text
stringlengths 0
128k
|
|---|
Board Thread:Roleplaying/@comment-3293219-20180408173218/@comment-3293219-20180414100339
"Aye, you would." Jerusalem shrugged, crossing her legs over.
"Though if you'd break me out as well as yourself, I would definitely reward you."
|
package parser
import (
"testing"
"github.com/ysugimoto/falco/ast"
"github.com/ysugimoto/falco/lexer"
"github.com/ysugimoto/falco/token"
)
func TestParseImport(t *testing.T) {
input := `// Leading comment
import boltsort; // Trailing comment`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.ImportStatement{
Meta: ast.New(T, 0, comments("// Leading comment"), comments("// Trailing comment")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "boltsort",
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestParseInclude(t *testing.T) {
input := `// Leading comment
include "feature_mod"; // Trailing comment`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.IncludeStatement{
Meta: ast.New(T, 0, comments("// Leading comment"), comments("// Trailing comment")),
Module: &ast.String{
Meta: ast.New(token.Token{}, 0),
Value: "feature_mod",
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestParseSetStatement(t *testing.T) {
t.Run("simple assign", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
set /* Host */ req.http.Host = "example.com"; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.SetStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1, comments("/* Host */")),
Value: "req.http.Host",
},
Operator: &ast.Operator{
Meta: ast.New(T, 1),
Operator: "=",
},
Value: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("with string concatenation", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
set /* Host */ req.http.Host = "example." req.http.User-Agent ".com"; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.SetStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1, comments("/* Host */")),
Value: "req.http.Host",
},
Operator: &ast.Operator{
Meta: ast.New(T, 1),
Operator: "=",
},
Value: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "example.",
},
Right: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.User-Agent",
},
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: ".com",
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
}
func TestParseIfStatement(t *testing.T) {
t.Run("only if", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ /* infix */"example.com") {
restart;
} // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1, comments("/* infix */")),
Value: "example.com",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2, comments(), comments("// Trailing comment")),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("logical and condtions", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com" && /* infix */req.http.Host == "foobar") {
restart;
} // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "&&",
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Right: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "==",
Left: &ast.Ident{
Meta: ast.New(T, 1, comments("/* infix */")),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "foobar",
},
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2, comments(), comments("// Trailing comment")),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("logical or condtions", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com" || req.http.Host == "foobar") {
restart;
}
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "||",
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Right: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "==",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "foobar",
},
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("if-else", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com") {
restart;
}
// Leading comment
else {
restart;
} // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
AlternativeComments: comments("// Leading comment"),
Alternative: &ast.BlockStatement{
Meta: ast.New(T, 2, comments(), comments("// Trailing comment")),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("if else if else ", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com") {
restart;
} else if (req.http.X-Forwarded-For ~ "192.168.0.1") {
restart;
} else {
restart;
}
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
Another: []*ast.IfStatement{
{
Meta: ast.New(T, 1),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.X-Forwarded-For",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "192.168.0.1",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
Alternative: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("if elseif else ", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com") {
restart;
} elseif (req.http.X-Forwarded-For ~ "192.168.0.1") {
restart;
} else {
restart;
}
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
Another: []*ast.IfStatement{
{
Meta: ast.New(T, 1),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.X-Forwarded-For",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "192.168.0.1",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
Alternative: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("if elsif else ", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
if (req.http.Host ~ "example.com") {
restart;
} elsif (req.http.X-Forwarded-For ~ "192.168.0.1") {
restart;
} else {
restart;
}
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.IfStatement{
Meta: ast.New(T, 1, comments("// Leading comment")),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
Another: []*ast.IfStatement{
{
Meta: ast.New(T, 1),
Condition: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "~",
Left: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.X-Forwarded-For",
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "192.168.0.1",
},
},
Consequence: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
Alternative: &ast.BlockStatement{
Meta: ast.New(T, 2),
Statements: []ast.Statement{
&ast.RestartStatement{
Meta: ast.New(T, 2),
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
}
func TestParseUnsetStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
unset req.http.Host; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.UnsetStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestParseAddStatement(t *testing.T) {
t.Run("simple assign", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
add req.http.Cookie:session = "example.com"; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.AddStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Cookie:session",
},
Operator: &ast.Operator{
Meta: ast.New(T, 1),
Operator: "=",
},
Value: &ast.String{
Meta: ast.New(T, 1),
Value: "example.com",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("with string concatenation", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
add req.http.Host = "example" req.http.User-Agent "com"; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.AddStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Host",
},
Operator: &ast.Operator{
Meta: ast.New(T, 1),
Operator: "=",
},
Value: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "example",
},
Right: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.User-Agent",
},
},
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "com",
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
}
func TestCallStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
call feature_mod_recv; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.CallStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Subroutine: &ast.Ident{
Meta: ast.New(T, 1),
Value: "feature_mod_recv",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestDeclareStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
declare local var.foo STRING; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.DeclareStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Name: &ast.Ident{
Meta: ast.New(T, 1),
Value: "var.foo",
},
ValueType: &ast.Ident{
Meta: ast.New(T, 1),
Value: "STRING",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestErrorStatement(t *testing.T) {
t.Run("without argument", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
error 750; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.ErrorStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Code: &ast.Integer{
Meta: ast.New(T, 1),
Value: 750,
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("with argument", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
error 750 "/foobar/" req.http.Foo; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.ErrorStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Code: &ast.Integer{
Meta: ast.New(T, 1),
Value: 750,
},
Argument: &ast.InfixExpression{
Meta: ast.New(T, 1),
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "/foobar/",
},
Operator: "+",
Right: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Foo",
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
t.Run("with ident argument", func(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
error var.IntValue; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.ErrorStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Code: &ast.Ident{
Meta: ast.New(T, 1),
Value: "var.IntValue",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
})
}
func TestLogStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
log {"syslog "}
{" fastly-log :: "} {" timestamp:"}
req.http.Timestamp
; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.LogStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Value: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Right: &ast.Ident{
Meta: ast.New(T, 1),
Value: "req.http.Timestamp",
},
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Right: &ast.String{
Meta: ast.New(T, 1),
Value: " timestamp:",
},
Left: &ast.InfixExpression{
Meta: ast.New(T, 1),
Operator: "+",
Right: &ast.String{
Meta: ast.New(T, 1),
Value: " fastly-log :: ",
},
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "syslog ",
},
},
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestReturnStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
return(deliver); // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.ReturnStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Ident: &ast.Ident{
Meta: ast.New(T, 1),
Value: "deliver",
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestSyntheticStatement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
synthetic {"Access "}
{"denied"}; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.SyntheticStatement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Value: &ast.InfixExpression{
Meta: ast.New(T, 1),
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "Access ",
},
Operator: "+",
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "denied",
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
func TestSyntheticBase64Statement(t *testing.T) {
input := `// Subroutine
sub vcl_recv {
// Leading comment
synthetic.base64 {"Access "}
{"denied"}; // Trailing comment
}`
expect := &ast.VCL{
Statements: []ast.Statement{
&ast.SubroutineDeclaration{
Meta: ast.New(T, 0, comments("// Subroutine")),
Name: &ast.Ident{
Meta: ast.New(T, 0),
Value: "vcl_recv",
},
Block: &ast.BlockStatement{
Meta: ast.New(T, 1),
Statements: []ast.Statement{
&ast.SyntheticBase64Statement{
Meta: ast.New(T, 1, comments("// Leading comment"), comments("// Trailing comment")),
Value: &ast.InfixExpression{
Meta: ast.New(T, 1),
Left: &ast.String{
Meta: ast.New(T, 1),
Value: "Access ",
},
Operator: "+",
Right: &ast.String{
Meta: ast.New(T, 1),
Value: "denied",
},
},
},
},
},
},
},
}
vcl, err := New(lexer.NewFromString(input)).ParseVCL()
if err != nil {
t.Errorf("%+v", err)
}
assert(t, vcl, expect)
}
|
User:Codysimpsonfann/Cody Simpson
Cody Robert Simpson is an Australian mucisian, born in Gold Coast, Queensland, Australia, born on January 11 1997. The currently 12 year old artist has one single, called "One". Cody has two siblings, his sister, Alli and brother, Tom. Cody, was discorved on www.youtube.com by his producer, Shawn Campbell Official Lyrics. Cody enjoys, singing, playing guitar, and surfing on the Austrailian Coast, when he can. Cody wrote and produced his hit single, "One".
|
Guiliana Rancic to Open Italian Restaurant
August 30, 2011
Giuliana Rancic is about to open her very own Italian restaurant in Chicago with her husband Bill.
The E! host says much of the inspiration for the restaurant came from her family.
"One of our inspirations is my Italian mom," Giuliana said. "Mama DePandi makes the most authentic Italian food and people cannot wait to get their hands on it ... She along with our chef, Doug Psaltis, will create mouthwatering dishes together."
So who does Giuliana want as her first celebrity patron? Well, LeAnn Rimes of course!
"She lost a lot of weight from all the stress in her life," Giuliana said. "She seems a little thin right now and I think she looks great when she's a bit curvier."
LeAnn was none to happy about the comments and took to her Twitter page to defend herself.
"@GiulianaRancic hey, we should go to dinner sometime," LeAnn wrote. "You get criticized all the time for how small you are. You can see just HOW much I eat and maybe put a stop to this crazy "shrinking" once and for all. Then we should workout together! Good luck with your restaurant!!!!"
The Rancics' restaurant is scheduled to open in January 2012.
Image Sources:
.
Categories:
|
package jenkins.plugins.elastest.submitters;
import static org.junit.Assert.assertEquals;
import static org.junit.Assert.assertTrue;
import static org.mockito.Matchers.any;
import static org.mockito.Mockito.atLeast;
import static org.mockito.Mockito.atLeastOnce;
import static org.mockito.Mockito.verify;
import static org.mockito.Mockito.when;
import java.io.ByteArrayOutputStream;
import java.net.URI;
import org.apache.commons.lang.CharEncoding;
import org.apache.http.HttpEntity;
import org.apache.http.StatusLine;
import org.apache.http.client.methods.CloseableHttpResponse;
import org.apache.http.client.methods.HttpPost;
import org.apache.http.entity.ContentType;
import org.apache.http.entity.StringEntity;
import org.apache.http.impl.client.CloseableHttpClient;
import org.apache.http.impl.client.HttpClientBuilder;
import org.junit.After;
import org.junit.Before;
import org.junit.Test;
import org.junit.runner.RunWith;
import org.mockito.Mock;
import org.mockito.runners.MockitoJUnitRunner;
@RunWith(MockitoJUnitRunner.class)
public class LogstashSubmitterTest {
LogstashSubmitter submitter;
@Mock
HttpClientBuilder mockClientBuilder;
@Mock
CloseableHttpClient mockHttpClient;
@Mock
StatusLine mockStatusLine;
@Mock
CloseableHttpResponse mockResponse;
@Mock
HttpEntity mockEntity;
LogstashSubmitter createSubmitter(String host, int port, String key,
String username, String password) {
return new LogstashSubmitter(mockClientBuilder, host, port, key,
username, password);
}
@Before
public void before() throws Exception {
int port = (int) (Math.random() * 1000);
submitter = createSubmitter("localhost", port, "logstash", "username",
"password");
when(mockClientBuilder.build()).thenReturn(mockHttpClient);
when(mockHttpClient.execute(any(HttpPost.class)))
.thenReturn(mockResponse);
when(mockResponse.getStatusLine()).thenReturn(mockStatusLine);
}
@After
public void after() throws Exception {
// verifyNoMoreInteractions(mockClientBuilder);
// verifyNoMoreInteractions(mockHttpClient);
}
@Test(expected = IllegalArgumentException.class)
public void constructorFailNullHost() throws Exception {
try {
createSubmitter(null, 8200, "logstash", "username", "password");
} catch (IllegalArgumentException e) {
assertEquals("Wrong error message was thrown",
"host name is required", e.getMessage());
throw e;
}
}
@Test(expected = IllegalArgumentException.class)
public void constructorFailEmptyHost() throws Exception {
try {
createSubmitter("http:// ", 8200, "logstash", "username",
"password");
} catch (IllegalArgumentException e) {
assertEquals("Wrong error message was thrown",
"Could not create uri", e.getMessage());
throw e;
}
}
@Test
public void constructorSuccess1() throws Exception {
// Unit under test
submitter = createSubmitter("localhost", 8200, "logstash", "username",
"password");
// Verify results
assertEquals("Wrong host name", "localhost", submitter.host);
assertEquals("Wrong port", 8200, submitter.port);
assertEquals("Wrong key", "logstash", submitter.key);
assertEquals("Wrong name", "username", submitter.username);
assertEquals("Wrong password", "password", submitter.password);
assertEquals("Wrong auth", "dXNlcm5hbWU6cGFzc3dvcmQ=", submitter.auth);
assertEquals("Wrong uri", new URI("http://localhost:8200/logstash/"),
submitter.uri);
}
@Test
public void constructorSuccess2() throws Exception {
// Unit under test
submitter = createSubmitter("localhost", 8200, "jenkins/logstash", "",
"password");
// Verify results
assertEquals("Wrong host name", "localhost", submitter.host);
assertEquals("Wrong port", 8200, submitter.port);
assertEquals("Wrong key", "jenkins/logstash", submitter.key);
assertEquals("Wrong name", "", submitter.username);
assertEquals("Wrong password", "password", submitter.password);
assertEquals("Wrong auth", null, submitter.auth);
assertEquals("Wrong uri",
new URI("http://localhost:8200/jenkins/logstash/"),
submitter.uri);
}
@Test
public void getPostSuccessNoAuth() throws Exception {
String json = "{ 'foo': 'bar' }";
submitter = createSubmitter("localhost", 8200, "jenkins/logstash", "",
"");
// Unit under test
HttpPost post = submitter.getHttpPost(json);
HttpEntity entity = post.getEntity();
assertEquals("Wrong uri",
new URI("http://localhost:8200/jenkins/logstash/"),
post.getURI());
assertEquals("Wrong auth", 0, post.getHeaders("Authorization").length);
assertEquals("Wrong content type", entity.getContentType().getValue(),
ContentType.APPLICATION_JSON.toString());
assertTrue("Wrong content class", entity instanceof StringEntity);
ByteArrayOutputStream stream = new ByteArrayOutputStream();
entity.writeTo(stream);
assertEquals("Wrong content", stream.toString(CharEncoding.UTF_8),
"{ 'foo': 'bar' }");
}
@Test
public void getPostSuccessAuth() throws Exception {
String json = "{ 'foo': 'bar' }";
submitter = createSubmitter("localhost", 8200, "logstash", "username",
"password");
// Unit under test
HttpPost post = submitter.getHttpPost(json);
HttpEntity entity = post.getEntity();
assertEquals("Wrong uri", new URI("http://localhost:8200/logstash/"),
post.getURI());
assertEquals("Wrong auth", 1, post.getHeaders("Authorization").length);
assertEquals("Wrong auth value", "Basic dXNlcm5hbWU6cGFzc3dvcmQ=",
post.getHeaders("Authorization")[0].getValue());
assertEquals("Wrong content type", entity.getContentType().getValue(),
ContentType.APPLICATION_JSON.toString());
assertTrue("Wrong content class", entity instanceof StringEntity);
ByteArrayOutputStream stream = new ByteArrayOutputStream();
entity.writeTo(stream);
assertEquals("Wrong content", stream.toString(CharEncoding.UTF_8),
"{ 'foo': 'bar' }");
}
@Test
public void pushSuccess() throws Exception {
String json = "{ 'foo': 'bar' }";
submitter = createSubmitter("http://localhost", 8200,
"/jenkins/logstash", "", "");
when(mockStatusLine.getStatusCode()).thenReturn(201);
// Unit under test
submitter.push(json);
verify(mockClientBuilder).build();
verify(mockHttpClient).execute(any(HttpPost.class));
verify(mockStatusLine, atLeastOnce()).getStatusCode();
verify(mockResponse).close();
verify(mockHttpClient).close();
}
@Test
public void pushFailStatusCode() throws Exception {
String json = "{ 'foo': 'bar' }";
submitter = createSubmitter("http://localhost", 8200,
"/jenkins/logstash", "username", "password");
when(mockStatusLine.getStatusCode()).thenReturn(500);
when(mockResponse.getEntity()).thenReturn(new StringEntity(
"Something bad happened.", ContentType.TEXT_PLAIN));
// Unit under test
submitter.push(json);
// Verify results
verify(mockClientBuilder).build();
verify(mockHttpClient).execute(any(HttpPost.class));
verify(mockStatusLine, atLeastOnce()).getStatusCode();
verify(mockResponse).close();
verify(mockHttpClient).close();
}
}
|
"use strict";
function _objectSpread(target) { for (var i = 1; i < arguments.length; i++) { var source = arguments[i] != null ? arguments[i] : {}; var ownKeys = Object.keys(source); if (typeof Object.getOwnPropertySymbols === 'function') { ownKeys = ownKeys.concat(Object.getOwnPropertySymbols(source).filter(function (sym) { return Object.getOwnPropertyDescriptor(source, sym).enumerable; })); } ownKeys.forEach(function (key) { _defineProperty(target, key, source[key]); }); } return target; }
function _defineProperty(obj, key, value) { if (key in obj) { Object.defineProperty(obj, key, { value: value, enumerable: true, configurable: true, writable: true }); } else { obj[key] = value; } return obj; }
function _toConsumableArray(arr) { return _arrayWithoutHoles(arr) || _iterableToArray(arr) || _nonIterableSpread(); }
function _nonIterableSpread() { throw new TypeError("Invalid attempt to spread non-iterable instance"); }
function _iterableToArray(iter) { if (Symbol.iterator in Object(iter) || Object.prototype.toString.call(iter) === "[object Arguments]") return Array.from(iter); }
function _arrayWithoutHoles(arr) { if (Array.isArray(arr)) { for (var i = 0, arr2 = new Array(arr.length); i < arr.length; i++) { arr2[i] = arr[i]; } return arr2; } }
(function () {
// Fixed Header
// Form Validation
// Object fit css backward compatibility fix
// Financial Table Indexing and Loader
////////// Fixed Header //////////
function headerFixed(fixedHeader, stickyPoint) {
if (window.pageYOffset > stickyPoint) {
var phantomHeight = $(fixedHeader).outerHeight();
$('.sticky-phantom').height(phantomHeight).show();
fixedHeader.classList.add('fixed-header');
} else {
$('.sticky-phantom').hide();
fixedHeader.classList.remove('fixed-header');
}
}
function responsiveWidthHeader(fixedHeader) {
var stickyPoint = fixedHeader.offsetTop;
if (window.innerWidth > 767) {
$(window).scroll(function () {
if (!!stickyPoint) {
headerFixed(fixedHeader, stickyPoint);
}
});
} else {
$(window).scroll(function () {
$('.sticky-phantom').hide();
fixedHeader.classList.remove('fixed-header');
});
}
}
window.onload = function () {
var fixedHeader = document.getElementsByClassName("navigation")[0];
responsiveWidthHeader(fixedHeader);
window.addEventListener("resize", function () {
responsiveWidthHeader(fixedHeader);
});
}; ////////// Form Validation //////////
var form_Validation_Model = {};
form_Validation_Model.validate = function () {
//Select Forms to be Validated
var toBeValidatedForm = new Array().slice.call(document.querySelectorAll(".needs-validation"));
toBeValidatedForm.forEach(function (element) {
return element.setAttribute("novalidate", "true");
});
function validateForm(event) {
if (document.querySelector(".btnGetCalculation")) {
var resultDisplayBox = document.querySelector(".calculate__inquiry__form__calculation");
event.preventDefault(); // Calculation Function present in each calculate components
calc();
resultDisplayBox.style.display = "inline-block";
resultDisplayBox.scrollIntoView({
behavior: "smooth",
block: "center",
inline: "nearest"
});
}
} //Check for Validation
var validation = Array.prototype.filter.call(toBeValidatedForm, function (form) {
form.addEventListener('submit', function (event) {
if (form.checkValidity() === false) {
event.preventDefault();
event.stopPropagation();
} else {
validateForm(event);
}
form.classList.add('was-validated');
}, false);
});
}; //Initialize on Form Included Pages
if (document.getElementsByClassName("needs-validation").length) {
form_Validation_Model.validate();
} ////////// Object fit css backward compatibility fix //////////
function ObjectFitCompat(objectPolyfillImages) {
objectPolyfillImages.forEach(function (element) {
var elementSrc = element.getElementsByTagName("img")[0].getAttribute("src");
if (elementSrc) {
element.style.backgroundImage = "url(" + elementSrc + ")";
element.classList.toggle("compat-object-fit");
}
});
}
function ObjectFitInit(objectFitSelector) {
if ('objectFit' in document.documentElement.style === false) {
var objectPolyfillImages = new Array().slice.call(document.querySelectorAll(objectFitSelector));
ObjectFitCompat(objectPolyfillImages);
}
}
var ObjectFitElem = [".carousel__client", ".carousel-item", ".single-notice--details__image"];
ObjectFitElem.map(ObjectFitInit); // Financial Table Indexing and Loader
function spinnerLoader() {
var loader = document.createElement("div");
loader.setAttribute("class", "spinnerLoader");
loader.innerHTML = "<div class=\"bounce1\"></div><div class=\"bounce2\"></div><div class=\"bounce3\"></div>";
return loader;
} // For multiple table separation inside financial page
function tableSeparator(element, index) {
element.classList.add("table", "table-hover", "table-bordered", "table-loader");
var tableContainer = document.createElement("div");
var targetContainer = document.querySelector(".reporttable");
if (targetContainer) {
tableContainer.classList.add("table-" + index);
tableContainer.append(element);
targetContainer.append(tableContainer);
}
}
if (document.querySelector("table")) {
var financialTableIndexing = document.querySelectorAll(".financial__section table");
var showLoading = document.querySelectorAll(".table-loader");
var index = 0;
var tableIndexing = new Array().slice.call(financialTableIndexing).forEach(function (element) {
tableSeparator(element, index);
index++;
});
var addLoader = new Array().slice.call(showLoading).forEach(function (element) {
var loaderIcon = spinnerLoader();
element.parentNode.append(loaderIcon);
});
}
if (document.querySelector(".barChartImplementation")) {
var tableCount = document.querySelectorAll("table");
var tableIndex = 0;
tableCount.forEach(function (element) {
var labels = [],
datasetsLine = [],
datasetsBar = [],
eachLabelBar,
eachTableTitle,
bottomLabelTitle;
var tableRows = new Array().slice.call(element.querySelectorAll("tbody tr"));
eachTableTitle = tableRows[0].cells[0].textContent;
bottomLabelTitle = tableRows[1].cells[0].textContent;
var thead = document.createElement("thead");
var theadTr = document.createElement("tr");
var theadEl = new Array().slice.call(tableRows[1].cells);
theadEl.forEach(function (el) {
var theadTh = document.createElement("th");
theadTh.innerHTML = el.textContent;
theadTr.append(theadTh);
});
element.querySelector("tbody").deleteRow(0);
element.querySelector("tbody").deleteRow(0);
thead.append(theadTr);
element.prepend(thead);
tableRows.shift();
tableRows.shift();
var rowData = element.querySelectorAll("thead th");
for (var i = 1; i < rowData.length; i++) {
labels.push(rowData[i].textContent);
}
for (var _i = 0; _i < tableRows.length; _i++) {
var datasetsVal = tableRows[_i].querySelectorAll("td");
var dataBar = [];
var datasetsBarObj = {};
for (var j = 0; j < datasetsVal.length; j++) {
if (j == 0) {
eachLabelBar = datasetsVal[j].textContent;
} else {
dataBar.push(parseFloat(datasetsVal[j].textContent.replace(/,/g, '')));
}
}
datasetsBarObj.label = eachLabelBar;
datasetsBarObj.backgroundColor = '#' + (Math.random() * 0xFFFFFF << 0).toString(16);
datasetsBarObj.data = dataBar;
datasetsBar.push(datasetsBarObj);
}
datasetsLine = datasetsBar[datasetsBar.length - 1];
datasetsLine.type = "line";
datasetsLine.borderColor = '#' + (Math.random() * 0xFFFFFF << 0).toString(16);
datasetsLine.lineTension = "0";
datasetsLine.fill = "false";
datasetsBar.pop();
datasetsBar.forEach(function (element) {
element.type = "bar";
});
datasetsBar.push(datasetsLine);
var targetElement = document.querySelector(".table-" + tableIndex);
var canvasContainerElement = document.createElement("div");
canvasContainerElement.setAttribute("id", "chartContainer" + tableIndex);
canvasContainerElement.setAttribute("class", "chartContainer");
var canvasElement = document.createElement("canvas");
canvasElement.setAttribute("id", "bar-chart-grouped" + tableIndex);
canvasElement.setAttribute("height", 470);
canvasContainerElement.appendChild(canvasElement);
targetElement.prepend(canvasContainerElement);
var chartdata = {
labels: labels,
datasets: datasetsBar
};
Chart.defaults.global.defaultFontColor = 'black';
Chart.defaults.global.defaultFontFamily = 'Georgia';
new Chart(document.getElementById("bar-chart-grouped" + tableIndex), {
type: 'bar',
data: chartdata,
options: {
responsive: true,
maintainAspectRatio: false,
title: {
display: true,
text: eachTableTitle
},
tooltips: {
callbacks: {
label: function label(tooltipItem, data) {
var value = data.datasets[tooltipItem.datasetIndex].data[tooltipItem.index];
value = value.toLocaleString();
return value;
} // end callbacks:
}
},
//end tooltips
scales: {
xAxes: [{
display: true,
scaleLabel: {
display: true,
labelString: "Year"
}
}],
yAxes: [{
display: true,
scaleLabel: {
display: true,
labelString: 'Value'
},
ticks: {
beginAtZero: true,
userCallback: function userCallback(value, index, values) {
value = value.toLocaleString();
return value;
}
}
}]
},
pan: {
enabled: true,
mode: "x",
speed: 10,
threshold: 10
},
zoom: {
enabled: true,
drag: false,
mode: "x",
limits: {
max: 10,
min: 0.5
}
}
}
});
tableIndex++;
});
} ////////// Mapbox //////////
// Branch Styling
function reArrangeBranchList(branches) {
var activeBranches = _toConsumableArray(branches).filter(function (el) {
return el.classList.contains('active');
});
var branchesList = activeBranches.length;
var i = 0;
for (i; i < branchesList; i++) {
activeBranches[i].style.marginLeft = "1%";
}
if (window.innerWidth <= 1024) {
var n = Math.floor(branchesList / 3);
if (n === 0) n = 1;
while (n > 0) {
var leftElement = 3 * n - 1;
if (activeBranches[leftElement]) {
activeBranches[leftElement].style.marginLeft = "26.5%";
}
n--;
}
}
if (window.innerWidth > 1024 && window.innerWidth <= 1280) {
var _n = Math.floor(branchesList / 5);
if (_n === 0) _n = 1;
while (_n > 0) {
var _leftElement = 5 * _n - 2;
if (activeBranches[_leftElement]) {
activeBranches[_leftElement].style.marginLeft = "17.5%";
}
_n--;
}
}
if (window.innerWidth > 1280) {
var _n2 = Math.floor(branchesList / 7);
if (_n2 === 0) _n2 = 1;
while (_n2 > 0) {
var _leftElement2 = 7 * _n2 - 3;
if (activeBranches[_leftElement2]) {
activeBranches[_leftElement2].style.marginLeft = "13.5%";
}
_n2--;
}
}
}
if (document.querySelector("#map")) {
var branchList = document.querySelectorAll('.branchcontainer li');
reArrangeBranchList(branchList);
window.addEventListener('resize', function () {
reArrangeBranchList(branchList);
});
} // Mapbox related Code
function getFeature(element) {
var coordinates = [];
var long = Number(element.dataset.long);
var lat = Number(element.dataset.lat);
var address = element.dataset.address;
var provinceoffice = element.dataset.province;
var headoffice = element.dataset.head;
coordinates.push(long);
coordinates.push(lat);
var currentFeature = {
"type": "Feature",
"geometry": {
"type": "Point",
"coordinates": coordinates
},
"properties": {
"address": address,
"province": provinceoffice,
"headoffice": headoffice
}
};
return currentFeature;
}
function flyToStore(currentFeature) {
map.flyTo({
center: currentFeature.geometry.coordinates,
zoom: 15
});
} // Add Remove method in the DOM element
if (!('remove' in Element.prototype)) {
Element.prototype.remove = function () {
if (this.parentNode) {
this.parentNode.removeChild(this);
}
};
}
function createPopUp(currentFeature) {
var popUpText = '<h3>Nepal Insurance</h3>' + '<h4>' + currentFeature.properties.address + '</h4>';
var popUps = document.getElementsByClassName('mapboxgl-popup'); // Check if there is already a popup on the map and if so, remove it
if (popUps[0]) {
popUps[0].remove();
}
;
var popup = new mapboxgl.Popup({
closeOnClick: false
}).setLngLat(currentFeature.geometry.coordinates).setHTML(popUpText).addTo(map);
} //Shows location on map when map icon clicked
function showOnMap(element) {
if (!!element.dataset.long && !!element.dataset.lat && !!element.dataset.address) {
var feature = getFeature(element);
flyToStore(feature);
createPopUp(feature);
}
}
if (document.querySelector("#map")) {
mapboxgl.accessToken = 'pk.eyJ1Ijoia25pZ2h0Y2FuZHkiLCJhIjoiY2pzbXhsYXV6MDZoczQ0cGRhdXM4cnliNSJ9.ld_oUwvkeT8a7lI5S7bsnQ';
var mapContainer = document.querySelector("#map");
var markerButtons = [].slice.call(document.querySelectorAll(".map-marker"));
markerButtons.forEach(function (element) {
if (element.dataset.lat && element.dataset.long) {
element.addEventListener('click', function () {
showOnMap(element);
mapContainer.scrollIntoView({
behavior: "smooth",
block: "center"
});
});
}
});
var geojsonData = [];
var _branchList = [].slice.call(document.querySelectorAll(".branch .map-marker"));
_branchList.forEach(function (element) {
var feature = getFeature(element);
geojsonData.push(feature);
});
var map = new mapboxgl.Map({
container: 'map',
style: 'mapbox://styles/mapbox/streets-v9',
center: [84.1240, 28.3949],
zoom: 6
});
var insurancejson = {
"type": "FeatureCollection",
"features": geojsonData
};
map.on('load', function (e) {
// Add the data to your map as a layer
map.addSource('places', {
type: 'geojson',
data: insurancejson
});
});
insurancejson.features.forEach(function (marker) {
var el = document.createElement('div');
el.className = 'marker marker-active marker-province ' + marker.properties.province; // el.className = 'marker marker-active marker-province ' + marker.properties.province;
if (marker.properties.headoffice === '1') {
el.className += ' marker-head';
el.style.width = "75px";
el.style.height = "75px";
} // By default the image for your custom marker will be anchored
// by its center. Adjust the position accordingly
// Create the custom markers, set their position, and add to map
new mapboxgl.Marker(el, {
offset: [0, -23]
}).setLngLat(marker.geometry.coordinates).addTo(map);
el.addEventListener('click', function (e) {
var activeItem = document.getElementsByClassName('active'); // 1. Fly to the point
flyToStore(marker); // 2. Close all other popups and display popup for clicked store
createPopUp(marker); // e.stopPropagation();
});
});
map.addControl(new mapboxgl.GeolocateControl({
positionOptions: {
enableHighAccuracy: true
},
trackUserLocation: true
}));
map.addControl(new mapboxgl.NavigationControl());
} // Mapbox Filter Buttons
function activeProvince() {
// let filterProvince = ['province-1', 'province-2', 'province-3', 'province-4', 'province-5', 'province-6', 'province-7'];
var filterProvince = [];
function showProvince(province) {
if (filterProvince.includes(province)) {
return filterProvince;
} else {
filterProvince.push(province);
return filterProvince;
}
}
function hideProvince(province) {
if (filterProvince.includes(province)) {
filterProvince = filterProvince.filter(function (el) {
return el !== province;
});
return filterProvince;
} else {
return filterProvince;
}
}
return {
show: showProvince,
hide: hideProvince
};
}
function hasClass(element, classArray) {
if (classArray.length > 0) {
return element.classList.contains(classArray[0]) || hasClass(element, classArray.slice(1));
}
return false;
}
function filteredProvince(locationContainer, provinces, markers) {
locationContainer.forEach(function (htmlEl) {
hasClass(htmlEl, provinces) ? htmlEl.classList.add('active') : htmlEl.classList.remove('active');
});
markers.forEach(function (markerEl) {
hasClass(markerEl, provinces) ? markerEl.classList.add('marker-active') : markerEl.classList.remove('marker-active');
});
}
function showLocationFilter(event, locationContainer, markers, provinceList) {
var targetBtn = event.target;
var filterVal = 'province-' + targetBtn.dataset.target;
var activationBtn = targetBtn.parentNode;
var btnIsActive = activationBtn.classList.contains('active');
if (btnIsActive) {
activationBtn.classList.remove('active');
var provinces = provinceList.hide(filterVal);
filteredProvince(locationContainer, provinces, markers);
} else {
activationBtn.classList.add('active');
var _provinces = provinceList.show(filterVal);
filteredProvince(locationContainer, _provinces, markers);
}
if (!document.querySelector('.btn-group-toggle .btn.active')) {
markers.forEach(function (el) {
el.classList.add('marker-active');
});
locationContainer.forEach(function (el) {
el.classList.add('active');
});
}
}
if (document.querySelector("#map")) {
var filterButtons = document.querySelectorAll('.btn-group-toggle input');
var markers = document.querySelectorAll('.marker');
var locationContainer = document.querySelectorAll('.branchcontainer li');
var provinceList = activeProvince();
filterButtons.forEach(function (btn) {
btn.addEventListener('click', function (event) {
showLocationFilter(event, locationContainer, markers, provinceList);
reArrangeBranchList(locationContainer);
});
});
}
})(); ////////// Jquery Dependencies //////////
$(document).ready(function () {
// Close Navbar Click Outside //
$(document).click(function (event) {
var clickover = $(event.target);
var opened = $(".navbar-collapse").hasClass("collapse show");
if (opened === true && !clickover.hasClass("navbar-toggler")) {
$("button.navbar-toggler").click();
}
}); //Show tooltip on Forms and Other Pages
if ($('[data-toggle="tooltip"]').length) {
$('[data-toggle="tooltip"]').tooltip();
} ////////// PopUp Start HomePage and hide for 10seconds using Cookie //////////
if (document.cookie.indexOf("homemodal=true") < 0) {
setTimeout(function () {
$("#popupModal").modal("show");
}, 500);
var date = new Date();
date.setTime(date.getTime() + 10 * 1000);
var expires = "expires=" + date.toUTCString();
document.cookie = "homemodal=true;" + expires + "; path=/";
} ////////// Expand Toggle Sub-Navigation //////////
$(window).resize(function () {
if (window.innerWidth > 767) {
visibleSubNav = false;
$("nav.nav").fadeIn(100);
}
});
var visibleSubNav = false;
$('.expand-toggle .btn').click(function () {
if (visibleSubNav) {
$(this).parent().next("nav").fadeOut(200);
$(this).find("i.fas")[0].classList.remove("rotate");
visibleSubNav = false;
} else {
$(this).find("i.fas")[0].classList.add("rotate");
$(this).parent().next("nav").fadeIn(200);
visibleSubNav = true;
}
}); ////////// Header Navigation Dropdown //////////
$('.headernav .dropdown').hover(function () {
$(this).find('.dropdown-menu').stop(true, true).delay(100).fadeIn(400);
}, function () {
$(this).find('.dropdown-menu').stop(true, true).delay(100).fadeOut(200);
}); ////////// Financial Section Table to Datatables //////////
var datatable_Model = {};
datatable_Model.datatableConfiguration = {
searching: false,
paging: false,
info: false,
responsive: true,
ordering: false,
dom: 'exportBtn',
// dom: 'Bfrtip',
buttons: ['excel', 'pdf']
};
datatable_Model.initDatatable = function (tableContainer) {
var config = arguments.length > 1 && arguments[1] !== undefined ? arguments[1] : this.datatableConfiguration;
$(tableContainer).on('init.dt', function () {
$(tableContainer).parent().find(".spinnerLoader").css("display", "none");
}).DataTable(config);
}; // Initialize table conversion to datatables
if (document.querySelector(".datatable table")) {
setTimeout(function () {
datatable_Model.initDatatable(".reporttable table");
}, 500);
} ////////// Gallery Image Justified and Lightbox//////////
var gallery_Model = {};
gallery_Model.justifiedConfiguration = {
rowHeight: 260,
lastRow: 'nojustify',
margins: 5
};
gallery_Model.initLightGallery = function (imageContainer) {
var $lightGallery = $(imageContainer);
$lightGallery.lightGallery({
share: false
});
$lightGallery.on('onAfterOpen.lg', function (event) {
$("body").css("overflow", "hidden");
});
$lightGallery.on('onCloseAfter.lg', function (event) {
$("body").css("overflow", "auto");
});
};
gallery_Model.initJustifiedGallery = function (imageContainer) {
$(imageContainer).justifiedGallery(this.justifiedConfiguration).on('jg.complete', function () {
this.initLightGallery(imageContainer);
}.bind(this));
}; // Initialize Justified Gallery and Lightbox
if ($(".gallery-lightbox").length) {
gallery_Model.initJustifiedGallery(".gallery-lightbox");
} //Gridder Management and Team Section
if ($(".gridder").length) {
$('.gridder').gridderExpander({
scroll: true,
scrollOffset: 30,
scrollTo: "panel",
animationSpeed: 400,
animationEasing: "easeInOutExpo",
showNav: true,
nextText: "<span></span>",
prevText: "<span></span>",
closeText: ""
});
} // View and Download Section //
function workaroundDownload(downloadButton) {
var targetFileLocation = $(downloadButton).attr("href");
window.open(targetFileLocation);
}
if ($("a[download]").length) {
var downloadAttrSupported = "download" in document.createElement("a");
if (!downloadAttrSupported) {
$("a[download]").each(function () {
$(this).on("click", function (e) {
e.preventDefault();
workaroundDownload(this);
});
});
}
}
function fileExists(url) {
var http = new XMLHttpRequest();
http.open('GET', url, false);
http.send();
return http.status != 404;
}
$("a.btnViewFile").on("click", function () {
var targetModal = $(this).data("modal");
var targetFile = $(this).data("target");
var targetTitle = $(this).data("title");
if (fileExists(targetFile)) {
$("#" + targetModal + " .modal-body").html("");
if (targetFile.toLowerCase().match(/\.(pdf)/g)) {
PDFObject.embed(targetFile, "#" + targetModal + " .modal-body");
} else {
var $viewContainer = document.createElement("embed");
$viewContainer.src = targetFile;
$($viewContainer).appendTo("#" + targetModal + " .modal-body");
}
} else {
$("#" + targetModal + " .modal-body").html("<div class='error'><p>File not found.</p></div>");
$("#" + targetModal + " .modal-body").css("background", "none");
}
$("#" + targetModal).find(".modal-title").text(targetTitle);
$("#" + targetModal).modal("show");
$('#' + targetModal).on('shown.bs.modal', function (e) {
e.target.style.paddingRight = 0;
});
}); ////////// Carousel Sliders //////////
var carousel_Model = {};
carousel_Model.carouselSettings = {
slidesToShow: 4,
slidesToScroll: 1,
nextArrow: "<span class='fa fa-angle-right rightslide'></span>",
prevArrow: "<span class='fa fa-angle-left leftslide'></span>",
responsive: [{
breakpoint: 1024,
settings: {
slidesToShow: 3,
slidesToScroll: 1,
autoplay: true
}
}, {
breakpoint: 768,
settings: {
slidesToShow: 2,
slidesToScroll: 1,
autoplay: true
}
}, {
breakpoint: 480,
settings: {
slidesToShow: 1,
slidesToScroll: 1,
autoplay: true
}
}]
};
carousel_Model.initCarousel = function (carouselContainer, config) {
$(carouselContainer).on('init', function () {
$(carouselContainer).parent().find(".spinnerLoader").css("display", "none");
});
config == null ? config = this.carouselSettings : "";
$(carouselContainer).slick(config);
};
var newsArticlesCarouselConfig = JSON.parse(JSON.stringify(carousel_Model.carouselSettings));
newsArticlesCarouselConfig.responsive[0].settings.arrows = false;
newsArticlesCarouselConfig.responsive[0].settings.autoplay = true;
carousel_Model.carouselContainers = {
client: {
container: ".client__list__carousel",
config: null
},
insurance: {
container: ".insuranceoptions__slider",
config: null
},
news: {
container: ".news__articles--carousel",
config: newsArticlesCarouselConfig
}
};
for (var key in carousel_Model.carouselContainers) {
var carouselContainers = _objectSpread({}, carousel_Model.carouselContainers);
if (carouselContainers.hasOwnProperty(key)) {
if ($(carouselContainers[key].container).length) {
carousel_Model.initCarousel(carouselContainers[key].container, carouselContainers[key].config);
}
}
}
});
|
Generate days row on the basis of date range column
I have a csv file comprises of two columns (Week and Data) and 100 rows.
Which look like this:
<table>
<tr>
<th>Week</th>
<th>Data</th>
</tr>
<tr>
<td>2009-01-04 - 2009-01-10</td>
<td> Some Data</td>
</tr>
</table>
But I want to convert the given range of date in rows of days. like this:
<table>
<tr>
<th>Week</th>
<th>Data</th>
</tr>
<tr><td>2009-01-04</td>
<td>Some Data</td></tr>
<tr><td>2009-01-05</td>
<td>Some Data</td></tr>
<tr><td>2009-01-06</td>
<td>Some Data</td></tr>
<tr><td>2009-01-07</td>
<td>Some Data</td></tr>
<tr><td>2009-01-08</td>
<td>Some Data</td></tr>
<tr><td>2009-01-09</td>
<td>Some Data</td></tr>
<tr><td>2009-01-10</td>
<td>Some Data</td></tr>
</table>
As I am new to pandas, is there a easy way to achieve this kind of thing?
My dataset contains 100 rows and each row has a Week column which is consist of range of dates.
please help me out I am stuck here.
Your help will be appreciated.
Thanks.
import datetime
from dateutil.parser import parse as parse_date
from pandas import DataFrame
df = DataFrame([['2009-01-04 - 2009-01-10','Some Data'],
['2009-01-11 - 2009-01-17','Some Data']])
df.columns = ['week','data']
def generate_dates(date_range):
day1_str, day2_str = date_range.split(' - ')
day1, day2 = parse_date(day1_str), parse_date(day2_str)
delta = day1 - day2
return [day1 + datetime.timedelta(days=x) for x in range(0, abs(delta.days + 1))]
def create_rows_from_row(row):
dates = generate_dates(row['week'])
return [[d, row['data']] for d in dates]
def create_new_df(df):
rows = []
for idx in range(len(df)):
rows.extend(create_rows_from_row(df.ix[idx]))
new_df = DataFrame(rows)
new_df.columns = ['week','data']
return new_df
create_new_df(df)
|
/**
* Copyright 2012 John W. Krupansky d/b/a Base Technology
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
package com.basetechnology.s0.agentserver.util;
import java.util.ArrayList;
import java.util.HashMap;
import java.util.Iterator;
import java.util.List;
import java.util.Map;
import com.basetechnology.s0.agentserver.AgentServerException;
public class NameValueList<T> implements Iterable<NameValue<T>> {
public List<NameValue<T>> nameValueList = new ArrayList<NameValue<T>>();
public Map<String, NameValue<T>> nameValueMap = new HashMap<String, NameValue<T>>();
public NameValueList(){
// Nothing needed
}
public NameValueList(List<NameValue<T>> nameValueList){
// Make a copy of the string list and build a map for lookup by name
for (NameValue<T> nameValue: nameValueList){
// Copy this string
NameValue<T> nameValueCopy = nameValue.clone();
// Add this string to the new string list
nameValueList.add(nameValueCopy);
// Add this string to map for lookup by its name
// TODO: Symbol has name and SymbolTable (and hence SymbolValues)
nameValueMap.put(nameValueCopy.name, nameValueCopy);
}
}
public boolean containsKey(String stringName){
return nameValueMap.containsKey(stringName);
}
public NameValue<T> add(String name, T value) throws AgentServerException {
// Check if name is already in list
if (containsKey(name))
// Treat as update rather than add
return put(name, value);
else {
// Add new name to the list
NameValue<T> newNameValue = new NameValue<T>(name, value);
nameValueList.add(newNameValue);
// Update the map
nameValueMap.put(name, newNameValue);
// Return the new name-value
return newNameValue;
}
}
public void clear(){
// Clear the list
nameValueList.clear();
// Clear the map
nameValueMap.clear();
}
public NameValue<T> get(int i){
return nameValueList.get(i);
}
public T get(String stringName){
NameValue<T> nameValue = nameValueMap.get(stringName);
if (nameValue == null)
return null;
else
return nameValue.value;
}
public NameValue<T> put(String stringName, NameValue<T> value) throws AgentServerException {
// Check if name is alread in list
if (containsKey(stringName)){
// Need to update list
// Get current name/value pair
NameValue<T> currentValue = nameValueMap.get(stringName);
// Find current name/value pair in list
int i = nameValueList.indexOf(currentValue);
if (i < 0)
throw new AgentServerException("Corrupted nameValueList for key: '" + stringName + "'");
// Update the existing list value
nameValueList.set(i, value);
} else {
// Need to add to list
nameValueList.add(value);
}
return nameValueMap.put(stringName, value);
}
public NameValue<T> put(String stringName, T value) throws AgentServerException {
return put(stringName, new NameValue<T>(stringName, value));
}
public NameValue<T> put(String stringName, String value) throws AgentServerException {
return put(stringName, new NameValue<T>(stringName, (T)value));
}
public Iterator<NameValue<T>> iterator(){
return nameValueList.iterator();
}
public NameValue<T> remove(String stringName){
// Get the current name/value from the map
NameValue<T> nameValue = nameValueMap.get(stringName);
// It may not exist
if (nameValue != null){
// Remove the name/value from the list
nameValueList.remove(nameValue);
// Remove the value from the map
return nameValueMap.remove(stringName);
} else
// Nothing to do for nonexistent value
return null;
}
public int size(){
return nameValueList.size();
}
}
|
/*
this class required to make an account in twilio website and fill the api information as following
1: you need to change line 15 to your ACCOUNT_SID
2: and change line 17 to your AUTH_TOKEN
*/
package model;
import com.twilio.Twilio;
import com.twilio.rest.api.v2010.account.Message;
import com.twilio.type.PhoneNumber;
public class SMS_API {
public static final String ACCOUNT_SID =
"ACCOUNT_SID";
public static final String AUTH_TOKEN =
"AUTH_TOKEN";
public static void send_sms(String message_value ,String number) {
Twilio.init(ACCOUNT_SID, AUTH_TOKEN);
Message message;
message = Message
.creator(new PhoneNumber("+97"+number), // to
new PhoneNumber("+12252172717"), // from
message_value)
.create();
System.out.println(message.getSid());
}
}
|
User:Jgmoxness
<EMAIL_ADDRESS>or Special:Emailuser/Jgmoxness
See also:
* www.TheoryOfEverything.org
See below for my content:
Images of higher order orbits of E8 (421, 241, 142)
E8 421 Petrie Projection
E8 241 Petrie Projection
E8 142 Petrie Projection (53% of inner edges culled)
* more detail on projections
Images of various orbits of H4 hulls
120-Cell Hulls
120-Cell showing the individual 8 concentric hulls and in combination.svg of Norm=$\sqrt{8}$.
Hulls 1, 2, & 7 are each overlapping pairs of Dodecahedrons.
Hull 3 is a pair of Icosidodecahedrons.
Hulls 4 & 5 are each pairs of Truncated icosahedrons.
Hulls 6 & 8 are pairs of Rhombicosidodecahedrons.]]
Overlay of regular and quasi-regular constructions of Snub Dodecahedra and Truncated Icosidodecahedra
Triakis icosahedron Hulls
600-Cell Hulls
24-Cell to 600-Cell H4 Animation
600-Cell to 120-Cell Animation
T alternate of the 120-cell
DualSnub24Cell
Snub24Prime
Snub24CellPrime-hulls
120Cell-M
Snub24Cell
H4Phi-Snub24Cell-4hulls-each
Images Dynkin Diagrams
Cell8+Cell16=Cell24
Images of Fano Planes
CoPrime graph
(talk) 02:52, 6 April 2010 (UTC)
|
Python - Insert newlines into text so text won't exceed max character width
I'm making an email in plain text. Now I have a string with text in it which I insert into the email. However, I want this text to have a max character width.
So input text is for example:
This is the input text. It's very boring to read because it's only an example which is used to explain my problem better. I hope you can help me.
And I want it to become:
This is the input text. It's very
boring to read because it's only
an example which is used to explain
my problem better. I hope you can
help me.
Of course we need to take into account that you can't split in the middle of a word. It may get pretty tricky when you have symols like ' and -, so I was wondering if there are tools that can do this for you? I've heard about NLTK but I couldn't find a solution there yet, and maybe it's a little bit overkill?
There is a textwrap library for just this:
http://docs.python.org/2/library/textwrap.html
Examples can be found there too. You likely want to use:
textwrap.fill(text, width)
A great, don't know why I couldn't find this. Thanks!
I now also found the preferred way to do this in a Django project (which I use). It's the built-in template tag wordwrap
{{ value|wordwrap:5 }}
https://docs.djangoproject.com/en/1.3/ref/templates/builtins/#wordwrap
|
package dev.chamindu.mongotime;
import java.time.LocalDateTime;
public class Event {
private LocalDateTime eventTime;
public LocalDateTime getEventTime() {
return this.eventTime;
}
public void setEventTime(LocalDateTime eventTime) {
this.eventTime = eventTime;
}
}
|
[SPARK-13264][Doc] Removed multi-byte characters in spark-env.sh.template
In spark-env.sh.template, there are multi-byte characters, this PR will remove it.
Can one of the admins verify this patch?
OK, but can you fix the other occurrence in serialize.R comments?
Thank you for reviewing, @srowen .
I fixed some files which are used multi-byte character.
ok to test.
Test build #51031 has started for PR 11149 at commit 5507bd0.
Test build #51031 has finished for PR 11149 at commit 5507bd0.
This patch passes all tests.
This patch merges cleanly.
This patch adds no public classes.
Merged build finished. Test PASSed.
Test PASSed.
Refer to this link for build results (access rights to CI server needed):
https://amplab.cs.berkeley.edu/jenkins//job/SparkPullRequestBuilder/51031/
Test PASSed.
Merged to master
|
<?php
include("../includes/database_connection.php");
include("../includes/session.php");
include("../includes/functions.php");
?>
<?php
if(logged_in())
header("Location : home.php");
?>
<?php
global $error;
if (isset($_POST['submit']))
{
$password = mysqli_real_escape_string($connection,(mysql_entities_fix_string($_POST['password'])));
$username = mysqli_real_escape_string($connection,(mysql_entities_fix_string($_POST['username'])));
$hash_password = password_hashing($password);
$found_user=attempt_login($username,$hash_password,$connection);
if($found_user)
{
$user_id=find_user_by_id($username,$connection);
$name=find_user_by_name($username,$connection);
$_SESSION['current_user_id']=$user_id;
$_SESSION['current_name']=$name;
$_SESSION['current_username']=$username;
redirect_to("home.php");
}
else
{
$error="Incorrect user details";
destroySession();
}
}
?>
<!DOCTYPE html>
<html lang="en" class="no-js">
<head>
<script src="js/jquery.min.js"></script>
<link href="css/login.css" rel="stylesheet" type="text/css" media="all"/>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1">
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<link href='//fonts.googleapis.com/css?family=Roboto+Condensed:400,700' rel='stylesheet' type='text/css'>
</head>
<body>
<div class="header">
<div class="header-main">
<h1>Welcome to FAVOR.ME !</h1>
<div class="header-bottom">
<div class="header-right w3agile">
<div class="header-left-bottom agileinfo">
<form action="login.php" method="post" autocomplete="on">
<input type="text" value="User name" name="username" onfocus="this.value = '';" onblur="if (this.value == '') {this.value = 'User name';}" required />
<input type="password" value="Password" name="password" onfocus="this.value = '';" onblur="if (this.value == '') {this.value = 'password';}" required />
<span style="color: red;"><?php echo $error?></span>
<div class="forgot">
<h6><a href="forgot_password.php">Forgot Password?</a></h6>
</div>
<div class="clear"> </div>
<input type="submit" name="submit" value="Login">
</form>
<div class="header-left-top">
<div class="sign-up"> <h2>or</h2> </div>
</div>
<div class="header-social wthree">
<a href="signup.php" class="face" style="text-align: center;"><h5>Sign up</h5></a>
<a href="about_us.html" class="twitt" style="text-align: center;"><h5>About Us</h5></a>
</div>
</div>
</div>
</div>
</div>
</div>
</body>
</html>
|
So Much Easier Than Throwing
So Much Easier Than Throwing is a PP trial in Dead Rising 3.
This PP trial requires you to create the Boom Cannon 50 times.
Once completed, the trial will yield 10,000 PP.
|
#!/usr/bin/env python
#-----------------------------------------------------------------------------
# $Id: plot_alt_profiles.py,v 1.3 2014/03/10 16:04:06 agburr Exp $
# plot_alt_profiles
#
# Author: Angeline G. Burrell, UMichigan, Oct 2013
#
# Comments: Routines to make linear and contour altitude plots.
#
# Includes: plot_single_alt_image - plots a single linear or location slice as
# a function of altitude
# plot_mult_alt_images - plot multiple locations of linear or 3D
# altitude slices
# plot_alt_slices - plot a single 3D altitude contour with
# several linear slices
# -----------------------------------------------------------------
# plot_linear_alt - plot the linear altitude dependence of a
# quantity
# plot_3D_alt - plot the altitude dependence of a quantity
# as the function of another spatiotemporal
# coordinate
#----------------------------------------------------------------------------
'''
Plot data from a 3D GITM file for different spatiotemporal coordinates
'''
# Import modules
import sys
import string
import math
import numpy as np
import matplotlib.pyplot as plt
import matplotlib.gridspec as gridspec
from matplotlib.cm import get_cmap
from matplotlib.colors import LogNorm
from matplotlib.ticker import FormatStrFormatter,MultipleLocator
import gitm_plot_rout as gpr
def plot_single_alt_image(plot_type, x_data, alt_data, z_data, x_name, x_scale,
x_units, alt_units, z_name="", z_scale="", z_units="",
xmin=None, xmax=None, amin=None, amax=None, zmin=None,
zmax=None, xinc=6, ainc=6, zinc=6, title=None,
tloc="t", figname=None, draw=True, color1="b",
color2="o", color3=":", xl=True, xt=True, yl=True,
yt=True, *args, **kwargs):
'''
Creates a rectangular or polar map projection plot for a specified latitude
range.
Input: plot_type = key to determine plot type (linear, contour, scatter)
x_data = 2D numpy array containing x-axis data
alt_data = 2D numpy array containing y-axis altitude data
z_data = 1D or 2D numpy array containing data to plot using a
color scale or an empty list for a linear plot
x_name = Name of x-axis data
x_scale = Plot x-axis data using a linear or exponetial scale?
x_units = x-axis data units
alt_units = y-axis altitude units (m or km)
z_name = Name of z-axis data (default="")
z_scale = Plot z-axis data using a linear or exponetial scale?
(default="")
z_units = z-axis data units (default="")
xmin = minimum value for x variable (default=None)
xmax = maximum value for x variable (default=None)
amin = minimum value for altitude (default=None)
amax = maximum value for altitude (default=None)
zmin = minimum value for z variable (default=None)
zmax = maximum value for z variable (default=None)
xinc = number of tick incriments for x variable (default 6)
ainc = number of tick incriments for altitude (default 6)
zinc = number of tick incriments for z variable (default 6)
title = plot title
tloc = title location (t=top, r=right, l=left, b=bottom,
default is top)
figname = file name to save figure as (default is none)
draw = draw to screen? (default is True)
xkey = for contour plots specify an x key (default dLat)
(options dLat/dLon/Latitude/Longitude)
color1 = linear color (default blue) or True/False for color/B&W
for the contour colorscale
color2 = linear marker type (default circles) or True/False for
including a colorbar
color3 = linear line type (default dotted) or True/False if the
colorscale using in the contour plot should be centered
about zero.
xl = Include x label (default is True)
xt = Include x ticks (default is True)
yl = Include y (altitude) label (default is True)
yt = Include y ticks (default is True)
'''
# Initialize the new figure
f = plt.figure()
ax = f.add_subplot(111)
if(string.lower(plot_type)=="linear"):
con = plot_linear_alt(ax, x_data, alt_data, x_name, x_scale, x_units,
alt_units, xmin=xmin, xmax=xmax, amin=amin,
amax=amax, xinc=xinc, ainc=ainc, title=title,
tloc=tloc, xl=xl, xt=xt, yl=yl, yt=yt,
color=color1, marker=color2, line=color3)
else:
con = plot_3D_alt(ax, x_data, alt_data, z_data, x_name, x_scale,
x_units, alt_units, z_name, z_scale, z_units,
xmin=xmin, xmax=xmax, amin=amin, amax=amax, zmin=zmin,
zmax=zmax, xinc=xinc, ainc=ainc, zinc=zinc, cb=color2,
color=color1, zcenter=color3, title=title, tloc=tloc,
xl=xl, xt=xt, yl=yl, yt=yt, plot_type=plot_type)
if draw:
# Draw to screen.
if plt.isinteractive():
plt.draw() #In interactive mode, you just "draw".
else:
# W/o interactive mode, "show" stops the user from typing more
# at the terminal until plots are drawn.
plt.show()
# Save output file
if figname is not None:
plt.savefig(figname)
return f, ax
# End plot_single_alt_image
def plot_mult_alt_images(plot_type, subindices, x_data, alt_data, z_data,
x_name, x_scale, x_units, alt_units, y_label=False,
z_name="", z_scale="", z_units="", xmin=None,
xmax=None, amin=None, amax=None, zmin=None, zmax=None,
xinc=6, ainc=6, zinc=6, title=None, tloc="t",
figname=None, draw=True, color1="b", color2="o",
color3=":", *args, **kwargs):
'''
Creates a linear or contour altitude map for a specified altitude range.
A list of latitude and longitude indexes should be specified. They may
be of equal length (for paired values), or for a constant value in one
coordinate, a length of list one can be specified.
Input: plot_type = key to determine plot type (linear, contour, scatter)
subindices = 2D or 3D list of lists containing the index or indices
to include in subplots. How it works:
subindices = [[1], [], [2, 3, 4]]
First index of data only uses index=1,
the third index of data will be used to
select data for linear plots with the
third data index= 2, 3, and 4. The second
data index includes all of the data.
subindices = [[1,2], [40, 50]]
Two subplots will be made, with the data
arrays using data[1,40], data[2,50]
for the two subplots, and the third index
will implicitly include all the data
x_data = 2D or 3D numpy array containing x-axis data
alt_data = 2D or 3D numpy array containing y-axis altitude data
z_data = 1D or 2D numpy array containing data to plot using a
color scale or an empty list for a linear plot
x_name = Name of x-axis data
x_scale = Plot x-axis data using a linear or exponetial scale?
x_units = x-axis data units
alt_units = y-axis altitude units (m or km)
y_label = List of right-side y-axis labels (labeling subplots)
or False to provide no labels (default=False)
z_name = Name of z-axis data (default="")
z_scale = Plot z-axis data using a linear or exponetial scale?
(default="")
z_units = z-axis data units (default="")
xmin = minimum value for x variable (default=None)
xmax = maximum value for x variable (default=None)
amin = minimum value for altitude (default=None)
amax = maximum value for altitude (default=None)
zmin = minimum value for z variable (default=None)
zmax = maximum value for z variable (default=None)
xinc = number of tick incriments for x variable (default 6)
ainc = number of tick incriments for altitude (default 6)
zinc = number of tick incriments for z variable (default 6)
title = plot title
tloc = title location (t=top, r=right, l=left, b=bottom,
default is top)
figname = file name to save figure as (default is none)
draw = draw to screen? (default is True)
xkey = for contour plots specify an x key (default dLat)
(options dLat/dLon/Latitude/Longitude)
color1 = linear color (default blue) or True/False for color/B&W
for the contour colorscale
color2 = linear marker type (default circles) or True/False for
including a colorbar
color3 = linear line type (default dotted) or True/False if the
colorscale using in the contour plot should be centered
about zero.
'''
module_name = "plot_mult_alt_images"
# Test the subindices input
slen = [len(i) for i in subindices]
pnum = max(slen)
if(pnum < 1):
print module_name, "ERROR: no subplot regions specified"
return
if(pnum == 1):
print module_name, "WARNING: only one region, better to use plot_single_alt_image"
for sl in slen:
if sl > 1 and sl != pnum:
print module_name, "ERROR: subindices input format is incorrect"
return
# Initialize the x,y,z variable limits if desired
if len(slen) == 1 or (len(slen) == 2 and slen[1] == 0):
if xmin == None:
xmin = np.nanmin(x_data[subindices[0]])
if xmax == None:
xmax = np.nanmax(x_data[subindices[0]])
if amin == None:
amin = np.nanmin(alt_data[subindices[0]])
if amax == None:
amax = np.nanmax(alt_data[subindices[0]])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[subindices[0]])
if zmax == None:
zmax = np.nanmax(z_data[subindices[0]])
elif len(slen) == 2 or (len(slen) == 3 and slen[2] == 0):
if slen[0] == 0:
if xmin == None:
xmin = np.nanmin(x_data[:,subindices[1]])
if xmax == None:
xmax = np.nanmax(x_data[:,subindices[1]])
if amin == None:
amin = np.nanmin(alt_data[:,subindices[1]])
if amax == None:
amax = np.nanmax(alt_data[:,subindices[1]])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[:,subindices[1]])
if zmax == None:
zmax = np.nanmax(z_data[:,subindices[1]])
else:
if slen[0] == pnum:
s0 = subindices[0]
else:
s0 = subindices[0][0]
if slen[1] == pnum:
s1 = subindices[1]
else:
s1 = subindices[1][0]
if xmin == None:
xmin = np.nanmin(x_data[s0,s1])
if xmax == None:
xmax = np.nanmax(x_data[s0,s1])
if amin == None:
amin = np.nanmin(alt_data[s0,s1])
if amax == None:
amax = np.nanmax(alt_data[s0,s1])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[s0,s1])
if zmax == None:
zmax = np.nanmax(z_data[s0,s1])
elif len(slen) == 3:
if slen[0] == 0 and slen[1] == 0:
if xmin == None:
xmin = np.nanmin(x_data[:,:,subindices[2]])
if xmax == None:
xmax = np.nanmax(x_data[:,:,subindices[2]])
if amin == None:
amin = np.nanmin(alt_data[:,:,subindices[2]])
if amax == None:
amax = np.nanmax(alt_data[:,:,subindices[2]])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[:,:,subindices[2]])
if zmax == None:
zmax = np.nanmax(z_data[:,:,subindices[2]])
elif slen[0] == 0:
if slen[1] == pnum:
s1 = subindices[1]
else:
s1 = subindices[1][0]
if slen[2] == pnum:
s2 = subindices[2]
else:
s2 = subindices[2][0]
if xmin == None:
xmin = np.nanmin(x_data[:,s1,s2])
if xmax == None:
xmax = np.nanmax(x_data[:,s1,s2])
if amin == None:
amin = np.nanmin(alt_data[:,s1,s2])
if amax == None:
amax = np.nanmax(alt_data[:,s1,s2])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[:,s1,s2])
if zmax == None:
zmax = np.nanmax(z_data[:,s1,s2])
elif slen[1] == 0:
if slen[0] == pnum:
s0 = subindices[0]
else:
s0 = subindices[0][0]
if slen[2] == pnum:
s2 = subindices[2]
else:
s2 = subindices[2][0]
if xmin == None:
xmin = np.nanmin(x_data[s0,:,s2])
if xmax == None:
xmax = np.nanmax(x_data[s0,:,s2])
if amin == None:
amin = np.nanmin(alt_data[s0,:,s2])
if amax == None:
amax = np.nanmax(alt_data[s0,:,s2])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[s0,:,s2])
if zmax == None:
zmax = np.nanmax(z_data[s0,:,s2])
else:
print module_name, "WARNING: Including restrictions in 3D will cause this program to crash unless the input data is 4D (for linear plots) or 5D (for contour/scatter plots)."
if slen[0] == pnum:
s0 = subindices[0]
else:
s0 = subindices[0][0]
if slen[1] == pnum:
s1 = subindices[1]
else:
s1 = subindices[1][0]
if slen[2] == pnum:
s2 = subindices[2]
else:
s2 = subindices[2][0]
if xmin == None:
xmin = np.nanmin(x_data[s0,s1,s2])
if xmax == None:
xmax = np.nanmax(x_data[s0,s1,s2])
if amin == None:
amin = np.nanmin(alt_data[s0,s1,s2])
if amax == None:
amax = np.nanmax(alt_data[s0,s1,s2])
if len(z_data) > 0:
if zmin == None:
zmin = np.nanmin(z_data[s0,s1,s2])
if zmax == None:
zmax = np.nanmax(z_data[s0,s1,s2])
else:
print module_name, "ERROR: subplot index out of range"
return
# Initialize the new figure
f = plt.figure()
ax = list()
tl = " "
f.text(0.01,0.55,"Altitude (${:s}$)".format(alt_units),rotation="vertical")
if title:
f.suptitle(title, size="medium")
# Adjust the figure height to accomadate the number of subplots
if(pnum > 2):
fheight = f.get_figheight()
f.set_figheight(fheight * 0.5 * pnum)
for snum in reversed(range(0, pnum)):
cl = False
xl = False
fnum = (pnum * 100) + 11 + snum
ax.append(f.add_subplot(fnum))
try:
yl = y_label[snum]
except:
yl = False
if(pnum == snum + 1):
xl = True
if(snum == 0):
cl = True
if len(slen) == 1 or (len(slen) == 2 and slen[1] == 0):
xdat = np.array(x_data[subindices[0][snum]])
altdat = np.array(alt_data[subindices[0][snum]])
if len(z_data) > 0:
zdat = np.array(z_data[subindices[0][snum]])
elif len(slen) == 2 or (len(slen) == 3 and slen[2] == 0):
if slen[0] == 0:
xdat = np.array(x_data[:,subindices[1][snum]])
altdat = np.array(alt_data[:,subindices[1][snum]])
if len(z_data) > 0:
zdat = np.array(z_data[:,subindices[1][snum]])
else:
if slen[0] == pnum:
s0 = subindices[0][snum]
else:
s0 = subindices[0][0]
if slen[1] == pnum:
s1 = subindices[1][snum]
else:
s1 = subindices[1][0]
xdat = np.array(x_data[s0,s1])
altdat = np.array(alt_data[s0,s1])
if len(z_data) > 0:
zdat = np.array(z_data[s0,s1])
elif len(slen) == 3:
if slen[0] == 0 and slen[1] == 0:
xdat = np.array(x_data[:,:,subindices[2][snum]])
altdat = np.array(alt_data[:,:,subindices[2][snum]])
if len(z_data) > 0:
zdat = np.array(z_data[:,:,subindices[2][snum]])
elif slen[0] == 0:
if slen[1] == pnum:
s1 = subindices[1][snum]
else:
s1 = subindices[1][0]
if slen[2] == pnum:
s2 = subindices[2][snum]
else:
s2 = subindices[2][0]
xdat = np.array(x_data[:,s1,s2])
altdat = np.array(alt_data[:,s1,s2])
if len(z_data) > 0:
zdat = np.array(z_data[:,s1,s2])
elif slen[1] == 0:
if slen[0] == pnum:
s0 = subindices[0][snum]
else:
s0 = subindices[0][0]
if slen[2] == pnum:
s2 = subindices[2][snum]
else:
s2 = subindices[2][0]
xdat = np.array(x_data[s0,:,s2])
altdat = np.array(alt_data[s0,:,s2])
if len(z_data) > 0:
zdat = np.array(z_data[s0,:,s2])
else:
print module_name, "WARNING: Including restrictions in 3D will cause this program to crash unless the input data is 4D (for linear plots) or 5D (for contour/scatter plots)"
if slen[0] == pnum:
s0 = subindices[0][snum]
else:
s0 = subindices[0][0]
if slen[1] == pnum:
s1 = subindices[1][snum]
else:
s1 = subindices[1][0]
if slen[2] == pnum:
s2 = subindices[2][snum]
else:
s2 = subindices[2][0]
xdat = np.array(x_data[s0,s1,s2])
altdat = np.array(alt_data[s0,s1,s2])
if len(z_data) > 0:
zdat = np.array(z_data[s0,s1,s2])
else:
print module_name, "ERROR: subplot index out of range"
return
if(string.lower(plot_type)=="linear"):
con = plot_linear_alt(ax[-1], xdat, altdat, x_name, x_scale,
x_units, alt_units, xmin=xmin, xmax=xmax,
amin=amin, amax=amax, xinc=xinc, ainc=ainc,
xl=xl, yl=yl, color=color1, marker=color2,
line=color3)
else:
con = plot_3D_alt(ax[-1], xdat, altdat, zdat, x_name, x_scale,
x_units, alt_units, z_name, z_scale, z_units,
xmin=xmin, xmax=xmax, amin=amin, amax=amax,
zmin=zmin, zmax=zmax, xinc=xinc, ainc=ainc,
zinc=zinc, cb=False, color=color1,
zcenter=color3, title=False, tloc=tloc,
xl=xl, yl=yl, plot_type=plot_type)
if plot_type.find("scatter") >= 0:
cax = con.axes
else:
cax = con.ax
cpr = list(cax.get_position().bounds)
if cl is True:
cpr[2] = new_width
cax.set_position(cpr)
else:
# Add and adjust colorbar
cbar = gpr.add_colorbar(con, zmin, zmax, zinc, "vertical",
z_scale, z_name, z_units)
bp = list(cbar.ax.get_position().bounds)
cp = list(cax.get_position().bounds)
new_width = cp[2] + 0.075
cp[2] = new_width
bp[1] = bp[1] + bp[3] * (float(pnum - 1) / 2.0)
bp[0] = bp[0] + 0.015
cbar.ax.set_position(bp)
cax.set_position(cp)
if draw:
# Draw to screen.
if plt.isinteractive():
plt.draw() #In interactive mode, you just "draw".
else:
# W/o interactive mode, "show" stops the user from typing more
# at the terminal until plots are drawn.
plt.show()
# Save output file
if figname is not None:
plt.savefig(figname)
return f, ax
# End plot_mult_alt_images
def plot_alt_slices(x_data, alt_data, z_data, xdim, x_indices, x_name, x_scale,
x_units, alt_units, z_name, z_scale, z_units, xmin=None,
xmax=None, amin=None, amax=None, zmin=None, zmax=None,
xinc=6, ainc=6, zinc=6, title=None, figname=None, draw=True,
color="k", marker="o", line=":", zcolor=True, zcenter=False,
plot_type="contour", *args, **kwargs):
'''
Creates a contour altitude map with several linear slices as a function of
altitude for a specified variable. A list of latitude and longitude
indexes should be specified. One list should consist of a single value,
the other will be the x variable in the contour plot. The degree flag
determines whether x will be ploted in radians or degrees.
Input: x_data = 3D numpy array containing x data for the contour plot
alt_data = 3D numpy array containing altitude data
z_data = 3D numpy array containing data to plot using a
color scale and as the x variable in the linear plots
xdim = index (0-2) of the dimension to hold the x data constant
x_indices = List of index values to plot alt and z at a constant x
x_name = Name of x data
x_scale = Plot x data using a linear or exponetial scale?
x_units = x data units
alt_units = altitude units (m or km)
z_name = Name of z data
z_scale = Plot z data using a linear or exponetial scale?
z_units = z data units
xmin = minimum value for x variable (default=None)
xmax = maximum value for x variable (default=None)
amin = minimum value for altitude (default=None)
amax = maximum value for altitude (default=None)
zmin = minimum value for z variable (default=None)
zmax = maximum value for z variable (default=None)
xinc = number of tick incriments for x variable (default 6)
ainc = number of tick incriments for altitude (default 6)
zinc = number of tick incriments for z variable (default 6)
title = plot title
figname = file name to save figure as (default is none)
color = line color for linear plots (default black)
marker = marker type for linear plots (default circle)
line = line type for linear plots (default dotted line)
zcolor = Color plot or B&W (default is True for color)
zcenter = Should the z range be centered about zero (default is
False, for uncentered)
plot_type = Make a contour or scatter plot
'''
module_name = "plot_alt_slices"
# Process the index lists
pnum = len(x_indices)
if(pnum < 1):
print module_name, "ERROR: no subplot slices specified"
return
# Initialize the x,y,z variable limits
if(xmin is None):
xmin = np.nanmin(x_data)
if(xmax is None):
xmax = np.nanmax(x_data)
if(zmin is None):
zmin = np.nanmin(z_data)
if(zmax is None):
zmax = np.nanmax(z_data)
if zcenter and abs(zmin) != zmax:
zmax = max(abs(zmin), zmax)
zmin = -1.0 * zmax
if(amin is None):
amin = np.nanmin(alt_data)
if(amax is None):
amax = np.nanmax(alt_data)
# Initialize the new figure
f = plt.figure()
if title:
f.suptitle(title, size="medium")
# Adjust the figure size to accomadate the number of subplots
if(pnum > 2):
fwidth = f.get_figwidth()
f.set_figwidth(fwidth * 0.5 * pnum)
# Display the 3D contour plot on top
gs = gridspec.GridSpec(2,pnum)
gs.update(hspace=.4)
axc = plt.subplot(gs[0,:])
con = plot_3D_alt(axc, x_data, alt_data, z_data, x_name, x_scale, x_units,
alt_units, z_name, z_scale, z_units, xmin=xmin, xmax=xmax,
amin=amin, amax=amax, zmin=zmin, zmax=zmax, xinc=xinc,
ainc=ainc, zinc=zinc, cb=True, cloc="t", color=zcolor,
zcenter=zcenter, plot_type=plot_type)
# Determine how many x tics to include in each linear slice
if(pnum > 4):
zinc *= 0.5
# Add the linear slices
y = [amin, amax]
axl = list()
for snum in reversed(range(0, pnum)):
xl = False
yl = False
axl.append(plt.subplot(gs[1,snum]))
if(snum == 0):
yl = True
if(math.floor(pnum * 0.5) == snum):
xl = True
if xdim == 0:
xloc = x_data[x_indices[snum]]
for i in range(len(x_data[x_indices[snum]].shape)):
xloc = xloc[0]
tl = "{:.2f} ${:s}$ {:s}".format(xloc, x_units, x_name)
x = [x_data[x_indices[snum]], x_data[x_indices[snum]]]
altdat = alt_data[x_indices[snum]]
zdat = z_data[x_indices[snum]]
elif xdim == 1:
xloc = x_data[0,x_indices[snum]]
for i in range(len(x_data[x_indices[snum]].shape)):
xloc = xloc[0]
tl = "{:.2f} ${:s}$ {:s}".format(xloc, x_units, x_name)
x = [x_data[0,x_indices[snum]], x_data[0,x_indices[snum]]]
altdat = alt_data[:,x_indices[snum]]
zdat = z_data[:,x_indices[snum]]
else:
tl = "{:.2f} ${:s}$ {:s}".format(x_data[0,0,x_indices[snum]],
x_units, x_name)
x = [x_data[0,0,x_indices[snum]], x_data[0,0,x_indices[snum]]]
altdat = alt_data[:,:,x_indices[snum]]
zdat = z_data[:,:,x_indices[snum]]
# Add a line to the contour plot
axc.plot(x, y, color=color, linestyle=line, linewidth=2)
# Add a linear slice below the contour plot
plot_linear_alt(axl[-1], zdat, altdat, z_name, z_scale, z_units,
alt_units, xmin=zmin, xmax=zmax, amin=amin, amax=amax,
xinc=zinc, ainc=ainc, title=tl, tloc="t", xl=xl, yl=yl,
color=color, marker=marker, line=line)
if draw:
# Draw to screen.
if plt.isinteractive():
plt.draw() #In interactive mode, you just "draw".
else:
# W/o interactive mode, "show" stops the user from typing more
# at the terminal until plots are drawn.
plt.show()
# Save output file
if figname is not None:
plt.savefig(figname)
return f, axc, axl
# End plot_alt_slices
def plot_linear_alt(ax, x_data, alt_data, x_name, x_scale, x_units, alt_units,
xmin=None, xmax=None, amin=None, amax=None, xinc=6, ainc=6,
title=None, tloc="t", xl=True, xt=True, yl=True, yt=True,
color="b", marker="+", line="-", *args, **kwargs):
'''
Creates a rectangular map projection plot for a specified latitude range.
Input: ax = axis handle
x_data = 2D numpy array containing x-axis data
alt_data = 2D numpy array containing y-axis altitude data
x_name = Name of x-axis data
x_scale = Plot x-axis data using a linear or exponetial scale?
x_units = x-axis data units
alt_units = y-axis altitude units (m or km)
xmin = minimum value for x variable
xmax = maximum value for x variable
amin = minimum altitude
amax = maximum altitude
xinc = number of x variable tick incriments (default 6)
ainc = number of alt variable tick incriments (default 6)
title = plot title (default is None)
tloc = Specify the title location (t=top, r=right, l=left,
b=bottom, default is top)
xl = Include x (z variable) label (default is True)
xt = Include x ticks (default is True)
yl = Include y label. By default this label is placed on
the left to label the altitude. If a non-Boolian value
is provided, this will be assumed to be a string to be
placed as a label on the right. (default is True)
yt = Include y ticks (default is True)
color = line/marker color (default b [blue])
marker = marker type (default +)
line = line type (default - [solid line])
'''
# Set the x, a, and z ranges
if(xmin is None):
xmin = np.nanmin(x_data)
if(xmax is None):
xmax = np.nanmax(x_data)
arange = xmax - xmin
xwidth = arange / xinc
if(amin is None):
amin = np.nanmin(alt_data)
if(amax is None):
amax = np.nanmax(alt_data)
arange = amax - amin
awidth = arange / ainc
# Plot the values
con = ax.plot(x_data, alt_data, color=color, marker=marker, linestyle=line)
# Configure axis
if yt:
ytics = MultipleLocator(awidth)
ax.yaxis.set_major_locator(ytics)
else:
ax.yaxis.set_major_formatter(FormatStrFormatter(""))
if yl is True:
ax.set_ylabel('Altitude ($km$)')
elif yl is not False:
ax.set_ylabel(yl)
ax.yaxis.set_label_position("right")
plt.ylim(amin, amax)
if x_scale.find("exponential") >= 0:
ax.set_xscale('log')
elif xt:
xtics = MultipleLocator(xwidth)
ax.xaxis.set_major_locator(xtics)
else:
ax.xaxis.set_major_formatter(FormatStrFormatter(""))
if xl:
if x_units is None:
ax.set_xlabel(r'{:s}'.format(x_name))
else:
ax.set_xlabel(r'%s ($%s$)' % (x_name, x_units))
plt.xlim(xmin, xmax)
# Set the title
if title:
rot = 'horizontal'
yloc = 1.05
xloc = .5
if(tloc == "l" or tloc == "r"):
xloc = -.1
yloc = .5
rot = 'vertical'
if(tloc == "r"):
xloc = 1.1
if(tloc == "b"):
yloc = -.1
ax.set_title(title,size='medium', rotation=rot, y=yloc, x=xloc)
return con
#End plot_linear_alt
def plot_3D_alt(ax, x_data, alt_data, z_data, x_name, x_scale, x_units,
alt_units, z_name, z_scale, z_units, xmin=None, xmax=None,
amin=None, amax=None, zmin=None, zmax=None, xinc=6, ainc=6,
zinc=6, cb=True, cloc="r", color=True, zcenter=False,
title=None, tloc="t", xl=True, xt=True, yl=True, yt=True,
plot_type="contour", *args, **kwargs):
'''
Creates a single polar projection, with the latitude center and range
determined by the input.
Input: ax = axis handle
x_data = 2D numpy array containing x-axis data
alt_data = 2D numpy array containing y-axis altitude data
z_data = 1D or 2D numpy array containing data to plot using a
color scale
x_name = Name of x-axis data
x_scale = Plot x-axis data using a linear or exponetial scale?
x_units = x-axis data units
alt_units = y-axis altitude units (m or km)
z_name = Name of z-axis data
z_scale = Plot z-axis data using a linear or exponetial scale?
z_units = z-axis data units
xmin = minimum value for x variable (default=None)
xmax = maximum value for x variable (default=None)
amin = minimum value for altitude (default=None)
amax = maximum value for altitude (default=None)
zmin = minimum value for z variable (default=None)
zmax = maximum value for z variable (default=None)
xinc = number of tick incriments for x variable (default 6)
ainc = number of tick incriments for altitude (default 6)
zinc = number of tick incriments for z variable (default 6)
cb = Add a colorbar (default is True)
cloc = Colorbar location (t=top, r=right, l=left, b=bottom,
default is right)
color = Color plot or B&W (default is True for color)
zcenter = Should the z range be centered about zero (default is
False, for uncentered)
title = plot title (default is none)
tloc = title location (t=top, r=right, l=left, b=bottom,
default is top)
xl = Include x label (default is True)
xt = Include x ticks (default is True)
yl = Include y label. This defaults to placing an altitude
label on the left axis. If a non-Boolian value is
provided, it is assumed to be a string that will be
used as a right axis label. (default is True)
yt = Include y ticks (default is True)
plot_type = Make a scatter or contour plot? (default=contour)
'''
# Set the x, a, and z ranges
if(xmin is None):
xmin = np.nanmin(x_data)
if(xmax is None):
xmax = np.nanmax(x_data)
arange = xmax - xmin
xwidth = arange / xinc
if(zmin is None):
zmin = np.nanmin(z_data)
if(zmax is None):
zmax = np.nanmax(z_data)
if zcenter and abs(zmin) != zmax:
arange = max(abs(zmin), zmax)
zmax = arange
zmin = -1.0 * arange
arange = zmax - zmin
zwidth = arange / zinc
if(amin is None):
amin = np.nanmin(alt_data)
if(amax is None):
amax = np.nanmax(alt_data)
arange = amax - amin
awidth = arange / ainc
# Determine the z scale
if z_scale.find("exp") >= 0:
v = np.logspace(math.log10(zmin), math.log10(zmax), zinc*10,
endpoint=True)
norm = LogNorm(vmin=zmin, vmax=zmax)
else:
norm = None
v = np.linspace(zmin, zmax, zinc*10, endpoint=True)
# Plot the data
col = gpr.choose_contour_map(color, zcenter)
if plot_type.find("scatter") >= 0:
con = ax.scatter(x_data, alt_data, c=z_data, cmap=get_cmap(col),
norm=norm, vmin=zmin, vmax=zmax, edgecolors="none",
s=10)
cax = con.axes
else:
con = ax.contourf(x_data, alt_data, z_data, v, cmap=get_cmap(col),
norm=norm, vmin=zmin, vmax=zmax)
cax = con.ax
# Configure axis
if yt:
ytics = MultipleLocator(awidth)
ax.yaxis.set_major_locator(ytics)
else:
ax.yaxis.set_major_formatter(FormatStrFormatter(""))
if yl is True:
ax.set_ylabel('Altitude ($km$)')
elif yl is not False:
ax.set_ylabel(yl)
ax.yaxis.set_label_position("right")
plt.ylim(amin, amax)
if x_scale.find("exponential") >= 0:
ax.set_xscale('log')
elif xt:
xtics = MultipleLocator(xwidth)
ax.xaxis.set_major_locator(xtics)
else:
ax.xaxis.set_major_formatter(FormatStrFormatter(""))
if xl:
ax.set_xlabel(r'%s ($%s$)' % (x_name, x_units))
plt.xlim(xmin, xmax)
# Set the title
if title:
rot = 'horizontal'
yloc = 1.05
xloc = 0.5
if tloc == "b":
yloc = -.1
elif tloc != "t":
rot = 'vertical'
yloc = 0.5
xloc = -.2
if tloc == "r":
xloc = 1.1
title = ax.set_title(title,y=yloc,size='medium',x=xloc,rotation=rot)
# Change the background color
ax.patch.set_facecolor('#747679')
# Add a colorbar
if cb:
orient = 'vertical'
if(cloc == 't' or cloc == 'b'):
orient = 'horizontal'
cbar = gpr.add_colorbar(con, zmin, zmax, zinc, orient, z_scale, z_name,
z_units)
if(cloc == 'l' or cloc == 't'):
bp = list(cbar.ax.get_position().bounds)
cp = list(cax.get_position().bounds)
if(cloc == 't'):
cp[1] = bp[1]
bp[1] = cp[1] + cp[3] + 0.085
else:
bp[0] = 0.125
cp[0] = bp[0] + 0.1 + bp[2]
cax.set_position(cp)
cbar.ax.set_position(bp)
return con
#End plot_3D_alt
#End plot_alt_profiles
|
What's the RMS voltage of this asymmetric rectangle function?
I recorded this asymmetric rectangle function:
I calculated the RMS voltage to be equal to the amplitude (4,10 V in this case)
However when I measured this exact signal with a TrueRMS multimeter, it showed 3,54 V.
Where is my error?
"MAX" is maximum and not RMS. The devil's in the small detail.
@Andyaka The oscilloscope is not directly measuring the rms with the Max-function, thats correct. However I did the calculation and for a bipolar rectangle signal, the rms is equal to the amplitude.
You need to detail how you made that calculation numerically. Your scope shot implies an RMS value of 4 volts (not 4.1 volts).
@Andyaka I will add my calculations to the question when I'm home. Wikipedia also lists an rms value of 1 for square waves, confirming my calculation. https://en.wikipedia.org/wiki/Crest_factor#Examples
You shouldn't use 4.1 volts as the effect peak signal. You should use 4 volts.
The function generator was actually set to 4,0 V. I think it's just the oscilloscopes Max-function that also picks up noise, as Tony mentioned. However wether it's 4,0 V or 4,1 V, my issue is what the multimeter shows.
Let's accept your peak amplitudes are +/- 4.1 V.
The true RMS of that waveform is exactly 4.1 V, it has the same heating effect as 4.1 V DC.
The mean DC of your signal is 2.05 V. If you remove the DC, you end up with a waveform with peaks of +6.15 V and -2.05 V. The RMS of this signal is 3.55 V.
I wonder if your meter is only measuring the AC component?
I had a look at the multimeters manual (MetraHit 2+) and it does not explicitly state wether it can only measure the AC component. Is it typical that multimeters can only measure the AC Component in AC-mode?
+1 Actually I think this is the most likely answer- the meter is AC-coupled so it has no knowledge of the DC component.
I don't have the exact multimeter on hand that I used for the measurement, but I just tested this with another multimeter and indeed, the AC mode seems to ignore the DC-component. Question solved, thanks everyone.
Well, assuming your wave is symmetric (that is, the positive as well as the negative part have the same magnitude), your calculation is right.
You don't know what that "TrueRMS" multimeter does, or what it does expect in a signal. Quite possibly it expects a signal composed of harmonic signals below some relatively low frequency (i.e. the meter has a bandwidth), whereas a square wave has infinite support in spectrum - all power above the point at which the meter's bandwidth ends is ignored; you get less power, and the square of the average power is thus also lower.
Nothing to see here, really - unspecified measurement devices doing unspecified things.
Regardless of duty cycle the power that can be dissipated into a resistive load for V+= |V-| the Vrms=Vpk.
But in your case if you applied +/- 4V and with noise on your measurement, the scope will read V+ + Vnoise = 4.1 , so eyeballing it, that appears to be closer to 4V or the average of each peak.
Putting the 20MHz filter on the noise may improve the scope reading on this low f signal.
Test your meter at different frequencies and check the manual specifications.
A rectangular wave has high frequency components that extend up to very high frequencies.
You have a fundamental (250Hz) that is pretty high in relation to mains to start with.
Typically cheap true-RMS meters don't bother to tell you that the frequency limit is for sinusoidal waves and non-sinusoidal will have less accuracy. A relatively good meter such as the Fluke 179 lists ACV accuracy as +/-4% + 3 digits up to 500Hz.
A cheaper meter such as the Extech EX411A lists ACV bandwidth as up to 1kHz and claims 1% accuracy (no mention of waveform).
You're seeing an error of -21%, which is large but plausible for an inexpensive meter.
Check the reading at lower frequency (such as 50Hz) and see if it is closer.
Edit: I think Neil's answer is correct- the meter is AC coupled and ignores the DC component. Easy to test, input a DC voltage and if it reads zero you have your answer.
I checked the multimeters manual and indeed it only has a bandwith of up to 1kHz. (it's a "MetraHit 2+")
|
Installation for the transferring of long objects to be used particularly for the service of machines for binding bars
ABSTRACT
A chair conveyor, specially for transferring elongated objects and/or serving machines for binding bundles of bars or sections. The conveyor has two parallel endless chains, means for imparting motion thereto and plates to interconnect the two endless chains. Spaced apart supports for the transported objects are provided which are connected to the interconnecting plates by pedestals. The chain conveyor can be associated to and loaded by a step by step conveyor whose movable beams may pass between adjacent supports in the chain conveyor.
United States Patent Inventor Hubert Elineau Versailles, France App]. No. 786,210 Filed Dec. 23, 1968 Patented June 15, 1971 Assignee Etablissements R. Sen ard 8: Fils Maromme, Seine-Maritime, France Priority Dec. 22, 1967 France 7 204 INSTALLATION FOR THE TRANSFERRIN G OF LONG OBJECTS TO BE USED PARTICULARLY FOR THE SERVICE OF MACHINES FOR BINDING BARS 2 Claims, 4 Drawing Figs.
U.S. Cl 198/106, 198/219 Int. Cl B65g 37/00 Field of Search 198/32, 219, 106; 263/6 A [56] References Cited UNITED STATES PATENTS 1,448,395 3/1923 Foe ll 198/219X 2,983,498 5/1961 MacGregor. 263/6(A) 3,168,190 2/1965 Nienstedt l98/106X 3,265,187 8/1966 Hein et al. 198/219X FOREIGN PATENTS 313,546 7/1919 Germany 198/219 Primary Examiner-Albert J. Ma kay Altorney-Sparrow and Sparrow ABSTRACT: A chair conveyor, specially for transferring elongated objects and/or serving machines for binding bundles of bars or sections. The conveyor has: two parallel endless chains, means for imparting motion thereto and plates to interconnect the two endless chains. Spaced apart supports for the transported objects are provided which are connected to the interconnecting plates by pedestals. The chain conveyor can be associated to and loaded by a step by step conveyor whose movable beams may pass between adjacent supports in the chain conveyor.
PATENTED JUM 5 l9?! SHEET 1 0F 2 2: INVENTOF? HUBERT ELINEAU ATENTEDJUNI 5197: 3584-130 SHEET 2 OF 2 Swarm; N1 gY u Toausv;
INSTALLATION FOR THE TRANSFERRING OF LONG OBJECTS TO BE USED PARTICULARLY FOR THE SERVICE OF MACHINES FOR BINDING BARS The present invention relates to a chair conveyor for the transfering of elongated objects such as rolled bars or bundles of bars to be used particularly for the service of machines for binding bundles of bars or sections.
For sewing of such machines, roller conveyors are generally used, the disadvantages of which is their rather complicated and very expensive construction, since the feed of the binding machines is performed in a discontinuous manner which results in a succession of starting and stopping of the conveyors requiring special equipment and causing a considerable waste of driving power.
The object of the present invention is to remove these disadvantages by providing a device which complies better than the 1 existing devices with the requirements of the practice. A
further object of the invention is to provide a chain conveyor disposed to be loaded by means of a rotating mechanism, such as the movable beams of a rack conveyor. Another object of the invention is to provide a device for transfering elongated objects and comprising a step by step conveyor and a chain conveyor disposed to be loaded by a rotating mechanism of said step conveyor.
According to the invention, the device for the transfering of elongated objects comprises a pilgrim '5 step" conveyor and a chain conveyor. According to the invention, the chain conveyor for transporting objects consists of two parallel endless chains, means for imparting motion thereto, plates substantially at right angles to the plane of, and interconnecting the endless chains, spaced apart supporting members for the objects and of pedestals to connect the supporting members to the plates. The paths given to objects by the conveyors having one common part owing to the fact that the ends of the mobile stringers of the pilgrims step conveyor, during their motion, pass between the chain conveyor members supporting the objects.
By way of example and in order to facilitate the understanding of the invention, a description is given hereinafter of particular embodiments of the invention, represented in a schematic and non limiting manner in the attached drawing in which:
FIGS. 1 and 2 respectively show in partial side elevational and plan views, the device for the transfer of elongated objects, according to the invention;
FIG. 2 shows a vertical section along the plane A.A. of FIG. 2; and v FIG. 4, analogous to FIG. 3, shows a vertical section of a variant of such installation.
With reference to the drawing there is shown a device comprising a chain conveyor according to the invention intended to serve a machine 1 for binding bundles of bars 30 or sections 31, i.e.'the device feeds unbound bars 30 or sections 31. To said machine. As is known, the bundles are held stationary in machine 1 at the required place and for the time necessary to the laying of the binding.
The device comprises a pilgrims step conveyor 2, consisting of a number of movable parallel beams 3 and of stationary beams 4. The movable beams 3 are supported by arms 5, 6 provided at their ends with bearings in which the trunnions of parallel cranks 7, 8 rotate, driven by a shaft 9 and by a suitable motor with one or several gears 10 ensuring the synchronous rotation of the cranks. The movement of movable beams 3 is therefore a motion of circular translation.
By any appropriate means, the bars 30, bundles of bars 32 or sections 31 are brought at point 11 at one end of conveyor 2 at a level above the lower part of the circular paths of the ends 12 of beams 3. Beams 3 and stationary beams 4 are provided with notches or hollows 13 on their part. Bars 30 and bundles 32 brought in at point I], raised in the notch of end 12 of the movable beams 3, are deposited in the first notch of in the notches of the movable and stationary beams alternating ly and eventually reach the end 14 of the beams 3 which move in the direction of the arrows 21.
According to the invention, a chain conveyor 15, running perpendicularly to the "pilgrims step" conveyor 2, is placed on the side of the ends 14 of beams 3. Conveyor 15 comprises two parallel endless chains 16,17, connected by metal plates 18 disposed substantially at right angles to said chains chains 16, 17 are driven through a suitable mechanism by a motor 15. Plates 18 support at certain distances through-like members 19 connected with plates 18 by pedestals 20.
According to the invention, the spacing between adjacent trough like members 19 and the height of pedestals 20 is selected in such manner that the ends 14 of movable beams 3 of step-by-step conveyor 2 are disposed to pass between two adjacent members 19 and connecting metal plates 18 and endless chains 16,17. The bundles contained in end notches 14 of movable beams 3 are thus deposited in members 19 and are transferred to the input of binding machine 1 by chain conveyor 15 conversely, objects may be transferred from chain conveyors 15 to step-by-step conveyor 2, with movable beams 3 moving in the opposite direction of the one shown by arrow 21. The previously described device may be complemented by another chain conveyor 23 similar to conveyor 15, placed in the alignment of the latter at the output end of machine 1 and driven by a motor 230 so that the transfer speed of conveyors 15 and 23 may be identical. In cooperation with conveyor 15 or alone, conveyor 23 empties the bundle of bars or sections bound by machine 1.
Of course, according to their size all the bars which will constitute the bundle to be bound, may be taken in at 11 by the notches of ends 12 of movable beams 3. In this case the conveyor 2 will make a single revolution per bound bundle.
As a variant, the upper surface of the stationary beams 24 and of the movable beams 25 of the pilgrims step conveyor 26 of this device may be plan which permits the transfer step-by step of bundles 27. In this case, the associated chain conveyor 28 is provided with flat plates 29 replacing the previously described through-like members. The chain conveyor according to the invention can be loaded by means of any rotating mechanism similar to the movable beams described above.
Compared with the known roller conveyors, the chain conveyor according to the invention has numerous advantages such as: a lower cost price, lower power consumption, a simplified construction due to the elimination of devices for stopping the bars an improved support and guiding for the transferred objects and thus eliminating accidental bending and warping of thin bars.
The invention is obviously not limited to the modes of application and embodiments described above but it is understood that various changes may be made within the spirit and scope of the appended claims.
What I claim is:
I. In a device for transferring substantially elongated objects such as metal bars or bundles of bars, said device comprising a step-by-step conveyor having parallel sets of both stationary and movable beams, first means to impart a motion to said movable beams in a closed curved path in a plane substantially parallel to said stationary and movable beams, a chain conveyor disposed substantially at right angle to said step-by-step conveyor, said chain conveyor comprising two parallel endless chains, second means for imparting motion thereto, a plurality of plates substantially at right angles to said chains, said plates disposed for interconnecting said two endless parallel chains, a plurality of spaced apart supporting troughs for said elongated objects and pedestals disposed for connecting said troughs to said interconnecting plates, the spacing between said troughs, and the height of said pedestals being determined to permit passing of the ends of said movable beams in said step-by-step conveyor between two of said adjacent troughs.
2. A device according to claim 1 for servicing a binding stationary beams 4, then raised again to progress step-by-step machine for metal bars, said device comprising a first chain disposed for synchronizing the transferring speeds of said first and said second conveyor.
1. In a device for transferring substantially elongated objects such as metal bars or bundles of bars, said device comprising a step-by-step conveyor having parallel sets of both stationary and movable beams, first means to impart a motion to said movable beams in a closed curved path in a plane substantially parallel to said stationary and movable beams, a chain conveyor disposed substantially at right angle to said step-by-step conveyor, said chain conveyor comprising two parallel endless chains, second means for imparting motion thereto, a plurality of plates substantially at right angles to said chains, said plates disposed for interconnecting said two endless parallel chains, a plurality of spaced apart supporting troughs for said elongated objects and pedestals disposed for connecting said troughs to said interconnecting plates, the spacing between said troughs, and the height of said pedestals being determined to permit passing of the ends of said movable beams in said step-by-step conveyor between two of said adjacent troughs.
2. A device according to claim 1 for servicing a binding machine for metal bars, said device comprising a first chain conveyor disposed for feeding said bars to the input of said binding machine, a second chain conveyor disposed for carrying said bars from the output of said machine, and means disposed for synchronizing the transferring speeds of said first and said second conveyor.
|
[Federal Register Volume 65, Number 85 (Tuesday, May 2, 2000)]
[Page 25485]
[FR Doc No: 00-10842]
-----------------------------------------------------------------------
FEDERAL COMMUNICATIONS COMMISSION
Notice of Public Information Collection(s) Being Submitted to OMB
for Review and Approval
April 24, 2000.
SUMMARY: The Federal Communications Commissions, as part of its
continuing effort to reduce paperwork burden invites the general public
and other Federal agencies to take this opportunity to comment on the
following information collection, as required by the Paperwork
Reduction Act of 1995, Public Law 104-13. An agency may not conduct or
sponsor a collection of information unless it displays a currently
valid control number. No person shall be subject to any penalty for
failing to comply with a collection of information subject to the
Paperwork Reduction Act (PRA) that does not display a valid control
number. Comments are requested concerning: (a) Whether the proposed
collection of information is necessary for the proper performance of
the functions of the Commission, including whether the information
shall have practical utility; (b) the accuracy of the Commission's
burden estimate; (c) ways to enhance the quality, utility, and clarity
of the information collected; and (d) ways to minimize the burden of
the collection of information on the respondents, including the use of
automated collection techniques or other forms of information
technology.
DATES: Written comments should be submitted on or before June 1, 2000.
If you anticipate that you will be submitting comments, but find it
difficult to do so within the period of time allowed by this notice,
you should advise the contact listed below as soon as possible.
ADDRESSES: Direct all comments to Les Smith, Federal Communications
Commission, Room 1-A804, 445 12th Street, SW., Washington, DC 20554 or
via the Internet to [email protected].
FOR FURTHER INFORMATION CONTACT: For additional information or copies
of the information collections contact Les Smith at (202) 418-0217 or
via the Internet at [email protected].
SUPPLEMENTARY INFORMATION:
OMB Control Number: 3060-0055.
Title: Application for Cable Television Relay Service Station
Authorization.
Form Number: FCC 327.
Type of Review: Extension of a currently approved collection.
Respondents: Business or other for-profit entities; Individuals or
households; State, Local, or Tribal Governments.
Number of Respondents: 973.
Estimate Time Per Response: 3.166 hours.
Frequency of Response: On occasion reporting requirement.
Total Annual Burden: 3,081 hours.
Total Annual Costs: $184,000.
Needs and Uses: Cable television system owners or operators and
MMDS operators use FCC Form 327 to apply for cable television relay
service station authorizations (CARS). The Commission uses the
information to determine whether applicants meet basic statutory
requirements and are qualified to become or continue as Commission
licensees.
OMB Control Number: 3060-0568.
Title: Commercial Leased Access Rates, Terms, and Conditions.
Form Number: N/A.
Type of Review: Extension of a currently approved collection.
Respondents: Business or other for-profit entities.
Number of Respondents: 6,330.
Estimate Time Per Response: 2 minutes to 10 hours.
Frequency of Response: On occasion reporting requirement; Third
party disclosure.
Total Annual Burden: 94,171 hours.
Total Annual Costs: $74,000.
Needs and Uses: The Commission and prospective leased access
programmers use this information to verify rate calculations for leased
access channels and to eliminate uncertainty in negotiations for leased
commercial access. The Commission's leased access requirements are
designed to promote diversity of programming and competition in
programming delivery as required by section 612 of the Cable Television
Consumer Protection and Competition Act of 1992.
Federal Communications Commission.
Magalie Roman Salas,
Secretary.
[FR Doc. 00-10842 Filed 5-1-00; 8:45 am]
BILLING CODE 6712-01-P
|
# WARCannon - Catastrophically powerful parallel WARC processing
WARCannon was built to simplify and cheapify the process of 'grepping the internet'.
With WARCannon, you can:
* Build and test regex patterns against real Common Crawl data
* Easily load Common Crawl datasets for parallel processing
* Scale compute capabilities to asynchronously crunch through WARCs at frankly unreasonable capacity.
* Store and easily retrieve the results
## How it Works
WARCannon leverages clever use of AWS technologies to horizontally scale to any capacity, minimize cost through spot fleets and same-region data transfer, draw from S3 at incredible speeds (up to 100Gbps per node), parallelize across hundreds of CPU cores, report status via DynamoDB and CloudFront, and store results via S3.
In all, WARCannon can process multiple regular expression patterns across 400TB in a few hours for around $100.
## Installation
WARCannon requires that you have the following installed:
* **awscli** (v2)
* **terraform** (v0.11)
* **jq**
* **jsonnet**
* **npm** (v12 or v14)
**ProTip:** To keep things clean and distinct from other things you may have in AWS, it's STRONGLY recommended that you deploy WARCannon in a fresh account. You can create a new account easily from the 'Organizations' console in AWS. **By 'STRONGLY recommended', I mean 'seriously don't install this next to other stuff'.**
First, clone the repo and copy the example settings.
```sh
$ git clone [email protected]:c6fc/warcannon.git
$ cd warcannon
warcannon$ cp settings.json.sample settings.json
```
Edit `settings.json` to taste:
* `backendBucket`: Is the bucket to store the terraform state in. If it doesn't exist, WARCannon will create it for you. Replace '< somerandomcharacters >' with random characters to make it unique, or specify another bucket you own.
* `awsProfile`: The profile name in `~/.aws/credentials` that you want to piggyback on for the installation.
* `nodeInstanceType`: An array of instance types to use for parallel processing. 'c'-types are best value for this purpose, and any size can be used. `["c5n.18xlarge"]` is the recommended value for true campaigns.
* `nodeCapacity`: The number of nodes to request during parallel processing. The resulting nodes will be an arbitrary distribution of the `nodeInstanceTypes` you specify.
* `nodeParallelism`: The number of simultaneous WARCs to process *per vCPU*. `2` is a good number here. If nodes have insufficient RAM to run at this level of parallelism (as you might encounter with 'c'-type instances), they'll run at the highest safe parallelism instead.
* `nodeMaxDuration`: The maximum lifespan of compute nodes in seconds. Nodes will be automatically terminated after this time if the job has still not completed. Default value is 24 hours.
* `sshPubkey`: A public SSH key to facilitate remote access to nodes for troubleshooting.
* `allowSSHFrom`: A CIDR mask to allow SSH from. Typically this will be `<yourpublicip>/32`
## Grepping the Internet
WARCannon is fed by [Common Crawl](https://commoncrawl.org/) via the [AWS Open Data](https://registry.opendata.aws/) program. Common Crawl is unique in that the data retrieved by their spiders not only captures website text, but also other text-based content like JavaScript, TypeScript, full HTML, CSS, etc. By constructing suitable Regular Expressions capable of identifying unique components, researchers can identify websites by the technologies they use, and do so without ever touching the website themselves. The problem is that this requires parsing hundreds of terabytes of data, which is a tall order no matter what resources you have at your disposal.
### Developing Regular Expressions
Grepping the internet isn't for the faint of heart, but starting with an effective seive is the first start. WARCannon supports this by enabling local verification of regular expressions against real Common Crawl data. First, open `lambda_functions/warcannon/matches.js` and modify the `regex_patterns` object to include the regular expressions you wish to use in `name: pattern` format. Here's an example from the default search set:
```javascript
exports.regex_patterns = {
"access_key_id": /(\'A|"A)(SIA|KIA|IDA|ROA)[JI][A-Z0-9]{14}[AQ][\'"]/g,
};
```
Strings matching this expression will be saved under the corresponding key in the results; `access_key_id` in this case. **Protip:** Use [RegExr](https://regexr.com) with the 'JavaScript' format to build and test regular expressions against known-good matches.
You also have the option of only capturing results from specified domains. To do this, simply populate the `domains` array with the FQDNs that you wish to include. It is recommended that you leave this empty `[]` since it's almost never worthwhile (the processing effort saved is very small), but it can be useful in some niche cases.
```javascript
exports.domains = ["example1.com", "example2.com"];
```
Once the `matches.js` is populated, run the following command:
```bash
warcannon$ ./warcannon testLocal <warc_path>
```
WARCannon will then download the warc and parse it with your configured matches. There are a few quality-of-life things that WARCannon does by default that you should be aware of:
1. WARCannon will download the warc to `/tmp/warcannon.testLocal` on first run, and will re-use the downloaded warc from then on even if you change the warc_path. If you wish to use a different warc, you must delete this file.
2. WARCs are large; most coming in at just over 1GB. WARCannon uses the CLI for multi-threaded downloads, but if you have slow internet, you'll need to exercise patience the first time around.
On top of everything else, WARCannon will attempt to evaluate the total compute cost of your regular expressions when run locally. This way, you can be informed if a given regular expression will significantly impact performance *before* you execute your campaign.
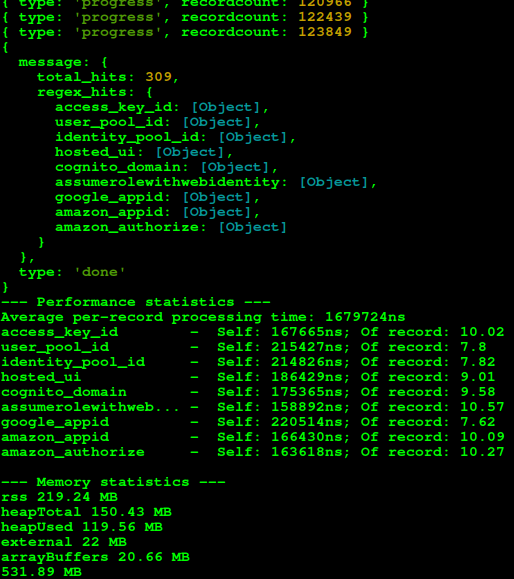
### Performing Custom Processing
Sometimes a simple regex pattern isn't sufficient on its own, and you need some additional steps to ensure you're returning the right information. In this case, simply adding a function to the `exports.custom_functions` object with the same key name allows you to perform any additional processing you see fit.
```javascript
exports.regex_patterns = {
"access_key_id": /(\'A|"A)(SIA|KIA|IDA|ROA)[JI][A-Z0-9]{14}[AQ][\'"]/g,
};
exports.custom_functions = {
"access_key_id": function(match) {
// Ignore matches with 'EXAMPLE' in the text, since this is common for documentation.
if (match.text(/EXAMPLE/) != null) {
// Returning a boolean 'false' discards the match.
return false
}
}
}
```
**Note: WARCannon is meant to crunch through text at stupid speeds.** While it's certainly *possible* to perform any type of operation you'd like, adding high-latency custom functions such as network calls can significantly increase processing time and costs. Network calls could also result in LOTS of calls against a website, which could get you in trouble. Be smart about how you use these functions.
### Performing a One-Off Test in AWS
The costs of AWS can be anxiety-inducing, especially when you're only looking to do some research. WARCannon is built to allow both one-off executions in addition to full campaigns, so you can be confident in the results you'll get back. Once you're happy with the results you get with `testLocal`, you can deploy your updated matches and run a cloud-backed test easily:
```bash
warcannon$ ./warcannon deploy
warcannon$ ./warcannon test <warc_path>
```
This will synchronously execute a Lambda function with the regular expressions you've configured, and immediately return the results. This process takes about 2.5 minutes, so don't be afraid to wait while it does its magic.
### Launching a Real Campaign
Once you're happy with the results you get in Lambda, you're ready to grep the internet for real. We'll first go over some basic housekeeping, then kick it off.
#### Clearing the Queue
WARCannon uses AWS Simple Queue Service to distribute work to the compute nodes. To ensure that your results aren't tainted with any prior runs, you can tell WARCannon to empty the queue:
```bash
warcannon$ ./warcannon emptyQueue
[+] Cleared [ 15 ] messages from the queue
```
You can then verify the state of the queue:
```bash
warcannon$ ./warcannon status
Deployed: [ YES ]; SQS Status: [ EMPTY ]
Job Status: [ INACTIVE ]
Active job url: https://d201offlnmhkmd.cloudfront.net
```
Verify the following before proceeding:
1. The SQS Queue is empty
2. The job status is 'INACTIVE'
#### Populating the Queue (Simple)
In order to create the queue messages that the compute nodes will consume, you must first populate SQS with crawl data. WARCannon has several commands to help with this, starting with the ability to show the available scans. In this case, let's look at the scans available for the year 2021:
```bash
warcannon$ ./warcannon list 2021
CC-MAIN-2021-04
CC-MAIN-2021-10
```
We have two scans matching the string "2021" to work with. We can now instruct WARCannon to populate the queue based on one of these scans. This time, we need to provide a parameter that uniquely identifies one of the scans. "2021-04" will do the trick. We could choose to populate only a partial scan by also specifying a number of chunks and a chunk size, but we'll skip that for now.
```bash
warcannon$ ./warcannon populate 2021-04
{Created 799 chunks of 100 from 79840 available segments"
"StatusCode": 200,
"ExecutedVersion": "$LATEST"
}
```
#### Populating the Queue via Athena (Advanced)
During deployment, WARCannon automatically provisions a database (warcannon_commoncrawl) and workgroup (warcannon) in Athena that can be used to rapidly query information from CommonCrawl. This can be especially useful for populating sparse campaigns based on certain queries. For example, the following query will search for WARCs that contain responses from 'example.com'
```sql
SELECT
warc_filename,
COUNT(url_path) as num
FROM
warcannon_commoncrawl.ccindex
WHERE
subset = 'warc' AND
url_host_registered_domain IN ('example.com') AND
crawl = 'CC-MAIN-2021-04'
GROUP BY warc_filename
ORDER BY num DESC
```
You can use the Athena console to fine-tune your results, but you must run the query from the WARCannon command line if you intend to populate a job with it:
```bash
./warcannon queryAthena "SELECT warc_filename, COUNT(url_path) as num FROM warcannon_commoncrawl.ccindex WHERE subset = 'warc' AND url_host_registered_domain IN ('example.com') AND crawl = 'CC-MAIN-2021-04' GROUP BY warc_filename ORDER BY num DESC"
[+] Query Exec Id: 0319486e-1846-491c-badf-2e23ae213974 .. SUCCEEDED
```
WARCannon can then use the results of a query to populate the queue, and does so based on the `warc_filename` column from the resultset. As such, it's recommended that you either `group by` this column or use `distinct()` to avoid duplicates. WARCannon will throw an error if this field isn't present. Populate the queue with Athena results by passing the Query Execution ID to the `populateAthena` command.
```bash
./warcannon populateAthena 0319486e-1846-491c-badf-2e23ae213974
{Created 26 chunks of 10 from 251 available segments"
"StatusCode": 200,
"ExecutedVersion": "$LATEST"
}
```
**Note: While populating a sparse job for a single domain might seem like a good idea, it often isn't.** The responses from a single domain tend to be spread widely across a large subset of WARCs. This can be seen clearly using the example query above to see that of the ~150,000 records in each WARC, the largest single hit for moderate-sized websites can be in the single-digits.
#### Firing the WARCannon
With the queue populated, we're ready to fire. WARCannon will do a few sanity checks to ensure everything is in order, then show you the configuration of the campaign and give you one last opportunity to abort before you finalize the order.
```bash
warcannon$ ./warcannon fire
[!] This will request [ 6 ] spot instances of type [ m5n.24xlarge, m5dn.24xlarge ]
lasting for [ 86400 ] seconds.
To change this, edit your settings in settings.json and run ./warcannon deploy
--> Ready to fire? [Yes]:
```
Pull the trigger by responding with 'Yes'.
```bash
--> Ready to fire? [Yes]: Yes
{
"SpotFleetRequestId": "sfr-03dd32b8-51f7-4c8e-802b-a702fc3c8c95"
}
[+] Spot fleet request has been sent, and nodes should start coming online within ~5 minutes.
Monitor node status and progress at https://d201offlnmhkmd.cloudfront.net
```
The response includes a link to your unique status URL, where you can monitor the progress of your campaign and the performance of each node.
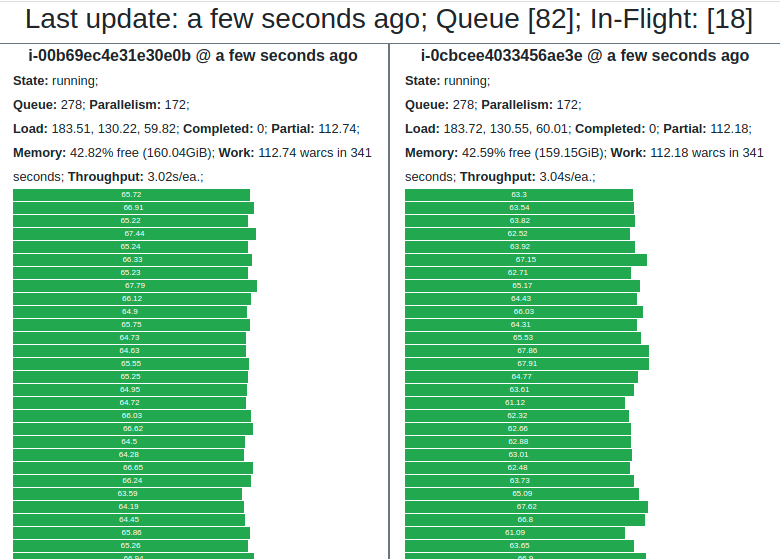
#### Obtaining Results
WARCannon results are stored in S3 in JSON format, broken down by each node responsible for producing the results. Athena results are stored in the same bucket under the `/athena/` prefix. You can sync the results of a campaign to the `./warcannon/results/` folder on your local machine using the `syncResults` command.
```bash
./warcannon syncResults
sync: s3://warcannon-results-202...
sync: s3://warcannon-results-202...
sync: s3://warcannon-results-202...
...
```
You can then empty the results buckets with `clearResults`
```bash
./warcannon clearResults
delete: s3://warcannon-results-202...
delete: s3://warcannon-results-202...
delete: s3://warcannon-results-202...
...
[+] Deleted [ 21 ] files from S3.
```
# Official Discord Channel
Come hang out on Discord!
[](https://discord.gg/7SDYBs65Zp)
|
JAMES ROLLIN SLONAKER
and fovea centralis, is observed at the optical axis. It appears as a local thickening of the chorioid at the axis, and is distinct from its general increase in thickness over the back of the eye. This increase is due to a greater number of blood-vessels. (See development of the fovea.) The formative cells of the scleral
TABLE 3
Showing the thickness of the different layers of the cornea, and the chorioid and sclerotic coats in the developing and the adult eyes. Also the axial and equatorial diameters of the whole eye at the same ages. 2 to 12 represent the ages in days of the embryos used; H-2, H-4 and H-fl, represent, respectively, hatched two days, four days, and just flying. All measurements were made in millimeters and as nearly at right angles to the surface as possible
pigment.
Two days after hatching (figs. 82 and 83) pigmentation of the chorioid has begun, more prominently near the lens than at the back of the eye. In this respect it corresponds to the pigmenta tion of the pigment layer of the retina which begins in the region of the lens at a much earher age (see development of the retina) .
|
Page:The deplorable history of the Catalans, from their first engaging in the war, to the time of their reduction. (1714).djvu/10
reduced by Declaration. However, there was hopes, that another Place might be more culpable. And considering likewise that the constant Difficulties which attend Descents in an Enemies Country, where the Hazard is ever great, and the Success, at least, but uncertain; an Expedient was therefore thought of, whereby we might gain an Inlet or Key into the Kingdom, and a conveniencyconvenience [sic] to land our Troops to carry on the War with a prospect of Success, and this was by engaging Portugal in an Alliance with us; which was happily effected, tho’though [sic] no means waswere [sic] left unessayedunattempted [sic] by France to overthrow it.
By this Treaty of Alliance, among other Things, it was stipulated, That the Arch DukeArchduke [sic] Charles, being undeniably entitled to the Spanish Monarchy, by virtue of a Renunciation from the Emperor his Father, and from the King of the Romans his elder Brother, should come in Person to Lisbon, attended by a Royal Fleet, and an Army of 12000 Men, two thirds English, and one Dutch, to which the King of Portugal was to join 13000 PortuguezePortuguese [sic], at the ExpenceExpense [sic] of the Allies, and 15000 more at his own.
In this manner a Scheme was laid by the Ministers at home, for a vigorous prosecution of the War in Spain- and their part of it performed, by sending his CatholickCatholic [sic] Majesty, (who had before been Proclaimed at Vienna) to Portugal, after his arrival in England, according to the Terms of the Treaty, without loss of time; for King Charles Landed at Portsmouth about the latter end of December 1703. and notwithstanding the several delays occasioned by the Winds, yet he was conveyed to Lisbon by the Confederate Fleet, by the end of February.
|
Thread:Doctor Ibrahim/@comment-28530195-20170709062356/@comment-26517142-20170721050202
And well...the enmasse thing is a part of my usual shtick. :D
|
ASP.NET UserControl OnError
UserControls in ASP.NET (4.0) inherit from System.Web.UI.UserControl. VisualStudio intellisense suggest OnError as valid override of TemplateControl. At runtime .NET ignores this error handling. Only the OnError at Page-Level gets invoked. Did i miss anything or is there a design issue?
public partial class Sample : System.Web.UI.UserControl
{
protected override void OnError(EventArgs e)
{
// Never reach ;o)
base.OnError(e);
}
}
Possibly related: http://stackoverflow.com/questions/341417/handling-web-user-control-error-on-asp-net-page
@deniz dogan: i could not use an errorhandling outside the control. it need to be an internal fallback. it's also not possible to attach on the error event in OnInit.
ah.. the elusive OnError
this page sheds some good light on the inner workings of this event:
http://weblogs.asp.net/vga/archive/2003/06/16/8748.aspx
it may be that some exceptions are caught w/out triggering OnError
Why do you want to override OnError? You'd probably be better off by using a try/catch block or subscribing to the Application_Error event.
because you'd need to wrap EVERY operation in try/catch.. OnError should automatically notify you of any problems, if that's what you're using it for. try/catch is suitable when you know what error might cause the exception and how to handle that situation.
|
<?php
defined('BASEPATH') OR exit('No direct script access allowed');
class All_model extends CI_Model {
//ambil semua data (select *)
public function getAll($table){
return $this->db->get($table);
}
//ambil data bersyarat (edit, delete, show detail)
public function getData($table, $where){
return $this->db->get_where($table, $where);
}
public function detailTrans(){
$this->db->select('d.*, m.nama_menu');
$this->db->from('detailtransaksi d');
$this->db->join('menu m', 'm.id = d.menu_id', 'left');
$this->db->where('d.status', '=', 0);
return $this->db->get();
}
//simpan data (store)
public function storeData($table, $data){
$this->db->insert($table, $data);
}
//simpan data edit (update)
public function updateData($table, $where, $data){
$this->db->where($where);
$this->db->update($table, $data);
}
//hapus data
public function deleteData($table, $where){
$this->db->where($where);
$this->db->delete($table);
}
// join tabel berdasarkan transaksi
public function fulltrans($id){
$this->db->select('t.id as transID, t.total_harga, t.tgl_trans, t.status_pembayaran, d.id as detailID, d.status, d.jumlah_pesanan, d.total, m.id as menuID, m.nama_menu, m.harga, j.id as mejaID, j.no_meja');
$this->db->from('menu m');
$this->db->join('detailtransaksi d', 'm.id = d.menu_id', 'left');
$this->db->join('transaksi t', 't.id = d.trans_id', 'left');
$this->db->join('meja j', 'j.id = t.meja_id', 'left');
$this->db->where('t.id', $id);
return $this->db->get();
}
public function transaksi($status = false){
$this->db->select('t.id, t.meja_id, m.no_meja, t.total_harga, t.tgl_trans, t.status_pembayaran');
$this->db->from('transaksi t');
$this->db->join('meja m', 'm.id = t.meja_id', 'left');
if ($status) {
$this->db->where('t.status_pembayaran', '=', 0);
}
$this->db->order_by('tgl_trans', 'desc');
return $this->db->get();
}
public function getTransaksiMonth($month, $nextMonth)
{
$this->db->select('COUNT(*) as bulan');
$this->db->from('transaksi t');
$this->db->where('t.tgl_trans BETWEEN '.strtotime($month).' AND '.strtotime($nextMonth));
return $this->db->get();
}
public function getTotalTransaksi($month, $nextMonth)
{
$this->db->select('sum(total_harga) as total');
$this->db->from('transaksi t');
$this->db->where('t.tgl_trans BETWEEN '.strtotime($month).' AND '.strtotime($nextMonth));
return $this->db->get();
}
public function getTotalPorsi($month, $nextMonth)
{
$this->db->select('sum(d.jumlah_pesanan) as total');
$this->db->from('detailtransaksi d');
$this->db->join('transaksi t', 't.id = d.trans_id', 'left');
$this->db->where('t.tgl_trans BETWEEN '.strtotime($month).' AND '.strtotime($nextMonth));
return $this->db->get();
}
}
?>
|
Talk:Rare Short Spiked Collar/@comment-36596554-20181220172412/@comment-37635716-20181220175423
everyone can get 20 with just spares so im pretty sure its more XP
|
using System;
using System.Globalization;
using Xamarin.Forms;
using Xamarin.Forms.Internals;
namespace ShoppingCart.Converters
{
/// <summary>
/// This class have methods to convert the Boolean values to string.
/// </summary>
[Preserve(AllMembers = true)]
public class BooleanToStringConverter : IValueConverter
{
/// <summary>
/// This method is used to convert the bool to string.
/// </summary>
/// <param name="value">Gets the value.</param>
/// <param name="targetType">Gets the target type.</param>
/// <param name="parameter">Gets the parameter.</param>
/// <param name="culture">Gets the culture.</param>
/// <returns>Returns the string.</returns>
public object Convert(object value, Type targetType, object parameter, CultureInfo culture)
{
if (value != null && parameter != null)
{
if (parameter.ToString() == "0")
{
if ((bool) value)
return "\ue72f";
return "\ue734";
}
if (parameter.ToString() == "1")
{
if ((bool) value)
return "\ue732";
return "\ue701";
}
}
return string.Empty;
}
/// <summary>
/// This method is used to convert the string to bool.
/// </summary>
/// <param name="value">Gets the value.</param>
/// <param name="targetType">Gets the target type.</param>
/// <param name="parameter">Gets the parameter.</param>
/// <param name="culture">Gets the culture.</param>
/// <returns>Returns the string.</returns>
public object ConvertBack(object value, Type targetType, object parameter, CultureInfo culture)
{
return true;
}
}
}
|
[Congressional Record Volume 145, Number 152 (Tuesday, November 2, 1999)]
[House]
[Pages H11218-H11231]
{time} 1145
FOREIGN NARCOTICS KINGPIN DESIGNATION ACT
Mr. GILMAN. Madam Speaker, I move to suspend the rules and pass the
bill (H.R. 3164) to provide for the imposition of economic sanctions on
certain foreign persons engaging in, or otherwise involved in,
international narcotics trafficking.
The Clerk read as follows:
H.R. 3164
Be it enacted by the Senate and House of Representatives of
the United States of America in Congress assembled,
SECTION 1. SHORT TITLE.
This Act may be cited as the ``Foreign Narcotics Kingpin
Designation Act''.
SEC. 2. FINDINGS AND POLICY.
(a) Findings.--Congress makes the following findings:
(1) Presidential Decision Directive 42, issued on October
21, 1995, ordered agencies of the executive branch of the
United States Government to, inter alia, increase the
priority and resources devoted to the direct and immediate
threat international crime presents to national security,
work more closely with other governments to develop a global
response to this threat, and use aggressively and creatively
all legal means available to combat international crime.
(2) Executive Order No. 12978 of October 21, 1995, provides
for the use of the authorities in the International Emergency
Economic Powers Act (IEEPA) (50 U.S.C. 1701 et seq.) to
target and apply sanctions to 4 international narcotics
traffickers and their organizations that operate from
Colombia.
(3) IEEPA was successfully applied to international
narcotics traffickers in Colombia and based on that
successful case study, Congress believes similar authorities
should be applied worldwide.
(4) There is a national emergency resulting from the
activities of international narcotics traffickers and their
organizations that threatens the national security, foreign
policy, and economy of the United States.
(b) Policy.--It shall be the policy of the United States to
apply economic and other financial sanctions to significant
foreign narcotics traffickers and their organizations
worldwide to protect the national security, foreign policy,
and economy of the United States from the threat described in
subsection (a)(4).
SEC. 3. PURPOSE.
The purpose of this Act is to provide authority for the
identification of, and application of sanctions on a
worldwide basis to, significant foreign narcotics
traffickers, their organizations, and the foreign persons who
provide support to those significant foreign narcotics
traffickers and their organizations, whose activities
threaten the national security, foreign policy, and economy
of the United States.
SEC. 4. PUBLIC IDENTIFICATION OF SIGNIFICANT FOREIGN
NARCOTICS TRAFFICKERS AND REQUIRED REPORTS.
(a) Provision of Information to the President.--The
Secretary of the Treasury, the Attorney General, the
Secretary of Defense, the Secretary of State, and the
Director of Central Intelligence shall consult among
themselves and provide the appropriate and necessary
information to enable the President to submit the report
under subsection (b). This information shall also be provided
to the Director of the Office of National Drug Control
Policy.
(b) Public Identification and Sanctioning of Significant
Foreign Narcotics Traffickers.--Not later than June 1, 2000,
and not later than June 1 of each year thereafter, the
President shall submit a report to the Permanent Select
Committee on Intelligence, and the Committees on the
Judiciary, International Relations, Armed Services, and Ways
and Means of the House of Representatives; and to the Select
Committee on Intelligence, and the Committees on the
Judiciary, Foreign Relations, Armed Services, and Finance of
the Senate--
(1) identifying publicly the foreign persons that the
President determines are appropriate for sanctions pursuant
to this Act; and
(2) detailing publicly the President's intent to impose
sanctions upon these significant foreign narcotics
traffickers pursuant to this Act.
The report required in this subsection shall not include
information on persons upon which United States sanctions
imposed under this Act, or otherwise on account of narcotics
trafficking, are already in effect.
(c) Unclassified Report Required.--The report required by
subsection (b) shall be submitted in unclassified form and
made available to the public.
(d) Classified Report.--(1) Not later than July 1, 2000,
and not later than July 1 of each year thereafter, the
President shall provide the Permanent Select Committee on
Intelligence of the House of Representatives and the Select
Committee on Intelligence of the Senate with a report in
classified form describing in detail the status of the
sanctions imposed under this Act, including the personnel and
resources directed towards the
imposition of such sanctions during the preceding fiscal
year, and providing background information with respect to
newly identified significant foreign narcotics traffickers
and their activities.
(2) Such classified report shall describe actions the
President intends to undertake or has undertaken with respect
to such significant foreign narcotics traffickers.
(3) The report required under this subsection is in
addition to the President's obligation to keep the
intelligence committees of Congress fully and completely
informed of the provisions of the National Security Act of
1947.
(e) Exclusion of Certain Information.--
(1) Intelligence.--Notwithstanding any other provision of
this section, the reports described in subsections (b) and
(d) shall not disclose the identity of any person, if the
Director of Central Intelligence determines that such
disclosure could compromise an intelligence operation,
activity, source, or methods of the United States.
(2) Law enforcement.--Notwithstanding any other provision
of this section, the reports described in subsections (b) and
(d) shall not disclose the name of any person if the Attorney
General, in coordination as appropriate with the Director of
the Federal Bureau of Investigation, the Administrator of the
Drug Enforcement Administration, and the Secretary of the
Treasury, determines that such disclosure could reasonably be
expected to--
(A) compromise the identity of a confidential source,
including a State, local, or foreign agency or authority or
any private institution that furnished information on a
confidential basis;
(B) jeopardize the integrity or success of an ongoing
criminal investigation or prosecution;
(C) endanger the life or physical safety of any person; or
(D) cause substantial harm to physical property.
(f) Notification Required.--(1) Whenever either the
Director of Central Intelligence or the Attorney General
makes a determination under subsection (e), the Director of
Central Intelligence or the Attorney General shall notify the
Permanent Select Committee on Intelligence of the House of
Representatives and the Select Committee on Intelligence of
the Senate, and explain the reasons for such determination.
(2) The notification required under this subsection shall
be submitted to the Permanent Select Committee on
Intelligence of the House of Representatives and the Select
Committee on Intelligence of the Senate not later than July
1, 2000, and on an annual basis thereafter.
(g) Determinations Not To Apply Sanctions.--(1) The
President may waive the application to a significant foreign
narcotics trafficker of any sanction authorized by this title
if the President determines that the application of sanctions
under this Act would significantly harm the national security
of the United States.
(2) When the President determines not to apply sanctions
that are authorized by this Act to any significant foreign
narcotics trafficker, the President shall notify the
Permanent Select Committee on Intelligence, and the
Committees on the Judiciary, International Relations, Armed
Services, and Ways and Means of the House of Representatives,
and the Select Committee on Intelligence, and the Committees
on the Judiciary, Foreign Relations, Armed Services, and
Finance of the Senate not later than 21 days after making
such determination.
(h) Changes in Determinations To Impose Sanctions.--
(1) Additional determinations.--(A) If at any time after
the report required under subsection (b) the President finds
that a foreign person is a significant foreign narcotics
trafficker and such foreign person has not been publicly
identified in a report required under subsection (b), the
President shall submit an additional public report containing
the information described in subsection (b) with respect to
such foreign person to the Permanent Select Committee on
Intelligence, and the Committees on the Judiciary,
International Relations, Armed Services, and Ways and Means
of the House of Representatives, and the Select Committee on
Intelligence, and the Committees on the Judiciary, Foreign
Relations, Armed Services, and Finance of the Senate.
(B) The President may apply sanctions authorized under this
Act to the significant foreign narcotics trafficker
identified in the report submitted under subparagraph (A) as
if the trafficker were originally included in the report
submitted pursuant to subsection (b) of this section.
(C) The President shall notify the Secretary of the
Treasury of any determination made under this paragraph.
(2) Revocation of determination.--(A) Whenever the
President finds that a foreign person that has been publicly
identified as a significant foreign narcotics trafficker in
the report required under subsection (b) or this subsection
no longer engages in those activities for which sanctions
under this Act may be applied, the President shall issue
public notice of such a finding.
(B) Not later than the date of the public notice issued
pursuant to subparagraph (A), the President shall notify, in
writing and in classified or unclassified form, the Permanent
Select Committee on Intelligence, and the Committees on the
Judiciary, International Relations, Armed Services, and Ways
and Means of the House of Representatives, and the Select
Committee on Intelligence, and the Committees on the
Judiciary, Foreign Relations, Armed Services, and Finance of
the Senate of actions taken under this paragraph and a
description of the basis for such actions.
SEC. 5. BLOCKING ASSETS AND PROHIBITING TRANSACTIONS.
(a) Applicability of Sanctions.--A significant foreign
narcotics trafficker publicly identified in the report
required under subsection (b) or (h)(1) of section 4 and
foreign persons designated by the Secretary of the Treasury
pursuant to subsection (b) of this section shall be subject
to any and all sanctions as authorized by this Act. The
application of sanctions on any foreign person pursuant to
subsection (b) or (h)(1) of section 4 or subsection (b) of
this section shall remain in effect until revoked pursuant to
section 4(h)(2) or subsection (e)(1)(A) of this section or
waived pursuant to section 4(g)(1).
(b) Blocking of Assets.--Except to the extent provided in
regulations, orders, instructions, licenses, or directives
issued pursuant to this Act, and notwithstanding any contract
entered into or any license or permit granted prior to the
date on which the President submits the report required under
subsection (b) or (h)(1) of section 4, there are blocked as
of such date, and any date thereafter, all such property and
interests in property within the United States, or within the
possession or control of any United States person, which are
owned or controlled by--
(1) any significant foreign narcotics trafficker publicly
identified by the President in the report required under
subsection (b) or (h)(1) of section 4;
(2) any foreign person that the Secretary of the Treasury,
in consultation with the Attorney General, the Director of
Central Intelligence, the Director of the Federal Bureau of
Investigation, the Administrator of the Drug Enforcement
Administration, the Secretary of Defense, and the Secretary
of State, designates as materially assisting in, or providing
financial or technological support for or to, or providing
goods or services in support of, the international narcotics
trafficking activities of a significant foreign narcotics
trafficker so identified in the report required under
subsection (b) or (h)(1) of section 4, or foreign persons
designated by the Secretary of the Treasury pursuant to this
subsection;
(3) any foreign person that the Secretary of the Treasury,
in consultation with the Attorney General, the Director of
Central Intelligence, the Director of the Federal Bureau of
Investigation, the Administrator of the Drug Enforcement
Administration, the Secretary of Defense, and the Secretary
of State, designates as owned, controlled, or directed by,
or acting for or on behalf of, a significant foreign
narcotics trafficker so identified in the report required
under subsection (b) or (h)(1) of section 4, or foreign
persons designated by the Secretary of the Treasury
pursuant to this subsection; and
(4) any foreign person that the Secretary of the Treasury,
in consultation with the Attorney General, the Director of
Central Intelligence, the Director of the Federal Bureau of
Investigation, the Administrator of the Drug Enforcement
Administration, the Secretary of Defense, and the Secretary
of State, designates as playing a significant role in
international narcotics trafficking.
(c) Prohibited Transactions.--Except to the extent provided
in regulations, orders, instructions, licenses, or directives
issued pursuant to this Act, and notwithstanding any contract
entered into or any license or permit granted prior to the
date on which the President submits the report required under
subsection (b) or (h)(1) of section 4, the following
transactions are prohibited:
(1) Any transaction or dealing by a United States person,
or within the United States, in property or interests in
property of any significant foreign narcotics trafficker so
identified in the report required pursuant to subsection (b)
or (h)(1) of section 4, and foreign persons designated by the
Secretary of the Treasury pursuant to subsection (b) of this
section.
(2) Any transaction or dealing by a United States person,
or within the United States, that evades or avoids, or has
the effect of evading or avoiding, and any endeavor, attempt,
or conspiracy to violate, any of the prohibitions contained
in this Act.
(d) Law Enforcement and Intelligence Activities Not
Affected.--Nothing in this Act prohibits or otherwise limits
the authorized law enforcement or intelligence activities of
the United States, or the law enforcement activities of any
State or subdivision thereof.
(e) Implementation.--(1) The Secretary of the Treasury, in
consultation with the Attorney General, the Director of
Central Intelligence, the Director of the Federal Bureau of
Investigation, the Administrator of the Drug Enforcement
Administration, the Secretary of Defense, and the Secretary
of State, is authorized to take such actions as may be
necessary to carry out this Act, including--
(A) making those designations authorized by paragraphs (2),
(3), and (4) of subsection (b) of this section and revocation
thereof;
(B) promulgating rules and regulations permitted under this
Act; and
(C) employing all powers conferred on the Secretary of the
Treasury under this Act.
(2) Each agency of the United States shall take all
appropriate measures within its authority to carry out the
provisions of this Act.
(3) Section 552(a)(3) of title 5, United States Code, shall
not apply to any record or information obtained or created in
the implementation of this Act.
(f) Judicial Review.--The determinations, identifications,
findings, and designations made pursuant to section 4 and
subsection (b) of this section shall not be subject to
judicial review.
SEC. 6. AUTHORITIES.
(a) In General.--To carry out the purposes of this Act, the
Secretary of the Treasury may, under such regulations as he
may prescribe, by means of instructions, licenses, or
otherwise--
(1) investigate, regulate, or prohibit--
(A) any transactions in foreign exchange, currency, or
securities; and
(B) transfers of credit or payments between, by, through,
or to any banking institution, to the extent that such
transfers or payments involve any interests of any foreign
country or a national thereof; and
(2) investigate, block during the pendency of an
investigation, regulate, direct and compel, nullify, void,
prevent, or prohibit any acquisition, holding, withholding,
use, transfer, withdrawal, transportation, placement into
foreign or domestic commerce of, or dealing in, or exercising
any right, power, or privilege with respect to, or
transactions involving, any property in which any foreign
country or a national thereof has any interest,
by any person, or with respect to any property, subject to
the jurisdiction of the United States.
(b) Recordkeeping.--Pursuant to subsection (a), the
Secretary of the Treasury may require recordkeeping,
reporting, and production of documents to carry out the
purposes of this Act.
(c) Defenses.--
(1) Full and actual compliance with any regulation, order,
license, instruction, or direction issued under this Act
shall be a defense in any proceeding alleging a violation of
any of the provisions of this Act.
(2) No person shall be held liable in any court for or with
respect to anything done or omitted in good faith in
connection with the administration of, or pursuant to, and in
reliance on this Act, or any regulation, instruction, or
direction issued under this Act.
(d) Rulemaking.--The Secretary of the Treasury may issue
such other regulations or orders, including regulations
prescribing recordkeeping, reporting, and production of
documents, definitions, licenses, instructions, or
directions, as may be necessary for the exercise of the
authorities granted by this Act.
SEC. 7. ENFORCEMENT.
(a) Criminal Penalties.--(1) Whoever willfully violates the
provisions of this Act, or any license rule, or regulation
issued pursuant to this Act, or willfully neglects or refuses
to comply with any order of the President issued under this
Act shall be--
(A) imprisoned for not more than 10 years,
(B) fined in the amount provided in title 18, United States
Code, or, in the case of an entity, fined not more than
$10,000,000,
or both.
(2) Any officer, director, or agent of any entity who
knowingly participates in a violation of the provisions of
this Act shall be imprisoned for not more than 30 years,
fined not more than $5,000,000, or both.
(b) Civil Penalties.--A civil penalty not to exceed
$1,000,000 may be imposed by the Secretary of the Treasury on
any person who violates any license, order, rule, or
regulation issued in compliance with the provisions of this
Act.
(c) Judicial Review of Civil Penalty.--Any penalty imposed
under subsection (b) shall be subject to judicial review only
to the extent provided in section 702 of title 5, United
States Code.
SEC. 8. DEFINITIONS.
As used in this Act:
(1) Entity.--The term ``entity'' means a partnership, joint
venture, association, corporation, organization, network,
group, or subgroup, or any form of business collaboration.
(2) Foreign person.--The term ``foreign person'' means any
citizen or national of a foreign state or any entity not
organized under the laws of the United States, but does not
include a foreign state.
(3) Narcotics trafficking.--The term ``narcotics
trafficking'' means any illicit activity to cultivate,
produce, manufacture, distribute, sell, finance, or transport
narcotic drugs, controlled substances, or listed chemicals,
or otherwise endeavor or attempt to do so, or to assist,
abet, conspire, or collude with others to do so.
(4) Narcotic drug; controlled substance; listed chemical.--
The terms ``narcotic drug'', ``controlled substance'', and
``listed chemical'' have the meanings given those terms in
section 102 of the Controlled Substances Act (21 U.S.C. 802).
(5) Person.--The term ``person'' means an individual or
entity.
(6) United states person.--The term ``United States
person'' means any United States citizen or national,
permanent resident alien, an entity organized under the laws
of the United States (including its foreign branches), or any
person within the United States.
(7) Significant foreign narcotics trafficker.--The term
``significant foreign narcotics trafficker'' means any
foreign person that plays a significant role in international
narcotics trafficking, that the President has determined to
be appropriate for sanctions pursuant to this Act, and that
the President has publicly identified in the report required
under subsection (b) or (h)(1) of section 4.
SEC. 9. EXCLUSION OF PERSONS WHO HAVE BENEFITED FROM ILLICIT
ACTIVITIES OF DRUG TRAFFICKERS.
Section 212(a)(2)(C) of the Immigration and Nationality Act
(8 U.S.C. 1182(a)(2)(C)) is amended to read as follows:
``(C) Controlled substance traffickers.--Any alien who the
consular officer or the Attorney General knows or has reason
to believe--
``(i) is or has been an illicit trafficker in any
controlled substance or in any listed chemical (as defined in
section 102 of the Controlled Substances Act (21 U.S.C.
802)), or is or has been a knowing aider, abettor, assister,
conspirator, or colluder with others in the illicit
trafficking in any such controlled or listed substance or
chemical, or endeavored to do so; or
``(ii) is the spouse, son, or daughter of an alien
inadmissible under clause (i), has, within the previous 5
years, obtained any financial or other benefit from the
illicit activity of that alien, and knew or reasonably should
have known that the financial or other benefit was the
product of such illicit activity,
is inadmissible.''.
SEC. 10. EFFECTIVE DATE.
This Act shall take effect on the date of enactment of this
Act.
The SPEAKER pro tempore (Mrs. Biggert). Pursuant to the rule, the
gentleman from New York (Mr. Gilman) and the gentleman from New York
(Mr. Crowley) each will control 20 minutes.
Mr. NADLER. Madam Speaker, I rise to claim the time in opposition
since I gather that both gentlemen from New York, Mr. Gilman and Mr.
Crowley, are in support.
The SPEAKER pro tempore. Is the gentleman from New York (Mr. Crowley)
in favor of the motion?
Mr. CROWLEY. Yes, I am, Madam Speaker.
The SPEAKER pro tempore. On that basis, pursuant to clause 1(c) of
rule XV, the gentleman from New York (Mr. Nadler) will control the 20
minutes reserved for the opposition.
The Chair recognizes the gentleman from New York (Mr. Gilman).
Mr. GILMAN. Madam Speaker, I am pleased to yield 10 minutes to the
gentleman from Florida (Mr. McCollum), and I ask unanimous consent that
he be permitted to control the time as he may deem appropriate.
The SPEAKER pro tempore. Is there objection to the request of the
gentleman from New York?
There was no objection.
Mr. NADLER. Madam Speaker, since this side ought to be represented in
support also, I yield 10 minutes to the gentleman from New York (Mr.
Crowley), and I ask unanimous consent that he be permitted to control
that time.
The SPEAKER pro tempore. Is there objection to the request of the
gentleman from New York?
There was no objection.
General Leave
Mr. GILMAN. Madam Speaker, I ask unanimous consent that all Members
may have 5 legislative days within which to revise and extend their
remarks on H.R. 3164.
The SPEAKER pro tempore. Is there objection to the request of the
gentleman from New York?
There was no objection.
Mr. GILMAN. Madam Speaker, I yield myself such time as I may consume.
Madam Speaker, the gentleman from Florida (Mr. Goss) and the
gentleman from Florida (Mr. McCollum) and our leadership are to be
complimented on moving forward on H.R. 3164. This important effort
improves the tools needed to tackle the critical problem of
international drug traffickers and those who knowingly transact and do
business with these kingpins.
This bill, by expanding and regularizing the authority for the
President to routinely block the property of major drug kingpins, after
the required June 1 listing of these kingpins, deprives them of access
to the United States market and to our financial system. It makes it
clear that our Nation is serious about confronting the threat that they
pose to our Nation and to its people.
After this bill becomes law, it is no longer going to be business as
usual for these global drug kingpins, for their relatives and business
associates and front companies.
Today we are moving forward with an important new initiative in our
war on drugs. Now we will routinely implement the application of
blocking assets
and denying these global drug traffickers and their associates access
to our markets and to our financial services.
There can be no more important tools in our arsenal against
international drug traffickers who target our Nation and its young
people than asset forfeiture, disruption of their business transaction
and their dealings.
With regard to the drug traffickers, there must be no safe havens or
untouched illicit assets for those who would destroy our communities
and the lives of our young people by shipping their poisons into our
Nation.
Three Presidents have called illicit drug trafficking a serious
national security threat to our Nation. Such a threat warrants a
serious response, including this expanded authority to maintain
economic pressure on these drug traffickers.
Greater international cooperation, the ability to bring to justice
here in the United States those who would violate our laws and would
destroy our communities, and taking away their illicit assets and
ability to do business are all vital tools in our war on drugs. These
tools must be expanded and enhanced even further in our fighting drugs.
Whether these drug kingpins be from Thailand, from Colombia, from
Mexico, or elsewhere around the globe, they must be held accountable to
the American people, to our institutions, and to all the laws they
violate, making us the targets of their criminal activity.
These drug traffickers, their families and business associates should
certainly not be able to benefit financially in their drug trade, for
example, seeking to enroll their children in our best schools and our
institutions of higher learning with their illicit proceeds from the
destruction they visit on our society.
Denying them the fruits of their crimes and entry visas for their
families to come to our Nation is another significant way to help
ensure that their illicit practice will be ended.
This bill will provide overall help, improve our efforts to hold
these major drug kingpins accountable. It will help take the profit and
benefit out of their deadly drug trade. For those relatives,
associates, and businesses that transact with these drug kingpins, the
bill before us indicates that our Nation is prepared to act and to take
the profit out of the drug trade.
Madam Speaker, I was honored to be an original cosponsor of this
proposal that has previously passed the Senate, and I am pleased to
help move forward with this proposal before we adjourn this first
session of the 106th Congress. Accordingly, I urge my colleagues to
join with us in this important initiative.
Madam Speaker, I yield the balance of my time to the gentleman from
Florida (Mr. McCollum), and I ask unanimous consent that he be
permitted to control that time.
The SPEAKER pro tempore. Is there objection to the request of the
gentleman from New York?
There was no objection.
Mr. NADLER. Madam Speaker, I yield myself such time as I may consume.
Madam Speaker, I rise in opposition to this legislation which I
believe possesses the threat of turning what Members of this House
would consider a laudable goal, cracking down on drug dealers, into a
much more dangerous enterprise.
This bill allows the President or the FBI or the Treasury Department
or the CIA to designate any person in the world as a drug kingpin, to
seize his or her assets, and to make an average American subject to a
decade in prison for doing business with such people.
The bill sets no standards for such a designation. The designation
requires no proof. The designation cannot, according to this bill, be
challenged or reviewed by a court of law. There is simply no way
provided to make the Government provide the proof we expect.
It also appears to bar the family, the American families of any such
individuals from entering the United States. Is this the America we
want, an America in which the President or some Federal bureaucrat can
simply designate someone as a bad guy and exclude American-born
individuals from the country, and freeze the assets of anyone they
desire, some of the assets which may be owed to law-abiding citizens?
Can we really suspend all judicial review and say to hell with due
process? What is the remedy if the bureaucracy gets the wrong person?
It would have been nice to have had a hearing on this bill and to
look at some of these questions in committee, but we did not. This bill
was not reviewed by the Committee on the Judiciary or by the
Subcommittee on the Constitution. It was rushed to the floor with no
adult supervision, which seems to mark every aspect of Republican rule
on Capitol Hill these days.
Real people will have to live with this bill. We owe all Americans a
duty to be careful and conscientious in the work we do, not to endow
the executive with untrammeled power over individual liberty in order
to make a statement.
This bill is an embarrassment to this House and a danger to our
freedoms. Constitutional liberty and due process are precious to this
country. Millions of our citizens have fought and died for liberty. In
the 1950s, the fear of Communism was used to justify invasions of our
traditional liberties. The Supreme Court overturned some of those
invasions.
Now that international Communism is no longer a threat to us, fear of
drugs is leading us down the same sad road to overturn our
constitutional liberties, to overturn the due process that alone
protects us and differentiates us from the Communist tyrannies we
opposed. In the name of the war against drugs, we should not overturn
liberty.
How can we say that the President or some bureaucrat can designate
anyone they want without any evidence, without any proof, without any
standards, and say that person will have his property seized, that
person can go to no court, can get no review, can confront no
witnesses? The court of Star Chamber would have been ashamed, and this
House should be ashamed and not pass this bill.
Madam Speaker, I reserve the balance of my time.
Mr. McCOLLUM. Madam speaker, I yield myself such time as I may
consume.
Madam Speaker, H.R. 3164, the Foreign Narcotics Kingpin Designation
Act of 1999, is a bill to identify, expose, isolate, and incapacitate
the businesses and the agents of major drug traffickers all over the
world and deny them access to the United States financial system and to
the benefits of trade and transactions involving U.S. businesses and
individuals.
United States individuals and companies are prohibited from engaging
in unlicensed transactions, including any commercial or financial
dealings, with any designated major drug trafficker or kingpin.
Properties and assets of these drug kingpins located in the United
States are blocked or frozen.
This bill is the product of several months of consultations involving
the Select Committee on Intelligence, Committee on International
Relations, the Committee on the Judiciary, and the Committee on Ways
and Means, as well as the detailed negotiations with the National
Security Council, the Treasury Department, the State Department, the
Justice Department, and the intelligence community. The Clinton
administration has carefully reviewed this legislation and now supports
this bill.
Madam Speaker, the gentleman from New York (Chairman Gilman) of the
House Committee on International Relations, the gentleman from Illinois
(Chairman Hyde) of the Committee on the Judiciary have each waived
jurisdiction and consideration of the bill in committee so that it can
come to the floor today prior to the conclusion of this session.
Although it did not receive referral on H.R. 3164, the Committee on
Ways and Means staff were consulted and offered language changes which
were incorporated into this bill.
I introduced an earlier version of this language with the gentleman
from Florida (Mr. Goss), the gentleman from New York (Mr. Rangel), and
the gentleman from New York (Mr. Gilman) last May. Senators Coverdell
and Feinstein did likewise on the Senate side and were successful in
attaching the proposal to the Intelligence Authorization bill by
unanimous consent of the Senate.
Unfortunately, the intelligence conference has been stalled due to
other
issues. In order to move the important national security legislation
that is involved here, the sponsors decided last week to offer this
bill as a stand-alone for consideration of all the Members.
Unlike earlier and more limited sanctions initiatives, the kingpins
bill is global in scope and focuses on major narco-trafficking groups
in Mexico, Colombia, the Caribbean, Southeast Asia, and Southwest Asia.
The legislation is carefully designed to focus our government's efforts
against the specific individuals most responsible for trafficking
illegal narcotics by attacking their sources of income and undermining
their efforts to launder their drug profits in legitimate business
activities.
The precedent for H.R. 3164 was the highly successful application of
sanctions since 1995 against the Cali Cartel narco-trafficking
organization and its key leaders. Executive Order 12978, issued by the
Clinton administration in October of 1995, has had the effect of
dismantling and defunding numerous business entities tied to the Cali
Cartel. The Specially Designated Narcotics Trafficker sanctions program
has been renewed every year, most recently this year, and has had
significant impact on both the Cali and the North Coast drug cartels in
Colombia.
As of October 21, 1999, the Colombian Special Designated Narcotics
Trafficking list totals 496 traffickers, comprised of 5 principals, 195
entities, and 296 individuals, with whom financial and business
dealings are prohibited and whose assets are blocked under Executive
Order 12978.
Of the 195 business entities designated, nearly 50 of these with an
estimated aggregate income of some $210 million had been liquidated or
were in the process of liquidation. These specific results augment the
less quantifiable but significant impact of denying the designated
individuals of entities of the Colombian drug cartels access to the
United States financial and commercial facilities.
Madam Speaker, I include for the RECORD the text of Executive Order
12978 of October 21, 1995, as well as a June 1998 Treasury document
entitled ``Impact of the Specially Designated Narcotics Traffickers
Program'' as follows:
[From the Federal Register, October 24, 1995]
Executive Order 12978 of October 21, 1995: Blocking Assets and
Prohibiting Transactions With Significant Narcotics Traffickers
By the authority vested in me as President by the
Constitution and the laws of the United States of America,
including the International Emergency Economic Powers Act (50
U.S.C. 1701 et seq.) (IEEPA), the National Emergency Act (50
U.S.C. 1601 et seq.), and section 301 of title 3, United
States Code.
I, WILLIAM J. CLINTON, President of the United States of
America, find that the actions of significant foreign
narcotics traffickers centered in Colombia, and the
unparalleled violence, corruption, and harm that they cause
in the national security, foreign policy, and economy of the
United States, and hereby declare a national emergency to
deal with that threat.
Section 1. Except to the extent provided in section 203(b)
of IEEPA (50 U.S.C. 1702(b)) and in regulations, orders,
directives, or licenses that may be issued pursuant to this
order, and notwithstanding any contract entered into or any
license or permit granted prior to the effective date, I
hereby order blocked all property and interests in property
that are or hereafter come within the United States, or that
are or hereafter come within the United States, or that are
or hereafter come within the possession or control of United
States persons, of:
(a) the foreign persons listed in the Annex to this order:
(b) foreign persons determined by the Secretary of the
Treasury, in consultation with the Attorney General and the
Secretary of State:
(i) to play a significant role in international narcotics
trafficking centered in Colombia; or
(ii) materially to assist in, or provide financial or
technological support for or goods or services in support of,
the narcotics trafficking activities of persons designated in
or pursuant to this order; and
(c) persons determined by the Secretary of the Treasury in
consultation with the Attorney General and the Secretary of
State, to be owned or controlled by, or to act for or on
behalf of, persons designated in or pursuant to this order.
Sec. 2 Further, except to the extent provided in section
203(b) of IEEPA and in regulations, orders, directives, or
licenses that may be issued pursuant to this order, and
notwithstanding any contract entered into or any license or
permit granted prior to the effective date. I hereby prohibit
the following:
(a) any transaction or dealing by United States persons or
within the United States in property or interests in property
of the persons designated in or pursuant to this order:
(b) any transaction by any United States person or within
the United States that evades or avoids, or has the purpose
of evading or avoiding, or attempts to violate, any of the
prohibitions set forth in this order.
Sec. 3. For the purposes of this order:
(a) the term ``person'' means an individual or entity;
(b) the term ``entity'' means a partnership, association,
corporation, or other organization, group or subgroup;
(c) the term ``United States person'' means any United
States citizen or national, permanent resident alien, entity
organized under the laws of the United States (including
foreign branches), or any person in the United States:
(d) the term ``foreign person'' means any citizen or
national of a foreign state (including any such individual
who is also a citizen or national of the United States) or
any entity not organized solely under the laws of the United
States or existing solely in the United States, but does not
include a foreign state; and
(e) the term ``narcotics trafficking'' means any activity
undertaken illicitly to cultivate, produce, manufacture,
distribute, sell, finance or transport, or otherwise assists,
abet, conspire, or collude with others in illicit activities
relating to, narcotic drugs, including, but not limited to,
cocaine.
Sec. 4. The Secretary of the Treasury, in consultation with
the Attorney General and the Secretary of State, is hereby
authorized to take such actions, including the promulgation
of rules and regulations, and to employ all powers granted to
the President by IEEPA as may be necessary to carry out this
order. The Secretary of the Treasury may redelegate any of
these functions to other officers and agencies of the United
States Government. All agencies of the United States
Government are hereby directed to take all appropriate
measures within their authority to carry out this order.
Sec. 5. Nothing contained in this order shall create any
right or benefit, substantive or procedural, enforceable by
any party against the United States, its agencies or
instrumentalities, its officers or employees, or any other
person.
Sec. 6. (a) This order is effective at 12:01 a.m. Eastern
Daylight Time on October 22, 1995.
(b) This order shall be transmitted to the Congress and
published in the Federal Register.
William J. Clinton,
The White House, October 21, 1995.
____
Impact of the Specially Designated Narcotics Traffickers Program
U.S. Department of the Treasury, Office of Foreign Assets Control,
International Programs Division, June 1998
the specially designated narcotics traffickers program
Executive Order 12978, signed by President Clinton on
October 21, 1995 under authority of the International
Emergency Economic Powers Act (``IEEPA''), found that the
activities of significant foreign narcotics traffickers
centered in Colombia and the unparalleled violence,
corruption, and harm that they cause constitute an unusual
and extraordinary threat to the United States' national
security, foreign policy and economy. Treasury's Office of
Foreign Assets Control (``OFAC'') enforces the narcotics
trafficking sanctions under Executive Order 12978. The
principal tool for implementing the sanctions is OFAC's list
of Specially Designated Narcotics Traffickers (``SDNTs'').
That list, known as ``la Lista Clinton'' (the Clinton list)
in Colombia, is developed by OFAC in close consultation with
the Justice and State Departments.
Companies and individuals are identified as SDNTs and
placed on the SDNT list if they are determined, (a) to play a
significant role in international narcotics trafficking
centered in Colombia, (b) to materially assist in or provide
financial or technological support for, or goods or services
in support of, the narcotics trafficking activities of
persons designated in or pursuant to the executive order, or
(c) to be owned or controlled by, or to act for or on behalf
of, persons designated in or pursuant to Executive Order
12978. The objectives of the SDNT program are to identify,
expose, isolate and incapacitate the businesses and agents of
the Colombian cartels and to deny them access to the U.S.
financial system and to the benefits of trade and
transactions involving United States businesses and
individuals.
U.S. individuals and companies are prohibited from engaging
in unlicensed transactions, including any commercial or
financial dealings, with any of the SDNTs. After designation
as an SDNT, all SDNT assets subject to U.S. jurisdiction are
blocked. This includes bank accounts, other property, and
interests in property. Violations carry criminal penalties of
up to $500,000 per violation for corporations and $250,000
for individuals, as well as imprisonment of up to 10 years.
Civil penalties of up to $11,000 per violation may be imposed
administratively.
summary
OFAC has listed 451 companies and individuals as SDNTs
against which the prohibitions and blocking authorities of
Executive Order 12978 apply. Since the inception of the SDNT
program in October 1995, OFAC has issued seven lists
identifying SDNTs. On May 26, 1998, the SDNT list was
expanded to
reach beyond the Cali cartel and now includes the names of
one of the leaders of Colombia's North Coast cartel, Julio
Cesar Nasser David, and 18 associated businesses and
individuals that Treasury has determined are acting as fronts
for the North Coast cartel. Work is underway on naming more
SDNTs.
The SDNT list is currently comprised of the four Cali
cartel kingpins named by President Clinton as significant
narcotics traffickers, the newly-designated significant North
Coast trafficker, Julio Cesar Nasser David, 154 companies,
and 292 additional individuals involved in the ownership or
management of the Colombian drug cartels' ``legitimate''
business empire. the SDNT businesses include a drugstore
chain, a supermarket chain, pharmaceutical laboratories, a
clinic, hotel and restaurant service companies, radio
stations, a communications company, poultry farms and
distributors, construction firms, real estate firms,
investment and financial companies, cattle ranches, and other
agricultural businesses. As a result of the SDNT program:
SDNTs have been forced out of business or are suffering
financially. Over 40 SDNT companies, with estimated combined
annual sales of over $200 million, were liquidated or in the
process of liquidation by February 1998.
DNTs are denied access to banking services in the U.S. and
Colombia, including bank accounts, loans, and credit cards;
and existing SDNT accounts have been terminated. OFAC has
identified nearly 400 closed Colombian accounts affecting
over 200 SDNTs.
SDNTs have been isolated and denied access to the benefits
of trade and transactions involving U.S. businesses, and
existing SDNT business relationships with U.S. firms have
been terminated. U.S. businessmen in Colombia have termed the
SDNT program as ``a good preventive measure'' that helps them
steer clear of the cartels' fronts and agents.
Individuals designated as SDNTs have suffered a ``civil
death.'' Many individuals named as SDNTs have lost their jobs
and have been blocked from entering the U.S. after their U.S.
visas were revoked. In addition, being an SDNT in Colombia
carries the overwhelming social stigma of being associated
with the drug cartels. Many Colombian businessmen have re-
evaluated their relationships with cartel fronts and agents
as a result of the sanctions.
SDNTs Forced Out of Business
SDNTs have been forced out of business or are suffering
financially since the implementation of the SDNT program in
October 1995. Over 40 SDNT companies, with estimated combined
annual sales of over U.S. $200 million, were liquidated or in
the process of liquidation by February 1998. Some SDNT
companies have attempted to continue operating through
changes in their company names and/or corporate structures.
To date, OFAC has placed a total of 18 of these successor
companies on the SDNT list under their new company names.
Copservir, the successor company to Drogas La Rebaja,
continues to suffer, even though its employees ostensibly
purchased the drugstore chain from Gilberto and Miguel
Rodriguez Orejuela and reorganized it under the new name.
Copservir has stated that it is forced to operate on a cash
basis and suffers financially because of the sanctions.
The SDNT poultry businesses owned by Helmer Herrera
Buitrago, among the largest poultry firms in Colombia, have
been forced to change names and reorganize in order to
continue operating. For example, one Herrera SDNT poultry
business, Valle de Oro S.A., with sales exceeding U.S. $8.5
million in 1995, has changed its name to Procesadora de
Pollos Superior S.A. and currently operates at a loss and is
deficient in working capital.
Six pharmaceutical laboratories owned by Miguel and
Gilberto Rodriguez Orejuela and designated as SDNTs have
liquidated or are in the process of liquidation. Three of the
six pharmaceutical laboratories reorganized under new company
names and corporate structures. OFAC listed these three
companies, Farmacoop, Pentacoop, and Cosmepop, as SDNTs in
April 1997. These three companies, however, all have a
reduced net worth and incomes and are deficient in working
capital.
An ``Iron Curtain'' between SDNTs and Financial Institutions
SDNTs are denied access to banking services in both the
U.S. and Colombia, including bank accounts, loans, and credit
cards; and existing SDNT accounts have been terminated. These
effects are in addition to the as yet unquantified, but very
real, costs to the SDNT companies and individuals of being
denied access to the U.S. financial and commercial systems.
As one prominent financial institution told OFAC, the SDNT
list has created an ``iron curtain'' between SDNTs and banks.
OFAC has identified nearly 400 closed accounts affecting
over 200 SDNTs. Anecdotal evidence points to hundreds more
closed accounts affecting SDNTs. This suggests that, in the
financial community as a whole, the vast majority of SDNTs
have lost access to banking services in Colombia as well as
in the U.S.
The Rodriguez Orejuela businesses of the Cali cartel have
been particularly damaged by the banks' actions. Copservir,
the successor company to SDNT Drogas La Rebaja, is now
operating largely on a cash basis because most banks refuse
to provide it services. Blocking actions by U.S. banks were
the primary reason for the liquidation of Laboratorios
Kressfor. Laboratorios Genericos Veterinarios de Colombia's
bank accounts were closed because of the sanctions, and the
company is now in liquidation.
Most Colombian banks have incorporated the SDNT list into
their internal compliance programs.
SDNTs are Isolated Commercially
SDNT have been isolated and denied access to the benefits
of trade and transactions involving U.S. businesses, and
existing SDNT business relationships with U.S. firms have
been terminated since the sanctions went into effect in
October 1995. U.S. businessmen in Colombia have termed the
SDNT program as ``a good preventive measure'' that helps them
steer clear of the cartels' fronts and agents. Copservir has
stated that, ``As a result of the economic sanctions . . . no
United States entity would conduct any business with the
[Drogas La Rebaja] chain stores.'' Specific examples of the
impact of the sanctions program on SDNT business
relationships include:
Alert letters sent by OFAC to major U.S. companies, both to
the parents in the U.S. and to their subsidiaries in
Colombia, resulted in the cooperation of U.S. subsidiaries in
terminating business relationships with SDNTs. One company
sought OFAC's assistance in identifying companies trying to
hide their connections to SDNTs, U.S. firms, including
subsidiaries, have complied with the requirements of the SDNT
program.
Alert letters sent by OFAC to nearly 5000 Colombian firms,
suppliers of SDNTs prior to the implementation of sanctions
in October 1995, resulted in pledges of cooperation and
promises of compliance from many of the recipients. One
Colombian chemical company, with several U.S. chemical
manufacturing licenses, directed its subsidiaries to
terminate all dealings with SDNTs.
A U.S. pharmaceutical company declined a purchase request
from a suspect Colombian firm, based on information published
in the SDNT list. A major European pharmaceutical company
publicly announced that it would review its business
relationship with an SDNT, after the press reported that it
was selling drugs to an SDNT.
SDNT Individuals Suffer a ``Civil Death''
Individuals designated as SDNTs have suffered a ``civil
death.'' Before an individual is permitted to open a new
account, banks check ``the Clinton list.'' Many individuals
named as SDNTs have lost their jobs. Many Colombian
businessmen have re-evaluated their relationships with cartel
fronts and agents as a result of the sanctions.
SDNTs have been blocked from entering the U.S. after losing
their U.S. visas. Under State Department procedures, U.S.
visas of newly-designated individuals will be revoked and any
application for a U.S. visa for an SDNT individual may be
denied.
Being an SDNT in Colombia carries the overwhelming social
stigma of being associated with the drug cartels. William
Rodriguez, the son of imprisoned Cali cartel leader Miguel
Rodriguez Orejuela, has publicly stated that ``being a
Rodriguez these days (i.e., being on the SDNT list) is worse
than having AIDS.''
The Drogas La Rebaja drugstore chain, listed as an SDNT
business since the inception of the SDNT program in October
1995, has been the lynchpin of the ``legitimate'' business
activity of imprisoned Cali cartel leaders Gilberto and
Miguel Rodriguez Orejeula. The Drogas La Rebaja drugstore
chain, with annual profits for 1995 of over U.S. $16.3
million, saw its profits plummet in 1996. By early July 1996,
William Rodriquez, the son of Cali cartel leader Miguel
Rodriguez Orejuela, told a Colombian news magazine that
cartel-linked companies cannot get service at local banks and
said ``businesses like Drogas La Rebaja . . . may have shut
down.''
In an effort to evade the sanctions and distance itself
from its cartel owners, Drogas La Rebaja was ostensibly sold
to its 4,000 employees for approximately U.S. $32 million on
July 31 1996. Copservir, the new name of the employee-owned
drugstore chain, continued to use Drogas La Rebaja as a trade
name and attempted to open local bank accounts and establish
business ties with U.S. firms after the purchase. In April
1997, OFAC listed Copservir as an SDNT. As a result of the
sanctions, Copservir is forced to operate on a cash basis and
suffers financially.
DROGAS LA REBAJA'S EARNINGS
[In millions of US dollars]
------------------------------------------------------------------------
Sales Profits
-----------------------------------
1995 1996 1995 1996
------------------------------------------------------------------------
Drogas La Rebaja (Eight regions).... 139.1 111.3 16.3 4.9 *
------------------------------------------------------------------------
* 1996 data for Cali region is unavailable.
Source: Public records.
Madam Speaker, the administration has indicated that this list will
continue to be expanded to include additional drug trafficking
organizations centered in Colombia and their fronts.
Madam Speaker, I include for the Record the October 19, 1999, message
from the President transmitting notification that the national
emergency regarding significant narcotics traffickers centered in
Colombia is to continue for an additional year, as well as the October
20, 1999, message from the President transmitting a 6-month periodic
report on significant narcotics traffickers centered in Colombia, as
follows:
National Emergency Regarding Significant Narcotics Traffickers Centered
in Colombia
message from the president of the united states transmitting
notification that the emergency declared with respect to significant
narcotics traffickers centered in Colombia is to continue in effect for
one year beyond October 21, 1999, pursuant to 50 u.s.c. 1622(d):
To the Congress of the United States:
Section 202(d) of the National Emergencies Act (50 U.S.C.
1622(d)) provides for the automatic termination of a national
emergency unless, prior to the anniversary date of its
declaration, the President publishes in the Federal Register
and transmits to the Congress a notice stating that the
emergency is to continue in effect beyond the anniversary
date. In accordance with this provision, I have sent the
enclosed notice to the Federal Register for publication,
stating that the emergency declared with respect to
significant narcotics traffickers centered in Colombia is to
continue in effect for 1 year beyond October 21, 1999.
The circumstances that led to the declaration on October
21, 1995, of a national emergency have not been resolved. The
actions of significant narcotics traffickers centered in
Colombia continue to pose an unusual and extraordinary threat
to the national security, foreign policy, and economy of the
United States and to cause unparalleled violence, corruption,
and harm in the United States and abroad. For these reasons,
I have determined that it is necessary to maintain in force
the broad authorities necessary to maintain economic pressure
on significant narcotics traffickers centered in Colombia by
blocking their property subject to the jurisdiction of the
United States and by depriving them of access to the United
States market and financial system.
William J. Clinton.
The White House, October 19, 1999.
Notice
Continuation of Emergency With Respect to Significant Narcotics
Traffickers Centered in Colombia
On October 21, 1995, by Executive Order 12978, I declared a
national emergency to deal with the unusual and extraordinary
threat to the national security, foreign policy, and economy
of the United States constituted by the actions of
significant foreign narcotics traffickers centered in
Colombia, and the unparalleled violence, corruption, and harm
that they cause in the United States and abroad. The order
blocks all property and interests in property of foreign
persons listed in an Annex to the order, as well as foreign
persons determined to play a significant role in
international narcotics trafficking centered in Colombia, to
materially assist in, or provide financial or technological
support for or goods or services in support of, the narcotics
trafficking activities of persons designated in or pursuant
to the order, or to be owned or controlled by, or to act for
or on behalf of, persons designated in or pursuant to the
order. The order also prohibits any transaction or dealing by
United States persons or within the United States in such
property or interests in property. Because the activities of
significant narcotics traffickers centered in Colombia
continue to threaten the national security, foreign policy,
and economy of the United States and to cause unparalleled
violence, corruption, and harm in the United States and
abroad, the national emergency declared on October 21, 1995,
and the measures adopted pursuant to respond to that
emergency, must continue in effect beyond October 21, 1999.
Therefore, in accordance with section 202(d) of the National
Emergencies Act (50 U.S.C. 1622(d)), I am continuing the
national emergency for 1 year with respect to significant
narcotics traffickers centered in Colombia.
This notice shall be published in the Federal Register and
transmitted to the Congress.
William J. Clinton.
The White House, October 19, 1999.
____
Six Month Periodic Report on Significant Narcotics Traffickers Centered
in Colombia
message from the president of the united states transmitting a 6-month
periodic report on the national emergency with respect to significant
narcotics traffickers centered in colombia that was declared in
executive order no. 12978 of october 21, 1995, pursuant to 50 u.s.c.
1703(c)
To the Congress of the United States:
As required by section 401(c) of the National Emergencies
Act, 50 U.S.C. 1641(c), and section 204(c) of the
International Emergency Economic Powers Act (IEEPA), 50
U.S.C. 1703(c), I transmit herewith a 6-month periodic report
on the national emergency with respect to significant
narcotics traffickers centered in Colombia that was declared
in Executive Order 12978 of October 21, 1995.
William J. Clinton.
The White House, October 20, 1999.
PRESIDENT'S PERIODIC REPORT ON THE NATIONAL EMERGENCY WITH RESPECT TO
SIGNIFICANT NARCOTICS TRAFFICKERS CENTERED IN COLOMBIA
I hereby report to the Congress on the developments since
my last report concerning the national emergency with respect
to significant narcotics traffickers centered in Colombia
that was declared in Executive Order No. 12978 of October 21,
1995. This report is submitted pursuant to section 401(c) of
the National Emergencies Act, 50 U.S.C. 1641(c), and section
204(c) of the International Emergency Economic Powers Act
(``IEEPA''), 50 U.S.C. 1703(c).
1. On October 21, 1995, I signed Executive Order 12978,
``Blocking Assets and Prohibiting Transactions with
Significant Narcotics Traffickers'' (the ``Order'') (60 Fed.
Reg. 54579, October 24, 1995). The Order blocks all property
subject to U.S. jurisdiction in which there is any interest
of four significant foreign narcotics traffickers, two of
whom are now deceased, who were principals in the so-called
Cali drug cartel centered in Colombia. These four principals
are listed in the annex to the Order. The Order also blocks
the property and interests in property of foreign persons
determined by the Secretary of the Treasury, in consultation
with the Attorney General and the Secretary of State: (a) to
play a significant role in international narcotics
trafficking centered in Colombia; or (b) materially to assist
in or provide financial or technological support for, or
goods or services in support of, the narcotics trafficking
activities of persons designated in or pursuant to the Order.
In addition, the Order blocks all property and interests in
property subject to U.S. jurisdiction of persons determined
by the Secretary of the Treasury, in consultation with the
Attorney General and the Secretary of State, to be owned
or controlled by, or to act for or on behalf of, persons
designated in or pursuant to the Order (collectively
``Specially Designated Narcotics Traffickers'' or
``SDNTs'').
The Order further prohibits any transaction or dealing by a
United States person or within the United States in property
or interests in property of SDNTs, and any transaction that
evades or avoids, has the purpose of evading or avoiding, or
attempts to a violate, the prohibition contained in the
Order.
Designations of foreign persons blocked pursuant to the
Order are effective upon the date of determination by the
Director of the Department of the Treasury's Office of
Foreign Assets Control (``OFAC'') acting under authority
delegated by the Secretary of the Treasury. Public notice of
blocking is effective upon the date of filing with the
Federal Register, or upon prior actual notice.
2. On October 24, 1995, the Department of the Treasury
issued a Notice containing 76 additional names of persons
determined to meet the criteria set forth in Executive Order
12978 (60 Fed. Reg. 54582, October 24, 1995). Additional
Notices expanding and updating the list of SDNTs were
published on November 29, 1995 (60 Fed. Reg. 61288), March 8,
1996 (61 Fed. Reg. 9523), and January 21, 1997 (62 Fed. Reg.
2903).
Effective February 28, 1997, OFAC issued the Narcotics
Trafficking Sanctions Regulations (``NTSR'' or the
``Regulations''), 31 C.F.R. Part 536, to further implement
the President's declaration of a national emergency and
imposition of sanctions against significant foreign narcotics
traffickers centered in Colombia (62 Fed. Reg. 9959, March 5,
1997).
On April 17, 1997 (62 Fed. Reg. 19500, April 22, 1997),
July 30, 1997 (62 Fed. Reg. 41850, August 4, 1997), September
9, 1997 (62 Fed. Reg. 48177, September 15, 1997), and June 1,
1998 (63 Fed. Reg. 29608, June 1, 1998), OFAC amended
appendices A and B to 31 C.F.R. chapter V, revising
information concerning individuals and entities who have been
determined to play a significant role in international
narcotics trafficking centered in Colombia or have been
determined to be owned or controlled by, or to act for or on
behalf of, or to be acting as fronts for the Cali cartel in
Colombia.
On May 27, 1998 (63 Fed. Reg. 28896, May 27, 1998), OFAC
amended appendices A and B to 31 C.F.R. chapter V, by
expanding the list for the first time beyond the Cali cartel
by adding the name of one of the leaders of Colombia's North
Coast cartel, Julio Cesar Nasser David, who has been
determined to play a significant role in international
narcotics trafficking centered in Colombia, and 14 associated
businesses and four individuals acting as fronts for the
North Coast cartel. Also added were six companies and one
individual that have been determined to be owned or
controlled by, or to act for or on behalf of, or to be acting
as fronts for the Cali cartel in Colombia. These changes to
the previous SDNT list brought it to a total of 451
businesses and individuals.
On June 25, 1999, OFAC amended appendix A to 31 C.F.R.
chapter V by adding the names of eight individuals and 41
business entities acting as fronts for the Cali or North
Coast cartels and supplementary information concerning 44
individuals already on the list (64 Fed. Reg. 34984, June 30,
1999). The entries for four individuals previously listed
as SDNTs were removed from appendix A because OFAC had
determined that these individuals no longer meet the
criteria for designation as SDNTs. These actions are part
of the ongoing interagency implementation of Executive
Order 12978 of October 21, 1995. The addition of these 41
business entities and eight individuals to appendix A (and
the removal of four individuals) brings the total number
of SDNTs to 496 (comprised of five principals, 195
entities, and 296 individuals) with whom financial and
business dealings are prohibited and whose assets are
blocked under the 1995 Executive Order. The SDNT list will
continue to be expanded to include additional drug
trafficking organizations centered in Colombia and their
fronts.
3. OFAC has disseminated and routinely updated details of
this program to the financial, securities, and international
trade communities by both electronic and conventional media.
In addition to bulletins to banking institutions via the
Federal Reserve System and the Clearing House Interbank
Payments Systems (CHIPS), individual notices were provided to
all relevant state and federal regulatory agencies, automated
clearing houses, and state and independent banking
associations across the country. GFAC contacted all major
securities industry associations and regulators. It posted
electronic notices on the Internet, more than ten computer
bulletin boards and two fax-on-demand services, and provided
the same material to the U.S. Embassy in Bogota for
distribution to U.S. companies operating in Colombia.
4. As of September 15, 1999, GFAC had issued 14 specific
licenses pursuant to Executive Order No. 12978. These
licenses were issued in accordance with established Treasury
policy authorizing the completion of pre-sanction
transactions, the receipt of payment of legal fees for
representation of SDNTs in proceedings within the United
States arising from the imposition of sanctions, and certain
administrative transactions. In addition, a license was
issued to authorize a U.S. company in Colombia to make
certain payments to two SDNT-owned entities in Colombia
(currently under the control of the Colombian government) for
services provided to the U.S. company in connection with the
U.S. company's occupation of office space and business
activities in Colombia.
5. The narcotics trafficking sanctions have had a
significant impact on the Colombian drug cartels. SDNTs have
been forced out of business or are suffering financially. Of
the 195 business entities designated as SDNTs as of September
7, 1999, nearly 50, with an estimated aggregate income of
more than $210 million, had been liquidated or were in the
process of liquidation. Some SDNT companies have attempted to
continue to operate through changes in their company names
and/or corporate structures. OFAC has placed a total of 27 of
these successor companies on the SDNT list under their new
company names.
As a result of OFAC designations, Colombian banks have
closed nearly 400 SDNT accounts, affecting nearly 200 SDNTs.
One of the largest SDNT commercial entities, a discount
drugstore with an annual income exceeding $136 million, has
been reduced to operating on a cash basis. Another large SDNT
commercial entity, a supermarket with an annual income
exceeding $32 million, entered liquidation in November 1998
despite changing its name to evade the sanctions. An SDNT
professional soccer team was forced to reject and invitation
to play in the United States, two of its directors resigned,
and the team now suffers restrictions affecting its
business negotiations, loans, and banking operations.
These specific results augment the less quantifiable but
significant impact of denying the designated individuals
and entities of the Colombian drug cartels access to U.S.
financial and commercial facilities.
Various enforcement actions carried over from prior
reporting periods are continuing and new reports of
violations are being aggressively pursued. Since the last
report, OFAC has collected no civil monetary penalties but is
continuing to process a case for violations of the
Regulations.
6. The expenses incurred by the Federal Government in the
six-month period from October 21, 1998 through April 20,
1999, that are directly attributable to the exercise of
powers and authorities conferred by the declarations of the
national emergency with respect to Significant Narcotics
Traffickers, are estimated at approximately $650,000.
Personnel costs were largely centered in the Department of
the Treasury (particularly in the Office of Foreign Assets
Control, the U.S. Customs Service, and the Office of the
General Counsel, the Department of Justice, and the
Department of State. These data do not reflect certain costs
of operations by the intelligence and law enforcement
communities.
7. Executive Order 12978 provides this Administration with
a tool for combating the actions of significant foreign
narcotics traffickers centered in Colombia and the
unparalleled violence, corruption, and harm that they cause
in the United States and abroad. The Order is designed to
deny these traffickers the benefit of any assets subject to
the jurisdiction of the United States and to prevent United
States persons from engaging in any commercial dealings with
them, their front companies, and their agents. Executive
Order 12978 and its associated SDNT list demonstrate the
United States' commitment to end the damage that such
traffickers wreak upon society in the United States and
abroad. The SDNT list will continue to be expanded to include
additional Colombian drug trafficking organizations and their
fronts.
The magnitude and the dimension of the problem in
Colombia--perhaps the most pivotal country of all in terms of
the world's cocaine trade--are extremely grave. I shall
continue to exercise the powers at my disposal to apply
economic sanctions against significant foreign narcotics
traffickers and their violent and corrupting activities as
long as these measures are appropriate, and will continue to
report periodically to the Congress on significant
developments pursuant to 50 U.S.C. 1703(c).
Madam Speaker, H.R. 3164 is closely modeled on the precedents and
procedures established under the Executive Order just mentioned. The
kingpins bill codifies the interagency designation process and ensures
proper and timely congressional oversight of such designations by the
various committees of jurisdiction and is involved in this matter.
Our intent is to use the success of the Colombia Specially Designated
Narcotics Traffickers program to apply these methods on a global basis
against all the significant drug traffickers.
The bill blocks or freezes all property or assets subject to U.S.
jurisdiction with which there is any interest of significant foreign
narcotics traffickers.
{time} 1200
It also blocks the property and interests in property of foreign
persons determined by the Secretary of the Treasury, in consultation
with the Attorney General, the Director of Central Intelligence, the
Director of the Federal Bureau of Investigation, the Administrator of
the Drug Enforcement Administration, the Secretary of State, and the
Secretary of Defense, A, to play a significant role in international
narcotics trafficking; or, B, to materially assist in or provide
financial or technological support for, or goods or services in support
of, the narcotics trafficking activities of persons designated by the
executive branch or pursuant to this legislation.
In addition, the bill blocks all property and interests in property
subject to U.S. jurisdiction of foreign persons determined by the
Secretary of Treasury to be owned or controlled by, or to act for or on
behalf of persons designated bay the executive branch pursuant to this
legislation.
The bill carries criminal penalties of up to 10 years in prison and
$10 million in fines for somebody who violates this act, or for anyone
who refuses or willfully neglects to comply with any presidential order
under the bill. Officers or agents of corporations or other entities
could get up to 30 years in prison, and there are civil fines.
The kingpins bill will ensure congressional input and oversight of
this designation in the sanctions process. Starting next June 1, and
every June 1 thereafter, the President will be required to submit to
Congress an unclassified report that publicly identifies the foreign
persons that the President determines are appropriate for sanctions
under the act and publicly details the President's intent to impose
sanctions on these significant foreign narcotics traffickers.
The President will further be required to submit a classified report
to the congressional intelligence committees on July 1 of each year
detailing the status of the sanctions, including personnel and
resources directed toward the imposition of such sanctions during the
preceding year, with background information with respect to newly
identified significant foreign narcotics traffickers and their
activities. This report, the classified one, will describe any and all
actions the President intends to undertake or has undertaken against
such narcotics traffickers.
The kingpins process is carefully structured to protect intelligence
and law enforcement community sources and methods from exploitation by
persons linked to these groups. Designations of foreign persons blocked
pursuant to the legislation will be effective upon the date of
determination by the director of the Treasury's Office of Foreign
Assets Control, acting under the authority of the Secretary of the
Treasury. Public notice of the blocking is effective upon the date of
the filing with the Federal Register or upon actual notice. The Office
of Foreign Assets Control has disseminated and routinely updates
details of the Colombian program and certainly can do so here as well.
With respect to the Colombian program that exists now, the Office of
Foreign Assets Control contacted all major securities industry
associations and regulators, posted electronic notices on the Internet
and computer bulletin boards, and two fax-on-demand services, and
provided the same material to the U.S. Embassy in Bogota, and I would
expect them to do so under this bill.
The kingpins process is intended to supplement not replace United
States policy of annual certification of countries based on their
performance in
combating narcotics trafficking. Its sponsors' intent is that the
implementation of this bill will require additional resources in
personnel from intelligence and law enforcement communities to make it
a truly global process. It is my hope the administration will request
additional funding for fiscal year 2001 for all of those concerned to
make this process work. The success of the Colombian program has
largely been the product of close U.S. cooperation with Colombian law
enforcement and regulatory agencies, and we would expect the same with
all of the other countries today.
I strongly urge the support of this bill and the adoption of it.
Mr. Speaker, I reserve the balance of my time.
Mr. CROWLEY. Mr. Speaker, I yield 4 minutes to the gentleman from New
York (Mr. Rangel).
(Mr. RANGEL asked and was given permission to revise and extend his
remarks.)
Mr. RANGEL. Mr. Speaker, I have been in the Congress for close to 3
decades. I have heard more presidents declare war against drugs, and
the results really have been declaring war against young people.
If we were to take a look at the results of this war, we will find
that we have about 2 million young people locked up in jail. Most all
of these people come from minority communities that have been addicted
to drugs, they have been arrested and, in most cases, have had
mandatory sentences, where judges do not even consider the facts and
circumstances surrounding the violation of the law.
These are not drug traffickers or kingpins or people that we were
supposed to declare war against. And more often than not, we find that
the public school systems located in the areas where we find the most
arrests are systems that are not providing education to these people.
Is it right? Is it legal? Of course not. Should it be dealt with? Of
course it should. But the war that has not been declared is the war
against those people that manipulate our republic, that manipulate the
bank system, that are able to do these things because they have the
funds and they do not end up in jail.
It seems to me that what this legislation says, which I am an
original sponsor of, is that we are going to declare war against those
people that not only violate our law but are a threat to our national
security. When before have we heard that we are reaching out for the
strong resources of these United States, the President, the Justice
Department, which includes the FBI, and we are talking about the CIA
and all of the forces that are supposed to protect the United States of
America, to get to the people, like terrorists, who do not deserve the
support of the United States Constitution? We are asking the President
to declare war, to bring in the Department of Defense, and not to allow
people to use our system in order to bring the poison into the United
States where weak people and untrained people become the ultimate
person that is being destroyed.
We see right now that we are building more jails than we are schools,
and State legislatures all over the country are fighting for prisons to
be located in their rural districts rather than support for farmers.
And what we are seeing right now is that international drug traffickers
who use our banks, who use our systems are a threat to our system.
Now, we can get some people who want to find out what their
constitutional rights are, but I tell my colleagues this, it just seems
to me that we should not just concentrate on those who violate the laws
on our streets and are arrested in the streets, but those who violate
our national law and the international law. The people that we find
doing the 5 and the 10 and the 20 and the 30 years are not the people
who are banking and financing the drug trafficking in this country.
They do not grow the drugs, they do not manufacture the drugs, they do
not process the drugs, they do not use our banking system. They are
guilty. They are guilty of using the drugs and selling the drugs in
order to maintain their habits, and they should go to jail. But that
should not be the direction in which we have our national drug policy.
We should go after the worst of the lot; those who are sober, those
who have clear thinking, those who have no regard at all for their
fellow man, those that use the system, make the money, hire the lawyers
and manipulate the United States of America. I hope what this means is
when the President declares war, he is bringing all of the people that
have the intelligence, that have the power to take these people, take
their assets, and let them know, ``Not in our country can they do
that.''
Mr. NADLER. Mr. Speaker, I yield myself such time as I may consume.
Mr. Speaker, the distinguished gentleman from New York (Mr. Rangel)
put his finger on several of the aspects of this bill. He is quite
right, we should not be jailing drug users for 20 and 30 years. Those
are silly laws. And we should go after the drug kingpins, clearly. But
then he said we should declare war against people who do not deserve
the protection of the United States Constitution, unquote.
Everybody deserves the protection of the United States Constitution,
Mr. Speaker. Everybody who is in this country or has property in this
country deserves the protection of the United States Constitution. That
is the basis of constitutional liberty. Once we say that someone, no
matter how heinous a criminal or vile a villain does not deserve due
process of law, once we say that we can tear down the laws that we have
erected for the protection of our liberties to get at the devil, then,
as Sir Thomas More says, there is no protection for anybody.
That is what this bill does. This bill says that if the President or
the Secretary of the Treasury declares so-and-so a drug kingpin, we
will seize that person's property, without any due process of law,
without any hearing, without any evidence or without any proof. And he
has no recourse. No lawyer on his behalf may go into court and say the
Secretary's wrong; that they have the wrong person, there is no
evidence he is a drug kingpin. Perhaps the President really designated
him because he did not like his political views or he did not give a
large enough campaign contribution, assuming some future villainous
president.
The fact is there has to be due process, no matter how vile the
villain. We do not believe in lynch laws. We do not string up the
rapist until after he has a fair trial. And this bill goes against
this.
The gentleman from New York (Mr. Rangel) said, ``They are guilty.''
Yes, the drug kingpins are guilty, but is the individual designated
really a drug kingpin? Do we not need evidence; do we not need some due
process?
Again, in the name of wars, we often destroy liberty. In the name of
the drug war, we are going further and further down a road to destroy
the liberty that we hold so precious. This bill is a large step in that
direction.
Why does the bill say there shall be no judicial review of the
designation or the determination by the President; because we do not
trust the courts or because we want to cut corners, and getting a drug
kingpin is more important than protecting our liberty? If we did not
have that paragraph in this bill, if judicial review were allowed to
people whose property is going to be seized because the President or
the Secretary of State thinks they are a drug kingpin, maybe this bill
would be defensible. But as it is, it is simply a bill that says let us
tear up the Constitution, let us go back before the Magna Carta, the
king is always right, no one can question him, the President is a king.
This bill should not be passed.
Mr. Speaker, I reserve the balance of my time.
Mr. McCOLLUM. Mr. Speaker, I yield 4 minutes to the gentleman from
Florida (Mr. Goss), coauthor of this bill and chairman of the Permanent
Select Committee on Intelligence.
(Mr. GOSS asked and was given permission to revise and extend his
remarks.)
Mr. GOSS. Mr. Speaker, I am pleased to join my colleague, the
distinguished gentleman from Florida (Mr. McCollum), in offering H.R.
3164, the Foreign Narcotics Kingpin Designation Act, for the House's
consideration this morning. It is an important piece of legislation.
Since its attachment by Senators Coverdell and Feinstein to the
Senate version of the intelligence authorization bill last July, the
kingpins bill has been the subject of extensive negotiation among the
committees of jurisdiction and the Clinton administration.
Because this provision has now been caught up with some unrelated
problems in the intelligence conference and the intelligence bill, we
felt it important that the extensive work that has been done to perfect
this legislation not be lost in the waning days of this session and,
thus, here we are.
As a result, the House today has a chance to endorse an even better
bill, sending a strong signal that we intend to win the war on drugs by
going after the criminals who make themselves rich at the expense of
America's young people and so many other unsuspecting victims and
helpless addicts around the world.
The kingpins legislation takes the successful model of the Colombia
kingpin program that was established under Executive Order 12978 in
1995, and creates an annual kingpin designation process, global in
scope and subject to rigorous congressional oversight. I repeat,
rigorous congressional oversight. The kingpins list will be the result
of a tested and continuing interagency review process that incorporates
verifiable information from the law enforcement and intelligence
communities on the illicit activities of significant foreign narcotics
trafficking entities.
The process includes safeguards that are present to protect the
innocent. An unclassified listing of kingpins, their business
associates, and their related entities will be sent to the Congress on
an annual basis beginning on June 1, 2000. A classified report on the
specific activities and findings of the kingpins program will be
provided to the intelligence committees beginning on July 1, 2000.
Our goal is simple: To identify kingpins and their supporting
organizations in Latin America, the Caribbean, Southeast and Southwest
Asia, Europe, the former Soviet Union, Africa, and elsewhere. Following
identification, the process will then seek to disrupt and dismantle
these foreign criminal cartels.
In my view, the kingpins mechanism represents a proven and a powerful
capability for the President and the Congress to improve the counter-
drug performance of ourselves and our allies in the war against drugs.
As important, it intensifies the legal and financial pressure on
significant multinational criminal organizations. And, third, it
encourages greater cooperation and information sharing between the
United States agencies and our foreign counterparts, who are indeed
very helpful on the war on drugs.
In the case of Colombia, for example, the program has been singularly
successful against the Cali cartel because of the assistance furnished
by Colombian law enforcement and regulatory agents.
Mr. Speaker, I will insert for the Record an August 27, 1999 op-ed
from the New York Times on the kingpins bill and an October 13, 1999
letter to Senator Coverdell on the kingpins provision be included in
the Record. These are especially instructive pieces of commentary.
In a recent Southwest Florida town meeting on what our communities
can do to better fight the war on drugs, I stressed the many levels on
which we need to wage battle.
{time} 1315
We have to look at the demand and we have to look at supply and
everything in between and what is going on in our community and what is
happening halfway around the world. So we have this bill today which
sends a very clear strong message to our kids that we will go to the
mat for them, that we are sending a clear signal to the narcotics bad
guys that we are coming after them where it hurts them most, in their
pocketbook, going after their profits. I think that is sort of
critical.
I wish to commend all those who have worked in this effort, starting
particularly at the very top with the gentleman from Illinois (Speaker
Hastert), whose leadership and consistent commitment to this effort has
been unwavering, as has been his support.
I urge all Members to take a good close look at this resolution. I
cannot imagine any reason in the world to vote against it. I think
there is every reason to vote for it. I urge their support after their
careful consideration.
Mr. Speaker, I include the following statements for the Record:
[From the New York Times, August 27, 1999]
Vote on Drugs
(By A.M. Rosenthal)
Notice to the public:
Vote now on drugs, one of the only two ways.
1. If you support the war against drugs, vote now for
pending Congressional legislation designed to wound major
drug lords around the world. It cuts them off from all
commerce with the U.S., now a laundry for bleaching the blood
from drug-trade billions and turning them into investments in
legitimate businesses.
Vote by telling your members of Congress that when the
House-Senate bill authorizing intelligence funds comes up for
final decision, probably next month, you want them to vote
for the section called ``blocking assets of major narcotics
traffickers.''
Insist they start now to tell the Administration not to try
to water it down to satisfy any country for diplomatic or
economic reasons--including Mexico, the biggest drug entry
point for America, already complaining about ``negative
consequences'' of the proposal.
Turn yourself and your civil, labor or commercial
organization, or religious congregation, into lobbies for the
bill--counterweight to the lobbies of drug-transfer nations
and American companies beholden to them.
2. If you are against the war on drugs or just don't care
about what drugs are doing to our country, then don't do a
thing. That is a vote, too.
That's the way it is in Washington. Members of Congress
introduce legislation, committees discuss it for months,
votes are taken and then when the time comes to work out
House-Senate differences, administrations on the fence and
under professional lobbyists' pressure use their power to try
to mold the legislation to their liking. That is exactly the
time for ordinary Americans around the country to do their
own lobbying.
The bill targeting drug lords extends throughout their
vicious world the economic sanctions already directed at
Colombian drug lords, by President Clinton's executive order.
It will prohibit any U.S. commerce by specifically named drug
operators, seize all their assets in the U.S., and ban
trading with them by American companies.
The bill specifies that every year the U.S. Government list
the major drug lords of the world, by name and nation. The
lists are certain to include top drug traders from countries
such as Afghanistan, Jamaica, the Dominican Republic,
Thailand and Mexico.
In the Senate it was introduced by Paul Coverdell, a
Georgia Republican, and Dianne Feinstein, Democrat from
California, and passed with bipartisan support. In the House
it also has support in both parties, including Porter Goss of
Florida, a Republican and chairman of the House Intelligence
Committee, and Charles Rangel, the New York Democrat. It
waits the final September House-Senate Joint Intelligence
Committee vote.
For awhile I heard from within the Administration the kind
of mutters that preceded the Clinton certification last year
that Mexico was carrying out anti-drug commitments
satisfactorily, which was certainly a surprise to Mexican
drug lords.
Then, yesterday, the White House told me that it favored
some target sanctions.
Its objection to the bill was that the Administration would
have to list all major drug lords for the President to choose
targets, and that could endanger investigations. The White
House said it would be better for the President to select
targets without having to choose from a list.
Bit of a puzzle. The bill already gives him the right to
decide which of the drug lords to target from the
Administration's unpublished list. But some members of
Congress think the motive is to avoid a list that might
include just a little too many from a ``sensitive country.''
No one bill will end the drug war. Only the determination
of Americans to use every sort of resource will do that--
parental teaching, law enforcement with some compassion
toward first offenders and none for career drug criminals,
enough money for therapy in and out of jails, targeting drug
lords--and passionate leadership.
That would preclude Presidential candidates who mince
around about whether they used drugs when they were younger--
unless they grow up publicly and quickly.
Dr. Mitchell S. Rosenthal, head of the Phoenix House
therapeutic communities, says that the bill ``reflects the
kind of values that we don't hear enough these days.'' So
vote--one way or the other.
____
Department of the Treasury,
Washington, DC, October 13, 1999.
Hon. Paul Coverdell,
U.S. Senate, Washington, DC.
Dear Senator Coverdell: You have requested the views of the
Office of Foreign Assets Control regarding two specific
provisions in draft legislation to impose sanctions against
significant foreign narcotics traffickers contained in the
intelligence Authorization Bill (that has been characterized
to us as the Senate Intelligence Committee version). We
discuss each of those below without addressing the larger
issues of the proposed legislation that are being addressed
separately by the Administration.
``knowing'', Willful'', or ``Intentional''
We object to the addition of any of the following words
into the administrative process
for identifying significant foreign narcotics traffickers and
their organizations: ``knowing'', ``willful'', or
``intentional''. It has been proposed to insert ``knowing and
willful'' (alternatively ``intentional'') into section
703(a)(1)(A) [page 4, line 20], and into the definition of
``significant foreign narcotics trafficker'' in section
708(5) [page 20, lines 25-26].
The use of ``knowing'', ``willful'', or ``intentional''
would impose an unreasonable additional obstacle to the
designation of foreign narcotics kingpins and their
organizations. It sets a higher evidentiary threshold, making
it more difficult for the Secretary to compile a sufficient
record upon which to recommend significant foreign narcotics
traffickers and their organizations for designation by the
President. Documenting the state of mind of a foreign
narcotics trafficker is likely to be difficult, if not
impossible, even when there is, in fact, no doubt about that
person's narcotics trafficking activities. In the case of a
trafficker's organization, there is no viable means to assert
that an organization has a ``state of mind'' much less to
prove what constitutes that organization's ``state of mind.''
We believe that the existing standards for designation are
rigorous enough to avoid arbitrary and capricious actions
under the proposed law.
The findings and purpose provisions of sections 701 and 702
make clear that the proposed sanctions legislation is
attempting to follow the model established by the IEEPA
program against Colombian cartels. Such sanctions are not
aimed at proving or prosecuting the specific narcotics
trafficking cases of other crimes of the kingpins and their
organizations. They are directed at denying the traffickers
and their organizations (including their business enterprises
and agents) access to the benefits of trade and transactions
involving the United States and, specifically, U.S.
businesses and individuals. To accomplish this sanctions
objective, we need to identify and prohibit transactions with
the kingpins and their organizations, not because they are
engaged in narcotics trafficking or other crimes per se, but
because the totality of their activities poses a threat to
the national security, foreign policy and economy of the
United States.
judicial review
We also object to the judicial review provision as drafted.
The judicial review exception in paragraph (f)(2) of section
704 is too broadly drawn. As drafted, the provision allows
the U.S. person to seek review of the blocking of any assets
of its foreign partner, whether or not those assets are
jointly owned. Thus, in the guise of a process for review of
an assets blocking involving a U.S. party's interests, it
would permit judicial review of the Treasury secretary's
designation determination regarding that foreign party. This
would circumvent the limitations on that review that are
provided in subsection (f)(1). The Administrative Procedure
Act already provides for judicial review of final agency
actions; and, therefore, additional judicial review
provisions are unnecessary.
I am at your disposal to discuss these or any other matters
relating to the pending bill or to the Specifically
Designated Narcotics Traffickers program being used against
the Colombian drug cartels under E.O. 12978 and IEEPA. My
telephone number is 202-622-2510.
Sincerely,
R. Richard Newcomb,
Director, Office of Foreign Assets Control.
____
Office of Foreign Assets Control, U.S. Department of the Treasury
Evidentiary Requirements for the SDNT Program, September 16, 1999
All Specially Designated Nationals (``SDN'') programs
require that our designations pass an ``arbitrary and
capricious'' test; and all designations are based upon a non-
criminal standard of ``reasonable cause to believe'' that the
party is owned or controlled by, or acts, or purports to act,
for or on behalf of the sanctioned country or non-state
party. Furthermore, the IEEPA-SDNT Executive order has an
additional designation basis for foreign firms or individuals
that ``materially . . . assist in or provide financial or
technological support for or goods or services in support of,
the narcotics trafficking activities'' of the named drug
kingpins or other, already designated SDNTs.
In implementing the Colombia IEEPA-SDNT program, OFAC
analysts identify and research foreign targets that can be
linked by evidence to individuals or entities already
designated pursuant to E.O. 12978. To establish sufficient
linkage, OFAC initially was dependent upon a significant body
of documentary evidence developed through criminal law
enforcement raids and seizures. For most of the continuing
designations under E.O. 12978 (that now total 496 with the
June 8 addition of 41 entities and 8 individuals to the SDNT
list), OFAC has not used criminal law enforcement information
and instead has depended upon OFAC's own research and
information collection.
The President's involvement was required in the designation
of only the original four Cali cartel kingpins named in the
annex to E.O. 12978. Additional kingpins are developed by
close coordination between OFAC and Justice, and the
preponderance of the SDNTs are designated as the result of
OFAC's research and collection efforts.
OFAC reaches designation determinations after extensive
reviews of the evidence internally and with the Department of
Justice. In the SDNT program, E.O. 12978 requires that the
State and Justice Departments be consulted by Treasury prior
to a designation; and, as noted above, Justice is deeply
involved in examining the sufficiency of the evidence that
occurs before any parties are added to the list.
OFAC regulations provide for post-designation review and
remedies. The usual forum for considering removal of a
designation (such as a change in circumstances or behavior)
is one in which the named party petitions OFAC for removal.
Most petitioners initiate the review process simply by
writing us.
Exchanges of correspondence, additional fact-finding, and,
often, meetings occur before OFAC decides whether there is a
basis for removal. Most parties seeking removal have followed
this approach. Although a number of persons have been removed
through this means, overall only a very few parties on the
SDNT and other SDN lists have ever petitioned for removal.
Federal courts have held that no pre-deprivation hearing is
required in blocking of assets because of the Executive
Branch's plenary authority to act in the area of foreign
policy and the obvious need to take immediate action upon
designation to avoid dissipation of affected assets.
OFAC actions are reviewable in Federal court under the
Administrative Procedure Act. There have been few such cases
in the history of the SDN programs; and no court has struck
down any of OFAC's designations. A U.S. District Court case
(Copservir v. Newcomb) brought on behalf of SDNT companies of
the Rodriguez-Orejuela cartel (Miguel and Gilberto Rodriguez-
Orejuela, ``MRO-GRO'') was dismissed. It has now been
appealed. An associated SDNT lawsuit involving 21 individual
SDNTs connected to the MRO-GRO businesses (Arbelaez v.
Newcomb), is currently pending before the same Federal court
that dismissed the Copservir case. Under the APA, the
Government must demonstrate that OFAC's action was neither
arbitrary nor capricious.
Evidence to support designations is acquired through
research and investigation by OFAC and other Federal
agencies; and it involves a broad spectrum of sources. All of
OFAC's designation programs adhere to a process of thorough
evidentiary development and review and are consistent with
U.S. statutes and the decisions of our courts. Designation
decisions are coordinated in all programs. In the IEEPA-SDNT
program against Colombian traffickers, the State and Justice
Departments must be consulted prior to a designation; and
OFAC works closely with them and with other interested
investigative and information-collecting agencies.
____
OFAC's Current Practices
Designations, notice and awareness. The IEEPA-SNDT program
against Colombian traffickers is our working model for a
procedure. Designations of foreign persons under this
program, particularly the derivative designations of foreign
businesses, are kept secret until they have occurred to
ensure that assets within U.S. jurisdiction may be blocked
and that the designation investigation about the entity and
related inquiries about other persons are not compromised.
When a designation is effected, several actions occur
either simultaneously or in close sequence to one another.
After concurrence from Justice and State, OFAC's director
makes the designation. Shortly thereafter, the following will
occur:
Actual notice. OFAC provides actual notice of blocking and
designation to specific financial institutions or other
businesses that are believed to have accounts or other assets
of the designated narcotics trafficker or to be handling or
engaging in transactions involving that target.
Cyberspace notice. OFAC simultaneously initiates a set of
electronic notifications, including updates to the SDNT list
and public information brochures on its web site, that notify
the financial community and the public at large that these
parties have been designated and that the prohibitions of the
program are in effect with respect to them. Specific steps
include:
Electronic Fedwire alert to 5,000 on-line financial
institutions.
Electronic CHIPS alert to the 250 money center banks.
Uploading of the OFAC web site SDNT list with the new names
and an updated comprehensive SDNT list (a visual alert to new
SDNTs is featured on the web site) and updated OFAC public
information brochures.
Uploading of the new designations and the expanded SDNT
list to other web sites (Treasury Electronic Library; GPO
Federal Bulletin Board; Commerce's Economic Bulletin Board;
Office of the Comptroller of the Currency's fax-on-demand
service; Commerce's STAT-USA/FAX, a fax-on-demand service.
Updating OFAC's own fax-on-demand service.
Telephone and/or fax notifications to federal bank
regulatory agencies.
Federal Register publication. Constructive legal notice is
effected through publication of the new SDNTs in the Federal
Register.
Publicity. Press announcement by Treasury or the White
House is common in order to have the broadest effective
notice and impact on the targeted foreign parties.
Counter-narcotics community. Other federal counter-narcotic
elements are notified, too. Commonly, classified cables have
been sent in advance to U.S. embassies in affected foreign
countries to make them aware that an SDNT action is about to
occur. In the Colombia SDNT context, the U.S. embassy and
OFAC (which has an officer assigned to Bogota) coordinate
closely throughout the process.
Host government. To the extent feasible, the USG
coordinates carefully with the host government concerning the
designated parties, and it works cooperatively with
appropriate host government authorities to pursue additional
measures and leads against the significant foreign narcotics
traffickers and the SDNTs.
U.S. businesses. When U.S. firms are believed to have on-
going, previously lawful dealings with the designated foreign
party, they are notified promptly by OFAC, directed to cease
the now prohibited activities and to block any SDNT assets
within their control, and advised of their rights and
responsibilities under IEEPA and OFAC's regulations.
Relationships between U.S. firms and SDNTs have usually been
discovered after the fact, and there have been very few cases
where post-designation transactions were discovered. In
helping U.S. firms comply with the SDNT program., OFAC has
followed a practice of disseminating:
Program awareness letters to U.S. businesses that are
starting to do business with Colombian firms. (To date, three
such letters have been sent in the SDNT program.)
Specific awareness letters to U.S. firms and their
Colombian subsidiaries that are believed to have had pre-
designation dealings with SDNTs. (To date, 32 such letters
have been sent.)
Specific alert letters, including cease and desist
instructions, to U.S. firms and their foreign subsidiaries
that have been found to have post-designation dealings with
SDNT companies or their successor firms. (To date, 15 such
letters have been sent to U.S. firms and their foreign
subsidiaries.)
In the rare case where apparently willful post-designation
dealings by a U.S. firm with an SDNT were to be discovered, a
referral for preliminary criminal investigation would be made
to U.S. Customs.
With regard to U.S. businesses, banks and individuals, the
purpose of the SDNT program is not to create criminal
jeopardy for unwitting U.S. businesses; it is to inform U.S.
persons of the identities of the prohibited foreign parties.
OFAC works to identify and expose the SDNTs in order to
prevent prohibited transactions and dealing with the SDNTs,
to block their identifiable assets, and to deny the SDNTs
access to the U.S. financial and commercial systems and to
the benefits of trade and transactions involving U.S.
businesses and individuals.
Legitimate foreign banking and business sector. OFAC also
seeks voluntary compliance with the U.S. sanctions programs
by the legitimate foreign banks and businesses in Colombia.
OFAC's director and officers have met regularly with
Colombian bankers and business groups from the beginning of
the SDNT program in a successful effort to develop a
cooperative working relationship and voluntary compliance
with the U.S. sanctions in isolating the drug kingpins and
their business enterprises and operatives. These measures,
which are being expanded upon, have included:
More than 450 general alert letters to Colombian firms that
had pre-sanctions supply or other business relationships with
SDNT firms.
Other specific alert letters to Colombian banking
authorities about SDNT accounts.
Numerous meetings with Colombian bankers and businessmen.
Ownership and control. Designations under OFAC's SDNT
program and its other nine programs that employ the SDN
concept are based upon a non-criminal standard of
``reasonable cause to believe'' that the party is owned or
controlled by, or acts, or purports to act, for or on behalf
of the sanctioned country or, as in the case of the
significant narcotics traffickers centered in Colombia, the
sanctioned non-state party. The IEEPA/SDNT narcotics
Executive order has an additional designation basis where
foreign persons ``materially . . . assist in or provide
financial or technological support for or goods or services
in support of, the narcotics trafficking activities'' of one
of the named drug kingpins or another of the already-named
SDNTs (emphasis supplied).
OFAC has an established practice for reaching
determinations of ownership or control. It is not an
inflexible formula but is, rather, a judicious assessment of
the nature and quality of the indicia of control drawn from
the totality of available information about the entity in
question. Prominent, but not exhaustive, criteria used in
determining SDNT control of and entity are:
Exercise of voting power: size of equity holdings; direct
and indirect shareholding percentages; existence of voting
trusts, supermajority voting requirements, or other
mechanisms to consolidate voting power or block initiatives
of other shareholders.
Exercise of managed authority: identities of the board of
directors, executive committees, and other managed bodies
controlling the business policies of the entity; ability to
designate officers or directors.
Exercise of operating authority: identities of major
officials and senior managers with day-to-day operating
authority or control over the types of transactions conducted
by the business.
History of operations: objective indications that the
business is run for the benefit of SDNTs.
The courts have held that OFAC's interpretations are
consistent with the premise of the Executive Order, which
lies in the recognition that the four principal narcotics
traffickers named in the annex to the E.O. have invested
their vast drug fortunes in ostensibly legitimate companies.
Mr. CROWLEY. Mr. Speaker, I yield myself such time as I may consume;
and I rise in support of H.R. 3164, the Foreign Narcotics Kingpin
Designation Act.
Mr. Speaker, the legislation before the House today is part of our
constant battle to get a grip on the flow of illegal narcotics into the
United States.
This bill will give the President additional tools to combat
international narcotics traffickers, to freeze their assets in the
U.S., to prohibit them from conducting business in the U.S., and
exclude them from entering this country.
Given the negative impact of illegal drug use on our citizens, this
legislation could not come at a more appropriate time. Illegal drug use
is destroying our children and ruining lives, making our streets
unsafe, and contributing to the substantial growth of the U.S. prison
population.
Illegal drug use in the U.S. has also generated huge profits for
international drug cartels. These cartels then use that money to branch
out into other areas of international crime and to destabilize foreign
governments that seek to crack down on illegal drug production.
In short, the U.S. must continue to move aggressively to crack down
on the international narcotics kingpins which keep the drugs flowing
into the U.S.
The bill before us today will help the President wage that war. The
legislation requires the Secretaries of Treasury, Defense, and State,
the Attorney General, and the CIA Director to provide a list to the
President of significant foreign narcotics traffickers. The President
would then be required to impose sanctions against narcotics
traffickers on the list and others that lend them material support,
including freezing the traffickers' assets in the U.S., blocking
transactions between U.S. citizens and the drug traffickers, and
prohibiting the traffickers from receiving visas to come to our
country.
It would also provide the President with a national security interest
waiver, as well as the ability to provide information to Congress in a
classified format to protect intelligence and law enforcement
information.
The administration supports this legislation, in part because it is
based on a similar initiative launched by President Clinton against
Colombian narcotics traffickers.
In October of 1995, President Clinton issued an executive order which
targeted and applied sanctions to four international narcotics
traffickers and organizations that operate out of Colombia. The bill
before us today will expand that initiative to other countries, as
well.
I urge my colleagues to support H.R. 3164, the Foreign Narcotics
Kingpin Designation Act.
Mr. Speaker, I reserve the balance of my time.
Mr. NADLER. Mr. Speaker, I yield 1\1/2\ minutes to the distinguished
gentleman from North Carolina (Mr. Watt).
Mr. WATT of North Carolina. Mr. Speaker, I rise in opposition to the
bill not because I do not support the objective of trying to cut back
on drugs and illegal drug activity in this country, but because I am
concerned that we are giving the President and the administration far,
far too much authority and subjecting them to far, far too little
review.
The notion that we in this Congress can oversee the designation of
who is designated a drug kingpin effectively is just nonsense. We do
not have the ability to do that. The appropriate place to do that is
not in the Congress of the United States. The appropriate place to do
that is in the courts of the United States.
This provision, which denies any judicial review to the
determinations made by the administration under this bill, is just un-
American. I mean, I have never seen the ability of the President to
take and block assets of people who are living in this country and then
say in a law the determinations, identifications, findings, and
designations made pursuant to section 4 and subsection (b) of this
section shall not be subject to judicial review.
That is what the courts are for. We are not saying that there should
not be a designation. But if the designation is
wrong, the people have to have the right to the court.
Mr. McCOLLUM. Mr. Speaker, I yield 2 minutes to the gentleman from
Arkansas (Mr. Hutchinson).
Mr. HUTCHINSON. Mr. Speaker, I thank the gentleman for yielding me
the time.
Mr. Speaker, I rise in support of this legislation for a couple of
reasons. We have to look very carefully as to what it does.
First of all, it directs the Secretary of the Treasury to designate
foreign narco-traffickers. A very simple designation. The argument was
made by the gentleman from North Carolina (Mr. Watt), well, there ought
to be some review of this.
The second step is what is reviewable. And that is that those so
designated would not be permitted to own or transfer property in the
United States or engage in U.S. financial transactions. That, under the
Administrative Procedures Act, would be appealable, would be
reviewable. And so, if the administration maintained a list of narco-
traffickers, which they are entitled to do, which is appropriate to do,
then if they seize those assets, then that would be subject to
administrative review.
The third thing that is very, very important is that it only applies
to foreign individuals and entities. This is the linchpin of this
legislation, is not to American citizens but it is to foreign entities
and individuals. If their assets are blocked, then, once again, that
would be subject to administrative review.
Why is all of this important? It is important because we are
attacking the sources of income and the ability to launder money.
I have been down to Colombia. I have been to Puerto Rico. I have been
through these hearings. And whether we talk to the DEA or whether we
talk to the narco-traffickers, they indicate that the other side, the
narco-traffickers, have greater resources and we have to hit them where
it hurts and where we can make a difference.
The third thing I think that is important is that it has been proven
to be successful. We are not experimenting in the dark here. The 1995
sanctions against the Cali cartel were successful. They had the effect
of dismantling the business entities tied to the Cali cartel. And that
is what we are trying to do, not just in Colombia but worldwide. We are
looking at the foreign entities that we can determine are engaged in
trafficking.
I want to express my appreciation to the gentleman from New York (Mr.
Rangel) for the comment that he made that this is exactly the direction
that we go in. So I ask my colleagues to support it.
Mr. NADLER. Mr. Speaker, I yield myself 30 seconds.
Mr. Speaker, the gentleman was incorrect in his statement to the
bill. The bill says the determinations, identifications, findings, and
designations made pursuant to, et cetera, shall not be subject to
judicial review. Designating an individual as a significant foreign
trafficker is not, under this bill, subject to judicial review.
So the President or the bureaucrat has the absolute authority to say
he is a foreign narcotics trafficker. If he thinks he is not, his
lawyers in the United States cannot appeal it in court and no evidence
is necessary. And that is simply, as was said before, un-American.
Mr. CROWLEY. Mr. Speaker, may I inquire as to how much time we have
remaining?
The SPEAKER pro tempore (Mr. Sununu). The gentleman from New York
(Mr. Crowley) has 3 minutes remaining. The gentleman from New York (Mr.
Nadler) has 2\1/2\ minutes remaining. The gentleman from Florida (Mr.
McCollum) has 1\1/2\ minutes remaining.
Mr. CROWLEY. Mr. Speaker, I yield 1 minute to the gentleman from New
York (Mr. Rangel).
Mr. RANGEL. Mr. Speaker, I did not mean to infer that he wanted to
bend the Constitution so badly that we would suffer from it now and in
the future. But in the period of time that we are living today, where
terrorism is actually a threat to our everyday life, I cannot imagine
that we would apply to a court in order to find out how we can keep
some of these bums out of our country or to keep them from destroying
our property and our lives.
I take this war on drugs pretty seriously. We have lost lives not
only to drug addiction but to our prison system. There is no question
in my mind that most Americans believe if we wanted to stop this that
we can but that big dollars prevent us from doing it. We go all over
the world telling other countries that they really are not going after
their drug traffickers, they will not extradite, they will not put them
in jail, they will not do anything.
Now is the time for us to do something. Now is the time to bring the
best minds that we have in the United States, those who have the
constitutional mandate to protect the American citizens.
Obviously, the President has overlooked this legislation, the
Judiciary has overlooked the legislation, and they feel that we stand
on sound constitutional ground. But the whole idea that we cannot
protect ourselves against those people who use our system, who infringe
upon our rights to bring this poison into the United States, who
threaten our national security, who have 2 million people locked up, at
least over half of them for drug-related crimes, it seems to me that we
are yielding to legal questions rather than questions that in times of
war we find answers to.
So I think this is a giant step forward. And if there are problems
with it, I hope they come back to this House and to the Congress so
that we can deal with it. But I think the mere fact that we are going
to pass this law sends a message to the foreign drug traffickers.
Mr. NADLER. Mr. Speaker, I yield 1 minute to the distinguished
gentleman from Virginia (Mr. Scott).
Mr. SCOTT. Mr. Speaker, Amendment 5 of the Bill of Rights says that
``no person shall be held to answer for a capital or otherwise infamous
crime unless on a presentment or indictment of a grand jury except,''
and then it goes on to say, ``nor to be deprived of life, liberty, or
property without due process of law.''
Now, the designation by the President is not due process of law.
Usually we have a trial. There is no judicial review in this situation.
And even the designation as a foreigner, if they happen to be a citizen
and are designated as a foreigner, they have no judicial review and no
|
When i click a button, it displays many alerts, stacks and overlaps
i want to sync the task, which when i click sync on the side menu, it will call the function in data.service.ts and it will display alert.
private async presentAlert(message) {
const alert = await this.alertCtrl.create({
message: message,
buttons: ['OK']
});
await alert.present();
}
this is the code, where i want to sync the task on data.service.ts
sync_task()
{
let body = new FormData();
body.append('access_token', localStorage.getItem('access_token'));
this.apiService.syncDataFromForm('/tasks', body)
.then((result: any) => {
if(result.data)
{
let form_data = result.data;
console.log("task synced");
console.log(form_data);
this.deleteTask();
this.deleteTaskList();
this.deleteBuildingDetails();
console.log(form_data);
for(let data of result.data) {
var submission_id = data.submission_id;
var project_name = data.project_name;
var status = '0';
var building_submission_id = data.building.submission_id;
var building_data = JSON.stringify(data.building.data);
console.log("building_data");
console.log(building_data);
this.insertTask(submission_id, project_name, status);
for(let formData of data.data)
{
console.log("all form data");
console.log(formData);
var form_id = formData.form_id;
var data_id = formData.id;
var form_name = formData.form_name;
var submission_group = formData.submission_group;
console.log("form_id");
console.log(formData.form_id);
this.insertTaskList(submission_id, data_id, form_id, form_name,submission_group);
}
this.insertBuildingDetails(submission_id, building_submission_id, building_data);
}
this.authState.next(false);
this.presentAlert('Successfully synced!');
this.menuCtrl.close();
this.router.navigateByUrl('home');
} else {
this.presentAlert('Uh oh!, sync failed! ');
}
});
}
this code in side menu
sync_task()
{
this.data.sync_task();
}
i don't know why the alert display too many times. the alert stacking up until the background turns dark. and i need to click ok too many times to clear that.
It depends where do you call this chunk of code, maybe this is in an ionViewWillEnter method that will subscribe every time you visit the page (you can revisit it multiple times)... What you need to do is to put a counter inside the subscribe method so that you can check how many subscriptions are there.
Please share the full block from where this.presentAlert() is being called. Are you sure that that method is not getting called multiple times?
i have edit my code. @arif08
Do you get repeated console.log as well?
yes. every data sync, the alert repeated as well, how to display one alert only@arif08
|
// This file uses jQuery. A valid jQuery object must be passed to the
// function returned by requiring this file.
module.exports = function($) {
var Data = require('../../core/data.js');
// if parseXML method already has been defined, which would be the case if this
// function was previously called, just return immediately
if (typeof(Data.parseXML)==="function") { return Data; };
// <data>
// <variables
// missingvalue="DATAVALUE"
// missingop="COMPARATOR">
// <variable
// id="STRING!"
// column="INTEGER"
// type="DATATYPE(number)"
// missingvalue="STRING"
// missingop="COMPARATOR">
// </variable>
// </variables>
// <repeat period="STRING"/>
// <values>
// </values>
// <csv
// location="STRING!">
// </csv>
// <service
// location="STRING!"
// format="STRING">
// </service>
// </data>
Data.parseXML = function (xml, multigraph, messageHandler) {
var ArrayData = require('../../core/array_data.js'),
DataVariable = require('../../core/data_variable.js'),
DataMeasure = require('../../core/data_measure.js'),
PeriodicArrayData = require('../../core/periodic_array_data.js'),
CSVData = require('../../core/csv_data.js')($),
WebServiceData = require('../../core/web_service_data.js')($),
Multigraph = require('../../core/multigraph.js')($),
pF = require('../../util/parsingFunctions.js'),
variables_xml,
defaultMissingvalueString,
defaultMissingopString,
dataVariables = [],
data,
adap, adapter = ArrayData;
if (xml) {
adap = pF.getXMLAttr($(xml),"adapter");
if (adap !== undefined && adap !== "") {
adapter = Multigraph.getDataAdapter(adap);
if (adapter === undefined) {
throw new Error("Missing data adapater: " + adap);
}
}
// parse the <variables> section
variables_xml = xml.find("variables");
defaultMissingvalueString = pF.getXMLAttr(variables_xml,"missingvalue");
defaultMissingopString = pF.getXMLAttr(variables_xml,"missingop");
var variables = variables_xml.find(">variable");
if (variables.length > 0) {
$.each(variables, function (i, e) {
dataVariables.push( DataVariable.parseXML($(e)) );
});
}
// check to see if we have a <repeat> section, and if so, grab the period from it
var haveRepeat = false,
period,
repeat_xml = $(xml.find(">repeat"));
if (repeat_xml.length > 0) {
var periodString = pF.getXMLAttr($(repeat_xml),"period");
if (periodString === undefined || periodString === "") {
messageHandler.warning("<repeat> tag requires a 'period' attribute; data treated as non-repeating");
} else {
period = DataMeasure.parse(dataVariables[0].type(),
periodString);
haveRepeat = true;
}
}
// if we have a <values> section, parse it and return an ArrayData instance:
var values_xml = $(xml.find(">values"));
if (values_xml.length > 0) {
values_xml = values_xml[0];
var stringValues = adapter.textToStringArray(dataVariables, $(values_xml).text());
if (haveRepeat) {
data = new PeriodicArrayData(dataVariables, stringValues, period);
} else {
data = new ArrayData(dataVariables, stringValues);
}
}
// if we have a <csv> section, parse it and return a CSVData instance:
var csv_xml = $(xml.find(">csv"));
if (csv_xml.length > 0) {
csv_xml = csv_xml[0];
var filename = pF.getXMLAttr($(csv_xml),"location");
data = new CSVData(dataVariables,
multigraph ? multigraph.rebaseUrl(filename) : filename,
messageHandler,
multigraph ? multigraph.getAjaxThrottle(filename) : undefined);
}
// if we have a <service> section, parse it and return a WebServiceData instance:
var service_xml = $(xml.find(">service"));
if (service_xml.length > 0) {
service_xml = $(service_xml[0]);
var location = pF.getXMLAttr(service_xml,"location");
data = new WebServiceData(dataVariables,
multigraph ? multigraph.rebaseUrl(location) : location,
messageHandler,
multigraph ? multigraph.getAjaxThrottle(location) : undefined);
var format = pF.getXMLAttr(service_xml,"format");
if (format) {
data.format(format);
}
}
}
if (data) {
if (defaultMissingvalueString !== undefined) {
data.defaultMissingvalue(defaultMissingvalueString);
}
if (defaultMissingopString !== undefined) {
data.defaultMissingop(defaultMissingopString);
}
data.adapter(adapter);
}
return data;
};
return Data;
};
|
Attractive Bent Gender
Everything About Fiction You Never Wanted to Know.
Jump to navigation Jump to search
Jerry: Oh, you don't understand, Osgood! Ehhhh... I'm a man.
Osgood: Well, nobody's perfect.
Whenever a male is turned into a female (or sometimes just when he dresses as one), he/she will almost always be extremely attractive, especially to members of his inner circle and close associates.
This may result in awkwardness for all concerned. The sex-changed character will often examine her new form and find it to be very... attractive. Only to promptly Squick herself out when she realizes what she's thinking.
Attractive Bent Gender operates in tandem with the First Law of Gender Bending to leave the world more attractive than it had been before. Or at least no less attractive. A handsome man may become a beautiful woman... but so will an unattractive man. In true Gender Bender or Easy Sex Change situations, one rarely encounters a handsome man who becomes an unattractive woman.
The trope may also apply to scenarios where a male is Disguised in Drag or crossdressing. Sometimes this is played straight, but (particularly when the crossdressing is Played for Laughs) it's often a case of Informed Attractiveness. In such scenarios, despite the "new woman" looking mannish and homely to the audience and most characters, someone will unaccountably be smitten with "her." Hilarity Ensues as the crossdressed hero tries to fend off the advances of an unwanted suitor.
This trope frequently leads up to the Second Law of Gender Bending. Sweet on Polly Oliver is a subtrope where a woman crossdressing is found attractive by guys. Frequently accompanies Something's Different About You Now. See also Rule 63, which basically exists because of this trope. When they actually are both genders, it becomes Everybody Wants the Hermaphrodite.
Contrary to stereotype, this can be Truth in Television.
Examples of Attractive Bent Gender include:
Advertising[edit | hide | hide all]
• In the '70s or thereabouts, there was a commercial for either a razor or an electric shaver featuring a cop who needed a really clean shave to pose as a woman for a stakeout. At the end of the ad, another cop studies him and remarks, "Face is terrific!" Grimace: "But that body!"
Anime and Manga[edit | hide]
• Ranma ½. Among the many things that rile Akane up about Ranma is that his girl form has a larger bust than she does. Note that he is already considered handsome as a male.
• Ranma is also one of the only guys turned girls that really didn't get turned on looking at herself naked. When ending up naked in a bathtub with a mirror-generated duplicate, he finds the situation vaguely odd, but not much else. The clone, on the other hand...
• Ryoga gets distracted by Ranma fairly easily, save for when he and s/he first end up in the bathroom together—most likely because of Ryoga's sheer rage at Ranma at the time and discovering that Ranma truly was responsible for causing Ryoga to receive his Jusenkyo curse. He's more vulnerable when he's not aware that Ranma is the girl currently almost-naked or flirting with him, but unless things are really serious, he's still not exactly happy at seeing Ranma's girl-form naked.
• The female form being incredibly attractive is possibly part of the curse as both another person and a monkey affected were equally good-looking. Though, at one point it is mentioned that female Ranma looks almost identical to her Hot Shounen Mom and the other guy was almost undoubtedly Bishonen, so maybe that was just one very good specimen of monkey
• Oddly enough, apparently Rumiko Takahashi herself also preferred the female Ranma, as she shows up in Fan Service scenes, and "cute" cover art (emphasizing the femininity of the character,) more often than any other character in the series.
• Wholesome Crossdresser Konatsu makes quite a beautiful woman, especially compared to god-awful looking step-family. This is justified by being quite Bishonen, and the one time he wore male clothes the girls were all over him.
(Then again, all of his disguises are pretty convincing... at first.)
• The crossdressing version of this was also subverted when Shinnosuke, his grandfather, Ryoga and male-Ranma try to distract a girl-eating monster by dressing as girls. They all look horrible, at least in part because their outfits are ridiculous.
• Subverted in Bleach, where the guys are blackmailed by Rangiku into doing her evil bidding, but don't look good at all, except for Kira, who pulls off the Shrinking Violet look well.
• Makoto in El-Hazard and El-Hazard 2. He just happens to look exactly like Princess Fatora.
• Code Geass had this shot from the first season's picture dramas.
• Jun from Happiness!!, a Wholesome Crossdresser who wants to be a girl to marry his (straight male) childhood friend and dresses and acts accordingly. This causes another student to remark on one occasion that "The number one beauty in this school is a guy." At one point, he is actually turned into a girl by wild magic (with very little outward change), which has the side effect of making every male in the school become obsessively attracted to him/her.
• Ryuunosuke from Urusei Yatsura is a girl forced to dress up as a boy. Despite all of the school knowing of her situation, she still gets more Valentine's chocolates and love letters from the girls than all of the other boys.
• Subverted in Romeo X Juliet when Genki Girl actress Emilia convinces her friend Odin to crossdress for the Rose Ball and notes that the end result is very pretty... completely unaware that Odin actually * is* a girl.
• Shiratori Ryuushi of Mahoraba. Tamimi and Momono (who dressed him up in his sleep in the first place) knew he would since he was fairly girlish and were still amazed at "Ryuko". When one of his classmates sees "her" he falls in love and becomes depressed at not being able to see her until Shiratori finds out and takes up the disguise again to say "she's" not available.
• Persona 4: The Animation has Naoto who wins a beauty pageant and has at least one boy and at least one off screen girl with a crush on her. Teddie also counts, winning the cross dressing pageant by a landslide.
• Subverted in Macross Frontier: main character Alto was a kabuki actor specializing in princess or feminine characters, and is nicknamed "Princess" by his classmate/wingmate Miguel. He absolutely hates this part of his life, and resents his father for dragging him into the business.
• He also happens to share Ranma's last name, Saotome; this may be a Shout-Out on the producers' part.
• Somewhat Lampshaded and subverted near the end of Hana Kimi: when Mizuki (who spends almost all the manga as a Bifauxnen and has to "crossdress back" in certain key occasions) is discovered by the rest of her classmates, many of them only find The Reveal shocking because they think of Mizuki as just cute and hoped that, if there was really a girl crossdressing in their male school, she must be incredibly gorgeous and sexy.
• Hazumu from Kashimashi: Girl Meets Girl gets a lot more more romantic attention after being transformed from a boy to a girl - mostly from other girls too. This causes problems with her male best friend who comically is conflicted about his undeniable attraction to her despite the fact he knew her as a boy until the gender switch.
• In Girls Bravo, the main character Yukinari is forced to dress as a girl, in order to host a gaming tournament. His disguise is so convincing that even the local pervert Fukuyama mistakes him for a pretty girl. This makes for one of the most humorous scenes in anime when Fukuyama finds out his true gender.
• Taken to a extreme in Vandread, where the titular ship's second-in-command, named BC, is a male, surgically changed into a woman's body and infiltrated into the crew to act as a spy for the males. Does a good enough job (with the aid of a voice-changer) that one of the captured crew, Bart, falls in love with him. The reveal in Vandread: Second Stage is well-done.
• Even after learning that she's a man, Bart still proclaims his love. It's not very disturbing for Bart to love a cross-dresser, as he lived all his life on a planet populated entirely of men. Ho Yay indeed.
• Haku from Naruto, who is a very attractive girl in all respects save his actual gender. He was able to convince Naruto that he was a girl simply by removing his mask and changing his clothes, and it came as no small shock to Naruto when he discovered the ruse.
• Naruto's Sexy/Harem Jutsu has this effect, although this is usually intentional.
• Gren, from Cowboy Bebop, is a man who suffers from a severe hormone imbalance due to experimental drug treatments and subsequently gained breasts and a female body. He occasionally finds call to dress up as a woman, and is considered attractive by both genders. He also temporarily unsettles Faye when she bursts in on him in the shower, sees his breasts (and body), and thinks he's a woman. Then her eyes scroll down.
• Inverted in Ouran High School Host Club, with Bifauxnen Haruhi Fujioka, who is a Wholesome Crossdresser more or less by accident.
• Also averted in a chapter where the half of the male members of the Host Club dressed up as women and just looked like men in dresses, makeup, and wigs. This is notably surprising in that, had it been any other manga, they would have been gorgeous.
• That's just because their costumes and makeup were gaudy and ridiculous, otherwise they probably would make pretty good woman.
• Watch Kyoya in that scene. He's not wearing any ridiculous make-up. He literally looks like a woman. It's the same deal at the end of the Haruhi in Wonderland episode, where he's cross dressing for some reason while the rest of the hosts are dressed as male characters.
• The Zuka Club.
• James is no stranger to cross-dressing in Pokémon (so much so that in some fanfic universes it's considered to be part of Team Rocket's basic training), but in an episode that was banned for years in the United States, he enters a women's bikini contest wearing a particularly convincing full-body, flesh-tone bodysuit with inflatable breasts.[1]
• Ash Ketchum himself has dressed as a girl on three different occasions in the series so far, one of them during the episode Pokemon Scent-sation as Ashley.
• Every season of Slayers has a crossdressing episode (and it's always episode 17). Gourry looks very attractive - men (and lesbians) hit on him, and in Slayers Try a sea monster mistakes him for a beautiful princess. And of course, there's Zelgadis ("Miss Lulu") on episode 17 of Slayers Next. His friends just stare at him for a few seconds, he just looks so damn hot.
• One wonders if the trend began because of Slayers' Idiosyncratic Episode Naming . Episode 17 was the "Q" episode ("Question?" in this case), and one has to wonder if they were trying to slip "Queer" past the radar in the process.
• Johan in Monster.
• Aoi Futaba from You're Under Arrest. Lampshaded in Episode 5, where the Bokuto squad attempt to "masculinize" him by putting him through martial arts training and dressing him in a male officer's uniform, with unfortunate results.
Aoi: So... how do I look?
Ken, Natsumi, Miyuki, Yoriko: (various pained expressions)
Miyuki: He actually looks better in a skirt...
• In CUTExGUY Sumi Takaoko is a generically cute girl who has been turned into a improbably hot, tall man, and promptly gets hit on by just about everyone interested in hot, tall males, especially The Vamp-ish school nurse. She uses it as a opportunity to hang out with the guy she has a crush on as a friend.
• Ryo in Penguin Revolution is so good at cross-dressing that his female persona "Ryoko" is The Ojou of his school, and widely agreed to be gorgeous. Towards the end of the series, he plays highly successful female roles in a movie and a play (and frets that he's going to have to make his living as an actress instead of as an actor).
• Likewise, in volume 5, Yuzuru Narazaki dresses up as a woman for an event held by Peacock and looks good enough to make at least one man very uncomfortable.
• Masashi Rando effortlessly passes as Yuna Kurimi in Pretty Face.
• Although it's justified since it's not simple crossdressing or gender bending, but major reconstructive surgery.
• In one episode of Natsume Yuujinchou, Natsume briefly gets possessed by a female spirit. Because of that, he begins to exhibit feminine qualities (sometimes seemingly having longer hair), and all of his friends start finding themselves disturbingly attracted to him.
• Yuki from No Bra easily passes as a girl, to the point where the only cast member who knows the truth is his Unlucky Childhood Friend and roommate Masato. Much to his embarrassment, several of his friends quickly develop crushes on this new "girl" at their school. Made even funnier in that Yuki never actually claims to be a girl (he even tries to explain it, but is ignored), just dresses and acts like one. It doesn't help that he has a very feminine build including what seem to be breasts.
• Rito from To LOVE-Ru is changed into a girl on four separate occasions, with his best male friend apparently suffering a case of love at first sight. He does make a pretty cute girl.
• When the title character of Hayate the Combat Butler is accidentally cursed to dress like a girl, he actually looks disturbingly attractive. Attractive enough to convince Izumi's butler that he really is female (he even lies and says his name is Hermione Ayasaki, and the butler lampshades that it sounds like a wizard's name). Then, Izumi recognizes him and tells the butler the truth, which causes him to look at Hayate's chest and realize that she's right. Better yet, he goes from being dressed like a maid to being dressed up like a bunny, and then accidentally reveals himself in public to all of the people he knows.
• Note that Hayate actually turned said butler, Kotetsu Segawa, completely gay for him. Ever since then he has rather aggressively pursued Hayate, once even challenging him to ping-pong at an onsen resort on the condition that if he won Hayate would have to go into the bath with him (He later threw the match to Maria, who made her condition that the two of them would have to do her chores...dressed as maids. We haven't yet seen this but we have seen Maria excitedly preparing maid outfits for it.)
• He's been forced to cross-dress numerous times over the course of the manga and so far Nagi, Maria, Isumi, Sakuya, Miki, Risa, Izumi, Chiharu, Ayumu, and Hinagiku have all seen him this way. When Sakuya needed to find a maid she lamented that Hayate was a butler and not a maid, Nagi and Maria (with evil grins) commented that they preferred him as a maid too. Isumi seems to think that cross-dressing is a hobby of his (and doesn't mind at all) while Risa was more than willing to help Maria force him into girl's clothes in Greece. Ayumu and Chiharu were there when Nagi made Hayate wear Ayumu's street clothes and both found him very attractive (Ayumu even told him to keep the outfit because he looked so good in it). Hinagiku admitted that she found him disturbingly attractive as well, but so far has been the only one to prefer as a guy. Shame Hina's mom tried to get the poor guy to wear a frilly dress that Hina wouldn't wear for her within an hour of meeting him.
• Hell it was literally a plot point that if someone meets him when he is crossdressed they would never be able to tell that Hayate is a guy. And it's been proven twice so far.
• Wandering Son's Shuuichi Nitori inadvertently stole the attention of the boy his older sister liked after he saw Shuu dressed as a girl.
• Nitori has quite the harem, from both boys and girls. On the other side of the spectrum, Takatsuki is quite the looker too.
• Makoto, AKA Mako-chan from Minami-ke. You wouldn't think that a hairclip and skirt could turn an average looking boy into a cute girl.
• In Mahou Sensei Negima, an Instant Cosplay Surprise turns Negi into a surprisingly cute fox girl.
• Simiarly, Kouta in Midori Days falls victim to a female gang who decide to put him in a cute dress. The effect is so striking the entire gang falls in love with him.
• Not to mention when Seiji dresses up like a girl to catch a molester on a train, prompting his (male) friend to unknowingly hit on him. Said friend later shows off a picture he took on his phone. Seiji responds by eating the phone.
• Tsubasa from Girls Saurus is male, but so feminine-looking that people even subconsciously visualise him as a woman (complete with rather ample breasts), and even the main character, who fears all women, keep falling for him in weaker moments... even after the reveal. He goes to an all-male school, but practically everyone else thinks he's a girl in disguise, and has vowed to never reveal 'her' secret since they find the idea of a sweet Polly Oliver romantic. (They don't even peek in the shared showers, so the ruse continues on.) When he finds out, he's thoroughly upset about the whole deal.
• In Mobile Suit Gundam 00 one of the Trinity brothers points out that if Tieria Erde were a woman he would be extremely attractive. Later on Tieria has a somewhat infamous scene in which he gets longer hair, artifical breasts (though considering he is an entirely artificial person this is perhaps somewhat redundant), and a flattering dress. The result is so stunning that that some male fans admit they would go for even knowing that he is, in fact, a guy.
• Mariya Shidou from Maria Holic is a boy crossdressing, but you'd never guess in a million years. This is endlessly frustrating to Kanako, who's not only a lesbian but fears boys so much they make her break out in hives. She's intensely attracted to Mariya as a girl, and has to keep reminding herself he isn't one.
• At the beginning of +Anima, Husky is dressed as a Mermaid Princess. Looking back later in the series, Cooro mentions that 'Husky was pretty as the Mermaid Princess.' When Nana knocks Husky out and puts him in a dress, someone (probably Cooro again, since Senri never talks), says that it's pretty. When Husky is bought by Lord Hashas and shows up at his mansion dressed like a black-haired pre-teen girl, he finds 'her' "exquisite", and when Nana and Cooro rescue him from said Lord, Nana coos and fawns over how 'pretty' and 'amazing' he looks.
• Then again, Husky often gets mistaken for a girl even when he isn't dressed up like one. Nana even believes he's a girl secretly crossdressing as a boy in the beginning.
• Happens often in Here Is Greenwood. Shun Kusanagi and his little brother look like girls, which is disturbing/amusing/arousing to the general populace of the all-male Greenwood dorm. Various other male characters don drag at different points in the manga (mostly for cultural/sports festivals), and attract various admirers. This is not including the alternative-dimension Cherrywood where everyone male is female.
• Shima Katsuki in Misae's arc in Clannad: After Story is forced to crossdress to sneak into the school to see Misae by her friends. Needless to say, the school's males are lovestruck with Moe Moe.
• In Fushigi Yuugi, the beautiful courtesan Nuriko is revealed to be a man. A very pretty man. (Hotohori, already a gorgeous male, actually is a little jealous at the start.) Later on in the manga, all the Suzaku warriors are temporarily forced to cross-dress, and Chichiri turns himself into a very sweetly gorgeous young woman - possibly the the best-looking out of all of them, to which Nuriko does not react very well.
• One of the OVA specials features the Suzaku and Seryuu groups and their respective priestesses going on a vacation trip to what turns out to be an all-women's bath (which they find out only when they arrive there), forcing the males to dress as females. Of course it's a no-brainer for Nuriko, while Hotohori is just so bishounen it's no problem for him, and Tomo merely wonders how much make-up needs changing. As for the others, some of them end up looking good, ranging from cute (Chiriko) to gorgeous (Nakago and Chichiri), others end up looking ridiculous (Tamahome and Tasuki), while Mitsukake, who's face was censored, ended up giving everyone a big scare.
• Possibly one of the most amazing instances occurs in St Luminous Mission High School where the lead male's best friend, Ryuzo Tanami, spends all but maybe 15 minutes of the series in drag. (Hey, he said he wanted to attend an all-girl's school...) Not only is 'she' very good-looking, with instantly & natural long hair and no telltales, one of 'her' classmates who thought she was straight falls in love with 'her' and doesn't take the subsequent questioning of her sexuality very well...
• In Season 2 of Genshiken Kousaka (who is pretty much Stupid Sexy Flanders as is) cosplays as a character from Kujibiki Unbalance for Comi Fes, causing shocked reactions from the other guys from the group.
Ohno: Do you think it's generally erotic, or just catering to a particular fetish?
Madarame: I think we should stop talking about this...
• Ivankov from One Piece. Dear Lord. When Ivankov is a man he is ugly, and barely even human-looking. When he is a woman she is beautiful. Why?
• He defeated a man in a fight by turning him both body and mind into that of a woman's.
• Ivankov's power lets him control anything about a persons body, be it himself or anyone else by controlling hormones, so if he wanted to he could probably have changed into an unattractive woman, an attractive man, or a freaking goat. Hell, his power is probably how he has his usual appearance of a vaguely bowling-pin shaped giant.
• Yubisaki Milk Tea's main character Yoshinori Ikeda sorts through his coming of age issues by cross dressing. His best friend falls for him, and one of his love interests starts out only being comfortable around him when he's in drag.
• Ciel Phantomhive from Black Butler, who wore a fancy, pink ballgown. He does make a real cute girl. Well, cute enough that he would get kidnapped by the handsome Viscount Druitt.
• Alois also dresses up as a female maid and Ciel is shown to look at him in awe because he thinks he's a girl and blush.
• Yellow Dancer/Belmont from Robotech/GenesisClimberMospeada who once gets mistaken for a woman even while not cross dressing.
• Ranmaru, Takenaga, and Yuki.
• Kämpfer: Natsuru gets this. And both genders LOVE HIM/HER!!! Doesn't help that his Gender Bender side is VERY beautiful.
• Hibiki Amasawa really does make a convincing woman, even if it is just to get a job as a Gym Teacher.
• Megumi, the Gender Bender protagonist of the The Day of Revolution. Justified in that she always was a girl (albeit an intersexed one) and even the guys wanted him before he Jumped The Gender Barrier.
• Parodied somewhat in Gintama. Gintoki and Katsura end up being forced to work in a crossdressing club after offending the leader of the crossdressers, Fierce God Mademoiselle Saigou. Due to the somewhat bishonen nature of the main characters, they look pretty good. The other crossdressers however are..... a bit more realistic.
• Gilbert and Break (but especially Gilbert) are quite lovely when the mangaka puts them in pretty pretty dresses in the Pandora Hearts omake.
• The Angel Chromosome-XX figure of Tabris from Neon Genesis Evangelion shows that Kaworu is an attractive sort, regardless of gender.
• Megumi Amatsuka from Tenshi na Konamaiki (AKA Cheeky Angel) is a boy cursed to be a girl by a trickster genie twisted his wish to become a 'man among men' She is generally regarded to be the most attractive girl in the school despite her tendency to inflict violence on her more adamant male admirers. Later subverted when it turns out Megumi always was a girl.
• Kinoshita Hideyoshi enjoys a similar status in the fandom as Jun Watarese of Happiness! (see above), due to the Ambiguous Gender factor.
• Yuuji Fukunaga of Liar Game is a male-to-female transsexual. And you'd never believe it if everybody else didn't keep using male pronouns when referring to him.
• Sora Aoi of Aki Sora. Every girl in his life takes any possible opportunity to make him crossdress, and he looks waaay too cute every single time.
• Hanaukyo Maid Tai
• Episode 15. Taro looks very nice in his maid costume.
• La Verite episode 5. Taro looks quite beautiful in his Mahoromatic cosplay costume.
• Kyo Aizawa, a girl cross-dressing in order to join a high school basketball team makes such an attractive boy in Girl Got Game that she manages to get more chocolate on Valentine's Day than the Team's captain.
• In Heroman, when Joey is forced to cross dress in episode 19 it comes as no surprise that he makes an attractive looking girl. What does come as a surprise is that so does his best friend Psy, after taming his wild shock of hair.
• Hiro gets hit on by a couple of gangsters in the Non Sequitur Episode of Ookamikakushi.
• This is the main premise of Princess Princess, where three bishonen in an all boys school are chosen to crossdress in order to make up for the lack of girls.
• Played with in the manga Usotsuki Lily. En Shinohara is a male, man-hating Wholesome Crossdresser. He's cute enough that the male student body actually doesn't believe he's male until his uniform blouse gets wet and transparent. However, this doesn't completely remove the problem, as at least one guy afterward is quoted as saying "Even those he's a guy, cute things are cute! (His transparent shirt was erotic!)"
• Pandora Hearts: When Oz dresses up as a maid, Gil says he looks "gorgeous" and a male servant of the Barma household seems to approve as well.
• The five protagonists in Ame Nochi Hare.
• In Axis Powers Hetalia, Italy is captured by the Allies after he hits on a pretty girl, who takes him prisoner. The 'girl' in question is actually a very male France in disguise.
• Examples from The World God Only Knows:
• Not only does Keima have the charm and looks to seduce and make the targeted girl fall in love with him, he can make random passerbys comment what a cute "girl" he is when he was dressed as a girl. This is what he looks like as a girl.
• Also Yui, who prefers to wear boy's clothes after her capture by Keima.
• Mizuki and her boyfriend Akira in Ai Ore Love Me. They're androgynous though, so they look the same whatever they're wearing; though Mizuki looks a little overly masculine even when wearing female clothing.
• The female lead Jeudi in the Honoo no Alpen Rose manga. She has to cut her hair and crossdress to escape the Count, and a girl named Liesl hits on "him". Then people are unsettled with reveals, much to Liesl's disapppointment. A while later, Liesl confesses to Jeudi that she miiiight be a little infatuated with her still, and lampeents that Jeudi's not a guy.
• Peppo of Gankutsuou.
• Tadakuni in Daily Lives of High School Boys was tricked into crossdressing in High School Boys and Skirts.
• Mizutama in Pump Up, when they dress him as Cinderella for a play.
• When he was younger the protagonist of Kuroneko Guardian used to model in girl's clothes. He now finds it incredibly embarrassing.
• In Rurouni Kenshin, when Kamatari first appears in front of Misao and Kaoru, everyone agrees that "she" is more attractive than them—before finding out that Kamatari is a cross-dressing man.
Comic Books[edit | hide]
• An unusual variant in the Marvel Universe Elseworld 1602. Scotius Summerisle (Cyclops) is in a relationship with Sweet Polly Oliver "John" Grey (Jean) and grows increasingly jealous of the time Werner (Angel) spends with her. Following her death, he realises that Werner never saw through the disguise and apologises. Werner refuses the apology, explaining, "I believed she was a boy, but I was in love with that boy."
• In Gorsky and Butch, the only female among the main cast in Maciek, a swat policeman re-drawn into a girl while trying to arrest the authors of the comic. He is very attractive, in an Action Girl way.
• When Tim Drake from Batman dressed up like a girl, "she" was almost immediately asked out on a date by someone that had no idea she was Robin, the Boy Wonder.
• The Ultimate Spider-Man version of the "Clone Saga" resulted in a number of clones of Spidey being created. One of Peter's clones, known as Jessica, was female and was meant to have her former memories erased and rewritten with memories suitable for a female secret agent. Jessica escaped before this reprogramming could occur, however. From her perspective, it as if she had been Peter Parker for her entire life, then suddenly woke up one day as a girl. Hilariously, Jessica had to deal with the fact that Johnny Storm found her attractive, and they even started dating, which really freaked out the "original" Peter Parker.
• Jimmy Olsen, on more than one occasion!
• Thor has, in some alternate universes, becomes a very beautiful woman.
In this case, as it turned out, it was partly because he was inhabiting the goddess Sif's body, but the trickster god has used shapeshifting and illusion for similar effect on other occasions.
• In one Beetle Bailey strip, General Halftrack found the company sitting in a clearing watching a beautiful girl in a skimpy bikini parade about. Sergeant Snorkel explained it was a lesson in camouflage: the "girl" was Lieutenant Fuzz. The strip was itself a rehash of an older strip, which had Sarge himself camouflaged as the gorgeous woman.
• When Shade the Changing Man became a woman, she was a stunningly beautiful one. Justified in that he was already such a pretty boy that he had masculinity issues with his image.
• Zatanna's beautiful assistant Mikey (who can fill out Zatanna's stage costume quite nicely in a pinch) apparently was once a burly male Teamster type.
• Averted for Laughs in Valhalla, when Thor is forced to dress like a woman to infiltrate a Jotun wedding (as the bride). He looks pretty much like himself in a dress, with a veil covering the beard. And the less said about Loki's initial disguise (which is toned down to the one on the picture), the better.
Fan Fiction[edit | hide]
• This Neon Genesis Evangelion fic features Shinji cross-dressing as a major plot point. He proves to be so attractive when doing this that many of his straight schoolmates begin questioning their sexualities.
• Another fic consisted of a list of things Misato was no longer allowed to do. Most are Noodle Incidents, including a pair of items stating Misato may no longer dress Shinji in girls' clothes, even if he makes it look good.
• In a particularly interesting example, this Yu-Gi-Oh! fanfic manages to invoke this trope twice. Besides the fact that one of the otherwise male characters (Namely Seto Freaking Kaiba) has been re-written as a woman. An incredibly attractive young woman who also happens to be crossdressing so well that those who don't know otherwise find her to be an incredibly attractive young man... All as planned of course.
• The Harry Potter fanfic Jade Green Eyes and Beyond Expectations feature Harry crossdressing to hide from the wizarding world after the war ends and he becomes a star. Cue Male Gaze.
• In a Spider-Man fanfic Blessing in Disguise Peter finds that she makes a rather attractive girl after the shock and denial winds down somewhat after being turned into one.
• As Sarah called out Jareth[2] about it in fancomic Roommates:
• It was already established before this incident that at least James looks good in female clothing. Thanks to a time manipulating "friend" and later to a French girlfriend and way too much absinthe.
Film[edit | hide]
• Leslie Cheung: in various films like this
• The classic Hollywood version of this trope is Some Like It Hot, whose final lines provide the page quote.
• Goodbye Charlie has a dead mobster come back to life as the beautiful Debbie Reynolds. In a 1984 failed pilot for a TV series, he's Suzanne Somers.
• Switch (a loose and unofficial remake of Goodbye Charlie) has Perry King "trading up" to Ellen Barkin.
• Though it's more a case of a handsome man becoming an attractive woman.
• Dil in The Crying Game - and, in fact, the actor who plays her - makes a stunningly beautiful woman.
• Angel from RENT
• Barry Watson (and some would say Michael Rosenbaum) in Sorority Boys.
• In Back to The Future Part II, Michael J. Fox plays several of Marty's family members, including his future daughter. He makes a pretty good looking girl.
• Rare example of a female to male, but in Boys Don't Cry about the real life murder of Brandon Teena, who was a trans man, Hillary Swank not only looked convincingly male, but was not bad-looking.
• Breakfast On Pluto goes to show that Cillian Murphy makes an awfully pretty girl.
• Cillian also cross-dresses in the movie Peacock. He is...alluring.
• Dustin Hoffman as Tootsie. Charles Durning's character said something near the end of the movie to the effect of "The only reason you're still alive is that I never kissed you."
• Subverted in Victor/Victoria, with the man dressed as a woman actually being a woman dressed as a man dressed as a woman. (and when a man dons one of her outfits, he is certainly not convincingly female.)
• In Willow, where Madmartigan briefly dresses as a woman after a tryst, pretending to be a cousin of the married woman he just bedded, to avoid being pounded by the lunker of a husband. The husband, after looking him over, offers the immortal line, "Wanna breed?"
• This is pretty much the central theme of the film Zerophilia, which centers around a character whose sex changes back and forth several times throughout.
• Billy Crudup made quite the popular and attractive lady when he played one of the last of the Restoration era boy players Ned Kynaston in Stage Beauty.
• Stephen Dorff in I Shot Andy Warhol.
• With all due respect to Calpernia Addams, Lee Pace in Soldier's Girl is much prettier as Calpernia Addams than she is.
• Tilda Swinton has done this twice:
• As the title character in Orlando. Orlando starts off as a rather attractive man in Renaissance England when, enamoured by his beauty, Queen Elizabeth I grants him immortality. Roughly 150 years later, Orlando goes into a days-long sleep, only to wake and find himself transformed into a woman.
• She played the archangel Gabriel in Constantine as a divine, genderless being.
• In Thunderbolt And Lightfoot Jeff Bridges has to dress up like a woman as part of a robbery plot. He looks at himself in the mirror and muses that he looked so good he would do him himself!
• The titular character of Mulan has this at times, most notably in "A Girl Worth Fighting For".
Yao: Bet the local girls thought you were quite the charmer.
Literature[edit | hide]
• Mary Russell is occasionally called upon to dress as a man (given her spouse's occupation, quite frequently) and is still rather Bishonen doing so. As can be understood. And in a situation that might otherwise have been Sweet on Polly Oliver, this trope holds truer—during O, Jerusalem, when she's dressed as a teenage boy, her would-be rapists are in no way dissuaded by her revealing her gender.
• Subverted in Terry Pratchett's Jingo, where after explaining the 'universal law' of this trope, it goes on to say "In this case, the laws were fighting against the fact of Corporal Nobby Nobbs, and gave up."
• In Naomi Novik's short story The Wreck of the Amphidragora, Lady Araminta looks much the same as a man as she did as a woman, which is still fairly attractive. Her captor finds her attractive enough that he would have tried to seduce "Lord Aramin" if Araminta hadn't solicited him first.
• Older Than Print: The Arabian Nights story "Prince Camaralzaman and Princess Badoura" tells of a Prince and Princess whose beauty so captivates a pair of djinn that they argue over which is the most beautiful mortal alive. Their attempt to settle the question leads to the Prince and Princess falling in love. It becomes a plot point that the two are almost identical, to the point where the Princess can dress up as the Prince, fool a cohort of her father's guards who are escorting them, and then fool a King and his daughter. Enough that the King proposes marriage and the daughter accepts.
• In The Wheel of Time the Dark One intentionally gives the formerly male Balthamel a beautiful female body as Aran'gar because Balthamel was a pervert, and the Dark One has a sense of humor.
• In Lamb the Gospel According To Biff, there's a scene when Biff has to disguise himself as a woman (he lost the coin toss) to help save the daughter of an Indian outcast (widowed) he had just met. Said Indian outcast doesn't let the fact that it's a man stop him from hitting on "her".
• Matthew (or should I say 'Blossom'?) in The Rose Of The Prophet trilogy. He is supposed to be androgynous-verging-on-the-feminine anyway, but damn it's harped on.
• This photo, depicting Stephen Colbert as Raven from Wigfield. His brother Jay was completely fooled by the picture, asked Stephen how he knew 'her' and was "a little disturbed" when told he was drooling over his little brother.
• In John Varley's Steel Beach, protagonist Hildy Johnson starts out as a fairly standard looking male but, after a high tech sex-change (a common motif in Varley's work), becomes a stunning woman.
• Mentioned in Starfighters of Adumar. The four members of Red Flight have to disguise themselves as women to get past the people hunting them.
Wes: "So. Who's best-looking in women's dress? I vote for myself."
• Averted in Last Call, when the protagonist goes Disguised in Drag to infiltrate a poker game. Justified, as in this case he's only concealing his identity rather than his sex, so it's sufficient that he passes for a drag queen, not a woman.
• George Alec Effinger's Marid Audran series takes place in the Budayeen, a Red Light District of a 23rd century Cyberpunk Muslim/Arab city. The Easy Sex Change is commonplace, and Attractive Bent Gender is the rule more than the exception. To the point that it's considered noteworthy that one character, a German girl, is exceptionally attractive... despite the fact that she's just a "real girl!"
• Orlando, upon turning into a woman, is amazingly good-looking; she's just as physically fit as she was when she was a man, but has all sorts of feminine beauty on top of that.
• The Star Trek short story "The Procrustean Petard" features a device which changes the sex of every member of the Enterprise crew (except for Spock, whose Half-Human Hybrid nature causes him to suffer from Extra Y, Extra Violent). Kirk is somewhat taken aback by how hot he is as a woman.
• Leviathan has Deryn/Dylan Sharp,who a number of teenage females in the books (plus Alek) consider extremely handsome, even moreso because she's a heroic airman.
• In Georgette Heyer's The Masqueraders, Robin Merriot has, ahem, political reasons for wanting to change his identity until the heat dies down. Being fairly short, slim, and fine-featured, he makes a very pretty "Kate," while his sister Prudence disguises herself as "Peter," Kate's handsome brother. Robin is confident enough in his masculinity that his only misgiving is that he can't very well court the girl he's fallen for when he looks like a girl himself. He even shows no qualms about pretending to flirt with a man who's seen through both deceptions (but is going along with them while courting Prudence).
Live Action TV[edit | hide]
• Occurs several times in Blackadder:
• An extreme example, to the point of parody, is the scene in Blackadder II where Lord Percy falls for Baldrick in a dress—despite him retaining his usual beard and level of cleanliness.
• Baldrick in a dress also works for Lord Flasheart (the beard gives him "something to hang on to!")
• Plus, of course, Bob's "Bob" was a very attractive woman who dressed as such an attractive man that Blackadder falls in love before even finding out that Bob is a woman, shortly after admitting that he had feelings for him.
• Parodied in Blackadder Goes Forth, when General Melchett falls for the square-jawed, Perma Stubbled "Georgina". Taken to insane extremes when he sees "Bob" in a pretty dress and assumes it's a tawdry drag act (Which "Georgina" was intended to be all along).
• Due South Season 2 Episode 12 "Some Like It Red", Benton Fraser volunteers to go undercover to an all-girls school, requiring him to crossdress. He looks quite fetching, with a strong resemblance to Lucy Lawless. Even the girls at the all-girl school are amazed that "Ms. Fraser" is a man, deciding that "he" must be a woman on the inside, at least.
• In the Halloween episode of News Radio, Dave Foley is said to look better in Lisa's dress than Lisa does. Then again, Foley knew about it as a member of The Kids in The Hall where this was a comedic plot point from time to time...
• Examples from Saved by the Bell:
• In the original series' S:1-E:2, "Screech's Girl", Zack tries to cheer up Screech, who feels depressed because he doesn't think any girl could love him, by claiming he could find Screech a girl. Since he can't he then claims to have found a girl, but that she's very shy. He calls Screech every day and talks to him as "Bambi". He does it so well that not only is Screech convinced, but Slater hits on him, realises that it's Zack then compliments his legs. Even Kelly is convinced. Finally, Screech decides that he's better off now, knowing that he's able to date women, but claims not to be ready for commitment yet.
• In Saved By the Bell: The New Class S:1-E:2, "The Slumber Party", new main character Scott dresses up as a girl so that he can attend a slumber party with his female friends. However, a jock from school catches sight of him, and is immediately smitten.
• Something similar happens in a classic episode of Happy Days where the Fonz unknowingly takes a liking to a cross-dressing Richie. They slow dance.
• Vince Noir ("the great confuser") from The Mighty Boosh is a prime example, though not everyone is smitten. One character refers to him as "Howard Moon['s]...ugly girlfriend." This becomes part of a running gag in which Vince is often referred to as Howard's wife or girlfriend. Believe it or not, Vince isn't the Butt Monkey of the show.
• Davina has a quite large fanbase.
• Doctor Who, The Master turns the entire human population into clones of himself, resulting in various disturbingly gorgeous Drag!Masters. The original script even had a cut scene where the original Master flirted with Abigail!Master.
• In Jeeves and Wooster - the TV series, not in the books - Jeeves has to dress up as a female American novelist for one of their Zany Schemes. D'Arcy Cheesewright falls in love with him and moves to New York in order to find her again.
• Cops on Barney Miller sometimes have to go undercover:
• Detective Harris (played by Ron Glass) is a snappy dresser. When he is assigned to do undercover work wearing women's drag, he spends the whole show getting ready, even shaving off his 'stash. In the end, everyone is stunned at how great he looks as a woman.
• In another episode, the much less attractive Fish does the same undercover detail and gains a male admirer who continues to be drawn to Fish even after he finds out he's not a lady.
• Massively averted with Dietrich, who was gung-ho about undercover work, but just ended up looking like a man in a dress.
• Justified in the Argentinian/Spanish soap opera Lalola.
• In Silver Spoons, Rick dresses as a girl so that his best friend wouldn't be embarrassed by not having a date to a party. Ricky Schroeder actually made a pretty good looking girl.
• Boy Meets World Season 4 Episode 15 "Chick Like Me" (the title refers to the book "Black Like Me" which inspired the episode) featured a crossdressing Rider Strong, who looked quite fetching as "Veronica Wasboysky". This was commented on in the show and was genuinely true. Cory, who was originally going to be the crossdresser is definitely not an example. It may be more understandable than most examples, since Shawn admits to having thought about crossdressing before this ever became a plot. He even has a preferred female name, has practised female mannerisms and has a wig already.
• Boy Meets World Season 7 Episode 11 "What A Drag!" is more debatable. Jack is supposed to be considered, in universe, an attractive girl and Eric, in universe, is definitely not. In actual terms, however, Jack is clearly a boy in a dress, while Eric actually looks like just a larger than average girl. Of course, that may be because Jack is so squeamish about pretending to be a woman and over-compensates, as Shawn tries to explain at the end. Eric, on the other hand, asks for and listens to Shawn's expert advice, implying that Shawn never did stop being Veronica from time to time.
• One episode of Are You Being Served had Mr. Humphries dressing in drag for a store beauty contest. Not only did "she" win, but Mr. Grace asked "her" to accompany him on a cruise on his yacht! Mr. Humphries looked horrified as he was dragged away, and the viewer was left to imagine the hilarity that no doubt ensued.
• A few episodes of The Suite Life of Zack and Cody had either Zack and/or Cody in a dress. And they did look pretty convincing. This example might be considered a surprising allusion for a Disney show to a previous role played by the Sprouse twins in The Heart Is Deceitful Above All Things.
• In 30Rock, Tracy disguises himself, badly, as a woman, then asks Frank if he finds him attractive. Frank replies, "Tracy, I know it's you...yes, yes I do."
• While in Monty Python's Flying Circus, one of the Pythons crossdressing for a skit is fairly obvious and played for laughs, Eric Idle actually looks pretty attractive. For example...
• Scrubs has played with this occasionally with Turk and J.D.: "You'd make a pretty girl."
• In the Legend of the Seeker episode "Princess", Zedd dresses up as a prim and proper elderly countess and gets hit on by an elderly herald. The exchange between him and Cara makes the situation even more hilarious:
Cara: It seems you have an admirer.
Zedd: [Indignantly] Is there any reason why I shouldn't?
• The Japanese Reality Show Crossdress Paradise (turn on "closed captioning" for subtitles), which features cute high school boys in drag, and has a segment where they must "pass" in public and flirt with passerby. On the other hand, the intended audience for the show is clearly young women.
• In Wizards of Waverly Place Uncle Kelbo is Shakira.
• Every time Jack Tripper dressed up as a woman, men fell in love with him.
• The Miniseries adaptation of the acclaimed Brazilian book The Devil to Pay In The Backlands has a really good example of the female-to-male kind, with the protagonist's love interest Diadorim.
• The Monkees had two examples:
• In "The Chaperone", when the chaperone for the guys' party passes out drunk right before it starts, Micky does himself up as "Mrs. Arcadian" to appease the father of the girl Davy is in love with. Hilarity Ensues. Mrs. Arcadian's attractiveness is questionable in absolute terms, but the father finds her to be rather fetching.
• In "Some Like It Lukewarm" (the title being a direct reference to Some Like It Hot), Davy dresses as a girl so the boys can enter a contest for mixed gender groups. He looks like, well, Davy Jones in a dress. However, the radio personality emceeing the contest thinks he's the most gorgeous woman he's ever laid eyes on.
• "Alberta" from He's A Lady.
• RuPaul's Drag Race runs on this trope.
• The killer in an episode of Criminal Minds. As a split personality killer where one personality is a woman, this was going to happen at some point. And boy, does it happen.
• In a fourth season episode of The A-Team, Murdock, with help from special guest Boy George, dresses as a pregnant woman to gain access to the rest of the team who have had to barricade themselves in the sheriff's office. Not only does he managed to convince a lynch mob to let him through without anyone questioning that he wasn't a she, but Face mentions that Murdock looked better to him as a woman than he did as a man.
• Done in F Troop when Corporal Agarn, dressed as an "Indian maid", coaxes the Loco Brothers out of their cave. Made funnier by the fact that Wrangler Jane, an actual woman, had failed in an earlier bid to do the same. Made famous to younger viewers as the clip shown on Freakazoid!.
• In the Star Trek: Deep Space Nine episode "Profit and Lace", Quark is forced to do a gender-swap and pose as a female. Every male Ferengi he encounters (even his own family) comments on what a lovely female he makes, to the point where the Nagus (who knows he's really Quark) can't keep his hands off him and a prominent businessman is completely smitten with him (even after being told Quark is really male).
Brunt (pointing at naked gender swapped Quark): "I tell you, that is not a female!"
Nilva: "Close enough for me…"
• Ivan a drag king played by Kelly Lynch on The L Word.
• In Wingin' It, a Canadian Disney show, the main character Carl is turned into quite an attractive girl in order to understand women, after taking his new Angel in Training girlfriend Denise out on a terrible date. part 1 part 2
• In one episode of The Red Green Show, the gang has to make it seem like there are women at the lodge, so Harold and Dalton disguise themselves as women. Despite not looking feminine, Harold is asked out on a date.
Mythology[edit | hide]
• Norse Mythology has some interesting examples:
• The gods Odin and Thor have been able to pass themselves off as women. While the fact that Thor and Odin make attractive women may make one wonder what the hell women looked like in the Northlands, Thor's disguise as a woman makes a lot of sense, when you look at the symbolism behind the story. The Jotun steal his hammer and hide it. As the price for returning it, they want Freyja in exchange. She, of course, is none too pleased by the Aesir's willingness to sell her down the river for Thor's hammer. The hammer is, of course, more than just a hammer, and so, with his * ahem* giant-bashing stick taken away, Thor is metaphorically a woman. Interesting guys, the old Norse. (Yes, this does mean the hammer is his penis.)
• Thor pulled it off only by hiding his face with a veil, and Loki had to talk fast to explain away his completely unwomanly appetite and fierce eyes.
• The Norse Trickster Loki has shapeshifted and not just passed as female, but given birth. To a horse. With eight legs. No, really. He and the other Norse gods had to lure away a horse to keep a wall from being built on time, and Loki was "it." (Certainly, there are few legends in mythology more aggressively Squick-y than Sleipnir's origin story. We feel bad for Sleipnir's dad.)
• In Hindu Mythology, Vishnu's female incarnation as the enchantress Mohini is so gorgeous Shiva falls for her. They even had a child, the culture-hero Ayyappan, and in some versions this was their way around a No Man of Woman Born clause.
Radio[edit | hide]
Dennis Day: You know, I saw Charleys Aunt this summer, and somebody just told me that pretty lady in it was you!
Jack Benny: Oh, well, i-it was me! It was me, it was my character in the picture. And now ladies and gentlemen--
Dennis: Holy smoke! You know, I thought it was a real girl!
Jack: No. No, Dennis, it was me. And um... And now, ladies and gentlemen--
Dennis: I sent you a love letter. Forget about it.
Theater[edit | hide]
• Shakespeare's entire life's work, pretty much.
• Sometimes it works both ways, too. When Viola dresses up as a man in Twelfth Night, the woman she's supposed to woo for her lord instead falls for her male persona. (Good thing she has a Half Identical Twin.)
• As You Like It: And let us not forget fair Rosalind, who once did dress to become Ganymede. A shepherdess, Phebe, then fell for "him", and Rosalind did try to rebuff her.
• There is a musical adaptation of Twelfth Night called All Shook Up. The music is all Elvis Presley all the time. And lots of attractive gender bending.
• In The Taming of the Shrew, the man who finally manages to woo the eponymous shrew(ish woman) is a crossdresser. His relative attractiveness as a man or a woman is not mentioned, but usually the part is played as either comically manly even when crossdressing or fitting this trope to the point of fake Les Yay between the romantic leads.
• The cross-dresser in RENT, Angel.
• In Der Rosenkavalier, the Baron von Ochs starts hitting on the chambermaid "Mariandel" the moment he first sees her. When they have arranged a tête à tête, he suddenly notices the resemblance between her and Octavian, whom he has every reason to hate at that point, but dismisses it. And after the tête à tête turns into a trap and the situation culminates in the Baron scandalously abrogating his impending Arranged Marriage to Sophie, he turns to "Mariandel" proposing marriage, whereupon the maid excuses herself with a very amusing secret to tell the Inspector.
• Peter Pan productions in the United Kingdom, including the original concept. Normally, British theatre is known its panto Dames; respectable male actors who perform the role of an older woman in the play, whether the original story had one or not, and perform it as a Drag Queen. But in the Peter Pan productions, they are replaced with an attractive young woman playing the role of the prepubescent boy Peter Pan. This is traditional in honour of the original Peter Pan, who was played by the author's children's Nanny when they first devised the story to entertain the kids while they were bedridden with illness over Christmas.
• M. Butterfly. Song Li-ling—especially when played by the right actor. The original Song was played by BD Wong who really pulled it off.
Video Games[edit | hide]
• Cloud from Final Fantasy VII, if you get the right items for the preceding quest. Although the polycount is too low to allow the player to judge for themselves, he is treated as if he were a very attractive woman in-game.
• Given his character design in the Compilation, it's no longer hard to imagine what Cloud would look like as a woman. Now I just want to know what he'd look like as a man.
• The answer is something like this
• Forget imagination. If Cloud-in-drag looked anything like THIS in the crossdressing sequence of the original FFVII game, it's no wonder Don Corneo decided to pick Cloud instead of Aeris and Tifa.
• Even when they forgot to include any sort of stuffing for Clouds blouse, which Tifa, and even Aeris, has a-plenty...
• Maybe he likes Pettankos? He later kidnaps Yuffie...
• The main character of Final Fantasy XIII, Lightning, is deliberately something of his Distaff Counterpart. She's not just, presumably, similar to him personality wise, she has his face, and the crazy thing? While she's not as feminine or delicate as most other Square Enix girls, she's still quite pretty.
• To put it bluntly, Lightning is Cloud if / when he cross dresses. Toriyama's guidelines to Nomura was to make her "strong and beautiful" - a "female version of Cloud." And considering what Lightning looks like, who wouldn't want to bang Cloud when he's dressed like a girl?
• Bridget from the Guilty Gear series of games, who is the basis of an internet meme for this very reason.
• Mori Ranmaru is a male figure from Japanese history who is frequently portrayed in fiction as having a very feminine appearance. Particularly in the Samurai Warriors video games, Mori looks like a girl and is even voiced by a woman.
• Which makes the quote he makes upon seeing you in Warriors Orochi, "I am as dangerous as I am manly!" rather amusing in itself.
• In addition to that, in Samurai Warriors 2, during Oichi's Dream stage, he will eventually join the battle to decide who the most beautiful woman in Japan is.
• Dimitri Maximov from Darkstalkers has a super move called "Midnight Bliss", which changes attractive (or even unattractive) male or female characters into attractive females. His appearance in SNK vs Capcom: Chaos spawned a fanart industry consisting of female versions of male video game characters, who are referred to as being "Midnight Blissed".
• Jun Kurosu from Persona 2: Innocent Sin, who is rather androgynous-looking. His official profile states that crossdressing is one of his talents and that he looks prettier in a dress then most girls. In addition, one of his demon negotiation contacts is a group contact with Lisa Silverman, one of the other party members, who ambushes him and puts makeup on him...and then proceeds to get very depressed over him being prettier then she is.
• There's a lot of this going on in Persona 4. Naoto is pretty attractive as a guy, and later on Teddie handily wins a crossdressing competition.
• Poor, poor Shika in Kira Kira. He was forced into drag once in tenth grade and was so cute that a guy fell in love with him. His childhood friend brings this up to their fellow (female) bandmates, who decide to get out his wig and force him to dress up as a girl. Much hilarity is had. Shika swears never to crossdress again—but then he has to dress up as a girl to get into a friend's house because of her overprotective grandfather. And Kirari continues to force him into drag for concerts and her general amusement. One thing leads to another, and Shika spends about a third of the game forced into women's clothing and a wig. Even in the sequel, for the return of the original d2b, his fellow ex-band members conspire against him to crossdress once more for their last performance.
• Lucifer Louisa Ferre in Strange Journey.
• In Majin Tensei II, BEELZEBUB, of all things, shows up looking like an attractive woman in bondage gear with a fly motif.
• Circuits Edge, the 1989 CRPG based on George Alec Effinger's Marid Audran novels (see Literature, above), likewise featured this trope.
• Poison from Final Fight is either a post-op or pre-op transsexual, depending on who you ask. Word of God is that she's pre-op in Japan and post-op elsewhere. It's like She's a Man In Japan, but... more complicated depending on personal definitions. In any case, she makes a lovely woman.
Webcomics[edit | hide]
"I wish I could say this was my worst date ever. I totally do."
• Charlie from Khaos Komix (though she's a transgirl, not a crossdresser) looks damn hot in a corset and skirt. Even Natalie Geln is jealous.
• She looked great when she had long hair too. On the other side of the spectrum, Tom (a Transsexualism female-to-male) is Mr. Fanservice at its finest. And he's not even on hormones.
• RPG World polled readers to find out which character in the comic would win a swimsuit competition. After the results were tallied, it was revealed that character with the second highest number of votes ("Red Haired NPC Girl") was really just Hero, the lead male character, dressed like a girl.
• Sparkling Generation Valkyrie Yuuki has this as its premise, basically. When Yuuki gets his first good look at his new female body (which has the same face as his old one) he chides himself for his perverted thoughts. And then...
• Subverted in Order of the Stick, when Roy puts on the Belt of Gender Changing, she's still bald. Played straight when donning a (mop) wig is enough to get a dwarf assassin to invite himher back to his room. Subverted again when Belkar can smell that the woman is Roy but hits on him just because it makes him uncomfortable.
• Given that it's a dwarf that he seduces, it's not really played straight even that once...dwarven women are pretty manly to begin with. A human male may well be more feminine that a dwarven female!
• Ash from Misfile has managed to attract both boys and girls (not surprising, considering her mother's a Lingerie Model) but can't quite deal with the Squick factor.
• Subverted in a story arc of Bruno the Bandit, wherein a sorceress' curse turns Bruno, the Bruce Campbell-esque title character, into an equally Bruce Campbell-esque woman. Subverted again when a minor character shows up looking to propose marriage to his ladylove Octavia, who looks exactly as Bruno looks now.
• In Eight Bit Theater, the airship of the Light Warriors crashes on a female barracks, and to get out of them without being slaughtered by the elves, the LW dress themselves as women. And one of the elf guards finds one of them cute - the one with the obscured face (which would actually drive him insane if he ever actually saw), which his comrades usually mention is smelly and fat, Black Mage (and we didn't even mention his personality).
• Subverted/Inverted in The Dragon Doctors with Mori, a woman who gets turned into very handsome man, much to the discomfort of his/her recently gender-swapped, formerly-male colleagues. Mori's colleagues are also fairly good looking, but not extremely attractive like him/her.
• Basically the entire plot of MaterialGirl; just add unwilling crossdressing. (This example needs some Wiki Magic.)
• Dillon of Ménage à 3 dresses up as Black Canary for a part in a play. He's so convincing that apparently his male co-actor playing Green Lantern doesn't realise even after kissing him.
• The "Anomalie" storyline in Its Walky! had Joyce and Walky swap genders. Tony mistakes her for Sal (which considering that they're Half-Identical Twins, is understandable). When everything returns to normal, Robin reveals that she wanted to kiss "Jayce."
• Reversing the usual genders of the trope, in Keychain of Creation, Marena, a happily promiscuous shapeshifting Lunar Exalt, is just as attractive when she changes into a male form.
• Appears frequently in Jet Dream Remix Comic stories:
• The men of the Thunderbird Squadron were all transformed into attractive women, but they were mostly attractive men beforehand. The exception is the former T-Bird "teen mascot," Rolf Jarl Cook. As a boy, he was a short, skinny kid with glasses, but as a T-Girl renamed "Cookie Jarr," she's extremely attractive, to the point that Even the Girls Want Her.
• Also enforced in the Cookie Jarr stories that feature Teen Superspy organization J.E.T. T.E.E.N. The crossdressing young Elle-Boys are all quite beautiful and have very feminine figures, regardless of what they might look like in their male guises.
• In a side plot of Twokinds the slave Mike has an illusion cast upon him that makes him appear as an attractive female to himself and others. Chaos ensues.
• Given the reactions of various characters, Sonja and Robyn seem to fall under this category in The Wotch.
• Every significant male character of Black Adventures has gotten a crossdressing fanservice scene now.
• Simon of Double K has spent all but two panels dressed in drag. And apparently, several people in universe find his disguise attractive. And some out of universe as well.
• In Murry And Lewy, both of the main characters get a Gender Bender. Murry, who was a slightly attractive guy, turned into one heck of a good looking lady, while his partner was average looking at best in both states.
Web Original[edit | hide]
• The online serial novel The Saga of Tuck does this straight (if you pardon the expression) and deadly serious - it causes Tuck to panic when Travis starts showing serious interest in him, out of fear of what Travis would do if he found out, and later, when s/he reluctantly begins dating him, the realization that s/he is attracted to him. Travis later reveals that a mutual friend had spilled the beans before they started seeing each other regularly (mostly; Travis believes at first that Tuck has had sex-reassignment surgery, which is believable because, as they determine later, Tuck is biologically intersexed).
• One of Gaia Online's minigames features a Bizarro Universe in which the Handsome Lech Liam is a Lia instead. She has a bombshell body, but her face is still very plainly Liam's (albeit with a ton of makeup plastered on), both playing this trope straight and averting it.
• Most main characters in the Whateley Universe, it's not just the gender benders though: half the mutants who have a physical change when they manifest are extremely attractive while the other half, including two of the protagonist genderbenders, don't look human anymore.
• In the Paradise setting, in which an unknown cause is changing humans into Funny Animals (and sometimes changing their gender at the same time), it is explicitly stated in some of the stories that the gender-Changed get a special "bonus" in the attractiveness department (especially as regards Breast Expansion), even beyond the ordinary such enhancements that Changed get in general.
• A rare justified example in Metamor Keep - the Transgender curse victims are intentionally made to be attractive to the opposite sex, and originally, it's because they were to be turned into sex slaves.
• While many people already found Joe Walker attractive when he played Voldemort in A Very Potter Musical, many more believed that him playing Umbridge in A Very Potter Sequel only made him hotter.
• Lauren Lopez makes a very adorable Draco Malfoy, too. Sango Taijima (usually Lavender) makes a really cute boy.
• This is inevitable in any story in the Transsexuals and Crossdressers section of Literotica, for obvious reasons.
• "Spoonette" seems to be rather popular with the boys....
• The entire (insulting) point of the "It's a trap!" meme.
Western Animation[edit | hide]
• The Fairly OddParents, "The Boy Who Would Be Queen": Wanda changes Timmy into a girl, who his best friend A.J. falls for, and tries to win "her" over with a dead frog.
• Timmy's Dad once dressed as a woman to enter Miss Dimmsdale pageant. Adam West fell in love with him and knowing the truth did nothing to change the feeling.
• Played with in the Futurama episode "War is the H-Word", when Leela disguises herself as a decidedly un-handsome man named "Lee Lemon." Even though she doesn't look like much, Zapp Brannigan is strangely attracted to "him" and, in the end, after fighting Lee, losing, and finding out who "he" really is, proclaims that he's never been so happy to have been beaten up by a woman.
• In another episode, Bender passes himself off as a female robot to enter the Robot Olympics and attracts the attention of Show Within a Show actor Calculon. Fridge Logic ensues.
• Clone High has an episode which follows almost exactly the same lines as the first Futurama episode mentioned above, with Joan of Arc and JFK in Leela and Zap's respective roles.
• Additionally, Cleopatra comes onto Joan and is shocked when she is rejected. And intrigued when she finds out the truth.
• In Cybersix, the title character is a woman who dresses as a man in her secret identity, an English teacher, and has a female student lusting after him/her. The disguise is provided by Clark Kenting. When The Glasses Come Off, evil gets an ass-whuppin'.
Just like the Futurama example, a man who lusted after her as a woman (in this case, Jerry), is just as attracted when she's a man, with predictable confusion and self-doubt on Jerry's part.
• In one episode of SpongeBob SquarePants, Patrick disguises himself as a woman and becomes part of a Love Triangle between Squidward and Mr. Krabs.
• Bugs Bunny frequently cross-dresses as part of his Karmic Trickster hijinks:
• In the classic cartoons, Bugs's "victim" invariably regards the result as attractive, although it looks rather silly to the audience. 'Cause everyone agrees it's funny.
• Referenced in Wayne's World where Garth asks Wayne if he ever found Bugs Bunny attractive when he dressed up as a girl bunny. Wayne laughs his "no" incredulously for a moment, then says seriously "No", to which Garth responds "Me neither, I was just wondering". Considering Garth's overall character, he may have been serious.
• Discussed in a Basic Instructions strip, with one character squicking out another by pointing out that none of the female characters in the Classic Disney Shorts (Minnie, Daisy, Clarabelle) is as attractive as Bugs Bunny in drag. The other character requests Brain Bleach, but nonetheless admits that this is true.
• Set up similarly, but subverted in Duck Dodgers, where Dodgers dresses a woman to fool some guards but they both think "she" is ugly and quite easily figure him out to be a guy. Dodgers then has to simply bribe them. (But played straight in an episode where Cadet is disguised as a female alien to seduce X-2 and retrieve information.)
• Bugs's drag act is subverted on The Looney Tunes Show. Most characters say he makes an ugly woman, though Daffy and Speedy have found him attractive.
• In the 1952 Looney Tunes "Fowl Weather" Sylvester gives himself a very basic disguise as a hen—and attracts the attention of a rooster.
You're different! (drags Sylvester off) You'll be my favorite!
The female Garrison looks nearly identical to the male version, save for lopsided breasts and a slightly smaller build.
• This happened in another episode in which Cartman suffered a case of amnesia and believed himself to be a Vietnamese woman named "Ming Lee". Wanting money, his friends had "Ming Lee" earn it for him. At least one of the clients liked it so much he didn't even become upset upon recognizing Cartman as Ming Lee.
• In another episode, Cartman's hand was Hennifer Lopez. She likes tacos and burritos. Ben Affleck left Jennifer for Hennifer, and Cartman, who apparently couldn't control his hand, got Affleck spooge all over him.
• The guy-dresses-as-woman variant has happened to Lumpus a couple times on Camp Lazlo. The first time, after leaving a restaurant without paying, he and Slinkman must sneak back in dressed as women. Sure enough, an employee falls for Lumpus even after he bangs on the men's room door, shouting in his normal voice for Lazlo to let him in. It was done hilariously later on in the series, when Jane, the love of his life, was engaged to the most disgusting character on the series. Lumpus happens to be in a dress when he finally confesses his love for her...and everyone thinks he's a lady confessing her love for Jane's fiance, who simply says, "Sorry, Jane, she's hot," and chases Lumpus.
• The Venture Brothers: Dean Venture finds himself in ?derland while wearing a Princess Leia slave girl costume (it was for a costume contest, the group theme being Star Wars). The dictator of the nation, Dr. Venture's "official" arch-nemesis, hauls off the rest of the Ventures but falls instantly for Dean. (Cue all the jokes about how Dean is a pretty wimpy guy.)
• On the Stoked episode "Mr. Wahine", Reef is first forced to dress up like a girl by the senior staff members, but then when he finds out that there's an all-girl surf contest going on, he decides to keep his disguise on for a chance to beat his rival-slash-love interest Fin. Disguised as "Sandy Beaches", he discovers to his horror that the manager of the hotel is immediately crushing on him.
• Alvin and The Chipmunks did a Sherlock Holmes spoof where Simon played Sherlock, Theodore played Dr. Watson and Alvin played Moriarty. In one scene Holmes disguises himself as a Cockney barwench and was able to fool Watson enough that he came on to him.
• Because there isn't enough subtext in that relationship already, chipmunks or otherwise.
• Stanley Chan makes quite a convincing lady when he needs to play the part, and in episode 3 one man found his hula girl self so attractive he proposed to "her"!
• On Family Guy Brian has hit on both a Disguised in Drag Stewie and Quagmire's father.
• That other Seth MacFarlane show has Roger Smith, who apparently looks so good disguised as a teenage girl even his old friend Steve is fooled. They even dated for a while and he never even tumbled to the truth.
• Kid Flash of Young Justice can't help but find Miss Martian attractive when she assumes the shape of a female version of himself.
• There are at least two episodes of The Flintstones where Fred dresses as a woman, and in both someone inexplicably finds him irresistably attractive. (Well, inexplicably if you discount "because it complicates the plot" as a viable reason.)
• Parodied in The Amazing World of Gumball, where Gumball wears his mother's wedding dress to school and not only does everyone including his brother and father find him impossibly beautiful despite him not changing his voice or mannerisms at all, they think the same of anything wearing the dress, including a balloon with a face scribbled on it and a fire hydrant. Apparently, it was just a really nice dress. (Given the world they live in world where animals and objects spontaneously becoming intelligent, clothes may really be the only thing they can use as a standard of beauty.)
• An episode of The Garfield Show has this happening to Garfield and Odie, resulting in them looking like elderly ladies (to be fair, though, this is imposed on them). Nermal gets smitten the moment he sees Garfield in this fashion, but lucky for him he never finds out the truth.
• Tom and Jerry examples:
• An episode of the Tom and Jerry comedy show featured Jerry getting a robot dog to protect him from Tom. Tom hid the robot and disguised himself to look like it. The robot fell in love.
• When Tom was tasked with guarding the garden against a gopher, he disguised himself as a female gopher. It would have worked except that Jerry warned the gopher, who then played along.
• "Flirty Birdy" (1945): Tom uses a Paper-Thin Disguise to entice an eagle who is also after Jerry for eating. Things Go Horribly Right and it ends with Tom sitting on a nest of eggs!
• In the Chuck Jones era, Tom disguised himself as a female mouse. It worked too well.
• The Simpsons examples:
• In "Marge in Chains," Bart plans to use this trope against the prison warden.
• In "Camp Feare", Abe developed feminine attributes due to not taking his medication. Another old man flirted with "her". Abe would have told the truth but changed his mind when his suitor told "her" his dating plans.
• In another episode, there was a Stargate SG 1 convention. When the lights were out, MacGyver-obsessed fans Selma and Patty abducted Richard Dean Anderson. The people attending the convention concluded that there must be a real Stargate in the convention hall, and started looking for it until someone pointed out something more incredible: there was a girl in there. The "girl" was Groundskeeper Willy, who tried to explain he wasn't a girl and was wearing a kilt but was told he's the best they hoped to get.
Real Life[edit | hide]
• Isis King of America's Next Top Model fame.
• Some people are primarily attracted to transgendered individuals, an orientation known as transromanticism. Example: one couple thought, at first, that they were both lesbians. After a while, one of them realized he was a trans man, and his partner realized she was specifically attracted to trans men.
• YouTube vloggers CandiFLA, sweetnsexyts, and a good number of others. (Candi does voicetraining videos and has been known to bend back using her male voice, resulting in some amusingly jarring videos.)
• People are often surprised to find out that Pikmin Link, the internet's most famous Link cosplayer, is actually female—almost always just after asking where they can find more pictures of "that really hot guy dressed as Link."
• Also applies to cosplay where the demographic watchers/players/readers are mostly female and the same goes for males who have very delicate features.
• F. Scott Fitzgerald was actually voted "most beautiful show girl" for his role in the the 1916 Princeton Triangle Club show, The Evil Eye.
1. The dubbed version, when it finally aired, had the breast scenes cut.
2. (It wasn't even his fault. Poor guy had a cold.)
|
<?php
namespace Vhnh\Cart\Tests\Fakes;
use Vhnh\Cart\Contracts\Buyable;
class Product implements Buyable
{
public function __construct($attributes = [])
{
$this->attributes = $attributes;
}
public function fill(array $attributes)
{
$this->attributes = $attributes;
return $this;
}
public function ean()
{
return $this->attributes['ean'];
}
public function vat()
{
return $this->attributes['vat'];
}
public function price()
{
return $this->attributes['price'];
}
public function toArray()
{
return $this->attributes;
}
}
|
add support to generate Pojos from Json Schema
please add support to generate Pojos from Json Schema like xjc does within jaxb.
it doesn't, cause it doesn't support urn:jsonschema for now: https://github.com/joelittlejohn/jsonschema2pojo/issues/412
|
User:Matthewkson
About Me Hey guys, I'm a fellow Wikipedia user (Matthewkson) by the name of Matthew. I'm a student who enjoys playing soccer, writing, drawing, and experimenting with html and C++. I'm also an avid fan of the soccer team Real Madrid. More later. Matthew
|
<?php
/**
* Created by IntelliJ IDEA.
* User: VictorRentea
* Date: 9/18/2017
* Time: 12:40 AM
*/
namespace victor\training\oo\creational\abstractfactory\lego;
use victor\training\oo\creational\abstractfactory\spi\BlockFactory;
use victor\training\oo\creational\abstractfactory\spi\Board;
use victor\training\oo\creational\abstractfactory\spi\Cube;
class LegoFactory implements BlockFactory
{
function createCube(): Cube
{
return new LegoCube();
}
function createBoard(): Board
{
return new LegoBoard();
}
function __toString()
{
return "Lego Factory";
}
}
|
/sdcard has encryption enabled and files are not useable
After booting into the recovery and browsing the filesystem, everything looks a little bit "garbled". Especially the /sdcard doesn't seem to be alright. Here you can only see folders with "GUID"-like names and no contents. Also there are two drives with zero bytes able to select when trying to change between external and internal memory.
My guess is, that the fstab is either not compatible or flat out wrong. Maybe a switch to that ominous fstab v2 format could fix it, but I need to do some more research.
https://github.com/ADeadTrousers/twrp_device_Unihertz_Atom_XL/commit/78cb78abda554bbbe44a95b6330865f11921d9f6
Still no luck in getting decryption to work.
Still no luck in getting decryption to work.
According to https://github.com/PeterCxy/android_device_umidigi_F1/tree/twrp-9.0 and https://github.com/Vgdn1942/android_device_blackview_bv9500plus one would need a keystore*.so file but I couldn't find any in the stock rom.
1c54597e6008364eba9e6b909985750dc62db5e9
Latest try prevents a successful boot so as a workaround I deactivated /data completely. Can't factory reset now though.
The trustkernel daemon (teed) seems to be operational now: 6a79d27a39a9dabb12995af7c24666a36b2e44d1
I'm more and more convinced that the Atom L/XL uses FBE instead of FDE and according to some sources on the net TWRP only supports FDE.
Ok, I need to revoke my previous comment: There is a FBE switch in TWRP e590bd635c0cb3bc2368b05f215370fae3a55aea
It's just not working though.
By logging through the code I came to the function "decryptWithKeymasterKey" in "KeyStorage.cpp" which fails.
So it seems that the problem lies with correctly registering keymaster service. I'm looking at you manifest.xml and compatibility_matrix.xml.
Including them at the correct patch ".../etc/vintf" lets TWRP freeze on boot. So something must be going on there. Need more intel.
ErrorCode in Keymaster4.cpp in function Keymaster::begin at mDevice->begin is -33.
According to hardware/interfaces/keymaster/4.0/types.hal this means ErrorCode::INVALID_KEY_BLOB
Could it be that a 'wrong' keymaster instance is being used?
Maybe a little bit more elaboration:
According to KeyStorage.cpp the keyfile is stored in /data/unencrypted/key/keymaster_key_blob.
A little bit of research brought me to https://forum.xda-developers.com/t/rom-official-nightly-lineageos-16-0-for-oneplus-3-3t.3866517/post-80122746
So there seems to be a problem with formatting of the key blob.
Finally!
Decryption is working now. One needs to set PLATFORM_SECURITY_PATCH 4376593c79c5cd133e30ed3e18a8af8329ada8d9
Now the ErrorCode::KEY_REQUIRES_UPGRADE is thrown. I believe that's because the key blob is created with a lower timestamp than 2099-12-31. Anyway now TWRP logs that it was able to decrypt /data. Checking with File Manager or adb shell confirms that.
BUT
Everything in the user scope /data/media/0 is still encrypted. According to the logs the file /data/system/gatekeeper.pattern.key is missing. Only that this file doesn't even exists when the system boots and that encrypts just fine.
So my guess is that it is either named differently, located somewhere else or another authentication method than gatekeeper is used by LineageOS.
I'm pretty sure now that LOS (Stock Android 10?) is using the synthetic password method. According to Decrypt.cpp all information is stored in /data/system_de/<userid>. Checking this folder from LOS I can see various key and pwd files but navigating to it from TWRP it's still garbled (= encrypted). As I now already have a decrypted /data/system there needs to be another step in decryption that is still missing for /data/system_de.
|
use common::{Day, Part};
use regex::Regex;
use std::fmt;
pub fn main() {
let mut data: Vec<String> = vec![];
if common::load_data("data/day-12-input.txt", &mut data).is_ok() {
let part_1 = Part::new(part_1);
let part_2 = Part::new(part_2);
let mut day = Day::new(part_1, part_2);
day.run(&data);
assert_eq!(362, day.part_1.result);
assert_eq!(29895, day.part_2.result);
println!("{}", day.to_string());
} else {
eprintln!("cannot open data/day-12-input.txt");
std::process::exit(1);
}
}
enum Command {
North(i32),
South(i32),
East(i32),
West(i32),
Left(i32),
Right(i32),
Forward(i32),
}
#[derive(Clone, Copy, Debug, PartialEq)]
struct Point {
lat: i32,
lon: i32,
}
impl fmt::Display for Point {
fn fmt(&self, f: &mut fmt::Formatter<'_>) -> fmt::Result {
write!(f, "({},{})", self.lat, self.lon)
}
}
impl Point {
fn new(lat: i32, lon: i32) -> Point {
Point { lat, lon }
}
fn origin() -> Point {
Point { lat: 0, lon: 0 }
}
fn manhattan_distance_from(&self, other: Point) -> i32 {
(self.lat - other.lat).abs() + (self.lon - other.lon).abs()
}
fn rotate_around(&mut self, other: &Point, angle: i32) {
let delta_lat = self.lat - other.lat;
let delta_lon = self.lon - other.lon;
match normalize_angle(angle) {
0 => {}
90 => {
self.lat = other.lat - delta_lon;
self.lon = other.lon + delta_lat;
}
180 => {
self.lat = other.lat - delta_lat;
self.lon = other.lon - delta_lon;
}
270 => {
self.lat = other.lat + delta_lon;
self.lon = other.lon - delta_lat;
}
angle => panic!("unexpected angle: {}", angle),
}
}
}
struct ShipMk1 {
location: Point,
heading: i32,
}
impl ShipMk1 {
fn new() -> ShipMk1 {
ShipMk1 {
location: Point::new(0, 0),
heading: 90,
}
}
fn execute(&mut self, command: Command) {
match command {
Command::North(distance) => self.location.lat += distance,
Command::South(distance) => self.location.lat -= distance,
Command::East(distance) => self.location.lon += distance,
Command::West(distance) => self.location.lon -= distance,
Command::Left(angle) => self.heading = normalize_angle(self.heading - angle),
Command::Right(angle) => self.heading = normalize_angle(self.heading + angle),
Command::Forward(distance) => match self.heading {
0 => self.execute(Command::North(distance)),
90 => self.execute(Command::East(distance)),
180 => self.execute(Command::South(distance)),
270 => self.execute(Command::West(distance)),
angle => panic!("unexpected heading: {}", angle),
},
}
}
}
struct ShipMk2 {
location: Point,
waypoint: Point,
}
impl ShipMk2 {
fn new() -> ShipMk2 {
ShipMk2 {
location: Point::new(0, 0),
waypoint: Point::new(1, 10),
}
}
fn execute(&mut self, command: Command) {
match command {
Command::North(distance) => self.waypoint.lat += distance,
Command::South(distance) => self.waypoint.lat -= distance,
Command::East(distance) => self.waypoint.lon += distance,
Command::West(distance) => self.waypoint.lon -= distance,
Command::Left(angle) => self.waypoint.rotate_around(&Point::origin(), -angle),
Command::Right(angle) => self.waypoint.rotate_around(&Point::origin(), angle),
Command::Forward(distance) => {
self.location.lat += self.waypoint.lat * distance;
self.location.lon += self.waypoint.lon * distance;
}
}
}
}
pub fn part_1(data: &[&str]) -> u64 {
let mut ship = ShipMk1::new();
for line in data {
if let Some(command) = interpret_command_line(line) {
ship.execute(command);
}
}
ship.location.manhattan_distance_from(Point::new(0, 0)) as u64
}
pub fn part_2(data: &[&str]) -> u64 {
let mut ship = ShipMk2::new();
for line in data {
if let Some(command) = interpret_command_line(line) {
ship.execute(command);
}
}
ship.location.manhattan_distance_from(Point::new(0, 0)) as u64
}
fn interpret_command_line(line: &str) -> Option<Command> {
let regex = Regex::new(r"([EFLNRSW])(\d+)").unwrap();
if let Some(captures) = regex.captures(line) {
let command_selector: &str = captures.get(1).unwrap().as_str();
let amount: i32 = captures.get(2).unwrap().as_str().parse().ok().unwrap();
let command = match command_selector {
"N" => Command::North(amount),
"S" => Command::South(amount),
"E" => Command::East(amount),
"W" => Command::West(amount),
"L" => Command::Left(amount),
"R" => Command::Right(amount),
"F" => Command::Forward(amount),
other => panic!("unexpected command selector: {}", other),
};
Some(command)
} else {
None
}
}
fn normalize_angle(angle: i32) -> i32 {
let mut new_angle = angle;
while new_angle < 0 {
new_angle += 360;
}
new_angle % 360
}
#[cfg(test)]
mod tests {
use super::*;
#[test]
fn test_part_1() {
let data = vec!["F10", "N3", "F7", "R90", "F11"];
assert_eq!(part_1(&data), 25);
}
#[test]
fn test_part_2() {
let data = vec!["F10", "N3", "F7", "R90", "F11"];
assert_eq!(part_2(&data), 286);
}
#[test]
fn test_point_manhattan_distance() {
let point = Point::new(0, 0);
assert_eq!(point.manhattan_distance_from(Point::new(17, 8)), 25);
assert_eq!(point.manhattan_distance_from(Point::new(17, -8)), 25);
assert_eq!(point.manhattan_distance_from(Point::new(-17, 8)), 25);
assert_eq!(point.manhattan_distance_from(Point::new(-17, -8)), 25);
}
#[test]
fn test_point_rotate_around() {
let mut point = Point::new(4, 10);
let origin = Point::new(0, 0);
point.rotate_around(&origin, 90);
assert_eq!(point, Point::new(-10, 4));
point.rotate_around(&origin, -90);
assert_eq!(point, Point::new(4, 10));
point.rotate_around(&origin, 180);
assert_eq!(point, Point::new(-4, -10));
point.rotate_around(&origin, 0);
assert_eq!(point, Point::new(-4, -10));
}
}
|
HRFWiki2 talk:Wiki Stuff
* Oh, okay. B H S · Talk to me 20:34, September 1, 2012 (EDT)
Duplicate Pages
|
Wikipedia:Articles for deletion/Robert Weiner
The result was delete. Jo-Jo Eumerus (talk, contributions) 11:09, 15 December 2016 (UTC)
Robert Weiner
* – ( View AfD View log Stats )
Does not meet WP:GNG or notability for coaches Chrissymad ❯❯❯ Talk 18:23, 7 December 2016 (UTC)
* Delete High school football coaches are almost never notable.John Pack Lambert (talk) 21:03, 10 December 2016 (UTC)
* Delete - High school sports is inevitably a local endeavor; I suppose a certain small number of coaches rack up sufficient state titles to become noteworthy for the achievement, but this does not seem to be the case here. For better or worse, WP's notability standards are heavily skewed towards professional athletics, to the level even of college-level players. It is hard to see this as a special case. The 404 link in the footnotes does nothing to bolster my sentiment that this subject does not meet GNG at this time. Carrite (talk) 12:38, 14 December 2016 (UTC)
|
Proxy doesn't work
When I try to execute this:
`
credentials = client.SignedJwtAssertionCredentials(
SERVICE_ACCOUNT_EMAIL,
key,
scope='https://www.googleapis.com/auth/androidpublisher')
httplib2.debuglevel=4
myproxy = httplib2.ProxyInfo(proxy_type = httplib2.socks.PROXY_TYPE_HTTP, proxy_host='http://proxy.my.comp', proxy_port=8080)
myhttp = httplib2.Http(proxy_info=myproxy)
authorization = credentials.authorize(myhttp)
service = build('androidpublisher', 'v2', http=authorization)
`
I get this error:
httplib2.ServerNotFoundError: Unable to find the server at accounts.google.com
I also tried to set the proxy as env-variables. For basic stuff like installing via pip it works fine, but it doesn't work with the client. But I assume it should use the environment variables if nothing is set as proxy_info in the code.
Any suggestions on this?
Thanks!
Just wasnt aware that I have to add RDNS = true. (my company doesnot support DNS-Request to outside from the local machine so I have to force httplib2 to do the DNS-Request through the proxy and not from local)
Here is working with environment variables:
http_proxy=http://proxy_ip:proxy_port
and
https_proxy=http://proxy_ip:proxy_port
|
Native San Franciscan, Giants Fan, 49ers Fan, Golden State Warriors Fan, Father, Husband, Traveler, Car Enthusiast, Project Manager, Salesman, Perfectionist, and Eager Student are just some examples of the hats I have worn in the past and present. Though, I will be adding one more hat to that list, Front-end Web Development.
I'm a former Project Mangager for a signage company. I've managed sign projects for many companies in San Francisco as well as across the nation and even globally for many years. I can drive through most neighborhoods in San Francisco and spot a sign that I helped make, which makes me feel proud. I'm proud of the fact that the result of my work is appreciated and utilized by everyone, whether it be a small start-up, a property owner, a non-profit organization, medium-sized businesses, sports teams or large corporations.
Now, I'm a budding Front End Web Developer looking for that same prideful feeling, but on a different platform. Let my expertise with HTML5, CSS3, and Twitter Bootstrap create seamless and streamlined web sites that your users will love to interact with. Allow me to help you and your company reach another level.
|
Test 040 methods
Tests for 040 methods in variable_fields.rb
[ ] multiple_no_040?
[ ] multiple_no_040b?
[ ] missing_040c?
[ ] fix_040b
https://www.loc.gov/marc/bibliographic/bd040.html
Duplicate issue. Closed.
|
Thread:Sailor*Moon*Star/@comment-3247345-20121007213233/@comment-3247345-20121008152324
@Seddieicarlyforever Thank you for being one of the few voices of reason here.
Now that I've said that I have to go to class. I'll deal with the rest of this nonsense later.
|
#!/bin/bash
INPUT=$1
OUTPUT=$2
SIZE=$3
if [ -z "$SIZE" ];
then
SIZE=200
fi
notify-send "Thumbnailing $INPUT to $OUTPUT"
unzip -p "$INPUT" "QuickLook/Thumbnail.png" | convert - -resize $SIZEx$SIZE\> "$OUTPUT"
|
// Copyright (c) 2020 Siemens AG
//
// Permission is hereby granted, free of charge, to any person obtaining a copy of
// this software and associated documentation files (the "Software"), to deal in
// the Software without restriction, including without limitation the rights to
// use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of
// the Software, and to permit persons to whom the Software is furnished to do so,
// subject to the following conditions:
//
// The above copyright notice and this permission notice shall be included in all
// copies or substantial portions of the Software.
//
// THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
// IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS
// FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR
// COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
// IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
// CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
//
// Author(s): Jonas Plum
package sqlitefs
import (
"io/ioutil"
"os"
"path"
"path/filepath"
"reflect"
"strings"
"testing"
"time"
"github.com/spf13/afero"
)
func setup(t *testing.T) string {
name := strings.ReplaceAll(t.Name(), "\\", "_")
name = strings.ReplaceAll(name, "/", "_")
dir, err := ioutil.TempDir("", name)
if err != nil {
t.Fatal(err)
}
return dir
}
func cleanup(t *testing.T, directories ...string) {
for _, directory := range directories {
err := os.RemoveAll(directory)
if err != nil {
t.Fatal(err)
}
}
}
func dummyFS(t *testing.T, dir string) (*FS, error) {
// create database
fs, err := New(filepath.Join(dir, "test.db"))
if err != nil {
t.Fatal(err)
}
// create file
err = afero.WriteFile(fs, "/myfile1.txt", []byte(strings.Repeat("test", 1000)), 0666)
if err != nil {
t.Fatal(err)
}
// create directories
err = fs.MkdirAll("/dir/subdir", 0666)
if err != nil {
t.Fatal(err)
}
// create 2. file
err = afero.WriteFile(fs, "/dir/subdir/myfile2.txt", []byte("test2"), 0666)
if err != nil {
t.Fatal(err)
}
return fs, err
}
func TestFS_Chmod(t *testing.T) {
type args struct {
name string
mode os.FileMode
}
tests := []struct {
name string
args args
wantErr bool
}{
{"set mode", args{name: "/myfile1.txt", mode: 0}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.Chmod(tt.args.name, tt.args.mode); (err != nil) != tt.wantErr {
t.Fatalf("Chmod() error = %v, wantErr %v", err, tt.wantErr)
}
info, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if info.Mode() != tt.args.mode {
t.Errorf("Chmod() error = got %v, want %v", info.Mode(), tt.args.mode)
}
})
}
}
func TestFS_Chtimes(t *testing.T) {
myTime := time.Now()
type args struct {
name string
atime time.Time
mtime time.Time
}
tests := []struct {
name string
args args
wantErr bool
}{
{"set time", args{name: "/myfile1.txt", atime: myTime, mtime: myTime}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.Chtimes(tt.args.name, tt.args.atime, tt.args.mtime); (err != nil) != tt.wantErr {
t.Errorf("Chtimes() error = %v, wantErr %v", err, tt.wantErr)
}
info, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if info.ModTime().Unix() != tt.args.mtime.Unix() {
t.Errorf("Chtimes() error = got %v, want %v", info.ModTime(), tt.args.mtime)
}
})
}
}
func TestFS_Create(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
wantErr bool
}{
{"create file", args{"/f3.txt"}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
got, err := fs.Create(tt.args.name)
if (err != nil) != tt.wantErr {
t.Errorf("Create() error = %v, wantErr %v", err, tt.wantErr)
return
}
exists, err := afero.Exists(fs, tt.args.name)
if err != nil {
t.Fatal(err)
}
if !exists {
t.Fatal("file was not created")
}
err = got.Close()
if err != nil {
t.Fatal(err)
}
})
}
}
func TestFS_Mkdir(t *testing.T) {
type args struct {
name string
perm os.FileMode
}
tests := []struct {
name string
args args
wantErr bool
}{
{"mkdir", args{"/mydir", 0700}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.Mkdir(tt.args.name, tt.args.perm); (err != nil) != tt.wantErr {
t.Errorf("Mkdir() error = %v, wantErr %v", err, tt.wantErr)
}
exists, err := afero.Exists(fs, tt.args.name)
if err != nil {
t.Fatal(err)
}
if !exists {
t.Fatal("file was not created")
}
})
}
}
func TestFS_MkdirAll(t *testing.T) {
type args struct {
p string
perm os.FileMode
}
tests := []struct {
name string
args args
wantErr bool
}{
{"parent, child", args{"/foo/bar", 0700}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.MkdirAll(tt.args.p, tt.args.perm); (err != nil) != tt.wantErr {
t.Errorf("MkdirAll() error = %v, wantErr %v", err, tt.wantErr)
}
parent, _ := path.Split(tt.args.p)
exists, err := afero.Exists(fs, parent)
if err != nil {
t.Fatal(err)
}
if !exists {
t.Fatalf("parent %s was not created", parent)
}
exists, err = afero.Exists(fs, tt.args.p)
if err != nil {
t.Fatal(err)
}
if !exists {
t.Fatal("p was not created")
}
})
}
}
func TestFS_Name(t *testing.T) {
tests := []struct {
name string
want string
}{
{"name", "SQLiteFS"},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if got := fs.Name(); got != tt.want {
t.Errorf("Name() = %v, want %v", got, tt.want)
}
})
}
}
func TestFS_Open(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
want []byte
wantErr bool
}{
{"open", args{"/myfile1.txt"}, []byte(strings.Repeat("test", 1000)), false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
got, err := fs.Open(tt.args.name)
if (err != nil) != tt.wantErr {
t.Errorf("Open() error = %v, wantErr %v", err, tt.wantErr)
return
}
if err != nil {
return
}
defer got.Close()
b, err := afero.ReadAll(got)
if err != nil {
t.Fatal(err)
}
if !reflect.DeepEqual(b, tt.want) {
t.Errorf("Open() got = %v, want %v", b, tt.want)
}
})
}
}
func TestFS_OpenFile(t *testing.T) {
type args struct {
name string
flag int
perm os.FileMode
}
tests := []struct {
name string
args args
want []byte
wantErr bool
}{
{"open", args{"/myfile1.txt", 0, 0755}, []byte(strings.Repeat("test", 1000)), false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
got, err := fs.OpenFile(tt.args.name, tt.args.flag, tt.args.perm)
if (err != nil) != tt.wantErr {
t.Errorf("OpenFile() error = %v, wantErr %v", err, tt.wantErr)
return
}
if err != nil {
return
}
defer got.Close()
b, err := afero.ReadAll(got)
if err != nil {
t.Fatal(err)
}
if !reflect.DeepEqual(b, tt.want) {
t.Errorf("OpenFile() got = %v, want %v", b, tt.want)
}
})
}
}
func TestFS_Remove(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
wantErr bool
}{
{"remove", args{"/myfile1.txt"}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.Remove(tt.args.name); (err != nil) != tt.wantErr {
t.Errorf("Remove() error = %v, wantErr %v", err, tt.wantErr)
}
exists, err := afero.Exists(fs, tt.args.name)
if err != nil {
t.Fatal(err)
}
if exists {
t.Fatal("file still exists")
}
})
}
}
func TestFS_RemoveAll(t *testing.T) {
type args struct {
path string
}
tests := []struct {
name string
args args
wantErr bool
}{
{"removeall", args{"/dir"}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.RemoveAll(tt.args.path); (err != nil) != tt.wantErr {
t.Errorf("RemoveAll() error = %v, wantErr %v", err, tt.wantErr)
}
exists, err := afero.Exists(fs, tt.args.path)
if err != nil {
t.Fatal(err)
}
if exists {
t.Fatal("file still exists")
}
})
}
}
func TestFS_Rename(t *testing.T) {
type args struct {
oldname string
newname string
}
tests := []struct {
name string
args args
wantErr bool
}{
{"rename", args{"/myfile1.txt", "2.txt"}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
if err := fs.Rename(tt.args.oldname, tt.args.newname); (err != nil) != tt.wantErr {
t.Errorf("Rename() error = %v, wantErr %v", err, tt.wantErr)
}
exists, err := afero.Exists(fs, tt.args.oldname)
if err != nil {
t.Fatal(err)
}
if exists {
t.Fatal("file still exists")
}
exists, err = afero.Exists(fs, tt.args.newname)
if err != nil {
t.Fatal(err)
}
if !exists {
t.Fatal("file does not exist")
}
})
}
}
func TestFS_Stat(t *testing.T) {
info := Info{
name: "myfile1.txt",
sz: 4000,
mode: 0666,
mtime: time.Time{},
dir: false,
}
type args struct {
name string
}
tests := []struct {
name string
args args
want *Info
wantErr bool
}{
{"stat", args{"/myfile1.txt"}, &info, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
got, err := fs.Stat(tt.args.name)
if (err != nil) != tt.wantErr {
t.Errorf("Stat() error = %v, wantErr %v", err, tt.wantErr)
return
}
got.(*Info).mtime = time.Time{}
if !reflect.DeepEqual(got, tt.want) {
t.Errorf("Stat() got = %v, want %v", got, tt.want)
}
})
}
}
func TestFileInfo_IsDir(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
want bool
}{
{"dir", args{"/dir"}, true},
{"file", args{"/myfile1.txt"}, false},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.IsDir(); got != tt.want {
t.Errorf("IsDir() = %v, want %v", got, tt.want)
}
})
}
}
func TestFileInfo_ModTime(t *testing.T) {
mytime := time.Now()
type args struct {
name string
}
tests := []struct {
name string
args args
want time.Time
}{
{"/dir", args{"/dir"}, mytime},
{"file", args{"/myfile1.txt"}, mytime},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
fs.Chtimes(tt.args.name, mytime, mytime)
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.ModTime(); !reflect.DeepEqual(got.Unix(), tt.want.Unix()) {
t.Errorf("ModTime() = %v, want %v", got, tt.want)
}
})
}
}
func TestFileInfo_Mode(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
want os.FileMode
}{
{"/dir", args{"/dir"}, 0666},
{"file", args{"/myfile1.txt"}, 0666},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.Mode(); got != tt.want {
t.Errorf("Mode() = %v, want %v", got, tt.want)
}
})
}
}
func TestFileInfo_Name(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
}{
{"dir", args{"/dir"}},
{"file", args{"/myfile1.txt"}},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.Name(); got != path.Base(tt.args.name) {
t.Errorf("Name() = %v, want %v", got, path.Base(tt.args.name))
}
})
}
}
func TestFileInfo_Size(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
want int64
}{
{"dir", args{"/dir"}, 0},
{"file", args{"/myfile1.txt"}, 4000},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.Size(); got != tt.want {
t.Errorf("Size() = %v, want %v", got, tt.want)
}
})
}
}
func TestFileInfo_Sys(t *testing.T) {
type args struct {
name string
}
tests := []struct {
name string
args args
want interface{}
}{
{"dir", args{"/dir"}, nil},
{"file", args{"/myfile1.txt"}, nil},
}
for _, tt := range tests {
t.Run(tt.name, func(t *testing.T) {
tempDir := setup(t)
defer cleanup(t, tempDir)
fs, err := dummyFS(t, tempDir)
if err != nil {
t.Fatal(err)
}
defer fs.Close()
i, err := fs.Stat(tt.args.name)
if err != nil {
t.Fatal(err)
}
if got := i.Sys(); !reflect.DeepEqual(got, tt.want) {
t.Errorf("Sys() = %v, want %v", got, tt.want)
}
})
}
}
|
@INCLUDE_COMMON@
echo
echo ELEKTRA CHECK CONFLICTS SCRIPTS TESTS
echo
check_version
FILE=`mktemp`
cleanup()
{
rm -f $FILE
}
#needed to have job control:
set -m
#TODO: should use resolver-debug (mount it)
#multiple resolvers missing, so you have to recompile and uncomment next
#line
exit 0
# heat up the config file (create it)
$KDB set $USER_ROOT value1 1>/dev/null 2>/dev/null
fg %1 1>/dev/null 2> /dev/null
fg %1 1>/dev/null 2> /dev/null
[ $? = "0" ]
succeed_if "should be successful"
[ "x`$KDB get $USER_ROOT 2> /dev/null`" = "xvalue1" ]
succeed_if "could not get correct value1"
echo "Doing first test before locking happens"
$KDB set -v $USER_ROOT value2 1>/dev/null 2>/dev/null
$KDB set -v $USER_ROOT value3 1>/dev/null 2>$FILE
#in the non-locking race condition we need a different timestamp
sleep 1
fg %1 1>/dev/null
fg %1 1>/dev/null
[ $? = "0" ]
succeed_if "should be successful"
fg %2 1>/dev/null
fg %2 1>/dev/null
[ $? != "0" ]
succeed_if "should fail (time mismatch error)"
grep '(#30)' $FILE > /dev/null
succeed_if "error number not correct"
grep 'found conflict' $FILE > /dev/null
succeed_if "error message not correct"
[ "x`$KDB get $USER_ROOT 2> /dev/null`" = "xvalue2" ]
succeed_if "could not get correct value2"
echo "Doing second test during locking"
$KDB set -v $USER_ROOT value4 1>/dev/null 2>/dev/null
$KDB set -v $USER_ROOT value5 1>/dev/null 2> $FILE
fg %1 1> /dev/null
fg %2 1> /dev/null
[ $? != "0" ]
succeed_if "should fail (unable to get lock)"
fg %1
[ $? = "0" ]
succeed_if "should be successful"
grep '(#30)' $FILE > /dev/null
succeed_if "error number not correct"
grep 'found conflict' $FILE > /dev/null
succeed_if "error message not correct"
[ "x`$KDB get $USER_ROOT 2> /dev/null`" = "xvalue4" ]
succeed_if "could not get correct value4"
$KDB rm $USER_ROOT 1>/dev/null 2>/dev/null
fg %1 1> /dev/null
fg %1 1> /dev/null
[ $? = "0" ]
succeed_if "remove should be successful"
end_script check conflicts
|
using System.Collections.Generic;
using System.IO;
using System.Linq;
using System.Text;
using Titanium.Web.Proxy.Models;
using Titanium.Web.Proxy.Extensions;
using System;
namespace Titanium.Web.Proxy.Http
{
/// <summary>
/// Http(s) response object
/// </summary>
public class Response
{
public string ResponseStatusCode { get; set; }
public string ResponseStatusDescription { get; set; }
internal Encoding Encoding { get { return this.GetResponseCharacterEncoding(); } }
/// <summary>
/// Content encoding for this response
/// </summary>
internal string ContentEncoding
{
get
{
var hasHeader = ResponseHeaders.ContainsKey("content-encoding");
if (hasHeader)
{
var header = ResponseHeaders["content-encoding"];
return header.Value.Trim();
}
return null;
}
}
internal Version HttpVersion { get; set; }
/// <summary>
/// Keep the connection alive?
/// </summary>
internal bool ResponseKeepAlive
{
get
{
var hasHeader = ResponseHeaders.ContainsKey("connection");
if (hasHeader)
{
var header = ResponseHeaders["connection"];
if (header.Value.ToLower().Contains("close"))
{
return false;
}
}
return true;
}
}
/// <summary>
/// Content type of this response
/// </summary>
public string ContentType
{
get
{
var hasHeader = ResponseHeaders.ContainsKey("content-type");
if (hasHeader)
{
var header = ResponseHeaders["content-type"];
return header.Value;
}
return null;
}
}
/// <summary>
/// Length of response body
/// </summary>
internal long ContentLength
{
get
{
var hasHeader = ResponseHeaders.ContainsKey("content-length");
if (hasHeader == false)
{
return -1;
}
var header = ResponseHeaders["content-length"];
long contentLen;
long.TryParse(header.Value, out contentLen);
if (contentLen >= 0)
{
return contentLen;
}
return -1;
}
set
{
var hasHeader = ResponseHeaders.ContainsKey("content-length");
if (value >= 0)
{
if (hasHeader)
{
var header = ResponseHeaders["content-length"];
header.Value = value.ToString();
}
else
{
ResponseHeaders.Add("content-length", new HttpHeader("content-length", value.ToString()));
}
IsChunked = false;
}
else
{
if (hasHeader)
{
ResponseHeaders.Remove("content-length");
}
}
}
}
/// <summary>
/// Response transfer-encoding is chunked?
/// </summary>
internal bool IsChunked
{
get
{
var hasHeader = ResponseHeaders.ContainsKey("transfer-encoding");
if (hasHeader)
{
var header = ResponseHeaders["transfer-encoding"];
if (header.Value.ToLower().Contains("chunked"))
{
return true;
}
}
return false;
}
set
{
var hasHeader = ResponseHeaders.ContainsKey("transfer-encoding");
if (value)
{
if (hasHeader)
{
var header = ResponseHeaders["transfer-encoding"];
header.Value = "chunked";
}
else
{
ResponseHeaders.Add("transfer-encoding", new HttpHeader("transfer-encoding", "chunked"));
}
ContentLength = -1;
}
else
{
if (hasHeader)
{
ResponseHeaders.Remove("transfer-encoding");
}
}
}
}
/// <summary>
/// Collection of all response headers
/// </summary>
public Dictionary<string, HttpHeader> ResponseHeaders { get; set; }
/// <summary>
/// Non Unique headers
/// </summary>
public Dictionary<string, List<HttpHeader>> NonUniqueResponseHeaders { get; set; }
/// <summary>
/// Response network stream
/// </summary>
internal Stream ResponseStream { get; set; }
/// <summary>
/// response body contenst as byte array
/// </summary>
internal byte[] ResponseBody { get; set; }
/// <summary>
/// response body as string
/// </summary>
internal string ResponseBodyString { get; set; }
internal bool ResponseBodyRead { get; set; }
internal bool ResponseLocked { get; set; }
/// <summary>
/// Is response 100-continue
/// </summary>
public bool Is100Continue { get; internal set; }
/// <summary>
/// expectation failed returned by server?
/// </summary>
public bool ExpectationFailed { get; internal set; }
public Response()
{
this.ResponseHeaders = new Dictionary<string, HttpHeader>(StringComparer.OrdinalIgnoreCase);
this.NonUniqueResponseHeaders = new Dictionary<string, List<HttpHeader>>(StringComparer.OrdinalIgnoreCase);
}
}
}
|
Get lost in so many "that, and, in proportion to" in this sentence
I read a paper about lake and got confused about the following sentence (lower left in page 11256), because it has so many "and", "that", "in proportion to". I do not know which part of the sentence belongs to which word above.
Short-term bioassays indicated that C-limited (i.e., carbon limited) photosynthesis and algal growth and did not predict the continued growth of algal biomass in proportion to P (i.e., phosphorus).
From the view of English grammar instead of knowledge of environmental science, how can I decompose this sentence? It is frustrating that I konw the meaning of every word in this sentence, but I cannot understand this sentence.
No wonder you can't understand it. It is not grammatical. There is no verb in the first clause.
If I had to guess, I'd guess that the second 'and' should be removed.
@Jim I'd guess that that should be removed.
@StoneyB - Hmm, that doesn't clarify it for me. I might have thought 'limited' should be a verb instead of being hyphenated, but the parenthetical seems to preclude that.
@Jim "Indicated" is often used in scientific contexts to signify "indicated the presence of".
@StoneyB - Ahh!! Perfect. Makes sense now.
We need the previous sentence (or perhaps more) to see if 'that' is meant to be a determiner or complementiser here.
@StoneyB: I don't see how the (medical jargon?) usage His symptoms indicate [that pathogen] directly relates to OP's text. Apart from a typo (in the original) that I corrected, I really can't see anything that needs "explaining" here.
I'm voting to close this question as off-topic because it's apparently predicated on a typo.
StoneyB has a point. It could be "Short-term bioassays indicated C-limited (i.e., carbon limited) photosynthesis and algal growth and did not predict the continued growth of algal biomass in proportion to P (i.e., phosphorus)," in other words, short-term bioassays indicated that the critical factor was the availability of carbon, and did not predict etc. I skimmed the paper but I'm not sure which correction is what was intended. I recommend that this question be migrated over to Biology.
I suppose @StoneyB is right. Following parts constitiute this sentence : (1) Short-term bioassays indicated the presence of C-limited (i.e., carbon limited) photosynthesis and algal growth; (2) Short-term bioassays did not predict the continued growth of algal biomass in proportion to P (i.e., phosphorus).
PS: The biological meaning of Sentence (2) means that “There is no presence of P-limited photosynthesis and algal growth.”
I think the comments by StoneyB and the OP have it more correct than the existing answers...
It's not really fair to try to read this sentence without context.
For the first five years (1969–1974), the ratio of N to P in fertilizer was added at 12: 1 by weight, well above the Redfield ratio, to ensure that phytoplankton had adequate N and P supplies during the period when we were testing the C limitation hypothesis
The sentence you refer to involves data from 1969-1974, with adequate N and P.
I would rewrite the sentence as:
(Short-term bioassays) indicated (carbon-limited photosynthesis and algal growth), and (therefore) did not predict the continued growth of algal biomass in proportion to P (i.e., phosphorus).
Or, maybe in English that is more clear:
Algae were carbon-limited so the level of phosphorus didn't affect algal growth.
I think what probably happened is that in editing they went from:
Short-term bioassays indicated that carbon limited photosynthesis
(meaning their tests showed carbon was limiting photosynthesis)
to
Short-term bioassays indicated carbon-limited photosynthesis
(meaning their tests showed the lake was in a state called 'C-limited/carbon-limited photosynthesis'...which has the same overall meaning as above)
and left in the "that" when converting to the compound adjective.
Caveat: I'm a neuroscientist, and plants don't have brains, so this is typically a bit outside my wheelhouse... I'm giving this answer as someone familiar with science writing, not someone familiar with lake eutrophication except as a childhood neighbor to a eutrophic lake with a terrible phosphorus problem resulting from nearby farms.
Such a great answer! Thanks to explain one possible way how this "strange that" came from. I will improve my ability of science writing. Also hope I can do something for the eutrophic lake near your childhood house in the future (if I can be a specialist).
@TX So far alum treatments, carp removal, stocking better fish, and raising the water level by a foot and a half to match historical levels has helped a bit.
From the view of English grammar, it looks like you have a surplus "and" that creates a loose end in the sentence, or like you're missing part of the sentence that lists a third factor for predicting growth of algal biomass.
It should look like one of the two options:
Eliminating the surplus "and": Short-term bioassays indicated that C-limited photosynthesis and algal growth did not predict the continued growth of algal biomass in proportion to P.
Adding a third factor: Short-term bioassays indicated that C-limited photosynthesis and algal growth and N-fixing cyanobacteria did not predict the continued growth of algal biomass in proportion to P.
Disclaimer: For the third factor, I just picked up something random from the text...
Short-term bioassays indicated that C-limited (i.e., carbon limited)
photosynthesis and algal growth and did not predict the continued
growth of algal biomass in proportion to P (i.e., phosphorus).
"That" above is being used to indicate the particular C-limited photosynthesis previously mentioned. It is not being used as a conjunction. Were you reading it aloud, "that" would be pronounced to rhyme with the word "bat," not to rhyme with the word "bet."
Short-term bioassays indicated that C-limited (i.e., carbon
limited) photosynthesis and algal growth and did not predict the
continued growth of algal biomass in proportion to P (i.e.,
phosphorus).
"In proportion to" means "to a relative size comparable with." It's saying that short-term bioassays didn't forecast the ongoing increase of algal biomass in a manner proportionate to P.
Or it could be an example of incorrect grammar (which looks the favourite to me; your reading is grammatical, but doesn't seem to construe well). Obviously, more context is needed to decide.
Thanks! I think your explanation about "that" not being a conjunction is appropriate. In addition, I suppose StoneyB's comment can also be helpful.
Either "that" or "and" is superfluous. The presence of "that" means that the photosynthesis and growth have some effect which is not stated if "and" is present as well. If "that" is omitted then indication of photosynthesis and growth are one outcome of the studies and the prediction is another.
|
English Student's Monasticon. By the Rev. Mackenzie E. C. Walcott, B.D. Two Vols., crown 8vo, cloth extra, with Map and Ground-Plans, 14s.
Kingdom. Containing Notices of
the Descent, Birth, Marriage, Educa tion, &c., of more than 12,000 dis tinguished Heads of Families, their Heirs Apparent or Presumptive, the Offices they hold or have held, their Town and Country Addresses, Clubs, &c. Twenty-fourth Annual Edition, for 1884, clotk, full gilt, 50s. [Shortly.
The Shilling Peerage (1884). Con taining an Alphabetical List of the House of Lords, Dates of Creation, Lists of Scotch and Irish Peers, Addresses, &c. 32mo, cloth. Is. Published annually.
The Shilling Baronetage (1884). Containing an Alphabetical List of the Baronets of the United Kingdom, short Biographical Notices, Dates of Creation, Addresses, &c. 321110, cloth, Is. Published annually.
The Shilling House of Commons
(1884). Containing a List of all the Members of the British Parliament, their Town and Country Addresses, &c. 32mo, cloth. Is. Published
Angler; or. The Contemplative Man's Recreation ; being a Discourse ot Rivers, Fishponds, Fish and Fishing, written by Izaak Walton ; and In structions how to Angle for a Trout or Grayling in a clear Stream, by Charles Cotton. With Original Memoirs and Notes by Sir Harris Nicolas, and 61 Copperplate Illustrations. Large crown 8vo, cloth antique, 7s. 61.
Tavern Anecdotes and Sayings
Including the Origin of Signs, and Reminiscences connected with Ta verns, Coffee Houses, Clubs, &c. By Charles Hindley. With Illusts.
|
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
'''
.. module:: examples.benchmarks.144_000_example_2
:platform: Agnostic, Windows
:synopsis: Test for IGES type 144 form 0
.. Created on 01/08/2013
.. codeauthor:: Rod Persky <rodney.persky {removethis} AT gmail _DOT_ com>
.. Licensed under the Academic Free License ("AFL") v. 3.0
.. Source at https://github.com/Rod-Persky/pyIGES
.. figure:: 144-000-example-2.png
:scale: 70 %
:height: 507 px
:width: 1191 px
:alt: 142 type
:align: center
A more involved example of |BENCH_142|_ for |BENCH_144|_ on a 3D geometry.
The geometry however isn't complex - just more involved.
+--------------+-----------------+
| Stage 2, | Stage 1, |
| |BENCH_142| | Create Elements |
+==============+=================+
| |IGES_142| | |IGES_106| |
+--------------+-----------------+
| | |IGES_110| |
+--------------+-----------------+
| | |IGES_120| |
+--------------+-----------------+
This example draws a number of horizontally square slots
though a cone. In comparison to example 1, this is somewhat
more involved as tracing on a conical surface is tedious -it's not
particularly trivial though. The image on the left is an extension to
the task, having revolved the cutting profile - this illustrates
exactly why benchmarks need to be made (this is just too creative and
achieves nothing).
The code to make hole though a cone is:
.. literalinclude:: 144_000_example_2.py
:pyobject: iges_144_000
:linenos:
:emphasize-lines: 27-29, 92-95, 99
'''
import os
import sys
import math
sys.path.append(os.path.abspath('../../../'))
import examples.benchmarks
def cyl_to_rect(cyl_system):
#data is in format [[r], [theta], [z]]
rect_system = [[], [], []] # [[x], [y], [z]]
for i in range(0, len(cyl_system[0])):
rect_system[0].append(math.cos(math.radians(cyl_system[1][i])) * cyl_system[0][i])
rect_system[1].append(math.sin(math.radians(cyl_system[1][i])) * cyl_system[0][i])
rect_system[2].append(cyl_system[2][i])
return rect_system
def iges_144_000():
import pyiges.IGESGeomLib as IGES
from pyiges.IGESCore import IGEStorage
from pyiges.IGESGeomLib import IGESPoint
filename = "144-000-example-2.igs"
system = IGEStorage()
examples.benchmarks.standard_iges_setup(system, filename)
# Setup a cone like surface, the cone is boring but whatever!
cone_surface_profile = IGES.IGESGeomPolyline(IGESPoint(-10, 0, 0),
IGESPoint(0, 0, 10))
system.Commit(cone_surface_profile)
# The centre of the revolve
center_line = IGES.IGESGeomLine(IGESPoint(0, 0, 0),
IGESPoint(0, 0, 10))
system.Commit(center_line)
# Make the surface from the profile, this is to be trimmed
cone_surface = IGES.IGESRevolve(cone_surface_profile, center_line)
system.Commit(cone_surface)
#Setup the surface we are to put holes into, we're using the whole surface,
# as indicated by the 0 in the outer profile parameter
trimmed_surface = IGES.IGESTrimmedParaSurface(cone_surface,
0)
trimmed_surface.N1 = 0
hole = []
hole_copse = []
# We're going to put a bunch of holes into the surface, because we don't
# care about the index of the hole we can get away with specifying -8 to 8
for holenum in range(-8, 8):
hole.append(IGES.IGESGeomPolyline())
hole_data = [[], [], []]
# Top line following the cone profile
for i in range(21 * holenum, 20 + 21 * holenum):
hole_data[0].append(3)
hole_data[1].append(i)
hole_data[2].append(7)
# Line down the cone profile
hole_data[0].append(7)
hole_data[1].append(hole_data[1][-1])
hole_data[2].append(3)
# Bottom line following the cone profile
for i in range(20 + 21 * holenum, 21 * holenum, -1):
hole_data[0].append(7)
hole_data[1].append(i)
hole_data[2].append(3)
# Line back to start of the cone profile
hole_data[0].append(hole_data[0][0])
hole_data[1].append(hole_data[1][0])
hole_data[2].append(hole_data[2][0])
# Convert to rectangular coordinate system
hole_rect_cs = cyl_to_rect(hole_data)
# Push the points into the common format
for i in range(0, len(hole_rect_cs[0])):
hole[-1].AddPoint(IGESPoint(hole_rect_cs[0][i],
hole_rect_cs[1][i],
hole_rect_cs[2][i]))
# Commit this hole
system.Commit(hole[-1])
# Lets make a really very crazy looking thing!
# And revolve the cutting profile by a bit
# Setup Revolve Line data
random_line_data = cyl_to_rect([[-10, 10],
[(20 * holenum) + 90, (20 * holenum) + 90],
[10, 10]])
# Make revolve line
revolve_line = IGES.IGESGeomLine(IGESPoint(random_line_data[0][0], random_line_data[1][0], random_line_data[2][0]),
IGESPoint(random_line_data[0][1], random_line_data[1][1], random_line_data[2][1]))
# Commit revolve line
system.Commit(revolve_line)
# Make the revolve
system.Commit(IGES.IGESRevolve(hole[-1], revolve_line, -1, 0))
# Create the Curve on Parametric Surface
hole_copse.append(IGES.IGESCurveOnParametricSurface(cone_surface,
hole[-1],
hole[-1],
2))
system.Commit(hole_copse[-1])
# Lets put that holes in!
trimmed_surface.add_bounding_profile(hole_copse[-1])
# commit that surface!
system.Commit(trimmed_surface)
system.save(filename)
if not os.environ.get('READTHEDOCS', None):
print(system)
os.startfile(filename)
if __name__ == "__main__":
iges_144_000()
|
Align Series and DataFrame in assignlevel
Tests are still assuming the index is not taken into account, either we need to be smarter or fix the tests.
Codecov Report
Patch coverage: 100.00% and project coverage change: +0.14% :tada:
Comparison is base (e64085d) 79.16% compared to head (5521e0b) 79.31%.
Additional details and impacted files
@@ Coverage Diff @@
## main #38 +/- ##
==========================================
+ Coverage 79.16% 79.31% +0.14%
==========================================
Files 9 9
Lines 720 725 +5
Branches 194 196 +2
==========================================
+ Hits 570 575 +5
Misses 125 125
Partials 25 25
Files Changed
Coverage Δ
src/pandas_indexing/core.py
86.37% <100.00%> (+0.23%)
:arrow_up:
:umbrella: View full report in Codecov by Sentry.
:loudspeaker: Have feedback on the report? Share it here.
|
<div align="center">
<br>
<a href="https://almogtavor.github.io/date-range-picker">
<img src="images/../src/images/title.svg" width="800" height="400" alt="Click for Demo">
</a>
<br>
</div>
<sup>
<br />
<p align='center'>
<a href="https://www.npmjs.com/package/dates-picker"><img alt="NPM" src="https://img.shields.io/badge/v1.0.3-npm-orange"></a>
<p align='center'>⚛️📆 Flexible React date range picker calendar with no dependencies</p>
</p>
<br />
<br />
</sup>

## Demo
Demo page at <https://almogtavor.github.io/date-range-picker/>
<details>
<summary>Read More</summary>
## Main Features
* Pick method - an option of configuring the component to be date picker, range picker, or ranges picker.
* Days amount tab - an option of selecting a number of days backward from the current date immediately by choosing a number.
* Colors palette - an option of determining the component's color (can be disabled removed).
* Language - English and Hebrew support.
* Select all button - an option of selecting all of the current board's dates. Whether viewing dates, months, or years.
* Boards number - an option of configuring components to be in one board or two boards.
## Installation
```sh
$ npm i dates-picker
```
## Usage
```javascript
function callbackFunction(dates) {
console.log(`The range of dates that got picked is: ${dates.text}`);
console.log(`The min date that got picked is: ${dates.minDate}`);
console.log(`The max date that got picked is: ${dates.maxDate}`);
console.log(`The number of days that got picked is: ${dates.numberOfDaysPicked}`);
console.log(`All dates: ${dates.allDates}`);
}
function MyComponent() {
return (
<DateRangePicker
callback={callbackFunction}
/>
)
}
}
```
## Options
Property | Type | Allowed Values | Default Value | Description
-------------------------------------|-----------|------------------|----------------------|-----------------------------------------------
language | String | `English`, `Hebrew` | `English` | component's language. currently support English and Hebrew. Notice Languages such Hebrew changes the whole component from left to right to right to left.
colorsPalette | String | `enabled`, `disabled` | `enabled` | by enabling colors palette you can choose the component's color.
format | String | any combination of 2 Ds, 2 Ms and 2\4 Ys with other | `DD-MM-YYYY` | the format of the dates.
selectAllButton | String | `enabled`, `disabled` | `enabled`| depends on current board's view (dates, months, or years), select all enabled items.
startDate | date | date object | `new Date(1900, 0, 0)` | calendar's start date.
endDate | date | date object | `new Date(2025, 0, 0)` | calendar's end date.
firstDayOfWeekIndex | int | 0 - 6 | 0 (sunday) | first day of the week (etc monday, sunday).
pickMethod | String | `date`, `range`, `ranges` | `range` | date means picking one day (on one board). range is to peak dates two dates. ranges is to pick an array of ranges (with view option on hover).
defaultColor | String | any color format item | `#2196f3` | default component's color. becomes the first option on colors palette.
daysAmountTab | String | `enabled`, `disabled` | `disabled` | by enabling, there will be a button on the left that you can open and choose prepared range, or days amount up to today.
boardsNum | int | 1, 2 | 2 | by specifing you can choose the component's boards number.
## Future Plans
* Add simple and intuitive time picker option (by list\ or visual clock\ both).
* Tooltips for buttons explanation (for example on select all button).
* On non-component-screen click, close component.
* Go back button on non-dates mode (or on all modes for previous). When the user is in month's or year's mode, add an option to return to dates mode without choosing any value.
* Component & button sizes parameters
* Border radius parameter
* An option to cancel picked range from the input label
</details>
|
Page:A Compilation of the Messages and Papers of the Confederacy, Including the Diplomatic Correspondence, 1861-1865, Volume I.djvu/674
642 Messages and Papers of the Confederacy. War, Prisoners of (Continued): Treatment of — Letter of President Davis to President Lincoln regarding, "5- Referred to, 121. Retaliation — Measures of, proclaimed, 269. Discussed, 2S9. Threatened, 115, 120, 141. War, Secretary of: Appropriations recommended by. (See Appropriations.) Communication from, transmitted, 147. Report of, transmitted and dis- cussed, 73, 78, 138, 151, 190, 194, J 95» !99. 200, 201, 235, 294, 369, 447, 49i- War Tax: Appropriation recommended to re- fund excess of, paid by — Louisiana, 253. North Carolina, 239. Propriet v of providing for payment of loans by, discussed, 259. War Vessels. (See Vessels, Naval.) Washington and New Orleans Tele- graph Company, shares held in, by alien enemies discussed, 30S, 309- Watkins, Oscar M., resolution of thanks tendered command of, 338. Webb, W. A., mentioned, 19S. Weed, Thurlow, mentioned, 95. Weldon Railroad, Va., Seizure of. While operating against Richmond and Petersburg, Va., in June, 1S64, the Federals, under Gen. Grant, attempted to, capture this road from the Confederates, under Gen. Lee. The latter were attacked on June 22 bv Federals, under the imme- diate command of Generals Birney and Wright, who were repulsed with heavy loss. August 18, another attack was made by forces under Gen. Warren, the Con- federal s being under command of Gen. Mahone, with a Federal loss of 4,500. On the 25th, at Reams Station, an assault was made on the Second Army Corps and Gregg's cavalry while destroying the railroad, and they were driven off with heavy losses. Wheat's Louisiana Battalion, disband- ing of, referred to, 261. Wheeler, Joseph, resolution of thanks tendered command of, 33S. Whiting, William H. C: Correspondence with, regarding defense of Wilmington, N. C, transmitted, 402. Report of, regarding running blockade of Wilmington, N. C, transmitted, 382. Wilderness, Va., Battle of. (See also Spottsylvania Court House, Bat- tle of.) A battle in the Wilderness region in Virginia, south of the Rapidan River, May S, 6, 1S64. The Federals, 120,000 men and 300 guns, were commanded by Gen. Grant and Gen. Meade; the Confed- erates, 65,000, by Gen. Lee. The Confed- erates attacked on the 5th, and the fight- ing was severe through that day and the next. Federal losses, near 20,000, includ- ing 5,000 prisoners; Confederate loss, about 10,000. The Federals withdrew, and marched to near Spottsylvania Court House. The Confederates met them there, and the battle of Spottsylvania Court House was fought. Willcox, 0. B., correspondence in peace negotiations, 521. Williams, John S., report of, on opera- tions at Blue Springs, Henderson, and Rheatown transmitted, 402. Williamsburg, Va., Battle of. A battle at Williamsburg, Va., May6, 1862. The Federals were commanded by Generals Hooker and Heintzelman; the Confederates, by Gen. Magruder. The Federals attacked and were repulsed, with a loss of 450 killed and i,Soo wound- ed and missing; Confederate loss, includ- ing killed and wounded, 1,500. Wilmington, N. C: Defense of, referred to, 402. Running blockade of, referred to, 382. Wilson's Creek, Mo., Battle of. A battle near Springfield, Mo., Aug. 10, 1861. The Federals were command- ed by Generals Lyon and Sigel; the
|
// Copyright 2017 Archos SA
//
// Licensed under the Apache License, Version 2.0 (the "License");
// you may not use this file except in compliance with the License.
// You may obtain a copy of the License at
//
// http://www.apache.org/licenses/LICENSE-2.0
//
// Unless required by applicable law or agreed to in writing, software
// distributed under the License is distributed on an "AS IS" BASIS,
// WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
// See the License for the specific language governing permissions and
// limitations under the License.
package com.archos.mediascraper.preprocess;
import android.net.Uri;
import android.text.TextUtils;
import java.text.Normalizer;
/**
* Holds search relevant information for movies
* Title & Year specifically
*/
public class MovieSearchInfo extends SearchInfo {
private final String mName;
private final String mYear;
/** package private, use {@link SearchPreprocessor} */
MovieSearchInfo(Uri uri, String name, String year) {
super(uri);
mName = Normalizer.normalize(name, Normalizer.Form.NFC);
mYear = TextUtils.isEmpty(year) ? null : year;
}
public String getName() {
return mName;
}
public String getYear() {
return mYear;
}
@Override
protected String createSearchSuggestion() {
if (mYear != null)
return mName + " " + mYear;
return mName;
}
@Override
public boolean isTvShow() {
return false;
}
}
|
[Congressional Record Volume 151, Number 146 (Monday, November 7, 2005)]
[House]
[Page H9701]
ANNOUNCEMENT BY THE SPEAKER PRO TEMPORE
The SPEAKER pro tempore. Pursuant to clause 8 of rule XX, the Chair
will postpone further proceedings today on motions to suspend the rules
on which a recorded vote or the yeas and nays are ordered, or on which
the vote is objected to under clause 6 of rule XX.
Record votes on postponed questions will be taken after 6:30 p.m.
today.
____________________
|
trench taken out around them deep enough to sever all roots, filling up the trench again firmly. About one-third the distance from the stem the trees spread is proper for the trench. It will probably cause the trees to form fruit buds. Allow one Strawberry layer to a plant, all others should be pinched off as they appear. Club-root in Cabbag-es ( Amateur ).—It is in some cases very diffi¬ cult to deal with. The best preventive is to dress the ground with gaslime at the rate of a bushel per rod (30J square yards') some months in advance of putting in the crop, for when applied at the time or shortly in advance of the planting it is injurious to them. It should be spread evenly on the surface, and be merely raked or very lightly pointed in. A dressing of nitrate of soda is also good. It may be applied a fortnight in advance of the crop, at the rate of 1 lb. per rod. Super¬ phosphate of lime may,be used advantageously at the rate of 3 to 4J lbs. per rod. When, planting out, any. Cabbages found with a protuberance at the root should be thrown away, or the club opened and the grub destroyed : those and all the other plants dipped in a thick solution of soot water. Terhaps the best material for dipping is to mix 1 oz. Calvert’s No 5 carbolic acid w T ith two gallons of soapsuds, adding sufficient clay or loam to form a thin paste. Well stir the mixture and dip the whole of the plants before planting, which must be in ilaniD soil, so as to render watering unnecessary. Petroleum may be used in a similar manner as the carbolic acid. Bee Orchis Treatment (J. 7?.).—The Ophrys apifera may be grown in pots, which should be well drained, using pieces of chalk, and a compost of sandy loam, but not very light, intermixed with about a fourth of chalk in moderate sized pieces. The tuberous roots should be placed beside or between pieces of chalk, care being taken to fill in the interstices with the loam. The plants may be stood on ashes in a cold frame, but are preferably plunged in that material to the rim. They require to have the soil always moist, but little water will be needed during the resting period, whilst, w r hen'growing and until the growth matures, water must be afforded copiously. They are the better for slight shade. Admit air on all favourable occasions, and draw the lights off whenever the weather is mild. They may also be grown in pots plunged in ashes with a little protective material in winter, such as dry hay. A position where they will have plenty of light with slight shade from hot sun is the best for these plants. The b.est mode of culture is to plant at the foot of rockwork alongside limestone or chalk, with rock or other prominence that will afford shade from the powerful rays of summer sun. Care should be taken not to allow them to suffer from lack of moisture. Ammonia for Vines (7f. S. 71).—Time after time it has been stated in " Work for the Week,” in articles, and in answers in this column, that ammonia can be beneficially applied to Vines in the form of strong guano water sprinkled in the house and placed in troughs on the pipes. We are. most willing to. advise you at all times, but have often observed you apply for information that has been given a few weeks before, and consequently a few weeks • too late for your deriving full benefit from the replies that we can give on a subject. Mix one or two ounces of guano in a gallon of water, and make every available plant of the house wet with it every evening when you close the sashes. You cannot very well use too much of this in hBt weather until the Grapes colour, but open the lights an inch or two at the top before nightfall, and the front lights also on sultry nights, and leave them open, giving more air very early in the morning,in advance of the rising temperature—that is. to prevent the heat, rushing up suddenly, then having to throw open the ventilators to reduce it. This latter practice, which is much too common, is the cause of many failures. The night temperature you name is quite 5° higher than is recommended in the Journal; in fact 10°, and.we fear you do not read attentively. If the thermometer registers 65° the first thing in the morning the house will be quite warm enough, but there must always be a free circulation of air. Shallow vessels may still be kept filled with water in hot weather, but the ammonia applications had better cease when the Grapes are fairly colouring, and before they are ripe. As has frequently been stated, this should commence when the berries are about stoning. Names of Fruits. —The names and addresses of senders of fruit to be named must in all cases be enclosed with the specimens, whether letters referring to the fruit are sent by post or not. The names are not necessarily required for publication, initials sufficing for that. Only six specimens can be named at once, and any beyond that number cannot be preserved. (J. S.')-— The box did not reach us till Monday, and as it was only half filled with fruit the contents resembled jam, hence the varieties were totally beyond identification. Names of Plants. —We only undertake to name species of plants, not varieties that have originated from seed and termed florists’ flowers. Flowering specimens are necessary of flowering plants, and Fern fronds should bear spores. Specimens should arrive in a fresh state in firm boxes. Slightly damp moss or soft green leaves form the best packing, d ry cotton wool the worst. Not more than six specimens can be named at once. ( 7 J . 7 ?.). —As you will see by our standing notification we do not under¬ take to name varieties of florists’ flowers. Possibly most of those you send never had names ; the flaked and mottled flowers are inferior. If you purchased the plants as named varieties you had better send flowers to the vendor for him to name. ( J 72. S. 67.).—Melilotus officinalis. (II. A'.).— 1, Lotus corniculatus; 2, Medicago maculata ; 3, Trifolium pratense. (IF. J3. 72.).--1, Shone Armeria ; 2, Centranthus ruber. (77.67). —We do not undertake to name Roses, and the other two specimens, both apparently Spineas, were not in good condition for determination. COYENT GARDEN MARKET.— August 1st. A brisk business dome:, with heavy supplies. Prices remain the same with theexception of house fruit, which is lower. FRUIT.
A WET SUMMER.
After the dry weather of May a dripping June was gladly welcomed, as being admirably calculated to promote free growth and bring on the corn crops in readiness to derive full benefit from the hot summer weather which we had reasonable hope would follow in July. But such hopes were doomed to disappointment, for the cold wet weather of July, 1888, was so remarkable that it will certainly be remembered for many years to come ; not, we hope, for any disastrous results arising from it, but rather for its phenomenal character alone. True it is that people are not wanting who assert that the effects of week after week of cold, wet, sunless weather in July must prove the reverse of beneficial for the corn ; that the Wheat could not “ cast ”— i.e., set its blossom and develope grain—without
|
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace Demo_5
{
class Queue
{
static public Node Enqueue(Node queue, string value)
{
//Add to tail
return List.Add(queue, value, -1);
}
static public Node Dequeue(Node queue, out string value)
{
return Stack.Pop(queue, out value);
}
static public string Peek(Node queue)
{
return Stack.Peek(queue);
}
}
}
|
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Dataflow;
namespace Jsonm
{
public class ParserErrorReporter : ErrorReporter
{
public List<ErrorInformation> Errors { get; set; }
public ParserErrorReporter()
{
Errors = new List<ErrorInformation>();
}
protected override void OnError(ErrorInformation errorInformation)
{
string msg = string.Format(errorInformation.Message, errorInformation.Arguments.ToArray());
throw new ParserErrorException(errorInformation.Location.Span.Start.Line,
errorInformation.Location.Span.Start.Column,
errorInformation.Location.Span.Length,
msg);
//throw new FormatException(
// string.Format("Syntax error at [{0}, {1}]: {2}",
// errorInformation.Location.Span.Start.Line,
// errorInformation.Location.Span.Start.Column,
// msg));
}
}
}
|
Engine induction valve with reduced backflow
ABSTRACT
This invention is an effective engine induction valve which provides a decrease in engine blowback while maintaining engine power. This valve uses a moveable member made from a heat-setting material, this member being bent into an elliptical curve when the member is in the closed position. This elliptical curve has an included angle at the edge of the member which opens toward the engine, this orientation being beneficial in reducing blowback. Using springs to limit the force attaching the moveable member to the valve body prevents unwanted buckling of this member when exposed to elevated temperature and fuel. An embodiment is described which provides a valve with a uniform frequency response at various operating conditions, especially different temperatures.
BACKGROUND
[0001] 1. Field of Invention
[0002] This invention is an improved engine induction one-way valve to control intake mass flow in primarily two-stroke cycle engines. In one embodiment of this invention, a reed embodiment, the moveable sealing member is a reed; in another embodiment, a poppet embodiment, it is a spring-loaded curved plate. The moveable sealing member is bent against a curved seat preferably being a segment of an ellipse and having a relatively small average radius of curvature. The convex side of this curve always faces the incoming flow to the engine thereby presenting an aerodynamic surface for this flow; the concave side always faces the engine to minimize backflow. In order to minimize the pop-off pressure of this valve which would normally be associated with bending to this small radius of curvature, the moveable sealing member is made from a material which stress relieves and takes a set when exposed to a process which usually includes elevated temperature.
[0003] 2. Description of Prior Art
[0004] Induction valves have been used extensively to control mass (air and sometimes fuel) flow into an engine, primarily two-stroke cycle engines. These two-stroke cycle engines are normally crankcase-scavenged wherein the reciprocating motion of the piston in the cylinder changes the effective crankcase volume, thus causing a pumping action. When the cylinder piston rises in its cylinder, effective crankcase volume increases creating a vacuum which causes a mass flow into the crankcase; the descending motion of the piston on the power stroke decreases crankcase volume causing an increase in crankcase pressure, this increase being used to force mass into the engine cylinder for combustion. This increase in crankcase pressure also tends to force mass flow out of the crankcase through the induction tract through which it just entered, this reverse mass flow being called backflow, reversion, or blowback. It is desirable to minimize this backflow for engine power, emissions, and fuel economy considerations.
[0005] Several methods of controlling this reverse flow have been employed; one method uses a reed valve placed in the induction tract. The reed valve design which has gained wide acceptance for crankcase-scavenged two-stroke cycle engines uses reeds firmly clamped to a reed cage, the reeds and reed cage looking much like a pup tent with the apex of the tent facing the engine. FIG. 1 of applicant's co-pending application 09/812337 shows a commonly used reed assembly. The included angle of a reed valve is defined herein as the angle between two lines tangent to the reed ends when in the closed position. This angle by choice will be 180 degrees or less. Typically, this included angle in a conventional reed valve is in a range of 60 to 120 degrees, with the open side of the included angle facing away from the engine (toward the throttle) and its apex pointing toward the engine. Therefore, in the case of a conventional reed valve, the included angle is the angle between the two panels of the “tent” with the floor of the tent being on the side away from the engine and the peak of the tent pointing toward the engine.
[0006] The reed cage contains usually three or four openings in each side of the “tent” with reed petals which rest against seats formed into the tent, thereby closing the valve. The reed petals bend away from the seats to open the valve upon application of an opening pressure. The seats are normally flat and therefore the reeds in the closed position resting against the seats are flat. The reed petals are usually made from stainless steel, fiberglass, or carbon fiber, the latter being most widely used today. A guard plate is used in clamping the reeds to the reed cage, this guard plate limiting the maximum bending of the reed to help prevent reed damage.
[0007] Observation of open carburetors on operating engines using conventional reeds shows considerable blowback at almost all throttle positions and conditions of engine loading. This prompted this action to develop an improved induction valve which would reduce this blowback.
[0008] Several modifications in the basic design of these reed valves have been developed. U.S. Pat. No. 4,076,047 to Akahori (1978) describes using a reed petal seat which causes a slight bend in the reed in its closed position, thus creating a pre-load in the reed which aids in sealing. This pre-load in bending, however, causes an increase in the reed pop-off pressure, the pressure which must be applied to the reed to initiate an opening movement. For best operation of a reed valve in admitting mass flow into the engine with minimal entropy increase, it is desirable that this pop-off pressure be minimized. Therefore, in U.S. Pat. No. 4,076,047, an angle between the reed seat and its clamping surface in the range of 1 degree to 3 degrees is described as preferable, this small angle being a compromise between improved sealing and increased pop-off pressure.
[0009] Other reed assemblies, such as described in U.S. Pat. Nos. 2,612,882 to Kiekhaefer (1952), 3,008,459 to Kaufinan (1961), and 4,408,579 to Kusche (1983) show reed valve assemblies for internal combustion engines which use a reed securely mounted to a reed cage or block in which the reed forms an included angle described above of 180 degrees. In other words, the reed seats are positioned such that the plane containing the seats (and the reeds in the closed position) lies essentially perpendicular to the engine induction passage. The tangent lines to the reed ends are therefore co-linear and the included angle is 180 degrees. These seats are also shown as being flat.
[0010] U.S. Pat. No. 5,601,112 to Sekiya et al. (1997) describes a valve which has a moveable sealing member which is flexible and spring-loaded. The open area of the valve and hence the valve flow rate for any pressure across the valve is determined by a combination of translational movement of the disc and flexing of the disc. If the flexibility of the disc material changes with temperature, the operation of the valve will not be uniform at various operating temperatures. Also a stopper is used which blocks a substantial portion of the dynamic pressure associated with a backflow from impacting the disc. Also shown is a disc which is essentially flat across most of its area when in the closed position; this flat portion is not an aerodynamic shape for forward flow and thus impedes forward flow through the valve.
[0011] Also, a flow control device called a liquid scroll diode is known in the art which uses no moving parts to provide asymmetric flow characteristics. These diodes provide a flow path which is offset in passing through a circular shaped cavity. The offset is positioned in the cavity to cause minimal flow momentum direction change in a forward direction. The position of the offset, however, together with the circular cavity, causes some backward flow to “scroll” around the circular cavity, ending up with a momentum which is in the opposite direction to which it started, namely against the original flow momentum direction. These scrolling vortices essentially reverse the momentum direction of a portion of the backward flow, directing this reversed momentum against the backward flow. This momentum reversal interferes severely with backward mass flow through the diode, providing the asymmetrical flow characteristic. It was felt that the principles used in these liquid scroll diodes could be applied to an engine induction valve to reduce blowback.
[0012] Objects and Advantages
[0013] It is an object of this invention to provide an engine induction valve having a moveable sealing member with a curved shape having a convex side facing away from the engine at all operating conditions presenting an aerodynamic surface to incoming mass flow and the opposite concave side always facing the engine to cause a scrolling vortex action to outward flow thereby reducing blowback.
[0014] It is a further object of this invention to provide an engine induction valve with a moveable sealing member having an included angle between lines tangent to its ends in the closed position of less than 180 degrees with the angle opening facing toward the engine and its apex pointing away from the engine.
[0015] It is a further object of this invention to provide an engine induction valve having a uniform frequency response at various temperatures while using a moveable sealing member made from a material whose elastic modulus changes with temperature.
[0016] It is a further object of this invention to provide an engine induction valve having a moveable sealing member mounting which has more than one mounting point but allows volume expansion of the member in all directions.
[0017] It is a further object of this invention to provide an engine induction valve which uses a moveable sealing member which is forced to bend against a seat, thereby inducing a stress in the member, but being constructed of a material in which this stress is consequently diminished upon application of a process containing elevated temperature, for instance.
[0018] It is a further object of this invention to provide an engine induction valve which uses a moveable member to seal against a curved seat, this curved seat having a decreasing radius of curvature as the distance from a central axis of the member increases.
[0019] Still further objects and advantages will become apparent from a consideration of the ensuing description and drawing.
DRAWING FIGURES
[0020]FIG. 1 shows an isometric view of a preferred reed valve embodiment of this invention. FIGS. 2 and 3 show cross sectional views of this reed valve taken in a plane containing the axis of a reed attachment bolt, FIG. 2 having the reed in the closed position, FIG. 3 having the reed in the open position. FIG. 4 shows an isometric view of a preferred poppet valve embodiment of this invention. FIGS. 5 and 6 show cross sectional views of this poppet valve taken in a plane containing the axis of a mounting stud, FIG. 5 having the moveable member in the closed position, FIG. 6 having the member in the open position.
REFERENCE NUMERAL IN THE DRAWINGS
[0021] 10 induction valve housing
[0022] 12 valve housing outlet conduit
[0023] 20 inlet manifold
[0024] 22 inlet manifold conduit
[0025] 24 arrow showing valve inlet flow direction
[0026] 70 arrow showing reverse flow scroll vortex streamline
[0027] 100 reed valve assembly
[0028] 120 reed valve body
[0029] 122 reed opening
[0030] 126 reed seat
[0031] 130 reed petal in closed position
[0032] 130′ reed petal in open position
[0033] 131 elongated mounting hole
[0034] 132 reed petal sealing edge
[0035] 133 reed petal pivot edge
[0036] 142 mounting screw
[0037] 144 mounting spring
[0038] 146 mounting rod
[0039] 147 mounting rod threaded hole
[0040] 148 lock nut
[0041] 200 poppet valve assembly
[0042] 220 poppet valve body
[0043] 222 poppet body opening
[0044] 226 poppet seat
[0045] 230 moveable sealing member in closed position
[0046] 230′ moveable sealing member in open position
[0047] 231 elongated mounting hole
[0048] 232 moveable member primary sealing edge
[0049] 233 moveable member secondary sealing edge
[0050] 242 mounting stud
[0051] 244 control spring
[0052] 246 guide rod
[0053] 248 nut
DESCRIPTION AND OPERATION—FIGS. 1, 2, and 3
[0054]FIGS. 1, 2, and 3 show a reed valve assembly 100 of this invention. Reed assembly 100 is normally clamped between an induction valve housing 10 and an inlet manifold 20 using a suitable clamping means (not shown). Valve housing 10 is normally cast as part of an engine (not shown) and contains an outlet conduit 12 which transfers the mass which has passed through valve 100 into the engine. Inlet manifold 20 is normally a metal or rubber member which connects reed assembly 100 to a throttle body or carburetor (not shown) and contains an inlet conduit 22. Inward mass flow direction is shown by direction arrow 24; streamlines of reverse air flow scroll vortices are shown illustrative ly by arrows 70.
[0055] Assembly 100 contains a body 120 normally machined or cast from a metal such as aluminum or a plastic such as acetal or nylon. Body 120 has an opening 122 in a seat 126, seat 126 having a preferred contour.
[0056] A reed petal in a closed position is shown as 130; a reed petal in an open position is shown as 130′. Petal 130 contains an elongated mounting hole 131, a sealing edge 132, and an edge generally perpendicular to sealing edge 132 called a pivot edge 133.
[0057] Reed 130 is positioned relative to body 120 using screws 142, springs 144, a mounting rod 146 with threaded holes 147, and optional lock nuts 148. Reed 130 as it opens to reed 130′ bends and pivots against rod 146 creating the reed action.
[0058] Operation of FIGS. 1, 2, and 3 is as follows. Reciprocating motion of a piston in the engine creates pressure pulses in the engine crankcase, these pressure pulses resulting in a pressure difference across reed valve assembly 100. When the engine piston is on its upward stroke, a reduced pressure appears in outlet conduit 12 relative to the pressure existing in inlet conduit 22. Once this pressure difference exceeds the reed's pop-off pressure, this pressure difference causes reed petal 130 in the closed position against seat 126 to move away from seat 126 and eventually move to an open position shown as reed petal 130′. Shortly after the engine piston begins its descent on the power stroke, the pressure in outlet conduit 12 rises relative to the pressure in inlet conduit 22. This change in pressure difference, aided by the bending stress existing in reed petal 130′, causes petal 130′ to move toward seat 126 eventually effectively sealing opening 122. The movement of petal 130′ to seat 126 essentially prevents further mass escape, or blowback, out of the engine crankcase. This description describes the operation of reed assembly 100 and is similar to the operation of conventional reed assemblies.
[0059] Several parameters affect reed valve operation in allowing relatively unrestricted mass inflow to the engine but relatively restricted outflow. Aerodynamic considerations for the reed assembly are very important; reed operation will be improved if it has good aerodynamic properties in the forward direction, but poor aerodynamic properties in the reverse direction. Other considerations involve the reed itself; the density and elastic modulus of the material, and the thickness and length of the reed from its pivot point. A mass flow system which allows mass flow with small entropy increase can be said to have good aerodynamic properties; a system which causes relatively large entropy increase can be said to have poor aerodynamic properties. A valve which has poorer aerodynamic flow properties into an engine and/ or better aerodynamic flow properties out of an engine will cause an engine to lose power.
[0060] Conventional reeds presently used, namely reeds with their included angle facing away from the engine, are fairly aerodynamic in the forward direction, the inside of the reed “tent” collecting or “funneling” the incoming mass and directing it toward the reed opening for smooth flow into the engine. Conventional reeds are actually also fairly aerodynamic in the reverse direction, however, which is not desirable. When conventional reeds are in the open position, there is a direct path for mass flow through the open reed in the backward direction, and the flow relatively easily adjusts to exit through the reed opening as it travels out of the engine crankcase. Some of the outward mass flow, however, “misses” the reed opening, pressurizing the area between the open reed and the reed housing. The area between the open reed and the reed housing is essentially a “dead end street”. The mass stream which passes the open end of the conventional reed passes into this “dead air” space where essentially all its momentum is lost and not reversed. The momentum of the mass which has missed the reed end has therefore minimal effect in reducing backflow.
[0061] Reed assembly 100 of this invention has good aerodynamic properties in the forward direction, even with the reed having an included angle which faces the engine. The inward flow aerodynamic properties associated with the curved surface of reed 130 (and 130′) are better than those existing with a flat surface. Dynamometer testing has shown that this shape flows well due to the fact that there is essentially no loss in engine power with reed assembly 100 compared to a conventional reed assembly.
[0062] Reed assembly 100 has poor aerodynamic flow characteristics in the reverse direction, this being desirable. As mentioned above, observing open carburetors on a running engine shows considerable blowback when using conventional reed assemblies. The open carburetors on a twin cylinder engine have been observed while run on a dynamometer with a conventional reed installed on one cylinder and a reed assembly similar to assembly 100 of this invention on the other cylinder. It was observed that while there was little or no decrease in horsepower compared to the same engine run with two conventional reeds, the carburetor containing the reed assembly similar to assembly 100 had minimal blowback at any throttle position or engine loading, but the carburetor with the conventional reed installed had significant blowback at almost all conditions.
[0063] It is felt that this reduction in blowback is partially the result of the scroll vortex effect described above. Open reed petal 130′ (and even its eventual change to closed reed 130) in FIG. 3 is shown to have the ability to create this same circular vortex to impede mass outflow from the engine through reed assembly 100. When the pressure in conduit 12 is greater than the pressure in conduit 22, mass flow in conduit 12 is in a direction toward reed petal 130′, namely away from the engine. Even a relatively short distance from petal 130′, the flow is fairly uniform across the area of conduit 12. Due to the fact that the opening at sealing edge 132 of reed petal 130′ is offset relative to the center of conduit 12 and due to the momentum or dynamic pressure of the moving mass in conduit 12, there is a tendency for some of the mass to impinge upon the concave engine side of reed petal 130′ and “scroll” due to the curved shape of petal 130′, creating a flow streamline shown by arrow 70. This scrolling mass flow leaves sealing edge 132 of reed petal 130′ shown by the end of arrow 70. The direction of the momentum of this mass flow at the end of arrow 70 has a component which is reversed from that existing in conduit 12, this reversed momentum opposing mass flow past sealing edge 132 thereby reducing blowback. In other words, the shape of reed assembly 100 performs similarly to a scroll liquid diode in that the flow path in the backward direction is offset, a portion of the backward flow contacts a curved surface, namely the concave engine side of reed 130′, causing this flow portion to “scroll”, interfering with and limiting reverse mass flow past sealing edge 132 of open reed 130′.
[0064] It is also important to note that this scroll effect which reduces backflow is most effective if the backward flow momentum, or dynamic pressure, is able to directly impinge on the back side of moveable member 130′. This enables the scroll to exit near sealing edge 132 where it is most effective in reducing backflow past this edge. The presence of a stopper, a fixed member which prevents excessive movement of reed 130′, would interfere with the dynamic pressure associated with this backflow from impinging on reed 130′. It is conceivable that a stopper could be designed with its own curved surface to create a scrolling effect, but due to the fact that it is fixed, would only be most effective in reducing backflow when reed 130′ was in the fully open position and edge 132 was adjacent to the stopper. At other partially open positions, edge 132 would be spaced away from the edge of the stopper which is causing the scrolling, and therefore its beneficial effect would be diminished. Therefore, it can be seen that reed 130′ of assembly 100 provides in essence a moveable “scrolling edge”, namely sealing edge 132, which has maximum benefit in reducing backflow past itself. A fixed stopper which prevents a substantial portion of the backward dynamic pressure from impinging on member 130′ would also slow down the closing of member 130′ to position 130. This is due to the diminished closing force on member 130′ due to the loss of the dynamic pressure impact on 130′ caused by the shielding effect of a fixed stopper.
[0065] This design did present some obstacles which had to be overcome. It is preferable to design reed assembly 100 to fit into existing valve housings 10 to enable replacement of conventional reed assemblies. Therefore the length of pivot edge 133 of reed 130 is limited by the existing space available. One-half the length of pivot edge 133, which can be called the pivot length of reed 130, considered in relation to the movement away from seat 126 of sealing edge 132, determines the average radius of curvature required in open reed 130′ required for sufficient mass flow past edge 132. Conventional reeds, primarily because of the orientation of their included angles and the fact that they are clamped at the base of the reed cage “tent”, have pivot lengths in the range of 38 mm (1.5 inches); the pivot length of reed 130′ of assembly when installed in an existing reed housing 10 is limited to a length of approximately 19 mm (0.75 inches). Therefore, to achieve a similar opening area for mass flow past sealing edge 132, reed 130 of this invention must deflect to a smaller average radius of curvature than that required for a conventional reed.
[0066] As mentioned earlier, existing reeds used today primarily use carbon fiber in their construction, other materials being fiberglass and stainless steel. These materials are relatively rigid and would excessively fatigue or actually break when bent in the small radius required in assembly 100. A material with the elastic properties of a rubber, in other words a material having a Poisson's ratio (the ratio between the strain perpendicular to an applied stress and the strain parallel to the stress) in the range of 0.4 to 0.8 is desirable for this application because of its ability to be repeatedly bent to a relatively small radius of curvature.
[0067] A material which worked well for this reed assembly 100 was polyurethane having a durometer of 90 Shore A and a thickness of 1.5 mm (0.06 inches). This material has a low specific gravity, about 1.1, a relatively high tensile strength, good abrasion resistance, and long life under continuous flexing.
[0068] Another problem which arose when using this material was its thermal expansion and expansion caused by impregnation when exposed to elevated temperatures in the presence of fuel and lubricating oil. This expansion was found to be in the range of about 5%. When a reed 130 made from polyurethane was rigidly clamped by mounting rod 146 to body 120 and subsequently exposed to elevated temperature in the presence of fuel and oil, reed 130 permanently buckled, especially at sealing edge 132; it couldn't easily lengthen due to the rigid clamping. This buckling prevented reed 130 from effectively sealing against seat 126 and the operation of valve 100 was impaired.
[0069] The solution to this problem was to spring load attachment screws 142 using mounting springs 144 and to use elongated holes 131 in reed 130 for the penetration of screws 142 through member 130 as shown in FIG. 1. By adjusting the torque on screws 142, springs 144 were set with a sufficient initial load to hold and position reed 130 against body 120 but, with elongated holes 131, still allowed reed 130 to lengthen, thereby preventing the buckling described above.
[0070] Testing and computer simulations of this system indicate that in all cases it is desirable to minimize the pre-load on reed 130 consistent with satisfactory sealing. In other words it is beneficial to minimize the pop-off pressure of reed 130. The reed design of this invention shown in FIGS. 1,2, and 3 at first inspection would indicate that its pop-off pressure would be relatively high. The pop-off pressure of reed 160, using a reed made of the above mentioned material and which is initially flat, does exhibit a relatively high pop-off pressure when first installed against curved seat 126. A reed assembly similar to assembly 100 with an initially flat “new” polyurethane reed was tested for power on an engine, and there was a power decrease compared to that obtained with conventional reed assemblies on the same engine.
[0071] It was found, however, that after repeated operation and heat soaking in the presence of fuel, engine power increased. Also, after removal of this “used” reed from body 120, it had stress-relieved, taking a set. Reed 130 after removal from body 120 had approximately the shape of seat 126, having only slightly less curvature than seat 126 after removal. This stress relief, therefore, would also mean a decrease in pop-off pressure with the consequent improvement in engine power. It should be noted that this stress relief can occur in service, or reed 130 can be pre-set by application of a suitable process such as bending and subjection to elevated temperature (in the presence of a suitable solvent if desired).
[0072] A seat 126 shape which worked particularly well, especially for a reed which took a set, was a curve whose radius of curvature became progressively less as the dimension from mounting rod 146 along pivot edge 133 increased. This helped insure that the primary sealing edge of reed 130, namely edge 132, sealed against seat 126 in the closed position. A curve that fits this description of course is an ellipse An elliptically curved seat 126 is easily obtained by machining body 120 using an inclined circular mill. A suitable seat 126 was milled into body 120 for a valve similar to assembly 100 by clamping body 120 horizontally in a mill and machining with a mill of diameter 80 mm (3.15″) with its axis inclined at an angle of 40 degrees to vertical.
[0073] Lines tangent to reed 130 near opposite edges 132 which define the end of the curve in reed 130 establish the included angle for this design. Using the seat and reed pivot length described above, this yielded an included angle for closed reed 130 of approximately 140 degrees. This included angle has its opening toward the engine and its apex pointing away from the engine. This included angle of course progressively decreased as reed 130 bent to reed 130′, attaining an included angle of approximately 120 degrees at an open position.
DESCRIPTION AND OPERATION—FIGS. 4, 5, and 6
[0074]FIGS. 4, 5, and 6 show a poppet valve assembly 200 of this invention. Poppet assembly 200 is normally clamped between an induction valve housing 10 and an inlet manifold 20 using a suitable clamping means (not shown). Valve housing 10 is normally cast as part of an engine (not shown) and contains an outlet conduit 12 which transfers the mass which has passed through valve 200 into the engine. Inlet manifold 20 is normally a metal or rubber member which connects assembly 200 to a throttle body or carburetor (not shown) and contains an inlet conduit 22. Inward mass flow direction is shown by direction arrow 24; streamlines of reverse air flow scroll vortices are shown illustrative ly by arrows 70.
[0075] Assembly 200 contains a body 220 normally machined or cast from a metal such as aluminum or a plastic such as acetal or nylon. Body 220 has an opening 222 in a seat 226, seat 226 preferably having an elliptical contour.
[0076] A moveable sealing member in a closed position is shown as 230; in an open position it is shown as 230′. Member 230 contains elongated mounting holes 231, a primary sealing edge 232, and an edge generally perpendicular to sealing edge 232 called secondary sealing edge 233. Moveable sealing member 230 is positioned relative to body 220 using studs 242, springs 244, guide rods 246, and nuts 248.
[0077] Operation of FIGS. 4, 5, and 6 is similar to the operation of reed assembly 100. As in assembly 100, reciprocating motion of the engine piston causes pressure differences to appear across assembly 200. When the pressure in outlet conduit 12 is less than the pressure in inlet conduit 22, member 230 is urged to compress springs 244, moving along guide rods 246 away from seat 226 thereby allowing mass flow through opening 222. In this case, the pop-off pressure valve 200 is primarily determined by the initial set-up force in springs 244; once this pop-off pressure is exceeded, movement of member 230 occurs. When the pressure in outlet conduit 12 increases relative to the pressure in inlet conduit 22, the force built up in compressed springs 244 along with the force on moveable member 230′ due to static and dynamic pressure acting on it, moves member 230′ along guide rods 246 toward seat 226, eventually contacting seat 226 and effectively sealing opening 222.
[0078] Poppet assembly 200, like reed assembly 100, has good aerodynamic properties in the forward direction, enabled in part to the initial bend, or curve, in member 230. This initial bend over the entire surface of member 230 will make assembly 200 possess better forward aerodynamic properties than a similar poppet valve having a portion of its surface flat. These good aerodynamic properties exist at all positions of member 230.
[0079] Assembly 200, like assembly 100, has poor reverse flow aerodynamic properties. Poppet valves similar to assembly 200 were run on an engine; blowback quantity was observed to be minimal compared to conventional reed valves with essentially no loss in engine power. Like assembly 100, this improved performance of assembly 200 is believed to partially be attributable to the scrolling of the reverse air flow shown by arrows 70 in FIG. 6. As in assembly 100, the engine side of valve 200 is designed without any stoppers or baffles to hinder backward mass flow momentum and its associated dynamic pressure from impinging on the engine side of member 230. This allows the scrolling action shown by arrow 70 to occur near edge 232, thereby being most effective in reducing backward mass flow past edge 232. Edge 232, like edge 132 in assembly 100, is a moveable “scrolling edge”.
[0080] In testing reed assemblies similar to assembly 100, increased blowback was observed when reed 130 was hot. This is caused by a reduction at elevated temperatures in the elastic modulus of the polyurethane used to construct reed 130. This reduction in elastic modulus makes reed 130 more flexible, reduces the natural frequency of the reed, and consequently lowers the frequency response of the valve, thereby allowing more blowback.
[0081] In assembly 200 an essentially constant frequency response was obtained by making moveable member 230 “stiff” relative to the total spring rate of springs 244. This was obtained primarily by three methods. First, a polyurethane of a higher durometer, namely 95 Shore A, was used compared to the 90 durometer used in reed assembly 100. This higher durometer material has a higher elastic modulus thereby making member 230 stiffer in bending. Another change was to make the length of secondary sealing edge 233 in member 230 shorter than the length of pivot edge 133 of reed 130. This shorter length also makes member 230 stiffer in bending along edge 233 than petal 130 in bending along edge 133. Minimizing the total moving mass in assembly 200, principally the mass of member 230, also minimizes the spring rate of springs 244 for any given frequency response, also helping make them relatively weak compared to the flexibility of member 230. Using these design considerations in a valve similar to assembly 200 there was no noticeable difference in frequency response of the valve at various operating temperatures for any spring rate value selected for springs 244.
[0082] Moveable member 230 has an essentially rectangular shape, and it is therefore necessary that the angular orientation of 230 relative to body 220 by maintained correctly to insure proper closing of opening 222 by member 230. Since member 230 is not rigidly clamped to body, more than one coupling point is required to maintain the proper orientation. Member 230 was provided with two holes to allow two guide rods 246 to penetrate member 230. Moveable member 230 of assembly 200, because of its spring 244 mounting, its frequent movement from seat 226, and its elongated holes 231, also overcomes the problem of buckling caused by volume swell of member 230 even though multiple mounting points are used. Furthermore, it has been found that elongated holes 231 can be replaced with sufficiently oversized round holes relative to the diameter of guide rods 246, and can be further improved if these holes are located such that their position is correct relative to guide rods 246 after normal swelling of member 230 has occurred. It was also found that due to the good abrasion resistance of the polyurethane used in member 230, no bushings in holes 231 were required; holes 231 in the polyurethane were their own bushings.
[0083] Member 230 of assembly 200 was designed to have minimum bending due to opening pressure compared to reed petal 130 of assembly 100. Therefore, to insure improved aerodynamic properties in the forward direction, seat 226 was designed to have a smaller average radius of curvature than that used in seat 126 of assembly 100. This was accomplished by using a milling cutter having a smaller diameter than that used for seat 126 of assembly 100. A suitable seat 226 was milled into body 220 for a valve similar to assembly 200 by clamping body 220 horizontally in a mill and machining with a mill of diameter 48 mm (1.9″) with its axis inclined at an angle of 45 degrees to vertical. Using the seat described above with a length for secondary sealing edge 233 of 34 mm (1.3″), this gave an included angle for member 230 of approximately 110 degrees. This included angle has its opening facing toward the engine and its apex pointing away from the engine.
SUMMARY, RAMIFICATION, AND SCOPE
[0084] Accordingly, the reader will see that this invention provides an engine induction valve which is an effective replacement for conventional reed valves which, partially due to a curve in its moveable member, provides a reduction in engine blowback while delivering essentially equal engine power. Proper spring selection and moveable member shape and material selection allow this valve to maintain an essentially uniform frequency characteristic even if the moveable member material changes stiffness with temperature change. Proper spring loaded attachment of the moveable body to the valve body allows expansion of the moveable member without buckling. Construction of the moveable member from a material which takes a set after exposure to a combination of heat and fuel allows the member to be significantly bent to improve the aerodynamic characteristics of the valve while maintaining a low pop-off pressure.
[0085] Although the description above contains many specificities, these should not be construed as limiting the scope of the invention but as merely providing illustrations of some of the presently preferred embodiments of this invention. For instance, o-rings have successfully been used for the mounting springs in the reed embodiment of this invention. Also, discussed here is a reed embodiment where the moveable member acts like a reed and moves only in flexing, and a poppet embodiment where the moveable member moves essentially only in translation. A combination of these two embodiments is possible where both moveable member flexing and translation are important in the valve operation. Also, even though the moveable member in either the reed or poppet valve embodiment is described as one piece of material, there could be some instances where manufacture of the moveable member in several pieces may be desirable, which could still fall under the essence of this invention. Thus, the scope of the invention should be determined by the appended claims and their legal equivalents, rather than by the examples given.
I claim:
1. A valve for mass flow control in an induction tract of an internal combustion engine, said engine induction tract including: a first direction of said mass flow toward said engine, a second direction of said mass flow away from said engine, a first pressure urging said mass flow in said first direction toward said engine, a second pressure urging said mass flow in said second direction away from said engine, said valve including: a body with a seat having a curved surface, a moveable member which has a closed position which effectively closes said valve when operationally covering said seat but which is able to move away from said seat in response to said first pressure to open said valve, said moveable member having a curved shape, said curved shape having a first side which is always convex and a second side which is always concave, an attachment means which is effective in positioning said moveable member relative to said body and said seat, wherein said first convex side always faces away from said engine and wherein said curve in said first convex side is always effective in creating good aerodynamic mass flow properties in first direction toward said engine, and wherein said second concave side always faces toward said engine and is always effective in reducing said mass flow in said second direction away from said engine.
2. The valve of claim
1. wherein said moveable member has a first shape which can be deformed by a force into a second shape and can return to essentially said first shape after removal of said force, and wherein said moveable member has said first shape, is deformed by said force into said second shape, is subjected to a process, and after removal of said force has a third shape distinctly different from said first shape.
3. The valve of claim
2. wherein said process includes application of elevated temperatures.
4. The valve of claim
2. wherein said process includes the application of a fuel of said engine.
5. The valve of claim
2. wherein said process includes operation in said induction tract of said engine.
6. The valve of claim
2. wherein said moveable member is made from polyurethane.
7. The valve of claim
2. wherein said second shape is the shape of said moveable member when in said closed position, and wherein said valve has a first magnitude of said first pressure which causes said moveable member in said second shape before application of said process to move incrementally from said closed position, a second magnitude of said first pressure which causes said moveable member in said second shape after application of said process to move incrementally from said closed position, and wherein said first magnitude is operationally greater than said second magnitude.
8. The valve of claim
2. wherein said attachment means penetrates said moveable member in multiple locations, and wherein said attachment means has an operationally effective spring rate to limit the force between said moveable member and said body allowing operationally effective movement of said moveable member in all directions thereby preventing detrimental buckling of said moveable member after application of an operationally possible process.
9. The valve of claim
1. wherein said mass flow in said second direction away from said engine has a momentum in said second direction and is effective in applying dynamic pressure to said second side of said moveable member which is always concave and always facing toward said engine, and whereby said second side of said moveable member which is always concave and always facing toward said engine is effective in causing reversal of a portion of said momentum in said second direction to a momentum having a component in said first direction toward said engine, whereby said mass flow in said second direction away from said engine is impeded.
10. The valve of claim
9. wherein an operationally effective portion of said mass flow in said second direction away from said engine impacts said second side of said moveable member which is always concave and always facing toward said engine and wherein said effective portion of said mass flow in said second direction consequently contains streamlines which are scroll vortices located near an edge of said moveable member thereby impeding said mass flow in said second direction away from said engine past said edge of said moveable member.
11. The valve of claim
10. wherein said streamlines which are scroll vortices operationally move in response to movement of said moveable member.
12. The valve of claim
1. wherein said moveable member has a flexibility, said attachment means has an operationally finite spring rate, and wherein said flexibility in said moveable member is effective in determining movement of said moveable member in response to said first pressure and wherein said spring rate of said attachment means is operationally ineffective in determining said movement.
13. The valve of claim
1. wherein said moveable member has a flexibility, said attachment means has a spring rate, and wherein said flexibility in said moveable member is operationally ineffective in determining movement of said moveable member in response to said first pressure and wherein said spring rate of said attachment means is effective in determining said movement.
14. The valve of claim
1. wherein said moveable member has a flexibility, said attachment means has a spring rate, and wherein said flexibility in said moveable member and said spring rate of said attachment means are effective in determining movement of said moveable member in response to said first pressure.
15. A valve for mass control in a n induction tract of a n internal combustion engine, said valve including: a body with a seat having a curve d surface, a moveable member which effectively closes said valve when operationally covering said seat but which is able to move away from said seat in response to said first pressure to open said valve, said curved surface in said seat having a first radius of curvature near a central axis of said moveable member and a second radius of curvature near an edge of said moveable member, wherein said first radius of curvature is greater than said second radius of curvature.
16. The valve of claim
15. wherein said curved surface in said seat contains a segment of an ellipse.
17. The valve of claim
1. wherein said moveable member has an included angle defined by two lines tangent to surfaces of said moveable member at opposite edges which define the ends of said curved shape of said moveable member, the value of said included angle being less than 180 degrees and wherein said included angle opens toward said engine and said included angle has its apex pointing away from said engine.
18. The valve of claim
17. wherein said included angle has a value between 50 and 150 degrees.
19. A valve for mass flow control in an induction tract of an internal combustion engine, said engine induction tract including: a first direction of said mass flow toward said engine, a second direction of said mass flow away from said engine, a first pressure urging said mass flow in said first direction toward said engine, a second pressure urging said mass flow in said second direction away from said engine, said valve including: a body with a seat, a moveable member which effectively closes said valve when operationally covering said seat but which is able to move away from said seat in response to said first pressure to open said valve, an attachment means which is effective in positioning said moveable member relative to said body and said seat, said moveable member having a flexibility, said flexibility in said moveable member being effective in determining movement of said moveable member, said attachment means being ineffective in determining said movement of said moveable member, said moveable member having an included angle defined by lines tangent to said moveable member near opposite edges of said moveable member, the value of said included angle being less than 180 degrees, and wherein said included angle opens toward said engine and said included angle has its apex pointing away from said engine.
20. The valve of claim
19. wherein said included angle has a value between 50 and 150 degrees.
|
Non-Hodgkin lymphoma (NHL) is a common B/NK/T cell lymphoma with 509,590 new cases and 248,724 deaths around the world in 2018 \[[@CIT0001]\]. According to the report from National Central Cancer Registry of China, there were 88,200 new cases of lymphoma and myeloma in 2015 which accounted for 2.1% of all new cancer cases, whereas the case number of deaths from lymphoma and myeloma was 52,100 which accounted for 1.9% of all cancer deaths in 2015 \[[@CIT0002]\]. In 2016, more than 260,000 people were diagnosed with lymphoma in China, indicating that there were approximately 20 patients with lymphoma per 100,000 people \[[@CIT0003]\].
The increase in overall survival rates of NHL was largely ascribed to the progress in several treatment studies and the application of the relevant research achievements \[[@CIT0004]\], which included monoclonal antibody (mAbs) \[[@CIT0010]\], mAbs linked to anti-tubulin or DNA damaging agents \[[@CIT0013]\], small molecule inhibitors \[[@CIT0014],[@CIT0015]\] and the targeted chimeric antigen receptor T cells (CAR-T) \[[@CIT0016]\]. However, recently the mortalities of NHL are still high and even remain increasing in some regions. And the distribution trend of incidence and mortality of NHL varies depending on age, gender and country. Although several regional and national studies on the incidence and mortality of NHL have been performed, specific studies about the burden of NHL at a global level are scarce.
The aim of this study was to comprehensively analyse the distribution trends of NHL in different countries and regions by collecting data from Global Burden of Disease (GBD) study. It is necessary to get more detailed data on the incidence and mortality of NHL and the changing trends of NHL in different countries and regions, which could help policymakers to adopt policies more rationally based on the information. In GBD Study in 2017, countries and regions were divided into five major regions according to the social-demographic index (SDI). Therefore in this study, we collected detailed data about the incidence and mortality of NHL from GBD Study in 2017 and comprehensively assessed the disease burden of NHL at the global level and also analysed its current trends according to sex, age, SDI, country and region. We also collected data on human development index (HDI) of the national level in 2017 from the World Bank and evaluated the association between percentage change of incidence and mortality and HDI at the national level.
Materials and methods {#S0002}
Study data {#S0002-S2001}
We collected data from the Global Health Data Exchange (GHDx) on GBD Study in 2017 hosted by Institute for Health Metrics and Evaluation at Washington University, with the query tool (<http://ghdx.healthdata.org/gbd-results-tool>). Instruments for the tabulation and graphical visualization of the GLOBOCAN database for 195 countries can be found on the Global Cancer Observatory website. The 195 countries were divided into 21 regions, including Eastern, Western, South-Eastern, and South Central Asia; Eastern, Western, Southern, and Northern Europe; Northern and South Central America; Southern, Northern, Central, Eastern, and Western Africa; Oceanian; Australia/New Zealandand Caribbean \[[@CIT0001]\]. In GBD Study in 2017, countries and regions were divided into five major regions according to SDI as follows: low SDI, low-middle SDI, middle SDI, middle-high SDI and high SDI. SDI was calculated based on per capital income at the national level, the average educational years of people above 15 years old and the general fertility rate. General methods for GBD 2017 and the method for estimation of NHL burden have been detailed in other GBD studies \[[@CIT0019],[@CIT0020]\]. Briefly, data on the incidence and mortality of NHL were sought from individual cancer registries or aggregated databases of cancer registries. Since NHL is a fatal disease, we used incidence and mortality to assess its burden. The subjects in this study were patients with NHL which conform to an approved standard of The International Classification of Diseases such as 9th/10th revision codes pertaining to NHL (200--200.9, 202--202.98 and C82--C85.29, C85.7--C86.6, C96--C96.9, respectively).
Statistical analysis {#S0002-S2002}
The indices relating to age-standardized rate (ASR) are good indicators of changes in disease patterns of population distribution, as well as are clues of changes in risk factors. ASR is essential when we compare different groups of people with distinct age structures, so ASR of incidence and mortality was calculated to quantify the burden of NHL in this study. The ASR per 100,000 people was calculated using the method reported by previous study \[[@CIT0021]\]. In briefly, the age-specific rates and number of people in the same age subgroup of the standard people group were sum up, then be divided by the sum of standard population weights.
The change trends of incidence and mortality of NHL were assessed by percentage changes and estimated annual percentage changes (EAPCs). EAPC is a frequently used measure of the ASR trend over a time interval. A regression line was fitted to the natural logarithm of the ASR, i.e. y = a + Px + £, where y is the natural logarithm of the ASR, and x is the calendar year. The EAPC was calculated as 100 × (exp (P) −1), and its 95% confidence intervals (CIs) can also be obtained from the model.
Additionally, in order to explore the influential factor for incidence and mortality of NHL, we collected data on HDI at the national level in 2017 from the World Bank and analysed the correlation between percentage change of incidence and mortality and HDI at the national level.
All the statistics were performed with the R program (Version 3.5.3, R core team). A *p* value of less than 0.05 was considered statistically significant.
Global burden of non-Hodgkin lymphoma {#S0003-S2001}
Globally, the incidence of NHL varies considerably across the world, with the highest incidence observed in Lebanon (23.35 per 100,000 people; 95% UI: \[20.19--27.08\] in 2017), followed by Australia (15.95 per 100,000 people; 95% UI: \[14.1--17.89\]) and New Zealand (15.73 per 100,000 people; 95% UI: \[14.117.89\]). The lowest incidence was observed in Iraq (1.49 per 100,000 people, 95% UI: \[1.35--1.64\] in 2017), followed by Kyrgyzstan (1.68 per 100,000 people; 95% UI \[1.51--1.84\]) and Bangladesh (1.71 per 100,000 people; 95% UI: \[1.42--2.01\]) ([Figure 1](#F0001){ref-type="fig"} and [Table S1](https://doi.org/10.1080/07853890.2022.2039957)). As for the percentage change of incidence, Lebanon had witnessed more than one time of increment (174.03%) from 1990 to 2017, followed by South Korea (169.07%) and Georgia (147.17%). From 1990 to 2017, Iraq had fallen (−61.35%), followed by Burundi (−33.34%) and Rwanda (−31.25%) ([Figure 2](#F0002){ref-type="fig"} and [Table S2](https://doi.org/10.1080/07853890.2022.2039957)).
::: {#F0001 .fig}
The global disease burden of non-Hodgkin lymphoma for both sexes in 195 countries and territories in 2017. The age-standardized deaths rate (upper) and the age-standardized incidence rate (lower). The world map was created using R program package "maps" (version 3.3.0, <https://cran.r-project.org/web/packages/maps/index.html>).
::: {#F0002 .fig}
The age-standardized percentage change of incidence and mortality of non-Hodgkin lymphoma for both sexes in 195 countries and territories in 2017. The age-standardized percentage change of deaths (upper) and the age-standardized percentage change of incidence (lower). The world map was created using R program package "maps" (version 3.3.0, <https://cran.r-project.org/web/packages/maps/index.html>).
As for the mortality of NHL across the world, it was shown that the mortality in Malawi was the highest (11.79 per 100,000 people; 95% UI: \[9.65--14.02\] in 2017), followed by Lebanon (9.02 per 100,000 people; 95% UI: \[8.01--10.22\]) and Uganda (8.24 per 100,000 people; 95% UI: \[6.95--9.68\]). Besides, the lowest mortality was observed in Kyrgyzstan (1.22 per 100,000 people; 95% UI: \[1.12--1.33\] in 2017), followed by Iraq (1.26 per 100,000 people; 95% UI: \[1.14--1.38\]) and Kazakhstan (1.41 per 100,000 people; 95% UI: \[1.3--1.55\]) ([Figure 1](#F0001){ref-type="fig"} and [Table S3](https://doi.org/10.1080/07853890.2022.2039957)). In terms of the percentage change of death from 1990 to 2017, more increments was recorded in Georgia (104.74%), followed by Lithuania (59.94%) and Zimbabwe (59.22%), more reductions were recorded in Iraq (−64.62%), followed by Kazakhstan (−42.17%) and Bermuda (−41.44%) ([Figure 2](#F0002){ref-type="fig"} and [Table S4](https://doi.org/10.1080/07853890.2022.2039957)).
Regarding SDI regions, the incidence of NHL was increased in other SDI regions except the low SDI regions during the period from 1990 to 2017 ([Table 1](#t0001){ref-type="table"}). As for the geographical regions, absolute number of NHL cases was increased in almost all the regions ([Figure 3](#F0003){ref-type="fig"}). Significant or slight decreases in the percentage change incidence of NHL were reported in 50 countries or territories (including Iraq, Burundi, Rwanda, etc.) from 1990 to 2017. However, the percentage change incidence of NHL was reported as being significantly increased in 18 countries or territories including Lebanon, South Korea, Georgia, Estonia, etc. Additionally, 33 countries or territories including Seychelles, Romania, Mauritius, and Ireland showed a substantial increase. But steady or slight increase in the percentage change incidence of NHL was reported in 93 countries or territories, including France, UK, Philippines, Norway, North Korea, etc ([Figure 2](#F0002){ref-type="fig"}).
::: {#F0003 .fig}
The age-standardized incidence and mortality rate of non-Hodgkin lymphoma by SDI and gender from 1990 to 2017.
::: {#t0001 .table-wrap}
The age-standardized rate of incidence and death of non-Hodgkin lymphoma in 1990 and 2017, and age-standardized percentage change and EAPC of non-Hodgkin lymphoma from 1990 to 2017.
Location Death (1990, 95% UI) Death (2017, 95% UI) Incidence (1990, 95% UI) Incidence (2017, 95% UI) Percentage change death (1990--2017, 95% UI) Percentage change incidence (1990--2017, 95% UI) EAPC (death, 95% CI) EAPC (incidence, 95% CI)
------------------------------ ---------------------- ---------------------- -------------------------- -------------------------- ---------------------------------------------- -------------------------------------------------- -------------------------- --------------------------
Global 3.19 (3.1 to 3.34) 3.18 (3.11 to 3.24) 4.75 (4.62 to 4.93) 6.18 (6.06 to 6.29) −0.47% (−5.91 to 3.34) 30.12% (23.92 to 35.29)\* −0.19 (−0.28 to −0.1)\* 0.75 (0.62 to 0.88)\*
Low SDI 3.05 (2.59 to 3.76) 2.99 (2.66 to 3.21) 3.23 (2.69 to 4.06) 3.22 (2.86 to 3.46) −2.03% (−19.39 to 16.38) −0.55% (−20.15 to 21.92) −0.15 (−0.23 to −0.08)\* −0.1 (−0.19 to −0.02)\*
Low-middle SDI 2.57 (2.39 to 2.81) 2.96 (2.74 to 3.17) 2.76 (2.55 to 3.06) 3.41 (3.16 to 3.67) 15.13% (0.23 to 26.02)\* 23.42% (5.92 to 36.03)\* 0.5 (0.46 to 0.54)\* 0.74 (0.71 to 0.78)\*
Middle SDI 2.29 (2.2 to 2.37) 2.51 (2.42 to 2.61) 2.52 (2.43 to 2.61) 3.68 (3.54 to 3.83) 9.62% (3.86 to 17.01)\* 45.61% (37.23 to 55.26)\* 0.32 (0.21 to 0.43)\* 1.4 (1.19 to 1.61)\*
High-middle SDI 2.24 (2.16 to 2.32) 2.56 (2.49 to 2.64) 2.94 (2.84 to 3.05) 5.38 (5.19 to 5.56) 14.16% (7.96 to 20.82)\* 82.91% (71.85 to 93.49)\* 0.54 (0.45 to 0.63)\* 2.46 (2.21 to 2.7)\*
High SDI 4.47 (4.43 to 4.5) 3.84 (3.75 to 3.92) 9.11 (9.01 to 9.21) 12.07 (11.75 to 12.39) −14.04% (−15.99 to −12.17)\* 32.51% (28.71 to 36.27)\* −0.99 (−1.18 to −0.8)\* 0.58 (0.32 to 0.85)\*
Central Europe 2.56 (2.52 to 2.6) 2.88 (2.8 to 2.97) 3.86 (3.78 to 3.95) 7.1 (6.84 to 7.4) 12.46% (8.56 to 16.37)\* 83.91% (75.73 to 92.5)\* 0.51 (0.36 to 0.65)\* 2.5 (2.39 to 2.61)\*
Australasia 5.85 (5.72 to 5.99) 4.6 (4.2 to 4.99) 12.35 (11.96 to 12.75) 15.91 (14.31 to 17.54) −21.46% (−28.37 to −14.64)\* 28.85% (15.48 to 42.95)\* −1.46 (−1.69 to −1.24)\* 0.55 (0.33 to 0.77)\*
Central Asia 1.86 (1.7 to 1.98) 1.88 (1.79 to 1.97) 2.41 (2.22 to 2.55) 2.98 (2.83 to 3.14) 1.46% (−6.92 to 12.69) 23.82% (13.68 to 36.56)\* −0.09 (−0.2 to 0.02) 0.69 (0.5 to 0.88)\*
Central Latin America 2.57 (2.52 to 2.61) 2.66 (2.55 to 2.78) 2.87 (2.81 to 2.93) 3.82 (3.66 to 4.03) 3.78% (−0.84 to 9.38) 33.42% (27.33 to 40.66)\* 0.09 (0.01 to 0.16)\* 1.04 (0.96 to 1.12)\*
Tropical Latin America 2.71 (2.65 to 2.77) 2.74 (2.66 to 2.82) 3.05 (2.97 to 3.12) 3.77 (3.65 to 3.89) 1.11% (−2.58 to 4.84) 23.47% (18.7 to 28.08)\* −0.16 (−0.42 to 0.1) 0.62 (0.36 to 0.88)\*
Caribbean 4.01 (3.8 to 4.51) 3.45 (3.2 to 3.79) 4.92 (4.62 to 5.54) 5.35 (4.96 to 5.83) −14.08% (−19.91 to −8.3)\* 8.84% (0.43 to 17.15)\* −0.62 (−0.79 to −0.46)\* 0.3 (0.13 to 0.47)\*
Southern Sub-Saharan Africa 2.61 (2.35 to 2.9) 2.99 (2.78 to 3.19) 2.7 (2.45 to 2.97) 3.25 (3.01 to 3.47) 14.82% (3.88 to 27.99)\* 20.52% (10.18 to 33.53)\* 0.63 (0.15 to1.11)\* 0.76 (0.28 to 1.24)\*
Eastern Europe 2 (1.84 to 2.1) 2.57 (2.51 to 2.64) 3.5 (3.22 to 3.73) 6.14 (5.84 to 6.46) 28.62% (23.06 to 38.32)\* 75.3% (63.01 to 90.61)\* 1.18 (0.97 to 1.38)\* 2.6 (2.2 to 3)\*
Southern Latin America 3.67 (3.58 to 3.77) 3.62 (3.35 to 3.93) 4.21 (4.1 to 4.32) 5.48 (5.08 to 5.97) −1.52% (−8.93 to 7.12) 30.29% (20.53 to 41.76)\* −0.29 (−0.59 to 0.01) 0.76 (0.51 to 1.02)\*
Andean Latin America 3.63 (3.38 to 3.9) 4.02 (3.65 to 4.37) 3.86 (3.61 to 4.16) 5.09 (4.62 to 5.56) 10.73% (−1.11 to 23.24) 31.84% (16.83 to 47.17)\* 0.39 (0.16 to 0.63)\* 1.08 (0.87 to 1.3)\*
Southeast Asia 2.79 (2.58 to 3.04) 2.78 (2.61 to 2.94) 3 (2.76 to 3.29) 3.46 (3.24 to 3.67) −0.41% (−9.26 to 9.33) 15.1% (3.66 to 26.49)\* −0.06 (−0.13 to 0.01) 0.46 (0.41 to 0.5)\*
Western Europe 4.18 (4.13 to 4.22) 3.77 (3.63 to 3.91) 8.4 (8.23 to 8.56) 12.67 (12.11 to 13.24) −9.63% (−13.13 to −6.35)\* 50.95% (43 to 58.65)\* −0.79 (−0.99 to −0.58)\* 1.15 (0.87 to 1.42)\*
High-income Asia Pacific 3.09 (3.05 to 3.13) 3.18 (3.02 to 3.31) 5.08 (4.97 to 5.19) 8.61 (7.99 to 9.22) 2.89% (−2.09 to 7.55) 69.38% (57.2 to 81.34)\* −0.08 (−0.24 to 0.08) 2.09 (1.93 to 2.25)\*
South Asia 2.13 (1.94 to 2.36) 2.68 (2.5 to 2.83) 2.22 (2.02 to 2.48) 2.96 (2.76 to 3.13) 25.69% (10.35 to 39.58)\* 33.12% (15.42 to 47.55)\* 0.85 (0.79 to 0.9)\* 1.05 (0.98 to 1.12)\*
High-income North America 6.2 (6.13 to 6.27) 4.74 (4.62 to 4.87) 14.37 (14.12 to 14.61) 15.24 (14.77 to 15.75) −23.51% (−25.71 to −21.17)\* 6.05% (2.23 to 10.12)\* −1.58 (−1.81 to −1.35)\* −0.52 (−0.88 to −0.15)\*
East Asia 1.92 (1.82 to 2.01) 2.21 (2.12 to 2.31) 2.24 (2.12 to 2.34) 4.55 (4.32 to 4.76) 15.21% (6.99 to 24.96)\* 103.37% (87.02 to 120.8)\* 0.57 (0.25 to 0.9)\* 2.8 (2.27 to 3.33)\*
North Africa and Middle East 3.05 (2.76 to 3.46) 2.81 (2.67 to 2.99) 3.33 (3.03 to 3.82) 4.34 (4.12 to 4.63) −7.63% (−21.32 to 6.51) 30.29% (9.24 to 49.14)\* −0.25 (−0.34 to −0.16)\* 1.11 (1.06 to 1.17)\*
Oceania 2.59 (2.14 to 3.37) 2.77 (2.31 to 3.66) 2.81 (2.35 to 3.72) 3.11 (2.63 to 4.16) 7.27% (−5.35 to 21.8) 10.49% (−3.06 to 27.45) 0.41 (0.33 to 0.49)\* 0.51 (0.44 to 0.58)\*
Central Sub-Saharan Africa 2.49 (1.84 to 2.96) 2.08 (1.47 to 2.67) 2.56 (1.95 to 3.07) 2.16 (1.57 to 2.71) −16.46% (−32.18 to 2.34) −15.9% (−32.99 to 5.12) −0.75 (−0.92 to −0.58)\* −0.73 (−0.9 to −0.57)\*
Eastern Sub-Saharan Africa 6.57 (5.48 to 8.12) 5.63 (4.84 to 6.27) 6.9 (5.62 to 8.71) 5.96 (5.1 to 6.67) −14.29% (−34.81 to 9.76) −13.58% (−35.87 to 14.57) −0.79 (−0.9 to −0.68)\* −0.76 (−0.87 to −0.64)\*
Western Sub-Saharan Africa 3.26 (2.76 to 3.91) 3.17 (2.79 to 3.68) 3.6 (3 to 4.34) 3.56 (3.11 to 4.13) −2.57% (−20.26 to 16.92) −1.29% (−19.8 to 20.08) −0.29 (−.41 to −0.18)\* −0.27 (−0.4 to −0.13)\*
Results are for both sexes combined. \*Statistically significant increase or decrease.
The mortality was increased in the low-middle, middle and middle-high SDI regions during the period from 1990 to 2017. However, the mortality was reduced in the low and high SDI regions ([Table 1](#t0001){ref-type="table"}). One hundred countries or territories (such as Iraq, Kazakhstan, Bermuda, etc.) were shown as being significant or slight decreases in the percentage change death of NHL from 1990 to 2017. Moeover, substantial increase in the percentage change death was reported in five countries or territories including Lithuania, Zimbabwe, and Ukraine. Steady or slight increase in the percentage change death was shown in 89 countries or territories including Japan, South Africa, India, etc. ([Figure 2](#F0002){ref-type="fig"}).
The change in the incidence of NHL {#S0003-S2002}
At the global level, the incidence of NHL increased gradually, and it changed from 4.75 per 100,000 people (95% UI: 4.62--4.93) in 1990 to 6.18 per 100,000 (95% UI: 6.06--6.29) in 2017 ([Figure 3](#F0003){ref-type="fig"}). The percentage change incidence of NHL was 30.12%, while its EAPCs of the incidence was 0.75 (95% CI: 0.62--0.88) during the period from 1990 to 2017 ([Table 1](#t0001){ref-type="table"}). In terms of SDI level, as shown in [Figure 3](#F0003){ref-type="fig"} and [Table 1](#t0001){ref-type="table"}, the percentage change incidence and its EAPCs of the incidence decreased slightly in the low SDI region but they increased significantly in the other SDI regions. In the high-middle SDI region, EAPCs of the incidence increased dramatically by 2.46 (95% CI: 2.21 to − 2.7). EAPCs of the incidence in the other three SDI regions were on the increase.
From the viewpoint of the 21 territories in the world, the percentage change incidence of NHL in East Asia, High-income Asia Pacific, Eastern Europe and Central Europe increased significantly from 1990 to 2017. However, the percentage change incidence decreased in the following three territories such as Central, Eastern and Western sub-Saharan Africa ([Figure 4](#F0004){ref-type="fig"}). Besides, we observed positive correlations between HDI and incidence of NHL (*ρ* = 0.59, *p* \< 0.001) for both males (*ρ* = 0.57, *p* \< 0.001) and females (*ρ* = 0.56, *p* \< 0.001) ([Figure 5](#F0005){ref-type="fig"}).
::: {#F0004 .fig}
The age-standardized percentage change of incidence and mortality of non-Hodgkin lymphoma by SDI and gender from 1990 to 2017.
::: {#F0005 .fig}
The correlation between human development index (HDI) and age-standerdized percentage change of incidence and mortality of non-Hodgkin lymphoma from 1990 to 2017. The dots represent countries that were available on HDI data. The p indices and *p* values were derived from Pearson correlation analysis.
As for gender and age, the incidence of NHL in the males was higher than that in the females ([Figure 6](#F0006){ref-type="fig"}). For example, in 2017, the ASR of NHL incidence was 46.85 (95% UI: 45.29--48.44) and 32.86 (95% UI 31.67--33.89) per 100,000 people in males and females aged over 70, respectively. The ASR of NHL incidence was 17.54 (95% UI: 16.98--18.07) and 11.75 (95% UI: 11.35--12.12) per 100,000 people in males and females aged 50--69, respectively. The ASR of NHL incidence was 3.14 (95% UI: 3.02--3.25) and 2.14 (95% UI: 2.07--2.22) per 100,000 people in males and females aged 15--49, respectively. Globally, the male-to-female ratios of incidence were all more than 1.4 in the groups aged 15--49, 50--69 and over 70. Besides, the male-to-female ratios of incidence were greater in Middle SDI regions of all three age groups than those in low-middle SDI regions of all three age groups ([Figure 7](#F0007){ref-type="fig"}). Noticeably, the male-to-female ratio of incidence in high-middle SDI region had been increasing significantly since 2005 ([Figure 7](#F0007){ref-type="fig"}). In brief, the incidence of NHL in the young-aged group accounted for relatively low proportion in all the age groups, while the incidence of NHL was significantly higher in the males of old-aged groups than that in the females of old-aged groups ([Figure 6](#F0006){ref-type="fig"}).
::: {#F0006 .fig}
The incidence and mortality of non-Hodgkin lymphoma in different age groups in 1990, 2007 and 2017.
::: {#F0007 .fig}
The male to female ratio of incidence and mortality of non-Hodgkin lymphoma among different age groups from 1990 to 2017.
Overall, the male-to-female ratio of incidence tended to be on the increase from 1990 to 2017. However, there were also exceptions. In the group aged 15--49, the male-to-female ratio of incidence in high SDI regions gradually decreased, and that in low SDI regions were relatively stable. The male-to-female ratio of incidence in low-middle SDI regions of all three age groups was lower than those in the other four SDI regions of all three age groups. As regard to the level of GBD territories, the incidence rate of NHL showed an upward trend in four territories including East Asia, High-income Asia Pacific, Eastern Europe, and Central Europe, while a downward trend was observed in three territories including Central, Eastern, and Western sub-Saharan Africa.
The change in the mortality of NHL {#S0003-S2003}
At the global level, the mortality of NHL was stable with 3.19 per 100,000 people (95% UI: 3.1--3.34) in 1990 and 3.18 per 100,000 people (95% UI: 3.11--3.24) in 2017. However, the EAPCs of NHL significantly decreased by −0.19 (95% CI: from −0.28 to −0.1), and the percentage change mortality of NHL from 1990 to 2017 decreased by −0.47% (95% UI: from −5.91 to −3.34) ([Table 1](#t0001){ref-type="table"}). As for the analysis of NHL according to the SDI level and territories, the percentage change death in both low and high SDI regions decreased significantly during the period from 1990 to 2017, and its percentage change death was −2.03% (95% UI: from −19.39 to 16.38) and −14.04% (95% UI from −15.99 to −12.17) in low and high SDI, respectively ([Table 1](#t0001){ref-type="table"}). From 1990 to 2017, EAPCs of death in low and High SDI regions decreased slightly with −0.15 (95% CI: from −0.23 to −0.08) and − 0.99(95% CI: from −1.18 to −0.8), respectively. But the percentage change death of NHL and its EAPCs in other SDI regions increased from 1990 to 2017 ([Table 1](#t0001){ref-type="table"}). The mortality in males was higher than that in the females during this period ([Figure 3](#F0003){ref-type="fig"}). Moreover, the percentage change death of NHL and its EAPC were reported as being slightly decreased in 10 territories including Australasia, Caribbean, Southern Latin America, Southeast Asia, Western Europe, High-income North America, North Africa and the Middle East, Central Sub-Saharan Africa, Eastern Sub-Saharan Africa and Western Sub-Saharan Africa. And the percentage change death of NHL and its EAPC were shown as being steadily or slightly increased in eleven territories including Central Europe, Central Asia, Central Latin America, Tropical Latin America, Southern Sub-Saharan Africa, Eastern Europe, Andean Latin America, High-income Asia Pacific, South Asia, East Asia and Oceania ([Table 1](#t0001){ref-type="table"}). From the viewpoint of GBD territories, the mortality showed an upward trend in six territories (East Asia, South Asia, Eastern Europe, Central Europe, Andean Latin American, Southern Sub-Saharan Africa), a downward trend in eight territories (Australasia, High-income North American, Western Europe, Caribbean, North Africa and Middle East, Central Eastern and Western sub-Saharan Africa), and a stable trend in the other territories ([Figure 4](#F0004){ref-type="fig"}).
As for gender and age, the mortality of NHL had been gradually increasing with age since 1990, and the mortality of the males was higher than that of the females ([Figure 6](#F0006){ref-type="fig"}). For example, in 2017, the mortality of NHL in patients aged over 70 was 30.12 (95% UI: 29.32--30.83) and 20.78 (95% UI: 20.12--21.35) per 100,000 people for males and females, respectively. The mortality in patients aged 50--69 was 8.56 (95% UI: 8.29--8.78) and 5.16 (95% UI: 4.98 − 5.34) per 100, 000 people for the males and the females, respectively. The mortality of people aged 15--49 was 1.24 (95% UI: 1.19--1.29) and 0.79 (95% UI: 0.76 − 0.83) per 100,000 for the males and females, respectively. The male-to-female ratio of deaths displayed an increasing tendency in the age groups of 15--49, 50--69 and over 70 years from 1990 to 2017. However, in the group aged 15--49, the male-to-female ratios of deaths in high SDI regions gradually decreased.
In brief, the male-to-female ratios of deaths in the group aged over 70 were lower than that in the groups aged 15--49 and 50--69. Additionally, the mortality of NHL in the young-aged group accounted for relatively lower proportion in all the aged groups. And for the old-aged group, males showed a significantly higher mortality of NHL as compared to females. Moreover, the male-to-female ratios of deaths in Middle SDI regions were relatively higher than that in other regions in all three age groups. But low-middle SDI region showed a lower male-to-female ratio of deaths relative to other regions in all three age groups ([Figure 7](#F0007){ref-type="fig"}).
In the current study, we comprehensively analysed the current trends in the incidence and mortality of NHL at the global, regional, and national level. In general, both the incidence and mortality of NHL were increased during the period from 1990 to 2017. The trend, however, varied from region to region. On the basis of the objective evidence provided in this study, more rational studies on strategies, disease control and prevention may be conducted.
NHL is a heterogeneous group of lymphoid malignancies originating in B-lymphocytes, T-lymphocytes, or natural killer (NK) cells (NK/T-cell lymphomas are very rare). According to the classifications of NHL by World Health Organisation (WHO) in 2017, there were nearly 100 subtypes \[[@CIT0022]\]. The aetiology and risk factors responsible for NHL include gene rearrangement \[[@CIT0023]\], chromosome translocation \[[@CIT0024]\], and viruses such as Epstein-Barr virus (EBV) \[[@CIT0003],[@CIT0025]\], human immunodeficiency virus (HIV) \[[@CIT0026],[@CIT0027]\], hepatitis B/C virus (HBV/HCV) \[[@CIT0028]\], helicobacter pylori (HP) \[[@CIT0031]\] and human herpes virus (HHV8) \[[@CIT0032]\] infection. Therefore, the global distribution of NHL shows an inconsistent tendency. Despite an increasing understanding of the pathology and genetics of NHL, global reports on distribution characteristics of the incidence of NHL remained limited. We comprehensively analysed the temporal trends in the incidence and mortality of NHL at the global level from 1990 to 2017, so as to better formulate the management program of NHL and improve the survival rate of the disease.
Data about the incidence and mortality of diseases in many countries are available through the WHO, but the cause of deaths varied greatly in the accuracy of the record and the completeness of registrations. Overall, the incidence of NHL was high in Australia, High-income North America and Western Europe, but was low in Europe, Latin America and Africa. The heterogeneous pattern in risk factor exposures results in a markedly diverse in the incidence of NHL across the world, and makes the prevention of NHL be complex. Moreover, marked variations in incidence rates of NHL exist in population of each region around the world. So, special attention should be given to the role of endemic infections and environmental exposures in the incidence of NHL in some regions, particularly in Africa, Asia and Latin America. Additionally, the mortalities of NHL were high in Eastern Sub-Saharan Africa, High-income North America and Australia, but were low in East Asia, Central Asia and Central Sub-Saharan Africa. We found the phenomenon that the mortality of NHL was high in both the developed regions and underdeveloped areas, which may be ascribed to the so-called westernization of lifestyle, the different pathological subtype of lymphoma, and relatively high incidence of invasive NHL in both the developed and underdeveloped regions. The above analysis could provide the explanation for possible causes of the overall differences in the incidence and mortality of NHL in different regions. Next, we will analyse the percentage changes from 1990 to 2017, trends by gender, age and region, and the related factors that may have effects on these results.
In this study, we described the latest trends and patterns of global incidence, mortality and EAPC of NHL from 1990 to 2017 according to the results of GBD Study in 2017. The incidence and mortality of NHL were higher in males of all age groups than that in females of all age groups, which is partly attributed to some risk factors including smoking and infections. From the point of view of the global level, the incidence of NHL had gradually increased from 4.75 per 100,000 people in 1990 to 6.18 per 100,000 people in 2017. Over the past 28 years, the incidence and EAPCs of NHL had increased by 30.11% and 0.75, respectively. Additionally, we also found that the incidence and mortality of NHL in all the SDI regions were lower in young-aged group than those in the old-aged group. An upward trend of the incidence was shown in four territories including East Asia, High-income Asia Pacific, Eastern Europe, and Central Europe, which may be associated with the continuous advancement of diagnosis and treatment in these regions. For example, stem cell transplantation and novel agents such as small molecule inhibitors and immune checkpoint inhibitors \[[@CIT0033]\] could provide a new choice for those with refractory or recurrent NHL. With the development of new treatment strategies and palliative medicine, the survival period of patients with NHL is extended. Therefore, the increased incidence may reflect the improvements in the ability of early detection of subclinical lesions. However, a downward trend of the incidence was shown in three territories including Central, Eastern and Western sub-Saharan Africa, and this may be associated with wars and condition of economy and medicine in these regions. Our results also showed that EAPCs of incidence decreased most significantly by −0.1 in the low SDI region, while it increased most markedly by 2.46 in the high SDI region. In this study, we also analysed the disease burden according to the HDI which was created by the United Nations Development Program to highlight the importance of national policy in assessing outcomes of the development beyond the economic growth. We found that HDI was positively associated with the incidence of NHL, well demonstrating our presumption of the causes for the constant increase of the incidence.
Mortality is a better parameter for evaluating the effectiveness of cancer treatment as compared to the incidence or survival rate, since mortality is less affected by some biases derived from changes in detection practices of diseases \[[@CIT0034]\]. However, the advantage of mortality in assessing the efficacy of treatment is based on the premise that survival rate is steady between the groups to be compared. We found that from the viewpoint of global level, the EAPCs of death of NHL decreased significantly by −0.19 during the period from 1990 to 2017, while the percentage change of mortality of NHL decreased by −0.47 over the same period. Notably, the mortality of NHL in male subjects was higher than that in female subjects. Moreover, our results showed that the mortality of NHL was relatively stable around the world. Based on the above analysis, we should actively prevent or reduce the incidence of NHL other than providing better approaches for treatment of NHL, although there is a great challenge to complete the task.
There are some limitations in this study. First, the quality of data in some underdeveloped territories such as Africa and Tropical Latin America was not accurate, since there are not reliable systems providing the information about mortality of diseases in those regions and population-based cancer registries are rare there. Secondly, racial differences were neglected in the GBD Study. However, to a certain extent, racial differences have a profound impact on the onset and death of diseases. It is required to further investigate the aetiology and risk factors for NHL in our future study. This might help to better explain the changing trend and the distribution of pathogenic factors in the disease so as to develop more appropriate strategies of prevention and therapies of NHL.
###### Supplemental Material
Click here for additional data file.
We thank the Institute for Health Metrics and Evaluation (IHME) and its fundings to provide us with free access to the data on Global Burden of Disease (GBD) Study in 2017.
Ethical approval {#S0005}
The study was approved by Shaanxi Provincial Cancer Hospital, Affiliated Hospital of Medical College of Xi'an Jiaotong University. The data released from the Global Health Data Exchange query did not require informed patient consent.
Author contributions {#S0007}
HFS, LX and YHG were involved in acquisition and analysis of the data, and the drafting of the paper and revise it critically for intellectual content. JQD performed analysis and interpretation of the data. KJN and ML were involved in the conception and design, and revised it critically for intellectual content. All authors read and approved the final manuscript and all authors agree to be accountable for all aspects of the work.
Disclosure statement {#S0006}
No potential conflict of interest was reported by the author(s).
Data availability statement {#S0008}
The datasets generated during and/or analysed during the current study are available from the Global Health Data Exchange query tool (<http://ghdx>. healthdata.org/gbd-results-tool).
AbbreviationsNHLNon-Hodgkin lymphomamAbsmonoclonal antibodyCAR-Tantigen receptor T cellsGBDGlobal Burden of DiseaseGHDxGlobal Health Data ExchangeGBDGlobal Burden of DiseaseUIsuncertainty intervalsASRage-standardized rateCIsconfidence intervalsHDIhuman development indexSDIsocial-demographic indexNK cellsnatural killer cellsEAPCsEstimated annual percentage changesDLBCLdiffuse large B-cell lymphomaCLLchronic lymphocytic leukaemiaSLLsmall lymphocytic lymphomaFLfollicular lymphomaMZLmarginal zone lymphomaMCLmantle cell lymphomaPTCLperipheral T-cell lymphoma
Both these authors have contributed equally to this work.
[^2]: Supplemental data for this article can be accessed [[here]{.underline}](https://doi.org/10.1080/07853890.2022.2039957).
|
<?php
namespace App;
use Illuminate\Database\Eloquent\Model;
class Previousdisease extends Model
{
protected $fillable = ['disease_name','disease_notes', 'patient_id', 'clinic_id'];
// Relationships
public function patient()
{
return $this->belongsTo('App\Patient');
}
}
|
Broadband acoustic invisibility and illusions
The active manipulation of sound waves replaces physical with virtual media to create acoustic invisibility and illusions.
INTRODUCTION
Rendering objects invisible to acoustic, elastic, or electromagnetic waves (cloaking) or making objects appear where there are none (holography) is of immediate scientific and technological interest. Sophisticated cloaks and holograms relying on real-time wavefield manipulation ( Fig. 1) remained science fiction until theoretical advances, particularly in the field of transformation optics (1,2), enabled scientists to create the first physical invisibility and illusion devices (3)(4)(5)(6)(7)(8)(9). Existing devices rely on the control of wavefields with passive or active methods but have serious limitations. Passive methods (1,(5)(6)(7)(9)(10)(11)(12)(13)(14)(15) are based on tailored materials to manipulate impinging wavefields. While most of these approaches work efficiently only over narrow frequency bands and suffer from internal dissipation (16,17), some approaches, particularly those based on transformation acoustics and scattering cancellation (8,15,18), can be effective over a broader frequency range. However, passive methods require the meticulous design and construction of materials that manipulate the wavefield. Hence, they are inflexible and do not adapt to changing incident wavefields or requirements. Active methods (3,4,(19)(20)(21)(22)(23)(24) rely on the emission of a secondary wavefield that (destructively) interferes with the primary field. The secondary wavefield is typically created with control sources distributed on the boundary or across the area of interest (Fig. 1). Active methods provide a more flexible and dynamic control of wavefields and can, in principle, react to changes in the incident field in real time. However, existing active cloaking and holography devices have considerable limitations: They rely on a priori knowledge of the incident or scattered wavefields and hence fail if the characteristics of the primary energy sources change or are unknown (23)(24)(25), which is the case for many conceivable applications. In such a scenario, the signals for the control sources need to be estimated and updated in real time. To our knowledge, Friot et al. (4) are the only authors who have experimentally demonstrated active cloaking of acoustic waves without a priori knowledge of the incident wavefield beyond one dimension (1D). However, they used a control algorithm that relies on a nondeterministic optimization approach that reduces the scattered field in certain areas, while it actually increases the field in other locations. Moreover, in these experiments, the forward-scattered field is not controlled at all, the results are not spectrally broadband, and some knowledge of the signal emitted by the primary source is required. These assumptions compromise the cloak and limit its practical use.
We consider a fundamentally different approach to acoustic cloaking and holography that relies on virtually replacing part of a physical medium by a desired, virtual medium. We achieve this by complementing the acoustic waves propagating in the physical medium with a real-time simulation of the waves propagating in the virtual medium. The simulation is performed on a massively parallelized, low-latency control system based on field-programmable gate arrays [FPGAs; see (26) for details]. An active, fully deterministic, and global control loop [ (27)(28)(29) and Supplementary Materials] links the physical and virtual media in real time by extrapolating particle velocity and pressure wavefields from an acoustically transparent array of microphones to an array of control loudspeakers surrounding the region to be replaced (see Fig. 2 and the Supplementary Materials for details). Using this approach, we demonstrate in 2D acoustic experiments that a physical scattering object can be replaced with a virtual homogeneous background medium in real time, thereby hiding the object from broadband acoustic waves (cloaking). In a second set of experiments, we replace part of a physical homogeneous medium by a virtual scattering object, thereby creating an acoustic illusion of an object that is not physically present (holography). Because of the broadband nature of the control loop and in contrast to other cloaking approaches, this requires neither a priori knowledge of the primary energy source nor of the scattered wavefields, and the approach holds even for primary sources, whose locations change over time.
RESULTS
We first demonstrate cloaking of a quasi-rigid, circular scatterer with a diameter of 12.6 cm placed in the center of an air-filled, 2D acoustic waveguide. The boundary of the scatterer is lined with 20 secondary loudspeakers (Fig. 2E). A primary wavefield is emitted by eight individual loudspeakers located along the perimeter of the experiment across an arc of 96° (Fig. 3A). All loudspeakers emit the same broadband wavelet [described by the second derivative of a Gaussian function (30)] with a center frequency, f c , of 3 kHz but with an increasing time delay. This mimics a primary source that changes its location with an effective velocity of 173 m/s, sending a broadband pulse from each new location. First, the control loudspeakers surrounding the scatterer are inactive. Consequently, the rigid scatterer disturbs the incident wavefield, causing back scattering and forward scattering (Fig. 3, A, D, G, and J). In a second experiment, the primary loudspeakers emit the same primary wavefield, but this time, the control loudspeakers complement the scattered field based on the particle velocity field extrapolated in real time from two circular microphone arrays enclosing the scatterer (Fig. 3, B, E, H, and K). Since the Green's functions used for the extrapolation simulate a homogeneous, air-filled medium, the scattering object is effectively replaced by air through the emission of the secondary wavefield and therefore rendered acoustically invisible for an observer outside of the control loudspeaker array. For comparison, we emit the same primary field but remove the scattering object and secondary loudspeakers from the waveguide (Fig. 3, C, F, and I). The resulting acoustic wavefield closely resembles the wavefield obtained with enabled secondary loudspeakers, confirming that the scatterer is rendered acoustically invisible. Active cloaking suppresses not only the scattered field arising from the direct wave propagating between the primary source and the scattering object but also that caused by the echoes from the boundary of the waveguide at later times (see fig. S1). The cloak is effective over a broad range of frequencies and all angles with a reduction in mean scattered acoustic intensity of −8.4 dB (Eq. 1 and Fig. 3, L and M). Note that the scatterer remains acoustically invisible despite the change of location of the primary source, demonstrating that our approach does not rely on any a priori knowledge of the incident or scattered fields. Finite-element simulations (see Materials and Methods) replicating the three experiments are in excellent agreement with the experimental results (Fig. 3, G to I). In a second suite of experiments, we demonstrate the ability to create broadband acoustic holograms. For these experiments, the Green's functions used for the real-time wavefield extrapolation simulate wavefield interactions with virtual objects located within the control loudspeaker array. Since, in this case, no physical boundary exists at the location of the loudspeakers, wavefields are controlled at a sound-transparent emitting surface. This requires the dual emission (and extrapolation) of particle velocity and pressure as the signatures of collocated monopole and dipole sources [(29) and Supplementary Materials]. Consequently, in these experiments, the wavefield is controlled with two closely spaced circular loudspeaker arrays mounted flush with the planar boundary of the waveguide to create effective dipole and monopole sources (see Fig. 2F and Supplementary Materials). We choose extrapolation Green's functions that represent a virtual rigid scatterer with the same geometry as the physical scatterer used in the cloaking experiments (i.e., circular, 12.6 cm in diameter, and rigid boundary; geometry shown in Fig. 4A). This time, a single stationary loudspeaker placed at [0, 0.66] m emits a primary wavefield with a wavelet with f c = 3 kHz. The pressure field is measured by the microphone arrays and extrapolated to the sound-transparent emitting surface in real time, where the resulting virtually scattered field is emitted by the secondary loudspeakers. Consequently, a hologram of the virtual scatterer is created: The total wavefield now contains interactions of the primary loudspeaker with the virtual object. The resulting acoustic wavefield and angular distribution of virtually scattered intensity are in excellent agreement with measurements made with a physical scatterer inside the waveguide (Fig. 4, B to F), further underlining the successful creation of a broadband acoustic hologram.
DISCUSSION
We demonstrated the ability to replace part of a physical medium with a virtual medium through real-time and broadband wavefield control. In these experiments, we either replaced a physical scatterer by virtual air, thereby rendering the scatterer acoustically invisible, or created the illusion of a virtual rigid object located within the array of control loudspeakers. The presented results demonstrate effectiveness over a broad frequency range of more than 3.5 octaves, with upper frequency limits of 8.7 kHz (cloaking) and 5.9 kHz (holography), consistent with classical sampling theory (see Supplementary Materials for details). However, modifying the experimental setup can relax these limits.
Hardware perturbations from the ideal case are, of course, always present. For instance, results will deteriorate with malfunctioning sources or receivers. However, loudspeakers and microphones are usually very reliable; we have not observed failures during our work. Moreover, regular tests (e.g., subsequently emitting each source, recording on all microphones, and comparing the results to a set of reference measurements) can help to identify and replace such failing components. Some applications, however, might not allow ad hoc hardware replacements and require operation with a reduced number of sources or receivers. In this case, a modification of the extrapolation Green's functions can compensate for such drop-outs as long as the number of failing components is reasonable (e.g., every second loudspeaker failing, leading to 1.4 loudspeakers per wavelength), as was demonstrated in previous physical tests of the underlying control algorithm (31).
The proposed methodology opens up previously inaccessible research in wave physics, particularly because any desired virtual medium of arbitrary complexity, including nonlinear or nonphysical (e.g., energygaining) media, can be inserted into the physical medium within the loudspeaker arrays, as long as the medium can be described by an appropriate set of extrapolation Green's functions. By physically recording the scattering Green's functions of an existing object and using those Green's functions for the real-time extrapolation in the presented holography approach, physical objects can be acoustically cloned and reproduced in a different environment (see Supplementary Materials for details). Moreover, the methodology is not restricted to experiments in air. For instance, it can also be used to create underwater acoustic cloaks and illusions. While the substantially increased speed of sound in water dictates a smaller latency for the real-time wavefield extrapolation, moving the control receivers further away from the control sources or using hardware with flatter frequency responses (i.e., requiring shorter filters and thus less latency for their correction) counteracts these additional challenges. In principle, the methodology also extends to elastodynamic and electromagnetic waves, but a practical realization is considerably more challenging. The approach has immediate practical implications, including hiding arbitrary objects from interrogating devices, improving architectural acoustics, creating invisible sensors, and creating holograms for communication, educational, entertainment, and stealth purposes.
Experimental design
We use an air-filled acoustic waveguide composed of two parallel polymethyl methacrylate (PMMA) plates with a spacing of a = 2.5 cm for the presented cloaking and holography experiments. See Fig. 2 for photographs of the experimental setup and hardware components. The boundary of the experimental domain consists of a 3D printed ring with a radius of 66.2 cm made of the synthetic resin VeroWhite. The propagation of waves between the two PMMA plates can be considered 2D as long as the signals below the cutoff frequency of the fundamental mode are used, which is given by f c = 0.5ca −1 (32), where c is the speed of sound. For our experiments this results in f c ≈ 6.9 kHz. Instead of directly measuring the normal particle velocity and pressure on S rec , as dictated by the theory of the underlying control algorithm (see Supplementary Materials for details), we use two circular arrays of pressure microphones with radii of 35.3 and 37.3 cm, respectively, each consisting of 114 electret condenser microphones (SparkFun Electronics, BOB-12758 and COM-08635; Fig. 2C). The normal particle velocity is then approximated using the pressure gradient in the normal direction (26,33). All microphones are mounted flush with the inside of the front PMMA plate to minimize their impact on the pressure field. In the case of cloaking experiments, the rigid emitting boundary at S emt consists of a 3D printed ring with a radius of 6.4 cm, housing 20 loudspeakers (PUI Audio, AS01508MR-R; Fig. 2E). For the holography experiments, the transparent emitting boundary at S emt consists of two separate circular source arrays with radii of 7.4 and 9.4 cm, respectively, each consisting of 18 loudspeakers mounted flush with the front PMMA plate (Fig. 2F). We produced all holes in the PMMA plate with a computerized numerical control (CNC) milling machine to ensure high accuracy and precision. All microphones and the loudspeakers of the holography experiment are mounted into custommade, 3D printed supports (Fig. 2, C and F). The supports are wrapped with Teflon tape and then inserted into the holes in the PMMA plate. This ensures an accurate fit, closes holes, and reduces wavefield scattering. We validated the assumption of 2D wave propagation in the waveguide and the negligibility of scattering at the control hardware in previous experiments (31). The distance between S rec and S emt of approximately 30 cm allows a maximum total latency of about 870 s (for experiments in air). Of these, the wavefield extrapolation consumes 200 s, while the remaining 670 s are available for real-time hardware corrections and estimation of normal particle velocity from pressure recordings. A massively parallelized, low-latency data acquisition and control system enabled by more than 500 National Instruments FlexRIO FPGAs runs the nonlocal control algorithm. The system supports simultaneous recording of 800 analog input channels and simultaneous emission of 800 analog output channels while operating at a 20-kHz sample rate [more details of the system architecture can be found in (26)]. The experiments and data acquisition are performed with LabVIEW.
Numerical simulations
The numerical reference simulations in Figs. 3 and 4 and the computation of all extrapolation Green's functions are performed with the finite-element simulation software COMSOL Multiphysics (version 5.5, Acoustics Module). The simulation domain consists of air with a density of 1.225 kg/m 3 and a speed of sound of 347 m/s. The circular scatterer is simulated as a sound-hard (i.e., rigid) object. The Green's functions are obtained by simulating impulsive monopole and dipole sources at the location of the control loudspeakers, recording pressure and particle velocity at the location of the control microphones, and applying source-receiver reciprocity.
Scattered acoustic intensity and repeatability
We assess the effectiveness of the broadband active cloak in terms of the reduction in scattered acoustic intensity, I R , given by
|
THRIFT SHOP, INC., a corporation, d/b/a Mode O’Day, Francis X. Moesch and Hazel C. Moesch, Appellants, v. ALASKA MUTUAL SAVINGS BANK, a banking corporation, Appellee.
No. 509.
Supreme Court of Alaska.
Jan. 29, 1965.
r Francis J. Nosek, Jr.’, and Neil S. Mac-kay,' Anchorage, for appellants.
Richard O. Gantz and Robert C. Erwin, Hughes, Thorsness & Lowe, Anchorage, for appellee.
Before NESBETT, C. J., and DIMOND and AREÑD, JJ.
DIMOND, Justice.
This is a dispute over the right tó possession of some business property in'downtown Anchorage. Appellants claimed that appellee liad agreed to lease the property to them, and then had defaulted and leased it to- a third party. Without appellee’s knowledge or consent, appellants took possession'of the premises which they'were seeking to lease .by entering the building where those premises are located during the early morning hours of April 18, 1964. Appellee requested appellants to leave and, when they refused, brought this forcible entry .and detainer action to regain possession. The superior court held in favor of appellee and appellants have appealed.
The trial court’s basic holding was that appellants had no oral or written lease, no claim or color of title, and no right to possession to the premises in dispute. The principal question on this appeal is whether such holding was erroneous.
In January 1964 appellants commenced negotiations with appellee for a lease of the premises. These negotiations resulted in an understanding between the parties that appellants would lease approximately 1200 square feet of floor space from appel-lee. It was contemplated by both parties that they would execute a written lease. Appellee’s president, R. L. Rettig, testified that on March 17 or 18, 1964 the appellants picked up a draft of a lease which he had had prepared and was offering to appellants. Rettig had prepared the lease for execution not only by the appellant corporation, Thrift Shop, Inc., but also by the corporation’s officers, Francis and Hazel Moesch, in their individual capacities. Rettig testified that oil or about March 25 he telephoned Francis Moesch to see about getting the lease signed. Moesch told Rettig that he and his wife objected to signing the lease as individuals. Rettig said he heard nothing further from appellants until after the disastrous March 27th earthquake. On or about March 31 Francis and Hazel Moesch called on Rettig at his office. According to Rettig, they told him they were ready to go ahead with the written lease. .Rettig told them that he did not know whether he could rent to them because the building had been condemned on account of the earthquake, and because Rettig had started discussions with other persons .for a lease of the premises. The next day Hazel Moesch again came to Rettig’s' office; and at that time he told her that he would be unable to rent the property to her.
Francis Moesch testified that appellants had made an oral agreement with Rettig to lease the premises, and that they had made plans, which Rettig knew about, to make alterations in the space to be rented. Moesch also testified that in -reliance on such agreement, appellants had ordered over $14,000 worth of equipment and $10,-000 worth of merchandise to be placed in the store space they were renting from appellee. Finally, Moesch testified that when he and his wife called at Rettig’s office on March 31, he made a tender to Rettig of the rent and offered him the written lease which had been signed by the corporation and by Francis and Hazel Moesch as individuals. He testified that Rettig refused to accept the lease or the rent.
We cannot say that the trial judge erred in holding that there was no binding lease agreement between the parties. A contract to lease would not exist until the parties had manifested their mutual assent to its formation. It is true that words and acts of the parties may constitute sufficient manifestations of assent to make a binding oral contract, even though the parties also had contemplated that their agreement would later be reduced to writing. But such an oral contract would exist only if the parties had definitely agreed on the terms that they planned to incorporate into the writing, and had agreed that the final writing would contain those provisions and no others. If it is apparent that the parties intended that the determination of certain details were to be deferred until the writing was made out, or if an intention was manifested in any way that legal obligations arising between .the parties should be deferred until the writing was made, then the words and acts of the parties would amount to nothing more.than preliminary negotiations and agreements and would not constitute a contract.
From the testimony in this case it appears dear that an oral- contract to lease never came into existence. Appellee’s president, R. L. Rettig, was asked: “in these conversations did — did you ever arrive finally at what terms you would .rent to them for ?” He replied: “Yes. We had arrived at the general formula under which the lease would be entered into.” Appellant Francis Moesch was asked whether. during the negotiations he and Rettig finally came to an understanding- of what the terms of the lease were. * * * I told him we’d take the building. * * * I says, ‘we’ll take it’, and he said ‘Fine’, and when I got the lease I says, ‘Well, fine’.”
This testimony in no way establishes that the parties had orally agreed upon all of the essential terms they planned to incorporate into the written lease. Rather, this testimony creates a strong inference that the parties intended that the final and full expression of their mutual assent would be deferred ’ until the written .lease had been prepared and agreed upon. There was'no othér testimony that detracted from '.the validity of such an inference. The evidence would not support a finding that the parties intended there be a binding agreement prior to the execution of the written lease;
Nor would the evidence-support a finding that a contract was formulated when appellants tendered to appellee the signed lease and a check for the rent on March 31. Prior to that date, on March 17 or 18, appellee had offered to rent the premises according to the terms of a written lease which Rettig had had prepared and had presented .to appellants. In order for a contract to have been formed, it was essential that acceptance of this offer be unequivocal and in exact compliance with the requirements of the offer that appellee had made. That was not done here. One of the express requirements of the proposed written lease was-that it be executed, not only by the corporation, Thrift Shop, Inc., but also by Francis and Hazel Moesch as individuals. Appellee was advised by the Moesches on 'March 25 that they objected to signing the lease individually. This action on their part amounted either to a rejection of the offer made by appellee or, if it could be said that the lease was otherwise acceptable, to a counter-offer by the appellants. In either case, whether there was an outright rejection or a counter-offer, the effect was the same — the power to accept the offer that had been made by appellee was terminated. Appellants could not revive the proposal made by appellee by tendering an acceptance of it later on March 31. Their action in this respect did not bring a contract into existence.
Appellants argue that since this was an action to recover possession of property under the forcible entry and detainer statute, the court was limited to determining whether appellants’ entry of appellee’s premises was forcible or whether they unlawfully held possession by force. Appel-ants contend that the court had no right to inquire into the existence or non-existence of an agreement to lease, and that that question would have to he litigated in a separate action of ejectment. In support of this contention appellants cite the early Alaska cases of Steil v. Dessmore , decided in 1907, and Miners’ & Merchants’ Bank v. Brice , decided in 1915, which held that where there is no forcible entry or forcible detainer there is no cause of action, and that the proper remedy for one who claims the right to possession of the property is in a suit for ejectment.
These cases are not controlling. The practice and procedure in our courts today is not the same as that which prevailed in 1907 and 1915. Civil Rule 2 provides that “There shall be one form of action to be known as a ‘civil action.’ ” In Mitchell v. Land we held that in this one-form-of-action procedure, the parties should be granted the relief to which they are entitled, irrespective of the theory of their pleadings, and that a court is not justified in depriving a party of his rights because he mistakes the nature of his remedy. In this case evidence was presented by both parties which showed that no contract to lease had been created, and that appellants had no right to possession of the premises which they had occupied without appellee’s permission. Whether appellants had entered the premises by force or were unlawfully witholding possession by force is of no significance. The evidence showed that appellee was entitled to recover possession from the appellants. It would have been entirely contrary to the spirit and purpose of the rules of civil procedure to have forced appellee to resort to a separate action in ejectment in order to obtain the relief to which the proof showed it was entitled.
The procedure in a forcible entry and de-tainer action is more summary in nature than in an ordinary civil action. Under Civil Rule 85 the summons in a forcible entry and detainer action must be served not less than 2 nor more than 4 days before the day of trial, and no continuance may be granted for a longer period than 2 days “unless the defendant applying therefor shall give an undertaking to the adverse party, with sureties approved by the court, conditioned to the payment of the rent that may accrue if judgment is rendered against defendant.” It is true that if this action had been simply one to recover possession of property without reference to the forcible entry and detainer statute, Civil Rule 85 would not have been applicable. But appellants have not established that they were harmed by application of that rule. The only continuance they asked for was granted, and when the question of the existence of a contract to lease was being inquired into at the trial, appellants did not contend that they had been prejudiced by being summarily brought to trial.
Nor have appellants shown any prejudice arising from the fact that appellee’s complaint was limited to claiming relief under the forcible entry and detainer statute, whereas the scope of inquiry at the trial was extended beyond the narrow issues of whether appellants had used force in securing or retaining possession of the premises. Appellants not only did not object to testimony concerning the existence or non-existence of a lease, but offered testimony themselves on this point. They did not claim that this matter could not be gone into because of the nature of appellee’s complaint. Finally, appellants made no claim during the trial that because the action had been brought as one for forcible entry and detainer, they were prevented from introducing any evidence relevant and material to their claim that a binding contract to lease had been entered into.
The trial court was justified in holding that there was no lease agreement between the parties and that appellants had no right to possession of the premises in dispute. It is unnecessary to decide whether or not appellants’ entry or detention of the premises was forcible within the meaning of the statute. The proof showed that appellants were not entitled to possession, without regard to whether the element of force was present.
Appellants’ final point is that the court erred in awarding damages consisting of $25 a day as reasonable rental value of the premises during the time that appellants retained possession, together with the cost of hiring guards for that time at the rate of $156 a day. Appellants argue that appellee was limited to recovering arrears of rent or damage to the premises under that portion of the forcible entry and de-tainer statute which provides:
“The plaintiff may unite a cause of action for arrears of rent on the property in question or for damage to the premises and all the causes are considered to arise out of the same transaction.”
We do not interpret this statutory provision as limiting the recoverable damages where one’s real property has been withheld from his possession by another. This section of the law purports to deal only with practice and procedure, and not with the substantive law of damages. And in dealing with procedure, this section has no significance, because in providing what causes of action may be united it attempts to regulate a matter of practice and procedure covered by court rule. Civil Rule 18(a) provides that a plaintiff may join in his complaint, either alternately or independently, as many claims either legal or equitable as he may have against the defendant.
By unlawfully taking possession of ap-pellee’s property, appellants committed a tort and were liable as trespassers to ap-pellee. Such liability imposed on appellants an obligation to compensate appellee for the injury done to appellee’s rights. This obligation would be fulfilled by requiring appellants to pay appellee an amount of money which would place appel-lee in a position substantially equivalent in a pecuniary way to that which it would have occupied had the tort not been committed.
By reason of appellants’ unlawful invasion of appellee’s rights, appellee was denied the opportunity to collect rent for the property during the time that appellants had possession. In addition, appellee was required to hire guards for the building where the premises were located, because the building could not be kept locked while appellants occupied the premises. What appellee lost in rent and what it paid out for guards is the measure of compensation that appellants are obliged to pay for their invasion of appellee’s rights. The damages awarded to appellee were proper.
The judgment is affirmed.
. Century Ins. Agency, Inc. v. City Commerce Corp., Opinion No. 260, 396 P.2d 80, 81 (Alaska 1964).
. Restatement, Contracts § 26 (1932); In re ABC — Fed. Oil & Burner Co., 290 F.2d 886, 889 (3d Cir 1961).
. Restatement, Contracts § 26, comment a (1932). ... ...
. Restatement, -' Contracts §§ 58, • 59 (1932); United States v. Braunstein, 75 F.Supp. 137, 139 (S.D.N.Y.1947) appeal dismissed, 168 F.2d 749 (2d Cir. 1948); United States v. Mitchell, 104 F.2d 343, 346 (8th Cir. 1939).
. 1 Corbin, Contracts § 90 (1963); Beaumont v. Prieto, 249 U.S. 554, 556, 39 S.Ct. 383, 63 L.Ed. 770, 772 (1919). ■
. Beaumont v.' Prieto,' supra note 5. •
. AS 09.45.060-09.45.160.
. 3 Alaska 392, 399 (D.Alaska 1907).
. 5 Alaska 418, 420-421 (D.Alaska 1915).
.355 P.2d 682, 687 (Alaska 1960). See also Brayton v. City of Anchorage, 386 P.2d 832, 833 (Alaska 1963).
. AS 09.45.070(b).
. Silverton v. Marler, Opinion No. 186, 389 P.2d 3, 5-6 (Alaska 1964).
. Restatement, Torts § 158 (1934).
. Restatement, Torts §§ 901, 902, 903, comment a (1939).
|
import {component} from 'flightjs';
import $ from 'jquery';
import {Constants} from './traceConstants';
export default component(function spanPanel() {
this.$annotationTemplate = null;
this.$binaryAnnotationTemplate = null;
this.show = function(e, span) {
const self = this;
this.$node.find('.modal-title').text(
`${span.serviceName}.${span.spanName}: ${span.durationStr}`);
this.$node.find('.service-names').text(span.serviceNames);
const $annoBody = this.$node.find('#annotations tbody').text('');
$.each((span.annotations || []), (i, anno) => {
const $row = self.$annotationTemplate.clone();
if (anno.value === Constants.ERROR) {
$row.addClass('anno-error-transient');
}
$row.find('td').each(function() {
const $this = $(this);
const maybeObject = anno[$this.data('key')];
// In case someone is storing escaped json as an annotation value
// TODO: this class is not testable at the moment
$this.text($.type(maybeObject) === 'object' ? JSON.stringify(maybeObject) : maybeObject);
});
$annoBody.append($row);
});
$annoBody.find('.local-datetime').each(function() {
const $this = $(this);
const timestamp = $this.text();
$this.text((new Date(parseInt(timestamp, 10) / 1000)).toLocaleString());
});
const $binAnnoBody = this.$node.find('#binaryAnnotations tbody').text('');
$.each((span.binaryAnnotations || []), (i, anno) => {
const $row = self.$binaryAnnotationTemplate.clone();
if (anno.key === Constants.ERROR) {
$row.addClass('anno-error-critical');
}
$row.find('td').each(function() {
const $this = $(this);
const maybeObject = anno[$this.data('key')];
// In case someone is storing escaped json as binary annotation values
// TODO: this class is not testable at the moment
$this.text($.type(maybeObject) === 'object' ? JSON.stringify(maybeObject) : maybeObject);
});
$binAnnoBody.append($row);
});
this.$node.modal('show');
};
this.after('initialize', function() {
this.$node.modal('hide');
this.$annotationTemplate = this.$node.find('#annotations tbody tr').remove();
this.$binaryAnnotationTemplate = this.$node.find('#binaryAnnotations tbody tr').remove();
this.on(document, 'uiRequestSpanPanel', this.show);
});
});
|
Why radio button switching is not reflecting in redux state variable?
I am working on a react.js app where i am working with redux state management.I have created 2 radio buttons and I am switching between them and setting the state variable correspondingly.
Here's my active button:
<form >
<input type="radio" id="html" name="status" value="HTML" onClick={this.setClientStatus("Active")}/>
<label for="html">Active</label><br/>
<input type="radio" id="css" name="status" value="CSS" onClick={this.setClientStatus("InActive")}/>
<label for="css">InActive</label><br/>
</form>
Here's my dispatch method:
const mapDispatchToProps = dispatch => ({
setClientName: clientName=>dispatch(onSetClientName(clientName)),
setClientStatus:clientStatus=>dispatch(onSetClientStatus(clientStatus))
});
export default connect(mapStateToProps, mapDispatchToProps)(toReturn);
Here's my method to change the state:
constructor(props) {
super(props);
this.setClientStatus=this.setClientStatus.bind(this);
}
setClientStatus(status)
{
this.props.setClientStatus(status)
}
action.js
export const SET_STATUS='CLIENT/SET_STATUS'
actionCreator.js
export function onSetClientStatus(clientStatus)
{
// console.log(clientStatus)
return {type:Actions.SET_STATUS,clientStatus}
}
clientReducer.js
const initialState = {
clientStatus:"",
};
case Actions.SET_STATUS:{
{
console.log(action.clientStatus)
return Object.assign({},state,{clientStatus:action.clientStatus})}
}
Even when I try to log the status in actionCreator or reducer,without clicking on radio buttons I see toggling in value of status whenever the state of app changes due to other state variables.I am calling the setClientStatus method only on onClick of radio buttons but I dont know how they are getting logged on every state change in the app.
Here's my full working app.use npm start to run then go to add a client then just toggle between the radio buttons.
Github repo here
Thanks
In the onClick prop of both your inputs you are invoking the setClientStatus instead of passing a function. It happens on every render, that's why you see it being toggled on other state changes.
Instead of:
onClick={this.setClientStatus("Active")}
onClick={this.setClientStatus("InActive")}
you probably need to have:
onClick={() => this.setClientStatus("Active")}
onClick={() => this.setClientStatus("InActive")}
Thanks for this,cant believe I missed that
|
# coding: utf-8
from __future__ import absolute_import
from bitmovin_api_sdk.common import BaseApi, BitmovinApiLoggerBase
from bitmovin_api_sdk.common.poscheck import poscheck_except
from bitmovin_api_sdk.models.bitmovin_response import BitmovinResponse
from bitmovin_api_sdk.models.response_envelope import ResponseEnvelope
from bitmovin_api_sdk.models.response_error import ResponseError
from bitmovin_api_sdk.models.vorbis_audio_configuration import VorbisAudioConfiguration
from bitmovin_api_sdk.encoding.configurations.audio.vorbis.customdata.customdata_api import CustomdataApi
from bitmovin_api_sdk.encoding.configurations.audio.vorbis.vorbis_audio_configuration_list_query_params import VorbisAudioConfigurationListQueryParams
class VorbisApi(BaseApi):
@poscheck_except(2)
def __init__(self, api_key, tenant_org_id=None, base_url=None, logger=None):
# type: (str, str, str, BitmovinApiLoggerBase) -> None
super(VorbisApi, self).__init__(
api_key=api_key,
tenant_org_id=tenant_org_id,
base_url=base_url,
logger=logger
)
self.customdata = CustomdataApi(
api_key=api_key,
tenant_org_id=tenant_org_id,
base_url=base_url,
logger=logger
)
def create(self, vorbis_audio_configuration, **kwargs):
# type: (VorbisAudioConfiguration, dict) -> VorbisAudioConfiguration
"""Create Vorbis Codec Configuration
:param vorbis_audio_configuration: The Vorbis Codec Configuration to be created
:type vorbis_audio_configuration: VorbisAudioConfiguration, required
:return: Vorbis Audio Configuration
:rtype: VorbisAudioConfiguration
"""
return self.api_client.post(
'/encoding/configurations/audio/vorbis',
vorbis_audio_configuration,
type=VorbisAudioConfiguration,
**kwargs
)
def delete(self, configuration_id, **kwargs):
# type: (string_types, dict) -> BitmovinResponse
"""Delete Vorbis Codec Configuration
:param configuration_id: Id of the codec configuration
:type configuration_id: string_types, required
:return: Id of the codec configuration
:rtype: BitmovinResponse
"""
return self.api_client.delete(
'/encoding/configurations/audio/vorbis/{configuration_id}',
path_params={'configuration_id': configuration_id},
type=BitmovinResponse,
**kwargs
)
def get(self, configuration_id, **kwargs):
# type: (string_types, dict) -> VorbisAudioConfiguration
"""Vorbis Codec Configuration Details
:param configuration_id: Id of the codec configuration
:type configuration_id: string_types, required
:return: Vorbis Audio Configuration
:rtype: VorbisAudioConfiguration
"""
return self.api_client.get(
'/encoding/configurations/audio/vorbis/{configuration_id}',
path_params={'configuration_id': configuration_id},
type=VorbisAudioConfiguration,
**kwargs
)
def list(self, query_params=None, **kwargs):
# type: (VorbisAudioConfigurationListQueryParams, dict) -> VorbisAudioConfiguration
"""List Vorbis Configurations
:param query_params: Query parameters
:type query_params: VorbisAudioConfigurationListQueryParams
:return: List of Vorbis codec configurations
:rtype: VorbisAudioConfiguration
"""
return self.api_client.get(
'/encoding/configurations/audio/vorbis',
query_params=query_params,
pagination_response=True,
type=VorbisAudioConfiguration,
**kwargs
)
|
Sütterlinschrift
Etymology
., its designer.
Noun
* 1) script
Usage notes
* There is a (rare) plural.
|
ios UIViewController not calling viewDidUnload
When I simulate a memory warning, viewDidUnload should run on unused objects, right?
How do I go about figuring out WHY my UIView won't go away?
FYI I'm using ARC and every ivar is an IBOutlet and looks like:
@property (nonatomic, weak) IBOutlet UIView *someView;
What do you mean by "go away"? Are you expecting your view to have a nil value after viewDidUnload?
I want it to go out of memory, so in a roundabout way I suppose I do expect a nil value (or something similar). I'm ultimately just trying to make sure my memory management is in check.
What class are we looking at here? Only UIViewControllers release their view in case of a mem warning.
If this is a custom class or a custom added view, you should unload it yourself.
And the view is the 'main view' associated with this controller? Or is it a custom view you added yourself?
it's view I added my self. fyi this view is associated to it's OWN nib.
Views that you added and retained yourself will not be released in case of a memory warning. You need to do this yourself. That's what the viewDidUnload method` can be used for. But, it looks like you don't actually retain the view...
I'm using ARC so I would assume ARC would take care of the retain/release. Maybe I am mistaken?
|
Detachable and replaceable shock damper for use in structures
ABSTRACT
A shock damper includes a damper body installed in the frame of a structure and adapted to absorb earthquake shocks, and braces adapted to support the damper body in the frame of the structure, the damper body having a horizontal top plate, a horizontal bottom plate, and a vertical connecting device connected between the horizontal top plate and the horizontal bottom plate, the connecting device being a shaft formed of any of a variety of cross sections, or a plurality of plates of any of a variety of profiles.
BACKGROUND OF THE INVENTION
[0001] 1. Field of the Invention
[0002] The present invention relates to shock dampers for installation in a structure to absorb shocks and, more particularly, to a detachable and replaceable shock damper, which can be detachable and replaceable in a structure.
[0003] 2. Description of the Related Art
[0004] An earthquake is a shaking of the crust of the earth, caused by underground volcanic forces or by shifting of rock. When an earthquake occurs in a residential area, it may cause disaster. Therefore, there are special terms strictly defined according to the law to build structures in areas where earthquake may occur frequently, i.e., buildings in areas where earthquake may occur frequently must be strong enough to bear earthquake shocks of a certain grade. Various earthquake protective structural materials and techniques have been developed for this purpose.
SUMMARY OF THE INVENTION
[0005] The present invention has been accomplished under the circumstances in view. It is one object of the present invention to provide a shock damper for structures, which effectively absorbs earthquake shocks. It is another object of the present invention to provide a shock damper for structures, which is detachable and replaceable. To achieve these and other objects of the present invention, the shock damper comprises a damper body installed in the frame of a structure to absorb earthquake shocks, and braces to support the damper body in the frame of the structure, the damper body having a horizontal top plate, a horizontal bottom plate, and a vertical connecting device connected between the horizontal top plate and the horizontal bottom plate, the connecting device being a shaft formed of any of a variety of cross sections, or a plurality of plates of any of a variety of profiles.
[0006] The foregoing object and summary provide only a brief introduction to the present invention. To fully appreciate these and other objects of the present invention as well as the invention itself, all of which will become apparent to those skilled in the art, the following detailed description of the invention and the claims should be read in conjunction with the accompanying drawings. Throughout the specification and drawings, identical reference numerals refer to identical or similar parts.
[0007] Many other advantages and features of the present invention will become manifest to those versed in the art upon making reference to the detailed description and the accompanying sheets of drawings in which a preferred structural embodiment incorporating the principles of the present invention is shown by way of illustrative example.
BRIEF DESCRIPTION OF THE DRAWINGS
[0008]FIG. 1 is an exploded view of a shock damper constructed according to one embodiment of the present invention.
[0009]FIG. 2 shows one installation example of the shock damper shown in FIG. 1.
[0010]FIG. 3A is an installed view of an alternate form of the shock damper according to the present invention.
[0011]FIG. 3B is an installed view of another alternate form of the shock damper according to the present invention.
[0012] FIGS. 4A˜4H are installed views of other different alternate forms of the shock damper according to the present invention.
[0013] FIGS. 5A˜5F are installed views of still other different alternate forms of the shock damper according to the present invention.
[0014] FIGS. 6A˜6I are top views showing different alternate forms of the shock damper according to the present invention.
[0015] FIGS. 7A˜7H are perspective views showing different alternate forms of the damper body according to the present invention.
[0016]FIGS. 8A and 8B are exploded and perspective views of still another different alternate form of the damper body according to the present invention.
[0017]FIGS. 8C and 8D are exploded and perspective views of still another different alternate form of the damper body according to the present invention.
[0018]FIGS. 9A and 9B are exploded and perspective views of still another alternate form of the connecting device for the damper body according to the present invention.
[0019]FIGS. 10A and 10B are respective view of still another two alternate forms of the damper body according to the present invention.
[0020]FIG. 11 is shockwave curves obtained from an earthquake simulation vibration table with and without the effect of the present invention under the E1 Center 1940 Earthquake. The upper figures show shockwave curves without the effect of the present invention. The lower figures show shockwave curves with the effect of the present invention. It proves that most seismic energy is absorbed by the present invention.
[0021]FIG. 12 is shockwave curves obtained from an earthquake simulation vibration table with and without the effect of the present invention under the doubled E1 Center 1940 Earthquake. The upper figures show shockwave curves without the effect of the present invention. The lower figures show shockwave curves with the effect of the present invention. It proves that most seismic energy is absorbed by the present invention.
DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENT
[0022] For the purpose of promoting an understanding of the principles of the invention, reference will now be made to the embodiment illustrated in the drawings. Specific language will be used to describe the same. It will, nevertheless, be understood that no limitation of the scope of the invention is thereby intended, alterations and further modifications in the illustrated device, and further applications of the principles of the invention as illustrated herein being contemplated as would normally occur to one skilled in the art to which the invention relates.
[0023] Referring to FIG. 1, a shock damper is shown comprising a damper body 10 and braces 20 supporting the damper body 10. The damper body 10 is comprised of a horizontal top plate 11, a horizontal bottom plate 12, and a vertical connecting device 13 connected between the top plate 11 and the bottom plate 12. The top plate 11 and the bottom plate 12 are rectangular plates, each having four axle holes 111; 121 in the four comers thereof. The top plate 11 and the bottom plate 12 may be arranged in parallel, or in a crossed manner. According to the embodiment shown in FIG. 1, the top plate 11 and the bottom plate 12 are arranged at different elevations in a crossed manner. Referring to FIGS. 1 through 5, respective screws 40 are mounted in the axle holes 111 of the top plate 11 of the damper body 10 to fixedly secure the top plate 11 to the bottom of the structural beam 31 of the structure 30. A top locating plate 21 is closely attached to the bottom of the bottom plate 12 and fixedly fastened to the axle holes 121 of the bottom plate 12 by screws. The braces 20 are symmetrically arranged at two sides, each having a top end connected to the bottom of the locating plate 21, and a bottom end connected to a bottom locating plate 22, which is fixedly fastened to the inside of the column 32 or floor by respective studs 40. The braces 20 may be arranged in two sets to form a V-shaped profile or an inversely disposed V-shaped profile. Thus, the beam 31 and column 32 of the structure 30 and the damper body 10 and braces 20 of the shock damper of the present invention are joined together. When an earthquake occurs, the connecting device 13 is deformed to absorb earthquake energy, so the structure 30 bears little earthquake energy and, is free from damage by the earthquake. In order to fit different structures, the braces 20 may be tilted in one direction to support the damper body 10 against apart of the building (see FIGS. 3A, 3B, 4C, 4F, and 5B). The present invention may be variously embodied to fit different structural constructions. For example, the damper body 10 may be supported between two sets of braces 20 that are respectively arranged into a V-shaped profile or an inversely disposed V-shaped profile at the top or bottom side of the damper body 10, forming a shock damper with an X-shaped profile (see FIGS. 4D and 5C); two damper bodies 10 may be incorporated with braces 20 to form a shock damper of V-shaped profile or inversely disposed V-shaped profile (see FIG. 4E); damper bodies 10 may be installed in structures or shearing walls formed of beams 31 and braces 20 (see FIGS. 4G, 4H, 5E, and 5F).
[0024] Basically, the damper body 10 is formed of top plate 11, a bottom plate 12, and a connecting device 13 supported between the top plate 11 and the bottom plate 12. By means of braces 20, the damper body 10 is firmly secured to the beam 31 and column 32 of the structure 30. Upon an earthquake, the relatively lower strength of the connecting device 13 is deformed to absorb shock waves from the earthquake. The connecting device 13 may be variously embodied. For example, the connecting device 13 can be made having any of a variety of cross sections including oval cross section, double-trapezoidal cross section, rhombic cross section, circular cross section, triangular cross section, trapezoidal cross section, rectangular cross section, polygonal cross section, or the like. The connecting device 13 can also be made having a crossed structure connected between the top plate 11 and the bottom plate 12, as shown in FIG. 7B. According to the embodiment shown in FIG. 7C, the top plate 11 and the bottom plate 12 each are formed of two symmetrical plate members respectively bilaterally welded to the top and bottom sides of the connecting device 13. According to the embodiment shown in FIG. 7E, the connecting device 13 is shaped like an I-bar. According to the embodiment shown in FIG. 7F, the connecting device 13 is comprised of two V-shaped plates connected in parallel between the top and bottom plates, and the V-shaped plates of the connecting devices 13 each have a bottom end welded with a horizontally extended cylindrical rod (or a spherical member) 23 and pivoted to a hole 24 in the bottom plate. According to the embodiments shown in FIGS. 7G and 7H, the connecting device 13 is comprised of two Y-shaped or X-shaped plates. According to the embodiments shown in FIGS. From 8A˜8C, the top plate 11 and the bottom plate 12 each have a plurality of transversely or longitudinally extended locating grooves 112 or 122 on the bottom plate 12 or top plate 11, and the connecting device 13 is comprised of a plurality of I-bars respectively fitted with the respective horizontal top or bottom section 131 into the locating grooves 112 and 122 of the top plate 11 and the bottom plate 12. According to the embodiment shown in FIGS. 9A and 9B, the connecting device 13 is comprised of a stack of I-shaped plates fastened together by screw bolts. FIGS. 10A and 10B show that the top and bottom plates 11 and 12 each have a T-shaped profile, and the connecting device 13 is comprised of a stack of I-shaped plates connected between the T-shaped top plate 11 and the T-shaped bottom plate 12. Further, a transverse connecting member may be connected between each two adjacent plates of the connecting device 13 to keep the plates of the connecting device 13 in balance. As indicated above, the present invention provides a simple shock damper, detachable and replaceable, installed in a structure to absorb shocks.
[0025] A prototype of shock damper has been constructed with the features of FIGS. 1˜10. The shock damper functions smoothly to provide all of the features discussed earlier.
[0026] It will be understood that each of the elements described above, or two or more together, may also find a useful application in other types of methods differing from the type described above.
[0027] While certain novel features of this invention have been shown and described and are pointed out in the annexed claim, it is not intended to be limited to the details above, since it will be understood that various omissions, modifications, substitutions and changes in the forms and details of the device illustrated and in its operation can be made by those skilled in the art without departing in any way from the spirit of the present invention.
I claim:
1. A shock damper comprising: at least one damper body respectively installed in the frame of a structure and adapted to absorb shocks from the said structure, the said at least one damper body each comprising a horizontal top plate, a horizontal bottom plate, and a vertical connecting device connected between the said horizontal top plate and the said horizontal bottom plate, the said connecting device having any of a variety of cross sections and a structural strength weaker than the said horizontal top plate and the said horizontal bottom plate such that the said connecting device is deformed to absorb shocks when said structure encountering an earthquake; and supporting means adapted to secure the said at least one damper body to the beam and column of the frame of the said structure by studs, the said supporting means comprising a plurality of braces.
2. The shock damper of claim 1 wherein the horizontal top plate and horizontal bottom plate of each of the said at least one damper body are flat plate members each having a set of locating grooves respectively facing each other, and the connecting device of each of the said at least one damper body is comprised of a plurality of I-bars engaged into the said locating grooves and supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
3. The shock damper of claim 1 wherein the horizontal top plate and horizontal bottom plate of each of the said at least one damper body are rhombic plate members each having a set of locating grooves respectively facing each other, and the connecting device of each of the said at least one damper body is comprised of a plurality of plates respectively engaged into the said locating grooves and supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
4. The shock damper of claim 1 wherein the horizontal top plate and horizontal bottom plate of each of the said at least one damper body are rhombic plate members, and the connecting device of each of the said at least one damper body is comprised of a plurality of metal I-bars or plates with an I shaped cross section vertically connected between the horizontal top plate and horizontal bottom plate of the respective damper body.
5. The shock damper of claim 1 wherein the horizontal top plate and horizontal bottom plate of each of the said at least one damper body are flat plate members each having a set of locating grooves respectively facing each other, and the connecting device of each of the said at least one damper body is comprised of a plurality of triangular plates respectively engaged into the said locating grooves and supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
6. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of V-shaped plates vertically connected between the horizontal top plate and horizontal bottom plate of the respective damper body.
7. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of plates vertically supported between the horizontal top plate and horizontal bottom plate of the respective damper body, and the plates of the connecting device of each of the said at least one damper body each having a bottom side welded with a horizontally extended cylindrical rod member supported on the horizontal bottom plate of the respective damper body.
8. The shock damper of claim 7 wherein the said cylindrical rod member has a locating groove adapted to receive the respective plate of the respective connecting device.
9. The shock damper of claim 7 wherein the bottom plate of the connecting device of each of the said at least one damper body has a plurality of holes, and the cylindrical rod members of the plates of the connecting device of each of the said at least one damper body are respectively pivoted to the holes of the bottom plate of the connecting device of each of the said at least one damper body.
10. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of plates vertically supported between the horizontal top plate and horizontal bottom plate of the respective damper body, and the plates of the connecting device of each of the said at least one damper body each having a bottom side welded with a spherical member supported on the horizontal bottom plate of the respective damper body.
11. The shock damper of claim 10 wherein the said spherical member has a locating groove adapted to receive the respective plate of the respective connecting device.
12. The shock damper of claim 10 wherein the bottom plate of the connecting device of each of the said at least one damper body has a plurality of holes, and the spherical members of the plates of the connecting device of each of the said at least one damper body are respectively pivoted to the holes of the bottom plate of the connecting device of each of said at least one damper body.
13. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of X-shaped supporting members respectively supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
14. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of I-bars respectively fitted into respective grooves on the horizontal top plate and horizontal bottom plate of the respective damper device and then fixedly secured thereto by one of the fastening means including welding, adhesive means, and screw joints.
15. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a plurality of T-bars respectively supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
16. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a stack of I-shaped plates fastened together by screw bolts and supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
17. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a stack of I-shaped plates fastened together by screw bolts and supported between the horizontal top plate and horizontal bottom plate of the respective damper body and fixedly secured to the structure.
18. The shock damper of claim 1 wherein the connecting device of each of the said at least one damper body is comprised of a stack of T-shaped metal plates fastened together by one of the fastening means including welding, adhesive means, and screw joints, and supported between the horizontal top plate and horizontal bottom plate of the respective damper body.
|
Table tennis at the 2014 Summer Youth Olympics
Table tennis at the 2014 Summer Youth Olympics was held from 17 to 23 August at the Wutaishan Sports Center in Nanjing, China.
Qualification
Each National Olympic Committee (NOC) can enter a maximum of 2 competitors, 1 per each gender. As hosts, China is given the maximum quota should they not qualify an athlete and a further 8 spots, 4 in each gender, will be allocated by the Tripartite Commission, however one spot was unused and was reallocated. The remaining 54 places shall be decided in four qualification phases: the 2014 World Qualification Event, the Under-18 World Rankings, six Road to Nanjing series events and six continental qualification tournaments.
To be eligible to participate at the Youth Olympics athletes must have been born between 1 January 1996 and 31 December 1999.
Schedule
The schedule was released by the Nanjing Youth Olympic Games Organizing Committee.
* All times are CST (UTC+8)
|
With no explanation, chose the best option from "A", "B", "C" or "D". from which the claim arises with such particularity that the defendant or claimant will be able, without moving for a more definite statement, to commence an investigation of the facts and to frame a responsive pleading.” Id. Rule E(2)(a). “If the conditions for an in rem action appear to exist, the court must issue an order directing the clerk to issue a warrant for the arrest of the vessel or other property that is the subject of the action.” Id. Rule C(3)(a)(ii)(A). It is well settled that claims for breach of charter and cargo damage give rise to maritime liens. See Rainbow Line, 480 F.2d at 1027 (“The American law is clear that there is a maritime lien for the breach of a charter party....”); RR Caribbean, Inc. v. Dredge “Jumby Bay”, 147 F.Supp.2d 378, 381 (D.Vi.2001) (<HOLDING>); Demsey & Assocs., Inc. v. S.S. Sea Star, 461
A: holding that section 506d does not permit the strip down of a partially secured lien
B: recognizing that breach of contract cause of action accrues at time of the breach
C: holding party in breach could not maintain suit for breach of contract
D: recognizing a maritime lien for breach of a partially executed charter party
D.
|
namespace SLStudio
{
public abstract class StudioWorker : IStudioWorker
{
protected StudioWorker()
{
Name = GetType().Name;
}
public virtual string Name { get; }
}
}
|
package ru.ifmo.unbiased.algo;
import ru.ifmo.unbiased.Individual;
import ru.ifmo.unbiased.UnbiasedProcessor;
import ru.ifmo.unbiased.ops.Operator2;
import ru.ifmo.unbiased.ops.UnbiasedOperator;
import ru.ifmo.unbiased.util.ImmutableIntArray;
import static ru.ifmo.unbiased.Operators.*;
public final class OneMaxHandCrafted {
private OneMaxHandCrafted() {}
private static final UnbiasedOperator FLIP_TWO_SAME = new Operator2() {
@Override
protected void applyBinary(int sameBits, int differentBits) {
flipSame(2);
flipDifferent(0);
}
};
private static final UnbiasedOperator FLIP_FOUR_DIFFERENT = new Operator2() {
@Override
protected void applyBinary(int sameBits, int differentBits) {
flipSame(0);
flipDifferent(4);
}
};
private static final UnbiasedOperator FLIP_THREE_SAME = new Operator2() {
@Override
protected void applyBinary(int sameBits, int differentBits) {
flipSame(3);
flipDifferent(0);
}
};
private static final UnbiasedOperator FLIP_SEVEN_SAME = new Operator2() {
@Override
protected void applyBinary(int sameBits, int differentBits) {
flipSame(7);
flipDifferent(0);
}
};
private static final UnbiasedOperator FLIP_ONE_WHERE_ALL_THREE_SAME = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 1;
}
};
private static final UnbiasedOperator FLIP_ONE_WHERE_SECOND_DIFFERS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[1] = 1;
}
};
private static final UnbiasedOperator FLIP_ONE_WHERE_THIRD_DIFFERS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[2] = 1;
}
};
private static final UnbiasedOperator FLIP_TWO_WHERE_THIRD_DIFFERS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[2] = 2;
}
};
private static final UnbiasedOperator FLIP_ALL_WHERE_SECOND_DIFFERS_AND_ONE_WHERE_FIRST_DIFFERS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[1] = bitCounts.get(1);
result[3] = 1;
}
};
public static int runTernary(UnbiasedProcessor processor) {
processor.reset();
try {
int n = processor.getProblemSize();
Individual good = processor.newRandomIndividual();
Individual bad = good;
int sameCount = n;
//noinspection InfiniteLoopStatement
while (true) {
if (sameCount == 1) {
if (good.fitness() == n - 1) {
good = processor.query(FLIP_ONE_SAME, good, bad);
}
} else if (sameCount == 2) {
if (good.fitness() == n - 2) {
good = processor.query(FLIP_TWO_SAME, good, bad);
} else {
Individual flipOne = processor.query(FLIP_ONE_SAME, good, bad);
if (flipOne.fitness() == n - 2) {
good = processor.query(FLIP_ONE_WHERE_ALL_THREE_SAME, good, bad, flipOne);
} else {
good = flipOne;
}
}
} else {
Individual m = processor.query(FLIP_THREE_SAME, good, bad);
if (m.fitness() == good.fitness() + 3) {
good = m;
} else if (m.fitness() == good.fitness() - 3) {
bad = processor.query(XOR3, good, bad, m);
} else if (m.fitness() == good.fitness() + 1) {
Individual p = processor.query(FLIP_TWO_WHERE_THIRD_DIFFERS, good, bad, m);
if (p.fitness() == good.fitness() + 2) {
good = p;
} else {
Individual r = processor.query(
FLIP_ALL_WHERE_SECOND_DIFFERS_AND_ONE_WHERE_FIRST_DIFFERS, good, m, p);
if (r.fitness() == good.fitness() + 2) {
good = r;
} else {
good = processor.query(XOR3, good, p, r);
}
}
bad = processor.query(XOR3, good, bad, m);
} else {
Individual p = processor.query(FLIP_ONE_WHERE_THIRD_DIFFERS, good, bad, m);
if (p.fitness() == good.fitness() + 1) {
good = p;
} else {
Individual r = processor.query(FLIP_ONE_WHERE_SECOND_DIFFERS, good, m, p);
if (r.fitness() == good.fitness() + 1) {
good = r;
} else {
good = processor.query(XOR3, m, p, r);
}
}
bad = processor.query(XOR3, good, bad, m);
}
sameCount -= 3;
}
}
} catch (UnbiasedProcessor.OptimumFound found) {
return found.numberOfQueries();
}
}
public static int runQuaternary(UnbiasedProcessor processor) {
processor.reset();
try {
Individual first = processor.newRandomIndividual();
Individual second = first;
int sameCount = processor.getProblemSize();
int n = sameCount;
//noinspection InfiniteLoopStatement
while (true) {
if (sameCount < 7) {
//noinspection InfiniteLoopStatement
while (true) {
if (sameCount == 1) {
if (first.fitness() == n - 1) {
first = processor.query(FLIP_ONE_SAME, first, second);
}
} else if (sameCount == 2) {
if (first.fitness() == n - 2) {
first = processor.query(FLIP_TWO_SAME, first, second);
} else {
Individual flipOne = processor.query(FLIP_ONE_SAME, first, second);
if (flipOne.fitness() == n - 2) {
first = processor.query(Operators.ternary1SS, first, second, flipOne);
} else {
first = flipOne;
}
}
} else {
Individual m = processor.query(FLIP_THREE_SAME, first, second);
if (m.fitness() == first.fitness() + 3) {
first = m;
} else if (m.fitness() == first.fitness() - 3) {
second = processor.query(XOR3, first, second, m);
} else if (m.fitness() == first.fitness() + 1) {
Individual p = processor.query(Operators.ternary2SD, first, second, m);
if (p.fitness() == first.fitness() + 2) {
first = p;
second = processor.query(XOR3, first, second, m);
} else {
Individual r = processor.query(Operators.ternaryDS1DD, first, m, p);
if (r.fitness() == first.fitness() + 2) {
first = r;
second = processor.query(XOR3, first, second, m);
} else {
first = processor.query(XOR3, first, p, r);
second = processor.query(XOR3, first, second, m);
}
}
} else {
Individual p = processor.query(Operators.ternary1SD, first, second, m);
if (p.fitness() == first.fitness() + 1) {
first = p;
second = processor.query(XOR3, first, second, m);
} else {
Individual r = processor.query(Operators.ternary1DS, first, m, p);
if (r.fitness() == first.fitness() + 1) {
first = r;
second = processor.query(XOR3, first, second, m);
} else {
first = processor.query(XOR3, m, p, r);
second = processor.query(XOR3, first, second, m);
}
}
}
sameCount -= 3;
}
}
} else {
Individual a = processor.query(FLIP_SEVEN_SAME, first, second);
if (a.fitness() == first.fitness() + 7) {
first = a;
} else if (a.fitness() == first.fitness() - 7) {
second = processor.query(Operators.ternarySD, second, first, a);
} else {
if (a.fitness() - first.fitness() < 0) {
Individual b = processor.query(FLIP_FOUR_DIFFERENT, a, first);
if (first.fitness() == a.fitness() + 5) {
if (b.fitness() == a.fitness() + 2) {
Individual c = processor.query(Operators.ternary2SD, first, b, a);
if (c.fitness() == first.fitness()) {
Individual d = processor.query(FLIP_ONE_DIFFERENT, c, first);
if (d.fitness() == first.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.ternarySD, first, d, c);
second = processor.query(XOR3, second, a, first);
}
} else {
Individual d = processor.query(Operators.qua1SDS, first, b, a, c);
if (d.fitness() == first.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDSDSD, d, c, a, b);
second = processor.query(XOR3, second, a, first);
}
}
} else if (b.fitness() == a.fitness() + 4) {
Individual c = processor.query(Operators.ternary2SD, b, a, first);
if (c.fitness() == b.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, a, first);
} else {
Individual d = processor.query(Operators.ternary1DS, first, b, c);
if (d.fitness() == first.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSS, first, b, c, d);
second = processor.query(XOR3, second, a, first);
}
}
}
} else if (first.fitness() == a.fitness() + 3) {
if (b.fitness() == a.fitness()) {
Individual c = processor.query(Operators.ternary2SD, first, b, a);
if (c.fitness() == first.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, a, first);
} else if (c.fitness() == first.fitness()) {
Individual d = processor.query(Operators.qua1DSS1DDS, first, a, c, b);
if (d.fitness() == first.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, a, first);
} else if (d.fitness() == first.fitness()) {
Individual e = processor.query(XOR3, d, c, first);
if (e.fitness() == first.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSS, first, a, e, b);
second = processor.query(XOR3, second, a, first);
}
} else if (d.fitness() == first.fitness() - 2) {
first = processor.query(Operators.quaDSS, first, a, b, d);
second = processor.query(XOR3, second, a, first);
}
} else if (c.fitness() == first.fitness() - 2) {
first = processor.query(Operators.quaDSS, first, a, b, c);
second = processor.query(XOR3, second, a, first);
}
} else if (b.fitness() == a.fitness() + 2) {
Individual c = processor.query(Operators.ternary2DS2SD, b, a, first);
if (c.fitness() == b.fitness()) {
Individual d = processor.query(Operators.ternary1DS1SD, first, b, c);
if (d.fitness() == first.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, a, first);
} else if (d.fitness() == first.fitness()) {
Individual f = processor.query(Operators.quaSDDDSS, first, b, c, d);
if (f.fitness() == first.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDSDSD, first, b, c, d);
second = processor.query(XOR3, second, a, first);
}
} else if (d.fitness() == first.fitness() - 2) {
Individual f = processor.query(Operators.quaSDSDSS, first, b, c, d);
if (f.fitness() == first.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
Individual x = processor.query(Operators.ternary1DSSD, b, a, c);
if (x.fitness() == first.fitness() + 2) {
first = x;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDDDSS, b, a, c, x);
second = processor.query(XOR3, second, a, first);
}
}
}
} else if (c.fitness() == b.fitness() - 2) {
Individual e = processor.query(Operators.qua1DSS1DDS, first, a, b, c);
if (e.fitness() == first.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, a, first);
} else if (e.fitness() == first.fitness() - 2) {
first = processor.query(Operators.quaDSS, first, a, c, e);
second = processor.query(XOR3, second, a, first);
} else if (e.fitness() == first.fitness()) {
Individual f = processor.query(Operators.quaDSSSSD, first, b, c, e);
if (f.fitness() == first.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSS, first, a, c, f);
second = processor.query(XOR3, second, a, first);
}
}
} else if (c.fitness() == b.fitness() + 2) {
Individual d = processor.query(Operators.ternary1SD, c, a, b);
if (d.fitness() == first.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDS, c, a, b, d);
second = processor.query(XOR3, second, a, first);
}
}
} else if (b.fitness() == a.fitness() + 4) {
Individual c = processor.query(Operators.ternary2DD, first, a, b);
if (c.fitness() == first.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, a, first);
} else {
Individual d = processor.query(Operators.ternary1DS, b, first, c);
if (d.fitness() == first.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSS, b, first, c, d);
second = processor.query(XOR3, second, a, first);
}
}
}
} else if (first.fitness() == a.fitness() + 1) {
if (b.fitness() == a.fitness() + 4) {
first = b;
second = processor.query(XOR3, second, a, first);
} else if (b.fitness() == a.fitness() + 2) {
Individual c = processor.query(Operators.ternary2DS2DD, first, a, b);
if (c.fitness() == first.fitness()) {
Individual d = processor.query(Operators.qua1DSSDDD, first, a, b, c);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else if (d.fitness() == first.fitness() + 1) {
first = processor.query(Operators.quaDSSSDD, d, a, c, b);
second = processor.query(XOR3, second, a, first);
} else if (d.fitness() == first.fitness() - 1) {
Individual e = processor.query(Operators.ternary1DS1SD, b, first, c);
if (e.fitness() == b.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, a, first);
} else if (e.fitness() == b.fitness()) {
Individual f = processor.query(Operators.quaSDSDSD, b, e, c, first);
if (f.fitness() == b.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDSDSD, b, e, first, c);
second = processor.query(XOR3, second, a, first);
}
} else if (e.fitness() == b.fitness() - 2) {
first = processor.query(Operators.quaDSSSSD, b, first, e, c);
second = processor.query(XOR3, second, a, first);
}
}
} else if (c.fitness() == first.fitness() - 2) {
Individual d = processor.query(Operators.qua1DSS1SSD, b, first, c, a);
if (d.fitness() == b.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, a, first);
} else if (d.fitness() == b.fitness()) {
Individual e = processor.query(Operators.quaDSSSSD, b, a, c, d);
if (e.fitness() == b.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSSSSD, b, d, c, first);
second = processor.query(XOR3, second, a, first);
}
} else if (d.fitness() == b.fitness() - 2) {
Individual e = processor.query(Operators.quaDSS, b, a, c, d);
first = processor.query(Operators.quaDSS, e, first, c, d);
second = processor.query(XOR3, second, a, first);
}
} else if (c.fitness() == first.fitness() + 2) {
Individual d = processor.query(Operators.ternary1DD, c, first, b);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDDS, c, first, b, d);
second = processor.query(XOR3, second, a, first);
}
}
} else if (b.fitness() == a.fitness()) {
Individual c = processor.query(Operators.ternary2DS2SD, b, a, first);
if (c.fitness() == b.fitness() + 4) {
first = c;
second = processor.query(XOR3, second, a, first);
} else if (c.fitness() == b.fitness() + 2) {
Individual d = processor.query(Operators.quaDSDDDS, first, a, b, c);
if (d.fitness() == first.fitness() + 2) {
Individual e = processor.query(Operators.ternary1DS, d, first, b);
if (e.fitness() == first.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSS, d, first, b, e);
second = processor.query(XOR3, second, a, first);
}
} else if (d.fitness() == first.fitness() - 2) {
Individual e = processor.query(Operators.ternary1DS1SD, c, a, b);
if (e.fitness() == first.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, a, first);
} else if (e.fitness() == c.fitness()) {
Individual f = processor.query(Operators.quaSDSDSD, e, first, d, b);
if (f.fitness() == first.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, a, first);
} else if (f.fitness() == e.fitness() - 2) {
first = processor.query(Operators.quaDSSSDD, e, a, d, b);
second = processor.query(XOR3, second, a, first);
}
} else if (e.fitness() == c.fitness() - 2) {
first = processor.query(Operators.quaSDSDSS, c, a, b, e);
second = processor.query(XOR3, second, a, first);
}
}
} else if (c.fitness() == b.fitness()) {
Individual d = processor.query(Operators.quaDSSDDD, first, a, b, c);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
Individual e = processor.query(Operators.qua1DSS1SSD1SDS, first, b, c, d);
if (e.fitness() == first.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, a, first);
} else if (e.fitness() == first.fitness() + 1) {
Individual f = processor.query(Operators.quaSSDDDS, e, first, b, d);
if (f.fitness() == first.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
f = processor.query(Operators.quaDDSSSD, e, first, b, c);
if (f.fitness() == first.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDSDSD, e, first, b, d);
second = processor.query(XOR3, second, a, first);
}
}
} else if (e.fitness() == first.fitness() - 1) {
Individual f = processor.query(Operators.quaDSDSDSSSDDDS, e, first, b, d);
if (f.fitness() == first.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
f = processor.query(Operators.quaDSDSDSSSDDDS, e, first, b, c);
if (f.fitness() == first.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSDSDSSSDDDS, e, first, c, d);
second = processor.query(XOR3, second, a, first);
}
}
} else if (e.fitness() == first.fitness() - 3) {
first = processor.query(Operators.quaDSSSDSSSDDDS, b, d, c, e);
second = processor.query(XOR3, second, a, first);
}
}
} else if (c.fitness() == b.fitness() - 2) {
Individual d = processor.query(Operators.qua1DDSSDS, first, b, a, c);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDDDSS, d, c, b, a);
second = processor.query(XOR3, second, a, first);
}
}
} else if (b.fitness() == a.fitness() - 2) {
Individual c = processor.query(Operators.ternary2SD, first, b, a);
if (c.fitness() == first.fitness() + 2) {
Individual d = processor.query(Operators.ternary1SD, c, b, a);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaSDS, c, b, a, d);
second = processor.query(XOR3, second, a, first);
}
} else {
Individual d = processor.query(Operators.ternary1DSSD, c, b, a);
if (d.fitness() == first.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, a, first);
} else {
first = processor.query(Operators.quaDSSSDD, c, b, a, d);
second = processor.query(XOR3, second, a, first);
}
}
}
}
} else {
Individual b = processor.query(FLIP_FOUR_DIFFERENT, first, a);
if (a.fitness() == first.fitness() + 5) {
if (b.fitness() == first.fitness() + 2) {
Individual c = processor.query(Operators.ternary2SD, a, b, first);
if (c.fitness() == a.fitness()) {
Individual d = processor.query(FLIP_ONE_DIFFERENT, c, a);
if (d.fitness() == a.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.ternarySD, a, d, c);
second = processor.query(XOR3, second, first, a);
}
} else {
Individual d = processor.query(Operators.qua1SDS, a, b, first, c);
if (d.fitness() == a.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDSDSD, d, c, first, b);
second = processor.query(XOR3, second, first, a);
}
}
} else if (b.fitness() == first.fitness() + 4) {
Individual c = processor.query(Operators.ternary2SD, b, first, a);
if (c.fitness() == b.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, first, a);
} else {
Individual d = processor.query(Operators.ternary1DS, a, b, c);
if (d.fitness() == a.fitness() + 1) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSS, a, b, c, d);
second = processor.query(XOR3, second, first, a);
}
}
}
} else if (a.fitness() == first.fitness() + 3) {
if (b.fitness() == first.fitness()) {
Individual c = processor.query(Operators.ternary2SD, a, b, first);
if (c.fitness() == a.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, first, a);
} else if (c.fitness() == a.fitness()) {
Individual d = processor.query(Operators.qua1DSS1DDS, a, first, c, b);
if (d.fitness() == a.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, first, a);
} else if (d.fitness() == a.fitness()) {
Individual e = processor.query(XOR3, d, c, a);
if (e.fitness() == a.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSS, a, first, e, b);
second = processor.query(XOR3, second, first, a);
}
} else if (d.fitness() == a.fitness() - 2) {
first = processor.query(Operators.quaDSS, a, first, b, d);
second = processor.query(XOR3, second, first, a);
}
} else if (c.fitness() == a.fitness() - 2) {
first = processor.query(Operators.quaDSS, a, first, b, c);
second = processor.query(XOR3, second, first, a);
}
} else if (b.fitness() == first.fitness() + 2) { // �������� ����
Individual c = processor.query(Operators.ternary2DS2SD, b, first, a);
if (c.fitness() == b.fitness()) {
Individual d = processor.query(Operators.ternary1DS1SD, a, b, c);
if (d.fitness() == a.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, first, a);
} else if (d.fitness() == a.fitness()) {
Individual f = processor.query(Operators.quaSDDDSS, a, b, c, d);
if (f.fitness() == a.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDSDSD, a, b, c, d);
second = processor.query(XOR3, second, first, a);
}
} else if (d.fitness() == a.fitness() - 2) {
Individual f = processor.query(Operators.quaSDSDSS, a, b, c, d);
if (f.fitness() == a.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
Individual x = processor.query(Operators.ternary1DSSD, b, first, c);
if (x.fitness() == a.fitness() + 2) {
first = x;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDDDSS, b, first, c, x);
second = processor.query(XOR3, second, first, a);
}
}
}
} else if (c.fitness() == b.fitness() - 2) {
Individual e = processor.query(Operators.qua1DSS1DDS, a, first, b, c);
if (e.fitness() == a.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, first, a);
} else if (e.fitness() == a.fitness() - 2) {
first = processor.query(Operators.quaDSS, a, first, c, e);
second = processor.query(XOR3, second, first, a);
} else if (e.fitness() == a.fitness()) {
Individual f = processor.query(Operators.quaDSSSSD, a, b, c, e);
if (f.fitness() == a.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSS, a, first, c, f);
second = processor.query(XOR3, second, first, a);
}
}
} else if (c.fitness() == b.fitness() + 2) {
Individual d = processor.query(Operators.ternary1SD, c, first, b);
if (d.fitness() == a.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDS, c, first, b, d);
second = processor.query(XOR3, second, first, a);
}
}
} else if (b.fitness() == first.fitness() + 4) {
Individual c = processor.query(Operators.ternary2DD, a, first, b);
if (c.fitness() == a.fitness() + 2) {
first = c;
second = processor.query(XOR3, second, first, a);
} else {
Individual d = processor.query(Operators.ternary1DS, b, a, c);
if (d.fitness() == a.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSS, b, a, c, d);
second = processor.query(XOR3, second, first, a);
}
}
}
} else if (a.fitness() == first.fitness() + 1) {
if (b.fitness() == first.fitness() + 4) {
first = b;
second = processor.query(XOR3, second, first, a);
} else if (b.fitness() == first.fitness() + 2) {
Individual c = processor.query(Operators.ternary2DS2DD, a, first, b);
if (c.fitness() == a.fitness()) {
Individual d = processor.query(Operators.qua1DSSDDD, a, first, b, c);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else if (d.fitness() == a.fitness() + 1) {
first = processor.query(Operators.quaDSSSDD, d, first, c, b);
second = processor.query(XOR3, second, first, a);
} else if (d.fitness() == a.fitness() - 1) {
Individual e = processor.query(Operators.ternary1DS1SD, b, a, c);
if (e.fitness() == b.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, first, a);
} else if (e.fitness() == b.fitness()) {
Individual f = processor.query(Operators.quaSDSDSD, b, e, c, a);
if (f.fitness() == b.fitness() + 2) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDSDSD, b, e, a, c);
second = processor.query(XOR3, second, first, a);
}
} else if (e.fitness() == b.fitness() - 2) {
first = processor.query(Operators.quaDSSSSD, b, a, e, c);
second = processor.query(XOR3, second, first, a);
}
}
} else if (c.fitness() == a.fitness() - 2) {
Individual d = processor.query(Operators.qua1DSS1SSD, b, a, c, first);
if (d.fitness() == b.fitness() + 2) {
first = d;
second = processor.query(XOR3, second, first, a);
} else if (d.fitness() == b.fitness()) {
Individual e = processor.query(Operators.quaDSSSSD, b, first, c, d);
if (e.fitness() == b.fitness() + 2) {
first = e;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSSSSD, b, d, c, a);
second = processor.query(XOR3, second, first, a);
}
} else if (d.fitness() == b.fitness() - 2) {
Individual e = processor.query(Operators.quaDSS, b, first, c, d);
first = processor.query(Operators.quaDSS, e, a, c, d);
second = processor.query(XOR3, second, first, a);
}
} else if (c.fitness() == a.fitness() + 2) {
Individual d = processor.query(Operators.ternary1DD, c, a, b);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDDS, c, a, b, d);
second = processor.query(XOR3, second, first, a);
}
}
} else if (b.fitness() == first.fitness()) {
Individual c = processor.query(Operators.ternary2DS2SD, b, first, a);
if (c.fitness() == b.fitness() + 4) {
first = c;
second = processor.query(XOR3, second, first, a);
} else if (c.fitness() == b.fitness() + 2) {
Individual d = processor.query(Operators.quaDSDDDS, a, first, b, c);
if (d.fitness() == a.fitness() + 2) {
Individual e = processor.query(Operators.ternary1DS, d, a, b);
if (e.fitness() == a.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSS, d, a, b, e);
second = processor.query(XOR3, second, first, a);
}
} else if (d.fitness() == a.fitness() - 2) {
Individual e = processor.query(Operators.ternary1DS1SD, c, first, b);
if (e.fitness() == a.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, first, a);
} else if (e.fitness() == c.fitness()) {
Individual f = processor.query(Operators.quaSDSDSD, e, a, d, b);
if (f.fitness() == a.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, first, a);
} else if (f.fitness() == e.fitness() - 2) {
first = processor.query(Operators.quaDSSSDD, e, first, d, b);
second = processor.query(XOR3, second, first, a);
}
} else if (e.fitness() == c.fitness() - 2) {
first = processor.query(Operators.quaSDSDSS, c, first, b, e);
second = processor.query(XOR3, second, first, a);
}
}
} else if (c.fitness() == b.fitness()) {
Individual d = processor.query(Operators.quaDSSDDD, a, first, b, c);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
Individual e = processor.query(Operators.qua1DSS1SSD1SDS, a, b, c, d);
if (e.fitness() == a.fitness() + 3) {
first = e;
second = processor.query(XOR3, second, first, a);
} else if (e.fitness() == a.fitness() + 1) {
Individual f = processor.query(Operators.quaSSDDDS, e, a, b, d);
if (f.fitness() == a.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
f = processor.query(Operators.quaDDSSSD, e, a, b, c);
if (f.fitness() == a.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDSDSD, e, a, b, d);
second = processor.query(XOR3, second, first, a);
}
}
} else if (e.fitness() == a.fitness() - 1) {
Individual f = processor.query(Operators.quaDSDSDSSSDDDS, e, a, b, d);
if (f.fitness() == a.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
f = processor.query(Operators.quaDSDSDSSSDDDS, e, a, b, c);
if (f.fitness() == a.fitness() + 3) {
first = f;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSDSDSSSDDDS, e, a, c, d);
second = processor.query(XOR3, second, first, a);
}
}
} else if (e.fitness() == a.fitness() - 3) {
first = processor.query(Operators.quaDSSSDSSSDDDS, b, d, c, e);
second = processor.query(XOR3, second, first, a);
}
}
} else if (c.fitness() == b.fitness() - 2) {
Individual d = processor.query(Operators.qua1DDSSDS, a, b, first, c);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDDDSS, d, c, b, first);
second = processor.query(XOR3, second, first, a);
}
}
} else if (b.fitness() == first.fitness() - 2) {
Individual c = processor.query(Operators.ternary2SD, a, b, first);
if (c.fitness() == a.fitness() + 2) {
Individual d = processor.query(Operators.ternary1SD, c, b, first);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaSDS, c, b, first, d);
second = processor.query(XOR3, second, first, a);
}
} else {
Individual d = processor.query(Operators.ternary1DSSD, c, b, first);
if (d.fitness() == a.fitness() + 3) {
first = d;
second = processor.query(XOR3, second, first, a);
} else {
first = processor.query(Operators.quaDSSSDD, c, b, first, d);
second = processor.query(XOR3, second, first, a);
}
}
}
}
}
}
sameCount -= 7;
}
}
} catch (UnbiasedProcessor.OptimumFound found) {
return found.numberOfQueries();
}
}
private static class Operators {
static final UnbiasedOperator quaDDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = 0; // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSSDDD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = bitCounts.get(7); // DDD
}
};
static final UnbiasedOperator ternary1SS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 1; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = 0;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternarySD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = bitCounts.get(2);
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary2SD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = 2;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternaryDS1DD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = bitCounts.get(1);
result[2] = 0;
result[3] = 1; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary1DS1SD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 1;
result[2] = 1;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary1SD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = 1;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary1DS = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 1;
result[2] = 0;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary1DSSD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 1;
result[2] = bitCounts.get(2);
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary2DS2SD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 2;
result[2] = 2;
result[3] = 0; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary2DS2DD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 2;
result[2] = 0;
result[3] = 2; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary2DD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = 0;
result[3] = 2; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator ternary1DD = new UnbiasedOperator(3) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // flip nothing where (first == second), (first == third) => 00
result[1] = 0;
result[2] = 0;
result[3] = 1; // flip nothing where (first != second), (first != third) => 11
}
};
static final UnbiasedOperator qua1SDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = 1; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSDDDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = 0; // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = 0; // SSD
result[5] = bitCounts.get(5); // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSSSDD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = bitCounts.get(6); // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator qua1DDSSDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = 1; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaSDSDSS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaSDDDSS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = bitCounts.get(6); // SDD
}
};
static final UnbiasedOperator quaSDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator qua1DSS1SSD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 1; // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 1; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaSDSDSD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = bitCounts.get(5); // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator qua1DSS1DDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 1; // DSS
result[2] = 0; // SDS
result[3] = 1; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSSSSD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = bitCounts.get(4); // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaSSDDDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = 0; // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = bitCounts.get(4); // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator qua1DSSDDD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 1; // DSS
result[2] = 0; // SDS
result[3] = 0; // DDS
result[4] = 0; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = bitCounts.get(7); // DDD
}
};
static final UnbiasedOperator quaDDSSSD = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = 0; // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = bitCounts.get(4); // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator qua1DSS1SSD1SDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 1; // DSS
result[2] = 1; // SDS
result[3] = 0; // DDS
result[4] = 1; // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSDSDSSSDDDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = 0; // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = bitCounts.get(4); // SSD
result[5] = bitCounts.get(5); // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
static final UnbiasedOperator quaDSSSDSSSDDDS = new UnbiasedOperator(4) {
@Override
protected void applyImpl(ImmutableIntArray bitCounts, int[] result) {
result[0] = 0; // SSS
result[1] = bitCounts.get(1); // DSS
result[2] = bitCounts.get(2); // SDS
result[3] = bitCounts.get(3); // DDS
result[4] = bitCounts.get(4); // SSD
result[5] = 0; // DSD
result[6] = 0; // SDD
result[7] = 0; // DDD
}
};
}
}
|
<html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf8">
<title>intersting </title>
</head>
<body>
<form action="index2.php" method="post">
username: <input name="username" type="text" /><br/>
password: <input name="password" type="password"><br/>
<input name="submit" type="submit">
</form>
</body>
</html>
<?php
$dbhost = "localhost";
$dbuser = "root";
$dbpass = "12ytsdsg";
$db = "ctf";
$conn = mysql_connect($dbhost,$dbuser,$dbpass);
if($conn)
echo "connect is success";
else
echo "connect is fail ";
$vo=mysql_select_db($db,$conn);
function filter($str){
$filterlist = "/\(|\)|username|password|where|case|when|like|regexp|into|limit|=|for|;/";
if(preg_match($filterlist,strtolower($str))){
die(" stupid hacker .illegal input!");
}
return $str;
}
$username = isset($_POST['username'])?filter($_POST['username']):die("please input username!");
$paaword = isset($_POST['password'])?filter($_POST['password']):die("please input password!");
echo $username;
echo $paaword;
$sql = "select * from admin where username='$username' and password='$paaword'";
$res =mysql_query($sql,$conn);
if($result=mysql_fetch_array($res)){
echo $result['username'];
}else{
echo "the flag == password";
}
?>
|
OGMS-0001-A
OGMS-0001-A or "The_ghostisbehindyou"
was the first Myth to join the group
Facts
* died in a fire
* is a ghost
* also a hacker
* friends with c0mmunity and thepowerofthec0mmunity
* claims to have connection with noli but is so un active
Myth Friends
* 1) Iam_unkn0wn2
* 2) mrbutman5890
* 3) Deadm8te
* 4) Mythopias
|
Mold temperature controller
FIG. 1 is a front elevational view of the mold temperature controller showing my new design;
FIG. 2 is a rear elevational view thereof;
FIG. 3 is a left side elevational view thereof;
FIG. 4 is a right side elevational view thereof;
FIG. 5 is a top plan view thereof;
FIG. 6 is a bottom plan view thereof;
FIG. 7 is a perspective view taken from the top, front and right side ofthe mold temperature controller; and,
FIG. 8 is a perspective view taken from the top, rear and left side ofthe mold temperature controller.
The ornamental design for a mold temperature controller, as shown and described.
|
How to send an image to server automatically?
I want the user to upload an image to the server without hitting the submit button.
This is my html form:
<form>
<div class="entry">Upload image<input type="file" formmethod="post" formaction="/avatar_upload"/></div>
</form>
Is it possible to upload the file to the server without using the submit button?
So the question is how to submit a file upload without pressing a submit button?
Yes, that's exactly what I want.
So then, this is not about MongoDB.
Try to use onchange event of the input button to fire the save.
Sorry to ask you, but how exactly should I use it? I suppose I have to make post request in this situation?
Sample code in this fiddle https://jsfiddle.net/shubmittal/qhecy6fp/1/
You can also find examples in this stackoverflow discussion https://stackoverflow.com/questions/7231157/how-to-submit-form-on-change-of-dropdown-list
Change your markup like this (add id attributes):
<form id="form">
<div class="entry">Upload image
<input id="file" type="file" formmethod="post" formaction="/avatar_upload"/>
</div>
</form>
In Javascript (assuming jQuery is used):
$('#file').on('change', function () {
$('#form').submit();
});
|
Smoke test flake: turns off editor line numbers and verifies the live change
Build: https://dev.azure.com/monacotools/a6d41577-0fa3-498e-af22-257312ff0545/_build/results?buildId=231209
Changes: https://github.com/Microsoft/vscode/compare/088d730...079d0ab
1) VSCode Smoke Tests (Web)
Preferences
turns off editor line numbers and verifies the live change:
Error: Timeout: get elements '.line-numbers' after 20 seconds.
at Code.poll (/Users/runner/work/1/s/test/automation/src/code.ts:277:11)
at Code.waitForElements (/Users/runner/work/1/s/test/automation/src/code.ts:218:10)
at Context.<anonymous> (src/areas/preferences/preferences.test.ts:22:4)
2) VSCode Smoke Tests (Web)
Preferences
changes "workbench.action.toggleSidebarPosition" command key binding and verifies it:
Error: Timeout: get element '.part.activitybar.right' after 20 seconds.
at Code.poll (/Users/runner/work/1/s/test/automation/src/code.ts:277:11)
at Code.waitForElement (/Users/runner/work/1/s/test/automation/src/code.ts:222:10)
at ActivityBar.waitForActivityBar (/Users/runner/work/1/s/test/automation/src/activityBar.ts:28:3)
at Context.<anonymous> (src/areas/preferences/preferences.test.ts:33:4)
This actually looks like a real issue to me wrt settings. Both tests fail because settings have been written to in a way that renders them wrong. I wonder if our disposable work could have any impact here:
Ok wait, this is really bizarre: the playwright playback shows the custom title with command center in the beginning and then suddenly disappearing. I wonder if at that moment we issue a click that then ends up in the wrong location?
I cannot explain the removal of the custom title in this case. Are we running some kind of settings sync? The theme also seems to change.
Looks like a flake.
Actually, it turns out we configure the command center and layout actions to not be visible in smoke tests:
https://github.com/microsoft/vscode-smoketest-express/commit/f041f67cf235b1fd983780750d9e376fac6d1f74
This explains why the custom title area hides after a while. I think I will see to revert that change because it would mean that at anytime while the test runs, the entire workbench moves up by 22px...
|
from itertools import product
from .symbols import Variable, bool_to_machine
class InvalidFormula(BaseException):
pass
class Formula:
def __init__(self, list=[], replacements=None):
self._list = list
self._vars = []
for i in self._list:
if isinstance(i, Variable) and i not in self._vars:
self._vars.append(i)
used = []
if replacements is None:
self._reps = []
for i in self._list:
if i.machine not in used:
used.append(i.machine)
self._reps += i.replacements
else:
self._reps = replacements
def __getitem__(self, i):
return self._list[i]
def __len__(self):
return len(self._list)
def has_sub_tautology(self):
pass
def brackets_match(self):
pass
def get_variables(self):
return self._vars
def get_replacements(self):
return self._reps
def simplify(self, machine):
replacements = self.get_replacements()
while len(machine) > 1:
pre = machine
for i, j in replacements:
machine = j.join(machine.split(i))
if pre == machine:
raise InvalidFormula
return machine == "1"
def get_truth(self, values):
vars = self.get_variables()
assert len(vars) == len(values)
machine = self.as_machine()
for v, t in zip(vars, values):
machine = bool_to_machine(t).join(machine.split(v.machine))
return self.simplify(machine)
def is_tautology(self):
vars = self.get_variables()
for values in product([True, False], repeat=len(vars)):
if not self.get_truth(values):
return False
return True
def is_contradiction(self):
vars = self.get_variables()
for values in product([True, False], repeat=len(vars)):
if self.get_truth(values):
return False
return True
def is_valid(self):
try:
self.get_truth([True for i in self.get_variables()])
return True
except InvalidFormula:
return False
def as_ascii(self):
return "".join([i.ascii for i in self._list])
def as_tex(self):
return " ".join([i.tex for i in self._list])
def as_unicode(self):
return "".join([i.unicode for i in self._list])
def as_machine(self):
return "".join([i.machine for i in self._list])
def __str__(self):
return "".join(str(i) for i in self._list)
|
/**
* THIS IS EXAMPLE CODE. IT IS NOT PART OF THE API AND MAY CHANGE OR DISAPPEAR
* AT ANY POINT.
*
* This selector is meant to select only those tests that Chrome passes.
*/
import { TestHandling } from "../selection";
import { TestSpec } from "../test-spec";
import { Selection as WhatwgSelection } from "./whatwg";
//
// Most likely platform issues (i.e. issues outside the XML parser itself but
// with the JavaScript runtime, either due to the ES standard or the runtime's
// own quirks):
//
// - surrogate encoding:
//
// V8 goes off the rails when it encounters a surrogate outside a pair. There
// does not appear to be a workaround.
//
// - unicode garbage-in garbage-out:
//
// V8 passes garbage upon encountering bad unicode instead of throwing a
// runtime error. (Python throws.)
//
// - xml declaration encoding:
//
// By the time the parser sees the document, it cannot know what the original
// encoding was. It may have been UTF16, which was converted correctly to an
// internal format.
//
// These are genuine parser errors:
//
// - ignores wf errors in DOCTYPE:
//
// Even non-validating parsers must report wellformedness errors in DOCTYPE.
//
// - naming error with namespaces:
//
// The parser should error on an element name like a:b:c due to the two
// colons. Chrome currently just omits the elements that are not well-formed.
//
const PROBLEMATIC: Record<string, string> = {
"not-wf-sa-168": "surrogate encoding",
"not-wf-sa-169": "surrogate encoding",
"not-wf-sa-170": "unicode garbage-in garbage-out",
"ibm-not-wf-P02-ibm02n30.xml": "surrogate encoding",
"ibm-not-wf-P02-ibm02n31.xml": "surrogate encoding",
"ibm-not-wf-P82-ibm82n03.xml": "ignores wf errors in DOCTYPE",
"rmt-e2e-27": "surrogate encoding",
"rmt-e2e-61": "xml declaration encoding",
"rmt-ns10-013": "naming error with namespaces",
"rmt-ns10-016": "naming error with namespaces",
"rmt-ns10-026": "naming error with namespaces",
"x-ibm-1-0.5-not-wf-P04-ibm04n21.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04-ibm04n22.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04-ibm04n23.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04-ibm04n24.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04a-ibm04an21.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04a-ibm04an22.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04a-ibm04an23.xml": "surrogate encoding",
"x-ibm-1-0.5-not-wf-P04a-ibm04an24.xml": "surrogate encoding",
"hst-lhs-007": "xml declaration encoding",
};
export class Selection extends WhatwgSelection {
async getTestHandling(test: TestSpec): Promise<TestHandling> {
return PROBLEMATIC[test.id] !== undefined ? "skip" :
super.getTestHandling(test);
}
}
|
List of awards and nominations received by Michael Bay
The following is a list of awards and nominations received by American filmmaker Michael Bay. Bay has received five MTV Movie Awards: Best Movie and Best Summer Movie You Haven't Seen Yet for Transformers and Best Action Sequence for Pearl Harbor, Bad Boys II and The Rock. In 1994, Bay was honored by the Directors Guild of America with an award for Outstanding Directorial Achievement in Commercials. Bay received the ShoWest 2009 Vanguard Award for excellence in filmmaking at the confab of theater owners. In 2011 Bay was honored at the Transformers Hall of Fame for directing the Transformers live-action films.
|
Add types to Slots.
I think using private fields would be good at some point, but I'd worry that they're new enough that some downstream users may have trouble, even if they're polyfilled. Seems like it may make sense to wait a bit and refactor later. But I agree in general that this seems like a good direction to take.
BTW, @12wrigja and I were chatting and we may end up merging a fork of this PR instead that does some other nifty things like making HasSlot into a type guard function so that if (HasSlot(foo, TIME_ZONE)) { } will narrow foo to a ZonedDateTime inside the if block. I converted this PR to draft while we figure that out.
Closing this PR as @justingrant merged in a better version of these changes in #74 .
|
Dodge County, Nebraska Genealogy
United States > Nebraska > Dodge County
Parent County
1854--Dodge County was created 23 November 1854 as an original county. County seat: Fremont
Neighboring Counties
* Burt
* Butler
* Colfax
* Cuming
* Douglas
* Saunders
* Washington
Web Sites
* Family History Library Catalog
|
import EnemyType from "../const/EnemyType";
import Phaser, { Scene } from "phaser";
import { birdFlyAnimConfig } from "../Animation/Animation";
export default class Enemy extends Phaser.Physics.Arcade.Sprite {
canFly: boolean;
constructor(s: Scene, x: number, y: number, type: EnemyType) {
super(s, x, y, type.imgTexture);
this.scene.add.existing(this);
if (type.fly) {
this.canFly = true;
this.fly();
this.scene.anims.create(birdFlyAnimConfig(this));
this.play("enemy-dino-fly");
} else {
this.canFly = false;
}
this.setOrigin(0, 1);
}
fly() {
this.scene.tweens.add({
targets: this,
props: {
y: {
repeat: -1,
yoyo: true,
duration: 2000,
ease: "Sine.easeInOut",
value: {
getEnd: (target, key, value) => {
return Phaser.Math.Between(
<number>this.scene.game.config.height - 60 - this.height,
this.height
);
},
getStart: (target, key, value) => {
return this.height;
},
},
},
},
});
}
}
|
import { combineReducers, AnyAction } from "redux";
import { createAtomic, AtomicAction } from "../index";
export interface AtomicState {
title: string;
arrayOfStrings: string[];
counter: number;
subObject: {
title: string;
age: number;
};
}
const initialAtomicState: AtomicState = {
title: "",
arrayOfStrings: [],
counter: 0,
subObject: {
title: "",
age: 0
}
};
const increment = () => (state: AtomicState): AtomicState => {
return {
...state,
counter: state.counter + 1
};
};
const changeTitle = (title: string) => (state: AtomicState): AtomicState => {
return {
...state,
title
};
};
export const atomic1 = createAtomic("atomic1", initialAtomicState, { increment, changeTitle });
export const atomic2 = createAtomic("atomic2", initialAtomicState, { increment, changeTitle });
export const sampleApp = combineReducers<any>({
atomicOne: atomic1.reducer,
atomicTwo: atomic2.reducer
});
export const atomic1Actions = {
increment: atomic1.wrap(increment, "increment"),
changeTitle: atomic1.wrap(changeTitle, "changeTitle")
};
export const atomic2Actions = {
increment: atomic2.wrap(increment, "increment"),
changeTitle: atomic2.wrap(changeTitle, "changeTitle")
};
|
import { applyMiddleware, createStore, compose, combineReducers } from 'redux'
import createSagaMiddleware from 'redux-saga'
import { routerReducer, routerMiddleware } from 'react-router-redux'
import { createLogger } from 'redux-logger'
import { getReducers, getSagas } from '../utils/redux-decorators'
const reducer = combineReducers({
...getReducers(),
routing: routerReducer
})
const sagaMiddleware = createSagaMiddleware()
let createStoreWithMiddleware
if (process.env.NODE_ENV === 'production' || process.env.NODE_ENV === 'test') {
const logger = createLogger({
collapsed: true
})
createStoreWithMiddleware = compose(applyMiddleware(sagaMiddleware, routerMiddleware(), logger))(createStore)
} else {
createStoreWithMiddleware = applyMiddleware(sagaMiddleware, routerMiddleware())(createStore)
}
const store = createStoreWithMiddleware(reducer, {})
sagaMiddleware.run(getSagas)
export default store
|
function Zhill(data)
{
this.init(data);
}
(function () {
Zhill.scoringMethodOrder = [
'markov', 'trad', 'tradtwist', 'iter', 'itertwist'
];
Zhill.scoringMethods = {
'markov': 'Markov',
'trad': 'Trad.',
'tradtwist': 'Tweaked',
'iter': 'Iter.',
'itertwist': 'Tweaked iter.'
};
Zhill.tapeCount = 21;
Zhill.prototype.init = function(data)
{
this.progNames = data.progs;
this.commit = data.commit;
this.scoringMethod = data.scoringMethod;
var n = data.progs.length;
// build the result map and recompute points
var points = new Array(n);
for (var i = 0; i < n; i++)
points[i] = 0;
this.rawResults = {};
for (var a = 0; a < n-1; a++)
{
var res = {};
var rr = data.results[a];
for (var b = a+1; b < n; b++)
{
var dp = rr[b - (a+1)];
res[this.progNames[b]] = dp;
var s = 0;
for (var i = 0; i < dp.length; i++)
s += dp[i];
points[a] += s / (2*Zhill.tapeCount);
points[b] -= s / (2*Zhill.tapeCount);
}
this.rawResults[this.progNames[a]] = res;
}
// construct objectified list of programs
this.progNames = data.progs;
this.progMap = {};
this.progs = [];
for (var i = 0; i < n; i++)
{
var score = {};
for (var s in Zhill.scoringMethods)
score[s] = data.scores[s].score[i];
var name = this.progNames[i];
var shortName = name;
if (shortName.length > 16)
shortName = shortName.substring(0, 16) + '…';
var p = {
'name': name,
'shortName': shortName,
'points': points[i],
'score': score,
'rank': i,
'prevRank': data.prevrank[i]
};
this.progs.push(p);
this.progMap[this.progNames[i]] = p;
}
// helpful occasionally
this.progNameOrder = this.progNames.slice(0);
this.progNameOrder.sort();
};
Zhill.prototype.delta = function(prog)
{
if (typeof prog === 'string') prog = this.progMap[prog];
if (prog.prevRank === null)
return 'new';
var delta = prog.prevRank - prog.rank;
if (delta == 0)
return '--';
return (delta > 0 ? '+' : '') + delta;
};
Zhill.prototype.results = function(progA, progB)
{
if (typeof progA === 'string') progA = this.progMap[progA];
if (typeof progB === 'string') progB = this.progMap[progB];
if (progA.rank == progB.rank)
{
var res = new Array(2 * Zhill.tapeCount);
for (var i = 0; i < res.length; i++)
res[i] = 0;
return res;
}
if (progA.rank < progB.rank)
return this.rawResults[progA.name][progB.name];
var raw = this.rawResults[progB.name][progA.name];
var res = new Array(2 * Zhill.tapeCount);
for (var i = 0; i < res.length; i++)
res[i] = -raw[i];
return res;
};
})();
var zhill = new Zhill(zhillData);
zhillData = undefined;
|
How to initialise the Bresenham algorithm to display an hyperbole
I have an exam in graphics informatic and I am trying to understand the Bresenham algorithm. I understand displaying a line and a circle (I think) but when I do an exercise where I have to display a hyperbolic function I can't make it right.
The hyperbolic function has the equation y = 100/x and I converted it to x*y - 100 = 0. I assume that the currently displayed pixel is at (x_p, y_p) on the screen. I calculated the increments and I found I = 2y_p - 1 when the pixel to be displayed is the one at the right, and I = 2y_p - 2x_p - 5 when the pixel to be displayed is at the bottom right. But now I don't know how to initialise. In my courses, the initialisation for a line is made at x_0 = 0, y_0 = 0, for a circle of a radius R, it is x_0 = 0, y_0 = R, but what is it for my hyperbole ?
I want to trace the hyperbole from x = 10 up to x = 20
void trace (const int x1, const int y1, const int x2)
{
int x = x1;
int y = y1;
int FM = //what to put here ???
glVertex2i(x,y);
while (x < x2)
{
if (FM < 0)
{
++x; --y;
const int dSE = 2*y - 2*x - 5;
FM += dSE;
}
else
{
++x;
const int dE = 2*y - 1;
FM += dE;
}
glVertex2i(x,y);
}
}
so I called this function like that :
glBegin(GL_POINTS);
trace(10,10,20);
glEnd();
I know it is old OpenGL, I use it just for testing purposes.
As you're probably aware, the basic idea behind Bresenham-style algorithms is that you're taking a series of fixed steps, and at each step you're making a decision. In this particular case, the steps are x positions between 10 and 20, and the decision is whether the next y value should be y or y - 1.
To make this decision, you want to pick the y value that's going to be closest to the function value for the next x coordinate: 100 / (x + 1). So, you pick y if dist(y, 100 / (x + 1)) is smaller than dist(y - 1, 100 / (x + 1))... otherwise, pick y - 1. That decision is equivalent to deciding whether the following expression is negative:
err(x, y) = (y - 100 / (x + 1)) ^ 2 - (y - 1 - 100 / (x + 1)) ^ 2
= 2 * (y - 100 / (x + 1)) - 1
= 2 * y - 200 / (x + 1) - 1
Since x + 1 is positive for the range we are interested in, we can multiply through by it to get an equivalent decision value:
err(x, y) = 2 * y * x + 2 * y - 200 - x - 1
= 2 * y * x + 2 * y - x - 201
This is the decision value you want to use for each step, so it's also the formula you'd want to use to calculate the initial decision value. You can then calculate err(x + 1, y) - err(x, y) and err(x + 1, y - 1) - err(x, y) to get the incremental update formulas to be used in the loop.
There are, of course, other formulas that will also work, and any given formula may need some adaption if you:
swap the meaning of the y vs. y - 1 decision
decide to compute the decision value using the pre-update vs. post-update values of x and y
want to draw pixels with the closest centers to the function vs. pixels with the closest coordinate
Sample fiddle: https://jsfiddle.net/0e8fnk5h/
I managed to finally draw this hyperbola ty. But I have still some points I don't understand quite well. You initialized with y = 100/10 + 1/2 and it worked but I have an example where y is initialized with y = f(x) - 1/2 (for circles). When should I use one or the other? And also I always invert what to put when err > 0 and err < 0
In JavaScript, Math.floor() rounds down to the next integer, so Math.floor(x + 0.5) always returns the nearest integer to x. If you are in C/C++, coercing a float to an integer truncates, which means it rounds positive values down and negative values up. So y = f(x) - 0.5; would give you the nearest integer in the case where f(x) is a negative value and y has an integer type. I expect the circle code you are looking at is drawing an octant of the circle where y is negative. And yeah, if you're swapping the order of the y and y - 1 branches, you'd want to negate err.
Hey, it's been I wild since I posted this question, but thanks to your answer I managed to have 15/20 to the exam on this topic, so thanks you ;)
The control variable FM has to be initialized to the distance of the first mid-point to the curve. In this case, you measure distance by twice the value of the implicit function, i.e. we have
FM = 2 * F(x1 + 1, y1 + 1/2)
= 2 * [(x1 + 1) * (y1 + 1/2) - 100]
= 2 * x1 * y1 + 2 * y1 + x1 - 199
|
how to remove error while calling server request
I am getting this error while calling the webservice request .I am using restangular.js file .I am tring to call webservice .But While calling webservice I am getting error .could you please help me remov
Here is my code
http://goo.gl/tbVgkY
I am reading the documentation from here
https://github.com/mgonto/restangular#element-methods
Uncaught Error: [$injector:nomod] http://errors.angularjs.org/1.3.3/$injector/nomod?p0=app
angular.min.js:101 Error: [ng:areq] http://errors.angularjs.org/1.3.3/ng/areq?p0=IndexCtrl&p1=not%20a%20function%2C%20got%20undefined
at Error (native)
at https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:6:416
at Ob (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:19:417)
at pb (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:20:1)
at https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:75:177
at https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:57:112
at r (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:7:408)
at F (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:56:496)
at g (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:51:299)
at g (https://ajax.googleapis.com/ajax/libs/angularjs/1.3.3/angular.min.js:51:316)
IndexCtrl is undefined. To fix the error define IndexCtrl. You can't use console.debug as the call to the service will be asynchronous. For now just assign the result to scope
var IndexCtrl = function ($scope, Restangular){
$scope.data = Restangular.all("data").getList().$object;
};
angular
.module('app')
.controller('IndexCtrl', IndexCtrl);
IndexCtrl.$inject = ['$scope', "Restangular"];
There was also a problem with your service not being restful so I got another service url that was:
angular.module('app',["restangular", "ngRoute"])
.config(function (RestangularProvider) {
RestangularProvider.setBaseUrl('http://jsonplaceholder.typicode.com');
});
Plunkr
There's lots of other issues. I fixed the one you posted in the question. I'd suggest you read some tutorials before posting a question like this.
please help to remove error so that i will learn I try http://goo.gl/tbVgkY ..where Is issue .could you please help me removing error
What is RestangularProvider? It's not declared anywhere?
Actually I make example after study of this tutorial http://bahmutov.calepin.co/fast-prototyping-using-restangular-and-json-server.html he used RestangularProvider
did you use restangular.js file before ? Please look on this issue
did you find anything ..any problem
You should use plunkr. It's much better
Let us continue this discussion in chat.
i will use could you please help me why my webservice call not work
|
Method and apparatus for packet data service discovery
ABSTRACT
A method and device for packet data service discovery are described. A mobile device memory stores a packet data services blacklist and a historical blacklist. The packet data services blacklist identifies wireless networks that do not provide packet data services to the mobile device. The packet data services blacklist is based on previous packet data service authentication rejections, is distinct from a voice services blacklist, and is updated in response to newly received packet data service authentication information. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period. No advance knowledge of data services roaming agreements is required, and unnecessary network access can be avoided, which in turn saves network resources and capacity.
CROSS-REFERENCE TO RELATED APPLICATIONS
This application is a continuation of U.S. patent application Ser. No. 10/533,957 having a 371(c) date of May 4, 2005, and issued as U.S. Pat. No. 7,701,872 on Apr. 20, 2010, the '957 application being a 371 of International Application No. PCT/CA2003/000955 having an international filing date of Jun. 23, 2003, which itself claims the benefit of priority from U.S. Provisional Patent Application Ser. No. 60/423,355 filed on Nov. 4, 2002.
FIELD
The present application relates to the discovery of services provided for a mobile device in a wireless network without any a priori knowledge. The application relates particularly to the discovery of packet data services provided for mobile devices.
BACKGROUND
In a CDMA (Code Division Multiple Access) network, a system identifier (SID) identifies a service provider as well as a given geographical area. Networks within a system are given a network identifier or NID. A network is uniquely identified by the pair (SID, NID). FIG. 1 illustrates a network cloud 100 showing the relationship between various system identifiers and network identifiers.
A CDMA mobile device is typically pre-programmed by operators with an entity called a Preferred Roaming List (PRL). A PRL can also be downloaded to the mobile device using known over the air provisioning methods. FIG. 2 illustrates a simplified representation of a conventional preferred roaming list 102. The PRL, which comprises of a number of records, indicates which systems the mobile device is allowed to acquire. In this example, each record identifies a system by its (SID, NID) pair and provides the frequencies that the mobile device is to use when attempting to acquire the system. For each record, there can be an indicator of whether the system is preferred, the roaming status, the relative priority of the system, and its geographic region. As part of system acquisition, the mobile device searches for a CDMA Pilot Channel on a set of frequencies based on the PRL. The (SID/NID) information of the acquired system is conveyed to the mobile device on a Sync Channel once the mobile device has acquired the Pilot Channel. The PRL only contains the information about which systems the mobile device is allowed to acquire. It does not have any information about the type of services that are allowed on a given network. Typically, it only indicates that a certain degree of voice service is available on a network.
An “always-on always connected” mobile device needs to maintain data connectivity all the time to support seamless mobility. This requires the mobile device to re-establish its data connectivity whenever it changes systems. However, the mobile device has no a priori knowledge as to whether it is allowed to make a data call on a given system. Even if the network indicates that it is capable of supporting packet data services, there is no guarantee that the mobile device will be allowed to make any data calls. The mobile device can only find out about such information after it makes a data call origination attempt. A mobile device can only have true data mobility if a data roaming services agreement exists between the relevant service providers. A roaming agreement between operators does not necessarily cover all available services. For example, two operators may have a voice services roaming agreement, but no packet data services roaming agreement. Currently, there is no standardized mechanism to convey this information to the mobile device. As a result, the mobile device is forced to make blind data call origination attempts to find out whether it is allowed to make data calls or not. This has a significant impact on the battery life, especially in a geographical area where the mobile device goes in and out of a system where data calls are not allowed. Therefore, there is a need for a device capable of efficiently handling interactions with a network with respect to data service availability.
BRIEF DESCRIPTION OF THE DRAWINGS
Embodiments of the present application will now be described, by way of example only, with reference to the attached figures, wherein:
FIG. 1 illustrates a network cloud showing the relationship between various system identifiers and network identifiers;
FIG. 2 illustrates a simplified representation of a conventional preferred roaming list;
FIG. 3 illustrates a system used for authentication in a simple IP network;
FIG. 4 illustrates a system used for authentication in a mobile IP network;
FIG. 5 illustrates a mobile device according to an embodiment of the present application in the context of wireless network components and a home server of the mobile device;
FIG. 6A and FIG. 6B illustrate a flowchart showing steps in a method according to an embodiment of the present application;
FIG. 7 illustrates a representation of an exemplary current blacklist according to an embodiment of the present application; and
FIG. 8 illustrates the relationship between a conventional OSI network layer model and a layer model for a mobile device.
DETAILED DESCRIPTION
Generally, the present application provides a method and apparatus for packet data service discovery without any a priori knowledge. A current blacklist comprising entries for wireless networks not providing packet data services is kept in a mobile device's memory, in order to avoid unnecessary repeated requests to such networks. Current preferred roaming lists can identify whether a given wireless network can be acquired, but do not identify whether a data services roaming agreement exists. A mobile device, or mobile station, according to the application, or employing a method according to the application, dynamically “auto-discovers” the wireless networks on which it is permitted to make packet data calls. A list of wireless networks not providing packet data services (i.e. either not supporting the services or not having a packet data services roaming agreement) is kept in memory of the mobile device based on previous attempts to connect to such networks.
Specifically, a method and device for packet data service discovery are described. A mobile device memory stores a packet data services blacklist and a historical blacklist. The packet data services blacklist identifies wireless networks that do not provide packet data services to the mobile device. The packet data services blacklist is based on previous packet data service authentication rejections, is distinct from a voice services blacklist, and is updated in response to newly received packet data service authentication information. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period. No advance knowledge of data services roaming agreements is required, and unnecessary network access can be avoided, which in turn saves network resources and capacity.
In an embodiment, the present application provides a mobile device capable of supporting packet data services and voice services offered by wireless networks. The mobile device includes the following: a memory; a packet data services blacklist provided in the memory, the packet data services blacklist identifying wireless networks that do not provide packet data services to the mobile device, the packet data services blacklist being based on previous packet data service authentication rejections and being distinct from a voice services blacklist; a historical blacklist provided in the memory, distinct from the packet data services blacklist and the voice services blacklist, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period; and a processor for updating the packet data services blacklist in response to newly received packet data service authentication information.
The mobile device can further include a transceiver for exchanging packet data service authentication information with the wireless networks. The processor can determine whether a current system identifier is stored in the historical blacklist. The processor can perform the determination of whether the current system identifier is stored in the historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to a second device.
In another embodiment, the present application provides a packet data service authentication system including a mobile device capable of supporting packet data services and voice services offered by wireless networks, and a second device. The mobile device includes: a memory; a packet data services blacklist provided in the memory, the packet data services blacklist identifying wireless networks that do not provide packet data services to the mobile device, the packet data services blacklist being based on previous packet data service authentication rejections and being distinct from a voice services blacklist; a historical blacklist provided in the memory, distinct from the packet data services blacklist and the voice services blacklist, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period; and a processor for updating the packet data services blacklist in response to newly received packet data service authentication information, and for determining whether a current system identifier is stored in the historical blacklist.
The processor can perform the determination of whether the current system identifier is stored in the historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to the second device. The mobile device can further include a transceiver for exchanging packet data service authentication information with the wireless networks. The second device can be a home server. The machine readable memory can further include statements and instructions for execution by the processor to: notify the home server of a change in status of the current system identifier; and remove the current system identifier from the historical blacklist.
In a further embodiment, the present application provides a method of data service discovery for a mobile device having a packet data services blacklist. The method includes the following steps: examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if a detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to an other device. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist.
The method can further include detecting the wireless network. The other device can be a home server, in which case the method can further include: notifying the home server of a change in status of the current system identifier; and removing the current system identifier from the historical blacklist.
In a yet further embodiment, the present application provides a packet data service authentication system, including a mobile device having a memory, the memory storing a packet data services blacklist, and a second device. The mobile device is capable of supporting packet data services and voice services offered by wireless networks. The mobile device includes a machine readable memory having statements and instructions for execution by a processor to perform a method of data service discovery for the mobile device, the method including: examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if a detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to the second device. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist.
The second device can include a home server. The machine readable memory can further include statements and instructions for execution by the processor to: notify the home server of a change in status of the current system identifier; and remove the current system identifier from the historical blacklist. The method of data service discovery for the mobile device can further include detecting the wireless network.
In another embodiment, the present application provides a machine readable memory having statements and instructions for execution by a processor to perform a method of data service discovery for a mobile device having a packet data services blacklist, the method including: detecting a wireless network; examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if the detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to an other device. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist.
The other device can include a home server, and the method can further include: notifying the home server of a change in status of the current system identifier; and removing the current system identifier from the historical blacklist.
In a further embodiment, the present application provides a machine readable memory for use in a method of data service discovery for a mobile device, including a packet data services blacklist and a historical blacklist. The packet data services blacklist identifies wireless networks that do not provide packet data services to the mobile device. The packet data services blacklist is based on previous packet data service authentication rejections and is distinct from a voice services blacklist. The packet data services blacklist is updated in response to newly received packet data service authentication information. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period.
In a yet further embodiment, the present application provides a mobile device including a machine readable memory for use in a method of data service discovery for the mobile device, the machine readable memory a packet data services blacklist and a historical blacklist. The packet data services blacklist identifies wireless networks that do not provide packet data services to the mobile device. The packet data services blacklist is based on previous packet data service authentication rejections and is distinct from a voice services blacklist. The packet data services blacklist is updated in response to newly received packet data service authentication information. The historical blacklist is distinct from the packet data services blacklist and the voice services blacklist. The historical blacklist identifies wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period.
The present application provides at least one of the following advantages: no advance knowledge of data roaming agreements is required at the mobile device; no mobile device software change is required when a data roaming agreement changes; the mobile device can notify its home server regarding a change of status of any wireless network; significant power savings are realized at the mobile device; and unnecessary wireless network access is avoided in a network, which saves network resources and capacity.
The following paragraphs provide definitions for terms that will be used in the specification.
The term “mobile device” as used herein includes any electronic device having at least voice and data communication capabilities. The mobile device can be a two-way wireless communication device capable of supporting both voice services and packet data services. Although reference is made in the description to the use and provision of packet data services, the application can advantageously be used with other types of data services. Depending on the exact functionality provided, the mobile device may be referred to in the art by different terms, for example, as a data messaging device, a two-way pager, a wireless e-mail device, a cellular telephone with data messaging capabilities, a wireless Internet appliance, or a data communication device.
The term “wireless network” as used herein includes any network or system, or the operator or carrier of such a network or system, having at least one component that provides wireless or mobile services, for example packet data services, to a mobile device.
A wireless network that “supports” packet data services has the necessary hardware and software in place to be capable of offering packet data services to a mobile device. A wireless network that “does not support” packet data services does not have the necessary hardware and software in place to be capable of offering packet data services to a mobile device.
A wireless network “provides” packet data services to a mobile device when it supports packet data services and also permits, or allows, that mobile device to use the packet data services. This permission can be, for example, pursuant to a packet data services roaming agreement between carriers, service providers, or network operators. A wireless network that “does not provide” packet data services to a mobile device either does not support packet data services, or it supports packet data services, but the mobile device is not permitted to use the packet data services, for example due to a lack of a packet data services roaming agreement.
There are two main types of CDMA packet data networks with which embodiments of the present application can be used. The first type is a Simple IP (SIP) network in which a mobile device does not have a fixed Internet Protocol (IP) address. The IP address of a mobile device in a SIP network changes over time, with respect to location, etc. Once radio link protocol communication is established between the mobile device and a Radio Network (RN), the RN initiates an R-P interface between the RN and a Packet Data Serving Node (PDSN). The mobile device is authenticated by the serving PDSN via a RADIUS server and is subsequently assigned an IP address. The PDSN then provides the mobile device with connectivity, for instance to the Internet, an intranet (not shown), or generally an IP network. As the mobile device moves across PDSN boundaries, it is assigned new IP addresses, as necessary. An “always-on always connected” mobile device typically notifies its home server of its own IP address so that packets can be pushed to it from its own server (e.g. an enterprise server). Typically, the Home Server IP address is fixed and known to the mobile device.
The second type is a Mobile IP (MIP) network in which a mobile device can have a static IP address, which is assigned by its home wireless network. The Home Agent IP address is also programmed into the mobile device. As the mobile device roams to a foreign network and attempts to set up a data session, the Foreign Agent (which is in effect a PDSN) communicates with the mobile device's specified Home Agent and then assigns the mobile device a Care-of Address (CoA). The home IP address of a mobile device in a MIP network can remain the same regardless of location, time, etc. Other devices or servers sending data to the mobile device only need to know about its home IP address, not the CoA.
Specific examples of SIP and MIP networks will be described in further detail in relation to FIG. 3 and FIG. 4, respectively. FIG. 3 illustrates a system used for authentication in a simple IP network.
In FIG. 3, a mobile device 104 communicates with a Radio Network (RN) 106. The RN 106 performs functions such as call setup, handling handoff, performing tasks at a Radio Link Protocol (RLP) Layer and below. The RN 106 also communicates with a packet data serving node (PDSN) 108. A PDSN, used in third generation (3G) networks, has a range of IP addresses and performs IP address management, maintains a session, and may perform caching. A PDSN provides access to the Internet, intranets and Wireless Application Protocol (WAP) servers for mobile devices utilizing a RN. It provides foreign agent (FA) support in MIP networks and packet transport for virtual private networking.
A Remote Authentication Dial-In User Service (RADIUS) server 110 is responsible for performing functions related to authentication, authorization, and accounting (AAA) of packet data services. It is also known as an AAA server. The RADIUS server 110 is connected to IP network 112. The PDSN 108 communicates with other network entities, such as other RADIUS servers, via the IP network 112.
The authentication steps in a SIP system such as in FIG. 3, generally comprise system access authentication and data authentication. The system access authentication is performed by a home location register/authentication center (HLR/AC) as a first level of authentication. In a system access authentication step, the RN 106 sends a global challenge, and the mobile device 104 sends a response. This step is performed before the data session is established.
Next, a data authentication step is performed. This is typically done by means of known schemes such as Challenge-Handshake Authentication Protocol (CHAP) and Password Authentication Protocol (PAP).
If there is no data roaming agreement, one of the authentication steps (typically the data authentication step) will fail. Since there is no standard definition of what to do in such a case, the mobile device keeps trying. This is relevant to an “always-on, always connected” mobile device that is expected to maintain data connectivity at all times. Furthermore, according to the CDMA standard, a “dormant” mobile device is required to reconnect an existing dormant data connection every time there is a change in the NID, SID or packet zone identifier. A “dormant” mobile device has already established a PPP context with the network, but a reconnect attempt to a new wireless network can still fail. In addition, an “always-on, always connected” mobile device may be required to notify its Home Server if there is any change in the current SID in order to facilitate proper and efficient routing of data from the Home Server to the appropriate gateway. Repeated failed attempts to setup a data session in such conditions have the effect of unnecessarily increasing the amount of network traffic, and also reduce the battery life of the mobile device. In addition, if the mobile device is on the edge of a service area, there can be a “ping-pong” effect as the device alternates between trying to authenticate on a home network and on a foreign network.
FIG. 4 illustrates a system used for authentication in a MIP network. In FIG. 4, the mobile device 104 stores a fixed home IP address, a fixed home agent address, and may store a fixed home server address. The PDSN 108 in FIG. 4 can also be referred to as the foreign agent. The foreign agent 108 communicates with a home agent 114, which has its own RADIUS server 116. Once the foreign agent 108 finds out the necessary information to communicate with the home agent 114, the authentication is actually performed at the home agent 114. The home agent 114 receives all packets intended for the mobile device 104 and forwards them on to the foreign agent 108, which in turn forwards them to the mobile device. The home agent 114 stores a CoA for the mobile device 104 and maps the home IP address of the mobile device to the CoA. In FIG. 4, the RN of the PDSN serving node can communicate via a mobile station controller (MSC) 118 to a home location register (HLR) 120 via SS7 network 122.
The authentication steps in a MIP system include an initial system access authentication step, as is the case with SIP. However, in a MIP network, the subsequent data authentication step comprises a plurality of steps, such as: a foreign agent challenge (where the foreign agent sends a message asking the mobile device to respond); an MN-AAA_(H) authentication step; and an MN-HA authentication step, where MN represents a mobile node or mobile device, AAA_(H) represents a home RADIUS or AAA server, and HA represents a home agent. The data authentication step can comprise one or more of these levels of authentication. If any one of these authentication steps fails, this indicates that there is no data roaming agreement.
FIG. 5 illustrates a mobile device according to an embodiment of the present application in the context of wireless network components and a home server of the mobile device. The mobile device 104 communicates with the RN 106, which in turn can communicate with the PDSN 108, as described earlier. The PDSN 108 can communicate with a home server 128 associated with the mobile device by means of intermediary devices, such as illustrated in FIG. 5 by Router A 124 on the PDSN side and Router B 126 on the home server side.
FIG. 5 shows the mobile device having a current blacklist 122. A blacklist as used herein represents a collection of data identifying wireless networks that do not provide packet data services to the mobile device. The blacklist can be stored in a form in which each listed network can be uniquely identified, and will be described in further detail below. Such a blacklist is in contrast to a preferred roaming list, which is known in the art, in which a listing of systems or networks allowing voice services is typically kept. Storing and using a blacklist helps to avoid unnecessary attempts to repeatedly access data services on the same wireless network. The current blacklist 122 identifies wireless networks that do not currently provide packet data services to the mobile device and is stored in memory on the mobile device. The current blacklist 122 is based on previous data relating to packet data service availability. Such data can be obtained as follows.
The mobile device 104 typically has a processor and transceiver, which includes a transmitter and a receiver. The receiver is used to decode information frames received over the air from the wireless network. The information frames can carry higher layer protocol stack payload and may contain payload from different entities in the wireless network, such as a PDSN. The received information frames are passed to the processor, which then determines the next course of action. The transmitter is used to send over the air information frames to the wireless network as directed by the processor. The information frames carry payloads of higher layers in the protocol stack.
In terms of data authentication, the processor typically processes incoming packet data service authentication frames received from the wireless network, as well as outgoing packet data service authentication frames sent from the mobile device. The general steps relating to the exchange of such packet data service authentication frames is known in the art. For instance, an incoming packet data service authentication frame can contain a packet data service authentication request. In response to that request, the processor prepares the proper response. That response is sent by means of an outgoing packet data service authentication frame. The wireless network then performs authentication steps. Information relating to an authentication acceptance or rejection is typically sent to the mobile device. Of course, any of these exchanges can comprise, or be separated into, one or more information frames, packets or other unit of data transmission.
The exchange of packet data service authentication information between the mobile device and the wireless network is typically initiated in the context of the mobile device making a packet data call attempt on the wireless network. The authentication steps are simply a part of the data call process.
The current blacklist 122 is based on previous processed incoming packet data service authentication information. When packet data services are not provided to the mobile device, a packet data service authentication rejection is received from the wireless network. Therefore, the current blacklist is 122 is, in particular, based on received packet data service authentication rejections. The current blacklist 122 is also updated by the processor in response to newly received packet data service authentication rejections. The current blacklist 122 advantageously identifies a wireless network by its system identifier and network identifier pair, as will be described later in relation to FIG. 7.
In a particular embodiment, the current blacklist includes a timer value for each system that does not provide packet data services to the mobile device. The inclusion of a timer value is intended to provide an opportunity to send a subsequent packet data service authentication request at a suitable time, in order to determine if the situation has changed with respect to the wireless network not providing packet data services. The timer value can advantageously be implemented as an age timer, as is known to those skilled in the art. The selection of values to be used in the age timer 134 as shown in FIG. 7 can be based on knowledge of system parameters and the likelihood of change in such parameters. For instance, for a wireless network known to be having problems with or changes to its network equipment, the age timer can be set anywhere from a number of minutes to a number of days. For a wireless network which is the subject of negotiations to provide data roaming services, the age timer can be set anywhere from a number of days to a number of weeks or months, to monitor for any anticipated changes.
As described above, the mobile device maintains and updates its own current blacklist. This is advantageous since each mobile device can have its own particular abilities and requirements with respect to wireless networks it can acquire. The current blacklist is can be stored in memory on the mobile device. In another embodiment, information stored in the mobile device's current blacklist can be transmitted to a server. The current blacklist can include a flag indicating whether an identification of a blacklisted wireless network has been passed to a server. Any portion of a current blacklist can advantageously be sent from the mobile device to a remote server, such as its home server, where the information can then be stored.
The server can gather current information relating to various wireless networks from a plurality of mobile devices. The server can send a server-stored current blacklist to a mobile device in particular instances where such transmission would be beneficial. For example, if a mobile device loses the information in its current blacklist, rather than building it from scratch, it could receive a server-stored current blacklist. The server-stored current blacklist can be stored in a memory of the particular server, or another server with which the server is in communications. The server can build a composite current blacklist based on reports from different mobile devices. This stored information can then be re-sent to other mobile stations.
FIG. 6A and FIG. 6B illustrate a flowchart showing steps in a method according to an embodiment of the present application. In step 200, in FIG. 6A, a mobile device starts acquisition of a system, or wireless network, based on the information in the PRL and the setting of network scan mode as specified by the user. The system acquisition can be initiated by any one of a number of situations, such as: turning the mobile device's radio functions on, change/loss of service; attempt to receive better service; network-directed redirection; rescan for a preferred system; etc.
Once a system has been acquired, it can be determined in step 202 whether the mobile device is required to send CDMA registration. If the system requires registration, a registration attempt is initiated. In step 204, it is determined whether the CDMA registration attempt was successful. If yes, the method continues to step 206; if not, the method returns to the first step 200 and attempts to acquire a different system. Steps 200-204 are steps that are used in known methods of data service discovery.
In step 206, it is determined whether the acquired CDMA system, or network, supports or may support packet data services. The system will typically have an indicator to convey whether packet data services are supported. An example of such an indicator is the protocol revision of the RN, e.g. protocol revision greater than or equal to 6 in a CDMA2000 network.
However, such an indicator is not an absolute guarantee that packet data services are supported since a protocol revision of 6 (IS-2000 release 0) in such a network does not necessarily mean that packet data services are supported. Further steps in the method will confirm whether packet data services are provided, or permitted, with respect to the mobile device; this step simply rules out situations where such services are definitely not supported. If the network does not support packet data service (e.g. protocol revision<6 in a CDMAOne network), then, referring to step 208, the mobile device allows only voice and SMS traffic and notifies a user that packet data services are not available. If the network indicates that it supports or may support packet data services then the method proceeds to step 210.
In step 210, a determination is made as to whether the current system, or wireless network, is in a current blacklist. This is typically done by comparing the current SID with SID values stored in the current blacklist. If the current SID is found in the current blacklist, the method proceeds to step 212 in which the mobile device allows only voice and SMS traffic and notifies a user that packet data services are not provided by the current network. No data call attempt is made in such a case.
If the current SID is not in the current blacklist, the method proceeds to step 214 in FIG. 6B (if the mobile device does not already have an active data session). This is the case when the radio is turned ON or the mobile device cannot establish a data session on previously visited systems. In this step, the mobile device attempts to establish a data call. This can be achieved by the mobile device initiating a packet data call to setup a PPP session and attempting to get an IP address. If the mobile device has already established a data session, i.e. it is in a dormant state with an IP address, the method proceeds to step 215. In step 215, the mobile device attempts to reconnect the data session. The process is similar to step 214 with minor differences.
In step 216, a determination is made as to whether the network authentication has failed, i.e. a packet data service authentication rejection is received. In a SIP network, the mobile device is authenticated by the network using CHAP or PAP, which assume that the User Id and Password of the device are known by the network. If the device turns out to be an unknown entity to the network from a packet data services viewpoint, the authentication will fail and packet data services will be refused. If authentication fails, the method proceeds to step 218 where the mobile device enters, or adds, the SID of the system to current blacklist, starts a timer and stops trying to setup a data session on the system until the timer expires. The timer value can be an age timer. Following this step, the method proceeds to step 212 in FIG. 6A, where the device allows voice and SMS and informs the user that packet data services are not provided by the network.
When the device moves to another system, it first checks whether the new system supports packet data services or not. If it does, the device then checks whether the system is in its current blacklist, as outlined in the steps above. If yes, it refrains from making any data call attempts on that system. Otherwise, the device will try to reconnect to keep the data session alive. If it fails authentication, the new system will also be blacklisted and no data retry attempts will take place until the associated age timer expires.
If, in step 216, the network successfully authenticates the mobile device, it is determined that the network provides data services to the mobile device and the method proceeds to step 220. The method can also include within step 218 a step of marking the SID as “not reported”. Then, in step 220, it is determined whether any entry in the current blacklist has not been reported. The term “reporting” here is used to represent any communication of such an entry to a device other than the mobile device, such as a home server associated with the mobile device.
Therefore, if there is a non-reported entry in the current blacklist, in step 222 the home server is notified of the SID change and any “new” blacklisted SIDs are reported. If there are no non-reported entries in the current blacklist, step 224 can determine whether the current SID is stored in a “once blacklisted” table. The “once blacklisted” table is similar to the current blacklist in structure, as will be outlined below, except that it keeps a historical list of all SIDs that have been blacklisted within a particular time period. If the current SID is in the “once blacklisted” table, the method proceeds to notify the home server of a change in status of the current SID and it is removed from the “once blacklisted” list. If not, the method proceeds to step 228, where the mobile device has successfully established or re-established a packet data session and enters a dormant state whenever it is done sending or receiving data.
In an alternative embodiment, the method further includes a step of “pushing” a current blacklist from a home server to a mobile device. This can easily be accomplished since the home server can be kept up-to-date with respect to data roaming agreements for a given wireless service provider and all the mobile devices that have subscribed to its wireless service can be informed accordingly. In some cases, this blacklist can be a composite current blacklist formed at the home server based on the reports from the mobile devices that belong to the same carrier. If the information is pushed to the mobile device, then it provides advance warning to a mobile device entering a new system. When an mobile device powers up in a RN and registers with the server, the server can also forward the information of currently blacklisted systems so that the mobile device can avoid data originations in such RNs.
FIG. 7 illustrates a representation of an exemplary current blacklist according to an embodiment of the present application. The current blacklist 122 includes information relating to SIDs that are currently listed as the wireless networks where packet data services are not provided. The current blacklist can be stored as a table, with each entry, or row, and can include the following data: identification of SID 132; a timer value 134, such as an age timer; and a flag 136. The SID identification can include an identification of the corresponding NID. The associated timer starts when the SID is first blacklisted and counts down until its expiry, at which time the entry can be removed from the current blacklist. The flag 136 indicates whether the blacklisted SID has been passed to a server, such as a home server, with allowed values in an embodiment being YES and NO. An appropriate initial timer value can be selected, after which the SID will be removed from the blacklist, for example, one month. When a system with a formerly blacklisted SID is next encountered, the availability of packet data services is rechecked. In an alternative embodiment, the entire current blacklist can be reset or cleared when radio services on a mobile device are turned off.
There are two types of reset conditions under which a current blacklist, or a portion thereof, is cleared: a timer reset condition and a provisioning reset condition. The term “timer reset condition” is used to refer to any instance (such as expiry of an age timer, powering off of the mobile device or its radio) where an individual entry in the current blacklist is to be cleared. For example, a wireless network's entry in the current blacklist is cleared upon expiry of its age timer. After that point, the next time the mobile device encounters that wireless network, it attempts anew to acquire packet data services on the system, in case the situation has changed. A mobile device's current blacklist can alternatively be cleared when the mobile device is turned off, or when the device's radio is turned off.
The mobile device can also clear the entire current blacklist in response to a provisioning reset condition. A “provisioning reset condition” includes any change in provisioning or authentication parameters, such as user ID or password in SIP. Such a change occurs after a mobile device is provisioned for the first time, or re-provisioned with new parameters. The provisioning process can take place over the air or manually. In the case of the occurrence of a provisioning reset condition, the mobile device automatically clears the current blacklist as it may no longer be valid in light of the changed parameters.
Whenever the device re-establishes a data session after being refused service on one or more other wireless networks, it can send the list of blacklisted SIDs that has not yet been reported to the home server. In addition, the device also maintains a list of SIDs that were once blacklisted, but now provide packet data services. Once the device notifies the server of status change, the corresponding entries are cleared. When the server is notified of the status change of a wireless network and that the wireless network now provides packet data services, it can also notify other mobile devices of this status change so that all the other mobile devices can clear the entry of that wireless network and will not avoid data originations in that wireless network.
FIG. 8 illustrates the relationship between a conventional OSI network layer model 138 and a similar layer model 140 for a typical mobile device. A device driver layer 142, an operating system layer 144 and a radio layer 146 can collectively be referred to as a radio section. The Java/Radio Interface 148 facilitates communication between the layers in the radio section and those in the Java section. Although the applications in this example are shown as Java-based, they can be based on any other high level language. The Java section includes a Java Virtual Machine layer 150 and a Java Applications layer 152. The steps shown in FIG. 6 can be performed at the layers identified as the radio section, although they may alternatively be performed at the layers identified as a Java section.
The above-described embodiments of the present application are intended to be examples only. Alterations, modifications and variations may be effected to the particular embodiments by those of skill in the art without departing from the scope of the application, which is defined solely by the claims appended hereto.
What is claimed is:
1. A mobile device capable of supporting packet data services and voice services offered by wireless networks, the mobile device comprising: a memory; a packet data services blacklist provided in the memory, the packet data services blacklist identifying wireless networks that do not provide packet data services to the mobile device, the packet data services blacklist being based on previous packet data service authentication rejections and being distinct from a voice services blacklist; a historical blacklist provided in the memory, distinct from the packet data services blacklist and the voice services blacklist, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period; a processor for updating the packet data services blacklist in response to newly received packet data service authentication information, and for determining whether a current system identifier is stored in the historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to a second device.
2. The mobile device of claim 1 further comprising a transceiver for exchanging packet data service authentication information with the wireless networks.
3. A packet data service authentication system, comprising: a mobile device capable of supporting packet data services and voice services offered by wireless networks; and a second device, the mobile device including, a memory; a packet data services blacklist provided in the memory, the packet data services blacklist identifying wireless networks that do not provide packet data services to the mobile device, the packet data services blacklist being based on previous packet data service authentication rejections and being distinct from a voice services blacklist; a historical blacklist provided in the memory, distinct from the packet data services blacklist and the voice services blacklist, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period; and a processor for updating the packet data services blacklist in response to newly received packet data service authentication information, and for determining whether a current system identifier is stored in the historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to the second device.
4. The system of claim 3 wherein the mobile device further comprises a transceiver for exchanging packet data service authentication information with the wireless networks.
5. A packet data service authentication system, comprising: a mobile device capable of supporting packet data services and voice services offered by wireless networks; and a home server, the mobile device including, a memory; a packet data services blacklist provided in the memory, the packet data services blacklist identifying wireless networks that do not provide packet data services to the mobile device, the packet data services blacklist being based on previous packet data service authentication rejections and being distinct from a voice services blacklist; a historical blacklist provided in the memory, distinct from the packet data services blacklist and the voice services blacklist, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period; and a processor for updating the packet data services blacklist in response to newly received packet data service authentication information, and for determining whether a current system identifier is stored in the historical blacklist; the memory further comprising statements and instructions for execution by the processor to: notify the home server of a change in status of the current system identifier; and remove the current system identifier from the historical blacklist.
6. A method of data service discovery for a mobile device having a packet data services blacklist comprising: examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if a detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to an other device, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period, the historical blacklist being distinct from the packet data services blacklist and the voice services blacklist.
7. The method of claim 6 further comprising detecting the wireless network.
8. The method of claim 6 wherein the other device comprises a home server, and further comprising: notifying the home server of a change in status of the current system identifier; and removing the current system identifier from the historical blacklist.
9. A packet data service authentication system, comprising: a mobile device having a memory, the memory storing a packet data services blacklist; and a second device; the mobile device capable of supporting packet data services and voice services offered by wireless networks, the mobile device including a machine readable memory having statements and instructions for execution by a processor to perform a method of data service discovery for the mobile device, the method including: examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if a detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to the second device, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period, the historical blacklist being distinct from the packet data services blacklist and the voice services blacklist.
10. The system of claim 9 wherein the method of data service discovery for the mobile device further comprises detecting the wireless network.
11. The system of claim 9 wherein the second device comprises a home server.
12. The system of claim 11 wherein the machine readable memory further comprises statements and instructions for execution by the processor to: notify the home server of a change in status of the current system identifier; and remove the current system identifier from the historical blacklist.
13. A machine readable memory having statements and instructions for execution by a processor to perform a method of data service discovery for a mobile device having a packet data services blacklist, the method including: detecting a wireless network; examining the packet data services blacklist stored on the mobile device, the packet data services blacklist being distinct from a voice services blacklist; if the detected wireless network is listed in the packet data services blacklist, refraining from making any packet data call attempts for a predetermined period of time; otherwise, determining whether the wireless network provides packet data services to the mobile device, and adding the wireless network to the packet data services blacklist if the wireless network does not provide packet data services to the mobile device; determining whether a current system identifier is stored in a historical blacklist in response to a determination that there are no wireless networks newly blacklisted in relation to the mobile device for which an identification has not been communicated to an other device, the historical blacklist identifying wireless networks that are no longer in the packet data services blacklist and were once in the packet data services blacklist within a particular time period, the historical blacklist being distinct from the packet data services blacklist and the voice services blacklist.
14. The machine readable memory of claim 13 wherein the other device comprises a home server, and wherein the method further includes: notifying the home server of a change in status of the current system identifier; and removing the current system identifier from the historical blacklist.
|
# -*- coding: utf-8 -*-
# A simple python script for monitoring mouse traps using a Raspberry Pi
# Using Button / when_released for simplicity, could be made nicer I guess
# Written by Andreas Ottosson (https://github.com/andreasottosson)
from gpiozero import Button
from signal import pause
import os
import sys
import requests
import time
# Where is the traps connected on the Pi, there is one wire to the GPIO and one to ground and when that connection is broken ie the trap has sprung it triggeres when_released
trap_gpio_pins = [2,3,4,5,6,13,19,26]
traps = []
try:
os.environ["APP_KEY"]
except KeyError:
print("Please set the environment variable APP_KEY!")
sys.exit(1)
try:
os.environ["USER_KEY"]
except KeyError:
print("Please set the environment variable USER_KEY!")
sys.exit(1)
# Save basic stats in a text file
# def trap_stats(t):
# file = open('trap_stats.txt', 'a')
# file.write(t+'\n')
# file.close()
def trap_setup():
for p in trap_gpio_pins:
count = 1
globals()['trap'+str(count)] = Button(p, bounce_time=5)
globals()['trap'+str(count)].when_released = trap_triggered
traps.append(globals()['trap'+str(count)])
count = count + 1
def gpio_to_trap(pin):
gpio = str(pin).strip('GPIO') # pin = GPIO17 etc...
trap_nr = trap_gpio_pins.index(int(gpio))
trap_nr = trap_nr + 1
return f'trap{trap_nr}'
def trap_triggered(button_object):
t = gpio_to_trap(button_object.pin)
print(f'Trap {t} got triggered!')
# trap_stats(t)
try:
r = requests.post("https://api.pushover.net/1/messages.json", data = {
"token": os.environ["APP_KEY"],
"user": os.environ["USER_KEY"],
"message": "Trap {} got triggered! 🐭".format(t)
})
print('Notification sent!')
print(r)
except requests.exceptions.RequestException as e:
print('Error sending notification...')
print(e)
def check_traps():
unarmed_trap = False
for trap in traps:
if trap.value != 1:
unarmed_trap = True
t = gpio_to_trap(trap.pin)
print(f'Trap {t} is not armed!')
if unarmed_trap == True:
print('WARNING! Some traps are not armed.')
else:
print('All traps are armed and ready!')
trap_setup()
while True:
check_traps()
time.sleep(900)
|
Talk:United Aerospace Command/@comment-24142455-20141029020742/@comment-24142455-20141030002619
Can someone unlock the page? I think the RP break is over
|
Zend_Dojo_Form Elements aren't proper working
Now I tried a bit around with Zend_Dojo_Form. The elements do not work like expected. The only element which is working is the checkBox.
To see for everybody here a screenshot:
Here a snippet of my formclass:
$this->addElement('DateTextBox','datum',array(
'label' => 'datum',
'datePattern' => 'dd-MM-yyyy',
'required' => 'true'
));
$this->addElement('TimeTextBox','zeit',array(
'label' => 'Uhrzeit',
'timePattern' => 'HH:mm',
'required' => 'true'
));
$this->addElement('CheckBox','test',array(
'label' => 'ja Nein',
'checkedValue' => 'yes',
'uncheckedValue' => 'nein',
'checked' => 'true'
));
$this->addElement('editor','test1',array(
'label' => 'Editor',
'plugins' => array('redo',
'undo','|','bold','italic','underline'),
'editActionInterval' => 2,
'height' => '100px'
));
My form extends Zend_Dojo_Form
I want to use date and time, don't mind I tried the others also to see if Zend_Dojo is found.
The date and time elements don't drop down on click, they just show like in the screenshot an X and a second row.
EDIT:
I have the dojo like follows in my application.ini
resources.view.helperPath.Zend_Dojo_View_Helper = "Zend/Dojo/View/Helper"
In my layout.phtml:
if ($this->dojo()->isEnabled()){
$this->dojo()->setCdnBase(Zend_Dojo::CDN_BASE_GOOGLE);
$this->dojo()->setCdnDojoPath(Zend_Dojo::CDN_DOJO_PATH_GOOGLE);
//$this->dojo()->requireModule('dijit.form.DateTextBox');
echo $this->dojo();
}
Do I need something else?
can you check if dojo js library has been loaded?
how can I do that? I thought it is loaded because the checkBox works
now it works, because I tried around to solve my errors the stylesheet was missing. So I added in my layout.phtml the stylesheet:
$this->dojo()->addStyleSheetModule('dijit.themes.tundra');
|
const request = require("supertest");
const express = require("express");
const RedirectRoute = require("../Redirect");
describe("Redirect route", () => {
let route;
let app;
let inCookies = { redirect: "foobar" };
let outCookieName;
let outCookieValue;
let setCookie = jest.fn((name, value) => {
outCookieName = name;
outCookieValue = value;
});
beforeEach(async () => {
route = new RedirectRoute();
await route.init();
app = express();
app.use((req, res, next) => {
req.cookies = inCookies;
res.cookie = setCookie;
next();
});
app.use(route.router);
});
test("redirect to links", async () => {
return Promise.all([
request(app)
.get("/redirect/github")
.expect(302, /github\.com/),
request(app)
.get("/redirect/benchmarks")
.expect(302, /gtmetrix\.com/),
request(app)
.get("/redirect/responsiveness")
.expect(302, /material\.io/)
]);
});
test("self-redirect with resetting the cookie", async () => {
await request(app)
.get("/redirect")
.expect(302, /foobar/);
expect(outCookieName).toBe("redirect");
expect(outCookieValue).toBe("");
});
});
|
intergrate github repo stats
unit test for ExpressCheckout failed as a result of failed remote calls to the core express checkout API endpoint in daraja API
|
package club.quar.util.type;
import lombok.Getter;
import java.util.Collection;
import java.util.LinkedList;
/**
* A list which automatically evicts elements from the head of the queue when
* attempting to add new elements onto the queue and it is full. This queue orders elements FIFO
* (first-in-first-out). This data structure is logically equivalent to a circular buffer (i.e.,
* cyclic buffer or ring buffer).
*/
public final class EvictingList<T> extends LinkedList<T> {
@Getter
private final int maxSize;
public EvictingList(final int maxSize) {
this.maxSize = maxSize;
}
public EvictingList(final Collection<? extends T> c, final int maxSize) {
super(c);
this.maxSize = maxSize;
}
@Override
public boolean add(final T t) {
if (size() >= getMaxSize()) removeFirst();
return super.add(t);
}
public boolean isFull() {
return size() >= getMaxSize();
}
}
|
MAP27: Halls of Cocytus (Whispers of Satan)
Walkthrough
Essentials
Other points of interest
If you want a chaingun, head down the first hallway to the left.
Secrets
Things
This level contains the following numbers of things per skill level:
|
Ball sealer for hydrocarbon resource recovery, method for manufacturing same, and method for treating borehole using same
ABSTRACT
A ball sealer for hydrocarbon resource recovery, characterized by being obtained by coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin and by having a diameter of not less than approximately 25 mm (1 inch). This ball sealer has a large diameter, retains the property of being disintegrable after fracturing, and has impact resistance which makes the ball withstand high-velocity loading. The sealer is suitable for use in hydraulic fracturing, which is commonly used for recovering hydrocarbon resources including petroleum and gases.
This large-diameter ball sealer can be efficiently formed with high dimensional accuracy by a method including at least one insert injection molding step.
TECHNICAL FIELD
The present invention relates to a ball sealer as one type of tool for forming or maintaining a downhole (or borehole) for recovery of hydrocarbon resources such as petroleum and gas, and particularly relates to a ball sealer (a so-called frac ball) suitable for formation of a frac plug or frac sleeve (plug or pipe for hydraulic fracturing) as such a tool, and a method for manufacturing the same, and a method for treating a borehole using the same.
BACKGROUND ART
A downhole (borehole) is provided for recovery of hydrocarbon resources (typically called “petroleum” hereinafter) from a subterranean formation containing hydrocarbon resources such as petroleum and gas, but to accelerate the formation and maintenance thereof as well as resource recovery, there are many tools such as frac plugs, bridge plugs, ball sealers, isolation plugs, and packers (comprehensively called “downhole tools” hereinafter) that are disposed of by being disintegrated or dropped in the downhole as-is without being retrieved above ground after use (for examples of such downhole tools and modes of use thereof, see Patent Documents 1 to 6, for example). Therefore, for such disposable tools, it has also been recommended to form the entire tool or a component that constitutes a binding part for accelerating disintegration (component for downhole tool) from a disintegrable polymer. Examples of such disintegrable polymers include polysaccharides such as starch and dextrin; animal protein polymers such as chitin and chitosan; aliphatic polyesters such as polylactic acid (PLA, typically poly-L-lactic acid (PLLA)), polyglycolic acid (PGA), polybutyric acid, and polyvaleric acid; poly amino acids; polyethylene oxide; and the like (Patent Documents 1 and 2). Furthermore, it has also been proposed to pour in a fluid called a pad, such as diesel oil, on top of the frac balls after fracturing using frac balls made from a rigid resin such as polystyrene, to accelerate ball disintegration after fracturing (Patent Document 3).
To recover hydrocarbon resources (typically “petroleum”) from a nearby subterranean formation via a formed downhole, hydraulic fracturing is often employed.
Conventionally, as described above, there were many applications in which a ball sealer as an example of a downhole tool was used in hydraulic fracturing to block perforations directly, as a blocking material (also called perforation balls) for suppressing inflow of excess process water into perforations for recovering petroleum formed using a perforating gun or the like in the subterranean formation (for example, Patent Documents 4 and 5). As ball sealers used in such applications, to improve sealing ability by means of form-fitting deformation into perforations of indeterminate shape as necessary, relatively small ball sealers with a diameter of 16 to 32 mm (0.625 to 1.25 inches; Patent Document 4, column 2, lines 46 to 48) made from a non-disintegrable material such as aluminum or a non-disintegrable resin such as nylon or phenol resin which has been coated with a rubbery surface layer were used. Furthermore, to improve form-fitting deformability into perforations of indeterminate shape, perforation balls having a laminate structure of three or more layers have also been proposed (Patent Document 5).
However, the use of larger-diameter ball sealers as some of the material constituting the frac plug or frac sleeve (plug or pipe for hydraulic fracturing) used in hydraulic fracturing has also been recently proposed. More specifically, a high-pressure water stream is introduced into partitioned process areas by disposing ball seats having an opening at the center, together with frac plugs with incorporated ball sealers for closing the opening, in prescribed locations of the formed downhole, and the water stream is made to act in a direction straight through to the downhole, and the subterranean formation layer is fractured to form perforations for recovering petroleum (for example, Patent Documents 1 to 3).
Alternatively, a method has been proposed wherein a pipe (frac sleeve), in which a plurality of ball seats have been incorporated and disposed with separation therebetween, is inserted into a downhole, and then, in this frac sleeve, a perforation formation operation is continuously performed by successively fracturing the subterranean formation into which ball sealers are supplied to and disposed in the ball seats and then introducing a high-pressure water stream (for example, Patent Documents 6 and 3).
As the ball sealers (also called frac balls) that constitute part of such a frac plug or frac sleeve, in addition to those having the same diameter as the perforation balls used as direct blocking material of the perforation balls generally described above (for example, a diameter of approximately 25 to 100 mm (1 to 4 inches)), those having a larger diameter are often required. Additionally, frac balls require different deformation resistance than perforation balls due to the usage mode thereof. Specifically, in hydraulic fracturing treatment (fracturing) of a subterranean formation, since high water pressure of 7 to 70 MPa (1000 to 10,000 psi) acts on the frac ball, rigidity is required so that breakage or excessive deformation does not occur in order to assure seal ability between it and the ball seat. In particular, as shown in Patent Documents 3 and 6, in order to form as many fracturing zones as possible in a sleeve (cylindrical pipe) inserted in a downhole, the difference between the opening diameter of the seat seats that form adjacent seal parts and the diameter of the frac balls must be as small as possible, and the seal width (overlap, difference in radius) between the ball that forms one seal part and the seat seat must be held to a minimum. Naturally, a frac ball requires deformation resistance (rigidity), which is completely the opposite of the deformability of a perforation ball. For such reasons, conventionally, metal frac balls were mainly used, but it has also been proposed to use resin frac balls to save the labor of retrieval after fracturing (Patent Document 3).
In contrast, the present inventors found that a disintegrable resin frac ball containing, at least in part, an aliphatic polyester resin of which the rigidity (deformation resistance) has been improved by blending a reinforcing material as necessary can be used at least in conventional hydraulic fracturing. It has been established, however, that there are problems in further improving productivity. Specifically, in order to supply and dispose a frac ball of a prescribed size in a ball seat at a corresponding depth reaching 1,000 to 2,000 m from the ground surface, the frac ball must be conveyed over a certain period of time by a high-pressure water stream. This period of time depends completely on the flow rate of the high-pressure water stream, and at a flow rate of not greater than the conventional approximately 4 m/sec (for example, a flow rate of 15 barrels/min for a 4.5-inch pipe), the frac ball containing disintegrable resin described above can be used, but when a higher-rate high-pressure water stream is employed, there is risk that the frac ball will crack and sealing ability will be lost.
CITATION LIST Patent Literature
Patent Document 1: US 2005/0205266A Specification
Patent Document 2: US 2005/0205265A Specification
Patent Document 3: US 2012/0181032A Specification
Patent Document 4: US 7647964B Specification
Patent Document 5: US 2009/0101334A Specification
Patent Document 6: US 2010/0132959A Specification
SUMMARY OF INVENTION Technical Problem
In light of the above circumstances in background art, a primary object of the present invention is to provide a ball sealer for hydrocarbon resource recovery having a relatively large diameter and improved impact resistance, containing, at least in part, disintegrable aliphatic polyester resin.
Further objects of the present invention are to provide a manufacturing method that can form the aforementioned ball sealer for hydrocarbon resource recovery with good dimensional precision using a relatively simple process, and a method for treating a borehole using the ball sealer for hydrocarbon resource recovery.
Solution to Problem
The ball sealer for hydrocarbon resource recovery of the present invention is characterized by being obtained by coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin, and the diameter being not less than approximately 25 mm (1 inch). According to a preferred aspect, a polyglycolic acid resin is used as the disintegrable aliphatic polyester resin.
Furthermore, the method for manufacturing a ball sealer of the present invention is characterized by comprising coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin, to give a diameter of not less than approximately 25 mm (1 inch). According to a preferred aspect, the ball sealer is formed by a method comprising at least one insert injection molding step, in which the aforementioned spherical core or an inside core constituting the interior thereof is disposed as an insert, and a coating resin or outside core resin is injection-molded.
Furthermore, the borehole treatment method of the present invention is a method that comprises a fracturing cycle, in which a frac ball is supplied together with process fluid to a ball seat having an opening provided inside a long frac sleeve inserted into a borehole formed in a subterranean formation, and by sealing the opening of the ball seat disposed at a prescribed location, it forms a seal part and blocks the process fluid, and by causing the process fluid to spurt out from openings provided in the frac sleeve walls directly above the seal part, the borehole inner wall adjacent to the openings is drilled or completed, thereby forming perforations, and after that, the frac ball is disintegrated in situ; the method being characterized by using the ball sealer of the present invention as the frac ball. According to a preferred aspect, it is a method in which a fracturing cycle, in which a plurality of ball seats of gradually larger opening diameter are provided at prescribed intervals from the downstream side to the upstream side in the elongation direction in a long frac sleeve and a plurality of frac balls of gradually larger diameter are sequentially supplied together with process fluid, a seal part is formed, and perforations are formed, is sequentially performed from the downstream side to the upstream side, wherein the ball sealer of the present invention is used as at least some of the plurality of frac balls.
BRIEF DESCRIPTION OF DRAWINGS
FIG. 1 is a schematic cross-sectional view of an aspect of a ball sealer (frac ball) of the present invention.
FIG. 2 is a schematic cross-sectional view of another aspect of the ball sealer (frac ball) of the present invention.
FIG. 3 is a schematic cross-sectional view of a mold in an intermediate stage of frac ball manufacturing according to an aspect of the present invention.
FIG. 4 is a cross-sectional view of a downhole in which a frac sleeve has been inserted, for explaining an example of a fracturing operation performed using a frac sleeve in which the ball sealer (frac ball) of the present invention is incorporated.
DESCRIPTION OF EMBODIMENTS
The present invention will be described in detail hereinafter using preferred embodiments thereof.
As described above, a ball sealer for hydrocarbon resource recovery of the present invention is characterized by being obtained by coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin, and the diameter being not less than approximately 25 mm (1 inch).
Note that in the present specification, the term “disintegration” from which “disintegrable” is derived indicates various processes whereby the sealing function against a corresponding ball seat is no longer maintained, due to significant changes in the physical characteristics of the frac balls resulting from the various materials constituting the ball sealer (frac balls) of the present invention changing significantly at the frac ball environment temperature (normally from 0 to 200° C.) and under the surrounding fluid conditions after fracturing when the heat of the subterranean formation is also added. Those processes are not limited to (bio)degradation, which is generally known in regard to aliphatic polyesters, and also include disintegration, dissolution, and delamination, but are not limited thereto.
FIG. 1 is a schematic cross-sectional view of the most basic aspect of the ball sealer (frac ball) of the present invention. A frac ball 1 is formed by coating a core 2, made from a single resin material, with a resin material layer 3 having higher impact resistance than the core 2. FIG. 2 illustrates another aspect, in which a frac ball 1A is formed by coating a core 2A, having a two-layer structure of an outside core 2 a and an inside core 2 b, with a resin material layer 3 having higher impact resistance than the outside core 2 a.
The resin material that constitutes the core 2 of FIG. 1 or the outside core 2 a of FIG. 2 must have, at least at the frac fluid temperature (normally from 10 to 121° C.), compressive strength (ASTM-D-695) of not less than 30 MPa, preferably not less than 50 MPa, and more preferably not less than 70 MPa, and tensile strength (ASTM-D-882) of not less than 10 MPa, preferably not less than 30 MPa, and more preferably not less than 50 MPa. Such mechanical strength can be established even with a polyglycolic acid (PGA) alone, but in the case of other aliphatic polyester resins such as polylactic acid, it is preferably reinforced by blending a filler such as short fibers or an inorganic filler. This effect is similar for PGA resins as well, and blending of a filler is preferred when particularly high mechanical strength is desired. In the present invention, because impact strength is improved by the coating layer 3, the impact strength of the core 2 (or 2 a) need not be particularly regulated, but a coating layer 3 having a V-notched Izod impact strength according to ASTM-D-256 of approximately 10 to 100 J/m is generally used.
A polyglycolic acid resin (PGA resin) that is preferred as the aliphatic polyester resin also has the characteristics of excellent initial mechanical strength such as the highest level of compressive strength in thermoplastic resins, and has a large effect of suppressing the thickness reduction rate in water due to being a material in which short fiber reinforcing material has been blended. Examples of the polyglycolic acid resin (PGA resin) include glycolic acid homopolymers made from only glycolic acid (—OCH₂—CO—) used as the repeating unit (that is, polyglycolic acid (PGA)), as well as glycolic acid copolymers containing other monomer (comonomer) units, preferably hydroxycarboxylic acid units such as lactic acid, in a proportion of not greater than 50% by weight, preferably not greater than 30% by weight, and more preferably not less than 10% by weight. By using a copolymer that contains other monomer units, the hydrolysis rate, crystallinity, and the like of the polyglycolic acid resin can be adjusted to a certain degree.
A polyglycolic acid resin having a weight average molecular weight of not less than 70,000, and preferably from 100,000 to 500,000, is used. When the weight average molecular weight is less than 70,000, the initial mechanical strength characteristics required in frac balls are lost. On the other hand, when the weight average molecular weight is greater than 500,000, it is not preferred because molding processability is adversely affected. In consideration of injection molding characteristics, melt viscosity measured at the melting point plus 50° C. (270° C. for polyglycolic acid alone) at a shear rate of 120 sec⁻¹ (JIS K 7199) is preferably in the range of 20 to 2,000 Pa·s, and particularly preferably in the range of 200 to 1,500 Pa·s.
The PGA resin that constitutes the core 2 (FIG. 1) or outside core 2 a (FIG. 2) is normally used alone, but other thermoplastic resins such as other aliphatic polyesters, aromatic polyesters, and elastomers may also be blended with the objective of controlling its disintegrability and the like. The added amount thereof is an amount that does not hinder the polyglycolic acid resin from existing as a matrix resin necessary in order to exhibit its characteristic rigidity (compression resistant strength) and linear thickness decrease rate characteristics. More specifically, the added amount should be held to less than 30% by weight, preferably less than 20% by weight, and more preferably less than 10% by weight.
Filler
Examples of short fiber reinforcing materials as preferred examples of the filler (core reinforcing material) include inorganic fibrous substances such as glass fibers, carbon fibers, asbestos fibers, silica fibers, alumina fibers, zirconia fibers, boron nitride fibers, silicon nitride fibers, boron fibers, and potassium titanate fibers; metal fibrous substances such as stainless steel, aluminum, titanium, steel, and brass; and organic fibrous substances with a high melting point such as aramid fibers, kenaf fibers, polyamides, fluorine resins, polyester resins, and acrylic resins. Among these, those having a short diameter (D) from 0.1 to 1,000 μm, more preferably from 1 to 100 μm, and particularly preferably from 5 to 20 μm, and having an aspect ratio (L/D) from 2 to 1,000, more preferably from 3 to 300, and particularly preferably from 3 to 150, are used so as to provide a composition suitable for melt-molding. Typically, those fibers called milled fibers or chopped fibers are preferably used.
Examples of other filers that function as reinforcing materials include mica, silica, talc, alumina, kaolin, calcium sulfate, calcium carbonate, titanium oxide, ferrite, clay, glass powder, zinc oxide, nickel carbonate, iron oxide, quartz powder, magnesium carbonate, barium sulfate, and the like.
When a reinforcing material is blended, it is blended in a proportion of preferably from 2 to 100 parts by weight, more preferably from 10 to 90 parts by weight, and particularly preferably from 20 to 80 parts by weight, relative to 100 parts by weight of the resin that constitutes the core 2 (FIG. 1) or the outside core 2 a (FIG. 2). When it is less than 2 parts by weight, the effect of blending is poor, and when it is greater than 100 parts by weight, there is risk that it will be difficult to uniformly disperse the reinforcing material by melt-kneading.
The multilayer core structure of FIG. 2 is normally preferable to the single-layer core structure of FIG. 1. The first reason a multilayer core structure is preferred is that it enables use of separate materials on the inside and the outside. The high mechanical strength required in the core 2 lies especially in the surface layer thereof (the outside core 2 a in the example of FIG. 2), and in the present invention, a disintegrable aliphatic polyester resin, preferably PGA resin, in which a filler has been blended as necessary is used. In contrast, the inside core 2 b, which has low requirements for mechanical strength, may be formed of another general (bio)degradable resin, for example, aliphatic polyesters other than PGA resin, such as polylactic acid (PLA, typically poly-L-lactic acid (PLLA)), polybutyric acid, and polyvaleric acid; polysaccharides such as starch and dextrin; animal protein polymers such as chitin and chitosan; poly amino acids; polyethylene oxide; and the like. Alternatively, disintegrable materials in which, using these disintegrable resins as a binder, a filler is blended in a relatively large quantity as an extender having almost no reinforcing effect, and disintegrable non-resin materials which have few adverse effects on the natural environment may be used. Furthermore, in either case, whether the core is a single layer or multiple layers (FIG. 2), a hollow spherical core may be used as the single-layer core 2 (FIG. 1) or the inside core 2 b (FIG. 2), while keeping in mind the need to maintain mechanical strength, typified by compressive strength, of the frac ball as a whole.
The frac ball of the present invention is formed by coating the above-described single-layer core 2 (FIG. 1) or multilayer core 2A (FIG. 2) with a resin layer 3 made from a resin material having impact resistance strength greater than that of the disintegrable aliphatic polyester resin in which filler is blended as necessary that constitutes the core. It is preferable to select and use a coating layer material having sufficient impact resistance in accordance with the conveyance speed during use.
The V-notched Izod impact strength according to ASTM-D-256 is used as an indicator of the impact resistance required in the coating layer material.
Specifically, the required impact resistance of the ball coating layer material may differ depending on usage temperature and seat shape, but as V-notched Izod strength, not less than 20 J/m is preferred, not less than 50 J/m is more preferred, and not less than 100 J/m is particularly preferred. Since the maximum test strength has been set at 500 J/m, when a sample “does not break” in an Izod impact test, it is interpreted as having an impact strength greater than the value given above. The coating layer 3 material preferably has higher impact strength than the core 2 (or outside core 2 a), preferably not less than 10 J/m, and particularly not less than 30 J/m.
The impact resistance or impact mitigation characteristics required in the coating resin layer 3 may vary depending on the relative relationship with the disintegrable aliphatic polyester resin that constitutes the core 2 or its surface layer 2 a. For example, PGA resin, which is an excellent core constituent material having high hardness (compressive strength), has the tendency of low impact resistance strength due to its hardness, but aliphatic polyester resins other than PGA resin, such as polylactic acid resin which is relatively soft compared to PGA resin, is potentially a constituent material of the coating resin layer 3 having impact mitigation ability for coating a core made from PGA resin. Impact-resistant grade resin is particularly preferred.
Typical impact-resistant resin materials are rubbers and elastomers, but since they have excessive elastic deformability when used alone, they are used only in a limited thickness, for example, from 0.05 to 10 mm, when used as the surface layer material of frac balls, which require dimensional stability. As a coating layer 3 resin material that has both deformation resistance and impact resistance, a mixture of an aliphatic polyester (preferably PGA resin) and an elastomer is used, and a mixture of an aliphatic polyester resin in which a relatively small amount of elastomer, from 1 to 30% by weight and preferably from 2 to 20% by weight, has been blended is particularly preferred. Specific examples of the elastomer include styrene-based elastomers, olefin-based elastomers, vinyl chloride-based elastomers, urethane-based elastomers, polyester-based elastomers, amide-based elastomers, acrylic rubber-based core/shell-type elastomers, and the like. Most preferred among these are polyester-based elastomers made by combining a polyester hard segment and a polyether or polyester soft segment, which have good miscibility with aliphatic polyesters. Examples of commercially available products thereof include “Hytrel” manufactured by DuPont, which is a block copolymer of polybutylene terephthalate and polyether, and “Ecoflex” manufactured by BASF, which is a biodegradable polybutylene adipate-terephthalate block copolymer.
Blending of a short fiber reinforcing material is preferred in order to improve the impact resistance of the coating layer, and it is preferably blended such that the proportion of reinforcing material relative to the entire coating layer in which the reinforcing material has been blended is from 1 to 50% by weight.
In addition to the fillers (reinforcing materials) described above, various additives, such as thermal stabilizers, photostabilizers, plasticizers, desiccants, waterproofing agents, water-repellent agents, lubricants, degradation accelerators, degradation inhibitors, and the like, may also be added as necessary to the resin material that constitutes the core 2, the outside core 2 a, the inside core 2 b, or the coating layer 3, within a range consistent with the objectives of the present invention.
The frac ball of the present invention is formed as a sphere having a diameter as a whole, including the coating layer 3, of not less than approximately 25 mm (1 inch), and preferably not less than 38 mm (1.5 inches). (Furthermore, the upper limit of diameter is generally not greater than approximately 127 mm (5 inches), and preferably not greater than 114 mm (4.5 inches).) The diameter of the core 2 or the core 2A also varies considerably depending on the materials of the core 2 (or 2A) and the coating layer 3, but, for example, it is from 80 to 99.9% and preferably approximately from 90 to 99.9% of the frac ball diameter, and is not less than 20 mm and preferably not less than 25 mm.
The remainder is the coating layer, of which the thickness may also vary widely depending on the material and the extent of the need to improve impact resistance strength, but it varies widely from 0.05 to 20 mm, preferably from 0.1 to 10 mm.
To form such large frac balls with the required high dimensional precision, a method of performing injection molding using an insert in at least one step, developed in accordance with the method disclosed in the specification of WO2014/024827A (included in the specification of the present application as reference), is preferred.
Specifically, when a single-layer core 2 reaching a diameter of, for example, 1 inch, is integrally molded by, for example, injection molding, shrinkage occurs and high dimensional precision is difficult to obtain due to heat shrinkage after injection molding, which is also seen in general thermoplastic resins, and due to shrinkage accompanying crystallization of aliphatic polyester, which is generally crystalline although in varying degrees. Therefore, regardless of whether the same resin material or different resin materials are used in the outside core 2 a and the inside core 2 b, a problematic decrease in dimensional precision of the outside core 2 a can be markedly reduced when the core 2A is formed by the molding method of the present invention, which uses the inside core 2 b as an insert.
An aspect of manufacturing a multilayer core containing an outside core 2 a made from PGA resin by the method of the present invention which uses the insert molding method will be described in reference to FIG. 3.
FIG. 3 is a schematic cross-sectional view of a mold 10 in an intermediate stage of an aspect of the present invention. A spherical inside core 12 (2 b of FIG. 2) disposed inside a cavity 11 in the open state of a mold 10, which consists of an upper die 10 a and a lower die 10 b, is held by a plurality of support pins 13 which protrude in the vertical direction as illustrated in the drawing in the closed state of the mold 10, in which the upper die 10 a and lower die 10 b are joined with a boundary surface 10 c interposed. In this state, melted PGA resin is injected into the cavity 11 via a runner 14 and gate 15 of the mold, and at the same time that injection is complete (that is, immediately before injection is complete or at substantially the same time), the tips of the plurality of support pins 13 are retracted in the directions of the arrows from their respective core support positions illustrated in the drawing, and when injection is complete, retraction to the position of the inner surface 10 s of the mold is substantially complete.
After that, the molded article is cooled and crystallized in the mold. The mold temperature may be any temperature less than the melting point, but from the perspectives of cooling rate and crystallization rate, it is preferably from 50 to 150° C. When less than 50° C., there are the problems that cooling is too fast, the resin does not spread uniformly when injected, the degree of crystallization of the outside of the molded article relative to the inside is low, and uniformity of physical properties is lost. When not less than 150° C., a long time is required for cooling because the crystallization rate is slow.
After that, the mold is opened and the formed laminate molded article is taken out. The molded article may be water-cooled to cool it down as necessary. Furthermore, residual strain may be eliminated and the degree of crystallization may be made uniform by performing heat treatment at 100 to 200° C. for several minutes to several hours as necessary. Additionally, as necessary, slight surface irregularities corresponding to the gate 15, slight surface irregularities that may remain on the part corresponding to the support pin 13, and surface irregularities of the mold line corresponding to the boundary surface may be removed by polishing to finish the molded article to a smooth surface.
The number of support pins 13 is preferably from 3 to 20 each for the upper die 10 a and the lower die 10 b, and particularly approximately from 3 to 12. All of the support pins are preferably disposed upward and downward from the center of the spherical core such that the tip ends make contact within a range of 90° as the central angle θ. As the support pins, rod-like bodies having a round or slightly elliptical shape with a cross-sectional area of approximately 0.5 to 15 mm² are preferably used.
Thus, a core 2A of a frac ball, in which the outside core 2 a layer made from the above PGA resin is formed on the spherical inside core 2 b, is obtained. The material of the inside core 2 b may be PGA resin, but, as described above, any degradable material may be used for the inside core 2 b, which has low requirements for mechanical strength.
As described above, the thickness of the coating resin layer 3 can vary greatly from 0.05 to 20 mm, depending on the material thereof, and the material and strength of the core 2 or outside core 2 a. For a thickness of approximately 1 mm, the constituent resin material may be molded by a method such as repeatedly dip-coating or spray-coating and curing using a solution or dispersion-like paint obtained by combining it with a suitable solvent or dispersion medium. However, to form a coating layer 3 greater than 1 mm in a uniform thickness, it is still preferable to form it by injection molding with the core 2 or 2A as an insert using the insert injection molding method described above in reference to FIG. 3.
One preferred usage mode of the ball sealer (frac ball) for hydrocarbon resource recovery of the present invention is to use it as at least some of the frac balls having a plurality of diameters incorporated in a long frac sleeve. The fracturing operation using such a long frac sleeve will be described in reference to FIG. 4. FIG. 4 is a partial cross-sectional view of a frac sleeve 10 inserted in a downhole (borehole) D formed in a subterranean formation F. It illustrates a ball seat Bsn disposed at the nth position Sn from the tip direction of the frac sleeve 10, and a ball seat Bsm disposed at the mth position (m>n). When performing fracturing using this frac sleeve, a ball In with a relatively small diameter is supplied by riding on a water stream introduced along the X direction inside the sleeve, and when it is disposed on the ball seat Bsn, the tip of the ball seat Bsn moves to the position of the downstream stopper 2 n due to the water pressure thereof. As a result, a flush hole 3 n that was covered by the back edge of the ball seat Bsn is exposed, and perforations 4 n for petroleum recovery are formed in the subterranean formation at position Sn by the high-pressure water stream that spurts out via these flush holes 3 n. Then, a ball 1 m having a larger diameter than that of the ball 1 n is supplied to a position Sm further upstream, and the above fracturing operation is continued. After a series of fracturing operations, the frac balls . . . 1 n, . . . 1 m, . . . and the like remaining at positions . . . Bsn, . . . Bsm, . . . and the like disintegrate and disappear in a prescribed time according to the disintegrability of the constituent resin thereof under the action of subterranean formation heat and surrounding fluid.
Specifically, in the frac sleeve used in such an aspect, sometimes a long frac sleeve reaching several hundred to several thousand meters formed by adding intermediate tubes is required, and in order to continuously perform a series of fracturing operations using such a long frac sleeve, sometimes a set of numerous frac balls of different diameters, ranging from a small diameter of approximately 12.7 mm (0.5 inches) to a large diameter of approximately 127 mm (5 inches), is required. Therefore, one preferred aspect of application of the present invention is a set of a plurality of frac balls of different diameters in the range of approximately 12.7 mm (0.5 inches) to approximately 127 mm (5 inches), wherein at least some, preferably not less than half, have a diameter not less than approximately 25 mm (1 inch), and include the frac ball of the present invention having a laminate structure. As the remaining smaller-diameter frac balls, a molded ball formed by coating a single-layer core made from an aliphatic polyester such as polyglycolic acid resin as-is, or after coating with the coating resin of the present invention, is preferably used.
EXAMPLES
The present invention will be more specifically described hereinafter based on working examples and comparative examples. The characteristic values in the present specification, including the examples below, are based on values measured by the methods described below.
Impact Resistance Strength
A V-notched Izod impact test specimen was created and impact strength was measured in conformance with ASTM-D-256.
Loading Test
As a simulation test of durability of a frac ball when a frac ball is seated (loaded) by riding on a high-pressure water stream to a ball seat disposed in a frac sleeve inserted in a borehole, a ball seat (angle of ball bearing surface relative to horizontal is 60°) having an opening 0.25 inches smaller than the diameter of the test ball was set inside a vertical steel pipe of inner diameter 4.5 inches, and a test ball was supplied together with a water stream of 50 barrels/min (approximately 8 m/s as water flow rate), and a loading test was performed. The test was performed three times per test ball, and if no cracks occurred in any of three test balls, it was evaluated as acceptable.
Core Production Example 1
A PGA laminated core having a diameter of 1.5 inches was obtained by substantially the same method as Working Example 1 of WO2014/024827A specification.
Specifically, polyglycolic acid (PGA) (melt viscosity: 600 Pa·s at 270° C., 120 sec⁻¹; V-notched Izod impact strength: 27 J/m; manufactured by Kureha Corporation) was supplied to an injection molder (“SAV-100-75” manufactured by Sanjo Seiki Co., Ltd.) and melt-kneaded at a cylinder temperature of 250° C., and a PGA ball having a diameter of 0.5 inches (approximately 13 mm) was obtained using a mold set to 100° C. Then, the 0.5-inch PGA ball 12 produced as above was disposed as an inner-most layer core on three cylindrical support pins 13 having a cross-sectional area of 1.5 mm² of the lower die 10 b of the vertical insert injection molding mold 10 as illustrated in FIG. 3, and the mold was closed by lowering the upper die 10 a equipped with three of the same support pins 13, and the PGA ball core 12 was held in substantially the center of the formed cavity 11. In the state illustrated in FIG. 3, the mold temperature was set to 100° C., and the same PGA as above was supplied to the vertical injection molder, melt-kneaded at a cylinder temperature of 250° C., and injected into the 1.5-inch-diameter cavity 11 of the mold. At substantially the same time as injection was complete, the support pins 13 of the upper and lower dies were retracted to the inner surface position of the mold. After injection was complete, it was cooled for 35 seconds while being held in the 100° C. mold, and then the mold was opened, and a 1.5-inch-diameter PGA laminated ball core 1 was obtained by insert molding.
Core Production Example 2
Laminated ball cores 2 having a diameter of 1.5 inches were obtained in the same manner as Core Production Example 1 except that instead of PGA, a mixture of regular grade polylactic acid (PLLA 1; “4032D” manufactured by NatureWorks LLC; notched Izod impact strength: 16 J/m) and powdered talc filler (“Micro Ace L-1” manufactured by Nippon Talc Co., Ltd.; mean diameter: 5 μm) in a weight ratio of 70/30 (notched Izod impact strength of mixture: 15 J/m) was used.
Working Example 1
Frac balls with an elastomer-blended PGA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in substantially the same manner as Core Production Example 1 by using a mold having an inner diameter of 1.5 inches, with the 1.5-inch diameter PGA laminate ball cores 1 obtained in the above Core Production Example as an insert, and instead of PGA alone, using a mixture of PGA and a polybutylene terephthalate-polyether block copolymer (“Hytrel” manufactured by DuPont; V-notched Izod impact strength: did not break; called “Elastomer 1”) in a weight ratio of 90/10 (notched Izod impact strength of mixture: 50 J/m).
Working Example 2
Frac balls with a PLLA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, impact-resistant grade polylactic acid (PLLA 2; “3801X” manufactured by NatureWorks LLC; weight average molecular weight: 260,000; melting point: 170° C.; notched Izod impact strength: 144 J/m) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
Working Example 3
Frac balls with a coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, biodegradable polybutylene adipate-terephthalate block copolymer (“Ecoflex” manufactured by BASF; notched Izod impact strength: did not break (>500 J/m); called “Elastomer 2”) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
Working Example 4
Frac balls with a glass fiber-reinforced PGA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, a mixture of PGA and glass fiber (GF) (“GL-HF” manufactured by Owens Corning Corporation; short diameter: 10 μm; fiber length: 3 mm) in a weight ratio of 70/30 (notched Izod impact strength of mixture: 115 J/m) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
Working Example 5
Frac balls with an aramid fiber-reinforced PGA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, a mixture of PGA and aramid fiber (“Techno ra” manufactured by Teijin Ltd.; short diameter: 12 μm; fiber length: 3 mm) in a weight ratio of 90/10 (notched Izod impact strength of mixture: 120 J/m) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
Working Example 6
Frac balls with an impact-resistant grade PLLA coating layer having a final diameter of 2 inches were produced in the same manner as Working Example 2 except that instead of the PGA core, the filler-blended regular grade PLLA core obtained in Core Production Example 2 was used.
Working Example 7
Frac balls with a coating layer of PGA blended with GF and elastomer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, a mixture of PGA, the GF used in Working Example 4, and the elastomer 1 used in Working Example 1 in a weight ratio of 66/30/4 (notched Izod impact strength of mixture: 68 J/m) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in
Working Example 1.
Working Example 8
Frac balls with an impact-resistant PLLA coating layer having a final diameter of 2.5 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that further insert molding of PGA was performed using the 1.5-inch-diameter PGA laminate core obtained by Core Production Example 1 as an inside core, and a 2.0-inch-diameter laminate core having a 0.25-inch-thick PGA outside core was obtained, and this was used as an insert instead of the 1.5-inch-diameter PGA laminate ball core 1, and the impact-resistant grade PLLA 2 used in Working Example 2 was also used.
Comparative Example 1
Frac balls with a PGA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, PGA alone was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
Comparative Example 2
Frac balls with a regular grade PLLA coating layer having a final diameter of 2 inches were produced by performing insert injection molding in the same manner as Working Example 1 except that as the coating material, the regular grade PLLA 1 used in Core Production Example 2 (notched Izod impact strength: 16 J/m) was used instead of the mixture of PGA/elastomer 1 in a weight ratio of 90/10 that was used in Working Example 1.
The coated frac balls of Working Examples 1 to 8 having a coating layer with improved impact resistance obtained as described above did not incur any cracking in the three loading tests described above, whereas the frac balls of Comparative Examples 1 and 2 having a coating layer containing highly rigid PGA as the main component incurred cracking in at least one loading test out of three.
A summary of the working examples and comparative examples described above are shown collectively in the following Table 1.
TABLE 1 Compar- Compar- Working Working Working Working Working Working Working Working ative ative Example 1 Example 2 Example 3 Example 4 Example 5 Example 6 Example 7 Example 8 Example 1 Example 2 (Inside) PGA PGA PGA PGA PGA PLLA 1/ PGA PGA PGA PGA core *1 filler = 70/30 Core 1 1 1 1 1 2 1 1 1 1 production example Diameter 1.5 1.5 1.5 1.5 1.5 1.5 1.5 1.5 1.5 1.5 (inches) Outside core — — — — — — PGA — — Thickness — — — — — — 0.25 — — (inches) Coating PGA/ PLLA 2 Elastomer PGA/GF = PGA/ PLLA 2 PGA/GF/ PLLA 2 PGA PLLA 1 layer *1 elastomer 2 70/30 aramid elastomer 1 = 90/10 fiber = 1 = 90/10 66/30/4 Thickness 0.25 0.25 0.25 0.25 0.25 0.25 0.25 0.25 0.25 0.25 (inches) Final 2 2 2 2 2 2 2 2.5 2 2 diameter (inches) Loading Acceptable Acceptable Acceptable Acceptable Acceptable Acceptable Acceptable Acceptable Cracked Cracked results *1 Elastomer 1: Polybutylene terephthalate-polyether block copolymer Elastomer 2: Polybutylene adipate-terephthalate block copolymer PLLA 1: Regular grade PLLA PLLA 2: Impact-resistant grade PLLA
INDUSTRIAL APPLICABILITY
According to the present invention, as described above, a ball sealer having a large diameter suitable for use in hydraulic fracturing, which is widely used in recovery of hydrocarbon resources, and having impact resistance to withstand high flow rate loading while maintaining disintegrability after fracturing is provided, and an efficient method for manufacturing it and a borehole treatment method (fracturing method) using it are also provided.
1. A ball sealer for hydrocarbon resource recovery, the ball sealer being obtained by coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin, and the diameter being not less than 25.4 mm (1 inch).
2. The ball sealer according to claim 1, wherein the disintegrable aliphatic polyester resin is an aliphatic polyester resin that has been reinforced with a filler.
3. The ball sealer according to claim 1, wherein the disintegrable aliphatic polyester resin is a polyglycolic acid resin.
4. The ball sealer according to claim 2, wherein the disintegrable aliphatic polyester resin is a polylactic acid that has been reinforced with a filler.
5. The ball sealer according to claim 1, wherein the coating resin material comprises a disintegrable aliphatic polyester resin.
6. The ball sealer according to claim 5, wherein the coating resin material comprises a polylactic acid.
7. The ball sealer according to claim 1, wherein the coating resin material comprises an elastomer.
8. The ball sealer according to claim 1, wherein the coating resin material comprises a mixture of an elastomer and a polyglycolic acid resin.
9. The ball sealer according to claim 1, wherein the spherical core has a two-layer structure of an outside core and an inside core, the outside core comprising a disintegrable aliphatic polyester resin, and the inside core comprising a disintegrable material other than a polyglycolic acid resin.
10. A method for manufacturing the ball sealer for hydrocarbon resource recovery described in claim 1, the method comprising coating a spherical core that comprises at least one layer comprising a disintegrable aliphatic polyester resin with a resin material that has higher impact resistance than the aliphatic polyester resin, to form a sphere having a diameter of not less than 25.4 mm (1 inch).
11. The method for manufacturing a ball sealer according to claim 10, comprising a step of forming the spherical core, the spherical core having a two-layer structure of an outside core and an inside core, by disposing a spherical inside core in substantially a center in a mold cavity with support pins, and in that state, injection-molding an outside core resin around the inside core, and after retracting the support pins to the wall surface of the mold cavity in synchronization with completion of injection of the outside core resin, curing the outside core resin.
12. The method for manufacturing a ball sealer according to claim 10, comprising a step of forming a ball sealer by disposing the spherical core in substantially a center in a mold cavity with support pins, and in that state, injection-molding coating resin material around the core, and after retracting the support pins to the wall surface of the mold cavity in synchronization with completion of injection of the coating resin material, curing the coating resin material.
13. A method for treating a borehole comprising a fracturing cycle, the fracturing cycle comprising supplying a frac ball together with process fluid to a ball seat having an opening provided inside a long frac sleeve inserted into a borehole formed in a subterranean formation, and, by sealing the opening of the ball seat disposed at a prescribed location, the frac ball forming a seal part and blocking the process fluid, and, by causing the process fluid to spurt out from openings provided in a frac sleeve wall directly above the seal part, drilling or completing a borehole inner wall adjacent to the openings, thereby forming perforations, and after that, disintegrating the frac ball in situ; the method using the ball sealer described in claim 1 as a frac ball.
14. A method for treating a borehole, the method comprising a fracturing cycle, the fracturing cycle comprising providing a plurality of ball seats of gradually larger opening diameter at prescribed intervals from a downstream side to an upstream side in an elongation direction in a long frac sleeve and sequentially supplying frac balls of gradually larger diameter together with process fluid, forming a seal part, and forming perforations; the fracturing cycle being sequentially performed from the downstream side to the upstream side; the method using the ball sealer described in claim 1 as at least some of the plurality of frac balls.
|
offspring.
Paedogenesis. — Although sexual reproduction is usually carried on only by adults, this is not always the case, for there are certain species whose members have the remarkable power of reproducing sexually while they are in the larval ^ state. This reproduction by a larval animal is called -paedogenesis. Paedogenesis may be either parthenogenetic or bisexual.
Parthenogenetic paedogenesis occurs in certain species of flies. The larvae in these species (Fig. 134) produce ova which develop by partheno genesis into larvae before the oviducts are present. The latter generation of larvae escapes from the parent larva by rupture of the body wall. This results in the death of the parent. Several generations may be produced
Under certam conditions this animal attains sexual maturity and breeds while it is still in the larval form having gills. In some of the Mexican lakes this is said to be the usual occurrence, while in Kansas and Nebraska it is rare, and in many localities it probably does not occur at all.
Hermaphroditism. — Most animals — a very great majority of the metazoa — possess either male or female organs of reproduction but not both. Species which have the sexes thus separate are said to be dioecious (living in two houses), while those species whose individuals produce both eggs and spermatozoa are called monoecious (living in one house). Individuals with both male and female organs are said to be hermaphrodites.'^ Two common species of Hydra are hermaphroditic, as are most of the flatworms, most snails, and some roundworms. In many monoecious species the spermatozoa are produced first and later the ova, but in some species this condition is reversed. By developing the sexual products at different times, cross-fertilization, that is, fertilization of eggs by spermatozoa from another individual, is assured. In the earth worm, eggs and spermatozoa are produced in the same individual and
' A larva is a young independent individual which differs from the adult in the possession of organs not possessed by the adult, or in lacking certain organs which arc present in the adult (for example, a frog tad{K)le).
|
SELECT
ANU.Email UserEmail,
ANU.UserName UserName,
LR.Id LeaderboardRecordId,
LR.UserId ,
LR.TotalTime ,
LR.Created ,
LR.TotalAwards ,
LR.FavoriteActress ,
LR.FavoriteActor ,
LR.FavoriteGenre
FROM `mooviesboarddb`.LeaderboardRecords AS LR
INNER JOIN `mooviesboarddb`.AspNetUsers AS ANU ON ANU.Id = LR.UserId
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.